
Participants can earn up to $250,000 for demonstrating exploits in Microsoft Hyper-V client under the virtualization category, or up to $150,000 for Chrome and Edge exploits under the web browser category.
Congress Articles - H Congress Articles - H 2020 2019 2018 2017 Congress blog Congress blog
Pwn2Own 2021, more than $1,500,000 in cash and prizes for contestants
28.1.2021 Congress Securityaffairs
Trend Micro’s Zero Day Initiative announced the Pwn2Own Vancouver 2021 hacking competition that will also cover Zoom, MS Teams Exploits.
Trend Micro’s Zero Day Initiative (ZDI) on this week announced the forthcoming Pwn2Own Vancouver 2021 hacking competition that will take place on April 6-8.
The organizers provided information about the targets, prizes and rules for the competition.
Due to the ongoing COVID-19 pandemic, the event this year will be hybrid in the format, participants will submit their exploits remotely and the ZDI staff in Toronto (Canada) and Austin (Texas) will verify their efficiency.
People interested in the event can follow it through live streaming on YouTube and Twitch.
This year the overall prize pool is greater than $1.5 million in cash.
“As the workforce moves out of the office and goes remote, the tools needed to support that change become greater targets. That’s one reason we added this new category and teamed up with Zoom to have them in the contest. Microsoft Teams will also be a target. A successful demonstration of an exploit in either of these products will earn the contestant $200,000 – quite the payout for a new category.” reads the announcement published by ZDI. “Tesla returns for this year’s contest but driving off with a brand-new Model 3 will be more of a challenge this year. Of course, that means the rewards are greater as well, with the top prize going for $600,000 (plus the car itself).”
Other prizes include a Tesla Model 3 that will be assigned to participants that be involved in the hacking of vehicles. The hack of a Tesla could be awarded up to $600,000 to completely take over the vehicle.
The participants could be involved in the demonstration of working exploits for one of the following categories:
— Virtualization Category
— Web Browser Category
— Enterprise Applications Category
— Server Category
— Local Escalation of Privilege Category
— Enterprise Communications Category
— Automotive Category
The novelty is represented by the “enterprise communications category,” participants can earn up to $200,000 for demonstrating working exploits against Zoom or Microsoft Teams platforms.
“Our newest category focuses on tools that we have come to rely on as we evolved into a remote workforce. Zoom has become a partner for their inaugural Pwn2Own, and we’re happy to have them on board.” continues the announcement.
“A successful attempt in this category must compromise the target application by communicating with the contestant. Example communication requests could be audio call, video conference, or message,”

Participants can earn up to $250,000 for demonstrating exploits in Microsoft Hyper-V client under the virtualization category, or up to $150,000 for Chrome and Edge exploits under the web browser category.
The maximum prize for exploits under the enterprise application category is $100,000 for Microsoft 365 exploits, while the prize for exploits under the server category is up to $200,000 for Microsoft Exchange and Windows RDP exploits.
Other information is available here.
At last year’s event, the first edition of Pwn2Own affected by the pandemic, white hat hackers only earned a total of $270,000 for their exploits.
Pwn2Own 2021: Hackers Offered $200,000 for Zoom, Microsoft Teams Exploits
28.1.2021 Congress Securityweek
Trend Micro’s Zero Day Initiative (ZDI) on Tuesday announced the targets, prizes and rules for the Pwn2Own Vancouver 2021 hacking competition, a hybrid event scheduled to take place on April 6-8.
Pwn2Own Vancouver typically takes place during the CanSecWest conference in Vancouver, Canada, but due to the coronavirus pandemic, this year’s event will be hybrid — participants can submit their exploits remotely and ZDI staff in Toronto (Canada) and Austin (Texas) will run the exploits. The attempts will be live-streamed on YouTube and Twitch.
The prize pool for Pwn2Own 2021 exceeds $1.5 million in cash and other prizes, including a Tesla Model 3.
The car is being offered to those who participate in the automotive category. In this category, in addition to the vehicle, hackers can earn up to $600,000 for hacking a Tesla. There are three difficulty levels in this category and the Model 3 is being offered in each of them.
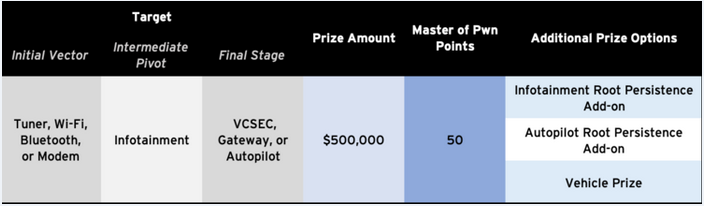
ZDI has also announced a new category for the upcoming event. As part of the new enterprise communications category, participants can earn up to $200,000 for demonstrating exploits against Zoom or Microsoft Teams.
“A successful attempt in this category must compromise the target application by communicating with the contestant. Example communication requests could be audio call, video conference, or message,” ZDI noted.
Other categories include virtualization, with a top prize of $250,000 for Microsoft Hyper-V client exploits, a web browser category, with a top prize of $150,000 for Chrome and Edge exploits, an enterprise application category, with a maximum prize of $100,000 for Microsoft 365 exploits, a server category, with up to $200,000 offered for Microsoft Exchange and Windows RDP exploits, and a local privilege escalation category, with $40,000 being the top prize for Windows 10 exploits.
Registration for the event closes on April 2. The complete rules are available on ZDI's website.
At last year’s event, the first edition of Pwn2Own affected by the pandemic, white hat hackers only earned a total of $270,000 for their exploits.
Unixfreaxjp at #R2CON2020 presented shellcode basics for radare2
17.11.20 Congress Securityaffairs
Shellcode play an essential role in cyber attacks, the popular expert Unixfreaxjp explained how to utilize radare2 for variation of shellcode analysis
Shellcode is having an important part in cyber intrusion activities and mostly spotted to be executed during the process/thread injection or during the exploitation of memory space that mostly related to a vulnerability. Either way, the purpose of shellcode is to utilize a small executable size so it can run and can trigger further steps of actions in a specifically targeted environment.
Depends on the nature of the shell code itself it can be made for a good purpose or bad one. The analysis of a shellcode requires know-how of which system library and functions will be invoked to help its execution, and depends on the operating system it can be a wide variation of commands from direct calls to an OS functions calls to the hash of the API of certain OS libraries. A good analysis tool can help you dissect a shellcode if the low-level language analysis operation is supported, as any shellcode is coded in assembly language. radare2 is one example of those tools.
In this presentation, I explain how to utilize radare2 for variation of shellcode analysis and will lead you as a tutorial from a basic know-how in analyzing shell code with multiple demonstrations.
I also state the definition of the shellcode to avoid misleading and adding up some samples on interesting cases that can help you to see how they can be utilized for any kind of (bad) purpose that is explaining the importance for all of us in learning how to analyze them. I was having only 30 minutes to present this rich content so I condensed the material in the video of the presentation so please read the slides and pause the video while you are watching, I hope you can learn something from this presentation.
Below the Q&A video published by Unixfreaxjp:
https://youtu.be/A9wodVpSFds
Google and Mozilla fixed issues exploited at 2020 Tianfu Cup hacking contest
12.11.20 Congress Securityaffairs
Mozilla and Google have already fixed the critical flaws in Firefox and Chrome exploited by bug bounty hunters at 2020 Tianfu Cup hacking contest.
Mozilla and Google have already addressed the critical Firefox and Chrome vulnerabilities that were recently exploited by white hat hackers at the 2020 Tianfu Cup hacking contest.
The vulnerability in Chrome exploited by hackers at the 2020 Tianfu Cup, tracked as CVE-2020-16016, is an inappropriate implementation issue that resided in the base component. Google addressed the flaw with the release of Chrome 86.
The CVE-2020-16016 flaw, along with the CVE-2020-26950 issue, was exploited by a team named “360 Enterprise Security and Government and (ESG) Vulnerability Research Institute,” which is part of the Chinese tech giant Qihoo 360 that won the competition. The team earned $744,500 of the total $1,210,000 jackpot.
The Firefox vulnerability, tracked as CVE-2020-26950, is related to write side effects in MCallGetProperty opcode not being accounted for.
“In certain circumstances, the MCallGetProperty opcode can be emitted with unmet assumptions resulting in an exploitable use-after-free condition,” reads the advisory published by Mozilla.
Mozilla addressed the issue with the release of Firefox 82.0.3, Firefox ESR 78.4.1 and Thunderbird 78.4.2.
