
Mitre ATT&CK Matrix Used to Evaluate Endpoint Detection and Response Product
24.10.2017 securityweek Safety
The growing acceptance that it is impossible to detect and block all malware at the perimeter requires some form of response to malware post-breach. Endpoint Detection and Response (EDR), using machine learning behavioral rules to detect an intrusion, is the security industry's reply.
Anti-malware testing, however, is still largely predicated on malware detection, leaving the efficiency of the response side of EDR less well understood. EDR firm Endgame has sought to address this by using the Mitre ATT&CK Matrix to emulate the post-breach tactics used by the China-based APT3 group.
Mitre's Adversarial Tactics, Techniques, and Common Knowledge (ATT&CK) Matrix is a curated framework that describes the techniques used by adversaries once they are inside a network. It lists, under 10 tactic categories, all known tactics, techniques, and procedures (TTPs) used by adversaries to make decisions, expand their foothold and execute their intentions. These 10 categories derive from the later stages (control, maintain, and execute) of Lockheed Martin's seven-stage cyber kill chain.
The ATT&CK categories comprise persistence, privilege escalation, defense evasion, credential access, discovery, lateral movement, and execution.
“To best understand what an adversary can do post-exploit,” explains Mitre's Frank Duff, “we released the ATT&CK framework. The next logical step is to show how ATT&CK can be actionable, and we have done so with ATT&CK-based adversary emulations. These emulations provide a method to prove the effectiveness of security solutions against known threats.”
It was the APT3 attack emulation against which Endgame was tested. Endgame, the firm announced today, successfully stopped APT3 in the emulation exercise before any data theft or damage would have occurred. “At Endgame,” commented CTO Jamie Butler “we're committed to holding ourselves to the highest standard of protection, which means going beyond malware-based testing regimens to include post-exploitation techniques. I encourage other security vendors to expand their measurement criteria to include the Mitre's ATT&CK Matrix to clearly demonstrate the true value of protections for customers.”
Endgame was founded in 2008 by Chris Rouland and other executives who previously worked with the CIA and Internet Security Systems. It originally concentrated on government customers, and is still strong in this area. The HB Gary leak of 2011 indicated that the early Endgame sold zero-day vulnerabilities. By 2014, the firm had ceased this involvement and used a $23 million Series B funding round followed by a $30 million Series C round to finance the growth of its commercial offering in both the federal and commercial market.
The firm has a tradition of innovation. It uses adversarial machine learning to probe (and improve) its own machine learning defense product. It was an early 'next-gen' adopter of 'traditional' third-party anti-malware testing, and became a member of the Anti-Malware Testing Standards Organization (AMTSO) in January 2017. “As advanced attacks become more pervasive,” said Endgame's director of threat research and adversary prevention Mark Dufresne at the time “it's critical that we establish objective testing methodologies that enable enterprises to make transparent buying decisions based on efficacy of solutions. We look forward to working closely with AMTSO.”
In December 2016 it was certified in an independent evaluation by SE Labs, scoring 100% efficacy. In June 2017 it achieved a 99.5% protection rate in a test conducted by AV Comparatives. This new expansion into using Mitre's ATT&CK Matrix is designed to highlight the ability of the 'response' side of EDR if (and when) detection fails.
SE Labs director Simon Edwards told SecurityWeek in an emailed statement, “We use a similar matrix when building targeted attacks and judging systems designed to detect/ protect against such attacks. We approached the project by analyzing real-world breaches and coming up with different criteria for each part of the attack chain. We did this independently of Mitre but the results are not very different.”
“We are engaging with the security industry to encourage this thinking,” added Mitre's Duff, “so that they can effectively articulate their capabilities to our government partners, as well as the public. We look forward to continuing to work with commercial vendors to articulate their capabilities in the future.”
DHS, FBI Warn of Ongoing APT Attack Against Critical Infrastructure
24.10.2017 securityweek BigBrothers
The Department of Homeland Security and Federal Bureau of Investigation have issued a joint technical alert warning that government entities and organizations in the energy, nuclear, water, aviation, and critical manufacturing sectors are subject to an ongoing attack campaign from an advanced actor, most probably Dragonfly (aka Crouching Yeti and Energetic Bear).
The alert was first distributed by email and is now published by US-CERT. It warns, “Since at least May 2017, threat actors have targeted government entities and the energy, water, aviation, nuclear, and critical manufacturing sectors, and, in some cases, have leveraged their capabilities to compromise victims' networks.” The attack is considered to be ongoing.
The alert does not itself attribute the attack to any specific attacker, but it does comment, “The report Dragonfly: Western energy sector targeted by sophisticated attack group, released by Symantec on September 6, 2017, provides additional information about this ongoing campaign.” Dragonfly's activities against western critical infrastructure -- and especially the energy sector -- have been known for many years. There have been many suggestions that the group operates out of Russia and may be connected to the Russian government.
This new alert from DHS/FBI would therefore suggest either an increase in tempo or growing success in Dragonfly's activities. It describes the attacks in relation to the seven-stage kill chain; but noticeably stops short of the final stage, 'actions on objective'. The implication is that the attacker is seeking a position for possible action against the critical infrastructure in the future.
The threat actors have chosen their targets rather than attacking targets of opportunity. Typically, this is followed by a spear-phishing campaign using email attachments to leverage Microsoft Office functions to retrieve a document using the Server Message Block (SMB) protocol. This sends the user's credential hash to the remote server, where “The threat actors then likely used password-cracking techniques to obtain the plaintext password. Once actors obtain valid credentials, they are able to masquerade as authorized users.”
Watering holes are also used to gather credentials. “The threat actors compromise the infrastructure of trusted organizations to reach intended targets,” notes the alert, adding, “Approximately half of the known watering holes are trade publications and informational websites related to process control, ICS, or critical infrastructure.”
When credentials have been gained, the attackers use these to access victims' networks where multi-factor authentication is not in use. Once inside the networks, the attackers download their tools from a remote server. In one example, the attacker downloaded multiple files, including INST.txt. This was renamed to INST.exe, run, and immediately deleted. “The execution of INST.exe,” says the alert, “triggered a download of ntdll.exe, and shortly after, ntdll.exe appeared in the running process list of a compromised system of an intended target.” In its earlier report, Symantec associated the MD5 hash of INST.exe to Backdoor.Goodor.
There is no direct indication in this report that critical infrastructure operation technology (OT) networks have been compromised -- but it does state clearly that the IT networks have been breached. “This APT actor's campaign has affected multiple organizations in the energy, nuclear, water, aviation, construction, and critical manufacturing sectors.”
The primary activity on the compromised networks seems to be reconnaissance, presumably to find OT weaknesses that could be exploited on demand. “Upon gaining access to intended victims, the threat actors conducted reconnaissance operations within the network. Specifically, the threat actors focused on identifying and browsing file servers within the intended victim's network. The threat actors viewed files pertaining to ICS or Supervisory Control and Data Acquisition (SCADA) systems.”
The report adds, “In one instance, the threat actors accessed workstations and servers on a corporate network that contained data output from control systems within energy generation facilities. In this same incident, the threat actors created a malicious scheduled task that invoked ‘scr.exe’ with the arguments ‘scr.jpg’. The MD5 hash of scr.exe matched the MD5 of ScreenUtil, a tool used by the threat actor, as reported in the Symantec Dragonfly 2.0 report.”
“The latest U.S. power company attacks,” warns David Zahn, GM at PAS, “are an escalation that should be a wakeup call for all critical infrastructure companies that we need to do more. Even basics like knowing what cyber assets are in a power plant or industrial facility are missing today. If you cannot see it, you cannot secure it. If you cannot secure it, then understand that it may get worse before it gets better. Additional attention and investment are needed if we are to get ahead of these threats.”
The US-CERT alert comes with a long list of network signatures and host-based rules that can be used to detect malicious activity associated with the threat actors' TTPs. Both the DHS and FBI recommend that network administrators review the IP addresses, domain names, file hashes, and YARA and Snort signatures provided, and add the IPs to their watch list to determine whether malicious activity is occurring within their organization.
Kaspersky Aims to Clear Its Name With New Transparency Initiative
24.10.2017 securityweek BigBrothers
Kaspersky Lab announced on Monday the launch of a new Global Transparency Initiative whose goal is to help the company clear its name following recent reports about its inappropriate ties to the Russian government.
There have been several media reports analyzing the company’s alleged connection to the Kremlin, which has led to many U.S. officials raising concerns regarding the use of Kaspersky products. It all culminated last month when the Department of Homeland Security (DHS) ordered all government agencies to identify and remove the firm’s security products.
The latest report on Kaspersky’s ties with Russia came from the Wall Street Journal, which claimed that Russian hackers had exploited Kaspersky software to steal NSA exploits. The news article did not provide too many details, but the main possible scenarios were that either Kaspersky colluded with the Russian government or that the hackers exploited vulnerabilities in the company’s products to access the NSA exploits.
Kaspersky has always denied any wrongdoing and it has often offered to allow governments to take a look at its source code to prove it. The company’s latest attempt to clear its reputation is the Global Transparency Initiative.
The first phase of the initiative includes an independent source code review that will be conducted by the first quarter of 2018. At a later time, the company’s software updates and threat detection rules will also be put under the microscope.
By Q1 2018, Kaspersky also wants an independent assessment of its secure development lifecycle processes, and its software and supply chain risk mitigation strategies. The firm has also proposed the development of additional controls to manage its data processing practices and confirmation of compliance with said controls by an independent party.
In order to give its partners – including government stakeholders – access to source code and other product components, Kaspersky plans on establishing three Transparency Centers in Asia, Europe and the United States. While the deadline for the three centers is 2020, the company wants to launch the first one next year.
Likely in response to the latest news report, which suggests that hackers may have stolen NSA files by exploiting a vulnerability in Kaspersky products, the security firm has promised to offer as much as $100,000 for severe vulnerabilities found in its products. The company currently offers $5,000 for serious flaws and wants to introduce the new maximum reward by the end of the year.
“Internet balkanization benefits no one except cybercriminals,” said Eugene Kaspersky, chairman and CEO of Kaspersky Lab. “Reduced cooperation among countries helps the bad guys in their operations, and public-private partnerships don’t work like they should. The internet was created to unite people and share knowledge.”
“Cybersecurity has no borders, but attempts to introduce national boundaries in cyberspace is counterproductive and must be stopped. We need to reestablish trust in relationships between companies, governments and citizens,” he added. “That’s why we’re launching this Global Transparency Initiative: we want to show how we’re completely open and transparent. We’ve nothing to hide. And I believe that with these actions we’ll be able to overcome mistrust and support our commitment to protecting people in any country on our planet.”
Eugene Kaspersky has been invited by the U.S. House of Representatives’ Oversight Subcommittee of the Committee on Science, Space, and Technology to testify and respond to the accusations brought against his company. However, the hearing was initially scheduled too soon, which did not give him enough time to obtain a U.S. visa. The hearing will be rescheduled for a later date, Kaspersky said on Twitter.
Russian Spies Lure Targets With NATO Cybersecurity Conference
24.10.2017 securityweek BigBrothers
A cyber espionage group linked to Russia has been trying to deliver malware to targeted individuals using documents referencing a NATO cybersecurity conference, Cisco’s Talos research team reported on Monday.
The attack has been linked to the notorious threat actor known as APT28, Pawn Storm, Fancy Bear, Sofacy, Group 74, Sednit, Tsar Team and Strontium.
The campaign was apparently aimed at individuals interested in the CyCon U.S. conference organized by the NATO Cooperative Cyber Defence Centre of Excellence (CCDCOE) in collaboration with the Army Cyber Institute at West Point on November 7-8 in Washington, D.C. The hackers created malicious documents with information that was copied from the official CyCon U.S. website.
The topic used as bait in this attack suggests that the threat actor targeted individuals with an interest in cyber security.
APT28 has been known to use zero-day exploits in its operations and, earlier this month, researchers noticed that the hackers had started leveraging a Flash Player vulnerability that Adobe had patched just two days prior. However, in the campaign analyzed by Cisco Talos, the attackers did not use any zero-days.
Instead, they relied on Office documents containing a VBA script. The goal was to deliver Seduploader, a piece of malware which has been used by the threat actor in other NATO-related attacks as well.
“In the previous campaign where adversaries used Office document exploits as an infection vector, the payload was executed in the Office word process. In this campaign, adversaries did not use any exploit. Instead, the payload is executed in standalone mode by rundll32.exe,” researchers explained.
Seduploader is a reconnaissance malware capable of capturing screenshots, collecting and exfiltrating information about the system, executing code, and downloading files. The variant used in these attacks is slightly different compared to previously known samples, which is likely an attempt to evade detection.
The CCDCOE published an alert on its website on Monday to warn people interested in the CyCon conference about the attack.
“This is clearly an attempt to exploit the credibility of Army Cyber Institute and NATO CCDCOE in order to target high-ranking officials and experts of cyber security,” the organization said.
APT28 is not the only threat actor to use cyber security conferences as a lure in their operations. Last year, Palo Alto Networks reported that a China-linked espionage group known as Lotus Blossom, Elise and Esile had used fake invitations to the company’s Cybersecurity Summit to trick users into installing malware.
EU ePrivacy Regulation Edges Closer to Fruition
24.10.2017 securityweek Privacy
The proposed European Union ePrivacy Regulation is on the verge of entering Trilogue. Trilogue is the series of informal discussions involving the European Parliament, the Council of Europe (that is, representatives from each member state), and the European Commission. It is Trilogue that defines the final shape of the legislation.
The all-important hurdle was the vote by 31 in favor to 24 against by the European Parliament's justice committee (LIBE) at the end of last week. LIBE is the lead committee in preparing this legislation.
The ePrivacy Regulation is intended to harmonize e-communications confidentiality laws across the member states by replacing the ePrivacy Directive passed in 2002 (and amended by the 'cookies directive' of 2009). In this way it is similar to the General Data Protection Regulation (GDPR) replacing the earlier Data Protection Directive -- and it carries the same potential sanction of up to 4% of global revenue.
Consistent enforcement will be achieved by assigning the related supervisory powers to the national independent authorities already competent to enforce the GDPR. The intention is to have the ePrivacy Regulation ready by the time GDPR becomes enforceable in May 2018.
However, the new regulation goes beyond simply harmonizing existing laws. These were put into effect before the rise of 'over-the-top' communication channels such as WhatsApp, Facebook, Messenger, and Skype -- which largely escape the confidentiality requirements imposed on mainstream telecommunications companies. The new regulation will apply to the provision of e-communications services to end-users in the EU, irrespective of whether it is a paid for or free service. Providers from outside of the EU will have to appoint a representative within the EU.
While expanding the scope to include the newer channels, the ePrivacy Regulation in its current form also increases the detail of confidentiality. For example, the new terminology is 'tracking technologies', which includes but is not limited to cookies. As with GDPR, consent must be freely and unambiguously given by the user, but can be expressed by a clear affirmative action.
Such 'affirmative action' could be at the browser settings level where technically feasible and possible -- and the wording of the proposal seems to imply that browsers will be required to include a 'no tracking' feature in all new software. Under the new proposal, service providers will not be able to prevent users from accessing a website if they refuse to accept cookies.
The regulation also specifically expands its core rules from content only to include metadata -- which is now generally accepted to include personal information.
However, it should be said that the Regulation is still in the proposal stage. It has already been weakened following extensive industry lobbying. The view of the marketing and advertising industry is that increased consumer protection will stifle innovation and reduce free services on the Internet. A new report from Corporate Europe Observatory (CEO) published October 17 notes that in 41 high-level EU Commission lobby meetings in 2016, 36 were with corporate interests. Only five were with civil society lobbyists.
Industry lobbying -- and in particular, the marketing industry -- will continue during Trilogue, and may well succeed in weakening the proposal further. “During the negotiations on the [GDPR],” notes CEO, “the industry lobby had repeatedly succeeded in having a considerable influence on the positions of the Member States. Due to the non-transparency of the Trilog method, this is particularly vulnerable to opaque manipulation attempts by lobbyists.”
Jan Philipp Albrecht, who was the EU rapporteur for the GDPR, warned about the continuing pressure from conservative MEPs and business interests. “Some conservatives have refused a compromise, despite the great concessions, the profit interests of large internet groups and the short-sighted deregulation fantasies of some industrial associations about the fundamental rights on data protection, privacy and communication secrecy and want to massively weaken the data protection in communication. Consumers want strong data protection of their communications.”
The marketing and ad industries will hope to achieve further concessions from the member states, while privacy activists will hope that the European Parliament and European Commission can hold steady.
Whole Foods Market confirms that nearly 100 locations were affected by card breach
24.10.2017 securityaffairs Incindent
According to the Whole Foods Market, crooks may have stolen payment cards at taprooms and full table-service restaurants at nearly 100 locations.
At the end of September, the Amazon-owned grocery chain Whole Foods Market notified customers a security breach. According to the security breach notification issued by the company, cybercriminals were able to gain unauthorized access to credit card information for customers who made purchases at certain venues like taprooms and full table-service restaurants located within some stores.
The Amazon-owned company notified customers last week that the payment systems security breach affected nearly 100 locations across the United States. The company published a page to provide users details about the allow them to check if the store they made was compromised by the hackers.
“Whole Foods Market has resolved the incident previously announced on September 28, 2017, involving unauthorized access of payment card information used at certain venues such as tap rooms and full table-service restaurants located within some stores.” states the company.
“These venues use a different point of sale system than the company’s primary store checkout systems, and payment cards used at the primary store checkout systems were not affected.”
According to the company, crooks may have stolen payment cards at taprooms and full table-service restaurants using a malware.
Whole Foods hired a cybersecurity forensics firm to conducted the investigation that discovered the intrusion occurred as early as March 10.
Crooks used a PoS malware designed to siphon card data, including cardholder names, account numbers, card expiration dates, and internal verification codes.
The affected locations are in various cities in Alabama, Arizona, Arkansas, California, Colorado, District of Columbia, Florida, Georgia, Hawaii, Idaho, Illinois, Indiana, Kansas, Maine, Michigan, Minnesota, Missouri, Nevada, New Hampshire, New Jersey, New Mexico, New York, North Carolina, Ohio, Oregon, Pennsylvania, Tennessee, Texas, Virginia, Washington and Wisconsin. The largest number of affected locations is in California.
“The investigation determined that unauthorized software was present on the point of sale system at certain venues. The software copied payment card information—which could have included payment card account number, card expiration date, internal verification code, and cardholder name—of customers who used a payment card at these venues at dates that vary by venue but are no earlier than March 10, 2017 and no later than September 28, 2017.” continues the firm.
The supermarket chain pointed out that payments made at primary store checkout systems were not affected, the breach does not impact Amazon.com.

