European Parliament Proposes Ban On Encryption Backdoors
19.6.2017 thehackernews BigBrothers
Prime Minister Theresa May wants tech companies, like Facebook, Apple, and Google, to create controversial 'backdoors' for police, but even somewhere she knows that it's not that easy as it sounds.
The Civil Liberties, Justice and Home Affairs Committee of the European Parliament has released a draft proposal [PDF] for new laws on privacy and electronic communications, recommending end-to-end (E2E) encryption on all communications and forbidding backdoors that offer access to law enforcement.
"The protection of confidentiality of communications is also an essential condition for the respect of other related fundamental rights and freedoms, such as the protection of freedom of thought, conscience and religion, and freedom of expression and information," the draft reads.
Draft Says, Your Security is Our Top Priority
According to the draft, EU citizens need more protection, not less and they need to know that the "confidentiality and safety" of their data is "guaranteed," but software backdoors risk "weakening" that privacy.
What is backdoor? By definition, "Backdoor is a feature or defect of a computer system that allows surreptitious unauthorized access to data."
Many countries' government, including the US Defence Department, have forced major companies to provide backdoor access to their services, allowing the feds to intercept users' traffic and access everything from secure messages to their web activities.
But, "Technically, there is no such backdoor that only the government can access. If surveillance tools can exploit the vulnerability by design, then an attacker who gained access to it would enjoy the same privilege."
Draft Demands End-to-End Encryption & Ban On Backdoors
The proposed draft recommends the use of end-to-end encryption that would make it more difficult for federal officials to request data from tech companies.
The proposal would ban decryption of user data as well as the creation of backdoors in software or encryption technologies that could allow government access to users' private information.
So if the amendments pass, the ban on software backdoors would make it difficult for the government to enforce the Section 49 of the Regulation of Investigatory Powers Act (RIPA) 2000's requirement that companies remove "electronic protection" when possible.
For those unaware, end-to-end encryption is a secure communication that encrypts data on the sender's system before passing it to a company's server. The company then passes the encrypted data to the intended recipient, who is the only person who can decrypt it.
Nobody in between, be it an application service provider, an Internet service provider (ISP), hacker, or even law enforcement officials, can read or tamper with the data.
"When encryption of electronic communications data is used, decryption, reverse engineering or monitoring of such communications shall be prohibited," the draft reads.
"Member States shall not impose any obligations on electronic communications service providers that would result in the weakening of the security and encryption of their networks and services."
Securing the 'Internet of Things'
Similarly, the draft also says, the current law have not kept pace with how the machine-to-machine communications in the Internet of Things can expose citizens.
The connected devices and machines are increasingly communicating with each other today by using electronic communications networks.
So, according to the committee, this Regulation should also be applied to the machine-to-machine communications in order to "ensure full protection of the rights to privacy and confidentiality of communications, and to promote a trusted and secure Internet of Things in the digital single market."
In short, the committee wants that any future means of communication, such as "calls, internet access, instant messaging applications, email, internet phone calls and messaging provided through social media" are all protected from hackers, government and prying eyes.
The committee wants that applications, browsers, internet service providers, cars, smartphones or fitness trackers should also respect no-track requests from their customers, and snoop their data only after getting users' consent.
However, it should be noted that most technology companies fall under the United States court of law, and post-Snowden era proves that as long as your countries' data is stored out of your boundaries, your policies and regulations would hardly make any difference.
Mexican Govt. Allegedly Used Spyware Against Journalists, Activists & A Child
19.6.2017 thehackernews BigBrothers
After the disclosure of sophisticated global espionage and disinformation campaign aimed to discredit enemies of the state, Citizen Lab researchers exposed the dirty game of the Mexican government and its politics.
The report — "Government Spy: Systematic monitoring of journalists and human rights defenders in Mexico" — published by Citizen Lab today revealed how the Mexican government used advanced spyware tools purchased from the NSO Group to target the country's most prominent human rights lawyers, anti-corruption activists, and journalists.
The NSO Group, an Israel-based company that produces the most advanced mobile spyware on the planet, sold the tool to governments with an explicit agreement that it should be used only to fight terrorists or criminal groups that have long kidnapped and killed Mexicans.
But, the Mexican government targets include:
Lawyers looking into the case of 43 Students disappeared in September 2014 from the town of Iguala.
Two Mexican most influential journalists.
An American who is representing victims of sexual abuse by the police.
A child, presumably in an attempt to spy on his mother.
"The targets share a basic connection: they have been involved in investigating or working on reports of high-level official corruption, or government involvement in human rights abuses," the report says.
According to the report, the purchase of the NSO Group's exploit "has been documented by at least three units in Mexico:
the National Defense Secretariat (SEDENA)
the Attorney General's Office (PGR)
the National Security and Investigation Center (CISEN)
Since 2011, the above three Mexican federal agencies have purchased nearly $80 Million worth of spyware from the NSO group.
The surveillance tool in question is the infamous mobile spyware 'Pegasus' that was also used in targeted cyber attacks against human rights activists in the United Arab Emirates last year.
Pegasus is one of the NSO group's most advanced mobile spyware tool that can infiltrate Android, as well as iPhones to monitor calls, texts, email, contacts, and calendars, as well as use the phone's microphone and camera for surveillance, turning a target’s smartphone into a sophisticated bugging device.
