
Fighting Back Against the Cyber Mafia
8.12.2017 securityweek CyberCrime
Four distinct groups of cybercriminals have emerged, serving as the new syndicates of cybercrime: traditional gangs, state-sponsored attackers, ideological hackers and hackers-for-hire. This is the central thesis of a new report titled 'The New Mafia: Gangs and Vigilantes'. In this report, the gangs are the criminals and the vigilantes are consumers and businesses -- and the vigilantes are urged to 'fight back'.
The report (PDF) is compiled by endpoint protection firm Malwarebytes. It is designed to explain the evolution of cybercrime from its earliest, almost innocuous, beginnings to the currently dangerous 'endemic global phenomenon'; and to suggest to consumers and businesses they don't need to simply accept the current state. They can fight back.
Fighting back, however, is not hacking back -- or in the more politically acceptable euphemism, active defense.
"This is not what was meant in our report," Jerome Segura, Malwarebytes' lead malware intelligence analyst told SecurityWeek. "Fighting back means being proactive and reporting scams or malware in order to help out the community at large. We need users to leverage their experiences in order to gain insights into the criminal rings operating with impunity."
The report explains the evolution and operational context of the four 'mafia' gangs. It should be noted, however, that this is a broad brush view -- the lines of distinction between the different groups is often and increasingly blurred.
Traditional gangs co-opt hackers-for-for hire and are behind cybercrime-as-a-service. State actors can sub-contract traditional gangs to hide behind plausible deniability. And state actors and law enforcement are not beyond using hacktivists for their own ends; for example, the FBI's alleged use of Hector Monsegur (aka Sabu) to convict Jeremy Hammond for and following the LulzSec hack of Stratfor in 2011.
Traditional gangs "have taken the motivations and acts of traditional organized crime gangs, theft and the sale of drugs, guns and stolen goods, to the online world." This is organized cybercrime: organized street crime co-opting tech savvy hackers. "The people at the top may be the same individuals leading drug cartels or pre-existing gangs," suggests the report; "or new kingpins that have risen to the top of organizations as the internet has grown." These people remain invisible -- if anything, it is the hackers who get caught.
State-sponsored attackers are not new, but have become more active, more subtle and more destructive in recent years. "Russian interference in the US Election and widespread hacks from North Korea are prominent examples," says the report. But it is not limited to 'rogue' states. Stuxnet "was deployed by Western nations to cause Iran's nuclear centrifuges to spin too quickly, destroying the centrifuges, and infecting 200,000 computers." The effect of state-sponsored hacking could "suggest a potential blurring of the distinction between cybercrime and cyberwarfare."
Ideological hackers are more commonly called hacktivists -- and perhaps Anonymous is the best known instance. But it is a much wider concern. Russian President Vladimir Putin suggested that Russian ideological hackers could have been behind the DNC hacks. Edward Snowden would be classified as an ideological hacker. "In this context," warn the reports authors, "groups at political extremes are more likely to firstly, disagree ideologically with political and business developments and secondly, attack the online presences of those they disagree with."
The fourth 'gang', hackers-for-hire, is in part the personification of the evolving service economy for cybercrime services. Ransomware-as-a-service is a visible and virulent example. "Interestingly," say the authors, hackers-for-hire "operate in a highly retail-oriented manner with an emphasis on customer service and reliability." Interestingly, this is the area of cybercrime that particularly worries Steve Durbin, managing director of the Information Security Forum. His concern is that cybercrime-as-a-service is introducing a large-scale unpredictable element of almost script kiddie wannabees -- the opposite, in fact, of 'organized crime'.
The Malwarebytes authors hope that by understanding the nature of cybercrime and cybercriminals, the fear-factor can be removed from consumers and businesses. Just as the criminals have become very organized in their sharing of information on the dark web, Malwarebytes believes that law-abiding citizens can fight back "by sharing their collective experiences to build knowledge and awareness. Creating an environment where the risks are better communicated and understood will enable individuals and businesses alike to better identify and ward off threats."
This proposal is not, however, limited to sharing information between businesses, and between business and government. The key is a better communication of risk within each organization. Underlying this is the need for business leaders to recognize that cybercrime is also a business, and not just a technological issue. This does not yet seem to be happening.
The report's authors point to the disparity between business leaders' perception of cybercrime, and their technologists' perception. According to PwC's global economic crime survey, say the authors, 74% of surveyed business stakeholders reported that they were not, or did not know if they were, victims of cybercrime. Malwarebytes' own research concentrating on technologists, however, indicated that less than 35% had not experienced cybercrime. The implication is that business leaders are still unaware of the extent of cybercrime even within their own organizations, and therefore unaware of the need to more proactively defend their business.
Malwarebytes believes that with better business understanding of the threat posed by cybercrime, and better sharing of threat information within and between businesses, consumers and government, the fight against cybercrime and cybercriminals will be strengthened.
"Knowledge, awareness and intelligence are our best weapons against the new gangs of cybercrime," says the report. "Given the fragmented, global nature of cybercrime, individuals and businesses have to play an important role alongside law enforcement agencies governments and other bodies in thwarting this activity."
Marcin Kleczynski, CEO of Malwarebytes, summarizes, "Through greater vigilance and a comprehensive understanding of the cybercrime landscape, businesses can support the efforts of legislators and law enforcement, while also taking action into their own hands."
Malwarebytes raised $50 million in a Series B funding round from Fidelity Management and Research Company in January 2016.
CVE-2017-11937 | Microsoft releases an emergency update to fix a flaw in Malware Protection Engine
8.12.2017 securityaffairs Vulnerebility
Microsoft issued an emergency Windows Security Update to address a critical flaw, tracked as CVE-2017-11937, that affects the Malware Protection Engine.
Microsoft issued an emergency Windows Security Update to address a critical vulnerability, tracked as CVE-2017-11937, that affects the Malware Protection Engine (MPE).
The emergency fix comes a few days before Microsoft is scheduled to roll out its December Patch Tuesday updates.
The critical RCE flaw could be exploited by an attacker to take full control of a victim’s PC. The Malware Protection Engine (MPE) is the main component of the Windows defense system and it implements basic features like scanning, detection, and cleaning.
The Windows Malware Protection Engine is enabled by default and it is used by Microsoft antivirus and antimalware software implemented in its solutions, including Windows Defender and Microsoft Security Essentials along with Endpoint Protection, Forefront Endpoint Protection, and Exchange Server 2013 and 2016, impacting Windows 7, Windows 8.1, Windows 10, Windows RT 8.1, and Windows Server.
The CVE-2017-11937 flaw is a memory corruption vulnerability that is triggered when the Malware Protection Engine scans a specially crafted file for a malicious code.
Triggering the flaw, the attacker can execute malicious code in the security context of the LocalSystem account and take full control of the target’s computer, this means that it could install further malicious code and create accounts with maximum privileges.
“A remote code execution vulnerability exists when the Microsoft Malware Protection Engine does not properly scan a specially crafted file, leading to memory corruption. An attacker who successfully exploited this vulnerability could execute arbitrary code in the security context of the LocalSystem account and take control of the system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights.” reads the security advisory published by Microsoft.
“To exploit this vulnerability, a specially crafted file must be scanned by an affected version of the Microsoft Malware Protection Engine.”
To trigger the flaw, a remote attacker could place a specially crafted malicious file in a location that is scanned by the Malware Protection Engine and this is possible to do in many ways. An attacker, for example, could set up a website to deliver a specially crafted file that is scanned when the victim visits the site.
Another possible attack vector is represented by email, the attacker could deliver a specially crafted file via emails, it is also possible to exploit Instant Messenger services for the same purpose.

“There are many ways that an attacker could place a specially crafted file in a location that is scanned by the Microsoft Malware Protection Engine.” continues Microsoft.
“For example, an attacker could use a website to deliver a specially crafted file to the victim’s system that is scanned when the website is viewed by the user. An attacker could also deliver a specially crafted file via an email message or in an Instant Messenger message that is scanned when the file is opened. In addition, an attacker could take advantage of websites that accept or host user-provided content, to upload a specially crafted file to a shared location that is scanned by the Malware Protection Engine running on the hosting server.”
Microsoft has released an out-of-band critical update to address the vulnerability is urging users to install it as soon as possible.
For enterprise deployments as well as end users, the default configuration in Microsoft antimalware software helps ensure that malware definitions and the Microsoft Malware Protection Engine are kept up to date automatically
The critical CVE-2017-11937 vulnerability was reported to Microsoft by the UK’s National Cyber Security Centre (NCSC), a division of the UK GCHQ intelligence agency.
Microsoft assured that the vulnerability was not exploited in attacks in the wild.
OpenSSL patches for the fourth time in 2017 its library, and it will likely be the last one
8.12.2017 securityaffairs Vulnerebility
The OpenSSL Project released the OpenSSL 1.0.2n version that addresses two vulnerabilities discovered by the Google researcher David Benjamin.
Benjamin discovered the vulnerabilities using the OSS-Fuzz fuzzing service.
The first “moderate severity” issue, tracked as CVE-2017-3737, is related to an “error state” mechanism implemented since OpenSSL 1.0.2b.
“OpenSSL 1.0.2 (starting from version 1.0.2b) introduced an “error state” mechanism. The intent was that if a fatal error occurred during a handshake then OpenSSL would move into the error state and would immediately fail if you attempted to continue the handshake.” reads the security advisory.
“This works as designed for the explicit handshake functions (SSL_do_handshake(), SSL_accept() and SSL_connect()), however due to a bug it does not work correctly if SSL_read() or SSL_write() is called directly.”
