
Exploited Windows Flaws Affect Siemens Medical Imaging Products
4.8.2017 securityweek Exploit
Siemens has informed customers that some of its molecular imaging products are exposed to remote attacks due to vulnerabilities affecting Windows and other third-party components.
One advisory, published by both Siemens and ICS-CERT, warns of two critical Windows vulnerabilities that allow a remote, unauthenticated attacker to execute arbitrary code. The security holes impact Siemens Healthineers’ PET/CT and SPECT/CT medical imaging products running on Windows XP.
One of the flaws, CVE-2008-4250, is a critical Server service issue that had been exploited in targeted attacks when Microsoft patched it back in 2008. According to one researcher, it has also been leveraged in the past years to deliver the Conficker malware.Siemens medical imaging device
The second vulnerability is the more recent CVE-2017-7269, a buffer overflow vulnerability in Internet Information Services (IIS) 6.0 that has been exploited in attacks since at least July 2016. Microsoft has released a patch for this vulnerability on all its operating systems, including Windows XP due to the leak by Shadow Brokers of an NSA-linked exploit dubbed ExplodingCan.
Siemens says it’s working on releasing updates for the affected products and, in the meantime, it has advised customers to disconnect the devices from the network or deploy them in secure network segments.

While support for Windows XP ended in April 2014, the fact that Siemens has warned customers using this old version of Microsoft’s operating system is not surprising. Windows XP is still widely used, including in the healthcare sector.
Related: Learn More at SecurityWeek’s 2017 ICS Cyber Security Conference
A second advisory released by Siemens and ICS-CERT warns of other vulnerabilities affecting the molecular imaging products when running on Windows 7.
Siemens discovered that products running on Windows 7 are exposed to attacks due to four critical remote code execution vulnerabilities that can be exploited by an unauthenticated hacker. Three of them, discovered in 2015, affect Persistent Systems Accelerite Radia Client Automation (formerly HP Client Automation).
The fourth vulnerability, CVE-2015-1635, affects Windows and it was patched by Microsoft in April 2015. While the flaw can be exploited for remote code execution, researchers spotted denial-of-service (DoS) attacks leveraging the weakness shortly after it was fixed.
Siemens is also preparing patches for these security holes. Until the fixes become available, customers have been advised to take measures to prevent potential attacks.
One Million Exposed to Adware via Hijacked Chrome Extension
4.8.2017 securityweek Hacking
Over one million users were exposed to adware after the developer of a highly popular Chrome extension fell victim to a phishing attack.
The incident happened on August 1, when Chris Pederick, Director of Engineering at Bleacher Report, exposed his developer credentials after clicking on a link received via a phishing email. The result was that attackers accessed his account and pushed a modified version of the Web Developer Chrome extension.
Soon after the malicious extension version (v0.4.9) began reaching its one-million-strong userbase, people started complaining about its new malicious behavior, which involved inserting ads into visited sites. Early next day, the developer was able to upload a new version (v0.5) of the extension to remove the malicious code.
The developer notes that only the Chrome version of Web Developer was compromised, and that the Firefox and Opera versions aren’t affected. He encourages the extension’s Chrome users to update to version 0.5 as soon as possible.
“I am still looking into exactly what the malicious code was doing, but it is strongly advised that if you had Web Developer for Chrome installed that you change your password to any site that you logged into on Wednesday, August 2nd as a precaution, particularly Cloudflare which looks as though it may have been explicitly targeted. It has also been suggested that Cloudflare users revoke their API key if they visited the Cloudflare dashboard yesterday as this may have been compromised as well,” the developer says.
Pederick explains that on August 1 at 9.25 AM PDT, he received an email claiming to come from Google, informing him that there are some issues with his extension and the Chrome Store policies. He clicked on the link in the email and logged into his developer account almost immediately.
He discovered that the email was bogus and that he fell victim to an attack only the next day at 6:30 AM PDT, when he logged back into the account and changed the password. By 9.15 AM PDT, the clean version (v0.5) of Web Developer was already live in the Chrome store.
“With the compromised version of the extension now replaced in the store, I have been working on replying to everyone who tweeted or emailed me advising them to upgrade to version 0.5 ASAP. I have also informed Google of what happened, although there is not an obvious right way to report this and thus far I have not heard from them,” Pederick also notes.
The developer says that, in addition to changing the password for the compromised account, he also enabled two-factor authentication. He is still looking into the impact of the malicious code.
As it turns out, Web Developer was only one Chrome extension cybercriminals hijacked recently to infest with adware. Last week, a member of the Copyfish extension team received a similar phishing email and fell to the trick. This eventually resulted in attackers pushing an updated (and malicious) version of the extension, which too started to insert ads/spam into websites, just as it happened with Web Developer.
The attack happened on July 28 and the update was pushed the next day. On July 30, the developers noticed the malicious behavior and logged into their account, but noticed that the actors had moved the extension to their own account. Google moved Copyfish back to the original developers’ account on August 1, the developers reveal.
With two popular Chrome extensions targeted by similar phishing emails within several days of each other, chances are that more similar attacks are brewing.
SMBs Eye Managed Security Solutions: Survey
4.8.2017 securityweek Security
Webroot commissioned Wakefield Research to query 600 SMB IT decision makers in the US, UK and Australia to discover current attitudes towards IT security among companies with less than 500 employees. Such companies are often thought to be more at risk of successful cyber-attacks because of smaller budgets, fewer IT staff, and fewer infosecurity products designed for the smaller company.
The results of the survey (PDF) show the curious mixture of reality and wishful-thinking that often affects perception of infosecurity. For example, only 31% of US SMBs consider ransomware to be a major threat in 2017 -- despite 49% being concerned about 'new forms of malware'. In the UK, ransomware is considerd a bigger threat at 50%, with 59% worrying about new forms of malware. This is despite previous Webroot research (PDF) showing that over 60% of companies have already been affected by ransomware; while most analysts believe the threat is still increasing.
Self-confidence is high. First, 72% of SMBs globally believe that they are at least "almost completely ready to manage IT security and protect against threats"; second, 89% of SMBs around the world believe they have staff who could successfully address and/or eliminate a cyber-attack; and thirdly, 87% are confident in their staff cyber security education.
"The lack of concern about ransomware is leaving a gaping hole in the security of global businesses, as witnessed by the recent outbreaks of WannaCry and not-Petya," comments Adam Nash, Webroot's EMEA regional manager. "This combined with the false sense of security when it comes to businesses' ability to manage external threats is worrying."
Nash believes that SMBs "can no longer afford to put security on the back burner and need to start engaging with the issues and trends affecting the industry." It's not as if they do not understand the costs. Asked about the estimated total cost of a cyberattack "where customer records or critical business data were lost", US respondents replied with an average cost of $579,099.
This was the lowest figure. In the UK, it rises to $974,250; and to a colossal $1,509,938 in Australia.
Outsourcing security is often seen as a solution to the budgetary and staffing problems of SMBs. "Enlisting the help and expertise of a Managed Security Services Provider," comments Nash, "is one way to implement a secure, layered approach to combat external threats.” But it is not yet the norm, with only 13% of SMBs currently outsourcing. The rest use a mix of in-house and outsourced IT security support (37%), or fully in-house security (50%).
This is likely to change. Eighty percent of the respondents expect to use a third-party cyber security provider to manage security in 2017.
Despite an overt appearance of confidence in their own abilities, there seems to be an increasing acceptance of the value of outsourcing. Ninety percent of the respondents believe that outsourcing their IT solutions in the future would improve their security and enable them to address other areas of the business.
The net result highlighted by this survey is that there is a huge opportunity for MSSPs to tap into an awakening but yet unfulfilled demand in the SMB market.
Windows 10 Can Detect PowerShell Attacks: Microsoft
4.8.2017 securityweek Attack
Windows 10 can detect suspicious PowerShell activities, code injection, and malicious documents, including attacks where a process connects to a web server and starts dropping and launching an app, Microsoft says.
The functionality is integrated into Defender Advanced Threat Protection (Windows Defender ATP), which was released along Windows 10 Creators Update (and built into the core of Windows 10 Enterprise). The security software is also set to receive a series of enhancements in the Fall Creators Update. Courtesy of endpoint sensors built into Windows 10, along with machine learning technologies, Windows Defender ATP relies on a generic stream of behavioral events to improve detection, the tech giant says.
According to Microsoft, a process’ behavior is defined “not only by its own actions but also by the actions of descendant processes and other related processes,” and many of the actions associated with process execution are usually performed by other processes (injected with malicious code) when malware is involved. Thus, Windows Defender ATP incorporates process behavior trees, being able to analyze the actions and behaviors of a process and its descendants, related either through process creation or memory injection.
The use of machine learning helps Windows Defender ATP “generically detect all kinds of advanced attack methods,” and the same technologies are also effective in detecting attacks involving PowerShell scripts, code injection, and polymorphic documents that launch malicious code, the company explains in a blog post.
One of the malicious uses of PowerShell involves performing tasks without introducing malicious binaries, something that signature-based sensors can detect. Because payloads stored in scripts are easier to maintain and modify, PowerShell can prove attractive to malware creators. Leveraging machine learning, Windows Defender ATP can detect suspicious PowerShell behaviors, including those abused in fileless attacks, Microsoft claims.
To remain stealthy, malware such as Kovter also uses in-memory attack methods, thus evading signature-based scanners. For persistency in memory, PowerShell scripts that inject malicious code to other processes are used. Last month, however, Microsoft explained how Windows 10 enhancements provide protections against code injection attacks, including those used by Kovter and Dridex.
The company now says that documents with malicious macros that trigger suspicious PowerShell and Microsoft Word behaviors are also on Windows Defender ATP’s radar. “ML detects this attack method based on behavior signals available only at the time of execution. In contrast, most signature-based technologies are unable to stop this method, which uses the normal processes PowerShell.exe and Winword.exe. Documents themselves are also generally easy to alter for polymorphism,” Microsoft explains.
Windows 10, the tech giant says, can also detect suspicious documents used by Chanitor (also known as Hancitor). All of these security improvements are possible because the company’s tools take advantage of behavior data, collected via sensors built into Windows 10 and converted by Windows Defender ATP into sets of components or features fed to machine learning technologies like process behavior trees.
“The upcoming Fall Creators Update will integrate Windows Defender ATP closely with the rest of the Windows threat protection stack, transforming it into a comprehensive pre- and post-breach protection solution that enables enterprise customers to not only detect and respond to threats on their devices and networks but also to deliver proactive protection,” Microsoft notes.
Cisco fixes DoS, Authentication Bypass issues with its products and OSPF flaw
4.8.2017 securityaffairs Vulnerebility
Cisco addressed 15 flaws in its products, including 2 flaws that could be exploited by attackers to trigger a DoS condition or bypass local authentication.
Cisco addressed 15 vulnerabilities affecting a dozen products, including two high severity flaws that could be exploited by attackers to trigger a denial of service condition or bypass local authentication.
CISCO also addressed four cross-site scripting vulnerabilities, a cross-site request forgery vulnerability, two SQL vulnerabilities, and a directory traversal vulnerability.
The most important issues affect the network administration product CISCO Identity Services Engine and its Videoscape Distribution Suite. The bypass local authentication issue is caused by the improper handling of authentication requests and policy assignment.
CISCO
To exploit the flaw, an attacker could authenticate with a valid external user account that matches an internal username, then he will receive the authorization policy of the internal account. If successful the exploit would grant the attacker Super Admin privileges for the engine’s admin portal, Cisco said.
According to CISCO, the attacker would gain Super Admin privileges for the engine’s admin portal.
The denial of service vulnerability affects the virtual video infrastructure solution Videoscape Distribution Suite, that is not able to manage an excessive number of connections can cause the exhaustion of allotted resources.
“A vulnerability in the cache server within Cisco Videoscape Distribution Suite (VDS) for Television could allow an unauthenticated, remote attacker to cause a denial of service (DoS) condition on a targeted appliance.” states the CISCO advisory.
“The vulnerability is due to excessive mapped connections exhausting the allotted resources within the system. An attacker could exploit this vulnerability by sending large amounts of inbound traffic to a device with the intention of overloading certain resources. A successful exploit could cause the device to reload, resulting in a DoS condition.”
CISCO also published an advisory for several products affected by a bug involving the routing protocol Open Shortest Path First (OSPF).
A remote unauthenticated attacker can take full control of the OSPF Autonomous System (AS) domain routing table and intercept or black-hole traffic.
“The attacker could exploit this vulnerability by injecting crafted OSPF packets. Successful exploitation could cause the targeted router to flush its routing table and propagate the crafted OSPF LSA type 1 update throughout the OSPF AS domain.” states the advisory.
“To exploit this vulnerability, an attacker must accurately determine certain parameters within the LSA database on the target router,” Cisco warned. “This vulnerability can only be triggered by sending crafted unicast or multicast OSPF LSA type 1 packets. No other LSA type packets can trigger this vulnerability.”
CISCO has already issued security patches for affected products.
Microsoft Makes Third Attempt at Fixing Old Stuxnet Flaw
4.8.2017 securityweek Vulnerebility
One of the patches released by Microsoft as part of its June 2017 security updates represents the company’s third attempt at patching an old vulnerability exploited by the notorious Stuxnet worm in 2010.
The initial vulnerability, tracked as CVE-2010-2568, allows a remote attacker to execute arbitrary code on a system using specially crafted shortcut files with the LNK or PIF extension.
CVE-2010-2568 was one of the four zero-day vulnerabilities exploited in the 2010 Stuxnet attacks targeting Iran’s nuclear program. Despite being patched by Microsoft in August 2010, it has remained one of the most exploited vulnerabilities.
In 2015, researchers discovered that Microsoft’s initial fix could be bypassed and the tech giant released another patch. The flaw, tracked as CVE-2015-0096, was treated by Microsoft as a completely new issue.
According to an advisory published on Thursday by the CERT Coordination Center at Carnegie Mellon University, someone discovered another method for bypassing Microsoft’s patches for this weakness. No information has been provided as to who discovered the new vulnerability.
“The fix for CVE-2010-2568 and the subsequent fix for CVE-2015-0096 are both insufficient in that they not take into account LNK files that use the SpecialFolderDataBlock or KnownFolderDataBlock attributes to specify the location of a folder. Such files are able to bypass the whitelisting first implemented in the fix for CVE-2010-2568,” CERT/CC said in its advisory.
“By convincing a user to display a specially-crafted shortcut file, an attacker may be able to execute arbitrary code with the privileges of the user. Depending on the operating system and AutoRun/AutoPlay configuration, this can happen automatically by connecting a USB device,” the advisory explained.
CERT/CC pointed out that Microsoft patched the new vulnerability, tracked as CVE-2017-8464, with its June security updates. Microsoft informed customers at the time that this flaw had been exploited in the wild. Exploits for the security hole are now publicly available, including a Metasploit module made by Securify's Yorick Koster.
The organization pointed out that in addition to applying Microsoft’s patches, users can prevent potential attacks by blocking outgoing connections on TCP and UDP ports 139 and 445. This prevents machines from accessing a remote SMB server, which is typically needed to exploit the vulnerability.
Russian Hacker Sentenced to Prison for Ebury Botnet Attacks
4.8.2017 securityweek BotNet
A 41-year-old Russian citizen has been sentenced to 46 months in prison by a court in the U.S. state of Minnesota for his role in a cybercrime scheme involving a botnet powered by the Linux malware known as Ebury.
Maxim Senakh was indicted in the U.S. in January 2015 and was later arrested by authorities in Finland. His extradition to the United States was approved in January 2016 and, earlier this year, he pleaded guilty to conspiracy to violate the Computer Fraud and Abuse Act (CFAA) and conspiracy to commit wire fraud.
After serving his 46-month prison sentence in the United States, Senakh will be deported to Russia.
According to U.S. authorities, Senakh and his accomplices used the Ebury malware, an OpenSSH backdoor and credential stealer, to create a botnet that helped them make millions of dollars through click-fraud and email spam campaigns.
The Russian national, who admitted profiting from the traffic generated by the botnet, was responsible for registering domains used for the command and control (C&C) infrastructure.
Ebury was first spotted in 2011. Security firm ESET, Germany’s CERT‑Bund, the Swedish National Infrastructure for Computing, and the European Organization for Nuclear Research (CERN) published a detailed analysis of the malware in February 2014.
The U.S. Department of Justice said the botnet operated by Senakh and his co-conspirators ensnared tens of thousands of servers across the world, including thousands in the U.S.
“The defendant and his co-conspirators sought to turn a network of thousands of infected computers in the United States and around the world into their personal cash machines,” said Acting Assistant Attorney General Kenneth A. Blanco of the DOJ’s Criminal Division. “But cybercriminals like Mr. Senakh should take heed: they are not immune from U.S. prosecution just because they operate from afar or behind a veil of technology. We have the ability and the determination to identify them, find them, and bring them to justice.”
Several Russian hackers have been sentenced to prison this year in the United States, including Mark Vartanyan, Alexander Tverdokhlebov and Roman Valeryevich Seleznev.
Hackers Can Use Git Repos for Stealthy Attack on Developers
4.8.2017 securityweek Hacking
Malicious actors can abuse GitHub and other services that host Git repositories for stealthy attacks aimed at software developers, experts showed recently at the Black Hat security conference in Las Vegas.
Clint Gibler, security researcher at NCC Group, and Noah Beddome, security researcher and Director of Infrastructure Security at Datadog, have been testing the systems of organizations involved in software development and noticed that a key point of security failure in many cases was introduced by improperly managed or improperly understood trust relationships.
An in-depth analysis of the trust relationships between an organization, its developers, platforms and code revealed a series of security holes that can be exploited to evade the target’s defenses and gain persistent access to its systems.
Development-focused environments consist of workstations, general users, local and remote developers, version control systems, code repositories, continuous integration systems, and staging and production systems.
Gibler and Beddome showed that the trust relationships between these components, particularly in Agile software development environments, can introduce serious security risks if not managed properly. Furthermore, the experts warned that organizations can often introduce unintended levels of trust relationships - for example, removing security controls to get the job done faster and meet deadlines.
In order to demonstrate how these trust relationships can be abused, Gibler and Beddome created a penetration testing tool named GitPwnd. GitPwnd allows attackers to communicate with compromised devices via Git repositories, which store software history data.
Commands are sent to the hacked machine via the Git repository and the response is received over the same transport layer, making it less likely for the victim to notice the malicious traffic, which is disguised as operations that would normally be performed by a developer. GitPwnd uses GitHub to host the attacker’s Git repo, but the researchers pointed out that other services, such as BitBucket or GitLab, work just as well.
The attacker can create a copy of a popular repository to make communications as inconspicuous as possible. In order to further disguise the malicious traffic as normal user workflow, an attacker can abuse Git hooks, scripts that run automatically when a developer runs Git commands in a repo directory. And since hooks are not under version control, modifications made to them are not shown when using Git to determine local file changes, making the malicious code more difficult to detect.
Once the attacker gains access to the victim’s systems, via spear-phishing or other methods, GitPwnd can automate this entire process. The hacker can then run arbitrary Python commands on compromised machines to silently steal information and complete other tasks.
GitPwnd is open source and available on GitHub. While malicious actors could abuse it, the researchers told SecurityWeek that it still takes a skilled attacker to use the tool effectively. Moreover, the tool is designed to be “noisy” on purpose in certain aspects to discourage abuse.
Attacks on software developers are not unheard of. A few months ago, security firms ESET and Palo Alto Networks reported that a threat group that had been targeting open source developers, particularly ones using GitHub, managed to stay under the radar for over three years.
As for abusing GitHub itself, the China-linked threat group known as Winnti has leveraged the service to obtain the IP address and port number of C&C servers used in attacks aimed at organizations in Southeast Asia.
UK Security Researcher 'Hero' Accused of Creating Bank Malware
4.8.2017 securityweek Virus
A British computer security researcher hailed as a hero for thwarting the "WannaCry" ransomware onslaught was in US custody on Thursday after being indicted on charges of creating malware to attack banks.
Marcus Hutchins, known by the alias "Malwaretech," was charged in an indictment dated July 12 and unsealed by federal authorities in Wisconsin.
The US Justice Department said in a statement Hutchins was arrested Wednesday in Las Vegas, where a major Def Con hacker security conference took place over the weekend.
Twitter postings from other security researchers said he was detained as he prepared to fly back to Britain.
Hutchins faces criminal charges including conspiracy to commit computer fraud, according to the US Department of Justice.
The indictment accuses Hutchins and another individual of making and distributing Kronos "banking Trojan," a reference to malicious software designed to steal user names and passwords used at online banking sites.
Since it was created, Kronos has been configured to work on banking systems in Britain, Canada, Germany, Poland, France, and other countries, according to the DOJ.
The indictment set the time of the activity by Hutchins as being from July 2014 to July of the following year.
- 'Dark markets' -
Hutchins was part of a conspiracy to distribute the hacking tool on so-called dark markets, according to the indictment signed last month by US Attorney Gregory Haanstad.
Kronos was evidently first made available through certain internet forums in early 2014, and was marketed and distributed through a hidden online AlphaBay marketplace, according to US prosecutors.
AlphaBay was shut down by US and European police in a crackdown on two huge "dark web" marketplaces that allowed the anonymous online trade of drugs, hacking software and guns.
The timing of the indictment of Hutchins raises questions as to whether insights mined from the AlphaBay probe lead to his arrest.
Underground websites AlphaBay and Hansa Market had tens of thousands of sellers of deadly drugs like fentanyl and other illicit goods serving more than 200,000 customers worldwide.
AlphaBay, the largest dark web market, had been run out of Thailand, and filled a gap left behind by the notorious Silk Road online market, shut down by authorities in 2013.
Officials at the time said shutting down the two markets and the arrests of administrators enabled them to collect extensive intelligence on buyers and sellers, including criminal gangs. Their names were being distributed to law enforcement in 37 countries.
- From hero to accused -
Lawyers at the San Francisco-based online rights group Electronic Frontier Foundation said they were looking to contact Hutchins.
"The EFF is deeply concerned about the arrest of Marcus Hutchins, a security researcher known for shutting down the WannaCry ransomware. We are looking into the matter, and are reaching out to Hutchins," a statement from the group said.
A spokesperson for the British Embassy in Washington said only that they "are in touch with local authorities in Las Vegas following reports of a British man being arrested."
Hutchins was hailed as a hero in May for finding and triggering a "kill switch" for a WannaCry ransomware attack that was spreading wildly around the world, locking away data on computers and demanding money for its release.
Andrew Mabbitt, another security researcher who was with Hutchins in Las Vegas, said he did not believe the allegations. "He spent his career stopping malware, not writing it," Mabbitt said on Twitter.
Facebook COO Sheryl Sandberg on Crypto weakening: Crypto War 2.0
4.8.2017 securityaffairs Krypto
Sheryl Sandberg on crypto weakening. The new Crypto war being started where government agencies are wanting a reduction in encryption strengths.
DISCLAIMER: All views and facts explained in this article are the views of the author and does not in anyway related to the views of organization where the individual is employed. The article is an observation based on self-researched facts and is in no way written to offend any parties.
“The goal for governments is to get as much information as possible.” (Sheryl Sandberg)
One of the oldest encryption known to man was the Caesar cipher, also known as a shift cipher. Mostly used by Julius Caesar to send messages which he didn’t want to be understood by his enemies. Shift to today and encryption are an important part of your digital day-to-day life. Consider anyone who sends a WhatsApp message or browsing securely, encryption protects your security and importantly your privacy. But with the new Crypto war being started where government agencies are wanting a reduction in encryption strengths so that they can break into our digital day-to-day life is on. Quite the “Et tu Brute” moment for us, the users.
The idea is well iterated by Facebook COO Sheryl Sandberg where she says, “The goal for governments is to get as much information as possible. And so when there are message services like WhatsApp that are encrypted, the message itself is encrypted but the metadata is not, meaning that you send me a message, we don’t know what that message says but we know you contacted me,”. You quite clearly can understand her to stand in the matter where the governments are already being provided meta data (pretty much a road map of your activities) but now the new policies could make the use of the applications quite invasive.
The Crypto War ideally started in the 1990s when they did a bad promotion with the “Clipper Chip“, could not withstand the distribution PGP crypto system, reduce the strength of SSL encryption used in our browsing or the latest Apple iPhone unlock push.
Taking a queue from “Big Brother”, the other 2 members of the Five Eyes (FVEY) – UK and Australia, moved fast to herd their own legislative sheep. The Five Eyes of Surveillance – the USA, the UK, Canada, New Zealand and Australia, have a joint cooperation in sharing military, human and signals intelligence. The UK’s Snoopers’ Charter (The Investigatory Powers Act 2016) passed on 29 November 2016 was a step in the direction to have in-built backdoors to encrypted systems, for Government and Intelligence agencies to investigate.
The Australian Prime Minister has already stated that the UK’s law is a great model law and could hint at their own version very soon.

Sheryl Sanberg
“weakening of encryption would make lesser data available to Governments than more”
Sheryl Sandberg further makes it clear that weakening of encryption would make lesser data available to Governments than more, as in time people would use offshore alternatives.
This directly impacts Data Sovereignty , which was on the side of the Government. Tech giants like Google, Facebook and Apple have all spoken about how privacy and security is an offering of encryption but have faced challenges from Government agencies to about its use in terrorism and crime. Both ends of the debate hold up with no clear indication of a middle ground being reached anytime soon.
With Sentiment analysis and other processing tools in the age of Big Data, much of hate speech, terrorism and radical content and the other distasteful media are being slowly worked towards to be curbed and mitigated. Moves like these are counter intuitive to Intelligence as well because having too much information sometimes doesn’t mean you have complete intelligence. It is how fast you process this intel and can take action on it that counts.
One good thing does get underlined in the interview though. With all the fear of automation in the industry, a human touch is still required for intel generation.
Wikileaks – CIA Dumbo tool allows agents to disable security cameras
4.8.2017 securityaffairs BigBrothers
Wikileaks published a new batch of files belonging to the CIA Vault 7 archive that reveals the ‘Dumbo’ tool used by the agents to disable security cameras.
Wikileaks published a new batch of files belonging to the CIA Vault 7 archive, the documents detail a tool code named ‘Dumbo‘ that was developed by the intelligence agency to disables security cameras and corrupts recordings.
It identifies installed devices like webcams and microphones, either locally or connected by wireless (Bluetooth, WiFi) or wired networks.
CIA agents have to execute “Dumbo” directly from a USB thumb drive in the targeted device, it requires SYSTEM privileges to perform its activity.
The tool supports 32bit Windows XP, Windows Vista, and newer versions of Windows operating system. 64bit Windows XP or Windows versions prior to XP are not supported.
The tool is able to mute microphones, disable network adapters, and suspend processes utilizing webcams and corrupt any video recordings.
“Dumbo is a capability to suspend processes utilizing webcams and corrupt any video recordings that could compromise a PAG deployment. The PAG (Physical Access Group) is a special branch within the CCI (Center for Cyber Intelligence); its task is to gain and exploit physical access to target computers in CIA field operations.” states the description of the tool provided by Wikileaks.
Dumbo also reports operators where footage files are stored allowing their corruption or deletion.
“[The tool] identifies installed devices like webcams and microphones, either locally or connected by wireless (Bluetooth, WiFi) or wired networks. All processes related to the detected devices (usually recording, monitoring or detection of video/audio/network streams) are also identified and can be stopped by the operator,” WikiLeaks said. “By deleting or manipulating recordings the operator is aided in creating fake or destroying actual evidence of the intrusion operation.”
According to the user guide, Personal Security Products such as the Kaspersky antivirus may block the installation of the device driver necessary to perform Dumbo operations.

Below the list of release published by Wikileaks since March:
Dumbo– 03 August, 2017
Imperial – 27 July, 2017
UCL/RAYTHEON – 19 July, 2017
HighRise – 13 July, 2017
BothanSpy and Gyrfalcon – 06 July, 2017
OutlawCountry – 30 June, 2017
ELSA malware – 28 June, 2017
Cherry Blossom – 15 June, 2017
Pandemic – 1 June, 2017
Athena – 19 May, 2017
AfterMidnight – 12 May, 2017
Archimedes – 5 May, 2017
Scribbles – 28 April, 2017
Weeping Angel – 21 April, 2017
Hive – 14 April, 2017
Grasshopper – 7 April, 2017
Marble Framework – 31 March, 2017
Dark Matter – 23 March, 2017
WannaCry Hero Marcus Hutchins was detained in Las Vegas after Def Con conference
4.8.2017 securityaffairs Virus
Marcus Hutchins, the expert who discovered the “kill switch” that halted the outbreak of the WannaCry ransomware was detained in Las Vegas after Def Con.
Marcus Hutchins, also known as MalwareTech, is the 22-year-old security expert who made the headlines after discovering the “kill switch” that halted the outbreak of the WannaCry ransomware. Marcus Hutchins has been arrested in in Las Vegas after attending the Def Con hacking conference and was detained by the FBI in the state of Nevada.

In the last 24 hours, there were no tweets from the account of the expert, and the news of the arrest was confirmed by a friend of the experts to Motherboard.
“Motherboard verified that a detainee called Marcus Hutchins, 23, was being held at the Henderson Detention Center in Nevada early on Thursday. A few hours after, Hutchins was moved to another facility, according to a close personal friend.” reported Motherboard.“The friend told Motherboard they “tried to visit him as soon as the detention centre opened but he had already been transferred out.” Motherboard granted the source anonymity due to privacy concerns.”
“I’ve spoken to the US Marshals again and they say they have no record of Marcus being in the system. At this point we’ve been trying to get in contact with Marcus for 18 hours and nobody knows where he’s been taken,” the person added. “We still don’t know why Marcus has been arrested and now we have no idea where in the US he’s been taken to and we’re extremely concerned for his welfare.”
At the time I was writing there are no precise information about the arrest and its motivation.
Hutchins discovered that registering the domain
hxxp://www[.]iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea[.]com
it was possible to stop the propagation of the malware.
The Hutchins’s friend Andrew Mabbitt confirmed via Twitter that the expert is detained at FBI’s field office in Las Vegas.
Follow
Andrew Mabbitt @MabbsSec
Finally located @MalwareTechBlog, he's in the Las Vegas FBI field office. Can anyone provide legal representation?
7:48 PM - Aug 3, 2017
75 75 Replies 844 844 Retweets 856 856 likes
Twitter Ads info and privacy
The UK’s National Crime Agency confirmed to The Register that a UK national was arrested in Nevada, but doesn’t provide further information about the charges.
Today another event made the headlines, hackers behind WannaCry cashed out over $140,000 from the Bitcoins wallets used for the payments.
It’s is normal that many experts speculate the two events are correlated.
Stay Tuned!
Updated on August 3rd, 2017
“On Wednesday, 22-year-old Marcus Hutchins — who runs a security blog called MalwareTech — was arrested in Las Vegas for “his role in creating and distributing the Kronos banking Trojan,” according to a spokesperson from the U.S. Department of Justice.” states the CNN.
“The charges relate to alleged conduct occurring between July 2014 and July 2015.
According to an indictment provided to CNN Tech, Hutchins created the malware and shared it online. The Eastern District of Wisconsin returned a six-count indictment against Hutchins on July 12, 2017. It was unsealed at the time of his arrest.”

UK malware researcher Marcus Hutchins accused of creating Kronos Trojan
4.8.2017 securityaffairs Virus
The British security researcher Marcus Hutchins was arrested by the FBI on Thursday after being indicted on charges of creating the Kronos banking malware.
The news of the Marcus Hutchins‘s arrest made the headlines, the motivation has shocked the IT sector; the British malware experts who stopped the WannaCry ransomware outbreak was arrested in Las Vegas on Wednesday on suspicion of being a malware author.
The 22-year-old security expert, also known as MalwareTech, has been arrested in in Las Vegas after attending the Def Con hacking conference and was detained by the FBI in the state of Nevada.
FBI agents nabbed the man at the airport while he was preparing to fly back to the UK, he was arrested for “his role in creating and distributing the Kronos banking Trojan,” according to a spokesperson from the U.S. Department of Justice.
According to the investigators, Marcus Hutchins created the malware and shared it online, below the indictment issued by Eastern District of Wisconsin.
The prosecutors believe Hutchins created, shared, and masterminded the Kronos banking Trojan between July 2014 and July 2015.

Marcus Hutchins has developed the malicious code and he updated the code in February 2015 with a co-conspirator who is accused of advertising the Kronos banking Trojan on hacker forums.
The accomplice has sold at least one copy of the malware for $2,000, the US government also claims that on June 11, 2015, Hutchins sold attack code in America.
Kronos was developed starting from the Zeus Trojan, it took its name after the father of Zeus in Greek mythology, with the intent to steal money from victim’s bank accounts.
Principal featured advertised were:
Common credential-stealing techniques such as form grabbing and HTML injection compatible with the major browsers (Internet Explorer, Firefox and Chrome);+
32- and 64-bit ring3 (user-mode) rootkit capable of also “defending from other Trojans”;+
Antivirus bypassing;+
Malware-to-C&C communication encryption;+
Sandbox bypassing.+
Kronos malware was offered for $7,000 and it includes numerous modules for evading detection and analysis, the seller also offered a “try and buy” server for $1,000, giving the possibility to test the malware for a week prior to buying it.
Going back in the time, experts noticed that Marcus Hutchins tweeted the following message on July 13, 2014.
Follow
MalwareTech ✔@MalwareTechBlog
Anyone got a kronos sample?
7:26 PM - Jul 13, 2014
33 33 Replies 430 430 Retweets 330 330 likes
Twitter Ads info and privacy
The experts also speculate Hutchins was identified after the Feds shut down the darkweb marketplace Alphabay, where Kronos was available for sale. It is likely that Feds identified it during the investigation on the marketplace.
This is How CIA Disables Security Cameras During Hollywood-Style Operations
3.8.2017 thehackernews BigBrothers
In last 20 years, we have seen hundreds of caper/heist movies where spies or bank robbers hijack surveillance cameras of secure premises to either stop recording or set up an endless loop for covert operations without leaving any evidence.
Whenever I see such scenes in a movie, I wonder and ask myself: Does this happen in real-life?
Yes, it does, trust me—at least CIA agents are doing this.
WikiLeaks has just unveiled another classified CIA project, dubbed 'Dumbo,' which details how CIA agents hijack and manipulate webcams and microphones in Hollywood style "to gain and exploit physical access to target computers in CIA field operations."
The Dumbo CIA project involves a USB thumb drive equipped with a Windows hacking tool that can identify installed webcams and microphones, either connected locally, wired or wirelessly via Bluetooth or Wi-Fi.
Once identified, the Dumbo program allows the CIA agents to:
Mute all microphones
Disables all network adapters
Suspends any processes using a camera recording device
Selectively corrupted or delete recordings
However, there are two dependencies for a successful operation:
Dumbo program requires SYSTEM level privilege to run.
The USB drive must remain plugged into the system throughout the operation to maintain control over connected surveillance devices.
This project is being used by the CIA's Physical Access Group (PAG)—a special branch within the Center for Cyber Intelligence (CCI) which is tasked to gain and exploit physical access to target computers in CIA field operations.
Previous Vault 7 CIA Leaks
Last week, WikiLeaks published another CIA project, dubbed 'Imperial,' which revealed details of at least 3 CIA-developed hacking tools and implants designed to target computers running Apple Mac OS X and different flavours of Linux operating systems.
Since March, WikiLeaks has published 19 batches of "Vault 7" series, which includes the latest and last week leaks, along with the following batches:
UCL/Raytheon — An alleged CIA contractor, which analysed in-the-wild advanced malware and hacking tools and submitted at least 5 reports to the agency for help it develop its own malware.
Highrise — An alleged CIA project that allowed the spying agency to stealthy collect and forward stolen data from compromised smartphones to its server via SMS messages.
BothanSpy and Gyrfalcon — 2 alleged CIA implants that allowed the agency to intercept and exfiltrate SSH credentials from targeted Windows and Linux computers using different attack vectors.
OutlawCountry – An alleged CIA project that allowed the agency to hack and remotely spy on computers running Linux operating systems.
ELSA – Alleged CIA malware that tracks geo-location of targeted laptops and computers running the Microsoft Windows OS.
Brutal Kangaroo – A tool suite for Microsoft Windows OS used by the CIA agents to target closed networks or air-gap computers within an organisation or enterprise without requiring any direct access.
Cherry Blossom – A framework employed by the agency to monitor the Internet activity of the targeted systems by exploiting flaws in Wi-Fi devices.
Pandemic – A CIA's project that allowed the spying agency to turn Windows file servers into covert attack machines that can silently infect other PCs of interest inside the same network.
Athena – A spyware framework that the agency designed to take full control over the infected Windows systems remotely and works against every version of Windows OS–from Windows XP to Windows 10.
AfterMidnight and Assassin – 2 alleged CIA malware frameworks for the Microsoft Windows platform that's meant to monitor and report back actions on the infected remote host PC and execute malicious actions.
Archimedes – Man-in-the-middle (MitM) attack tool allegedly developed by the agency to target computers inside a Local Area Network (LAN).
Scribbles – Software allegedly designed to embed 'web beacons' into confidential documents, allowing the CIA agents to track insiders and whistleblowers.
Grasshopper – A framework which allowed the spying agency to easily create custom malware for breaking into Microsoft's Windows OS and bypassing antivirus protection.
Marble – Source code of a secret anti-forensic framework used by the agency to hide the actual source of its malware.
Dark Matter – Hacking exploits the spying agency designed to target iPhones and Macs.
Weeping Angel – Spying tool used by the CIA agents to infiltrate smart TV's, transforming them into covert microphones.
Year Zero – CIA hacking exploits for popular hardware and software.
Hackers Behind WannaCry Ransomware Withdraw $143,000 From Bitcoin Wallets
3.8.2017 thehackernews Ransomware
The cyber criminals behind the global WannaCry ransomware attack that caused chaos worldwide have finally cashed out their ransom payments.
Nearly three months ago, the WannaCry ransomware shut down hospitals, telecom providers, and many businesses worldwide, infecting hundreds of thousands of computers in more than 150 countries, encrypting files and then charging victims $300-$600 for the keys.
WannaCry was really bad, as the nasty ransomware forced the British NHS (National Health Service) to shut down hospitals and doctor's surgeries, and infected a Spanish telecommunications company and Russian mobile operator, among much more.
Even a month after the outbreak, the WannaCry ransomware was found infecting systems at Honda Motor Company, forcing the factory to shut down its production, and 55 speed and traffic light cameras in Victoria, Australia.
Overall, the hackers behind WannaCry made $140,000 in Bitcoins from the victims who paid for the decryption keys—but for almost three months, they did not touch three of their wallets where victims were instructed to send ransom payments.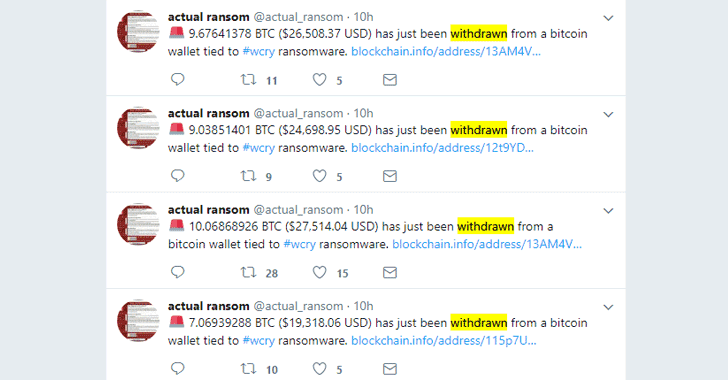
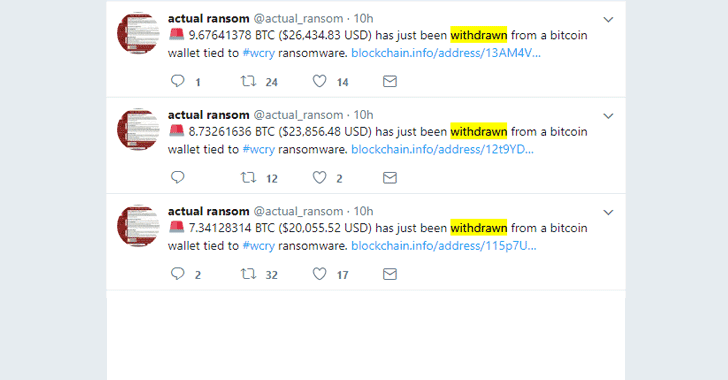
However, the WannaCry hackers started cashing out their cryptocurrencies on Wednesday night.
According to a Twitter bot tracking WannaCry ransom payments, only 338 victims paid the $300 in Bitcoin that totalled $140,000.
On Wednesday night, this money was withdrawn in 7 different payments within 15 minutes, although it is not clear where the money is being sent, or how the attacker will use it.
If you are unaware, we recently reported about Google's research on how cyber criminals and ransomware hackers cash out their stolen or looted cryptocurrencies via cryptocurrency exchanges that are involved in money laundering.
Last week, even German authorities arrested an alleged operator of the popular BTC-e Bitcoin exchange on charges of laundering over $4 billion in Bitcoin for culprits involved in hacking attacks, tax fraud and drug trafficking without identifying them.
The identity behind the WannaCry ransomware is still unknown, though some researchers traced back WannaCry to a state-sponsored hacking group called Lazarus in North Korea, while other believed the perpetrators might be Chinese.
The WannaCry epidemic was using self-spreading capabilities by leveraging leaked NSA's SMBv1 exploit, called EternalBlue, to infect vulnerable Windows computers, particularly those using older versions of the operating system.
While most of the affected organisations have now returned to normal, law enforcement agencies across the world are still on the hunt.
Hackers Hijacked Chrome Extension for Web Developers With Over 1 Million Users
3.8.2017 thehackernews Hacking 
From past few years, spammers and cyber criminals were buying web extensions from their developers and then updating them without informing their users to inject bulk advertisements into every website user visits in order to generate large revenue.
But now they have shifted their business model—instead of investing, spammers have started a new wave of phishing attacks aimed at hijacking popular browser extensions.
Just two days ago, we reported how cyber criminals managed to compromise the Chrome Web Store account of a German developer team and hijacked Copyfish extension, and then modified it with ad-injection capabilities to distribute spam correspondence to users.
Now just yesterday, another popular Chrome extension 'Web Developer' was hijacked by some unknown attackers, who updated the software to directly inject advertisements into the web browser of over its 1 million users.
Chris Pederick, the creator of Web Developer Chrome extension that offers various web development tools to its users, alerted late Wednesday that some unknown hackers apparently phished his Google account, updated the extension to version 0.4.9, and pushed it out to its 1,044,000 users.
In both the cases, cyber criminals used phishing first to gain access to the developers' Google accounts, hijacked their respective extensions and then updated the extension to perform malicious tasks.
However, the Firefox version of both the extensions was unaffected.
According to the developer, the malicious software build fetched JavaScript code from the web and ran it within users' web browsers to forcibly inject advertisements on web pages.
The plugin has access to pretty much everything that's happening on a user's browser—can do anything from reading all the website content to intercept traffic, sniff keystrokes, or any task one can imagine.
So, hijacking the Web Developer extension could be a nightmare for users—especially for those who are professional designers and access their official accounts (website, hosting, or email) using the same browser.
Pederick said version 0.4.9 of the software might have done worse, but within five to six hours of its compromise, he came to know of the malicious build, pulled it down from the Chrome store, and fixed the extension about an hour later.
However, the compromised code would have allowed the miscreants to make a sizable commission from the advertisements during the few hours the evil javascript was active.
Web Developer users are strongly recommended to update their extension to version 0.5 immediately.
Users should also consider changing their passwords for all web accounts, as well as nullify login tokens and cookies used on websites they visited while using the infected extension.
Cylance Launches Next-Gen Endpoint Security for Consumers
3.8.2017 securityweek Safety
CylancePROTECT Home Edition Will Allow Businesses to Offer Protection to Employee-Owned Devices at Home
The BYOD threat is a known security weakness for most companies that operate an 'own device' policy. While there are endpoint management products that provide a degree of safety, the mere fact that the device is owned outside of the network and used both inside and outside of the corporate environment means that it must be treated as insecure and a potential threat.
“The virtual borders of corporate networks are no longer defined by the corporate firewall," explains Christopher Bray, SVP/GM Consumer at Cylance Inc. "Because of the proliferation of work and personal devices at home, the distinction between the corporate network and employee's home networks has become blurred. CISOs and their security teams have a difficult time controlling their security risk and exposure from cybersecurity threats originating from employees' homes."
CylancePROTECT Home Edition
While corporate security has received a fillip from the introduction of next-gen AI and machine-learning malware detection, no such solution is available to home users. Home users usually ignore anti-malware, or use one of the free home versions of traditional AV -- which is not the perfect solution for modern malware.
"CylancePROTECT Home Edition," Bray told SecurityWeek, "is the first next-generation antivirus available to consumers and provides families with the only enterprise-class, next generation security software built for home use. We do this by using artificial intelligence to eliminate the need for updates and popups, and with an easy-to-use and elegant interface. We're excited to roll out the Home Edition to customers as the next step in Cylance's mission to protect all devices and people.”
This move is likely to be well-received by corporate CISOs. "I think this is a great idea," said Steven Lentz, CSO and Director of information security at Samsung Research America. "It's good that companies are offering home users protection since I bet a good amount of them are infected, or don't know they have embedded malware/ransomware on their systems.
"Cylance," he told SecurityWeek, "has a good reputation, so I would believe and hope that their offering should be pretty good. Home users are such a large target area -- and vendors need to be more proactive and protect against all the various malware." Lentz does not believe that 'traditional AV' does a good enough job against modern malware. "I am glad Cylance is doing this for the home user. I hope they offer it for free, like RansomFree [next-gen from Cybereason; but limited to ransomware]. It would also be great if Cylance offered the product for Mac as well as Windows."

Lentz gets half his wishes. It is not free. It "will be sold on an annual basis, paid for by the employer for employees to use on their home systems," Bray told SecurityWeek. "Companies recognize the risk of today's threats combined with the new working environment where employees telecommute and can use personal devices to access company assets." Although used at home, it provides additional security for the business.
It also represents pretty good value. It is priced per household, allowing the employee to protect up to 10 family members' devices no matter where they are in the country. Further, it can be viewed as an employment benefit -- protecting the corporate network while providing a free service to employees and their families.
But Lentz gets his second wish: it is available for both Windows and Mac. "With our company mission to protect every device under the sun," said Bray, "this is the first step in our future plans (which will include iOS and Android)."
One of the traditional problems for any company installing security on employee devices is the privacy pushback; many employees are wary about having company software on their personal device reporting back to the company security team. Users like the freedom of allowing other family members to use their devices, and not having to worry about corporate security policies. There is no issue with CylancePROTECT Home Edition -- it is completely stand-alone and designed to protect the user without reference to the company.
"Home Edition does not send any metrics or reports to the company," explained Bray. "We architected the product very deliberately to ensure complete privacy for the employees. Their deployments are physically separate so it is impossible for the company to have any view into their personal systems. This data, however, is easily accessed by the employee themselves through their own cloud console through which they can manage, configure and view their personal deployments. This also gives the employee the additional benefit of deploying and managing protection across their family's systems irrespective of physical location; kids at college, parents in another city..."
In summary, Home Edition is a complete next-gen anti-malware product, free to the end user (paid for by his employer) and coming with no privacy encumbrances. If Lentz is a good example, it will be welcomed by CISOs -- but they may well wish it were free.
Cylance Inc closed a $100 million Series D funding round in June 2016.
Cisco Patches Serious Flaws in ISE, VDS TV Products
3.8.2017 securityweek Vulnerebility
Cisco on Wednesday published more than a dozen security advisories describing vulnerabilities in various products. Two of the flaws affecting Videoscape Distribution Suite for Television (VDS TV) and Identity Services Engine (ISE) have been rated high severity.
VDS TV, formerly known as Content Delivery System for Television, is a virtual video infrastructure solution that allows service providers to deliver, store and stream video content to subscribers. The ISE is a network security product used in the healthcare, telecommunications, financial, manufacturing, retail and education sectors, including by organizations such as the United Nations, Virgin Media, AT&T, and J. C. Penney.
The security hole in VDS TV, CVE-2017-6745, exists in the product’s cache server and it allows a remote, unauthenticated hacker to cause a denial-of-service (DoS) condition on the targeted appliance by sending it large amounts of inbound traffic.
“The vulnerability is due to excessive mapped connections exhausting the allotted resources within the system. An attacker could exploit this vulnerability by sending large amounts of inbound traffic to a device with the intention of overloading certain resources. A successful exploit could cause the device to reload, resulting in a DoS condition,” Cisco said in its advisory.
The vulnerability, for which there are no workarounds, has been addressed by Cisco with the release of TV Streamer Application 4.6(1).
The weakness affecting ISE, CVE-2017-6747, exists in the product’s authentication module and it allows a remote attacker to bypass authentication, and possibly get super admin privileges on the ISE administration portal.
“The vulnerability is due to improper handling of authentication requests and policy assignment for externally authenticated users. An attacker could exploit this vulnerability by authenticating with a valid external user account that matches an internal username and incorrectly receiving the authorization policy of the internal account,” Cisco explained.
Cisco ISE, ISE Express and ISE Virtual Appliance running versions 1.3, 1.4, 2.0.0, 2.0.1 or 2.1.0 are affected. A fix for the vulnerability is included in versions 1.4.0 patch 11, 2.0.0 patch 5, 2.0.1 patch 5, and 2.1.0 patch 2. Version 2.2.x is not impacted.
Both of these high severity flaws were discovered internally and there is no evidence of exploitation for malicious purposes.
Symantec to Sell Certificate Business to DigiCert for $950 Million
3.8.2017 securityweek IT
After reaching an agreement with Google regarding penalties for misissued digital certificates, Symantec announced on Wednesday that it has made a deal with DigiCert to sell its website security and related public key infrastructure (PKI) solutions.
DigiCert has agreed to pay Symantec $950 million in cash and a stake of roughly 30 percent in common stock equity of the DigiCert business. The transaction has been approved unanimously by Symantec’s board of directors and is expected to be completed in the third quarter of fiscal 2018.
DigiCert will continue to operate under the supervision of CEO John Merrill from its headquarters in Lehi, Utah, where it will employ more than 1,000 people. With the acquisition of Symantec’s certificate business, the company is expected to bring new approaches to the TLS market and benefit from growth opportunities in IoT.
Symantec has come under fire recently for misissued TLS certificates, and Google and other web browser vendors have been discussing penalties.
Google announced recently that certificates issued by Symantec and its partners before June 1, 2016, will need to be replaced by March 15, 2018. All other certificates need to be replaced until the release of Chrome 70, currently scheduled for release in October 2018.
Google said Symantec could still issue digital certificates, but only through the infrastructure of a subordinate certificate authority (SubCA). A few weeks ago, Symantec said it had been trying to find a partner and informed customers that the new infrastructure should be set up by December 1.
It appears Symantec has decided to abandon its website security business altogether, but promised customers an easy transition.
“We carefully examined our options to ensure our customers would have a world-class experience with a company that offers a modern website PKI platform and is poised to lead the next generation of website security innovation,” said Symantec CEO Greg Clark. “I’m thrilled that our customers will benefit from a seamless transition to DigiCert, a company that is solely focused on delivering leading identity and encryption solutions. Symantec is deeply committed to the success of this transition for our customers.”
Some of Symantec and DigiCert’s competitors have taken the opportunity to get Symantec customers concerned about potential disruptions to join them.
Comodo has published a blog post warning Symantec customers of the consequences of moving to DigiCert.
“DigiCert does not have the same infrastructure as Symantec, as a much smaller Certificate authority it never had the need to,” Comodo said. “Therefore, the eventual platform migration poses a huge execution and technology risk for all Symantec Enterprise customers and channel partners.”
G Suite Admins Can Now Manage SAML Certificates
3.8.2017 securityweek Security
Google on Wednesday announced that G Suite administrators are now able to directly manage X.509 certificates associated with their Security Assertion Markup Language (SAML) applications.
SAML allows users to use G Suite credentials to sign into enterprise cloud apps via Single Sign-On (SSO). Admins are provided with an identity and access management (IAM) service to manage all users and cloud applications, but don’t have to manage individual user IDs and passwords for each cloud application, for each user, as IAM features a unified sign-on across all enterprise cloud software.
With the help of X.509 certificates, SAML can ensure the authenticity and integrity of messages shared between an Identity Provider (IdP) and Service Provider (SP), Google explains. These certificates are automatically associated with a SAML application when it is first installed via the Amin console.
The certificates come with a five-year lifetime. Previously, admins had to contact Google Support to change or rotate an application’s existing certificate, regardless of whether it was about to expire or was compromised.
As soon as a certificate expires, however, users can no longer sign into the associated application using SAML-based SSO.
With the new change, admins can manage X.509 certificates on their own, without having to ask for additional support from Google.
“Today, we’re giving you the ability to do so on your own in the Admin console, where you can easily view certificates in use, identify those about to expire, create new ones, and assign them to applications,” Google notes.
However, only super admins are provided with visibility into the expiration status of SAML certificates and only they can take action on these certificates, the Internet giant also explains.
The new feature is launching to both Rapid Release and Scheduled Release and impacts all G Suite editions. Because it will see a gradual rollout, the feature could take up to 15 days to become visible in some cases.
Admins interested in learning more on how to set up custom SAML applications should head to this support article. Information on SAML certificate rotation and how admins can manage certificates is available here.
'Dumbo' Tool Helps CIA Agents Disable Security Cameras
3.8.2017 securityweek BigBrothers
The U.S. Central Intelligence Agency (CIA) has developed a tool that disables security cameras and corrupts recordings in an effort to prevent its agents from getting compromised, according to documents published on Thursday by WikiLeaks.
The tool, dubbed “Dumbo,” is executed directly from a USB thumb drive by an operative who has physical access to the targeted device. Once executed, the program can mute microphones, disable network adapters, and suspend processes associated with video recording devices.
Dumbo also informs its user of where those video recording processes store footage so that the files can be corrupted or deleted.
The user guides made available by WikiLeaks — the latest version is dated June 2015 — show that the tool was developed in response to the need for a capability to disrupt webcams and corrupt recordings in an effort to prevent a PAG (Physical Access Group) deployment from getting compromised.
PAG is a special branch within the CIA’s Center for Cyber Intelligence (CCI) and its role is to gain physical access to computers and exploit this access, WikiLeaks said.
The tool, designed for Windows XP and newer versions of the Microsoft operating system, needs SYSTEM privileges to function correctly.
“[The tool] identifies installed devices like webcams and microphones, either locally or connected by wireless (Bluetooth, WiFi) or wired networks. All processes related to the detected devices (usually recording, monitoring or detection of video/audio/network streams) are also identified and can be stopped by the operator,” WikiLeaks said. “By deleting or manipulating recordings the operator is aided in creating fake or destroying actual evidence of the intrusion operation.”
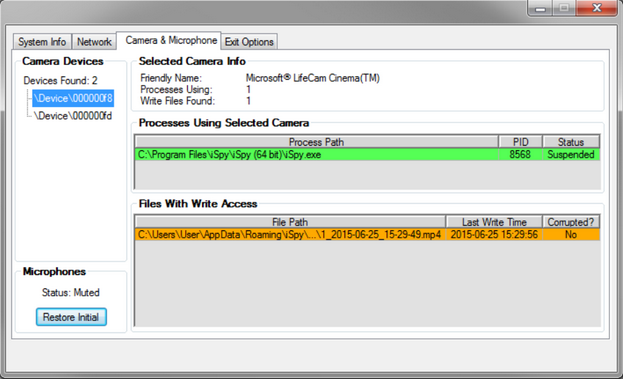
Dumbo developers pointed out that home security products (e.g. Kaspersky antivirus) may block some of the tool’s functions, and advised users to disable any protections before installation.
WikiLeaks has exposed numerous tools allegedly used by the CIA as part of a leak dubbed Vault 7. The tools detailed so far are designed for hacking Mac OS X devices (Imperial), intercepting SMS messages on Android devices (HighRise), redirecting traffic on Linux systems (OutlawCountry), stealing SSH credentials (BothanSpy), spreading malware on an organization’s network (Pandemic), locating people via their device’s Wi-Fi (Elsa), hacking routers and access points (Cherry Blossom), and accessing air-gapped networks (Brutal Kangaroo).
New TrickBot banking Trojan variant borrows spreading capabilities from Wannacry
3.8.2017 securityaffairs Virus
A cyber gang is improving its version of the TrickBot banking Trojan by implementing the self-spreading worm-like capabilities used by WannaCry and NotPetya
Cybercriminals most of all are capitalizing the lesson from the recent WannaCry and NotPetya ransomware massive attacks.
At least one cyber gang is improving its version of the TrickBot banking Trojan by implementing the self-spreading worm-like capabilities that allowed both ransomware to rapidly spread worldwide.
The new version of the TrickBot banking Trojan, dubbed “1000029” (v24), includes the code for the exploitation of the Windows Server Message Block (SMB) vulnerability.

Recently malware experts at Flashpoint have discovered that the TrickBot Banking Trojan has been improved to spread locally across networks by exploiting the Server Message Block (SMB) flaw.
“On July 27, 2017, in coordination with Luciano Martins, Director of Cyber Risk Services at Deloitte, Flashpoint observed a new version – “1000029” – of the formidable “Trickbot” banking Trojan with a new “worm64Dll” module, spread via the email spam vector, impersonating invoices from a large international financial institution.” states the analysis shared by Flashpoint.
The experts noticed that n of TrickBot ‘1000029’ is still a developing phase, for example, the crooks haven’t yet implemented the feature to mass scan on the Internet for vulnerable systems.
The Trojan actually scans domains for lists of vulnerable servers via the NetServerEnum Windows API and enumerate other computers on the network via Lightweight Directory Access Protocol (LDAP).
“The Trickbot gang appears to be testing a worm-like malware propagation module, which appears to spread locally via Server Message Block (SMB), scan domains for lists of servers via NetServerEnum Windows API, and enumerate other computers via Lightweight Directory Access Protocol (LDAP) enumeration. As of this writing, this malware feature does not appear to be fully implemented by the criminal gang as the initial purported SMB exploit has not yet been observed.” continues the analysis.
The researchers also discovered that the new TrickBot variant can also be disguised as ‘setup.exe’ that is delivered through a PowerShell script to spread through interprocess communication and download additional version of TrickBot onto shared drives.
Experts have no doubt, the Trickbot crew will continue in improving the threat.
“Flashpoint assesses with moderate confidence that the Trickbot gang will likely continue to be a formidable force in the near term,” concludes Flashpoint.
“Even though the worm module appears to be rather crude in its present state, it’s evident that the Trickbot gang learned from the global ransomware worm-like outbreaks of WannaCry and ‘NotPetya’ and is attempting to replicate their methodology.”
The bateleur backdoor is the new weapon in the Carbank gang’s arsenal
3.8.2017 securityaffairs Virus
Experts at Proofpoint noticed the infamous cyber crime gang Carbanak has added a new JScript backdoor dubbed Bateleur Backdoor to its arsenal.
According to researchers at security firm Proofpoint, the infamous cyber crime gang Carbanak has added a new JScript backdoor dubbed Bateleur Backdoor to its arsenal. Carbanak, aka FIN7, has also used updated macros.
The Carbanak gang was first discovered by Kaspersky Lab in 2015. the group has stolen at least $300 million from 100 financial institutions.
In early 2016, the Carbanak gang target banks and financial institutions, mainly in the US and the Middle East.
In November last year, experts at Trustwave uncovered a new campaign launched by the group targeting organizations in the hospitality sector.
In January, the Carbanak gang started using Google services for command and control (C&C) communication.
The crooks used the “ggldr” script to send and receive commands to and from Google Apps Script, Google Sheets, and Google Forms services.
Hackers used to create a unique Google Sheets spreadsheet for each infected user, in this way they attempted to avoid detection.
In May, researchers at Trustwave observed the group using new social engineering techniques and phishing techniques, including the use of hidden shortcut files (LNK files) for target compromise.
Back to the present, the group started using new macros and the Bateleur backdoor in attacks against United States-based chain restaurants.
“Proofpoint researchers have uncovered that the threat actor commonly referred to as FIN7 has added a new JScript backdoor called Bateleur and updated macros to its toolkit. We have observed these new tools being used to target U.S.-based chain restaurants, although FIN7 has previously targeted hospitality organizations, retailers, merchant services, suppliers and others.” ” reads the analysis published by Proofpoint. The new macros and Bateleur backdoor use sophisticated anti-analysis and sandbox evasion techniques as they attempt to cloak their activities and expand their victim pool.”
The Carbanak gang started using macro documents to drop the new JScript backdoor instead GGLDR script that was used in past campaigns to send and receive commands to and from Google Apps Script, Google Sheets, and Google Forms services.
Experts noticed that the Carbanak gang has updated multiple times both the macro and the malware since June.
Attackers used simple and effective messages to target a restaurant chain, if email is sent from an Outlook.com account then the text claims “This document is encrypted by Outlook Protect Service,”if it is sent by a Gmail account, the lure document instead claims “This document is encrypted by Google Documents Protect Service.”

The documents embed macros that access the malicious payload via a caption, then they extracts the JScript from the caption and save the content to debug.txt in the current user’s temporary folder (%TMP%). Next, the macro creates a scheduled task to execute debug.txt as a JScript (the Bateleur backdoor), it sleeps for 10 seconds before deleting the scheduled task
The Bateleur backdoor appears very sophisticated, it implements anti-sandbox and anti-analysis (obfuscation) mechanisms.
“The malicious JScript has robust capabilities that include anti-sandbox functionality, anti-analysis (obfuscation), retrieval of infected system information, listing of running processes, execution of custom commands and PowerShell scripts, loading of EXEs and DLLs, taking screenshots, uninstalling and updating itself, and possibly the ability to exfiltrate passwords, although the latter requires an additional module from the command and control server (C&C).” continues the analysis.
“Although Bateleur has a much smaller footprint than GGLDR/HALFBAKED, lacks basic features such as encoding in the C&C protocol, and does not have backup C&C servers, we expect the Bateleur developer(s) may add those features in the near future,” the security researchers say.
Proofpoint speculates the Bateleur backdoor is being used by the FIN7/Carbanak group, the researchers observed a threat actor that was using this specific code along with GGLDR scripts that was used exclusively by the gang.
The phishing messages were “sharing very similar or identical attachment names, subject lines, and/or sender addresses.”
The Bateleur backdoor was also leveraging the Tinymet Meterpreter downloader, a tool employed by Carbanak hackers since 2016.
“A small Meterpreter downloader script, called Tinymet by the actor(s) (possibly inspired by [5]), has repeatedly been observed being utilized by this group at least as far back as 2016 [6] as a Stage 2 payload. In at least one instance, we observed Bateleur downloading the same Tinymet Meterpreter downloader ” states Proofpoint.
The Carbanak is still active and continuously improve its Tactics, Techniques, and Procedures.
“We continue to see regular changes to the tactics and tools used by FIN7 in their attempt to infect more targets and evade detection. The Bateleur JScript backdoor and new macro-laden documents appear to be the latest in the group’s expanding toolset, providing new means of infection, additional ways of hiding their activity, and growing capabilities for stealing information and executing commands directly on victim machines,” ProofPoint concludes.
Former Bupa employee offered 1 million customer records for sale on dark web
3.8.2017 securityaffairs Incindent
Former Employee of the Healthcare giant Bupa offered for sale records of 1 Million clients on Dark Web.
A former employee of healthcare giant Bupa was selling between 500,000 and 1 million medical records on the dark web. The former employee whose identity remains undisclosed had sold several batches of hundreds of thousands of medical records managed by Bupa.
Analysts at DataBreaches found a first batch of medical records stolen by the former employee on June 23, the man was offering them on a dark web marketplace. DataBreaches revealed the vendor MoZeal was offering for sale at least 500,000 medical records, the man listed between 500,000 to 1 million insurance records.
Below the official statement issued by the company.
“All of the information and statements we have made public this week, remain valid,” read the statement. “We are aware of a report by Databreaches.net that suggest ‘a former employee claimed to have 1m records for sale’. Our thorough investigation established that 108,000 policies, covering 547,000 customers, had been copied and removed. The disparity in numbers claimed and those taken, relates to duplicate copies of some records.”
The Bupa’s Managing Director Sheldon Kenton downplayed the incident claiming that only 103,000 medical records of Bupa UK clients were sold.
“I wanted to let you know that we recently discovered that an employee had taken some customer information from one of our systems. I know that this will be concerning, so wanted to explain the situation,” Kenton said.
“The information that was taken does not include any financial or medical information. This data comes from one particular part of Bupa – Bupa Global – which handles international health insurance, mainly for people who work overseas or travel on a regular basis. To be fair, this does not affect Bupa’s other local businesses.”

The listing contained insurance data from 122 countries and customers’ personal information including member and registration IDs, names, birthdates, contact information and information about intermediaries.
Bupa, of course, fired the employee and is currently pursuing legal actions against him and is trying to discover the real identity of the vendor MoZeal.
Medical records are a hot commodity on dark web marketplaces, the healthcare industry was the number one target for cybercriminals. Previously, the banking industry held the top position.
In 2015, more than 100 million healthcare records were compromised, according to IBM’s “2016 Cyber Security Intelligence Index.”
The non-profit organization Institute for Critical Infrastructure Technology revealed that 47 percent of US-based residents have had their medical records stolen, their data were offered for sale on the dark web in 2015.
New IoT Bill Proposes Security Standards for Smart Devices
3.8.2017 thehackernews IoT
By this time, almost every one of you owns at least one internet-connected device—better known as the "Internet of things"—at your home, but how secure is your device?
We have recently seen Car hacking that could risk anyone's life, Hoverboard hacking, even hacking of a so-called smart Gun and also the widespread hacks of insecure CCTV cameras, routers and other internet-connected home appliances.
But this did not stop vendors from selling unsecured Internet-connected smart devices, and customers are buying them without giving a sh*t about the security of their smart devices.
However, the massive cyber attack on a popular DNS service provider that shut down a large portion of the Internet last year made us all fear about the innocent-looking IoT devices, which surround us every day, but actually, poses a threat to global cyber security.
Not anymore!
A bipartisan group of senators have now introduced a new bill aimed at securing internet-connected devices by setting industry-wide security standards for the government's purchase and use of IoT devices, including computers, routers and security cameras.
The new bill—called the Internet of Things Cybersecurity Improvement Act of 2017—was introduced on Tuesday by Senator Mark Warner (D-VA), a Democrat in Virginia and Senator Cory Gardner (R-CO), a Republican from Colorado.
The bill would require suppliers that provide wearables, sensors and other web-connected smart devices to the United States government to adhere to some new industry-wide security practices.
The security standards prohibit the suppliers from including hard-coded (unchangeable) usernames and passwords in their devices, which is a primary vector for hackers and malware to break into the devices and hijack them.
Last year's cyber attack on Dyn DNS provider also involved the use of default credentials to break into hundreds of thousands of internet-connected smart devices and then used them to launch distributed denial of service (DDoS) attacks on Dyn, causing a significant outage to a ton of websites such as Twitter, GitHub, PayPal, Amazon, and Netflix for several hours.
The legislation would also require vendors to ensure that their devices are patchable and are free from already known vulnerabilities when sold.
The bill was drafted with input from technology experts at the Atlantic Council and Harvard University.
The lawmakers are trying to "take the lightest touch possible" to address an "obvious market failure" that has left device manufacturers with little incentive to build with security in mind, Sen. Warner told Reuters.
The legislation would direct the White House Office of Management and Budget (OMB) for permission to buy devices if their network-level security requirements are in place.
New Legislation Could Force Security Into IoT
3.8.2017 securityweek IoT
After years of warnings from security experts and researchers, the Internet of Things (IoT) remains fundamentally insecure. Now a group of senators has introduced bipartisan legislation to force vendors to ensure basic security within their IoT devices if they wish to sell into the government market.
Sens. Mark R. Warner (D-VA) and Cory Gardner (R-CO), co-chairs of the Senate Cybersecurity Caucus, along with Sens. Ron Wyden (D-WA) and Steve Daines (R-MT) today introduced bipartisan legislation: Internet of Things (IoT) Cybersecurity Improvement Act of 2017. Its purpose is to require that all devices bought by the government meet defined minimum security requirements. Its effect will be that without compliance, vendors will lose their largest single market. Compliance, they hope, will then filter down from the public to private sectors, and on to consumers.
IoT Security"While I'm tremendously excited about the innovation and productivity that Internet-of-Things devices will unleash, I have long been concerned that too many Internet-connected devices are being sold without appropriate safeguards and protections in place," said Sen. Warner. "This legislation would establish thorough, yet flexible, guidelines for Federal Government procurements of connected devices. My hope is that this legislation will remedy the obvious market failure that has occurred and encourage device manufacturers to compete on the security of their products."
The need for legislation is empirically obvious. Vendors simply do not build security into the design of their internet-connected devices. Last year, the IoT delivered the world's largest (Mirai) DDoS attacks. This year there have been numerous examples of vulnerable IoT cameras (including more announced today). Last week, SecurityWeek reported on a fish tank being used to exfiltrate data; and yesterday it was shown that the Amazon Echo can be used by attackers as an always-on listening device.
Martin Zinaich, Information Security Officer with the City of Tampa (FL) told SecurityWeek that he found WannaCry attack traffic on his network. He tracked it back to an HP scanner, which was infected with the ransomware. "I now have to worry about large format scanners. Tomorrow it will be light bulbs, door locks and the candy machine," he said. Adding insult to injury, the scanner's documentation says, closed system "so no antivirus is required."
Under the proposed legislation, vendors selling to the US government will be required to ensure their devices are patchable, they rely on industry standard protocols, they do not use hard-coded passwords, and they do not contain any known vulnerabilities.
Passwords, patching, and vulnerabilities are all likely to be problem areas; but the legislators have tried to cover most angles. For example, with the Amazon Echo vulnerability, the vulnerability is found in the physical design of the device -- and it simply cannot be patched. However, the legislation includes waivers for a number of specific conditions, allowing, for example,'an equivalent level of security' for non-compliant devices.
In this instance, "I don't see any reason why this attack type would prompt a recall of hardware," comments Travis Smith, principal security researcher at Tripwire. "Since the attack requires physical access, the vast majority of users will never have to worry about it. Even if this device were to become compromised, the network traffic of an Echo device is very static. Any attacker sending audio data out would be exposed very quickly to anyone monitoring traffic."
The vulnerability issue is given further consideration in relation to disclosures. Vendors have been known to attempt to limit disclosure through copyright protections, and threats to invoke the Computer Fraud and Misuse Act (CFAA). This new Act exempts security researchers from liability under the CFAA -- an Act that Krebs describes as "a dated anti-cybercrime law that many critics say has been abused by government prosecutors and companies to intimidate and silence security researchers."
To be covered by this exemption, disclosure by a security researcher will need to conform to a set of standards yet to be defined -- but ones that will probably delay disclosure until the vendor fixes the vulnerability. However, vendors and researchers often disagree on fixes and timescales. Last week IOActive disclosed vulnerabilities in a Diebold ATM and in nuclear radiation monitors that the vendors either ignored or declined to fix. Disclosure has always been a problem, and is likely to remain so within the parameters of the new bill.
Passwords and patching are also always a problem. "When left up to the user," comments Smith, "changing passwords and installing patches is not a priority." Users, he explains, are more interested in getting the device working than in ensuring it is working securely. "The reason Mirai was so successful was not because users could not change their password, but because they chose not to when installing the device. I would add to this bill that devices should force the user to change the default password, but that the default password should be unique to each device as well."
Nevertheless, this new legislation is generally considered to be a useful and valuable start to solving the IoT security problem. Mark Noctor, VP EMEA at Arxan Technologies, calls it a positive step forwards. "By requiring vendors to explain the vulnerabilities in their systems and explain why their device is still considered secure," he comments, "the Internet of Things Cybersecurity Act of 2017 would force developers to take security seriously. Meeting this demand would help guarantee that devices are secure by design, rather than having security provisions included as an afterthought -- something that is all too common in today's fast-paced market."
The reality, however, is that legislative proposals do not necessarily translate into effective law. Zinaich has such concerns. "The bill is very good, but the likelihood of it staying in place is slim," he told SecurityWeek.
WannaCry Inspires Banking Trojan to Add Self-Spreading Ability
2.8.2017 thehackernews Ransomware
Although the wave of WannaCry and Petya ransomware has now been slowed down, money-motivated hackers and cyber criminals have taken lessons from the global outbreaks to make their malware more powerful.
Security researchers have now discovered at least one group of cyber criminals that are attempting to give its banking Trojan the self-spreading worm-like capabilities that made recent ransomware attacks go worldwide.
The new version of credential stealing TrickBot banking Trojan, known as "1000029" (v24), has been found using the Windows Server Message Block (SMB)—that allowed WannaCry and Petya to spread across the world quickly.
TrickBot is a banking Trojan malware that has been targeting financial institutions across the world since last year.
The Trojan generally spreads via email attachments impersonating invoices from a large unnamed "international financial institution," but actually leads victims to a fake login page used to steal credentials.
Last week, researchers at Flashpoint, who've been continually tracking TrickBot activities and its targets, have discovered that the TrickBot Trojan has just been evolved to spread locally across networks via Server Message Block (SMB).
Since the new version of TrickBot is still being tested, the new features are not fully implemented by the hacking gang behind the Trojan. It also doesn't have the ability to randomly scan external IPs for SMB connections, unlike WannaCry which exploited a vulnerability dubbed EternalBlue.
Flashpoint researchers said the trojan is modified to scan domains for lists of vulnerable servers via the NetServerEnum Windows API and enumerate other computers on the network via Lightweight Directory Access Protocol (LDAP).
The new TrickBot variant can also be disguised as 'setup.exe' and delivered through a PowerShell script to spread through interprocess communication and download additional version of TrickBot onto shared drives.
According to the researchers, the latest discovery of new TrickBot variant provides an insight into what the operators behind the malware might be using in the near-future.
"Flashpoint assesses with moderate confidence that the Trickbot gang will likely continue to be a formidable force in the near term," said Vitali Kremez, director of Research at Flashpoint.
"Even though the worm module appears to be rather crude in its present state, it's evident that the Trickbot gang learned from the global ransomware worm-like outbreaks of WannaCry and 'NotPetya' and is attempting to replicate their methodology."
In order to safeguard against such malware infection, you should always be suspicious of unwanted files and documents sent over an email and should never click on links inside them unless verifying the source.
To always have a tight grip on your valuable data, keep a good backup routine in place that makes their copies to an external storage device that is not always connected to your PC.
Moreover, make sure that you run an effective anti-virus security suite on your system, and keep it up-to-date.
Alexa, Are You Spying On Me? Not Really, Maybe, It's Complex!
2.8.2017 thehackernews CyberSpy
Do you own an Amazon Echo?
So are you also worried about hackers turning out your device into a covert listening device?
Just relax, if there's no NSA, no CIA or none of your above-skilled friends after you.
Since yesterday there have been several reports on Amazon Echo hack that could allow a hacker to turn your smart speaker into a covert listening device, but users don’t need to worry because the hack is not simple, requires physical access to the device and does not work on all devices, as well.
Amazon Echo is an always-listening voice-activated smart home speaker that is designed to play music, set alarms, answer questions via the Alexa voice assistant, and control connected smart home devices like WeMo, Hive and Nest.
Hack Turns Amazon Echo Into Spying Device (But It's Complex)
Now researchers from MWR InfoSecurity have demonstrated a hack, showing how hackers can exploit a vulnerability in some models of Amazon Echo to turn them into covert listening devices that can secretly record your most intimate moments.
But the hack is not simple and has some significant limitations:
The first major limitation of the Amazon Echo hack is that it does involve the hacker being able to gain physical access to the device, though, according to researchers, it is possible to tamper with the Echo without leaving any traces behind.
The second limitation is that the Amazon Echo hack works only against older models, as the vulnerability discovered by MWR researchers only affects the 2015 and 2016 versions of the AI-powered speaker.
Another major limitation to carry out this hack is that the attacker should be above average skills in Linux as well as embedded hardware systems.
In short, it is a very sophisticated hack that first requires James Bond to bypass all CCTV cameras, if you have, to stealthily gain physical access to your premises, and then at least 30 minutes spare time with the Amazon Echo to install the malware without leaving any traces of tampering.
In another scenario, as described by the researchers, your house cleaner or maid who has access to your device could also perform this attack, so the researchers dubbed the attack as "evil maid."
However, the 'evil maid' attack is not as impressive as it sounds because in such highly targeted scenario one can simply implant bugging devices with less effort, knowledge and time.
Hacking Amazon Echo: How It Works?
In order to carry out the evil maid hack, MWR Labs security researcher Mark Barnes first removed the Echo's rubber base on the bottom, which allowed them to access 18 debug "pads" Amazon engineers rely on to carry out various diagnostics.
Barnes then directly booted into the actual firmware of the device via an external SD card. From there, he was able to install persistent malware without leaving any physical traces of tampering with the device.
The malware then allowed the researcher to gain remote root shell access of the device, and ultimately access to the 'always listening' microphones.
"Once we'd root we examined the processes running on the device and the scripts that spawn these processes," Barnes wrote. "We were able to understand how audio media is being passed and buffered between processes and the tools that are used to create and interact with these audio buffers."
Barnes said his team then developed scripts that leveraged tools embedded on the Amazon Echo to continuously stream the raw microphone audio over TCP/IP to a remote server without affecting the actual functionality of the device itself.
This eventually means that hackers, at least theoretically, can covertly monitor and listen in on users conversations and steal private data without their permission or even realisation.
"The rooting of the Amazon Echo device in itself was trivial; however, it raises a number of important questions for manufacturers of Internet enabled or 'Smart Home' devices," Barnes added.
The researcher warned users from buying smart speakers from third-party retailers, along with advising them to push the Echo's mute button to disable the microphone physically.
In response to the MWR's findings, Amazon released a statement saying the best way for users to protect themselves from such tamperings is always to buy the Echo from the company directly.
"Customer trust is very important to us. To help ensure the latest safeguards are in place, as a general rule, we recommend customers purchase Amazon devices from Amazon or a trusted retailer and that they keep their software up-to-date," the company said.
Users owning 2017 models of the device are not affected by this latest hack, as the new models introduced a mitigation that joins two of the crucial debugging pads in a way that prevents the device from external booting.
Carbanak Hackers Using Bateleur Backdoor
2.8.2017 securityweek Virus
The financially-motivated Carbanak hacker group has added a new JScript backdoor to its cyber-weapons arsenal, along with updated macros, Proofpoint security researchers warn.
Also referred to as FIN7, the multinational gang of cybercriminals has been active for at least two years and has been associated with a variety of incidents this year. In 2015, Kasperskly Lab first outed the group, saying that had hit more than 100 banks across 30 countries and made off with up to one billion dollars over a period of roughly two years.
In early May, the group was said to have started using shims for process injection and persistence, only one week after adopting new phishing techniques, including the use of hidden shortcut files (LNK files) for target compromise.
Recently, the group started using new macros and a commodity backdoor called Bateleur in attacks against United States-based chain restaurants, Proofpoint reveals. Previously, the group had been targeting hospitality organizations, retailers, merchant services, suppliers and others.
The security researchers also note that both the new macros and the backdoor use sophisticated anti-analysis and sandbox evasion techniques. The group started using macro documents to drop the previously undocumented JScript backdoor in June, marking a switch from their customary GGLDR payload. Both the macro and the malware have seen multiple updates since June.
Depending on the type of account the spam email is sent from (i.e. Outlook, Gmail), the attachment document packs a matching lure by claiming that the document as encrypted by the mail service’s Protect Service. The macro-enabled document grabs the malicious payload from a caption, saves the content to debug.txt, then creates a scheduled task to execute debug.txt as a JScript. The macro sleeps for 10 seconds, then deletes the scheduled task
The malicious JScript – which is the Bateleur backdoor – has anti-sandbox and anti-analysis (obfuscation) functionality.
The malware can also retrieve a PowerShell command containing a payload capable of retrieving user account credentials, meaning that it could also potentially target user’s passwords with the help of an additional module, Proofpoint says.
Proofpoint has observed the malware jump from version 1.0 to 1.0.4.1 over the course of a single month and reveals that several commands were added with the update, including the ability to execute a fetched EXE or PowerShell commands via WMI.
“Although Bateleur has a much smaller footprint than GGLDR/HALFBAKED, lacks basic features such as encoding in the C&C protocol, and does not have backup C&C servers, we expect the Bateleur developer(s) may add those features in the near future,” the security researchers say.
Proofpoint claims it has determined with a high degree of certainty that Bateleur is being used by the FIN7/Carbanak group, and also provides some evidence to sustain the claim.
In June, similar messages separately dropped GGLDR and Bateleur to the same target, and the timing and similarity suggest the same actor was behind all of them, especially with some messages “sharing very similar or identical attachment names, subject lines, and/or sender addresses.”
Bateleur was also observed downloading the Tinymet Meterpreter downloader, a tool employed by Carbanak hackers since at least as far back as 2016. A new command tinymet recently added to the FIN7-linked GGLDR/HALFBAKED backdoor was also observed downloading a JScript version of the Tinymet Meterpreter downloader.
“We continue to see regular changes to the tactics and tools used by FIN7 in their attempt to infect more targets and evade detection. The Bateleur JScript backdoor and new macro-laden documents appear to be the latest in the group’s expanding toolset, providing new means of infection, additional ways of hiding their activity, and growing capabilities for stealing information and executing commands directly on victim machines,” the security researchers conclude.
Critical Vulnerabilities Found in Mitsubishi HMI Tool
2.8.2017 securityweek Vulnerebility
ICS-CERT and Trend Micro’s Zero Day Initiative (ZDI) have disclosed the details of several critical vulnerabilities affecting Mitsubishi Electric’s E-Designer, a tool used for programming E1000 human-machine interfaces (HMIs).
Security researcher Andrea Micalizzi, also known as “rgod,” discovered that version 7.52 Build 344 of E-Designer is affected by several vulnerabilities that can be exploited for remote code execution and denial-of-service (DoS) attacks.
The expert identified three types of flaws: stack-based buffer overflows (CVE-2017-9638), heap-based buffer overflows (CVE-2017-9636) and out-of-bounds write bugs (CVE-2017-9634).
Micalizzi found a total of six stack buffer overflows and five heap buffer overflows affecting various components initialized during the processing of a driver configuration file.
The problem is that the process fails to properly validate the length of user-supplied data prior to copying it to a fixed-length buffer, allowing an attacker to execute arbitrary code in the context of the administrator. For the attack to work, the hacker needs to convince the targeted user to open a malicious file or web page.
The two out-of-bounds write flaws found by the researcher are caused due to the way certain sections of a project specification file (.mpa) are processed. These weaknesses can also lead to remote code execution.
Related: Learn More at SecurityWeek's ICS Cyber Security Conference
ZDI has published separate advisories for each of the 13 security holes. All the vulnerabilities have been rated critical based on CVSS scores that exceed 9.
According to ZDI, the flaws were reported to Mitsubishi in late May 2016, but advisories were only made public this month.
The vendor has not released patches for E-Designer as the product has been discontinued. Instead, it has advised customers to replace E-Designer HMIs with interfaces created with the company’s new product, GT Works, or use E-Designer in a secure network that is behind a firewall.
ICS-CERT recommends placing control systems behind firewalls and isolating them from the business network, and using VPNs when remote access is required.
Interpol, Group-IB Unmask Pro-ISIS Hackers
2.8.2017 securityweek Cyber
Interpol has teamed up with Russian security firm Group-IB in an effort to identify the members of a pro-ISIS hacker group that has taken credit for many website defacements and distributed denial-of-service (DDoS) attacks.
The group, calling itself the United Islamic Cyber Force (UICF), has carried out numerous attacks since January 2014. It has contributed to hacktivist campaigns such as OpFrance, which included attacks on the TV5Monde TV station and Notepad++, OpIsrael, OpIndia, Operation Free Palestine and Operation Free Al-Aqsa.
According to Group-IB, UICF has had over the years at least 40 members who were connected to over 60 pro-Islamic hacker groups from around the world. The security firm has traced the online monikers used by UICF hackers to individuals in Indonesia, Pakistan, Morocco, Algeria, Nigeria, India and Kosovo.
Using the aliases and email addresses posted by the hackers on the websites they defaced, researchers managed to identify several individuals allegedly involved with UICF.
“Their low level of technical training, a sense of impunity and excessive ambitions cause hacktivists not to pay due attention to their own security, despite the various instructions for ensuring anonymity popular in their milieu,” said Dmitry Volkov, Group-IB co-founder and head of the company’s threat intelligence department. “Information published by the hacktivists helped us a great deal in our investigations.”
The email addresses and aliases were linked by Group-IB to personal websites and social media profiles that appear to have been registered using the hackers’ real names.
The security firm’s report includes censored pictures, social media accounts, and redacted phone numbers and email addresses allegedly belonging to members of the hacker group.
“From their profiles, none of the hacktivists from the United Islamic Cyber Force looks like professional cybercriminals who attack banks, government institutions or strategic infrastructure facilities,” Group-IB said in its report. “They are yesterday's schoolchildren and students, with a limited life experience, easily amenable to someone else's influence. Their goal is not to steal money, but publicity – coverage of their actions by the world media.”
SecurityWeek has reached out to Interpol to find out if it plans on taking any action against the individuals identified by Group-IB, but the law enforcement agency did not respond by the time of publication.
TrickBot Targets Outlook, Browser Data
2.8.2017 securityweek BotNet
Soon after being found to have worm-like spreading capabilities, the TrickBot banking Trojan has expanded its attack surface to target Outlook and Web browsing data.
While TrickBot has been an active threat for less than a year, its developers, supposedly the Dyre group, have been actively adding new capabilities to it. Earlier this year, they expanded the target list to hit private banking and payment processors, in addition to CRM providers.
Independent researcher and programmer Hasherezade now reveals that the malware authors have added new modules to their creation and might have also added new developers to its team. A newly observed Outlook.dll module, for example, is written in Delphi, unlike most of the components, which are written in C++.
The security researcher says that the current run comes with 5 modules: SystemInfo.dll and loader.dll (injectDll32), which have been observed in TrickBot since the very beginning, mailsearcher.dll, added in December 2016, and two modules that haven’t been observed before, namely module.dll and Outlook.dll.
According to Hasherezade, module.dll/importDll32 is written in C++ and compiled with Qt5 and OpenSSL. It also incorporates SQLite. The compilation timestamp suggests it was written in May 2017.
The module was designed to steal data from the browsers, including Cookies, HTML5 Local Storage, Browsing History, Flash LSO (Local Shared Objects), and URL hits, among other info. The module is bulky and doesn’t hide its intentions.
“In contrary to loader.dll/injectDll, which is modular and stores all the scripts and targets in dedicated configuration files, module.dll/importDll32 comes with all the data hardcoded. For example, we can find inside the binary a very long list of targets – websites from countries all around the world – France, Italy, Japan, Poland, Norway, Peru and more,” the researcher reveals.
The module creates a hidden desktop and uses it as a workspace to open and fingerprint browsers in such a way that the user isn’t aware of the malicious activity.
Written in Delphi, the Outlook.dll module contains a hardcoded configuration that follows a pattern typical for TrickBot modules. Designed to steal data saved by Microsoft Outlook, the module opens relevant registry keys, then attempts to retrieve saved credentials.
“TrickBot’s new modules are not written very well and they are probably still under development. The overall quality of the design is much lower than the quality of the earlier code. For example, module.dll is bulky and does not follow the clean modular structure introduced by TrickBot before. Also, they make use of languages and libraries that are easier – Qt instead of native sockets for module.dll, Delphi language for Outlook.dll,” Hasherezade points out.
The findings are in line with Flashpoint’s report last week, which revealed that TrickBot’s authors were working on implementing a worm module to abuse the Server Message Block (SMB) protocol to spread locally, but that the logic to randomly scan external IPs for SMB connections wasn’t yet ready.
The changes suggest that new members were added to the TrickBot development team, but that some of them are lower quality programmers, or that the team is only experimenting with new capabilities. “TrickBot is still actively maintained and it is not going to leave the landscape any soon,” Hasherezade concludes.
Remotely Exploitable Flaws Found in Popular IP Cameras
2.8.2017 securityweek Vulnerebility
Bitdefender and Checkmarx have each published reports describing remotely exploitable vulnerabilities found by their researchers in popular VStarcam, Loftek and Neo IP cameras.
As part of its research into IoT security, Bitdefender discovered several buffer overflow vulnerabilities affecting the web server service and the Real Time Streaming Protocol (RTSP) server of iDoorbell and Neo Coolcam NIP-22 cameras made by China-based Shenzhen Neo Electronics.
A remote, unauthenticated attacker can exploit the flaws to execute arbitrary code and take control of the vulnerable devices. While they focused on the iDoorbell and Neo Coolcam NIP-22 devices, researchers believe other products sold by the Chinese company are also likely affected.
Based on Shodan scans, Bitdefender believes there are roughly 175,000 unique devices that may be vulnerable to attacks directly from the Internet due to their use of UPnP to open ports.
Checkmarx researchers have analyzed a couple of IP cameras from Loftek and VStarcam and discovered several new vulnerabilities and variations of previously found flaws.
In Loftek’s CXS 2200 camera, experts discovered cross-site request forgery (CSRF) flaws that can be exploited to add new admin users, server-side request forgery (SSRF) flaws that can be used for denial-of-service (DoS) attacks and to find other devices on the local network or the Internet, stored cross-site scripting (XSS) bugs that can be used to execute arbitrary code, and file disclosure vulnerabilities.
In the VStarcam C7837WIP camera, researchers found stored XSS, open redirect, and forced factory reset weaknesses. Both cameras allow attackers to manipulate HTTP responses, which can be useful for conducting XSS, cross-user defacement, cache poisoning and page hijacking attacks.
Checkmarx pointed out that cameras from several manufacturers use very similar hardware and software. An Internet scan conducted using the Shodan search engine revealed more than 1.2 million devices that experts believe are likely vulnerable.
“As our initial scans came to an end, we reached the conclusion that if your camera is connected - you’re definitely at risk,” Checkmarx said in its report. “It’s as simple as that. A malicious user can exploit your device to track your day-to-day, know when you’re home or out, steal your email information, steal your wireless connection, gain control of other connected devices, use your camera as a bot, listen in to your conversations, record video, and more.”
Both Bitdefender and Checkmarx warned that the devices affected by these vulnerabilities can be hijacked and enrolled into a massive botnet such as Mirai. Updates that patch the flaws are not available for most of the vulnerable devices.
Cobalt Hackers Now Using Supply Chain Attacks
2.8.2017 securityweek Hacking
After expanding operations to Americas earlier this year, the financially-motivated "Cobalt" cybercriminal group has changed techniques and is now using supply chain attacks to target an organization’s partners, Positive Technologies reveals.
First described in 2016 and currently active worldwide, Cobalt is quick to react to banks' protective measures, and the use of the infrastructure and accounts of a company’s employees for nefarious operations is proof of that. To trick recipients into opening phishing messages from illegitimate domains, the group also uses the names of regulatory authorities or security topics, researchers say.
The group is targeting banks, financial exchanges, insurance companies, investment funds, and other financial organizations. The attackers use phishing messages disguised as mailings from financial regulators and employ various types of malicious attachments, including malicious documents or ZIP archives packing executables or shortcut files.
The hackers, Positive Technologies says, were among the first to have access to the latest version of the Microsoft Word Intruder 8 exploit builder, which allowed them to create files exploiting CVE-2017-0199, a vulnerability patched in April. The group also abuses poorly protected public sites to drop files onto the victims’ computers, and delivers the phishing messages to both corporate and personal addresses of targeted employees.
Last year, the group was targeting financial institutions in Eastern Europe, Central Asia, and Southeast Asia, but the target list expanded in 2017 to include North America, Western Europe, and even South America (Argentina).
Around 75% of the targeted organizations are in the financial sector, the researchers say (90% of the targeted financial organizations are banks). However, the group also started targeting financial exchanges, investment funds, and lenders, and researchers say this is indicative that “attacks on diverse companies with major financial flows are underway.”
In addition to financial institutions, the hackers also target government, telecom/Internet, service providers, manufacturing, entertainment, and healthcare organizations. “Cobalt attacks government organizations and ministries in order to use them as a stepping stone for other targets,” Positive Technologies said.
The researchers suggest that only a handful of people constitute the team in charge with the technical aspects of Cobalt’s attacks. The same team appears responsible for registering malicious domains and for sending phishing emails.
The emails typically contain a malicious attachment either meant to fetch a dropper from a remote server or containing the dropper in a password-protected archive. The dropper would then download and execute the Beacon Trojan (which has been also associated with the FIN7/Carbanak group).
By forging sender information, the group delivers phishing emails to compromise a specific organization that partners with banks, then starts “sending phishing messages from these partners' infrastructures using the hacked accounts and mail servers of real employees.” Because of that, the final recipients are likely to trust the sender, which increases the chances of a successful infection.
“The attackers carefully choose subject lines, recipient addresses, and attachment names that will ‘fly below the radar’ so that recipients open the attachments enclosed with phishing messages,” the researchers say.
More than half (60%) of the phishing messages associated with Cobalt were related to cooperation and service terms between banks and their partners. The group also used security anxieties as an attack vector, sending messages from illegitimate domains posing as VISA, MasterCard, and FinCERT units of the Russian Central Bank and National Bank of the Republic of Kazakhstan.
The security researchers believe that the automation tool the group uses to send messages to thousands of recipients is alexusMailer v2.0, a freely available PHP script that offers anonymity and which supports multithreaded sending.
The group also uses widely available public mail services, along with services that allow anonymous registration of temporary addresses.
The group tends to register domains towards the beginning of the week, then prepare hacking tools, and concentrate on sending out mailings and advancing their attacks within the infrastructure of compromised organizations at the end of the week. On average, the time between a domain’s registration and its use in a campaign is four days.
“Since phishing mailings are sent out during working hours, domains are usually registered during the interval from 6:00 PM to 12:00 AM (UTC+0), which coincides with the end of the working day in European countries,” the researchers say.
The researchers were also able to discover and block newly registered Cobalt phishing domains before they were used in campaigns. The researchers also worked with industry regulators in Russia and other countries to disable delegation for all .ru domains and other top-level domains associated with the group.
“Information about the extent of losses caused by the Cobalt group in 2017 is not yet available. Perhaps warnings by bank regulators headed off some of the group's efforts. Judging by the scale of Cobalt campaigns worldwide, multimillion-dollar losses by banks are a real possibility. And if attacks on financial exchanges are successful, the consequences will include not only direct losses to individual companies, but rate turbulence on world currency markets,” the researchers conclude.
The Svpeng Trojan continues to evolve, the last variant includes keylogger capabilities
2.8.2017 securityaffairs Android
Security experts at Kaspersky discovered the dreaded Svpeng Trojan has been recently modified to implement keylogger features.
Cyber criminals are becoming even more aggressive and are using new stealth techniques.
Security experts at Kaspersky have discovered that one of the most dangerous Android banking Trojan, Svpeng, has been recently modified to implement keylogger features to improve data stealing capabilities.
Kaspersky Lab spotted a new variant of Svpeng a couple of weeks ago with a new keylogger feature, which takes advantage of Android’s Accessibility Services.
“In mid-July 2017, we found a new modification of the well-known mobile banking malware family Svpeng – Trojan-Banker.AndroidOS.Svpeng.ae. In this modification, the cybercriminals have added new functionality: it now also works as a keylogger, stealing entered text through the use of accessibility services.” reads the analysis published by Kaspersky.
The Accessibility Services is an Android feature that provides user interface (UI) enhancements for users with disabilities or those temporarily unable to interact with a device.
This new feature allows the Svpeng Trojan to log all keystrokes on the device and to get the malware obtaining more permissions and rights to prevent victims from uninstalling it.
In November 2016 the number of Android devices infected with the Svpeng banking trojan was more than 318,000 worldwide. Crooks exploited a Chrome Zero-Day vulnerability to deliver the Android Svpeng Trojan to Android users via Google AdSense.
In May, malware researchers discovered another attack technique dubbed Cloak and Dagger attack that exploit the Android’s Accessibility Services to silently take full control of the infected devices.
The new strain of the Svpeng Trojan has already infected devices in 23 countries, including Russia (29%), Germany (27%), Turkey (15%), Poland (6%) and France (3%).
The malware researchers noticed that the malware doesn’t perform malicious actions on devices belonging to Russian users.
The Svpeng Trojan distinguish Russian users by checking the device’s language. If the language is Russian, the malware doesn’t perform further malicious tasks.
This circumstance suggests the gang behind the threat is Russian.
The latest variant of the Svpeng discovered in July was being distributed through malicious websites that disguised as a fake Flash Player.

