
- Apple -
Last update 09.10.2017 13:46:27
Introduction List Kategorie Subcategory 0 1 2 3 4 5 6 7 8
Apple Patches BroadPwn Bug in iOS 10.3.3
21.7.2017 Threapost Apple
Apple released iOS 10.3.3 Wednesday, which serves as a cumulative update that includes patches for multiple vulnerabilities including the high-profile BroadPwn bug that allowed an attacker to seize control of a targeted iOS device.
BroadPwn was revealed earlier this month as a flaw in Broadcom Wi-Fi chipsets used in Apple and Android devices. Apple said the vulnerability affected the iPhone 5 to iPhone 7, the fourth-generation iPad and later versions, and the iPod Touch 6th generation.
Exodus Intelligence discovered the flaw (CVE-2017-3544), which was patched earlier this month on Android when Google released its July Android Security Bulletin. Nitay Artenstein, the researcher with Exodus Intelligence who discovered the vulnerability, is scheduled to do a talk on the vulnerability at Black Hat next week.
Yesterday’s Apple security updates also included fixes for its tvOS, iTunes and iCloud for Windows, the Safari browser, watchOS and macOS Sierra.
In addition to patching the BroadPwn vulnerability, Apple addressed 13 arbitrary code execution vulnerabilities tied to everything from a buffer overflow bug found in the Contacts (CVE-2017-7062) app and a memory corruption issue (CVE-2017-7009) in the CoreAudio component of the OS.
The open source web browser engine WebKit was also patched by Apple. One WebKit vulnerability (CVE-2017-7011) allowed an attacker to use a malicious website that could lead to an “address bar spoofing” attack. A second (CVE-2017-7019) WebKit memory corruption issue allowed an attacker to maliciously craft web content that could lead to arbitrary code execution on a targeted iOS device.
“The issue involves the ‘WebKit Page Loading’ component. It allows remote attackers to execute arbitrary code or cause a denial of service (memory corruption and application crash) via a crafted web site,” wrote Apple regarding CVE-2017-7019.
On Wednesday, Apple also released patches for macOS Sierra 10.12.6, as well as Security Update 2017-003 for El Capitan and Security Update 2017-003 for Yosemite. Four CVEs were associated with a memory corruption issue tied to all macOS operating systems. The vulnerability (CVE-2017-7031) is an “issue that involves the ‘Foundation’ component. It allows remote attackers to execute arbitrary code or cause a denial of service (memory corruption and application crash) via a crafted file,” according to Apple.
Apple also released iCloud for Windows 6.2.2 that addressed almost a dozen CVEs tied to bugs found by Google Project Zero researchers. Researcher Ivan Fratric, with Google Project Zero, is behind eight of the CVEs. Most of the bugs he found are related to iCloud memory corruption issues in WebKit. The flaw allowed the processing of maliciously crafted web content within the app that could lead to arbitrary code execution.
Apple’s watchOS 3.2.3 release snuffed out a number of bugs including one interesting vulnerability tied to the operating system’s libxml2 library, responsible for manipulating XML content, that impacted all watch models. “Parsing a maliciously crafted XML document may lead to disclosure of user information,” described Apple (CVE-2017-7013).
A memory corruption bug was patched in Apple’s tvOS (CVE-2017-7008) that could lead to arbitrary code execution if a maliciously crafted movie file was played on the device, Apple said.
Apple Patches Vulnerabilities Across All Platforms
20.7.2017 securityweek Vulnerebility Apple
Apple this week released security patches for all four of its operating systems to resolve tens of security bugs in each of them.
The tech giant addressed 37 vulnerabilities with the release of macOS Sierra 10.12.6 (and Security Update 2017-003 El Capitan and Security Update 2017-003 Yosemite). The vast majority of the issues could result in arbitrary code execution. Impacted components include audio, Bluetooth, contacts, Intel graphics driver, kernel, libarchive, and libxml2, Apple reveals.
The release of iOS 10.3.3 adressed 47 vulnerabilities, many allowing for arbitrary code execution and some for unexpected application termination or information disclosure. WebKit was the most affected component, with over 20 bugs squashed in it. Kernel, Safari, messages, contacts, libarchive, and libxml2 were also among the affected components.
Tracked as CVE-2017-9417 and affecting Broadcom's BCM4354, 4358, and 4359 chips, one of the vulnerabilities could allow an attacker within range to execute arbitrary code on the Wi-Fi chip. Because said chips are used in various smartphones, including devices from HTC, LG, and Samsung, Google too addressed the issue with its latest Android patches.
Apple addressed 16 security flaws with the release of watchOS 3.2.3, including CVE-2017-9417. Kernel was affected the most, with 9 bugs resolved in it. Contacts, IOUSBFamily, libarchive, libxml2, libxpc, messages, and Wi-Fi were also impacted. These vulnerabilities could result in arbitrary code execution, unexpected application termination, information disclosure, or an app’s ability to read restricted memory.
Apple's tvOS 10.2.2 resolves 38 bugs, most of which affect WebKit and Kernel (they were addressed in iOS and watchOS as well). Most of these issues could lead to arbitrary code execution, in some cases with elevated privileges (kernel or system), Apple notes in its advisory.
Apple also released Safari 10.1.2 this week, addressing a bug in Safari Printing and 24 issues in WebKit or related to it. iTunes 12.6.2 for Windows patches 23 security issues (one in iTunes, another in libxml2, and 21 in WebKit), while iCloud for Windows 6.2.2 resolves 22 vulnerabilities (one in libxml2 and 21 in WebKit).
Apple Builds Data Center in China, Promises No Backdoors
12.7.2017 securityweek Apple
Apple opens data center in China - Image Credits: flickr.com/photos/nez
Apple on Wednesday announced the establishment of its first China-based data center in an effort to improve its services in the region and comply with recently implemented regulations, but the tech giant has promised not to build any backdoors into its systems.
The new data center is located in China’s Guizhou province, which Apple selected following a “careful study” – the company said it was impressed with the local government’s leadership and its focus on environmental sustainability. Officials from the Guizhou province visited Silicon Valley last year to promote big data opportunities as part of a pilot program.
