
BlackOasis APT and new targeted attacks leveraging zero-day exploit
25.10.2017 Kaspersky
More information about BlackOasis APT is available to customers of Kaspersky Intelligence Reporting Service. Contact: intelreports@kaspersky.com
Introduction
Kaspersky Lab has always worked closely with vendors to protect users. As soon as we find new vulnerabilities we immediately inform the vendor in a responsible manner and provide all the details required for a fix.
On October 10, 2017, Kaspersky Lab’s advanced exploit prevention systems identified a new Adobe Flash zero day exploit used in the wild against our customers. The exploit was delivered through a Microsoft Office document and the final payload was the latest version of FinSpy malware. We have reported the bug to Adobe who assigned it CVE-2017-11292 and released a patch earlier today:
So far only one attack has been observed in our customer base, leading us to believe the number of attacks are minimal and highly targeted.
Analysis of the payload allowed us to confidently link this attack to an actor we track as “BlackOasis”. We are also highly confident that BlackOasis was also responsible for another zero day exploit (CVE-2017-8759) discovered by FireEye in September 2017. The FinSpy payload used in the current attacks (CVE-2017-11292) shares the same command and control (C2) server as the payload used with CVE-2017-8759 uncovered by FireEye.
BlackOasis Background
We first became aware of BlackOasis’ activities in May 2016, while investigating another Adobe Flash zero day. On May 10, 2016, Adobe warned of a vulnerability (CVE-2016-4117) affecting Flash Player 21.0.0.226 and earlier versions for Windows, Macintosh, Linux, and Chrome OS. The vulnerability was actively being exploited in the wild.
Kaspersky Lab was able to identify a sample exploiting this vulnerability that was uploaded to a multi scanner system on May 8, 2016. The sample, in the form of an RTF document, exploited CVE-2016-4117 to download and install a program from a remote C&C server. Although the exact payload of the attack was no longer in the C&C, the same server was hosting multiple FinSpy installation packages.
Leveraging data from Kaspersky Security Network, we identified two other similar exploit chains used by BlackOasis in June 2015 which were zero days at the time. Those include CVE-2015-5119 and CVE-2016-0984, which were patched in July 2015 and February 2016 respectively. These exploit chains also delivered FinSpy installation packages.
Since the discovery of BlackOasis’ exploitation network, we’ve been tracking this threat actor with the purpose of better understanding their operations and targeting and have seen a couple dozen new attacks. Some lure documents used in these attacks are shown below:
Decoy documents used in BlackOasis attacks
To summarize, we have seen BlackOasis utilizing at least five zero days since June 2015:
CVE-2015-5119 – June 2015
CVE-2016-0984 – June 2015
CVE-2016-4117 – May 2016
CVE-2017-8759 – Sept 2017
CVE-2017-11292 – Oct 2017
Attacks Leveraging CVE-2017-11292
The attack begins with the delivery of an Office document, presumably in this instance via e-mail. Embedded within the document is an ActiveX object which contains the Flash exploit.
Flash object in the .docx file, stored in uncompressed format
The Flash object contains an ActionScript which is responsible for extracting the exploit using a custom packer seen in other FinSpy exploits.
Unpacking routine for SWF exploit
The exploit is a memory corruption vulnerability that exists in the “com.adobe.tvsdk.mediacore.BufferControlParameters” class. If the exploit is successful, it will gain arbitrary read / write operations within memory, thus allowing it to execute a second stage shellcode.
The first stage shellcode contains an interesting NOP sled with alternative instructions, which was most likely designed in such a way to avoid detection by antivirus products looking for large NOP blocks inside flash files:
NOP sled composed of 0x90 and 0x91 opcodes
The main purpose of the initial shellcode is to download second stage shellcode from hxxp://89.45.67[.]107/rss/5uzosoff0u.iaf.
Second stage shellcode
The second stage shellcode will then perform the following actions:
Download the final payload (FinSpy) from hxxp://89.45.67[.]107/rss/mo.exe
Download a lure document to display to the victim from the same IP
Execute the payload and display the lure document
Payload – mo.exe
As mentioned earlier, the “mo.exe” payload (MD5: 4a49135d2ecc07085a8b7c5925a36c0a) is the newest version of Gamma International’s FinSpy malware, typically sold to nation states and other law enforcement agencies to use in lawful surveillance operations. This newer variant has made it especially difficult for researchers to analyze the malware due to many added anti-analysis techniques, to include a custom packer and virtual machine to execute code.
The PCODE of the virtual machine is packed with the aplib packer.
Part of packed VM PCODE
After unpacking, the PCODE it will look like the following:
Unpacked PCODE
After unpacking the virtual machine PCODE is then decrypted:
Decrypted VM PCODE
The custom virtual machine supports a total of 34 instructions:
Example of parsed PCODE
In this example, the “1b” instruction is responsible for executing native code that is specified in parameter field.
Once the payload is successfully executed, it will proceed to copy files to the following locations:
C:\ProgramData\ManagerApp\AdapterTroubleshooter.exe
C:\ProgramData\ManagerApp\15b937.cab
C:\ProgramData\ManagerApp\install.cab
C:\ProgramData\ManagerApp\msvcr90.dll
C:\ProgramData\ManagerApp\d3d9.dll
The “AdapterTroubleshooter.exe” file is a legitimate binary which is leveraged to use the famous DLL search order hijacking technique. The “d3d9.dll” file is malicious and is loaded into memory by the legit binary upon execution. Once loaded, the DLL will then inject FinSpy into the Winlogon process.
Part of injected code in winlogon process
The payload calls out to three C2 servers for further control and exfiltration of data. We have observed two of them used in the past with other FinSpy payloads. Most recently one of these C2 servers was used together with CVE-2017-8759 in the attacks reported by FireEye in September 2017. These IPs and other previous samples tie closely to the BlackOasis APT cluster of FinSpy activity.
Targeting and Victims
BlackOasis’ interests span a wide gamut of figures involved in Middle Eastern politics and verticals disproportionately relevant to the region. This includes prominent figures in the United Nations, opposition bloggers and activists, and regional news correspondents. During 2016, we observed a heavy interest in Angola, exemplified by lure documents indicating targets with suspected ties to oil, money laundering, and other illicit activities. There is also an interest in international activists and think tanks.
Victims of BlackOasis have been observed in the following countries: Russia, Iraq, Afghanistan, Nigeria, Libya, Jordan, Tunisia, Saudi Arabia, Iran, Netherlands, Bahrain, United Kingdom and Angola.
Conclusions
We estimate that the attack on HackingTeam in mid-2015 left a gap on the market for surveillance tools, which is now being filled by other companies. One of these is Gamma International with their FinFisher suite of tools. Although Gamma International itself was hacked by Phineas Fisher in 2014, the breach was not as serious as it was in the case of HackingTeam. Additionally, Gamma had two years to recover from the attack and pick up the pace.
We believe the number of attacks relying on FinFisher software, supported by zero day exploits such as the ones described here will continue to grow.
What does it mean for everyone and how to defend against such attacks, including zero-day exploits?
For CVE-2017-11292 and other similar vulnerabilities, one can use the killbit for Flash within their organizations to disable it in any applications that respect it. Unfortunately, doing this system-wide is not easily done, as Flash objects can be loaded in applications that potentially do not follow the killbit. Additionally, this may break any other necessary resources that rely on Flash and of course, it will not protect against exploits for other third party software.
Deploying a multi-layered approach including access policies, anti-virus, network monitoring and whitelisting can help ensure customers are protected against threats such as this. Users of Kaspersky products are protected as well against this threat by one of the following detections:</p style=”margin-bottom:0!important”>
PDM:Exploit.Win32.Generic
HEUR:Exploit.SWF.Generic
HEUR:Exploit.MSOffice.Generic
More information about BlackOasis APT is available to customers of Kaspersky Intelligence Reporting Service. Contact: intelreports@kaspersky.com
Acknowledgements
We would like to thank the Adobe Product Security Incident Response Team (PSIRT) for working with us to identify and patch this vulnerability.
References
Adobe Bulletin https://helpx.adobe.com/security/products/flash-player/apsb17-32.html
Indicators of compromise
4a49135d2ecc07085a8b7c5925a36c0a
89.45.67[.]107
ATMii: a small but effective ATM robber
25.10.2017 Kaspersky Virus
While some criminals blow up ATMs to steal cash, others use less destructive methods, such as infecting the ATM with malware and then stealing the money. We have written about this phenomenon extensively in the past and today we can add another family of malware to the list – Backdoor.Win32.ATMii.
ATMii was first brought to our attention in April 2017, when a partner from the financial industry shared some samples with us. The malware turned out to be fairly straightforward, consisting of only two modules: an injector module (exe.exe, 3fddbf20b41e335b6b1615536b8e1292) and the module to be injected (dll.dll, dc42ed8e1de55185c9240f33863a6aa4). To use this malware, criminals need direct access to the target ATM, either over the network or physically (e.g. over USB). ATMii, if it is successful, allows criminals to dispense all the cash from the ATM.
exe.exe – an injector and control module
The injector is an unprotected command line application, written in Visual C with a compilation timestamp: Fri Nov 01 14:33:23 2013 UTC. Since this compilation timestamp is from 4 years ago – and we do not think this threat could have gone unnoticed for 4 years – we believe it is a fake timestamp. What’s also interesting is the OS that is supported by the malware: One more recent than Windows XP. We can see this in the image below, where the first argument for the OpenProcess() function is 0x1FFFFu.
OpenProcess call with the PROCESS_ALL_ACCESS constant
It is the PROCESS_ALL_ACCESS constant, but this constant value differs in older Windows versions such as Windows XP (see the picture below). This is interesting because most ATMs still run on Windows XP, which is thus not supported by the malware.
A list of PROCESS_ALL_ACCESS values per Windows version
The injector, which targets the atmapp.exe (proprietary ATM software) process, is fairly poorly written, since it depends on several parameters. If none are given, the application catches an exception. The parameters are pretty self-explanatory:
param short description
/load Tries to inject dll.dll into atmapp.exe process
/cmd Creates/Updates C:\ATM\c.ini file to pass commands and params to infected library
/unload Tries to unload injected library from atmapp.exe process, while restoring its state.
/load param
<exe.exe> /load
The application searches for a process with the name atmapp.exe and injects code into it that loads the “dll.dll” library (which has to be in the same folder as the exe.exe file). After it has been loaded it calls the DLLmain function.
/unload param
<exe.exe> /unload
As the name already suggests, it is the opposite of the /load parameter; it unloads the injected module and restores the process to its original state.
/cmd param
<exe.exe> /cmd [cmd] [params]
The application creates/updates C:\ATM\c.ini which is used by the injected DLL to read commands. The file is updated each time the .exe is run with the /cmd param.
Contents of c.ini after execution of “exe.exe /cmd info”
The executable understands the following set of commands:
command description
scan Scans for the CASH_UNIT XFS service
disp Stands for “dispense”. The injected module should dispense “amount” cash of “currency” (amount and currency are used as parameters)
info Gets info about ATM cash cassettes, all the returned data goes to the log file.
die Injected module removes C:\ATM\c.ini file
dll.dll injecting module
After injection and execution of the DllMain function, the dll.dll library loads msxfs.dll and replaces the WFSGetInfo function with a special wrap function, named mWFSGetInfo.
At the time of the first call to the fake WFSGetInfo function, C:\ATM\c.ini is ignored and the library tries to find the ATM’s CASH_UNIT service id and stores the result, basically in the same way as the scan command does. If the CASH_UNIT service is not found, dll.dll won’t function. However, if successful, all further calls go to the mWFSGetInfo function, which performs the additional logic (reading, parsing and executing the commands from the C:\ATM\c.ini file).
Contents of C:\ATM\c.ini after execution of “exe.exe /cmd disp RUB 6000”
Below is an output of the strings program uncovering some interesting log messages and the function names to be imported. The proprietary MSXFS.DLL library and its functions used in the ATMii malware are marked with red boxes.
“scan” command
Because of the architecture of XFS, which is divided into services, the injected library first needs to find the dispense service. This command must be successfully called, because the disp and info commands depend on the service id retrieved by scan. Scan is automatically called after the dll has been injected into atmapp.exe.
After collecting the WFS_INF_CDM_STATUS data, additional data gets added to the tlogs.log. An example can be found below:
…
(387):cmd_scan() Searching valid service
(358):FindValidService() Checking device index=0
(70):CheckServiceForValid() ————————————————
(72):CheckServiceForValid() Waiting for lock
(76):CheckServiceForValid() Device was locked
(86):CheckServiceForValid() WFSGetInfo Success 0
(182):CheckServiceForValid() Done-> szDevice: WFS_CDM_DEVONLINE, szDispenser: WFS_CDM_DISPOK, szIntermediateStacker: WFS_CDM_ISEMPTY, szSafeDoor: WFS_CDM_DOORCLOSED
(195):CheckServiceForValid() Unlocking device
(390):cmd_scan() Service found 0
…
Part of a tlogs.log possible log after successfully executed “scan” command
“info” command
Before the criminals can dispense cash, they first need to know the exact contents of the different cassettes. For this, they use the info command which provides exhaustive information on all cassettes and their contents. The list of used XFS API functions is the same as with the scan command, but this time WFSGetInfo is called with the WFS_INF_CDM_CASH_UNIT_INFO (303) constant passed as a param.
Below is an example of the data in log file returned by the info command.
…
(502):ExecuteCmd() Executing cmd
(506):ExecuteCmd() CMD = info
(402):cmd_info() ! hFoundGlobalService = 0
(213):GetDeviceInformation() ————————————————
(220):GetDeviceInformation() Device locked 0
(337):GetDeviceInformation() Module: C:\program files\dtatmw\bin\atmapp\atmapp.exe
Cash Unit # 1, name=SOMENAME
Type: 3
Status: HIGH
Currency ID: 0x52-0x55-0x42
Note Value: 5000
Notes Count: 3000
Notes Initial Count: 3000
Notes Minimum Count: 10
Notes Maximum Count: 0
…
Example5 Part of a tlogs.log possible log after successfully executed “info” command
“disp” command
The dispense command is followed by two additional params in the command file: currency and amount. Currency must contain one of the three-letter currency codes of notes kept in the CASH_UNIT_INFO structure (currency codes are described in ISO_4217 e.g. RUB, EUR). The amount code holds the amount of cash to dispense and this value must be a multiple of ten.
“die” command
Does nothing except deleting C:\ATM\c.ini command file.
Conclusion
ATMii is yet another example of how criminals can use legitimate proprietary libraries and a small piece of code to dispense money from an ATM. Some appropriate countermeasures against such attacks are default-deny policies and device control. The first measure prevents criminals from running their own code on the ATM’s internal PC, while the second measure will prevent them from connecting new devices, such as USB sticks.
ATM malware is being sold on Darknet market
25.10.2017 Kaspersky Virus
Disclaimer and warning
ATM systems appear to be very secure, but the money can be accessed fairly easily if you know what you are doing. Criminals are exploiting hardware and software vulnerabilities to interact with ATMs, meaning they need to be made more secure. This can be achieved with the help of additional security software, properly configured to stop the execution of non-whitelisted programs on ATMs.
Worryingly, it is very easy to find detailed manuals of ATM malware. Anybody can simply buy them for around 5000 USD on darknet markets.
More information about CutletMaker ATM malware is available to customers of Kaspersky Intelligence Reporting Service. Contact: intelreports@kaspersky.com
Introduction
In May 2017, Kaspersky Lab researchers discovered a forum post advertising ATM malware that was targeting specific vendor ATMs. The forum contained a short description of a crimeware kit designed to empty ATMs with the help of a vendor specific API, without interacting with ATM users and their data. The post links to an offer that was initially published on the AlphaBay Darknet marketplace, which was recently taken down by the FBI.
Advertisement post
An offer post on AlphaBay market
The price of the kit was 5000 USD at the time of research. The AlphaBay description includes details such as the required equipment, targeted ATMs models, as well as tips and tricks for the malware’s operation. And part of a detailed manual for the toolkit was also provided.
Screenshot of a description on AlphaBay market
Previously described ATM malware Tyupkin was also mentioned in this text. The manual “Wall ATM Read Me.txt” was distributed as a plain text file, written in poor English and with bad text formatting. The use of slang and grammatical mistakes suggests that this text was most likely written by a native Russian-speaker.
Apart of a manual with text formatting applied
The manual provides a detailed picture, though only a fragment of the complete manual is being shown. There is a description for each step of the dispense process:
Prepare an all tools, all the programs should be placed on a flash disk.
Tools are wireless keyboard, usb hub, usb cable, usb adapter usb a female to b female, Windows 7 laptop or a tablet ( to run code generator) and a drill.
Find an appropriate ATM
Open ATM door and plug into USB port.
Execute Stimulator to see full information of all the ATM cassettes.
Execute CUTLET MAKER to get it is code.
Execute password generator on a tablet or on a laptop and paste CUTLET MAKER code to it, put the result password to CUTLET MAKER.
Dispense the money from chosen cassette.
The manual provides usage descriptions for all parts of the toolset. The list of crimeware from the kit consists of CUTLET MAKER ATM malware, the primary element, with a password generator included and a Stimulator – an application to gather cash cassette statuses of a target ATM. The crimeware kit is a collection of programs possibly written by different authors, though CUTLET MAKER and Stimulator were protected in the same way, c0decalc is a simple terminal-based application without any protection at all.
Delicious cutlet ingredients: CUTLET MAKER, c0decalc and Stimulator
The first sample was named “CUTLET MAKER” by its authors and has been designed to operate the cash dispense process on specific vendor ATMs.
To answer the question of how a cook from the CUTLET MAKER interface and cutlets relate to stealing money from ATMs, we must explain the meaning of the word “Cutlet“. Originally, it means a meat dish, but as a Russian slang term “Cutlet” (котлета) means “a bundle of money”, suggesting that the criminals behind the malware might be native Russian speakers.
The “Cutlet Maker” malware functionality suggests that two people are supposed to be involved in the theft – the roles are called “drop” and “drop master”. Access to the dispense mechanism of CUTLET MAKER is password protected. Though there could be just one person with the c0decalc application needed to generate a password. Either network or physical access to an ATM is required to enter the code in the application text area and also to interact with the user interface.
Stimulator was possibly developed by the same authors. Its purpose is to retrieve and show the status information of specific vendor ATM cash cassettes (such as currency, value and the amount of notes).
CUTLET MAKER and c0decalc
CUTLET MAKER is the main module responsible for dispensing money from the ATM. The sample analysed in this research has the MD5 checksum “fac356509a156a8f11ce69f149198108” and the compilation timestamp Sat Jul 30 20:17:08 2016 UTC.
The program is written in Delphi and was packed with VMProtect, however it is possible that multiple packers might have been used.
Different versions of the main component were found while researching this toolset. The first known submission of the first version sent to a public multiscanner service took place on June 22nd 2016. All submissions discovered by Kaspersky Lab were performed from different countries, with Ukraine being the chronological first country of origin.
Known CUTLET MAKER filenames (according to public multiscanner service information):
cm.vmp.exe
cm15.vmp.exe
cm16F.exe
cm17F.exe
The following version information was captured from the application’s window caption, followed after a “CUTLET MAKER” name. Known versions at the time of research were:
1.0
1.02
1.0 F
The assumed development period is from 2016-06-22 to 2016-08-18, according to the first submission date of the earliest version and the last submission date of the latest version at the time of writing. The application requires a special library to operate, which is part of a proprietary ATM API, controlling the cash dispenser unit.
With all the dependencies in place, the interface shows a code.
CUTLET MAKER challenge code marked with red rectangle
In order to unlock the application, a password from c0decalc generator needs to be entered, thereby answering the given challenge code. If the password is incorrect, the interface won’t react to any further input.
Each “CHECK HEAT” and “start cooking!” button corresponds to a specific ATM cash cassette. Buttons labeled “CHECK HEAT” dispense one note, “start cooking!” dispenses 50 “cutlets” with 60 notes each. The “Stop!” button stops an ongoing “start cooking!” process. “Reset” is intended to reset the dispense process.
c0decalc a password generator for CUTLET MAKER
This tool is an unprotected command line application, written in Visual C. The purpose of this application is to generate a password for CUTLET MAKER’s graphical interface.
The compilation timestamp for this specific sample is Sun Nov 13 11:35:25 2016 UTC and was first uploaded to a public multiscanner service on December 7th 2016.
Example output for “12345678” input
Kaspersky Lab researchers checked the algorithm during the analysis and found “CUTLET MAKER” working with the passwords generated by “c0decalc”.
Stimulator
The Stimulator sample analysed in this research has the MD5 hash “27640bb7908ca7303d13d50c14ccf669”. This sample is also written in Delphi and packed the same way as “CUTLET MAKER”. The compilation timestamp is Sat Jul 16 18:34:47 2016 UTC.
The application is designed to work on specific vendor ATMs and also uses proprietary API calls.
Some additional symbols were found in the memory dump of a “Stimulator” process, pointing to an interesting part of the application. After execution and pressing the “STIMULATE ME!” button, the proprietary API function is used to fetch an ATM’s cassette status. The following cassette state results are used:
1CUR
2CUR
3CUR
4CUR
1VAL
2VAL
3VAL
4VAL
1NDV
2NDV
3NDV
4NDV
1ACT
2ACT
3ACT
4ACT
Each preceding number is mapped to an ATM cassette. The three character states are interpreted as follows:
nCUR cassette n currency (like “USD”, “RUB”)
nVAL cassette n note value (like 00000005, 00000020 )
nACT cassette n counter for specific notes in a cassette (value from 0 to 3000)
nNDV number of notes in the ATM for cassette n (value from 0 to 3000)
The result of “STIMULATE ME!” button press in proper environment
Each column, shown in the picture above, describes the state of one corresponding ATM cassette.
The background picture used in the application interface turns out to be quite unique, the original photo was posted on a DIY blog:
https://www.oldtownhome.com/2011/8/4/Knock-Knock-Whos-There-Merv-the-Perv/
Original picture as used in “Stimulator” application (photo by Alex Santantonio)
Conclusion
This type of malware does not affect bank customers directly, it is intended for the theft of cash from specific vendor ATMs. CUTLET MAKER and Stimulator show how criminals are using legitimate proprietary libraries and a small piece of code to dispense money from an ATM. Examples of appropriate countermeasures against such attacks include default-deny policies and device control. The first measure prevents criminals from running their own code on the ATM’s internal PC. It is likely that ATMs in these attacks were infected through physical access to the PC, which means criminals were using USB drives to install malware onto the machine. In such a case, device control software would prevent them from connecting new devices, such as USB sticks. Kaspersky Embedded Systems Security will help to extend the security level of ATMs.
Kaspersky Lab products detects this threats as Backdoor.Win32.ATMletcut, Backdoor.Win32.ATMulator, Trojan.Win32.Agent.ikmo
The Festive Complexities of SIGINT-Capable Threat Actors
25.10.2017 Kaspersky Security
To read the full paper and learn more about this, refer to “Walking in Your Enemy’s Shadow: When Fourth-Party Collection Becomes Attribution Hell”
Attribution is complicated under the best of circumstances. Sparse attributory indicators and the possibility of overt manipulation have proven enough for many researchers to shy away from the attribution space. And yet, we haven’t even discussed the worst-case scenarios. What happens to our research methods when threat actors start hacking each other? What happens when threat actors leverage another’s seemingly closed-source toolkit? Or better yet, what if they open-source an entire suite to generate so much noise that they’ll never be heard?
Thankfully, the 2017 VirusBulletin conference is upon us and, as in previous years, we’re taking the opportunity to dive into an exciting subject, guided by our experience from doing hands-on APT research.
During the past years, we discussed the evolution of anti-malware research into intelligence brokerage, the inherent problems with doing attribution based solely on fifth-domain indicators, and an attempt to have a balanced discussion between defensive cats and the sly mice that elude them. Continuing in this direction, this year we decided to put our heads together to understand the implications that the esoteric SIGINT practice of fourth-party collection could have on threat intelligence research.
A few types of SIGINT Collection
The means by which information is generated and collected is the most important part of an analyst’s work. One must be well aware of the means and source of the information analyzed in order to either compensate or exploit its provenance. For that reason, collection can be categorized by its means of generation in relation to the position of the parties involved, as discussed below. These definitions will serve as functional categories for our understanding as outsiders looking into the more complex spheres of collection dynamics.
To showcase the types of data collection, let’s imagine a competent entity named ‘Agency-A’ as a stand-in for a ‘God on the wire‘-style SIGINT agency interested in fourth-party collection.
There are multiple types of collection categories available to this entity. The more obvious being information collected by Agency-A directly (first-party) or shared with Agency-A by partner services (second-party). Third-party collection, or information collected via access to strategic organizations, whether they realize it or not, has gotten a lot of attention over the past few years. This would include ISPs, ad networks, or social media platforms that aggregate great troves of valuable data.
Similarly, we will use further entities Agency-B as a second semi-competent SIGINT agency upon which Agency-A can be recurringly predatory for the sake of explanation. When necessary an even less competent Agency-C will serve as prey.
Yet, things get most interesting when we start talking about:
“Fourth-party collection – …involves interception of a foreign intelligence service’s ‘computer network exploitation’ (CNE) activity in a variety of possible configurations. Given the nature of Agency-A as a cyber-capable SIGINT entity, two modes of fourth-party collection are available to it: passive and active. The former will take advantage of its existing visibility into data in transit either between hop points in the adversary’s infrastructure or perhaps in transit from the victim to the command-and-control servers themselves (whichever opportunity permits). On the other hand, active means involve the leveraging of diverse CNE capabilities to collect, replace, or disrupt the adversary’s campaign. Both present challenges we will explore in extensive detail further below.”
In less technical terms, fourth-party collection is the practice of spying on a spy spying on someone else. Or with age-old cryptographic interlocutors: Bob is obsessed with Alice. Alice is being spied on by her overzealous neighbour Eve. In order for Bob to be a creeper without arousing suspicion, he decides to spy on Eve with the purpose of getting to know Alice through Eve’s original privacy violation.
As you might expect there are different ways to do this and many of them enjoy the benefit of being near impossible to detect. Where possible, we have added examples of what to us looks like possible active attempts to collect on another’s collection. Otherwise, we have added thought experiments to help us wrap our heads around this shadowy practice. Two examples worth bringing to your attention (reproduced faithfully from our paper):
‘We heard you like popping boxes, so we popped your box so we can watch while you watch’
Attempting to highlight examples of fourth-party collection is a difficult exercise in the interpretation of shadows and vague remnants. While passive collection is beyond our ability to observe, active collection involves the risk of leaving a footprint in the form of artefacts. In the course of APT investigations, Kaspersky Lab’s Global Research and Analysis Team (GReAT) has encountered strange artefacts that defy immediate understanding in the context of the investigation itself. While we cannot be certain of the intent or provenance of these artefacts, they nonetheless fit a conceptual framework of active fourth-party collection. Here’s a few examples:
Crouching Yeti’s Pixelated Servers
In July 2014, we published our research on Crouching Yeti, also known as ‘Energetic Bear’, an APT actor active since at least 2010. Between 2010 and 2014, Crouching Yeti was involved in intrusions against a variety of sectors, including:
Industrial/machinery
Manufacturing
Pharmaceutical
Construction
Education
Information technology
Most of the victims we identified fell into the industrial and machine manufacturing sector, indicating vertical of special interest for this attacker.
To manage their victims, Crouching Yeti relied on a network of hacked websites which acted as command-and-control servers. For this, the attackers would install a PHP-based backend that could be used to collect data from or deliver commands to the victims. To manage the backend, the attackers used a control panel (also written in PHP) that, upon checking login credentials, would allow them to manage the information stolen from the victims.
In March 2014, while investigating one of the hacked sites used by Energetic Bear, we observed that for a brief period of time, the page for the control panel was modified to include an <img src> tag that pointed to a remote IP address in China. This remote 1×1 pixels wide image was likely intended to fingerprint the attackers as they logged into their control panel. The fingerprinting could have been used to collect attributory indicators. The usage of an IP address in China, which appeared to point to yet another hacked server, was most likely an attempt at a rudimentary false flag should this injection be discovered.
NetTraveler’s Most Leet Backdoor
While investigating the Nettraveler attacks, we obtained a disk image of a mothership server used by the threat actor. The mothership, a combination staging and relay server, contained a large number of scripts used by the attackers to interact with their malware, as well as VPN software and other IP masking solutions used to tunnel into their own hacking infrastructure.
Beyond the fortuitous boon of seizing such a content-rich server, GReAT researchers made a further unexpected discovery: the presence of a backdoor apparently placed by another entity.
We believe the backdoor was installed by an entity intent on maintaining prolonged access to the Nettraveler infrastructure or their stolen data. Considering that the NetTraveler operators had direct access to their mothership server and didn’t need a backdoor to operate it, we consider other possible interpretations less likely.
The artefact encountered is the following:
Name svchost.exe
MD5 58a4d93d386736cb9843a267c7c3c10b
Size 37,888
Interestingly, the backdoor is written in assembly and was injected into an empty Visual C executable that served as a template. This unusual implementation was likely chosen in order to confuse analysis or prevent detection by simple antivirus programs.
The backdoor is primitive and does nothing but listen to port 31337 (The most ‘LEET!’ port) and wait for a payload to be sent. The acceptable payload format is depicted here:
The assembly code is then executed and can perform any action chosen by the predatory attackers. The backdoor requires no authentication. Combining this sort of backdoor with Metasploit or other similar frameworks could have easily been used to control the system.
During the last years, we have seen a number of other peculiar incidents and cases which could constitute fourth party collection.”
To read the full paper and learn more about this, refer to “Walking in Your Enemy’s Shadow: When Fourth-Party Collection Becomes Attribution Hell”
Thirty Percent of CEO Email Accounts Exposed in Breaches: Study
25.10.2017 securityweek Spam
Thirty percent of CEOs from the world's largest organizations have had their company email address and password stolen from a breached service. Given the continuing tendency for users to employ simple passwords and reuse the same passwords across multiple accounts, the implication is that at least some of these CEOs are at risk of losing their email accounts to cyber criminals or foreign nation state hacking groups.
The statistic comes from a report (PDF) published today by F-Secure, whose researchers checked the email addresses of 200 CEOs from the world's largest organizations against a database of leaked credentials. It notes that the 30% figure increases to 63% for tech companies.
Email accounts are highly valuable to cybercriminals, often containing sensitive information. A case in point is the hack and breach of Colin Powell's Gmail account in 2016 and the public exposure of his candid thoughts during the presidential campaign. In one email, for example, he comments, “and [Hillary Clinton] once again looks shifty if not a liar.” Researchers have suggested that Powell's account was breached because he may have used the same email password as he had for his Dropbox account -- details of which were leaked just a few weeks previously.
Business email compromise (BEC) attacks also become very compelling if the finance director receives a transfer instruction that originates from the CEO's genuine email account.
F-Secure found, unsurprisingly, that the top breached services to which CEOs linked their company email addresses were the professional networking site, LinkedIn, and Dropbox. Together they account for 71% of the CEOs.

