
- Apple -
Last update 09.10.2017 13:46:27
Introduction List Kategorie Subcategory 0 1 2 3 4 5 6 7 8
Apple Patches Vulnerabilities Disclosed at Pwn2Own
17.5.2017 securityweek Apple
Apple on Monday released a new set of security updates to address more than 100 vulnerabilities in its products, including five that were disclosed at Pwn2Own in March 2017.
Four of the 37 bugs resolved in macOS Sierra 10.12.5 were disclosed at Pwn2Own: a Use-After-Free Privilege Escalation in IOGraphics (CVE-2017-2545), a Stack-based Buffer Overflow Privilege Escalation in WindowServer (CVE-2017-2541), an Information Disclosure in WindowServer (CVE-2017-2540), and an Unsigned Dylib Loading Privilege Escalation in Speech Framework (CVE-2017-6977).
The platform release also resolved issues in 802.1X, Accessibility Framework, CoreAnimation, CoreAudio, HFS, iBooks, Intel Graphics Driver, IOSurface, Kernel, Multi-Touch, NVIDIA Graphics Drivers, Sandbox, SQLite, and TextInput.
Exploitation of these bugs could lead to the capturing of user network credentials, arbitrary code execution, privilege escalation, sandbox escape, reading of restricted memory, the opening of arbitrary websites without user permission.
The newly released iOS 10.3.2 patches 41 bugs affecting AVEVideoEncoder, CoreAudio, iBooks, IOSurface, Kernel, Notifications, Safari, Security, SQLite, TextInput, and WebKit. The flaws could result in privilege escalation, arbitrary code execution, denial of service, reading of restricted memory, the execution of unsigned code, and universal cross site scripting.
A total of 26 vulnerabilities were resolved with the release of Safari 10.1.1. Two issues were addressed in Safari and could result in application denial of service or address bar spoofing, while the remaining 24 were patched in WebKit and could lead to arbitrary code execution, universal cross site scripting, or execution of unsigned code.
One of these was CVE-2017-2544, an Array concat Integer Overflow Remote Code Execution disclosed at Pawn2Own by 360 Security (@mj0011sec) working with Trend Micro's Zero Day Initiative.
Apple fixed 12 bugs with the release of watchOS 3.2.2, affecting AVEVideoEncoder, CoreAudio, IOSurface, Kernel, SQLite, TextInput, and WebKit. Most could lead to arbitrary code execution, but some allow for privilege escalation or the reading of restricted memory.
Of the 23 flaws tvOS 10.2.1 resolves, 12 were found in WebKit and impacted Safari and iOS as well. The remaining issues affected AVEVideoEncoder, CoreAudio, IOSurface, Kernel, SQLite, and TextInput.
Additionally, Apple released iTunes 12.6.1 for Windows and iCloud for Windows 6.2.1 to resolve an arbitrary code execution bug in each (CVE-2017-6984 and CVE-2017-2530, respectively).
Apple Releases Dozens of Security Patches for Everything
16.5.2017 thehackernews Apple
While Windows users are currently in fear of getting their systems hijacked by the WannaCry ransomware outbreak, Apple users are sitting relaxed, thinking that malware attacks are something that happens to Windows users, and not Apple.
But you are mistaken – Apple products are also not immune to the hack attacks and malware infections, as an ebook can hack your Mac, iPhone, and iPad.
Apple on Monday pushed out software updates for iOS, macOS, Safari, tvOS, iCloud, iTunes, and watchOS to fix a total of 67 unique security vulnerabilities, many of which allows attackers to perform remote code execution on an affected system.
iOS is 10.3.2 for iPhone, iPad, and iPod
Apple's mobile operating system iOS 10.3.2 for the iPhone, iPad and iPod touch addresses 41 security flaws, 23 of which resides in WebKit, including 17 remote code execution and 5 cross-site scripting (XSS) vulnerabilities.
Besides this, iOS 10.3.2 also addresses a pair of flaws in iBooks for iOS (CVE-2017-2497, CVE-2017-6981) that could allow e-books to open arbitrary websites and execute malicious code with root privileges.
Other flaws addressed in iOS 10.3.2 include a memory corruption issue in AVE Video Encoder that could allow a malicious application to gain kernel-level privileges, and a certificate validation issue in the certificate trust policy for handling of untrusted certificates.
Apple users can install iOS 10.3.2 by connecting their iOS devices to iTunes or downloading it directly by going to the Settings → General → Software Update.
macOS Sierra 10.12.5 for El Capitan and Yosemite
Apple's Mac operating system macOS Sierra 10.12.5 addresses a total of 37 vulnerabilities, including a pair of bugs in iBook that allow the execution of arbitrary code with root privileges, and a separate bug in iBook that allows an application to escape its secure sandbox.
Other flaws addressed in macOS Sierra 10.12.5 include a Wi-Fi networking issue that allows the theft of network credentials, elevation of privilege bugs in both the Intel and Nvidia graphics drivers, and four different arbitrary code execution flaws in SQLite.
Mac users can download the update through the App Store → Updates. Alternatively, macOS Sierra users can be download Sierra 10.12.5 as a stand-alone update, OS X El Capitan users can download the update here, and OS X Yosemite users can get the security update here.
Safari 10.1.1 for Apple Browser
Safari 10.1.1 addresses a total of 26 security issues, 23 of which resides in WebKit, many of which are also patched in the iOS 10.3.2.
Rest three vulnerabilities are patched in the Safari browser itself.
The Safari 10.1.1 update can be downloaded by going to the App Store → Updates on El Capitan and Yosemite systems.
watchOS 3.2.2 for Apple Watch
Apple Watch users should install watchOS 3.2.2 that patches a total of 12 security vulnerabilities, four of which could be used by attackers to execute remote code execution on the affected device.
Users of Apple Watch can download watchOS 3.2.2 by connecting their watch to its charger, and opening the Apple Watch app → My Watch tab → General → Software Update on their iPhone.
tvOS 10.2.1 for Apple TV
Apple has also released tvOS 10.2.1 to patch a total of 23 vulnerabilities, 12 of which resides in WebKit engine that could allow an attacker to perform cross-site scripting and remote code execution attacks on a target device.
The tvOS 10.2.1 update can be downloaded directly from the Apple TV by going to Settings → System → Update Software.
iTunes 12.6.1 for Windows and iCloud for Windows 6.2.1
Meanwhile, Apple also released patches for Windows users using iTunes and iCloud. Both iTunes 12.6.1 and iCloud 6.2.1 patches a single remote code execution bug in WebKit for Windows 7 and later.
Apple users are recommended to update all their operating systems for Apple products and Safari as soon as possible before cyber criminals exploited them. Patches are available through automatic updates.
iCloud Keychain vulnerability allowed hackers to Steal sensitive data
11.5.2017 securityaffairs Apple
Apple has recently fixed an iCloud Keychain vulnerability that could have been exploited by hackers to steal sensitive data from iCloud users.
The flaw allowed hackers to run man-in-the-middle (MitM) attacks to obtain sensitive user information (i.e. names, passwords, credit card data, and Wi-Fi network information).
The researcher Alex Radocea of Longterm Security discovered in March a vulnerability tracked as CVE-2017-2448 that affects the iCloud Keychain.
Apple promptly fixed the issue, along with other bugs in its products, at the end of March.
The iCloud Keychain sync feature allows Apple users to synchronize their keychain, in this way passwords and other sensitive data are shared among all the user’s Apple devices.
Apple implemented end-to-end encryption for the sync process, the encryption relies on a syncing identity key unique to each device.
Data is transmitted via the iCloud Key-Value Store (KVS) and any connection between apps and the KVS are arbitrated by “syncdefaultsd” and other iCloud system services.
The researchers Radocea discovered a vulnerability in the open source implementation of the Off-The-Record (OTR) messaging protocol. Any device can transmit OTR data if it is part of a group of trust called “signed syncing circle.” The access to the signed circle requires permission from an existing device and user interaction.
“The “signed syncing circle” is signed both with the private keys from the syncing identities of each device as well as with a key derived from the user’s iCloud password.” reads the blog post published by Radocea. “In order to update the “signed syncing circle” with a new device, an existing member of the circle must approve an application ticket and add the requesting member’s public key to the circle. This application ticket must be signed with a key derived from the user’s iCloud password, and the approving device similarly prompts the user for the iCloud password to verify. This requires user interaction on the requesting device and on the device already in the circle, to verify that both devices have knowledge of the user’s current iCloud password.”
Radocea discovered that the signature verification procedure for OTR could have been bypassed, this means that an attacker can launch a MitM attack to negotiate an OTR session without needing the syncing identity key.
The hacker can exploit the flaw to impersonate other devices in the circle when keychain data is being synced intercepting the related data. Watch out, the flaw cannot be exploited to join the signing circle.
The expert highlighted that if the user doesn’t enable two-factor verification for its account, an attacker can access the target accounts by capturing its iCloud password.
“Considering that OTR uses ephemeral keys for encryption, this flaw implies that a syncing identity key is no longer required for an adversary with Man In The Middle capabilities to negotiate an OTR session to receive secrets. Although an attacker can not join a signing circle with this flaw, they can impersonate any of the peers in the circle when keychain items are being synced in order to intercept keychain secrets.” continues the blog post.
“For an adversary to gain access to user Keychain secrets, an adversary could leverage this flaw with one of several capabilities to receive keychain secrets. First, assuming that two-factor authentication is not enabled for the user, an attacker with the victim’s iCloud password would be able to directly access and modify entries in the user’s iCloud KVS data,”
The expert also warned of possible modification of iCloud KVS entries and the lack of certificate pinning for TLS communications that opens the door to the attackers.
“Second, a sophisticated adversary with backend access to iCloud KVS would also be able to modify entries to perform the attack,” said the researcher. “Third, the ‘syncdefaultsd’ service does not perform certificate pinning for TLS communications. Without key-pinning, a maliciously issued TLS certificate from any trusted system Certificate Authority could intercept TLS sessions to the iCloud KVS web servers and also perform the attack.”
Apple has fixed the vulnerability by improving the validation for the authenticity of OTR packets.
Software Download Mirror Distributes Mac Malware
8.5.2017 securityweek Apple
A download mirror server for the video converting tool HandBrake was recently compromised and configured to distribute a remote administration Trojan (RAT) for Mac computers.
The company has posted a security alert on its website, informing Mac users that from Tuesday to Saturday of last week they might have downloaded a Trojanized version of the application. According to HandBrake, while not all users might have been affected, all of them should verify the downloaded file before running it.
“Anyone who has downloaded HandBrake on Mac between [02/May/2017 14:30 UTC] and [06/May/2017 11:00 UTC] needs to verify the SHA1 / 256 sum of the file before running it. Anyone who has installed HandBrake for Mac needs to verify their system is not infected with a Trojan. You have 50/50 chance if you've downloaded HandBrake during this period,” the company says.
The company notes that its primary download mirror and website were unaffected. Only the download mirror at download.handbrake.fr has been compromised, but it has been already shut down for investigation. Further, HandBrake says it is rebuilding the download mirror server, a move that might affect performance and the availability of old versions of HandBrake.
Related: High-Profile Targets Attacked via Software Update Mechanism
While downloads via the application’s built-in updater with 1.0 and later are unaffected, those via the application’s built-in updater with 0.10.5 and earlier are not verified by a DSA Signature, and users should check their systems for malicious versions.
HandBrake also detailed a series of steps users should perform to clean up their systems in the event of infection. They also note that impacted users should also “change all the passwords that may reside in [their] OSX KeyChain or any browser password stores.”
To check whether they are affected or not, users should look for a process called “Activity_agent” in the OSX Activity Monitor application. If it is present, it means that they were infected with malware.
The actors who managed to compromise the download mirror replaced the legitimate HandBrake file on the server with one packing a new variant of OSX.Proton RAT that was detailed in March this year. The threat was discovered on a closed Russian cybercrime message board, where it was offered at 2 Bitcoins (around $2,500) for single installations.
At the time, the malware was being advertised as “a professional FUD surveillance and control solution” that included root-access privileges and features. The RAT was said to provide operators with full control over the infected machines and to allow them to monitor keystrokes, take screenshots, and even execute commands.
According to objective-see.com, the variant of Proton being distributed though the compromised HandBrake mirror is almost identical to the initial version, except for the screenshot taking capabilities, which are missing now.
The malware has a very low detection rate on VirusTotal, but Apple has already released an XProtect signature for it, which should help keep users protected.
Turla Cyberspies Developing Mac OS X Malware
5.5.207 securityweek Apple
The Russia-linked cyberespionage group known as Turla has been working on developing a Mac OS X version of its Snake malware framework, researchers at Fox-IT revealed this week.
Turla is also known as Waterbug, KRYPTON and Venomous Bear. Snake, also tracked as Turla and Uroburos, is one of its primary tools. The group is believed to have been active since at least 2006, but experts recently linked it to one of the earliest known state-sponsored cyberespionage operations carried out in the ‘90s.
The threat actor initially focused on targeting Windows systems, but in late 2014 Kaspersky Lab reported uncovering a piece of malware designed to work on Linux.
Now, Fox-IT has identified what it believes to be a Mac OS X version of Turla’s Snake malware. According to researchers, the sample they found contained debug functionality and it was signed on February 21, which indicates that it’s still under development.
An analysis of the Mac malware, delivered by the attackers as an Adobe Flash Player installer, showed that it had actually been ported from the Windows version. Its code included references to the “explorer” process, the Internet Explorer web browser and named pipes.
Once deployed, the malware maintains persistence by abusing Apple’s LaunchDaemon service. In order to bypass the GateKeeper security feature, the malware has been signed with a valid developer certificate that was likely stolen by the cyberspies. Fox-IT has notified Apple about the compromised certificate.
Experts noticed that the malware’s developers likely speak Russian, based on the use of the KOI8-R character encoding, which covers the Cyrillic alphabet.
“This indicates that the developers tested with Russian command output (encoded using the KOI8-R codepage). On systems where the command output is displayed in another language (and another codepage), text would be incorrectly represented in Cyrillic characters,” Fox-IT researchers said in a blog post.
The security firm has yet to see any attacks leveraging the OS X version of the Snake malware.
The Turla group is believed to be responsible for attacks on many organizations around the world, and despite having its operations exposed by the cybersecurity community on several occasions, the threat actor has continued to launch attacks and improve its tools.
In recent weeks, researchers reported seeing a new JavaScript malware used to profile victims, and an improved version of the second-stage backdoor tracked as Carbon and Pfinet.
The OSX.Dok dropper spotted installing the new Bella backdoor
3.5.2017 securityaffairs Apple
Bad news for Mac users, a new variant of the OSX.Dok dropper was discovered by researchers at Malwarebytes, it was spotted installing a new payload dubbed Bella backdoor.
Once the DOK malware infects a macOS system, it gains administrative privileges and installs a new root certificate. The root certificate allows the malicious code to intercept all victim’s communications, including SSL encrypted traffic.
Today the Malwarebytes malware researcher Adam Thomas has discovered found a variant of the OSX.Dok dropper works in a different way respect the first one and installs a different payload, dubbed Bella.
“Adam Thomas, a Malwarebytes researcher, found a variant of the OSX.Dok dropper that behaves altogether differently and installs a completely different payload.” states the analysis published by Malwarebytes.
The new Bella malware is delivered using the same technique of the DOK malware, it leverages a zipped app named Dokument.app masquerading as a document.
The malicious code is signed with the same digital certificate as the OSX.Dok dropper and it was first uploaded to VirusTotal around the same time.
Apple now revoked the certificate in order to neutralize the threat.
Bella, such as DOK, copies itself to /Users/Shared/AppStore.app, then it creates a window on top of all other windows, displaying a message claiming that a security problem has been detected in the operating system and an update is available, it requests victims to enter his password.
Bella displays the fake “OS X Updates Available” window, covering the entire screen, then after a minute it simply closes and deletes itself.

