14.3.23 Virus The Hacker News
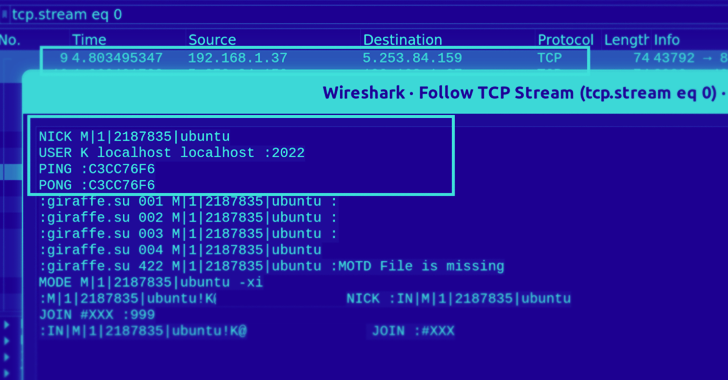
A new Golang-based malware dubbed GoBruteforcer has been found targeting web servers running phpMyAdmin, MySQL, FTP, and Postgres to corral the devices into a botnet.
GoBruteforcer: New Golang-Based Malware Breaches Web Servers Via Brute-Force Attacks
14.3.23 Virus The Hacker News
A new Golang-based malware dubbed GoBruteforcer has been found targeting web servers running phpMyAdmin, MySQL, FTP, and Postgres to corral the devices into a botnet.
"GoBruteforcer chose a Classless Inter-Domain Routing (CIDR) block for scanning the network during the attack, and it targeted all IP addresses within that CIDR range," Palo Alto Networks Unit 42 researchers said.
"The threat actor chose CIDR block scanning as a way to get access to a wide range of target hosts on different IPs within a network instead of using a single IP address as a target."
The malware is mainly designed to single out Unix-like platforms running x86, x64 and ARM architectures, with GoBruteforcer attempting to obtain access via a brute-force attack using a list of credentials hard-coded into the binary.
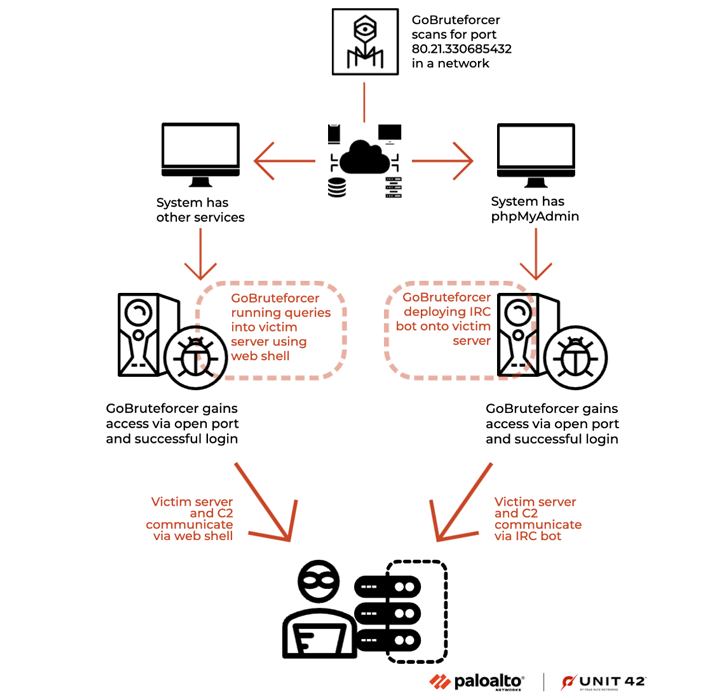
If the attack proves to be successful, an internet relay chat (IRC) bot is deployed on the victim server to establish communications with an actor-controlled server.
GoBruteforcer also leverages a PHP web shell already installed in the victim server to glean more details about the targeted network.
That said, the exact initial intrusion vector used to deliver both GoBruteforcer and the PHP web shell is undetermined as yet. Artifacts collected by the cybersecurity company suggest active development efforts to evolve its tactics and evade detection.
The findings are yet another indication of how threat actors are increasingly adopting Golang to develop cross-platform malware. What's more, GoBruteforcer's multi-scan capability enables it to breach a broad set of targets, making it a potent threat.
"Web servers have always been a lucrative target for threat actors," Unit 42 said. "Weak passwords could lead to serious threats as web servers are an indispensable part of an organization. Malware like GoBruteforcer takes advantage of weak (or default) passwords."