Tianfu Cup 2020 – 5 minutes to hack Windows 10, Ubuntu iOS, VMWare EXSi, and others
10.11.20 Congress Securityaffairs
Many popular OS and applications have been hacked during this year’s edition of the Tianfu Cup hacking competition.
This year’s edition of the Tianfu Cup hacking competition was very prolific, bug bounty hackers have discovered multiple vulnerabilities in multiple software and applications.
The Tianfu Cup is the most important hacking contest held in China, the total bonus of the contest this year was up to 1 million US dollars.
The third edition of the competition ended today and the winning team earned a total of $744,500.
The participants successfully tested their exploits against the following software:
iOS 14 running on an iPhone 11 Pro
Samsung Galaxy S20
Windows 10 v2004 (April 2020 edition)
Ubuntu
Chrome
Safari
Firefox
Adobe PDF Reader
Docker (Community Edition)
VMWare EXSi (hypervisor)
QEMU (emulator & virtualizer)
TP-Link and ASUS router firmware
This year fifteen teams of Chinese hackers took part in the competition, each team had three tries of five minutes to demonstrate a working exploit against a specific target.
Working exploits were already reported to software vendors that will address the vulnerabilities discovered by the experts in the coming weeks.
The team named “360 Enterprise Security and Government and (ESG) Vulnerability Research Institute,” which is part of the Chinese tech giant Qihoo 360, won the competition. The winning team earned $744,500 of the total $1,210,000 jackpot.
At the second place there is the AntFinancial Lightyear Security Lab followed by the security researcher Pang.
Tianfu Cup 2020 – 5 minutes to hack Windows 10, Ubuntu iOS, VMWare EXSi, and others
9.11.20 Congress Securityaffairs
Many popular OS and applications have been hacked during this year’s edition of the Tianfu Cup hacking competition.
This year’s edition of the Tianfu Cup hacking competition was very prolific, bug bounty hackers have discovered multiple vulnerabilities in multiple software and applications.
The Tianfu Cup is the most important hacking contest held in China, the total bonus of the contest this year was up to 1 million US dollars.
The third edition of the competition ended today and the winning team earned a total of $744,500.
The participants successfully tested their exploits against the following software:
iOS 14 running on an iPhone 11 Pro
Samsung Galaxy S20
Windows 10 v2004 (April 2020 edition)
Ubuntu
Chrome
Safari
Firefox
Adobe PDF Reader
Docker (Community Edition)
VMWare EXSi (hypervisor)
QEMU (emulator & virtualizer)
TP-Link and ASUS router firmware
This year fifteen teams of Chinese hackers took part in the competition, each team had three tries of five minutes to demonstrate a working exploit against a specific target.
Working exploits were already reported to software vendors that will address the vulnerabilities discovered by the experts in the coming weeks.
The team named “360 Enterprise Security and Government and (ESG) Vulnerability Research Institute,” which is part of the Chinese tech giant Qihoo 360, won the competition. The winning team earned $744,500 of the total $1,210,000 jackpot.
At the second place there is the AntFinancial Lightyear Security Lab followed by the security researcher Pang.
Routers, NAS Devices, TVs Hacked at Pwn2Own Tokyo 2020
9.11.20 Congress Securityweek
Bug bounty hunters have hacked routers, network-attached storage (NAS) devices and smart TVs at the Zero Day Initiative’s Pwn2Own Tokyo 2020 hacking competition.
Due to the COVID-19 pandemic, the competition has been turned into a virtual event and Pwn2Own Tokyo is actually coordinated by Trend Micro’s ZDI from Toronto, Canada, with participants demonstrating their exploits remotely.
Organizers have offered significant prizes for exploits targeting a wide range of mobile and IoT devices, but participants have only focused on routers, NAS products and TVs.
In total, participants were awarded $136,000 for 23 unique vulnerabilities across six different devices. Impacted vendors have been given 120 days to release patches before details are made public by ZDI.
A dozen teams and individuals signed up for this year’s Pwn2Own Tokyo. The winner was Team Flashback, which earned a total of $40,000 for hacking TP-Link AC175 and NETGEAR Nighthawk R7800 routers.
The second place team, named DEVCORE, earned $20,000 for successfully demonstrating an exploit against a Synology DiskStation DS418Play NAS product, and $17,500 for an exploit targeting a Western Digital My Cloud Pro Series PR4100 NAS device.
The Trapa Security team took home $20,000 for an exploit targeting the WD device, and $5,000 for a NETGEAR router hack. The same total amount was earned by the STARLabs team for exploits targeting the NETGEAR router and the Synology NAS device.
Participants also hacked Samgung and Sony smart TVs, but they didn’t earn any money since the vulnerabilities they leveraged had already been known.
At last year’s Pwn2Own Tokyo, participants earned a total of $315,000 for disclosing 18 vulnerabilities.
China’s Tianfu Cup hacking competition also took place over the weekend, with participants earning a total of over $1.2 million, including $180,000 for iPhone exploits, $180,000 for VMware ESXi exploits, and $80,000 for Samsung Galaxy S20 exploits.
Bug Bounty Hunters Earn $1.2 Million at Chinese Hacking Competition
9.11.20 Congress Securityweek
Bug bounty hunters have earned a total of more than $1.2 million over the weekend at the 2020 Tianfu Cup International PWN Contest, a major hacking competition that takes place every year in China.
Organizers of the event describe it as “China’s Pwn2Own” and this year the prize pool exceeded $1 million.
A total of 15 teams signed up for the 2020 Tianfu Cup and 8 of them earned money for their exploits. The winner was a team representing Chinese cybersecurity firm Qihoo 360, which earned over $740,000.
The Qihoo 360 team earned $100,000 for a Chrome exploit that achieved remote code execution with a sandbox escape, $180,000 for a VMware ESXi guest to host escape, $40,000 for a Firefox exploit, $60,000 for a Qemu exploit, and $18,000 for an Adobe Reader exploit.
The same team also hacked an iPhone 11 Pro with iOS 14 and earned $180,000 for an exploit that achieved remote code execution with a sandbox escape. They also targeted a Samsung Galaxy S20, which earned them $80,000 as they demonstrated an exploit that achieved remote code execution with root privileges.
The Qihoo 360 team also hacked Windows 10 and CentOS 8, which earned them $40,000 for each exploit chain.
Another team also hacked the iPhone 11 Pro and earned $180,000. It’s worth noting that the top prize for hacking the iPhone was $300,000, for a remote jailbreak.
Other participants targeted Safari, Docker, Adobe Reader, the Galaxy S20, Ubuntu, and Asus and TP-Link routers. Overall, organizers said, participants successfully hacked 11 of the 16 targets.
At last year’s event, participants earned over half a million dollars for hacking products from Apple, Google, Microsoft, VMware and others.
The Zero Day Initiative’s Pwn2Own Tokyo competition also took place last week, but participants only earned $136,000 for 23 unique vulnerabilities. White hat hackers remotely demonstrated their exploits against routers, NAS devices and smart TVs.
Windows 10, iOS, Chrome, Firefox and Others Hacked at Tianfu Cup Competition
9.11.20 Congress Thehackernews
Multiple software products from Adobe, Apple, Google, Microsoft, Mozilla, and Samsung were successfully pwned with previously unseen exploits in Tianfu Cup 2020, the third edition of the international cybersecurity contest held in the city of Chengdu, China.
"Many mature and hard targets have been pwned on this year's contest," the event organizers said. "11 out of 16 targets cracked with 23 successful demos."
The hacking competition showed off hacking attempts against a number of platforms, including:
Adobe PDF Reader
Apple iPhone 11 Pro running iOS 14 and Safari browser
ASUS RT-AX86U router
CentOS 8
Docker Community Edition
Google Chrome
Microsoft Windows 10 v2004
Mozilla Firefox
Samsung Galaxy S20 running Android 10
TP-Link TL-WDR7660 router
VMware ESXi hypervisor

The Tianfu Cup, analogous to Pwn2Own, was started in 2018 following a government regulation in the country that barred security researchers from participating in international hacking competitions because of national security concerns.
The two-day event, which happened over the weekend, saw white hat hackers from 15 different teams using original vulnerabilities to break into widely used software and mobile devices in 5 minutes over three attempts.
The idea, in a nutshell, is to use various web browsers to navigate to a remote URL or use a flaw in the software to control the browser or the underlying operating system.