The page set up by the company also provides suggestions to the customers on how to protect themselves from fraudulent activities involving their payment cards.
NetBSD security improved with the implementation of kernel ASLR (KASLR)
24.10.2017 securityaffairs Safety
The development team at NetBSD is going to implement the KASLR (kernel Address Space Layout Randomisation) for 64-bit AMD processors.
The KASLR coding technique allows randomizing the location of memory where the NetBSD kernel is loaded. The ASRL technique is widely adopted as a security measure to protect applications from the exploitation of vulnerabilities like buffer overflow because it is impossible for the attacker to predict the memory location that could be used to inject malicious code.
The current design decouples the bootloader and the kernel with an additional layer dubbed “prekern.”
“The current design is based on a specialized kernel called the “prekern“, which operates between the bootloader and the kernel itself. The kernel is compiled as a raw library with the GENERIC_KASLR configuration file, while the prekern is compiled as a static binary.” explained the developer Maxime Villard.
“When the machine boots, the bootloader jumps into the prekern. The prekern relocates the kernel at a random virtual address (VA), and jumps into it. Finally, the kernel performs some cleanup, and executes normally.”

The implementation is still incomplete, Villard anticipated the future work:
Randomise the kernel sections independently, and intertwine them;
Modify several kernel entry points not to leak kernel addresses to userland;
Randomise the kernel heap too (which is still static for now).”
All of the patches are already available in the current NetBSD, the post written by the developer also includes a link to the instructions on how to install and use this implementation.
This KASLR implementation will be available starting from NetBSD 9.
“Once it is stabilized, it may be backported to NetBSD 8. Until then, feel free to test it!”
Latest Russia-linked APT28 campaign targeting security experts
24.10.2017 securityaffairs APT
Russian cyber espionage group APT28 targeted individuals with spear-phishing messages using documents referencing a NATO cybersecurity conference.
Researchers with Cisco Talos have spotted a Russian cyber espionage group targeting individuals with spear-phishing messages using documents referencing a NATO cybersecurity conference.
Experts attributed the attack to the dreaded Russian APT28 group, aka Pawn Storm, Fancy Bear, Sofacy, Group 74, Sednit, Tsar Team and Strontium.
The hackers targeted individuals with a specific interest in the CyCon US cybersecurity conference organized by the NATO Cooperative Cyber Defence Centre of Excellence (CCDCOE) in collaboration with the Army Cyber Institute at West Point on November 7-8 in Washington, D.C.
The state-sponsored hackers used bait documents containing content copied from the official CyCon U.S. website, the attackers were clearly interested in spying on cybersecurity experts.
“Cisco Talos discovered a new malicious campaign from the well known actor Group 74 (aka Tsar Team, Sofacy, APT28, Fancy Bear…). Ironically the decoy document is a deceptive flyer relating to the Cyber Conflict U.S. conference. CyCon US is a collaborative effort between the Army Cyber Institute at the United States Military Academy and the NATO Cooperative Cyber Military Academy and the NATO Cooperative Cyber Defence Centre of Excellence.” states the report published by CISCO Talos.
“Due to the nature of this document, we assume that this campaign targets people with an interest in cyber security.”