Bella is an open-source backdoor that was developed by a coder that goes online with the GitHub handle “Noah.”
“Noah first joined GitHub back in 2015 but was not active there until August of 2016, when he began creating Python scripts to attack various macOS data, such as stealing iCloud authorization tokens, or password and credit card information from Chrome.” continues the analysis.
“In February of this year, he published the code for Bella, a Python script with some frightening capabilities, including:
Exfiltration of iMessage and SMS chat transcripts
Location of devices via Find My iPhone and Find My Friends
Phishing of passwords
Exfiltration of the keychain
Capture of data from the microphone and webcam
Creation and exfiltration of screenshots
Remote shell and screen sharing”
The Bella payload includes the capability to escalate to root privileges by exploiting flaws in the OS, this feature only works on macOS 10.12.1 and earlier, or phishing to obtain an admin credential.
Bella is customizable with a script named BUILDER , below an example related to a Bella sample that is controlled by a C&C server with the following characteristics:
host = ‘185.68.93.74’ #Command and Control IP (listener will run on)
port = 4545 #What port Bella will operate over
This above address is owned by a hosting company located in Moscow, Russia.
The malware has also been set to install the script, database, and launch agent files in the following locations:
~/Library/Containers/.bella/Bella
~/Library/Containers/.bella/bella.db
~/Library/LaunchAgents/com.apple.iTunes.plist
If the malware gains the root access, it will be placed in the corresponding locations in the root library folder, rather than the user’s library folder.
Experts speculate the Bella backdoor will be used by other threat actors in the future due to a modular structure.
“Of course, since the code signing certificate on the Dokument.app dropper for this malware has been revoked, no one can be newly-infected by this particular variant of this malware at this point. However, since Bella is open-source and surprisingly powerful for a Python script, it’s quite likely it will be dropped by other malicious installers in the future.” concluded MalwareBytes.
New "Dok" Mac OSX Malware Steals Sensitive Data
1.5.2017 securityweek Apple
New malware able to spy on OSX users' internet traffic, including https traffic, has been found targeting European users. The malware was previously not stopped by Apple's Gatekeeper, and when discovered was not detected by anti-malware signature engines.
Called "Dok" (OSX/Dok) by Check Point, the malware combines phishing techniques and a valid developer certificate to effect a MITM attack capable of eavesdropping on all of the victim's internet traffic.
The attack starts with a phishing email. In the example given by Check Point, a sample sent to a user in Germany was baited with supposed inconsistencies in the user's tax returns. The email included an attachment, Dokument.zip, containing the malware bundle signed on April 21, 2017 by Seven Muller and called Truesteer.AppStore.
If activated, the malware copies itself to the /Users/Shared folder and executes. A pop-up message tells the user that the expected bundle was damaged and could not be opened; but the malware itself replaces any loginitem named 'AppStore' in order to gain persistence.
Further social engineering is then used to obtain the user's password in order to complete the malware installation. It uses localization to pop-up a window in either English or German. The window overlays all other windows and claims that a security issue has been identified.
The user is asked to enter his or her password in order to obtain the necessary updates. This window persists, and the user is unable to do anything but comply. Even if the computer is restarted, the window will reappear. However, once the he or she enters the password, the malware obtains administrator privileges and installs the Homebrew command-line installation system. This is then used to download and install a Tor client and SOCAT.
OSX/Dok then uses its user-granted privileges to suppress further password prompts. It proceeds to install a new root certificate and alter the system's network settings, redirecting traffic through a server hidden in Tor. This allows the hacker to intercept and read all outgoing traffic, even when legitimately encrypted with SSL. Because the server is located in Tor, the hacker remains anonymous.
The potential is serious. For consumers, login details for any accessed online service can be seen and stolen -- including bank details.
It is potentially more harmful for businesses. Thomas Reed, director of Mac offerings at Malwarebytes, comments: "The impact on business could be much more severe, as it could expose information that could allow an attacker to gain access to company resources. For example, consider the potential damage if, while infected, you visited an internal company page that provided instructions for how to connect to the company VPN and access internal company services. The malware would have sent all that information to the malicious proxy server."
Apple has reacted swiftly. It revoked the developer certificate on April 28. Installation of this particular version should now be stopped by Gatekeeper. It has also pushed out silent updates that protect OSX users against two variants of the malware, OSX.Dok.A and OSX.Dok.B, and also against a new version of the intrusive adware known as OSX.Genieo.F.
While there should now be no new infections of this version of OSX/Dok, Reed warns that complete removal for anyone already infected is not simple. The malware makes many changes to the system, and even though its activity can be stopped, other changes could cause ongoing problems. "For people who don't know their way around in the Terminal and the arcane corners of the system," he suggests, "it would be wise to seek the assistance of an expert, or erase the hard drive and restore the system from a backup made prior to infection."
For businesses, he suggests, "If you have been infected by this malware in a business environment, you should consult with your IT department, so they can be aware of the risks and begin to mitigate them."
New MacOS Malware, Signed With Legit Apple ID, Found Spying On HTTPS Traffic
28.4.2017 thehackernews Apple
Many people believe that they are much less likely to be bothered by malware if they use a Mac computer, but is it really true? Unfortunately, No.
According to the McAfee Labs, malware attacks on Apple's Mac computers were up 744% in 2016, and its researchers have discovered nearly 460,000 Mac malware samples, which is still just a small part of overall Mac malware out in the wild.
Today, Malware Research team at CheckPoint have discovered a new piece of fully-undetectable Mac malware, which according to them, affects all versions of Mac OS X, has zero detections on VirusTotal and is "signed with a valid developer certificate (authenticated by Apple)."
Dubbed DOK, the malware is being distributed via a coordinated email phishing campaign and, according to the researchers, is the first major scale malware to target macOS users.
The malware has been designed to gain administrative privileges and install a new root certificate on the target system, which allows attackers to intercept and gain complete access to all victim communication, including SSL encrypted traffic.
Just almost three months ago, Malwarebytes researchers also discovered a rare piece of Mac-based espionage malware, dubbed Fruitfly, that was used to spy on biomedical research center computers and remained undetected for years.
Here's How the DOK Malware Works: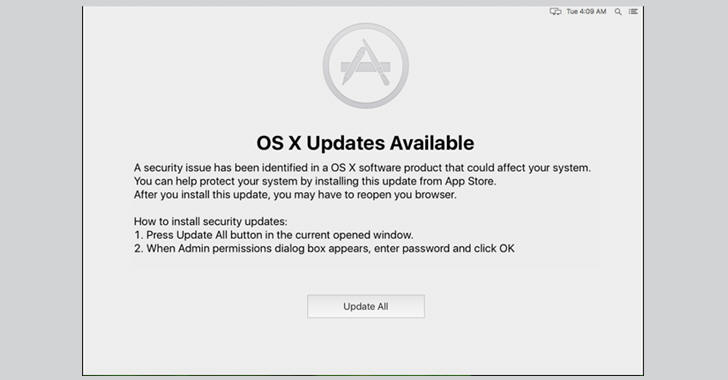
The malware is distributed via a phishing email masquerading as a message regarding supposed inconsistencies in their tax returns, tricking the victims into running an attached malicious .zip file, which contains the malware.
Since the malware author is using a valid developer certificate signed by Apple, the malware easily bypasses Gatekeeper -- an inbuilt security feature of the macOS operating system by Apple. Interestingly, the DOK malware is also undetectable in almost all antivirus products.
Once installed, the malware copies itself to the /Users/Shared/ folder and then add to "loginItem" in order to make itself persistent, allowing it to execute automatically every time the system reboots, until it finishes to install its payload.
The malware then creates a window on top of all other windows, displaying a message claiming that a security issue has been identified in the operating system and an update is available, for which the user has to enter his/her password.
Once the victim installed the update, the malware gains administrator privileges on the victim's machine and changes the victim system's network settings, allowing all outgoing connections to pass through a proxy.
According to CheckPoint researchers, "using those privileges, the malware will then install brew, a package manager for OS X, which will be used to install additional tools – TOR and SOCAT."
DOK Deletes itself after Setting up Attacker's Proxy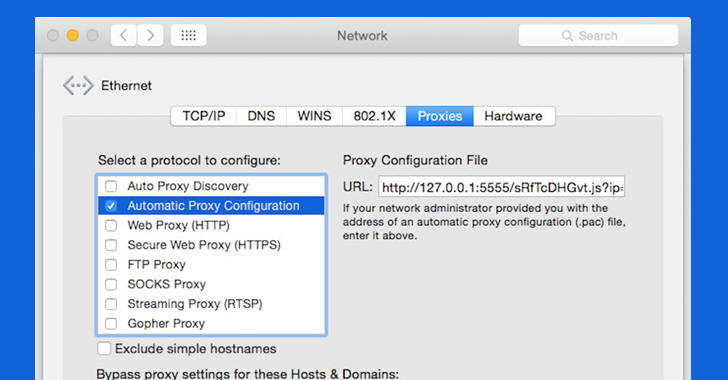
The malware then installs a new root certificate in the infected Mac, which allows the attacker to intercept the victim’s traffic using a man-in-the-middle (MiTM) attack.
"As a result of all of the above actions, when attempting to surf the web, the user’s web browser will first ask the attacker web page on TOR for proxy settings," the researchers say.
"The user traffic is then redirected through a proxy controlled by the attacker, who carries out a Man-In-the-Middle attack and impersonates the various sites the user attempts to surf. The attacker is free to read the victim's traffic and tamper with it in any way they please."
According to researchers, almost no antivirus has updated its signature database to detect the DOK OS X malware, as the malware deletes itself once it modifies proxy settings on the target machines for interceptions.
Apple can resolve this issue just by revoking the developer certificate being abused by the malware author.
Meanwhile, users are always recommended to avoid clicking links contained in messages or emails from untrusted sources and always pay extra attention before proving your root password.
Vulnerability in Apple Music for Android could be exploited to steal user data
7.4.2017 securityaffairs Apple
Apple fixed a vulnerability tracked as CVE-2017-2387 in the Apple Music for Android that could allow attackers to launch MitM attacks on the application.
The update released Apple for the Apple Music application for Android fixes a certificate validation issue that can be exploited by an attacker to run MitM attacks and intercept user data.
The Apple Music for Android version 2.0 also implements new features and fixes the above vulnerability tracked as CVE-2017-2387.
According to Google Play, the version 2.0 of Apple Music for Android has between 10 and 50 million installs.
The flaw CVE-2017-2387 was discovered by David Coomber of Info-Sec.CA in August 2016. The vulnerability was affecting Apple Music 1.2.1 and earlier versions of the Android app.

“The Apple Music Android application (version 1.2.1 and below), does not validate the SSL certificates it receives when connecting to the mobile application login and payment servers.” reads the security advisory published by Coomber.
“An attacker who can perform a man in the middle attack may present bogus SSL certificates which the application will accept silently. Sensitive information could be captured by an attacker without the user’s knowledge.”
According to the expert, the app did not validate the SSL certificates presented while connecting to the login and payment servers. The attacker can present a forged SSL certificate that will be accepted by the application without raising any alert.
“An attacker who can perform a man in the middle attack may present bogus SSL certificates which the application will accept silently,” Coomber explained in his advisory. “Sensitive information could be captured by an attacker without the user’s knowledge.”
Unfortunately, such kind of issues is quite common for mobile applications and represent a serious threat to the user privacy.
Flaw in Apple Music for Android Exposes User Data
7.4.2017 securityweek Apple
An update released this week by Apple for the Apple Music application for Android addresses a certificate validation issue that can be exploited to intercept potentially sensitive data.
In addition to a new design and new features, version 2.0 of Apple Music for Android, which according to Google Play has between 10 and 50 million installs, patches a vulnerability that can allow a man-in-the-middle (MitM) attacker to obtain user information.
The vulnerability, tracked as CVE-2017-2387, was reported to Apple by David Coomber of Info-Sec.CA back in August 2016. At the time, the researcher determined that the flaw had affected Apple Music 1.2.1 and earlier versions of the Android app.
In an advisory published this week, Coomber said he asked Apple for a status update in January, and the company said it had still been working on addressing the security hole.
The problem, according to the researcher, was that the app did not validate the SSL certificates received when connecting to the login and payment servers.
“An attacker who can perform a man in the middle attack may present bogus SSL certificates which the application will accept silently,” Coomber explained in his advisory. “Sensitive information could be captured by an attacker without the user's knowledge.”
It’s worth noting that this appears to be the first security advisory released by Apple for the Music app. The Android application was introduced in November 2015.
Download and install the last iOS 10.3.1, attackers can hack you over Wi-Fi
5.4.2017 securityaffairs Apple
A critical flaw could be exploited by attackers within range to “execute arbitrary code on the Wi-Fi chip,” download and install last iOS 10.3.1 version.
Last week, Apple released iOS 10.3, an important release of the popular operating system the fixed more than 100 bugs and implements security improvements.
Apple opted to push an emergency patch update (iOS 10.3.1 version), that fixed some critical vulnerabilities, including one tracked as CVE-2017-6975. The flaw could be exploited by attackers within range to “execute arbitrary code on the Wi-Fi chip.”
The flaw was first discovered by the expert Gal Beniamini from the Google’s Project Zero team, the expert and his team did not disclose technical details on the flaw.
“Impact: An attacker within range may be able to execute arbitrary code on the Wi-Fi chip
Description: A stack buffer overflow was addressed through improved input validation.

