Smart-security practices like not sharing passwords with anyone and multi-factor authentication (MFA) are two simple ways to prevent this type of personal insider threat, Dan Conrad, field strategist with One Identity, told Threatpost.
Social 2024 2023 2022 2021 2020
Tech Giants Lend WhatsApp Support in Spyware Case Against NSO Group
23.12.2020 Social Threatpost
Google, Microsoft, Cisco Systems and others want appeals court to deny immunity to Israeli company for its alleged distribution of spyware and illegal cyber-surveillance activities.
Facebook subsidiary WhatsApp has received new high-caliber support in its case against Israeli intelligence company NSO Group. The court case aims to hold NSO Group accountable for distributing its Pegasus spyware on the popular WhatsApp messaging service with the intent of planting its spyware on phones of journalists and human rights workers.
A group of companies–including tech giants Google, Microsoft and Cisco Systems–have filed a legal brief called an amicus to support WhatsApp against NSO’s alleged illegal cyber-surveillance activities, including selling “cyber-surveillance as a service” to foreign governments and other companies. VMWare and GitHub also signed the brief along with LinkedIn–a Microsoft subsidiary–and the Internet Association, which represents dozens of tech companies, including Amazon, Facebook and Twitter.
Meanwhile, the Electronic Frontier Foundation (EFF) filed an amicus brief of its own to support WhatsApp, asserting that the case is not merely a battle of tech companies, but has a potential outcome that will have “profound implications for millions of Internet users and other citizens of countries around the world.”
2020 Reader Survey: Share Your Feedback to Help Us Improve
Amicus briefs are known as “amicus curiae” in legal terms, which is Latin for “friend of the court.” The briefs are common in appellate cases to make points or provide new information that the principle litigators in the case may not have addressed.
In this case, the briefs are aimed at lending support to WhatsApp in an effort to convince the United States Court of Appeals for the Ninth Circuit to hold NSO accountable for its activities. The current case in front of the court is an appeal for immunity that the NSO filed after a federal judge allowed a suit WhatsApp originally filed in October 2019 to move forward earlier this year.
NSO President Shiri Dolev has defended the company, saying it should be protected against legal action since it sells its tools to governments and law enforcement who use them to go after criminals and find victims of disasters, among other benevolent activities.
Tech companies and the original judge in the case so far haven’t been convinced by this argument. “Even if the tools are sold to governments who use them for narrowly targeted attacks, there are a variety of ways they can still fall into the wrong hands,” Tom Burt, Microsoft corporate vice president of customer security and trust, said in a blog post published Monday supporting the amicus.
“The expansion of sovereign immunity that NSO seeks would further encourage the burgeoning cyber-surveillance industry to develop, sell and use tools to exploit vulnerabilities in violation of U.S. law,” he wrote. “Private companies should remain subject to liability when they use their cyber-surveillance tools to break the law, or knowingly permit their use for such purposes, regardless of who their customers are or what they’re trying to achieve.”
The EFF, which often butts heads against tech companies over privacy issues, in this case is aligned with them against NSO.
“Corporate complicity in human rights abuses is a widespread and ongoing problem, and the Ninth Circuit should not expand the ability of technology companies like NSO Group to avoid accountability for facilitating human rights abuses by foreign governments,” EFF senior staff attorneys Sophia Cope and Andrew Crocker wrote in a blog post also published Monday regarding the EFF’s amicus.
In the original case, WhatsApp sued NSO Group for allegedly creating tools such as Pegasus so its clients can spy on and read the protected WhatsApp messages of journalists and human rights workers. The case stemmed from the discovery in May 2019 of a zero-day vulnerability in WhatsApp’s messaging platform, exploited by attackers who were able to inject the Pegasus spyware onto victims’ phones in targeted campaigns.
The lawsuit alleges that NSO Group developed the surveillance code and used vulnerable WhatsApp servers to send malware to approximately 1,400 mobile devices, including those of more than 100 human-rights defenders, journalists and other members of civil society in at least 20 countries across the globe.
“As we gathered the information that we lay out in our complaint, we learned that the attackers used servers and internet-hosting services that were previously associated with NSO,” said Will Cathcart, head of WhatsApp, in a post when the lawsuit was filed. “In addition, as our complaint notes, we have tied certain WhatsApp accounts used during the attacks back to NSO. While their attack was highly sophisticated, their attempts to cover their tracks were not entirely successful.”
WhatsApp has claimed that the attack violates various U.S. state and federal laws, including the U.S. Computer Fraud and Abuse Act, and aims with the suit to bar NSO Group from using Facebook and WhatsApp services, among seeking other unspecified damages.
Nosy Ex-Partners Armed with Instagram Passwords Pose a Serious Threat
23.12.2020 Social Threatpost
A survey of single people found almost a third are still logging into their ex’s social-media accounts, some for revenge.
Breakups can be traumatic in all sorts of ways. Now we know they can pose a serious cybersecurity threat too. A new survey found that an alarming number of people are still accessing their exes’ accounts without their knowledge — a handful for malicious reasons.
The survey conducted during November for Reboot Digital PR Agency found that 70 percent of exes polled have logged into their former partner’s Instagram account in the past week. And a full 65 percent of those who report social-media snooping said it had become an “obsession.”
This kind of social-media stalking is primarily fueled by curiosity, according to the report, but in a handful of cases, these breaches can present a real threat.
2020 Reader Survey: Share Your Feedback to Help Us Improve
“Most exes claim that they still log into past partners’ social-media accounts to ‘see if they have met someone new,'” according to Reboot’s report, “with 59 percent of participants admitting this was the main reason.”
Curiosity is one thing, but troublingly, 13 percent confessed they logged in to “seek revenge.”
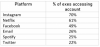
Common accounts for stalker exes to access, the report added, include Instagram, Netflix, Facebook, email, Spotify and Twitter.
The report said that they found only 23 percent of account-holders were aware their former partners still had access.
The report also discovered that many exes (32 percent) stop logging in about six months post-breakup, with others stopping around the 10 to 12-month mark (18 percent). Shockingly, however, 17 percent of participants admitted to logging into their ex’s social accounts 2 years after a breakup.
Exes’ Protection
Smart-security practices like not sharing passwords with
anyone and multi-factor authentication (MFA) are two simple ways to prevent this
type of personal insider threat, Dan Conrad, field strategist with One Identity,
told Threatpost.
Most common accounts accessed by exes. Source: Reboot.
“People assume that they should change their passwords after a big life event, however, if you’re following strong password hygiene practices, an individual’s password shouldn’t be affected by [this], as no one else should have access to the password in the first place,” Conrad said in an emailed response to the report.
“With many applications requiring MFA, passwords have become a part of the authentication process, making credentials no longer enough to break into an account,” Conrad said.
He added that research shows that the more frequently users change their passwords, the weaker those passwords tend to become.
Personal Threats Meet Professional
Much like at companies and other
organizations, insider threats can impact individuals and their personal data.
And with the pandemic continuing the blur the lines between both, an ex’s data
breach could quickly balloon into a serious professional problem too.
During a recent Threatpost webinar on insider threats Craig Cooper, Gurucul COO explained how dangerous insider Threats to business can be, including a threat actor targeting a specific employee.
“The question is often: What might they be looking at? And often, when you are talking about insider threats on the physical side, it could be someone targeting a specific person,” Cooper said. “That’s not very comfortable to think about, but that’s obviously something that could happen. This happens with workplace violence and those types of things.”
Employees with personal problems, like a breakup or divorce, have started to be identified by companies as “high risk,” for security breaches according to Code42’s CISO Jadee Hanson who spoke with Threatpost last March about the trend.
“There’s psychological studies that look at tone and language that employees use throughout the workday, and so if it’s negative in nature, the adversaries can absolutely take advantage of that and use that person,” Hansen said.
She explained companies have started monitoring social media accounts of its key credential holders for potential insider threats.
“Following certain security people or certain people that have sort of elevated access,” she said. “What are they saying in a public forum and trying to exploit them? Just knowing that they’re more of a disgruntled employee rather than your average employee.”
Access Mitigation
Cooper, along with Gurucul CEO Saryu Nayyar, explained that
the critical mitigation for businesses to protect from insider threats is paying
meticulous attention to permissions and who has access to important data. That
same advice, much like the threat itself, also applies to personal accounts.
Beyond not sharing passwords to your accounts and using MFA whenever possible, Conrad stressed the importance of using strong, unique passwords for every account.
“Instead of focusing on how often to change a password, it’s essential to focus on not only meeting complexity requirements but also ensuring the password is unique to each account,” Conrad warned. “To help juggle passwords, people should use a reputable password manager as these systems generate complex passwords for each account, alert the users if accounts have the same password and interject complex credentials when required. The bottom line is that how frequently you change a password isn’t as important as how strong your password is.”
Tech Giants Show Support for WhatsApp in Lawsuit Against Spyware Firm
23.12.2020
Social
Securityweek
Microsoft, Cisco, GitHub, Google, LinkedIn, VMware and the Internet Association have filed an amicus brief in support of WhatsApp in the legal case against the NSO Group.
Facebook-owned messaging service WhatsApp filed the lawsuit in October 2019 in California, accusing Israeli technology firm NSO Group of spying on journalists, human rights activists and others.
WhatsApp says that NSO Group attempted to infect approximately 1,400 devices with spyware in an effort to steal sensitive information from WhatsApp users.
NSO Group claims that its Pegasus spyware is in fact a legitimate cyber-surveillance tool meant to help government organizations fight terrorism and other type of crime.
However, security firms and other organizations have publicly disclosed a multitude of incidents in which Pegasus was used maliciously. The most recent of these involved the use of an iMessage zero-day exploit to infect the iPhones of Al Jazeera journalists.
The amicus brief that Microsoft and others filed in support of WhatsApp underlines that the trading of software such Pegasus is concerning due to possible misuse by threat actors, because NSO does not share information on vulnerabilities it finds in targeted platforms, and because NSO and similar companies threaten human rights.
According to Microsoft, due to cyber-surveillance companies like the NSO Group, which are called private-sector offensive actors (PSOAs), the number of countries using offensive cyber capabilities has increased from five between 2012 and 2015 to at least 18 in the present.
“Reporting also shows foreign governments are using those surveillance tools, bought from PSOAs, to spy on human rights defenders, journalists and others, including U.S. citizens,” Microsoft notes in a blog post.
Tools like Pegasus, the tech giant points out, enable the tracking of an individual’s whereabouts. They can be used to listen in on conversations, read texts and emails, access photos, steal contacts lists, download sensitive data, tap into internet search history, and more.
Microsoft also points out that privacy is fundamental for journalists to report on events, for dissidents to be able to make their voices heard, and for democracy to flourish. Cyber-surveillance tools such as Pegasus threaten all these, as well as individuals’ lives.
“The expansion of sovereign immunity that NSO seeks would further encourage the burgeoning cyber-surveillance industry to develop, sell and use tools to exploit vulnerabilities in violation of U.S. law. Private companies should remain subject to liability when they use their cyber-surveillance tools to break the law, or knowingly permit their use for such purposes, regardless of who their customers are or what they’re trying to achieve,” Microsoft says.
Nosy Ex-Partners Armed with Instagram Passwords Pose a Serious Threat
22.12.2020
Social
Threatpost
A survey of single people found almost a third are still logging into their ex’s social-media accounts, some for revenge.
Breakups can be traumatic in all sorts of ways. Now we know they can pose a serious cybersecurity threat too. A new survey found that an alarming number of people are still accessing their exes’ accounts without their knowledge — a handful for malicious reasons.
The survey conducted during November for Reboot Digital PR Agency found that 70 percent of exes polled have logged into their former partner’s Instagram account in the past week. And a full 65 percent of those who report social-media snooping said it had become an “obsession.”
This kind of social-media stalking is primarily fueled by curiosity, according to the report, but in a handful of cases, these breaches can present a real threat.
2020 Reader Survey: Share Your Feedback to Help Us Improve
“Most exes claim that they still log into past partners’ social-media accounts to ‘see if they have met someone new,'” according to Reboot’s report, “with 59 percent of participants admitting this was the main reason.”
Curiosity is one thing, but troublingly, 13 percent confessed they logged in to “seek revenge.”
Common accounts for stalker exes to access, the report added, include Instagram, Netflix, Facebook, email, Spotify and Twitter.
The report said that they found only 23 percent of account-holders were aware their former partners still had access.
The report also discovered that many exes (32 percent) stop logging in about six months post-breakup, with others stopping around the 10 to 12-month mark (18 percent). Shockingly, however, 17 percent of participants admitted to logging into their ex’s social accounts 2 years after a breakup.
Exes’ Protection
Smart-security practices like not sharing passwords with
anyone and multi-factor authentication (MFA) are two simple ways to prevent this
type of personal insider threat, Dan Conrad, field strategist with One Identity,
told Threatpost.
Most common accounts accessed by exes. Source: Reboot.
“People assume that they should change their passwords after a big life event, however, if you’re following strong password hygiene practices, an individual’s password shouldn’t be affected by [this], as no one else should have access to the password in the first place,” Conrad said in an emailed response to the report.
“With many applications requiring MFA, passwords have become a part of the authentication process, making credentials no longer enough to break into an account,” Conrad said.
He added that research shows that the more frequently users change their passwords, the weaker those passwords tend to become.
Personal Threats Meet Professional
Much like at companies and other
organizations, insider threats can impact individuals and their personal data.
And with the pandemic continuing the blur the lines between both, an ex’s data
breach could quickly balloon into a serious professional problem too.
During a recent Threatpost webinar on insider threats Craig Cooper, Gurucul COO explained how dangerous insider Threats to business can be, including a threat actor targeting a specific employee.
“The question is often: What might they be looking at? And often, when you are talking about insider threats on the physical side, it could be someone targeting a specific person,” Cooper said. “That’s not very comfortable to think about, but that’s obviously something that could happen. This happens with workplace violence and those types of things.”
Employees with personal problems, like a breakup or divorce, have started to be identified by companies as “high risk,” for security breaches according to Code42’s CISO Jadee Hanson who spoke with Threatpost last March about the trend.
“There’s psychological studies that look at tone and language that employees use throughout the workday, and so if it’s negative in nature, the adversaries can absolutely take advantage of that and use that person,” Hansen said.
She explained companies have started monitoring social media accounts of its key credential holders for potential insider threats.
“Following certain security people or certain people that have sort of elevated access,” she said. “What are they saying in a public forum and trying to exploit them? Just knowing that they’re more of a disgruntled employee rather than your average employee.”
Access Mitigation
Cooper, along with Gurucul CEO Saryu Nayyar, explained that
the critical mitigation for businesses to protect from insider threats is paying
meticulous attention to permissions and who has access to important data. That
same advice, much like the threat itself, also applies to personal accounts.
Beyond not sharing passwords to your accounts and using MFA whenever possible, Conrad stressed the importance of using strong, unique passwords for every account.
“Instead of focusing on how often to change a password, it’s essential to focus on not only meeting complexity requirements but also ensuring the password is unique to each account,” Conrad warned. “To help juggle passwords, people should use a reputable password manager as these systems generate complex passwords for each account, alert the users if accounts have the same password and interject complex credentials when required. The bottom line is that how frequently you change a password isn’t as important as how strong your password is.”
Email Address of Instagram Users Exposed via Facebook Business Suite
22.12.2020
Social
Securityweek
A researcher has earned over $13,000 for a flaw that exposed the email address and birth date of Instagram users via the Facebook Business Suite.
The issue was discovered in October by Saugat Pokharel, a researcher based in Nepal, and it was patched within hours by Facebook.
Pokharel identified the vulnerability while analyzing the Facebook Business Suite interface that the social media giant introduced in September. Facebook Business Suite is designed to make it easier for businesses to manage Facebook, Messenger, Instagram and WhatsApp from a single location.
Pokharel connected his Instagram account to the Business Suite and noticed that, when messaging an Instagram user, he could see that user’s email address, which should have been kept private. It’s worth noting that the email address was displayed on the right side of the chat window — obtaining the information did not require any actual hacking.
The researcher determined that the email address of every Instagram user was exposed, even those who had their accounts set to private and ones that did not accept direct messages from everyone.
Facebook quickly patched this issue, but while he was verifying the fix, Pokharel noticed that the birth date of Instagram users was exposed in the same way by the Facebook business tool. The social media company patched the birth date exposure within a week.
Pokharel said he received a total of $13,125 from Facebook for his findings.
A few months ago, cybersecurity firm Check Point disclosed the details of an Instagram vulnerability that could have been exploited to hijack accounts and turn the victim’s phone into a spying tool without any interaction.
3M Users Targeted by Malicious Facebook, Insta Browser Add-Ons
18.12.2020
Social Virus
Threatpost
Researchers identify malware existing in popular add-ons for Facebook, Vimeo, Instagram and others that are commonly used in browsers from Google and Microsoft.
Twenty-eight popular extensions for Google Chrome and Microsoft Edge browsers may contain malware and likely should be uninstalled by the more than 3 million people that already have downloaded them, security researchers said Thursday.
Extensions for the browsers that potentially could pose a security threat include Video Downloader for Facebook, Vimeo Video Downloader, Instagram Story Downloader, VK Unblock, as well as others in use for the two popular browsers, according to research from Avast Threat Intelligence.