Qihoo 360's Enterprise Security and Government (ESG) Vulnerability Research Institute came out top with $744,500 in prize money, followed by Ant-Financial Light-Year Security Lab ($258,000) and a security researcher named Pang ($99,500).
Patches for all the demonstrated bugs demonstrated are expected to be released in the coming days.
Pwn2Own Tokyo Day 3: Team Flashback crowned Master of Pwn
9.11.20 Congress Securityaffairs
On the third day of the Pwn2Own Tokyo 2020 bug bounty hunters hacked a Synology NAS and had multiple partial successes.
We are on day three of the popular Pwn2Own Tokyo hacking competition that due to the COVID-19 pandemic has been arranged as a virtual event.
The Pwn2Own Tokyo is actually coordinated by Zero Day Initiative from Toronto, Canada, and white hat hackers taking part in the competition have to demonstrate their ability to find and exploit vulnerabilities in a broad range of devices.
Let’s start with the only success of day 3 obtained by the STARLabs team targeting the Synology DiskStation DS418Play NAS.
The team of experts exploited a race condition and an OOB Read to get a root shell on the NAS. They earned $20,000 and 2 points towards Master of Pwn.
Day three has seen multiple partial successes, below the details of the attempts:
DEVCORE team targeting the Western Digital My Cloud Pro Series PR4100 – The team chained 6 bugs to gain code execution, but 2 flaws had previously been reported. They won $17,500 and 1.5 Master of Pwn points.
Gaurav Baruah targeting the Western Digital My Cloud Pro Series PR4100 – The expert was able to successfully get a root shell on the device exploiting a flaw that had been previously submitted. He earned 1 point towards Master of Pwn.
The Viettel Cyber Security team targeting the Sony X800 television – The team got a partial win because he was able to read sensitive files from a fully patched Sony X800 smart TV by using a bug that was publicly known. The team only earned 1 point towards Master of Pwn.
The only failure of the day was for an attampt of the Team Bugscale targeting the LAN interface on the NETGEAR Nighthawk R7800 router. The team failed in getting their exploit to work within the allotted timeframe.
The Master Pwn winner of Pwn2Own Tokyo is the Team Flashback, Congrats.
NETGEAR Router, WD NAS Device Hacked on First Day of Pwn2Own Tokyo 2020
7.11.20 Congress Securityweek
Bug bounty hunters hacked a NETGEAR router and a Western Digital network-attached storage (NAS) device on the first day of the Zero Day Initiative’s Pwn2Own Tokyo 2020 hacking competition.
Due to the coronavirus pandemic, the competition has been turned into a virtual event and Pwn2Own Tokyo is actually coordinated by ZDI from Toronto, Canada, with participants demonstrating their exploits remotely.
On the first day of the event, the NETGEAR Nighthawk R7800 router was targeted by Team Black Coffee, Team Flashback, and teams from cybersecurity firms Starlabs and Trapa Security.
Team Flashback earned $20,000 for what has been described as a very reliable remote code execution exploit that combined two bugs. The attack targeted the device via the WAN interface.
The Starlabs team achieved arbitrary code execution by combining two bugs and it earned $5,000. The Trapa Security team earned the same amount after using a command injection flaw to take control of the router.
The Western Digital My Cloud Pro series PR4100 NSA device was targeted by the Trapa Security team, which earned $20,000 for an exploit that combined an authentication bypass bug and a command injection vulnerability to gain root, and by 84c0 Team, which successfully demonstrated a remote code execution exploit, but their win was only partial since they leveraged a previously known flaw.
The top rewards for hacking routers and NAS devices at Pwn2Own Tokyo 2020 is $20,000. In the case of routers, this is the maximum reward for WAN attacks, while for LAN attacks participants can earn up to $5,000.
Also on the first day, the Viettel Cyber Security team targeted a Samsung smart TV, and while they managed to hack it and get a reverse shell on the device, the attack involved a known vulnerability so it did not earn them any money.
The second day of Pwn2Own Tokyo has already started. Over the next two days, participants will target TP-Link and NETGEAR routers, WD and Synology NAS devices, and Sony and Samsung TVs.
This year’s event is also sponsored by Facebook, which invited researchers to hack its Oculus and Portal devices. However, it seems Pwn2Own Tokyo 2020 will focus on routers, NAS products and TVs.
At last year’s Pwn2Own Tokyo, participants earned a total of $315,000 for disclosing 18 different vulnerabilities.
Black Hat Wrap-Up: IoT and Hardware Vulnerabilities Take the Spotlight
10.8.20 Congress Securityweek
The first entirely virtual edition of the Black Hat cybersecurity conference took place last week and researchers from tens of organizations presented the results of their work from the past year.
Some of the most interesting presentations focused on vulnerabilities affecting industrial, IoT, hardware and web products, but a few of the talks covered endpoint software security.
Here are some of the most interesting presentations from Black Hat:
Black Hat 2020 summary
Legacy programming languages can pose serious risks to industrial robots
Researchers from Trend Micro and the Polytechnic University of Milan have analyzed industrial programming languages and the risks they pose to robots and other programmable manufacturing machines. They have developed a worm to demonstrate the severity of their findings.
Variants of the Kr00k attack impact Wi-Fi chips from Qualcomm and MediaTek
The Kr00k vulnerability, which allows attackers to decrypt wireless communications, only affects Wi-Fi chips from Broadcom and Cypress, but ESET researchers discovered recently that similar vulnerabilities also exist in chips made by MedaTek and Qualcomm.
Mercedes-Benz E-Class hacked remotely by Chinese researchers
Researchers from Sky-Go, the vehicle cybersecurity unit of Chinese security firm Qihoo 360, have described the analysis process that resulted in the discovery of 19 vulnerabilities in a Mercedes-Benz E-Class, including flaws that can be exploited to remotely hack a car.
Lamphone attack allows spying via light bulb vibrations
A researcher from the Ben-Gurion University of the Negev has detailed a technique for remotely eavesdropping on the conversations in a room by analyzing a light bulb’s frequency response to sound.
Attacking industrial systems via protocol gateway vulnerabilities
Researchers from Trend Micro have analyzed several protocol gateways used in industrial environments and found that they are affected by vulnerabilities that can allow threat actors to obtain valuable information and disrupt critical processes.
Manipulating the energy market with high-wattage IoT botnets
A botnet powered by high-wattage IoT devices could be used, in theory, to manipulate the energy market the same way financial markets can be manipulated, according to researchers from the Georgia Institute of Technology.
Sophisticated macOS attack using Office document macros
Patrick Wardle, principal security researcher at Jamf, described an exploit chain that resulted in the delivery of malware to a macOS system using a Microsoft Office document containing macro code. For the exploit to be successful, the victim would simply have to open a document. No alerts are displayed to the victim.
Plundervolt: using CPU voltage modifications to steal data
Researchers from various universities have described Plundervolt, an attack method disclosed last year that leverages CPU voltage modifications to expose data stored using Intel Software Guard Extensions (SGX).
Google’s analysis of zero-day vulnerabilities finds “detection bias”
Google Project Zero has released a report on the vulnerabilities exploited in attacks in 2019, and its researchers have drawn some interesting conclusions regarding the detection of zero-days.
Over 30 vulnerabilities discovered across 20 CMS products
Researchers from GitHub and Micro Focus Fortify have discovered more than 30 vulnerabilities across 20 popular content management systems (CMS). The attacks targeted templates and focused on escaping template sandboxes and achieving remote code execution.
New HTTP request smuggling attacks
A SafeBreach researcher has detailed several new variants of HTTP request smuggling attacks, which apparently still haven’t been fully mitigated, despite the fact that the method has been known for more than a decade.
Bypassing firewalls and NATs with attack on Ethernet cables
Researchers from Armis have shown how malicious actors could leverage packet-in-packet attacks on Ethernet cables to bypass firewalls and NATs. This type of attack has been known for years, but until now it was considered impractical.
BlueRepli attack bypasses Bluetooth authentication on Android phones
Researchers from DBAPPSecurity have disclosed a new Bluetooth attack, named Bluethooth Replicant (BlueRepli), that can be used for stealthy access to Android phones.
More devices affected by Ripple20 vulnerabilities
Researchers from JSOF and Tenable discovered more devices affected by the vulnerabilities dubbed Ripple20. Ripple20 is the name given to 19 security holes affecting the Treck TCP/IP stack, which is used by millions of IoT devices.
Vulnerabilities in Kata Containers
Kata Containers are affected by vulnerabilities that can be exploited to escape a container, break out of the VM and compromise the host, a researcher from Palo Alto Networks has demonstrated.
