1.8.24 Social The Hacker News
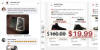
Facebook users are the target of a scam e-commerce network that uses hundreds of fake websites to steal personal and financial data using brand impersonation and malvertising tricks.
Social 2024 2023 2022 2021 2020
Telegram Agrees to Share User Data With Authorities for Criminal Investigations
24.9.24 Social The Hacker News
In a major policy reversal, the popular messaging app Telegram has announced it will give users' IP addresses and phone numbers to authorities in response to valid legal requests in an attempt to rein in criminal activity on the platform.
"We've made it clear that the IP addresses and phone numbers of those who violate our rules can be disclosed to relevant authorities in response to valid legal requests," Telegram CEO Pavel Durov said in a post.
To that end, the company now explicitly states -
"If Telegram receives a valid order from the relevant judicial authorities that confirms you're a suspect in a case involving criminal activities that violate the Telegram Terms of Service, we will perform a legal analysis of the request and may disclose your IP address and phone number to the relevant authorities."
Such data disclosures, it said, will be included in its periodic transparency reports. It further noted that the service may collect metadata such as IP address, devices and Telegram apps used, and the history of username changes to tackle spam, abuse, and other violations.
It's worth noting that a previous version of its policy limited user information sharing to cases involving terror suspects: "If Telegram receives a court order that confirms you're a terror suspect, we may disclose your IP address and phone number to the relevant authorities."
Accompanying the changes is an update to its search feature to remove problematic content from search results and a new mechanism for users to report illegal search terms and material through the @SearchReport bot for subsequent review and removal by a human moderation team.
The update to Telegram's Terms of Service and Privacy Policy is a major volte-face for the company which has refused to police the platform for years, turning it into a major haven for cybercrime and other illegal activities, including drug trafficking, child pornography, and money laundering.
The changes have also been driven by the arrest of Durov in France over allegations that the company turned a blind eye to various crimes flourishing unchecked on the platform. He was subsequently released on bail but has been ordered to stay in the country pending ongoing investigation.
Last week, the Ukrainian government said it was banning the use of Telegram by government officials, military personnel, and other defense and critical infrastructure workers, citing national security concerns.
Ukraine Bans Telegram Use for Government and Military Personnel
20.9.24 Social The Hacker News
Ukraine has restricted the use of the Telegram messaging app by government officials, military personnel, and other defense and critical infrastructure workers, citing national security concerns.
The ban was announced by the National Coordination Centre for Cybersecurity (NCCC) in a post shared on Facebook.
"I have always advocated and advocate for freedom of speech, but the issue of Telegram is not a question of freedom of speech, it is a matter of national security," Kyrylo Budanov, head of Ukraine's GUR military intelligence agency, said.
Ukraine's National Security and Defense Council (NSDC) said that Telegram is "actively used by the enemy" to launch cyber attacks, spread phishing messages and malicious software, track users' whereabouts, and gather intelligence to help the Russian military target Ukraine's facilities with drones and missiles.
To that end, the use of Telegram has been proscribed on official devices of employees of state authorities, military personnel, employees of the security and defense sector, as well as enterprises that are operators of critical infrastructure.
It's worth noting that the ban does not extend to personal phones, or people who use the app as part of their official duties.
In a statement shared with Reuters, Telegram said it has not provided any personal data to any country, including Russia, and that deleted messages are permanently deleted with no way of recovering them.
The development comes weeks after Telegram's CEO was arrested in France and then released on bail in connection with an investigation into the use of the popular messaging app for child pornography, drug trafficking, and fraud.
Telegram Founder Pavel Durov Arrested in France for Content Moderation Failures
25.8.24 Social The Hacker News
Pavel Durov, founder and chief executive of the popular messaging app Telegram, was arrested in France on Saturday, according to French television network TF1.
Durov is believed to have been apprehended pursuant to a warrant issued in connection with a preliminary police investigation.
TF1 said the probe was focused on a lack of content moderation on the instant messaging service, which the authorities took issue with, turning the app into a haven for various kinds of criminal activity, including drug trafficking, child pornography, money laundering, and fraud.
The hands-off approach to moderation on Telegram has been a point of contention, fueling cybercrime and turning the platform into a hub for threat actors to organize their operations, distribute malware, and peddle stolen data and other illegal goods
"This messaging app has transformed into a bustling hub where seasoned cybercriminals and newcomers alike exchange illicit tools and insights creating a dark and well-oiled supply chain of tools and victims' data," Guardio Labs said in a report earlier this year.
