28.5.23 Virus The Hacker News

A new strain of malicious software that's engineered to penetrate and disrupt critical systems in industrial environments has been unearthed.
New COSMICENERGY Malware Exploits ICS Protocol to Sabotage Power Grids
28.5.23 Virus The Hacker News
A new strain of malicious software that's engineered to penetrate and disrupt critical systems in industrial environments has been unearthed.
Google-owned threat intelligence firm Mandiant dubbed the malware COSMICENERGY, adding it was uploaded to the VirusTotal public malware scanning utility in December 2021 by a submitter in Russia. There is no evidence that it has been put to use in the wild.
"The malware is designed to cause electric power disruption by interacting with IEC 60870-5-104 (IEC-104) devices, such as remote terminal units (RTUs), that are commonly leveraged in electric transmission and distribution operations in Europe, the Middle East, and Asia," the company said.
COSMICENERGY is the latest addition to specialized malware like Stuxnet, Havex, Triton, IRONGATE, BlackEnergy2, Industroyer, and PIPEDREAM, which are capable of sabotaging critical systems and wreaking havoc.
Mandiant said that there are circumstantial links that it may have been developed as a red teaming tool by Russian telecom firm Rostelecom-Solar to simulate power disruption and emergency response exercises that were held in October 2021.
This raises the possibility that the malware was either developed to recreate realistic attack scenarios against energy grid assets to test defenses or another party reused code associated with the cyber range.
The second alternative is not unheard of, especially in light of the fact that threat actors are known to adapt and repurpose legitimate red team and post-exploitation tools for malicious ends.
COSMICENERGY's features are comparable to that of Industroyer – which has been attributed to the Kremlin-backed Sandworm group – owing to its ability to exploit an industrial communication protocol called IEC-104 to issue commands to RTUs.
"Leveraging this access, an attacker can send remote commands to affect the actuation of power line switches and circuit breakers to cause power disruption," Mandiant said.
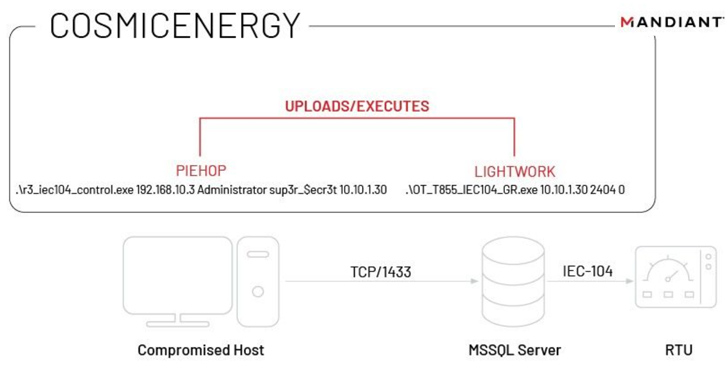
This is accomplished by means of two components called PIEHOP and LIGHTWORK, which are two disruption tools written in Python and C++, respectively, to transmit the IEC-104 commands to the connected industrial equipment.
Another notable aspect of the industrial control system (ICS) malware is the lack of intrusion and discovery capabilities, meaning it requires the operator to perform an internal reconnaissance of the network to determine the IEC-104 device IP addresses to be targeted.
To pull off an attack, a threat actor would therefore have to infect a computer within the network, find a Microsoft SQL Server that has access to the RTUs, and obtain its credentials.
PIEHOP is then run on the machine to upload LIGHTWORK to the server, which sends disruptive remote commands to modify the state of the units (ON or OFF) over TCP. It also immediately deletes the executable after issuing the instructions.
The fact that an ICS malware family has been identified prior to it being actively used in real-world attacks makes it an unusual find, Daniel Kapellmann Zafra, analysis manager at Google Cloud's Mandiant Intelligence division, told The Hacker News.
"While COSMICENERGY's capabilities are not significantly different from previous OT malware families', its discovery highlights several notable developments in the OT threat landscape," Mandiant said.
"The discovery of new OT malware presents an immediate threat to affected organizations, since these discoveries are rare and because the malware principally takes advantage of insecure by design features of OT environments that are unlikely to be remedied any time soon."
"One of the main lessons from COSMICENERGY is that defenders should be familiar with prior OT [operational technology] malware families, their capabilities, and how they work," Kapellmann Zafra said.
"Knowledge about this can help defenders to sustain threat hunting and detection programs that rigorously look for behaviors that are known to be suspicious in OT networks."