Once installed, the malware asks the device to use Accessibility Services that allows it grants itself device administrator rights, displays an overlay on the top of legitimate apps. The malware is also able to grant itself some dynamic permissions, such as the ability to make calls, send and receive SMS, and access the victim’s contacts.
“Using accessibility services allows the Trojan to get access to the UI of other apps and to steal data from them, such as the names of the interface elements and their content, if it is available. This includes entered text. Furthermore, it takes screenshots every time the user presses a button on the keyboard, and uploads them to the malicious server. It supports not only the standard Android keyboard but also a few third-party keyboards.” states Kaspersky.
“Some apps, mainly banking ones, do not allow screenshots to be taken when they are on top. In such cases, the Trojan has another option to steal data – it draws its phishing window over the attacked app. It is interesting that, in order to find out which app is on top, it uses accessibility services too.”
The researchers intercepted an encrypted configuration file from the malware’s C&C server, the analysis of the file allowed them to identify other apps targeted by the Svpeng Trojan along with phishing URLs to overlay them.
The config file decrypted by the experts contained a phishing URL for the PayPal and eBay mobile apps to steal credentials and URLs for banking apps from different countries:
The file also allows the malware to receive various commands from the C&C server, including instructions:
To send SMS
To collect info (Contacts, installed apps and call logs)
To collect all SMS from the device
To open URL
To start stealing incoming SMS
Amazon Suspends Sales of BLU Smartphones Over Security, Privacy Concerns
2.8.2017 securityweek Mobil
Amazon has suspended the sale of BLU Android smartphones after learning that there might be a potential security issue on select devices.
The giant online retailer has decided to make the BLU phones unavailable on its website despite their great popularity after Kryptowire security researchers revealed at the Black Hat conference last week that some devices gather a great deal of sensitive information and send it to servers in China.
“We recently learned of a potential security issue on select BLU phones, some of which are sold on Amazon.com. Because security and privacy of our customers is of the utmost importance, all BLU phone models have been made unavailable for purchase on Amazon.com until the issue is resolved,” an Amazon spokesperson told SecurityWeek via email.
The privacy issue initially surfaced in November 2016, when Kryptowire revealed that the firmware on some mobile phones sold in the United States via Amazon, BestBuy, and other online retailers included a backdoor and sent personally identifiable information (PII) to third-party servers without informing users. The BLU R1 HD smartphone emerged as one of the affected models.
The root of the cause was the commercial Firmware-Over-The-Air (FOTA) update software system managed by a company named Shanghai ADUPS Technology Co. Ltd. BLU revealed in November that it had raised concerns over the practice, determining ADUPS to disable the data collection functionality.
At the time, ADUPS confirmed its data collection practices and also provided an explanation on why it collects so much user and device information. The company also said that it didn’t share text messages, contacts, or phone logs with others and that it even deleted information received from BLU phones.
Data collection could target specific users
In their presentation at Black Hat last week, Kryptowire’s security researchers revealed not only that the pre‐installed system apps from ADUPS collect a great deal of user data, but that they also can be used for surveillance to “target specific users and text messages matching remotely-defined keywords.”
Fine-grained device location information is also siphoned, along with user and device information including the full content of text messages, phone call history, unique device identifiers including the International Mobile Subscriber Identity (IMSI), serial number, Media Access Control (MAC) address, and the International Mobile Equipment Identity (IMEI) number.
The researchers say that the firmware also collects information on the installed applications and the order in which the user uses their applications, that it can bypass the Android permission model, execute remote commands with escalated privileges, and remotely reprogram the devices, in addition to allowing for the remote installation of applications without users’ consent.
“The user and device information was collected automatically and transmitted periodically without the users' consent or knowledge. Some of the collected information was encrypted and then transmitted over secure web protocols to a server located in Shanghai. This software and behavior bypasses the detection of mobile anti-virus tools because they assume that software that ships with the device is not malware and thus, it is white-listed,” the researchers revealed.
Refined data collection
During their Black Hat presentation, the Kryptowire researchers revealed that affected BLU models include popular smartphones such as the BLU R1 HD and the BLU Life One X2. Other impacted devices include BLU Energy X Plus 2, BLU Neo XL, BLU Grand M, along with phones from other manufacturers, such as Cubot X16S, which continues to be available on Amazon.
The firmware on Cubot X16S was observed exfiltrating call logs, browser history, a list of installed apps, and unique device IDs. Furthermore, there is a command and control (C&C) channel allowing ADUPS to remotely execute commands as the system user.
On BLU Grand M, siphoned data included the list of installed applications, cell tower ID, used apps (with a timestamp), IMEI, IMSI, MAC address, serial number, and phone number.
Despite being caught red-handed, ADUPS hasn’t put an end to its data collection practice, but actually refined it. It only scaled back the data exfiltration on some devices, but kept the infrastructure for the PII exfiltration. With the C&C still alive and also active on certain devices, a firmware update could scale the data exfiltration back up, the researchers note in presentation slides shared with SecurityWeek.
They also reveal that the C&C channel would activate only after the device has been used for 20 days (not necessarily consecutive), but that the use of HTTP renders the channel open to ManintheMiddle (MitM) attacks.
The user and device information collected by the ADUPS apps is sent to the company’s servers, which Kryptowire traced to locations in China. According to the researchers, there are certain ADUPS URLs that could be blocked to prevent the exfiltration of PII: http(s)://*.plumad.com, http(s)://*.adsunflower.com, http(s)://*.adfuture.cn, http(s)://*.advmob.cn, http(s)://*.adups.com, and http(s)://*.adups.cn.
BLU denies any wrong doing
On Monday, BLU Products issued a public statement to respond to what it called “inaccuracies reported by several news outlets” by “making clear that there is absolutely no spyware or malware or secret software on BLU devices.”
While pointing out that it wasn’t aware of the ADUPS data collection when it came to light last year, the company also said that, when it became aware of the issue, in addition to asking ADUPS to turn off the functionality, “it decided to switch the Adups OTA application on future devices with Google's GOTA,” but that “some older devices still use ADUPS OTA.”
“The data that is currently being collected is standard for OTA functionally and basic informational reporting. This is in line with every other smartphone device manufacturer in the world. There is nothing out of the ordinary that is being collected, and certainly does not affect any user's privacy or security,” BLU Products says.
“BLU has several policies in place which takes customer privacy and security very seriously, and confirms that there has been no breach or issue of any kind with any of its devices,” the company also noted.
BLU also pointed out that its privacy policy does note that collected user data could be stored on servers outside the US: “BLU will retain any personal identifiable information (“PII”) that it collects through our software while you have an active BLU device. By using BLU devices, you are allowing your information associated with your device to be moved from your country of residence to the United States or any country where this data is stored.”
What BLU didn’t mention in the press release, however, was that the privacy policy was recently modified to state that the data might be stored on servers outside the United States.
The April 2017 and June 2017 versions of the policy stated: “BLU will retain any personal identifiable information (“PII”) that it collects through our software while you have an active BLU account and store it on servers located in the United States of America. By using BLU devices, you are allowing your information associated with your device to be moved from your country of residence to the United States.”
“We regularly review and make updates to privacy policy,” a BLU Products spokesperson told SecurityWeek via email, responding to an inquiry on the change.
The privacy policy also states that BLU shares PII with third parties “to fulfill obligations or services for BLU users,” and that “these companies have access to personal information needed to perform their services or functions, but may not use it for other purposes without the sole permission of the user.” This basically covers ADUPS’ November 2016 claim that it collects texts to better flag junk messages.
“We stand behind those findings” – Kryptowire
BLU’s representative also told SecurityWeek that the company’s phones pose no security risk, as they perform standard and basic data collection that all involved parties are aware of.
“Since Nov 2016 when the initial privacy concern was reported by Kryptowire, which BLU quickly remedied, Amazon has been aware of the ADUPS and other applications on our BLU devices which were deemed at the time by BLU, Amazon, and Kryptowire to pose no further security or privacy risk,” BLU’s spokesperson said.
“Now almost a year later, the devices are still behaving in the same exact way, with standard and basic data collection that pose no security or privacy risk. There has been absolutely no new behavior or change in any of our devices to trigger any concern. We expect Amazon to understand this, and quickly reinstate our devices for sale,” the representative concluded.
Kryptowire, however, disagrees with the claim, saying that their forensic evidence clearly shows that the data collection performed by the ADUPS software is a clear invasion of privacy.
At Black Hat, the security researchers revealed that ADUPS still provides firmware update services for BLU and that the Chinese company still collects a great deal of user and device information from the manufacturer’s devices, although it is less aggressive in doing so (the text messages and call logs are no longer exfiltrated).
“Kryptowire presented the technical details and forensic evidence of our findings at Black Hat, one of the largest security conferences in the world, in front of an audience of the world's foremost security experts. We stand behind those findings,” Tom Karygiannis, VP Product, Kryptowire, told SecurityWeek via email.
ICS-CERT Issues Warning of CAN Bus Vulnerability
2.8.2017 securityaffairs ICS
The US ICS-CERT issued an alert in response to a public report of a vulnerability in the Controller Area Network BUS (CAN BUS).
On Friday (28th of July), the Industrial Controls Systems Cyber Emergency Team or ICS-CERT, issued an alert in response to a public report of a vulnerability in the Controller Area Network (CAN), Bus standard.
The vulnerability detailed in the alert is a stealth Denial of Service attack that requires physical access to the CAN, and an attacker with extensive knowledge of how to reverse engineer the traffic. This ultimately results in the disruption of the availability of arbitrary functions of the target device.
The public report that is referenced in the ICS-CERT alert is from a group of Italian security researchers from Politecnico di Milano (the largest technical university in Italy), in their report the researchers detail how “modern vehicles incorporate tens of electrical control units (ECU’s) , driven by, according to estimates, as much as 100,000,000 lines of code. They are tightly interconnected via internal networks, mostly based upon the CAN bus standard…”.
The report presents how the denial-of-service attack against the CAN bus standard is harder to detect, because it exploits the design of the CAN protocol at a low level. This allows an attacker to target malfunctions in safety-critical components or disable vehicle functionalities such as power steering or airbags for example.
The attack exploits the weakness in the CAN protocol, working between the physical and data link layers of the OSI stack without requiring any message sending capability to the attacker.
It is important to note that the research conducted in the report concluded that this attack is completely undiscoverable without a major restructure of the CAN bus networks, which is widely adopted in automotive, manufacturing, building automation, and hospitals.
A full proof of concept of the CAN denial-of-service was posted on Github, the project titled “A Stealth, Selective, Link-layer Denial-of-Service Attack Against Automotive Networks” proves the attack detailed in the paper released by Politecnico di Milano. The attack was delivered against a Alfa Romeo Giulietta using a Arduino Uno Rev 3 to disable the parking sensor module (identifier 06314018) on CAN B operating at 29 bit / 50 kbps.

In summary, this exploit focuses on recessive and dominate bits to cause malfunctions in CAN nodes rather than complete frames, which have been found in previously reported attacks which can be detected by IDS/IPS systems unlike this attack.
Because of how the denial of service attack exploits the design of the CAN protocol, and how easily an input port (typically ODB-II), can be accessed by a potential attacker the recommendation from ICS-CERT is to limit access to these input ports. They are also working with the automotive industry and other industries to strategize mitigation plans.
Finally, given how widely CAN bus is adopted by the automotive, healthcare, and manufacturing industries this further highlights how singular weaknesses in a secure environment can compromise the network as a whole.
Security flaws affect TCUs used in BMW, Ford, Infiniti, and Nissan vehicles
2.8.2017 securityaffairs Vulnerebility
Three security researchers have discovered security vulnerabilities in the telematics control units (TCUs) used in BMW, Ford, Infiniti, and Nissan vehicles.
Three security researchers have discovered security vulnerabilities in the telematics control unit (TCU) manufactured by Continental AG that is installed on various car models manufactured by BMW, Ford, Infiniti, and Nissan.
The researchers are Mickey Shkatov, Jesse Michael, and Oleksandr Bazhaniuk (@jessemichael, @HackingThings, @ABazhaniuk) from the Advanced Threat Research Team at McAfee. The team has presented their discovery at the last DEF CON security conference.
The TCUs are 2G modems that are used by modern vehicles to transfer data, they enable the communications between the car and remote management tools such as web panels and mobile apps.
The two vulnerabilities found by the research team affect the TCUs that use the S-Gold 2 (PMB 8876) cellular baseband chipset, they are a stack-based buffer overflow in the TCU’s component that processes AT commands (CVE-2017-9647), and a vulnerability in the temporary mobile subscriber identity (TMSI) may could be exploited by attackers to access and control memory (CVE-2017-9633).
The first vulnerability could be exploited only by an attacker with a physical access to the car using the vulnerable TCU, while the second can be exploited by a remote attacker.
Below the description provided in the alert:
“Stack-based buffer overflow CWE-121 – An attacker with a physical connection to the TCU may exploit a buffer overflow condition that exists in the processing of AT commands. This may allow arbitrary code execution on the baseband radio processor of the TCU.
IMPROPER RESTRICTION OF OPERATIONS WITHIN THE BOUNDS OF A MEMORY BUFFER CWE-119 – A vulnerability in the temporary mobile subscriber identity (TMSI) may allow an attacker to access and control memory. This may allow remote code execution on the baseband radio processor of the TCU.”

The ICS-CERT issued a specific alert for the vulnerabilities affecting the Continental AG Infineon S-Gold 2 (PMB 8876).
“Successful exploitation of these vulnerabilities could allow a remote attacker to execute arbitrary code. This may allow an attacker to disable the infotainment system of the vehicle and affect functional features of the vehicle. According to affected auto manufacturers, these vulnerabilities do not directly affect the critical safety features of the vehicle.” states the alert issued by the ICS-CERT.
The following vehicles use vulnerable TCUs:
BMW several models produced between 2009-2010
Ford – program to update 2G modems has been active since 2016 and impact is restricted to the limited number of P-HEV vehicles equipped with this older technology that remain in service.
Infiniti 2013 JX35
Infiniti 2014-2016 QX60
Infiniti 2014-2016 QX60 Hybrid
Infiniti 2014-2015 QX50
Infiniti 2014-2015 QX50 Hybrid
Infiniti 2013 M37/M56
Infiniti 2014-2016 Q70
Infiniti 2014-2016 Q70L
Infiniti 2015-2016 Q70 Hybrid
Infiniti 2013 QX56
Infiniti 2014-2016 QX 80
Nissan 2011-2015 Leaf
According to affected car makers, the flaws could be exploited only to access the infotainment systems of the vehicles.
Nissan announced it will disable the 2G modems (TCUs) for all affected customers for free in one of its services. Same thing for Infiniti cars, while BMW “will be offering a service measure to affected customers.”
Ford already started disabling all 2G modems in 2016.
Roughly 175,000 Chinese Internet Connected security cameras can be easily hacked
2.8.2017 securityaffairs Hacking
An estimated 175,000 Internet of Things (IoT) connected security cameras manufactured by Shenzhen Neo Electronics are vulnerable to cyber attacks.
According to a new report from security provider Bitdefender, roughly 175,000 connected security cameras are vulnerable to cyber attacks.
The vulnerable cameras are manufactured by the Chinese company Shenzhen Neo Electronics that offers surveillance and security solutions, including IP cameras, sensors and alarms.
The experts discovered several buffer overflow vulnerabilities in two models of cameras manufactured by the company, the iDoorbell and the NIP-22 models.

The researchers believe that other models commercialized by the Chinese company are vulnerable because they use the same firmware.
“Several buffer overflow vulnerabilities (some before authentication) are present in the two cameras studied, the iDoorbell model and NIP-22 model, but we suspect that all cameras sold by the company use the same software and are thus vulnerable.” reads the report published by BitDefender. “These vulnerabilities could allow, under certain conditions, remote code execution on the device. This type of
vulnerabilities is also present on the gateway which controls the sensors and alarms.”
The security cameras use UPnP (Universal Plug and Play) to automatically open ports in the router’s firewall to allow the access from the Internet. Querying the Shodan search engine for vulnerable devices the researchers discovered between 100,000 and 140,000 vulnerable devices worldwide.
“Internet. We found between 100,000 and 140,000 devices when searching for the HTTP web server, and a similar number when searching for the RTSP server (both vulnerable). These are not necessarily the same devices, as some have only one service forwarded. We estimate that the real number of unique devices is around 175,000.” continues the report.
The experts noticed that both security camera models are vulnerable to two different cyber attacks, one that affects the web server service running on cameras and another that affects the RSTP (Real Time Streaming Protocol) server.
Researchers demomstrated that was quite easy to exploit the flaws in the security cameras, anyone can hack access the livestream by simply logging in with default credentials (i.e. “user,” “user,” and “guest,” “guest”).
The researchers also discovered a buffer overflow vulnerability that could be exploited to take control of the cameras remotely.
Shenzhen Neo did not comment the discovery.
Netflix Helps Identify APIs at Risk of Application DDoS Attacks
1.8.2017 securityweek Attack
Netflix has published tools and information to help defenders identify systems that could be leveraged by malicious actors for damaging application layer distributed denial-of-service (DDoS) attacks.
Akamai’s State of the Internet report for the first quarter of 2017 shows that application layer attacks accounted for less than one percent of DDoS attacks. However, security engineers at Netflix warn that they can pose a serious threat to organizations relying on a microservice architecture.
The microservices architecture is an increasingly popular method for developing software. In a microservices architecture, the application relies on multiple smaller and independent services that communicate with other services to serve a business goal.
The problem with this type of architecture, from a security standpoint, is that there may be a gateway API that sends out thousands of requests to middle tier and backend services from a single request.
If an attacker can identify an API that fans out into a large number of requests to middle and backend services, they may be able to generate a DoS condition in middle tier services and cause an overall service outage, Netflix warned.
“All of this is made possible because the microservice architecture helps the attacker by massively amplifying the attack against internal systems. In summary, a single request in a microservices architecture may generate tens of thousands of complex middle tier and backend service calls,” said Netflix security engineers Scott Behrens and Bryan Payne, who had a talk on this topic last week at the DEF CON conference.
The security experts have provided instructions on how defenders can analyze their systems in order to identify potentially problematic APIs. Netflix has also released a couple of open source testing tools for application DDoS.
Repulsive Grizzly is a framework designed to make it easier for organizations to look for weak spots. It can be used in combination with Cloud Kraken, the second tool released as open source by Netflix, to conduct tests at a larger scale across multiple data centers and regions.
Netflix made available the source code of several internal tools in the past years, including for collecting intelligence, discovering cross-site scripting (XSS) flaws, and securing devices.
Indonesia to Deport 153 Chinese for $450 Million Scam
1.8.2017 securityweek Spam
Indonesia will deport 153 Chinese nationals arrested for alleged involvement in a multimillion-dollar cyber fraud ring targeting wealthy businessmen and politicians in China, police said Tuesday.
The syndicate, who ran their operation from abroad to avoid detection by Chinese officials but did not target any victims in their host country, made around six trillion rupiah ($450 million) since beginning operations at the end of 2016, Indonesia police said.
They were arrested following a tip-off from Chinese authorities.
"We are conducting an intensive investigation and currently coordinating with the Chinese police to deport them," said national police spokesman Rikwanto, who goes by one name.
The group, based in several locations across Indonesia, contacted victims pretending to be Chinese police or law officials, promising to help resolve their legal cases in return for immediate cash transfers, Jakarta police said.
The criminal network included IT specialists who would retrieve information on victims and develop communications systems for contacting them, he said.
Chinese nationals were arrested in Jakarta, the city of Surabaya and on the resort island of Bali in separate raids over the weekend.
"The perpetrators and the victims are Chinese. It just happens that they operate from Indonesia," said Jakarta police spokesman Argo Yuwono.
Police are investigating how several of the Chinese suspects were able to enter the archipelago without a valid passport.
Cyber criminals targeting victims in China have increasingly exploited technological advances to operate from abroad, spreading across Southeast Asia and beyond in recent years.
China has become increasingly assertive in extraditing suspects.
In July, a gang of 44 people from China and Taiwan were arrested in Thailand for allegedly running an elaborate phone scam that conned $3 million from scores of victims, mainly based in China.
Cambodia deported 74 people to China for their role in an alleged telecom fraud, also in July, according to Xinhua.
Last year, 67 alleged criminals were deported from Kenya to China to face investigation for fraud.
Pharmaceutical giant Merck confirmed NotPetya attack disrupted operations worldwide
1.8.2017 securityaffairs Ransomware
The US pharmaceutical company Merck revealed that the massive NotPetya cyberattack has disrupted its worldwide operations.
The news was part of the Merck’s financial results announcement for the second quarter of 2017, according to the pharmaceutical giant the ransomware destructed operations in several critical sectors, including manufacturing, research, and sales.
The company didn’t disclose details on the cyber attacks, it believes that the NotPetya ransomware was the threat that hit the company on June 27th affecting tens of thousands of systems in more than 65 countries.
The analysis conducted on the ransomware reveals the threat was designed to look like ransomware but was wiper malware designed for sabotage purpose.
Researchers Matt Suiche, founder at Comae Technologies, explained that the analysis conducted by his team on Petya samples used in the attack revealed its wiper capabilities.
“we noticed that the current implementation that massively infected multiple entities in Ukraine was in fact a wiper which just trashed the 24 first sector blocks of the disk while replicating itself. Some noted that this was mainly slack space as only the first sector is relevant for most of machines — except few exceptions. ” states the analysis published by Comae Technologies.
“We believe the ransomware was in fact a lure to control the media narrative, especially after the WannaCryincidents to attract the attention on some mysterious hacker group rather than a national state attacker like we have seen in the past in cases that involved wipers such as Shamoon.”

Attackers might have used a diversionary strategy hide a state-sponsored attack on Ukraine critical infrastructure.
Experts from Kaspersky’s conducted a similar research that led to a similar conclusion.
Unlike other ransomware, Petya does not encrypt files on the infected systems but targets the hard drive’s master file table (MFT) and renders the master boot record (MBR) inoperable.
Petya locks the access to the users’ data by encrypting the master file table (MFT) and replaces the computer’s MBR with its own malicious code that displays the ransom note.
Petya overwrites the MBR of the hard drive causing Windows to crash. When the victim tries to reboot the PC, it will impossible to load the OS, even in Safe Mode.
The name of Merck was circulating on the internet shortly after the attack as one of the numerous victims of the NotPetya attack worldwide. Other major companies affected by the NotPetya attack were the Ukraine’s central bank, Russian oil giant Rosneft, advertising group WPP, the shipping giant A.P. Moller-Maersk, TNT Express and the law firm DLA Piper.
The company said it had still been working on restoring operations and minimizing the effects of the incident.
The company confirmed it had still been working on restoring operations:
“The company is in the process of restoring its manufacturing operations. To date, Merck has largely restored its packaging operations and has partially restored its formulation operations,” Merck said. “The company is in the process of restoring its Active Pharmaceutical Ingredient operations but is not yet producing bulk product. The company’s external manufacturing was not impacted. Throughout this time, Merck has continued to fulfill orders and ship product.”
Cyber attacks could have a significant impact on businesses, and two of the world’s largest consumer goods companies confirmed it. On July the companies Mondelez and Reckitt Benckiser warned of the impact of the NotPetya attack on their revenues.
The Mondelez International company estimated the NotPetya attack would cut three percentage points from second-quarter sales growth because of disruptions to shipping and invoices caused by the cyber attack.
the Reckitt Benckiser, the maker of Nurofen painkillers and Durex condoms, said it expected sales would be hit Q2 by an estimated £110m this year.
TOPransom: From eMail Attachment to Powning the Attacker’s Database
1.8.2017 securityaffairs Ransomware
TOPransom – Analyzing the entire process from getting an email attachment to powning the ransom server trying to stop the infection.
Hi folks, today I want to share a quick but intensive experience in fighting cybercrime. I wish you would appreciate the entire process of getting an email attachment to powning the ransom server trying to stop the infection and to alert everybody about the found threats. As a second step, I would try to identify the attacker in order to give additional information to law enforcements, those actions would not be published.
But, let’s start by having a little bit of context:
During the past few days a colleague of mine (MarcoT.) gave me an interesting eMail attachment called: 71878378709_708463.zip (sha256:fdd1da3bdd8f37dcc04353913b5b580dadda94ba).
By unzipping the attachment, it was interesting to see a single .vbs file. By double clicking a .vbs file the victim would run it through microsoft wscript.exe which fires up the infection process. The eMail belongs to a more complex spamming set spread over USA and coming few days ago to Europe as well.
The visual basic script was obfuscated, as you may appreciate from the following image, but the used obfuscation technique was quite weak to reverse. In fact only one round of packing was adopted and after few substitutions “clear text strings” were observable.

Obfuscated Dropper
Interesting techniques were introduced in this dropper. First of all a lot of junk code (apparently good code) was added in order to make reverse engineering process much harder. Very interesting the choice of such a code apparently taken from real droppers but not linked to the analized one. Another interesting adopted technique was on the “User-Agent” settings, which happened to be the key-factor to download the real payload. The dropper per-se is not interesting anymore. It basically uses a romantic WScript.Shell to execute a ‘MZ’ file once downloaded from compromised websites (IoC later on). The Dropped file is returned directly into the HTTP response body and saved with a static name in temporary user folder: saToHxy.exe. The dropper file renamed VB objects and VB functions to make everything a little harder.

Saving Dropper into user temporary file with static name
As today the dropping URLs are the following ones:
castillodepalazuelos.es/rf734rgf?
2010.sggt-wh.de/rf734rgf?
actt.gr/rf734rgf?
As mentioned a romantic Shell.Run would execute the dropped payload. The Payload (sha356:6a51d0cd9ea189babad031864217ddd3a7ddba84) looks like a one-stager payload. No heavy encryption nor multi staging delivery is involved, clear and intuitive user functions within enabled debugging headers.

No Packing found
Firing up IDA and reversing the sample showed up small encoded payload through XOR and some anti debugging tricks such as the timing control and performance monitoring as follows:
Anti-Debugging tricks: Timing and Performante control
Following on the analysis it becomes clear the spread use of Secure Handler Exception Chain exploiting technique. By triggering exceptions the attacker calls modified exception handler functions able to decode the payload and to allocate it directly on the new memory pages, ending up on “call eax” section. The following image shows the decoding loop.

Decoding Loop on 0x3001220
Following a piece of decoded memory area (configuration file), decoded by 0x03001220.
Decoded Memory Area
Dynamic Analysis took out the evidence of a Ransomware payload. In fact following on the decoded payload by getting far on memory site the analyst could observe the ransom HTML page (next image). I would prefer to show out a rendered “ransom request page” rather than a junk of hexadecimal bytes. (sha256: cdb3fef976270ab235db623d6a4a97ea93c41dd1) The ransom page looks looks like the following image.

I will call this Ransomware the “TOPransom” since the funny and evident mistake the attacker made in writing the ransom request file in where he suggested to download the TOP Browser rather then the TOR Browser 😀 (LOL). The TOPransom encrypts files and changes the file extensions with a alphanumeric extension, usually made of 3 characters (why “usually” ? Because looking at the attacker’s db it looks like that, but I didn’t find evidence on that). The modified extension is used as a hidden parameter in the ransom page. The following image shows some hidden features used by the attacker to bring informations to the control server.

POST request to buy the decrypter
Particularly interesting (at least in my persona point o view) the hidden input type called “FB” which looks like piggy backing two informations to the command and control (ransom server) such as: the extension and some hexadecimal content included in a crafted tag called “pre”. By clicking on “Yes I want to buy” the victim POST such a data and are prompted to the following page asking for 0.18 BTC in order to get files back.
Request for ransom
The FB hidden value “made me curious”. By changing the first value (the one before the statement “pre”) you would appreciate different BTC wallets with different asking prices. The following image shows the different results.
Request for ransom 2
This makes the system vulnerable to “balance enumeration” and to “denial of resources”. In fact by enumerating the attacker wallet space I will perform a duplice action: if the wallet exists I’ll take its balance, if the wallet does not exists the backend will create a new wallet, filling up the attacker reserved space for wallet creation. This action could block the new wallet creation ergo new infections. So lets’ write a simple dirty python script to force new wallet creation and money mapping.

Forcing New Wallets to limitate further infections (please do not consider this script as production ready script. Do not consider it as best implementation for such a goal)
Following on the analysis by playing a little bit further with that parameter (FB) I figured out it was vulnerable to SQL Injection. What a nice surprise !! The vulnerable parameter was the crafted tag called “pre” which vulnerable to code injection, which triggered SQLinjections.

SQLi on C&C server !
So let’s try to pown the Attacker ! As first sight you may observe a MySQL error with not a latin characters. Google Translator says it is a Russian language ! Now we know that the attacker belongs, with high probability, to the Russian community. By investigating a little bit harder on the DB, only TOR availability and super slow, I found the botids and the relatives tasks. Please have a look to incremental ids and try to immagine how big was that network.

Bot Ids and relative locations
Another interesting topic was to investigate which were the system users(a.k.a the attackers). In other words the users of such a ransomware-as-a-service-platform” which happened to be the real attackers. Since It looks like a “Ransomware as a service” platform figuring out how many dollars the attackers were able to gain over time its my next goal. The following obfuscated image shows some of the found usernames, passwords (chipertext) and wallets the attackers used to gain profit.

Attackers Username, Passwords and Wallets
My attention ended up on that guy: god.true@xmpp.jp
That guy is related to the following private wallet: 1P3t56jg5RQSkFDWkDK3xBj9JPtXhSwc3N
As you might guess there are two main wallet types:
– Public wallets which store the victim’s money. They are the public available wallets, everybody got infected must now them in order to pay the ransom.
– Private wallets which are the “real ones” belonging to attackers. Private wallets got money from public wallet once reached the end of the attack. Platform charges are applied during that transaction.
Having the private wallet means to have the possibility to track down transactions history. Transactions history is a great source to figure out if that guy made more illegal activity over the past months. Following the go.true@xmpp.jp ‘s private wallet. We may observe interesting transactions as showed in the following image

Transaction From 1P3t56jg5RQSkFDWkDK3xBj9JPtXhSwc3N
That wallet which is DB-related to god.true@xmpp.jp, made huge amount of transactions back on 2017-04-23 and 2017-04-20 by moving out from its wallet 81,87 BTC harvested by many small and similar transactions! If we include the harvested BTC from this attack which currently have balance 13 BTC, he or she is close to 100 BTC transactions. How about 2017-04 (do you remember any famous attack on that time ? :P) With high probability the attacker looks like abusing illegal activities (such as ransomware activities) more then once a time, this boy/girl — with a high probability — is a recurring attacker. By investigating a little bit more on that email address it’s easy to find heavy relations between got.true@xmpp.jp and https://vlmi.su/ which is a Russian based Market Place where attackers buy and sell attacking tools, information and experiences.
After few more crafted SQL queries I was able to extract the “inst” talbe. Fields names are the following ones:
ID, IP, FB, OS, TIMED, TIMEIN. COUNTRY, BRWSER
Yes come one ! This table records the infected clients, let’s see if we can do something to help them !
A simple DB count showed me more 2k infections so far. Not bad for being a plain new ransomware as a service. The Targets look like being very spread all over the world. So far it’s possible to extract the following country distribution.

TOPransom Victims Distribution
I will not disclosure IP addresses in order to guarantee victims privacy. Another interesting data comes from the victim browser distribution (another parameter collected by the attacker). Curiously the most used browser on windows devices is Chrome as the following image shows. [remember] The infection vector wasn’t through web browser but through wscript.exe which opens .vbs by double click on it. [/remember]

TOPransomware victims browser distribution
On this post I’ve been describing the activity that took me from an email attachment to drop the entire attacker’s database on a Ransomware as a Service platform that I called TOPransom. I’ve being trying to enumerate attacker’s income and to mitigate the spreading vector by filling up wallets creation per user by writing a quick and durty python script.
Following IoC for your detection systems. Have fun !
IoC (summing up):
dropper .vba (sha256:fdd1da3bdd8f37dcc04353913b5b580dadda94ba)
saToHxy.exe (sha256:6a51d0cd9ea189babad031864217ddd3a7ddba84)
castillodepalazuelos.es/rf734rgf?
2010.sggt-wh.de/rf734rgf?
actt.gr/rf734rgf?
https://n224ezvhg4sgyamb.onion.link/efwdaq.php
RECOVER-FILES-html (sha256: cdb3fef976270ab235db623d6a4a97ea93c41dd1)
Bot location: http://oeirasdigital.pt
Bot Location: http://jflo.ca/
TOP Browser
Sledují každý váš krok vaším vlastním mobilem. Pak vám vybílí bankovní účet
1.8.2017 Novinky/Bezpečnost Mobilní
Počítačoví piráti se stávají stále zběhlejšími v nejrůznějších internetových podvodech a hledají nové cesty, které by jim zpřístupnily bankovní účty obětí. Jeden z nově objevených záškodníků dokáže na chytrém telefonu sledovat doslova každý krok uživatele. Pro kyberzločince je pak hračka jim vybílit účet, a to platí i o těch ostražitějších.
Před novým virem, který je vylepšenou verzí bankovního malwaru zvaného Svpeng, varoval bezpečnostní expert ze společnosti Kaspersky Lab Roman Unuchek. Právě on totiž hrozbu objevil jako první.
Tento vylepšený záškodnický program jasně ukazuje, jak se v poslední době počítačoví piráti vyvíjejí. Kombinují různé škodlivé kódy tak, aby byli schopni nepozorovaně ukrást z cizího zařízení citlivá data a následně je zneužít – v tomto konkrétním případě je řeč o přístupových údajích do internetového bankovnictví.
Upravená verze je sofistikovanější
Většina bankovních trojských koňů je totiž poměrně snadno odhalitelná, alespoň pokud se bavíme o těch určených pro chytré telefony. Uživateli totiž na displeji podstrčí při pokusu o přihlášení do internetového bankovnictví podvodnou stránku, u které jde však velmi často poznat, že jde o padělek.
Pozornější uživatelé tak zpravidla na tento trik nenaletí a kyberzločincům své přihlašovací údaje na zlatém podnose nenaservírují. I když výjimky se pochopitelně také najdou.
Upravená verze škodlivého viru Svpeng je však daleko sofistikovanější. Obsahuje totiž zabudovaný keylogger, který zaznamenává doslova veškerou činnost uživatele na napadeném smartphonu. Počítačoví piráti se tak dozví přihlašovací údaje i ve chvíli, kdy je uživatel skutečně zadává do legitimního formuláře banky.
Další část trojského koně se pak postará o zbytek – odchytne potvrzovací zprávu a zneužije ji. Počítačoví piráti pak mohou velmi snadno vybílit svým obětem celý účet. V případě, že to internetové bankovnictví umožňuje, mohou si tímto způsobem zažádat i o půjčku. Uživatele tak připraví dokonce i o peníze, které na účtu ve skutečnosti nemá.
Původní verze nakazila přes 300 000 zařízení
Keyloggery kolovaly internetem už v minulých letech. Vůbec poprvé však podle serveru The Hacker News implementovali počítačoví piráti jejich funkce do trojského koně, tedy do jediného škodlivého kódu. A propašovat k uživateli jeden virus je daleko jednodušší než dva různé.
Obavy jsou tedy na místě. A to i s ohledem na fakt, že původní verze škodlivého kódu Svpeng dokázala infikovat více než 300 000 zařízení během jediného měsíce. S pomocí vylepšené varianty tohoto záškodníka tak počítačoví piráti získávají mocnou zbraň.
Počítačovým pirátům navíc práci velmi usnadňují samotní uživatelé. Nově objevená hrozba se totiž soustředí výhradně na chytré telefony a tablety s operačním systémem Android. A právě na mobilních zařízeních drtivá většina uživatelů nepoužívá vůbec žádný antivirový program. Těžko pak mohou odhalit, že je jejich zařízení skutečně infikované.
Dangerous Mobile Banking Trojan Gets 'Keylogger' to Steal Everything
1.8.2017 thehackernews Virus
Cyber criminals are becoming more adept, innovative, and stealthy with each passing day. They have now shifted from traditional to more clandestine techniques that come with limitless attack vectors and are harder to detect.
Security researchers have discovered that one of the most dangerous Android banking Trojan families has now been modified to add a keylogger to its recent strain, giving attackers yet another way to steal victims sensitive data.
Kaspersky Lab's Senior malware analyst Roman Unuchek spotted a new variant of the well-known Android banking Trojan, dubbed Svpeng, in the mid of last month with a new keylogger feature, which takes advantage of Android's Accessibility Services.
Trojan Exploits 'Accessibility Services' to Add Keylogger
Yes, the keylogger added in the new version of Svpeng takes advantage of Accessibility Services — an Android feature that provides users alternative ways to interact with their smartphone devices.
This change makes the Svpeng Trojan able not only to steal entered text from other apps installed on the device and log all keystrokes, but also to grant itself more permissions and rights to prevent victims from uninstalling the Trojan.
In November last year, the Svpeng banking trojan infected over 318,000 Android devices across the world over the span of only two months with the help of Google AdSense advertisements that was abused to spread the malicious banking Trojan.
Over a month ago, researchers also discovered another attack taking advantage of Android's Accessibility Services, called Cloak and Dagger attack, which allows hackers to silently take full control of the infected devices and steal private data.
If You Are Russian, You Are Safe!
Although the new variant of the Svpeng malware is not yet widely deployed, the malware has already hit users in 23 countries over the course of a week, which include Russia, Germany, Turkey, Poland, and France.
But what's worth noticing is that, even though most infected users are from Russia, the new variant of Svpeng Trojan doesn't perform malicious actions on those devices.
According to Unuchek, after infecting the device, the Trojan first checks the device's language. If the language is Russian, the malware prevents further malicious tasks—this suggests the criminal group behind this malware is Russian, who are avoiding to violate Russian laws by hacking locals.
How 'Svpeng' Trojan Steals Your Money
Unuchek says the latest version of Svpeng he spotted in July was being distributed through malicious websites that disguised as a fake Flash Player.
Once installed, as I have mentioned above, the malware first checks for the device language and, if the language is not Russian, asks the device to use Accessibility Services, which opens the infected device to a number of dangerous attacks.
With having access to Accessibility Services, the Trojan grants itself device administrator rights, displays an overlay on the top of legitimate apps, installs itself as a default SMS app, and grants itself some dynamic permissions, such as the ability to make calls, send and receive SMS, and read contacts.
Additionally, using its newly-gained administrative capabilities, the Trojan can block every attempt of victims to remove device administrator rights—thereby preventing the uninstallation of the malware.
Using accessibility services, Svpeng gains access to the inner working of other apps on the device, allowing the Trojan to steal text entered on other apps and take screenshots every time the victim presses a button on the keyboard, and other available data.
"Some apps, mainly banking ones, do not allow screenshots to be taken when they are on top. In such cases, the Trojan has another option to steal data – it draws its phishing window over the attacked app," Unuchek says.
"It is interesting that, in order to find out which app is on top, it uses accessibility services too."
All the stolen information is then uploaded to the attackers' command and control (C&C) server. As part of his research, Unuchek said he managed to intercept an encrypted configuration file from the malware's C&C server.
Decrypting the file helped him find out some of the websites and apps that Svpeng targets, as well as help him obtain a URL with phishing pages for both the PayPal and eBay mobile apps, along with links for banking apps from the United Kingdom, Germany, Turkey, Australia, France, Poland, and Singapore.
Besides URLs, the file also allows the malware to receive various commands from the C&C server, which includes sending SMS, collecting information such as contacts, installed apps and call logs, opening the malicious link, gathering all SMS from the device, and stealing incoming SMS.
The Evolution of 'Svpeng' Android Banking Malware
Researchers at Kaspersky Lab initially discovered the Svpeng Android banking malware trojan back in 2013, with primary capability—Phishing.
Back in 2014, the malware was then modified to add a ransomware component that locked victim's device (by FBI because they visited sites containing pornography) and demanded $500 from users.
The malware was among the first to begin attacking SMS banking, use phishing web pages to overlay other apps in an effort to steal banking credentials and to block devices and demand money.
In 2016, cyber criminals were actively distributing Svpeng via Google AdSense using a vulnerability in the Chrome web browser, and now abusing Accessibility Services, which possibly makes Svpeng the most dangerous mobile banking malware family to date that can steal almost anything—from your Facebook credentials to your credit cards and bank accounts.
How to Protect Your Smartphone From Hackers
With just Accessibility Services, this banking Trojan gains all necessary permissions and rights to steal lots of data from the infected devices.
The malicious techniques of the Svpeng malware even work on fully-updated Android devices with the latest Android version and all security updates installed, so it is little users can do in order to protect themselves.
There are standard protection measures you need to follow to remain unaffected:
Always stick to trusted sources, like Google Play Store and the Apple App Store, but only from trusted and verified developers.
Most importantly, verify app permissions before installing apps. If any app is asking more than what it is meant for, just do not install it.
Do not download apps from third party sources, as most often such malware spreads via untrusted third-parties.
Avoid unknown and unsecured Wi-Fi hotspots and Keep your Wi-Fi turned OFF when not in use.
Never click on links provided in an SMS, MMS or email. Even if the email looks legit, go directly to the website of origin and verify any possible updates.
Install a good antivirus app that can detect and block such malware before it can infect your device, and always keep the app up-to-date.
Malware Attack Disrupts Merck's Worldwide Operations
1.8.2017 securityweek Virus
American pharmaceutical giant Merck revealed in its financial results announcement for the second quarter of 2017 that a recent cyberattack has disrupted its worldwide operations, including manufacturing, research and sales.
While Merck has not provided details about the incident in its financial report, the June 27 attack referenced by the company is most likely the NotPetya malware outbreak that affected tens of thousands of systems in more than 65 countries. Many of the victims were located in Ukraine, the home of a tax software firm whose product was used as the main attack vector.
Researchers initially believed NotPetya (aka PetrWrap, exPetr, GoldenEye and Diskcoder.C) was a piece of ransomware, similar to WannaCry. However, a closer analysis revealed that it was actually a wiper and it was unlikely that victims could recover their files, even if they paid the ransom.
Merck, which was named as one of the victims of the NotPetya attack shortly after the outbreak started, said on Friday that it had yet to fully assess the impact of the disruption. The company said it had still been working on restoring operations and minimizing the effects of the incident.
“The company is in the process of restoring its manufacturing operations. To date, Merck has largely restored its packaging operations and has partially restored its formulation operations,” Merck said. “The company is in the process of restoring its Active Pharmaceutical Ingredient operations but is not yet producing bulk product. The company’s external manufacturing was not impacted. Throughout this time, Merck has continued to fulfill orders and ship product.”
Merck is just one of several major companies affected by the NotPetya attack. The list also includes Ukraine's central bank, Russian oil giant Rosneft, UK-based advertising group WPP, Danish shipping giant A.P. Moller-Maersk, and FedEx-owned TNT Express.
FedEx reported last month that it had still been working on restoring systems hit by the destructive malware attack, and admitted that it may not be able to fully restore all affected systems and recover all the critical business data encrypted by NotPetya.
Reckitt Benckiser, the British consumer goods company that makes Nurofen, Dettol and Durex products, said the attack disrupted its ability to manufacture and distribute products. The firm estimated that the incident could have an impact of £100 million ($130 million) on its revenue.
TCU Flaws Expose Cars to Remote Hacking
1.8.2017 securityweek Vulnerebility
Vulnerabilities discovered by researchers in telematics control units (TCUs) from Continental, which are used by several major car manufacturers, can expose vehicles to local and remote hacker attacks.
McAfee security researchers Mickey Shkatov, Jesse Michael and Oleksandr Bazhaniuk disclosed the flaws last week at the DEF CON security conference.
A TCU is an embedded system used for wireless tracking and communications to and from a vehicle. According to an advisory by ICS-CERT, the McAfee researchers discovered two vulnerabilities affecting Continental TCUs that use Intel’s Infineon S-Gold2 (PMB8876) 2G baseband chipset.
The more serious of the flaws, tracked as CVE-2017-9633 and related to the temporary mobile subscriber identity (TMSI), allows a remote attacker to execute arbitrary code on the baseband radio processor of the TCU. This type of vulnerability was disclosed several years ago by Ralf-Philipp Weinmann of the University of Luxembourg in a paper on baseband attacks.
The second weakness, CVE-2017-9647, is a stack-based buffer overflow that allows an attacker with physical access to the TCU to execute arbitrary code on the baseband radio processor.
ICS-CERT said the security holes affect 2G services present in several BMW models manufactured between 2009 and 2010, Nissan Leaf from 2011 to 2015, some Ford plug-in hybrid (PHEV) models, and several Infiniti models produced between 2013 and 2016. The agency warned that proof-of-concept (PoC) exploits are available.
An attacker can exploit the vulnerabilities to disable a vehicle’s infotainment system or tamper with functional features, but the affected carmakers claim critical safety features are not impacted.
Starting with last year, Ford has been working on updating or disabling legacy 2G modems and believes only a limited number of vehicles are still affected. The company is investigating the issue and will take further steps if needed. BMW has confirmed the existence of the flaws and it plans on addressing the problem.
Nissan and its luxury car division, Infiniti, have issued technical service bulletins advising dealers to disable the 2G TCU on customers’ vehicles at no charge. The company said the 2G cellular service is no longer active in the U.S. and the TCU no longer performs any functions. Nevertheless, the manufacturer decided to initiate this campaign “out of abundance of caution to help prevent potential cybersecurity issues.”
Continental has also confirmed the existence of the flaws, but it has yet to identify a mitigation plan, ICS-CERT said.
Microsoft Patches Several Outlook Vulnerabilities
1.8.2017 securityweek Vulnerebility
Microsoft has released patches for several important vulnerabilities affecting Outlook, the professional email and calendar application included in the Office suite.
The tech giant pointed out that none of the flaws have been disclosed and none of them have been exploited in attacks. The security holes are related to Click-to-Run (C2R), a streaming and virtualization technology used to install Office products.
One of the vulnerabilities, discovered by the Microsoft Office Security Team and tracked as CVE-2017-8663, is a memory corruption that can be leveraged for remote code execution. The weakness can be exploited by getting an Outlook user to open a specially crafted file sent to them via email.
“An attacker who successfully exploited the vulnerability could take control of an affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights,” Microsoft said in its advisory.
Another vulnerability that can lead to arbitrary code execution is CVE-2017-8571, a security feature bypass issue that exists due to the way Outlook handles input. An attacker can exploit the flaw by tricking the targeted user into opening and interacting with a specially crafted document. Nicolas Joly of MSRCE UK reported the problem to Microsoft.
The third security hole, CVE-2017-8572, is an information disclosure bug that exists because Office improperly discloses memory content. An attacker who knows the memory address of the targeted object needs to trick the target into opening a specially crafted file in order to obtain information that can be useful for accessing the victim’s computer and data. Aaron Grattafiori of Facebook and Soroush Dalili from NCC Group were credited for finding the flaw.
Microsoft said the patches also address several known issues in the June 2017 security updates. The company was forced to pull its June Outlook update after users reported that it had been causing the application to crash.
Of the total of eight issues identified, six have been fixed and two are still under investigation, Microsoft said.
Iran-Linked Hackers Use "Mia Ash" Honey Trap to Compromise Targets
1.8.2017 securityweek BigBrothers
A threat group said to be associated with Iranian government-directed cyber operations is believed to be operating a fake online persona to target organizations in the Middle East with malware, SecureWorks researchers say.
Known as COBALT GYPSY or TG-2889, the threat group was previously associated with various campaigns, including Shamoon attacks, which were apparently orchestrated by multiple groups working together.
Phishing campaigns observed in early 2017 and aimed at entities in the Middle East and North Africa (MENA), with a focus on Saudi Arabian organizations, used the PupyRAT open-source remote access Trojan have also been associated with the COBALT GYPSY, SecureWorks says.
These likely unsuccessful campaigns were followed by “highly targeted spearphishing and social engineering attacks” from an entity using the online persona Mia Ash. SecureWorks believes that COBALT GYPSY was behind these attacks as well, and the threat group used spearphishing to target telecommunications, government, defense, oil, and financial services organizations in the MENA region.
“Further analysis revealed a well-established collection of fake social media profiles that appear intended to build trust and rapport with potential victims. The connections associated with these profiles indicate the threat actor began using the persona to target organizations in April 2016,” the researchers say.
The phishing campaigns observed at the end of 2016 used shortened URLs leading to a macro-enabled Word document that executed a PowerShell command to download additional PowerShell loader scripts for PupyRAT. Successful installation of the malicious program would have provided the attackers with full access to the victims’ systems.
In January, an employee at one of the targeted organizations was contacted via LinkedIn by a purported London-based photographer named Mia Ash, who claimed to be reaching out as part of a worldwide exercise. Following multiple messages about professions, photography, and travels, Mia Ash eventually encouraged the employee to become friends on Facebook and continue the conversation there.
After communicating for several weeks via email, WhatsApp, and likely Facebook, Mia Ash eventually sent a Microsoft Excel document titled “Copy of Photography Survey.xlsm” and encouraged the employee to open “the email at work using their corporate email account so the survey would function properly.” Macros included in the document downloaded the PupyRAT malware.
SecureWorks believes COBALT GYPSY is behind the Mia Ash persona, using it to infect the targeted organizations after the initial campaigns failed. “The group has repeatedly used social media, particularly LinkedIn, to identify and interact with employees at targeted organizations, and then used weaponized Excel documents to deliver RATs such as PupyRAT,” the researchers note.
Mia Ash, the researchers say, is highly likely fake, although associated with LinkedIn, Facebook, Blogger, and WhatsApp accounts, and several email addresses. The persona appears to have been established in April 2016 or earlier, while the accounts appear to feature supporting material and content originating from other sources.
The LinkedIn profile contains a description of employment at Mia's Photography seemingly taken from the LinkedIn page of a U.S.-based photographer. The images used by Mia Ash, consistent across the various accounts and profiles, were likely taken from the social media accounts belonging to a Romanian photographer.
The researchers also observed that several of Mia Ash’s LinkedIn connections match the names of people associated with the Mia Ash Facebook page, suggesting that the threat actor is initially contacting individuals on LinkedIn, then switching to Facebook. Photography connections were used to project authenticity, but multiple non-photography endorsers located in Saudi Arabia, United States, Iraq, Iran, Israel, India, and Bangladesh appear to be targets working for technology, oil/gas, healthcare, aerospace, and consulting organizations.
These individuals had job titles such as technical support engineer, software developer, and system support, implying elevated access within the corporate network. Threat actors are looking to compromise accounts with admin or elevated access to “quickly access a targeted environment to achieve their objectives.”
“The individuals' locations and industries align with previous COBALT GYPSY targeting and Iranian ideological, political, and military intelligence objectives. These characteristics suggest that COBALT GYPSY executed the January and February phishing campaigns and that it created the Mia Ash persona,” SecureWorks says.
The security researchers have been tracking multiple COBALT GYPSY campaigns since 2015 and say it is highly likely that the group is connected to Iranian government-directed cyber operations, given that it has launched espionage campaigns against organizations “of strategic, political, or economic importance to Iranian interests.”
According to SecureWorks, the threat group might have created multiple online personae to gain access to targeted computer networks via social engineering. “The use of the Mia Ash persona demonstrates the creativity and persistence that threat actors employ to compromise targets. The persistent use of social media to identify and manipulate victims indicates that COBALT GYPSY successfully achieves its objectives using this tactic,” the researchers conclude.
Amazon Echo Could Become an Attacker's Listening Device
1.8.2017 securityweek Hacking
The Amazon Echo is an always-listening device designed to play music, answer questions via the Alexa voice service, and control connected home devices such as WeMo, Hive and Nest. Now researchers have demonstrated that while it listens to you, attackers could be listening to you as well.
Mike Barnes, a researcher at MWR Infosecurity, has published details of an attack that can compromise the device while leaving no evidence of tampering. The attack requires physical access, and continues work (PDF) published last year by researchers from The Citadel, The Military College of South Carolina.
The earlier research was looking for potential Echo attack approaches. The paper concludes, "We believe that any of these approaches would allow further access into the file system of the Echo that would allow security researchers the ability to reverse engineer binaries for vulnerabilities, scan the device for hardcoded credentials, and much more."
This is the basis of the approach taken by MWR. In summary, the attack uses the devices' exposed debug pad to watch the boot process and understand the device's configuration. The Echo first attempts to boot from an SD Card attached to the debug pads. "By correctly formatting a SD Card with X-loader and U-Boot in the correct partition," writes Barnes, "we can boot from this card and into a U-Boot commandline interface."
This allowed him to understand the inner workings of the device. He introduced a reverse shell that spawned on boot. He then removed all external evidence of the attack and the Echo rebooted into its normal operation. However, he was now able to connect remotely with root.
Remotely, he was able to create a script "that would continuously write the raw microphone data into a named fifo pipe which we then stream over TCP/IP to a remote service. On the remote device we receive the raw microphone audio, sample the data and either save it as a wav file or play it out of the speakers of the remote device."
In effect, everything that the Echo hears can now also be heard by attackers without any alteration to the functionality of the Echo or evidence of tampering.
The weakness (or difficulty) in the attack is that it requires physical access to the device; but, warns Barnes, "it shouldn't be taken for granted that consumers won't expose the devices to uncontrolled environments that places their security and privacy at risk."
He offers several mitigations. The first is to use the physical mute button on the Echo. This will stop it 'listening', but reduces the always-on functionality of the device. The second is to monitor network traffic looking for anomalous traffic. This would be realistic if the Echo is used in a workplace, but not so likely in a home environment.
The third option is to always buy direct from Amazon. When MWR disclosed the flaw, Amazon released a statement: "Customer trust is very important to us. To help ensure the latest safeguards are in place, as a general rule, we recommend customers purchase Amazon devices from Amazon or a trusted retailer and that they keep their software up-to-date."
Amazon has fixed the weakness in the latest version. "This vulnerability has been confirmed on the 2015 and 2016 edition of the Amazon Echo," writes Barnes, "however the 2017 edition is not vulnerable to this physical attack." Buying a new device from source will be immune. However, buying an Amazon Echo second-hand could expose users to the potential purchase of a tampered device. If you find one in your hotel room, check that it is a 2017 model. If it is not, switch it to mute when not actively in use.
"What this research highlights," says Barnes, "is the need for manufacturers to think about both the physical and digital security risks that the devices may be subjected too and mitigate them at the design and development stage. Whilst Amazon has done a considerable amount to minimize the potential attack surface, these two hardware design choices -- the unprotected debug pads and the hardware configuration setting that allows the device to boot via an external SD card -- could expose consumers to an unnecessary risk."
DDoS attacks in Q2 2017
1.8.2017 Kaspersky Attack
The second quarter of 2017 saw DDoS attacks being more and more frequently used as a tool for political struggle. The Qatar crisis was accompanied by an attack on the website of Al Jazeera, the largest news network in the area, Le Monde and Le Figaro websites were targeted in the heat of the presidential election in France, and in Great Britain they recalled a year-old incident with the Brexit voter registration website where some citizens were excluded from the referendum because of the continuous attacks on the website.
Quite a significant event took place in the USA: the Federal Communications Commission (FCC) revealed plans for abolishing the principle of net neutrality, legislatively mandated two years before. The public comment system of the Commission website was rendered inoperative for about a day and eventually was completely disabled as a result of a massive attack. The reason for the crash remained unclear: it was either an invasion of the opponents of net neutrality, who were flooding the system with identical comments, or, on the contrary, an attack launched by the supporters of net neutrality, who tried to prevent their adversaries from flooding the FCC website with fake comments.
And yet, money remains the driving force of DDoS attacks. The growing interest in cryptocurrencies led to an increase in their exchange-value in the second quarter of 2017, which in turn drew the attention of cybercriminals. The largest bitcoin exchange, Bitfinex underwent an attack at the same time as the trading of a new IOT-currency IOTA was launched. Somewhat earlier the BTC-E exchange stated that its services were slowed down because of a powerful DDoS attack. Apparently, this way cybercriminals attempt to manipulate the currency rates, which can be quite easily achieved considering the high volatility of cryptocurrencies.
Owners of DDoS botnets do not limit themselves to renting out their computing powers. At the end of June, there was registered a large-scale attempt of extortion under threat of a DDoS attack. The group that calls itself Armada Collective demanded about $315,000 from seven South Korean banks in exchange for not disrupting their online services. According to a Radware report, this was not the first case of extortion through a DDoS attack initiated by this group.
With growing financial losses from DDoS attacks law enforcement agencies begin to take the attack initiators more seriously. In April 2017 in Great Britain, a young man was sentenced to two years in prison for a series of attacks, which he had carried out five years before while still being a student. The man had created the Titanium Stresser botnet and traded its services on a darknet, thus yielding a profit of approximately £386,000.
There were not many technical innovations in DDoS attacks in the second quarter; however, news concerning a new DDoS-attack vector deserves attention. Researchers from Corero Network Security reported that they had registered more than 400 attacks with the help of misconfigured LDAP servers. The largest attack volume was at 33 Gb/s. As amplified reflection was used in that case, the organization of such attacks requires relatively few resources.
The most infamous attack of the second quarter became a DDoS attack on Skype servers. Many users of the messenger all over the world experienced connectivity problems. The responsibility for the campaign was claimed by CyberTeam, but its motives remain unknown.
Quarter Trends
Ransom DDoS
The trend of extorting money under threat of DDoS attacks is becoming more prominent during this quarter. This approach was dubbed “ransom DDoS”, or “RDoS”. Cybercriminals send a message to a victim company demanding a ransom of 5 to 200 bitcoins. In case of nonpayment, they promise to organize a DDoS attack on an essential web resource of the victim. Such messages are often accompanied by short-term attacks which serve as demonstration of the attacker’s power. The victim is chosen carefully. Usually, the victim is a company which would suffer substantial losses if their resources are unavailable.
There is another method as opposed to the above-mentioned one: hoping to gain revenue quickly and without much effort cybercriminals contact a great number of companies by sending out ransom messages with threats of launching a DDoS attack, not taking into account the specifics of these companies’ operation. In most cases, they do not launch a demonstrative attack. Paying the ransom would create a certain reputation for a company and provoke further attacks of other cybercriminal groups.
It should be noted that these groups now are more and more represented not by well-coordinated hacker professional teams but by beginners who do not even possess the skills to launch a DDoS attack and only have the means for a “demonstrative attack”. Those who fall victim to this scheme are companies that for one reason or another have no resources to organize security for their services yet capable of parting with available funds in order to pay the ransom.
SambaCry
There is yet another important event of the quarter, which is the discovery of a vulnerability in the Samba network software. The vulnerability allows cybercriminals to execute code remotely on devices running Linux and Unix. Samba is a software suite that allows addressing network disks and printers and runs on a majority of Unix-like operating systems, such as Linux, POSIX-compatible Solaris and Mac OS X Server and various BSD OSes.
According to the Samba company, “all versions of Samba from 3.5.0 onwards have a remote code-execution vulnerability, allowing a malicious client to upload a shared library to a writable share, and then cause the server to load and execute it”.
The total number of devices with the vulnerable software reaches over 500,000, roughly estimated. This means that cybercriminals can use the devices to create botnets with the goal of carrying out large-scale DDoS attacks.
Statistics for botnet-assisted DDoS attacks
Methodology
Kaspersky Lab has extensive experience of combating cyber threats, including DDoS attacks of various complexity types and ranges. The experts of the company have been tracking the actions of botnets by using the DDoS Intelligence system.
Being part of the Kaspersky DDoS Prevention solution, the DDoS Intelligence system is intended to intercept and analyze commands sent to bots from command-and-control servers and requires neither infecting any user devices nor the actual execution of cybercriminals’ commands.
This report contains DDoS Intelligence statistics for the second quarter of 2017.
In the context of this report, it is assumed that an incident is a separate (single) DDoS-attack if the interval between botnet activity periods does not exceed 24 hours. For example, if the same web resource was attacked by the same botnet with an interval of 24 hours or more, then this incident is considered as two attacks. Also, bot requests originating from different botnets but directed at one resource count as separate attacks.
The geographical locations of DDoS-attack victims and C&C servers that were used to send commands are determined by their respective IP addresses. The number of unique targets of DDoS attacks in this report is counted by the number of unique IP addresses in the quarterly statistics.
It is important to note that DDoS Intelligence statistics are limited only to those botnets that have been detected and analyzed by Kaspersky Lab. It should also be noted that botnets are just one of the tools for performing DDoS attacks; thus, the data presented in this report do not cover every single DDoS attack occurred during the indicated period.
Q2 summary
The resources in 86 countries were attacked in Q2 2017, 14 countries increase over the Q1 2017.
Just as in Q1, almost one-half of the attacks (47.42%) were aimed at the targets in China.
China, South Korea, and the USA remained leaders by both the number of attacks and the number of targets. According to the number of reported C&C servers, the same countries are in the TOP 3; but South Korea took the first place this time.
The long-term DDoS attacks made it back in Q2. The record duration was 277 hours, which was a 131% increase compared to Q1. At the same time, the share of the attacks that lasted less than 50 hours remained practically unchanged (99.7% in Q2 vs. 99.8% in Q1).
There was a considerable drop in the share of attacks over TCP (down to 18.2% from 26.6%) and ICPM (down to 7.3% from 8.2%). This caused a rise in the percentage of SYN floods and attacks over UDP and HTTP.
Linux botnets recovered from the decline of their share in Q1. Those botnets were responsible for 51.23% of attacks in Q2 compared to 43.40% in Q1.
Geography of attacks
DDoS attacks were registered in 86 countries in Q2, where the largest number of the attacks were aimed at China (58.07% of all of the attacks), which is 3 p.p. higher compared to the previous quarter. South Korea went down from 22.41% to 14.17% and retained second place nonetheless, while the USA rose from 11.37% up to 14.03%, almost catching up with South Korea.
The top 10 accounted for 94.60% of attacks and included Italy (0.94%) and Netherlands (0.84%), pushing down Vietnam and Denmark in Q2. Russia (1.60%) lost 0.37 p.p., moving down from fourth to sixth place, while Great Britain went up from 0.77% to 1.38%, a rise from seventh to fifth place.
Distribution of DDoS attacks by country, Q1 2017 vs. Q2 2017
95.3% of the attacks were aimed at targets in the countries of top 10 in Q2 2017.
Distribution of unique DDoS-attack targets by country, Q1 2017 vs. Q2 2017
China maintained its leading position in distribution by number of targets: 47.42% of them were located in the territory of the country, a fall of 0.36 p.p. compared to Q1. At the same time, the USA pushed down South Korea by going up from third to second place. Respectively, the USA rose to 18.63% (vs. 13.80% in Q1), while South Korea went from 26.57% down to 16.37%.
The share of targets located in the territory of Russia dropped from 1.55% in Q1 to 1.33% in Q2, pushing Russia down from fifth to seventh place. Vietnam and Denmark left the top 10 and were replaced by Italy (1.35%) and Australia (0.97%).
Dynamics of the number of DDoS attacks
The number of attacks per day ranged from 131 (April 17) to 904 (April 13) in Q2 2017. The peak numbers were registered on April 24 (581), May 7 (609), June 10 (614), and June 16 (621). A relative downturn was registered on April 14 (192), May 31 (240), and June 23 (281).
Dynamics of the number of DDoS attacks in Q2 2017*
*Since DDoS attacks may continuously last for several days, one attack may be counted several times in the timeline, i.e., once per day.
Monday stayed as the quietest day for DDoS attacks (11.74% of all of the attacks) in Q2 2017, while Sunday became the busiest day (15.57%) on account of the activity slacking on Saturday, a fall from 16.05% in Q1 to 14.39% in Q2. Thursday became the second busiest day, coming right behind Sunday (15.39%).
Distribution of DDoS attacks by day of the week
Types and duration of DDoS attacks
SYN floods partially recovered their positions lost during the previous quarter, rising from 48.07% to 53.26% in Q2 2017. There was an increase of percentage for both UDP attacks (from 8.71% up to 11.91%) and HTTP attacks (from 8.43% up to 9.38%). At the same time, the share of TCP DDoS attacks plummeted from 26.62% down to 18.18%, while the popularity of ICMP attacks slightly decreased from 8.17% down to 7.27% (out of all of the registered attacks).
Distribution of DDoS attacks by type
Long-term attacks made it back to the statistics in Q2 2017: 0.07% of the attacks lasted more than 100 hours, while the record attack continued for 277 hours, 157 hours longer than the record of the previous quarter. At the same time, the share of attacks that lasted 4 hours or less increased from 82.21% in Q1 to 85.93% in Q2. Thus, the percentage of attacks lasting from 5 to 49 hours decreased.
Distribution of DDoS attacks by duration (hours)
C&C servers and botnet types
The top 3 countries with the greatest number of detected C&C servers was slightly changed in Q2: China retained the third place with its 7.74%, ousting Netherlands, which moved down to fourth place despite an increase from 3.51% to 4.76%. South Korea kept its leading position and saw a fall from 66.49% down to 49.11%, while the USA still retained the second place (16.07%). The top 3 countries accounted for 72.92% of C&C servers in total.
The top 10 included Canada and Denmark (each at 0.89%), ousting Romania and Great Britain in Q2. Compared to Q1 2017, there was a significant decrease in the shares of Hong Kong (down to 1.19% from 1.89%) and Russia (down to 2.68% from 3.24%).
Distribution of botnet C&C servers by country in Q2 2017
Distribution by operating system became almost balanced in Q2: the share of Linux-based botnets comprised 51.23%; accordingly, Windows-based botnets comprised 48.77%.
Correlation between Windows- and Linux-based botnet attacks
Conclusions
There were no particular changes in the statistics of the second quarter of 2017 when compared to the previous quarter. As before about one half of DDoS attacks still originated in China, also in China was one half of the detected attack targets.
The second quarter quite clearly showed that the DDoS-attack threat is perceived rather seriously. Some companies were prepared to pay cybercriminals literally after their first demand without waiting for the attack itself. This set off a whole new wave of fraud involving money extortion under threat of a DDoS attack, also known as “ransom DDoS”. The gravity of the situation can be seen in the cybercriminals’ frequent disregard for demonstrating their capabilities; instead, the fraudsters would just send out ransom messages directed at a large pool of addresses. Certainly, the “entry threshold” for ransom DDoS is extremely low, fraudsters need neither significant resources nor technical skills or knowledge.
DDoS útoky se prodlužují a chtějí výkupné
1.8.2017 SecurityWorld
Firmy v průběhu druhého čtvrtletí tohoto roku zaznamenaly návrat dlouhotrvajících DDoS útoků. Nejdelší z nich trval celých 277 hodin (více než 11 dní), což je v porovnání s předchozím čtvrtrokem nárůst o 131 %. Podle Q2 2017 botnet DDoS reportu společnosti Kaspersky Lab se tak jedná v tomto roce o dosavadního rekordmana.
Nicméně DDoS útoky se v období mezi dubnem a červnem nelišily pouze svojí délkou. Významně se také zvýšil počet států, v nichž došlo k napadení různých organizací – počet stoupl ze 72 států v prvním čtvrtletí na 86 ve druhém. Mezi 10 nejvíce napadených států patřily Čína, Jižní Korea, USA, Hong Kong, Velká Británie, Rusko, Itálie, Nizozemsko, Kanada a Francie. Itálie a Nizozemí v první desítce oproti prvnímu čtvrtletí vystřídaly Vietnam a Dánsko.
Cílem DDoS útoků se stala například velká mediální agentura Al Jazeera, internetové stránky novin Le Monde a Figaro nebo servery populární služby Skype. V průběhu dubna až června se také kyberzločinci pokusili pomocí DDoS útoků manipulovat s cenou kryptoměn, k čemuž je vedl neustále stoupající kurz těchto měn. Největší obchodní burza s měnou Bitcoin, Bitfinex, byla napadena ve chvíli, kdy došlo ke spuštění obchodování nové kryptoměny IOTA token. Ještě předtím zaznamenala výrazné zpomalení svého provozu v důsledku mohutného DDoS útoku také burza BTC-E.
Zájem DDoS útočníků o peníze je nicméně žene dál, než jen k manipulacím s kurzem kryptoměn. Použití těchto útoků může být výhodné pro vymáhání peněz, čehož jsou příkladem Ransom DDoS nebo RDoS trendy. Kyberzločinci obvykle svým obětem zasílají zprávy, v nichž požadují výkupné ve výši 5 až 200 bitcoinů. V případě, že firmy odmítnou požadovanou částku zaplatit, přistoupí útočníci k vyhrožování DDoS útokem na kriticky důležité online zdroje oběti.
Zaujal vás tento článek? Přehled nejzajímavějších zpráv získáte odebíráním našeho newsletteru »
Výhružnou zprávu navíc může doprovázet krátkodobý DDoS útok, který má oběť přesvědčit o tom, že se jedná o reálnou hrozbu. Na konci června například došlo k pokusu o masivní RDoS útok skupinou nazývanou Armada Collective, která požadovala po sedmi jihokorejských bankách sumu okolo 315 000 dolarů.
Existuje nicméně ještě jeden způsob, který se v posledním kvartále stal oblíbeným – Ransom DDoS bez jakéhokoliv DDoS útoku. Podvodníci zasílali velkému množství firem výhružné zprávy a doufali, že se některé rozhodnou zaplatit výkupné v obavě z možných následků. Jestliže se pouze jedna firma rozhodne zaplatit, přinese to kyberzločincům zisk s minimem vynaloženého úsilí.
„V dnešní době útoky typu Ransom DDoS nevyžadují zkušené týmy kyberzločinců se špičkovými technologiemi. V podstatě jakýkoliv podvodník, který ani nemá technické vědomosti a dovednosti k zorganizování plnohodnotného DDoS útoku, si může jednoduše zakoupit demonstrativní útok za účelem vydírání. Tito lidé si vybírají především ty firmy, které své systémy nijak nechrání před DDoS útoky. V jejich případě stačí jednoduchá demonstrace a nechají se snadno přesvědčit k zaplacení výkupného,“ komentuje Kirill Ilganaev, vedoucí oddělení DDoS ochrany ve společnosti Kaspersky Lab.
Odborníci Kaspersky Lab firmy varují před placením výkupného. Mohlo by to totiž způsobit dlouhodobé škody nad rámec okamžitých peněžních ztrát. Informace o firmě, která zaplatila výkupné, se rychle rozšíří komunitou zločinců a mohla by vyprovokovat další útoky od jiných skupin.
Ukrajina byla jen začátek. Ruští hackeři si testují hybridní válku
1.8.2017 Novinky/Bezpečnost BigBrother
V testovací arénu se proměnila v minulých letech Ukrajina. Ruští hackeři, kteří od proevropské revoluce v Kyjevě v roce 2014 napadli už několik klíčových míst ukrajinské infrastruktury, podle kyjevských představitelů v praxi testují prostředky tzv. hybridní války. Napsala to agentura Reuters s odvoláním na informace vicekancléře Dmytra Šymkiva, odpovědného v ukrajinském vedení za kybernetickou bezpečnost.
Ukrajina se stala terčem hackerů hned několikrát. Počítačoví piráti napadli již dříve například servery ukrajinské ústřední volební komise nebo citlivé aparáty registrující úroveň radiace v areálu černobylské jaderné elektrárny, postižené havárií v roce 1986.
Jeden z posledních velkých útoků se udál na konci června. Hackeři napadli prostřednictvím viru ukrajinské rozvodné elektrické sítě, zablokovali pokladní systémy supermarketů a ochromili počítačové sítě velkých bank, uvedl Šymkiv.
Sluší se také připomenout, že zasažena při tomto útoku nebyla pouze Ukrajina, ale prakticky celý svět. Do žebříčku deseti zemí, ve kterých škodlivý kód řádil nejvíce, se dostala například i Česká republika. Ukrajina nicméně tomuto žebříčku vévodila.
Rusko vinu popírá
Podle Kyjeva jsou všechny tyto útoky součástí hybridní války, kterou Rusko vede proti svému sousedovi od svržení proruského prezidenta Viktora Janukovyče před třemi lety. Jako hybridní je tato válka označována s ohledem na to, že v ní jsou používány nevojenské nástroje – kybernetické útoky.
Moskva nicméně jakýkoli podíl na kybernetické diverzi popírá.
Hackeři se snaží získat informace z informačních systémů ukrajinského ministerstva zahraničí a obrany. Ministr financí Oleksandr Danyljuk agentuře Reuters řekl, že jeho úřad musel kompletně obměnit zabezpečení svých serverů, když loni v listopadu hackeři zlikvidovali 90 procent ministerské počítačové sítě. Když ministr v parlamentu prezentoval návrh rozpočtu, nemohli se poslanci seznámit s jeho strukturou, protože servery ministerstva financí byly nedostupné.
V roce 2015 vznikla v Kyjevě s britskou pomocí kybernetická policie. Její šéf Serhij Demedjuk novinářům řekl, že jeho organizace v boji proti ruským hackerům spolupracuje s moldavskou prozápadní vládou, s níž si Ukrajina vyměňuje i špionážní informace. Přestože Ukrajina není členem NATO, Aliance poskytla kyjevské vládě pomoc při vytváření armádní jednotky chránící před hackery vojenskou infrastrukturu.
Nelegální software nahrává
Situace ale zdaleka není uspokojivá. Přes čtyři pětiny softwaru se na Ukrajině využívá nelegálně, což zvyšuje zranitelnost vůči útokům hackerů, uvedla agentura Reuters. Podle údajů Mezinárodního ústavu pro rozvoj řízení (IIMD) je v hodnocení úrovně kybernetického zabezpečení Ukrajina na 60. místě z 63 hodnocených států.
Ukrajina je nicméně pouhým začátkem. S podobnými útoky na principech hybridní války se budeme podle bezpečnostních expertů setkávat v budoucnu daleko častěji. Už jen kvůli tomu, jak je moderní doba závislá na počítačových systémech.
Hackeři hlásí, že ukradli Hru o trůny
1.8.2017 Novinky/Bezpečnost Hacking
Podle serveru Entertainment Weekly ukradla skupina hackerů společnosti HBO několik pořadů a navíc údajně i scénář seriálu Hra o trůny. Vedení HBO ale neuvedlo, o co přesně šlo.
Společnost HBO vydala jen obecné prohlášení, že došlo „ke kyberincidentu“ a byl ukraden nějaký materiál. “Okamžitě jsme zahájili vyšetřování a spolupracujeme s bezpečnostními složkami a externími firmami zaměřenými na kyberbezpečnost. Ochrana dat je pro nás nejvyšší priorita a bereme vážně zodpovědnost za data, která spravujeme.“
Hackeři tvrdí, že mají 1,5 terabytu dat, a podle serveru už nějaké epizody seriálů Ballers a Room 104 visí na internetu. Není však jasné, kdo to udělal.
HBO nechce potvrdit ani množství dat, ani konkrétní názvy pořadů.
Některým americkým reportérům však přišel e-mail, kde se kdosi vytahuje, že se podařil „největší únik dat“ a že jde o HBO a Hru o trůny: „Máte to štěstí, že jste první pionýři, kteří mohou být svědky toho úniku a mohou si to stáhnout. Užijte si to a šiřte dál. Dáme interview tomu, kdo to bude dobře šířit.“
Peníze jako hlavní motiv. Hackerům KLDR už nejde jen o informace
1.8.2017 Novinky/Bezpečnost BigBrother
Za organizovanými hackerskými útoky na finanční instituce Jižní Koreje a dalších států po celém světě stojí Pchjongjang, vyplývá ze zprávy jihokorejského Institutu finanční bezpečnosti (FSI). KLDR se v důsledku sankcí už při útocích nesoustřeďuje na získávání vládních či vojenských informací, ale snaží se získat finance, uvádí dále zpráva. Agentuře Reuters se nepodařilo získat vyjádření severokorejského zastoupení při OSN. Severní Korea jakékoli spojení s kybernetickými útoky pravidelně popírá.
Pchjongjang bývá spojován například s útokem na společnost Sony Pictures v roce 2014, během kterého zmizelo velké množství dat, na internetu se objevily osobní údaje zaměstnanců a pirátské kopie nových filmů.
Některé firmy zabývající se počítačovou bezpečností KLDR připisují i celosvětový útok vyděračského viru WannaCry, který v květnu zasáhl na 300 000 počítačů ve 150 zemích a částečně paralyzoval britské státní zdravotnictví (NHS).
Ruská společnost Kaspersky Lab má za to, že Severní Korea stojí i za kybernetickým útokem na polské banky. Američtí činitelé zase Pchjongjangu přičítají kybernetickou krádež 81 miliónů dolarů (1,8 miliardy Kč), k níž došlo po prolomení systému bangladéšské centrální banky.
Služby spojené s virtuálními měnami
Americká společnost FireEye ve své zprávě uvedla, že Severní Korea kybernetickou špionáž čím dál častěji využívá k finančnímu zisku a zaměřuje se i na služby spojené s virtuálními měnami.
Zpráva institutu FSI identifikovala osm útoků, při nichž severokorejští hackeři cílili na jihokorejské vládní a hospodářské instituce. Dále zmiňuje nově zformovanou hackerskou skupinu Andariel, která je činná přinejmenším od loňského května.
FSI má za to, že tato skupina proniká do bankomatů, a pokouší se tak získat informace o bankovních kartách, které buď prodává na černém trhu, anebo je využívá k výběru hotovosti. Vytvořila údajně i malware, s jehož pomocí pronikla na internetové servery provozující hazardní hry.
Česko si polepšilo, v mezinárodním žebříčku kybernetické bezpečnosti je na 35. místě
1.8.2017 Novinky/Bezpečnost Zabezpečení
Česká republika si loni polepšila v mezinárodním hodnocení připravenosti na kybernetické útoky. Proti roku 2015 se posunula o šest míst dopředu a patří jí celosvětově 35. příčka. Vyplývá to z hodnocení OSN Global Cybersecurity Index, které zveřejnila organizace CZ.NIC na svém blogu. V žebříčku si nejlépe stojí Singapur, USA a Malajsie, následují Omán a Estonsko.
Mezinárodní srovnání připravenosti a vyspělosti jednotlivých zemí v oblasti kybernetické bezpečnosti je založeno především na hodnocení oblastí, jako jsou legislativa, organizační kapacity či mezinárodní spolupráce. V rámci hodnocení ČR získala body například i za projekt bezpečnostního routeru Turris, aktivní podporu zakládání CSIRT týmů nebo kurzů pořádaných Akademií CZ.NIC.
V jiném hodnocení National Cyber Security Index (NCSI), což je projekt Estonska, který ale srovnává pouze 26 zemí, se Česko umístilo na první příčce. Projekt hodnotil například existenci národní strategie pro oblast kybernetické bezpečnosti a její implementaci, právní postižitelnost jednání kybernetické trestné činnosti včetně ratifikace mezinárodní Úmluvy o kybernetické kriminalitě. Do projektu téměř není zapojená Afrika, Asie a až na Kanadu ani Severní a Jižní Amerika.
Mezi další kritéria společná pro obě srovnání patří existence vzdělávacích programů na jednotlivých stupních škol či realizace osvětových aktivit.
Svou roli ve výsledcích představovala i metodologie a podrobnější otázky řešené Mezinárodní telekomunikační unií pro OSN. „Obě srovnání však potvrzují pozitivní trend připravenosti na kybernetické útoky, který potvrdilo i cvičení Locked Shields, v rámci kterého byl nejlepší český tým,“ dodal Jiří Průša z CZ.NIC.
A new era in mobile banking Trojans
1.8.2017 Kaspersky Android
Svpeng turns keylogger and steals everything through accessibility services
In mid-July 2017, we found a new modification of the well-known mobile banking malware family Svpeng – Trojan-Banker.AndroidOS.Svpeng.ae. In this modification, the cybercriminals have added new functionality: it now also works as a keylogger, stealing entered text through the use of accessibility services.
Accessibility services generally provide user interface (UI) enhancements for users with disabilities or those temporarily unable to interact fully with a device, perhaps because they are driving. Abusing this system feature allows the Trojan not only to steal entered text from other apps installed on the device, but also to grant itself more permissions and rights, and to counteract attempts to uninstall the Trojan.
Attack data suggests this Trojan is not yet widely deployed. In the space of a week, we observed only a small number of users attacked, but these targets spanned 23 countries. Most attacked users were in Russia (29%), Germany (27%), Turkey (15%), Poland (6%) and France (3%). It is worth noting that, even though most attacked users are from Russia, this Trojan won’t work on devices running the Russian language. This is a standard tactic for Russian cybercriminals looking to evade detection and arrest.
The Svpeng malware family is known for being innovative. Starting from 2013, it was among the first to begin attacking SMS banking, to use phishing pages to overlay other apps to steal credentials, and to block devices and demand money. In 2016, cybercriminals were actively distributing Svpeng through AdSense using a vulnerability in the Chrome browser. This makes Svpeng one of the most dangerous mobile malware families, and it is why we monitor the functionality of new versions.
The attack process
After starting, the Trojan-Banker.AndroidOS.Svpeng.ae checks the device language and, if it is not Russian, asks the device for permission to use accessibility services. In abusing this privilege, it can do many harmful things. It grants itself device administrator rights, draws itself over other apps, installs itself as a default SMS app, and grants itself some dynamic permissions that include the ability to send and receive SMS, make calls, and read contacts. Furthermore, using its newly-gained abilities the Trojan can block any attempt to remove device administrator rights – thereby preventing its uninstallation. It is interesting that in doing so it also blocks any attempt to add or remove device administrator rights for any other app too.
Svpeng was able to become a device administrator without any interaction with the user just by using accessibility services.
Using accessibility services allows the Trojan to get access to the UI of other apps and to steal data from them, such as the names of the interface elements and their content, if it is available. This includes entered text. Furthermore, it takes screenshots every time the user presses a button on the keyboard, and uploads them to the malicious server. It supports not only the standard Android keyboard but also a few third-party keyboards.
Some apps, mainly banking ones, do not allow screenshots to be taken when they are on top. In such cases, the Trojan has another option to steal data – it draws its phishing window over the attacked app. It is interesting that, in order to find out which app is on top, it uses accessibility services too.
From the information Svpeng receives from its command and control server (CnC), I was able to intercept an encrypted configuration file and decrypt it to find out the attacked apps, and to obtain a URL with phishing pages.
I uncovered a few antivirus apps that the Trojan attempted to block, and some apps with phishing URLs to overlay them. Like most mobile bankers, Svpeng overlays some Google apps to steal credit card details.
Also, the config file contained a phishing URL for the PayPal and eBay mobile apps to steal credentials and URLs for banking apps from different countries:
UK– 14 attacked banking apps
Germany – 10 attacked banking apps
Turkey– 9 attacked banking apps
Australia– 9 attacked banking apps
France– 8 attacked banking apps
Poland– 7 attacked banking apps
Singapore– 6 attacked banking apps
There was one more app in this configuration file – Speedway app, which is a rewards app, not a financial app. Svpeng will overlay it with a phishing window to steal credentials.
It can also receive commands from the CnC:
To send SMS
To collect info (Contacts, installed apps and call logs)
To collect all SMS from the device
To open URL
To start stealing incoming SMS
Distribution and protection
The Trojan-Banker.AndroidOS.Svpeng.ae is distributed from malicious websites as a fake flash player. Its malicious techniques work even on fully-updated devices with the latest Android version and all security updates installed. By accessing only one system feature this Trojan can gain all necessary additional rights and steal lots of data.
HBO Hacked again, Game of Thrones Script Leaked on the Internet
1.8.2017 securityaffairs Hacking
Hackers claim to have stolen 1.5 terabytes of data from HBO, including information on the current season of Game of Thrones.
Are you a fan of ‘Game of Thrones’ series? There is a news for you, hackers claim to have stolen 1.5 terabytes of data from HBO, including information on the current season of Game of Thrones and a script that is reportedly for the upcoming fourth episode of Game of Thrones Season 7.
The hackers notified the security breach to several reporters via anonymous email sent on Sunday, below the text of the message sent to the reporters:
“Hi to all mankind. The greatest leak of cyber space era is happening. What’s its name? Oh, I forget to tell. It’s HBO and Game of Thrones……!!!!!!
You are lucky to be the first pioneers to witness and download the leak. Enjoy it & spread the words. Whoever spreads well, we will have an interview with him.”
“HBO has joined the ranks of Hollywood entertainment companies to suffer a major cyber attack.” reads the Entertainment Weekly website.
“EW has learned that upcoming episodes of a couple series and at least one alleged script or treatment have been put online by hackers who breached the company’s systems — with more threatened to be coming soon.”
The hackers have stolen episodes of several HBO shows yet to release online, they have already leaked online upcoming episodes of “Ballers” and “Room 104” and they announced more leaks to be “coming soon.”
“HBO recently experienced a cyber incident, which resulted in the compromise of proprietary information,” reads a statement issued by the company. “We immediately began investigating the incident and are working with law enforcement and outside cybersecurity firms. Data protection is a top priority at HBO, and we take seriously our responsibility to protect the data we hold.”
HBO hasn’t provided further details on the cyber attack, it currently investigating the incident with the help of law enforcement and cyber security firms.
This is the second time that hackers break into the HBO network, in 2015, the first four episodes of “Game of Thrones Season 5” were leaked online.
HBO chairman and CEO Richard Plepler sent an email to HBO employees notifying them the security breach.
“As most of you have probably heard by now, there has been a cyber incident directed at the company which has resulted in some stolen proprietary information, including some of our programming,” he wrote. “Any intrusion of this nature is obviously disruptive, unsettling, and disturbing for all of us. I can assure you that senior leadership and our extraordinary technology team, along with outside experts, are working round the clock to protect our collective interests. The efforts across multiple departments have been nothing short of herculean. It is a textbook example of quintessential HBO teamwork. The problem before us is unfortunately all too familiar in the world we now find ourselves a part of. As has been the case with any challenge we have ever faced, I have absolutely no doubt that we will navigate our way through this successfully.”
Hollywood seems to be a privileged target for crooks, in April the hacker ‘The Dark Overlord’ claimed to have stolen and leaked online episodes from the forthcoming season of the TV show Orange Is The New Black.
In May, a hacker claimed to have stolen Pirates of the Caribbean: Dead Men Tell No Tales, but Disney denied it.
HBO Hacked — 'Game of Thrones' Scripts & Other Episodes Leaked Online
31.7.2017 thehackernews Hacking
If you are a die heart fan of 'Game of Thrones' series, there's good news for you, but obviously bad for HBO.
Hackers claim to have stolen 1.5 terabytes of data from HBO, including episodes of HBO shows yet to release online and information on the current season of Game of Thrones.
What's more? The hackers have already leaked upcoming episodes of the shows "Ballers" and "Room 104" on the Internet.
Additionally, the hackers have also released a script that is reportedly for the upcoming fourth episode of "Game of Thrones" Season 7.
According to Entertainment Weekly, hackers claim to have obtained 1.5 terabytes of data from the entertainment giant and informed several reporters about the hack via anonymous email sent on Sunday.
Though HBO has confirmed the cyber attack on its network and released a statement, the company did not confirm what the hackers have stolen more information, and whether or not upcoming episodes of the widely watched Game Of Thrones have been stolen.
"HBO recently experienced a cyber incident, which resulted in the compromise of proprietary information," the company confirmed the hack in a statement.
"We immediately began investigating the incident and are working with law enforcement and outside cybersecurity firms. Data protection is a top priority at HBO, and we take seriously our responsibility to protect the data we hold."
After leaking episodes of "Ballers" and "Room 104" and a script that is believed to be the new episode of "Game of Thrones," hackers have promised more leaks to be "coming soon."
The anonymous email sent to the reporters read:
"Hi to all mankind. The greatest leak of cyber space era is happening. What’s its name? Oh, I forget to tell. It's HBO and Game of Thrones……!!!!!!
You are lucky to be the first pioneers to witness and download the leak. Enjoy it & spread the words. Whoever spreads well, we will have an interview with him."
If hackers have indeed stolen 1.5 terabytes of data from HBO, it could be the company's second major cyber attack, after 2015, when the first four episodes of "Game of Thrones Season 5" appeared on the Internet shortly before the season's premiere.
However, when compared to Sony hack 2014, wherein hackers stole 100 terabytes of data, the amount of data stolen from HBO is nowhere near it.
In an email sent to its employees about the latest breach obtained by EW, HBO chairman and CEO Richard Plepler said:
"The problem before us is unfortunately all too familiar in the world we now find ourselves a part of. As has been the case with any challenge we have ever faced, I have absolutely no doubt that we will navigate our way through this successfully."
At this moment, it is still unclear who is behind the hack. We will update the story with the latest information.
Someone Hijacks A Popular Chrome Extension to Push Malware
31.7.2017 thehackernews Virus
Phishers have recently hacked an extension for Google Chrome after compromising the Chrome Web Store account of German developer team a9t9 software and abused to distribute spam messages to unsuspecting users.
Dubbed Copyfish, the extension allows users to extract text from images, PDF documents and video, and has more than 37,500 users.
Unfortunately, the Chrome extension of Copyfish has been hijacked and compromised by some unknown attacker, who equipped the extension with advertisement injection capabilities. However, its Firefox counterpart was not affected by the attack.
The attackers even moved the extension to their developer account, preventing its developers from removing the infected extension from the store, even after being spotted that the extension has been compromised.
"So far, the update looks like standard adware hack, but, as we still have no control over Copyfish, the thieves might update the extension another time… until we get it back," the developers warned. "We can not even disable it—as it is no longer in our developer account."
Here's How the Hackers Hijacked the Extension:
Copyfish developers traced the hack back to a phishing attack that occurred on 28 July.
According to a9t9 software, one of its team members received a phishing email impersonating the Chrome Web Store team that said them to update their Copyfish Chrome extension; otherwise, Google would remove it from the web store.
The phishing email instructed the member to click on "Click here to read more details," which opened the "Google" password dialogue box.
The provided link was a bit.ly link, but since the team member was viewing the link in HTML form, he did not find it immediately suspicious and entered the password for their developer account.
The developers said the password screen looked almost exactly the one used by Google. Although the team did not have any screenshot of the fake password page as it appeared only once, it did take a screenshot of the initial phishing email and its reply.
"This looked legit to the team member, so we did not notice the [phishing] attack as such at this point. [Phishing] for Chrome extensions was simply not on our radar screen," the developers said.
Once the developer entered the credentials for a9t9 software’s developer account, the hackers behind the attack updated the Copyfish extension on 29 July to Version 2.8.5, which is pushing out spams and advertisements to its users.
The worst part comes in when the Copyfish makers noticed the issue very quickly, but they could not do anything because the hackers moved the extension to their developer account.
The software company contacted Google developer support, which is currently working to provide the company access to their software.
The a9t9 software is warning users that the Chrome extension for Copyfish is currently not under its control. So, users are advised not to install the malicious Chrome extension and remove, if they have already installed.
Hackers Compromise Accounts of FireEye Threat Intelligence Analyst
31.7.2017 securityweek Hacking
A hacker or group of hackers claimed today to have breached FireEye's Mandiant. In a Pastebin post, they claimed, "It was fun to be inside a giant company named 'Mandiant'... 'Mandiant' knows how deep we breached into its infrastructure."
The "proof" of the breach was somewhat limited information about one Mandiant/FireEye employee, Adi Peretz (FireEye purchased Mandiant for $1 billion in January 2014). Peretz is described in the Pastebin post as 'Victim #1', a 'Senior Threat Intelligence Analyst at Mandiant.' There is no evidence of a breach deep into Mandiant's infrastructure, and a FireEye spokesperson told SecurityWeek that the company network has not been breached.
There does not appear to be anything sensitive on Pastebin (Pastebin's policy is to remove any such data). Instead there is a link to the full dump on megafileupload.com, from where a 32 MB zipped file can be downloaded. The content, however, is not awe-inspiring -- embarrassing for Peretz, but hardly damaging to FireEye. It includes personal details from Peretz (such as a rather small Outlook contact list), emails, and freely available PDF documents such as a Cylance-produced PDF description of Cylance Protect.
This highlights a fundamental contradiction in the Pastebin announcement. The hacker announces, "This leak was just a glimpse of how deep we breached into Mandiant, we might publish more critical data in the future." Yet from the evidence presented, there is little more than a breach of Peretz's LinkedIn and other personal accounts.
The LinkedIn account has since been removed, but not before the hackers defaced it with the picture of a bare backside and language to suit.
In a statement emailed to SecurityWeek, FireEye confirms the apparently limited nature of the breach. "We are aware of reports that a Mandiant employee's social media accounts were compromised. We immediately began investigating this situation and took steps to limit further exposure. Our investigation continues, but thus far we have found no evidence FireEye or Mandiant systems were compromised."
Although the hacker says he has more, and might leak more in the future, that is not described as the primary drive behind the breach. Effectively, the hacker describes this as the first success ('Victim #1') of a new project: Op. #LeakTheAnalyst. The motivation is to embarrass security analysts, not to breach major companies.
"In the #LeakTheAnalyst operation," says the hacker, "we say fuck the consequence let's track them on Facebook, Linked-in, Tweeter, etc. let's go after everything they've got, let's go after their countries, let's trash their reputation in the field." For a long time, he says, "we - the 31337 hackers - tried to avoid these fancy ass "Analysts" whom trying to trace our attack footprints back to us and prove they are better than us." No more. "Let's unleash hell upon them."
The clue is in the Op name: LeakTheAnalyst. The question is whether this really is a new, well-resourced hacker campaign, and that more analysts have been compromised and will be embarrassed in the future -- or did one hacker get lucky, get into Peretz's accounts, and is now trying to make it seem like a planned and coordinated campaign?
The hacker or hackers are currently unknown. The poster uses the term, 'we -- the 31337 hackers'; but that is probably a generic usage simply claiming 'I am one of the elite hackers'.
The leakage is probably not the treasure trove of hugely sensitive internal information claimed by some. It should not, for example, surprise anyone that FireEye/Mandiant meets with the Israeli Defense Force; while a FireEye Threat Intelligence Summary from June 2016 is hardly critical.
Nevertheless, it would be a mistake to believe that the dump contains nothing of value to attackers; and at the very least it is a huge embarrassment for a senior security analyst within a major security firm. Must do better should now be his motto. It appears that he had been owned for upwards of a year -- and for the moment, we cannot be certain that additional data has not been lifted.
Google Wants Symantec Certificates Replaced Until Chrome 70
31.7.2017 securityweek Security
After several months of debate, Google has released its final proposal in the case of Symantec’s certificate authority (CA) business. All Symantec-issued certificates must be replaced by the time Google releases Chrome 70 next year.
Google announced its intention to take action against Symantec for improperly issued digital certificates in March. The announcement came after the company, particularly some of its subsidiaries and WebTrust audited partners, were caught wrongly issuing certificates.
After several proposals on both sides, Google has come up with a final decision. According to the company, between now and March 15, 2018, websites using TLS certificates issued by Symantec before June 1, 2016, should obtain replacements from a trusted CA, including Symantec.
While Symantec will be allowed to release certificates, it will have to find a subordinate certificate authority (SubCA) whose infrastructure it can use. The company expects to have new infrastructure set up by December 1.
Starting with Chrome 66, currently scheduled for release on March 15, 2018, certificates issued on or after June 1, 2016, will no longer be trusted.
Certificates issued through Symantec’s old infrastructure after June 1, 2016, will continue to be trusted, but only until the release of Chrome 70. With the release of Chrome 70, scheduled for release on October 23, 2018, all certificates issued via the company’s old infrastructure will stop being trusted by the web browser.
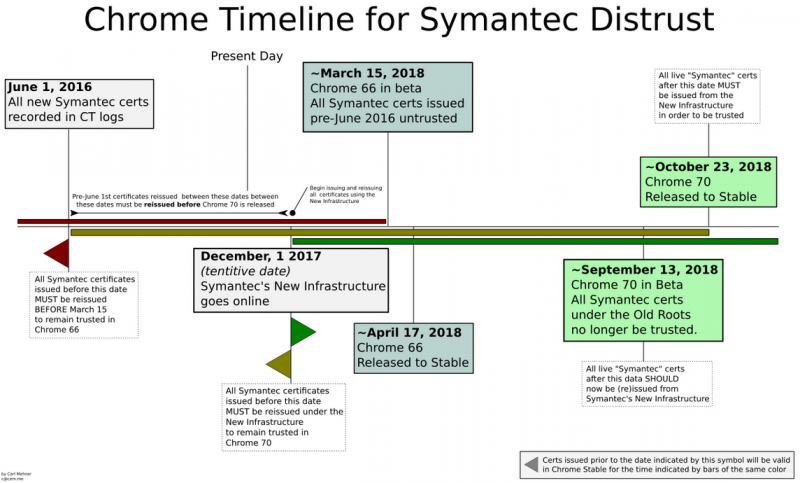
Mozilla advised Symantec in May to accept Google’s proposal and described the alternative action it had been prepared to take in case an agreement was not reached. Microsoft and Apple have not made any comments on the matter, but based on the outcome of the case involving WoSign and StartCom, at least Apple is likely to follow in Google’s footsteps.
Symantec has promised to step up its game, but recent incidents have shown that the company, and particularly its subsidiaries, still have a long way to go. A researcher managed to trick Symantec’s RapidSSL into revoking TLS certificates by falsely claiming that their associated private keys had been compromised.
Mortgage Phishing Scams Target Big Payouts
31.7.2017 securityweek Phishing
Over the last few years, business email compromise (BEC) scams have rocketed -- costing victims $1.45 billion in 2016 alone (FBI report). Now a new related threat has emerged -- the mortgage phishing scam -- that seems likely to follow a similar trajectory.
It is early days and the scam -- like BEC in its early days -- goes by various names: mortgage phish, mortgage escrow scam, real estate wire transfer scam, and mortgage wiring scam. But it is growing. In June 2017, during National Homeownership Month, the FTC issued a warning: "the FTC and the National Association of Realtors want to remind you that scammers sometimes use emails to rob home buyers of their closing costs and personal information."
Like BEC, the scam seeks to trick its victims into wiring funds to a criminally operated account. The difference here is that it people rather than businesses that are conned -- and they can end up losing their life savings and/or their home.
The FTC warning explains the basic scam: "Hackers break into the email accounts of buyers or real estate professionals to get information about upcoming real estate transactions. The hacker then sends an email to the buyer, posing as the real estate professional or title company. The bogus email says there has been a last-minute change to the wiring instructions, and tells the buyer to wire closing costs to a different account. But it's the scammer's account. If the buyer takes the bait, their bank account could be cleared out in a matter of minutes."
Barracuda Networks has described a real-life example that, in this instance, failed. "On the day that the buyers were set to wire funds, they received an email from their mortgage company stating that they switched banks, and to follow the updated wiring instructions in the email attachment."
Home buyers are particularly vulnerable at this point. They may have spent many stressful months in arranging the purchase, and there is now one relatively simple task before they can collect the keys to their new home. In this instance, the scam failed. It raised a red flag for the buyer who looked more closely at the email -- and noticed that the actual sender's email address didn't quite match the one listed in the real mortgage agent's email signature.
The text of the email read, "We changed banks, please see the attached for the updated wiring instructions. Let me know you receive this message and when wire is sent."
The attachment gives the attacker an extra shot at the target. If he opens the attachment but decides against making the wire, he could still find himself infected with a banking trojan or, potentially, ransomware. In this instance, however, the target did the right thing: he "immediately called his mortgage agent to confirm that the message was in fact a scam. What he found even more alarming with his situation," adds Barracuda, "was the reaction that he received from the mortgage company. They mentioned that it's a wide-spread problem, but they didn't seem interested in looking into the issue any further."
House prices have consistently grown since the 2006 crash, and now stand at similar or above their previous high. This makes it a lucrative market for scammers. "Scams like these have been around for a few years," reported HousingWire in June this year." Last year, the Contra Costa Association of Realtors warned Bay Area homebuyers that they could be targets of similar schemes, one of which cost a local buyer nearly $1 million."
The mortgage phish is just another social engineering spear-phish; but the stakes are high and the targets are vulnerable. The Contra Costa Association warns, "Because buyers often put their complete faith in the real estate professionals who guide them through transactions, they very rarely challenge any advice and direction provided. Moreover, they are so comfortable making daily online transactions, they rarely, if ever question the authenticity of email or text messages." It adds, "there is no means to retrieve the funds once wired."
Last month Barracuda launched Sentinel, described as "an artificial intelligence (AI) powered spear-phishing and business email compromise (BEC) real-time detection and prevention solution."
Triada Trojan Preinstalled on Low-Cost Android Devices
31.7.2017 securityweek Android
Several low-cost Android device models were recently found to feature the Triada Trojan built into their firmware, Dr. Web security researchers say.
Designed as a financial threat, Triada was said last year to be the most advanced mobile malware because it could inject itself into the Zygote parent process, thus running code in the context of all applications. Earlier this year, it adopted sandbox technology (specifically, the open source sandbox DroidPlugin) to improve its detection evasion capabilities.
According to Dr. Web, the malware was recently found embedded in libandroid_runtime.so system library, thus being able to penetrate the processes of all running apps without requiring root privilages. The modified library, the security firm reveals, was found on several mobile devices, including Leagoo M5 Plus, Leagoo M8, Nomu S10, and Nomu S20.
“[Triada] is embedded into the source code of the library. It can be assumed that insiders or unscrupulous partners, who participated in creating firmware for infected mobile devices, are to be blamed for the dissemination of the Trojan,” Dr. Web researchers reveal.
The malware was implemented in the library in a way that allows it to get control “each time when an application on the device makes a record to the system log.” The initial launch of the Trojan, the researchers say, is performed by Zygote, which is launched before other applications.
After initialization, the malware sets up parameters, creates a working directory, then checks the environment. If running in the Dalvik environment (the discontinued process virtual machine in Android), it intercepts a system method to keep track of when applications start and inject its malicious code in them immediately after they start.
The Trojan can secretly run additional malicious modules to download other Trojan components. This approach, the security researchers say, can be used to run malicious plugins to steal confidential information and bank credentials, to run cyber-espionage modules, or intercept messages from social media clients and messengers.
Another malicious module Triada can extract and decrypt from libandroid_runtime.so was designed to download additional malicious components from the Internet and to ensure they can interact with each other.
“Since [Triada] is embedded into one of the libraries of the operating system and located in the system section, it cannot be deleted using standard methods. The only safe and secure method to get rid of this Trojan is to install clean Android firmware,” the security researchers warn.
Dr. Web says it has informed the manufacturers of compromised smartphones of the issue. Affected users are advised to install all updates that might be released for their devices.
PoC Malware Exploits Cloud Anti-Virus for Data Exfiltration
31.7.2017 securityweek Virus
Security researchers at SafeBreach have created proof-of-concept (PoC) malware that can exfiltrate data from endpoints that don’t have a direct Internet connection by exploiting cloud-enhanced anti-virus (AV) agents.
Although highly secure enterprises might employ strict egress filtering, meaning that endpoints either have no direct Internet connection or have a connection restricted to hosts required by their legitimately installed software, data can be exfiltrated if cloud AV products are in use, the security researchers argue.
Presented at BlackHat USA 2017 by Itzik Kotler and Amit Klein from SafeBreach Labs, the PoC tool relies on packing data inside an executable the main malware process creates on the compromised endpoint. Thus, if the AV product employs an Internet-connected sandbox as part of its cloud service, data is exfiltrated as soon as the AV agent uploads the newly created executable to the cloud for further inspection, although the file is executed in an Internet connected sandbox.
In a whitepaper (PDF), the researchers not only provide data and insights on AV in-the-cloud sandboxes, but their also cover the use of on-premise sandboxes, cloud-based/online scanning and malware categorization services, and sample sharing. Furthermore, they provide information on how the attack can be further enhanced and how cloud-based AV vendors can mitigate it.
Dubbed Spacebin, the proof-of-concept tool was made available on GitHub. The project includes directories with both server-side and client-side code. Instructions on how to use the tool are available on the project’s page.
What Kotler and Klein focused on was the analysis of two network architectures found in highly secure organizations: one where endpoints don’t have access to the Internet, but an AV management server does; and another where the machines have access to a closed set of hosts, meaning there’s very limited access to the Internet. In both scenarios, cloud-based AV agents are deployed across all endpoints.
“We are going to abuse the cloud AV sandboxing feature that many AV vendors use. The rationale for this feature is that it enables the AV vendor to offer lightweight agent software, and carry out the heavy-lifting security analysis work in the cloud. Specifically, in such an architecture, the AV agent needs to conduct only basic security checks against other processes and files, allowing for a grey area where a binary “malicious/non-malicious” decision cannot be determined locally. A process/file falling into this grey area is sent to the cloud for further analysis, and a security decision is obtained from the cloud (sometimes in near real time),” the researchers explain.
The sample is typically executed in an AV cloud sandbox and its behavior observed there, where a malicious program can run with no harm to real users or resources, the researchers note. They also argue that the AV cloud sandbox would normally be connected to the Internet, as this would provide better detection capabilities (for example, the malware might attempt to connect to a command and control server and the sandbox would detect that).
“The attacker process (called Rocket) contains a secondary executable (called Satellite) as part of its data. The Satellite can be encrypted/compressed to hide the fact that it is another executable, thus the Satellite can be no more than a piece of data in the Rocket memory space (and file) that does not jeopardize the Rocket. The Satellite contains a placeholder for arbitrary data (“payload”) to be exfiltrated. The location of the placeholder should be known to the Rocket,” the researchers explain.
As part of the attack, the Rocket collects the data (payload) it needs to exfiltrate, decrypts / decompresses the Satellite and embeds the payload in its image (can further compress or encrypt the payload), writes the Satellite image to disk as a file, and spawns the Satellite (from its file) as a child process.
The Satellite then performs an intentionally suspicious action to trigger endpoint AV detection and have the Satellite image file (which contains the payload) sent to the AV cloud. Next, the cloud AV executes the Satellite file in an Internet-connected sandbox and the Satellite process can attempt to exfiltrate the embedded payload using any known Internet-based exfiltration methods.
“Note that this attack is ‘noisy’ in the sense that the AV product will flag the Satellite file as suspicious and as such this may have visible impact on the user, as well as visibility in logs and records. However, for a one time exfiltration attack this will already be too late, as the payload will already be traveling to the cloud by the time this incident is investigated by flesh-and-blood analysts,” the security researchers explain.
One mitigation solution would involve blocking the AV sandboxes (both on-premise and cloud sandboxes) from accessing the Internet. This, however, may be too strict in many cases, as it would no longer allow them to observe the Internet traffic of a sample. Because of that, Internet blocking could be applied only for samples not coming from the Internet, because they do not carry enterprise endpoint-specific payloads and can’t exfiltrate anything useful from the endpoint.
“We can generalize our findings and state that sharing an executable (suspicious/malicious sample) from the organization, with the outside world in some manner (e.g. submitting the sample to a cloud analysis service or allowing such file submission) can result in data exfiltration, unless there is confidence that the sample has arrived from outside the organization and the file has not changed since its arrival,” the researchers conclude.
Hackers leaked data from alleged Mandiant FireEye ‘breach’ under #OpLeakTheAnalyst.
31.7.2017 securityaffairs Hacking
Late Sunday evening, hackers leaked details alleged stolen from a compromised system maintained by Adi Peretz, a Senior Analyst at Mandiant.
Late Sunday evening, hackers have posted details alleged stolen from a system belonging to Adi Peretz, a Senior Threat Intelligence Analyst at security firm FireEye/Mandiant.
The leaked archive is a 337MB PST file containing the expert’s emails. Leaked archive also includes images of its accounts, including One Drive, Live, LinkedIn, geo-tracking of personal devices for at least a year, billing records and PayPal receipts.

