Research Finds Microsoft Edge Has Privacy-Invading Telemetry
15.3.2020 Bleepingcomputer OS Privacy
While Microsoft Edge shares the same source code as the popular Chrome browser, it offers better privacy control for users. New research, though, indicates that it may have more privacy-invading telemetry than other browsers.
According to Microsoft, telemetry refers to the system data that is uploaded by the Telemetry components or browser's built-in services. Telemetry features aren't new to Microsoft and the company has been using Telemetry data from Windows 10 to identify issues, analyze and fix problems.
Professor Douglas J Leith, Chair of Computer Systems at Trinity College in Ireland, tested six web browsers to determine what data they were sharing. In his research, he pitted Chromium-based Microsoft Edge, Google Chrome, Brave, Russia's Yandex, Firefox and Apple Safari.
Unfortunately, Microsoft Edge didn't perform well in various privacy tests.
Too much telemetry in Microsoft Edge
When testing the Edge Browser, Leith saw that every URL that was typed into Edge would be sent back to Microsoft sites.
For example, every URL typed into the address bar is shared with Bing and other Microsoft services such as SmartScreen. This was confirmed by BleepingComputer who used Fiddler to see the JSON data being sent to Microsoft.
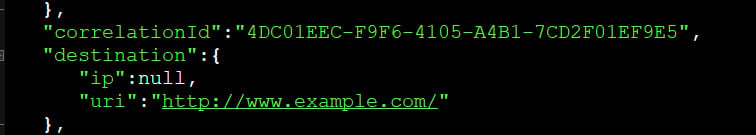
Unhashed URL being sent to SmartScreen
This could be fixed by using a technique similar to Google's Safe Browsing implementation that downloads a a list of known malicious sites and saves it locally. This list is the checked by the browser and if any data needs to be sent to Google's servers, will only send a hashed partial URL fingerprint that can be used to track browsing behavior.
The browser also sends unique hardware identifiers to Microsoft, which is a "strong and enduring identifier" that cannot be easily changed or deleted.
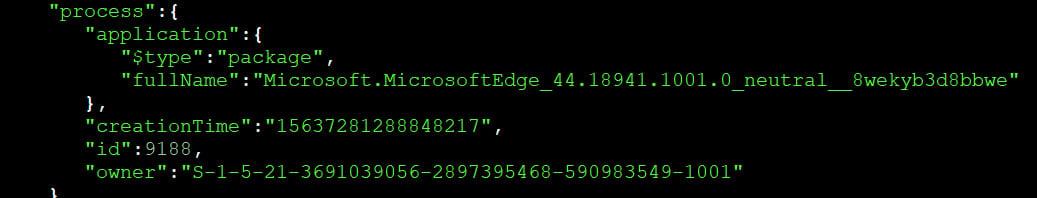
User tracking information being sent
Russian web browser Yandex is also engaged in similar anti-privacy activities:
From a privacy perspective Microsoft Edge and Yandex are qualitatively different from the other browsers studied. Both send persistent identifiers than can be used to link requests (and associated IP address/location) to back end servers. Edge also sends the hardware UUID of the device to Microsoft and Yandex similarly transmits a hashed hardware identifier to back end servers. As far as we can tell this behaviour cannot be disabled by users. In addition to the search autocomplete functionality that shares details of web pages visited, both transmit web page information to servers that appear unrelated to search autocomplete.
It's important to note that Microsoft Edge for Enterprise gives administrators a lot of control in deployments to disable all these trackers, but the trackers are enabled by default in all Edge installations.
While Microsoft Edge didn't fare well in the tests, the researcher has also questioned Chrome's and other browser's behaviour.
Users have previously noticed that Chrome scans the entire computer and reports hashes of executable programs back to Google to build Chrome's Safe Browsing platform.
Chrome, Firefox and Safari share details of every webpage you visit with their services. All these browsers use autocomplete feature to send web addresses to their services in realtime.
Firefox's telemetry transmissions, which is silently enabled by default, can potentially be used to link these over time. In Firefox, there is also an open WebSocket for push notifications and it is linked to a unique identifier, which could be used for tracking, according to the researcher.