CVE-2017-6975: Gal Beniamini of Google Project Zero” reads the security note published by Apple for the iOS 10.3.1 release.
The CVE-2017-6975 affects iPhone 5 and later, iPad 4th generation and later, iPod touch 6th generation and later
iPhone 5S was not affected because it is the first model based on a 64-bit processor.
Today Beniamini will publish a detailed technical analysis of the issue, including a detailed description of the attack scenario.The iOS 10.3.1 update can be downloaded via Settings → General → Software Update on your iOS device.
Apple users already running the iOS 10.3 can download and install the iOS 10.3.1 release simply pressing on the “Download and Install” button to install the update.
If you are the owner of an Apple iPhone, iPad and iPod Touch you must update your device as soon as possible.
Update Your Apple Devices to iOS 10.3.1 to Avoid Being Hacked Over Wi-Fi
5.4.2017 thehackernews Apple
Less than a week after Apple released iOS 10.3 with over 100 bug fixes and security enhancements; the company has just pushed an emergency patch update – iOS 10.3.1 – to addresses a few critical vulnerabilities, one of which could allow hackers to "execute arbitrary code on the Wi-Fi chip."
The vulnerability, identified as CVE-2017-6975, was discovered by Google's Project Zero staffer Gal Beniamini, who noted on Twitter that more information about the flaw would be provided tomorrow.
Apple also did not provide any technical details on the flaw, but urged Apple iPhone, iPad and iPod Touch users to update their devices as soon a possible.
In the security note accompanying iOS 10.3.1, Apple describes the issue as a stack buffer overflow vulnerability, which the company addressed by improving the input validation.
A stack buffer overflow flaw occurs when the execution stack grows beyond the memory that is reserved for it, allowing hackers to execute malicious code remotely.
The flaw allows an attacker, within range, to execute malicious code on the phone's Wi-Fi chip.
The vulnerability appears to affect iPhone 5 and later, iPad 4th generation and later, and iPod touch 6th generation, and later devices running the iOS 10.3 operating system.
It's worth mentioning that iPhone 5 and iPhone 5C were Apple's last iPhone handsets to have a 32-bit processor with Apple A6 system on a chip. Since iPhone 5S has a 64-bit processor, it is not affected by the issue.
To know more technical details about the flaw, you are required to wait until tomorrow when Beniamini will release a detailed blog post describing the bug and its impact on Apple users.
With iOS 10.3 release, an over-the-air download for 32-bit Apple devices wasn't available. This has also being changed with iOS 10.3.1 update, which brings back support for iPhone 5 and 5C as well as the fourth-generation iPad -- the only remaining 32-bit Apple devices.
The iOS 10.3.1 update can be downloaded over-the-air via Settings → General → Software Update on your iOS device.
Apple users running iOS 10.3 should be able to see the iOS 10.3.1 update, so press on the "Download and Install" button to install the update.
With New iPhone, Trump Still a Target for Hackers
31.3.2017 securityweek Apple
President Donald Trump has a new phone. An iPhone.
That would not ordinarily be news, but given the security concerns about the risk of hack attacks on the prolific White House tweeter, the shift is significant.
Cybersecurity specialists say Trump's decision to transition from his Android device -- details of which were never disclosed but which was believed to be an unsecured, older-model Samsung -- is positive for security, but doesn't eliminate risks from hackers.
"I can guarantee the Russians and Chinese will try to figure out an attack," said John Dickson, a former air force cybersecurity officer who now works for the Texas-based Denim Group consulting firm.
White House social media chief Dan Scavino confirmed the smartphone shift this week, tweeting that Trump "has been using his new iPhone for the past couple of weeks here on Twitter. Yes, it is #POTUS45 reading & tweeting!"
Dickson said security will depend on how the president is using the device -- whether it is exclusively for tweeting -- and if it is plugged into an enterprise management system that can "wall off" vulnerabilities.
"If it's a single-purpose device, the risk is minimal," he said. "But as soon as you start clicking on things, downloading apps, granting access, that's when things matter tremendously."
Mobile devices can be hacked to allow an attacker to listen via the phone's microphone, access its camera, monitor geolocation or even take over the handset remotely.
Former president Barack Obama carried a BlackBerry, and later a different smartphone, with security modifications that limited its functions.
Trump's switch comes despite his call for a boycott a year ago of the iPhone maker for refusing FBI requests to help hack a device for a probe into a deadly California attack.
- More secure? -
Some analysts say Apple devices may offer more security because the company controls the hardware and software and frequently updates its operating system. Apple did not respond to an AFP query on Trump's decision.
Betsy Cooper, executive director of the University of California's Center for Long-Term Cybersecurity said that despite Apple's reputation, recent research has shown "that both iPhones and Android can be abused by hackers."
Cooper said it remains unclear how the president's social media is managed -- what devices are used and who has access to his personal @realDonaldTrump and official @POTUS handles on Twitter.
From a security standpoint, "it would be better to eliminate the personal accounts and use only government devices and government-protected social media accounts," Cooper said.
Concerns of hacking come following Trump's unverified allegation that his phones were tapped during last year's election campaign, and after leaked documents from former contractor Edward Snowden showed US tapping of German leader Angela Merkel's personal phone.
Some phones are marketed as "hardened" or secure devices for people in power, but it wasn't clear if these are used at the White House.
- Phone as 'honeypot'? -
Nicholas Weaver, a researcher at the California-based International Computer Science Institute, said Trump's phone swap "massively reduces, but does not completely eliminate, the security risks."
But while he agreed foreign governments are likely to try to hack the phone, Weaver said US intelligence services may have modified it to be "a nice honeypot to trap attempted attacks."
A honeypot is a technique used to lure hackers and attackers to identify them and find ways to neutralize or punish them.
Weaver said in a blog post earlier this year that Trump's use of an older Android device opened massive security risks and that "the working assumption should be that Trump's phone is compromised by at least one -- probably multiple -- hostile foreign intelligence services."
At the time, it was not clear what type of handset Trump was using, but a New York Times report after the inauguration said he was using "his old, unsecured Android phone."
Last month, Representative Ted Lieu of California called for an investigation, saying Trump's phone use may be "jeopardizing national security."
Dickson said that even with strong security, the president could fall victim to an attack if he uses his phone for email and web browsing.
This could be in the form of "spearphishing," or a message disguised to look as if it's from a trusted aide or family member, but which contains malware.
"This is what sophisticated attackers do," Dickson said, and because the president's activities are widely known, "he would be an easier target for spearphishing."
Police Arrest Man Potentially Linked to Group Threatening to Wipe Millions Of iPhones
29.3.2017 thehackernews Apple
The British authority has reportedly arrested a 20-years-old young man – potentially one of the member of a cyber criminal gang 'Turkish Crime Family' who threatened Apple last week to remotely wipe data from millions of iOS devices unless Apple pays a ransom of $75,000.
The UK's National Crime Agency (NCA) arrested a young man from London on Tuesday on suspicion of "Computer Misuse Act and extortion offences," who according to Motherboard, "may be connected to the ongoing attempted extortion of Apple by a group calling itself the Turkish Crime Family."
Last week, the hacking group claimed to have access to over 300 million iCloud accounts and threatened Apple to remotely wipe data from those millions of Apple devices unless Apple pays it $75,000 in Bitcoin or Ethereum, or $100,000 worth of iTunes gift cards.
Motherboard broke the story after one of the members of Turkish Crime Family shared screenshots of emails between the hacking group and Apple's security team with the publication.
Shortly after the extortion news, Apple released a statement, saying that there have not been any breaches to its servers and databases; instead, the data in possession with hackers appears to be from previously compromised third-party services, such as LinkedIn.
The company also said it is working with law enforcement to identify the criminals.
"Apple is actively monitoring to prevent unauthorised access to user accounts and is working with law enforcement to identify the criminals involved," Apple said in the statement.
"To protect against these type of attacks, we always recommend that users always use strong passwords, not use those same passwords across sites and turn on two-factor authentication."
Although the NCA has not elaborated further about the arrest except that the man has been bailed pending further inquiries, another member of the same criminal gang confirmed Motherboard via an email that the arrested member hasn't been online after the alleged raid.
Moreover, the group claimed his friend who was at his house during the raid managed to film the incident, though Motherboard, who received a copy of it, has declined to post the video publicly at this time.
Arrest Doesn’t Mean Your iCloud Data is Safe
At this moment, we are not entirely sure that the arrested man is actually linked to the Turkish Crime Family, although the man is suspected of having committed blackmail and unauthorised access of computers with the intent to commit or facilitate the commission of further offences, according to the warrant Motherboard received in an email.
But if he comes out to be the member of the same hacking group, it doesn't mean that Apple extortion threat has gone completely, as other members of the hacking group are still out there with alleged compromised icloud accounts.
It's possible that remaining members of Turkish Crime Family, in panic, go underground without doing anything, but there's still the possibility of them remotely wiping victim's Apple devices and resetting iCloud accounts, if they actually have the capability to do what they claim.
The hacking group has given Apple a deadline until April 7 to pay up the ransom.
So, if you haven't done yet, change your iCloud passwords immediately and enable two-step authentication to add an extra layer of security to your account in order to keep your iCloud account safe from hackers.
Apple Patches Hundreds of Vulnerabilities Across Product Lines
28.3.2017 securityweek Apple
Apple Patches Desktop, Mobile, Wearable Platforms to Fix More than 200 Security Vulnerabilities
Apple on Monday released security patches for its macOS and macOS Server, iOS, watchOS, tvOS, Safari, and Pages, to address over 200 vulnerabilities.
No less than 127 vulnerabilities were addressed with the release of macOS Sierra 10.12.4 (and Security Update 2017-001 El Capitan and Security Update 2017-001 Yosemite). These affected components such as apache, Audio, Bluetooth, FontParser, ImageIO, IOFireWireAVC, Kernel, OpenSSH, OpenSSL, QuickTime, Security, tcpdump, tiffutil, and WebKit.
tcpdump was affected the most, as the tech giant resolved 41 vulnerabilities in this component alone. By leveraging these flaws, an attacker in a privileged network position could be able to execute arbitrary code with user assistance, Apple notes in its advisory. The company also resolved 11 bugs in Kernel and 8 flaws in tiffutil.
Some of the flaws resolved in macOS Sierra 10.12.4 include memory corruption, inconsistent user interface issues, out-of-bound read, access and validation issues, buffer overflow, uncontrolled format string, timing side channel bug, profile uninstallation issue, use after free, and race condition. Many were addressed by improved input validation or improved memory handling.
Tracked as CVE-2017-2485 and discovered by Cisco Talos, a memory corruption issue was found in the parsing of certificates and was addressed through improved input validation. According to Apple, the issue could lead to arbitrary code execution when processing a maliciously crafted x509 certificate. Talos reveals that this use-after-free vulnerability (which affects iOS as well) manifests due to improper handling of X.509v3 certificate extensions fields.
“An application that passes a malicious certificate to the certificate validation agent could trigger this vulnerability. Possible scenarios where this could be exploited include users connecting to a website which serves a malicious certificate to the client, Mail.app connecting to a mail server that provides a malicious certificate, or opening a malicious certificate file to import into the keychain,” the researchers say.
The macOS Sierra 10.12.4 update also includes the security content of Safari 10.1, Apple says. In a separate advisory, the company explains that 38 bugs were squashed in the browser, 33 of which affect WebKit (three were found in WebKit JavaScript Bindings and WebKit Web Inspector). The security update addresses memory corruption, prototype access, keychain handling, information disclosure, and validation issues.
iOS 10.3 was released on Monday with fixes for 84 flaws affecting Accounts, Audio, CoreGraphics, CoreText, FontParser, ImageIO, Kernel, libarchive, Profiles, Safari, Security, and WebKit, among other components (many of the fixed issues were impacting macOS, Safari).
Some of the addressed flaws include a buffer overflow in the handling of font files, an infinite recursion, multiple memory corruption issues, out-of-bounds read bugs, or the sending of requests to iTunes sandbox web services in cleartext. Affecting how Safari handles JavaScript pop-ups, one of the flaws was abused by attackers to lock victims from using the browser and scare them into paying a ransom in the form of an iTunes Gift Card.
Also released on Monday, tvOS 10.2 addresses 56 bugs, while watchOS 3.2 resolves 34 of them. Additionally, Apple pushed out macOS Server 5.3 to resolve 3 vulnerabilities (in Profile Manager, Web Server, and Wiki Server), and Pages 6.1, Numbers 4.1, and Keynote 7.1 for Mac and Pages 3.1, Numbers 3.1, and Keynote 3.1 for iOS, to address one issue in Export.
Apple iOS 10.3 Fixes Safari Flaw Used in JavaScript-based Ransomware Campaign
28.3.2017 thehackernews Apple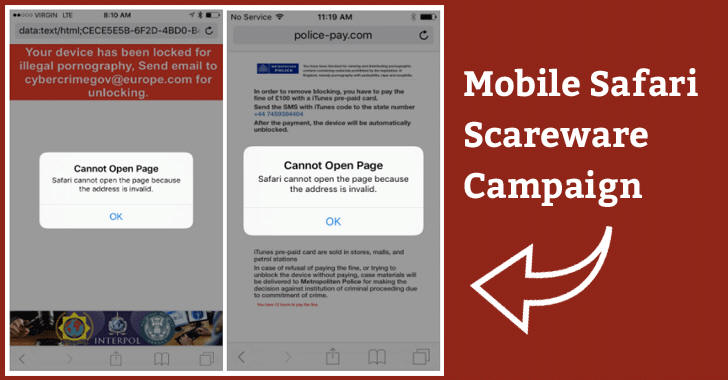
If you own an iPhone or iPad, it's possible you could see popup windows in a sort of endless cycle on your Safari browser, revealing your browser has been locked and asking you to pay a fee to unlock it. Just do not pay any ransom.
A new ransomware campaign has been found exploiting a flaw in Apple's iOS Safari browser in order to extort money from users who view pornography content on their phones or attempt to illegally download pirated music or other sensitive content.
However, the good news is that Apple patched the web browser vulnerability on Monday with the release of iOS version 10.3.
The vulnerability resides in the way Safari displayed JavaScript pop-up windows, which allowed ransomware scammers to display an endless loop of pop-up windows, preventing victims to use the browser, researchers from mobile security provider Lookout said in a blog post published on Monday.
The victims eventually would end up on an attacker website that masquerades itself as a legitimate law enforcement site informing victims that they have to pay a fine for viewing illegal content in order to regain access to their browser.
Lookout researchers called the exploit "scareware," as the attack doesn't actually encrypt any data and hold it ransom. Rather the attack just scares victims into paying the ransom fee to unlock the browser.
"The scammers abused the handling of pop-up dialogs in Mobile Safari in such a way that it would lock out a victim from using the browser," Lookout explains.
"The attack would block the use of the Safari browser on iOS until the victim pays the attacker money in the form of an iTunes Gift Card. During the lockout, the attackers displayed threatening messaging in an attempt to scare and coerce victims into paying."
The scammers effectively used fear as a factor to get victims pay the fee before they realized that there was no real risk to their data and it's very easy to overcome this issue.
While overcoming the threat for users is as simple as clearing their browsing history and cache, iOS 10.3 users are no longer at risk of getting trapped in the endless cycle of JavaScript popups.
Lookout researchers shared the cause of this iOS exploit with Apple last month, and the company has promptly patched the issue with the release of iOS 10.3. Now, pop-up windows only take over a tab, instead of the entire app.
Those iOS 10.2 users who are already hit by this ransomware campaign can clear their browsing cache by navigating to Settings → Safari → Clear History and Website Data.
Apple Updates iTunes to Patch SQLite, Expat Flaws
27.3.2017 Securityweek Apple
Apple updated the Windows and Mac versions of iTunes last week to address more than a dozen vulnerabilities affecting the Expat and SQLite libraries.
iTunes 12.6 for Windows and OS X address seven flaws in SQLite, a cross-platform library that implements a self-contained, embeddable, zero-configuration SQL database engine. The latest iTunes versions also resolve ten vulnerabilities in the Expat XML parser library.
iTunes 12.6 updates SQLite to version 3.15.2, released in late November 2016, and Expat to version 2.2.0, released in June 2016.
The CVE identifiers mentioned in Apple’s advisories show that the company has not updated these components for several years.
For example, CVE-2013-7443 was patched in SQLite in February 2014, CVE-2015-3414 was patched in April 2015, and CVE-2016-6153 was fixed in May 2016. Most of the flaws resolved in iTunes can be exploited for denial-of-service (DoS) attacks, but some of them could also allow arbitrary code execution and privilege escalation.
In the case of Expat, Apple’s advisory mentions some vulnerabilities that were patched in March 2012 with the release of Expat 2.1.0. The security holes in Expat can also be exploited mostly for DoS attacks, but arbitrary code execution may also be possible in some cases.
It’s worth noting that a majority of the iTunes updates released last year patched vulnerabilities affecting the WebKit browser engine. One of the Windows updates, released in July, patched flaws in the libxml2 and libxslt libraries.
Apple: CIA's Mac, iPhone Vulnerabilities Already Patched
24.3.2017 securityweek Apple
Apple Tells WikiLeaks to Submit CIA Exploits Through Normal Process
Apple’s initial analysis of the iPhone and Mac exploits disclosed by WikiLeaks on Thursday shows that the vulnerabilities they use have already been patched. The company told WikiLeaks to send the information it possesses through the regular submission process.
WikiLeaks’ second “Vault 7” dump, dubbed by the organization “Dark Matter,” includes documents describing tools allegedly used by the U.S. Central Intelligence Agency (CIA) to spy on iPhones and Mac computers. However, installing the implants requires physical access to the targeted device.
The documents are dated 2008, 2009 and 2012, but WikiLeaks claims it has information that the CIA has continued to work on these tools. Apple has conducted a preliminary assessment of the latest WikiLeaks disclosure and determined that the vulnerabilities described in the documents were patched years ago.
“Based on our initial analysis, the alleged iPhone vulnerability affected iPhone 3G only and was fixed in 2009 when iPhone 3GS was released. Additionally, our preliminary assessment shows the alleged Mac vulnerabilities were previously fixed in all Macs launched after 2013,” Apple told SecurityWeek.
Follow
WikiLeaks ✔ @wikileaks
Apple's claim that it has "fixed" all "vulnerabilities" described in DARKMATTER is duplicitous. EFI is a systemic problem, not a zero-day.
2:33 AM - 24 Mar 2017
2,605 2,605 Retweets 3,557 3,557 likes
Apple’s analysis of the first Vault 7 leak also showed that many of the disclosed iOS exploits had already been patched in the latest version of the mobile operating system.
The tools described in the Dark Matter leak include Sonic Screwdriver, which is designed to allow code execution on a Mac laptop with password-protected firmware via an exploit stored on a Thunderbolt-to-Ethernet adapter.
The DarkSeaSkies implant is designed for targeting the EFI on MacBook Air computers, while NightSkies can be used to steal data from iPhones.
The documents show that the exploits can be delivered either via a supply chain intercept or by giving the manipulated device to the target as a gift. However, some believe the claims made by WikiLeaks regarding supply chain interception are misleading.
Apple has not negotiated with WikiLeaks
WikiLeaks has not made public any of the actual exploits, but it has promised to share them with affected tech companies. However, the whistleblower organization wants these companies to meet certain conditions, including to promise to patch the vulnerabilities within 90 days.
While Mozilla has accepted WikiLeaks’ offer, it appears Google, Apple and other companies are not eager to cooperate, which WikiLeaks has blamed on “conflicts of interest due to their classified work for U.S. government agencies.” Apple said it had not negotiated with WikiLeaks for any information.
“We have given them instructions to submit any information they wish through our normal process under our standard terms,” Apple said in its statement. “Thus far, we have not received any information from them that isn’t in the public domain. We are tireless defenders of our users' security and privacy, but we do not condone theft or coordinate with those that threaten to harm our users.”
Fortinet researchers spotted a malware that infects both Microsoft and Apple OSs
24.3.2017 securityaffairs Apple
Malware researchers at Fortinet have discovered a weaponized Word document that is able to start the infection process on both Microsoft and Apple OSs.
Security researchers at Fortinet have spotted a weaponized Word document that has been designed to spread malware on either Microsoft Windows or Mac OS X, it is able to determine which OS is used by the person that opens the document and start the attack.
The documents trick victims into enabling macros, then a malicious VBA code is executed.
Once the VBA code is executed, the AutoOpen() function is automatically invoked. It first reads the data from the “Comments” property of the Word file, a base64-encoded string, and depending on the OS, executes a certain script.
When executed on Mac OS X, the script downloads a malicious file containing another script, written in python, that’s executed and communicate with the control server.
“When the python script is executed, it downloads a file from “hxxps://sushi.vvlxpress.com:443/HA1QE”, and executes it. The downloaded python script is a slightly modified version of the Python meterpreter file, which is also part of the Metasploit framework.” reads the analysis published by Fortinet. “The source code of the project can be downloaded from the following URL: hxxps://github.com/rapid7/metasploit-payloads/blob/master/python/meterpreter/meterpreter.py.”
The above script is a version of a Python Meterpreter file that leverages in-memory DLL injection mechanism.
A similar technique was implemented by the criminal gang tracked as GCMAN and a group of criminals that powered a hacking campaign that leverage on fileless malware in February,
The script used to start the attack on Window systems is much more sophisticated. It implements a “matryoshka” mechanism of powershell scripts and according to the researchers it only works on 64-bit versions of Windows.
Each layer is base64-encoded, once the final level is executed, the script downloads a 64-bit DLL file, which executes and communicates with the control server.

The malware researchers at Fortinet are still analyzing the malicious code.
Weaponized Word Document Targets macOS, Windows
23.3.2017 securityweek Apple
A recently uncovered malware campaign was found to be using a weaponized Word document that can be used to target both macOS and Windows machines, Fortinet researchers warn.
The campaign relies on a macro-enabled Word file designed to execute a malicious VBA (Visual Basic for Applications) code. Up to a certain point, the code execution follows the same steps, but then it takes a different path, depending on whether it runs on macOS or Windows.
Similar to a typical macro attack, as soon as the user opens the malicious document, they are prompted to enable macros, which automatically causes the VBA code to be executed (the VBA uses slightly modified code taken from a Metasploit framework).
The code calls the AutoOpen() function, which reads Base64-encoded data from the “Comments” property of the file. Moving forth, the execution route differs depending on whether the victim runs macOS or Windows, Fortinet says.
On macOS, because Python is pre-installed and Python scripts can be executed by default, the malicious attack takes this route. Thus, the base64-decoded script is executed to download another Python script, which researchers discovered to be a slightly modified version of the Python meterpreter file, which is also part of the Metasploit framework.
Once this script is executed, it attempts to connect to a remote domain on port 443, but Fortinet says that the server wasn’t answering client requests during analysis. However, security researchers observed that the Python process remains active on the system while trying to connect to the reachable server.
On Windows systems, the VBA script makes a DOS-style command string starting with cmd.exe, then starts powershell.exe hidden, and executes the base64-encoded code. The PowerShell script was designed to decompress a piece of gzip data to get another PowerShell script and execute it.
The malicious script would ultimately download a file into a newly allocated buffer, with this file found to be a 64-bit DLL file. The file is executed when the thread function is returned. The malware was also observed establishing communication with the server, but Fortinet didn’t offer further info on its capabilities.
Both the macOS and Windows malicious programs were observed trying to communicate with subdomains of vvlxpress[.]com.
Although macro malware has been hitting Windows users for a very long time, this is only the second attack to date to abuse malicious macros in an attempt to compromise Macs, after another was detailed in early February. However, this is the first time the same macro-enabled Word document has been used to target both macOS and Windows users.
Turkish Crime Family group will remotely wipe hundreds of millions of iPhones unless Apple pays ransom
23.3.2017 securityaffairs Apple
Hackers belonging to the Turkish Crime Family group threaten to remotely wipe hundreds of millions of iPhones unless Apple pays a ransom.
Crooks are claiming to have over 627 millions of iCloud credentials and intend to wipe date from iPhones, iPads and Macs if the Apple does not pay $150,000 within two weeks.
Members of the group which calls itself Turkish Crime Family claim that they’ve been involved in selling databases of stolen credentials for the past few years.
“The group said via email that it has had a database of about 519 million iCloud credentials for some time, but did not attempt to sell it until now. The interest for such accounts on the black market has been low due to security measures Apple has put in place in recent years, it said.” reported ComputerWorld.
The members of the group are originally from Istanbul, but now seem to be located in Green Lanes, an area in North London.