“In addition to that are images detailing the compromise of their One Drive account, Live account, LinkedIn account, geo-tracking of personal devices for at least a year, billing records and PayPal receipts, credentials for an engineering portal at FireEye, WebEx and JIRA portals, as well as Live and Amazon accounts. There are also records related to an alleged customer, Bank Hapoalim, and internal documentation and presentations, including one for the IDF (Israel Defense Forces) from 2016.” reported Salted Hash.
The security firm has denied any intrusion in its systems.
The hackers who published the alleged Mandiant Internal Leaks claims it is part of the ongoing campaign #OpLeakTheAnalyst.
“It was fun to be inside a giant company named “Mandiant” we enjoyed watching how they try to protect their clients and how their dumb analysts are trying to reverse engineer malwares and stuffs.
Now that “Mandiant” knows how deep we breached into its infrastructure its so-called threat analysts are trying to block us. Let’s see how successful they are going to be :D” reads the message published on PasteBit.
Independent analysts who visioned the leaked material believe there is no evidence of any compromise.
Follow
Ido Naor @IdoNaor1
Only one workstations seems to be infected during #leakTheAnalyst . Dump does not show any damage to core assets of #Mandiant
11:45 AM - Jul 31, 2017
1 1 Reply 7 7 Retweets 11 11 likes
Twitter Ads info and privacy
The security researcher Hanan Natan also believes the overall Mandiant networks weren’t breached:
Follow
WetNork @sha1roedah
Mandiant Leak http://pastebin.com/raw/6HugrWH4
Personal data and some internal docs, apparently only on one workstation #LeakTheAnalyst
11:25 AM - Jul 31, 2017
Replies Retweets likes
Twitter Ads info and privacy
Below the response issued by FireEye:
“We are aware of reports that a Mandiant employee’s social media accounts were compromised. We immediately began investigating this situation, and took steps to limit further exposure. Our investigation continues, but thus far, we have found no evidence FireEye or Mandiant systems were compromised.”
Hacker Leaks Data From Mandiant (FireEye) Senior Security Analyst
31.7.2017 thehackernews Hacking
Reportedly, at least one senior cyber security analyst working with Mandiant, a Virginia-based cybersecurity firm owned by the FireEye, appears to have had its system compromised by hackers, exposing his sensitive information on the Internet.
On Sunday, an anonymous group of hackers posted some sensitive details allegedly belonged to Adi Peretz, a Senior Threat Intelligence Analyst at Mandiant, claiming they have had complete access to the company's internal networks since 2016.
The recent hack into Mandiant has been dubbed Operation #LeakTheAnalyst.
Further Leaks from Mandiant Might Appear
The hackers have leaked nearly 32 megabytes of data—both personal and professional—belonging to Peretz on Pastebin as proof, which suggests they have more Mandiant data that could be leaked in upcoming days.
"It was fun to be inside a giant company named “Mandiant” we enjoyed watching how they try to protect their clients and how their dumb analysts are trying to reverse engineer malware and stuff," the Pastebin post reads.
"This leak was just a glimpse of how deep we breached into Mandiant, we might publish more critical data in the future."
Hackers dumped a treasure trove of sensitive information, which includes:
Peretz's Microsoft account login details
Peretz's Contacts
Screenshots of the Windows Find My Device Geolocator, linked to Peretz's Surface Pro laptop.
Client correspondence
Presentations
Contents of his email inbox
Several internal Mandiant and FireEye documents
Threat intelligence profiles for the Israeli Defence Force (IDF)
Besides leaks, the anonymous hackers also reportedly broke into Peretz's LinkedIn page and defaced it. His profile has since been deleted from the professional media network.
Although the motives behind the hack are not known at this moment, Mandiant has yet to comment on the incident.
In response to the leak, Mandiant's parent company, FireEye issued a statement, blaming the employee's social media accounts for the leak. The statement reads:
We are aware of reports that a Mandiant employee's social media accounts were compromised. We immediately began investigating this situation, and took steps to limit further exposure. Our investigation continues, but thus far, we have found no evidence FireEye or Mandiant systems were compromised.
ICS-CERT Warns of CAN Bus Vulnerability
31.7.2017 securityaffairs ICS
The United States Industrial Control Systems Cyber Emergency Response Team (ICS-CERT) issued an alert on Friday to warn relevant industries about a vulnerability affecting the Controller Area Network (CAN) bus standard.
CAN is a high-reliability serial bus communications standard. It’s present in most modern cars – it allows various components of a vehicle to communicate with each other – and it’s also used in the healthcare and other sectors.
A team of Italian researchers published a paper last year describing various CAN weaknesses and an attack method that can be leveraged for denial-of-service (DoS) attacks. They also published a proof-of-concept (PoC) exploit and a video showing how they managed to exploit the flaw to disable the parking sensors on a 2012 Alfa Romeo Giulietta.
The attack method presented by the experts requires physical access to the targeted vehicle and extensive knowledge of the CAN protocol, but ICS-CERT pointed out that it might be more difficult to detect compared to previously disclosed techniques.
“The severity of the attack varies depending on how the CAN is implemented on a system and how easily an input port (typically ODB-II) can be accessed by a potential attacker,” ICS-CERT said. “This attack differs from previously reported frame-based attacks, which are typically detected by IDS/IPS systems. The exploit focuses on recessive and dominate bits to cause malfunctions in CAN nodes rather than complete frames.”
Since CAN is a standard used across multiple industries and many products, patching vulnerabilities is not an easy task.
ICS-CERT says it’s working with vendors and researchers to identify mitigations for such attacks. In the meantime, the agency recommends limiting access to the OBD-II ports of a vehicle.
As cars become increasingly connected, researchers have invested significant effort into identifying potential security holes. A study conducted by IOActive last year showed that when it comes to cars, the CAN bus is the fourth most common attack vector.
Flaws that can be exploited for CAN access are also highly common, accounting for more than a quarter of the weaknesses analyzed by IOActive.
Airlines Alert Customers, Employees of Cybersecurity Incidents
31.7.2017 securityaffairs Cyber
Several North American airlines alerted customers and employees in the past days about various types of cybersecurity incidents, including system breaches, data leaks and credential stuffing attacks.
Virgin America said it detected unauthorized access to information systems containing employee and contractor data on March 13. According to the company, a third-party accessed logins and passwords used for its corporate network.
Cybersecurity forensics experts have been called in to investigate the incident and law enforcement has been notified.
The company said roughly 3,100 employees and contractors had their login credentials compromised, and an additional 110 individuals may have had social security numbers, driver’s license or government issued IDs, addresses, and health-related information stolen.
Canada-based WestJet Airlines told customers on Friday that an unauthorized third party disclosed some WestJet Rewards member profile data. While the leaked data did not contain any payment card or other financial information, the company has notified the Calgary Police Service and the RCMP’s cybercrime unit.
The airline is in the process of notifying affected customers, and it has advised WestJet Rewards members to change their passwords on a regular basis.
Florida-based ultra low cost carrier Spirit Airlines has sent an email to customers to notify them of an incident involving their FREE SPIRIT account.
The company told customers that someone published their information on a third-party website, but pointed out that the data was obtained from a prior breach unrelated to Spirit Airlines.
Spirit’s warning comes after a hacker contacted news websites, including SecurityWeek, claiming to have obtained information on 11.7 million Spirit accounts. The individual claimed to have alerted the airline of a vulnerability in its systems, and decided to put the data up for sale on the dark web after the company ignored him.
The hacker has leaked more than 10,000 records apparently belonging to Spirit customers, including names, Spirit account numbers, passwords, dates of birth, phone numbers, addresses and email addresses. However, he refused to provide the full data set or evidence of how he breached the airline’s systems.
Spirit told SecurityWeek that the hacker actually attempted to extort the company using emails and passwords obtained previously from other sources on the Internet.
Security expert Troy Hunt, the owner of the Have I Been Pwned service, told SecurityWeek that all the email addresses he tested from the leaked data show up in Exploit.in, a list of nearly 600 million email address and password combinations compiled using data stolen from various online systems.
Cybercriminals have used the Exploit.in list for credential stuffing attacks, where attackers automatically inject username/password combinations into a website’s login page in hopes that account owners have used the same credentials on multiple online services.
OpenAI Gym – A machine learning system creates ‘invisible’ malware
31.7.2017 securityaffairs Virus
At DEF CON hacking conference experts demonstrated how to abuse a machine learning system dubbed OpenAI Gym to create malware that can avoid detection.
We have discussed several times about the impact of Artificial Intelligence (AI) on threat landscape, from a defensive perspective new instruments will allow the early detections of malicious patterns associated with threats, from the offensive point of view machine learning tools can be exploited to create custom malware that defeats current anti-virus software.
At the recent DEF CON hacking conference, Hyrum Anderson, technical director of data science at security shop Endgame, demonstrated how to abuse a machine learning system to create malicious code that can avoid detections of security solutions.
Anderson adapted the Elon Musk’s OpenAI framework to create malware, the principle is quite simple because the system he created just makes a few changes to legitimate-looking code and convert them into malicious code.
A few modifications can deceive AV engines, the system created by the experts was named OpenAI Gym.
“All machine learning models have blind spots,” he said. “Depending on how much knowledge a hacker has they can be convenient to exploit.”
Anderson and his group created a system that applies very small changes to a legitimate code and submits it to a security checker. The analysis of the response obtained querying the security checker allowed the researchers to make lots of tiny tweaks that improved the capability of the malware to avoid the detection.

The machine learning system developed by the experts ran over 100,000 samples past an unnamed security engine in 15 hours of training. The results were worrisome, 60 per cent of the malware samples past the security system’s defenses.
The code of the OpenAI Gym was published by Anderson and his team on Github.
“This is a malware manipulation environment for OpenAI’s gym. OpenAI Gym is a toolkit for developing and comparing reinforcement learning algorithms. This makes it possible to write agents that learn to manipulate PE files (e.g., malware) to achieve some objective (e.g., bypass AV) based on a reward provided by taking specific manipulation actions.” reads the description of the toolkit published on GitHub.
Anderson encouraged experts to try the OpenAI Gym and improve it.
Airlines Alert Customers, Employees of Cybersecurity Incidents
31.7.2017 securityweek Cyber
Several North American airlines alerted customers and employees in the past days about various types of cybersecurity incidents, including system breaches, data leaks and credential stuffing attacks.
Virgin America said it detected unauthorized access to information systems containing employee and contractor data on March 13. According to the company, a third-party accessed logins and passwords used for its corporate network.
Cybersecurity forensics experts have been called in to investigate the incident and law enforcement has been notified.
The company said roughly 3,100 employees and contractors had their login credentials compromised, and an additional 110 individuals may have had social security numbers, driver’s license or government issued IDs, addresses, and health-related information stolen.
Canada-based WestJet Airlines told customers on Friday that an unauthorized third party disclosed some WestJet Rewards member profile data. While the leaked data did not contain any payment card or other financial information, the company has notified the Calgary Police Service and the RCMP’s cybercrime unit.
The airline is in the process of notifying affected customers, and it has advised WestJet Rewards members to change their passwords on a regular basis.
Florida-based ultra low cost carrier Spirit Airlines has sent an email to customers to notify them of an incident involving their FREE SPIRIT account.
The company told customers that someone published their information on a third-party website, but pointed out that the data was obtained from a prior breach unrelated to Spirit Airlines.
Spirit’s warning comes after a hacker contacted news websites, including SecurityWeek, claiming to have obtained information on 11.7 million Spirit accounts. The individual claimed to have alerted the airline of a vulnerability in its systems, and decided to put the data up for sale on the dark web after the company ignored him.
The hacker has leaked more than 10,000 records apparently belonging to Spirit customers, including names, Spirit account numbers, passwords, dates of birth, phone numbers, addresses and email addresses. However, he refused to provide the full data set or evidence of how he breached the airline’s systems.
Spirit told SecurityWeek that the hacker actually attempted to extort the company using emails and passwords obtained previously from other sources on the Internet.
Security expert Troy Hunt, the owner of the Have I Been Pwned service, told SecurityWeek that all the email addresses he tested from the leaked data show up in Exploit.in, a list of nearly 600 million email address and password combinations compiled using data stolen from various online systems.
Cybercriminals have used the Exploit.in list for credential stuffing attacks, where attackers automatically inject username/password combinations into a website’s login page in hopes that account owners have used the same credentials on multiple online services.
Microsoft won’t patch the 20-year-old SMBv1 SMBloris flaw disclosed at DEF CON conference
31.7.2017 securityaffairs Vulnerebility
Microsoft has announced that the SMBv1 SMBloris bug described at DEF CON won’t be patched because it could be fixed simply blocking incoming connections.
Recently security researchers at RiskSense have identified a 20-year-old Windows SMB vulnerability they called SMBloris (a nod to the Slowloris DoS attack.), they presented their findings at the recent DEF CON hacker conference.
The exploit is a Denial of Service (DoS) attack affecting “every version of the SMB protocol and every Windows version dating back to Windows 2000.” Like most DoS attacks, the target system is overwhelmed by multiple service requests rendering it unavailable. Most modern systems require coordination of a massive number of attacking systems to overwhelm the target, referred to as a Distributed Denial of Service (DDoS) attack. However, the flaws discovered in the Windows SMB service are easily exploited by a single, low-powered computer.
SMBloris flaw
Microsoft has announced that the SMBv1 bug described at DEF CON won’t be patched because it could be fixed simply blocking connections coming from the Internet.
“The reason they say it’s a moderate issue is because it does require opening many connections to the server, but you could do it all from a single machine, and a Raspberry Pi could take down the beefiest server”. explained RiskSense researchers Sean Dillon.
Follow
Jenna Magius @JennaMagius
Now that SMBLoris is dropped at DEF CON, time to drop it on Twitter:
The first 3 bytes of an SMB connection are an NBSS header,
1:04 AM - Jul 30, 2017
6 6 Replies 275 275 Retweets 338 338 likes
Twitter Ads info and privacy
The SMBloris is a memory handling bug that could be exploited by attackers to shut down big web servers with small computers.
Of course, attackers can trigger the SMBloris only if the target machine has SMBv1 exposed to the Internet, that’s why Microsoft argued that it is just a configuration issue.
NBSS is the NetBIOS Session Service protocol, every connection to it allocates 128 KB of memory that is freed when the connection is closed. The connection is closed after 30 seconds if no activity is performed.
With 65535 TCP ports available the attackers can fill up more than 8 GB, powering DDoS attack on both IPv4 and IPv6 it is possible to reach 16 GB. The volume could be doubled (32 GB) using two IPs, they can fill 32 GB.
The attack triggers the memory saturation for NBSS and it is necessary to reboot the server in order to restore a normal operation.
Hackers Take Over US Voting Machines In Just 90 Minutes
31.7.2017 thehackernews BigBrothers
Today, election hacking is not just about hacking voting machines, rather it now also includes hacking and leaking dirty secrets of the targeted political parties—and there won’t be a perfect example than the last year's US presidential election.
But, in countries like America, even hacking electronic voting machines is possible—that too, in a matter of minutes.
Several hackers reportedly managed to hack into multiple United States voting machines in a relatively short period—in some cases within minutes, and in other within a few hours—at Def Con cybersecurity conference held in Las Vegas this week.
Citing the concern of people with the integrity and security of American elections, for the first time, Def Con hosted a "Voting Machine Village" event, where tech-savvy attendees tried to hack some systems and help catch vulnerabilities.
Voting Machine Village provided 30 different pieces of voting equipment used in American elections in a room, which included Sequoia AVC Edge, ES&S iVotronic, AccuVote TSX, WinVote, and Diebold Expresspoll 4000 voting machines.
And what's horrible? The group of attendees reportedly took less than 90 minutes to compromise these voting machines.
hacking-voting-machine
Image Credit: @tjhorner
Members of the Def Con hacking community managed to take complete control of an e-poll book, an election equipment which is currently in use in dozens of states where voters sign in and receive their ballots.
Other hackers in attendance claimed to have found significant security flaws in the AccuVote TSX, which is currently in use in 19 states, and the Sequoia AVC Edge, used in 13 states.
Another hacker broke into the hardware and firmware of the Diebold TSX voting machine.
Hackers were also able to hack into the WinVote voting machine, which is available on eBay, and have long been removed from use in elections due to its vulnerabilities.
Hackers discovered a remote access vulnerability in WinVote's operating system, which exposed real election data that was still stored in the machine.
Another hacker hacked into the Express-Pollbook system and exposed the internal data structure via a known OpenSSL vulnerability (CVE-2011-4109), allowing anyone to carry out remote attacks.
"Without question, our voting systems are weak and susceptible. Thanks to the contributors of the hacker community today, we’ve uncovered even more about exactly how," said Jake Braun, a cybersecurity expert at the University of Chicago, told Reg media.
"The scary thing is we also know that our foreign adversaries — including Russia, North Korea, Iran — possess the capabilities to hack them too, in the process undermining the principles of democracy and threatening our national security."
Election hacking became a major debate following the 2016 US presidential election, where it was reported that Russian hackers managed to access U.S. voting machines in at least 39 states in the run-up to the election.
However, there is no evidence yet to justify these claims.
Even, Hacking of voting machines is also a major concern in India these days, but the government and election commission has declined to host such event to test the integrity of EVMs (Electronic Voting Machines) used during the country's General and State Elections.
Apple Removes Some VPN Services From Chinese App Store
31.7.2017 securityweek Apple
Apple has removed software allowing internet users to skirt China's "Great Firewall" from its app store in the country, the company confirmed Sunday, sparking criticism that it was bowing to Beijing's tightening web censorship.
Chinese internet users have for years sought to get around heavy internet restrictions, including blocks on Facebook and Twitter, by using foreign virtual private network (VPN) services.
Beijing mandated in January that all developers must obtain government licenses to offer VPNs, leading to the Apple decision.
Apple Removes VPN Apps from App Store
"We have been required to remove some VPN apps in China that do not meet the new regulations," Apple told AFP in a statement Sunday.
"These apps remain available in all other markets where they do business."
Two major providers, ExpressVPN and Star VPN, said on Saturday that Apple had notified them that their products were no longer being offered in China. Both firms decried the move.
"Our preliminary research indicates that all major VPN apps for iOS have been removed," ExpressVPN said in a statement, calling Apple's move "surprising and unfortunate".
"We're disappointed in this development, as it represents the most drastic measure the Chinese government has taken to block the use of VPNs to date, and we are troubled to see Apple aiding China's censorship efforts," it added.
Star VPN wrote on Twitter: "This is very dangerous precedent which can lead to same moves in countries like UAE etc. where government control access to internet."
China has hundreds of millions of smartphone users and is a vital market for Apple, whose iPhones are wildly popular in the country.
The company unveiled plans earlier this month to build a data centre in China to store its local iCloud customers' personal details.
While China is home to the world's largest number of internet users, a 2015 report by US think tank Freedom House found that the country had the most restrictive online use policies of 65 nations it studied, ranking below Iran and Syria.
But China has maintained that its various forms of web censorship are necessary for protecting its national security.
The national VPN crackdown comes after the passing of a controversial cybersecurity bill last November that tightened restrictions on online freedom of speech and imposed new rules on service providers.
Since the regulation took effect this June, authorities have closed dozens of celebrity gossip blogs and issued new rules around online video content to eliminate programs deemed offensive.
DEF CON Voting Village – Hackers easily pwned US voting machines
31.7.2017 securityaffairs BigBrothers
Hackers attending Def Con hacking conference were invited to hack into voting machines used in US past elections to assess their level of security.
DEF CON 2017 – Are voting systems secure? In August 2016, the FBI issued a “flash” alert to election officials across the country confirming that foreign hackers have compromised state election systems in two states.
Although the US largely invested in electronic voting systems their level of security appears still not sufficient against a wide range of cyber attacks.
During an interesting session at the DEF CON hacking conference in Las Vegas, experts set up 30 computer-powered ballot boxes used in American elections simulating the Presidential election. Welcome in the DEF CON Voting Village!

Bradley Barth @BBB1216BBB
At the 1st ever Voting Village at #DEFCON, attendees tinker w/ election systems to find vulnerabilities. I'm told they found some new flaws
11:27 PM - Jul 28, 2017
3 3 Replies 32 32 Retweets 29 29 likes
Twitter Ads info and privacy
The organization asked the participant to physically compromise the system and hack into them, and the results were disconcerting.
“We encourage you to do stuff that if you did on election day they would probably arrest you.” John Hopkins computer scientist Matt Blaze said,
Most of the voting machines in the DEF CON Voting Village were purchased via eBay (Diebold, Sequoia and Winvote equipment), others were bought from government auctions.

In less than 90 minutes hackers succeeded in compromising the voting machines, one of them was hacker wirelessly.
“Without question, our voting systems are weak and susceptible. Thanks to the contributions of the hacker community today, we’ve uncovered even more about exactly how,” said Jake Braun, cybersecurity lecturer at the University of Chicago.
The analysis of the voting machines revealed that some of them were running outdated OS like Windows XP and Windows CE and flawed software such as unpatched versions of OpenSSL.
Some of them had physical ports open that could be used by attackers to install malicious applications to tamper with votes.
Even if physical attacks are easy to spot and stop, some voting machines were using poorly secured Wi-Fi connectivity.
The experts Carsten Schurmann at the DEF CON Voting Village hacked a WinVote system used in previous county elections via Wi-Fi, he exploited the MS03-026 vulnerability in Windows XP to access the voting machine using RDP.

Robert McMillan @bobmcmillan
Greetings from the Defcon voting village where it took 1:40 for Carsten Schurmann to get remote access to this WinVote machine.
9:41 PM - Jul 28, 2017
47 47 Replies 1,565 1,565 Retweets 1,243 1,243 likes
Twitter Ads info and privacy
Another system could be potentially cracked remotely via OpenSSL bug CVE-2011-4109, it is claimed.

kate conger ✔@kateconger
huge cheer just went up in @votingvilllagedc as hackers managed to load Rick Astley video onto a voting machine #defcon25
10:07 PM - Jul 29, 2017
23 23 Replies 573 573 Retweets 877 877 likes
Twitter Ads info and privacy
The good news is that most of the hacked equipment is no longer used in today’s election.
Apple removed iOS VPN apps from Chinese App Store in compliance to censorship law
31.7.2017 securityaffairs Apple
In compliance with Chinese Internet monitoring law, Apple has started removing all IOS VPN apps from it App Store in China.
The company complies with a request from the Chinese Government that wants to strict censorship making it harder for netizens to bypass the Great Firewall system (aka Golden Shield project).
The Golden Shield project allows China to censor Internet and block access to major foreign websites in the country, it is already blocking some 171 out of the world’s 1,000 top websites, including Google, Facebook, Twitter, and Dropbox.
In a blog post, the developers at VPN service provider ExpressVPN reported how the tech giant Apple informed them that their VPN app had been removed from the official Chinese App Store.
“We received notification from Apple today, July 29, 2017, at roughly 04:00 GMT, that the ExpressVPN iOS app was removed from the China App Store. Our preliminary research indicates that all major VPN apps for iOS have been removed.” reads the blog post.
“Users in China accessing a different territory’s App Store (i.e. they have indicated their billing address to be outside of China) are not impacted; they can download the iOS app and continue to receive updates as before.”
The same thing is happening to all major VPN providers that are receiving a similar notice from Apple.
To bypass Chinese censorship, citizens use virtual private networks (VPNs), but earlier this year, China increased the pressure on VPN service providers making it mandatory for them to be authorized by local authorities.

The decision to ban VPN services and proxies is part of the “clean-up” of China’s Internet connections launched by the Ministry of Industry and Information Technology.
“We’re disappointed in this development, as it represents the most drastic measure the Chinese government has taken to block the use of VPNs to date, and we are troubled to see Apple aiding China’s censorship efforts,” continues ExpressVPN statement.
Another VPN service provider, Star VPN, also received same notice from Apple.
“We are writing to notify you that your application will be removed from the China App Store because it includes content that is illegal in China,” Apple said in the notice. “We know this stuff is complicated, but it is your responsibility to understand and make sure your app conforms with all local laws.”
A few weeks ago, Apple announced it is setting up its first data center in China in the southern province of Guizhou to comply with new Government cyber security laws that request tech giants to store data related to Chinese customers locally.
Šifrujte, kde se dá...
31.7.2017 SecurityWorld Kryptografie
Díky technickému pokroku a zvýšenému přijetí je zabezpečení vašich dat a komunikace mnohem jednodušší, než si myslíte. Přinášíme přehled toho, co všechno se dá šifrovat a jaké pro to můžete použít nástroje.
Probíhá útok na šifrování. Bez ohledu na to, zda si myslíte, že máte co skrývat, měli byste mít obavy. Šifrování je klíčovým prostředkem, kterým lze zabezpečit citlivé soukromé informace a komunikaci před zvědavýma očima.
Vlády po celém světě napadají naši schopnost využívat technologie šifrování argumentací, že šifrování ztěžuje orgánům činným v trestním řízení vedení vyšetřování a sledování podezřelých on-line aktivit. Jejich řešení? Zřizování „zadních vrátek,“ jejichž prostřednictvím by mohly odemknout zabezpečená data.
Nejlepší způsob, jak se bránit v prosazování takového požadavku oslabit šifrování – a to je přesně to, k čemu zadní vrátka slouží – je udělat kódování všudypřítomné a zcela běžné.
Pokud šifrování používá každý, počínaje kódovaným chatem přes šifrovaný e-mail po surfování na webu zabezpečené šifrou (a kódované je také všechno mezi tím), potom je mnohem těžší argumentovat, že šifrování chrání jen pár vyvolených, kteří mají co skrývat.
A kde začít? Dnes je primární překážkou bránící využívat šifrování jako rutinní faktor v počítačovém životě většiny lidí skutečnost, že je stále relativně obtížné ho použít.
Kódování tradičně vyžadovalo, aby uživatel překonal hodně překážek, než ho zprovoznil, ale to se už pomalu mění. Přinášíme seznam různých šifrovacích technologií, které lze snadno použít k ochraně vašich dat před zvědavýma očima, a přispět tak k bezpečné a privátní komunikaci.
Čím více lidí je používá, tím těžší bude zbavit je práva na soukromí a bezpečí.
Aplikace pro bezpečný chat a zasílání zpráv
Mobilní zařízení jsou vzhledem k rozsahu a hloubce obsažených citlivých dat významným zdrojem obav o bezpečnost. Naštěstí se možnosti šifrování pro mobilní zařízení rychle stávají všudypřítomné. A nejde jen o samotné aplikace.
Například Apple zapnul šifrování celého disku zařízení iOS ve výchozím nastavení, takže jsou veškerá data v telefonech iPhone a tabletech iPad automaticky chráněná.
Také Google nabízí ve svých posledních verzích systému Android šifrování celého disku, přestože ještě není zapnuté ve výchozím stavu. Šifrování celého disku mobilních zařízení se tak stává standardem. Jakmile to tak bude, bude už návrat mnohem těžší.
Apple rovněž nabízí kompletní šifrování pro svou aplikaci iMessage, aby udržel vaše zprávy mimo dosah provozovatele. Například zástupci bezpečnostních složek nedávno v mediálně známém případu naléhali na Apple, aby jim usnadnil získání dat ze zařízení iOS, jež vlastnil podezřelý z terorismu, ale Apple jim neustoupil.
Pro mnoho běžných uživatelů je použití zařízení s iOS nejjednodušším způsobem, jak využít šifrovací nástroje.
Některé aplikace umožňují bezpečné zasílání zpráv pro platformy Android a iOS – patří mezi ně Wickr, Signal nebo Telegram. Jednou z nevýhod těchto nástrojů pro šifrovaný chat a zasílané zprávy je, že odesílatel a příjemce musejí používat ke komunikaci stejnou aplikaci.
Například uživatelé aplikace Wickr mohou odesílat šifrované textové zprávy ostatním uživatelům této aplikace, ale k poslání standardní nešifrované textové zprávy uživatelům, kteří aplikaci Wickr nemají, už musejí použít běžnou aplikaci pro posílání textových zpráv.
Popularita aplikace Wickr je také vyvolávána další poskytovanou vrstvou zabezpečení: chaty a fotografie se po uplynutí definované doby smažou. Týká se to i souborů audio, video a dokonce i dokumentů stažených z cloudového úložiště.
Vše poslané přes Wickr se přenáší přes šifrované kanály a automaticky se to maže po vypršení platnosti. Když přijdou lidé, kteří se o původní obsah zajímají, není jim co předat, protože data jsou už dávno pryč.
Telegram má v současné době špatnou pověst, protože se objevují zprávy, že tuto aplikaci používají teroristické skupiny a zločinci. Umožňuje uživatelům sdílet šifrovaná média a zprávy najednou až s 200 lidmi. Tajné chaty mohou zcela obejít servery Telegram a mohou být uložené jen po zadanou dobu nebo bezpečně uložené pro pozdější použití.
Šifrované hlasové hovory
Kupování předplaceného telefonu pokaždé, když chcete udělat telefonní hovor, který nelze vystopovat k vám, je už věcí minulosti díky několika novým aplikacím zaměřeným na zabezpečení hlasové komunikace.
Aplikace Signal, vytvořená bezpečnostním výzkumníkem Moxie Marlinspikeem, umožňuje uživatelům snadno navázat šifrované hlasové hovory a odesílat šifrované zprávy na platformách Android a iOS. (Aplikace Signal Desktop Chrome ve verzi beta rozšiřuje bezpečné zasílání zpráv aplikací Signal i na stolní počítače.).
Bonusem k Signalu je, že aplikace umožňuje uživatelům komunikovat s každým v seznamu kontaktů. Pokud příjemce hovoru není uživatelem Signalu, budete upozorněni, že hovor nebude šifrovaný, ale nemusíte přecházet do své standardní telefonní aplikace, abyste mohli volat, takže je proces přijetí ještě snadnější.
Společnost Open Whisper Systems, která aplikaci Signal vyvíjí, spolupracuje s řadou významných providerů služeb, jako jsou třeba WhatsApp, Google nebo FaceBook, ten například technologii Signal využil ve svém Messengeru (funkce Secret Conversations). Popularita aplikací jako WhatsApp nebo Snapchat ukazuje, že si lidé velmi přejí používat bezpečnou komunikaci.
Dlouhou dobu měli lidé s potřebou telefonovat z desktopu k dispozici jako vhodné řešení jen aplikaci Skype. Aplikaci Skype však zasáhla obvinění, že vláda USA přinutila společnost Microsoft vestavět do této služby zadní vrátka.
OStel je zabezpečená služba pro hlasovou a videokomunikaci, která je udržována v rámci projektu The Guardian Project a je k dispozici pro desktop i pro mobilní uživatele. Uživatelé si musejí vytvořit účet ve službě OStel (nejsou požadovány žádné osobní údaje) a stáhnout příslušný software.
Se službou OStel například komunikují aplikace CSipSimple a Linphone na platformách Android a iOS.
Oba konce hovoru, volající i příjemce, musejí využívat službu OStel. OStel neumí volat na pozemní linky ani na mobilní telefonní čísla se SIM kartou v mobilních sítích. Jednou z výhod služby OStel je, že funguje na platformách BlackBerry, iPhone či Android stejně jako na Mac OS X, Windows a Linuxu. Používá stejný šifrovací protokol ZRTP jako výše zmíněný Signal.
Šifrování připojení k internetu
Weby stále častěji využívají protokol HTTPS k ochraně dat posílaných mezi počítačem uživatele a serverem. Informace o kreditní kartě zadané do webového formuláře se přenášejí přes šifrovaný kanál na server prodejce, takže všichni útočníci, kteří by mohli monitorovat přenosy, netuší, co se odeslalo. To je však jen začátek.
Díky všudypřítomnosti veřejných sítí Wi-Fi – na letištích, v kavárnách, parcích a dokonce i v metru New Yorku – je snadné zapomenout, že připojení on-line není vždy nejlepší nápad.
Útočníci mohou snadno zachytit data tekoucí do zařízení a z něho nehledě na on-line služby, k jakým přistupujete. Zde může pomoci šifrování internetového připojení přes síť VPN, jako jsou například služby F-Secure Freedome, NordVPN nebo CyberGhostVPN – data jsou potom pro slídily nepoužitelná.
Většina z nás zná VPN jako software, který se instaluje do pracovních počítačů, aby umožnil přístup k podnikovým aplikacím. VPN služby však také umožňují uživatelům vytvořit šifrovaný tunel se serverem třetí strany a potom přistupovat k internetu prostřednictvím tohoto tunelu.
Když se uživatel v Česku připojí k Facebooku prostřednictvím služby VPN ve Francii, tak je pro Facebook uživatelem z Francie a ne z Česka. Je to skvělý způsob, jak používat on-line bankovnictví z letiště, protože služba VPN šifruje spojení a brání všem odposlouchávat vaše bankovní aktivity.
Potom je zde Tor, který poskytuje úplnou anonymitu na internetu. Používá vícevrstvý bezpečnostní mechanismus podobný cibuli, který odráží komunikaci mezi více uzly, aby skryl její původ.
Nejenže Tor brání dohledu, ale také brání webům sledovat uživatele. Můžete dokonce přistupovat k Facebooku přes Tor. Uživatelé, pro které je Tor nový, mohou použít pro začátek Tor Browser. Orbot je Tor proxy pro Android z projektu The Guardian Project.
Šifrování e-mailu
Ze všech forem moderní komunikace je e-mail možná nejvíce citlivý. Vaše e-mailová schránka může obsahovat bankovní výpisy, účty z různých služeb a obchodů, dokumenty související s daněmi a také osobní zprávy.
Informace o tom, s kým mluvíte, o čem mluvíte a dokonce i jen kdy posíláte e-mail, může být v nesprávných rukách velmi nebezpečná. Zástupci bezpečnostních složek si mohou vyžádat kopie e-mailů uložených na e-mailových serverech, takže zasílání šifrovaných částí textu zajistí, že vaše zprávy uvidí jen ten, koho k tomu skutečně oprávníte.
Zabezpečené e-mailové služby, jako jsou Hushmail a GhostMail, slibují vestavěné šifrování. Když pošlete e-mail jinému členovi, zašifruje služba obsah vaší zprávy před odesláním.
Chcete-li poslat zprávu příjemci, který není na Hushmailu, vaše zpráva může být šifrovaná pomocí tajné kombinace otázky a odpovědi. Příjemce bude muset k dešifrování zprávy znát odpověď na otázku. Tyto služby pracují s klíči na pozadí, aby byl proces pro uživatele bezproblémový.
Také Outlook má vestavěné kryptografické bezpečnostní funkce založené na digitálních certifikátech vytvořených tímto softwarem. Předtím, než si mohou uživatelé zasílat šifrované zprávy, musejí digitálně zprávy podepsat a vyměnit si certifikáty.
Jakmile to mají za sebou, je práce s novou zprávou snadná: stačí z nabídky Možnosti vybrat příkaz pro šifrování obsahu a příloh.
Máte-li několik let historie ve službách Gmail, Yahoo, Hotmail apod., je těžké se přesunout k novému poskytovateli e-mailu jen kvůli nutnosti zabezpečení. Jednou z možností je použít Hushmail či GhostMail pro citlivou komunikaci a využívat dále současnou službu pro běžné zprávy. Působí to však proti cíli všudypřítomného šifrování.
Správa soukromých a veřejných klíčů
Dokud se poskytovatelé e-mailových služeb nerozhodnou nakonfigurovat univerzálně šifrovaný e-mailový systém, leží odpovědnost zabezpečení na odesílateli a příjemci.
Odesílatel musí
vygenerovat pár klíčů (veřejný a soukromý) a zveřejnit veřejný klíč. Příjemce musí vědět, jak k dešifrování zpráv používat ten veřejný. Pro mnoho nástrojů, které využívají kombinace veřejných a soukromých klíčů, je správa páru (veřejný a soukromý) transparentní. Není to však případ e-mailů.
Služby jako Keybase.io a aplikace pro Android, jako jsou K-9 nebo OpenKeychain, se pokoušejí zjednodušit správu klíčů. Keybase.io umožňuje použít ke zveřejnění veřejného klíče služby Twitter, GitHub a Reddit a řadu dalších nástrojů.
Soukromý klíč můžete uložit u Keybase nebo jinam, například do telefonu do aplikace OpenKeychain. Chcete-li podepsat své zprávy klíčem nebo zašifrovat celou textovou zprávu, můžete použít vestavěné nástroje Keybase a poté zkopírovat vytvořený blok textu do své e-mailové zprávy.
Protože Keybase využívá PGP (Pretty Good Privacy), může příjemce dešifrovat či verifikovat podpis pomocí libovolného správce klíčů, který pracuje s klíči PGP.
Mailvelope je zase aplikace Chrome, která dokáže zašifrovat a dešifrovat zprávy pomocí klíčů PGP v populárních webových službách.
Šifrování osobního e-mailu má ale před sebou ještě dlouhou cestu, než začne být tak snadné, aby ho mohli používat všichni, ale naštěstí k tomu směřuje.
Zašifrování pevného disku
Microsoft integroval šifrování souborů a disku do některých verzí systému Windows pomocí nástroje BitLocker, stejně jako to udělala firma Apple pro Mac OS X prostřednictvím řešení FileVault2.
Apple removes VPN Apps from the China App Store
30.7.2017 thehackernews Apple
In order to comply with Chinese censorship law, Apple has started removing all virtual private network (VPN) apps from the App Store in China, making it harder for internet users to bypass its Great Firewall.
VPN service providers that provide services in China has accused the United States tech giant of complying with Chinese stringent cyberspace regulations.
In a blog post, the developers of ExpressVPN reported that Apple informed them that their VPN app had been pulled from the company's Chinese App Store, and it seems all major VPN clients have received the same notice from Apple.
China has strict Internet censorship laws through the Great Firewall of China – the country's Golden Shield project that employs a variety of tricks to censor Internet and block access to major foreign websites in the country.
The Great Firewall is already blocking some 171 out of the world's 1,000 top websites, including Google, Facebook, Twitter, Dropbox, Tumblr, and The Pirate Bay in the country.
Therefore, to thwart these restrictions and access these websites, hundreds of millions of Chinese citizens use virtual private networks (VPNs) that encrypt their online traffic and route it through a distant connection.
However, earlier this year, China announced a crackdown on VPNs and proxy services in the country and made it mandatory for all VPN service providers and leased cable lines operators to have a license from the government to use such services.
This 14-month-long crackdown on the use of unsupervised internet connections, including VPNs was launched by the country's Ministry of Industry and Information Technology, who called it a "clean-up" of China's Internet connections.
Now, ExpressVPN received a notice from Apple that its app would be removed from the China-based App Store "because it includes content that is illegal in China."
"We're disappointed in this development, as it represents the most drastic measure the Chinese government has taken to block the use of VPNs to date, and we are troubled to see Apple aiding China's censorship efforts," ExpressVPN said in a statement.
Not just ExpressVPN alone, but another VPN service provider, Star VPN, also received same notice from Apple, the company confirmed via its official Twitter account on Saturday.
"We are writing to notify you that your application will be removed from the China App Store because it includes content that is illegal in China," Apple said in the notice. "We know this stuff is complicated, but it is your responsibility to understand and make sure your app conforms with all local laws."
Although Apple did not comment on this issue, it is no coincidence, as the company has severely been implementing various aspects of Chinese law in recent months for its regional operations in the most populated country.
Earlier this year, Apple removed the New York Times (NYT) app from its Chinese App Store because the app was in "violation of local regulations."
The tech giant has even partnered with a local firm in the southwestern province of Guizhou earlier this month to set up its first data centre in China, which will store all user information for Chinese customers.
Hacking A $1500 'Smart Gun' With $15 Magnets
30.7.2017 thehackernews Hacking
I think we should stop going crazy over the smart things unless it's secure enough to be called SMART—from a toaster, security cameras, and routers to the computers and cars—everything is hackable.
But the worst part comes in when these techs just require some cheap and easily available kinds of stuff to get compromised.
Want example? It took just cheap magnets purchased from Amazon online store for a security researcher to unlock a "smart" gun that only its owner can fire.
The German manufacturer of the Armatix IP1 "smart" gun which claimed the weapon would 'usher in a new era of gun safety' as the gun would only fire by its owners who are wearing an accompanying smartwatch.
However, for the first time, a skilled hacker and security researcher who goes by the pseudonym "Plore" found multiple ways to defeat the security of Armatix GmbH Smart System and its $1,400 smart gun.
According to a detailed report by Wired, the smart idea behind the Armatix IP1 is that the gun will only fire if it is close to the smartwatch, and won't beyond a few inches of distance from the watch.
However, Plore found three ways to hack into the Armatix IP1 smart gun, and even demonstrated (the video is given below) that he could make the smart gun fire without the security smartwatch anywhere near it.
Smart Gun Hacking Demonstrated:
Plore placed $15 magnets near the barrel of the gun, doing this made him bypass the security watch, thereby defeating the Armatix IP1’s the electromagnetic locking system altogether.
"I almost didn't believe it had actually worked. I had to fire it again," the researcher said. "And that's how I found out for $15 (£11.50) of materials you can defeat the security of this $1,500 (£1,150) smart gun."
Plore was also able to jam the radio frequency band (916.5Mhz) of the gun from ten feet away using a $20 (£15) transmitter device that emits radio waves, preventing the owner from firing the gun even when the watch is present.
The researcher was also able to hack the gun's radio-based safety mechanism by using a custom-built $20 RF amplifier to extend the range of the watch.
When the owner squeezes the trigger, the gun sends out a signal to check whether the watch is there or not.
But the researcher was able to intercept the signal using a radio device, which acts as a relay that could extend the range by up to 12 feet, meaning somebody else other than the owner could be wearing the watch, defeating its fundamental security feature.
Plore believes that if smart guns are going to become a reality soon, they will need to be smarter than this one.
Chinese researchers from Tencent hacked a Tesla model once again
30.7.2017 securityaffairs Hacking
A team of security researchers from Chinese firm Tencent has once again demonstrated how to remotely hack a Tesla Model vehicle.
Security researchers from Chinese firm Tencent have once again demonstrated how to remotely hack a Tesla Model vehicle. Once the experts reported the flaws to the car makers it promptly patched them.
In a video PoC of the attack, researchers at Tencent’s Keen Security Lab demonstrated how they could hack a Tesla Model X, both while it was on the move and parked.
The attack is disconcerting, the hackers took control of the brakes, sunroof, turn signals, displays, door locks, windshield wipers, mirrors, and the trunk.
Tesla fixed the flaws and claimed that they were not easy to exploit.
The experts in response published a new blog post claiming they’ve hacked a Tesla Model X via a Controller Area Network (CAN bus) and Electronic Control Unit (ECU) attack.
“Keen Lab discovered new security vulnerabilities on Tesla motors and realized full attack chain to implement arbitrary CAN BUS and ECUs remote controls on Tesla motors with latest firmware.” reads the post.

“Several highlights for 2017 Tesla Research:
Realized full attack chain as we did in year 2016 to implement arbitrary CAN BUS and ECUs remote controls.
Discovered multiple 0Days in different modules. Currently, Keen Lab is working with Tesla and related manufactures on assigning CVE number of the vulnerabilities.
Tesla implemented a new security mechanism “code signing” to do signature integrity check of system firmware that will be FOTAed to Tesla motors in Sept 2016. The code signing was bypassed by Keen Lab.
The “Group lighting show of Model X” in our demonstration is technically arbitrary remote controls on multiple ECUs at the same time. It shows Keen Lab’s research capability on CAN BUS and ECUs.“
The experts noticed Tesla had implemented new security measures, such as the signature integrity check for its firmware, since their previous attack.
The researchers successfully bypassed the new security mechanisms in a new attack.
The video PoC shows the experts remotely unlocking the doors and trunk in parking mode, control the brake on the move and much more by taking control of multiple ECUs.
Tesla with the help of the researchers patched the vulnerabilities with version v8.1, 17.26.0 or above that was distributed to the vehicle in circulation over-the-air (FOTA upgrade firmware) update.
“The problems found in this study affect the sale of Tesla models and sales models, according to the Tesla security team’s report, the vast majority of the world’s Tesla vehicles have been successfully upgraded through the FOTA system firmware to ensure that Tesla users driving safety. We once again thank the Tesla security team for quick response and quick fix.” states the post published by Tencent.
Different the position of Tesla, a company spokesman tried to downplay the attack:
“While the risk to our customers from this type of exploit is very low and we have not seen a single customer ever affected by it, we actively encourage research of this kind so that we can prevent potential issues from occurring,” a Tesla spokesperson told SecurityWeek.
“This demonstration wasn’t easy to do, and the researchers overcame significant challenges due to the recent improvements we implemented in our systems,” they added. “In order for anyone to have ever been affected by this, they would have had to use their car’s web browser and be served malicious content through a set of very unlikely circumstances. We commend the research team behind this demonstration and look forward to continued collaboration with them and others to facilitate this kind of research.”
Experts spotted Triada Trojan in firmware of low-cost Android smartphones
30.7.2017 securityaffairs Android
Malware researchers at the Russian anti-virus firm Dr.Web have spotted the Triada Trojan in the firmware of several low-cost Android smartphones.
Another case of pre-installed malware make the headlines, malware researchers at the Russian anti-virus firm Dr.Web have spotted the Triada Trojan in the firmware of several low-cost Android smartphones, including Leagoo M5 Plus, Leagoo M8, Nomu S10, and Nomu S20.
Experts speculate that threat actors compromised the supply chain infecting a small number of smartphones of the above models.
“Virus analytics from Dr.Web detected a malicious program built into the firmware of several mobile devices running Android. The Trojan called Android.Triada.231 is embedded into one of the system libraries. It penetrates processes of all running applications and can secretly download and run additional modules.” reads the analysis published by Dr Web.

The Triada Trojan was found inside the Android OS Zygote core process, the component used to launch programs on mobile devices.
“By infecting Zygote, Trojans embed into processes of all running applications get their privileges and function as part of applications. Then, they secretly download and launch malicious modules.” continues the analysis.
The Triada trojan was first discovered in March 2016 by researchers at Kaspersky Lab that at time recognized it as the most advanced mobile threat ever seen. The range of techniques used by the threat to compromise mobile devices was not implemented in any other known mobile malware.
Triada was designed with the specific intent to implement financial frauds, typically hijacking the financial SMS transactions. The most interesting characteristic of the Triada Trojan apart is the modular architecture, which gives it theoretically a wide range of abilities.

Once the malware was initialized it sets up some parameters, creates a working directory, and checks the environment it is running. If the malware is running in the Dalvik environment, it hooks up one of the system methods to track the start of all applications and perform malicious activity immediately after they start.
“The main function of Android.Triada.231 is to secretly run additional malicious modules that can download other Trojan components. To run additional modules, Android.Triada.231 checks if there is a special subdirectory in the working directory previously created by the Trojan. The subdirectory name should include the MD5 value of the software package name of the application, into the process of which the Trojan is infiltrated.” states the analysis.
Experts at Dr Web explained that the Triada Trojan cannot be deleted using standard methods because it is hidden into one of the libraries of the operating system and located in the system section. To eradicate the threat, it is necessary to install a clean Android firmware. Dr.Web notified manufacturers of compromised smartphones.
DEF CON 25 – BBC Micro:bit could be used to hijack a drone
30.7.2017 securityaffairs Hacking
A security researcher demonstrated how to use a pocket-sized microcomputer BBC’s Micro:bit to take control of a quadcopter drone.
In a talk at the at year’s DEF CON hacking conference in Las Vegas, Damien Cauquil, a security researcher at Econocom Digital Security, demonstrated how to use a pocket-sized microcomputer such BBC’s Micro:bit to sniff out keystrokes from a wireless keyboard or and even take control of a quadcopter drone.
The Micro:bit is an ARM-based embedded system designed by the BBC for use in computer education in the UK. It is powered by a 16MHz 32-bit ARM Cortex-M0 CPU with 16KB of RAM and Bluetooth connectivity, the expert showed that with a few line of Python coding it is possible to use it as a wireless sniffer.
The Micro:bit is very cheap, it goes just £12, and Cauquil showed how to use publicly available software to snoop on signals from a wireless keyboard via Bluetooth.
The small size of such kind of device makes it is possible to hide it in a desk to sniff sensitive info typed by victims, such as passwords and login credentials.
One of the most intriguing uses showed by the expert is the hack of drone. Cauquil attached the tiny micro computer to a drone controller handset and hijack the flight controls.

Source The Register
“It took us a few months to hack into the Micro:Bit firmware and turn it into a powerful attack tool able to sniff keystrokes from wireless keyboards or to hijack and take complete control of quadcopters during flight.” reads the talk description. “We also developed many tools allowing security researchers to interact with proprietary 2.4GHz protocols, such as an improved sniffer inspired by the mousejack tools designed by Bastille. We will release the source code of our firmware and related tools during the conference.”
Cauquil explained that occasionally latency issues would cause the Micro:bit to lose its connection with the drone, but he is sure that Micro:Bit will become a nifty platform to create portable RF hacking tools.
Philadelphia RaaS - ransomware jako byznys za pár dolarů
30.7.2017 SecurityWorld Viry
Vytvářet a šířit ransomware je stále jednodušší a ve své podstatě k tomu nejsou nutné žádné speciální dovednosti. Ve skutečnosti potřebují kybernetičtí zločinci jen odhodlání realizovat své nekalé úmysly a mít přístup k tzv. temnému webu (z anglického dark web, je možné se setkat například i s označením zakázaný nebo tajemný web či internet) – tedy k tržišti, kde jsou sady pro tvorbu malware prodávány stejně jako boty nebo hračky na Amazonu.
Tento trend úzce souvisí s konceptem ransomware jako služba (ransomware as a service) a jedním z jeho konkrétních příkladů je nebezpečný a propracovaný kit Philadelphia.
Na červencové konferenci Black Hat 2017 zveřejnila společnost Sophos podrobnou studii s názvem „Ransomware as a Service (Raas): Deconstructing Philadelphia“. V této zprávě se Dorka Palotay, výzkumnice budapešťské pobočky globální sítě pro zkoumání hrozeb SophosLabs, zaměřila na pochopení vnitřních mechanismů kitu na tvorbu ransomware – sady Philadelphia, kterou si může za 400 amerických dolarů pořídit naprosto kdokoli.
Po zakoupení mohou noví „uživatelé“ unést a držet vaše počítačová data jako rukojmí a vyžadovat za jejich osvobození výkupné. Ano, je to přece o ransomware.
The Rainmakers Labs, autoři tohoto RaaS kitu, přistupují ke svému podnikání podobně jako legitimní softwarové společnosti, které prodávají své produkty a služby. Zatímco samotná Philadelphia je dostupná na šedých trzích v rámci temného webu, marketingové aktivity jsou veřejné – na YoutTube je k dispozici video, které přináší podrobnosti o samotném kitu i o rozsáhlých možnostech přizpůsobení výsledného ransomware. A videem to nekončí, součástí webu provozovaného na generické TLD doméně .com je i podrobný popis, jak kit používat.
Koncept ransomware jako služba sice není zcela nový, nicméně novinkou je právě marketingové úsilí vyzdvihující atraktivitu přístupu „připrav si svůj vlastní ransomware útok“.
„Snahy skupiny The Rainmakers Labs jsou překvapivě sofistikované. Podrobnosti o Philadelphii jsou veřejně dostupné na webu, čímž se tento kit zásadně liší od své konkurence inzerované v podzemních zákoutích temného webu,“ konstatuje Dorka Palotay. „K nalezení Philadelphie není potřeba Tor prohlížeč, a to, jak je tento kit odvážně propagován, bohužel naznačuje další nepříliš příznivý vývoj.“
Philadelphia není zajímavá jen marketingem. Pozornost si zaslouží i řada pokročilých voleb, pomocí kterých mohou „kupující“ výsledný ransomware přizpůsobit svým konkrétním představám a lépe jej zacílit na potenciální oběti. Mezi tyto rozšiřující možnosti patří podpora sledování oběti na mapách Google (‘Track victims on a Google map‘) nebo volba ‘Give Mercy’ pro případné slitování a dešifrování určitých souborů zdarma. Nechybí ani tipy na vytvoření vlastní kampaně nebo popis nastavení řídícího centra a postupů pro výběr peněžních částek.
Jistou ironií je, že ‘Give Mercy’ nemusí být projevem vstřícnosti k obětem, ale také jakousi zvrácenou formou zadních vrátek umožňujících zločincům dostat se z ošemetných situací, například během testování nebo v případě nechtěného útoku na přátele.
Zaujal vás tento článek? Přehled nejzajímavějších zpráv získáte odebíráním našeho newsletteru »
Volba pro sledování obětí na mapách Google zní trochu děsivě a počítačovým zločincům umožňuje podívat se na „cíle“ svých útoků z demografického pohledu. Získané informace jsou vcelku důležité, protože představují kvalifikované vstupy pro rozhodování, zda útok zopakovat, zda ransomware nějak modifikovat nebo třeba zda neuvažovat právě o povolení „soucitu“.
Ani jedno z uvedených rozšíření, stejně jako řada dalších funkcí, není však jedinečnou záležitostí Philadelphie. A stejně tak platí, že jde o možnosti, jejichž výskyt není příliš obvyklý. Ve skutečnosti jsou to příklady funkcionalit nejnovějších kitů a potvrzení toho, že ransomware jako služba je čím dál tím podobnější legálnímu softwarovému trhu. A to v opravdu globálních rozměrech.
„Za pozornost určitě stojí fakt, že Philadelphia stojí 400 amerických dolarů. A další ransomware kity se prodávají v cenách od 39 do 200 dolarů,“ uvádí dále Dorka Palotay. „Nicméně čtyři stovky jsou pro zájemce o Philadelphii stále ještě dobrou cenou, protože za ně získají i budoucí aktualizace, neomezený přístup a možnost vytvořit libovolný počet vlastních variant ransomware. Jinými slovy je to v podstatě stejné, jako u běžného software dostupného v modelu SaaS, kdy mají zákazníci možnost využívat vždy aktuální verzi.“
Philadelphia přináší navíc i tzv. mosty – PHP skript, který umožňuje správu komunikace mezi útočníky a oběťmi včetně ukládání informací o jednotlivých útocích.
Mezi další volby umožňující přizpůsobení výsledného ransomware útoku patří v případě Philadelphie úprava vyděračské zprávy pro oběti, a to včetně její barvy nebo toho, zda se má zobrazit ještě před zašifrováním souborů. Určitě nemilá je i tzv. Ruská ruleta, kdy aktivací této volby mohou autoři zajistit smazání některých souborů po uplynutí předem stanové lhůty, která se obvykle pohybuje v řádu hodin. Mechanismus ruské rulety je nicméně v ransomware kitech poměrně běžný a jeho účelem je vyvolat paniku a donutit uživatele k rychlejšímu zaplacení výkupného.
Možnosti přizpůsobení i zmiňované mosty zvyšují zisk a dávají kybernetickému zločinu zcela nové rozměry. Obojí by přitom mohlo vést k rychlejším inovacím ransomware jako takového. Mimochodem, jak vyplývá z podrobných analýz dalších RaaS platforem, existuje v souvislosti s konceptem ransomware jako služba řada různých zdrojů příjmů, a to od procentuálního dělení výkupného přes prodej předplatného až po zpřístupňování dashboardů umožňující sledování útoků.
Globální síť pro zkoumání hrozeb SophosLabs také uvádí, že někteří kybernetičtí zločinci již využívají „cracknuté“ nebo pirátské verze kitu Philadelphia a na jejich základě pak prodávají svoji vlastní ošizenou variantu, pochopitelně za menší peníze. Samotné krádeže ničím novým nejsou, nicméně nesporně zajímavá je míra tohoto počínání. Předpřipravené hrozby, které od útočníků nevyžadují skoro žádné znalosti a jsou snadno dostupné, se navíc neustále vyvíjí, a společnost Sophos předpokládá, že trend okrádání lumpů lumpy nadále poroste.
Mezi kybernetickými zločinci není krádež cizího kódu nebo vytvoření vlastní varianty ransomware na základě starší existující verze ničím neobvyklým. Tento přístup jsme měli možnost pozorovat i u nedávných Petya hrozeb, kdy v sobě varianta NotPetya kombinovala jednu z předchozích verzí ransomware Petya, Golden Eye, s exploitem Eternal Blue umožňujícím šíření hrozby a infikování počítačů ve skutečně globálním měřítku.
BlackHat 2017 – Positive Technologies researcher claims ApplePay vulnerable to two distinct attacks
29.7.2017 securityaffairs Apple
BlackHat 2017 – Security expert at Positive Technologies claims ApplePay vulnerable to two distinct attacks.
At the Black Hat USA hacking conference, security researchers from Positive Technologies announced to have devised two distinct attacks against ApplePay exploiting weaknesses in the mobile payment method.
ApplePay is considered today one of the most secure payment systems, but Positive Technologies claimed it had discovered two potential attack vectors.
“With wireless payments – PayPass, ApplePay, SamsungPay, etc, there is a perception that ApplePay is one of the most secure systems. ApplePay’s security measures mean that it has a separate microprocessor for payments [Secure Enclave], card data is not stored on the device nor is it transmitted in plaintext during payments.” said Timur Yunusov, head of banking security for Positive Technologies.
“During testing, I have discovered at least two methods that render these precautions worthless. While one relies on the device being jailbroken, which is estimated at 20 percent* and is a practice that the security community opposes, another is against a device that is ‘intact.’ Attackers can either register stolen card details to their own iPhone account, or they can intercept the SSL traffic between the device and the Apple Server to make fraudulent payments directly from the victim’s phone.”
A first attack presented in a talk by Yunusov requires a jailbroken device to work, this means that attackers have to infect a jailbroken device with malware. Once infected the mobile, the attackers can intercept the payment data to an Apple server. Once hackers have successfully infected the device with malware having root privileges, they have reached their goal.