“If SSL_read()/SSL_write() is subsequently called by the application for the same SSL object then it will succeed and the data is passed without being decrypted/encrypted directly from the SSL/TLS record layer,” OpenSSL said in its advisory.
The flaw has been rated “moderate severity” because the targeted application would need to be affected by a bug that causes a call to SSL_read() or SSL_write() after getting a fatal error.
This issue was reported to OpenSSL on 10th November 2017 by David Benjamin that also proposed a fix that was implemented by Matt Caswell of the OpenSSL.OpenSSL

The second flaw tracked as CVE-2017-3738 is an overflow vulnerability that could be exploited by an attacker to access TLS-protected communications. The flaw was rated as “low severity” because it is very difficult to trigger in a real attack scenario.
“There is an overflow bug in the AVX2 Montgomery multiplication procedure used in exponentiation with 1024-bit moduli. No EC algorithms are affected. Analysis suggests that attacks against RSA and DSA as a result of this defect would be very difficult to perform and are not believed likely.” continues the advisory. “Attacks against DH1024 are considered just feasible, because most of the work necessary to deduce information about a private key may be performed offline. The amount of resources required for such an attack would be significant.”
The OSS-Fuzz tool also allowed Google researchers to find two low and medium severity, tracked CVE-2017-3736 and CVE-2017-3732, vulnerabilities in early November.
This is the fourth OpenSSL security update in 2017, and it will likely be the last one.
NiceHash: security breach leads to 60 million lost – Iceman is behind?
8.12.2017 securityaffairs Incindent
NiceHash has been hacked, roughly to 60$ million (4,736.42 BTC) have been stolen while the bitcoin is crossing the 14k$ mark for the first time.
A dark day for cryptocurrency miners, NiceHash has been hacked. Closely to 60$ millions (4,736.42 BTC) have been stolen while the bitcoin is crossing the 14k$ mark for the first time.
The hacker’s bitcoin address cleary shows the steal of 4,736.42 BTC in a window of 48 hours:https://bitinfocharts.com/bitcoin/address/1EnJHhq8Jq8vDuZA5ahVh6H4t6jh1mB4rq
NiceHash users are furious by the time of reaction of the team. It took about 24 hours to realize that big amounts have been stolen.
I’ve contacted a member of Iceman and knowing this security breach for some reason he explained that NiceHash actually owned their users’ bitcoin wallets in order to save transactions fees and collect unclaimed BTC. This issue leads to a massive security breach which allows access to all NiceHash wallets. He claimed that by reverse engineering of their miner client, Iceman group was able to access their API.
Is Iceman really behind this attack?
About the Author: Marc Miller
Marc Miller is a web journalist, focused on cybercrime.
He started a blog called: THE PURPLE HAT – Cyber Gangs NAKED, dedicated to exposing the methods and works of cybercrime gangs such as “CARBANAK” or similar sophisticated syndicated Cybercrime organizations.
In the past. he worked as a web front-end programmer. Also, he is passionate about hardware, hacking, security and marketing.
Major Banking Applications were found vulnerable to MiTM attacks over SSL
8.12.2017 securityaffairs Mobil
Security experts discovered a critical vulnerability in major mobile banking applications that left banking credentials vulnerable to hackers.
A group of security researchers has discovered a critical vulnerability in major mobile banking applications that left banking credentials vulnerable to hackers.
The vulnerability was discovered by researchers of the Security and Privacy Group at the University of Birmingham, who analyzed hundreds of iOS and Android banking apps.
The experts discovered that several of them were vulnerable to man-in-the-middle attacks.
The list of affected banking apps includes Allied Irish bank, Co-op, HSBC, NatWest, and Santander.
An attacker sharing the same network segment of the victim could intercept SSL connection and retrieve the user’s banking credentials even if the apps are using SSL pinning feature.
The SSL pinning provides an additional level of protection against man-in-the-middle attacks, the certificate pinning is implemented to avoid detection of security solutions that use their own certificates to inspect the traffic.
“If a single CA acted maliciously or were compromised, which has happened before (see e.g. DigiNotar in 2011 [15]), valid certificates for any domain could be generated allowing an attacker to Man-in-the-Middle all apps trusting that CA certificate.” states the research paper.
Researchers found that due to the wrong implementation of the authentication process the apps were vulnerable to MITM attacks. The lack of hostname verification left many banking applications open to attacks because they were not able to check if they connected to a trusted source.
The apps fail to check that they connect to a URL having the hostname that matches the hostname in the digital certificate that the server exposes.
“Automated tools do exist to test a variety of TLS flaws. Lack of certificate signature verification can be tested for by serving the client a self-signed certificate, lack of hostname verification by serving a valid certificate for a different hostname, and lack of certificate pinning can be checked for by adding a custom CA to the device’s trust store. ” continues the paper.
“These tests have been shown to be effective at finding vulnerabilities in apps [10] and poor TLS certificate validation [5]. However, none of these tools can detect the possibility that an app will pin to the root or intermediate certificate used but fail to validate the hostname”
The experts created a new automated tool, dubbed Spinner, to test hundreds of banking apps quickly and without requiring purchasing certificates.
The tool leverages Censys IoT search engine for finding certificate chains for alternate hosts that only differ in the leaf certificate.
“Given the certificate for a target domain, the tool queries for certificate chains for alternate hosts that only differ in the leaf certificate. The tool then redirects the traffic from the app under test to a website which has a certificate signed by the same CA certificate, but of course a different hostname (Common Name),” continues the paper.
“If the connection fails during the establishment phase then we know the app detected the wrong hostname. Whereas, if the connection is established and encrypted application data is transferred by the client before the connection fails then we know the app has accepted the hostname and is vulnerable.”
The security experts with the help of the National Cyber Security Centre (NCSC) notified all affected banks that addressed the issues before they publicly disclosed their findings.
Organizations Getting Better at Detecting Breaches: Report
8.12.2017 securityweek Virus
Organizations have become slightly better at detecting cyber intrusions, but malicious actors are constantly working on improving their tactics and techniques, according to CrowdStrike’s 2017 Cyber Intrusion Services Casebook.
The report is based on data collected by the security firm from more than 100 investigations. Four of these cases are analyzed in detail in the report, including a SamSam ransomware attack on a commercial services organization, a cybercrime operation aimed at a manufacturer’s e-commerce application, a PoS malware incident targeting a large retailer, and a NotPetya infection.
CrowdStrike has determined that organizations continue to improve their ability to detect intrusions on their own. The percentage of firms that self-detected a breach increased to 68 percent, up from 57 percent in the previous year.
As for dwell time, which is the number of days between the initial intrusion and detection, the average has decreased slightly to 86 days. CrowdStrike pointed out that it still takes some organizations as much as 800 to 1,000 days to detect a breach, but these cases are an exception.
“Regardless of dwell time duration, automated systems may eventually detect an intrusion, but by the time human staff is alerted and aware it’s often too late: the attackers must be stopped before they can achieve their objectives,” CrowdStrike said in its report.
Of the attacks analyzed by CrowdStrike, the most prevalent were aimed at stealing intellectual property, stealing money, stealing personally identifiable information (PII), and ransom or extortion.
In more than one-third of attacks, hackers gained access to the targeted organization’s systems using web server, web application or web shell exploits, or file uploaders. Other commonly seen attack vectors were remote access via RDP or VPN (23%), supply chain compromise (12%), social engineering and phishing (11%), and cloud-based service exploits (11%).
Roughly two-thirds of the attacks analyzed by the security firm were fileless – they involved malicious code being written to and executed from memory, harvesting credentials via phishing or social engineering, remote logins via stolen credentials, and exploits targeting web applications.
CrowdStrike also noticed that tactics and techniques typically used by nation-state actors have been increasingly leveraged by cybercrime groups.
“These include fileless malware and ‘living off the land’ techniques involving processes native to the Windows operating system, such as PowerShell and WMI (Windows Management Instrumentation),” CrowdStrike said. “Many also employ anti-forensics tools and methods in an effort to erase signs of their presence and increase dwell time. Brute-force attacks on RDP (remote desktop protocol) servers are also prevalent in these cases.”
Attackers are also increasingly turning to self-propagating malware, particularly in the case of ransomware such as the notorious WannaCry. These attacks are often successful due to organizations failing to update critical systems and deploying comprehensive security technologies.
Process Doppelgänging: New Malware Evasion Technique Works On All Windows Versions
8.12.2017 thehackernews Virus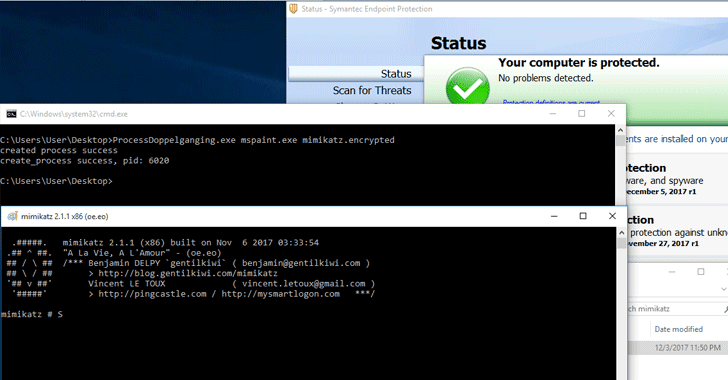
A team of security researchers has discovered a new malware evasion technique that could help malware authors defeat most of the modern antivirus solutions and forensic tools.