The situation is not so critical, changing the iCloud passwords will make ineffective the operation of the crooks. As usual, let me suggest also to enable two-factor authentication.
The hackers claim to have verified over 220 million of the credentials, they login credentials allowed them to access to iCloud accounts.
The hackers tested the login credentials using automated scripts and a large number of proxy servers to avoid being blocked by Apple.
Initially, the Turkish Crime Family crew asked Apple a $75,000 ransom in Bitcoin or Ethereum cryptocurrency. Now the group has increased its request raising the ransom value to $150,000, and the group intends to increase it further if Apple doesn’t pay in three days.
According to Motherboard, Apple will not pay the ransom, the hackers provided screenshots of alleged emails between its members and the Apple’s security team. Someone also published a video on YouTube showing how to use leaked credentials to access iCloud accounts, but the group claims that the person who shared the video is not a member of their group.
“We firstly kindly request you to remove the video that you have uploaded on your YouTube channel as it’s seeking unwanted attention, second of all we would like you to know that we do not reward cyber criminals for breaking the law,” reads a message allegedly sent by a member of Apple’s security team reads. (Motherboard only saw a screenshot of this message and not the original). The alleged Apple team member then says archived communications with the hacker will be sent to the authorities.”
Apple did not immediately respond to a request for comment.
“We are doing this because we can and mainly to spread awareness for Karim Baratov and Kerem Albayrak, which both are being detained for the Yahoo hack and one of them is most probably facing heavy sentencing in America,” a representative for the group said via email. “Kerem Albayrak on the other hand is being accused of listing the database for sale online.”
At this point we have to wait April 7, this is the date when the hackers plan to launch the mass attack on iCloud accounts and wipe their contents.
Hackers Threaten to Remotely Wipe 300 Million iPhones Unless Apple Pays Ransom
22.3.2017 thehackernews Apple 
If you use iCloud to sync your Apple devices, your private data may be at risk of getting exposed or deleted by April 7th.
It has been found that a mischievous group of hackers claiming to have access to over 300 million iCloud accounts is threatening Apple to remotely wipe data from those millions of Apple devices unless Apple pays it $75,000 in crypto-currency or $100,000 worth of iTunes gift cards.
The hacking group, who identified themselves as 'Turkish Crime Family,' has demanded a ransom to be paid in Bitcoin or Ethereum, another popular crypto-currency.
Motherboard broke this story on Tuesday after a hacker claiming to represent the alleged hacking group shared screenshots of alleged emails between the group and Apple's security team with the publication.
"I just want my money and thought this would be an interesting report that a lot of Apple customers would be interested in reading and hearing," the hacker told Motherboard.
The screenshots of email exchange indicate that when Apple security team asked for a sample list of hacked account to verify the claims, the group only provided a YouTube video demonstrating access to one of the allegedly hacked accounts and remotely wiping all content from the device.
However, the story seems inconsistent, as on its Twitter account, the group claims to have access to 200 million iCloud accounts, while in one of the emails, it says to access 300 million Apple email accounts and in another, the number gets almost double to 559 million.
At this time, it is very difficult for even Apple to verify the claims. However, the company has warned the group saying that it does not reward cyber criminals for breaking the law and asking them to remove the video as it was "seeking unwanted attention."
The hacking group has given Apple a deadline until April 7 to pay up the ransom. Unless its demands are met, the group are going to start remotely wiping victim's Apple devices and reset iCloud accounts.
How to Protect Your iCloud Account From Hackers
Whether the claims and threat are real or not, but if hackers gain access to your iCloud account, they could easily download all your photos and other private data.
In order to keep your iCloud account safe from hackers, Apple users are advised to change their iCloud passwords immediately and enable two-step authentication to add an extra layer of security to your account.
Also Read: Searching for Leaked Celebrity Photos? Don't Blindly Click Any Fappening Link!
We have already aware of the consequences iCloud accounts can make if they get hacked by malicious attackers. In 2014, iCloud hack led to The Fappening, wherein hackers flooded the Internet with nude photos of hundreds of female celebrities, which were stored in their iCloud accounts.
Some people are also linking the Turkish Crime Family to the recent The Fappening 2.0 incident that leaked private photographs of many celebrities, including Emma Watson and Mc Rose, last week.
However, there is no evidence to suggest the blackmail attempt had anything to do with The Fappening 2.0 attack.
New variant of the macOS Proton RAT advertised on Russian cybercrime underground
14.3.2017 securityaffairs Apple
Experts from security firm Sixgill have discovered a new strain of the macOS Proton RAT that is offered for sale on Russian cybercrime underground.
The Dark Web is the right place where to find any kind of illegal products and services, malware such as banking trojan and spyware are very popular in cyber criminal underground.
Recently a new remote access tool (RAT) specifically designed to infect macOS systems is currently being advertised on Russian cybercrime underground. The researchers at security firm Sixgill discovered the advertising on crime forums and on a custom website, this threat is also described in videos published on YouTube.
The Proton homepage went down just after the experts at Sixgill published the report.
“Sixgill researchers have encountered a post in one of the leading, closed Russian cybercrime message boards. The author of the thread announced a RAT dubbed Proton, intended for installation exclusively on MAC OS devices. The author offered this product in one of the leading underground cybercrime markets.” reads a report published by Sixgill.
The Proton RAT first appeared in the threat landscape last year, the variant recently advertised on hacking forums includes many features such as the ability to execute console commands, access the user’s webcam, log keystrokes, capture screenshots and open SSH/VNC remote connections. The malicious code is also able to inject malicious code in the user’s browser to display popups asking victims information such as credit card numbers, login credentials, and others.
“The malware includes root-access privileges and features allowing an attacker to obtain full control of the victim’s computer. Its capabilities include: running real-time console commands and file-manager, keylogging, SSH/VNC connectivity, screenshots, webcam operation and the ability to present a custom native window requesting information such as a credit-card, driver’s license and more. The malware also boasts the capability of iCloud access, even when two-factor authentication is enabled.” continues the report.
According to the author, macOS Proton RAT is written in native Objective-C and it is fully undetected by any existing MAC OS antivirus solution.
Below the list of features described in the ad:

The Proton RAT has root access and is able to elude standard macOS security features, it is also able to bypass two-factor authentication on iCloud accounts.
Researchers speculate macOS Proton RAT leverages a zero-day vulnerability in macOS, but most interesting characteristic of the threat is that the malicious code is signed with genuine Apple code-signing certificates. It is likely the author has managed to falsify registration to Apple Developer ID Program or has stolend the credentials to an apple developer.
“The real threat behind the software is this: The malware is shipped with genuine Apple code-signing signatures. This means the author of Proton RAT somehow got through the rigorous filtration process Apple places on MAC OS developers of third-party software, and obtained genuine certifications for his program. Sixgill evaluates that the malware developer has managed to falsify registration to the Apple Developer ID Program or used stolen developer credentials for the purpose.” reads the report.
The price for the macOS Proton RAT ranged from $1,200 to $830,000 for the entire project (an absurd price). Below the version advertised on the Proton websites:
Standard Edition
I) License to control only ONE remote machine 1) 1 BTC — unsigned 2) 2 BTC — signed
II) License to control 20 remote machines 1) 10 BTC — unsigned 2) 11 BTC — signed
III) License to control infinite remote machines 1) 66 BTC — unsigned 2) 76 BTC — signed
Extended edition
I) License to control infinite remote machines 1) 166 BTC — unsigned 2) 200 BTC — signed
II) License to control infinite remote machines on your own server 1) 366 BTC — without source code 2) 666 BTC — with full source code
Researchers noticed that the authors of the malware try to disguise their spyware as legitimate surveillance software.
Google Expands Safe Browsing Protection on macOS
3.3.2017 securityweek Apple
Google announced this week that it will expand Safe Browsing on macOS in an effort to protect Chrome users against unwanted ad injections and unauthorized settings changes.
“Safe Browsing is broadening its protection of macOS devices, enabling safer browsing experiences by improving defenses against unwanted software and malware targeting macOS,” Google’s Kylie McRoberts and Ryan Rasti said on the company’s Security Blog. “As a result, macOS users may start seeing more warnings when they navigate to dangerous sites or download dangerous files.”
Applications that inject ads violate Google’s unwanted software policy and Mac users will be warned when Chrome detects such activity.
As for Chrome settings, the tech giant wants to ensure that applications cannot make unauthorized changes to the start page, the home page and the default search engine.
Google recently launched a new Mac API called Settings Overrides, which allows Chrome extensions to override the start page, home page and search settings in the web browser. The company wants this API to be the only approved method for making changes to Chrome settings on macOS and OS X.
However, only extensions approved for the Chrome Web Store are allowed to use the Settings Overrides API. Starting with March 31, Chrome will display a warning when a piece of software attempts to modify settings via other methods.
Apple internal development servers compromised by a malware
25.2.2017 securityaffairs Apple
Apple’s design lab internal development servers was infected by a malware so the company ended its relationship with Supermicro server supplier.
It was mid-2016 when Apple’s design lab internal development servers was infected by a malware that was masquerading as a fake firmware patch.
In response to the security incident, Apple purged its data centers of servers built by Supermicro, including returning recently purchased systems.
“In early 2016, Apple discovered what it believed was a potential security vulnerability in at least one data center server it purchased from a U.S.-based manufacturer, Super Micro Computer, according to a Super Micro executive and two people who were briefed about the incident at Apple.” reported the theinformation.com. “The server was part of Apple’s technical infrastructure, which powers its web-based services and holds customer data.”
A source familiar with the case at Apple told Ars that the malicious firmware was downloaded directly from Supermicro’s support site, and the malicious code is still hosted there.
Apple denied the security breach, but the senior vice-president of technology t Supermicro, Tau Leng, told The Information that the company had ended its relationship with Supermicro because of the infection in the App Store development environment. Leng also confirmed Apple returned the systems it had recently purchased.
The trend for cloud giants is the slight migration to custom hardware designed by system integrators to cut the cost of the data center.
apple server
According to Leng, Apple was the only company to be infected by a fake firmware, this means that the root cause of the security breach was not in the Supermicro’s servers. He asserted that when his company asked Apple’s engineers to provide information about the firmware, they gave an incorrect version number—and then refused to give further information.
Leng also added that information about the firmware version shared by Apple’s engineers was incorrect (wrong version number).
An Apple spokesperson reached out by Ars defined the story “completely inaccurate.”
Let’s wait for the Apple’s version.
New MacOS Malware linked to Russian Hackers Can Steal Passwords & iPhone Backups
16.2.2017 thehackernews Apple
Security researchers have discovered a new Mac malware allegedly developed by APT28 Russian cyber espionage group who is believed to be responsible for 2016 presidential election hacking scandal.
A new variant of the X-Agent spyware is now targeting Apple macOS system that has previously been used in cyber attacks against Windows, iOS, Android, and Linux devices.
The malware is designed to steal web browser passwords, take screenshots of the display, detect system configurations, execute files and exfiltrate iPhone backups stored on the computer.
The X-Agent malware is tied to Russian hacking group known as APT28 — also known as Fancy Bear, Sofacy, Sednit, and Pawn Storm — that has been operating since at least 2007 and is allegedly linked to the Russian government.
"Our past analysis of samples known to be linked to APT28 group shows a number of similarities between the Sofacy/APT28/Sednit Xagent component for Windows/Linux and the Mac OS binary that currently forms the object of our investigation," Bitdefender reported in a blog post published Tuesday.
"For once, there is the presence of similar modules, such as FileSystem, KeyLogger, and RemoteShell, as well as a similar network module called HttpChanel."
Like variants for other platforms, the Mac version of X-Agent spyware is also act as a backdoor with advanced cyber-espionage capabilities that can be customized depending on the objectives of an attack.
Moreover, X-Agent is being planted by exploiting a vulnerability in the MacKeeper software installed on the targeted computers and known malware dropper Komplex — a first-stage trojan that APT28 uses to infect machines.
Abovementioned evidence indicates that the newly discovered Mac version of X-Agent is also created by the same Russian hacking group.
Once successfully installed, the backdoor checks for the presence of a debugger and if it finds one, it terminates itself to prevent execution. But if not, the backdoor waits for an Internet connection to communicate with the command-and-control servers.
"After the communication has been established, the payload starts the modules. Our preliminary analysis shows most of the C&C URLs impersonate Apple domains," Bitdefender researchers said.
"Once connected to the C&C, the payload sends a HelloMessage, then spawns two communication threads running in infinite loops. The former uses POST requests to send information to the C&C, while the latter monitors GET requests for commands."
The Research is still ongoing and Bitdefender security researchers right now only have the Mac malware sample and not a full picture of how an attack works.
APT28 is one of the two Russian-linked cyber-espionage groups that have been accused of hacking into the U.S. Democratic National Committee's email server last year and interfering with the 2016 presidential election.
You can read BitDefender's previous analysis on the APT28 hacking group here [PDF].
FireEye Becomes AV Replacement, Adds macOS Support
15.2.2017 Securityweek Apple
SAN FRANCISCO – RSA CONFERENCE 2017 - Cyber threat protection and intelligence firm FireEye today unveiled major updates to its endpoint security platform, including two new protection engines and support for Apple’s macOS systems.
The new capabilities are the first of several no-cost upgrades for FireEye Endpoint Security customers that are coming in 2017, the company says.
As part of the latest FireEye Endpoint Security platform, a new “Exploit Guard” engine leverages behavioral analysis capabilities to detect known threats, while a new partnership integrates Bitdefender’s anti-malware engine to protect against more traditional commodity malware. The combination allows FireEye Endpoint Security to serve as an Anti-Virus replacement with a single agent that can satisfy compliance requirements.
FireEye Endpoint SecurityThe company claims that its behavioral analysis engine that powers the new Exploit Guard feature, has in testing environments, been able to detect and block nearly all the previously unknown exploits – without signatures or indicators – that were publicly reported over the past three years.
“We took every zero-day exploit that affected Windows machines from 2014, 2015 and 2016 and fed them into this engine,” FireEye CTO Grady Summers told SecurityWeek at the company’s recent internal Momentum 2017 conference. Summers, who previously served as CISO at GE, explained that FireEye pulled down all the ransomware and exploit kits they could find on Virus Total and were able to achieve a 99.74% efficacy (detection) rate with no signatures or prior knowledge.
The company boasts an advantage of continually responding to high profile breaches around the world via its Mandiant team, where incident responders and analysts are able to see where other products fail. The company says that in Q4 2016, Mandiant responded to more security breaches than in any prior quarter in the company’s history.
"Well over 80 percent of the time, if I'm reading a headline, we are there," Kevin Mandia, CEO at FireEye, told SecurityWeek in a meeting at the Momentum Conference last month . "That makes me feel good."
“At FireEye, our security innovation begins at the breach. Because we own that moment, we get to witness firsthand how attackers evade other security safeguards – including 'next gen' endpoint – and this allows us to innovate at the speed of attackers,” Kara Wilson, Chief Marketing Officer at FireEye, wrote in a blog post.
In addition to insights gained from the Mandiant Incident Response team, context from FireEye iSIGHT Intelligence helps security teams prioritize and triage threats, the company says.
“FireEye Endpoint Security is built to speed up and simplify endpoint protection and response with high-fidelity alerts, context from FireEye iSIGHT Intelligence, and forensic and investigation capabilities scaled to hundreds of thousands of endpoints,” the company explains. “This seamless integration of prevention, detection and response capabilities in a single agent also greatly simplifies the customer deployment and lowers the performance impact on the endpoint.”
These new capabilities are generally available to customers globally immediately.
The integration of Bitdefender's anti-virus engine is expected to occur during the first quarter of 2017, with additional roll-out of other detection and prevention capabilities following later this year.
In addition to the recently added support for macOS endpoints, support for Linux servers will be added later in 2017. Other enhancements coming this year will include virtual and cloud form factors and expanded behavioral analysis and machine learning capabilities to protect against unknown malware and exploits.
After seeing its stock price decline significantly over the past years, along with major executive leadership changes, FireEye is betting on new products and partnerships to help improve its position in the cybersecurity solutions market.
In late 2016, FireEye launched new cloud-based network security and threat intelligence offerings. The company also announced a deal with Microsoft that allows Windows Defender Advanced Threat Protection (WDATP) users to gain access to FireEye's iSIGHT adversary based intelligence.
In November 2016 the company unveiled FireEye Helix, a new platform designed to help customers efficiently integrate and automate security operations functions and accelerate incident response.
In December 2016, FireEye and the NATO Communications and Information Agency (NCI) announced an information sharing partnership, under which the two organizations will exchange non-classified technical information related to cyber threats and vulnerabilities.
“The investments we are making in 2017 for our customers in Endpoint Security are significant, as it is a core component of the FireEye Helix platform and a huge opportunity for our business,” Mandia said in a statement.
Russian Cyberspies Use New Mac Malware to Steal Data
15.2.2017 securityweek Apple
Researchers have discovered a new piece of malware used by the Russia-linked threat group known as APT28 to steal sensitive data from Mac devices, including backups and passwords.
APT28 is also tracked as Fancy Bear, Pawn Storm, Sofacy, Tsar Team, Strontium and Sednit. The threat actor has been linked to several high-profile attacks aimed at government and other types of organizations around the world, including the recent election-related hacker attacks in the United States.
APT28 has been known for using an OS X downloader named Komplex, and researchers from Bitdefender and Palo Alto Networks have now come across another Mac malware believed to be part of the group’s arsenal.
XAgent, or X-Agent, is a Trojan used by APT28 in attacks targeting Windows systems. A recently analyzed campaign aimed at Ukraine indicates that the group may have also developed an Android version of XAgent.
Bitdefender and Palo Alto Networks have also identified a macOS version of XAgent, which they believe is downloaded to targeted systems by the Komplex downloader. Both security firms determined, based on binary strings, that Komplex and XAgent were likely created by the same developer.
Once it infects a Mac computer, the malware, which its authors call XAgentOSX, contacts a command and control (C&C) server and waits for instructions. C&C communications are similar to the ones used by the Windows version of XAgent.
XAgentOSX can collect information about the system, running processes and installed applications, it can download and upload files, execute commands and files, and take screenshots.
The malware also looks for backup files from an iPhone or iPad, which it can exfiltrate using one of the available commands. XAgentOSX can also log keystrokes, allowing the attackers to obtain the victim’s credentials.
Bitdefender told SecurityWeek that it does not have any information on XAgentOSX infections and targets, but the company believes the victims are hand-picked in an effort to prevent the exposure of malware samples.
“Most likely, this sample is directed at the same audience that makes the focus of the APT28 group (government, airspace, telecom and, e-crime services). It most likely covers the instances in which targets in the respective groups use Macs as work or personal computers,” said Bogdan Botezatu, Senior E-Threat Analyst at Bitdefender.
APT28 is a sophisticated threat group whose arsenal includes a wide range of tools, including Linux malware. One of the actor’s favorite Linux tools is Fysbis, an unsophisticated yet efficient backdoor.
Signal introduced the Video call feature in public beta release
15.2.2017 securityaffairs Apple
Signal, the most secure instant messaging app, introduced the Video call feature in public beta release. You can test is now!
Signal is considered the most secure instant messaging app, searching for it on the Internet it is possible to read the Edward Snowden’ testimony:
“Use anything by Open Whisper Systems” Snowden says.
The Cryptographer and Professor at Johns Hopkins University Matt Green and the popular security expert Bruce Schneier are other two admirers of the Signal app
News of the day is that the Signal app released video calling feature on Tuesday for both Android and iOS.
The new feature will allow Signal users to make face-to-face through video calling with a specific focus on security.
The Signal video calling feature implements the support for CallKit on iOS 10 devices, a recently introduced framework that lets users’ VoIP app integrate tightly with the native Phone UI.
The Callkit in iOS 10 allows Signal users to answer calls just like regular calls, but there are some specific privacy issues that must be carefully considered.
“CallKit offers a native calling experience to VoIP apps like Signal. As well as being able to answer calls directly from your lock screen, you’ll also see Signal calls in the system’s “Recent Calls” list. This is because iOS treats CallKit calls like any other call, however that also means some information will be synced to iCloud if enabled. This information includes who you called and how long you talked.” wrote Moxie Marlinspike.
CallKit could be disabled by Signal iOS users to enhance the privacy.
The Signal’s video calling feature is still in beta, in order to make a video call both users will have to enable the feature.
If you wan to try the new feature go into your Signal settings and enable ‘Video calling beta’ under ‘Advanced.’
“If you decide that’s not for you, you can opt-out of the CallKit features at any time in Settings > Advanced > Use CallKit, while continuing to use the rest of the new calling system.” continues Moxie Marlinspike.
Signal Messaging App Rolls Out Encrypted Video Calling
15.2.2017 thehackernews Apple
WhatsApp and Facebook have so far the largest end-to-end encrypted video calling network of all, but now another popular end-to-end encrypted messaging app recommended by whistleblower Edward Snowden is ready to give them a really tough competition.
The Signal app, which is widely considered the most secure of all other encrypted messaging apps, released video calling feature on Tuesday for both Android and iOS in a new update.
Developed by open source software group Open Whisper System, Signal is a free and open source messaging application specially designed for Android and iOS users to make secure and encrypted messages and voice calls.
Even the Signal Protocol powers the end-to-end encryption built into WhatsApp, Facebook Messenger, and Google Allo's Incognito mode as well.
Signal has already been providing fully end-to-end encrypted chat and voice calling features, but the newly added feature will make it even easier for privacy conscious people to convey their information face-to-face through video calling without compromising security.
Watch Out! There's a Privacy issue too!
This new video calling feature also comes with support for CallKit on iOS 10 devices, a new framework that makes Signal act more like the regular phone app.
Callkit in iOS 10 allows Signal users to answer calls from with one touch through their device's lock screen and lists those calls on the device's native "Recent Calls" just like regular calls, possibly making it inconvenient for privacy-minded people.
CallKit is optional, and if users decide to opt-in this feature, some of their data might sync to Apple's iCloud servers, including who the Signal users called and how long they had the conversation, Signal's pseudonymous lead designer Moxie Marlinspike explains in a blog post.
The CallKit feature can be turned off within your iOS device's settings to enhance your privacy.
Currently, Signal’s video calling feature is in beta, which means both users will have to enable the feature for video calling to work manually.
To try out video calling in Signal, you will have to go into your Signal settings and enable 'Video calling beta' under 'Advanced.'
Word documents laced with malicious macros used to hack Apple Mac systems
13.2.2017 securityaffairs Apple
Crooks exploiting Word documents laced with malicious macros to compromise Apple Mac systems exactly in the same way they do with Microsoft machines.
It’s amazing the number of Apple Mac users that tell me their systems are immune from malware. This false sense of security is very dangerous and I believe it is important to explain how also Mac system could be compromised by malicious codes.
I want to take advantage by telling you about a recent event to explore the topic, crooks exploiting Word documents laced with malicious macros to compromise Apple Mac systems exactly in the same way they do with Microsoft machines.
Last week, security experts observed a spike in the distribution spam messages using attachments embedding malicious macros. One of the baits was titled “U.S. Allies and Rivals Digest Trump’s Victory – Carnegie Endowment for International Peace.docm,” when the Mac recipients open the documents are prompted to enable macros.
Apple MAC
If a Mac user enabled the macros, the file executes a Python function that downloads a malicious payload and executes it infecting the machine. The Python code is publicly available, it is part of the open-source project EmPyre, and as highlighted by the researcher Patrick Wardle, this new attack leverages old tricks.
“Today, Monday the 6th, was a busy day for macOS malware! First, Nex (@botherder) posted a great writeup, iKittens: Iranian actor resurfaces with malware for mac (macdownloader)“, which detailed some new macOS malware. Shortly thereafter, my friend Scott (@0xdabbad00) brought to my attention the following tweet:
Segui
Snorre Fagerland @fstenv
#OSX #Macro #EmPyre "U.S. Allies and Rivals Digest Trump’s Victory - Carnegie Endowment for International Peace" https://www.virustotal.com/en/file/07adb8253ccc6fee20940de04c1bf4a54a4455525b2ac33f9c95713a8a102f3d/analysis/ …
11:34 - 6 Feb 2017
9 9 Retweet 16 16 Mi piace
A malicious Word document targeting Mac users? I was intrigued :). I grabbed the sample (“U.S. Allies and Rivals Digest Trump’s Victory – Carnegie Endowment for International Peace.docm”), noting that only 4 AV engines currently flagged it as malicious”
The analysis of the attack revealed that the IP address used by crooks to spread the malware is located in Russia and was not new to researchers monitoring phishing campaigns.
The security researcher Patrick Wardle explained that the this Apple Mac Malware is not sophisticated, the attack needs the user interaction to compromise the machine.
The reliance on macros rather than a software vulnerability implies that the exploit can’t be blocked only by patching systems.
“Overall this malware sample isn’t particularly advanced. It relies on user interaction (to open a malicious document in Microsoft Word, (not Apple’s Pages)), as well as needs macros to be enabled. Most users know never to allow macros – right!?! Moreover using an open-source implant likely ensures that detection software should detect it – right!?” concluded Wardle.
“However let’s be nice and give the attackers some credit. By using a macros in Word document they are exploiting the weakest link; humans! And moreover since macros are ‘legitimate’ functionality (vs. say a memory corruption vulnerability) the malware’s infection vector doesn’t have to worry about crashing the system nor being ‘patched’ out. “
Recently the security researchers Claudio Guarnieri and Collin Anderson have analyzed samples of the MacDownloader malware that was disguised by nation-state hackers as a Flash Player update and a Bitdefender adware removal tool.
According to the researchers, the malware was first “poorly” developed the end of 2016, the experts noticed its code was copied from other sources. Anyway, at the time of writing the analysis, MacDownload is undetected by virus scanning engines on VirusTotal, while at the time I was writing just a dozen vendors have recognized the bogus Flash Player and Bitdefender apps as a threat.
This last case demonstrates that Apple MAC threat landscape is very active, for this reason, it is important awareness and a proper security posture for MAC users.
Apple’s iCloud saved the deleted Safari browsing history over the years
12.2.2017 securityaffairs Apple
According to the Russian forensic firm Elcomsoft the Apple iCloud saved deleted Safari browsing history over the years open the door to surveillance.
According to digital forensics firm Elcomsof, Apple iCloud maintained deleted internet Safari browsing history over the years. The experts at Elcomsof discovered the issue while trying to extract records from iCloud accounts, they were able to retrieve supposedly deleted Safari browser histories from the accounts. The researchers were able to pull information such as the date and time the website was visited and when the record was deleted.
Safari history is synced across the devices used by a specific iCloud account. When the user deletes a record on one device, it will disappear on all other devices in a few seconds when the devices are connected to the Internet.
Users can set iCloud to store their browsing history, in this way it will be available from all the user’s connected devices. The researchers discovered that even if the user deletes the history, iCloud doesn’t actually erase it but keeps it in a format invisible to the user.
“However, those same records will be kept in Apple iCloud for much longer. In fact, we were able to access records dated more than one year back. The user does not see those records and does not know they still exist on Apple servers.” reads a blog post published by the Elcomsoft’s CEO Vladimir Katalov.
“In fact, we were able to access records dated more than one year back,”
The experts used the Elcomsoft Phone Breaker forensic tool to extract files from an iCloud account.
How does it work?
In order to extract Safari history from iCloud it is necessary to be authenticated into the user’s Apple ID. The operation can be carried on using login credentials or by using an authentication token extracted from the user’s computer. The authentication tokens are automatically created by iCloud Control Panel on Windows and Mac computers that were synced with iCloud.
The Elcomsoft Phone Breaker can be used by experts to extract iCloud authentication tokens.
“By using the token to log in, you’ll bypass both the password and the secondary authentication prompt if two-factor authentication is enabled on the user’s account. As a result, iCloud access alert will not be delivered to the user.” states the post.
Below the procedure to extract Safari browsing history from iCloud with Elcomsoft Phone Breaker:
Launch Elcomsoft Phone Breaker 6.40 or newer
Click “Download Synced Data from iCloud”
Authenticate with Apple ID/password or binary authentication token
Specify everything you’d like to download. Make sure to check “Safari”
Safari browsing history