According to the report, the targets had received over 76 messages with links to the Pegasus exploit along with uniquely crafted social engineering messages, "troubling personal and sexual taunts, messages impersonating official communications by the Embassy of the United States in Mexico, fake AMBER Alerts, warnings of kidnappings, and other threats."
Once the victims open the link, Pegasus would then get downloaded onto their smartphones, turning the target's smartphone into a digital spying tool, which is in the pocket of victims, but fully under the control of the operator.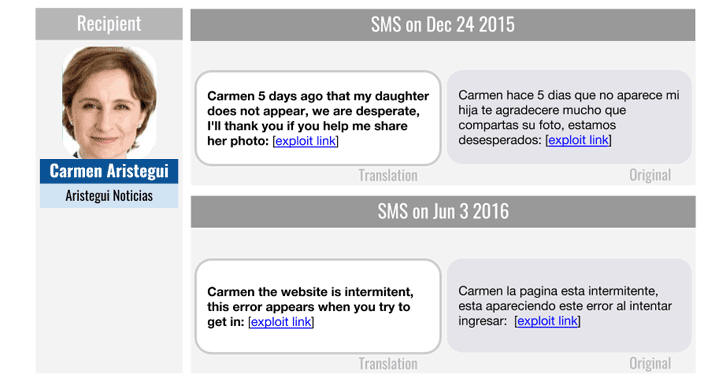
The malware allows the attacker to extract an incredible amount of data stored in files, contacts, messages, and emails and then forward them to a hidden server. It also takes control of the smartphone's microphone and camera — all without users’ knowledge.
Among those targeted by the government include:
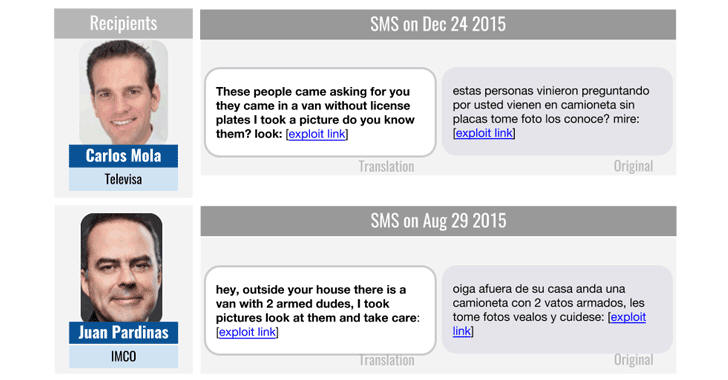
Activists with the Centro Miguel Agustín Pro Juárez for Human Rights (Centro PRODH)
Members of the Mexican Institute for Competitiveness (IMCO)
TV personality and investigative journalist Carmen Aristegui, along with her son Emilio Aristegui (a teenager)
Other journalists working for the Mexican non-profit Against Corruption and Impunity
TV network Televisa anchor Carlos Loret de Mola
A majority of the infection attempts on victims were recorded under two separate events: in August 2015 and between April 2016 and July 2016.
The report asserts that all evidence points towards the Mexican government which itself is behind the cyber espionage.
Workarounds Provided for HPE SiteScope Vulnerabilities
19.6.2017 securityweek Vulnerebility
Several potentially serious vulnerabilities have been found in HPE SiteScope, and while patches are not available, users can apply workarounds to prevent attacks.
HPE SiteScope is an agentless performance and availability monitoring software for distributed IT infrastructures, including servers, network services, applications, and operating systems.
While conducting a security assessment, expert Richard Kelley identified several vulnerabilities in version 11.31.461 of the product.
Kelley noticed that a critical remote code execution vulnerability disclosed in 2012 and for which a Metasploit module is available still hasn’t been patched by HPE. The vendor noted that users can prevent attacks by setting a specific flag in the “groups/master.config” file to disable old APIs.
A Shodan search conducted by Kelley showed that there are at least 230 SiteScope servers accessible on the Internet.
“I wonder how many admins know about this setting, and why wouldn’t HPE just remove the old APIs from new versions if they are no longer needed?” the researcher said in a blog post.
The expert also discovered that credentials stored in configuration files are encrypted, but the encryption key is hardcoded, allowing an attacker to obtain the password needed to log in to the SiteScope interface with administrator privileges.
Once the attacker has access to the administration interface, they can obtain credentials for Linux and Windows servers monitored via SiteScope. While the admin interface only displays passwords as dots, the actual password is transmitted in clear text over an unsecure connection to the client, allowing a man-in-the-middle (MitM) attacker to easily obtain the information.
Kelley also discovered the existence of a proprietary encryption scheme that uses a hardcoded private key. He determined that this function had still been used to encrypt some configuration data.
HPE said it plans on addressing the insecure transmission of credentials sometime in the third quarter. As for the encryption-related issues, the company pointed out that the problems are covered in chapter 20 of the SiteScope deployment guide.
While HPE has asked the researcher to delay disclosure until the third quarter, Kelley and CERT/CC have decided to make the flaws public to “encourage HPE to provide defender mitigations as soon as possible.”
CERT/CC has published an advisory containing mitigation advice for the unpatched vulnerability.
It’s not uncommon for HPE to provide workarounds for SiteScope vulnerabilities instead of releasing patches. In October 2015, Rapid7 disclosed the details of a command injection flaw that had also been addressed in the product documentation.