Download numbers from the browser store show that several million people worldwide currently may be using the extensions, researchers said. Moreover, while Avast Threat Intelligence began investigating the threat in November, it may have gone unnoticed for years. Reviews on the Chrome Web Store show evidence of this, as they mention link hijacking from as far back as December 2018, researchers noted.
Avast Threat Intelligence discovered the malware after following up on research by Czech researcher Edvard Rejthar at CZ.NIC, who first identified the threat originating in browser extensions on his system, Avast senior writer Emma McGowan wrote in a blog post published Thursday.
Noticing some “non-standard” behavior coming from his computer, Rejthar went hunting for the source in browser add-ons, which tend to be “the most common vulnerability of a user’s computer in addition to phishing,” he wrote.
Rejthar set a trap to catch the culprit in action and found malicious scripts coming from certain browser extensions. The malware entered the system through localStorage, the general data repository that browsers make available to sites and add-ons, he reported.
Avast researchers investigated further and found that infected JavaScript-based extensions contain malicious code that open the door to downloading even more malware to a person’s computer, according to McGowan’s post. They also manipulate all links that the victims click on after downloading the extensions, she wrote.
“For example, links in Google Search lead users to other, seemingly random, sites,” according to the post. “This includes phishing sites and ads.”
Clicking on the links also causes the extensions to send info to the attacker’s control server, ostensibly creating a log of all of someone’s clicks. That log is then sent to third-party websites and can be used to collect a user’s personal information, including birth date, email addresses, device information, first sign-in time, last login time, name of his or her device, operating system, browser used and version, and IP address, according to Avast.
Researchers surmised that either the extensions were created deliberately with built-in malware, or the threat actor waited for the extensions to become popular and then pushed out a malicious update, Avast researcher Jan Rubin said.
“It could also be that the author sold the original extensions to someone else after creating them and then his client introduced the malware afterwards,” he said in the post.
Further, the domains used in the campaign are likely not owned by the cybercriminals; rather, the domain owners probably pay the cybercriminals for every re-direction, Rubin added.
At the time of this writing, the infected extensions are still available for download, according to Avast, which recommends that users disable and uninstall them and scan for malware before continuing to use them.
Avast said researchers have reported the issue to both Google and Microsoft. Neither company responded immediately to request for comment about whether they are aware of the extensions and plan to investigate and/or remove them.
Threatpost has reached out to Avast to get a full list of the identified extensions and will update this post accordingly.
Of the two companies, Google at least is no stranger to responding to news of malicious browser extensions. In June, the company removed 106 Chrome browser extensions from its Chrome Web Store in response to a report that they were being used to siphon sensitive user data.
Experts spotted browser malicious extensions for Instagram, Facebook and others
18.12.2020
Social Virus
Securityaffairs
Avast researchers reported that three million users installed 28 malicious
Chrome or Edge extensions that could perform several malicious operations.
Avast Threat Intelligence researchers spotted malicious Chrome and Edge browser
extensions that were installed by over 3 million users.
The extensions were designed to steal user’s data (i.e. birth dates, email addresses, and active devices) and redirect the victims to ads and phishing sites.
Many of these applications are still available on the Chrome Web Store and the Microsoft Edge Add-ons portal.
“The extensions which aid users in downloading videos from these platforms include Video Downloader for Facebook, Vimeo Video Downloader, Instagram Story Downloader, VK Unblock, and other browser extensions on the Google Chrome Browser, and some on Microsoft Edge Browser.” reads the analysis published by Avast. “The researchers have identified malicious code in the Javascript-based extensions that allows the extensions to download further malware onto a user’s PC. “
The tainted extensions pose as helper add-ons for Vimeo, Instagram, Facebook, and other popular online services.
Experts pointed out that the malware is quite difficult to detect since its ability to “hide itself,” it is able to detect if the user is googling one of its domains or if the user is a web developer and in these cases, it won’t perform any malicious activities on the victim’s browser. It is interesting to note that the malware avoids infecting web developers because they could unmask the malicious code in the extensions.
The malicious extensions are part of a campaign aimed at hijacking user traffic for financial motivation.
“Avast researchers believe the objective behind this is to monetize the traffic itself. For every redirection to a third party domain, the cybercriminals would receive a payment.” Avast said.
The extensions were discovered in November, but experts highlighted that some of them had been active since at least December 2018 and had tens of thousands of installs. To evade detection the malicious extensions only start to exhibit malicious behavior days after installation
Avast shared its findings with both Google and Microsoft that are scrutinizing the extensions.
Below the full list of tainted extensions:
Direct Message for Instagram
Direct Message for Instagram™
DM for
Instagram
Invisible mode for Instagram Direct Message
Downloader for
Instagram
Instagram Download Video & Image
App Phone for Instagram
App
Phone for Instagram
Stories for Instagram
Universal Video Downloader
Universal Video Downloader
Video Downloader for FaceBook™
Video Downloader
for FaceBook™
Vimeo™ Video Downloader
Vimeo™ Video Downloader
Volume
Controller
Zoomer for Instagram and FaceBook
VK UnBlock. Works fast.
Odnoklassniki UnBlock. Works quickly.
Upload photo to Instagram™
Spotify
Music Downloader
Stories for Instagram
Upload photo to Instagram™
Pretty Kitty, The Cat Pet
Video Downloader for YouTube
SoundCloud Music
Downloader
The New York Times News
Instagram App with Direct Message DM
If you have installed one of the above extensions uninstall and remove it from
your browsers.
New Backdoors Used by Hamas-Linked Hackers Abuse Facebook, Dropbox
11.12.2020
APT
Social
Virus
Securityweek
Two new backdoors have been attributed to the Molerats advanced persistent threat (APT) group, which is believed to be associated with the Palestinian terrorist organization Hamas.
Likely active since at least 2012 and also referred to as Gaza Hackers Team, Gaza Cybergang, DustySky, Extreme Jackal, and Moonlight, the group mainly hit targets in the Middle East (including Israel, Egypt, Saudi Arabia, the UAE and Iraq), but also launched attacks on entities in Europe and the United States.
In early 2020, security researchers at Cybereason's Nocturnus group published information on two new malware families used by the APT, namely Spark and Pierogi. Roughly a month later, Palo Alto Networks revealed that the group had expanded its target list to include insurance and retail industries, in addition to the previously targeted government and telecommunications verticals.
Now, Cybereason reveals that Molerats has expanded its toolset with the addition of two backdoors named SharpStage and DropBook, along with a downloader called MoleNet. All three malware families allow attackers to run arbitrary code and collect data from the infected machines and have been used in an espionage campaign actively targeting Arab-speaking individuals in the Middle East.
What makes the backdoors stand out is the use of legitimate online services for nefarious purposes. For example, both use a Dropbox client for data exfiltration and for storing espionage tools, while DropBook is controlled through fake Facebook accounts. Google Drive is also abused for payload storage.
The security researchers also identified new activity targeting Turkish-speaking entities with the Spark backdoor, as well as a separate campaign in which a new Pierogi variant is used against targets also infected with DropBook, SharpStage, and Spark. The overlap suggests a close connection between Molerats and APT-C-23 (Arid Viper), both considered sub-groups of Gaza Cybergang.
“The newly discovered backdoors were delivered together with the previously reported Spark backdoor, which along with other similarities to previous campaigns, further strengthens the attribution to Molerats,” Cybereason notes.
The malware families were used to target political figures and government officials in the Palestinian Territories, Egypt, Turkey, and UAE, among other Middle East regions. Phishing lures used in these attacks include Hamas elections, Israeli-Saudi relations, Palestinian politicians, and other political events.
Observed samples of SharpStage, a .NET backdoor, show compilation timestamps between October 4 and November 29, 2020. The malware can capture screenshots, download and execute files, execute arbitrary commands, and unarchive data fetched from the C&C.
Built by the developer behind JhoneRAT, DropBook is a Python-based backdoor capable of performing reconnaissance, executing shell commands, and downloading and executing additional malware. The threat only executes if WinRAR and an Arabic keyboard are present on the infected system.
The malware can fetch and run a broad range of payloads, including an updated version of itself, the MoleNet downloader, Quasar RAT, SharpStage, and ProcessExplorer (legitimate tool used for reconnaissance and credential dump).
Previously undocumented, the MoleNet downloader appears to have been in use since 2019, while its infrastructure might have been active since 2017. The heavily obfuscated .NET malware can perform WMI commands for reconnaissance, check the system for debuggers, restart the system, send OS info to the C&C, download additional payloads, and achieve persistence.
“The discovery of the new cyber espionage tools along with the connection to previously identified tools used by the group suggest that Molerats is increasing their espionage activity in the region in light of the current political climate and recent events in the Middle East,” Cybereason concludes.
Spotify Users Hit with Rash of Account Takeovers
24.11.20 Social Threatpost
Users of the music streaming service were targeted by attackers using credential-stuffing approaches.
Subscribers of Spotify streaming music service may have experienced some disruption, thanks to a likely credential-stuffing operation.
Credential stuffing takes advantage of people who reuse the same passwords across multiple online accounts. Attackers will use IDs and passwords stolen from another source, such as a breach of another company or website, that they then try to use to gain unauthorized access to other accounts, trying the stolen logins against various accounts using automated scripts. Cybercriminals have successfully leveraged the approach to steal data from various popular companies, including most recently, the North Face.
vpnMentor’s research team spotted an open Elasticsearch database containing more than 380 million individual records, including login credentials and other user data, actively being validated against Spotify accounts. The database in question contained over 72 GB of data, including account usernames and passwords verified on Spotify; email addresses; and countries of residence.
“The exposed database belonged to a third party that was using it to store Spotify login credentials,” the firm said. “These credentials were most likely obtained illegally or potentially leaked from other sources.”
It added, “Working with Spotify, we confirmed that the database belonged to a group or individual using it to defraud Spotify and its users.”
In response, Spotify initiated a rolling reset of passwords, making the information in the database relatively useless. The attacks ultimately affected between 300,000 and 350,000 music-streamers, vpnMentor said – a small fraction of the company’s user base of 299 million active monthly users.
“The origins of the database and how the fraudsters were targeting Spotify are both unknown,” according to the company, in a Monday posting. “The hackers were possibly using login credentials stolen from another platform, app or website and using them to access Spotify accounts.”
The exposed database could also be used for more than credential-stuffing attacks on Spotify, according to vpnMentor.
“[This could lead to] many criminal schemes, not just by the fraudsters who built it, but also by any malicious hackers who found the database, as we did,” according to the posting. “Any of these parties could use the PII data exposed to identify Spotify users through their social media accounts, and more. Fraudsters could use the exposed emails and names from the leak to identify users across other platforms and social media accounts. With this information, they could build complex profiles of users worldwide and target them for numerous forms of financial fraud and identity theft.”
Ameet Naik, security evangelist at PerimeterX, said via email that hackers run credential-stuffing attacks to check the validity of these credentials against multiple services.
“These automated attacks, also known as account takeover (ATO), are growing in size and scope, up 72 percent over the prior year,” he said via email. “Businesses need to protect their login pages from ATO attacks using bot management solutions. Users must use strong, unique passwords on each service and use multi-factor authentication where possible.”
Anyone who has reused a Spotify password on any other accounts should also change it immediately, researchers said.
“This exposure goes to illustrate that criminals don’t need sophisticated technical hacking abilities to compromise accounts, rather, they can take advantage of lax security practices on behalf of users,” said Javvad Malik, security awareness advocate at KnowBe4. “Credentials are a particular area in which users are left exposed because they either choose weak passwords, or reuse them across different sites. It’s why it’s important that users understand the importance of choosing unique and strong passwords across their accounts and where available enable and use multifactor authentication (MFA). That way, even if an account is compromised, it won’t be possible for attackers to use those credentials to breach other accounts.”
TikTok fixed security issues that could have led one-click account takeover
24.11.20
Social
Securityaffairs
TikTok has addressed a couple of security issues that could have been chained to
led account takeover.
The first issue addressed by the social media platform
is a reflected XSS security flaw that has been reported by the bug bounty hunter
Muhammed “milly” Taskiran via the bug bounty platform HackerOne.
The Cross-Site-Scripting flaw affected the company domains www.tiktok.com and m.tiktok.com and its exploitation could have lead to data exfiltration.
“The researcher discovered a URL parameter reflecting its value without being properly sanitized and was able to achieve reflected XSS. In addition, researcher found an endpoint which was vulnerable to CSRF.” reads the description published by HackerOne. “The endpoint allowed to set a new password on accounts which had used third-party apps to sign-up. Researcher combined both vulnerabilities to achieve a “one click account takeover”.”
Using a fuzzing testing approach, the expert discovered a URL parameter reflecting its value without being properly sanitized. The white-hat hacker was able to achieve reflected XSS and also found an endpoint that was vulnerable to Cross-site request forgery (CSRF).
“The endpoint enabled me to set a new password on accounts which had used third-party apps to sign-up.” Taskiran explained. “I combined both vulnerabilities by crafting a simple JavaScript payload – triggering the CSRF – which I injected into the vulnerable URL parameter from earlier, to archive a “one click account takeover.”
Taskiran created a simple JavaScript payload that chained the XSS and the CSRF vulnerabilities. The script first triggers the CSRF issue, then injected into the vulnerable URL parameter leading to a one-click account takeover.
Taskiran received a $3,860 payout for the reported vulnerabilities.
Facebook Messenger Bug Allows Spying on Android Users
21.11.20 Social Threatpost
The company patched a vulnerability that could connected video and audio calls without the knowledge of the person receiving them.
Facebook has patched a significant flaw in the Android version of Facebook Messenger that could have allowed attackers to spy on users and potentially identify their surroundings without them knowing.
Natalie Silvanovich, a security researcher at Google Project Zero, discovered the vulnerability, which she said existed in the app’s implementation of WebRTC, a protocol used to make audio and video calls by “exchanging a series of thrift messages between the callee and caller,” she explained a description posted online.
In a normal scenario, audio from the person making the call would not be transmitted until the person on the other end accepts the call. This is rendered in the app by either not calling setLocalDescription until the person being called has clicked the “accept button,” or setting the audio and video media descriptions in the local Session Description Protocol (SDP) to inactive and updating them when the user clicks the button, Silvanovich explained.
“However, there is a message type that is not used for call set-up, SdpUpdate, that causes setLocalDescription to be called immediately,” she explained. “If this message is sent to the callee device while it is ringing, it will cause it to start transmitting audio immediately, which could allow an attacker to monitor the callee’s surroundings.”
Silvanovich provided a step-by-step reproduction of the issue in her report. Exploiting the bug would only take a few minutes; however, an attacker would already have to have permissions—i.e., be Facebook “friends” with the user–to call the person on the other end.
Silvanovich disclosed the bug to Facebook on Oct. 6; the company fixed the flaw on Nov. 19, she reported. Facebook has had a bug bounty program since 2011.
In fact, Silvanovich’s identification of the Messenger bug—which earned her a $60,000 bounty–was one of several that the company highlighted in a blog post published Thursday celebrating the program’s 10th anniversary.
“After fixing the reported bug server-side, our security researchers applied additional protections against this issue across our apps that use the same protocol for 1:1 calling,” Dan Gurfinkel, Facebook security engineering manager, wrote in the post. He added that Silvanovich’s award is one of the three highest ever awarded, “which reflects its maximum potential impact.”
Facebook recently bolstered its bug bounty offering with a new loyalty program that the company claims is the first of its kind. The program, called Hacker Plus, aims to further incentivize researchers to find vulnerabilities in its platform by offering bonuses on top of bounty awards, access to more products and features that researchers can stress-test, and invites to Facebook annual events.
Silvanovich chose to donate the “generously awarded” bounty to GiveWell, a nonprofit that organizations charitable donations to ensure their maximum impact, she disclosed on Twitter.
Silvanovich is among a number of Google Project Zero researchers who have been active lately at identifying serious vulnerabilities in popular apps. In the past month, researchers from the group have not only discovered significant zero-day vulnerabilities in Google’s own Chrome browser, but also in Apple’s mobile devices and Microsoft Windows.
Facebook Pays $60,000 for Vulnerability in Messenger for Android
20.11.20
Social
Securityweek
Facebook this week addressed a vulnerability in Facebook Messenger for Android that could have allowed an attacker to connect to an audio call without user interaction.
Discovered by Google Project Zero security researcher Natalie Silvanovich, the issue exists because an attacker can send a crafted message that would trick the receiver’s Messenger into automatically enabling audio, even if the call was not actually answered.
In Facebook Messenger, Silvanovich explains, audio and video are set up in WebRTC through a series of thrift messages exchanged between the caller and the receiver.
Typically, audio from the receiver is transmitted only after the user has consented to accepting the call, by clicking on the accept button (at which point setLocalDescription is called).
“However, there is a message type that is not used for call set-up, SdpUpdate, that causes setLocalDescription to be called immediately,” the security researcher explains.
If an attacker sends that message to the receiver’s device while it is ringing, the audio will start transmitting immediately, thus allowing the attacker to spy on the targeted user.
To reproduce the issue, both the attacker and the receiver need to be logged into Facebook Messenger on their devices. Furthermore, the target needs to be logged into Facebook in a browser, with the same account, which “will guarantee call set-up uses the delayed calls to setLocalDescription strategy,” the researcher explains.