Headquartered in Dubai, Telegram has over 950 million monthly active users as of July 2024. It recently launched an in-app browser and a Mini App Store, effectively turning it into a super app, mirroring Tencent's WeChat.
(This is a developing story. Please check back for more updates.)
Facebook Ads Lead to Fake Websites Stealing Credit Card Information
1.8.24 Social The Hacker News
Facebook users are the target of a scam e-commerce network that uses hundreds of fake websites to steal personal and financial data using brand impersonation and malvertising tricks.
Recorded Future's Payment Fraud Intelligence team, which detected the campaign on April 17, 2024, has given it the name ERIAKOS owing to the use of the same content delivery network (CDN) oss.eriakos[.]com.
"These fraudulent sites were accessible only through mobile devices and ad lures, a tactic aimed at evading automated detection systems," the company said, noting the network comprised 608 fraudulent websites and that the activity spans several short-lived waves.
A notable aspect of the sophisticated campaign is that it exclusively targeted mobile users who accessed the scam sites via ad lures on Facebook, some of which relied on limited-time discounts to entice users into clicking on them. Recorded Future said as many as 100 Meta Ads related to a single scam website were served in a day.
The counterfeit websites and ads have been found to mainly impersonate a major online e-commerce platform and a power tools manufacturer, as well as single out victims with bogus sales offers for products from various well-known brands. Another crucial distribution mechanism entails the use of fake user comments on Facebook to lure potential victims.
"Merchant accounts and related domains linked to the scam websites are registered in China, indicating that the threat actors operating this campaign likely established the business they use to manage the scam merchant accounts in China," Recorded Future noted.
This is not the first time criminal e-commerce networks have sprung up with an aim to harvest credit card information and make illicit profits off fake orders. In May 2024, a massive network of 75,000 phony online stores – dubbed BogusBazaar – was discovered to have made more than $50 million by advertising shoes and apparel by well-known brands at low prices.
Then last month, Orange Cyberdefense revealed a previously undocumented traffic direction system (TDS) called R0bl0ch0n TDS that's used to promote affiliate marketing scams through a network of fake shop and sweepstake survey sites with the goal of obtaining credit card information.
"Several distinct vectors are used for the initial dissemination of the URLs that redirect through the R0bl0ch0n TDS, indicating that these campaigns are likely carried out by different affiliates," security researcher Simon Vernin said.
The development comes as fake Google ads displayed when searching for Google Authenticator on the search engine have been observed redirecting users to a rogue site ("chromeweb-authenticators[.]com") that delivers a Windows executable hosted on GitHub, which ultimately drops an information stealer named DeerStealer.
What makes the ads seemingly legitimate is that they appear as if they are from "google.com" and the advertiser's identity is verified by Google, according to Malwarebytes, which said "some unknown individual was able to impersonate Google and successfully push malware disguised as a branded Google product as well."
Malvertising campaigns have also been spotted disseminating various other malware families such as SocGholish (aka FakeUpdates), MadMxShell, and WorkersDevBackdoor, with Malwarebytes uncovering infrastructure overlaps between the latter two, indicating that they are likely run by the same threat actors.
On top of that, ads for Angry IP Scanner have been used to lure users to fake websites, and the email address "goodgoo1ge@protonmail[.]com" has been used to register domains delivering both MadMxShell and WorkersDevBackdoor.
"Both malware payloads have the capability to collect and steal sensitive data, as well as provide a direct entry path for initial access brokers involved in ransomware deployment," security researcher Jerome Segura said.
Meta Settles for $1.4 Billion with Texas Over Illegal Biometric Data Collection
31.7.24 Social The Hacker News
Meta, the parent company of Facebook, Instagram, and WhatsApp, agreed to a record $1.4 billion settlement with the U.S. state of Texas over allegations that it illegally collected biometric data of millions of users without their permission, marking one of the largest penalties levied by regulators against the tech giant.
"This historic settlement demonstrates our commitment to standing up to the world's biggest technology companies and holding them accountable for breaking the law and violating Texans' privacy rights," Attorney General Ken Paxton said. "Any abuse of Texans' sensitive data will be met with the full force of the law."
The development arrived more than two years after the social media behemoth was sued for unlawfully capturing facial data belonging to Texas without their informed consent as is required by the law. The Menlo Park-based company, however, did not admit to any wrongdoing.
Cybersecurity
Tag Suggestions, as the feature was originally called when it was introduced in 2010, was marketed as a way for users to easily tag photos shared on Facebook with the names of people in them. However, it was enabled by default without giving adequate explanation as to how it worked.
