The Microsoft Teams iOS app
After the 2.0.10 build will be published on the App Store, affected users can update their Teams app to remediate the problems.
iOS Articles - 1 2
iOS Exploit Allows 'Unfettered Access' to iPhone User Data Over Wi-Fi
2.12.2020 iOS Securityweek
Google Details iPhone Zero-Click Exploit Allowing Theft of User Data, Including Photos, Emails
Google Project Zero has disclosed the details of an iOS exploit that allows an attacker to hack iPhones remotely over Wi-Fi and steal sensitive data, without any user interaction.
The exploit was uncovered by Google Project Zero researcher Ian Beer — who over the past year has found numerous critical vulnerabilities in Apple products — as a result of a six-month analysis conducted earlier this year. The expert described his findings and the process that led to the discovery in a lengthy blog post published on Tuesday.
According to Beer, the exploit leverages a single memory corruption vulnerability that can be used against an iPhone 11 Pro device to bypass mitigations and achieve native code execution and kernel memory reading and writing.iPhone 11 Pro exploit details
The exploit abuses Apple Wireless Direct Link (AWDL), a Wi-Fi based mesh networking protocol designed for connecting Apple devices in ad-hoc peer-to-peer networks.
Since the exploit requires AWDL to be enabled, the researcher used a technique involving Bluetooth low energy (BLE) advertisements to force the targeted device to enable AWDL without any user interaction and without the attacker having too much information about the targeted device. AWDL can also be remotely enabled, for example, by sending a voicemail, but that requires knowledge of the target’s phone number.
Beer’s exploit leveraged a buffer overflow vulnerability in AWDL to remotely gain access to a device and execute an implant as root. He has published videos showing how an attacker can launch the calculator on a phone, and how they can use the deployed implant to steal user data. The expert pointed out that the implant has full access to the targeted user’s information, including photos, emails, messages, and keychain data.
While his exploit in its current form takes a couple of minutes to execute, he believes that with more resources it could be reduced to just a few seconds.
Beer said Apple patched the vulnerability before the launch of its COVID-19 contact tracing system in iOS 13.5 in May.
The researcher said he was not aware of any attacks exploiting the vulnerability, but pointed out that the patch implemented by Apple was quickly noticed by Mark Dowd, co-founder of Azimuth Security, a small Australian company that provides hacking tools to law enforcement and intelligence agencies.
“This has been the longest solo exploitation project I've ever worked on, taking around half a year,” Beer explained. “But it's important to emphasize up front that the teams and companies supplying the global trade in cyberweapons like this one aren't typically just individuals working alone. They're well-resourced and focused teams of collaborating experts, each with their own specialization. They aren't starting with absolutely no clue how bluetooth or wifi work. They also potentially have access to information and hardware I simply don't have, like development devices, special cables, leaked source code, symbols files and so on.”
Unc0ver is the first jailbreak that works on all recent iOS versions since 2014
25.5.2020 Securityaffairs iOS
A team of hackers and cyber-security researchers have released a new jailbreak package dubbed Unc0ver for iOS devices.
A team of cyber-security researchers and hackers have released a new jailbreak package dubbed Unc0ver (from the name of the team that devised it) that works on all recent iOS versions.
Jailbreaking an iOS mobile device it is possible to remove hardware restrictions implemented by the Apple’s operating system, Jailbreaking gives users root access to the iOS file system and manager, this allows them to download and install applications and themes from third-party stores.
By default, Apple does not allow users to have full control over their iPhones and other iOS devices, citing security reasons.
The Unc0ver team today released Unc0ver 5.0.0, the latest version of their jailbreak, which can root and unlock all iOS devices, even those running the latest iOS v13.5.
The jailbreak exploits a zero-day vulnerability in the iOS operating system that was discovered by Pwn20wnd, a member of the Unc0ver team, and that has yet to be addressed by Apple.
Pwn20wnd states that #unc0ver v5.0.0 will be a big milestone for jailbreaking because it is the first zero-day jailbreak released since iOS 8 that was released in September 2014.
Other jailbreak applications released since iOS 9 used 1-day exploits and and did not work on the current iOS version.
The new Unc0ver 5.0.0 jailbreak can be used from iOS, macOS, Linux, and Windows devices.
The Unc0ver team published instructions on their website.
“unc0ver is designed to be stable and enable freedom from the moment you jailbreak your device. Built-in runtime policy softener allows running code without Apple’s notarization and pervasive restrictions.” reads the website.
