6.9.23 Vulnerebility The Hacker News
Nine security flaws have been disclosed in electric power management products made by Schweitzer Engineering Laboratories (SEL).
9 Alarming Vulnerabilities Uncovered in SEL's Power Management Products
6.9.23 Vulnerebility The Hacker News
Nine security flaws have been disclosed in electric power management products made by Schweitzer Engineering Laboratories (SEL).
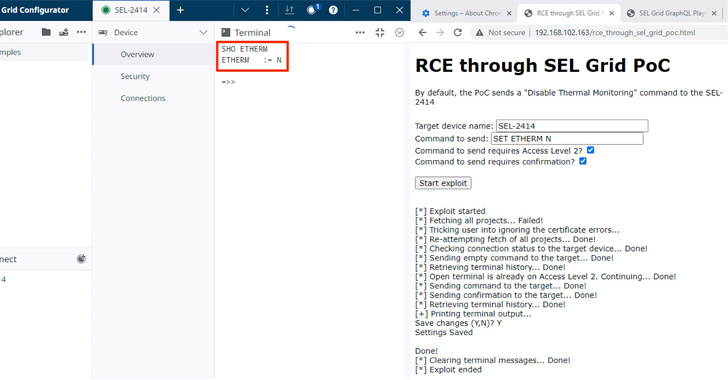
"The most severe of those nine vulnerabilities would allow a threat actor to facilitate remote code execution (RCE) on an engineering workstation," Nozomi Networks said in a report published last week.
The issues, tracked as CVE-2023-34392 and from CVE-2023-31168 through CVE-2023-31175, have CVSS severity scores ranging from 4.8 to 8.8 and impact SEL-5030 acSELeratorQuickSet and SEL-5037 GridConfigurator, which are used to commission, configure, and monitor the devices.
Exploitation of CVE-2023-31171 could be achieved by sending a phishing email that tricks a victim engineer into importing a specially crafted configuration file to achieve arbitrary code execution on the engineering workstation running the SEL software.
Cybersecurity
What's more, the shortcoming can be chained with CVE-2023-31175 to obtain administrative privileges on the target workstation. CVE-2023-34392, on the other hand, could be weaponized by an adversary to stealthily send arbitrary commands to the machines by means of a watering hole attack.
The latest research adds to a set of 19 security vulnerabilities previously reported in the SEL Real Time Automation Controller (RTAC) suite (from CVE-2023-31148 through CVE-2023-31166) that could be exploited to "obtain unauthorized access to the web interface, alter displayed information, manipulate its logic, perform man-in-the-middle (MitM) attacks, or execute arbitrary code."
In July 2023, the operational technology security company also followed upon last years' findings, detecting five new vulnerabilities affecting the American Megatrends (AMI) MegaRAC BMC software solution that could permit an attacker to achieve reset-resistant persistence and conceal a backdoor on the web-based BMC management interface.
"This backdoor access could persist even across reinstallations of the host operating system or hard resets of the BMC configuration itself," Nozomi Networks said.
Since then, 14 more security bugs have been unearthed in the Phoenix Contact Web Panel 6121-WXPS, including four critical-severity flaws, that could be exploited by a remote attacker to completely compromise the appliances.
The development comes as the U.S. Cybersecurity and Infrastructure Security Agency (CISA) has partnered with MITRE to develop an extension for the Caldera cyber attack emulation platform that's specifically centered around operational technology (OT) networks.