Researcher Demonstrates Several Zoom Vulnerabilities at DEF CON 28
10.8.20 Congress Thehackernews
Popular video conferencing app Zoom has addressed several security vulnerabilities, two of which affect its Linux client that could have allowed an attacker with access to a compromised system to read and exfiltrate Zoom user data—and even run stealthy malware as a sub-process of a trusted application.
According to cybersecurity researcher Mazin Ahmed, who presented his findings at DEF CON 2020 yesterday, the company also left a misconfigured development instance exposed that wasn't updated since September 2019, indicating the server could be susceptible to flaws that were left unpatched.
After Ahmed privately reported the issues to Zoom in April and subsequently in July, the company issued a fix on August 3 (version 5.2.4).
It's worth noting that for some of these attacks to happen, an attacker would need to have already compromised the victim's device by other means. But that doesn't take away the significance of the flaws.
In one scenario, Ahmed uncovered an issue with the Zoom Launcher for Linux that could allow an adversary to run unauthorized software owing to the manner it launches the "zoom" executable.
"This breaks all of the protection of application whitelisting, allows malware to run as a subprocess of a trusted vendor (Zoom), and is a bad design/security practice by all means," Ahmed said in an analysis.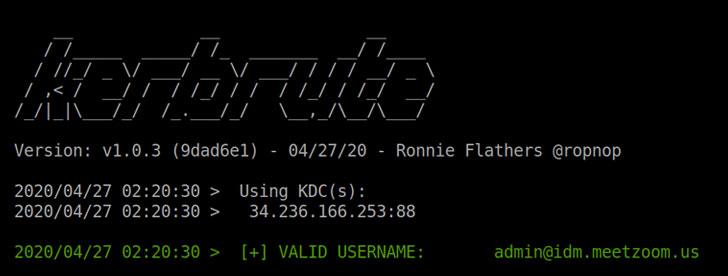
That's not all. In a similar vein, an attacker with access to the victim's machine can read and exfiltrate Zoom user data and configuration by navigating to the local database and even accessing chat messages stored on the system in plaintext format.
Two other flaws involved an externally accessible Kerberos authentication service ("ca01.idm.meetzoom.us") and a TLS/SSL issue that lets malware inject custom certificate fingerprints into the local Zoom database.
"This is per user certificate pinning and intentionally allows for the user to allow custom certificates," Zoom said of the certificate injection flaw. "The user can write to their own database, but no other non-root users can. It's common best practice to have user applications run at their privilege level, as requiring Zoom to run as root would introduce unnecessary security risks to Zoom and our customers."
But it gets more interesting. Ahmed went on to highlight a memory leak vulnerability by exploiting the profile picture feature on Zoom to upload a malicious GIF image, download the rendered file, and extract data from it to leak portions of system memory.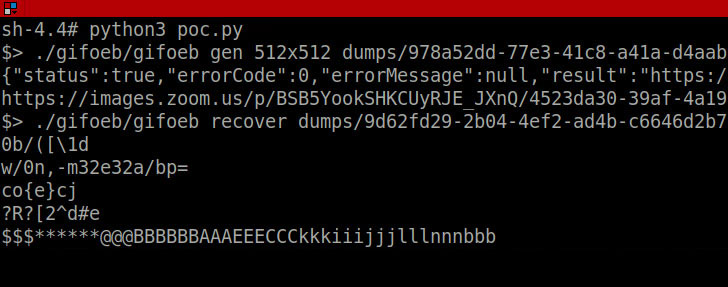
"After an internal investigation, we've concluded that the behavior was not a memory leak but just our image utility's best effort at converting a malformed gif into a jpeg," the company said.
Although Ahmed believes this to be a consequence of a known flaw in ImageMagick image conversion software (CVE-2017-15277), Zoom has said it doesn't use the utility to convert GIFs uploaded as profile pictures into JPEG format.
In response to the disclosures, Zoom has taken down the exposed Kerberos authentication server to prevent brute-force attacks, while also acknowledging that it's working on addressing the lack of encryption while storing the chat logs.
It's recommended that users update Zoom to the latest version to mitigate any risk arising out of these issues.
The development came as the company resolved a security flaw last month. It allowed attackers to crack the numeric passcode used to secure private meetings on the platform and eavesdrop on participants.
Black Hat 2020: Satellite Comms Globally Open to $300 Eavesdropping Hack
7.8.20 Congress Threatpost
Attackers can listen in on internet traffic for high-value targets a continent away, like shipping fleets and oil installations, using some basic home-television gear.
Satellite internet communications are susceptible to eavesdropping and signal interception by far-flung attackers located in a different continent or country from their victims. And all they need is $300 worth of off-the-shelf equipment to pull it off.
That’s the word from James Pavur, an academic researcher and doctoral candidate at Oxford University, speaking at Black Hat 2020 on Wednesday.
Satellite ISPs provide connectivity in places where terrestrial communications aren’t possible. For instance, at oil rigs in the Gulf, or to pilots in-flight. Commercial shipping vessels, fishing boats, cruise passengers, terrestrial explorers camping in the wilderness, Arctic observation camps, weather stations and others all rely on satellite to connect to the outside world.
The first thing to know is that the way satellite communications work provides for a wide geographical attack area, the researcher explained. When a satellite ISP makes an internet connection for a customer, it beams that customer’s signals up to a satellite in geostationary orbit within a narrow communications channel; that signal is then sent back down to a terrestrial receiving hub and routed to the internet. However, when the response signals are sent back along the same path (just in reverse), that transmission downlink between the satellite and the user will be a broadcast transmission, containing many customers’ traffic simultaneously.
“A critical difference is that we’re going to send [downstream signals] in a really wide beam, because we want to cover as many customers as possible, and satellites are very expensive,” according to Pavur. “So radio waves carrying a response to a Google search will reach our customer in the middle of the Atlantic Ocean; but they will also hit an attacker’s dish in, say, Ghana.”
Essentially what this means is that if they were able to perform an interception, adversaries could eavesdrop on vast sections of the globe.
The $300 Listening Station
The common assumption is that for an attacker to pull off this kind of signal interception, it takes money. And indeed, there are specialized modems for intelligence-collection purposes that allow governments to listen in on satellite communications, Pavur noted; they’re installed in multimillion-dollar ground stations worldwide. However, for those without nation-state assistance, the researcher demonstrated that the same kind of attack can be accomplished with basic home-television consumer equipment.
“We purchased this simple flat panel satellite dish — although honestly any satellite dish would do, even something that’s already resting on your roof, or off of Craigslist or Gumtree for basically free,” Pavur said. “And then we used a PCIe satellite tuner card. These are widely available for people who want to watch satellite television on their computer.”
Higher-end professional PCIe tuner cards cost between $200 and $300, but there are cheaper versions in the $50 to $80 price range. The downside of the cheaper ones, Pavur explained, is that there will be a lack of reliability in listening in on certain feeds.
With the equipment in hand, eavesdroppers then need to decide where to point their dishes (the locations of comms satellites are public information), and then go about discovering internet feeds. To do that, Pavur’s team used a software tool called EPS Pro, which is designed to help people find satellite television channels.
“We’re going to point our satellite dish at a spot in the sky that we know has a satellite, and we’re going to scan the Ku band of the radio spectrum to find signals against the background noise,” Pavur explained. “The way we’ll identify channels is by looking for distinct humps in the radio spectrum; because they stick out against the background noise, we can guess that there’s something going on there. We’ll tell our card tune to this one, and treat it as a digital video broadcasting for satellite feed. After a few seconds we get a lock on that feed, meaning we successfully found a connected satellite.”
The next step is to make a short recording of the feed; depending on the signal-to-noise ratio, the amount of data captured could range from a megabyte to a terabyte. In any event, attackers would then examine the data to discover whether they’ve found internet traffic or a TV feed.
“There’s no dark magic to this process, I’m just going to look through that raw binary file for the string HTTP, which we’d expect to see an internet capture, but wouldn’t expect to see in a television feed,” Pavur explained.
Once an internet connection is identified, it’s possible to record it and then parse it for information. But there’s one other obstacle to this process, according to the research. The feed might be transmitted in one of two protocols: The MPEG video streaming format (which is easy to parse using commonly available tools like Wireshark), or a newer protocol known as generic stream encapsulation (GSE).