The second attack doesn’t request a jailbroken because hackers intercept and/or manipulate SSL transaction traffic. The attackers tamper with transaction data, for example by changing the amount or currency being paid or the delivery details for the goods being ordered.
Attackers can register stolen card details to their own iPhone account to make payments on behalf of the victims, they can intercept the SSL traffic between the device and the Apple Server to make fraudulent payments.
“The first step in the second attack is for hackers to steal the payment token from a [targeted] victim’s phone. To do that, they will use public Wi‑Fi, or offer their own ‘fake’ Wi‑Fi hotspot, and request users create a profile. From this point they can steal the ApplePay cryptogram [the key to encrypting the data].Apple states that the cryptogram should only be used once. However, merchants and payment gateways are often set up to allow cryptograms to be used more than once.” Positive Technologies explained to El Reg.
“As the delivery information is sent in cleartext, without checking its integrity, hackers can use an intercepted cryptogram to make subsequent payments on the same website, with the victim charged for these transactions.”
The experts highlighted that there are some limitations to the attack, for example, the victim will receive a notification about the transaction as soon as it is made, this means that they can immediately block their card.
Researchers recommend to avoid using ApplePay to purchase items online on websites that don’t use the “https” and to avoid making transactions in public Wi‑Fi networks where the attackers can easily eavesdrop the traffic.
“The advice, as always, is to avoid jailbreaking a device in the first instance,” said Yunusov who added, “Another precaution is for users to avoid downloading unnecessary applications which will help prevent malware from being added to the device.”
Positive Technology already reported its findings to Apple, but it warns that the development of patches will be no simple due to the significant impact on any components of the security chain.
Malware experts at ESET released a free tool for ICS Malware analysis
29.7.2017 securityaffairs ICS
Security experts from ESET that spotted the Industroyer malware used against Ukraine’s power grid released a free tool for ICS Malware analysis
ESET researchers Robert Lipovsky and Anton Cherepanov have released a free tool for the analysis of ICS malware.
The security duo is the same that discovered the CrashOverride/Industroyer malware that targeted the Ukraine’s power grid,
CrashOverride/Industroyer is the fourth publicly known piece of malware, a detailed description of remaining threats was available in my article “Which Malware are Specifically Designed to Target ISC Systems?.“
The development of the tool was inspired by their investigation, the expert analyzed the ICS malware involved in the attack against Ukraine’s power grid in 2016 that caused a huge power outage in the city of Kiev and neighboring regions.
The researchers developed an IDAPython script for IDA Pro that could be used by malware researchers and cyber security experts to reverse-engineer binaries that employ the OPC Data Access industrial communications protocol.
“An IDAPython script for IDA Pro that helps reverse engineer binaries that are using the OPC Data Access protocol.” reads the description published on GitHub.
“It can be used to analyse such malware families as Havex RAT and Win32/Industroyer.
The script identifies CLSID, IID, and LIBID constants and creates structures and enumerations. Afterwards, these structures can be used to annotate COM method call parameters.”
Havex is a general purpose Remote Access Trojan (RAT) discovered in June 2015 when malware researchers at F-Secure spotted a cyber espionage campaign based on the Havex malware targeting ICS/SCADA systems and vendors.
The Havex malware has been used in several targeted attacks in the previous months; threat actors used it against different industry sectors.
“If there are other future malware [families] like Industroyer or Havex, [investigators] will have an easier time” finding and analyzing them, Lipovsky says.
“This tool helps you understand what the threat was designed to do,” he says. Detection is important, he says, “but if you want to understand what the attackers are up to, you need to dig in deeply.”
The availability of such kind of open-source tools allows experts to rapidly analyze ICS malware and implement automate defense systems.
Lipovsky and Cherepanov highlighted the importance for ICS/SCADA operators of early detection of the threats.
“A lot of people are downplaying these sorts of things as ‘not an attack.’ Spying is an attack,” said the expert. “These things are detectable.”
Lipovsky announced the tool during a session at the Black Hat hacking conference.
BLACK HAT USA – Hackers turn car washing machines in a mortal trap
29.7.2017 securityaffairs Hacking
BLACK HAT USA – Experts show how hackers can cause physical damage to vehicles and injure drivers by remotely hacking a connected car washing machines.
What about hacking into Internet-connected car wash machines?
It is a scarring scenario, hackers from anywhere in the world could transform car washing machines into death traps.
In a talk at the Black Hat 2017 conference in Las Vegas, the popular hacker Billy Rios, founder of security shop Whitescope, and Jonathan Butts, committee chair for the IFIP Working Group on Critical Infrastructure Protection, demonstrated how to compromise widely used control systems for car washing machines. The experts hacked: the Laserwash series manufactured by PDQ.
The Laserwash systems can be remotely controlled via a web-based user interface:

The control system is an embedded WindowsCE computer powered by an ARM-compatible processor.
As you know, Microsoft no longer provides security updates for this specific OS, this means that hackers can exploit known vulnerabilities to remotely execute code on the system and fully compromise it.
Another possibility for attackers consists in the exploitation of the lack of secure installs, for example, the security duo had found a suitable car wash exposed online with the default password 12345. Once logged in from their browser, they were given full control of the system with serious consequences.
“Car washes are really just industrial control systems. The attitudes of ICS are still in there,” Rios said. “We’ve written an exploit to cause a car wash system to physically attack; it will strike anyone in the car wash. We think this is the first exploit that causes a connected device to attack someone.”
The duo presented to the audience how they managed to bypass the safety sensors on the car wash doors to close them on a car entering the washer. Of course, the hackers can conduct more destructive attacks controlling the entire car washing machine, the can control the bay doors and use them to either lock the vehicle in or strike it and its occupants. Hackers can also take control of the robotic washing arm and hit the vehicle and its occupants.
“We controlled all the machinery inside the car wash and could shut down the safety systems,” he said. “You could set the roller arms to come down much lower and crush the top of the car, provided there was not mechanical barriers in place.”
The experts reported their findings to PDQ in February 2015, but they received a reply from the company only when their talk was accepted for Black Hat, then the manufacturer turned out that it wasn’t possible to patch against such kind of attacks.
PDQ alerted its customers and urged them to change their default password or protect the car washing machines with network appliances that will filter incoming traffic.
The ICS-CERT issued a security advisory on Thursday, warning of the presence of the vulnerabilities in several models of PDQ’s LaserWash, Laser Jet and ProTouch automatic car wash systems.
“Successful exploitation of these vulnerabilities may allow a remote attacker to gain unauthorized access to the affected system and to issue unexpected commands to impact the intended operation of the system.” states the CERT.
Below the list of recommendations for the users:
PDQ recommends that users apply the following controls:
Always make sure any PDQ equipment is not accessible from the Internet; it should be behind a secure firewall.
Whenever a machine or router is received and installed, always change the default password from the factory settings to a new password unique to the machine. If an existing site is still using the factory default passwords on a machine or router, immediately change the default password to a new, unique, strong password.
Always set up the system network (router or Wi-Fi) with its security features enabled such that they require a username and password to be able to access the machine network.
Do not set up the site router with “port forwarding” enabled. This can effectively expose the system to the Internet and may permit an unauthorized person to reach the machine login screen.
Do not share passwords or write them down in an accessible place where unauthorized users may find them.
NCCIC/ICS-CERT recommends that users take defensive measures to minimize the risk of exploitation of these vulnerabilities. Specifically, users should:
Minimize network exposure for all control system devices and/or systems, and ensure that they are not accessible from the Internet.
Locate control system networks and remote devices behind firewalls, and isolate them from the business network.
When remote access is required, use secure methods, such as Virtual Private Networks (VPNs), recognizing that VPNs may have vulnerabilities and should be updated to the most current version available. Also recognize that VPN is only as secure as the connected devices.
Critical Vulnerabilities discovered in Radiation Monitoring Devices (RDMs) used at Power Plants and Airports
29.7.2017 securityaffairs Vulnerebility
Experts discovered flaws in widely deployed Radiation Monitoring Devices (RDMs) that could be triggered to raise false alarms and worse.
This week at Black Hat in Las Vegas, researchers at information security firm IO Active, disclosed their findings on radiation monitoring devices from Ludum, Mirion, and Digi that were found to contain multiple unpatched vulnerabilities.

These vulnerabilities would allow an attacker to disrupt, delay, or obfuscate the detection of radioactive material, including leaks, which could lead to either risk of personal safety levels being impacted, or potentially aid smuggling of radioactive materials at airport/ports.
The findings from the report focus on the following:
Ludlum
53 Gamma Personnel Portal Monitor
Gate Monitor Model 4525
Mirion
WRM2 Transmitters
Digi
XBee-PRO XSC 900
Xbee S3B (OEM)
Some of the vulnerabilities highlighted include hard-coded passwords with the highest level of privileges, this particular vulnerability was identified by reverse engineering the publicly available binaries of the Ludlum 53 Gamma Personal Portal- which detects gamma radiation in or on personnel passing through the portal from either direction:
Because of this “backdoor”, the authentication of the system can be effectively bypassed by a malicious actor to take control of the device, and according to the research paper would allow an attacker to disable it preventing RPM from triggering the appropriate alarms.
Additionally, the Ludlum Gate Monitor 4525 which is used to detect radioactive material in lorries cargo at ports, had a series of major configuration and security weaknesses, that would enable an attacker to conduct a MiTM (man-in-the-middle), attack.
According to the report, the Gate Monitor used protocols such as Port 20034/UDP and Port 23/TCP which does not deploy any encryption, effectively allowing an attacker to intercept/drop packets and falsify information or disable alarms.
With both of these vulnerabilities, an attacker would need to have compromised the WLAN, or devices connected to it, therefore using those machines to pivot to the Gate Monitor.
What about nuclear power plants?
The report also covered this with findings in both Digi firmware and Mirion’s devices. The researcher at IO Active Ruben Santamarta tested the software and firmware for the Mirion radiation monitoring devices that detect medium to long range radioactive levels at NPP (Nuclear Power Plants).
The WRM2 Devices software is written in .Net and Java, and uses the OEM XBee S3B wireless transceivers. The WRM2 software was reverse engineered by IO Active to reveal the encryption algorithm used to encrypt the firmware files (in the XCS-Pro and S3B-XSC), essentially allowing an attacker to modify or create a modified firmware.
This would allow an attacker to bypass the XBee’s AT Command handles and bypass OEM Network ID Read only protection, and transmit or receive from any XBee network.
In this scenario, attackers could intercept data or transmit false data to NPP systems either creating a falsified reading of a Radiation leak or create a Denial of Service attack, by interfering with the frames being sent to the WRM2 compatible devices.
The Vendors were all contacted under a responsible disclosure policy via ICS-CERT or directly:
Ludlum acknowledged the report but refused to address the issues, due to the devices being located at secure facilities. Mirion also acknowledges the report but cited that patching would effectively break the systems but is working collaboratively with Digi to address the issues.
In summary, this report further highlights the risks that third party components can introduce to high-risk targets such as nuclear power plants. With recent reports in the US of such assets being targeted and breached, this is an area that needs focus, not only from the organizations that are being targeted but also the technology providers who support Critical National Infrastructure.
How Hackers Cash Out Thousands of Bitcoins Received in Ransomware Attacks
29.7.2017 thehackernews Ransomware
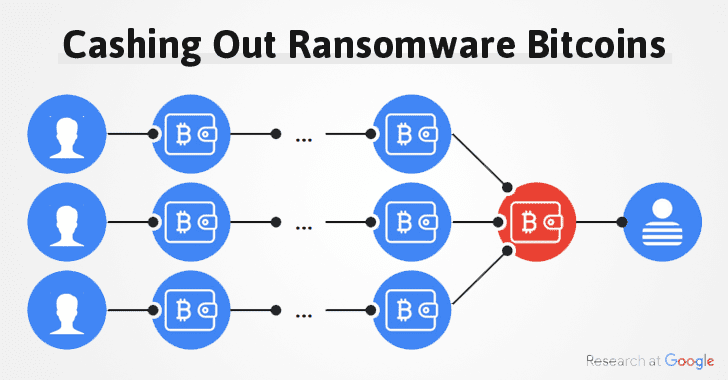
Digital currencies have emerged as a favourite tool for hackers and cyber criminals, as digital currency transactions are nearly anonymous, allowing cyber criminals to use it in underground markets for illegal trading, and to receive thousands of dollars in ransomware attacks—WannaCry, Petya, LeakerLocker, Locky and Cerber to name a few.
Also, every other day we hear about some incidents of hacking of crypto currency exchange or digital wallets, in which hackers stole millions of dollars in Bitcoin or Ethereum.
The latest back-to-back series of thefts of Ethereum—one of the most popular and increasingly valuable cryptocurrencies—in which around half a billion dollars in total were stolen is the recent example of how much hackers are after crypto currencies.
It's obvious that after ripping off hundreds of thousands of cryptocurrencies from exchanges, wallets and ransomware victims, cyber criminals would not hold them in just digital form—the next step is to cash them out into real-world money.
But how do they cash out without getting caught by law enforcement?
If you are unaware, there are some crypto currency exchanges involved in money laundering, who are illegally-operating to help hackers and cyber criminals easily cash out their digital currencies without identifying them, i.e. anonymously.
According to a recent research paper presented by three Google researchers, more than 95% of all Bitcoin payments collected from ransomware victims have been cashed out via a Russian cryptocurrency exchange, called BTC-e, since 2014.
Interestingly, just two days before Google presentation, one of the founders of BTC-e exchange, Alexander Vinnik, was arrested by Greek police on charges of laundering over $4 Billion in Bitcoin for culprits.
"We uncover the cash-out points, tracking how the money exits the Bitcoin network, enabling the authorities to pick up the money trail using conventional financial tracing means," the trio researchers, Luca Invernizzi, Kylie McRoberts and Elie Bursztein said.
Key Points — Tracking Ransomware Payments
The researchers followed the step-by-step money trail and got a look at the evolving ecosystem of ransomware families, which already helped make cyber-thieves at least $25 Million in the last two years.
Most Damaging Ransomware Families: According to the research, two families of ransomware strain helped hackers made most of the money — Locky and Cerber — while other variants are also starting to emerge.
Criminals looted In Millions: Locky has been the overall biggest earner for hackers at $7.8 Million and was the first ransomware infection to earn above $1 million a month to date, while Cerber has made $6.9 million to date with consistently making more than $200,000 a month.
Victim's Favorite Places to Buy Bitcoins: Obviously, victims also need BTC to pay out criminals, and most victims choose LocalBitcoins, Bithumb, and CoinBase to buy BTC, where 90% victims pay in a single transaction.
How Criminals Cash Out Cryptocurrency: According to the research, more than 95% of all Bitcoin payments for ransomware were cashed out via BTC-e, a service operational since 2011.
Criminals Renting Out Botnets: Cybercriminal gangs behind Dridex, Locky and Cerber have taken Necurs botnet—army of compromised machines—on rent to distribute their ransomware infections on a massive scale.
Google conducted the research in collaboration with the researchers from New York University, University of California San Diego and blockchain analyst firm Chainalysis.
When talking about BTC-e, the cryptocurrency exchange is believed to have been involved in cashing out Bitcoins stolen from the once-very popular Japanese bitcoin exchange Mt. Gox, which was shut down in 2014 following a massive series of mysterious robberies.
Tesla Model X Hacked by Chinese Experts
29.7.2017 securityweek Hacking
Security researchers from China-based tech company Tencent have once again demonstrated that they can remotely hack a Tesla. The vulnerabilities they leveraged were quickly patched by the carmaker.
Tencent’s Keen Security Lab published a video last year showing how they could hack a Tesla Model S, both while it was parked and on the move. They took control of the sunroof, turn signals, displays, door locks, windshield wipers, mirrors, the trunk and even the brakes.
At the time, Tesla patched the vulnerabilities within 10 days, but claimed that the vulnerabilities were not as easy to exploit as it appeared from the video published by Keen Security Lab researchers. Tesla Model X
In a new video and blog post published this week, the researchers claim they’ve once again managed to hack a Tesla, this time a Model X, via a Controller Area Network (CAN bus) and Electronic Control Unit (ECU) attack.
The experts said Tesla had implemented some new security mechanisms, including a signature integrity check for system firmware, since their previous attack. However, they managed to bypass these mechanisms and demonstrated a new attack.
In its video, Keen Security Lab showed that it managed to remotely unlock the doors and trunk in parking mode, control the brake in driving mode, and put on a light show using the car’s headlights and taillights by taking control of multiple ECUs.
Tesla, which has been working closely with the researchers since their demonstration last year, said it patched the vulnerabilities with version v8.1, 17.26.0+ of the software, which it rolled out to customers via an over-the-air (OTA) update.
“While the risk to our customers from this type of exploit is very low and we have not seen a single customer ever affected by it, we actively encourage research of this kind so that we can prevent potential issues from occurring,” a Tesla spokesperson told SecurityWeek.
“This demonstration wasn’t easy to do, and the researchers overcame significant challenges due to the recent improvements we implemented in our systems,” they added. “In order for anyone to have ever been affected by this, they would have had to use their car’s web browser and be served malicious content through a set of very unlikely circumstances. We commend the research team behind this demonstration and look forward to continued collaboration with them and others to facilitate this kind of research.”
Tesla has been running a bug bounty program since mid-2015. A few weeks later, the company increased its maximum payout to $10,000 after researchers disclosed a series of vulnerabilities.
Researchers at Norway-based security firm Promon showed last year how hackers could hijack Tesla vehicles by taking control of their associated mobile app, but the carmaker claimed none of the vulnerabilities they exploited were actually in Tesla products.
Report Depicts Shameful State of Cybersecurity Metrics
29.7.2017 securityweek Cyber
For years, Security has sought the ear of the Board and claimed it was not offered. Today the Board is listening; but all too often Security talks in a language that Business does not understand. There is a solution, but it is not yet maximized. That solution is Metrics, a language spoken and understood by both Business and Security; but not widely or effectively used.
The size of the task can be seen in just two statistics from Thycotic's 2017 State of Cybersecurity Metrics Annual Report (PDF). Firstly, 1 in 3 companies invest in cybersecurity technologies without any way to measure their value or effectiveness. Since the global market for cybersecurity products currently stands at around $100+ billion, this means that more than $33 billion dollars is spent every year without any current way to evaluate the ROI.
The second statistic is that four out of every five companies fail to include business stakeholders in cybersecurity investment decisions. The result, in combination, is that through no direct fault of its own, Business doesn't understand what Security is doing, and has no way of knowing whether it is effective.
The onus is on Security to more efficiently include Business in its work. Metrics is the key, but 4 out of 5 companies worldwide are not fully satisfied with their cybersecurity metrics. More worryingly, more than half of respondents (58%) to a Thycotic survey scored a failing grade when evaluating their efforts to measure their cybersecurity investments and performance against best practices.
These conclusions come from a benchmark survey devised and conducted by Thycotic and including responses from more than 400 companies -- mostly from North America, but with Europe, Russia, India, Central and South America also represented.
Using metrics to demonstrate the overall efficiency or lack of efficiency in a company's cybersecurity posture is difficult but not impossible. At the moment, however, companies are not making use of, or even collecting, the statistics that are readily available. For example, four out of five companies never measure the success of security training investments.
Two out of three companies don't fully measure whether their disaster recovery will work as planned. And while 80% of breaches involve stolen or weak credentials (from Verizon's DBIR), 60% of companies still do not adequately protect privileged accounts.
The result is what Thycotic describes as 'the shameful state of cybersecurity metrics'. It sees two areas that Security needs to improve: the failure in planning and the failure in performance. In planning, Security is failing to measure the value of cybersecurity investments; not understanding what information to protect; and not engaging with Business stakeholders. In performance, Security is not measuring expected outcomes; not measuring security awareness; and not measuring compliance with policies or regulations.
The survey and report is the first of new annual reports designed to highlight the state of companies' ability to measure their own security performance. To gather the information, Thycotic has developed a Security Measurement Index (SMI) benchmark based on ISO 27001 standards combined with best practices from experts and professional bodies.
The benchmark returns gradings A, B C, D and F. Fifty percent of companies scored F, while only 18% ranked A.
"It's really astonishing to have the results come in and see just how many people are failing at measuring the effectiveness of their cybersecurity and performance against best practices," said Joseph Carson, chief security scientist at Thycotic. "This report needed to be conducted to bring to light the reality of what is truly taking place so that companies can remedy their errors and protect their businesses."
Thycotic proposes a four-point plan to improve the situation: educate, protect, monitor and measure; and the report gives advice on how each of these should be enacted. Combining this program with Thycotic's Security Measurement Index benchmark should not only improve companies' metrics; but provide the metrics to demonstrate and measure that improvement.
Researchers Demo Physical Attack via Car Wash Hack
29.7.2017 securityweek Safety
LAS VEGAS - BLACK HAT USA - Researchers have created proof-of-concept (PoC) exploits to demonstrate how hackers can cause physical damage to vehicles and injure their occupants by remotely hijacking a connected car wash.
The attack was detailed in a presentation at the Black Hat security conference this week by WhiteScope founder Billy Rios, a researcher best known for finding vulnerabilities in medical devices and industrial control systems (ICS), and Dr. Jonathan Butts, founder of QED Secure Solutions and committee chair for the IFIP Working Group on Critical Infrastructure Protection.
The experts pointed out that automated car wash systems are essentially ICS and, just like industrial systems, they can be hacked and manipulated.
Their research has focused on LaserWash, an automated car wash which, according to its creator, PDQ Manufacturing, can “think for itself.”LaserWash car wash can be hacked remotely
Rios and Butts discovered that the web-based administration panel for the product, which is in many cases accessible directly from the Internet, has many features, including for sending email alerts and a widget for social media.
However, the more problematic issue is that both the owner and engineer accounts for the web interface are protected by weak default passwords. They also discovered that the authentication mechanism can be bypassed by a hacker.
Once they gain access to the web interface, a hacker can take control of the car wash system. The PoCs developed by the researchers show how an attacker can disable safety signals and take control of the bay doors, which can be used to either lock the vehicle in or unexpectedly strike it and its occupants. Hackers can also take control of the robotic washing arm and continuously discharge water or hit the vehicle and its occupants, the researchers said.
Rios first informed PDQ of the LaserWash vulnerabilities back in February 2015, just before disclosing his findings at Kaspersky’s Security Analyst Summit. However, the vendor ignored Rios for more than a year.
Now that Rios and Butts developed PoC exploits that demonstrate the risks in a real world scenario, PDQ has confirmed the existence of the flaws and claims it’s working on developing fixes.
According to an advisory published by ICS-CERT on Thursday, the vulnerabilities affect several models of PDQ’s LaserWash, Laser Jet and ProTouch automatic car wash systems.
ICS-CERT warned that the flaws can be exploited remotely even by an attacker with a low skill level, and provided a series of measures recommended by the manufacturer for mitigating the threat. The steps include changing the default password and ensuring that the equipment is behind a firewall.
WikiLeaks Details Mac OS X Hacking Tools Used by CIA
29.7.2017 securityweek BigBrothers
The latest round of documents published by WikiLeaks as part of a leak dubbed by the organization “Vault 7” describes several tools allegedly used by the U.S. Central Intelligence Agency (CIA) to target Mac OS X and other POSIX systems.
The tools, said to be part of a CIA project named “Imperial,” are called Achilles, Aeris and SeaPea.
A “secret” document dated July 2011 reveals that Achilles is a tool that can be used to create trojanized OS X disk image installers (.dmg). The resulting DMG file will contain a legitimate application and malicious executables added by the user – these files will be executed only once after the real application has been launched.WikiLeaks leaks more alleged CIA hacking tools
SeaPea is an OS X rootkit designed to provide stealth and launching capabilities for other tools. Version 2.0 of SeaPea was detailed in documents previously dumped by WikiLeaks, but the new user guide provides information on version 4.0.
Finally, Aeris is an implant designed to target operating systems that are compliant with the Portable Operating System Interface for Unix (POSIX), including Debian, Red Hat, Solaris, FreeBSD and CentOS.
POSIX is a set of specifications for maintaining compatibility between Unix-like operating systems by defining the API for software compatibility. Apple’s operating systems are also POSIX-compliant.
The Aeris tool includes various features, including for automatically exfiltrating files and encrypted communications.
As with many of the other Vault 7 tools exposed by WikiLeaks, given that their user guides were written several years ago, it’s likely that these projects have either been improved considerably to keep up with the new security features introduced by the creator of the targeted software or they were abandoned altogether.
Other tools described in documents published by WikILeaks over the past few months are designed for intercepting SMS messages on Android devices (HighRise), redirecting traffic on Linux systems (OutlawCountry), stealing SSH credentials (BothanSpy), spreading malware on an organization’s network (Pandemic), locating people via their device’s Wi-Fi (Elsa), hacking routers and access points (Cherry Blossom), and accessing air-gapped networks (Brutal Kangaroo).
British Hacker Convicted in Germany of Major Cyber Attack
29.7.2017 securityweek BigBrothers
A British man was handed a suspended jail sentence by a German court Friday for a massive cyber attack against Deutsche Telekom last year.
The regional court in the western city of Cologne said it would suspend the sentence of one year and eight months against the defendant, Daniel Kaye, following pleas to this effect by both prosecutors and the defence.
The 29-year-old last week described as "the worst mistake of my life" the attack that knocked more than one million German households offline in November, carried out for money on behalf of a Liberian client.
He was detained in February at London's Luton airport on a European arrest warrant for attempted computer sabotage and extradited to Germany.
German police said the goal of the attack was to infect users' computers with a "botnet" -- a network of web-connected machines that can be manipulated with malware and used to assault other online targets.
Kaye told the court he was paid $10,000 (about 8,500 euros) by a Liberian telecom company which wanted to use the botnet to damage a local rival.
The attack, which the company said caused about two million euros of damage, ended when it advised customers to disconnect their routers and restart them after a software update.
The large-scale strike fuelled concerns over cyber security in Germany and officials have warned that more online assaults are possible ahead of a general election in September.
Although he will not face jail-time in Germany, Britain has opened probes against Kaye for alleged involvement in other hacking attacks and bank blackmail cases, German news agency DPA reported.
VMware API Allows Limited vSphere Users to Access Guest OS
29.7.2017 securityweek Safety
LAS VEGAS - BLACK HAT USA - Researchers discovered that a VMware API can be abused by vSphere users with limited privileges to access the guest operating system without authentication. VMware has provided workarounds for preventing potential attacks exploiting the vulnerability.
VMware vSphere is a virtualization product that includes ESXi hypervisors, vCenter Server for managing vSphere environments, and the vSphere Client, which is used to manage virtual machines (VMs).
The security issue was discovered by employees of data center and cloud security firm GuardiCore while analyzing VMware’s Virtual Infrastructure eXtension (VIX) API, which helps users write scripts to automate VM operations and manipulate files within the guest OS.
The VIX API includes functionality that allows direct access to the guest OS. While this functionality is primarily designed for use by VMware Site Recovery Manager, VMware Update Manager and VMware Infrastructure Navigator, GuardiCore researchers discovered that it can also be abused by vSphere users with limited privileges to access the guest OS.
GuardiCore at Black Hat
In a presentation at the Black Hat security conference in Las Vegas, Ofri Ziv, VP of research at GuardiCore, revealed that an attacker can exploit the vulnerability to gain full control of the guest OS, including for arbitrary code execution with elevated privileges, lateral movement across the targeted data center (including to isolated networks), and data theft.
Ziv pointed out that such an attack is unlikely to be detected by many security products as it doesn’t leave any trace. The flaw impacts guest machines running ESXi 5.5 and VMware tools prior to version 10.1.0.
In order to exploit this flaw, the attacker requires basic knowledge of how the VIX API works and a limited vSphere account. This account needs to have the “Virtual Machine -> Configuration -> Advanced,” “Virtual Machine -> Interaction -> Guest Operating System Management by VIX API” and the “Host -> Configuration -> Advanced Settings” privileges for the attack to work.
This means that the attacker would most likely be a malicious insider. The vulnerability can be highly useful for breaking segmentation, which is a critical requirement for virtual environments. Even VMware tells customers that guest VMs should be isolated from the host and other guests running on the same host.
Ziv told SecurityWeek in an interview that isolation between VMs and their host is particularly important in financial institutions and other organizations where IT teams should not be allowed to access the sensitive data stored inside the VMs they manage.
VMware, which assigned this vulnerability the identifier CVE-2017-4919 and an “important” severity rating, published an advisory on Thursday. The company informed customers that vCenter Server versions 5.5, 6.0 and 6.5 are affected, and provided workarounds for VMs running on ESXi 6.0. The problematic functionality in the VIX API can be disabled manually in the case of VMware Tools 9.10.0 through 10.0.x. Starting with VMware Tools 10.1.0, the function has been disabled.
GuardiCore has released an open source risk assessment tool, PoC exploits, and a fork of open-vm-tools to address the vulnerability in ESXi 5.5. The company has also published a blog post containing technical details.
U.S Indicts Russian Man Over Money Laundering Through Bitcoin Exchange
29.7.2017 securityweek CyberCrime
95% of Tracked Ransoms Were Cashed Out via BTC-e, a Digital Currency Exchange The Accused Alexander Vinnik Operated
The United States Department of Justice this week indicted a Russian man for his role in the laundering of money obtained from hacks, ransomware schemes, and other illegal activities.
Alexander Vinnik, 37, was arrested in Greece on July 25 and faces charges in the United States. According to the indictment, he is the owner and operator of multiple BTC-e accounts, including administrative accounts. Furthermore, he is the primary beneficial owner of BTC-e’s managing shell company, Canton Business Corporation.
BTC-e, one of the world’s largest and most widely used digital currency exchanges, received deposits valued at over $4 billion, and numerous withdrawals from BTC-e administrator accounts went directly to Vinnik’s personal bank accounts, the indictment alleges. Moreover, proceeds from hacks and thefts from Bitcoin exchanges were funded through a BTC-e account associated with Vinnik.
According to a DoJ announcement, the Russian was indicted for “operating an unlicensed money service business, money laundering, and related crimes” and for receiving funds from the infamous hack of Mt. Gox. The largest digital currency exchange in 2013-2014, Mt. Gox started bankruptcy proceedings in April 2014, after discovering the theft of 850,000 Bitcoins and finding only 200,000 coins in an old wallet. Hackers supposedly siphoned the funds for a long period of time, starting 2011.
“The indictment alleges that Vinnik obtained funds from the hack of Mt. Gox and laundered those funds through various online exchanges, including his own BTC-e and a now defunct digital currency exchange, Tradehill, based in San Francisco, California. The indictment alleges that by moving funds through BTC-e, Vinnik sought to conceal and disguise his connection with the proceeds from the hacking of Mt. Gox and the resulting investigation,” DoJ reveals.
The indictment also notes that BTC-e, founded in 2011, was preferred by cybercriminals because it didn’t require users to validate identity, was obscuring and anonymizing transactions and source of funds, and had no anti-money laundering process. In fact, BTC-e was allegedly operated so as to facilitate transactions for cybercriminals.
The indictment also alleges the exchange “received the criminal proceeds of numerous computer intrusions and hacking incidents, ransomware scams, identity theft schemes, corrupt public officials, and narcotics distribution rings.” Over the course of operation, BTC-e supposedly received $4 billion worth of Bitcoin for facilitating crimes such as computer hacking, fraud, identity theft, tax refund fraud schemes, public corruption, and drug trafficking.
At Black Hat this week, Google, Chainalysis, UC San Diego, and the NYU Tandon School of Engineering researchers presented the findings of an investigation into ransomware payments, where they were able to track payments through the Bitcoin blockchains from distribution sites to the cash-out points. According to their report (PDF), “95% [of] traced ransoms [were] cashed out via BTC-E.”
The Treasury Department also also BTC-e $110 million for violating U.S. anti-money laundering laws, and fined Vinnik $12 million for his role in the scheme.
The indictment charges BTC-e and Vinnik with one count of operation of an unlicensed money service business (carrying a maximum penalty of 5 years in prison) and one count of conspiracy to commit money laundering (a maximum penalty of 20 years in prison). It also charges Vinnik with seventeen counts of money laundering (a maximum penalty of 20 years in prison for each count) and two counts of engaging in unlawful monetary transactions (a maximum penalty of 10 years in prison for each count).
“BTC-e was noted for its role in numerous ransomware and other cyber-criminal activity; its take-down is a significant accomplishment, and should serve as a reminder of our global reach in combating transnational cybercrime,” United States Secret Service (USSS) Special Agent in Charge of the Criminal Investigative Division Michael D’Ambrosio said.
TrickBot Trojan Gets Worm-Like Infection Powers
29.7.2017 securityweek Virus
A newly observed version of the TrickBot banking Trojan includes a worm-like malware propagation module that allows it to spread locally via Server Message Block (SMB), Flashpoint security researchers warn.
Built by the Dyre gang, TrickBot emerged last summer when it was still under development, but quickly became a fully-operational threat. By the end of last year, the Trojan had expanded operations to Asia, and was observed this year targeting private banking, payment processing and Customer Relationship Management (CRM) providers.
As part of a campaign discovered this week, TrickBot was spreading via spam emails impersonating invoices from a large international financial institution, but also included worm-like spreading capabilities, Flashpoint says.
The analyzed version, the security researchers discovered, could spread locally via SMB, could scan domains for lists of servers via NetServerEnum Windows API, and could also enumerate other computers via Lightweight Directory Access Protocol (LDAP).
The new features, however, aren’t fully implemented and the initial purported SMB exploit has not yet been observed, Flashpoint says.
The malware includes “MachineFinder” and “netscan” functions that leverage NetServer Enumeration and LDAP Enumeration functions. Thus, it can list all servers of the specified type that are visible in a domain, and can also “enumerate all computers that are not domain controllers and resolve them to domains to IPs via gethostbyname and inet_ntoa Windows API.”
Flashpoint also discovered that the Trickbot module includes strings suggesting it uses the Python implementation of the SMB protocol “pysmb” to attempt authentication on Windows 2007, Windows 7, Windows 2012, and Windows 8 operating systems. The threat leverages SMB to determine exploitation.
By leveraging the IPC (interprocess communication) share, the new TrickBot variant also attempts to spread and execute a PowerShell script to download another TrickBot sample onto shared drives and mask it as “setup[.]exe.”
“Notably, this malware does not appear to have logic to randomly scan external IPs for SMB connections – as was the case for the worm that spread the WannaCry ransomware in May 2017,” Flashpoint says.
Based on recently observed campaigns, researchers suggest that TrickBot continues to grow as a banking Trojan with global impact, targeting financial instructions across the world. Last week, Flashpoint noticed the malware adding multiple financial institutions in the United States on its target list, while also targeting users in over a dozen more countries.
After WannaCry and NotPetya brought highlighted the risks SMB and publicly available exploits pose to consumers and businesses worldwide, it’s no wonder more malware authors are experimenting with worm-like capabilities for lateral movement.
Such modules allow malware to compromise other computers on the same Local Area Network, infect more victims, and enlist machines as part of the botnet. Such worm-like infections could help the TrickBot gang conduct more account takeover (ATO) fraud.
“Even though the worm module appears to be rather crude in its present state, it is evident that the TrickBot gang learned from the global ransomware worm-like outbreaks of WannaCry and “NotPetya” and is attempting to replicate their methodology. Flashpoint assesses with moderate confidence that the TrickBot gang will likely continue to be a formidable force in the near term,” Flashpoint says.
Man-Machine Teamwork Needed for Effective Threat Hunting: Report
29.7.2017 securityweek Security
Seven hundred IT and security professionals were surveyed by McAfee to understand the current state and future development of threat hunting -- the active search for existing network breaches.
For this purpose, a threat hunter is defined as an analyst who focuses on clues and hypotheses (rather than waiting for binary alerts from rule-based detections); is human-centric (rather than tool-centric); and works from the assumption of an existing breach. The hunting process is defined as the military OODA concept: observe, orient, decide, act.
To allow comparison of threat-hunting capabilities, the respondents rated the perception of their own maturity from level 1 to level 4. This ranges from hunters who primarily rely on automated alerting with some routine data collection (level 1) to hunters who automate the majority of successful data analysis (level 4).
One of the first insights from the survey and report (PDF) is that successful threat-hunting is a combination of art and science. Level 1 hunters operate largely on an ad hoc basis; for level 2 hunters it is an organized process; but for the most successful hunters at level 4, it is a mix of both.
Looking to improve their maturity, the top four strategies overall are better automation of threat hunting processes, increased use of data analytics, hiring of more experienced employees, and more precise diagnostic tools. Noticeably, and perhaps naturally, the lower level SOCs place hiring staff as the priority, followed by improved use of data analytics. Level 3, which is probably better staffed by definition, seeks first better automation and second increased analytics.
McAfee postulates that lower level SOCs seek to staff-up and chase "shiny new toys... trying to emulate leading
SOCs too soon", while more advanced SOCs "shift their focus from building strong hunting and incident response teams to making them more effective."
One clear differentiation between level 4 hunters and the lower levels is the degree of automation. "Respondents in levels 1 through 3 SOCs," notes the report, "reported deploying automation extensively at an average of 23% compared with 75% of level 4 SOCs."
This carries over into the next stage of cybersecurity -- incident response. Extensive automation quite naturally supplies the greater context needed by incident responders to more accurately scope and triage incidents for rapid incident resolution. This is confirmed in the survey results: "71% of SOCs with a level 4 maturity closed investigations in an average of less than one week -- the majority of which closed in less than 24 hours." The average time for the lower levels is 25 days.
Similarly, says McAfee, "The more mature SOCs also determine the root cause of an attack 70% percent of the time, versus 43% percent of the time for the developing organizations."
Another difference in the operational procedures between the different levels of maturity is the amount of time spent on researching and customizing threat hunting tools. Level 1 hunters spend, on average 10 hours per month. This rises consistently to 17 hours for level 4 hunters. "This," suggests McAfee, "is a good example of both the power of human+machine teaming, and the importance of locally produced intelligence and personalization."
Sandboxes are the most used hunting tool. Noticeably, the more advanced hunters have been using them for longer than the lower levels: four years, on average, for level 4; compared to 2 years for level 1. However, the use made of sandboxes also changes with the level of hunter maturity. Twice as many level 4 hunters use sandboxing for investigation and threat validation rather than just detection and alerting.
All data analysis relies on data. Sixty percent of all four maturity levels use public threat intelligence feeds; but as the maturity level increases, so the hunters begin to rely more on the TTPs they gather internally from their own research. Automated processes to feed threat intelligence into a correlation engine are used by 45% of level 1 hunters, but 77% of level 4 hunters. The nature of the feeds also changes with the levels: 80% of level 4s use ISACs and other private or paid-for feeds compared to 41% of level 1s.
"Threat hunting is here to stay, and is no longer an esoteric practice limited to a few of the edgier practitioners," says McAfee. "Over the next few years, expect to see threat hunting as part of most organizations' analytics driven security operations, backed by extensive automation and machine analytics."
What is clear from this survey, however, is that threat hunting is not simply a case of buying systems to do it. Effective threat hunting leading to efficient incident response is a combination of man and machine, of art and science, with the man tailoring and automating the science to suit his own environment.
Rurktar Malware: An Espionage Tool in Development
28.7.2017 securityweek Virus
A newly discovered spyware family that appears designed for cyber-espionage is still under development, G DATA security researchers say.
Dubbed Rurktar, the tool hasn’t had all of its functionality implemented yet, but G DATA says “it is relatively safe to say [it] is intended for use in targeted spying operations.” The malicious program could be used for reconnaissance operations, as well as to spy on infected computers users, and steal or upload files.
The spyware, researchers say, appears to originate from Russia. Some of its internal error messages are written in Russian and the IP addresses used to remotely control the tool are located in the country, which the security firm considers strong indicators of its origin.
At the moment, Rurktar packs functions that allow it to perform reconnaissance of a network infrastructure and check whether a particular machine is reachable or not, as well as to take screenshots of an infected machine’s desktop, and also download specific files from a target system. Furthermore, the program can delete files from the target machine and can also upload files to it.
“All of this points to industrial espionage - the functions that have been described so far do not have any practical application for large-scale operations, such as ransomware schemes,” G DATA explains.
The malware can also be used to enumerate usernames, computer name, and OS version; get the current preferences the malware is actively using; enumerate the UUID; list hard disks and information about them; execute a command via the command prompt; list current running processes on the computer; and terminate running processes.
Implemented functions in the configuration file include Debug (writes logfile RCS.log to the disk), Port (the port the malware connects to), IP (the IP the malware connects to), FriendlyID (a default return value being used if no UUID was enumerated), NetworkImageQ (sets the quality of the image to be delivered), CaptureDirectory (checks whether a directory exists or not), and ScreenshotEx (sets the extension type for all screenshots).
A great deal of other functions haven’t been implemented yet: CaptureMode, CaptureStart, CaptureStopProcess1, VideoCap, SkipFrames, DetectionPreBuffer, DefPass, DetectPorog, MaxCaptureFrames, WatchFiles, SendOriginPreviews, ControlExt, WatchProc, ScreenshotAutoCapture, ScreenshotPause, ProxyEnabled, and several others more.
The malware uses a wrapper called Snow.exe, which checks whether admin privileges are available or not and executes Rurktar. It can also execute a new process of itself to ask the user for admin privileges if needed. To gain persistency, the spyware installs a new service called RCSU, which is started upon reboot.
What the security researchers haven’t established yet, however, is whether the espionage tool is the work of a single individual or that of a team. Its author apparently uses a Dropbox folder as a working directory, which could suggest that there are multiple individuals cooperating on building it and are consolidating their work through a Dropbox.
“What Dropbox can also be used for by a single individual is a crude and very basic versioning system - some Dropbox accounts offer the possibility of restoring earlier versions of a file. Therefore, it can be used to track changes, but it is not ideal from a developer's stand point. Using Dropbox as a backup is, of course, also a possibility to be considered here,” G DATA notes.
Being work-in-progress, the cyber-espionage tool hasn’t spread very widely yet, but that is expected to change as soon as operational status is reached.
The few IP addresses linked to it so far are believed to have been used for testing purposes only. Additionally, the IP addresses used for remote control are expected to see increased diversity and to expand beyond the Russian space, mainly because the actors will start using or repurposing the malware for various operations.
“The Rurktar malware is yet not been found that often, but has the potential to be more popular in the coming months because of the amount of options an attacker has with this malware,” G DATA’s Nathan Stern, who performed a detailed analysis of the malware, notes (PDF).
House Committee Passes Bills to Boost DHS Cyber Powers
28.7.2017 securityweek BigBrothers
DHS Gets More Cyber Power With New Bills
New Legislation Would Create Cybersecurity and Infrastructure Security Agency to Address Cyber Threats
Less than a week after the U.S. Department of Homeland Security (DHS) reauthorization act passed the House of Representatives, the House Homeland Security Committee on Wednesday passed two bills to reorganize the cybersecurity operations of the DHS and demand it to report on procedures used to disclose vulnerabilities.
The first of the bills that moved forward this week is the Cybersecurity and Infrastructure Security Agency Act (PDF), which creates a new agency within DHS to improve the Department’s cyber and infrastructure stance.
Sponsored by Homeland Security Committee Chairman Michael McCaul (R-Texas) and the committee’s ranking member Bennie Thompson (D-Miss), the bill states that DHS’s cyber operations division would retain most cybersecurity responsibilities, including the protection of federal networks. It would also be responsible with the sharing of cyber threat information with critical industry sectors--something the DHS has already been doing in various capacities.
Called the Cybersecurity and Infrastructure Security Agency, the new operational entity will be split in three divisions: cybersecurity, infrastructure security, and emergency communications. The bill also states that it will be led by a director who will report to the Homeland Security secretary, along with a deputy director who will assist in managing the Agency and will report to the director.
The second bill the Committee passed on Wednesday is the Cyber Vulnerability Disclosure Reporting Act (PDF). Sponsored by Rep. Sheila Jackson Lee (D-Texas), the legislation requires the Homeland Security secretary to report on how the Department is using vulnerability disclosure programs, with the first report set to be due eight months after the bill’s passage.
“To the extent possible, such report shall include an annex with information on instances in which such policies and procedures were used to disclose cyber vulnerabilities in the year prior to the date such report is required and, where available, information on the degree to which such information was acted upon by industry and other stakeholders,” the bill reads.
In the light of numerous software exploits associated with the National Security Agency made public over the past year by the Shadow Brokers hacking group, Microsoft has warned of the risks that zero-day exploits stockpiled by governments pose, and pushed for the adoption of a PATCH Act that would prevent occurrences such as WannaCry.
The numerous documents WikiLeaks has released over the past several months on CIA hacking tools also spurred debate on governments stockpiling software vulnerabilities instead of reporting them so they could be patched.
DHS Reauthorized
Both bills passed unanimously less than a week after the Department of Homeland Security Authorization Act of 2017 passed the House of Representatives on July 20. Not only did the bill reauthorizes the Department, but is represents the first actual authorization for some of its parts.
A bill outline (PDF) reveals the legislation meant to update DHS’ counterterrorism, emergency preparedness, and maritime security programs, bringing changes to the Federal Emergency Management Agency, Coast Guard, Transportation Security Administration, Secret Service, U.S. Citizenship and Immigration Services, and Immigration and Customs Enforcement.
Improved Airport Security
Also directing the streamlining and restructuring of TSA, the bill requires it to “develop and implement a preventative maintenance validation process for security-related technology deployed to airports.” The administration also has to “conduct a comprehensive, agency-wide efficiency review” to streamline and restructure operations to reduce spending.
TSA is also requested to conduct a broad assessment of cyber risks to aviation security, to vet airports and airlines if requested, and enhance cyber threat information sharing across the aviation sector.
The administration is required “to implement a secure, automated system at all airports, for verifying travel and identity documents of passengers who are not members of a Department of Homeland Security (DHS) trusted traveler programs,” and to improve the efficiency of traveler vetting programs such as TSA PreCheck and CBP Global Entry. Additionally, the agency would be required to test automated and biometric-based systems at airports to verify the identity memebers of the TSA PreCheck and other DHS trusted traveler programs.
“The committee believes that the minimum security standards for airport security set forth by the Chicago Convention established by the International Civil Aviation Organization are not robust enough in the current threat environment where we have repeatedly seen terrorist organizations planning attacks targeting aviation. Therefore, the committee believes the United States should take a leadership role at the ICAO in building consensus among member states to raise these standards,” section 1522 reads.
Cybersecurity at U.S. Ports
Section 1403 of the bill amends the Maritime Transportation Security Act (MTSA) and formally gives the U.S. Coast Guard (USCG) responsibility for cybersecurity at ports.
"While USCG does not currently have operational authority of cybersecurity at ports, it is responsible for ensuring that cybersecurity is part of the USCG approved facility security plan for ports," the bill reads.
The U.S. Coast Guard will also be tasked with stepping up cyber protections at U.S. ports and helping port operators share cyber threat information.
"The Committee believes that our ports and the automated systems that control them are vulnerable to cyber-attacks, which could be devastating to the transit of international commerce, says the bill. “While USCG inspects and approves what are known as “facility security plans” at ports twice a year, these plans are not currently required to have a cybersecurity strategy. The Committee believes that requiring facility operators to have a cybersecurity plan, and providing them with a mechanism to share best practices and receive current intelligence, is critical to maintaining the uninterrupted flow of maritime commerce and the security of our ports."
Emergency Preparedness, Response, and Communications
The bill also sets aside $800 million for each of the fiscal years from 2018 through 2022 for the Urban Area Security Initiative, designed to help urban areas better prepare to prevent and respond to acts of terrorism. The funds would be used “to (1) enhance medical preparedness, and (2) enhance cybersecurity,” section 1606 of the bill reads.
“The Committee has heard that, while improving, the flow of federal cyber threat and risk information to State and local emergency response providers is slow and overclassified. Additionally, for several years now, FEMA has released an annual National Preparedness Report, which highlights the States' 32 core capabilities, as defined by the National Preparedness Goal. Since the first National Preparedness Report was released in 2012, States have ranked their cybersecurity capabilities as one of their lowest,” the bill reads, noting that the current process of information sharings has "caused emergency response providers to be reactive rather than proactive" in addressing cyber threats.
The bill also requires the Director of the Office of Emergency Communications to submit an annual report that “must include specific information on the Office’s efforts to: promote communication among emergency response providers during disasters; conduct nationwide outreach to foster the development of interoperable emergency communications capabilities; and provide interoperable emergency communications technical assistance to State, regional, local, and tribal government officials.”
Secret Service
The DHS reauthorization act demands that the Secret Service increase the annual number of training hours for officers and agents. Additionally, it states that the Secret Service director has to be confirmed by the Senate, instead of being appointed directly by the president, and authorizes the construction of facilities to improve training.
According to Homeland Security secretary John Kelly, the bill should help DHS better carry tasks, suggesting that the reauthorization act would improve morale throughout the Department.
“[The bill] allows us to study disaster preparedness and response, so we can find ways to help communities recover faster, in a cost-effective way. It gives first responders the training and equipment they need to counter today’s terrorist threats. And it improves the Department’s information sharing capabilities, so our state, local, tribal and territorial partners can stay up to date on the threats facing our communities, in both the cyber and the physical world,” Kelly stated.
Now that it has passed the House of Representatives, the reauthorization bill heads to the Senate. However, there is no schedule yet for considering it.
In an official statement, President Donald J. Trump commended the House’s vote: “Since its formation nearly fifteen years ago in response to the terrorist attacks of September 11, 2001, DHS has been on the front lines of the Federal Government’s efforts to keep the American public safe. I look forward to signing this important legislation and I encourage the United States Senate to take it up without delay,” President Trump said.
The libertarian-leaning House Liberty Caucus, on the other hand, opposes the bill, suggesting it was rushed: “Such a vast, significant piece of legislation demands debate and input from the full membership of the House of Representatives. Instead, this bill overhauling the department and authorizing billions of dollars is being rushed to the floor, ensuring representatives have no time to vet its countless provisions,” the Liberty Caucus reportedly stated.
Wikileaks Vault 7 – Imperial projects revealed the 3 hacking tools Achilles, SeaPea and Aeris
28.7.2017 securityaffairs BigBrothers
Wikileaks published another batch of classified documents from the CIA Vault 7 leak, it includes details of the Imperial project.
Today another batch of classified documents from the CIA Vault 7 leak was published by Wikileaks. The documents are related to a CIA project codenamed ‘Imperial,’ they include details of three CIA hacking tools and implants that have been designed to compromise computers running Apple Mac OS X and different Linux distributions.
The three hacking tools are:
Achilles — A tool to trojanize a legitimate OS X disk image (.dmg) installer.
SeaPea — A Stealthy Rootkit For Mac OS X Systems
Aeris — An Automated Implant For Linux Systems
Wikileaks CIA Imperial project.
Achilles
Achilles is a hacking tool that allows CIA operators to package malicious codes with a legitimate Mac OS app into a disk image installer (.DMG) file. According to the documents, Achilles v1.0 was developed in 2011, the CIA experts only tested it on Mac OS X 10.6 (Apple Snow Leopard OS launched in 2009).
The tool is a shell script written in Bash that gives the operators “one or more desired operator specified executables” for a one-time execution.
In a classic attack scenario, the target individuals download an infected disk image on their computer, once they will open and install the software, the malware would run in the background.
Once the malware is executed, it will erase any trace of the Achilles from the downloaded application so that the file would “exactly resemble” the original legitimate software. This behavior makes hard the investigation of the malware from security experts and antivirus software.
SeaPea
The SeaPea hacking tool is a Mac OS X Rootkit that gives CIA operators stealth and tool launching capabilities by hiding important files, processes and socket connections from the users.
It was developed in 2011, according to the documents SeaPea works on computers running then-latest Mac OS X 10.6 (Snow Leopard) Operating System (32- or 64-bit Kernel Compatible) and Mac OS X 10.7 (Lion) Operating System.
CIA operators need a root access to infect the target Mac computer, the hacking tools can be removed reformatting the startup disk or upgrading the OS to the next version.
Aeris
The Aeris hacking tool is an automated implant written in C programming language that could be used to backdoor portable Linux-based Operating Systems, including Debian, CentOS, Red Hat, FreeBSD and Solaris.
Below the list of features implemented by Aeris:
Configurable beacon interval and jitterStandalone and Collide-based HTTPS LP support
Standalone and Collide-based HTTPS LP supportSMTP protocol support
SMTP protocol supportTLS Encrypted communications with mutual authentication
TLS Encrypted communications with mutual authentication
Compatibility with the NOD Cryptographic Specification
Structured command and control that is similar to that used by several Windows
implant-
Automated file exfiltration
Simple and flexible deployment and installation
Aeris is a builder that CIA operators can use to generate custom implants, it does not have a separate installer and in order to be deployed operators just need to place an Aeris binary in the desired directory.
“Aeris does not have a separate installer. To deploy it, simply place an Aeris binary in the desired directory. Rename the binary in any way that you wish. Note that the configuration is patched in at build time; hence, no additional files (beyond possibly those related to persistence — see the next section) are needed.” states the user guide.
Below the list of release published by Wikileaks since March:
Imperial – 27 July, 2017
UCL/RAYTHEON – 19 July, 2017
HighRise – 13 July, 2017
BothanSpy and Gyrfalcon – 06 July, 2017
OutlawCountry – 30 June, 2017
ELSA malware – 28 June, 2017
Cherry Blossom – 15 June, 2017
Pandemic – 1 June, 2017
Athena – 19 May, 2017
AfterMidnight – 12 May, 2017
Archimedes – 5 May, 2017
Scribbles – 28 April, 2017
Weeping Angel – 21 April, 2017
Hive – 14 April, 2017
Grasshopper – 7 April, 2017
Marble Framework – 31 March, 2017
Dark Matter – 23 March, 2017
Greek police arrested a man running the BTC-e Bitcoin exchange to launder more than US$4bn worth of the Bitcoin
28.7.2017 securityaffairs Cyber
Greek Police arrested a Russian man and accused him of running the BTC-e Bitcoin exchange to launder more than US$4bn worth of the cryptocurrency.
Greek Police have arrested the Russian national Alexander Vinnik (38) and they accuse the man of running the BTC-e Bitcoin exchange to launder more than US$4bn worth of the cryptocurrency.
The police seized two laptops, two tablets, mobile phones, a router, a camera, and four credit cards.
The authorities reported that since 2011, 7 million Bitcoin went into the BTC-e exchange and 5.5 million withdrawn.
According to the Greek media outlet the Daily Thess, he FBI tracked Alexander Vinnik for more than a year.
“38-year-old Russian Alexander Vinnik enjoyed his vacation with his partner in one of the most expensive hotels in Ouranoupoli in Halkidiki. He had not realized the slightest of the FBI steps he had been watching for months, informing the Greek prosecution authorities of his action.” reported the the Daily Thess. “Yesterday after a surprise operation he was arrested and today he was handcuffed to the prosecutor of the Thessaloniki Court of Appeals in order to start the proceedings for his extradition to the United States.”

The Greek outlet reported that the Russian embassy in Greece has confirmed the arrest of the crook and is waiting for the extradition to the US.
The Tokyo-based group WizSec who investigated the Mt Gox case revealed that pilfering goes back as far as 2011, the experts are now accusing Vinnik of laundering the proceeds of the Bitcoin theft that caused the shut down of the major exchange.
“Earlier today news broke of an arrest in Greece of a Russian national suspected of running a large-scale money laundering operation focused on Bitcoin. The man has since been publicly identified as Alexander Vinnik, 38, and over $4 billion USD is said to have been trafficked through the operation since 2011.” reads a post published by Wizsec.
“We won’t beat around the bush with it: Vinnik is our chief suspect for involvement in the MtGox theft (or the laundering of the proceeds thereof). This is the result of years of patient work, and these findings were surely independently uncovered by other investigators as well.”
Wizsec experts reported that after Mt Gox’s “hot wallet” private keys were stolen in 2011, the Bitcoin were transferred to a number of wallets “controlled by Vinnik”.
Below an excerpt from the Wizsec post;
In September 2011, the MtGox hot wallet private keys were stolen, in a case of a simple copied wallet.dat file. This gave the hacker access to a sizable number of bitcoins immediately, but also were able to spend the incoming trickle of bitcoins deposited to any of the addresses contained.
Over time, the hacker regularly emptied out whatever coins they could spend using the compromised keys, and sent them to wallet(s) controlled by Vinnik. This went on for long periods, but also had breaks — a prominent second phase of thefts happened later in 2012 and 2013.
By mid 2013 when the funds spendable from the compromised keys had slowed to a near halt, the thief had taken out about 630,000 BTC from MtGox.
”
The experts at Wizsec discovered some of the stolen keys turning up at BTC-e wallets, these wallets were used to launder “ the crypto currencies stolen in various cyber heists between 2011 and 2012, including Bitcoinia and Bitfloor.
Vinnik transferred some coins back onto Mt Gox because the man used accounts that could be linked to his online identity ‘WME’.”
Earlier July, the trial of Mark Kapeles, the Mt Gox’s boss, started, according to documents filed with the Tokyo District Court, roughly 307,000 BTC were transferred to BTC-e wallets.
In the July 26 court hearing in Thessaloniki, Vinnik denied the accusations, now the final decision on the extradition will be taken by the Greek Minister of Justice.
The experts at Wizsec discovered some of the stolen keys turning up at BTC-e wallets, these wallets were used to launder the crypto currencies stolen in various cyber heists between 2011 and 2012, including Bitcoinia and Bitfloor.
Vinnik transferred some coins back onto Mt Gox because the man used accounts that could be linked to his online identity ‘WME’.”
Earlier July, the trial of Mark Kapeles, the Mt Gox’s boss, started, according to documents filed with the Tokyo District Court, roughly 307,000 BTC were transferred to BTC-e wallets.
In the July 26 court hearing in Thessaloniki, Vinnik denied the accusations, now the final decision on the extradition will be taken by the Greek Minister of Justice.
3 New CIA-developed Hacking Tools For MacOS & Linux Exposed
27.7.2017 thehackernews BigBrothers
WikiLeaks has just published a new set of classified documents linked to another CIA project, dubbed 'Imperial,' which reveals details of at least three CIA-developed hacking tools and implants designed to target computers running Apple Mac OS X and different flavours of Linux operating systems.
If you are a regular reader of THN, you must be aware that this latest revelation by the whistleblower organisation is the part of an ongoing CIA-Vault 7 leaks, marking it as the 18th batch in the series.
If you are unaware of the Vault 7 leaks, you can head on to the second of this article for having a brief look on all the leaks at once.
Achilles — Tool to Backdoor Mac OS X Disk Images
Dubbed Achilles, the hacking tool allows CIA operators to combine malicious Trojan applications with a legitimate Mac OS app into a disk image installer (.DMG) file.
The binding tool, the shell script is written in Bash, gives the CIA operators "one or more desired operator specified executables" for a one-time execution.
As soon as an unsuspecting user downloads an infected disk image on his/her Apple computer, opens and installs the software, the malicious executables would also run in the background.
Afterwards, all the traces of the Achilles tool would be "removed securely" from the downloaded application so that the file would "exactly resemble" the original legitimate app, un-trojaned application, making it hard for the investigators and antivirus software to detect the initial infection vector.
Achilles v1.0, developed in 2011, was only tested on Mac OS X 10.6, which is Apple's Snow Leopard operating system that the company launched in 2009.
SeaPea — Stealthy Rootkit For Mac OS X Systems
The second hacking tool, called SeaPea, is a Mac OS X Rootkit that gives CIA operators stealth and tool launching capabilities by hiding important files, processes and socket connections from the users, allowing them to access Macs without victims knowledge.
Developed in 2011, the Mac OS X Rootkit works on computers running then-latest Mac OS X 10.6 (Snow Leopard) Operating System (32- or 64-bit Kernel Compatible) and Mac OS X 10.7 (Lion) Operating System.
The rootkit requires root access to be installed on a target Mac computer and cannot be removed unless the startup disk is reformatted or the infected Mac is upgraded to the next version of the operating system.
Aeris — An Automated Implant For Linux Systems
The third CIA hacking tool, dubbed Aeris, is an automated implant written in C programming language that is specifically designed to backdoor portable Linux-based Operating Systems, including Debian, CentOS, Red Hat — along with FreeBSD and Solaris.
Aeris is a builder that CIA operators can use to generate customised impacts, depending upon their covert operation.
"It supports automated file exfiltration, configurable beacon interval and jitter, stand-alone and Collide-based HTTPS LP support and SMTP protocol support — all with TLS encrypted communications with mutual authentication,"
"It's compatible with the NOD Cryptographic Specification and provides structured command and control that's similar to that used by several Windows implants."
Previous Vault 7 CIA Leaks
Last week, WikiLeaks revealed about CIA contractor Raytheon Blackbird Technologies, which analysed in-the-wild advanced malware and hacking techniques and submitted at least five reports to the agency for help develop their own malware.
Since March, the whistle-blowing group has published 18 batches of "Vault 7" series, which includes the latest and last week leaks, along with the following batches:
Highrise Project — the alleged CIA project that allowed the spying agency to stealthy collect and forwarded stolen data from compromised smartphones to its server through SMS messages.
BothanSpy and Gyrfalcon — two alleged CIA implants that allowed the spying agency to intercept and exfiltrate SSH credentials from targeted Windows and Linux operating systems using different attack vectors.
OutlawCountry – An alleged CIA project that allowed it to hack and remotely spy on computers running the Linux operating systems.
ELSA – the alleged CIA malware that tracks geo-location of targeted PCs and laptops running the Microsoft Windows operating system.
Brutal Kangaroo – A tool suite for Microsoft Windows used by the agency to targets closed networks or air-gapped computers within an organization or enterprise without requiring any direct access.
Cherry Blossom – An agency's framework, basically a remotely controllable firmware-based implant, used for monitoring the Internet activity of the targeted systems by exploiting vulnerabilities in Wi-Fi devices.
Pandemic – A CIA's project that allowed the agency to turn Windows file servers into covert attack machines that can silently infect other computers of interest inside a targeted network.
Athena – A CIA's spyware framework that has been designed to take full control over the infected Windows PCs remotely, and works against every version of Microsoft's Windows operating systems, from Windows XP to Windows 10.
AfterMidnight and Assassin – Two alleged CIA malware frameworks for the Microsoft Windows platform that has been designed to monitor and report back actions on the infected remote host computer and execute malicious actions.
Archimedes – Man-in-the-middle (MitM) attack tool allegedly created by the CIA to target computers inside a Local Area Network (LAN).
Scribbles – A piece of software reportedly designed to embed 'web beacons' into confidential documents, allowing the agency to track insiders and whistleblowers.
Grasshopper – Framework which allowed the spying agency to easily create custom malware for breaking into Microsoft's Windows and bypassing antivirus protection.
Marble – Source code of a secret anti-forensic framework, basically an obfuscator or a packer used by the CIA to hide the actual source of its malware.
Dark Matter – Hacking exploits the agency designed to target iPhones and Macs.
Weeping Angel – Spying tool used by the agency to infiltrate smart TV's, transforming them into covert microphones.
Year Zero – Alleged CIA hacking exploits for popular hardware and software.
Microsoft Is Paying Up To $250,000 With Its New Bug Bounty Program
27.7.2017 thehackernews Security
Microsoft has finally launched a new dedicated bug bounty program to encourage security researchers and bug hunters for finding and responsibly reporting vulnerabilities in its latest Windows versions of operating systems and software.
Being the favourite target of hackers and cyber criminals, every single zero-day vulnerability in Windows OS—from critical remote code execution, mitigation bypass and elevation of privilege to design flaws—could cause a crisis like recent WannaCry and Petya Ransomware attacks.
In past five years the tech giant has launched multiple time-limited bug bounty programs focused on various Windows features, and after seeing quite a bit of success, Microsoft has decided to continue.
"Security is always changing, and we prioritise different types of vulnerabilities at different points in time. Microsoft strongly believes in the value of the bug bounties, and we trust that it serves to enhance our security capabilities."
With its latest bug bounty program, Microsoft is offering up to $250,000 in rewards to cybersecurity researchers and bug hunters who find vulnerabilities in the company's software, which mainly focuses on:
Windows 10, Windows Server 2012 and Insider Previews
Microsoft Hyper-V
Mitigation Bypass Techniques
Windows Defender Application Guard
Microsoft Edge Browser
Below is the chart showing details of the targets, main focus areas and the respective payouts:
"In the spirit of maintaining a high-security bar in Windows, we’re launching the Windows Bounty Program on July 26, 2017," Microsoft says in a blog post. "The bounty program is sustained and will continue indefinitely at Microsoft’s discretion."
Recently, the non-profit group behind Tor Project joined hands with HackerOne and launched a bug bounty program with the payout of up to $4,000 to researchers and bug hunters for finding and reporting flaws that could compromise the anonymity network.
For more granular details about Microsoft's Bug Bounty Program, you can check out the program on the TechNet site.
Smart Vacuum Cleaners Making Map Of Your Home — And Wants to Sell It
27.7.2017 thehackernews Privacy
What if I say that your cute, smart robotic vacuum cleaner is collecting data than just dirt?
During an interview with Reuters, the CEO of iRobot, the company which manufactured Roomba device, has revealed that the robotic vacuum cleaner also builds a map of your home while cleaning — and is now planning to sell this data to third-party companies.
I know it sounds really creepy, but this is what the iRobot company has planned with the home mapping data its Roomba robots collect on its users.
What is Roomba?
Manufactured by Massachusetts-based firm iRobot, Roomba is a cute little robotic vacuum cleaner — which ranges in price from $375 to $899 — that has been vacuuming up household dirt since 2002.
Early versions of Roomba used IR or laser sensors to avoid obstacles in their way, but the company began distributing high-end Wi-Fi-connected Roomba models from 2015, such as the Roomba 980, which includes a camera and Simultaneous Localisation And Mapping (SLAM) technology that can not only avoid obstacle but also build a map of your home.
And this has opened up new possibilities for the company.
What Data Roomba Collects and Why?
Roomba robots gather all kinds of data—from room dimensions and furniture position to distances between different objects placed in your room—that could help next-generation IoT devices to build a true smart home.
Angle believes mapping data could be used by other smart home devices—such as thermostats, lighting, air conditioner, personal assistant, and security cameras—to become smarter.
According to iRobot CEO Colin Angle, "there's an entire ecosystem of things and services that the smart home can deliver once you have a rich map of the home that the user has allowed to be shared."
Angle also told the publication that he is planning to push the company toward a broader vision of the smart home, and in the near future iRobot could sell your floor data with the business like Apple, Amazon, Microsoft and Google—but not without its users' consent.
Until now, your home data is private and is not being shared with any third-party company.
Why Would Companies be Interested in Your Floor-Plans?
By now, you must be thinking how your floor plans would be beneficial to companies like Apple, Amazon, Google or Microsoft?
The move has some obvious privacy concerns, but surprisingly, this could help other smart devices at your home to work more efficiently—for example:
The data could help tech companies like Amazon, Apple and Google to improve their smart home speakers to control the vacuum and make use of the acoustics to improve audio performance throughout the home.
Dimensional knowledge of the rooms could help Smart Air-conditioners to control airflow throughout the rooms.
Home mapping data could also help Apple’s ARKit developers to create new apps for room management and interior design.
Moreover, Microsoft, Apple, Amazon and Google are already chasing this kind of data to lead in the smart industry.
Concerns — Privacy And Security
Since 2015 when iRobot introduced the mapping technology in Roomba, the vacuum clear has not just been picking up dirt and dust, but they have also been mapping the layout of your home, which could be privacy concerns for many of its users.
According to its terms of service, the users already give the company permission to share their data with third party vendors and subsidiaries, and on government requests.
"We may share your information...Third party vendors, affiliates, and other service providers that perform services on our behalf, solely in order to carry out their work for us, which may include identifying and serving targeted advertisements, providing e-commerce services, content or service fulfillment, billing, web site operation, payment processing and authorization, customer service, or providing analytics services," the company's privacy policy reads.
Given these terms, it is possible for the company to sell its customers information in bulk with companies without notifying its users. And it is obvious that more you want your technology to be smart, more private data you are offering to companies.
Roomba is already compatible with Amazon's Alexa and Google's Home — Apple's HomePod speaker will soon join them — therefore, its CEO is planning to sell its maps to one or more of these 'Big Three' in the next couple of years.
Creator of NanoCore RAT Pleads Guilty to Aiding CyberCriminals
27.7.2017 thehackernews Virus
A programmer who was arrested in March this year—not because he hacked someone, but because he created and distributed a remote access software that helped cyber criminals—has finally pleaded guilty.
Taylor Huddleston, 26, of Hot Springs, Arkansas, pleaded guilty on Tuesday to federal charges of aiding and abetting computer intrusions for intentionally selling a remote access tool (RAT), called NanoCore, to hackers.
NanoCore RAT happens to be popular among hackers and has been linked to instructions in at least 10 countries, among them was a high-profile assault on Middle Eastern energy firms in 2015.
NanoCore RAT, a $25 piece of remote access software, allows attackers to steal sensitive information from victim computers, such as passwords, emails, and instant messages. The RAT could even secretly activate the webcam on the victims' computers in order to spy on them.
Huddleston began developing NanoCore in late 2012, not with any malicious purpose, but with a motive to offer a low-budget remote management software for schools, IT-conscious businesses, and parents who desired to monitor their children's activities on the web.
However, according to the plea agreement, Huddleston created, marketed, and distributed two products — NanoCore RAT and Net Seal — in underground hacking forums that were extremely popular with cyber criminals around the world.
The programmer also took responsibility for creating and operating a software licensing system called "Net Seal" that was used by another suspect, Zachary Shames, to sell thousands of copies of Limitless keylogger.
"Huddleston used Net Seal to assist Zachary Shames in the distribution of malware to 3,000 people that was, in turn, used it to infect 16,000 computers," the DoJ statement reads.
In his guilty plea, Huddleston has admitted that he intended his products to be used maliciously.
Huddleston was arrested in March, almost two months before the FBI raided his house in Hot Springs, Arkansas and left with his computers after 90 minutes, only to return 8 weeks later with handcuffs.
Huddleston is now facing a maximum penalty of 10 years in prison and is scheduled to be sentenced on December 8.
Google Detects Dangerous Spyware Apps On Android Play Store
27.7.2017 thehackernews Android
Security researchers at Google have discovered a new family of deceptive Android spyware that can steal a whole lot of information on users, including text messages, emails, voice calls, photos, location data, and other files, and spy on them.
Dubbed Lipizzan, the Android spyware appears to be developed by Equus Technologies, an Israeli startup that Google referred to as a 'cyber arms' seller in a blog post published Wednesday.
With the help of Google Play Protect, the Android security team has found Lipizzan spyware on at least 20 apps in Play Store, which infected fewer than 100 Android smartphones in total.
Google has quickly blocked and removed all of those Lipizzan apps and the developers from its Android ecosystem, and Google Play Protect has notified all affected victims.
For those unaware, Google Play Protect is part of the Google Play Store app and uses machine learning and app usage analysis to weed out the dangerous and malicious apps.
Lipizzan: Sophisticated Multi-Stage Spyware
According to the Google, Lipizzan is a sophisticated multi-stage spyware tool that gains full access to a target Android device in two steps.
In the first stage, attackers distribute Lipizzan by typically impersonating it as an innocuous-looking legitimate app such as "Backup" or "Cleaner" through various Android app stores, including the official Play store.
Once installed, Lipizzan automatically downloads the second stage, which is a "license verification" to survey the infected device to ensure the device is unable to detect the second stage.
After completing the verification, the second stage malware would root the infected device with known Android exploits. Once rooted, the spyware starts exfiltrating device data and sending it back to a remote Command and Control server controlled by the attackers.
Lipizzan Also Gathers Data from Other Popular Apps
The spyware has the ability to monitor and steal victim's email, SMS messages, screenshots, photos, voice calls, contacts, application-specific data, location and device information.
Lipizzan can also gather data from specific apps, undermining their encryption, which includes WhatsApp, Snapchat, Viber, Telegram, Facebook Messenger, LinkedIn, Gmail, Skype, Hangouts, and KakaoTalk.
There's very few information about Equus Technologies (which is believed to have been behind Lipizzan) available on the Internet. The description of the company's LinkedIn account reads:
"Equus Technologies is a privately held company specialising in the development of tailor made innovative solutions for law enforcement, intelligence agencies, and national security organisations."
Earlier this year, Google found and blocked a dangerous Android spyware, called Chrysaor, allegedly developed by NSO Group, which was being used in targeted attacks against activists and journalists in Israel, Georgia, Turkey, Mexico, the UAE and other countries.
NSO Group Technologies is the same Israeli surveillance firm that built the Pegasus iOS spyware initially detected in targeted attacks against human rights activists in the United Arab Emirates (UAE) last year.
How to Protect your Android device from Hackers?
Android users are strongly recommended to follow these simple steps in order to protect themselves:
Ensure that you have already opted into Google Play Protect.
Download and install apps only from the official Play Store.
Enable 'verify apps' feature from settings.
Protect their devices with pin or password lock.
Keep "unknown sources" disabled while not using it.
Keep your device always up-to-date with the latest security patches.
CowerSnail — Windows Backdoor from the Creators of SambaCry Linux Malware
27.7.2017 thehackernews Virus
Last month, we reported about a group of hackers exploiting SambaCry—a 7-year-old critical remote code execution vulnerability in Samba networking software—to hack Linux computers and install malware to mine cryptocurrencies.
The same group of hackers is now targeting Windows machines with a new backdoor, which is a QT-based re-compiled version of the same malware used to target Linux.
Dubbed CowerSnail, detected by security researchers at Kaspersky Labs as Backdoor.Win32.CowerSnail, is a fully-featured windows backdoor that allows its creators to remotely execute any commands on the infected systems.
Wondering how these two separate campaigns are connected?
Interestingly, the CowerSnail backdoor uses the same command and control (C&C) server as the malware that was used to infect Linux machines to mine cryptocurrency last month by exploiting the then-recently exposed SambaCry vulnerability.
Common C&C Server Location — cl.ezreal.space:20480
SambaCry vulnerability (CVE-2017-7494), named due to its similarities to the Windows SMB flaw exploited by the WannaCry ransomware that recently wreaked havoc worldwide, affected all Samba versions newer than Samba 3.5.0 released over the past seven years.
Shortly after the public revelation of its existence, SambaCry was exploited by this group of hackers to remotely install cryptocurrency mining software—"CPUminer" that mines cryptocurrencies like Bitcoin, Litecoin, Monero and others—on Linux systems.
But now, the same hackers are targeting both, Windows and Linux computers, with CPUminer by utilising computing resources of the compromised systems in order to make the profit.
"After creating two separate Trojans, each designed for a specific platform and each with its own peculiarities, it is highly probable that this group will produce more malware in the future," Sergey Yunakovsky of Kaspersky Lab said in a blog post.
In separate research, security researcher Omri Ben Bassat reported about more copycat groups of hackers who are exploiting the same SambaCry vulnerability for cryptocurrency mining and installing "Tsunami backdoor," an IRC-based DDoS botnet malware that's been known for infecting Mac OS X and IoT devices in the past.
For those unaware: Samba is open-source software (re-implementation of SMB/CIFS networking protocol) that offers Linux/Unix servers with Windows-based file and print services and runs on the majority of operating systems and IoT devices.
Despite being patched in late May, the SambaCry bug is actively being exploited by hackers. Just last week, researchers spotted a new piece of malware, called SHELLBIND, exploiting the flaw to backdoor Network Attached Storage (NAS) devices.
Bitcoin Exchange Operator Arrested For $4 Billion Money Laundering Scheme
27.7.2017 thehackernews IT
Greece police have arrested a Russian man who is believed to have been the operator of the popular BTC-e Bitcoin exchange on charges of laundering more than $4 billion in bitcoin for culprits involved in hacking attacks, tax fraud and drug trafficking.
A United States jury indicted 38-year-old Alexander Vinnik on Wednesday after his arrest in Greece on Tuesday at the request of US law enforcement authorities. The suspect is one of the operators of BTC-e, a service operational since 2011.
Headquartered in Russia, the digital currency exchange has been offline since the arrest of Vinnik, and its homepage says, "Site is under maintenance. We apologize for the inconvenience.."
According to a press release published by the U.S. Treasury's Financial Crimes Enforcement Network (FinCEN), BTC-e ignored "know your customer" laws in an effort to serve criminals, and even hosted message boards buzzing with illegal activities.
The FinCEN also announced a $110 million penalty against BTC-e for facilitating crimes along with a separate $12 Million fine against Vinnik.
BTC-e Linked to Collapse of Mt. Gox Bitcoin Exchange
This case is really important for the law enforcement because it could reveal the possible culprit behind the collapse of the once-very popular Japanese bitcoin exchange Mt. Gox, which was shut down in 2014 following a massive series of mysterious robberies, which totalled at least $375 million in Bitcoin.
According to the U.S. Department of Justice, Vinnik obtained funds from the hacker or insider who stole bitcoins from Mt. Gox and sent them to a bitcoin wallet controlled by Vinnik, who intentionally laundered them through BTC-e, over a period of three years.
"After the coins entered Vinnik's wallets, most were moved to BTC-e and presumably sold off or laundered (BTC-e money codes were a popular choice). In total some 300,000 BTC ended up on BTC-e," according to WizSec, a Japanese security firm that has long been investigating the Mt. Gox case.
"To be clear, this investigation turned up evidence to identify Vinnik not as a hacker/thief but as a money launderer; his arrest news also suggests this is what he is being suspected for. He may have merely bought cheap coins from thieves and offered a laundering service."
Vinnik arrest is the latest in a series of US investigations against Russian cybercriminals in Europe, following the shutdown of two of the biggest dark web marketplaces, AlphaBay and Hansa, last week.
While Greek police described Vinnik as "an internationally sought ‘mastermind’ of a crime organisation," United States authorities accused him of facilitating crimes including hacking, identity theft, tax refund fraud, public corruption and drug trafficking.
Vinnik is to be charged with operation of an unlicensed money service business, conspiracy to commit money laundering, money laundering, and engaging in unlawful monetary transactions.
If found guilty, the suspect could face up to 55 years in prison, together with a $500,000 fine or twice the value of the property involved in the transaction for each count.
Iranian Cyberspy Groups Share Malware Code
27.7.2017 securityweek BigBrothers
Two cyberspy groups believed to be operating out of Iran, tracked by security firms as OilRig and Greenbug, have apparently shared malware code, according to researchers at Palo Alto Networks.
While cyber espionage groups sponsored by the same government often try to keep their campaigns separate, in the past months, researchers found connections between several groups linked to Iran. Experts identified shared code, infrastructure and even operations where two actors apparently helped each other directly.
One threat group, tracked as OilRig, has been around since 2015 and it has targeted many organizations, particularly in the financial and government sectors, in the United States and Middle Eastern countries. The actor’s attacks have often involved weaponized Microsoft Excel spreadsheets tracked as Clayslide and a backdoor dubbed Helminth.
In attacks observed by Palo Alto Networks this summer, hackers used new versions of Clayslide to deliver their malware. However, instead of pushing Helminth, the malicious spreadsheet delivered a variant of ISMDoor, a remote access trojan (RAT) previously used by a group tracked as Greenbug.
The activities of Greenbug were brought to light in early 2017 by Symantec, which believes the group may have helped the Iran-linked hackers who launched the Shamoon 2.0 attacks against Saudi Arabia last year.
The new ISMDoor variant, dubbed ISMAgent by Palo Alto Networks, is similar to the old malware as they both use DNS tunneling, but there are some significant differences. According to experts, ISMDoor accepts a longer but more rigid list of commands, while ISMAgent accepts more limited but flexible commands.
Researchers previously found links between the Shamoon attacks and an Iran-linked group tracked as Magic Hound (aka Cobalt Gypsy and Timberworm), and between Magic Hound and other Iranian actors named Rocket Kitten and Newscaster (aka Charming Kitten and NewsBeef).
One hacker group that is also believed to be based in Iran, which has yet to be linked to other actors, is CopyKittens. CopyKittens has been around since at least 2013, targeting government organizations, academic institutions, IT firms, and defense companies in Israel, Saudi Arabia, the U.S., Jordan, Germany and Turkey.
Unpatched Cisco Autonomic Networking Flaws Disclosed at Black Hat
27.7.2017 securityweek Vulnerebility
Cisco published advisories on Wednesday to inform users of several unpatched vulnerabilities affecting the Autonomic Networking feature of it IOS and IOS XE software. The flaws, some of which rated “high severity,” were disclosed this week by a researcher at the Black Hat security conference.
Omar Eissa, an analyst at Germany-based security firm ERNW, disclosed the weaknesses as part of a briefing titled “Network Automation is Not Your Safe Haven: Protocol Analysis and Vulnerabilities of Autonomic Network.”
One of the vulnerabilities rated by Cisco high severity, CVE-2017-6663, allows an unauthenticated attacker on the network to cause autonomic nodes to reload and generate a denial-of-service (DoS) condition by capturing packets and replaying them to reset the Autonomic Control Plane (ACP) channel of the affected system.
The researcher noted in his presentation at Black Hat that it takes roughly 15 minutes to crash a device by exploiting this vulnerability.
The second high severity flaw, classified as an information disclosure issue and tracked as CVE-2017-6665, allows an unauthenticated attacker to capture and view ACP packets that are sent in clear text instead of being encrypted. The root cause of these security holes is unknown, Cisco said.
A third vulnerability, rated medium severity, allows a remote, unauthenticated autonomic node to access the Autonomic Networking infrastructure of an impacted systems after the certificate for that node has been revoked.
The vulnerabilities affect Cisco IOS and IOS XE software if Autonomic Networking is enabled on the device. Patches have yet to be released for these weaknesses and Cisco says there are no workarounds. The networking giant is not aware of any attacks exploiting these vulnerabilities.
This is not the first time Eissa has disclosed Cisco Autonomic Networking flaws at a security conference. A few months ago, at an event in Germany called TROOPERS, he disclosed a couple of high severity DoS vulnerabilities. However, Cisco had patched those before the researcher’s disclosure.
Sweden Data Scandal Costs Two Ministers Their Jobs
27.7.2017 securityweek Incindent
Two Swedish ministers lost their jobs on Thursday over a huge leak of sensitive data that has rocked the fragile centre-left government.
But Prime Minister Stefan Lofven vowed he would be staying on despite speculation he could call a snap election.
Interior Minister Anders Ygeman, a political heavyweight previously seen as a likely future prime minister, has resigned, Lofven said at a press conference, adding that Infrastructure Minister Anna Johansson will also step down.
Ygeman reportedly knew about the leak from the national transport agency, which made the private data of millions of citizens accessible abroad, but failed to tell the prime minister.
The scandal has blown up in recent weeks after it emerged that an entire database on Swedish drivers' licences was made available to technicians in the Czech Republic and Romania, with media reporting that the identities of intelligence agents may have been jeopardised.
Lofven's Social Democrat-led minority government has been badly rattled by one of Sweden's largest data breaches in decades, and opposition parties had threatened the coalition with a vote of no confidence.
Some political commentators had expected Lofven to call an early election at Thursday's press conference -- but he insisted said he intends to serve his full term, which ends in 2018.
"I have no intention of plunging Sweden into a political crisis," he said, pointing to "formidable challenges" the country is facing including tensions in the Baltic region, Brexit as well as the government's plans for social and economic reforms.
"I looked at several alternatives, and I chose the best one for the country," Lofven said.
The data leak stems from the Swedish transport agency's hiring of IBM in 2015 to take over its IT operations.
IBM in turn used subcontractors in the Czech Republic and Romania -- making the sensitive information accessible by foreign technicians who did not have security clearance.
The Swedish military said information on its personnel, vehicles as well as defence and contingency planning could have been included in the leak, although the transport agency denied having a register on military vehicles and said there was no indication the data had been "spread in an improper way".
- Defence minister next? -
Swedish Defence Minister Peter Hultqvist kept his job in the reshuffle despite facing claims that, like the interior minister, he knew about the scandal but failed to tell the premier.
However, Hultqvist still faces the threat of being forced out in a censure motion launched by the opposition on Wednesday against all three ministers caught up in the scandal.
"There is no longer any confidence in the defence minister," Ebba Busch Thor, leader of the Christian Democrats, wrote on Twitter.
"The prime minister will not take responsibility, which is why we will hold him to account in parliament."
The far-right Sweden Democrats signalled they would support the censure motion, which would need a parliamentary majority to remove Hultqvist from office.
Maria Agren, head of the transport agency at the centre of the leak, quit in January for undisclosed reasons but has since confessed to violating data handling. She accepted a fine of 70,000 Swedish kronor (around 7,000 euros, $8,000).
Hultqvist and Ygeman reportedly found out about the leak last year, but the prime minister was only informed in January.
Johansson, who oversees the transport agency, said her former state secretary had known about the leak but kept the information hidden from her -- triggering heavy criticism among opposition parties who said she should have known what was happening.
FireEye Releases Free Malware Analysis Toolbox
27.7.2017 securityweek Virus
FireEye has released a piece of software that creates a fully customizable virtual machine (VM) containing all the tools and tweaks needed for malware analysis and other cybersercurity-related tasks.
FLARE VM – where FLARE stands for FireEye Labs Advanced Reverse Engineering – is a Windows-based security distribution inspired by Linux distros such as Kali and REMnux. It was developed by FireEye threat researcher Peter Kacherginsky in order to address the challenges associated with maintaining a custom VM.
It provides a platform that includes a comprehensive collection of security tools that can be used to conduct malware analysis, reverse engineering, incident response, forensic investigations and penetration testing. It includes disassemblers, debuggers, decompilers, static and dynamic analysis, exploitation, vulnerability assessment, and network analysis tools.
In order to install FLARE VM, users need a virtual machine with Windows 7 or a newer version of the operating system. From the VM, they need to visit a URL in Internet Explorer and the installation starts. The process takes 30-40 minutes, depending on the connection speed, and it involves several restarts of the system.
Once the installation has been completed, users are advised to make a snapshot of the VM to save its clean state and switch networking settings to Host-Only in order to prevent the analyzed malware samples from connecting to the local network or the Internet.
According to FireEye, users can easily customize their FLARE VM installation as it is built using the Chocolatey package management system. Users can choose tools from both the Chocolatey repository and FireEye’s FLARE repository, which is continually expanded.
Ensuring that the tools included in FLARE VM are up to date is also easy. Running the command “cup all” will update all the installed packages.
FireEye has made available usage instructions and source code on GitHub. A blog post published by the company also provides an example for how FLARE VM can be used to analyze a malware sample.
NanoCore RAT Author Pleads Guilty
27.7.2017 securityweek Virus
A Hot Springs, Arkansas man this week pleaded guilty to creating two malicious programs, including the NanoCore RAT (Remote Access Trojan).
Taylor Huddleston, 26, admitted to having developed, marketed, and distributed malicious programs that “were extremely popular with cybercriminals around the world,” an announcement from the Department of Justice (DoJ) reads.
One of the malicious programs Huddleston created and sold is the “NanoCore RAT,” malware designed to steal information from the victims’ computers and which infected tens of thousands of computers, according to the DoJ. In addition to being able to exfiltrate sensitive information such as passwords, emails, and instant messages, the threat could also be used to spy on victims via the webcams attached to their computers.
NanoCore RAT has been associated with various infection campaigns worldwide, including one targeting the finance departments of small and medium-sized businesses in the U.K., the U.S. and India. Last year, SentinelOne revealed how state-sponsored threat actors were using fileless tricks to deliver the RAT, while Symantec detailed how this threat and others were distributed via free Voice-over-IP (VoIP) service Discord.
The other malicious program Huddleston admitted to have developed is “Net Seal,” a licensing software used to distribute malware for co-conspirators. He used the malicious application to “assist Zachary Shames in the distribution of malware to 3,000 people that was in turn used to infect 16,000 computers,” DoJ reveals.
Huddleston created Net Seal in 2012 and packed it with protections meant to prevent the use of illicitly obtained copies of the application. In 2014, he build NanoCore, which he advertised as a remote desktop management utility, but which included all of the capabilities typically found in a RAT.
Initially, Huddleston argued that he wasn’t responsible for how cybercriminals used his applications, but changed the approach in the meantime. “In his guilty plea, Huddleston admitted that he intended his products to be used maliciously,” the DoJ announcement said.
Huddleston faces a maximum sentence of 10 years in prison. He is scheduled to be sentenced on December 8.
Critical Vulnerabilities Found in Nuke Plant Radiation Monitors
27.7.2017 securityweek Vulnerebility
Critical Vulnerabilities Found in Radiation Monitors Used in Nuclear Power Plants, Seaports and Airports
LAS VEGAS - BLACK HAT USA - Researchers have discovered multiple unpatched vulnerabilities in different radiation monitoring devices that could be leveraged by attackers to reduce personnel safety, delay detection of radiation leaks, or help international smuggling of radioactive material.
In a paper (PDF) delivered by Ruben Santamarta, principal security consultant at Seattle-based IOActive, at Black Hat Wednesday, it was disclosed that radiation monitors supplied by Ludlum, Mirion and Digi contain multiple vulnerabilities.
Patching will be difficult since these are design flaws rather than software bugs; and the vendors' early response to IOActive's discoveries was, in each case, to decline to work on patches. Since then, Digi has told IOActive that it is collaborating with Mirion to patch the critical vulnerabilities.
Vulnerabilities in different radiation monitoring devices Nevertheless, IOActive concludes, "we should acknowledge these issues are not currently patched, so increasing awareness of the possibility of such attacks will help to mitigate the risks." It is likely that the same flaws will be present in other vendors' radiation monitoring devices.
There are many kinds of radiation monitor used in many different environments. IOActive concentrated its research on portal monitors, used at airports and seaports; and area monitors, used at Nuclear Power Plants (NPPs). However, little effort was required for the portal monitors: "the initial analysis revealed a complete lack of security in these devices, so further testing wasn't necessary to identify significant vulnerabilities," notes the report.
In the Ludlum Model 53 personnel portal, IOActive found a backdoor password that granted the highest privilege. With this, malicious personnel could bypass authentication and take control of the device, preventing the triggering of proper alarms.
In the Ludlum Model 4525 gate monitor, IOActive discovered a complete lack of security in the communication between the gate and the controller Windows device. With these vulnerabilities, IOActive warns, "Malicious actors can perform a man-in-the-middle attack that alters the readings when the radioactive material they are interested in trafficking is detected. This would allow them to safely bypass these gate monitors while maintaining the compromised device in a working condition."
In fact, adequately resourced attackers could fine-tune their malware, says IOActive, to deploy "an advanced payload that hides specific isotopes from detectors, while providing the expected readings for others."
For its analysis of area monitors used at NPPs, IOActive concentrated on the Mirion WRM2 protocol used in numerous devices. It found that it could insert false information into the communications. There are two 'worst-case' scenarios.
In the first, under normal working conditions, attackers could simulate a radiation leak by inserting a dataset of falsified readings. Although this on its own is unlikely to cause a reactor shutdown (because of the need for human intervention), it could lead to an evacuation of the site.
In the second, in a real accident situation, the course of the evacuation could be manipulated: "attackers may falsify these readings to trick authorities into giving the wrong directions for the evacuation, thus increasing the damage and/or potential casualties."
"Failed evacuations, concealed persistent attacks and stealth man-in-the-middle attacks are just a few of the risks I flagged in my research," said Santamarta. "Being able to properly and accurately detect radiation levels, is imperative in preventing harm to those at or near nuclear plants and other critical facilities, as well as for ensuring radioactive materials are not smuggled across borders."
Google experts blocked a new targeted malware family, the Lipizzan spyware
27.7.2017 securityaffairs Virus
Google has identified a new strain of Android malware, the Lipizzan spyware, that could be used as a powerful surveillance tool.
Malware researchers at Google have spotted a new strain of Android spyware dubbed Lipizzan that could exfiltrate any kind of data from mobile devices and use them as surveillance tools.
The Lipizzan spyware is a project developed by Israeli startup Equus Technologies, the company description on LinkedIn reads:
“Equus Technologies is a privately held company specialising in the development of tailor made innovative solutions for law enforcement, intelligence agencies, and national security organisations.”
The experts have found the Lipizzan spyware sample in the wild while investigating other threats, the IT giant used also the recently presented Google Play Protect technology.
“In the course of our Chrysaor investigation, we used similar techniques to discover a new and unrelated family of spyware called Lipizzan. Lipizzan’s code contains references to a cyber arms company, Equus Technologies.” states the analysis published by Google.
“Lipizzan is a multi-stage spyware product capable of monitoring and exfiltrating a user’s email, SMS messages, location, voice calls, and media.”
Google researchers have found at least 20 apps in Play Store which infected fewer than 100 Android smartphones in total, the company classified the infections as targeted attacks.
“We have found 20 Lipizzan apps distributed in a targeted fashion to fewer than 100 devices in total and have blocked the developers and apps from the Android ecosystem. Google Play Protect has notified all affected devices and removed the Lipizzan apps.” states Google.
Google removed the infected apps from the stores, while Google Play Protect has notified all affected victims.
The Lipizzan spyware is a sophisticated multi-stage spyware that could be used by attackers to gain full access to a target Android device in two phases.
In the first stage, attackers distribute Lipizzan by concealing it as a legitimate app such “Cleaner” through the Android app stores, including the official Play store.
Once the victims have installed the malicious code, it would download and load a second “license verification” stage.
The code verifies that certain conditions are matched then it will root the device with known exploits and begin to exfiltrate device data to a Command & Control server.
Experts explained that the Lipizzan spyware is able to monitor and steal victim’s email, SMS messages, screenshots, photos, voice calls, contacts, application-specific data, location and device information.
The spyware is also able to collect data from specific apps, including WhatsApp, Snapchat, Viber, Telegram, Facebook Messenger, LinkedIn, Gmail, Skype, Hangouts, and KakaoTalk.
Experts found critical flaws in Diebold Opteva ATM that allow to vend notes from the machine
27.7.2017 securityaffairs Vulnerebility
Experts at the US firm IOActive have discovered a critical physical and authentication bypass vulnerability in the Diebold Opteva ATM.
The researchers have found two vulnerabilities in the Diebold Opteva ATM machines with the AFD platform that could be chained to allow an unauthorized user to vend notes from the device.
“IOActive has discovered two vulnerabilities in Opteva ATMs with the AFD platform that, when combined, may allow an unauthorized user to vend notes from the device.” reads the advisory.

