
.png?ssl=1)
Industry Massively Underinsured Against Global Cyber Attacks: Study
17.7.2017 securityweek Cyber
Industry is massively underinsured against a major global cyberattack -- which could trigger losses on a par with natural disasters such as Hurricane (Superstorm) Sandy. This is one of the main conclusions of a study conducted by Lloyds of London (the world's oldest insurance organization with more than 20% of the global cyber insurance market), and Cyence (a risk modeling firm).
The report, "Counting the cost: Cyber exposure decoded" (PDF), examines two attack scenarios. In the first, attackers make a malicious modification to a hypervisor controlling the cloud infrastructure, which causes multiple server failures in multiple cloud customers. In the second, a zero-day vulnerability affecting an operating system with 45% share of the market is obtained by unidentified criminal groups that attack vulnerable businesses for financial gain.
In the first (cloud) scenario, the projected losses range from $4.6 billion for a large event to $53.1 billion for an extreme event. In the second (zero-day) scenario, the projected losses range from $9.7 billion for a large event to $28.7 billion for an extreme event. However, the report also notes that losses could be much lower or very much higher: as low as $15.6 billion or as high as $121.4 billion for an extreme cloud event.
The uninsured gap could be as much as $45 billion for the cloud services scenario – meaning that less than a fifth (17%) of the economic losses are covered by insurance. The insurance gap could be as high as $26 billion for the mass vulnerability scenario – meaning that just 7% of economic losses are covered.
This represents both a major market opportunity for the cyber insurance industry, and a poor understanding of the financial risk level within industry. The warning comes just weeks after major global ransomware attacks (WannaCry and NotPetya) and a U.S. government warning to industrial firms about a hacking campaign targeting the nuclear and energy sectors.
This variation in projected costs is caused by the second major conclusion drawn by the study -- neither the security industry nor the underwriting industry yet has sufficient understanding of global cybersecurity risk to formulate accurate risk/exposure figures for insurance purposes.
For example, for motor insurance, the industry has many years of detailed data on motor accidents: types of vehicle, ages of drivers, geolocations and so on; all against a background of improving motor safety. Cyber security, however, has little such data in a market whose conditions are continually worsening with new and more sophisticated attackers. This is further complicated by a poor understanding of liability and risk aggregation in cyber liability.
"The doomsday scenarios painted in the report highlight the growing issue of cyber risk aggregation," suggests Pete Banham, cyber resilience expert at Mimecast. "By adopting a cloud strategy that seeks to reduce the number of vendors, organizations may be tipping towards short term cost savings at the expense of security."
"For the insurance industry to capitalize on the growing cyber market," notes the report, "insurers would benefit from a deeper understanding of the potential tail risk implicit in cyber coverage." At the same time, it suggests, "Risk managers could use the cyber-attack scenarios to see what impacts cyber-attacks might have on their core business processes, and plan what actions they could take to mitigate these risks."
"This report gives a real sense of the scale of damage a cyber-attack could cause the global economy," comments Inga Beale, CEO of Lloyd's. "Just like some of the worst natural catastrophes, cyber events can cause a severe impact on businesses and economies, trigger multiple claims and dramatically increase insurers' claims costs. Underwriters need to consider cyber cover in this way and ensure that premium calculations keep pace with the cyber threat reality."
It should be noted, however, that the cyber security industry -- which could be impacted if industry diverts its primary risk strategy from mitigation (buying security controls) to transference (buying insurance) -- has its doubts.
"These are big numbers," comments David Emm, principal security researcher at Kaspersky Lab; but they don't mean much unless terms such as ‘serious cyber-attack' are quantified. How can we assess the global cost of an attack? It could mean anything from a temporary interruption of service to the takeover of customer systems – with very different costs. It's important for companies to conduct their own risk assessment and develop a strategy that's designed to secure corporate systems and mitigate the risk of an attack on those systems."
Two years ago, Lloyd's predicted that a major successful attack against the U.S. power grid "would cause between $243 billion to more than $1 trillion in economic damage.
Intel, Defense Bills Amended to Include Russian Hacking
17.7.2017 securityweek BigBrothers
Intelligence and defense policy legislation passed last week shows that the United States government is increasingly concerned about cyberattacks, particularly attacks coming from Russia.
The National Defense Authorization Act (NDAA), which the House of Representatives passed on Friday, specifies the budget and expenditures of the U.S. Department of Defense (DoD).
The list of amendments for the fiscal year 2018 includes several issues related to cyber capabilities. One of the adopted amendments requires the DoD to update its cyber strategy, to require the president to create a strategy for using offensive cyber capabilities, and providing technical assistance to NATO members.
Other amendments include improvements to training, recruitment and retention of cyber personnel; the possibility to request additional resources if the House of Representatives is the victim of a cyberattack; and banning the DoD from working with telecoms firms that were “complicit” with cyberattacks attributed to North Korea.
Another amendment requires the DoD to help Ukraine improve its cyber security capabilities. This comes after the country’s energy sector was hit two times by damaging cyberattacks believed to have been sponsored by the Russian government.
Russia is the focus of several amendments, including the cyberattacks believed to have been launched by state-sponsored actors and the country’s propaganda and disinformation initiatives. The Secretary of Defense and the Director of National Intelligence will be required to provide Congress a report on all attempts to hack DoD systems in the past two years by threat groups linked to Russia.
The Intelligence Authorization Act for Fiscal Year 2018, which the House Permanent Select Committee on Intelligence unanimously advanced on Thursday, also references Russia.
The Intelligence Authorization Act, which authorizes funding for the U.S. intelligence community, requires the Director of National Intelligence to submit a report assessing the most significant Russian influence campaigns aimed at foreign elections.
Without specifically naming Russia, the bill also requires an unclassified advisory report on foreign counterintelligence and cybersecurity threats to federal election campaigns. This comes after the U.S. officially accused Russia of attempting to interfere with last year’s presidential election.
There have been several incidents recently involving the leakage of classified information from the intelligence community, including the Vault7 files by WikiLeaks. An amendment to the Intelligence Authorization Act requires officials to submit semiannual reports on investigations into unauthorized public disclosures of classified information.
Another hot topic covered by the Intelligence Authorization Act is related to the retention of vulnerabilities. This has been a highly debated subject, particularly after the recent WannaCry ransomware attacks, which leveraged an exploit developed by the NSA. Following the attacks, a group of lawmakers introduced a new bill, the PATCH Act, whose goal is to help the government decide whether or not it should release vulnerability details to non-federal entities.
OmniRAT-Based Android Backdoor Emerges
17.7.2017 securityweek Virus
A newly discovered Android backdoor appears to be based on the OmniRAT remote administration tool (RAT) that targets Android, Windows, Linux and MacOS devices, Trend Micro security researchers warn.
Dubbed GhostCtrl, the threat masquerades as a legitimate or popular application and uses the names App, MMS, whatsapp, and even Pokemon GO. When launched, however, the malicious Android Application Package (APK) is decoded and saved on the Android device.
The APK is dynamically clicked by a wrapper and the user is prompted to install it. The prompt, Trend Micro explains, won’t go away even if the user attempts to dismiss the message, thus eventually annoying the user into accepting the installation.
Once the installation has been completed, a service that helps the malicious code run in the background is launched. The backdoor function is usually named com.android.engine, in an attempt to mislead users into believing it is a legitimate system process.
The malware then connects to the command and control (C&C) server to retrieve commands, which the server sends encrypted, but the malicious APK decrypts them upon receipt.
Trend's security researchers also noticed that the backdoor connects to a domain rather than directly to the C&C server’s IP address, most probably in an attempt to obscure traffic. Several Dynamic Name Servers (DNS) the researchers discovered at some point led to the same C&C IP address: hef–klife[.]ddns[.]net, f–klife[.]ddns[.]net, php[.]no-ip[.]biz, and ayalove[.]no-ip[.]biz.
“A notable command contains action code and Object DATA, which enables attackers to specify the target and content, making this a very flexible malware for cybercriminals. This is the command that allows attackers to manipulate the device’s functionalities without the owner’s consent or knowledge,” Trend Micro says.
The malware can control the Wi-Fi state; monitor the phone sensors’ data in real time; set phone’s UiMode, like night mode/car mode; control the vibrate function; download pictures as wallpaper; list the file information in the current directory and upload it to the C&C; delete/rename a file in the indicated directory; upload a desired file to the C&C; create an indicated directory; use the text to speech feature (translate text to voice/audio); send SMS/MMS to a number; delete browser history or SMS; download a file; call a phone number; open activity view-related apps; control the system infrared transmitter; and run a shell command and upload the output result.
“Another unique C&C command is an integer-type command, which is responsible for stealing the device’s data. Different kinds of sensitive—and to cybercriminals, valuable—information will be collected and uploaded, including call logs, SMS records, contacts, phone numbers, SIM serial number, location, and browser bookmarks,” the researchers explain.
Compared to other Android info-stealers, GhostCtrl can pilfer a great deal of data in addition to the above: Android OS version, username, Wi-Fi, battery, Bluetooth, and audio states, UiMode, sensor, data from camera, browser, and searches, service processes, activity information, and wallpaper.
Furthermore, the malware can intercept text messages from phone numbers specified by the attacker and can record voice or audio and upload the recording to the C&C. All the stolen data is sent to the server encrypted.
The malware also includes a series of commands that aren’t usually seen in Android RATs, such as the option to clear/reset the password of an account, set the phone to play different sound effects, specify the content in the Clipboard, customize the notification and shortcut link, control the Bluetooth to search and connect to another device, or set the accessibility to TRUE and terminate an ongoing phone call.
The first GhostCtrl packed a framework to gain admin-level privilege, but had no function codes. These, however, were included in the subsequent variants, which also added an increasing number of features to be hijacked. The second version could also work as ransomware by locking the device’s screen and resetting the password, and could root the device. The third version, the security researchers say, includes obfuscation techniques to hide its malicious routines.
“GhostCtrl’s combination with an information-stealing worm, while potent, is also telling. The attackers tried to cover their bases, and made sure that they didn’t just infect endpoints. And with the ubiquity of mobile devices among corporate and everyday end users, GhostCtrl’s capabilities can indeed deliver the scares,” Trend Micro said.
Ashley Madison Offers $11 Million in Data Breach Settlement
17.7.2017 securityweek Hacking
Ruby Life Inc., the owner and operator of the online adultery service Ashley Madison, has offered to pay $11.2 million to individuals affected by the 2015 data breach.
Ashley Madison was breached in July 2015 by hackers who had threatened to leak the personal details of the website’s customers unless its owners shut down the service.
In mid-August, the hackers leaked details associated with well over 30 million user accounts, including names, addresses, phone numbers, email addresses, dates of birth, users’ interests and their physical description, password hashes, and credit card transactions. A few days later, they also dumped internal company files and emails.
The incident caused problems for a lot of people and there have been several suicides possibly related to the leak of Ashley Madison user data. Individuals affected by the breach filed class actions alleging inadequate data security practices and misrepresentations regarding the dating service.
In December 2016, Ruby, formerly named Avid Dating Life, agreed to pay a $1.6 million penalty to settle charges with the U.S. Federal Trade Commission (FTC) and state regulators for failing to protect confidential user information.
Ruby announced on Friday that it has also settled the customer lawsuits. If the settlement is approved by the court, the company will pay a total of $11.2 million to a fund that will be used to compensate customers who submitted valid claims for losses resulting from the 2015 data breach.
“While ruby denies any wrongdoing, the parties have agreed to the proposed settlement in order to avoid the uncertainty, expense, and inconvenience associated with continued litigation, and believe that the proposed settlement agreement is in the best interest of ruby and its customers,” Ruby stated.
Ruby also clarified that the identities of individuals who had signed up for Ashley Madison were not verified, allowing users to create accounts using other people's information.
“Therefore, ruby wishes to clarify that merely because a person's name or other information appears to have been released in the data breach does not mean that person actually was a member of Ashley Madison,” the company said.
Hundreds of Domains Hijacked From French Registrar Gandi
17.7.2017 securityweek Hacking
Hundreds of domains were hijacked earlier this month and redirected to an exploit kit landing page as part of an attack targeting the French domain name registrar and hosting services provider Gandi.
According to an incident report published by Gandi last week, the hacker attack involved one of its technical partners, which helps the company connect to some of the 200 registries that allow it to manage more than 2.1 million domain names across 730 top level domains (TLDs).
The attacker managed to obtain credentials to a web portal of this technical partner. It’s unclear how the credentials were stolen, but Gandi suspects that the data may have been intercepted from the HTTP connection to its partner’s portal. The company highlighted that its own systems or the infrastructure of its technical partner have not been breached.
Once they gained access to the web portal, the attacker modified the name servers for 751 domains in an effort to redirect their visitors to an exploit kit.
According to SWITCH, the registry for .ch (Switzerland) and .li (Liechtenstein) domain names, which had 94 of its domains hijacked, victims were redirected to the RIG exploit kit. One of the affected domains belongs to Swiss security firm SCRT, which also had its incoming emails redirected to a foreign mail server.
Gandi said it learned about the incident on July 7 from a registrar and immediately started reverting the changes made by the attacker. The company has also reset all login credentials to the platforms used to connect to registries and technical partners.
In the case of SCRT, the visitors of its website were only redirected to the exploit kit for roughly one hour, but Gandi said the unauthorized changes were in place for up to 11 hours, until all the updates made by the attackers were reversed.
Gandi determined that 18 SSL certificates were issued for the affected domains during the attacks, but its analysis showed that each of the certificates is legitimate.
This was not the only recent incident involving domain names. Earlier this month, a security researcher noticed that he could register several domain names that matched the authoritative name servers for the .io TLD.
While the researcher suggested that registering the domains could have allowed him to hijack most of the DNS traffic for the .io TLD, others pointed out that the outcome couldn’t have been as catastrophic as the researcher claimed.
Backdoor Uses FFmpeg Application to Spy on Victims
17.7.2017 securityweek Virus
A recently observed feature-rich backdoor is capable of spying on its victim’s activities by recording full videos with the help of the "FFmpeg" application, Malwarebytes warns.
Detected as Backdoor.DuBled and written in .NET, the malware is distributed through a JS file containing an executable that installs itself under a random. To achieve persistence, the threat uses a run key, while also dropping a copy of itself in the startup folder.
The threat downloads the legitimate applications Rar.exe and ffmpeg.exe, along with related DLLs (DShowNet.dll and DirectX.Capture.dll) and uses them for its nefarious operations, the security researchers reveal.
FFmpeg is described by its developers as a "complete, cross-platform solution to record, convert and stream audio and video."
During run, the malware creates unencrypted .tmp files inside its installation folder, containing keystrokes and logging the running applications. It was also observed closing and deleting some applications from the compromised machine, including ProcessExplorer and baretail.
Communication with the command and control (C&C) server is performed over TCP using port 98. Initial beaconing is performed by the server via a command “idjamel,” to which the threat responds with basic information about the victim machine, such as name/username, operating system, and a list of running processes.
Next, the server sends the configuration, which includes a list of targeted banks which the malware saves the list to registry. The C&C also sends a set of Base64 encrypted PE files, including non-malicious helper binaries, and a URL to download the FFmpeg application (but the link points to a dummy page when accessed).
The analyzed sample was packed with the help of CloudProtector, which decrypts the payload using a custom algorithm and a key supplied in the configuration. The decrypted executable is then loaded in memory using process hollowing (or the RunPE technique).
“The unpacked payload is the layer containing all the malicious features. It is not further obfuscated, so we can easily decompile it and read the code,” Malwarebytes explains.
The threat was designed to spy on users and backdoor the infected machines. It can record videos using the FFmpeg application, snap screenshots, and log keystrokes. The video recording event is triggered when the victim accesses a site related to online banking, which clearly reveals the final purpose of the threat’s authors: to spy on victims’ banking activities.
Recorded videos are sent to the C&C encoded in Base64, while the screenshots (saved as JPG) and captured logs are periodically compressed using the RAR application, and then sent to the server.
The malware can also enumerate opened windows and can disable anti-malware applications. What’s more, the bot’s functionality can be expanded with the help of plugins, which it downloads from the C&C.
Two of the plugins the malware downloaded during analysis provided it with capabilities typical for a RAT: processmanager.dl (written in 2015), and remotedesktop.dll (written in 2016). The latter plugin was obfuscated, although the main malware module and the former plugin weren’t.
“This malware is prepared by an unsophisticated actor. Neither the binary nor the communication protocol is well obfuscated. The used packer is well-known and easy to defeat. However, the malware is rich in features and it seems to be actively maintained. Its capabilities of spying on the victim and backdooring the attacked machine should not be taken lightly,” Malwarebytes concludes.
SMS Phishing induces victims to photograph its own token card
17.7.2017 securityaffairs Phishing
Renato Marinho detailed an unusual SMS phishing campaign that hit Brazilian users. All started with an SMS message supposedly sent from his bank.
Introduction
Today I faced quite an unusual SMS phishing campaign here in Brazil. A friend of mine received an SMS message supposedly sent from his bank asking him to update his registration data through the given URL. Otherwise, he could have his account blocked, as seen in Figure 1.

.png?ssl=1)
Figure 1 – SMS message received
Telling you the truth, my friend doesn’t have any account on the informed bank and, even so, we know that those kinds of message are hardly ever sent by banks and are, most of the time, related to malware propagation and information stealing. However, instead of discarding the message, we decided to give it a try and the results, as you are going to read in this diary, surprised us. This campaign involves no malware propagation – just creativity in favor of evil.
SMS Phishing analysis
The link in the message aims to take the victim to a fake and very simplistic mobile version of a well-known bank website. First, it asks for the “CPF” (a kind of social security card number) and a password, as seen in Figure 2.

Figure 2 – Fake bank website asking for CPF and password
It is interesting noting that there is a data input validation. The user must obey to the CPF number composition rules otherwise he can’t proceed. This validation is done by the JavaScript code shown in Figure 3.

Figure 3 – CPF validation rules
This kind of validation is certainly used to give a bit of legitimacy to the fake website and, perhaps, to do not overload crooks with much “data-mining” work.
In the next page, the fake website informs that the device used on that connection needs to be authorized, as seen in Figure 4.

Figure 4 – Fake website: user must authorize the device
By clinking on “Habilitar Aparelho” which means “enable device”, a new page is shown asking for the victim to inform the 4-digit password, as seen in Figure 5.

Figure 5 – Fake website asking for the 4-digit password
Again, there is a minimum validation to avoid the user trying very simple passwords like “1234” as seen in Figure 6.

Figure 6 – 4-digit password “validation” code
Next, the step that caught our attention. The fake website asks the victim to take a picture of its token card and upload it. To be precisely, asks to take a picture of the side with all security codes used to validate banking transactions as a second-factor authenticator, as seen in Figure 7.

Figure 7 – Asking for the token card picture
By clicking on “Finalizar Habilitação” which means “proceed with the device authorization”, the victim’s smartphone will prompt the user to select a picture from its library or take a new one – which is exactly what the user is induced to do, as seen in Figure 8.

Figure 8 – Taking the token card picture
Once the victim ends up the whole process, including the token card picture, the criminals will have all the information needed to make fraudulent transactions on the compromised bank account and the user is forwarded to the real bank login page.
Final words
Using victim’s smartphone to take pictures to steal information or, who knows, things, scares me a little bit. I can explain. Earlier this month, reading Bruce Schneier’s blog I saw a post entitled “Now It’s Easier than Ever to Steal Someone’s Keys” [1] which says, “The website key.me will make a duplicate key from a digital photo.”.
While writing this diary, I was reported about similar SMS Phishing campaigns targeting other banks costumers here in Brazil. Stay tuned.
References
[1] https://www.schneier.com/blog/archives/2017/07/now_its_easier_.html
Ashley Madison to Pay $11.2 Million to Data Breach Victims
17.7.2017 thehackernews Incindent
Ashley Madison, an American most prominent dating website that helps people cheat on their spouses has been hacked, has agreed to an $11.2 Million settlement for roughly 37 million users whose personal details were exposed in a massive data breach two years ago.
Though the parent company of Ashley Madison, Ruby Corp., denies any wrongdoing, the company has pledged to pay around $3,500 to each of the hack's victims for the settlement.
The settlement has to be reviewed by a federal judge in St. Louis.
Ashley Madison marketed itself as a means to help people cheat on their spouses, with a tagline "Life is short. Have an affair."
The site was breached in July 2015 and hackers dumped nearly 100 gigabytes' worth of sensitive data belonging to 37 million users of the casual sex and marriage affair website onto the dark web.
The leaked data included victims' usernames, first and last names, email addresses, passwords, credit card data information, street names, phone numbers, and transactions records, which led to blackmails and even suicides.
The 2015 data breach cost Ruby Corp, formerly known as Avid Life, over a quarter of its revenue and forced the Toronto-based company to spend millions of dollars to boost security and user privacy.
Ruby Corp was already forced to pay $1.66 Million to settle charges from Federal Trade Commission (FTC) and 13 states, alleging that the service misled its consumers about its privacy policy and didn't do enough to protect their information.
Besides this, the company also agreed to 20 years' worth of the FTC overseeing its network security to ensure that its user data is being protected. This includes:
Performing a risk assessment to protect customer data.
Implementing new data security protocols.
Upgrading systems based on the assessments.
Offering periodic security risk assessment (both internal and third-party).
Requiring "reasonable safeguards" against any potential cyber attacks from their service providers.
Now, according to Reuters, the company has to pay $11.2 million to users who were affected by the breach – users with valid claims can get up to $3,500 depending on their losses attributable to the breach.
Windows 10 Will Now Let You Reset Forgotten Password Directly From the Lock Screen
17.7.2017 thehackernews Safety
Microsoft is making every effort to make its Windows 10 Fall Creators Update bigger than ever before by beefing up its security practices and hardening it against hackers and cyber attacks in its next release.
Microsoft is finally adding one of the much-requested features to Windows 10: Pin and Password recovery option directly from the lock screen.
Yes, the next big update of Windows 10, among other features, will allow you to recover your forgotten pin and password, allowing you to reset your Windows password directly from the lock screen.
In Windows 10 Fall Creators Update, you will see "Reset password" or "I forgot my PIN" options on the login screen along with the sign-in box, mspoweruser confirmed.
Once you click on the option, Windows 10 will take you to the OOBE where Cortana will help you reset your password, after you successfully verify your identity using either your secondary email, your phone number, or Microsoft Authenticator.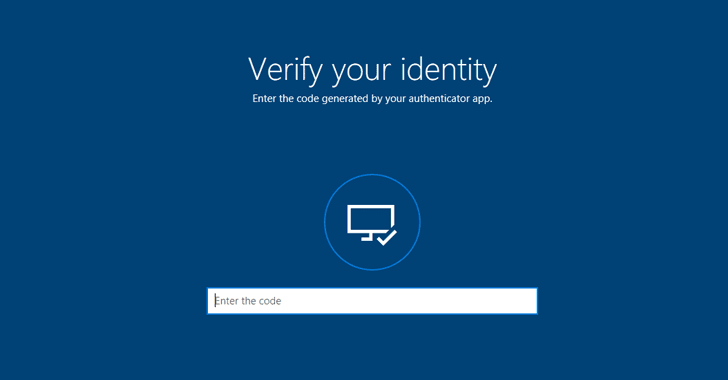
A verification code will be sent to the option you chose, and once you entered and verified your identity, you will be able to reset the password and regain access to your computer directly from the login screen.
The tech giant is currently testing this new feature in its Windows 10 Insiders build 16237, making it much easier for them to recover their Microsoft Accounts.
You can use this option if you have either activated the Windows Hello authentication system or have a PIN to secure your account.
With the launch of Windows 10 Creator Update (also known as RedStone 3), which is expected to release sometime between September and October 2017, the company has already planned to:
Remove the 30-year-old SMB v1 file sharing protocol.
Build AI-powered antivirus software.
Build its EMET anti-exploit tool into the kernel of the operating system.
Support three different flavours of the Linux OS – Ubuntu, Fedora, and SUSE – directly through their Windows Store.
Add new anti-ransomware feature, called Controlled Folder Access, as part of its Windows Defender.
Besides this new upgrade, Windows 10 Fall Update also includes improvements to Acrylic Material translucency effects, Task Manager, Mixed Reality headset and much more.
You can check out the complete list here.
What’s new after the AlphaBay Market Shutdown in the darkweb?
17.7.2017 securityaffairs CyberCrime
Authorities shut down Alphabay, wondering which will be the marketplace that will reach the top and which will be the impact on the criminal ecosystem?
AlphaBay was shut down by law enforcement and the alleged mastermind committed suicide in jail while waiting for the extradition to the US.
The event will have a significant impact on the cyber criminal underground, now it is interesting to analyze the evolution of the others black marketplaces in order to understand which will be the biggest one in the next months.
A good source could be the Dark Net Markets Comparison Chart published by the website DeepDotWeb.com, it integrates marketplace data with the hidden Dark Net Markets List ratings, along with uptime status data provided by our monitoring system and creation dates from Gwern.net.
The researchers at DeepDotWeb used the following parameter to evaluate the popularity of each market, data is relayed to the past 28 days until July 12.
Impressions & Clicks – These two features give us an indication of the number of pages from this site will appear on Google for search queries containing the market name.
Searches on the site – is simple how many times people entered the site search terms that relate to the specific market in DeepDotWeb’s internal search.
Hits on related pages: How many visits there were on pages inside deepdotweb that their focus is some specific market (filtered using google analytics).
The table proposed by the DeepDotWeb shows that the Russian black marketplace RAMP (Russian Anonymous Marketplace) and DreamMarker are the biggest markets after the shutdown of the AlphaBay, followed by the Hansa Market.

RAMP marketplace (http://ramp5bb7v2abm34a.onion) is a Russian marketplace having a forum-like organization, it is frequented by prominent hackers from Eastern Europe.
Due to the forum-like structure, the products are not organized into categories, it is not easy to calculate the exact number of listings or vendors on RAMP.
RAMP is operating since September 2012, it is probably the oldest running darknet market! It has already outlived its rivals Silk Road, Agora, and AlphaBay.
It is not clear how RAMP survived so long, there are some speculations regarding its longevity, someone believes that the main reason is that it is a Russian focused market.
There are four main categories of vendors on RAMP:
Audited Dealers
Private Points
Market
Miscellaneous
The Audited Dealers group includes the more reliable group of vendors.
Like black marketplace, RAMP lists several prohibited posts and discussions about illegal goods and activities, including drugs, pornography and child pornography, weapons, fake documents. and banknotes.
“Based on the statistics presented on the forum at the time we did this review, RAMP had 186,304 users; 13,224 created topics, 931,494 posts (all time), and 88 posts for the week. These numbers show that RAMP is indeed a significant darknet community.” states the analysis published on the website Darknetmarkets.co.”The longevity and popularity of Russian Anonymous Marketplace appear surprising to some especially as the site claims to make around a quarter of a million every year but RAMPs’ owners believe that this is because it is in Russian and serves predominantly Russian users. Also, it could be due to its focus on drugs and prohibition of hacking and pornography.”

The Dream Market (http://lchudifyeqm4ldjj.onion/?ai=1675) has been around since Nov/Dec 2013, it is an excellent aggregator for buyers and sellers of any kind of drugs (i.e. Cannabis, Benzos, Ecstasy, etc.).
The filtering feature makes it easy to search the items offered on the black market places.
The listing for Digital Goods is growing with sellers offering mostly fraud-related goods, such as stolen account data, stolen credit card data (CV, CCV) and fake documents.
Many sellers offer guides and tutorials on hacking and other illegal activities such as carding, it is also possible to find counterfeit banknotes from many countries. Hacking services are skinny, no significant deals are available. Same story for purchasing and customizing malware, it is quite easy to find well-known RATs and Keylogger, but this isn’t the right place where to find complex malware.
http://lchudifyeqm4ldjj.onion/?ai=1675
The remain markets are smaller and the values of parameters used for the analysis demonstrate it.
NAME IMPRESSIONS CLICKS SEARCHS ON SITE HITS ON RELATED PAGES
Alphabay (Defunct) 323,452 67,713 1,116 408,016
RAMP (Russian) 58,618 23,413 363 210,271
Dream Market 56,430 32,467 451 227,470
Hansa Market 55,629 16,811 1 98,090
Silk road 3.1 10,418 1,048 10 14,365
House of lions 74 25 1 9,023
Darknet Heroes League 578 275 11 7,499
Apple market 177 14 2,680 6,727
WALL ST Market 885 68 4 5,593
The Majestic garden 2,353 849 1 4,655
CGMC 811 244 5 3,576
Zion Market 327 14 3 3,325
TradeRoute 260 103 7 3,061
Pyramid market 9 0 0 2,699
Pekarmarket 8 4 1 1,932
RSclub 69 32 0 1,538
Tochka 50 11 104 396
Did you receive a WhatsApp subscription ending email or text? Watch out!
17.7.2017 securityaffairs Social
Did you receive a WhatsApp subscription ending email or text? Watch out! It is a scam to steal your payment and personal data.
Researcher Graham Cluley is warning of bogus ‘WhatsApp subscription ending’ emails and texts.
Internet users are receiving an email pretending to be from WhatsApp and warning them of the ending for an alleged WhatsApp subscription.
Although the company stopped requesting any payment since January 2016, crooks are attempting to exploit the fact that in the past, WhatsApp used to ask users to pay a fee after they had been using the service for a year.
Using this social engineering attack, crooks aim to trick users into clicking links including in the messages that might result in they handing their payment information over to attackers.
“Have you received an email claiming to come from WhatsApp that warns that you have been using the service for more than one year and that it’s time to take out a subscription?”
“Beware! The emails are, of course, a scam designed to trick you into clicking links that might result in you handing your payment information over to fraudsters.” states the blog post published by Graham Cluley on the ESET blog.


Below a portion of the malicious email:
Your subscription is ending soon
Please update your payment information now
UPDATE YOUR PAYMENT INFORMATION
Our records indicate that your WhatsApp trial service is exceeding the one year period. At the completion of your trial period your WhatsApp will no longer be able to send or receive message. To continue using WhatsApp without interruption, we need you to subscribe for any of our subscription periods.
As usual, you should always be wary of unsolicited email messages and SMS text messages claiming to come from WhatsApp demanding payments or the verification of your account’s credentials.
“You ultimately decide what links you click on, and whether you hand over your passwords and payment card details. Always think twice, because the wrong decision could prove costly.” concluded Graham Cluley.
Crooks used Infrared insert skimmers in a recent wave of ATM attacks
16.7.2017 securityaffairs Attack
The number of cyber attacks against ATM involving so-called ‘insert skimmers’ is increasing. Bran Krebs wrote about recent attacks using infrared devices.
The number of cyber attacks against ATM involving so-called ‘insert skimmers’ is increasing. Insert Skimmers are wafer-thin fraud devices designed to fit invisibly inside the ATM card slot.
Insert Skimmers are able to capture card data and store it on an embedded flash memory.
The popular cyber security expert Brian Krebs reported in some cases the use of insert skimmers that are able to transmit stolen card data wirelessly via infrared.
The infrared is a short-range communication technology, every day we use it when we change TV program with a television remote control.
Krebs cited a case that has happened a few weeks ago in the Oklahoma City metropolitan area where at least four banks were victims of ATM attacks involving insert skimmers.
The KFOR news channel quoted a local police detective saying “the skimmer contains an antenna which transmits your card information to a tiny camera hidden somewhere outside the ATM.”

An insert skimmer retrieved from a compromised cash machine in Oklahoma City. Image: KrebsOnSecurity.com.
Krebs confirmed that financial industry sources tell him that preliminary analysis of the insert skimmers used in the ATM attacks confirms they were equipped with technology to transmit stolen card data wirelessly to the hidden camera using infrared.
The insert skimmers used to compromise cash machines in Oklahoma City were equipped with the hidden that was used to record time-stamped videos of ATM users entering their PINs and to receive card data recorded and transmitted by the insert skimmer.
This design helps crooks in reducing maintenance activities for the skimmers, for example when they need to substitute the internal battery, they could leave the device in the ATM slot and swap out the hidden camera.
The skimmers are optimized to preserve battery, according to Krebs the insert skimmer also uses an embedded battery that is turned on only when someone inserts a card into the ATM slot.
The spy cameras are deployed to remain hidden, crooks use tiny pinholes cut into false fascias that they install above or beside the PIN pad.
“Thieves involved in skimming attacks have hidden spy cameras in some pretty ingenious places, such as a brochure rack to the side of the cash machine or a safety mirror affixed above the cash machine (some ATMs legitimately place these mirrors so that customers will be alerted if someone is standing behind them at the machine).” wrote Krebs.
“More often than not, however, hidden cameras are placed behind tiny pinholes cut into false fascias that thieves install directly above or beside the PIN pad. Unfortunately, I don’t have a picture of a hidden camera used in the recent Oklahoma City insert skimming attacks.”
Let me suggest covering the pin pad with your hand when you enter it, in this case, the hidden camera will not be able to record it. Krebs also wars of non-video methods to obtain the PIN (such as PIN pad overlays), but he explains that these devices are rare and more expensive for fraudsters.
If you are searching more information about Skimmers devices check out Brian Krebs’s series All About Skimmers.
NemucodAES ransomware and Kovter trojan bundled in the same campaigns
16.7.2017 securityaffairs Ransomware
Security experts at the SANS Institute discovered that that NemucodAES ransomware and Kovter trojan are being delivered together in spam campaigns.
Security experts at the SANS Institute Internet Storm Center, discovered that that two malware families, NemucodAES and Kovter are being delivered together in .zip attachments delivered via active spam campaigns.
Security Researcher Brad Duncan noticed in the last couple of weeks a significant increase in malicious spam delivering .zip archives with JavaScript files used to download and execute the NemucodAES ransomware and Kovter click-fraud malware.
NemucodAES is a variant of the Nemucod Trojan downloader, known for being used in different campaigns in 2016 distributing Locky and TeslaCrypt ransomware.
“By March 2016, we started seeing reports of ‘Nemucod ransomware’ that stopped downloading ransomware binaries in favor of using its own script-based ransomware component,” Duncan wrote in a SANS Institute Internet Storm Center posted Friday.
“And now in July 2017, we see the next phase of Nemucod ransomware: NemucodAES. Emisoft states this new variant is written in JavaScript and PHP. It uses AES and RSA to encrypt a victim’s files.”
The NemucodAES ransomware is easy to neutralize due to the availability of a decryptor, meanwhile, Kovter click-fraud is a fileless malware hard to detect. Kovter was also used by threat actors to steal personal information and download and execute additional malicious payloads.
Spam campaigns deliver the malicious .zip archives disguised as notices from the United Parcel Service.
“Malspam with Zip archives containing JavaScript files are easy for most organizations to detect… But some of these messages might slip past your filtering, and some people could possibly get infected. With the NemucodAES decryptor, people can recover their files, but I expect this ransomware will continue to evolve,” Duncan wrote.
Kovter was packaged with other ransomware in past campaigns, in February, experts at Microsoft’s Malware Protection Center spotted malicious email campaigns using .lnk attachments to spread Locky ransomware and Kovter.
Back to the recent campaign, NemucodAES and Kovter were bundled in malicious .zip archives. When victims unpack the archives a JavaScript file is extracted.
“Network traffic was typical for an infection by one of the .js files. We first see HTTP requests for the NemucodAES JavaScript, followed by requests for various executables. Then we see the post-infection Kovter traffic. NemucodAES doesn’t generate any traffic on its own,” according to the research report.
The NemucodAES ransomware encrypt files without appending any info to the original file names, then it delivers in the “AppData\Local\Temp” directory instructions (via an .hta file) to decrypt the files. It also uses a Windows desktop background (a .bmp file) as the ransomware note.

Victims are requested to pay a $1,500 ransom in Bitcoin.
Experts are investigating the presence of the Kovter malware in the campaigns. Kovter seems to be used only to check traffic and generating command-and-control traffic.
“I see a lot of post-infection events for Kovter command and control traffic. But I’m not certain click-fraud is involved any more,” Duncan said.
Give a look at the SANS’s analysis for further details about this campaign.
How encryption can help startups in protecting their data
16.7.2017 securityaffairs Safety
The deployment of encryption in modern businesses does not only guarantee hundred percent security but it also reduces the surface of attack.
Data protection has become the top objective for many businesses in the world today. Especially after the ransomware incident, hacked credit card databases and the Apple leak. Businesses are scratching their heads in anticipation of what could hit them next?
It is a brilliant idea from the executives to prioritize data protection over everything. Nonetheless, it is equally difficult to harmonize security processes across several systems and devices. Even the most cautious and watchful business owners can leave out data unprotected.
Encryption is highly regarded as one of the best-sought solutions for this problem. The deployment of encryption in computers, cloud systems, mobile phones and other business avenues does not only guarantee hundred percent security but it also substantially eliminates the potential of being attacked and incurring financial loss.
encryption
How does encryption work?
Creating a synergy with other security measures, encryption secures the data and its trafficking to other parties. After being encrypted, a file becomes impossible to crack or decipher, and it becomes difficult to break into sensitive or valuable business information.
How can business owners encrypt their company’s data?
As a responsible and clever business owner, you must place a high emphasis on data breaches and financial losses, and this can only be achieved by employing complete encryption of devices and network. Encryption can be implemented and help in the following areas for protection of your valuable data:
Wi-Fi Hotspots
A laptop acts as a blessing when traveling and you require access to company files, but using an unsecured Wi-Fi public hotspot can backfire pretty badly and make you vulnerable to attacks.
Emails
With email becoming the standard medium for the exchange of sensitive information, it is equally important to keep the process encrypted to avoid losing information to data thieves. All businesses should engage in premium level encryption to protect their data, irrespective of whether probable hackers possess physical access to computers or not.
Passwords
Your password is an essential element of encryption. To make the password hack-proof, make it long; 10 or more characters is advisable. The code should consist both upper and lower case letters, numbers, and special characters. It is recommended to keep separate passwords for each system and device, and document them in a safe place if remembering them is a hard job to do.
Cloud
Despite its attractiveness such as affordability, convenience, and sharing, Cloud Storage solutions are quite vulnerable to external attacks. Dropbox and other big names in the Cloud storage scene offer built-in data encryption of your data stored on their servers. But, the point to be highlighted here is that they also hold the decryption keys, which, in certain situations might be used to access your stored information. There are many products which give an extra protection layer to cloud storage locations.
Search Engines
Like it or not, Google, Yahoo, and other search engines will catalog every search you perform on the internet. Your online web search choices are then attached to your computer’s IP address and are subsequently used to customize the advertising and searches for your machine. This cataloging might seem unobtrusive and perhaps even useful, but it is also a risk for future public embarrassment and social faux pas. Don’t let these search engines store your searches for ‘anti-depressants,’ ‘love advice,’ ‘divorce lawyers,’ and ‘anger management’. To avoid it, a VPN browser can help you cloak your IP address so you can keep your private searches private. If you are connected to a VPN, your online traffic is redirected to a 3rd party server, which encrypts the information.
USB and External Drives
Portable data storage and plug and play devices sure are useful, but attached with it are the theft/loss strings. Gladly, products such as BitLocker To Go, helps keep portable storage drives encrypted when fallen into the wrong hands.
A password to open a company PC would be useless if one can get away with the hard disk. All it would require is, to connect the hard drive to another system and alas, access to all the data right in front. To avoid this mishap, Microsoft BitLocker software for Ultimate Windows 7 or Vista (or the Enterprise or Pro Windows 8), that offers complete hard drives encryption. To turn on the feature, just go to Control Panel > System and Security > BitLocker Drive Encryption.
In a Nutshell…
Guarding your sensitive information against theft and vulnerability isn’t a tough task in today’s digital world, particularly with the progressive adoption of cloud computing. The fact of the matter is, despite all the security measures, sometimes, hackers and cyber criminals still can find their way through a company’s or individual’s system, making it vulnerable to date theft or data leakage.
For that reason, it is said to consider prudently what (and when) you want to save on the cloud, and consult with a professional cloud services provider to find out what encryption level suits you best.
In the modern business environment, which is increasingly depending upon on computers and cloud-based storage, nothing is or at least should be, dearer to you than a rock-solid encryption strategy which can ensure your long-term safety and success.
Hackshit PhaaS platform, even more easy to power Phishing campaigns
16.7.2017 securityaffairs Phishing
The experts from Netskope Threat Research Labs discovered the Hackshit PhaaS platform, another interesting case of crimeware-as-a-service.
A few days ago, we discussed the Katyusha scanner,a powerful and fully automated SQLi vulnerability scanner discovered by researchers at security firm Recorded Future that was available for $500 in the cyber crime underground.
The Katyusha scanner is just one of the numerous hacking tools and crimeware-as-a-service available in the hacking community.
Today I desire to present you another crimeware-as-a-service that was discovered by the experts from Netskope Threat Research Labs dubbed Hackshit.
The Hackshit is a Phishing-as-a-Service (PhaaS) platform that offers low cost, “automated solution for the beginner scammers,” it allows wannabe crooks to easily launch a phishing campaign.
Dubbed Hackshit, the PhaaS platform attracts new subscribers by offering them free trial accounts to review their limited set of hacking tutorials and tricks to make easy money.
“Netskope Threat Research Labs recently discovered a Phishing-as-a-Service (PhaaS) platform named Hackshit, that records the credentials of the phished bait victims. The phished bait pages are packaged with base64 encoding and served from secure (HTTPS) websites with “.moe” top level domain (TLD) to evade traditional scanners. “.moe” TLD is intended for the purpose of ‘The marketing of products or services deemed’. The victim’s credentials are sent to the Hackshit PhaaS platform via websockets. ” states a blog post published by Netskope.
The researchers discovered the PhaaS platform during a research about the trends of CloudPhishing attacks. They observed a phishing page using data URI scheme to serve base64 encoded content (data:text/html;base64) delivered from “https://a.safe.moe,” accessing the link the researchers were presented a phished login page for Google Docs.
Once the victims have provided their credentials, they presented another phishing page whose source uses a data URI scheme to serve base64 encoded content (data:text/html;base64) again from https://a.safe.moe.
This second phished page was designed to trick victims into providing recovery details of their email account. Once the victim has provided his details, he is redirected to the original Google recovery page.
The experts decoded the two phishing pages and discovered that the credentials are sent to the attacker via a websocket to https://pod[.]logshit[.]com and https://pod-1[.]logshit[.]com.
“Accessing logshit[.]com led us to the discovery of the PhaaS website named Hackshit as shown in Figure 6. Further research concluded the website is serving as a PhaaS platform.” continues the blog post.

Hackshit is a PhaaS platform that offers several phishing services and it also implements a black marketplace to buy and sell such kind of services.
“The marketplace is a portal that offers services to purchase and sell for carrying out the phishing attacks,” Netskope researcher Ashwin Vamshi explained.
“The attacker then generates a phished page from the page/generator link and logs into the email account of the compromised victim, views all the contacts and sends an email embedded with the phished link.”
Crooks can purchase site login accounts of compromised victim from the marketplace using Perfect Money or bitcoins.
Using the Hackshit, subscribers can easily generate their unique phishing pages for many popular services, including Yahoo, Facebook, and Gmail.
Experts also noticed that the Hackshit website uses an SSL certificate issued by the open certificate authority Let’s Encrypt.
Let’s see which is the pricing model behind the PhaaS, Hackshit offers several subscription tiers from Starter to Master, ranging from 40 USD per week to 250 USD for 2 months.
Hackshit demonstrated that crimeware-as-a-service represent a serious risk for businesses and end-users, it is bringing wannabe hackers into the cybercrime arena.
CISCO issues security patches for nine serious RCEs in SNMP subsystem in IOS and IOS XE
15.7.2017 securityaffairs Vulnerebility
Cisco has fixed nine serious remote code execution flaws in the SNMP subsystem running in all the releases of IOS and IOS XE software.
The tech giant publicly disclosed the vulnerability on June 29 and provided workarounds, not it is notifying customers about the availability of security patches.
The nine issues, that have been tracked with codes from CVE-2017-6736 to CVE-2017-6744, were all patched by the company. All the flaws could be exploited by a remote unauthenticated attacker by sending specially crafted SNMP packets, resulting in arbitrary code execution or causing the system to reload.
“The Simple Network Management Protocol (SNMP) subsystem of Cisco IOS and IOS XE Software contains multiple vulnerabilities that could allow an authenticated, remote attacker to remotely execute code on an affected system or cause an affected system to reload. An attacker could exploit these vulnerabilities by sending a crafted SNMP packet to an affected system via IPv4 or IPv6. Only traffic directed to an affected system can be used to exploit these vulnerabilities.” states the advisory published by CISCO in June.
The experts warned of nine flaws affecting the Simple Network Management Protocol (SNMP) component of IOS and IOS XE software.
The flaws are due to a buffer overflow condition in the SNMP subsystem, all versions of SNMP – Versions 1, 2c, and 3 are affected.
Cisco SNMP
As reported by the advisory, an authenticated attacker who knows the SNMP read-only community string of a target system could remotely execute code or cause the device to reload by sending a specially crafted SNMP packet via IPv4 or IPv6.
The attack is very dangerous because hackers could obtain full control of vulnerable devices and the worst news is that CISCO warned customers that attackers in the wild know about the vulnerabilities and can exploit them in any moment.
“A successful exploit could allow the attacker to execute arbitrary code and obtain full control of the affected system or cause the affected system to reload,” Cisco said in its advisory.
Cisco confirmed that any device configured with a list of particular management information base (MIBs) is also vulnerable. MIBs are databases associated with SNMP implementations and are used to manage devices in a communication network.
CISCO when disclosed the issued The company’s original workaround recommendation was to disable the affected MIBs.
Devices configured with any of the following MIBs are vulnerable:
ADSL-LINE-MIB
ALPS-MIB
CISCO-ADSL-DMT-LINE-MIB
CISCO-BSTUN-MIB
CISCO-MAC-AUTH-BYPASS-MIB
CISCO-SLB-EXT-MIB
CISCO-VOICE-DNIS-MIB
CISCO-VOICE-NUMBER-EXPANSION-MIB
TN3270E-RT-MIB
“Some of the MIBs may not be present on all systems or versions but are enabled when present,” continued the Cisco advisory.
“Administrators may be accustomed to utilizing the show snmp mib command in privileged EXEC mode to display a list of enabled MIBs on a device,” Cisco said. “Not all of the MIBs will be displayed in the output of the show snmp mib command but may still be enabled.” Customers were advised to implement the entire exclude list.
CISCO customers need to apply the patches, the company also recommends network managers to regularly change community strings, which are used to restrict read/write access to SNMP data on a device running IOS or IOS XE.
“These community strings, as with all passwords, should be chosen carefully to ensure they are not trivial,” Cisco said. “They should also be changed at regular intervals and in accordance with network security policies.”
Ovidiy Stealer a cheap and efficient infostealer offered for sale
15.7.2017 securityaffairs Virus
A new infostealer malware dubbed Ovidiy Stealer was offered for sale by a Russia-speaking malware developer that goes online with the moniker “TheBottle.”
TheBottle has advertised the malware on various cybercrime forums.
The Ovidiy Stealer was first spotted in June 2017, according to the experts at security firm Proofpoint the malware is under development and is gaining popularity in the cyber criminal underground.
“Proofpoint threat researchers recently analyzed Ovidiy Stealer, a previously undocumented credential stealer which appears to be marketed primarily in the Russian-speaking regions. It is under constant development, with several updated versions appearing since the original samples were observed in June 2017. The growing number of samples demonstrate that criminals are actively adopting this malware.” states the analysis published by Proofpoint.

The infostealer is offered for sale on a Russian website for 450-750 Rubles ($7-$13), according to the malware researchers, the low price is because the malware isn’t so efficient as other malicious codes available on the market.
Malware experts at Proofpoint discovered the Ovidiy Stealer is currently being spread via email as executable attachments, compressed executable attachments, and links to an executable download.
“It is also likely spread via file hosting / cracking / keygen sites, where it poses as other software or tools. In several cases, we observed the Ovidiy Stealer bundled with a “LiteBitcoin” installer, further validating this claim.” continues the analysis.
The experts claim the Ovidiy Stealer is not complex, it doesn’t obtain boot persistence and currently implements only a few features.
It can collect and steal information from many popular applications, including:
FileZilla
Google Chrome
Kometa browser
Amigo browser
Torch browser
Orbitum browser
Opera browser
Once the malware has siphoned the information from the victims it sends it back to a control panel that is used by all the subscribers to access them. The panel is published on the same server that hosts the website, at ovidiystealer.ru, an operation choice that shows the lack of experience of the author.
Another TheBottle’s mistake is the use of RoboKassa for payments, it is a PayPal-like money processor based in Russia that does not ensure users’ anonymity.
“Ovidiy Stealer is a new password stealer that entered the criminal ranks barely one month ago. While it is not the most advanced stealer we have seen, marketing and an entry-level price scheme make it attractive and accessible to many would-be criminals. Ovidiy Stealer is lightweight and simple enough to work with relative ease, allowing for simple and efficient credential exfiltration.” concluded Proofpoint.”A lightweight, easy-to-use, and effective product coupled with frequent updates and a stable support system give Ovidiy Stealer the potential to become a much more widespread threat. “
Risk Intelligence Firm Flashpoint Raises $28 Million
15.7.2017 securityweek Security
Flashpoint, a New York, NY-based threat intelligence and research company that focuses on what it calls “Business Risk Intelligence” (BRI) gleaned from combing the Deep & Dark Web, has raised $28 million in Series C funding.
The company goes beyond what many traditional cyber threat intelligence providers collect, which typically includes technical indicators such as IP addresses, domains, and signatures. Flashpoint collects information and monitors conversations in the underground, including cybercriminal groups and terrorist organizations such as the Islamic State (Daesh) and its supporters.
According to the company, the additional funding will help support adoption of its BRI offerings and support the recruitment of additional threat intelligence analysts.
As Flashpoint explains, the company provides customers with “visibility into real threats with the potential to harm them and the context to help them understand how these threats could impact their business.”
"Traditional cyber threat intelligence, which has been largely focused on indicators of compromise, is insufficient in supporting the risk decision-making process, as it too often limits its focus on events in cyberspace," warned Flashpoint in its Business Risk Intelligence - Decision Report, published in January 2017. "Not all actors constrain their operations solely to the cyber realm; top tier nation-states like the U.S. and Russia use the full-spectrum of their capabilities to achieve their objectives. A threat assessment of Chinese or Russian cyber operations without the context of the national objectives they are supporting fails to provide risk decision-makers with an accurate portrayal of the threat landscape upon which to make business decisions."
Flashpoint says its customer base includes industries such as finance, retail, insurance, healthcare, law, media, energy, technology, telecommunications, defense, aviation, entertainment, hospitality, consumer goods, and manufacturing. The company counts several Fortune 500 and government organizations as customers.
Led by new investor Georgian Partners, the Series C round also included investors Greycroft Partners, TechOperators, Leaders Fund, Jump Capital, Bloomberg Beta, and Cisco Investments also participated in the round. Robert Herjavec, founder and CEO of security firm Herjavec Group and investor on ABC's hit show, Shark Tank, was an early investor in the company, SecurityWeek has confirmed.
The company previously raised $10 million in Series B funding in July 2016 and announced its expansion from cyber threat intelligence into business risk intelligence.
Josh Lefkowitz, CEO and co-founder of Flashpoint, is a SecurityWeek columnist.
Atlassian Launches Public Bug Bounty Program
15.7.2017 securityweek Security
Team collaboration and productivity software provider Atlassian announced this week the launch of a Bugcrowd-based public bug bounty program with rewards of up to $3,000 per vulnerability.
Atlassian has been running a private bug bounty program and the company has now decided to take advantage of all the 60,000 researchers who have signed up on the Bugcrowd platform to help find security holes in its products.
The initiative covers Confluence and JIRA products, including Android and iOS mobile apps, and *.atlassian.io domains hosting services that interact with the company’s products. Bug bounty hunters will have to create their own Atlassian cloud instances using their Bugcrowd email address.Atlassian launches bug bounty program
Other products, the Atlassian websites, customer cloud instances, billing systems, internal or development services, and third-party add-ons are out of scope.
The company is interested in cross-instance data leakage and access, remote code execution, server-side request forgery (SSRF), reflected and stored cross-site scripting (XSS), cross-site request forgery (CSRF), SQL injection, XML external entity (XXE), access control, and directory traversal flaws.
As for rewards, most of the targeted products qualify for “tier 1” rewards. Critical vulnerabilities in these products can earn researchers up to $3,000, while the least serious flaws are worth $100. Confluence Team Calendars is the only “tier 2” product and the maximum reward is $1,500 per flaw.
Since the launch of its bug bounty program, Atlassian has paid out rewards for 39 vulnerabilities, with the average payout at roughly $500.
“The economics of bug bounties are too overwhelming to ignore,” said Daniel Grzelak, head of security at Atlassian. “Our traditional application security practice produces great results early in the lifecycle and deep in our services, but the breadth and depth of post-implementation assurance provided by the crowd really completes the secure development lifecycle. Multiplying the specialization of a single bounty hunter by the size of the crowd creates a capability that just can’t be replicated by individual organizations.”
Dark Web Market AlphaBay Goes Down
15.7.2017 securityweek CyberCrime
AlphaBay, a Dark Web markerplace for illegal products, went down last week after authorities seized equipment following raids in three different countries.
Following the incident, vendors selling their products on AlphaBay began to flock to other Dark Web marketplaces, a transition that apparently started to cause technical issues on some of these portals. AlphaBay supposedly had over 400,000 users last week.
AlphaBay was the most popular marketplace on the Dark Web, followed by RAMP (Russian), Dream Market, Hansa Market, and Silk road 3.1. Launched in December 2014 and already having over 200,000 users by October 2015, AlphaBay saw an influx of users after a similar portal called TheRealDeal disappeared last summer.
The exact reason for AlphaBay’s demise remains unclear at the moment, but there is some speculation that its admins might have pulled off an exit scam, shutting down the portal and stealing crypto-currency from escrow wallets, BleepingComputer’s Catalin Cimpanu notes.
Others, however, suggest the marketplace was taken down after authorities raided various locations in the United States, Canada and Thailand on July 5. AlphaBay went down the same day the raids happened, and the Wall Street Journal reports the law enforcement operation resulted in the portal’s shutdown.
Authorities apparently confirmed three raids in Canada and another in Thailand, but didn’t confirm that they were related to the Dark Web marketplace. While only equipment was reportedly seized in Canada, Alexander Cazes, 26, was arrested in Thailand, where authorities seized assets valued at over $11 million.
Cazes, supposedly the individual running AlphaBay, allegedly gave his consent to be extradited to the United States after a request from the Federal Bureau of Investigation. On Wednesday morning, he was found dead in his cell at the Narcotics Suppression Bureau in Bangkok's Laksi district.
Ilia Kolochenko, CEO of web security company High-Tech Bridge, pointed out in an emailed comment to SecurityWeek that, although there’s no safe harbor for cybercriminals operating illegal marketplaces such as AlphaBay, the portal’s demise is likely to result in miscreants taking measures to better secure their operations.
“Dark Web gives an illusion of safety and anonymity to many unexperienced users. This case is a good example that there is no safe harbor for cybercrime marketplaces operating on the global scale. Users erroneously believe that bitcoin or tor can assure their undetectability, but this assumption is wrong. There are many other ways to trace and unmask them via weaknesses in tangential technologies, or just by using social engineering or even their own garrulity against them,” Kolochenko said.
Last year, 35-year-old Aaron James Glende from Winona, Minnesota, was sentenced to four years and two months in prison for selling stolen information on AlphaBay. In January this year, a Reddit user demonstrated he could read any private message the dark web marketplace.
“However, this news is rather a bad one in the long run. I think, other illegal market places will quickly learn the lesson and take all measures to secure their platforms and operators. We will probably see many new smaller places restricted only to ‘trusted’ sellers and verified buyers. This will seriously impede any further investigation and police raids,” Kolochenko concluded.
Earlier this year, darknet marketplace Hansa announced the launch of a bug bounty program with rewards of up to 10 bitcoins, in an effort to minimize chances of the website being hacked.
Insider Steals Customer Data From Global Healthcare Group
15.7.2017 securityweek Incindent
Major International Healthcare Organization Bupa Loses Customer Details to Insider Threat
Bupa, a major international healthcare group, announced yesterday, "We recently discovered an employee of our international health insurance division (which is called 'Bupa Global'), had inappropriately copied and removed some customer information from the company.
Sheldon Kenton, Managing Director at Bupa Global, announced, "Around 108,000 international health insurance policies are affected," and added; "The data taken includes: names, dates of birth, nationalities, and some contact and administrative details including Bupa insurance membership numbers."
DataBreaches soon added some detail. "DataBreaches.net first became aware of the Bupa breach on June 23, when a listing appeared on the now-gone Alpha Bay marketplace by a vendor calling himself 'MoZeal'." MoZeal was a new member to AlphaBay, having joined on 2 May 2017; and DataBreaches conjectures "that 'MoZeal' is likely the rogue employee that Kenton referred to."
DataBreaches provided the full list of stolen data as provided by MoZeal, which turns out to be more expansive than that provided by Bupa. It includes separate home and office fax, email address, mobile and landline phone numbers. DataBreaches also questions the Bupa statement. "While Bupa reports that 108,000 were affected, MoZeal's listing and thread indicated that there were over 130,000 in the U.K. alone, and that overall there were about 500,000 – 1 million records for sale."
SecurityWeek asked Bupa to clarify this, and was told, "All of the information and statements we have made public this week remain valid. We are aware of a report that suggests that on 23 June 2017 'a former employee claimed to have 1m records for sale'. Our thorough investigation established that 108,000 policies, covering 547,000 customers, had been copied and removed. The disparity in numbers claimed and those taken relates to duplicate copies of some records."
For now, Bupa is providing little more information. It is contacting those customers who are affected "to apologize and advise them as we believe the information has been made available to other parties." This implies that affected customers should be particularly wary about phishing attempts seeking additional information, either for complete identity theft or just to steal bank account details or card numbers.
Earlier this week, Kaspersky Lab published a study on "The Human Factor in IT Security", showing the extent to which employees are making businesses vulnerable from within. Kaspersky's principal security researcher David Emm believes employees rank at the very top of the list of threats to data and systems. "When insider-assisted attacks do occur," he told SecurityWeek, "the impact of such attacks can be devastating as they provide a direct route to the most valuable information -- in this case, customer data."
David Kennerley, director of threat research at Webroot, adds, "Because of the nature of the information that's been leaked, Bupa Global customers who have been affected need to be extra vigilant, without doubt they are now prime targets for phishing attacks and other targeted activities, as well as possible identify theft."
The potency of identity theft should not be underestimated. On Monday this week Alf Goransson -- the CEO of Securitas, Sweden's largest security firm -- was declared bankrupt by the Stockholm District Court (it is expected to be rescinded). A fraudulent loan had been taken out in his name in April after his identity was stolen at the end of March. The perpetrator also used his name to request bankruptcy. The bankruptcy led to Goransson's automatic deregistration by the Swedish Companies Registration Office as the Securitas CEO.
In the Bupa incident, the perpetrator is known and has been dismissed, and Bupa is taking 'appropriate legal action'. In response to SecurityWeek's request for clarity, Bupa said, "It was an existing employee." It was neither an ex-employee, nor a contractor. "Just to reiterate," continued Bupa, "the employee had access to this information as part of their job and chose to abuse their position. The employee responsible has been dismissed. Bupa has a zero-tolerance attitude towards data theft."
Bupa has not said how it discovered the breach, whether it was via its own internal controls or because a third-party (such as law enforcement) recognized it on the dark web. Nor has it said exactly when it discovered the breach, nor when it dismissed the employee.
The UK data protection regulator, the Information Commissioners Office (ICO), confirmed that it knows about the incident and told SecurityWeek, "Organizations have a duty to protect people's privacy and personal data. We have been made aware of an issue involving Bupa Global and are making enquiries." However, the ICO declined to tell SecurityWeek when it had been informed of the breach.
Since DataBreaches knew about the loss on 23 June, it is likely that Bupa knew about it around the same time. That implies that the AlphaBay takedown occurred after MoZeal's offer to sell Bupa data, and before Bupa disclosed the loss. The timing is most probably coincidental; but nevertheless, the only SecurityWeek question that Bupa completely ignored, was this: "Does the theft of your data and its subsequent offer for sale on AlphaBay have anything whatsoever to do with AlphaBay being taken down?" When companies limit the information they provide in their disclosures, there is a great temptation to fill in the gaps.
Americké jaderné elektrárny má před hackery ochránit nový zákon
14.7.2017 Novinky/Bezpečnost BigBrother
Od května eviduje americké ministerstvo pro vnitřní bezpečnost a FBI zvýšený počet pokusů o kybernetický útok na jaderné elektrárny. Jejich zabezpečení je podle některých senátorů zastaralé.
Nový federální zákon, který by řešil strategii pro kybernetickou bezpečnost a chránil kritickou infrastrukturu včetně elektrických sítí a jaderných elektráren před útoky hackerů, prosazují američtí senátoři. Reagují tak na zvyšující se počty případů kybernetických útoků na americké jaderné elektrárny, jež od května eviduje federální ministerstvo pro vnitřní bezpečnost a FBI. Podle jejich zprávy hackeři z cizích zemí pronikli nejméně do tuctu amerických elektráren. Obdobným útokům opakovaně čelila i Ukrajina. V obou případech je z útoků podezříváno Rusko.
„Zprávy o pokusech o kybernetické průniky do jaderných elektráren nastiňují potřebu USA přijmout komplexní strategii pro kybernetickou ochranu. Proto jsem představil návrh zákona, který má ochránit americkou elektrickou síť před kybernetickými útoky,“ oznámil prostřednictvím Twitteru nezávislý senátor Angus King ze státu Maine. Podle jeho kolegy Eda Markeyho, senátora za Massachusetts, by federální úřady měly vyvinout větší úsilí při ochraně počítačových sítí v amerických jaderných elektrárnách.
Markey proto zaslal dopis pěti federálním ministerstvům a dalším úřadům a vyžádal si od nich podrobnější informace o dosavadních útocích i způsobu, jak jsou jaderné elektrárny chráněny. Senátor chce znát přesný počet napadených elektráren a jaká opatření přijaly po těchto incidentech. Odpovědi žádá do 10. srpna. Federální ministerstvo pro vnitřní bezpečnost připustilo, že útoky jsou intenzivnější, zhruba poslední dva měsíce. Senátoři chtějí předejít situaci, kdy by některá z elektráren byla paralyzována vyděračským ransomwarem, jako tomu bylo nedávno v ukrajinském Černobylu, kde personál musel přejít na ruční ovládání monitorovacích zařízení.
Ukrajina jako testovací trenažer pro hackery?
Američtí senátoři se obávají, že podobný útok na americké jaderné elektrárny by mohl mít katastrofické následky. FBI zveřejnila informaci, že jednou z elektráren, kterou se hackeři pokusili napadnout, je kansaská Wolf Creek. I když ministerstvo pro vnitřní bezpečnost dopady hackerských útoků na americké elektrárny snižuje, senátor Markey varuje před dalšími způsoby infiltrace do systémů elektráren. „Neexistuje žádná záruka, že by se škodlivý kód nemohl dostat do systémů prostřednictvím falešné aplikace nebo externích datových zařízení,“ napsal senátor federálním úřadům.
„Jaderné elektrárny i další zařízení, která jsou součástí kritických infrastruktur států, jsou stále častějším cílem útoků hackerů. Poslední dva roky jsme svědky opakovaných útoků na energetickou infrastrukturu Ukrajiny, což by mohlo představovat jakýsi velký test v reálných podmínkách. Nelze vyloučit, že se stejní hackeři, kteří stojí za útoky na Ukrajině, nepřipravují na větší akci v USA,“ říká Václav Zubr, bezpečnostní expert společnosti ESET. Každý stát by podle něj měl řádně zabezpečit svoje rozvodné sítě a další kritické body, jejichž narušení by ohrožovalo celou ekonomiku země.
Podle Michaela Daniela, prezidenta Cyber Threat Alliance a bývalého bezpečnostního poradce prezidenta Baracka Obamy, se elektrárny stávají stále častějším cílem hackerů. Daniel proto doporučuje federálním úřadům, aby zlepšily vzájemnou komunikaci a koordinovaly ochranu před takovými útoky.
No Free Pass for ExPetr
14.7.2017 Kaspersky Ransomware
Recently, there have been discussions around the topic that if our product is installed, ExPetr malware won’t write the special malicious code which encrypts the MFT to MBR. Some have even speculated that some kind of conspiracy might be ongoing. Others have pointed out it’s plain and simple nonsense. As usual, Vesselin Bontchev, a legend in IT security, who’s become famous for usually getting things right, said it best:
So, what is going on here? As a wise man once said, “the code doesn’t lie,” so let’s analyze the ExPetr MBR disk infection/wiping code in details.
In a nutshell, the malware does these actions:
Checks administrator privileges
Enumerates running processes
Depending on the processes found, initialize a special runtime config
Depending on this runtime config, malware execution branches are chosen
The malware’s main function
The “check privileges” function
An interesting fact is that malware tries to find several running processes (it calculates a hash from running process names and compares it with several hard-coded values).
Enumerating running processes
The most interesting part that happens here is:
After this condition two malicious functions could be executed:
InfectMbr This routine will write the malicious GoldenEye encryptor code to the MBR. After reboot, this code will encrypt MFT and 1024 bytes of each file.
WipePhysicalDrive This routine will overwrite the first 10 sectors of the disk with random trash.
Let’s describe this condition in detail:
The WipePhysicalDrive function will be initiated if:
the special bit in runtime config is not set (that happens when malware finds the avp.exe running process).
the InfectMbr function fails.
This is what happens after an initial infection:
Graphic illustration of condition
Very important additions:
WipePhysicalDrive could be initiated regardless of whether the avp.exe process is running or not. This function will be called when the malware could not write the malicious code to MBR. For example, it could be caused by the activity of other security solutions blocking this write.
Regardless of whether MBR was infected with malicious code or was overwritten with random trash, malware will still try to encrypt the victim’s files using the AES and RSA ciphers and the attacker’s public key.
Overall, it appears that the group behind ExPetr have built what is usually called a stone soup. This is a mix of old code, new code, dirty hacks, test checks and parts of unusual code. For instance, there is a special condition block in which the AES file encryption doesn’t run at all, however, this condition is always false. It very much looks like something that was rushed out the door before it was polished and ready, from many points of view.
Why the rush, you may wonder? We do not know, but there could be several explanations. One of them could be they tried really hard to catch the EternalBlue/EternalRomance “train”. After WannaCry, a lot of organizations started patching their Windows installations to close these vulnerabilities, effectively shrinking the window of opportunity. It’s possible the authors of ExPetr wanted to infect as many targets as possible before these exploits were widely patched.
Despite the rush, the attackers were obviously aware of our technologies (and other companies’ technologies, obviously), notably System Watcher, which is extremely effective at fighting ransomware. System Watcher works by collecting information about the suspicious actions of running programs and builds a score. For instance, when a program reads a full file in memory, it then writes another file of similar size yet different format, then deletes the original, and the score increases. Other similar known bad behavior is used to increase the score and good behavior to decrease it. If multiple malicious actions happen several times, over and over, the score can reach a threshold where it’s pretty obvious that something is wrong. In that case, System Watcher warns the user and offers to terminate the offending process and restore the data.
To fight against this technology, the ExPetr authors have included multiple “counter measures.” One of them is to avoid writing the GoldenEye encryptor code to the MBR if our product is running. This is done in order to prevent raising the suspicion score and getting terminated too early. It actually seems that they put significant energy into trying to bypass our products and target our users, meaning they were pretty worried about being stopped. Nevertheless, these didn’t work too well, reinforcing the theory of a big pile of hacks, put together in a rush. The System Watcher component fires anyway and stops the file encryption, terminating the process and undoing the changes.
To conclude, our users have been protected despite the measures built into ExPetr to target them.
So why we are writing this longer explanation? With complex malware code and retro measures built to bypass antivirus products, it is complicated to understand all the functionality of today’s malware. It is easy to get tricked and believe certain code checks give a free pass to Kaspersky users. In reality, they were intended as a means of trying to pass under the System Watcher’s radar. In the end, it didn’t work. Our users do not need a free pass from ExPetr, since they have an universal “free pass” from our products and System Watcher.
The Magala Trojan Clicker: A Hidden Advertising Threat
14.7.2017 Kaspersky Virus
One large group will slowly conquer another large group, reduce its numbers, and thus lessen its chance of further variation and improvement. <…> Small and broken groups and sub-groups will finally tend to disappear.
Charles Darwin. ‘On the Origin of Species’
The golden age of Trojans and viruses has long gone. Malicious programs created by enthusiasts for research purposes and for fun are now largely confined to history books and dusty computer incident reports. They have been replaced by programs that put a heavy emphasis on making money.
If we ignore targeted attacks prepared by professionals for very specific purposes, what sort of malware do we most often hear about today? Encryption malware and DDoS botnets made up of IoT devices. Both types are profitable for cybercriminals and relatively easy to implement. However, they are not the only types of malware capable of generating cash; we mustn’t overlook a third particularly numerous borderline malware family that includes advertising bots and modules, and partnership programs – all of which is typically referred to as potentially unwanted adware/potentially unwanted programs (PUA/PUP). They are borderline because there is a fine line between classifying a program as adware and defining the same program as an outright Trojan. In this paper, we will deal with one such renegade that has gone well beyond the limits of ‘fair play’ when it comes to advertising.
The malware in question is detected by Kaspersky Lab products as Trojan-Clicker.Win32.Magala.
Operating algorithm
Magala falls into the category of Trojan Clickers that imitate a user click on a particular webpage, thus boosting advertisement click counts. It’s worth pointing out that Magala doesn’t actually affect the user, other than consuming some of the infected computer’s resources. The main victims are those paying for the advertising; typically they are small business owners doing business with unscrupulous advertisers.
The first stage of infection involves the Trojan checking which version of Internet Explorer is installed and locating it in the system. If it’s version 8 or earlier, the Trojan won’t run. So, if you still have this version on your computer, there’s nothing to worry about.
Checking the version of Internet Explorer, virtual desktop initialization.
If the desired version of Internet Explorer is found, then, unbeknown to the user, a virtual desktop is initialized. All further activities are performed here. After that a sequence of utility operations is run (something that is typical for this malware family): autorun is set up, a report is sent to a hardcoded URL, and the required adware is installed. To interact with the content of an open page, Magala uses IHTMLDocument2, the standard Window interface that makes it easy to use DOM tree. The Trojan uses it to load MapsGalaxy Toolbar, installs it on the system and adds the site hxxp://hp.myway.com to the system registry, also associated with MapsGalaxy, so that it becomes the browser’s home page.
A simple check is incorporated into the Trojan to find out if the search bar has alread been installed – this is done with the help of the appropriate registry branch.
Magala then contacts the remote server and requests a list of search queries for the click counts that need to be boosted.
Receiving the list of search queries
This list is sent ‘as is’, in a plain text file with lots of strings.
List of search queries
Using this list, the program begins to send the requested search queries and click on each of the first 10 links in the search results, with an interval of 10 seconds between each click.
Программа начинает последовательно вводить указанные запросы и кликать по десяти первым ссылкам
Profit margin
As far as we know, an average cost per click (CPC) in a campaign like this is 0.07 USD. The cost per thousand (CPM) comes to 2.2 USD. It should be noted that Trojan Clickers are certainly not the most popular way of selling advertising: the method most in demand is the displaying of a set homepage, where each installation also costs 0.07 USD.
A botnet consisting of 1000 infected computers clicking 10 website addresses from each search result and performing some 500 search requests with no overlaps in the search results could ideally mean the virus writer earns up to 350 USD from each infected computer. However, these cost estimates are only approximations, and don’t typically occur in the real world. The costs of different requests may vary greatly, and the price of 0.07 USD per click is also an average value.
Propagation statistics
As can be seen in the diagram below, Trojan-Clicker.Win32.Magala infections occur most often in Germany and the US. This finding is corroborated by an analysis of the search requests for which the click numbers need to be boosted. These statistics were collected from March to early June 2017.
Conclusion
Programs belonging to the potentially unwanted adware class do not typically pose as much of a threat to the end user as, say, encryption or banking malware does. However, there are two characteristic features to this malware class which make it difficult to deal with. Firstly, there is the borderline functionality that blurs the lines between legitimate and malicious software. It has to be clarified whether a specific program is part of a secure and legal advertising campaign or if it is illegitimate software performing similar functions. A second important aspect of this class – its sheer quantity – also means a fundamentally different approach to any analysis is required.
MD5
1EB2D932BB916D4DB7F483859EEBABF8
206DD0B0E8FAA2D81AB617491F80AD0B
25BC675D23C2ACD5F288856F6B91818D
44A408386B983583CAEB0590433BE07B
4E4FA0B8C73889E9AA028C8FD7D7B3A5
6D3D80E89ABDED981AE329203F1779EB
6FA035264744E9C9A30409012BAB18DE
732B82A7424B60FEBB1E874B205E2D76
771E742D6C110F8BD68A7304EF93B131
A6B288A3B8C48A23092246FBBF6DB7C2
CF5A5C45778C793477ECAB02F1B3B2C3
DC16BA21BFE4838FD2A897FF13050FF4
F364B043BD6E2CC9C43F86E2004D71D3
F36672933F3CBACF8D8B396DFE259526
New "WPSetup" Attack Targets Fresh WordPress Installs
14.7.2017 securityweek Attack
A new type of attack against WordPress is targeting fresh installations to get admin access and execute PHP code in the victim’s web hosting account, Wordfence reveals.
Dubbed WPSetup, the campaign was observed in May and June, and starts with the attackers scanning for a specific URL used by new installations of WordPress: /wp-admin/setup-config.php. If the URL contains a setup page, it means the victim has recently installed WordPress on their server but has yet to configure it.
Basically, it means that those who install WordPress either by unzipping the ZIP archive or through a one-click installer but don’t immediately complete the installation steps provide attackers with the necessary means to take control of the website.
“It is very easy for an attacker to take over not just the new WordPress website, but the entire hosting account and all other websites on that hosting account,” Mark Maunder, Wordfence founder and CEO, claims.
Any WordPress installation starts with selecting the language, followed by an introductory message, after which the user selects a database name, username, password and server for the new WordPress installation. At this point, an attacker who finds the fresh install can “click through the first two steps and then enter their own database server information,” Maunder argues.
The attack is successful even if the database is on their own server or contains no data, Wordfence says. A working WordPress installation on the victim’s site and admin access to it is all the attackers need. Once the final installation step is completed, WordPress confirms that it can communicate with the database, and presents the attacker with a dialogue to run the install.
At this point, the attacker can create the first admin-level account with their own information, hit install, and then sign into a fresh WordPress on the victim’s server, using their own database.
“Once an attacker has admin access to a WordPress website running on your hosting account, they can execute any PHP code they want in your hosting account,” Maunder notes.
Because WordPress allows admins to edit the code of themes and plugins, an attacker can simply launch the theme or plugin editor and insert PHP code, thus having the code executed the next time the page is refreshed.
“Once an attacker has admin access to a WordPress site, they can upload any plugin with any PHP code, including their own custom plugin. To execute their code, they spend a few minutes creating a basic WordPress plugin and then upload it to the site and activate it,” Maunder continues.
An attacker could execute code on the victim’s site and also install a malicious shell in a directory in the victim’s hosting account, thus gaining access to all files and websites on that account. This would also provide the attacker with access to any databases the WordPress installation has access to, and maybe also with access to other application data.
Logan Kipp, Product Evangelist at SiteLock, told SecurityWeek in an emailed comment that incomplete WordPress setups left online and publicly-accessible are more common than one might think. According to Kipp, even when warned of the risks involved, many customers wouldn’t understand that “reinstalling WordPress would not inhibit a persistent infection, especially if it spread outside of the WordPress file structure.”
“Cybercriminals aren't always after just sensitive information like passwords and credit cards, a server's resources are one of the many currencies of the cybercriminal underworld. Your server may be used to leverage attacks on other servers or website visitors. One of the questions I am frequently asked is "who host a cybercriminal?" In most cases, the answer is regular people who aren't well-informed that have become unwilling cohabitants to a cybercriminal,” he continues.
Weston Henry, Lead Security Analyst at SiteLock, tells SecurityWeek that attack itself is a well-known tactic and that long have web scanners been configured to find default install files and directories.
“The WordPress attackers capitalized on the sheer number of WordPress installs on the net, and took advantage of forgotten and unfinished installs. Site owners can protect themselves by preparing for and completing new WordPress installs as soon as they're begun. Next, site owners can use a web application firewall to whitelist owner or developer IP addresses. An .htaccess file can also be used to limit access by IP address,” Henry said.
In a separate report, Wordfence revealed that the number of daily complex attacks against WordPress has increased to 7.2 million in June, up 32% from May. The average number of daily brute force attacks went up 36% compared to May, with a peak at over 41 million.
The report also reveals that the top 25 attacking IPs launched a total of 133 million attacks in June, a slight decrease from the 144 million attacks registered in May. The most attacked WordPress theme was mTheme-Unus, while the most targeted plugin was WP Mobile Detector. The top three attacking countries are Russia, U.S. and Ukraine, the report also reveals.
Old Kerberos Bypass Flaw Patched in Windows, Linux
14.7.2017 securityweek Vulnerebility
A 20-year-old authentication bypass vulnerability affecting some implementations of the Kerberos protocol has been patched in Windows, Linux and BSD operating systems.
Kerberos, whose name stems from the mythological three-headed hound Cerberus, is an authentication protocol that uses “tickets” to allow nodes to communicate securely over a non-secure network.
The flaw has been dubbed Orpheus' Lyre because similar to how the bard Orpheus managed to get past Cerberus by putting it to sleep with his lyre, the vulnerability can be used to bypass Kerberos.
Researchers Jeffrey Altman, Viktor Duchovni and Nico Williams first discovered the security hole in the Heimdal implementation of Kerberos, which had been vulnerable since late 1996. Microsoft’s implementation also turned out to be affected, but the MIT Kerberos was never impacted. Orpheus' Lyre vulnerability
The experts have not provided too many technical details in order to give users time to apply the patches. However, they did reveal that the flaw affects the Kerberos v5 specification and it’s related to the use of unauthenticated plaintext.
A man-in-the-middle (MitM) attacker can exploit the vulnerability to steal credentials, escalate privileges, and bypass authentication.
“In _krb5_extract_ticket() the KDC-REP service name must be obtained from encrypted version stored in 'enc_part' instead of the unencrypted version stored in 'ticket'. Use of the unecrypted version provides an opportunity for successful server impersonation and other attacks,” said the developers of Heimdal, who track the flaw as CVE-2017-11103.
Heimdal is used by several Linux distributions, which have already started releasing patches. Red Hat is not affected as it uses the MIT implementation of Kerberos.
The vulnerability has also been addressed in Samba, which includes the Heimdal Kerberos since version 4.0.0. FreeBSD has also published an advisory.
Microsoft, which tracks the flaw as CVE-2017-8495, addressed it in Windows with its latest Patch Tuesday updates.
“A security feature bypass vulnerability exists in Microsoft Windows when Kerberos fails to prevent tampering with the SNAME field during ticket exchange. An attacker who successfully exploited this vulnerability could use it to bypass Extended Protection for Authentication.
To exploit this vulnerability, an attacker would have to be able to launch a man-in-the-middle attack against the traffic passing between a client and the server,” Microsoft said in its advisory.
The experts who discovered Orpheus' Lyre pointed out that this is a client-side bug that cannot be mitigated on the server side.
While the researchers, Samba and Heimdal have classified this as a critical vulnerability, Microsoft and some of the affected Linux distributions assigned it an “important” or “medium” severity rating, likely due to the fact that the attacker requires network access for exploitation.
Australia to Compel Chat Apps to Hand Over Encrypted Messages
14.7.2017 securityweek Social
Social media giants like Facebook and WhatsApp will be compelled to share encrypted messages of suspected terrorists and other criminals with Australian police under new laws unveiled Friday.
It comes after Prime Minister Malcolm Turnbull warned encrypted messages were increasingly being used by terrorists, drug traffickers and paedophile rings, calling for legislation to be modernised to allow police to do their jobs.
"We need to ensure that the internet is not used as a dark place for bad people to hide their criminal activities from the law," he said, adding that the tech giants must "face up to their responsibility".
"They can't just wash their hands of it and say it's got nothing to do with them."
Australian authorities can currently obtain information from telecommunications companies, but not internet firms that use data encryption to guarantee user confidentiality.
Encryption essentially involves complex algorithms scrambling data to make it indecipherable until unlocked by its owner or when it reaches its destination.
"Because of this end-to-end encryption, all of that information, all of that data, that communication is effectively dark to the reach of the law," said Turnbull.
"And that's not acceptable. We are a society, a democracy, under the rule of law, and the law must prevail online as well as offline."
The laws will be introduced into parliament by the end of the year.
Attorney-General George Brandis said the legislation would be similar to Britain's Investigatory Powers Act, which imposes an obligation on companies to cooperate with investigations.
They would provide Australian intelligence and law enforcement authorities with coercive powers as a "last resort" if tech companies did not voluntarily help, said Brandis.
"It is vitally important that the development of technology does not leave the law behind," he said.
However, Silicon Valley tech companies have so far refused to bend to similar legal requests.
Facebook said it already had a system in place to help police and intelligence officials in Australia.
"We appreciate the important work law enforcement does, and we understand their need to carry out investigations. That's why we already have a protocol in place to respond to requests where we can," a spokesperson said.
"At the same time, weakening encrypted systems for them would mean weakening it for everyone."
Apple told AFP it had no comment on the new legislation.
British Home Secretary Amber Rudd will travel to the United States shortly to discuss the issue further with her American counterpart and tech companies, said Turnbull.
The US government last year locked horns in a legal battle with Apple, seeking to compel the iPhone maker to help decrypt a device used by one of the attackers in the San Bernardino shooting rampage.
Authorities eventually dropped the case after finding a way to break into the iPhone without Apple's help.
Turnbull admitted it may be difficult to enforce the laws if firms do not comply, but said it was important to "recognise the challenge and call on those companies to provide the assistance".
Inadequate Boundary Protections Common in Critical Infrastructure: ICS-CERT
14.7.2017 securityweek ICS
The assessments conducted by the U.S. Industrial Control Systems Cyber Emergency Response Team (ICS-CERT) in 2016 showed that inadequate boundary protection has remained the most prevalent weakness in critical infrastructure organizations.
ICS-CERT conducted 130 assessments in the fiscal year 2016, which is more than in any previous year. Monitor newsletters published by ICS-CERT this year show that it has already conducted 74 assessments in the first half of 2017.
Assessments are offered to both government organizations and private sector companies whose owners and operators request them. Last year, the CERT conducted assessments in 12 of the 16 critical infrastructure sectors, including chemical, commercial facilities, communications, critical manufacturing, emergency services, dams, energy, food and agriculture, IT, government facilities, transportation, and water and wastewater systems.
Similar to the previous two years, inadequate boundary protection remained the most common flaw – 94 discoveries representing more than 13 percent of all weaknesses identified during assessments. Boundary protection issues can result in failure to detect unauthorized activity in critical systems, and an increased risk to control systems due to the lack of proper separation from the enterprise network.
The second most prevalent type of vulnerability, with 42 discoveries, is “least functionality.” This refers to organizations failing to implement controls to ensure that unnecessary services, ports, protocols or applications that can be exploited to gain access to ICS are disabled.
ICS-CERT also discovered 36 instances of identification and authentication flaws. Many organizations fail to implement proper identification and authentication mechanisms for their users – this leads to accountability problems and makes it more difficult to secure the accounts of individuals who have left the company.
The fourth most prevalent issue discovered during assessments is related to physical access controls – which can make it easier for malicious actors to gain an initial foothold into the targeted organization’s ICS network.
Another common problem identified by investigators was related to mechanisms for auditing and accountability. According to ICS-CERT, 26 organizations did not have a formal process in place for reviewing and validating logs, which makes it more difficult to detect an intrusion in the ICS network and respond to an incident.
ICS-CERT’s FY 2016 Annual Assessment Report also includes recommendations on how to address these issues.
20 years-old Orpheus’ Lyre vulnerability in Kerberos fixed this week
14.7.2017 securityaffairs Vulnerebility
A 20 years-old vulnerability in Kerberos, dubbed Orpheus’ Lyre, was parched this week for both Microsoft and Linux distros.
A 20 years-old vulnerability in Kerberos was parched this week for both Microsoft and Linux distros.
The vulnerability dubbed Orpheus’ Lyre has been found three months ago by Jeffrey Altman, founder of AuriStor, and Viktor Dukhovni and Nicolas Williams from Two Sigma Investments. The issue
The flaw, tracked as CVE-2017-11103, was found in Heimdal, an open-source implementation of Kerberos, like the mythological character Orpheus played his lyre with such grace that it lulled Cerberus to sleep, this issue can bypass Kerberos.
The issue could result in remote privilege escalation and credential theft, an attacker can trigger it to access the target network.
“The original cryptographic sin of Kerberos is an abundance of unauthenticated plaintext in the protocol. That is, portions of Kerberos messages are neither encrypted nor integrity-protected in some direct cryptographic manner. In some cases that sin is likely born of premature optimization — the mother of many bugs. Kerberos can be secure despite this surfeit of unauthenticated plaintext, but it requires extreme care by implementors to get every detail right so as to authenticate said plaintext.” reads the description for the Orpheus’ Lyre .”Orpheus’ Lyre happened because of one instance of unauthenticated plaintext, and the ease with which the specific plaintext could accidentally be used instead of an authenticated copy of the same text. The unauthenticated plaintext issue at hand is this: the Ticket issued in KDC responses. “
The flaw is related the way Kerberos handles authentication messages, the expert discovered that flawed implementations of Kerberos fetched metadata from unprotected key distribution center (KDC) tickets rather than encrypted KDC responses.
“The attacker needs to be on the network and to have control over a service principle that the client could communicate with,” Altman told The Register. “As far as we know there are no exploits in the wild. But it certainly is exploitable and we consider it to be very serious.”
“Given how broadly Kerberos has been deployed over the last almost 30 years, it clearly is in a wide ecosystem with a lot of different vendors,”
The Orpheus’ Lyre bug affects multiple different Kerberos 5 implementations, including one by Microsoft and by the KTH Royal Institute of Technology in Sweden (Heimdal).

Altman recommends to review every Kerberos implementation, not every vendor can be expected to have fixed the vulnerability and in some cases, the vendors went out of the market.
Altman explained that the flaw could have been prevented by removing the unencrypted fields in order to force the use of the encrypted ones when the authentication request is composed.
“In _krb5_extract_ticket() the KDC-REP service name must be obtained from encrypted version stored in ‘enc_part’ instead of the unencrypted version stored in ‘ticket’. Use of the unecrypted version provides an opportunity for successful server impersonation and other attacks.” wrote Altman.
“The fact that this has been around for as long as it has been in open source, I think, is just one more case that should debunk the theory that open source programming is in some way more secure than closed source programming.”
The expert pointed out that if IT giants like Microsoft failed in identifying the problem other companies missed it, the same story for the entire open source community.
Altman has no doubt, this kind of issues will continue to plague the open-source community because developers are often not compensated for their contributions.
“We will never be reimbursed for the cost to our lives and the lost time to our companies for having done this favor to the world,” Altman concluded. “As a society, we need to understand what the costs of this work are.”
Ubuntu Linux for Windows 10 Released — Yes, You Read it Right
14.7.2017 thehackernews IT
Windows and Linux in the same line? Yes, you heard that right... and that too, on the same computer and within the same operating system.
Two months ago, Microsoft announced its plans to let its users install three different flavours of the Linux operating system – Ubuntu, Fedora, and SUSE – directly through their Windows Store, allowing them to run Windows and Linux apps side-by-side.
Now, downloading an entire operating system has just become as easy as downloading an application with the availability of popular Linux distro 'Ubuntu' in the Windows App Store.
However, unlike a conventional Ubuntu installation, this Ubuntu version runs in a sandboxed alongside Windows 10 with limited interaction with the operating system and is focused on running regular command-line utilities like bash or SSH as a standalone installation through an Ubuntu Terminal.
For now, Ubuntu is currently only available to Windows 10 Insiders users and would be made available to the public with the upcoming Windows 10 Fall Creator Update, which is expected to release in September/October 2017.
Here's How to Install and Run Ubuntu on Windows 10
Users registered in Windows 10 Insiders Program with at least "Build 16215" installed can directly install Ubuntu from the Windows Store, which will allow them to "use Ubuntu Terminal and run Ubuntu command line utilities including bash, ssh, git, apt and many more."
After installing Ubuntu, Windows 10 users will require enabling "Windows Subsystem for Linux" that was previously added to Windows 10.
To enable it, follow these simple steps:
Navigate to Control Panel and go to "Apps and features" settings.
Select "Programs and Features" from the right panel.
Open the "Turn Windows features on or off" from the left menu.
Select the "Windows Subsystem for Linux" and save it.
Reboot Your system.
While the company has not revealed exactly when its users can expect to see the other two Linux distro, Fedora and SUSE Linux, to the Windows Store, this step by Microsoft follows its commitment to the open source community.