“In partnership with a local internet services company, Guizhou on the Cloud Big Data, we’re proud of the fact the facility will be fully powered by 100 percent renewable energy like all of our other data centers around the world,” Apple said in a statement sent to SecurityWeek.
"Our Chinese customers love using iCloud to store their photos, videos, documents and apps securely, and to keep them updated across all of their devices. We're committed to continuously improving the user experience, and the addition of this data center will allow us to improve the speed and reliability of our products and services while also complying with newly passed regulations,” Apple added.
The said cybersecurity regulations, adopted last year and implemented on June 1, impose new rules for online services providers. Trade groups opposed the initiative – whose initial version even required companies to submit source code for verification – arguing that it offered an unfair advantage to Chinese businesses.
The new law is largely focused on protecting China’s networks and private user information, and it requires cloud services to be operated by local companies. As a result, Apple has teamed up with government-owned Guizhou-Cloud Big Data to offer its iCloud service.
While some may be concerned about the location of the data center given the Chinese government’s track record, Apple has promised to maintain its strong data privacy and security protections and not create any backdoors into its systems.
Apple’s announcement comes just weeks after Chinese authorities reported uncovering a massive underground operation run by Apple employees who had abused the company’s internal systems to collect and sell customers’ personal details.
OSX DoK Malware linked to Operation Emmental used to target Swiss Banks again
11.7.2017 securityaffairs Apple
Crooks behind the Operation Emmental hacking campaign have started targeting the Swiss banks using a variant of the DoK Mac OS X malware.
In July 2014, malware researchers at Trend Micro published a report on the hacking campaign “Operation Emmental” that was targeting Swiss bank accounts whit a multi-faceted attack that allowed crooks to bypass two factor authentication implemented by the financial organization to protect its customers.
According to the experts, the Operation Emmental has been around since at least 2012.
The experts dubbed the campaign “Operation Emmental” because of the numerous holes in the security implemented by the Swiss banks, exactly like the popular Swiss Emmental cheese.
The hackers used a malware which was able to intercept SMS tokens used to authorize operations and change domain name system settings to hijack victims to rogue bank websites, which were a replica of legitimate ones, used for phishing attacks.
The threat actors targeted bank customers’ accounts in different countries, including in Switzerland, Austria, Japan and Sweden. Investigators suspected that Russian-speaking individuals were responsible for the Operation Emmental due clues discovered in the source code analyzed.
The hackers behind the Operation Emmental have continued to improve their malicious codes. The hackers used on Android malware and a Windows banking Trojan tracked as Retefe and WERDLOD.
The novelty in the operation of the group is represented by the usage of a new variant of the Dok malware in a new wave of attacks against the Swiss banks.
The malicious code is delivered via email, once the DOK malware infects a macOS system, it gains administrative privileges and installs a new root certificate. The root certificate allows the malicious code to intercept all victim’s communications, including SSL encrypted traffic.
According to researchers at Trend Micro, the malware variant tracked as OSX_DOK.C is configured to hijack traffic only if the victim’s external IP is located in Switzerland. OSX_DOK.C redirects users to bogus login pages for the financial organizations whose domain is included in a hardcoded list.
“The OSX_DOK malware (Detected by Trend Micro as OSX_DOK. C) showcases sophisticated features such as certificate abuse and security software evasion that affects machines using Apple’s OSX operating system.” reads the analysis published by Trend Micro.
The Dok sample detected by Trend Micro was considered by the malware researchers the Mac version of Retefe/WERDLOD.
“While WERDLOD and OSX_DOK.C use different codes (since they target different operating systems), they have similar proxy settings and script formats.”
“Comparing it to OSX_DOK.C, we can see that it uses the same script format” Trend Micro researchers said in a blog post.
“Given the connection between WERDLOD and OSX_DOK.C, it is reasonable to assume that the latter is also a part of the Operational Emmental campaign,”

The researchers observed that the latest versions of the Dok malware leverage a bug in the Ultimate Packer for Executables (UPX) tool to pack the Trojan and avoid detection.
'Dok' Mac Malware Used to Target Swiss Banks
10.7.2017 securityweek Apple
The cybercriminals behind the campaign known as Operation Emmental have apparently started targeting the customers of Swiss banks using a variant of the Mac OS X malware tracked as Dok.
Operation Emmental has been around since at least 2012 and the individuals who run it – experts determined that they are likely Russian speakers – have continued to improve their malware. The group has been known to leverage Android malware, designed to bypass two-factor authentication (2FA) and lock victims out of their smartphones, and a Windows banking Trojan tracked as Retefe and WERDLOD.
However, researchers believe a variant of the Dok malware has also been used in Operation Emmental to target Swiss banks.
Dok, a piece of malware typically delivered via email, is designed to spy on victims by installing a new root certificate and modifying the infected device’s network settings in order to redirect traffic through Tor.
According to Trend Micro, in the Operation Emmental attacks, the malware is configured to hijack traffic only if the victim’s external IP is located in Switzerland. Tracked by the security firm as OSX_DOK.C, the Trojan redirects users to a fake online banking login page if they visit the website of a financial organization whose domain is specified in a hardcoded list.
An analysis by Trend Micro and others showed that Dok actually appears to be the Mac version of Retefe/WERDLOD. Experts pointed out that both pieces of malware kill the web browser process before installing fake certificates, they share proxy settings and script formats, and they target mostly the same Swiss banks.
“Given the connection between WERDLOD and OSX_DOK.C, it is reasonable to assume that the latter is also a part of the Operational Emmental campaign,” Trend Micro researchers said in a blog post.
The security firm also pointed out that more recent versions of the Dok malware leverage a bug in the Ultimate Packer for Executables (UPX) tool to pack the Trojan and make it more difficult for security products to detect the threat.
MACSPY – Remote Access Trojan as a service on Dark web
15.6.2017 securityaffairs Apple
Reporters for the online service “Bleeping Computer” have uncovered a new threat to Apple being offered on the dark web, it is the MACSPY RAT.