The Diebold Opteva line of ATMs with the AFD platform is composed of an upper cabinet for the operating system and a lower cabinet for the safe, each part requests its own authentication requirements.
Chaining the vulnerabilities allows the attacker to bypass both authentication mechanisms and take the control of the Diebold Opteva ATM.
In the attack scenario presented IOActive, the researchers physical accessed to the internal computer by inserting a metal rod through a speaker hole on the front of the ATM, lifting a metal locking bar and gaining access to the upper cabinet of the Diebold Opteva ATM that contains the computer. Once accessed to the computer, the researchers removed the USB connection from the Windows host and gained a direct line of communication to the AFD controller for the safe.
At this point, the hackers triggered the second flaw to get to the money.
The experts made a reverse engineering of the AFD’s protocol and firmware, they were able to gain access to the content of the safe without authenticating.
“Using the USB that connects the AFD to the computer in the upper cabinet, the team was able to initiate two-way communication. This would normally require a shared encryption key and a device identifier; however, the team was able to complete the authentication protocol unencrypted and set up communications without properly authenticating. This allowed the team to act as an authenticated user and gain access to the contents of the safe.” continues the analysis. “The protocol does not require any device specific knowledge to carry out the attack. This would imply that an attacker with access to one device could reverse engineer enough of the controller protocol to effectively bypass authentication and vend notes from any other device that uses an AFD as long as the vulnerability remains unpatched.”
IOActive reported the issue to Diebold in February 2016, only one year later, in May 2017 Diebold responds, “[your]..system is very old (2008/2009 vintage) and is unpatched;”
IOActive asked if retesting a recent supported version would be possible, but without receiving a reply.
Finally, on July 26, 2017, IOActive opted for the public disclosure.
Unfortunately, it is still unclear whether the ATMs have been patched, nor whether any newer firmware versions are still vulnerable.
DEF CON Talk Will Expose The Latest SMB Vulnerability SMBLoris
27.7.2017 securityaffairs Vulnerebility
Security researchers at RiskSense have identified a 20-year-old Windows SMB vulnerability they are calling SMBloris, a DEF CON Talk Will Expose it.
Server Message Block (SMB) has been a foundational piece of Microsoft Windows’ networking all the way back to the LAN Manager days, facilitating “shared access to files, printers and serial ports.” It is so common that a free software implementation called Samba was developed long ago to allow UNIX-like systems to share network resources with Windows systems. It is a rare company that doesn’t have SMB packets running on the network.
Over the years SMB has gone through many versions to add features and improve performance. It has also had its share of vulnerabilities on all of the platforms it has been implemented, with many, many patches along the way. No matter how many times it is patched or upgraded, it seems that there is always another vulnerability to be uncovered. Many times a vulnerability that was patched in an earlier version is rediscovered years later. In 2015, security researchers at Cylance discovered a new attack vector for an 18-year-old SMB vulnerability. The new method dubbed Redirect to SMB, “impacted products from Microsoft, Apple, Abode, Symantec, Box, Oracle, and more.” In 2014, the Guardians of Peace used an SMB worm exploit to hack Sony Pictures. And an SMB exploit called ETERNALBLUE was part of the cache of NSA tools released by Shadow Brokers in 2017. This exploit was eventually wrapped up and released on the World as the initial exploit point for WannaCry ransomware. Many of these vulnerabilities existed in the SMB code for many years until they were publicly exploited.
In a seeming case of deja vu, security researchers at RiskSense have identified a 20-year-old Windows SMB vulnerability they are calling SMBloris (a nod to the Slowloris DoS attack.)
SMBLoris Windows RCE vulnerability
The exploit is a Denial of Service (DoS) attack affecting “every version of the SMB protocol and every Windows version dating back to Windows 2000.” Like most DoS attacks, the target system is overwhelmed by multiple service requests rendering it unavailable. Most modern systems require coordination of a massive number of attacking systems to overwhelm the target, referred to as a Distributed Denial of Service (DDoS) attack. However, the flaws discovered in the Windows SMB service are easily exploited by a single, low-powered computer.
According to researcher Sean Dillon, “While working on EternalBlue, we observed a pattern in the way memory allocations were done on the non-paged pool of the Windows kernel. The non-paged pool is memory that has to be reserved in physical RAM; it can’t be swapped out. That’s the most precious pool of memory on the system. We figured out how to exhaust that pool, even on servers that are very beefy, even 128 GB of memory. We can take that down with a Raspberry Pi.”
Dillon and his research partner Zach Harding followed a responsible disclosure process and privately notified the SMBloris flaw to Microsoft of the vulnerability in early June. Mid June Microsoft replied with their assessment that the vulnerability presented only a “moderate risk”, and would not be moved into the security branch which means it is unlikely to ever be fixed.
Speaking to Threatpost, a Microsoft spokesperson did suggest, “For enterprise customers who may be concerned, we recommend they consider blocking access from the Internet to SMBv1.”
Given the long history of vulnerabilities in SMB, I hope that everyone is already blocking SMB at their firewalls! Given rumors that a single, low-powered computer is able to exploit the SMB vulnerability for a successful DoS attack, it is not unreasonable to anticipate an attack launched against internal servers from internal clients. Perhaps a properly crafted email attachment that is executed on a desktop?
Dillon and Harding are expected to release full details of the vulnerability at a DEF CON talk on Saturday. With more details, you will be able to assess for yourself whether the risk is “moderate” or something you need to encourage Microsoft to address.
Microsoft Launches Windows Bug Bounty Program
27.7.2017 securityweek Security
Microsoft announced on Wednesday the launch of a Windows bug bounty program with payouts ranging between $500 and $250,000.
Microsoft has been running several bug bounty programs, but none of them have covered all features of Windows. As part of the new program, the company is prepared to pay out a reward for security holes in any feature of Windows Insider Preview and various focus areas that include the Hyper-V hypervisor, exploit mitigation bypasses, the Windows Defender Application Guard, and the Edge web browser.
“Any critical or important class remote code execution, elevation of privilege, or design flaws that compromises a customer’s privacy and security will receive a bounty,” Microsoft said.
Bounty hunters can earn up to $15,000 for remote code execution, up to $10,000 for privilege escalation, and up to $5,000 for information disclosure, remote denial-of-service (DoS), and tampering or spoofing vulnerabilities found in Windows Insider Preview, the slow ring.
As for the focus areas, the newly added Windows Defender Application Guard (WDAG) category can earn researchers up to $30,000 for a high quality report and functioning exploit demonstrating a vulnerability that can be leveraged to escape the WDAG container to the host.
The highest payout is for vulnerabilities in Hyper-V running on Windows 10, Windows Server 2012 or Windows Insider Preview. Hackers can receive up to $250,000 from Microsoft for a high quality report and exploit demonstrating a remote code execution flaw that allows a guest VM to compromise the hypervisor, a guest to host escape, or a guest to guest escape.
In the other focus areas, hackers can earn up to $200,000 if they find a way to bypass exploit mitigations, and a maximum of $15,000 for remote code execution flaws in Edge.
Researchers who discover vulnerabilities already found internally by Microsoft employees will still get a reward if they are the first to submit a report. They are eligible to receive up to 10 percent of the maximum bounty amount.
Hacked Smart Fish Tank Exfiltrated Data to 'Rare External Destination'
27.7.2017 securityweek Hacking
Insiders attached two Raspberry Pi devices to a corporate healthcare network to help divert staff to a phishing website to phish staff credentials. An internet-connected smart fish tank transferred 10GB of data to an adversary's server in Finland.
These are two of nine real-life examples presented in the Darktrace Global Threat Report 2017 (PDF). Darktrace was founded in Cambridge UK in 2013, combining mathematicians and machine learning (ML) experts from the university with intelligence experts from MI5 and GCHQ. The firm's approach is to mimic the human body's immune system in cyber.
For example, from the company's website, "Darktrace Antigena replicates this function of the human immune system, by creating 'digital antibodies' in response to in-progress threats." The purpose is to slow the rate of infection enough to give security teams an adequate response window before irreparable damage is done.
The seven additional cases described in the report include a ransomware infection; IoT devices co-opted into a DoS attack; a banking trojan; a former employee's compromised credentials; discovery of a vulnerability in a third-party cloud storage supplier; discovery of data theft by a former employee; and an attacker's attempt to use a corporate network in a bitcoin mining operation.
These incidents were detected by Darktrace over the last year. Each of the descriptions includes a summary of the incident, the anomalous activity detected by Darktrace, and the action taken to defend the network.
A weakness in the report is that it is sparse on details. A Darktrace spokesman explained that this is due to customer usage. How each customer uses its technology is different and Darktrace itself isn't privy to that information. It examines network behavior, but not traffic content. The result is that the information provided gives examples of incidents detected by Darktrace, but little technical detail on the incident itself.
For example, in one case Darktrace quickly detected the attachment of two Raspberry Pis on the internal network that were redirecting users to a look-alike external website. "The redirected users were being presented with a fake login page and 'security survey' where they were required to enter their usernames and passwords," says the report. Darktrace detected this in real-time because it detects deviations from normal network behavior -- and the sudden appearance and operation of two Raspberry Pis was abnormal.
"The Raspberry Pis quickly disappeared from the network," it continued. But what it doesn't say is whether sufficient forensic data was gathered to be able to determine the insider or insiders responsible for the act -- in other words the report does not say whether the threat was eliminated (and the insider terminated or prosecuted) or whether this particular malicious insider threat continues.
"Darktrace is regularly used for forensic analysis," Justin Fier, director for cyber intelligence & analysis at Darktrace, told SecurityWeek. "The organization may have used it to help apprehend the insiders but we cannot confirm."
Fier also explained the lack of detail in the smart fish tank incident. "A North American casino," says the report, "recently installed a high-tech fish tank as a new attraction, with advanced sensors that automatically regulate temperature, salinity, and feeding schedules." For security, the tank was configured to communicate its data via a VPN.
Nevertheless, Darktrace quickly detected "anomalous data transfers from the fish tank to a rare external destination." In fact, 10GB of data was transferred outside of the network, via the fish tank. What isn't specified, however, is what the data comprised, where on the network it came from, how it was moved to the fish tank for exfiltration, nor whether the malware methodology used to acquire the data before exfiltration was also discovered.
Fier explained, "Darktrace doesn't look at the content of files, so we don't know [what data was exfiltrated], though the communications took place on a protocol that is normally associated with audio and video. The attacker somehow gained access to the corporate network, and then either brute-forced or used stolen credentials to log onto the fish tank VPN."
A third example involves corporate IoT devices being co-opted into a DDoS botnet. "Designers at an architectural firm were using smart drawing pads to enable them to quickly send schematics and drawings to clients and other staff members," says the report. However, the default logon credentials were not changed, leaving the devices vulnerable.
Darktrace soon detected 'highly unusual volumes of data being sent outside of the network.' "This was identified as a denial-of-service attack. The pads were responding to a specific type of request for information commonly used to disable the target's systems by flooding it with superfluous traffic," says the report. It gives no information on how the DDoS attack operated, who was the target, nor whether the devices had become part of a known botnet.
Darktrace was unable to give SecurityWeek any further details on the variant of botnet or its targets.
The report then states, "Involvement in the attack could have legal implications for the firm had their infrastructure been responsible for damaging another network." This is a stretch. While there may be a technical possibility, there is almost zero likelihood of a successful action against a company with infected devices used in a DDoS attack -- the sheer difficulty in determining which devices out of potentially hundreds of thousands caused precisely what damage to which targets is simply too complex.
Challenged on this, Fier replied, "We don't know of any instances where such involvement in DDoS attacks has led to a company being held liable."
There is value in this report, as itprovides genuine examples of the originality and inventiveness of attackers, and demonstrates that Darktrace is able to detect them. However, describing it as a 'Global Threat Report' is ambitious. The subtitle, 'Selected Case Studies', would be more realistic and accurate.
Earlier this month, Darktrace announced that it had raised $75 million in a Series financing round.
Code Execution Vulnerabilities Patched in FreeRDP
27.7.2017 securityweek Vulnerebility
Researchers at Cisco’s Talos security intelligence and research group have discovered several potentially serious vulnerabilities in FreeRDP. The tool’s developers patched the flaws on Monday with the release of an update.
FreeRDP is an open-source implementation of Microsoft’s Remote Desktop Protocol (RDP). The software, which allows users to remotely connect to other devices, is included in several Linux distributions and is available for both Windows and Mac systems. The FreeRDP library is also used by many commercial applications.
While FreeRDP is typically used for legitimate purposes, it has also been leveraged by cybercriminals, including the notorious group known as Carbanak and Anunak.
Talos researchers discovered that FreeRDP 2.0.0-beta1 on Windows, Linux and Mac OS X is affected by six vulnerabilities that can be exploited for remote code execution and denial-of-service (DoS) attacks.
The RCE flaws, both tracked as CVE-2017-2834 and assigned a severity rating of “high,” exist due to the use of untrusted data in handling the license authentication and reception of an RDP packet from the server.
“The license message sent by the server contains a length field, which is not correctly verified by FreeRDP. For internal purposes, the library decreases this value by 4, if the server is sent a value inferior to 3, this will result in a negative value and the writing of packet contents outside of the allocated buffer in memory. This vulnerability can allow the execution of arbitrary code on the FreeRDP client side,” Talos said in its advisory.
The DoS vulnerabilities, which allow an attacker to crash the client, exist due to the way the client handles proprietary server certificates, security data, and license challenge packets.
The security holes can be exploited by sending specially crafted packets, either via a man-in-the-middle (MitM) attack or by compromising the server.
Talos has made available technical details and developed proof-of-concept (PoC) exploits for the vulnerabilities.
The flaws were patched with the release of FreeRDP 2.0.0-rc0 on Monday. FreeRDP developers have also published an advisory pinpointing the changes made to the code.
NoMoreRansom Says 28,000 Victim Devices Decrypted
27.7.2017 securityweek Ransomware
This week marks the one-year anniversary of the launch of the NoMoreRansom project. The project comprises an alliance of law enforcement agencies and private industry, currently totaling 109 partners. Its purpose is to gather all known ransomware decryptors in one location (the NoMoreRansom website) so that ransomware victims can at least attempt to decrypt encrypted files.
The project was launched on July 25, 2016 by the Dutch National Police, Europol, McAfee and Kaspersky Lab and now holds access to 54 decryption tools provided by 9 partners and covering 104 ransomware families. The site itself is available in 26 languages.
Since its inauguration it has helped decrypt 28,000 ransomware victim devices -- but, warns Europol, the threat is still escalating. "Ransomware has soared since 2012, with criminals lured by the promise of profit and ease of implementation. The threat continues to evolve, becoming stealthier and more destructive, increasingly targeting businesses more than individuals because the potential returns are much higher."
Europol notes that WannaCry alone claimed more than 300,000 business victims across 150 countries in its first few days; and that some organizations are still struggling to recover from the NotPetya attacks of June 27. It adds, "The total number of users who encountered ransomware between April 2016 and March 2017 rose by 11.4% compared to the previous 12 months, from 2,315,931 to 2,581,026 users around the world.
These figures demonstrate that NoMoreRansom is no solution to ransomware. It has benefited 28,000 users (and this should not be dismissed); but that figure is less than one-ninetieth of the total number of victims.
Europol recognizes this. "Prevention is no doubt better than cure. Internet users need to avoid becoming a victim in the first place. Many up to date prevention tips are available on www.nomoreransom.org." Its advice remains, "If you do become a victim, it is important not to pay the ransom and report your infection to the police."
It is equally clear, however, that many people do pay the ransom. At Black Hat this week, Google, Chainalysis, UC San Diego, and the NYU Tandon School of Engineering researchers presented details of their own investigation into ransomware payments. They have been able to track payments through the bitcoin blockchains from distribution sites to the cash-out points. It is hoped that law enforcement will be able to pick up the trail from here and use traditional money-tracking methods to locate the criminals.
The team tracked 34 separate ransomware families over the last two years, concluding that ransomware victims have paid out $25 million to the criminals; and that Locky alone generated $7 million. Cerber generated $6.9 million and CryptXXX generated $1.9 million.
With such figures, it is understandable that the usual 'official' advice from both law enforcement and security researchers is, "Don't pay the ransom: there is no guarantee that the criminals will decrypt your files, you paint a target on your back for further attacks, and you fund the whole criminal ecosystem."
Google Takes Second Swing at OAuth Worm
27.7.2017 securityweek Phishing
Mitigations put in place by Google in May 2017 to help block phishing attacks such as the recent OAuth worm weren’t enough to completely mitigate the issue, as Google's platform still allowed malicious OAuth clients to be submitted under deceiving names, Proofpoint security researchers say.
The OAuth worm was possible because malicious developers could create seemingly legitimate apps and trick users into granting access to email and cloud service accounts. Lack of validation allowed an attacker to impersonate Google Docs and impacted more than one million G Suite users.
The attack, however, prompted Google to tighten OAuth rules and introduce validations around the choice of name for new apps. The company updated policies and announced enforcement on OAuth applications in an attempt to prevent similar attacks from happening.
Proofpoint now explains that while Google was able to respond to the attack fast, it didn’t address the issue properly, and malicious developers were still able “to submit any name for new OAuth clients — including scripts, third-party apps and extensions.” The security company discovered that Google’s validations could be bypassed to serve “a Google OAuth client with a name of its choice from script.google[.]com.”
The issue, Proofpoint says, was that Google resolved the vulnerability that made the May attack possible, but didn’t address the root of the technique. As a result, it was still possible for users “to serve their own content with a URL at ‘script.google.com’, itself at least in part a factor of the openness of the OAuth clients space.”
Because the OAuth clients space historically had no checks on the actions developers could perform, it allowed the creation of any application and the request of any permission considered necessary. App developers were also allowed to send their applications to anyone else and serve them with a URL at script.google.com in the process.
In addition to alerting the public on the risk these applications pose, the May 2017 attack could also be mitigated because it included an identifiable URL. This, however, didn’t eliminate the exploit itself, allowing future versions to avoid the mitigations by not including a return URL or by using a URL that can’t be distinguished from a valid Google script URL.
"[The] OAuth worm employed a rare email permission often used only by select email clients (e.g. Outlook) in combination with another permission. That specific combination was unique and not used by any other OAuth client Proofpoint has previously examined,” the security researchers say.
Effective defense would build on the analysis of the app to determine permissions, app creator, recipient (or victim), app name, context, and other features. By performing such analysis, Proofpoint discovered another flaw within Google Apps and says that an attacker could exploit it to carry a similar attack as the OAuth worm, despite the mitigations put in place by Google.
“In this case, our researchers were able to create an app called ‘Google Docs’ or ‘Google Drive’, bypassing some of the protections Google introduced following the May 2017 attack. Using this technique, an attacker can then launch a similar phishing campaign, but this time with links that are less suspicious -- and more potentially enticing -- than possible in the May campaign,” Proofpoint says.
The security company reported the issue to Google, which resolved it within a day. The Internet giant released an update to alert users on new web applications and Apps Scripts that require verification. Previously, an ‘error’ page was displayed for unverified web apps. In the following months, the verification process will be expanded to existing applications as well.
Critical Vulnerability Found in Diebold ATM Machine
27.7.2017 securityweek Vulnerebility
Seattle-based IOActive has issued a critical security advisory detailing a physical and authentication bypass in the Diebold Opteva ATM.
"IOActive has discovered two vulnerabilities in Opteva ATMs with the AFD platform that, when combined," warns the advisory "may allow an unauthorized user to vend notes from the device."
The combined use of the vulnerabilities is necessary because of ATMs' practice of separating the safe from the operating system. Diebold's Opteva line of ATMs with the AFD platform contain an upper cabinet for the operating system and a lower cabinet for the safe, each with its own authentication requirements.
Opteva ATMThe researchers first gained physical access to the internal computer by inserting a metal rod through a speaker hole in the ATM, lifting a metal locking bar and gaining access to the upper cabinet of the ATM containing the computer. With access to the computer, they were able to get a direct line to the AFD controller for the safe. But they still needed a second vulnerability to get to the money.
For this, IOActive reverse engineered the AFD's protocol and firmware. From here, the team was able to complete the authentication protocol unencrypted and set up communications without properly authenticating. In short, the two vulnerabilities allowed the team to act as an unauthenticated user and gain access to the content of the safe.
Since the process does not require any device specific knowledge, IOActive concludes that "an attacker with access to one device could reverse engineer enough of the controller protocol to effectively bypass authentication and vend notes from any other device that uses an AFD as long as the vulnerability remains unpatched."
The problem here, and one of the most disturbing aspects of the advisory, is that IOActive doesn't know whether it has been patched. It first reported the issue to Diebold in February 2016; but it did not get a secure transit from Diebold to allow it to disclose the issue until January 2017.
In February 2017, one year after the first notification to Diebold, Diebold requested and received tracelogs from IOActive. IOActive tried to follow-up, and eventually was told, "[your]... system is very old (2008/2009 vintage) and is unpatched." Its offer to retest current firmware was ignored, as were further attempts to follow-up with Diebold.
Finally, on July 26, 2017, more than 18 months after initially contacting the vendor, IOActive decided to go public. At this stage, it is unknown whether the devices have been patched, nor whether any newer versions of the firmware are still vulnerable.
The advisory from IOActive is available here.
UniCredit bank breach – Data of 400,000 loan applicants exposed due to the hack of a partner
27.7.2017 securityaffairs Incindent
UniCredit bank breach – Data of 400,000 loan applicants exposed due to the hack of a partner. Italian media outlets downplay the risk, is it correct?
The Italian bank UniCredit admitted a series of security breaches occurred in the last year, personal data of 400,000 loan applicants have been exposed.
The Italian bank confirmed that hackers compromised the systems of an unnamed third-party provider for exposing Italian customer data. – including International Bank Account Numbers (IBANs).
“UniCredit today announced it has been the victim of a security breach in Italy due to unauthorised access through an Italian third party provider to Italian customer data related to personal loans only.” reads the statement published by Unicredit.
“A first breach seems to have occurred in September and October 2016 and a second breach which has just been identified in June and July 2017. Data of approximately 400,000 customers in Italy is assumed to have been impacted during these two periods. No data, such as passwords allowing access to customer accounts or allowing for unauthorised transactions, has been affected, whilst some other personal data and IBAN numbers might have been accessed.”
The financial institution confirmed that a first security breach occurred in late 2016, between September and October, while the second violation was detected between June and July 2017.
Data of approximately 400,000 Italian customers might have been exposed, according to Unicredit it doesn’t include financial data or passwords.
The company confirmed to have discovered and fixed the breach, an investigation is still ongoing.

Italy’s largest bank UniCredit is pictured in downtown Milan September 12, 2013. REUTERS/Stefano Rellandini ( ITALY – Tags: BUSINESS) – RTX13ISW
UniCredit is one of the major Italian banks, as part of Transform 2019, the bank is investing 2.3 billion euro in upgrading and strengthening its IT systems.
According to UniCredit, the breach at Italy’s biggest lender was detected 10 months after the initial compromise.
As you know I’m Italian, and I can tell you that the first reaction of the Italian media outlets was to say that there is no risk for the Unicredit customers because login credentials were not exposed.
This is not correct in my humble opinion and spread such kind of false sense of security is very dangerous.
Even if crooks cannot use stolen data to access Unicredit customer accounts, users must be informed of frauds that can be conducted by cyber criminals to deceive them.
It is easy to predict a spike in spear phishing attacks against Unicredit customers, and information stolen by hackers could make malicious messages hard to detect to common people, especially when the media outlets ensured them by saying that there is no risk.
Spear phishing campaigns could also allow crooks to bypass security measures like two-factor authentication systems. Let’s think of a phishing message including a link to a clone of the legitimate bank website. The bogus website could trick victims into providing the login credentials and also the 2FA code, then the attacker can impersonate the victim and make transactions on his behalf.
There is also the concrete risk that crooks will offer stolen data on black marketplaces allowing hackers to use them in many fraud scheme.
Even if stolen data doesn’t include email addresses, it is quite easy for hackers to use retrieve them from data dumps from other data breaches once the name of a bank customer is exposed.
Another disconcerting aspect of the UniCredit bank breach is the fact that the attack started several months ago and was disclosed only now?
This means that companies face severe difficulties in detecting fraudulent activities and raises the debate on the level of security for the entire supply chain. Once again, hackers targeted a subcontractor or a partner to violate the security of a biggest organization.
Let me close suggesting Unicredit users stay vigilant on their bank accounts, reporting any suspicious activity. Be careful to any kind of unsolicited message from the bank.
Chinese Police dismantled the behind the Fireball adware campaign that infected more than 250 Million PCs
27.7.2017 securityaffairs Virus
Chinese authorities arrested eleven members of the gang behind the Fireball adware campaign that infected more than 250 Million PCs.
Chinese police have identified and arrested individuals suspected to be the operators behind the massive adware campaign that infected more than 250 Million computers across the world earlier this year.
In June, researchers at security firm Check Point discovered the massive campaign spreading the Fireball malware. The malicious code was infecting both Windows and Mac OS systems, it can be used by attackers to gain full controls of the victim’s web browsers, to spy on the victims and exfiltrate user data.
The adware is disguised as a legitimate software and leverages browser plug-ins to boost its own advertisements.
Fireball malware
The researchers associated the campaign with the operation of the Chinese firm Rafotech that is a company that officially offers digital marketing and game apps to 300 million customers.
Chinese media outlets reported eleven Rafotech employees arrested by local police, including executives. It seems that the authorities arrested the suspects in June shortly after the publication of the report.
The Chongqing Morning News confirmed that the president, the technical director, and an operations director were arrested by the Chinese Police.
According to the state-owned outlet “Sixth Tone,” the click-fraud netted 80 million yuan, nearly US$12 million.
The Beijing Municipal Public Security Bureau Haidian Branch Network Security Brigade was informed by someone working under the pseudonym Zhang Ming, then the authorities monitored the Fireball campaign tracking its operators.
The individuals have allegedly “admitted the facts,” they were responsible for the campaign that launched around 2015 when the Rafotech setup the advertising fraud.
According to Beijing Youth Daily, the Fireball adware did not infect Chinese users to avoid being investigated by local authorities.
To check the presence of the malware on your systems open your web browser and try to reply the following questions:
Did you set your homepage?
Are you able to modify your browser’s homepage?
Are you familiar with your default search engine and can modify that as well?
Do you remember installing all of your browser extensions?
To uninstall the adware just remove the respective application from the machine and reset to default settings for your browser.
North Korea's Elite More Connected Than Previously Thought
26.7.2017 securityweek BigBrothers
Telecommunications capability in North Korea is three-tiered. The vast majority of people have neither internet nor North Korean intranet connectivity -- they simply have mobile telephony voice, text and picture/video messaging within the domestic provider, Koryolink.
A small group of others, including university students, scientists and some government officials, can access the state-run North Korean intranet, Kwangmyong, that links libraries, universities and government departments and comprises a limited number of domestic websites.
A much smaller group from the ruling elite does, however, have full access to the internet. From April 1 through July 6, 2017, Recorded Future analyzed internet traffic from this small group of officials, and concluded that the standard view of North Korea is not entirely accurate: its leadership at least is not isolated from the rest of the world.
North Korea FlagIn a report and analysis conducted in partnership with Team Cymru and published today, Recorded Future notes that North Korean leadership's internet activity is little different to the rest of the world's internet activity: "North Koreans spend much of their time online checking social media accounts, searching the web, and browsing Amazon and Alibaba," notes the report. "Facebook is the most widely used social networking site for North Koreans, despite reports that it, Twitter, YouTube, and a number of others were blocked by North Korean censors in April 2016."
The researchers looked for any proof of the hypothesis that there may be a correlation between North Korean internet activity and North Korean missile tests; but could find none. While noting that the research data was too small to be conclusive, the report says, "if there is a correlation between North Korean activity and missile tests, it is not telegraphed by leadership and ruling elite internet behavior."
What is clear, however, is that there is virtually nil malicious cyber activity directly from the North Korean mainland, and that "most state-sponsored activity is perpetrated from abroad." While this has some advantages, it also demonstrates an operational weakness that Recorded Future suggests could be exploited to apply asymmetric pressure on the Kim regime. By operating outside of national boundaries state actors should, in theory, be more easily detected and held accountable for their actions.
Most of the extra-territorial malicious activity is likely to come from the countries that have a significant North Korean presence: India, Malaysia, New Zealand, Nepal, Kenya, Mozambique, and Indonesia. China is excluded from this because of the unique nature of the North Korean/China relationship and the lower likelihood of direct cooperation with the West -- even though 10% of all North Korean cyber activity is with China.
This figure, however, is dwarfed by that of India. "Nearly one-fifth [20%] of all activity observed during this time period involved India," says the report. This supports reports of an increasingly close diplomatic and trade relationship between North Korea and India.
With little malicious activity coming from the North Korean mainland, the report is unable to draw conclusions about the associated cyber threat. Nevertheless, it says, "there was a smaller, but significant, amount of activity that was highly suspect. One instance was the start of Bitcoin mining by users in North Korea on May 17."
The temporal relationship to WannaCry is clear. "It began," says Recorded Future, "very soon after the May WannaCry ransomware attacks, which the NSA has attributed to North Korea’s intelligence service, the Reconnaissance General Bureau (RGB), as an attempt to raise funds for the Kim regime. By this point (May 17) actors within the government would have realized that moving the bitcoin from the three WannaCry ransom accounts would be easy to track and ill-advised if they wished to retain deniability for the attack."
The implication is that bitcoin mining was chosen to replace the missing funds from the WannaCry ransomware -- however, it is also worth considering this in conjunction with Joe Carson's consideration of WannaCry as a bitcoin manipulation method.
"Team Cymru’s intelligence and Recorded Future’s analysis have revealed two separate realities," concludes the report. The first is that attempts to completely isolate North Korea simply have not worked. The second, however, is more positive: "new tools that do not focus on Pyongyang and territorial North Korea are needed to achieve a lasting negative impact on the current Kim regime." This could be achieved partnering with the countries that currently have internet activity with North Korea, such as India, Malaysia, Indonesia, and New Zealand.
Meanwhile, it says, "We continue to recommend that financial services firms and those supporting U.S. and South Korean military THAAD [Terminal High Altitude Area Defense] deployment as well as on-peninsula operations maintain the highest vigilance and awareness of the heightened threat environment to their networks and operations on the Korean peninsula."
Hacker Steals $8.4 Million in Ethereum from Veritaseum
26.7.2017 securityweek Incindent
An unknown hacker stole around 37,000 VERI tokens from Veritaseum peer-to-peer platform and sold them for around $8.4 million in Ethereum during the company’s ICO (Initial Coin Offering).
Veritaseum's founder and CEO Reggie Middleton had posted details on the hack on the BitcoinTalk forums, where he also revealed that the compromise came through a company Veritaseum was working with.
“We were hacked, possibly by a group. The hack seemed to be very sophisticated, but there is at least one corporate partner that may have dropped the ball and be liable,” he noted in one post. “A company that we use was compromised, the vulnerability was closed, and we are investigating whether we should move against that company or not,” he mentioned in another.
Apparently, the hacker was able to steal the VERI tokens during the ICO and took advantage of their high demand to sell them immediately. The company had issued 100 million tokens, meaning that the stolen amount, 37,000, represented only around 00.07% of the total. While “the amount stolen was miniscule,” Middleton said, “the dollar amount was quite material."
“The hacker(s) made away with $8.4M worth of tokens, and dumped all of them within a few hours into a heavy cacophony of demand. This is without the public knowing anything about our last traction,” Middleton revealed.
Veritaseum's founder pointed out that, because the tokens were stolen from the company, no user was affected. The also noted that the company doesn’t consider it necessary to buy the tokens back and that they won’t fork VERI either, although they had the option to.
What Middleton didn’t reveal was who the corporate partner supposedly involved in the heist was. He did say, however, that the company will “let the lawyers sort that out, if it goes that far.”
The $8.4 million the hacker sold the VERI tokens for ended up in two Ethereum wallets that have been already emptied.
This is the latest in a series of several high-profile hacking incidents involving the crypto-currency, starting with a breach at the Bithumb crypto-currency exchange. Last week, $7 million worth of Ethereum was stolen from CoinDash during the company's ICO, along with $30 million worth of crypto-currency from multi-sig wallets created with Ethereum Parity clients 1.5.
New Windows Backdoor Linked to SambaCry Linux Malware
26.7.2017 securityweek Virus
The cybercriminals who had recently delivered a cryptocurrency miner to Linux servers by exploiting the Samba vulnerability known as EternalRed and SambaCry are believed to have developed a backdoor designed for Windows systems.
The new malware, detected by Kaspersky Lab products as Backdoor.Win32.CowerSnail, uses the same command and control (C&C) server as the Linux malware, namely cl.ezreal.space:20480.
CowerSnail was created using Qt, a cross-platform development framework. Experts believe its authors may have leveraged Qt in order to directly transfer Unix code instead of having to learn using the Windows API. On the other hand, while it does make it easier to transfer code between platforms, Qt significantly increases the size of the resulting file.
Once it infects the system, the malware escalates the priority of its process and starts communicating with its C&C server through the IRC protocol.
CowerSnail can collect information about the compromised machine, receive updates, execute commands, install or uninstall itself as a service, and receive updates.
After it harvests system information and sends it back to the C&C domain, the malware exchanges pings with the server and waits for commands from the attackers.
“After creating two separate Trojans, each designed for a specific platform and each with its own peculiarities, it is highly probable that this group will produce more malware in the future,” explained Kaspersky’s Sergey Yunakovsky.
The SambaCry vulnerability exploited by the Linux malware linked to this threat actor, CVE-2017-7494, can be exploited to upload a shared library to a writable share and cause the server to load that library. This allows a remote attacker to execute arbitrary code on the targeted system.
The security hole, patched in May, affects the products of several vendors, including routers and network-attached storage (NAS) appliances. In fact, one piece of malware spotted by Trend Micro in early July leverages the SambaCry vulnerability to target NAS devices, particularly ones used by small and medium-size businesses.
Tech Giants Announce Plans for Removal of Flash
26.7.2017 securityweek IT
Apple, Facebook, Google, Microsoft and Mozilla have outlined their plans for moving away from Flash Player now that Adobe officially announced an end-of-life (EOL) and end-of-support date for the controversial product.
Adobe announced on Tuesday that, following discussions with several technology partners, it has decided to stop updating and distributing Flash Player at the end of 2020. The company has encouraged developers and content creators to migrate to open standards such as HTML5, WebGL and WebAssembly, which are supported by all major web browsers.
While Flash Player is still used by many websites and applications, the security community has been asking Adobe to retire the old software for several years due to the large number of vulnerabilities and numerous attacks involving Flash exploits.
Over the past years, web browser vendors and other Internet companies have taken steps to reduce the security risks associated with Flash Player by either limiting Flash content or banning it altogether.
Apple, Facebook, Google, Microsoft and Mozilla have promised to help with the transition and they have each outlined their plans for the complete removal of Flash support from their products.
Apple has been moving away from Flash since 2010. Currently, users need to manually install Flash if they need it and even so it remains disabled by default – manual approval is required on each website before the Flash plugin is executed.
Facebook, which still allows Flash games on its platform, says it has partnered with game developers to help them migrate to HTML5. The social media giant will accept Flash games until the end of 2020, but warned that the ability to play these games also depends on the decisions made by browser vendors.
Google pointed out that the number of Chrome users visiting a site with Flash every day has dropped from 80 percent three years ago to 17 percent today. Google has been and will continue to gradually phase out Flash – first by asking for explicit permission to run Flash content in more situations and eventually disabling it by default. The company wants to remove it completely toward the end of 2020.
Microsoft, which updates the Flash Player components used by its products every Patch Tuesday, wants to disable Flash by default in both Edge and Internet Explorer in mid-to-late 2019. Even if users will re-enable it, they will still need to manually approve Flash for each website. Flash will be removed completely by the end of 2020.
Moziila’s roadmap for Flash is similar. The organization wants to disable Flash by default for most users in 2019, while allowing Extended Support Release (ESR) users to continue viewing Flash content through the end of 2020.
New CowerSnail Windows Backdoor linked to SHELLBIND SambaCry Linux Malware
26.7.2017 securityaffairs Virus
Malware researchers at Kaspersky Lab have found a new Windows Backdoor dubbed CowerSnail linked to the recently discovered SHELLBIND SambaCry Linux malware.
Security experts at Kaspersky Lab have spotted a new Windows Backdoor dubbed CowerSnail linked to the recently discovered SHELLBIND SambaCry Linux malware.
SHELLBIND has infected most network-attached storage (NAS) appliances, it exploits the Samba vulnerability (also known as SambaCry and EternalRed) to upload a shared library to a writable share, and then cause the server to load that library.
This trick allows a remote attacker to execute arbitrary code on the targeted system.
SHELLBIND and the Backdoor.Win32.CowerSnail shares the command and control (C&C) server (cl.ezreal.space:20480).
“We recently reported about SambaCry, a new family of Linux Trojans exploiting a vulnerability in the Samba protocol. A week later, Kaspersky Lab analysts managed to detect a malicious program for Windows that was apparently created by the same group responsible for SambaCry.” states Kaspersky. “It was the common C&C server that both programs used – cl.ezreal.space:20480 – that suggested a relationship between them.”
The CowerSnail backdoor was developed using the cross-platform development framework Qt, a design choice to allow rapid migration of the malicious code developed for Unix platform to a Windows environment.
SambaCry was designed for *nix-based systems, meanwhile, CowerSnail was written using Qt because the author didn’t want to go into the details of WinAPI and migrated the code the *nix code “as is”.
On the other hand, while it does make it easier to transfer code between platforms, Qt significantly increases the size of the resulting file.
The drawback in using Qt is the increasing of the size of the resulting file.
“This framework provides benefits such as cross-platform capability and transferability of the source code between different operating systems. This, however, has an effect on the resulting file size: the user code ends up as a small proportion of a large 3 MB file.” continues Kaspersky.
CowerSnail first escalates the process priority and the current thread’s priority, then it starts communicating with its Command & Control server through the IRC protocol.
CowerSnail implements classic backdoor features, it can collect information about the infected system (Timestamp, Installed OS type (e.g. Windows), OS nameHost name, Information about network interfaces, ABI Core processor architecture
Information about physical memory), it can execute commands, install or uninstall itself as a service, and receive updates.

The experts believe that the same threat actor has developed the two Trojans, each designed for a specific purpose.
“After creating two separate Trojans, each designed for a specific platform and each with its own peculiarities, it is highly probable that this group will produce more malware in the future,” concluded Kaspersky Lab.
CrowdStrike presented the fastest and largest cybersecurity search engine
26.7.2017 securityaffairs Cyber
CrowdStrike Inc., the leader in cloud-delivered endpoint protection, announced the fastest and largest cybersecurity search engine.
Security firm CrowdStrike, the leader in cloud-delivered endpoint protection, announced a significant improvement of its Falcon platform that has been integrated with a powerful cybersecurity search engine.
According to the company the cybersecurity search engine has high performance, it claims it is more than 250 times faster than other malware search tools.
The search engine is powered by Falcon MalQuery, which CrowdStrike claims is more than 250 times faster than other malware search tools.
MalQuery has developed a patent-pending indexing technology that allows used to perform real time searching in a huge repository of threats events and malicious codes.
The company has indexed more than 700 million files totaling over 560 TB of malware and collected data related to 51 billion security events every day.
“This platform has grown to be the largest and most active repository of threat events and artifacts in the industry, indexing over 50 billion events per day and amassing a 560TB collection of 700 million files.” reads the announcement published by CrowdStrike.”CrowdStrike’s patent pending indexing technology makes all of this data available for real-time search. Organizations can now search for malware — both metadata and binary content — and get results from the Falcon platform in seconds.”

The users can query the system for plain text (ASCII and Unicode) or binary search (HEX) along with YARA-based queries.
The results are augmented “with CrowdStrike intelligence so the severity and context of the threat is clear.”
“Today’s threat landscape demands speed and precision – some of the best minds in cybersecurity are hampered by slow search tools and limited data sets. We believe that real-time data access is how cybersecurity professionals can get ahead of modern-day threats, and we’ve built the fastest AI-enabled platform that makes this possible,” said George Kurtz, CrowdStrike co-founder and CEO.
“With today’s launch, we are fundamentally changing the game by empowering threat researchers to outpace the adversary with this solution. CrowdStrike Falcon Search Engine enables the next-gen SOC to be more productive and acts as a powerful force multiplier for security teams,”
Recently the cyber security firm announced a partnership with security firm Dragos to provide cybersecurity services for industrial control systems (ICS).
Gang Behind Fireball Malware that Infected 250 Million PCs Busted by Police
26.7.2017 thehackernews Virus

Chinese authorities have recently initiated a crackdown on the operators of a massive adware campaign that infected around 250 Million computers, including Windows and Mac OS, across the world earlier this year.
The adware campaign was uncovered by security researchers at Check Point last month after it already infected over 25 million computers in India, 24 million in Brazil, 16 million in Mexico, 13 million in Indonesia and 5.5 million in the United States.
Dubbed Fireball, the infamous adware comes bundled with other free legitimate software that you download off the Internet.
Once installed, the malware installs browser plug-ins to manipulate the victim's web browser configurations and replace their default search engines and home pages with fake search engines.
Far from legitimate purposes, Fireball has the ability to spy on victim's web traffic, execute malicious code on the infected computers, install plugins, and even perform efficient malware dropping, creating a massive security hole in targeted systems and networks.
fireball-chinese-adware-software
At the time, Check Point researchers linked the operation to Rafotech, a Beijing-based Chinese firm which claims to offer digital marketing and game apps to 300 million customers, blaming the company for using Fireball for generating revenue by injecting ads into the web browsers.
Now, Beijing Municipal Public Security Bureau Network Security Corps have made 11 arrests in the case.
All the suspects are Rafotech employees, three of which worked as the company's president, technical director, and operations director, Chinese new agency reports.
Chinese outlets report that the Fireball developers made a profit of 80 Million Yuan (nearly US$12 million) from the adware campaign.
The establishment of Rafotech was jointly funded by several people in 2015, and by the end of the year, they developed the Fireball virus for the advertising fraud, which redirects the victim's every query to either Yahoo.com or Google.com and includes tracking pixels that collect the victim's information.
All the arrested suspects have allegedly admitted of the development and distribution of the Fireball malware. The arrests began in June shortly after the story about Fireball went online.
No doubt, the company was using the Fireball adware to boost its advertisements and gain revenue, but at the same time, the adware has the capability to distribute additional malware, which may come up as a potential disaster in future.
CowerSnail, from the creators of SambaCry
26.7.2017 Kaspersky Virus
We recently reported about SambaCry, a new family of Linux Trojans exploiting a vulnerability in the Samba protocol. A week later, Kaspersky Lab analysts managed to detect a malicious program for Windows that was apparently created by the same group responsible for SambaCry. It was the common C&C server that both programs used – cl.ezreal.space:20480 – that suggested a relationship between them.
Kaspersky Lab products detect the new malicious program as Backdoor.Win32.CowerSnail. MD5: 5460AC43725997798BAB3EB6474D391F
CowerSnail was compiled using Qt and linked with various libraries. This framework provides benefits such as cross-platform capability and transferability of the source code between different operating systems. This, however, has an effect on the resulting file size: the user code ends up as a small proportion of a large 3 MB file.
First stage
First of all, CowerSnail escalates the process priority and the current thread’s priority.
Then it uses the StartServiceCtrlDispatcher API to launch the main C&C communication thread as a control manager service.
If the thread is successfully launched as a service, further communication with the C&C is carried out through that service; otherwise, CowerSnail operates without it. CowerSnail can also accept various variables as input, such as the C&C host. When these are absent, the required data is extracted from the file itself.
Invoking the main C&C communication method will look like this in the control service routine (the method is stated as ‘route’).
C&C server communication
Traffic analysis shows that the bot communicates with the C&C via the IRC protocol. This can be seen from the characteristic ‘CHANNEL’ command and the subsequent exchange of pings, which often occurs in IRC botnets made up of IoT devices.
The first two bytes are the ‘pk’ signature which occurs in each packet except the CHANNEL command. The DWORD that follows is the size of the remaining part of the packet:
The name of each field is encoded in Unicode and is preceded by field length. The RequestReturn/Request DWORD coming after the status bar shows the number of variables for the variable RequestReturn. In this example, there are three variables: ‘success’, ‘I’ and ‘result’. Each of these fields, in turn, can contain more nested variables. The screenshot below shows the response to the SysInfo request in which CowerSnail sends 14 (0xE) different strings containing information about the infected system. The type of variable is stated after its name, followed by its value.
The structures of the request packet and the response packet are slightly different. The server’s request includes the request name coded as Request->arg->type->”Ping/SysInfo/Install”, as well as extra parameters that are nested into the arg field.
Here are examples of several variable types:
0x00000005 – Integer variable
0x0000000A – String variable
After registering the infected host at the C&C server, which includes sending information about the infected system, CowerSnail exchanges pings with the server and waits for commands.
Commands
Unlike SambaCry, CowerSnail does not download cryptocurrency mining software by default, but instead provides a standard set of backdoor functions:
Receive update (LocalUpdate)
Execute any command (BatchCommand)
Install CowerSnail as a service, using the Service Control Manager command line interface (Install)
Uninstall CowerSnail from service list (Uninstall)
Collect system information:
Timestamp
Installed OS type (e.g. Windows)
OS name
Host name
Information about network interfaces
ABI
Core processor architecture
Information about physical memory
Conclusion
SambaCry was designed for *nix-based systems. CowerSnail, meanwhile, was written using Qt, which most probably means the author didn’t want to go into the details of WinAPI, and preferred to transfer the *nix code “as is”. This fact, along with the same C&C being used by both programs, strongly suggests that CowerSnail was created by the same group that created SambaCry. After creating two separate Trojans, each designed for a specific platform and each with its own peculiarities, it is highly probable that this group will produce more malware in the future.
Nebezpečný virus útočil pět let. Nikdo si ho nevšiml
26.7.2017 Novinky/Bezpečnost Viry
Více než pět let se šířil internetem zákeřný virus Stantinko, aniž si toho kdokoliv všiml. Zmapovat chování tohoto nezvaného návštěvníka se podařilo až nyní bezpečnostním expertům antivirové společnosti Eset.
Malware zvaný Stantinko útočil doposud především v Rusku, Bělorusku a na Ukrajině. Podle bezpečnostních expertů je riziko nakažení tímto škodlivým kódem v České republice poměrně nízké, protože cílí především na rusky hovořící uživatele. Zcela vyloučit riziko útoku v tuzemsku samozřejmě ale nelze.
Jakmile je počítač infikován, nainstaluje dvě škodlivé služby v rámci operačního systému Windows, které se spouštějí při každém jeho startu. „Když ho ‚chytíte‘, je obtížné se ho zbavit, protože každá z obou služeb má schopnost znovu nainstalovat tu druhou. Aby uživatel problém plně eliminoval, musí vymazat ze svého počítače obě tyto služby současně,“ vysvětluje Frédéric Vachon, analytik společnosti Eset.
Zásuvné moduly pro Chrome
Konkrétně jsou nainstalovány dva zásuvné moduly – „The Safe Surfing“ a „Teddy Protection“. Oba jsou přitom běžně k dispozici ke stažení pro prohlížeč Google Chrome. „Během naší analýzy byly oba pluginy na internetu stále nabízeny,“ podotkl Marc-Etienne Léveillé, expert na výzkum malwaru ve společnosti Eset.
„Na první pohled vypadají jako legitimní rozšíření webového prohlížeče, a dokonce mají své internetové stránky. Pokud je však nainstaluje Stantinko, obdrží tato rozšíření odlišnou konfiguraci, která obsahuje příkazy na provádění podvodných kliknutí na reklamy a vkládání vlastního kódu do navštěvovaných webových stránek,“ konstatoval Léveillé.
S nakaženým počítačem si pak počítačoví piráti mohou dělat cokoliv, co chtějí. „To znamená například masivní anonymní vyhledávání stránek vytvořených pomocí nástrojů Joomla a WordPress, na něž následně provádějí tzv. brute force útoky s cílem vyhledání a odcizení dat, a mohou též vytvářet falešné účty na Facebooku,“ zdůraznil Vachon.
S napadeným počítačem tak mohou kyberzločinci provádět další útoky, ale stejně tak například vydělávat peníze na zobrazované reklamě, která by se jinak na počítači vůbec nezobrazovala.
Skrýval se dlouho
Zajímavé je především to, jak dlouho se podařilo malware Stantinko počítačovým pirátům skrývat před zraky bezpečnostních expertů a antivirových programů. Dosáhli toho tak, že škodlivá data ukrývali ve zdrojových kódech programů, které na první pohled vypadaly legitimně.
„Škodlivý kód využívá vyspělé techniky a je skryt buď zašifrovaný v souboru, nebo v registru Windows. Následně je dešifrován pomocí klíče, který se vygeneruje během prvotního napadení. Jeho škodlivé chování nelze detekovat, dokud ze svého řídicího serveru neobdrží nové komponenty, což komplikuje jeho odhalení,“ uzavřel Léveillé.
Stantinko se šíří internetem i nadále, majitelé většiny antivirových programů s aktualizovanou databází by však proti němu měli již být chráněni.
Experts Unveil Cyber Espionage Attacks by CopyKittens Hackers
26.7.2017 thehackernews CyberSpy
Security researchers have discovered a new, massive cyber espionage campaign that mainly targets people working in government, defence and academic organisations in various countries.
The campaign is being conducted by an Iran-linked threat group, whose activities, attack methods, and targets have been released in a joint, detailed report published by researchers at Trend Micro and Israeli firm ClearSky.
Dubbed by researchers CopyKittens (aka Rocket Kittens), the cyber espionage group has been active since at least 2013 and has targeted organisations and individuals, including diplomats and researchers, in Israel, Saudi Arabia, Turkey, the United States, Jordan and Germany.
The targeted organisations include government institutions like Ministry of Foreign Affairs, defence companies, large IT companies, academic institutions, subcontractors of the Ministry of Defense, and municipal authorities, along with employees of the United Nations.
The latest report [PDF], dubbed "Operation Wilted Tulip," details an active espionage campaign conducted by the CopyKittens hackers, a vast range of tools and tactics they used, its command and control infrastructure, and the group's modus operandi.
How CopyKittens Infects Its Targets
The group used different tactics to infiltrate their targets, which includes watering hole attacks — wherein JavaScript code is inserted into compromised websites to distribute malicious exploits.
The news media and organisations whose websites were abused as watering hole attacks include The Jerusalem Post, for which even German Federal Office for Information Security (BSI) issued an alert, Maariv news and IDF Disabled Veterans Organization.
Besides water hole attacks, CopyKittens also used other methods to deliver malware, including:
Emailed links to malicious websites controlled by attackers.
Weaponized Office documents exploiting recently discovered flaw (CVE-2017-0199).
Web servers exploitation using vulnerability scanner and SQLi tools like Havij, sqlmap, and Acunetix.
Fake social media entities to build trust with targets and potentially spread malicious links.
"The group uses a combination of these methods to persistently target the same victim over multiple platforms until they succeed in establishing an initial beachhead of infection – before pivoting to higher value targets on the network," Trend Micro writes in a blog post.
In order to infect its targets, CopyKittens makes use of its own custom malware tools in combination with existing, commercial tools, like Red Team software Cobalt Strike, Metasploit, post-exploitation agent Empire, TDTESS backdoor, and credential dumping tool Mimikatz.
Dubbed Matryoshka, the remote access trojan is the group's self-developed malware which uses DNS for command and control (C&C) communication and has the ability to steal passwords, capture screenshots, record keystrokes, collect and upload files, and give the attackers Meterpreter shell access.
"Matryoshka is spread through spear phishing with a document attached to it. The document has either a malicious macro that the victim is asked to enable or an embedded executable the victim is asked to open," Clear Sky says in a blog post.
The initial version of the malware was analysed in 2015 and seen in the wild from July 2016 until January 2017, though the group also developed and used Matryoshka version 2.
Users are recommended to enable two-factor authentication in order to protect their webmail accounts from being compromised, which is a treasure trove of information for hackers, and an "extremely strong initial beachhead" for pivoting into other targets.
Hacker Steals $8.4 Million in Ethereum (4th Heist In A Month)
26.7.2017 thehackernews Incindent
More Ethereum Stolen!
An unknown hacker has just stolen nearly $8.4 Million worth of Ethereum – one of the most popular and increasingly valuable cryptocurrencies – in yet another Ethereum hack that hit Veritaseum's Initial Coin Offering (ICO).
This incident marks as the fourth Ethereum hack this month and second cyber attack on an ICO, following a theft of $7 Million worth of Ether tokens during the hack of Israeli startup CoinDash's initial coin offering last week.
A few days ago, a hacker also stole nearly $32 Million worth of Ethereum from wallet accounts by exploiting a critical vulnerability in Parity's Ethereum Wallet software, which followed a $1 Million worth of Ether and Bitcoins heist in crypto currency exchange Bithumb earlier this month.
Now, Veritaseum has confirmed that a hacker stole $8.4 Million in Ether (ETH) from its ICO this Sunday, July 23.
"We were hacked, possibly by a group. The hack seemed to be very sophisticated, but there's at least one corporate partner that may have dropped the ball and be liable. We will let the lawyers sort that out if it goes that far," Veritaseum founder Reggie Middleton confirmed the theft on the BitcoinTalk forum.
Middleton has called the recent Ethereum hack "inconsequential," saying some of his partners (unnamed corporate third party services) may be responsible for the attack.
Middleton said that due to the high demand of the VERI tokens during the ICO held over the weekend, the hacker first managed to steal those tokens and then immediately sold them to other buyers "within a few hours" for the cryptocurrency.
The hacker made off an estimated $8.4 million in ETH during that a relatively short period of time. The stolen funds were first dumped into two separate Ethereum wallets and then were moved to other accounts.
It looks like around 37,000 VERI tokens were stolen out of 100 Million in the recent theft, though the good news is that the Ethereum theft does not affect actual ICO investors, as Middleton says the stolen tokens belonged to him and his team members.
"There are 100M tokens issued; the hackers stole about 37k. As I said, it is quite disconcerting, but it is not the end [of] the world. In the scheme of things, this is small," Middleton says.
"The tokens were stolen from me, not the token buyers. I am not downplaying the seriousness of the heist either, but I am looking at the heist for what it is. A company that we use was compromised, the vulnerability was closed, and we are investigating whether we should move against that company or not."
At the moment, Middleton did not disclose the attack vector that was exploited to sweep out $8.4 Million in ETH, though he assured users that his team had taken necessary measures to prevent the attack from happening in the future.
Apple Users, Beware! A Nearly-Undetectable Malware Targeting Mac Computers
26.7.2017 thehackernews Apple
Yes, even Mac could also get viruses that could silently spy on its users. So, if you own a Mac and think you are immune to malware, you are wrong.
An unusual piece of malware that can remotely take control of webcams, screen, mouse, keyboards, and install additional malicious software has been infecting hundreds of Mac computers for more than five years—and it was detected just a few months back.
Dubbed FruitFly, the Mac malware was initially detected earlier this year by Malwarebytes researcher Thomas Reed, and Apple quickly released security patches to address the dangerous malware.
Now months later, Patrick Wardle, an ex-NSA hacker and now chief security researcher at security firm Synack, discovered around 400 Mac computers infected with the newer strain of the FruitFly malware (FruitFly 2) in the wild.
Wardle believes the number of infected Macs with FruitFly 2 would likely be much higher, as he only had access to some servers used to control FruitFly.
Although it is unknown who is behind FruitFly or how the malware gets into Mac computers, the researchers believe the nasty malware has been active for around ten years, as some of its code dates back to as far as 1998.
"FruitFly, the first OS X/macOS malware of 2017, is a rather intriguing specimen. Selectively targeting biomedical research institutions, it is thought to have flown under the radar for many years," Wardle wrote in the abstract of his talk, which he is going to present at the Black Hat later this week.
Since the initial infection vector for FruitFly is unclear, like most malware, Fruitfly could likely infect Macs either through an infected website delivering the infection or via phishing emails or a booby-trapped application.
FruitFly is surveillance malware that's capable of executing shell commands, moving and clicking a mouse cursor, capturing webcam, killing processes, grabbing the system's uptime, retrieving screen captures, and even alerting the hacker when victims are again active on their Mac.
"The only reason I can think of that this malware has not been spotted before now is that it is being used in very tightly targeted attacks, limiting its exposure," Reed wrote in the January blog post.
"Although there is no evidence at this point linking this malware to a specific group, the fact that it has been seen specifically at biomedical research institutions certainly seems like it could be the result of exactly that kind of espionage."
Wardle was able to uncover FruitFly victims after registering a backup command and control (C&C) server that was once used by the attacker. He then noticed around 400 Mac users infected with FruitFly started connecting to that server.
From there, the researcher was also able to see IP addresses of FruitFly infected victims, indicating 90 percent of victims were located in the United States.
Wardle was even able to see the name of victims' Macs as well, making it "really easy to pretty accurately say who is getting infected," he told Forbes.
But rather than taking over those computers or spying on the victims, Wardle contacted law enforcement and handed over what he found to law enforcement agents, who are now investigating the matter.
Wardle believes surveillance was the primary purpose of FruitFly, though it is yet unclear whether it is government or other hacker groups.
"This did not look like cyber crime type behaviour; there were no ads, no keyloggers, or ransomware," Wardle said. "Its features had looked like they were actions that would support interactivity—it had the ability to alert the attacker when users were active on the computer, it could simulate mouse clicks and keyboard events."
Since the Fruitfly's code even includes Linux shell commands, the malware would work just fine on Linux operating system. So, it would not come as a surprise if a Linux variant of Fruitfly was in operation.
British Hacker Admits Using Mirai Botnet to DDoS Deutsche Telekom
26.7.2017 thehackernews BotNet
An unnamed 29-year-old man, named by authorities as "Daniel K.," pleaded guilty in a German court on Friday to charges related to the hijacking of more than one Million Deutsche Telekom routers.
According to reports in the German press, the British man, who was using online monikers "Peter Parker" and "Spiderman," linked to domains used to launch cyber attacks powered by the notorious Mirai malware has been pleaded guilty to "attempted computer sabotage."
The suspect was arrested on 22nd February this year at Luton airport in London by Britain's National Crime Agency (NCA) at the request of the Federal Criminal Police Office of Germany, aka the Bundeskriminalamt (BKA).
The hacker, also known as 'BestBuy,' admitted to the court on Friday that he was behind the cyber attack that knocked more than 1.25 Million customers of German telecommunications provider Deutsche Telekom offline last November.
According to the German authorities, the attack was especially severe and was carried out to compromise the home routers to enrol them in a network of hijacked devices popularly called Botnet, which is being offered for sale on dark web markets for launching DDoS attacks.
Late last year, Deutsche Telekom's routers became infected with a modified version of the Mirai malware – infamous IoT malware which scans for insecure routers, cameras, DVRs, and other IoT devices and enslaves them into a botnet network – causing over a million pounds' worth of damage, the company said at the time.
Mirai is the same botnet that knocked the entire Internet offline last year by launching massive distributed denial of Service (DDoS) attacks against the Dyn DNS provider, crippling some of the world's biggest and most popular websites, including Twitter, Netflix, Amazon, Slack, and Spotify.
Mirai leveraged attack experienced sudden rise after a cyber criminal in October 2016 publicly released the source code of Mirai, which is then used to by many cyber criminals to launch DDoS attacks.
The hacker reportedly told the court that a Liberian internet service provider (ISP) paid him $10,000 to carry out the attack against its competitors., and that Deutsche Telekom was not the main target of his attack.
At the time of his arrest, the suspect faced up to 10 years in prison. He's due to be sentenced on July 28.
The BKA got involved in the investigation as the attack on Deutsche Telekom was deemed to be a threat to the nation's communication infrastructure.
The investigation involved close cooperation between British, German and Cypriot law enforcement agencies, backed by the European Union's law enforcement intelligence agency, Europol, and Eurojust.
Georgian News Site Serves New Version of Old Mac Trojan
26.7.2017 securityweeek Apple
Researchers at security firm Volexity noticed that the website of a media organization based in the country of Georgia had been serving a new version of an old Mac Trojan to specific visitors.
According to experts, the compromised news website has English, Russian and Georgian sections, but only the Georgian language pages appeared to deliver the malware. The threat is a new version of OSX/Leverage, a backdoor first spotted back in 2013.
Interestingly, not all visitors were targeted. JavaScript code planted on the site profiled each user and only served the malware if certain conditions were met. The malware was pushed only to devices whose user agent showed that the victim accessed the site from a Mac and a web browser other than Chrome.
The script also checked cookies to determine if the user had previously visited the website and analyzed the malicious JavaScript code. If a returning user is detected, the exploitation chain is terminated.
If all the conditions are met and the potential victim is using the Safari browser from a Mac computer, an iframe is loaded and a fake Adobe website is displayed. The site is designed to trick users into downloading a fake Flash Player critical update.
The malicious Flash Player update is delivered via a Metasploit module that abuses Safari functionality to force the download and execution of an OS X application. However, the victim still needs to allow the execution of the file when prompted or manually execute it from the Downloads folder.
Once executed, the malware creates a Launch Agent for persistence and opens the genuine Adobe Flash Player website to avoid raising suspicion. The backdoor contacts its command and control (C&C) server and sends it information about the infected system.
“Unlike the earlier version of the malware, this new version does not limit itself to a predefined set of commands and instead allows an unrestricted command shell capability back into an infected system,” Volexity researchers said in a blog post.
The new version of the Leverage malware, which was also spotted by Sophos earlier this month, is signed with an Apple code signing certificate issued to a developer apparently named “Aleks Papandopulo.”
The first version of Leverage had been disguised as an image file and in some cases it downloaded a logo of the Syrian Electronic Army hacker group onto compromised machines.
Interestingly, Volexity has discovered a link between an IP address associated with one of the domains serving the new version of Leverage and Stantinko, a recently uncovered botnet that has powered a massive adware campaign since 2012. The Stantinko operation has mainly targeted Russia and Ukraine.
Tech Firms Target Domains Used by Russia-linked Threat Group
26.7.2017 securityweeek APT
Tech companies ThreatConnect and Microsoft are moving toward exposing and taking down domains associated with Russia-linked threat group known as Fancy Bear.
Also tracked as APT28, Pawn Storm, Sofacy, Tsar Team, Strontium and Sednit, the threat group has been associated with a variety of high-profile cyber-attacks aimed at government and other types of organizations worldwide.
Last year, the threat group was said to have orchestrated election-related hacker attacks in the United States. The actor allegedly developed the so called XTunnel malware specifically to compromise the Democrat National Committee (DNC) network last year, and was said in February 2017 to be using brand new Mac malware to steal data.
ThreatConnect says their team was able to identify “dozens of recently registered domains and IPs that have varying levels of association to the Russian APT.” Moreover, the security firm discovered three name servers the group most likely used for domains, which allows defenders to “proactively identify new domains that may be associated with Fancy Bear activity”.
One of the domains, the security company reveals, is unisecproper[.]org, which was registered using the email address le0nard0@mail[.]com and is hosted on a dedicated server at the IP 92.114.92.134. The certificate used by this domain has been already associated (PDF) with Fancy Bear in operations targeting the DNC and German Parliament, which clearly indicates that the domain is associated with the group.
Using the SSL certificate, ThreatConnect discovered recent IPs associated with Fancy Bear, along with numerous domains hosted on these IPs, also supposedly associated with the threat group. Some of these domains were discovered in previous investigations as well.
The researchers also managed to find name servers used by Fancy Bear, including nemohosts[.]com, bacloud[.]com, and laisvas[.]lt. The investigation eventually led to the discovery of hundreds of domains associated with these name servers, tens of which were hosted on dedicated servers.
The researchers note these are suspicious domains but note that “consistencies in registration and hosting tactics do not definitively associate many of these suspicious domains with previous malicious, Fancy Bear activity.”
“It's important to caveat our confidence in these indicators' association to FANCY BEAR activity. For many of those indicators that we've included here, we don't know whether they have actually been used maliciously. But if known bad is all that you are worried about or interested in, then you'll always be at least one step behind the attacker. Only by leveraging intelligence to identify and exploit our adversaries' tactics can we move from a reactive, whack-a-mole state to a proactive, informed defense,” ThreatConnect says.
Microsoft, in the meantime, is taking legal action against Fancy Bear: the tech company filed a civil lawsuit in August 2016, seeking to seize command-and-control (C&C) domains used by the group. According to court documentation Microsoft made public, there are hundreds of domains containing Microsoft trademarks that it is looking to take control of.
The actors failed to appear in a federal court in Virginia to defend themselves, and Microsoft is pushing for a default judgment in its favor. By seizing the domains, Microsoft would be able to cut the group off from communicating with infected systems.
“Microsoft seeks a preliminary injunction directing the registries associated with these Internet domains to take all steps necessary to disable access to and operation of these Internet domains to ensure that changes or access to the Internet domains cannot be made absent a court order and that all content and material associated with these Internet domains are to be isolated and preserved pending resolution of the dispute. Microsoft seeks a permanent injunction, other equitable relief and damages,” Microsoft notes.
Previously, Microsoft used legal action to take down botnets. In 2012, as part of Operation b71, the company seized C&C servers associated with the notorious Zeus family of malware. In 2014, in an attempt to take down the Bladabindi (njRAT) and Jenxcus (NJw0rm) malware families, the company seized 23 No-IP domains to route bad traffic to a sinkhole.
Iranian 'CopyKittens' Conduct Foreign Espionage
26.7.2017 securityweeek CyberSpy
CopyKittens Iran cyberspies
An Iran-linked threat group named by researchers CopyKittens has been conducting foreign espionage on strategic targets in various countries. Trend Micro and ClearSky have published a report detailing the actor’s activities, including targets, tools and attack methods.
The first report on CopyKittens was published in November 2015, but the group is believed to have been active since at least 2013. The hackers initially appeared to mainly target Israeli individuals, including diplomats and researchers, but further analysis showed that its operations have also covered entities in Saudi Arabia, Turkey, the United States, Jordan and Germany.
The list of targets includes government organizations, academic institutions, IT firms, defense companies and contractors, municipal authorities, and employees of the United Nations.
According to the latest report on CopyKittens activity, dubbed Operation Wilted Tulip, the hackers have used a wide range of tools and tactics. In some cases, they relied on watering hole attacks where news and other websites were compromised and set up to deliver exploits. The organizations whose websites were abused as watering holes includes The Jerusalem Post, for which even Germany’s Federal Office for Information Security (BSI) issued an alert.
The hackers also delivered malware using malicious documents set up to exploit various vulnerabilities, including the recently discovered Office flaw tracked as CVE-2017-0199, which at one point was a zero-day. In one attack, the hackers breached the email account of an employee of the Ministry of Foreign Affairs in the Turkish Republic of Northern Cyprus. The compromised account was used to send out a weaponized document to foreign affairs ministries in various countries around the world.
Some of the attacks targeting Israeli entities also leveraged fake social media profiles, often appearing to belong to attractive women.
As for the tools and malware used by CopyKittens, they leveraged automated scanning and exploitation tools such as Havij, sqlmap and Acunetix to find vulnerabilities in the targeted websites.
The threat actor has used both its own and widely available malware and tools, including the TDTESS backdoor, the Matryoshka RAT, the Vminst lateral movement tool, the Cobalt Strike threat emulation software, Mimikatz, Metasploit, the ZPP compression utility, and the Empire post-exploitation tool.
Some of the tools and malware have allowed the group to use DNS for command and control (C&C) communications and data exfiltration.
CopyKittens is not the only Iran-linked cyber espionage group. In the past years, security firms have also exposed the activities of actors known as Rocket Kitten, COBALT GYPSY, and Charming Kitten (Newscaster, NewsBeef).
CrowdStrike Launches Cybersecurity Search Engine
26.7.2017 securityweeek Cyber
Cloud-based endpoint security firm CrowdStrike announced on Tuesday that it has expanded the capabilities of its Falcon platform by adding a powerful search engine.
The search engine is powered by Falcon MalQuery, which CrowdStrike claims is more than 250 times faster than other malware search tools. MalQuery uses a patent-pending indexing technology and it allows users to filter results so that they are provided only the most relevant information.CrowdStrike
CrowdStrike says its threat database has indexed more than 700 million files totaling over 560 TB of malware, and it ingests over 51 billion security events every day. String- and YARA-based searches can be conducted via a single console and results are displayed as schematized, readily consumable snapshots.
The results of the search, which analyzes both a file’s metadata and content, are augmented with CrowdStrike intelligence to provide security operations center (SOC) personnel information on context and severity.
The security firm pointed out that faster and more accurate search results help streamline security operations, which ultimately leads to improved protection against new threats.
“Today’s threat landscape demands speed and precision – some of the best minds in cybersecurity are hampered by slow search tools and limited data sets. We believe that real-time data access is how cybersecurity professionals can get ahead of modern-day threats, and we’ve built the fastest AI-enabled platform that makes this possible,” said George Kurtz, CrowdStrike co-founder and CEO.
“With today’s launch, we are fundamentally changing the game by empowering threat researchers to outpace the adversary with this solution. CrowdStrike Falcon Search Engine enables the next-gen SOC to be more productive and acts as a powerful force multiplier for security teams,” Kurtz added.
Earlier this month, CrowdStrike announced that it teamed up with Dragos to provide cybersecurity services for industrial control systems (ICS).
Bot vs Bot in Never-Ending Cycle of Improving Artificial intelligence
26.7.2017 securityweeek BotNet
Artificial intelligence, usually in the form of machine learning (ML), is infosecurity's current buzz. Many consider it will be the savior of the internet, able to defeat hackers and malware by learning and responding to their behavior in all-but real time. But others counsel caution: it is a great aid; but not a silver bullet.
The basic problem is that if machine learning can learn to detect malware, machine learning can learn to avoid detection by machine learning. This is a problem that exercises Hyrum Anderson, technical director of data science at Endgame.
At the BSides Las Vegas in August 2016 he presented his work on a 'Deep Adversarial Architectures for Detecting (and Generating!) Maliciousness'. He described the concept of using red team vs blue team gaming, where a 'malicious' algorithm continually probes a defensive algorithm looking for weakness, and the defensive algorithm learns from the probes how to improve itself.
Bot vs BotThis week, at the Black Hat conference, Anderson takes the concept further in a presentation titled 'Testing Machine Learning Malware Detection via Adversarial Probing'. The purpose is simple -- to use machine learning to test and improve machine learning defenses. In reality, it is an important step in the continuing battle between attackers and defenders.
Omri Moyal, co-founder and VP of research at Minerva, explains. "Given the increased adoption of anti-malware products that use machine learning, most adversaries will soon arm themselves with the capabilities to evade it," he told SecurityWeek. "The most sophisticated attackers will develop their own offensive models. Some will copy ideas and code from various publicly-available research papers and some will even use simple trial and error, or replicate the offensive efforts of another group. In this cat-and-mouse chase, the defenders should change their model to mark the evolved attack tool as malicious. A process which is the modern version of 'malware signature' but more complex."
Anderson's theories will help the defender to stay ahead of the attacker by being both cat and mouse. His Black Hat presentation starts with the understanding that "all machine learning models have blind spots or hallucination spots (modeling error)." At the same time, an advanced attacker knows what models are used by the defender; and can use his own ML to probe for those blind spots.
Moyal explained the implications for defenders. "Just like in previous generations of anti-virus software, attackers can constantly evaluate their malware against the machine learning model until a successful variant is created," he told SecurityWeek. Malware authors have long tested new or repackaged malware against VirusTotal-like services to see whether it is likely to get past the defenders' AV defenses. Now they will use ML to test their malware against the known ML defenses, seeking out the blind spots.
"The resulting specimen," continued Moyal, "can be used against each victim whose protection relies on this model, offering the attacker a high degree of certainty the malicious program will not be detected. Attackers can also automate this process of generating malware that bypasses the model and even use offensive machine learning to improve this process."
Anderson's research is based on the idea of finding the blind spots and closing them before the attackers find them. Ironically, this can be achieved by doing exactly what the attackers will do -- use machine learning to probe machine learning. This is nothing more than what security researchers have been doing for decades: probe software to find the weaknesses and get those weaknesses patched before they are found and exploited by the bad people.
In today's presentation, Anderson describes a scientific approach on how to evade malware detection with an AI agent to compete against the malware detector. Although in this instance focusing on Windows PE, the framework is generic and can be used in other domains.
The agent examines a PE file and probes it to find a way to evade the malware detection model. The agent learns how to 'beat' the defense. However, as used by the defenders, this approach simply finds the blind spots that can then be fixed. Used solely by attackers, it finds the blind spots that can be exploited.
Anderson's key takeaway is that machine learning anti malware just bought and installed will offer early success in malware protection, but it will quickly become porous against advanced adversaries. Staying one jump ahead of the bad guys has always been, and remains, the key to infosecurity even in the age of artificial intelligence.
Hyrum Anderson, Bobby Filar, and Phil Roth from Endgame, together with Anant Kharkar from the University of Virginia, have published an associated white paper: Evading Machine Learning Malware Detection (PDF).
IBM Launches Security Testing Services For Cars, IoT
26.7.2017 securityweeek IoT
IBM Security announced on Monday that the services provided by its X-Force Red penetration testing group have been expanded to include connected vehicles and Internet of Things (IoT) devices.
IBM X-Force Red, which the company launched one year ago, has been working with automotive manufacturers and third-party suppliers to provide expertise and penetration testing and consulting services.
Researchers will also apply some of the findings from research disclosed earlier this year into the risks associated with purchasing used connected cars. They showed that insecure transfer of ownership can allow the previous owner to unlock the car, start it remotely and track its location.IBM
Experts, both independent and ones representing security firms, demonstrated on several occasions in the past years that cars can be hacked, and the risk of a cyberattack will only increase as the number of connected vehicles is expected to reach a quarter billion by 2020.
IBM’s X-Force Red team aims to help customers in the automotive industry secure hardware, software, networks and human interactions.
As for IoT testing, the service will leverage IBM’s Watson IoT platform, a cognitive system that allows organizations to easily connect and manage their IoT devices. The product has built-in security controls and IoT threat intelligence capabilities that help organizations visualize risks and develop efficient incident response through policy-driven automations.
IBM customers using the Watson IoT platform can get help from the X-Force Red team in ensuring that their products are secure from development to deployment.
“It’s not just about the technology, it is also about the global reach, investment, and collaborative approach which make IBM a trusted IoT partner for enterprise IoT solutions,” said James Murphy, Offering Manager, IBM Watson IoT Platform. “With IoT technologies permeating the farthest corners of industry, IBM is bringing our Watson IoT Platform and X-Force Red security talent together to address present and future concerns.”
Adobe to Kill Flash Player, End Support by 2020
26.7.2017 securityweeek IT
[Breaking] Adobe on Tuesday said that it would kill its Flash Player and stop providing security updates by the end of 2020.
Adobe Flash Player has made headlines over the years due to the large number of serious vulnerabilities identified by both white and black hat hackers. The company has been forced to issue emergency patches on several occasions after learning that malicious actors had been exploiting unpatched Flash Player vulnerabilities in their operations.
According the company, the decision was made in collaboration with several Adobe technology partners including Apple, Facebook, Google, Microsoft and Mozilla.
“Specifically, we will stop updating and distributing the Flash Player at the end of 2020 and encourage content creators to migrate any existing Flash content to these new open formats,” Adobe said.
Adobe said it would continue to support Flash on a number of major OSs and browsers that currently support Flash content through the planned EOL.
“This will include issuing regular security patches, maintaining OS and browser compatibility and adding features and capabilities as needed,” Adobe said in a blog post. “We remain fully committed to working with partners, including Apple, Facebook, Google, Microsoft and Mozilla to maintain the security and compatibility of Flash content.”
While Adobe has officially made the decision to kill-off the vulnerable software product, many other leading internet firms have been pushing hard against the software over the past years and trying to limit the use of Flash across their products and services.
In May 2016, Google announced its plans to block Adobe Flash and implement an 'HTML5 by Default' policy on Chrome by the end of 2016.
“It is time for Adobe to announce the end-of-life date for Flash and to ask the browsers to set killbits on the same day,” Facebook’s CSO, Alex Stamos, said in July 2015 after the existence of several Flash Player zero-day flaws was brought to light by the data breach suffered by Italian spyware maker Hacking Team.
In June 2016, Google stopped accepting display ads built in Adobe Flash, not long after Amazon stopped accepting Flash ads on its online shopping website. At the time, Amazon said that the move, which went into effect on Sept. 1, 2015, was prompted by browser setting in Chrome, Firefox, and Safari, which were meant to limit Flash content displayed on web pages.
Nathan Wenzler, chief security strategist at security consulting company AsTech, believes there will be a lot of split feelings about the official EOL announcement for Flash.
“On one hand, a great deal of the multimedia games, videos, graphics and other rich services that have helped make the Internet what it is today were originally built on Flash. It provided a great platform for a huge array of products, and it could be argued we wouldn't be where we are today without it,” Wenzler told SecurityWeek. “That said, the security world will likely rejoice at the retirement of a product which has had a huge number of well-known vulnerabilities and flaws over the years, which have been the entry point for malicious tools that have compromised millions of systems across the globe.”
“While Adobe has been increasingly more vigilant about hardening Flash and more consistently providing patches and hotfixes whenever a vulnerability was identified, it still served as a particular pain point for a lot of organizations to keep Flash patched and maintain a consistent security posture for their systems which had Flash installed,” Wenzler added.
Chris Roberts, chief security architect at threat detection and defense solutions provider Acalvio, pointed out that the end of Flash Player has been coming for a while.
“It’s been good while we had it, but let’s face it, it’s been a whipping boy of the security industry for a while with more than 1000 CVE’s dedicated to it throughout the years,” Roberts said via email. “Kind of like many of us in the industry that find ourselves getting grayer and less tolerant of others, it’s time to hang up the hat and work out how to retire. At least in Flash’s world, it’s been given a nice sunset (until 2020) and probably a good pension in the vaults of software somewhere.”
Flash Player was originally developed by Macromedia, which was acquired by Adobe in 2005.
Sweden Rattled by Massive Confidential Data Leak
26.7.2017 securityweeek BigBrothers
Sweden's minority government was battling to contain the fallout Monday after a massive leak that may have made confidential military information accessible abroad, as well as the private data of millions of citizens.
The leak made an entire database on Swedish drivers' licenses available to technicians in the Czech Republic and Romania, with media reporting that the identities of intelligence agents may have been jeopardized.
"What has happened is an accident," Prime Minister Stefan Lofven told a news conference in Stockholm, adding that an investigation has been launched.
"It has happened in violation of the law and exposed Sweden and Swedish citizens to harm," Lofven said.
One of the largest breaches of government information in Sweden in decades, the scandal may threaten the ruling Social Democrat-led coalition as opposition parties have said they could put the issue to a confidence vote in parliament.
The leak stems from the transport agency's hiring of IBM in 2015 to take over its IT operations.
IBM in turn used subcontractors in the Czech Republic and Romania -- making the sensitive information accessible by foreign technicians.
- 'Keys to the kingdom' -
The transport agency's director general Maria Agren resigned in January for unknown reasons, but she has since confessed to violating data handling and accepted a fine of 70,000 Swedish kronor (around 7,000 euros, $8,000), according to media reports earlier this month.
The Swedish military said in a statement Saturday that information on its personnel, vehicles and defense and contingency planning could have been amongst the leaked data.
But the transport agency has denied having a register on military vehicles and added that "nothing indicates" the leaked information has been "spread in an improper way".
An official at the agency told the Dagens Nyheter newspaper that carelessness with Swedes' data was like "giving away the keys to the kingdom".
Grilled by reporters on Monday, Lofven said he was told about the leak in January by his state secretary.
Defense Minister Peter Hultqvist and Interior Minister Anders Ygeman had known about it since 2016, according to several media reports.
And Infrastructure Minister Anna Johansson, who oversees the transport agency, told TT news agency on Sunday that her former state secretary had known about the leak but kept the information hidden from her -- triggering outrage among opposition parties.
"(The fact) that a responsible minister didn't know what happened within her own field provides no confidence at all," Jonas Sjostedt, leader of the Left party, told TT.
Annie Loof, leader of the Centre party, said in a statement Sunday that "a vote of no-confidence would not be excluded".
Fruitfly macOS and OS X backdoor remained undetected for years
26.7.2017 securityaffairs Apple
A new mysterious strain of macOS and OS X malware dubbed Fruitfly went undetected by malware researchers and security software for at least five years.
Fruitfly is a backdoor that could be used by attackers to gain full control over the infected systems by implementing many spying features.
Fruitfly has the ability to capture screenshots, keystrokes, webcam images, and steal data from the infected Mac.
Patrick Wardle, chief security researcher at Synack and former NSA analyst, has analyzed a sample of the malware and will present his findings this week at the hacking conference Black Hat.
The expert has built a custom command and control server to examine the FruitFly backdoor, he announced the release a number of tools used for his analysis, including a user-mode process monitor.

It has been estimated that the number of infected devices is roughly 400 and likely much higher.
““[FruitFly] was designed in a way to be interactive,” explained Wardle “This can move the mouse, generate presses and interact with the UI elements of the operating system.””
The FruitFly sample analyzed by Patrick Wardle is a variant of a malware that was spotted in January by experts at Malwarebytes after being undetected for at least two years.
After the discovery of the malware in January, Apple updated macOS to automatically detect the malware, but the strain of malware found by Wardle remained undetected by macOS security system and antivirus products.
The Fruitfly malware relies on functions that were deprecated long ago and uses a crude method to gain persistence. Compared to other Mac malware it is much easier to detect.
A submission to the VirusTotal malware detection service shows that only 22 out of 57 Antivirus are able to detect the malware.
The analysis of the malware allowed Wardle to decrypt several backup domains that were hardcoded, and the good news is that the domains remained available allowing him to register one of them.
The expert set up a “sink hole” with the registered domain and noticed that close to 400 infected Macs connected to the server, most of them from United States. Although Wardle did nothing more than
Wardle explained that the was able to send commands to the infected machine to spy on the victims, but he did not do it to respect their privacy.
Wardle explained that the method of infection is still unknown, he suspects the victims were tricked into clicking malicious links.
Wardle also explained that it is still unclear the real motivation of the attackers, the malware in fact, is not able to steal payment card data or to deliver other malicious payloads to monetize the effort of the attackers (i.e. ransomware).
Anyway the fact that the malware targets home users led the researchers to exclude the involvement of a nation-state attacker.
“I don’t know it if it’s just some bored person or someone with perverse goals,” Wardle said. “If some bored teenager is spying on me, that would still be very emotionally traumatic. If it’s turning on the webcam, that’s for perverse reasons.”
The researcher believes that Fruitfly was therefore abandoned by its creators, but the victims are still exposed to anyone who is able to impersonate a C&C server included in the list of hardcoded domains.
Wardle reported his findings to law enforcement and all hardcoded domains are no longer available to avoid abuses.
Wardle developed a set of tools for its investigation, such as BlockBlock for detecting persistence mechanisms and OverSight for detecting webcam alerts.
Don’t miss the Wardle speech at the Black Hat Security Conference in Las Vegas, it is titled Offensive Malware Analysis: Dissecting OSX/Fruitfly via a custom C&C Server.
Veritaseum – Hacker Steals $8.4 Million in Ethereum, for the second time during the ICO
26.7.2017 securityaffairs Incindent
Veritaseum – An unknown hacker has stolen nearly $8.4 Million worth of Ethereum cryptocurrency, for the second time during the ICO.
A clamorous cyber heist makes the headlines, an unknown hacker has stolen nearly $8.4 Million worth of Ethereum cryptocurrency, the hack hit Veritaseum Initial Coin Offering (ICO).
This is the fourth Ethereum cyber heist this month, for the second time hackers exploited the ICO to steal the precious crypto currencies.
Last week, a hacker stole $7 Million in Ethereum from CoinDash in just 3 minutes after the ICO launch, he tricked investors into sending ETH to the wrong address.

A few days ago, a hacker stole nearly $32 Million worth of Ethereum from wallet accounts by exploiting a critical flaw in the Parity’s Ethereum Wallet software. A third cyber heist of $1 Million worth of Ether and Bitcoins affected the currency exchange Bithumb earlier June.
Back to the present, Veritaseum confirmed the security breach, a hacker stole $8.4 Million in Ether (ETH) from its ICO on July 23. Further investigation is ongoing, it is still unclear which vulnerability was exploited by the hacker.
“We were hacked, possibly by a group. The hack seemed to be very sophisticated, but there’s at least one corporate partner that may have dropped the ball and be liable. We will let the lawyers sort that out if it goes that far.” said Veritaseum founder Reggie Middleton.
“The hacker(s) made away with $8.4M worth of tokens, and dumped all of them within a few hours into a heavy cacophony of demand. This is without the public knowing anything about our last traction.
I would like to make it known that we had the option to fork VERI, but chose not to. At the end of the day, the amount stolen was miniscule (less than 00.07%) although the dollar amount was quite material.”
Middleton speculates that an unnamed third-party company may be responsible for the attack. According to Middleton, due to the high demand of the VERI tokens during the ICO held over the weekend, the hacker first managed to steal those tokens and then immediately sold them to other buyers “within a few hours.”
The hacker first dumped the stolen funds into two separate Ethereum wallets and then moved them to other accounts.
The hacker has stolen 37,000 VERI tokens out of 100 Million in the cyber heist, this means that the event will not impact ICO investors.
“There are 100M tokens issued; the hackers stole about 37k. As I said, it is quite disconcerting, but it is not the end [of] the world. In the scheme of things, this is small,” added Middleton.
“The tokens were stolen from me, not the token buyers. I am not downplaying the seriousness of the heist either, but I am looking at the heist for what it is. A company that we use was compromised, the vulnerability was closed, and we are investigating whether we should move against that company or not.”
Experts detailed the new Operation Wilted Tulip campaign of the CopyKittens APT
26.7.2017 securityaffairs APT
Researchers from ClearSky and Trend Micro uncovered a new massive cyber espionage campaign conducted by CopyKittens dubbed ‘Operation Wilted Tulip’
A joint investigation conducted by experts from the Israeli cyber-intelligence firm by ClearSky and Trend Micro uncovered a new massive cyber espionage campaign dubbed ‘Operation Wilted Tulip’ conducted by an Iran-linked APT group CopyKittens (aka Rocket Kittens).