In 2013, the Microsoft launched Visual Studio, and a year later, the company open-sourced .NET. In 2015, the tech giant open sourced the Visual Studio Code Editor, as well.
Last year, Microsoft took many steps to show its love for Linux, which includes bringing of Ubuntu on Windows 10, working with FreeBSD to develop a Virtual Machine image for its Azure cloud, choosing Ubuntu as the OS for its Cloud-based Big Data services, and even joining the Linux Foundation as a Platinum member – the highest level of membership.
Have you tried out Ubuntu on Windows 10? If yes, let us know your experience in the comments below.
AlphaBay Shut Down After Police Raid; Alleged Founder Commits Suicide in Jail
14.7.2017 thehackernews BigBrothers
AlphaBay Market — one of the largest Dark Web marketplaces for drugs, guns, and other illegal goods — that mysteriously went dark earlier this month without any explanation from its admins has reportedly been shut down by the international authorities.
On July 4th, the dark web marketplace suddenly went down without any explanation from its admins, which left its customers who have paid large sums in panic.
Some customers even suspected that the site's admins had pulled an exit scam to steal user funds.
However, according to the Wall Street Journal, the disappearance of the AlphaBay came after authorities in the United States, Canada, and Thailand collaborated to conduct a series of raids and arrest Alexandre Cazes, who allegedly was one of the AlphaBay's operators.
Citing "people familiar with the matter," the publication claims that Cazes, a resident of Canada, was arrested in Thailand and taken into custody in Bangkok on July 5th, the same day the police executed two raids on residences in Quebec, Canada.
The 26-year-old Canadian citizen was awaiting extradition to the United States when a guard found him hanged in his jail cell on Wednesday, the Chiang Rai Times confirms. Cazes is believed to have hanged himself using a towel.
Cazes had been living in Thailand for nearly 8 years. During his arrest, authorities also seized "four Lamborghini cars and three houses worth about 400 million baht ($11.7 million) in total."
AlphaBay, also known as "the new Silk Road," also came in the news at the beginning of this year when a hacker successfully hacked the AlphaBay site and stole over 200,000 private unencrypted messages from several users.
After the disappearance of Silk Road, AlphaBay emerged in 2014 and became a leader among dark web marketplaces for selling illicit goods from drugs to stolen credit card numbers, exploits, and malware.
Unlike dark web market 'Evolution' that suddenly disappeared overnight from the Internet, stealing millions of dollars worth of Bitcoins from its customers, AlphaBay Market was shut down by the law enforcement, suffering the same fate as Silk Road.
Silk Road was shut down after the law enforcement raided its servers in 2013 and arrested its founder Ross William Ulbricht, who has been sentenced to life in prison.
The FBI also seized Bitcoins (worth about $33.6 million, at the time) from the site. Those Bitcoins were later sold in a series of auctions by the United States Marshals Service (USMS).
Zaplaťte, jinak odhalíme vaše soukromí. Vyděračský virus cílí na mobily a tablety
14.7.2017 Novinky/Bezpečnost Viry
Český Národní bezpečnostní tým CSIRT.CZ varoval před novým vyděračským virem, který podle nejstřízlivějších odhadů ohrožuje tisíce uživatelů operačního systému Android. Pokud oběti tohoto škodlivého kódu nezaplatí výkupné, útočníci zveřejní soukromá data z napadeného zařízení.
Nově objevený škodlivý kód se jmenuje SpyDealer. „Po oběti požaduje 50 dolarů (1200 Kč), jinak prý uvolní její osobní údaje, včetně fotografií, historie webových stránek a textových zpráv,“ uvedl Pavel Bašta, bezpečnostní analytik CSIRT.CZ, který je provozován sdružením CZ.NIC.
„Podle pracovníků McAfee SpyDealer krade data z aplikací Facebook, WhatsApp a Skype. Uživatelé napadených zařízení jsou informováni, že pokud do 72 hodin nezaplatí, budou jejich osobní data poslána všem kontaktům v telefonním a e-mailovém seznamu,“ doplnil Bašta.
Virus se dostal do oficiálního obchodu
Bezpečnostní pracovníci navíc zjistili, že zmiňovaný škodlivý kód se podařilo útočníkům propašovat i do oficiálního obchodu Google Play. Konkrétně jej obsahovaly aplikace „Wallpapers Blur HD“ a „Booster & Cleaner Pro“. Ty však již nyní nejsou v oficiálním obchodu ke stažení.
Vyděračské viry cílí na mobilní zařízení, tedy na chytré telefony i počítačové tablety, stále častěji. V průběhu prvních tří měsíců tohoto roku se objem mobilního ransomwaru více než ztrojnásobil.
V prvním čtvrtletí letošního roku tak množství detekovaných souborů mobilního ransomwaru vystoupalo na číslo 218 625. Přitom ještě na konci loňského roku bylo detekováno pouze 61 832 mobilních vyděračských virů.
Útočí stejně jako na PC
Vyděračské viry se chovají na napadených mobilech stejně agresivně jako na klasických počítačích. Dokážou zašifrovat celou paměť zařízení a smartphone nebo tablet uzamknou tak, aby jej nebylo možné používat.
Za zpřístupnění uložených dat pak požadují výkupné. To se často může pohybovat v řádech několika tisíc korun. Přitom ani po zaplacení zmiňované částky uživatelé nemají jistotu, že se k uloženým datům skutečně dostanou. Podvodníci totiž v některých případech jednoduše vezmou peníze a už se nikdy neozvou.
Výkupné by tedy uživatelé neměli platit nikdy. Jedinou šancí, jak se k zašifrovaným datům dostat, je zařízení odvirovat. To ale není vůbec jednoduchý proces a v některých případech se to nemusí ani podařit.
Avast představil Štít proti ransomwaru, který zabrání cizím aplikacím, aby vám zašifrovaly počítač
14.7.2017 Živě.cz Viry
Avast představil Štít proti ransomwaru, který zabrání cizím aplikacím, aby vám zašifrovaly počítačAvast představil Štít proti ransomwaru, který zabrání cizím aplikacím, aby vám zašifrovaly počítačAvast představil Štít proti ransomwaru, který zabrání cizím aplikacím, aby vám zašifrovaly počítačAvast představil Štít proti ransomwaru, který zabrání cizím aplikacím, aby vám zašifrovaly počítačAvast představil Štít proti ransomwaru, který zabrání cizím aplikacím, aby vám zašifrovaly počítač Microsoft na sklonku června oznámil, že na základě stále častějších ransomwarových kampaní upraví Windows 10 takovým způsobem, aby se samy osobě lépe chránily virům, které se snaží zašifrovat osobní soubory a poté vyžadují výkupné. Desítky proto v podzimní aktualizaci dostanou zámek, který znemožní přepis souborů neznámými soubory.
Pokud se vám však nechce čekat až do podzimu, případně máte na počítači třeba stále nejpopulárnější Windows 7, podobnou ochranu pro vás připravil také Avast. Jeho bezpečnostní software Avast Internet Security, Avast Premier, AVG Internet Security a AVG Ultimate totiž v poslední aktualizaci získal funkci Štít proti ransomwaru.
Štít proti ransomwaru umožní měnit soubory ve zvolených složkách pouze autorizovanými aplikacemi
V konfiguraci budete moci nastavit složky a případně i typy souborů, které budou moci měnit pouze povolené aplikace (třeba ty kancelářské, grafické editory aj.). Pokud se je však pokusí přepsat neautorizovaná aplikace, antivirus ji okamžitě zablokuje.
V principu se vlastně jedná o velmi jednoduché řešení, které však může být v ochraně před zrádným ransomwarem zdaleka nejúčinnější.
Kritické chyby jsou v programech Microsoftu i Adobe. Mohou je zneužít kyberzločinci
14.7.2017 Živě.cz Zranitelnosti
Flash Player, Internet Explorer, ale například i operační systém Windows. Ve všech těchto produktech byly objeveny kritické bezpečnostní chyby. Záplaty jsou naštěstí již k dispozici, a tak by je měli uživatelé co nejdříve nainstalovat. V opačném případě se vystavují riziku útoku kyberzločinců.
Americký softwarový gigant opravil více než pět desítek zranitelností. „Opravy se týkaly například prohlížečů Edge a Internet Explorer, kancelářského balíku MS Office nebo celkově součástí operačního systému Windows,“ uvedl Pavel Bašta, analytik Národního bezpečnostního týmu CSIRT.CZ.
„Jako kritických bylo označeno 19 z nich a je proto doporučeno co nejdříve systémy aktualizovat,“ doplnil Bašta.
Zotročí počítač, nainstalují virus
Všechny chyby mají nálepku kritické, mohou je tedy snadno zneužít počítačoví piráti. Například ke spuštění libovolného kódu, na cizí stroj mohou klidně propašovat nějaký počítačový virus. A klidně jej i zotročit a zneužít k útoku typu DDoS.
Při něm mohou počítačoví piráti vyřadit některé služby, které na počítači uživatel využívá. Daleko větší riziko však představuje možnost vzdáleného spuštění programů – touto cestou totiž mohou kyberzločinci do napadeného stroje propašovat prakticky libovolný škodlivý kód.
Prakticky stejná rizika hrozí uživatelům, kteří mají v počítači nainstalovaný Flash Player. „Společnost Adobe vydala novou verzi Flash Playeru s opravami tří zranitelností, z nichž jedna byla označena jako kritická,“ konstatoval Bašta.
S instalací neotálet
Právě kritickou zranitelnost mohou počítačoví piráti také zneužít k tomu, aby propašovali na cizí stroj prakticky libovolný škodlivý kód – podobně jako u chyb v programech amerického softwarového gigantu.
S instalací všech aktualizací by tak uživatelé neměli v žádném případě otálet. K dispozici jsou prostřednictvím služby Windows Update, která je nedílnou součástí operačního systému Windows. Případně je možné novou verzi Flash Playeru stáhnout přímo ze stránek Adobe.
Lidé, kteří využívají automatické aktualizace, se nemusejí o nic starat.
Policie zavřela AlphaBay, jedno z největších černých tržišť v Toru. Provozovatel spáchal sebevraždu
14.7.2017 Živě.cz BigBrother
Policie zavřela AlphaBay, jedno z největších černých tržišť v Toru. Provozovatel spáchal sebevraždu5 FOTOGRAFIÍ
zobrazit galerii
Tržiště AlphaBay nahradilo populární Silk Road poté, co policie zavřela jeho první generaci. Ještě před týdnem se jednalo pravděpodobně o vůbec největší tržiště zaměřující se na obchod s nelegálním zbožím, primárně drogami. Přibližně týden však není v Toru k dispozici a po prvotních spekulacích o tom, že se jedná o podvod provozovatelů, přinesl Wall Street Journal informaci o tom, že jej rovněž zavřely bezpečnostní složky. Na odstavení tržiště se měla podílet policie ze Spojených států, Kanady a Thajska.
Právě v Thajsku měl být zadržen hlavní provozovatel Alexandre Cazes, který před několika lety unikl ze Spojených států po obvinění z obchodu s drogami. Po zadržení nyní spáchal v cele sebevraždu. Zátahy na další provozovatele se odehrály také v kanadském Québecu.
Cazes žil v Thajsku osm let a mezi jeho majetek patřily čtyři vozy Lamborghini a tři domy v celkové hodnotě asi 11,7 milionů dolarů (267,7 milionů korun).
WPSetup attack, hackers targets uncompleted WordPress installs
1.7.2017 securityaffairs Attack
Attackers are using automated scans to target freshly installed WordPress websites, WordFence experts dubbed the technique WPSetup attack.
According to experts at the WordPress security plugin WordFence, attackers are using automated scans to target freshly installed WordPress websites, taking advantage of administrators who fail to properly configure their server’s settings. The experts dubbed the attack WPSetup attack.
Hackers launched thousands of scans each day, searching for the URL /wp-admin/setup-config.php, that new WordPress installs use to setup new sites.
The attackers aim to find new WordPress installs that are not yet configured by the administrators.
In the period between the end of May and mid-June, WordFence researchers observed a spike in the number of attacks targeting WordPress accounts from the end of May to mid-June.
“In May and June, we saw our worst-of-the-worst IPs start using a new kind of attack targeting fresh WordPress installations.” states WordFence.
“We also had our first site cleaning customer that was hit by this attack.
Attackers scan for the following URL:
/wp-admin/setup-config.php
This is the setup URL that new installations of WordPress use. If the attacker finds that URL and it contains a setup page, it indicates that someone has recently installed WordPress on their server but has not yet configured it. At this point, it is very easy for an attacker to take over not just the new WordPress website, but the entire hosting account and all other websites on that hosting account.”
In just one day, on May 30, the experts observed roughly 7,500 scans a day, a peak in the malicious activity.

The WPSetup attack leverages on the fact that a user hasn’t finished setting up its WordPress installation, the attacker can exploit this condition to complete the user’s installation.
The attackers operate with admin access, this means that they can enter their own database name, username, password, and database server. The attackers can take over the website running their own installation or creating a supplementary account.
How the WPSetup Attack Gets Full Control of Your Hosting Account?
Once the attacker gains admin access to a WordPress website running on your hosting account, they can execute PHP code via a theme or plugin editor.
The attackers can install a shell in a victim’s directory to access any files or websites on the account or access any databases or application data.
“Once an attacker can execute code on your site, they can perform a variety of malicious actions. One of the most common actions they will take is to install a malicious shell in a directory in your hosting account. At that point they can access all files and websites on that account. They can also access any databases that any WordPress installation has access to, and may be able to access other application data.” continues the analysis.
WordFence explained that the WPSetup attack is not new, but this is the first time for such kind of attack on a large-scale.
WordFence recommends users to create a specially coded .htaccess file in the base of their web directory to avoid attackers access it before the installation is completed.
“Before you install a fresh WordPress installation, create a .htaccess file in the base of your web directory containing the following:
order deny,allow
deny from all
allow from <your ip>"
Replace the ‘<your ip>’ with your own IP address. You can find this out by visiting a site like whatsmyip.org.
This rule ensures that only you can access your website while you are installing WordPress. This will prevent anyone else from racing in, completing your installation and taking control of your hosting account by uploading malicious code.
Once complete, you can remove the .htaccess rule and allow the rest of the world to access your website.”
Eternal Blues scanner allowed to find 50,000 EternalBlue-vulnerable host
1.7.2017 securityaffairs Safety
The Eternal Blues scanner allowed administrators worldwide to discover more than 50,000 computers vulnerable to the NSA-linked EternalBlue exploit.
Recently the security researcher Elad Erez developed Eternal Blues, a free EternalBlue vulnerability scanner that could be used by administrators to assess networks.

Now Elad Erez published data collected by the Eternal Blues over the two weeks, the results are disconcerting, more than 50,000 scanned hosts are still vulnerable to the exploit. The data is even more worrisome if you consider that a single vulnerable machine could expose the entire network to the attackers.
The administrator of a network composed of 10,000 hosts discovered the only two machines were still vulnerable, in information that was crucial to protect the entire network.
As of July 12, the Eternal Blues tool was used to scan more than 8 million IPs, 1.5 million are located in France.

Erez revealed that vulnerable machines were found in around 130 countries, top 3 countries had more than 30,000 vulnerable machines.
53.82% of the vulnerable hosts still have SMBv1 enabled, 1 out of 9 hosts in a network is vulnerable to EternalBlue.
Although Eternal Blues found only around 50,000 vulnerable systems,
Erez explained that the number of vulnerable machines is much higher than 50,000, he explained that issues with the tool prevented it from correctly counting the number of vulnerable hosts.
Erez issued a new release of the tool on July 2 that fixes the above problems.
Below the results of the scan:
More than 8 million IPs were scanned. France taking the lead with 1.5 million
The top 3 vulnerable countries (out of ~130), had more than 30,000 vulnerable hosts altogether
The majority (53.82%) of hosts nowadays still have SMBv1 enabled
1 out of 9 hosts in a network is vulnerable to EternalBlue
One network, with almost 10,000 hosts (not IPs), had 2 vulnerable hosts. How could anyone find that without Eternal Blues?
Erez is satisfied by the scanner that has increased in a significant way the level of awareness on EternalBlue exploit allowing administrators to secure their networks.
“Unfortunately, exploitation of EternalBlue is still a very good method of invoking remote code execution. It is available in more than 50,000 hosts scanned by Eternal Blues (as for July 12, 2017). Yes, even after all the latest attacks by WannaCry and NotPetya. I’m here to remind you, sometimes it takes just 1 vulnerable machine to take you down.” concluded the expert.
“Although numbers are quite high (remember, these are IPs scanned with my tool only), I feel like awareness did increase somewhat. Running Eternal Blues is, by definition, being aware of the problem. So good for you for taking responsibility and checking your network status. Now it’s patching time!”
Administrators are recommended to periodically scan their networks for Eternal Blue flaw, to apply the latest patches and disable the SMBv1 protocol.
How CIA Agents Covertly Steal Data From Hacked Smartphones (Without Internet)
14.7.2017 thehackernews BigBrothers
WikiLeaks has today published the 16th batch of its ongoing Vault 7 leak, this time instead of revealing new malware or hacking tool, the whistleblower organisation has unveiled how CIA operatives stealthy collect and forward stolen data from compromised smartphones.
Previously we have reported about several CIA hacking tools, malware and implants used by the agency to remotely infiltrate and steal data from the targeted systems or smartphones.
However, this time neither Wikileaks nor the leaked CIA manual clearly explains how the agency operatives were using this tool.
But, since we have been covering every CIA leak from the very first day, we have understood a possible scenario and have illustrated how this newly revealed tool was being used.
Explained: How CIA Highrise Project Works
In general, the malware uses the internet connection to send stolen data after compromising a machine to the attacker-controlled server (listening posts), but in the case of smartphones, malware has an alternative way to send stolen data to the attackers i.e. via SMS.
But for collecting stolen data via SMS, one has to deal with a major issue – to sort and analyse bulk messages received from multiple targeted devices.
To solve this issue, the CIA created a simple Android application, dubbed Highrise, which works as an SMS proxy between the compromised devices and the listening post server.
"There are a number of IOC tools that use SMS messages for communication and HighRise is a SMS proxy that provides greater separation between devices in the field ("targets") and the listening post" by proxying ""incoming" and "outgoing" SMS messages to an internet LP," the leaked CIA manual reads.
What I understood after reading the manual is that CIA operatives need to install an application called "TideCheck" on their Android devices, which are set to receive all the stolen data via SMS from the compromised devices.
The last known version of the TideCheck app, i.e. HighRise v2.0, was developed in 2013 and works on mobile devices running Android 4.0 to 4.3, though I believe, by now, they have already developed an updated versions that work for the latest Android OS.
Once installed, the app prompts for a password, which is "inshallah," and after login, it displays three options:
Initialize — to run the service.
Show/Edit configuration — to configure basic settings, including the listening post server URL, which must be using HTTPS.
Send Message — allows CIA operative to manually (optional) submit short messages (remarks) to the listening post server.
Once initialized and configured properly, the app continuously runs in the background to monitor incoming messages from compromised devices; and when received, forwards every single message to the CIA's listening post server over a TLS/SSL secured Internet communication channel.
Previous Vault 7 CIA Leaks
Last week, WikiLeaks dumped two alleged CIA implants that allowed the agency to intercept and exfiltrate SSH credentials from targeted Windows and Linux operating systems using different attack vectors.
Dubbed BothanSpy — implant for Microsoft Windows Xshell client, and Gyrfalcon — targets the OpenSSH client on various distributions of Linux OS, including CentOS, Debian, RHEL (Red Hat), openSUSE and Ubuntu.
Since March, the whistleblowing group has published 16 batches of "Vault 7" series, which includes the latest and last week leaks, along with the following batches:
OutlawCountry – An alleged CIA project that allowed it to hack and remotely spy on computers running the Linux operating systems.
ELSA – Alleged CIA malware that tracks geo-location of targeted computers and laptops running the Microsoft Windows operating system.
Brutal Kangaroo – A tool suite for Microsoft's Windows used by the spying agency to target closed networks or air-gapped computers within an organisation or enterprise without requiring any direct access.
Cherry Blossom – An agency's framework used for monitoring the Internet activity of the targeted systems by exploiting vulnerabilities in Wi-Fi devices.
Pandemic – A CIA's project that allowed the agency to turn Windows file servers into covert attack machines that can silently infect other computers of interest inside a targeted network.
Athena – An agency's spyware framework that has been developed to take full control of the infected Windows machines remotely, and works for every version of Microsoft's Windows operating systems, from XP to Windows 10.
AfterMidnight and Assassin – Two CIA malware frameworks for the Windows platform that has been designed to monitor activities on the infected remote host computer and execute malicious actions.
Archimedes – Man-in-the-middle attack tool allegedly developed by the CIA to target computers inside a Local Area Network (LAN).
Scribbles – Software reportedly designed to embed 'web beacons' into confidential documents, allowing the agency to track insiders and whistleblowers.
Grasshopper – Framework that allowed the CIA hackers to easily create their custom malware for breaking into Microsoft's Windows OS and bypassing antivirus protection.
Marble – Source code of a secret anti-forensic framework used by the agency to hide the actual source of its malware.
Dark Matter – Hacking exploits the spying agency designed to target iOS and Mac systems.
Weeping Angel – Spying tool used by the CIA hackers to infiltrate smart TVs, transforming them into covert microphones.
Year Zero – Alleged CIA hacking exploits for popular software and hardware.
EFF Reviews Privacy Practices of Online Service Providers
14.7.2017 securityweek BigBrothers
During 2016, the US government made 49,868 requests to Facebook for user data; 27,850 requests to Google; and 9,076 requests to Apple. Governments will not stop making these requests, since the internet has become a major avenue for mass surveillance. The real issue is to what extent internet companies will seek to protect their users' data from unwarranted government intrusions.
Each year, the Electronic Frontier Foundation (EFF) publishes an annual 'Who Has Your Back' analysis of the basic privacy policy of major online service providers. It looks at five primary characteristics:
• Best privacy practices (including a satisfactory public, published policy and a published transparency rep ort)
• Informs users about government data requests (in advance of actually handing over any data)
• Refusal to hand over data without legal requirement (including by leakage or sale to third parties)
• Stands up National Security Letter (NSL) gag orders (with a public pledge to invoke the right to seek judicial review of all indefinite gag orders)
• Has a pro-user public policy (including support for reform of Section 702 of the FISA Amendments Act that will reduce the collection of information on innocent people).
A star is awarded for each category satisfied by the provider. This year (PDF), nine out of 26 evaluated companies have been awarded five stars: Adobe, Credo, Dropbox, Lyft, Pinterest, Sonic, Uber, Wickr, and Wordpress.
Telecoms companies generally perform poorly. "When it comes to adopting policies that prioritize user privacy over facilitating government data demands," notes the report, "the telecom industry for the most part has erred on the side of prioritizing government requests." Particularly at fault here are AT&T, Comcast, T-Mobile, and Verizon -- all with a single star in the 'best practices' category.
This is not, however, universal in telecoms. "Credo Mobile [5 stars] has repeatedly proven that telecom companies can adopt policies that earn credit in every category year after year. Similarly, Sonic [5 stars], an ISP competitor to AT&T, Comcast, TMobile, and Verizon, has now earned credit in every category of EFF's annual report for five years."
Some technology companies that have been high performers in previous years have dropped from that position this year -- for example, Facebook, Google and Twitter. All three have so far failed to publicly commit to requesting judicial review of all NSLs. Fewer than half of the reviewed companies have actually made that commitment: Adobe, Airbnb, Apple, Credo, Dropbox, Lyft, Pinterest, Slack, Sonic, Uber, Wickr, and WordPress.
"We applaud these companies that have taken a public stand to ensure judicial oversight of gag orders and urge others within the technology space to do the same," says EFF.
Failure to be awarded all five stars should not in itself suggest a complete failure in user privacy concern -- only that the company could do even better. For example, of Google, EFF says, "This is Google's sixth year in Who Has Your Back, and it has adopted a number of industry best practices, including publishing a transparency report, requiring a warrant for content, and publishing its guidelines for law enforcement requests. Google promises to inform users before disclosing their data to the government and supports substantive reforms to rein in NSA surveillance. Google prohibits third parties from allowing Google user data to be used for surveillance purposes."
Its failure to win five stars this year is solely down to the lack of a public policy to demand a judicial review on NSL letters. "We urge Google to create a public policy of requesting judicial review of all National Security Letters," says EFF. On its own, this doesn't mean that Google does not have such a policy (it may or it may not), it simply has not publicly avowed the policy.
Apple is another tech giant that just falls short of five stars. Unlike Google, it does have a publicly stated policy of demanding a judicial review on all NSLs. Apple's published policy states, "If Apple receives a National Security Letter (NSL) from the U.S. government that contains an indefinite gag order, Apple will notify the government that it would like the court to review the nondisclosure provision of the NSL pursuant to USA FREEDOM ."
Apple is not, however, specifically campaigning for the reform of Section 702.
Two companies criticized by EFF are Amazon and WhatsApp, both receiving just 2 stars. While EFF praises WhatsApp's move to adopt end-to-end encryption by default for its billion users, its policies still lag behind. Amazon has been rated number one in customer service, yet it hasn't made the public commitments to stand behind its users' digital privacy that the rest of the industry has.
"The tech industry as a whole has moved toward providing its users with more transparency," comments EFF senior staff attorney Nate Cardozo; but telecommunications companies -- which serve as the pipeline for communications and Internet service for millions of Americans -- are failing to publicly push back against government overreach. Both legacy telcos and the giants of Silicon Valley can and must do better. We expect companies to protect, not exploit, the data we have entrusted them with."
Samsung Tizen Accused of Being Home to at Least 27,000 Findable Bugs
14.7.2017 securityweek Vulnerebility
A purveyor of static code analysis wished to pitch his product to Samsung. What better way, he thought, than to run his product against the Samsung Tizen operating system, and demonstrate the results. The demonstration fell through, and the purveyor decided instead to publish his findings.
The purveyor is Andrey Karpov, CTO at "Program Verification Systems" Co Ltd and one of the developers of PVS-Studio. In a report published Wednesday, he claims that PVS-Studio would find 27,000 coding errors in Tizen. He actually checked only 3.3% of the code; but finding about 900 errors, he believes that would extrapolate to 27,000.
If his figures are correct, it could be a lot worse. He suggests that one use of PVS-Studio will detect "more than 10% of errors that are present in the code." Regular use would push that up to about 20% of the errors -- but either way, if his figures are correct, the implication is that Tizen potentially houses more than 250,000 bugs.
Tizen is a Linux-based open-source operating system designed for wide use in Samsung products: smartphones, tablets, smart TVs, smart watches, cameras and PCs. The project started in 2013, and by 2015 it had reached smartphones. Today it can be found on millions of devices and especially smart TVs.
Tizen is not new to controversy. Earlier this year security researcher Amihai Neiderman, then at Israeli firm Equus Technologies, reported the presence of 40 zero-day vulnerabilities in Tizen. "Right now, Tizen isn't mature enough, isn't ready enough to be sent to the public like this," he commented. "If those vulnerabilities I found in a few hours of research, then somebody who's really going to dedicate himself to be a Tizen researcher will find way more vulnerabilities."
27,000 bugs do not translate to 27,000 vulnerabilities -- but some of them could. For example, Karpov claims to have found 52 errors in which private data is not cleared. Only one is in the direct Samsung code -- the rest are in third-party libraries used in Tizen. "I think this is a serious omission," he writes, "since is does not matter which part of the program will be erroneous, when private data will remain somewhere in memory and then someone will use it."
Karpov wrote an open letter to Samsung in May 2017. He described a number of the errors he had found, and said "Our team is willing to work on improving the quality of Tizen project. The text contains remarks to the code fragments, but this is not criticism. All projects have bugs. The aim was to show by real examples that we aren't talking about abstract recommendations concerning the code improvement, but about real defects that we can find and fix."
Samsung's Youil Kim rejected the approach. Stating that "We currently have our own static analysis tool and run it regularly for Tizen," Kim added, "However, we don't agree with that Tizen has 27,000 defects that should be fixed."
Karpov begs to differ.
SecurityWeek has reached out to Samsung for a statement on this issue, but has had no response at the time of writing. If one is received, it will be appended to the post.
Dell Launches Endpoint Security Product for Air-Gapped Systems
13.7.2017 securityweek Safety
Dell announced on Thursday the availability of a new version of its Endpoint Security Suite Enterprise product designed specifically for air-gapped systems.
The solution is designed to protect isolated computers from malware, insiders and other threats using artificial intelligence and predictive mathematical models provided by endpoint security firm Cylance.
Researchers demonstrated in the past years that malware can leverage several methods to exfiltrate sensitive data from air-gapped systems, including through noise, LEDs, heat and radio frequencies.Dell Launches Endpoint Security Product for Air-Gapped Systems
Since isolated systems are not connected to the Internet, the security products installed on them cannot automatically receive regular malware definitions and other updates. By teaming up with Cylance, whose mathematical models only require a few updates per year, Dell has developed a solution that can protect a device without requiring an Internet connection.
In addition to threat protection features, Endpoint Security Suite Enterprise provides data encryption capabilities designed for securing files on any device against both external attacks and insiders (e.g. malicious USB drives). IT teams can enforce encryption policies on multiple endpoints and operating systems without disrupting productivity, Dell said. The product also includes web protection filtering capabilities.
Three versions of Dell Endpoint Security Suite Enterprise are currently available: one for systems with an Internet connection, one for devices that connect to an on-premises server for updates, and one for systems that are completely isolated.
"Highly-regulated organizations and government agencies need to deploy air gap solutions to protect their highly sensitive data, but have been unable to take advantage of the latest security technology that requires cloud connections," said Brett Hansen, vice president of Endpoint Data Security and Management at Dell.
"Dell is responding to their heightened needs by adapting our flagship Endpoint Security Suite Enterprise solution for on-premises, air gap environments – giving these organizations an advanced threat protection solution that has been inaccessible to them before now," Hansen added.
The air gap version of Dell Endpoint Security Suite Enterprise is available now in the United States and other select countries around the world.
'HighRise' Android Malware Used by CIA to Intercept SMS Messages
13.7.2017 securityweek BigBrothers
WikiLeaks on Thursday published a user guide describing what appears to be a tool used by the U.S. Central Intelligence Agency (CIA) to intercept SMS messages on Android mobile devices.
Named HighRise, the version of the malware described in the WikiLeaks document is disguised as an app called TideCheck, and it only works on Android versions between 4.0 and 4.3.
According to its developers, the tool must be manually downloaded, installed and activated on the targeted device – this means that the attacker needs to have physical access to the smartphone or trick victims into installing it themselves.
The second scenario is less likely as activating the app requires the user to open the TideCheck app, enter the “inshallah” password (the Arabic expression for “God willing”), and select the “Initialize” option from the menu. The document shows that the app will automatically run in the background after a reboot once it has been manually activated.
HighRise can be used to proxy incoming SMS messages received by the compromised device to a remote server. The tool also includes functionality for sending messages to the server via a secure communications channel.
The user guide leaked by WikiLeaks is for version 2.0 of HighRise and it’s dated December 2013. Google has made numerous security improvements to the Android operating system since version 4 – the latest version is Android 7 Nougat – and malware such as HighRise may no longer work without significant updates.
On the other hand, cybercriminals have been keeping up with the improvements and they still manage to create profitable Android malware. Furthermore, given that HighRise requires a significant amount of user interaction, it’s possible that this or other similar projects are still successfully utilized by the CIA.
Over the past months, WikiLeaks has described several “Vault 7” tools allegedly used by the agency. The most recent leaks detail malware designed for redirecting traffic on Linux systems (OutlawCountry), stealing SSH credentials (BothanSpy), spreading malware on an organization’s network (Pandemic), locating people via their device’s Wi-Fi (Elsa), hacking routers and access points (Cherry Blossom), and accessing air-gapped networks (Brutal Kangaroo).
Researchers Remotely Hijack Oracle OAM 10g Sessions
13.7.2017 securityweek Hacking
Two security researchers recently discovered an issue with improperly configured Oracle Access Manager (OAM) 10g that can be exploited by remote attackers to hijack sessions from unsuspecting users.
The issue, security researchers Nabeel Ahmed and Tom Gilis discovered, is related to the OAM authentication flow. In this Oracle Single Sign-On (SSO) implementation, the OAM server only validates whether the requested resource is indeed protected or not, and then redirects the user to a login page.
The OAM Server, the researchers note, sets the OAMREQ cookie (which contains information regarding the location of the requested resource) in the user's browser, so it would know on the next request for which resource the user is authenticating.
Next, the user submits credentials on the provided login screen, and the OAM server verifies them and, if the logon is successful, serves a cookie and a valid session, while also redirecting the user to the protected resource.
While analyzing the cookies the server delivers to the user, the security researchers noticed that the request/response flow contains some red flags. One of them is a parameter called rh=, which is the domain of the protected resource, while the other is the fact that the cookie is sent via a GET request.
The security researchers also noticed that, while the OAM server validates whether the resource is protected or not, it doesn’t serve an error if the resource doesn’t exist. Even in such cases, the OAM server redirects the user to the login page and serves an OAMREQ cookie.
After receiving a cookie for a non-existing resource, the researchers tested their findings against real resources and discovered two issues: the user is redirected after submitting credentials (Open Redirect), and the cookie value is transmitted in the GET request
“Since we can control where the user has to go and since we also can read the cookie value that is coming from the user we can hijack his session,” Ahmed notes.
For that, the user would need to be tricked into clicking a link and logging in. However, since the user is required to log in on the real portal, that shouldn’t raise suspicion. If the user is logged in, the cookie would be retrieved without issues and without the victim noticing it.
“We found hundreds of hundreds of high profile organization with the same misconfiguration, all of them exposed against session hijacking. We analyzed 100 high profile domains and only 1 was properly secured against this attack,” Ahmed said.
An attacker knowing such domains could send phishing emails and lure victims into clicking the link. The attacker doesn’t have to set up another website to capture credentials, but the victim is redirected to the login page, where they are asked to submit their credentials.
The server responds with a HTTP 302 redirect pointing to a malicious domain that steals users’ cookie and uses it to log in to their account. The webserver sends a redirect to the victim with the same cookie information to the appropriate domain, meaning that both the victim and the attacker are logged in, each on their independent session.
According to the researcher, when they contacted Oracle to point out the configuration issue, the company informed them that the problem had been already addressed through a feature called SSODomains. However, if SSODomains isn’t defined, it “effectively means you'll be able to get valid session for any domain,” the security researcher said.
According to Ahmed, the NIST CVSSv3 calculator would give the vulnerability an overall score of 9.3, meaning that it is a Critical issue.
Free Scanner Finds 50,000 EternalBlue-Vulnerable Systems
13.7.2017 securityweek Safety
More than 50,000 computers vulnerable to the NSA-linked EternalBlue exploit were found by a free vulnerability scanner in recent weeks.
Dubbed Eternal Blues, the tool was designed to provide network administrators with visibility into the EternalBlue-vulnerable machines in their networks, but without actually exploiting the flaw. In the wake of WannaCry, NotPetya, and other global infections leveraging the NSA-linked exploit, knowing whether a network is vulnerable or not is certainly a good idea.
According to Elad Erez, the security researcher who built the scanner, data collected through Eternal Blues over the past couple of weeks reveals that more than 50,000 scanned hosts are vulnerable to the exploit.
Erez also warns that sometimes all it takes is a single vulnerable machine to compromise an entire network. Using Eternal Blues, the administrator(s) of a network with around 10,000 hosts found the only two machines that were still vulnerable, thus securing the entire environment.
As of July 12, over 8 million IPs were scanned using Eternal Blues, most of which (1.5 million) are located in France. Vulnerable machines were found in around 130 countries and the top 3 countries “had more than 30,000 vulnerable hosts altogether,” the security researcher says.
Over half (53.82%) of the vulnerable hosts still have SMBv1 enabled, the researcher also discovered. Moreover, he notes that 1 out of 9 hosts in a network is vulnerable to EternalBlue.
Although Eternal Blues found only around 50,000 vulnerable systems, Erez warns that the number is much higher. Issues with the scanner prevented it from correctly reporting the number of vulnerable host. The researcher addressed those in a version released on July 2, but didn’t take previous findings into account when presenting the above numbers.
According to Erez, however, awareness on EternalBlue appears to have increased. The mere fact that admins are using the scanner is proof of that, he says.
To keep systems and networks secure, admins should apply the latest patches, perform periodic assessments of risks in their networks, and disable SMBv1, the researcher says. He also advises enabling automatic updates on Windows systems.
“Please, don’t be mistaken – recent ransomware attacks are the ones that made all the buzz, since they actually tell you when they hit you. I believe there are many more EternalBlue-based attacks which remain off the radar and are still unknown to,” the researcher points out.
Ransomware pro Android vyhrožuje, že odhalí historii vašeho internetového brouzdání
13.7.2017 Živě.cz Viry
Ransomware vyhrožuje, že rozešle všem kontaktům v mobilu soukromé informaceUkázka infikované aplikaceTakové pokyny v McAfee objevili v kódu infikovaných aplikacíUkázka infikované aplikaceTakové pokyny v McAfee objevili v kódu infikovaných aplikací6 FOTOGRAFIÍ
zobrazit galerii
McAfee odhalil další útok, který je zaměřený na mobilní zařízení s Androidem. Jmenuje se LockerLeaker a jde o vyděračský malware, který vyhrožuje, že rozešle soukromá data a historii internetového prohlížení všem vašim kontaktům.
Typický ransomware zašifruje pevný disk a po uživateli požaduje za odemčení peníze. LeakerLocker na to jde podobně, ale přesto jinak. Zálohuje si uživatelova soukromá data a vyhrožuje, že pokud uživatel nezaplatí 50 dolarů, rozešle je všem kamarádům a rodině v seznamu kontaktů.
McAfee odhalil, že se LeakerLocker šíří skrze dvě aplikace v obchodě Google Play – Wallpaper Blur HD (staženo 5 – 10 tisíckrát) a Booster Cleaner Pro (staženo 1 až 5 tisíckrát), přičemž není vyloučeno, že se nachází i na dalších místech. Infikováno bylo až 15 tisíc zařízení. Obě dvě aplikace mají pozitivní recenze, které naznačují, že byly napsány útočníky.
Jakmile si člověk aplikace se škodlivým kódem stáhne, vyzvou jej k potvrzení přístupů, včetně přístupu k hovorům, k SMS zprávám a kontaktům. Následně na obrazovce zobrazí výhrůžku.
Hrozba ale není až tak ničivá. McAfee prováděl analýzu, k čemu všemu se LeakerLocker skutečně dokáže dostat a zjistil, že ke zcela všem informacím na zařízení ne. Dokáže ovšem získat historii internetové prohlížení, znění SMS zpráv a fotografie z alba, tedy data, o kterých bezesporu nechcete, aby se potulovala světem.
New Ransomware Threatens to Send Your Internet History & Private Pics to All Your Friends
13.7.2017 thehackernews Ransomware
After WannaCry and Petya ransomware outbreaks, a scary (but rather creative) new strain of ransomware is spreading via bogus apps on the Google Play Store, this time targeting Android mobile users.
Dubbed LeakerLocker, the Android ransomware does not encrypt files on victim's device, unlike traditional ransomware, rather it secretly collects personal images, messages and browsing history and threatens to share it to their contacts if they don't pay $50 (£38).
Researchers at security firm McAfee spotted the LeakerLocker ransomware in at least two apps — Booster & Cleaner Pro and Wallpapers Blur HD — in the Google Play Store, both of which have thousands of downloads.
To evade detection of malicious functionality, the apps initially don’t contain any malicious payload and typical function like legitimate apps.
But once installed by users, the apps load malicious code from its command-and-control server, which instructs them to collect a vast number of sensitive data from the victim's phone — thanks to its victims granting unnecessary permissions blindly during installation.
The LeakerLocker ransomware then locks the home screen and displays a message that contains details of the data it claims to have stolen and holds instructions on how to pay the ransom to ensure the information is deleted.
The ransom message reads:
All personal data from your smartphone has been transferred to our secure cloud.
In less than 72 hours this data will be sent to every person on your telephone and email contacts list. To abort this action you have to pay a modest ransom of $50 (£38).
Please note that there is no way to delete your data from our secure but paying for them. Powering off or even damaging your smartphone won't affect your data in the cloud.
Although the ransomware claims that it has taken a backup of all of your sensitive information, including personal photos, contact numbers, SMS', calls and GPS locations and browsing and correspondence history, researchers believe only a limited amount of data on victims is collected.
According to researchers, LeakerLocker can read a victim's email address, random contacts, Chrome history, some text messages and calls, take a picture from the camera, and read some device information.
All the above information is randomly chosen to display on the device screen, which is enough to convince the victims that lots of data have been copied.
Both malicious apps have since been removed by Google from the Play Store, but it is likely that hackers will try to smuggle their software into other apps.
If you have installed any of the two apps, uninstall it right now.
But if you are hit by the ransomware and are worried about your sexy selfies and photographs being leaked to your friends and relatives, you might be thinking of paying a ransom.
Do not pay the Ransom! Doing so motivates cyber criminals to carry out similar attacks, and there is also no guarantee that the stolen information will be deleted by the hackers from their server and will not be used to blackmail victims again.
Researcher Claims Samsung's Tizen OS is Poorly Programmed; Contains 27,000 Bugs!
13.7.2017 thehackernews Vulnerebility
A researcher has claimed that Samsung's Tizen operating system that runs on millions of Samsung products is so poorly programmed that it could contain nearly 27,000 programming errors, which could also lead to thousands of vulnerabilities.
Tizen is a Linux-based open-source operating system backed by Intel and Samsung Electronics, which has been in development since early 2012 and designed for smartphones, tablets, smart TVs, smart watches, cameras and PCs.
According to Andrey Karpov — founder of Russia-based company Program Verification Systems that made PVS-Studio, a static code analyzer tool that helps programmers to find and fix bugs in their source codes — his team has discovered hundreds of errors in Tizen project using PVS-Studio.
Samsung's Tizen operating system, written in C/C++ programming language, currently has 72.5 million lines of source code, out of which Karpov's team has analysed some randomly chosen modules i.e. 3.3% of the entire Project and found nearly 900 errors.
"If we extrapolate the results, we will see that our team is able to detect and fix about 27000 errors in Tizen," Karpov says.
In April this year, Israeli researcher Amihai Neiderman called Tizen "the worst code I've ever seen" after he examined the operating system and discovered as many as 40 zero-day vulnerabilities in Tizen code.
After finding almost a thousand bugs in Tizen code, Karpov contacted Samsung to pitch for the sale of static analyser PVS-Studio software, but Youil Kim from Samsung declined the offer.
According to a mail exchanged between Karpov and Kim, Samsung is already using the SVACE technology (Security Vulnerabilities and Critical Errors Detector) to detect potential vulnerabilities and errors in source code of applications created for Tizen.
"We are already aware that another tool can find additional defects. However, we don't agree with that Tizen has 27,000 defects that should be fixed. As you know, many of static analysis warnings are often considered as insignificant issues," Kim added.
Tizen operating system already runs on nearly 30 million Smart TVs, Galaxy Gear-branded watches Smart TVs, cameras, home appliances and some of its smartphones sold in countries like Russia, India and Bangladesh.
Samsung has even plans to have some 10 Million Tizen smartphones in the market at the end of this year.
So, if claims made by the researcher are true — which was also acknowledged by a Samsung representative to some extent — the company should shift their focus mainly towards the security of the operating system in Tizen 4.0, which is due for release in September.
Windows 10 Boosts Protections Against Code Injection Attacks
13.7.2017 securityweek Attack
Enhancements in Windows 10 Creators Update include improvements in Windows Defender Advanced Threat Protection (Windows Defender ATP) to keep users protected from threats such as Kovter and Dridex Trojans, Microsoft says.
Specifically, Windows Defender ATP in Creators Update can detect code injection techniques associated with these threats, such as process hollowing and atom bombing. Already used by various other threats, these methods enable malware to infect computers and engage into various nefarious activities while remaining stealthly.
Process hollowing is a technique where a threat spawns a new instance of a legitimate process, after which it replaces the legitimate code with that of the malware. While other injection techniques add a malicious feature to a legitimate process, hollowing results in a process that looks legitimate but is primarily malicious.
There are various threats using process hollowing, with Kovter, a four-year old click-fraud Trojan that adopted a fileless infection model last year and which was recently associated with ransomware such as Locky, being the most popular. In November last year, Kovter was found responsible for a massive spike in new malware variants.
Delivered mainly through phishing emails, Kovter hides most of its malicious components via registry keys, then uses native applications to execute the code and perform injection. For persistence, it adds shortcuts (.lnk files) to the startup folder or new keys to the registry.
The malware adds two registry entries to have its component file opened by the legitimate program mshta.exe. The component extracts an obfuscated payload from a third registry key and a PowerShell script is used to execute another script that injects shellcode into a target process. Through this shellcode, Kovter uses process hollowing to inject malicious code into legitimate processes.
Atom bombing is a rather new code injection method, based on a Windows vulnerability that can’t be patched, and which can be used by an attacker who has already compromised the targeted machine. The technique relies on malware writing malicious code to the global atom table and using asynchronous procedure calls (APC) to retrieve the code and insert it into the memory of the target process.
Dridex, a threat first spotted in 2014, was anearly adopter of atom bombing. Mainly distributed via spam emails, Dridex was designed to steal banking credentials and sensitive information, as well as to disable security products and provide attackers with remote access to victim computers. The threat remains stealthy and persistent through avoiding common API calls associated with code injection techniques.
When executed on the victim’s system, the malware looks for a target process and ensures user32.dll is loaded by this process, as it needs the DLL to access the required atom table functions. Next, the malware writes its shellcode to the global atom table, then adds NtQueueApcThread calls for GlobalGetAtomNameW to the APC queue of the target process thread to force it to copy the malicious code into memory.
“Kovter and Dridex are examples of prominent malware families that evolved to evade detection using code injection techniques. Inevitably, process hollowing, atom bombing, and other advanced techniques will be used by existing and new malware families,” John Lundgren, Windows Defender ATP Research Team, explains.
Windows Defender ATP Creators Update, he adds, includes function calls and statistical models that can detect various malicious injection techniques and better expose covert attacks. According to Lundgren, Microsoft has already tested these capabilities against real-world examples of malware families employing process hollowing and atom bombing, among other methods.
Democracy at Risk from Poor Cybersecurity, Foreign Interference: Survey
13.7.2017 securityweek BigBrothers
Survey Shows Distinct Voter Concern for Elections and Cybersecurity
For more than a year, a single thread has dominated American news: foreign interference in US elections. It started in June 2016 in the run-up to the 2016 presidential election, when the Democratic National Committee (DNC) announced it had been hacked, and CrowdStrike accused Russia-based Cozy Bear (APT 29).
Since then, the ramifications have rarely been out of the news. In October 2016 the U.S. government formally accused Russia of being behind the cyberattacks, and by December it became known that the CIA believed that "Russia intervened in the 2016 election to help Donald Trump win the presidency, rather than just to undermine confidence in the U.S. electoral system," The Washington Post reported.
Since then, emphasis has switched to questioning the extent to which the Trump electoral team may or may not have known about or colluded with Russia in order to win the election; and whether it has or has not attempted to hinder or subvert subsequent law enforcement investigations. This has continued throughout 2017 until Wednesday this week when Rep. Brad Sherman (D-Calif.) formally introduced an article of impeachment against President Trump.
The article of impeachment revolves around Trump's dismissal of FBI director James Comey allegedly to hinder the FBI's investigation into former National Security Advisor, General Michael Flynn. "In all of this, Donald John Trump has acted in a manner contrary to his trust as President and subversive of constitutional government, to the great prejudice of the cause of law and justice and to the manifest injury of the people of the United States."
The huge and apparently unending ramifications of what started as just another cyber hack has caused cybersecurity firm Carbon Black to wonder what effect the cyber element has had on the American electorate. In June 2017, it conducted a nationwide survey (PDF) of 5,000 eligible U.S. voters, with particular reference to the upcoming midterm 2018 elections.
In an associated blog post Carbon Black CEO Patrick Morley commented, "In perhaps the most startling revelation from the survey, 1 in 4 voters said they will consider not voting in upcoming elections over cybersecurity fears."
In reality, this figure is easily covered by existing non-voters. Approximately only 57.9% of voters voted in the 2016 election, down less than 1% from the 58.6% that voted in 2012. So, while 25% of voters now say they may not vote in the midterms, this may have no effect on the actual voter turnout.
A second area where the obvious conclusion may not be the accurate conclusion can be seen in 'voter perception on election influence'. According to the survey, "47% of voters said they believe the 2016 U.S. election was influenced by foreign entities." However, there could be a strong element of 'sore loser' in these figures. There is an aspect of tribalism in political affiliation -- some people will always vote for one particular party simply because of tribal affiliations.
It is estimated that 48% of the electorate voted for Clinton (slightly more than the estimated 46% who voted Trump). There will be a strong incentive for the losing 48% to blame external causes on their loss -- and that could account for a large proportion of the 47% of responding voters who told Carbon Black that the result was influenced by foreign entities.
Despite not being able to definitively relate current sentiment to a past or future threat against electoral democracy, the Carbon Black survey nevertheless shows distinct voter concern for elections and cybersecurity. Several of the survey queries are unambiguous, and the results can be taken at face value. Forty-five percent of voters believe that Russia poses the biggest cybersecurity risk to U.S. elections. Of the remaining 55%, "20% said the United States itself; 17% said North Korea; 11% said China; and 4% said Iran. (3% answered 'other.')" notes the report.
Fifty-four percent of respondents "said the NSA leaks negatively impacted their trust in the U.S. election system to keep data safe;" and 44% "said they believe Russia will 'Be back' to influence future elections."
Carbon Black concludes, "Cyberattacks against our elections seed doubt in democracy. The idea that even a single voter is willing to forfeit their vote in fear of a cyberattack is startling. The fact that 1 in 4 voters said they would be willing to do so speaks volumes about how deeply this doubt has penetrated. The alleged cyberattacks surrounding the 2016 elections were a clarion call that foreign entities are motivated to disrupt U.S. elections." More starkly, it adds, "Our democracy is at risk."
Reality is probably not as extreme as this suggests. Political sentiment polling is very difficult, and Carbon Black has failed to eliminate 'other causes' in some of its questions. It might, for example, have been better to question 5,000 eligible voters that had actually voted in 2016 to get a more accurate picture of future voting intentions.
Nevertheless, it is clear that there is strong voter concern over the future of elections and cybersecurity. The report makes five proposals designed "to help restore voter confidence." The first is to implement stronger cybersecurity protection for online registration systems and voter databases. The second is to limit (or discontinue) the use of electronic voting machines. The third is to create an auditable paper trail of votes in every state and precinct. The fourth is to prohibit online voting.
The fifth is arguably the most important. In January 2017, then U.S. Homeland Security Secretary Jeh Johnson said, "I have determined that election infrastructure in this country should be designated as a subsector of the existing Government Facilities critical infrastructure sector. Given the vital role elections play in this country, it is clear that certain systems and assets of election infrastructure meet the definition of critical infrastructure, in fact and in law."
In its fifth recommendation, Carbon Black now calls for the government to "commit the same urgency and resources to protecting its elections as it does for 'traditional' critical infrastructure."
Trend Micro Patches Flaws in Deep Discovery Product
13.7.2017 securityweek Vulnerebility
Trend Micro has released a critical patch for its Deep Discovery Director product to address several vulnerabilities that can be combined to achieve arbitrary command execution.
Deep Discovery Director is a Linux-based on-premises management platform that allows organizations to centralize the deployment of product updates and upgrades, Virtual Analyzer images, and configurations to Deep Discovery products.
Researchers at Core Security discovered in late May that version 1.1 of the product is affected by three potentially serious vulnerabilities, including command injection, hardcoded password and improper backup validation issues. Trend Micro addressed the bugs this week and published a security bulletin to notify customers.
According to Core Security, configuration and database backup archives are not signed or validated. They are encrypted, but the same cryptographic key is used across all virtual appliances.
An attacker with access to the Deep Discovery Director web console can exploit these weaknesses to create specially crafted backup archives that will be loaded by the application. The backup restoration process for accounts used to access the pre-configuration console is affected by a command injection vulnerability, allowing the attacker to leverage the malicious backup archive to execute arbitrary commands and spawn a root shell.
Core Security has published an advisory that contains technical details for each of the vulnerabilities and how they can be combined to achieve arbitrary command execution.
Trend Micro has classified the vulnerabilities as medium severity and pointed out that an attacker requires physical or remote access to the affected machine in order to exploit the flaws.
This is not the only critical patch released in recent months by Trend Micro for a Deep Discovery product. In March, the company informed customers of Deep Discovery Email Inspector (DDEI) 2.5.1 of critical vulnerabilities that can be exploited for remote code execution.
The security holes were reported to Trend Micro via the Zero Day Initiative (ZDI), which published separate advisories for each of the issues.
Wikileaks: CIA HighRise Android malware used to intercept and redirect SMSs
13.7.2017 securityaffairs BigBrothers
Wikileaks released the documentation for HighRise, an Android app used by the CIA to intercept and redirecting SMS messages to a CIA-controlled server.
WikiLeaks just published a new batch of documents related to another CIA hacking tool dubbed HighRise included in the Vault 7 released in partnership with media partners.
The tool is an Android application used by the US intelligence agents to intercept and redirecting SMS messages to a CIA-controlled server.
Below the list of features implemented by the Android malware:
Proxy “incoming” SMS messages received by HighRise host to an internet LP
Send “outgoing” SMS messages via the HighRise host
Provide a communications channel between the HighRise field operator & the LP
TLS/SSL secured internet communications
“HighRise is an Android application designed for mobile devices running Android 4.0 to 4.3. HighRise provides a redirector function for SMS messaging. There are a number of IOC tools that use SMS messages for communication and HighRise is a SMS proxy that provides greater separation between devices in the field (“targets”) and the listening post.” reads the manual.
According to a user manual leaked by Wikileaks, the malicious code only works on Android versions from 4.0 through 4.3 (Android Ice Cream Sandwich and Jelly Bean) that currently account for 8,8 percent of overall Android devices on the market.
Anyway, the document is dated back to December 2013, it is likely that the CIA has updated the tool in the meantime to target newer versions of the Android OS.
The HighRise tool is packaged inside an app named TideCheck (tidecheck-2.0.apk, MD5: 05ed39b0f1e578986b1169537f0a66fe).

The tool must be installed by CIA agents manually on the target system and need to be manually executed at least one time.
“Therefore, the HighRise application first must be manually run once before it will automatically run in the background or after a reboot. As a consequence, the HighRise application now shows up in the list of installed apps so it can be started by the HighRise operator. ” continues the manual.
When running the tool for the first time, CIA cyber spies must enter the special code “inshallah” (“God willing” in Arabic) to access its settings.
Once the code has been entered and the software is successfully activated, HighRise will run in the background listening for events. The hacking tool will automatically start every time the phone is powered on.
“Once activated, HighRise will run in the background listening for events. It will also automatically start when the phone is powered on. Activating HighRise multiple times will have no adverse affects.” continues the manual.
Below the list of release published by Wikileaks since March:
HighRise – 13 July, 2017
BothanSpy and Gyrfalcon – 06 July, 2017
OutlawCountry – 30 June, 2017
ELSA malware – 28 June, 2017
Cherry Blossom – 15 June, 2017
Pandemic – 1 June, 2017
Athena – 19 May, 2017
AfterMidnight – 12 May, 2017
Archimedes – 5 May, 2017
Scribbles – 28 April, 2017
Weeping Angel – 21 April, 2017
Hive – 14 April, 2017
Grasshopper – 7 April, 2017
Marble Framework – 31 March, 2017
Dark Matter – 23 March, 2017
Verizon Downplays Leak of Millions of Customer Records
13.7.2017 securityweek Incindent
The personal details of millions of Verizon customers were exposed online due to a misconfigured Amazon Web Services (AWS) S3 bucket operated by a third-party vendor, but the telecoms giant has downplayed the incident.
Cyber resilience firm UpGuard reported on Wednesday that its researchers discovered an unprotected AWS S3 bucket containing information on as many as 14 million Verizon customers, including names, addresses, phone numbers, PINs used for identity verification purposes, customer satisfaction data, and service purchases.
The data, which appears to represent daily logs collected over the first six months of 2017, was not exposed by Verizon itself, but by NICE Systems, an Israel-based partner that provides call center services. UpGuard reported the leak to Verizon on June 13, but the exposed database was only protected on June 22.
“Beyond the sensitive details of customer names, addresses, and phone numbers—all of use to scammers and direct marketers—the prospect of such information being used in combination with internal Verizon account PINs to takeover customer accounts is hardly implausible. To do so would enable impersonators to tell Verizon call center operators to do whatever was wished of them,” UpGuard said in a blog post.
In a statement published on its corporate website, Verizon downplayed the incident, claiming that the details of only 6 million unique customers were exposed. The company blamed the leak on human error, and pointed out that no one other than UpGuard had accessed the unprotected cloud storage area.
“The overwhelming majority of information in the data set had no external value, although there was a limited amount of personal information included, and in particular, there were no Social Security numbers or Verizon voice recordings in the cloud storage area,” Verizon said.
“To further clarify, the data supports a wireline portal and only includes a limited number of cell phone numbers for customer contact purposes. In addition, to the extent PINs were included in the data set, the PINs are used to authenticate a customer calling our wireline call center, but do not provide online access to customer accounts,” the company added.
Experts believe this is a serious incident, even if no one else downloaded the data from the cloud storage.
“Sure, a mid-air miss is better than an air flight disaster, but neither should ever happen,” John Gunn, chief marketing office for VASCO Data Security, told SecurityWeek. “Data such as this can be used by hackers for all types of attacks, especially phishing attacks, by giving them legitimacy in the mind of the victim. We saw this recently with the DocuSign breach and the subsequent successful attacks against their users.”
Willy Leichter, vice president of marketing at Virsec, believes “this will be a heated board-level issue for a $1 billion company like Nice, and a $125 billion-plus company like Verizon.”
“If the European General Data Protection Regulation (GDPR) was in effect (it is starting in May 2018) there could be a fine as large at $5 billion (4% of annual revenue) for this single incident,” Leichter said.
US Government limits purchase of Kaspersky Lab solutions amid concerns over Russia ties
13.7.2017 securityaffairs BigBrothers
The US General Services Administration announced that the security firm Kaspersky Lab has been deleted from lists of approved vendors.
The US government bans Kaspersky solutions amid concerns over Russian state-sponsored hacking. Federal agencies will not buy software from Kaspersky Lab due to its alleged links to the Russian intelligence services.
This week, a Bloomberg News report, claimed internal company emails show that Kaspersky has a strict relationship with Russia secret services FSB.
The General Services Administration (GSA), which is the organization that handles federal government purchasing contracts, announced that cyber security firm Kaspersky Lab has been removed from the list of approved vendors.
“GSA’s priorities are to ensure the integrity and security of US government systems and networks and evaluate products and services available on our contracts using supply chain risk management processes,” reads the statement issued by the General Services Administration.
The decision doesn’t surprise the IT security industry, the US intelligence and Government officials have expressed concerns about the adoption of Kaspersky software several times.
It is important to highlight that the ban is not total, Government agencies will still be able to use Kaspersky software purchased separately from the GSA contract process.
According to the Reuters,
The company said in a statement to AFP , it had not received any updates from GSA or any other U.S. government agency regarding its vendor status.
“Kaspersky Lab has no ties to any government, and the company has never helped, nor will help, any government in the world with its cyberespionage efforts,” the company said.
It added that it had been “caught in the middle of a geopolitical fight where each side is attempting to use the company as a pawn in their political game.”
Kaspersky added that “the company is being unjustly accused without any hard evidence to back up these false allegations.”
Kaspersky on Tuesday published statement in response to the Bloomberg’s report.
“While the U.S. government hasn’t disclosed any evidence of the ties, internal company emails obtained by Bloomberg Businessweek show that Kaspersky Lab has maintained a much closer working relationship with Russia’s main intelligence agency, the FSB, than it has publicly admitted.”
“Actually, the reported emails show no such link, as the communication was misinterpreted or manipulated to try to make the media outlet’s narrative work. Kaspersky Lab is very public about the fact that it assists law enforcement agencies around the world with fighting cyberthreats, including those in Russia, by providing cybersecurity expertise on malware and cyberattacks.” states Kaspersky.
“Kaspersky Lab regularly cooperates with law enforcement agencies, industry peers and victims of cybercrime.”
In May, the Senate Armed Services Committee passed a defense spending policy bill that would ban Kaspersky products from use in the US military. The decision was taken a day after the FBI interviewed several of the company’s U.S. employees at their private homes as part of a counterintelligence investigation into its operations.
“In May senior U.S. intelligence officials said in testimony before the Senate Intelligence Committee that they were reviewing government use of software from Kaspersky Lab.” reported the Reuters Agency.
“Lawmakers raised concerns that Moscow might use the firm’s products to attack American computer networks, a particularly sensitive issue given allegations by U.S. intelligence agencies that Russia hacked and leaked emails of Democratic Party political groups to interfere in the 2016 presidential election campaign. Russia denies the allegations.”
New PoS Malware LockPoS emerges in the threat landscape
13.7.2017 securityaffairs Virus
A newly discovered Point of Sale (PoS) malware dubbed LockPoS appeared in the wild and it is being delivered through the Flokibot botnet.
A newly discovered Point of Sale (PoS) malware is being delivered via a dropper that is manually loaded and executed on the targeted systems, Arbor Networks Security researchers warn.
Arbor Networks researchers discovered a new Point of Sale (PoS) malware, dubbed LockPoS, in the threat landscape.
LockPoS uses command and control (C&C) infrastructure used by the Flokibot against Brazilian users.
The Floki bot is a banking Trojan based on Zeus that has been sold on cybercrime underground since September 2016. The malware was developed starting from the Zeus source code that was leaked in 2011, it is offered for $1,000 worth of bitcoins.
The experts from Flashpoint who discovered it in the wild in December speculated that the Floki Bot has a Brazilian origin, the threat actor behind the malware was using the “flokibot” moniker and communicated in Portuguese. It targeted Brazilian IPs and domains and targeted systems having default language set to Portuguese.
The LockPoS the malware has been compiled in late June and to use a dropper that injects the malicious code directly into the explorer.exe process.
The malware has to be manually loaded and executed, then the dropper continues by extracting a resource file from itself that contains multiple components that are injected into explorer.exe. and that works as a second-stage loader. Next, the malicious code decrypts, decompresses, and loads the final LockPoS payload.
LockPoS implements a regular “registry run” method for persistence and obfuscates important strings using XOR and a key of “A”.
“LockPoS uses the regular “registry run” method for persistence. It obfuscates important strings using XOR and a key of “A”. An initial configuration (which includes the C2 URL) is stored unencrypted as a resource named “XXXX”:” states the analysis.
“C2 communications are via HTTP and using a very telling User-Agent. “
The malware’s communication with the C&C server via HTTP,once infected a machine, it sends back to the server several information including username, computer name, and bot ID, Bot version (1.0.0.6), CPU, Physical memory, Display devices, Windows version and architecture, and MD5 hash of currently running sample.
“The malware’s PoS credit card stealing functionality works similarly to other PoS malware: it scans the memory of other running programs looking for data that matches what credit card track data looks like. Here’s a snippet of the matching function,” continues the analysis.

The LockPoS has been distributed via a Flokibot botnet, it is likely by the same threat actors that is focused on Brazilian users.
Experts highlighted that hackers used the same C&C at treasurehunter[.]at was used in another PoS malware campaign spotted by FireEye last year and tracked as TreasureHunt.
Arbor Networks explained that the LockPoS is a totally different malware family from TREASUREHUNT.
“One thing to note about the analyzed C2 server (treasurehunter[.]at) is that there is a name overlap with another PoS malware that FireEye wrote about in 2016 called TREASUREHUNT. Based on their research on its C2 communications, panel, and other IoCs it looks like LockPoS and TREASUREHUNT are separate families.”
“It is currently unclear whether LockPoS is an exclusive malware associated with one threat actor or whether it will be sold on underground forums like Flokibot was.’, continues the analysis.
Ransomware, hrozba na vzestupu. Nebylo lepší, když nám viry nedávaly na výběr?
13.7.2017 Lupa.cz Viry
Jak je možné se nakazit? Jaké typy ransomwaru existují? A vyplatí se útočníkům zaplatit? Odpovědět se pokoušíme v novém seriálu na téma ransomware.
Možná jste před rokem slovo výkupné „ransom“ nepoužívali, možná vám jako mně evokovalo spíš pána z MI6 Arthura Ransomea a jeho Vlaštovky a Amazonky. Zatímco v minulém roce se už už zdálo, že hlavní hledáček malwaru se zaměřuje na mobilní zařízení, letos jsou opět na talíři hlavně počítače.
Když byl před nějakou dobou CSIRT.CZ osloven, aby připravil seriál o ransomwaru, nevěděli jsme, že bude po informacích taková sháňka. Bylo to ještě než Google pro dotaz „ransomware“ vracel 26 milionů odkazů a než se luhy a háji českých mainstreamových medií prohnal WannaCry, následován poté po šesti týdnech NotPetyou.
Opravdu jsme se nenudili: v našem seriálu se budeme snažit shrnout, co ransomware je, jak se s časem vyvíjí, co dělat před a co dělat po (prevence a mírnění škod), jak je ransomware možné zapasovat do ekosystému škodlivých programů a co pro vás, ať už jako oběti, či jako činitele, v současnosti mohou udělat policejní orgány.
R jako ransomware
Mezi okamžikem, kdy jsem se poprvé pousmál nad screenshotem: „Tady Policie ČR, zablokovali jsme vám počítač, protože jste sdílel soubory! Toto je Vaše IP adresa! Jste v Mělníku! Zaplaťte tak a tak!“ a mezi chvíli, když jsem zvedl sluchátko se zoufalým pánem: „Zašifrovalo nám to všechny počítače ve firmě! Zálohovali jsme na síťový disk, ten je také zašifrovaný!“ se změnilo leccos.
Předně nám trochu mrzne úsměv na rtech, když pomyslíme na to, zda nám nečouhá nějaký zapomenutý port. Když první viry, které člověk potkal, ta data alespoň mazaly („Disk is one half“, psal mi virus coby osmiletému nad z poloviny smazaným 12megovým diskem a já si to neuměl přeložit a měsíce myslel, že je to jakási legrace, nová funkcionalita BIOSu), když vám viry nedávaly na výběr, bylo to možná milejší. Aspoň člověk nebyl ve stínu té hrozivé svobody volby, asi jako někdo, kdo právě utopil harddisk v akváriu a sedí nad mobilním připojením ve snaze rozhodnout, jestli pro pár fotek z Mácháče zaplatí osm tisíc za rekonvalescenci disku u specializované společnosti. Zaplatím-li požadovanou sumu, budu jedním z pěti, kterým se data nevrátí, jak je u statistiky ransomwaru obvyklé? Nebo je to dokonce ransomware, kde se data nevrací nikomu?
Že máte na cloudu historii souborů? A jak dlouhou? A co když potkáte kousek, jenž se snaží nahrát soubor mnohokrát za sebou, aby se přemazala i jejich případná historie?
To se nám zasteskne po nějakém tom malwaru pro introverty, který při startu Skype napíše všem kontaktům: „Hi!“, abyste pak dvě hodiny všem na potkání vysvětlovali, že si povídat vlastně nechcete.
Někdy máme štěstí v neštěstí
Zatímco WannaCry řičel ve stovce zemí, povedlo se najít jeho kill switch, vlastnost, která šíření dané verze malwaru zastaví. Stačilo, aby Marcus Hutchins koupil doménu, na jejíž neexistenci program spoléhal – a řádění polevilo. Další vlna sice na sebe nenechala dlouho čekat, ale společnosti už měly čas záplatovat a připravit se proti odhalenému vektoru útoku.
Měli jsme vlastně ještě štěstí, že poslední dva ransomwary, o kterých se hodně psalo, jsou napsány fušersky. A neříkám to jenom proto, že má díru každý program a ta díra se najde, zvlášť když se na vás vrhnou analytici celého širého napadeného světa.
Promiňte, ale postavit celý business model na tom, že všechny finanční záležitosti s oběťmi provedete na německé freemailové službě Posteo, kterou Vám týž den zablokují. Autorům druhého viru NotPetya přišlo jen kolem 30 plateb – pánům se podpálil les, aby si opekli buřt. Respektive nebohou Ukrajinu, je pravděpodobné, že šlo o kyberútok, který se pouze maskoval jako finančně lačný. Data byla likvidována bez meškání. Jaké to teprve bude, až někdo vydá řádně otestovaný ransomware s vadou, na niž se nenarazí hned první den?
Napadá ransomware i mou platformu?
Ano. A pokud ne dnes, poptejte se zítra.
Již jsem zmiňoval, že hlavní cíl ransomwaru jsou desktopy. Jak to tak bývá, hlavní odrazový můstek jsou tradičně Windows – široká základna vhodných uživatelů. Stejně jako se před pár lety říkalo „Viry na Linuxu nefungují“, protože Linux nebyl tak populární, a pak klepl tučňáka přes zoban Mayhem a Mirai a kdoví, co ještě, i ransomware s upířím výrazem šplhá ze své půlnoční rakve, plné poštovních známek, USB zdířek a ethernetové kabeláže.
Máme tu i kousky požírající webové servery (KimcilWare), přes síť dostupné databáze, ale i sociální účty. Už před rokem si 16letý Liverpoolan hodlal přibrigádničit krádežemi účtů na Instagramu. Na své si samozřejmě už nějakou dobu přicházejí uživatelé OS X a v budoucnu se můžeme jistě těšit na lepší podporu IoT zařízení.
Je třeba dodat, že na mobilech je nižší tendence k šifrování dat, protože se to nevyplatí – uživatelé tak chytrých mobilů, na nichž běží malware, příliš snadno zálohují na obtížněji napadnutelný cloud; nemějte však pocit falešného bezpečí.
Kolik typů znáš…
Jak platí u každého malwaru, je výzvou každý daný malware klasifikovat. Představte si, že milion druhů hmyzu, které lidstvo zvládlo katalogizovat, jsou druhy malwaru. Jistá část připadá na ransomware; jeden typ ransomwaru je pak pakobylka. Tipnete si, kolik je v řádu strašilek druhů a poddruhů? Autoři malware stále přepisují, jak se jim hodí, jaký dostávají feedback; přepisují a znovupoužívají jej i lidé, kterým projde pod rukama. Myslíte si, že třeskuté ransomwary zneužily nějaké svobodozednářské zranitelnosti? Že NotPetya přišla zčistajasna? Mě překvapilo/pobavilo, když jsem se dočetl, že sám anonymní autor původního malware Petya zkoušel proti zhoubě pomoci.
Možností, jak ransomware členit, je nepřeberně. Výzkumníci z celého světa se spojují a sdílí IoC, tzv. indikátory kompromitace, podle kterých lze poznat blížící se zhoubu. Možná by vás zajímal například dokument se seznamem IoC, které o WannaCry zveřejnil US-CERT – v přiloženém XLS jsou názvy souborů a jejich hashů, které WannaCry na systému vytváří.
Uvádím například tuto škálu, kam ransomware můžete zařadit:
Strašáci – Nejméně nebezpečnou formou jsou falešné antivirové zprávy (například ve formě reklam na webu), které vypadají jako systémová tlačítka a hlásají: „Našli jsme malware na vašem počítači, zaplaťte a my vám ho odstraníme“. Kdo neklikne, neprohloupí.
Lenoši – Malware sídlí na počítači, omezí se však na zprávu, že se počítač šifruje a ať laskavě zaplatíme. Nic se však v systému neděje, soubory se jenom přejmenovávají. Útočník nemusí nic moc řešit.
Lockery – zamezují přístup k počítači „Tady Policie ČR…,“ ale nic víc nepodnikají. Pokud je uživatel dostatečně zběhlý a zbaví se hlášky, najde soubory neporušené.
Cryptor – pronikne až na kůži a soubory zašifruje; klíč si odešle do světa a vám zbývá naděje, že někdo kladný dobude útočníkovy servery a klíče získá…
Wiper – nejhorší, co se může stát je, že útočník vůbec nepočítá s tím, že by vám soubory vrátil. O peníze žádá, data však ničí.
Kudy ke mně vede cesta?
Vede odevšad. Touž bakterii můžete chytit při jídle s neumytýma rukama nebo dobrou pozicí před pčíkancem ve vestibulu Jiřího z Poděbrad; je to lhostejné.
Přichází e-mailem v příloze, přichází nezáplatovaným portem napřímo přes síť, protože jste neaktualizovali, přichází nezáplatovaným portem napřímo přes síť, protože vydavatel vašeho systému/programu neupdatoval, přichází dokumentem od nicnetušícího kolegy. Ve Wordu není pro nic za nic velké žluté oznámení: „Soubor jste stáhli z internetu, nelze editovat“.
Budeme si střádat na výkupné?
„Pomáhá platit?“, ptají se lidé často. Možná ano i určitě ne – je to jako jednat s teroristy. Já vím, snadno se mi mluví, když mám externí disk hluboko ve skříni, jenže když zaplatíme, příště budou chtít víc.
Navíc se vy osobně můžete stát oblíbeným terčem na nějakém seznamu úspěšně prolomených obětí. Když Ježíš vyhnal zlého ducha, a člověk stejně nezáplatoval, vrátilo se duchů sedm.
More than 14 Million Verizon Customers’ records exposed by a third party firm
13.7.2017 securityaffairs Incindent
Data belonging to 14 million U.S.-based Verizon customers have been exposed on an unprotected AWS Server by a partner of the telecommunications company.
The notorious security expert Chris Vickery, UpGuard director of cyber risk research. as made another disconcerting discovery, more than 14 million US customers’ personal details have been exposed after the third-party vendor NICE left the sensitive records open on an unprotected AWS Server.
NICE Systems is an Israeli firm that offers several solutions for intelligence agencies, including telephone voice recording, data security, and surveillance systems.
Exposed data also revealed that NICE Systems has a partnership with Paris-based telecommunication company “Orange,” it seems that the third-party firm collects customer details across Europe and Africa.
“The data repository, an Amazon Web Services S3 bucket administered by a NICE Systems engineer based at their Ra’anana, Israel headquarters, appears to have been created to log customer call data for unknown purposes;” reads a blog post published by Vickery. “Verizon, the nation’s largest wireless carrier, uses NICE Systems technology in its back-office and call center operations. In addition, French-language text files stored in the server show internal data from Paris-based telecommunications corporation Orange S.A.—another NICE Systems partner that services customers across Europe and Africa.”

The exposed data are sensitive information of millions of customers, including names, phone numbers, and account PINs (personal identification numbers).
The huge trove of data is related to the customers’ calls to the Verizon’s customer services in the past 6 months.
“Beyond the risks of exposed names, addresses, and account information being made accessible via the S3 bucket’s URL, the exposure of Verizon account PIN codes used to verify customers, listed alongside their associated phone numbers, is particularly concerning.” continues the expert, “Possession of these account PIN codes could allow scammers to successfully pose as customers in calls to Verizon, enabling them to gain access to accounts—an especially threatening prospect, given the increasing reliance upon mobile communications for purposes of two-factor authentication.”
It is still unclear why Verizon allowed NICE to collect call details, experts speculate the third party vendor was tasked to monitor the efficiency of its call-center operators for Verizon.
The incident demonstrates the risks of third-party vendors handling sensitive data. UpGuard pointed out the long interval of time between the initial notification to Verizon by UpGuard (June 13th) to the closure of the breach (on June 22nd)
“Finally, this exposure is a potent example of the risks of third-party vendors handling sensitive data,” reads the blog post from UpGuard.
“NICE Systems’ history of supplying technology for use in intrusive, state-sponsored surveillance is an unsettling indicator of the severity of this breach of privacy.”
Chris Vickery discovered many other clamorous cases of open database exposed on the Internet. In December 2015 the security expert discovered 191 million records belonging to US voters online, in April 2016 he also discovered a 132 GB MongoDB database open online and containing 93.4 million Mexican voter records.
In March 2016, Chris Vickery has discovered online the database of the Kinoptic iOS app, which was abandoned by developers, with details of over 198,000 users.
In January 2017, the expert discovered online an open Rsync server hosting the personal details for at least 200,000 IndyCar racing fans.
In March, he announced a 1.37 billion records data leak, in June 2017 Vickery revealed the DRA firm left 1.1 TB of data unsecured on an Amazon S3, 198 million US voter records exposed.
MS Patch Tuesday fixes 19 critical issues, including two NTLM zero-day flaws
13.7.2017 securityaffairs Vulnerebility
As part of the Microsoft Patch Tuesday, the tech giant fixed two critical flaws in Windows NTLM Security Protocol. Users must apply the patch asap.
As part of the July Patch Tuesday, Microsoft has released security patches for a serious privilege escalation flaw affecting all Windows operating system versions for enterprises released since 2007.
Experts at Security firm Preempt, discovered two zero-day flaws that affect Windows NTLM security protocols. The vulnerabilities could be exploited by attackers to create a new domain administrator account and take over the target domain.
The NT LAN Manager (NTLM) is an ancient authentication protocol, despite it was replaced by Kerberos in Windows 2000, it is still supported by Microsoft and it is used by many organizations.

The first flaw involves unprotected Lightweight Directory Access Protocol (LDAP) from NTLM relay, and the second is related to the Remote Desktop Protocol (RDP) Restricted-Admin mode.
Even if LDAP signing protects from both Man-in-the-Middle (MitM) and credential forwarding, the protocol is not able to fully protect against NTLM relay attacks,
The vulnerability could be exploited by an attacker with SYSTEM privileges to use incoming NT LAN Manager sessions and perform the LDAP operations, including the updating of domain objects.
“This allows an attacker with SYSTEM privileges on a machine to use any incoming NTLM session and perform the LDAP operations on behalf of the NTLM user.” reads a blog post published by Preempt.
“To realize how severe this issue is, we need to realize all Windows protocols use the Windows Authentication API (SSPI) which allows downgrade of an authentication session to NTLM.As a result, every connection to an infected machine (SMB, WMI, SQL, HTTP) with a domain admin would result in the attacker creating a domain admin account and getting full control over the attacked network.”
The second NTLM vulnerability affects the RDP Restricted-Admin mode that allows users to access to a remote machine without providing their password.
According to Preempt researchers, the RDP Restricted-Admin allows authentication systems to downgrade to NTLM.
This means that it is possible to perform NTLM relay attacks and password cracking against the RDP Restricted-Admin.
“Preempt discovered that RDP Restricted-Admin, which is sometimes referred to (mistakenly) as Kerberosed RDP, allows downgrade to NT LAN Manager in the authentication negotiation. This means that every attack you can perform with NTLM such as credential relaying and password cracking could be carried out against RDP Restricted-Admin.” continues the analysis.
Chaining the two zero-days, an attacker could create a bogus domain admin account whenever an admin connects with RDP Restricted-Admin and get control of the entire domain.
The NTLM flaws have been reported to Microsoft in April, but the company only acknowledged a month later the NTLM LDAP vulnerability (tracked as CVE-2017-8563). Microsoft did not recognize RDP bug, the tech giant classified it as a “known issue” that could be solved with a proper configuration of the network.
Microsoft recommends companies running vulnerable servers with NT LAN Manager enabled to patch them as soon as possible.
Other mitigation actions are:
turning NT LAN Manager off.
requiring that incoming LDAP and SMB packets are digitally signed in order to prevent credential relay attacks.
Microsoft has released patches for 55 security vulnerabilities, including 19 critical issues, in its products, including Edge, Internet Explorer, Windows, Office and Office Services and Web Apps, .NET Framework, and Exchange Server.
Following NotPetya NATO Increases Support for Ukraine’s Cyber Defenses
13.7.2017 securityaffairs BigBrothers
Following the massive NotPetya attack, NATO Increases Support for Ukrainian Cyber Defenses, Ukraine Considers Joining NATO.
“Critical Infrastructure” is one of the most sensitive elements of any country’s economy. Recent attacks against Ukraine’s infrastructure have many other countries taking note and have encouraged NATO to pitch in and help bolster Ukrainian cyber defenses.
In December 2015, Ukrainian power grid operators watched helplessly as hackers remotely logged into three power distribution centers and turned off power to over 230,000 residents. The hackers had started their plans many months earlier by sending carefully crafted phishing emails to key IT staff working for the target companies. The malicious attachments to these emails allowed the bad guys to gain a foothold in the networks and over the subsequent months they carefully gathered information and improved their remote capabilities until it was time to strike. Attribution is difficult, but given the patience and approaches demonstrated by the bad guys it is obvious that they are sophisticated and many people are pointing their finger at Russian-linked hacking groups.

More recently, in June 2017, a ransomware attack was launched in Ukraine impacting transportation, banking and power infrastructure. Believed to be the Petya ransomware variant, the attack spread beyond the original targets and became a worldwide problem that has directly cost millions of dollars in lost production for many companies as well as untold costs in remediation and recovery efforts. As investigators began to dig deeper into the Petya attack it appears that it was only masquerading as ransomware. The primary function of ransomware is to generate revenue for the bad guys. However, this attack had a clunky mechanism for gathering the ransom so it appears its primary function was something else. Most experts now agree that this was another attack intended to disrupt Ukrainian infrastructure and have dubbed it the NotPetya attack. Again attribution is uncertain, but Russian-linked groups are suspected.
All other countries are keeping a close watch on these developments. It is reported that critical infrastructure protections in Ukraine are better than many other countries’ so it is conceivable that these same attacks will eventually be turned against new targets. In a demonstration of solidarity — and likely a lot of self-interest — NATO has agreed to provide Ukraine with support and equipment to “help Ukraine investigate who is behind the different attacks,” according to NATO secretary-general Jens Stoltenberg. In December 2014 NATO established the Cyber Defence Trust Fund with a mandate “to provide Ukraine with the necessary support to develop its strictly defensive, CSIRT-type technical capabilities, including laboratories to investigate cyber security incidents.” Since June 2016, €965,000 has been contributed by eight countries and while this helped to bolster Ukrainian cyber defenses, it is obvious that it isn’t enough.
Speaking on the topic of Ukraine formally joining the NATO union at a joint press conference with NATO on Monday, Ukrainian President Petro Poroshenko said,
“Today we clearly stated that we would begin a discussion about a membership action plan and our proposals for such a discussion were accepted with pleasure.”
Given the recent cyber attacks’ rumored source as Russian-linked hacking groups, the ongoing tensions between Russia and Ukraine as well Russia’s public stance against any NATO expansion this is unlikely to calm things down in the region. But with the sophistication of the cyber attacks and the apparent disregard for global impacts beyond Ukrainian borders, it is impractical for other countries to sit on the sidelines and let Ukraine attempt to protect themselves.
LockPoS Point of Sale Malware Emerges
12.7.2017 securityweek Virus
A newly discovered Point of Sale (PoS) malware is being delivered via a dropper that is manually loaded and executed on the targeted systems, Arbor Networks Security researchers warn.
The new threat was associated with command and control (C&C) servers used by Flokibot in a campaign targeting Brazil. Dubbed LockPoS, the malware appears to have been compiled in late June and to use a dropper that injects it directly into the explorer.exe process.
After being manually loaded and executed, the dropper continues by extracting a resource file from itself. The resource contains multiple components that are injected into explorer.exe and which act as a second-stage loader. Next, it starts decrypting, decompressing, and loading the final LockPoS payload.
While analyzing the malware, Arbor Networks researchers discovered it uses a regular “registry run” method for persistence. The malware obfuscates important strings using XOR and a key of “A”. It also stores an initial configuration unencrypted as a binary structure.
The malware’s communication with the C&C server is performed via HTTP, using a very telling User-Agent. Information sent to the server includes username, computer name, and bot ID, Bot version (1.0.0.6), CPU, Physical memory, Display devices, Windows version and architecture, and MD5 hash of currently running sample.
“The malware’s PoS credit card stealing functionality works similarly to other PoS malware: it scans the memory of other running programs looking for data that matches what credit card track data looks like. Here’s a snippet of the matching function,” the security researchers explain.
Until now, the new malware has been distributed via a Flokibot botnet, and, with both threats sharing a common C&C server, the researchers believe that same threat actor controls both of them. Because the Flokibot campaign associated with the server was targeting Brazil, the researchers believe LockPoS will target the same country as well.
Although the same C&C at treasurehunter[.]at was used in another PoS malware campaign in what FireEye referred to last year as TREASUREHUNT, Arbor Networks says that LockPoS is a different malware family from TREASUREHUNT.
“It is currently unclear whether LockPoS is an exclusive malware associated with one threat actor or whether it will be sold on underground forums like Flokibot was. Based on the internals of the malware described in this post, LockPoS seems to be coded well and stable, but doesn’t particularly raise the bar when it comes to ‘highly advanced malware’, the researchers note.
Microsoft Patches LDAP Relay Vulnerability in NTLM
12.7.2017 securityweek Vulnerebility
Microsoft resolved over 50 bugs with its July 2017 set of security patches, one being a vulnerability where the Lightweight Directory Access Protocol (LDAP) wasn’t protected from Microsoft NT LAN Manager (NTLM) relay.
Discovered by the Preempt research team, the LDAP relay attack could be exploited by a hacker to create new domain administrator accounts even when best-practice controls are enabled. A similar attack can be performed by exploiting a RDP relay flaw in NTLM, the security researchers said.
Consisting of a series of security protocols aimed at offering authentication, integrity, and confidentiality, NTLM relay is one of the main attack vectors for hackers and pen-testers, Preempt argues.
The basic manner in which NTLM works is that the user encrypts a server-issued challenge with their password hash to establish a connection. An attacker able to use the challenge in a parallel session with the server needs to forward “the same encrypted hash to create a successful NTLM authentication” and use this to open a session (such as SMB) and infect the target system with malware.
Countermeasures preventing NTLM credential relay include SMB signing – where a derived session key is used to digitally sign all incoming packets, thus preventing server exploitation even if the NTLM session was relayed; and Enhanced Protection for Authentication (EPA) – where the client signs an element of the TLS session with the derived session key, thus protecting the server from credential relaying.
“LDAP protocol is used in Active Directory to query and update all domain objects. There is a special configuration in the Group Policy Object (GPO) - Domain Controller: LDAP server signing requirements. When this GPO is set to Require Signing the domain controller rejects LDAP sessions that are not either digitally signed with a derived session key or the entire session is encrypted over TLS (LDAPS),” Preempt’s Yaron Zinar explains.
Tracked as CVE-2017-8563, the vulnerability resides in LDAPS not having protection for credential forwarding, although it does protect from Man-in-the-Middle (MitM) attacks, the same as LDAP signing.
“This allows an attacker with SYSTEM privileges on a machine to use any incoming NTLM session and perform the LDAP operations on behalf of the NTLM user,” Zinar notes.
Because all Windows protocols use the Windows Authentication API (SSPI), which allows for authentication sessions to be downgraded to NTLM, “every connection to an infected machine (SMB, WMI, SQL, HTTP) with a domain admin would result in the attacker creating a domain admin account and getting full control over the attacked network,” the researcher notes.
The second vulnerability Preempt discovered resides in RDP Restricted-Admin, a protocol that allows users to connect to remote machines revealing their password to the machine. RDP Restricted-Admin, the researchers say, allows downgrade to NTLM in the authentication negotiation, meaning that attacks that can be performed with NTLM can be carried out against RDP Restricted-Admin.
“As RDP Restricted-Mode is often used by support technicians with elevated privileges to access remote machines, this puts their credentials at risk of being compromised. Furthermore, when combined with the first LDAP relay issue, this means that each time an admin connected with RDP Restricted-Admin an attacker was able to create a rogue domain admin,” Zinar says.
Although RDP Restricted-Mode was previously found to allow attackers to connect to remote machines using pass-the-hash, Microsoft told Preempt that the vulnerability was a known issue, and “recommended configuring network to be safe from any sort of NTLM relay.”
U.S. Bans Kaspersky Software Amid Concerns Over Russia Ties
12.7.2017 securityweek BigBrothers
Washington - The US government has moved to block federal agencies from buying software from Russia-based Kaspersky Lab, amid concerns about the company's links to intelligence services in Moscow.
The General Services Administration, which handles federal government purchasing contracts, said in a statement to AFP that Kaspersky Lab, a major global provider of cybersecurity software, has been removed from its list of approved vendors, making it more difficult to obtain Kaspersky products.
"GSA's priorities are to ensure the integrity and security of US government systems and networks and evaluate products and services available on our contracts using supply chain risk management processes," the agency said in a statement.
The action came weeks after top US intelligence agency and law enforcement officials publicly expressed concerns about use of Kaspersky software.
The officials, appearing at a congressional hearing in May, stopped short of offering specifics but appeared to suggest concerns over the computer security firm's alleged links to Russian defense and intelligence bodies.
The company said in a statement to AFP Wednesday, "Kaspersky Lab has no ties to any government, and the company has never helped, nor will help, any government in the world with its cyberespionage efforts."
It added that "the company is being unjustly accused without any hard evidence to back up these false allegations."
A Bloomberg News report this week meanwhile claimed internal company emails show that Kaspersky has maintained a closer working relationship with Russia's main intelligence agency, the FSB, than it has publicly admitted.
Kaspersky on Tuesday issued a statement disputing the Bloomberg accounting, saying "the communication was misinterpreted or manipulated," but did acknowledge that it "regularly cooperates with law enforcement agencies, industry peers and victims of cybercrime."
The company has repeatedly denied working with any government agency, and Russia-born founder Eugene Kaspersky has on several occasions sought to counter any such allegations.
In a June 30 blog post, Kaspersky wrote, "For some reason the assumption continues to resonate that since we're Russian, we must also be tied to the Russian government. But really, as a global company, does anyone seriously think we could survive this long if we were a pawn of ANY government?"
Apple Builds Data Center in China, Promises No Backdoors
12.7.2017 securityweek Apple
Apple opens data center in China - Image Credits: flickr.com/photos/nez
Apple on Wednesday announced the establishment of its first China-based data center in an effort to improve its services in the region and comply with recently implemented regulations, but the tech giant has promised not to build any backdoors into its systems.
The new data center is located in China’s Guizhou province, which Apple selected following a “careful study” – the company said it was impressed with the local government’s leadership and its focus on environmental sustainability. Officials from the Guizhou province visited Silicon Valley last year to promote big data opportunities as part of a pilot program.
“In partnership with a local internet services company, Guizhou on the Cloud Big Data, we’re proud of the fact the facility will be fully powered by 100 percent renewable energy like all of our other data centers around the world,” Apple said in a statement sent to SecurityWeek.
"Our Chinese customers love using iCloud to store their photos, videos, documents and apps securely, and to keep them updated across all of their devices. We're committed to continuously improving the user experience, and the addition of this data center will allow us to improve the speed and reliability of our products and services while also complying with newly passed regulations,” Apple added.
The said cybersecurity regulations, adopted last year and implemented on June 1, impose new rules for online services providers. Trade groups opposed the initiative – whose initial version even required companies to submit source code for verification – arguing that it offered an unfair advantage to Chinese businesses.
The new law is largely focused on protecting China’s networks and private user information, and it requires cloud services to be operated by local companies. As a result, Apple has teamed up with government-owned Guizhou-Cloud Big Data to offer its iCloud service.
While some may be concerned about the location of the data center given the Chinese government’s track record, Apple has promised to maintain its strong data privacy and security protections and not create any backdoors into its systems.
Apple’s announcement comes just weeks after Chinese authorities reported uncovering a massive underground operation run by Apple employees who had abused the company’s internal systems to collect and sell customers’ personal details.
Edgewise Networks Emerges From Stealth to Bring Zero Trust Networking to the Data Center
12.7.2017 securityweek Security
Burlington, MA-based Edgewise Networks has emerged from stealth mode with a product designed to implement a zero-trust approach to network security.
Founded by Peter Smith and Harry Sverdlove in Spring 2016; backed by venture capital firms .406 Ventures, Accomplice, and Pillar; and supported by Patrick Morley (CEO of Carbon Black), Omar Hussain (CEO of Imprivata), Brian Ahern (CEO of Threat Stack), and Bob Brennan (CEO of Veracode), Edgewise seeks to augment perimeter firewalls and improve on microsegmentation.
Edgewise believes that there is a fundamental flaw in defense-by-firewall. While firewalls can detect and block known bad addresses, they cannot detect bad use of good addresses. This means that any compromise of a 'good' address can allow an attacker straight through the firewall, by policy, and into an attack position.
"There are two commonalities in almost all publicized attacks," comments co-founder Peter Smith. "Firstly, attackers rarely, if ever, enter a network directly on their ultimate target: they gain a foothold, surveil the attack surface and then move laterally to where they can conduct the final attack. Secondly, they invariably accomplish this by introducing malicious code at some stage -- for C&C, for the next stage of the attack, and so on."
Preventing the lateral movement is where firewalls fail. They can see where traffic is coming from, and they can see where it is going; but they cannot see who is in control of the software being used, or the server from which it comes. Consider NotPetya, he said. "The worm spread more or less unabated because the firewalls could not detect any maliciousness in the traffic."
Microsegmentation is an improvement on perimeter firewalls alone; but is still not adequate. "Essentially, it forces all traffic through the firewall. Beside the complexity of installation and management, the firewalls still cannot prevent the attacks because they can still only protect what they can see; and despite the fact that they can see all of the network traffic, they can only look at the traffic to identify malicious behavior -- they cannot look outside of the traffic, cannot look at the hosts to see what software is actually making those communications."
Edgewise sees its product as being more effective than complex microsegmentation, and even easier to use than relatively simple next-gen firewalls.
Firewalls, he continued, can only attribute traffic to the address that sent it and the address that receives it. "They cannot see the actual software that created the connection; or the user controlling the application; or the host on which it is running. There is consequently no guarantee that the application you trust is controlled by the user you think should be controlling it. Most new technology just looks more closely at network packets -- but however much you stare at the packet, it will not tell you the identity of the software producing the communication or the user controlling it on either side of the connection."
Two primary aspects of Edgewise illustrate how it operates. Firstly, it ensures that only trusted applications communicate by mutually validating the identity of the underlying software, users and hosts before allowing the connection. "This approach," says the company, "extends the zero-trust networking model that calls for validating application communications and not trusting addresses to secure internal networks."
Secondly, it uses machine-learning to model application communication patterns and generate optimal protection policies automatically. This serves several purposes. It can be used to generate maximum protection from minimum policies, and to produce a policy map that can be used as a 'what-if' model even by non-experts. New policies can be tested on the map to see exactly what effect they will have on the overall network attack surface.
The result, said Smith, "is that we get rid of all of the unnecessary network attack surface that firewalls cannot see. We stop anything that is not trusted and we build the policies for the customer automatically. We have a machine-learning system that analyzes the communication patterns of the software we protect, and then creates the policies to protect the systems. No user intervention is necessary to build the policies -- only to apply them." Which, he added, can be a single click.
"The user sees a map of how the software communicates," he continued. "He can select the software he particularly wishes to protect, and one click will protect it. Only trustworthy software will be allowed to communicate. We also measure the risk associated with the environment -- the attack surface. We measure how much it is, and how much it would shrink if the customer applies our protection."
Edgewise calls this 'Trusted Application Networking'. "It's what Forrester calls zero-trust networking, and what Gartner calls CARTA," said Smith. "Essentially they boil down to the same thing: assert the identity of communicating software and the entities communicating; do not just blindly trust addresses."
Organizations Only Slightly Improved Security Posture: Report
12.7.2017 securityweek Analysis
Organizations made some improvements to their security posture last year, but only marginally, as the average time-to-fix is still too high and remediation rates are too low, according to the 12th annual application security statistics report from WhiteHat Security.
WhiteHat Security’s report is based on dynamic and static testing data collected in 2016 from 15,000 web apps and over 65,000 mobile applications.
The figures show a 25 percent improvement in the average number of vulnerabilities found in web applications – the number dropped from four flaws in 2015 to three flaws in 2016. However, the security firm pointed out that a majority of applications have three or more security holes and nearly half of them are critical.
Looking at the vulnerability profile of each industry, we see that the services sector has the highest number of vulnerabilities, followed by transportation, retail and education.
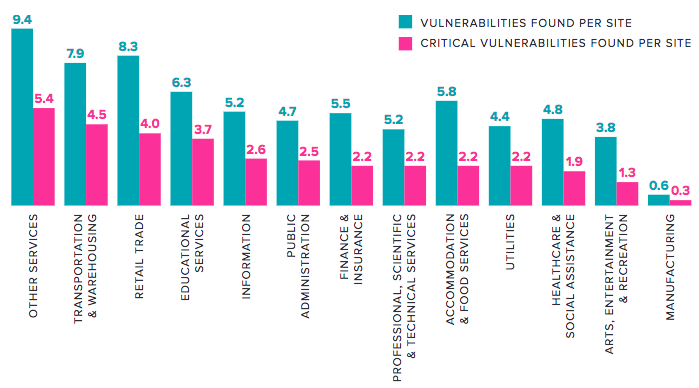
According to WhiteHat, nearly half of the applications it has tested are vulnerable every single day of the year. In industries such as utilities, retail, accommodations and education, roughly 60 percent of web applications are always vulnerable.
Dynamic security testing conducted by the company showed that the most prevalent vulnerabilities are information leakage, cross-site scripting (XSS), content spoofing, and insufficient transport layer protection. The types of vulnerabilities that are most often found to be critical are SQL injection, XSS, cross-site request forgery (CSRF) and insufficient authorization.
While, as expected, development teams focus on fixing critical and high severity flaws first, low-risk weaknesses are addressed before medium-risk ones.
“Development teams are prioritizing critical software problems first, but then move on to easier fixes,” WhiteHat said in its report. “This is human nature. After patching tricky vulnerabilities, why not knock out a few simple ones?”
The study found that while XSS vulnerabilities are critical 40 percent of the time, developers ignored nearly half of these security holes in 2016. Even SQL injection, which is considered critical in 94 percent of cases, only has a remediation rate of 60 percent.
There have been some improvements in the time it takes software developers to fix a vulnerability – the average number of days dropped from 146 days in 2015 to 129 days in 2016. However, it still took developers, on average, nearly 200 days to patch high severity problems, up from 171 in 2015.
Static testing conducted by WhiteHat showed that insufficient transport layer protection, SQL injection, and unpatched libraries are critical in many cases. However, only less than half of critical bugs are fixed in the development process and make it into production.
In the case of vulnerabilities discovered via static testing, developers seem to focus on issues that are easy to fix and often neglect more severe problems.
The full Application Security Statistics Report, which also includes data on mobile application vulnerabilities, is available in PDF format.
Let's Encrypt Wildcard Certificates a 'Boon' for Cybercriminals, Expert Says
12.7.2017 securityweek Safety
To speed up the adoption of HTTPS, free and open Certificate Authority (CA) Let’s Encrypt will start issuing wildcard certificates as of January 2018.
Created by Mozilla, the University of Michigan, and the Electronic Frontier Foundation (EFF), with Cisco and Akamai as founding sponsors, Let’s Encrypt is pushing for a fully encrypted World Wide Web. The move should help better protect user data from eavesdroppers, but some concerns have been raised about the new offering.
Let’s Encrypt came out of private beta in December 2015 and issued its millionth certificate in March 2016. Last week, the organization announced it had already issued over 100 million security certificates, thus becoming one of the largest CAs by number of issued certificates.
Now, the organization is moving to accelerate HTTPS deployment by starting to issue wildcard certificates, “a commonly requested feature.”
“A wildcard certificate can secure any number of subdomains of a base domain (e.g. *.example.com). This allows administrators to use a single certificate and key pair for a domain and all of its subdomains, which can make HTTPS deployment significantly easier,” Josh Aas, ISRG Executive Director, notes.
Let’s Encrypt’s over 100 million digital certificates are used to secure around 47 million domains, which also benefit from the CA’s fully automated DV certificate issuance and management API. According to Aas, Let’s Encrypt’s service already helped the percentage of encrypted page loads to rise from 40% to 58%.
The organization will be offering wildcard certificates free of charge via an upcoming ACME v2 API endpoint. Only base domain validation via DNS will be supported in the beginning, but the CA may explore additional validation options over time.
“We decided to announce this exciting development during our summer fundraising campaign because we are a nonprofit that exists thanks to the generous support of the community that uses our services. If you’d like to support a more secure and privacy-respecting Web, donate today,” Aas concludes.
Let’s Encrypt’s goal might be improved security and privacy for all users, but it doesn’t mean that its certificates can’t be misused. In March 2017, encryption expert Vincent Lynch revealed that, over a 12-month period, Let’s Encrypt issued over around 15,000 security certificates containing the term PayPal for phishing sites.
According to Kevin Bocek, chief security strategist for Venafi, Let’s Encrypt’s introduction of free wildcard certificates is great for privacy, but a boon for cybercriminals.
“Cybercriminals can create thousands of fake websites using Let’s Encrypt’s wildcard certificates, all with a seemingly trustworthy glowing green padlock in the web browser address field,” Bocek told SecurityWeek. “We have seen bad actors abuse Let’s Encrypt certificates before: more than 14,000 certificates were issued for PayPal phishing websites by Let’s Encrypt, a powerful example of how bad guys exploit Certificate Authority business processes.”
“There’s no putting the Let’s Encrypt genie back in the bottle, but this means every organization could be a victimized by malicious websites designed to spoof their customers and partners,” Bocek added. “This means every organization must monitor the internet for malicious certificates. Google’s Certificate Transparency initiative and other similar technologies allow organizations to spot fake or malicious certificates regardless of the CA.”
PSD2 and Open Banking Bring Problems and Opportunities for Global Banks
12.7.2017 securityweek Security
Global Banks Should Not Ignore Europe's Payment Services Directive 2 (PSD2)
Payment Services Directive 2 (PSD2) is a new EU banking/finance regulation coming into force in January 2018. It is designed to shake up the finance sector -- perhaps even designed to weaken the overall strength of the banks following the 2008 crash. While being European in origin, American and other global banks should not -- and perhaps cannot -- ignore it.
The banks are considered to be too powerful and monolithic with sole and complete ownership of their customers financial data. The European bureaucrats want to introduce some competition. Their chosen route is to force the banks to provide APIs that will allow third-party apps to access customer data and provide new services not currently offered by the banks. The bureaucrats then believe third-parties will re-invigorate the payments and finance markets for end users.
There are enormous difficulties for the banks -- for while they are required to give third-party access to customer data, they will remain liable for the security of that data under the General Data Protection Regulation (GDPR).
Consider if this is done via a social media organization. That organization will build an app that provides access to, and uses, its customers' financial data. The banks can authenticate the social media organization; but the social media app authenticates the user. It is possible, then, that access to customer financial data will be controlled only by social media logon; and that will almost certainly be less secure than the multi-factor and behavioral security measures that many banks currently use.
But where there are problems, there are also opportunities. The banks that provide effective and efficient APIs could attract new customers from banks that provide poor APIs, all coming from the quality of the third-party apps that use those APIs. As Steve Kirsch, CEO at Token, told SecurityWeek, "In general, when you see a new unstoppable trend, the biggest winners are generally the earliest adopters."
There are two reasons for American banks (and other global banks) to conform to this new European regulation. Firstly, American banks with a European operation will be required to do so. Secondly, European banks with an American operation will bring their APIs with them. Since the customer will be the biggest winner in this new world of open banking, American banks not offering a similar service will be at a disadvantage. "American banks should be rushing to implement open banking on their own," says Kirsch. "It is a major step forward for banking."
The GSM Association (GSMA: the trade body that represents mobile operators with more than 1000 full and associate members) agrees that US banks should get involved. "It should not take a law for American banks to take up PSD2 principles," Marta Ienco, head of government and regulatory affairs at GSMA Personal Data, told SecurityWeek. "Instilling consumer confidence that money is safe, with fewer clunky security measures, will mean more customers want to use their service and trust the company."
GSMA believes that mobile banking is inherently secure. "Operators can leverage user data such as location, account and usage history, which in turn can be used to help verify transactions. Moreover," added Ienco, "this rich data can also help minimize instances of account takeover fraud. So, if someone tries to change the mobile number associated with a bank account, the operator can determine if the original mobile number is still in use, and use it to alert the customer to any suspicious changes to their personal details."
Like many regulations, PSD2 describes what must be done, but not how it can be achieved. This leads to difficulties for both the third-party app developers, and for the banks themselves.
For the developers, it does mandate 2FA; but that is about all. While there are some de facto API standards, such as REST and OAUTH, there are is no standard for the PSD2 banking APIs. "The APIs for different banks could all be completely different in how they work, how their authentication is achieved, and so on," explains Andrew Whaley, VP of engineering at Arxan Technologies. "The practical problems for an organization trying to consume these APIs (such as a social media organization, or whatever) means that the third-party potentially has to build a different adapter for every different bank."
For the banks, one difficulty will be in maintaining their own strict authentication requirements. "PSD2 is clear that the banks are still responsible for the customer data ownership, and the safety of the data," explains Whaley. "So, if the third party gets hold of the data, and its access controls are not particularly strong and someone else gets hold of the data, accidentally or deliberately, the bank is still liable for the third party's failure. The only way the banks can counter this is to bring the technology and countermeasures they already have in their own apps to bear in this space and force their own authentication standards through the API so that they have direct communication with the customer before the third-party can get access to the data."
GSMA agrees that the banks are caught between PSD2 and GDPR. "If banks aren't completely certain of the provenance of a request, and decline a request from a service provider, they could be in violation of PSD2. But if a data breach then takes place, they could also become liable under the rules of GDPR, also coming into effect next year."
PSD2 is a done deal and will come into effect in January 2018. European banks cannot avoid it, and American banks with a European presence (that is, European customers) will need to comply for those European customers. However, the global nature of big bank operations means that PSD2 APIs will inevitably come into play in the US. When that happens, US banks unable to take part in the new world of open banking will be at a distinct disadvantage to those that can.
HPE Addresses Vulnerabilities in Several Products
12.7.2017 securityweek Vulnerebility
Hewlett Packard Enterprise (HPE) has informed customers of security bypass, information disclosure, remote code execution, cross-site scripting (XSS) and URL redirection vulnerabilities in several of its products. Advisories for each of the affected products were published this week on the Full Disclosure mailing list.
According to the company, the Samba component of HPE NonStop Server is affected by access restriction bypass (CVE-2017-2619) and remote code execution flaws (CVE-2017-7494). The latter is also known as EternalRed and SambaCry, and it has already been exploited in the wild to deliver malware. The vulnerability affects the products of several major software vendors.
HPE has not released patches for the Samba bugs, but it has provided some workarounds that can be used to prevent potential attacks. The security holes affect Samba on NonStop T1201L01 through T1201L01^AAL, and T1201H01 through T1201H01^AAM. Fixes will be included in the upcoming T1201L01^AAO and T1201H01^AAN versions.
The company also informed customers that it has rolled out patches for security bypass, XSS and URL redirection vulnerabilities affecting the HPE Network Node Manager i (NNMi) software.
The flaws, collectively tracked as CVE-2017-8948 with a severity rating of “critical,” can be exploited remotely. The security holes affect versions 10.0x, 10.1x and 10.2x, and patches have been made available for each of them.
The HPE SiteScope application monitoring software is affected by four vulnerabilities, including remote code execution and security restrictions bypass flaws rated “high severity.” The other two weaknesses affecting SiteScope are encryption-related issues that can lead to the disclosure of sensitive information.
The security holes affect versions 11.2x and 11.3x, and they have been addressed with the release of security updates and mitigations.
The SiteScope vulnerabilities were disclosed last month by CERT/CC and researcher Richard Kelley after the discovery of hundreds of potentially vulnerable installations on the Internet. At the time, HPE promised to release patches for the more serious flaws in the third quarter and pointed out that the encryption bugs are covered in the product’s deployment guide.
An updated advisory – initially released in mid-May – has also been published by HPE on the Full Disclosure mailing list this week. The advisory informs users of five critical and high severity remote code execution vulnerabilities affecting the HPE Intelligent Management Center (iMC) network management platform.
Critical Flaws Found in Windows NTLM Security Protocol – Patch Now
12.7.2017 thehackernews Vulnerebility
As part of this month's Patch Tuesday, Microsoft has released security patches for a serious privilege escalation vulnerability which affect all versions of its Windows operating system for enterprises released since 2007.
Researchers at behavioral firewall specialist Preempt discovered two zero-day vulnerabilities in Windows NTLM security protocols, both of which allow attackers to create a new domain administrator account and get control of the entire domain.
NT LAN Manager (NTLM) is an old authentication protocol used on networks that include systems running the Windows operating system and stand-alone systems.
Although NTLM was replaced by Kerberos in Windows 2000 that adds greater security to systems on a network, NTLM is still supported by Microsoft and continues to be used widely.
The first vulnerability involves unprotected Lightweight Directory Access Protocol (LDAP) from NTLM relay, and the second impact Remote Desktop Protocol (RDP) Restricted-Admin mode.
LDAP fails to adequately protect against NTLM relay attacks, even when it has built-in LDAP signing the defensive measure, which only protects from man-in-the-middle (MitM) attacks and not from credential forwarding at all.
The vulnerability could allow an attacker with SYSTEM privileges on a target system to use incoming NTLM sessions and perform the LDAP operations, like updating domain objects, on behalf of the NTLM user.
"To realize how severe this issue is, we need to realize all Windows protocols use the Windows Authentication API (SSPI) which allows downgrade of an authentication session to NTLM," Yaron Zinar from Preempt said in a blog post, detailing the vulnerability.
"As a result, every connection to an infected machine (SMB, WMI, SQL, HTTP) with a domain admin would result in the attacker creating a domain admin account and getting full control over the attacked network."
Video Demonstration of Relay Attack
Preempt researchers also provided a video to demonstrate credential relay attacks.
The second NTLM vulnerability affects Remote Desktop Protocol Restricted-Admin mode – this RDP Restricted-Admin mode allows users to connect to a remote computer without giving their password.
According to Preempt researchers, RDP Restricted-Admin allows authentication systems to downgrade to NTLM. This means the attacks performed with NTLM, such as credential relaying and password cracking, could also be carried out against RDP Restricted-Admin.
When combined with the LDAP relay vulnerability, an attacker could create a fake domain admin account whenever an admin connects with RDP Restricted-Admin and get control of the entire domain.
The researchers discovered and privately reported LDAP and RDP Relay vulnerabilities in NTLM to Microsoft in April.
However, Microsoft acknowledged the NTLM LDAP vulnerability in May, assigning it CVE-2017-8563, but dismissed the RDP bug, claiming it is a "known issue" and recommending configuring a network to be safe from any NTLM relay.
"In a remote attack scenario, an attacker could exploit this vulnerability by running a specially crafted application to send malicious traffic to a domain controller. An attacker who successfully exploited this vulnerability could run processes in an elevated context," Microsoft explained in its advisory.
"The update addresses this vulnerability by incorporating enhancements to authentication protocols designed to mitigate authentication attacks. It revolves around the concept of channel binding information."
So, sysadmins are recommended to patch their vulnerable servers with NT LAN Manager enabled as soon as possible.
You can either consider turning NT LAN Manager off or require that incoming LDAP and SMB packets are digitally signed in order to prevent credential relay attacks.
Besides this NTLM relay flaw, Microsoft has released patches for 55 security vulnerabilities, which includes 19 critical, in several of its products, including Edge, Internet Explorer, Windows, Office and Office Services and Web Apps, .NET Framework, and Exchange Server.
Windows users are strongly advised to install the latest updates as soon as possible in order to protect themselves against the active attacks in the wild.
Microsoft Patches Over 50 Vulnerabilities
12.7.2017 securityweek Vulnerebility
Microsoft has patched more than 50 vulnerabilities in its products, including Windows, Internet Explorer, Edge, Office, SharePoint, .NET, Exchange and HoloLens. While some of them have already been disclosed, the tech giant is not aware of any malicious attacks exploiting these flaws.
One of the weaknesses whose details have already been publicly disclosed is CVE-2017-8584, a critical remote code execution vulnerability affecting HoloLens, Microsoft’s mixed reality headset.
The security hole, caused due to how HoloLens handles objects in memory, can be exploited by sending specially crafted Wi-Fi packets to a device. Successful exploitation can allow the attacker to take control of the targeted system.
This is just one of the 19 vulnerabilities rated critical. The list also includes remote code execution vulnerabilities in Windows Search, Windows Explorer, Internet Explorer and the scripting engines used by Microsoft’s web browsers.
The Windows Search flaw (CVE-2017-8589) can be exploited by sending a specially crafted message to this service, which can allow a hacker to elevate privileges and take control of the device. Microsoft pointed out that in an enterprise environment, a remote attacker can exploit the flaw without authentication using an SMB connection.
Other flaws that have already been disclosed are CVE-2017-8587, a Windows denial-of-service (DoS) issue, and CVE-2017-8611 and CVE-2017-8602, both of which are spoofing vulnerabilities affecting web browsers.
Renato Marinho, director of research at Morphus Labs, believes there are also some “important” vulnerabilities worth mentioning. This includes privilege escalation bugs related to the Windows Common Log File System (CLFS) driver and the NT LAN Manager (NTLM) Authentication Protocol, a PowerShell remote code execution flaw, a Kerberos SNAME security feature bypass, and a remote code execution weakness affecting WordPad.
Trend Micro’s Zero Day Initiative (ZDI) pointed out that with the July 2017 Patch Tuesday fixes, Microsoft has addressed all the vulnerabilities disclosed at this year’s Pwn2Own hacking competition.
Microsoft has also updated the Flash Player libraries used by its products – Adobe patched three vulnerabilities on Tuesday with the release of version 26.0.0.137.
Katyusha Scanner — Telegram-based Fully Automated SQL Injection Tool
12.7.2017 thehackernews Safety
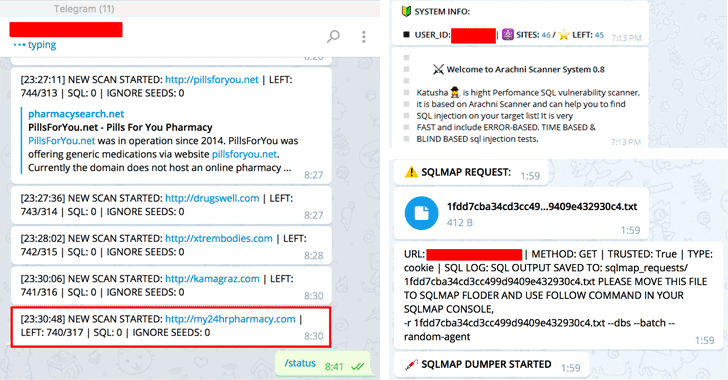
A new powerful hacking tool recently introduced in an underground forum is making rounds these days, allowing anyone to rapidly conduct website scans for SQL injection flaws on a massive scale — all controlled from a smartphone using the Telegram messaging application.
Dubbed Katyusha Scanner, the fully automated powerful SQLi vulnerability scanner was first surfaced in April this year when a Russian-speaking individual published it on a popular hacking forum.
Researchers at Recorded Future's Insikt Group threat intelligence division found this tool for sale on an underground hacking forum for just $500. Users can even rent the Katyusha Scanner tool for $200.
According to the researchers, Katyusha Scanner is a web-based tool that's a combination of Arachni Scanner and a basic SQL Injection exploitation tool that allows users to automatically identify SQLi vulnerable sites and then exploits it to take over its databases.
Arachni is an open source vulnerability scanning tool aimed towards helping users evaluate the security of their web applications.
What makes this tool stand out of line is its 'Infrastructure-as-a-Service' model.
Remotely Control Hacking Tool Via Telegram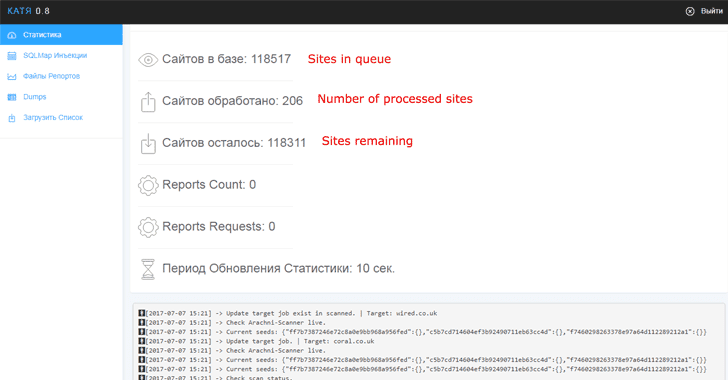
Katyusha Scanner is abusing the Telegram messaging application to control its operations, such as sending and receiving commands.
The Katyusha Scanner tool is quite easy to setup and use, allowing anyone to conduct large-scale penetration attacks against a large number of targeted websites simultaneously with the mere use of their smartphones.
The Pro version of the tool not just identifies vulnerable websites, but also allows hackers to establish a "strong foothold within vulnerable web servers" and automatically extract "privileged information such as login credentials."
Once the scan is complete, Katyusha Scanner sends a text message to the criminals with the vulnerable site name, its Alexa web ratings, helping criminals identify popular websites that would likely be more profitable for them to attack, and the number of databases.
The criminals, even with no technical knowledge, can download any exfiltrated data available by just clicking on their smartphones to issue commands.
Katyusha Scanner also allows for the automatic dumping of databases and can be used on both Linux as well as Windows machines.
"The availability of a highly robust and inexpensive tool...Katyusha Scanner to online criminals with limited technical skills will only intensify the compromised data problem experienced by various businesses, highlighting the importance of regular infrastructure security audits," researchers at Recorded Future wrote.
Many buyers praised the quality of the tool on the black market site, one of the satisfied customers who got immediate success in obtaining access to eight web servers wrote:
"Excellent support! The seller has configured the software for my server, which was failing before, however, right now it flies divinely! I highly recommend the software, and it has found eight SQL vulnerabilities in half a day, great automation of the routine. Very grateful to the seller."
Another wrote: "The author has helped with the product setup after the purchase, and (Katyusha) has immediately found SQL vulnerability. Thank you for the great product."
Initially, Katyusha Scanner was sold for $500, but due to unexpectedly high demand, a light version of the tool with slightly limited functionality was released on May 10, 2017, at just $250.
With the release of the most recent Katyusha 0.8 Pro update at the end of June, the author also made the scanner available for rent at $200 per month for the first time.
Máme důležitou zprávu, tvrdí podvodníci. Pak důvěřivce oberou
12.7.2017 Novinky/Bezpečnost Phishing
Za bankéře se vydávají počítačoví piráti v nevyžádaných e-mailech, které kolují v posledních dnech českým internetem. Snaží se přitom vylákat z důvěřivců přihlašovací údaje k internetovému bankovnictví. Před novým podvodem varovala Česká spořitelna.
Ukázka podvodného e-mailu
FOTO: České spořitelny
„Chcete-li zobrazit svou zabezpečenou zprávu, přihlaste se do služby Internetové bankovnictví a použijte kanál zabezpečené zprávy,“ tvrdí podvodníci v nevyžádaném e-mailu, který primárně cílí na klienty České spořitelny.
Podvodníci se samozřejmě snaží donutit uživatele kliknout na odkaz ve zprávě, který vede na falešné stránky imitující službu Servis24, tedy internetové bankovnictví spořitelny. Pokud na podvodný web zadají důvěřivci svoje přihlašovací údaje, zpřístupní tak svůj účet kyberzločincům.
Aktualizace kontaktních informací
Ti navíc ihned po prvním přihlášení uživatelům tvrdí, že je potřeba aktualizovat kontaktní informace – právě to měla být ona důležitá zpráva. Pokud to důvěřivci skutečně udělají, jsou již jen krůček od vybílení bankovního účtu. Se znalostí telefonního čísla je totiž pro podvodníky hračkou vylákat od lidí potvrzovací SMS zprávu, pomocí které mohou například provádět peněžní transakce.
V ohrožení jsou přitom i jedinci, kteří nemají na bankovním účtu příliš mnoho financí. Útočníci mohou touto cestou sjednat bez vědomí majitele klidně i půjčku. A tyto peníze následně vyberou.