Reporters for the online service “Bleeping Computer” have uncovered a new threat to Apple being offered on the dark web. Thru their efforts the researchers for AlienVault were able to obtain a copy of the new “MacSpy” program, described as the most sophisticated malware for Mac OS-x operating system to date.
The hackers offering MacSpy on the dark net are not selling it but in fact – giving it away at no cost. The software combines with a provided TOR portal to enable users to hack into and obtain surveillance information from targeted MAC computers.
The authors of the malware claim that they created it because Apple products have grown so popular. It is this popularity of Apple products that appears to have driven their desire to create the remote access Trojan (RAT) program. The free version of the MacSpy malware is designed to monitor Apple users, record data on the Mac system and then covertly spin it back to the controller who launched the attacks. MacSpy is can capture screen image and has an embedded keylogger. In addition, MacSpy can also capture ICloud synced data such as photos, provide voice recording surveillance, extract clipboard contents and download browser information.
Much like contemporary software providers; the MacSpy developers offers a “paid” version with enhanced features for customers. The paid version of MacSpy has many similar features seen inside programs developed by the CIA as shown in the Wikileaks Vault 7 releases. The remote controller can update the Trojan silently, extract any file, encrypt whole user directories, deliver scheduled dumps of an entire infected system, and extract social media and email data for surveillance.

According to the AlienVault, the MacSpy program is currently “completely undetected by various AV companies and products”. The program also includes a feature to disable the ability of users to analyze, debug and understand its operation. The anti-analysis designs include a series of hardware checks against the CPU chips to ensure the program is not being executed in a virtual mode or on a minimal “sand-box” system to be examined. It also calls the Apple “ptrace” function with the proper options to prevent debuggers from attaching to the process itself.
Once the system has passed the anti-analysis features it installs itself, deletes the installation files for stealth and links up to a TOR proxy in order to begin the process of data surveillance. MacSpy does attach itself to start up files so the system will re-establish a link to the TOR proxy at the beginning of each reboot.
MacSpy transmits the data it collects by sending a POST request through the TOR proxy, and then repeatedly sends POST commands for the selected data that the malware has stolen from the infected target system. Once it has completed its download the malware deletes the temporary files containing the data it sent.
There are some bright sides to the MacSpy story. The developers appear to have copied much of their code from the Stack Overflow website for programmers. In addition, the MacSpy payload is not digitally signed and may trigger an alert on properly configured Mac OS systems.
However, according to AlienVault, the MacSpy malware is a sign that there is a dark future for Apple users.
“People generally assume when they are using Macs they are relatively safe from malware,” notes AlienVault in its dissection of the MacSpy Trojan.
“This has been a generally true statement, but this belief is becoming less and less true by the day, as evidenced by the increasing diversity in mac malware along with this name family.”
Scammers Are Using Fake Apple In-App Subscriptions to Make Lot of Money
13.6.2017 thehackernews Apple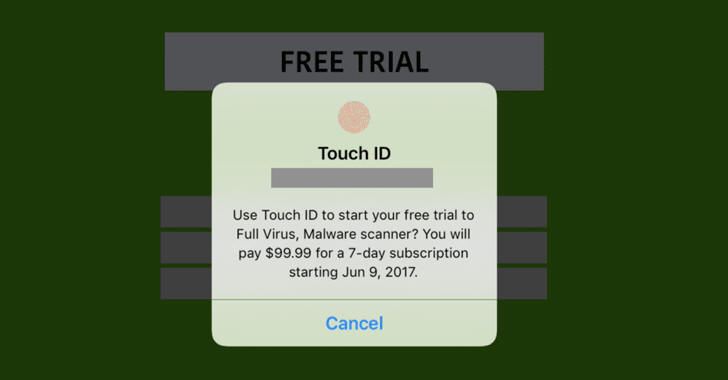
In this year's annual event, Apple announced that the company had paid out $70 Billion to developers in the App Store's lifetime and that $21 Billion of the amount was paid in the last year alone.
But has all this money gone to the legitimate app developers?
Probably not, as app developer Johnny Lin last week analyzed the Apple's App Store and discovered that most of the trending apps on the app store are completely fake and are earning their makers hundreds of thousands of dollars through in-app purchases and subscriptions.
Scammers Use 'Search Ads' Platform to Boost App Ranking
Shady developers are abusing Apple's relatively new and immature App Store Search Ads, which was launched at last year's Worldwide Developers Conference (WWDC), to promote their app in the store by using a few strategically chosen search ads and a bit of SEO.
"They're taking advantage of the fact that there's no filtering or approval process for ads, and that ads look almost indistinguishable from real results, and some ads take up the entire search result's first page," Lin wrote in his lengthy Medium post.
"I dug deeper to find that unfortunately, these aren't isolated incidents, they're fairly common in the app store's top grossing lists. And this isn't just happening with security related keywords. It seems like scammers are bidding on many other keywords."
Watch Out, Don't fall for Fake Apple In-App Subscriptions
One of the top earning apps Lin found was named "Mobile Protection: Clean & Security VPN" that tricked users into signing up for a $99.99 per week subscription for a complete garbage service by just laying their thumb on the Touch ID.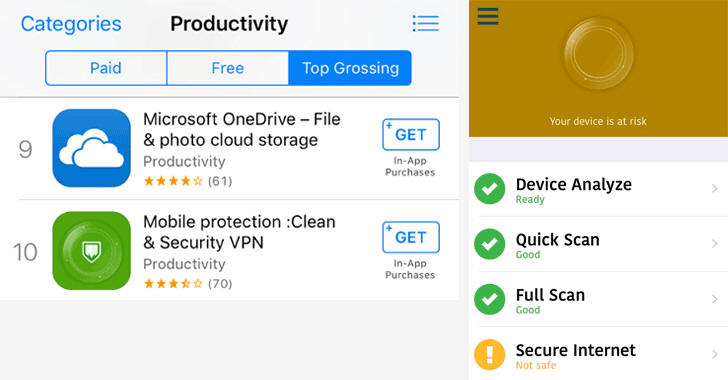
According to Lin, this app alone has earned its developer an estimated $80,000 per month, according to data from marketing firm Sensor Tower.