Dubbed Process Doppelgänging, the new fileless code injection technique takes advantage of a built-in Windows function and an undocumented implementation of Windows process loader.
Ensilo security researchers Tal Liberman and Eugene Kogan, who discovered the Process Doppelgänging attack, presented their findings today at Black Hat 2017 Security conference held in London.
Process Doppelgänging Works on All Windows Versions
Apparently, Process Doppelgänging attack works on all modern versions of Microsoft Windows operating system, starting from Windows Vista to the latest version of Windows 10.
Tal Liberman, the head of the research team at enSilo, told The Hacker New that this malware evasion technique is similar to Process Hollowing—a method first introduced years ago by attackers to defeat the mitigation capabilities of security products.
In Process Hollowing attack, hackers replace the memory of a legitimate process with a malicious code so that the second code runs instead of the original, tricking process monitoring tools and antivirus into believing that the original process is running.
Since all modern antivirus and security products have been upgraded to detect Process Hollowing attacks, use of this technique is not a great idea anymore.
On the other hand, Process Doppelgänging is an entirely different approach to achieve the same, by abusing Windows NTFS Transactions and an outdated implementation of Windows process loader, which was originally designed for Windows XP, but carried throughout all later versions of Windows.
Here's How the Process Doppelgänging Attack Works:
Before going further on how this new code injection attack works, you need to understand what Windows NTFS Transaction is and how an attacker could leverage it to evade his malicious actions.
NTFS Transaction is a feature of Windows that brings the concept of atomic transactions to the NTFS file system, allowing files and directories to be created, modified, renamed, and deleted atomically.
NTFS Transaction is an isolated space that allows Windows application developers to write file-output routines that are guaranteed to either succeed completely or fail completely.
According to the researcher, Process Doppelgänging is a fileless attack and works in four major steps as mentioned below:
Transact—process a legitimate executable into the NTFS transaction and then overwrite it with a malicious file.
Load—create a memory section from the modified (malicious) file.
Rollback—rollback the transaction (deliberately failing the transaction), resulting in the removal of all the changes in the legitimate executable in a way they never existed.
Animate—bring the doppelganger to life. Use the older implementation of Windows process loader to create a process with the previously created memory section (in step 2), which is actually malicious and never saved to disk, "making it invisible to most recording tools such as modern EDRs."
Process Doppelgänging Evades Detection from Most Antiviruses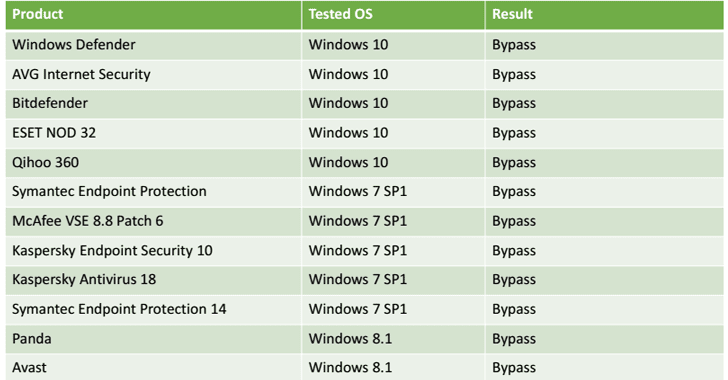
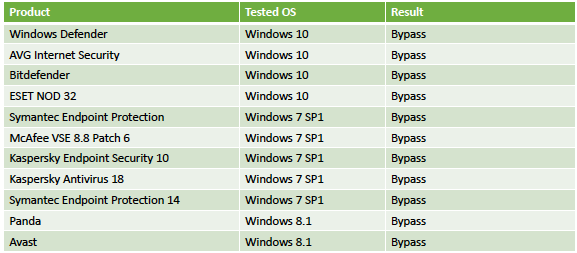
Liberman told The Hacker News that during their research they tested their attack on security products from Windows Defender, Kaspersky Labs, ESET NOD32, Symantec, Trend Micro, Avast, McAfee, AVG, Panda, and even advance forensic tools.
In order to demonstrate, the researchers used Mimikatz, a post-exploitation tool that helps extract credentials from the affected systems, with Process Doppelgänging to bypass antivirus detection.
When the researchers ran Mimikatz generally on a Windows operating system, Symantec antivirus solution caught the tool immediately, as shown below: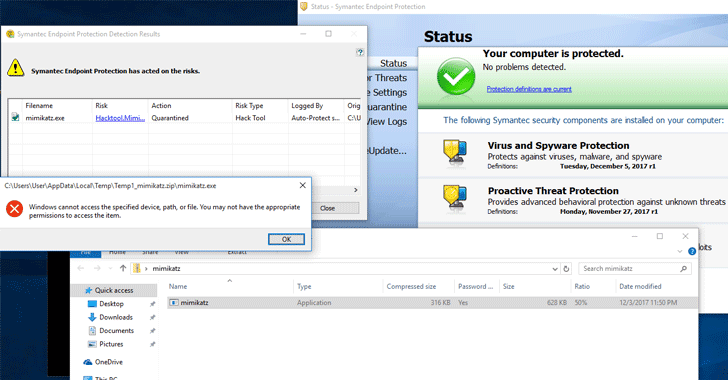
However, Mimikatz ran stealthy, without antivirus displaying any warning when executed using Process Doppelgänging, as shown in the image at top of this article.
Liberman also told us that Process Doppelgänging works on even the latest version of Windows 10, except Windows 10 Redstone and Fall Creators Update, released earlier this year.
But due to a different bug in Windows 10 Redstone and Fall Creators Update, using Process Doppelgänging causes BSOD (blue screen of death), which crashes users' computers.
Ironically, the crash bug was patched by Microsoft in later updates, allowing Process Doppelgänging to run on the latest versions of Windows 10.
I don't expect Microsoft to rush for an emergency patch that could make some software relying on older implementations unstable, but Antivirus companies can upgrade their products to detect malicious programs using Process Doppelgänging or similar attacks.
This is not the very first time when enSilo researchers have discovered a malware evasion technique. Previously they discovered and demonstrated AtomBombing technique which also abused a designing weakness in Windows OS.
In September, enSilo researchers also disclosed a 17-year-old programming error in Microsoft Windows kernel that prevented security software from detecting malware at runtime when loaded into system memory.
Massive Breach Exposes Keyboard App that Collects Personal Data On Its 31 Million Users
8.12.2017 thehackernews Mobil
In the digital age, one of the most popular sayings is—if you're not paying, then you're not the customer, you're the product.
While downloading apps on their smartphones, most users may not realize how much data they collect on you.
Believe me; it’s way more than you can imagine.
Nowadays, many app developers are following irresponsible practices that are worth understanding, and we don't have a better example than this newly-reported incident about a virtual keyboard app.
A team of security researchers at the Kromtech Security Center has discovered a massive trove of personal data belonging to more than 31 million users of the popular virtual keyboard app, AI.type, accidentally leaked online for anyone to download without requiring any password.
Founded in 2010, Ai.type is a customizable and personalizable on-screen keyboard for mobile phones and tablets, with more than 40 million users worldwide.
Apparently, a misconfigured MongoDB database, owned by the Tel Aviv-based startup AI.type, exposed their entire 577 GB of the database online that includes a shocking amount of sensitive details on their users, which is not even necessary for the app to work.
"...they appear to collect everything from contacts to keystrokes."
The leaked database of over 31 million users includes:
Full name, phone number, and email address
Device name, screen resolution and model details
Android version, IMSI number, and IMEI number
Mobile network name, country of residence and even user enabled languages
IP address (if available), along with GPS location (longitude/latitude).
Links and the information associated with the social media profiles, including birth date, emails, photos.
"When researchers installed Ai.Type they were shocked to discover that users must allow 'Full Access' to all of their data stored on the testing iPhone, including all keyboard data past and present," the researchers say.
What's more?
Moreover, the leaked database also reveals that the virtual keyboard app is also stealing users' contact books, including the contacts' names and phone numbers—and already scraped more than 373 million records.
"There was a range of other statistics like the most popular users’ Google queries for different regions. Data like average messages per day, words per message, the age of users, words_per_day': 0.0, 'word_per_session and a detailed look at their customers," the researchers say.
Researchers go on to raise a question that "why would like a keyboard, and emoji application need to gather the entire data of the user's phone or tablet?"
Even the recent data breaches have taught us that once our personal data gets in the hands of cybercriminals, it makes us vulnerable forever.
Therefore, the best defense to protect yourself is always—awareness.
New TeamViewer Hack Could Allow Clients to Hijack Viewers' Computer
8.12.2017 thehackernews Hacking
Do you have remote support software TeamViewer installed on your desktop?
If yes, then you should pay attention to a critical vulnerability discovered in the software that could allow users sharing a desktop session to gain complete control of the other's PC without permission.
TeamViewer is a popular remote-support software that lets you securely share your desktop or take full control of other's PC over the Internet from anywhere in the world.
For a remote session to work both computers—the client (presenter) and the server (viewer)—must have the software installed, and the client has to share a secret authentication code with the person he wants to share his desktop.
However, a GitHub user named "Gellin" has disclosed a vulnerability in TeamViewer that could allow the client (sharing its desktop session) to gain control of the viewer's computer without permission.
TeamViewer Hack Could Be Used By Anyone—Server Or Client
Gellin has also published a proof-of-concept (PoC) code, which is an injectable C++ DLL, which leverages "naked inline hooking and direct memory modification to change TeamViewer permissions."