“unc0ver Team strongly cautions against installing any iOS software update that breaks unc0ver as you can’t re-jailbreak on versions of iOS that are not supported by unc0ver at that time.”
The Unc0ver team tested the jailbreak on iOS 11 through iOS 13.5, the software did not work on iOS versions 12.3 to 12.3.2 and 12.4.2 to 12.4.5.
What makes this jailbreak outstanding is that according to Pwn20wnd it doesn’t impact Apple’s iOS security features.
Let’s see when Apple will release security updates to address the zero-day vulnerability exploited by the Unc0ver team.
Zerodium will no longer acquire certain types of iOS exploits due to surplus
15.5.20 Securityaffairs iOS
The popular zero-day broker Zerodium announced new limitations it the submission of certain types of iOS exploits due to surplus.
The exploit broker Zerodium announced that it’s no longer accepting certain types of iOS exploits due to surplus, this implies that prices for them will drop in the near future.
The company announced via Twitter that it would no longer accept submissions for iOS local privilege escalation, Safari remote code execution, and sandbox escape exploits, at least for the next months.
Zerodium argued that it has taken this decision due to the high number of submissions, an information that could give us an idea of how is prolific the hacking community.
We will NOT be acquiring any new Apple iOS LPE, Safari RCE, or sandbox escapes for the next 2 to 3 months due to a high number of submissions related to these vectors.
Prices for iOS one-click chains (e.g. via Safari) without persistence will likely drop in the near future.
— Zerodium (@Zerodium) May 13, 2020
Company experts believe that the prices for iOS one-click chains (e.g. via Safari) without persistence will likely drop in the next months.
Zerodium CEO Chaouki Bekrar criticized the current level of iOS security that is evidently going to zero.
“Let’s hope iOS 14 will be better,” said Chaouki Bekrar.
iOS Security is fucked. Only PAC and non-persistence are holding it from going to zero…but we're seeing many exploits bypassing PAC, and there are a few persistence exploits (0days) working with all iPhones/iPads. Let's hope iOS 14 will be better.https://t.co/39Kd3OQwy1
— Chaouki Bekrar (@cBekrar) May 13, 2020
The decision of the company is coherent with the announcement made in September 2019 when Zerodium updated the price list for both Android and iOS exploits, with Android ones having surpassed the iOS ones for the first time.
Announcement: We've updated our prices for major Mobile exploits. For the first time, we will be paying more for Android than iOS. We've also increased WhatsApp & iMessage (0-click) but reduced the payout for iOS (1-click) in accordance with market trends:https://t.co/0NBRnq4I4y pic.twitter.com/XqpmAKmmKF
— Zerodium (@Zerodium) September 3, 2019
For the first time, the price for Android exploits is higher than the iOS ones, this is what has emerged from the updated price list published by the zero-day broker Zerodium.
Currently a zero-click exploit chain for Android would be rewarded with up to $2.5 million, while an exploit chain for iOS only $2 million.
The tech giant is running a public bug bounty program through which it’s prepared to pay out up to $1 million for exploits that achieve persistence, bypass PAC and require no user interaction.
Microsoft Teams call drops on desktop caused by iOS bug
10.5.2020 Bleepingcomputer iOS
Microsoft urges users not to update their Microsoft Teams iOS client to the latest version as it comes with a bug that causes intermittent call drops on the desktop client after answering if logged in with the same account.
Users who haven't updated their Teams iOS app to the 2.0.9 build will not experience any issues as this is the only version containing the bug.
"We've identified that Teams iOS client build 2.0.9 contains the problem and previous builds will not cause the issue," Microsoft explained.
"We encourage users to refrain from manually updating the app until a new version is released."
We've identified that Teams iOS client build 2.0.9 contains the problem and previous builds will not cause the issue. We encourage users to refrain from manually updating the app until a new version is released. See TM212147 in the admin center for details.
— Microsoft 365 Status (@MSFT365Status) May 7, 2020
According to the TM212147 admin center announcement, the impact of this issue is "specific to users that are signed into Teams on the affected iOS build and any other Microsoft Teams endpoint simultaneously."
The call drop issues for desktop users are caused by a recent change in the iOS client made to a component designed to facilitate made to users logged on multiple endpoints with the same account.
Microsoft says that a fix for the issue is included in version 2.0.10 of the Teams iOS client which has already been submitted for review and approval to the iOS App Store, to be available for download later this week.
Until the patched app version will be published, Microsoft says that "signing out of the mobile client with the affected build should prevent the issue from occurring on the desktop version."