With spell and grammatical errors and fake reviews, 'Mobile Protection: Clean & Security VPN' claimed to be a Virus scanner, prompting users to "Instantly use full of smart anti-virus" by offering them a "FREE TRIAL."
But as soon as a victim tapped on the free trial, Touch ID screen appeared that read:
"Use Touch ID to start your free trial to Full Virus, Malware Scanner? You will pay $99.99 for a 7-day subscription starting June 9, 2017."
Usually, users who landed on the Touch ID screen making their mind for a free trial accidentally pressed their thumb on the Touch ID, which netted nearly $400 per month from just one user.
Therefore, the shady app developer needed just 200 people to be tricked into paying for the junk service to earn them $80,000 per month, which means $960,000 annually, according to Lin's calculations.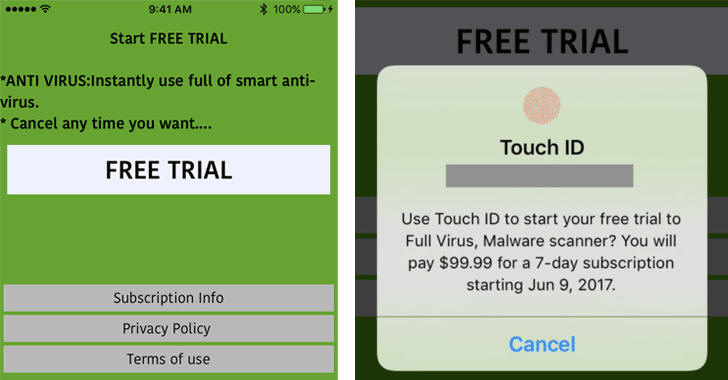
Lin explained how shady developers are abusing the App Store Search Ads service and "taking advantage of the fact that there's no filtering or approval process for ads, and that ads look almost indistinguishable from real results."
Though Apple removed the app, and several other apps that Lin highlighted in his post, but its App Store is still full of shady apps that use in-app purchases and misleading descriptions to trick users into spending lots of money on garbage.
Affected? Here's How to Cancel App Subscriptions
However, if you, unfortunately, downloaded any of the shady apps in question and paid for an expensive subscription, you can follow these steps to cancel all future payments:
Open Settings app and go to iTunes & App Store → Apple ID → View Apple ID.
Enter your Apple ID password or press against Touch ID when prompted.
Click on Subscriptions and then tap on the subscriptions you want to cancel, and tap Confirm.
Now once your current subscription period ends, you'll not charge.
Lin has also provided a long list of recommendation for Apple to implement to make its App Store safe for users, which includes steps to make better UI on Touch ID subscriptions, stricter Review of subscriptions, easier cancellation of subscriptions, fraud- and abuse-proof Search Ads, and remove scams and refund users.
MacSpy Malware Offered as Free Service
13.6.2017 securityweek Apple Virus
Just days after MacRansom Ransomware-as-a-service (RaaS) was uncovered, the first malware-as-a-service (MaaS) targeting Mac users was discovered on an undground forum available for free, AlienVault reveals.
Dubbed MacSpy and claiming to be the "most sophisticated Mac spyware ever”, the threat was built out of a “need of such programs on MacOS,” the malware’s author claims. The developers advertise the malware as free and advanced, but don’t appear to have set a specific price for the latter.
The free variant includes support for anonymous communication over the TOR network, can capture screenshots, log keystrokes, record voice, retrieve clipboard content and browser data, and grab iCloud photos during the syncing process. Moreover, it is advertised as being completely untraceable courtesy of low memory and CPU usage, AlienVault discovered.
The paid variant supposedly also allows users to adjust capture and recording intervals remotely, and can retrieve any files and data from the Mac, encrypt the entire user directory within seconds, and disguise the malware as a legitimate file format. Further, it supports daily archive of collected files, access to emails and social network accounts, and benefits from updates and code signing.
The MaaS, however, doesn’t appear polished, as wannabe criminals can’t automatically sign up for the service, but need to email the author with the preferred username and password instead. After creating the account, the author sends a zipped file to the new user, along with unzipping instructions.
Users can apparently infect machines by placing MacSpy’s unzipped folder onto a USB drive and manually executing a 64-bit executable called 'updated' when needed. The executable isn’t signed and doesn’t seem to be detected by the various AV companies on VirusTotal.
In addition to the 'updated' file, the archive contains a 64-bit executable 'webkitproxy', a 64-bit dynamically linked shared library 'libevent-2.0.5.dylib', and a config file. Given that webkitproxy and libevent-2.0.5.dylib are signed by TOR, the researchers concluded they are related to the function of Tor Onion routing.
The malware also includes anti-analysis capabilities, such as debugger and virtualization checks (CPU code count, amount of memory on the host). It also checks if it runs on a Mac, the same as MacRansom. For persistency, the threat creates a launch entry in ~/Library/LaunchAgents/com.apple.webkit.plist, ensuring it runs at every start up.
After execution, the malware copies itself and associated files to “~/Library/.DS_Stores/” and deletes the original folder. Next, it uses the curl command to contact the command and control (C&C) server, and sends collected data to it using POST requests through the TOR proxy. It also deletes the temporary files it uses to collect data.
The web portal is a “very bare bones directory listing containing a folder labeled the most recent date of the malware executing on a system in the YYYYMM format, followed by a folder in the DD format.” The folder includes directories resembling the directory naming on the victim system and containing the data collected from the victim.
MacSpy, AlienVault notes, shows an increased focus on MacOS, which has been generally considered relatively safe from malware.
“While this piece of Mac malware may not be the stealthiest program, it is feature rich and it goes to show that as OS X continues to grow in market share, we can expect malware authors to invest greater amounts of time in producing malware for this platform,” the security researchers conclude.
MacRansom: The first Mac ransomware offered as a RaaS Service
12.6.2017 securityaffairs Ransomware Apple
Malware researchers at security firm Fortinet have spotted MacRansom, it is the first Mac ransomware offered as a RaaS Service.
Malware researchers at security firm Fortinet have spotted a new strain of ransomware dubbed MacRansom that targets Mac machines.