Proof-of-concept code has been released as well, on the Project Zero portal. The code was tested on Facebook Messenger for Android version 284.0.0.16.119.
Silvanovich reported the vulnerability to Facebook in early October, and a patch was released on November 17.
The social media platform awarded the researcher $60,000 for her finding, which she is donating to charity. Facebook says it too will donate the same amount, to the same charity.
Facebook Messenger Bug Lets Hackers Listen to You Before You Pick Up the Call
20.11.20
Social
Thehackernews
Facebook has patched a bug in its widely installed Messenger app for Android that could have allowed a remote attacker to call unsuspecting targets and listen to them before even they picked up the audio call.
The flaw was discovered and reported to Facebook by Natalie Silvanovich of Google's Project Zero bug-hunting team last month on October 6 with a 90-day deadline, and impacts version 284.0.0.16.119 (and before) of Facebook Messenger for Android.
In a nutshell, the vulnerability could have granted an attacker who is logged into the app to simultaneously initiate a call and send a specially crafted message to a target who is signed in to both the app as well as another Messenger client such as the web browser.
"It would then trigger a scenario where, while the device is ringing, the caller would begin receiving audio either until the person being called answers or the call times out," Facebook's Security Engineering Manager Dan Gurfinkel said.
According to a technical write-up by Silvanovich, the flaw resides in WebRTC's Session Description Protocol (SDP) — which defines a standardized format for the exchange of streaming media between two endpoints — allowing an attacker to send a special type of message known as "SdpUpdate" that would cause the call to connect to the callee's device before being answered.
Audio and video calls via WebRTC typically does not transmit audio until the recipient has clicked the accept button, but if this "SdpUpdate" message is sent to the other end device while it is ringing, "it will cause it to start transmitting audio immediately, which could allow an attacker to monitor the callee's surroundings."

In some ways, the vulnerability bears similarity to a privacy-eroding flaw that
was reported in Apple's FaceTime group chats feature last year that made it
possible for users to initiate a FaceTime video call and eavesdrop on targets by
adding their own number as a third person in a group chat even before the person
on the other end accepted the incoming call.
The gaffe was deemed so severe that Apple pulled the plug on FaceTime group chats altogether before it addressed the issue in a subsequent iOS update.
But unlike the FaceTime bug, exploiting the issue isn't that easy. The caller would have to already have the permissions to call a specific person — in other words, the caller and the callee would have to be Facebook friends to pull this off.
What's more, the attack also necessitates that the bad actor uses reverse engineering tools like Frida to manipulate their own Messenger application to force it to send the custom "SdpUpdate" message.
Silvanovich was awarded a $60,000 bug bounty for reporting the issue, one among Facebook's three highest bug bounties to date, which the Google researcher said she was donating to a non-profit named GiveWell.
This not the first time Silvanovich has found critical flaws in messaging apps, who has previously unearthed a number of issues in WhatApp, iMessage, WeChat, Signal, and Reliance JioChat, some of which have found the "callee device to send audio without user interaction."
Peiter 'Mudge' Zatko Named Head of Security at Twitter
17.11.20
Social
Securityweek
Social media giant Twitter has appointed security expert Peiter Zatko as its head of security.
Better known under his hacker name "Mudge," Zatko is an expert in network security, an open-source programmer, and a writer, and was the most prominent member of the high-profile hacker group L0pht.
On Monday, shortly after Reuters broke the news, Zatko confirmed on Twitter that he has joined the social media platform’s executive team.
Previously, Zatko handled security at Stripe. Before that, he worked at Google and the Defense Advanced Research and Projects Agency (DARPA). His career in computer security, however, started in the 1990s.
The news comes roughly a month and a half after Twitter appointed Rinki Sethi as chief information security officer (CISO). Over the past couple of years, the platform went through three CISOs.
The new appointment underlines Twitter’s focus on improving its security posture following the significant data breach that resulted in the takeover of multiple high-profile accounts in July 2020.
Exposed Database Reveals 100K+ Compromised Facebook Accounts
17.11.20 Social Threatpost
Cybercriminals left an ElasticSearch database exposed, revealing a global attack that compromised Facebook accounts and used them to scam others.
Researchers have uncovered a wide-ranging global scam targeting Facebook users, after finding an unsecured database used by fraudsters to store the usernames and passwords of at least 100,000 victims.
Researchers said that the cybercriminals behind the scam were tricking Facebook victims into providing their account login credentials by using a tool that pretended to reveal who was visiting their profiles.
The fraudsters then “used the stolen login credentials to share spam comments on Facebook posts via the victims’ hacked account, directing people to their network of scam websites,” according to researchers with vpnMentor on Friday. “These websites all eventually led to a fake Bitcoin trading platform used to scam people out of ‘deposits’ of at least €250 [$295].”
Researchers said they have no evidence about whether the data was accessed or leaked by any other malicious parties.
Threatpost has reached out to Facebook for further comment.
The Database
The unsecured Elasticsearch database was 5.5 gigabytes and
contained 13,521,774 records of at least 100,000 Facebook users. It was open
between June and September of this year; it was discovered on Sept. 21 and
closed on Sept. 22.
The data in the exposed database included credentials and IP addresses; text outlines for comments the fraudsters would make on Facebook pages (via a hacked account) that directed people to suspicious and fraudulent websites; and personally identifiable information (PII) data such as emails, names and phone numbers of the Bitcoin scam victims.
Researchers said that in order to confirm that the database was live and real, they entered fake login credentials on one of the scam web pages and verified they had been recorded.
The day after they discovered the database, researchers believe it was attacked by the ongoing widespread Meow cyberattack, which completely wiped all its data. A Meow attack refers to ongoing attacks that started earlier in July and left 1,000 unsecured databases permanently deleted. The attack leaves the word “meow” as its only calling card, according to researcher Bob Diachenko. Meow hackers also recently targeted a Mailfire server that was misconfigured and left open.
“The database went offline the same day and was no longer accessible,” said researchers. “We believe the fraudsters did this following the Meow attack, but can’t confirm.”
The Scam
The global scam targeting Facebook users starts with a network of
websites owned by fraudsters, which trick Facebook users into providing their
credentials by promising they would show targets a list of people who had
recently visited their profiles.
It’s unclear how visitors were driven to these websites. Researchers found 29 domains tied to this network; websites had names such as: askingviewer[.]com, capture-stalkers[.]com and followviewer[.]com.
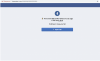
The scam page. Credit: vpnMentor
The website tells victims “There were 32 profile visitors on your page in the last 2 days! Continue to view you list,” and points them to a button that says “Open List!” When the victim clicks on the button, they are sent to a fake Facebook login page, where they are asked to input their login credentials. After they do so, a fake loading page appears, promising to share the full list, and the victim is redirected to the Google Play page for an unrelated Facebook analytics app.
“In the process, the fraudsters saved the victim’s Facebook username and password on the exposed database for future use in their other criminal activities,” said researchers. “These were stored in cleartext format, making it easy for anyone who found the database to view, download and steal them.”
The attackers then use the victims’ credentials for the next phase of the attack – taking over accounts and commenting on Facebook posts published in the victims’ network, with links to a different network of scam websites that are owned by the fraudsters. These sites relate to a Bitcoin fraud scheme. When a victims’ Facebook friend visits the one of the sites, they are directed to sign up for a free Bitcoin trading account and to deposit $295 to start trading.
“By including links to fake news websites, the fraudsters hoped to bypass and confuse Facebook’s fraud and bot detection tools,” said researchers. “If the hacked accounts only posted the same links to a Bitcoin scam over and over, they’d quickly be blocked by the social network.”
Researchers told Facebook users that if they think they have been a victim of the fraud effort, to change their login credentials immediately.
“Furthermore, if you reused your Facebook password on any other accounts, change it immediately to protect them from hacking,” said researchers. “We recommend using a password generator to create unique, strong passwords for every private account you have, and changing them periodically.”
Unprotected database exposed a scam targeting 100K+ Facebook accounts
17.11.20
Social
Securityaffairs
Researchers discovered an ElasticSearch database exposed online that contained
data for over 100000 compromised Facebook accounts.
Researchers at vpnMentor
discovered an ElasticSearch database exposed online that contained an archive of
over 100.000 compromised Facebook accounts. The archive was used by crooks as
part of a global hacking campaign against users of the social network.
“We discovered the scam via an unsecured database used by the fraudsters to store private data belonging to 100,000s of their victims.” reads the analysis published vpnMentor.
“The people running the scam were tricking Facebook users into providing login credentials for their private accounts via a tool pretending to reveal who was visiting their profiles.”
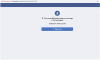
The fraudsters used the stolen login credentials to access Facebook accounts and
share spam comments on posts. The comments all eventually led to a fake Bitcoin
trading platform used to scam people out of ‘deposits’ of at least €250.
“By
including links to fake news websites, the fraudsters hoped to bypass and
confuse Facebook’s fraud and bot detection tools,” said researchers. “If the
hacked accounts only posted the same links to a Bitcoin scam over and over,
they’d quickly be blocked by the social network.”
Fraudsters were tricking Facebook users into providing their account login credentials by providing a tool that pretended to reveal who was visiting their profiles. Personally Identifiable Information (PII) data included in the archive also included emails, names, and phone numbers for the victims who’d registered at a fraudulent Bitcoin site also run by the fraudsters. Experts also discovered tens of domains employed by the fraudsters in this scam campaign.
The archive also included technical information about how the cybercriminals had automated their processes.
It is not clear if the exposed data was accessed or leaked by other third parties.
The size of the archive was over 5.5 GB and contained a total of 13,521,774, it
remained open between June and September of this year. According to the experts
at least 100,000 Facebook users were exposed in the Facebook scam.
vpnMentor
pointed out Facebook accounts were not hacked, the exposed database belonged to
a third party using it to process account login credentials obtained illegally
via a group of scam websites targeting Facebook users
The researchers notified the social network of their discovery, they also confirmed that the database was live and real.
The day after the discovery of the unsecured database, it was likely targeted by a Meow attack, which wiped its data, them the database went offline. Since July, experts observed dozens of unsecured Elasticsearch and MongoDB instances exposed online that were inexplicably wiped by threat actors as part of a campaign tracked as Meow attack.
“If you’re a Facebook user and think you’ve been a victim of this fraud, change your login credentials immediately.” concludes the report.
“Furthermore, if you reused your Facebook password on any other accounts, change it immediately to protect them from hacking. We recommend using a password generator to create unique, strong passwords for every private account you have, and changing them periodically.”
Below the investigation timeline:
Database discovered: 21st September, 2020
Date Facebook contacted: 21st
September, 2020
Database server closed*: 22nd September, 2020
Amazon Sues Instagram, TikTok Influencers Over Knockoff Scam
14.11.20
Social
Threatpost
‘Order This, Get This’: Social-media influencers are in Amazon’s legal crosshairs for promoting generic Amazon listings with the promise to get prohibited counterfeit luxury items instead.
Instagram and TikTok social-media influencers Kelly Fitzpatrick and Sabrina Kelly-Krejci are among 13 defendants in a lawsuit filed by Amazon, which alleges that they participated in an an online scam to sell counterfeit luxury goods.
Counterfeit goods are strictly forbidden in the Amazon marketplace, but generic products — often called “dupes” — are allowed. A dupe may look like a designer item, but lack logos or other trademarked aspects.
Here’s how Amazon said the scheme worked: The influencers would promote items on their Instagram and TikTok accounts and point followers to an Amazon listing for a seemingly generic product. But that’s where the legitimacy allegedly ends.
“Often, the Amazon pages display only a generic, seemingly non-infringing product; the counterfeit nature of the product is revealed only to those who order and receive the product,” according to the lawsuit. “As Fitzpatrick routinely instructs her followers in social media posts: ‘Order this/Get this!'”
The lawsuit alleges the group sold a range of bootleg goods, including Gucci belts and bag knockoffs.
Here’s an Instagram post from @styleeandgrace directing followers to swipe up for a link to a generic listing on Amazon to a “trusted seller.”
Fitzpatrick had already been booted from Amazon’s Influencer Program for selling counterfeit goods outright, according to the company’s announcement of the lawsuit. She then allegedly pivoted to this scheme to keep the sales going.
Threatpost was unable to contact either of the defendants for comment.
Counterfeit Crimes
Amazon takes selling dupes on the site very seriously.
Amazon seller account terms strictly prohibit the sale of counterfeit goods. The
company said in 2019 it spent more than $500 million to get counterfeit goods
off the marketplace, which drive down the price of legit luxury brands and hurts
big sellers.
“These defendants were brazen about promoting counterfeits on social media and undermined the work of legitimate influencers,” said Cristina Posa, associate general counsel and director, Amazon Counterfeit Crimes Unit. “This case demonstrates the need for cross-industry collaboration in order to drive counterfeiters out of business. Amazon continues to invest tremendous resources to stop bad actors before they enter our store, and social-media sites must similarly vet, monitor and take action on bad actors that are using their services to facilitate illegal behavior.”
This high-profile crackdown comes at a time when Amazon is expanding its business in the luxury retail space. The company announced the launch of Luxury Stores in September, accessible by invitation only, with its first collection from Oscar de la Renta.
Counterfeit Sellers ‘On Notice’
COVID-19 has boosted online shopping, and the
market for counterfeit luxury goods along with it. In late October, the Korean
Intellectual Property Office (KIPO) announced it was cracking down after a surge
of bootleg goods on the market jumped by 204 percent from January to August
year-over-year, Hypebeast reported.
For its part, Amazon is helping retailers keep fakes off the market with lawsuits like these to deter copycat sellers. The company also has a full time Amazon Counterfeit Crime Unit working across the globe to stop counterfeit, launched last summer.
“Every counterfeiter is on notice that they will be held accountable to the maximum extent possible under the law, regardless of where they attempt to sell their counterfeits or where they’re located,” Dharmesh Mehta, vice president of Customer Trust and Partner Support for Amazon, said at the time the unit was launched. “We are working hard to disrupt and dismantle these criminal networks, and we applaud the law-enforcement authorities who are already part of this fight. We urge governments to give these authorities the investigative tools, funding and resources they need to bring criminal counterfeiters to justice because criminal enforcement – through prosecution and other disruption measures.”
‘Copyright Violation’ Notices Lead to Facebook 2FA Bypass
29.10.20 Social Threatpost
Fraudulent Facebook messages allege copyright infringement and threaten to take down pages, unless users enter logins, passwords and 2FA codes.
Scammers have hatched a new way to attempt to bypass two-factor authentication (2FA) protections on Facebook.
Cybercriminals are sending bogus copyright-violation notices with the threat of taking pages down unless the user attempts to appeal. The first step in the “appeal?” The victim is asked to submit a username, password and 2FA code from their mobile device, according to Sophos researcher Paul Ducklin, allowing fraudsters bypass 2FA.
2FA is an added layer of protection on top of a username and password that usually involves sending a unique code to a mobile device, which must be entered to access a platform. But crooks are increasingly finding ways around it.
Ducklin explained in a recent post about his findings that Sophos regularly receives social media copyright infringement scam emails, but this one distinguished itself by launching a plausible attack using fraudulent pages generated on Facebook, giving their phishing emails an added air of legitimacy.
“None of these tactics are new — this scam was just an interesting and informative combination,” Ducklin wrote to Threatpost in an email about his findings. “Firstly, the email is short and simple; secondly, the link in the email goes to a legitimate site, namely Facebook; thirdly, the workflow on the scam site is surprisingly believable.”
The fake Facebook emails offer clues that they’re not legit, but Ducklin points out it’s convincing enough to goad social-media administrators into wanting to gather more information on the supposed copyright violation complaints, which means clicking on the phishing link in the email.
The email’s message threatens to delete the victim’s page unless an appeal is filed within 24 hours.
“You’ll see when you hover over the ‘continue’ [it] does indeed take you to facebook.com,” he said. “The catch is that the Facebook address is the fraudulent page set up to look like an official Facebook page dedicated to handling copyright violation issues.”
From there, even though the linked text looks like clicks are sent to another Facebook page — ostensibly so victims can file an “appeal” — Ducklin looked and found the target URL is different from the linked text. It instead sends the victim to a .CF domain based in the Central African Republic.
“That’s an old trick used by crooks – and even by some legitimate sites,” Ducklin added.
The site was set up temporarily on a cloud web hosting service, which generates an HTTPS certificate once the site is online, making detection a bit trickier, he added.
“The certificate’s validity started at midnight today, and the scam email we received arrived at 01:53 UTC, which is early evening on the West Coast of America, and late evening on the East Coast,” Ducklin wrote. “As you can see, cybercrooks move fast!”
Once on the site, users were asked to enter their password, twice, access the Facebook app on their mobile device and enter in the 2FA code, which is found in the “Settings & Privacy > Code Generator” section of the app. Ducklin wrote this could result in “potentially giving them a one-shot chance to login as you, directly from their server, even if you have 2FA enabled.”
Once they have access to a victim’s Facebook credentials, the attackers can sell off the info on the dark web, use it to hijack or take down pages, hold user data for ransom or even make fraudulent in-app purchases.