But it's not just email addresses and password hashes that are exposed in leaked breaches. Eighty-one percent of the CEOs, say the researchers, “have their emails and other details such as physical addresses, birthdates and phone numbers exposed in the form of spam lists and leaked marketing databases.” A mere 18% of CEO email addresses are not associated with any leak or hack.
The reality is that the CEO's email account is a prized target for attackers, and CEOs need to take particular care over protecting them. One approach is to use a private account and personal phone number to disguise the company association -- but F-Secure warns that there are drawbacks in terms of defense in the later stages of the kill chain.
“When using a private email, a personal phone number or a home address to register for a service that the CEO uses to conduct official business, the CEO effectively denies the company's IT, communications, IPR, legal, and security teams a chance to protect the credentials, monitor their misuse or attempts to compromise them and makes it nearly impossible to recover them later,” comments F-Secure CISO, Erka Koivunen. “To an attacker, a CEO who uses private email to register for a service they use in an official capacity, spells a loner - someone who goes it alone and doesn't bother to rely on his/her staff to provide protection.”
The bottom line is that CEOs and their companies need to take particular care in protecting their email account passwords. F-Secure's advice is well-known good password practice. Use unique, long, illogical passwords that do not comprise words that could be found in hackers' word lists. Use a password manager to generate them (but, “Be wary of cloud-based password managers that don’t require access to the device in order to log into them”). Avoid social logins (if you lose the social media account, all of the associated accounts are also lost). Always use multi-factor authentication where it is available (avoiding SMS passcodes if possible: “Offline authenticators or hardware-based tokens are always preferred”).
Key is the password itself. “Use fully random password strings that are as long as a particular service allows, typically 32 characters,” F-Secure Labs lead researcher Jarno Niemela told SecurityWeek. “Passwords like these are secure as long as the service provider is not storing passwords in plain text;” absent, he adds, the possibility of an intelligence agency with a really big budget which could, theoretically, find an MD5 collision.
Even this remote possibility could be limited, he says, if the service provider makes strong efforts to protect the passwords. “Password cracking,” that is, obtaining the plaintext password from a stolen hash, “can be pretty much eliminated by using forced computation, also known as key stretching. This means that the service uses PBKDF2, scrypt, bcrypt or some other scheme that iterates the password hash verification up to millions of times. It effectively makes password cracking millions of times slower -- and even relatively simple passwords will become rather unfeasible, provided that they are not directly in some word list.”
Kaspersky May Have Found How Russian Hackers Stole NSA Data
25.10.2017 securityweek BigBrothers
Security firm Kaspersky Lab has shared preliminary results from its investigation following media reports that Russian hackers used its software to steal sensitive NSA data from a contractor’s computer back in 2015.
The Wall Street Journal reported earlier this month that a threat group working for the Russian government stole information on how the U.S. hacks foreign networks and how it defends against cyberattacks. The files were allegedly taken in 2015 from the personal computer of an NSA contractor who had been using a security product from Kaspersky Lab.
The article suggested that Kaspersky either knowingly helped the Russian government obtain the files or that the hackers exploited vulnerabilities in the company’s software without the firm knowing about the attack.
Kaspersky immediately launched an internal investigation into the matter and it has now shared preliminary results.
Kaspersky revealed in June 2015 that its own systems had been breached as part of an attack involving Duqu 2.0 malware, which has been linked to Israeli intelligence. The company’s latest investigation has found no evidence of additional intrusions.
As for the 2015 event reported by WSJ, the starting point of Kaspersky’s investigation is an APT-related incident that occurred in 2014. At the time, the company’s systems detected what appeared to be source code for malware used by the Equation Group, a threat actor believed to be associated with the NSA. At this point, the firm had not made its Equation Group research available to the public.
A Kaspersky home product had detected what appeared to be new Equation Group malware samples on a device in the United States. The antivirus had been configured to automatically send new malware samples back to the company for analysis.
The user in question later intentionally downloaded malware-laden piracy software, specifically a Microsoft Office key generator, and temporarily disabled the Kaspersky product on the machine as it would have prevented the installation of the tool. The malware, detected as Backdoor.Win32.Mokes.hvl, remained on the device for an unspecified period and it opened a backdoor on the system, giving hackers easy access to the computer.
When the antivirus was re-enabled, it detected both Backdoor.Win32.Mokes.hvl and other pieces of malware linked to the Equation Group. One of the files, a 7zip archive, was automatically sent to Kaspersky Lab for analysis, but the company’s CEO, Eugene Kaspersky, ordered the removal of the files from all systems after determining that it was Equation malware source code. The files were not shared with third parties before being deleted, Kaspersky said.
According to the company, no other malware was detected by its products on that device in 2015. After the activities of the Equation Group were made public by the company in February 2015, Equation Group malware was detected on several other IPs in the same range as the initial infection, but the devices appeared to be configured as honeypots and Kaspersky said it did not process the detections in any special way.
The company said it did not detect any other related incident since. It also claimed that an analysis of its software confirmed that it had not created any detection rules for non-malicious documents containing keywords such as “classified” or “top secret” – this aims to reinforce its initial statement that it does not intentionally spy for the Russian government.
Kaspersky also pointed out that it routinely informs the U.S. government about active APT attacks detected in the county.
“We believe the above is an accurate analysis of this incident from 2014. The investigation is still ongoing, and the company will provide additional technical information as it becomes available,” Kaspersky said.
Several recent media reports focused on Kaspersky’s alleged connection to the Kremlin, which has led to many U.S. officials raising concerns regarding the use of company’s products. Last month, the Department of Homeland Security (DHS) ordered all government agencies to identify and remove the firm’s security products.
In an effort to clear its name, Kaspersky announced the launch of a new transparency initiative that involves giving partners access to source code and paying significantly larger bug bounties for vulnerabilities found in the firm’s products.
Offshore Legal Firm Appleby Hacked, financial details of rich clients is set to be released
25.10.2017 securityaffairs Hacking
The Financial details of some of the world’s richest people are set to be published after the Offshore Legal Firm Appleby suffered a data security incident.
A new financial data leak made the headlines, financial details of clients of an offshore a legal firm is set to be published. The news was reported on Wednesday by a British newspaper, the Bermuda-based offshore firm Appleby was hacked and data could be available online very soon.
The Telegraph reported the news saying “some of the world’s richest people were braced for their financial details to be exposed”.
“It is understood the leak involves some of Britain’s wealthiest people, who were instructing lawyers and public relations companies in an effort to protect their reputations,” added the newspaper.
The Offshore law firm Appleby confirmed it has received inquiries from the International Consortium of Investigative Journalists in relation to the leaked documents.
The Telegraph added that “global consortium of left-leaning media organisations” is set to release the information “in the coming days.”.
The ICIJ is a global network of investigative journalists that made the headlines in 2015 after the release of the Panama Papers, the huge trove of documents stolen from Panamanian law firm Mossack Fonseca.
The Appleby firm said the inquiries “have arisen from documents that journalists claim to have seen and involve allegations made against our business and the business conducted by some of our clients.”
“Appleby has thoroughly and vigorously investigated the allegations and we are satisfied that there is no evidence of any wrongdoing, either on the part of ourselves or our clients,” said the law firm, which has multiple offices in locations including Bermuda and the Cayman Islands.
“We refute any allegations which may suggest otherwise and we would be happy to cooperate fully with any legitimate and authorised investigation of the allegations by the appropriate and relevant authorities.”