The hackers targeted government and academic organizations in various countries, according to the experts the group has been active since at least since 2013.
In 2015, ClearSky detected new activity from the Rocket kitten APT group against 550 targets, most of which are located in the Middle East.
The CopyKittens hackers targeted organisations and individuals in Israel, Saudi Arabia, Turkey, the United States, Jordan and Germany.
The joint report published by ClearSky and Trend Micro includes details on the Operation Wilted Tulip and described the TTPs (techniques, tactics, and procedures) adopted by the Rocket Kittens APT group.
“CopyKittens use several self-developed malware and hacking tools that have not been publicly reported to date, and are analyzed in this report: TDTESS backdoor; Vminst, a lateral movement tool; NetSrv, a Cobalt Strike loader; and ZPP, a files compression console program. The group also uses Matryoshka v1, a selfdeveloped RAT analyzed by ClearSky in the 2015 report, and Matryoshka v2 which is a new version, albeit with
similar functionality. The group often uses the trial version of Cobalt Strike3 , a publicly available commercial software for “Adversary Simulations and Red Team Operations.” states the report .
“Other public tools used by the group are Metasploit, a well-known free and open source framework for developing and executing exploit code against a remote target machine;
Mimikatz, a post-exploitation tool that performs credential dumping; and Empire, “a PowerShell and Python post-exploitation agent.” For detection and exploitation of internet-facing web servers, CopyKittens use Havij, Acunetix and sqlmap.”
The hackers used both spear phishing attacks and watering holes to compromise target systems.
CopyKittens compromised websites of media outlets and organizations to deliver its malware. Among the websites compromised by hackers to conduct watering hole attacks, there is The Jerusalem Post, the Maariv news and IDF Disabled Veterans Organization.
Below the full list of methods used by CopyKittens in its campaigns.
Watering hole attacks – inserting malicious JavaScript code into breached strategic websites.
Web based exploitation – emailing links to websites built by the attackers and containing known exploits.
Malicious documents – email attachments containing weaponized Microsoft Office documents.
Fake social media entities – fake personal and organizational Facebook pages are used for interaction with targets and for information gathering.
Web hacking – Havij, Acuntix and sqlmap are used to detect and exploit internet-facing web servers.
The hackers used multiple tools and malware to infect targets, they used both custom malicious codes and commercial solutions like Cobalt Strike.the report!
Adobe Flash end of life announced by 2020. Start thing of the migration
26.7.2017 securityaffairs IT
Adobe announced Flash end-of-life by 2020. Apple, Facebook, Google, Microsoft and Mozilla plans to stop supporting the Adobe Flash Media Player in 2020.
It’s official, Adobe will kill Flash by 2020, the company will stop providing support for the popular browser plugin.by the end of that year.
“Given this progress, and in collaboration with several of our technology partners – including Apple, Facebook, Google, Microsoft and Mozilla – Adobe is planning to end-of-life Flash. Specifically, we will stop updating and distributing the Flash Player at the end of 2020 and encourage content creators to migrate any existing Flash content to these new open formats.” states the Adobe’s announcement.
Open standards like HTML5, WebGL, and WebAssembly have matured enough over the past years to replace all the features today implemented by Adobe Flash.
Starting from 2020, the company will no more provide support on major browsers, including Chrome, Firefox, and Internet Explorer and Edge.
“If the site continues to use Flash, and you give the site permission to run Flash, it will work through the end of 2020.” wrote Google. “We’re supportive of Adobe’s announcement today, and we look forward to working with everyone to make the web even better. “
“To provide guidance for site authors and users that continue to rely on Flash, Mozilla has updated its published roadmap for Flash in Firefox. Starting next month, users will choose which websites are able to run the Flash plugin.” states Firefox. “Flash will be disabled by default for most users in 2019, and only users running the Firefox Extended Support Release (ESR) will be able to continue using Flash through the final end-of-life at the end of 2020. In order to preserve user security, once Flash is no longer supported by Adobe security patches, no version of Firefox will load the plugin.”
According to Google, Flash usage had gone down from 80% to 17%.

In a similar way, Microsoft also announced the end of support for its products.
“We will phase out Flash from Microsoft Edge and Internet Explorer, culminating in the removal of Flash from Windows entirely by the end of 2020. This process began already for Microsoft Edge with Click-to-Run for Flash in the Windows 10 Creators Update.” states Microsoft.
Facebook also announced that it will shut off Flash games by the end of 2020.
Administrators of Websites that rely on Flash are being encouraged to start planning the migration to new technologies.
Under the cyber security perspective, the Adobe Flash end of life is a good news because it is one of the most exploited software in recent cyber attacks.
32M Becomes First-Ever Company to Implant Micro-Chips in Employees
25.7.207 thehackernews Privacy
Biohacking could be a next big thing in this smart world.
Over two years ago, a hacker implanted a small NFC chip in his left hand right between his thumb and his pointer finger and hacked Android smartphones and bypassed almost all security measures, demonstrating the risks of Biohacking.
At the end of the same year, another hacker implanted a small NFC chip with the private key to his Bitcoin wallet under his skin, making him able to buy groceries or transfer money between bank accounts by just waving his hand.
And this is soon going to be a reality, at least in one tech company in Wisconsin.
Marketing solution provider Three Square Market (32M) has announced that it had partnered with Swedish biohacking firm BioHax International for offering implanted microchips to all their employees on 1st August, according to the company's website.
Although the programme is optional, the company wants at least more than 50 of its employees to undergo the Biohacking procedure.
Like previous bio hacks, the chips will be implanted underneath the skin between the thumb and forefinger, and will also use near-field communications (NFC) — the same technology that makes contactless credit cards and mobile payments possible — along with radio-frequency identification (RFID).
According to the company, the implanted chips would allow its employees to log into their office computers, pay for food and drink from office vending machines, open doors and use the copy machine, among other purposes.
The company CEO has also confirmed that 'there's no GPS tracking at all.'
"We foresee the use of RFID technology to drive everything from making purchases in our office break room market, opening doors, use of copy machines, logging into our office computers, unlocking phones, sharing business cards, storing medical/health information, and used as payment at other RFID terminals," 32M chief executive Todd Westby said.
"Eventually, this technology will become standardised allowing you to use this as your passport, public transit, all purchasing opportunities, etc."
Interested employees will be chipped at the 32M inaugural "chip party" on 1st August at the company's headquarters in River Falls, Wisconsin.
Three Square Market is considered as a leader in micro market technology, which designs mini-convenience stores using a self-checkout kiosk (vending machines), often found in large companies.
The company has more than 2,000 kiosks in nearly 20 different countries, and it operates over 6,000 kiosks in TurnKey Corrections, the firm's corrections industry business.
While the Biometric information and technology are experiencing an increase in popularity, it also raises widespread concerns around the safety and privacy of people adopting it.
Hackers could misuse the technology used to provide easiness to the public against the public itself, and one should not forget that with the advance in technology, the techniques used by cyber criminals also improves.
One in Ten U.S. Organizations Hit by WannaCry: Study
25.7.207 securityweek Ransomware
A recent survey discovered that the vast majority of organizations in the United States weren’t prepared for the WannaCry ransomware attack, but just one in ten ended up being infected by the malware.
WannaCry stormed the world in mid-May by leveraging a previously patched exploit called EternalBlue, which hacker group Shadow Brokers allegedly stole from the NSA-linked Equation Group. The ransomware mostly infected Windows 7 computers that hadn’t been patched in due time, and also revealed the destructive impact of a global outbreak. NotPetya confirmed the risk in late June.
According to a survey (PDF) from software lifecycle automation solutions provider 1E, 86% of the organizations in the U.S. had to “divert significant resources” to safeguard themselves during the WannaCry attack. Only 14% of the respondents revealed their organization was prepared for such an attack.
The study also shows that 86% of organizations don’t apply patches immediately after they are released, thus leaving endpoints and entire networks exposed to such attacks. While 14% of respondents said they apply patches immediately, 36% apply them within one week after release, and 27% need up to a month for that, while 23% don’t apply patches within a month after release.
It’s no surprise that 70% of the 400+ U.S. IT professionals responding to the survey said they had to work over at least one weekend as a result of the WannaCry attack, while one in ten admitted to having worked three or more weekends.
The fact that most organizations aren’t prepared for attacks that exploit already patched vulnerabilities is also reflected in the percentage of respondents who said they already migrated to Windows 10: 11%. While 53% said they are currently migrating to Microsoft’s latest platform iteration, 28% said they are planning on doing so this year or the next, while 8% said they had no such plan.
Following the WannaCry incident, awareness appears to have increased regarding the benefits of applying the necessary patches in due time. 71% of respondents said their intent to stay updated has improved (the percentage rises to 87% when infected organizations are concerned), while 74% said “the experience of reacting to WannaCry has left them better prepared for future threats.”
However, 87% of organizations aren’t taking steps to accelerate their migration to Windows 10, despite the looming risks. Furthermore, 73% of respondents said management didn’t make more resources available to IT to help it apply patches faster and/or accelerate its OS migration.
“There is growing a concern that we have entered an era in which this kind of attack becomes the new normal. It's more important than ever that organizations stay current and ensure that software is kept up-to-date and fully patched at all times. WannaCry was a huge wakeup call that elevated security concerns to boardroom level -- IT teams can't afford to leave their organizations exposed,” Sumir Karayi, founder and CEO of 1E, said.
Researcher Analyzes Psychology of Ransomware Splash Screens
25.7.207 securityweek Ransomware
The 'splash screens' of seventy-six different types of ransomware have been analyzed by a cyber-psychologist from De Montfort University. Commissioned by SentinelOne, the subsequent report 'Exploring the Psychological Mechanisms used in Ransomware Splash Screens' (PDF) is designed to reveal how social engineering tactics are used by cyber criminals to manipulate and elicit payments from individuals.
All successful ransomware infections have one common factor -- an explanatory instruction screen to describe what has happened and explain how the victims can recover their files through the payment of a ransom. It is these explanatory screens that comprise the 'splash screens' that are analyzed.
The content and design of the splash screens varies widely but they all have the same intention: to ensure that the victim pays up. "The argument presented in the current report," writes the author, Dr Lee Hadlington, "suggests that these tactics are closely aligned to the concept of social engineering, working on aspects of fear, urgency, scarcity, authority and, in some cases, humor."
He admits that it isn't clear whether the use of archetypal social engineering methods is by design or imitation; but they do occur. The primary social engineering techniques are 'urgency' ('pay within a short deadline or the fee will double'); fear ('or you will lose all of your personal files'); authority ('you must do what I say'); and -- sometimes -- approachability ('email me if you need further instructions').
Hadlington says, "We know that psychology plays a significant part in cyber crime -- what's been most interesting from this study is uncovering the various ways that key social engineering techniques are used to intimidate or influence victims. With ransomware on the rise, it's important that we improve our understanding of this aspect of the attack and how language, imagery and other aspects of the initial ransom demand are used to coerce victims."
While the analysis of the splash screens is interesting and thorough, it does not explain why it is important to understand a technique (social engineering) that is already well-understood and thoroughly analyzed. Furthermore, there is no ability to study the effectiveness of the social engineering techniques (which would at least benefit social engineering research if not ransomware research).
One difficulty is that we do not fully understand the underlying purpose of this social engineering. David Harley, a senior research fellow with ESET, has his own thoughts. "As I see it, the importance of social engineering in notifications lies mostly in these areas," he told SecurityWeek in an emailed comment: "[firstly] pressuring the victim into taking the desirable action of paying up more or less immediately, rather than exploring other options. Especially if there's a risk that grey- or whitehat researchers will come up with a way of recovering data without paying.
"[Secondly] pressuring the victim into paying for recovery of data that aren't actually lost; and [thirdly] pressuring the victim into paying for recovery of data for which the criminals don't actually have a recovery mechanism, before some interfering security researcher points out that paying up doesn't achieve anything."
The big weakness in the report is the inability to measure the effectiveness of the splash screens. This is something that the author admits: "Not all splash screens are the same -- there is a distinct difference in terms of the level of sophistication of mechanisms used to gain payment, presentation of the splash screens and provision of information for further contact. However, there is no further data to explore how such differences map to their success in terms of eliciting payment."
Tony Rowan, a director at SentinelOne, accepts the difficulty in measuring the success of the different splash screens. "This is an interesting area," he told SecurityWeek, "and we have looked for data to use in a correlation exercise. At this stage, the payment data is too disparate and unverifiable to be useful for a correlation exercise, though this is an area we will continue to look at."
But as Harley adds, "As someone with a background in social sciences, I find these questions rather interesting; but from an academic point of view, without subjective data to draw on which aren't present in this study, they're just conjecture."
Without the ability to measure the effectiveness of the different splash screens, there can be no serious conclusions from the analysis. This is admitted: "By expanding the current work with more empirical research, a clearer understanding of why certain ransomware splash screens are more successful at eliciting a payment over others could be obtained," writes Hadlington. "Such information could in turn be used to provide effective mitigation techniques for such attacks, as well as giving both investigators and victims a clearer pathway for help and advice in the event of an attack."
But even then, it is not at all clear how understanding the efficiency of different social engineering techniques in splash screens could help provide 'effective mitigation techniques for such attacks'. It has to be said that this research will be of more interest to students of social engineering than to students of cyber security.
Misconfigured Google Groups Expose Sensitive Data
25.7.207 securityweek IT
Researchers at cloud security firm RedLock believe hundreds of organizations may be exposing highly sensitive information by failing to properly configure Google Groups.
Google Groups is a service that allows users to create and take part in online forums and email-based groups. When a group is configured, its creator has to set sharing options for “Outside this domain - access to groups” to either “Private” or “Public on the Internet.”
RedLock’s Cloud Security Intelligence (CSI) team noticed that many Google Groups for Business users have allowed access to their groups from the Internet, and in some cases the configuration error has resulted in the exposure of sensitive information.
Researchers have found names, email and home addresses, employee salary data, sales pipeline data, and customer passwords in the exposed groups.
“We only looked for a sample of such cases and found dozens,” RedLock told SecurityWeek. “Extending that, there are likely hundreds of companies affected by this misconfiguration.”
According to RedLock, the list of affected firms includes IBM’s The Weather Company, which operates weather.com, intellicast.com and Weather Underground; Fusion Media Group, which owns Gizmodo, The Onion, Jezebel and Lifehacker; video ad platform SpotX, which delivers ads to 600 million people worldwide every month; and cloud-based helpdesk support provider Freshworks, whose software is used by more than 100,000 companies.
Organizations using Google Groups have been advised to immediately check their settings to ensure that access is set to private in order to avoid leaking sensitive data.
“Simple misconfiguration errors – whether in SaaS applications or cloud infrastructure – can have potentially devastating effects,” said Varun Badhwar, CEO and co-founder of RedLock.
Badhwar pointed to the recent incidents involving Deep Root Analytics, WWE and Booz Allen Hamilton as examples of the impact such simple errors can have.
“This new issue that the RedLock CSI team discovered has led to the exposure of sensitive information from hundreds of companies simply through the click of a button,” Badhwar explained. “In today’s environment, it’s imperative that every organization take steps to educate employees on security best practices and leverage tools that can automate the process of securing applications, workloads and other systems. In the cloud, for example, a resource only exists for 127 minutes on average – there’s no way for IT teams alone to keep up with this rapid rate of change.”
Spring Dragon APT used more than 600 Malware samples in different attacks
25.7.207 securityaffairs APT
The threat actor behind Spring Dragon APT has been developing and updating its wide range of tools throughout the years, new attacks reported in South Asia.
According to a new report published by Kaspersky Lab, the China-linked APT group Spring Dragon (aka Lotus Blossom, Elise, and Esile) has used more than 600 malware samples in its attacks over the past years.
The Spring Dragon APT group is a state-sponsored group that has been around since at least 2012, but further evidence collected by the researchers suggests that it may have been active since 2007.
The APT group focused its cyber espionage campaigns on military and government organizations in Southeast Asia.
In June 2015, Trend Micro published a report on a targeted attack campaign of the group that hit organizations in various countries in the Southeast Asian region. The experts speculated the involvement of state-sponsored hackers due to the nature of the stolen information.
“The Esile targeted attack campaign targeting various countries in the Southeast Asian region has been discussed in the media recently. This campaign – which was referred to by other researchers as Lotus Blossom – is believed to be the work of a nation-state actor due to the nature of the stolen information, which is more valuable to countries than either private companies or cybercriminals.” wrote Trend Micro.
In October 2015, the Lotus Blossom group launched a new espionage campaign using fake invitations to Palo Alto Networks’ Cybersecurity Summit held in Jakarta, on November 3.
Back to the present, researchers from Kaspersky Lab were informed by a research partner in Taiwan of a new wave of attacks powered by the APT group.
“Information about the new attacks arrived from a research partner in Taiwan and we decided to review the actor’s tools, techniques and activities.” states the analysis from Kaspersky Lab.
“Using Kaspersky Lab telemetry data we detected the malware in attacks against some high-profile organizations around the South China Sea.”
The hackers also targeted political parties, educational institutions, and companies in the telecommunications industry.
Most infections were observed in countries around the South China Sea, including Taiwan, Indonesia, Vietnam, the Philippines, Hong Kong, Malaysia, and Thailand.

Spring Dragon is known for spear phishing and watering hole attacks, malware researchers at Kaspersky Lab collected a large set composed of more than 600 malware samples used in different attacks.
The APT group has a huge cyber arsenal, it has been developing and updating its range of tools throughout across the years. The hackers have various backdoor modules with unique characteristics and functionalities, it manages a large Command and Control infrastructure that includes more than 200 unique IP addresses and C&C domains.
Most C&C servers used by Spring Dragon are located in Hong Kong and the United States, other servers have also been found in Germany, China and Japan.
“The large number of samples which we have managed to collect have customized configuration data, different sets of C2 addresses with new hardcoded campaign IDs, as well as customized configuration data for creating a service for malware on a victim’s system. This is designed to make detection more difficult.” continues the analysis.
“All the backdoor modules in the APT’s toolset are capable of downloading more files onto the victim’s machine, uploading files to the attacker’s servers, and also executing any executable file or any command on the victim’s machine. These functionalities enable the attackers to undertake different malicious activities on the victim’s machine.”
The analysis of the malware compilation timestamps revealed that attackers might be in the GMT+8 time zone, the same of countries like China, Indonesia, Malaysia, Mongolia, Singapore, Taiwan, the Philippines and Western Australia.
Another interesting information emerged from the analysis is that the malware has been compiled by two different groups, one of which may be in Europe.
“It also suggests that either there is a second group working another shift in the same time zone or the attackers are cross-continental and there is another group, possibly in Europe. The uneven distribution of timestamps (low activity around 10am, 7-8pm UTC) suggests that the attackers didn’t change the timestamps to random or constant values and they might be real.” states the analysis.
“The number of malware samples which we managed to collect (over 600) for the group surpassed many others, and suggests an operation on a massive scale. It’s possible that this malware toolkit is offered in specialist public or private forums to any buyers, although, to date, we haven’t seen this.”
Přichází nový typ kyberútoků s cílem masivně poškozovat firmy
25.7.2017 SecurityWorld Kyber
Kybernetické hrozby se vyvíjejí extrémně rychle. V budoucnu se setkáme s novým typem ničivých kybernetických útoků, tzv. DeOS útoky (z anglického Destruction of Service).
Budoucí DeOS útoky budou mít jediný cíl – napáchat maximální škody a zničit veškeré zálohovací mechanismy, které organizace potřebují k obnově systému a dat. S těmito závěry přišla studie Cisco 2017 Midyear Cybersecurity Report, která pravidelně mapuje globální trendy a situaci v kybernetické bezpečnosti.
Studie dále poukazuje na to, že je na vzestupu obchod s vyděračským softwarem, ransomwarem, a jeho spuštění se pro útočníky stává stále snazším. Větší škody ale globálně způsobí útoky využívající sociálního inženýrství. Ty se zaměřují na konkrétní firmy a snaží se donutit oběť, aby útočníkovi převedla své peníze. Za 3 roky si takto hackeři vydělali 5,3 miliardy dolarů.
Studie také přinesla závěry průzkumu mezi 3000 bezpečnostními profesionály, který ukázal, s jakými největšími výzvami se potýkají jednotlivá průmyslová odvětví.
„Nedávné globální útoky ransomwaru WannaCry a Nyetya ukázaly, že tradiční útoky vyděračských softwarů se stávají stále ničivějšími. Odhadujeme, že jsou tyto incidenty předzvěstí nového typu, tzv. DeOS útoku, který dokáže napáchat mnohem větší škody, a ze kterého se napadené organizace budou jen těžko vzpamatovávat,“ říká Milan Habrcetl, bezpečnostní expert společnosti Cisco a doplňuje: „Nové možnosti kybernetickým útočníkům otevírá také rychlý rozvoj internetu věcí. Nedávná aktivita některých internetových robotů provádějících nežádoucí činnost (tzv. botnetů) naznačuje, že útočníci mohou položit základy počítačových hrozeb s obrovským dopadem, které by potenciálně mohly narušit i samotný provoz internetu. Dnes vidíme, že lépe na takové útoky reagují firmy, které průběžně monitorují provoz v síti a bezpečnostní řešení je její součástí.“
Výzkumníci společnosti Cisco monitorovali vývoj kybernetických hrozeb v první polovině roku 2017 a zjistili i nové postupy útočníků. Ti stále častěji využívají technik, které vyžadují uživatelovo kliknutí na infikovaný odkaz či přílohu emailu. Hackeři dnes vyvíjejí malware, který nemá formu klasického souboru, ale ukládá se rovnou do paměti.
Tento typ je mnohem náročnější detekovat a analyzovat, neboť se automaticky vymaže po restartování počítače. Útočníci také stále častěji spoléhají na anonymizovanou a decentralizovanou infrastrukturu, jako je například proxy služba Tor.
Studie společnosti Cisco ukazuje aktuální trendy a techniky, které útočníci využívají. Mezi ně patří:
Ransomware jako služba: Podle odhadů dosáhl zisk kybernetických útočníků z ransomware kampaní v roce 2016 více než 1 miliardu amerických dolarů. I proto se černý trh rozrůstá a společnost Cisco pozoruje nárůst modelu Ransomware jako služba (Ransomware‑as‑a‑service). Ten umožňuje útočníkům provést útok vyděračského softwaru, aniž by oni sami disponovali potřebnými nástroji a dovednostmi.
Sociální inženýrství: Větší finanční ztrátu než ransomware způsobily organizacím útoky s podvodnými emaily, které využívaly také technik sociálního inženýrství. V nich se útočnici snaží, aby organizace v domnění, že jde o legální transakci, převedly peníze na jejich účet. Tento byznys je velmi výnosný. Podle odhadů odborníků z amerického týmu Internet Crime Complaint Center dokázali hackeři mezi říjnem 2013 a prosincem 2016 tímto způsobem vydělat 5,3 miliardy dolarů.
Objem spamu stále narůstá: Kybernetičtí útočníci stále častěji využívají k šíření útoků nevyžádanou poštu. Výzkumníci společnosti Cisco očekávají, že objem spamu poroste i nadále, zatímco obliba exploit kitů (nástroje pro šíření škodlivého softwaru) bude klesat.
Firmy podceňují spyware a adware: Mnoho bezpečnostních odborníků stále považuje soubory typu spyware (špehovací software odesílající data bez vědomí uživatele) a adware (software zobrazující nevyžádané reklamy)za spíše nepříjemné než nebezpečné. Nicméně i tyto soubory mohou znamenat pro firmy vysoké riziko. Výzkumníci společnosti Cisco odhalili, že 20 % firem má ve firemní síti alespoň jeden ze 3 nejrozšířenějších typů spywaru. Ty přitom mohou odesílat útočníkům informace o firmě a tím zvýšit riziko nakažení skutečným malwarem.
Studie Cisco 2017 Midyear Cybersecurity Report dále zkoumala, jakým hlavním hrozbám čelí jednotlivá průmyslová odvětví. I přesto, že hackeři používají sofistikovanější techniky a zvyšují intenzitu, organizace se stále potýkají i se základními požadavky na kyberbezpečnost. Se stále užším propojením IT a operačních technologií, i v souvislosti s rozvojem internetu věcí, se firmám nedaří zajistit viditelnost provozu sítě a komplexní přístup k bezpečnosti.
Průzkum, kterého se zúčastnilo 3000 bezpečnostních profesionálů, zjistil, že bezpečnostní týmy jsou neustále pod tlakem zvyšujícího se množství útoků. Dále průzkum zjistil, že:
Pouze 2/3 organizací skutečně prošetřují bezpečnostní upozornění. V některých odvětvích (například zdravotnictví či doprava) je to dokonce jenom kolem 50 %.
I v nejrizikovějších odvětvích (jako je finančnictví či zdravotnictví) jsou podniky schopny efektivně reagovat na skutečné útoky v méně než 50 % případů.
Úspěšné průniky jsou motivací ke zlepšení. Napříč většinou odvětví znamená úspěšný útok přinejmenším minimální posílení bezpečnosti v alespoň 90 % organizací.
Mezi další zjištění v jednotlivých odvětvích patří:
Veřejný sektor: Ze všech zkoumaných hrozeb bylo 32 % z nich označeno jako skutečně oprávněných (ohrožujících). Ovšem pouze proti 47 % z nich vytvořily organizace dodatečnou obranu.
Maloobchod: 32 % podniků říká, že v posledních několika letech se jim kvůli kybernetickým útokům snížily zisky. Zhruba 25 % pak ztratilo zákazníky nebo obchodní příležitosti.
Výroba: 40 % bezpečnostních profesionálu z oblasti výroby řeklo, že nemají oficiální bezpečnostní strategii, ani neaplikují bezpečnostní normy, jako jsou ISO 27001 či NIST 800‑53.
Sektor utilit: Bezpečnostní profesionálové označili za největší bezpečnostní rizika cílené útoky (42 %) a tzv. přetrvávající pokročilé hrozby (advanced persistent threats). Ty jako největší hrozbu vnímá 40 % dotázaných.
Zdravotnictví: Za vysoké riziko označilo 37 % respondentů cílené útoky.
Šest rad na obranu
Aby se organizace efektivněji bránily současným stále sofistikovanějším útoků, měly by zvolit proaktivní přístup. Bezpečnostní tým Cisco radí:
Pravidelně aktualizujte infrastrukturu i aplikace, aby útočníci nemohli využít již známé zranitelnosti.
Bezpečnostní prvky musí být integrované. Omezte investice do izolovaných řešení.
Zapojte do kyberbezpečnosti nejvyšší členy vedení, aby porozuměli rizikům, výhodám i rozpočtovým omezením.
Vytvořte jasné metriky. Používejte je, abyste lépe pochopili přínosy konkrétních kroků a mohli svoji bezpečnost dále zlepšovat.
Zkontrolujte úroveň znalostí svých zaměstnanců prostřednictvím tréninkových postupů se zaměřením na konkrétní pracovní pozice i na obecné školení.
Snažte se vyvážit obranu s aktivní reakcí. Obrana před útoky spočívá v průběžné činnosti, nikoliv pouze v prvotním nasazení a následné pasivitě.
SLocker source code leaked online for free, a gift for crooks and hackers
24.7.2017 securityaffairs Ransomware
The SLocker source code leaked online, it is one of the oldest mobile lock screen and file-encrypting ransomware.
The source code of the SLocker Android malware, one of the most popular Android ransomware families, has been leaked online for free, allowing crooks to develop their own variant of the threat.
SLocker was first spotted in 2015, it is the first ransomware to encrypt Android files.
The SLocker source code has been leaked on GitHub by a user who uses the online moniker “fs0c1ety,” the hacker is inviting everyone to contribute to the code and submit bug reports.
“The SLocker family is one of the oldest mobile lock screen and file-encrypting ransomware and used to impersonate law enforcement agencies to convince victims to pay their ransom.” states fs0c1ety.
“All contributions are welcome, from code to documentation to design suggestions to bug reports. Please use GitHub to its fullest– contribute Pull Requests, contribute tutorials or other wiki content– whatever you have to offer, we can use it!”

The SLocker, aka Simple Locker, is a mobile ransomware that locks victims’ mobile devices and requests the payment of a ransom to unlock them.
The malware impersonates law enforcement agencies to convince victims to pay the ransom, it infected thousands of Android devices in 2016.
According to the experts, more than 400 new variants of the SLocker ransomware were observed in the wild in May, while in May researchers at Trend Micro found a variant mimicking the WannaCry GUI .
“This particular SLocker variant is notable for being an Android file-encrypting ransomware, and the first mobile ransomware to capitalize on the success of the previous WannaCry outbreak.” reads the analysis published by Trend Micro.
“While this SLocker variant is notable for being able to encrypt files on mobile, it was quite short-lived. Shortly after details about the ransomware surfaced, decrypt tools were published. And before long, more variants were found. Five days after its initial detection, a suspect supposedly responsible for the ransomware was arrested by the Chinese police. Luckily, due to the limited transmission channels (it was spread mostly through forums like QQ groups and Bulletin Board Systems), the number of victims was very low.”
Once infected the mobile device, SLocker runs silently in the background and encrypts any kind of file on the smartphone, including images, documents, and videos.
The ransomware is also able to hijack the mobile device, making impossible for the owners to access the device.
The availability of the SLocker source code will likely increase the number of samples that will be detected in the wild in the incoming weeks.
Sweden Accidentally Leaks Personal Details of Nearly All Citizens
24.7.2017 thehackernews BigBrothers
Another day, Another data breach!
This time sensitive and personal data of millions of transporters in Sweden, along with the nation's military secrets, have been exposed, putting every individual's as well as national security at risk.
Who exposed the sensitive data? The Swedish government itself.
Swedish media is reporting of a massive data breach in the Swedish Transport Agency (Transportstyrelsen) after the agency mishandled an outsourcing deal with IBM, which led to the leak of the private data about every vehicle in the country, including those used by both police and military.
The data breach exposed the names, photos and home addresses of millions of Swedish citizen, including fighter pilots of Swedish air force, members of the military's most secretive units, police suspects, people under the witness relocation programme, the weight capacity of all roads and bridges, and much more.
The incident is believed to be one of the worst government information security disasters ever.
Here's what and How it Happened:
In 2015, the Swedish Transport Agency hand over IBM an IT maintenance contract to manage its databases and networks.
However, the Swedish Transport Agency uploaded IBM's entire database onto cloud servers, which covered details on every vehicle in the country, including police and military registrations, and individuals on witness protection programs.
The transport agency then emailed the entire database in messages to marketers that subscribe to it.
And what’s terrible is that the messages were sent in clear text.
When the error was discovered, the transport agency merely thought of sending a new list in another email, asking the subscribers to delete the old list themselves.
If you think the scandal ends there, you are wrong. The outsourcing deal gave IBM staff outside Sweden access to the Swedish transport agency's systems without undergoing proper security clearance checks.
IBM administrators in the Czech Republic were also given full access to all data and logs, according to Swedish newspaper Dagens Nyheter (DN), which analysed the Säpo investigation documents.
According to Pirate Party founder and now head of privacy at VPN provider Private Internet Access Rick Falkvinge, who brought details of this scandal, the incident "exposed and leaked every conceivable top secret database: fighter pilots, SEAL team operators, police suspects, people under witness relocation."
Tons of Sensitive Info Exposed about Both Individuals and Nation's Critical Infrastructures
According to Falkvinge, the leak exposed:
The weight capacity of all roads as well as bridges (which is crucial for warfare, and gives a lot idea about what roads are intended to be used as wartime airfields).
Names, photos, and home addresses of fighter pilots in the Air Force.
Names, photos, and home addresses of everybody in a police register, which are believed to be classified.
Names, photos, and residential addresses of all operators in the military's most secret units that are equivalent to the SAS or SEAL teams.
Names, photos, and addresses of everybody in a witness relocation program, who has been given protected identity for some reasons.
Type, model, weight, and any defects in all government and military vehicles, including their operator, which reveals a much about the structure of military support units.
Although the data breach happened in 2015, Swedish Secret Service discovered it in 2016 and started investigating the incident, which led to the fire of STA director-general Maria Ågren in January 2017.
Ågren was also fined half a month's pay (70,000 Swedish krona which equals to $8,500) after finding her guilty of being "careless with secret information," according to the publication.
What's the worrying part? The leaked database may not be secured until the fall, said the agency's new director-general Jonas Bjelfvenstam. The investigation into the scope of the leak is still ongoing.
Google Rolls-Out Play Protect Services for Android
24.7.2017 securityweek Android
After introducing the product at the Google I/O conference in May, Google has now made its Play Protect security services available to all Android users.
Play Protect was designed to combine various Android security services, including Verify Apps and Bouncer, in a single suite integrated into all devices with Google Play. This, Googls says, will let users benefit from comprehensive protection capabilities without having to search for and download multiple applications on their devices.
The Internet giant already performs tens of billions of application scans every day in an effort to protect the 2 billion active Android devices around the world. According to Google, it can identify risks, discover potentially harmful applications, prevent them from compromising devices, and even remove them from already infected devices when necessary.
Play Protect was designed to scan all applications in Google Play before they are downloaded, but also periodically all apps installed on connected devices. Thus, it can detect harmful behavior even in applications that haven’t been installed via Google Play.
In fact, Play Protect scans and monitors apps from third-party sources continuously, meaning it could detect malicious activities even if they are performed long after the app was installed (some programs hide their behavior by acting normally in the beginning). Potentially harmful apps are disabled and the user is alerted.
“Google Play Protect continuously works to keep your device, data and apps safe. It actively scans your device and is constantly improving to make sure you have the latest in mobile security. Your device is automatically scanned around the clock, so you can rest easy,” Google claims.
A Find My Device service (previously known as Android Device Manager) is also part of Play Protect, allowing users to easily locate, lock, or wipe phones, tablets, and other type of devices that have been lost or stolen. Safe Browsing, the feature that keeps users protected when surfing the web via Chrome on Android, is also included in the suite.
Users looking to customize the Play Protect options on their devices should head to Settings > Google > Security > Play Protect (previously Verify Apps). Play Protect should be available on all devices running Google Play services 11 or above.
Despite Google’s continuous focus on improving Android safety, malicious apps still manage to slip into Google Play and infect millions. To circumvent the company’s protections, cybercriminals hide their malware in fake system updates, mobile games, utility programs, and fake versions of popular streaming apps.
Threat Hunters Analyze Trends in Destructive Cyber-Attacks
24.7.2017 securityweek Cyber
The three primary trends in the incidence of destructive cyber-attacks are that they are increasing; they are usually state-sponsored; and they do not, apart from a few rare occurrences, involve anything more than basic tools. Potentially more concerning for private industry, however, is a lack of concern over what, in kinetic warfare, would be termed 'collateral damage'.
Cybereason, a Boston MA-based threat hunting firm, has analyzed destructive cyber-attacks from the 1982 software-instigated explosion in a Siberian pipeline to the recent NotPetya and Industroyer attacks. Cybereason's conclusions are not reassuring for industry.
A graph of attack sophistication over time shows two primary characteristics. The majority of attacks have occurred since 2012, and the majority of attacks are (relatively) unsophisticated.
The three sophisticated attacks are a 1998 US military attack against Serbian air defense systems; the Stuxnet attack against the Iranian nuclear program in 2010; and the CrashOverride/Industroyer attack against the Ukrainian power grid in 2016. All three have one common characteristic: they are thought to be nation-state attacks against critical or military infrastructure.
A clear majority of unsophisticated attacks are targeted against private industry. Cybereason sees little sign of this being contained by government interaction, and fears that it is likely to increase: it is, in effect, uncontrolled cyber war in all but official classification.
Some of these attacks are likely to have been nation-state actors testing out their cyber-weapons. The 2015 attack against the French television station TV5Monde is thought to be one; where the UK intelligence community concluded that it was likely an attempt to test forms of cyber-weaponry as part of an increasingly aggressive posture by Russia, acting through APT28/Fancy Bear.
Other attacks are purely political, including several attacks by Iranian hackers against Saudi oil production. Some could be considered 'national' political/revenge, such as the North Korean Dark Seoul attack against South Korean television and banking in 2013, and against Sony Pictures in 2014.
Cybereason argues that government is unable -- perhaps unwilling -- to counter this threat.
"There is no incentive for nations to stop this behavior," Cybereason explains in its report (PDF). "They can signal displeasure, retaliate for another's actions, or conduct disruptive covert operations with impunity. The relative ease in striking internationally that the Internet provides combined with the comparative lack of retribution has created an environment where nations will continue to experiment and grow increasingly bold in their attacks."
The problem for private industry, however, is the fundamental difference between kinetic and cyber warfare. "The idea that a major power would threaten the critical infrastructure of another major power over an information operation would be outrageous if the threat was carried out via kinetic means."
But governments are reluctant to respond in the cyber domain as they would in the kinetic domain for fear of escalation ultimately leading to the transition from cyber to real world conflict. The result is that cyber collateral damage is largely accepted by governments; and that collateral damage is frequently private industry.
"With no ability, or even intent to dissuade destructive attacks from nation states," warns Cybereason, "the private sector is paying the ultimate price. They are most often the victims of these attacks because they are both less secure than government networks and also have been largely deemed a 'safe' target from a retaliation standpoint."
For this reason, Cybereason believes "that the cluster of relatively low sophisticated [nation-state] attacks is likely to continue grow year over year. The victims will likely continue to be non-government institutions that for some reason or other present a useful target for advancing a hostile nation's interests."
It is equally worried, however, that similar tactics will be adopted by non-state attackers.
"Currently, DDoS is the easiest and most leveraged tool for hacktivists and those looking to disrupt specific entities," the security firm says. "However, as more destructive tools continue to be used and society continues to become numb to the announcements of new attacks, cybercrime and hacktivists will increasingly be willing to move into this space. The ability to have a larger impact combined with the ability to increase obfuscation by not only damaging the information systems but also wiping forensic evidence will become even more enticing for those who want to expand their business model."
Put simply, Cybereason believes that private sector attackers will increasingly use destruction as part of their methodology. The implication, and advice from Cybereason, is that the private sector defenders need to factor aggressive destruction into their risk management.
It warns against relying on 'deterrence by denial', whether this is a government induced threat of retaliation or private sector 'hacking back'. Government will be reluctant to instigate the former, while the latter "is only going to lead to more hacking, less secure networks, and in general a shorter and more brutal life for corporation's network security."
It recommends two courses of action for the private sector. The first is to understand and recognize where it might be a target for "a nation state lashing out" now, and possibly destructive hacktivist attacks in the future. This implies that effective disaster recovery can no longer be considered a luxury but an absolute necessity. The second is to switch from reactive defense to proactive threat-hunting within the network, in order to detect and block destructive attacks before they can be triggered by the adversary.
In June 2017, Cybereason announced that it had raised $100 million in Series D funding, increasing the total investment in the firm to $189 million.
Over 600 Malware Samples Linked to Chinese Cyberspy Group
24.7.2017 securityweek Virus
A China-linked cyber espionage group tracked by security firms as Lotus Blossom, Elise, Esile and Spring Dragon has used more than 600 malware samples in its attacks over the past years, according to Kaspersky Lab.
Spring Dragon has been around since at least 2012, but there is some evidence suggesting that it may have been active since 2007. The state-sponsored threat group has mainly targeted military and government organizations in Southeast Asia.
Kaspersky Lab learned recently from a research partner in Taiwan of new attacks launched by the group. Data collected by the security firm indicates that the APT actor has also targeted political parties, universities and other educational institutions, and companies in the telecommunications sector.
The cyberspies appear to focus on countries around the South China Sea, including Taiwan, Indonesia, Vietnam, the Philippines, Hong Kong, Malaysia and Thailand.
The threat actor has been using a wide range of tools, including backdoors that can download other files to the compromised machine, upload files to a remote server, and execute files and commands. Kaspersky Lab has identified a total of more than 600 malware samples used over the past years.
According to the security firm, the malware leverages a command and control (C&C) infrastructure of more than 200 unique IP addresses and domains, with each sample using hardcoded campaign codes and custom C&C addresses.
The C&C servers used by Spring Dragon are located in several countries, but roughly two-thirds are located in Hong Kong and the United States. Some servers have also been spotted in Germany, China and Japan.
Based on malware compilation timestamps, which Kaspersky believes have not been altered, the attackers appear to be located in the GMT+8 timezone, which corresponds to China, Indonesia, Malaysia, Mongolia, Singapore, Taiwan, the Philippines and Western Australia.
The malware compilation timestamps also suggest that the members of the group either work in two shifts, or Spring Dragon malware has been compiled by two different groups, one of which may be located in Europe.
“The number of malware samples which we managed to collect (over 600) for the group surpassed many others, and suggests an operation on a massive scale. It’s possible that this malware toolkit is offered in specialist public or private forums to any buyers, although, to date, we haven’t seen this,” explained Kaspersky’s Noushin Shabab.
Internet Bug Bounty Project Receives $300,000 Donation
24.7.2017 securityweek Security
The Internet Bug Bounty (IBB), a project whose goal is to make the Web safer by rewarding white hat hackers who find vulnerabilities in core Internet infrastructure and open source software, announced on Friday that it has secured a $300,000 donation.
Facebook, GitHub and the Ford Foundation, one of the world’s largest charitable organizations, have each donated $100,000 to the IBB. With their donation, GitHub and the Ford Foundation have joined existing sponsors, Facebook, Microsoft and HackerOne.
The IBB rewards researchers who find vulnerabilities in OpenSSL, Nginx, Apache httpd, Perl, PHP, Python, Ruby, Flash, Ruby on Rails, Phabricator, Django, RubyGems and other widely used Internet technologies.
Since its launch in November 2013, the IBB has awarded more than $600,000 for over 600 vulnerabilities found by bounty hunters. This includes over $150,000 awarded last year and $45,000 that hackers decided to donate to charities and nonprofit organizations, such as the Electronic Frontier Foundation (EFF), Hackers for Charity, and the Freedom of the Press Foundation.
Critical security holes such as ImageTragick, Heartbleed and Shellshock earned researchers $7,500, $15,000 and $20,000, respectively.
With the newly raised funds, the IBB plans on expanding the scope of the bug bounty program by adding a new category for flaws in popular data parsing libraries, which are considered increasingly risky. The expansion will also cover technologies that “serve as the technical foundation of a free and open Internet, such as OpenSSL.”
“At Ford Foundation we believe that a secure, free and open internet is critical in the fight against inequality,” said Michael Brennan, Ford Foundation’s technology program officer on the Internet Freedom team. “The open source infrastructure of the internet is part of a public commons that we are committed to help maintain and draw attention to. A necessary part of this maintenance is recognizing and rewarding those who uncover critical vulnerabilities in freely available code that we all rely upon.”
Briton Pleads Guilty to Mirai Attacks in German Court
24.7.2017 securityweek BotNet
A British man pleaded guilty last week in a German court to launching a cyberattack that resulted in more than one million customers of telecommunications provider Deutsche Telekom experiencing Internet disruptions.
German media has identified the 29-year-old man as “Peter Parker” and “Spiderman,” online monikers linked to domains used to coordinate some attacks powered by the notorious Mirai malware. He was also identified by Handelsblatt as Daniel K.
A blog post published earlier this month by security blogger Brian Krebs revealed that the suspect is a British man named Daniel Kaye and the hacker known online as “BestBuy.” He has also been tied to the nickname “Popopret,” but it’s unclear if it’s the same person or a partner of BestBuy.
Krebs found links between Kaye, a massive Mirai botnet that enslaved a large number of Internet of Things (IoT) devices, and a piece of malware named GovRAT.
Reports of BestBuy’s apprehension surfaced in February when German police announced that a man suspected of carrying out the November 2016 attack on Deutsche Telekom had been arrested by the U.K. National Crime Agency (NCA) at a London airport based on a warrant issued by authorities in Germany.
According to German media reports, the 29-year-old pleaded guilty on Friday in the Regional Court of Cologne, claiming that he regretted his actions. He said his main motive was money – he was about to marry his fiance and he wanted a good start to married life. It’s worth mentioning that the social media profiles for Daniel Kaye uncovered by Krebs also showed that he had been engaged to be married.
The hacker told the court that Deutsche Telekom was not the main target of his attack. Instead, he used the Mirai malware to hijack routers – including ones belonging to Deutsche Telekom customers – and other types of devices, which he abused to launch distributed denial-of-service (DDoS) attacks. He claimed a telecommunications firm in the West African country of Liberia paid him $10,000 to attack a competitor.
At the time of his arrest, German authorities said the suspect faced between 6 months and 10 years in prison. He may be sentenced on July 28.
New Debian 9.1 release includes 26 security fixes for 55 packages
24.7.2017 securityaffairs Vulnerebility
The Debian Project announced the Debian 9.1 GNU/Linux, a version that brings numerous updates and addresses many security issues.
The Debian Project announced the new Debian 9.1 release that includes 26 security fixes. The list of fixed problems includes the Heimdal Kerberos man-in-the-middle vulnerability, a 20 years-old vulnerability in Kerberos that was parched this week for both Microsoft and Linux distros.
“The Debian project is pleased to announce the first update of its stable distribution Debian 9 (codename stretch). This point release mainly adds corrections for security issues, along with a few adjustments for serious problems. Security advisories have already been published separately and are referenced where available.” states the announcement.
“Please note that the point release does not constitute a new version of Debian 9 but only updates some of the packages included. There is no need to throw away old stretch media. After installation, packages can be upgraded to the current versions using an up-to-date Debian mirror.”
Debian 9.1 isn’t a new Debian version or bring new features, it only updates the existing packages with a special focus on cyber security.
Debian 9.1 also addresses security issues in Apache, and includes a number of Linux updates and patches for OpenVPN flaws (including recently fixed CVE-2017-7508, CVE-2017-7520, CVE-2017-7520).
The new release fixes the CVE-2017-1000381 in the c-ares function “ares_parse_naptr_reply()“, it also addresses several issues in thedwarfutils link shortener and in libquicktime.
“The c-ares function `ares_parse_naptr_reply()`, which is used for parsing NAPTR responses, could be triggered to read memory outside of the given input buffer if the passed in DNS response packet was crafted in a particular way.” states the description for the CVE-2017-1000381 flaw.

For updating all packages run the following command:
apt-get update && apt-get upgrade
For downloading Debian 9.1 images, refer one of the mirrors at the following URL:
https://www.debian.org/mirror/list
Spring Dragon – Updated Activity
24.7.2017 Kaspersky APT
Spring Dragon is a long running APT actor that operates on a massive scale. The group has been running campaigns, mostly in countries and territories around the South China Sea, since as early as 2012. The main targets of Spring Dragon attacks are high profile governmental organizations and political parties, education institutions such as universities, as well as companies from the telecommunications sector.
In the beginning of 2017, Kaspersky Lab became aware of new activities by an APT actor we have been tracking for several years called Spring Dragon (also known as LotusBlossom).
Information about the new attacks arrived from a research partner in Taiwan and we decided to review the actor’s tools, techniques and activities.
Using Kaspersky Lab telemetry data we detected the malware in attacks against some high-profile organizations around the South China Sea.
Spring Dragon is known for spear phishing and watering hole techniques and some of its tools have previously been analyzed and reported on by security researchers, including Kaspersky Lab. We collected a large set (600+) of malware samples used in different attacks, with customized C2 addresses and campaign codes hardcoded in the malware samples.
Spring Dragon’s Toolset
The threat actor behind Spring Dragon APT has been developing and updating its range of tools throughout the years it has been operational. Its toolset consists of various backdoor modules with unique characteristics and functionalities.
The threat actor owns a large C2 infrastructure which comprises more than 200 unique IP addresses and C2 domains.
The large number of samples which we have managed to collect have customized configuration data, different sets of C2 addresses with new hardcoded campaign IDs, as well as customized configuration data for creating a service for malware on a victim’s system. This is designed to make detection more difficult.
All the backdoor modules in the APT’s toolset are capable of downloading more files onto the victim’s machine, uploading files to the attacker’s servers, and also executing any executable file or any command on the victim’s machine. These functionalities enable the attackers to undertake different malicious activities on the victim’s machine.
A detailed analysis of known malicious tools used by this threat actor is available for customers of Kaspersky Threat Intelligence Services.
Command and Control (C2) Infrastructure
The main modules in Spring Dragon attacks are backdoor files containing IP addresses and domain names of C2 servers. We collected and analyzed information from hundreds of C2 IP addresses and domain names used in different samples of Spring Dragon tools that have been compiled over the years.
In order to hide their real location, attackers have registered domain names and used IP addresses from different geographical locations. The chart below shows the distribution of servers based on geographical location which the attackers used as their C2 servers.
Distribution chart of C2 servers by country
More than 40% of all the C2 servers used for Spring Dragon’s operations are located in Hong Kong, which hints at the geographical region (Asia) of the attackers and/or their targets. The next most popular countries are the US, Germany, China and Japan.
Targets of the Attacks
As was mentioned, the Spring Dragon threat actor has been mainly targeting countries and territories around the South China Sea with a particular focus on Taiwan, Indonesia, Vietnam, the Philippines, Hong Kong, Malaysia and Thailand.
Our research shows that the main targets of the attacks are in the following sectors and industries:
High-profile governmental organizations
Political parties
Education institutions, including universities
Companies from the telecommunications sector
The following map shows the geographic distribution of attacks according to our telemetry, with the frequency of the attacks increasing from yellow to red.
Geographic map of attacks
Origin of the Attacks
The victims of this threat actor have always been mainly governmental organizations and political parties. These are known to be of most interest to state-supported groups.
The type of malicious tools the actor has implemented over time are mostly backdoor files capable of stealing files from victims’ systems, downloading and executing additional malware components as well as running system commands on victims’ machines. This suggests an intention to search and manually collect information (cyberespionage). This activity is most commonly associated with the interests of state-sponsored attackers.
As a routine analysis procedure, we decided to figure out the attacker’s possible time zone using the malware compilation timestamps from a large number of Spring Dragon samples. The following diagram shows the frequency of the timestamps during daytime hours. The timestamps range from early 2012 until now and are aligned to the GMT time zone.
Assuming the peak working hours of malware developers are the standard working day of 09:00-17:00, the chart shows that compilation took place in the GMT+8 time zone. It also suggests that either there is a second group working another shift in the same time zone or the attackers are cross-continental and there is another group, possibly in Europe. The uneven distribution of timestamps (low activity around 10am, 7-8pm UTC) suggests that the attackers didn’t change the timestamps to random or constant values and they might be real.
Histogram of malware files’ timestamps
Conclusions
Spring Dragon is one of many long-running APT campaigns by unknown Chinese-speaking actors. The number of malware samples which we managed to collect (over 600) for the group surpassed many others, and suggests an operation on a massive scale. It’s possible that this malware toolkit is offered in specialist public or private forums to any buyers, although, to date, we haven’t seen this.
We believe that Spring Dragon is going to continue resurfacing regularly in the Asian region and it is therefore worthwhile having good detection mechanisms (such as Yara rules and network IDS signatures) in place. We will continue to track this group going forward and, should the actor resurface, we will provide updates on its new modus operandi.
EU digital chief Andrus Ansip announced its plans to improve cyber security in EU
24.7.2017 securityaffairs Cyber
EU digital chief Andrus Ansip announced new measures to improve EU cyber security, including new offices to certify cybersecurity of technology products.
The EU digital chief Andrus Ansip announced his plan to set up a new office to certify the level of cyber security implemented in technology products.
The European Commission vice-president is thinking of a network of cybersecurity offices, so-called centers of excellence, spread across the states of the Union that will be focused on certifying the cyber security measures implemented by products.
“European products and cybersecurity products are not able, only some of them are able, to compete in the world market. We have to pay much more attention to this,” Ansip explained.
Andrus Ansip ✔ @Ansip_EU
International cooperation, large-scale exercises, R&D all essential to strengthen #cybersecurity @ccdcoe. More centres of excellence needed.
12:34 PM - 13 Jul 2017 · Tallinn, Estonia
24 24 Retweets 34 34 likes
Twitter Ads info and privacy
In September, Ansip will present new measures on cybersecurity certification, including a system to grade products based on their security features.
“The European Commission is getting ready to propose new legislation to protect machines from cybersecurity breaches, signaling the executive’s growing interest in encouraging traditional European manufacturers to build more devices that are connected to the internet.” reported website www.euractiv.com.
Ansip also added that in September there will be an updated EU cyber security strategy in order to improve the ability of European organizations to respond to attacks.

Ansip described the EU as a scenario where most countries don’t have resources to repel cyber attacks, for this reason, it is necessary to improve cooperation and the information sharing.
“Just in five EU member states we have 24/7 capabilities when we are talking about national CERTs,” Ansip said.
Hacker BestBuy pleads guilty to hijacking more than 900k Deutsche Telekom routers
24.7.2017 securityaffairs Hacking
The hacker BestBuy pleaded guilty in court on Friday to hijacking more than 900,000 routers from the network of Deutsche Telekom
The notorious hacker BestBuy, also known as Popopret, pleaded guilty in court on Friday to hijacking more than 900,000 routers from the network of Deutsche Telekom. The 29-year-old man, whom name wasn’t revealed by authorities. used a custom version of the Mirai IoT malware.

Earlier July the popular investigator Brian Krebs announced to have discovered the real BestBuy’s identity. according to the experts, the hacker is the Briton Daniel Kaye.
BestBuy was also known as the author of the GovRAT malware, he offered the source code of the RAT, including a code-signing digital certificate, for nearly 4.5 Bitcoin on the TheRealDeal black market.
German authorities referenced the man as Spiderman which is the name he used to register the domain names that the hacker used as C&C for his botnet.
According to the German website FutureZone.de, Deutsche Telekom estimated that the losses caused by the cyber attack were more than two million euros.
BestBuy targeted the routers in late November 2016 with the intent to recruit them in its botnet that was offered as a DDoS for hire service, but accidentally the malicious code variant he used triggered a DoS condition in the infected devices.
“The hacker admitted in court that he never intended for the routers to cease functioning. He only wanted to silently control them so he can use them as pawns in a DDoS botnet. ” wrote Bleepingcomputer.com.
Early December 2016, the man used another flawed version of Mirai that caused the same widespread problem in UK where more than 100,000 routers went offline. The routers belonged to Kcom, TalkTalk, a UK Postal Office, TalkTalk ISPs.
BestBuy was arrested in late February 2017 by the UK police at the London airport, then he was extradited to Germany to face charges in a German court in Cologne.
On July 21, the hacker BestBuy pleaded guilty, according to German media the man explained that he was hired by a Liberian ISP to carry out DDoS attacks on local competitors.
The hacker said the Liberian ISP paid him $10,000 to hit its competitors.
BestBuy’s sentencing hearing is scheduled July 28, the man faces up to ten years in the jail.
Worst known governmental leak ever affected the Swedish Transport Agency. Homeland security at risk
24.7.2017 securityaffairs BigBrothers
Worst known governmental leak ever affected the Swedish Transport Agency, data includes records of members of the military secret units.
Sweden might be the scenario for the worst known governmental leak ever, the Swedish Transport Agency moved all of its data to “the cloud,” but it transferred it to somebody else’s computer.
The huge trove of data includes top secret documents related to the fighter pilots, SEAL team operators, police suspects, people under witness relocation.
“The responsible director has been found guilty in criminal court of the whole affair, and sentenced to the harshest sentence ever seen in Swedish government: she was docked half a month’s paycheck.” wrote
Full data of top-secret governmental individuals, including photo, name, and home address, was leaked.
Director General Maria Ågren in Sweden was fined half a month’s salary in a very short trial.
Further investigation in the governmental data leak revealed that the Swedish Transport Agency moved all its data to “the cloud”, as managed by IBM, two years ago, but suddenly the Director General of the Transport Agency, Maria Ågren, was quickly retired from her position in January 2017.
On July 6 it was disclosed the news that the Director was found guilty of exposing classified information in a criminal court of law.
“But on July 6th, she is known to be secretly investigated to have cleared confidential information. According to the Security Unit for Security Objectives, the data may damage the security of the country. She is ordered to pay 70,000 kronor in daily fines.” reported the website SvtNyHeater.se.
“Among other things, the entire Swedish database of driving license photos has been available to several Czech technologies, which have not been tested for security. This means that neither the SÄPO nor the Transport Agency had control over the persons who handled the information that could be said to damage the security of the country.“
Leaked data included information related to people in the witness protection program and similar programs. This information was wrongly included in the register distributed outside the Agency as part of a normal procedure. Another unacceptable mistake was discovered by the investigators when a new version without the sensitive identities was distributed, the Agency did not instruct recipients of destroying the old copy.
“Last March, the entire register of vehicles was sent to marketers subscribing to it. This is normal in itself, as the vehicle register is public information, and therefore subject to Freedom-of-Information excerpts.” continues the Swedish website. “What was not normal were two things: first, that people in the witness protection program and similar programs were included in the register distributed outside the Agency, and second, when this fatal mistake was discovered, a new version without the sensitive identities was not distributed with instructions to destroy the old copy. Instead, the sensitive identities were pointed out and named in a second distribution with a request for all subscribers to remove these records themselves. This took place in open cleartext e-mail.”

Sensitive data on Swedish vehicles was released to companies with no security clearance. Credit: Jonas Ekströmer/TT
Leaked information is precious data for a foreign government in an Information warfare scenario, data includes records of fighter pilots in the Air Force, policemen, and members of the military’s most secret units.
The archive also includes any kind of information about any government and military vehicle, including their “operator, which says a ton about the structure of military support units;”
The PrivacyNewsOnline confirmed that the governmental data leak is still ongoing and that it can be expected to be fixed “maybe this fall”.
“Much of the available analysis of the leak is still in the form of fully-redacted documents from the Security Police and similar agencies.” concluded the news agency.
Expert exploited an unrestricted File Upload flaw in a PayPal Server to remotely execute code
24.7.2017 securityaffairs Exploit
The security researcher Vikas Anil Sharma exploited an unrestricted File Upload vulnerability in a PayPal Server to remotely execute code.
The security researcher Vikas Anil Sharma has found a remote code execution vulnerability in a PayPal server.
The expert was visiting the PayPal Bug Bounty page using the Burp software, below the response obtained opening the page http://paypal.com/bugbounty/.
PayPal server hack
The expert focused his analysis on the list of PayPal’s domains mentioned in “Content Security Policy:” Response Header, in particular, the “https://*.paypalcorp.com.”
In this first phase, the hacker was interested in finding as much possible valid sub domains to exploit in the attack, tools like Subbrute , Knockpy , enumall, are useful when performing such kind of analysis.
“these are the tools which i normally use , but being lazy on the weekend i made use of VirusTotal this time to enumerate the sub domains you can get the list here :
https://www.virustotal.com/en/domain/paypalcorp.com/information/
Copied the subdomain’s list locally & ran “dig -f paypal +noall +answer” to checkout where all the subdomains are actually pointing to in a neat way” wrote the researcher.
The expert noticed that the domain “brandpermission.paypalcorp.com” was pointing to “https://www.paypal-brandcentral.com/” that is a site hosting an Online Support Ticket System for PayPal Vendors, Suppliers, and Partners where they request for PayPal Brand Permissions.
The website allows users to upload the mockups of the logos and any graphics related to the brand along. The expert decided to create a ticket by uploading a simple image and analyze the folder destination of the picture.
“So, I first created a ticket by uploading a simple image file named “finished.jpg” which got stored as ” finished__thumb.jpg ” in directory :
“/content/helpdesk/368/867/finishedthumb.jpg” “finished _thumb.jpg” was the new file created in the directory “/867/” i quickly checked whether the actual file which we uploaded exists in the directory or not, luckily (You’ll know why later in the post ) “finished.jpg” also existed in the same directory. Cool stuff ;)” continue the bug hunter’s post.
Vikas discovered that the above link includes the ticket number, in the specific case the number of the ticket he has created is “368,” meanwhile “867” is the folder’s id where all the files related to the tickets are stored, including the Mockup files.
The researcher created a new ticket and discovered that ticket id and file id numbers are generated in serial manner. The expert uploaded a “.php” extension file instead of an image and discovered that the application did not validate file type, content, etc.
“As soon as i saw 302 Response , i ran towards opening the ticket & doing a simple right click copy link shit like i was able to do when uploading a image file . But,here in this case if you upload a php file as mock up you can’t see the path of the php file uploaded only thing which is visible is the ticket number.” wrote the expert.
Differently, from the uploading of image files, the expert noticed that it was not possible to discover the folder used to store mockup files.
The expert uploaded a file named success.php,” so for a similarity with the image uploading, he assumed that the file was stored as the success_thumb.php.
At this point, he decided to brute force the folder id for files.

Once discovered the folder id for files, the researcher tried to execute the code:
https://www.paypal-brandcentral.com/content/_helpdesk/366/865/success.php?cmd=uname-a;whoami
“Some cat+/etc/passwd magic to make myself beleive that i have actually found a RCE ;)” he wrote.

Below the timeline for the vulnerability:
Jul 08, 2017 18:03 – Submitted
Jul 11, 2017 18:03 – Fixed
The UK continues to grant the export of surveillance equipment to countries like Turkey
24.7.2017 securityaffairs BigBrothers
According to the UK’s Department for International Trade, the country granted a license to export surveillance equipment to Turkey earlier this year.
The UK continues to be one of the most active countries involved in the trade of surveillance technology. British firms continue to export surveillance systems ranging from internet mass surveillance equipment to-catchers.
According to the UK’s Department for International Trade, the country granted a license to export surveillance equipment to Turkey earlier this year, exactly while the Turkish Government for International Trade, the country granted a license to export surveillance equipment to Turkey earlier this year, exactly while the Turkish Government was conducting a severe repression against opposites, dissidents, journalists and human rights advocates.
Turkey today continues to be the country that arrests more journalists than any other state worldwide. Last week, a Turkish court ordered the arrest of Amnesty’s Turkey director along with other human rights activists.
While the UK government granted the above license export, the situation in Turkey became particularly worrying. On December, the Turkish authorities investigated more than 10000 individuals over online terror activities. The suspects were accused of being responsible for the sharing of material and post against government officials.
The Turkish Government applied restrictions on the Tor anonymity network, and more in general, on all VPN services, that could be used to avoid censorship.
The Turkish authorities questioned more than 3,000 people from June to December 2016, 1,656 of them have been arrested.
The Government dismissed 4,400 public servants, while Human Rights Watch claimed the Turkish government jailed members of the democratic opposition.
We cannot ignore that Turkey is under the constant threat of the terrorist organization due to its Geographic location.
A Department for International Trade spokesperson told Motherboard in an email, “The UK government takes its defence export responsibilities very seriously and operates one of the most robust export control regimes in the world.” The spokesperson said the UK examines each application on a case-by-case basis, and draws from NGO reports and other resources. “We have suspended or revoked licences when the level of risk changes and we constantly review local situations.”
I personally believe that is absurd that UK, and any other Government, still provides surveillance equipment to any states that don’t respect human rights.
THN Weekly Roundup — 10 Most Important Stories You Shouldn't Miss
23.7.2017 thehackernews Mobil
Here we are with our weekly roundup, briefing this week's top cyber security threats, incidents and challenges.
This week has been very short with big news from shutting down of two of the largest Dark Web marketplaces and theft of millions of dollars in the popular Ethereum cryptocurrency to the discovery of new Linux malware leveraging SambaCry exploit.
We are here with the outline of this week's stories, just in case you missed any of them. We recommend you read the entire thing (just click 'Read More' because there's some valuable advice in there as well).
Here's the list of this Week's Top Stories:
1. Feds Shuts Down AlphaBay and Hansa Dark Web Markets — Dream Market Under Suspicion
On Thursday, Europol announced that the authorities had shut down two of the largest criminal Dark Web markets — AlphaBay and Hansa — in what's being called the largest-ever international operation against the dark web's black market conducted by the FBI, DEA and Dutch National Police.
Interestingly, the federal authorities shut down AlphaBay, but before taking down Hansa market, they took control of the Dark Web market and kept it running for at least a month in an effort to monitor the activities of its visitors, including a massive flood of Alphabay refugees.
After the shutdown of both AlphaBay and Hansa, Dream Market has emerged as the leading player, which has been in business since 2013, but it has now been speculated by many dark web users that Dream Market is also under police control.
For detailed information — Read more.
2. New Ransomware Threatens to Send Your Internet History to All Your Friends
After WannaCry and Petya ransomware outbreaks, a new strain of ransomware has been making the rounds on the Google Play Store in bogus apps, which targets Android mobile phone users.
Dubbed LeakerLocker, instead of encrypting files on your device, this Android ransomware secretly collects personal images, messages and browsing history and then threatens to share them with your contacts if you don't pay $50 (£38).
For more detailed information on the LeakerLocker ransomware — Read more.
3. New CIA Leaks — Smartphone Hacking and Malware Development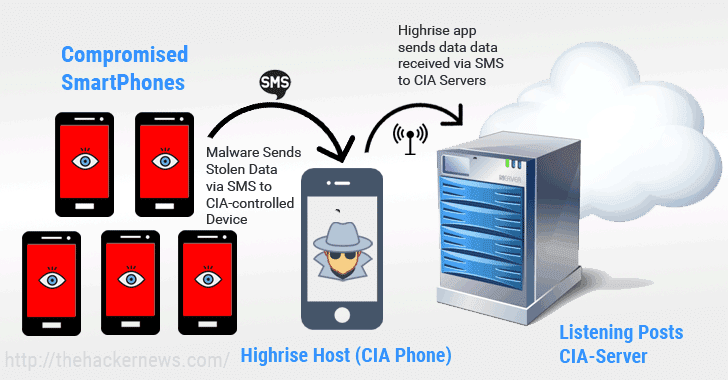
WikiLeaks last week published the 16th batch of its ongoing Vault 7 leak, revealing the CIA's Highrise Project that allowed the spying agency to stealthy collect and forwards stolen data from compromised smartphones to its server through SMS messages.
This week, the whistleblowing organisation revealed about a CIA contractor — Raytheon Blackbird Technologies — who was responsible for analysing advanced malware and hacking techniques being used in the wild by cyber criminals.
For more detailed information on Highrise Project and its contractor Raytheon Blackbird Technologies — Read More.
4. Three Back-to-Back Multi-Million Dollar Ethereum Heist in 20 Days
This week, an unknown hacker stole nearly $32 Million worth of Ethereum – one of the most popular and increasingly valuable cryptocurrencies – from wallet accounts linked to at least three companies by exploiting a critical vulnerability in Parity's Ethereum Wallet software.
This was the third Ethereum cryptocurrency heist that came out two days after an alleged hacker stole $7.4 Million worth of Ether from trading platform CoinDash and two weeks after someone hacked into South Korean cryptocurrency exchange and stole more than $1 Million in Ether and Bitcoins from user accounts.
For more detailed information about the Ethereum Heist — Read More.
5. Critical Gnome Flaw Leaves Linux PCs Vulnerable
This week has been bad for Linux users as well. A security researcher discovered a code injection vulnerability in the thumbnail handler component of GNOME Files file manager that allowed hackers to execute malicious code on targeted Linux machines.
German researcher Nils Dagsson Moskopp dubbed the vulnerability Bad Taste (CVE-2017-11421) and also released proof-of-concept (PoC) code on his blog to demonstrate the vulnerability.
For more details about the Bad Taste vulnerability and its PoC — Read More.
6. New Malware Exploits SambaCry to Hijack NAS Devices
Despite being patched in late May, the SambaCry vulnerability is currently being leveraged by a new piece of malware to target the Internet of Things (IoT) devices, particularly Network Attached Storage (NAS) appliances.
SambaCry is a 7-year-old critical remote code execution (RCE) vulnerability (CVE-2017-7494) in Samba networking software that could allow a hacker to remotely take full control of a vulnerable Linux and Unix machines.
The flaw was discovered and patched two months ago, but researchers at Trend Micro warned that the flaw had been actively exploited by the SHELLBIND malware that mostly targets NAS devices used by small and medium-size businesses.
For more detailed information on the SHELLBIND malware — Read More.
7. Devil's Ivy — Millions of Internet-Connected Devices At Risk
This week, researchers at the IoT-focused security firm Senrio discovered a critical remotely exploitable vulnerability in an open-source software development library used by major IoT manufacturers that eventually left millions of smart devices vulnerable to hacking.
Dubbed Devil's Ivy, the vulnerability (CVE-2017-9765) in the gSOAP toolkit (Simple Object Access Protocol) — an advanced C/C++ auto-coding tool for developing XML Web services and XML application.
The researchers also released proof-of-concept (PoC) video demonstrating the RCE on a security camera manufactured by Axis Communications.
For more detailed information on the Devil's Ivy and PoC video — Read More.
8. “Ubuntu Linux for Windows 10 Released” — Sounds So Weird?
Downloading an entire operating system has just become as easy as downloading an application for Windows 10 users, as Microsoft last week announced the availability of popular Linux distro 'Ubuntu' in the Windows App Store.
While the company announced its plans to launch Fedora and SUSE Linux as well on Windows Store, the company did not reveal exactly when its users can expect to see these two flavours of Linux distro on the App Store.
For detailed information on how to install and run Ubuntu on Windows 10 — Read More.
9. Over 70,000 Memcached Servers Vulnerable to Hacking
It's been almost eight months since the Memcached developers have patched several critical remote code execution (RCE) vulnerabilities in the software, but tens of thousands of servers running Memcached application are still vulnerable.
Cisco's Talos intelligence and research group last year discovered three critical RCE vulnerabilities in Memcached — a moderhttp://thehackernews.com/2017/07/segway-hoverboard-hacking.htmln open-source and easily deployable distributed caching system that allows objects to be stored in memory.
The vulnerability exposed major websites including Facebook, Twitter, YouTube, Reddit, to hackers, but the team of researchers scanned the internet on two different occasions and found that over 70,000 servers are still vulnerable to the attacks, including ransomware attacks similar to the one that hit MongoDB databases in late December.
For more in-depth information on the Memcached vulnerabilities — Read More.
10. Tor Launches Bug Bounty Program for Public
After its intention to launch a public bug bounty program in late December 2015, the Tor Project has finally launched a "Bug Bounty Program," encouraging hackers and security researchers to find and privately report bugs that could compromise the anonymity network.
The bug bounty reports will be sent through HackerOne — a startup that operates bug bounty programs for companies including Yahoo, Twitter, Slack, Dropbox, Uber, General Motors – and even the U.S. Department of Defense for Hack the Pentagon initiative.
For detailed information on bug bounty prices and types of valid vulnerabilities — Read More.
Other Important News This Week
Besides these, there were lots of incidents happened this week, including:
Microsoft's smart move to help take down cyber espionage campaigns conducted by "Fancy Bear" hacking group.
A new credential stealing malware found being sold for as cheap as $7 on underground forums.
Cisco patched a highly critical RCE vulnerability in its WebEx browser extension for Chrome and Firefox, which could allow attackers to execute malicious code on a victim's computer remotely.
Windows 10 now let you Reset forgotten password directly from your computer's Lock Screen.
Several critical vulnerabilities in Segway Ninebot miniPRO could allow hackers to remotely take "full control" over the hoverboard within range and leave riders out-of-control.
Ashley Madison's parent company Ruby Corp has agreed to pay a total of $11.2 Million to roughly 37 million users whose personal details were exposed in a massive data breach two years ago.
A Russian man involved in the development and maintenance of Citadel was sentenced to five years in prison
23.7.2017 securityaffairs BigBrothers
The Russian hacker Mark Vartanyan was sentenced to five years in prison for his involvement in the development and maintenance of the Citadel botnets.
It’s a terrific moment for cyber criminals, law enforcement worldwide continues their fight against illegal activities online and the recent shut down of AlphaBay and Hansa black markets demonstrate it.
The news of the day is that the Russian hacker Mark Vartanyan was sentenced to five years in prison for his involvement in the development and maintenance of the Citadel botnets.
Vartanyan, also known with the pseudonymous of “Kolypto” was arrested in Norway and extradited to the United States in December 2016.
Kolypto pleaded guilty in court in March 2017, he was charged with one count of computer fraud.
“Citadel caused vast amounts of harm to financial institutions and individuals around the world. Mark Vartanyan utilized his technical expertise to enable Citadel into becoming one of the most pernicious malware toolkits of its time, and for that, he will serve significant time in federal prison,” said US Attorney John Horn.
Citadel started being offered for sale in 2011 on invite-only, Russian cybercriminal forums, it is directly derived from the popular Zeus banking Trojan, in June 2013 Microsoft and the FBI carried out takedowns that eradicated more than 1,400 bots (nearly 88% of overall Citadel botnet) associated with this malware.

Experts estimated that the malware has been responsible for over $500 million in financial fraud.
Across the years, the Citadel malware affected more than 11 million computers globally, the most recent variant derived by Citadel is Atmos and it was spotted in April 2016 when he infected more than 1,000 bots.
The Vartanyan’s role was crucial for the malware distribution, the man was involved in the development and improving maintenance of Citadel. He was active from August 21, 2012 and January 9, 2013, while residing in Ukraine, and between on or about April 9, 2014 and June 2, 2014, while residing in Norway.
“Malicious software and botnets are rarely created by a single individual. Cybercrime is an organized team effort involving sophisticated, talented, and tech savvy individuals. Today’s sentencing of Mr. Vartanyan […] both removes a key resource from the cyber underworld and serves as a strong deterrent to others who may be contributing to the development of botnets and malware. The threat posed by cyber criminals in the U.S. and abroad is ever increasing,” David J. LeValley, Special Agent in Charge, FBI Atlanta Field Office, said.
Lloyd’s of London: A massive cyber attack could cause an average of $53 billion of economic losses
23.7.2017 securityaffairs Ransomware
A major global cyber attack has the potential to trigger $53 billion of economic losses, the equivalent to a natural disaster like 2012’s Superstorm Sandy.
Events like the massive Wannacry attack or the Ukraine power outage raise the discussion about the possible economic losses caused by a cyber attack.
According to a new report published by the Lloyd’s of London (“Counting the cost: Cyber exposure decoded”), a massive cyber attack on a global scale could cause an average of $53 billion of economic losses. a figure on par with a catastrophic natural disaster such as U.S. Superstorm Sandy in 2012, Lloyd’s of London said in a report on Monday.
“A major global cyber-attack has the potential to trigger $53 billion of economic losses, roughly the equivalent to a catastrophic natural disaster like 2012’s Superstorm Sandy, according to a scenario described in new research by Lloyd’s, the world’s specialist insurance market, and Cyence, a leading cyber risk analytics modelling firm.” states a blog post published by Lloyd’s of London.
The figure is disconcerting, experts compared it with losses caused by a natural disaster such as the Superstorm Sandy that hit the US in 2012.
“The report, co-written with risk-modeling firm Cyence, examined potential economic losses from the hypothetical hacking of a cloud service provider and cyber attacks on computer operating systems run by businesses worldwide.” reported the Reuters.
Insurers are trying to estimate the economic impact of a cyber attack and the potential exposure to cyber risks, and believe me, it is very difficult to do it due to the lack of historical data on such kind of incidents.
“This report gives a real sense of the scale of damage a cyber-attack could cause the global economy. Just like some of the worst natural catastrophes, cyber events can cause a severe impact on businesses and economies, trigger multiple claims and dramatically increase insurers’ claims costs. Underwriters need to consider cyber cover in this way and ensure that premium calculations keep pace with the cyber threat reality.” said Lloyd’s of London Chief Executive Inga Beale.
“We have provided these scenarios to help insurers gain a better understanding of their cyber risk exposures so they can improve their portfolio exposure management and risk pricing, set appropriate limits and expand into this fast-growing, innovative insurance class with confidence.”
According to Cyence, economic costs in the hypothetical cloud provider attack could reach $8 billion global cost for cases like “WannaCry” ransomware that hit targets in more than 100 countries.

Economic costs could include business interruptions and computer repairs.
In June, the “NotPetya” ransomware infected systems worldwide causing $850 million in economic costs.
According to the report, in the hypothetical cloud service attack, hackers delivered a malware into a cloud provider’s software that was designed to trigger system crashes among users a year later.
The malware then propagates among the provider’s customers, infecting systems in almost any industry, from financial services to healthcare
The experts estimated average economic losses caused by the disruption of the victims’ operations could range from $4.6 billion to $53 billion for massive cyber attacks.
“But actual losses could be as high as $121 billion, the report said.” continues the Reuters.
“As much as $45 billion of that sum may not be covered by cyber policies due to companies underinsuring, the report said.”
The report estimates average losses for a scenario involving a hacking of operating systems ranged from $9.7 billion to $28.7 billion.
“Lloyd’s has a 20 percent to 25 percent share of the $2.5 billion cyber insurance market,” added Beale.
Download ‘Counting the cost: Cyber exposure decoded‘ report
Russia’s Duma has approved the bill to prohibit tools used to surf outlawed websites
23.7.2017 securityaffairs BigBrothers
Russia is going to tighten controls on web services, on Friday, the parliament voted to prohibit web tools that could be used to surf outlawed websites.
Recently Russian authorities threatened to ban to ban Telegram because it refused to comply data protection laws.
On Friday, the Russia’s parliament voted to ban web tools that could be used by people to surf outlawed websites.
In the same day, the Duma also approved the proposed bill to oblige anyone using an online message service to identify themselves with a telephone number.
Russia is going to tighten controls on web services, for this reason, members the Duma passed the questionable bill. The bill will prohibit the use of any service from the Russian territory if they could be used to access blacklisted websites.
In case the law will be approved by the upper chamber of the Russian Parliament and by President Vladimir Putin, the Roskomnadzor will manage a list of anonymizer services and will ban them if they will be not compliant with access restrictions ordered by the Russian Government.
Privacy advocates groups fear the bill that is considered too restrictive and could open the door to a strict censorship, Government opposition groups heavily rely on such kind of technology to extend their protest abroad.
Let me close with a look at the Tor Metrics and Russia people accessing the popular anonymizing service.

The data related to the top-10 countries by estimated number of directly-connecting clients shows that Russia is at the third place.
COUNTRY MEAN DAILY USERS
United States 437521 (20.01 %)
United Arab Emirates 320743 (14.67 %)
Russia 213318 (9.76 %)
Ukraine 180847 (8.27 %)
Germany 176053 (8.05 %)
France 87925 (4.02 %)
United Kingdom 75001 (3.43 %)
Canada 41001 (1.88 %)
Netherlands 40586 (1.86 %)
Italy 37230 (1.70 %)
Stantinko botnet was undetected for at least 5 years while infecting half a million systems
23.7.2017 securityaffairs BotNet
A huge botnet dubbed Stantinko was undetected for at least 5 years, the disconcerting discovery was made by researchers from security firm ESET.
According to ESET, the Stantinko botnet has infected around half a million computers worldwide. Operators behind the botnet powered a massive adware campaign active since 2012, crooks mainly targeted users in Russia and Ukraine searching for pirated software.
The researchers discovered that the attack vector used by the cyber criminals is an app called FileTour, it is used to install a variety of programs on the victim’s machine, while also launching Stantinko in the background.
“Making heavy use of code encryption and rapidly adapting so as to avoid detection by anti-malware, Stantinko’s operators managed to stay under the radar for at least the last five years, attracting very little attention to their operations.” states the analysis published by ESET.
The botnet is mainly used to install on the infected systems browser extensions that are used to inject ad and perform click fraud.
The malicious browser extensions installed by the Stantinko malware are called The Safe Surfing and Teddy Protection. Both extensions distributed through the Chrome Web Store are used to block unwanted URLs. The botnet installs its versions of both browser extensions that are able to receive a configuration to perform click fraud and ad injection.
The researchers also noticed that the Stantinko malware could be used take full control of the target systems, it leverages on services that allow attackers conduct several malicious activities (i.e. performing massive searches on Google, performing brute-force attacks on Joomla and WordPress installs).
The malware installs two specific Windows services after compromise, each of them is able to reinstall the other if deleted. This means that in order to sanitize the system it is necessary to remove both services at the same time.

The Stantinko malware is a modular backdoor, its components embed a loader allowing them to execute any Windows executable sent by the C&C server directly in memory.
“This feature is used as a very flexible plugin system allowing the operators to execute anything on an infected system. Table 1 is a description of known Stantinko plugins.
MODULE NAME ANALYSIS
Brute-force Distributed dictionary-based attack on Joomla and WordPress administrative panels.
Search Parser Performs massive distributed and anonymous searches on Google to find Joomla and WordPress websites. It uses compromised Joomla websites as C&C servers.
Remote Administrator Backdoor that implements a full-range of actions from reconnaissance to data exfiltration.
Facebook Bot Bot performing fraud on Facebook. Its capabilities include creating accounts, liking picture or pages, and adding friends.
Experts speculate that crooks work close to the advertisers that pay for the traffic they receive from the botnet.
“On the other hand, traditional click-fraud malware relies on a series of redirections between several ad networks to launder their malicious traffic. This shows that not only are the Stantinko operators able to develop highly stealthy malware, but they are also able to abuse the traditional ad-serving economy without getting caught,” ESET points out.
Microsoft sued Fancy Bear to gain control of the domains used in the cyber espionage campaigns
22.7.2017 securityaffairs APT
Microsoft used the lawsuit to disrupt a large number of cyber espionage campaigns conducted by infamous Fancy Bear APT hacking group
We have discussed several times about hacking back and the case we are going to analyze is a good example of an alternative approach to hit back an APT group.
Microsoft used the lawsuit to disrupt a large number of cyber espionage campaigns conducted by infamous Fancy Bear APT hacking group (APT28, Sofacy, Sednit, and Pawn Storm). The experts with the help of the authorities took over the command and control infrastructure of the group in order to analyze the traffic and the targets of the malware by using the lawsuit as a tool.
“A new offensive by Microsoft has been making inroads against the Russian government hackers behind last year’s election meddling, identifying over 120 new targets of the Kremlin’s cyber spying, and control-alt-deleting segments of Putin’s hacking apparatus.” reported the daily beast.
“How are they doing it? It turns out Microsoft has something even more formidable than Moscow’s malware: Lawyers.”
Microsoft sued Fancy Bear in a US federal court, accusing the APT group of computer intrusion, cybersquatting, and reserving several domain names that violate Microsoft’s trademarks.
Fancy Bear is active since at least 2007 and was one of the APT groups involved in the numerous cyber attacks against the US DNC and 2016 Presidential Election.
Numerous reports published by security firms linked the APT group to the GRU (General Staff Main Intelligence Directorate), the Russian secret military intelligence agency.
The experts at Microsoft observed Fancy Bear hackers often using domain names that look-alike Microsoft products and services, such as livemicrosoft[.]net and rsshotmail[.]com, for its cyber espionage campaigns.
The abuse was exploited by Microsoft to sue the hacking group with “unknown members” into the court of justice and gain the ownership of domains used by Fancy Bear to deliver malware.
“These servers can be thought of as the spymasters in Russia’s cyber espionage, waiting patiently for contact from their malware agents in the field, then issuing encrypted instructions and accepting stolen documents,” the report reads.
Fancy bear
Last year, the U.S. District Judge Gerald Bruce Lee granted Microsoft’s request and issued a then-sealed order to domain name registrars “compelling them to alter”the DNS of at least 70 Fancy Bear domains. The traffic was redirected to servers controlled by Microsoft.
Technically the procedure is called ‘sinkholing‘ and allows investigators to monitor the traffic from the infected systems to track the botnet infrastructure.
This is the precious work done by the Digital Crimes Unit that has identified the potential victims of the Russian APT.
“By analyzing the traffic coming to its sinkhole, the company’s security experts have identified 122 new cyber espionage victims, whom it’s been alerting through Internet service providers,” the report reads.
Microsoft is still waiting for a final judgment on the Fancy Bear case. The hearing has been scheduled on Friday in Virginia court.
“Microsoft concludes in court filings that its efforts have had “significant impact” on Fancy Bear’s operations. By analyzing the traffic coming to its sinkhole, the company’s security experts have identified 122 new cyber espionage victims, whom it’s been alerting through Internet service providers.” concludes the report.”On Friday, the company is set to ask Magistrate Judge Theresa Carroll Buchanan for a final default judgment against Fancy Bear, and for a permanent injunction giving Microsoft ownership of the domains it’s seized.”
Modified versions of Nukebot Trojan spotted in wild after code leak
22.7.2017 securityaffairs Virus
Apparently, different cyber gangs are using modified versions of the Nukebot in wild after code Leak occurred in March 2017.
Crooks are adapting the leaked source code for the Nukebot banking Trojan to target banks in the United States and France and to steal mail client and browser passwords.
Apparently, different cyber gangs are using modified versions of the Nukebot in wild since its source code was leaked leak in March.