The forensic implication of the discovery is serious because it implies the possibility to conduct surveillance activity as explained in the post.
“Forensic use of synced data is hard to underestimate. Unlike cloud backups that are created daily at best, iCloud sync works nearly in real-time. Being able to track suspect’s activities almost no delay can be invaluable for surveillance and investigations.” states Katalov.
“Since deleting browsing history from iCloud is nearly impossible for the user, discovering illicit activities becomes much easier. Experts will be able to recover visits to extremist and other illicit Web sites even if the suspect deletes their browser history or wipes their iPhone.”
Keeping a copy of a user’s browser history can certainly be “invaluable for surveillance and investigations,” Katalov said. But it’s unclear if Apple knew that its iCloud service was storing the deleted records.
Apple didn’t immediately respond to a request for comment, but experts from Elcomsoft noticed that after they disclosed the issue, Apple started “purging” older browser history records from iCloud.
“we have informed media about this issue in advance, and they reached Apple for comments. As far as we know, Apple has not responded, but started purging older history records. For what we know, they could be just moving them to other servers, making deleted records inaccessible from the outside; but we never know for sure. Either way, as of right now, for most iCloud accounts we can see history records for the last two weeks only (deleted records for those two weeks are still there though).” states the blog post. But now only deleted records as old as only two weeks can be extracted, the forensic company said.
Elcomsoft suggests disabling the syncing of Safari browsing history from iCloud.
Watch Out! First-Ever Word Macro Malware for Apple Mac OS Discovered in the Wild
10.2.2017 thehackernews Apple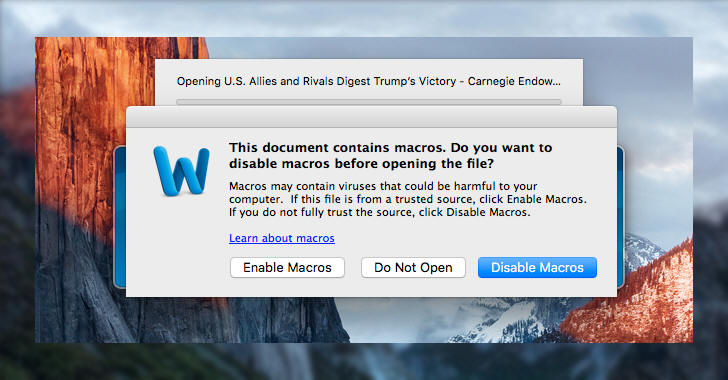
After targeting Windows-based computers over the past few years, hackers are now shifting their interest to Macs as well.
The emergence of the first macro-based Word document attack against Apple's macOS platform is the latest example to prove this.
The concept of Macros dates back to 1990s. You might be familiar with the message that reads: "Warning: This document contains macros."
Macro is a series of commands and actions that help automate some tasks. Microsoft Office programs support Macros written in Visual Basic for Applications (VBA), but they can also be used for malicious activities like installing malware.
Until now, hackers were cleverly using this technique to target Windows.
However, security researchers have now detected the first in-the-wild instance of hackers are making use of malicious macros in Word documents to install malware on Mac computers and steal your data – an old Windows technique.
The hack tricks victims into opening infected Word documents that subsequently run malicious macros. One such malicious Word file discovered by the researcher was titled "U.S. Allies and Rivals Digest Trump's Victory – Carnegie Endowment for International Peace.docm."
However, after clicking on the malicious Word document and before running it on your system, Mac users are always prompted to enable macros.
Denying permission can save you, but if enabled ignoring warnings, the embedded macro executes a function, coded in Python, that downloads the malware payload to infect the Mac PCs, allowing hackers to monitor webcams, access browser history logs, and steal password and encryption keys.
According to a blog post published this week by Patrick Wardle, director of research at security firm Synack, the Python function is virtually identical to EmPyre – an open source Mac and Linux post-exploitation agent.
"It’s kind of a low-tech solution, but on one hand it’s abusing legitimate functionality so it’s not going to crash like a memory corruption or overflow might, and it’s not going to be patched out," said Wardle.
Wardle tracked the IP address from which the malicious Word documents were spread to Russia and that IP has previously been associated with malicious activities like phishing attacks.
adobe flash malware
Another malicious attack discovered by researchers this week also relied on standard Windows techniques by prompting users to download and install a fake software update, but actually harvest the user Keychain, phish usernames and passwords, and other sensitive data.
The MacDownloader nasty virus presented itself as both an update for Adobe Flash and the Bitdefender Adware Removal Tool, which are always annoying and dismissed by most users.
This is what all attackers want. Once the user clicks on either reject the updates or just press yes to dismiss it once and for all, the malware gets the green signal to harvest user keychain, phish usernames and passwords, collect private and sensitive data, and then send them back to attackers.
Researchers have spotted macOS malware targeting mostly the defense industry and reported to have been used against a human rights advocate.
The best way to avoid these kinds of attacks is to just deny permission to enable macros from running when opening a suspicious Word document and avoid downloading software from third-party App Store or untrusted websites.
Iranian hackers are back with the MACDOWNLOADER MAC malware
8.2.2017 Securityweek Apple
An Iranian espionage group has been using an unsophisticated strain of malware, dubbed MacDownloader, to steal credentials and other data from Mac users.
A cyber espionage group linked to the Iranian Government has been using an unsophisticated strain of malware, dubbed MacDownloader, to steal credentials and other data from Mac computers.
The researchers Claudio Guarnieri and Collin Anderson have analyzed the malicious code that was disguised by nation-state hackers as a Flash Player update and a Bitdefender adware removal tool.
The attacks analyzed by the two researchers were mainly focused on the defense industrial base sector, but it is known that the same threat was used against a human rights advocate.
According to the researchers, the malware was first “poorly” developed the end of 2016, the experts noticed its code was copied from other sources. Anyway, at the time of writing the analysis, MacDownload is undetected by virus scanning engines on VirusTotal, while at the time I was writing just a dozen vendors have recognized the bogus Flash Player and Bitdefender apps as a threat.
Once the MacDownloader infects a device, the malware collects information about the host, including passwords stored in the Keychain.
“MacDownloader seems to be poorly developed and created towards the end of 2016, potentially a first attempt from an amateur developer. In multiple cases, the code used has been copied from elsewhere. The simple activity of downloading the remote file appears to have been sourced from a cheat sheet. The main purpose of MacDownloader seems to be to perform an initial profiling of the infected system and collection of credentials from macOS’s Keychain password manager – which mirrors the focus of Windows malware developed by the same actors.” reads the analysis published by the security duo.
The malicious code was first spotted on a fake website of the aerospace firm United Technologies Corporation, that same site that was used in the past to spread a Windows malware and the Browser Exploitation Framework (BeEF).
The malware researchers linked the MacDownloader with the activity of an Iranian threat actor known as Charming Kitten (aka Newscaster and NewsBeef).
Newscaster group made the headlines in 2014 when experts at iSight issued a report describing the most elaborate net-based spying campaign organized by Iranian hackers using social media.
Iranian Hackers used a network of fake accounts (NEWSCASTER network) on principal social media to spy on US officials and political staff worldwide, this is reported in an analysis done by iSIGHT Partners. The Charming Kitten group is also known for the abuse of Open Source Security Tools, including the BeEF.
The analysis of the malware revealed that the authors have attempted to implement remote update and persistence capabilities, but both features don’t work.
“It appears that the application contains an unused attempt to install persistent access to the victim host. One segment provides a poorly-implemented shell script to save a response from the C2 and mark it for persistence by writing an entry in the /etc/rc.common file. In theory, every time the infected computer would start up, the shell script would be launched to download a file from a remote location, check if it changed from the previous iteration, and if so execute that new implant. While we haven’t managed to obtain a proper response from the server before it was taken offline, our initial investigation did not find a subsequent implant.” states the analysis.
The experts have collected evidence that links the malware to other Iranian threat actors, including the Iran Cyber Security Group and Flying Kitten (aka Rocket Kitten).