The Microsoft Teams iOS app
After the 2.0.10 build will be published on the App Store, affected users can update their Teams app to remediate the problems.
While the iOS App Store doesn't list the number of app users, the Microsoft Teams iOS client is the third most popular app in the Business category and it has 557.1K ratings.
Microsoft Teams is Redmond's cloud collaboration platform that recently reached 75 million daily active users (DAUs) as announced on March 30 because of the influx of remote workers caused by the COVID-19 pandemic, representing a 70% increase since March 19 when it reported 44 million DAUs.
The Microsoft Teams Windows client was patched against image-based account takeover vulnerability last month that allowed attackers to use GIFs to gain access to multiple accounts at once to steal conversations and threads.
New iOS zero-days actively used against high-profile targets
25.4.2020 Bleepingcomputer iOS
Two zero-day vulnerabilities affecting iPhone and iPad devices were found by cybersecurity startup ZecOps after the discovery of a series of ongoing remote attacks that have targeted iOS users since at least January 2018.
"The attack’s scope consists of sending a specially crafted email to a victim’s mailbox enabling it to trigger the vulnerability in the context of iOS MobileMail application on iOS 12 or maild on iOS 13," ZecOps researchers said.
Successfully exploiting the security flaws — an Out-of-bounds Write (OOB Write) and a Remote Heap Overflow — enables the attackers to run remote code on the compromised iPhone and iPad devices allowing them to gain access to, leak, edit, and delete emails.
"Additional kernel vulnerability would provide full device access – we suspect that these attackers had another vulnerability," ZecOps further explained.
You’ve Got (0-click) Mail! Unassisted iOS Attacks via MobileMail/Maild in the Wild via @ZecOps Blog https://t.co/tHbq1ZUuom
— ZecOps (@ZecOps) April 22, 2020
Nation-state hackers behind ongoing attacks
The researchers discovered the remote attacks following a routine iOS Digital Forensics and Incident Response (DFIR) investigation while they were targeting against iOS 11.2.2 users through the default Mail application.
While initial signs pointed at the attacks going as far as January 2018, it is possible that the zero-day was used in related attacks even earlier.
"We believe that these attacks are correlative with at least one nation-state threat operator or a nation-state that purchased the exploit from a third-party researcher in a Proof of Concept (POC) grade and used ‘as-is’ or with minor modifications," ZecOps said.
ZecOps detected multiple highly-targeted attacks exploiting these iOS zero-days including:
• Individuals from a Fortune 500 organization in North America
• An executive from a carrier in Japan
• A VIP from Germany
• MSSPs from Saudi Arabia and Israel
• A Journalist in Europe
• Suspected: An executive from a Swiss enterprise
Although ZecOps didn't want to attribute the attacks to a specific threat actor, the researchers said that they are aware of at least one organization "selling exploits using vulnerabilities that leverage email addresses as a main identifier."
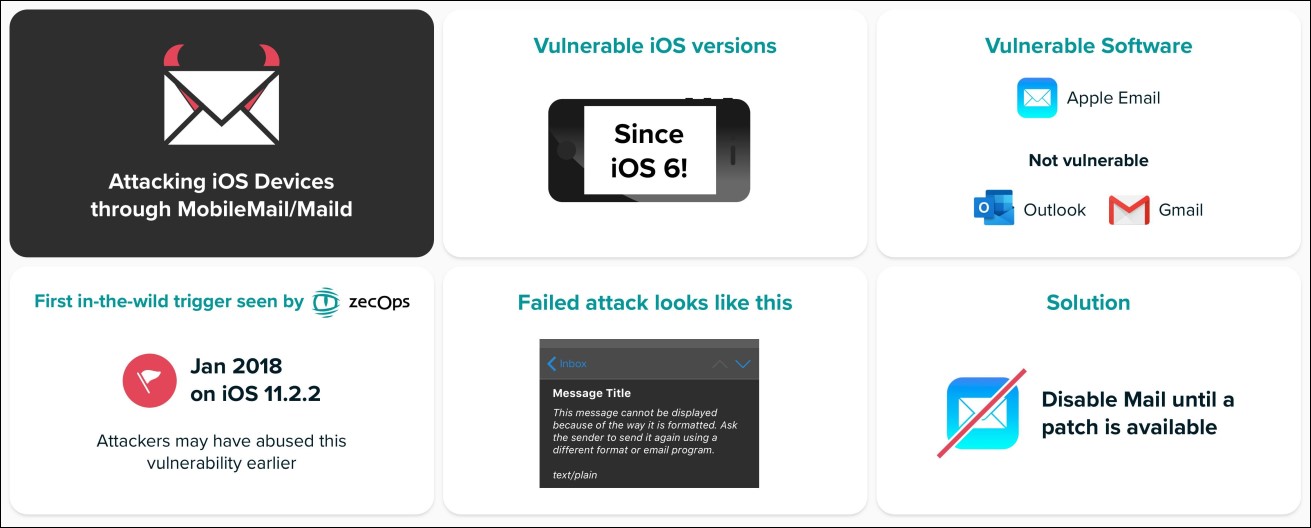
Image: ZecOps
All devices running iOS 6 and later are vulnerable
All iPhones and iPad iOS 6 or above — including the latest version iOS 13.4.1 — are vulnerable to attacks, although iOS devices running even older versions could also be exposed given that ZecOps stopped testing after iOS 6.