“GSE is much simpler in theory; it takes an IP payload and wraps it in a generic GSE stream which has a bunch of different fragments, and then puts that into a digital video broadcasting feed,” explained the researcher. “This is particularly popular we found among enterprise customers, who rent an entire satellite transponder for their networks. But, the signals they send have more complicated modulations that are hard for cheap hardware to keep up with.”
As a result, the team found they were often losing big chunks of these types of GSE internet feeds, resulting in corrupted files. There was a fix however: they wrote a forensic tool called GC Extract that can reconstruct meaningful IP data out of a corrupted GSE recording – problem solved.
Encryption Issues
The Oxford team took their set-up and applied it to real satellite internet connections, finding that generally speaking, the satellite ISPs they examined did not seem to be employing encryption by default. As a result, they were able to listen in on feeds from a wide range of victim types, on land, at sea and in the air – as if they were the ISP themselves.
“What this means is that an attacker who’s listening to your satellite signal gets to see what your internet service provider would expect to see: Every packet that comes to your modem, every BitTorrent you download, every website you visit,” Pavur said. “But it gets even worse if we look at enterprise customers, because a lot of them were operating what was essentially a corporate land network over the satellite feeds. For example, imagine a cruise line that has a bunch of Windows devices aboard it ships. This Windows local area network with all that internal LDAP traffic and SDP traffic will be broadcast over the satellite link, giving an eavesdropper perspective from behind the firewall.”
Even users whose own traffic is encrypted are susceptible, Pavur explained.
“Our ISP vantage point gives us some unique perspectives on what you’re doing – for example, your DNS queries are likely still sent unencrypted, so we can piece together your internet browsing history, and which websites you’re visiting,” the analyst noted. “Even those TLS certificates which are protecting the contents of your traffic are also fingerprinting the servers you’re talking to, and the services you’re connecting to.”
Victim Impact
Pavur also offered a few examples of what the team was able to pick up. For instance, they intercepted an email conversation that a lawyer in Spain was having with a client, about an upcoming court case.
“Now, obviously, this raises serious concerns for attorney client privilege and personal communications privacy,” said the researcher. “But in our threat model, it gets even worse, because at this point, we have access to the contents of this email inbox, we know his email address. So we can say hey, this guy goes to paypal.com, and we can also go to PayPal and use the ‘forgot my password’ function to steal his PayPal account or any other account.”
In another example, the team found that many wind turbines use satellite, and that they have connected terminals with a control panel for changing the settings of the power station.
“The credentials for these were often being sent in clear text over the satellite link, meaning that anyone on the internet could see that and start messing around with electricity infrastructure,” Pavur said. “There may be a second layer of protection behind this login page that we didn’t account for, but it’s at least intuitively concerning that these credentials are being broadcast in clear text.”
In a maritime use case, the eavesdropping picked up multiple terabytes of information from ships, but it wasn’t immediately clear which packets were coming from which vessel.
“So we picked 100 random IP addresses and devised a basic fingerprint consisting of DNS queries, TLS certificates and some strings from the first couple of bytes of their traffic, to see if we could actually de-anonymize these IP addresses and tie them to specific ships in the ocean,” Pavur explained, adding that they were successful for about 10 percent of the vessels the team looked at.
One was a fishing boat that was using software to tell it where fish could be found, over the satellite feed, while another was a massive container ship, “one of the larger ships in the world for one of the largest shipping companies in the world.”
Other successful targets for interception included a subsea repair ship, operated by a major petroleum company, which had a vulnerable box running Windows Server 2003; a port authority transmitting cargo-ship lists of all crew members, dates of birth and passport numbers, in clear text; and communications from a Greek billionaire’s yacht.
In the case of the vulnerable server, Pavur cautioned that this could be a pathway to attacking the operational technology on board the ship.
As for the latter, “one day, his captain forgot his Microsoft account login,” Pavur said. “And so the account-reset password was sent over clear text on the satellite feed. At this point, we had a route where we could have potentially hijacked this captain’s account and targeted an extremely high net-worth individual via targeted social-engineering attacks.”
Notification and Mitigation
The Oxford team disclosed their findings to all impacted entities, both the test victims and ISPs – but won’t be “naming and shaming” anyone.
“We don’t want this to be a report about X cruise line leaking your personal information; we want to talk about a systemic issue that affects almost every customer of satellite geostationary broadband,” said Pavur. “We of course responsibly disclose these vulnerabilities, reaching out to some companies as much as a year ago, as well as the customers who are most affected by these breaches. Generally people were pretty receptive.”
The Federal Bureau of Investigation also released a private threat-intelligence notification in response to the research.
On the mitigation front, the response is more complicated than simply adding encryption. Users that employ standard end-to-end encryption will find themselves taking a big performance hit, according to the research.
“It turns out that traffic is really slow over those satellite feeds because of all the hops you have to make in the sky,” Pavur explained. “And so as a result, satellite internet service providers have built a tool called a performance-enhancing proxy, which is essentially a benevolent man-in-the-middle that intercepts and modifies your TCP sessions on both sides of the satellite link to make it feel fast. Unfortunately, if you use standard end to end encryption, this will stop the ISP from being able to engage in that benevolent man-in-the-middle attack, and it will slow your satellite speeds to a crawl.”
An alternative is to use a TLS-encrypted email client which would eliminate the performance difference, but would protected at least email-related communications. And also, ISPs could improve on their end, with encryption or tweaks that disallow traffic to be parsed.
The takeaway, according to Pavur, is that internet users should always remember that the next hop is unknown.
“The internet is a weird web with devices and systems that are connected in ways that you can never predict, you might connect to a secure Wi-Fi hotspot or a cell tower, but the next hop could be a satellite link or wiretapped Ethernet cable,” Pavur cautioned. “Having the right, the ability and the knowledge to encrypt your own data, and to choose to do that, is critical to protecting against this class of attack, whatever domain you think about it in.”
Black Hat 2020: ‘Zero-Click’ MacOS Exploit Chain Uses Microsoft Office Macros
7.8.20 Congress Threatpost
At Black Hat 2020, Patrick Wardle disclosed an exploit chain that bypasses Microsoft’s malicious macros protections to infect MacOS users.
A new “zero-click” MacOS exploit chain could allow attackers to deliver malware to MacOS users using a Microsoft Office document with macros. The attack bypasses security measures that both Microsoft and Apple have put in place to protect MacOS users from malicious macros.
The exploit chain, revealed by Patrick Wardle, principal security researcher with Jamf, at Black Hat USA 2020, runs macros without an alert or prompt from the Microsoft Office application that prompts explicit user approval – meaning that when a user opens the document, the macro is automatically executed.
“As the current [macros-based] attacks are lame… I wanted to make them ‘better’ to raise awareness about this attack vector, and also highlight how it could easily be worse,” Wardle told Threatpost. “I found a sandbox escape and a bypass of Apple’s new notarization requirements, and combined that with another zero day (from another researcher) to make a full ‘zero-click’ exploit chain.”
Wardle notified both Microsoft and Apple about his findings. Apple patched the flaws with the release of MacOS 10.15.3, but told Wardle “this issue does not qualify for a CVE.” Microsoft meanwhile told Wardle that the exploit chain was an issue “on the Apple side.”
Current Macro-Based Attacks
A macro is a snippet of executable code that can be added to Microsoft Office documents, generally used to accomplish a task automatically. However, macros are also commonly abused by cybercriminals, who use them for delivering a malicious payload to the endpoint because they can be allowed with a simple, single mouse-click on the part of the user when prompted.

Credit: Patrick Wardle
Microsoft has attempted to block macros-based attacks. The tech giant has disabled them in Microsoft Office by default, so a user gets an alert if they are enabling macros. Microsoft also debuted a feature that sandboxed more recent versions of Microsoft Office applications that are running on modern versions of macOS – so even if (malicious) macros are inadvertently allowed to run, they will find themselves running in a highly restrictive sandbox.
From Apple’s end, the company has created notarization checks to prevent potentially malicious code – downloaded from the internet – from executing on MacOS systems. Notarizing is an automated system that scans software for malicious content and checks for code-signing issues. Due to these current protections, previous macros-based exploits have had little success.
However, Wardle’s exploit chain bypassed all of these security protections.
Exploit Chain
The first step in Wardle’s chain was a previously-disclosed high-severity vulnerability, CVE-2019-1457, which is a security bypass in Microsoft Office by not enforcing macro settings on an Excel document. The vulnerability results in XML macros that are in the symbolic link (SYLK) file format being automatically executed in Office 11 for Mac. This vulnerability still affects more recent versions of Office for Mac (if users enabled the “disable all macros without notification” options), the CERT Coordination Center warned last year.