The firm confirmed that the expected publication of sensitive documents is the result of a security incident occurred last year.
“We are committed to protecting our clients’ data and we have reviewed our cybersecurity and data access arrangements following a data security incident last year which involved some of our data being compromised,” the statement said. “These arrangements were reviewed and tested by a leading IT forensics team and we are confident that our data integrity is secure.”
At the time there are no details about the hack or system affected.
The Daily Telegraph added that Appleby is notifying the security breach to its customers, the law firm denied that any of the allegations leveled against its clients involved misconduct.
Last year, the ICIJ released the Panama Papers, it was an earthquake in financial and political elites.
Na Ukrajinu zaútočil zlý králík. Schytalo to kijevské metro i letiště v Oděse
25.10.2017 Živě.cz Kyber
Falešná aktualizace Flash PlayeruPřivítání zavirovaného počítačeDialog s odpočtem pro zaplacení výkupného skrze bitcoinZákeřný
Na některé země východní Evropy a Turecko zaútočil nová varianta ransomwaru Win32/Diskcoder.D (Not-Petya) s označením Bad Rabbit (zlý králík). Rozšiřuje se docela svižně, přičemž nejlépe se mu daří na Ukrajině a v Rusku. Ransomware například zašifroval některé počítače kijevského metra tamního ministerstva dopravy nebo třeba letiště v Oděse. Případy nakažení se podle Národního úřadu pro kybernetickou a informační bezpečnost a Esetu objevily i v Bulharsku, Turecku a Japonsku.
Rychlostí, jakou se Bad Rabbit šíří, připomíná podle expertů jarní kampaň ransomwaru WannaCry, který zasáhl i některé počítače v Česku. A s WannaCry má společný i postup útoku. Jakmile jej na počítači spustíte, zašifruje data a za odemknutí požaduje výkupné ve výši 0,05 bitcoinu, což po přepočtu činí okolo 6 000 korun.
Podzimní update Windows 10 přinesl nový Defender, který obsahuje dílčí ochranu před ransomwarem. Do vybraných složek se dostanou pouze povolené programy.
Podle Esetu se zlý králík šiří hlavně skrze falešné aktualizace Flash Playeru a protokol SMB (port 445) na Windows XP a vyšších.
„Účinnou prevencí (vakcinací) před nakažením ransomwarem Bad Rabbit je vytvoření souborů c:\windows\infpub.dat a c:\windows\cscc.dat a odebrání všech oprávnění k těmto souborům,“ píše na svých stránkách NÚKIB,
Roste trend kybernetické špionáže, varovalo Vojenské zpravodajství
25.10.2017 Novinky/Bezpečnost BigBrother
Vojenské zpravodajství v roce 2016 zaznamenalo rostoucí trend kybernetické špionáže. Soustředila se na získání tajných informací o obraně státu. Ve výroční zprávě za rok 2016 to uvedlo Vojenské zpravodajství (VZ). Píše v ní také, že cizí tajné služby získávaly spolupracovníky z řad občanských sdružení, nevládních organizací a zbrojního průmyslu, uvedlo Vojenské zpravodajství.
Podle zpravodajců zahraniční zpravodajské služby působily na českém území s posláním a úkoly, které odpovídaly velikosti Česka, jeho poloze a vojenskému významu jako členské země NATO. "Modus operandi" tajných služeb se podle Vojenského zpravodajství nezměnil. „Zpravodajské služby cizích mocí nadále tipovaly, rozpracovávaly a získávaly své spolupracovníky z řad občanských sdružení a spolků, nevládních a neziskových organizací a zaměstnanců působících ve zbrojním průmyslu," uvedlo VZ.
Cizí agenti se zaměřili na získávání citlivých údajů o záměrech Česka v oblasti obrany a o plánech na modernizaci české armády. „Vzhledem k otevřenosti našeho demokratického systému v přístupu k informacím shromažďovali příslušníci zpravodajských služeb, působící pod diplomatickým krytím, neutajované, avšak zpravodajsky využitelné informace o stavu obranyschopnosti a kritické infrastruktuře ČR," poznamenalo Vojenské zpravodajství.
Phishingové kampaně a vyděračský malware
Zaznamenali opět také rostoucí trend kybernetické špionáže, která se soustředila na získání utajovaných i citlivých informací související s obranou státu a jeho kritickou infrastrukturou. Zpravodajci podotkli, že mnohé kybernetické útoky byly velmi obtížně detekovatelné, často zůstávaly delší dobu neodhalené a bylo nesnadné identifikovat skutečné pachatele.
„Útočníci ke kybernetické špionáži zneužívali zranitelná místa informačních a komunikačních systémů, ale také lidského faktoru," uvedlo VZ. V České republice zaregistrovalo zejména phishingové kampaně nebo použití vyděračského malware. Na začátku letošního roku rozsáhlý kybernetický útok, který měl trvat měsíce, oznámilo české ministerstvo zahraničí.
Účinnost a nebezpečnost kybernetických útoků provedených teroristy a extremisty byly podle zpravodajců v roce 2016 na nízké úrovni. Internet používali hlavně pro získávání nových členů, pro propagandu a pro komunikaci.
Šéf FBI: Mírně řečeno, šifrování je obrovský, obrovský problém
25.10.2017 Živě.cz BigBrother
Šifrování se stává samozřejmou součástí práce s počítačem
Vyšetřovatelé i tajné služby se toho ale děsí
Podle šéfa FBI se schyluje k obrovskému problému
Ředitel FBI Christopher WrayŘeditel FBI Christopher WrayŠéf FBI: Mírně řečeno, šifrování je obrovský, obrovský problémŠéf FBI: Mírně řečeno, šifrování je obrovský, obrovský problémŠéf FBI: Mírně řečeno, šifrování je obrovský, obrovský problém10 FOTOGRAFIÍ
End-to-end šifrování, tedy šifrování, nad kterým nemá poskytovatel prakticky žádnou moc, se v posledních letech stává stále dostupnější funkcí jak na mobilních telefonech, tak zejména ve všemožných instantních komunikátorech.
Důvodů je celá řada počínaje všeobecným zvyšováním standardu zabezpečení napříč technologiemi (třeba zavádění HTTPS) a konče obecnými obavami z odposlechu, které před lety zesílila mimo jiné i aféra okolo Edwarda Snowdena a uniklých materiálů NSA.
Šifrování se stává normou
Z šifrování, na které jsme ještě před pár lety hleděli jako na speciální funkci pro speciální případy, se tak stává standardní součást komunikačních protokolů a naše internetová společnost je tím pádem i lépe zabezpečená proti útokům z všemožných stran.
Klepněte pro větší obrázek Klepněte pro větší obrázek Klepněte pro větší obrázek Klepněte pro větší obrázek Klepněte pro větší obrázek
End-to-end šifrování jako volitelná funkce v komunikátoru Facebook Messenger. Šifrovací klíč mají pouze koncové aplikace, provozovatel tedy obsah komunikace nemůže vidět, ani kdyby k tomu dostal soudní příkaz.
Jenže zároveň platí to B. Šifrování nás sice chrání třeba před nezvanými čtenáři naší pošty, nicméně stejně tak brání policejním orgánům po celém světě sbírat důkazy pro svá vyšetřování. Kdyby šly některé figury českých korupčních kauz jen trošku více s dobou a používaly ke komunikaci end-to-end šifrování, českou veřejnost by se nejspíše nikdy nebavily třeba memy s krabicí od vína.
Šéf FBI: Do poloviny zabavených mobilů se vůbec nedokážeme dostat
Prekérní situaci potvrzuje i americký úřad vyšetřování FBI, který se musí nejen s end-to-end šifrováním potýkat v mnohem větší míře než malé Česko. Nepříjemně to ilustrují čísla, se kterými se o víkendu pochlubil šéf úřadu Christopher Wray. Agenti FBI se během letošního roku nedostali do více než poloviny mobilních zařízení, ke kterým nezískali klíč a staly součástí vyšetřování.
Klepněte pro větší obrázek Klepněte pro větší obrázek
Kompletní šifrování telefonu na Androidu je sice k dispozici už roky, ve výchozím stavu je ale aktivní jen na několika modelech s dostatkem výkonu. Na iPhonech je dnes mnohem rozšířenější.
V absolutních číslech se jednalo o více než 6 900 mobilních telefonů. Pravděpodobně šlo především o iPhony, i když silné šifrování je k dispozici i na novějších verzích Androidu. Většinou je však ve výchozím stavu vypnuté – zvláště na slabších telefonech, protože si řekne o pořádný díl procesorového výkonu.
„Mírně řečeno, je to obrovský, obrovský problém“ – Christopher Wray, ředitel FBI
„To put it mildly, this is a huge, huge problem,“ popsal podle AP situaci Wray a dodal, že vestavěné end-to-end šifrování i podobné techniky zabezpečení v IM komunikátorech si oblíbila celá kriminální scéna počínaje drogovými dealery a konče těžkým organizovaným zločinem.
Bláznivý nápad: Šifrování, které nikdo neprolomí. Tedy až na stát
Nikdo přitom neví, jak takový problém vyřešit, a tak mnozí střílejí naslepo jako třeba americký zástupce nejvyššího žalobce Rod Rosenstein, který navrhuje jakési odpovědné šifrování (responsible encryption, PDF).
Mělo by se jednat o šifrování, které naprosto nikdo nerozlouskne... Tedy až na vyšetřovatele FBI. V případě end-to-end šifrování, kdy nemá klíč provozovatel, ale pouze majitel dat, telefonu aj., by to v praxi znamenalo, že by musel autor techniky zavést do systému zadní vrátka.
Vysoký federální úředník obhajuje princip zadních vrátek do šifrování
A jakmile jsou někde jakákoliv zadní vrátka, představuje to potenciální zranitelnost, kterou dříve či později rozlousknou hackeři – ať už ti hodní, nebo zlí. Suma sumárum, šifrování se zadními vrátky není principiálně bezpečné, nehledě na to, že by bylo hotovou parodií v jakémkoliv režimu, kde by jen náznakem hrozilo i riziko zneužití ze strany státu.
Neprolomitelné šifrování jako právo občana EU? Možná
Jasno v každém případě nemají pouze v USA, ale i na starém kontinentu. Zatímco fanoušci rychlých řešení volají v rámci boje proti terorismu po zákazu neprolomitelného šifrování, jiní chtějí naopak end-to-end šifrování povznést na úroveň práva obyvatel Evropské unie.
Právě s tím na jaře přišel Výbor pro občanské svobody, spravedlnost a vnitřní věci Evropského parlamentu a právo na šifrování chce dostat do evropské politiky elektronického soukromí (ePrivacy). V praxi by mohli Evropané šifrovat vše, co se jim zlíbí a nikdo by jim to neměl komplikovat jakýmikoliv zadními vrátky.
Podobné nápady se nicméně asi nebudou příliš zamlouvat telekomunikačním operátorům, kteří naopak na základě politik data retention ukládají data o uskutečněných hovorech aj. Na sklonku loňského léta proto prolétla médii zpráva, že by se legislativa data retention mohla jednou rozšířit i na webové služby, kterým by tak bylo elegantně znemožněno nasadit end-to-end šifrování, protože by nemohli ukládat metadata o uskutečněné komunikaci.
„Daň“ za svobodnou společnost
Surfaři však mohou zatím zůstat klidní, zůstalo pouze u slov, problém šifrování totiž skutečně už z principu nemá řešení a vyšetřovatelé ve svobodné a technologicky vyspělé společnosti budou nejspíše muset i nadále hledat jiné způsoby, jak získat důkazy. Na tom se ostatně na sklonku září shodli i experti na kybernetickou bezpečnost, kteří se sjeli na brněnskou konferenci CyberCon 2017.
Česká spořitelna varovala před novým útokem na bankovní účty
25.10.2017 Novinky/Bezpečnost Phishing
Počítačoví piráti neustále hledají cesty, jak se dostat na cizí bankovní účty. Tentokrát to zkouší přes zasílání zabezpečené zprávy uživatelům. Samozřejmě jde ale o podvod. Před novým typem útoku varovala Česká spořitelna.
Phishingový útok, při kterém počítačoví piráti doslova loví důvěřivé uživatele na udičku jako ryby, cílí právě na klienty spořitelny. Jeho cílem je vylákat přihlašovací údaje k internetovému bankovnictví, tedy ke službě Servis 24.
„Vy máte nové zprávy on-line. Chcete-li zobrazit svou zabezpečenou zprávu, přihlaste se do služby Internetového bankovnictví,“ tvrdí podvodníci vydávající se za bankéře v e-mailu, který v posledních dnech koluje českým internetem.