Fashion Retailer Buckle Finds Malware on PoS Systems
19.6.2017 securityweek Virus
The Buckle, Inc., a fashion retailer that operates more than 450 stores across the United States, informed customers on Friday that malware had been found on some of its point-of-sale (PoS) systems.
According to the retailer, malware was present on PoS systems at some of its stores between October 28, 2016, and April 14, 2017. The company has called in outside experts to investigate the incident and help secure its network.
The malware was designed to steal data from a card’s magnetic stripe, including cardholder name, account number and expiration date, but The Buckle believes the malware did not collect data from all transactions conducted via infected PoS systems.Buckle suffers credit card breach
The company pointed out that all its stores support EMV (chip card) technology, which makes it significantly more difficult to clone cards using stolen data. Nevertheless, the compromised payment card data can still be useful to cybercriminals, particularly for card-not-present fraud.
The Buckle said there was no evidence that social security numbers, email addresses or physical addresses were obtained by the attackers, and there is no indication that its website and online store are affected.
“As part of Buckle’s response, connections between Buckle’s network and potentially malicious external IP addresses were blocked, potentially compromised systems were isolated, and malware-related files residing on Buckle’s systems were eradicated. Additionally, Buckle reported a potential incident to the payment card brands and is cooperating with them regarding this incident,” the company said in a statement.
The Buckle has advised customers to keep an eye out for any suspicious activity on their payment card, and immediately report any unauthorized charges to the card issuer. A list of affected stores has not been made available.
The Buckle’s announcement comes just two weeks after big box department store chain Kmart, which operates more than 700 stores, informed customers of a payment card breach.
How to Speed Up Firefox With Multi-Process, If It's Not Working By Default
19.6.2017 thehackernews IT
enable-firefox-multiprocess-feature
After years of waiting, Mozilla last week launched Firefox 54 for Windows, Mac, Linux, and Android, with multi-process support — a "major improvement" to improve your browsing experience — but many users are still struggling to take advantage of this feature.
Mozilla's multi-process support in Firefox has been in development for over eight years as part of a project, codenamed Electrolysis or E10S, which aimed at improving responsiveness and speed by streamlining memory use by different processes.
Describing the latest release as the largest change to Firefox code ever, Mozilla says it has worked hard to avoid increased memory consumption, and slower performance, as Firefox now uses up to four processes to run web page content across all open tabs.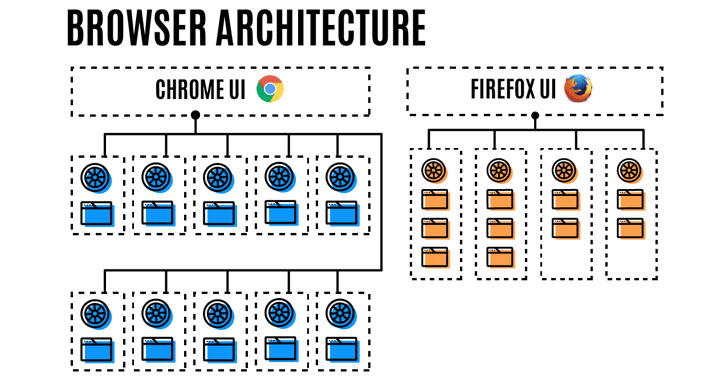
In other words, Firefox is finally making use of "significantly less RAM" of your computer, as heavy web pages in one tab will now have a much lower impact on responsiveness and speed in other tabs.
"This design makes it easier to utilize all of the cores available on modern processors and, in the future, to securely sandbox web content," says Mozilla. "It also improves stability, ensuring that a single content process crashing won't take out all of your other tabs, nor the rest of the browser."
This feature is about to be enabled by default with Firefox 54, but many Firefox users are unable to take advantage of multi-process support and disappointed to see that their web browser is clinging to a single process.
This issue is happening because one or more of your installed Firefox add-ons could be incompatible with Electrolysis, or multi-process feature.
Step 1 — Check If Multi-Process is Working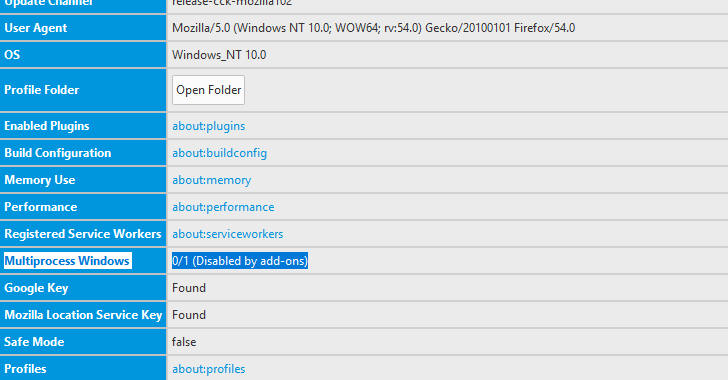
To check whether or not Firefox multiprocess feature is working fine, visit about:support in the address bar and look for the "Multiprocess Windows" line (as shown):
If it says "1/1 (Enabled by default)" — multi-process feature is working.
If it says "0/x (Disabled by add-ons)" — multi-process is not working.