Credit: Patrick Wardle
Next, Wardle leveraged a sandbox escape that was released in mid-2018. This sandbox escape abused a sandbox exception in Office app’s sandbox profile. When it was first released, Microsoft patched the flaw by only denying file creations (deny file-write) in the user’s Application Scripts and LaunchAgents directory.
However, “this means that from the sandbox (e.g. via macro code), we can still create files (ending in ~$something) almost anywhere,” said Wardle.
Finally, the exploit chain ended with a full bypass of Apple’s notarization requirements. Wardle was able to do so by abusing the Archive Utility app in MacOS. He used a login item zip archive ~/Library/~payload.zip that was automatically extracted (outside the sandbox) via the Archive Utility.
“If the LaunchAgent directory does not exist (which it does not on a default install of macOS), it will be created, with our launch agent inside it,” he said. “In other words, we’ve just found a way to create a launch agent, that on the next login will automatically executed by macOS. With an ability to create a launch agent (that will launch an interactive remote shell), it’s game over.”
What this exploit chain means for an end user is that if they receive a Microsoft Office document and attempt to open it, the executable will automatically run: “Triggered by simply opening a malicious (macro-laced) Office document, no alerts, prompts nor other user interactions were required in order to persistently infect even a fully-patched macOS Catalina system,” Wardle said.
More MacOS Macros-Based Attacks
Wardle warned that macros-based attacks, while traditionally targeting Windows users, have become increasingly more common on MacOS systems.
For instance, in 2019 the infamous Lazarus APT group was observed using macro-laden Office documents to target macOS users. In 2017, researchers uncovered a malicious Word document, designed to spread malware on either Mac OS X or Microsoft Windows, depending on where it’s opened.
“In the world of Windows, macro-based Office attacks are well understood (and frankly are rather old news). However, on macOS, though such attacks are growing in popularity and are quite en vogue, they have received far less attention from the research and security community,” said Wardle.
Black Hat 2020: Using Botnets to Manipulate Energy Markets for Big Profits
7.8.20 Congress Threatpost
Black Hat 2020 session discusses how high-wattage connected devices like dishwashers and heating systems can be recruited into botnets and used to manipulate energy markets.
Researchers are warning that a new class of botnets could be marshaled and used to manipulate energy markets via zombie armies of power-hungry connected devices such as air conditioners, heaters, dryers and digital thermostats. A coordinated attack could cause an energy stock index to predictably go up or down – creating an opportunity for a rogue operator to cash in.
Researchers with the Georgia Institute of Technology laid out the scenario in a Black Hat 2020 virtual session Wednesday. They warned, high-wattage IoT devices are vulnerable to takeover by threat actors who can hijack them in the same way that millions of CCTV cameras, DVRs and home routers are recruited into botnet armies to conduct distributed denial-of-service attacks and mine cryptocurrency.
“If an attacker can just slightly affect electricity market prices in their favor, it would be like knowing today what’s going to happen in tomorrow’s stock market,” said Tohid Shekari, a graduate research assistant in the School of Electrical and Computer Engineering at the Georgia Institute of Technology.
Shekari was joined by Raheem Beyah, professor, vice president for Interdisciplinary Research, at Georgia Institute of Technology, during the session. They explained that energy markets are split into either a day-ahead or real-time. Energy producers work with resellers who deliver electricity to end users. The ecosystem is ripe for manipulation by threat actors, they said.
“To meet the demand for electrical energy, utility companies must predict future demand and purchase power from the day-ahead wholesale energy market at competitive prices,” according to a Georgia Tech report on the research. “If the predictions turn out to be wrong, the utilities may have to pay more or less for the energy they need to meet the demands of their customers by participating in the real-time market.”
Those real-time markets are more volatile and subject to price fluctuation. “Creating erroneous demand data to manipulate forecasts could be profitable to the suppliers selling energy to meet the unexpected demand, or the retailers or utilities buying cheaper energy from the real-time market,” the report said.
Manipulation of this energy ecosystem can also allow a rogue investor to accurately predict a shift in market value and capitalize on ups and downs.
During the Black Hat session, Beyah estimated that the number of hijacked IoT devices needed to carry out an attack might be 50,000 within a single market. That would enable what he called an “IoT Skimmer” attack. Using a botnet to increase or decrease power consumption by just 1 percent would be enough to manipulate prices and be extremely hard to detect.
Bigger swings in power consumption, researchers pointed out, could also be used to sabotage an energy supplier.
“By turning the compromised equipment on or off to artificially increase or decrease power demand, botnets made up of these energy-consuming devices might help an unscrupulous energy supplier or retailer (electric utility) alter prices to create a business advantage, or give a nation-state a way to remotely harm the economy of another country by causing financial damage to its electricity market,” according to the Georgia Tech report.
IoT Skimmer Attacks: Hypothetical
While the damage wrought by botnets and botnet malware like Mirai, Hydra and BASHLITE is not hypothetical, the IoT Skimmer attacks are. Researchers said they are unaware of any specific attacks designed to manipulate energy markets.
Separately, the energy sector is often targeted by way of disruptive attacks. In January, researchers identified the threat actor group APT33, dubbed Magnallium, targeting global oil-and-gas industry and electric companies in North America. Months before that campaign was uncovered, another advanced persistent threat group (APT34), also known as ZeroCleare, was bent on destruction and disruption of the Middle East oil industry.
Destructive intent aside, researchers estimate a three-month IoT Skimmer campaign could yield attackers $24 million a year. A malicious IoT Skimmer attack, on the other hand, could cause $350 million per year in economic damage to the U.S. energy sector, the researchers estimated.
The Georgia Tech research was based on one year of real-world data analysis of the two largest electricity markets in the U.S. – New York and California, Shekari and Beyah said.
Mitigating against these types of attacks, the researchers said, will take comprehensive monitoring of high-wattage IoT-connected devices and any unexpected spikes or dips in power consumption would need to trigger alarm bells.
Black Hat 2020: Linux Spyware Stack Ties Together 5 Chinese APTs
6.8.20 Congress Threatpost
The groups, all tied to the Winnti supply-chain specialist gang, were seen using the same Linux rootkit and backdoor combo.
A stack of Linux backdoor malware used for espionage, compiled dynamically and customizable to specific targets, is being used as a shared resource by five different Chinese-language APT groups, according to researchers.
According to an analysis from BlackBerry released at Black Hat 2020 on Wednesday, those five groups have turned out to all be splinters of the Winnti Group. Active since at least 2011, Winnti is known for high-profile supply-chain attacks against the software industry, with the aim of spreading trojanized software (such as CCleaner, ASUS LiveUpdate and multiple malicious video games).
The Linux toolset uncovered by BlackBerry was used in a series of targeted attacks. It contains six different pieces, according to Kevin Livelli, director of threat intelligence at the firm. Speaking during a Wednesday session, he noted that the tools start with an installer bash script, compressed inside of another shell script, whose job it is to work with a remote build server. That build server, which is the second item in the bundle, custom-compiles a malware package for a specific target on the fly, which would then be downloaded to the victim by the installer.
This custom malware payload consists of items three and four: A rootkit and a backdoor, complete with an installation script for the target. As for the rootkit, BlackBerry researchers found two variants, both designed to work with an associated backdoor.
“We saw them tailored for different kernel versions, with up-to-date command-and-control (C2), so we knew older kernel versions were still in use – likely a reflection of the fact that many Linux sysadmins are too slow to update for various reasons,” Livelli said. “We found examples of malware that targeted Red Hat Enterprise, CentOS and Debian, but it’s a good bet, given their custom nature, and on the fly combination, that there are others out there.”
The fifth item is an attacker control panel, capable of managing both Windows and Linux targets simultaneously, with its own graphical user interface, Livelli said. And finally, the sixth item is the Linux XOR DDoS botnet, which is the largest known Linux botnet, first coming to notice in 2015.
As far as C2 activity, Livelli said that BlackBerry observed hard-coded network callback data inside the attacked organization it investigated, which suggests that the group had already established infrastructure inside the target before deploying the Linux stack.
“It’s highly likely that all the Linux malware that we found was not first-stage malware, but rather a persistence tool, a beachhead, if you would, and that the compromise of the targets ran much deeper and was much more well established,” Livelli said. “We also saw extensive abuse of legitimate cloud provider infrastructure [for C2].”
In addition to the C2 infrastructure and the Linux stack, it’s worth noting that other malware also infested the systems observed.