Facebook responded to Threatpost’s request for comment, saying the company recommends being careful to not click on any suspicious links, adding if a user does get hacked, they can get help securing their account at facebook.com/hacked. The company added that they recommend using a third-party authenticator app as a primary security method. Facebook also has a list of tips to avoid phishing attempts on its platform.
Is 2FA Broken?
Bypassing 2FA has emerged as a disturbing trend.
Cybercriminal group Rampant Kitten was discovered just last month, after years of operating undetected, to have developed Android malware that gathers 2FA security codes sent to devices in addition to Telegram login information, while launching Google phishing attacks.
At about the same time a trojan called “Alien” targeted banks with a novel notification sniffer which gave scammers the ability to access new device updates, including 2FA codes, to bypass the protection.
In May, another attack on Office 365 attempted to trick users into granting permissions to a rogue application, which would then bypass 2FA protections.
The list of 2FA breaches goes on. It remains up to the user to make sure they don’t fall for these types of phishing scams. Ducklin added that using a web filter and avoiding email requests for login details are also good policies to follow.
“2FA has never been a silver bullet that will eliminate phishing and fraud — but it does make things harder for the crooks, and it gives you one more opportunity to stop and think when you are logging in, ‘Do I really want to put my password and my login code in *on this very site*?” Ducklin said. Always check where emails came from and where web links have taken you — because the only thing worse than being scammed is being scammed and then realizing that the telltale signs were there all along.”
He added, “As any carpenter will tell you: measure twice; cut once.”
Researchers: LinkedIn, Instagram Vulnerable to Preview-Link RCE Security Woes
28.10.20 Social Threatpost
Popular chat apps, including LINE, Slack, Twitter DMs and others, can also leak location data and share private info with third-party servers.
UPDATE
Link previews in popular chat apps on iOS and Android are a firehose of security and privacy issues, researchers have found. At risk are Facebook Messenger, LINE, Slack, Twitter Direct Messages, Zoom and many others. In the case of Instagram and LinkedIn, it’s even possible to execute remote code on the companies’ servers through the feature, according to an analysis.
Link previews are standard in most chat apps, and they can be very useful. When a user sends a link through, it renders a short summary and a preview image in-line in the chat, so other users don’t have to click the link to see what it points to.
Unfortunately, there’s a downside. According to independent researchers Talal Haj Bakry and Tommy Mysk, the feature can leak IP addresses, expose links sent in end-to-end encrypted chats and has been caught “unnecessarily downloading gigabytes of data quietly in the background.”
The issues go back to how the previews are generated, according to the researchers. There are three ways to do that: The sender can generate it; the receiver can generate it; or the server can generate it. The last two are problematic, with the server-generated version being the most concerning.
“How does the app know what to show in the summary?” Bakry and Mysk explained. “It must somehow automatically open the link to know what’s inside. But is that safe? What if the link contains malware? Or what if the link leads to a very large file that you wouldn’t want the app to download and use up your data.”
Sender-Generated Links
If the sender generates the preview, the app will go
and download what’s in the link, create a summary and a preview image of the
website, and it will send this as an attachment along with the link.
A typical link preview. Source: Google.
“When the app on the receiving end gets the message, it’ll show the preview as it got from the sender without having to open the link at all,” explained the researchers, in a posting this week. “This way, the receiver would be protected from risk if the link is malicious.”
iMessage, Signal (if the link preview option is turned on in settings), Viber and WhatsApp all follow this best-practice approach, they noted. But, there is a caveat when it comes to Viber.
“If you send a link to a large file, your phone will automatically try to download the whole file even if it’s several gigabytes in size,” researchers noted.
They added, “it’s also worth mentioning that even though Viber chats are end-to-end encrypted, tapping on a link will cause the app to forward that link to Viber servers for the purposes of fraud protection and personalized ads.”
Receiver-Generated Links
When the receiver generates the preview, it means
that the app will open any link that’s sent to it, automatically, with no user
interaction needed.
“This one is bad,” said the researchers, noting that the process can leak location data.
“Let’s briefly explain what happens when an app opens a link,” they wrote. “First, the app has to connect to the server that the link leads to and ask it for what’s in the link. This is referred to as a GET request. In order for the server to know where to send back the data, the app includes your phone’s IP address in the GET request.”
They added, “If you’re using an app that follows this approach, all an attacker would have to do is send you a link to their own server where it can record your IP address. Your app will happily open the link even without you tapping on it, and now the attacker will know where you are [down to a city block].”
A second issue is that a link could potentially point to a large video or archive file.
“A buggy app might try to download the whole file, even if it’s gigabytes in size, causing it to use up your phone’s battery and data plan,” the researchers warned.
Server-Generated Links
Finally, in the third approach, the app sends the link
to an external server and asks it to generate a preview, then the server will
send the preview back to both the sender and receiver.
While this avoids the IP address-leaking issue found in the receiver-generating scenario, it potentially exposes information to third parties, according to the researchers, and can allow for code execution if the link points to a malicious website with JavaScript.
As far as data exposure, the server will need to make a copy (or at least a partial copy) of what’s in the link to generate the preview.
“Say you were sending a private Dropbox link to someone, and you don’t want anyone else to see what’s in it,” researchers wrote. “The question becomes…are the servers downloading entire files, or only a small amount to show the preview? If they’re downloading entire files, do the servers keep a copy, and if so for how long? And are these copies stored securely, or can the people who run the servers access the copies?”
Multiple apps use this approach for previewing links. But in testing, they vary widely in terms of how much data the servers downloaded, researchers said:
Discord: Downloads up to 15 MB of any kind of file.
Facebook Messenger:
Downloads entire files if it’s a picture or a video, even files gigabytes in
size.
Google Hangouts: Downloads up to 20 MB of any kind of file.
Instagram: Just like Facebook Messenger, but not limited to any kind of file.
The servers will download anything no matter the size.
LINE: Downloads up to
20 MB of any kind of file.
LinkedIn: Downloads up to 50 MB of any kind of
file.
Slack: Downloads up to 50 MB of any kind of file.
Twitter: Downloads
up to 25 MB of any kind of file.
Zoom: Downloads up to 30 MB of any kind of
file.
“Though most of the app servers we’ve tested put a limit on how much
data gets downloaded, even a 15 MB limit still covers most files that would
typically be shared through a link (most pictures and documents don’t exceed a
few MBs in size),” the researchers noted. “So if these servers do keep copies,
it would be a privacy nightmare if there’s ever a data breach of these servers.”
The issue is of particular concern to LINE users, according to Bakry and Mysk, because LINE claims to have end-to-end encryption where only the sender and receiver can read the messages.
“When the LINE app opens an encrypted message and finds a link, it sends that link to a LINE server to generate the preview,” according to the researchers. “We believe that this defeats the purpose of end-to-end encryption, since LINE servers know all about the links that are being sent through the app, and who’s sharing which links to whom. Basically, if you’re building an end-to-end encrypted app, please don’t follow [the server-generated] approach.”
After the researchers sent a report to the LINE security team, the company updated its FAQ to include a disclosure that they use external servers for preview links, along with information on how to disable them.
Facebook Messenger and its sister app Instagram Direct Messages are the only ones in the testing that put no limit on how much data is downloaded to generate a link preview. Facebook responded to the researchers’ concerns, saying that it considers the feature to be working as intended, but did not confirm how long it holds onto the data. Twitter gave the same response.
“As we explained to the researcher weeks ago, these are not security vulnerabilities,” a facebook company spokesperson told Threatpost. “The behavior described is how we show previews of a link on Messenger or how people can share a link on Instagram, and we don’t store that data. This is consistent with our data policy and terms of service.”
Slack meanwhile confirmed that it only caches link previews for around 30 minutes, which is also explained in its documentation.
Zoom told the researchers that it is looking into the issue and that it’s discussing ways to ensure user privacy.
The researchers also contacted Discord, Google Hangouts and LinkedIn to report their findings, but said they have not received a response from these two.
Remote Code-Execution Woes
As far as the code-execution issue, the
researchers posted a video with a proof-of-concept of how hackers can run any
JavaScript code on Instagram servers. And in LinkedIn Messages case, the servers
were also vulnerable to running JavaScript code, which allowed them to bypass
the 50 MB download limit in a test.
“You can’t trust code that may be found in all the random links that get shared in chats,” Bakry and Mysk explained. “We did find, however, at least two major apps that did this: Instagram and LinkedIn. We tested this by sending a link to a website on our server which contained JavaScript code that simply made a callback to our server. We were able to confirm that we had at least 20 seconds of execution time on these servers. It may not sound like much, and our code didn’t really do anything bad, but hackers can be creative.”
When reached via Twitter DM, Mysk told Threatpost that “In our testing, an attacker can run any JavaScript code on these servers. While it may not be immediately obvious how this can cause real harm, allowing JavaScript code to run leaves the door wide open for a team of dedicated attackers. The simplest attack would be something like mining cryptocurrencies on these servers and using up their resources.”
Neither company responded to the researchers’ concerns. But the Facebook spokesperson told Threatpost that the feature works as intended, and that it’s not a security vulnerability. The person added that way the functionality is presented does not take into account industry-standard security measures that Instagram has put in place to protect against code-execution risks, and that when the concern was reported, it “found no risk of RCE.”
As for LinkedIn, a spokesperson told Threatpost via email: “To help keep our members safe, we use a sandbox environment to evaluate the security risk of the links being shared. These environments are ephemeral and have strict access controls that are designed to discover malicious code execution. To this end, we do execute JavaScript in the URL contents for completeness of evaluation. We also don’t cache the content of these URLs. All these steps are taken to inspect content of link for safety.”
But Mysk noted that such protections may not be good enough.
“Server-side mitigations such as running JavaScript code in a sandbox environment is effective in thwarting most attacks, but more sophisticated attacks could allow the attacker to leave the sandbox and execute code outside the protected environment, which could potentially allow the attacker to steal data and secret keys,” he told Threatpost. “We’ve seen many successful attempts to escape the JavaScript sandbox in apps like Chrome, and these link preview servers are no different.”
Looking for Safety
The link-preview issue is just one more concern when it
comes to the security of the collaboration apps that have become intrinsic to
the work-from-home reality caused by the COVID-19 pandemic.
The good news is that some apps don’t render previews at all, such as Signal (if the link preview option is turned off in settings), Threema, TikTok and WeChat.
“This is the safest way to handle links, since the app won’t do anything with the link unless you specifically tap on it,” researchers noted.
However, they also warned that link previews are a widespread phenomenon: “There are many email apps, business apps, dating apps, games with built-in chat, and other kinds of apps that could be generating link previews improperly, and may be vulnerable to some of the problems we’ve covered.”
Twitter Hack: 24 Hours From Phishing Employees to Hijacking Accounts
16.10.20
Social
Securityweek
New York Financial Regulator Concludes Investigation Into Twitter Hack
Hackers needed roughly 24 hours to take over high-profile Twitter accounts in the July attack, a report from the New York Department of Financial Services reveals.
The attack started on July 14 and was over the next day, when it became apparent that numerous high-profile accounts, including those of Bill Gates, Elon Musk, Barack Obama, and Jeff Bezos, were hijacked and leveraged to promote a cryptocurrency scam.
The hackers, which were identified shortly after the incident, leveraged internal Twitter systems to change email addresses and login credentials for targeted accounts and take control of them. A total of 130 accounts were targeted and the passwords for 45 of them were changed.
A couple of weeks after the incident, Twitter revealed that hackers targeted some employees with phone phishing until gaining access to the account support tools they needed.
In a report summarizing an investigation into the incident, the New York Department of Financial Services, which launched a probe on July 16, reveals that the attack lasted roughly 24 hours from when the phishing calls were placed until the targeted accounts were compromised.
“It was surprising how easily the Hackers were able to penetrate Twitter’s network and gain access to internal tools allowing them to take over any Twitter user’s account. The extraordinary access the Hackers obtained with this simple technique underscores Twitter’s cybersecurity vulnerability and the potential for devastating consequences,” the report reads.
The attack was allegedly carried out by 17-year-old Graham Ivan Clark (aka Kirk#5270), of Tampa, Florida, who is said to be the mastermind behind the incident, 19-year-old Mason John Sheppard (aka Chaewon and “ever so anxious#001”) of the United Kingdom, and 22-year-old Nima Fazeli (aka Rolex, Rolex#0373, and Nim F) of Orlando, Florida.
In the afternoon of July 14, pretending to be calling from the IT department at Twitter in response to some issues with the VPN (not uncommon, due to the massive switch to remote working), the hackers called several of the social platform’s employees and directed them to enter credentials on a phishing page. The page would also generate a fake multi-factor authentication notification.
“The Department found no evidence the Twitter employees knowingly aided the Hackers. Rather, the Hackers used personal information about the employees to convince them that the Hackers were legitimate and could, therefore, be trusted. While some employees reported the calls to Twitter’s internal fraud monitoring team, at least one employee believed the Hackers’ lies,” the report reveals.
While the first victim did not have access to the targeted internal systems, the hackers used their credentials to navigate the network and identify employees that did. On July 15, they targeted such employees, including some of those who were responsible for dealing with sensitive global legal requests.
Soon after gaining the ability to take over Twitter accounts (including OG – “original gangster” accounts), the hackers started discussing the sale of OG usernames, and then began publicly demonstrating their access to Twitter’s internal systems: on July 15, just before 2:00 p.m., they hijacked multiple OG accounts and posted screenshots of a Twitter internal tool.
Next, the hackers switched to verified accounts, likely aiming to make their demands for cryptocurrency seem legitimate, the report points out. Within the next couple of hours, they hit the accounts of cryptocurrency trader @AngeloBTC, crypto-exchange Binance, and ten other cryptocurrency-related accounts, such as Coinbase, Gemini Trust Company, and Square, Inc.
Over the next couple of hours, the hackers started tweeting from verified accounts that had millions of followers, including those of Apple, Uber, Bill Gates, Elon Musk, Kanye West, Kim Kardashian West, Joseph R. Biden, Jr., Warren Buffet, and Floyd Mayweather Jr.
“The Hackers also used some of the compromised accounts to resend the same bitcoin scam tweets multiple times. Given the number of followers for each high-profile user account, the fraudulent tweets reached millions of potential victims across the globe. The Hackers stole approximately $118,000 worth of bitcoin through the Twitter Hack,” the report notes.
In their report, which provides a visual timeline of the events, the Department of Financial Services also points out that the non-public information of some users was compromised and that Twitter failed to publicly report real-time updates on the incident – although the company “severely limited or revoked its employees’ access to its internal systems” to contain the breach.
The report also underlines the incident’s impact on cryptocurrency-related entities and their customers, dissects the cybersecurity weaknesses that made the hack possible, and provides details on the best practices critical institutions should adopt to prevent or mitigate similar incidents.
“The Twitter Hack brought a social media giant to its knees. The David to this Goliath was a group of unsophisticated cyber crooks who exploited social media to create widespread disruption for hundreds of millions of users. The election weeks away puts a spotlight on the need to improve cybersecurity to prevent misuse of social media platforms,” the report concludes.
Australian social news platform leaks 80,000 user records
6.10.20
Social
Securityaffairs
Cybernews has found an exposed data bucket that belongs to the Australian news
sharing platform Snewpit containing around 80,000 user records.
Original post
at
https://cybernews.com/security/australian-social-news-platform-leaks-80000-user-records/
To increase efforts to secure user data, Snewpit will be reviewing “all server logs and access control settings” to confirm that no unauthorized access took place and to ensure that “user data is secure and encrypted.”
The CyberNews investigations team discovered an exposed data bucket that belongs to Snewpit, an Australian news sharing platform. The unsecured bucket contains close to 80,000 user records, including usernames, full names, email addresses, and profile pictures.
The files that contain the records were stored on a publicly accessible Amazon Web Services (AWS) server, which means that anyone with a direct URL to the files could access and download the data that was left out in the open.
On September 24, the sensitive files in the Snewpit bucket were secured by the company and are no longer accessible.
To see if your email address has been exposed in this or other security breaches, use ourpersonal data leak checker.
What data is in the bucket?
The exposed Snewpit Amazon AWS bucket contained
26,203 files, including:
256 video files filmed and uploaded by Snewpit users and developers
23,586
image files of photos documenting local events that were apparently uploaded by
the users
4 CSV files, one of which contained 79,725 user records, including
full names, email addresses, usernames, user descriptions, last login times, and
total time spent in the Snewpit app, among other metrics
Aside from the user
records, the bucket also contained thousands of user profile pictures.
Examples of exposed records
Here are some examples of the user records,
videos, and images left on the exposed Snewpit bucket.
The CSV file contains user records for what we assume to be users who downloaded and installed the Snewpit app, which currently has 50,000+ installs on Apple’s App Store and Google’s Play store.
The video files stored in the bucket seem to show raw footage from news posts, including criminal incidents.
There were also user profile pictures among the files stored in the bucket.
Who owns the bucket?
The publicly available Amazon bucket appears to belong
to Snewpit, a software company based in Australia. Snewpit is a map-based
peer-to-peer app that allows users to create, find, and share real-time news
updates, as well as receive notifications for news posted within 5 kilometers of
their location.
According to the developers, the app is aimed at helping users “form a worldwide community of citizen journalists, reporting and discovering local news and events happening around them.”
The app is mostly used by Australians, with small userbases currently located in the US and the UK.