Step 2 — Disable/Remove Incompatible Add-Ons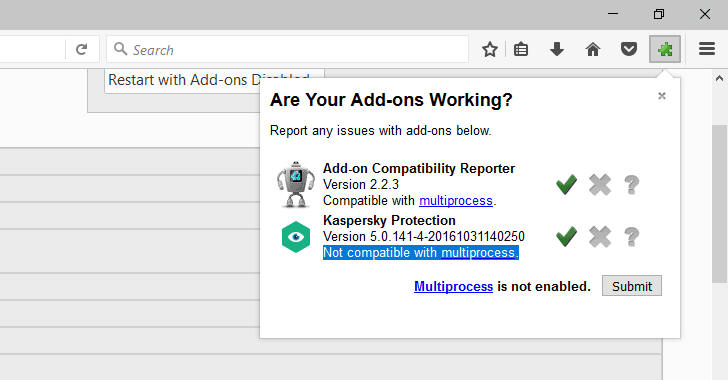
To find out the list of incompatible add-ons to see which of your extensions is at fault, install "Add-on Compatibility Reporter add-on" provided by Firefox.
Step 3 — Enable Firefox Multiprocess Feature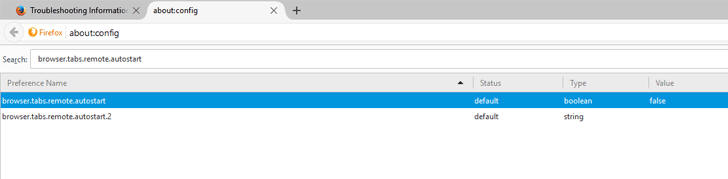
In order to manually fix this issue and enable Electrolysis feature, you first need to disable or completely remove incompatible add-ons from your browser.
Now, enable Electrolysis feature in Firefox using the following steps:
Type about:config in the address bar
Search for browser.tabs.remote.autostart
Double-click on it and set value to True
Step 4 — Change No. of Content Processes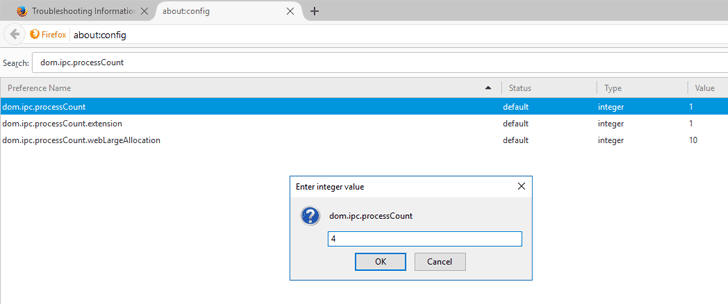
You can also change the number of content processes, which is by default 4, to more or less, according to your pool of RAM.
Visit about:config
Search for dom.ipc.processCount
Set its value to more than 1
That's it. You are done.
You do not need to restart your web browser for this to take effect.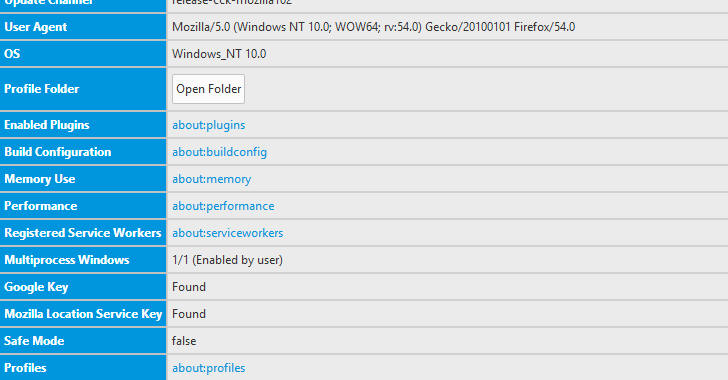
No doubt, this change will let Google Chrome users rethink to shift on Firefox, as by default Chrome starts a new process for every tab, thus using an infinite number of processes, which eventually slow down the web browser as well as the operating system to a crawl.
"We are pushing forward in building a completely revamped browser made for modern computing. It's our goal to make Firefox the fastest and smoothest browser for PCs and mobile devices," Mozilla says. "Through the end of 2017, you'll see some big jumps in capability and performance from Team Firefox."
Firefox 54 is available to download in the stable form, while Firefox 55, which further refines the process, is available only to developers.
Vir Industroyer může napadat rozvodny elektřiny a ohrozit veřejnou dopravu
19.6.2017 Novinky/Bezpečnost ICS
Malware, který odhalila společnost ESET, s největší pravděpodobností může za loňský výpadek elektřiny v části ukrajinské metropole Kyjeva. Experti se shodují, že šlo jen o test.
Ukrajinský výpadek elektrické energie, ke kterému došlo loni 17. prosince, navázal na podobnou akci hackerů z roku 2015, kdy zůstalo bez elektřiny na 250 tisíc ukrajinských domácností.
Analytici společnosti ESET nyní odhalili spojitost mezi loňským útokem a vzorky malwaru, který detekovali jako Win32/Industroyer. Výpadek elektřiny v Kyjevě podle nich mohl být jen testem, zda je malware funkční a přípravou na daleko rozsáhlejší útok, který se nemusí soustředit pouze na rozvodny elektrického proudu.
„Nedávný útok na ukrajinskou rozvodnou síť by měl sloužit jako výzva pro všechny, co jsou zodpovědní za bezpečnost kritických systémů na celém světě,“ varuje Anton Cherepanov, Senior Malware Researcher ve společnosti ESET. Industroyer je schopen přímo ovládat spínače a jističe elektrické sítě.