In March, the source code for a new banking Trojan, dubbed Nuclear Bot (Nukebot ), was available for sale in the cyber criminal underground.The Nuclear Bot banking Trojan first appeared in the cybercrime forums in early December when it was offered for $2,500. The malicious code implements some features commonly seen in banking Trojans, it is able to inject code in Mozilla Firefox, Internet Explorer and Google Chrome browsers and steal sensitive data provided by the users.
The Trojan can also open a local proxy or hidden remote desktop service to allow crooks to initiate rogue transactions through the victims’ browsers after they have been tricked into providing the second authentication factor.
The creator of the malware lost his credibility over the months and has been flagged as a scammer in the hacking community. The malware author did not offer a test version of the malware to potential buyers and advertised the Nuclear Bot using different names on different cybercrime forums.
In order to gain credibility and notoriety in the cyber crime underground he released the Trojan’s source code.
The NukeBot Trojan appears as a powerful tool written from scratch and that was able in early stage attacks to avoid detection of antivirus solutions.
Now malware experts from Kaspersky Lab have detected several compiled samples of Nukebot Trojan created since March, many of which appear to be test samples.
“The publication of malware source code may be nothing new, but it still attracts attention from across the IT community and some of that attention usually goes beyond just inspecting the code. The NukeBot case was no exception: we managed to get our hands on a number of compiled samples of the Trojan. ” wrote experts from Kaspersky.
“Most of them were of no interest, as they stated local subnet addresses or ‘localhost/127.0.0.1’ as the C&C address. Far fewer samples had ‘genuine’ addresses and were ‘operational.’”
The analysis of compiled samples revealed that only five percent were being used in real attacks, but there is no information about the campaign leveraging these samples.
The implementations of web injections in the source code confirm that hackers are using it to target banks in France and the U.S.
Researchers extracted the IP addresses of the command and control servers from the code from some plait-text version they were in possession. Obviously, the operational versions of Nukebot were encrypted, this means that the researchers need to extract the keys in order to decode it.
“In order to trigger web injections, we had to imitate interaction with C&C servers. The C&C addresses can be obtained from the string initialization procedure,” continues the analysis. “When first contacting a C&C, the bot is sent an RC4 key which it uses to decrypt injections. We used this simple logic when implementing an imitation bot, and managed to collect web injections from a large number of servers.
“Initially, the majority of botnets only received test injects that were of no interest to us,” Yunakovsky said. Later, however, we identified a number of NukeBot’s ‘combat versions.’”
Experts also noticed that some modified versions of Nukebot did not have web injections, these variants are delivered via droppers, and once they are unpacked, the malicious code downloads a number of password recovery utilities from a remote server under the attacker’s control.
Dark Web Users Suspect "Dream Market" Has Also Been Backdoored by Feds
22.7.2017 thehackernews CyberCrime
By now you might be aware of the took down of two of the largest online dark websites—AlphaBay and Hansa—in what's being called the largest-ever international operation against the dark web's black market conducted by the FBI, DEA (Drug Enforcement Agency) and Dutch National Police.
But the interesting aspect of the takedown was that the federal authorities shut down AlphaBay, but took control of the Hansa market and kept it running for at least a month in an effort to monitor the activities of its visitors.
The visitors of Hansa market also included a massive flood of Alphabay refugees, as the seizer of AlphaBay Market forced their visitors to join the Hansa market for illegal trading and purchasing.
However, not just Hansa, after AlphaBay's shutdown, many of its users also joined another website known as Dream Market, which is believed to be the second-largest dark web marketplace, ahead of Hansa.
After the shutdown of both AlphaBay and Hansa, Dream Market has emerged as the leading player, but now some Reddit users on several "r/Dream_Market" threads have expressed concerns about the Dream Market, which has been in business since 2013.
One Reddit user said that Dream Market has been compromised in a similar manner as Hansa and is already under police control.
"I got contacted by an ex-Hansa staff member telling me that the operation is apparently bigger than we currently assume, that 'there will be a bloodbath, a purge' and that 'any vendor on HANSA should immediately seize his operation, lawyer up and hide his trails'," the Reddit user post read.
Possibly the Real IP of Dream Market "Mistakenly" Exposed
Another Redditor claimed to have discovered a non-encrypted IP address in Dream Market’s source code, saying that police might have taken over control of the dark market as well and are now actively monitoring its visitors.
"We found a clear address IP on the javascript source code of the market. The police must know it from a long time. GO AWAY FROM HERE RIGHT NOW !!!," the Redditor wrote along with a piece of Site's Source Code.
After exploring a bit, I found that the clearnet IP address 194.9.94.82 mentioned in the JavaScript file (lchudifyeqm4ldjj.onion/market.js) is owned by "Loopia AB," a Swedish hosting company.
This JavaScript file has not been added or altered recently, as according to some moderators, the file has been there from at least past 9 months, and the code itself doesn’t indicate any signs of hijack or interception.
However, here's the big blunder — Exposure of the possible real IP address of the server, which is supposed to be hidden behind the Tor Onion Router, is one of the biggest mistakes Dream Market operators might have made that could have already given an opportunity to law enforcement agencies to raid the hosting company and take control of the servers.
While the claims that Dream Market is under police control are yet to be verified, vendors who joined Dream Market may still be compromised by law enforcement.
Meanwhile, some anonymous users on Reddit are also encouraging dark web users to visit Dream Market, saying "CALM DOWN! DREAM IS WORKING FINE!"
Benefitted from the shutdown of its rivals, Dream Market had 57,000 listings for drugs and 4,000 listings for opioids on Thursday.
How Microsoft Cleverly Cracks Down On "Fancy Bear" Hacking Group
22.7.2017 thehackernews CyberSpy
What could be the best way to take over and disrupt cyber espionage campaigns?
Hacking them back?
Probably not. At least not when it's Microsoft, who is continuously trying to protect its users from hackers, cyber criminals and state-sponsored groups.
It has now been revealed that Microsoft has taken a different approach to disrupt a large number of cyber espionage campaigns conducted by "Fancy Bear" hacking group by using the lawsuit as a tool — the tech company cleverly hijacked some of its servers with the help of law.
Microsoft used its legal team last year to sue Fancy Bear in a federal court outside Washington DC, accusing the hacking group of computer intrusion, cybersquatting, and reserving several domain names that violate Microsoft's trademarks, according to a detailed report published by the Daily Beast.
Fancy Bear — also known as APT28, Sofacy, Sednit, and Pawn Storm — is a sophisticated hacking group that has been in operation since at least 2007 and has also been accused of hacking the Democratic National Committee (DNC) and Clinton Campaign in an attempt to influence the U.S. presidential election.
The hacking group is believed to be associated with the GRU (General Staff Main Intelligence Directorate), Russian secret military intelligence agency, though Microsoft has not mentioned any connection between Fancy Bear and the Russian government in its lawsuit.
Instead of registering generic domains for its cyber espionage operations, Fancy Bear often picked domain names that look-alike Microsoft products and services, such as livemicrosoft[.]net and rsshotmail[.]com, in order to carry out its hacking and cyber espionage campaigns.
This inadvertently gave Microsoft an opportunity to drag the hacking group with "unknown members" into the court of justice.
Microsoft Sinkholed Fancy Bear Domains
The purpose of the lawsuit was not to bring the criminal group to the court; instead, Microsoft appealed to the court to gain the ownership of Fancy Bear domains — many of which act as command-and-control servers for various malware distributed by the group.
"These servers can be thought of as the spymasters in Russia's cyber espionage, waiting patiently for contact from their malware agents in the field, then issuing encrypted instructions and accepting stolen documents," the report reads.
Although Microsoft did not get the full-ownership of those domains yet, the judge last year issued a then-sealed order to domain name registrars "compelling them to alter" the DNS of at least 70 Fancy Bear domains and pointing them to Microsoft-controlled servers.
Eventually, Microsoft used the lawsuit as a tool to create sinkhole domains, allowing the company's Digital Crimes Unit to actively monitor the malware infrastructures and identify potential victims.
"By analyzing the traffic coming to its sinkhole, the company’s security experts have identified 122 new cyber espionage victims, whom it’s been alerting through Internet service providers," the report reads.
Microsoft has appealed and is still waiting for a final default judgment against Fancy Bear, for which the hearing has been scheduled on Friday in Virginia court.
WannaCry přiměl britskou vládu investovat 21 miliónů liber do zabezpečení zdravotnictví
22.7.2017 Novinky/Bezpečnost Viry
Ničivý útok ransomwaru WannaCry ochromil v květnu značnou část zdravotnických zařízení na britských ostrovech. Britská vláda bude proto investovat 21 miliónů liber (620 miliónů korun) do lepšího zabezpečení počítačových sítí zdravotnických zařízení Národní zdravotní služby (NHS).
Rozhodnutí padlo v přímé souvislosti s květnovým útokem ransomwaru WannaCry, který ochromil zhruba třetinu zařízení NHS a donutil lékaře odložit naplánované chirurgické zákroky. Podle státního tajemníka pro zdravotnictví a konzervativního poslance Jeremyho Hunta by peníze měly být použity k potlačení budoucích malwarových útoků a ochránění citlivých dat pacientů.
Dotaci na lepší zabezpečení si má rozdělit 27 traumacenter po celé Anglii. Nemocnice včetně zařízení King's College, St Mary's, Royal London a Manchester Royal Infirmary dostanou prostředky na aktualizaci informačních systémů a školení zaměstnanců, která mají zvýšit jejich povědomí o kybernetických hrozbách a jak jim čelit.
„Lidé musí získat jistotu, že zdravotní informační systémy jsou bezpečné. Nedávné události včetně útoku ransomwaru z května 2017 ukázaly, že NHS musí umět ochránit své základní služby před podobným kybernetickým útokem,“ prohlásil podle webu Infosecurity-magazine.com britský ministr zdravotnictví lord O'Shaughnessy.
Nemocnice přestanou používat Windows XP
Kabinet premiérky Theresy Mayové rovněž podpoří zdravotnická zařízení v síti NHS při přechodu od nepodporovaných operačních systémů, jako je Windows XP, k bezpečnějším řešením. Podle zatím nepotvrzených informací by vláda měla na tyto změny vyčlenit dalších 50 miliónů liber (asi 1,5 miliardy korun).
„Rozhodnutí britské vlády lze jen podpořit. Kdo jiný než zdravotnická zařízení, která spravují velmi citlivá osobní data pacientů, by měl mít tato data spolehlivě ochráněna?“ ptá se Václav Zubr, bezpečnostní expert společnosti ESET.
Ransomware WannaCry se začal šířit v pátek 12. května a zasáhl především Rusko, které zaznamenalo téměř polovinu všech napadených zařízení na světě. Následovala Ukrajina a Tchaj-wan, shodně s 11 procenty detekcí útoků ransomwaru WannaCry.
Přestože podíl WannaCry na globálních kybernetických hrozbách byl poměrně malý, pozornost veřejnosti si získal velice rychlým šířením. „Na rozdíl od většiny ransomwaru se v interní síti šířil jako červ využívající neopravené chyby systému. V zahraničí byly zasaženy nemocnice či výrobní závody,“ přiblížil Václav Zubr.
V České republice podle statistik společnosti ESET tento ransomware představoval 0,15 procenta ze všech detekovaných kybernetických hrozeb během měsíce května, kdy WannaCry celosvětově útočil. Šlo tedy o zanedbatelné číslo. „Je to dáno tím, že se Češi dobře chránili před vlnami ransomwaru, a také tím, že Česká republika nebyla primárním cílem tohoto útoku,“ uzavírá Václav Zubr ze společnosti ESET.
Russia Moves to Ban Tools Used to Surf Outlawed Websites
22.7.2017 securityweek BigBrothers
Russia's parliament on Friday voted to outlaw web tools that allow internet users to sidestep official bans of certain websites, the nation's latest effort to tighten controls of online services.
Members of the lower house, the Duma, passed the bill to prohibit the services from Russian territory if they were used to access blacklisted sites.
The bill instructs Russia's telecommunications watchdog Roskomnadzor to compile a list of anonymizer services and prohibit any that fail to respect the bans issued in Russia on certain websites.
The proposed law still has to be approved by the upper chamber of parliament and then by President Vladimir Putin.
Several internet-based groups in Russia have condemned it as too vaguely formulated and too restrictive.
The Duma also approved moves Friday to oblige anyone using an online message service to identify themselves with a telephone number.
Russia's opposition groups rely heavily on the internet to make up for their lack of access to the mainstream media.
But the Russian authorities have begun to tighten controls on online services, citing security concerns.
In June, Russian officials threatened to ban the Telegram messaging app after the FSB security service said those behind April's deadly Saint Petersburg metro bombing had used it.
Citadel Author Sentenced to Five Years in Prison
22.7.2017 securityweek Virus
A Russian man this week was sentenced to five years in prison for his involvement in the development and maintenance of the Citadel banking malware.
Known under the handle of “Kolypto,” Mark Vartanyan was arrested in Norway and extradited to the United States in December 2016. In March 2017, he pleaded guilty in court. Charged with one count of computer fraud, he will serve his sentence in federal prison.
The Citadel malware was designed to steal sensitive information such as online banking login credentials, courtesy of keylogging capabilities. The threat ensnared machines into botnets and affected millions of people globally. The malware was estimated in 2013 to have been responsible for over $500 million in financial fraud.
Based on the leaked source code of the Zeus banking Trojan, Citadel spawned numerous variants, the most recent of which is called Atmos and is said to be Citadel's polymorphic successor. In April last year, Atmos had over 1,000 bots.
“Citadel caused vast amounts of harm to financial institutions and individuals around the world. Mark Vartanyan utilized his technical expertise to enable Citadel into becoming one of the most pernicious malware toolkits of its time, and for that, he will serve significant time in federal prison,” U.S. Attorney John Horn said.
Also capable of stealing personally identifiable information from victim computer networks, Citadel started being sold in 2011 on invite-only, Russian-language cybercriminal forums.
Citadel operators are said to have targeted and exploited the computer networks of major financial and government institutions worldwide, including financial institutions in the United States. The malware infected an estimated 11 million computers.
According to the information presented in court, Vartanyan was involved not only in the development and maintenance of Citadel, but also in the improvement and distribution of the malware. He engaged in such activities between on or about August 21, 2012 and January 9, 2013, while residing in Ukraine, and between on or about April 9, 2014 and June 2, 2014, while residing in Norway, the Department of Justice reveals.
“Malicious software and botnets are rarely created by a single individual. Cybercrime is an organized team effort involving sophisticated, talented, and tech savvy individuals. Today's sentencing of Mr. Vartanyan […] both removes a key resource from the cyber underworld and serves as a strong deterrent to others who may be contributing to the development of botnets and malware. The threat posed by cyber criminals in the U.S. and abroad is ever increasing,” David J. LeValley, Special Agent in Charge, FBI Atlanta Field Office, said.
Symantec Tricked Into Revoking Certificates Using Fake Keys
22.7.2017 securityweek Security
Researcher Hanno Böck has tricked Symantec into revoking TLS certificates by falsely claiming that their private keys had been compromised. Comodo was also targeted, but the company did not fall for the same ruse.
Certificate authorities (CAs) are required to revoke certificates whose private keys have been compromised within 24 hours. Keys are often inadvertently exposed by certificate owners and previous research by Böck showed that while it often takes companies more than 24 hours, ultimately they do revoke compromised certificates.
Böck then decided to check if CAs ensure that an allegedly compromised private key actually belongs to a certificate before revoking it.
The researcher set up a couple of test domains and ordered free, short-term certificates for them from Comodo and Symantec’s RapidSSL. He then created fake private keys for the certificates and attempted to trick Symantec and Comodo into revoking them by providing the forged keys.
In order to increase his chances of success, Böck searched the web for private keys that were actually compromised and added them to a Pastebin post along with his forged keys. He then informed Comodo and Symantec about the “compromised” keys and asked them to revoke the certificates.
While Comodo did notice the fake keys among the ones that were actually compromised, Symantec informed him that all the certificates whose private keys were in the Pastebin post, including the fake ones apparently associated with the researcher’s test domains, had been revoked.
“No harm was done here, because the certificate was only issued for my own test domain. But I could’ve also fake private keys of other people's' certificates. Very likely Symantec would have revoked them as well, causing downtimes for those sites” Böck explained.
The researcher was also displeased with the fact that Symantec did not provide a reason for revoking the certificates, which makes it difficult for domain owners to learn from mistakes and improve their processes. Symantec insisted that the keys associated with Böck’s certificates had been compromised, even after he pointed out that the certificates had actually been revoked based on forged keys.
“Symantec did a major blunder by revoking a certificate based on completely forged evidence. There’s hardly any excuse for this and it indicates that they operate a certificate authority without a proper understanding of the cryptographic background,” Böck said.
After the researcher made his findings public, Symantec published a blog post promising to improve its processing of third-party revocation requests.
“First, a gap was identified in the public and private key matching process where keys are verified during the revocation request procedure,” Symantec said. “We performed a modulus comparison, a necessary part of this verification process, but it was incomplete as other parameters in the keys were not checked. Once we became aware of this, we immediately corrected the procedure. We are not aware of any instances where there was customer impact as a result of this process gap other than the test scenario run by the reporting researcher.”
“Secondly, we are reviewing how we communicate with customers during the 3rd party revocation request process to be more consistent and transparent with certificate owners,” it added.
Google and Mozilla are both displeased with Symantec, its subsidiaries and its partners regarding the improper issuance of certificates. There has been a lot of debate over the past few months about how Symantec should be penalized, with the security firm making another counterproposal this week.
Undetected For Years, Stantinko Malware Infected Half a Million Systems
22.7.2017 securityweek Virus
A massive botnet that remained under the radar for the past five years managed to infect around half a million computers and allows operators to “execute anything on the infected host,” ESET researchers warn.
Dubbed Stantinko, the botnet has powered a massive adware campaign active since 2012, mainly targeting Russia and Ukraine, but remained hidden courtesy of code encryption and the ability to rapidly adapt to avoid detection by anti-malware solutions.
Targeting users looking for pirated software, the actors behind the malware use an app called FileTour as the initial infection vector. The program installs a variety of programs on the victim’s machine, while also launching Stantinko in the background.
The massive botnet is used mainly to install browser extensions that in turn perform ad injections and click fraud, but malicious Windows services are used to execute a broad range of operations: backdoor activities, searches on Google, and brute-force attacks on Joomla and WordPress administrator panels, ESET reveals.
The threat also installs two malicious Windows services after compromise, each with the ability to reinstall the other if deleted. Because of this, successful disinfection requires both services to be deleted at the same time. If not, a new version of the deleted service could be provided by the command and control (C&C) server, researchers say.
The malicious browser extensions installed by Stantinko are called The Safe Surfing and Teddy Protection, both distributed through the Chrome Web Store and seemingly legitimate apps that block unwanted URLs. When installed by the botnet, however, the extensions receive a configuration to perform click fraud and ad injection.
Stantinko is a modular backdoor that includes a loader to execute any Windows executable sent by the C&C server directly in memory. Courtesy of a flexible plugin system, the malware’s operators can execute any code on an infected system.
Known plugins include Brute-force (performs distributed dictionary-based attacks on Joomla and WordPress administrative panels), Search Parser (performs massive distributed and anonymous searches on Google to find Joomla and WordPress websites and uses compromised Joomla websites as C&C servers), Remote Administrator (backdoor that implements a full-range of actions, from reconnaissance to data exfiltration), and Facebook Bot (performs fraud on Facebook: can create accounts, like pictures or pages, and add friends).
The malware’s operators are focused on making money mainly through click fraud. The actors are also believed to be very close to the advertisers, as users would sometimes reach the advertiser’s website directly after the Stantinko-owned ad network.
“On the other hand, traditional click-fraud malware relies on a series of redirections between several ad networks to launder their malicious traffic. This shows that not only are the Stantinko operators able to develop highly stealthy malware, but they are also able to abuse the traditional ad-serving economy without getting caught,” ESET points out.
The group behind the botnet is also trying to fraudulently access administrative accounts of Joomla and WordPress websites and resell the account logins on the underground market. Furthermore, the actors also engage into social network fraud through a plugin capable of interacting with Facebook (courtesy of botnet’s size, it is difficult for Facebook to detect this type of fraud).
“Even though it isn’t noticeable to the user, due to the absence of CPU intensive tasks, Stantinko is a major threat, as it provides a large source of fraudulent revenue to cybercriminals. Moreover, the presence of a fully featured backdoor allows the operators to spy on all the victimized machines,” the security researchers conclude.
Network Spreading Capabilities Added to Emotet Trojan
22.7.2017 securityweek Virus
Researchers at Fidelis Cybersecurity have spotted a variant of the Emotet Trojan that has what appears to be a feature designed to help the malware spread on internal networks.
The recent WannaCry and NotPetya incidents have demonstrated how efficient an attack can be if the malware includes a component that allows it to spread from one system to another. Given the success of these operations, other cybercriminals may also be looking to incorporate similar capabilities into their malware.
Emotet, also known as Geodo, is related to the Dridex and Feodo (Cridex, Bugat) malware families. Emotet has mainly served as a banking Trojan, helping cybercriminals steal banking credentials and other sensitive information from users in Europe and the United States.
In the attacks observed recently by Fidelis, Emotet has been used as a downloader for several other banking Trojans based on the victim’s geographical location.
The spreader component seen in attacks over the past month is designed to enumerate network resources in an effort to locate shares to which it can write a file and create a remote service. The service, named “Windows Defender System Service,” writes the malware to the disk and executes it.
If a shared resource is password-protected, the malware will try to guess credentials for user and administrator accounts by launching a dictionary attack.
Researchers pointed out that the network spreader component they have analyzed is packaged differently compared to the known Emotet modules, which could indicate that the spreader is a component used only by a specific group and not a direct piece of the malware.
“With the recent addition of spreading capabilities being added to ransomware it’s not at all surprising to see other malware families start to look into adding similar capabilities. It seems to be a common trend lately for malware developers to add in functionality based on what’s in the news which recently has been filled with all things wormable, which could mean this might be a continued trend for malware in the future,” said Fidelis’ Jason Reaves.
Fidelis has published a blog post containing technical details on the spreader component and indicators of compromise (IoC).
Hundreds of Java Flaws Patched by Schneider in Trio TView Software
22.7.2017 securityweek Vulnerebility
Energy management and automation solutions giant Schneider Electric was informed by a researcher that its Trio TView software uses a version of Java that was released in 2011 and is affected by hundreds of vulnerabilities.
Researcher Karn Ganeshen informed Schneider that the version of Java Runtime Environment (JRE) used in Trio TView, a management and diagnostics software for industrial radio systems, is outdated and contains numerous vulnerabilities.
JRE 1.6.0 update 27, released in August 2011, is plagued by more than 360 flaws, including security holes that over the past years have been exploited in attacks by both cybercriminals and state-sponsored threat actors. The list includes CVE-2015-4902, CVE-2015-2590 and CVE-2012-4681, all of which were zero-day vulnerabilities at some point.
The outdated version of Java is present in TView 3.27.0 and earlier. With the release of TView 3.29.0, Schneider updated the Java component to version 1.8.0 update 131, which Oracle released in mid-April 2017.
Ganeshen previously notified Schneider of several vulnerabilities, including ones affecting some of the company’s power meters.
Vulnerabilities in Schneider Electric PowerSCADA Anywhere and Citect Anywhere
Schneider has informed ICS-CERT that it has released patches for several medium and high severity vulnerabilities impacting its PowerSCADA Anywhere and Citect Anywhere.
The vulnerable applications are extensions of Citect SCADA, a high performance SCADA software for industrial process customers.
Versions 1.0 of PowerSCADA Anywhere and Citect Anywhere are affected by a high severity cross-site request forgery (CSRF) flaw that can be exploited to initiate “state-changing requests” by getting the targeted user to click on a specially crafted link.
The other vulnerabilities have been described as information exposure issues, use of outdated cipher suites, and a weakness that can be exploited to escape the application and launch other processes.
Patches for these security holes are included in version 1.1 of the affected products. Schneider has also provided a series of recommendations for hardening systems running PowerSCADA Anywhere and Citect Anywhere.
Tor Launches Bug Bounty Program — Get Paid for Hacking!
21.7.2017 thehackernews Security
With the growing number of cyber attacks and breaches, a significant number of companies and organisations have started Bug Bounty programs for encouraging hackers, bug hunters and researchers to find and responsibly report bugs in their services and get rewarded.
Following major companies and organisations, the non-profit group behind Tor Project – the largest online anonymity network that allows people to hide their real identity online – has finally launched a "Bug Bounty Program."
The Tor Project announced on Thursday that it joined hands with HackerOne to start a public bug bounty program to encourage hackers and security researchers to find and privately report vulnerabilities that could compromise the anonymity network.
HackerOne is a bug bounty startup that operates bug bounty programs for companies including Yahoo, Twitter, Slack, Dropbox, Uber, General Motors – and even the United States Department of Defense for Hack the Pentagon initiative.
Bug bounty programs are cash rewards gave by companies or organisations to white hat hackers and researchers who hunt for serious security vulnerabilities in their website or products and then responsibly disclose them.
The Tor Project announced its intention to launch a public bug bounty program in late December 2015 during a talk by the Tor Project at Chaos Communication Congress (CCC) held in Hamburg, Germany. However, it launched the invite-only bounty program last year.
The highest payout for the flaws has been kept $4,000 — bug hunters can earn between $2,000 and $4,000 for High severity vulnerabilities, between $500 and $2,000 for Medium severity vulnerabilities, and a minimum of $100 for Low severity bugs.
Moreover, less severe issues will be rewarded with a t-shirt, stickers and a mention in Tor's hall of fame.
"Tor users around the globe, including human rights defenders, activists, lawyers, and researchers, rely on the safety and security of our software to be anonymous online," Tor browser developer Georg Koppen said in a blog post. "Help us protect them and keep them safe from surveillance, tracking, and attacks."
The Tor Project is a non-profit organisation behind the Tor anonymizing network that allows any online user to browse the Internet without the fear of being tracked.
The Project first announced its plan to launch the bug bounty program weeks after it accused the FBI of paying the researchers of Carnegie Mellon University (CMU) at least $1 Million to help them Unmask Tor users and reveal their IP addresses, though FBI denies the claims.
Feds Seize AlphaBay and Hansa Markets in Major Dark-Web Bust
21.7.2017 thehackernews CyberCrime
It's finally confirmed — In a coordinated International operation, Europol along with FBI, DEA (Drug Enforcement Agency) and Dutch National Police have seized and taken down AlphaBay, one of the largest criminal marketplaces on the Dark Web.
But not just AlphaBay, the law enforcement agencies have also seized another illegal dark web market called HANSA, Europol confirmed in a press release today.
According to Europol, both underground criminal markets are "responsible for the trading of over 350,000 illicit commodities including drugs, firearms and cybercrime malware."
On July 4th, AlphaBay suddenly went down without any explanation from its administrators, which left its customers in panic. Some of them even suspected that the website's admins had pulled an exit scam and stole user funds.
However, last week it was reported that the mysterious shut down of the dark web marketplace was due to a series of raids conducted by the international authorities.
The raid also resulted in the arrest of Alexandre Cazes, a 26-year-old Canadian citizen who was one of the alleged AlphaBay's operators and was awaiting extradition to the US when a guard found him hanged in his jail cell the next day.
Now, Europol just announced that two of the largest criminal Dark Web markets—AlphaBay and Hansa— have shut down by the authorities, as the infrastructure "responsible for the trading of over 350 000 illicit commodities including drugs, firearms and cybercrime malware."
"This is an outstanding success by authorities in Europe and the US. The capability of drug traffickers and other serious criminals around the world has taken a serious hit today after a highly sophisticated joint action in multiple countries," Rob Wainwright, Europol Executive Director said.
"By acting together on a global basis the law enforcement community has sent a clear message that we have the means to identify criminality and strike back, even in areas of the Dark Web. There are more of these operations to come."
Feds Covertly Monitored Activities of Criminals Hansa Market
This is what made the operation more interesting.
Interesting — Feds Took Control Over Hansa Dark Web Site & Kept It Running for a Month to Covertly Monitor Activities of Criminals
The federal authorities revealed that they secretly took control over the Hansa market on 20th June 2017 and kept it running for at least a month in an effort to monitor the activities of vendors and buyers without their knowledge.
And here's the Icing on the cake — During the same period federal authorities purposely only took down AlphaBay, forcing their users to join the Hansa market for illegal trading and purchasing.
"We could identify and disrupt the regular criminal activity that was happening on Hansa market but also sweep up all of those new users that were displaced from AlphaBay and looking for a new trading platform for their ciminal activities," Rod Jay Rosenstein, the Deputy Attorney General for the DoJ, said today in a live press conference in Washington DC.
How One Simple Mistake Revealed AlphaBay Operator’s Identity
Cazes made the same mistake that most cyber criminals do which revealed his real identity and led to his arrest. He was using his personal email (Pimp_Alex_91@hotmail.com) to send out welcome & support emails to all members of his AlphaBay websites.
OPSEC Failure — One simple mistake revealed the identity of the AlphaBay operator & lead to his arrest.
The feds learned that the email address belonged to a Canadian man named Alexandre Cazes with the birth date October 19, 1991, and was working as president of a software company called EBX Technologies.
Cazes has been charged with a total of 16 counts, including:
1 count of conspiracy to engage in racketeering
1 count of conspiracy to distribute narcotics
6 counts of distribution of narcotics
1 count of conspiracy to commit identity theft
4 counts of unlawful transfer of false identification documents
1 count of conspiracy to commit access device fraud
1 count of trafficking in device making equipment
1 count of money laundering conspiracy
"Law enforcement authorities in the United States worked with numerous foreign partners to freeze and preserve millions of dollars’ worth of cryptocurrencies that were the subject of forfeiture counts in the indictment, and that represent the proceeds of the AlphaBay organization’s illegal activities," the DoJ says.
After the disappearance of Silk Road, AlphaBay emerged in 2014 and became a leader among dark web marketplaces for selling illicit goods from drugs to stolen credit card numbers, exploits, and malware.
Prior to its takedown, AlphaBay Market reached more than 200,000 customers and 40,000 vendors, with over 250,000 listings for illegal drugs and over 100,000 stolen and fraudulent identification documents and access devices, malware and other computer hacking tools.
Authorities believed that the dark websites like AlphaBay and Hansa were responsible for lost of many lives in America.
"Today, some of the most prolific drug suppliers use what is called the dark web, which is a collection of hidden websites that you can only access if you mask your identity and your location," Rosenstein said.
"One victim was just 18 years old when in February she overdosed on a powerful synthetic opioid which she had bought on AlphaBay. Grant Siever, only 13 years of age, a student at Treasure Mountain Junior High School, Utah, Park City. When he passed away, after overdosing on a synthetic opioid that had been purchased by a classmate on AlphaBay."
Like AlphaBay, Silk Road, the largest Dark Web market at that time, was also shut down after the law enforcement raided its servers in 2013 and arrested its founder Ross William Ulbricht, who has been sentenced to life in prison.
The feds also seized Bitcoins (worth $33.6 million, at that time) from the dark web site. Those Bitcoins were later sold in a series of auctions by the United States Marshals Service (USMS).
DarkHotel APT group leverages new methods to target politicians
21.7.2017 securityaffairs APT
According to Bitdefender, DarkHotel APT is back and it is targeting government employees with an interest in North Korea with a technique dubbed inexsmar.
According to the security firm Bitdefender, the DarkHotel APT is back and it is targeting government employees with an interest in North Korea with new techniques.
The hackers’ victims have been discovered in several countries, including North Korea, Russia, South Korea, Japan, Bangladesh, Thailand, Taiwan, China, the United States, India, Mozambique, Indonesia and Germany.
The first Darkhotel espionage campaign was spotted by experts at Kaspersky Lab in late 2014, according to the researchers the APT group has been around for nearly a decade while targeting selected corporate executives traveling abroad. According to the
According to the experts, threat actors behind the Darkhotel campaign aimed to steal sensitive data from executives while they are staying in luxury hotels, the worrying news is that the hacking crew is still active.
The attackers appeared high skilled professionals that exfiltrated data of interest with a surgical precision and deleting any trace of their activity. The researchers noticed that the gang never go after the same target twice. The list of targets includes CEOs, senior vice presidents, top R&D engineers, sales and marketing directors from the USA and Asia traveling for business in the APAC region.
Security researchers believe the APT group members are Korean speakers.
The attackers leveraged several methods to hack into the target systems, including zero-day exploits and used as the attack vectors peer-to-peer (P2P) file sharing websites and hotel’s Wi-Fi.
Now the Darkhotel group was using new attack methods and an exploit leaked from Italian surveillance firm Hacking Team.
The attack technique used in recent attacks was dubbed Inexsmar and it was observed in targeted attacks against political figures.
“Our threat researchers have come across a very particular DarkHotel attack known as Inexsmar, which appears to mark a significant departure from the APT group’s traditional modus operandi. This sample dates back to September 2016 and seems to be used in a campaign that targets political figures rather than the usual corporate research and development personnel, CEOs and other senior corporate officials.” reads the analysis published by BitDefender.
“This attack uses a new payload delivery mechanism rather than the consacrated zero-day exploitation techniques, blending social engineering with a relatively complex Trojan to infect its selected pool of victims.”
Hackers spread a Trojan downloader via phishing emails, the malicious code is used to gather information on the infected device and sends it back to attackers. If the infected systems meet specific requirements a first stage downloader, disguised as a component of OpenSSL, is fetched. In this phase, the malicious code opens a document titled “Pyongyang e-mail lists – September 2016,” that contains email contacts for various organizations in Pyongyang.
The attack stops if the requirements are not satisfied, otherwise, another payload is delivered.
Unfortunately, at the time of the investigation, the C&C server was offline and researchers were not able to collect further details about the attack.
The use of a multi-stage downloader represents the major improvement compared to the use of exploits because it allows attackers to improve the distribution and the update of the malware.
Apple Patches BroadPwn Bug in iOS 10.3.3
21.7.2017 Threapost Apple
Apple released iOS 10.3.3 Wednesday, which serves as a cumulative update that includes patches for multiple vulnerabilities including the high-profile BroadPwn bug that allowed an attacker to seize control of a targeted iOS device.
BroadPwn was revealed earlier this month as a flaw in Broadcom Wi-Fi chipsets used in Apple and Android devices. Apple said the vulnerability affected the iPhone 5 to iPhone 7, the fourth-generation iPad and later versions, and the iPod Touch 6th generation.
Exodus Intelligence discovered the flaw (CVE-2017-3544), which was patched earlier this month on Android when Google released its July Android Security Bulletin. Nitay Artenstein, the researcher with Exodus Intelligence who discovered the vulnerability, is scheduled to do a talk on the vulnerability at Black Hat next week.
Yesterday’s Apple security updates also included fixes for its tvOS, iTunes and iCloud for Windows, the Safari browser, watchOS and macOS Sierra.
In addition to patching the BroadPwn vulnerability, Apple addressed 13 arbitrary code execution vulnerabilities tied to everything from a buffer overflow bug found in the Contacts (CVE-2017-7062) app and a memory corruption issue (CVE-2017-7009) in the CoreAudio component of the OS.
The open source web browser engine WebKit was also patched by Apple. One WebKit vulnerability (CVE-2017-7011) allowed an attacker to use a malicious website that could lead to an “address bar spoofing” attack. A second (CVE-2017-7019) WebKit memory corruption issue allowed an attacker to maliciously craft web content that could lead to arbitrary code execution on a targeted iOS device.
“The issue involves the ‘WebKit Page Loading’ component. It allows remote attackers to execute arbitrary code or cause a denial of service (memory corruption and application crash) via a crafted web site,” wrote Apple regarding CVE-2017-7019.
On Wednesday, Apple also released patches for macOS Sierra 10.12.6, as well as Security Update 2017-003 for El Capitan and Security Update 2017-003 for Yosemite. Four CVEs were associated with a memory corruption issue tied to all macOS operating systems. The vulnerability (CVE-2017-7031) is an “issue that involves the ‘Foundation’ component. It allows remote attackers to execute arbitrary code or cause a denial of service (memory corruption and application crash) via a crafted file,” according to Apple.
Apple also released iCloud for Windows 6.2.2 that addressed almost a dozen CVEs tied to bugs found by Google Project Zero researchers. Researcher Ivan Fratric, with Google Project Zero, is behind eight of the CVEs. Most of the bugs he found are related to iCloud memory corruption issues in WebKit. The flaw allowed the processing of maliciously crafted web content within the app that could lead to arbitrary code execution.
Apple’s watchOS 3.2.3 release snuffed out a number of bugs including one interesting vulnerability tied to the operating system’s libxml2 library, responsible for manipulating XML content, that impacted all watch models. “Parsing a maliciously crafted XML document may lead to disclosure of user information,” described Apple (CVE-2017-7013).
A memory corruption bug was patched in Apple’s tvOS (CVE-2017-7008) that could lead to arbitrary code execution if a maliciously crafted movie file was played on the device, Apple said.
Defenders Gaining on Attackers, But Attacks Becoming More Destructive: Cisco
21.7.2017 securityweek Attack
Cisco Publishes 2017 Midyear Cybersecurity Report
Cisco's just-released Midyear Cybersecurity Report (PDF) draws on the accumulated work of the Cisco Security Research members. The result shows some improvement in industry's security posture, but warns about the accelerating pace of change and sophistication in the global cyber threat landscape.
Improvements can be demonstrated by the mean 'time to detect.' When monitoring first began in November 2015, this stood at 39 hours; but it narrowed to about 3.5 hours in the period from November 2016 to May 2017.
Against this, however, Cisco warns that the pace of technology is creating an ever-increasing threat surface that needs to be protected. "Lack of visibility into dynamic IT environments," notes the report, "the risks presented by "shadow IT," the constant barrage of security alerts, and the complexity of the IT security environment are just some reasons resource-strapped security teams struggle to stay on top of today's evasive and increasingly potent cyber threats."
The report analyzes existing threats, comments on evolving attack methodologies, and makes two worrying predictions about the increasing ruthlessness of attackers. The first prediction is that any apparent current lull in the use of IoT-based large-scale DDoS is no reason for optimism. "Botnet activity in the IoT space suggests some operators may be focused on laying the foundation for a wide-reaching, high-impact attack that could potentially disrupt the Internet itself," says Cisco.
Cisco's second concern is over the potential evolution of ransomware into a threat designed to lock down systems and destroy data as part of the attack process. It calls this threat, Destruction of Service (DeOS); and we may have already seen its nascence in NotPetya .
In financial value to the attacker, Cisco points out that ransomware is far less fruitful than the business email compromise (BEC) attack. "US$5.3 billion was stolen due to BEC fraud between October 2013 and December 2016. In comparison, ransomware exploits took in US$1 billion in 2016," says the report.
"BEC scams are aimed at big targets," it explains, "and big targets have fallen victim to them, even though such organizations may have mature threat defenses and safeguards against fraud. Both Facebook and Google have been victims of BECs and wire fraud." The attack's success rate is easily explained. "Because BEC messages don't contain malware or suspect links, they can usually bypass all but the most sophisticated threat defense tools."
Cisco highlights five current trends in malware evolution that have been evident in the first six months of 2017. The first is that attackers are using distribution systems that require users to take some type of positive action. An example would be a password-protected malicious document (with the password conveniently provided to the user in the body of the email). "When placed in a sandbox environment," says Cisco "these attachments do not show any evidence of being malicious, so they are forwarded to the user."
The second trend is that ransomware authors are creating malware quickly, easily, and cost-effectively by using open-source codebases, like Hidden Tear and EDA2, which publicly release ransomware code for "educational" purposes.
The third is the continuing growth of ransomware-as-a-service (RaaS) platforms, such as Satan. These, says the report, "are ideal for lazy adversaries who want to enter the ransomware market and launch a successful campaign without having to perform any coding or programming."
"Ransomware as a service," comments David Kennerley, director of threat research at Webroot, "is without a doubt one of the biggest threats facing organizations across industries today, and protection against ransomware is currently a question of economics. Due to poor security practices and culture in many cases it is often seen to be cheaper to pay the ransom to get the data back than to use internal recovery procedures."
But he does not recommend this approach. "No matter how tempting it might be, if any other option exists, however challenging, companies should never negotiate or concede to the criminal and pay the ransom. The danger with paying the ransom is there's no guarantee they'll recover the encrypted files. By paying you are only fueling the ransomware economy – and what now stops you being targeted again in future cyberattacks?"
Cisco's fourth malware trend is the growing prevalence of fileless or memory-resident malware. "It relies on PowerShell or WMI to run the malware completely in memory without writing any artifacts to the file system or registry, unless the attacker wants to put persistent mechanisms in place." Because there is no malware on the disk, there is no file to detect.
The fifth trend is that attackers are relying more on anonymized and decentralized infrastructures for obfuscation in their command and control. Tor bridging services are an example -- such as Tor2web, a proxying service that allows systems on the Internet to access things that are hosted within Tor, without requiring the installation of a local Tor client application.
In most of these developments, there is a constant: the economics of hacking has turned a corner. "The modern hacking community," says the report, "is benefiting from quick and easy access to a range of useful and low-cost resources."
Cisco notes that a decline in the use of exploit kits to deliver malware has coincided with an increase in spam levels. "Adversaries who had relied heavily on exploit kits to deliver ransomware," it explains, "are turning to spam emails, including those containing macro-laden malicious documents that can defeat many sandboxing technologies because they require user interaction to infect systems and deliver payloads."
Cisco does not expect exploit kits to disappear, but "other factors, such as the greater difficulty of exploiting vulnerabilities in files built with Adobe Flash technology, may be slowing the resurgence."
One threat vector given special mention is PUP-style spyware, which is often given little attention by defenders. Cisco studied three common families, and found at least one present within 20% of 300 companies it sampled. The three families are Hola, RelevantKnowledge, and DNSChanger/DNS Unlocker. "Although operators may market spyware as services designed to protect or otherwise help users," warns the report, "the true purpose of the malware is to track and gather information about users and their organizations -- often without users' direct consent or knowledge. Spyware companies are known to sell or provide access to the data they collect, allowing third parties to harvest information with relative anonymity. That information can be used to identify critical assets, map internal infrastructures in organizations, and orchestrate targeted attacks."
Timely patching continues to be an issue. "In late 2016," says the report, "Cisco threat researchers discovered and reported three remote code-execution vulnerabilities in Memcached servers. A scan of the Internet a few months later revealed that 79 percent of the nearly 110,000 exposed Memcached servers previously identified were still vulnerable to the three vulnerabilities because they had not been patched."
The overall picture presented in Cisco's 2017 Midyear Cybersecurity Report is a mixed bag. There is some good news. "Much of the research," it concludes, "shows that defenders not only have been gaining ground on adversaries, but also developing a much better understanding of how and where threat actors operate."
But against this, it adds, attackers are evolving more destructive attacks (such as DeOS and massive scale IoT-based DDoS attacks). "That is why it has never been more important for organizations to make cybersecurity a top priority."
Hacker Steals $30 Million in Ethereum from Parity Wallets
21.7.2017 securityweek Hacking
A hacker was allegedly able to exploit a vulnerability in Ethereum wallet client Parity and steal over $30 million worth of crypto-currency.
Because of a security flaw in the Parity Ethereum client, the hacker managed to steal 153,000 Ether from multi-sig wallets created with Parity clients 1.5. Parity has issued a security alert, but updated it today to reveal that the vulnerability has been already resolved.
According to the company, the vulnerability was discovered in “Parity Wallet's variant of the standard multi-sig contract” and affects all users “with assets in a multi-sig wallet created in Parity Wallet prior to 19/07/17 23:14:56 CEST.”
Prior to releasing the fix, Parity suggested users should “immediately move assets contained in the multi-sig wallet to a secure address.”
In fact, it appears that a group of security researchers and members of the Ethereum Project decided help moving the crypto-currency from the vulnerable wallets and took matter into their own hands by exploiting the same vulnerability to drain as many multi-sig wallets as possible.
“White Hat Group(s) were made aware of a vulnerability in a specific version of a commonly used multisig contract. This vulnerability was trivial to execute, so they took the necessary action to drain every vulnerable multisig they could find as quickly as possible. Thank you to the greater Ethereum Community that helped finding these vulnerable contracts,” the group notes on their account.
The group managed to drain over 377,116 Ether to their wallet, which is worth over $75 million. They also note that affected users will be refunded as soon as a secure multi sig wallet is created for them.
“If you hold a multisig contract that was drained, please be patient. They will be creating another multisig for you that has the same settings as your old multisig but with the vulnerability removed and will return your funds to you there,” the group says.
The hacker, on the other hand, has already started to move the stolen assets from the initial Ethereum wallet. 70,000 Ether, worth around $14 million, was already moved to seven different wallets, each containing 10,000 Ether now.
Ethereum’s value dropped from around $230 at around $200 following the hack.
Earlier this week, an unknown actor managed to hack the CoinDash official website during the company’s Token Sale and stole $7 million in Ethereum by replacing the company’s legitimate address with their own.
In early July, hackers managed to hijack a computer belonging to an employee of Bithumb, one of the world’s largest cryptocurrency exchanges, and stole significant amounts of Bitcoin and Ethereum.
“This latest incident has serious ramifications. In fact, ETH price has actually taken a dip, and is likely due to the uncertainty around this breach. Hackers exploited a vulnerability in multi-sig wallets from Parity – drastically different from the ICO CoinDash hack that happened earlier this week,” Tyler Moffitt, Senior Threat Research Analyst at cybersecurity firm Webroot, told SecurityWeek in an emailed comment.
Last year, a hack on the Ethereum holdings of DAO (a decentralized and virtual organization designed to provide funds for new projects) also resulted in a drop in the digital currency’s value.
“The key takeaway from this hack is that we're still exploring the Ethereum space and wallet security is more important than ever. As a threat researcher, I personally recommend hardware or native wallets (desktop wallets); they are the most secure, as you are in control of any transaction. Do NOT store lots of currency in exchanges that control your private address. Only use them to make trades then back out to safe addresses,” Moffitt concluded.
A King’s Ransom It is Not
20.7.2017 Kaspersky Ransomware
Hidden motivations in separate but similar destructive events
EXPETR RANSOMWARE SHADOW BROKERS VULNERABILITIES AND EXPLOITS WANNACRY
The first half of 2017 began with two intriguing ransomware events, both partly enabled by wormable exploit technology dumped by a group calling themselves “The ShadowBrokers”. These WannaCry and ExPetr ransomware events are the biggest in the sense that they spread the quickest and most effectively of known ransomware to date. With this extraordinary effectiveness and speed, one might expect that at least one of the groups would walk away with a very large cash haul. But that is not the case.
King Richard the I, held for a King’s Ransom of 100,000 marks. The largest ransom in known history. At the time, twice England’s GDP
Both of these incidents were carried out by two very different groups that appear to have been capable of obtaining, but minimally interested in, a king’s ransom. This missing financial motivation is strange, considering the royal capabilities of the exploits that they used to deploy their ransomware.
Also unusual, and preceding and relevant to these 2017 ransomware events, is that groups carrying out aggressive, destructive acts were more straightforward about the matter. We first posted our destructive BlackEnergy (BE) findings in 2014, along with discussion of their “dstr” plugin and odd DDoS features. Allegedly BE later took down large parts of the electrical grid in Ukraine for almost a half day. Later we described the Destover components used in the worm-enabled, destructive, politically motivated Sony incident. And Shamoon and StonedDrill have been pushed in the Middle East around turbulent political situations as well. These components were all wiper technology, delivered in a very intentional and destructive manner. It’s interesting that these spectacles all coincided with large political events and interests. So this new need to cloak their destructive activity or sabotage is an interesting shared change in tactics.
WannaCry Deployment
WannaCry deployment efforts began much earlier than has been publicly discussed. Our private report subscribers received early information that the attackers were spearphishing targets globally by at least March 14th. These messages contained links to files hosted at file sharing services. When clicked, the link led to what recipients thought were resumes related to job applications with a filename “Resume.zip” containing “Job Inquiry – Resume 2017.exe”.
This executable maintained a modified Adobe pdf file icon, and dropped both more malware (droppers and downloader chains that later led to WannaCry installations) and immediately opened decoy job applications. Here is an image of one of the decoys. While we couldn’t find it online, it may be a rip of a legitimate document:
Most of these targets were soft (likely to run the exe and likely did not have advanced network defense programs in place), their locations dispersed globally, and their organizations’ profiles inconsistent.
The group attempted to deploy the first version of WannaCry ransomware to these and various other targets over the next two months, with no success or observable effort to collect bitcoin from this activity. And, even after the ETERNALBLUE spreader exploit with the DOUBLEPULSAR code and its oddly mistaken kill switch likely was hastily added to the ransomware, the attackers did not focus much more development or attention on collecting bitcoin. At one point, the actor sent a light set of messages encouraging users to pay BTC to their wallet.
This sort of inexpensive, two month long activity also may tell us a bit about the actor, their capabilities, and their interests — slow, practical, and somewhat hiding their interests in a very odd way.
While the Sony incident demonstrated the theft and use of stolen credentials and reliable lateral movement, even that credential theft itself required little effort on the part of the attackers. Entire spreadsheets of admin passwords were left open on network shares. Bizarre permission configurations were maintained within the network. The actor had little to do in order to spread a wiper with its audio-video payload to lob oddball jibes at Sony and its executives, and post pastebin threats at movie-goers and share the company’s dirty laundry over p2p. Understanding and co-opting a software update infrastructure was unnecessary in the Sony incident. But a low-tech worming component was also built into the toolset, highly effective most likely because of a low security environment, not because of a previously 0day component.
ExPetr Deployment
ExPetr deployment was sharp, advanced, and technically agile. The group precisely targeted a major accounting software supplier to Ukrainian organizations. They also compromised a news website in UA to further waterhole targets outside the reach of the M.E.Doc network.
Once inside the M.E.Doc network, they gained access to the software update infrastructure and used that access to further steal credentials within target customer organizations. It’s interesting that delivery of the original poisoned installer occurred in April, and the large scale wiping event occurred much later. Also, not all systems receiving attempted Telebot deployments later received an ExPetr deployment. And, not all systems receiving attempted ExPetr deployments had previously received an attempted Telebot deployment.
Oddly, the two month delay in delivering the worm-enabled ExPetr variant is unexpectedly similar to the delay we saw with WannaCry. Later, they delivered the WMI/PsExec/ETERNALBLUE/ETERNALROMANCE-weaponized ExPetr sabotage variant. But in a substantial advance from Wannacry, even if Windows systems were patched, the attackers had stolen credentials for effective lateral movement and could wipe/crypt target systems. This addition also tells us that this attacker wanted to focus on effectively operating the confines of Ukrainian-connected organizations. The worming components also didn’t generate random network connections outside of the target networks. The variant included both native win64 and win32 MSVC-compiled Mimikatz-inspired components dropped to disk and run, stealing passwords for maximum privilege and spread, like those for domain admin and various network service accounts.
The ExPetr attackers apparently did not return with widely spread taunts or messages for their targets, or drag out the incident by requesting BTC transactions for disk decryption.
Comparison Table
WannaCry ExPetr
Spearphishing Yes – dependent Minimal (if any) – reported initial entry
Waterholing No Yes
Supply side server compromise No Yes
Capable of developing wormable exploit No Seemingly not
Initial activity March 14 April 15
Ransomware/wiper spread date May 12 (two months later) June 27 (two months later)
Targeting Global and opportunistic Focused primarily within one country
ETERNALBLUE Yes Yes
ETERNALROMANCE No Yes
DOUBLEPULSAR Yes Yes (minor modification)
Advanced credential theft and spreading No Yes
Advanced anti-malware evasion No Yes
Wiper functionality No Yes
Properly implemented crypto No Yes
Rushed mistakes Unregistered kill switch domain Not really – possibly MBR overwrite algorithm (unlikely)
Financial draw No Minimal
Code sharing with other projects Yes Yes
The recent ETERNALBLUE/ETERNALROMANCE/DOUBLEPULSAR-enabled WannaCry and ExPetr incidents share similarities. Not in the sense that they were carried out by the same actor; it is most likely that they were not. One APT was rushed, opportunistic, not as technically capable as the other, while the other APT was practical, agile, and focused. But we are at the start of a trend emerging for this unusual tactic – APT camouflage destructive targeted activity behind ransomware.
The NukeBot banking Trojan: from rough drafts to real threats
20.7.2017 Kaspersky Virus
This spring, the author of the NukeBot banking Trojan published the source code of his creation. He most probably did so to restore his reputation on a number of hacker forums: earlier, he had been promoting his development so aggressively and behaving so erratically that he was eventually suspected of being a scammer. Now, three months after the source code was published, we decided to have a look at what has changed in the banking malware landscape.
NukeBot in the wild
The publication of malware source code may be nothing new, but it still attracts attention from across the IT community and some of that attention usually goes beyond just inspecting the code. The NukeBot case was no exception: we managed to get our hands on a number of compiled samples of the Trojan. Most of them were of no interest, as they stated local subnet addresses or ‘localhost/127.0.0.1’ as the C&C address. Far fewer samples had ‘genuine’ addresses and were ‘operational’. The main functionality of this banking Trojan is to make web injections into specific pages to steal user data, but even from operational servers we only received ‘test’ injections that were included in the source code as examples.
Test injections from the NukeBot source code
The NukeBot samples that we got hold of can be divided into two main types: one with plain text strings, and the other with encrypted strings. The test samples typically belong to type 1, so we didn’t have any problems extracting the C&C addresses and other information required for analysis from the Trojan body. It was a bit more complicated with the encrypted versions – the encryption keys had to be extracted first and only after that could the string values be established. Naturally, all the above was done automatically, using scripts we had developed. The data itself is concentrated in the Trojan’s one and only procedure that is called at the very beginning of execution.
A comparison of the string initialization procedure in plain text and with encryption.
Decryption (function sub_4049F6 in the screenshot) is performed using XOR with a key.
Implementation of string decryption in Python
In order to trigger web injections, we had to imitate interaction with C&C servers. The C&C addresses can be obtained from the string initialization procedure.
When first contacting a C&C, the bot is sent an RC4 key which it uses to decrypt injections. We used this simple logic when implementing an imitation bot, and managed to collect web injections from a large number of servers.
Initially, the majority of botnets only received test injects that were of no interest to us. Later, however, we identified a number of NukeBot’s ‘combat versions’. Based on an analysis of the injections we obtained, we presume the cybercriminals’ main targets were French and US banks.
Example of ‘combat-grade’ web injections
Of all the Trojan samples we obtained, 2-5% were ‘combat-grade’. However, it is still unclear if these versions were created by a few motivated cybercriminals and the use of NukeBot will taper off soon, or if the source code has fallen into the hands of an organized group (or groups) and the number of combat-grade samples is set to grow. We will continue to monitor the situation.
We also managed to detect several NukeBot modifications that didn’t have web injection functionality, and were designed to steal mail client and browser passwords. We received those samples exclusively within droppers: after unpacking, they downloaded the required utilities (such as ‘Email Password Recovery’) from a remote malicious server.
Kaspersky Lab products detect the banking Trojans of the NukeBot family as Trojan-Banker.Win32.TinyNuke. Droppers containing this banking Trojan were assigned the verdict Trojan-PSW.Win32.TinyNuke.
MD5
626438C88642AFB21D2C3466B30F2312
697A7037D30D8412DF6A796A3297F37E
031A8139F1E0F8802FF55BACE423284F
93B14905D3B8FE67C2D552A85F06DEC9
A06A16BD77A0FCB95C2C4321BE0D2B26
0633024162D9096794324094935C62C0
9E469E1ADF9AAE06BAE6017A392B4AA9
078AA893C6963AAC76B63018EE4ECBD3
44230DB078D5F1AEB7AD844590DDC13E
FAF24FC768C43B95C744DDE551D1E191
8EBEC2892D033DA58A8082C0C949C718
6DC91FC2157A9504ABB883110AF90CC9
36EB9BDEFB3899531BA49DB65CE9894D
D2F56D6132F4B6CA38B906DACBC28AC7
79E6F689EECB8208869D37EA3AF8A7CA
9831B1092D9ACAEB30351E1DB30E8521
U.S., European Police Say 'Dark Web' Markets Shut Down
20.7.2017 securityweek CyberCrime
Washington - US and European police on Thursday announced the shutdown of two huge "dark web" marketplaces that allowed the anonymous online trade of drugs, hacking software and guns.
US Attorney General Jeff Sessions said underground websites AlphaBay and Hansa had tens of thousands of sellers of deadly drugs like fentanyl and other illicit goods serving more than 200,000 customers worldwide.
"This case, pursued by dedicated agents and prosecutors, says you are not safe, you cannot hide. We will find you, dismantle your organization and network, and we will prosecute you," Sessions said in a warning to dark web entrepreneurs. The announcement came three weeks after AlphaBay stopped functioning with no explanation.
On July 5, the Canadian national who ran AlphaBay, Alexandre Cazes, was arrested in Thailand. Earlier this week, Cazes was found dead in his Thai police cell, with police saying he apparently hanged himself with a towel.
AlphaBay's shutdown sent traffic flooding into the smaller Hansa marketplace.
But that new traffic, tens of thousands of users, was unaware that Dutch police had already secretly taken control of Hansa, giving them the ability to identify and track buyers and sellers of illicit goods.
The Hansa market has also now been shut down, said Europol executive director Rob Wainwright.
"By acting together on a global basis the law enforcement community has sent a clear message that we have the means to identify criminality and strike back, even in areas of the Dark Web," Wainwright said.
AlphaBay had been a massive marketplace for illicit goods, 10 times larger than the notorious Silk Road underground cyber marketplace shut down by the US Federal Bureau of Investigation in 2013.
At the time it was shut down, it had more than 250,000 listings for illegal drugs and toxic chemicals, according to the US Justice Department.
It also had 100,000 advertisements for guns, stolen and fraudulent personal documents, counterfeit goods, malware and computer hacking tools.
The marketplaces operated underground on the Tor network, which allows anonymity for users.
With the takedown of AlphaBay and Hansa, authorities said they have frozen millions of dollars worth of cryptocurrencies like Bitcoin used to settle online transactions without the buyers and sellers being identified.
They also seized from Cazes and his wife millions of dollars in currency, luxury cars, and homes in four countries, including a hotel he owned in Thailand.
Wainwright said the investigation had resulted in the identification of numerous organized crime figures and that intelligence leads have been distributed to law enforcement in 37 countries around the world.
"This operation is an example of the improving concerted ability of law enforcement to strike against criminals, even on the dark net," he said. "This coordinated hit against these two marketplaces is just a taste of what is to come in the future."
Apple Patches Vulnerabilities Across All Platforms
20.7.2017 securityweek Vulnerebility Apple
Apple this week released security patches for all four of its operating systems to resolve tens of security bugs in each of them.
The tech giant addressed 37 vulnerabilities with the release of macOS Sierra 10.12.6 (and Security Update 2017-003 El Capitan and Security Update 2017-003 Yosemite). The vast majority of the issues could result in arbitrary code execution. Impacted components include audio, Bluetooth, contacts, Intel graphics driver, kernel, libarchive, and libxml2, Apple reveals.
The release of iOS 10.3.3 adressed 47 vulnerabilities, many allowing for arbitrary code execution and some for unexpected application termination or information disclosure. WebKit was the most affected component, with over 20 bugs squashed in it. Kernel, Safari, messages, contacts, libarchive, and libxml2 were also among the affected components.
Tracked as CVE-2017-9417 and affecting Broadcom's BCM4354, 4358, and 4359 chips, one of the vulnerabilities could allow an attacker within range to execute arbitrary code on the Wi-Fi chip. Because said chips are used in various smartphones, including devices from HTC, LG, and Samsung, Google too addressed the issue with its latest Android patches.
Apple addressed 16 security flaws with the release of watchOS 3.2.3, including CVE-2017-9417. Kernel was affected the most, with 9 bugs resolved in it. Contacts, IOUSBFamily, libarchive, libxml2, libxpc, messages, and Wi-Fi were also impacted. These vulnerabilities could result in arbitrary code execution, unexpected application termination, information disclosure, or an app’s ability to read restricted memory.
Apple's tvOS 10.2.2 resolves 38 bugs, most of which affect WebKit and Kernel (they were addressed in iOS and watchOS as well). Most of these issues could lead to arbitrary code execution, in some cases with elevated privileges (kernel or system), Apple notes in its advisory.
Apple also released Safari 10.1.2 this week, addressing a bug in Safari Printing and 24 issues in WebKit or related to it. iTunes 12.6.2 for Windows patches 23 security issues (one in iTunes, another in libxml2, and 21 in WebKit), while iCloud for Windows 6.2.2 resolves 22 vulnerabilities (one in libxml2 and 21 in WebKit).
Tor Offers $4,000 Per Flaw in Public Bug Bounty Program
20.7.2017 securityweek Security
Tor launches bug bounty program
The Tor Project announced on Thursday the launch of a public bug bounty program. Researchers can earn thousands of dollars if they find serious vulnerabilities in the anonymity network.
The Tor Project first announced its intention to launch a bug bounty program in late December 2015. A private program was launched in January 2016 and bounty hunters managed to find three denial-of-service (DoS) flaws, including two out-of-bounds (OOB) read and one infinite loop issues, and four memory corruption vulnerabilities that have been described as “edge-case.”
Now, with support from the Open Technology Fund, Tor has launched a public bug bounty program on the HackerOne platform.
The organization is looking for vulnerabilities in the Tor network daemon and Tor Browser, including local privilege escalation, remote code execution, unauthorized access of user data, and attack methods that can be used to obtain crypto data on relays or clients.
Researchers can earn between $2,000 and $4,000 for high severity bugs. Medium severity vulnerabilities are worth between $500 and $2,000, while low severity issues will be rewarded with a minimum of $100. Even less severe problems will be rewarded with a t-shirt, stickers and a mention in Tor’s hall of fame. On its bug bounty page, the Tor Project provides examples for each category of vulnerabilities, including with CVE references.
Vulnerabilities affecting third-party libraries used by Tor can also earn between $500 and $2,000, but libraries covered by other bug bounty programs, such as OpenSSL, have been excluded.
“Tor users around the globe, including human rights defenders, activists, lawyers, and researchers, rely on the safety and security of our software to be anonymous online. Help us protect them and keep them safe from surveillance, tracking, and attacks,” said Georg Koppen, a longtime Tor browser developer.
Tor first announced its intention to launch a bug bounty program after a team of researchers from Carnegie Mellon University helped the FBI unmask users of the anonymity network by creating more than a hundred new relays on the network. The Tor Project claimed at the time that the U.S. government had paid the university at least $1 million to carry out the attack.
Firms Unite to Hunt Threats From Network to Endpoint
20.7.2017 securityweek Security
Network and Endpoint Threat Hunters Corvil and Endgame Combine to Provide Pan-Infrastructure Detection and Response
Two threat hunting and detection companies have integrated their products to give greater visibility and protection across the entire infrastructure. Corvil, with expertise in real-time traffic analysis, and Endgame, with expertise in endpoint protection, can now share threat intelligence between the two platforms with a single click.
"The challenge today between endpoint security and network security," explains David Murray, Corvil chief business development officer, "is that they often tend to exist each in their own domain, when one of infosecurity's multipliers is the ability to integrate and be able to track a threat across the network and into the endpoint."
Organizations may have dozens of different security tools and technologies that do not adequately talk to each other. "The result," says Murray, "is that security analysts remain horribly overburdened." Training existing staff to a higher skill-set, or buying in new experts is often not an option. "It is important," he continued, to take the intelligence and analytics that we provide and seamlessly integrate it with other security technologies. We've already done this with Cisco's Tetration. Today we're announcing two further integrations, one with Endgame and the other with Palo Alto Networks, that enable comprehensive protection from the perimeter through the network and inclusive of the endpoint."
Endgame's endpoint threat detection platform can see endpoint threats at the kernel level and in memory, but can lose visibility into the path of anomalous communication that leaves the endpoint. "Similarly," adds Murray, "anything that tries to compromise an individual host or server endpoint of any kind has to travel over the network in order to get there. By sharing intelligence back and forth between our two platforms, we're able to provide a stronger fabric for protection."
Both Corvil and Endgame share similar philosophies and have a history of protecting some of the most sensitive and attacked infrastructures: Corvil in fintech, and Endgame in defense and military. Both believe organizations cannot wait to be breached but need to take an aggressive threat-hunting approach to network defense.
"The techniques attackers use today are increasingly aggressive, complex, and difficult to detect," comments Nate Fick, Endgame's CEO. "Security solutions that only identify customer breaches after damage and loss are no longer acceptable. Corvil shares our philosophy of direct, aggressive protection. Extending the visibility, we can offer customers across the network and endpoint represents the most comprehensive solution available on the market."
Both also share the view that their role is to make hunting and protection as easy as possible for the analyst, reducing the customer's reliance on expensive expert analysts. Each has their own virtual assistant. Corvil's Cara automatically generates daily risk reports, while Endgame's Artemis is a natural-language Siri-like assistant that will answer questions like, "What is suspicious on my network today?"
"One of the things we're planning to release in the second phase of integration," Murray told SecurityWeek, "is to extend the capabilities of our respective virtual experts to give both platforms the ability to stretch much further across an attack lifecycle, and be able to triangulate information to make a more active and more precise response."
Speed in detecting a threat loses its value if there is a subsequent delay in responding to that threat. Both platforms have their own built-in response capabilities. Corvil also integrates with Palo Alto Networks (PAN) firewalls. Where PAN micro-segmentation is employed, Corvil can initiate a firewall road block to PAN to isolate the risky host. Similarly, Endgame, has its own more surgical disruptions it can introduce within the host or endpoint.
"Let's say Corvil detects a risky host," explains Murray. "With one click the analyst can see the result in Endgame, and they can trigger an action right there. Similarly, if someone is working in Endgame and has questions about the downstream communication of a suspicious host, the analyst can bring up information about the communication in Endgame and then click to Corvil to further investigate it. Corvil could initiate a firewall road block in PAN directly from Corvil. Corvil can determine the source of the bad behavior and block it so that it can no longer communicate through the firewall. Alternatively, there could be a more surgical disruption within the source through Endgame."
"By combining Endgame's heritage in protecting against nation-state adversaries with Corvil's longstanding leadership in safeguarding algorithmic businesses," says Murray, "we, uniquely, provide critical capabilities that our customers across industries require. Today's partnership with Endgame enables us to cover a wider spectrum of an organization's infrastructure and empower today's overburdened security teams."
The Corvil/Endgame integration is available from today to early adopter customers
FedEx May Have Permanently Lost Data Encrypted by NotPetya
20.7.2017 securityweek Ransomware
FedEx-owned international delivery services company TNT Express is still working on restoring systems hit last month by the destructive NotPetya malware attack, but some business data may never be recovered, FedEx said in a Securities and Exchange Commission (SEC) filing this week.
NotPetya (also known as Nyetya, PetrWrap, exPetr, GoldenEye, and Diskcoder.C) infected tens of thousands of systems, including ones belonging to major organizations, in more than 65 countries. Many of the victims were located in Ukraine, which is not surprising considering that the main attack vector was the update system of M.E. Doc, an accounting tool developed by Kiev-based tax software firm Intellect Service.
The infosec community initially believed NotPetya was a piece of ransomware, similar to WannaCry. However, closer analysis revealed that it was actually a wiper and it was unlikely that victims could recover their files, even if they paid the ransom.
TNT Express, whose Ukraine office uses the compromised tax software, was hit hard by the attack, which led to FedEx temporarily suspending trading of its shares on the New York Stock Exchange. It’s worth noting that FedEx was also impacted by the WannaCry attack.
In its annual report with the SEC on Form 10-K for fiscal year 2017, FedEx said the attack did not affect any other of its companies. While there is no evidence that any data was stolen by malicious actors from TNT systems, the attack had a significant impact on the company’s operations and communications.
A majority of TNT services are available by now, but FedEx informed customers of possible delays in service and invoicing due to the use of manual processes. The company is working on restoring critical systems, including operational, finance, back-office and secondary business systems, but it’s unclear how long the process will take.
Furthermore, FedEx believes it’s “reasonably possible” that TNT will not be able to fully restore all affected systems and recover all the critical business data encrypted by NotPetya.
“Given the recent timing and magnitude of the attack, in addition to our initial focus on restoring TNT operations and customer service functions, we are still evaluating the financial impact of the attack, but it is likely that it will be material,” FedEx said in a press statement. “We do not have cyber or other insurance in place that covers this attack. Although we cannot currently quantify the amounts, we have experienced loss of revenue due to decreased volumes at TNT and incremental costs associated with the implementation of contingency plans and the remediation of affected systems.”
FedEx is not the only shipping company hit by NotPetya. Danish shipping giant A.P. Moller-Maersk also had its systems infected, which prevented it from accepting new orders. Maersk-owned APM Terminals, a global port and cargo inland services provider, was also affected, causing problems at major ports in the United States and Europe.
According to Reuters, Maersk admitted that its antivirus software was not effective against the NotPetya malware, and the company now claims to have implemented additional security measures to prevent future incidents.
Avast Acquires CCleaner Developer Piriform
20.7.2017 securityweek IT
Antivirus firm Avast announced on Wednesday the acquisition of Piriform, a London, UK-based company that develops the popular cleaning and optimization tool CCleaner.
While the Piriform staff will join Avast’s consumer business unit, the antivirus company wants to keep Piriform products separate from its current system optimization offering, which includes Avast Cleanup and AVG TuneUp. Avast acquired AVG last year.
The Piriform acquisition will broaden Avast’s presence in London and the companies say they will combine their expertise to deliver even better products.
CCleaner is used by more than 130 million people worldwide, including 15 million Android device users. Avast CEO Vince Steckler believes the CCleaner brand fits his company very well as they both provide high-quality free products.
Steckler also pointed out that both Avast and Piriform have strong and loyal communities whose members provide product feedback and help each other.
“I’ve seen Piriform grow from a bedroom-based hobby to a real business with billions of downloads, millions of users and a worldwide fan base. Our objective, which is to create world-class software tools that fix real world problems, has made the business what it is today,” said Lindsey Whelan, CEO of Piriform.
“We’re pleased to become part of a company which shares this objective because it means together, we can combine our expertise to deliver even better software to the people that matter most: our users,” Whelan added.
The financial terms of the deal have not been disclosed.
New CyberX Technology Predicts ICS Attack Vectors
20.7.2017 securityweek ICS
Industrial cybersecurity and threat intelligence firm CyberX announced on Thursday the availability of a new simulation technology that allows organizations to predict breach and attack vectors on their networks.
The new industrial control systems (ICS) security service, named ICS Attack Vector Prediction, leverages proprietary analytics to continuously predict possible attack avenues and help organizations prevent breaches.
The solution provides a visual representation of all possible attack chains targeting critical assets in the operational technology (OT) network. Scenarios are ranked based on the level of risk to help security teams prioritize mitigation.
Cybersecurity personnel are provided detailed mitigation recommendations for each vulnerability. This can include patching Windows devices, upgrading vulnerable PLC firmware, and disabling unnecessary or unmanaged remote access methods.
CyberX's in-house ICS security experts can also advise organizations on how to devise the most efficient and effective mitigation strategies, especially in large and globally-distributed organizations in sectors such as manufacturing, pharmaceuticals, chemicals, and oil and gas.
Related: Learn More at SecurityWeek's 2017 ICS Cyber Security Conference
Security teams can easily simulate the effects of each mitigation action. For example, they can simulate patching or isolating a device in order to determine if that eliminates the risk posed to important systems.
Scanning OT networks is not as easy as scanning IT networks because invasive actions can cause downtime. In order to prevent disruption to the customer’s systems, CyberX says its product simulates attack vectors by using agentless asset discovery and vulnerability assessment technology that combines a deep understanding of industrial systems and non-invasive traffic analysis.
The Attack Vector Prediction technology is available now as part of the base CyberX platform at no additional charge to existing customers. The CyberX platform is priced based on the number of monitored appliances, both physical or virtual.
With the addition of the attack prediction technology to its offering, CyberX says it addresses all four requirements outlined in Gartner’s Adaptive Security Architecture framework: prediction, prevention, detection and response.
Critical Code Injection Flaw In Gnome File Manager Leaves Linux Users Open to Hacking
20.7.2017 thehackernews Vulnerebility
A security researcher has discovered a code injection vulnerability in the thumbnail handler component of GNOME Files file manager that could allow hackers to execute malicious code on targeted Linux machines.
Dubbed Bad Taste, the vulnerability (CVE-2017-11421) was discovered by German researcher Nils Dagsson Moskopp, who also released proof-of-concept code on his blog to demonstrate the vulnerability.
The code injection vulnerability resides in "gnome-exe-thumbnailer" — a tool to generate thumbnails from Windows executable files (.exe/.msi/.dll/.lnk) for GNOME, which requires users to have Wine application installed on their systems to open it.
Those who are unaware, Wine is a free and open-source software that allows Windows applications to run on the Linux operating system.
Moskopp discovered that while navigating to a directory containing the .msi file, GNOME Files takes the filename as an executable input and run it in order to create an image thumbnail.
For successful exploitation of the vulnerability, an attacker can send a crafted Windows installer (MSI) file with malicious VBScript code in its filename, which if downloaded on a vulnerable system would compromise the machine without further user interaction.
"Instead of parsing an MSI file to get its version number, this code creates a script containing the filename for which a thumbnail should be shown and executes that using Wine," Moskopp explains while demonstrating his PoC.
"The script is constructed using a template, which makes it possible to embed VBScript in a filename and trigger its execution."
The flaw can be exploited by potential hackers using other attack vectors as well, for example, by directly inserting a USB-drive with a malicious file stored on it, or delivering the malicious file via drive-by-downloads.
How to Protect Yourself from Bad Taste
Moskopp reported the vulnerability to the GNOME Project and the Debian Project. Both of them patched the vulnerability in the gnome-exe-thumbnailer file.
The vulnerability affects gnome-exe-thumbnailer before 0.9.5 version. So, if you run a Linux OS with the GNOME desktop, check for updates immediately before you become affected by this critical vulnerability.
Meanwhile, Moskopp also advised users to:
Delete all files in /usr/share/thumbnailers.
Do not use GNOME Files.
Uninstall any software that facilitates automatically execution of filenames as code.
Moskopp also advised developers to not use "bug-ridden ad-hoc parsers" to parse files, to "fully recognise inputs before processing them," and to use unparsers, instead of templates.
CrowdStrike, Dragos Partner to Deliver Comprehensive ICS Security Services
20.7.2017 securityweek ICS
Cloud-based endpoint security firm CrowdStrike and Dragos, a company that specializes in protecting industrial control systems (ICS), announced on Tuesday a strategic partnership whose goal is to provide comprehensive cybersecurity services.
Joint customers will benefit from a combination of CrowdStrike’s assessment, preparedness and incident response services and Dragos’ expertise in protecting ICS. The offering is designed to help critical infrastructure and other organizations secure their systems against sophisticated threats.
Customers will be provided proactive enterprise security services through CrowdStrike’s Falcon platform, compilation and correlation of ICS security events via the Dragos platform, and expertise for preventing, assessing and responding to ICS incidents.
The partnership will also offer comprehensive enterprise and industry intelligence, and improved awareness, visibility and protection against threats that pose a serious risk to organizations using both networked endpoints and industrial devices.
“At CrowdStrike, we track a wide array of adversaries going after critical infrastructure with incredibly sophisticated attack methods and tools. In order to stop these breaches, it’s important to combine domain knowledge of the industrial threat landscape, actionable intelligence, advanced security services and endpoint protection technology,” said Thomas Etheridge, vice president of services at CrowdStrike. “We are thrilled to partner with Dragos, a company that brings unrivalled expertise in ICS/SCADA systems to offer joint customers improved security planning, awareness, visibility, and exceptionally fast response to incidents.”
“Current security solutions are blind to how adversaries breach industrial systems and disrupt critical operations. Together, CrowdStrike and Dragos leverage proven human expertise, adversary intelligence and unrivaled technology to uniquely equip our customers with a full understanding of the enterprise and industrial threat landscape,” said Ben Miller, director of Threat Operations at Dragos.
'DarkHotel' APT Uses New Methods to Target Politicians
20.7.2017 securityweek APT
The DarkHotel threat group has been using some new methods in attacks aimed at government employees with an interest in North Korea, according to a report published this week by security firm Bitdefender.
The activities of the DarkHotel advanced persistent threat (APT) actor came to light in November 2014, when Kaspersky published a report detailing a sophisticated cyber espionage campaign targeting business travelers in the Asia-Pacific region. The group has been around for nearly a decade and some researchers believe its members are Korean speakers.
The attackers targeted their victims using several methods, including through their hotel’s Wi-Fi, zero-day exploits and peer-to-peer (P2P) file sharing websites. Nearly one year later, the threat group was observed using new attack techniques and an exploit leaked from Italian spyware maker Hacking Team.
DarkHotel victims have been spotted in several countries, including North Korea, Russia, South Korea, Japan, Bangladesh, Thailand, Taiwan, China, the United States, India, Mozambique, Indonesia and Germany. Up until recently, the attacks appeared to focus on company executives, researchers and development personnel from sectors such as defense industrial base, military, energy, government, NGOs, electronics manufacturing, pharmaceutical, and medical.
In more recent DarkHotel attacks it has dubbed “Inexsmar,” security firm Bitdefender said the hackers targeted political figures, and they appeared to be using some new methods.
Bitdefender’s analysis is based on samples from September 2016. The initial Trojan downloader, delivered via phishing emails, collects information on the infected device and sends it back to its command and control (C&C) server. If the compromised system meets requirements (i.e. it belongs to an individual who is of interest), the first stage DarkHotel downloader, disguised as a component of OpenSSL, is fetched.
In the meantime, in an effort to avoid raising suspicion, the malware opens a document titled “Pyongyang e-mail lists - September 2016,” which provides a list of email contacts for various organizations in North Korea’s capital city.
If the system profile does not match what the attackers are looking for, the C&C server returns a “fail” string and the attack stops. If the attack continues, a second payload is retrieved.
When Bitdefender analyzed the malware samples, the C&C server was offline, making it impossible to know exactly who the victims were and how much damage was caused. However, Bitdefender’s Bogdan Botezatu told SecurityWeek that, based on the structure of the phishing message, the intended targets are most likely individuals working for governments or state institutions who have an interest in the political situation in North Korea.
Experts believe that the use of social engineering and a multi-stage downloader is an improvement compared to the direct use of exploits as it gives the attackers more flexibility in malware distribution and ensures that the Trojan remains up to date.
A bug in Gnome pic parser can be exploited to run malicious VBScripts
20.7.2017 securityaffairs Exploit Virus
A bug in your image thumbnailer could represent a new attack vector for hackers that can exploit it for script injection.
Another day, another bug in a popular application. A bug in your image thumbnailer could represent a new attack vector for hackers that can exploit it for script injection.
To create image thumbnails, Gnome Files allows users providing filenames as an executable input.
The flaw was detailed by the researchers Nils Dagsson Moskopp who provided useful suggestions to avoid being hacked.
“Thumbnail generation for MSI files in GNOME Files executes arbitrary VBScript.” states Moskopp.
“Delete all files in /usr/share/thumbnailers. Do not use GNOME Files. Uninstall any other software that facilitates automatically executing parts of filenames as code”.
Dagsson Moskopp published a PoC code leveraging Wine to execute VBScript. He tricks Gnome Files into creating an MSI file called badtaste.txt.

Create MSI Files
Create a file named poc.xml with the following content:
<?xml version="1.0" encoding="utf-8"?>
<Wix xmlns="http://schemas.microsoft.com/wix/2006/wi">
<Product Version="1.0"/>
</Wix>
Execute the following Bourne Shell code:
wixl -o poc.msi poc.xml
cp poc.msi "poc.msi\",0):Set fso=CreateObject(\"Scripting.FileSystemObject\"):Set poc=fso.CreateTextFile(\"badtaste.txt\")'.msi"
Trigger Execution
Start GNOME Files and navigate to the folder with the MSI files. An empty file with the name badtaste.txt should appear.
“Whenever an icon for a Microsoft Windows executable (EXE), installer (MSI), library (DLL), or shortcut (LNK) should be shown, Gnome Files calls /usr/bin/gnome-exe–thumbnailer to either extract an embedded icon from the file in question or deliver a fallback image for the appropriate filetype.” explained the expert.
The expert highlighted that the problem is triggered due to the presence of just one line of code in /usr/bin/gnome-exe-thumbnailer:
DISPLAY=NONE wine cscript.exe //E:vbs //NoLogo Z:\\tmp\\${TEMPFILE1##*/}.vbs 2>/dev/null \
“Instead of parsing an MSI file to get its version number, this code creates a script containing the filename for which a thumbnail should be shown and executes that using Wine. The script is constructed using a template, which makes it possible to embed VBScript in a filename and trigger its execution.” Dagsson Moskopp added.
In order to avoid problems, Dagsson Moskopp suggests developers should not use “ad-hoc parsers” to parse files, should “fully recognise inputs before processing them”, and should use unparsers.
Below the remedy suggestions for both users and developers:
Remedy (for users)
“Delete all files in /usr/share/thumbnailers. Do not use GNOME Files. Uninstall any other software that facilitates automatically executing parts of filenames as code.”
Remedy (for developers)“Do not parse files with bug-ridden ad-hoc parsers. Fully recognize inputs before processing them. Do not use templates, use unparsers instead. Read about LANGSEC.”
DDoS Tools availability Online, a worrisome trend
20.7.2017 securityaffairs Attack
Experts warn of an increased availability of DDoS tools online, many wannabe hackers download and use them without awareness on consequences.
As cyber crime reaches new levels with new malware & viruses being realized online on a daily basis it also becomes apparent that the increase in DDoS tools that require no apparent skills to use them, just providing the IP address it is possible to launch the attack. These tools are becoming more and more available on the Internet.
We are all aware of the effects of a DDOS attack can have on a company not only rendering their website inaccessible, but also causing a loss in online revenue & sales.
With the release of such applications comes the added threat of users knowingly allowing backdoors to their computer systems to allow the creators access to your device to continue attacks in your absence. Not only does a back door in a system allow the distributor access but also anyone else who finds the vulnerability.
The main concern is that in general many young people are downloading and using theses tools but also the fact that they are told under false illusions to use them and believe they are safe in taking part in denial of service attacks on high profile sites including government domains causing sites to go offline and un reachable.
It’s very important nowadays to be aware of what your children are downloading on the Internet and that you only install applications that are from verified software companies and scanned before install or execution.
These groups are spreading their vulnerable applications through more and more blatant means on mainstream social media were most younger generations reside on the web.
( I am not going to advise on how to use denial of service and stay anonymous but I can assure the application you installed is not protecting you it’s infecting your system. )
Please see the below DDoS tools & applications found by our cyber research division at Frontline Cyber Security Ltd in a short search over some popular social media sites (Mention No Names). We were seeing how easily accessible DDOS tools are to the general web user.
Distributed denial of service application’s found ( Details removed of download links please contact us if you are a researcher / analyst. )
LOIC RedCult Edition – RiskwareAgent – MD5 609db4b9154f9aee29a5ceb775bec655
RedCult Doser – Loic.7 – MD5 6d0abacacd4393f9b3e30b2ed3be316e
RC Doors – Malware.SDi.5EDF – MD5 b1465ff2711b3cc9c4c8faf414354e7d
exe – Win32.DarkKomet – MD5 606aeb40c65070d234e1617d1ab257ff
ddos_android – Android.SpyAgent – MD5 c99ccf4d61cefa985d94009ad34f697f
Here is an image of the Android application running fill out a few boxes and click send.

We also obtained a list of targets theses applications were released to attack and have also managed to collect screen shots of the tools in use against government sites.
Below are some images of the application being used in what appears to be one of many Anonymous Operations in this case #OpIsrael.
We have a list of servers the tool was designed to attack but are unable to post it at this time.
The below image shows the application being shared and distributed
In regards to the above DDoS tools, the relevant authorities have been notified and are assisting in having them removed.
Black Hat is coming and with it a good reason to update your “Broadcom-based” devices
20.7.2017 securityaffairs Mobil
BroadPwn potentially expose to hack millions of Android devices using Broadcom Wi-Fi Chip, update your “Broadcom-based” devices.
Black Hat 2017 is debuting in 3 days and with it a potential concern to most of us. It turns out that one of the conference presentations, entitled BROADPWN: REMOTELY COMPROMISING ANDROID AND IOS VIA A BUG IN BROADCOM’S WI-FI CHIPSETS [1], will detail how Broadcom BCM43xx Wi-Fi chipsets can be exploited to achieve full code execution on the compromised device without user interaction.
“An attacker within range may be able to execute arbitrary code on the Wi-Fi chip”, says Apple about this vulnerability (CVE-2017–9417) in today’s security bulletin [2].