The lawsuit accused Meta of violating the state's Capture or Use of Biometric Identifier (CUBI) Act and the Deceptive Trade Practices Act.
"Unbeknownst to most Texans, for more than a decade Meta ran facial recognition software on virtually every face contained in the photographs uploaded to Facebook, capturing records of the facial geometry of the people depicted," according to a press statement from the Attorney General's office.
"Meta did this despite knowing that CUBI forbids companies from capturing biometric identifiers of Texans, including records of face geometry, unless the business first informs the person and receives their consent to capture the biometric identifier."
In November 2021, Meta said it was discontinuing its "Face Recognition" system altogether and deleting a huge collection of more than a billion users' facial recognition templates as part of a wider initiative to limit the use of the technology across its products.
That same year, it agreed to pay a $650 million settlement in a 2015 class-action lawsuit in Illinois under the Biometric Information Privacy Act (BIPA) over similar allegations related to its face-tagging system.
Meta is not the only party being targeted by Texas over the collection of biometric data. The state also sued Google in October 2022 for allegedly violating the same biometric privacy law by gathering voice and facial data through products like Google Photos, Google Assistant, and Nest Hub Max. The case is currently underway.
Meta Removes 63,000 Instagram Accounts Linked to Nigerian Sextortion Scams
26.7.24 Social The Hacker News
Meta Platforms on Wednesday said it took steps to remove around 63,000 Instagram accounts in Nigeria that were found to target people with financial sextortion scams.
"These included a smaller coordinated network of around 2,500 accounts that we were able to link to a group of around 20 individuals," the company said. "They targeted primarily adult men in the U.S. and used fake accounts to mask their identities."
In cases where some of these accounts attempted to target minors, Meta said it reported them to the National Center for Missing and Exploited Children (NCMEC).
Separately, Meta said it also removed 7,200 assets, including 1,300 Facebook accounts, 200 Facebook Pages and 5,700 Facebook Groups, based in Nigeria that were used to organize, recruit and train new scammers.
"Their efforts included offering to sell scripts and guides to use when scamming people, and sharing links to collections of photos to use when populating fake accounts," it said.
Meta attributed the second cluster to a cybercrime group tracked as Yahoo Boys, which came under the radar earlier this year for orchestrating financial sextortion attacks targeting teenagers from Australia, Canada, and the U.S.
A subsequent report from Bloomberg exposed sextortion-fueled suicides, revealing how scammers are posing as teenage girls on Instagram and Snapchat to lure targets and entice them into sending explicit photos, which are then used to blackmail victims in exchange for money or risk getting their images forwarded to their friends.
Back in April, the social media giant said it has devised new methods to identify accounts that are potentially engaging in sextortion, and that it's enacting measures to prevent these accounts from finding and interacting with teens.
"Financial sextortion is a horrific crime that can have devastating consequences," Meta said. "This is an adversarial space where criminals evolve to evade our ever-improving defenses."
Meta's actions come as INTERPOL said it conducted a global law enforcement operation referred to as Jackal III that targeted West African organized crime groups such as Black Axe, leading to scores of arrests and the seizure of $3 million in illegal assets, including cryptocurrencies and luxury items.
The effort, which took place between April 10 and July 3, 2024, spanned 21 countries and was orchestrated with an aim to dismantle transnational organized crime syndicates involved in cyber fraud, human trafficking, drug smuggling, and violent crimes both within Africa and globally.
"The annual operation resulted in some 300 arrests, the identification of over 400 additional suspects, and the blocking of more than 720 bank accounts," INTERPOL said in a press statement.
The development also follows a wave of other law enforcement actions from across the world designed to tackle cybercrime -
Vyacheslav Igorevich Penchukov (aka father and tank), who pleaded guilty at the start of the year for his role in the Zeus and IcedID malware operations, was sentenced by a U.S. court to nine years in prison and three years of supervised release. He was also ordered to pay $73 million in restitution.
The Ukrainian Cyber Police announced the arrest of two people in connection with financial theft attacks targeting "leading industrial enterprises" in the country, leading to losses amounting to $145,000 (six million hryvnias). If found guilty, they face up to 12 years in prison.
Spain's La Guardia Civil arrested three suspected members of NoName057(16), prompting the pro-Russian hacktivist group to declare a "holy war" on the country. The individuals have been accused of participating in "denial-of-service cyber attacks against public institutions and strategic sectors of Spain and other NATO countries." The group called the arrests a "witch hunt" by Russophobic authorities.