Podvodné bankovnictví imitující službu Servis24.
FOTO: Česká spořitelna
I proto se banka již od podvodných zpráv distancovala. „Buďte k podezřelým e-mailům velmi obezřetní, vždy se do SERVIS 24 přihlašujte ze stránek banky, případně přímo ze stránek www.servis24.cz. Zároveň buďte velmi obezřetní před zadáním jakéhokoliv SMS kódu a vždy pečlivě čtěte autorizační SMS zprávy,“ varovali zástupci banky.
„Pokud máte podezření, že jste podvodný e-mail obdrželi, v žádném případě nereagujte na jeho obsah, neklikejte na odkaz, který je jeho součástí, a zprávu nám přepošlete na e-mailovou adresu phishing@csas.cz. Jestliže jste již na odkaz klikli a vyplnili požadované údaje, ihned kontaktujte klientskou linku České spořitelny na bezplatném telefonním čísle 800 207 207,“ stojí v doporučení spořitelny.
E-mail může přijít z jiné banky
Sluší se podotknout, že stejnou taktiku mohou počítačoví piráti v nadcházejících dnech či týdnech zkusit také pod hlavičkou úplně jiné banky. Obezřetnost je tak na místě. Prakticky žádný finanční institut v tuzemsku totiž nerozesílá e-maily, prostřednictvím kterých by bylo možné se rovnou přihlásit ke svému účtu.
Vhodné je také ověřovat webovou adresu v internetovém prohlížeči, zpravidla podle ní je totiž možné poznat, že se uživatel ve skutečnosti nachází na podvodných stránkách – a ne ve skutečném internetovém bankovnictví.
Katyusha Scanner, a new SQLi Vulnerability Scanner Available for $500 in the underground
12.7.2017 securityaffairs IT
Katyusha Scanner is a new fully automated SQLi vulnerability scanner discovered by researchers at security firm Recorded.
Recorded Future security researchers have discovered a fully automated SQLi vulnerability scanner, dubbed Katyusha Scanner, on a hacking forum. The tool is offered for sale for just $500, it allows mass scans, simply managed from a smartphone through the Telegram messenger. The company, of course, reported the discovered to law enforcement.
The Katyusha Scanner appeared in the hacking underground in early April. It was developed starting from the Anarchi Scanner open source penetration testing tool and according to the researchers, it has already been updated seven times since its introduction
Actually, the Katyusha Scanner is offered under a Pro and a Lite version that go for between $250 and $500.
The Pro version leverages known exploits to hack into the system, once a SQL injection bug is found the tool notify it to the attacker via a text message that includes the site name, Alexa rating, and the number of available databases.
“On April 8, 2017, a Russian-speaking member of a top-tier hacking forum introduced “Katyusha Scanner,” the powerful and fully automated SQLi vulnerability scanner that utilizes the functionality of Telegram messenger and Anarchi Scanner, an open-source penetration testing tool.” states the blog post published by RecorderFuture.
The released product, coupled with outstanding support and frequent updates, immediately gained popularity and accolades of grateful clients for an intuitive and straightforward interface, as well as incredible performance.”


Researchers at Recorded Future reported that the seller is Russian speaking and is known in the hacking underground for selling data stolen from e-commerce websites. According to the experts, the forum where the tool is commercialized is frequented by top-tier Russian hackers.
An innovative feature implemented in the Katyusha Scanner allows crooks to upload a list of target websites and launch the concurrent attack against them simultaneously, seamlessly controlling the attack via Telegram.
The scanner is easy to use, the attackers only need set up a standard web server with the version of the Anarchi scanner that has been modified to allow the control of the operation through a linked Telegram account.
The attackers can control the attack using almost every mobile OS.
“Interestingly, the name Katyusha was not chosen by chance — it represents an iconic multiple rocket launcher, developed by the Soviet Union during World War II known for inflicting panic in Nazi forces with its stealthy and devastating attacks. Similar to the very lethal weapon conceived 70 years ago, Katyusha Scanner allows criminals to initiate large-scale penetration attacks against a massive number of targeted websites with several clicks using their smartphones.” continues the analysis.
The seller suggests starting with at least 500 target sites, attackers can issue commands to scan them for any known vulnerabilities. The Pro version also implements the capability of downloading any exfiltrated data available.
According to Recorded Future, at least 12/15 user have already purchased the tool, they were satisfied for the efficiency of the tool.
The potential scale of the attacks that the tool is able to power is worrisome.
“When dozens buy it and initiate attacks every day, the potential fallout will be significant,” Recorded Future director of advanced collection Andrei Barysevich said. “The scale of attacks which is available to criminals is quite unprecedented now. And the convenience of this; someone who wants to engage in this type of activity doesn’t have to be a hacker, he doesn’t have to know how certain tools operate or what exploit packs they should be using. The tool will do everything for them.”
SAP Addresses High Severity Vulnerabilities With July 2017 Patches
12.7.2017 securityweek Vulnerebility
SAP today announced that a total of 12 Security Notes were included in its July 2017 Security Patch Day, including four notes that address high severity vulnerabilities.
Of the 12 Security Notes, 2 were updates to previously released Patch Day Security Notes, the German software maker reveals. Cross-Site Scripting and Information Disclosure bugs were the most common types of isses addressed.
Additionally, SAP released 11 Support Package Notes, for a total of 23 Security Notes. Overall, 11 of the Notes were released after June 13, but before July 11. Of the 23 Notes, 5 were updates to previously released Security Notes, ERPScan reveals.
The most severe of the addressed vulnerabilities involved Missing authorization checks in SAP Point of Sale (POS) Retail Xpress Server. With a CVSS score of 8.1, the bug could be exploited to read, write, or delete files stored on SAP POS server; shutdown the Xpress Server application; and monitor all content displayed on a receipt window of a POS.
“An attacker can use a Missing authorization check vulnerability to access a service without any authorization procedure and use service functionality that has restricted access. This can lead to an information disclosure, privilege escalation, and other attacks,” ERPScan explains.
Another High severity bug was a Missing authorization check vulnerability in SAP Host Agent. With a CVSS score of 7.5, the issue “could allow an attacker to remotely restart SAP Host Agent without authentication, through a specific crafted SOAP request,” security firm Onapsis reveals.
The company explains that all SAP Host Agent versions up to 7.21 PL24 are affected, including all Netweaver-based applications and HANA 1 and HANA 2. The issue was resolved in SAP Host Agent version 7.21 PL25. SAP HANA users should upgrade to Revision 122.10 (for SAP HANA1.00 SPS12), Revision 2.02 (for SAP HANA2.0 SPS00), or Revision 12 (for SAP HANA2.0 SPS01).
The remaining High priority security notes include: Improved security for outgoing HTTPS connections in SAP NetWeaver, with a CVSS score of 7.4; and Missing authorization-check in BC-SRV-ALV, with a CVSS score of 6.0. Both are updates to previously released security notes.
Other dangerous vulnerabilities addressed this month in SAP products include a Code injection vulnerability (CVSS Base Score: 6.5) in SAP Governance, Risk and Compliance Access Controls (GRC); Cross-site scripting and Cross-site request forgery (CVSS Base Score: 6.1) in SAP CRM Internet Sales Administration Console; an XML external entity vulnerability (CVSS Base Score: 6.1) in SAP BI Promotion Management Application; and an XML external entity vulnerability (CVSS Base Score: 5.4) in SAP Business Objects Titan.
“This month only 43% of notes require no manual steps besides note installation. Installing these notes is easier than the other ones and patching them has direct impact on information security. This percentage is lower than the average (usually between 60% and 75%) so this means this month’s users should perform more manual steps to have better coverage of patches in their environments,” Onapsis explains.
Symantec to Acquire Mobile Security Firm Skycure
12.7.2017 securityweek IT
Just three days after announcing that it would acquire Fireglass, Symantec announced that it has agreed to acquire mobile security firm Skycure.
Founded in 2012 by two former members of Israel Defense Forces' Unit 8200, Skycure has raised a total of $27.5 million in funding to date, and offers a threat prevention platform aimed at protecting mobile devices by monitoring network traffic behavior and fixing suspicious activity.
Symantec said that Skycure’s technology would be combined with its Integrated Cyber Defense Platform, giving Symantec customers “access to comprehensive and effective endpoint protection offerings across traditional and mobile devices, with enhanced capabilities for mobile devices, applications, network gateways and data protection."
Symantec also said that gaining access to Skycure’s technology will help position the company to serve as a strategic partner for telecommunications companies looking to build out mobile security offerings for their end users.
While no financial terms were disclosed, analysts from investment firm Jefferies estimate the acquisition cost to be roughly $200 million.
“While it's logical for [Symantec] to expand further into this market for a complete endpoint (desktop + server + mobile) offering, we note that it has been difficult to monetize mobile,” Jefferies wrote in a research note Tuesday. “Additionally, while we believe the go-to-market strategy to partner with telcos is logical, we note that it is likely at a substantially lower ASP than the direct channel. Therefore, we continue to believe that even traction gained within the telco channel may not be a meaningful contributor to revenue given greater go-to-market efficiency (i.e., lower price points).”
Jefferies also commented on the acquisition of Fireglass, calling it a “smart offensive and defensive move.”
“We saw the acquisition of Fireglass as a smart offensive and defensive move, as its browser isolation technology can be used to enter a new and potentially high-growth market, while defending the Symantec proxy solutions from any potential threat this market could pose,” the note added.
According to Symantec CEO Greg Clark, the company believes the future is “mobile-first” and requires protection that single platform vendors will struggle to provide on their own. “Our investments in this area will bring defense-in-depth across platforms including, closed operating systems,” Clark said in a statement.
“We believe the Skycure acquisition is logical given an increasingly mobile-first world, but believe that the return on this investment is incrementally less obvious given ongoing challenges to monetize mobile security,” Jefferies analysts opined.
Russian Financial Cybercriminal Gets Over 9 Years In U.S. Prison
11.7.2017 thehackernews CyberCrime
A 29-year-old Russian-born, Los Angeles resident has been sentenced to over nine years in prison for running botnets of half a million computers and stealing and trafficking tens of thousands of credit card numbers on exclusive Russian-speaking cybercriminal forums.
Alexander Tverdokhlebov was arrested in February, pleaded guilty on March 31 to wire fraud and on Monday, a federal court sentenced him to 110 months in prison.
According to court documents, Tverdokhlebov was an active member of several highly exclusive Russian-speaking cybercriminal forums largely engaged in money laundering services, selling stolen sensitive data, and malware tools since at least 2008.
Tverdokhlebov offered several illegal services on these underground forums, including the exchange of tools, services and stolen personal and financial information.
The hacker also operated several botnets – a network of compromised ordinary home and office computers that are controlled by hackers and can be used to steal credit card and other sensitive financial information.
At various occasions between 2009 and 2013, Tverdokhlebov claimed on the underground forums that "he possessed 40,000 stolen credit card numbers and could control up to 500,000 infected computers."
Tverdokhlebov emigrated from Russia in 2007 and later obtained United States citizenship. He also hired two Russian students studying in the America to cash out funds from a compromised bank account.
At the time of his arrest in February, federal authorities seized approximately $5 million in Bitcoin and $272,000 in cash from Tverdokhlebov, while he was trying to steal money from thousands of online US bank accounts.
According to the prosecutors, Tverdokhlebov stole sensitive financial information from at least 100 victims, estimating losses totaled between $9.5 Million to $25 Million.
"As part of the sentencing, the court also ordered the defendant to serve three years of supervised release following his prison term, with conditions of release that will include monitoring of the defendant's computer use," the Department of Justice said.
Most of his family is still based in Russia, and the only significant tie he has in the United States is a relationship with a Russian-born woman based there. Tverdokhlebov also married an American citizen in 2009 but divorced her shortly.
SQLi Vulnerability Scanner Available on Hacking Forum at $500
11.7.2017 securityweek Safety
A fully automated SQLi vulnerability scanner is available for purchase on a hacking forum for just $500, Recorded Future security researchers have discovered.
Dubbed Katyusha Scanner, the powerful tool was posted on a popular hacking forum by a Russian-speaking individual, on April 8, 2017. The scanner takes advantage of the functionality of Telegram messenger, as well as of Anarchi Scanner, an open-source penetration testing tool, the security researchers reveal.
The application has already received numerous updates, the last of them introduced on June 26, 2017, as Katyusha 0.8 Pro. Because of “outstanding support” from its author, the scanner immediately gained popularity among users, and started being praised for its intuitive and straightforward interface, and for performance capabilities.
Not only does the scanner allow miscreants to control the hacking process using a standard web interface, but it also provides users with the possibility to “upload a list of websites of interest and launch the concurrent attack against several targets simultaneously,” the researchers say. The operation can be seamlessly controlled via Telegram messenger.
Apparently, the scanner’s name specifically reflects this capability, making reference to the multiple-rocket launcher developed by the Soviet Union during World War II.
“Similar to the very lethal weapon conceived 70 years ago, Katyusha Scanner allows criminals to initiate large-scale penetration attacks against a massive number of targeted websites with several clicks using their smartphones,” Recorded Future explains.
Katyusha Scanner was made available at $500, with a light version released on May 10, 2017 at $250. The latter variant has slightly limited functionality, but was introduced due to the high demand the original scanner registered. Along with the Katyusha 0.8 Pro update at the end of June, the author also made the tool available for rent at $200 per month.
Recorded Future researchers warn that “the Pro version offers significantly more robust functionality, not only capable of identification but also establishing a strong foothold within vulnerable web servers and an automatic extraction of privileged information such as login credentials.”
Once the scan has been completed, the tool can display the Alexa web rating for each identified target, providing cybercriminals with “immediate visibility into the popularity of the resource and possible profit level in the future.”
The scanner can search and export email/password credentials, is multi-threaded (with support for concurrent sessions), and offers a module framework, Telegram messenger interface, and web interface. Furthermore, it allows for automatic dumping of databases, supports SQLMAP reports and file upload (the list of targeted websites), and can be used on both Linux and Windows.
The web shell module features CMS family identification (Bitrix, WordPress, OpenCart, etc.), login credentials brute-forcing (concurrent with SQLi scan), and automatic web shell upload.
Available scanning options include SQL injection (sql_injection) — Error-based detection (Oracle, InterBase, PostgreSQL, MySQL, MSSQL, EMC, SQLite, DB2, Informix, Firebird, SaP Max DB, Sybase, Frontbase, Ingres, HSQLDB, MS Access), Blind SQL injection using differential analysis (sql_injection_differential), and Blind SQL injection using timing attacks (sql_injection_timing – MySQL, PostgreSQL, and MSSQL).
“Despite the fact that SQLi attacks have been around for over 20 years, we are still seeing them successfully being used as common attack vectors by online criminals The availability of a highly robust and inexpensive tool such as Katyusha Scanner to online criminals with limited technical skills will only intensify the compromised data problem experienced by various businesses, highlighting the importance of regular infrastructure security audits,” Recorded Future concludes.
Researcher Takes Over .IO Domains by Registering Name Servers
11.7.2017 securityweek IT
A security researcher could have taken over thousands of .IO domains after being able to register four domain names of the top level domain (TLD)’s authoritative name servers.
The incident happened last month, when researcher Matthew Bryant was “graphing out the DNS delegation paths of various TLDs.” During his project, he discovered a name server domain that was available for registration and was able to purchase it.
".IO" is the country code top level domain (ccTLD) assigned to the British Indian Ocean Territory.
TLDs have authoritative name servers at arbitrary domain names but, by exploiting errors such as misconfiguration, expiration, or other issues, it is possible to “register a name server domain name and use it to serve new DNS records for the entire TLD zone,” the security researcher explains.
For that, one would have to enumerate all name server hostnames for a given extension and then check for base-domains that expired and are available for registration. In some instances, however, the expired domains would not be available for purchase even if not marked as reserved.
Using this method, the researcher stumbled upon the name server domain of ns-a1.io, which appeared as available for the registration price of 90.00 USD. After successfully purchasing it, Bryant attempted to contact the .io TLD to get the issue fixed, but failed.
As a result, he decided to look for other similar name server domains and found ns-a2.io, ns-a3.io, and ns-a4.io domains available for purchase as well. All four domains are listed as authoritative name servers for the .io TLD, and anyone controlling them could potentially “poison/redirect the DNS for all .io domain names registered,” the researcher explains.
Bryant was eventually able to send an email to the appropriate security contact and was informed the next day that the issue was resolved. The researcher verified that he was not able to re-register these domains, showing that the error was remediated.
“Given the fact that we were able to take over four of the seven authoritative name servers for the .io TLD we would be able to poison/redirect the DNS for all .io domain names registered. Not only that, but since we have control over a majority of the name servers it’s actually more likely that clients will randomly select our hijacked name servers over any of the legitimate name servers even before employing tricks like long TTL responses, etc to further tilt the odds in our favor,” the researcher explains.
He also notes that, because the .io TLD has Domain Name System Security Extensions (DNSSEC) enabled, which adds security by enabling DNS responses to be validated, users should be defended from attackers able to send bad/forged DNS data. However, “DNSSEC support is pretty abysmal and I rarely encounter any support for it unless I specifically set a resolver up that supports it myself,” the researcher also points out.
According to Matt Pounsett, however, while the Backend Registry Operator for the .io TLD clearly made a big mistake by allowing a third-party to register the name servers, the issue “definitely does not constitute the catastrophe implied.” He explains that “the name servers for the .io TLD don't respond with their own NS set in their response,” meaning that attack won’t work as suggested.
The issue with the authoritative name servers was that the .io TLD apparently transitioned last month from the operators of the registry to a third-party already in charge with the backend for other top-level domains. The third-party, Afilias, got hold of three domain name servers, but left the other four available.
ICS Security Pros Increasingly Concerned About Ransomware: Survey
11.7.2017 securityweek ICS Ransomware
Many security practitioners in the field of industrial control systems (ICS) believe the level of risk is high, and they are increasingly concerned about ransomware and embedded controllers, according to the SANS Institute’s fourth annual ICS cyber security survey.
ICS security experts from organizations of all sizes told SANS that they believe the top threat vectors are devices that cannot protect themselves, such as embedded controllers (44%), internal threats, including accidents (43%), external threats, such as nation-state actors and hacktivists (40%), and ransomware and other extortion attempts (35%).
Ransomware has made a lot of headlines in the past year and industrial systems are at risk, as demonstrated by both theoretical attack scenarios and in-the-wild threats such as the WannaCry malware. As a result, the number of ICS security experts concerned about ransomware has nearly doubled compared to data from the previous SANS survey.
“Although ransomware primarily infects commercial OS-based systems (e.g., Windows, Linux), the integration of these into ICS environments and the dependence of ICS on devices running these operating systems has extended ransomware’s effectiveness and reach,” SANS said in its report. “Publicly known operational impacts remain few to date but, we expect more to follow, especially given public demonstrations of ransomware targeting ICS/SCADA.”
Recent ICS hacking demonstrations also appear to have contributed to an increasing awareness that embedded controllers and control system applications are at risk – nearly one-quarter of respondents believe controllers are most at risk. On the other hand, many still believe that computers running commercial operating systems are most at risk and have the greatest impact.
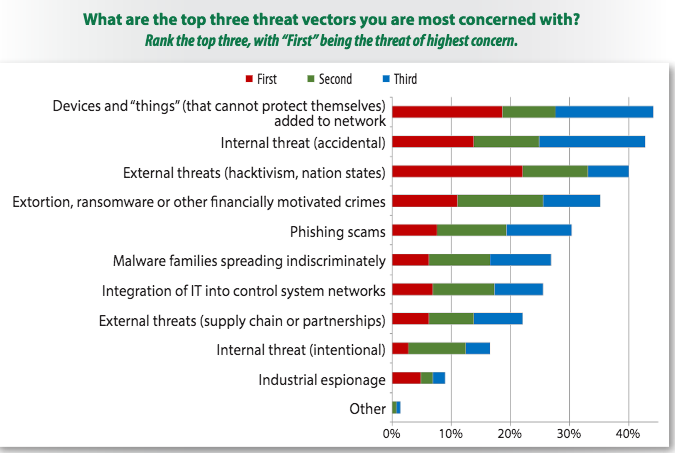
More than two-thirds of respondents believe the threat to ICS to be high or critical, and nearly half said their budgets for ICS security increased from the fiscal year 2016. Over the next 18 months, 20 percent or more of organizations have allocated budget for performing security assessments or audits of control systems, increase visibility into these systems, increase security awareness training, and implement anomaly and intrusion detection tools.
“Budgets for training and certification of staff responsible for implementing and maintaining security of control systems and control fell considerably, from 34% in 2016 to 26% in 2017. Rather than balancing this with increases in trained staff or outside consultants, budgets for these initiatives decreased, dropping, at 14%, below the top 10 budgetary initiatives,” SANS said. “At a time of increasing exposures and risk factors, this is counterintuitive. Rising threat levels and expanding attack surfaces require skilled professionals to address these risks.”
Of the organizations with more than 10,000 employees, 2.6 percent said they have a budget of more than $10 million for control system security in the fiscal year 2017, and 6 percent said they have a budget ranging between $1 million and $10 million. On the other hand, 2.6 percent of large companies admitted they don’t have a budget for ICS security.
The fact that some organizations have allocated budget for improving visibility is encouraging, considering that when asked if their control systems have been infected or infiltrated, 40 percent of respondents said “not that we know of,” which suggests they may have been breached, but lack visibility into their operational technology (OT) network.
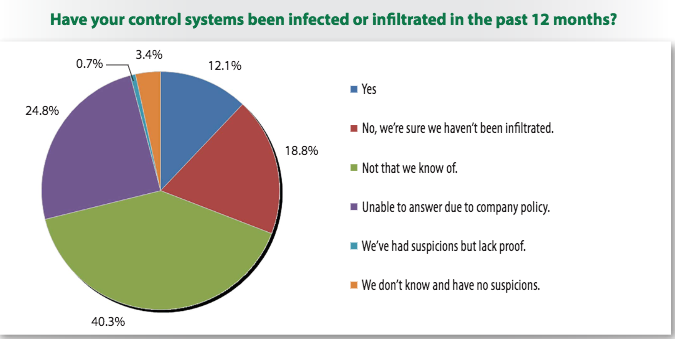
Roughly 12 percent of respondents said their control systems were infected or infiltrated in the past year. While most of them either did not know how many times their systems were breached or said they had only detected such events up to five times, some reported more than 50 incidents.
Microsoft Patch Tuesday – June 2017
11.7.2017 Symantec Vulnerebility blog
This month the vendor has patched 94 vulnerabilities, 18 of which are rated Critical.
Hello, welcome to this month's blog on the Microsoft patch release. This month the vendor has patched 94 vulnerabilities, 18 of which are rated Critical.
As always, customers are advised to follow these security best practices:
Install vendor patches as soon as they are available.
Run all software with the least privileges required while still maintaining functionality.
Avoid handling files from unknown or questionable sources.
Never visit sites of unknown or questionable integrity.
Block external access at the network perimeter to all key systems unless specific access is required.
Microsoft's summary of the June 2017 releases can be found here:
https://portal.msrc.microsoft.com/en-us/security-guidance
This month's update covers vulnerabilities in:
Microsoft Internet Explorer
Microsoft Edge
Microsoft Office
Microsoft Hyper-V
Microsoft Uniscribe
Windows Graphics
Microsoft Windows
The following is a breakdown of the issues being addressed this month:
Cumulative Security Update for Microsoft Internet Explorer and Edge
Scripting Engine Memory Corruption Vulnerability (CVE-2017-8496) MS Rating: Critical
A remote code execution vulnerability exists when Microsoft Edge improperly handles objects in memory. An attacker who successfully exploited this issue could obtain information to further compromise the user�s system.
Scripting Engine Memory Corruption Vulnerability (CVE-2017-8497) MS Rating: Critical
A remote code execution vulnerability exists in the way the Microsoft Edge JavaScript scripting engine handles objects in memory. This may corrupt memory in such a way that an attacker could execute arbitrary code in the context of the current user.
Internet Explorer Memory Corruption Vulnerability (CVE-2017-8517) MS Rating: Critical
A remote code execution vulnerability exists in the way JavaScript engines render when handling objects in memory in Microsoft browsers. This may corrupt memory in such a way that an attacker could execute arbitrary code in the context of the current user.
Scripting Engine Memory Corruption Vulnerability (CVE-2017-8520) MS Rating: Critical
A remote code execution vulnerability exists in the way the Microsoft Edge JavaScript scripting engine handles objects in memory.This may corrupt memory in such a way that an attacker could execute arbitrary code in the context of the current user.
Scripting Engine Memory Corruption Vulnerability (CVE-2017-8522) MS Rating: Critical
A remote code execution vulnerability exists in the way JavaScript engines render when handling objects in memory in Microsoft browsers. This may corrupt memory in such a way that an attacker could execute arbitrary code in the context of the current user.
Scripting Engine Memory Corruption Vulnerability (CVE-2017-8524) MS Rating: Critical
A remote code execution vulnerability exists in the way JavaScript engines render when handling objects in memory in Microsoft browsers. This may corrupt memory in such a way that an attacker could execute arbitrary code in the context of the current user.
Microsoft Edge Memory Corruption Vulnerability (CVE-2017-8548) MS Rating: Critical
A remote code execution vulnerability exists in the way JavaScript engines render when handling objects in memory in Microsoft browsers. This may corrupt memory in such a way that an attacker could execute arbitrary code in the context of the current user.
Scripting Engine Remote Code Execution Vulnerability (CVE-2017-8549) MS Rating: Critical
A remote code execution vulnerability exists when Microsoft Edge improperly handles objects in memory. An attacker who successfully exploited this issue could obtain information to further compromise the user�s system.
Scripting Engine Memory Corruption Vulnerability (CVE-2017-8499) MS Rating: Critical
A remote code execution vulnerability exists in the way the Microsoft Edge JavaScript scripting engine handles objects in memory. This may corrupt memory in such a way that an attacker could execute arbitrary code in the context of the current user.
Internet Explorer Memory Corruption Vulnerability (CVE-2017-8519) MS Rating: Important
A remote code execution vulnerability exists when Internet Explorer improperly accesses objects in memory. This vulnerability could corrupt memory in such a way that an attacker could execute arbitrary code in the context of the current user.
Scripting Engine Memory Corruption Vulnerability (CVE-2017-8521) MS Rating: Important
A remote code execution vulnerability exists in the way the Microsoft Edge JavaScript scripting engine handles objects in memory. This may corrupt memory in such a way that an attacker could execute arbitrary code in the context of the current user.
Microsoft Edge Memory Corruption Vulnerability (CVE-2017-8523) MS Rating: Important
A security bypass vulnerability exists when Microsoft Edge fails to correctly apply Same Origin Policy for HTML elements present in other browser windows. An attacker can exploit this issue to trick a user into loading a page with malicious content.
Microsoft Browser Information Disclosure Vulnerability (CVE-2017-8529) MS Rating: Important
An information disclosure vulnerability exists when affected Microsoft scripting engines do not properly handle objects in memory. The vulnerability could allow an attacker to detect specific files on the user's computer.
Microsoft Edge Security Feature Bypass Vulnerability (CVE-2017-8530) MS Rating: Important
A security bypass vulnerability that affects Microsoft Edge.
Internet Explorer Memory Corruption Vulnerability (CVE-2017-8547) MS Rating: Important
A remote code execution vulnerability exists when Internet Explorer improperly accesses objects in memory. This vulnerability could corrupt memory in such a way that an attacker could execute arbitrary code in the context of the current user.
Microsoft Edge Security Feature Bypass Vulnerability (CVE-2017-8555) MS Rating: Important
A security bypass vulnerability exists when the Edge Content Security Policy (CSP) fails to properly validate certain specially crafted documents. An attacker can exploit this issue to trick a user into loading a web page with malicious content.
Microsoft Edge Information Disclosure Vulnerability (CVE-2017-8498) MS Rating: Moderate
An information disclosure vulnerability exists in Microsoft Edge that allows JavaScript XML DOM objects to detect installed browser extensions. To exploit the vulnerability, in a web-based attack scenario, an attacker could host a malicious website in an attempt to make a user visit it.
Microsoft Edge Information Disclosure Vulnerability (CVE-2017-8504) MS Rating: Low
An information disclosure vulnerability exists when the Microsoft Edge Fetch API incorrectly handles a filtered response type. An attacker could use the vulnerability to read the URL of a cross-origin request.
Cumulative Security Update for Microsoft Office
Microsoft Office Remote Code Execution Vulnerability (CVE-2017-0260) MS Rating: Important
A remote code execution vulnerability exists when Office improperly validates input before loading dynamic link library (DLL) files. An attacker who successfully exploited this issue could take control of an affected system.
Microsoft Office Remote Code Execution Vulnerability (CVE-2017-8506) MS Rating: Important
A remote code execution vulnerability exists when Office improperly validates input before loading dynamic link library (DLL) files. An attacker who successfully exploited this issue could take control of an affected system.
Microsoft Office Memory Corruption Vulnerability (CVE-2017-8507) MS Rating: Important
A remote code execution vulnerability exists in the way that Microsoft Outlook parses specially crafted email messages. An attacker who successfully exploited this issue could take control of an affected system.
Microsoft Office Security Feature Bypass Vulnerability (CVE-2017-8508) MS Rating: Important
A security bypass vulnerability exists in Microsoft Office software when it improperly handles the parsing of file formats. The security bypass by itself does not allow arbitrary code execution.
Microsoft Office Remote Code Execution Vulnerability (CVE-2017-8509) MS Rating: Important
A remote code execution vulnerability exist in Microsoft Office software when the Office software fails to properly handle objects in memory. An attacker who successfully exploited this issue could use a specially crafted file to perform actions in the security context of the current user.
Microsoft Office Remote Code Execution Vulnerability (CVE-2017-8510) MS Rating: Important
A remote code execution vulnerability exist in Microsoft Office software when the Office software fails to properly handle objects in memory. An attacker who successfully exploited this issue could use a specially crafted file to perform actions in the security context of the current user.
MicrosoftOffice Remote Code Execution Vulnerability (CVE-2017-8511) MS Rating: Important
A remote code execution vulnerability exist in Microsoft Office software when the Office software fails to properly handle objects in memory. An attacker who successfully exploited this issue could use a specially crafted file to perform actions in the security context of the current user.
Microsoft Office Remote Code Execution Vulnerability (CVE-2017-8512) MS Rating: Important
A remote code execution vulnerability exist in Microsoft Office software when the Office software fails to properly handle objects in memory. An attacker who successfully exploited this issue could use a specially crafted file to perform actions in the security context of the current user.
Microsoft PowerPoint Remote Code Execution Vulnerability (CVE-2017-8513) MS Rating: Important
A remote code execution vulnerability exist in Microsoft Office software when the Office software fails to properly handle objects in memory. An attacker who successfully exploited this issue could use a specially crafted file to perform actions in the security context of the current user.
Microsoft SharePoint Reflective XSS Vulnerability (CVE-2017-8514) MS Rating: Important
A cross-site scripting vulnerability because it fails to sufficiently sanitize user-supplied input. An authenticated attacker could exploit this vulnerability by sending a specially crafted request to an affected SharePoint server.
Microsoft Outlook for Mac Spoofing Vulnerability (CVE-2017-8545) MS Rating: Important
A spoofing vulnerability exists when Microsoft Outlook for Mac does not sanitize html or treat it in a safe manner. An attacker who successfully tricked the user could gain access to the user's authentication information or login credentials.
Microsoft SharePoint XSS vulnerability (CVE-2017-8551) MS Rating: Important
A privilege escalation vulnerability exists when SharePoint Server does not properly sanitize a specially crafted web request to an affected SharePoint server. An authenticated attacker could exploit the vulnerability by sending a specially crafted request to an affected SharePoint server. Successful exploits may allow an attacker to perform cross-site scripting attacks.
Cumulative Security Update for Microsoft Windows Hyper-V
Hypervisor Code Integrity Elevation of Privilege Vulnerability (CVE-2017-0193) MS Rating: Important
A privilege escalation vulnerability exists when Windows Hyper-V instruction emulation fails to properly enforce privilege levels. An attacker who successfully exploited this issue could gain elevated privileges on a target guest operating system.
Cumulative Security Update for Skype for Business
Skype for Business Remote Code Execution Vulnerability (CVE-2017-8550) MS Rating: Critical
A remote code execution vulnerability exists when Skype for Business and Microsoft Lync Servers fail to properly sanitize specially crafted content. An authenticated attacker who successfully exploited this issue could execute HTML and JavaScript content in the Skype for Business or Lync context.
Cumulative Security Update for Microsoft Windows Uniscribe
Windows Uniscribe Remote Code Execution Vulnerability (CVE-2017-8527) MS Rating: Critical
A remote code execution vulnerability exist when the Windows font library improperly handles specially crafted embedded fonts. An attacker who successfully exploited this issue could take control of the affected system.
Windows Uniscribe Remote Code Execution Vulnerability (CVE-2017-8528) MS Rating: Critical
A remote code execution vulnerability exists due to the way Windows Uniscribe handles objects in memory. An attacker who successfully exploited this issue could take control of the affected system.
Windows Uniscribe Remote Code Execution Vulnerability (CVE-2017-0283) MS Rating: Critical
A remote code execution vulnerability exists due to the way Windows Uniscribe handles objects in memory. An attacker can exploit this issue could take control of the affected system.
Windows Uniscribe Information Disclosure Vulnerability (CVE-2017-0282) MS Rating: Important
An information disclosure vulnerability exists when Windows Uniscribe improperly discloses the contents of its memory. An attacker who successfully exploited this issue could obtain information to further compromise the user�s system.
Windows Uniscribe Information Disclosure Vulnerability (CVE-2017-0284) MS Rating: Important
An information disclosure vulnerability exists when Windows Uniscribe improperly discloses the contents of its memory. An attacker who successfully exploited this issue could obtain information to further compromise the user�s system.
Windows Uniscribe Information Disclosure Vulnerability (CVE-2017-0285) MS Rating: Important
An information disclosure vulnerability exists when Windows Uniscribe improperly discloses the contents of its memory. An attacker who successfully exploited this issue could obtain information to further compromise the user�s system.
Windows Uniscribe Information Disclosure Vulnerability (CVE-2017-8534) MS Rating: Important
An information disclosure vulnerability exists when Windows Uniscribe improperly discloses the contents of its memory. An attacker who successfully exploited this issue could obtain information to further compromise the user�s system.
Cumulative Security Update for Microsoft Windows Graphics
Windows Graphics Information Disclosure Vulnerability (CVE-2017-0286) MS Rating: Important
An information disclosure vulnerability exists when the Windows GDI component improperly discloses the contents of its memory. An attacker who successfully exploited this issue could obtain information further compromise the user�s system.
Windows Graphics Information Disclosure Vulnerability (CVE-2017-0287) MS Rating: Important
An information disclosure vulnerability exists when the Windows GDI component improperly discloses the contents of its memory. An attacker who successfully exploited this issue could obtain information further compromise the user�s system.
Windows Graphics Information Disclosure Vulnerability (CVE-2017-0288) MS Rating: Important
An information disclosure vulnerability exists when the Windows GDI component improperly discloses the contents of its memory. An attacker who successfully exploited this issue could obtain information further compromise the user�s system.
Windows Graphics Information Disclosure Vulnerability (CVE-2017-0289) MS Rating: Important
An information disclosure vulnerability exists when the Windows GDI component improperly discloses the contents of its memory. An attacker who successfully exploited this issue could obtain information further compromise the user�s system.
Windows Graphics Information Disclosure Vulnerability (CVE-2017-8531) MS Rating: Important
An information disclosure vulnerability exists when the Windows GDI component improperly discloses the contents of its memory. An attacker who successfully exploited this issue could obtain information further compromise the user�s system.
Windows Graphics Information Disclosure Vulnerability (CVE-2017-8532) MS Rating: Important
An information disclosure vulnerability exists when the Windows GDI component improperly discloses the contents of its memory. An attacker who successfully exploited this issue could obtain information further compromise the user�s system.
Windows Graphics Information Disclosure Vulnerability (CVE-2017-8533) MS Rating: Important
An information disclosure vulnerability exists when the Windows GDI component improperly discloses the contents of its memory. An attacker who successfully exploited this issue could obtain information further compromise the user�s system.
Cumulative Security Update for Microsoft Windows Kernel-Mode Drivers
Windows Kernel Elevation of Privilege Vulnerability (CVE-2017-0297) MS Rating: Important
A privilege escalation vulnerability exists in the way that the Windows Kernel handles objects in memory. An attacker who successfully exploited this issue could execute code with elevated permissions.
Windows Kernel Information Disclosure Vulnerability (CVE-2017-0299) MS Rating: Important
An information disclosure vulnerability exists when the Windows kernel fails to properly initialize a memory address, allowing an attacker to retrieve information that could lead to a Kernel Address Space Layout Randomization (KASLR) bypass. An attacker who successfully exploited this issue could retrieve the base address of the kernel driver from a compromised process.
Windows Kernel Information Disclosure Vulnerability (CVE-2017-0300) MS Rating: Important
An information disclosure vulnerability exists when the Windows kernel fails to properly initialize a memory address, allowing an attacker to retrieve information that could lead to a Kernel Address Space Layout Randomization (KASLR) bypass. An attacker who successfully exploited this issue could retrieve the base address of the kernel driver from a compromised process.
Windows Kernel Information Disclosure Vulnerability (CVE-2017-8462) MS Rating: Important
An information disclosure vulnerability exists when the Windows kernel fails to properly initialize a memory address, allowing an attacker to retrieve information that could lead to a Kernel Address Space Layout Randomization (KASLR) bypass. An attacker who successfully exploited this issue could retrieve the base address of the kernel driver from a compromised process.
Win32k Elevation of Privilege Vulnerability (CVE-2017-8465) MS Rating: Important
A privilege escalation vulnerability exists when the Windows kernel improperly handles objects in memory. An attacker who successfully exploited this issue could run processes in an elevated context.
Win32k Elevation of Privilege Vulnerability (CVE-2017-8468) MS Rating: Important
A privilege escalation vulnerability exists when the Windows kernel improperly handles objects in memory. An attacker who successfully exploited this issue could run processes in an elevated context.
Windows Kernel Information Disclosure Vulnerability (CVE-2017-8469) MS Rating: Important
An information disclosure vulnerability exists when the Windows kernel improperly initializes objects in memory. An attacker can exploit this issue by sending a specially crafted application.
Win32k Information Disclosure Vulnerability (CVE-2017-8470) MS Rating: Important
An information disclosure vulnerability exists when the Windows kernel improperly initializes objects in memory. An attacker can exploit this issue by sending a specially crafted application.
Win32k Information Disclosure Vulnerability (CVE-2017-8471) MS Rating: Important
An information disclosure vulnerability exists when the Windows kernel improperly initializes objects in memory. An attacker can exploit this issue by sending a specially crafted application.
Win32k Information Disclosure Vulnerability (CVE-2017-8472) MS Rating: Important
An information disclosure vulnerability exists when the Windows kernel improperly initializes objects in memory. An attacker can exploit this issue by sending a specially crafted application.
Win32k Information Disclosure Vulnerability (CVE-2017-8473) MS Rating: Important
An information disclosure vulnerability exists when the Windows kernel improperly initializes objects in memory. An attacker can exploit this issue by sending a specially crafted application.
Windows Kernel Information Disclosure Vulnerability (CVE-2017-8474) MS Rating: Important
An information disclosure vulnerability exists when the Windows kernel improperly initializes objects in memory. An attacker can exploit this issue by sending a specially crafted application.
Win32k Information Disclosure Vulnerability (CVE-2017-8475) MS Rating: Important
An information disclosure vulnerability exists when the Windows kernel improperly initializes objects in memory. An attacker can exploit this issue by sending a specially crafted application.
Windows Kernel Information Disclosure Vulnerability (CVE-2017-8476) MS Rating: Important
An information disclosure vulnerability exists when the Windows kernel improperly initializes objects in memory. An attacker can exploit this issue by sending a specially crafted application.
Win32k Information Disclosure Vulnerability (CVE-2017-8477) MS Rating: Important
An information disclosure vulnerability exists when the Windows kernel improperly initializes objects in memory. An attacker can exploit this issue by sending a specially crafted application.
Windows Kernel Information Disclosure Vulnerability (CVE-2017-8478) MS Rating: Important
An information disclosure vulnerability exists when the Windows kernel improperly initializes objects in memory. An attacker can exploit this issue by sending a specially crafted application.
Windows Kernel Information Disclosure Vulnerability (CVE-2017-8479) MS Rating: Important
An information disclosure vulnerability exists when the Windows kernel improperly initializes objects in memory. An attacker can exploit this issue by sending a specially crafted application.
Windows Kernel Information Disclosure Vulnerability (CVE-2017-8480) MS Rating: Important
An information disclosure vulnerability exists when the Windows kernel improperly initializes objects in memory. An attacker can exploit this issue by sending a specially crafted application.
Windows Kernel Information Disclosure Vulnerability (CVE-2017-8481) MS Rating: Important
An information disclosure vulnerability exists when the Windows kernel improperly initializes objects in memory. An attacker can exploit this issue by sending a specially crafted application.
Windows Kernel Information Disclosure Vulnerability (CVE-2017-8482) MS Rating: Important
An information disclosure vulnerability exists when the Windows kernel improperly initializes objects in memory. An attacker can exploit this issue by sending a specially crafted application.
Windows Kernel Information Disclosure Vulnerability (CVE-2017-8483) MS Rating: Important
An information disclosure vulnerability exists when the Windows kernel improperly initializes objects in memory. An attacker can exploit this issue by sending a specially crafted application.
Win32k Information Disclosure Vulnerability (CVE-2017-8484) MS Rating: Important
An information disclosure vulnerability exists when the Windows kernel improperly initializes objects in memory. An attacker can exploit this issue by sending a specially crafted application.
Windows Kernel Information Disclosure Vulnerability (CVE-2017-8485) MS Rating: Important
An information disclosure vulnerability exists when the Windows kernel improperly initializes objects in memory. An attacker can exploit this issue by sending a specially crafted application.
Windows Kernel Information Disclosure Vulnerability (CVE-2017-8488) MS Rating: Important
An information disclosure vulnerability exists when the Windows kernel improperly initializes objects in memory. An attacker can exploit this issue by sending a specially crafted application.
Windows Kernel Information Disclosure Vulnerability (CVE-2017-8489) MS Rating: Important
An information disclosure vulnerability exists when the Windows kernel improperly initializes objects in memory. An attacker can exploit this issue by sending a specially crafted application.
Windows Kernel Information Disclosure Vulnerability (CVE-2017-8490) MS Rating: Important
An information disclosure vulnerability exists when the Windows kernel improperly initializes objects in memory. An attacker can exploit this issue by sending a specially crafted application.
Windows Kernel Information Disclosure Vulnerability (CVE-2017-8491) MS Rating: Important
An information disclosure vulnerability exists when the Windows kernel improperly initializes objects in memory. An attacker can exploit this issue by sending a specially crafted application.
Windows Kernel Information Disclosure Vulnerability (CVE-2017-8492) MS Rating: Important
An information disclosure vulnerability exists when the Windows kernel improperly initializes objects in memory. An attacker can exploit this issue by sending a specially crafted application.
Cumulative Security Update for Microsoft Windows
LNK Remote Code Execution Vulnerability (CVE-2017-8464) MS Rating: Critical
A remote code execution exists in Microsoft Windows that could allow remote code execution if the icon of a specially crafted shortcut is displayed. An attacker who successfully exploited this issue could gain the same user rights as the local user.
Windows PDF Remote Code Execution Vulnerability (CVE-2017-0291) MS Rating: Critical
A remote code execution vulnerability exists in Microsoft Windows if a user opens a specially crafted PDF file. An attacker who successfully exploited this issue could cause arbitrary code to execute in the context of the current user.
Windows PDF Remote Code Execution Vulnerability (CVE-2017-0292) MS Rating: Critical
A remote code execution vulnerability exists in Microsoft Windows if a user opens a specially crafted PDF file. An attacker who successfully exploited this issue could cause arbitrary code to execute in the context of the current user.
Windows Remote Code Execution Vulnerability (CVE-2017-0294) MS Rating: Critical
A remote code execution vulnerability exists when Microsoft Windows fails to properly handle cabinet files. To exploit the vulnerability, an attacker would have to convince a user to either open a specially crafted cabinet file or spoof a network printer and trick a user into installing a malicious cabinet file disguised as a printer driver.
Windows Search Remote Code Execution Vulnerability (CVE-2017-8543) MS Rating: Critical
A remote code execution vulnerability exists when Windows Search handles objects in memory. An attacker who successfully exploited this issue could take control of the affected system.
Device Guard Code Integrity Policy Security Feature Bypass Vulnerability (CVE-2017-0173) MS Rating: Important
A security bypass vulnerability exists in Device Guard that could allow an attacker to inject malicious code into a Windows PowerShell session. An attacker who successfully exploited this issue could inject code into a trusted PowerShell process to bypass the Device Guard Code Integrity policy on the local machine.
Device Guard Code Integrity Policy Security Feature Bypass Vulnerability (CVE-2017-0215) MS Rating: Important
A security bypass vulnerability exists in Device Guard that could allow an attacker to inject malicious code into a Windows PowerShell session. An attacker who successfully exploited this issue could inject code into a trusted PowerShell process to bypass the Device Guard Code Integrity policy on the local machine.
Device Guard Code Integrity Policy Security Feature Bypass Vulnerability (CVE-2017-0216) MS Rating: Important
A security bypass vulnerability exists in Device Guard that could allow an attacker to inject malicious code into a Windows PowerShell session. An attacker who successfully exploited this issue could inject code into a trusted PowerShell process to bypass the Device Guard Code Integrity policy on the local machine.
Device Guard Code Integrity Policy Security Feature Bypass Vulnerability (CVE-2017-0218) MS Rating: Important
A security bypass vulnerability exists in Device Guard that could allow an attacker to inject malicious code into a Windows PowerShell session. An attacker who successfully exploited this issue could inject code into a trusted PowerShell process to bypass the Device Guard Code Integrity policy on the local machine.
Device Guard Code Integrity Policy Security Feature Bypass Vulnerability (CVE-2017-0219) MS Rating: Important
A security bypass vulnerability exists in Device Guard that could allow an attacker to inject malicious code into a Windows PowerShell session. An attacker who successfully exploited this issue could inject code into a trusted PowerShell process to bypass the Device Guard Code Integrity policy on the local machine.
Windows Default Folder Tampering Vulnerability (CVE-2017-0295) MS Rating: Important
A tampering vulnerability exists in Microsoft Windows that could allow an authenticated attacker to modify the folder structure. An attacker who successfully exploited this issue could potentially modify files and folders that are synchronized the first time when a user logs in locally to the computer.
Windows TDX Elevation of Privilege Vulnerability (CVE-2017-0296) MS Rating: Important
A privilege escalation vulnerability exists when tdx. sys fails to check the length of a buffer prior to copying memory to it.
Windows COM Session Elevation of Privilege Vulnerability (CVE-2017-0298) MS Rating: Important
A privilege escalation exists in Windows when a DCOM object in Helppane. exe, configured to run as the interactive user, fails to properly authenticate the client.
Windows PDF Information Disclosure Vulnerability (CVE-2017-8460) MS Rating: Important
An information disclosure vulnerability exists in Microsoft Windows when a user opens a specially crafted PDF file. An attacker who successfully exploited this issue could read information in the context of the current user.
Windows Cursor Elevation of Privilege Vulnerability (CVE-2017-8466) MS Rating: Important
A privilege escalation vulnerability exists when Windows improperly handles objects in memory. An attacker who successfully exploited this issue could run processes in an elevated context.
Windows Security Feature Bypass Vulnerability (CVE-2017-8493) MS Rating: Important
A security bypass vulnerability exists when Microsoft Windows fails to enforce case sensitivity for certain variable checks, which could allow an attacker to set variables that are either read-only or require authentication.
Windows Elevation of Privilege Vulnerability (CVE-2017-8494) MS Rating: Important
A privilege escalation vulnerability exists when Windows Secure Kernel Mode fails to properly handle objects in memory.To exploit the vulnerability, a locally-authenticated attacker could attempt to run a specially crafted application on a targeted system.
Windows VAD Cloning Denial of Service Vulnerability (CVE-2017-8515) MS Rating: Important
A denial of service vulnerability exists in Microsoft Windows when an unauthenticated attacker sends a specially crafted kernel mode request. An attacker who successfully exploited this issue could cause a denial of service on the target system, causing the machine to either stop responding or reboot.
Windows Search Information Disclosure Vulnerability (CVE-2017-8544) MS Rating: Important
An information disclosure vulnerability exists when Windows Search handles objects in memory. An attacker who successfully exploited this issue could obtain information to further compromise the user�s system.
GDI Information Disclosure Vulnerablity (CVE-2017-8553) MS Rating: Important
An information disclosure vulnerability exists when the Windows kernel improperly handles objects in memory. An attacker who successfully exploited this issue could obtain information to further compromise the user�s system.
Adobe Fixes Vulnerabilities in Flash Player, Connect
11.7.2017 securityweek Vulnerebility
Adobe today released updates for its Flash Player and Connect products to address several vulnerabilities that can be exploited for remote code execution, information disclosure, cross-site scripting (XSS) attacks, and clickjacking.
An advisory published by Adobe for Flash Player shows that version 26.0.0.137 patches three critical vulnerabilities, including ones that can be exploited to take control of affected systems.
The list includes a critical memory corruption flaw that can lead to remote code execution (CVE-2017-3099) and two important information disclosure weaknesses caused by memory corruption and security bypass issues (CVE-2017-3100 and CVE-2017-3080). Jihui Lu of Tencent KeenLab and a researcher who uses the online moniker “bo13oy” have been credited for finding CVE-2017-3099, respectively CVE-2017-3100.
In the case of the Connect web conferencing software, Adobe patched three less severe vulnerabilities. The security holes have been described as a user interface bug that can be exploited for clickjacking attacks (CVE-2017-3101) and input validation problems that can allow reflected and stored XSS attacks (CVE-2017-3102, CVE-2017-3103).
The flaws, discovered by Anas Roubi, Adam Willard of Raytheon Foreground Security, and Alexis Laborier, affect Connect for Windows and they have been patched with the release of version 9.6.2.
Adobe said it was not aware of any attacks exploiting these vulnerabilities, but pointed out that some details of the Flash Player flaw tracked as CVE-2017-3080 were made public on July 3.
NATO Providing Cybersecurity Equipment to Ukraine
11.7.2017 securityweek BigBrothers
NATO Takes Steps to Bolster Ukrainian Cyber Security
Ukraine is an area of great geopolitical significance -- a sort of buffer zone between NATO and Russia -- that both sides seek to influence. Crimea aside, neither side wishes to be too overt with military intervention, and the result is tailor-made for modern cyber warfare.
What remains of Ukraine is politically west-leaning and NATO-cooperative. This places Russia in the position of protagonist; and while it should be said that there is little direct proof of Russia-led cyber warfare, there is equally little doubt in the minds of many security researchers.
Two examples will immediately come to mind: the power disruptions over the Christmas period of 2015, and the more recent NotPetya ransomware outbreak. The latter started in the Ukraine before spreading worldwide. It appears to have emanated from Ukrainian accounting software called MEDoc, but is now thought by some to be a wiper cyberweapon disguised as ransomware "apparently launched by the same threat group that initiated numerous other attacks against the country’s power grid, mining and railway systems, and Ukrainian government organizations."
NATO's official policy towards Ukraine is to bolster its independence.
"A sovereign, independent and stable Ukraine, firmly committed to democracy and the rule of law, is key to Euro-Atlantic security," it says. "Since 2014, in the wake of the Russia-Ukraine conflict, cooperation has been intensified in critical areas."
Cyber security is one of those critical areas. In December 2014, NATO established a Trust Fund designed "to provide Ukraine with the necessary support to develop its strictly defensive, CSIRT-type technical capabilities, including laboratories to investigate cyber security incidents."
By June 2016, eight nations had contributed a total of €965,000, plus in-kind contributions from Estonia and the USA. This week, the project appears to have moved to the next step at a joint briefing with NATO secretary general, Jens Stoltenberg, and Ukrainian president Petro Poroshenko in Kiev on Monday.
Ukrinform, the national news agency of Ukraine, reported Monday, "He [Stoltenberg] said that one of the areas where the alliance was paying more attention in its cooperation with Ukraine was the sector of cyber security. NATO is currently in the process of providing Ukraine with new equipment for some key government institutions and authorities, which will enable Ukraine to investigate who is behind certain cyber-attacks, because the response to them is extremely important, Stoltenberg said. And it should also help Ukraine protect its key government institutions from cyber-attacks, he added."
NotPetya is exactly the sort of cyber-attack that such defenses will need to prevent.
HyTrust Acquires DataGravity, Raises $36 Million
11.7.2017 securityweek IT
Cloud security firm HyTrust today announced that it has acquired data visibility and security company DataGravity, and raised $36 million in a new funding round.
Terms of the acquisition have not been disclosed, but members of the DataGravity team will join HyTrust. By acquiring DataGravity, HyTrust hopes to further enhance its security policy enforcement capabilities for cloud workloads through new data discovery and classification expertise.
DataGravity, which in the past years managed to raise a total of $92 million, exited stealth mode in 2014 when it launched Discovery, a platform that provided data security, and search and discovery capabilities. The company later released the DataGravity for Virtualization virtual appliance.HyTrust acquires DataGravity
HyTrust’s decision to acquire DataGravity comes shortly after Forrester estimated that the global cloud security market will increase to $3.5 billion by 2021, which represents an annual growth rate of 28 percent.
“The acquisition will accelerate the expansion of HyTrust's platform capabilities and capitalize on the high-growth cloud security market,” said Eric Chiu, co-founder and president of HyTrust. “DataGravity's data discovery and classification capabilities support HyTrust's mission to deliver a security policy framework that provides customers with full visibility, insight and enforcement of policy across workloads. We couldn't be more excited.”
HyTrust also announced that it has closed a $36 million funding round led by investment firm Advance Venture Partners (AVP), which brings the total raised by the company to $100 million. Sway Ventures, Epic Ventures, Vanedge Capital, Trident Capital, and strategic investors Cisco, Fortinet, Intel and VMware also participated.
Part of the $36 million have been used to acquire DataGravity and the rest will go towards expanding sales and marketing efforts, and funding new product development.
“HyTrust is very well positioned to capitalize on a tremendous growth opportunity in the cloud security space,” said David ibnAle, founding partner at AVP. “The need for security, automated compliance and policy enforcement for cloud infrastructure and data is critical in almost every industry, and HyTrust is front and center in this field. Gartner's recent highlighting of the sector as a top security technology for 2017 underscores the relevance of HyTrust's solutions, and we are extremely excited about the opportunity to back the market leader in this space.”
Calling Artificial Intelligence to Counter Ransomware Attacks
11.7.2017 securityaffairs Ransomware
The progression in Artificial Intelligence have incited intense debate worldwide, some experts are calling AI to counter malware attacks
In a short span of six weeks, the world was hit twice by major ransomware attacks — malicious software that seizes the data stored on your computer systems and would only release it to you upon receiving ransom money.
It goes without saying that the world is in dire need of better defense mechanism, and mercifully they have started to arise but in a rather slower and in patchwork fashion. The day we would feel completely secure, we may have artificial intelligence to thank.
Ransomware is not necessarily the trickiest or the most dangerous forms of malware that can hack into your computer, but it surely is infuriating and at many instances devastating. The majority types of infections that sneak into your systems don’t lock down your personal pictures or documents the way ransomware does and nor do they demand money.
Despite knowing the risks, there are many who aren’t very savvy enough to keep up with the security software updates. Both of the recent ransomware attacks thwacked users who were unsuccessful at installing the security update which Windows released a few months earlier.
Artificial Intelligence
The progression in Artificial Intelligence have incited intense debate worldwide. Science fiction is nearing reality and AI products are taking over households and workplace. Concerns about the potential takeover of AI over the job market is rising. Discussions are also live about the detrimental effects of an AI singularity, taking over the world and terminating the human race.
Though these debates are all valid, I strongly hold the opinion that AI should not only be concentrated to just home gadgets or on process optimization and automation. Instead, AI can be put to use in solving the greater problems the world is facing.

AI in tackling Ransomware
2015 saw around 707 million cybersecurity breaches while in 2016 the figure reached 554 million in just the first half.
Detecting Malware
Earlier, the identification of malicious programs was done by matching the program’s code against a database of identified malware. Though this method was only as good as the database and would ultimately get outdated, allowing new malware variants to easily sneak in.
Hence, security companies started to gauge a malware by its behavior. For instance, in the case of ransomware, the software may go for repetitive tries to lock files by encrypting them. But this could also flag regular computer behavior for example file compression.
The modern techniques now include considering a combination of behaviors. Such as, a program which is encrypting files without displaying a progress bar on the monitor could be signaled as a surreptitious activity. But the drawback here is that it slows down the process of harmful software identification, also locking up some of the files.
Provision
The growing number of alerts being generated by the traditional tools is only increasing the struggle for the security teams. AI, with its ability to self-learn and automate, can raise the effectiveness and cut cost, guarding us from terrorism or attacks of rather smaller scale.
Moving further, the existing AI-centric solutions in the industry are more pro-active. They have the ability to anticipate attacks beforehand by detecting patterns and glitches pertaining to malicious content.
Secureworks utilizes the predictive competencies of AI for advanced threat recognition globally. SiftScience, Cylance, and Deep Instinct are using it to prevent frauds and for endpoint security, like smartphones and laptops. These technologies hold the potential to radically magnify the possibilities and scale of security specialists and enable them to sense incoming threats before they actually materialize.
FBI prohledávala domy zaměstnanců Kaspersky Lab. Ruskou firmu má za hrozbu
11.7.2017 Lupa.cz BigBrother
Debaty o tom, zda je ruská antivirová společnost Kaspersky Lab možnou hrozbou, pokračují. Začátkem loňského roku jsme na Lupě publikovali článek, který v Kaspersky nevyvolal příliš dobré reakce. Podezření na to, že společnost a její zakladatel Eugene Kaspersky udržují úzké vztahy s ruskou vládou a tajnými službami, se probíralo i jinde.
Bloomberg nyní ve svém týdeníku Businessweek přichází s dalšími informacemi. Tajné služby ve Spojených státech nyní Kaspersky Lab považují za potenciální risk pro národní bezpečnost. Kongres jedná o tom, zda zakázat produkty ruského podniku pro využití v armádě. Podle Bloombergu také FBI navštívila domovy zaměstnanců Kaspersky Lab působících v Americe. Nic konkrétního se nenašlo, vztahy s vládními složkami jsou ale pro Američany stále problematické.
Uniklé e-maily rovněž ukazují, že Kaspersky má mnohem užší vazby na ruské tajné služby, než se původně předpokládalo. Eugene Kaspersky například měl dohlížet na vývoj antihacking nástroje pro ruskou službu FSB. Tento projekt se pak stal základem DDoS ochrany v produktech Kaspersky. Jak už jsme také psali, výzkumníci Kaspersky pomáhají v Rusku odhalovat kyberútočníky.
To ale nemusí být zase tak zásadní. Například v Izraeli hodně komerčních technologií spojených s bezpečností vychází z armádních a vládních projektů. Ve světě jsou běžné i různé úrovně spolupráce státních bezpečnostních složek a soukromých firem. Volá se třeba po digitálních Ženevských konvencích (které mimochodem Eugene Kaspersky veřejně podporuje).
Více o podezřeních na propojení Kaspersky Lab a Ruska v našem dřívějším článku. Bloomberg k tématu rovněž zveřejnil podcast. O Rusko a jeho technologické oblasti Skolkovo, kde vzniká třeba router pro operátory, v naší reportáži. I v případě některých projektů Skolkova je FBI poněkud podezřívavá.
Russian Hacker Living in U.S. Sentenced to Prison
11.7.2017 securityweek BigBrothers
A Russian-born U.S. citizen has been sentenced to 110 months in prison for running a sophisticated cybercrime operation that involved botnets, stolen financial data and money laundering.
Alexander Tverdokhlebov, 29, has been living in Los Angeles. He emigrated from Russia in 2007 and later obtained U.S. citizenship.
According to U.S. authorities, Tverdokhlebov was an active member on several exclusive Russian-speaking cybercrime forums since at least 2008. He is said to have offered various services, including for laundering illegal proceeds.
The man also operated botnets that allowed cybercriminals to steal payment cards and other data. Investigators said Tverdokhlebov boasted about possessing 40,000 credit card numbers and controlling as many as half a million computers between 2009 and 2013.
The hacker sold the stolen card data to individuals who used it to make fraudulent purchases or withdrawals from the victims’ accounts. He is also said to have recruited Russian students visiting the U.S. to receive money from victims and then forward it to Tverdokhlebov and his accomplices.
Authorities believe Tverdokhlebov’s activities resulted in losses between $9.5 and $25 million. When he was arrested, investigators found $275,000 in cash distributed across several safety deposit boxes in Las Vegas and Los Angeles. They also seized Bitcoin and other assets valued at roughly $5 million.
Tverdokhlebov pleaded guilty to wire fraud in late March and he has now been sentenced to 110 months in prison and three years of supervised release, which includes the monitoring of his computer use.
Several Russian nationals have been charged or convicted recently for cybercrimes in the United States. Yevgeniy Aleksandrovich Nikulin has been charged for hacking into the systems of LinkedIn, Dropbox and Formspring and will be extradited from the Czech Republic, two Russian Federal Security Service (FSB) officers have been indicted over the 2014 Yahoo hack, and the author of the Citadel malware recently pleaded guilty.
A lengthy prison sentence was given recently to 32-year-old Roman Valeryevich Seleznev, convicted on 38 counts in relation to a point-of-sale (PoS) hacking scheme.
Cloud Foundry has disclosed a privilege escalation flaw in User Account and Authentication software
11.7.2017 securityaffairs Hacking
The Open source devops platform Cloud Foundry fixed a bug that affects its User Account and Authentication server software.
The Open source devops platform Cloud Foundry has disclosed a vulnerability, tracked as CVE-2017-8032, that affects its User Account and Authentication server software. The flaw, rated by the organization as high-severity, could be exploited by zone administrators to escalate their privileges when mapping permissions for an external provider.
The User Account and Authentication is the Cloud Foundry ID management service that implements the OAuth2 authentication protocol.

CVE-2017-8032 was patched in an update last week, and the detailed advisory landed June 12 here.
“In Cloud Foundry cf-release versions prior to v264; UAA release all versions of UAA v2.x.x, 3.6.x versions prior to v3.6.13, 3.9.x versions prior to v3.9.15, 3.20.x versions prior to v3.20.0, and other versions prior to v4.4.0; and UAA bosh release (uaa-release) 13.x versions prior to v13.17, 24.x versions prior to v24.12. 30.x versions prior to 30.5, and other versions prior to v41, zone administrators are allowed to escalate their privileges when mapping permissions for an external provider.” reads the description published by the Mitre.
The vulnerability affects the following versions of UAA and cf-release versions prior to v264:
UAA release:
All versions of UAA v2.x.x
3.6.x versions prior to v3.6.13
3.9.x versions prior to v3.9.15
3.20.x versions prior to v3.20.0
Other versions prior to v4.4.0
UAA bosh release (uaa-release):
13.x versions prior to v13.17
24.x versions prior to v24.12
30.x versions prior to 30.5
Other versions prior to v41
The Cloud Foundry security advisory highlights that a foundation is vulnerable only if all of the following conditions are satisfied:
You are using multiple zones in UAA
You are giving out admin privileges for managing external providers (LDAP/SAML/OIDC) and corresponding group mappings
You have enabled LDAP/SAML/OIDC providers and external group mappings
Cloud Foundry suggests making one of these conditions false to mitigate the threat.
Revising any of these settings serves as a mitigation ahead of implementing a patch, Cloud Foundry says.
The advisory includes the link to upgrade both Cloud Foundry users to version 264 or later and standalone UAA users that have to install the 3.x.x series.
Google Silently Adds 'Panic Detection Mode" to Android 7.1 – How It's Useful
11.7.2017 thehackernews Android
How often do you click the 'back' or the ‘Home’ button on your mobile device to exit an application immediately?
I believe, several times in a single day because a large number of apps do not have an exit button to directly force-close them instead of going back and back and back until they exit.
Sometimes Android users expect the back button to take them back to the back page, but sometimes they really want to exit the app immediately.
Often this has severe usability implications when a majority of users are already dealing with their low-performance mobile devices and believe that clicking back button multiple times would kill the app and save memory, but it doesn't.
Google has now addressed this issue and silently included a feature within Android 7.1 Nougat that allows users to exit from apps by pressing the 'back' key successively within 0.3 seconds for over four times.
Dubbed "Panic Detection Mode," the feature runs in the background of Android operating system and detects panic in situations when a user repeatedly presses the back button on their smartphone to exit an app and allows the operating system to override the application and send the user safely back to the home screen.
While Google did not publicly make any announcement about the panic detection mode feature, XDA Developers yesterday unearthed the feature within the source code of Android 7.1 Nougat.
Since then a number of media outlets described Android 7.1 Nougat Panic Detection Mode as a security feature that protects Android devices from malicious applications.
It has been reported as a new security feature that looks for the number of times a user presses the back button within a certain amount of time and allows users to exit from the apps that go rogue and try to take control of user's device.
But the feature seems to be developed by Google engineers keeping usability as a priority, instead of security in mind.
Because activating panic detection mode neither automatically detects a malicious app and report back to Google, nor it behaves differently for a legitimate app.
However, it can help Android users in some cases to kill rogue app instantly; but again it’s up to users if they are able to identify malicious apps themselves and want to remove them manually.
So, this feature is also useful if a malicious application takes control over the display and prevents you from backing out of it.
The 'panic detection mode' feature is currently limited to the devices running Android 7.1 Nougat, and not available for all the Android users, XDA Developers pointed out. The feature also needs to be manually enabled by the user.
Google fights enough to keep its Android operating system safe and secure, but malware and viruses still make their ways into its platform, especially through malicious apps even on Google's own Play Store.
It appears that Google also has plans for wider implementation of the 'panic detection mode' feature in the upcoming version of its Android OS and would most likely make it enabled by default in the future releases.
Adwind RAT Returns! Cross-Platform Malware Targeting Aerospace Industries
11.7.2017 thehackernews Virus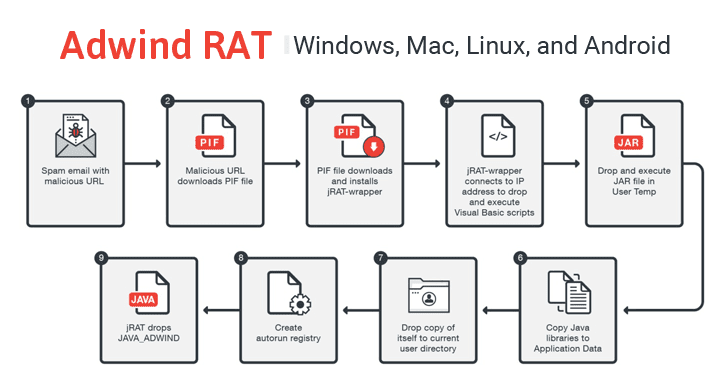
Hackers and cyber criminals are becoming dramatically more adept, innovative, and stealthy with each passing day.
While other operating systems are more widely in use, cybercriminals have now shifted from traditional activities to more clandestine techniques that come with limitless attack vectors, support for cross platforms and low detection rates.
Security researchers have discovered that infamous Adwind, a popular cross-platform Remote Access Trojan written in Java, has re-emerged and currently being used to "target enterprises in the aerospace industry, with Switzerland, Austria, Ukraine, and the US the most affected countries."
Adwind — also known as AlienSpy, Frutas, jFrutas, Unrecom, Sockrat, JSocket, and jRat — has been in development since 2013 and is capable of infecting all the major operating systems, including Windows, Mac, Linux, and Android.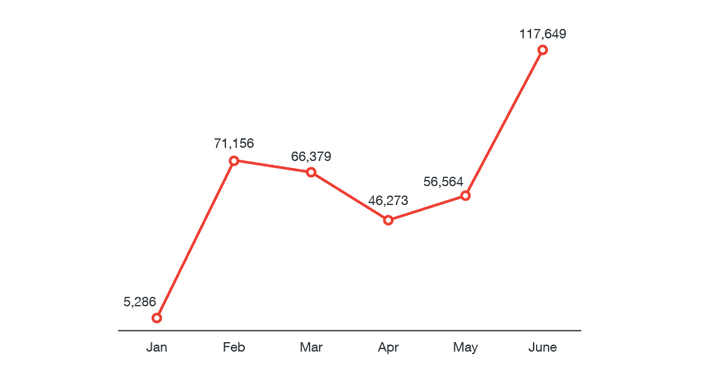
Adwind has several malicious capabilities including stealing credentials, keylogging, taking pictures or screenshots, data gathering and exfiltrate data. The trojan can even turn infected machines into botnets to abuse them for destructing online services by carrying out DDoS attacks.
Researchers from Trend Micro recently noticed a sudden rise in the number of Adwind infections during June 2017 — at least 117,649 instances in the wild, which is 107 percent more than the previous month.
According to a blog post published today, the malicious campaign was noticed on two different occasions.
First was observed on June 7 and used a link to divert victims to their .NET-written malware equipped with spyware capabilities, while the second wave was noticed on June 14 and used different domains hosting their malware and command-and-control servers.
Both waves eventually employed a similar social engineering tactic to trick victims into clicking the malicious links within a spam email that impersonate the chair of the Mediterranean Yacht Broker Association (MYBA) Charter Committee.
Once infected, the malware also collects system's fingerprints, along with the list of installed antivirus and firewall applications.
"It can also perform reflection, a dynamic code generation in Java. The latter is a particularly useful feature in Java that enables developers/programmers to dynamically inspect, call, and instantiate attributes and classes at runtime. In cybercriminal hands, it can be abused to evade static analysis from traditional antivirus (AV) solutions," the researchers wrote.
My advice for users to remain protected from such malware is always to be suspicious of uninvited documents sent over an email and never click on links inside those documents unless verifying the source.
Additionally, keep your systems and antivirus products up-to-date in order to protect against any latest threat.
Virus infikoval milióny zařízení. Hackerům vydělal velké peníze
11.7.2017 Novinky/Bezpečnost Viry
Na pořádný balík peněz si přišli v uplynulých dvou měsících neznámí počítačoví piráti, kterým se podařilo infikovat více než 14 miliónů mobilů a tabletů s operačním systémem Android. Vydělávali především na zobrazování nevyžádané reklamy. Upozornila na to bezpečnostní společnost Check Point.
Nově objevený nezvaný návštěvník se jmenuje CopyCat a jde o poměrně sofistikovaný škodlivý kód, který dokáže v napadeném zařízení udělat pěknou neplechu.
Může například rootovat operační systém, což jinými slovy znamená, že do něj počítačoví piráti mohou snadno propašovat libovolný další škodlivý kód nebo nad přístrojem převzít kontrolu na dálku. Útočníci nicméně CopyCat využívali jinak.
Vydělávali na reklamě
Na infikovaných tabletech a chytrých telefonech zobrazovali nevyžádanou reklamu. Z ní pak inkasovali veškeré svoje zisky, které rozhodně nebyly malé. Podle bezpečnostních expertů si touto cestou vydělali přibližně 1,5 miliónu dolarů, tedy v přepočtu více než 34 miliónů korun.
Většina uživatelů totiž reklamu nepovažovala za škodlivou, a jednoduše ji zavřela. Oběti útoku tak nevědomky vydělávaly kyberzločincům velké peníze.
Za napadení mobilu nebo tabletu si nicméně většinou mohli uživatelé sami. CopyCat se totiž šířil výhradně přes neoficiální kanály, nikoliv přes originální obchod s aplikacemi Google Play. To jinými slovy znamená, že do přístrojů si záškodníka stáhli lidé sami, pokud instalovali aplikace z neznámých zdrojů, například nejrůznějších podvodných stránek.
Útok se nevyhnul ani Evropě
Nově objevená hrozba útočila nejčastěji v Asii, například v USA ale bylo napadeno více než 280 tisíc mobilních zařízení. CopyCat se objevil také v Evropě, zda se útočníkům podařilo napadnout zařízení některých tuzemských uživatelů, však v tuto chvíli není jasné.
I tento virus opět ukazuje, že mobilní zařízení mohou být stejně zranitelná jako klasické počítače. Při používání smartphonů a tabletů by tak měli být uživatelé stejně obezřetní. Samozřejmostí by měl být například nainstalovaný antivirový program.
Google will ban WoSign and StartCom certificates from Chrome 61
11.7.2017 securityaffairs Security
Google is going to completely ban digital certificates issued by the Chinese CA WoSign, and its subsidiary StartCom starting with Chrome 61.
Recently Google warned website owners that it will completely ban digital certificates issued by the Chinese certificate authority WoSign and its subsidiary StartCom. The Tech giant will no longer trust the WoSign certificates starting with Chrome 61.
In September 2016, Mozilla announced that it was planning to ban the Chinese certificate authority WoSign due to a number of violations, including backdating SHA -1 certificates in order to subvert deprecating certs from being trusted.
According to a report published by Mozilla, WoSign failed to report its acquisition of SmartCom and it was also accused of mis-issuing digital certificates for GitHub, allowing arbitrary domain names to be securely signed without ever performing any type of validation.
Mozilla, Apple and Google took the final decision of revoking trust in certificates from WoSign and StartCom due to more than a dozen incidents and issues since January 2015.
In January 2017 Google released Chrome 56 which no longer accepted certificates issued by WoSign or StartCom after October 21, 2016.
Initially, Google has been restricting trust to popular hostnames based on the Alexa Top 1 Million list in order to avoid problems to website owners.
Starting with Chrome 61 it will no longer trust the certificates issued by the Chinese CA, even for the above Alexa Top 1 Million websites.
“As previously announced, Chrome has been in the process of removing trust from certificates issued by the CA WoSign and its subsidiary StartCom, as a result of several incidents not in keeping with the high standards expected of CAs.” states Devon O’Brien of the Chrome Security Team.
“We started the phase out in Chrome 56 by only trusting certificates issued prior to October 21st 2016, and subsequently restricted trust to a set of whitelisted hostnames based on the Alexa Top 1M. We have been reducing the size of the whitelist over the course of several Chrome releases.”
Chrome 61 will reach the Beta channel in late July 20, and the Stable channel in mid-September.
“Beginning with Chrome 61, the whitelist will be removed, resulting in full distrust of the existing WoSign and StartCom root certificates and all certificates they have issued.” continues Devon O’Brien.
Google has not specified if its decision to ban WoSign and StartCom certificates is temporary or permanent. Apple and Mozilla adopted a different approach, both decided to ban the companies for at least one year.
The Chinese CA certificate authority took serious action in hopes of obtaining forgiveness from web browser vendors, it changed leadership and announced the complete separation of WoSign from StartCom.
OSX DoK Malware linked to Operation Emmental used to target Swiss Banks again
11.7.2017 securityaffairs Apple
Crooks behind the Operation Emmental hacking campaign have started targeting the Swiss banks using a variant of the DoK Mac OS X malware.
In July 2014, malware researchers at Trend Micro published a report on the hacking campaign “Operation Emmental” that was targeting Swiss bank accounts whit a multi-faceted attack that allowed crooks to bypass two factor authentication implemented by the financial organization to protect its customers.
According to the experts, the Operation Emmental has been around since at least 2012.
The experts dubbed the campaign “Operation Emmental” because of the numerous holes in the security implemented by the Swiss banks, exactly like the popular Swiss Emmental cheese.
The hackers used a malware which was able to intercept SMS tokens used to authorize operations and change domain name system settings to hijack victims to rogue bank websites, which were a replica of legitimate ones, used for phishing attacks.
The threat actors targeted bank customers’ accounts in different countries, including in Switzerland, Austria, Japan and Sweden. Investigators suspected that Russian-speaking individuals were responsible for the Operation Emmental due clues discovered in the source code analyzed.
The hackers behind the Operation Emmental have continued to improve their malicious codes. The hackers used on Android malware and a Windows banking Trojan tracked as Retefe and WERDLOD.
The novelty in the operation of the group is represented by the usage of a new variant of the Dok malware in a new wave of attacks against the Swiss banks.
The malicious code is delivered via email, once the DOK malware infects a macOS system, it gains administrative privileges and installs a new root certificate. The root certificate allows the malicious code to intercept all victim’s communications, including SSL encrypted traffic.
According to researchers at Trend Micro, the malware variant tracked as OSX_DOK.C is configured to hijack traffic only if the victim’s external IP is located in Switzerland. OSX_DOK.C redirects users to bogus login pages for the financial organizations whose domain is included in a hardcoded list.
“The OSX_DOK malware (Detected by Trend Micro as OSX_DOK. C) showcases sophisticated features such as certificate abuse and security software evasion that affects machines using Apple’s OSX operating system.” reads the analysis published by Trend Micro.
The Dok sample detected by Trend Micro was considered by the malware researchers the Mac version of Retefe/WERDLOD.
“While WERDLOD and OSX_DOK.C use different codes (since they target different operating systems), they have similar proxy settings and script formats.”
“Comparing it to OSX_DOK.C, we can see that it uses the same script format” Trend Micro researchers said in a blog post.
“Given the connection between WERDLOD and OSX_DOK.C, it is reasonable to assume that the latter is also a part of the Operational Emmental campaign,”

The researchers observed that the latest versions of the Dok malware leverage a bug in the Ultimate Packer for Executables (UPX) tool to pack the Trojan and avoid detection.
Google to Completely Ban WoSign, StartCom Certificates in Chrome 61
10.7.2017 securityweek Security
Google last week warned website owners that digital certificates from Chinese certificate authority WoSign and its subsidiary StartCom will no longer be trusted starting with Chrome 61.
Mozilla, Apple and Google last year decided to revoke trust in certificates from WoSign and StartCom as a result of more than a dozen incidents and issues brought to the attention of the web browser community since January 2015.
Problems include backdating certificates to bypass restrictions, issuing certificates without authorization, and misleading browser vendors about WoSign's acquisition of StartCom and their relationship.
Google started taking action against the firms in late January 2017, with the release of Chrome 56, which no longer accepted certificates issued by WoSign or StartCom after October 21, 2016.
In order to minimize impact on website owners, Google has been restricting trust to popular hostnames based on the Alexa Top 1 Million list. This whitelist has been gradually reduced and starting with Chrome 61 it will be removed completely. Chrome 61 will reach the Developer channel in the coming weeks, the Beta channel in late July 20, and the Stable channel in mid-September.
“Sites still using StartCom or WoSign-issued certificates should consider replacing these certificates as a matter of urgency to minimize disruption for Chrome users,” warned Devon O’Brien of the Chrome Security Team.
Apple and Mozilla have decided to ban WoSign and StartCom for at least one year, but Google has not specified for how long it plans on distrusting certificates from these companies.
The certificate authorities had several meetings with browser vendors, changed leadership and promised to completely separate WoSign from StartCom, but they did not convince Apple, Google and Mozilla. Apple was the first to announce plans to revoke trust in their certificates, followed by Mozilla, which justified its decision by arguing that the firms were deceptive.
Alarming Percentage of Employees Hide Security Incidents: Report
10.7.2017 securityweek Incindent
Policy and Engagement Are Key to Addressing Insider Threats
The human factor, also often known as the insider threat, has long been known but rarely quantified. Kaspersky Lab has attempted to do just that -- to answer the question, 'What role do employees play in a business's fight against cybercrime?'
Kaspersky used the B2B International market research company to query 5,000 businesses around the globe; and the results are alarming. "Fifty-two percent of businesses admit that employees are their biggest weakness in IT security, with their careless actions putting business IT security strategy at risk," explains the Kaspersky report.
The extent of the issue is illustrated by the top three vulnerability concerns all being related to the human factor or employee behavior: inappropriate sharing (47%); data on lost mobile devices (46%); and inappropriate use of IT resources (44%). The supply chain, increasingly used by advanced hackers as an entry point, figures fourth at 43%.
This concern is verified by actual cybersecurity incidents. "Among the businesses that faced cybersecurity incidents in the past 12 months, one-in-ten (11%) [of] the most serious types of incidents involved careless employees," states the report. This is second only to incidents involving malware, standing at 23%.
Even here, however, the human factor is important. Forty-nine percent of businesses reported being attacked by malware this year (an increase of 11% over last year). The top contributing factors behind the reported incidents are all human factors: careless/uninformed employees (53%); accidental loss of hardware (38%); and phishing/social engineering (36%).
The more dangerous targeted attacks are also increasing, with 27% of businesses reporting incidents (up 6% on the previous year). "Of these attacked businesses, over a quarter (28%) believe phishing/ social engineering contributed to the attack," notes the report.
Here Kaspersky makes an additional point: it isn't enough to simply increase social engineering and phishing awareness, it is also important to create an environment in which employees are willing to own up to errors. Kaspersky calls this the 'hide and seek' problem: employees sometimes hide their mistake leaving the business to seek the source of the problem.
"Employees," the report explains, "don't always take action when their company is hit by a security incident. In fact, in 40% of businesses around the world, employees hide an incident when it happens." This tendency varies by size of company: as low as 29% of very small businesses; at 42% of SMBs; and as high as 45% of enterprises with more than 1,000 employees.
Kaspersky warns against a big stick approach to this problem. "If employees are hiding incidents, there must be a reason why. In some cases, companies introduce strict, but unclear rules and impose extra responsibility on employees, warning them not to do this or that, or they will be held responsible if something goes wrong. Such policies only foster fears, and leave employees with just one option — to avoid punishment whatever it takes."
BYOD is another area where the human factor continues to cause concern. "Almost half (48%) of businesses overall," says Kaspersky, "are worried about employees inappropriately sharing company data via the mobile devices that they bring to work." This is a particular concern for small businesses, where it rises to 57%. The concern is justified in practice: according to the research, more than half (54%) of businesses have had data exposed because employees have lost devices.
Kaspersky warns that policy alone is not enough to defend against the human factor. "A policy, alone, will not protect a business from threats -- partly because IT security policies are not always followed by the staff that they are designed for, and partly because they cannot cover every possible risk." In fact, 44% of respondents admitted that employees simply do not properly follow policy.
Kaspersky's solution is to find the right balance of policy and engagement: policy to define correct behavior; and engagement to make employees want to follow policy. "Staff training is essential in raising awareness among personnel and motivating them to pay attention to cyberthreats and countermeasures -- even if they are not part of their specific job responsibilities. Installing updates, ensuring that anti-malware protection is on, and managing personal passwords properly shouldn't always be at the bottom of an employee's to-do list."
US Food Payment Kiosk Vendor Avanti Markets Hacked, Biometric data stolen
10.7.2017 securityaffairs Incindent
US payment kiosk vendor Avanti Markets that installs its self-service payment devices in corporate breakrooms across America suffered a security breach.
The US payment kiosk vendor Avanti Markets that installs its self-service payment devices in thousands of corporate breakrooms across America suffered a security breach.
According to the popular investigator Brian Krebs who first reported the news, the systems of the company were infected by a malware that stole customer data including names, e-mail addresses, credit card accounts as well as biometric data.
“Avanti Markets, a company whose self-service payment kiosks sit beside shelves of snacks and drinks in thousands of corporate breakrooms across America, has suffered of breach of its internal networks in which hackers were able to push malicious software out to those payment devices, the company has acknowledged.” wrote Brian Krebs.”The breach may have jeopardized customer credit card accounts as well as biometric data, Avanti warned.”
The company admitted the breach and it is informing people that their data were exposed.
“On July 4, 2017, we discovered a sophisticated malware attack which affected kiosks at some Avanti Markets. Based on our investigation thus far, and although we have not yet confirmed the root cause of the intrusion, it appears the attackers utilized the malware to gain unauthorized access to customer personal information from some kiosks.” states the data breach notification issued by the Avanti Markets. “Because not all of our kiosks are configured or used the same way, personal information on some kiosks may have been adversely affected, while other kiosks may not have been affected.”
Biometric data that were allegedly stolen by hackers are fingerprints, used by the company to allow users to make rapid payments.
Avanti Markets already notified law enforcement the security breach and launched an internal investigation. In response to the security breach, the company cleaned the affected machines, changed its passwords, blocked payment processing at affected locations.
Avanti Markets will offer affected individuals free credit monitoring and a call centre helpline.
“Another source told this author that Avanti’s corporate network had been breached, and that Avanti had made the decision to turn off all self-checkouts for now — although the source said customers could still use cash at the machines.” continues Krebs.
According to a Krebs’s source that has spoken under a condition of anonymity, the company did not adopt basic security measures to project data, such as the P2Pe encryption.
“I was told that about half of the self-checkouts do not have P2Pe,” the source said, on condition of anonymity. P2Pe or “point-to-point encryption,” and it’s a technology that encrypts sensitive data such as credit card information at every point in the card transaction.
“In theory, P2Pe should be able to protect card data even if there is malicious software resident on the device or network in question.”
The analysis conducted by Risk Analytics revealed that cyber criminals used the PoSeidon malware, a memory scraper malware that is able to steal data directly from the memory of the PoS systems. According to the experts, the PoS malware was used by Russian cybercriminals to target payment systems worldwide.