“State-backed attackers almost always target multiple platforms,” Livelli said. “This time, we found some of the same group of attackers in command of some Android malware, and others wielding some Windows malware. We found an excellent vantage point on an entire malware suite and good evidence of a cross-platform approach to espionage.”
That type of undertaking is not for the under-resourced, he added.
“The attackers took a lot of time to set this up, establish a foothold in the target, devise a way to quickly compile sophisticated malware for multiple combinations of Linux distributions and kernel versions, and then install it,” Livelli said. “That’s a lot of love, tension and development time, plus testing and refinement. And on top of that you’ve got to take care of the kids, go grocery shopping and walk the dog and you know, there’s COVID-19 social-distancing to do.”
Linux for Stealth
Further investigation also showed that the Linux malware set has likely been in the wild for nearly a decade. One reason for its longevity, Livelli said, is because Linux tends to fly under the radar when it comes to those holding the cyber-defense purse strings in any organization.
“Think for a minute about the people who sign the paychecks or make the big decisions,” he said. “How often does the word ‘Linux’ enter their conversations. Second, for those of us who’ve had the opportunity to work for vendors, how [deep] are the offerings for Linux compared to the offerings for Mac and Windows. I’m willing to wager that in general, security industry support of the myriad Linux distro and kernel combinations out there pales in comparison to the support given to Windows. It’s just economics, you supply the engineering and marketing and sales effort behind the platform that creates the most demand.”
As a consequence of that reality, Linux malware can slip through the cracks – while giving cybercriminals deep access to sensitive information.
“Our conclusion was that the targeting of these Linux servers was strategic in nature,” Livelli said. “I don’t have to tell anybody in this audience why the always-on, always-available nature of Linux makes it a great beachhead. How often do you take your web server or your database server offline? Is it somewhere in the neighborhood of never?”
He added that Linux-run servers constitute a deep bench of critical infrastructure within the government agencies and businesses that make up modern society.
“Linux runs not just web servers and database servers, but also proxy servers, file servers, VPN servers, stock exchange servers, it’s embedded in IoT, it’s embedded in network appliances, it’s embedded in cars,” he said. “And I don’t have to point out to this audience that Linux-run web servers are perfect for hiding massive amounts of exfiltrated data.”
Hence, APT interest in Linux is not a completely unknown quantity. According to Livelli, “Linux malware in the hands of government-backed groups has been written about before – Kaspersky Lab has documented its use by the Russian Turla and American Equation Group, and among the Chinese groups we’ve seen Linux malware research on Deep Panda and APT41…[including by] our colleagues at Chronicle. The point here is that we should be watching for this kind of thing.”
All Trails Lead to Winnti
The five individual groups found using the Linux stack were linked to Winnti and to each other in some way, Livelli noted.
For instance, “we followed a C2 trail for [one of the groups] and found some domain crossover, which led to our sample, a file that had the string called ‘wavedancer,'” he explained. “And as we took it apart, parsing some XML strings coughed up some other C2 information, which led to dual domains, which led to a domain that was registered by the same email address as had been used in lots of other PassCV work we’ve been following.”
Also, each of the groups employed a familiar Winnti technique. “Students of Winnti know that one of their hallmarks is the use of code-signing certificates, stolen from video-game companies and [more recently] certs taken from adware companies,” the researcher said.”[This] is probably the easiest common denominator to identify across these groups.”
Livelli believes that “Winnti” as a handle is actually an umbrella term that may describe shared resources rather than act as a moniker for any single APT crew. He said that he believes it’s probably a group of civilian contractors whose assembled tools are shared and that the targets are split up. Alternatively, it could be that the Chinese government is offering various groups levels of tools and support—an arrangement that FireEye called a “digital quartermaster” model.
“Whether these groups are actively collaborating, casually sharing, if they comprise some of the same members, or in actuality are smaller parts of some larger group, it’s beyond our means of analysis,” Livelli said. “But one thing is clear: This isn’t a single crew, with a one trick pony. We are looking at a long-standing, well-thought-out, richly resourced intelligence collection operation, with a sizable software engineering team to build and maintain all these tools.”
Black Hat 2020: Open-Source AI to Spur Wave of ‘Synthetic Media’ Attacks
6.8.20 Congress Threatpost
The explosion of open-source AI models are lowering the barrier of entry for bad actors to create fake video, audio and images – and Facebook, Twitter and other platforms aren’t ready.
An abundance of deep-learning and open-source technologies are making it easy for cybercriminals to generate fake images, text and audio called “synthetic media”. This type of media can be easily leveraged on Facebook, Twitter and other social media platforms to launch disinformation campaigns with hijacked identities.
At a Wednesday session at Black Hat USA 2020, researchers with FireEye demonstrated how freely-available, open-source tools – which offer pre-trained natural language processing, computer vision, and speech recognition tools – can be used to create malicious the synthetic media.
Synthetic media includes fake videos, voices and images that can be used in various malicious cases. For instance, cybercriminals can use generative text to forge legitimate-looking spearphishing emails. And at a bigger scale, this fake media can be used to create more malicious content, such as “fake porn” videos weaponized to harass targeted women. In other cases, synthetic media can be used to sway public opinion, like a wide-scale disinformation campaigns using phony, but recognizable, personas.
“Fine tuning for generative impersonation in the text, image, and audio domains can be performed by nonexperts… [and] can be weaponized for offensive social media-driven information operations,” said Philip Tully, staff data scientist at FireEye, and Lee Foster, senior manager of information operations analysis at FireEye during a Wednesday session.
Low Barrier to Entry
The world is currently facing the “calm before the storm” when it comes to the malicious use of synthetic media, Tully warned.
For one, social media has also “greased the wheels” for this type of synthetic content to actually have a malicious impact, said Tully. Social media companies often do not require high bars of credibility, and offer a platform for content to go viral, allowing anyone to create fake media that is believable.
Secondly, the technology for creating synthetic media is becoming cheaper, easier, more pervasive and more credible – “drastically reducing the amount of time that it takes to make this happen,” he said. One such concept lowering the barrier to entry is called “transfer learning.” Previously, researchers using deep learning models to create fake content had to train two different data models. But in transfer learning, neural network models learn one task, and then the learning from that first task is used to fine tune the second task.
This concept has paved the way to a “rich open source model ecosystem,” said Tully. While these open-source models have many advantages – including for research and detection against malicious AI bots – they are also leading to real-world, malicious, fake content found on social media platforms.
black hat FireEye deepfake session
Click to Expand.
For instance, FireEye researchers uncovered a widespread influence campaign that impersonated and fabricated U.S. politicians and journalists on social media – with pro-Iranian interests (the campaign led to Facebook, Instagram and Twitter taking action against over 40 accounts). In another instance, Foster said, networks of inauthentic social media accounts were discovered amplifying political narratives, such as pro-China networks targeting protestors in Hong Kong and pushing COVID-19 pandemic narratives.
Black Hat Demonstration
Researchers demonstrated various open-source models that are providing both good and bad actors with the means to create synthetic media content. For instance, for the creation of fake images they pointed to the style-based GAN architecture (StyleGAN), which allows data-driven unconditional generative image modeling. The GAN architecture consists of a “mapper” stage, which embeds inputs as visual features; a “generator” that synthesizes image from scratch, and a “discriminator,” which predicts whether real images and generated images are real or fake.
Researchers demonstrated voice cloning with SV2TTS, a three-stage deep learning framework enabling them to create a numerical representation of a voice from a few seconds of audio, and to use it for fake output. At a technical level, this starts with the input of a dataset into a “speaker encoder,” which embeds a speaker’s utterance. In the second phase, a text-to-speech platform called Tacotron2 generates a spectrogram from text that is conditioned on these utterances; and finally, a tool called WaveRNN model infers audio waveform from these spectrograms. Voice impersonation is another top threat that cybercriminals are focusing on – with a voice “deep fake” last year swindling one company out of $243,000.
Researchers finally demonstrated the generation of “synthetic text,” which can be achieved by fine-tuning the open source language model known as GPT-2. GPT-2 is an open source deep neural network that was trained in an unsupervised manner on the causal language modeling task. The model is trained so it can predict the next word in a sentence accurately – and ultimately form full sentences.
Researchers said, a bad actor could put an “input” of open source social media posts from the Russian Internet Research Agency (IRA), which they describe as a social media “troll factory.” This input would then create fine-tuned text generations as an output, which can then be posted by troll accounts as part of disinformation campaigns online – such as “It’s disgraceful that our military has to be in Iraq and Syria.”