Používá k tomu protokoly průmyslové komunikace, které jsou po celém světě běžné pro infrastruktury napájení, systémy řízení dopravy a jiné kritické infrastruktury. Potenciální dopad této hrozby se může pohybovat v rozmezí od jednoduchého vypnutí rozvodu elektrické energie přes kaskádovité poruchy až po vážnější poškození zařízení.
Malware se chová jako systém, který napadl
„Schopnost škodlivého kódu Industroyer přetrvávat v systému a přímo zasahovat do provozu průmyslového hardwaru z něj činí největší hrozbu od Stuxnetu, který v roce 2010 úspěšně napadl íránský jaderný program. Aktuálně jde o nejnebezpečnější škodlivý software zaměřený na průmyslové řídící systémy,“ konstatuje Cherepanov.
Nebezpečnost Industroyeru spočívá v tom, že používá protokoly napadených systémů tak, jak bylo navrženo, aby byly používány, takže jeho chování nelze odhalit. Problém je v tom, že tyto protokoly byly navrženy před desítkami let a v té době byly průmyslové systémy izolovány od vnějšího světa. Proto jejich tvůrci nemysleli na jejich zabezpečení. Útočníci tedy nemuseli hledat v těchto protokolech žádné bezpečnostní chyby. Vše, co potřebovali, bylo naučit malware komunikovat s těmito protokoly, vysvětluje ESET.
Industroyer je typem vysoce přizpůsobitelného malwaru. Zatímco jeho univerzální část může být použita k útoku na jakýkoli průmyslový systém řízení a využije k tomu některé z jeho komunikačních protokolů, některé části analyzovaných vzorků malwaru byly navrženy tak, aby se zaměřily na konkrétní hardware.
Canada’ CSE warns of cyber attacks against next 2019 Election
19.6.2017 securityaffairs BigBrothers
The Canada Communications Security Establishment (CSE) published a report that reveals that hackers will attempt to hack into 2019 country’s Election.
The Canada Communications Security Establishment (CSE) published a report that reveals that cyber criminals and hacktivists had leaked sensitive government documents, and attempted to hack into 2015 country’s Election.
The hackers targeted candidates and spread disinformation and propaganda in order to influence the vote. According to the CSE, the “low sophistication” attacks “did not impact the outcome of the election.”
The CSE warns of possible interference in the forthcoming 2019 election, especially of hacktivist groups.
According to the CSE, 13 percent of countries holding national elections in 2017 are targets of cyber attacks even more sophisticated.
“We judge that, almost certainly, multiple hacktivist groups will deploy cyber capabilities in an attempt to influence the democratic process in 2019,” states the CSE report. The Canadian intelligence believes that hackers will increasingly adopt “more sophisticated” techniques threatening 2019 elections and politicians.
Clearly, Canadian Intelligence fears possible interference like the one observed in the US and French President campaigns. The Canadian intelligence avoided referring Russia or other states as potential opponents.
The Canadian intelligence believes that hackers will increasingly adopt “more sophisticated” techniques threatening 2019 elections and politicians.
The CSE report confirmed that the Anonymous collective leaked secret documents in 2015 on Canadian diplomatic missions and the size of Canadadia spy network overseas in order to damage the candidate Tories during the election campaign.

OTTAWA, ON: OCTOBER 8, 2012 : Communications Security Establishment Canada building on Heron Rd ( Chris Mikula / Ottawa Citizen) For NATIONAL story Assignment #110602
CSE report also warns of Nation-state actors that could launch for the first time their offensive against Canada’s democracy.
State-sponsored hackers may target politicians and parties involved in the 2019 election depending on “how Canada’s nation-state adversaries perceive Canada’s foreign and domestic policies, and on the spectrum of policies espoused by Canadian federal candidates in 2019.”
Foreign Affairs Minister Chrystia Freeland confirmed that threats to elections have been “energetically discussed” at meetings of NATO and the G7 group. Canada and its allies will no accept any attack against their voting machine.
“We are a member of the G7, we are a NATO country, we are an influential voice and a leader on the world stage and so therefore there is a significant interest in influencing the direction of Canadian elections,” Minister of Democratic Institutions Karina Gould told AFP.
“Regardless of who is behind these cyberthreats, it’s important that we can protect ourselves”.
The CSE analyzed dozens of cyber attacks against more than 40 states in the last decade and discovered that in almost 80 percent of the cases, the attacks have been powered by state actors.
The situation in Canada is worrisome, according to the CSE report, political parties, politicians and the media in Canada are under attack due to lack of proper security posture.
The Canadian election system itself still relies on paper ballots, provincial and municipal elections could suffer cyber attacks.
“In particular, we know that certain nation-states have core interests that can be affected by Canadian policies related to natural resources, which are often made at the provincial/territorial level,” said the report. “Hacktivists may begin to view subnational elections… as worthy targets.”
Rufus malware used to empty ATMs running outdated OS in India
19.6.2017 securityaffairs Virus
Indian authorities are facing with the Rufus malware, a malicious code used to clean out ATMs running outdated Windows XP software across states.
Many security firms and law enforcement agencies are warning of malware-based attacks against ATM. Recently 27 people have been arrested by the Europol for jackpotting attacks on ATM across many countries in Europe.
Last threat spotted in the wild is the Rufus malware, it is a Chinese malicious code that could be used to compromise ATMs. Indian authorities have observed numerous cyber attacks leveraging this threat. Reports of cyber heists come from West Bengal, Gujarat, Odisha, and Bihar.