The injectable C++ DLL (hack) can be used by both, the client and the server, which results as mentioned below:
If exploited by the Server—the hack allows viewers to enable "switch sides" feature, which is only active after the server authenticated control with the client, eventually allowing the server to initiate a change of control/sides.
If exploited by the Client—the hack allows the client to take control of the mouse and keyboard of the server "with disregard to servers current control settings and permissions."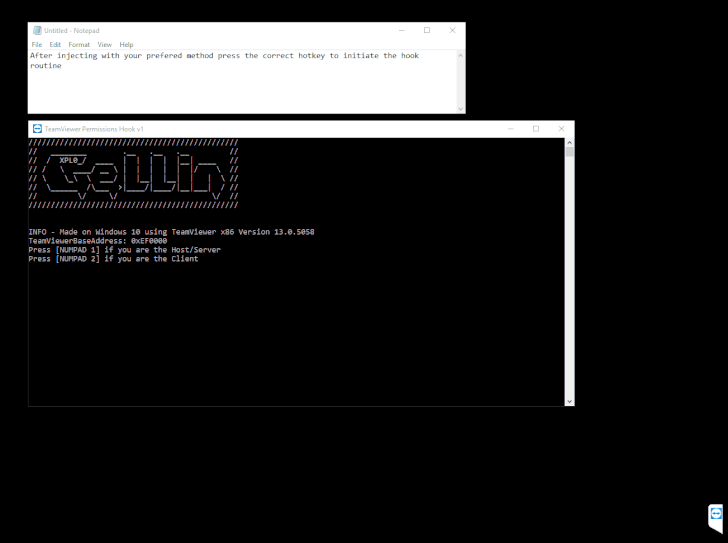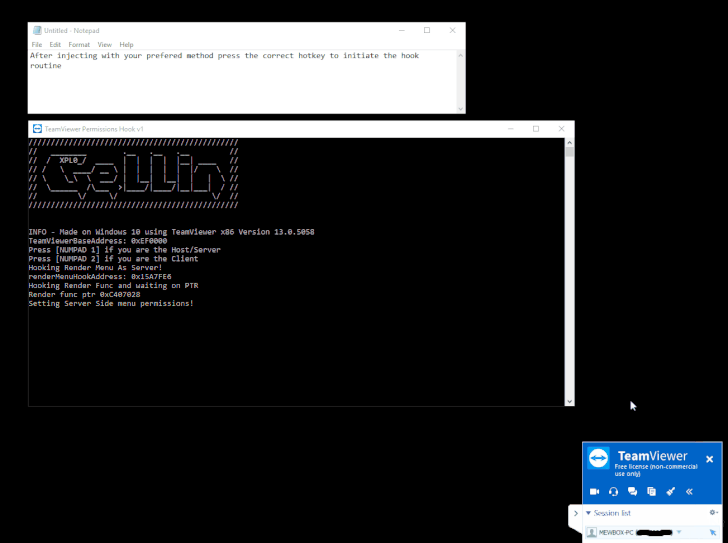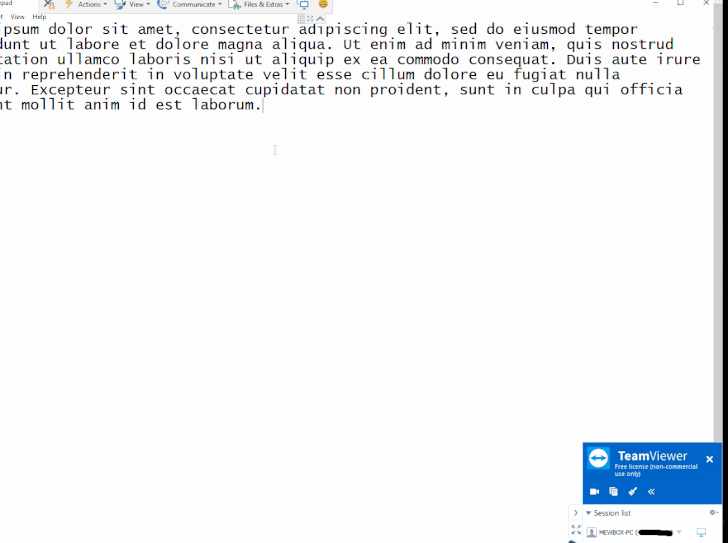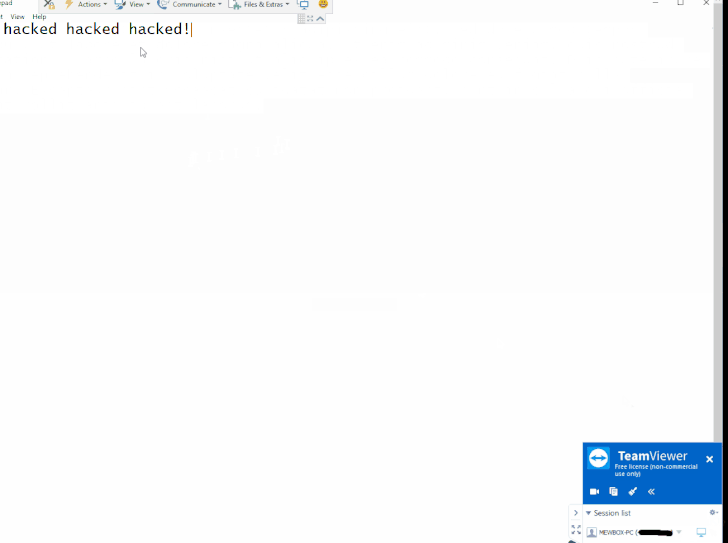
This vulnerability impacts TeamViewer versions running on Windows, macOS as well as Linux machines.
A Reddit user "xpl0yt," who first publicized this vulnerability, claimed to have been in contact with the TeamViewer security team, who confirmed him the existence of the vulnerability in its software and released a patch for Windows.
A TeamViewer spokesperson told The Hacker News, "We are patching versions 11-13. Windows is already available, whereas MacOS and Linux are expected later today."
TeamViewer users are recommended to install the patched versions of the software as soon as they become available. Patches will be delivered automatically to those users who have configured their TeamViewer software to receive automatic updates.
Largest Crypto-Mining Exchange Hacked; Over $70 Million in Bitcoin Stolen
8.12.2017 thehackernews Hacking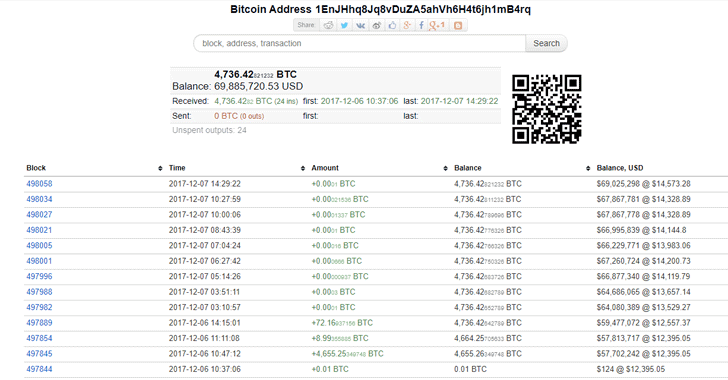
Bitcoin is breaking every record—after gaining 20% jump last week, Bitcoin price just crossed the $14,800 mark in less than 24 hours—and there can be no better reason for hackers to put all of their efforts to steal skyrocketing cryptocurrency.
NiceHash, the largest Bitcoin mining marketplace, has been hacked, which resulted in the theft of more than 4,700 Bitcoins worth over $57 million (at the time of breach).
And guess what? You'll be surprised to know that the stolen BTC now worth over $70 million—in less than 24 hours.
Founded in 2014, NiceHash is a cloud-based crypto-mining marketplace that connects people from all over the world to rent out their spare computing power to other in order to create new coins.
On Wednesday, several NiceHash users reported that their BTC wallets had been emptied, which was later confirmed by NiceHash after its service went offline claiming to be undergoing maintenance.
At the time of writing, the NiceHash service is still offline with a post on its website, confirming that "there has been a security breach involving NiceHash website," and that hackers stole the contents of the NiceHash Bitcoin wallet.
The company did not provide any further details about the security incident, but it did say that NiceHash has paused its operations for next 24 hours while it figures out exactly how many numbers of BTC were swiped from its website and how it was taken.
Although NiceHash has not confirmed the number of bitcoins stolen from its virtual wallet, some of its customers have circulated a wallet address that suggests around 4,736 BTC—worth more than $70 million based on today's price—in total were drained from the company's wallet.
NiceHash has initiated an investigation into the matter, and has reported the incident to the "relevant authorities and law enforcement" and has been "co-operating with them as a matter of urgency."
The company also assured its customers that it is "fully committed to restoring the NiceHash service with the highest security measures at the earliest opportunity," but it's still unclear how the company will manage to settle everything if it is unable to compensate the total loss.
"We understand that you will have a lot of questions, and we ask for patience and understanding while we investigate the causes and find the appropriate solutions for the future of the service. We will endeavor to update you at regular intervals," the company says.
Following the security incident, NiceHash is recommending its customers to change their passwords—both on NiceHash and other services, if they are using the same credentials.
NiceHash is the latest cryptocurrency company to suffer a significant blow in recent months. Another major hack took place last month due to a flaw in Parity's wallet that caused over $160 million in ETH (Ether) to be frozen, while nearly $32 million in ETH was stolen by hackers in July.
Critical Flaw in Major Android Tools Targets Developers and Reverse Engineers
8.12.2017 thehackernews Vulnerebility
Finally, here we have a vulnerability that targets Android developers and reverse engineers, instead of app users.