FOTO: Česká spořitelna
Pozornější uživatelé si na první pohled mohou všimnout, že zpráva je psaná s chybami a některá slova jsou dokonce špatně vyskloňovaná. Odkaz v e-mailu navíc nevede na oficiální stránky služby Servis 24, nýbrž na podvodný web, což je patrné z adresního řádku.
Po přihlášení kyberzločinci důvěřivcům tvrdí, že je potřeba aktualizovat kontaktní informace – právě to měla být ona důležitá zpráva. Pokud to důvěřivci skutečně udělají, jsou již jen krůček od vybílení bankovního účtu. Se znalostí telefonního čísla je totiž pro podvodníky hračkou vylákat od lidí potvrzovací SMS zprávu, pomocí které mohou například provádět peněžní transakce.
V ohrožení jsou přitom i jedinci, kteří nemají na bankovním účtu příliš mnoho financí. Útočníci mohou touto cestou sjednat bez vědomí majitele klidně i půjčku. A tyto peníze následně vyberou.
E-mail může přijít z jiné banky
Není navíc vyloučeno, že znění podvodné zprávy útočníci upraví a že začne kolovat internetem i bez gramatických chyb. Stejně tak mohou e-mail podvodníci cílit na klienty dalších českých bank.
Opatrnost je tedy na místě. „Buďte k podezřelým e-mailům velmi obezřetní, vždy se do SERVIS 24 přihlašujte ze stránek banky, případně přímo ze stránek www.servis24.cz. Zároveň buďte velmi obezřetní před zadáním jakéhokoliv SMS kódu a vždy pečlivě čtěte autorizační SMS zprávy,“ doporučili zástupci České spořitelny.
Ti zároveň zdůraznili, že lidé by neměli na zprávy reagovat. „Pokud máte podezření, že jste podvodný e-mail obdrželi, v žádném případě nereagujte na jeho obsah, neklikejte na odkaz, který je jeho součástí, a zprávu nám přepošlete na e-mailovou adresu phishing@csas.cz. Jestliže jste již na odkaz klikli a vyplnili požadované údaje, ihned kontaktujte klientskou linku České spořitelny na bezplatném telefonním čísle 800 207 207,“ uzavřeli zástupci spořitelny.
Hacker Hijacks CoinHive's DNS to Mine Cryptocurrency Using Thousands of Websites
25.10.2017 thehackernews Hacking
Hacker Hijacks CoinHive's DNS to Mine Cryptocurrency Using Thousands of Websites
When yesterday I was reporting about the sudden outbreak of another global ransomware attack 'Bad Rabbit,' I thought what could be worse than this?
Then late last night I got my answer with a notification that Coinhive has been hacked — a popular browser-based service that offers website owners to embed a JavaScript to utilise their site visitors' CPUs power to mine the Monero cryptocurrency for monetisation.
Reportedly an unknown hacker managed to hijack Coinhive's CloudFlare account that allowed him/her to modify its DNS servers and replace Coinhive's official JavaScript code embedded into thousands of websites with a malicious version.
https://coin-hive[.]com/lib/coinhive.min.js
Hacker Reused Leaked Password from 2014 Data Breach
Apparently, hacker reused an old password to access Coinhive's CloudFlare account that was leaked in the Kickstarter data breach in 2014.
"Tonight, Oct. 23th at around 22:00 GMT our account for our DNS provider (Cloudflare) has been accessed by an attacker. The DNS records for coinhive.com have been manipulated to redirect requests for the coinhive.min.js to a third party server." Coinhive said in a blog post today.
"This third-party server hosted a modified version of the JavaScript file with a hardcoded site key."
As a result, thousands of sites using coinhive script were tricked for at least six hours into loading a modified code that mined Monero cryptocurrency for the hacker rather than the actual site owners.
"We have learned hard lessons about security and used 2FA [Two-factor authentication] and unique passwords for all services since, but we neglected to update our years old Cloudflare account."
Your Web-Browsers Could Be Mining Cryptocurrencies Secretly for Strangers
Coinhive gained media attention in last weeks after world's popular torrent download website, The Pirate Bay, caught secretly using this browser-based cryptocurrency miner on its site.
Immediately after that more than thousands of other websites also started using Coinhive as an alternative monetisation model by utilising their visitors' CPU processing power to mine digital currencies.
Even hackers are also using Coinhive like services to make money from compromised websites by injecting a script secretly.
Well, now the company is also looking ways to reimburse its users for the lost revenue due to breach.
How to Block Websites From Hijacking Your CPU to Mine Cryptocoins
Due to concerns mentioned above, some Antivirus products, including Malwarebytes and Kaspersky, have also started blocking Coinhive script to prevent their customers from unauthorised mining and extensive CPU usage.
You can also install, No Coin Or minerBlock, small open source browser extensions (plug-ins) that block coin miners such as Coinhive.
DUHK Attack Lets Hackers Recover Encryption Key Used in VPNs & Web Sessions
25.10.2017 thehackernews Attack
DUHK — Don't Use Hard-coded Keys — is a new 'non-trivial' cryptographic implementation vulnerability that could allow attackers to recover encryption keys that secure VPN connections and web browsing sessions.
DUHK is the third crypto-related vulnerability reported this month after KRACK Wi-Fi attack and ROCA factorization attack.
The vulnerability affects products from dozens of vendors, including Fortinet, Cisco, TechGuard, whose devices rely on ANSI X9.31 RNG — an outdated pseudorandom number generation algorithm — 'in conjunction with a hard-coded seed key.'
Before getting removed from the list of FIPS-approved pseudorandom number generation algorithms in January 2016, ANSI X9.31 RNG was included into various cryptographic standards over the last three decades.
Pseudorandom number generators (PRNGs) don’t generate random numbers at all. Instead, it is a deterministic algorithm that produces a sequence of bits based on initial secret values called a seed and the current state. It always generates the same sequence of bits for when used with same initial values.
Some vendors store this 'secret' seed value hard-coded into the source code of their products, leaving it vulnerable to firmware reverse-engineering.
Discovered by cryptography researchers — Shaanan Cohney, Nadia Heninger, and Matthew Green — DUHK, a 'state recovery attack,' allows man-in-the-middle attackers, who already know the seed value, to recover the current state value after observing some outputs.
Using both values in hand, attackers can then use them to re-calculate the encryption keys, allowing them to recover encrypted data that could 'include sensitive business data, login credentials, credit card data and other confidential content.'
"In order to demonstrate the practicality of this attack, we develop a full passive decryption attack against FortiGate VPN gateway products using FortiOS version 4." researchers said.
"Our scans found at least 23,000 devices with a publicly visible IPv4 address running a vulnerable version of FortiOS."
Here below you can check a partial list (tested by researchers) of affected devices from various vendors:
crack-prng-encryption-key
The security researchers have released a brief blog post and technical researcher paper on a dedicated website for DUHK attack.
Bad Rabbit: New Ransomware Attack Rapidly Spreading Across Europe
25.10.2017 thehackernews Ransomware
A new widespread ransomware attack is spreading like wildfire around Europe and has already affected over 200 major organisations, primarily in Russia, Ukraine, Turkey and Germany, in the past few hours.
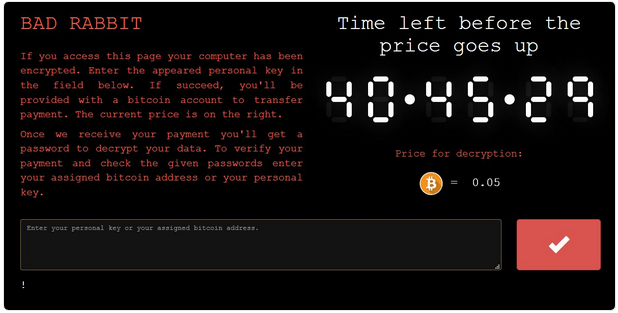
Dubbed "Bad Rabbit," is reportedly a new Petya-like targeted ransomware attack against corporate networks, demanding 0.05 bitcoin (~ $285) as ransom from victims to unlock their systems.
According to an initial analysis provided by the Kaspersky, the ransomware was distributed via drive-by download attacks, using fake Adobe Flash players installer to lure victims' in to install malware unwittingly.
"No exploits were used, so the victim would have to manually execute the malware dropper, which pretends to be an Adobe Flash installer. We’ve detected a number of compromised websites, all of which were news or media websites." Kaspersky Lab said.
However, security researchers at ESET have detected Bad Rabbit malware as 'Win32/Diskcoder.D' — a new variant of Petya ransomware, also known as Petrwrap, NotPetya, exPetr and GoldenEye.
Bad Rabbit ransomware uses DiskCryptor, an open source full drive encryption software, to encrypt files on infected computers with RSA 2048 keys.
bad-rabbit-ransomware
ESET believes the new wave of ransomware attack is not using EternalBlue exploit — the leaked SMB vulnerability which was used by WannaCry and Petya ransomware to spread through networks.
Instead it first scans internal network for open SMB shares, tries a hardcoded list of commonly used credentials to drop malware, and also uses Mimikatz post-exploitation tool to extract credentials from the affected systems.
The ransom note, shown above, asks victims to log into a Tor onion website to make the payment, which displays a countdown of 40 hours before the price of decryption goes up.
The affected organisations include Russian news agencies Interfax and Fontanka, payment systems on the Kiev Metro, Odessa International Airport and the Ministry of Infrastructure of Ukraine.
Researchers are still analyzing Bad Rabbit ransomware to check if there is a way to decrypt computers without paying ransomware and how to stop it from spreading further.
How to Protect Yourself from Ransomware Attacks?
Kaspersky suggest to disable WMI service to prevent the malware from spreading over your network.
Most ransomware spread through phishing emails, malicious adverts on websites, and third-party apps and programs.
So, you should always exercise caution when opening uninvited documents sent over an email and clicking on links inside those documents unless verifying the source to safeguard against such ransomware infection.
Also, never download any app from third-party sources, and read reviews even before installing apps from official stores.
To always have a tight grip on your valuable data, keep a good backup routine in place that makes their copies to an external storage device that isn't always connected to your PC.
Make sure that you run a good and effective anti-virus security suite on your system, and keep it up-to-date.
Bad Rabbit Linked to NotPetya, but Not as Widespread
25.10.2017 securityweek Ransomware
The Bad Rabbit ransomware attack that hit Russia and Ukraine on Tuesday has been linked to the recent NotPetya outbreak, but the number of infections appears to be far smaller.
Several cybersecurity firms have conducted an initial analysis of the threat, including Cisco Talos, Kaspersky, Malwarebytes, ESET, McAfee, Bitdefender and Trend Micro.
Bad Rabbit distribution
Researchers say the malware spreads via watering hole attacks that deliver a fake Flash Player installer. The malicious file has been delivered from compromised websites in Denmark, Ireland, Bulgaria, Turkey and Russia.
Researchers pointed out that victims need to manually launch the fake Flash installer to get infected, and the file needs to obtain administrative privileges, which causes Windows to display a User Account Control (UAC) prompt. The attackers have not made any effort to bypass UAC.
Once executed, the dropper copies the main module (infpub.dat) to the Windows folder and executes it through rundll32.exe, a Windows component used to run code in DLL files. Scheduled tasks, which have been given dragon names from the “Game of Thrones” TV show, are used to execute other malware components and reboot the system.
The ransom note is displayed in both text files dropped onto the system and via a bootlocker screen.
Bad Rabbit
Similar to NotPetya, Bad Rabbit does appear to rely on SMB to spread, but, contrary to initial reports, it does not use the NSA-linked EternalBlue exploit.
The malware scans the internal network for open SMB shares with a specific name. The threat relies on the Mimikatz post-exploitation tool to harvest credentials, but it also includes a hardcoded list of usernames and passwords.
Bad Rabbit file encryption
Once it infects a system, Bad Rabbit encrypts more than 100 file types, including archives, backups, databases, images, documents, source code, and virtual disk images. The encrypted files are given a .encrypted extension. Kaspersky’s Costin Raiu pointed out that the file types are similar to the ones targeted by NotPetya, but not identical.
Bad Rabbit clears security logs and deletes the update sequence number (USN) change journal, which logs all changes made to files on the volume, to prevent recovery.
The encryption relies on DiskCryptor, an open source full disk encryption software, and the attackers have used the AES-128-CBC cipher and an RSA-2048 public key.
It’s still unclear if files can be recovered without paying the ransom. However, unlike NotPetya, which made it impossible to decrypt files even if the ransom had been paid, researchers confirmed that data encrypted by Bad Rabbit is recoverable with the right key.
Victims are asked to pay 0.05 bitcoin, worth roughly $280, to get their files back, but the amount increases if the ransom is not paid within two days.
A majority of the victims are in Russia, where the ransomware hit several media outlets, including Interfax and Fontanka. A significant number of Infections has also been observed in Ukraine, where the malware reportedly hit the airport in Odessa, the Kiev subway, the State Aviation Service of Ukraine, and the Transport Ministry of Ukraine. Infections have also been spotted in Bulgaria, Turkey, Germany, Japan and other countries.
Some of the organizations whose systems have been compromised reported suffering significant disruptions.
Unlike the NotPetya attack, which hit tens of thousands of systems in more than 65 countries, Kaspersky reported that it had only seen roughly 200 victims. The security firm believes this may have been a targeted attack aimed at corporate networks.
Bad Rabbit links to NotPetya
Several security firms have classified Bad Rabbit as a variant of NotPetya, the malware that hit numerous organizations in late June and caused losses of millions of dollars for several major companies. NotPetya has also been tracked as Diskcoder, Petya, Petrwrap, exPetr and GoldenEye.
While NotPetya initially also appeared to be a piece of ransomware, researchers noticed that the encrypted files could not have been recovered even if the ransom had been paid. The malware was later reclassified as a wiper.
The list of similarities between NotPetya and Bad Rabbit includes the fact that both use SMB to spread, they create scheduled tasks to reboot the system, the ransom screen is very similar, both use .dat files as the main component, and some of the functionality and code is almost identical.
On the other hand, unlike NotPetya, Bad Rabbit does not use the EternalBlue exploit, its encryption functionality works properly and a more advanced crypter is used, it uses a different kernel and bootloader, and the attacks appear to have been more targeted. Another significant difference is the fact that NotPetya was delivered via a Ukraine-based company’s update server, while Bad Rabbit leverages drive-by attacks.
DUHK Attack allows attackers recover encryption keys used to secure VPN connections and web browsing sessions
25.10.2017 securityaffairs Attack
DUHK is a vulnerability that allows attackers to recover secret encryption keys used to secure VPN connections and web browsing sessions
After the disclosure of the KRACK and ROCA attacks, another attack scenario scares IT community. It is the DUHK vulnerability (Don’t Use Hard-coded Keys), it is the last cryptographic implementation vulnerability that could be exploited by attackers to recover encryption keys used to secure VPN connections and web browsing sessions.
The DUHK vulnerability was reported by the cryptography researchers Shaanan Cohney, Nadia Heninger, and Matthew Green.
The group researchers have published technical details about the attack on a dedicated website.
“DUHK (Don’t Use Hard-coded Keys) is a vulnerability that affects devices using the ANSI X9.31 Random Number Generator (RNG) in conjunction with a hard-coded seed key.” wrote the researchers.
“The ANSI X9.31 RNG is an algorithm that until recently was commonly used to generate cryptographic keys that secure VPN connections and web browsing sessions, preventing third parties from reading intercepted communications.”
The DUHK vulnerability affects a wide range of products from dozens of vendors, including CISCO, Fortinet, and TechGuard. The vulnerability affects every device the relies on the outdated pseudorandom number generation algorithm ANSI X9.31 RNG ‘in conjunction with a hard-coded seed key.’
The bad news is that the ANSI X9.31 RNG was included into several cryptographic standards over the last three decades until January 2016 when it was removed from the list of FIPS-approved pseudorandom number generation algorithms.
The problem is related to the fact that Pseudorandom number generators are not able to generate random numbers and the knowledge of initial secret value (seed) could be used to determine the number generated by the algorithm.
Unfortunately, some vendors store the seed value hard-coded into the source code of their solutions. An attacker can obtain the seed by a reverse-engineering of the source code of the products.
The DUHK is described as ‘state recovery attack,’ an attacker with the knowledge of the seed value can power a man-in-the-middle attack to recover the current state value after observing some outputs.
Attackers can then use the values to re-calculate the encryption keys and decrypt data potentially exposing sensitive data, including login credentials, credit card data, and other confidential information.
“In order to demonstrate the practicality of this attack, we develop a full passive decryption attack against FortiGate VPN gateway products using FortiOS version 4.” researchers said.
“Our scans found at least 23,000 devices with a publicly visible IPv4 address running a vulnerable version of FortiOS.”
Below a partial list of affected devices tested by the researchers:

Further technical details are included in the paper “Practical state recovery attacks against legacy RNG implementations.”
Bad Rabbit ransomware rapidly spreads, Ukraine and Russia most targeted countries
25.10.2017 securityaffairs Ransomware
A new strain of malware dubbed Bad Rabbit ransomware has been found rapidly spreading in Russia, Ukraine and elsewhere.
A new massive ransomware campaign is rapidly spreading around Europe, the malware dubbed Bad Rabbit has already affected over 200 major organizations mainly in Russia, Ukraine, Germany, Japan, and Turkey in a few hours.
The Bad Rabbit ransomware has infected several big Russian media outlets, the Interfax news agency and Fontanka.ru confirmed they were hit by the malware.
According to Kaspersky, the Odessa International Airport has reported on a cyberattack on its information system, but it is still unclear it is the same attack.
“In some of the companies, the work has been completely paralysed – servers and workstations are encrypted,” head of Russian cyber-security firm Group-IB, Ilya Sachkov, told the TASS news agency.
According to the malware experts, Bad Rabbit ransomware is Petya-like malware that is targeting corporate networks.
The malicious code demands 0.05 bitcoin ransom (~ $280) from victims to unlock their systems.
Experts from Kaspersky that analyzed the malware, believe the Dab Rabbit ransomware is spread via drive-by download attacks, attackers are using fake Adobe Flash players installer to trick victims into installing the malware.
“On October 24th we observed notifications of mass attacks with ransomware called Bad Rabbit. It has been targeting organizations and consumers, mostly in Russia but there have also been reports of victims in Ukraine. Here’s what a ransom message looks like for the unlucky victims:” reported Kaspersky Lab.

“No exploits were used, so the victim would have to manually execute the malware dropper, which pretends to be an Adobe Flash installer. We’ve detected a number of compromised websites, all of which were news or media websites.” continues the analysis published by Kaspersky Lab.
The experts from security firm ESET tracked the Bad Rabbit ransomware as ‘Win32/Diskcoder.D‘. According to ESET, the malware is a new variant of Petya ransomware. it relies on the open-source encryption software DiskCryptor, files are encrypted RSA 2048 keys.
The researchers excluded the new ransomware uses the EternalBlue exploit, instead, it first scans the target network for open SMB shares, tries to access them using hardcoded list of credentials to drop the malicious code, then uses the Mimikatz tool to extract credentials from the target.
“Win32/Diskcoder.D has the ability to spread via SMB. As opposed to some public claims, it does notuse the EthernalBlue vulnerability like the Win32/Diskcoder.C (Not-Petya) outbreak. First, it scans internal network for open SMB shares.” reads the analysis published by ESET.
“Mimikatz is launched on the compromised computer to harvest credentials. A hardcoded list username and password is also present.”