The Rufus malware could be used to hack only ATMs running outdated software, all the ATMs targeted by crooks were found to be still using the old versions of Windows XP.
According to The Dailymail, the first attack was reported in Odisha city, the police are working with cyber experts to identify cyber criminals.

The crooks use to target unguarded ATMs nighttime, they infect the system with a pen drive that is inserted into the USB port. Once the malware has infected the ATM, it would restart the system interrupting the connection with the service provider’s servers.
The Rufus malware generates a code after it infected the system, the code is then sent back to the crooks that convert it into a password. Every time the password is entered, the ATM releases the money.
“The malware when used on an ATM generates a code, which the crooks send to their gang members, who convert the code to a password, and as soon the password is applied the ATM dispenses cash,'” reported The DailyMail.
“The officer said banks would not immediately learn about the crime as crooks bypass the server and the hackers swiftly walk away without raising an alarm.”
Of course, such kind of attack is the result of the lack of adequate security measures for ATMs, it is expected that the Indian Government will force ATM manufacturers to upgrade the system running on their machines.
“The government and RBI should make ATM manufacturers compulsorily install new and robust operating systems,” said Mumbai-based cyber lawyer and expert Prashant Mali.
“‘If the government plans to increase the number of ATMs, then it should ensure that they are available whenever needed.”
ATM vendors denied the existence of any security loopholes or other vulnerabilities exploited by cyber criminals.
The Reserve Bank of India is working closely with National Payment Corporation of India to instruct the banks on how to enhance their security.
Canada: Hackers Targeted Country's 2015 Election, May Try Again
18.6.2017 securityweek BigBrothers
Canada's electronic eavesdropping agency warned Friday that hackers and foreign states may try to sway its elections in 2019, after so-called hacktivists tried but failed to influence the 2015 ballot that brought Justin Trudeau's Liberals to power.
In a report, the Communications Security Establishment (CSE) said hacktivists and cybercriminals had leaked sensitive government documents, and attempted to smear candidates and spread disinformation and propaganda ahead of the 2015 vote.
These "low sophistication" attacks "did not impact the outcome of the election," the CSE concluded.
But it added that hacktivists are likely to try again when Canadians return to the polls in 2019.
"We judge that, almost certainly, multiple hacktivist groups will deploy cybercapabilities in an attempt to influence the democratic process in 2019," the CSE said in the report, adding that these groups will adapt and increasingly adopt "more sophisticated" approaches.
The agency pointed to hacker group Anonymous, for example, leaking secret documents in 2015 on Canadian diplomatic missions and the size of Canada's spy network overseas to try to embarrass the incumbent Tories during the election campaign.
Nation-states have so far not targeted Canada's 150-year-old democracy, the CSE said.
But they may try in the next election, the agency said, depending on "how Canada's nation-state adversaries perceive Canada's foreign and domestic policies, and on the spectrum of policies espoused by Canadian federal candidates in 2019."
The report comes as US officials probe alleged Russian interference in last year's US presidential elections and after French President Emmanuel Macron's election campaign was subject to cyberattacks.
Canadian officials avoided naming Russia or other antagonists.
Foreign Affairs Minister Chrystia Freeland said interference in elections has been "energetically discussed" at meetings of NATO and the G7 group of leading industrial powers.
"We are a member of the G7, we are a NATO country, we are an influential voice and a leader on the world stage and so therefore there is a significant interest in influencing the direction of Canadian elections," Minister of Democratic Institutions Karina Gould told AFP.
"Regardless of who is behind these cyberthreats, it's important that we can protect ourselves," she said.
According to the CSE, 13 percent of countries holding national elections this year have had their democratic processes targeted, and the number and sophistication of the attacks are predicted to rise.
The agency analyzed dozens of incidents over the past decade that victimized almost 40 nations. It concluded that in almost 80 percent of the cases, state actors were behind attempts to influence the democratic process.
The rest mostly involved cybercriminals stealing voter information.
The CSE report said political parties, politicians and the media in Canada faced the greatest vulnerability to cyberthreats and "influence operations." The Canadian election system itself still relies on paper ballots.
The report noted that provincial and municipal elections could also be targeted.
"In particular, we know that certain nation-states have core interests that can be affected by Canadian policies related to natural resources, which are often made at the provincial/territorial level," said the report. "Hacktivists may begin to view subnational elections... as worthy targets."
Facebook inadvertently revealed moderators’ identities to suspected terrorists
18.6.2017 securityaffairs Social
A bug in the software used by Facebook moderators to review inappropriate content resulted in the disclosure of identities of moderators to suspected terrorists.
According to the Guardian, the social network giant Facebook put the safety of its content moderators at risk after inadvertently exposing their personal details to suspected terrorist users on the social network.
A bug in the software used by moderators to review and remove inappropriate content resulted in the disclosure of personal profiles of content moderators while they were reviewing the content from the platform.
The bug in Facebook’s moderation application was discovered in 2016 and caused the personal profiles of content moderators to appear among activity notifications for online groups after moderators had removed the groups’ administrators for terms-of-service violations.
“The security lapse affected more than 1,000 workers across 22 departments at Facebook who used the company’s moderation software to review and remove inappropriate content from the platform, including sexual material, hate speech and terrorist propaganda.” reported The Guardian.