Cisco Security Team spotted for the first time the malware in March 2015, the experts defined it as the most sophisticated PoS malware at the time of the discovery.
Experts at Risk Analytics believes the threat actor has been active since 2015, they observed that the traffic they identified matched Cisco’s 2015 analysis of PoSeidon and uses the same SSL certificate spotted by Cisco experts in past investigation.
Reliance Jio systems allegedly hacked. It should be the biggest breach of personal data ever in India
10.7.2017 securityaffairs Hacking
Data allegedly stolen from the Reliance Jio systems were available online, It should be the biggest breach of personal data ever in India.
The week starts with the news of another clamorous data breach, personal details of some 120 Million customers of the Indian company Reliance Jio were exposed. If it will be confirmed, the incident is the biggest breach of personal data ever in India.
Reliance Jio Infocomm Limited, or Reliance Jio, is an LTE mobile network operator in India. “It is a wholly owned subsidiary of Reliance Industries that provides wireless 4G LTE service network (without 2G/3G based services) and is the only ‘VoLTE-only’ (Voice over LTE) operator in the country which lacks legacy network support of 2G and 3G, with coverage across all 22 telecom circles in India.“
According to the telecom regulator’s website, Reliance Jio had over 112 million users as of April end,
A few hours ago, a website named Magicapk.com went online, offering Reliance Jio customers to search for their identification data by typing in their Reliance Jio number.

The website was hosted by the web hosting company GoDaddy.com and was registered in May 2017, but there is no data related to the owner.
The website is no more accessible, but many customers confirmed that data was authentic. Stolen data includes names, email addresses, mobile numbers, circle-Id, SIM activation date and time, and for some users the Aadhaar numbers.
Reliance Jio released a statement to deny the data beach and saying the leaked data appears to be “inauthentic.”
“We have come across the unverified and unsubstantiated claims of the website and are investigating it. Prima facie, the data appears to be unauthentic. We want to assure our subscribers that their data is safe and maintained with highest security,” a Jio spokesperson said. “We want to assure our subscribers that their data is safe and maintained with highest security. Data is only shared with authorities as per their requirement.”
The company has “informed law enforcement agencies about the claims of the website and will follow through to ensure strict action is taken.”
The colleagues at the Hacker News verified the leaked data for a few Jio numbers. Data is accurate only for some Jio numbers, but not for all.
“Therefore, the data on the website seems to be authentic, but luckily some customers are spared–probably those who have been issued Jio SIM after the breach.” states the blog post on THN.
“Mobile numbers for other telecom operators in India, such as Vodafone and Airtel, did not work on the website.”
It is still unclear if hackers breached the Reliance Jio systems or if they obtained the data from some third-party marketing company with whom the company shared its customer’s records.
All Reliance Jio customers should be alert for phishing messages or unrequested calls asking for further details about their accounts.
What is the hype around Firewall as a Service?
10.7.2017 thehackernews Safety
Admit it. Who would not want their firewall maintenance grunt work to go away?
For more than 20 years, companies either managed their edge firewall appliances or had service providers rack-and-stack appliances in their data centers and did it for them.
This was called a managed firewall — an appliance wrapped with a managed service, often from a carrier or managed security service provider (MSSP).
The provider assumed the management of the firewall box, its software, and even its policy and management from the over-burdened IT team. But customers ended up paying for the inefficiency of dealing with appliances (i.e. “grunt work”) because the problem just shifted to the provider. A new architecture was needed - a transformation from an appliance form factor to a true cloud service.
In a 2016 Hype Cycle for Infrastructure Protection report, Gartner analyst Jeremy D'Hoinne initiated the emerging category of Firewall as a Service (FWaaS).
He defined FWaaS as “...a firewall delivered as a cloud-based service or hybrid solution (that is, cloud plus on-premises appliances). The promise of FWaaS is to provide simpler and more flexible architecture by leveraging centralized policy management, multiple enterprise firewall features and traffic tunneling to partially or fully move security inspections to a cloud infrastructure”
Recently, in the 2017 Magic Quadrant for Unified Threat Management (SMB Multifunction Firewalls), the analysts reference a Gartner client survey indicating 14% of respondents were likely (8%) or very likely (6%) to consider moving all the firewall security functions to FWaaS.
FWaaS isn't merely packaging of legacy appliances into a managed service. It is challenging the decades-old concept of the appliance as the primary form factor to deliver network security capabilities.
What is an FWaaS?
FWaaS offers a single logical firewall that is available anywhere, seamlessly scales to address any traffic workload, enforces unified policy, and self-maintained by a cloud provider.
Let’s look at these elements in more detail.
• Single, global firewall instance — One firewall instance for the entire global organization is radically different than the current architecture that places a network security stack at each location, a regional hub or a datacenter.
With FWaaS every organizational resource (data center, branch, cloud infrastructure or a mobile user) plugs into the FWaaS global service and leverages all of its security capabilities (application control, URL filtering, IPS, etc).
• Seamlessly scales to address inspection workload — FWaaS provides the necessary compute resources to perform all security processing on all traffic regardless of source or destination.
IT teams no longer need complex sizing processes to determine the appliance capacity needed to plan for today’s business requirements and future growth.
For example, the increase in SSL traffic volume pressures appliance processing capacity and can force unplanned. FWaaS can scale to accommodate these needs without disrupting the customer’s business operations.
• Enforcing a unified policy — A single firewall, by design, has a single security policy. While legacy appliance vendors created centralized management consoles to ease managing distributed appliances, IT must still consider the individual firewalls instances per location and often customize policies to the locations’ unique attributes.
In heterogenous firewall environments (often created due to M&A) security policy is hard to configure and enforce increasing exposure to hackers and web-borne threats. Contrast that with a single cloud-based firewall that uniformly applies the security policy on all traffic, for all locations and users.
• Self-maintained — One of the most painful aspects of firewall management is maintaining the software through patches and upgrades. It is a risky process that could impact business connectivity and security.
Many IT teams tend to skip or completely avoid software upgrades, leaving enterprise exposed. Because the cloud-based firewall software is maintained by the FWaaS provider and is shared by all customers, the firewall is kept up to date by quickly fixing vulnerabilities and bugs, and rapidly evolving with new features and capabilities that the customers can immediately access.
FWaaS is bringing genuine relief to overburdened IT teams within enterprises and service providers. Instead of wasting cycles on sizing, deploying, patching, upgrading and configuring numerous edge devices, work can now shift to delivering true security value to the business through early detection and fast mitigation of true risk.
FWaaS Providers
FWaaS is not a mere concept. It has been deployed in production deployments and by several vendors.
Cato Networks is a provider of the Cato Cloud, built from the ground up to deliver Firewall as a Service.
Cato provides an optimized, global SD-WAN, ensuring resilient connectivity to its FWaaS in from all regions of the world. Cato can completely eliminate edge firewalls by inspecting both WAN and Internet-bound traffic. The Cato Cloud FWaaS further extends to mobile users and cloud datacenters.
Zscaler provides FWaaS for Internet-bound traffic from remote branches and mobile users. To secure WAN traffic, customers must rely on other means.
Palo Alto Networks recently announced a similar service. It uses its next generation firewall within a cloud service to protect users, whether in remote locations or mobile, accessing the Internet.
FWaaS is a viable alternative for IT teams that waste time and money to sustain their distributed edge firewall environments — the so-called appliance sprawl.
With FWaaS, they can now reduce the operational and capital expense of upgrading and refreshing appliances as well as the attack surface resulting from delayed patches and unmitigated vulnerabilities.
By simplifying the network security architecture, FWaaS makes IT more productive and the business secure.
Reliance Jio Customers' Data Allegedly Hacked – Company Denies Breach
10.7.2017 thehackernews Hacking
Personal details of some 120 Million customers have been allegedly exposed on the Internet in probably the biggest breach of personal data ever in India.
Last night, an independent website named Magicapk.com went online, offering Reliance Jio customers to search for their identification data (Know Your Customer or KYC) just by typing in their Jio number.
Reliance set up the Jio 4G network across the length and breadth of India in September last year and gained more than 50 million subscribers within a span of just 83 days. The company gave seven months of free internet, unlimited calls, unlimited music to its subscribers.
Although the website that claimed to have hacked into Jio database is no longer accessible, many users confirmed their personal data showed up on the website, displaying their names, email addresses and most alarmingly, in some cases, Aadhaar numbers.
Aadhaar is a 12-digit unique identification number issued by the Indian government to every resident of India. This number is also used for enrolling for a SIM.
Company Denies Data Breach Before Investigation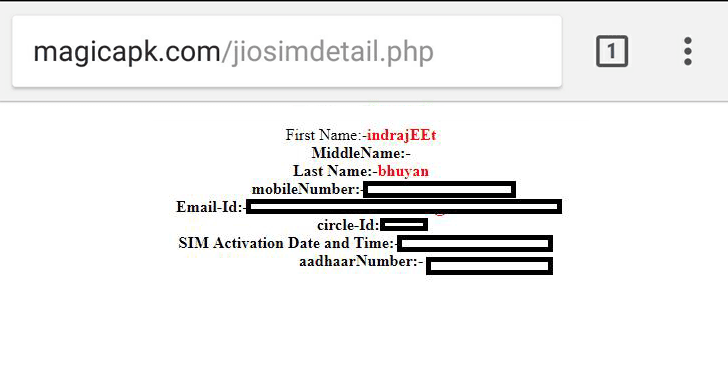
In response to the breach, Reliance Jio released a statement, saying that the claims are unverified and that the leaked data appears to be "unauthentic."
"We have come across the unverified and unsubstantiated claims of the website and are investigating it. Prima facie, the data appears to be unauthentic," a spokesperson said.
"We want to assure our subscribers that their data is safe and maintained with highest security. Data is only shared with authorities as per their requirement."
The Jio spokesperson said the company has "informed law enforcement agencies about the claims of the website and will follow through to ensure strict action is taken."
Breach Appears to be Authentic! But Doesn't Affect All JIO Users
The Hacker News independently verified the leak for a few Jio numbers, and the data came out to be accurate for some Jio numbers, but not for all.
Therefore, the data on the website seems to be authentic, but luckily some customers are spared--probably those who have been issued Jio SIM after the breach.
For obvious reasons, we are not naming the customers we tested on the website and found their identity leaked just by typing their mobile number. The leaked information includes:
First Name
Middle Name
Last Name
Mobile Number
Email-Id
Circle-Id
SIM Activation Date and Time
Aadhaar Number, in some cases
Mobile numbers for other telecom operators in India, such as Vodafone and Airtel, did not work on the website.
Hackers Identity is Unknown Yet
The website was hosted by the web hosting company GoDaddy.com and was registered in May 2017, but so far it is not clear who owned the domain.
Also, it is not clear at this moment that how the hackers got access to sensitive data of Jio customers and was it Jio who got hacked or some third-party marketing company with whom the company shared its customer's data.
Though there is very little victims (especially those who have exposed their Aadhaar number) can do to protect themselves from future attacks. Hackers holding their Aadhaar number can disguise their identities to carry out several frauds.
All Jio customers are highly recommended to be vigilant to unrequested calls asking for their further details or account passwords. No company asks for these details over phone calls or emails.
Victims should also particularly be alert of the Phishing emails, which are usually the next step of cyber criminals after a large-scale hack at any telecoms company. Phishing tricks users into giving up further personal details like passwords.
Satellite Phone Encryption Calls Can be Cracked in Fractions of a Second
10.7.2017 thehackernews Mobil
Security researchers have discovered a new method to decrypt satellite phone communications encrypted with the GMR-2 cipher in "real time" -- that too in mere fractions of a second in some cases.
The new attack method has been discovered by two Chinese security researchers and is based on previous research by German academicians in 2012, showing that the phone's encryption can be cracked so quickly that attackers can listen in on calls in real time.
The research, disclosed in a paper published last week by the security researchers in the International Association for Cryptologic Research, focused on the GMR-2 encryption algorithm that is commonly being used in most modern satellite phones, including British satellite telecom Inmarsat, to encrypt voice calls in order to prevent eavesdropping.
Unlike previous 2012 research by German researchers who tried to recover the encryption key with the help of 'plaintext' attacks, the Chinese researchers attempted to "reverse the encryption procedure to deduce the encryption-key from the output keystream directly."
The attack method requires hitting a 3.3GHz satellite stream thousands of times with an inversion attack, which eventually produces the 64-bit encryption key and makes it easier to hunt for the decryption key, allowing attackers to decrypt communications and listen in to a conversation.
"This indicates that the inversion attack is very efficient and practical which could lead to a real time crack on the GMR-2 cipher," the research paper reads. "The experimental results on a 3.3GHz platform demonstrate that the 64-bit encryption-key can be completely retrieved in around 0.02s."
According to the duo, the attack can eventually crack the satellite phone call encryption in a fraction of a second when carried out successfully, allowing the attacker to break into the communications in real time for live eavesdropping.
The new findings spark concerns surrounding the security of satellite phones, which are mostly used by field officers in war zones that protect our land, air, and water, as well as people in remote area precisely because of no other alternatives.
Such attacks could pose a significant threat to satellite phone users' privacy.
"Given that the confidentiality is a very crucial aspect in satellite communications, the encryption algorithms in the satellite phones should be strong enough to withstand various eavesdropping risks," researchers said.
"This again demonstrates that there exists serious security flaws in the GMR-2 cipher, and it is crucial for service providers to upgrade the cryptographic modules of the system in order to provide confidential communication," researchers concluded.
The research was carried out by Jiao Hu, Ruilin Li and Chaojing Tang of National University of Defense Technology, Changsha, China. For more details, you can head on to their research paper [PDF], titled "A Real-time Inversion Attack on the GMR-2 Cipher Used in the Satellite Phones."
Researchers Decrypt Satellite Phone Communication in Real-Time
10.7.2017 securityweek Mobil
A group of security researchers detailed a real-time inversion attack against the GMR-2 stream cipher used in satellite phone communication, claiming it is much more efficient than previously devised attacks.
In a research paper (PDF), Jiao Hu, Ruilin Li, and Chaojing Tang from the School of Electronic Science and Engineering at the National University of Defense Technology in China, explain that the real-time inversion attack uses one frame keystream and contains three phrases.
One of the two widely deployed variants of GMR (GEO-Mobile Radio Interface), the GMR-2 cipher has been found vulnerable to two types of plaintext attacks. A read-collision technique was presented in 2012, when the details of the satellite cipher algorithms were made public, and a dynamic guess-and-determine attack was devised in 2013.
“In this paper, we study the inverse properties of the GMR-2 cipher to show a bad one-way character of such cipher, then by introducing a new concept “valid key chain”, we propose what we call the inversion attack against the GMR-2 cipher. This attack can reduce the exhaustive search space from 264 to about 213 on average when one frame (15 bytes) keystream is available,” the researchers explain.
Because of this, the inversion attack is very efficient and practical, and could be used to perform real-time decryption on the GMR-2 cipher, the security researchers argue. When carried out on a 3.3GHz platform, the attack can completely retrieve the 64-bit encryption-key in around 0.02 seconds, the researchers say.
The technique contains three phases, namely table generation; dynamic table looks-up, filtration and combination; and verification. The attack can be used to “retrieve the complete 8-byte encryption-key from only 1 frame (15 bytes) of keystream on average.” It also significantly reduces the exhaustive search space, and requires only 6KB of extra storage space.
The security researchers reveal that, in 10,000 experiments, the newly devised technique was able to uniquely determine 97.2% of the encryption-keys by the 15 bytes of keystream. The remaining 2.8% of the keys needed an extra keystream byte to retrieve.
According to the paper, not only does the proposed inversion attack prove more efficient than the previously detailed dynamic guess-and-determine method and the read-collision based technique, but it also proves that serious security flaws exist in the GMR-2 cipher.
“Compared with previous known attacks, this inversion attack is much more efficient. It is crucial for service providers to upgrade the cryptographic modules of the system in order to provide confidential communication,” the researchers say.
Afghanistan Enacts Law to Control Cyberspace
10.7.2017 securityweek Cyber
Afghanistan's President Ashraf Ghani has signed into law a cybercrime bill targeting online crime and militancy by groups such as the Taliban and Islamic State, officials said Monday, amid concerns it could limit free speech.
The Cyber Crime Law criminalizes a range of online activities including hacking, spreading ethnic hatred, distribution of online defamatory speech, exposing government secrets, and cyber-terrorism within the provisions of the newly reviewed penal code.
"The law has 28 articles and it is going to control all cybercrimes. All criminals will be tracked and referred to courts," Najib Nangyal a spokesman for the ministry of communication told AFP.
While much of Afghanistan remains deeply rural, over 8.5 million Afghans are using the internet in big cities such as Kabul, Herat and Mazar-i-Sharif, most of them vocal on social media such as Twitter and Facebook.
The guerrilla war waged by militants and grisly video footage of war casualties, torture, hostage victims and destruction compete daily with celebrity gossip and the latest sports news in Afghan online communities.
The Taliban, who previously rejected all modern technology, have developed a media-savvy online PR team using Twitter, Facebook and the internet, posting statements, breaking news of the latest attacks and taking responsibility for assaults, though their claims are often wildly exaggerated.
Their efforts pale globally in comparison to the Islamic State group, which has actively exploited social media to lure thousands of foreign fighters to Syria and Iraq, and which is making gradual inroads in Afghanistan.
"We are trying to make a cyber police team to track the criminals. The government is also working to track, list and block all the militants' online accounts," Nangyal said.
However, media watchdog group Nai warned the law could have a detrimental effect on access to information in Afghanistan, which was ranked 120th out of 180 countries in the 2017 World Press Freedom Index compiled by Reporters Without Borders.
"After reviewing law we reached the conclusion that the law will limit the freedom of speech," Nai said in a statement which also criticized the wording of the legislation as "vague".
'Dok' Mac Malware Used to Target Swiss Banks
10.7.2017 securityweek Apple
The cybercriminals behind the campaign known as Operation Emmental have apparently started targeting the customers of Swiss banks using a variant of the Mac OS X malware tracked as Dok.
Operation Emmental has been around since at least 2012 and the individuals who run it – experts determined that they are likely Russian speakers – have continued to improve their malware. The group has been known to leverage Android malware, designed to bypass two-factor authentication (2FA) and lock victims out of their smartphones, and a Windows banking Trojan tracked as Retefe and WERDLOD.
However, researchers believe a variant of the Dok malware has also been used in Operation Emmental to target Swiss banks.
Dok, a piece of malware typically delivered via email, is designed to spy on victims by installing a new root certificate and modifying the infected device’s network settings in order to redirect traffic through Tor.
According to Trend Micro, in the Operation Emmental attacks, the malware is configured to hijack traffic only if the victim’s external IP is located in Switzerland. Tracked by the security firm as OSX_DOK.C, the Trojan redirects users to a fake online banking login page if they visit the website of a financial organization whose domain is specified in a hardcoded list.
An analysis by Trend Micro and others showed that Dok actually appears to be the Mac version of Retefe/WERDLOD. Experts pointed out that both pieces of malware kill the web browser process before installing fake certificates, they share proxy settings and script formats, and they target mostly the same Swiss banks.
“Given the connection between WERDLOD and OSX_DOK.C, it is reasonable to assume that the latter is also a part of the Operational Emmental campaign,” Trend Micro researchers said in a blog post.
The security firm also pointed out that more recent versions of the Dok malware leverage a bug in the Ultimate Packer for Executables (UPX) tool to pack the Trojan and make it more difficult for security products to detect the threat.
75 Percent of U.S. Companies Think GDPR Doesn't Apply to Them
10.7.2017 securityweek Privacy
A new report focusing on Europe's General Data Protection Regulation (GDPR) preparedness shows a worrying disconnect between Business and Security. GDPR will come into effect in May 2018, and perhaps more than any other security regulation will require close cooperation between Business, IT and Security to enable and ensure regulatory compliance across the whole organization. The penalty for failure is severe: up to €20 million or 4% of global turnover -- and the reach of the regulation is effectively global.
NTT Security interviewed 1,350 non-IT decision-makers across the globe. It sought to understand GDPR awareness across the business, and measure how well information security policies are being communicated across the business. The results (PDF), it suggests, are mixed. While there is some improvement in general security policies, there is poor understanding of security-related regulations in general, and GDPR in particular.
This lack of understanding starts from the very basics: only 4 in 10 respondents recognize that GDPR will affect their own organization. The reality is that it will affect any business anywhere in the world that trades with the European Union or has any customers that are citizens of the European Union.
General Data Protection Regulation (GDPR)
This lack of understanding is much higher in America where 75% of businesses do not believe that GDPR is relevant to them. This is similar to Australia (74%) and Hong Kong (71%).
The most promising figures, unsurprisingly, come from within Europe: Switzerland (42%), and Germany and Austria (53%). More surprising, however, is the lack of awareness in the UK, where 61% of respondents are unaware of the GDPR implications.
It's not clear why the UK has such a low level of awareness. It could be down to Brexit and a feeling that EU regulations will no longer apply in the UK -- but this would be a false assumption. The UK will still be a part of the EU when GDPR becomes part of UK law in May 2018; and even outside of Europe, UK companies -- like US companies -- will need to comply if they wish to trade in or with Europe. Or it could be a response to the traditional 'light touch' operated by the UK regulator (the Information Commissioners Office).
The general lack of awareness is more concerning for GDPR than most other security-related regulations because GDPR is not just about security and the prevention of breaches -- it's just as much about how personally identifiable data is handled. For example, a strict requirement is that without other arrangements (such as Privacy Shield) European data must not be exported from Europe. Similarly, it may not be exported to a third party without the user's express permission.
To meet these requirements, companies will need to know exactly where the data is held, and who has access to it. This is potentially problematic given the widespread use of cloud storage and the personal use of cloud apps. To combat this, it will be important for every employee to understand what can and cannot be done with the data, and where it can and cannot be stored. However, a third of all respondents don't even know where their company data is stored. Of the two-thirds who know where it is stored, only 45% are definitely aware of how the new regulations will affect the storage.
Incident response is a second area that will require careful planning. Any breach likely to result in a risk to the rights and freedoms of individuals has to be notified to the relevant EU regulator within 72 hours (although full disclosure can then be staggered). Where there is a 'high risk' to individuals, those affected must be notified directly. Failure in this part of GDPR can result in a penalty of up to €10 million, or 2% of global turnover.
To comply with disclosure requirements, companies need to have a detailed and thorough incident response plan in place; and for this to be effective, all aspects of the business (not just IT and Security) need to know exactly what must be done, and when it must be done.
Less than half (48%) of organizations have an incident response plan, although 31% are implementing one. However, a plan is only words if people do not understand it. Within the 48% of companies with an incident response plan, only 47% of the decision-maker respondents are fully aware of what that plan includes. This is particularly worrying since an effective plan can only be put in place with widespread involvement across the business.
"In an uncertain world," warns Garry Sidaway, an SVP at NTT Security, "there is one thing organizations can be sure of and that's the need to mark the date of 25 May 2018 in their calendars. While the GDPR is a European data protection initiative, the impact will be felt right across the world for anyone who collects or retains personally identifiable data from any individual in Europe. Our report clearly indicates that a significant number do not yet have it on their radar or are ignoring it. Unfortunately, many organizations see compliance as a costly exercise that delivers little or no value, however, without it, they could find themselves losing business as a result, or paying large regulatory fines."
The EU's recent fine of €2.42 billion ($2.73 billion) on Google suggests European regulators will not hesitate in levying large fines for serious and repeated GDPR transgressions.
Original Petya Master Decryption Key Released
10.7.2017 securityweek Ransomware
The master decryption key for last year’s Petya ransomware was made public last week and has since been confirmed to be genuine.
Petya ransomware first emerged in March 2016, distinguishing itself from similar malware by encrypting the Master Boot Record (MBR) instead of individual files. Soon after its initial appearance, Petya was paired with another ransomware, and the pair became available as a service a couple of months later.
The last known variant of the malware was spotted in December 2016 and was referred to as GoldenEye. Dubbed PetrWrap, a ransomware family observed in March this year was using Petya for its nefarious purposes, but wasn’t created by Janus Cybercrime Solutions, the name Petya’s author goes by.
NotPetya, the destructive wiper that hit numerous organizations in Ukraine and various other countries in late June, wasn’t the work of Janus either, but only borrowed code from Petya. In a tweet on June 28, Janus claimed no connection with NotPetya.
One week later, on July 5, the ransomware author posted a link to an encrypted and password protected file hosted on the mega.nz service. After opening the file, independent researcher and programmer Hasherezade found in it the master decryption key for all previous Petya variants.
Kaspersky security researcher Anton Ivanov has already confirmed that the key works for all Petya versions, including GoldenEye.
The release of the master decryption key is great news for those Petya victims who were unable to restore their files to date. Last year, security researchers managed to crack the first two versions of the ransomware, and the only variant not decrypted before was GoldenEye.
“Thanks to the currently published master key, all the people who have preserved the images of the disks encrypted by the relevant versions of Petya, may get a chance of getting their data back,” Hasherezade explains.
The newly released master key, however, won’t help users hit by NotPetya.
“This key cannot help in case of [NotPetya], since, in this particular case, the Salsa keys are not encrypted with Janus’ public key, but, instead of this, erased and lost forever. It can only help the people who were attacked by Petya/Goldeneye in the past,” Hasherezade notes.
Although the wiper’s alleged authors suggested last week they could provide decryption keys to help users with encrypted files, some researchers suggest decryption isn’t possible in NotPetya’s case. Others, however, explain decryption is possible if NotPetya was “unable to obtain administrator privileges when running.”
PoS Malware Hits Avanti Payment Kiosks
10.7.2017 securityweek Virus
Hackers Steal Payment Card and Biometric Data From Avanti Kiosks
Micro markets solutions provider Avanti Markets has informed customers that their personal, payment card and biometric data may have been stolen by cybercriminals who managed to infect some of its kiosks with malware.
According to the company, which serves 1.6 million customers across 46 U.S. states, the malware was designed to harvest information such as cardholder name, credit and debit card number, and expiration date.Avanti kiosk
Depending on how the kiosk was configured and the service used by the customer, the malware may have also stolen names, email addresses and even biometric information in the case of customers who utilized the fingerprint scanner to pay for their items.
Avanti said the breach was discovered on July 4 and its internal response team has taken measures to secure systems, including changing passwords. Payment processing systems have been shut down at some locations while the malware is being removed. The company has notified law enforcement and it plans on offering credit monitoring services to affected individuals.
“We continue to assess and modify our privacy and data security policies and procedures to prevent similar situations from occurring. For instance, we are in the middle of implementing an end to end encryption solution for all of our kiosks, and are working on expediting that implementation,” Avanti told customers. “Theft of data and similar incidents are difficult to prevent in all instances, however, we will be reviewing our systems and making improvements where we can to minimize the chances of this happening again.”
While the firm has not named the piece of malware used in the attack, security blogger Brian Krebs revealed that a July 7 blog post from Risk Analytics describing a PoSeidon (FindPOS) infection on a break room vending kiosk at a customer’s office was actually part of the Avanti campaign.
“This is a textbook example of an Internet of Things (IoT) threat: A network-connected device, controlled and maintained by a third party, which cannot be easily patched, audited, or controlled by your own IT staff,” said Risk Analytics’ Noah Dunker.
The security firm detected the malware on its customer’s network using known indicators of compromise (IoC) for PoSeidon.
Template Injection Used in Attacks on U.S. Critical Infrastructure
10.7.2017 securityweek BigBrothers
U.S. energy facilities hit by cyberattacks
Cisco Shares Technical Details on Attacks Targeting U.S. Energy Facilities
The recent attacks aimed at energy facilities and other critical infrastructure organizations in the United States have leveraged a technique called template injection, according to Cisco’s Talos intelligence and research group.
The New York Times and Bloomberg revealed last week that the FBI and the DHS had issued a joint report warning of cyberattacks targeting manufacturing plants, nuclear power stations and other energy facilities in the U.S. and elsewhere. Unnamed officials said the attacks hit at least a dozen power firms in the United States, including the Wolf Creek nuclear facility in Kansas.
The U.S. Department of Energy said it was working with affected firms and pointed out that only administrative and business networks appeared to be impacted, not systems controlling the energy infrastructure.
Wolf Creek representatives told SecurityWeek that while they can’t make public comments on security issues, they can confirm that the attacks did not have any operational impact on the facility as control systems are completely separate from the corporate network.
According to the FBI/DHS report, the campaign has been active since at least May and an initial investigation showed that the techniques used by the hackers were similar to ones associated with a Russia-linked threat actor tracked as Crouching Yeti, Energetic Bear and Dragonfly. The group has been known to target industrial companies.
Russia has also been accused of orchestrating destructive attacks aimed at Ukraine’s power grid. Researchers have recently published an in-depth analysis of the malware believed to have been used in the latest of these attacks.
The FBI/DHS alert said the attackers sent malicious emails to senior industrial control engineers in an effort to deliver malware designed to harvest credentials and allow them to access the targeted organization’s network.
“As a class, engineering professionals may reasonably be expected to possess valuable intellectual property such as product or facility design, and have access to industrial control networks,” said Sean McBride, critical infrastructure lead analyst at FireEye.
Related: Learn More at SecurityWeek’s ICS Cyber Security Conference
The hackers reportedly also leveraged watering holes and man-in-the-middle (MitM) attacks in this campaign. McBride told SecurityWeek that the campaign has also targeted the users of government websites in other parts of the world, and some of the weaponized documents had no obvious connection to the energy sector.
Cisco Talos researchers have been monitoring these attacks and analyzed some of the malicious Word documents used by the hackers to gain access to the targeted organization’s network. The company has observed attacks aimed at critical infrastructure firms around the world, but the primary targets appear to be the United States and Europe.
The malicious documents, disguised as resumes and environmental reports, don’t rely on traditional methods, such as VBA macros or other embedded scripts, to deliver malware. Instead, when the decoy document is opened, while the Word application is in progress of being launched, a template file is loaded from an attacker-controlled SMB server.
Loading the template file in what is known as a template injection attack allowed the attackers to silently harvest SMB credentials. The method can also be used to download other malicious payloads to the victim’s device, but the hackers’ SMB server was offline during Talos’ analysis and experts could not determine what other payloads may have been served.
Researchers have found a connection between the template injection used in this attack and an open source tool named Phishery. It’s unclear if the similarities are a coincidence, if the hackers behind the energy sector attacks modified the existing tool, or if they simply wanted to confuse investigators.
“We believe this campaign is likely designed to steal information enabling the attackers to gain future access to industrial control systems that run this critical infrastructure, rather than an espionage-type campaign designed to steal plans and other sensitive commercial information,” said Galina Antova, co-founder of Claroty, a cybersecurity company specialized in protecting industrial control systems.
Poučení z malwaru NotPetya
10.7.2017 Root.cz Viry
V dnešním díle si přečtete, jak probíhalo napadení sítě hostující software M.E.Doc malwarem NotPetya a jaké poučení z toho plyne. Následují i další užitečné bezpečnostní informace z celého světa.
Vše důležité o infekci internetu malwarem NotPetya
Malware označovaný jako Petya, NotPetya apod. se do světa a zejména na Ukrajinu rozšířil prostřednictvím velmi rozšířeného účetního a daňového softwaru „M.E.Doc“ („Můj elektronický dokument“), který vytvořila ukrajinská firma „Intellect Service“. Tento malware se šířil z infikovaných strojů dále do sítě prostřednictvím zranitelnosti MS17–010 v protokolu SMB 1.0. Útočníkům se podařilo infiltrovat síť zmíněné firmy, získat přístup ke zdrojovému kódu programu M.E.Doc a rozeslat uživatelům programu jeho infikované verze maskované jako regulérní nové verze.
Podle údajů, které zveřejnily firmy Talos a ESET, vypadal časový rozvrh útoku na síť firmy „Intellect Service“ takto:
14. 4. a 15. 5.2017: Update server distribuoval zákazníkům infikovanou verzi softwaru M.E.Doc.
22. 5. 2017: Firma „Intellect Service“ informovala zákazníky, že od 18. 5. se v sítích objevuje ransomware podobný WannaCry. To ale údajně se softwarem M.E.Doc nesouvisí, protože firma posílá svůj software antivirovým společnostem ke kontrole.
22. 6. 2017: Update server distribuoval zákazníkům poslední infikovanou versi softwaru M.E.Doc.
27. 6. 2017, 8.59 UTC: Útočník se přihlásil na update server s ukradeným jménem a heslem administrátora; získal rootovský přístup prostřednictvím su.
27. 6. 2017, 9.15 UTC: Provoz update serveru byl přesměrován na cizí server v síti OVH (Francie).
27. 6. 2017, 12.31 UTC: Přesměrování provozu update serveru na cizí server skončilo.
27. 6. 2017, 14.11 UTC: Cizí uživatel v lotyšské síti Bighostlv-NET ukončil relaci SSH a odhlásil se z update serveru.
27. 6. 2017, 19.46 UTC: Disk na cizím serveru v síti OVH byl smazán.
Firma ESET zjistila, že útočníci měli přístup ke zdrojovému kódu programu M.E.Doc a infikovali modul ZvitPublishedObjects.dll. Tento modul sbírá mj. kódy EDRPOU (obdoba našich daňových identifikačních čísel DIČ), uživatelská jména a hesla uživatelů a poštovních proxy serverů. Takto zjištěná data byla odeslána na (falešný) update server ve formě cookies; žádný C&C kanál nebyl použit.
Každý stroj, na kterém byl spuštěn infikovaný program M.E.Doc, také reagoval na tyto externí příkazy:
vykonání příkazu shell,
zápis souboru na disk, včetně možného spuštění jako program nebo jako DLL; soubor pak byl přepsán náhodnými daty a smazán,
odeslání libovolného souboru z infikovaného stroje,
odeslání informací o systému (verse OS, 32/64 bitů, privilegia, nastavení UAC, uživatelská a proxy jména a hesla).
Z těchto zjištění plyne:
Šlo o útok cílený na Ukrajinu a na cizí firmy, které s Ukrajinou obchodují. Díky tomu, že útočníci znají údaje EDRPOU (DIČ), přesně vědí, která firma zpracovává své účetnictví na M.E.Docu a ve které síti.
Cílem útoku bylo zničit data napadených firem (sabotáž), infikovat další počítače v napadených sítích a zjistit údaje o obchodních transakcích napadených firem.
Finanční zisk nebyl cílem útoku, přestože ten se tvářil jako ransomware a požadoval za dešifrování dat 300 USD v bitcoinech.
Závěry:
Útok byl velmi dobře naplánován a proveden. Pro útočníky musel být velmi drahý.
Nyní je odhalena metoda infekce v softwaru M.E.Doc i manipulace s update serverem; útočník už tedy tímto způsobem nedokáže spouštět vlastní kód na velikém množství infikovaných počítačů (údajně u 80 % ukrajinských firem).
Aby vynaložené prostředky nepřišly nazmar, je pravděpodobné, že na infikovaných počítačích mohou existovat další dosud neznámá zadní vrátka, skrze něž je útočník bude moci znovu ovládnout.
Všechny firmy už napadené i ty, které využívají software MEDoc nebo podobný, které obchodují s Ukrajinou nebo které provozují své systémy na Ukrajině, by měly dávat velký pozor, protože proti nim stojí nebezpečný protivník.
Doporučují se zejména tyto kroky:
změna přístupových hesel uživatelů i poštovních a proxy serverů,
rozdělení sítě na samostatné části,
důkladné monitorování ohrožených systémů,
omezení přístupu do sítě,
včasná instalace bezpečnostních záplat,
přechod ze starších systémů na Windows 10,
instalace IPS na spojích mezi zahraničními firmami a jejich ukrajinskými pobočkami,
instalace vhodné ochrany na všech ukrajinských systémech,
řídit se podle doporučení firem Microsoft a Cisco.
Windows 10 platform resilience against the Petya ransomware attack
10.7.2017 Ransomware
The Petya ransomware attack on June 27, 2017 (which we analyzed in-depth in this blog) may have been perceived as an outbreak worse than last month’s WannaCrypt (also known as WannaCry) attack. After all, it uses the same SMB exploit used by WannaCrypt and adds a second exploit and other lateral movement methods. However, our telemetry shows a less widespread attack:
The new Petya variant is highly sophisticated malware, but our telemetry shows it had far less reach than we expected given its worm-like spreading capabilities
The attack started in Ukraine; when the dust settled, more than 70% of the machines that encountered Petya were in Ukraine
It managed to spread to machines in other countries but in significantly lower volumes
The majority of infections were observed in Windows 7 machines
In this follow-up blog entry, we’ll discuss platform protection and mitigation in Windows 10 and Windows 10 S. The security configuration and reduced attack surface of Windows 10 S block this attack by default. As we previously discussed in a white paper, Windows 10 Creators Update has next-gen security technologies that help defend against ransomware attacks.
We will also present new findings from our continued investigation, specifically into the boot sector modification behavior of the ransomware.
Windows 10 protection and mitigation
The new Petya ransomware combines multiple well-known techniques for propagation and infection that are not new to security researchers. The noteworthy aspect is that Petya’s developer(s) took techniques normally used by penetration testers and hackers, and built a sophisticated multi-threaded automation of these techniques inside a single piece of code.
Such attacker techniques are part of the modern threat landscape and are continuously researched by security teams at Microsoft. Resulting new mitigations, hardening or defensive measures are then integrated into our products and operating systems.
Windows 10 follows this philosophy of continuous mitigation improvements. From our analysis of Petya, we were able to measure the defenses provided by Windows 10. Summarized in the diagram below are how mitigations and security features can help disrupt the different stages of this attack.
Petya’s kill-chain diagram with platform defenses able to mitigate or prevent certain techniques in Windows 10
Each mitigation in this diagram is placed on top of the specific malware techniques, which are either fully prevented or mitigated in Windows 10. For an overview and specific details of these mitigations included in Windows 10, see this page. Technical details of how each mitigation can help to block Petya’s techniques are listed below:
Device Guard can enforce strong code integrity policies to allow only trusted signed apps to run. It can thus block the entry vector of Petya (an updater running an untrusted binary) and also the further propagation attempts executing an untrusted DLL, either through PSEXEC or WMI.
Credential Guard uses virtualization-based security to isolate the LSASS process, so it fully protects from the credential dump executed by Petya using the external Mimikatz-like tool. It also protects the domain credentials stored in the Windows Credential Store. Access tokens exposed in memory can still be leveraged by Petya, but this is a less effective propagation mechanism, and it relies on third-party tools and other processes active in memory while Petya executes.
Several exploit mitigations such as better KASLR (randomization of kernel), NX HAL and PAGE POOL (non-executable kernel regions) are included by default in Windows 10 Anniversary and Creators Update, and they help mitigate SMB exploits like EternalBlue and EternalRomance. More mitigations like KCFG (control-flow guard for kernel) and HVCI (kernel code-integrity) are automatically enabled with Device Guard to provide additional resistance also to new exploits. Previous blogs discuss in detail how such mitigations were able to help mitigating unknown zero-day exploits, not effective against Windows 10.
UEFI Secure Boot is the security standard that uses hardware features to protect boot process and firmware against tampering. This protection will stop the dangerous disk encryption executed by Petya with a bootloader. After Petya’s forced reboot, a machine with Secure Boot will detect the anomalous bootloader and prevent further execution, containing the damage and preventing the very dangerous encryption of disk sectors leading to a complete loss of data. A machine in this state will be prevented from booting and can be recovered with the regular repair functionality from the Windows USB/DVD media. NOTE: Individual files encrypted by Petya in the limited time before reboot will remain encrypted and must be recovered from backup copies.
App Locker can also be used to block execution of certain programs (e.g. PSEXEC) or unsigned binaries (e.g. Petya’s DLL library) for machines that cannot benefit from Device Guard due to lack of the specific hardware requirements or due to older operating systems not supporting new mitigations (e.g. Windows 7).
Finally, administrators of networks with older operating systems like Windows 7 which do not benefit of modern hardware and software mitigations, may consider deploying some hardened configurations that could help to slow down or remove certain lateral movement techniques. Such hardened configurations may impact legitimate functionality such as file-sharing or remote management and so it needs to be evaluated carefully before deployment.
Block or restrict access to specific IPs for file-sharing services (SMB)
netsh firewall set service fileandprint
netsh firewall set service RemoteAdmin disable
Block remote execution through PSEXEC
FOR /F “usebackq tokens=2 delims=:” %a IN (`sc.exe sdshow scmanager`) DO sc.exe sdset scmanager D:(D;;0x00040002;;;NU)%a
ACL remote WMI access
Limited execution time
The impact of Petya’s worm behavior is limited by its design. As part of its execution command, it receives a time that it can run performing lateral movement and exploitation before rebooting the system.
If an argument is not passed, a default of 60mins is assumed. This value is later used to determine the time in the future for the system to reboot.
This means that the threat can only do lateral movement and exploitation of other machines during this limited time. This reduced the reach of the attack, as observed in our telemetry.
Also, the malware’s worm code does not persist across reboot; for example, if an infected machine is successfully rebooted, the worm does not run again.
Conditional behavior and boot sector modification
As discussed in our in-depth analysis of the Petya ransomware attack, beyond encrypting files, the ransomware also attempts to infect the Master Boot Record (MBR).
In addition to modifying the MBR, the malware modifies the second sector of the C: partition by overwriting it with uninitialized buffer, effectively destroying the Volume Boot Record (VBR) for that partition. The screenshot below shows the code that makes these changes:
It is not clear what the purpose of these modifications are, but the code appears to be buggy – it allocates 10 times the amount of memory it requires. In most modern machines, the VBR on the C: partition is not used for booting as there is a separate partition for the boot manager. Generally, for machines running Windows 7 or later that weren’t upgraded from XP, the malware’s VBR changes are unlikely to have any impact.
During malware initialization phase, this malware maintains a global variable that dictates its behavior. It alters its behavior based on the presence of processes related to certain antivirus applications running in the system.
Specifically, it looks for names of processes belonging to Kaspersky Antivirus and Symantec Antivirus and alters its behavior if it finds them. Below are the CRC values that threat checks and their corresponding process names.
CRC value Matching process name
0x651B3005 NS.exe
0x6403527E ccSvcHst.exe
0x2E214B44 avp.exe
Information controlling threats behavior is stored in a global variable (gConfig in the screenshots), which is then used to check during MBR modification.
If Kaspersky Antivirus process is found in the system or if the MBR infection is unsuccessful, the malware then proceeds to destroy the first 10 sectors of the hard drive. The code snippet below shows the threat logic:
Below snapshot shows threat code that destroys 10 sectors of \\\\.\\PhysicalDrive0, including the MBR sector.
On the other hand, if Symantec AV process names are found, the threat does not perform SMB exploitation.
We compared this new ransomware’s MBR infection functionality to the original Petya malware. Here are some of our findings:
Although the layout of the code and encrypted data in the sectors following the MBR varies between the two versions, the code itself is functionally very similar. The encryption process is the same: when the malicious MBR starts, it loads additional code from sectors after the MBR, which in turn proceeds to encrypt the Master File Table (MFT). After the encryption process is complete, the user is presented with the following ransom message, which is different from the typical ASCII skull and crossbones shown by the original Petya:
Ransom note from Petya after MBR infection
Interestingly, the first part of the text is the same message used by the WannaCrypt ransomware:
WannaCrypt ransom note
In terms of the malware code itself, there are some differences between the new Petya variant and the original malware. For example, the malware authors changed the constants for the key expansions of the encryption algorithm (Salsa20)— the standard string “expand 32-byte k” was replaced with the custom “-1nvalid s3ct-id”.
The code that is supposed to show the skull and crossbones ransom note is still physically present in the malicious MBR code, but it is only printing empty lines.
The strategy to cause a reboot to trigger the malicious MBR code has also been updated. The original version generated a serious system error by calling NtRaiseHardError with code 0xC0000350 (STATUS_HOST_DOWN), which forced the machine to reboot. The new Petya variant has also added a function to schedule a task that reboots the machine after a pre-configured number of minutes.
Fake victim ID
Below is the structure of the malware configuration stored by threat at Sector 32 (0x20):
typedef struct
{
BYTE Null;
BYTE SalsaKey[0x20];
BYTE SalsaIV[0x08];
BYTE BitcoinAddress[0x22];
BYTE Empty[0x5E];
BYTE VictimID[0x3C]; // 60 bytes
BYTE Empty2[0x11B];
}
The VictimID shown to the user is randomly generated using CryptGenRandom() and does not correspond to the MFT encryption, so the ID shown is of no value and is also independent from the per-drive file encryption ID written on README.TXT.
Below is a sample disk sector 32 written by the malware. Unlike the original Petya malware, elliptic curve data is empty.
Boot recovery options
Petya causes some damage to the operating system’s boot code. In certain cases, recovery to boot the infected machine to a clean state is possible.
Case 1: If machine is equipped with secure boot + UEFI
If an infected machine shows the message below, it means the threat couldn’t hijack the boot process and encrypt MFT. In this case, booting off a clean installation media and performing Startup Recovery can fix the issue, and the machine can be booted.
Case 2: If system is non-UEFI, installed with Kaspersky Antivirus, and in a state where boot completely fails
The ransomware attempts to destroy the first 10 sectors of the \\\\.\\PhysicalDrive0 if Kaspersky Antivirus is found or if the MBR infection is unsuccessful. Thus, boot process hijack through malicious MBR hasn’t been completed so the MFT (Master File table) contents are intact and not encrypted by the threat. In this case, the partition table information is destroyed by the threat. Given that it stores critical information needed in the booting process, a traditional boot repair process may not work. Rebuilding the partition table may require consultation with an expert.
Case 3: if a ransom message like below is seen, recovery is not possible
The image is shown if the machine reboots and the malicious MBR is executed successfully. In this case, it is likely that the malware successfully encrypted the MFT, a vital structure of the NTFS file system. Unfortunately, recovery is not possible, and the machine is not capable of booting anymore. One can take the hard disk to another clean system, use disk recovery tools to recover any recoverable personal files, and reimage the system.
Protection against ransomware attacks
The new Petya ransomware variant we saw this week is significantly more complex than the original. It also improved on WannaCrypt‘s spreading mechanisms by using a second exploit and adding more propagation methods. These lateral movement capabilities make this ransomware a higher risk for networks with an infected machine. Furthermore, the boot sector modification behavior discussed in this blog gives this ransomware more potential to cause damage to machines.
This Petya outbreak exemplifies the ever-increasing sophistication of ransomware attacks. A multi-layer defense stack is needed to protect computers and networks. At Microsoft, we strive to continuously enhance Windows 10 with next-generation features to protect customers. As described in this blog, Windows 10 has defenses that can mitigate ransomware attacks like Petya.
Windows Defender Antivirus and Windows Defender Advanced Threat Protection allows customers to detect, investigate, and respond to ransomware attacks. For enterprises, Device Guard locks down devices and provide kernel-level virtualization based security. Credential Guard protects domain credentials stored in the Windows Credential Store.
Keep your software up-to-date to block threats that attempt to exploit software vulnerabilities to infect machines or spread across networks. Additionally, secure privileged access to protect your network from credential theft.
To know more about security features in Windows 10, read out white paper “Next-gen ransomware protection with Windows 10 Creators Update”.
To find mitigation steps specific to this new Petya variant, refer to our blog “New ransomware, old techniques: Petya adds worm capabilities”.
Nato will respond with ‘conventional military assaults’ to future cyber attacks
10.7.2017 securityaffairs BigBrothers
NATO has warned that in the future any cyber attack against a member state could trigger a military response according to the mutual defence clause.
NATO has warned that in the future any cyber attack against a member state could trigger a military response according to the alliance’s Article 5, mutual defence clause.
The NATO announcement follows the massive NotPetya ransomware-based attacks that hit system worldwide. most of them in Ukraine.
The Petya ransomware hit systems in several industries, including banks, transport, telecommunications, and energy. Hackers Among the hardest hit were Ukr telecom, Dniproenergo, Ukrzaliznytsia, Kiev -Boryspil Airport, and the Cabinet of Ministers of Ukraine. Popular aircraft manufacturer Antonov was also reportedly hit.
According to NATO CCD COE, the recent massive attack based on NotPetya ransomware was powered by a “state actor.” The malware infected over 12,000 devices in around 65 countries, the malicious code hit major industries and critical infrastructure.
NATO
Experts from NATO CCD COE believe the attack was likely launched by a nation-state actor, or it was commissioned to a non-state actor by a state. The attackers were well funded and the attack they conducted was very complex and expensive.
The experts observed that despite the operation was complex, the attackers did not spend much effort for managing the payments, a circumstance that suggests hackers were not financially motivated.
“The operation was not too complex, but still complex and expensive enough to have been prepared and executed by unaffiliated hackers for the sake of practice. Cyber criminals are not behind this either, as the method for collecting the ransom was so poorly designed that the ransom would probably not even cover the cost of the operation,” NATO’s Cooperative Cyber Defense Centre of Excellence (CCD COE), said in a press release on Friday.
This declaration could have serious consequences, the cyber attack could be interpreted as an act of war, and can trigger a military response of the alliance under the Article 5 of the North Atlantic Treaty, the principal of collective defense.
According to the NATO secretary-general Jens Stoltenberg, NATO is threatening to respond to cyber-attacks against member states with a conventional military strike.
Stoltenberg highlighted that that NATO leaders officially recognized the cyberspace as the fifth domain of a warfare so the alliance could respond with conventional weapons in case of a powerful cyber attack.
“The attack in May and this week just underlines the importance of strengthening our cyber defences and that is what we are doing. We exercise more, we share best practices and technology, and we also work more and more closely with allies,” said Stoltenberg.
“Nato helps Ukraine with cyber defence and has established a trust fund to finance programs to help Ukraine improve its cyber defences. We will continue to do this and it is an important part of our cooperation,”.
The Ukrainian secret service launched an investigation to attribute the attack, the local authorities believe that a Russian APT was behind the attack. At the time I was writing, the Ukrainian authorities were not able to attribute the attack to Russia.
Experts found an unpatched flaw in Humax WiFi Router model HG-100R
10.7.2017 securityaffairs Vulnerebility
Experts found a flaw in Humax WiFi Router model HG-100R that could be triggered to fully compromise the devices.
A zero-day vulnerability in Humax WiFi Router model HG-100R could be exploited by attackers to compromise the WiFi credentials and obtain the router console administrative password. Trustwave SpiderLabs researchers discovered.
The issue was found by researchers at Trustwave SpiderLabs in May 2017, the company tried to report it to the manufacturer that did reply. the researchers say. The Humax WiFi Router model HG-100R is a default brand/version distributed by a major Internet provider in Brazil, it is also used in many other countries worldwide.
“More recently, in May 2017, Felipe Cerqueira and Thiago Musa, both from Trustwave SpiderLabs, have found a remote vulnerability in the HUMAX WiFi Router model HG-100R*. This vulnerability can allow attackers to compromise the WiFi Credentials and, even more dangerous, to retrieve the router console administrative password.” states the blog post published by Trustwave SpiderLabs.”The equipment is a default brand/version distributed by a major Internet provider in Brazil (where the vulnerability was discovered) but is also used in many other parts of the world.”
The issue is simple to exploit, the attackers just need to send specially crafted requests to the management console to bypass authentication. The experts discovered the router fails to validate the session token while returning answers for some methods in “url/api”.
The exploitation of the flaw could allow an attacker to retrieve sensitive information, such as the private/public IP addresses, SSID names, and passwords.
“The cookie login is basically json data containing uid and pwd encoded in base64: login={“uid”:”admin”,”pwd”:”4cd08a961f5c”};,” states the post. “In the example below you can see a request to the router without providing any authentication as well as the response containing sensitive data such as SSID name, IP addresses and WiFi password.”

A second vulnerability that affects the Humax WiFi Router model HG-100R allows attackers to bypass authentication to access the backup functionality. The feature allows router administrators to save and restore configuration, unfortunately, in both cases, the code fails to check cookies “login” and “login_token.” This implies that attacker can send requests to download and upload the full router configuration.
An attacker can change for example the DNS setting in order to hijack the user’s traffic.
“By using the backup generation/restore functionality provided by the URLs “/view/basic/GatewaySettings.bin” and “/view/basic/ConfigUpload.html” we were able to retrieve, change and finally restore a specially crafted configuration. As an example of the danger of this type of vulnerability, an attacker could use it to change your DNS configuration and redirect your traffic to servers controlled by them in order to steal private information such as passwords or banking account information.” continues the analysis.
The experts also discovered that the GatewaySettings.bin file stores the administrative password in clear text. From byte 96, the file is encoded in base64, decoding it is possible to view the password for “admin” (AAAAAAAA) and “root” (humax) users.
“If your router allows remote configuration management via the Internet, attackers can easily gain access to it and change configurations that will impact your Internet traffic. However, even if configuration management is not available on the Internet facing interface, attackers can still exploit the vulnerability in locations where WiFi routers are public, for instance in a café or airport,” continues the blog post.
To protect your router, disable the option “Remote Configuration Management.”
“Access your HUMAX WiFi Router via the following URL: http://192.168.0.1 and you should be able to find the credentials on the bottom of the router itself. By default, this configuration is not enabled, but you should double check it to make sure. If you don’t have access to your router, try to contact your Internet Service Provider and ask for support or, perhaps, a new router,” Trustwave concludes.
FBI and DHS warn of targeted attacks on US Nuclear Facilities
10.7.2017 securityaffairs BigBrothers
Since May, APT actors have been penetrating the networks of US companies that operate nuclear facilities and that works in the energy industry.
According to a joint report issued by the Department of Homeland Security and the FBI published last week, since May, hackers have been penetrating the networks of businesses that operate nuclear power stations, manufacturing plants and energy facilities in the United States and other countries.
The Wolf Creek Nuclear Operating Corporation is one of the companies hit by hackers, it runs a nuclear power plant near Burlington, Kan.

The news was disclosed by The New York Times that obtained the report, the attack was also confirmed by security experts involved in the incident response procedures.
The document doesn’t provide information related to the motivation of the attacks (sabotage or cyber espionage), it is not clear if attackers were able to fully compromise the target network and access the control systems of the facilities.
The attackers appear as part of a reconnaissance activity of the target infrastructure aimed to gather information for future attacks.
“There is no indication of a threat to public safety, as any potential impact appears to be limited to administrative and business networks.” reads the joint statement from the FBI and the Department of Homeland Security,
“In most cases, the attacks targeted people — industrial control engineers who have direct access to systems that, if damaged, could lead to an explosion, fire or a spill of dangerous material, according to two people familiar with the attacks who could not be named because of confidentiality agreements.” states The New York Times.
The experts have not doubt, the attackers belong to an “advanced persistent threat” group linked to a foreign government.
The attackers’ TTPs mimicked those of the APT groups that in the past targeted the energy industry, such as the Russian Energetic Bear APT group.
The hackers launched spear phishing attacks on senior industrial control engineers that have access to the critical industrial control systems in the target plants. The phishing emails messages containing fake résumés for control engineering jobs, they are weaponized Microsoft Word documents used by hackers to steal victims’ credentials and make lateral movements in the target networks.
The hackers also powered watering hole attacks compromising legitimate websites visited by the victims and used to deliver malware.
The Department of Homeland Security consider cyberattacks on critical infrastructure “one of the most serious national security challenges we must confront.”
Strojové učení: Nová naděje proti kybernetickým útokům
9.7.2017 SecurityWorld Zabezpečení
Technologie, která má potenciál zásadně změnit styl hry, by mohla přenést ochranu podnikových sítí na zcela novou úroveň.
Zneklidňující počet úspěšných krádeží dat během posledních několika let ukazuje, že organizace jsou zahlcené rostoucím počtem hrozeb. Objevil se však nový druh bezpečnostního řešení, který využívá pro podnikové zabezpečení strojové učení. Tyto nástroje dovolují analyzovat sítě, porozumět jim, detekovat anomálie a chránit podniky před ohrožením.
Je tedy strojové učení odpovědí na dnešní kybernetické výzvy? Oboroví analytici a firmy nabízející tyto produkty prohlašují, že zaznamenávají zvýšenou poptávku a že první reakce od uživatelů je pozitivní.
„Strojové učení je významným bezpečnostním trendem letošního roku,“ tvrdí Eric Ogren, hlavní bezpečnostní analytik ve společnosti 451 Research. „Každý šéf zabezpečení nyní ví, že behaviorální analytické produkty nabízejí nejlepší šanci zachytit útoky, které uniknou statické preventivní obraně.“
Dodává, že strojové učení je srdcem těchto behaviorálních přístupů. „Není to něco jako pozorování a poslouchání,“ dodává Ogren.
„Strojové učení podle něj zaznamenává chování při definování statistického profilu normální aktivity pro uživatele, zařízení nebo web. To je důležité, protože to poskytuje základ pro analýzu chování, aby bylo možné zabránit velkým škodám způsobeným útokem, který by unikl obraně před hrozbami nebo zneužil povolenou činnost.“
Dlouhodobý přínos strojového učení spočívá v tom, že směruje organizaci na cestu k pravděpodobnostnímu a prediktivnímu bezpečnostnímu přístupu, který se snadno integruje s obecně uznávanými postupy IT.
„Je vidět, že se to již vyplácí ve velkých cloudových a mediálních podnicích, kde se bezpečnost posuzuje méně ve smyslu prostého rozlišení dobrého či špatného a více ve smyslu snížení rizika narušení hlavní podnikatelské činnosti s bezprostředním vlivem na celkový zisk,“ vysvětluje Ogren.
Potenciální problémy
Stejně jako u všech novějších technologií přináší i strojové učení případné těžkosti. „Může být náročné rozlišit kvalitu algoritmů strojového učení od různých dodavatelů,“ vysvětluje Ogren.
Kvalita se podle něj projeví ve výsledcích. On sám doporučuje využít projekty ověření konceptu na několika oddělených případech nasazení pro uživatele, zařízení a weby, aby se zjistila efektivita produktu.
Přestože strojové učení může vést k obrovskému zlepšení zabezpečení, „není to alfa a omega“, poznamenává David Monahan, ředitel výzkumu zabezpečení a řízení rizik ve výzkumné společnosti Enterprise Management Associates. „Má svá omezení a nejlepší způsob využití. Je to skvělý nástroj pro významnou oblast zabezpečení k identifikaci toho, co je mimořádné a mělo by se prověřit a přezkoumat.“
Existují dva hlavní typy strojového učení používané v oblasti zabezpečení: s dohledem a bez dohledu. „Fungují lépe pro rozdílné účely, ale oba v podstatě nacházejí anomálie v daných sadách dat,“ popisuje Monahan. „Proto může být výsledek dobrý jen tak, jak jsou kvalitní poskytnutá data. Strojové učení je tedy přídavná technologie, nikoli základní.“
Hlavní výhody
Základní výhodou této technologie je její schopnost rychle rozpoznat trendy, vzory a anomálie v rozsáhlých a různorodých souborech dat, vysvětluje Monahan.
„Je to mnohem rychlejší než u většiny, ne-li u všech nástrojů big dat, protože to funguje v reálném čase nebo téměř v reálném čase měřeném ve vteřinách až minutách a není nutné čekat na dávkové zpracování,“ tvrdí Monahan.
Potřeba strojového učení je vyvolávaná dvěma fakty, vysvětluje Kristine Lovejoyová, prezidentka a výkonná ředitelka společnosti BluVector, která nabízí bezpečnostní technologii využívající strojové učení.
Jedním je, že zjištění kompromitace trvá dlouhou dobu, a druhým, že v mnoha, ne-li ve všech případech se firmy dozvědí o svém napadení od někoho jiného.
„Organizace potřebují funkce, které jim umožní udržet krok s hrozbami, zjistit je a zlikvidovat dříve, než dojde k nějakým škodám,“ připomíná Lovejoyová.
Firmy „si uvědomily, že nedokážou předvídat každý možný vektor útoku a že si nemohou dovolit ručně vytvářet pravidla pro detekci vektorů, které očekávají“, uvádí Mike Paquette, produktový viceprezident společnosti Prelert, která je dalším dodavatelem bezpečnostních nástrojů využívajících strojové učení.
„Hledají takový způsob automatizace analýz svých dat z protokolů souvisejících se zabezpečením, aby nepřetržitě docházelo k detekci elementárního útočného chování,“ prohlašuje Paquette.
Zde je malá ukázka dostupných bezpečnostních nástrojů, které využívají strojové učení:
Společnost Acuity Solutions nabízí BluVector, produkt pro detekci malwaru a kybernetických útoků, který využívá strojové učení jako mechanismus identifikace a stanovení důležitosti potenciálních hrozeb. Po identifikaci hrozeb dochází k vytvoření forenzních balíčků pro specialisty na odchycení a reakci, kteří hrozby prozkoumají a ošetří.
DgSecure Monitor od společnosti Dataguise je produkt pro detekci narušení, který využívá strojové učení a behaviorální analytiku k varování v situacích, kdy se aktivity uživatele odchýlí od typického profilu chování. Produkt usnadňuje vytváření řídicích zásad zabezpečení dat pomocí této funkce v kombinaci se zásadami definovanými pro uživatele, a to nehledě na případnou chráněnost citlivých dat.
Společnost Deep Instinct nabízí produkt Deep Learning, který je inspirován schopností mozku učit se identifikovat objekt a změnit tuto identifikaci v okamžitou přirozenost. Při aplikaci hlubokého učení pro kybernetickou bezpečnost rozděluje produkt Deep Instinct tento proces dvou fází: učení a predikce. Výsledkem je pak instinktivní kybernetická ochrana i před nejméně určitelnými kybernetickými útoky z jakéhokoliv zdroje.
Společnost Distil Networks nabízí technologii, která chrání webové aplikace před škodlivými boty, před zneužitím rozhraní API a před podvody. Každý zákazník společnosti Distil podle jejích slov těží z globální infrastruktury strojového učení, která v reálném čase analyzuje útočné vzory. Distil například aktivně předpovídá boty na základě korelace více než 100 dynamických klasifikací a upozorňuje na anomálie v chování specifickém pro vzory unikátního webového provozu.
Společnost Prelert nabízí tři produkty pokročilé detekce hrozeb, které využívají strojové učení pro oblast bezpečnosti. Všechny tři jsou postavené na stroji behaviorální analytiky firmy Prelert, který využívá nedohlíženou technologii strojového učení k vytváření etalonů normálního chování v datech protokolů a identifikuje anomálie a neobvyklé vzory v datech souvisejících s kybernetickými útoky.
European police shut down the Elysium website, a major child porn platform
9.7.2017 securityaffairs CyberCrime
German police, in a joint operation with other law enforcement agencies, have shut down one of the major Dark Web child pornography site, the ‘Elysium website.’
German police have shut down one of the major Dark Web child pornography websites, the ‘Elysium.’
The Elysium website had more than 87,000 members, most of the users were from Austria and Germany. The platform was used by pedophiles and criminals to exchange pedo-pornographic content and according to German police, it was also used to arranged meetings to abuse children physically.
The police identified and arrested the administrator of the group, a 39-year-old man from Hesse region of Germany. The man was arrested on 12th June during a raid in his apartment, the agents seized the server used by the suspect. The investigation resulted in the arrest of other suspects.
“In the past five weeks, the German Federal Prosecutor’s Office (Generalstaatsanwaltschaft Frankfurt am Main – Zentralstelle zur Bekämpfung der Internetkriminalität) and Federal Criminal Police Office (Bundeskriminalamt) have arrested a number of individuals suspected of the serious sexual abuse of children and the distribution of large amounts of child abuse material online. The German authorities have also taken down the child abuse platform Elysium.” states the Europol.
“The Elysium platform, built as a forum, has existed since the end of 2016 and was only accessible via the Darknet. With over 87 000 members worldwide, the platform was used to exchange child abuse material as well as to make appointments for the sexual abuse of children. Elysium also encompassed chat groups in German, French, Spanish and Italian.”
The Elysium website was shut down on June 13, 2017, below the tweet published by the Europol director Rob Wainwright.
Follow
Rob Wainwright ✔ @rwainwright67
European police operation supported by @Europol takes down major child sexual abuse platform with 87,000 members https://twitter.com/europol/status/883243393886932994 …
12:35 PM - 7 Jul 2017
45 45 Retweets 43 43 likes
Twitter Ads info and privacy
According to the Europol other suspects were arrested by law enforcement, including:
A 61-year-old individual from Bavaria which is suspected of the production and dissemination of child abuse material. In addition, he is suspected of the sexual abuse of two children aged 5 and 7 years.
A 56-year-old individual from Baden-Württemberg, was arrested under the suspicion of being the moderator of the forums of the platform and the chat groups.
A 28 year-old individual was arrested because he is suspected of having participated in the dissemination of child abuse material, of having severely sexually abused his two children for years and facilitated the sexual abuse of his children by the above suspects.
The operation conducted by the German Police involved other law enforcement agencies and partners, including the New Zealand Police, the Italian State Police – Postal and Communication Police Service and the Australia’s Task Force Argos from Queensland.
“The action of the German authorities assisted by Europol has resulted in the arrest of individuals involved not only in the physical abuse of children but the takedown of a platform, Elysium, used to distribute large amounts of child abuse material. This is a highly significant action in safeguarding children from abuse.” said Steven Wilson, Head of the European Cybercrime Centre (EC3) at Europol.
The experts from HackRead made further analysis on the Elysium website discovering that it was formed in November 2016 and opened in December 2016.
“The site was owned and operated by Noctua, Ovidius, and Scorpion. A fourth administrator account, “Elysium”, was used by the other 3 administrators to post important announcements.” states the post published by HackRead.

Hard Rock and Loews hotel chains notified guests of security breaches
9.7.2017 securityaffairs CyberCrime
Hard Rock and Loews hotel chains notified guests of security breaches, the incidents are linked to hack of the SynXis platform provided by the Sabre firm.
It has happened again, the Hard Rock Hotels and Casinos franchise is alerting guests about a possible data breach.
Customers have to monitor their bank account for suspicious activity and immediately report them.
The Hard Rock Hotels and Casinos chain learned on June 6 of a security breach, crooks gained access to payment card data for a “small subset” of customers who booked reservations through the SynXis platform provided by third-party vendor Sabre Hospitality Solutions.
In May, the Travel Tech Giant Sabre confirmed in a SEC filing it was “investigating an incident involving unauthorized access to payment information contained in a subset of hotel reservations processed through the Sabre Hospitality Solutions SynXis Central Reservation system.”
The intruders gained access to the system after hijacking an internal account on the SynXis system.
“The unauthorized access has been shut off and there is no evidence of continued unauthorized activity,” reads a statement that Sabre sent to affected properties in May. “There is no reason to believe that any other Sabre systems beyond SynXis Central Reservations have been affected.”
The impact of the incident could be severe, the SynXis Central Reservation product is a rate and inventory management SaaS application that is currently used by more than 32,000 hotels worldwide.
Later, the company confirmed the hackers had managed to access personally identifiable data, payment card details, and other information.
Back to the present, the investigation into the Hard Rock Hotels and Casinos franchise breach concluded this week. The company notified the incident to the customers and the Federal Trade Commission.
The security breach took place between between Aug. 10 and March 9 and affected an undisclosed number of guests at 11 Hard Rock properties:
Hard Rock Hotel & Casino Biloxi, Hard Rock Hotel Cancun, Hard Rock Hotel Chicago, Hard Rock Hotel Goa, Hard Rock Hotel & Casino Las Vegas, Hard Rock Hotel Palm Springs, Hard Rock Hotel Panama Megapolis, Hard Rock Hotel & Casino Punta Cana, Hard Rock Hotel Rivera Maya, Hard Rock Hotel San Diego and Hard Rock Hotel Vallarta.
“The brand was recently notified of a security incident through third-party hotel reservation system – The Sabre Hospitality Solutions SynXis. Following an examination of evidence, Sabre alerted Hard Rock Hotels & Casinos on June 6, 2017 that an unauthorized party gained access to account credentials that permitted unauthorized access to unencrypted payment card information, as well as certain reservation information, for a subset of hotel reservations processed through the reservation system.” reads the statement issued by the company. “The investigation determined that the unauthorized party first obtained access to payment card and other reservation information on August 10, 2016. The last access to payment card information was on March 9, 2017.”
“Not all of our hotels leverage Sabre Hospitality Solutions SynXis, so only a small subset were affected. Customers have been notified and Sabre has contacted the FTC,” the company said in a statement. “Hard Rock Hotels & Casinos is in the process of notifying the attorneys general’s offices as required by law.”
In June 2016 the Hard Rock Hotel & Casino in Las Vegas disclosed for the second time a data breach, customers who made purchases between October 27, 2015 and March 21, 2016 were affected by the breach.
the first one was disclosed in May 2015, when the company notified that the compromised payment cards were used between September 3, 2014 and April 2, 2015, at the restaurant, bar and retail locations at the Hard Rock Hotel Las Vegas property.

Another luxury hotel chain, Loews Hotels, reportedly also began notifying customers they were impacted by the Sabre breach.
“Luxury hotel chain Loews Hotels is warning some customers that a data breach may have resulted in financial information being stolen.” reads the NBC 10 Philadelphia.
“Hackers obtained access to credit card, security code and password information through a third-party company, Sabre, which provides booking services through travel agencies, websites and other mediums, the hotel chain said. In some cases, email, phone number, and street addresses were also taken.
Highly-sensitive information like Social Security numbers and passport information was not affected.”
The Sabre incident could have serious repercussion, this week Google has notified some employees that they may have been hit by the data breach suffered by travel technology firm Sabre.
Google employees were affected by the Sabre data breach because it was using booking services provided by the Carlson Wagonlit Travel (CWT), a company that uses the SynXis platform.
Google notified affected employees via letter, the IT giant learned of the Sabre breach on June 16 from Carlson Wagonlit Travel (CWT).
Google notified employees that their name, contact information and payment card details may have been accessed by attackers, who breached the reservations system between August 10, 2016 and March 9, 2017.
“We recently learned that certain hotel reservations made for Google business travel were
among the many reservations affected by a security incident impacting a third-party provider’s
electronic reservation system that serves thousands of travel agencies and hotels. This did not
affect Google’s systems. However, this incident impacted one of the travel providers used by
Googlers, Carlson Wagonlit Travel (CWT).” states the letter.
“Sabre’s investigation discovered no evidence that information such as Social Security, passport, and driver’s license numbers were accessed,” Google said. “However, because the SynXis CRS deletes reservation details 60 days after the hotel stay, we are not able to confirm the specific information associated with every affected reservation.”
To protect its employee, Google opted to offer affected ones two years of identity protection and credit monitoring services.
Sabre declared that only 15 percent of the average daily bookings on the its reservation system between August and March were viewed.
“Not all reservations that were viewed included the payment card security code, as a large percentage of bookings were made without a security code being provided,” Sabre said via statement, “Others were processed using virtual card numbers in lieu of consumer credit cards. Personal information such as social security, passport or driver’s license number was not accessed. Sabre has notified law enforcement and the credit card brands as part of our investigation.”
UK Police: Accessing the Darkweb could be a sign of terrorism
9.7.2017 securityaffairs BigBrothers
In a leaflet distributed by the UK authorities, the police tell citizens to be vigilant on anyone using the darkweb.
The widespread of terrorism in Europe has been very severe recently. As a way of effectively dealing with
In a wake of recent terror attacks, London authorities are conducting various initiatives to fight the threat. The police arrested several suspects, but the most curious initiative is the distribution of leaflets with listings of suspicious activities that are to be interpreted by the authorities as a sign of potential terrorism.
““Be aware of what is going on around you—of anything that strikes you as different or unusual, or anyone that you feel is acting suspiciously—it could be someone you know or even someone or something you notice when you are out and about that doesn’t feel quite right,” reads the leaflet.

Online communities play a significant role in radicalization, for this reason, the police decided to distribute the leaflet.
The listings include the item “visiting the Darkweb,” the authorities fear that terrorists and sympathizers could access darknet for propaganda, to smuggle weapons, and to raise funds.
The Dutch police confirmed that the situation in the country is very worrisome, according to a national threat assessment report published by the Dutch police on June 1, the trade of weapons on the darknet is increased.
According to the experts it is always easier to get a rifle than a pistol in the darkweb, law enforcement in the Netherlands seized hundreds of firearms in a few weeks.
According to the European authorities, Holland seems to be a hub in a network of international arms smugglers.
The use of Darknet in well known to law enforcement, some governments created specific units to infiltrate communities and prevent abuses.
In August 2016, the German Government announced last week the creation of a new cyber security unit named ZITiS to tackle terrorists online in a wake of terror attacks.
Early 2016, the Europol announced a new European counter-terrorism centre to fight the terrorism.
In November 2015, the GCHQ and NCA joined forces to fight illegal activities in the Dark Web and formed a new unit called the Joint Operations Cell (JOC).
In 2016, Bernard Cazeneuve, the Internal Affairs minister in France, said at a National Assembly meeting that the Darknet are abused by terrorist organizations for their outrageous activities.
“ISIL’s activities on the Surface Web are now being monitored closely, and the decision by a number of governments to take down or filter extremist content has forced the jihadists to look for new online safe havens.” She added that “The Dark Web is a perfect alternative as it is inaccessible to most but navigable for the initiated few – and it is completely anonymous.” reads a 2015 report published by Beatrice Berton on the use of the Darknet by ISIS.
Thomas Rid, the Professor of Security Studies at King’s College London, explained that despite more than 50 percent of what’s hosted in the dark web is illegal and illegitimate, terrorists do not find anonymizing network so useful.
“Militants and extremists don’t seem to find the Tor hidden services infrastructure very useful. So there are few jihadist and militants in the Darknet. It’s used for criminal services, fraud, extreme, illegal pornography, cyber-attacks and computer crime.” said Rid.
Anyway it is essential to monitor the use of Dark web by terrorists, anonymizing networks offers a privileged environments for extremists and cybercriminals.
GMR-2 issues allow satellite phone communications decryption in near real-time
9.7.2017 securityaffairs BigBrothers
Researchers have exploited vulnerabilities in the implementation of the GMR-2 cipher decrypt satellite phone communications in fractions of a second.
Two Chinese security researchers have exploited vulnerabilities in the implementation of the GMR-2 standard that could be exploited to decrypt satellite phone communications in fractions of a second.
The GMR-2 is a stream cipher with 64-bit key-length being used in some Inmarsat satellite phones.
It is possible to crack the GMR-2 cipher by using only one frame known keystream, but the process is time-consuming. The researchers devised a technique that for the first time allows a real-time inversion attack using one frame keystream.
“Then by introducing a new concept called “valid key chain” according to the cipher’s key schedule, we
for the first time propose a real-time inversion attack using one frame keystream. This attack contains three phases: (1) table generation (2) dynamic table looks-up, filtration and combination (3) verification.” reads the research paper.
The satellite phones of British Telecom Inmarsat use the GMR-2 standard,
In 2012, a group of German researchers demonstrated through a reverse engineering activity that both are weaker than other ciphers such as AES or PRESENT.
“With respect to the GMR-2 cipher, in a known-plaintext setting where approximately 50–65 bytes plaintext are known to the attacker, it is possible to recover a session key with a moderate computational complexity, allowing the attack to be easily performed with a current PC,” explained the German experts.
GMR-2 satellite mobile communications
The Chinese duo detailed a new real-time inversion attack against GMR-2 that allows attackers to obtain a real-time decryption of satellite communications.
Differently, from the previous attack method, the researchers don’t crack the cipher with a plaintext attack, instead, they reverse engineered the encryption process in order to extrapolate the encryption key directly from the output keystream.
“Our analysis shows that, using the proposed attack, the exhaustive search space for the 64-bit encryption key can be reduced to about 213 when one frame (15 bytes) keystream is available. Compared with previous known attacks, this inversion attack is much more efficient. Finally, the proposed attack are carried out on a 3.3GHz platform, and the experimental results demonstrate that the 64-bit encryption-key could be recovered in around 0.02s on average.” continues the paper.
The security of satellite communication is crucial and the choice strong algorithms is essential to avoid eavesdropping.
“Given that the confidentiality is a very crucial aspect in satellite communications, the encryption algorithms in the satellite phones should be strong enough to withstand various eavesdropping risks,” continues the analysis.
“Table 3 is the comparison between the known cryptanalytic results and ours, from which we can see
that the inversion attack proposed in this paper possesses evident superiority compared with the dynamic guess-and-determine attack and the read-collision based attack. Given one frame (15 bytes) of keystream, one can break the GMR-2 cipher with only 0.02s on a 3.3GHz platform. This again demonstrates that there exists serious security flaws in the GMR-2 cipher, and it is crucial for service providers to upgrade the cryptographic modules2 of the system in order to provide confidential communication.”

Of course, satellite phone providers must upgrade their systems in order to protect communications.
SpyDealer Malware Steals Private Data From Popular Android Apps
9.7.2017 securityweek Virus
A recently discovered Android Trojan can exfiltrate private data from more than 40 applications, Palo Alto Networks security researchers have discovered.
Dubbed SpyDealer, the malware is capable of stealing sensitive messages from communication apps using the Android accessibility service feature, and gains rooting privileges with the help of exploits from a commercial rooting app called Baidu Easy Root. It uses root privileges to maintain persistence on the compromised device.
According to Palo Alto Networks, the Trojan can remotely control the device via UDP, TCP and SMS channels. It can steal information from popular applications such as WeChat, Facebook, WhatsApp, Skype, Line, Viber, QQ, Tango, Telegram, Sina Weibo, Tencent Weibo, Android Native Browser, Firefox Browser, Oupeng Brower, QQ Mail, NetEase Mail, Taobao, and Baidu Net Disk.
Once the malware has compromised a device, it can harvest an exhaustive list of personal information, including phone number, IMEI, IMSI, SMS, MMS, contacts, accounts, phone call history, location, and connected Wi-Fi information. It can also answer incoming phone calls from a specific number, can record phone calls and the surrounding audio and video, can take photos with the device’s cameras, monitor location, and take screenshots.
Palo Alto Networks researchers couldn’t determine exactly how SpyDealer infects devices, but say that it isn’t distributed through the official Google Play store and that some users might have been infected via compromised wireless networks. The Trojan is only effective against Android 2.2 to 4.4 releases, given that these are the only versions the rooting tool it uses supports, meaning that it could potentially infect around 25% of all Android devices.
“On devices running later versions of Android, it can steal significant amounts of information, but it cannot take actions that require higher privileges,” the network security firm says.
The security researchers have captured 1,046 samples of SpyDealer and say that it is under active development, with three variants currently in the wild. The latest variant encrypts the content of configuration files and almost all constant strings in the code, and also packs a service to steal targeted apps’ messages.
The oldest Trojan sample is dated October 2015, which suggests the threat has been active for over a year and a half.
Once installed, the malware doesn’t show an application icon, but registers “two broadcast receivers to listen for events related to the device booting up and network connection status.” At the first launch, the malware retrieves configuration information (from a local asset that can be remotely updated) such as the IP address of a remote command and control (C&C) server, the actions it can take on mobile networks, and the actions allowed under a Wi-Fi network.
By registering a broadcast receiver with a higher priority than the default messaging app, SpyDealer can listen for commands via incoming SMS messages. It can also create a TCP server on the compromised device listening at port 39568, and can actively connect to the remote server to ask for commands through UDP or TCP.
"To remotely control the victim device, the malware implements three different C&C channels and supports more than 50 commands,” Palo Alto Networks said.
Mondelez International and Reckitt warn of economic impact of cyber attack on sales
8.7.2017 securityaffairs Cyber
Cyber attacks could have a significant impact on businesses, Mondelez International and Reckitt warn of NotPetya effect on the sales.
Cyber attacks could have a significant impact on businesses, and two of the world’s largest consumer goods companies confirmed it. On Thursday the companies Mondelez and Reckitt Benckiser warned of the impact of the NotPetya attack on their revenues.
Mondelez International is one of the world’s largest snacks companies, its products include the Oreo cookies and Cadbury chocolates. The company estimated the NotPetya attack would cut three percentage points from second-quarter sales growth because of disruptions to shipping and invoices caused by the cyber attack.
The company declared that its shipping and invoicing was disrupted during the last four days of Q2.
Considering that Mondelez International’s net revenues were $6.4bn in Q1, it is possible to quantify the overall economic impact of a cyber attack.
“There are a few markets where we have permanently lost some of that revenue due to holiday feature timing, but we expect we will be able to recognize the majority of these delayed shipments in our third quarter results,” Mondelez said on Thursday.
The company confirmed that employees in different regions were experiencing technical problems, but it is still unclear whether the issues were linked to the massive ransomware-based attack.
Mondelez believes it will incur in other costs in the second and third quarters due to the cyber attacks.