Jiri Kropac @jiriatvirlab
#ESET confirms Discoder/#Petya/#BadRabbit campaign live today, incorporating #Mimikatz distribuded via fake flash. More info soon.
4:42 PM - Oct 24, 2017
10 10 Replies 248 248 Retweets 147 147 likes
Twitter Ads info and privacy
Researchers from ESET reported that the payment website is hosted on the Tor network, the ransom note provided instructions to make the payment while displaying a countdown of 40 hours before the price of decryption increase.
Security experts are still analyzing the Bad Rabbit ransomware, meantime, malware researchers from Kaspersky are suggesting to disable WMI service to prevent the malware from spreading over the target network and to block the execution of files c:\windows\infpub.dat and c:\Windows\cscc.dat.
As usual stay vigilant when opening unsolicited mail containing documents or clicking on embedded links.
Credentials (UN)Management in home banking.
25.10.2017 securityaffairs Security
Introduction
Out of the five main information security pillars, namely confidentiality, integrity, availability, authenticity and irrefutability, common users give more attention to the first one. But in real life even though in general people agree with the importance of backup, not many actually implement this security mechanism. What one says and what one do is not the same.
Nowadays, the concern with espionage acts grew with Snowden´s case, and that fact can be easily checked with media coverage of the case. From the mass coverage media such as The Huffington Post, The Washington Post, through information security expert Bruce Schneier, all bring insight about the impact of the information disclosed by the former NSA employee.
With that in mind, one can ask himself the question “how secret is my secret?”.
This paper is a brief of the full research The leakage of passwords from home banking sites: A threat to global cyber security? –Jounal of Payments Strategy and Systems Vol 11 Number 2 By Rodrigo Ruiz; Rogério Winter; Kil Jin Brandini Park; Fernando Amatte
We Got Something…
Account information of various websites were recovered. AS A CLEAR TEXT!

Figure 1 – Citibank USA account information (“&username=userciti” and “&password=citipaswt”) recovered from disk.
Web Forms
Web forms defines the way users can interact with a website. The user enters some data, text or numbers in specific fields, clicks the submit button and waits for a response. All forms share this basic behavior and HTML commands are standard. Each development framework have its own way to generate forms, but they are not responsible to provide any kind of security on it.
A basic html web form will look like this:
HTML code
<form method="POST" action="">
<br>User : <input type="text" name="user" size="20">
<br>Password: <input type="password" name="password" size="20">
<br><input type="submit">
</form>
Considering this basic HTML form, one question remains: where is the security behind it?
Who Should Worry?
Users, developers, companies, and organizations of any size.
One should think about the implications of a password disclosure. The effects vary, according to the service, but ranges from espionage, sabotage and even unlawful money transfers.
Thus anyone that own, manage or use websites that requires identification and authentication should worry, since with this method if an attacker acquires access to the user machine he can easily search for those account information in a matter of hours.
Am I Really Protected?
Usually, the traffic of data is the main concern when the focus is in confidentiality. Thus, the encryption of the communication channel is largely used.
As an example, in the application network layer, the HTTPS protocol is used to provide that confidentiality.
Another safety measure is to forbid the use of weak passwords and to avoid plain text storage of passwords on servers.
But none of the above really matters if username and passwords are recorded as plain text on the client side. And in this paper, we proved that this happens with many internet web service providers.
How Was The Job Done?
First, it is important to notice that we need physical access to the disk for this method to work. We will discuss this matter further on the topic of possible protection from this flaw.
After navigation and authentication on the tested sites, we began by searching for a previously known string (the bogus password) on the disk. For the test performed we chose passwords that were not previously used on the tested machine in order to avoid false positives.
For that end we used a tool to search for strings on the disk with raw access, not caring for the particularities of the file structures or filesystem.
Making it Automatic
After the proof of concept, we tried to extract signatures for each service tested (websites visited).
We began with some bogus account information on various websites. With that, we extracted account signatures of some websites as see in Table 1:

Table 1 – Signature of the Account Identification for Some of the Tested Sites.
The signatures allowed the carving of data from the disk, through the usage of the Foremost program, a forensic tool for extraction of files – “data carving” – of different formats.
This tool works as follows: It reads a block of data in memory, disk or files and looks for signatures related to files of well-known formats. The search showed the possibility of unveiling username and password previously used on the system:
The tests are still happening, and the same results were gathered from other sites like webmail (Figure 2), banking, government and military sites:

Figure 2 – Login Information from Gmail (“mail?gxlu=inprivate.rfk%40gmail.com”)
Where Did We Find it?
In Internet Explorer´s case, the following directories and files contained the recovered information about authentication:
\users\user\appdata\local\microsoft\internet Explorer\recovery\last active\
\users\usuário\appdata\local\microsoft\windows\temporary internet files\low\content.ie5\
\Pagefile.sys
In Chrome, Firefox and Safari´s case, the only file that contained the recovered information about authentication was Pagefile.sys. That proves that in their case the leakage of login information is due to the operating system´s paging process.
In the tests conducted with a Brazilian banking site, the following files contained the recovered information about authentication:
\Program Data\gpplugin\cef\bank.gbl.??
\users\usuário\appdata\local\microsoft\windows temporary\wk9???\adsadclient31.htm
About the Inspiration of This Research
From some previous work, the authors demonstrated that the browser’s functionality that promises anonymous browsing (e.g Internet Explorer´s In Private, Firefox´s Private Browsing, Chrome´s Incognito Mode and Safari´s Private Mode) show in certain circumstances flaws that allow an attacker to extract information about sites visited by the users.
In the first paper, “Tornando Pública a Navegação In Private”(Making InPrivate Navigation as public), published on the proceedings of the seventh international conference on forensic computer science, we tested for several conditions the anonymous browsing functionality of the browsers Internet Explorer 8 and Firefox 8.0.1 running inside virtual machines. We were able to recover, using data carving forensic techniques, images and page fragments that allowed the identification of the pages visited by the users as see in Figure 3:

Figure 3 – One of the images recovered from disk after user navigation. The image was completely recovered but for copyright reasons is only partially displayed.
It is possible to see a fragment of a webpage recovered from disk after user navigation. Source: Tornando Pública a Navegação In Private (RUIZ, AMATTE and PARK).
<h2><a href=”http://www.simpsons.com.br/?p=148”
rel=”bookmark” title=”Permanent Link to Ned
Flanders e Edna Krabappel”>Ned Flanders e Edna
Krabappel</a></h2>
<div class=”post-title-info”>Autor: Felipe |
Categoria: <a href=”http://www.simpsons.com.br/?cat=5”
title=”Ver todos os posts em Informa
<p><ahref=”http://thesimpsons.com/nedna/”><img
src=”http://thesimpsons.com/nedna/collectibles/pronedna-
facebook-icon01.jpg” alt=”A favor” /></a> <a
href=”http://thesimpsons.com/nedna/”><img src=”http://
thesimpsons.com/nedna/collectibles/no-nedna-facebookicon01.
jpg” alt=”Contra” /></a></p>
This work was extended and published on the proceedings of the International Conference on Information Security and Cyber Forensics as Opening the “Private Browsing” Data – Acquiring Evidence of Browsing Activities. The paper included the following browsers: Internet Explorer 10, Firefox 24.0_1, Google Chrome 30.0.159969M_1 and Safari 5.1.7_1. The base guest virtual machine for each browser was replicated 4 times, each to be used in the four different tests performed on each browser:
Test S (Shutdown): Consists of visiting a web site available on the internet, making operations to interact with the site, finish the execution of the browser correctly and generating the virtual machine image for analysis.
Test F (Freeze): Consists of visiting a web site available on the Internet, making operations to interact with the site and with the browser still active, generating the virtual machine image for analysis.
Test K (Kill process): Consists of visiting a web site available on the internet, making operations to interact with the site, requesting that the operating system interrupts the browser execution and generating the virtual machine image for analysis.
Test P (Power down): Consists of visiting a web site available on the internet, making operations to interact with the site, requesting the virtualizer to turn off the virtual machine – simulating a power outage – generating the virtual machine image for analysis.
The results obtained showed no significant changes from the first research:
Table 2 – Results for Safari Browser
F Test K Test P Test S Test
Page address recover Yes Yes Yes Yes
Pic recover No Yes Yes Yes
Table 3 – Results for Fire Fox Browser
Teste F Teste K Teste P Teste S
Page address recover Yes Yes Yes Yes
Pic recover No Yes Yes Yes
Table 4 – Results for Chrome Browser
F Test K Test P Test S Test
Page address recover Yes Yes Yes Yes
Pic recover No Yes Yes Yes
Table 5 – Results for IE10
F Test K Test P Test S Test
Page address recovery Yes Yes No Yes
Pic recovery No No Yes No
How to Avoid It?
As previously stated, physical access to the disk is needed for this method. That could lead to the assumption that the use of cryptography would render the method useless. But this is not entirely true.
It is easy to notice that a malware running in the user machine could collect and send the banking account information gathered while the machine is in use (and thus with decrypted data in memory and disk).
So it becomes clear that other techniques are needed in order to avoid it.
Why Use a KeyLogger?
From that perspective, it is easy to notice that instead of a keylogger (that would need to wait until the user typed the account information), it is more effective to develop a malware that will search the disk for the signatures extracted. As a matter of fact, we already have a proof of concept, implemented using the Foremost forensic tool, that does exactly this.
More on the Subject
We also conducted tests on Linux and Safari and on mobile Android systems and were able to recover username and passwords on them.
It is important to notice that no unlawful actions were conducted, as no penetration tests were done. All username and password tested were personal or invalid/bogus.
Also noteworthy is the fact that when possible, we contacted the companies and organizations about this issue.
Conclusions
As previously stated, no amount of safety measures is enough when account information is stored as plaintext on the client side. We proved that this happens with major internet service providers.
Because of this finding, banking account information can be easily disclosed, and a keylogger is no longer needed. It is easier and more effective to carve the data from the disk.
Offshore Legal Firm Hacked, Braces for Media Leaks
24.10.2017 securityweek Hacking
Financial details of some of the world's richest people are set to be published after a Bermuda-based offshore firm suffered a data breach, a British newspaper reported Wednesday.
The legal firm, Appleby, said it was bracing for documents to be published after being approached by the media network behind the Panama Papers.
The US-based International Consortium of Investigative Journalists (ICIJ) and affiliated media raised allegations against the company's operations and its clients, following information being leaked.
"Appleby has thoroughly and vigorously investigated the allegations and we are satisfied that there is no evidence of any wrongdoing, either on the part of ourselves or our clients," said the law firm, which has multiple offices in locations including Bermuda and the Cayman Islands.
"We refute any allegations which may suggest otherwise and we would be happy to cooperate fully with any legitimate and authorised investigation of the allegations by the appropriate and relevant authorities."
The expected publication of Appleby documents follows "a data security incident last year which involved some of our data being compromised," the firm said, without giving further details.
Appleby is yet to feature in a report by the ICIJ, which last year released the Panama Papers setting in motion a scandal which shook political and financial elites.
The publication of 11.5 million digital records from the Panamanian law firm Mossack Fonseca revealed how many of the world's wealthy used offshore companies to stash assets, leading to at least 150 inquiries or investigations in 79 countries as of March 2017.
The Telegraph put the Appleby case on its front page Wednesday, saying "some of the world's richest people were braced for their financial details to be exposed".
"It is understood the leak involves some of Britain's wealthiest people, who were instructing lawyers and public relations companies in an effort to protect their reputations," the newspaper said.
A "global consortium of left-leaning media organisations" is set to release the information "in the coming days," added the conservative daily.
'Bad Rabbit' Ransomware Attack Hits Russia, Ukraine
24.10.2017 securityweek Ransomware
Several major organizations in Russia and Ukraine were hit in the past few hours by a ransomware named “Bad Rabbit.” The incident reminds of the massive attack involving NotPetya malware, which ended up costing companies millions of dollars.
Few details are known so far about the Bad Rabbit attack, which has the potential to cause significant damage.
Infected computers display a screen informing users that their files have been encrypted and instructing them to access a website over the Tor anonymity network. The Tor site tells victims to pay 0.05 bitcoin, worth roughly $283, to obtain the key needed to recover the encrypted files. However, the price goes up if the ransom is not paid within two days.

The list of organizations reportedly hit by the Bad Rabbit ransomware includes Russian media outlets Interfax and Fontanka, the airport in Odessa, the Kiev subway, the State Aviation Service of Ukraine, and the Transport Ministry of Ukraine. Interfax and others said the attack disrupted their operations.
Researchers are still analyzing the malware, but initial reports claim Bad Rabbit has been distributed via fake Flash Player updates. Some said the ransomware also leverages the Mimikatz post-exploitation tool for lateral movement within the compromised network. Kaspersky’s Anton Ivanov revealed that the threat uses code from a legitimate disk encryption utility named DiskCryptor.
Security firm ESET said the malware appears to be a new variant of NotPetya, also known as Diskcoder, Petya, Petrwrap, NotPetya, exPetr and GoldenEye. However, this has not been confirmed by other researchers. ESET reported that while most infections are in Russia and Ukraine, some compromised machines were also detected in Turkey, Bulgaria and other countries.
There are also some reports that Bad Rabbit uses SMB – specifically the NSA-linked EternalBlue exploit – to spread, just like NotPetya. However, this hasn’t been confirmed either.
The attack does remind of NotPetya, which started spreading via a software update from a Ukrainian company. However, NotPetya turned out to be a wiper instead of ransomware.
The fact that another major attack has hit Ukraine is not surprising considering that the country’s Security Service warned earlier this month about a possible large-scale cyberattack on state organizations and private companies. The agency said the purpose of the attack would be to disrupt IT systems and destabilize the situation in the country.
VPN, Web Sessions Exposed to DUHK Crypto Attack
24.10.2017 securityweek Attack
A vulnerability in the outdated ANSI X9.31 random number generator (RNG) can allow attackers to recover encryption keys and read data passing through VPN connections and encrypted web browser sessions, researchers warned.
The vulnerability has been dubbed DUHK (Don’t Use Hard-coded Keys) and it has been found to affect the products of at least a dozen vendors. The issue was discovered by cryptography experts Shaanan Cohney, Nadia Heninger, and Matthew Green.
ANSI X9.31 is a pseudorandom number generator that was standardized in 1985 and it was compliant with the Federal Information Processing Standards (FIPS) requirements until January 2016. The RNG relies on a static key to generate random numbers and that key must remain secret in order for the system to be secure.DUHK attack
However, some companies implemented X9.31 with a static key that has been stored directly in the source code of the product. This allows an attacker to obtain the key from the application’s source code or binary and use it to decrypt communications associated with that product.
In some cases, an attacker may be able to recover the private key in just a few seconds via the DUHK attack, which works only if the RNG is used directly to generate crypto keys and if the attacker can obtain some of the generated numbers.
The weakness has been known since 1998, but neither NIST nor entities involved in the FIPS standardization process specified a method for securely generating the key.
An analysis of hundreds of products that implemented the X9.31 RNG revealed that 12 of them had used static hardcoded keys in the source code, leaving their users vulnerable to attacks.
The list of affected products included the BeCrypt Cryptographic Library, Cisco Aironet, DeltaCrypt FIPS Module, Fortinet’s FortiOS, MRV Communications’ LX-4000T/LX-8020S, Neoscale’s CryptoStor, Neopost’s Postal Security Devices, Renesas’ AE57C1, TechGuard’s PoliWall-CCF, Tendyron’s OnKey193, ViaSat’s FlagStone Core, and the Vocera Cryptographic Module. Many of the affected vendors have since removed the use of X9.31 from their products.
The researchers tested the practicality of the attack method against Fortinet’s FortiGate VPN gateway products, which run the FortiOS operating system. An Internet scan conducted this month showed that there are more than 25,000 Fortinet devices that are vulnerable and exploitable.
“And this count is likely conservative, since these were simply the devices that bothered to answer us when we scanned. A more sophisticated adversary like a nation-state would have access to existing VPN connections in flight,” Green explained in a blog post.
The vulnerability affects Fortinet devices running FortiOS versions 4.3.0 through 4.3.18. The vendor addressed the issue, which it tracks as CVE-2016-8492, last year with the release of versions 4.3.19 and 5.0.
There is no evidence of DUHK attacks in the wild and the researchers who discovered the flaw say they don’t plan on releasing any code used in their implementation of the method.
Furthermore, while the actual key recovery might be easy, a real-world attack exploiting this vulnerability is difficult to conduct. However, the flaw could be highly useful for a state-sponsored actor such as the NSA, which has far greater capabilities compared to the average threat group. It’s also worth mentioning that the attack is passive so it would not be easy to detect, researchers said.
A few years ago, the NSA was accused of promoting the use of the backdoored Dual Elliptic Curve Deterministic Random Bit Generator (Dual EC DRBG). However, experts have now pointed out that Dual EC was not as widely used as X9.31.
Microsoft Drops Lawsuit as U.S. Govt Limits Use of Gag Orders
24.10.2017 securityweek BigBrothers
Microsoft is dropping a lawsuit against the US government after the Department of Justice issued new rules limiting the use of secrecy orders that prevent firms from telling customers law enforcement has accessed their data.
The tech giant sued the government in April last year, but declared victory Monday and said it was ending its case after the DOJ announced it would revise its rules.
Brad Smith, Microsoft's chief legal officer, said the company had achieved "an unequivocal win for our customers" that protected the constitutional rights of US citizens.
"Until now, the government routinely sought and obtained orders requiring email providers to not tell our customers when the government takes their personal email or records," he wrote in a blog post.
"Sometimes these orders don't include a fixed end date, effectively prohibiting us forever from telling our customers that the government has obtained their data."
Smith acknowledged that secrecy orders were sometimes required for legitimate reasons -- such as protecting individuals at risk from harm or ensuring an investigation was not thwarted.
But, he added, at the time the lawsuit was filed, "the government appeared to be overusing secrecy orders in a routine fashion - even where the specific facts didn't support them".
"When we filed our case we explained that in an 18-month period, 2,576 of the legal demands we received from the U.S. government included an obligation of secrecy, and 68 percent of these appeared to be indefinite demands for secrecy," he said.
But in a memo issued last week, Deputy Attorney General Rod Rosenstein said any such gag order "should have an appropriate factual basis" and "should extend only as long as necessary to satisfy the government's interest".
While lauding the DOJ's decision, Microsoft repeated its call on US Congress to amend the 1986 Electronic Communications Privacy Act that regulates government access to contemporary electronic communications.
It comes as the US Supreme Court last week announced it would hear a separate privacy case that pits the Trump administration against Microsoft.
The case examines whether US law enforcement should be allowed to access evidence held on servers overseas during an investigation.
It comes after Microsoft refused to hand over emails during a US drug trafficking investigation on the basis the police's warrant did not extend to Ireland, where the messages were stored.
'Bad Rabbit' Ransomware Attack Hits Russia, Ukraine
24.10.2017 securityweek Ransomware
Several major organizations in Russia and Ukraine were hit in the past few hours by a ransomware named “Bad Rabbit.” The incident reminds of the massive attack involving NotPetya malware, which ended up costing companies millions of dollars.
Few details are known so far about the Bad Rabbit attack, which has the potential to cause significant damage.
Infected computers display a screen informing users that their files have been encrypted and instructing them to access a website over the Tor anonymity network. The Tor site tells victims to pay 0.05 bitcoin, worth roughly $283, to obtain the key needed to recover the encrypted files. However, the price goes up if the ransom is not paid within two days.