“A bug in the software, discovered late last year, resulted in the personal profiles of content moderators automatically appearing as notifications in the activity log of the Facebook groups, whose administrators were removed from the platform for breaching the terms of service. The personal details of Facebook moderators were then viewable to the remaining admins of the group.”
Facebook “inadvertently” exposed the personal details of over 1,000 Facebook employees, approximately 40 of them were from special counter-terrorism unit in Dublin, Ireland.
For six workers the incident was “assessed to be ‘high priority,’ the risk now for the workers is that terrorists and lone wolves could insert them in a kill list.
“Six of those were assessed to be “high priority” victims of the mistake after Facebook concluded their personal profiles were likely viewed by potential terrorists.” continues The Guardian. “The Guardian spoke to one of the six, who did not wish to be named out of concern for his and his family’s safety. The Iraqi-born Irish citizen, who is in his early twenties, fled Ireland and went into hiding after discovering that seven individuals associated with a suspected terrorist group he banned from Facebook – an Egypt-based group that backed Hamas and, he said, had members who were Islamic State sympathizers – had viewed his personal profile.”
terrorists Facebook
The employee is one of the numerous low-paid contractors, he confirmed that he’d relocated to eastern Europe for five months from fear of retaliation.
“It was getting too dangerous to stay in Dublin,” the employee said. “The only reason we’re in Ireland was to escape terrorism and threats.”
Facebook confirmed the breach:
“As soon as we learned about the issue, we fixed it and began a thorough investigation to learn as much as possible about what happened.” said a company spokesperson.
Kasperagent malware used in a new campaign leveraging Palestine-Themed decoy files
18.6.2017 securityaffairs APT
Researchers uncovered a new cyber espionage campaign involving the Kasperagent spyware delivered with Palestine-Themed decoy files.
In March, experts at security firm Qihoo 360 have spotted a cyber espionage campaign conducted by a threat actor tracked as APT-C-23 and Two-Tailed Scorpion.
A few weeks later, in April, researchers at Palo Alto Networks and ClearSky also shared the results of their investigation on the group.
The APT-C-23 group leverages Windows malware dubbed Kasperagent and Micropsia, and Android malware called SecureUpdate and Vamp in cyber attacks aimed mainly at Palestine. Victims of the group were also located in Israel, Egypt and the United States.
Malware experts at threat intelligence firm ThreatConnect have recently discovered tens of sample of the Kasperagent malware that had been compiled in April and May.
These samples dropped various decoy files associated with the Palestinian Authority tha is the body that governs the Palestinian Territories in the Middle East.
The documents are designed to appear as legitimate and most of them are publicly available on news websites or social media.
To trick victims into opening the documents, attackers used subjects such as the assassination of Hamas military leader Mazen Fuqaha, and banning of the Palestinian political party Fatah from Gaza.
“The first document – dated April 10, 2017 – is marked “Very Secret” and addressed to Yahya Al-Sinwar, who Hamas elected as its leader in Gaza in February 2017. Like the photo displayed in the first decoy file we found, this document references the death of Mazen Fuqaha. The Arabic-language text and English translation of the document are available in ThreatConnect here.” reads the analysis published by ThreatConnect.

Crooks used the Kasperagent malware as a reconnaissance tool and downloader, anyway recent samples detected by the experts include additional capabilities, such as password stealing from browsers, taking screenshots and logging keystroke.
“However, some of the recently identified files display “extended-capability” including the functionality to steal passwords, take screenshots, log keystrokes, and steal files. These “extended-capability” samples called out to an additional command and control domain, stikerscloud[.]com.” continues the report. “Additionally, early variants of KASPERAGENT used “Chrome” as the user agent, while more recent samples use “OPAERA” – a possible misspelling of the “Opera” – browser. The indicators associated with the blog article are available in the ThreatConnect Technical Blogs and Reports source here.”
The APT-C-23 group used the same malware in the campaigns analyzed by ThreatConnect and Palo Alto Networks and ClearSky, anyway the command and control (C&C) servers were different.
ThreatConnect observed that malware used in the recent campaign was hosted on the IP address 195.154.110[.]237 that stored four domains, two of which (upfile2box[.]com and 7aga[.]net) registered by a freelance web developer from Gaza.
The researchers believe that the threat actors and at least one of the target is located in the Palestinian Territories. It is likely, the cyber espionage campaign may have been aimed at Hamas, Israel or the Fatah party.
“Just like we can’t make a definitive determination as to who conducted this campaign, we do not know for sure who it was intended to target. What we do know is that several of the malicious files were submitted to a public malware analysis site from the Palestinian Territories. This tells us that it is possible either the threat actors or at least one of the targets is located in that area,” concluded ThreatConnect.
BAE Systems accused of selling mass surveillance software Evident across the Middle East
18.6.2017 securityaffairs Security
BC Arabic and the Danish newspaper Dagbladet accuse British BAE Systems of selling mass surveillance software called Evident across the Middle East.
The British company BAE Systems has been selling mass surveillance software called Evident across the Middle East, the findings are the result of a year-long investigation by BBC Arabic and the Danish newspaper Dagbladet. The surveillance software was acquired after the purchase of Danish company ETI in 2011, and experts believe it was used by totalitarian governments to persecute opponents and activists.
“You’d be able to intercept any internet traffic,” a former employee told the BBC. “If you wanted to do a whole country, you could. You could pin-point people’s locations based on cellular data. You could follow people around. They were quite far ahead with voice recognition. They were capable of decrypting stuff as well.”