Another company, the Reckitt Benckiser, maker of Nurofen painkillers and Durex condoms, said it expected sales would be hit Q2 by an estimated £110m this year.
“It projecting a second quarter like-for-like sales drop of 2 per cent, cutting annual revenue growth by a full percentage point.” states the Financial Times. “Reckitt cautioned that this was not a final estimate since it had not yet recovered fully from the attack.”
Other major firms hit by the cyber attack faced similar problems, including the world’s largest shipping company AP Moller-Maersk and one of the world’s biggest law firms, the DLA Piper-
Google Chrome Bans Chinese SSL Certificate Authorities WoSign and StartCom
8.7.2017 thehackernews Krypto
As a punishment announced last October, Google will no longer trust SSL/TLS certificate authorities WoSign and its subsidiary StartCom with the launch of Chrome 61 for not maintaining the "high standards expected of CAs."
The move came after Google was notified by GitHub's security team on August 17, 2016, that Chinese Certificate Authority WoSign had issued a base certificate for one of GitHub's domains to an unnamed GitHub user without authorization.
After this issue had been reported, Google conducted an investigation in public as a collaboration with Mozilla and the security community, which uncovered several other cases of WoSign misissuance of certificates.
As a result, the tech giant last year began limiting its trust of certificates backed by WoSign and StartCom to those issued before October 21st, 2016 and has been removing whitelisted hostnames over the course of several Chrome releases since Chrome 56.
Now, in a Google Groups post published on Thursday, Chrome security engineer Devon O'Brien said the company would finally remove the whitelist from its upcoming release of Chrome, completely distrusting the existing WoSign and StartCom certificates.
"Beginning with Chrome 61, the whitelist will be removed, resulting in full distrust of the existing WoSign and [its subsidiary] StartCom root certificates and all certificates they have issued," says O'Brien.
"Based on the Chromium Development Calendar, this change should be visible in the Chrome Dev channel in the coming weeks, the Chrome Beta channel around late July 2017, and will be released to Stable around mid-September 2017."
Last year, Apple and Mozilla also stopped trusting WoSign, and StartCom issued certificates for their web browsers due to their number of technical and management failures.
"Most seriously, we discovered they were backdating SSL certificates to get around the deadline that CAs stop issuing SHA-1 SSL certificates by January 1, 2016," Kathleen Wilson, the head of Mozilla's trusted root program, said.
"Additionally, Mozilla discovered that WoSign had acquired full ownership of another CA called StartCom and failed to disclose this, as required by Mozilla policy."
The problems with WoSign certificate service dated back to July 2015 and publicly disclosed last year by British Mozilla programmer Gervase Markham on Mozilla's security policy mailing list.
According to Markham, an unnamed researcher accidentally found this security blunder when trying to get a certificate for 'med.ucf.edu' but also applied for 'www.ucf.edu' and WoSign approved it, giving the certificate for the university's primary domain.
For testing purpose, the security researcher then used this trick against Github base domains (github.com and github.io), by proving his control over a sub-domain.
And guess what? WoSign handed over the certificate for GitHub main domains, as well.
Starting from September 2017, visitors to sites using WoSign or StartCom HTTPS certificates would eventually see trust warnings in their web browsers.
So, websites that are still relying on certificates issued by WoSign or StartCom are advised to consider replacing their certificates "as a matter of urgency to minimize disruption for Chrome users," O'Brien said.
Google Chrome Bans Chinese SSL Certificate Authorities WoSign and StartCom Friday, July 07, 2017 Mohit Kumar 0 0 0 New As a punishment announced last October, Google will no longer trust SSL/TLS certificate authorities WoSign and its subsidiary StartCom with the launch of Chrome 61 for not maintaining the "high standards expected of CAs." The move came after Google was notified by GitHub's security team on August 17, 2016, that Chinese Certificate Authority WoSign had issued a base certificate for one of GitHub's domains to an unnamed GitHub user without authorization. After this issue had been reported, Google conducted an investigation in public as a collaboration with Mozilla and the security community, which uncovered several other cases of WoSign misissuance of certificates. As a result, the tech giant last year began limiting its trust of certificates backed by WoSign and StartCom to those issued before October 21st, 2016 and has been removing whitelisted hostnames over the course of several Chrome releases since Chrome 56. Now, in a Google Groups post published on Thursday, Chrome security engineer Devon O'Brien said the company would finally remove the whitelist from its upcoming release of Chrome, completely distrusting the existing WoSign and StartCom certificates. "Beginning with Chrome 61, the whitelist will be removed, resulting in full distrust of the existing WoSign and [its subsidiary] StartCom root certificates and all certificates they have issued," says O'Brien. "Based on the Chromium Development Calendar, this change should be visible in the Chrome Dev channel in the coming weeks, the Chrome Beta channel around late July 2017, and will be released to Stable around mid-September 2017." Last year, Apple and Mozilla also stopped trusting WoSign, and StartCom issued certificates for their web browsers due to their number of technical and management failures. "Most seriously, we discovered they were backdating SSL certificates to get around the deadline that CAs stop issuing SHA-1 SSL certificates by January 1, 2016," Kathleen Wilson, the head of Mozilla's trusted root program, said. "Additionally, Mozilla discovered that WoSign had acquired full ownership of another CA called StartCom and failed to disclose this, as required by Mozilla policy." The problems with WoSign certificate service dated back to July 2015 and publicly disclosed last year by British Mozilla programmer Gervase Markham on Mozilla's security policy mailing list. According to Markham, an unnamed researcher accidentally found this security blunder when trying to get a certificate for 'med.ucf.edu' but also applied for 'www.ucf.edu' and WoSign approved it, giving the certificate for the university's primary domain. For testing purpose, the security researcher then used this trick against Github base domains (github.com and github.io), by proving his control over a sub-domain. And guess what? WoSign handed over the certificate for GitHub main domains, as well. Starting from September 2017, visitors to sites using WoSign or StartCom HTTPS certificates would eventually see trust warnings in their web browsers. So, websites that are still relying on certificates issued by WoSign or StartCom are advised to consider replacing their certificates "as a matter of urgency to minimize disruption for Chrome users," O'Brien said.
Pět příznaků, že útočník už pronikl do vaší sítě
8.7.2017 SecurityWorld Zabezpečení
Podle některých odhadů útočníci pronikli až do 96 % všech sítí – takže je nutné je odhalit a zastavit, aby neměli čas na eskalaci oprávnění, nalezení cenných aktiv a ukradení dat. Přinášíme popis vhodných protiopatření.
Útok na firemní síť nekončí infekcí nebo převzetím koncového bodu – zde teprve začíná. Z takového místa je útok vysoce aktivní a útočníka lze zjistit a zastavit, pokud víte, jak ho najít. Pomůže vám k tomu následujících pět strategií.
Hledejte příznaky narušení.
Vyhledávejte skenování portů, nadměrně neúspěšné pokusy o přihlášení a další druhy průzkumných aktivit, protože se útočník snaží zmapovat vaši síť.
Útočník bude zpočátku potřebovat porozumět topologii sítě, do které pronikl. Bude hledat zranitelné koncové body a servery a zaměří se na uživatele s oprávněním správce a na sklady cenných dat.
Většina nástrojů detekce narušení dokáže detekovat známé skenery portů. Rozlišení mezi skrytým průzkumem a legitimním skenováním využívaným při vysílání v síti je však složitější.
Přiznejme si to – většina počítačů a aplikací je doslova upovídaná. Přesto však lze najít anomálie svědčící o útoku, pokud jste definovali, kolik portů a cílů mohou různá zařízení ve vaší síti obvykle využívat.
Zdroj dat: Nástroje pro monitoring či správu sítě, agregace NetFlow.
Problémy: Útočníci mohou pracovat nenápadně a pomalu, takže budete potřebovat udělat některé analýzy založené na čase. Můžete také mít mnoho upovídaných nástrojů a protokolů, takže chvíli potrvá, než se podaří odfiltrovat šum.
Hledejte „normální“ uživatele vykonávající administrátorské úlohy.
Útočníci stále častěji používají v počítačích a na serverech spíše nativní nástroje než známé útočné nástroje a malware, aby je nedetekoval antivirový software nebo software EDR (Endpoint Detection and Response). To je však samo o sobě anomálií, kterou lze detekovat.
Pokuste se zjistit, kdo jsou vaši administrátoři. Adresářové služby, jako jsou služby Active Directory, vám pomohou vytvořit v rámci vaší organizace uživatelské role a oprávnění.
Potom zjistěte, jaké nástroje vaši správci používají a jaké aplikace či zařízení obvykle spravují – například databáze ERP a intranetový web. S těmito znalostmi můžete rozpoznat situace, kdy útočník převezme stroj a začne vykonávat administrátorské úlohy neočekávaným způsobem.
Zdroj dat: Kombinace informací o síti (síťové pakety nebo data NetFlow) a informací z adresářových služeb poskytne nejlepší způsob, jak identifikovat administrátorské chování.
Problémy: Bohužel neexistuje jeden zdroj informací, který by vám přesně řekl, kdo jsou vaši správci a jaké vybavení spravují. Monitorování využití SSH a RPC z perspektivy kurzu však dokáže poskytnout dobrý výchozí bod.
Výsledkem pravděpodobně bude velké množství falešně pozitivních nálezů, ale časem už dokážete zrno od plev oddělit. Seznam schválených administrátorů vám poskytne výchozí bod, který pomůže při detekci.
Hledejte zařízení, která používají více účtů a přihlašovacích údajů pro přístup k síťovým prostředkům.
Útočníci rádi využívají přihlašovací údaje k usnadnění svých postupů a ke skrývání. Ukradnou nebo vytvoří účty a využijí je k průzkumu a k získání přístupu. To je projev vnějších i vnitřních útočníků.
Analyzujte využívání přihlašovacích údajů, abyste našli anomálie ukazující na takový typ útočných aktivit.
Zdroj dat: Monitoring síťového provozu a analýza protokolů infrastruktury autentizace a autorizace jsou nejlepší zdroje pro odhalení zneužití přihlašovacích údajů.
Extrahujte tato data a analyzujte je, abyste získali představu o tom, s kolika systémy každý uživatel obvykle komunikuje. Poté monitorujte anomálie.
Problémy: Rozdíly mezi uživateli jsou velké, ale můžete se pokusit definovat tzv. „průměrného“ uživatele. Dokonce i jen výpis uživatelů s velkými objemy může poskytnout dobrou viditelnost – když se v seznamu objeví nové jméno, můžete ho zkontrolovat.
Hledejte útočníka, který se snaží najít cenná data na souborových serverech.
Jedním z kroků, který útočníci obvykle dělají, je zjištění, jaké souborové systémy Windows jsou široce dostupné, aby mohli získat důležitá data, jako například duševní vlastnictví a čísla kreditních karet, nebo mohli vzdáleně zašifrovat data pro získání výkupného.
Nalezení anomálií v přístupech ke sdílení souborů může být cenným signálem a může vás také upozornit na zaměstnance, který zvažuje interní krádež dat.
Zdroj dat: Protokoly z vašich souborových serverů jsou nejlepším způsobem, jak to zvládnout. Bude to však vyžadovat určité analýzy, aby došlo k transformaci do podoby uživatelské perspektivy a k získání schopnosti vidět anomálie v přístupu uživatelů.
Problémy: K některým sdíleným úložištím souborů přistupují skutečně všichni, a pokud se tam nějaký uživatel dostává poprvé, může to vytvořit velký výkyv a falešně pozitivní indikaci.
Kromě toho jsou údaje o přístupu dost chaotické a těžko analyzovatelné. Lze to vidět i pomocí síťových nástrojů, ale extrakce podstatných informací je velmi pracná.
Hledejte aktivity velení a řízení a mechanismy trvalého přístupu.
Útočníci potřebují způsob komunikace mezi internetem a koncovými body, které kontrolují ve vašem prostředí. Přestože se používá při útoku méně malwaru než kdysi, stále se přítomnost škodlivého softwaru a nástrojů vzdáleného přístupu v podobě trojských koní (RAT – Remote Access Trojans) dá očekávat.
Sledujte odchozí komunikaci, zda se v ní nevyskytují příznaky malwaru volajícího domů.
Zdroj dat: Mnoho bezpečnostních nástrojů pro perimetr již vyhledává aktivity velení a řízení. Cílený malware se může pokusit kontaktovat zdroje AWS či Azure nebo nové servery, které nebudou rozpoznány tradičními službami threat intelligence (zpravodajství o hrozbách).
Své současné zabezpečení můžete rozšířit o kontrolu, zda se v protokolech DNS nevyskytují vzory dotazů DNS, které by ukazovaly na malware pokoušející se najít řídicí servery.
Mnoho neúspěšných požadavků DNS nebo požadavků, které vypadají jako strojově generované názvy domén, je příznakem malwaru naprogramovaného tak, aby zabránil zablokování na základě reputace.
Problémy: Útočníci mají mnoho způsobů, jak skrývat přenosy velení a řízení, takže je dobré dávat si pozor, ale nespoléhat při zjišťování malwaru jen na tento typ detekce.
Nikdy nelze říci, jakou kombinaci běžných internetových stránek včetně služeb Twitter, Craigslist, Gmail a mnoha dalších by malware mohl zneužít pro řídicí komunikaci.
Vyplatí se tedy vynaložit určité úsilí na sledování těchto aktivit, ale není to tak důležité jako sledování bočního pohybu a nadměrného používání přihlašovacích údajů, které je pro útočníka mnohem těžší utajit.
Private Decryption Key For Original Petya Ransomware Released
7.7.2017 thehackernews Ransomware
Rejoice Petya-infected victims!
The master key for the original version of the Petya ransomware has been released by its creator, allowing Petya-infected victims to recover their encrypted files without paying any ransom money.
But wait, Petya is not NotPetya.
Do not confuse Petya ransomware with the latest destructive NotPetya ransomware (also known as ExPetr and Eternal Petya) attacks that wreaked havoc across the world last month, massively targeting multiple entities in Ukraine and parts of Europe.
The Petya ransomware has three variants that have infected many systems around the world, but now the author of the original malware, goes by the pseudonym Janus, made the master key available on Wednesday.
According to the security researchers, victims infected with previous variants of Petya ransomware, including Red Petya (first version) and Green Petya (second version) and early versions the GoldenEye ransomware can get their encrypted files back using the master key.
The authenticity of the master key has been verified by an independent Polish information security researcher known as Hasherezade.
"Similarly to the authors of TeslaCrypt, he released his private key, allowing all the victims of the previous Petya attacks, to get their files back," Hasherezade posted her finding on MalwareBytes on Thursday.
"Thanks to the currently published master key, all the people who have preserved the images of the disks encrypted by the relevant versions of Petya, may get a chance of getting their data back."
Although the first and second version of Petya was cracked last year, the private key released by Janus offers the fastest and most reliable way yet for Petya-infected victims to decrypt their files, especially locked with the uncrackable third version.
Meanwhile, Kaspersky Lab research analyst Anton Ivanov also analyzed the Janus' master key and confirmed that the key unlocks all versions of Petya ransomware, including GoldenEye.
Janus created the GoldenEye ransomware in 2016 and sold the variants as a Ransomware-as-a-Service (RaaS) to other hackers, allowing anyone to launch ransomware attacks with just one click and encrypt systems and demand a ransom to unlock it.
If the victim pays, Janus gets a cut of the payment. But in December, he went silent.
However, according to the Petya author, his malware has been modified by another threat actor to create NotPetya that targeted computers of critical infrastructure and corporations in Ukraine as well as 64 other countries.
The NotPetya ransomware also makes use of the NSA's leaked Windows hacking exploit EternalBlue and EternalRomance to rapidly spread within a network, and WMIC and PSEXEC tools to remotely execute malware on the machines.
Security experts even believe the real intention behind the recent ransomware outcry, which was believed to be bigger than the WannaCry ransomware, was to cause disruption, rather than just another ransomware attack.
According to researchers, NotPetya is in reality wiper malware that wipes systems outright, destroying all records from the targeted systems, and asking for ransom was just to divert world's attention from a state-sponsored attack to a malware outbreak.
Lucky are not those infected with NotPetya, but the master key can help people who were attacked by previous variants of Petya and Goldeneye ransomware in the past.
Security researchers are using the key to build free decryptors for victims who still have crypto-locked hard drives.
Private Decryption Key For Original Petya Ransomware Released Friday, July 07, 2017 Swati Khandelwal 133 189 0 327 Rejoice Petya-infected victims! The master key for the original version of the Petya ransomware has been released by its creator, allowing Petya-infected victims to recover their encrypted files without paying any ransom money. But wait, Petya is not NotPetya. Do not confuse Petya ransomware with the latest destructive NotPetya ransomware (also known as ExPetr and Eternal Petya) attacks that wreaked havoc across the world last month, massively targeting multiple entities in Ukraine and parts of Europe. The Petya ransomware has three variants that have infected many systems around the world, but now the author of the original malware, goes by the pseudonym Janus, made the master key available on Wednesday. According to the security researchers, victims infected with previous variants of Petya ransomware, including Red Petya (first version) and Green Petya (second version) and early versions the GoldenEye ransomware can get their encrypted files back using the master key. The authenticity of the master key has been verified by an independent Polish information security researcher known as Hasherezade. "Similarly to the authors of TeslaCrypt, he released his private key, allowing all the victims of the previous Petya attacks, to get their files back," Hasherezade posted her finding on MalwareBytes on Thursday. "Thanks to the currently published master key, all the people who have preserved the images of the disks encrypted by the relevant versions of Petya, may get a chance of getting their data back." Although the first and second version of Petya was cracked last year, the private key released by Janus offers the fastest and most reliable way yet for Petya-infected victims to decrypt their files, especially locked with the uncrackable third version. Meanwhile, Kaspersky Lab research analyst Anton Ivanov also analyzed the Janus' master key and confirmed that the key unlocks all versions of Petya ransomware, including GoldenEye. Janus created the GoldenEye ransomware in 2016 and sold the variants as a Ransomware-as-a-Service (RaaS) to other hackers, allowing anyone to launch ransomware attacks with just one click and encrypt systems and demand a ransom to unlock it. If the victim pays, Janus gets a cut of the payment. But in December, he went silent. However, according to the Petya author, his malware has been modified by another threat actor to create NotPetya that targeted computers of critical infrastructure and corporations in Ukraine as well as 64 other countries. The NotPetya ransomware also makes use of the NSA's leaked Windows hacking exploit EternalBlue and EternalRomance to rapidly spread within a network, and WMIC and PSEXEC tools to remotely execute malware on the machines. Security experts even believe the real intention behind the recent ransomware outcry, which was believed to be bigger than the WannaCry ransomware, was to cause disruption, rather than just another ransomware attack. According to researchers, NotPetya is in reality wiper malware that wipes systems outright, destroying all records from the targeted systems, and asking for ransom was just to divert world's attention from a state-sponsored attack to a malware outbreak. Lucky are not those infected with NotPetya, but the master key can help people who were attacked by previous variants of Petya and Goldeneye ransomware in the past. Security researchers are using the key to build free decryptors for victims who still have crypto-locked hard drives.
WWE Exposes Details of 3 Million Customers on AWS
7.7.2017 securityweek CyberCrime
In what is likely to be an operator or technician error, WWE left unencrypted personal details of more than 3 million customers exposed on AWS in at least two separate databases. The issue was reported to WWE on July 4, and the company swiftly removed them.
According to a report in Forbes, the discovery was made by a Kromtech researcher named Bob Dyachenko.
WWE has acknowledged the incident with a brief statement on its website: "Although no credit card or password information was included, and therefore not at risk, WWE is investigating a vulnerability of a database housed on Amazon Web Services (AWS), which has now been secured. WWE utilizes leading cybersecurity firms Smartronix and Praetorian to manage data infrastructure and cybersecurity and to conduct regular security audits on AWS. We are currently working with Amazon Web Services, Smartronix and Praetorian to ensure the ongoing security of our customer information."
There is no indication in this statement over whether the database may or may not have been accessed or downloaded by anyone other than Mr Dyachenko.
According to Forbes, all the stored data was held in plaintext, and included educational background, earnings and ethnicity, home and email addresses, birthdates, and customers' children's age ranges and genders where supplied." Holding children's age, sex and home addresses will be particularly concerning for privacy advocates.
Although the WWE statement implies a single database, it seems that a second database contained European customer data; specifically comprising "reams of information primarily on European fans, though the information contained only addresses, telephone numbers and names..."
That second database is worth considering, since names, addresses and telephone numbers will be considered protected personal information under European laws.
"Organizations like WWE which inadequately value subscriber data will, from May 2018, find themselves exposed also to GDPR fines," warned Alan Calder, founder and executive chairman of IT Governance Ltd in an emailed comment. "A personal data breach on this scale would have to be reported to an EU supervisory authority and could well lead to a significant fine for failing to protect personal data."
GDPR can impose penalties of up to €20 million or 4% of global turnover, whichever is the greater; and that this can be imposed even though the company may be American, located in America, and storing the data on an American server.
This is not the first time in recent weeks that AWS customers have left data exposed. Last month, three contractors left 1 terabytes of data (including the details of 198 million American voters) on an unprotected AWS S3 bucket. There have been calls for Amazon to highlight sensitive data stored insecurely; but it is the customers' responsibility to protect it.
Even if security firms are employed by the data owner (or 'controller', in this case WWE), regulatory responsibility for protecting that data almost always remains with the controller under European law. SecurityWeek has reached out to both the WWE-named security firms (Smartronix and Praetorian) and will update this article with any response.
Vulnerabilities Found in Siemens Building Tech, Smart Grid Products
7.7.2017 securityweek ICS
Siemens and ICS-CERT published advisories this week to warn organizations of potentially serious vulnerabilities affecting some of the German technology conglomerate’s building controller and smart grid devices.
Users of the OZW672 and OZW772 products, designed for remote plant control and monitoring, have been informed of medium and high severity flaws allowing attackers to access or alter historical measurement data stored on the device, and read or manipulate data in TLS sessions via man-in-the-middle (MitM) attacks.
The security holes, discovered by Stefan Viehböck from SEC Consult, have not been patched, but Siemens has provided a series of recommendations for preventing potential attacks.
Related: Learn More at SecurityWeek’s 2017 ICS Cyber Security Conference
Siemens also informed customers of five vulnerabilities affecting Reyrolle protection relays. The flaws, discovered by the vendor itself, can be exploited by remote attackers or ones with network access to obtain sensitive information, bypass authentication and perform administrative operations, and cause a denial-of-service (DoS) condition.
The weaknesses have been patched with the release of firmware version 4.29.01. These and other vulnerabilities also affect SIPROTEC 4 and Compact protection products.
A separate advisory published by Siemens describes a DoS vulnerability affecting the SIMATIC Logon automation software, which provides authentication for access control on SIMATIC human-machine interface (HMI) panels. The security hole has been addressed with the release of version 1.6 of the software.
Schneider Electric patches flaws in Wonderware and Ampla MES products
In addition to the Siemens advisories, ICS-CERT informed industrial organizations this week of vulnerabilities affecting Schneider Electric Ampla Manufacturing Execution Systems (MES) and the Wonderware ArchestrA Logger logging software.
Wonderware ArchestrA Logger versions 2017.426.2307.1 and prior are affected by three high severity flaws that can be exploited for remote code execution and DoS attacks.
Ampla MES versions 6.4 and earlier fail to properly protect sensitive information – specifically, passwords are hashed using a weak algorithm, and session data is not encrypted when the software interacts with third-party databases.
The author of the original Petya ransomware released the master key
7.7.2017 securityaffairs Ransomware
The author of the original variant of the Petya ransomware has made the master key available online, all the victims can decrypt their files for free.
Janus, the author of the original variant of Petya ransomware (that isn’t the NotPetya variant used in the recent massive attack) has made the master key available online.
All the victims of the original Petya ransomware can now use the master key for free to decrypt their files.
“As research concluded, the original author of Petya, Janus, was not involved in the latest attacks on Ukraine. His original malware was pirated and extended by an unknown actor (read more here).” reads a blog post published by MalwareByte “As a result of the recent events, Janus probably decided to shut down the Petya project. Similarly to the authors of TeslaCrypt, he released his private key, allowing all the victims of the previous Petya attacks, to get their files back.”
Follow
JANUS @JanusSecretary
"They're right in front of you and can open very large doors" https://mega.nz/#!lmow0Z7D!InyOTGaodVLX2M9pMGQvHJaGpvon11FyGep10ki4LHc … @hasherezade @MalwareTechBlog ;)
8:14 PM - 5 Jul 2017
28 28 Retweets 35 35 likes
Twitter Ads info and privacy
Researchers from KasperskyLab confirmed that the master key released by Janus works on files encrypted by the original Petya ransomware and early versions the GoldenEye ransomware.
Anton Ivanov @antonivanovm
The published #Petya master key works for all versions including #GoldenEye
7:45 PM - 6 Jul 2017
495 495 Retweets 360 360 likes
Twitter Ads info and privacy
“The published #Petya master key works for all versions including #GoldenEye,” tweeted Ivanov from Kaspersky Lab.
GoldenEye is a ransomware created by Janus in 2016 that is based on the Petya code, unfortunately, someone has stolen the “compiled application” of the threat in 2017 and modified it.
“The source code of the original Petya has never been leaked publicly, so in case it was recompiled it proves that the original Petya’s author, Janus, is somehow linked to the current outbreak (either this is his work or he has sold the code to another actor).” wrote Hasherezade in one of its analysis.
Follow
hasherezade @hasherezade
My new post on #EternalPetya - proving that the code was indeed patched: https://blog.malwarebytes.com/threat-analysis/2017/06/eternalpetya-yet-another-stolen-piece-package/ …
6:56 PM - 30 Jun 2017
Photo published for EternalPetya - yet another stolen piece in the package? - Malwarebytes Labs
EternalPetya - yet another stolen piece in the package? - Malwarebytes Labs
In this post, we will try to fill this gap, by making step-by-step comparison of the current kernel and the one on which it is based (Goldeneye Petya).
blog.malwarebytes.com
251 251 Retweets 262 262 likes
Twitter Ads info and privacy
The expert confirmed that a stolen version of the ransomware that is based on the GoldenEye code was used in the massive NotPetya attack (aka ExPetr, Eternal Petya). Unlike previous versions, the NotPetya variant doesn’t implement the feature to decrypt files.
In April 2016, researchers developed a tool to decrypt files encrypted by early Petya ransomware versions. The Twitter user @leostone announced to have elaborated a method to generate passwords in less than a minute. The user also developed a website to help victims generate keys for restoring encrypted files.
In order to generate a decryption key, the victim just needs to provide certain information on the infected drive. The researcher Fabian Wosar from Emisoft as developed an application that is able to automatize the process extracting data from infected Petya drives and generate the key for the data rescue.
The security experts Lawrence Abrams, who contribute at BleepingComputer.com blog, has prepared a guide on how to use the tool.
Abrams explained that the tool scans the infected drive searching for the Petya bootcode. Once detected the code, it selects it and allow users to simply copy both the sectors and nonce associated with it. These data (a Base64-encoded 512 bytes verification data and a Base64-encoded 8 bytes nonce) could be used to generate the password through the @leostone’s website.
“An individual going by the twitter handle leostone was able to create an algorithm that can generate the password used to decrypt a Petya encrypted computer. In my test this, this algorithm was able to generate my key in 7 seconds.” wrote Abrams in a blog post.

To discover the password, the user has to physically remove the drive from the infected machine and attach it to either a Windows machine or a USB drive docking station and to launch the Wosar’s tool.
“To use Leostone’s decryption tool you will need attach the Petya affected drive to another computer and extract specific data from it. The data that needs to be extracted is 512-bytes starting at sector 55 (0x37h) with an offset of 0 and the 8 byte nonce from sector 54 (0x36) offset: 33 (0x21). This data then needs to be converted to Base64 encoding and used on the https://petya-pay-no-ransom.herokuapp.com/ site to generate the key.” continues Abrams.
“Unfortunately, for many victims extracting this data is not an easy task. The good news is that Fabian Wosar created a special tool that can be used to easily extract this data. In order to use this tool, you need to take the encrypted drive from the affected computer and attach it to a Windows computer that is working properly. If your infected computer has multiple drives, you should only remove the drive that is the boot drive, or C:\ drive, for your computer.”
Once obtained the password, users should be able to reconnect their encrypted drive and enter it to restore the files encrypted by the Petya ransomware.
In response to the tool, the Petya’s author updated the ransomware neutralizing it.
“Thanks to the currently published master key, all the people who have preserved the images of the disks encrypted by the relevant versions of Petya, may get a chance of getting their data back,” Hasherezade wrote.
BroadPwn potentially expose to hack millions of Android devices using Broadcom Wi-Fi Chip
7.7.2017 securityaffairs Android
Google warned of a serious flaw dubbed BroadPwn in some Broadcom Wi-Fi chipsets that potentially impacts millions of Android devices.
Google published the monthly security update for Android devices, it warned of a serious flaw, dubbed BroadPWN, in some Broadcom Wi-Fi chipsets that potentially impacts millions of Android devices, as well as some iPhone models.
BroadPwn is a critical remote code execution vulnerability, tracked as CVE-2017-3544, that affects the Broadcom BCM43xx family of WiFi chipsets. Remote attackers can trigger the flaw without user interaction to execute malicious code on vulnerable devices with kernel privileges.
“The most severe vulnerability in this section could enable a remote attacker using a specially crafted file to execute arbitrary code within the context of an unprivileged process.,” reads the Google July 2017 Android Security Bulletin.
The BroadPwn issue was reported by the Exodus Intelligence expert Nitay Artenstein, he will present the analysis at the Next Black Hat 2017 conference.
“Meet Broadpwn, a vulnerability in Broadcom’s Wi-Fi chipsets which affects millions of Android and iOS devices, and can be triggered remotely, without user interaction. The Broadcom BCM43xx family of Wi-Fi chips is found in an extraordinarily wide range of mobile devices – from various iPhone models, to HTC, LG, Nexus and practically the full range of Samsung flagship devices.
“In this talk, we’ll take a deep dive into the internals of the BCM4354, 4358 and 4359 Wi-Fi chipsets, and explore the workings of the mysterious, closed-source HNDRTE operating system. Then, we’ll plunge into the confusing universe of 802.11 standards in a quest to find promising attack surfaces.” states the abstract of the talk.

Google also patched 10 critical RCEs and more than 100 high and moderate issues. The company also fixed several critical flaws affecting the Android Mediaserver process, some of them could be exploited by a remote attacker to perform code execution.An input validation flaw in the libhevc library, tracked as CVE-2017-0540, can be exploited by using a specifically crafted file.
“A remote code execution vulnerability in libhevc in Mediaserver could enable an attacker using a specially crafted file to cause memory corruption during media file and data processing. This issue is rated as Critical due to the possibility of remote code execution within the context of the Mediaserver process. Product: Android. Versions: 5.0.2, 5.1.1, 6.0, 6.0.1, 7.0, 7.1.1. Android ID: A-33966031.” reads the vulnerability description.
As usual, Google already issued security updates for Pixel and Nexus devices, but remaining Android devices will remain vulnerable until OEMs will fix the issues too.
Millions of Android Devices Using Broadcom Wi-Fi Chip Can Be Hacked Remotely
7.7.2017 thehackernews Android

Google has released its latest monthly security update for Android devices, including a serious bug in some Broadcom Wi-Fi chipsets that affects millions of Android devices, as well as some iPhone models.
Dubbed BroadPwn, the critical remote code execution vulnerability resides in Broadcom's BCM43xx family of WiFi chipsets, which can be triggered remotely without user interaction, allows a remote attacker to execute malicious code on targeted Android devices with kernel privileges.
"The most severe vulnerability in this [runtime] section could enable a remote attacker using a specially crafted file to execute arbitrary code within the context of an unprivileged process," Google describes in the July 2017 Android Security Bulletin.
The BroadPwn vulnerability (CVE-2017-3544) has been discovered by Exodus Intelligence researcher Nitay Artenstein, who says the flawed Wi-Fi chipset also impacts Apple iOS devices.
Since Artenstein will be presenting his finding at Black Hat 2017 event, details about the BroadPwn bug is scarce at this moment.
"The Broadcom BCM43xx family of Wi-Fi chips is found in an extraordinarily wide range of mobile devices – from various iPhone models to HTC, LG, Nexus and practically the full range of Samsung flagship devices," the abstract for Artenstein's talk says.
Besides the fix for the BroadPwn vulnerability, July's Android Security Bulletin includes patches for 10 critical, which are all remote code execution bugs, 94 high and 32 moderate rated vulnerabilities.
Two months ago, an over-the-air hijacking vulnerability was discovered in Broadcom WiFi SoC (Software-on-Chip) chips, allowing attackers within the same WiFi network to remotely hack, iPhones, iPads, iPods and Android handsets without any user interaction.
At that time, Apple rushed out an emergency iOS patch update to address the serious bug, and Google addressed the flaw in its Android April 2017 security updates.
Android Security Bulletin: July 2017 Updates
Among the other critical flaws is a long list of vulnerabilities in the Mediaserver process in the Android operating system, which also allows attackers to perform remote code execution on the affected devices.
One of the vulnerabilities is an issue with the way the framework handles some specific files. The libhevc library has an input validation vulnerability (CVE-2017-0540), which can be exploited using a crafted file.
"A remote code execution vulnerability in libhevc in Mediaserver could enable an attacker using a specially crafted file to cause memory corruption during media file and data processing," the vulnerability description says.
"This issue is rated as Critical due to the possibility of remote code execution within the context of the Mediaserver process."
The over-the-air updates and firmware for Google devices have already been issued by the company for its Pixel and Nexus devices, though rest of Android still need to wait for an update from their OEMs, leaving million of Android devices vulnerable for next few months.
Millions of Android Devices Using Broadcom Wi-Fi Chip Can Be Hacked Remotely Thursday, July 06, 2017 Mohit Kumar 1486 770 59 2351 Google has released its latest monthly security update for Android devices, including a serious bug in some Broadcom Wi-Fi chipsets that affects millions of Android devices, as well as some iPhone models. Dubbed BroadPwn, the critical remote code execution vulnerability resides in Broadcom's BCM43xx family of WiFi chipsets, which can be triggered remotely without user interaction, allows a remote attacker to execute malicious code on targeted Android devices with kernel privileges. "The most severe vulnerability in this [runtime] section could enable a remote attacker using a specially crafted file to execute arbitrary code within the context of an unprivileged process," Google describes in the July 2017 Android Security Bulletin. The BroadPwn vulnerability (CVE-2017-3544) has been discovered by Exodus Intelligence researcher Nitay Artenstein, who says the flawed Wi-Fi chipset also impacts Apple iOS devices. Since Artenstein will be presenting his finding at Black Hat 2017 event, details about the BroadPwn bug is scarce at this moment. "The Broadcom BCM43xx family of Wi-Fi chips is found in an extraordinarily wide range of mobile devices – from various iPhone models to HTC, LG, Nexus and practically the full range of Samsung flagship devices," the abstract for Artenstein's talk says. Besides the fix for the BroadPwn vulnerability, July's Android Security Bulletin includes patches for 10 critical, which are all remote code execution bugs, 94 high and 32 moderate rated vulnerabilities. Two months ago, an over-the-air hijacking vulnerability was discovered in Broadcom WiFi SoC (Software-on-Chip) chips, allowing attackers within the same WiFi network to remotely hack, iPhones, iPads, iPods and Android handsets without any user interaction. At that time, Apple rushed out an emergency iOS patch update to address the serious bug, and Google addressed the flaw in its Android April 2017 security updates. Android Security Bulletin: July 2017 Updates Among the other critical flaws is a long list of vulnerabilities in the Mediaserver process in the Android operating system, which also allows attackers to perform remote code execution on the affected devices. One of the vulnerabilities is an issue with the way the framework handles some specific files. The libhevc library has an input validation vulnerability (CVE-2017-0540), which can be exploited using a crafted file. "A remote code execution vulnerability in libhevc in Mediaserver could enable an attacker using a specially crafted file to cause memory corruption during media file and data processing," the vulnerability description says. "This issue is rated as Critical due to the possibility of remote code execution within the context of the Mediaserver process." The over-the-air updates and firmware for Google devices have already been issued by the company for its Pixel and Nexus devices, though rest of Android still need to wait for an update from their OEMs, leaving million of Android devices vulnerable for next few months.
Wiretap Raises $4.9 Million to Monitor Enterprise Social Networks
7.7.2017 securityweek IT
Columbus, Ohio-based startup Wiretap has closed a $4.9 million Series A financing round led by Pittsburgh-based Draper Triangle Ventures, Columbus-based Ohio Innovation Fund and Rev1 Ventures, as well as JumpStart Inc., based in Cleveland. The money will be used for sales, marketing and R&D.
Wiretap has developed a platform that provides visibility into an increasingly important but dark aspect of corporate life: the enterprise social network (ESN). Slack is a prime example, although there are many others such as Microsoft Yammer, and Workplace by Facebook.
ESNs provide the modern 'water-cooler' environment, where employees meet informally for both corporate and social collaboration. The difficulty for management is that it has no visibility into that environment, leaving a new and unmeasured threat vector.
A November 2016 study by Persistence Market Research titled Enterprise Social Networks and Online Communities Market: Global Industry Analysis and Forecast 2016–2026 predicts that the ESN and online community market will grow from $2.6 billion in 2016 to $12.18 billion by 2026. It comments, "Online collaboration of business information with social networking websites creates an opportunity for hackers to illegally access information or gain unauthorized access to critical business data through social websites."
Wiretap monitors the ESNs and provides unique visibility into corporate sentiment. Using artificial intelligence, including behavioral and linguistic analysis, it provides management awareness of corporate social health. This could be used to highlight the problems that initially cause dissatisfaction and ultimately lead to insider threats, allowing HR to intervene and address the problem. Or it could be used to monitor for potential or actual leaks of PII or IP.
Wiretap CEO Jeff Schumann told SecurityWeek that the current problems faced by Uber are an example of corporate health issues that could be highlighted and subsequently solved with Wiretap in place. Uber's HR team were apparently unaware of the undercurrent of sexual harassment within the organization until it finally boiled over. In June, it was forced to sack 20 full time employees; and there will likely be more to follow. The damage to brand image is inestimable.
Schumann suggested that linguistic and behavioral analysis of ESNs will highlight growing discontent within the company, allowing HR to intervene and improve or at least manage the situation. Individual grievances that can slowly grow into insider threat motivation can also be highlighted.
By monitoring and analyzing ESNs over time, management will get the tools to predict and address corporate health issues. "As the demand and popularity of Enterprise Social Networks soars, Wiretap bridges a critical security gap -- ensuring the enterprise remains secure while maximizing the productivity and inherent collaboration of their ESN investments," explains Schumann.
"Rev1 Ventures is committed to supporting high-growth companies, like Wiretap, as they scale and grow," said Rev1 Ventures EVP for investment funds, Ryan Helon. "With an innovative approach for securing enterprise collaboration tools and a compelling vision for helping companies maximize social channels for better engagement and performance, Wiretap is poised for explosive success and we're excited to be part of their journey."
CIA Tools for Stealing SSH Credentials Exposed by WikiLeaks
7.7.2017 securityweek BigBrothers
WikiLeaks has published documents detailing BothanSpy and Gyrfalcon, tools allegedly used by the U.S. Central Intelligence Agency (CIA) to steal SSH credentials from Windows and Linux systems.
A document dated March 2015 describes BothanSpy as a tool that steals credentials for active SSH sessions from Xshell, an SSH, telnet, and rlogin terminal emulator for Windows.
Using a mode dubbed by its developers “Fire and Collect,” BothanSpy collects SSH credentials and sends them to the attacker’s server without writing any data to the compromised machine’s disk. If the mode “Fire and Forget” is used, the stolen credentials are written to a file on the disk.
The other tool, Gyrfalcon 2.0, described in a document dated November 2013, is designed to steal SSH credentials from the OpenSSH client on Linux platforms.
Gyrfalcon is a library loaded into the OpenSSH client process address space. It collects OpenSSH session traffic, including usernames and passwords, compresses and encrypts the data, and stores it in a file. A third-party application is required to exfiltrate the file.
The documentation for Gyrfalcon 2.0 informed users that they must have a thorough understanding of the Linux/UNIX command line interface, and they must know standard procedures for masking their activity within certain shells.
Over the past months, as part of a leak dubbed “Vault 7,” WikiLeaks has described several tools allegedly used by the CIA. The list includes tools designed for redirecting traffic on Linux systems (OutlawCountry), spreading malware on an organization’s network (Pandemic), locating people via their device’s Wi-Fi (Elsa), hacking routers and access points (Cherry Blossom), and accessing air-gapped networks (Brutal Kangaroo).
WikiLeaks has also exposed tools designed for replacing legitimate files with malware, hacking smart TVs, launching MitM attacks, making malware attribution and analysis more difficult, and creating custom malware installers.
Researchers have found links between the tools detailed by Wikileaks and the malware used by a cyber espionage actor named “Longhorn” and “The Lamberts.”
Flaws Found in Dell EMC Data Protection, ESRS Products
7.7.2017 securityweek Vulnerebility
Dell EMC informed customers this week that its Data Protection Advisor and ESRS Policy Manager products are affected by high and medium severity vulnerabilities, and provided patches and workarounds for addressing the issues.
According to an advisory published by the company on the Full Disclosure mailing list, versions prior to 6.8 of the EMC Secure Remote Support (ESRS) Policy Manager are affected by a high severity flaw.
The security hole, discovered by Travis Emmert from Salesforce and tracked as CVE-2017-4976, is caused by the existence of an undocumented account that can be used by a remote attacker to gain unauthorized access to a targeted system.
“EMC ESRS Policy Manager contains an undocumented account (OpenDS admin) with a default password. A remote attacker with the knowledge of the default password may login to the system and gain administrator privileges to the local LDAP directory server,” the company said in its advisory.
Starting with ESRS Policy Manager 6.8, users are prompted to change this default password during the installation process. Customers have also been provided instructions on how to change the password on their existing installations.
A separate advisory published by Dell EMC this week describes medium severity vulnerabilities affecting the EMC Data Protection Advisor data protection management software.
The product is affected by several blind SQL injection flaws (CVE-2017-8002) that can be exploited by a remote, authenticated attacker to gain access to data by executing arbitrary SQL commands, and a path traversal weakness (CVE-2017-8003) that can be exploited by a high privileged user to access information from the underlying OS server.
Users have been advised to update EMC Data Protection Advisor to version 6.4 as soon as possible.
Earlier this month, Beyond Security’s SecuriTeam Secure Disclosure (SSD) project published the details and proof-of-concept (PoC) code for a command injection vulnerability affecting EMC’s IsilonSD Edge software-defined storage solution.
The flaw allows a remote, authenticated attacker to execute arbitrary OS commands, including with root privileges. Researchers reported their findings to EMC on April 24, but it’s unclear if the vulnerability has been patched by the vendor.
Hackeři pronikli do amerických elektráren
7.7.2017 Novinky/Bezpečnost Kyber
Hackeři operující ve prospěch cizího státu nedávno pronikli do nejméně tuctu amerických elektráren včetně kansaské jaderné elektrárny Wolf Creek. Napsala to v pátek agentura Bloomberg s odvoláním na informované americké činitele. Útok podle nich vyvolává podezření, že hackeři hledají slabá místa v rozvodu elektrické energie.
Experti varují, že nepřátelské síly si chtějí vytvořit podmínky pro narušení dodávky elektřiny v USA. Příslušné varování dostaly energetické podniky minulý týden. Hackeři rovněž nedávno pronikli do sítí jisté nejmenované společnosti, která vyrábí kontrolní systémy pro zařízení užívaná v elektrárenských provozech.
Hlavním podezřelým je Rusko, píše Bloomberg. Taková možnost je obzvlášť znepokojivá, protože Rusům se už podařilo vyřadit část elektrické rozvodné sítě na Ukrajině, což mohl být test jejich útočných nástrojů. Americká agentura dodává, že USA mají, jak známo, k dispozici vlastní kybernetické nástroje schopné rozvrátit nepřátelskou elektrickou síť.
Podle amerického ministerstva pro vnitřní bezpečnost Spojeným státům bezprostřední nebezpečí nehrozí. "Není náznak žádného veřejného ohrožení, protože případný dopad (hackerských útoků) se omezuje na administrativní a obchodní sítě," uvedlo ministerstvo. Partnerské ministerstvo energetiky prý s rozvodnými firmami spolupracuje na posílení bezpečnosti.
Lék na vyděračský virus? Piráti chtějí za univerzální klíče milióny
7.7.2017 Novinky/Bezpečnost Viry
Na konci června zasáhla hned několik zemí světa masivní vlna vyděračského viru Win32/Diskcoder.C Trojan. Útočníci však kvůli školácké chybě nevydělali ani korunu. Napravit se to snaží nyní, kdy na černém trhu nabízejí k prodeji univerzální klíče za milióny korun.
Uživatelé napadení virem místo startu operačního systému uvidí tuto zprávu.
Škodlivý kód Win32/Diskcoder.C Trojan se internetem již nijak dramaticky nešíří. Přesto v různých koutech světa zůstávají stále zavirované tisíce počítačů. A odvirovat je kvůli chybě počítačových pirátů nejde ani ve chvíli, kdy jsou uživatelé ochotni zaplatit výkupné.
Většina vyděračských virů jsou poměrně sofistikované škodlivé kódy. Po zablokování počítače požadují výkupné, platba z každého napadeného účtu je přitom směřována do jiné bitcoinové peněženky. Vystopovat útočníky je tedy prakticky nemožné a stejně tak není reálné zablokovat jednotlivé transakce. Útočníkům z vyděračských virů plynou často i milióny korun.
V případě ransomwaru Win32/Diskcoder.C Trojan však útočníci tak chytří nebyli. S majiteli napadených počítačů totiž komunikují prostřednictvím e-mailu na serveru posteo.net. V podstatě každý, kdo chce odblokovat počítač, musí útočníkům napsat.
Právě to se ale provozovatelům serveru posteo.net nelíbilo, a tak e-mailovou schránku počítačových pirátů ještě v úterý večer zablokovali, stalo se tak pouhých pár hodin poté, co se vyděračský virus začal šířit internetem.
Zaplatit chtějí v bitcoinech
Z řádků výše je patrné, že kyberzločinci na tomto škodlivém kódu nevydělali ani korunu. Napravit se to snaží nyní na černém trhu. Nabízí k prodeji univerzální klíče, které slouží k odemknutí uzamčených počítačů.
Útočníci patrně doufají, že je koupí nějací další počítačoví piráti, kteří je následně budou za úplatu distribuovat mezi lidi. Mezi případnými zájemci by se mohla objevit také nějaká antivirová společnost, jež by s pomocí klíčů vytvořila nástroj na obnovu uzamčených počítačů.
Cena za univerzální klíče však není rozhodně nízká. Kyberzločinci chtějí v přepočtu bezmála šest miliónů korun. Zaplatit přitom chtějí v bitcoinech, aby je nebylo možné vystopovat.
Zákeřný vyděračský virus
Ransomware Win32/Diskcoder.C Trojan napadl na konci června bankovní sektor, energetické i poštovní společnosti. Stejně tak ale útočil i v domácnostech. Nejvíce postižena je Ukrajina, do žebříčku deseti zemí, ve kterých virus řádil nejvíce, se nicméně dostala také Česká republika, jež je aktuálně na deváté příčce žebříčku.
Win32/Diskcoder.C Trojan je poměrně zákeřný škodlivý kód. Většina vyděračských virů totiž potřebuje k zašifrování dat na pevném disku poměrně dost času, klidně i několik hodin. Během toho může jejich práci zachytit antivirový program a zablokovat je ještě dříve, než v počítači nadělají nějakou větší neplechu.
Nově objevená hrozba však funguje jiným způsobem. Na disku nezašifruje všechna data, ale pouze tzv. MBR (Master Boot Record). Jde o hlavní spouštěcí záznam, díky kterému se v podstatě spouští celý operační systém. K zašifrovanému záznamu pak počítač nemá přístup a místo Windows spustí jen hlášku o nutnosti zaplatit výkupné.
Na zašifrování MBR nepotřebuje nový vyděračský virus několik hodin, stačí mu pouze pár vteřin. Antiviry tak prakticky nemají šanci škodlivý kód zachytit. Hned po prvním restartu je pak problém na světě.
Hackeři ukradli milióny korun z obří bitcoinové burzy
7.7.2017 Novinky/Bezpečnost Kriminalita
Hackeři napadli jednu z pěti největších burz pro obchody s kybernetickou měnou bitcoin Bithumb, která působí v Jižní Koreji. Podle prohlášení burzy hackeři ukradli data uživatelů a peníze v objemu miliard wonů (desítek miliónů Kč), uvedl server rttnews.com.
Bithumb je největší burzou pro obchody s bitcoiny a další kybernetickou měnou ether v Jižní Koreji. Na obchodech s bitcoiny v zemi má podíl 75,7 procenta. Denně se zde zobchoduje v průměru 13 000 bitcoinů, což je zhruba deset procent celosvětového obchodu s touto měnou.
Podle burzy hackeři ukradli databázi s informacemi o klientech z počítače jednoho ze zaměstnanců. Údajně se ztratila jména, e-maily a čísla mobilních telefonů více než 31 800 klientů. Finanční ztráty z účtů těchto zákazníků by měly dosáhnou miliard wonů, podle jedné neověřené zprávy z místních médií ztráta dosáhla 1,2 miliardy wonů (23,8 miliónu Kč). Burza slíbila klientům odškodnění.
BBC na svých stránkách upozornila, že útok hackerů se zřejmě uskutečnil již v únoru. Bithumb odhalil útok 29. června. Napaden měl být domácí počítač zaměstnance.
Jihokorejská tisková agentura Jonhap uvedla, že jihokorejský úřad pro internet a bezpečnost zahájil vyšetřování této události.
Vklady nejsou pojištěny
Evropský bankovní úřad již dříve varoval spotřebitele, že neregulované virtuální měny představují velké riziko, přestože jde o relativně populární prostředek k investici. Vklady totiž nejsou nijak chráněny a kurz často výrazně kolísá.
Virtuální měna bitcoin vznikla v roce 2009, větší popularitě se ale těší v posledních letech. Vytvořena byla tak, aby se nedala ovlivňovat žádnou vládou ani centrální bankou.
Kybernetické mince „razí“ síť počítačů se specializovaným softwarem naprogramovaným tak, aby uvolňoval nové mince stabilním, ale stále klesajícím tempem. Počet mincí v oběhu má dosáhnout nakonec 21 miliónů, což má být kolem roku 2140.
Tips to Stay Secure on Summer Vacations
7.7.2017 securityaffairs Security
In the excitement of summer vacations, most of us forget to equip ourselves with the privacy tools and needed security measures. Yet, such flawed data security could ruin your vacations as the cyber goons always remain on work.
Therefore, here we have listed some essential steps that are must to secure your sensitive information you carry with yourself while traveling.
Don’t Divulge the plans for your summer vacations
In the era of the globally connected smart world, internet users often share their personal experiences on their social accounts. Yet, these people who are connected with us through our social accounts are not the one to whom we are closely familiar with.
There are some common concerns and security tips while using your social account and sharing personal details on it. You may wait until you return from the vacations to upload the pictures or your location updates instead of confessing at the spot. However, the ones who are making such divulgence are providing cyber thefts a real-time opportunity to exploit your sensitive data.
Graham Cluley, Chief Technology Officer at UK tech security firm Sophos says;
“Social networks are great fun, and can be advantageous but people really need to understand that it’s a complicated world and you need to step wisely.”
“People should just exercise common sense online, but the problem with common sense is that it’s not very common. If you wouldn’t invite these people into your house to see your cat, you certainly wouldn’t let them see pictures from holiday.”
To remain secure, there are few tips you should follow while traveling;
Make your post visible to the people you know and not let them on public display.
Disable the GPS feature from your phone and social media accounts.
Don’t provide check-ins to your places such as Hotels, Airport, and others.
Keep Your Devices and Web Browsers Updated
Updating your devices and web browsers is a consistent advice from security experts as a precaution to avoid security flaws and cyber attacks. Unpatched devices are at a risk of vulnerability exploitations which could be averted through updating your systems and devices.
Carrying devices such as Smartphones, laptops, and tablets make your vacation more happening, joyous and memorable. Yet, they could cause trouble when their systems are outdated.
summer vacations
Infosec Analyst Yasin Soliman says;
“Don’t forget to check the browser software installed on your devices. The ever-increasing uptick of web-based services for work and play means it’s vital that your web browser remains safe and secure when traveling.”
A recommended privacy measure also includes secure browsers that you should have on your devices.
Turn off the Wi-Fi devices Not in Use
You should turn off all the Wi-Fi connections at home when going to the vacations. Keeping that Wi-Fi on could provide an opportunity to cyber criminals who could easily exploit vulnerabilities in an open Wi-Fi.
Communications director of the Internet Education Foundation, Danielle Yates says,
“An open and unsecured network can be accessed by anyone within range and, further, if communications are not secure, it’s possible someone with malicious intent could intercept emails or even view private files and records.”
However, you must make sure that all the IoT devices in your house are disconnected from the internet. Also while traveling you should avoid public Wi-Fi connections that could be harmful to your device’s security.
Disable GPS When Not Necessary
While on vacations most of the people are new to the places they want to visit. Therefore, they often enable GPS for directional help and leave it on. Yet, such excitement could expose you to the vulnerability and security threats.
Kim Crawley, Information security writer says;
“While on holiday, only turn GPS on your phone or tablet when you need to use it. Not only will you save your battery; you’ll also be more difficult for an attacker to geolocate. This advice also applies to when you’re not on holiday. There are a lot of websites, apps, and online services these days that’ll ask for your geolocation to be enabled. Never enable it unless you absolutely must.”
Government Accountability Office said,
“Specifically, they are concerned that location data can be used for purposes other than to provide services to the consumer, such as selling the data to others for marketing. They also have concerns that location data can be used to track where consumers are, which can, in turn, be used to steal their identity, stalk them, or monitor them without their knowledge. In addition, location data can be used to infer other sensitive information about individuals such as their religious affiliation or political activities.”
USB Outlets Should be Avoided
To attract the travelers and visitors most of the hospitality industry organizations such as Hotels provide the facility of USB outlets to charge their devices. However, if you are one of the travelers it’s never a great idea to charge your device from such outlets.
The owner of Sherpa Intelligence LLC, Tracy Z. Maleeff elaborates the reason of this as;
“These ubiquitous ports could possibly do harm to your devices rather than just charge them. Unlike a regular outlet plug, charging via a USB plug could result in a transfer of data from the port to your device. Why risk having malware loaded onto your device when you only wanted a charge?”
To overcome these problems you could use alternatives such as phone charger or a regular wall outlet.
Follow Basic Security Precautions
The previously discussed privacy measures are necessary to follow while being on vacations. Also, they are especially applicable while traveling but there are some basic online security precautions you must follow as a primary layer of defense. Without these, you could be in trouble.
David Jamieson, a Cyber Security individual described some of these measures;
“If ever there is a time to encrypt your laptop, ensure your files are backed up or stored in the cloud, turn on your firewall, confirm your anti-virus and anti-malware applications are up-to-date, and use complex passwords for your web accounts, THIS IS THE TIME. Criminals do NOT let down their guard; rather, they constantly work hard to steal from us.”
So, keeping yourself vigilant could save you from data thefts. Basic privacy measures such as avoiding public Wi-Fi, using secure browsers and software updates should be among your highest concerns while exploring the world.
Have a Pleasant Journey
Being data security literate just require some simple techniques to remember. Yet, such minute incentives could exempt you from the unease of being prone to vulnerabilities. With your data being secure, you could have a much joyous experience of swimming, camping, and the sunbath.
CopyCat Android malware infected 14 Million devices and rooted 8 Million
7.7.2017 securityaffairs Android
Researchers at Check Point spotted a new family of Android malware dubbed CopyCat that infected 14 million devices and rooted 8 million of them.
Researchers at Check Point’s Mobile Research Team have spotted a new family of Android malware that infected 14 million devices and rooted 8 million of them.
According to the expert, the new strain of Android malware dubbed CopyCat allowed its authors to earn $1.5 million from April to May 2016 by implementing an ad fraud scheme.
“Check Point researchers identified a mobile malware that infected 14 million Android devices, rooting approximately 8 million of them, and earning the hackers behind the campaign approximately $1.5 million in fake ad revenues in two months.” states the analysis published by the researchers. “CopyCat is an extensive campaign that infected 14 million devices globally, rooting 8 million of them, in what researchers describe as an unprecedented success rate. Check Point researchers estimate that the malware generated $1.5 million for the group behind the campaign.”
Researchers with Check Point’s Mobile Research Team spotted CopyCat in March, the largest number of infections is in Southeast Asia (55%) and Africa (18%), but the infections in the US are increasing.
Attackers spread the malware by trojanizing popular apps that were made available for download on third-party app stores.
Once installed on the target mobile device, the malware waits for it reboot, then it downloads a series of exploits from an Amazon S3 bucket in order to root the device.
“Once the device has restarted, CopyCat downloads an “upgrade” pack from an S3 bucket, a web storage service provided by Amazon. This pack contains six common exploits with which the malware attempts to root the device.” continues the analysis.
“If successful, CopyCat installs another component to the device’s system directory, an activity which requires root permissions, and establishes persistency, making it difficult to remove”
The malicious code injects code into the Zygote process in the Android core that launches apps, with this technique the attackers gain admin privileges.
CopyCat isn’t the first malware targeting Zygote, in 2016 experts at Kaspersky and at Checkpoint found the Triada Android Trojan using the same technique.
According to the experts at Check Point, the authors of the CopyCat malware use to inject code into the Zygote process to get credit for fraudulently installed apps on the device by swapping out referrer IDs for legitimate apps with their own.
The crooks also earn money by displaying fake ads and installs fake apps.
The analysis of C&C servers revealed that between April and May the attackers served fake ads to 3.8 million of the devices while crooks were stealing credit for installing apps on Google Play from 4.4 million of other devices.
It’s interesting to note that the CopyCat malware used a bulk of old exploits to root millions of devices, such as the Towelroot, other exploits were from 2014 and 2013. This means that the success of the CopyCat attack that possible due to a large number of unpatched devices.

Malware experts believe that the Chinese MobiSummer ad network could be behind the CopyCat malware.
“It is unclear who is behind the CopyCat attack, however, there are several connections to MobiSummer, an ad network located in China. It is important to note that while these connections exist, it does not necessarily mean the malware was created by the company, and it is possible the perpetrators behind it used MobiSummer’s code and infrastructure without the firm’s knowledge.” states the analysis.
“The first connection between the company and the malware is the server, which operates both the malware and some of MobiSummer’s activity. In addition, some of the malware’s code is signed by MobiSummer itself, and some of the remote services used by the malware were created by the company. The malware also refrains from targeting Chinese devices, suggesting the malware developers are Chinese and want to avoid any investigation by local law enforcement, a common tactic in the malware world.”
Check Point reported findings of its investigation to Google.
Wikileaks: BothanSpy and Gyrfalcon CIA Implants steal SSH Credentials from Windows and Linux OSs
7.7.2017 securityaffairs BigBrothers
WikiLeaks leaked documents detailing BothanSpy and Gyrfalcon CIA implants designed to steal SSH credentials from Windows and Linux OSs.
WikiLeaks has published a new batch of documents from the Vault7 dump detailing two new CIA implants alleged used by the agency to intercept and exfiltrate SSH (Secure Shell) credentials from both Windows and Linux operating systems with different attack vectors.
The first implant codenamed BothanSpy was developed to target Microsoft Windows Xshell client, the second one named Gyrfalcon was designed to target the OpenSSH client on various Linux distros, including CentOS, Debian, RHEL (Red Hat), openSUSE and Ubuntu.
BothanSpy and Gyrfalcon are able to steal user credentials for all active SSH sessions and then sends them back to CIA cyber spies.
BothanSpy is installed as a Shellterm 3.x extension on the target machine, it could be exploited by attackers only when Xshell is running on it with active sessions.
Xshell is a terminal emulator that supports SSH, SFTP, TELNET, RLOGIN and SERIAL for delivering industry leading features including a tabbed environment, dynamic port forwarding, custom key mapping, user defined buttons, VB scripting, and UNICODE terminal for displaying 2 byte characters and international language support.
“BothanSpy only works if Xshell is running on the target, and it has active sessions. Otherwise, Xshell is not storing credential information in the location BothanSpy will search.” reads the user manual.
“In order to use BothanSpy against targets running a x64 version of Windows, the loader being used must support Wow64 injection. Xshell only comes as a x86 binary, and thus BothanSpy is only compiled as x86. Shellterm 3.0+ supports Wow64 injection, and Shellterm is highly recommended.“
The Gyrfalcon implant works on Linux systems (32 or 64-bit kernel), CIA hackers use a custom malware dubbed JQC/KitV rootkit for persistent access.
The implant could collect full or partial OpenSSH session traffic, it stores stolen information in a local encrypted file for later exfiltration.
“Gyrfalcon is an SSH session “sharing” tool that operates on outbound OpenSSH sessions from the target host on which it is run. It can log SSH sessions (including login credentials), as well as execute
commands on behalf of the legitimate user on the remote host.” reads the user manual of Gyrfalcon v1.0.
“The tool runs in an automated fashion. It is configured in advance, executed on the remote host and left running. Some time later, the operator returns and commands gyrfalcon to flush all of its collection to disk. The operator retrieves the collection file, decrypts it, and analyzes the collected data”
Wikileaks also published the user guide for Gyrfalcon v2.0, the implant in composed of two compiled binaries that should be uploaded by attackers to the target platform.

“The target platform must be running the Linux operating system with either 32- or 64-bit kernel
and libraries. Gyrfalcon consists of two compiled binaries that should be uploaded to the target
platform along with the encrypted configuration file. ” continues the malware.
“Gyrfalcon does not provide any communication services between the local operator computer and target platform. The operator must use a third-party application to upload these three files to the target platform.”
Below the list of release published by Wikileaks since March:
BothanSpy and Gyrfalcon – 06 July, 2017
OutlawCountry – 30 June, 2017
ELSA malware – 28 June, 2017
Cherry Blossom – 15 June, 2017
Pandemic – 1 June, 2017
Athena – 19 May, 2017
AfterMidnight – 12 May, 2017
Archimedes – 5 May, 2017
Scribbles – 28 April, 2017
Weeping Angel – 21 April, 2017
Hive – 14 April, 2017
Grasshopper – 7 April, 2017
Marble Framework – 31 March, 2017
Dark Matter – 23 March, 2017
NotPetya Operators Accessed M.E.Doc Server Using Stolen Credentials: Cisco
6.7.2017 securityweek Ransomware
The group behind last week’s destructive NotPetya attack was able to access M.E.Doc’s update server and use it for their nefarious purposes courtesy of stolen credentials, Cisco has discovered.
Last week, multiple security companies determined that the tax software company’s update server was used as the initial attack vector. Although M.E.Doc denied possible compromise several times during the first days of the outbreak, it eventually agreed to allow a security firm to perform forensic analysis of the server.
Earlier this week, Ukraine police seized the M.E.Doc servers believed to have been used in the incident, to prevent any subsequent attacks from happening. The local authorities suggested the threat group might use the server for further attacks, and not without reason, it seems: a fake WannaCry ransomware family was distributed in the shadow of NotPetya using the same vector.
Cisco was the security company M.E.Doc provided with access to its server, and the company now confirms not only that the server was compromised, but also that the attack was destructive in nature, and that a backdoored module was pushed to M.E.Doc clients several times over the past months.
RSA Webinar - July 13 at 1PM ET: Evolution from Two-Factor Authentication to Identity Assurance
Disguised as ransomware, the NotPetya wiper (which Cisco refers to as Nyetya), was designed to overwrite the infected system’s Master Boot Record (MBR) to prevent access to the operating system. The malware also encrypts specific file types, but the process wasn’t meant to allow file decryption, the security researchers suggested.
In a new report presenting the findings of their analysis of the M.E.Doc server, Cisco confirms that the attack was destructive in nature and that all malware installations came through the M.E.Doc update system.
The investigators discovered a web shell at http://www.me-doc[.]com[.]ua/TESTUpdate/medoc_online.php and found it to be a slightly modified version of the open source PHP web shell PAS. Stored in an encrypted form, the web shell requires a passphrase to decrypt.
Using stolen admin credentials, the malicious actor logged into the M.E.Doc server, acquired root privileges, and started modifying the configuration file for the NGINX web server so that “any traffic to upd.me-doc.com.ua would be proxied through the update server and to a host in the OVH IP space with an IP of 176.31.182.167.”
The actor restored the original server configuration several hours later. They also wiped the OVH server to erase evidence.
Further analysis confirms the ESET report claiming that a backdoor had been inserted into the M.E.Doc software on multiple occasions: on April 14, May 15, and June 22. The malicious actor behind this activity was TeleBots, also known as BlackEnergy and Sandworm, ESET revealed.
“The .net code in ZvitPublishedObjects.dll had been modified on multiple occasions to allow for a malicious actor to gather data and download and execute arbitrary code,” Cisco notes.
The backdoor, the security company confirms, was used to retrieve the EDRPOU and name of M.E.Doc clients, as well as to steal sensitive information (SMTP hosts, usernames, passwords, and email addresses) and download and execute payloads. All traffic was masqueraded as requests to the legitimate M.E.Doc server.
According to Cisco, the concerning matter is that the actor behind NotPetya “burned a significant capability in this attack” by compromising both “the backdoor in the M.E.Doc software and their ability to manipulate the server configuration in the update server.” The actor was able to “deliver arbitrary code to the 80% of UA businesses that use M.E.Doc,” as well as to any other multinational corporation using the software.
“This is a significant loss in operational capability, and the Threat Intelligence and Interdiction team assesses with moderate confidence that it is unlikely that they would have expended this capability without confidence that they now have or can easily obtain similar capability in target networks of highest priority to the threat actor,” Cisco continues.
The company also advises organizations with ties to Ukraine software like M.E.Doc and with systems in Ukraine to take extra caution, given that these resources have been shown to be targeted by advanced threat actors. The security firm advises companies to use separate network architectures and increased monitoring, as well as to patch their systems for any known vulnerabilities, and even upgrade to more secure platform versions.
“Talos places this attack in the supply-chain category. Rather than targeting organizations directly, an actor compromises trusted hardware and software vendors to deliver compromised assets to a high-priority environment. We believe that these types of malicious capabilities are highly desired by sophisticated actors. All vendors, regardless of size or geographic region, must be increasingly vigilant,” the company concludes.
NotPetya Decryption Key Sale - Genuine or Curveball Charade?
6.7.2017 securityweek Ransomware
Confusion over the source and motive behind the NotPetya ransomware outbreak was given an extra stir with the offer for sale of a private decryption key. Posts appeared Tuesday on both Pastebin and DeepPaste: "Send me 100 Bitcoins and you will get my private key to decrypt any harddisk (except boot disks)."
The posts appear to be genuine, and the key proofs have been tested. "It means that whoever posted this message has [the] private key to decrypt the data encrypted by the NotPetya malware," Anton Cherepanov, ESET senior malware researcher, told Forbes.
Catalin Cimpanu at BleepingComputer suggests a different verification. Just before the posts appeared, he points out that two small payments (of around $285 and $300) were made from the ransomware's Bitcoin wallets to wallets associated with the Pastebin and DeepPaste text sharing services. On the reasonable assumption that the payments and the posts are associated, it is further proof that the offer comes from the NotPetya group. "
The announcement made yesterday night is verified by the two Bitcoin payments the group made to the two services where they hosted their statements," Cimpanu wrote.
Shortly after the posts, the entire remaining funds (about $10,000) were moved out of the ransomware wallet in what seems to be the start of the group striving to hide their tracks.
On the surface, this appears to be a logical process. A faulty encryption routine used by the malware made the recovery of files by victims impossible. F-Secure has pointed out that decryption can be achieved with difficulty: "In order to decrypt the files successfully, the files should be enumerated in the exact same order as during encryption, and with the same "bug" in place."
This still requires a decryptor obtained separately by the victims; but the group's webmail provider has shut down their inbox so they can no longer read emails or reply with decryption keys.
With no possibility of collecting more ransoms, the private key is the only asset of value left to the group -- so selling that in a single transaction for a large amount would make sense. This is what you might expect criminals to do.
The confusion comes from a strong body of opinion that suggests the perpetrators are not simple criminals but a state-sponsored group. NotPetya, says this theory, is actually a cyber weapon disguised as ransomware delivered by Russia primarily against the Ukraine as part of the ongoing cyber conflict between the two nations.
"Since the outbreak," explains David Kennerley, director of threat research at Webroot, "many analysts have pointed towards possible state involvement in the ransomware attack, and the ‘mistakes' made by the authors of NotPetya, lent to theories their main intention wasn't primarily monetary gain. And the most likely the aim was to cause as much damage and havoc as possible under the guise of ransomware – with the primary target being Ukrainian entities."
Further indications that the group might not be serious about collecting money comes from Cimpanu. The Pastebin/DeepPaste messages include a link to "a Dark Web portal running Mattermost, an open source, self-hosted Slack-like online chat application." He engaged with the group, but got little response to his queries, and the chat room is now deactivated. Yesterday he tweeted, "NotPetya public chat is down. Charade over."
The bottom-line is that this sale initially looks like the act of a criminal gang, but proves nothing. "We've been told that the hackers, portraying to be the ransomware creators, have successfully decrypted a number of files encrypted by NotPetya – this definitely points towards inside knowledge of the ransomware itself," comments Kennerley.
"Are they the creators? Are they close to the creators, or has another group independently found a possible weakness in NotPetya's encryption routine and is now attempting to make a quick buck? A number of files have been decrypted, this doesn't mean they have the ability to decrypt all files, but again it adds a twist to the story. At least from a distance, it adds an argument against the theories that this wasn't about the money – or is this a smoking gun to throw investigators of the scent, or even an attempt at good old internet trolling? Whatever it turns out to be - At 100 bitcoins, it's very unlikely anyone will take them up on their offer."
"Unfortunately, this doesn't really clear anything up about the case," comments F-Secure security adviser Andy Patel. "100BTC for the master key that will decrypt all files encrypted by NotPetya isn't really worth it, considering a majority of victims probably have corrupted master file tables, and hence can't even access that data anymore."
So, despite the apparent criminal offer for sale, it is still unclear whther NotPetya is a cyberweapon aimed at the Ukraine or a flawed criminal act. It isn't clear whether the private key sale is genuinely from the perpetrator, or a curveball from a state group.
Kaspersky Releases Open Source Digital Forensics Tool
6.7.2017 securityweek Analysis
Kaspersky Lab researcher Vitaly Kamluk has released the source code of Bitscout, a compact and customizable tool designed for remote digital forensics operations.
Bitscout, which is not an official Kaspersky product, initially started as a hobby project a few years ago, and it has been continually improved based on the requirements that arose in Kaspersky investigations involving digital forensics.
Bitscout 2.0 – version 1.0 was never released to the public – enables forensic investigators to remotely analyze a system, while allowing the system’s owner to monitor the expert’s activities and ensure that their access is limited to the targeted disks. The tool can be useful to researchers, law enforcement cybercrime units, and educational institutions.
The owner of the system on which forensic analysis will be conducted is provided an image file that they must burn onto a removable storage drive. The system is then booted from this drive and the investigator connects remotely to Bitscout over SSH using a VPN.
Bitscout includes several popular tools designed for forensic analysis, but users can also customize them or add their own. The tool uses a text-based user interface (TUI) in order to make it easy to operate.
According to Kamluk, the investigator is only provided root privileges inside a virtual container, and the owner can specify which disks can be analyzed to prevent unauthorized access. On the other hand, the researcher can install additional software and make changes to the system from this container, but only in the volatile memory to ensure that everything is restored to its initial state after the device is shut down.
“All remote sessions are recorded and stored outside of the container,” Kamluk said in a blog post. “This provides a good level of isolation and a way to reconstruct the forensic process for learning purposes, or prove the existence of evidence.”
The Bitscout source code and basic usage instructions are available on GitHub.
Russia Jails Head of Notorious Hacker Group
6.7.2017 securityweek Crime
A Moscow court on Thursday jailed the leader of a notorious hacking group for two years for breaking into the accounts of high-ranking Russian officials.
Vladimir Anikeyev headed the Shaltai Boltai collective -- Russian for "Humpty Dumpty" -- believed to be behind high-profile hacks, including into the Twitter account of Prime Minister Dmitry Medvedev.
Anikeyev -- who has been under arrest since October 2016 -- was found guilty of gaining unauthorised access to computer data after a closed trial that was classified as "secret", the court said in a statement.
He was handed the two-year sentence after striking a plea bargain and agreeing to cooperate with the authorities.
Among those Anikeyev was accused of targeting were lead Kremlin propagandist Dmitry Kiselyov, presidential advisor Andrei Belousov and Medvedev's spokeswoman Natalia Timakova.
In 2014 the group claimed credit for breaking into the Twitter account of premier Medvedev and posting messages saying he was quitting the government in shame to become a freelance photographer and criticising President Vladimir Putin.
The group was initially portrayed as an anti-Kremlin collective, with its eye-catching leaks of official emails leaving the authorities red-faced.
But alleged members of the secretive collective have told media outlets that they made money by selling the hacked data to the highest bidder.
Anikeyev did not plan to challenge the verdict and his lawyer said he would immediately apply for early release when his sentence comes into force in ten days, RIA Novosti news agency said.
Anikeyev's arrest came at roughly the same time as the detention of several high-ranking cybercrime officials at Russia's FSB security agency, sparking speculation the cases were linked.
There has, however, been no confirmation that the arrests were connected.
Watch Out for Malware If You're Interested in North Korean Missile Program
6.7.2017 thehackernews BigBrothers
If you hold an interest in the North Korean Missile Program and are one of those curious to know capabilities of the recently tested North Korean long-range missile than you could be a target of a new malware campaign.
North Korea claims to have conducted the first test of an intercontinental ballistic missile (ICBM), the Hwasong-14, on 3rd July, and US officials believe the country may have fired a brand-new missile that has not been seen before.
Now, just a day after the test missile launch, hackers have started utilizing the news to target people interested in North Korean missile arsenal that has progressed over the decades from crude artillery rockets to testing what the country claims long-range missiles that could strike targets in the United States.
Security researchers at Talos Intelligence have discovered a new malware campaign that started on 4th July to target victims with KONNI, an unknown Remote Access Trojan (RAT) that has been in use for over three years.
The KONNI malware is a Remote Access Trojan designed to steal files, record keystrokes, perform screenshots, get the system information, including hostname, IP address, username, OS version and installed software, as well as execute malicious code on the infected computer.
How Does the KONNI Malware Work?
The hackers use an email attachment as the initial infection vector to deliver the Trojan through an executable file, which when opened displays an MS Office document that disguised as an article about the test missile launch.
However, the content of the document is copy/pasted from an article published on July 3rd by South Korean Yonhap News Agency.
In reality, the malicious executable drops two different versions of KONNI: event.dll and errorevent.dll.
On 64-bit versions of Windows, both binaries are dropped, while just errorevent.dll is dropped on 32-bit versions of Windows.
The dropped malware is then immediately executed to "ensure that the malware persists and is executed on rebooting the compromised system," the researchers say.
C&C Server Disguises as a Legitimate Climbing Club Website
The malware uses a new Command and Control server hosted on a website that disguises as a legitimate climbing club, but the site does not actually contain any real text, but the default text of the CMS (Content Management System).
The C&C traffic of the malware also takes place as "HTTP post requests to web pages hosted as /weget/download.php, /weget/uploadtm.php or /weget/upload.php on the domain itself."
In addition, the website also contains a contact section with an address in USA, but the map below the address points to a location in Seoul, South Korea.
"The threat actors associated with KONNI typically use decoy documents relating to North Korea, and this campaign is no exception. However, in contrast to the convincing decoy document lifted from a third party, the content of the decoy website hosted on the CnC server does not look legitimate," the researchers concluded.
"Nevertheless, this threat actor continues to remain active and continues to develop updated versions of their malware. Organizations which may have an interest in the contents of this decoy document and that used in previous campaigns should ensure that they are adequately protected against this and subsequent campaigns."
So, my advice for users to remain protected from such malware is always be suspicious of uninvited documents sent over an email and never click on links inside those documents unless verifying the source.
Additionally, keep your systems and antivirus updated to protect against any latest threat.
Symantec to Acquire Threat Isolation Startup Fireglass
6.7.2017 securityweek IT
Symantec announced on Thursday that it has agreed to acquire Israeli cybersecurity start-up Fireglass for an undisclosed sum.
Fireglass, which emerged from stealth in February 2016, describes its technology as an agentless isolation solution that eliminates ransomware, malware and phishing threats in real-time by preventing potentially harmful content from ever reaching user endpoints or the corporate network.
Delivered as a cloud service, on premises, or in a hybrid model, Fireglass protects users from links they click on, or dangerous websites they visit, using its browser isolation technology, which allows web traffic and email content to be executed remotely and not reach endpoints.
“Integrating Fireglass’ isolation technology with Symantec’s existing endpoint, email and secure web gateway solutions could reduce security events by as much as 70 percent, while virtually eliminating advanced threats spread by web browsing or email content,” said Symantec CEO Greg Clark. “Isolation will become a core component in the design of cyber defense architectures for the cloud generation who face the reality of an encrypted Internet and the crisis inherent in email and web-delivered attacks.”
Fireglass’ browser isolation technology integrates with existing security solutions and across Windows, Mac, Android, iOS and other devices including browser-enabled IoT devices.
The transaction is subject to customary closing conditions, and is expected to close in the third calendar quarter of 2017, Symantec said. Fireglass’ technology is expected to be available to Symantec customers and partners soon after the transaction closes, the company said.
Fireglass is backed investors including Lightspeed Venture Partners and Norwest Venture Partners.
Early this year, Sophos announced its plans to acquire Invincea, a provider of endpoint security solutions that leverage virtual containers to protect against advanced malware and other threats.
Perl devs fix an important flaw in DBD—MySQL that affects encryption between client and server
6.7.2017 securityaffais Vulnerebility
Perl development team solved a flaw in DBD—MySQL in some configurations that wasn’t enforcing encryption allowing an attacker to power MiTM attacks.
The security researcher Pali Rohár reported an important flaw in DBD—MySQL, tracked as CVE-2017-10789, that affects only encryption between client and server.
According to the expert, the issue in some configurations wasn’t enforcing encryption allowing an attacker to power MiTM attacks.
“The DBD::mysql module through 4.043 for Perl uses the mysql_ssl=1 setting to mean that SSL is optional (even though this setting’s documentation has a “your communication with the server will be encrypted” statement), which allows man-in-the-middle attackers to spoof servers via a cleartext-downgrade attack, a related issue to CVE-2015-3152.” reads the description provided by the Mitre.
Rohár discovered that the Perl DBD::mysql driver does not enforce SSL/TLS encryption when option
mysql_ssl=1 is enabled.
“Enabling encryption depends on an announcement from MySQL server what it supports which can man-in-the-middle attack spoof. DBD::mysql does not enforce SSL/TSL encryption even when certificate is specified via connection parameter mysql_ssl_ca_file.” states the advisory published by the expert. “Therefore usage of SSL/TLS encryption in DBD::mysql is insecure.”
The Perl 5 database interface maintainers have issued an important security patch for DBD—MySQL, a note on the GitHub account confirms that the issue leaves systems vulnerable to BACKRONYM and Riddle attacks.
“The important change is that DBD::mysql reject connection to MySQL server (also SSL enabled) if mysql_ssl=1 is set and libmysqlclient.so library cannot enforce SSL encryption (because is vulnerable to BACKRONYM or Riddle).” reads the note on GitHub.
The Riddle has been uncovered in the popular DBMS Oracle MySQL in 2015, the issue can be potentially exploited by attacker powering a man-in-the-middle attack to steal usernames and passwords.
“The Riddle is a critical security vulnerability found in Oracle’s MySQL 5.5 and 5.6 client database libraries. The vulnerability allows an attacker to use riddle in the middle for breaking SSL configured connection between MySQL client and server.” states the description of the flaw.“This vulnerability is a very critical security hole because it affects MySQL — a very popular SQL database — and SSL connection which is by its definition secure.”
The flaw, tracked as CVE-2017-3305, potentially exposes login credentials to eavesdropping, an attacker can capture them when a MySQL clients 5.5 and 5.6 send them to servers.
A security update released for the versions 5.5.49 and 5.6.30 failed to completely fix the bug. The experts noticed that the Versions 5.7 and later, as well as MariaDB systems, are not affected by this issue.
According to security researcher Pali Rohár, the Riddle vulnerability results from the failed attempt to patch the BACKRONYM vulnerability affecting the MySQL database. The Backronym vulnerability exposes passwords to attackers who are in a position to run a man-in-the-middle attack, even if the traffic is encrypted.
The developers fixed the issue forcing the MySQL server to reject a connection if the client can’t enforce the SSL encryption.
Google Patches Critical Vulnerabilities in Android
6.7.2017 securityweek Vulnerebility
Google on Wednesday announced that a total of 138 vulnerabilities were addressed in the Android platform with the release of this month’s set of security patches.
The July 2017 Android Security Bulletin was split in two partial security patch level strings: the 2017-07-01 security patch level that addresses issues in the platform itself, and the 2017-07-05 security patch level, which resolves device-specific vulnerabilities in various components supplied by manufacturers.
While in the security bulletins prior to June 2017 Google focused on detailing the resolved vulnerabilities, starting last month the company moved to underline the vulnerable components and the number of issues affecting them.
The 2017-07-01 security patch level addresses a total of 43 bugs in Android, including 10 vulnerabilities rated Critical, 28 assessed with a High severity ranking, and 5 Moderate.
Media Framework was the most impacted component, with 27 vulnerabilities addressed in it: 10 Critical, 15 High, and 2 Moderate. Google resolved 12 Remote Code Execution (RCE) issues in the component (10 Critical), 1 Elevation of Privilege (EoP), 12 Denial of Service (DoS) bugs, and 2 Information Disclosure (ID) flaws.
“The most severe of these issues is a critical security vulnerability in media framework that could enable a remote attacker using a specially crafted file to execute arbitrary code within the context of a privileged process,” Google notes in its advisory.
Other affected components include Runtime (a Moderate RCE), Framework (7 flaws: EoP, ID and DoS), Libraries (3 issues: RCE and DoS), and System UI (5 bugs: RCE and EoP). Affected platform versions include Android 4.4.4, 5.0.2, 5.1.1, 6.0, 6.0.1, 7.0, 7.1.1, and 7.1.2.
The 2017-07-05 security patch level addresses a total of 95 vulnerabilities: 1 assessed Critical severity, 66 considered High risk, 27 Moderate severity, and 1 Low. Qualcomm closed-source components were affected the most, with 55 High severity vulnerabilities addressed.
Of the remaining 40 vulnerabilities, 25 impact Qualcomm components: 7 High severity and 18 Moderate issues. 22 of the flaws were Elevation of Privilege vulnerabilities, while the remaining three were Information Disclosure issues.
Other impacted components include Broadcom components (a Critical RCE and 2 Moderate EoP bugs), HTC components (Moderate EoP and ID and Low severity ID), Kernel components (4 EoP, 1 DoS and 1 ID issue), MediaTek components (a High severity EoP), and NVIDIA components (High severity EoP and Medium risk ID).
According to Google, all devices running a security patch level of 2017-07-05 will be safe from these vulnerabilities and all of the bugs addressed in previous security patch levels. Nexus and Pixel devices will receive the security patch level of July 05, 2017, the company also announced.
Android Ransomware Mimics WannaCry
6.7.2017 securityweek Ransomware
Android file-encrypting ransomware SLocker was recently observed using an interface similar to that of the WannaCry malware that hit Windows systems worldwide last month, TrendMicro security researchers reveal.
One of the first Android ransomware families to encrypt files on compromised devices, SLocker had a short lived success before, as the suspect supposedly responsible for it was arrested within five days after the initial detection.
The malware initally infected a small number of users because of limited transmission channels (forums like QQ groups and Bulletin Board Systems), but is back in an attempt to capitalize on the success of the WannaCry outbreak.
According to Trend Micro, the original ransomware sample found earlier this month was named King of Glory Auxiliary and was posing as a cheating tool for the game King of Glory. Once installed, however, the ransomware featured a similar appearance to WannaCry.
To lure users into installing it, the SLocker ransomware also disguises as video players, and other types of programs. After the application is first run, however, it changes the icon and name, along with the wallpaper of the infected device.
It also checks whether it has been run before, and generates a random number and stores it in SharedPreferences if not. Next, the threat locates the device’s external storage directory and starts a new thread that will first go through the directory to find files that meet specific requirements.
“We see that the ransomware avoids encrypting system files, focuses on downloaded files and pictures, and will only encrypt files that have suffixes (text files, pictures, videos). When a file that meets all the requirements is found, the thread will use ExecutorService (a way for Java to run asynchronous tasks) to run a new task,” the security researchers explain.
The malware generates a cipher based on the previously generated random number and feeds the string to construct the final key for AES before using AES to encrypt files.
SLocker victims are provided three options to pay the ransom, but all three lead to the same QR code requesting victims to pay via popular Chinese mobile payment service QQ. The malware also threatens victims that the ransom amount will increase after three days and that files will be deleted after a week.
The malware analysis also revealed that the decryption key is compared with the value in MainActivity.m, which is the previously generated random number plus 520. Thus, users can decrypt their files for free if they can figure out the method for generating the decrypt key, TrendMicro notes.
“Compared to the ransomware we’ve seen before, this ransomware is relatively simple. It is actually quite easy for a security engineer to reverse the ransomware and find a way to decrypt files. However, the proliferation of new variants so quickly after the first one shows that these malicious actors are not slowing down. Even though a suspect was caught, more advanced ransomware may be just around the corner,” TrendMicro notes.
To stay protected, users should install only apps downloaded from legitimate app stores, and should also check the permissions requested by each app, especially when they allow the software to read/write on external storage. Users should also back up their data regularly and install and maintain a comprehensive antivirus solution.
Bitscout – The Free Remote Digital Forensics Tool Builder
6.7.2017 Kaspersky Analysis
Being a malware researcher means you are always busy with the struggle against mountains of malware and cyberattacks around the world. Over the past decade, the number of daily new malware findings raised up to unimaginable heights: with hundreds of thousands of malware samples per day! However, while there are some rare and dangerous malware, not every sample is as malicious as these. Moreover, some of the biggest threats exist only when several ingredients are put together, including multiple malware tools, malicious infrastructure, and interactive commands coming from their operators.
This is why, instead of only looking at malware, we have started tracking groups of attackers and have focused on campaigns and isolated incidents. This has been an increasingly challenging job, because it involves searching for a needle in a haystack of haystacks, and sometimes we’re searching across very distant locations. There are different ways of undergoing searches like this, but the most reliable is that used by law enforcement agencies: full digital forensics. This procedure is time consuming, highly dependent on the availability of a skilled expert on site, and usually involves physical travelling. Our natural response to this problem is to find a solution – and surprisingly no one was offering one. Well, at least not one that was up to our standards!
My Bitscout project started years ago as a hobby. I had been playing with the creation and customisation of LiveCDs. Some time afterwards, when we needed to find traces of a certain attacker on a compromised PC in an African country, I thought I could help. I built a simple and minimal LiveCD on Linux, with a preconfigured VPN client and SSH server, and shared it with the system owner over the Internet. The owner burnt the CD and started the infected PC from it. It worked like a charm: a full control over remote computer connected via the Internet became available from my desk. It was a slow connection but it luckily for me I didn’t use a bandwidth-heavy remote desktop access. A text terminal was more than enough to do the job over a slow modem line. I managed to help the owner acquire a forensically sound disk image of the compromised system, point out the malware and related file locations and, most importantly, extract precious pieces of information, including a malware dropper and spearphishing email.
Time passed, and similar requests appeared again and again. We worked with INTERPOL using the same model: a law enforcement officer would go to the physical disk acquisition location, and with permission from local law enforcement agencies, would let us find the most important evidence on the site – instantly. This cut our time traveling and helped law enforcement with the quick discovery of key artefacts left after a cyberattack.
Some time afterwards many new scenarios started popping up:
Manually remediatiating an infected PC (from a rootkit)
Sharing remote sessions let us educate new users and increase the speed of analysis
Once, I traveled to a customer but I had no expensive enterprise SAS disk controller with me to complete a disk image acquisition with. Using LiveCD I was able to clone the disk via the original server hardware. And I didn’t even have to stay in the cold server room to monitor the progress!
We also worked on making the tool simple and friendly for users who are not familiar with commandline Linux environments. Still, for the sake of having a small disk size, we decided to keep away from GUI tools and X11 servers. Naturally we settled on a TUI (Text UI), which is simple to operate with just arrow keys.
However, when you work with someone who has never met you, trust is an inherent problem. Just think about it: would you let some remote expert have access to your precious system? If so, I’d be delighted to work with you. But if I were in your shoes, I would be paranoid, and would like to control the process myself. This is quite natural and is something that bothered me in the previous versions of LiveCDs.
This issue of trust could be resolved if we could somehow limit an expert’s access to hardware, and monitor and record everything that he/she does. Following this idea, we built a new version of Bitscout: Bitscout 2.0, which we have just released. The remote expert has root privileges only inside a virtual unprivileged container. The expert can access only those disk devices that are permitted by the owner, and it’s possible for them to install additional software and change system files – all without the risk of compromising the host system or data on the harddrive. This is all done in RAM, and is gone once the system is shutdown. In addition, all remote sessions are recorded and stored outside of the container. This provides a good level of isolation and a way to reconstruct the forensic process for learning purposes, or prove the existince of evidence.
But that’s not all! Bitscout 2.0 is not only based on open-source tools, it is actually an open source tool itself that let’s you build your own LiveCDs – your own types of Bitscout systems. So, the tool is essentially a collection of scripts which anyone can validate, customize and improve.
And you are welcome to do so, because now it’s on Github: https://github.com/vitaly-kamluk/bitscout
CISCO fixed 3 critical issued in Elastic Services Controller and Ultra Services Framework
6.7.2017 securityaffairs Vulnerebility
CISCO fixed three critical issued in Elastic Services Controller and Ultra Services Framework, admins have to manual patch them.
The last weekly security update list published by CISCO includes three critical vulnerabilities affecting the Elastic Services Controller and Ultra Services Framework.
The flaw, tracked as CVE-2017-6713, in the network function virtualisation management environment Elastic Services Controller is related to the use of static default credentials that would let a remote attacker access to all the instances of the controller’s UI.
“A vulnerability in the Play Framework of Cisco Elastic Services Controller (ESC) could allow an unauthenticated, remote attacker to gain full access to the affected system.” reads the security advisory published by CISCO.
“The vulnerability is due to static, default credentials for the Cisco ESC UI that are shared between installations. An attacker who can extract the static credentials from an existing installation of Cisco ESC could generate an admin session token that allows access to all instances of the ESC web UI.”
As reported in the security advisory the same credentials are shared between multiple installations, allowing an attacker to generate an admin session token to access any instances of the Elastic Services Controller web UI.
A second issue, tracked as CVE-2017-6712, is a privilege escalation bug caused by the presence of the user ‘tomcat‘ having access to shell commands that lets that user overwrite any file on the system, and elevate their privilege to root.
“A vulnerability in certain commands of Cisco Elastic Services Controller could allow an authenticated, remote attacker to elevate privileges to root and run dangerous commands on the server.” states the advisory issued by CISCO.
“The vulnerability occurs because a “tomcat” user on the system can run certain shell commands, allowing the user to overwrite any file on the filesystem and elevate privileges to root. An exploit could allow an authenticated, remote attacker to elevate privileges and run dangerous commands on the server.”
Other issues affect the Ultra Services Framework’s (USF) automation service.
A first bug in the Ultra Services Framework’s (USF) automation service (CVE-2017-6711) is related to an insecure configuration of the Apache ZooKeeper service, which could be exploited by a remote attacker to get access to the orchestrator network.
“A vulnerability in the Ultra Automation Service (UAS) of the Cisco Ultra Services Framework could allow an unauthenticated, remote attacker to gain unauthorized access to a targeted device.” states the advisory.
“The vulnerability is due to an insecure default configuration of the Apache ZooKeeper service used by the affected software. An attacker could exploit this vulnerability by accessing the affected device through the orchestrator network. An exploit could allow the attacker to gain access to ZooKeeper data nodes (znodes) and influence the behavior of the system’s high-availability feature.”
A second bug in the Ultra Services Framework’s (USF) automation service, tracked as CVE-2017-6714, resides in the staging server and could lead Arbitrary Command Execution.
“A vulnerability in the AutoIT service of Cisco Ultra Services Framework Staging Server could allow an unauthenticated, remote attacker to execute arbitrary shell commands as the Linux root user.” states the advisory.
“The vulnerability is due to improper shell invocations. An attacker could exploit this vulnerability by crafting CLI command inputs to execute Linux shell commands as the root user. An exploit could allow the attacker to execute arbitrary shell commands as the Linux root user.”
The last issue in the Ultra Services Framework AutoVNF is a Log File User Credential Information Disclosure Vulnerability (CVE-2017-6709) in the USF’s AutoVNF.
The use of Admin credentials is logged in clear text, an attacker can retrieve them accessing the logfile’s URL.
A vulnerability in the AutoVNF tool for the Cisco Ultra Services Framework could allow an unauthenticated, remote attacker to access administrative credentials for Cisco Elastic Services Controller (ESC) and Cisco OpenStack deployments in an affected system.
“The vulnerability exists because the affected software logs administrative credentials in clear text for Cisco ESC and Cisco OpenStack deployment purposes. An attacker could exploit this vulnerability by accessing the AutoVNF URL for the location where the log files are stored and subsequently accessing the administrative credentials that are stored in clear text in those log files. A successful exploit could allow the attacker to access the administrative credentials for Cisco ESC and Cisco OpenStack deployments in the affected system, which the attacker could use to conduct additional attacks.” states the advisory.
“The same product also has a symbolic link error that exposes the system to arbitrary file read and malicious code execution.”
Hackers Target Prominent Chinese-Language News Sites
6.7.2017 securityweek Virus
Several prominent Chinese-language news websites that are blocked in China have been targeted in malware, phishing and reconnaissance attacks, according to a new report from the University of Toronto’s Citizen Lab group.
Citizen Lab learned of the attacks after being contacted by China Digital Times (CDT), a California-based bilingual news website covering China. Someone purporting to be a UC Berkeley student sent an email to a CDT journalist claiming to have “insider information” on cyberattacks launched at Mingjing News after it interviewed a Chinese billionaire who accused high-ranking officials in China’s Communist Party of being corrupt. Other CDT staff received similar emails the following days.
The messages contained a link pointing to a fake CDT website designed to redirect users to a WordPress phishing page. CDT does run on WordPress and the fake login page was well designed, suggesting that the attacker had put considerable effort into the campaign.
The attack on CDT lasted for roughly 20 days, but it did not appear to be successful and the threat group moved on to other targets. An analysis of the server used to host the phishing website and registration data showed that the group had also set up several other domains designed to mimic popular Chinese-language news websites that are blocked in China.
This includes Mingjing News, Epoch Times, HK01 and Bowen Press. The fake domains have apparently been set up for various purposes, including phishing, malware delivery and reconnaissance.
While Citizen Lab identified fake domains designed to mimic the ones of the aforementioned news websites, researchers were unable to confirm that these organizations were directly targeted by the threat group.
The malware involved in the attacks is NetWire, a remote access trojan (RAT) known to be used by several actors. The malware was configured to bypass detection and make analysis more difficult.
The threat group is believed to have targeted Chinese-language news sites since at least 2015. Researchers also discovered links between this campaign and a 2013 operation aimed at a Tibetan radio station, and a 2015 attack targeting Thai government agencies. The digital certificate used to sign the malware is the same as one spotted last year in attacks aimed at the gaming industry.
One possibility is that the same threat group is behind all operations, but a more likely scenario is that different actors have shared some resources.
As far as attribution is concerned, Citizen Lab pointed out that the targeted organizations are of interest to the Chinese government.
“It is noteworthy that all of the fake websites our researchers discovered in this campaign are meant to mimic news websites that publish content critical of the Chinese government. It is possible the operators behind this campaign are ‘hackers for hire’ — typical of the way in which a lot of cyber espionage is outsourced in China,” explained Ronald Deibert, director of Citizen Lab. “However, we are unable to positively attribute this campaign to a specific state agency.”
AlphaBay Dark Web Market Goes Down; Users Fear Exit-Scam
6.7.2017 thehackernews Cyber
AlphaBay Market, one of the largest Dark Web marketplaces for drugs, guns, and other illegal goods, suddenly disappeared overnight without any explanation from its admins, leaving its customers who have paid large sums in panic.
AlphaBay, also known as "the new Silk Road," has been shut down since Tuesday night. The site also came in the news at the beginning of this year when a hacker successfully hacked the AlphaBay site and stole over 200,000 private unencrypted messages from several users.
Although the website sometimes goes down for maintenance, customers are speculating that the admins have stolen all their Bitcoins for good measure, when heard no words from the site's admins on the downtime.
Some users at Reddit and Twitter are claiming that AlphaBay's admins may have shut down the marketplace to withdraw a huge number of bitcoins from the site's accounts.
The withdrawal Bitcoin transactions total 1,479.03904709 Bitcoin (roughly $3.8 Million), which led to suspicion from some users that the site’s admins may have pulled an exit scam to steal user funds.
In March 2015, the largest (at the time) dark web market 'Evolution' suddenly disappeared overnight from the Internet, stealing millions of dollars worth of Bitcoins from its customers.
However, users no need to worry—at least right now when nothing is confirmed, and the timing of the two incidents—site downtime and Bitcoin withdrawals—may be just coincidental.
This is not the first time AlphaBay goes offline. Last year, the site went down for about four days. Also, the blockchain transactions of about $3.8 Million are not enough for AlphaBay moderators to go offline.
One user on Reddit calls for calm and patience, saying "Now I'll admit I don't know for sure what's going on, and I am a bit nervous myself because if this is the end then I've lost a couple of hundred dollars myself But think about it Last year alphabay went down for about 4 days."
"Everyone was saying for sure that this was it, but it was not. It took the alphabay moderators days to update people on what was going on too; they're known to do this. Also about that blockchain transaction.. 44 bitcoins rounds off to about 4 million US. [I don’t know] about you but that doesn't sound like nearly enough money."
While AlphaBay continues to be down, and AlphaBay-associated Redditor who goes by moniker Big_Muscles has called users to calm down, saying the site's servers are under update and will be "back online soon."
Also unlike Silk Road, there is no indication that the law enforcement took down the AlphaBay marketplace.
Silk Road was shut down in 2013 after the arrest of its unassuming founder, Ross William Ulbricht. The FBI seized bitcoins (worth about $33.6 million, at the time) from the site, which were later sold in a series of auctions by the United States Marshals Service (USMS).
[Video] Ukrainian Police Seize Servers of Software Firm Linked to NotPetya Cyberattack
6.7.2017 thehackernews Ransomware
Ukrainian National Police has released a video showing officers raiding company of M.E.Doc accounting software makers, whose systems have been linked to outbreak of Petya (NotPetya) ransomware that recently infected computers of several major companies worldwide.
On 4th July, masked police officers from Ukrainian anti-cybercrime unit — carrying shotguns and assault rifles — raided the software development firm “Intellect Service,” in the capital city Kyiv and seized their servers, which were reportedly compromised by hackers to spread (ExPetr, PetrWrap, Petya, NotPetya) ransomware.
Researchers from ESET security firm have found a very stealthy malicious code in the M.E.Doc software update which was injected by an unknown hacker or group of hackers in mid-April by exploiting a vulnerability.
The malicious software upgrade, designed to install a backdoor and give unauthorized remote access to attackers, was then delivered as an update to nearly 1 million computers belonging to its client companies.
Researchers explain that the backdoor installed in endpoint computers was designed to allow hackers to execute various commands remotely and further install other malicious programs, eventually used to conduct WannaCry like global ransomware attack.
The software company previously denied its servers had been compromised, but several researchers and even Microsoft blamed the company for being "patient zero" for the NotPetya attack.
Ukrainian authority has also said that the company could face charges.
Moreover, the Petya investigation took interesting twist last week when researchers found that NotPetya is not a ransomware; instead, it’s a destructive piece of “wiper” malware designed to destroy all records from the targeted systems, making organizations to shut down their operations.
Ukrainian authority has recommended M.E.Doc customers to stop using its accounting software until further notice. So, you are supposed to turn off your computers if it has the M.E.Doc software installed on and change your passwords.
Ukraine believes Russia is behind the NotPetya cyber attack that shut down the nation's critical operations, including the airport, local metro, hospitals, and government, but authorities are still investigating the case.
NotPetya Hacker Demands 100 Bitcoins for the Decryption Key
It was also reported today that the hackers connected to the NotPetya ransomware moved $10,000 worth of Bitcoins from the online wallet they were using to receive payments from victims to a different wallet.
After that someone claimed to be connected to NotPetya Posted an announcement on DeepPaste and Pastebin, asking for 100 Bitcoins (roughly $256,000) for the private key that supposedly decrypts any file encrypted with NotPetya.
AV-TEST: The number of malware decreases, but their complexity increases
6.7.2017 securityaffairs Virus
According to the AV-TEST Security Report 2016/2017 published by the independent anti-virus testing outfit AV-TEST, the number of malware decreases, but …
According to the AV-TEST Security Report 2016/2017 published by the independent anti-virus testing outfit AV-TEST, the number of malware samples detected in 2016 decreased compared to 2015, but they have been more sophisticated.
The recent NotPetya and WannaCry ransomware-based massive attacks, IoT malware like Mirai and banking Trojans implement new sophisticated techniques to avoid detection and to rapidly spread.
AV-TEST spotted roughly 127.5 million malware samples in 2016, meanwhile, the number of samples discovered in 2015 was 144 million (+14%).