Privacy Concerns Raised Over New Google Chrome Feature
24.2.2020 Bleepingcomputer Privacy
With the release of Google Chrome 80, Google quietly slipped in a new feature that allows users to create a link directly to a specific word or phrase on a page. A Brave Browser researcher, though, sees this as a potential privacy risk and is concerned Google added it too quickly.
In February 2019, we reported about a new web feature created by Google called 'Scroll To Text Fragment' that allows users to create links to a specific word on a web page and automatically highlight it.
To use this feature, users would need to create a special URL using the https://example.com#:~:text=prefix-,startText,endText,-suffix format as outlined in the Scroll To Text Fragment WICG draft.
As text fragment URLs can be a bit complicated to make, Google Chrome developer Paul Kinlan created a bookmarklet that makes the task easy.
As an example, to create a link to the phrase "man with a beret" in the XKCD Wikipedia article, you would use the https://en.wikipedia.org/wiki/Xkcd#:~:text=man%20with%20a%20beret URL.
When Chrome 80 users click on this link, they will be brought directly to this phrase and the phrase will automatically be highlighted as shown below.
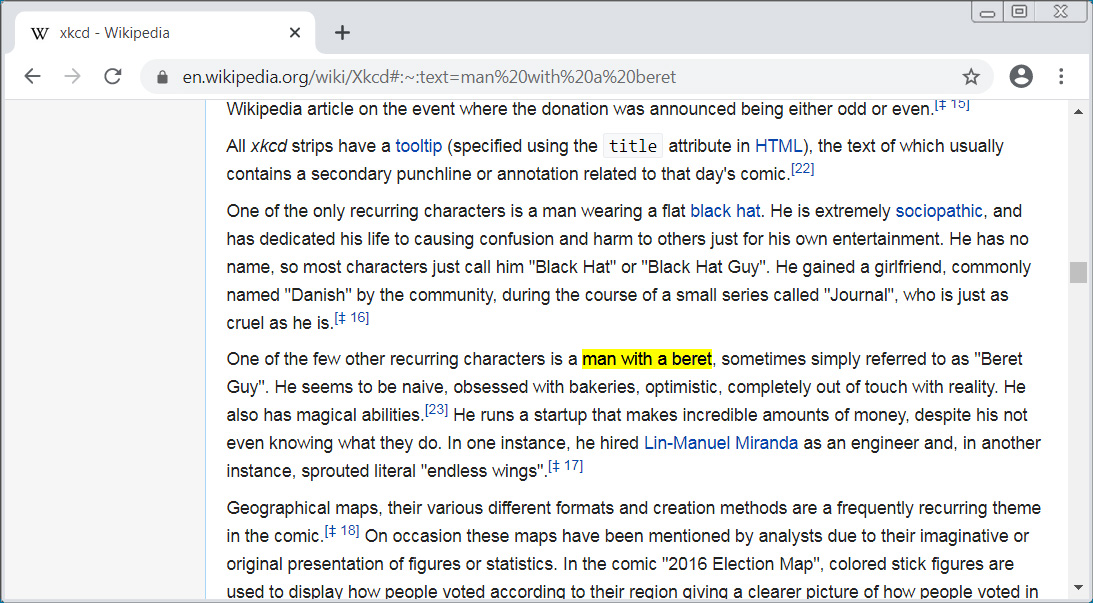
TextFragment URL
At first glance, this feature seems very useful as it makes it easy to share specific locations on a web page with someone else.
Brave Browser security researcher Peter Snyder, though, thinks this feature introduces privacy risks that Google did not address before making the feature live.
Scroll To Text Fragment feature could leak data
Major browser developers are part of the W3C’s Web Platform Incubator Community Group (WICG), which is used to propose new web platform features before they are added to browsers.
While a browser developer does not have to use this process to determine if they will add a feature, it does allow other developers and security researchers to raise any technical, security, or privacy concerns that they may have.
As part of the discussion for the 'ScrollToTextFragment' feature, Snyder raised concerns that it could allow an attacker under certain conditions to determine if the particular text appears on a page.