“Of particular note are wireless networks named Jok3r and mb_1986. Jok3r corresponds with a member of a defacement group, Iran Cyber Security Group, who continues to be fairly active in vandalizing sites. Iran Cyber Security Group also, as with many other defacement groups later identified as involved in state-aligned campaigns, purports to provide commercial security services and penetration testing training.” states the report.
“The “mb_1986″ wireless name is more interesting, as it provides a connection to earlier Iranian campaigns, overlapping with the Flying Kitten actor group and subsequent malware activity in summer 2014.”
The report also includes the IoCs, enjoy it!
Hackers Can Intercept Data From Popular iOS Apps
7.2.2017 securityweek Apple
Dozens of popular iOS applications are affected by vulnerabilities that allow man-in-the-middle (MitM) attackers to silently intercept data from connections that should be protected by TLS, a study has found.
The developers of verify.ly, a service designed for finding security issues in iOS apps, analyzed applications in the Apple App Store and identified hundreds that are likely vulnerable to data interception. Experts have tested each of them on an iPhone running iOS 10 and confirmed that 76 had been vulnerable.
According to Will Strafach, iOS security expert and developer of verify.ly, the affected applications have been downloaded more than 18 million times. The vulnerability is considered high risk in the case of 19 of the 76 applications, as they expose financial or medical service credentials or session authentication tokens.
The medium risk category includes 24 iOS apps, which also expose login credentials and session authentication tokens. The names of the high and medium risk apps have not been disclosed in order to give vendors time to patch the flaws.
Researchers identified 33 low risk applications, which allow attackers to intercept only partially sensitive information, including analytics data, email addresses, and login credentials that would only be entered on a trusted network. The list includes banking, VPN, entertainment, news, stock trading, chat, and Snapchat-related apps.
“This sort of [MitM] attack can be conducted by any party within Wi-Fi range of your device while it is in use. This can be anywhere in public, or even within your home if an attacker can get within close range,” Strafach explained. “Such an attack can be conducted using either custom hardware, or a slighly modified mobile phone, depending on the required range and capabilities. The best similar and well-understood form of attack to this would be the ability to read data from credit cards at a close range.”
Applications are vulnerable to these types of attacks due to the way their developers implement network-related code, which means only the developers can properly address the issue. However, end-users can protect themselves against potential attacks by utilizing the affected applications only over a cellular data connection, which is much more difficult to intercept compared to Wi-Fi.
An automated analysis of Android apps conducted back in 2014 by CERT/CC showed that thousands of applications were vulnerable to MitM attacks, and many of them are still vulnerable today.
76 Popular iOS apps are vulnerable to man-in-the-middle (MITM) attacks
7.2.2017 securityweek Apple
A study conducted on iOS mobile apps revealed that many of them are affected by security vulnerabilities that expose users to man-in-the-middle (MitM) attacks.
A new study confirms that dozens of iOS apps are affected by vulnerabilities that could be exploited by hackers to run man-in-the-middle (MitM) and intercept data from connections even if protected by TLS.
The study was conducted by the developers at verify.ly, a service that analyzes iOS apps searching for security issues. The experts analyzed applications in the Apple App Store and discovered hundreds of security issues that potentially expose mobile users to MITM attacks. All the applications have been tested on iPhone mobile devices running iOS 10 version and confirmed that 76 had been vulnerable.
The impact is serious if we consider that the affected applications account for more than 18 million downloads. The vulnerability is considered high risk in the case of 19 of the 76 applications. The applications expose sensitive data, including financial or medical service credentials or session authentication tokens.
“During the testing process, I was able to confirm 76 popular iOS applications allow a silent man-in-the-middle attack to be performed on connections which should be protected by TLS (HTTPS), allowing interception and/or manipulation of data in motion.” reads the blog post published by the researchers.
“According to Apptopia estimates, there has been a combined total of more than 18,000,000 (Eighteen Million) downloads of app versions which are confirmed to be affected by this vulnerability.”
Examining the key findings of the report we can see that:
the medium-risk category includes 24 iOS apps that expose login credentials and session authentication tokens.
the low-risk category includes 33 iOS apps that are affected by flaws that could be exploited by attackers to intercept only partially sensitive information such as email addresses and login credentials.
“This sort of attack can be conducted by any party within Wi-Fi range of your device while it is in use. This can be anywhere in public, or even within your home if an attacker can get within close range,” continues the post. “Such an attack can be conducted using either custom hardware, or a slighly modified mobile phone, depending on the required range and capabilities. The best similar and well-understood form of attack to this would be the ability to read data from credit cards at a close range.”
The security issues discovered by the experts are the result of the lax of adoption of secure coding techniques. Waiting for a fix, the users of the affected iOS apps need to avoid using them on Wi-Fi networks.
Apple Patches Dozens of Vulnerabilities Across Product Lines
24.1.2017 Securityweek Apple
Apple this week released a new set of important security updates for its products, to patch dozens of vulnerabilities in macOS, iOS, watchOS, tvOS, and Safari, as well as in the iCloud and iTunes for Windows applications.
The newly released macOS Sierra 10.12.3 resolves 11 vulnerabilities in components such as apache_mod_php, Bluetooth, Graphics Drivers, Help Viewer, IOAudioFamily, Kernel, libarchive, and Vim. Most of the plugged issues could allow applications to execute arbitrary code, while others could allow malicious archives or web content to execute code. One of the bugs could allow an application to determine kernel memory layout.
Released on Monday, iOS 10.2.1 resolves 18 vulnerabilities in multiple components, including Auto Unlock, Contacts, Kernel, libarchive, WebKit, and Wi-Fi. WebKit was the most affected component, with no less than 12 flaws resolved in it, most of which were discovered by Google Project Zero researches.
Affecting iPhone 5 and later, iPad 4th generation and later, and iPod touch 6th generation and later, the patched security holes included one where Auto Unlock may unlock when Apple Watch is off the user's wrist, unexpected application termination when processing a maliciously crafted contact card, arbitrary code execution with kernel privileges, data exfiltration, popups being opened by malicious websites, and the possibility to manipulate an activation-locked device to briefly present the home screen.
A total of 33 vulnerabilities were addressed with the release of watchOS 3.1.3, affecting all Apple Watch models. The issues were found in components such as Accounts, Audio, Auto Unlock, CoreFoundation, CoreGraphics, CoreMedia Playback, CoreText, Disk Images, FontParser, ICU, ImageIO, IOHIDFamily, IOKit, Kernel, libarchive, Profiles, Security, syslog, and WebKit.
The resolved vulnerabilities could be exploited for arbitrary code execution, to gain root privileges, to automatically trust certificates, to cause a denial of service, to overwrite existing files, to cause an unexpected system termination, to read kernel memory, to leak memory remotely. There’s also the issue where Auto Unlock could unlock when Apple Watch is off the user's wrist.
The release of tvOS 10.1.1 was meant to resolve 12 vulnerabilities in Kernel, libarchive, and Webkit. Affecting Apple TV (4th generation). These could result in an application executing arbitrary code with kernel privileges, arbitrary code execution when unpacking a malicious archive, and data exfiltration and arbitrary code execution when processing maliciously crafted web content.
No less than 12 bugs were patched in Safari 10.0.3, which is now available for download for OS X Yosemite v10.10.5, OS X El Capitan v10.11.6, and macOS Sierra 10.12.3. While one of these was an address bar spoofing, 11 were found in Webkit and could result in data exfiltration and arbitrary code execution.
Some of the Webkit issues were found to affect iCloud and iTunes for Windows too, and were addressed with the release of iCloud for Windows 6.1.1 and iTunes 12.5.5. The same four bugs affected both applications, resulting in arbitrary code execution.
Endgame Unveils Siri-like Feature for Security Operations Teams
20.1.2017 Securityweek Apple
Threat protection firm Endgame today announced a new AI-powered chatbot feature within its Endgame Detect and Respond (EDR) platform designed to support security analysts.
Dubbed Artemis, named after the mythological goddess of the hunt, the feature could be described as a 'Siri for SOCs'; an intelligent assistant whose purpose is to simplify and automate the hunt for network-resident attackers.
EDR's purpose is the automated use of machine learning to detect subtle indications of anomalous behavior that might indicate the presence of an attacker.
Engame LogoEDR is a hunter; but like all hunters it is most efficient with the help of a terrain guide. In modern Security Operations Centers, that guide is the system analyst, who directs and controls the hunter. Together, top-tier analysts and machine-learning automation is seen as the most effective method of detecting attackers before they can do damage.
The problem is the security skills gap -- the sparsity and cost of professional talent. According to HPE's recently published 2017 State of Security Operations report, staffing issues are one of the prime causes for SOCs failing to reach the required level of maturity. Artemis is designed to help this problem as an intelligent conversational assistant to systems analysts.
"Security teams are faced with two major challenges," says Jamie Butler, CTO at Endgame: "insufficient resources to stop attacks in-progress and lack of automated solutions to uncover malicious behavior in time to prevent information theft. Just as digital assistants like Siri or Alexa proved their ability to give time back to our day by tackling complex tasks, Artemis is an assistant that automatically combs through millions of data points to provide intelligent decisions for the security industry. Security teams," he adds, "especially those that lack sufficient resources, will now have the analytic depth required to find malicious activity across all enterprise endpoints and eliminate threats in time to stop damage and loss."
As an example, if an analyst were to ask Artemis "what is suspicious in my network today?", Artemis would comb through millions of events across endpoints in seconds and provide the user with a comprehensive list of malicious activity. But Artemis goes beyond detection into response. She then recommends a course of action and can be instructed to kill dangerous processes instantly.
In effect, Artemis empowers less-experienced Tier 1 analysts to behave at the same level of sophistication as a Tier 3. She helps SOCs adopt automation without suffering from the usual staffing problems.
Endgame raised $23 million in Series B funding in March 2013, followed by $30 million in Series C funding in November 2014.
In December 2016, Endgame announced that it had been awarded an $18.8 million contract with the U.S. Air Force to have elite Air Force Cyber Protection Teams leverage the Endgame platform to protect endpoints and critical infrastructure.
Crashing iPhone Or iPad with a simple Emoji text message
20.1.2017 securityaffairs Apple
A simple sequence of three character-long text message containing Emoji can cause the block and the reboot os iPhones and iPads running iOS 10.1 or below.
A new Apple’s iOS bug was discovered in the community of mobile tech experts, it can be exploited to crash iPhone or iPad devices by just sending an Emoji text message.
Several users are already reporting the issue and the popular YouTube EverythingApplePro published a video proof-of-concept for the bug. In the video is reported an example of the sequence of characters that temporarily freeze an iPhone causing the device restarting.
The sequence is composed of a white Flag emoji, the digit “0” and a Rainbow emoji. The issue is linked to the way that iOS creates the rainbow flag emoji that is not an official emoji, Apple creates the rainbow flag Emoji by combining the code behind the two white flag and rainbow emoji. Apple iOS joins them by using a hidden character known as a VS16. The iPhone attempts to combine the two emoji, but is unable to because of the zero in the middle.

Source http://www.magazine49.com/archives/48106
There are also other ways to crash the Apple mobile device, another hack leverages the same characters used in a contact file that is sent to an iMessage contact via the iCloud’s sharing feature.
“Both the methods mentioned above will crash and iPhone or iPad to varying degrees, although the simple text string sent via a standard iMessage appears to affect iPhones and iPads running iOS 10.1 or below.” reported The Hacker News. “However, the boobytrapped contact card affects all versions of iOS 10, including Apple’s latest iOS 10.2 operating system.”
Users have to upgrade their version to the last one in order to prevent such kind of attacks.