The technique to use cyber security conferences as a lure in cyber espionage operations is well known, other threat actors in the past used the same tactic. Last year, a Chinese cyber espionage group known as Lotus Blossom attempted to lure victims with fake invitations to a Palo Alto Networks’ Cybersecurity Summit.
The attackers didn’t use any zero-day vulnerabilities in this last campaign, instead, they relied on weaponized Office documents containing VBA scripts used to deliver a new variant of Seduploader (also known as GAMEFISH backdoor, Sednit, JHUHUGIT and Sofacy).
The Seduploader malware, also known as GAMEFISH backdoor, Sednit, JHUHUGIT and Sofacy, is a strain of malware that has been already used by the threat actor in other campaigns against NATO representatives.
“In the previous campaign where adversaries used Office document exploits as an infection vector, the payload was executed in the Office word process. In this campaign, adversaries did not use any exploit. Instead, the payload is executed in standalone mode by rundll32.exe,” continues the report.
The Seduploader is a reconnaissance malware that was used for years by APT28, it is composed of 2 files: a dropper and a payload. The experts noticed that dropper and the payload are quite similar to the previous versions but the author modified some public information such as MUTEX name, obfuscation keys.
Hackers made these modifications to avoid detection of security solutions.
The CCDCOE published an alert on its website to warn people interested in the CyCon conference about the attack.
“Information from CyCon U.S. website has been used in a Word document with an intent to deliver malware. This type of attack, where legitimate information is used to attract the attention of victims, is rather common and normally detected and prevented in information systems with widely used safeguards.” reads the alert.
“This is clearly an attempt to exploit the credibility of Army Cyber Institute and NATO CCDCOE in order to target high-ranking officials and experts of cyber security,”
Data z protokolů odkrývají neznámé skutečnosti
24.10.2017 SecurityWorld Zabezpečení
I ten nejmenší tým IT může využívat správu protokolů pro hladší provoz a silnější zabezpečení.
Malé týmy IT stejně jako ty velké závisejí při odstraňování problémů, vyšetřování bezpečnostních incidentů a dalších důležitých úlohách na aktuálnosti informací.
Zvýraznění a rychlé a efektivní přednostní vyřešení problémů může znamenat rozdíl mezi krizí a úspěšným provozem firmy, bez ohledu na velikost. Velká část těchto důležitých aktuálních informací přichází v podobě dat protokolů (log).
Je důležité si uvědomit, že „malý tým IT“ neznamená malý objem dat. Mnoho menších IT týmů a jejich systémy generují každý den mnoho gigabajtů protokolů. S omezením rozpočtu a personálu však menší týmy IT čelí specifickým problémům, pokud jde o analýzy protokolů.
Drobné IT týmy jsou, a není divu, zcela běžné ve soustě malých firem (a dokonce i v některých velkých organizacích). Podle nedávné zprávy společnosti Spicework o trendech přijetí technologií mají společnosti s méně než 99 zaměstnanci obvykle mezi svými pracovníky průměrně jen dva až tři IT profesionály.
Data protokolů jsou jakýmsi supermanem IT údajů: slabá a neokázalá zvenku, ale skrývají nesmírnou sílu. Protokoly zachycují životně důležité skutečnosti týkající se vaší firmy. Poskytují rozhodující záznamy veškerého dění od oblíbenosti produktů až po stav zabezpečení a výkonu vaší sítě.
Analýza dat protokolu správně transformuje způsob rozhodování a dokonce i způsob fungování firmy. Tato data až příliš často leží bez užitku na serverech a čekají, až je někdo objeví. Ale tak to nemusí být – malé organizace a týmy IT prostě potřebují způsob, jak je využít.
Pochopení dat protokolů
Jedním z největších problémů, kterým týmy IT čelí v souvislosti s daty protokolů, je prostá agregace dat a nalezení vzájemných souvislostí. Neexistují zde žádné datové standardy.
Každá zakázková aplikace má vlastní protokoly. Dostupné nástroje často mají vážná omezení, jako je například omezení znaků pro soubory protokolu, které se vracejí.
Když máte mezi zaměstnanci jen dva až tři IT profesionály, stávají se agregace a korelace všech dat protokolů vytvářených ve společnosti kolosálním úkolem.
Tato úloha se dále ztěžuje současnými technologiemi, které pracují tak rychle, že se nová data protokolů vytvářejí nepřetržitě 24 hodin denně 7 dní v týdnu, a to v každé aplikaci a systému ve vaší infrastruktuře.
Chce-li váš tým IT úspěšně využívat data protokolů, musíte nejprve najít vhodný způsob jejich správy.
Shromažďování a centralizace
Agregace dat protokolů do jednoho místa – protože jsou generovaná aplikacemi, infrastrukturou a distribuovanými prostředími – je k získání komplexního pohledu na IT nezbytná.
Nutnost prohledávat jednotlivé oddělené sklady dat a ručně hledat souvislosti může být časově náročná, zejména když nefunguje klíčová služba.
Například posílání všech protokolů syslog a událostí Windows do jednoho místa znamená, že se můžete zbavit nutnosti používat při řešení problému několik jednotlivých nástrojů.
Automatizace sběru dat protokolu a centralizace je výchozím bodem k získání větší hodnoty z vašich dat. (Viz tabulku s příklady dat, která oddělení IT potřebují shromažďovat a centralizovat.)
Většina nástrojů a ručních přístupů vyžaduje, aby uživatelé normalizovali či vybírali konkrétní data ze souborů protokolů, což zabírá čas a ztrácí se tím podstatný kontext. Lepším přístupem je shromažďovat a v reálném čase uchovávat data v jejich nezpracované podobě v nativním formátu, aby bylo možné zodpovědět nečekané otázky.
To však může být náročné. Neexistují žádné standardní formáty pro data protokolů. Téměř každý systém, aplikace a zařízení zabezpečení bude mít jiný formát dat protokolu.
Tabulkové kalkulátory a nástroje BI nelze přímo použít k analýze dat protokolů z různorodých systémů. Ve chvíli, kdy se vytvoří schéma nebo se data vloží do řádků a sloupců, čeká uživatele tabulkových kalkulátorů a nástrojů BI hora práce nad rámec pouhého přidání dat protokolu z dalších systémů.
Nejhorším scénářem je pak požadavek kontextu z originálního souboru protokolu, jen aby se zjistilo, že při normalizaci dat či při jejich extrakci, transformaci a načítání (ETL) došlo ke ztrátě kontextu.
Hledání a monitoring
Prohledávání dat protokolů s cílem najít problém se v podstatě rovná hledání jehly v kupce sena. A stejně, jako by někdo mohl použít magnet při hledání té jehly, potřebují malé týmy IT snadný způsob, jak vybrat potřebné soubory protokolů. Měly by to být soubory, které ukazují, že se něco pokazilo, že došlo k chybě systému nebo k narušení zabezpečení.
Řešení tohoto problému je jednoduché a známe ho velmi dobře všichni – hledání. Dostupnost vyhledávací funkce, která dokáže prozkoumat centralizovaná data protokolů, odstraňuje nutnost používat grep nebo tabulkový kalkulátor ke hledání IT problémů.
Představte si, že jednoduše zadáte slovo „error“ nebo „fail*“ a dostanete jako odpověď všechny relevantní soubory protokolů ze všech vašich systémů.
Přestože schopnost hledat problémy významně šetří čas a snižuje náklady, skutečný přínos spočívá v přechodu mezi reaktivním a proaktivním přístupem. Proaktivním vyhledáváním událostí obsahujících klíčová slova „error“ nebo „fail*“ a varováním v případě, když se vyskytnou, mohou týmy IT identifikovat a řešit problémy dříve, než se rozrostou do podoby plnohodnotného požárního poplachu.
Vizualizace a reporty
Vytvoření informačních panelů a reportů pro všechna relevantní data poskytuje rychlý přehled o zdravotním stavu IT a problémech. Například vytvoření vizualizací chyb pomůže týmu IT lépe stanovit priority a řešit nejprve největší závady.
Přirozeným vývojem je přejít od jednotlivých vizualizací k informačním panelům, které zahrnují několik vizualizací na základě zobrazení živých a historických dat. Informační panely jsou základnou pro týmy IT pro monitorování více prahových hodnot a podmínek na bázi trendů.
Je důležité si uvědomit, že identifikace a detailní zkoumání problémů přímo z informačních panelů je základem pro efektivní pracovní postupy při správě a využívání dat protokolů. Možnost proklikat se z tabulky či grafu přímo k surovým datům snižuje čas potřebný k řešení problémů a pomáhá týmům přejít z reaktivního přístupu na proaktivní.
Centrální shromažďování a analýza dat protokolů jsou pouze výchozím bodem. Skutečný přínos začne poté, co se týmům podaří vymanit se z režimu podobnému požárnímu cvičení a proces zautomatizovat.
Eliminace manuálního vyhledávání
Posun za hranice, které představují grep a manuální vyhledávání v protokolech, sníží průměrnou dobu potřebnou na řešení problémů a uvolní personál IT k práci na důležitějších projektech.
Pamatujte, že schopnost přistupovat k datům protokolů a eliminovat separaci, kterou tvoří datová sila, jež se vyskytují ve všech systémech a aplikacích, je rozhodující pro získání přehledu potřebného k řešení problémů a k pochopení plné hodnoty dat protokolů.
Hledání v jedné či dvou aplikacích, nebo dokonce jen v jednom systému může skončit odstraněním symptomů problému, a nikoli hlavní příčiny. Kromě toho zkoumání jednotlivých protokolů a zdrojů snižuje přínos efektivity, která plyne z odstranění manuálního procesu.
Monitoring systémů, aplikací a KPI
Prevence je příslovečně tisíckrát efektivnější než řešení následků. Proaktivní sledování, zda se v datech webu a aplikací nevyskytují problémy, pomůže týmům IT vymanit se z režimu hašení požárů.
Monitorování výskytu problémů a spouštění upozornění, když není splněn klíčový ukazatel výkonu nebo je systém nefunkční, zásadním způsobem transformuje fungování týmů IT z reaktivního na proaktivní.
Tato transformace hraje významnou roli v pomoci týmům IT, aby využívaly své omezené zdroje na identifikaci příležitostí k optimalizaci systémů a aplikací, a ne až k reakcím na problémy.
Přechod na proaktivní režim v konečném důsledku umožní týmu, aby se více věnoval strategické práci, jako je například zvýšení zabezpečení IT.
Zlepšení zabezpečení IT
Protože data protokolů obsahují rozhodující záznamy o aktivitě v celé vaší infrastruktuře a sítích, mají také informace, které by mohly indikovat podvody, narušení a útoky APT. Použití dat protokolů k podpoře zabezpečení IT může urychlit šetření v oblasti zabezpečení a pomoci určit příčinu narušení.
Použití tabulkového kalkulátoru nebo jiného nástroje využívajícího řádky a sloupce pro data protokolů může zpomalit vyšetřování narušení, nebo může dokonce způsobit neúmyslné odstranění dat, která jsou pro případ klíčová, protože důležitá data někdy nezapadají do určitého schématu.
Řešení problémů se zabezpečením může být také časově citlivé. Schopnost rychlého vyhledávání v datech protokolů a obdržení varování při výskytu anomální aktivity představuje stěžejní funkce pro prevenci a zastavení útoku.
Stejně jako Clark Kent, který vyrostl z mírného mladíka ze Středozápadu a stal se z něj plnohodnotný superhrdina – Superman, by měla i data protokolů projít transformací ze skromné zpětné vazby k mocnému nástroji pomáhajícímu pochopit a řešit složité problémy.
Pamatujte si: Jenom to, že jste malou firmou nebo máte malý tým IT, ještě neznamená, že nemůžete přeskočit vysokou budovu nebo letět rychleji než vlak.
***Tabulka 1:
Ukázka typů dat, která oddělení IT potřebují centralizovat
Příklad typu dat
Původ
Protokoly clickstream
Webové servery, směrovače, proxy servery, reklamní servery
Protokoly aplikací
Lokální soubory protokolů, log4j, log4net, WebLogic, WebSphere, JBoss, .Net, PHP
Syslog
Směrovače, přepínače, síťová zařízení
Protokoly Windows
Protokoly aplikací Windows, zabezpečení a systému
Exclusive – CSE ZLab experts spotted a new Wonder botnet in the wild
23.10.2017 securityaffairs BotNet
The CSE CybSec Z-Lab Malware Lab spotted a new botnet, dubbed Wonder botnet, while it was investigating malicious code in the dark web.
While investigating the malicious code in the dark web, ZLab experts discovered a “NetflixAccountGenerator.exe” that promises to generate a premium account for Netflix services for free. Unfortunately, the software downloaded does not work as expected because it installs a BOT rather than create a desiderated account!
The malware researchers analyzed this “exe” file and discovered that the malware is not indexed yet: only one site on the Clearnet identified it as a threat after it was uploaded for the first time around September 20th, probably by the author in order to test its ability to remain stealth.
The analysis of the malware revealed it is a bot that belongs to an alive botnet dubbed by the experts Wonder botnet. The Command and Control is hidden behind a site that is the mirror of another one:

Figure 1 – On the left the fake site; on the right the original site
Experts verified that the fake page “support.com” at the link “wiknet.wikaba.com” on the left side, point to the front-end of the botnet’s C2C. The interesting thing is that every link on it refers to the original page, clicking on one links the researchers were redirected to the corresponding page on “support.com”.
The experts also discovered some hidden paths that contain the information and the commands used by the bots.
The malware is composed of two parts:
A Downloader: it is a .NET executable with the only purpose of downloading and executing the real bot code, uploaded on “pastebin.com/raw/E8ye2hvM”.
The real Bot: when it is downloaded and executed, it infects the host setting its persistence mechanisms and starts its malicious behavior schematized in the following figure: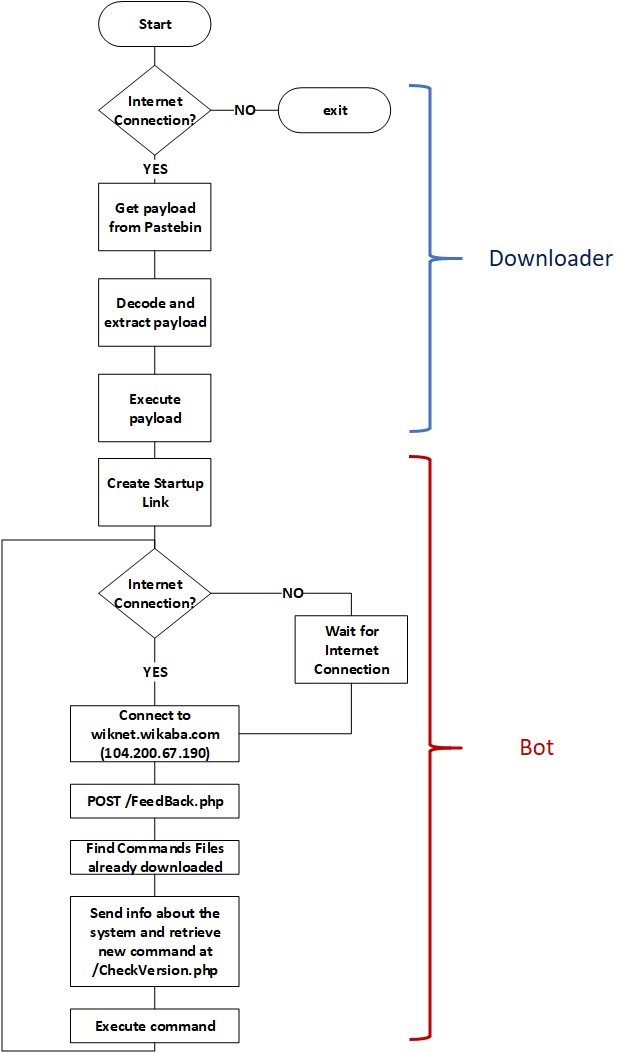
Figure 2 – Wonder Botnet’s behavior scheme
Further technical details, including IoCs and Yara rules are included in the report published by CSE Cybsec ZLab. PDF
Assemblyline – Canada’s CSE intelligence Agency releases its malware analysis tool
23.10.2017 securityaffairs BigBrothers
Canada’s Communications Security Establishment (CSE) intel agency has released the source code for one of its malware analysis tools dubbed Assemblyline.
The Canada’s Communications Security Establishment (CSE) intelligence agency has released the source code for one of its malware detection and analysis tools dubbed Assemblyline.
The Assemblyline tool is written in Python and was developed under the CSE’s Cyber Defence program.
“This tool was developed within CSE’s Cyber Defence program to detect and analyse malicious files as they are received. As the Government of Canada’s centre of excellence in cybersecurity, CSE protects and defends the computer networks and electronic information of greatest importance to the Government of Canada.” states the Communications Security Establishment.”Our highly skilled staff works every day to protect Canada and Canadians from the most advanced cyber threats. Assemblyline is one of the tools we use.”

The Canadian intelligence agency described the analysis process as a conveyor belt, the files arrive in the system and are triaged in a sequence composed of the following phases:
Assemblyline generates information about each file and assigns a unique identifier that travels with the file as it flows through the system.
Users can add their own analytics, which we refer to as services, to Assemblyline. The services selected by the user in Assemblyline then analyze the files, looking for an indication of maliciousness and/or extracting features for further analysis.
The system can generate alerts about a malicious file at any point during the analysis and assigns the file a score.
The system can also trigger automated defensive systems to kick in. Malicious indicators generated by the system can be distributed to other defence systems.
Assemblyline recognizes when a file has been previously analysed.
The CSE decided of releasing the Assemblyline tool allowing anyone to customize the tools and deploy their own analytics into it.
The tool allows users to focus their efforts on the most harmful files, reducing the number of non-malicious files that experts have to inspect.
“The strength of Assemblyline is the ability of users to scale the system to their needs and the way that Assemblyline automatically rebalances its workload depending on the volume of files.” CSE added.” It reduces the number of non-malicious files that security analysts have to inspect, and permits users to focus their time and attention on the most harmful files, allowing them to spend time researching new cyber defence techniques,” CSE added.
The Assemblyline source code is available on BitBucket, users can modify it according to their needs.
Other intelligence agencies also released open source tools in the past, In November 2016, peers at the GCHQ released the CyberChef tool to analyze encryption, compression and decompression, and data formats.
Proton malware spreading through supply-chain attack, victims should wipe their Macs
23.10.2017 securityaffairs Apple
The dreaded Proton malware was spreading through a new supply-chain attack that involved the Elmedia apps, victims should wipe their Macs
Bad news for Mac users, a new malware is threatening them of a complete system wipe and reinstall.
Crooks are distributing the malware in legitimate applications, the popular Elmedia Player and download manager Folx developed by the Elmedia Player who confirmed the threat. The latest versions of both apps came with the OSX.Proton malware.
The Proton malware is a remote access tool (RAT) available for sale on some cybercrime forums, it first appeared in the threat landscape last year. The malicious code includes many features such as the ability to execute console commands, access the user’s webcam, log keystrokes, capture screenshots and open SSH/VNC remote connections. The malicious code is also able to inject malicious code in the user’s browser to display popups asking victims’ information such as credit card numbers, login credentials, and others.
The Proton malware can hack into a victim’s iCloud account, even if two-factor authentication is used, and in March it was offered for sale at $50,000.
Experts at security firm ESET discovered that the Proton malware is spreading through supply chain attacks, hackers injected the malicious code into downloads of the applications.
“During the last hours, ESET researchers noticed that Eltima, the makers of the Elmedia Player software, have been distributing a version of their application trojanized with the OSX/Proton malware on their official website. ESET contacted Eltima as soon as the situation was confirmed. Eltima was very responsive and maintained an excellent communication with us throughout the incident.” reported ESET.
ESET promptly alerted Elmedia, hackers compromised the developer’s servers and implanted the Proton malware into the download files.
Below the timeline of the attack:
2017-10-19 : Trojanized package confirmed
2017-10-19 10:35am EDT: Eltima informed via email
2017-10-19 2:25pm EDT: Eltima acknowledged the issue and initiated remediation efforts
2017-10-19 3:10pm EDT: Eltima confirms their infrastructure is cleaned up and serving the legitimate applications again
2017-10-19 10:12am EDT: Eltima publishes an announcement about the event
2017-10-20 12:15pm EDT: Added references to Folx that was also distributed with the Proton malware
If you want to check your installation do a scan for the following file and directories:
/tmp/Updater.app/
/Library/LaunchAgents/com.Eltima.UpdaterAgent.plist
/Library/.rand/
/Library/.rand/updateragent.app/
“The presence of any of the files above is an indication that your system may have been infected by the trojanized Elmedia Player or Folx application which means your OSX/Proton is most likely running. If you downloaded Elmedia Player or Folx on the 19th of October 2017, your system is likely affected.” reads the security advisory published by Eltima.
The Proton malware has already infected a computer if any of those files and directories exist. Even if the malware is recognized by antivirus software, it’s difficult to remove.
“If you have downloaded that software on October 19th before 3:15pm EDT and run it, you are likely compromised.” states ESET.
“As with any compromission with a administrator account, a full OS reinstall is the only sure way to get rid of the malware. Victims should also assume at least all the secrets outlined in the previous section are compromised and take appropriate measures to invalidate them.”

The company Eltima is also suggesting a total system OS reinstall to rid the infected systems of this malware.
“A total system OS reinstall is the only guaranteed way to totally rid your system of this Malware,” it warned. “This is a standard procedure for any system compromise with the affection of administrator account.”
A leaked document raises a doubt about NSA knew the #Krack attack since 2010
23.10.2017 securityaffairs BigBrothers
An NSA leaked document about the BADDECISION hacking tool raises the doubt about National Security Agency knew the Krack attack since 2010.
Security experts are questioning the NSA about the recently disclosed Krack attack the allows an attacker to decrypt information included in protected WPA2 traffic.
Security experts believe that the National Security Agency was aware of the flaw and its arsenal included a specific exploit.
An NSA spokesperson did not comment the claims, this is normal for the US intelligence agencies, but according to ZDNet, rumors that it knew something about the vulnerability in the WPA2 protocol are circulating in the intelligence community.
In some cases, the US intelligence even is informed of a vulnerability doesn’t disclose it in the attempt to exploit it for intelligence operations.
According to a top secret document leaked by the Edward Snowden and dated back 2010, the NSA arsenal included a hacking tool called BADDECISION classified as an “802.11 CNE tool. that used a true Man-in-the-middle attack and frame injection technique to redirect a target client to a FOXACID server.”