The list of organizations reportedly hit by the Bad Rabbit ransomware includes Russian media outlets Interfax and Fontanka, the airport in Odessa, the Kiev subway, the State Aviation Service of Ukraine, and the Transport Ministry of Ukraine. Interfax and others said the attack disrupted their operations.
Researchers are still analyzing the malware, but initial reports claim Bad Rabbit has been distributed via fake Flash Player updates. Some said the ransomware also leverages the Mimikatz post-exploitation tool for lateral movement within the compromised network. Kaspersky’s Anton Ivanov revealed that the threat uses code from a legitimate disk encryption utility named DiskCryptor.
Security firm ESET said the malware appears to be a new variant of NotPetya, also known as Diskcoder, Petya, Petrwrap, NotPetya, exPetr and GoldenEye. However, this has not been confirmed by other researchers. ESET reported that while most infections are in Russia and Ukraine, some compromised machines were also detected in Turkey, Bulgaria and other countries.
There are also some reports that Bad Rabbit uses SMB – specifically the NSA-linked EternalBlue exploit – to spread, just like NotPetya. However, this hasn’t been confirmed either.
The attack does remind of NotPetya, which started spreading via a software update from a Ukrainian company. However, NotPetya turned out to be a wiper instead of ransomware.
The fact that another major attack has hit Ukraine is not surprising considering that the country’s Security Service warned earlier this month about a possible large-scale cyberattack on state organizations and private companies. The agency said the purpose of the attack would be to disrupt IT systems and destabilize the situation in the country.
UK Probes Equifax Hacking
24.10.2017 securityweek Hacking
Britain's financial watchdog on Tuesday said it was investigating a massive hack of the US consumer credit rating service Equifax that affected potentially almost 700,000 British customers.
In a short statement, the Financial Conduct Authority said "it is investigating the circumstances surrounding a cybersecurity incident that led to the loss of UK customer data held by Equifax Ltd on the servers of its US parent".
The hack between May and July resulted in the theft of personal information from around 145 million US customers and led to the resignation of Equifax chief executive Richard Smith.
Smith blamed a combination of human and technical error for the serious breach.
One-Third of Industrial Networks Connected to Internet: Study
24.10.2017 securityweek Security
Many industrial and critical infrastructure systems are connected to the Internet, and the operational technology (OT) networks of some organizations have already been compromised, according to a new study from industrial security firm CyberX.
What makes the CyberX study interesting is the fact that it’s not based on a survey. Instead, the company used data obtained after passively monitoring traffic from 375 OT networks over the past 18 months. The organizations whose networks have been analyzed are from a variety of sectors – including manufacturing, energy and utilities, oil and gas, and pharmaceuticals and chemicals – in the United States, Europe and the Asia-Pacific region.
Organizations have often downplayed the risks associated with the presence of vulnerable industrial control systems (ICS) on their networks, claiming that devices are isolated, or air-gapped, and cannot be accessed remotely from the Internet.
However, CyberX’s study revealed that roughly one-third of organizations had industrial networks connected to the public Web. These systems are often accessible remotely for convenience, including for remote management, performing software updates, and even web browsing and email from the OT network.
More than 80% of industrial sites are running a remote management protocol such as RDP, VNC or SSH, allowing attackers on the OT network to remotely access and control other devices on the network via standard administration tools. Misconfigured wireless access points (WAPs) can also be leveraged as an attack vector, and one in five of the analyzed companies had at least one WAP.
CyberX also found that 76% of analyzed industrial sites have machines running obsolete versions of Windows, such as Windows 2000 and Windows XP, on their OT networks. Both Windows devices and industrial systems such as programmable logic controllers (PLCs) had vulnerabilities in 28% of cases.
Furthermore, many organizations haven’t made sure that strong authentication mechanisms are in place. In nearly 60% of cases, CyberX has seen plaintext passwords crossing the network, allowing man-in-the-middle (MitM) attackers to obtain valuable information.
The analysis shows that Modbus is the most widely used industrial protocol (58%), followed by Ethernet IP (28%), Siemens’ S7, OPC, OSIsoft PI and MMS.
Researchers also found that almost half of industrial sites did not have even basic antivirus protection on Windows endpoints.
“We’ve heard from customers that adding AV software to endpoints such as HMI workstations can sometimes void the warranty provided by their OT vendors. Vendors are concerned that the overhead of AV scanning software will impact the performance or reliability of their workstations,” CyberX said in its report. “Nevertheless, lack of AV protection increases the risk of having known malware on these systems — such as Conficker, WannaCry, and NotPetya — without even knowing about it.”
As a matter of fact, CyberX did see malware in 10% of the analyzed OT networks. The security firm has observed Conficker infections, which is one of the most widespread pieces of malware and it has been known to infect even critical infrastructure organizations. CyberX told SecurityWeek that it also noticed some threats that exhibited behavior consistent with the EternalBlue exploit, which has been used by both the WannaCry ransomware and the NotPetya wiper.
The data shows little difference between the security scores of various industries – there is only a +/- 5% variation from the median score of 61% across the analyzed sectors.
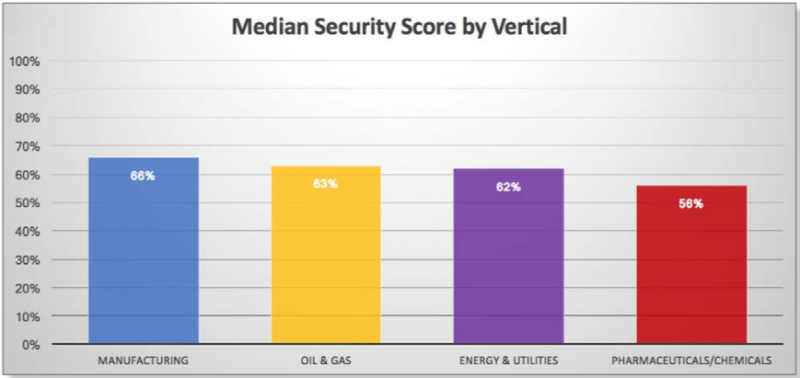
Simulated Phishing Firm KnowBe4 Raises $30 Million
24.10.2017 securityweek Phishing
Security awareness training and simulated phishing firm KnowBe4 has secured $30 million in Series B financing led by Goldman Sachs Growth Equity (GS Growth), with existing investor Elephant participating. It brings the total financing raised by KnowBe4 to $44 million.
“KnowBe4 has separated itself as a leader in the cyber-security awareness training market, with their platform becoming a ‘need to have’ for businesses across sectors and geographies in the fight against cyber-threats,” said Hans Sherman, a Vice President in Goldman Sachs’ Merchant Banking Division, who will join the KnowBe4 board of directors in connection with the investment. “Our financing will support the company’s continuing growth as they expand globally and develop new products to serve this fast-growing market.”
KnowBe4 was formed in 2010. By 2014 it still lagged behind its big competitors, PhishMe and Wombat. Since then it has grown rapidly. Chief evangelist and strategy officer, Perry Carpenter, claims that it is now the fastest growing vendor in the market.
He told SecurityWeek the rapid growth is a combination of three primary factors: being priced for SMBs while being technologically targeted for large enterprises; a growing market readiness to use staff training to counter the emergence of ransomware and business email compromise (BEC) fraud; and the need for staff training to counter the insider threat (to prevent naive actions and help detect malicious actions). KnowBe4 uses a combination of awareness training and simulated phishing on what is now a well-proven and stable platform.
KnowBe4 raises $30 million
“The confidence in our company demonstrated by GS Growth’s investment shows the strength of the new-school security awareness training market, and support for KnowBe4’s approach and dedication to mobilizing an organization’s last line of defense, its employees, to make smarter security decisions and reduce overall company risk,” said Stu Sjouwerman, KnowBe4 Founder and CEO.
KnowBe4's training combines simulated phishing attacks, case studies, demonstration videos and tests with real-world scenarios to help employees understand the mechanisms of spam, phishing, spear phishing, malware and social engineering. Earlier this month, the company published its Q3 2017 list of top-clicked phishing email subjects from its enterprise training sessions. The top three are 'official data breach notification', 'UPS delivery', and 'password expiry notification'.
“In the wild,” Carpenter told SecurityWeek, “things like coupons for free pizzas are almost always in the top ten because it's self-interest. It's, literally, feeding an appetite. Suspicious activity in your bank feeds fear.” Phishing usually plays on a small number of human characteristics, such as self-interest, curiosity, FUD (fear, uncertainty and doubt) and urgency. The intent is to spark an emotional knee-jerk reaction from the targets -- to get them to click the link automatically and reactively.
The purpose of continuous training, said Carpenter, is to 'train-out' that knee-jerk reaction and give staff the emotional permission to slow down and think about things: “to mentally scan the content for suspicious phrases and links.” He likens this to creating muscle memory, like learning how to catch a ball. “It's awkward at first, but the only way to get better at it is to subject yourself frequently. Quarterly simulated phishing isn't really training -- it's quarterly baselining. You need to do the training almost continuously -- at least every two weeks -- and then you're conditioning behavioral response.”
Carpenter sees scalability as the current trend in targeted phishing. “Social media is being scraped for data, engines are being used to analyze the data, and botnets are used to deliver targeted phishing emails.”
KnowBe4, said Carpenter, tries to replicate this in its training. “We have an AI-driven agent that takes on a personality. We have a Facebook support agent; we're training one to be a dental receptionist, and so on. They have these personas and they try to engage people through an email: 'Hey, this is Bob at Facebook Security and we've noticed some suspicious activity on your account... click on this link and we can sort it out.’ If they click on the link, they've been owned and we do the training there and then.”
But if they ignore it, then a few hours later the agent will send a text message: “Hi; hope you got my email. Plz check it out and take the appropriate action.” If they don't respond to that, then the agent can move over to a voice mail. “It's kind of chat box-based,” explained Carpenter, “where the AI has been trained in more than 50,000 question and answer pairs so that if someone responds to it, it can have a conversation. That conversation is all about trying to drive the user to take the action that the social engineer would want them to take.”
Phishing awareness training is difficult, but necessary. “Phishing attacks are responsible for more than 90 percent of successful cyber attacks and the level of sophistication hackers are now using makes it nearly impossible for a piece of technology to keep an organization protected against social engineering threats,” said Carpenter. “It is clear that humans are the weakest link in an organization's security program. Simulated phishing helps CISOs and IT Managers reduce the human error within their organization, thus reducing their social engineering attack surface.”
APNIC Whois-related problem led to accidental exposure of authentication data
24.10.2017 securityaffairs Incindent
APNIC Deputy Director General Sanjaya confirmed that Whois data were accidentally exposed online included authentication details.
The Asia-Pacific Network Information Centre (APNIC) is a non-profit organization that provides Internet addressing services in the Asia-Pacific region. The APNIC made the headlines because it was informed about a Whois-related security incident that led to the exposure of authentication data.
According to the APNIC Deputy Director General Sanjaya, Whois data exposed online included authentication details for Maintainer and IRT objects. The incident was discovered on October when a member of the eBay Red Team reported that a third-party website had been republishing downloadable Whois data.
The incident affected Maintainer and Incident Response Team (IRT) objects in the APNIC Whois database.
Both Maintainer and IRT objects include an “auth” attribute that specifies a hashing format and stores an access password in the specified format. The “auth” hashes were accidentally included in downloadable data.
“A Maintainer (mntner) is an object in the APNIC Whois Database. Every object in the APNIC Whois Database is protected by a Maintainer via the ‘mnt-by’ attribute. This ensures that only authorized people that have access to this Maintainer can make changes to other objects that are protected by this Maintainer.” reported the APNIC in a blog post.
“An Incident Response Team (IRT) object is an object in the APNIC Whois Database that contains contact information for an organization’s administrators responsible for receiving reports of network abuse activities.
The ‘auth’ attribute in a Maintainer or IRT object specifies the hashing format used and stores the password in its hashed format.
The error that occurred saw the ‘auth’ hashes included in the downloadable whois data feed (not published on APNIC’s whois itself).”

The problem was promptly fixed, the exposed data included hashed passwords that could be cracked by threat actors to modify Whois data.
The good news is that according to the APNIC there is any evidence of abuse.
The organization warned of the potential risks related to any unauthorized changes of the data.
“Although password details are hashed, there is a possibility that passwords could have been derived from the hash if a malicious actor had the right tools.
If that occurred, whois data could potentially be corrupted or falsified for misuse. Our investigations to date have found no evidence of this occurring.” continues the security organization.
“It is important to note, however, that any public misrepresentation of registry contents on whois would not result in a permanent transfer of IP resources, as the authoritative registry data is held internally by APNIC.”
The non-profit organization has been working with affected users urging them to change passwords, the process was completed on Monday.
“All Maintainer and IRT passwords have now been reset, so there is no need to change them again if you are an APNIC resource holder,” Sanjaya added. “However, if you wish to change the new passwords to something more memorable, you should not choose the previous password (and if the old password was being used elsewhere on other systems, you should change those passwords).”
APNIC is currently working to determine the root cause of the incident.
Researcher spotted flaws in the web-based version of popular Sarahah app
24.10.2017 securityaffairs Vulnerebility
A security researcher discovered a number of embarrassing vulnerabilities in the popular anonymous feedback app Sarahah.
The anonymous feedback app Sarahah makes the headlines once again, according to the according to security researcher Scott Helme, the web-based version of the app is plagued with security flaws.
Sarahah mobile app allows users to receive anonymous feedback messages from friends and co-workers, but according to the Helme is vulnerable to web-based attacks such as Cross-Site Request Forgery (CSRF) and cross-site scripting.
An attacker can launch a Cross-Site Request Forgery (CSRF) attacks to force an end user to execute unwanted actions on a vulnerable web application.
Helme discovered that it was “trivially easy” to bypass Cross-Site Request Forgery (CSRF) protection implemented by the developers of the app.