Security researchers have discovered an easily-exploitable vulnerability in Android application developer tools, both downloadable and cloud-based, that could allow attackers to steal files and execute malicious code on vulnerable systems remotely.
The issue was discovered by security researchers at the Check Point Research Team, who also released a proof of concept (PoC) attack, which they called ParseDroid.
The vulnerability resides in a popular XML parsing library "DocumentBuilderFactory," used by the most common Android Integrated Development Environments (IDEs) like Google's Android Studio, JetBrains' IntelliJ IDEA and Eclipse as well as the major reverse engineering tools for Android apps such as APKTool, Cuckoo-Droid and more.
The ParseDroid flaw, technically known as XML External Entity (XXE) vulnerability, is triggered when a vulnerable Android development or reverse engineering tool decodes an application and tries to parse maliciously crafted "AndroidManifest.xml" file inside it.
In order words, all an attacker need to trigger the vulnerability is trick the developers and reverse engineers into loading a maliciously crafted APK file.
"By simply loading the malicious 'AndroidManifest.xml' file as part of an Android project, the IDEs starts spitting out any file configured by the attacker," the researchers said.
Demonstration: XML External Entity (XXE) to Remote Code Execution
Besides this, the XXE vulnerability can also be used to inject arbitrary files anywhere on a targeted computer to achieve full remote code execution (RCE), which makes the attack surface-wide and various.
Moreover, the attacker doesn't require to target their victims directly, as the researchers suggest "another attack scenario that can be used in the wild to attack a massive range of Android developers by injecting a malicious AAR (Android Archive Library) containing our XXE payload into repositories."
For educational and demonstration purpose, researchers have also created an online APK decoder tool that can extract the malicious file from an APK (in this case they used a PHP web shell), allowing the attacker to execute system commands on the web application server, as shown in the video.
"The way we chose to demonstrate this vulnerability, of course, is just one of many possible attack methods that can be used to achieve full RCE," the Check Point researchers wrote. "Indeed, the Path Traversal method lets us copy any file to any location on the file system, making the attack surface-wide and various."
Check Point researchers Eran Vaknin, Gal Elbaz, Alon Boxiner and Oded Vanunu discovered this issue in May 2017 and reported them to all major IDEs and tools developers, including Google, JetBrains, Eclipse and APKTool owner.
Most of the developers, including Google, JetBrains and APKTool owner, have since fixed the issue and released patched versions.
Since all the attack methods demonstrated by the researchers are cross-platform, developers and reverse engineers are highly recommended to update their tools, if they haven't yet.
Uber Paid 20-Year-Old Florida Hacker $100,000 to Keep Data Breach Secret
8.12.2017 thehackernews Crime
Last year, Uber received an email from an anonymous person demanding money in exchange for the stolen user database.
It turns out that a 20-year-old Florida man, with the help of another, breached Uber's system last year and was paid a huge amount by the company to destroy the data and keep the incident secret.
Just last week, Uber announced that a massive data breach in October 2016 exposed personal data of 57 million customers and drivers and that it paid two hackers $100,000 in ransom to destroy the information.
However, the ride-hailing company did not disclose identities or any information about the hackers or how it paid them.
Now, two unknown sources familiar with the incident have told Reuters that Uber paid a Florida man through HackerOne platform, a service that helps companies to host their bug bounty and vulnerability disclosure program.
So far, the identity of the Florida man was unable to be obtained or another person who helped him carry out the hack.
Notably, HackerOne, who does not manage or plays any role in deciding the rewards on behalf of companies, receives identifying information of the recipient (hackers and researchers) via an IRS W-9 or W-8BEN form before payment of the award can be made.
In other words, some employees at Uber and HackerOne definitely knows the real identity of the hacker, but choose not to pursue the case, as the individual did not appear to pose any future threat to the company.
Moreover, the sources also said that Uber conducted a forensic analysis of the hacker's computer to make sure that all the stolen data had been wiped, and had the hacker also sign a nondisclosure agreement to prevent further wrongdoings.
Reportedly, the Florida man also paid some unknown portion of the received bounty to the second person, who was responsible for helping him obtain credentials from GitHub for access to Uber data stored elsewhere.
Originally occurred in October 2016, the breach exposed the names and driver license numbers of some 600,000 drivers in the United States, and the names, emails, and mobile phone numbers of around 57 million Uber users worldwide, which included drivers as well.
However, other personal details, like trip location history, dates of birth, credit card numbers, bank account numbers, and Social Security numbers, were not accessed in the attack.
Former Uber CEO Travis Kalanick learned of the cyber attack in November 2016 and chose not to involve authorities, believing the company can easily and more effectively negotiate directly with the hackers to limit any harm to its customers.
However, this secret dealing with the hackers eventually cost Uber security executives their jobs for handling the incident.
Now Uber CEO Dara Khosrowshahi has reportedly fired Uber Chief Security Officer Joe Sullivan, and one of his deputies, Craig Clark, who worked to keep the data breach quiet.
"None of this should have happened, and I will not make excuses for it. While I cannot erase the past, I can commit on behalf of every Uber employee that we will learn from our mistakes," Khosrowshahi said.
"We are changing the way we do business, putting integrity at the core of every decision we make and working hard to earn the trust of our customers."
Last week, three more top Uber security managers resigned, including Sullivan's chief of staff Pooja Ashok, senior security engineer Prithvi Rai, and physical security chief Jeff Jones.
Chrome obsahuje kritickou chybu. V ohrožení jsou milióny uživatelů
8.12.2017 Novinky/Bezpečnost Zranitelnosti
Kritická bezpečnostní trhlina byla odhalena v oblíbeném internetovém prohlížeči Chrome od společnosti Google. Vzhledem k tomu, že zranitelnost se týká všech podporovaných operačních systémů, v ohrožení jsou desítky miliónů uživatelů z celého světa.
Chrome je aktuálně nejpopulárnějším webovým prohlížečem, což dokazuje i početná skupina uživatelů, která se podle nejstřízlivějších odhadů počítá na desítky miliónů. Právě proto se ale na něj vcelku pravidelně zaměřují počítačoví piráti.
Kritické zranitelnosti, které mohou zneužít hackeři, tak u tohoto internetového browseru bývají odhaleny zpravidla alespoň jednou měsíčně. Koneckonců v ohrožení byli uživatelé Chromu již v listopadu.
Oprava je již k dispozici
A jak je nyní zřejmé, ani v prosinci tomu nebude jinak. Tvůrci totiž tento týden ohlásili, že prohlížeč obsahuje kritickou bezpečnostní chybu. To jinými slovy znamená, že je počítačoví piráti mohou zneužít k tomu, aby do počítače propašovali prakticky libovolný škodlivý kód. Stejně tak ale mohou přistupovat k nastavení napadeného stroje či uloženým datům na pevném disku.
Ohroženi jsou majitelé prakticky všech aktuálně dostupných operačních systémů. Chyba se totiž týká verzí tohoto browseru pro operační systémy Windows, Mac OS a Linux.
Google naštěstí již trhlinu v nejnovější verzi opravuje, stejně jako řadu dalších chyb. Ty však již nemají nálepku „kritické“, ale pouze „důležité“. Pro uživatele by tak neměly představovat žádné velké bezpečnostní riziko, jsou určeny spíše ke zlepšení funkčnosti jednotlivých součástí internetového prohlížeče.
S instalací neotálet
V každém případě není příliš rozumné s instalací updatu otálet. V případě, že uživatelé nemají nastavenou automatickou instalaci aktualizací, neměli by s jejich stažením otálet. V opačném případě nechávají pro počítačové piráty otevřena zadní vrátka do svých počítačů.
Nainstalovat aktualizaci manuálně je možné prostřednictvím nápovědy, konkrétně v části „O aplikaci Chrome“. Po rozkliknutí této nabídky se uživateli automaticky nabídne instalace nejnovější verze.
Chrome není jediným prohlížečem, který trápí nebezpečné chyby. Tento týden byla kritická zranitelnost opravena například také ve Firefoxu.
Two Vulnerabilities Patched in OpenSSL
8.12.2017 securityweek Vulnerebility
The OpenSSL Project announced on Thursday the availability of OpenSSL 1.0.2n, a version that patches two vulnerabilities discovered by a Google researcher.
The flaws were identified by Google’s David Benjamin using the search giant’s OSS-Fuzz fuzzing service.
One of the security holes, CVE-2017-3737, is related to an “error state” mechanism introduced with OpenSSL 1.0.2b. The mechanism is designed to trigger an immediate failure if there is an attempt to continue a handshake after a fatal error has occurred. The problem is that if the SSL_read() or SSL_write() functions are called directly, the mechanism doesn’t work properly.
“If SSL_read()/SSL_write() is subsequently called by the application for the same SSL object then it will succeed and the data is passed without being decrypted/encrypted directly from the SSL/TLS record layer,” OpenSSL said in its advisory.
While this vulnerability could have serious implications, it has only been rated “moderate severity” due to the fact that the targeted application would need to have a bug that causes a call to SSL_read() or SSL_write() after getting a fatal error.
Another vulnerability reported to the OpenSSL Project by Benjamin is CVE-2017-3738, an overflow bug that could allow an attacker to access TLS-protected communications. However, an attack is very difficult to carry out, which is why the issue has been classified as “low severity.”
CVE-2017-3738 is similar to CVE-2017-3736 and CVE-2017-3732, two other vulnerabilities discovered using the OSS-Fuzz tool and patched last month, and CVE-2015-3193, an issue fixed in December 2015.