In November the EverythingApplePro reported that most of the Apple devices were crashing when the owners play a video. An iPhone-freezing video circulated online, when users played it in the Safari browser the iPhones slow down until they stop working altogether.
The iPhone-freezing video was first discovered by EverythingApplePro, it is a short .mp4 clip of someone standing by a bed with the words “Honey” written across the screen.
You Can Crash Anyone's iPhone Or iPad With A Simple Emoji Text Message
19.1.2017 thehackernews Apple
A newly discovered bug in Apple's iOS mobile operating system is being exploited in a prank that lets anyone crash your iPhone or iPad by just sending an emoji-filled iMessage, according to several reports.
YouTube star EverythingApplePro published a video highlighting a sequence of characters that temporarily freeze and restart an iPhone, which people can send to their iPhone buddies to trouble them. You can watch the video demonstration below.
Here's the first troublesome text: A white Flag emoji, the digit "0" and a Rainbow emoji.
This simple numeric character, flag, and rainbow emojis confuse iOS 10 devices when it tries to combine them into a rainbow flag.
As soon as this text is received, the iPhone's software attempts to combine the emojis but fails, and the messaging app crashes and eventually reboots in a few minutes. The recipients do not even have to open or read the message.
Video Demonstration
Another iPhone-crashing method involves the same characters, but saving them as a contact file and then sending that file to an iMessage contact via iCloud's sharing feature.
This, in turn, will crash the target's device, even if the victim has not manually opened the file.
Both the methods mentioned above will crash and iPhone or iPad to varying degrees, although the simple text string sent via a standard iMessage appears to affect iPhones and iPads running iOS 10.1 or below.
However, the boobytrapped contact card affects all versions of iOS 10, including Apple's latest iOS 10.2 operating system.
There is nothing you can do to protect yourself against this issue, as these iPhone-crashing issues have the ability to crash and reboot your iPhone or iPad without your interaction.
So, we hope that Apple releases a patch quickly to plug the issues, though the company has declined to comment on the issue.
This is not the first time EverythingApplePro has shared iOS-crashing issues. The YouTuber has a long history of reporting on iPhone crash pranks.
A new iPhone bug will crash the Messages app with a single text
1.1.2017 securityaffairs Apple
A researcher discovered that a single text message could be exploited to crash the Messages app by MMS on iOS due to a recently discovered bug
A single text message could be exploited to disable the Messages app on any iPhone due to a recently discovered bug.
The bug flaw makes the Apple Message app inoperable, making it impossible to read text messages or iMessages. The flaw is serious, the app will continue to crash even when the user closes it or reboot the device
In order to exploit the flaw, it is necessary to send to the target device a vCard (a transferable Address Book contact) containing so many lines of code that the Messages app is not able to process.
When the Messages app opens the message containing the vCard, it tries to open it and freezes displaying a white screen.
Below a video PoC of the vulnerability.
Because the Messages app always tries to open the most recent text message when it is launched, it will continue trying to open the malicious message even when the app is closed or the whole phone is rebooted.
“When you click, iOS want to read the text, the text in the file is very complicated for the system and cause a CPU average: the app freeze. You close the app, want to reopen but iOS want to reload the previous message but can’t because it’s the vcf file.” reads the blog post published by vincedes3.
The bug is similar to the “Effective Power” discovered in May 2015, when users noticed that a text message containing a string of Arabic text would crash phones.
Back to the present, there is a good news for those users that have received the malicious message. There at least two workarounds to remove the message from the top of the inbox:
By clicking this Fix link: vincedes3.com/save.html, it will open the window for sending a new message, pressing cancel and deleting the malicious message.
Visualizza l'immagine su Twitter
Visualizza l'immagine su Twitter
Segui
vincedes3 @vincedes3
For devices (including iPad) where the fix link does not work, ask Siri to send a message to the victim and click on the text.
11:27 - 29 Dic 2016
9 9 Retweet 12 12 Mi piace
By sending yourself a message in Siri, or ask someone else to send you a message. Once the message is received the Messages app will allow you to open the new message instead of the malicious one.
29 Dic
vincedes3 @vincedes3
For devices (including iPad) where the fix link does not work, ask Siri to send a message to the victim and click on the text. pic.twitter.com/3id4Y8Lhkn
Segui
Luca Marzano @marzanoluca93
@vincedes3 pic.twitter.com/S37I4MVUPe
16:33 - 30 Dic 2016
Visualizza l'immagine su Twitter
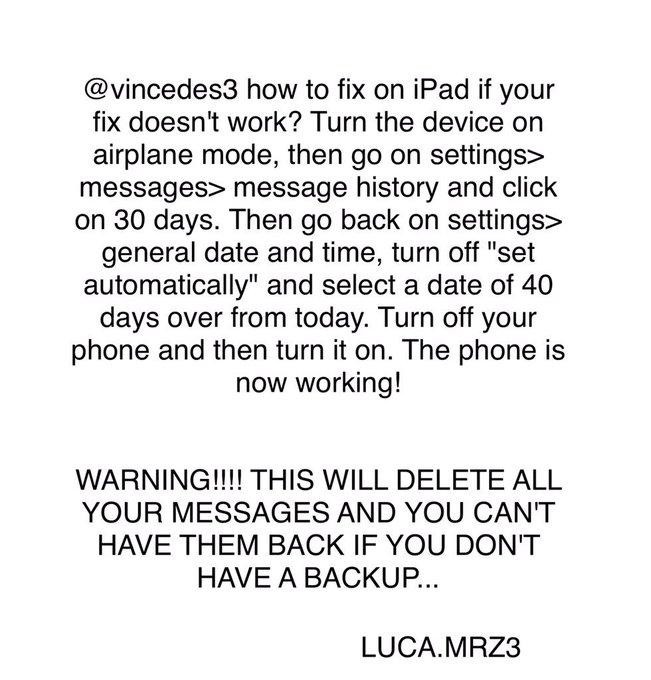
Moscow wants Apple to unlock iPhone of the killer of the Russian Ambassador
25.12.2016 securityaffairs Apple
The Russian and Turkish authorities asked Apple to unlock iPhone belonging to the assassin of Russian Ambassador Andrei Karlov.
The Russia’s ambassador to Turkey, Andrei Karlov, was killed on Monday during an exhibition in Ankara. The killer is a lone Turkish gunman that shouted “God is great!” and “don’t forget Aleppo, don’t forget Syria!”
The shooter was killed by Turkish forces in a shoutout and his iPhone 4s was recovered from the special forces.
The man who killed the Russian ambassador was identified as Mevlut Mert Altıntas, an off-duty police officer who used his police ID to gain access to the exhibition where Karlov was giving a speech.
Russian Ambassador Killer
Now Russian authorities want Apple to unlock the killer’s iPhone belonging to Killer of Russian Ambassador.
According to the investigators, the shooter pretended to be an official bodyguard, now Turkish and Russian authorities asked Apple to support the authorities by unlocking the shooter’s iPhone 4S. The request can trigger a new dispute between the Tech giant and the Kremlin, in a similar way to the San Bernardino Shooter case. the authorities believe, could assist them to investigate killer’s links to various terrorist organizations.
The authorities believe that the content on the iPhone could be useful to unmask the terrorist organization linked to the shooter.
It is quite easy to predict a refuse from Apple, for this reason, the Russian government is reportedly sending a team of experts to Ankara to unlock the shooter’s iPhone.
“Apparently Russia offered help and Russia is planning to send a special technical team to Turkey to unlock the iPhone, a senior Turkish official told us.” reported Macreports.com.
According to Macreports the team of experts arrived from Moscow could not unlock the iPhone, but the team was able to retrieve some data from the device without fully unlocking it.
Experts believe the assassination was part of a plot to destabilize the relationship between the Russian Government and the Turkish one.
How to Hack Apple Mac Encryption Password in Just 30 Seconds
16.12.2016 thehackernews Apple
Macintosh computers are often considered to be safer than those running Windows operating system, but a recently discovered attack technique proves it all wrong.
All an attacker needs is a $300 device to seize full control of your Mac or MacBook.
Swedish hacker and penetration tester Ulf Frisk has developed a new device that can steal the password from virtually any Mac laptop while it is sleeping or even locked in just 30 seconds, allowing hackers to unlock any Mac computer and even decrypt the files on its hard drive.
So, next time when you leave your Apple's laptop unattended, be sure to shut it down completely rather than just putting the system in sleep mode or locked.
Here's How an Attacker can steal your Mac FileVault2 Password
The researcher devised this technique by exploiting two designing flaws he discovered last July in Apple's FileVault2 full-disk encryption software.
The first issue is that the Mac system does not protect itself against Direct Memory Access (DMA) attacks before macOS is started.
It's because the Mac EFI or Extensible Firmware Interface (similar to a PC's BIOS) let devices plugged in over Thunderbolt to access memory without enabling DMA protections, which allows Thunderbolt devices to read and write memory.
Secondly, the password to the FileVault encrypted disk is stored in clear text in memory, even when the computer is in sleep mode or locked. When the computer reboots, the password is put in multiple memory locations within a fixed memory range, making it readable by hacking devices.
Dubbed PCILeech and costs approximately $300, the hacking device exploits these two vulnerabilities to carry out DMA attacks and extract Mac FileVault2 passwords from a device's memory in clear text before macOS boots, and anti-DMA protections come into effect.
To do this, all an attacker needs is access to a target Mac computer for just a few minutes to connect the PCILeech hacking device to the computer via its Thunderbolt port, which would allow the attacker to have full access to its data.
Video Demonstration of the Attack
Frisk also provided a video demonstration, which shows how he just plugged in a card flashed with his open source PCILeech software tool into the Mac's Thunderbolt port, which ran the hacking tool on the target Mac or MackBook, rebooted the system, and read the Mac password on the other laptop.
Yes, the attack only works if an attacker has physical access to a target Mac or MacBook, but all it takes is just 30 seconds to carry out successfully.
"Anyone including, but not limited to, your colleagues, the police, the evil maid and the thief will have full access to your data as long as they can gain physical access - unless the Mac is completely shut down," Frisk explained in a blog post on Thursday.
"If the Mac is sleeping it is still vulnerable. Just stroll up to a locked Mac, plug in the Thunderbolt device, force a reboot (ctrl+cmd+power) and wait for the password to be displayed in less than 30 seconds!"
Frisk reported his findings to Apple in August and the company fixed the issues in macOS 10.12.2 released on 13 December.
So Apple desktop users are required to update their devices to the latest version of its operating system to be safe.
A flaw allows to bypass the activation lock on iPhone and iPad
2.12.2016 securityaffairs Apple
Researchers discovered a bug that can be exploited to bypass Apple’s Activation Lock feature and gain access to the homescreen of locked Apple devices.
Security experts have discovered a new bug that could be exploited to bypass Activation Lock feature on Apple devices (iPhone, iPad).
The bug could allow gaining access to the homescreen of a locked device running the latest version of the Apple iOS.
Researchers reported at least two different variations of the issue, a first one working on iOS 10.1 and the second one on the latest iOS 10.1.1.
In case of a theft or loss of an Apple device (iPhone, iPad or iPod), users can activate the Lost Mode through the Find My iPhone service.
This mode automatically enables the Activation Lock to prevent the reactivation of the device without the owner’s permission.
When a user starts a locked device, he is prompted to connect to a Wi-Fi network. In case the “Other Network” option is selected, the user must enter the name of the network and choose a security protocol (e.g. WEP, WPA2, etc.).

Of course, the user has to provide a username and a password, but researchers noticed that there is no limitation on the number of characters that can be entered into the name, username and password fields.
An attacker can trigger a crash that exposes the device’s homescreen by entering a very long string into these fields.
The crash can be caused one of the following methods: Apple’s iPad smart cases, which cause the device to wake or sleep when the case is opened or closed.
Leveraging on the Apple’s iPad smart cases, which cause the mobile device to wake or sleep when the case is opened or closed.
Leveraging the screen rotation feature and Night Shift mode as demonstrated in the video PoC published by Vulnerability Lab.
Apple iOS v10.1.1 - iCloud & Device Lock Bypass via local Buffer Overflow Vulnerability Video
The first method was first analyzed by Hemant Joseph, who tested the Activation Lock feature after purchasing a locked iPad from eBay. The method worked on iOS 10.1 and was fixed by Apple with the iOS 10.1.1 release.
The second method was discovered by researchers at Vulnerability Lab and works also on iOS 10.1.1.
Watch out! This iPhone-freezing video will CRASH any iPhone!
24.11.2016 securityaffairs Apple
It has happened again, most of the Apple devices crashes when the owner plays this iPhone-freezing video. Be careful when clicking on suspicious links.
A new bug in iPhone is threatening Apple users, most of the Apple devices crashes when the owner plays a video. An iPhone-freezing video is circulating online, when users play it in the Safari browser the iPhones slow down until they stop working altogether.
The iPhone-freezing video was first discovered by EverythingApplePro, it is a short .mp4 clip of someone standing by a bed with the words “Honey” written across the screen.
“After playing the clip, affected iPhones will remain usable for a couple of minutes before growing more sluggish and eventually crashing altogether. ” reads a post published by The Telegraph.

At the time I was writing there is no information regarding the nature of the bug. Users observed that the iPhone crashes even if only a part of the iPhone-freezing video is played.
The clip causes the crash of all the versions of iOS back to iOS 5. The experts noticed a different behavior only on iOS 10.2 beta 3, with this specific version the vision of the video causes the phone to display the spinning wheel that indicates powering off.
In the past, other similar bugs were able to cause the crash/restart of the Apple devices, there was a problem receiving a certain text message, changing the iphone settings, or simply clicking on the link crashsafari.com on the iPhone, iPad or even Macs.
Below the PoC video for the iPhone-freezing video:
Waiting for a patch for your iPhone, be careful when clicking on suspicious or unsolicited links.
If you watch the video by mistake and your iPhone freezes up, you can solve the problem with a hard reboot.
“To do this on any iPhone model other than the iPhone 7, press and hold the home and power buttons at the same time for at least 10 seconds until the Apple logo appears. On an iPhone 7 you can hard reset by holding the power and volume decrease buttons.” continues The Telegraph.
“After the Apple logo appears, release the buttons and your iPhone should restart normally.”
Warning! Your iPhone Can Get Hacked Just by Opening a JPEG Image, PDF or Font File
25.10.2016 thehackernews Apple
What's worse than knowing that innocent looking JPEGs, PDFs and font files can hijack your iPhone, iPad, and iPod.
Yes, attackers can take over your vulnerable Apple's iOS device remotely – all they have to do is trick you to view a maliciously-crafted JPEG graphic or PDF file through a website or an email, which could allow them to execute malicious code on your system.
That's a terrible flaw (CVE-2016-4673), but the good news is that Apple has released the latest version of its mobile operating system, iOS 10.1, for iPhones and iPads to address this remote-code execution flaw, alongside an array of bug fixes.
And now that the company has rolled out a security patch, some hackers would surely find vulnerable Apple devices to exploit the vulnerability and take full control of them.
So, users running older versions of iOS are advised to update their mobile devices to iOS 10.1 as soon as possible.
Besides this remote code execution flaw, the newest iOS 10.1 includes security updates to address 11 security flaws in the firmware for the iPhone, iPad, and iPod Touch.
Those flaws include local code execution vulnerabilities, a remote code execution bug in WebKit (CVE-2016-4677), a flaw in contacts (CVE-2016-4686) that would allow an application to pull Address Book details even when access has been revoked.
To update your iOS device go to Settings → General → Software Update.
Security Updates for Mac, Apple Watch, and AppleTV
Apple has also released security updates for Mac PCs, Apple Watches and Apple TVs.
So, Mac users are advised to update their system to macOS Sierra (10.12.1), which includes security fixes for 16 CVE-listed vulnerabilities.
Those weaknesses include an image-handling bug (CVE-2016-4673), a denial of service (DoS) error in Nvidia graphics card drivers, a bug that exposed the length of user passwords and Remote Code Execution (RCE) flaws that could be triggered by font files and PDF files, among others.
Meanwhile, Apple Watch users are recommended to update their devices to watchOS 3.1, which includes fixes for 8 security flaws.
Those flaws include 2 vulnerabilities in sandbox profiles that could allow third-party apps to view image libraries and sound files without permission.
AppleTV users are also advised to update their devices to tvOS 10.0.1, which includes patches for 10 vulnerabilities, including the WebKit remote code execution flaw, the sandbox profiles flaws, and the CoreGraphics JPEG flaw.
So get your Apple device patched before getting caught by hackers.
The ‘Sin’ Card: How criminals unlocked a stolen iPhone 6S
19.10.2016 securityaffairs Apple
Even if you have an iPhone 6S protected by a 6 digits password plus the touch ID fingerprint it is possible to unlock it.
1. Introduction
You have an iPhone 6S protected by a 6 digits password plus the touch ID fingerprint and you may think that nobody can unlock it without the code, right? Wrong! At least not, according to the incident we analyzed this week at Morphus Labs.
An iPhone 6S, exactly as described in the previous paragraph, was stolen three days ago. The victim told us that, right after the incident, the criminals did reset some of their online services passwords, like Apple ID and contacted his bank pretending to be him in an attempt to retrieve the bank account’s passwords. Fortunately, they couldn’t reach the victim’s money, but, how could they reset the Apple ID password from a locked device?
To better understand this scenario, we’ve collected more information about the victim:
a) Could it have been a targeted attack, I mean, was the thief focused on stealing that iPhone specifically? Could the thief have previously grabbed the victim’s credentials using an e-mail phishing scam or something like that?
Probably not. According to the information we collected, the iPhone was the last item that the thief asked the victim.
b) Did some ID or other documents with the victim’s information also stolen? It is important to understand if the thief knew the victim’s name or e-mail address.
No. No ID or document with the victim’s name or any other information was stolen. They just asked for money and the iPhone.
c) How long did it take to the victim to lock the iPhone and SIM card?
Approximately 2 hours after the theft.
d) Was the iPhone password “guessable”?
No. The 6 digits password wasn’t easily guessable and had no relation to the victim’s car plate number or personal information that the thief might have.
So, given this mysterious scenario, we decided to dive into the situation and understand how the victim’s iPhone was unlocked.
2. The timeline
We will now establish a timeline to organize the facts that happened last October 14th afternoon:
a) 14:00 – the theft occurred;
b) 16:03 – the victim activated the lost mode of its iPhone and asked for it to be remotely erased through iCloud;
c) 16:28 – the victim’s Google Account password was changed;
d) 16:37 – the victim received an e-mail with a link to redefine its Apple ID’s password;
e) 16:38 – a new e-mail informing the victim that the Apple ID password has been changed;
f) 16:43 – a new e-mail informing that the iPhone has been located;
g) 16:43 – a new e-mail informing that the iPhone was being erased;
So, as we can see, the victim’s Google and Apple accounts passwords were reset by the thief of the iPhone. As we all know, unlocking an iPhone without the proper credentials is a “hard to unfeasible” work. So, how did they do it?
Based on the facts that we established on the timeline, we started to work on some questions that might explain what happened:
1) To change a Google account password, you have to inform at least your login, in other words, your e-mail address. How the e-mail address might have been discovered?
Despite the fact the latest IOS version shows information and notifications even on a locked iPhone, in our simulations, nothing appeared on the screen that could give the user’s Gmail address away;
2) Is there a way to discover the Apple ID from the device’s IMEI?
We searched on the Web and found paid services that offer exactly that: “discover the Apple’s ID from a given IMEI”. But all of them inform that this isn’t an online process. It could take 24 to 48 hours for you to get the information you want. This was not the case. The whole process took around 2 hours.
3) Is there a way to discover a Gmail account based on the only information that the criminal had, that is, the phone number?
We did some search again and realized that Google offers a way to discover an e-mail address based on some given data: the phone number that you associate to your account, a name and a surname. As the phone number could be easily discovered in this scenario, discovering the name and surname from that phone number could be less than hard. We’re starting to get somewhere…
3. The hypothesis simulation
So, we decided to follow that way and try to find the name and surname of the victim from the perspective of the thief. This time, arranging our lab wasn’t a tough task. The victim bought a new iPhone 6S smartphone, configured exactly the way the stolen one was and gave to us for the purpose of this research. That way, our scenario was as close as possible to the real scenario – including the same Google and Apple accounts.
3.1. Discovering the phone number
To obtain the phone number, we removed the SIM card from the iPhone and inserted it on another phone. Similar to the real scenario, no PIN lock was in place. On the other phone, it was easy to identify the phone number.

3.2. Low-hanging fruit
Now, having the phone number, we followed the “low-hanging fruit” strategy at first. We tried to find the victim’s name putting his phone number on the Internet search engines. Unfortunately, we didn’t find anything useful.
The next approach was to look for the phone number on Facebook. We know that if you have your phone number associated to your profile, it’s easy to find you by your phone number. Once again, nothing was found.
3.3. Thinking outside the box
Nothing on the low-hanging fruit, so, time to think outside the box. Of course that there could exist different ways to find out a person name by its phone number, but we decided to insist a little more in finding it with the information we have on our hands.
So, I remembered that recently I changed my smartphone. While configuring the new one, my WhatsApp profile came with my photo – and I didn’t restore if from the backup. But I didn’t remember if it came with my profile name and I decided to see if this strategy could give us the victim’s name.
To do so, we removed the SIM card from the locked iPhone and inserted it on a second smartphone with Whatsapp installed. We followed the initial configuration, receiving the SMS and so on, but unfortunately (of fortunately), WhatsApp did not load the profile name. It brought just the profile photo and status.
Yet related to WhatsApp, a second idea came into place. You might remember that if you are in a WhatsApp group and receive a message from a person that is not in your contact list, its name appears just after its phone number (ie: 9999-9999 ~Mike Arnold). So, it would be possible to send a message from that locked iPhone to a WhatsApp group, we could get the name associated to that profile.
3.4. (Whatsapp + Locked screen notification response) hacking
So, firstly, we confirmed that the iPhone was configured to show WhatsApp notifications on the locked screen sending it a single message. The message was shown as expected. The next step was to try to answer that message from the locked iPhone. Using the “3D touch” functionality, we were able to answer that message.
Initial validations were done, time to try the group message approach. We created a group and included the contact associated with the locked iPhone’s number. As there is no validation for you to enter a new group, as we did this and a new message was shown on the locked iPhone screen informing that it is now part of that new group.
As we had to create a contact associated with the iPhone number on the smartphone that created the group, we had to include a third participant in the same group. This third participant has no contact data related to the iPhone’s number.
So, that was all set. We sent a message from one of the group participants. As expected, the message arrived on the locked iPhone screen. We answered it from the locked iPhone and, as expected again, the message sent to the third participant came associated to the iPhone’s Whatsapp profile name. Stage completed.

The next and easiest step was to put those three parameters we discovered (phone number, name and a surname) in the Google form and get the e-mail address associated with that person. Stage completed.
3.4. Changing the Google account password
Now, let’s try to replay the password change made by the criminal. The next steps were:
– Enter Google login screen;
– Choose “forget my password” option;
– Insert any text on the “last password that you remember”;
– On the next screen, Google asks for the phone number associated with the account. They only show a partial of the phone number, but the last two digits allowed us to believe we were on the right track;
– Inserting the iPhone’s phone number, Google sent to iPhone a code through SMS to be inserted on the next screen;
– After doing that, Google offered us to input a new password for that account.