The Sarahah app allows users to send anonymous messages to the users, of course, ill-intentioned can abuse this feature to send insults and flaming. The app implements only rudimentary filtering to prevent abuse of other members. Helme pointed out that there isn’t rate limiting allowing attackers to anonymously send hundreds of messages.
“The app does deploy native CSRF protection but it turns out that in a lot (almost all) circumstances it’s fairly trivial to bypass. Endpoints like /Messages/FavoriteAjax and /Messages/DeleteAjax can be called as GET requests instead of POST requests and only require the id parameter in most cases. This makes it pretty trivial to craft a link to send to someone or launch a CSRF attack from any page you can get the victim to visit. ” wrote the expert.
“The application doesn’t seem to deploy rate limiting anywhere on the site and this is especially problematic when sending messages. Given the nature of the site and the ability to send totally anonymous messages, I was able to send several hundred abusive messages to Kate in just a couple of seconds. With no way to bulk delete messages Kate would have to sit there and delete each of these one by one.”
The issues discovered by Helme are unusual in a well-developed application, Sarahah is one of the most popular apps today, it is the number one app on Apple’s App Store and is number one in more than 10 countries on Google Play too.
Helme spotted many other vulnerabilities in the application, including password reset procedure account lockout issues.
“My biggest worry is that this is a brand new application and the issues were not difficult to find at all,” Helme told El Reg.. “They are basic issues I wouldn’t expect to find in a new app and as a result I’m concerned the app hasn’t undergone any security testing prior to release. If it has then I’d be raising some very serious questions with the firm that did the testing as to why such fundamental flaws were missed.”
Sarahah acknowledged the results of the Helme’s assessment and confirmed that its development team is already working to fix them.
The researcher attempted to report the flaws in early August, he was disappointed by the fact that the company did reply very fast, Helme highlights the importance of privacy and security issues for such kind of applications.
“An app of this nature should be very security and privacy-focused,” he explained. “I was disappointed at how difficult it was to contact the firm to responsibly disclose these issues that affect their users and how poor the response and handling was once I made contact.”
Kaspersky nechá prověřit svůj antivirový software. Kvůli obavám ze šmírování
24.10.2017 Novinky/Bezpečnost BigBrother
Ruská antivirová společnost Kaspersky Lab požádá nezávislý orgán, aby prověřil bezpečnost jejího antivirového softwaru, který Spojené státy označily za hrozbu pro svou národní bezpečnost. Firma v prohlášení uvedla, že bezpečnostním expertům a vládním představitelům poskytne zdrojový kód svého softwaru a následné aktualizace produktů.
Jevgenij Valentinovič Kasperskij, šéf společnosti Kaspersky Lab a vývojař antivirových programů.
Firma také slíbila, že umožní vnějším orgánům přezkoumat další aspekty svého podnikání, včetně vývoje softwaru. Revize softwaru, který je po celém světě nainstalován na zhruba 400 miliónech počítačů, má být zahájena v prvním čtvrtletí příštího roku.
„Nemáme co skrývat," řekl zakladatel a ředitel podniku Jevgenij Kasperskij. „Těmito kroky bychom měli být s to nedůvěru překonat," citovala jej agentura Reuters. Nezávislý revizní orgán, který má kontrolu provést, firma nejmenovala.
Vládní úřady v USA antivirus smazaly
Administrativa amerického prezidenta Donalda Trumpa v září nařídila vládním úřadům v USA odstranit z počítačů produkty společnosti Kaspersky.
Ministerstvo vnitřní bezpečnosti vyjádřilo znepokojení nad "vazbami mezi některými činiteli podniku a ruskými zpravodajskými službami a dalšími vládními agenturami a podmínkami ruského práva, které ruským zpravodajským službám umožňují požadovat nebo vymáhat spolupráci od společnosti Kaspersky a zaznamenávat komunikaci, která prochází ruskými sítěmi". Senát krok administrativy podpořil.
Izraelská zpravodajská služba uvedla, že objevila ruské vládní hackery používající antivirový software Kaspersky k odcizení tajných materiálů americké Národní agentury pro bezpečnost (NSA).
Světové špičky v oblasti kybernetické bezpečnosti nejsou jednotné v názoru, zda se ruské tajné služby zmocnily softwaru Kaspersky, aniž by o tom firma věděla, zda je spoluviníkem samotný podnik, nebo některý z jeho zaměstnanců.
Ruská společnost už dříve několikrát popřela, že má vazby na jakoukoliv vládu. Tvrdila také, že nikdy žádné vládě nepomůže s kybernetickou špionáží. Firma ale podle Reuters v minulosti připustila, že spolupracovala s ruskou tajnou službou FSB. Zakladatel a ředitel podniku Jevgenij Kasperskij navštěvoval školu KGB.
Kaspersky Lab se svleče do naha. Kvůli podezření ze spolupráce s ruskými úřady spouští unikátní transparentní iniciativu
24.10.2017 Živě.cz BigBrother
Ruský antivirový specialista Kaspersky Lab se musel v posledním roce potýkat s podezřením, že až příliš úzce spolupracuje s ruskou bezpečnostní službou FSB, což vedlo mimo jiné k nařízení, aby produkty od Kaspersky Lab zmizely z počítačů amerických federálních úřadů, které se obávaly případné špionáže. Nebylo to nicméně poprvé, podobný osud totiž v minulosti potkal i mnohé přední výrobce z Číny – třeba Huawei.
Aby se Kaspersky Lab vypořádal s pošramocenou pověstí, spouští poměrně unikátní transparentní iniciativu, která se skládá ze čtyř bodů:
Nezávislý audit zdrojových kódů: V 1. čtvrtletí příštího roku hodlá společnost vpustit do svých kódů respektovanou mezinárodní autoritu, která by provedla jeho audit.
Nezávislý audit vnitřních procesů: Stejně tak firma sama projde nezávislým auditem svých interních procesů
Tři transparentní centra v Evropě, Asii a USA: Do třetice hodlá Kaspersky Lab otevřít tři speciální centra, kde umožní klíčovým klientům, organizacím i vládám nahlížet do zdrojových kódů svých produktů a opět i dalších vnitřních procesů
Bug Bounty až 100 000 dolarů: Firma nakonec navýší svůj program hledání chyb. Nezávislí hackeři tak budou moci získat až 100 tisíc dolarů, pokud v produktech Kaspersky Lab objeví kritickou zranitelnost.
Adware a Defender zpomalí váš počítač nejvíce, Eset a F Secure naopak nejméně
24.10.2017 CNEWS Zabezpečení
Který antivirus je nejméně hospodárný a který naopak při používání počítače skoro nepocítíte?
Pokud jste ještě na antiviry nezanevřeli, mohlo by vás zajímat, jak si dnešní bezpečnostní produkty vedou v otázce výkonu. Právě na výkon se zaměřili na AV-Comparatives ve svém posledním testu antivirů.
Dle autorského týmu bylo testování provedeno na počítači Lenovo E560 s aktuálním systémem Windows 10 v 64bitové edici. Počítač obsahoval procesor Core i5-6200U, 8 GB operační paměti a blíže neurčené SSD.
K tématu: Souboj bezpečnostních expertů. Jsou antiviry přínosné, nebo je máme zahodit?
Jen tradičně upozorňuji, že výsledky se mohou lišit v závislosti na softwarové i hardwarové konfiguraci počítače, navíc může být používání každého člověka odlišné od automatizovaného testu, který AV-Comparatives provedlo.
Výsledky testování
Testování bylo rozděleno do dvou částí. Za provozu antivirů byly měřeny některé praktické operace jako kopírování souborů, komprimace apod. Ve druhé části byl spuštěn syntetický benchmark PC Mark 10. Dosažená skóre shrnuje následující tabulka. Shrnujícím a pro většinu lidí nejdůležitějším výsledkem je skóre dopadu, tj. poslední sloupec.
Vlastní testování AV-C PC Mark Celkem Skóre dopadu
Eset Internet Security 11.0 88 99,2 187,2 2,8
F-Secure Safe 17.0 88 99 187 3
Vipre Advanced Security 10.1 88 98,4 186,4 3,6
Bitdefender Internet Security 22.0 88 97,8 185,8 4,2
BullGuard Internet Security 18.0 88 97,1 185,1 4,9
Seqrite Endpoint Security 17.0 85 99,5 184,5 5,4
McAfee Internet Security 20.2, Panda Free Antivirus 18.3 85 97,7 182,7 7,3
Kaspersky Internet Security 18.0 85 96,9 181,9 8,1
Avira Antivirus Pro 15.0 83 98,5 181,5 8,5
Symantec Norton Security 22.11 85 96,3 181,3 8,7
Avast Free Antivirus 17.7, AVG Free Antivirus 17.7, eScan Corporate 360 14.0 85 96,1 181,1 8,9
Tencent PC Manager 12.3 85 93 178 12
Emsisoft Anti-Malware 2017.8 78 97 175 15
CrowdStrike Falcon Prevent 3.4 75 98,5 173,5 16,5
Trend Micro Internet Security 12.0 78 95,4 173,4 16,6
Fortinet FortiClient 5.6 s FortiGate 75 98,3 173,3 16,7
Windows Defender 4.11 63 96,6 159,6 30,4
Adaware Antivirus Pro 12.2 55 95,9 150,9 39,1
Ten obsahuje finální propočet, přičemž nižší číslo znamená nižší dopad na výkon počítače. Jako již mnohokrát dopadl velmi špatně integrovaný antivirus od Microsoftu. Testován byl zřejmě Windows 10 Creators Update, protože ve Fall Creators Updatu je obsažen Defender ve verzi 4.12. Největšího zpomalení byste měli „úspěšně“ dosáhnout instalací antiviru Adaware. Naopak nejlépe si vede Eset. Jen o kousek horší je v otázce zátěže F-Secure.
Na posledních příčkách si můžete všimnout velikých rozdílů. Adware bylo výrazně horší než Defender, který byl pro změnu výrazně horší než Fortinet. Následně se již výsledky zlepšují vcelku lineárně, snad s jednou výjimkou. Avast, AVG a eScan byli znatelně lepší než Tencent a produkty za ním. Mimochodem, minule dopadla Avira výrazně lépe, hůře naopak F-Secure. Produkty se vyvíjí, na výsledky ovšem může mít vliv též rozdílnost v metodice testování.
Změní PIN a zašifruje data. Trojský kůň DoubleLocker cílí na mobily
24.10.2017 Novinky/Bezpečnost Viry
Na chytré telefony s operačním systémem Android cílí trojský kůň zvaný DoubleLocker, před kterým varovala antivirová společnost Eset. Ta upozornila, že tento nezvaný návštěvník dokáže změnit na mobilním zařízení přístupový PIN kód a navíc ještě zašifrovat uložená data. Za jejich zpřístupnění pak požaduje výkupné.
DoubleLocker se tedy na napadeném zařízení chová úplně stejně jako vyděračské viry, které jsou označovány souhrnným názvem ransomware.
„DoubleLocker zneužívá služby Android Accessibility, což je oblíbený trik mezi kybernetickými zločinci. Jakmile je podvodná aplikace spuštěna, zažádá si o aktivaci služby zpřístupnění, která se v tomto případě vydává za aplikaci Google Play Service,“ přiblížili bezpečnostní experti útok škodlivého kódu.
Útočník získá administrátorská práva
Problém nastane ve chvíli, kdy uživatel na svém zařízení potvrdí aktivaci této služby. Útočník tak totiž získá administrátorská práva k zařízení, tedy jinými slovy může s napadeným přístrojem dělat na dálku prakticky cokoliv.
Podle bezpečnostních expertů se tento malware šíří především v Evropě a Turecku. Konkrétně byl jeho výskyt zaznamenán v Polsku a Německu, ojediněle pak v Bělorusku a Estonsku. Uživatele v České republice zatím nenapadl.
Na chytré telefony a počítačové tablety se počítačoví piráti zaměřují pravidelně. Lidé je totiž zpravidla nechávají bez jakékoliv obrany, tedy bez nainstalovaného antivirového programu. A tím nevědomky pomáhají počítačovým pirátům, pro ně je totiž v takovém případě velmi snadné nechráněné zařízení napadnout.
Vypátrat původ útoku na volební weby bude obtížné, zní z úřadu pro kyberbezpečí
24.10.2017 Novinky/Bezpečnost BigBrother
Vypátrat pachatele sobotního útoku na volební weby Českého statistického úřadu (ČSÚ) bude velmi obtížné. Uvedl to mluvčí Národního úřadu pro kybernetickou a informační bezpečnost (NÚKIB) Radek Holý. Útok dočasně znepřístupnil informační stránky pro veřejnost, volební výsledky ale neovlivnil.
Úřad podle Holého obdržel hlášení o incidentu od ČSÚ i operátora O2, který statistikům zajišťoval připojení. „Obě strany potvrdily, že se jednalo o útok DDoS. Podle našich informací se ČSÚ obrátil i na Policii ČR, která věc bude šetřit," uvedl.
Právě internetová síť O2 byla hackerským útokem postižena, a proto zmiňované weby v sobotu nefungovaly. [celá zpráva]

FOTO: repro volby.cz
Útok trval 2,5 hodiny. „Poprvé se náznaky útoku objevily kolem 14. hodiny a v průběhu odpoledne několikrát vyřadily z provozu prezentační web volby.cz. Situaci jsme začali okamžitě řešit a v 16:30 se podařilo útoky definitivně odklonit,“ uvedla na dotaz Novinek mluvčí O2 Lucie Pecháčková.
Případem se zabývá policie
ČSÚ zatím nechtěl útoky komentovat, protože je vyšetřuje policie a NÚKIB.
„Dle dostupných informací jde v případě tohoto DDoS útoku o víceméně dobře zvládnutý bezpečnostní incident. Výsledky voleb dle našeho názoru nemohl ovlivnit," podotkl ředitel bezpečnostní divize DCIT Karel Miko.
Podle technického ředitele antivirové firmy Eset Miroslava Dvořáka se dá podobným útokům čelit dostatečně robustní infrastrukturou v kombinaci s filtračními mechanismy. Lze to zajistit vlastními silami či využitím nabídek externích společností, tzv. scrubingových center. Vždy se zohledňuje nákladová efektivita takové ochrany.
ČSÚ: Za výpadek volebních webů může DDoS na infrastrukturu O2 [AKTUALIZOVÁNO]
24.10.2017 Živě.cz BigBrother
Přechodnou nedostupnost webů, na kterých Český statistický úřad (ČSÚ) publikoval průběžné výsledky sčítání hlasů ve víkendových parlamentních volbách, nejprve úřad vysvětloval technickými problémy. V neděli ale za příčinu potíží označil DDoS útok.
„Na základě podrobné analýzy, kterou si ČSÚ okamžitě vyžádal, byly uvedené problémy specifikovány. Bylo zjištěno, že v průběhu zpracování došlo k cílenému DDoS útoku na infrastrukturu společnosti O2 používanou pro zajištění voleb. V důsledku byla dočasně omezena dostupnost serverů volby.cz a volbyhned.cz,“ vysvětluje ČSÚ.
O2 přitom podle smluv zveřejněných v Registru smluv pro letošní volby ČSÚ dodalo posílenou ochranu webu volby.cz právě proti DDoS útokům. Služba AntiDDoS Advanced podle smlouvy zahrnuje nasazení systému Arbor APS na tzv. poslední míli přípojky ČSÚ. Operátor také posílil linku pro připojení vybraných médií na dedikovaný server ČSÚ z 10 Mb/s na 20 Mb/s.
Aktualizace 14:15 – doplňujeme vyjádření O2: Operátor ani po dotazech Lupy například na sílu DDoS, jeho cíle a trvání odmítl prozradit jakékoli technické podrobnosti. „Díky našemu technickému řešení se podařilo ochránit zpracování volebních výsledků, které útoky nijak neohrozily. Díky opatřením se pak i další prvky, jako například server volby.cz, podařilo plně obnovit už v 16:30. Nyní spolupracujeme se statistickým úřadem i dalšími subjekty a i vzhledem k probíhajícímu šetření nezveřejňujeme technické detaily,“ odpověděla Lupě na dotazy mluvčí O2 Lucie Pecháčková.
Aktualizace 15:30 – Podle mapy digitálních útoků, na kterou na Twitteru upozornil bezpečnostní expert Michal Špaček, v sobotu do Česka skutečně mířil zvýšený datový tok:
Autor: Digital Attack Map
Zajímavé je, že mapa čerpá údaje o DDoS útocích právě od společnosti Arbor, jejíž antiDDoS zařízení O2 pro ČSÚ nasadilo.
TIP: Jak IP kamery „rozbily internet“. Co víme o obřím DDoS útoku na Dyn?
Weby volby.cz a volbyhned.cz nebyly nějakou dobu dostupné během sobotního sčítání hlasů. ČSÚ na nich jednak zveřejňuje tabulky s průběžnými výsledky voleb, jednak přes ně poskytuje data pro média a další zájemce o zpracování výsledků.
Podle ČSÚ zahlcení serverů žádným způsobem neovlivnilo posílání dat z volebních okrsků ani jejich sčítání: „Útok žádným způsobem neovlivnil infrastrukturu používanou pro přenos výsledků voleb z přebíracích míst do centrály ČSÚ ani nezávislé zpracování dat.“
DDoS útokem se teď má zabývat policie a Národní úřad pro kybernetickou a informační bezpečnost. Provedení DDoS je přitom poměrně jednoduché, útoky se dokonce dají koupit jako služba „na klíč“. Ceny v závislosti na síle útoku začínají už na jednotkách dolarů.
Hackerský útok na volební weby trval 2,5 hodiny. Experti řeší, odkud přišel
24.10.2017 Novinky/Bezpečnost BigBrother
Zhruba 2,5 hodiny trval v sobotu DDoS útok na prezentační volební weby volby.cz a volbyhned.cz, na kterých se zobrazovaly aktuální volební výsledky počítané Českým statistickým úřadem (ČSÚ). Novinkám to v pondělí potvrdila mluvčí O2 Lucie Pecháčková.
Právě internetová síť O2 byla hackerským útokem postižena, a proto zmiňované weby v sobotu nefungovaly. [celá zpráva]
„Je třeba zdůraznit, že DDoS útoky díky technickému řešení nijak neovlivnily sčítání hlasů ani systémy statistického úřadu,“ uvedla na dotaz Novinek Pecháčková.
Útok začal po uzavření volebních místností
Přiblížila, jak se útoky po uzavření volebních místností uskutečnily. „Poprvé se náznaky útoku objevily kolem 14. hodiny a v průběhu odpoledne několikrát vyřadily z provozu prezentační web volby.cz. Situaci jsme začali okamžitě řešit a v 16:30 se podařilo útoky definitivně odklonit,“ zdůraznila Pecháčková.