CVE-2017-3738 affects both the 1.0.2 and 1.1.0 branches of OpenSSL. However, because it’s low severity, OpenSSL 1.1.0 has not been updated on this occasion. The vulnerability will be patched in OpenSSL 1.1.0h when it becomes available.
This is the fourth OpenSSL update from 2017 that patches security bugs and, unless a critical issue is discovered, it will likely be the last. OpenSSL security updates were also announced in January and February.
Chrome Improves Security for Enterprise Use
8.12.2017 securityweek Security
Chrome's Site Isolation Feature Renders Each Web Site in a Separate Process
Google is boosting the security of its browser with the release of Chrome 63, which brings a host of enhancements aimed at enterprises and also addresses 37 vulnerabilities.
The new browser iteration, Google says, can better protect enterprises from potential dangers like ransomware, malware, and other vulnerabilities. This is possible because of better process isolation, support for more advanced security standards, and the adoption of new policies.
One of the major enhancements Chrome 63 introduces is Site Isolation, where content for each open website is rendered in a separate process, isolated from the processes of other websites. The browser already includes sandboxing technology, but the new feature should deliver stronger security boundaries between websites.
Now, Chrome also allows IT admins to configure a new policy and restrict access to extensions based on the permissions required. Thus, they can block all extensions that require the use of a webcam or microphone, or those that want to access and modify data on the websites visited.
In an attempt to ensure more secure communication, the new browser release also enables Transport Layer Security (TLS) 1.3 for Gmail. TLS 1.3 support will be expanded to the broader web in 2018, Google reveals.
While Chrome browser users should not be impacted, IT admins can post feedback on any systems that are not interoperable with TLS 1.3. “As admins prepare for the wider use of TLS 1.3, they can configure this policy for network software or hardware that will not transit TLS 1.3 connections,” Google notes.
For the next year, the Internet giant also plans support for the NTLMv2 authentication protocol in Chrome 64, including Extended Protection for Authentication (EPA) on Mac, Android, Linux and Chrome OS. Thus, the same level of security as in Chrome on Windows will be available on all platforms performing NTLM authentication.
IT admins can already enable the feature in chrome://flags/#enable-ntlm-v2, but Google plans on making NTLMv2 the default NTLM protocol starting with Chrome 65. The update makes Chrome the only browser to support NTLMv2 with EPA on non-Windows platforms.
The Internet search company also plans on improving the browser’s stability by blocking third-party software from injecting code into Chrome on Windows.
Because some businesses rely on code injection, however, a new policy set to be introduced in the coming months should provide admins with extended support for critical apps. To check whether their software is injecting into Chrome, admins can visit chrome://conflicts.
Google also included patches for 37 vulnerabilities in Chrome 63, including 19 security flaws reported by external researchers. These include 1 Critical severity, 6 High risk, 7 Medium severity, and 5 Low risk bugs.
The company paid over $46000 to the reporting researchers. The highest bounties were paid for a Critical Out of bounds write in QUIC ($10500), a Heap buffer overflow in PDFium ($6337), two Use after free in PDFium issues ($5000 each), an Out of bounds write in Skia ($5000), and a Use after free in libXML ($3500).
Iranian Cyberspies Exploit Recently Patched Office Flaw
8.12.2017 securityweek CyberSpy
A cyber espionage group linked to Iran has been using a recently patched Microsoft Office vulnerability to deliver malware to targeted organizations, FireEye reported on Thursday.
The threat actor, tracked as APT34 by FireEye and OilRig by other companies, has been active since at least 2014, targeting organizations in the financial, government, energy, telecoms and chemical sectors, particularly in the Middle East.
Back in April, researchers noticed that APT34 had started exploiting an Office vulnerability (CVE-2017-0199) in attacks aimed at Israeli organizations shortly after Microsoft released a patch.
The cyberspies have now also started leveraging CVE-2017-11882, an Office vulnerability patched by Microsoft on November 14. FireEye said it had spotted an attack exploiting this flaw less than a week after the fix was released.
The remote code execution vulnerability affects the Equation Editor (EQNEDT32.EXE) component of Office and it has been around for 17 years. Some believe Microsoft may have addressed the security hole by directly modifying the executable, suggesting that the company may have lost its source code.
Proof-of-concept (PoC) exploits were made available for CVE-2017-11882 shortly after Microsoft released a patch and, in late November, researchers reported that a cybercrime group tracked as Cobalt had started exploiting the vulnerability.
However, FireEye saw the first attempt to exploit CVE-2017-11882 less than a week after Microsoft released a fix. The attack was aimed at a government organization in the Middle East.
In July 2017, FireEye observed an APT34 attack using CVE-2017-0199 to deliver a backdoor tracked by the company as POWRUNER, and a downloader with DGA (domain generation algorithm) functionality named BONDUPDATER. In November, the group switched to using CVE-2017-11882 to deliver these PowerShell-based pieces of malware.
The attackers used specially crafted RTF documents delivered to targeted users via spear phishing emails. When opened, the file triggers the Office vulnerability and initiates an infection process that ends with the execution of the backdoor and the downloader.
POWRUNER allows attackers to collect information about the infected machine, download and upload files, and capture screenshots. Once it receives commands from its command and control (C&C) server, the malware stops running.
The BONDUPDATER downloader is APT34’s first attempt at implementing a DGA for generating subdomains that are used for C&C communications.
“We assess that APT34’s efforts to continuously update their malware, including the incorporation of DGA for C2, demonstrate the group’s commitment to pursuing strategies to deter detection,” FireEye said in a blog post. “We expect APT34 will continue to evolve their malware and tactics as they continue to pursue access to entities in the Middle East region.”
This is not the first time FireEye has analyzed APT34’s activities. In May 2016, the security firm published a report detailing some of its attacks on banks in the Middle East, but at the time it did not attribute the operation to any group.
Palo Alto Networks reported in October that OilRig had started using a new Trojan in attacks aimed at entities in the Middle East.
Keylogger Found on 5,500 WordPress Sites
8.12.2017 securityweek Virus
Thousands of WordPress sites have been infected with a piece of malware that can log user input, Sucuri warns.
The infection is part of a campaign the security researchers detailed in April, when they revealed that websites were being infected with a piece of malware called cloudflare.solutions. The malware packed cryptominers at the time, and is now adding keyloggers to the mix as well.
At the moment, the cloudflare.solutions malware is present on 5,496 websites, and the number appears to be going up.
The injected Cloudflare[.]solutions scripts are added to a queue to WordPress pages using the theme’s function.php, and a fake CloudFlare domain is used in the URLs. One of the URLs loads a copy of a legitimate ReconnectingWebSocket library.
The main page of the domain claims “the server is part of an experimental science machine learning algorithms project,” the researchers reveal.
A cors.js script used there loads the Yandex.Metrika (Yandex’s alternative to Google Analytics), most likely to track the infected sites.
The researchers also discovered two cdnjs.cloudflare.com URLs with long hexadecimal parameters, with both of them belonging to CloudFlare. However, they are not legitimate and one doesn’t even exist, but link to payloads delivered in the form of hexadecimal numbers after the question mark in the URLs.
The script was designed to decode the payloads and inject the result into web pages, which results in the aforementioned keylogger.
“This script adds a handler to every input field on the websites to send its value to the attacker (wss://cloudflare[.]solutions:8085/) when a user leaves that field,” Sucuri explains.
The keylogger allows the actors behind this campaign to steal payment details, if the WordPress site has some ecommerce functionality and embeds a checkout form, as well as login credentials, given that the cloudflare[.]solutions keylogger is injected to login pages as well.
Because the malicious code resides in the function.php file of the WordPress theme, removing the add_js_scripts function and all the add_action clauses that mention add_js_scripts should prevent the attack.
“Given the keylogger functionality of this malware, you should consider all WordPress passwords compromised so the next mandatory step of the cleanup is changing the passwords (actually it is highly recommended after any site hack),” Sucuri notes.
Because the cloudflare.solutions malware also injects coinhive cryptocurrency miner scripts, site admins are also advised to check their websites for other infections as well.
'Process Doppelgänging' Helps Malware Evade Detection
7.12.2017 securityweek Virus
Researchers at enSilo have identified a new method that can be used by hackers to execute a piece of malware on any supported version of Windows without being detected by security products.
The new technique, dubbed “Process Doppelgänging,” is similar to process hollowing, a code injection method that involves spawning a new instance of a legitimate process and replacing the legitimate code with malicious one. This technique has been used by threat actors for several years and security products are capable of detecting it.
enSilo says it has now come up with a similar but more efficient method for executing malicious code, including ransomware and other types of threats, in the context of a legitimate process. Process Doppelgänging abuses the Windows loader to execute code without actually writing it to the disk, which makes it more difficult to detect an attack.
According to researchers, when Process Doppelganging is used, the malicious code is correctly mapped to a file on the disk, just like in the case of a legitimate process – modern security solutions typically flag unmapped code. The method can also be leveraged to load malicious DLLs.
Experts have successfully tested the technique on Windows 7, Windows 8.1 and Windows 10 against security products from Microsoft, AVG, Bitdefender, ESET, Symantec, McAfee, Kaspersky, Panda Security and Avast.
Doppelganging relies on transactional NTFS, which is designed to make it easier for app developers and administrators to handle errors and preserve data integrity. enSilo has found a way to make changes to an executable file via NTFS transactions without actually committing those modifications to the disk. Undocumented functionality of the Windows process loader is then abused to load the modified executable. The changes made to the original file are reverted in order to avoid leaving any trace.