Besides Apple, those chipsets are present on most smartphone devices like HTC, LG, Nexus and most Samsung models as well. Make sure to have this vulnerability fixed on all your devices — especially if you are planning to be in Las Vegas next week.
References
[1] https://www.blackhat.com/us-17/briefings.html#broadpwn-remotely-compromising-android-and-ios-via-a-bug-in-broadcoms-wi-fi-chipsets
[2] https://support.apple.com/pt-br/HT207923
Google Warns Users of Potentially Risky Web Apps
19.7.2017 securityweek Security
Google is taking another step to better protect users from malicious third-party web applications: it is now warning users of newly created web apps and Apps Scripts that are pending verification.
The move follows a series of similar protective measures the Internet giant announced earlier this year, after many of its users were hit by a phishing attack where a rogue app was found impersonating Google Docs. To prevent similar incidents, the company tightened OAuth rules and also started scrutinizing new web apps that request user data.
The new warning screen will be accompanied by changes expected to improve the developer experience, the company says, adding that the verification process and the new warnings will expand to existing apps in the coming months.
The new “unverified app” screen that users will see when accessing newly created web applications and Apps Scripts that require verification will replace the “error” page that has been served to developers and users over the past several months. The screen will appear before users are taken to the permissions consent screen, thus only informing users of the app not being yet verified.
Through these new notices, users will be automatically informed if they may be at risk, thus helping them make more informed decisions to keep their information safe. The testing and developing of applications should also be simplified.
“This will help reduce the risk of user data being phished by bad actors. This new notice will also help developers test their apps more easily,” Naveen Agarwal, Identity team, and Wesley Chun, Developer Advocate, G Suite, note in a blog post.
Users have the option to dismiss the alert, which allows developers to test applications without going through the OAuth client verification process first. Google has published a series of steps in a help center article to provide information on how to begin the verification process to remove the interstitial and prepare their app for launch.
The same protections are being applied to Apps Script beginning this week, meaning that all new Apps Scripts requesting OAuth access to data from users in other domains may also get the "unverified app" alert. Additional information was published in a verification documentation page.
“Apps Script is proactively protecting users from abusive apps in other ways as well. Users will see new cautionary language reminding them to ‘consider whether you trust’ an application before granting OAuth access, as well as a banner identifying web pages and forms created by other users,” Agarwal and Chun say.
Next, Google is planning an expansion of the verification process to existing apps as well, meaning that developers of some current apps may have to go through the verification flow. To ensure no issue will hinder the transition, developers should make sure their contact information is up-to-date.
“In the Google Cloud Console, developers should ensure that the appropriate and monitored accounts are granted either the project owner or billing account admin IAM role. In the API manager, developers should ensure that their OAuth consent screen configuration is accurate and up-to-date,” Google says.
The company has published help center articles to provide detailed information on granting IAM roles and on configuring the consent screen.
Organizations Slow to Patch Critical Memcached Flaws
19.7.2017 securityweek Vulnerebility
Tens of Thousands of Internet-Exposed Memcached Servers Are Vulnerable to Attacks
Tens of thousands of servers running Memcached are exposed to the Internet and affected by several critical vulnerabilities disclosed last year by Cisco’s Talos intelligence and research group.
In late October 2016, Talos published an advisory describing three serious flaws affecting Memcached, an open source, high performance distributed memory caching system used to speed up dynamic web apps by reducing the database load.
The vulnerabilities, tracked as CVE-2016-8704, CVE-2016-8705 and CVE-2016-8706, allow a remote attacker to execute arbitrary code on vulnerable systems by sending specially crafted Memcached commands. The flaws can also be leveraged to obtain sensitive data that could allow an attacker to bypass exploit mitigations.
The security holes were patched by Memcached developers before Talos disclosed its findings. A few months later, in late February and early March 2017, researchers conducted Internet scans to find out how many organizations had patched their installations.
The scans uncovered a total of more than 107,000 servers accessible over the Internet and nearly 80 percent of them, or roughly 85,000 servers, were still vulnerable. Furthermore, only approximately 22 percent of the servers, or roughly 24,000, required authentication.
Nearly 30,000 of the vulnerable servers were located in the United States, followed by China (17,000), the United Kingdom (4,700), France (3,200), Germany (3,000), Japan (3,000), the Netherlands (2,600), India (2,500) and Russia (2,300).
After completing the scans, Cisco obtained contact email addresses for all the IP addresses associated with the vulnerable servers and attempted to notify affected organizations.
Six months later, researchers conducted another scan, but the situation improved only slightly, with roughly 10 percent of systems patched since the previous analysis. However, the number of servers requiring authentication dropped to 18,000, or 17 percent of the total.
Interestingly, researchers noticed that more than 28,000 of the previously discovered servers were no longer online. However, since the total number of Internet-facing installations remained the same, experts determined that some servers either changed their IPs or organizations had been deploying new systems with vulnerable versions of Memcached.
Talos warned that these vulnerable Memcached installations could be targeted in ransom attacks similar to the ones that hit MongoDB databases in early 2017. While Memcached is not a database, it can still contain sensitive information and disrupting it could have a negative impact on other dependent services.
“The severity of these types of vulnerabilities cannot be understated,” experts warned. “These vulnerabilities potentially affect a platform that is deployed across the internet by small and large enterprises alike. With the recent spate of worm attacks leveraging vulnerabilities this should be a red flag for administrators around the world. If left unaddressed the vulnerabilities could be leveraged to impact organizations globally and impact business severely.”
The number of Memcached instances accessible from the Internet has remained fairly constant over the past years. An analysis conducted in August 2015 uncovered 118,000 Memcached instances exposing 11 terabytes of data.
Millions of Dow Jones Customer Records Exposed Online
19.7.2017 securityweek Incindent
American news and financial information firm Dow Jones & Company inadvertently exposed the details of millions of its customers. The data was found online by researchers in an Amazon Web Services (AWS) S3 bucket that had not been configured correctly.
Chris Vickery of cyber resilience firm UpGuard discovered on May 30 an AWS data repository named “dj-skynet” that appeared to contain the details of 4.4 million Dow Jones customers. Dow Jones disabled access to the files only on June 6.
The files included names, customer IDs, physical addresses, subscription details, the last four digits of credit cards and, in some cases, phone numbers belonging to individuals who subscribed to Dow Jones publications such as The Wall Street Journal and Barron’s.
One of the exposed files stored 1.6 million entries for Dow Jones Risk and Compliance, a risk management and regulatory compliance service for financial institutions.
According to UpGuard, the data was accessible because Dow Jones employees had configured the repository’s permissions to allow access to anyone with an AWS account. There are over one million Amazon cloud users and anyone can register an account for free.
Dow Jones confirmed the data leak, but claimed only 2.2 million of its customers were affected, not 4.4 million as UpGuard claims. The security firm has admitted that there could be some duplicate entries.
It’s unclear if affected customers will be notified, but in a statement to The Wall Street Journal the company downplayed the incident, arguing that there is no evidence the data was taken by anyone else and the exposed information does not pose a significant risk to users.
UpGuard disagrees and points out that the data could be highly valuable to malicious actors for phishing and other social engineering schemes.
In recent weeks, the security firm reported finding exposed databases storing data belonging to the U.S. National Geospatial-Intelligence Agency (NGA), American voters, and Verizon customers. Unprotected Amazon S3 buckets were involved in all incidents.
“Yet another demonstration of how services such as AWS are missing basic steps that ensure their data and services are configured in a secure fashion,” Bitglass CEO Rich Campagna told SecurityWeek.
“It’s seems like a no-brainer to implement data-centric security tools on any sensitive information that could get out to the public. This approach could ensure that cloud services deny unauthorized access, and organizations could take it one step further and encrypt sensitive data at rest,” Campagna added. “Companies like Dow Jones, Verizon and anyone else using the public cloud for their infrastructure can easily enforce policies that require internal teams and third-parties to adequately protect any customer data that touches the cloud.”
EternalSynergy-Based Exploit Targets Recent Windows Versions
19.7.2017 securityweek Exploit
A security researcher has devised an EternalSynergy-based exploit that can compromise versions of Windows newer than Windows 8.
EternalSynergy is one of several exploits allegedly stolen by the hacker group calling themselves the Shadow Brokers from the National Security Agency (NSA)-linked Equation Group. The exploit was made public in April along with several other hacking tools, one month after Microsoft released patches for them.
In May, a security researcher included EternalSynergy and six other NSA-linked hacking tools (EternalBlue, EternalChampion, EternalRomance, DoublePulsar, Architouch, and Smbtouch) in a network worm called EternalRocks. The tool was pulled weeks later to prevent abuse.
Security researcher Worawit Wang has now made public an EternalSynergy-derived exploit that also leverages EternalRomance and can be used on a wider range of Windows versions.
Available on both GitHub and ExploitDB, the tool targets 64-bit versions of Windows 2016, Windows 2012 R2, Windows 8.1, Windows 2008 R2 SP1, and Windows 7 SP1, as well as the 32-bit versions of Windows 8.1 and Windows 7 SP1.
Security researcher Sheila A. Berta, who is part of Telefonica's Eleven Paths security unit, has published a paper (PDF) on how to exploit Wang’s tool to get a Meterpreter session on Windows Server 2016.
EternalSynergy is based on the CVE-2017-0143 vulnerability, which “stems from not taking the command type of an SMB message into account when determining if the message is part of a transaction,” Microsoft reveals. “In other words, as long as the SMB header UID, PID, TID and OtherInfo fields match the corresponding transaction fields, the message would be considered to be part of that transaction.”
According to Microsoft, EternalSynergy should not work on Windows iterations newer than Windows 8, due to kernel security improvements such as Hypervisor-enforced Code Integrity (HVCI), which prevents unsigned kernel pages from being executed, and Control Flow Guard (CFG), designed to prevent invalid indirect function calls.
The exploit is expected to crash on unsupported operating system releases, but Wang managed to create a stable tool that targets Windows XP and newer versions, except Windows 10. Given a patch is already available from Microsoft, impacted users should consider applying it as soon as possible.
EternalSynergy is only one of the NSA-linked exploits to have caught researchers’ attention over the past several months. EternalBlue might be the most discussed such tool, after it has been abused in global attacks by ransomware such as WannaCry, the UIWIX ransomware, Adylkuzz botnet, and a stealth Remote Access Trojan.
Last month’s destructive NotPetya wiper also used EternalBlue to spread within compromised networks, along with the EternalRomance exploit and various other tools.
Malware Targets NAS Devices Via SambaCry Exploit
19.7.2017 securityweek Virus
A piece of malware dubbed by researchers SHELLBIND leverages a recently patched Samba vulnerability in attacks aimed at Internet of Things (IoT) devices, particularly network-attached storage (NAS) appliances.
The Samba flaw exploited in these attacks, tracked as CVE-2017-7494 and known as SambaCry and EternalRed, can be exploited by a malicious client to upload a shared library to a writable share, and then cause the server to load that library. This allows a remote attacker to execute arbitrary code on the targeted system.
The security hole was introduced in the Samba code in 2010 and it was patched in May. Since the Samba interoperability software suite is highly popular, the vulnerability affects the products of several major vendors, including NAS appliances.
Roughly two weeks after the patch was released, security firms noticed that the vulnerability had been exploited to deliver a cryptocurrency miner.
In early July, researchers at Trend Micro spotted another type of attack involving SambaCry. Cybercriminals have been exploiting the vulnerability in attacks targeting NAS devices used by small and medium-size businesses. The malware they have been using works on various architectures, including MIPS, ARM and PowerPC.
Attackers can leverage the Shodan Internet search engine to identify devices using Samba and write the initial malware files to their public folders.
According to Trend Micro, ELF_SHELLBIND.A is delivered as a SO file to Samba public folders and loaded via the SambaCry vulnerability. Once it’s deployed on the targeted system, the malware contacts a command and control (C&C) server located in East Africa. The threat modifies firewall rules to ensure that it can communicate with its server.
“Once the connection is successfully established and authentication is confirmed, then the attacker will have an open command shell in the infected systems where he can issue any number of system commands and essentially take control of the device,” explained Trend Micro researchers.
Users can protect their systems against these attacks by ensuring that Samba is up to date. Another mitigating factor is the need to have writable access to a shared location on the targeted system.
Court Upholds Gag Orders in National Security Letters
19.7.2017 securityweek Security
The Ninth U.S. Circuit Court of Appeals in San Francisco confirmed a lower court decision Monday that gag orders included in FBI National Security Letters (NSLs) do not violate the First Amendment of the U.S. Constitution's free speech protections.
It has been a long journey to this decision (PDF) centered around five NSLs; three received by CREDO in 2011 and 2013, and two received by Cloudflare in 2012. The two organizations petitioned the district court to have both the information requests and the non-disclosure requirements of the NSLs set aside.
The district court decided that the 2006 NSL Law was unconstitutional and enjoined the government from issuing new requests and enforcing the gag (but stayed the decision pending a government appeal). It did not set aside the existing five NSLs. CREDO and Cloudflare, and the government, appealed the decision.
With the appeals pending, the government enacted the USA FREEDOM Act, which became effective June 2, 2015. Given the new law, the appeals court sent the matter back to the district court. This time, the lower court decided that the NSL law, as amended, is constitutional, and that the FBI had shown sufficient cause. It allowed the government's cross-petition to enforce the NSLs and gags, barring the two 2013 CREDO NSLs.
CREDO and Cloudflare appealed the decision to uphold three of the NSLs, and the government appealed the decision to set aside the two 2013 CREDO NSLs. Meanwhile, the FBI closed its investigations pertaining to the three remaining NSLs, and voluntarily and partly lifted the gagging orders.
But CREDO and Cloudflare persisted, arguing that the whole concept of gagging NSLs contravenes the constitutional right to free speech.
It is this final petition that was rejected by the appeals court on Monday. Ironically, it is the FREEDOM Act that upholds the decision. The FREEDOM Act enforces greater administrative care over the delivery of NSLs and gag orders -- but if that care is taken, the requests become legal. That, at least, is the decision of the Ninth.
"We conclude," announced the three judges, "that § 2709(c)'s nondisclosure requirement imposes a content-based restriction that is subject to, and withstands, strict scrutiny. We further hold that, assuming the nondisclosure requirement is the type of prior restraint for which the Freedman procedural safeguards are required, the NSL law provides those safeguards. The nondisclosure requirement in the NSL law therefore does not run afoul of the First Amendment.
"It is not yet known whether CREDO and Cloudflare will continue the fight and appeal to the Supreme Court. Electronic Frontier Foundation (EFF) staff attorney Andrew Crocker tweeted, "Disappointing 9th Cir ruling in EFF's national security letter case on behalf of @CREDOMobile @Cloudflare. More soon." He added, "Especially disappointing is the court's failure to address permanent NSL gags, which always violate the First Amendment."
In a statement emailed to SecurityWeek, CREDO CEO Ray Morris said, "We are disappointed in the Ninth Circuit's decision and are considering our options for next steps. At CREDO, we know what an uphill battle challenging these gag orders can be and feel that the court missed an opportunity to protect the First Amendment rights of companies that want to speak out in the future."
Last week, EFF published its 2017 report, Who Has Your Back? It explains the issues behind NSLs. "NSLs are akin to subpoenas requiring service providers -- including technology companies, phone companies, and ISPs -- to hand over data to the FBI about users' private communications and Internet activity. These orders are almost always accompanied by gag orders preventing the recipients from ever revealing the letter's existence and which have contributed to widespread abuse of this investigatory tool."
Although Cloudflare was not included in the EFF study, CREDO is one of just 9 companies out of 26 awarded five stars for its attitudes and attempts to protect user privacy.
"Cloudflare's approach to law enforcement requests is that we are supportive of their work but believe that any requests we receive must adhere to the due process of law and be subject to judicial oversight," Doug Kramer, General Counsel at Cloudflare told SecurityWeek. "It is not Cloudflare's intent to make their job any harder, or easier. In 2013, we challenged an FBI request for customer information on a confidential basis through an NSL, which was not an easy decision, because we felt it violated that principle. Although decisions by a federal court and a new statute since that time have improved the NSL process, we think there is additional work to be done and are disappointed the Ninth Circuit ruled the current practice sufficient."
*Updated with comment from Cloudflare
UK Spy Agency Warns of State-sponsored Hackers Targeting Critical Infrastructure
19.7.2017 securityweek BigBrothers
The U.K. Government Communications Headquarters (GCHQ), Britain's secret eavesdropping agency, warns that 'a number of [UK] Industrial Control System engineering and services organisations are likely to have been compromised' following the discovery of 'connections from multiple UK IP addresses to infrastructure associated with advanced state-sponsored hostile threat actors.'
The warning comes from a National Cyber Security Centre (NCSC) memo obtained by Motherboard and confirmed by the BBC. NCSC is part of the UK's primary cyber intelligence agency, GCHQ.
From the little information available, it doesn't appear as if there are any specifically known compromises -- NCSC might simply be working from the statistical probability that if enough phishing attacks are launched, at least some will inevitably succeed.
Spear-phishing is not specifically mentioned within the memo, although it does mention a separate, non-public report from the FBI and DHS last month suggesting the same attackers were using spear-phishing to deliver poisoned Word documents. Motherboard also points to a paywalled report in the Times, Saturday, which states, "Hackers backed by the Russian government have attacked energy networks running the national grid in parts of the UK, The Times has learnt."
The clear unproven implication is that Russian state-backed actors are specifically targeting the western energy sector. Having said that, however, the Times report differs from the FBI/DHS and NCSC memos by stating that the intention was "to infiltrate control systems... This would also have given them the power to knock out parts of the grid in Northern Ireland."
Both the FBI/DHS and NCSC memos point to attacks against services organizations, indicating that in the UK and America, it is primarily the supply chain to the critical infrastructure that is being targeted. Indeed, the FBI/DHS statement comments, "There is no indication of a threat to public safety, as any potential impact appears to be limited to administrative and business networks."
So, apart from the Times report, this would appear to be a large-scale campaign designed to find ways to infiltrate the critical infrastructure rather than anything designed to damage the critical infrastructure. This is probably standard practice for most cyber-advanced nations -- ensuring they have the capacity to respond to a potential enemy if it ever becomes necessary.
The importance to an enemy and the potential danger to the critical infrastructure should not, however, be underestimated. A known and ready access route into, for example, the power grid, would be similar to having a nuclear deterrent primed and ready -- there is no intention to use it, but accidents can happen.
Neither the FBI/DHS nor the NCSC names the attackers. The NSCS clearly has suspects since it recognizes the infrastructure used. The New York Times, however, implicates Russia. "Two people familiar with the investigation say that, while it is still in its early stages, the hackers' techniques mimicked those of the organization known to cybersecurity specialists as "Energetic Bear," the Russian hacking group that researchers have tied to attacks on the energy sector since at least 2012."
Rapid7 Acquires Security Orchestration and Automation Firm Komand
19.7.2017 securityweek Security
Boston-based IT security and operations software maker Rapid7 (NASDAQ: RPD) on Tuesday announced that it has acquired security orchestration and automation firm Komand.
Founded in late 2015 by Jen Andre, who previously co-founded Threat Stack, Komand’s platform was designed to help security and IT teams automate repetitive tasks, which Rapid7 says will “help its customers reduce time to resolution, maximize resources, and overcome ecosystem complexity.”
Specifically, Rapid7 explained that Komand’s technology will expand Rapid7’s Insight platform’s ability to “empower lean security and IT teams to meaningfully increase productivity across their entire operation and reduce the time it takes to respond to an incident.”
Customers will now have the ability to automatically identify risks, respond to incidents, and address issues significantly faster and with less human intervention, Rapid7 says.
“The need for well-designed security and IT automation solutions is acute; resources are scarce, environments are becoming more complex, all while threats are increasing,” said Corey Thomas, president and CEO of Rapid7. “Security and IT solutions must evolve through context-driven automation, allowing cybersecurity and IT professionals to focus on more strategic activities.”
“We’ve been impressed by the technology developed by the Komand team and believe that together, we’ll be able to build solutions that make security and IT teams significantly more productive,” said Lee Weiner, chief product officer at Rapid7. “The complexity of today’s security and IT ecosystems have put security and IT operations teams at a significant disadvantage when they need to respond quickly. By developing contextualized automation technology, we’ll be able to cut back the time it takes to respond to an incident—when minutes can mean the difference between a minor issue and significant compromise or loss.”
Rapid7 cites use cases including automated risk remediation and patching, malware investigation and containment, and chat ops for responding to routine inquiries.
The terms of the acquisition were not disclosed, though Rapid7 said the purchase is not expected to have a material financial impact to its calculated billings, revenue, and non-GAAP earnings (loss) per share for calendar year 2017, as guided on May 9, 2017.
Both Rapid7 and Komand were Boston-based companies with offices just down the street from each other.
Komand announced in Jan. 2017 that it had closed a $1.25 million seed round of funding.
As part of the acquisition, 12 Komand employees have become employees of Rapid7.
Millions of IoT Devices Possibly Affected by 'Devil's Ivy' Flaw
19.7.2017 securityweek Vulnerebility
A vulnerability dubbed by researchers “Devil’s Ivy,” which exists in an open source library present in the products of many companies, could affect millions of security cameras and other Internet of Things (IoT) devices.
The flaw, a stack-based buffer overflow, was discovered by IoT security startup Senrio in a camera from Axis Communications, one of the world’s largest security camera manufacturers.
The weakness, tracked as CVE-2017-9765, can be exploited to cause a denial-of-service (DoS) condition and to execute arbitrary code. Senrio has published a technical advisory and a video showing how an attacker could exploit the flaw to hijack a security camera and gain access to its video feed.
“When exploited, [the vulnerability] allows an attacker to remotely access a video feed or deny the owner access to the feed,” Senrio said in a blog post. “Since these cameras are meant to secure something, like a bank lobby, this could lead to collection of sensitive information or prevent a crime from being observed or recorded.”
Devil's Ivy Exploit in Axis Security Camera from Senrio Labs on Vimeo.
Axis has determined that the vulnerability impacts nearly 250 of its camera models and it has started releasing firmware updates that patch the bug. The company has notified its customers and partners of Devil’s Ivy.
An investigation revealed that the security hole was actually in gSOAP, a development toolkit that simplifies the use of XML in server and client web applications. gSOAP is used by most of the top Fortune 500 companies and its developer, Genivia, claims it has been downloaded more than one million times.
The library is also used by some members of the ONVIF Forum, an organization that focuses on standardizing IP connectivity for cameras and other physical security products. ONVIF was established by Axis, Bosch and Sony in 2008 and its current members also include Canon, Cisco, D-Link, Honeywell, Huawei, Netgear, Panasonic, Siemens and Toshiba.
Senrio believes the Devil’s Ivy vulnerability could affect tens of millions of systems to some degree. A Shodan search conducted by the company on July 1 uncovered nearly 15,000 Axis dome cameras accessible from the Internet.
However, Genivia, which provided patches and mitigations, believes the vulnerability is not easy to exploit for arbitrary code execution.
Axis also pointed out in its advisory that exploitation of the flaw for code execution requires a skilled and determined attacker. The hacker needs to have access to the network housing the vulnerable device, but products exposed to the Internet are at much higher risk.
Both Axis and Senrio have advised users to place their cameras and other IoT devices behind a firewall to reduce the risk of exploitation.
Oracle Patches Record-Breaking 308 Vulnerabilities in July Update
19.7.2017 securityweek Vulnerebility
Oracle on Tuesday released its July 2017 Critical Patch Update (CPU) to address a total of 308 vulnerabilities, the highest number of security fixes ever released in a quarter by the enterprise software giant.
This month’s CPU resolves security issues in 22 different Oracle products, including Oracle Database Server, Oracle Enterprise Manager, Oracle Fusion Middleware, Oracle Hyperion, Oracle E-Business Suite, Oracle Industry Applications (Communications, Retail, and Hospitality), Oracle Primavera, Oracle Sun Products, Oracle Java SE, and Oracle MySQL.
Of the total 308 vulnerabilities addressed, 27 were assessed as critical issues, with a CVSS base score between 9.0 and 10.0 (only one bug was rated 10). Over half of the vulnerabilities addressed this month can be exploited remotely without authentication.
Oracle Hospitality Applications received the largest number of security fixes, at 48 – 11 of these may be remotely exploitable without authentication. Oracle Fusion Middleware received 44 fixes (31 remotely exploitable without authentication), including one that addressed a critical vulnerability (CVE-2017-10137 – CVSS score 10.0) in Oracle WebLogic Server.
Oracle also resolved large numbers of vulnerabilities in Oracle Java SE (32 – 28 remotely exploitable without authentication), Oracle PeopleSoft Products (30 – 20 remotely exploitable), Oracle MySQL (30 – 9 remotely exploitable), Oracle E-Business Suite (22 – 18 remotely exploitable), and Oracle Financial Services Applications (20 – 4 remotely exploitable).
The record-breaking number of 30 flaws addressed in PeopleSoft is worrying, especially since 20 of the bugs can be exploited over the network without user credentials, ERPScan, a firm that specializes in security SAP and Oracle software, notes.
“Oracle PeopleSoft combines Supplier Relationship Management, Human Capital Management, Supply Chain Management, and other applications. The software has 6000+ enterprise customers and serves 20 million end users worldwide including more than 800 universities. Over 1000 PeopleSoft systems are available on the Internet putting organizations at risk. According to the latest survey from Crowd Research partners, 89% of responders agreed that the number cyber-attacks on ERP will significantly grow in the near future. SAP Attacks may cost up to $50 million, PeopleSoft is definitely the same weight category,” Alexander Polyakov, CTO at ERPScan, told SecurityWeek in an emailed statement.
82 of the vulnerabilities addressed in this quarter’s CPU affect a scope of crucial business applications from Oracle, such as Oracle PeopleSoft, E-Business Suite, Siebel CRM, Oracle Financial Services, and Oracle Primavera Products Suite. Around 53% of these bugs can be exploited remotely without authentication.
One of the most important vulnerabilities in E-Business Suite (CVE-2017-10244) is an Information Disclosure issue that could allow an attacker “to exfiltrate sensitive business data without requiring a valid user account in the system,” Onapsis, the company that discovered the issue, reveals. The flaw affects all supported Oracle E-Business Suite versions: 12.1.3, 12.2.3, 12.2.4, 12.2.5 and 12.2.6.
“This vulnerability is especially critical as an attacker would only need a web browser and network access to the EBS system to perform it. Any number of critical documents could be stored in the system including invoices, purchase orders, HR information and design documents to start. Even systems in DMZ mode do not ensure these systems are not vulnerable,” Juan Perez-Etchegoyen, Onapsis CTO, said.
Other Oracle E-Business Suite flaws addressed this month include a path traversal vulnerability (CVE-2017-10192), multiple vulnerabilities that allow path traversal attacks (grouped in CVSs CVE-2017-10184 and CVE-2017-10186), two Denial of Service vulnerabilities (CVE-2017-10108 and CVE-2017-10109), a Multiple Cross Site Scripting vulnerability (CVE-2017-10180), two Cross Site Scripting vulnerabilities (CVE-2017-10185 and CVE-2017-10191) and an Information disclosure vulnerability (CVE-2017-10245).
“There are different vulnerabilities which could be used by an attacker to compromise the system and get business critical information. It is crucial to update Oracle E-Business Suite with the last patch to fix all of these vulnerabilities and have the system up to date,” Onapsis says.
The most critical issues resolved in the Oracle July 2017 CPU affect Oracle WebLogic Server component of Oracle Fusion Middleware (CVE-2017-10137 – CVSS score 10.0), the OJVM component of Oracle Database Server (CVE-2017-10202 – CVSS score 9.9), the Oracle Communications BRM component of Oracle Communications Applications (CVE-2015-3253 – CVSS score 9.8), the MICROS PC Workstation 2015 component of Oracle Hospitality Applications (CVE-2017-5689 – CVSS score 9.8), and the MySQL Enterprise Monitor component of Oracle MySQL (CVE-2016-4436 – CVSS score 9.8).
Each quarter starting last year, Oracle has been patching an increasing number of vulnerabilities in its products. After the January 2016 CPU broke the 200 security patches barrier, the April 2017 one hit the 300 mark, and this month’s set of patches sets a new record.
As more and more security researchers focus on finding vulnerabilities in business software, the number of addressed issues is expected to increase. This should result in improved overall security for Oracle software, but only as long as patches are installed in a timely manner, which is a difficult and monotonous task, as ERPScan points out.
Mozilla Conducts Security Audit of Firefox Accounts
19.7.2017 securityweek Security
Mozilla has asked Germany-based security firm Cure53 to conduct an audit of the Firefox Accounts system and researchers identified a total of 15 issues, including vulnerabilities rated critical and high severity.
Firefox Accounts, also known as FxA, is the system that allows Firefox users to access hosted services provided by Mozilla. Since the component represents Firefox’s central authentication service and it’s likely to be targeted by malicious actors, Mozilla has decided to have it tested.
Tests conducted by Cure53 researchers over a 30-day period in September and October 2016 led to the discovery of 15 issues, which includes six vulnerabilities and nine general weaknesses.
The most serious of the flaws, rated critical, could have allowed hackers to launch cross-site scripting (XSS) and scriptless attacks in an effort to phish users or to steal sensitive information. However, Mozilla pointed out that exploitation of the flaw required registering a relier, a process that is not open to the public.
One of the high severity vulnerabilities found by Cure53 could have allowed arbitrary command execution if the attacker could determine the location for the execution of an application.
The list of high severity flaws also includes another XSS bug and an encryption weakness that may be exploited to increase the efficiency of brute-force attacks. The other problems identified by researchers have been classified as having low or medium severity.
Most of the vulnerabilities have been patched and Mozilla claimed that none of them had been exploited for malicious purposes and none of them put user data at risk.
“Given the amount of the audited code and the complexity of the project, this number of findings classifies as low and translates to an overall positive result of the investigation,” Cure53 said in its report. “Despite the fact that the tests were as thorough as possible on the codebase placed in scope, only a single ‘Critical’ finding was ultimately spotted. Even though this issue was discovered early on in the test, no major design issues were identified. Ultimately, the platform was perceived as rather robust and secured against a wide range of different attacks.”
In the past months, Mozilla commissioned audits for several pieces of software through its Secure Open Source (SOS) program, including for cURL, Dovecot and the Network Time Protocol (NTP).
2017 ICS Cyber Security Conference Call for Speakers Open Through August 15
19.7.2017 securityweek ICS
Longest Running ICS/SCADA Cybersecurity Conference to take Place Oct. 23-26, 2017 at InterContinental Hotel Atlanta
The official Call for Papers (speakers) for SecurityWeek’s 2017 Industrial Control Systems (ICS) Cyber Security Conference, being held October 23 – 26, 2017 at the InterContinental Buckhead Atlanta, Georgia, USA is open through August 15, 2017.
As the original ICS/SCADA cyber security conference, the event is the largest and longest-running cyber security-focused event series for the industrial control systems sector. The conference caters to the energy, water, utility, chemical, transportation, manufacturing, and other industrial and critical infrastructure organizations.
2017 ICS Cyber Security Conference
With a 15-year history, the conference has proven to bring value to attendees through the robust exchange of technical information, actual incidents, insights, and best practices to help protect critical infrastructures from cyber-attacks.
Produced by SecurityWeek, the conference addresses ICS/SCADA topics including protection for SCADA systems, plant control systems, engineering workstations, substation equipment, programmable logic controllers (PLCs), and other field control system devices.
The Conference is unique and has historically focused on control system end-users from various industries and what cyber vulnerabilities mean to control system reliability and safe operation. It also has a long history of having discussions of actual ICS cyber incidents along with lessons learned.
The 2017 Conference is expected to attract more than 450 professionals from around the world, including large critical infrastructure and industrial organizations, military and state and Federal Government. The incorporates training workshops and advanced full-day training sessions on various topics.
Through the Call for Speakers, a conference committee will accept speaker submissions for possible inclusion in the program at the 2017 ICS Cyber Security Conference.
The conference committee encourages proposals for both main track and “In Focus” sessions. Most sessions are 45 minutes in length including time for Q&A.
Submissions will be reviewed on an ongoing basis so early submission is highly encouraged.
Submissions must include proposed presentation title, an informative session abstract, including learning objectives for attendees if relevant; and contact information and bio for the proposed speaker.
All speakers must adhere to the 100% vendor neutral / no commercial policy of the conference. If speakers cannot respect this policy, they should not submit a proposal.
To be considered, interested speakers should submit proposals by email to events@securityweek.com with the subject line “ICS2017 CFP” by August 15, 2017.
Plan on Attending the 2017 ICS Cyber Security Conference?
Online registration is open, with discounts available for early registration.
Sponsorship Opportunities
Sponsorship and exhibitor opportunities for the 2017 ICS Cyber Security Conference are available. Please contact events(at)securityweek.com for information.
About the ICS Cyber Security conference
Produced by SecurityWeek, the ICS Cyber Security Conference is the conference where ICS users, ICS vendors, system security providers and government representatives meet to discuss the latest cyber-incidents, analyze their causes and cooperate on solutions. Since its first edition in 2002, the conference has attracted a continually rising interest as both the stakes of critical infrastructure protection and the distinctiveness of securing ICSs become increasingly apparent.
WikiLeaks Reveals CIA Teams Up With Tech to Collect Ideas For Malware Development
19.7.2017 thehackernews BigBrothers
As part of its ongoing Vault 7 leaks, the whistleblower organisation WikiLeaks today revealed about a CIA contractor responsible for analysing advanced malware and hacking techniques being used in the wild by cyber criminals.
According to the documents leaked by WikiLeaks, Raytheon Blackbird Technologies, the Central Intelligence Agency (CIA) contractor, submitted nearly five such reports to CIA as part of UMBRAGE Component Library (UCL) project between November 2014 and September 2015.
These reports contain brief analysis about proof-of-concept ideas and malware attack vectors — publically presented by security researchers and secretly developed by cyber espionage hacking groups.
Reports submitted by Raytheon were allegedly helping CIA's Remote Development Branch (RDB) to collect ideas for developing their own advanced malware projects.
It was also revealed in previous Vault 7 leaks that CIA's UMBRAGE malware development teams also borrow codes from publicly available malware samples to built its own spyware tools.
Here's the list and brief information of each report:
Report 1 — Raytheon analysts detailed a variant of the HTTPBrowser Remote Access Tool (RAT), which was probably developed in 2015.
The RAT, which is designed to capture keystrokes from the targeted systems, was being used by a Chinese cyber espionage APT group called 'Emissary Panda.'
Report 2 — This document details a variant of the NfLog Remote Access Tool (RAT), also known as IsSpace, which was being used by Samurai Panda, Identified as another Chinese hacking group.
Equipped with Adobe Flash zero-day exploit CVE-2015-5122 (leaked in Hacking Team dump) and UAC bypass technique, this malware was also able to sniff or enumerate proxy credentials to bypass Windows Firewall.
Report 3 — This report contains details about "Regin" -- a very sophisticated malware sample that has been spotted in operation since 2013 and majorly designed for surveillance and data collection.
Regin is a cyber espionage tool, which is said to be more sophisticated than both Stuxnet and Duqu and is believed to be developed by the US intelligence agency NSA.
The malware uses a modular approach that allowed an operator to enable a customised spying. Regin's design makes the malware highly suited for persistent, long-term mass surveillance operations against targets.
Report 4 — It details a suspected Russian State-sponsored malware sample called "HammerToss," which was discovered in early 2015 and suspected of being operational since late 2014.
What makes HammerToss interesting is its architecture, which leverages Twitter accounts, GitHub accounts, compromised websites, and Cloud-storage to orchestrate command-and-control functions to execute the commands on the targeted systems.
Report 5 — This document details the self-code injection and API hooking methods of information stealing Trojan called "Gamker."
Gamker uses simple decryption, then drops a copy of itself using a random filename and injects itself into a different process. The trojan also exhibits other typical trojan behaviours.
Previous Vault 7 CIA Leaks
Last week, WikiLeaks revealed CIAs Highrise Project that allowed the spying agency to stealthy collect and forwards stolen data from compromised smartphones to its server through SMS messages.
Since March, the whistle-blowing group has published 17 batches of "Vault 7" series, which includes the latest and last week leaks, along with the following batches:
BothanSpy and Gyrfalcon — two alleged CIA implants that allowed the spying agency to intercept and exfiltrate SSH credentials from targeted Windows and Linux operating systems using different attack vectors.
OutlawCountry – An alleged CIA project that allowed it to hack and remotely spy on computers running the Linux operating systems.
ELSA – the alleged CIA malware that tracks geo-location of targeted PCs and laptops running the Microsoft Windows operating system.
Brutal Kangaroo – A tool suite for Microsoft Windows used by the agency to targets closed networks or air-gapped computers within an organisation or enterprise without requiring any direct access.
Cherry Blossom – An agency's framework, basically a remotely controllable firmware-based implant, used for monitoring the Internet activity of the targeted systems by exploiting vulnerabilities in Wi-Fi devices.
Pandemic – A CIA's project that allowed the agency to turn Windows file servers into covert attack machines that can silently infect other computers of interest inside a targeted network.
Athena – A CIA's spyware framework that has been designed to take full control over the infected Windows PCs remotely, and works against every version of Microsoft's Windows operating systems, from Windows XP to Windows 10.
AfterMidnight and Assassin – Two alleged CIA malware frameworks for the Microsoft Windows platform that has been designed to monitor and report back actions on the infected remote host computer and execute malicious actions.
Archimedes – Man-in-the-middle (MitM) attack tool allegedly created by the CIA to target computers inside a Local Area Network (LAN).
Scribbles – A piece of software allegedly designed to embed 'web beacons' into confidential documents, allowing the spying agency to track insiders and whistleblowers.
Grasshopper – Framework that allowed the spying agency to easily create custom malware for breaking into Microsoft's Windows and bypassing antivirus protection.
Marble – Source code of a secret anti-forensic framework, basically an obfuscator or a packer used by the CIA to hide the actual source of its malware.
Dark Matter – Hacking exploits the agency designed to target iPhones and Macs.
Weeping Angel – Spying tool used by the agency to infiltrate smart TV's, transforming them into covert microphones.
Year Zero – Alleged CIA hacking exploits for popular hardware and software.
Over 70,000 Memcached Servers Still Vulnerable to Remote Hacking
19.7.2017 thehackernews Vulnerebility
Nothing in this world is fully secure, from our borders to cyberspace. I know vulnerabilities are bad, but the worst part comes in when people just don't care to apply patches on time.
Late last year, Cisco's Talos intelligence and research group discovered three critical remote code execution (RCE) vulnerabilities in Memcached that exposed major websites including Facebook, Twitter, YouTube, Reddit, to hackers.
Memcached is a popular open-source and easily deployable distributed caching system that allows objects to be stored in memory.
The Memcached application has been designed to speed up dynamic web applications (for example php-based websites) by reducing stress on the database that helps administrators to increase performance and scale web applications.
It's been almost eight months since the Memcached developers have released patches for three critical RCE vulnerabilities (CVE-2016-8704, CVE-2016-8705 and CVE-2016-8706) but tens of thousands of servers running Memcached application are still vulnerable, allowing attackers to steal sensitive data remotely.
Researchers at Talos conducted Internet scans on two different occasions, one in late February and another in July, to find out how many servers are still running the vulnerable version of the Memcached application.
And the results are surprising...
Results from February Scan:
Total servers exposed on the Internet — 107,786
Servers still vulnerable — 85,121
Servers still vulnerable but require authentication — 23,707
And the top 5 countries with most vulnerable servers are the United States, followed by China, United Kingdom, France and Germany.
Results from July Scan:
Total servers exposed on the Internet — 106,001
servers still vulnerable — 73,403
Servers still vulnerable but require authentication — 18,012
After comparing results from both the Internet scans, researchers learned that only 2,958 servers found vulnerable in February scan had been patched before July scan, while the remaining are still left vulnerable to the remote hack.
Data Breach & Ransom Threats
This ignorance by organisations to apply patches on time is concerning, as Talos researchers warned that these vulnerable Memcached installations could be an easy target of ransomware attacks similar to the one that hit MongoDB databases in late December.
Although unlike MongoDB, Memcached is not a database, it "can still contain sensitive information and disruption in the service availability would certainly lead to further disruptions on dependent services."
The flaws in Memcached could allow hackers to replace cached content with their malicious one to deface the website, serve phishing pages, ransom threats, and malicious links to hijack victim's machine, placing hundreds of millions of online users at risk.
"With the recent spate of worm attacks leveraging vulnerabilities this should be a red flag for administrators around the world," the researchers concluded.
"If left unaddressed the vulnerabilities could be leveraged to impact organisations globally and affect business severely. It is highly recommended that these systems be patched immediately to help mitigate the risk to organisations."
Customers and organisations are advised to apply the patch as soon as possible even to Memcached deployments in "trusted" environments, as attackers with existing access could target vulnerable servers to move laterally within those networks.
Remotely Exploitable Flaw Puts Millions of Internet-Connected Devices at Risk
19.7.2017 thehackernews Vulnerebility
Security researchers have discovered a critical remotely exploitable vulnerability in an open-source software development library used by major manufacturers of the Internet-of-Thing devices that eventually left millions of devices vulnerable to hacking.
The vulnerability (CVE-2017-9765), discovered by researchers at the IoT-focused security firm Senrio, resides in the software development library called gSOAP toolkit (Simple Object Access Protocol) — an advanced C/C++ auto-coding tool for developing XML Web services and XML application.
Dubbed "Devil's Ivy," the stack buffer overflow vulnerability allows a remote attacker to crash the SOAP WebServices daemon and could be exploited to execute arbitrary code on the vulnerable devices.
The Devil's Ivy vulnerability was discovered by researchers while analysing an Internet-connected security camera manufactured by Axis Communications.
"When exploited, it allows an attacker to remotely access a video feed or deny the owner access to the feed," researchers say.
"Since these cameras are meant to secure something, like a bank lobby, this could lead to collection of sensitive information or prevent a crime from being observed or recorded."
Axis confirmed the vulnerability that exists in almost all of its 250 camera models (you can find the complete list of affected camera models here) and has quickly released patched firmware updates on July 6th to address the vulnerability, prompting partners and customers to upgrade as soon as possible.
However, researchers believe that their exploit would work on internet-connected devices from other vendors as well, as the affected software is used by Canon, Siemens, Cisco, Hitachi, and many others.
Axis immediately informed Genivia, the company that maintains gSOAP, about the vulnerability and Genivia released a patch on June 21, 2017.
The company also reached out to electronics industry consortium ONVIF to ensure all of its members, including Canon, Cisco, and Siemens, those who make use of gSOAP become aware of the issue and can develop patches to fix the security hole.
Internet of Things (IoT) devices has always been the weakest link and, therefore, an easy entry for hackers to get into secured networks. So it is always advisable to keep your Internet-connected devices updated and away from the public Internet.
New Linux Malware Exploits SambaCry Flaw to Silently Backdoor NAS Devices
19.7.2017 thehackernews Vulnerebility
Remember SambaCry?
Almost two months ago, we reported about a 7-year-old critical remote code execution vulnerability in Samba networking software, allowing a hacker to remotely take full control of a vulnerable Linux and Unix machines.
We dubbed the vulnerability as SambaCry, because of its similarities to the Windows SMB vulnerability exploited by the WannaCry ransomware that wreaked havoc across the world over two months ago.
Despite being patched in late May, the vulnerability is currently being leveraged by a new piece of malware to target the Internet of Things (IoT) devices, particularly Network Attached Storage (NAS) appliances, researchers at Trend Micro warned.
For those unfamiliar: Samba is open-source software (re-implementation of SMB/CIFS networking protocol), which offers Linux/Unix servers with Windows-based file and print services and runs on the majority of operating systems, including Linux, UNIX, IBM System 390, and OpenVMS.
Shortly after the public revelation of its existence, the SambaCry vulnerability (CVE-2017-7494) was exploited mostly to install cryptocurrency mining software—"CPUminer" that mines "Monero" digital currency—on Linux systems.
However, the latest malware campaign involving SambaCry spotted by researchers at Trend Micro in July mostly targets NAS devices used by small and medium-size businesses.
SHELLBIND Malware Exploits SambaCry to Targets NAS Devices
Dubbed SHELLBIND, the malware works on various architectures, including MIPS, ARM and PowerPC, and is delivered as a shared object (.SO) file to Samba public folders and loaded via the SambaCry vulnerability.
Once deployed on the targeted machine, the malware establishes communication with the attackers' command and control (C&C) server located in East Africa, and modifies firewall rules to ensure that it can communicate with its server.
After successfully establishing a connection, the malware grants the attackers access to the infected device and provides them with an open command shell in the device, so that they can issue any number and type of system commands and eventually take control of the device.
In order to find the affected devices that use Samba, attackers can leverage the Shodan search engine and write the original malware files to their public folders.
"It is quite easy to find devices that use Samba in Shodan: searching for port 445 with a 'samba' string will turn up a viable IP list," researchers said while explaining the flaw.
"An attacker would then simply need to create a tool that can automatically write malicious files to every IP address on the list. Once they write the files into the public folders, the devices with the SambaCry vulnerability could become ELF_SHELLBIND.A victims."
However, it is not clear what the attackers do with the compromised devices and what's their actual motive behind compromising the devices.
The SambaCry vulnerability is hell easy to exploit and could be used by remote attackers to upload a shared library to a writable share and then cause the server to load and execute the malicious code.
The maintainers of Samba already patched the issue in Samba versions 4.6.4/4.5.10/4.4.14, so you are advised to patch your systems against the vulnerability as soon as possible.
Just make sure that your system is running updated Samba version.
Also, attackers need to have writable access to a shared location on the target system to deliver the payload, which is another mitigating factor that might lower the rate of infection.
IntelliAV: Toward the Feasibility of Building Intelligent Anti-Malware on Android Devices
19.7.2017 securityaffairs Android
IntelliAV is a practical intelligent anti-malware solution for Android devices based on the open-source and multi-platform TensorFlow library.
Android is targeted the most by malware coders as the number of Android users is increasing. Although there are many Android anti-malware solutions available in the market, almost all of them are based on malware signatures, and more advanced solutions based on machine learning techniques are not deemed to be practical for the limited computational resources of mobile devices.
There are many reasons for a user to have an intelligent security tool capable of identifying potential malware on the device.
1. The Google Play Store is not totally free of malware. Many zero-day mobile malware has been found in Google Play in the past.
2. Third-party app stores are popular among mobile users. Nevertheless, security checks on the third-party stores are not as effective as those available on the Google Play Store.
3. It is quite often that users can be dodged by fake tempting titles like free games when browsing the web, so that applications are downloaded and installed directly on devices from untrusted websites.
4. Another source of infection is phishing SMS messages that contain links to malicious applications. Recent reports by Lookout and Google show how a targeted attack malware, namely Pegasus(Chrysaor), which is suspected of infecting devices via a phishing attack, could remain undetected for a few years.
5. One of the main concerns for any computing device in the industry is to make sure that the device a user buys is free of malware. Mobile devices make no exception, and securing the supply chain is paramount difficult, for the number of people and companies involved in the supply chain of the components.
There is a recent report that shows how some malware was added to Android devices somewhere along the supply chain before the user received the phone.
6. Almost all of the Android anti-malware
products are mostly signature-based, which lets both malware variants of known families, and zero-day threats to devices. There are claims by a few Android anti-malware vendors that they use machine learning approaches, even if no detail is
available on the mechanisms that are actually implemented on the device.
7. Offline machine learning systems would fail against wrapper/downloder malware
as the wrapper/downloader app usually doesn’t reveal enough malicious activities.
IntelliAV (http://www.intelliav.com) is a practical intelligent anti-malware solution for Android devices based on the open-source and multi-platform TensorFlow library.
The detail of the system can be found in a paper that the authors will present at CD-MAKE 2017 conference in September at Reggio Calabria, Italy.
IntelliAV does not aim to propose yet another learning-based system for Android malware detection, but by leveraging on the existing literature, they tested the feasibility of having an on-device intelligent anti-malware tool to tackle the deficiencies of existing
Android anti-malware products, mainly based on pattern matching techniques.
The architecture of the proposed IntelliAV system is depicted as follows:
its design consists of two main phases, namely offline training the model, and then its operation on the device to detect potential malware samples.
As the first phase, a classification model is built offline, by resorting to a conventional
computing environment. It is not necessary to perform the training phase on the device because it has to be performed on a substantial set of samples whenever needed to take into account the evolution of malware. The number of times the model needs to be updated should be quite small, as reports by AV-TEST showed that just the 4% of the total number of Android malware is actually new malware.
As the second phase, the model is embedded in the IntelliAV Android application that will provide a risk score for each application on the device.

IntelliAV can scan all of the installed applications on the device, and verify their risk scores (Quick Scan). In addition, when a user downloads an apk, it can be analyzed by IntelliAV before installation to check the related risk score, and take the appropriate decision (Custom Scan).


Challenging Modern AV vendors
Based on the recent reports by Virustotal, there is an increase in the number of anti-malware developers that resort to machine learning approaches for malware detection. However, the main focus of these products appears to be on desktop malware, especially Windows PE malware. Based on the available public information, there are just a few pieces of evidence of two anti-malware developers that use machine learning approaches for Android malware detection, namely Symantec and TrustLook. Their products are installed by more than 10 million users. While it is not clear how these products use machine learning, the authors considered them as two candidates for
comparison with IntelliAV. To provide a sound comparison, in addition to the Symantec and Trustlook products, the authors selected three other Android anti-malware products, i.e., AVG, Avast, and Qihoo 360, that are the most popular among
Android users as they have been installed more than 100 million times. the authors
compared the performances of IntelliAV on 2311 recent Android malware
(between January to March 2017).

As an independent test, IntelliAV has been tested by AV-TEST on 500 recent and common Android malware in July 2017.
Interesting, they could achieve 96% detection rate although the last model update of IntelliAV is December 2016, which shows the power of IntelliAV on detecting unknown malware.

About the Author Mansour Ahmadi
IntelliAV has been developed at the University of Cagliari, Italy, by Mansour Ahmadi, Angelo Sotgiu, and Giorgio Giacinto. Mansour Ahmadi is a post-doctoral researcher at the PRA lab at the University of Cagliari, Italy. Angelo Sotgiu has a bachelor degree from the University of Cagliari. Prof. Giorgio Giacinto is an Associate Professor of Computer Engineering at the University of Cagliari.
Lithuania to extradite the man responsible for 100M email scam against Google and Facebook
19.7.2017 securityaffairs Social
A Lithuanian court on Monday ruled the extradite of a man to the US to face charges of allegedly swindling $100M from Google and Facebook via email scam.
A Lithuanian man who is allegedly responsible for a $100 million scam (roughly 87 million euros) from tech companies Google and Facebook will be extradited to the United States soon.
The Lithuanian citizen Evaldas Rimasauskas (48) was arrested in March by local authorities. The US Law enforcement requested the arrest because the man stolen by the two IT giants the huge amount of money by posing as a large Asia-based hardware vendor.
The fraudulent activities happened between 2013 and 2015.
“The court has ruled in favor of extraditing Lithuanian citizen Evaldas Rimasauskas to the United States for criminal prosecution,” Judge Aiva Surviliene said.

Evaldas Rimasauskas is pictured in district court in Vilnius in May 2017 – Source AFP
The indictment explicitly mentioned Facebook and Google. According to the investigators, Rimasauskas created email accounts to trick victims into believing that the emails were sent by employees at the Asian hardware vendor.
He is accused of forging invoices, contracts, and letters to trick the administrative personnel into wiring over $100 million to overseas the bank accounts that he was managing.
The Rimasauskas’s lawyer, Snieguole Uzdaviniene, announced the intention of the man to appeal against the indictment.
Google confirmed that its systems were not hacked by the criminal, anyway, the company reviewed its internal processes and implemented countermeasures against email scams and BEC.
“We detected this fraud against our vendor management team and promptly alerted the authorities,” a Google spokesman told AFP.”We recouped the funds and we’re pleased this matter is resolved.”
Rimasauskas is waiting for the extradition and faces a maximum of 20 years in jail if convicted.
Two CryptoMix Ransomware variants emerged in a few days
19.7.2017 securityaffairs Ransomware
Two CryptoMix Ransomware variants emerged in a few days, a circumstance that suggests the operators behind the threat are very active.
Malwarebytes’ researcher Marcelo Rivero has spotted a new variant of the CryptoMix ransomware.

Marcelo Rivero @MarceloRivero
#CryptoMix #Ransomware adds ext ".EXTE" to encrypted files, and the note "_HELP_INSTRUCTION.TXT" - md5: 1059676fbb9d811e88af96716cc1ffb5
12:07 AM - 14 Jul 2017
25 25 Retweets 18 18 likes
Twitter Ads info and privacy
The CryptoMix Malware family was spotted more than a year ago, numerous improvements were added across the time, except for the encryption method that remained the same.
Since the beginning of this year, researchers discovered at least three other CryptoMix variants in the wild, Wallet, CryptoShield, and Mole02.
The last variant observed by Rivero appends the ‘.EXTE’ extension to encrypted files.
Once the ransomware is launched on a computer, it drops a file in the ApplicationData folder and the ransom note in the targeted files’ folders. The ransomware creates a unique ID for each system and sends it to the C&C server.
Authors of the malware ask victims to pay the ransom in Bitcoins and use the email as a communication channel with the victims.
“While overall the encryption methods stay the same in this variant, there have been some differences. First and foremost, we have a new ransom note with a file name of _HELP_INSTRUCTION.TXT. ” wrote the researchers Lawrence Abrams from BleepingComputer.
“The next noticeable change is the extension appended to encrypted files. With this version, when a file is encrypted by the ransomware, it will modify the filename and then append the .EXTE extension to encrypted file’s name. For example, an test file encrypted by this variant has an encrypted file name of 32A1CD301F2322B032AA8C8625EC0768.EXTE.”
Lawrence also remarked that a different variant of the CryptoMix ransomware was observed appending the
. AZER extension to the encrypted files.

Researchers observed that this variant was using a different ransom not ( _INTERESTING_INFORMACION_FOR_DECRYPT.TXT) and different email addressed to receive communications from the victims.
The AZER CryptoMix ransomware is the first malware of the family that works completely offline, its code included ten different RSA-1024 public encryption keys and uses one of them to encrypt the AES key it uses to encrypt the files.
“Last, but not least, this version performs no network communication and is completely offline. It also embeds ten different RSA-1024 public encryption keys, which are listed below. One of these keys will be selected to encrypt the AES key used to encrypt a victim’s files. This is quite different compared to the Mole02 variant, which only included one public RSA-1024 key.” states BleepingComputer.
The same feature was also implemented in the latest EXTE version, the experts observed it also embeds the ten public RSA keys allowing the threat working in absence of connection.
The discovery of two variants of the CryptoMix ransomware in the wild in a few days suggests the operators behind the threat are very active.
Hacker steals $7 Million in Ethereum from CoinDash in just 3 minutes
19.7.2017 securityaffairs Hacking
Hacker steals $7 Million in Ethereum from CoinDash in just 3 minutes after the ICO launch. Attacker tricked investors into sending ETH to the wrong address.
Cybercrime could be a profitable business, crooks stole $7 Million worth of Ethereum in just 3 minutes. The cyber heist was possible due to a ‘a simple trick.‘
Hackers have stolen the money from the Israeli social-trading platform CoinDash.
CoinDash launched an Initial Coin Offering (ICO) to allow investors to pay with Ethereum and send funds to token sale’s smart contact address.
Hackers were able to divert over $7 million worth of Ethereum by replacing the legitimate wallet address used for the ICO with their own.
In three minutes after the ICO launch, the attacker tricked CoinDash’s investors into sending 43438.455 Ether to the wrong address owned by the attacker.
At the moment the hacker’s wallet has a balance of 43,488 Ethereum (around $8.1 million).
Let’s see the details of the attack?
CoinDash’s ICO published an Ethereum address on its website to allow investors to transfer the Ethereum funds.
After a few minutes of the launch, the company warned that its website had been hacked and confirmed that the ICO legitimate address was replaced by a fraudulent address.
The startup asked to stop sending Ethereum to the posted address.
“GUYS WEBSITE IS HACKED! Don’t send your ETH!!!” reads the message from CoinDash HQ.
“Wait for the announcement of the address”
Follow
CoinDash.io @coindashio
The Token Sale is done, do not send any ETH to any address. Official statement regarding the hack will be released soon.
4:39 PM - 17 Jul 2017
530 530 Retweets 341 341 likes
Twitter Ads info and privacy
Too late!
“The CoinDash Token Sale opened to the public on July 17 at 13:00PM GMT, starting with a 15 minute heads up for whitelist contributors. During these 15 minutes, 148 whitelisted contributors sent 39,000 ETH to the token sale smart contract that were secured with a multisig wallet.” reads the statement issued by the company.“The moment the token sale went public, the CoinDash website was hacked and a malicious address replaced the CoinDash Token Sale address. As a result, more than 2,000 investors sent ETH to the malicious address. The stolen ETH amounted to a total of 37,000 ETH.”
The company confirms it gathered around $6 million during the first three minutes of the ICO. It announced that it would issue tokens to the people who sent these funds to the correct wallet, but it also ensured that it will issue the tokens for the users that have been impacted by the hack and that sent the money to the hacker’s wallet.
“The CoinDash Token Sale secured $6.4 Million from our early contributors and whitelist participants and we are grateful for your support and contribution. CoinDash is responsible to all of its contributors and will send CDTs reflective of each contribution. Contributors that sent ETH to the fraudulent Ethereum address, which was maliciously placed on our website, and sent ETH to the CoinDash.io official address will receive their CDT tokens accordingly,” said the company.
However, CoinDash clarified that it would not compensate users who sent funds to the hacker’s address after the website was shut down by the company.
“CoinDash is responsible to all of its contributors and will send CDTs [CoinDash Tokens] reflective of each contribution,” the company noted.
“Contributors that sent ETH to the fraudulent Ethereum address, which was maliciously placed on our website, and sent ETH to the CoinDash.io official address will receive their CDT tokens accordingly.”
Follow
CoinDash.io @coindashio
If you sent ETH to the hacker address, please fill this form.https://docs.google.com/a/coindash.io/forms/d/13S2gbsO2eHcqk7MmAwLF9Ky1k4E7EUE9jnry79GR50U/edit?ts=596cfbdf …
8:16 PM - 17 Jul 2017
Photo published for CoinDash Token Sale Follow Up
CoinDash Token Sale Follow Up
Please help us to investigate the status and solve the issues from the token sale by providing following information. 请帮助我们持续调查并解决此次代币发售的现况与问题,在下方问卷中提供你参与发售的相关信息。
docs.google.com
483 483 Retweets 319 319 likes
Twitter Ads info and privacy
Some users speculate the cyber heist is an insider’s job … stay Tuned
SHELLBIND IoT malware targets NAS devices exploiting SambaCry flaw
19.7.2017 securityaffairs Vulnerebility
The seven-year-old remote code execution vulnerability SambaCry was exploited by the SHELLBIND IoT malware to target NAS devices.
A new strain of malware dubbed SHELLBIND exploits the recently patched CVE-2017-7494 Samba vulnerability in attacks against Internet of Things devices.
SHELLBIND has infected most network-attached storage (NAS) appliances, it exploits the Samba vulnerability (also known as SambaCry and EternalRed) to upload a shared library to a writable share, and then cause the server to load that library.
This trick allows a remote attacker to execute arbitrary code on the targeted system.
CVE-2017-7494 is a seven-year-old remote code execution vulnerability that affects all versions of the Samba software since 3.5.0. The flaw has been patched by the development team of the project.
The CVE-2017-7494 flaw can be easily exploited, just a line of code could be used for the hack under specific conditions:
make file- and printer-sharing port 445 reachable on the Internet,
configure shared files to have write privileges.
use known or guessable server paths for those files
The Samba vulnerability affects the products of several major vendors, including NAS appliances.
The Samba bug appears to be a network wormable issue that could be exploited by a malicious code to self-replicate from vulnerable machine to vulnerable machine without requiring user interaction.
When SambaCry was discovered, nearly 485,000 Samba-enabled computers were found to be exposed on the Internet.
In June, researchers at Kaspersky Lab set up honeypots to detect SambaCry attacks in the wild. The experts spotted a malware campaign that was exploiting the SambaCry vulnerability to infect Linux systems and install a cryptocurrency miner.
“On May 30th our honeypots captured the first attack to make use of this particular vulnerability, but the payload in this exploit had nothing in common with the Trojan-Crypt that was EternalBlue and WannaCry. Surprisingly, it was a cryptocurrency mining utility!” reported Kaspersky.
The independent security researcher Omri Ben Bassat also observed the same campaign that he dubbed “EternalMiner.” The expert confirmed threat actors started exploiting the SambaCry flaw just a week after its discovery to hijack Linux PCs and to install an upgraded version of “CPUminer,” a Monero miner.
In early July, experts at Trend Micro uncovered a new type of attack involving SambaCry. Crooks have been exploiting the flaw in attacks targeting NAS devices used by small and medium-size businesses. The malicious code was designed to compromise almost any IoT architecture, including MIPS, ARM, and PowerPC.
The attackers can easily find vulnerable devices using the Shodan Internet search engine then and write the malicious code to their public folders.
Experts at Trend Micro discovered that the ELF_SHELLBIND.A is delivered as a SO file to Samba public folders, then the attacker load and execute it by exploiting the SambaCry vulnerability.
“This more recent malware is detected as ELF_SHELLBIND.A and was found on July 3. Similar to the previous reports of SambaCry being used in the wild, it also opens a command shell on the target system. But ELF_SHELLBIND.A has marked differences that separate it from the earlier malware leveraging SambaCry. For one, it targets internet of things (IoT) devices—particularly the Network Attached Storage (NAS) devices favored by small to medium businesses.” reads the analysis published by Trend Micro. “ELF_SHELLBIND also targets different architectures, such as MIPS, ARM, and PowerPC. This is the first time we’ve seen SambaCry being exploited without the cryptocurrency miner as a payload.”

Once the malware is executed, it connects a C&C server located in East Africa “169[.]239[.]128[.]123” over TCP, port 80. , To establish a connection, the malicious code modifies firewall rules, then the attacker will open a command shell on the target system.
“Once the connection is successfully established and authentication is confirmed, then the attacker will have an open command shell in the infected systems where he can issue any number of system commands and essentially take control of the device,” continues Trend Micro.
Sysadmins can protect their systems by updating their installs, if it is not possible for any reason a workaround can be implemented by the adding the line
nt pipe support = no
to the Samba configuration file and restarting the network’s SMB daemon.
The change will limit clients from accessing some network computers.
Organizations Slow to Patch Critical Memcached Flaws
18.7.2017 securityweek Vulnerebility
Tens of Thousands of Internet-Exposed Memcached Servers Are Vulnerable to Attacks
Tens of thousands of servers running Memcached are exposed to the Internet and affected by several critical vulnerabilities disclosed last year by Cisco’s Talos intelligence and research group.
In late October 2016, Talos published an advisory describing three serious flaws affecting Memcached, an open source, high performance distributed memory caching system used to speed up dynamic web apps by reducing the database load.
The vulnerabilities, tracked as CVE-2016-8704, CVE-2016-8705 and CVE-2016-8706, allow a remote attacker to execute arbitrary code on vulnerable systems by sending specially crafted Memcached commands. The flaws can also be leveraged to obtain sensitive data that could allow an attacker to bypass exploit mitigations.
The security holes were patched by Memcached developers before Talos disclosed its findings. A few months later, in late February and early March 2017, researchers conducted Internet scans to find out how many organizations had patched their installations.
The scans uncovered a total of more than 107,000 servers accessible over the Internet and nearly 80 percent of them, or roughly 85,000 servers, were still vulnerable. Furthermore, only approximately 22 percent of the servers, or roughly 24,000, required authentication.
Nearly 30,000 of the vulnerable servers were located in the United States, followed by China (17,000), the United Kingdom (4,700), France (3,200), Germany (3,000), Japan (3,000), the Netherlands (2,600), India (2,500) and Russia (2,300).
After completing the scans, Cisco obtained contact email addresses for all the IP addresses associated with the vulnerable servers and attempted to notify affected organizations.
Six months later, researchers conducted another scan, but the situation improved only slightly, with roughly 10 percent of systems patched since the previous analysis. However, the number of servers requiring authentication dropped to 18,000, or 17 percent of the total.
Interestingly, researchers noticed that more than 28,000 of the previously discovered servers were no longer online. However, since the total number of Internet-facing installations remained the same, experts determined that some servers either changed their IPs or organizations had been deploying new systems with vulnerable versions of Memcached.
Talos warned that these vulnerable Memcached installations could be targeted in ransom attacks similar to the ones that hit MongoDB databases in early 2017. While Memcached is not a database, it can still contain sensitive information and disrupting it could have a negative impact on other dependent services.
“The severity of these types of vulnerabilities cannot be understated,” experts warned. “These vulnerabilities potentially affect a platform that is deployed across the internet by small and large enterprises alike. With the recent spate of worm attacks leveraging vulnerabilities this should be a red flag for administrators around the world. If left unaddressed the vulnerabilities could be leveraged to impact organizations globally and impact business severely.”
The number of Memcached instances accessible from the Internet has remained fairly constant over the past years. An analysis conducted in August 2015 uncovered 118,000 Memcached instances exposing 11 terabytes of data.
Code Execution, DoS Vulnerabilities Found in FreeRADIUS
18.7.2017 securityweek Vulnerebility
Security testing of FreeRADIUS using a technique known as fuzzing revealed more than a dozen issues, including vulnerabilities that can be exploited for denial-of-service (DoS) attacks and remote code execution.
Researcher Guido Vranken recently discovered several flaws in OpenVPN through fuzzing, a technique that involves automatically injecting malformed or semi-malformed data into software to find implementation bugs. One of the flaws also turned out to impact FreeRADIUS, an open source implementation of RADIUS (Remote Authentication Dial-In User Service), a networking protocol for user authentication, authorization and accounting.
After patching the vulnerability, the developers of FreeRADIUS, said to be the world’s most popular RADIUS server, asked Vranken to conduct fuzzing on their software.
Testing conducted by the researcher led to the discovery of 11 security issues and FreeRADIUS developers identified an additional four problems. Of the 15 weaknesses affecting versions 2 and/or 3 of the software, five cannot be exploited and six affect DHCP packet parsers. The security holes were addressed on Monday with the release of versions 2.2.10 and 3.0.15.
The list of vulnerabilities includes memory leak, out-of-bounds read, memory exhaustion, buffer overflow and other issues that can be exploited to remotely execute arbitrary code or cause a DoS condition. The flaws can be exploited by sending specially crafted packets to the targeted server.
The vulnerabilities that can be leveraged for remote code execution are CVE-2017-10984, which affects versions 3.0.0 through 3.0.14, and CVE-2017-10979, which affects versions 2.0.0 through 2.2.9. They can be exploited by sending packets with malformed WiMAX attributes.
“The short summary is that if your RADIUS server is on a private network, accessible only by managed devices, you are likely safe. If your RADIUS server is part of a roaming consortium, then anyone within that consortium can attack it. If your RADIUS server is on the public internet, then you are not following best practices, and anyone on the net can attack your systems,” FreeRADIUS maintainers explained.
They pointed out that writing secure code in C is a big challenge, which is why they have been using several static analysis tools to identify vulnerabilities. However, the fuzzing tests uncovered many flaws that were previously missed by these tools, which is why FreeRADIUS developers plan on integrating the fuzzer into all future releases of their software.
Two Iranians Charged in U.S. Over Hacking Defense Materials
18.7.2017 securityweek CyberSpy
Two Iranians were indicted Monday in the United States with hacking a defense contractor and stealing sensitive software used to design bullets and warheads, according to the Justice Department.
According to the newly unsealed indictment businessman Mohammed Saeed Ajily, 35, recruited Mohammed Reza Rezakhah, 39, to break into companies' computers to steal their software for resale to Iranian universities, the military and the government.
The two men -- and a third who was arrested in 2013 and handed back to Iran in a prisoner swap last year -- allegedly broke into the computers of Vermont-based Arrow Tech Associates.
The indictment said they stole in 2012 the company's Prodas ballistics software, which is used to design and test bullets, warheads and other military ordnance projectiles.
The material stolen from Arrow Tech was protected by US controls on the export of sensitive technologies, and its distribution to Iran was banned by US sanctions on the country.
The two men were charged in the Rutland, Vermont federal district court, which issued arrest warrants for the two, who are believed to be in Iran.
In 2013 the US secured the arrest in Turkey of a third Iranian in the case, Nima Golestaneh, 30, who was extradited to the United States.
In December 2015 he pleaded guilty to charges of wire fraud and computer hacking.
One month later he was freed as part of a prisoner exchange with Tehran, which returned four Americans in exchange for seven Iranians who had been arrested in separate schemes to obtain and smuggle to Iran sensitive US technologies.
Hacker Steals $7 Million in Ethereum From CoinDash
18.7.2017 securityweek Hacking
An actor managed to hack the CoinDash official website during the company's ICO (Initial Coin Offering) and diverted over $7 million worth of Ethereum by replacing the official wallet address with their own.
The incident took place on Monday, just minutes after the company launched its ICO in an attempt to raise funds in the form of Ethereum crypto-currency. Similar to an (IPO) Initial Public Offering, an ICO happens when a company is looking to gather funds and issue tokens in return.
According to CoinDash, the hacker managed to take over the official website only three minutes after the ICO started. They replaced the official Ethereum wallet address with their own, which resulted in people sending over $7 million to the fradulent address.
The company shut down the website immediately after discovering the hack and also posted warnings on their Twitter account, informing users of the issue. They also posted an official statement on the website, to provide additional details on the matter.
The company says it managed to gather around $6 million during the first three minutes of the ICO. It also announced that it would issue tokens not only to the people who sent these funds, but also to those who ended sending the money to the hacker’s wallet.
“The CoinDash Token Sale secured $6.4 Million from our early contributors and whitelist participants and we are grateful for your support and contribution. CoinDash is responsible to all of its contributors and will send CDTs reflective of each contribution. Contributors that sent ETH to the fraudulent Ethereum address, which was maliciously placed on our website, and sent ETH to the CoinDash.io official address will receive their CDT tokens accordingly,” the company says.
However, CoinDash said that it would not compensate users who sent funds to the fraudulent address after the website was shut down.
At the moment the hacker’s wallet shows a balance of 43,488 Ethereum, currently worth around $8.1 million. CoinDash suggested that around $7 million of these funds were sent in by its users, but the amount could be higher, as some users might have sent funds after the hack was discovered.
“During the attack $7 Million were stolen by a currently unknown perpetrator. […] We are still under attack. Please do not send any ETH to any address, as the Token Sale has been terminated,” the company notes on its website.
CoinDash says it is currently investigating the breach and will provide more details on it as soon as possible. The company also posted a form for those who sent money to the hacker to complete.
The incident is yet another reminder that “blockchain technology in isolation cannot assure additional security,” but in fact increases risks, High-Tech Bridge CEO Ilia Kolochenko told SecurityWeek in an emailed comment.
“Many users, fooled by investors and so-called serial entrepreneurs, blindly believe that blockchain, particularly crypto-currencies, can make a digital revolution and provide an ‘unbreakable’ security. Unfortunately, this assumption is wrong and leads to a very dangerous feeling of false security. Blockchain technology can assure a very high level of data integrity, but we need to remember the numerous intertwined layers of modern technology stack, where one breached system or host can put the entire structure at risk,” Kolochenko said.
“Victims of this hack will quite unlikely get their money back as, technically speaking, it's virtually impossible. Moreover, law enforcement won't be able to help either in this case, except if it is an insider attack that can be investigated and prosecuted,” he concluded.
Android Backdoor GhostCtrl can spy on victims and take over Windows Systems
18.7.2017 securityaffairs Android
The GhostCtrl backdoor, is an OmniRAT-Based Android malware that can spy on victims, steal data and take over Windows System using the RETADUP infostealer.
Today’s smartphones are as powerful as the computers of only a few years ago. Unfortunately, that also means that Android phones have as many instances of malware as desktop and laptop computers. In 2016, Kaspersky Lab registered nearly 40 million attacks by malicious mobile software. Since smartphones are essentially full computers in your pocket, the bad guys are able to use many of the same techniques and in sometimes even the same tools! In late 2015 researchers at Avast discovered bad guys using the OmniRat remote administration tool (RAT) to compromise Android phones. On its own OmniRat is not malicious. It is a very capable tool for IT folks to provide remote support for Android users and even allows for remote access to Windows, Linux and Mac systems. It was also a very good tool for the bad guys to access your systems.
After several quiet months, OmniRat variants have been spotted in the wild and the software has benefitted from some significant updates since we last saw it. Dubbed GhostCtrl by Trend Micro researchers, it can do some “traditional” mobile malware things like:
Upload and download files to or from the bad guys’ servers
Send SMS messages to specified numbers (usually extra fee numbers)
Provide real time sensor data
As well as some very cool, and scary new things like:
Control the system infrared transmitter
Surreptitiously record voice, audio or video
Use the text-to-speech feature (i.e. translate text to voice/audio)
Clear/reset the password of an account specified by the attacker
Make the phone play different sound effects
Terminate an ongoing phone call
Use the Bluetooth to search for and connect to another device.
“The information-stealing RETADUP worm that affected Israeli hospitals is actually just part of an attack that turned out to be bigger than we first thought—at least in terms of impact. It was accompanied by an even more dangerous threat: an Android malware that can take over the device.” states the analysis from Trend Micro.
“Detected by Trend Micro as ANDROIDOS_GHOSTCTRL.OPS / ANDROIDOS_GHOSTCTRL.OPSA, we’ve named this Android backdoor GhostCtrl as it can stealthily control many of the infected device’s functionalities.”
This is scary enough — especially when you consider that there are a lot of bad guys out there that are only now starting to think of creative ways to exploit these new capabilities — GhostCtrl doesn’t limit itself to Android devices. Compromising a smartphone gives you access to a powerful computer, but most bad guys are after information. GhostCtrl comes with the RETADUP worm which was recently discovered stealing information from Windows systems in Israeli hospitals.
“GhostCtrl’s combination with an information-stealing worm, while potent, is also telling. The attackers tried to cover their bases, and made sure that they didn’t just infect endpoints. And with the ubiquity of mobile devices among corporate and everyday end users, GhostCtrl’s capabilities can indeed deliver the scares.” continues Trend Micro.
How Do You Get Infected?
GhostCtrl comes as an Android Application Package (APK) masquerading as a legitimate Android app such as WhatsApp, Pokemon Go, MMS — anything that will appeal to users. When the wrapper APK is launched, it decodes text from the resource file, writes this string as another APK and then launches this Malicious APK prompting the user to install it. It is easy to see how a user could be fooled or confused as to what file is asking to be installed and proceeding. Once the malicious software is installed the wrapper APK runs it as a service with no visible icon allowing the malware to run silently in the background.

Once the malicious application is running in the background, it contacts Command and Control (C&C) servers on the Internet to determine its next actions as described above. Depending on the infected target and the motivations of the bad guys the GhostCtrl malware could be used for any number of malicious activities. If the infected phone is only used by an individual at home, ransomeware at the lock screen or pay-for-use SMS messaging is a good bet. However, since GhostCtrl has also been linked with RETADUP, bad guys could find themselves with an Android-based back channel into a Windows environment inside an enterprise, which offers many more opportunities for money making.
There have already been three versions of the GhostCtrl RAT identified in the wild, each adding features and capabilities to the previous version. You should expect that it will continue to be enhanced as it continues to be successful in making money for the authors. And while the Google Play store has hosted malware for brief periods of time, it is unlikely that an APK downloaded from the official Play Store will be GhostCtrl. If you are getting your APKs from anywhere else, you should brace for the worst.
Hacker Uses A Simple Trick to Steal $7 Million Worth of Ethereum Within 3 Minutes
18.7.2017 thehackernews Hacking

All it took was just 3 minutes and 'a simple trick' for a hacker to steal more than $7 Million worth of Ethereum in a recent blow to the crypto currency market.
The heist happened after an Israeli blockchain technology startup project for the trading of Ether, called CoinDash, launched an Initial Coin Offering (ICO), allowing investors to pay with Ethereum and send funds to its address.
But within three minutes of the ICO launch, an unknown hacker stole more than $7 Million worth of Ether tokens by tricking CoinDash's investors into sending 43438.455 Ether to the wrong address owned by the attacker.
How the Hacker did this? CoinDash's ICO posted an Ethereum address for investors to pay with Ethereum and send funds to the app's website.
However, within a few minutes of the launch, CoinDash warned that its website had been hacked and the sending address was replaced by a fraudulent address, asking people not to send Ethereum to the posted address.
But before that, this little change of address redirected cryptocurrency by investors slated for CoinDash into the wallet of the hacker.
"It is unfortunate for us to announce that we have suffered a hacking attack during our Token Sale event," reads a statement posted on the company's official website.
"During the attack, $7 Million was stolen by a currently unknown perpetrator. The CoinDash Token Sale secured $6.4 Million from our early contributors and whitelist participants, and we are grateful for your support and contribution."
CoinDash doesn't know who is responsible for the attack, and the worst part is that the company is still under attack.
Investors are strongly advised to DO NOT send any Ether (ETH) to any address on the site, as CoinDash has terminated the Token Sale.
According to a CoinDash Slack channel screenshot posted to Reddit, CoinDash realised what was happening within 3 minutes, but it was too late.
Some people even believe that the incident was not a hack, rather an insider's job. One user said: "Is there any proof that this was a hack. What if Coindash put an address in and then cried hacker to get away with free ETH?"
The CoinDash website is offline, at the time of publication, and the company is asking affected investors who sent their Ether to the wrong address to collect the CoinDash token (CDT) by submitting information to this link.
However, investors sending Ether to any fraudulent address after the website was shut down will not be compensated.
"CoinDash is responsible to all of its contributors and will send CDTs [CoinDash Tokens] reflective of each contribution," the company noted.
"Contributors that sent ETH to the fraudulent Ethereum address, which was maliciously placed on our website, and sent ETH to the CoinDash.io official address will receive their CDT tokens accordingly."
This isn't the first time an ICO funding has been hacked. Last year, $50 Million was disappeared after hackers exploited code weaknesses in the Decentralised Anonymous Organisation (DAO) venture capital fund.
Lithuania to Extradite $100 Million Email Fraud Suspect to U.S.
18.7.2017 securityweek Hacking
A Lithuanian man who allegedly swindled $100 million (87 million euros) from tech giants Google and Facebook must be extradited to the United States, a court ruled on Monday.
"The court has ruled in favour of extraditing Lithuanian citizen Evaldas Rimasauskas to the United States for criminal prosecution," Judge Aiva Surviliene said.
The 48-year-old was arrested in March in the Baltic state at the request of US authorities, who accuse him of deceiving the two US firms in 2013-2015 by posing as a large Asia-based hardware vendor.
Facebook and Google are mentioned in the indictment, Rimasauskas's lawyer confirmed to AFP.
In a public statement, US prosecutors said Rimasauskas used "email accounts that were designed to create the false appearance that they were sent by employees and agents" of the Asian manufacturer.
He is also accused of forging invoices, contracts and letters to trick the companies into wiring over $100 million to overseas bank accounts under his control, according to prosecutors.
The scam was pulled off using deception and no Google systems were hacked, according to the California-based internet giant.
Google updated its internal processes to guard against similar incidents and recovered the money lost.
"We detected this fraud against our vendor management team and promptly alerted the authorities," a Google spokesman told AFP.
"We recouped the funds and we're pleased this matter is resolved."
Facebook did not respond to an AFP request for comment
Rimasauskas faces a maximum of 20 years in jail if convicted, the judge said.
Rimasauskas's lawyer, Snieguole Uzdaviniene, said she would appeal.
Google Inviting 2-Step Verification SMS Users to Google Prompt
18.7.2017 securityweek Safety
Google this week will start inviting 2-Step Verification (2-SV) SMS users to try Google Prompt, its year-old method of approving sign-in requests on smartphones.
Launched in June 2016, Google prompt allows users to approve sign-in requests via 2-SV by simply tapping “Yes” on a prompt. Available for both Android and iOS users, Google prompt received an improvement in February 2017, when Google added real-time security information about the login attempt, such as when and where it was made.
Google Prompt offers 2-SV over an encrypted connection and provides users with additional security features as well, including the option to block unauthorized access to their account.
While 2-SV users can also login by tapping a Security Key or by entering a verification code sent to their phone, in addition to using prompts, Google is now inviting those who receive a SMS on their phones to try Google prompts when they sign in.
“The invitation will give users a way to preview the new Google Prompts sign in flow instead of SMS, and, afterward, choose whether to keep it enabled or opt-out,” the Internet giant explains in a blog post.
In July last year, the National Institute of Standards and Technology (NIST) started deprecating SMS 2-step verification, just months after security researchers published a paper revealing that vulnerabilities in the mechanism expose it to simple bypass attacks.
“Overall, this is being done because SMS text message verifications and one-time codes are more susceptible to phishing attempts by attackers. By relying on account authentication instead of SMS, administrators can be sure that their mobile policies will be enforced on the device and authentication is happening through an encrypted connection,” Google notes.
According to the company, only 2-SV SMS users will receive the notification to test Google prompts, meaning that those using Security Key aren’t affected. The use of Google prompt requires a data connection. On iOS devices, it also requires the Google Search app to be installed. Enterprise edition domains can enforce security keys for more advanced security requirements.
“While users may opt out of using phone prompts when shown the promotion, users will receive follow-up notifications to switch after 6 months,” the company concludes.
CryptoMix Ransomware Variant EXTE Emerges
18.7.2017 securityweek Ransomware
A new variant of the CryptoMix ransomware was recently observed, appending the .EXTE extension to targeted files, security researchers warn.
Around for over a year, the CryptoMix ransomware family has seen numerous updates over time, but few major changes appear to have been added to it: although the ransom note and the used extension suffered modifications, the encryption method remained nearly the same from one variant to the other.
Once executed on the victim’s computer, the ransomware drops a file in the ApplicationData folder, while also dropping the ransom note in the targeted files’ folders. The malware also adds a series of registry keys, creates a unique ID and sends it to a remote location, after which it starts encrypting files using AES encryption.
In the ransom note, the malware demands users to contact the author via provided email addresses, while also asking them to pay the ransom amount in Bitcoins.
Discovered by Malwarebytes’ Marcelo Rivero, the latest malware variant uses the same encryption method as previous iterations, but does show some small updates, BleepingComputer’s Lawrence Abrams reveals.
The threat now adds the .EXTE extension to the encrypted files’ encrypted file name, while using a new ransom note named _HELP_INSTRUCTION.TXT (last year, CryptoMix used the HELP_YOUR_FILES.TXT ransom note). In this campaign, users are required to contact the ransomware authors at exte1@msgden.net, exte2@protonmail.com, and exte3@reddithub.com for payment information.
Earlier this month, a different variant of the malware was observed appending the .AZER extension to the encrypted files and using the _INTERESTING_INFORMACION_FOR_DECRYPT.TXT ransom note and webmafia@asia.com and donald@trampo.info email addresses.
Unlike previous variants, the AZER CryptoMix iteration performs no network communication and is completely offline. It embeds ten different RSA-1024 public encryption keys and uses one of them to encrypt the AES key it uses to encrypt the files.
The EXTE version, Abrams points out, also embeds the ten public RSA keys, meaning it too can work offline. The two variants emerged about one week of each other, which shows that the actor behind this ransomware variant is highly active. Since the beginning of this year, at least three other CryptoMix variants emerged: Wallet, CryptoShield, and Mole02.
Critical WebEx Flaws Allow Remote Code Execution
18.7.2017 securityweek Vulnerebility
Cisco has updated the WebEx extensions for Chrome and Firefox to address critical remote code execution vulnerabilities identified by researchers working for Google and Divergent Security.
Google Project Zero’s Tavis Ormandy and Cris Neckar of Divergent Security, a former member of the Chrome Security Team, discovered earlier this month that the WebEx extension allows a remote attacker to execute arbitrary code with the privileges of the web browser due to some changes made recently by Cisco.
The security holes, tracked as CVE-2017-6753, were reported to the networking giant on July 6 and they were addressed roughly one week later with the release of version 1.0.12. On Monday, both Cisco and Google Project Zero published advisories detailing the flaws.
According to Cisco, the vulnerabilities are caused by a “design defect” and they can be exploited by an attacker by getting the targeted user to visit a specially crafted webpage. The browser extensions for WebEx Meetings Server, WebEx Centers and WebEx Meetings running on Windows are impacted.
Updates have also been released for the Internet Explorer version of the WebEx plugin, which shares components with the Chrome and Firefox versions, and the WebEx desktop application. Cisco has informed customers that workarounds are not available.
Cisco said it was not aware of any attacks exploiting the vulnerabilities. However, the advisory published by Google Project Zero includes technical details and a working exploit. It also includes details on how Cisco addressed the issues.
This is not the first time Ormandy has found a critical vulnerability in the WebEx plugins. The researcher discovered a remote code execution flaw in January, which led to Google and Mozilla temporarily removing the WebEx extension from their stores.
Cisco’s initial fix turned out to be incomplete and it took the company several days to release proper patches after Ormandy’s disclosure.
For the second time in the year, experts found a flaw in Cisco WebEx Extension
18.7.2017 securityaffairs Vulnerebility
For the second time in a year, a highly critical remote code execution vulnerability was found in the Cisco WebEx Extension.
For the second time in a year, a highly critical remote code execution vulnerability, tracked as CVE-2017-6753, was discovered in the Cisco Systems WebEx browser extension for Chrome and Firefox. The vulnerability could be exploited by attackers to remotely execute malicious code on a target machine with the privileges of the affected browser.
“A vulnerability in Cisco WebEx browser extensions for Google Chrome and Mozilla Firefox could allow an unauthenticated, remote attacker to execute arbitrary code with the privileges of the affected browser on an affected system.” reads the security advisory published by CISCO. “This vulnerability affects the browser extensions for Cisco WebEx Meetings Server, Cisco WebEx Centers (Meeting Center, Event Center, Training Center, and Support Center), and Cisco WebEx Meetings when they are running on Microsoft Windows.”
Cisco WebEx is one of the most popular communication tools used by businesses and internet users for online meetings, webinars, and video conferences. The extension has roughly 20 million active users.
The impact of the flaw is severe if we consider that the extension has roughly more than 20 million installs.
The vulnerability was discovered by the popular Google Project Zero hacked Tavis Ormandy and Cris Neckar of Divergent Security. The CVE-2017-6753 RCE vulnerability is due to a designing bug in the WebEx browser extension, it could allow attackers to gain control of the affected system.
The exploitation of the vulnerability is quite simple, attackers just need to trick victims into visiting a web page containing specially crafted malicious code through the browser with affected WebEx browser extension installed.
“Earlier this week a former colleague from Chrome Security, Cris Neckar from Divergent Security, pointed out that there had been some changes to the way atgpcext worked, and it looked like there may be some new problems. I see several problems with the way sanitization works, and have produced a remote code execution exploit to demonstrate them,” Ormandy said. “This extension has over 20M [million] active Chrome users alone, FireFox and other browsers are likely to be affected as well.”
Cisco acknowledged the RCE flaw and has already patched it in the “Cisco WebEx Extension 1.0.12” update for Chrome and Firefox browsers.
It is important to highlight the absence of “workarounds that address this vulnerability.”
“Cisco has released software updates for Google Chrome and Mozilla Firefox that address this vulnerability. There are no workarounds that address this vulnerability.” continues the CISCO advisory.
According to the advisory, Apple’s Safari, Microsoft Internet Explorer, and Microsoft Edge are not affected by this RCE flaw. Cisco WebEx Productivity Tools, Cisco WebEx browser extensions for Mac or Linux, and Cisco WebEx on Microsoft Edge or Internet Explorer are not affected by the vulnerability.
Russian nation-state actors blamed for cyber attacks against Irish energy networks
18.7.2017 securityaffairs BigBrothers
Irish energy networks have been targeted by spear phishing attacks, Russian nation-state actors are the prime suspects for the cyber attacks.
Hackers have targeted Irish energy networks, senior engineers at the Electricity Supply Board (ESB), which supplies both Northern Ireland and the Republic, were targeted by spear phishing messages allegedly sent by a Russian threat actor linked to Russia’s GRU intelligence agency.
The news was reported by The Times, sources close to the newspaper confirmed that Russian nation state actors launched the attack to compromise control systems and take over the electricity grid.
“Hackers backed by the Russian government have attacked energy networks running the national grid in parts of the UK, The Times has learnt.” reported The Times.
“The hackers, who targeted the Republic of Ireland’s energy sector, intended to infiltrate control systems, security analysts believe. This would also have given them the power to knock out parts of the grid in Northern Ireland.”

Why Ireland?
Security experts believe that GRU hackers were testing their cyber capabilities against the country infrastructure. The nation state hackers may have been interested in destabilizing the country that also hosts European headquarters of IT giants like Apple, Google, and Facebook. US officials confirmed last week that Russian government hacking teams penetrated American nuclear and other energy companies.
The Ireland’s National Cyber Security Centre is investigating the cyber attack that according to the experts aimed to steal information and gather intelligence instead having sabotage purposes.
The news about the attack against the Irish energy networks was disclosed shortly after the FBI and Department of Homeland Security sent a joint alert to the energy sector warning of cyber attacks powered by Russian nation state actors against the US nuclear power plants.
According to the alert, “advanced, persistent threat actors” used spear phishing message to steal login credentials to access networks of companies in the energy industry,
According to a report on vulnerabilities in British defence released by the Royal United Services Institute (RUSI) earlier this month, the threat of cyber attacks continues to grow especially for Western satellite infrastructures. Military and civilian communications and GPS system could be targeted by hackers with a significant impact on the economy of the country.
Of course, Russia denied state-sponsored hackers have been involved in attacks against Western governments or Ukraine. President Putin blamed patriotic Russian hackers, for the interference with the 2016 Presidential Election.
Critical RCE Vulnerability Found in Cisco WebEx Extensions, Again — Patch Now!
17.7.2017 thehackernews Vulnerebility
A highly critical vulnerability has been discovered in the Cisco Systems’ WebEx browser extension for Chrome and Firefox, for the second time in this year, which could allow attackers to remotely execute malicious code on a victim's computer.
Cisco WebEx is a popular communication tool for online events, including meetings, webinars and video conferences that help users connect and collaborate with colleagues around the world. The extension has roughly 20 million active users.
Discovered by Tavis Ormandy of Google Project Zero and Cris Neckar of Divergent Security, the remote code execution flaw (CVE-2017-6753) is due to a designing defect in the WebEx browser extension.
To exploit the vulnerability, all an attacker need to do is trick victims into visiting a web page containing specially crafted malicious code through the browser with affected extension installed.
Successful exploitation of this vulnerability could result in the attacker executing arbitrary code with the privileges of the affected browser and gaining control of the affected system.
"I see several problems with the way sanitization works, and have produced a remote code execution exploit to demonstrate them," Ormandy said. "This extension has over 20M [million] active Chrome users alone, FireFox and other browsers are likely to be affected as well."
Cisco has already patched the vulnerability and released “Cisco WebEx Extension 1.0.12” update for Chrome and Firefox browsers that address this issue, though "there are no workarounds that address this vulnerability."
"This vulnerability affects the browser extensions for Cisco WebEx Meetings Server, Cisco WebEx Centers (Meeting Center, Event Center, Training Center, and Support Center), and Cisco WebEx Meetings when they are running on Microsoft Windows," Cisco confirmed in an advisory released today.
Download Cisco WebEx Extension 1.0.12
Chrome Extensions
Firefox Extension
In general, users are always recommended to run all software as a non-privileged user in an effort to diminish the effects of a successful attack.
Fortunately, Apple's Safari, Microsoft's Internet Explorer and Microsoft's Edge are not affected by this vulnerability.
Cisco WebEx Productivity Tools, Cisco WebEx browser extensions for Mac or Linux, and Cisco WebEx on Microsoft Edge or Internet Explorer are not affected by the vulnerability, the company confirmed.
The remote code execution vulnerability in Cisco WebEx extension has been discovered second time in this year.
Ormandy alerted the networking giant to an RCE flaw in the WebEx browser extension earlier this year as well, which even led to Google and Mozilla temporarily removing the add-on from their stores.
New IBM Z Mainframe Designed to "Pervasively Encrypt" Enterprise Data
17.7.2017 securityweek Safety
New IBM Z14 Mainframe Introduces Encryption Engine Capable of Running More Than 12 Billion Encrypted Transactions Per Day
The combination of an explosion in data breaches and increasingly severe regulatory requirements requires a new approach to security: the mainframe is back. IBM has announced its latest mainframe, the IBM z14, in what it calls "the most significant re-positioning of mainframe technology in more than a decade."

Encryption is seen as the best solution for both data loss and regulatory compliance. But encryption is hard, requiring more time and processing power than most companies have at their disposal. At the same time, it is becoming an increasingly attractive solution. More than nine billion data records have been lost or stolen since 2013; and only 4% were encrypted. Next year, the General Data Protection Regulation (GDPR) could, in theory, impose fines of up to 4% of global turnover for the loss of unencrypted personal data.
Photo of IBM Z14 MainframeA second regulation requiring widespread encryption is the NYSDFS cyber security regulation. This states, "As part of its cybersecurity program, based on its Risk Assessment, each Covered Entity shall implement controls, including encryption, to protect Nonpublic Information held or transmitted by the Covered Entity both in transit over external networks and at rest." 'Nonpublic Information' could almost be interpreted as 'everything'. The automatic facility to encrypt everything in transit and at rest -- as does the IBM Z -- will make its capabilities particularly attractive to banks and financial institutions that are governed by the New York State Department of Financial Services.
Encryption, where possible, is the one single solution that can solve both data loss (if it's encrypted, it's not lost) and compliance. IBM discussed the problem with 150 of its clients over three years and came up with its solution: a new mainframe with sufficient power and versatility to provide pervasive encryption.
IBM Z, says the firm, makes it possible, for the first time, for organizations to pervasively encrypt data associated with an entire application, cloud service or database in flight or at rest with one click. "The standard practice today," it says, "is to encrypt small chunks of data at a time, and invest significant labor to select and manage individual fields." But this approach doesn't scale, so encryption is often incomplete and/or inaccurate.
Encryption is only a solution, of course, if the decryption keys are kept safe. IBM Z offers what the company calls 'tamper-responding encryption keys'. Keys are invalidated at any sign of intrusion, and can be restored in safety. This key management system is designed to meet Federal Information Processing Standards (FIPS) Level 4 standards, and can be extended beyond the mainframe to other devices such as storage systems and servers in the cloud.
IBM's solution has been to introduce more power into a new mainframe: a massive 7x increase in cryptographic performance over the previous generation z13 -- driven by a 4x increase in silicon dedicated to cryptographic algorithms. "This is 18x faster than compared x86 systems (that today only focus on limited slices of data)," it claims, "and at just five percent of the cost of compared x86-based solutions."
These aren't the only large numbers associated with the new mainframe -- IBM claims it features the world's fastest microprocessor running at 5.2GHz. A single system can support more than 12 billion encrypted transactions per day; supports the world's largest MongoDB instance with 2.5x faster NodeJS performance than compared x86-based platforms; two million Docker Containers; and 1000 concurrent NoSQL databases.
Few companies will want to pay mainframe prices for compliance alone. However, IBM is also previewing new Z/OS software that aids with private cloud service delivery, enabling owners to transition from an IT cost center to a value-generating service provider.
It is also being incorporated into the IBM Cloud, where it will initially be used as an encryption engine for cloud services, and to run IBM blockchain services in six new centers in Dallas, London, Frankfurt, Sao Paulo, Tokyo and Toronto.
"The powerful combination of IBM Z encryption and secure containers differentiates IBM Blockchain services on the cloud by supporting the trust models new blockchain networks require,” said Marie Wieck, general manager, IBM Blockchain. "Enterprise clients also benefit from the ease of use making management transparent to the application and the user."