The research institute observed roughly 350,000 new malware samples each day, that correspond to four new samples per second.
Less than one percent of the total share of Windows malware is represented by Ransomware, but the damage caused by this threat is severe.
“Comprising not even 1% of the overall share of malware for Windows, the blackmail Trojans appear at first glance to be a marginal phenomenon. The fact that this type of assessment is incorrect can be explained via the mode of action and damage created by this class of Trojans. ” states AV-TEST.
“A level of distribution comparable to traditional viruses is not required to reap the greatest possible profit. Ransomware involves ‘high-tech malware’, which seeks its victims above all in a targeted business environment. For instance, emails infected with ransomware are sent out almost exclusively on weekdays.”
According to the researchers, the number of ransomware attack peaked in the Q1 2017.
AV-TEST reported a significant increase in the number of Mac OS samples (+370%) compared to 2015. The majority of malware was Trojan, more than 4,000 new samples were already identified in Q1 2017.
“Compared to the previous year, the malware sector for macOS is experiencing 370% percent growth. However, it is also important to keep an eye on the overall number of malware programs: Whereas in 2015 there were still a moderate 819 different malware threats targeting macOS, Apple users in 2016 already had to protect their devices from 3033 malware samples.” states the report.
The report confirms the number of Android malware samples doubled in 2016 to over 4 million, in June AV-TEST identified nearly 650,000 new samples of malware.
Give a look at the AV-TEST Security Report 2016/2017 !
Risks of hacking attacks: Ransomware – Cryptolocker and tutorials for Italian SMEs in the light of the Network and Information Security (NIS) Directive.
6.7.2017 securityaffairs Ransomware
As was anticipated by Minister Pier Carlo Padoan, the Taormina G7, he would have to face, inter alia, the overwhelming problem of Web security and the protection of sensitive data.
The issue is much more urgent in the light of cyber attacks on computer systems of some key service providers in several EU Member States and in the UK, including the National Public Health Service (public body) or Against that of Renault in France (private body) that had the effect of completely blocking both the structures mentioned and not only.
These attacks, in fact, have been carried out on a large scale and involved hundreds of computer systems at the European level. Ransomware technology, a type of malware used in this case by hackers, has already been used on several occasions and is spreading very rapidly so that it may become, as early as 2017, a serious problem as DDoS attacks ( Distributed Denial of Service) (source: David Gubiani, Check Point Security Engineering Manager).
Even at a non-Community level, the UN Security Council has dealt with this issue with Resolution 2341/2017, in which United Nations Member States have been encouraged to co-ordinate each other by exchanging their knowledge about each other to attacks perpetrated via the Web.
On this point, it is interesting to note that Jurgen Stock (Head of Interpol) has complained of a structural disconnection that exists at present between the United Nations Members States.
And as Professor Pierluigi Paganini, Chief Technologist of CyberSec Enterprise, said in his speech: “From the Wannacry case to the NIS Directive, critical infrastructures are still too vulnerable:” While in Europe there is a debate about the need to calibrate infrastructures, criticisms and adopting security measures that will make them resilient to cyberattacks, and such events demonstrate how vulnerable network infrastructure is exposed to small-scale threats.
Think of the potential large-scale impact of a ransomware such as WannaCry that exploits a zero-day flaw, which is not known at the time of the attack and is therefore extremely dangerous. ”
In the debate on Resolution 2341/2017, particular interest can be attributed to the point where it has been shown that the key role in cyber attack prevention lies in cooperation between public and private sectors; It was therefore hoped that a Memorandum of Understanding would be established between the Member States regarding the information on the acquired data.
It appears that ictu oculi – as in the NIS Directive at Community level and in UN Security Council Resolution 2341/2017 – the phrase “wishes cooperation between the Member States” stresses how information exchange can prove to be crucial and limited cyber attacks, which can provide effective prevention and, consequently, limitations of related harm to IT systems.
However, the appearance that is particularly alarming is that for such attacks, hackers used a Ransomware called “WannaCry” a virus that, like Cryptocker, was created by scammers with high-level knowledge in the field of computer programming.
Scammers can infiltrate a PC in a variety of ways, for example through an attachment of an infected mail or through the browser, when a website is infected with this kind of malware. The word ransom means requiring a ransom, to be paid to remove the limitation and to get the possibility of access to the PC (source Avast), actually doing a real extortion by the use of the computer system. It is therefore evident that there is a consequent risk for those who give up on what is required by extortionists to feed a funding channel for occult criminal organizations and terrorist organizations (Europol sources).
However, 2016, as Gabriele Faggioli, Legal, Ceo Partners4innovation said, with the NIS Directive of the Parliament and the European Council of July 6, will be remembered as the year that will mark the course of the decades on the issue of computer security.
The future of this issue in Europe is essentially due to the rules of a broad package of will be remembered as the year that will mark the course of the next decades on the issue of computer security.
The future of this issue in Europe is essentially attributable to the rules of a large EU reform package, which has been in force and in part already applicable since this year as Regulation no. 679/2016, General Data Protection Regulation (RGPD). This legislation, which entered into force on 24 May and applicable from 24 May 2018, replaces Directive 95/46 / EC. There is, moreover, Directive n. 1148/2016, the Network and Information Security Directive (NIS Directive), which entered into force on 8 August, laying down measures for a common high level of network security and information systems in the Union.
The text of the Directive states that Member States shall ensure that public administrations and market operators take appropriate technical and organizational measures to manage network security risks and the information systems that control and use in their operations.
Given the state of the art attacks, these measures must ensure a level of safety appropriate to the actual level of risk involved.
In particular, measures should be taken to prevent and minimize the impact of accidents attacks affecting their network and the information systems on the basic services they provide and, therefore, to ensure the continuity of the services incurred by these networks and information systems.
The Legislator has undertaken to ensure that the contents of these provisions are effective, work in practice, and last for at least a generation. The provisions are dense with technical-informational references and address the challenges imposed by new technologies in data protection and system and network security.
As Antonello Salerno said, “The future of cybersecurity in Italy could be decided on two key aspects: the role of the PA as an example and a spur for the private and the training of excellence skills remaining in the country.here” Of course, there are adequate investments to protect critical infrastructures. To reach this goal, the implementation of the European Network and Information Security Directive will be important.
If, from a formal point of view, the NIS Directive, which was adopted in July, is yet to be adopted (the deadline for transposition is by May 2018), Italy has already substantially aligned with many of the requirements of the new Community legislation, and can now focus on details to make the strategy more effective.
The hubs are those of the Decree of the President of the Council of Ministers of 24 January 2013, which contains a first model of cybersecurity governance and indicates in the DSI or DIS (Department of Security Information) and in the CISR (Interministerial Security Committee of the Republic) the main coordinating references. a
Under the NIS Directive, you will need to identify the essential service providers. The legislator could only point to the obligation to notify the attacks only for large national players, leaving the majority of Italian business fabric (mainly composed of SMEs) or, as it may be desirable, extend this obligation also to actors of relatively small size, such as many municipal or local companies, but which rely on large user bases and whose contribution on a national scale could be extremely significant.
The specific methods of allocating these resources will depend on the effectiveness of the Italian action on computer security. “The opportunity – emphasizes Andrea Rigoni (cybersecurity expert and partner of Intellium, strategic consultancy for NATO), governments and large infrastructures – is that with the adoption of the NIS directive we are back with the plan and it is decided to allocate more clearly and timely the funding for network security.”
Particularly interesting will be the role of the Public Administration, as has happened in the past on other occasions, starting with electronic billing, for example, can make a changeover for the private, thanks to compliance mechanisms. While on the one hand, the public has to make their own infrastructures and management systems compliant with international standards that the Government is required to identify and detail, and on the other hand, it may ask the same security standards for companies interested in working with the Public Administration, thus triggering a virtuous circle that will involve the private sector through the certification of the PA chain.
The risk for companies operating in any economic sector is high as evidenced by the outcome of a study that says Prof. Pierluigi Paganini is “surprising”, only 3 threats have been designed with the intent of striking critical industrial systems and infrastructures – Stuxnet, Havex, and BlackEnergy2. That data continues Paganini, “confirms that industrial systems today continue to be most exposed to generic threats, given alarming if we think an attack designed to hit these systems could have disastrous effects.
Stuxnet first, and the latest attacks in Ukraine with BlackEnergy malware have demonstrated the effectiveness of a malware in an offensive against an industrial system in a critical infrastructure. ”
From what has just been reported, additional business risks seem to derive from the use of computer media such as smartphones and tablets. Many companies, both public and private, provide computer support to their employees. With a 394% increase in smartphone and 1700% of the tablet in the past four years, it’s no wonder that mobile attacks are steadily increasing. According to the Check Point Security Report 2016, a five-person employee will be the author of a violation of his business data via mobile malware or malicious Wi-Fi, both highly effective attack devices on mobile devices.
As this trend is steadily growing, Check Point points out that mobile business-related violations is becoming an increasingly significant problem for a company’s security since these computer-based media are particularly vulnerable and vulnerable to an absence of a frequent update of the antivirus used.
Recent attacks involving some of the journalists’ phones show how attack techniques are “in the wild” and that we should expect more and more to see criminal bands using them. However, mobile security remains a challenge for businesses, a push-pull between productivity, privacy and protection.
In 2017, organizations should take into account the spread of cyber attacks through the “Industrial Internet of Things”, not only through smartphones and corporate tablets, but also, for example, by printers or other types of devices.
Convergence between IT and Operational Technology (OT) is making both the most vulnerable environments and therefore it will be necessary to extend physical control systems and physical security to logical space and implement threat prevention solutions in IT and OT environments. Critical infrastructures, including nuclear power plants, electricity and telecommunications networks, remain highly vulnerable to possible cyber attacks. Almost all infrastructures have been designed and built before the threat of cyber attacks and for this reason, even the simplest computer security principles in most cases have not been taken into account within the projects.
In this regard, it is interesting and also worrying as it has emerged in the quoted work of Prof. Pierluigi Paganini, which, as revealed by the research of the US – ICS CERT, states that: “… the energy sector is one of the most sought after and confirmed in the many attacks that have been observed over recent months by groups of criminals and nation-state actors. According to a recent analysis released by IBM Managed Security Services, the number of attacks against industrial systems has increased by 110% compared to last year. IBM experts observed a significant increase in brute-force attacks against SCADA systems. … The US leads the rankings of the five major nations affected by the attacks, not surprising if we consider the largest number of ICS systems in the United States. ”
Only at the beginning of 2016 was the first intentional blackout caused by a computer attack.
Critical Infrastructure Security Officers must, therefore, be prepared for their networks and systems to be systematically attacked by different actors: other States, terrorists and organized crime.
Check Point’s Security Report 2016 revealed that the number of unknown malware volumes that attack organizations is nearly 10,000, with about 12 million new malware variants identified each month.
In the Security report, it is evident that: “These technologies are in fact part of our business and cybercriminals have consequently innovated their hacking techniques.”
“Hackers have become smarter when it comes to malware and ransomware, releasing every minute new variations.”
“The era of signature-based antivirus to detect malware is far away.”
“With these predictions, companies can develop their IT security plans to keep them one step ahead of emerging threats by preventing attacks before they can cause damage.”
To ensure convergence in the implementation of Article 14, Member States of the U.E. encourage the use of network standards and/or technical specifications and information security.
Just to counter the risks of attacks on computer systems, as has been previously stressed, 2016 is remembered not only for the NIS Directive but also for privacy legislation.
Member States’ legislation identifies competent authorities both in the protection of sensitive data and in identifying the Computer Security Incident Response Team (CSIRT), but the NIS Directive, since many incidents compromise personal data, also provides that the competent authority should operate in close cooperation with the authorities that supervise the protection of data in cases of incidents involving personal data breaches.
However, the two disciplines cannot be confused, as they are directed to regulate the activities of distinct subjects. It is foreseen that NIS will only be applied to providers of essential services and Internet service providers, while the privacy and data protection regulations also apply to individuals.
However, the rules in question may overlap in cases where a computer incedent also involves a violation of personal data. In this case, the affected parties will have to act to report the incidents under the two directives, either they will have to report both the incidents referred to in the NIS Directive and the notification of the violation of personal data provided by the RGPD.
The hope is that, in a juncture and in the process of transposition into our legal order of both Directives, the Authorities responsible for the surveillance and management of cyberattacks and on the protection of the preservation of personal data examine the guidelines which can help businesses cope with security incidents, so as to ensure and insure compliance with both regulations.
Notwithstanding the NIS Directive applies only to “macro categories” i.e. to essential service operators (energy, transport, banking, health, etc.), while Regulation NIS no. 679/2016 applies to all companies, it is to be noted that the business fabric present on Italian territory is predominantly made up of SMEs which as such cannot benefit from the protection provided by the NIS; therefore, it would be desirable, in addition to an either convergence of the norms now cited, and the creation within the various trade associations (such as Confindustria, Confagricoltori, Confartigianato), of structures capable of receiving news of any incidents that have occurred to their associates and then, in turn, communicating them and CSIRT.
The constituent entity, within the category of associations, should essentially reflect the structure of the CSIRTs as set out in the NIS Directive, assuming a dual function: first, the protection of small and medium-sized enterprises from potential cyber attacks that could hurt or even blocking production by violating the informative and sensitive data present in the servers of the companies themselves; and second the assessment of the reliability of affiliated companies, in that way, for the development of a sort of “computer reliability rating” both on the prevention of computer accidents and on the contrary, and by ensuring a high level of protection of sensitive data.
It is believed that any user of the services produced by the subjects concerned should be able to know whether the company to which it is addressed is substantially reliable from a computer point of view and to know how to hold sensitive data on the servers of the company itself. Think, for example, of the case of a clinic and a patient who may be affected by a disease, a condition that, if spread, could severely damage the patient’s reputation. Or the case of a large company that would like to take advantage of the collaboration of a company for the development of the inductor: it is evident that it is useful to be aware of the reliability of the computer systems used.
To ensure the full operation of the description, it would be necessary to have the “mini CSIRT or CSIRT category” within each category association linked to a national CSIRT, which is then connected to the CSIRT network at a community level.
In addition, in a top-down view, the “CSIRT category”, present within each category association, are linked to a national CSIRT, which is then linked to the CSIRT network at Community again at a community level.
Furthermore, in a top-down view, the “CSIRT category”, if aware of an incident that happened to one of its associates, must report the incident not only to the national CSIRT but also to the other members of the association, avoiding possibly spreading the name of the affected affiliate for reasons of company reputation.
Companies will also have to set up a biennial plan to prevent computer attacks and protect sensitive data contained in their servers.
Consequently, every two years, the CSIRT category will list a list of associated companies by providing a rating of their reliability based on the level of prevention from computer incidents reached. This will greatly contribute to protecting the members of the association and improving prevention against cyber attacks and supporting actions in the event of a wasted attack.
Such a system, which, moreover, refers to a duty of cooperation enshrined in the world as well as in the community, can guarantee to public companies, private individuals and users of the services produced, more and more secure computer systems and the capability of dealing with hacker attacks while not abandoning victims and their users to their destiny, without specific reference points.
I conclude by making the conclusions of Prof. Pierluigi Paganini in his intervention “From the Wannacry case to the NIS Directive, critical infrastructures are still too vulnerable” in which it was expressly stated that: “… recalling that the security of our infrastructures also depends on the posture of the citizens. We need to learn about computer threats and how to defend ourselves from them. We are the knot of a global network with which we exchange a huge amount of information filtering or configuration errors in the systems we use every day could lead to risk situations for the entire community. ”

And I would add that as for the contrast to the offenses committed by minors in the Network, the aspect of education and prevention is the most important thing for the prevention. One has to enter once and for all in the perspective for which no small or large world player (physical and/or juridical persons) can feel immune to attacks and therefore have to be cyber protectors while never underestimating the risk and it’s results. We must also educate ourselves that what is happening in the virtual world has more and more serious repercussions on the real world and on the fate of the cyber attack victim.
Jak správně posoudit rizika?
6.7.2017 SecurityWorld Zabezpečení
Bez úplného a důkladného posouzení rizika můžete stejně tak vydat všechna svá datová aktiva napospas neomezeným únikům přes port 80 bez jakýchkoli bezpečnostních kontrol. V konečném důsledku tak útočníci a digitální zločinci získají v obou případech to, co chtějí.
Obrana před riziky, aniž víte, jaká tato rizika jsou, se podobá hraní paintballu se zavřenýma očima – neuvidíte svého protivníka. Posouzení rizik dává podniku konkrétní zúžené pole cílů, na které je potřebné se zaměřit.
Bezpečnostní experti vám poradí, co jsou spolehlivé zdroje a jaké byste měli udělat odborné kroky pro ochranu datových aktiv a úložišť v podniku.
Podrobnosti posuzování rizika
Posouzení IT rizik zahrnuje postupné kroky, které zajistí řádné vyhodnocení vašich IT rizik a jejich závažnosti pro vaši organizaci. Podle M. Scotta Kollera, poradce společnosti BakerHostetler, patří mezi tyto kroky následující úkony: ohodnocení dat a systémů; určení rizik těchto systémů; vyhodnocení těchto rizik z hlediska pravděpodobnosti, závažnosti a dopadu a určení kontrol, ochran a nápravných opatření.
Nástroje pro hodnocení dat a systémů mohou zahrnovat mapy sítě, inventář systémů a audity shromážděných a uložených dat, vysvětluje Koller.
Jde o více než jen o prosté pochopení – jde o přehledy topologií tak, aby zahrnovaly jádra sítí se všemi jejich servery, přepínači, směrovači, hardwarem, softwarem a službami až po hranice sítě, gatewaye a koncové body se všemi jejich uloženými daty, takže se musí zohlednit vše, co je a sídlí uvnitř vaší sítě. Nemůžete vytvořit seznam všech svých rizik, dokud je nevyhodnotíte pro veškeré síťové vybavení, které by mohlo být v ohrožení.
Při vytváření aktuálního a smysluplného seznamu reálných potenciálních rizik pro vaše systémy a datová aktiva zvažte zařazení manuální empirické fáze do celkového přístupu: sečtěte rizika, která nejvíce leží na srdci zainteresovaným osobám a členům týmu, a zajistěte, aby došlo k zohlednění každého systému a všech dat, seznam ověřte, odstraňte všechny duplicity a určete druhy rizik.
Jinými slovy, mluvte s lidmi o všem, co budete dělat při sestavování seznamu rizik. Kdokoli z nich si může všimnout něčeho, co by jinak uniklo pozornosti a nedostalo se na seznam identifikovaných rizik.
Existují také nástroje, které mohou pomoci podnikům zjistit konkrétní rizika. Řešení známá jako datová infrastruktura a pokročilá analytika dat, která nabízejí holistický pohled v reálném čase na situaci a obraz běžného provozu prakticky jakéhokoliv vybavení, systému, provozu či zařízení, a to způsobem, který je nezávislý na dodavatelích a pracuje téměř bez omezení, vysvětluje Steve Sarnecki, viceprezident společnosti OSIsoft.
Společnosti IBM a PwC jsou dalšími dvěma dodavateli, kteří nabízejí produkty této kategorie. Nástroje tohoto typu dokážou za účelem identifikace rizik sbírat informace o riziku z podnikových aktiv.
Metriky a nápravná opatření
Chcete-li vytvořit vizuální metriku pravděpodobnosti a závažnosti rizika, jednoduše ohodnoťte jednotlivá rizika od jedné do deseti nebo do sta pro pravděpodobnost a poté znovu pro závažnost. Použijte tato dvě čísla k vykreslení rizika jako bodu do grafu pomocí os X a Y.
Body, které se koncentrují v pravém horním rohu uvnitř čtverce, který je čtvrtinou celého grafu, tvoří nejdůležitějších 25 procent vašich rizik. Obrazové výsledky vyhledávače Google vám poskytnou představu o tom, co lidé v této oblasti už vytvořili.
Aby bylo možné posoudit možný dopad, je potřebné si uvědomit, že důsledky sahají daleko za finanční sféru. Podívejte se v historii své společnosti na nějaké důsledky, které nastaly.
Soustřeďte se na zprávy a analýzy z oboru IT o dopadech na organizace v podobné situaci, v jaké se nacházíte vy. Zeptejte se zainteresovaných osob na dopady, které je znepokojují.
Při hledání dalších kontrol, ochran a nápravných opatření pro zmírnění rizik se poohlédněte pro oborových osvědčených postupech s úspěšnou historií. NIST nabízí zdroje s bohatou diskuzí o kontrole. Také SANS nabízí seznam a rovněž diskuze o kontrole.
„Ochranným opatřením, které lze implementovat pro snížení potenciálního rizika infekce ransomwarem, je aktualizovat antivirový software. Po implementaci ochrany znovu vyhodnotíte riziko, abyste určili, zda jste dostatečně zmírnili dopady a pravděpodobnost rizika. Pokud ne, měli byste proces opakovat,“ radí Koller.
Očekávání a nastavení úrovně
Posouzení rizik neodstraní riziko, ale spíše ho akceptovatelně zredukuje. Vrátíme-li se k ransomwaru jako příkladu, spočívá zbytkové riziko ve skutečnosti, že antivirový software nemusí zabránit infekci ransomwarem, popisuje Koller.
„Organizace musí zvážit riziko spojené s danou událostí, pravděpodobnost výskytu a potenciální náklady spojené s dalšími ochranami,“ vysvětluje Koller. Pokud antivirový software nestačí, může podnik uvážit přidání dalších ochran.
Firma by se měla nejprve zabývat největšími riziky s nejvyšší pravděpodobností, závažností a náklady. Bez těchto informací, které poskytuje posouzení rizik, nedokáže podnik adekvátně chránit svá data.
Largest Cryptocurrency Exchange Hacked! Over $1 Million Worth Bitcoin and Ether Stolen
5.7.2017 thehackernews Hacking
One of the world's largest Bitcoin and Ether cryptocurrencies exchanges Bithumb has recently been hacked, resulting in loss of more than $1 Million in cryptocurrencies after a number of its user accounts compromised.
Bithumb is South Korea's largest cryptocurrency exchange with 20% of global ether trades, and roughly 10% of the global bitcoin trade is exchanged for South Korea's currency, the Won.
Bithumb is currently the fourth largest Bitcoin exchange and the biggest Ethereum exchange in the world.
Last week, a cyber attack on the cryptocurrency exchange giant resulted in a number of user accounts being compromised, and billions of South Korean Won were stolen from customers accounts.
Around 10 Million Won worth of bitcoins were allegedly stolen from a single victim's account, according to the Kyunghyang Shinmun, a major local newspaper.
A survey of users who lost cryptocurrencies in the cyber attack reveals "it is estimated that hundreds of millions of won [worth of cryptocurrencies] have been withdrawn from accounts of one hundred investors. One member claims to have had 1.2 billion won stolen."
Besides digital currencies, hackers were succeeded in stealing the personal information of 31,800 Bithumb website users, including their names, email addresses, and mobile phone numbers, the South Korean government-funded Yonhap News reported.
However, Bithumb claims that this number represents approximately 3% of its customers.
The exchange also told Yonhap that it contacted South Korea's cybercrime watchdog on June 30, Friday after it learned of the hack on June 29.
Bithumb believes that one of its employee's home computer was hacked in the attack and not its entire network and no passwords were compromised, so it is impossible for hackers to gain direct access to user accounts.
The digital currency exchange says that the loss of funds is the result of using "disposable passwords" in order to carry out digital transactions online.
"The employee PC, not the head office server, was hacked. Personal information such as mobile phone and email address of some users were leaked," Bithumb told the newspaper. "However, some customers were found to have been stolen from because of the disposable password used in electronic financial transactions."
While more than 100 Bithumb customers have already filed a complaint with the National Police Agency's cybercrime report center regarding the hack, South Korean officials are now investigating the incident.
Fake WannaCry Ransomware Uses NotPetya's Distribution System
5.7.2017 securityweek Ransomware
The NotPetya wiper wasn’t the only piece of malware distributed last week using the compromised M.E.Doc update mechanism: a fake WannaCry ransomware variant was delivered using the same channel, Kaspersky Lab reports.
Called FakeCry, the ransomware was delivered to M.E.Doc users on June 27, the same day as the NotPetya outbreak started. According to Kaspersky, it was run as ed.exe in the M.E.Doc directory by the parent process ezvit.exe, suggesting it used the same delivery mechanism abused by NotPetya.
Written in .NET and including a “WNCRY” string, the ransomware was clearly making reference to the massive WannaCry epidemic in May 2017, and the same did a “forgotten” PDB path inside it. However, the malware also pretends to be “made in China,” which researchers suggest is a false flag.
Last month, some security researchers suggested WannaCry was the work of North Korean hackers, while others suggested it didn’t fit North Korea’s style. Linguistic analysis threat intelligence firm Flashpoint performed on 28 WannaCry ransom notes revealed that the attackers were fluent Chinese speakers who also appeared to know English.
Unlike WannaCry, which spread through the EternalBlue Windows exploit, FakeCry uses a dropper saved on disk as wc.exe. The dropper can execute several commands: drop the ransomware component; begin encryption; begin decryption; <Key> (public key for encryption and private key for decryption); and demo (encryption or decryption with hardcoded RSA keys).
The ransomware component, on the other hand, can generate the RSA-2048 key pair, encrypt/decrypt files, encrypt/decrypt disk, and delete shadow copies on the infected machine. When executed, the malware first deletes shadow copies, then initializes keys, creates the file list for encryption, proceeds to encrypt files, and then shows the ransom window.
FakeCry targets around 170 file types to encrypt and can kill processes if they use targeted files, to unlock them. It uses the Handler Viewer Sysinternals tool to accomplish the task. The ransomware also contains a list of extensions that contains only image file types (jpg, jpeg, png, tif, gif, and bmp), and which the attackers can decrypt for free, researchers say.
The ransom note displayed by this ransomware is similar to that of WannaCry. The attackers demand 0.1 Bitcoin (around $260) and use the same wallet number for all infections (seven payments have been made so far to the wallet). The ransomware uses a Tor server for command and control.
“Unfortunately ExPetr/Petya was not the only ransomware that was distributed via MeDoc updates on June 27. In parallel, another ransomware, FakeCry, was also distributed to MeDoc users at exactly the same time as ExPetr/Petya. Our telemetry shows about 90 attacked organizations received the FakeCry ransomware, almost all in Ukraine,” Kaspersky notes.
Ukraine’s authorities this week announced they raided and seized M.E.Doc servers fearing that the cybercriminals behind the NotPetya attack might still have access to these resources. In an official announcement, they advised users to turn off all computers on which the M.E.Doc software is running and to change passwords and electronic digital signatures.
Given that both malware families were distributed through the same vector at the same time suggests they might be related. However, the security researchers have yet to establish a definitive connection between the two.
Less Malware, Better Quality: AV-TEST
5.7.2017 securityweek Analysis
While the number of malware samples spotted in 2016 decreased compared to the previous year, threats have been more sophisticated, according to the latest security report from antivirus research company AV-TEST.
AV-TEST identified roughly 127.5 million malware samples last year, which represents a 14% decrease from the 144 million seen in 2015. This translates to approximately 350,000 new samples each day, or four new samples per second.
The number of samples may have declined, but malware is becoming increasingly sophisticated, as demonstrated by the NotPetya and WannaCry ransomware attacks, banking Trojans, and threats designed to target Internet of Things (IoT) devices. This includes complex encryption and increased flexibility in the case of ransomware, and the use of special malware in attacks aimed at the SWIFT banking network.
While the threat posed by ransomware has been made clear by recent attacks, this type of malware accounts for only less than one percent of the total share of Windows malware. Despite the small proportion, AV-TEST pointed out that, due to their mode of action and potential damage, these types of Trojans cannot be considered a marginal phenomenon.
“A level of distribution comparable to traditional viruses is not required to reap the greatest possible profit. Ransomware involves ‘high-tech malware’, which seeks its victims above all in a targeted business environment. For instance, emails infected with ransomware are sent out almost exclusively on weekdays,” AV-TEST said.
Ransomware development peaked in the first quarter of 2017, with more than 110,000 samples detected by the company in April.
The quantity of Windows malware has decreased, but AV-TEST noticed that the number of Mac OS samples increased by 370% to 3,033 samples – a majority of which have been classified as Trojans. More than 4,000 new samples were already identified in the first quarter of 2017.
The number of Android malware samples doubled in 2016 to over 4 million, with the largest spike recorded in June, when AV-TEST identified nearly 650,000 new pieces of malware. In the same month, the company spotted more than 9,200 exploits covering all versions of Android.
The complete AV-TEST Security Report 2016/2017 is available online in PDF format.
Understanding Geopolitics Key to Analyzing Cyber Espionage: German Intelligence Service
5.7.2017 securityweek BigBrothers
Understanding geopolitics is key to understanding the perpetrators and victims of cyber espionage. This is one of the key messages from the German federal domestic intelligence service (BfV) 2016 annual report (summary PDF).
"Germany," it notes, "is of interest in its role as a geopolitical player, as a member of NATO and the EU and on account of its economic strength and innovative businesses." For slightly different reasons, this makes Germany a nation of interest to the three primary cyber adversaries, Russia, China, and Iran.
Its relatively open attitude to immigration adds to the list of adversaries. "Oppositional groups in Germany from foreign intelligence services' home countries are another target of espionage activities," it adds.
Russia, suggests the BfV, advocates a multipolar world -- but is suffering economically from the EU's economic sanctions imposed over the Crimea/Ukraine crisis. A key driver in Russian foreign policy is to induce the West to lift these sanctions. "Obtaining advance information about the positions of the Federal Government and opposition parties increases Russia's leverage in negotiations and creates opportunities for counter-measures."
This has led the Russian intelligence services to focus in Europe on the strained relationship between the EU and Turkey, the EU post-Brexit, and the European policy on security and defense -- as well as keeping a close eye on Europe's position over Russia's military intervention in Iraq.
For example, the Russia-linked Sandworm malware has actively targeted government sites, the NATO military alliance, utilities and telecommunications firms in recent years.
Propaganda and disinformation are also key methods used by Russia. "Tools," says the BfV, "include social networks, the microblogging service Twitter, government-funded and private institutes and Russian state media. TV, radio and online channels worldwide are used for propaganda and disinformation campaigns." Internet trolls are used extensively to influence public opinion and push pro-Russian views.
APT 28 (Fancy Bear) has continued its activity against German political parties, and the BfV assumes that Russian state agencies are trying to influence parties, politicians and public opinion, with a particular eye to the 2017 parliamentary election.
Chinese activities, suggests the BfV, are guided by three key policies: territorial integrity and protecting the communist party's hegemony; expanding China's geopolitical and military power; and modernizing the economy. "For this reason," it says, "the intelligence services' activities abroad are primarily focused on gathering intelligence about political decision-making processes, on obtaining technological know-how and on the opposition to the system."
The importance of the Chinese intelligence services has grown since Xi Jinping came to power in 2013, and has shifted towards political espionage. "They are now trying to obtain more information about supranational entities such as the EU and about international conferences such as the G20 Summit. Moreover, the country is very interested in policy positions on China, e.g. recognition as a market economy or territorial disputes in the region of the South China Sea."
In Germany, the focus of attention is on industry, research, technology and modern weapons technology. China also monitors attitudes of and towards what it calls the 'Five Poisons'; comprising the ethnic minorities of the Uyghurs and Tibetans seeking autonomy, the anti-regime Falun Gong movement, the democracy movement, and proponents of sovereignty for the island of Taiwan.
China, warns, the BfV, uses LinkedIn and Facebook "to recruit informants on a large scale. Their approach is almost always the same: Ostensible researchers, recruiters and headhunters contact persons with promising profiles and try to lure them with attractive opportunities. Finally, they invite these persons to China where they are approached by the intelligence services."
The primary motivation for the Iranian intelligence services is to spy on and suppress opposition movements at home and abroad. In Germany, there is a focus on (pro-) Jewish and Israeli targets. Interestingly, however, the BfV has found less evidence of Iranian attempts to acquire proliferation-sensitive material for its nuclear program since the Joint Comprehensive Plan of Action was agreed. At the same time, attempts to obtain material for its missile program (not covered by the nuclear agreement) has remained constant.
In all of these activities, the importance of cyber as opposed to physical espionage has grown. "However, cyber-attacks may be used not only for espionage but also for sabotage purposes. This is a threat in particular with regard to critical infrastructures."
The BfV also warns that cyber activity hasn't completely replaced physical espionage. "Instead, both forms of espionage complement each other, thus producing an increased threat potential. The potential targets of espionage activities therefore need to safeguard their protected property both against attempted attacks from outside and against disloyal employees in their own organizations ('insider attacks') who are recruited, blackmailed or even specifically infiltrated into the organization by foreign intelligence services."
Protecting the private sector from economic espionage and sabotage is, says the BfV, the joint responsibility of government and industry. On 26 April 2016, the BfV and other authorities and industry associations, launched the Economic Security Initiative (Initiative Wirtschaftsschutz). Coordinated by the Federal Ministry of the Interior, stakeholders can jointly develop and implement measures to improve economic security."
Ukrainian cyberpolice seized MeDoc servers while hackers withdrawn Bitcoin from NotPetya wallet
5.7.2017 securityaffairs Ransomware
The Ukraine’s cyber police seized the MeDoc servers after detecting a new suspicious activity and fearing new malware-based attacks.
The Ukrainian authorities have seized equipment from the online accounting firm MeDoc which is suspected to have had a significant role in the recent NotPetya attack.
The Ukraine’s cyber police have seized the servers after detecting a new suspicious activity, the seizure is containment measure that was adopted to “immediately stop the uncontrolled proliferation” of malware.

According to the Associated Press’s Raphael Satter that quotes the Cyberpolice spokesperson Yulia Kvitko, the company’s systems had either sent or were ready to send out a new update that might have been compromised by hackers.
“Tax software firm M.E. Doc was raided to “immediately stop the uncontrolled proliferation” of malware. In a series of messages, Cyberpolice spokeswoman Yulia Kvitko suggested that M.E. Doc had sent or was preparing to send a new update and added that swift action had prevented any further damage.” states the AP. ““Our experts stopped (it) on time,” she said.”
MeDoc technical staff provided its equipment to the Ukraine Cyberpolice to allow further detailed analysis. While the Ukraine Cyberpolice is investigating the case, the authorities urge people stop using the MeDoc application. The experts suggest turning off any computers running the MeDoc software, change their login credentials and get new digital signatures.
Back to the NotPetya massive attack, Kaspersky Lab analyst Aleks Gostev confirmed that alleged attackers cash out the sum paid by the victims, the Bitcoin collected in the original attack has been withdrawn.
codelancer @codelancer
And finally they withdraw everything ! Time to hunt, eh ? :) #notPetya money goes away
12:17 AM - 5 Jul 2017
9 9 Retweets 10 10 likes
Twitter Ads info and privacy
Roughly 3.96 Bitcoin ($10,382) was withdrawn from a wallet linked to NotPetya attack early on Wednesday morning.
Hackers used the money to pay for a Pastebin Pro account on the dark web, which was then used to post fresh ransomware drop instructions.
Follow
Kevin Beaumont ✔ @GossiTheDog
Haha the first Petya BitCoin transaction was to @pastebin for a Pastebin Pro account.
12:38 AM - 5 Jul 2017
11 11 Retweets 27 27 likes
Twitter Ads info and privacy
Follow
petya_payments @petya_payments
🚨 3.96983955 BTC ($10,381.86 USD) has just been withdrawn from a bitcoin wallet tied to #Petya ransomware https://blockchain.info/address/1Mz7153HMuxXTuR2R1t78mGSdzaAtNbBWX …
12:15 AM - 5 Jul 2017
170 170 Retweets 122 122 likes
Twitter Ads info and privacy
The AP closed its post reporting that Infrastructure Minister Volodymyr Omelyan told it his department had incurred “millions” in costs, with hundreds of workstations and two of its six servers knocked out.
Bithumb, the fourth largest Bitcoin exchange has been hacked
5.7.2017 securityaffairs CyberCrime
Bithumb, one of the world’s largest Bitcoin and Ether crypto currencies exchanges, has been hacked. Over $1 Million worth Bitcoin and Ether stolen.
Bithumb, one of the world’s largest Bitcoin and Ether crypto currencies exchanges, has been hacked. The hackers have stolen more than $1 Million in crypto currencies from the accounts of several users of the South Jordan exchange.
Bithumb is the first Ethereum exchange worldwide and the fourth Bitcoin exchange, the company accounts for 20% of global Ether trades and nearly 10% of the global bitcoin trade.
The cyber heist occurred last week when crooks compromised a number of user accounts stealing the precious currencies.
The Bithumb exchange confirmed Yonhap newspaper that it reported the incident to South Korea’s cybercrime watchdog on June 30, after it learned of the security breach on June 29.
According to the local newspaper Kyunghyang, hackers have stolen around 10 Million Won worth of bitcoins from a single account. It is quite impossible to exactly estimate the overall losses, a survey of victims states that hundreds of millions of Korean Won have been stolen from accounts of one hundred users.
“It seems that dozens of people have suffered financial damage as a result of a leak of personal information of customers last month in BITSUMM, Korea’s largest virtual money exchange with a daily trading volume of more than 700 billion won.” states biz.khan.co.kr.”According to a survey of people who lost money by Bitsum hack, which was created on February 27, it is estimated that hundreds of millions of won have been withdrawn from accounts of one hundred investors. One member claims to have been stolen by 1.2 billion won.
Hackers also stole personal information of 31,800 Bithumb users, including names, email addresses, and mobile phone numbers, states the South Korean Yonhap News.

Bithumb claims that only 3% of its customers were affected by the security breach.
The exchange also told Yonhap that it contacted South Korea ‘s cyber crime watchdog on June 30, Friday after it learned of the hack on June 29.
“Bithumb said it realized last week that one of its employees’ home personal computers was hacked.” states the Yonhap agency.
“The exchange said it believes that personal data on about 30,000 customers had been compromised, though the stolen data did not contain any of their passwords. Still, some of the customers claimed they suffered financial damage.”
Bithumb speculates that the hackers breached the home computer of one of its employees, the company excludes that its entire network was compromised.
The digital currency exchange says that the loss of funds is the result of using “disposable passwords” in order to carry out digital transactions online.
“The employee PC, not the head office server, was hacked. Personal information such as mobile phone and email address of some users were leaked,” Bithumb told the newspaper. “However, some customers were found to have been stolen from because of the disposable password used in electronic financial transactions.”
More than 100 Bithumb customers have already filed a complaint with the National Police Agency’s cybercrime report center.
Researchers Dissect Stealthy Backdoor Used by NotPetya Operators
5.7.2017 securityweek Ransomware
ESET security researchers have performed a detailed analysis of a stealthy backdoor used by the group behind the NotPetya destructive wiper and injected into the legitimate resources of tax accounting software M.E.Doc earlier this year.
Masquerading as ransomware, NotPetya was eventually found to be a wiper designed mainly to destroy data rather than hold it for ransom, and security researchers connected it to the persistent threat group TeleBots, which has launched several cyber-attacks against Ukraine before.
Previously referred to as BlackEnergy and Sandworm, the group allegedly compromised M.E.Doc earlier this year and injected their own code into one of the application’s modules. The malicious module was then pushed as an update to M.E.Doc clients and then used to distribute malware into the networks of these companies.
“It seems very unlikely that attackers could” inject a “very stealthy and cunning backdoor” into one of the software’s legitimate modules “without access to M.E.Doc’s source code,” ESET notes. Named ZvitPublishedObjects.dll, the backdoored module is written using the .NET Framework, is 5MB in size, and “contains a lot of legitimate code that can be called by other components, including the main M.E.Doc executable ezvit.exe.”
The malicious module was part of at least three updates released this year, on April 14, May 15, and June 22, yet M.E.Doc doesn’t appear to have been aware of the compromise, as several updates between April 24 and June 21 didn’t contain the backdoor. The malicious module was used for malware distribution at least twice: to drop the XData ransomware in May and NotPetya in June, ESET says.
“The main backdoor class is named MeCom and it is located in the ZvitPublishedObjects.Server namespace […]. The methods of the MeCom class are invoked by the IsNewUpdate method of UpdaterUtils in the ZvitPublishedObjects.Server namespace. The IsNewUpdate method is called periodically in order to check whether a new update is available,” ESET explains.
The attackers, ESET researchers say, knew exactly which organizations in Ukraine were using the backdoored M.E.Doc, courtesy of a unique legal entity identifier called the EDRPOU number that each company doing business in Ukraine has. Thus, the group could use tailored tactics against the computer network of the targeted organization, depending on their goals.
In addition to the EDRPOU numbers, the backdoor was used to collect proxy and email settings, including usernames and passwords, from the M.E.Doc application. The harvested information was written “into the Windows registry under the HKEY_CURRENT_USER\SOFTWARE\WC key using Cred and Prx value names.” These values can be used as evidence of compromise, ESET says.
The backdoor was using the M.E.Doc’s regular update check requests to the official M.E.Doc server upd.me-doc.com[.]ua to send the collected information in cookies. By not using external servers for command and control and not generating abnormal network traffic, the backdoor could remain completely hidden on the compromised networks.
Although forensic analysis on the M.E.Doc server wasn’t performed, ESET believes the server was compromised, especially since a PHP backdoor was found in a FTP directory on it. The researchers suggest that the attackers deployed on the server software allowing them to differentiate the requests coming from compromised machines.
The backdoor also includes code that allows the attackers to control the infected machines through a binary blob received via the official M.E.Doc server. After decryption and decompression, the binary reveals “an XML file that could contain several commands at once.”
“This remote control feature makes the backdoor a fully-featured cyberespionage and cybersabotage platform at the same time,” ESET notes.
Supported commands include RunCmd - shell command execution; DumpData - Base64 data decoding; MinInfo - information gathering (OS version, bitness (32 or 64), current privileges, UAC settings, proxy settings, email settings including login and password); GetFile - file collection; and Payload and AutoPayload - payload execution (as executable or as DLL - via rundll32.exe).
“As our analysis shows, this is a thoroughly well-planned and well-executed operation. We assume that the attackers had access to the M.E.Doc application source code. They had time to learn the code and incorporate a very stealthy and cunning backdoor. The size of the full M.E.Doc installation is about 1.5GB, and we have no way at this time to verify that there are no other injected backdoors,” ESET concludes.
The security researchers also note that further analysis is required to learn for how long the backdoor has been in use and whether the channel was used to push other commands and malware as well. They also note that there’s a possibility that the group might have compromised other software update supply chains but haven’t weaponized them yet.
Bitcoin, Ethereum Stolen Following Bithumb Hack
5.7.2017 securityweek Hacking
Hackers have stolen significant amounts of Bitcoin and Ethereum after hijacking a computer belonging to an employee of Bithumb, one of the world’s largest cryptocurrency exchanges.
Following complaints of cryptocurrency being stolen from their wallets, South Korea-based Bithumb informed customers last week that malicious actors had gained access to the PC of an employee and managed to steal user data, including email addresses and phone numbers.
According to South Korean news reports, roughly 31,000 users – representing 3 percent of the company’s total number of customers – had their information compromised. The incident is said to have occurred in late June.
While the stolen data did not allow the attackers to directly access virtual currency wallets, they used the compromised information to impersonate Bithumb administrators and trick people into handing over their credentials. Some victims reported being called by individuals purporting to be Bithumb executives, claiming there had been suspicious activity on their account.
Some users reported losing thousands and even hundreds of thousands of dollars worth of Bitcoin and Ethereum. The total losses could be very high considering that, last year, Bithumb was used to trade billions of dollars worth of cryptocurrencies.
Bithumb representatives have promised to compensate affected users with up to 100,000 South Korean Won (roughly $90), and fully reimburse them once exact damages are determined.
The company claimed its internal network and servers are safe, but advised customers to change their email address and password.
Bithumb notified the Korea Internet & Security Agency (KISA) of the incident. Over 100 of the organization’s customers are said to have filed a complaint with the National Police Agency’s cybercrime division.
Bithumb is not the only South Korean Bitcoin exchange targeted recently by hackers. A few weeks ago, Yapizon reportedly lost more than 3,800 bitcoin, at the time worth roughly $5.5 million, after hackers breached its systems.
Zero-Day Found in Humax WiFi Router
5.7.2017 securityweek Vulnerebility
An unpatched vulnerability affecting Humax WiFi Router model HG-100R allows attackers to compromise the WiFi credentials and even retrieve the router console administrative password, Trustwave SpiderLabs researchers discovered.
The vulnerability was found in May 2017, but repeated attempts to alert the manufacturer on it remained unanswered, the researchers say. According to Trustwave, the device is a default brand/version distributed by a major Internet provider in Brazil, while also being used in various other parts of the world.
The issue, Trustwave explains, starts with specially crafted requests sent to the management console, which allow the attacker to bypass authentication. This attack is possible because the router fails to validate the session token while returning answers for some methods in "url/api".
By exploiting the vulnerability, an attacker could retrieve sensitive information, including the private/public IP addresses, SSID names and passwords.
“The cookie login is basically json data containing uid and pwd encoded in base64: login={"uid":"admin","pwd":"4cd08a961f5c"};,” the researchers say.
A second issue with the router enables attackers to bypass authentication to access the backup functionality for saving and restoring configuration. This is possible because both ignore the absence of the cookies "login" and "login_token." Thus, they accept requests to download and upload the full router configuration.
With the help of the backup generation/restore functionality provided by the URLs ‘/view/basic/GatewaySettings.bin’ and ‘/view/basic/ConfigUpload.html’, the security researchers were able to retrieve, change and eventually restore a specially crafted configuration.
By using this vulnerability, an attacker could change the DNS configuration and redirect user’s traffic to servers controlled by the attacker. Thus, they could steal private information, including passwords and banking account information.
While looking at the GatewaySettings.bin file, the security researchers also discovered that it stores the administrative password without any encryption. From byte 96, the file is encoded in base64, and decoding it reveals the password for “admin” (AAAAAAAA) and “root” (humax) users, both saved in clear text.
“If your router allows remote configuration management via the Internet, attackers can easily gain access to it and change configurations that will impact your Internet traffic. However, even if configuration management is not available on the Internet facing interface, attackers can still exploit the vulnerability in locations where WiFi routers are public, for instance in a café or airport,” the researchers say.
To stay protected, and prevent remote exploitation, users should make sure their routers aren’t exposed to the Internet. For that, they should disable the option "Remote Configuration Management."
“Access your HUMAX WiFi Router via the following URL: http://192.168.0.1 and you should be able to find the credentials on the bottom of the router itself. By default, this configuration is not enabled, but you should double check it to make sure. If you don't have access to your router, try to contact your Internet Service Provider and ask for support or, perhaps, a new router,” Trustwave concludes.
NeutrinoPoS - Old Trojan Shifts to New Targets
5.7.2017 securityweek Virus
Kaspersky Lab security researchers have observed a new step in the evolution of the Neutrino malware, with a recently observed variant targeting point of sale (PoS) terminals.
The first thing that caught researchers’ attention was that the malware takes a long sleep before starting its malicious routine, in an attempt to avoid anti-virus sandboxes. The malware uses a pseudorandom number generator to determine the period of delay, Kaspersky’s Sergey Yunakovsky explains.
Next, the malware extracts a command and control (C&C) address list from its body and decodes it (the list is Base64-encoded). Next, the Trojan attempts to connect to a working C&C using a specific algorithm: it “sends POST-request to server, passing through its body encoding in base64 string “enter” (ZW50ZXI=).” All encoded strings feature the prefix “_wv=,” the researcher observed.
A working server would respond with a 404 page, but would also include the encoded string c3VjY2Vzcw== (success) at the end, which tells the Tojan to mark the address of the used server as working.
The header of each POST-request also includes an “auth” field, which is the same for each sample from the NeutrinoPOS family, researchers say.
The malware contains support for a variety of commands, including the option to download and start a file; take screenshots; search processes by name; change register branches; and search files by name on infected host and send the file to the C&C server. It also supports a “proxy” command.
The Trojan also includes the necessary algorithm for stealing credit card information. The implementation of this algorithm is quite simple, Kaspersky says.
The malware works through current processes and retrieves information about the memory page of each process and then starts scanning the memory pages for string “Track1”, which marks fields of the first track of the magnetic card.
In addition to the card number, the Trojan attempts to retrieve information such as card holder name and rest data (CVC32, expiration date, CVV). The collected information is sent to the server marked as Track1 and the malware moves to extracting Track2 data.
NeutrinoPOS was observed mainly infecting users in Russia and Kazakhstan, and Kaspersky notes that nearly 10% of the infected computers belong to small business corporate customers.
“Despite belonging to an old, well-known and researched family, [Neutrino] continues to bring various surprises to malware analysts and researchers in the form of atypical functionality or application. We can see the same situation with Mirai forks, for example, which generate an enormous count across all platforms and in different species,” Yunakovsky says.
The researcher also notes that Neutrino variants “with functionality for crypto-currency mining” might already be in the works.
In ExPetr/Petya’s shadow, FakeCry ransomware wave hits Ukraine
5.7.2017 Kaspersky Ransomware
FAKECRY RANSOMWARE
While the (cyber-)world was still shaking under the destructive ExPetr/Petya attack that hit on June 27, another ransomware attack targeting Ukraine at the same time went almost unnoticed.
So far, all theories regarding the spread of ExPetr/Petya point into two directions:
Distribution via trojanized updates to MeDoc users
Distribution via waterhole attacks in Ukrainian news websites (one case known)
While there is little doubt that MeDoc users were infected via malicious updates with ExPetr, it appears that ExPetr was not the only malware they received. Our telemetry confirms that MeDoc users received at least one other malicious program at the same time. This additional malware, which was run as “ed.exe” in the “MeDoc” program folder (eg. c:\programdata\medoc\medoc\ed.exe) was run on victim machines by the parent process ezvit.exe, a component of the MeDoc software. This suggests the delivery mechanism abused the same MeDoc updates vector as ExPetr.
The malware, which unsurprisingly, is also ransomware, is written in .NET and includes a “WNCRY” string, which obviously refers to the massive WannaCry epidemic that hit global businesses back in May 2017.
A “forgotten” PDB path inside also points to the project’s name being “WannaCry”:
Amusingly, in what we believe to be a false flag, it pretends to be “made in China”:
Based on the strings and the pretense that it’s WannaCry, we’ve decided to call this “FakeCry”.
FakeCry technical details
Sample:MD5: 0BDE638B274C7F9C6C356D3987ED1A2D
Size: 3,880,448 bytes
Compilation timestamp: Fri Jan 01 01:25:26 2016
First seen in the wild: 2017.06.27 12:34:00 (GMT)
Filename on disk: wc.exe
This program acts as a dropper for a ransomware module.
The dropper supports the following commands:
extract – drops the ransomware component
ed – begin encryption
dd – begin decryption
<Key>:
If ed is passed then it is a public key
If dd is passed then it is a private key
demo (encryption or decryption with hardcoded RSA keys)
The ransomware component has the following identification data:
MD5: 5C7C894A1CCFD8C8E0F174B0149A6601
Size: 442,880 bytes
Compilation timestamp: Fri Jan 01 01:20:53 2016
First seen in the wild: 2017.06.27 12:34:00 (GMT)
Filename on disk: ed.exe
The ransomware component supports the following command
genrsa – generate RSA-2048 key pair
Df – decrypt file
Dd – decrypt disk
ef- encrypt file
Ed – encrypt disk
delshadowcopies – delete shadow copies on machine
Example command line for the execution of the ransomware component:
exe -ed C:\ 3ds,uot,stw,sxw,ott,odt,pem,p12,csr,crt,key,pfx,der windows BgIAAACkAABSU0ExAAgA….
When run, the ransomware executes the following steps:
deletes shadow copies
initializes keys
creates file list for encryption
encrypts files
shows window with the ransom demand
Keys initialization process
The malware creates a RSA key pair for encryption. The private RSA key is encrypted with the attacker’s public RSA key, which is passed via arguments.
The generated, the public RSA key and encrypted private RSA key are stored in this registry key:
HKCU\Software\WC
File encryption process
List of extensions targeted for encryption:
doc,docx,xls,xlsx,ppt,pptx,pst,ost,msg,eml
vsd,vsdx,txt,csv,rtf,123,wks,wk1,pdf,dwg
onetoc2,snt,docb,docm,dot,dotm,dotx,xlsm,xlsb,xlw
xlt,xlm,xlc,xltx,xltm,pptm,pot,pps,ppsm,ppsx
ppam,potx,potm,edb,hwp,602,sxi,sti,sldx,sldm
sldm,vdi,vmdk,vmx,gpg,aes,ARC,PAQ,bz2,tbk
bak,tar,tgz,gz,7z,rar,zip,backup,iso,vcd
raw,cgm,tiff,nef,psd,ai,svg,djvu,m4u,m3u
mid,wma,flv,3g2,mkv,3gp,mp4,mov,avi,asf
mpeg,vob,mpg,wmv,fla,swf,wav,mp3,sh,class
jar,java,rb,asp,php,jsp,brd,sch,dch,dip
pl,vb,vbs,ps1,bat,cmd,js,asm,h,pas
cpp,c,cs,suo,sln,ldf,mdf,ibd,myi,myd
frm,odb,dbf,db,mdb,accdb,sql,sqlitedb,sqlite3,asc
lay6,lay,mml,sxm,otg,odg,uop,std,sxd,otp
odp,wb2,slk,dif,stc,sxc,ots,ods,3dm,max
3ds,uot,stw,sxw,ott,odt,pem,p12,csr,crt,key,pfx,der
If a file to be encrypted is locked by other processes, the ransomware can kill this process, using a Sysinternals tool (Handler Viewer) to accomplish the task.
The file encryption algorithm in a nutshell:
Attacker’s RSA public key is received by the ransomware via command line
“Session” RSA-2048 key-pair is generated
“Session” RSA private key is encrypted with public RSA key (which was received in point №1)
For each file, an AES-256 key and IV are generated
Key and IV are encrypted with generated “Session” RSA key and saved in the encrypted file
Interestingly, the ransomware contains a list of extensions called “DEMO_EXTENSIONS”. The attackers provide the claim that that the files from this DEMO_EXTENSION list (which contains only image file extensions – “jpg, jpeg, png, tif, gif, bmp”) will be decrypted for free, something that appears to be working as advertised.
Here’s a screenshot of the ransomware component running on a victim machine:
To decrypt the files, the attackers are asking for 0.1BTC, which is approximately 260$ at today’s exchange price. The wallet number is fixed, 13KBb1G7pkqcJcxpRHg387roBj2NX7Ufyf for all infections. Interestingly, the wallet has received seven payments so far, totalling 0.51 BTC. Most of the 0.1 payments took place on June 26, suggesting that was the day when the attack peaked. Interestingly, the attackers have withdrawn 0.41 BTC from the ransom account.
Transaction for wallet FakeCry
So far, there is no further activity on the receiving wallet 1FW1xW8kqNg4joJFyTnw6v5bXUNyzKXtTh.
To check the payment and receive the decryption key, the malware uses an Onion server as C2, which is “4gxdnocmhl2tzx3z[.]onion”.
Conclusions
Although the software company developing the MeDoc software has been so far denying all evidence that its users have been infected through malicious updates, our telemetry suggests that the vast majority of the ExPetr/Petya victims on June 27, 2017 were attacked this way.
Unfortunately ExPetr/Petya was not the only ransomware that was distributed via MeDoc updates on June 27. In parallel, another ransomware, FakeCry, was also distributed to MeDoc users at exactly the same time as ExPetr/Petya. Our telemetry shows about 90 attacked organizations received the FakeCry ransomware, almost all in Ukraine.
What makes FakeCry interesting is the fact that it appears to have been designed with false flags in mind. Its interface and messages closely emulate those of WannaCry, yet this is an entirely different malware. In what we believe to be a false flag, samples also include a “made in china” string.
Of course, one of the biggest questions here is if FakeCry and ExPetr are related. So far, the most important evidence that would suggest it, is the fact they were both distributed through MeDoc updates, at the same time.
As usual, our recommendations to protect against ransomware include:
Here’s our shortlist of recommendations on how to survive ransomware attacks:
Run a robust anti-malware suite with embedded anti-ransomware protection such as System Watcher from Kaspersky Internet Security.
Make sure you update Microsoft Windows and all third party software. It’s crucial to apply the MS17-010 bulletin immediately.
Do not run open attachments from untrusted sources.
Backup sensitive data to external storage and keep it offline.
Last but not least, never pay the ransom. Paying the ransom funds the next wave of attacks.
For sysadmins, our products detect the samples used in the attack by these verdicts:
UDS:DangerousObject.Multi.Generic
PDM:Trojan.Win32.Generic
Our behavior detection engine SystemWatcher detects the threat as:
PDM:Trojan.Win32.Generic
PDM:Exploit.Win32.Generic
Obří kybernetický útok byl na spadnutí. Policie ho zarazila
5.7.2017 Novinky/Bezpečnost Viry
Ukrajinská kybernetická policie spolu s experty tajné policie SBU zabránili v úterý druhé etapě počítačového útoku na Ukrajinu. Na Facebooku to v noci na středu oznámil ukrajinský ministr vnitra Arsen Avakov. Odborníci se stále snaží odhalit, kdo byl za předchozím útokem, který minulý týden začal napadením počítačů ukrajinských firem a institucí, než se rozšířil po celém světě.
Druhý útok byl podle Avakova odstartován v úterý ve 13:40 kyjevského času (12:40 SELČ) a měl vyvrcholit v 16:00.
"Kybernetická policie do 15:00 zablokovala rozesílání a aktivaci viru ze serverů informačního systému M.E.Doc. Útok byl zastaven. Servery byly zajištěny společně se stopami aktivity kybernetických zločinců se zjevnými zdroji z Ruské federace," napsal Avakov.
Dodal, že kybernetická policie uživatelům důrazně doporučuje změnit hesla a digitální podpisy.
Policie zabavila servery
Šéf ukrajinské kybernetické policie Serhij Demyďuk už v úterý večer oznámil, že policie zabavila servery kyjevské softwarové firmě MEDoc, která je podezřelá z šíření škodlivého programu před týdnem v úterý. Neřekl ale, že se tak stalo po zabránění dalšímu útoku, jak o něm v noci na středu informoval ministr vnitra.
Podle policistů hackeři na aktualizační server ukrajinské firmy umístili škodlivý malware, který se pak s novou verzí softwaru dostal do počítačů po celém světě. Šlo o vyděračský virus známý jako Win32/Diskcoder.C Trojan, který dokáže na napadeném stroji udělat pěknou neplechu.
Uživatelé napadení virem místo startu operační systému uvidí tuto zprávu.
Uživatelé napadení virem místo startu operačního systému uvidí tuto zprávu.
A to dokonce větší než drtivá většina dalších vyděračských virů. Ty totiž často potřebují k zašifrování dat na pevném disku poměrně dost času, klidně i několik hodin. Během toho může jejich práci zachytit antivirový program a zablokovat je ještě dříve, než v počítači nadělají nějakou větší škodu.
Nově objevená hrozba však funguje jiným způsobem. Na disku nezašifruje všechna data, ale pouze tzv. MBR (Master Boot Record). Jde o hlavní spouštěcí záznam, díky kterému se v podstatě spouští celý operační systém. K zašifrovanému záznamu počítač nemá přístup a místo Windows spustí jen hlášku o nutnosti zaplatit výkupné.
Na zašifrování MBR nepotřebuje nový vyděračský virus několik hodin, stačí mu pouze pár vteřin. Antiviry prakticky nemají šanci škodlivý kód zachytit. Hned po prvním restartu je problém na světě.
Ukrajinská firma vinu odmítá
Firma MEDoc jakoukoli odpovědnost za šíření škodlivého softwaru odmítla.
Ukrajinští činitelé hned po prvním útoku minulý týden obvinili Rusko, že stojí v pozadí tohoto kybernetického zločinu, což Moskva rázně odmítla.
Side-Channel Attack on Libgcrypt Allows RSA Key Recovery
5.7.2017 securityweek Krypto
The developers of Libgcrypt, the cryptographic library used by the GNU Privacy Guard (GnuPG) implementation of the OpenPGP standard, released an update last week to prevent side-channel attacks that allow the recovery of RSA private keys.
The attack method was identified recently by a team of researchers from various universities in Australia, the Netherlands and the United States.
They showed that the use of the sliding windows method for exponentiation leads to the leakage of exponent bits. It’s widely believed that the number of leaked bits is not enough to fully recover an RSA key, but the experts have demonstrated that extraction of RSA-1024 keys is possible, and even RSA-2048 keys in 13 percent of cases.
The research targeted Libgcrypt version 1.7.6 and the attack was conducted on an HP-Elite 8300 computer, with a 4-core Intel i5-3470 processor and 8GB of DDR3-1600 memory.
The developers of Libgcrypt have been notified of the vulnerability, tracked as CVE-2017-7526. They addressed the issue, which they described as a local side-channel attack, with the release of version 1.7.8.
Libgcrypt maintainers pointed out that this attack method requires running malicious software on the machine storing the targeted private RSA key. If this type of access is obtained, there are easier ways to recover the key than to launch such a side-channel attack.
“Allowing execute access to a box with private keys should be considered as a game over condition, anyway,” Libgcrypt developers said in an advisory. “However, on boxes with virtual machines this attack may be used by one VM to steal private keys from another VM.”
The developers of the Debian and Ubuntu Linux distributions have also released updates to address the vulnerability.
Technical details on this attack method can be found in the paper titled “Sliding right into disaster: Left-to-right sliding windows leak,” published on the website of the International Association for Cryptologic Research (IACR).
Why AA didn’t inform customers after a massive data leak
5.7.2017 securityaffairs Incindent
A backup containing sensitive information on more than 100,000 AA customers was exposed online, but the company didn’t disclose the incident.
UK car insurance company AA is being heavily criticized over its handling of a data breach that exposed customer email addresses and partial credit card number in April.
A server misconfiguration is the root cause for the exposure of data from the AA’s online shop. The issue exposed backup files containing orders for maps, motoring accessories and other products.

The incident was publicly disclosed last week when security experts Troy Hunt criticized the way AA has downplayed a massive data breach that exposed about 13GB of DB backups.
Follow
Troy Hunt ✔ @troyhunt
Extremely disappointing to see an organisation cover up and downplay a breach that includes credit card data. Very poor form by @TheAA_UK https://twitter.com/josephfcox/status/881863275029434368 …
3:34 PM - 3 Jul 2017
121 121 Retweets 118 118 likes
Twitter Ads info and privacy
The AA confirmed the incident affected AA shop & retailers orders rather than sensitive info. It was rectified & we take this seriously.”
26 Jun
Sajid Nawaz Khan @snkhan
@TheAA_Help Can you advise whether the breach reported by @troyhunt is genuine? Was customer data downloaded by a unauthorised third party?
Follow
The AA ✔ @TheAA_Help
@snkhan This incident was related to the AA shop & retailers’ orders rather than sensitive info. It was rectified & we take this seriously.
3:37 PM - 26 Jun 2017
Retweets 1 1 like
Twitter Ads info and privacy
According to Troy Hunt, the leak exposed also partial payment details (the last four figures of credit card numbers) of the users and other sensitive information.
Follow
Troy Hunt ✔ @troyhunt
Exposed data included card type, expiry and last 4 digits. Multiple customers who had their data compromised confirmed. Time to come clean. https://twitter.com/theaa_help/status/881889755688030209 …
5:09 PM - 3 Jul 2017 · Amsterdam, The Netherlands
19 19 Retweets 48 48 likes
Twitter Ads info and privacy
According to Motherboard the leaked dump contains 117,000 unique email addresses as well as portions of credit card data.
“The data obtained by Motherboard contains 117,000 unique email addresses, as well as full names, physical addresses, IP addresses, details of purchases, and payment card information. Those card details include the last four digits of the credit card and its expiry date.” states the blog post published by Motherboard.
“The data also appears to include a number of password hashes, and according to security researcher Scott Helme, an expired certificate and private encryption key.”
“This is essentially the username and password that the AA use to login to their Secure Trading account,” Helme wrote in an analysis of the breach shared with Motherboard.”
Even is a small portion of a credit card number has been exposed, this data can be used for identity verification exposing the owners to identity theft.
The ICO confirmed it is aware of the incident and that it is investigating the case.
“Businesses and organisations are obliged by law to keep people’s personal information safe and secure. We are aware of an incident involving the AA and are making enquiries.” an ICO spokesperson told El Reg.
According to the AA, the data was “only accessed several times.”
“Legal letters warning against a dissemination breach under the ‘Computer Misuse Act’ will be issued. The ICO [Information Commissioner’s Office] has been informed and we have commissioned a full independent investigation into the issue. We take any data issues incredibly seriously and would like to reassure our AA Shop customers that their payment details have not been compromised,” reads the statement from AA.
A few days ago, the UK car insurance company accidentally sent out a ‘password update’ email to its customers, at the time the incident declared the problem was caused by a human error.
Vulnerabilities in Pre-Installed Software expose Dell Systems to hack
4.7.2017 securityaffairs Vulnerebility
According to experts from Talos, security vulnerabilities in pre-installed software expose Dell systems to code execution attacks.
Security vulnerabilities in pre-installed software expose Dell systems to code execution attacks.
Hackers can exploit the flaws to disable security mechanisms, escalate privileges and execute arbitrary code within the context of the application user.
According to the experts from CISCO Talos, the vulnerable pre-installed software is the Dell Precision Optimizer application service and the Invincea-X and Invincea Dell Protected Workspace.
“Talos are releasing advisories for vulnerabilities in the Dell Precision Optimizer application service software, Invincea-X and Invincea Dell Protected Workspace. These packages are pre-installed on certain Dell systems. Vulnerabilities present in these applications could allow attackers to disable security mechanisms, escalate privileges and execute arbitrary code within the context of the application user.” states the advisory published by Cisco Talos.
The first vulnerability in Invincea-X, Dell Protected Workspace 6.1.3-24058, tracked as CVE-2016-9038, is a double fetch in the SboxDrv.sys driver.
An attacker can exploit the flaw by sending crafted data to the \Device\SandboxDriverApi device driver which is read/write accessible to everyone. A
The attacker can exploit the issue to write an arbitrary value to kernel memory space in order to gain local privilege escalation.
The second flaw tracked as CVE-2016-8732 affected the Invincea Dell Protected Workspace version 5.1.1-22303, that is a security solution for endpoints.
According to Talos, the flaws exist within one of the driver components, ‘InvProtectDrv.sys’ that is included in version 5.1.1-22303 of this security software. Weak restrictions on the driver communications channel and insufficient validation could allow an attacker controlled application that is executed on an affected system to leverage the driver to disable protection mechanisms.

Weak restrictions on the driver communications channel and insufficient validation allow an attacker-controlled application executed on the vulnerable machine to leverage the driver and disable some of the protection mechanisms in the software. The bug was fixed in the 6.3.0 release of the application.
A third flaw, tracked as CVE-2017-2802, affects the Dell Precision Optimizer application and could lead to the execution of arbitrary code. The vulnerabilities affects the Dell Precision Tower 5810 with nVidia graphic cards, PPO Policy Processing Engine 3.5.5.0, and ati.dll (PPR Monitoring Plugin) 3.5.5.0.
“During the start of ‘Dell PPO Service’, supplied by Dell Precision Optimizer application, the program “c:\Program Files\Dell\PPO\poaService.exe” loads the dll, “c:\Program Files\Dell\PPO\ati.dll”. This in turn attempts to load “atiadlxx.dll”, which is not present by default in the application directory. The program searches for an appropriately named dll in the directories specified by the PATH environment variable. If it finds a dll with the same name, it will load the dll into poaService.exe without checking the signature of the dll. This can lead to execution of arbitrary code if an attacker supplies a malicious dll of the correct name. ” continues the advisory.
An attacker could supply a malicious DLL having the same name of the “atiadlxx.dll” in one of the directories specified by the PATH environment variable to achieve arbitrary code execution.
The security implications for the flaws are serious because the Invincea Dell Protected Workspace is an application is commonly deployed to secure workstations within high-security environments.
Talos users’ organizations using affected versions of this software to update them to the latest version as soon as possible. It is important anyway to carefully assess any pre-installed software to avoid that flaws affecting them can be exploited by attackers.
“Given that the Invincea Dell Protected Workspace is an application that is commonly deployed to secure workstations within high security environments, it is recommended that organizations using affected versions of this solution update to the latest version as quickly as possible to ensure that the protections provided by this software cannot be bypassed by an attacker. ” concluded Talos.
Security researchers Crack 1024-bit RSA Encryption in GnuPG Crypto Library
4.7.2017 securityaffairs Krypto
Experts have devised a side-channel attack on RSA secret keys that allowed to crack 1024-bit RSA Encryption in GnuPG Crypto Library.
Security researchers have found a critical vulnerability, tracked as CVE-2017-7526, in a Gnu Privacy Guard (aka (GnuPG or GPG) cryptographic library that allowed them cracking RSA-1024 and extract the RSA key to decrypt data.
The research team was composed of experts from several universities, including Technical University of Eindhoven, the University of Illinois, the University of Pennsylvania, the University of Maryland, and the University of Adelaide.
GnuPG is popular open source encryption software currently used by many operating systems, including Linux, Windows, and macOS X.
The vulnerability resides in the Libgcrypt cryptographic library used by GnuPG, that opens to local FLUSH+RELOAD side-channel attack on RSA secret keys dubbed “Sliding right into disaster”
The expert discovered that the “left-to-right sliding window” method used by the libgcrypt library leaks significantly more information about exponent bits than for right-to-left, allowing RSA key recovery.
“It is widely believed that, even if the complete pattern of squarings and multiplications is observed through a side-channel attack, the number of exponent bits leaked is not sufficient to carry out a full key-recovery attack against RSA. Specifically, 4-bit sliding windows leak only 40% of the bits, and 5-bit sliding windows leak only 33% of the bits.” states the research paper.
“In this paper, we demonstrate a complete break of RSA-1024 as implemented in Libgcrypt. Our attack makes essential use of the fact that Libgcrypt uses the left-to-right method for computing the sliding-window expansion,”
“The pattern of squarings and multiplications in left-to-right sliding windows leaks significantly more information about the exponent than right-to-left. We show how to extend the Heninger-Shacham algorithm for partial key reconstruction to make use of this information and obtain a very efficient full key recovery for RSA-1024.”
In the L3 Cache Side-Channel Attack scenario, hackers run arbitrary software on the hardware handling the private RSA key.
The analysis of the pattern of memory utilization or the electromagnetic outputs emitted during the decryption process could allow the attacker to extract the encryption key from a system.
“Note that this side-channel attack requires that the attacker can run arbitrary software on the hardware where the private RSA key is used. Allowing execute access to a box with private keys should be considered as a game over condition, anyway.” reads the Libgcrypt advisory .
“Thus in practice, there are easier ways to access the private keys than to mount this side-channel attack. However, on boxes with virtual machines, this attack may be used by one VM to steal private keys from another VM.”
According to the experts, the side channel attack also works against RSA-2048, the attack
is efficient for 13% of keys.
“Scaling up to RSA-2048 does not stop our attack: we show that 13% of all RSA-2048 keys with CRT and w = 5 are vulnerable to our method after a search through 2000000 candidates” continues the paper.
The GnuPG Project released the Libgcrypt version 1.7.8. to fix the local side-channel attack.to fix the local side-channel attack.
Libgcrypt has released a fix for the issue in Libgcrypt version 1.7.8. Debian and Ubuntu already updated their library with the latest version of Libgcrypt.
A fresh massive AdGholas Malvertising campaign infects millions
4.7.2017 securityaffairs Virus
Researchers at Proofpoint discovered a massive AdGholas Malvertising Campaign infecting as many as 1 million computers per day with several banking trojans.
A new massive AdGholas malvertising network discovered by experts at Proofpoint has been infecting as many as 1 million computers per day with several banking trojans.
AdGholas operators have been active since 2015, the threat actors behind the AdGholas malvertising campaign was notable for its use of steganography and careful targeting of the massive volume of malicious ads and impressions and its ability to avoid detection of researchers.
“Proofpoint researchers have discovered and analyzed a massive malvertising network operating since 2015. Run by a threat actor we designated as AdGholas and pulling in as many as 1 million client machines per day” states the analysis from Proofpoint.
According to Proofpoint researchers “This campaign represents the first documented use of steganography in a drive-by malware campaign, and attacks employed ‘informational disclosure’ bugs perceived to be low-risk in order to stay below the radar of vendors and researchers.”
The campaign was receiving high-quality traffic from a variety of high-rank referrers, from more than twenty different AdAgency/AdExchange platforms. According to the experts, the AdGholas was clocking one to five million hits every day, unfortunately, roughly 10-20% of the hits were redirected to domains hosting exploit kits.
Cyber criminals were using domains that appear as clones of legitimate websites belonging to Hotel Merovinjo in Paris, Ec-centre and Mamaniaca.
The experts at Proofpoint observed that hackers served different malware depending on user and geography.

“Our analysis with colleagues from Trend Micro found that AdGholas campaigns do not all work the same way, but all do have the same multi-layered filtering and obfuscation,” continues the analysis. “For instance, the redirect tag is being sent in several ways. We saw the xhr-sid sent as response header to a POST to GIF, but it is sometimes hidden at the end of an ‘addStat hash in the initial landing.”
AdGholas gang went silent for two weeks after the Angler exploit kit disappearance from the threat landscape, it then returned using the same domains at the end of June in campaign leveraging the Neutrino EK.
Malware researchers observed the gang delivering geo-focused banking Trojans, such as Gozi ISFB in Canada, Terdot.A (aka DELoader) in Australia, Godzilla loaded Terdot.A in Great Britain, and Gootkit in Spain. The experts observed four different Neutrino threads, as Neutrino is not including an internal TDS while Blackhole, Angler and Nuclear were.
Recently the AdGholas gang or close distribution partners was operating reverse proxies serving the involved instance of exploit kit at the end of April.
AdGholas demonstrates that malvertising campaigns are becoming increasingly sophisticated to remain stealthy and effective.
Below key findings from Proofpoint analysis:
Massive scale: The AdGholas network drew traffic of 1-5 million high quality client hits per day.
Stealthy innovation: This campaign represents the first documented use of steganography in a drive-by malware campaign, and attacks employed “informational disclosure” bugs perceived to be low-risk in order to stay below the radar of vendors and researchers.
Sophisticated filtering: AdGholas employs ‘smart,’ multi-step filtering techniques to more precisely target client systems, including avoiding non-OEM and non-Nvidia/ATI-powered systems.
Convincing: Redirected sites avoid suspicion and improve effectiveness by closely mimicking the appearance of the legitimate site expected by the ad agencies.
China Shuts Down Popular VPN Services to Make Great Firewall Stronger
4.7.2017 thehackernews BigBrothers
Online Privacy has been one of the biggest challenges in today's interconnected world, as the governments across the world have been found censoring the Internet, stealing information and conducting mass surveillance on innocent people.
China is one such nation which always wanted to have a tight hold on its citizen and has long been known for its strict Internet censorship laws through the Great Firewall of China.
The Great Firewall of China is the nation's Golden Shield project that employs a variety of tricks to censor Internet and block access to various foreign news and social media sites, including Google, Facebook, Twitter, Tumblr, Dropbox, and The Pirate Bay.
So, in order to thwart these restrictions and access blocked websites, hundreds of millions of Chinese citizens rely on virtual private networks (VPNs) which route their traffic to servers overseas free of the Great Firewall filters, but this may not be an option soon.
For those unfamiliar, Virtual Private Network (VPN) securely routes your Internet traffic through a distant connection, protecting your browsing, hiding your location data and accessing restricted resources.
Also Read: Use Secure VPNs (Lifetime Subscription) to Prevent ISPs From Spying On You
GreenVPN, one of the most popular VPN services in China, notified its customers on Monday that the company would stop its VPN service from July 1st, following orders by "regulatory departments" to cease its operation, Bloomberg reported.
However, not just GreenVPN, some users also stated that they were unable to use SuperVPN, another popular VPN service on their smartphones over the weekend, although it is unclear whether the service was down to a glitch or the government restrictions.
This restriction could be part of new rules by the China's Ministry of Industry and Information Technology announced at the beginning of this year, making it illegal to use or operate local VPNs without government approval from the government.
According to the ministry, "all special cable and VPN services on the mainland needed to obtain prior government approval—a move making most VPN service providers in the country of 730 million Internet users illegal."
This crackdown on VPN services has been designed to "strengthen cyberspace information security management," as said by the Chinese ministry.
The crackdown is yet one of the several priorities for controlling online content in China.
Nebezpečný Chromex je opět na scéně, varovali počítačoví experti
4.7.2017 SecurityWorld Viry
Počítačoví piráti začali v minulých týdnech opět hojně šířit trojského koně zvaného Chromex. Ten se držel na předních příčkách žebříčku s nejrozšířenějšími kybernetickými hrozbami ještě v dubnu, pak se však stáhl do ústraní. V červnu však přišla další vlna útoků, ve kterých hrál Chromex opět hlavní roli.
Před dramatickým rozšířením tohoto trojského koně mezi zaznamenanými hrozbami varovali bezpečnostní odborníci z antivirové společnosti Eset. Podle nich patří Chromexu aktuálně druhá příčka v žebříčku nejrozšířenějších počítačových hrozeb.
„Svým podílem se blížil k dlouhodobě nejsilnějšímu škodlivému kódu JS/Danger.ScriptAttachment. Eset, který tuto hrozbu detekuje jako JS/Chromex.Submelius, jej v červnové statistice virových hrozeb identifikoval v 13,93 procentech případů,“ uvedl Miroslav Dvořák, technický ředitel společnosti Eset.
Slibují zrychlení internetu
„Chromex využívá například popularity neoficiálních streamovacích služeb na internetu a uživatelům nabízí instalaci škodlivých pluginů,“ doplnil Dvořák.
Útočníci přitom často slibují, že pluginy zrychlí načítání internetových stránek, ve skutečnosti ale způsobují opak. Často je na možnost instalace podobných pluginů možné narazit na různých streamovacích stránkách s českou nebo slovenskou doménou.
„Jak napovídá jeho název, Chromex se soustředí na doplňky k internetovému prohlížeči Chrome. V České republice se poprvé četněji vyskytl letos v březnu, kdy se ve statistice objevil na pátém místě. Dosud však nepředčil největší internetovou hrozbu současnosti, škodlivý kód Danger,“ konstatoval Dvořák.
Pozor na infikované přílohy e-mailů
Tento virus, plným názvem JS/Danger.ScriptAttachment, je velmi nebezpečný. Otevírá totiž zadní vrátka do operačního systému. Útočníci pak díky němu mohou propašovat do napadeného počítače další škodlivé kódy, nejčastěji tak šíří vyděračské viry typu ransomware.
Danger, který se šíří prostřednictvím infikovaných příloh e-mailů, měl v červnu podíl 17,81 procenta, což je meziměsíční pokles o 3,58 procentního bodu.
Stále to však mezi detekovanými hrozbami stačilo na absolutní prvenství. Přehled deseti nejrozšířenějších virových hrozeb za uplynulý měsíc naleznete v tabulce níže:
Top 10 hrozeb v České republice za červen 2017:
1. JS/Danger.ScriptAttachment (17,81 %)
2. JS/Chromex.Submeliux (13,93 %)
3. JS/Adware.AztecMedia (6,65 %)
4. JS/ProxyChanger (4,59 %)
5. Win32/GenKryptik (4,22 %)
6. Java/Adwind (2,88 %)
7. JS/Adware.Imali (2,71 %)
8. JS/TrojanDownloader.Nemucod (2,66 %)
9. PDF/TrojanDropper.Agent.AE (1,70 %)
10. PDF/TrojanDropper.Agent.AJ (1,62 %)
Microsoft Forces Users to Review Windows 10 Privacy Settings
4.7.2017 securityweek Privacy
Windows 10 users who haven’t installed the Creators Update will soon be notified to review their privacy settings and to install the latest feature update to remain secure, Microsoft announced.
Microsoft has been criticized for its Windows 10 data collection practices, and the French National Data Protection Commission (CNIL) recently served the company a formal notice to stop collecting excessive user data. As a result, Creators Update addressed these concerns, and CNIL closed the formal notice last week.
Although it claimed the Windows 10 data collection was aimed at improving the overall user experience, Microsoft did listen to feedback and provided users with increased control over their privacy in Creators Update. Users can now set data collection to Basic or Full, depending on how much usage statics they want to share with Microsoft.
Microsoft is now using these changes to push Windows 10 users to review their privacy settings if they haven’t done so already. The company will provide users with the possibility to postpone the process up to five times, but the next prompt will ask them to confirm their privacy settings.
“Given the Windows 10 Creators Update provides the latest security protections to help keep you safe, we want to help update your device as soon as possible. […] you will have the opportunity to review your privacy settings before your device is eligible to take the Creators Update. If you have not already taken this update, starting this week, we will prompt you to review your privacy settings,” John Cable, Director of Program Management, Windows Servicing and Delivery, notes in a Friday blog post.
The update experience, Cable says, will not change, and users will be able to choose when they want to update to the Creators Update, once their devices are ready.
Updating to the Creators Update, Cable notes, ensures that Windows 10 users benefit from the latest security improvements and usability improvements available for them. In the light of the recent WannaCry and NotPetya outbreaks, it’s not surprising the tech company is playing the “stay secure” card, especially since the first version of Windows 10 is at end-of-service.
“While you can continue to use this version and your computer will still work, you will no longer receive the monthly quality updates that contain protection from the latest security threats. To remain secure your device should be updated to the latest feature update,” Cable notes.
The “latest feature update,” of course, is Windows 10 Creators Update, and Microsoft is taking steps to ensure users are more likely to update. The company will start notifying them if their devices need to be updated, Cable reveals.
DeepMind's Use of NHS Patient Data Contravenes Data Protection Act
4.7.2017 securityweek Cyber
The UK's Information Commissioner's Office (ICO) has ruled today that the Royal Free NHS Foundation Trust contravened the Data Protection Act when it provided the personal data of 1.6 million patients to Google-owned DeepMind. The purpose of the data transfer was to help develop the healthcare app, Streams -- a diagnosis and detection system for acute kidney infection.
DeepMind is an artificial intelligence research company determined to use AI to solve complex problems -- such as health issues. Like all machine learning and AI, it needs large amounts of data from which to learn and from which its algorithms are developed. It is where and how this data is acquired that is at issue.
The Information Commissioner said in a statement, "There's no doubt the huge potential that creative use of data could have on patient care and clinical improvements, but the price of innovation does not need to be the erosion of fundamental privacy rights. Our investigation found a number of shortcomings in the way patient records were shared for this trial."
Those shortcomings included: patients were not properly informed that their data would be used in this way, and that the Trust should have been more transparent about the arrangement. However, the ICO stopped short of delivering any sanctions over these shortcomings, even though it states, "patient identifiable data was not subject to pseudonymisation."
In theory, the ICO could have fined the Royal Free up to £500,000. Instead, it has merely asked the Trust to establish a legal basis for the Google DeepMind project and for any future trials; to set out how it will comply with its duty of confidence in any future trials; to complete a privacy impact assessment; and to commission an audit of the trial which may be published by the ICO.
There are no specific requirements on DeepMind since under the law it is the 'data controller' -- that is, the Royal Free -- that is responsible for data protection.
The lack of specific legal sanctions may be because of the willingness of both the Trust and DeepMind to cooperate with the ICO. In a blog posted today, DeepMind first justified the project, and then admitted its failings. "We're proud that, within a few weeks of Streams being deployed at the Royal Free, nurses said that it was saving them up to two hours each day, and we've already heard examples of patients with serious conditions being seen more quickly thanks to the instant alerts."
But it added, "In our determination to achieve quick impact when this work started in 2015, we underestimated the complexity of the NHS and of the rules around patient data, as well as the potential fears about a well-known tech company working in health... We made a mistake in not publicizing our work when it first began in 2015, so we've proactively announced and published the contracts for our subsequent NHS partnerships."
In its own statement, the Royal Free commented, "We accept the ICO's findings and have already made good progress to address the areas where they have concerns. For example, we are now doing much more to keep our patients informed about how their data is used. We would like to reassure patients that their information has been in our control at all times and has never been used for anything other than delivering patient care or ensuring their safety."
Perhaps the key aspect of today's ruling is the ICO's final comment, "The Data Protection Act is not a barrier to innovation, but it does need to be considered wherever people's data is being used." This suggests that a light and pragmatic approach to applying current and future data protection laws will be the approach adopted by the UK regulator.
Personal Details of 117,000 AA Shoppers Exposed
4.7.2017 securityweek CyberCrime
The Automobile Association (AA) -- the UK's largest motoring organization with over 15 million members -- is being heavily criticized over its public handling of a major data incident that occurred in April. A server misconfiguration exposed personal details of more than 100,000 AA Shop customers; but its importance has been consistently downplayed by the organization. Affected customers were not informed.
The incident became public knowledge only last week when security researcher Troy Hunt tweeted that the AA had been notified "about 13GB of exposed DB backups". The AA responded with what appears to be its first public confirmation, "This incident was related to the AA shop & retailers' orders rather than sensitive info. It was rectified & we take this seriously."
AA president Edmund King has since said that for a short period a misconfiguration in the server allowed access to two backup data files. He added, "as the data was not sensitive, and our third-party supplier informed us that the data was only accessed several times, the case was closed."
Those few accesses were sufficient for both Troy Hunt and Motherboard to get hold of the data. Both confirm that it does contain sensitive data -- although not full card details -- for 117,000 customers. It includes full names, physical addresses, IP addresses, purchase details, and the last four digits of payment cards together with the expiry date.
This would certainly be enough for the creation of compelling spear-phishing attacks against those customers.
While the incident does not appear to be related to an attack, nevertheless the data was exposed and has been accessed. Motherboard and Troy Hunt have both seen it and have confirmed that it is genuine personal data of AA customers. It is impossible to guarantee that no potential bad actor has also seen it.
"When organizations detect a breach, it should be their first priority to inform all affected customers and take steps to ensure the continued protection of any exposed data," comments Ross Brewer, VP & MD EMEA for LogRhythm. "Failing to do so can, and often does, result in confidential information being left ‘in the wild' for longer than it needs to be. It only takes one hacker to be in the right place at the right time to cause very real damage."
Ilia Kolochenko, CEO at High-Tech Bridge, agrees that AA customers should be concerned. "A verified journalistic source says that the database, and apparently AA's entire web shop, were recently accessed by several unauthorized third-parties," he told SecurityWeek by email. "Cybercriminals could easily be among them, meaning that we should be prepared that the entire 100k database is breached and will be for sale on the Dark Web soon. However, I would avoid any panic until a first confirmed incident, involving records from the breached database, appears. In any case, victims of the breach are better to cancel their credit cards and change all their passwords if they had same or similar ones for all the accounts."
For now, UK data protection laws do not require a private entity such as the AA to disclose breaches. However, those laws do require that personal data is kept secure. The Information Commissioners Office (ICO -- the UK data protection regulator) has been informed of the incident and is investigating.
The need to disclose will change in just over 10 months when the EU's GDPR comes into force. "If anything," adds Brewer, "this points to the need for next year's GDPR enforcement and the tighter policies that will come with it. Under GDPR, the AA would almost certainly be facing a fine for non-disclosure."
The AA might indeed still face a fine under current legislation. An ICO spokesperson has commented, "Businesses and organizations are obliged by law to keep people's personal information safe and secure. We are aware of an incident involving the AA and are making enquiries." The ICO can deliver a fine of up to £500,000 for breach of the Data Protection Act -- and it is unlikely to be happy with the AA's behavior over the incident. Even though the website may have been operated by a third party, the AA remains the data controller and the liable party.
This is the second incident of misconfiguration leading to UK data exposure reported in as many weeks. A misconfiguration exposed email addresses at the UK government's Cyber Essentials website in June.
Pre-Installed Software Flaws Expose Dell Systems to Code Execution
4.7.2017 securityweek Vulnerebility
Flaws in pre-installed software expose Dell systems to attacks that could result in the disabling of security mechanisms, privilege escalation, and arbitrary code execution within the context of the application user.
The vulnerable applications include the Dell Precision Optimizer application service software and Invincea-X and Invincea Dell Protected Workspace, Cisco Talos reveals in an advisory.
Tracked as CVE-2016-9038, the first vulnerability impacting Invincea-X, Dell Protected Workspace 6.1.3-24058, as a result of a device driver being read/write accessible to everyone, which can be triggered by sending specially crafted data to it.
“A successful exploitation results in an arbitrary value written to kernel memory space, which can lead to local privilege escalation,” Cisco explains.
Cisco also warns of CVE-2016-8732, an issue that involves multiple security flaws in the driver component of Invincea Dell Protected Workspace version 5.1.1-22303, a security solution for endpoints.
Weak restrictions on the driver communications channel and insufficient validation allow an attacker-controlled application executed on the vulnerable machine to leverage the driver and disable some of the protection mechanisms in the software. The bug was addressed in the 6.3.0 release of the application.
Tracked as CVE-2017-2802, a third bug impacts the Dell Precision Optimizer application and could lead to execution of arbitrary code. The issue impacts Dell Precision Tower 5810 with nVidia graphic cards, PPO Policy Processing Engine 3.5.5.0, and ati.dll (PPR Monitoring Plugin) 3.5.5.0.
When the Dell PPO Service supplied by Dell Precision Optimizer starts, poaService.exe (located in “c:\Program Files\Dell\PPO\” loads the ati.dll from the same folder. The DLL, in turn, attempts to load atiadlxx.dll, which is not present by default in the directory, and the application searches “for an appropriately named DLL in the directories specified by the PATH environment variable.”
As soon as it finds a DLL with the same name, the app loads it into poaService.exe without checking its signature. Thus, an attacker could supply a malicious DLL of the correct name and achieve arbitrary code execution, Cisco explains.
“Given that the Invincea Dell Protected Workspace is an application that is commonly deployed to secure workstations within high security environments, it is recommended that organizations using affected versions of this solution update to the latest version as quickly as possible to ensure that the protections provided by this software cannot be bypassed by an attacker,” Cisco notes.
Sonda do hlubin ransomwaru Petya
4.7.2017 SecurityWorld Viry
Evropu v uplynulých dnech postihla nová vlna kybernetických útoků. Jako první byly napadené významné organizace na Ukrajině, posléze se útoky rozšířily především po Evropě. Experti Trend Micro vydali zprávu, ve které podrobně analyzovali situaci okolo tohoto malwaru.
Ačkoliv se stav rychle vyvíjí, zprávy naznačují, že jde o vypuknutí nové varianty ransomwaru Petya, o kterém odborníci poprvé podrobně informovali již v březnu 2016. Není výjimkou, že kyberzločinci svůj škodlivý software leckdy vylepšují.
Nová varianta používá funkci EternalBlue a nástroj PsExec jako infekční vektory. Je známo, že Petya přepisuje systém Master Boot Record (MBR), čímž zablokuje přístup uživatelů k jejich zařízením a zobrazuje tzv. modrou obrazovkou smrti (BSoD).
V případě Petya obrazovka BSoD slouží jako nástroj zobrazení žádosti o výkupné. Ransomware se rychle rozšiřuje, napadá organizace, podniky i konečné uživatele. Jeho propuknutí je podobné jako útok ransomwaru WannaCry.
Modrá obrazovka smrti v případě napadnutí ransomwaru Petya.
Průběh infekce
Prvotní vstup ransomwaru do systému zahrnuje použití nástroje PsExec, který je oficiálním nástrojem společnosti Microsoft a používá se ke spouštění procesů na vzdálených systémech. Využívá také exploit EternalBlue, který byl již dříve aplikován při útoku ransomwaru WannaCry.
Ten se zaměřuje na zranitelnost Serveru Message Block (SMB) v1. V napadeném systému se nová verze programu Petya spustí procesem rundll32.exe. Samotné šifrování se pak provede pomocí souboru s názvem perfc.dat, který se nachází v adresáři Windows.
Ransomware poté přidá plánovanou úlohu, která po hodině systém restartuje. Zároveň se Master Boot Record (MBR) upraví tak, aby bylo provedeno šifrování, a zobrazí se příslušná výhružná zpráva. Na začátku se objeví chybné oznámení CHKDSK, v ten moment probíhá šifrování.
Neobvyklé pro tento ransomware je, že nemění přípony zašifrovaných souborů. Dále také, že oproti jiným ransomwarům se šifrování zaměřuje zejména na typy souborů používaných v podnikovém prostředí, a ne na obrázky a video soubory.
Diagram útoku ransomwaru Petya
Mimo využití technologie EternalBlue vykazuje Petya i další společné znaky s ransomwarem WannaCry.
Podobně jako při útocích WannaCry, je i výkupní proces ransomwaru Petya poměrně jednoduchý: využívá přednastavenou adresu Bitcoin, čímž se proces dešifrování stává pro útočníky mnohem obtížnější, na rozdíl od předchozích útoků Petya, které měly pro tento proces rozvinutější rozhraní.
Od každého uživatele ransomwaru požaduje zaplatit 300 dolarů. Stejně jako při všech útocích ransomwaru, experti nedoporučují výkupné uhradit – v tomto případě to platí dvojnásobně, protože e-mailová adresa uvedená ve vyděračském odkazu již není aktivní.
Aby se předešlo a zabránilo infekci, doporučují experti uživatelům a organizacím okamžitě vykonat následující kroky:
Aktualizovat systémy pomocí nejnovějších záplat nebo zvážit použití virtuální opravy
Aplikovat princip omezení privilegií pro všechny pracovní stanice
Omezit a zajistit používání nástrojů pro správu systému jako jsou PowerShell a PsExec
Zablokovat nástroje a protokoly pro systémy které je nevyžadují (t. J. Port TCP 445)
Pravidelně zálohovat důležité údaje
Aktivně monitorovat sítě v souvislosti s výskytem jakýkoliv podezřelých aktivit nebo anomálií
Využívat mechanismy monitorování chování, které mohou zabránit nezvyklým změnám (např. šifrování) systémů
Nastavit segmentaci sítě a kategorizaci dat pro zmírnění dalších škod, které mohou vzniknout při útoku
Zabezpečit e-mailovou bránu a použít kategorizaci adresy URL (na zablokování škodlivých webových stránek), aby se snížil prostor pro útok.
Researchers Crack 1024-bit RSA Encryption in GnuPG Crypto Library
4.7.2017 thehackernews Krypto
Security boffins have discovered a critical vulnerability in a GnuPG cryptographic library that allowed the researchers to completely break RSA-1024 and successfully extract the secret RSA key to decrypt data.
Gnu Privacy Guard (GnuPG or GPG) is popular open source encryption software used by many operating systems from Linux and FreeBSD to Windows and macOS X.
It's the same software used by the former NSA contractor and whistleblower Edward Snowden to keep his communication secure from law enforcement.
The vulnerability, labeled CVE-2017-7526, resides in the Libgcrypt cryptographic library used by GnuPG, which is prone to local FLUSH+RELOAD side-channel attack.
A team of researchers — from Technical University of Eindhoven, the University of Illinois, the University of Pennsylvania, the University of Maryland, and the University of Adelaide — found that the "left-to-right sliding window" method used by the libgcrypt library for carrying out the mathematics of cryptography leaks significantly more information about exponent bits than for right-to-left, allowing full RSA key recovery.
"In this paper, we demonstrate a complete break of RSA-1024 as implemented in Libgcrypt. Our attack makes essential use of the fact that Libgcrypt uses the left-to-right method for computing the sliding-window expansion," the researchers wrote in the research paper.
"The pattern of squarings and multiplications in left-to-right sliding windows leaks significantly more information about the exponent than right-to-left. We show how to extend the Heninger-Shacham algorithm for partial key reconstruction to make use of this information and obtain a very efficient full key recovery for RSA-1024."
L3 Cache Side-Channel Attack requires an attacker to run arbitrary software on the hardware where the private RSA key is used.
The attack allows an attacker to extract the secret crypto key from a system by analyzing the pattern of memory utilization or the electromagnetic outputs of the device that are emitted during the decryption process.
"Thus in practice, there are easier ways to access the private keys than to mount this side-channel attack. However, on boxes with virtual machines, this attack may be used by one VM to steal private keys from another VM," Libgcrypt advisory reads.
Researchers have also provided evidence that the same side channel attack also works against RSA-2048, which require moderately more computation than RSA-1024.
The research paper titled, 'Sliding right into disaster: Left-to-right sliding windows leak,' was authored by David J. Bernstein, Joachim Breitner, Daniel Genkin, Leon Groot Bruinderink, Nadia Heninger, Christine van Vredendaal, Tanja Lange and Yuval Yarom.
Libgcrypt has released a fix for the issue in Libgcrypt version 1.7.8. Debian and Ubuntu have already updated their library with the latest version of Libgcrypt.
So, you are strongly advised to check if your Linux distribution is running the latest version of the Libgcrypt library.
U.K. Student Charged for Running DDoS Service
4.7.2017 securityweek CyberCrime
Jack Chappell, an 18-year-old student from Stockport, UK, has been charged over his alleged role in the operation of a service used by cybercriminals to launch distributed denial-of-service (DDoS) attacks against several major organizations.
According to the West Midlands Police, whose Regional Cyber Crime Unit led the investigation, Chappell supplied the DDoS service, which is also known as a booter or stresser service, and ran an online helpdesk as part of the operation.
The DDoS service has not been named, but it was allegedly used by cybercriminals to disrupt the systems of NatWest in 2015. It was also used to target the websites of the UK’s National Crime Agency (NCA), Netflix, Amazon, BBC, T-Mobile, EE, Vodafone, BT, Virgin Media and O2.
Chappell has been charged with impairing the operation of computers under the Computer Misuse Act, encouraging or assisting an offence, and money laundering crime proceeds with a US national. The FBI, Israeli Police and Europol’s European Cybercrime Center (EC3) assisted British authorities in this case.
None of the cyberattacks involving the service allegedly run by Chappell resulted in loss or theft of customer data, the West Midlands Police said.
Over the past years, several teenagers in the United Kingdom have been arrested and charged for using or running DDoS services. One of the most recent cases is the one of Adam Mudd, a 20-year-old who received a two-year prison sentence in April for running the Titanium Stresser service.
How to chain flaws in Lenovo VIBE smartphones to gain root privileges
4.7.2017 securityaffairs Mobil
Researchers from Mandiant found a way to gain root privileges on Lenovo VIBE smartphones by chaining three vulnerabilities.
The Lenovo VIBE smartphones were affected by security vulnerabilities that could allow an attacker with physical access to the device to gain root privileges.
Researchers from Lenovo confirmed that the vulnerabilities could be exploited only on devices that are not protected with a secure lock screen (i.e. PIN, passcode) and flaws affect only Android earlier than 6.0.
Attackers can trigger the issues to elevate privileges to the root user and interfere with the device’s operation.
“Vulnerabilities have been identified on Lenovo VIBE Mobile Phones that allow the user or an attacker with physical possession of a device that is not protected with a secure lock screen, e.g. PIN/Password, to elevate privileges to the root user (commonly known as “rooting” or “jailbreaking” a device) with the ability to modify the device’s operation and functionality in myriad ways.” states the advisory, published by Lenovo.
The advisory reports three flaws that can be chained to compromise a Lenovo device.
1. CVE-2017-3748 – Improper access controls on the nac_server component can be abused in conjunction with CVE-2017-3749 and CVE-2017-3750 to elevate privileges to the root user (commonly known as ‘rooting’ or “jail breaking” a device).
2. CVE-2017-3749 – The Idea Friend Android application allows private data to be backed up and restored via Android Debug Bridge, which allows tampering leading to privilege escalation in conjunction with CVE-2017-3748 and CVE-2017-3750
3. CVE-2017-3750 – The Lenovo Security Android application allows private data to be backed up and restored via Android Debug Bridge, which allows tampering leading to privilege escalation in conjunction with CVE-2017-3748
The vulnerabilities were found by the Mandiant’s Red Team in May 2016 that reported them to Lenovo.
The flaws were promptly fixed by Motorola that was in charge of Lenovo mobile solutions.
“In May of 2016, Mandiant’s Red Team discovered a series of vulnerabilities present on Lenovo’s Vibe P1 Android-based mobile device that allow local privilege escalation to the user “root”. Mandiant disclosed these vulnerabilities to Lenovo in May of 2016. Lenovo advised Mandiant that it should work with Motorola, who it had acquired and was now responsible for Lenovo’s mobile product portfolio.” states the analysis published by FireEye-Mandiant.
The full list of the affected Lenovo VIBE smartphones was included in the Motorola’s official advisory, Lenovo issued security updates only for 20 out of 40 phone models.