The malware is available with Ransomware-as-a-service (RaaS) model through a hidden service in the TOR network. Experts believe this is the first time a Mac ransomware is offered as RaaS.
“Just recently, we here at FortiGuard Labs discovered a Ransomware-as-a-service (RaaS) that uses a web portal hosted in a TOR network which has become a trend nowadays. However, in this case it was rather interesting to see cybercriminals attack an operating system other than Windows. And this could be the first time to see RaaS that targets Mac OS.” states the analysis published by Fortinet.
Despite the threat is not sophisticated like other similar threats it could cause serious problems to the victims because it encrypts victim’s files. The availability of MacRansom as RaaS makes it easy to arranges ransomware campaign to crooks that have no specific skills.
MacRansom variant is not readily available through the Tor portal, would-be crooks can contact the author of the ransomware in order to receive their version of the threat.
“This MacRansom variant is not readily available through the portal. It is necessary to contact the author directly to build the ransomware. At first, we thought of it as a scam since there was no sample but to verify this we dropped the author an email and unexpectedly received a response.” continues the analysis.

MacRansom implements symmetric encryption with a hard-coded key and the ransomware only encrypts a maximum of 128 files, it demands 0.25 bitcoin (around $700) for decryption keys.
Researchers found two sets of symmetric keys used by the ransomware:
ReadmeKey: 0x3127DE5F0F9BA796
TargetFileKey: 0x39A622DDB50B49E9
The ReadmeKey is used to decrypt ._README_ file that contains the ransom notes and instructions, while the TargetFileKey is used to encrypt and decrypt the victim’s files.
The malicious code implements anti-analysis activity, the first thing the ransomware does is to check if the sample is being run in a non-Mac environment or if it is running in debugged environment.
The author gives 30 per cent to the Bitcoin address of the customer once the victim has paid the ransom.
Customers just have to spread the threat, for example delivering it via spam emails on through drive-by download attacks.
The author discourages drive-by download attacks or other approaches that involve uploading customized versions of MacRansom.
“It is not every day that we see new ransomware specifically targeting Mac OS platform. Even if it is far inferior from most current ransomware targeting Windows, it doesn’t fail to encrypt victim’s files or prevent access to important files, thereby causing real damage.” concluded Fortinet.
“Last but not the least, this MacRansom variant is potentially being brewed by copycats as we saw quite a lot of similar code and ideas taken from previous OSX ransomware. Even though it utilizes anti-analysis tricks, which differs from previous OSX ransomware, these are well-known techniques widely deployed by many malware authors. MacRansom is yet another example of the prevalence of the ransomware threat, regardless of the OS platform being run.”
22 Apple Distributors Arrested for Selling Customers’ Data in $7.4 Million
9.6.2017 thehackernews Apple
Image Source: South China Morning Post
Chinese authorities have announced the arrest of around 22 distributors working as Apple distributors as part of a $7 million operation, who stole customers’ personal information from an internal Apple database and illegally sold it to Chinese black market vendors.
According to a report from Chinese media, this underground network reportedly consisted of employees working in direct Apple suppliers, and other outsource firms in the Zhejiang, a province in eastern China.
These employees had access to Apple databases along with other tools containing sensitive information about its customers.
They allegedly used their company's internal computer system to gather data includes usernames, email addresses, phone numbers, and Apple IDs, and then sold it in the underground market for between 10 yuan ($1.47) and 80 yuan ($11.78) per data point.
So far, the network has made a total of 50 million yuan (around $7.36 million). However, it is unclear if the data sold by the suspects belonged to only Chinese Apple users or users elsewhere as well.
apple-store-data-sell
Much details about the arrest have not been revealed by the Chinese authorities at this moment, though the police statement suggests the Chinese authorities across four provinces, including Guangdong, Jiangsu, Zhejiang, and Fujian, arrested 22 suspects over the weekend, following a few months of investigation.
The authorities dismantled their online network and seized all "criminal tools," and announced Thursday that the suspects have been "detained on suspicion of infringing individuals’ privacy and illegally obtaining their digital personal information."
Wondering how this spamming operation can affect you?
As I mentioned above, your personal data is profitable both for marketing companies to deliver targeted advertisements to you, and for hackers to carry out malicious hacking campaigns, including phishing attacks and other email scams.
Police are trying to capture and destroy the scammers' network, but users are advised to be vigilant while opening attachments in emails, clicking links in messages from unknown numbers and giving out any details on phone calls.
50 hashes per hour
8.6.2017 Kaspersky Apple
How often do you turn off your computer when you go home from work? We bet you leave it on so you don’t have to wait until it boots up in the morning. It’s possible that your IT staff have trained you to lock your system for security reasons whenever you leave your workplace. But locking your system won’t save your computer from a new type of attack that is steadily gaining popularity on Raspberry Pi enthusiast forums.
We previously investigated the security of charging a smartphone via a USB port connection. In this research we’ll be revisiting the USB port – this time in attempts to intercept user authentication data on the system that a microcomputer is connected to. As we discovered, this type of attack successfully allows an intruder to retrieve user authentication data – even when the targeted system is locked. It also makes it possible to get hold of administrator credentials. Remember Carbanak, the great bank robbery of 2015, when criminals were able to steal up to a billion dollars? Finding and retrieving the credentials of users with administrative privileges was an important part of that robbery scheme.
In our research we will show that stealing administrator credentials is possible by briefly connecting a microcomputer via USB to any computer within the corporate perimeter. By credentials in this blogpost we mean the user name and password hash and we won’t go into detail how to decipher the retrieved hash, or how to use it in the pass-the-has types of attacks. What we’re emphasizing is that the hardware cost of such an attack is no more than $20 and it can be carried out by a person without any specific skills or qualifications. All that’s needed is physical access to corporate computers. For example, it could be a cleaner who is asked to plug “this thing” into any computer that’s not turned off.