The NSA exploit was designed to target wireless networks by using a man-in-the-middle attack within range of the network, according to the Top-Secret slides it works for WPA and WAP2 networks, this implies that BADDECISION could bypass the encryption.
The FOXACID platform allows NSA operators to automatically supply the best malware for a specific target.
The slide said the hacking tool “works for WPA/WPA2,” suggesting that BADDECISION could bypass the encryption.
Cue the conspiracy theories. No wonder some thought the hacking tool was an early NSA-only version of KRACK.
Is BADDECISION the Krack attack tool?
Difficult to say, but many security researchers believe BADDECISION doesn’t exploit the KRACK attack.
According to former NSA staffers cited by ZDNet the NSA BADDECISION exploit is a sort of Ettercap tool that conducts man-in-the-middle attacks to carry out address resolution protocol (ARP) spoofing or poisoning.
Anyway, even if NSA BADDECISION doesn’t rely on the Krack attack, it is impossible to totally exclude that the agency was not aware of the vulnerability recently disclosed.
APT28 group is rushing to exploit recent CVE-2017-11292 Flash 0-Day before users apply the patches
23.10.2017 securityaffairs APT
The APT28 group is trying to exploit the CVE-2017-11292 Flash zero-day before users receive patches or update their systems.
Security experts at Proofpoint collected evidence of several malware campaigns, powered by the Russian APT28 group, that rely on a Flash zero-day vulnerability that Adobe patched earlier this week.
According to the experts who observed attacks on organizations across Europe and in the US, the APT28 group is trying to exploit the CVE-2017-11292 zero-day before users receive patches or update their systems.
The state-sponsored hackers focused their attacks on state departments and private-sector businesses in the aerospace industry.
“On Tuesday, October 18, Proofpoint researchers detected a malicious Microsoft Word attachment exploiting a recently patched Adobe Flash vulnerability, CVE-2017-11292. We attributed this attack to APT28 (also known as Sofacy), a Russian state-sponsored group.” states the report published by Proofpoint.
“Targeting data for this campaign is limited but some emails were sent to foreign government entities equivalent to the State Department and private-sector businesses in the aerospace industry. The known geographical targeting appears broad, including Europe and the United States. The emails were sent from free email services.”
The patch was released on Monday, October 16, at that time Kaspersky detected attacks leveraging the CVE-2017-11292 allegedly conducted by the BlackOasis APT group.
Researchers believe that APT28 was also in possession of the exploit (whether purchased, discovered on their own, or reverse engineered from the BlackOasis attack), and is trying to use it in targeted attacks.
The APT28 rushed to assemble the exploit and the distribution campaign, reusing code from past attacks, the APT28 hackers did the same in May after Microsoft patched three zero-days flaws exploited by the Russian APT group.
Back to the present, researchers believe the APT28 found a way to exploit the CVE-2017-11292, it is unclear if they purchased the zero-day or reverse engineered it from the BlackOasis attack.
The researchers noticed that the recent attacks exploiting the CVE-2017-11292 flaw employed the same old DealersChoice malware, a Flash exploit framework also used by the APT28 group against Montenegro.
When the target user opens these the weaponized files, DealersChoice contacts the remote server to download the CVE-2017-11292 exploit code and execute it.
“The document “World War 3.docx” contacts DealersChoice.B, APT28’s attack framework that allows loading exploit code on-demand from a command and control (C&C) server. DealersChoice has previously been used to exploit a variety of Flash vulnerabilities, including CVE-2015-7645, CVE-2016-1019, CVE-2016-4117, and CVE-2016-7855 via embedded objects in crafted Microsoft Word documents.” continues the report.

The Proofpoint researcher Kafeine, confirmed his company currently trying to take down C&C servers associated with the DealersChoice attack framework used in the CVE-2017-11292 attacks.
“APT28 appears to be moving rapidly to exploit this newly documented vulnerability before the available patch is widely deployed. Because Flash is still present on a high percentage of systems and this vulnerability affects all major operating systems, it is critical that organizations and end users apply the Adobe patch immediately. ” concluded Proofpoint.
Further technical details are available in the report published by Proofpoint, including the IOCs.
DHS and FBI warn of ongoing attacks on energy firms and critical infrastructure
23.10.2017 securityaffairs BigBrothers
The US DHS and the FBI have issued a warning that APT groups are actively targeting energy firms and critical infrastructure.
The US Department of Homeland Security (DHS) and the FBI have issued a warning that APT groups are actively targeting government departments, and firms working in the energy, nuclear, water, aviation, and critical manufacturing sectors.
The warning was sent to the organization via email on Friday to inform them of Advanced Persistent Threat Activity targeting energy and other critical infrastructure sectors since at least May 2017.
“Since at least May 2017, threat actors have targeted government entities and the energy, water, aviation, nuclear, and critical manufacturing sectors, and, in some cases, have leveraged their capabilities to compromise victims’ networks.” reads the alert.
“Analysis by DHS, FBI, and trusted partners has identified distinct indicators and behaviors related to this activity. Of specific note, the report Dragonfly: Western energy sector targeted by sophisticated attack group, released by Symantec on September 6, 2017, provides additional information about this ongoing campaign. “

The hackers use to target third-party suppliers and contractors (“staging targets”) to hit intended institution.
The attackers leverage the staging targets’ networks as pivot points and malware repositories when launching the attacks on their final intended victims.
According to the warning, the campaign is still ongoing, the government experts believe it is operated by the Dragonfly hacking group (aka Energetic Bear) that has been active since at least 2011 when it targeted defense and aviation companies in the US and Canada. Only in a second phase Dragonfly has focused its effort on US and European energy firms in early 2013.
In 2014, security experts at Symantec uncovered a new campaign targeting organizations located in the US, Italy, France, Spain, Germany, Turkey, and Poland.
Dragonfly gang conducted a cyber espionage campaign against energy grid operators, major electricity generation firms, petroleum pipeline operators, and energy industry industrial equipment providers.
According to the JAR report published by the US Department of Homeland Security, Dragonfly was Russian APT actor linked to the Government.
The infamous group remained under the radar since December 2015, but now the researchers pointed out Dragonfly targeted energy companies in Europe and the US.
In September 2017, the attackers aimed to control or even sabotage operational systems at energy facilities.
Back to the ongoing campaign, the attackers launched a spear-phishing campaign.
“Throughout the spear-phishing campaign, threat actors used email attachments to leverage legitimate Microsoft Office functions to retrieve a document from a remote server using the Server Message Block (SMB) protocol. (An example of this request is: file[:]//<remote IP address>/Normal.dotm). As a part of the standard processes executed by Microsoft Word, this request authenticates the client with the server, sending the user’s credential hash to the remote server prior to retrieving the requested file.” states the alert. “(Note: It is not necessary for the file to be retrieved for the transfer of credentials to occur.) The threat actors then likely used password-cracking techniques to obtain the plaintext password. Once actors obtain valid credentials, they are able to masquerade as authorized users.”
APT28 hackers also used spear-phishing emails with a generic contract agreement in the form of a PDF that even if doesn’t include a malicious code prompts the victim to click a link which (via a shortened URL) downloads a malicious file.
The weaponized attachments may refer to legitimate curricula vitae CVs or resumés for industrial control systems personnel, invitations or policy documents designed to entice users into clicking on the attachment.
“The emails leveraged malicious Microsoft Word attachments that appear to be legitimate résumés or curricula vitae (CVs) for industrial control systems personnel, as well as invitations and policy documents that entice the user to open the attachment. The list of file names has been published in the IOC.” continues the alert.
Attackers also used watering hole attacks, attackers compromise trade publications and informational websites related to process control, ICS, or critical infrastructure.
Much more detail, including indicators of compromise, filenames used in the attacks, and MD5 hashes, can be found in the alert published on US-CERT.
AhMyth Android RAT, another open source Android RAT Tool available on GitHub
23.10.2017 securityaffairs Virus
The source code of a new Android Remote Administration Tool is available on GitHub, it is dubbed AhMyth Android RAT. You just have to download and test it.
The source code of a new Android Remote Administration Tool is available on GitHub, it is dubbed AhMyth Android RAT.
The malicious code is still in beta version, the AhMyth Android RAT consists of two parts:
The Server side: desktop application based on electron framework (control panel)
The Client side: Android application (backdoor)
According to the author, the unique prerequisites from the source code are:
Electron (to start the app)
Java (to generate apk backdoor)
Electron-builder and electron-packer (to build binaries for (OSX,WINDOWS,LINUX))
meanwhile the prerequisites from the binaries:
Download a binary from https://github.com/AhMyth/AhMyth-Android-RAT/releases
Java (to generate apk backdoor)