On iOS 13, exploiting the vulnerabilities requires no user interaction, while on iOS 12 users have to click on the email to have their iPhone or iPad hacked.
Attackers can also try to exploit the security issue multiple times with no apparent signs on iOS 13 besides a temporary slowdown, while on iOS 12 the Mail application will suddenly crash.
If the attacks fail, the targets will see no signs on iOS 13, while on iOS 12 emails with "This message has no content" messages will show up in the inbox.
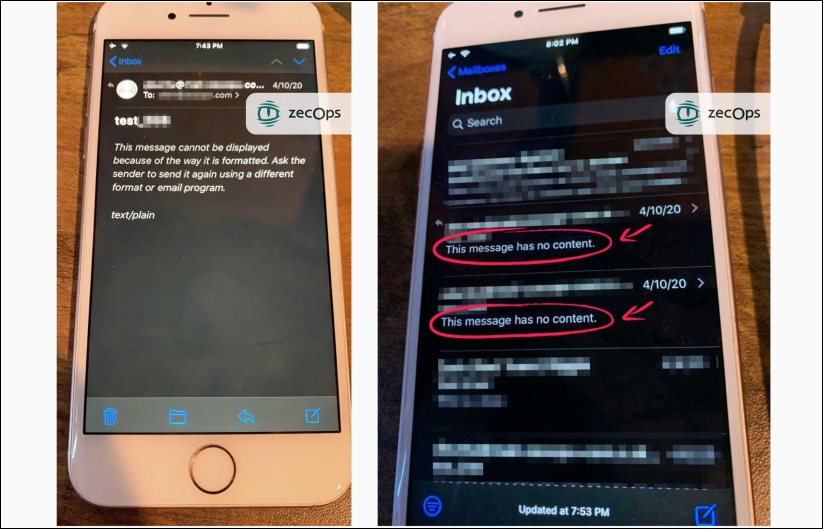
Failed attacks (ZecOps)
"If you cannot patch to this version, make sure to not use Mail application – and instead to temporarily use Outlook or Gmail which, at the time of this writing, were not found to be vulnerable," ZecOps advises.
"With very limited data we were able to see that at least six organizations were impacted by this vulnerability – and the full scope of abuse of this vulnerability is enormous. We are confident that a patch must be provided for such issues with public triggers ASAP."
Apple has already included a patch for the zero-days in iOS 13.4.5 beta 2 released on April 15, with a security fix to be made available for users of stable iOS versions soon.
iOS zero-days
Zero-day (aka 0day or 0-day) vulnerabilities are security bugs unknown or not yet patched by the vendor thus exposing devices running the vulnerable software or using the vulnerable hardware to attacks.
The iOS zero-days discovered by ZecOps aren't the first ones Apple has had to patch so far, with two actively exploited ones having been patched in iOS 12.1.4 and a couple of others receiving fixes after being exploited in the wild as part of five privilege escalation exploit chains.
Zero-day exploit acquisition platform Zerodium decreased payouts for iOS zero-days in September 2019, with Apple iOS full chain (1-Click) exploits with persistence dropping to $1,000,000 from $1,500,000, while iMessage RCE + LPE (1-Click) exploits without persistence got a $500,000 reduced price tag from the previous one of $1,000,000.
Zerodium's CEO Chaouki Bekrar told BleepingComputer at the time that "the last few months, we have observed an increase in the number of iOS exploits, mostly Safari and iMessage chains, being developed and sold by researchers from all around the world. The zero-day market is so flooded by iOS exploits that we've recently started refusing some [of] them."