We used a Raspberry Pi Zero in our experiments. It was configured to enumerate itself as an Ethernet adapter on the system it was being plugged into. This choice was dictated by the popularity of Raspberry Pi Zero mentions on forums where enthusiasts discuss the possibility of breaking into information systems with single-board computers. This popularity is understandable, given the device capabilities, size and price. Its developers were able to crank the chip and interfaces into a package that is slightly larger than an ordinary USB flash drive.
Yes, the idea of using microcomputers to intercept and analyze network packets or even as a universal penetration testing platform is nothing new. Most known miniature computing devices are built on ARM microprocessors, and there is a special build of Kali Linux that is specifically developed for pen testing purposes.
There are specialized computing sticks that are designed specifically for pen testing purposes, for example, USB Armory. However, with all its benefits, like integrated USB Type A connector (Raspberry Pi requires an adapter), USB Armory costs much more (around $135) and absolutely pales in comparison when you look at its availability vs. Raspberry Pi Zero. Claims that Raspberry Pi can be used to steal hashes when connected via USB to a PC or Mac surfaced back in 2016. Soon there were claims that Raspberry Pi Zero could also be used for stealing cookies fromh3 browsers – something we also decided to investigate.
So, armed with one of the most widespread and available microcomputers at the moment, we conducted two series of experiments. In the first, we attempted to intercept user credentials within the corporate network, trying to connect to laptop and desktop computers running different operating systems. In the second, we attempted to retrieve cookies in a bid to restore the user session on a popular website.
Experiment 1: stealing domain credentials
Methodology
The key principle behind this attack is emulation of the network adapter. We had absolutely no difficulties in finding the module emulating the Ethernet adapter under Raspbian OS (for reference, at the time of writing, we hadn’t found a similar module for Kali Linux). We made a few configuration changes in the cmdline.txt and config.txt files to load the module on boot.
A few extra steps included installing the python interpreter, sqlite3 database library and a special app called Responder for packet sniffing:
apt-get install -y python git python-pip python-dev screen sqlite3
pip install pycrypto
git clone https://github.com/spiderlabs/responder
And that wasn’t all – we set up our own DHCP server where we defined the range of IP addresses and a mask for a subnet to separate it from the network we’re going to peer into. The last steps included configuring the usb0 interface and automatic loading of Responder and DHCP server on boot. Now we were ready to rock.
Results
Just as soon as we connected our “charged” microcomputer to Windows 10, we saw that the connected Raspberry Pi was identified as a wired LAN connection. The Network Settings dialogue shows this adapter as Remote NDIS Internet sharing device. And it’s automatically assigned a higher priority than others.
Responder scans the packets that flow through the emulated network and, upon seeing the username/password hash pairs, directs them to a fake HTTP/HTTPS/NTLM (it supports v1 and v2) server. The attack is triggered every time applications, including those running in the background, send authentication data, or when a user enters them in the standard dialogue windows in the web browser – for example, when user attempts to connect to a shared folder or printer.
Intercepting the hash in automatic mode, which is effective even if the system is locked, only works if the computer has another active local network connection.
As stated above, we tried this proof of concept in three scenarios:
Against a corporate computer logged into a domain
Against a corporate computer on a public network
Against a home computer
In the first scenario we found that the device managed to intercept not only the packets from the system it’s connected to via USB but also NTLM authentication requests from other corporate network users in the domain. We mapped the number of intercepted hashes against the time elapsed, which is shown in the graph below:
Playing around with our “blackbox” for a few minutes, we got proof that the longer the device is connected, the more user hashes it extracts from the network. Extrapolating the “experimental” data, we can conclude that the number of hashes it can extract in our setting is around 50 hashes per hour. Of course, the real numbers depend on the network topology, namely, the amount of users within one segment, and their activity. We didn’t risk running the experiment for longer than half an hour because we also stumbled on some peculiar side effects, which we will describe in a few moments.
The extracted hashes are stored in a plain-text file:
In the second scenario we were only able to extract the connected system’s user credentials: domain/Windows name and password hash. We might have gotten more if we had set up shared network resources which users could try to access, but we’re going to leave that outside the scope of this research.
In the third scenario, we could only get the credentials of the owner of the system, which wasn’t connect to a domain authentication service. Again, we assume that setting up shared network resources and allowing other users to connect to them could lead to results similar to those we observed in the corporate network.
The described method of intercepting the hashes worked on Mac OS, too. When we tried to reach an intranet site which requires entering a domain name, we saw this dialogue warning that the security certificate is invalid.
Now, the interesting side effect we mentioned above was that when the device was connected to a[ny] system in the network, tasks sent out to the network printer from other machines in the same network were put on hold in the printer queue. When the user attempted to enter the credentials in the authentication dialogue window, the queue didn’t clear. That’s because these credentials didn’t reach the network printer, landing in the Raspberry Pi’s flash memory instead. Similar behavior was observed when trying to connect to remote folders via the SMB protocol from a Mac system.
Bonus: Raspberry Pi Zero vs. Raspberry Pi 3
Once we saw that the NTLM systems of both Windows and Mac had come under attack from the microcomputer, we decided to try it against Linux. Furthermore, we decided to attack the Raspberry Pi itself, since Raspbian OS is built on the Debian Weezy core.
We reproduced the experiment, this time targeting Raspberry Pi 3 (by the way, connecting it to the corporate network was a challenging task in itself, but doable, so we won’t focus on it here). And here we had a pleasant surprise – Raspbian OS resisted assigning the higher priority to a USB device network, always choosing the built-in Ethernet as default. In this case, the Responder app was active, but could do nothing because packets didn’t flow through the device. When we manually removed the built-in Ethernet connection, the picture was similar to that we had observed previously with Windows.
Similar behavior was observed on the desktop version of Debian running on Chromebook – the system doesn’t automatically set the USB Ethernet adapter as default. Therefore, if we connect Raspberry Pi Zero to a system running Debian, the attack will fail. And we don’t think that creating Raspberry Pi-in-the-middle attacks is likely to take off, because they are much harder to implement and much easier to detect.
Experiment 2: stealing cookies
Methodology
While working on the first experiment, we heard claims that it’s possible to steal cookies from a PC when a Raspberry Pi Zero is connected to it via USB. We found an app called HackPi, a variant of PoisonTap (an XSS JavaScript) with Responder, which we described above.