Who had access to the data?
According to Snewpit founder Charlie Khoury, the
bucket has been exposed for 5 weeks since the development team made server
changes to the system reporting. While Snewpit have not noticed any suspicious
activity, the company is reviewing all server logs to confirm that this is the
case.
”We will be reviewing all access control settings and ensuring our user data is secure and encrypted. We take our data and security seriously and will endeavour to make sure this does not happen again.” -Charlie Khoury
With that said, the files were stored on a publicly accessible Amazon S3 server, and bad actors can find unprotected Amazon buckets relatively easily. Since these buckets lack any sort of protection from unauthorized access, there is a possibility that the data may have been accessed by bad actors for malicious purposes during the 5-week period.
What’s the impact of the leak?
Fortunately, the files stored in the exposed
Snewpit bucket don’t contain any deeply sensitive information like personal
document scans, passwords, or social security numbers. However, even this data
can be enough for bad actors to abuse for a variety of malicious purposes:
Contact details like full names and email addresses can be used by phishers and
scammers to commit targeted attacks against the exposed Snewpit users by sending
them malicious spam emails
Particularly determined cybercriminals can combine
the data found in this bucket with previous breaches in other verticals in order
to build more accurate profiles of potential targets for identity theft
What
happened to the data?
We discovered the Snewpit bucket on September 24 and
immediately reached out to the company in order to help secure the bucket. The
Snewpit team responded within minutes and secured the files containing user
records on the same day.
What to do if you’ve been affected by the leak?
If you have a Snewpit
account, there is a high chance that your records may have been exposed in this
breach. To secure your data and avoid any potential harm from bad actors, we
recommend doing the following:
Use our personal data leak checker to see if your email address has been leaked.
Immediately change your email password and consider using a password manager.
Enable two-factor authentication (2FA) on your email and other online accounts.
Look out for incoming spam emails and phishing messages. Don’t click on anything
that looks even remotely suspicious, including emails from senders you do not
recognize.
Years-Long ‘SilentFade’ Attack Drained Facebook Victims of $4M
3.10.20
Social
Threatpost
Facebook detailed an
ad-fraud cyberattack that’s been ongoing since 2016, stealing Facebook
credentials and browser cookies.
Facebook has detailed a wide-scale Chinese malware campaign that targeted its ad platform for years and siphoned $4 million from users’ advertising accounts.
Dubbed SilentFade (short for “Silently running Facebook Ads with Exploits”), the malware compromised Facebook accounts and used them to promote malicious ads, steal browser cookies and more. The social-media giant said that the Chinese malware campaign started in 2016, but it was first discovered in December 2018, due to a suspicious traffic spike across a number of Facebook endpoints. After an extensive investigation, Facebook shut down the campaign and pursued legal action against the cybercriminals behind the attack in December 2019.
“Our investigation uncovered a number of interesting techniques used to compromise people with the goal to commit ad fraud,” said Sanchit Karve and Jennifer Urgilez with Facebook, in a Thursday analysis unveiled this week at the Virus Bulletin 2020 conference. “The attackers primarily ran malicious ad campaigns, often in the form of advertising pharmaceutical pills and spam with fake celebrity endorsements.”
Facebook said that SilentFade was not downloaded or installed by using Facebook or any of its products. It was instead usually bundled with potentially unwanted programs (PUPs). PUPs are software programs that a user may perceive as unwanted; they may use an implementation that can compromise privacy or weaken user security. In this case, researchers believe the malware was spread via pirated copies of popular software (such as the Coreldraw Graphics graphic design software for vector illustration and page layout, as seen below).
Once installed, SilentFade stole Facebook credentials and cookies from various browser credential stores, including Internet Explorer, Chromium and Firefox.
“Cookies are more valuable than passwords because they contain session tokens, which are post-authentication tokens,” said researchers. “This use of compromised credentials runs the risk of encountering accounts that are protected with two-factor authentication, which SilentFade cannot bypass.”
facebook malware campaign silentfade
An example of a web page leading to the
download of SilentFade. Credit: Facebook
The malware itself consists of three to four components, with the main downloader component being included in PUP bundles, researchers said. This downloader component is either a standalone malware component or a Windows service (installed as either “AdService” or ‘”HNService”). It’s responsible for persistence across reboots and for dropping 32-bit and 64-bit version dynamic library links (DLLs) in Chrome’s application directory, which are usually named winhttp.dll and launch DLL hijacking attacks.
“The DLL proxies all make requests to the real winhttp.dll but makes requests to facebook.com through the Chrome process, evading dynamic behavior-based anti-malware detection by mimicking innocuous network requests,” said researchers.
After stealing credentials, the malware retrieves the metadata about the Facebook account (such as payment information and the total amount previously spent on Facebook ads), using the Facebook Graph API, which is a legitimate Facebook feature allowing users to read and write data to and from the Facebook social graph. This data is then sent back to the malware’s C2 servers (as an encrypted JSON blob through custom HTTP headers).
SilentFade has varying persistence and detection-evasion tactics, including code to detect virtual machines (checking the description field of all available display drivers against “Virtual” or “VM” ) and halt execution when detected. It also disables Facebook notification alerts from compromised accounts, which could potentially alert the victim of suspicious activity.
And, in a unique anti-detection tactic, the C2 server stores the data and logs the IP address of the incoming request for the purpose of geolocation. “This was crucial as the attackers intentionally used the stolen credentials from the same or a nearby city to the infected machine to appear as though the original account owner has traveled within their city,” said researchers.
facebook malware campaign silentfade
Ad fraud process using cloaking and
legitimate user sessions retrieved by SilentFade. Credit: Facebook
While users’ Facebook credentials are valuable, users with credit cards linked accounts (for business accounts, for instance) also gave cybercriminals the ability to use those payment cards to promote malicious ads on Facebook.
However, “it should be noted that payment-information details (such as bank account and credit card numbers) were never exposed to the attackers, as Facebook does not make them visible through the desktop website or the Graph API,” said researchers.
As part of its investigations into SilentFade, Facebook also uncovered other Chinese malware campaigns, including ones dubbed StressPaint, FacebookRobot and Scranos. Some of these malware attacks remained active as recently as June, Facebook warned.
The company has faced security and privacy issues over the past year, and on Thursday filed a lawsuit in the U.S. against two companies that used scraping to engage in an international data harvesting operation, including scraping data from Facebook, Instagram, Twitter, YouTube, LinkedIn and Amazon, to sell “marketing intelligence.” The data involved includes names, user IDs, genders, dates of birth, relationship status, location information and more.
In the midst of all this, Facebook warns that it expects cybercriminals to continue to up the ante when it comes to launching attacks on its platform.
“We anticipate more platform-specific malware to appear for platforms serving large and growing audiences, as the evolving ecosystem targeting Facebook demonstrates,” said Facebook. “Only through user education and strong partnerships across the security industry will we measure the scale of malicious campaigns and effectively respond to them.”
Facebook Details Malware Campaign Targeting Its Ad Platform
2.10.20
Social Virus
Securityweek
Facebook on Thursday released a detailed technical report on a malware campaign that targeted its ad platform for years.
Referred to as SilentFade (Silently running Facebook ADs with Exploits), the malware was identified in late 2018 and the vulnerability it was exploiting to stay undetected was patched soon after. Facebook took legal action against the malware operators in December 2019.
The malware exploited a server-side flaw to persistently suppress notifications and ensure that the infected users would not be made aware of suspicious activity related to their accounts. This allowed SilentFade to abuse the compromised accounts and run malicious ads without the victims noticing anything.
Although the malware was first detected in the final week of 2018, the cyber-crime group behind it is believed to have been operating since 2016, constantly adapting to new Facebook features and likely expanding to other social platforms and web services as well.
Distribution channels for SilentFade include potentially unwanted program (PUP) bundles within pirated copies of legitimate software and other malware families. The PUP bundles would include a downloader component that would fetch a standalone malware component meant to achieve persistence and download malicious DLLs into Chrome’s application directory, to perform DLL hijacking.
Next, the malware would steal Facebook login credentials from Internet browsers, would retrieve metadata about the Facebook account, and send the information to the command and control (C&C) servers. The victim’s IP address was logged as well, for geolocation purposes.
“Based on a review of the data collected by SilentFade, it’s likely that compromised user accounts that had at least a linked payment method were deemed more valuable. SilentFade, or its customers, would then be able to use the compromised user’s payment method (credit card, bank account, or PayPal account) to run malicious ads on Facebook,” the social media platform explains.
If no page or linked payment information was attached to the account, the attackers used stolen credit card data to create pages and run ads. According to Facebook, however, no user payment information details were exposed to the attackers.
The malware included anti-VM checks and targeted Facebook-specific credentials and cookies stored on the local machine only. It also leveraged access to the Graph API to gather additional information on the victim, and took specific action to get around the security checks that Facebook had in place, such as asking for user permission.
Notification alerts were completely turned off for the compromised accounts, thus preventing users from receiving alerts on the suspicious activity taking place. Login alerts and Facebook Business pages were blocked as well.
After identifying the malicious activity, Facebook patched a server-side validation flaw, reverted the blocked notification state on all affected accounts, forced password resets, invalidated sessions, added more fixes and detection mechanisms, and reimbursed affected users.
Facebook’s investigation into SilentFade, which saw collaboration from Radware, Bitdefender, Atlassian/BitBucket and Google/VirusTotal, enabled attribution, and in December 2019 the company sued Chinese firm ILikeAd Media International Company Ltd. and two of its employees, namely Chen Xiao Cong and Huang Tao, for creating and operating the malware.
SilentFade authors, however, modified their code to ensure it can work even with Facebook’s new mechanisms in place, and started employing obfuscation to hinder detection.
The social platform also discovered additional Chinese malware that are part of an ecosystem targeting Facebook users and says that such attacks were active as of June 2020. Some of the names it mentions in a report made public on Thursday include StressPaint, FacebookRobot, and Scranos.
“We believe this ecosystem spread its wings again in early 2019 with the release of two newer malware families, ‘Scranos’ and ‘FacebookRobot’, first seen in April and June 2019, respectively,” the company notes.
Twitter Removes Iran-Linked Accounts Aimed at Disrupting U.S. Presidential
Debate
1.10.20
APT Social
Securityweek
Twitter on Wednesday announced that it removed 130 accounts originating from Iran that were aimed at disrupting the first 2020 U.S. presidential debate.
The accounts, the social media platform reveals, were removed after the Federal Bureau of Investigation (FBI) alerted it on the suspicious activity.
“Based on intel provided by the @FBI, last night we removed approximately 130 accounts that appeared to originate in Iran. They were attempting to disrupt the public conversation during the first 2020 US Presidential Debate,” Twitter announced.
The social platform also explains that it was able to quickly identify the accounts and remove them. The accounts had low engagement and weren’t able to impact the public conversation.
The company says that, once its investigation into these accounts has been completed, it will publish all of the necessary details on its Transparency portal.
“As standard, the accounts and their content will be published in full once our investigation is complete. We’re providing this notice to keep people updated in real time about our actions. We wish to thank the @FBI for their assistance,” Twitter said.
The removal of these accounts comes roughly one month after Microsoft warned of attempts from state-sponsored threat actors, including Iranian ones, to disrupt the 2020 U.S. presidential elections. Iran responded swiftly, claiming the allegations were absurd.
Last week, Facebook announced that it shut down a network of fake accounts out of China that were aiming at the US presidential race.
In June, Twitter announced the removal of a total of 30,000 state-linked accounts originating from China, Turkey, and Russia that engaged in manipulation.
Over the past couple of weeks, the FBI and CISA issued several alerts to warn of disinformation campaigns aimed hurting the population’s trust in the election results and the security of voting systems.
Twitter Says Bug Leading to API Key Leak Patched
28.9.20
Social
Securityweek
Twitter last week started sending emails to developers to inform them of a vulnerability that might have resulted in the disclosure of developer information, including API keys.
The issue, which has been fixed, potentially resulted in details about Twitter developer applications being stored in the browser’s cache when the app builders visited the developer.twitter.com website, the company said in an email sent to developers, which was shared online.
Designed to provide developers using the Twitter platform and APIs with access to documentation, community discussion, and other type of information, the portal also offers app and API key management functionality.
In the email sent to developers, Twitter revealed that the addressed issue resulted in app keys and tokens being stored in the browser’s cache, thus potentially resulting in their leak.
An attacker could abuse private keys and tokens to interact with Twitter on behalf of the developer, while access tokens would allow them to log into a developer’s account without knowing the credentials.
“Prior to the fix, if you used a public or shared computer to view your developer app keys and tokens on developer.twitter.com, they may have been temporarily stored in the browser’s cache on that computer. If someone who used the same computer after you in that temporary timeframe knew how to access a browser’s cache, and knew what to look for, it is possible they could have accessed the keys and tokens that you viewed,” Twitter told developers.
According to the company, app consumer API keys, along with user access tokens and secrets for the developers’ own Twitter accounts might have been affected by the issue. Those who did not use a shared computer to access the developer portal should not be impacted.
The social media platform claims that it has no evidence that the developer app keys and tokens were compromised, but that it decided to inform the affected parties of the issue, so they could take the necessary measures to ensure their apps and accounts are kept secure.
“We changed the caching instructions that developer.twitter.com sends to your browser to stop it from storing information about your apps or account so this won’t happen any longer,” Twitter also said.
Affected developers are advised to regenerate app keys and tokens, to avoid further data leaks.
In early August, Twitter revealed that an issue with the Android application might have resulted in private data being exposed to malicious apps. In April, the company said that the manner in which Firefox stored cached data might have resulted in the personal data of Twitter users being exposed.
Twitter warns developers of possible API keys leak
26.9.20
Social
Securityaffairs
Twitter is warning developers that their API keys, access tokens, and access
token secrets may have been exposed in a browser’s cache.
Twitter is sending
emails to developers to warn them that their API keys, access tokens, and access
token secrets may have been exposed in a browser’s cache.
According to the social media firm, the browser used by developers may have cached the sensitive data while accessing certain pages on developer.twitter.com.
The developer.twitter.com portal allows developers to manage their apps and
attached API keys, along with the access token and secret key for their account.
The social media firm has already fixed the problem by preventing the data to be
cached in the browser, but his notification aims at informing users that other
users accessed the machine used by developers in the past might have been able
to access security tokens and API keys.
Obtaining security tokens and API keys could allow an app to access data for a
specific account.
“Prior to the fix, if you used a public or shared computer to view your developer app keys and tokens on developer.twitter.com, they may have been temporarily stored in the browser’s cache on that computer.” reads the message send by Twitter via mail. “If someone who uses the same computer after you in that temporary timeframe knew how to access a browser’s cache, and knew what to look for, it is possible they could have accessed the keys and tokens that you viewed.”
“Depending on what pages you visited and what information you looked at, this could have included your app consumer API keys, as well as the user access token and secret for your own Twitter account.”
The company pointed out that there is no evidence that developer app keys and tokens were compromised, anyway, it recommends users to regenerate API keys and access tokens.
A similar issue was disclosed by Twitter in April, at the time the company announced that some private files sent via direct messages might have stored in the browser cache of Firefox browsers.
Instagram Remote Account Takeover Required No Action From Victim
25.9.20
Social
Securityweek
A vulnerability in Instagram allowed an attacker to take over an Instagram account and turn the victim's phone into a spying tool by simply sending a malicious image by any media exchange platform.
Researchers at Check Point, who discovered the vulnerability, have now published a detailed explanation on the vulnerability, how it was discovered, and how it could be exploited.
The vulnerability has since been patched.
Check Point Research decided to examine Instagram because of its size and popularity. It has more than 1 billion users with more than 100 million photos uploaded every day. The researchers chose to examine some of the third-party open source projects used within the Instagram app -- and focused on Mozjpeg. This is an open source Jpeg encoder developed by Mozilla to maximize compression over performance for web images.
The researchers used a fuzzer on images sent to the Mozjpeg decompression function, and decided to concentrate on one specific crash caused by an out-of-bounds write. They found that they could use an integer overflow leading to a heap buffer overflow. Successful exploitation of such bugs requires precise positioning of heap objects to enable useful adjacencies for memory corruption.
They were able to use a function that performs a raw malloc with a size under their control. This allowed them to place the overflowed buffer at a position of their choice on the heap. Putting everything together, reported the researchers, they could "(1) construct an image with malformed dimensions that (2) triggers the bug, which then (3) leads to a copy of our controlled payload that (4) diverts the execution to an address that we control."
Exploiting this vulnerability would give the attacker full control over the Instagram app, enabling the attacker to take actions without the user's consent -- including reading all direct messages on the Instagram account, deleting or posting photos at will, or manipulating account profile details. All that is required is for the attacker to send the crafted malicious image to the victim. If this is saved to the victim's phone (WhatsApp does this automatically by default), merely opening the Instagram app will trigger the exploitation and give the attacker full access for remote takeover.
Check Point reported its findings to Facebook towards the end of 2019. Facebook acknowledged the vulnerability and assigned it the CVE-2020-1895 reference number. NVD gives it a severity rating of 7.8. Facebook patched the vulnerability in February 2020, and Check Point delayed publishing its account of the vulnerability a further six months to give Instagram users enough time to update their apps. Facebook comments that the issue is fixed, and it has seen no evidence of associated abuse.
