RIDL and Fallout Attacks
Fallout: Reading Kernel Writes From User Space pdf
Fallout exploits a fourth vulnerability in Intel CPUs to leak data from Store Buffers, which is used when a CPU pipeline needs to store any type of data. This attack works against the Kernel Address Space Layout Randomization (KASLR) protection against memory corruption bugs.
The attack was developed by researchers at the University of Michigan, the University of Adelaide, Worcester Polytechnic Institute, Data61, Graz Institute of Applied Information Processing and Communications (IAIK), and the Catholic University in Leuven (KU Leuven).
The researchers say that the threat actor running a Fallout attack can choose the type of data to leak from the CPU's Store buffer.
Fallout also impacts all modern Intel processors, including those of the 9th generation, which include in-silicon mitigations for Meltdown.
This protection, however, "makes them more vulnerable to Fallout, compared to older generation hardware," say the developers of the attack.
Intel has been informed of the security flaws and provided microcode updates along with mitigation recommendations for operating system (and hypervisor) software. It is recommended to install the software updates as they come from vendors.
Lenovo has rolled out updates at the beginning of the month for ThinkPad P1 (Type 20MD, 20ME) and ThinkPad X1 Extreme for fixing three of the four MSD vulnerabilities.
"If you disable hyperthreading and at the same time you use Intel’s proposed mitigation (that is, using the very instruction) the MDS vulnerabilities are mitigated on old Intel processors," VUSec's Pietro Frigo told BleepingComputer.
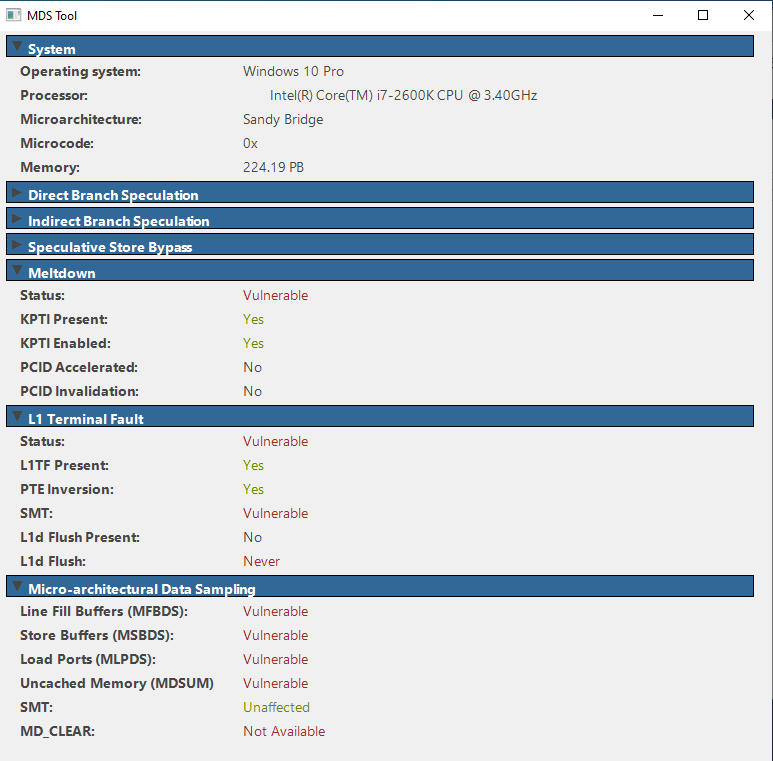
The four MDS vulnerabilities exploited by RIDL and Fallout have the following identifiers:
CVE-2018-12126: Microarchitectural Store Buffer Data Sampling (MSBDS) - CVSS score 6.5: Medium, exploited by Fallout attack
CVE-2018-12127: Microarchitectural Load Port Data Sampling (MLPDS) - CVSS score 6.5: Medium, exploited by RIDL attack
CVE-2018-12130: Microarchitectural Fill Buffer Data Sampling (MFBDS) - CVSS score 6.5: Medium, exploited by RIDL attack
CVE-2019-11091: Microarchitectural Data Sampling Uncacheable Memory (MDSUM) - CVSS score 3.8: Low, exploited by RIDL attack
The MSD vulnerabilities were reported to Intel independently by multiple security researchers starting June 2018 (Giorgio Maisuradze). In August, Bitdefender alerted the company of a Foreshadow (L1TF) mitigation bypass (MFBDS). The next month, Volodymyr Pikhur notified Intel of another L1TF mitigation bypass (MDSUM).
VUSec reported the three glitches they exploit via RIDL in September 2018 and in late January the researchers that developed the Fallout attack contacted Intel about MSBDS. Intel coordinated the release of the research details and disclosure of the vulnerabilities with the researchers, and today published a security advisory.
The VUSec team working on RIDL is composed of: Stephan van Schaik, Alyssa Milburn, Sebastian Österlund, Pietro Frigo, Kaveh Razavi, Herbert Bos, and Cristiano Giuffrida.
They made available a tool for users to test their systems against RIDL and Fallout attacks as well as other speculative execution vulnerabilities. It is available for Windows and Linux, and its source code has been published here.

VUSec set up a website describing the impact of the vulnerabilities leveraged by both RIDL and Fallout and offering information about the research, its impact and possible mitigations against the attacks.
A research paper with technical details about RIDL is also available and Fallout details are present in a separate paper.