The microcomputer in this experiment was configured just like in the previous one. HackPi works even better at establishing itself as a network adapter because it has an enhanced mechanism of desktop OS discovery: it is able to automatically install the network device driver on Windows 7/8/10, Mac and –nix operating systems. While in the first series of experiments, an attack could fail on Windows 7, 8 or Vista if the Remote NDIS Internet sharing device didn’t install itself automatically (especially when the PC is locked). And, unlike in the previous series, HackPi never had trouble assigning itself the default network adapter priority under Mac OS either.
What differs from the first experiment is that the cookies are stolen using the malicious Java Script launched from the locally stored web page. If successful, PoisonTap’s script saves the cookies intercepted from sites, a list of which is also locally stored.
Results
If the computer is not locked and the user opens the browser, Java Script initiates the redirecting of web requests to a malicious local web page. Then the browser opens the websites from the previously defined list. It is indeed quite spectacular:
If the user does nothing, Raspberry Pi Zero launches the default browser with URL go.microsoft.com in the address line after a short timeout. Then the process goes ahead as described. However, if the default browser has no cookies in the browser history, the attackers gain nothing.
Among the sites we’ve seen in the list supplied with the script were youtube.com, google.com, vk.com, facebook.com, twitter.com, yandex.ru, mail.ru and over 100 other web addresses. This is what the log of stolen cookies looks like:
We checked the validity of stolen cookies using the pikabu.ru website as an example by pasting the info into a clean browser field on other machines and were able to get hold of the user’s account along with all the statistics. On another website belonging to a railroad company vending service, we were able to retrieve the user’s token and take over the user’s account on another computer, because authentication protocol used only one LtpaToken2 for session identification.
Now this is more serious, because in this case the criminals can get information about previous orders made by the victim, part of their passport number, name, date of birth, email and phone number.
One of the strong points of this attack is that enthusiasts have learned how to automatically install the network device driver on all systems found in today’s corporate environments: Windows 7/8/10, Mac OS X. However, this scenario doesn’t work against a locked system – at least, for now. But we don’t think you should become too complacent; we assume it’s only a matter of time before the enthusiasts overcome this as well. Especially given that the number of these enthusiasts is growing every day.
Also, the malicious web page is blocked by all Kaspersky Lab products, which detect it as Trojan.JS.Poisontap.a. We also assume that this malicious web page will be blocked by the products of all other major anti-malware vendors.
Conclusions
There is already a wide array of single-board microcomputers: from the cheap and universal Raspberry Pi Zero to computing sticks specifically tuned for penetration testing, which cannot be visually differentiated from USB flash drives. To answer the main question of just how serious this threat is, we can say that at the moment it is overrated. However, we don’t advise underestimating the capabilities of IoT enthusiasts and it’s better to assume that those obstacles which we discovered in our experiment, have already been overcome.
Right now we can say that Windows PCs are the systems most prone to attacks aimed at intercepting the authentication name and password with a USB-connected Raspberry Pi. The attack works even if the user doesn’t have local or system administrator privileges, and can retrieve the domain credentials of other users, including those with administrator privileges. And it works against Mac OS systems, too.
The second type of attack that steals cookies only works (so far) when the system is unlocked, which reduces the chances of success. It also redirects traffic to a malicious page, which is easily blocked by a security solution. And, of course, stolen cookies are only useful on those websites that don’t employ a strict HTTP transport policy.
Recommendations
However, there are a number of recommendations we’d like to give you to avoid becoming easy prey for attackers.
Users
1. Never leave your system unlocked, especially when you need to leave your computer for a moment and you are in a public place.
2. On returning to your computer, check to see if there are any extra USB devices sticking out of your ports. See a flash drive, or something that looks like a flash drive? If you didn’t stick it in, we suggest you remove it immediately.
3. Are you being asked to share something via external flash drive? Again, it’s better to make sure that it’s actually a flash drive. Even better – send the file via cloud or email.
4. Make a habit of ending sessions on sites that require authentication. Usually, this means clicking on a “Log out” button.
5. Change passwords regularly – both on your PC and the websites you use frequently. Remember that not all of your favorite websites may use mechanisms to protect against cookie data substitution. You can use specialized password management software for easy management of strong and secure passwords, such as the free Kaspersky Password Manager.
6. Enable two-factor authentication, for example, by requesting login confirmation or with a hardware token.
7. Of course, it’s strongly recommended to install and regularly update a security solution from a proven and trusted vendor.
Administrators
1. If the network topology allows it, we suggest using solely Kerberos protocol for authenticating domain users. If, however, there is a demand for supporting legacy systems with LLNMR and NTLM authentication, we recommend breaking down the network into segments, so that even if one segment is compromised, attackers cannot access the whole network.
2. Restrict privileged domain users from logging in to the legacy systems, especially domain administrators.
3. Domain user passwords should be changed regularly. If, for whatever reason, the organization’s policy does not involve regular password changes, please change the policy. Like, yesterday.
4. All of the computers within a corporate network have to be protected with security solutions and regular updates should be ensured.
5. In order to prevent the connection of unauthorized USB devices, it can be useful to activate a Device Control feature, available in the Kaspersky Endpoint Security for Business suite.
6. If you own the web resource, we recommend activating the HSTS (HTTP strict transport security) which prevents switching from HTTPS to HTTP protocol and spoofing the credentials from a stolen cookie.
7. If possible, disable the listening mode and activate the Client (AP) isolation setting in Wi-Fi routers and switches, disabling them from listening to other workstations’ traffic.
8. Activate the DHCP Snooping setting to protect corporate network users from capturing their DHCP requests by fake DHCP servers.
Last, but not least, you never know if your credentials have been leaked from a site you’ve been to before – online or physical. Thus, we strongly recommend that you check your credentials on the HaveIbeenPwned website to be sure.
Chinese Apple Staff Suspected of Selling Private Data
8.6.2017 securityweek Apple
Beijing - Chinese authorities say they have uncovered a massive underground operation run by Apple employees selling computer and phone users' personal data.