Server Volby.cz
FOTO: repro volby.cz
S ohledem na probíhající vyšetřování však zatím nechtěla komentovat žádné další podrobnosti. Experti O2 se nicméně samotným útokem – a například i tím, odkud přišel – již zabývají. „Nyní jsme připraveni úřadům poskytnout maximální součinnost při šetření,“ doplnila mluvčí operátora.
Celým případem se nyní bude zabývat policie a Národní úřad pro kybernetickou a informační bezpečnost.
Útokům čelilo Česko už dříve
Masivním útokům typu DDoS čelily v roce 2013 některé tuzemské servery. Směrovány byly nejprve na zpravodajské weby, potom na portál Seznam.cz, servery bank a telefonních operátorů.
Podle bezpečnostních expertů šlo tehdy o největší kybernetický útok v celé historii Česka.
Výpadek volebních webů byl hackerský útok
24.10.2017 Novinky/Bezpečnost BigBrother
Za sobotní nedostupnost prezentačních volebních webů volby.cz a volbyhned.cz mohli kybernetičtí nájezdníci. V neděli to potvrdili zástupci Českého statistického úřadu (ČSÚ) s tím, že zmiňované servery čelily tzv. DDoS útoku.
FOTO: repro volby.cz
neděle 22. října 2017, 17:16
(Aktualizováno: neděle 22. října 2017, 17:31 )
Útok DDoS (Distributed Denial of Service) má vždy stejný scénář. Stovky tisíc počítačů začnou přistupovat v jeden okamžik na konkrétní server. Ten zpravidla nezvládne tak vysoké množství požadavků zpracovat a spadne. Pro běžné uživatele se pak takto napadená webová stránka tváří jako nedostupná.
A přesně to bylo příčinou výpadku webů volby.cz a volbyhned.cz. „Výpadky prezentačních serverů, které ČSÚ zaznamenal v sobotu 21. října odpoledne, vznikly na straně externího dodavatele komunikačních služeb. Podle původního oficiálního sdělení dodavatele byly příčinou technické problémy v jeho infrastruktuře,“ připomněla mluvčí ČSÚ Petra Báčová s tím, že nakonec byl výpadek způsoben úplně něčím jiným.
Došlo k cílenému DDoS útoku na infrastrukturu společnosti O2 používanou pro zajištění voleb.
mluvčí ČSÚ Petra Báčová
„Na základě podrobné analýzy, kterou si ČSÚ okamžitě vyžádal, byly uvedené problémy specifikovány. Bylo zjištěno, že v průběhu zpracování došlo k cílenému DDoS útoku na infrastrukturu společnosti O2 používanou pro zajištění voleb. V důsledku byla dočasně omezena dostupnost serverů volby.cz a volbyhned.cz,“ prohlásila Báčová.
Ta zároveň přiblížila, jak se provoz dotčených serverů podařilo obnovit. „Díky přijatým opatřením se podařilo útoky zcela eliminovat a zajistit obnovení všech služeb. Útok žádným způsobem neovlivnil infrastrukturu používanou pro přenos výsledků voleb z přebíracích míst do centrály ČSÚ ani nezávislé zpracování dat,“ uzavřela mluvčí ČSÚ.
Celým případem se nyní bude zabývat policie a Národní úřad pro kybernetickou a informační bezpečnost.
Útokům čelilo Česko už dříve
Masivním útokům typu DDoS čelily v roce 2013 některé tuzemské servery. Směrovány byly nejprve na zpravodajské weby, potom na portál Seznam.cz, servery bank a telefonních operátorů.
Podle bezpečnostních expertů šlo tehdy o největší kybernetický útok v celé historii Česka.
Nový botnet se rychle rozrůstá. Může shodit celý internet
24.10.2017 Živě.cz BotNet
Nový botnet se rychle rozrůstá. Může shodit celý internet
Přesně před rokem způsobil botnet Mirai rozsáhlou nedostupnost více předních internetových stránek a služeb. Nyní tým expertů odhalil jeho následovníka, který sdružuje až 20násobně více infikovaných zařízení. Vyvstávají tak opodstatněné obavy, že díky jeho síle by mohli útočníci „shodit celý internet“. Informace o potenciální hrozbě zveřejnil TechSpot.
Každým dnem se výrazně rozrůstá
Nový botnet s názvem IoT_reaper, případně IoT Troop, odhalili už v září výzkumníci z čínské bezpečnostní společnosti Qihoo 360 a izraelští experti z firmy Check Point. Za tento čas se však jeho velikost enormním tempem rozrostla. V době výzkumu totiž ovládal už více než dva miliony infikovaných IoT zařízení, přičemž se každý den rozroste minimálně o dalších 10 tisíc zařízení.
Výzkumníci uvedli, že botnet využívá část kódu z jeho předchůdce Mirai, ale obsahuje i několik nových funkcí. Výrazným rozdílem je zejména způsob infiltrace. Mirai vyhledával zařízení s otevřeným Telnetem a následně testoval nejpoužívanější, respektive výchozí přihlašovací řetězce (jméno a heslo) pro získání přístupu.
Botnetu se zjednodušeně říká Reaper. Ke svému rozšiřování využívá působivou sbírku známých zranitelností v IoT.
Kvůli bezpečnostním chybám dokáží neznámí útočníci jednoduše získat plnou kontrolu nad neaktualizovaným zařízením a připojit jej k botnetu. Drtivá většina z uvedených chyb byla sice už dávno opravená, ale uživatelé často zanedbávají aktualizaci. Kvůli nedbalosti se tak i jejich zařízení stávají jedním z článků budoucích útoků.
Na seznamu konkrétně figurují routery D-Link 850L , D-Link DIR-600/300 , Netgear DGN , Linksys E1500 / E2500 , kamerové systémy Netgear ReadyNAS Surveillance , JAWS , Vacron , AVTech a IP kamery Goahead . Podle expertů ze společnosti Check Point jsou ohroženy i routery Mikrotik, TP-Link, NAS zařízení Synology a neaktualizované linuxové servery. Kompletní přehled zneužívaných modelů najdete na tomto odkazu .
Síla botnetu může být ohromující
Experti se domnívají, že botnet Reaper je zatím ve fázi vývoje. Aktuálně se jeho provozovatelé snaží infikovat co možná nejvíce zranitelných zařízení a získat nad nimi kontrolu. Podle dostupných informací nebyl zatím zahájen žádný DDoS útok.
Problémem však je jeho gigantická velikost spolu s více než 100 DNS resolvery, které zajistí rapidně zesílení případného útoku. Nikdo zatím netuší, jaké jsou úmysly útočníků, zda jim jde o způsobení chaosu, finanční zisk nebo jsou jejich cílem specifické zájmy. Faktem však je, že útok může přijít kdykoliv a s rozsáhlými následky.
Pro ilustraci, botnet Mirai disponoval šířkou pásma asi 1 Tbps, což útočníkům umožnilo odstavit weby Disqus, GitHub, HBO Now, Imgur, IndieGoGo, Netflix, PayPal, Pinterest, PlayStation Network, Reddit, SoundCloud, Spotify, Twitter, Yelp a jiné. Reaper je však mnohem propracovanější, přičemž má potenciál zahájit útoky se silou několika desítek Tbps. To ve finále může odstavit klíčové služby internetu a prvky jeho infrastruktury. Naštěstí jen dočasně.
Nejsme napojení na ruskou vládu, říká Kaspersky a poskytne důkaz
24.10.2017 CNEWS BigBrother

Slavná ruská bezpečnostní společnost pojmenovaná dle svého zakladatele a šéfa tvrdí, že nemá co skrývat. Zakládá proto „globální transparentní iniciativu“ v rámci níž chce prokázat, že její software není napojen na místní vládu ani neobsahuje zadní vrátka. Reaguje tak na sílící tlak, který před měsícem vyvrcholil zákazem využívání produktů Kaspersky Lab u amerických federálních úřadů. Viz Spojené státy úřadům zakázaly používat ruský software.
Že nejde jen o prázdná slova, chce Kaspersky dokázat během příštího roku. Od prvního čtvrtletí 2018 poskytne nezávislým expertům zdrojové kódy k prověření softwaru a vyhledání možných bezpečnostních rizik. K nezávislým auditům bude podávat též veškeré softwarové aktualizace.
Otevřeností chce uklidnit investory i zákazníky. Nástroje Kaspersky Lab chrání přes 400 milionů uživatelů a 270 000 firem. Společnost navíc zvyšuje odměny za nalezení chyb v jejím softwaru. Vyplácet bude až 100 000 dolarů, dvojnásobek oproti minulosti.
Google to add "DNS over TLS" security feature to Android OS
24.10.2017 thehackernews Android
No doubt your Internet Service Provides (ISPs), or network-level hackers cannot spy on https communications.
But do you know — ISPs can still see all of your DNS requests, allowing them to know what websites you visit.
Google is working on a new security feature for Android that could prevent your Internet traffic from network spoofing attacks.
Almost every Internet activity starts with a DNS query, making it a fundamental building block of the Internet. DNS works as an Internet's phone book that resolves human-readable web addresses, like thehackernews.com, against their IP addresses.
DNS queries and responses are sent in clear text (using UDP or TCP) without encryption, which makes it vulnerable to eavesdropping and compromises privacy.
ISPs by default resolve DNS queries from their servers. So when you type a website name in your browser, the query first goes to their DNS servers to find the website's IP address, which eventually exposes this information (metadata) to your ISPs.
Moreover, DNS Security Extensions — widely known as DNSSEC — only offers data integrity, not privacy.
To address this problem, Internet Engineering Task Force (IETF) last year proposed an experimental feature called — DNS over TLS (RFC 7858), which works approximately the same way https does.
Just like Transport Layer Security (TLS) encrypted protocol secures HTTPS connections cryptographically, DNS-over-TLS dramatically enhances privacy and security with end-to-end authenticated DNS lookups.
Google is reportedly adding "DNS over TLS" support to the Android Open Source Project (AOSP), currently at an experimental stage, to allow smartphone users to turn on or off "DNS over TLS" feature under Developer Options settings.
"Presumably, if such an option is being added to Developer Options, then that means it is in testing and may arrive in a future version of Android such as version 8.1." Xda-developers said in a blog post.
However, just enabling "DNS over TLS" feature would not prevent your ISP to know what websites you visit.
Server Name Indication (SNI) — an extension of the TLS protocol — also indicates ISPs that which hostname is being contacted by the browser at the beginning of the 'handshake' process.
So to enjoy full anonymity, users are still required to use a trusted secure VPN service in combination with DNS-over-TLS protocol.
New Rapidly-Growing IoT Botnet Threatens to Take Down the Internet
24.10.2017 thehackernews IoT
Just a year after Mirai—biggest IoT-based malware that caused vast Internet outages by launching massive DDoS attacks—completed its first anniversary, security researchers are now warning of a brand new rapidly growing IoT botnet.
Dubbed 'IoT_reaper,' first spotted in September by researchers at firm Qihoo 360, the new malware no longer depends on cracking weak passwords; instead, it exploits vulnerabilities in various IoT devices and enslaves them into a botnet network.
IoT_reaper malware currently includes exploits for nine previously disclosed vulnerabilities in IoT devices from following manufactures:
Dlink (routers)
Netgear (routers)
Linksys (routers)
Goahead (cameras)
JAWS (cameras)
AVTECH (cameras)
Vacron (NVR)
Researchers believe IoT_reaper malware has already infected nearly two million devices and growing continuously at an extraordinary rate of 10,000 new devices per day.
This is extremely worrying because it took only 100,000 infected devices for Mirai to took down DNS provider Dyn last year using a massive DDoS attack.
Besides this, researchers noted that the malware also includes more than 100 DNS open resolvers, enabling it to launch DNS amplification attacks.
"Currently, this botnet is still in its early stages of expansion. But the author is actively modifying the code, which deserves our vigilance." Qihoo 360 researchers say.
Meanwhile, researchers at CheckPoint are also warning of probably same IoT botnet, named "IoTroop," that has already infected hundreds of thousands of organisations.
"It is too early to guess the intentions of the threat actors behind it, but with previous Botnet DDoS attacks essentially taking down the Internet, it is vital that organisations make proper preparations and defence mechanisms are put in place before attack strikes." researchers said.
According to CheckPoint, IoTroop malware also exploits vulnerabilities in Wireless IP Camera devices from GoAhead, D-Link, TP-Link, AVTECH, Linksys, Synology and others.
At this time it is not known who created this and why, but the DDoS threat landscape is skyrocketing and could reach tens of terabits-per-second in size.
"Our research suggests we are now experiencing the calm before an even more powerful storm. The next cyber hurricane is about to come." CheckPoint researchers warned.
You need to be more vigilant about the security of your smart devices. In our previous article, we have provided some essential, somewhat practical, solutions to protect your IoT devices.
Kaspersky Opens Antivirus Source Code for Independent Review to Rebuild Trust
24.10.2017 thehackernews BigBrothers
Kaspersky Lab — We have nothing to hide!
Russia-based Antivirus firm hits back with what it calls a "comprehensive transparency initiative," to allow independent third-party review of its source code and internal processes to win back the trust of customers and infosec community.
Kaspersky launches this initiative days after it was accused of helping, knowingly or unknowingly, Russian government hackers to steal classified material from a computer belonging to an NSA contractor.
Earlier this month another story published by the New York Times claimed that Israeli government hackers hacked into Kaspersky’s network in 2015 and caught Russian hackers red-handed hacking US government with the help of Kaspersky.
US officials have long been suspicious that Kaspersky antivirus firm may have ties to Russian intelligence agencies.
Back in July, the company offered to turn over the source code for the U.S. government to audit.
However, the offer did not stop U.S. Department of Homeland Security (DHS) from banning and removing Kaspersky software from all of the government computers.
In a blog post today the company published a four-point plan:
Kaspersky will submit its source code for independent review by internationally recognised authorities, starting in Q1 2018.
Kaspersky also announced an independent review of its business practices to assure the integrity of its solutions and internal processes.
Kaspersky will establish three transparency centres in next three years, "enabling clients, government bodies & concerned organisations to review source code, update code and threat detection rules."
Kaspersky will pay up to $100,000 in bug bounty rewards for finding and reporting vulnerabilities in its products.
"With these actions, we will be able to overcome mistrust and support our commitment to protecting people in any country on our planet." Kaspersky's CEO Eugene said.
However, infosec experts' twitter commentary shows that the damage has already been done.
"Code review is absolutely meaningless. All Russian intelligence need is an access to KSN, Kaspersky's data lake which is a treasure trove of data. Even open sourcing the entire product won't reveal or even help with revealing that." Amit Serper, the security researcher at Cybereason, tweeted.
Now it is important to see whether these actions will be enough to restore the confidence of US government agencies in Kaspersky or the company will be forced to move its base out of Russia.
APNIC Whois Error Led to Exposure of Passwords
24.10.2017 securityweek Incindent
The Asia-Pacific Network Information Centre (APNIC), the non-profit organization that provides Internet addressing services in the Asia-Pacific region, informed the community on Monday of a Whois-related security incident that led to the exposure of authentication data.
According to APNIC Deputy Director General Sanjaya, downloadable Whois data included authentication details for Maintainer and IRT objects. APNIC discovered the incident on October 12 after a member of eBay’s Red Team reported that a third-party site had been republishing downloadable Whois data. The issue was resolved the next day.
The exposed data included password hashes that attackers may have been able to crack and use to falsify or corrupt Whois data.
APNIC says it has not found any evidence of abuse, but it’s still analyzing logs. The organization pointed out that any unauthorized changes would only result in public misrepresentation of Whois data and not actually cause the transfer of IP resources.
Sanjaya said the incident was related to Maintainer and Incident Response Team (IRT) objects in the APNIC Whois database. The role of the Maintainer is to protect objects in the database against unauthorized access, while the IRT contains contact information for reporting abuse to an organization.
Both Maintainer and IRT have an “auth” attribute that specifies a hashing format and stores an access password in the specified format. An error during the upgrade of the APNIC Whois database caused the “auth” hashes to be included in downloadable data.
Since learning of the leak, APNIC has been working with affected users to have the exposed passwords changed. The process was completed on Monday.
“All Maintainer and IRT passwords have now been reset, so there is no need to change them again if you are an APNIC resource holder,” Sanjaya said. “However, if you wish to change the new passwords to something more memorable, you should not choose the previous password (and if the old password was being used elsewhere on other systems, you should change those passwords).”
APNIC is now trying to determine what led to the error and what can be done to prevent such incidents when upgrades are performed in the future.
Nearly 100 Whole Foods Locations Affected by Card Breach
24.10.2017 securityweek Incindent
Amazon-owned Whole Foods Market informed customers last week that a recent hacker attack aimed at its payment systems affected nearly 100 locations across the United States.
Whole Foods has set up a webpage where customers are being provided some details about the breach. The page allows users to check if the store they made purchases in has been hit.
According to the company, cybercriminals may have stolen payment cards used at taprooms and full table-service restaurants in various cities in Alabama, Arizona, Arkansas, California, Colorado, District of Columbia, Florida, Georgia, Hawaii, Idaho, Illinois, Indiana, Kansas, Maine, Michigan, Minnesota, Missouri, Nevada, New Hampshire, New Jersey, New Mexico, New York, North Carolina, Ohio, Oregon, Pennsylvania, Tennessee, Texas, Virginia, Washington and Wisconsin. The largest number of affected locations is in California.Whole Foods hacked
Whole Foods said it had learned of unauthorized access to some payment systems on September 23 and replaced affected point-of-sale (PoS) devices by September 28. However, the investigation conducted by the firm in collaboration with cybersecurity forensics experts revealed that hackers had gained access to some stores in as early as March 10.
The malware planted on PoS systems was designed to collect cardholder names, account numbers, card expiration dates, and internal verification codes.
The supermarket chain pointed out that the incident only impacted payment systems at taprooms and restaurants within stores. Payments made at primary store checkout systems were not affected. The company has also highlighted that the breach does not impact Amazon.com, which uses separate systems.
The web page set up by the company to provide information about the breach includes recommendations on how customers can protect themselves and how to avoid being liable for any fraudulent charges on their credit and debit cards.
Fast food restaurant chain Sonic Drive-In also confirmed this month that it had suffered a payment card breach. It’s unclear how many locations are affected, but some experts reported that millions of cards may have been stolen in the attack.
Websites Increasingly Use HTTPS: Google
24.10.2017 securityweek Safety
Over 60% of Sites Loaded via Chrome Use HTTPS, Says Google
The number of websites that protect traffic using HTTPS has increased considerably in the past months, according to data shared by Google last week.
The tech giant says 64% of websites loaded via Chrome on Android are now protected by HTTPS, up from 42% one year ago. There is also a significant improvement in the case of Mac and Chrome OS – in both cases, 75% of Chrome traffic is protected, up from 60% and 67%, respectively.
Data from Google shows that 67% of Chrome traffic on Windows goes through an HTTPS connection, up from 40% in July 2015 and nearly 50% in July 2016.
As for popular websites, Google says 71 of the top 100 sites on the Web use HTTPS by default, compared to 37 one year ago.
When analyzed based on geographical location, the data shows significant improvements in several countries, including the United States (from 59% to 73%), Japan (from 31% to 55%) and Brazil (from 50% to 66%).
Google’s efforts to boost HTTPS adoption include displaying warnings in Chrome for sites that use HTTP when receiving user data, sponsoring the Let’s Encrypt certificate authority, and adding statistics on HTTPS to its transparency report.
“HTTPS is easier and cheaper than ever before, and it enables both the best performance the web offers and powerful new features that are too sensitive for HTTP. There’s never been a better time to migrate!” Emily Schechter, Chrome Security Product Manager, said in a blog post.
While the number of legitimate websites using HTTPS has increased in the past months, so has the number of phishing sites leveraging HTTPS. Netcraft reported in May that the proportion of phishing websites using HTTPS had increased from roughly 5% to 15% since late January.
Google has made several security-related announcements recently, including the expansion of its HSTS preload list, stronger security for “high risk” users, and new phishing protections.