The U.K. National Crime Agency (NCA) said it infiltrated and took down digitalstress[.]su, a DDoS-for-hire (aka booter) service linked to "tens of thousands of attacks every week" globally. The site's suspected owner, who goes by the name Skiop, has also been arrested. The takedown, part of an ongoing coordinated effort dubbed Operation PowerOFF, came after German police disrupted the Stresser.tech DDoS attack service in April 2024.
Telegram App Flaw Exploited to Spread Malware Hidden in Videos
25.7.24 Social The Hacker News
A zero-day security flaw in Telegram's mobile app for Android called EvilVideo made it possible for attackers to malicious files disguised as harmless-looking videos.
The exploit appeared for sale for an unknown price in an underground forum on June 6, 2024, ESET said. Following responsible disclosure on June 26, the issue was addressed by Telegram in version 10.14.5 released on July 11.
"Attackers could share malicious Android payloads via Telegram channels, groups, and chat, and make them appear as multimedia files," security researcher Lukáš Štefanko said in a report.
It's believed that the payload is concocted using Telegram's application programming interface (API), which allows for programmatic uploads of multimedia files to chats and channels. In doing so, it enables an attacker to camouflage a malicious APK file as a 30-second video.
Users who click on the video are displayed an actual warning message stating the video cannot be played and urges them to try playing it using an external player. Should they proceed with the step, they are subsequently asked to allow installation of the APK file through Telegram. The app in question is named "xHamster Premium Mod."
"By default, media files received via Telegram are set to download automatically," Štefanko said. "This means that users with the option enabled will automatically download the malicious payload once they open the conversation where it was shared."
While this option can be disabled manually, the payload can still be downloaded by tapping the download button accompanying the supposed video. It's worth noting that the attack does not work on Telegram clients for the web or the dedicated Windows app.
It's currently not clear who is behind the exploit and how widely it was used in real-world attacks. The same actor, however, advertised in January 2024 a fully undetectable Android crypter (aka cryptor) that can reportedly bypass Google Play Protect.
Hamster Kombat's Viral Success Spawns Malicious Copycat#
The development comes as cyber criminals are capitalizing on the Telegram-based cryptocurrency game Hamster Kombat for monetary gain, with ESET discovering fake app stores promoting the app, GitHub repositories hosting Lumma Stealer for Windows under the guise of automation tools for the game, and an unofficial Telegram channel that's used to distribute an Android trojan called Ratel.
The popular game, which launched in March 2024, is estimated to have more than 250 million players, according to the game developer. Telegram CEO Pavel Durov has called Hamster Kombat the "fastest-growing digital service in the world" and that "Hamster's team will mint its token on TON, introducing the benefits of blockchain to hundreds of millions of people."
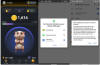
Ratel, offered via a Telegram channel named "hamster_easy," is designed to impersonate the game ("Hamster.apk") and prompts users to grant it notification access and set itself as the default SMS application. It subsequently initiates contact with a remote server to get a phone number as response.
In the next step, the malware sends a Russian language SMS message to that phone number, likely belonging to the malware operators, to receive additional instructions over SMS.
"The threat actors then become capable of controlling the compromised device via SMS: The operator message can contain a text to be sent to a specified number, or even instruct the device to call the number," ESET said. "The malware is also able to check the victim's current banking account balance for Sberbank Russia by sending a message with the text баланс (translation: balance) to the number 900."
Ratel abuses its notification access permissions to hide notifications from no less than 200 apps based on a hard-coded list embedded within it. It's suspected that this is being done in an attempt to subscribe the victims to various premium services and prevent them from being alerted.
The Slovakian cybersecurity firm said it also spotted fake application storefronts claiming to offer Hamster Kombat for download, but actually directs users to unwanted ads, and GitHub repositories offering Hamster Kombat automation tools that deploy Lumma Stealer instead.
"The success of Hamster Kombat has also brought out cybercriminals, who have already started to deploy malware targeting the players of the game," Štefanko and Peter Strýček said. "Hamster Kombat's popularity makes it ripe for abuse, which means that it is highly likely that the game will attract more malicious actors in the future."
BadPack Android Malware Slips Through the Cracks#
Beyond Telegram, malicious APK files targeting Android devices have also taken the form of BadPack, which refer to specially crafted package files in which the header information used in the ZIP archive format has been altered in an attempt to obstruct static analysis.