The author of the malware also published a video PoC:
Several malware researchers already noticed the availability of the malware online, such as Lukas Stefanko, a malware researcher at ESET, which is focused on Android security and Android malware.
View image on Twitter
View image on Twitter
Follow
Lukas Stefanko @LukasStefanko
Another open source Android RAT ● AhMyth ● available on GitHubhttps://github.com/AhMyth
11:55 AM - Oct 21, 2017
2 2 Replies 66 66 Retweets 136 136 likes
Energy Regulator Acts to Improve Power Grid Security
21.10.2017 securityweek CyberCrime
With growing concern over nation-state cyber attacks comes an increasing need to secure the critical infrastructure. In the Quadrennial Energy Review published in January 2017, the U.S. Energy Department wrote, “Cyber threats to the electricity system are increasing in sophistication, magnitude, and frequency.” The reliability of the electric system underpins virtually every sector of the modern U.S. economy, it warned.
In response to such concerns, the Federal Energy Regulatory Commission (FERC) yesterday proposed new cyber security management controls to enhance the reliability and resilience of the nation’s bulk electric system.Energy Regulator Acts to Improve Power Grid Security
“FERC proposes to approve Critical Infrastructure Protection (CIP) Reliability Standard CIP-003-7 (Cyber Security ñ Security Management Controls), which is designed to mitigate cyber security risks that could affect the reliable operation of the Bulk-Power System,” it announced.
The new standard will particularly improve on existing standards for access control, “by clarifying the obligations that pertain to electronic access control for low-impact cyber systems; adopting mandatory security controls for transient electronic devices, such as thumb drives and laptop computers; and requiring responsible entities to have a policy for declaring and responding to CIP exceptional circumstances related to low-impact cyber systems.”
The FERC statement also proposes that the North American Electric Reliability Corp (NERC) should develop criteria for mitigations against the risks resulting from any malware that could come from third-party transient devices. “These modifications will address potential gaps and improve the cyber security posture of entities that must comply with the CIP standards,” said FERC.
While there have been few known successful attacks against the U.S. critical infrastructure, concern has grown dramatically with increasing geopolitical tensions, and the more open attribution of specific cyber attacks to specific foreign nations. The activities of Russia, Iran and North Korea are concerning. Russia is openly blamed for the DNC breaches, NotPetya and the attacks against the Ukrainian power systems; North Korea has been blamed for the Sony breach and numerous attacks against South Korea; and Iran has been accused of attacks against aerospace and energy companies.
Locky Uses DDE Attack for Distribution
21.10.2017 securityweek Attack
While continuing to spread via spam emails sent by the Necurs botnet, the Locky ransomware has switched to new attack techniques in recent campaigns, in an attempt to evade detection and improve infection rate.
One of the methods involves the use of the Dynamic Data Exchange (DDE) protocol, which has been designed to allow Windows applications to transfer data between them. Consisting of a set of messages and guidelines, it uses shared memory to exchange data between applications.
Malicious actors found a way to use DDE with Office documents and automatically run malware without the use of macros. DDE, which allows an Office application to load data from another Office application, was replaced by Microsoft with Object Linking and Embedding (OLE), but continues to be supported.
The technique was previously observed being employed by the FIN7 hacking group in recent DNSMessenger malware attacks, and Internet Storm Center (ISC) handler Brad Duncan says it could also be associated with a Hancitor malware campaign spotted earlier this week.
Now, Duncan reveals that Locky too has adopted the use of Office documents and DDE for infection. Delivered through spam emails originating from Necurs, the documents were attached to messages posing as invoices.
The analyzed attack used a first-stage malware that achieved persistence on the compromised system. The Locky binary, on the other hand, was deleted post-infection.
The use of DDE for infection, however, is only one of the methods Locky employs. As Trend Micro points out, Necurs also distributed the ransomware through HTML attachments posing as invoices, Word documents embedded with malicious macro code or Visual Basic scripts (VBS), malicious URLs in spam emails, and VBS, JS, and JSE files archived via RAR, ZIP or 7ZIP.
“The continuous changes in Locky’s use of file attachments are its way of adjusting its tools to evade or bypass traditional security. But despite the seeming variety, there are common denominators in Locky’s social engineering, particularly in the email subjects and content. They appear to have the same old flavors, but with relatively different twists,” the security researchers explain.
Recent Necurs-fueled distribution campaigns were also observed dropping the TrickBot banking Trojan via the same attachments carrying Locky.
Booz Allen to Acquire AI-based Morphick
21.10.2017 securityweek IT
Contracting giant Booz Allen is to acquire cybersecurity firm Morphick. Few details have been made public -- there is no statement on the price involved nor the future of existing Morphick staff. Nevertheless, this seem to be a good fit for both companies, with Morphick gaining access to more customers, and Booz Allen moving further along its published plan to expand its commercial presence.
Morphick is located in Cincinatti with a staff of around 40 cybersecurity specialists. Booz Allen has its global headquarters in McLean, Virginia, and employs around 23,000 people. The acquisition is expected to close in the third quarter of Fiscal Year 2018, and is subject to customary closing conditions.
"The acquisition bolsters Booz Allen's growth strategy in its U.S. Commercial business, where the focus is on expanding clients' access to scalable, on-demand managed threat services. The addition of the Morphick team and technology further solidifies the firm's ability to solve increasingly advanced cyber challenges," said Horacio Rozanski, president and CEO of Booz Allen. "Under our long-term growth strategy, Vision 2020, Booz Allen has been moving closer to the center of our clients' missions, fusing our consulting heritage with expert capabilities in cyber, digital solutions, engineering and analytics," he added.
At least part of Morphick's technology comes from AI firm, Endgame. "The Morphick Managed EDR service, powered by Endgame," announced Endgame in January 2017, "combines Morphick's best-in-class managed detection and response services with Endgame's unparalleled EDR platform to provide customers with earliest prevention, accelerated detection and response, and automated hunt of next-gen attacks."
Booz Allen is moving straight to 'next-gen' threat detection with AI and machine-learning detection capabilities rather than signature-based detection -- and calls it 'an adaptive approach to threat detection'. "Morphick's technology is differentiated by an adaptive approach to threat detection that addresses the growing challenge of highly evolved cyber threats and determined attackers, empowering companies to protect themselves and respond more effectively," says Booz Allen. "The platform, which analyzes the motivation and actions of attackers to thwart their attacks, assists companies in mitigating the challenges of the shortage of skilled cyber professionals and limitations of traditional, static defenses."
Existing Morphick staff will also complement Booz Allen's current market presence. Describing its own alliance with Morphick, Endgame commented, "Core to the service offering are Morphick's seasoned security analysts and NSA-accredited incident response teams, whose deep expertise enables them to identify and terminate the efforts of latent attackers targeting organizations' intellectual property, business systems, or other key assets. These analysts will leverage Endgame's EDR platform to prevent, detect, and rapidly respond to advanced attacks without the reliance on signatures."
Endgame's involvement in Morphick technology will continue beyond the acquisition. "Endgame and Morphick are committed to continuing our relationship following the Booz Allen Hamilton transaction," an Endgame spokesperson told SecurityWeek. "Morphick has realized tremendous value for itself and its customers thanks to its use of the Endgame platform, and Morphick will continue to use and market the platform for their customers following the acquisition."
Unpatched Microsoft Word DDE Exploit Being Used In Widespread Malware Attacks
21.10.2017 thehackernews Vulnerebility

A newly discovered unpatched attacking method that exploits a built-in feature of Microsoft Office is currently being used in various widespread malware attack campaigns.
Last week we reported how hackers could leveraging an old Microsoft Office feature called Dynamic Data Exchange (DDE), to perform malicious code execution on the targeted device without requiring Macros enabled or memory corruption.
DDE protocol is one of the several methods that Microsoft uses to allow two running applications to share the same data.
The protocol is being used by thousands of apps, including MS Excel, MS Word, Quattro Pro, and Visual Basic for one-time data transfers and for continuous exchanges for sending updates to one another.
The DDE exploitation technique displays no "security" warnings to victims, except asking them if they want to execute the application specified in the command—although this popup alert could also be eliminated "with proper syntax modification."
Soon after the details of DDE attack technique went public, Cisco's Talos threat research group published a report about an attack campaign actively exploiting this attack technique in the wild to target several organisations with a fileless remote access trojan (RAT) called DNSMessenger.
Necurs Botnet Using DDE Attack to Spread Locky Ransomware
Now, hackers have been found using the Necurs Botnet—malware that currently controls over 6 million infected computers worldwide and sends millions of emails—to distribute Locky ransomware and TrickBot banking trojan using Word documents that leverage the newly discovered DDE attack technique, reported SANS ISC.
Locky ransomware hackers previously relied on macros-based booby-trapped MS Office documents, but now they have updated the Nercus Botnet to deliver malware via the DDE exploit and gain an ability to take screenshots of the desktops of victims.
"What’s interesting about this new wave is that the downloader now contains new functionality to gather telemetry from victims," Symantec said in a blog post.
"It can take screen grabs and send them back to a remote server. There’s also an error-reporting capability that will send back details of any errors that the downloader encounters when it tries to carry out its activities."
Hancitor Malware Using DDE Attack
Another separate malware spam campaign discovered by security researchers has also been found distributing Hancitor malware (also known as Chanitor and Tordal) using Microsoft Office DDE exploit.
Hancitor is a downloader that installs malicious payloads like Banking Trojans, data theft malware and Ransomware on infected machines and is usually delivered as a macro-enabled MS Office document in phishing emails.
How to Protect Yourself From Word DDE Attacks?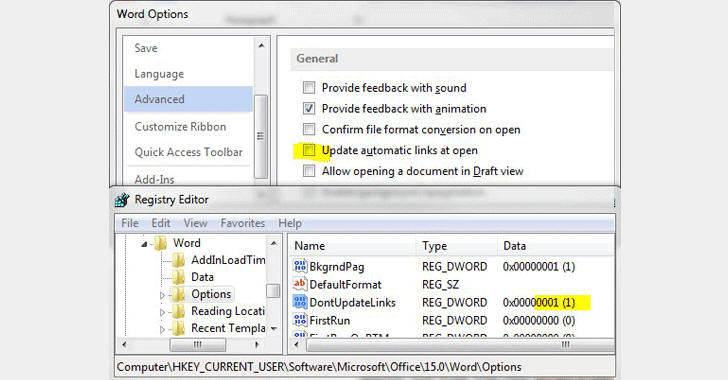
Since DDE is a Microsoft's legitimate feature, most antivirus solutions do not flag any warning or block MS Office documents with DDE fields, neither the tech company has any plans of issuing a patch that would remove its functionality.
So, you can protect yourself and your organisation from such attacks by disabling the "update automatic links at open" option in the MS Office programs.
To do so, Open Word → Select File → Options → Advanced and scroll down to General and then uncheck "Update Automatic links at Open."
However, the best way to protect yourself from such attacks is always to be suspicious of any uninvited document sent via an email and never click on links inside those documents unless adequately verifying the source.
Necurs botnet now spreading the Locky Ransomware via DDE Attacks
21.1.2017 securityaffairs BotNet
Operators behind Locky ransomware campaigns have switched to new attack techniques to evade detection leveraging the DDE protocol.
Security experts are continuing to observe the Locky ransomware spreading via spam campaigns that rely on the Necurs botnet. Now operators behind Locky ransomware campaigns have switched to new attack techniques to evade detection.
One of the new techniques adopted by the crooks is the use of the Dynamic Data Exchange (DDE) protocol designed to allow data transferring between applications.
“The DDE protocol is a set of messages and guidelines. It sends messages between applications that share data and uses shared memory to exchange data between applications. Applications can use the DDE protocol for one-time data transfers and for continuous exchanges in which applications send updates to one another as new data becomes available.” states Microsoft.