The Future of ‘Synthetic Media’
There are various technical mitigations that protect against deepfakes. These include machine learning-based forgery detection, which may include looking at eye alignment, teeth abnormalities, ear asymmetry, no blinking, and other factors in multi-media content.
Social media platforms can also adopt content authentication measures, such as verifying accounts or moderating content for fact-checking. Facebook, Microsoft and a number of universities have meanwhile joined forces to sponsor a contest promoting research and development to combat deepfakes. And, Google and other tech firms have released a dataset containing thousands of deepfake videos to aid researchers looking for detection techniques.
However, the “detection, attribution, and response is challenging in scenarios where actors can anonymously generate and distribute credible fake content using proprietary training datasets,” said the researchers. “We as a community can and should help AI researchers, policy makers, and other stakeholders mitigate the harmful use of open source models.”
Black Hat and DEF CON security conferences go virtual due to pandemic
10.5.2020 Bleepingcomputer Congress
DEF CON and Black Hat announced today that their upcoming security conferences in Las Vegas this summer will no longer be in-person and are instead moving to an all-virtual event.
Every summer, large groups of security researchers, law enforcement, government agencies, security companies, the media, and hackers descend upon Las Vegas for the Black Hat and DEF CON security conferences where they learn about the latest security research and threats.
Black Hat 2020 was scheduled for August 1st - 6th, and DEF CON 28 was to follow it on August 7th - 9th.

Black Hat 2016
Due to the global pandemic and the concerns that there is no safe way of conducting the conferences, both Black Hat and DEF CON have announced today that they are switching to an all-virtual conference format.
"We have been continuously reviewing the best ways to serve the information security community over the past few months as the global health situation continues to develop. While we will not be meeting in person, we are moving forward with a plan to transform Black Hat USA into an all-virtual event in order to best serve our community," Black Hat stated in an announcement.
DEF CON, who has a running joke every year that their conference is being canceled, have actually gone through with it and has now entered "Safe Mode with Networking" as they switch to an online conference.
"Even though our in-person Las Vegas event is canceled, we will run DEF CON 28 Safe Mode August 7-9 (Friday through Sunday) with 101 orientation Thursday - all of it remote. We will use the DEF CON Forums to coordinate all the various ways you to participate. That is where everyone can announce their plans, do signups, post pictures and videos and get people involved," DEF CON also announced.
Black Hat has not announced how they plan on performing the virtual conference and have stated they will post more information soon.
DEF CON has stated that they plan on using their Discord server to organize the virtual conference and that their events will continue in an online format.
While this is sure to disappoint many people who look forward to the annual summer security festivities, for those who were not able to attend, they may now have the opportunity to do so remotely.
Tech Conferences in Asia On Hold Due To Coronavirus Outbreak
16.2.2020 Bleepingcomputer Congress
This week, organizers of Black Hat Asia and DEF CON China security conferences announced that the coronavirus outbreak in the region is forcing them to put the events on hold.
Unlike this year's edition of Mobile World Congress (MWC) in Barcelona, which is no longer taking place, the two conferences have been postponed until the epidemic is contained.
C-virus got Black Hat and DEF CON
Starting Friday, the page for Black Hat Asia ostensibly shows the postpone notification for this year's edition. For the moment, few details are available as organizers are probably working on setting up the new date.
"After careful consideration of the health and safety of our attendees and partners, we have made the difficult decision to postpone Black Hat Asia 2020 due to the coronavirus outbreak."
Originally scheduled between March 31- April 3 at Marina Bay Sands in Singapore, the conference has been delayed to an unspecific date "in the fall this year," the organizers say. They will follow up with the specific dates for the event as soon as they are decided.
The announcement comes after the Singapore Ministry of Health on February 7 raised the risk assessment DORSCON Orange, the second-highest severity status before Red. At that date, 32 cases of coronavirus (2019-nCoV) infections had been recorded in the country.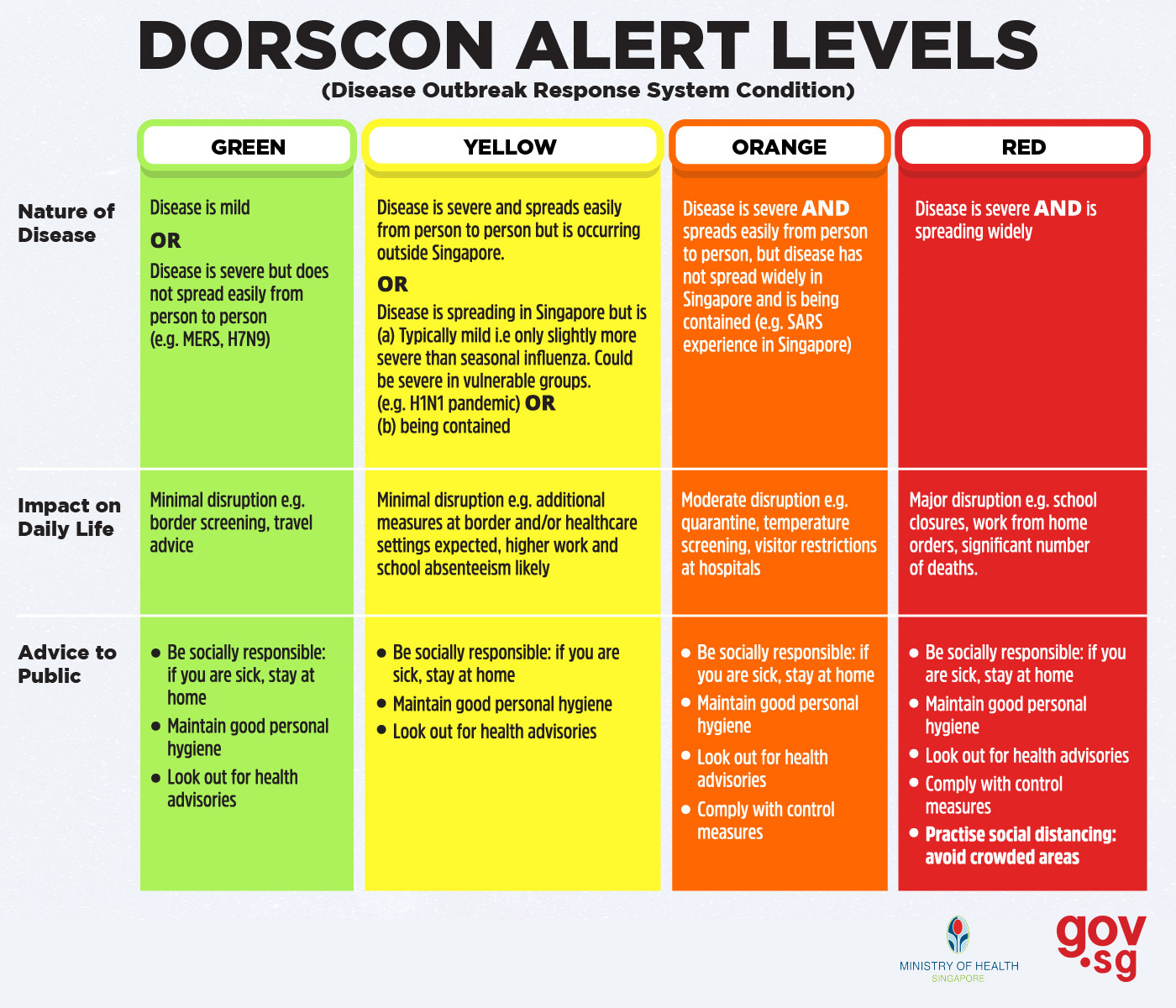
Postponing Black Hat Asia this year is in line with the Singapore government's advice to cancel or put off large-scale events.
"We understand the inconvenience this may cause and will follow up directly with all of those who are scheduled to attend and exhibit to determine appropriate next steps." - Black Hat Asia 2020
Early registration price for the conference ended on January 24 and was SGD1,700 (around $1,200). At this moment, there are no details about reimbursing those that may not be able to participate in autumn.
Organizers of Machine Learning Conference, focused on innovation in the field of machine learning, were also forced to postpone it for the same reason. Held in Singapore, the event was programmed for March 24- 26th.
DEF CON China 2.0 announced at the end of January the decision to postpone the event due to the coronavirus outbreak. It was planned between 17-19 April in Beijing and an alternative date is still to be released.
The organizers accept refund requests from participants that already got their tickets. Those that still want to attend don't have to do anything as their reservations are still valid.