Twenty-two people have been detained on suspicion of infringing individuals' privacy and illegally obtaining their digital personal information, according to a statement Wednesday from local police in southern Zhejiang province.
Of the 22 suspects, 20 were Apple employees who allegedly used the company's internal computer system to gather users' names, phone numbers, Apple IDs, and other data, which they sold as part of a scam worth more than 50 million yuan ($7.36 million).
The statement did not specify whether the data belonged to Chinese or foreign Apple customers.
Following months of investigation, the statement said, police across more than four provinces -- Guangdong, Jiangsu, Zhejiang, and Fujian -- apprehended the suspects over the weekend, seizing their "criminal tools" and dismantling their online network.
The suspects, who worked in direct marketing and outsourcing for Apple in China, allegedly charged between 10 yuan ($1.50) and 180 yuan ($26.50) for pieces of the illegally extracted data.
The sale of personal information is common in China, which implemented on June 1 a controversial new cybersecurity law aimed at protecting the country's networks and private user information.
In December, an investigation by the Southern Metropolis Daily newspaper exposed a black market for private data gathered from police and government databases.
Reporters successfully obtained a trove of material on one colleague -- including flight history, hotel checkouts and property holdings -- in exchange for a payment of 700 yuan ($100).
Defendant punished with 6-Months jail for refusing to give Police his iPhone Passcode
5.6.2017 securityaffairs Apple
US judges have other opinions to punish suspects that decide to don’t collaborate with police giving the iPhone passcode to unlock their devices.
Forgetting passwords for an electronic device could be an option for suspects to avoid complying with a court order, but sometimes things can go wrong.
US judges have other opinions to punish suspects that decide to don’t collaborate with law enforcement refusing to unlock their smartphones.
Last week, a defendant was punished with six months jail for allegedly refusing to reveal his iPhone passcode, while a second defendant walks through after he claimed he forgot his passcode.
A Florida court judge ruled last week that child abuse defendant Christopher Wheeler, 41, must serve 180 days in jail for not handing over his correct iPhone passcode to police. The man insisted that the passcode he provided to the police to unlock the mobile phone was correct.
“I swear, under oath, I’ve given [the detectives] the password,” Wheeler said.
Wheeler is accused of mistreatment against her daughter, the man was arrested and he was taken into custody in a Broward Circuit Court on Tuesday after the police were not able to access the content of his iPhone using the passcode he provided.
Investigators believe that the iPhone may contain photos of Wheeler child’s injuries,
“Detectives believe that his phone contains images of repeated injuries to the child, which could prove evidence in the case. A Broward judge earlier authorized a search warrant for Wheeler’s iPhone, but detectives had been unable to get in.” states the Miami Herald
“When a judge ordered him to provide the pass code, it didn’t work. Rothschild held him in criminal contempt earlier this month.”
This isn’t the unique case in which defendant refused to give the passcode.
In a different court, a Florida judge was facing an extortion case in which defendant that claimed to have forgotten the passcode for his BlackBerry phone.
In this second case, Wesley Victor and his girlfriend Hencha Voigt (a reality TV star) are accused of threatening to release sex tapes stolen from local social media celeb YesJulz unless she paid $18,000.
The sex tapes were published online, but in order to demonstrate that Victor and Voigt posted them online investigators need to access the iPhone.
“The judge made the right call,” Victor’s lawyer Zeljka Bozanic said. “My client testified he did not remember. It’s been almost a year. Many people, including myself, can’t remember passwords from a year ago.”
According to the Fifth Amendment, defendants have the rights to not to say anything that could be used against them. A passcode or any other personal information are protected by the amendment, considering that the number of similar cases is increasing it is expected a final judgment from the United States Supreme Court before.
Man Jailed 6 Months for Refusing to Give Police his iPhone Passcode
5.6.2017 securityaffairs Apple

Remember Ramona Fricosu? A Colorado woman was ordered to unlock her encrypted Toshiba laptop while the FBI was investigating alleged mortgage fraud in 2012, but she declined to decrypt the laptop saying that she did not remember the password.
Later the United States Court ruled that Police can force defendants to decrypt their electronic devices, of course, as it does not violate the Fifth Amendment that prevents any citizen from having to incriminate themselves.
Forgetting passwords for your electronic devices could be a smart move to avoid complying with a court order, but not every time, as US judges have different opinions on how to punish those who do not compel the order to unlock their phones.
On a single day last week, one defendant got six months jail for allegedly refusing to reveal his iPhone passcode, while a second defendant walks through after he claimed he forgot his passcode.
A Florida circuit court judge ruled last week that child abuse defendant Christopher Wheeler, 41, must serve 180 days in jail for not handing over the correct 4-digit code to unlock his iPhone to police, while he insisted that the passcode he gave to officers was correct.
"I swear, under oath, I've given [the detectives] the password," Wheeler said.
Wheeler was arrested earlier this year for allegedly hitting and scratching his daughter. He was taken into custody in a Broward Circuit Court on Tuesday after the cops were not able to access the phone using the passcode provided by him.
Investigators believe that the defendants iPhone may contain photos of his child's injuries, according to the Miami Herald.
However, in a different court, another Florida judge let off an extortion case defendant, even though he also claimed to have forgotten the passcode for his BlackBerry phone.
Wesley Victor and his girlfriend Hencha Voigt (a reality TV personality) both are accused of threatening to release sex tapes stolen from local social media celeb YesJulz unless she paid $18,000.
"The judge made the right call," Victor's lawyer Zeljka Bozanic said. "My client testified he did not remember. It's been almost a year. Many people, including myself, can't remember passwords from a year ago."
The sex tapes of YesJulz ended up on the Internet, but there is no evidence Victor or Voigt posted them online.
Voigt is also facing contempt of court charges and scheduled to appear in front of a judge next week because the passcode she provided to authorities for her phone was incorrect.
The Fifth Amendment gives defendants rights to not to say anything that could be used against them and a secret password or passcode is personal information protected by this amendment, but the above cases underscore the dilemma faced by law enforcement officials in dealing with the password and encryption issue.
It seems like the final word on passwords and encryption will likely have to come from the United States Supreme Court before.