According to experts at the security firm Sensepost, attackers have devised a method to achieve the execution of malicious code embedded in Office documents without user’s interaction by using DDE.
The DDE protocol allows an Office application to load data from another Office application, it was replaced by Microsoft with Object Linking and Embedding (OLE), but it is still supported.
The technique was implemented by several threat actors such as the FIN7 APT group in DNSMessenger malware attacks, and the operators behind the Hancitor malware campaign spotted earlier this week and detailed by Internet Storm Center (ISC) handler Brad Duncan.
According to Duncan, the recent Locky campaign used spam messages with Office documents posing as invoices. The threat actors delivered the spam messages through the Necurs botnet.
The Necurs Botnet malspam pushes Locky using DDE technique, in a first-stage of the attack the malware achieved persistence on the compromised system, in the second stage the Locky ransomware infects the system.
“I opened one of the Word documents in my lab environment and found a 1st stage malware (presumably a downloader) and a 2nd stage malware (Locky) during the infection. Today’s diary reviews the traffic and malware.” wrote Duncan.
According to the experts at Trend Micro, The Locky ransomware was also spread by the Necurs botnet through HTML attachments posing as invoices, Word documents embedded with malicious macro code or Visual Basic scripts (VBS), malicious URLs in spam emails, and VBS, JS, and JSE files archived via RAR, ZIP or 7ZIP.
The use of DDE for infection, however, is only one of the methods Locky employs. As Trend Micro points out, Necurs also distributed the ransomware through HTML attachments posing as invoices, Word documents embedded with malicious macro code or Visual Basic scripts (VBS), malicious URLs in spam emails, and VBS, JS, and JSE files archived via RAR, ZIP or 7ZIP.
Some of the recent lures observed by the experts at Trend Micro are:
Fake voice message notifications (vishing, or the use of voice-related systems in phishingattacks)
HTML attachments posing as invoices
Archive files masquerading as business missives from multinationals, e.g., audit and budget reports
Fraudulent emails that involve monetary transactions such as bills, parcel/delivery confirmations, and payment receipts
A new Mirai-Like IoT Botnet is growing in a new mysterious campaign
21.1.2017 securityaffairs BotNet
Malware researchers at Check Point have uncovered a new massive IoT botnet that presented many similarities with the dreaded Mirai.
The new thing bot emerged at the end of September and appears much more sophisticated, according to the experts the malware already infected more than one million organizations worldwide.
The malicious code tries to exploit many known-vulnerabilities in various IP camera models, including GoAhead, D-Link, TP-Link, AVTECH, NETGEAR, MikroTik, Linksys, and Synology.
The experts speculate that the malware once compromised a device use it to spread itself.
“With each passing day the malware was evolving to exploit an increasing number of vulnerabilities in Wireless IP Camera devices such as GoAhead, D-Link, TP-Link, AVTECH, NETGEAR, MikroTik, Linksys, Synology and others. It soon became apparent that the attempted attacks were coming from many different sources and a variety of IoT devices, meaning the attack was being spread by the IoT devices themselves.” reads the report published by Check Point.

“So far we estimate over a million organizations have already been affected worldwide, including the US, Australia and everywhere in between, and the number is only increasing,” continues Check Point.
While investigating the compromise of a GoAhead device the experts noticed that the attackers accessed the System.ini file. This file would contain the credentials of the user, but on the compromised IoT device it contained a ‘Netcat’ command to open a reverse shell to the attacker’s IP.
The attackers triggered the CVE-2017-8225 to hack into the IoT device. The experts verified that the botnet relies on compromise bots to sending out the infection.
“These attacks were coming from many different types of devices and many different countries, totaling approximately 60% of the corporate networks which are part of the ThreatCloud global network,” Check Point notes.