However, the Check Point researchers, while noting that fuzzing the exposed code turned up new vulnerabilities that have since been fixed, it is "likely that other bugs remain or will be introduced in the future. As such, continuous fuzz-testing of this and similar media format parsing code, both in operating system libraries and third-party libraries, is absolutely necessary."
Yaniv Balmas, Head of Cyber Research at Check Point said: "This research has two main takeaways. First, 3rd party code libraries can be a serious threat. We strongly urge developers of software applications to vet the 3rd party code libraries they use to build their application infrastructures and make sure their integration is done properly. 3rd party code is used in practically every single application out there, and it`s very easy to miss out on serious threats embedded in it. Today it's Instagram, tomorrow -- who knows?"
Second, he continued, "People need to take the time to check the permissions any application has on your device. This 'application is asking for permission' message may seem like a burden, and it's easy to just click 'Yes' and forget about it. But in practice this is one of the strongest lines of defense everyone has against mobile cyber-attacks, and I would advise everyone to take a minute and think, do I really want to give this application access to my camera, my microphone, and so on?"
Instagram uses should ensure that they are using version 128.0.0.26.128 or later.
Major Instagram App Bug Could've Given Hackers Remote Access to Your Phone
24.9.20
Social
Thehackernews
Ever wonder how
hackers can hack your smartphone remotely?
In a report shared with The Hacker
News today, Check Point researchers disclosed details about a critical
vulnerability in Instagram's Android app that could have allowed remote
attackers to take control over a targeted device just by sending victims a
specially crafted image.
What's more worrisome is that the flaw not only lets attackers perform actions on behalf of the user within the Instagram app—including spying on victim's private messages and even deleting or posting photos from their accounts—but also execute arbitrary code on the device.
According to an advisory published by Facebook, the heap overflow security issue (tracked as CVE-2020-1895, CVSS score: 7.8) impacts all versions of the Instagram app prior to 128.0.0.26.128, which was released on February 10 earlier this year.
"This [flaw] turns the device into a tool for spying on targeted users without their knowledge, as well as enabling malicious manipulation of their Instagram profile," Check Point Research said in an analysis published today.
"In either case, the attack could lead to a massive invasion of users' privacy and could affect reputations — or lead to security risks that are even more serious."
After the findings were reported to Facebook, the social media company addressed the issue with a patch update released six months ago. The public disclosure was delayed all this time to allow the majority of Instagram's users to update the app, thereby mitigating the risk this vulnerability may introduce.
Although Facebook confirmed there were no signs that this bug was exploited globally, the development is another reminder of why it's essential to keep apps up to date and be mindful of the permissions granted to them.
A Heap Overflow Vulnerability
According to Check Point, the memory corruption
vulnerability allows for remote code execution that, given Instagram's extensive
permissions to access a user's camera, contacts, GPS, photo library, and
microphone, could be leveraged to perform any malicious action on the infected
device.
As for the flaw itself, it stems from the way Instagram integrated MozJPEG — an open-source JPEG encoder library which aims to lower bandwidth and provide better compression for images uploaded to the service — resulting in an integer overflow when the vulnerable function in question ("read_jpg_copy_loop") attempts to parse a malicious image with specially crafted dimensions.
In doing so, an adversary could gain control over the size of the memory allocated to the image, the length of the data to be overwritten, and lastly, the contents of the overflowed memory region, in turn giving the attacker the ability to corrupt specific locations in a heap and divert code execution.
The consequence of such a vulnerability is that all a bad actor needs to do is send a corrupted JPEG image to a victim via email or WhatsApp. Once the recipient saves the image to the device and launches Instagram, the exploitation takes place automatically, granting the attacker full control over the app.
Even worse, the exploit can be used to crash a user's Instagram app and render it inaccessible unless it's removed and reinstalled all over again on the device.
If anything, the vulnerability is indicative of how incorporating third-party
libraries into apps and services can be a weak link for security if the
integration is not done right.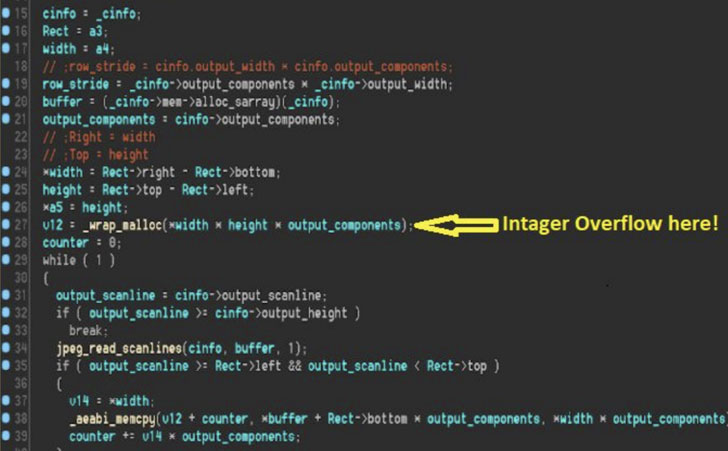
"Fuzzing the exposed code turned up some new vulnerabilities which have since been fixed," Check Point's Gal Elbaz said. "It is likely that, given enough effort, one of these vulnerabilities can be exploited for RCE in a zero-click attack scenario.
"Unfortunately, it is also likely that other bugs remain or will be introduced in the future. As such, continuous fuzz-testing of this and similar media format parsing code, both in operating system libraries and third-party libraries, is absolutely necessary."
Yaniv Balmas, the head of cyber research at Check Point, provided the following safety tips for smartphone users:
Update! Update! Update! Make sure you regularly update your mobile application
and your mobile operating systems. Dozens of critical security patches are being
shipped out in these updates every week, and each one can potentially have a
severe impact on your privacy.
Monitor permissions. Pay better attention to
applications asking for permission. It's effortless for app developers to ask
the users for excessive permissions, and it's also very easy for users to click
'Allow' without thinking twice.
Think twice about approvals. Take a few
seconds to think before you approve anything. Ask: "do I really want to give
this application this kind of access, do I really need it?" if the answer is no,
DO NOT APPROVE.
Facebook Says Fake Accounts From China Aimed at US Politics
23.9.20
BigBrothers Social
Securityweek
Facebook said Tuesday it derailed a network of fakes accounts out of China that had recently taken aim at the US presidential race.
The takedown came as part of the social networks fight against "coordinated inauthentic behavior" and marked the first time Facebook had seen such a campaign based in China targeting US politics, according to head of security policy Nathaniel Gleicher.
Facebook did not connect the campaign to the Chinese government, saying its investigation found links to individuals in the Fujian province of China.
In the takedown, Facebook removed 155 accounts, 11 Pages, 9 Groups and 6 Instagram accounts for violating its policy against foreign interference in deceptive schemes.
The campaign out of China focused primarily on the Philippines and South East Asia more broadly, and just a bit on the US, according to Gleicher.
Posts particularly commented about naval activity in the South China Sea, including US Navy ships, Facebook said.
The account holders would have had to use techniques to circumvent China's "Great Firewall," which bans the US social network. Gleicher said the people running the pages posed as locals in places they targeted, and tried to hide their locations using virtual private network software.
The network posted in South East Asia about Beijing's interest in the South China Sea; Hong Kong, and in support of Philippines President Rodrigo Duterte, Facebook said.
The network had evidently been active since at least 2018, only recently starting to post content both in for and against US President Donal Trump and his Democratic challenger Joe Biden, according to Gleicher.
"The operation had been running a while aimed at Southeast Asia; its aim at the US seemed nascent and ineffective," Gleicher said during a briefing with journalists.
"These actors had hardly posted anything; it looked like audience building."
About 133,000 people followed one or more of the campaigns Facebook pages, and around 61,000 people had joined one or more of its online Groups, according to the California-based social network.
The campaign had only spent about $60 on ads at Facebook, paid for in Chinese yuan, Gleicher said.
Twitter announces measures to protect accounts of people involved in 2020
Presidential election
19.9.20
Social
Securityaffairs
Twitter announced that it will adopt new security measures to protect
high-profile accounts during the upcoming election in the United States.
Twitter announced new measures to protect high-profile accounts during the
upcoming US Presidential election.
The types of accounts that are in this designated group are:
US Executive Branch and Congress
US Governors and Secretaries of State
Presidential campaigns, political parties and candidates with Twitter Election
Labels running for US House, US Senate, or Governor
Major US news outlets and
political journalists
Twitter will use an internal notification service to
alert owners of accounts associated with people in the above group.
“Voters, political candidates, elected officials and journalists rely on Twitter every day to share and find reliable news and information about the election, and we take our responsibility to them seriously.” reads the post published by the company. “As we learn from the experience of past security incidents and implement changes, we’re also focused on keeping high-profile accounts on Twitter safe and secure during the 2020 US election.”
The platform will provide recommendations about account security measures that
the owners of the accounts have to enable to secure their accounts.
One of these measures is the use of strong passwords, the owner of the accounts using weak passwords will be forced to change it.
In order to avoid that threat actors could change the passwords for high-profile accounts, Twitter enabled the password reset protection, this means that users have to confirm their identity via email or phone before resetting the password.
Twitter also recommends owners of high-profile accounts involved in the upcoming US Presidential election to enable two-factor authentication (2FA).
Twitter also plans to roll out more sophisticated detections and alerts features to rapidly respond to suspicious activity.
The company will implement better defenses against account takeover and expedited account recovery support.
“While we’re requiring some accounts do this given the unique sensitivities of the election period, everyone on Twitter can take advantage of these security measures, (and we encourage them to do so!),” continues the announcement. “Implementing these security measures is a critical preventative step, and you will continue to see us introduce new protections and features to help safeguard accounts on Twitter.”
In July, the social media platform suffered one of the biggest cyberattacks in its history, multiple high-profile accounts were hacked, including those of Barak Obama, US presidential candidate Joe Biden, Amazon CEO Jeff Bezos, Bill Gates, Elon Musk, Uber, and Apple.
Spyware Labeled ‘TikTok Pro’ Exploits Fears of US Ban
10.9.20 BigBrothers Social Virus Threatpost
Malware can take over common device functions as well as creates a phishing page to steal Facebook credentials.
Researchers have discovered a new Android spyware campaign pushing a “Pro” version of the TikTok app that is exploiting fears among its young and gullible users that the popular social media app is on the cusp of being banned in the United States. The malware can take over basic device functions—such as capturing photos, reading and sending SMS messages, making calls and launching apps—as well as uses a phishing tactic to steal victims’ Facebook credentials.
The rogue app called TikTok Pro is being promoted by threat actors using a variant of a campaign already making the rounds, which urges users via SMS and WhatsApp messages to download the latest version of TikTok from a specific web address, said Zscaler CISO and VP of security Shivang Desai in a report published Tuesday.
The first wave of the campaign spread a fake app, containing malware dubbed “TikTok Pro,” which asks for credentials and Android permissions–including camera and phone permissions—and resulted in the user being bombarded with advertisements, he said.
Threatpost Webinar Promo Bug Bounty
Click to Register
The new wave has leveled up with a completely new app delivering “full-fledged spyware with premium features to spy on victim with ease,” Desai wrote.
Once installed and opened, the new “Tik Tok Pro” spyware launches a fake notification which then disappears along with the app’s icon. “This fake notification tactic is used to redirect the user’s attention, meanwhile the app hides itself, making the user believe the app to be faulty,” he said in his report.
The malware also has another anti-detection capability in that it has an additional payload stored under the /res/raw/ directory, “a common technique used by malware developers to bundle the main payload inside the Android package,” Desai wrote. The payload is just a decoy rather than possesses actual app functionality, he added.
The spyware’s main execution capability comes from an Android service named MainService, which acts as the “brain” of the spyware and controls its functionality—”from stealing the victim’s data to deleting it,” Desai wrote.
In addition to having the ability to take over common smartphone functions—such as capturing photos, sending SMS messages, executing commands, capturing screenshots, calling phone numbers and launching other apps on the device—the spyware also has a unique feature it uses to steal Facebook credentials.
Similar to phishing campaigns, “Tik Tok Pro” launches a fake Facebook login page that, as soon as the victim tries to log in, stores the victim’s credentials in /storage/0/DCIM/.fdat. An additional command, IODBSSUEEZ, then sends the stolen credentials to the malware’s command and control server.
Desai noted that this type of phishing tactic can be extended to steal other critical user credentials, such as bank-account or financial log-in data, though this type of activity wasn’t seen in the observed campaign.
Moreover, the new spyware has numerous functionalities similar to other more well-known versions of this type of malware, such as Spynote and Spymax, “meaning this could be an updated version of these Trojan builders, which allow anyone, even with limited knowledge, to develop full-fledged spyware,” Desai noted.
However, the Facebook credential-stealing capability is unique to “Tik Tok Pro” and not something that’s been observed before with these spyware apps, he said.
The persistence of using the TikTok brand to spread malware is likely the result of the current controversy over the popular video-sharing app, which is owned by China’s ByteDance and has been criticized for its questionable data-collection tactics.
President Trump has threatened to ban in the app in the United States and several U.S. companies—including Microsoft and Wal-Mart—are eyeing a purchase of the app. India recently banned TikTok as well as many other Chinese apps over a political dispute.
“Users looking forward to using the TikTok app amidst the ban might look for alternative methods to download the app,” Desai wrote in his report. “In doing so, users can mistakenly install malicious apps, such as the spyware mentioned in this blog.”
Desai reiterated the usual warnings to Android users not to trust unknown links received in SMS or other messages and to only install apps from official stores like Google Play to avoid falling victim to the new spyware campaign.
Another mitigation tactic is to keep the “Unknown Sources” option disabled in the Android device, which won’t let a device install apps from unknown sources, he added.
To check to see if the new spyware is running undetected on an Android device, users can search for the app in device settings by going to Settings -> Apps -> Search for icon that was hidden and search for “TikTok Pro,” Desai advised.
The Twitter account of Indian Prime Minister Modi was hacked
4.9.20
Social
Securityaffairs
The Twitter account of the Indian Prime Minister Modi was hacked, attackers sent
a series of tweets asking followers to donate cryptocurrency to a relief fund.
The Twitter account for the personal website of the Indian Prime Minister
Narendra Modi (@narendramodi_in) has been hacked. The hackers have sent a series
of tweets asking the followers to donate cryptocurrency to the PM National
Relief Fund.
“Yes this account is hacked by John Wick,” reads one tweets.
“I appeal to you
all to donate generously to PM National Relief Fund for Covid-19, Now India
begin with crypto currency,” states another tweet.
Twitter quickly detected malicious activity and secured the compromised account locking out the hackers, the fraudulent messages were also deleted.
A Twitter spokesman confirmed the company was “aware of this activity and have taken steps to secure the compromised account.””We are actively investigating the situation,”
Unfortunately, such kind of incident is not rare, recently several high-profile Twitter accounts have been breached by hackers, including those of Barak Obama, US presidential candidate Joe Biden, Amazon CEO Jeff Bezos, Bill Gates, Elon Musk, Uber, and Apple.
The official Modi’s personal website account has more than 2.5 million followers, while the personal account of the Indian Prime Minister with more than 61 million followers was not affected.
“We are actively investigating the situation. At this time, we are not aware of additional accounts being impacted,” a Twitter spokeswoman told the BBC in an emailed statement.
The tweets, which have now been taken down, asked followers to donate cryptocurrency to the PM National Relief Fund.
The apparent scam spread to mainstream celebrity accounts such as Kim Kardashian West and those of corporations Apple and Uber.
Twitter pointed out that hackers did not breached its systems, they likely targeted Modi ‘s collaborators who where managing the account and used their administrative privileges to send out the tweets.
At the time, it is still unclear who is behind the attack.
Hackers use e-skimmer that exfiltrates payment data via Telegram
3.9.20
Social
Securityaffairs
Researchers observed a new tactic adopted by Magecart groups, the hackers used
Telegram to exfiltrate stolen payment details from compromised websites.
Researchers from Malwarebytes reported that Magecart groups are using the
encrypted messaging service Telegram to exfiltrate stolen payment details from
compromised websites.
Attackers encrypt payment data to make identification more difficult before
transferring it via Telegram’s API into a chat channel.
“For threat actors,
this data exfiltration mechanism is efficient and doesn’t require them to keep
up infrastructure that could be taken down or blocked by defenders,” explained
Jérôme Segura of Malwarebytes. “They can even receive a notification in real
time for each new victim, helping them quickly monetize the stolen cards in
underground markets.”
The new technique was first publicly documented by the security researcher @AffableKraut who spotted a credit card skimmer using Telegram to exfiltrate the data. The experts used data shared by security firm Sansec.
Threat actors deploy the e-skimmers on shopping websites by exploiting known vulnerabilities or using stolen credentials.
The software skimmer looks for fields of interest, such as billing, payment,
credit card number, expiration, and CVV. The skimmer also checks for the usual
web debuggers to prevent being analyzed by security researchers.
The use of Telegram represents the novelty of the Magecart attacks analyzed by Malwarebytes.
“The fraudulent data exchange is conducted via Telegram’s API, which posts payment details into a chat channel,” continues Segura. “That data was previously encrypted to make identification more difficult.”