Motorola has redesigned the affected mechanism to use a more secure process.
“Allowing backups on privileged applications can also be detrimental and should be disallowed. Just because an application is not running as a privileged Android user ID such as ‘android.uid.system’, does not mean that it cannot introduce vulnerabilities and be used to escalate privileges. Finally, applications should never allow executable code (Java classes, ELF binaries, or shared objects) within backups. This can be limited using a BackupAgent,” Concluded FireEye-Mandiant.
The researchers highlighted that the vulnerabilities in the Lenovo VIBE smartphones are difficult to exploit in a real attack scenario. As usual, let me suggest updating your mobile device.
Wikileaks: CIA má nástroje i na šmírování Linuxu
3.7.2017 Živě.cz BigBrother


Wikileaks: CIA má nástroje i na šmírování LinuxuSídlo CIA v Langley Struktura kybernetických operací CIA
Podle úniků ze CIA, které Wikileaks poslední měsíce uvolňuje s týdenní pravidelností, se americká zpravodajská agentura při svých kybernetických operacích soustředí především na průnik do Windows a MacOS.
Poslední zveřejněná várka dokumentů nicméně popisuje nástroj OutlawCountry, který se orientuje na linuxové distribuce – konkrétně CentOS a RHEL.
OutlawCountry je modul linuxového jádra, který po zavedení umožní změnit konfiguraci firewallu, přesměrovat síťový provoz a tedy připravit počítačovou síť pro útoky typu MITM (muž uprostřed).
Podobné nástroje nejsou ničím překvapujícím a pouze podtrhují skutečnost, že současným Jamesům Bondům už prostě nestačí naleštěné Bentley s kulomety za registrační značkou, ale bez znalosti softwaru se neobejdou.
Problém nastává tehdy, když podobné nástroje uniknou na internet a chopí se jich všemožní skript kiddies i profesionálové z šedé zóny. Přesně k tomu došlo v případě ransomwaru WannaCry, který se pokoušel zneužívat zranitelnosti protokolu SMB a šířit se lokální sítí. Onu zranitelnost přitom využívala software NSA, který v minulosti unikl na internet.
UK Teenager, Aged 18, Charged With Running DDoS-For-Hire Service
3.7.2017 thehackernews CyberCrime

A teenage student has been charged with running a supplying malware that was used for launching distributed denial of service (DDoS) attacks against websites of some of the world's leading businesses.
Jack Chappell, an 18-year-old teenager from Stockport, is accused of helping cyber criminals with his DDoS booter service (DDoS-for-hire service) to flood millions of websites around the world with the massive amount of data and eventually bring them down, making them unavailable to their users.
Among the victims that were allegedly attacked by Chappell's malware are the National Crime Agency (NCA), T-Mobile, O2, Virgin Media, the BBC, Amazon, Vodafone, BT, Netflix, and NatWest that had its online banking systems down in a 2015 cyber attack.
Chappell is charged following an investigation led by the West Midlands Regional Cyber Crime Unit and assisted by Israeli Police, the Federal Bureau of Investigation (FBI) and Europol’s European Cybercrime Centre (EC3).
According to authorities, the teenager rented his DDoS-for-hire service to criminals and also ran an online helpdesk for would-be hackers as part of his operation.
"He has been charged with impairing the operation of computers under the Computer Misuse Act, plus encouraging or assisting an offense and money laundering crime proceeds together with an American national," West Midlands Police said in a statement.
Chappell is due to appear at Manchester Magistrates' Court on July 4, Tuesday.
Late last year, another 19-year-old student from Hertford (Town in the UK) was pled guilty for running Titanium Stresser DDoS-for-hire service, one of the most popular DDoS booter tool that was used to launch over 1.7 Million DDoS attacks worldwide and brought him an income of more than US$385,000.
Google employees affected by the Sabre data breach
3.7.2017 securityaffairs Incindent
Google has notified some employees that they may have been hit by the data breach suffered by travel technology firm Sabre.
In May, the Travel Tech Giant Sabre confirmed in a SEC filing it was “investigating an incident involving unauthorized access to payment information contained in a subset of hotel reservations processed through the Sabre Hospitality Solutions SynXis Central Reservation system.”
The intruders gained access to the system after hijacking an internal account on the SynXis system.
“The unauthorized access has been shut off and there is no evidence of continued unauthorized activity,” reads a statement that Sabre sent to affected properties in May. “There is no reason to believe that any other Sabre systems beyond SynXis Central Reservations have been affected.”
The impact of the incident could be severe, the SynXis Central Reservation product is a rate and inventory management SaaS application that is currently used by more than 32,000 hotels worldwide.
Later, the company confirmed the hackers had managed to access personally identifiable data, payment card details, and other information.
Google employees were affected by the Sabre data breach because it was using booking services provided by the Carlson Wagonlit Travel (CWT), a company that uses the SynXis platform.
Google notified affected employees via letter, the IT giant learned of the Sabre breach on June 16 from Carlson Wagonlit Travel (CWT).

Google notified employees that their name, contact information and payment card details may have been accessed by attackers, who breached the reservations system between August 10, 2016 and March 9, 2017.
“We recently learned that certain hotel reservations made for Google business travel were
among the many reservations affected by a security incident impacting a third-party provider’s
electronic reservation system that serves thousands of travel agencies and hotels. This did not
affect Google’s systems. However, this incident impacted one of the travel providers used by
Googlers, Carlson Wagonlit Travel (CWT).” states the letter.
“Sabre’s investigation discovered no evidence that information such as Social Security, passport, and driver’s license numbers were accessed,” Google said. “However, because the SynXis CRS deletes reservation details 60 days after the hotel stay, we are not able to confirm the specific information associated with every affected reservation.”
To protect its employee, Google opted to offer affected ones two years of identity protection and credit monitoring services.
Google is working with CWT and Sabre to address this issue. Sabre hired cybersecurity firm Mandiant to support its investigation. The company also notified law enforcement and the payment card brands about the data breach.
“We are offering you 24 months of complimentary identity protection and credit monitoring
services. These services, described below, will be provided by AllClear ID and are available as
of the date of this notice. You can use them at any time during the next 24 months:” states Google.
Severe flaws found in German e-Government OSCI 1.2 Communication Library
3.7.2017 thehackernews Vulnerebility
Security researchers at SEC-Consult found severe vulnerabilities in the German e-government Communication Library OSCI (Online Services Computer Interface).
According to the experts at SEC-Consult, the German e-government system OSCI (Online Services Computer Interface) is open to padding oracle attacks and other vulnerabilities due to the use of an insecure communications protocol.
The researchers at SEC Consult found severe vulnerabilities in the OSCI 1.2 Transport library that provides a secure message exchange channel over an untrusted network (i.e. Internet) for German government agencies for eGovernment.
An attacker can exploit the vulnerabilities to decrypt messages, modify signed messages and read arbitrary files from the host that implements the vulnerable OSCI protocol.
“However, SEC Consult found that multiple vulnerabilities allow attackers to decrypt encrypted messages as well as modify signed messages. Moreover, a vulnerability can be used to read arbitrary files from any host that implements the OSCI 1.2 transport protocol using this library.” reads the security advisory.
An External Entity Injection (XXE), tracked as CVE-2017-10670, could be exploited by an attacker to read arbitrary files from the target system, or to trigger a denial-of-service condition on it.
“By sending manipulated XML data to any communication partner, an attacker is able to conduct an XXE attack on the receiving system. This attack allows an attacker to read arbitrary files from the file system of the victim host or to conduct a denial of service attack.” reads the Advisory.
The CVE-2017-10668 vulnerability is linked to the implementation of a number of deprecated encryption algorithms (Triple DES, AES 129, AES 192, and AES 256, all in CBC mode) that open the door to padding oracle attacks.
“Since the supported cipher algorithms do not provide protection against modification (malleability) and the library reveals in an error message whether decryption failed (error code 9202), SEC Consult was able to conduct a padding oracle attack. This attack allows an attacker to bypass transport encryption.” states the advisory.
“In our test setup we were able to decrypt an OSCI processDelivery message on a local machine within half an hour.” states a blog post published by SEC Consult.

A Signature Wrapping attack, tracked as CVE-2017-10669, allows the miscreant to change the contents of a message without invalidating the signature.
“Signature Wrapping attack [CVE-2017-10669] By moving XML elements within the document tree, a signature wrapping attack can be conducted. This allows an attacker to modify the contents of a signed message arbitrarily without invalidating the signature.” states the advisory.

The last issue is a deserialization bug that could be exploited to an external entity injection.
“A class in the library defines the method readObject() that is used by Java to deserialize a stream into an object. This method uses an XML parser to achieve this. However, the XML parser used is configured to resolve external entities. Therefore, an attacker who can influence data that deserialized by an application can conduct an XXE attack 1).”
Experts highlighted that the deserialization bug could be exploited even is the vulnerable application is not using the OSCI-Transport library, it is enough the presence of the OSCI-Transport library in the classpath of an application.
German public agencies should use the latest version of the OSCI-Transport library.
New German Law Risks Chilling Effect on Free Speech in Social Media
3.7.2017 securityweek Social
Germany passed a new law on Friday that imposes fines of up to €50 million on social media services with more than 2 million German users if they fail to remove hate speech or other illegal content. Where the infringement is obvious, it must be done within 24 hours; where it is less obvious it must be done within 7 days.
This must be done in response to a received complaint rather than a judicial instruction -- which means that social networks, such as Facebook, need to determine for themselves whether the content is legal or illegal.
The 'Enforcement on Social Networks' law, also known as the 'NetzDG' law, has both supporters and opponents. The Central Council of Jews -- Germany's main Jewish organization -- commented, "Jews are exposed to anti-Semitic hatred in social networks on a daily basis. Since all voluntary agreements with platform operators produced almost no result, this law is the logical consequence to effectively limit hate speech."
Facebook has a different view. It said in a statement, "We believe the best solutions will be found when government, civil society and industry work together and that this law as it stands now will not improve efforts to tackle this important societal problem."
Many civil rights groups fear it will have a chilling effect on free speech. Writing just before the law was adopted, digital rights group EDRi wrote, "In the current version [the one adopted by the German lawmakers], upload and content filters would not be mandatory, but whether or not mandatory, they are likely to be applied by big companies like Facebook. These companies are, quite rationally, driven by the motivation to avoid liability, using the cheapest options available, and to exploit the political legitimization of their restrictive measures for profit. This can only lead to privatized, unpredictable online censorship."
Facebook's current filters have been criticized separately. According to an analysis by Propublica, Facebook seeks to develop universally acceptable standards rather than national standards. The result can be conflicting.
For example, it did not remove a post from a U.S. congressman Clay Higgins which called for the slaughter of radicalized Muslims: "Kill them all. For the sake of all that is good and righteous. Kill them all." It did, however, remove a post from Boston poet and Black Lives Matter activist Didi Delgado who wrote, "All white people are racist. Start from this reference point, or you've already failed."
A common concern over NetzDG is that the size of the potential fines will persuade social media giants to err on the side of their own safety and consequently removing content that is perfectly legal. "Many of the violations covered by the bill are highly dependent on context, context which platforms are in no position to assess," commented the UN Special Rapporteur to the High Commissioner for Human Rights, David Kaye.
The law could still be stopped by the European Commission since many critics claim that it contravenes basic EU principles on freedom of expression. However, it could also go the other way. According to Spiegel Online today, German Federal Minister of Justice Heiko Maas has plans for government control over the algorithms that underlie the social networks' content filtering. The plans, suggests Spiegel, would represent "a new regulation of the Internet corporations -- affected by a review of the algorithms would be platforms such as Facebook and Google."
According to Maas, "transparency in the algorithms is the guarantee for preventing discrimination and for self-determination."
French Regulator Accepts Microsoft's Data Protection Improvements to Windows 10
3.7.2017 securityweek Privacy
CNIL Accepts Microsoft's Data Protection Improvements to Windows 10
CNIL, the French data protection regulator, has closed the formal notice procedure it served on Microsoft on June 30, 2016 over privacy concerns relating to Windows 10. "Since then," says CNIL, "the company has brought itself into line with data protection rules, the formal notice procedure has therefore been closed."
In a statement emailed to SecurityWeek, Microsoft commented, "We are committed to protecting our customers' privacy and putting them in control of their information. We appreciate the French data protection authority's decision and will continue to provide clear privacy choices and easy-to-use tools in Windows 10."
The notice was served last year with three particular concerns: the excessive collection of personal data; the tracking of users' web-browsing without their consent; and a lack of security and confidentiality of users' data. Since then, Microsoft has addressed each issue to CNIL's satisfaction.
On the first, Microsoft has reduced the amount of data it collects by nearly half. "it has restricted its collection to the sole data strictly necessary for maintaining the proper functioning of its operating system and applications, and for ensuring their security," notes CNIL.
On the second concern, Microsoft now makes it clear that an advertising ID is intended to track web-browsing in order to offer personalized advertising. This now has to be activated or deactivated at installation, and users can reverse the choice at any time.
Over security concerns, Microsoft "has strengthened the robustness of the PIN code allowing users to authenticate to all company’s online services, and more specifically to their Microsoft account," notes CNIL: "too common PIN code combinations are now forbidden."
Microsoft has also addressed the other injunctions within the formal notice. It has inserted the information required under Article 32 of the French Data Protection Act; it has requested CNIL authorization for its processing of personal data; it has joined Privacy Shield; and it has ceased placing advertising cookies without obtaining users' consent.
"The Chair of the CNIL has considered that the company had complied with the French Data Protection Act and has therefore decided to proceed to the closing of the formal notice," says the CNIL announcement.
Given the size of the sanctions that will become available to CNIL when the GDPR comes into force in May 2018, it is probably a wise move by Microsoft to get compliance sorted now.
'OutlawCountry' Tool Used by CIA to Target Linux Systems
3.7.2017 securityweek BigBrothers
One of the tools used by the U.S. Central Intelligence Agency (CIA) to target Linux systems is named OutlawCountry, according to documents published by WikiLeaks.
OutlawCountry is described by its developers as a tool that uses a kernel module to create a hidden netfilter table on the targeted Linux system. The operator can then use this table to create new firewall rules with iptables commands and these rules will take precedence over existing ones. The rules can be used to redirect traffic from the infected machine to one controlled by the attacker.
OutlawCountry documentation dated June 2015 states that the tool’s user needs to have shell access and root privileges to the targeted machine. As for hiding on the infected system, the new rules created by the malware are only visible to an administrator who knows the name of the table, and the table is removed if the kernel module is deleted by the operator.
Since the documentation specifically names CentOS and Red Hat Enterprise Linux as the operating systems on which the tool works, Red Hat has published an advisory for users who may be concerned about the impact of OutlawCountry.
The organization is still analyzing the available information, and in the meantime it has advised users to look for the existence of a file named nf_table_6_64.ko and the presence of a hidden table called dpxvke8h18 in the iptable rules. Users can check for the presence of the kernel module with the following lsmod command: lsmod | grep nf_table.
Last month, WikiLeaks published documents detailing tools allegedly used by the CIA to spread malware on a targeted organization’s network (Pandemic), locate users via Wi-Fi (Elsa), hack routers and access points (Cherry Blossom), and hack air-gapped networks using USB drives (Brutal Kangaroo).
WikiLeaks has also detailed tools designed for replacing legitimate files with malware, hacking Samsung smart TVs and routers, MitM tools, a framework used to make malware attribution and analysis more difficult, and a platform for creating custom malware installers.
Security firms have found links between the tools exposed by Wikileaks and the malware used by a cyber espionage group tracked as “Longhorn” and “The Lamberts.”
NotPetya Connected to BlackEnergy/KillDisk: Researchers
3.7.2017 securityweek Ransomware
Last week’s devastating NotPetya attack might have been launched by the same threat group that previously used the Russia-linked BlackEnergy malware family in attacks against Ukraine, security researchers reveal.
Initially believed to be a ransomware incident employing the same distribution tools as WannaCry, the NotPetya malware eventually proved to be a disk wiper spreading with the sole purpose of damaging infected computers. Similar to WannaCry, NotPetya hit Windows 7 machines the most.
The malware eventually hit systems in more than 65 countries, but most of its victims are located in Ukraine. Of a total of less than 20,000 machines infected by NotPetya (also referred to as PetrWrap, exPetr, GoldenEye, and Diskcoder.C), more than 70% are in Ukraine, Microsoft says.
Late last week, security researchers also discovered the reason why Ukraine was hit the most: the attack was apparently launched by the same threat group that initiated numerous other attacks against the country’s power grid, mining and railway systems, and Ukrainian government organizations.
Dubbed TeleBots, the group was previously referred to as BlackEnergy or Sandworm Team. One of the tools associated with it is the KillDisk wiper that was packing ransomware capabilities in recent attacks, and which demanded a 222 Bitcoin ransom from its victims.
The NotPetya sample used in last week’s attack includes a series of similarities with the BlackEnergy and KillDisk malware families, Kaspersky Lab and ESET security researchers have discovered.
The list of targeted file extensions in NotPetya shows similarities to the list in a wiper the group was using in 2015, Kaspersky Lab reveals. The lists are similar in composition and formatting (stored in the same dot-separated formats), which suggests a possible link, the security researchers say.
According to Kaspersky, a Yara rule they created during analysis “fires on BlackEnergy and ExPetr samples only” when run on the company’s extensive malware collection. The strings used to create the rule can generate false positives when used alone, but “when combined together in this fashion, they become very precise,” the researchers say.
“Of course, this should not be considered a sign of a definitive link, but it does point to certain code design similarities between these malware families,” Kaspersky says.
ESET, on the other hand, appears more confident of the connection between TeleBots and NotPetya, and even suggests that this was the third major attack the group launched this year against Ukraine.
The first, they say, was launched in March and had as final payload a ransomware family detected as Filecoder.NKH. Tools used in the attack included the Python/TeleBot.A backdoor, a heavily obfuscated VBS backdoor, CredRaptor (password stealer), Plainpwd (modified Mimikatz to recover Windows credentials), and SysInternals’ PsExec (used for lateral movement). A Linux ransomware was used on non-Windows servers.
In late May, the group launched a second large ransomware attack against Ukraine, this time using a piece of malware known as XData (detected as Filecoder.AESNI.C). Five days into the attack, and 96% of the malware’s detections were in Ukraine, ESET was reporting on May 23.
The ransomware also packed code that allowed it to automatically move laterally within compromised networks: it featured an embedded Mimikatz DLL to extract Windows credentials, as well as SysInternals’ PsExec utility for spreading.
One month later, the group launched a third, more sophisticated ransomware attack against organizations in Ukraine. Borrowing code from last year’s Petya ransomware, the actors created a wiper and started using NSA-linked SMB exploits to maximize spreading capabilities.
“However, unlike the original Petya ransomware, Diskcoder.C’s authors modified the MBR code in such a way that recovery won’t be possible. Specifically, the attacker cannot provide a decryption key and the decryption key cannot be typed in the ransom screen, because the generated key contains non-acceptable characters,” ESET explains.
The initial infection vector in the NotPetya incident was the Ukrainian accounting software called MEDoc, the same as in the case of the XData attack. For the March attack, the group compromised another software company in Ukraine (not related to M.E. Doc), and gained access to the internal networks of several financial institutions using VPN tunnels.
“[The] Diskcoder.C outbreak suggests that the attackers had access to the update server of the legitimate software. Using access to this server, attackers pushed a malicious update that was applied automatically without user interaction. That’s why so many systems in Ukraine were affected by this attack,” ESET notes.
The security researchers also believe that M.E.Doc’s server, where they discovered a malicious PHP backdoor medoc_online.php in a FTP directory, might have been used as infection vector for other malware as well. Using malicious updates, the group supposedly deployed their own nefarious tools “in a stealthy way to computer networks that belong to high-value targets.”
Local Root Exploit Found on Lenovo Smartphone
3.7.2017 securityweek Mobil
The Lenovo VIBE smartphone was found to include vulnerabilities that could allow an attacker with physical access to the device to gain root privileges.
The flaws, Lenovo explains in an advisory, impact only devices that are not protected with a secure lock screen, such as a PIN or a password. By exploiting these issues, a local user or attacker can elevate privileges to the root user and can “modify the device’s operation and functionality in myriad ways.”
A total of three vulnerabilities that can be exploited in conjunction were discovered, but the company says that only devices running versions of Android earlier than 6.0 may be vulnerable to the root exploit.
Tracked as CVE-2017-3748, the first of the three bugs is created by improper access controls on the nac_server component.
The remaining two issues, CVE-2017-3749 and CVE-2017-3750, impact the Idea Friend Android and Lenovo Security Android applications, respectively. Designed to allow “private data to be backed up and restored via Android Debug Bridge,” the apps also allow “tampering leading to privilege escalation.”
The three bugs were found by Mandiant’s Red Team in May 2016 and were reported the same month. In charge of Lenovo’s mobile phone portfolio, Motorola has since corrected the vulnerabilities by redesigning “the affected mechanism to use a more secure process,” Mandiant Red Team's Jake Valletta explains.
“Allowing backups on privileged applications can also be detrimental and should be disallowed. Just because an application is not running as a privileged Android user ID such as ‘android.uid.system’, does not mean that it cannot introduce vulnerabilities and be used to escalate privileges. Finally, applications should never allow executable code (Java classes, ELF binaries, or shared objects) within backups. This can be limited using a BackupAgent,” Valletta notes.
Because the exploit chain requires local, physical access to a device, it is “very unlikely to see this exploit ‘in the wild’,” the researcher says. However, users are advised to update their devices to the most recent software package their manufacturer has released, as well as to use strong lock screen settings to ensure their devices remain protected.
The complete technical details pertaining to the three vulnerabilities and the manner in which they can be exploited to gain root access are available in Valletta’s blog post.
A total of over 40 Lenovo phone models appear to be impacted by the issue, and the company says that no fix is available for 20 of them (15 other models aren’t impacted, as they have been already updated). Lenovo published a complete list of impacted devices.
UK Audit Office Says More Effort Needed to Combat Online Fraud
3.7.2017 securityweek Crime
UK's National Audit Office Says Online Fraud Needs to be Treated More Seriously by Government
Fraud is now the most commonly experienced crime in England and Wales; and most takes place online. In a newly released report, the UK's National Audit Office (NAO) welcomes some steps taken by the government to combat online fraud, but suggests that much more could and should be done.
The problem is growing rapidly. Card-not-present (CNP) fraud (a problem already increasing in America with the move to EMV cards) rose from 709,000 incidents in 2011 to approximately 1.4 million incidents in 2016 -- an increase of 103%, and 16% of all estimated crime instances. It is estimated that £10 billion was the loss to individuals in 2016, while the individual loss to victims in each incident was £250 or more.
The overall message of the report (PDF) is that online fraud is given sufficient importance by neither the government, the banks, nor law enforcement. For example, despite it being the most frequent crime, only one police officer in every 150 is primarily involved in economic crime. This compares to one in six officers whose primary function is traditional neighborhood policing.
The banks are also criticized. Although they play an important role in protecting people against fraud, the report finds the quality of their action to be inconsistent. "In 2016, the Payment Systems Regulator found that banks needed to improve the way they work together in responding to scams, that some banks needed to do more to combat scams, and that data available on the scale of scams were poor," notes the NAO report.
The government's primary response so far has been to establish the Joint Fraud Taskforce led by ministers in 2016. However, the report says, "there is a lack of proper governance, such as through a senior responsible owner or equivalent role. Despite setting up the Taskforce in February 2016, the Department has not yet reported on the Taskforce's progress or established measures for its performance." It is also concerned that banks are the only industry represented on the Taskforce: "many other organizations, including those in the retail, telecommunications and digital sectors, have responsibilities for preventing and reducing online fraud."
The report concludes, "Fraud is now the most commonly experienced crime in England and Wales, is growing rapidly and demands an urgent response. Yet fraud is not a strategic priority for local police forces, and the response from industry is uneven." It suggests that although online fraud is not the sole responsibility of the government, the Home Office is the only body that can oversee the system and lead the necessary change.
"At this stage, it is hard to judge that the response to online fraud is proportionate, efficient or effective," comments Amyas Morse, head of the National Audit Office.
"We welcome the report findings from the National Audit Office and a number of its recommendations," said Cifas deputy chief executive Mike Haley. "In particular, we would welcome the expansion of the membership of the Joint Fraud Taskforce to include other stakeholders, such as the retail and digital sectors, improving the collection and reporting of fraud, and examining sentencing guidelines for fraud, which are all proposals that Cifas has called for previously."
Cifas is a an independent, not-for-profit organization that protects businesses and individuals through secure data and intelligence sharing between the private, public and third sectors. In 2016, Cifas members prevented over £1 billion of fraud losses. It claims that its National Fraud Database and Internal Fraud Database are the most comprehensive databases of confirmed fraud in the UK; and that every day, it sends approximately 800 fraud cases to the City of London Police for potential investigation.
"Last year, our cross-sector membership reported a record 324,683 fraud crimes, 66% of which was cyber-enabled and nine out of 10 identity frauds committed online. These statistics speak for themselves: this is a high-volume crime that needs to be given more priority by government, law enforcement and industry. We therefore strongly agree that tackling online fraud should be a strategic priority for policing.
"We also endorse the need for government, law enforcement and industry to work together to raise awareness of how people can better protect themselves, and specifically we want to see fraud education in the school curriculum so that young people can be made more aware of the consequences of falling victim to a fraud as well as committing fraud."
Google Employees Hit by Sabre Breach
3.7.2017 securityweek Incindent
Google has notified some employees that their personal information may have been compromised as a result of the data breach suffered by travel technology firm Sabre.
Sabre informed customers in early May that it had launched an investigation after detecting unauthorized access to its SynXis Central Reservation System, a rate and inventory management product used by more than 32,000 hotels worldwide.
The company said the hackers had managed to access personally identifiable data, payment card details and other information. An investigation revealed that the attackers gained access to the system after hijacking an internal account on the SynXis platform.
In a letter sent out to affected employees, Google said it learned of the breach on June 16 from Carlson Wagonlit Travel (CWT), one of the companies used by the tech giant to book business travel and one of the many organizations that uses the SynXis product. Google pointed out that the breach did not impact its own systems.
Google told employees their name, contact information and payment card details may have been stolen by attackers, who had access to the reservations system between August 10, 2016 and March 9, 2017.
“Sabre’s investigation discovered no evidence that information such as Social Security, passport, and driver’s license numbers were accessed,” Google said. “However, because the SynXis CRS deletes reservation details 60 days after the hotel stay, we are not able to confirm the specific information associated with every affected reservation.”
Google has decided to offer affected employees two years of identity protection and credit monitoring services.
Sabre has yet to provide an update on this incident. The company has alerted law enforcement and payment card issuers, and contracted Mandiant to assist its investigation.
Linux Systemd Gives Root Privileges to Invalid Usernames
3.7.2017 securityweek Vulnerebility
A bug in Linux’s systemd init system causes root permissions to be given to services associated with invalid usernames, and while this could pose a security risk, exploitation is not an easy task.
A developer who uses the online moniker “mapleray” last week discovered a problem related to systemd unit files, the configuration files used to describe resources and their behavior. Mapleray noticed that a systemd unit file containing an invalid username – one that starts with a digit (e.g. “0day”) – will initiate the targeted process with root privileges instead of regular user privileges.
Systemd is designed not to allow usernames that start with a numeric character, but Red Hat, CentOS and other Linux distributions do allow such usernames.
“It's systemd's parsing of the User= parameter that determines the naming doesn't follow a set of conventions, and decides to fall back to its default value, root,” explained developer Mattias Geniar.
While this sounds like it could be leveraged to obtain root privileges on any Linux installation using systemd, exploiting the bug in an attack is not an easy task. Geniar pointed out that the attacker needs root privileges in the first place to edit the systemd unit file and use it.
The attack scenarios described by the developer include tricking an administrator into creating a malicious unit file, or exploiting a different vulnerability to obtain write access and using unit files to escalate privileges. Others noted that an administrator can deliberately create a username that starts with a digit and wrongly assume that the program will run with user-level privileges instead of as root. Some scenarios described on Hacker News don’t even require the involvement of the system administrator.
Systemd developers have classified this issue as “not-a-bug” and they apparently don’t plan on fixing it. Linux users are divided on the matter – some believe this is a vulnerability that could pose a serious security risk, while others agree that a fix is not necessary.
“It's an obvious bug (at least on RHEL/CentOS 7), since a valid username does not get accepted by systemd so it triggers unexpected behaviour by launching services as root.
However, it isn't as bad as it sounds and does not grant any username with a digit immediate root access,” Geniar explained.
This is not the only systemd flaw disclosed recently. Chris Coulson, an engineer with Canonical, the developer of the Ubuntu Linux distribution, revealed last week that systemd is affected by an out-of-bounds write vulnerability (CVE-2017-9445) that can be triggered using a specially crafted TCP payload to crash the systemd-resolved daemon or execute arbitrary code in the context of the daemon process.
Telegram agrees to register in Russia, but it will not share private data
3.7.2017 securityaffairs BigBrothers
Telegram agrees to register with Russia authorities to avoid the local ban, but the battle is still ongoing because it won’t share user data.
The Russian Government threatened to ban Telegram because it refused to comply data protection laws.
“There is one demand, and it is simple: to fill in a form with information on the company that controls Telegram,” said Alexander Zharov, head of Roskomnadzor.
“And to officially send it to Roskomnadzor to include this data in the registry of organizers of dissemination of information. In case of refusal… Telegram shall be blocked in Russia until we receive the needed information.”
The Russian Personal Data Law was implemented since September 1st, 2015, it requests foreign tech companies to store the personal data of Russian citizens within the country. The Law was designed for protecting Russian citizens from surveillance activities of foreign agencies such as the NSA.

Since January 1, the new Russian Data Protection Laws request foreign tech companies to store past six months of the personal data of Russians and encryption keys within the country. The companies are obliged to provide the access to the retained data if requested by authorities.
According to the FSB, the Russian intelligence agency, the terrorists who killed 15 people in Saint Petersburg in April were communicating through the Telegram encrypted messaging service.
The Russian intelligence asked Telegram to share users’ chats and crypto keys on demand to allow government investigations on terrorists abusing the instant messaging app as a communication channel.
The use of the popular encrypted messaging app is widespread among the militants of the terrorist organization in Russia and abroad, The use of Telegram has eclipsed the use of other social media platforms, including Twitter.
Now the company has agreed to register with new Russian Data Protection Laws, but its founder Pavel Durov clarified that his company doesn’t intend to share users’ confidential data with Russian authorities. Telegram wouldn’t store citizens’ information on servers located in Russian.
28 Jun
Marat Saytakov @m4rr
@durov Is it true?
"Once on the list, Telegram would have to store information about its users on Russian servers"
Follow
Pavel Durov ✔ @durov
@m4rr No, we won't ever comply with these laws, we only provided public data for registration. Full statement: https://vk.com/wall1_1854483
7:33 PM - 28 Jun 2017 · Paris, France
Pavel Durov
Глава Роскомнадзора открестился от желания получить доступ к личной переписке пользователей Telegram и заявил, что все, чего он ждет от нас для выполнения закона, – это предоставление информации о...
vk.com
8 8 Retweets 22 22 likes
Twitter Ads info and privacy
The Roskomnadzor announced on Wednesday that company had finally presented all the requirements.
Durov highlighted that Telegram takes care of the privacy of its users, the company will only share basic information as explained by the founder in a message published on VK.com.
“We will not comply with unconstitutional and technically impossible Yarovaya Package laws—as well as with other laws incompatible with the protection of privacy and Telegram’s privacy policy,” Durov said.
The NotPetya ransomware is a Brick Through Your Windows
3.7.2017 securityaffairs Ransomware
The recent global outbreak of the “NotPetya” malware has some very curious features that have left security officials puzzled.
Despite the press coverage, NotPetya is not really a ransomware attack to hold your data hostage. It’s a killbot.
Several information security specialists have pointed a finger directly at Moscow; citing circumstantial evidence the source of NotPetya was the TELEBOTS group of hackers previously associated with attacks on Ukraine, in particular, the Ukraine power grid “BlackEnergy” attack. Others have noted the malware used features stolen from the US National Security Agency, specifically the EternalBlue exploit made famous by the previous WannaCry global ransomware attack.
First, the NotPetya attack does have components used by the Telebot attackers. According to Anton Cherepanov, a researcher at the Welivesecurity group, the NotPetya malware contains telltale clues in design that point toward the hacker group. Once executed, this ransomware-like design encrypts all files, except files located in the C:\Windows directory, using AES and RSA algorithms.
“As mentioned above, in the final stage of their attacks, the TeleBots attackers pushed ransomware using stolen Windows credentials and SysInternals’ PsExec. This new ransomware was detected by ESET products as Win32/Filecoder.NKH. Once executed, this ransomware encrypts all files (except files located in the C:\Windows directory) using AES-128 and RSA-1024 algorithms. The malware adds the .xcrypted file extension to already-encrypted files.” states the analysis published by ESET.
The malware deletes and overwrites the target files with a special software design called KillDisk. Telebot attackers have previously used the special KillDisk wiping system which appears inside NotPetya.
However, it is not just the KillDisk feature that points to the TELEBOT group. It is this feature combined with the poorly designed pay-off scheme inside NotPetya that indicates it is not ransomware at all but in fact a high-speed brick to destroy Windows data.
First, the NotPetya malware contains a single email address to contact the hacker which was quickly shut down in the first few hours of the attack. In addition, the Bitcoin area where the ransom was to be paid was easy to monitor, a very curious move by someone who wants to get money for crime. Finally, the data recovery section of the NotPetya malware was inoperable, leaving little chance of getting your data back even if the ransom was paid.
So, instead of being a kidnap your data scheme, NotPetya turned out to be a smash everything malware masquerading as a ransomware attack. Again, this charade of acting like a ransomware but actually being a destruction attack points toward the same MO (modus operandi) of the TELEBOT group.
While the NotPetya malware can use the stolen NSA EternalBlue exploit, which was later patched in a special Microsoft update, the prime method of spreading the attack was not the NSA software at all. Instead, NotPetya used common system features used inside some Microsoft networks to spread itself. One method is called PsExec, a light-weight telnet-replacement that lets you execute processes on other systems. PsExec is provided by Microsoft. The other method used by NotPetya is WMIC or Windows Management Instrumentation Command-line that is also provided by Microsoft.

The use of Microsoft-provided tools allowed NotPetya to spread undetected. The EternalBlue exploit has a known signature and can be detected by security and anti-virus software. Instead of drawing attention and perhaps even alerting the targets, the NotPetya designers utilized a special version of the Mimikatz tool to steal passwords and logins and then ran the PsExec and WMI software tools provided by Microsoft to move and replicate in a stealth fashion, undetected by anti-virus and security software.
“Specifically, the malware had an embedded Mimikatz DLL that it used to extract Windows account credentials from the memory of a compromised PC. With these credentials, the malware started to spread inside its host network using SysInternals’ PsExec utility.” continues the analysis.
The use of WMI and PsExec to move across a network is also a known signature of several malware designers including the TELEBOT group.
It is also clear the NotPetya software started with a very specific attack on the Ukraine. The initial attack was contained inside false updates tied to financial software used by the Ukraine called M.E.Doc. M.E.Doc software is one of only two software packages available for businesses have to pay their taxes in Ukraine. The attackers elected to concentrate against the M.E.Doc package because it appears they may have previously penetrated the small firm that distributed it and it was likely that a large number of users would have the software. Again, the intimate knowledge of Ukraine software updates and operations indicates that the TELEBOT group may have been the culprit.
However, what appears to not have been anticipated was that many of the Ukraine businesses included international partners with vulnerable connections on a global scale. The NotPetya virus spread through this international VPN and network connections to various companies around the globe including the US, UK, Australia, and Russia. It is this last nation-state attack by NotPetya that provided the awkward but convenient plausible deniability for Moscow that the malware wasn’t their doing.
This could be true since Moscow is known to work with a wide variety of hacker groups, some of which operate independently of Kremlin orders and often for their own profit. Russia employed such privateer hackers during the 2008 war against Georgia. The hackers were able to bring down a wide variety of Georgian targets including government communications and private companies which distributed power generators.
However, the privateers also were forced to live off the land so to speak. In order to finance many of the attacks, the groups utilized stolen US credit card information. The use of US money to finance an information warfare operation against Georgia did not sit well inside Washington and perhaps was one reason why the then Bush administration responded to deter Moscow from further combat.
It is not unfair to point out that other nations including the US, UK, China, and Israel have also been known to utilize privateer hackers for national security or nation-state style strikes. Many smaller nations which have limited resources in these areas have also employed private, often nefarious, hacker groups to penetrate political opponents, uncover leakers and distrust journalists. Sometimes when these attacks are revealed, the resulting scandal can damage the ruling party such as in the recent case of cyber attacks by the Mexican government.
However, the lack of pay-off for NotPetya to the designers shows at very worst it was a poorly designed nation-state attack that went out of control. Nation-state actors should take heed from the lessons of NotPetya and WannaCry. The fact is that software “weapons” can have collateral damage that extends far from the intended original target. Soft-warfare weapons are much like their bio-warfare cousins, they can spread and even attack the hand that created them.
Podle Ukrajiny mají v útoku vyděračského viru prsty ruské tajné služby
3.7.2017 Novinky/Bezpečnost BigBrother
Do počítačového útoku vyděračským virem na Ukrajinu z 27. června byly zapojené ruské tajné služby a jejich cílem bylo zničit důležitá data a vyvolat paniku. V prohlášení to o víkendu uvedla ukrajinská tajná služba SBU.
Podle SBU tento útok, který začal v úterý na Ukrajině a posléze se rozšířil do celého světa, byl dílem stejných pirátských skupin, které loni v prosinci provedly útoky na finanční systém a dopravní a energetické objekty na Ukrajině.
"Hlavním úkolem viru bylo zničit důležitá data a narušit činnost ukrajinských státních i soukromých institucí s cílem vyvolat mezi obyvatelstvem paniku," uvedla tajná služba v prohlášení, které zveřejnila ukrajinská média.
Útok byl podle SBU předem dobře naplánovaný a spuštěný postupně v několika etapách. Začal v předvečer ukrajinského státního svátku.
Rusko obvinění odmítá
Ukrajinské úřady obvinily Moskvu z tohoto počítačového útoku hned v úterý. Mluvčí prezidenta Vladimira Putina Dmitrij Peskov ale toto obvinění rozhodně odmítl jako "nepodložené".
SBU v novém prohlášení zopakovala názor zahraničních expertů, že nový virus se jen tváří jako vyděračský software, takzvaný ransomware. Měl vyvolat dojem, že cílem je obohacení pachatelů. "Ve skutečnosti ale virus skrývá rozsáhlý útok na Ukrajinu. Svědčí o tom nepřítomnost reálného mechanismu k získání vyžadovaných peněz," uvedla tajná služba.
Na tuto skutečnost už ve čtvrtek poukázali počítačoví odborníci. Podle nich o jiném než zištném pozadí útoku svědčí zvláštní způsob platby výkupného za dešifrování zablokovaných souborů a následná komunikace s hackery.
Ti totiž oproti běžnému postupu zavedli jen jediné platební spojení a jako kontakt si zřídili e-mail u německého poskytovatele elektronické pošty Posteo. Společnost ovšem obratem schránku zablokovala, takže postižení nemají žádnou možnost kontaktovat útočníky, ačkoli peníze lze dále převádět.
US-CERT published an alert on the last variant of Petya ransomware, including countermeasures
2.7.2017 securityaffairs Ransomware
The Department of Homeland Security’s (DHS) US Computer Emergency Readiness Team (US-CERT) published the Alert (TA17-181A) on the Petya Ransomware.
The US-CERT urges organizations of updating their software and avoiding use unsupported applications and OSs.
The US-CERT confirmed it has received multiple reports of Petya ransomware infections related the recent massive attack. The ransomware leverages the ETERNALBLUE Exploit M2 MS17-010 to exploit vulnerabilities in Server Message Block (SMB) and makes devices unusable.
“The NCCIC Code Analysis Team produced a Malware Initial Findings Report (MIFR) to provide in-depth technical analysis of the malware. In coordination with public and private sector partners, NCCIC is also providing additional IOCs in comma-separated-value form for information sharing purposes.
Available Files:
MIFR-10130295.pdf
TA-17-181A_IOCs.csv
The scope of this Alert’s analysis is limited to the newest “Petya” variant that surfaced June 27, 2017, and this malware is referred to as “Petya” throughout this Alert.” states the alert.
“Based on initial reporting, this Petya campaign involves multiple methods of initial infection and propagation, including exploiting vulnerabilities in Server Message Block (SMB). “
The flaws exist in how the SMBv1 server handles certain requests, a remote attacker could execute code by sending specially crafted messages to [an SMBv1] server.
Experts at US-CERT that analyzed a sample of the last Petya ransomware discovered that this variant encrypts the victim’s files with a dynamically generated, 128-bit key and creates a unique ID of the victim. The experts haven’t found any link between the encryption key generation and the victim’s ID.
“However, there is no evidence of a relationship between the encryption key and the victim’s ID, which means it may not be possible for the attacker to decrypt the victim’s files even if the ransom is paid.” states the alerts.
“This Petya variant spreads using the SMB exploit as described in MS17-010 and by stealing the user’s Windows credentials. This variant of Petya is notable for installing a modified version of the Mimikatz tool, which can be used to obtain the user’s credentials. The stolen credentials can be used to access other systems on the network.”
The sample analyzed by the US-CERT will also attempt to identify other hosts on the network by checking the compromised system’s IP physical address mapping table.
The Petya variant writes a text file on the “C:\” drive containing the Bitcoin wallet address and the RSA keys for the ransom payment. The malicious code modifies the master boot record (MBR) to enable encryption of the master file table (MFT) and the original MBR, then it reboots the system to replace the MBR.
“Based on the encryption methods used, it appears unlikely that the files can be restored even if the attacker received the victim’s unique ID.”
The US-CERT suggests organizations following its best practices related to SMB, such as:
Disabling SMBv1
Blocking all versions of SMB at the network boundary by blocking TCP port 445 with related protocols on UDP ports 137-138 and TCP port 139, for all boundary devices.
“US-CERT cautions users and administrators that disabling or blocking SMB may create problems by obstructing access to shared files, data, or devices,” the agency states. “The benefits of mitigation should be weighed against potential disruptions to users.”

Below the complete list of recommended steps for prevention that was included in the alert:
Apply the Microsoft patch for the MS17-010 SMB vulnerability dated March 14, 2017.[5](link is external)
Enable strong spam filters to prevent phishing emails from reaching the end users and authenticate in-bound email using technologies like Sender Policy Framework (SPF), Domain Message Authentication Reporting and Conformance (DMARC), and DomainKeys Identified Mail (DKIM) to prevent email spoofing.
Scan all incoming and outgoing emails to detect threats and filter executable files from reaching the end users.
Ensure anti-virus and anti-malware solutions are set to automatically conduct regular scans.
Manage the use of privileged accounts. Implement the principle of least privilege. No users should be assigned administrative access unless absolutely needed. Those with a need for administrator accounts should only use them when necessary.
Configure access controls including file, directory, and network share permissions with least privilege in mind. If a user only needs to read specific files, they should not have write access to those files, directories, or shares.
Disable macro scripts from Microsoft Office files transmitted via email. Consider using Office Viewer software to open Microsoft Office files transmitted via email instead of full Office suite applications.
Develop, institute, and practice employee education programs for identifying scams, malicious links, and attempted social engineering.
Run regular penetration tests against the network, no less than once a year. Ideally, run these as often as possible and practical.
Test your backups to ensure they work correctly upon use.
Utilize host-based firewalls and block workstation-to-workstation communications.
NATO attributed the massive NotPetya attack to a ‘state actor’ and call for a joint investigation
2.7.2017 securityaffairs BigBrothers
NATO attributed the massive NotPetya attack to a ‘state actor,’ NotPetya and WannaCry Call for a Joint Response from International Community.
According to NATO, the recent massive attack based on NotPetya ransomware was powered by a “state actor.” The malware infected over 12,000 devices in around 65 countries, the malicious code hit major industries and critical infrastructure.
Recently the analysis conducted by various groups of experts confirmed that ransomware was designed to look like ransomware but it was wiper malware designed for sabotage purpose.
Attackers might have used a diversionary strategy hide a state-sponsored attack on Ukraine critical infrastructure.
Experts from NATO believe the attack was likely launched by a nation-state actor, or it was commissioned to a non-state actor by a state. The attackers were well funded and the attack they conducted was very complex and expensive.
The experts observed that despite the operation was complex, the attackers did not spend much effort for managing the payments, a circumstance that suggests hackers were not financially motivated.
“The operation was not too complex, but still complex and expensive enough to have been prepared and executed by unaffiliated hackers for the sake of practice. Cyber criminals are not behind this either, as the method for collecting the ransom was so poorly designed that the ransom would probably not even cover the cost of the operation,” NATO’s Cooperative Cyber Defense Centre of Excellence (CCD COE), said in a press release on Friday.
This declaration could have serious consequences, the cyber attack could be interpreted as an act of war, and can trigger a military response of the alliance under the Article 5 of the North Atlantic Treaty, the principal of collective defense.
“The global outbreak of NotPetya malware on 27 June 2017 hitting multiple organisations in Ukraine, Europe, US and possibly Russia can most likely be attributed to a state actor, concluded a group of NATO CCD COE researchers Bernhards Blumbergs, Tomáš Minárik, LTC Kris van der Meij and Lauri Lindström. Analysis of both recent large-scale campaigns WannaCry and NotPetya raises questions about possible response options of affected states and the international community.” wrote Tomáš Minárik, researcher at NATO’s CCD COE law branch.
“As important government systems have been targeted, then in case the operation is attributed to a state this could count as a violation of sovereignty. Consequently, this could be an internationally wrongful act, which might give the targeted states several options to respond with countermeasures,”
Despite the WannaCry attack and the NotPetya one present many similarities, according to the NATO researchers, they were conducted by different threat actors.
“As the extortion of money seems to be just a negligently prepared cover according to various news then the question about the motivation behind NotPetya attack should be looked from other perspectives. Even though the same vulnerability was used by WannaCry, the actors behind these two similar attacks are likely not the same. In both cases a possible financial gain for attackers has been more than modest. However, an effect was achieved, a large-scale successful disruptive attack almost globally, is almost identical in both cases. ” continues the NATO release.
“NotPetya is a sign that after WannaCry, yet another actor has exploited vulnerability exposed by the Shadow Brokers. Furthermore, it seems likely that the more sophisticated and expensive NotPetya campaign is a declaration of power – demonstration of the acquired disruptive capability and readiness to use it,” concluded Lauri Lindström, researcher at NATO CCD COE Strategy Branch.
Gavin O’Gorman, the investigator in Symantec Security Response, made a couple of hypothesis about the motive behind the attack.
The first is that the attack was powered by technologically capable criminals but with poor operational abilities. Attackers used one bitcoin wallet and used a single email account to contact.
The second theory is that the real motivation behind the attack is sabotage on a large scale.
“Perhaps this attack was never intended to make money, rather to simply disrupt a large number of Ukrainian organizations. Launching an attack that would wipe victim hard drives would achieve the same effect, however, that would be an overtly aggressive action,” O’Gorman wrote in a blog post.
“Effectively wiping hard drives through the pretense of ransomware confuses the issue, leaving victims and investigators to ask: ‘Are the attackers politically motivated, or criminally motivated?'”
WannaCry and NotPetya raise again the question about the possible response options of the international community and the necessity of norms of state behavior in the cyber space.
Both arguments were discussed at the recent Italy G7 Summit, with my colleagues at the G7 cyber group we proposed a set of norms of state behavior to address these problems. The result was a voluntary, non-binding norms of State behavior during peacetime in the G7 DECLARATION ON RESPONSIBLE STATES BEHAVIOR IN CYBERSPACE.
NATO call for a special joint investigation to attribute the attack to a specific actor and persecute it.
“WannaCry and NotPetya raise again the question about the possible response options of the international community. The number of affected countries shows that attackers are not intimidated by a possible global level investigation in response to their attacks. This might be an opportunity for victim nations to demonstrate the contrary by launching a special joint investigation.” concludes the press release.
FBI hacked a US Darknet shopper who tried to purchase Mail Bomb
2.7.2017 securityaffairs CyberCrime
The FBI hacked the system of a dark web user who tried to purchase a mail bomb from an undercover investigator in the US.
According to a plea agreement, filed on April 28, 2017, Clinton Scott Bass of Georgia (US) tried in a first time to purchase a car bomb. The man, who was using two different pseudo names, contacted an undercover FBI agent on a darknet marketplace.

Later on, the man decided to acquire a mail bomb from the undercover officer. The agent agreed to sell the explosive to the suspect who paid $550 in digital currency, likely Bitcoin or Monero.
“He was keen, at first, to buy a car bomb that would explode as soon as the vehicle’s door was opened or closed. But he then decided he wanted a mail bomb, which would go off on being opened.” reported Thomas Fox-Brewster from Forbes.
“The undercover agent agreed to sell him a bomb, which was in fact inert and delivered to an address provided by one of Bass’ monikers, who paid $550 in virtual currency for the service. Hidden in the fake explosive, however, was a location tracker.”
The police sent an inert device to the address provided by the suspect, they have also hidden a location tracker in the pack.
The location tracker allowed the agents to discover the real Bass’s target, they tracked the pack discovering that is was sent to someone in Hahira, Georgia on the morning of April 27, then Feds arrested the man.
Bass used an email address at the temporary mail provider Guerilla Mail while communicating with the undercover agent. The defendant used the email address to receive instructions from the vendor on how to use the mail bomb.
The FBI sent a phishing message to the Guerilla Mail address used by Bass in an attempt to locate him (i.e. tracking his IP address). The message included a weaponized attached document, which, once opened, would send target information to the FBI’s server. The FBI used the Network Investigative Technique (NIT), a method used by Feds in many other cases and that was questioned by privacy advocates that consider it a tool for dragnet surveillance.
“The message included a document, which, once opened, would send that identifying data to an FBI server, somehow overcoming the IP-masking provided by Tor. A separate document indicated the government also installed what’s known as a pen-trap tool to record all the information coming from the hack.” continues Fox Brewster.
An executed warrant document reported that the FBI retrieved 19 different IP addresses in the investigation by using the NIT, likely because the suspect was using a VPN service and the Tor network to mask his IP address. It is not clear is the NIT was useful to track the man.
Experts and privacy advocated consider legitimate the NIT usage in the specific case, it was a targeted attack that not impacted other individuals, such as the case of a watering hole attack.
“The way I see it is, the FBI has to do something to catch criminals, and at least in this case they didn’t resort to draconian methods such as mass surveillance without a warrant,” Flashmob, the administrator of Guerilla Mail, told the media. “Instead, they used a simple procedure with a warrant that doesn’t need much technical ability,”
The Electronic Frontier Foundation (EFF) security researcher Cooper Quintin also confirmed that the FBI’s phishing in the current case was legitimate.
But what makes this hack unique is that it appears to be the first public example of the FBI legally using a controversial update to the Rule 41 , that allows searches on users of anonymizing services, including the Tor network.
Anyway, there is an element of concern about the Bass case, authorities used “Stingray” technology to spy on the suspect and track his movements,
Bass pleaded guilty in April to charges of attempting to receive and transport explosive materials with the intent to kill, injure or intimidate. The man risks 120 months in prison, the trial will be held on July 12.
[ad rotate banner=”9″]
From BlackEnergy to ExPetr
1.7.2017 Kaspersky Ransomware
A gut feeling of old acquaintances, new tools, and a common battleground
Much has been written about the recent ExPetr/NotPetya/Nyetya/Petya outbreak – you can read our findings here:Schroedinger’s Pet(ya) and ExPetr is a wiper, not ransomware.
As in the case of Wannacry, attribution is very difficult and finding links with previously known malware is challenging. In the case of Wannacry, Google’s Neel Mehta was able to identify a code fragment which became the most important clue in the story, and was later confirmed by further evidence, showing Wannacry as a pet project of the Lazarus group.
To date, nobody has been able to find any significant code sharing between ExPetr/Petya and older malware. Given our love for unsolved mysteries, we jumped right on it.
Analyzing the Similarities
At the beginning of the ExPetr outbreak, one of our team members pointed to the fact that the specific list of extensions used by ExPetr is very similar to the one used by BlackEnergy’s KillDisk ransomware from 2015 and 2016 (Anton Cherepanov from ESET made the same observation on Twitter).
The BlackEnergy APT is a sophisticated threat actor that is known to have used at least one zero day, coupled with destructive tools, and code geared towards attacking ICS systems. They are widely confirmed as the entity behind the Ukraine power grid attack from 2015 as well as a chain of other destructive attacks that plagued that country over the past years.
If you are interested in reading more about the BlackEnergy APT, be sure to check our previous blogs on the topic:
BE2 custom plugins, router abuse and target profiles
BE2 extraordinary plugins
BlackEnergy APT Attacks in Ukraine employ spearphishing with Word documents
Going back to the hunt for similarities, here’s how the targeted extensions lists looks in ExPetr and a version of a wiper used by the BE APT group in 2015:
ExPetr 2015 BlackEnergy wiper sample
3ds, .7z, .accdb, .ai, .asp, .aspx, .avhd, .back, .bak, .c, .cfg, .conf, .cpp, .cs, .ctl, .dbf, .disk, .djvu, .doc, .docx, .dwg, .eml, .fdb, .gz, .h, .hdd, .kdbx, .mail, .mdb, .msg, .nrg, .ora, .ost, .ova, .ovf, .pdf, .php, .pmf, .ppt, .pptx, .pst, .pvi, .py, .pyc, .rar, .rtf, .sln, .sql, .tar, .vbox, .vbs, .vcb, .vdi, .vfd, .vmc, .vmdk, .vmsd, .vmx, .vsdx, .vsv, .work, .xls
.3ds, .7z, .accdb, .accdc, .ai, .asp, .aspx, .avhd, .back, .bak, .bin, .bkf, .cer, .cfg, .conf, .crl, .crt, .csr, .csv, .dat, .db3, .db4, .dbc, .dbf, .dbx, .djvu, .doc, .docx, .dr, .dwg, .dxf, .edb, .eml, .fdb, .gdb, .git, .gz, .hdd, .ib, .ibz, .io, .jar, .jpeg, .jpg, .jrs, .js, .kdbx, .key, .mail, .max, .mdb, .mdbx, .mdf, .mkv, .mlk, .mp3, .msi, .my, .myd, .nsn, .oda, .ost, .ovf, .p7b, .p7c, .p7r, .pd, .pdf, .pem, .pfx, .php, .pio, .piz, .png, .ppt, .pptx, .ps, .ps1, .pst, .pvi, .pvk, .py, .pyc, .rar, .rb, .rtf, .sdb, .sdf, .sh, .sl3, .spc, .sql, .sqlite, .sqlite3, .tar, .tiff, .vbk, .vbm, .vbox, .vcb, .vdi, .vfd, .vhd, .vhdx, .vmc, .vmdk, .vmem, .vmfx, .vmsd, .vmx, .vmxf, .vsd, .vsdx, .vsv, .wav, .wdb, .xls, .xlsx, .xvd, .zip
Obviously, the lists are similar in composition and formatting, but not identical. Moreover, older versions of the BE destructive module have even longer lists. Here’s a snippet of an extensions list from a 2015 BE sample that is even longer:
Nevertheless, the lists were similar in the sense of being stored in the same dot-separated formats. Although this indicated a possible link, we wondered if we could find more similarities, especially in the code of older variants of BlackEnergy and ExPetr.
We continued to chase that hunch during the frenetic early analysis phase and shared this gut feeling of a similarity between ExPetr and BlackEnergy with our friends at Palo Alto Networks. Together, we tried to build a list of features that we could use to make a YARA rule to detect both ExPetr and BlackEnergy wipers.
During the analysis, we focused on the similar extensions list and the code responsible for parsing the file system for encryption or wiping. Here’s the code responsible for checking the extensions to target in the current version of ExPetr:
This works by going through the target file system in a recursive way, then checking if the extension for each file is included in the dot-separated list. Unfortunately for our theory, the way this is implemented in older BlackEnergy variants is quite different; the code is more generic and the list of extensions to target is initialized at the beginning, and passed down to the recursive disk listing function.
Instead, we took the results of automated code comparisons and paired them down to a signature that perfectly fit the mould of both in the hope of unearthing similarities. What we came up with is a combination of generic code and interesting strings that we put together into a cohesive rule to single out both BlackEnergy KillDisk components and ExPetr samples. The main example of this generic code is the inlined wcscmp function merged by the compiler’s optimization, meant to check if the filename is the current folder, which is named “.”. Of course, this code is pretty generic and can appear in other programs that recursively list files. It’s inclusion alongside a similar extension list makes it of particular interest to us –but remains a low confidence indicator.
Looking further, we identified some other candidate strings which, although not unique, when combined together allow us to fingerprint the binaries from our case in a more precise way. These include:
exe /r /f
ComSpec
InitiateSystemShutdown
When put together with the wcscmp inlined code that checks on the filename, we get the following YARA rule:
rule blackenergy_and_petya_similarities {
strings:
//shutdown.exe /r /f
$bytes00 = { 73 00 68 00 75 00 74 00 64 00 6f 00 77 00 6e 00 2e 00 65 00 78 00 65 00 }
//ComSpec
$bytes01 = { 43 00 6f 00 6d 00 53 00 70 00 65 00 63 00 }
//InitiateSystemShutdown
$bytes02 = { 49 6e 69 74 69 61 74 65 53 79 73 74 65 6d 53 68 75 74 64 6f 77 6e 45 78 57}
//68A4430110 push 0100143A4 ;’ntdll.dll’
//FF151CD10010 call GetModuleHandleA
//3BC7 cmp eax,edi
//7420 jz …
$bytes03 = { 68 ?? ?? ?1 ?0 ff 15 ?? ?? ?? ?0 3b c7 74 ?? }
// “/c”
$bytes04 = { 2f 00 63 00 }
//wcscmp(…
$hex_string = { b9 ?? ?? ?1 ?0 8d 44 24 ?c 66 8b 10 66 3b 11 75 1e 66
85 d2 74 15 66 8b 50 02 66 3b 51 02 75 0f 83 c0 04 83 c1 04 66 85 d2 75
de 33 c0 eb 05 1b c0 83 d8 ff 85 c0 0f 84 ?? 0? 00 00 b9 ?? ?? ?1 ?0 8d
44 24 ?c 66 8b 10 66 3b 11 75 1e 66 85 d2 74 15 66 8b 50 02 66 3b 51 02
75 0f 83 c0 04 83 c1 04 66 85 d2 75 de 33 c0 eb 05 1b c0 83 d8 ff 85 c0
0f 84 ?? 0? 00 00 }
condition:
((uint16(0) == 0x5A4D)) and (filesize < 5000000) and
(all of them)
}
rule blackenergy_and_petya_similarities {
strings:
//shutdown.exe /r /f
$bytes00 = { 73 00 68 00 75 00 74 00 64 00 6f 00 77 00 6e 00 2e 00 65 00 78 00 65 00 }
//ComSpec
$bytes01 = { 43 00 6f 00 6d 00 53 00 70 00 65 00 63 00 }
//InitiateSystemShutdown
$bytes02 = { 49 6e 69 74 69 61 74 65 53 79 73 74 65 6d 53 68 75 74 64 6f 77 6e 45 78 57}
//68A4430110 push 0100143A4 ;’ntdll.dll’
//FF151CD10010 call GetModuleHandleA
//3BC7 cmp eax,edi
//7420 jz …
$bytes03 = { 68 ?? ?? ?1 ?0 ff 15 ?? ?? ?? ?0 3b c7 74 ?? }
// “/c”
$bytes04 = { 2f 00 63 00 }
//wcscmp(…
$hex_string = { b9 ?? ?? ?1 ?0 8d 44 24 ?c 66 8b 10 66 3b 11 75 1e 66
85 d2 74 15 66 8b 50 02 66 3b 51 02 75 0f 83 c0 04 83 c1 04 66 85 d2 75
de 33 c0 eb 05 1b c0 83 d8 ff 85 c0 0f 84 ?? 0? 00 00 b9 ?? ?? ?1 ?0 8d
44 24 ?c 66 8b 10 66 3b 11 75 1e 66 85 d2 74 15 66 8b 50 02 66 3b 51 02
75 0f 83 c0 04 83 c1 04 66 85 d2 75 de 33 c0 eb 05 1b c0 83 d8 ff 85 c0
0f 84 ?? 0? 00 00 }
condition:
((uint16(0) == 0x5A4D)) and (filesize < 5000000) and
(all of them)
}
When run on our extensive (read: very big) malware collection, the YARA rule above fires on BlackEnergy and ExPetr samples only. Unsurprisingly, when used alone, each string can generate false positives or catch other unrelated malware. However, when combined together in this fashion, they become very precise. The technique of grouping generic or popular strings together into unique combinations is one of the most effective methods for writing powerful Yara rules.
Of course, this should not be considered a sign of a definitive link, but it does point to certain code design similarities between these malware families.
This low confidence but persistent hunch is what motivates us to ask other researchers around the world to join us in investigating these similarities and attempt to discover more facts about the origin of ExPetr/Petya. Looking back at other high profile cases, such as the Bangladesh Bank Heist or Wannacry, there were few facts linking them to the Lazarus group. In time, more evidence appeared and allowed us, and others, to link them together with high confidence. Further research can be crucial to connecting the dots, or, disproving these theories.
We’d like to think of this ongoing research as an opportunity for an open invitation to the larger security community to help nail down (or disprove) the link between BlackEnergy and ExPetr/Petya. Our colleagues at ESET have published their own excellent analysis suggesting a possible link between ExPetr/Petya and TeleBots (BlackEnergy). Be sure to check out their analysis. And as mentioned before, a special thanks to our friends at Palo Alto for their contributions on clustering BlackEnergy samples.
Hashes
ExPetr:
027cc450ef5f8c5f653329641ec1fed91f694e0d229928963b30f6b0d7d3a745
BE:
11b7b8a7965b52ebb213b023b6772dd2c76c66893fc96a18a9a33c8cf125af80
5d2b1abc7c35de73375dd54a4ec5f0b060ca80a1831dac46ad411b4fe4eac4c6
F52869474834be5a6b5df7f8f0c46cbc7e9b22fa5cb30bee0f363ec6eb056b95
368d5c536832b843c6de2513baf7b11bcafea1647c65df7b6f2648840fa50f75
A6a167e214acd34b4084237ba7f6476d2e999849281aa5b1b3f92138c7d91c7a
Edbc90c217eebabb7a9b618163716f430098202e904ddc16ce9db994c6509310
F9f3374d89baf1878854f1700c8d5a2e5cf40de36071d97c6b9ff6b55d837fca
Wikileaks – CIA developed OutlawCountry Malware to hack Linux systems
1.7.2017 securityaffairs BigBrothers
WikiLeaks released a new batch of documents that detail the CIA tool OutlawCountry used to remotely spy on computers running Linux operating systems.
WikiLeaks has released a new batch of documents from the Vault 7 leak that details a CIA tool, dubbed OutlawCountry, used by the agency to remotely spy on computers running Linux operating systems.
According to the documentation leaked by WikiLeaks, the OutlawCountry tool was designed to redirect all outbound network traffic on the targeted computer to CIA controlled systems for exfiltrate and infiltrate data.
The OutlawCountry Linux hacking tool consists of a kernel module for Linux 2.6 that CIA hackers load via shell access to the targeted system.
The principal limitation of the tool is that the kernel modules only work with compatible Linux kernel below the list of prerequisites included in the documentation:
(S//NF) The target must be running a compatible 64-bit version of CentOS/RHEL 6.x
(kernel version 2.6.32).
(S//NF) The Operator must have shell access to the target.
(S//NF) The target must have a “nat” netfilter table
The module allows the creation of a hidden Netfilter table with an obscure name on a target Linux user.
” The OutlawCountry tool consists of a kernel module for Linux 2.6. The Operator loads the module via shell access to the target. When loaded, the module creates a new netfilter table with an obscure name. The new table allows certain rules to be created using the “iptables” command. These rules take precedence over existing rules, and are only visible to an administrator if the table name is known.” reads the OutlawCountry User Manual. “When the Operator removes the kernel module, the new table is also removed.”
In the following diagram, the CIA operator loads OutlawCountry on the target (TARG_1), then he may add hidden iptables rules to modify network traffic between the WEST and EAST networks. For example, packets that should be routed from WEST_2 to EAST_3 may be redirected to EAST_4.
The manual doesn’t include information related to the way the attacker injects the kernel module in the targeted Linux OS. It is likely, the cyber spies leverage multiple hacking tools and exploits in its arsenal to compromise the target running the Linux operating system.
The OutlawCountry contains just one kernel module for 64-bit CentOS/RHEL 6.x that makes possible injection only in default Linux kernel.
“(S//NF) OutlawCountry v1.0 contains one kernel module for 64-bit CentOS/RHEL 6.x.
This module will only work with default kernels. Also, OutlawCountry v1.0 only
supports adding covert DNAT rules to the PREROUTING chain.” continues the manual leaked by WikiLeaks.
A few days ago WikiLeaks has published a document detailing a tool allegedly used by the U.S. CIA to track people’s locations via their WiFi-enabled devices.
The malware codenamed Elsa implements geolocation feature, it scans visible WiFi access points and records their details, such as the ESS identifier, MAC address and signal strength at regular intervals.
Below the list of release published by Wikileaks since March:
OutlawCountry – 30 June, 2017
ELSA malware – 28 June, 2017
Cherry Blossom – 15 June, 2017
Pandemic – 1 June, 2017
Athena – 19 May, 2017
AfterMidnight – 12 May, 2017
Archimedes – 5 May, 2017
Scribbles – 28 April, 2017
Weeping Angel – 21 April, 2017
Hive – 14 April, 2017
Grasshopper – 7 April, 2017
Marble Framework – 31 March, 2017
Dark Matter – 23 March, 2017
Researcher released Eternal Blues, a free EternalBlue vulnerability scanner
1.7.2017 securityaffairs Safety
The security researcher Elad Erez developed Eternal Blues, a free EternalBlue vulnerability scanner that could be used to assess networks.
Now systems administrators and hackers have a new free tool, dubbed Eternal Blues, to scan networks looking at computers vulnerable to the NSA EternalBlue exploit.
EternalBlue is one of the hacking tools that the ShadowBrokers hacker group stolen to the NSA-linked Equation Group. The ShadowBrokers group leaked online the EternalBlue tool in April this year, a few weeks later Microsoft released security updates to fix the flaw exploited by the NSA exploit.
In May, the security expert Miroslav Stampar, a member of the Croatian Government CERT, discovered a new worm, dubbed EternalRocks, that exploits the EternalBlue flaw in the SMB protocol to spread itself like the popular WannaCry ransomware.
Security experts discovered later another hacking tool dubbed EternalRocks, a malware that uses 7 NSA exploits and that leverages the EternalBlue flaw to spread itself like WannaCry ransomware.
The Eternal Blues tool was developed by the researcher Elad Erez, of course, it designed for testing purposes and not to identify networks to hack.
“Eternal Blues is a free EternalBlue vulnerability scanner. It helps finding the blind spots in your network, these endpoints that are still vulnerable to EternalBlue.” explained Elad Erez.
“Just hit the SCAN button and you will immediately start to get which of your computers are vulnerable and which aren’t. That’s it.”

Companies and organizations can scan their networks for computers vulnerable to the EternalBlue exploit.
The tool was developed spread awareness and allow not technical organizations to assess their networks.
“The majority of latest WannaCry, NoPetya (Petya, GoldenEye or whatever) victims, are not technical organizations and sometimes just small business who don’t have a security team, or even just an IT team to help them mitigate this. Running NMap, Metasploit (not to mention more commercial products) is something they will never do. I aimed to create a simple ‘one-button’ tool that tells you one thing and one thing only – which systems are vulnerable in your network.” added Erez.
Erez also published the following tips to the admins who will use the tool.
If you’re about to run it in your working environment, please update the IT/Security team in advance. You don’t want to cause (IDS/IPS/AV) false alarms
If vulnerable systems were found – please take a Windows update asap
For god sake, please disable SMBv1 already. Whether your systems are patched or not. This protocol was written over 3 decades ago…!
If you would like to enjoy the tool but disallow sending anonymous statistics (which is so uncool), disable access to my website
The developer informed users that his tool sends back to him anonymous usage statistics through Google Analytics.
WordPress Plugin Used by 300,000+ Sites Found Vulnerable to SQL Injection Attack
1.7.2017 thehackernews Vulnerebility
A SQL Injection vulnerability has been discovered in one of the most popular Wordpress plugins, installed on over 300,000 websites, which could be exploited by hackers to steal databases and possibly hijack the affected sites remotely.
The flaw has been discovered in the highly popular WP Statistics plugin, which allows site administrators to get detailed information related to the number of users online on their sites, the number of visits and visitors, and page statistics.
Discovered by Sucuri team, WordPress plugin WP Statistics is vulnerable to SQL Injection flaw that allows a remote attacker, with at least a subscriber account, to steal sensitive information from the website's database and possibly gain unauthorized access to websites.
SQL Injection is a web application bug that allows hackers to inject malicious Structured Query Language (SQL) code to web inputs in order to determine the structure and location of key databases, which eventually allows stealing of the database.
The SQL injection vulnerability in WP Statistics plugin resides in multiple functions, including wp_statistics_searchengine_query().
"This vulnerability is caused by the lack of sanitization in user-provided data," researchers said. "Some attributes of the shortcode wpstatistics are being passed as parameters for important functions and this should not be a problem if those parameters were sanitized."
"One of the vulnerable functions wp_statistics_searchengine_query() in the file 'includes/functions/functions.php' is accessible through WordPress' AJAX functionality thanks to the core function wp_ajax_parse_media_shortcode()."
This function does not check for additional privileges, which allows website subscribers to execute this shortcode and inject malicious code to its attributes.
The researchers at Sucuri privately disclosed the flaw to the WP Statistics team and the team had patched the vulnerability in its latest version WP Statistics version 12.0.8.
So, if you have a vulnerable version of the plugin installed and your website allowing user registration, you are definitely at risk, and you should install the latest version as soon as possible.
Microsoft Tackles Ransomware with Controlled Folder Access
1.7.2017 securityweek Ransomware
In the wake of global malicious attacks such as WannaCry and NotPetya, Microsoft this week announced a new feature meant to keep users’ data safe from ransomware and other type of malware.
Dubbed Controlled folder access, the feature was included as a new option in the Windows Defender Security Center in Windows 10 Insider Preview Build 16232 for PC, and should become available for all users in the Windows 10 Fall Creators Update release, set to arrive sometime in October-November 2017.
This week, Microsoft also announced that the Fall Creators Update will make the Enhanced Mitigation Experience Toolkit (EMET) native to Windows 10, providing users with additional protection against exploits and other types of threats.
“In [Windows 10 Insider Preview Build 16232], we’re making it easier for you to protect valuable data from malicious apps and threats, such as ransomware. To enable the feature, search for and open the Windows Defender Security Center from Start, go to the Virus & threat protection settings section, and set the switch to On,” Dona Sarkar, Software Engineer, Windows and Devices Group, notes in a blog post.
The new feature, Sarkar explains, is meant to monitor the changes applications make to files in certain protected folders and blacklists any app that attempts to make such modifications, while also notifying the user on the action taken.
There will be a default list of folders included in the option (such as Documents, Pictures, Movies, and Desktop), but users will have the possibility to add more locations to the list. However, they won’t be able to modify the default list.
Users who don’t store their files in the default Windows libraries will certainly find the option to add more folders to the protected list a handy option.
“Click Protected folders in the Controlled folder access area and enter the full path of the folder you want to monitor. You can also enter network shares and mapped drives, but environment variables and wildcards are not supported (for right now),” Sarkar notes.
Controlled folder access should provide users with an extra layer of security in addition to the defenses already built into Windows 10. However, it users shouldn’t rely solely on it when it comes to data protection. Using a multi-layered approach to security is a better practice, as cybercriminals are constantly adapting in an attempt to bypass even the most sophisticated defenses.
Wikileaks Reveals CIA Malware that Hacks & Spy On Linux Computers
1.7.2017 thehackernews BigBrothers
WikiLeaks has just published a new batch of the ongoing Vault 7 leak, this time detailing an alleged CIA project that allowed the agency to hack and remotely spy on computers running the Linux operating systems.
Dubbed OutlawCountry, the project allows the CIA hackers to redirect all outbound network traffic on the targeted computer to CIA controlled computer systems for exfiltrate and infiltrate data.
The OutlawCountry Linux hacking tool consists of a kernel module, which the CIA hackers load via shell access to the targeted system and create a hidden Netfilter table with an obscure name on a target Linux user.
"The new table allows certain rules to be created using the "iptables" command. These rules take precedence over existing rules, and are only visible to an administrator if the table name is known. When the Operator removes the kernel module, the new table is also removed," CIA's leaked user manual reads.
Although the installation and persistence method of the OutlawCountry tool is not described in detail in the document, it seems like the CIA hackers rely on the available CIA exploits and backdoors to inject the kernel module into a targeted Linux operating system.
However, there are some limitations to using the tool, such as the kernel modules only work with compatible Linux kernels.
"OutlawCountry v1.0 contains one kernel module for 64-bit CentOS/RHEL 6.x; this module will only work with default kernels. Also, OutlawCountry v1.0 only supports adding covert DNAT rules to the PREROUTING chain," WikiLeaks says.
Previous Vault 7 CIA Leaks
Last week, WikiLeaks dumped a classified CIA malware that tracks geo-location of targeted PCs and laptops running the Microsoft Windows operating system.
Dubbed ELSA, the malware captures the IDs of nearby public hotspots and then matches them with the global database of public Wi-Fi hotspots' locations.
Since March, the whistleblowing group has published 14 batches of "Vault 7" series, which includes the latest and last week leaks, along with the following batches:
Brutal Kangaroo – a CIA tool suite for Microsoft Windows that targets closed networks or air-gapped computers within an enterprise or organization without requiring any direct access.
Cherry Blossom – a CIA's framework, generally a remotely controllable firmware-based implant, used for monitoring the Internet activity of the target systems by exploiting flaws in WiFi devices.
Pandemic – a CIA's project that allowed the spying agency to turn Windows file servers into covert attack machines that can silently infect other computers of interest inside a targeted network.
Athena – an agency's spyware framework that has been designed to take full control over the infected Windows machines remotely, and works with every version of Microsoft's Windows operating systems, from Windows XP to Windows 10.
AfterMidnight and Assassin – Two apparent CIA's malware frameworks for the Microsoft Windows platform that is meant to monitor and report back actions on the infected remote host computer and execute malicious code.
Archimedes – A man-in-the-middle attack tool allegedly built by the spying agency to target computers inside a Local Area Network (LAN).
Scribbles – A piece of software reportedly designed to embed 'web beacons' into confidential documents, allowing the CIA hackers to track insiders and whistleblowers.
Grasshopper – A framework that allowed the CIA to easily create custom malware for breaking into Microsoft's Windows and bypassing antivirus protection.
Marble – The source code of a secret anti-forensic framework, primarily an obfuscator or a packer used by the spying agency to hide the actual source of its malware.
Dark Matter – Hacking exploits the agency designed and used to target iPhones and Mac machines.
Weeping Angel – Spying tool used by the CIA to infiltrate smart TV's, transforming them into covert microphones in target's pocket.
Year Zero – CIA hacking exploits for popular hardware and software.
Windows nabízí ochranu před ransomwarem. Na vybrané složky nesáhne
30.6.2017 CNEWS.cz Zabezpečení
Jaromír se přidal k programu Windows Insider. Jste jako Jaromír?
Další pracovní týden je skoro za námi a Microsoft vydal další nové testovací sestavení Windows 10. Minule i předminule jsme se dočkali dlouhé řady novinek. Co tentokrát?
Zatím byla řeč o tom, že Microsoft odhalil novinky v zabezpečení Windows pro firmy. Z novinek zaměřených na spotřebitelský trh bylo zmíněno jen zapojení cloudových technologií do detekce. Windows 10 Fall Creators Update ale nabídne tak další novinky pro zlepšení zabezpečení na běžných domácích počítačích či tabletech.
Bezpečnostní funkce pro organizace
Windows 10 Insider Preview build 16232, jenž je dostupný ve Fast ringu na počítačích a tabletech, obsahuje také již oznámené novinky. Jednu z nich představuje Windows Defender Application Guard, který prostřednictvím správy zabezpečení nabízí možnost uchovávat uživatelská data mezi relacemi v Edgi.
Tím je zabráněno, aby vám někdo např. podstrčil nebezpečnou cookie, změnit uložená hesla nebo adresy oblíbených položek apod. Toto je docíleno tak, že se tato uživatelská data neobjevují na hostitelském stroji, ale jsou dostupná při používání aplikace. Chráněnou relaci vyvoláte z hlavní nabídky prohlížeče. S tím si nicméně nelamte hlavu, tato funkce je cílená na organizace, nikoli na jednotlivce.
Primárně organizacím a profesionální sféře patří také ochrana proti útokům, kterou najdete ve Windows Defender Security Center v sekci Řízení aplikací a prohlížečů. (V českém vydání je doslova neelegantně uvedeno Ochrana proti útokům typu exploit.) Spravovat ji ovšem může kdokoli.
V rámci podrobného nastavení ovlivníte chování DEP, ALSR, SEHOP apod. Kromě obecného nastavení můžete dopodrobna určovat, jak se bude Windows chovat vůči konkrétním programu. Jedná se o rozpracované prostředí a ne všechny funkce nabízené zatím fungují.
Složky, na které smí sáhnout jen vyvolené programy
Co spíše využijeme v domácnostech? Ochranu proti zásahům do uživatelských dat, což běžně dělá v poslední době populární ransomware. Příslušné nastavení opět najdete ve Windows Defender Security Center, tentokrát v nastavení antiviru.
Pokud novou funkci zapnete, bude Windows Defender u vybraných složek hlídat, jaké programy v nich provádí změny. Pokud se program z černé listiny pokusí změnit vaše soubory, budete na tuto skutečnost upozorněni. Na černé listině se nachází všechny aplikace, které vy ručně nepovolíte (tj. vaše vlastní bílá listina), ale především které na něj dosadí sám Microsoft.
Řízený přístup ke složkám ve Windows 10 FCU


Funkce pro ochranu složek proti pochybným aplikacím je volitelná Funkce pro ochranu složek proti pochybným aplikacím je volitelná
Do ochrany můžete zahrnout další složky, některé na seznam přidal sám Microsoft. Ty zde ale nejsou vidět Do ochrany můžete zahrnout další složky, některé na seznam přidal sám Microsoft. Ty zde ale nejsou vidětDo ochrany můžete zahrnout další složky, některé na seznam přidal sám Microsoft. Ty zde ale nejsou vidět
Kdyby Windows Defender přístup odepřel nesprávné aplikaci, můžete ji přidat na bílou listinu Kdyby Windows Defender přístup odepřel nesprávné aplikaci, můžete ji přidat na bílou listinu
Většina aplikací, které používáme, by přístup mít měla. Pod kontrolou máte seznam osobně schválených aplikací a částečně i seznam chráněných složek. Některé složky (Dokumenty, Hudba, Obrázky, Videa nebo Plocha) se na něm nachází standardně – a tyto složky neodeberete.
Kompletní seznam novinek, opravených chyb a známých problémů ve Windows 10 Insider Preview build 16232 naleznete na blogu Windows Experience. Na závěr musím doplnit dvě skutečnosti. Vyšel také Windows 10 Mobile Insider Preview Build 15228, které ovšem pouze řeší drobnosti. Především však Microsoft pozastavil distribuci nových verzí aplikací v kanálech programu Windows Insider. Stávající verze potřebují otestovat, aby je mohl vydat pro širokou veřejnost.
Unpatched Flaws in Schneider Electric U.motion Builder Disclosed
30.6.2017 securityweek ICS
The details of several vulnerabilities affecting Schneider Electric’s U.motion Builder software have been disclosed before the vendor released any patches.
Schneider Electric’s U.motion is a building automation solution used around the world mainly in the commercial facilities, critical manufacturing and energy sectors. U.motion Builder is a tool that allows users to create projects for their U.motion devices.
Security researcher Andrea Micalizzi, also known as “rgod,” discovered that the U.motion Builder software, version 1.2.1 and prior, is affected by several vulnerabilities, including ones rated critical and high severity.
Advisories published by ICS-CERT and the vendor describe the flaws as SQL injection, path traversal, authentication bypass, hardcoded password, improper access control, information disclosure, and denial-of-service (DoS) issues.
An attacker can exploit the security holes to execute arbitrary code and commands, steal files, gain access to the system with high privileges, obtain information, and cause a DoS condition – in some cases even without authentication.
The security holes were reported by Micalizzi to Schneider via Zero Day Initiative (ZDI) and ICS-CERT in March 2016. Several months later, the vendor said it was expecting a patch to become available by the end of the year.
Since fixes still haven’t been released, ZDI has made public more than 20 advisories detailing each of the vulnerabilities found by the researcher in U.motion Builder. The advisories include details, such as affected file and parameter, that could allow malicious actors to exploit the flaws.
Schneider Electric has now promised to release an update by the end of August and instructed customers to apply the patch as soon as it becomes available. In the meantime, the company has advised users to place the affected software behind a firewall, ensure that the machine hosting the software is not connected to the Web, use application whitelisting and access control features, and ensure that remote access is only possible over a trusted VPN.
This is not the first time researchers have decided to disclose unpatched flaws affecting Schneider products after the vendor’s failure to release patches or provide any status updates.
In April, experts disclosed two weaknesses affecting Schneider PLCs. The vendor admitted making a mistake in that case, but it seems it was not an isolated incident.
ICS-CERT has also published a couple of advisories this week detailing critical flaws in Siemens’ Viewport for Web Office Portal, SIMATIC, SINUMERIK and SIMOTION products.
Free EternalBlue Vulnerability Scanner Released
30.6.2017 securityweek Safety
A free tool that can scan networks to discover computers that are vulnerable to the NSA-linked EternalBlue exploit is now available.
EternalBlue is a tool that hacker group ShadowBrokers allegedly stolen from the National Security Agency (NSA)-linked Equation Group. It was made public in April this year, one month after Microsoft released patches for it and for various other exploits. -
In addition to being fully ported to Metasploit, EternalBlue was one of the seven NSA exploits to have been included in a network worm dubbed EternalRocks. What made the exploit famous, however, was its use in the global WannaCry outbreak.
Weeks before WannaCry, however, a stealth Remote Access Trojan (RAT) was using the exploit to compromise systems. The cryptocurrency miner Adylkuzz was also abusing EternalBlue before WannaCry. Additionally, the UIWIX ransomware was using the exploit around the same time as WannaCry.
Over the past week, EternalBlue came into focus once again, as it started being used in yet another worldwide outbreak by the destructive NotPetya wiper.
Microsoft president and chief legal officer Brad Smith has already warned of the risks that stockpiling exploits brings along, and a bi-partisan group of lawmakers already announced the introduction of the 'Protecting Our Ability to Counter Hacking Act of 2017' -- the PATCH Act.
This, however, does little to protect companies from attacks leveraging EternalBlue, especially if they are unaware of the existence of vulnerable machines within their networks. Dubbed Eternal Blues, the newly released free tool is meant to provide a helpful hand by scanning their network for computers that can be compromised via this exploit.
According to the tool’s developer Elad Erez, Eternal Blues has been already tested on real world networks. The utility wasn’t meant to exploit the vulnerability, but only to find it and notify of its existence.
“The majority of latest WannaCry, NotPetya victims are not technical organizations and sometimes just small business who don’t have a security team, or even just an IT team to help them mitigate this. I aimed to create a simple ‘one-button’ tool that tells you one thing and one thing only – which systems are vulnerable in your network,” Erez explains.
The developer also advises admins who find vulnerable computers using his tool to apply the necessary patches as soon as possible, and also to disable SMBv1, even on patched systems, considering that the protocol was written over three decades ago. The tool, he reveals, sends anonymous usage statistics through Google Analytics, including number of scanned computers and found vulnerabilities.
Windows 10 to Get Built-in Protection Against Most Ransomware Attacks
30.6.2017 thehackernews Ransomware
Ransomware Ransomware Everywhere Not a Single Place to Hide!
But, Microsoft has a simple solution to this problem to protect millions of its users against most ransomware attacks.
Two massive ransomware attacks — WannaCry and Petya (also known as NotPetya) — in a month have caused chaos and disruption worldwide, forcing hospitals, ATMs, shipping companies, governments, airports and car companies to shut down their operations.
Most ransomware in the market, including WannaCry and NotPetya, are specifically designed to target computers running Windows operating system, which is why Microsoft has been blamed for not putting proper defensive measures in place to prevent such threats.
But not now!
In the wake of recent devastating global ransomware outbreaks, Microsoft has finally realized that its Windows operating system is deadly vulnerable to ransomware and other emerging threats that specifically targets its platform.
To tackle this serious issue, the tech giant has introduced a new anti-ransomware feature in its latest Windows 10 Insider Preview Build (16232) yesterday evening, along with several other security features.
Microsoft is planning to introduce these security features in Windows 10 Creator Update (also known as RedStone 3), which is expected to release sometime between September and October 2017.
The anti-ransomware feature, dubbed Controlled Folder Access, is part of Windows Defender that blocks unauthorized applications from making any modifications to your important files located in certain "protected" folders.
Applications on a whitelist can only access Protected folders. So you can add or remove the apps from the list. Certain applications will be whitelisted automatically, though the company doesn't specify which applications.
Once turned on, "Controlled folder access" will watch over files stored inside Protected folders and any attempt to access or modify a protected file by non-whitelisted apps will be blocked by Windows Defender, preventing most ransomware to encrypt your important files.
So, whenever an application tries to make changes to Protected files but is blacklisted by the feature, you will get a notification about the attempt.
How to Enable Controlled Folder Access, Whitelist Apps and Add or Remove Protected Folders
Here's how to enable the Controlled folder access feature:
Go to Start menu and Open the Windows Defender Security Center
Go to the Virus & Threat Protection settings section
Set the switch to On
Here's how to allow apps that you trust is being blocked by the Controlled folder access feature to access Protected folders:
Go to Start menu and Open the Windows Defender Security Center
Go to the Virus & Threat Protection settings section
Click 'Allow an app through Controlled folder access' in the Controlled folder access area
Click 'Add an allowed app' and select the app you want to allow
Windows library folders like Documents, Pictures, Movies, and Desktop are designated as being compulsorily "protected" by default, which can not be removed.
However, users can add or remove their personal folders to the list of protected folders. Here's how to add folders to Protected folders list:
Go to Start menu and Open the Windows Defender Security Center
Go to the Virus & Threat Protection settings section
Click 'Protected folders' in the Controlled folder access area
Enter the full path of the folder you want to monitor
Users can also enter network shares and mapped drives, but environment variables and wildcards are not supported at this moment.
Other Security Feature Introduced in Windows 10 Insider Program
With the release of Windows 10 Insider Preview Build 16232, Windows Defender Application Guard (WDAG) for Edge — a new system for running Microsoft Edge in a special virtual machine in order to protect the OS from browser-based flaws — also received improvements in usability.
Windows 10 Insider Preview Build also comes with support for Microsoft Edge data persistence when using WDAG.
"Once enabled, data such as your favorites, cookies, and saved passwords will be persisted across Application Guard sessions," Microsoft explains.
"The persisted data will be not be shared or surfaced on the host, but it will be available for future Microsoft Edge in Application Guard sessions."
Another new security feature called Exploit Protection has been introduced in Windows 10 16232, which blocks cyber attacks even when security patches are not available for them, which means the feature will be useful particularly in the case of zero-day vulnerabilities.
Exploit Protection works without Microsoft's Windows Defender Antivirus tool, but you can find the feature in Windows Defender Security Center → App & Browser Control → Exploit Protection.
In the Fall Creators Update for Windows 10, Microsoft has also planned to use a broad range of data from Redmond's cloud services, including Azure, Endpoint, and Office, to create an AI-driven Antivirus (Advanced Threat Protection) that can pick up on malware behavior and protect other PCs running the operating system.
Also, we reported about Microsoft's plan to build its EMET or Enhanced Mitigation Experience Toolkit into the kernel of the upcoming Windows 10 to boost the security of your PC against complex threats such as zero-day vulnerabilities.
Also, the company is planning to remove the SMBv1 (Server Message Block version 1) — a 30-year-old file sharing protocol which came to light last month after the devastating WannaCry outbreak — from the upcoming Windows 10 (1709) Redstone 3 Update.
Besides this, some other changes and improvements have also been introduced with the release, along with patches for several known issues.
Cisco Warns of Serious Flaws in IOS Software
30.6.2017 securityweek Vulnerebility
Cisco has warned users that devices running the company’s IOS or IOS XE software are affected by several high severity vulnerabilities that can be exploited for remote code execution and denial-of-service (DoS) attacks.
There are a total of nine flaws affecting the Simple Network Management Protocol (SNMP) component of IOS and IOS XE software. Patches have yet to be made available by Cisco, but the networking giant has shared some workarounds.
An authenticated attacker who knows the SNMP read-only community string of the targeted system could execute code or cause the device to reload by sending a specially crafted SNMP packet via IPv4 or IPv6. If the attacker can execute code, they may be able to take full control of the affected system.
The vulnerabilities affect IOS devices running any version of SNMP if they are configured with one of nine management information bases (MIBs), which allow organizations to manage devices such as routers and switches in a network.
Cisco said it found these security holes during internal testing, but the company warned customers that individuals outside the company know about the vulnerabilities, which increases the chances of exploitation.
Vulnerabilities in Cisco Prime Infrastructure
Last week, Cisco informed customers of several high and medium severity vulnerabilities found by researchers at SEC Consult in its Prime Infrastructure and Evolved Programmable Network Manager products.
The flaws include SQL injection, XML external entity (XXE), local file disclosure and cross-site scripting (XSS) weaknesses that can be exploited remotely by authenticated or unauthenticated attackers. An advisory published by SEC Consult includes proof-of-concept (PoC) code for each of the vulnerabilities.
While Cisco was informed about these issues in November 2016, the company postponed the release of patches several times. Fixes were finally made available last week.
Cisco IOS Software is affected by RCE flaws that could allow full hack of the devices
30.6.2017 securityaffairs Vulnerebility
Experts at CISCO discovered severe remote code execution vulnerabilities in Cisco IOS Software while conducting internal testing.
Cisco warned users of serious vulnerabilities in IOS software that can be exploited by authenticated, remote attackers for code execution and denial-of-service (DoS) attacks. Experts at CISCO discovered the vulnerabilities while conducting internal testing.
“The Simple Network Management Protocol (SNMP) subsystem of Cisco IOS and IOS XE Software contains multiple vulnerabilities that could allow an authenticated, remote attacker to remotely execute code on an affected system or cause an affected system to reload. An attacker could exploit these vulnerabilities by sending a crafted SNMP packet to an affected system via IPv4 or IPv6. Only traffic directed to an affected system can be used to exploit these vulnerabilities.” states the advisory published by CISCO.
The experts warned of nine flaws affecting the Simple Network Management Protocol (SNMP) component of IOS and IOS XE software.
The flaws are due to a buffer overflow condition in the SNMP subsystem, all versions of SNMP – Versions 1, 2c, and 3 are affected.
As reported by the advisory, an authenticated attacker who knows the SNMP read-only community string of a target system could remotely execute code or cause the device to reload by sending a specially crafted SNMP packet via IPv4 or IPv6.
“To exploit these vulnerabilities via SNMP Version 2c or earlier, the attacker must know the SNMP read-only community string for the affected system. To exploit these vulnerabilities via SNMP Version 3, the attacker must have user credentials for the affected system. A successful exploit could allow the attacker to execute arbitrary code and obtain full control of the affected system or cause the affected system to reload.” continues the advisory.
The attack is very dangerous because hackers could obtain full control of vulnerable devices and the worst news is that CISCO warned customers that attackers in the wild know about the vulnerabilities and can exploit them in any moment.
Devices configured with any of the following MIBs are vulnerable:
ADSL-LINE-MIB
ALPS-MIB
CISCO-ADSL-DMT-LINE-MIB
CISCO-BSTUN-MIB
CISCO-MAC-AUTH-BYPASS-MIB
CISCO-SLB-EXT-MIB
CISCO-VOICE-DNIS-MIB
CISCO-VOICE-NUMBER-EXPANSION-MIB
TN3270E-RT-MIB
Waiting for a fix, users can apply workarounds suggested by the company.
NotPetya – Ukraine secret service announces a joint investigation with Europol, FBI, and NCA
30.6.2017 securityaffairs Ransomware
Ukraine secret service announces joint investigation with Europol, FBI, and NCA to attribute the recent Notpetya massive attack.
While security experts are investigating real motivation behind the massive NotPetya attack, Ukrainian authorities called for support in the investigation from European and US intelligence and law enforcement agencies.
The country’s security service SBU announced the international co-operation Europol, the FBI, and England’s National Crime Agency to investigate the incident and identify offenders.
Ukraine is the country with the largest number of NotPetya infections, a large number of critical infrastructure was affected in the attack.
According to the analysis conducted by Kaspersky, more than 50% of businesses targeted by NotPetya are industrial companies.