The security researchers provided a list of IoT devices targeted by the malware, even if the attackers’ motivation is unclear experts speculate the botnet could be used to power DDoS attacks.
Visa Makes Biometrics Easier for Financial Institutions
20.10.2017 securityweek Safety
The acceptance and adoption of biometrics as a primary or second factor in multi-factor authentication has been considerably slower than expected. There are signs now, however, that it is finally gathering pace. Apple has long included TouchID with the iPhone, and has now added FaceID to the new iPhone X. It is particularly strong in the financial sector: HSBC and MasterCard allow selfies; Barclays allows voice authentication; and the Bank of Montreal allows selfies or fingerprints.
Now, payment giant Visa has announced the launch of a new platform, Visa ID Intelligence. It will allow Visa card issuers, acquirers and merchants to adopt new biometric methods of their own preference. Users are becoming more comfortable with using biometrics; but the technology is not without critics.
Passwords alone are no longer considered adequate: they are too easily stolen or guessed. Furthermore, they do not prove the identity of the user, only ownership of the password. One-time passwords sent to the user via a separate channel are more secure, but very inconvenient with a high friction factor for the user.
Biometrics solve many of these problems: they prove identity and have a very low user friction factor -- but they can still be stolen if stored in an external database. “Traditional methods for authenticating a customer can create frustration or are simply not designed for the new ways people are shopping and paying,” explained Mark Nelsen, senior vice president of risk and authentication products at Visa. “We built Visa ID Intelligence to help accelerate smarter and easy-to-use authentication solutions for any commerce environment -- to better protect against fraud and to move closer to a world without passwords.”
Visa launches new biometrics platform
The platform currently has two features: ID documents and biometrics. The document side can prove identity by matching a 'selfie' to a photo ID (such as a driver's license, a passport or a military ID). The purpose is to allow financial institutions to make faster and smarter decisions. Uses include creating new accounts, requesting and issuing replacement cards, and an alternative to support calls for password resets.
The biometrics feature allows Visa's clients to choose and use biometric authentication such as eyes, face, voice or fingerprints for consumer authentication. The intention is to increase speed and reduce user friction while improving security.
Visa ID Intelligence is currently partnering with Daon, a privately held biometric software firm. “Visa ID Intelligence is revolutionary in both scope and implementation, and will benefit consumers who are growing more and more frustrated by an antiquated password system,” said Tom Grissen, CEO, Daon. “Visa understands it is critical to provide both security and convenience, and that's what Daon delivers through our proven biometrics platform, IdentityX.”
However, not all security experts are completely happy with biometrics as a form of authentication. One problem is that they may not be as secure as we are told. “The security and reliability of biometric authentication,” Tom Van de Wiele, F-Secure's principal security consultant, told SecurityWeek, “has being overplayed by industry for quite some time.” One concern is that all biometrics can be spoofed.
“Biometric authentication as part of the ‘something you are’ property of access control,” he said, “can be used against you. For example, asleep on the plane someone can re-use your finger; your picture might be taken from Facebook and used against a facial recognition technology; and your voice can be recorded from any source the attacker has access to.” His concern is that biometrics (something you are) still needs to be supported by a PIN or password (something you know).
Van de Wiele points to a further problem with biometrics. Biometrics shifts the burden of security onto the user. It is “asking the customer to keep their iris/fingerprints/voice safe and that is not something people care about or even think about.”
Another problem is persistence. “Biometric data, unlike a username or password, is persistent: we carry it with us for life,” explains Kaspersky Lab's principal security researcher, David Emm. “There's one major downside to its use - stored by a service provider, biometric data is just as valuable as a database containing usernames and passwords. However, any security breach resulting in leakage of this information is likely to have much more serious consequences than the theft of a password: after all, we can change a weak password, but we can't change a compromised fingerprint, iris scan or other biometric.”
The recent Equifax breach illustrates the cybersecurity quandary. Although the primary cause of the breach is linked to a failure to adequately patch a vulnerable system, Comodo subsequently reported, “From third-party (non-company system) sources, we uncovered that Equifax's chief privacy officer, CIO, VP of PR and VP of Sales, used all lowercase letters, no special symbols, and easily guessable words like spouses' names, city names, and even combinations of initials and birth year. This reveals that they didn't follow basic security best practices and were lacking a complex password requirement.”
This demonstrates the weakness in password authentication -- but it also demonstrates its primary strength. If those executives were aware that their passwords had been stolen, they could very easily change them. However, the danger in the data stolen from Equifax is primarily in the persistence of the data: birthdates, Social Security numbers, addresses, last names. None of these are easily changed, and criminals can use them as part of identity theft for many years to come. The same applies to biometrics.
The bottom line is that financial institutions need to be easier to use than their competitors or lose customers to those competitors. “The trade-off is between security and usability, and this is a hard choice,” says Van de Wiele.
Google Offers Bonus Bounties for Flaws in Popular Android Apps
20.10.2017 securityweek Security
Google announced on Thursday that it’s prepared to offer a bonus of $1,000 to researchers who find serious vulnerabilities in some of the popular applications present on Google Play.
The new Google Play Security Reward Program was launched by Google in partnership with HackerOne. For the time being, the project only covers a handful of applications whose developers have opted in to the program.
The list includes Alibaba’s AliExpress, Dropbox, Mail.ru, Snapchat, Tinder, the Duolingo language learning app, meditation app Headspace, and the Line messenger app. All of the Android apps developed by Google itself are also eligible for a bonus reward. Other applications may be added in the future.
Researchers who discover a serious vulnerability in one of these Android apps need to report their findings to the respective developer via their HackerOne page or their self-managed bug bounty program. Once the flaw has been fixed, the bounty hunter can request a bonus reward from Google via its Play Security Reward Program.
For the time being, only remote code execution vulnerabilities are eligible for the $1,000 bonus, but other types of security holes may be added in the future. The report must include a proof-of-concept (PoC) and it must work on Android 4.4 and later, but it’s not required to achieve a sandbox escape.
Google noted that the bonus bounty needs to be requested within 90 days of a patch being made available by the developer.
“The program is limited to a select number of developers at this time to get initial feedback. Developers can contact their Google Play partner manager to show interest,” Google employees said in a blog post. “All developers will benefit when bugs are discovered because we will scan all apps for them and deliver security recommendations to the developers of any affected apps.”
Flaws found in Google’s own Android apps can be reported via the Google Vulnerability Reward Program and there is no need to separately request the bonus bounty once the issue has been addressed.
Russian Hackers Exploit Recently Patched Flash Vulnerability
20.10.2017 securityweek Exploit
The Russia-linked cyber espionage group known as APT28 has been using a recently patched Adobe Flash Player vulnerability in attacks aimed at government organizations and aerospace companies, security firm Proofpoint reported on Thursday.
The Flash Player flaw in question, CVE-2017-11292, was patched by Adobe on October 16. At the time when the patch was released, the vulnerability had a zero-day status, as it had been exploited in targeted attacks by a Middle Eastern threat actor named BlackOasis to deliver FinFisher spyware.
APT28, which is also known as Fancy Bear, Pawn Storm, Strontium, Sofacy, Sednit and Tsar Team, started launching attacks using CVE-2017-11292 on October 18, Proofpoint said. It’s unclear if APT28 discovered the exploit on its own, purchased it, or reverse engineered the one used in the BlackOasis attack.
Nevertheless, Proofpoint pointed out that the cyberspies are likely trying to take advantage of the recently fixed vulnerability before Adobe’s patch is widely deployed by users.
The attacks observed by the security firm were aimed at organizations in the United States, Europe and other countries. The targets included foreign government organizations with responsibilities similar to the U.S. State Department, and private-sector aerospace companies.
The messages delivering the exploits were highly targeted and they were sent out using free email services, Proofpoint said. The attackers leveraged malicious documents and their previously known Flash Player exploit platform named DealersChoice to deliver the first-stage implant, specifically a reconnaissance tool.
While CVE-2017-11292 affects Windows, Mac and Linux systems, APT28 apparently only launched attacks against Windows users. Tests conducted by researchers showed that the exploit works on systems with Windows 7 or Windows 10 with Microsoft Office 2013. The exploit, however, fails to execute on 64-bit systems running Windows 10 Fall Creators Update (RS3) and Office 2016.
“APT28 is a sophisticated state-sponsored group that is using the vulnerability to attack potentially high-value targets but it is likely that other threat actors will follow suit and attempt to exploit this vulnerability more widely, whether in exploit kits or via other attack vectors,” Proofpoint researchers explained.
The security firm has been working on taking down the command and control (C&C) domains used in these attacks.
Supply Chain Attack Spreads macOS RAT
20.10.2017 securityweek Apple
Proton, a remote access tool (RAT) that emerged in early 2017, has once again compromised a legitimate software’s distribution channel to spread, ESET warns.
Discovered in March this year, Proton was designed to execute any bash command under root, monitor keystrokes, upload/download files to/from the victim’s machine, grab screenshots or webcam captures, get updates, and also send notifications to the attacker. It can also help the attacker connect via SSH/VNC to the target machine.
In May, the malware’s operators managed to compromise a download mirror of the popular video converting tool HandBrake and configured it to distribute the RAT via a trojanized version of the legitimate app.
Now, the attackers were able to hack Eltima, the makers of the Elmedia Player software, and replaced the legitimate application binaries available for download with trojanized iterations. Thus, Eltima ended up distributing the OSX/Proton malware via their official website.
The attack was observed on Thursday, October 19, and Eltima was able to clean the infected application binaries within hours after being informed on the incident, ESET says.
All users who downloaded the Elmedia Player software recently should check their systems for possible compromise. For that, they should verify for the presence of the following files or directories: /tmp/Updater.app/, /Library/LaunchAgents/com. Eltima.UpdaterAgent.plist, /Library/.rand/, and /Library/.rand/updateragent.app/.
“If any of them exists, it means the trojanized Elmedia Player application was executed and that OSX/Proton is most likely running,” ESET notes.
Apparently only the application version downloaded through the company’s website was compromised, while the version distributed through the built-in automatic update mechanism was supposedly unaffected.
Once installed on a compromised machine, the malware can steal operating system details, browser information from Chrome, Safari, Opera, and Firefox (including history, cookies, bookmarks, and login data), cryptocurrency wallets (Electrum, Bitcoin Core, and Armory), SSH private data, macOS keychain data, Tunnelblick VPN configuration, GnuPG data, 1Password data, and a list of all installed applications.
Proton’s operators aren’t the only cybercriminals out there attempting to infect users via supply chain attacks. Last year, Mac Bittorrent client Transmission was hacked twice to spread the OSX/KeRanger ransomware and OSX/Keydnap password stealer, respectively.
Another incident of global impact was the compromise of the updater process of tax accounting software MEDoc to distribute the NotPetya wiper. Spreading fast to organizations worldwide, the attack resulted in millions of dollars in losses, as some organizations were unable to recover data following the incident.
Canada's CSE Spy Agency Releases Malware Analysis Tool
20.10.2017 securityweek BigBrothers
Canada’s Communications Security Establishment (CSE) agency announced this week that the source code for one of its malware detection and analysis tools has been made public.
The Python-based tool released as open source by the spy agency is named Assemblyline and it was created within the CSE’s Cyber Defence program. The organization says this is one of the tools it uses to protect the country’s computer systems against advanced cyber threats.
Assemblyline allows defenders to automate the analysis of malicious files. The analysis process, which has been compared to a conveyor belt, involves assigning a unique identifier to files as they travel through the system, looking for signs of malicious functionality and extracting features for further analysis, generating alerts for malicious files and assigning them a score, and sending data to other protection systems so that identified threats can be neutralized.Assemblyline
Users can also add their own analytics, including custom-built software and antiviruses, to enhance Assemblyline’s capabilities.
“The strength of Assemblyline is the ability of users to scale the system to their needs and the way that Assemblyline automatically rebalances its workload depending on the volume of files. It reduces the number of non-malicious files that security analysts have to inspect, and permits users to focus their time and attention on the most harmful files, allowing them to spend time researching new cyber defence techniques,” CSE said.
The Assemblyline source code is available on BitBucket. Organizations can modify it to suit their needs or integrate it into existing solutions.
The CSE is a security and intelligence organization focused on collecting intel in support of the government’s priorities, and protecting the country’s most critical computer networks. While the spy agency has often been described as “super secret,” some insight into its activities was revealed by documents leaked a few years ago by former NSA contractor and whistleblower Edward Snowden.
The documents showed that the CSE had been analyzing a foreign espionage operation that it had linked to French intelligence. The campaign has since been investigated by many researchers and cybersecurity firms.
The CSE is not the only spy agency to release open source tools. Last year, the UK’s Government Communications Headquarters (GCHQ) made available CyberChef, a tool that allows both technical and non-technical people to analyze encryption, compression and decompression, and data formats.
New Mirai-Linked IoT Botnet Emerges
20.10.2017 securityweek BotNet
A new, massive botnet is currently recruiting improperly secured Internet of Things (IoT) devices such as IP wireless cameras, Check Point warns.
Some of the technical aspects of the botnet, the security researchers say, reveal a possible connection to Mirai, which stormed the world a year ago. However, this is an entirely new threat and the campaign that is rapidly spreading worldwide is much more sophisticated.
The new threat first emerged at the end of September, but Check Point says that over one million organizations globally might have been already hit. What is yet unclear is the purpose of this massive network of ensnared devices.
To compromise devices, the malware attempts to exploit a large number of vulnerabilities commonly found in various IP camera models. Targeted vendors include GoAhead, D-Link, TP-Link, AVTECH, NETGEAR, MikroTik, Linksys, Synology and others.
Because the attempted attacks were coming from different sources and a variety of IoT devices, the researchers concluded that the compromised devices themselves were spreading the malware.
“So far we estimate over a million organizations have already been affected worldwide, including the US, Australia and everywhere in between, and the number is only increasing,” Check Point says.
The analysis of an infected device revealed that the attackers accessed the System.ini file to check for compromise. Normally, that file would contain the credentials of the user, but on the hacked device it contained a ‘Netcat’ command to open a reverse shell to the attacker’s IP instead.
Thus, the researchers concluded that the machine, a GoAhead device that was compromised using the CVE-2017-8225 vulnerability, was transmitting the infection after being infected itself.
“Upon further research, it was found that numerous devices were both being targeted and later sending out the infection. These attacks were coming from many different types of devices and many different countries, totaling approximately 60% of the corporate networks which are part of the ThreatCloud global network,” Check Point notes.
The security researchers provided a list of device types – per vendor – that are supposedly targeted by the botnet. They also suggest that the actor behind this threat might be getting ready for massive, global attacks, possibly distributed denial of service (DDoS).
With over 20 billion devices expected to be connected to the Internet by 2020, the threat of insecure IoT devices is growing bigger every day. Europol too warns of the security challenges this continuously expanding market faces.
“The Internet of Things is a wide and diverse ecosystem where interconnected devices and services collect, exchange and process data in order to adapt dynamically to a context. In simpler words, it makes our cameras, televisions, washing machines and heating systems ‘smart’ and creates new opportunities for the way we work, interact and communicate, and how devices react and adapt to us,” Europol says.
The agency also underlines the importance of properly securing these devices and of implementing adequate protections to keep IoT devices safe from cyber threats. Europol notes that the fast adoption of IoT also raised new legal, policy, and regulatory challenges that require cooperation across different sectors to tackle.
“Internet of Things is not only here to stay but expected to significantly expand as more and more households, cities and industries become connected. Insecure IoT devices are increasingly becoming tools for conducting cyber criminality. We need to act now and work together to solve the security challenges that come with the IoT and to ensure the full potential,” Rob Wainwright, Executive Director of Europol, commented.
Google Prompt Now Primary Choice for 2-Step Verification
20.10.2017 securityweek Security
Google has taken yet another step toward improving the security of its users by making Google prompt the primary choice for 2-Step Verification (2SV), instead of SMS.
Launched in June last year, Google prompt was designed to improve the security of the login process by informing users of any login attempts on accounts with 2SV enabled. Instead of receiving an SMS message, the user is greeted with a pop-up on the smartphone, and they can log in by simply clicking the “Yes” button.
Considering that it is a more secure 2SV method compared to SMS, Google started inviting users to enable Google prompt this July. The functionality is available for both Android and iOS users, and has been designed to deliver 2SV over an encrypted connection, in addition to providing options such as the blocking of unauthorized access attempts.
“Google prompt is an easier and more secure method of authenticating an account, and it respects mobile policies enforced on employee devices,” the Internet giant claims.
Now, the company has decided to push Google prompt to all users, and is making it the first 2SV choice for them, instead of SMS. Once they enable 2SV, however, users will still be able to use options such as SMS, the Google Authenticator app, backup codes, and Security Keys as their alternative second step.
The change, Google says, will only impact users who haven’t set up two-step verification yet, while those who have won’t be affected. Furthermore, users who attempt to set up 2SV but don’t have a compatible mobile device will be prompted to use SMS instead. To enable 2SV, users should head to their My Account page.
The use of Google prompt, the Internet company points out, requires a data connection. On iOS devices, the feature requires the Google app. For more advanced security requirements, Suite Enterprise domains can enforce Security Keys.
Google prompt is currently rolling out to all users, but it might take up to two weeks before it becomes available everywhere.
Watch out! European Consumer Organisation warns of some kid GPS smartwatches have security flaws
20.10.2017 securityaffairs Vulnerebility
Some kid smartwatches available for sale in Europe pose security and privacy risks, including potentially allowing hackers to take control over them.
The European Consumer Organisation (BEUC) warns that most children’s GPS-tracking smartwatches represent a threat for them. Many devices are affected by security vulnerabilities that could be exploited by an attacker to take control over the smartwatches, spy on conversations, or abuse the smartwatch camera to take picture and clips. An attacker can track GPS location, spoof GPS coordinates sent to watch’s paired app, misleading parents about the exact location of their children.
BEUC issued a public service announcement on the security and privacy risks related the children’s smartwatches. BEUC also pointed out that SOS button on some of these smartwatches is not reliable because hackers could replace the emergency phone number with their own.
The European Consumer Organization report has been drawn up by the Norwegian Consumer Council, it includes findings of security audits for popular brands of children’s smartwatches such as Gator 2, Tinitell, Viksfjord, and Xplora.
“What we see with these connected products is they are brought to the market too quickly, and they are not in line with EU laws when it comes to privacy and security,” said Johannes Kleis, the director of the communications department at BEUC.
Smartwatches represent a serious threat also for child’s privacy, vendors are potentially allowed to collect child data without giving parents the ability to monitor and stop these activities.
“These watches should not find their way into our shops,” Monique Goyens, Director General of BEUC, said in a press release.
“Parents buy them to protect their children. However, they are probably unaware that instead of protecting them they are making their children more vulnerable,” she added. “The EU urgently needs to regulate mandatory security standards for connected products. Producers should immediately fix these flaws or they should find their products withdrawn from the market.”
The security researcher Roy Solberg also published an analysis of the Gator 2 that includes details of security flaws he discovered.
“Gator Watch – a GPS watch for kids – is leaking data in all ends and anyone on the Internet can live track your kid. We’re not talking about a security vulnerability, we’re talking about non-existing security.” wrote Solberg.

Source: BBC
This isn’t the first time that security experts warn of dangers related to kid smartwatches, in February 2016, security firm Rapid7 published a report on a vulnerability found in hereO kids’ GPS-tracking watches.