The attackers use Telegram to avoid setting up a dedicated C2 infrastructure to collect the stole payment details from the infected sites, the choice makes more difficult the detection of malicious traffic within compromised organizations.
Another advantage consists in the possibility to receive a notification in real time for each new victim, in this way threat actors can quickly monetize the stolen cards in the cybercrime ecosystem.
“For threat actors, this data exfiltration mechanism is efficient and doesn’t
require them to keep up infrastructure that could be taken down or blocked by
defenders.” concluded the post.
“Defending against this variant of a skimming
attack is a little more tricky since it relies on a legitimate communication
service. One could obviously block all connections to Telegram at the network
level, but attackers could easily switch to another provider or platform (as
they have done before) and still get away with it.”
New Web-Based Credit Card Stealer Uses Telegram Messenger to Exfiltrate Data
2.9.20
Social
Thehackernews
Cybercriminal groups
are constantly evolving to find new ways to pilfer financial information, and
the latest trick in their arsenal is to leverage the messaging app Telegram to
their benefit.
In what's a new tactic adopted by Magecart groups, the
encrypted messaging service is being used to send stolen payment details from
compromised websites back to the attackers.
"For threat actors, this data
exfiltration mechanism is efficient and doesn't require them to keep up
infrastructure that could be taken down or blocked by defenders," Jérôme Segura
of Malwarebytes said in a Monday analysis. "They can even receive a notification
in real time for each new victim, helping them quickly monetize the stolen cards
in underground markets."
The TTP was first publicly documented by security
researcher @AffableKraut in a Twitter thread last week using data from Dutch
cybersecurity firm Sansec.
Injecting e-skimmers on shopping websites by exploiting a known vulnerability or
stolen credentials to steal credit card details is a tried-and-tested modus
operandi of Magecart, a consortium of different hacker groups who target online
shopping cart systems.
These virtual credit card skimmers, also known as
formjacking attacks, are typically JavaScript code that the operators stealthily
insert into an e-commerce website, often on payment pages, with an intent to
capture customers' card details in real-time and transmit it to a remote
attacker-controlled server.
But over the last few months, they have stepped
up in their efforts to hide card stealer code inside image metadata and even
carry out IDN homograph attacks to plant web skimmers concealed within a
website's favicon file.
What's novel this time around is the method of exfiltrating the data (such as
name, address, credit card number, expiry, and CVV) itself, which is done via an
instant message sent to a private Telegram channel using an encoded bot ID in
the skimmer code.
"The fraudulent data exchange is conducted via Telegram's
API, which posts payment details into a chat channel," Segura said. "That data
was previously encrypted to make identification more difficult."
The
advantage of using Telegram is that threat actors no longer have to bother with
setting up a separate command-and-control infrastructure to transmit the
collected information nor risk facing the possibility of those domains being
taken down or blocked by anti-malware services.
"Defending against this
variant of a skimming attack is a little more tricky since it relies on a
legitimate communication service," Segura said. "One could obviously block all
connections to Telegram at the network level, but attackers could easily switch
to another provider or platform (as they have done before) and still get away
with it."
TikTok Surreptitiously Collected Android User Data Using Google-Prohibited
Tactic
13.8.20
Social
Threatpost
App concealed the practice of gathering device unique identifiers using an added layer of encryption.
TikTok has been collecting unique identifiers from millions of Android devices
without their users’ knowledge using a tactic previously prohibited by Google
because it violated people’s privacy, new research has found.
The app
concealed the practice, which can track users online without their consent, with
an added layer of encryption, according to analysis by and a report in the Wall
Street Journal (WSJ). TikTok, owned by Beijing-based parent company ByteDance
Ltd., appears to have stopped the practice in November, according to the report.
The identifiers collected by TikTok are called MAC addresses, which are unique to a device and used as its network address in a network segment. They are typically assigned by device manufacturers and aren’t usually changed or altered. For this reason, they are valuable to companies and third parties wanting to send targeted advertising to mobile device users, as they provide unique insight into customer behavior.
WSJ research found that TikTok collected MAC addresses for at least 15 months, ending with an update released Nov. 18 of last year. The app bundled the MAC address with other device data and sent it to ByteDance upon the app’s first installation and opening on a new device, according to the report.
That data bundle also included the device’s advertising ID, which is a 32-digit number aimed at allowing advertisers to track consumer behavior while still allowing the user to maintain some anonymity and control over their information, the WSJ found.
Indeed, mobile apps collect various data on users for advertising purposes, which has always been a point of contention for privacy advocates. Companies have defended the practice as helping them provide a personalized experience for their users.
TikTok is an enormously popular video-sharing app, especially in the United States. Its popularity has surged even higher since the beginning of the coronavirus pandemic in March, when stay-at-home orders were first put in place and people began using social-media mobile apps even more than usual to stay in touch.
The WSJ’s finding is not the first time TikTok has been accused of dodging data-collection practices and come at a critical time in the investigation and scrutiny of these tactics.
President Trump recently threatened to ban the app in the United States out of fear that it’s surreptitiously collecting data on U.S. government employees and contractors to use in China’s cyber activities against the United States. His comments came at a time when companies such as Microsoft, among others, were seeking to purchase the app, which would make it subject to U.S. laws on privacy and data collection.
TikTok has said it doesn’t share data with the Chinese government and would not violate user privacy even if asked, according to the WSJ. However, many security experts have warned that due to the security flaws of the app and China’s stance on cybersecurity, it’s likely the Chinese government has access to whatever data the app does.
TikTok not only has been targeting Android devices with its alleged shady data-collection practices. The app previously came under fire for reading Apple iPhone users’ cut-and-paste data, something that was discovered in February and which TikTok’s owners promised the app would stop doing in March.
However, in late June, a new iPhone privacy feature in Apple iOS 14 that shows a banner alert to let people known if a mobile app is pasting from the clipboard seemed to reveal that the practice was still going on.
Porn Video Interrupts US Court Hearing for Accused Twitter Hacker
6.8.20
Social
Securityaffairs
A court hearing held via Zoom for a US teenager accused of masterminding a stunning hack of Twitter was interrupted Wednesday with rap music and porn, a newspaper reported.
The purpose of the hearing was to discuss reducing bail terms set for the 17 year old Tampa resident arrested last Friday over the hack last month of the accounts of major US celebrities.
But the interruptions with music, shrieking and pornography became so frequent that Judge Christopher Nash ended up suspending it for a while, the Tampa Bay Times said.
Investigators view the youth -- AFP has chosen not to release his name because he is a minor -- as the brains behind the mid-July cyberattack that rocked Twitter.
Hackers accessed dozens of Twitter accounts of people such as Barack Obama, Joe Biden and Elon Musk, after gaining access to the system with an attack that tricked a handful of employees into giving up their credentials.
The hack affected at least 130 accounts, with tweets posted by the usurpers duping people into sending $100,000 in Bitcoin, supposedly in exchange for double the amount sent.
Bail for the 17 year old was set for $725,000 and in the hearing his lawyers were seeking to reduce it.
After the judge suspended the hearing, and eventually resumed it, hackers went at it again -- with interruptions that disguised their user names as organizations such as CNN and BBC.
In the end, judge Nash ruled against reducing the youth's bail.
He was arrested along with two others, aged 19 and 22, one of whom lives in Britain, and was charged with cyber fraud.
Porn Video Interrupts US Court Hearing for Accused Twitter Hacker
6.8.20
Social
Securityweek
A court hearing held via Zoom for a US teenager accused of masterminding a stunning hack of Twitter was interrupted Wednesday with rap music and porn, a newspaper reported.
The purpose of the hearing was to discuss reducing bail terms set for the 17 year old Tampa resident arrested last Friday over the hack last month of the accounts of major US celebrities.
But the interruptions with music, shrieking and pornography became so frequent that Judge Christopher Nash ended up suspending it for a while, the Tampa Bay Times said.
Investigators view the youth -- AFP has chosen not to release his name because he is a minor -- as the brains behind the mid-July cyberattack that rocked Twitter.
Hackers accessed dozens of Twitter accounts of people such as Barack Obama, Joe Biden and Elon Musk, after gaining access to the system with an attack that tricked a handful of employees into giving up their credentials.
The hack affected at least 130 accounts, with tweets posted by the usurpers duping people into sending $100,000 in Bitcoin, supposedly in exchange for double the amount sent.
Bail for the 17 year old was set for $725,000 and in the hearing his lawyers were seeking to reduce it.
After the judge suspended the hearing, and eventually resumed it, hackers went at it again -- with interruptions that disguised their user names as organizations such as CNN and BBC.
In the end, judge Nash ruled against reducing the youth's bail.
He was arrested along with two others, aged 19 and 22, one of whom lives in Britain, and was charged with cyber fraud.
Four individuals charged for the recent Twitter hack
1.8.2020
Social
Securityaffairs
Four suspects were charged for their alleged involvement in the recent Twitter
hack, announced the Department of Justice.
US authorities announced the
arrest of 17-year-old Graham Ivan Clark from Tampa, Florida, it is suspected to
have orchestrated the recent Twitter hack. The arrest is the result of an
operation coordinated by the FBI, the IRS, and the Secret Service.
The arrest of Clark, who is suspected to be the “mastermind” behind the attack, was first reported by Florida news outlet WFLA-TV.
“Hillsborough State Attorney Andrew Warren filed 30 felony charges against the teen this week for “scamming people across America” in connection with the Twitter hack that happened on July 15.” states WFLA-TV. “The charges he’s facing include one count of organized fraud, 17 counts of communications fraud, one count of fraudulent use of personal information with over $100,000 or 30 or more victims, 10 counts of fraudulent use of personal information and one count of access to computer or electronic device without authority.”
Hillsborough State Attorney Andrew Warren filed charges against Clark for being the “mastermind” behind the attack that compromised 130 accounts.
The teen is believed to have gained access to Twitter’s backend, then he used an internal tool to take over several high-profile accounts and promote a cryptocurrency scam. The attackers posted messages urging the followers of the hacked accounts to send money to a specific bitcoin wallet address to receive back larger sums.
The hackers were able to take control of 45 of them sending out some posts on behalf of the owners, and downloaded data from eight.
The list of hacked accounts includes Barrack Obama, Joe Biden, Bill Gates, Elon Musk, Jeff Bezos, Apple, Uber, Kanye West, Kim Kardashian, Michael Bloomberg, and others.
With this fraudulent scheme, threat actors obtained nearly $120,000 worth of
bitcoins (approximately 12.86 bitcoins were amassed by attackers in “accounts
associated with Clark”) from the unaware followers of the hacked accounts.
Below some of the charges reported in a press release from Warren’s office:
organized fraud (over $50,000) – 1 count
communications fraud (over $300) –
17 counts
fraudulent use of personal information (over $100,000 or 30 or more
victims) – 1 count
fraudulent use of personal information – 10 counts
access computer or electronic device without authority (scheme to defraud) – 1
count
In a separate announcement, the US Department of Justice announced
additional charges against two Clark’s accomplices, Mason Sheppard (19), aka
“Chaewon,” and Nima Fazeli (22), aka “Rolex,” from Orlando, Florida.
“Mason
Sheppard, aka “Chaewon,” 19, of Bognor Regis, in the United Kingdom, was charged
in a criminal complaint in the Northern District of California with conspiracy
to commit wire fraud, conspiracy to commit money laundering, and the intentional
access of a protected computer.” states the DoJ.
“Nima Fazeli, aka “Rolex,” 22, of Orlando, Florida, was charged in a criminal complaint in the Northern District of California with aiding and abetting the intentional access of a protected computer.
The third defendant is a juvenile. With exceptions that do not apply to this case, juvenile proceedings in federal court are sealed to protect the identity of the juvenile.”
Twitter: Epic Account Hack Caused by Mobile Spearphishing
1.8.2020
Attack Social
Threatpost
Hackers “mislead certain employees” to gain access to internal tools to take over high-profile accounts and push out a Bitcoin scam.
A mobile spearphishing attack targeting “a small number of employees” is what led to the unprecedented, major attack earlier in the month on high-profile Twitter accounts to push out a Bitcoin scam.
The company posted an update late Thursday on the situation, which has been unfolding since July 15, when 130 accounts of high-profile users such as Bill Gates, Elon Musk, Apple and Uber each were hijacked at the same time to promote a bogus advance-fee cryptocurrency deal.
“This attack relied on a significant and concerted attempt to mislead certain employees, and exploit human vulnerabilities, to gain access to our internal systems,” the company said in its update. “This was a striking reminder of how important each person on our team is in protecting our service.”
On the day of the attack, Twitter revealed that the accounts fell victim to a compromise of the company’s internal systems by a group of unidentified hackers that managed to access Twitter company tools and secure employee privileges. Until Thursday, Twitter had not yet confirmed exactly how attackers got access to those internal tools, a point that the company has now clarified.
The attack required threat actors to obtain access to both Twitter’s internal network via specific employee credentials, the company said Thursday.
Since not all of the employees that were initially targeted had permissions to use the account management tools key to the attack, the attackers used a two-step approach to hack their way in, according to Twitter. First they used the initial credentials they phished to access some of Twitter’s internal systems and learn information about company processes, according to the post.
“This knowledge then enabled them to target additional employees who did have access to our account-support tools,” the company said. “Using the credentials of employees with access to these tools, the attackers targeted 130 Twitter accounts, ultimately tweeting from 45, accessing the [direct messages (DM)] inbox of 36, and downloading the Twitter Data of seven.”
An elected official in the Netherlands was one of those whose DMs (direct messages) were leaked; however, attackers did not access data for any of the former U.S. elected officials whose accounts were breached, the company said.
Once it was aware of the attack, Twitter immediately locked down thousands of verified accounts belonging to elite Twitter users and high-profile companies to try to prevent hackers from perpetrating the scam. The attack involved sending tweets from each of the hijacked accounts to promote a bogus Bitcoin deal, which promised to double the value of Bitcoin currency sent to one specific wallet.
Twitter acknowledged Thursday that there has been “concern following this incident around our tools and levels of employee access,” and said that it’s taking steps and updating its account tools to make them more “sophisticated” to prevent such a breach in the future.
Those steps include significantly limiting access to internal tools and systems to ensure ongoing account security while the company completes its investigation. This unfortunately will result in some disruption of user account service, including limiting access to the Twitter Data download feature and other processes, Twitter acknowledged.
“We will be slower to respond to account support needs, reported tweets and applications to our developer platform,” the company said in the update. “We’re sorry for any delays this causes, but we believe it’s a necessary precaution as we make durable changes to our processes and tooling as a result of this incident.”
The company continues to investigate the attack and work with “appropriate authorities” to identify and those responsible. In the meantime, there continues to be widespread speculation and reported evidence about who may be behind the hack, but no solid conclusions.
Some of the strongest evidence about the potential perpetrators was published in a number of reports pointing to the sale of Twitter account access by hackers obsessed with so-called “OG handles,” which are short-character profile names that confer a measure of status and wealth in certain online communities.
Another plausible theory also emerged around screenshots of Twitter’s internal tools that appeared on underground forums ahead of the attacks due to a bribe of a lone rogue Twitter employee, but Twitter later refuted this claim.
The FBI is said to be taking the lead in the investigation due to the massive privacy, legislative and business ramifications of the incident.
NSO Group Impersonates Facebook Security Team to Spread Spyware — Report
22.5.2020 Threatpost CyberCrime
Social
An investigation traces an NSO Group-controlled IP address to
a fake Facebook security portal.
According to an investigative journalist team, the Israeli authors of the infamous Pegasus mobile spyware, NSO Group, have been using a spoofed Facebook login page, crafted to look like an internal Facebook security team portal, to lure victims in.
The news comes as Facebook alleges that NSO Group has been using U.S.-based infrastructure to launch espionage attacks. Both issues are relevant to Facebook’s quest to hold NSO accountable under U.S. laws (specifically the Computer Fraud and Abuse Act) for a spate of WhatsApp hacks that came to light last year.
Pegasus, which infects both Android and Apple smartphones, contains a host of spy features. After scanning the target’s device, it installs the necessary modules to read the user’s messages and mail, listen to calls, capture screenshots, log pressed keys, exfiltrate browser history and contacts and carry out other surveillance tasks as needed. It’s widely believed to have been involved in spying on murdered Saudi dissident Jamal Khashoggi, journalists investigating cartel activity in Mexico and more.
“A former NSO employee provided Motherboard with the IP address of a server setup to infect phones with NSO’s Pegasus hacking tool,” according to a Motherboard investigative report this week. “The IP address provided to Motherboard related to a one-click installation of Pegasus, the former employee said.”
Motherboard’s investigation, partnering with DomainTools and RiskIQ, involved a review of passive domain name server (DNS) records to uncover where the IP address controlled by NSO Group resolved to.
“Throughout 2015 and 2016, the IP address resolved to 10 domains,” the team wrote, one of which impersonated Facebook’s security team. The others were designed to appear as innocuous unsubscribe links, and others were crafted to look like package-tracking links from FedEx.
“Mobile devices are designed for accessibility, convenience and speed – extra security gets in the way of those benefits,” Colin Bastable, CEO of Lucy Security, told Threatpost. “Facebook’s brand property makes it ideal for exploitation by hackers, and in this case the use of a site designed to emulate the Facebook security team is especially adroit.”