In doing so, the idea is to prevent the AndroidManifest.xml file – a crucial file that provides essential information about the mobile application – from being extracted and properly parsed, thereby allowing malicious artifacts to be installed without raising any red flags.
This technique was extensively documented by Kaspersky earlier this April in connection with an Android trojan referred to as SoumniBot that has targeted users in South Korea. Telemetry data gathered by Palo Alto Networks Unit 42 from June 2023 through June 2024 has detected nearly 9,200 BadPack samples in the wild, although none of them have been found on Google Play Store.
"These tampered headers are a key feature of BadPack, and such samples typically pose a challenge for Android reverse engineering tools," Unit 42 researcher Lee Wei Yeong said in a report published last week. "Many Android-based banking Trojans like BianLian, Cerberus and TeaBot use BadPack."
Update#
In a statement shared with The Hacker News, Telegram said the exploit is not a vulnerability in the platform and it deployed a server-side fix on July 9, 2024, to secure users.
"It would have required users to open the video, adjust Android safety settings and then manually install a suspicious-looking 'media app,'" the company said, emphasizing that the exploit only poses a security risk when users install the app after bypassing the security feature.
Google said Android users are automatically secured against trojans via Google Play Protect, which is enabled by default on all devices with Google Play Services. "Google Play Protect can warn users or block apps known to exhibit malicious behavior, even when those apps come from sources outside of Play," it said.
Meta Given Deadline to Address E.U. Concerns Over 'Pay or Consent' Model
24.7.24 Social The Hacker News
Meta has been given time till September 1, 2024, to respond to concerns raised by the European Commission over its "pay or consent" advertising model or risk-facing enforcement measures, including sanctions.
The European Commission said the Consumer Protection Cooperation (CPC) Network has notified the social media giant that the model adopted for Facebook and Instagram might potentially violate consumer protection laws.
It described the new practice as misleading and confusing, with authorities expressing worries that consumers might have been pressured into choosing quickly between either paying for a monthly subscription or consenting to their personal data being used for targeted advertising.
This, the agency said, could have been motivated by fears that they "would instantly lose access to their accounts and their network of contacts."
Meta, which introduced a subscription plan for European Union (E.U.) users in late 2023, has run into hot water over offering what's essentially not a choice at all and for extracting a "privacy fee" to exercise their data protection rights.
As per the E.U. Digital Markets Act (DMA), companies in gatekeeper roles are required to seek users' express consent before utilizing their data for offering services that go beyond their core functionality (e.g., advertising) or provide access to a less personalized but equivalent version of the platforms for those who refuse to opt in.
"Gatekeepers cannot make use of the service or certain functionalities conditional on users' consent," the Commission noted earlier this month, stating that Meta's model is in violation of the DMA.
The Commission further called out Meta for using vague terms and branding the service as "free" when, in reality, it forces consumers to agree to their data used for personalized ads, not to mention making the experience confusing by making them "navigate through different screens" to determine how their data is used and processed for advertising purposes.
Meta, however, considers the paid version a legitimate business model, and has pointed to a ruling from the Court of Justice of the European Union (CJEU) last July that a company may offer an equivalent alternative version of its service "for an appropriate fee" that does not rely on data collection for ads.
That said, it bears noting here that the judgment pertains to in the context of users signing up for Meta's services, and not to existing users (which is where the aforementioned issues associated with changes to the consent model come from). It remains to be seen if it can be interpreted as a legal precedent.
"Consumers must not be lured into believing that they would either pay and not be shown any ads anymore, or receive a service for free, when, instead, they would agree that the company used their personal data to make revenue with ads," Didier Reynders, E.U. Commissioner for Justice, said.
"Traders must inform consumers upfront and in a fully transparent manner on how they use their personal data. This is a fundamental right that we will protect."
The development comes days after Nigeria's Federal Competition and Consumer Protection Commission (FCCPC) fined Meta $220 million after an investigation showed that the company's data sharing on Facebook and WhatsApp violated local consumer, data protection, and privacy laws by collecting users' information without their consent.
"Meta Parties shall immediately and forthwith stop the process of sharing WhatsApp user's information with other Facebook companies and third parties, until such a time when users have actively and voluntarily consented to each and every component of the liberties Meta parties intend to exercise with respect to the information of the data subjects," a final order issued last week read.
Earlier this May, the Turkish competition board imposed a $37.20 million penalty against the American tech giant over its data-sharing practices across Facebook, Instagram, Threads, and WhatsApp.