“We overwrite a legitimate file in the context of [an NTFS transaction],” enSilo said. “We then create a section from the modified file (in the context of the transaction) and create a process out of it. It appears that scanning the file while it's in transaction is not possible by the vendors we checked so far (some even hang) and since we rollback the transaction, our activity leaves no trace behind.”
“There are a lot of technical challenges involved in making it work,”researchers explained. “One of the hardest challenges is that in order to run a process out of a section (not a file on disk) the process needs to be created using NtCreateProces, which means that most of the initialization must be done manually, which requires knowing a lot of undocumented details on process creation.”
enSilo says its products can detect such an attack, which means other vendors can implement detection mechanisms as well, especially if the technique will be exploited in the wild. However, since the method abuses legitimate features, experts say it cannot be patched.
The security firm disclosed its findings this week at the Black Hat Europe conference in London. Technical details and proof-of-concept (PoC) code will be made available shortly.
The Worst Password Offenders of 2017
7.12.2017 securityweek Security
Password management firm Dashlane has published a list of what it believes are the top ten password offenders for 2017. It comprises six 'government' entries (including the President of the United States and the entire UK Government), and four organizations. Topping the list is Donald Trump, joined by Paul Manafort at #9 and Sean Spicer at #10.
To be fair, it is as much Trump the administration as it is Trump the person that is being called out. Dashlane points to a Channel 4 News investigation in January 2017 that said "Passwords used by Donald Trump's incoming cyber security advisor Rudy Giuliani and 13 other top staff members have been leaked in mass hacks."
In reality, the majority of people have had at least one password exposed by the many mass hacks that have plagued the internet this decade, so the biggest problem is not whether a password appears in the dark web listings, but whether it is still being used by the user of that password. Dashlane comments, "many of the top staff members Trump handpicked, including multiple cabinet secretaries, senior policy directors -- even cybersecurity advisor Rudy Giuliani -- were reusing insecure, simple passwords."
Paul Manafort, who was indicted in October by a federal grand jury as part of Robert Mueller's investigation into the Trump campaign, had been using 'Bond007' as his password for multiple personal accounts, including Dropbox and Adobe. Sean Spicer makes the list at #10 because, says Dashlane, "the former Press Secretary sent numerous Tweets of what appeared to be his very own passwords."
While the Democratic Party experienced several cybersecurity incidents last year, other U.S. government entities that made Dashlane's 2017 list include the Department of Defense (DOD at #4) and the Republican Party (at #5). For the DOD, Dashlane comments, "Defense contractor Booz Allen Hamilton left the Pentagon severely exposed by leaving critical files on a non-password protected Amazon server. Included in the exposed data were several unencrypted passwords that could have been used to access classified D.O.D. information."
The Republican Party is included for a similar reason: the exposure of sensitive data (by one of its analytics firms) of 198 million U.S. voters on an unprotected Amazon server.
Related: Clinton Email Server Vulnerable for 3 Months
It's not just U.S. political entities in the list, however. Coming in at #3 is the entire 'UK Government'. In March, the National Cyber Security Center (NCSC) chief executive Ciaran Martin wrote to political parties warning, "This is not just about the network security of political parties' own systems. Attacks against our democratic processes go beyond this and can include attacks on Parliament, constituency offices, think tanks and pressure groups and individuals' email accounts."
In June, the Times reported, "Passwords belonging to British cabinet ministers, ambassadors and senior police officers have been traded online by Russian hackers, an investigation by The Times has found." Again, the lists of passwords were probably aggregated from numerous earlier mass hacks -- but disturbingly, the most common password was 'password'.
Following these events it would be logical for members of parliament and IT administrators to have tightened password management. But in early December, several members tweeted that they routinely share their work computer password with staff, including interns http://www.securityweek.com/uk-members-parliament-share-passwords-staff .
Four commercial organizations make Dashlane's worst offenders list: Equifax (#2), Google (#6), HBO (#7) and Imgur (#8). Equifax is included not because of its loss of the personal details of 145.5 million people (basically a patching issue http://www.securityweek.com/equifax-confirms-apache-struts-flaw-used-hack rather than a password issue), but because of what appears to be a generally lax attitude towards password hygiene. A smaller and less well known Equifax breach this year occurred -- in Equifax's own disclosure letter to the Attorney General of New Hampshire -- because "unauthorized third-party(ies) gained access to the accounts primarily by successfully answering personal questions about the affected employees in order to reset the employees' PINs (i.e., the password to access the online portal)."
Compounding this, researchers discovered that an Equifax server in Argentina was protected by 'admin/admin'. Anyone guessing these credentials would be able to access the server and find and modify employees' user accounts. Obscured, but not encrypted, the user's credentials were a plain text user name with a password comprising the user's surname.
Google makes the list because of the May phishing attack http://www.securityweek.com/google-tightens-oauth-rules-combat-phishing that compromised an unknown number of Google users' login credentials.
HBO http://www.securityweek.com/hbo-hackers-demand-millions-ransom-note is included because following a series of hacks and breaches in 2017, "employees came forward with reports of terrible cybersecurity practices, including the reuse of passwords for personal and work accounts." One stolen and leaked Word document actually contains the personal email address and passwords of an HBO SVP.
Imgur is included because of a breach that occurred in 2014 but was only discovered this year. "The company admitted that at the time of the hack it was using an outdated algorithm to encrypt its users' passwords," explains Dashlane. "Although it updated its encryption last year, the damage was already done as 1.7 million user passwords were potentially compromised."
What is clear from this list is that despite all of the warnings and breaches, people and organizations who should be setting an example for everyone else are still demonstrating very poor password hygiene for both themselves and their users. Multi-factor authentication wherever possible will certainly help users protect themselves; but the first and primary line of defense is to use and never reuse very strong unique passwords -- and to hope that the service that requires them will never store them in plaintext.
Apple Patches Vulnerabilities in macOS, watchOS, and tvOS
7.12.2017 securityweek Apple
Apple this week released security updates for macOS, watchOS, and tvOS, as well as updated versions of the Safari browser and the iTunes for Windows application.
The company addressed a total of 22 vulnerabilities with the release of macOS High Sierra 10.13.2 this week (some of the patches were also included in Security Update 2017-002 Sierra and Security Update 2017-005 El Capitan).
Affected components included apache, curl, Directory Utility, Intel Graphics Driver, IOAcceleratorFamily, IOKit, Kernel, Mail, Mail Drafts, OpenSSL, and Screen Sharing Server. Kernel was impacted the most, with 8 bugs addressed in it.
Many of these flaws could result in attackers or malicious applications executing arbitrary code with either kernel or system privileges. Other vulnerabilities, however, could result in disclosure of process memory, administrator authentication bypass, and system termination, or could allow applications to read restricted memory.
Impacting macOS High Sierra 10.13.1, the flaw in Mail could result in an S/MIME encrypted email being inadvertently sent unencrypted if the receiver's S/MIME certificate was not installed, Apple notes in an advisory.
A total of 9 vulnerabilities were addressed with the release of watchOS 4.2. One of the bugs impacts IOSurface, another affects Wi-Fi, while the remaining 7 were resolved in Kernel. Most of the bugs could result in an application executing arbitrary code with kernel privileges or reading restricted memory.
Affecting Apple Watch (1st Generation) and Apple Watch Series 3, the Wi-Fi bug allowed an attacker in Wi-Fi range to force nonce reuse in WPA multicast/GTK clients.
The issue, known as Key Reinstallation Attacks or KRACK, was discovered earlier this year in the Wi-Fi standard itself, thus impacting all implementations, industrial networking devices included. Apple addressed the bug in most of its products in late October.
Released on Monday, tvOS 11.2 resolves 10 vulnerabilities: one in IOSurface, another in Wi-Fi, and 8 in Kernel. Essentially, it fixes the 9 bugs addressed with watchOS 4.2, along with one other issue in Kernel.
These 10 security vulnerabilities, along with 4 others (one in IOKit, one in IOMobileFrameBuffer, one in Mail, and another in Mail Drafts), were also addressed in iOS with the release of iOS 11.2 on December 2.
On Wednesday, December 6, Apple also released Safari 11.0.2 and iTunes 12.7.2 for Windows, but hasn’t provided information on the security content of these updates.
In late November, Apple released a security update for macOS High Sierra in an effort to patch a critical authentication bypass vulnerability that can be easily exploited to gain root access to a system.
Thousands of WordPress sites infected with a Keylogger and cryptocurrency miner scripts
7.12.2017 securityaffairs Virus
Nearly 5,500 WordPress websites are infected with a malicious script that logs keystrokes and in some loads a cryptocurrency miner in the visitors’ browsers.
The experts from security firm Sucuri observed that that malicious script is being loaded from the “cloudflare.solutions” domain, that anyway is not linked with Cloudflare.
According to PublicWWW, this malicious script version is currently active on 5,496 sites.
The script running on compromised WordPress websites logs anything that visitors type inside form fields.
“We also mentioned a post written back in April that described the cloudflare.solutionsmalware, which came along with the cryptominers. At this moment, PublcWWW reports there are 5,482 sites infected with this malware. It seems that this evolving campaign is now adding keyloggers to the mix.” reads the analysis published by Sucuri.

The script is a serious threat especially for WordPress installs configured to run as online stores, in these cases attackers can log credit card data and personal user details.
“This script adds a handler to every input field on the websites to send its value to the attacker (wss://cloudflare[.]solutions:8085/) when a user leaves that field.” continues the analysis.