Meanwhile, Facebook is in the process of suing the NSO Group over its alleged use of a zero-day exploit for Facebook-owned WhatsApp. In May 2019, a zero-day vulnerability was found in WhatsApp’s messaging platform, exploited by attackers who were able to inject the Pegasus spyware onto victims’ phones in targeted campaigns.
The lawsuit alleges that NSO Group used vulnerable WhatsApp servers to send malware to approximately 1,400 mobile devices. CitizenLab, which assisted Facebook’s investigation into the issue, said that it identified over 100 cases of abusive targeting of human-rights defenders and journalists in at least 20 countries across the globe stemming from NSO Group’s spyware.
Facebook also claims to have evidence that NSO Group launched some of its
WhatsApp hacks last year from cloud infrastructure hosted in the U.S.: Court
documents filed by Facebook in April detailing alleged specific U.S. IP
addresses used by NSO Group, hosted by California-based QuadraNet as well as
Amazon.
Facebook also recently filed a lawsuit against related U.S.-based domain registrars Namecheap and Whoisguard, for registering more than 45 domains spoofing Facebook and its services. In a related link to the NSO Group situation, the IP address provided to Motherboard by the NSO Group former employee allegedly resolved to domains registered with Namecheap, including the fake Facebook security portal, Motherboard noted.
Lucy Security’s Bastable pointed out that at the heart of this lies what are essentially phishing pages – even though NSO Group’s activity might be nation-state-level in terms of sophistication, the real exploit at work is of people.
“CISOs need to stop thinking of mobile devices as end-points: the real end-points are the people holding those devices,” he noted. “All the tech in the world is not going to protect users from determined attackers, but teaching people not to click on potentially dangerous links and to be suspicious of uninvited SMS messages and emails would save many people a lot of grief.”
For its part, NSO Group maintains that it is not a highest-bidder black-market exploit broker, that it’s not in the illicit spy business, and that it offers its wares only to legitimate governments for legitimate uses.
“Revisiting and recycling the conjecture of NSO’s detractors, such as CitizenLab, doesn’t change the overall truth of our position, which we have stated to the U.S. Federal Court in California,” an NSO spokesperson told Motherboard. “Our factual assertions have been provided as part of the official court record, and we do not have anything else to add at this time.”
Facebook Unveils Scam Warnings for Messenger Users
22.5.2020
Securityweek Social
Facebook on
Thursday said that its Messenger app will be watching behind the scenes for
scammers using the smartphone communication system.
Safety notices will pop up in Messenger text chats if activity taking place in the background is deemed suspicious by artificial intelligence software, according to director of privacy and safety product management Jay Sullivan.
He said the new safety feature "will help millions of people avoid potentially harmful interactions and possible scams without compromising their privacy."
The feature began rolling out to the Messenger app tailored for Android-powered smartphones in March and will head to Messenger on iPhones next week, according to Facebook.
"Too often people interact with someone online they think they know or trust, when it’s really a scammer or imposter," Sullivan said.
"These accounts can be hard to identify at first and the results can be costly."
Artificial intelligence software scans for scammers based on account behavior, such as sending messages in bulk targeting demographics or geographies, according to Facebook.
Warning notices pop up before people respond to messages of possibly dubious origins.
Since the feature does not involve looking at what is in messages, it should continue to add a layer of safety when Messenger takes to encrypted missives as planned by Facebook.
"As we move to end-to-end encryption, we are investing in privacy-preserving tools like this to keep people safe without accessing message content," Sullivan said.
Messenger already uses software tools to fight spam and thwart efforts by adults to contact minors they don't appear to know.
Messenger has been ramping up capabilities and security as use of online tools to communicate and socialize surges due to restrictions of movement during the pandemic.
Facebook recently unveiled a new video chat service with virtual "rooms" where people can pop in to visit friends, aiming at users turning to the popular Zoom platform during the pandemic.
Facebook Chief Wants EU Not China to Lead on Tech Rules
18.5.2020
Securityweek BigBrothers
Social
Facebook founder Mark Zuckerberg on Monday urged the European
Union to take the lead in setting global standards for tech regulation or risk
seeing countries follow China as a model.
"I think right now a lot of other countries are looking at China... and saying: 'Hey, that model looks like maybe it might work. Maybe it gives our government more control?'," Zuckerberg said, during a video debate with EU commissioner Thierry Breton.
Under the Beijing model, "you don't have to respect human rights quite as much in how the society gets run," he added.
"I just think that that's really dangerous and I worry about that kind of model spreading to other countries," Zuckerberg said in the talk, organised by the Centre on Regulation in Europe
"I think that the best antidote to that is having a clear regulatory framework that comes out of Western democratic countries, and that can become a standard around the world," he argued.
"When Europe sets policies, they often become the standards around the world," he said, citing the EU's GDPR data protection legislation, which has been widely replicated.
Breton, one of the EU's top officials on tech policy, said that Facebook and other big tech companies must also live up to certain values.
If you want to have the right regulation "you have to have a clear set of values and in Europe we have these values," he said, hinting Facebook sometimes fell short, especially on controlling illegal content or paying fair taxes.
"At the end of the day, if we cannot find a way, we will regulate, of course," he warned
- Lobbying drive -
"It is extremely important that when you are CEO, at the end of the day, you are the only one to be responsible," Breton said.
"The mission of a CEO is to listen to everyone and then to take the decision. At the end of the day, it will be Mark who will be responsible, nobody else."
The debate came as Facebook embarks on a European lobbying campaign.
The European Commission is ramping up towards a Digital Service Act, a major piece of EU lawmaking intended to curb the powers of US big tech.
The law would include all aspects of the digital world, including cracking down on hate speech, protecting user data and preventing big companies from abusing their dominant market positions.
Silicon Valley firms are preparing a furious lobbying counterattack to limit its reach.
Left unchecked, the law could force Facebook, Google, Amazon or Apple to split their businesses, provide rivals access to their data and act more as public utilities and not profit-seeking innovators.
The law would also make the giants liable for illegal content -- such as hate speech or pirated music -- reversing a laissez faire policy they say fueled the internet revolution.
NortonLifeLock Releases Free Tool for Detecting Bots on Twitter
16.5.2020
Securityweek
Social
NortonLifeLock this week released the beta version of a free
browser extension that allows Twitter users to easily identify bots on the
social media platform.
The tool, named BotSight, is currently available for Chrome, Chromium-based Brave, and Firefox for users in the US, UK, Australia and New Zealand. Its developers also plan on creating a smartphone app and a version that works with Microsoft Edge.
BotSight was created by the NortonLifeLock Research Group, formerly known as Symantec Research Labs — the NortonLifeLock brand was created after Symantec sold its enterprise security unit and Symantec brand to Broadcom for $10.7 billion.
NortonLifeLock says BotSight, which it describes as a research prototype, uses a machine learning model to detect Twitter bots with a high degree of accuracy, including in tweets displayed in the user’s timeline, search and trending topics. It analyzes more than 20 features to determine if a Twitter account is a bot, including the account name and description, and its follower increase rate.
When users install the BotSight extension, they will see a percentage and a green, yellow or red icon next to the name of each profile, including ones mentioned in a tweet. This icon indicates the likelihood of an account being a human or bot.
The company has so far analyzed more than 100,000 accounts and found that roughly 5% of tweets are posted by bots.
“In our analysis of recent coronavirus-related tweets, we found that between 6-18% of users tweeting on this subject were bots, depending on which time period we sampled, while a random sample of the Twitter stream indicates 4-8% bot activity by volume over the same time period. This contrast shows that bots are strategic about their behaviour: favoring current events to maximize their impact,” said Daniel Kats, principal researcher at the NortonLifeLock Research Group.
NortonLifeLock this week reported a $614 million revenue for the fourth quarter of fiscal year 2020, slightly lower than the $617 million reported one year ago.
Login with Facebook Bug Earns $20K Bounty
15.5.20 Threatpost Social
The cross-site scripting vulnerability could have allowed trivial account takeover.
Facebook has awarded a security researcher $20,000 for discovering a cross-site scripting (XSS) vulnerability in the Facebook Login SDK, which is used by developers to add a “Continue with Facebook” button to a page as an authentication method. Exploitation could allow threat actors to hijack accounts.
Security researcher Vinoth Kumar identified a Document Object Model-based (DOM) XSS flaw in the window.postMessage() method of the platform’s code. This method is supposed to enable secure cross-origin communication between Windows objects.
Kumar said he discovered the flaw when he went digging for client-side vulnerabilities—more specifically, XSSI, JSONP and postMessage issues, according to a recent blog post.
However, many of these flaws proved difficult to find, so he narrowed his focus to postMessage vulnerabilities, “as this is mostly ignored by security researchers, but it’s very easy to debug and no need to bypass firewalls,” he wrote in the post.
Kumar also created a Chrome extension to view/log cross-window communication happening on the page to make his search easier, he said.
The researcher first began exploring Facebook’s third-party plug-ins on its developer site to try to find iframe issues. iframes are used to embed one document within another, current HTML document. He discovered an issue there in the Facebook Login SDK for JavaScript.
He found that the SDK was creating a proxy iframe v6.0/plugins/login_button.php for cross-domain communication, while the proxy frame renders the “Continue with Facebook” button.
“The interesting thing was the JavaScript SDK sends [a] payload to the proxy frame, which contains the button’s click URL,” he explained. So, when the user clicks the “Continue with Facebook” button, the URL from the postMessage payload executes in the proxy iframe, which leads to the execution of the JavaScript on Facebook.com.
However, “there’s no URL/schema validation in the JavaScript” to check that the URL request is coming from the legitimate source, he explained, thus opening the door for malicious hijacking.
“So if we send a payload with [the] URL ‘javascript:alert(document.domain)’ to the https://www.facebook.com/v6.0/plugins/login_button.php iframe and the user clicks the ‘Continue With Facebook’ button, javascript:alert(document.domain) would be executed on facebook.com domain,” Kumar explained in his post.
Kumar outlined two ways to exploit the vulnerability. One is by opening a pop-up window, and the other is by opening an iframe — and then communicating with either. He provided code samples for both of these exploits, and posted a YouTube video proof of concept. The result of either of the attacks is that an attacker can hijack and take over someone’s account.
Kumar initially notified Facebook of the vulnerability on April 17. The company three days later pushed out a fix for it that adds a facebook.com regex domain and schema check in the payload URL parameter, he said.
On April 29, Facebook confirmed that the bug was fixed and paid Kumar his bug bounty on May 1.
Facebook has had a bug-bounty program in place since 2011. According to the program’s guidelines, $20,000 is a significant sum of money to be paid for the identification of a vulnerability.
The highest bounty that Facebook has paid to date has been $50,000, to a researcher who identified a bug in Facebook’s developer subscription mechanism that could allow for a misuse in notifications on certain types of user activity.
Facebook Awards Researcher $20,000 for Account Hijacking Vulnerability
13.5.2020
Securityweek
Social
Security researcher Vinoth Kumar says Facebook awarded him $20,000 after he discovered and reported a Document Object Model-based cross-site scripting (DOM XSS) vulnerability that could have been exploited to hijack accounts.
The researcher says he discovered the vulnerability in the window.postMessage() method, which is meant to safely enable cross-origin communication between Window objects.
The process of identifying the vulnerability, the researcher says, began with the Facebook Login SDK for JavaScript, which creates a proxy iframe v6.0/plugins/login_button.php for cross-domain communication.
What Kumar discovered was that the login SDK sends an initial payload to the proxy iframe, and that the payload contains the click URL of the 'Continue with Facebook' button, which is rendered in the proxy iframe.
When the user clicks the 'Continue with Facebook' button, the URL from the postMessage payload is executed in the proxy iframe, which leads to JavaScript being executed on Facebook.com.
The researcher identified two manners in which the vulnerability could be exploited, one involving opening a pop-up window and then communicating with it, and the other relying on opening an iframe and communicating with it.
Successful exploitation of the vulnerability would have allowed an attacker to obtain the victim’s session cookies and hijack their account.
“Due to an incorrect post message configuration, someone visiting an attacker-controlled website and clicks login with the Facebook button would trigger XSS on facebook.com domain behalf of logged-in user. This would have let to 1-click account takeover,” Kumar explains.
He has published a video to demonstrate the attack:
Facebook was informed about the discovery on April 17. The social media platform addressed the vulnerability three days later by “adding facebook.com regex domain and schema check in the payload url param.” The company awarded the researcher a $20,000 bug bounty two weeks later.
Why a single online name and social cards will be the new norm
12.5.2020 Net-security Social
Each day, online users provide companies, organizations, and other individuals with vital personal information without much thought. As social networks and brands began to use this data to make money, people have lost their control over how their data is handled.
Just last year, data breaches hit an all-time high with a 17% rise from 2018. Many of these leaks have exposed the private data of hundreds of millions of individuals who shared it with financial institutions, healthcare providers, or social media platforms.
Over the last decade, the rise of social media giants sparked one of the most relevant conversations about privacy. The truth is that not much has changed in how platforms collect and handle our information. As users realize data is a commodity, they will start taking much more control of the usage, ownership, and value of their information than ever before.
A movement based on the principle of letting people own their digital identity
is brewing. Users are looking for ways to control their online persona, with
single online names and social cards becoming the norm — but what exactly are
these tools, and how do they empower consumers that want to take back control of
their data?
Your identity online – centralized
Every new service or subscription a person signs up for requires them to give out essential data, whether it’s healthcare information, social security numbers, age, gender, or income — all of which can be easily misused if found in the wrong hands. Just last year, one of the biggest data breaches in history took place. First American Corporation, a title settlement service company, had 885 million real estate documents compromised.
The integrity of your social information is not in safe hands either. Just two years ago, Facebook famously faced one its biggest scandals by allowing a third-party app to gather the information of more than 50 million people; said data ended up in the hands of Cambridge Analytica, a controversial firm, who used it to work with election campaign teams in many countries all over the world.
But the tides are turning: With new movements and demands for greater user privacy, we have seen various solutions emerge on the market. Investors are driving developments of decentralized data platforms, and supporting efforts to democratize data in unseen ways.
Taking control of one’s digital identity can be done through self-sovereign
identity (SSI). This is, in essence, a movement based on the idea that users
should be in control of their information, deciding how and with whom they share
it.
How do SSI cards work?
Current data storage methods are not only dangerous but inefficient for consumers. Using social cards allows the users to always be in control of their private information in a more flexible way, as it gives individuals the ability to set parameters on what others get to see. People may only permit employers to access their professional credentials, while their friends and family members get permission to their social information. It’s a matter of letting everyone decide to which degree of privacy they feel comfortable with.
The idea of self-sovereign identity – that is, a credential owned by an individual, to be accessed only with the individual’s express consent – has existed for years; yet it’s only with the expansion of blockchain technology that it has become a feasible concept for consumers. Blockchain, along with platforms like IPFS and Hyperledger allows for a decentralized solution directly tackling the privacy issues of vulnerable data storage, given the encrypted nature of these tools.
This blockchain identity is both verifiable and immutable; there’s no chance of
misinformation when users know exactly who’s requesting their data and what that
data says. The path toward a self-sovereign identity is difficult to predict.
There are many challenges related to governance, policy, and trust frameworks
that have not been tackled. However, each day SSI gains more traction, and this
discussion becomes inevitable.
Peek behind the curtain
One of the biggest challenges is the standardization of SSI, which is a conversation that is bound to happen on a government level as the number of individuals adopting said technology grows. This adoption may take time, but with pressures both from top stakeholders and consumers, we’re moving towards widespread adoption.
By 2030, the United Nations wants to provide a universal identity for all human beings on the planet. This blockchain-powered solution could allow each person to hold a credential tied to their fingerprints, birth date, medical records, education, travel, bank accounts, and more. Although the extent of the Self Sovereign part is still under discussion, the technology could provide a secure and trackable ID to everyone.
While the future is uncertain, the way consumers perceive and handle their data is changing fast. Suggesting blockchain as a miracle solution for any issue is often criticized, but decentralizing online identity is one of its strongest features. Hopefully a transition to self-sovereign identity could help individuals gain back control of where their personal information is located, letting them have authority over themselves.
Twitter warns of legacy site theme shutting down on June 1
10.5.2020
Bleepingcomputer
Social
Twitter is warning users impersonating unsupported browsers to enable the original site theme that the legacy version will be shut down on June 1st, 2020.
In July 2019, Twitter began rolling out a new site interface that many, including myself, was greatly inferior to the legacy template.
It was quickly discovered that if you installed a browser extension to trick Twitter into thinking you were running Internet Explorer 11, which is unsupported, Twitter would continue to show you the older site template.
For those who are using this trick to impersonate Internet Explorer 11, Twitter has started to display a warning that states this trick is going to stop working on June 1st, 2020, when they will shut down the original legacy version of Twitter.
"This is the legacy version of twitter.com. We will be shutting it down on June 1, 2020. Please switch to a supported browser, or disable the extension which masks your browser. You can see a list of supported browsers in our Help Center."
New Twitter warning about legacy version
The help article states that
Twitter's supported browsers are Firefox, Edge, Safari, and Google Chrome.
While it has been a good run, it looks like we all get to experience Twitter's new theme, whether we want it or not, starting on June 1st, 2020.