It also follows a report that Oracle has agreed to pay $115 million to settle a class-action lawsuit in the U.S. accusing the database software and cloud computing company of breaching users' privacy by collecting their personal information and selling it to third-parties.
Google, meanwhile, has become the subject of a new probe initiated by the Italian data protection authority over how it gets users' consent prior to combining personal data from different services and if it provides adequate information to influence that choice.
"Google may use techniques and methods for requesting consent, and also for setting up the mechanisms for obtaining consent itself, which could condition the freedom of choice of the average consumer," the Garante alleged.
"Indeed, the customer would be induced to take a commercial decision that he/she would not have taken otherwise, by consenting to the combination and cross-use of his/her personal data among the plurality of services offered."
Meta's 'Pay or Consent' Approach Faces E.U. Competition Rules Scrutiny
2.7.24 Social The Hacker News
Meta's decision to offer an ad-free subscription in the European Union (E.U.) has faced a new setback after regulators accused the social media behemoth of breaching the bloc's competition rules by forcing users to choose between seeing ads or paying to avoid them.
The European Commission said the company's "pay or consent" advertising model is in contravention of the Digital Markets Act (DMA).
"This binary choice forces users to consent to the combination of their personal data and fails to provide them a less personalized but equivalent version of Meta's social networks," the Commission said.
It also noted that companies in gatekeeper roles must seek users' permission to combine their personal data between designated core platform services and other services (e.g., advertising) and that users who refuse to opt in should have access to a less personalized but equivalent alternative.
Cybersecurity
On top of that, Meta's approach does not allow users to choose a service that uses less of their personal data, stating it doesn't permit users to exercise their right to freely consent to combine their data from its services to target them with personalized online ads, the Commission said.
"Users who do not consent should still get access to an equivalent service which uses less of their personal data, in this case for the personalisation of advertising," it added.
Meta first announced its plans for an ad-free option to access Facebook and Instagram for users in the E.U., European Economic Area (EEA), and Switzerland in October 2023 as a way to comply with the strict privacy laws in the region.
But in the intervening months, the American tech giant has faced criticism for essentially not offering real choices for customers to opt from, instead forcing them to either consent to tracking for advertising purposes or pay up every month to avoid seeing personalized ads altogether.
"European users now have the 'choice' to either consent to being tracked for personalized advertising – or pay up to €251.88 a year to retain their fundamental right to data protection on Instagram and Facebook," Austrian privacy non-profit noyb said late last year.
"Not only is the cost unacceptable, but industry numbers suggest that only 3 percent of people want to be tracked – while more than 99 percent decide against a payment when faced with a 'privacy fee.'"
Cybersecurity
Should the preliminary findings be confirmed, Meta could be fined up to 10% of its total worldwide turnover, a number that can go up to 20% for systematic infringement of the rules.
"Subscription for no ads follows the direction of the highest court in Europe and complies with the DMA," Meta was quoted as saying in a statement shared with the Associated Press. It further said it will engage in "constructive dialogue" with the Commission as part of the investigation.
The development comes as a Norwegian court has confirmed that online dating app Grindr violated GDPR data protection laws in the E.U. by sharing user data with advertisers, requiring it to pay a fine of €5.7 million ($6.1 million).
Telegram Offers Premium Subscription in Exchange for Using Your Number to Send OTPs
29.3.24 Social The Hacker News
In June 2017, a study of more than 3,000 Massachusetts Institute of Technology (MIT) students published by the National Bureau for Economic Research (NBER) found that 98% of them were willing to give away their friends' email addresses in exchange for free pizza.
"Whereas people say they care about privacy, they are willing to relinquish private data quite easily when incentivized to do so," the research said, pointing out a what's called the privacy paradox.
Now, nearly seven years later, Telegram has introduced a new feature that gives some users a free premium membership in exchange for allowing the popular messaging app to use their phone numbers as a relay for sending one-time passwords (OTPs) to other users who are attempting to sign in to the platform.
The feature, called Peer-to-Peer Login (P2PL), is currently being tested in selected countries for Android users of Telegram. It was first spotted by tginfo in February 2024 (via @AssembleDebug).
According to Telegram's Terms of Service, the phone number will be used to send no more than 150 OTP SMS messages – including international SMS – per month, incurring charges from the user's mobile carrier or service provider.
That said, the popular messaging app notes that it "cannot prevent the OTP recipient from seeing your phone number upon receiving your SMS" and that it "will not be liable for any inconvenience, harassment or harm resulting from unwanted, unauthorized or illegal actions undertaken by users who became aware of your phone number through P2PL."