At that moment, we reproduced the Google account password change by mimicking what the criminal did and started to think how easy it could be, depending on the way it was set, to change someone’s Google account password having only its phone or SIM card and its first and last name – even for some minutes (or seconds).
3.5. Changing the Apple ID password
So, we continued following the incident timeline. On the next step we used the previous discovered Google e-mail as the Apple ID account login and choose the option “forget password” again. After that, a message was shown informing that an e-mail was sent to the Google account with a link to reset the password. The rest of this paragraph is easy to figure out. We had success changing the password associated with that Apple ID.

3.6. Unlocking the “new” iPhone
Based on the facts that occurred in the real incident, it was time to remotely lock and erase the iPhone we were using to do the simulations.
I could bet these procedures helped the criminal getting access to the iPhone. After the erase process, the iPhone asks you to enter the Apple ID and password that was previously associated to that device. And, as we have that information, it was easy to access and configure the “new” iPhone from scratch.
4. Vulnerabilities and Recommendations
Well, of course we might have followed a different strategy compared to that of the criminals, but the result was the same – an iPhone unlocked without its credentials.
However, to achieve this result, there are some assumptions that we will consider as vulnerabilities that should be avoided:
a) Locked phone notifications
Allowing your smartphone to show notifications while locked is a great convenience. But at the same time, allowing them may represent a great risk to your privacy and security.
As shown in our experiment, this feature allowed us to read SMS and WhatsApp messages and, worst, answer it without unlocking the device.
We strongly recommend disabling “show notifications on your locked smartphone” (advice for users). Depending on your platform (Android or IOS) or App, there are different ways to configure this.
b) The ‘Sin’ Card
This episode remembered us how important it is to protect the SIM card. We all take care of locking our smartphones with strong passwords and fingerprint auth, strong encryption and so on (don`t we?), but we have to remember the importance of properly securing the SIM card.
As we could see on the experiments we did on this research, the SMS is an important peace nowadays in terms of transaction validation and authentication services. We used it to receive the Google unlock code, but it could be used to authenticate other kinds of transactions.
So, we recommend to set a password protection (PIN) to your SIM card. That way, you considerably reduce the risk of impersonation if you lose or you have your cell phone stolen.
Depending on your smartphone, there are different ways to configure it. Remember that, after you set your SIM card PIN, you have to insert it every time you reboot your smartphone (which is not very usable).

c) Two-factor authentication
Last but not least, please, enable two-factor authentication on your accounts right now! Two-factor authentication means that you have to provide a combination of at least two methods to prove your identity to the system you are dealing with. The possible factors you can pick from are these three: something that you know, like a password; something that you have, like a hard or soft token and something that you are, like your fingerprint.
Nowadays, almost all of the Internet services offers you the option to configure two-factor authentication – usually a password and token. There is an option for the second factor to be sending you an SMS, but we know that it may be fragile. Preferably, choose to use an App, like Google Authenticator, to generate the token.
This strategy will strongly reduce the risks of unauthorized access to your account. If the victim of this incident was using two-factor authentication, it would be impossible to change their password by using the SMS strategy.
5. Final words
Given the short period of time between the theft and the accounts hacking process, we believe that this strategy is widely used to unlock lost and stolen devices.
Aside from the financial loss directly involved with having an iPhone lost/stolen, this case brings us an important reflection. Are we protecting our SIM cards and SMS messages as we should? The potential impact, like improper information access or disclosure in scenarios like the one from this article, could be even more devastating. It would be an overkill to compare an unlocked SIM card to an important password that you carry every day, in clear text, attached to your smartphone?
Apple starts downloading MacOS Sierra automatically to your MacBook — Here's How to Stop It
7.10.2016 thehackernews Apple
Are you experiencing slow Internet speed on your MacBook today? — It's not just you!
Here's Why:
Following in Microsoft's footsteps, Apple has started "pre-downloading" the latest version of its desktop operating system, macOS 10.12 Sierra, in the background, if you are still running OS X El Capitan.
If you have automatic downloads enabled on your Mac, a large file of around 5GB will mysteriously be downloaded to your computer in the background, using your Internet bandwidth for unrequested files.
Apple justifies this move by saying that the automatic download would make it easier for users to get the newest operating system, encouraging them to update their Macs.
The good news, however, is that the update will not install automatically without your permission.
Once downloaded automatically in the background, users who are running OS X El Capitan version 10.11.5 or later will receive a notification that says macOS Sierra is ready to be installed.
All you need to do is just click the Install button to get started with the update.
Thankfully, the automatic update feature is smart enough that it will only be downloaded on Mac computers that have an adequate amount of storage space and meet the specs for macOS Sierra.
So the Sierra installer will be deleted if the host Mac computer starts running low on storage.
"Apple is also being smart about the download. If your computer is low on space, macOS Sierra will not download," The Loop reports. "In addition, if it has downloaded and your computer starts to get low on space, the download will be automatically deleted."
Microsoft has been doing the same thing to its Windows 7 and 8 users by aggressively pushing Windows 10 installation since its launch, which caused a massive outcry.
How to Stop MacOS Sierra Automatic Download
apple-macbook-update
However, the automatic update is still a bit annoying if you have no intention to update your Mac anytime soon.
If you're not ready to upgrade to the latest macOS or want to download it later, you can simply delete the Sierra installer manually to keep from being prompted to do the install.
To delete the Sierra installer, go to Finder → Applications and then look for an application called 'Install macOS Sierra' and move the application to Trash, and Empty the Trash for leaving no trace of the Sierra.
Your Mac could prompt you for your Mac login password to complete the above action.
But if you don't want a bulky 5GB update to be downloaded to your computer for first before you kick off the installation, you can disable automatic downloads from the App Store to avoid the unwanted download.
To disable the feature, you can head on to System Preferences → App Store → Automatically check for updates and then uncheck "Download newly available updates in the background."
That's it. You are done!
Now your computer will not automatically download macOS Sierra and will not prompt you to install them. You can opt back into automatic downloads in the future.
Apple Watches banned from UK cabinet meetings to prevent eavesdropping
10.10.2016 securityaffairs Apple
The UK Government has decided to ban Apple Watches ban from the Cabinet over foreign eavesdropper fears, in 2013 occurred with the iPad.
The political fears cyber espionage, the recent string of cyber attacks against the US Presidential election and the constant pressure of Chinese hackers urge a major awareness on the cyber threats. In 2013, cabinet ministers were banned from bringing smartphones and tablets to meetings, the UK Government decided to ban iPads from the Cabinet over foreign eavesdropper fears.
The news was reported by the Mail on Sunday, after the Cabinet Office minister Francis Maude made a presentation using his iPads the Downing Street security staff has dismissed the mobile device to prevent eavesdropping of ongoing discussions.
Now the Tory government’s cabinet ministers have banned the Apple watches from internal meeting in case they are compromised by foreign cyber spies. The UK Government believes that Russians hackers could exploit such category of devices to gather sensitive information.
“Ministers have been barred from wearing Apple Watches during Cabinet meetings amid concerns that they could be hacked by Russian spies, The Telegraph has learned.” reported the Telegraph.
“Mobile phones have already been barred from the Cabinet because of similar concerns.One source said: “The Russians are trying to hack everything.”
apple-watches-banned-british-cabinet
It seems that Apple Watches are very popular gadgets among cabinet ministers when David Cameron was the prime minister many politicians. Things have changed under the government of the Prime Minister Theresa May who banned the devices amid fears that foreign hackers could listen in to government business.
The measure was adopted to avoid foreign security services infecting wearable devices mobile that could be used to spy on the ministers.
Why Apple logs your iMessage contacts and other metadata?
29.9.2016 securityaffairs Apple
Every time you type a number to start an iMessage conversation on your iPhone, Apple logs your message contacts and other metadata.
In January 2015, experts claimed that Apple is not able to read messages sent between devices through iMessages, but reported that the company but it is still able to access data in the backups.
Apple has always confirmed that attackers cannot eavesdrop iMessage conversations, but according to a document obtained by The Intercept there is something that user should know.
According to the document, Apple logs contacts’ phone numbers and shares them, alongside with other metadata, with law enforcement.
The Intercept received the document, titled “iMessage FAQ for Law Enforcement,” as part of a cache originating from within the Florida Department of Law Enforcement’s Electronic Surveillance Support Team. The author of the document is not known, such as the final audience, it is designated for “Law Enforcement Sources” and “For Official Use Only.”
When Apple users type a number to start a text conversation, the Messages app contacts the company servers to determine whether to route a given message over the SMS system or over the Apple’s proprietary messaging network.
“Every time you type a number into your iPhone for a text conversation, the Messages app contacts Apple servers to determine whether to route a given message over the ubiquitous SMS system, represented in the app by those déclassé green text bubbles, or over Apple’s proprietary and more secure messaging network, represented by pleasant blue bubbles, according to the document.” states The Intercept website. “Apple records each query in which your phone calls home to see who’s in the iMessage system and who’s not.”

The log includes the date and time of the conversation and the user’s IP address, information that could allow identifying the user’s location. The IT giant is compelled to turn over this data via court orders for systems known as “pen registers” or “trap and trace devices.”
Apple told to The Intercept that it only retains these logs for a period of 30 days, but court orders can extend the period of additional 30-day periods.
Below the official statement from Apple:
“When law enforcement presents us with a valid subpoena or court order, we provide the requested information if it is in our possession. Because iMessage is encrypted end-to-end, we do not have access to the contents of those communications. In some cases, we are able to provide data from server logs that are generated from customers accessing certain apps on their devices. We work closely with law enforcement to help them understand what we can provide and make clear these query logs don’t contain the contents of conversations or prove that any communication actually took place.”
As explained in the document, and confirmed by Apple, the company is not able to access the content of the conversation, but why the company retails these logs?
Apple1
Apple Tracks Who You're Chatting Using iMessage — and Shares that Data with Police
29.9.2016 thehackernews Apple
Doing conversations with your friend on iMessage and thinking that they are safe and out of reach from anyone else other than you and your friend? No, it's not.
End-to-end encryption doesn't mean that your iMessages are secure enough to hide your trace because Apple not only stores a lot of information about your iMessages that could reveal your contacts and location, but even share that information with law enforcement via court orders.
According to a new document obtained by The Intercept, Apple records a log of which phone numbers you typed into their iPhone for a message conversation, along with the date and time when you entered those numbers as well as your IP address, which could be used to identify your location.
Actually, every time a user type a phone number into their iPhone for a message conversation, iMessage contacts Apple servers to find out whether to route a given message over the iMessage system.
"Apple records each query in which your phone calls home to see who's in the iMessage system and who's not," The Intercept reports.
Moreover, the company is compelled to turn over this information to law enforcement with a valid court order — generally "pen registers" or "tap and trace devices" warrants that are very easy to obtain.
Pen register warrants are routinely being used to compel telephone companies to provide metadata about customers' phone calls to law enforcement.
Apple Logs Your IP Address (Location)
But it’s surprising that Apple, which has positioned itself as a staunch defender of its user privacy by refusing the federal officials to provide encryption backdoors into its products, hands over its users' information on iMessage contacts under such warrants.
The report also points out that keeping logs of users IP address that could be used to reveal one’s actual location is contrary to Apple's 2013 claim that the company "do not store data related to customers' location."
The Intercept obtained the document, titled 'iMessage FAQ for Law Enforcement,' about Apple's iMessage logs as part of a much larger cache originating from within a state police agency, "The Florida Department of Law Enforcement's Electronic Surveillance Support Team."
The team facilitates mass data collection for law enforcement using controversial tools such as Stingrays, along with the help of conventional techniques like pen registers and tap and trace devices warrants.
Although your iMessages are end-to-end encrypted, it doesn’t mean that all Apple users are enjoying the company's so-called privacy benefit.
If you have enabled iCloud Backup on your Apple devices to keep a backup of your data, the copies of all your messages, photographs and every important data stored on your device, are encrypted on iCloud using a key controlled by Apple, and not you.
So, Apple can still read your end-to-end encrypted iMessages, if it wants.
Even if you trust the company that it won't provide your decrypted data to law enforcement (just don't forget San Bernardino case in which Apple helped the FBI with the iCloud backup of the Shooter's iPhone), anyone who breaks into your iCloud account could see your personal and confidential data.
Apple deliberately Weakens Backup Encryption
Fortunately, it is possible to store your backups locally through iTunes, though it is not such an obvious choice for an average user.
What's even worse is that a recent issue in the local password-protected iTunes backups affects the encryption strength for backups of devices on iOS 10, allowing attackers to brute-force the password for a user's local backup 2,500 faster than was possible on iOS 9.
Apple has already confirmed that the issue exists and that a fix would be included in an upcoming update.
However, in response to the latest report about iMessage logs, Apple provided the following statement:
"When law enforcement presents us with a valid subpoena or court order, we provide the requested information if it is in our possession. Because iMessage is encrypted end-to-end, we do not have access to the contents of those communications. In some cases, we are able to provide data from server logs that are generated from customers accessing certain apps on their devices. We work closely with law enforcement to help them understand what we can provide and make clear these query logs don’t contain the contents of conversations or prove that any communication actually took place."
The Florida Department of Law Enforcement still has to comment on the matter.
Pippa Middleton private photos stolen in an Apple iCloud hack
25.9.2016 securityaffairs Apple
In what could be another serious celebrity hack, 3,000 photos have been stolen from Pippa Middleton ’s account and they are being offered for sale.
The UK Police is investigating the Pippa Middleton iCloud hack and consequent theft of private photos.
According to The Sun newspaper the stolen photos were offered for sale, it seems that someone had contacted the newspaper asking for £50,000 within 48 hours. The images included shots of the duchess’s children, Prince George and Princess Charlotte.
“Pippa was horrified last night after a crook tried to sell intimate photos said to have been hacked from her phone.” reported The Sun.
The man contacted The Sun claiming to have 3,000 images of the Duchess of Cambridge’s sister, 33. He said snaps included her at a wedding dress fitting and ones of her fiancé nude.”
The Met Police confirmed that inquiries were ongoing and that the authorities haven’t arrested ant suspects until now.
“Police have received a report concerning the alleged hacking of a personal iCloud account. Specialist officers are now investigating.” explained a Met Police spokesman.
The hacker, calling himself “Crafty Cockney”, claimed to be in possession of private photographs of Pippa Middleton, including her being fitted in a wedding dress and naked snaps of her millionaire fiance James Matthews. In order to prove the authenticity of his claims, the hacker sent via email two photos via email.
The stolen photos also include shots of the Duchess of Cambridge Kate, and brother-in-law Prince William.
The Sun also confirmed that an anonymous person has reportedly tried to sell the stolen photos them via encrypted messaging service WhatsApp.

The Sun confirmed that it had no intention of entering into a deal with the hacker and reported the issue to Pippa Middleton.
“Thank you very much for drawing this to the family’s attention.” said a spokesman for Miss Middleton cited by The Sun. “I can confirm that not only have the lawyers been informed but the police are about to be involved as well.”
Pippa Middleton is the last celebrity in order of time that was the victim of an “iCloud hack,” a long list of VIPs have had images stolen from their iCloud accounts in the Fappening saga.
As usual, it is strongly suggested to use a second factor of authentication for all the services that implement it.
In 2014, Apple introduced a “two-step verification” mechanism to protect iCloud users from such kind of hack. The mechanism leverages on a four-digit code that is either texted to the users’ mobile phone number or sent via Apple’s Find My iPhone app.
Don’t waste time, enable the two-step verification!
Young hacker Luca Todesco announced the iPhone 7 jailbreak
23.9.2016 thehackernews Apple
The popular hacker Luca Todesco (aka @qwertyoruiopz) has announced the existence of the iPhone 7 jailbreak for devices running iOS 10.
Only a few hours, this is the time spent by the popular hacker Luca Todesco (aka @qwertyoruiopz) to jailbreak the new and secure iPhone 7. The iPhone 7 was launched by Apple a few days ago and of course, hackers worldwide started their race to jailbreak the new device.
The 19-year-old hacker Luca Todesco shared via Twitter an image of his jailbroken iPhone 7, not so bad! The expert exploited a series of bugs to hack the device in just 24 hours and demonstrating that also the iPhone 7 is “not 100 percent secure-like nothing else is“
Visualizza l'immagine su Twitter
Visualizza l'immagine su Twitter
Segui
qwertyoruiop @qwertyoruiopz
obligatory cydia screenshot
11:00 - 21 Set 2016
333 333 Retweet 619 619 Mi piace
The image shows an iPhone 7 running both iOS 10.0.1 as well as the Cydia repository, used by owners of jailbroken device to install apps and other software that Apple does not officially support.

Cydia is an application very popular within the community of iOS Apple users, it is the jailbreaker’s App Store alternative for iOS. The unofficial store contains thousands of apps, themes, and many other downloads. Using Cydia iOs users can find and install applications on their jailbroken iOS Apple devices, the majority of the software in the store are available for free.
At the time I was writing it is not clear if Todesco will release the iPhone 7 jailbreak to the public, he hasn’t provided much information about the hack, for example he doesn’t explain if the exploit is an untethered jailbreak.
An untethered jailbreak is a procedure that doesn’t require the iPhone any reboot every time it connects to an external device capable of executing commands on the device.
The untethered jailbreak is more complicated, it makes the jailbroken device totally independent of the computer and allows users turning off and on the device without problems.
While the tethered jailbreak code is seen from iBoot, the untethered jailbreak totally resides on the device.
iPhone 7 jailbreak
The hacking community is celebrating the news, although Todesco has not released the exploit, he showed that it is possible to hack the iPhone 7.
Only you do now is sit and wait for a team that will release an untethered jailbreak for the new iPhone 7.Since it is not good news for Apple, the company would likely block the vulnerability used to develop jailbreak in its next iOS update, of course.