Newly Uncovered ThirdEye Windows-Based Malware Steals Sensitive Data
30.6.23 Virus The Hacker News
A previously undocumented Windows-based information stealer called ThirdEye has been discovered in the wild with capabilities to harvest sensitive data from infected hosts.
Fortinet FortiGuard Labs, which made the discovery, said it found the malware in an executable that masqueraded as a PDF file with a Russian name "CMK Правила оформления больничных листов.pdf.exe," which translates to "CMK Rules for issuing sick leaves.pdf.exe."
The arrival vector for the malware is presently unknown, although the nature of the lure points to it being used in a phishing campaign. The very first ThirdEye sample was uploaded to VirusTotal on April 4, 2023, with relatively fewer features.
The evolving stealer, like other malware families of its kind, is equipped to gather system metadata, including BIOS release date and vendor, total/free disk space on the C drive, currently running processes, register usernames, and volume information. The amassed details are then transmitted to a command-and-control (C2) server.
A notable trait of the malware is that it uses the string "3rd_eye" to beacon its presence to the C2 server.
There are no signs to suggest that ThirdEye has been utilized in the wild. That having said, given that a majority of the stealer artifacts were uploaded to VirusTotal from Russia, it's likely that the malicious activity is aimed at Russian-speaking organizations.
"While this malware is not considered sophisticated, it's designed to steal various information from compromised machines that can be used as stepping-stones for future attacks," Fortinet researchers said, adding the collected data is "valuable for understanding and narrowing down potential targets."
The development comes as trojanized installers for the popular Super Mario Bros video game franchise hosted on sketchy torrent sites are being used to propagate cryptocurrency miners and an open-source stealer written in C# called Umbral that exfiltrates data of interest using Discord Webhooks.
"The combination of mining and stealing activities leads to financial losses, a substantial decline in the victim's system performance, and the depletion of valuable system resources," Cyble said.
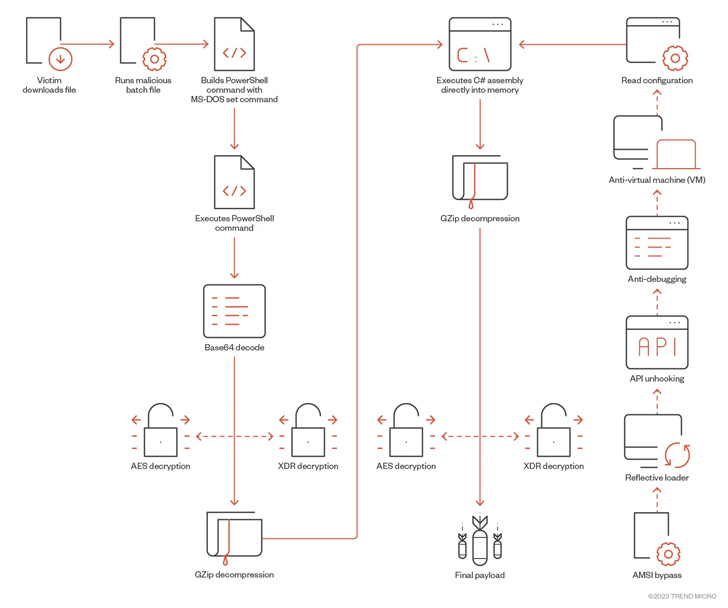
SeroXen infection chain
Video game users have also been targeted with Python-based ransomware and a remote access trojan dubbed SeroXen, which has been found to take advantage of a commercial batch file obfuscation engine known as ScrubCrypt (aka BatCloak) to evade detection. Evidence shows that actors associated with SeroXen's development have also contributed to the creation of ScrubCrypt.
Cybersecurity
The malware, which was advertised for sale on a clearnet website that was registered on March 27, 2023, prior to its shutdown in late May, has further been promoted on Discord, TikTok, Twitter, and YouTube. A cracked version of SeroXen has since found its way to criminal forums.
"Individuals are strongly advised to adopt a skeptical stance when encountering links and software packages associated with terms such as 'cheats,' 'hacks,' 'cracks,' and other pieces of software related to gaining a competitive edge," Trend Micro noted in a new analysis of SeroXen.
"The addition of SeroXen and BatCloak to the malware arsenal of malicious actors highlights the evolution of FUD obfuscators with a low barrier to entry. The almost-amateur approach of using social media for aggressive promotion, considering how it can be easily traced, makes these developers seem like novices by advanced threat actors' standards."