According to Sucuri experts, the threat actors behind this hacking campaign are active at least since April 2017. Sucuri has tracked at least three different malicious scripts hosted on the same cloudflare.solutions domain across the months.
The first attack leveraging on these scripts was observed in April when hackers used a malicious JavaScript file to embed banner ads on hacked sites.
In November, experts from Sucuri reported the same attackers were loading malicious scripts disguised as fake jQuery and Google Analytics JavaScript files that were actually a copy of the Coinhive in-browser cryptocurrency miner. By November 22, the experts observed 1,833 sites compromised by the attackers.
Back to the present, the script that was discovered on the compromised WordPress sites still includes in-browser cryptocurrency miner abilities and it also includes the keylogger component.
The malicious script resides in the function.php file of the WordPress theme, this means that it is possible to neutralize it by removing the add_js_scripts function and all the add_action clauses that refer add_js_scripts.
“As we already mentioned, the malicious code resides in the function.php file of the WordPress theme. You should remove the add_js_scripts function and all the add_action clauses that mention add_js_scripts.” concludes the anaysis.
“Given the keylogger functionality of this malware, you should consider all WordPress passwords compromised so the next mandatory step of the cleanup is changing the passwords (actually it is highly recommended after any site hack).”
Process Doppelgänging Attack allows evading most security software on all Windows Versions
7.12.2017 securityaffairs Attack
Experts devised a new attack technique dubbed Process Doppelgänging, that could be implemented by vxers to bypass most antivirus solutions.
A group of security researchers from Ensilo discovered a new malware evasion technique, dubbed Process Doppelgänging, that could be implemented by vxers to bypass most antivirus solutions and security software.
The technique is a fileless code injection method that exploits a built-in Windows function and an undocumented implementation of the Windows process loader.
The Process Doppelgänging technique works on almost any Windows version starting from Windows Vista to the latest version of Windows 10.
The security duo from Ensilo, Tal Liberman and Eugene Kogan, presented the Process Doppelgänging at Black Hat 2017 Security conference held in London.
Process Doppelgänging presents similarities to another technique dubbed Process Hollowing, but it relies upon the Windows mechanism of NTFS Transactions.
The Process Hollowing could be used by attackers to replace the memory of a legitimate process with a malicious code, in this way security software are tricked into believing that the legitimate process is running.
Fortunately, all modern security software are able to detect Process Hollowing attacks.The Process Doppelgänging leverages the Windows NTFS Transactions and an outdated implementation of Windows process loader originally designed for Windows XP to carry on the attack.
NTFS Transaction is a Windows feature that was implemented to integrate transactions into the NTFS file system, allowing it easier for application developers to handle errors and preserve data integrity, and of course to manage files and directories.
The NTFS Transaction is an isolated space that allows Windows application developers to write file-output routines which result could be always reconducted to a failure or success state.
The Process Doppelgänging fileless attack works in four steps that are:
Transact—process a legitimate executable into the NTFS transaction and then overwrite it with a malicious file.
Load—create a memory section from the modified (malicious) file.
Rollback—rollback the transaction (deliberately failing the transaction), resulting in the removal of all the changes in the legitimate executable in a way they never existed.
Animate—bring the doppelganger to life. Use the older implementation of Windows process loader to create a process with the previously created memory section (in step 2), which is actually malicious and never saved to disk, “making it invisible to most recording tools such as modern EDRs.”
“The goal of the technique is to allow a malware to run arbitrary code (including code that is known to be malicious) in the context of a legitimate process on the target machine,” said the security duo.
“Very similar to process hollowing but with a novel twist. The challenge is doing it without using suspicious process and memory operations such as SuspendProcess, NtUnmapViewOfSection.”
“In order to achieve this goal we leverage NTFS transactions. We overwrite a legitimate file in the context of a transaction. We then create a section from the modified file (in the context of the transaction) and create a process out of it. It appears that scanning the file while it’s in transaction is not possible by the vendors we checked so far (some even hang) and since we rollback the transaction, our activity leaves no trace behind.”
According to the tests conducted by the researchers, which used Process Doppelgänging to run the well-known password-stealing utility Mimikatz without being detected, the technique evades detection from most antiviruses as reported in the following table:

Liberman explained that the Process Doppelgänging works on even the latest version of Windows 10, except Windows 10 Redstone and Fall Creators Update, both released earlier this year. On these later releases, the attack triggers a BSOD (blue screen of death) condition.
Fortunately, it is technically challenging to power Process Doppelgänging attacks due to the need to know “a lot of undocumented details on process creation.”
The bad news is that the attack “cannot be patched since it exploits fundamental features and the core design of the process loading mechanism in Windows.”
Česko patří mezi nejbezpečnější země. Na Slovensku se počítačové viry šíří více
7.12.2017 Novinky/Bezpečnost Bezpečnost
Česko je z pohledu kybernetických hrozeb jednou z nejbezpečnějších zemí na světě. Podstatně horší je situace například v sousedním Slovensku, které podle počtu počítačových útoků naopak patří spíše mezi nebezpečné země. Vyplývá to z analýzy antivirové společnosti Check Point.
„Česká republika patřila i v říjnu mezi nejbezpečnější země, když se v Indexu hrozeb podruhé za sebou umístila na 119. příčce,“ uvedl Peter Kovalčík, SE Manager ve společnosti Check Point.
Podle něj se naopak Slovensko posunulo o kousek mezi nebezpečnější země a z 90. místa poskočilo na 75. pozici. U našich východních sousedů je tedy riziko nákazy nějakým škodlivým kódem citelně vyšší než u nás.
Zcela nejhorší je ale situace v Dominikánské republice, které patří ve sledovaném období naprosté prvenství. Mezi pět nejnebezpečnějších míst s ohledem na počet kybernetických útoků patří také Indie, Čína, USA a Hongkong.
„Největší skok mezi nebezpečné země zaznamenali Nová Kaledonie, Tanzanie a Kuvajt. Naopak Uruguay se posunula z 53. příčky na bezpečnější 118. pozici,“ doplnil Kovalčík.
Viry těží kybernetické mince
Při šíření virů jde přitom počítačovým pirátům stále častěji o zisk. Do cizích počítačů se snaží podstrčit podvodné aplikace, s jejichž pomocí budou moci těžit kybernetické mince, které pak smění za skutečné peníze.
„V říjnu se škodlivý kód CoinHive vyhoupl na 6. místo mezi nejpoužívanějším malwarem, což potvrzuje trend, na který upozornil nedávný výzkum společnosti Check Point, podle kterého mohou útočníci využít pro těžbu kryptoměn až 65 % celkových zdrojů CPU koncového uživatele, aniž by o tom věděl,“ uvedl bezpečnostní expert.
Zmiňovaný CoinHive je navržen pro těžbu kryptoměny Monero a implantuje JavaScript, který využívá procesor koncových uživatelů a negativně ovlivňuje výkon stroje těžbou kryptoměn.
„Vzestup škodlivého kódu CoinHive znovu ukazuje na nutnost pokročilých preventivních bezpečnostních technologií při ochraně sítí před kyberzločinci. Těžba kryptoměn je nová, tichá a sílící hrozba, která je pro útočníky velmi výnosná a způsobuje významný pokles výkonu koncových zařízení a sítí,“ uzavřel Kovalčík.
Těžařský gigant NiceHash přišel o 1,3 miliardy korun. Ukradli je hackeři
7.12.2017 Novinky/Bezpečnost Hacking
Těžařský gigant NiceHash, který sdružuje statisíce novodobých zlatokopů těžících virtuální měny, se stal terčem hackerů. Ti vysáli všechny uložené peníze. A jde o pořádný balík – 60 miliónů dolarů, tedy v přepočtu zhruba o 1,3 miliardy korun. Informovali o tom zástupci uskupení NiceHash.
Virtuální měny se těší tak velké popularitě především pro své vysoké a rychle rostoucí kurzy. Například jedna mince bitcoinu, což je aktuálně nejpopulárnější kryptoměna, má nyní hodnotu 14 300 dolarů (310 500 Kč).
Popularitě nicméně nahrává také fakt, že za pořízení virtuálních mincí nemusí uživatelé zaplatit ani korunu. Pokud mají dostatečně výkonný počítač, mohou si nainstalovat speciální software a s jeho pomocí kryptoměny doslova těžit – tento program totiž používá předem nastavené výpočty, jejich výsledkem je zisk virtuálních mincí. Za ty je pak možné nakupovat prakticky cokoliv.
A právě proto vzniklo uskupení NiceHash. Jde v podstatě o těžební gigant, do kterého se dobrovolně přihlašují lidé a nabízejí výkon svých počítačů pro těžbu bitcoinů. Zisk si pak spravedlivě rozdělují mezi sebe.
Zmizely všechny bitcoiny
Jenže jak teď vedení uskupení NiceHash sdělilo, nyní si nebude co rozdělovat. Počítačoví piráti doslova vybílili úplně celou virtuální peněženku tohoto těžařského gigantu. Jak již bylo uvedeno výše, šlo v přepočtu o rekordních 1,3 miliardy korun.
Zločinci a počítačoví piráti se na virtuální měny, především tedy populární bitociny zaměřují velmi často. Využívají totiž toho, že transakce v této měně nejsou jakkoli vystopovatelné. A proto je velmi nepravděpodobné, že by se podařilo dopadnout kyberzločince, kteří stojí za tímto útokem na NiceHash.
Vedení těžařského gigantu zatím mlčí o tom, jak bude celou situaci řešit. Plány prý budou jednotlivým uživatelům oznámeny později.