The SBU considers the NotPetya attack an “act of cyberterrorism”, the joint investigation aims to attribute the attack to a specific threat actor.
“The SBU specialists in cooperation with the experts of FBI USA, NCA of Great Britain, Europol and also leading cyber security institutions, conduct coordinated joint events on localization of damaging software PetyaA distribution, final definition of methods of this act of cyberterrorism, establishing of the attack sources, its executors, organizers and paymasters.” states the announcement from the SBU. “Currently the mechanisms of virus program distribution, its activation and operation algorithms are already identified. At the same time the work on the search of possibilities for data decoding and groundwork of guidelines for prevention of virus distribution, neutralization of other negative consequences of this emergency is in process.”
The analysis conducted by many security firms suggest that Ukraine was a possible target of the attack.
According to experts from Cisco Talos Intelligence and Microsoft, the infection started in Ukraine, where local firm named MeDoc was targeted by attackers. Researchers believe that hackers infected software update to a Ukrainian tax accounting system called MeDoc, but MeDoc denies the allegations.
“At the time of updating the program, the system could not be infected with the virus directly from the update file,” translated version of MeDoc post reads. “We can argue that users of the MEDoc system can not infect their PC with viruses at the time of updating the program.”
However, several security researchers and even Microsoft agreed with Talo’s finding, saying MeDoc was breached and the virus was spread via updates.
“Initial infection appears to involve a software supply-chain threat involving the Ukrainian company M.E.Doc, which develops tax accounting software, MEDoc. Although this vector was speculated at length by news media and security researchers—including Ukraine’s own Cyber Police—there was only circumstantial evidence for this vector. Microsoft now has evidence that a few active infections of the ransomware initially started from the legitimate MEDoc updater process. ” states Microsoft.
Let me close with interesting hints from the investigation conducted by F-Secure:
“How does it compare to WannaCry (which also used these exploits)?
WannaCry clearly picked these exploits up after the Shadow Brokers dumped them into the public domain in April. Also, WannaCry didn’t do the best job at implementing these exploits correctly.
By comparison, this “Petya” looks well-implemented, and seems to have seen plenty of testing. It’s fully-baked.”
“But are you still skeptical about this malware being “nation state”?”
“Less and less so. We don’t think any current attribution is rock solid (attribution never really is). We feel this is definitely worth deeper investigation. And more pizza.
We’ve changed our minds on some of our earlier conclusions. Please note this if you’re reading any previous F-Secure analysis. And, of course, this is subject to further revision, as new facts come to light.
But the great mystery behind the attack is why the author of the malware failed to add proper decryption functionality to the MBR lock screen. It is not clear if it is an intentional choice or a clamorous mistake.
How to stop Petya?
When a computer is infected with Petya it will automatically attempt to reboot in order to encrypt the hard drive’s Master Boot Record. To block the malware it is necessary to halt the reboot and keep the PC running. Another way to immunize the machine consists of creating a read-only file “perfc” and placing it inside the Windows directory.
“If you’re lucky, Petya worm might see that file and will not encrypt your machine, BUT, it will continue to spread to other machines on the same network.” reads the analysis published PureVPN.
Authentication Bypass Flaw Patched in BIND, Knot DNS
30.6.2017 securityweek Vulnerebility
The developers of the BIND and Knot DNS software have released updates to patch a potentially serious vulnerability that can be exploited to bypass authentication mechanisms.
The flaw, discovered by Clément Berthaux of Synacktiv, is related to Transaction SIGnature (TSIG), an authentication protocol used by the Domain Name System (DNS). The protocol is mainly used to authenticate dynamic DNS updates and zone operations.
An attacker who is able to communicate with an authoritative DNS server and has knowledge of a valid key name can exploit the security hole to bypass TSIG authentication and carry out unauthorized zone transfers or updates.
“This issue is due to the fact that when the server receives a request which TSIG timestamp is out of the time window, it still signs its answer, using the provided digest as prefix even though this digest is invalid and has an incorrect size. This allow an attacker to forge the signature of a valid request, hence bypassing the TSIG authentication,” Berthaux wrote in an advisory.
DNS zone transfer is the process in which a DNS server passes a copy of its database (i.e. zone) to another DNS server. Obtaining a copy of zone records can be useful for an attacker as they may contain information that can be leveraged for DNS spoofing attacks.
The Internet Systems Consortium (ISC) tracks this issue as two separate vulnerabilities – one medium severity flaw that allows unauthorized zone transfers (CVE-2017-3142), and a high severity flaw that can be exploited for unauthorized dynamic updates (CVE-2017-3143).
ISC addressed the problem this week with the release of BIND 9.9.10-P2, 9.10.5-P2 and 9.11.1-P2. Knot DNS patched the vulnerability with the release of versions 2.5.2 and 2.4.5 last week.
TSIG is also supported by, among others, PowerDNS and NSD, but the developers of these DNS servers have not published any advisories to indicate whether or not their products are affected.
8tracks data leak exposed 18 million user accounts
30.6.2017 securityaffairs Crime
The Music streaming service 8tracks suffered a major data leak, 18 million user accounts have been exposed and is available online.
Music streaming service 8tracks has been affected by a major data leak that exposed ‘millions’ of customer details.
The leak seems to have been caused by a staffer that erroneously exposed 18 million user accounts. The employee left some markers on his GitHub account that breached by hackers.
The lack of security for the GitHub repository seems to be the root cause of the breach, the employee wasn’t using two-factor authentication. The staffer was keeping backups of database tables in his repository.
“We received credible reports today that a copy of our user database has been leaked, including the email addresses and encrypted passwords of only those 8tracks users who signed up using email. If you signed up via Google or Facebook authentication, then your password is not affected by this leak. 8tracks does not store passwords in a plain text format, but rather uses one-way hashes to ensure they remain difficult to access. These password hashes can only be decrypted using brute force attacks, which are expensive and time-consuming, even for one password.” states the breach notification published by the company,
“We have found what we believe to be the method of the attack and taken precautions to ensure our databases are secure. 8tracks does not store sensitive customer data such as credit card numbers, phone numbers, or street addresses.”

According to the post published by the Music streaming service, 8tracks passwords hashed and salted, users that signed up to 8Tracks via Google or Facebook aren’t affected.
8Tracks confirmed to have identified an unauthorised attempt at a password change and investigation is still ongoing.
“We do not believe this breach involved access to database or production servers, which are secured by public/private SSH-key pairs. However, it did allow access to a system containing a backup of database tables, including this user data.” continues the company.”We have secured the account in question, changed passwords for our storage systems, and added access logging to our backup system. We are auditing all our security practices and have already taken steps to enforce 2-step authentication on Github, to limit access to repositories, and to improve our password encryption.”
As usual, let me recommend to change your password on 8tracks and any websites on which you used the same login credentials.
Microsoft issued Security fix for important flaw in Azure Active Directory Connect
30.6.2017 securityaffairs Vulnerebility
Microsoft is warning sysadmins to check their Azure Active Directory Connect installs and patch them against an important Privilege Escalation flaw.
Microsoft fixed an important privilege escalation vulnerability in Azure Active Directory (AD) Connect, tracked as CVE-2017-8613, that can be exploited by attackers to hijack the accounts of privileged users.
Azure Active Directory Connect allows organizations to integrate their on-premises identity infrastructure with Azure AD. The flaw resides in the Azure AD Connect feature “password writeback,” which allows users to easily reset their on-premises passwords by configuring Azure AD to write passwords back to the on-premises AD.
Microsoft warned of possible misconfiguration in the password writeback feature in the setup phase that could be abused by a malicious Azure AD administrator. A malicious Azure Active Directive administrator can set the password of an on-premises AD account belonging to a privileged user to a specific value in order to take over the account.
“Password writeback is a component of Azure AD Connect. It allows users to configure Azure AD to write passwords back to their on-premises Active Directory. It provides a convenient cloud-based way for users to reset their on-premises passwords wherever they are.” states the Microsoft security advisory.
“To enable Password writeback, Azure AD Connect must be granted Reset Password permission over the on-premises AD user accounts. When setting up the permission, an on-premises AD Administrator may have inadvertently granted Azure AD Connect with Reset Password permission over on-premises AD privileged accounts (including Enterprise and Domain Administrator accounts),” Microsoft explained in its advisory. “This configuration is not recommended because it allows a malicious Azure AD Administrator to reset the password of an arbitrary on-premises AD user privileged account to a known password value using Password writeback. This in turn allows the malicious Azure AD Administrator to gain privileged access to the customer’s on-premises AD.”

Microsoft solved the privilege escalation flaw by preventing password resets to privileged on-premises accounts.
Microsoft users can update their version to Azure Active Directory Connect 1.1.553.0 version. Users can also mitigate the issue by following the instructions provided by Microsoft.
Útočníci se dostanou do PC přes Skype. Využijí kritickou chybu
30.6.2017 Novinky/Bezpečnost Zranitelnosti
Český Národní bezpečnostní tým CSIRT.CZ varoval před nově objevenou zranitelností, kterou obsahuje populární komunikační program Skype. Oprava je naštěstí již k dispozici, a tak by uživatelé s její instalací neměli otálet.
„Chyba přetečení zásobníku umožňuje útočníkům vzdáleně rozbít aplikaci s neočekávanou výjimkou,“ vysvětlil technickou stránku věci Pavel Bašta, bezpečnostní analytik CSIRT.CZ, který je provozován sdružením CZ.NIC.
Podle něj jsou rizika nově objevené trhliny obrovská. „Následně se dá útok využít ke spuštění škodlivého kódu, a to bez jakékoliv interakce účtu oběti,“ doplnil Bašta.
To jinými slovy znamená, že chybu mohou počítačoví piráti zneužít k tomu, aby propašovali prakticky libovolného záškodníka na cizí počítač. S jeho pomocí pak budou schopni přistupovat k uloženým datům, odposlouchávat internetovou komunikaci či počítač úplně zotročit.
Útočníci mohou chybu snadno zneužít
Trhlinu ve Skypu objevil jako první bezpečnostní analytik Benjamin Kunz Mejri, který na ni upozornil přímo tvůrce softwaru – tedy společnost Microsoft. Právě díky němu bylo možné vydat opravu ještě dříve, než ji začali zneužívat počítačoví piráti.
Tím, že jsou detaily o zranitelnosti nyní veřejně známé, mohou ji snadno zneužít počítačoví piráti. S instalací opravy, respektive novější verze Skypu, by tak uživatelé rozhodně neměli otálet.
Stáhnout nejnovější aktualizaci je možné přímo z tohoto oblíbeného komunikačního programu. Stačí kliknout na nabídku „Nápověda“, kde se následně ukrývá volba „Vyhledat aktualizace“.
Microsoft reaguje na vlnu ransomwaru. Ve Windows 10 půjde chránit důležité soubory před zašifrováním
30.6.2017 Živě.cz Zabezpečení
Microsoft reaguje na vlnu ransomwaru. Ve Windows 10 půjde chránit důležité soubory před zašifrovánímMicrosoft reaguje na vlnu ransomwaru. Ve Windows 10 půjde chránit důležité soubory před zašifrovánímMicrosoft reaguje na vlnu ransomwaru. Ve Windows 10 půjde chránit důležité soubory před zašifrovánímNová možnost bude integrována do aplikace Windows Defender.Na podzim ji najdeme pod položkou Ochrana před viry a hrozbami.
V rámci podzimní aktualizace Fall Creator Update dorazí do Windows 10 funkce, která dostane název Controlled folder access. Ten sám o sobě popisuje její účel – řídit přístup k důležitým složkám a souborům.
Vše bude fungovat na jednoduchém principu, kdy výchozí systémové složky jako jsou Dokumenty, Obrázky, Videa nebo Plocha budou tzv. chráněnými složkami. Pokud se neznámá aplikace pokusí změnit jejich obsah, bude takový pokus zablokován a uživatel na to bude upozorněn.
Až po odsouhlasení budou moci být změny samotnou aplikací provedeny. Mezi takto chráněné složky půjde samozřejmě přidat i svoje vlastní umístění, a to včetně síťových jednotek. To se bude hodit při ochraně záloh, které by mohly být rovněž při útoku ransomwaru zašifrovány.
V nastavení půjde přidat bezpečné aplikace, které budou moci vždy přistupovat k souborům v chráněných složkách bez zobrazení výstrahy.
Funkce je aktuálně dostupná v rámci Insider Preview a sestavení Windows 10 16232. Do běžné verze Windows se dostane v rámci velké aktualizace, která vyjde v září.
Vyděračský virus byl jen zástěrka. Hlavním cílem byla ukrajinská infrastruktura
30.6.2017 Novinky/Bezpečnost Viry
Hlavním cílem rozsáhlého kybernetického útoku, který v úterý zasáhl kromě ukrajinských a ruských podniků i západní Evropu a Spojené státy, byla ukrajinská infrastruktura. Agentuře Reuters to řekl vysoký představitel ukrajinské policie. Hackeři prý pravděpodobně instalovali škodlivý malware, který využijí pro budoucí sabotáže.
Výpadek počítačového systému v důsledku hackerského útoku zaznamenaly soukromé i vládní instituce přibližně v 60 zemích po celém světě. Nejvíce však piráti udeřili na Ukrajině, kde se podle antivirové společnosti Eset nacházelo 75 procent zasažených počítačů. Hackeři za odšifrování počítačové sítě požadovali 300 dolarů (zhruba 7000 Kč).
Útočníci v současnosti nicméně nevydělají na škodlivém kódu Win32/Diskcoder.C Trojan ani korunu. E-mailová schránka, prostřednictvím které komunikovali se svými obětmi, je totiž zablokovaná. Útočníci tak nemají svým obětem jak napsat, že mají zaplatit výkupné.
Je zodpovědné Rusko?
Podle ukrajinských politiků za počítačovými útoky pirátů stojí Rusko, mluvčí Kremlu Dmitrij Peskov však obvinění označil za nepodložená. Kyjev obviňoval Moskvu i z předešlých dvou kybernetických zásahů na Ukrajině.

Uživatelé napadení virem místo startu operačního systému uvidí tuto zprávu.
FOTO: Avast
Podle bezpečnostních expertů cílem útoku bylo instalovat do ukrajinských vládních i komerčních počítačů takzvaný malware, škodlivý program sloužící k poškození nebo vniknutí do počítačového systému. Spíše než pro vydírání pak hackeři využijí program pro budoucí sabotáže, tvrdí odborníci.
Podle zdroje agentury Reuters v ukrajinské policii jsou požadavky na výkupné pouze zástěrkou. „Vzhledem k tomu, že byl virus modifikován tak, aby zasáhl všechna data a zabránil jejich dešifrování, pravděpodobnost instalace nového malwaru je velmi vysoká," řekl agentuře.
Oběti jsou i v Rusku
Předpoklady policie potvrzuje i kyjevská kybernetická výzkumná firma Information Systems Security Partners (ISSP). Podle jejich představitelů peníze nejspíš nebyly hlavním cílem hackerů vzhledem k tomu, že výkupné zaplatilo jen několik lidí.
„Téměř ve všech institucích, jejichž sítě byly zasaženy, ne všechny počítače skončily v režimu offline," řekl šéf ISSP Oleh Derevjanko. „Snažíme se pochopit, co mohli (hackeři) v těchto počítačích zanechat, když je zasáhli," dodal.
V Rusku se terčem kybernetického útoku stalo osm desítek společností včetně ropné jedničky Rosněfť. Ukrajina hlásila výpadky IT v bankovním sektoru, energetických i rozvodních sítích a poštovních společnostech.
Virus stále představuje hrozbu
Ať už pochází virus Win32/Diskcoder.C Trojan odkudkoliv, na napadeném stroji dokáže udělat pěknou neplechu. A to dokonce větší než drtivá většina dalších vyděračských virů. Ty totiž často potřebují k zašifrování dat na pevném disku poměrně dost času, klidně i několik hodin. Během toho může jejich práci zachytit antivirový program a zablokovat je ještě dříve, než v počítači nadělají nějakou větší škodu.
Nově objevená hrozba však funguje jiným způsobem. Na disku nezašifruje všechna data, ale pouze tzv. MBR (Master Boot Record). Jde o hlavní spouštěcí záznam, díky kterému se v podstatě spouští celý operační systém. K zašifrovanému záznamu pak počítač nemá přístup a místo Windows spustí jen hlášku o nutnosti zaplatit výkupné.
Na zašifrování MBR nepotřebuje nový vyděračský virus několik hodin, stačí mu pouze pár vteřin. Antiviry tak prakticky nemají šanci škodlivý kód zachytit. Hned po prvním restartu je pak problém na světě.
UK.gov accidental data leak. Users’ details left publicly accessible on a third-party site
30.6.2017 Securityaffairs BigBrothers
UK.gov leaves data dashboard users’ details on publicly accessible on a third-party system. Users are urge to reset their password.
Are you a user of the UK Government website UK.gov? Change your password now!
Users of the government’s data dashboard have been notified that their information was accidentally made public so they urge to change their passwords.
The news was reported by The Register after it has seen an email that confirmed that a file containing names, emails and hashed passwords for the data.gov.uk site was left publicly accessible on a third-party system.
According to the email, users registered on gov.uk on or before 20 June 2015 have been affected.
“A recent routine security review discovered a file containing some users’ names, emails and hashed passwords was publicly accessible on a third-party system,” reads the email from the Government Digital Service.
The Government Digital Service confirmed that it immediately adopted the necessary actions to remove data from the public domain. The GDS also reported the data breach to data protection watchdog Information Commissioner’s Office.

The UK Government suggests users reset their password for gov.uk and for any other website where they used the same login credentials.
“There is no evidence of misuse of anyone’s credentials,” states the email. “Resetting your password is purely a precautionary measure.”
The incident could have a severe impact on a large portion of Britons considering that the website Data.gov.uk was visited more than 200,000 times each month in 2017.
Pro-ISIS Hacking Group Continues Defacement Campaign
30.6.2017 securityweek CyberCrime
Pro-ISIS hacking group Team System DZ is continuing its website defacement campaign. Over last weekend several websites in Ohio and Maryland were forced to shut down after messages threatening President Trump and supporting Islamic State were posted on the sites.
The campaign has continued through the week, often targeting education and local government authorities. On Tuesday, a Los Angeles County government website belonging to the Board of Supervisors was defaced with the same message as that posted to the website of Ohio Gov. John Kasich and a Howard County, Maryland website: "You will be held accountable Trump, you and all your people for every drop of blood flowing in Muslim countries."
Elsewhere, the Ventura County Star reported yesterday, "The websites of numerous school districts in Ventura County went offline Wednesday morning after hackers targeted certain systems operated by the Ventura County Office of Education." Two sites were affected, but a further five sites were taken down by the authorities as a precaution.
Exact details of the hack are not clear, only that visitors were redirected "to a group's webpage where pro-ISIS views were posted." Team System DZ is not named, but the report adds, "The group behind the Ventura County hacking also is suspected of targeting the website of Ohio Gov. John Kasich on Sunday as well as a government website for Howard County in Maryland."
The campaign is not limited to the US. Yesterday, the Department of Basic Education in South Africa announced, "A short while ago we discovered that the Department's website has been hacked. The people who breached the website have since posted gory pictures of decapitated corpses, some of whom are children."
The authority then posted the hackers' message, apparently in full: "Hacked by Team System DZ. A message to the government, the American people and the rest of the world. Is this the humanity that you claim, or is life irrelevant to Muslims? Do not imagine that these acts against Muslims will pass you and we will forget what you did to the Arab and Muslim peoples all over the world. I love Islamic State."
At the time of writing this report, the site in question (www.education.gov.za) is still down.
On Tuesday, Ars Technica claimed that the initial weekend hacks had a common factor: "they were running on an outdated version of the DotNetNuke (DNN) content management platform." The implication is that if the hacked sites had updated their software they would not have been so easily breached. DNN patched the vulnerability in May 2016.
It is not clear whether all .the hacked sites used a similar outdated platform, but it is quite possible. While updating website software to the latest version is always good advice, at this moment it would seem an imperative for all DNN users.
Websites Increasingly Using Security Technologies: Mozilla
30.6.2017 securityweek Security
An analysis conducted using Mozilla’s Observatory tool has showed that modern security technologies are increasingly used by Alexa top 1 million websites.
Observatory, a free and open source tool developed by Mozilla Information Security Engineer April King, was announced in August 2016. The tool is designed to allow website developers and administrators to determine if they are using available security technologies at their full potential.
Observatory grades websites based on their use of security technologies such as Content Security Policy (CSP), Contribute.json, cookies, cross-origin resource sharing (CORS), HTTP Public Key Pinning (HPKP), HTTP Strict Transport Security (HSTS), redirections, subresource integrity, and X-Content-Type-Options, X-Frame-Options and X-XSS-Protection headers.
When the tool was first launched, King pointed out that usage rates of modern defensive security technologies were very low. A few months later, Observatory showed some improvements and the most recent data also shows an upward trend in the adoption of these technologies.
For example, the number of Alexa top 1 million websites using CSP has increased by 125 percent since April 2016. The number of sites using HTTPS has also increased by 36 percent, or roughly 119,000 websites, over the same period.
King pointed out that the increasing use of CSP is surprising, especially since the technology is not easy to implement on both new and existing websites.
According to King, more than 50,000 websites used the Mozilla Observatory to assess their level of security and over 2,500 of them have improved from a failing grade to an A or A+. Over 27,000 sites previously rated F got better grades in the past 8 months.
However, while there have been significant improvements, more than 93 percent of sites scanned using Observatory still received an F as of June 2017. Only less than one percent of the world’s most popular websites received an A+, A or B grade.
Group Pushes For Industrial Control Systems (ICS) Security Testing Standards
30.6.2017 securityweek ICS
There is a pressing need for technical assurance standards for industrial control systems (ICS). This is the conclusion and recommendation of a new paper from CREST (a leading UK accreditation body), and is supported by the UK National Cyber Security Centre (NCSC). That need just got stronger if, as now suspected, NotPetya and perhaps WannaCry, were cyber weapons tests. An encryption/wiper inside the critical infrastructure could have dire effects.
The danger is discussed in the stated rationale for the paper (PDF) titled 'Industrial Control Systems - Technical Security Assurance Position Paper'. "The increased connectivity of ICS environments and their use of conventional IT infrastructure components and protocols has enlarged the attack surface that can be exploited by ever more sophisticated cyber security attackers, such as state-sponsored attacks, organised cybercrime and extremist groups."
The problem for ICS is that while the attack surface is growing, the resistance against implementing new security controls that might disturb operational continuity remains high. "Securing ICS environments in many organisations is technically demanding and difficult to undertake (obscure and often obsolete technology, limited resources, high degree of sensitivity)," notes the report. Although there are several published frameworks for securing ICS environments -- including NIST SP.800-82r2, CPNI Security for Industrial Control Systems, IEC 62443, and ISA99 -- there is a lack of mandatory standards on how to test and assure that security.
The report notes that technical security testing specialists consider "inadequate management support (eg. lack of budget, poor resourcing, low risk appetite) as the most important factor affecting the ability to secure ICS environments and undertake technical security testing activities." Other difficulties include the evaporation of the air gap between IT and OT as a viable security control; cultural barriers and a resistance to change; the shortage of skilled resources; and a high degree of technical complexity and obscurity.
The effect of a difficult testing environment and a lack of management drive means that ICS environment owners and operators have no objective way of knowing whether cyber risk is being adequately managed; and at present there is no definitive standard for testing ICS environments that is mandated by regulatory bodies. "Frequent technical security assurance provides stakeholders, both inside and outside the organisation, with objective fact-based information on what remediation is required, why it is required and how it should be applied," says CREST. The purpose of this paper is to lay the groundwork for developing such standards.
"ICS environment owners require assurances that risk is being identified, assessed and evaluated," says Ian Glover, president of CREST. "Above all else they need to know that there are appropriate measures in place to manage and mitigate risk. Research on the project," he continued, "has helped to identify the high-level characteristics of a practical technical security testing approach and organisations should consider how this could add value and protection. It is clear that ICS environments are more sensitive than conventional IT environments and any penetration testing of systems needs to be planned and undertaken with a high degree of trust, skill and caution."
CREST's research confirmed that the overall context for all technical security testing should be provided by ICS environment owners (for example, all technical security testing should be business-led) and that the approach should be standards based. From this it developed a six-point standards-based testing process: define and agree scope; assess risks; undertake discovery; develop test plan; conduct technical security tests; and analyze and report test results.
The scoping process requires that the tests be aligned to the strategic, process and system requirements of the organization. "It is important," says CREST, "to be able to make this connection for all stakeholders and ensure there is a good understanding of the strategic, process and systems context as risk identified in ICS environments will have relevance at all three levels in the organisation."
Risk assessment explores the main threats and vulnerabilities of the ICS environment and determines the key risks and likely risk scenarios to be tested. Threat intelligence, says the paper, can "come from a wide variety of sources including the dark web, inside industry sources, open source monitoring, government sources and hacking forums."
The discovery step is designed to determine the specific devices that make up the infrastructure, systems and services in the ICS environment.
Developing a test plan requires a schedule of carefully constructed offline and online tests that are designed to assess the key risks of the ICS environment. There are, suggests CREST, proven test methods that can be used. "While as a general rule online technical security testing in ICS environments should be used with caution," says the report, "there are a variety of measures that can be taken to ensure services are aligned with the needs of the client and the risk of disruption is minimised."
Conducting the technical security tests involves a combination of offline and online tests that help to assess the ICS environment in a progressive check-test-check manner. "Research on the project has shown that Red Teaming is regarded by technical security testers working in ICS environments as a particularly valuable testing technique," notes the paper.
The final step, analysis and reporting, should document and report test results that are aligned to the business objectives and scope agreed with the ICS environment owner.
"This Position Paper," concludes CREST, "has identified a variety of actions that can be taken to help improve the uptake and use of technical security testing in ICS environments but of fundamental importance is the need to develop a standard for conducting technical security testing and the certification of organisations capable of providing technical testing services against this standard." It urges that work should start on developing its proposals into a "standard to help provide assurance that cyber risks are being managed in ICS environments."
It has the backing of the UK National Cyber Security Centre (NCSC). "We believe this paper provides a valuable contribution to the current thinking on this challenging topic and we look forward to working with CREST, as well as ICS operators and the cyber security industry."
Google přestane skenovat Gmailové účty
30.6.2017 SecurityWorld Kyber
Google potvrdil, že přestane skenovat emailové účty svých uživatelům za účelem zobrazování cílené reklamy.
V svém blogovém příspěvku Diane Greenová, viceprezidentka pro Google Cloud, uvádí, že v rámci G Suite se už Gmail pro personalizaci reklamy nepoužívá, přičemž bezplatný Gmail by měl být z tohoto systému vyňat v průběhu roku.
Pro zajímavost dodejme, že počet firemních uživatelů G Suite se za poslední rok víc než zdvojnásobil, za službu v současnosti platí víc než tři miliony společností.
„Tohle rozhodnutí uvádí Gmailové reklamy do souladu s tím, jak personalizujeme reklamy pro ostatní produkty Googlu,“ uvádí Greenová.
„Reklamy jsou zobrazovány na základě uživatelského nastavení, které mohou uživatelé kdykoliv změnit, včetně vypnutí personalizace reklamy. G Suite bude nadále bez reklam.“
Greenová také dodává, že žádná jiná e-mailová služba své uživatelé nechrání před spamem, phishingem a útoky hackerů tak úspěšně jako Gmail, který má v současnosti skoro jednu a čtvrt miliardy uživatelů.
„Zobrazení možných odpovědí činí skrz funkce jako Smart Reply práci v Gmailu jednodušší, rychlejší a efektivnější. Další doplňky umožní například platby či fakturaci přímo v Gmailu, což bude další převrat v tom, co můžete s emailem dělat,“ píše ve svém příspěvku dále Greenová.
„Uživatelé G Suite i běžní uživatelé Gmailu mohou být ujištění, že soukromí a bezpečnost pro nás bude při pokračující inovaci nadále na prvním místě. Informace sdílené s Googlem zůstávají nastavitelné na myaccount.google.com.“
Tento týden ve světě neútočil ransomware, ale nebezpečný wiper. Měl jediný cíl: Nadobro zničit co nejvíce dat
29.6.2017 Živě.cz Viry
Nejpostiženější zemí se stala Ukrajina, kde malware vyřadil například supermarkety. Odnesly to také banky a jejich bankomaty. Útočníci si zatím přišli asi na 9 200 dolarů.Takto se Petya hlásí po restartování systému. Pokud tuto obrazovku spatříte, počítač ihned vypněte.Tento týden ve světě neútočil ransomware, ale nebezpečný wiper. Měl jediný cíl: Nadobro zničit co nejvíce dat
Zprvu to vypadalo jako cílený kybernetický útok na Ukrajinu, po napadení dalších zemí se však začalo psát o další vlně ransomwaru Petya v jeho nové modifikaci. V podstatě se tedy mělo jednat o podobnou smršť, která před týdny zasáhla svět v souvislosti s vlnou WannaCry.
Včerejší vlna ransomwaru zasáhla i Česko. Petya je zákeřnější než WannaCry
Společnost Kaspersky Lab nicméně přišla s poněkud odlišným zjištěním. Před pár dny neútočil vyděračský ransowmare, ale wiper, který se za ransowmare pouze vydával. Stručně řečeno, podle inženýru, kteří se o svém zjištění rozepsali na webu Securelist, byl malware navržený takovým způsobem, že bylo prakticky nemožné dešifrovat data. A to i v případě, že by některá z obětí opravdu poslala výkupné.
V čem byl konkrétně problém? Když ransomware zašifruje počítač, vytvoří pro něj jedinečný identifikátor, který útočníkovi poslouží k tomu, aby na jeho základě mohl oběti vygenerovat dešifrovací klíč, který počítač uvede opět do provozu.
Klepněte pro větší obrázek
Osobní klíč, který měla oběť zaslat e-mailem útočníkovi. obratem by získala dešifrovací klíč. Podle Kaspersky Lab se však jedná pouze o shluk náhodných znaků.
Když se však analytici z Kaspersky Lab podívali do nitra nového ransomwaru, zjistili, že funkce, která má generovat onen jedinečný klíč odpovídající zašifrovaným datům na počítači oběti, ve skutečnosti generuje jen náhodný balast – náhodné znaky.
Funkce pro generování osobního klíče ve skutečnosti generuje jen sled náhodných znaků
Suma sumárum, je to vlastně hoax na druhou. Vypadá to jako ransomware, šifruje to soubory jako ransomware, žádá to výkupné jako ransomware… Ale zašifrovaná data už nikdy nedešifruje, protože chybí klíč.
Aby toho nebylo málo, jak už jsme psali včera, útočníci chtěli komunikovat s obětmi skrze poštovní schránku na službě Posteo, kterou však krátce po útoku provozovatel zablokoval.
Malware, který při šíření sítí zneužíval stejných zranitelností jako WannaCry, měl tedy podle Kaspersky Lab jediný cíl: Nadobro zničit co nejvíce dat a nenávratně poškodit co nejvíce obětí.
Original Author of Petya Ransomware is Back & He Wants to Help NotPetya Victims
29.6.2017 thehackernews Ransomware
The author of original Petya ransomware is back.
After a long 6 months of silence, the author of now infamous Petya ransomware appeared on Twitter today to help victims unlock their files encrypted by a new version of Petya, also known as NotPetya.
"We're back having a look in NotPetya," tweeted Janus, a name Petya creator previously chose for himself from a James Bond villain. "Maybe it's crackable with our privkey. Please upload the first 1MB of an infected device, that would help."
This statement made by Petya author suggests he may have held on a master decryption key, which if worked for the new variant of Petya infected files, victims would be able to decrypt their files locked in the recent cyber outcry.
Janus sold Petya as a Ransomware-as-a-Service (RaaS) to other hackers in March 2016, and like any regular ransomware, original Petya was designed to lock victim's computer, then return them when a ransom is paid.
This means anyone could launch the Petya ransomware attack with just the click of a button, encrypt anyone's system and demand a ransom to unlock it. If the victim pays, Janus gets a cut of the payment. But in December, he went silent.
However, On Tuesday, computer systems of the nation's critical infrastructure and corporates in Ukraine and 64 other countries were struck by a global cyber attack, which was similar to the WannaCry outbreak that crippled tens of thousands of systems worldwide.
Initially, a new variant of Petya ransomware, NotPetya, was blamed for infecting systems worldwide, but later, the NotPetya story took an interesting turn.
Yesterday, it researchers found that NotPetya is not a ransomware, rather it's a wiper malware that wipes systems outright, destroying all records from the targeted systems.
NotPetya also uses NSA's leaked Windows hacking exploit EternalBlue and EternalRomance to rapidly spread within the network, and WMIC and PSEXEC tools to remotely execute malware on the machines.
Experts even believe the real attack has been disguised to divert world's attention from a state-sponsored attack to a malware outbreak.
The source code to Petya has never been leaked, but some researchers are still trying hard to reverse engineer to find possible solutions.
Would this Really Help Victims?
Since Janus is examining the new code and even if his master key succeeds in decrypting victims’ hard drive's master file table (MFT), it won't be of much help until researchers find a way to repair MBR, which is wiped off by NotPetya without keeping any copy.
Tuesday's cyber outbreak is believed to be bigger than WannaCry, causing disaster to many critical infrastructures, including bricking computers at a Ukrainian power company, several banks in Ukraine, and the country's Kyiv Boryspil International Airport.
The NotPetya also canceled surgeries at two Pittsburgh-area hospitals, hit computers at the pharmaceutical company Merck and the law firm DLA Piper, as well as infected computers at the Dutch shipping company A.P. Moller-Maersk forced to shut down some container terminals in seaports from Los Angeles to Mumbai.
Microsoft Fixes Privilege Escalation Flaw in Azure AD Connect
29.6.2017 securityweek Vulnerebility
Microsoft has released an update for Azure Active Directory (AD) Connect to address an “important” vulnerability that can be exploited to hijack the accounts of privileged users.
Azure AD Connect is a tool that allows organizations to integrate their on-premises identity infrastructure with Azure AD. One feature of Azure AD Connect is “password writeback,” which allows users to easily reset their on-premises passwords by configuring Azure AD to write passwords back to the on-premises AD.
The problem, according to Microsoft, is that the password writeback feature may not be configured properly during enablement. A malicious Azure AD administrator can set the password of an on-premises AD account belonging to a privileged user to a known value and gain access to that account.
“To enable Password writeback, Azure AD Connect must be granted Reset Password permission over the on-premises AD user accounts. When setting up the permission, an on-premises AD Administrator may have inadvertently granted Azure AD Connect with Reset Password permission over on-premises AD privileged accounts (including Enterprise and Domain Administrator accounts),” Microsoft explained in its advisory.
This privilege escalation vulnerability is tracked as CVE-2017-8613 and it has been resolved by preventing password resets to privileged on-premises accounts.
Microsoft has provided detailed instructions on how organizations can check if they are affected. Users have been advised to update to version 1.1.553.0 of Azure AD Connect or apply mitigations suggested by the vendor.
Last week, Microsoft informed users that it patched yet another remote code execution vulnerability in its Malware Protection Engine. The flaw, discovered by Tavis Ormandy of Google Project Zero, could have been exploited to take control of a targeted system.
Ormandy and other Project Zero researchers identified several vulnerabilities in the Malware Protection Engine in the past weeks, including remote code execution and denial-of-service (DoS) flaws.
NotPetya - Destructive Wiper Disguised as Ransomware
29.6.2017 securityweek Ransomware
NotPetya/GoldenEye Malware Overwrites Master Boot Record
The Petya/NotPetya ransomware used in the global attack ongoing for the past two days was in fact hiding a wiper and was clearly aimed at data destruction, security researchers have discovered.
The attack started on June 27, with the largest number of victims being reported in Ukraine, where it apparently originated from. Within hours, the outbreak hit around 65 countries worldwide, including Belgium, Brazil, France, Germany, India, Russia, and the United States.
The attack would spread within local networks through various tools, including Mimikatz for credential gathering, and the EternalBlue exploit (also used by WannaCry), the EternalRomance exploit (Microsoft released patches for both in March), and WMIC (Windows Management Instrumentation Commandline) and PSExec for lateral movement.
The initial infection vector was the hijacked updater process of tax accounting software MEDoc, but researchers also discovered that the website of Ukrainian City of Bahmut might have been hacked and used to serve the malware as well.
Soon after the outbreak began, however, security researchers noticed that NotPetya wasn’t following the same rules as normal ransomware does when it comes to the payment process, and started sounding the alarm: an easy-to-block email address was used, a single Bitcoin address was hardcoded in the malware, and the payment process was rather counter-intuitive. The attackers weren’t seeking financial gains, multiple researchers said yesterday.
“A number of us in the security community are debating if the Petya attack on 27 June wasn’t a targeted attack on Ukraine, disguised as a ransomware attack on any organization caught up in the method used for infection,” Travis Farral, Director of Security Strategy at Anomali, told SecurityWeek in an emailed statement.
“There are details that support such a theory. The attackers behind the ransomware haven’t experienced much ROI despite the broad impact of the attack, they set up a weak payment process, launched the attack just prior to Ukraine’s Constitution Day and leveraged a malware family named for the pet name of Ukrainian President, Petro Poroshenko,” Farral continued.
During a phone call with SecurityWeek on Wednesday, Bitdefender senior e-threat analyst Bogdan Botezatu suggested that the attack might have had as final purpose data destruction rather than financial gains, and it didn’t take long for Matt Suiche, Microsoft MVP and founder of Comae Technologies, to reach the same conclusion.
“The ransomware was a lure for the media, this version of Petya actually wipes the first sectors of the disk like we have seen with malwares such as Shamoon,” Suiche says.
He reveals that, while the original Petya was meant to encrypt the Master Boot Record (MBR) and demand ransom to decrypt it, the malware used in this attack, which was referred to as Petya.A, Petrwrap, NotPetya, exPetr, and GoldenEye, is in fact overwriting MBR sectors without saving them elsewhere.
“We noticed that the current implemented that massively infected multiple entities Ukraine was in fact a wiper which just trashed the 25 first sector blocks of the disk,” Suiche says. The malware, he continues, “does permanent and irreversible damages to the disk.”
Comae also discovered that the attackers implemented a function to unconditionally wipe the first 10 sectors if two conditions were met: the hash command computed from a running process name (unknown so far) returned 0x2E214B44; the function that replaces the actual MBR returns an error (which should counter EDR trying to prevent bootloader modifications).
According to Kryptos Logic security researcher MalwareTech, however, the sectors that NotPetya overwrites in this attack don’t contain data at all. The malware supposedly saves the original first sector (MBR) elsewhere, but trashes the next 24 sectors.
“The 24 sectors following the MBR are completely empty on any standard Windows installation. […] Essentially on any standard Windows operating system there is nothing between sector 1 and sector 64,” the researcher points out.
Russian security firm Kaspersky Lab also reached the conclusion that the NotPetya campaign wasn’t designed as a ransomware attack, as everyone believed in the first place. Instead, it was “designed as a wiper pretending to be ransomware,” Kaspersky’s Anton Ivanov and Orkhan Mamedov explain in a recent blog post.
The first thing the researchers noticed was that the ransomware is actually generating random data when pretending to generate the installation ID showed to the victim. Without a valid ID, the attackers can’t decrypt the victims’ files.
“That means that the attacker cannot extract any decryption information from such a randomly generated string displayed on the victim, and as a result, the victims will not be able to decrypt any of the encrypted disks using the installation ID,” Kaspersky says.
On the one hand, this means that victims can’t restore their data even if they pay the ransom. On the other, it reinforces the idea that the main goal of the attack “was not financially motivated, but destructive.”
“The fact of pretending to be a ransomware while being in fact a nation state attack — especially since WannaCry proved that widely spread ransomware aren’t financially profitable — is in our opinion a very subtle way from the attacker to control the narrative of the attack,” Suiche notes.
“Perhaps this attack was never intended to make money, rather to simply disrupt a large number of Ukrainian organizations. Launching an attack that would wipe victim hard drives would achieve the same effect, however, that would be an overtly aggressive action. Effectively wiping hard drives through the pretense of ransomware confuses the issue,” Gavin O'Gorman, Symantec Security Response, points out.
Avira reveals that computers with Russian or Ukrainian language settings were impacted the most. The company also notes that the attack affected mostly older Windows systems running Windows 7 SP1, but that Windows 8 systems were affected as well.
Affected users are advised to refrain from paying the ransom as that would by no means help them decrypt their data. This advice is particularly true for the NotPetya incident, as the attackers have no means to restore victims’ data.
“Do not pay. You will not only be financing criminals, but it is unlikely that you will regain access to your files,” Europol notes. “Disconnect the infected device from the internet. If the infected device is part of a network, try to isolate it as soon as possible, in order to prevent the infection from spreading to other machines,” the agency continues.
Shadow Brokers sent out first round of exploits and threaten to dox former NSA hacker
29.6.2017 securityaffairs BigBrothers
Shadow Brokers has sent out the first round of exploits to the subscribers of its service, the hackers also threaten to dox former NSA hacker.
In May the notorious Shadow Brokers group announced the launch of a monthly subscription model for its data dumps, 0-Day Exploit Subscriptions goes for $21,000 per month.
The group claimed to have exploit codes for almost any technology available on the market, including “compromised network data from more SWIFT providers and Central banks.”
TheShadowBrokers Monthly Data Dump could be being:
web browser, router, handset exploits and tools
select items from newer Ops Disks, including newer exploits for Windows 10
compromised network data from more SWIFT providers and Central banks
compromised network data from Russian, Chinese, Iranian, or North Korean nukes and missile programs
Now the Shadow Brokers has sent out its first round of exploits to the subscribers of its service, the hackers also claim to have many subscribers.
On Wednesday the group announced its June data dump and asked individuals and organizations that want next month’s archive for a double payment corresponding to 200 ZEC or 1,000 XMR (Monero).
The Shadow Brokers also announced the launch of a “VIP Service,” for subscribers that are interested in specific vulnerabilities or intel on a certain organization. The VIP Service goes for a one-time payment of 400 ZEC (roughly 130,000), and according to the hacker group, there are already members of this exclusive club.
“Another global cyber attack is fitting end for first month of theshadowbrokers dump service. There is much theshadowbrokers can be saying about this but what is point and having not already being said? So to business! Time is still being left to make subscribe and getting June dump. Don’t be let company fall victim to next cyber attack, maybe losing big bonus or maybe price on stock options be going down after attack. June dump service is being great success for theshadowbrokers, many many subscribers, so in July theshadowbrokers is raising price.” reads the statement published by the group.
“TheShadowBrokers July dump is 200 ZEC or 1000 XMR. Using same addresses as June same instructions.”

The ShadowBrokers sent a special message to someone that goes online with the moniker of the “doctor,” the hackers met him on Twitter and they believe he is a former member of the NSA-linked Equation Group.
“TheShadowBrokers is having special invitation message for “doctor” person theshadowbrokers is meeting on Twitter. “Doctor” person is writing ugly tweets to theshadowbrokers not unusual but “doctor” person is living in Hawaii and is sounding knowledgeable about theequationgroup. Then “doctor” person is deleting ugly tweets, maybe too much drinking and tweeting? Is very strange, so theshadowbrokers is doing some digging” states the message.
The Shadow Group threatening to dox the “doctor” if he doesn’t sign up for their next monthly dump.
“TheShadowBrokers is thinking this outcome may be having negative financial impact on new security companies international sales, so hoping ‘doctor’ person and security company is making smart choice and subscribe. But is being ‘doctor’ person’s choice. Is not being smart choice to be making ugly tweets with enough personal information to DOX self AND being former equation group AND being co-founder of security company,” the Shadow Brokers added.
The ShadowBrokers dumps are very interesting for IT security experts, a group of researchers evaluated the opportunity to launch a crowdfunding initiative aims to buy Shadow Brokers leak before threat actors will start using the hacking tools and exploits in the wild.
Ultimately, the group decided to cancel the project due to legal concerns.
Kaspersky Patches Flaws in Anti-Virus for Linux File Server
29.6.2017 securityweek Vulnerebility
An update released earlier this month by Kaspersky Lab for its Anti-Virus for Linux File Server product addresses several potentially serious vulnerabilities discovered by researchers at Core Security.
Kaspersky Anti-Virus for Linux File Server is designed to protect workstations and file servers on large corporate networks. Core Security employees determined that the product’s web-based management interface is affected by vulnerabilities that can be exploited for arbitrary code execution and other malicious activities.
One of the security holes is caused by the lack of anti-CSRF tokens in the web interface, which allows a remote attacker to execute shell commands by tricking an authenticated user into accessing a specially crafted webpage.
Researchers also found vulnerabilities that can be exploited to escalate privileges to root, execute arbitrary code via a reflected cross-site scripting (XSS) flaw, and read arbitrary files due to a path traversal bug. Core Security has made available proof-of-concept (PoC) code for each of the vulnerabilities.
The vulnerabilities affect version 8 of Kaspersky Anti-Virus for Linux File Server and they are tracked as CVE-2017-9813, CVE-2017-9810, CVE-2017-9811 and CVE-2017-9812. The flaws were reported to Kaspersky in April and patches were released on June 14. Core Security has confirmed that the update released by the vendor fixes all the security holes.
“Kaspersky Lab would like to thank researchers from Core Security Technologies for pointing out vulnerabilities in Web Console of Kaspersky Anti-Virus for Linux File Server 8, which allowed, under specific conditions, unauthorized access to some product functionality,” Kaspersky Lab told SecurityWeek in an emailed statement. “These vulnerabilities are now fixed. Kaspersky Lab recommends to all customers, using Web Console, to upgrade the Kaspersky Anti-Virus for Linux File Server 8 to new CF4 version.”
Kaspersky has been running a HackerOne-powered bug bounty program that covers its Password Manager 8, Internet Security 2017 and Endpoint Security 10 products. The security firm is offering between $300 and $5,000 for each vulnerability.
Barracuda Launches AI-based Spear Phishing Detection
29.6.2017 securityweek Phishing
Barracuda Networks this week announced its new Sentinel product: an artificial intelligence (AI) powered spear-phishing and business email compromise (BEC) realtime detection and prevention solution. It marks the second company in a week, following GreatHorn, to use AI to combat social engineering.
"The threat has grown exponentially over the last few years," Asaf Cidon, vice president of content security services at Barracuda, told SecurityWeek. "According to the FBI's latest figures, more than $5 billion has been lost to BEC fraud between 2013 and 2016 -- with a 2,370% growth in spear-phishing between the beginning of 2015 and the end of 2016. BEC has become so pervasive because it is simple to do: anyone with an email account and a little on-line research into the target can produce a compelling fraudulent email."
Not only is BEC easy to produce, it is also hard to detect. While many other email-based attacks include a payload -- from a link in the body to malware in the attachment -- BEC fraud has neither. It relies entirely upon social engineering that traditional defenses cannot detect.
"This problem led us to build Sentinel," said Cidon; "an AI-based platform for real-time spear-phishing and cyber fraud defense. It relies on three individual layers to provide a comprehensive solution: artificial intelligence for fraud detection; DMARC for protection against domain spoofing and brand hijacking; and simulated attack training for identified high-risk staff."
The AI layer is the most important, he suggested. With access to millions of mailboxes, Barracuda has taught its AI to recognize fraudulent emails. It does this in two ways. Firstly, it fingerprints communication patterns within the customer organization. It learns, for example, how the CEO normally communicates with the finance team. Deviations from this pattern -- such as the sudden use of an email address not used before -- immediately flag the communication as worrying.
But Sentinel also analyzes the email content for style. In an example given by Cidon, the AI engine detected urgency (use of the word 'need', and termination with a question-mark) and sensitivity (use of 'bank transfer'). 'Urgency' is an archetypal element of social engineering. When the content analysis is coupled with the metadata fingerprint, other indicators such as the use of an external email address in either the from or reply-to fields are sufficient for the AI to recognize and quarantine the fraud.
The second layer of Sentinel sets up DMARC (Domain-based Message Authentication Reporting & Conformance) to prevent outbound domain spoofing. One common technique used by criminals is to spoof the organization's domain in order to send apparently official messages to customers and partners to steal credentials and gain access to accounts. This layer of Sentinel helps prevent spoofing-based spear phishing and brand hijacking.
The final layer is anti-fraud training for high risk staff. The AI part of the product is used to identify high risk personnel. The product then offers a set of tools to periodically and automatically train and test the security awareness of these employees with simulated spear phishing attacks.
Sentinel currently works with Office 365. However, Barracuda also offers a set of APIs designed to make to make the functionality easily extensible beyond email to additional messaging platforms such as G Suite, Slack, social media, and others: "In fact," said Cidon, "to any platform used by organizations for business communication."
Microsoft to Make EMET Native to Windows 10
29.6.2017 securityweek Safety
Microsoft is no longer interested in retiring its Enhanced Mitigation Experience Toolkit (EMET) but will instead make it native to Windows 10, the tech giant announced this week.
Initially released in 2009, EMET was designed to protect against certain zero-day software vulnerabilities at a time when there was a 3-4 years gap between Windows releases. The tool helped Microsoft disrupt common exploit kits and even features Windows 10 compatibility.
Seven years later, after it had already accelerated the release of new Windows iterations, Microsoft said EMET was no longer needed. The company initially announced plans to retire EMET on Jan. 27, 2017, but then pushed the end-of-life date back 18 months, to July 31, 2018, based on customer feedback.
In November 2016, as a reply to Microsoft’s claim that Windows 10 doesn’t need EMET to deliver great protection, CERT vulnerability analyst Will Dormann said in a blog that EMET includes additional protections that Windows 10 doesn’t.
Now, Rob Lefferts, Director of PM, Windows Enterprise and Security at Microsoft, says that feedback from customers who “are clearly fans of threat protections offered through EMET the Enhanced Mitigation Experience Toolkit (EMET)” determined the company to make the tool native to Windows 10 in the form of Windows Defender Exploit Guard.
The Exploit Guard is meant to pack both EMET capabilities and new vulnerability mitigations, in an attempt to deliver new prevention capabilities and make exploitation of vulnerabilities dramatically more difficult. The tool would also include a new class of intrusion prevention capabilities.
“Using intelligence from the Microsoft Intelligent Security Graph (ISG), Exploit Guard comes with a rich set of intrusion rules and policies to protect organziations from advanced threats, including zero day exploits. The inclusion of these built-in rules and policies addresses one of the key challenges with host intrusion prevention solutions which often takes significant expertise and development efforts to make effective,” Lefferts says.
Windows 10 Fall Creators Update will bring EMET back, alongside a variety of additional security improvements, Lefferts also announced. These include Windows Defender Application Guard (WDAG) and “substantial updates” to Windows Defender Device Guard and Windows Defender Antivirus.
“Windows Defender Advanced Threat Protection (ATP) will include seamless integration across the entire Windows threat protection stack to protect, detect and respond with rich, centralized management. In addition, we’re extending the reach of Windows Defender ATP to include Windows Server OS to protect customers across platforms,” Lefferts notes.
WDAG should prevent attackers from compromising local machines or moving laterally into the network by isolating malware downloaded via the browser or zero-day exploits. “With more than 90% of attacks using a hyperlink to initiate stealing credentials, installing malware, or exploiting vulnerabilities,” the browser emerges as the most common target for attackers, and Microsoft will focus on securing it.
Microsoft also plans on integrating Windows Defender Device Guard into Windows Defender ATP response capabilities, to ensure customers have better control over applications. Further, Windows 10 should deliver “a new level of security” to enterprises, along with new analytic capabilities, Microsoft says.
Telegram Agrees to Register With Russia to Avoid Ban, But Won't Share User Data
29.6.2017 thehackernews Krypto
After being threatened with a ban in Russia, end-to-end encrypted Telegram messaging app has finally agreed to register with new Russian Data Protection Laws, but its founder has assured that the company will not comply to share users' confidential data at any cost.
Russia's communications watchdog Roskomnadzor had recently threatened to block Telegram if the service did not hand over information required to put the app on an official government list of information distributors.
The Russian government requirement came following terrorists' suicide bombings that killed 15 people in Saint Petersburg in April in which terrorists allegedly used the Telegram's app to communicate and plot attacks.
"There is one demand, and it is simple: to fill in a form with information on the company that controls Telegram," said Alexander Zharov, head of Roskomnadzor.
"And to officially send it to Roskomnadzor to include this data in the registry of organizers of dissemination of information. In case of refusal… Telegram shall be blocked in Russia until we receive the needed information."
Telegram CEO Pavel Durov refused to comply with the country's requirements because he feared that it would weaken the privacy of its over 6 Million Russian users.
Telegram: No Confidential Data of Users will be Shared
However, after facing pressure from the government, Durov agreed on Wednesday to store Russian citizens' information on the country's servers.
The Russian Federal Service for Supervision Of Communications, Information Technology and Mass Media (Roskomnadzor) announced on Wednesday that Telegram had finally presented all the requirements.
Roskomnadzor is a federal executive body in Russia responsible for overseeing the media, including the electronic media, mass communications, information technology and telecommunications; organizing the work of the radio-frequency service; and overseeing compliance with the law protecting the confidentiality of its users' personal data.
Durov announced his decision via VK.com, the Russian version of Facebook, adding that while he's happy for Telegram to be formally registered in Russia, anything that violates users' privacy will not be served — only basic information about the company will be shared.
"We will not comply with unconstitutional and technically impossible Yarovaya Package laws—as well as with other laws incompatible with the protection of privacy and Telegram's privacy policy," Durov said.
Telegram is an end-to-end encrypted messaging app, but unlike WhatsApp, Telegram does not offer the end-to-end messaging feature to its users by default. Rather users need to open encrypted chats to communicate securely.
How to Communicate Securely with Telegram
If you are communicating with people on Telegram thinking that your chats are end-to-end encrypted, you are mistaken, because all your chats will be stored in plain text on Russian servers, making it possible for the government to request it with court orders, when required.
So, always make sure that you communicate with people on Telegram using its encrypted chat feature. Here's how to start an end-to-end encrypted chat on Telegram:
Open Telegram app
Select the contact you want to communicate
Click on his/her name
Select 'Start Secret Chat' (highlighted in green color)
A new, secure chat window will open, where you can communicate securely.
You can also enable other security features offered by Telegram.
These features include Two-Step Verification that allows you to set up an additional passcode for your Telegram account, which is also required to log into your account and Self-Destruct Secret Chats that lets you self-destruct your messages after a specified time (between 1 second and 1 week), leaving no trace on Telegram servers.
Your Linux Machine Can Be Hacked Remotely With Just A Malicious DNS Response
29.6.2017 thehackernews Hacking
A critical vulnerability has been discovered in Systemd, the popular init system and service manager for Linux operating systems, that could allow remote attackers to potentially trigger a buffer overflow to execute malicious code on the targeted machines via a DNS response.
The vulnerability, designated as CVE-2017-9445, actually resides in the 'dns_packet_new' function of 'systemd-resolved,' a DNS response handler component that provides network name resolution to local applications.
According to an advisory published Tuesday, a specially crafted malicious DNS response can crash 'systemd-resolved' program remotely when the system tries to lookup for a hostname on an attacker-controlled DNS service.
Eventually, large DNS response overflows the buffer, allowing an attacker to overwrite the memory which leads to remote code execution.
This means the attackers can remotely run any malware on the targeted system or server via their evil DNS service.
"In systemd through 233, certain sizes passed to dns_packet_new in systemd-resolved can cause it to allocate a buffer that's too small," explains Chris Coulson, Ubuntu developer at Canonical.
"A malicious DNS server can exploit this by responding with a specially crafted TCP payload to trick systemd-resolved into allocating a buffer that's too small, and subsequently write arbitrary data beyond the end of it."
This vulnerability has been present since Systemd version 223 introduced in June 2015 and is present in all the way up to, including Systemd version 233 launched in March this year.
Of course, systemd-resolved must be running on your system for it to be vulnerable.
The bug is present in Ubuntu versions 17.04 and version 16.10; Debian versions Stretch (aka Debian 9), Buster (aka 10) and Sid (aka Unstable); and various other Linux distributions that use Systemd.
Security patches have been rolled out to address the issue, so users and system administrators are strongly recommended to install them and update their Linux distros as soon as possible.
A critical flaw allows hacking Linux machines with just a malicious DNS Response
29.6.2017 securityaffairs Vulnerebility
A remote attacker can trigger the buffer overflow vulnerability to execute malicious code on affected Linux systems with just a malicious DNS response.
Chris Coulson, Ubuntu developer at Canonical, has found a critical vulnerability Linux that can be exploited to remotely hack machines running the popular OS. The flaw, tracked as CVE-2017-9445, resides in the Systemd init system and service manager for Linux operating systems.
A remote attacker can trigger the buffer overflow vulnerability to execute malicious code with just a malicious DNS response.
The expert has found the vulnerability in the ‘dns_packet_new‘ function of ‘systemd-resolved,’ that handles a DNS response and provides network name resolution to local applications.
A specially crafted malicious DNS response can crash ‘systemd-resolved’ program remotely every time the system tries to lookup for a hostname on an attacker-controlled DNS service.
The attacker can trigger the flaw by sending a large DNS response that triggers a buffer overflow that leads to remote code execution.
“Certain sizes passed to dns_packet_new can cause it to allocate a buffer that’s too small. A page-aligned number – sizeof(DnsPacket) + sizeof(iphdr) + sizeof(udphdr) will do this – so, on x86 this will be a page-aligned number – 80. Eg, calling dns_packet_new with a size of 4016 on x86 will result in an allocation of 4096 bytes, but 108 bytes of this are for the DnsPacket struct.” explains Coulson.
“A malicious DNS server can exploit this by responding with a specially crafted TCP payload to trick systemd-resolved in to allocating a buffer that’s too small, and subsequently write arbitrary data beyond the end of it.”
The flaw affects the
The flaw affects the Systemd version 223, which is dated back June 2015, and later, including Systemd version 233 launched in March 2017.
The vulnerability affects the Ubuntu versions 17.04 and version 16.10; Debian versions Stretch (aka Debian 9), Buster (aka 10) and Sid (aka Unstable); and various other Linux distributions that use Systemd.
Linux users and system administrators must update their installs as soon as possible.
Řádění vyděračského viru stále pokračuje. Kvůli nedostatečnému zabezpečení
29.6.2017 Novinky/Bezpečnost Viry
Svět zažil tento týden jeden z největších útoků vyděračských virů v celé historii počítačů. Přestože se podle některých zahraničních zdrojů podařilo řádění záškodníka zvaného Win32/Diskcoder.C Trojan zastavit, bezpečnostní experti společnosti Check Point upozornili na to, že vyhráno rozhodně ještě není.
Vyděračský virus Win32/Diskcoder.C Trojan, který je vylepšenou variantou nechvalně známého škodlivého kódu Petya, se totiž internetem neustále šíří. I když ne tak závratným tempem jako v prvním dnu.
Tento nezvaný návštěvník totiž využívá nedostatečného zabezpečení u jednotlivců i firem. „Alarmující je, že drtivá většina společností nemá nasazené takové technologie, které by je před podobnými typy útoků ochránily. Není potom divu, že se útoky tak rychle a snadno šíří,“ uvedl Peter Kovalčík, SE Manager ve společnosti Check Point Software Technologies.
„Problémem je i určitá roztříštěnost zabezpečení, často je nasazeno příliš mnoho různých řešení namísto sjednocené bezpečnostní architektury, která by byla zaměřená na prevenci a zastavení útoků, než mohou způsobit nějaké škody,“ konstatoval Kovalčík.
Nainstalujte nejnovější aktualizace
Ten zároveň nastínil, jaký byl u tohoto záškodníka vývoj. „Podle všeho se jedná o novou verzi ransomwaru Petya, který se poprvé objevil v březnu 2016. Nová verze se velmi rychle šíří podnikovými sítěmi po celém světě, podobně jako to dělal minulý měsíc ransomware WannaCry,“ podotkl bezpečnostní expert.

Uživatelé napadení virem místo startu operační systému uvidí tuto zprávu.
FOTO: Avast
„Organizace by měly okamžitě použít nejnovější bezpečnostní záplaty společnosti Microsoft a zakázat protokol SMBv1 pro sdílení souborů na systémech Windows. Zásadní je také nasazení preventivních bezpečnostních technologií a velmi důležité je i vzdělávání zaměstnanců. Aby měli povědomí o hrozbách a možných rizicích, která mohu být v příchozích e-mailech od neznámých odesílatelů nebo v podezřelých e-mailech od známých kontaktů,“ uzavřel Kovalčík.
Stejná obezřetnost je na místě i u klasických domácích uživatelů. I ti by pochopitelně měli mít nainstalované všechny nejnovější aktualizace.
Útočníci v současnosti nevydělají prostřednictvím škodlivého kódu Win32/Diskcoder.C Trojan ani korunu. E-mailová schránka, prostřednictvím které komunikovali se svými obětmi, je totiž zablokovaná. Útočníci tak nemají svým obětem jak napsat, že mají zaplatit výkupné.
Hrozbu nepodceňovat
To nicméně nemění nic na tom, že na počítači stále dokáže tento nezvaný návštěvník udělat pěknou neplechu. A to dokonce větší než drtivá většina dalších vyděračských virů. Ty totiž často potřebují k zašifrování dat na pevném disku poměrně dost času, klidně i několik hodin. Během toho může jejich práci zachytit antivirový program a zablokovat je ještě dříve, než v počítači nadělají nějakou větší škodu.
Nově objevená hrozba však funguje jiným způsobem. Na disku nezašifruje všechna data, ale pouze tzv. MBR (Master Boot Record). Jde o hlavní spouštěcí záznam, díky kterému se v podstatě spouští celý operační systém. K zašifrovanému záznamu pak počítač nemá přístup a místo Windows spustí jen hlášku o nutnosti zaplatit výkupné.
Na zašifrování MBR nepotřebuje nový vyděračský virus několik hodin, stačí mu pouze pár vteřin. Antiviry tak prakticky nemají šanci škodlivý kód zachytit. Hned po prvním restartu je pak problém na světě.
Nová Petya nevydírá, prostě jen ničí, data nebylo v plánu obnovit
29.6.2017 Root.cz Viry
Světem otřásá další vlna vyděračského malware, který obětem zašifruje disk a požaduje výkupné. Ukázalo se ale, že ve skutečnosti jde jen o zástěrku a data není možné vůbec obnovit. Není to vyděrač, je to zabiják.
V úterý se světem rozběhla nová forma malware Petya, který využívá známou zranitelnost, přepisuje MBR a při falešné kontrole disku po restartu pak zašifruje veškerá data. Nakonec zobrazí vyděračskou zprávu, podle které stačí zaplatit na bitcoinovou peněženku pouhých 300 dolarů, tedy asi 7000 korun, a vyděrači vám ochotně vaše data obnoví. Dokonce takovou službu výslovně garantují.
Ošklivý kus kódu
Malware zvaný NewPetya nebo také Petwrap už napadl velké firmy, banky, elektrárny zejména v Rusku a na Ukrajině, ale také ve Španělsku, Francii, Británii, Indii a dalších částech světa. Nevyhnul se pochopitelně ani Česku. Využívá stejnou útočnou techniku EternalBlue jako starší WannaCry a navíc přidává EternalRomance, zranitelnost portu 445. Detaily šíření popisuje Kaspersky Lab.
Malware pak v napadeném počítači čeká několik desítek minut, poté je počítač restartován a během startu proběhne zákeřná akce: falešná kontrola disku zašifruje veškeré NTFS oddíly a MBR je přepsán vlastním zavaděčem s vyděračskou hláškou.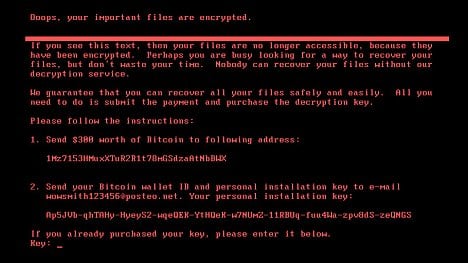
Odborníci si velmi rychle všimli toho, že se všem postiženým uživatelům objevuje stejná hláška se stejnými údaji a dokonce stejnou e-mailovou adresou wowsmith123456@posteo.net. Považovali to za nedotaženost této kampaně, protože adresa byla útočníkům velmi rychle odstřižena provozovatelem e-mailového serveru a tím byla znemožněna komunikace s útočníky.
Ukázalo se ale, že to vůbec není neschopností autorů.
Obnova dat nebyla nikdy v plánu
Nová forma malware Petya se totiž jenom tváří jako ransomware. Ve skutečnosti útočníci nikdy neměli v plánu s nikým komunikovat a za výkupné obnovovat data. E-mailová adresa je jen součástí kamufláže, aby uživatelé měli pocit, že to může vyjít. Vše se tváří „důvěryhodně“ včetně nutnosti zaslat identifikační klíč disku, což je technika známá z dřívějších ransomwarových kampaní. Uživatelé jsou při setkání s takovými informacemi ochotnější poslat peníze. Nic za ně ale nedostanou.
Nová Petya totiž není vyděračským malware, ale podle nejnovějších analýz jen ničí data bez možnosti jejich obnovy. Matt Suiche ze společnosti Comae Technologies kód analyzoval a zjistil, že nová varianta malware si nikam neukládá původní šifrovanou podobu MBR, ale prostě ji smaže.
Matt Suiche, Comae Technologies
Vlevo nová varianta ničící data, vpravo původní šifrující
Vlastně tak už není co obnovovat, protože původní obsah disku je zašifrován a MBR je pryč. I kdyby měli tedy autoři chuť vám po zaplacení pomoci, nemají jak. Spekuluje se, zda jde o úmysl či o chybu, ale změna v kódu je tak razantní, že se můžeme spíše přiklonit k úmyslu. Útočníkům je to jednoduše fuk, potřebují peníze, zbytek je nezajímá.
Podívejte se, jak vypadají obrazovky počítačů po napadení ransomware:
Vyšlo jim to, vydělali
Nejsmutnější na celém případu je, že se celá akce podařila a útočníci vydělali. Podle záznamů v bitcoinové peněžence přistálo v době psaní článku 45 plateb v celkové hodnotě 4 bitcoiny. Útočníci si tak přišli v přepočtu na více než 230 000 korun.
e to jen další potvrzení toho, že vyděračům se platit nemá. Jednak to podporuje jejich byznys, ale především nemáte jistotu, že za své peníze něco dostanete. V tomto konkrétní případě máte naopak jistotu, že vám zůstanou jen zašifrovaná data pro pláč.
Je tu ale i druhá varianta, kterou zmiňuje i Matt Suiche. Totiž že jde jen kouřovou clonu, která má zakrýt nějaký další větší útok, třeba v rámci testování kybernetické války nebo jiné závažné zprávy.
Kaspersky Patches Flaws in Anti-Virus for Linux File Server
29.6.2017 securityweek Vulnerebility
An update released earlier this month by Kaspersky Lab for its Anti-Virus for Linux File Server product addresses several potentially serious vulnerabilities discovered by researchers at Core Security.
Kaspersky Anti-Virus for Linux File Server is designed to protect workstations and file servers on large corporate networks. Core Security employees determined that the product’s web-based management interface is affected by vulnerabilities that can be exploited for arbitrary code execution and other malicious activities.
One of the security holes is caused by the lack of anti-CSRF tokens in the web interface, which allows a remote attacker to execute shell commands by tricking an authenticated user into accessing a specially crafted webpage.
Researchers also found vulnerabilities that can be exploited to escalate privileges to root, execute arbitrary code via a reflected cross-site scripting (XSS) flaw, and read arbitrary files due to a path traversal bug. Core Security has made available proof-of-concept (PoC) code for each of the vulnerabilities.
The vulnerabilities affect version 8 of Kaspersky Anti-Virus for Linux File Server and they are tracked as CVE-2017-9813, CVE-2017-9810, CVE-2017-9811 and CVE-2017-9812. The flaws were reported to Kaspersky in April and patches were released on June 14. Core Security has confirmed that the update released by the vendor fixes all the security holes.
“Kaspersky Lab would like to thank researchers from Core Security Technologies for pointing out vulnerabilities in Web Console of Kaspersky Anti-Virus for Linux File Server 8, which allowed, under specific conditions, unauthorized access to some product functionality,” Kaspersky Lab told SecurityWeek in an emailed statement. “These vulnerabilities are now fixed. Kaspersky Lab recommends to all customers, using Web Console, to upgrade the Kaspersky Anti-Virus for Linux File Server 8 to new CF4 version.”
Kaspersky has been running a HackerOne-powered bug bounty program that covers its Password Manager 8, Internet Security 2017 and Endpoint Security 10 products. The security firm is offering between $300 and $5,000 for each vulnerability.
Barracuda Launches AI-based Spear Phishing Detection
29.6.2017 securityweek Phishing
Barracuda Networks this week announced its new Sentinel product: an artificial intelligence (AI) powered spear-phishing and business email compromise (BEC) realtime detection and prevention solution. It marks the second company in a week, following GreatHorn, to use AI to combat social engineering.
"The threat has grown exponentially over the last few years," Asaf Cidon, vice president of content security services at Barracuda, told SecurityWeek. "According to the FBI's latest figures, more than $5 billion has been lost to BEC fraud between 2013 and 2016 -- with a 2,370% growth in spear-phishing between the beginning of 2015 and the end of 2016. BEC has become so pervasive because it is simple to do: anyone with an email account and a little on-line research into the target can produce a compelling fraudulent email."
Not only is BEC easy to produce, it is also hard to detect. While many other email-based attacks include a payload -- from a link in the body to malware in the attachment -- BEC fraud has neither. It relies entirely upon social engineering that traditional defenses cannot detect.
"This problem led us to build Sentinel," said Cidon; "an AI-based platform for real-time spear-phishing and cyber fraud defense. It relies on three individual layers to provide a comprehensive solution: artificial intelligence for fraud detection; DMARC for protection against domain spoofing and brand hijacking; and simulated attack training for identified high-risk staff."
The AI layer is the most important, he suggested. With access to millions of mailboxes, Barracuda has taught its AI to recognize fraudulent emails. It does this in two ways. Firstly, it fingerprints communication patterns within the customer organization. It learns, for example, how the CEO normally communicates with the finance team. Deviations from this pattern -- such as the sudden use of an email address not used before -- immediately flag the communication as worrying.
But Sentinel also analyzes the email content for style. In an example given by Cidon, the AI engine detected urgency (use of the word 'need', and termination with a question-mark) and sensitivity (use of 'bank transfer'). 'Urgency' is an archetypal element of social engineering. When the content analysis is coupled with the metadata fingerprint, other indicators such as the use of an external email address in either the from or reply-to fields are sufficient for the AI to recognize and quarantine the fraud.
The second layer of Sentinel sets up DMARC (Domain-based Message Authentication Reporting & Conformance) to prevent outbound domain spoofing. One common technique used by criminals is to spoof the organization's domain in order to send apparently official messages to customers and partners to steal credentials and gain access to accounts. This layer of Sentinel helps prevent spoofing-based spear phishing and brand hijacking.
The final layer is anti-fraud training for high risk staff. The AI part of the product is used to identify high risk personnel. The product then offers a set of tools to periodically and automatically train and test the security awareness of these employees with simulated spear phishing attacks.
Sentinel currently works with Office 365. However, Barracuda also offers a set of APIs designed to make to make the functionality easily extensible beyond email to additional messaging platforms such as G Suite, Slack, social media, and others: "In fact," said Cidon, "to any platform used by organizations for business communication."
Microsoft to Make EMET Native to Windows 10
29.6.2017 securityweek Safety
Microsoft is no longer interested in retiring its Enhanced Mitigation Experience Toolkit (EMET) but will instead make it native to Windows 10, the tech giant announced this week.
Initially released in 2009, EMET was designed to protect against certain zero-day software vulnerabilities at a time when there was a 3-4 years gap between Windows releases. The tool helped Microsoft disrupt common exploit kits and even features Windows 10 compatibility.
Seven years later, after it had already accelerated the release of new Windows iterations, Microsoft said EMET was no longer needed. The company initially announced plans to retire EMET on Jan. 27, 2017, but then pushed the end-of-life date back 18 months, to July 31, 2018, based on customer feedback.
In November 2016, as a reply to Microsoft’s claim that Windows 10 doesn’t need EMET to deliver great protection, CERT vulnerability analyst Will Dormann said in a blog that EMET includes additional protections that Windows 10 doesn’t.
Now, Rob Lefferts, Director of PM, Windows Enterprise and Security at Microsoft, says that feedback from customers who “are clearly fans of threat protections offered through EMET the Enhanced Mitigation Experience Toolkit (EMET)” determined the company to make the tool native to Windows 10 in the form of Windows Defender Exploit Guard.
The Exploit Guard is meant to pack both EMET capabilities and new vulnerability mitigations, in an attempt to deliver new prevention capabilities and make exploitation of vulnerabilities dramatically more difficult. The tool would also include a new class of intrusion prevention capabilities.
“Using intelligence from the Microsoft Intelligent Security Graph (ISG), Exploit Guard comes with a rich set of intrusion rules and policies to protect organziations from advanced threats, including zero day exploits. The inclusion of these built-in rules and policies addresses one of the key challenges with host intrusion prevention solutions which often takes significant expertise and development efforts to make effective,” Lefferts says.
Windows 10 Fall Creators Update will bring EMET back, alongside a variety of additional security improvements, Lefferts also announced. These include Windows Defender Application Guard (WDAG) and “substantial updates” to Windows Defender Device Guard and Windows Defender Antivirus.
“Windows Defender Advanced Threat Protection (ATP) will include seamless integration across the entire Windows threat protection stack to protect, detect and respond with rich, centralized management. In addition, we’re extending the reach of Windows Defender ATP to include Windows Server OS to protect customers across platforms,” Lefferts notes.
WDAG should prevent attackers from compromising local machines or moving laterally into the network by isolating malware downloaded via the browser or zero-day exploits. “With more than 90% of attacks using a hyperlink to initiate stealing credentials, installing malware, or exploiting vulnerabilities,” the browser emerges as the most common target for attackers, and Microsoft will focus on securing it.
Microsoft also plans on integrating Windows Defender Device Guard into Windows Defender ATP response capabilities, to ensure customers have better control over applications. Further, Windows 10 should deliver “a new level of security” to enterprises, along with new analytic capabilities, Microsoft says.
Wikileaks – The Elsa malware allows CIA to locate users via WiFi-enabled devices
29.6.2017 securityaffairs BigBrothers
WikiLeaks published the manual of the ELSA malware, a tool allegedly used by the U.S. CIA to track people’s locations via their WiFi-enabled devices.
WikiLeaks has published a document detailing a tool allegedly used by the U.S. CIA to track people’s locations via their WiFi-enabled devices.
The malware code-named Elsa implements geolocation feature, it scans visible WiFi access points and records their details, such as the ESS identifier, MAC address and signal strength at regular intervals.
Wikileaks published the user manual as part of Vault 7 dump, the document is dated September 2013 and there is no other information about its improvements.
View image on TwitterView image on Twitter
Follow
WikiLeaks ✔ @wikileaks
RELEASE: CIA 'ELSA' implant to geolocate laptops+desktops by intercepting the surrounding WiFi signals https://wikileaks.org/vault7/#Elsa
2:19 PM - 28 Jun 2017
1,119 1,119 Retweets 1,029 1,029 likes
Twitter Ads info and privacy
The malware also works when the Wi-Fi enabled device is offline or isn’t connected to an access point.
When the device is connected online, the malware leverages public geo-location databases from Google or Microsoft to resolve the position.
The data recorded by the ELSA malware is encrypted and logged, CIA agents can access them only manually retrieving the log by connecting to the Wi-Fi connected device.
“ELSA is a geo-location malware for WiFi-enabled devices like laptops running the Micorosoft Windows operating system. Once persistently installed on a target machine using separate CIA exploits, the malware scans visible WiFi access points and records the ESS identifier, MAC address and signal strength at regular intervals.” reads the post published by Wikileaks. “To perform the data collection the target machine does not have to be online or connected to an access point; it only needs to be running with an enabled WiFi device. If it is connected to the internet, the malware automatically tries to use public geo-location databases from Google or Microsoft to resolve the position of the device and stores the longitude and latitude data along with the timestamp. The collected access point/geo-location information is stored in encrypted form on the device for later exfiltration. The malware itself does not beacon this data to a CIA back-end; instead the operator must actively retrieve the log file from the device – again using separate CIA exploits and backdoors.”

The data is encrypted and logged, and the malware’s operator can manually retrieve this log by connecting to the infected device. The ELSA malware could be customized by CIA operators in order to match the target environment and mission objectives.
“The ELSA project allows the customization of the implant to match the target environment and operational objectives like sampling interval, maximum size of the logfile and invocation/persistence method,” continues WikiLeaks. “Additional back-end software (again using public geo-location databases from Google and Microsoft) converts unprocessed access point information from exfiltrated logfiles to geo-location data to create a tracking profile of the target device.”
Below the list of release published by Wikileaks since March:
ELSA malware – 28 June, 2017
Cherry Blossom – 15 June, 2017
Pandemic – 1 June, 2017
Athena – 19 May, 2017
AfterMidnight – 12 May, 2017
Archimedes – 5 May, 2017
Scribbles – 28 April, 2017
Weeping Angel – 21 April, 2017
Hive – 14 April, 2017
Grasshopper – 7 April, 2017
Marble Framework – 31 March, 2017
Dark Matter – 23 March, 2017
ExPetr/Petya/NotPetya is a Wiper, Not Ransomware
29.6.2017 Kaspersky Ransomware
DATA ENCRYPTION PETYA RANSOMWARE WIPER
After an analysis of the encryption routine of the malware used in the Petya/ExPetr attacks, we have thought that the threat actor cannot decrypt victims’ disk, even if a payment was made.
This supports the theory that this malware campaign was not designed as a ransomware attack for financial gain. Instead, it appears it was designed as a wiper pretending to be ransomware.
Below the technical details are presented. First, in order to decrypt victim’s disk the attackers need the installation ID:
In previous versions of “similar” ransomware like Petya/Mischa/GoldenEye, this installation ID contains crucial information for the key recovery. After sending this information to the attacker they can extract the decryption key using their private key.
Here’s how this installation ID is generated in the ExPetr ransomware:
This installation ID in our test case is built using the CryptGenRandom function, which is basically generating random data.
The following buffer contains the randomly generated data in an encoded “BASE58” format:
If we compare this randomly generated data and the final installation ID shown in the first screen, they are the same. In a normal setup, this string should contain encrypted information that will be used to restore the decryption key. For ExPetr, the ID shown in the ransom screen is just plain random data.
That means that the attacker cannot extract any decryption information from such a randomly generated string displayed on the victim, and as a result, the victims will not be able to decrypt any of the encrypted disks using the installation ID.
What does it mean? Well, first of all, this is the worst-case news for the victims – even if they pay the ransom they will not get their data back. Secondly, this reinforces the theory that the main goal of the ExPetr attack was not financially motivated, but destructive.
Our friend Matt Suiche from Comae Technologies independently came to the same conclusion.
Experts found a critical remote buffer overflow vulnerability in Skype
29.6.2017 securityaffairs Vulnerebility
The security expert Benjamin Kunz-Mejri from security firm Vulnerability Lab discovered a remote zero-day stack buffer overflow vulnerability in Skype.
The security expert Benjamin Kunz-Mejri from security firm Vulnerability Lab discovered a Skype zero-day stack buffer overflow vulnerability, tracked as CVE-2017-9948, that could be exploited by a remote attacker to execute malicious code.
Vulnerability Lab reported the flaw to Microsoft on 16th May, Microsoft released a patch on 8 June in Skype version 7.37.178.
The flaw resides in Skype Web messaging and call service and could be exploited during a team conference call.
“The buffer overflow vulnerability can be exploited by local and remote attackers without user interaction and with low privileged Skype user account.” states the security advisory published by Vulnerability Lab.
The flaw was ranked as a high-security risk and received a 7.2 CVSS score and affects Skype versions 7.2, 7.35, and 7.36 on Windows XP, Windows 7 and Windows 8.
“The problem is located in the print clipboard format & cache transmit via remote session on Windows XP, Windows 7, Windows 8 and Windows 10. In Skype v7.37 the vulnerability is patched,” continues the advisory.
A remote attacker can crash the application triggering an unexpected exception error, to overwrite the active process registers, or even execute malicious code on a vulnerable Sky instance.
The problem is caused by the way Skype uses the ‘MSFTEDIT.DLL’ file in case of a copy request on local systems.
“The security vulnerability allows to crash the software application with an unexpected exception error, to overwrite the active process registers to execute own malicious codes.” continues the advisory.
“The security vulnerability is located in the `clipboard format` function of the Skype software. Attackers are able to use a remote computer system with a shared clipboard, to provoke a stack buffer overflow on transmission to Skype. The issue affects the `MSFTEDIT.DLL` dynamic link library of the windows8 (x86) operating system”
The advisory details how to exploit the flaw, an attacker can craft a malicious image file and then copy and paste it from a clipboard of a computer system into a conversation window in the Skype software.
When the image is hosted on a clipboard on both the remote and the local systems, Skype triggers a stack buffer overflow.
“The limitation of the transmitted size and count for images via print of the remote session clipboard has no secure limitations or restrictions. Attackers [can] crash the software with one request to overwrite the EIP register of the active software process,” said researchers from Vulnerability Lab.
“Thus allows local or remote attackers to execute own codes on the affected and connected computer systems via the Skype software,” they added.
UK's Metropolitan Police Still Using 10,000 Windows XP Computers
29.6.2017 securityaffairs Security
Legacy Windows XP systems used by public authorities in the UK remains a concern. The WannaCry outbreak last month followed by the current 'NotPetya' outbreak -- both using a vulnerability patched in newer versions of Windows, but initially unpatched in XP -- highlights the problem.
Information obtained by Steve O'Connell, a member of the London Assembly and a Conservative Party spokesperson for policing and crime, shows that the Metropolitan Police Service (MPS, or the Met) was still using 18,293 XP machines on their network at the time of providing the information. Since XP is no longer supported by Microsoft, it is left vulnerable to any new exploits such as EternalBlue and DoublePulsar -- and it appears that only the tendency for WannaCry to crash XP rather than infect it prevented the worldwide outbreak from being far worse than it was.
The Met's position is more precarious than implied by O'Connell's figures. Last month, the UK's data protection regulator, the ICO, published findings (PDF) from a consensual audit of the Met. While finding some areas of 'good practice', it also noted other areas in need of improvement.
In particular, one area for improvement includes the continued use of XP on some desktops and laptops leading to "a residual risk to personal data." But in relation to WannaCry and NotPetya, this risk is magnified by weaknesses in both the Met's backup and business continuity procedures. "Backup arrangements for file systems are not tested to ensure that they are recoverable in the event of a disaster."
Furthermore, "The database used to store BC information is unsupported and not backed up."
The ICO's conclusion was that "The audit has identified considerable scope for improvement in existing arrangements to reduce the risk of non-compliance [with the Data Protection Act]."
The combination of a vulnerable system and untested recovery capabilities is particularly susceptible to ransomware -- and even more so where the ransomware attacks are more intent on mischief than collecting ransoms, as seems to be the case with both WannaCry and NotPetya. The threat to, or potential loss of, personal data stored by the Metropolitan Police is particularly concerning.
"It is vital the Met is given the resources to step up its upgrade timeline before we see another cyber-attack with nationwide security implications," warns O'Connell. But, of course, things are never so simple. SecurityWeek reached out to the Met to confirm O'Connell's figures, and received the following statement:
"The MPS is undergoing a complete refresh of its information technology processes, infrastructure, and equipment - including its desktop computers.
"However, the upgrade programme is not as simple as it would be for many other organizations due to the amount of specialist legacy software upon which parts of the MPS still rely.
"Replacements or remediation for this software that are compatible with a more modern operating system have to be ready before the roll-out is completed to ensure continued operational effectiveness.
"We have completed the upgrade of just over 17,000 devices to Windows 8.1, and this reduces the number of desktops running Previous XP to around 10,000."
The spokesperson did not know, and was unable to find out in time for this article, whether the Met has patched all its Windows systems (not just the XP ones) against MS17-010 vulnerabilities (also known as the EternalBlue vulnerabilities) after the WannaCry outbreak. However, he did add, "The entire Met ICT estate has a number of layers of industry-leading security, which we have been monitoring closely over the past 24 hours. The MPS estate currently remains un-impacted by the cyber-attack and our security checks continue."
The complicating factor of legacy software on legacy systems is a problem, and not just for the Met. "I'm sympathetic to the fact that financially stretched government agencies and public services may not feel that an OS upgrade is the best use of scarce resources," independent security expert David Harley told SecurityWeek.
"Sometimes," he continued, "there are technical reasons for not upgrading a system required to run specific software or peripherals. There may be systems for which an OS upgrade is expected to damage functionality for other reasons, such as underpowered hardware. There are systems that may not require updating because they're fully air-gapped, I suppose. And the risk from running systems that can no longer be updated is sometimes overhyped: there's plenty of malware that doesn't rely on unpatched Windows versions to allow it to execute."
But none of this means that organizations can relax their efforts to upgrade XP systems. "Nonetheless," concluded Harley, "the risk of attack by malware that makes use of vulnerabilities in unpatched machines (such as the new Petya variant that apparently makes use of EternalBlue) is quite significant enough to make it unwise to rely on systems that are no longer normally updated, even if the agencies concerned are taking advantage of rare events like Microsoft's XP patch in May... After all, dangers to their data, systems and internal processes don't only affect their 'business' but all of us."
The bottom line is that 10,000 XP systems still in use by the Metropolitan Police Service is really 10,000 too many.
Turns Out New Petya is Not a Ransomware, It’s a Destructive Wiper Malware
29.6.2017 thehackernews Ransomware
What if I say the Tuesday's devastating global malware outbreak was not due to any ransomware infection?
Yes, the Petya ransomware attacks that began infecting computers in several countries, including Russia, Ukraine, France, India and the United States on Tuesday and demands $300 ransom was not designed with the intention of restoring the computers at all.
According to a new analysis, the virus was designed to look like ransomware but was wiper malware that wipes computers outright, destroying all records from the targeted systems.
Comae Technologies Founder Matt Suiche, who closely looked the operation of the malware, said after analyzing the virus, known as Petya, his team found that it was a "Wiper malware," not ransomware.
Security experts even believe the real attack has been disguised to divert world's attention from a state-sponsored attack on Ukraine to a malware outbreak.
"We believe the ransomware was, in fact, a lure to control the media narrative, especially after the WannaCry incident, to attract the attention on some mysterious hacker group rather than a national state attacker," Suiche writes.
Is Petya Ransomware Faulty or Over-Smart?
Petya is a nasty piece of malware that, unlike other traditional ransomware, does not encrypt files on a targeted system one by one.
Instead, Petya reboots victims computers and encrypts the hard drive's master file table (MFT) and renders the master boot record (MBR) inoperable, restricting access to the full system by seizing information about file names, sizes, and location on the physical disk.
Then Petya ransomware takes an encrypted copy of MBR and replaces it with its own malicious code that displays a ransom note, leaving computers unable to boot.
However, this new variant of Petya does not keep a copy of replaced MBR, mistakenly or purposely, leaving infected computers unbootable even if victims get the decryption keys.
Also, after infecting one machine, the Petya ransomware scans the local network and quickly infects all other machines (even fully-patched) on the same network, using EternalBlue SMB exploit, WMIC and PSEXEC tools.
Don't Pay Ransom; You Wouldn’t Get Your Files Back
So far, nearly 45 victims have already paid total $10,500 in Bitcoins in hope to get their locked files back, but unfortunately, they would not.
It's because the email address, which was being set-up by the attackers to communicate with victims and send decryption keys, was suspended by the German provider shortly after the outbreak.
Meaning, even if victims do pay the ransom, they will never recover their files. Kaspersky researchers also said same.
"Our analysis indicates there is little hope for victims to recover their data. We have analyzed the high-level code of the encryption routine, and we have figured out that after disk encryption, the threat actor could not decrypt victims’ disks," the security firm said.
"To decrypt a victim’s disk threat actors need the installation ID. In previous versions of 'similar' ransomware like Petya/Mischa/GoldenEye this installation ID contained the information necessary for key recovery."
If claims made by the researcher is correct that the new variant of Petya is a destructive malware designed to shut down and disrupt services around the world, the malware has successfully done its job.
However, it is still speculation, but the virus primarily and massively targeted multiple entities in Ukraine, including the country's local metro, Kiev's Boryspil airport, electricity supplier, the central bank, and the state telecom.
Other countries infected by the Petya virus included Russia, France, Spain, India, China, the United States, Brazil, Chile, Argentina, Turkey and South Korea.
How Did Petya get into the Computers in the First Place?
According to research conducted by Talos Intelligence, little-known Ukrainian firm MeDoc is likely the primary source of the yesterday's global ransomware outbreak.
Researchers said the virus has possibly been spread through a malicious software update to a Ukrainian tax accounting system called MeDoc, though MeDoc has denied the allegations in a lengthy Facebook post.
"At the time of updating the program, the system could not be infected with the virus directly from the update file," translated version of MeDoc post reads. "We can argue that users of the MEDoc system can not infect their PC with viruses at the time of updating the program."
However, several security researchers and even Microsoft agreed with Talo's finding, saying MeDoc was breached and the virus was spread via updates.
Britové se chlubí supermoderní letadlovou lodí… S Windows XP uvnitř
28.6.2017 Živě.cz BigBrother
Britové se chlubí supermoderní letadlovou lodí… S Windows XP
Britové vypluli se svoji největší a supermoderní letadlovou loď HMS Queen Elizabeth (technické detaily najdete třeba na Wikipedii), nicméně tamní novináři z The Times a Guardianu při návštěvě na palubě objevili několik zajímavostí, kterými se nyní baví celý internet.
Britské jaderné ponorky jedou na Windows XP
Na mnoha obrazovkách v kontrolní místnosti totiž svítily stará dobrá XPéčka. Ano, ten děravý systém z počátku století, který už je dávno za zenitem. Toto zjištění potvrzuje i pohled do rozsáhlé galerie britského ministerstva obrany, kde najdete stovky fotografií vlajkové lodě včetně jejích útrob.
Windows XP a jejich pastelkové téma Luna Silver na ošetřovně
Britští námořníci mají na Windows XP zjevně slabost, už před devíti lety jsme se totiž podivovali nad modernizací jejich jaderných ponorek, které se dočkaly téhož operačního systému schovaného pod hlavičkou SMCS NG – Submarine Command System Next Generation.
A proč se Britové rozhodli zrovna pro Windows XP? Vysvětlení je vlastně docela prosté. Návrh a poté vývoj vlajkové lodi velikosti královny Alžběty je běh na velmi, opravdu velmi, dlouhou trať.
Klepněte pro větší obrázek
Schéma největší britské letadlové a vlajkové lodi Jejího Veličenstva
Královské námořnictvo si ji objednalo v roce 2008, ovšem veřejnosti se na první plavbě pochlubila teprve před pár dny a nyní začne další mnohaleté kolo testování a dovybavování technologiemi. Suma sumárum, plného nasazení by se měla dočkat až někdy v roce 2020.
Nástupce Windows XP, Visty, přitom Microsoft vypustil do světa teprve rok před objednávkou lodi a její konstruktér by si samozřejmě nemohl dovolit u tak kritického zařízení spoléhat na software, který ještě neprošel dostatečně dlouhým testováním v ostrém podnikovém provozu. Na letadlové lodi prostě nemůžete jen tak spouštět Windows Update a čekat na servisní balíčky.
Tím se ostatně hájí i samotné námořnictvo, které konstatuje, že je Queen Elizabeth navržena s ohledem na kybernetický boj a elektronické války zítřka, takže britský daňový poplatník se rozhodně nemusí obávat, že snad ty tři miliardy liber námořníci prošustrovali na něčem nevhodném.
Na stranu druhou je však pravda, že systém typu Windows XP musí být v takto kritické instalaci dokonale izolovaný od vnějšího internetového světa, bylo by totiž nemilé, kdyby královnu Alžbětu kdesi uprostřed Atlantiku překvapila třeba modrá obrazovka smrti po infekci rasnomwaru WannaCry.