Even worse, the mechanism – which largely relies on a honor system – doesn't prohibit users from contacting strangers to whose number the OTP authentication SMS was sent, and vice versa, potentially leading to an increase in spam calls and texts.
Telegram said it reserves the right to unilaterally terminate an account from the P2PL program if participants are found sharing personal information about recipients. It also warns users not to contact any OTP recipients or reply to them even if they message them.
As of March 2024, Telegram has more than 900 million monthly active users. It launched the Premium subscription program in June 2022, allowing users to unlock additional features like 4 GB file uploads, faster downloads, and exclusive stickers and reactions.
With online services still relying on phone numbers to authenticate users, it's worth keeping in mind the privacy and security risks that could arise from partaking in the experiment.
Meta in Legal Crosshairs for Intercepting Snapchat Traffic#
The development comes as newly unsealed court documents in the U.S. alleged that Meta launched a secret project called Ghostbusters to intercept and decrypt the network traffic from people using Snapchat, YouTube, and Amazon to help it understand user behavior and better compete with its rivals.
This was accomplished by leveraging custom apps from a VPN service called Onavo, which Facebook acquired in 2013 and shut down in 2019 after it came under scrutiny for using its products to track users' web activity related to its competitors and secretly paying teens to capture their internet browsing patterns.
The data-interception scheme has been described as a "man-in-the-middle" approach, in which Facebook essentially paid people between ages 13 and 35 up to $20 per month plus referral fees for installing a market research app and giving it elevated access to inspect network traffic and analyze their internet usage.
The tactic relied on creating "fake digital certificates to impersonate trusted Snapchat, YouTube, and Amazon analytics servers to redirect and decrypt secure traffic from those apps for Facebook's strategic analysis."
The apps were distributed through beta testing services, such as Applause, BetaBound, and uTest, to conceal Facebook's involvement. The program, which later came to be known as In-App Action Panel (IAAP), ran from 2016 to 2018.
Meta, in its response, said there is no crime or fraud, and that "Snapchat's own witness on advertising confirmed that Snap cannot 'identify a single ad sale that [it] lost from Meta's use of user research products,' does not know whether other competitors collected similar information, and does not know whether any of Meta's research provided Meta with a competitive advantage."
Meta Details WhatsApp and Messenger Interoperability to Comply with EU's DMA Regulations
8.3.24 Social The Hacker News
Meta has offered details on how it intends to implement interoperability in WhatsApp and Messenger with third-party messaging services as the Digital Markets Act (DMA) went into effect in the European Union.
"This allows users of third-party providers who choose to enable interoperability (interop) to send and receive messages with opted-in users of either Messenger or WhatsApp – both designated by the European Commission (EC) as being required to independently provide interoperability to third-party messaging services," Meta's Dick Brouwer said.
DMA, which officially became enforceable on March 7, 2024, requires companies in gatekeeper positions – Apple, Alphabet, Meta, Amazon, Microsoft, and ByteDance – to clamp down on anti-competitive practices from tech players, level the playing field, as well as compel them to open some of their services to competitors.
As part of its efforts to comply with the landmark regulations, the social media giant said it expects third-party providers to use the Signal Protocol, which is used in both WhatsApp and Messenger for end-to-end encryption (E2EE).
The third-parties are also required to package the encrypted communications into message stanzas in eXtensible Markup Language (XML). Should the message contain media content, an encrypted version is downloaded by Meta clients from the third-party messaging servers using a Meta proxy service.
The company is also proposing what's called a "plug-and-play" model that allows third-party providers to connect to its infrastructure for achieving interoperability.
"Taking the example of WhatsApp, third-party clients will connect to WhatsApp servers using our protocol (based on the Extensible Messaging and Presence Protocol – XMPP)," Brouwer said.
"The WhatsApp server will interface with a third-party server over HTTP in order to facilitate a variety of things including authenticating third-party users and push notifications."
Furthermore, third-party clients are mandated to execute a WhatsApp Enlistment API when opting into its network, alongside providing cryptographic proof of their ownership of the third-party user-visible identifier when connecting or a third-party user registers on WhatsApp or Messenger.
The technical architecture also has provisions for a third-party provider to add a proxy or an intermediary between their client and the WhatsApp server to provide more information about the kinds of content their client can receive from the WhatsApp server.
"The challenge here is that WhatsApp would no longer have direct connection to both clients and, as a result, would lose connection level signals that are important for keeping users safe from spam and scams such as TCP fingerprints," Brouwer noted.