"For example: Consider a situation where I can view DNS traffic (e.g. company network), and I send a link to the company health portal, with #:~:text=cancer. On certain page layouts, i might be able tell if the employee has cancer by looking for lower-on-the-page resources being requested"
Snyder further illustrates his concerns with a possible way for an attacker to determine if a person is friends with or follows someone on social networks like Facebook and Twitter.
"Besides the #:~:text=cancer example, Im certain the same approach could be used to figure out if you're facebook friends with someone twitter.com#:~:text=@handle or many many other things.
The root of all these issues is that this is a SOP violation, where a separate origin can control the initial state of an unrelated origin. As long as thats in place, there will be all sorts of sneaking-infromation-across-origins related-attacks possible."
Furthermore, by enabling this feature by default for all sites rather than allowing sites to opt into the feature, it automatically imposes this potential privacy risk on all sites.
With these privacy concerns raised, it was surprising to learn that Google went ahead and enabled this feature by default in Chrome 80 without any further discussion in the raised privacy issue on GitHub or in their release notes.
"Yes, this is shipping in M80 without a flag. We discussed this and other issues with our security team and, to summarize, we understand the issue but disagree on the severity so we're proceeding with allowing this without requiring opt-in (though we are still working on adding an opt in/out)," stated Google Chrome developer David Bokan when asked if the feature is now live.
With Google enabling the feature without further discussion, Snyder raised an important issue on Twitter. What is the point of using WICG to propose new web platform features if the developers for the most widely used browser, Google Chrome, adds these features regardless of the expressed concerns or at least giving a final response to open issues?
"But more broadly, I appreciate that we disagree about the degree of privacy risk here, but sincerely, what is the point of introducing things in WICG if they're going to ship unflagged in the majority browser w/o out the issues at *least* being closed / `wontfix`?," Snyder tweeted last week.
The good news is that Google appears to be considering an opt-in option for sites to allow this feature and hopes to have it ready in Chrome 82.
Avast Shuts Down Jumpshot After Getting Caught Selling User's Data
2.2.2020 Bleepingcomputer Privacy
Avast has announced that they are shutting down their Jumpshot subsidiary that was selling user data collected by Avast's antivirus software products.
In a joint investigation by PCMag and Motherboard, we learned this week that Avast has been collecting user data through their antivirus products and then repackaging it and selling it to other companies through a subsidiary called Jumpshot.
This web browsing data could include Google searches, what videos are watched, what sites are visited, and what files are downloaded.
Avast collecting user data is nothing new as four of their browser extensions were recently delisted from the Google and Mozilla extension sites after being caught tracking copious amounts of data.
After making changes to their extensions so that users would be alerted that their web history is tracked, Google and Mozilla allowed the extensions back into the store.
Avast Tracking Notice
This latest revelation that the security company was also using their antivirus software to track the data of over 400 million users and repackage for sale to other companies is not what many would call good security.
Jumpshot shut down
In an open letter by Avast CEO Ondrej Vlcek, the antivirus company apologizes to its users and announced that they will be shutting down the Jumpshot subsidiary.
"Protecting people is Avast’s top priority and must be embedded in everything we do in our business and in our products. Anything to the contrary is unacceptable. For these reasons, I – together with our board of directors – have decided to terminate the Jumpshot data collection and wind down Jumpshot’s operations, with immediate effect," Vlcek stated in a message posted to Avast's blog.
Avast also emphasized that Jumpshot was 100% GDPR compliant and operated independently with their own management and board of directors who built their services from the data feed shared by Avast.
"Jumpshot has operated as an independent company from the very beginning, with its own management and board of directors, building their products and services via the data feed coming from the Avast antivirus products," Vlcek continued. "During all those years, both Avast and Jumpshot acted fully within legal bounds – and we very much welcomed the introduction of GDPR in the European Union in May 2018, as it was a rigorous legal framework addressing how companies should treat customer data. Both Avast and Jumpshot committed themselves to 100% GDPR compliance. "
This announcement may be too late to avoid a serious hit to the company.
While it may not have much of an effect on their free antivirus offerings whose users have become numb to companies abusing their data, it could lead to an exodus of enterprise customers who are concerned about this type of behavior.