Warning: AI-generated YouTube Video Tutorials Spreading Infostealer Malware
13.3.23 Virus The Hacker News 
Threat actors have been increasingly observed using AI-generated YouTube Videos to spread a variety of stealer malware such as Raccoon, RedLine, and Vidar.
"The videos lure users by pretending to be tutorials on how to download cracked versions of software such as Photoshop, Premiere Pro, Autodesk 3ds Max, AutoCAD, and other products that are licensed products available only to paid users," CloudSEK researcher Pavan Karthick M said.
Just as the ransomware landscape comprises core developers and affiliates who are in charge of identifying potential targets and actually carrying out the attacks, the information stealer ecosystem also consists of threat actors known as traffers who are recruited to spread the malware using different methods.
One of the popular malware distribution channels is YouTube, with CloudSEK witnessing a 200-300% month-over-month increase in videos containing links to stealer malware in the description section.
These links are often obfuscated using URL shorteners like Bitly and Cuttly, or alternatively hosted on MediaFire, Google Drive, Discord, GitHub, and Telegram's Telegra.ph.
In several instances, threat actors leverage data leaks and social engineering to hijack legitimate YouTube accounts and push malware, often targeting popular accounts to reach a large audience in a short span of time.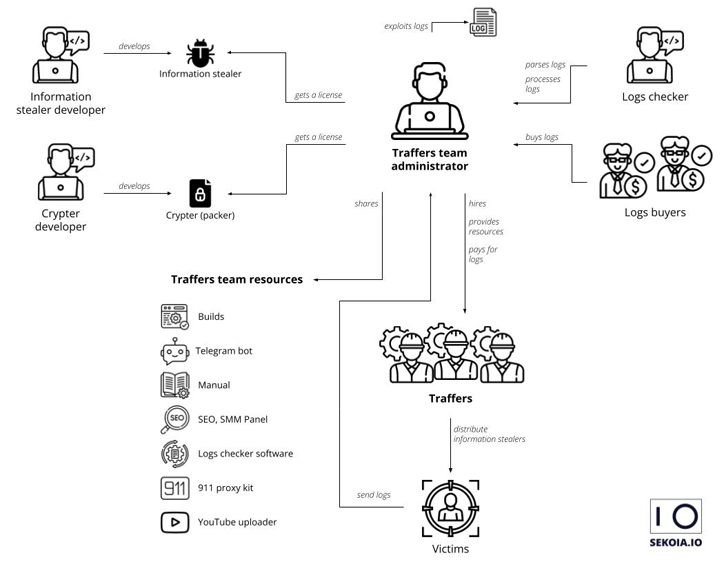
"Uploading to such accounts lends video legitimacy as well," Karthick explained. "However, such Youtubers will report their account taker to YouTube and gain access back to their accounts within a few hours. But in a few hours, hundreds of users could have fallen prey."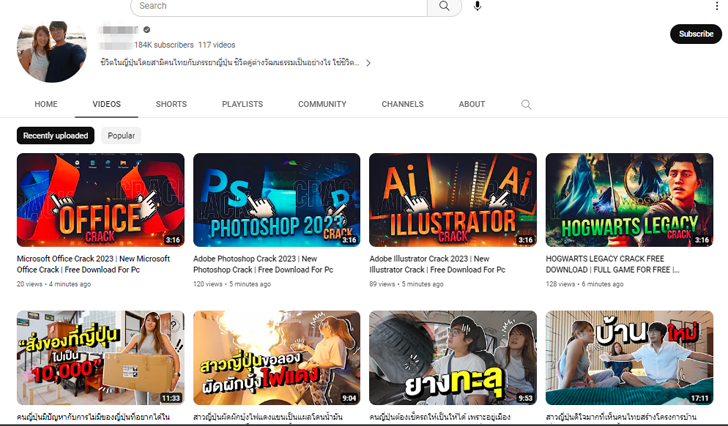
More ominously, anywhere between five to 10 crack download videos are uploaded to the video platform every hour, with the threat actors employing search engine optimization (SEO) poisoning techniques to make the videos appear at the top of the list.
Threat actors have also been observed to add fake comments to the uploaded videos to further mislead and entice users into downloading the cracked software.
The development comes amid a surge in new information stealer variants like SYS01stealer, S1deload, Stealc, Titan, ImBetter, WhiteSnake, and Lumma that are offered for sale and come with capabilities to plunder sensitive data under the guise of popular apps and services.
The findings also follow the discovery of a ready-to-use toolkit called R3NIN Sniffer that can enable threat actors to siphon payment card data from compromised e-commerce websites.
To mitigate risks posed by stealer malware, users are recommended to enable multi-factor authentication, refrain from clicking on unknown links, and avoid downloading or using pirated software.