"This approach also exposes all the chat metadata to the proxy server, which increases the likelihood that this data could be accidentally or intentionally leaked."
New 'VietCredCare' Stealer Targeting Facebook Advertisers in Vietnam
21.2.24 Social The Hacker News
Facebook advertisers in Vietnam are the target of a previously unknown information stealer dubbed VietCredCare at least since August 2022.
The malware is "notable for its ability to automatically filter out Facebook session cookies and credentials stolen from compromised devices, and assess whether these accounts manage business profiles and if they maintain a positive Meta ad credit balance," Singapore-headquartered Group-IB said in a new report shared with The Hacker News.
The end goal of the large-scale malware distribution scheme is to facilitate the takeover of corporate Facebook accounts by targeting Vietnamese individuals who manage the Facebook profiles of prominent businesses and organizations.
Facebook accounts that have been successfully seized are then used by the threat actors behind the operation to post political content or to propagate phishing and affiliate scams for financial gain.
VietCredCare is offered to other aspiring cybercriminals under the stealer-as-a-service model and advertised on Facebook, YouTube, and Telegram. It's assessed to be managed by Vietnamese-speaking individuals.
Customers either have the option of purchasing access to a botnet managed by the malware's developers, or procure access to the source code for resale or personal use. They are also provided a bespoke Telegram bot to manage the exfiltration and delivery of credentials from an infected device.
The .NET-based malware is distributed via links to bogus sites on social media posts and instant messaging platforms, masquerading as legitimate software like Microsoft Office or Acrobat Reader to dupe visitors into installing them.
One of its major selling points is its ability to extract credentials, cookies, and session IDs from web browsers like Google Chrome, Microsoft Edge, and Cốc Cốc, indicating its Vietnamese focus.
It can also retrieve a victim's IP address, check if a Facebook is a business profile, and assess whether the account in question is currently managing any ads, while simultaneously taking steps to evade detection by disabling the Windows Antimalware Scan Interface (AMSI) and adding itself to the exclusion list of Windows Defender Antivirus.
"VietCredCare's core functionality to filter out Facebook credentials puts organizations in both the public and private sectors at risk of reputational and financial damages if their sensitive accounts are compromised," Vesta Matveeva, head of the High-Tech Crime Investigation Department for APAC, said.
Credentials belonging to several government agencies, universities, e-commerce platforms, banks, and Vietnamese companies have been siphoned via the stealer malware.
VietCredCare is also the latest addition to a long list of stealer malware, such as Ducktail and NodeStealer,that has originated from the Vietnamese cyber criminal ecosystem with the intent of targeting Facebook accounts.
That having said, Group-IB told The Hacker News there is no evidence at this stage that suggests connections between VietCredCare and the other strains.
"With Ducktail, the functions are different, and while there are some similarities with NodeStealer, we note that the latter uses a [command-and-control] server instead of Telegram, plus their choice of victims is different," the company said.
"The stealer-as-a-service business model enables threat actors with little to no technical skills to enter the cybercrime field, which results in more innocent victims being harmed."
Signal Introduces Usernames, Allowing Users to Keep Their Phone Numbers Private
21.2.24 Social The Hacker News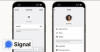
End-to-end encrypted (E2EE) messaging app Signal said it's piloting a new feature that allows users to create unique usernames (not to be confused with profile names) and keep the phone numbers away from prying eyes.
"If you use Signal, your phone number will no longer be visible to everyone you chat with by default," Signal's Randall Sarafa said. "People who have your number saved in their phone's contacts will still see your phone number since they already know it."
Setting a new username requires account holders to provide two or more numbers at the end of it (e.g., axolotl.99) in an effort to keep them "egalitarian and minimize spoofing." Usernames can be changed any number of times, but it's worth noting that they are not logins or handles.
Put differently, a username is an anonymous way to initiate conversations on the chat platform without having to share phone numbers. The feature is opt-in, although Signal said it's also taking steps to hide by default users' phone numbers from others who do not have them saved in their phone's contacts.
In addition, users can control who can find them by their numbers using another setting, restricting people from messaging them even if they are in possession of the phone numbers.
Both these options can be toggled via the following steps -
Settings > Privacy > Phone Number > Who Can See My Number > Everybody / Nobody
Settings > Privacy > Phone Number > Who Can Find Me By Number > Everybody / Nobody
"Your phone number will no longer be visible to people you chat with on Signal, unless they have it in their phone's contacts," Sarafa said. "You will also be able to configure a new privacy setting to limit who can find you by your phone number on Signal."