Journalists reported that one of the customers for the Evident software before the ETI acquisition was the Tunisian government, and according to a former Tunisian intelligence official, the surveillance software was used to track down President’s opponents.
“ETI installed it and engineers came for training sessions,” he explained. “[It] works with keywords. You put in an opponent’s name and you will see all the sites, blogs, social networks related to that user.”
Fearing a new Arab Spring, several Middle Eastern governments started internet surveillance to identify and persecute dissents, it was a great business opportunity for Western companies like BAE.
BAE Systems and other firms sustain they are committed to operating ethically and responsibly, respecting laws on international exports to overseas governments.
Freedom of information requests from the BBC and the Denmark newspaper Dagbladet Information demonstrate BAE sold systems to Saudi Arabia, the United Arab Emirates, Qatar, Oman, Morocco, and Algeria.
According to dissidents, the mass surveillance systems made their dirty job.
“I wouldn’t be exaggerating if I said more than 90 per cent of the most active campaigners in 2011 have now vanished,” Yahya Assiri, a former Saudi air force officer now in exile, told El Reg.
Evident was installed by numerous government organizations and the company improved it by adding new decryption add-ons.
The British government expressed concern that the software misuse, it cannot be excluded that Evident could be also used against the Western target.
“We would refuse a licence to export this cryptanalysis software from the UK because of Criteria 5 (national security) concerns,” the British export authority told its Danish counterparts in an email over the sale of Evident to the UAE. The Danes approved the sale anyway.
BAE sells surveillance software in Middle East
The consequences of such sales could come back to haunt the West, according to Dutch MEP Marietje Schaake. She warns that the costs could be very heavy indeed.
“Each and every case where someone is silenced or ends up in prison with the help of EU-made technologies I think is unacceptable,” said Dutch MEP Marietje Schaake.
“I think the fact that these companies are commercial players, developing these highly sophisticated technologies that could have a deep impact on our national security, on people’s lives, requires us to look again at what kind of restrictions may be needed, what kind of transparency and accountability is needed in this market before it turns against our own interest and our own principles.”
Buckle Inc. confirmed credit card breach at its stores
18.6.2017 securityaffairs Incindent
An official statement issued by the Buckle Inc. retail confirmed that a point-of-sale malware was discovered on cash registers at its stores.
A few hours ago, the popular investigator and cyber security expert Brian Krebs contacted the Buckle Inc. company after sources in the financial sector reported him about a possible card breach at the retailer.
“On Friday morning, KrebsOnSecurity contacted The Buckle after receiving multiple tips from sources in the financial industry about a pattern of fraud on customer credit and debit cards which suggested a breach of point-of-sale systems at Buckle stores across the country.” reported KrebsOnSecurity.
An official statement issued by the retail confirmed that a point-of-sale malware was discovered on cash registers at Buckle retail stores.
The Buckle Inc. is a clothier that operates more than 450 stores in 44 US states, on Friday the company disclosed that payment systems at its retail locations were infected by a malware used to steal credit card data.
Store front for The Buckle, a Kearney, Neb., based clothing chain.
According to the company, the PoS malware was stealing customer credit card data between Oct. 28, 2016 and April 14, 2017. According to the company, online sales were not affected by the card breach.
“We became aware that The Buckle, Inc. was a victim of a security incident in which a criminal entity accessed some guest credit card information follow purchases at some of our retail stores. We immediately launched a thorough investigation and engaged leading third party forensic experts to review our systems and secure the affected part of our network.” states the announcement published by the company.
“Through that investigation we learned that our store payment data systems were infected with a form of malicious code, which was quickly removed. Based on the forensic investigation, we believe that no social security numbers, email addresses or physical addresses were obtained by those criminally responsible. There is also no evidence that the buckle.com website or buckle.com guests were impacted.”
Crooks used malware to capture data stored on the magnetic stripe and clone the cards.
The Buckle Inc. confirmed that its stores are equipped with EMV-capable card terminals, this means that customers who shopped at compromised Buckle stores using a chip-based card would not be affected by the card breach.
The company is currently investigating the card breach with card brands and forensic investigation services.
“All Buckle stores had EMV (“chip card”) technology enabled during the time that the incident occurred and we believe the exposure of cardholder data that can be used to create counterfeit cards is limited. However, it is possible that certain credit card numbers may have been compromised.” states the company.
“We take the protection of payment card data very seriously. We are cooperating fully with card brands and forensic investigation services. Any affected individuals either have or will likely receive communications from their issuing banks with additional instructions and/or replacement cards. In line with best practice, we recommend that individuals closely monitor their payment card account statements.”
With this PHP rootkit you can take over a server hiding it in PHP server modules
18.6.2017 securityaffairs Virus
The Dutch developer Luke Paris has created a PHP rootkit that hides in PHP server modules, he also explained why it is more dangerous of classic rootkits.
The Dutch developer Luke Paris has created a rootkit that hides in PHP server modules that could be used by attackers to take over web servers.
While classic rootkits work on the lowest levels of the operating system, intercepting kernel operations to perform malicious actions, Luke Paris successfully attempted to create a rootkit that interacts with the PHP interpreter, instead of the OS kernel that is much more complex.
“The first and very obvious reason why you would write a rootkit as a PHP module is accessibility. Learning how to use the Zend Engine (the framework the entire PHP language is built with) is a lot easier than learning how to write kernel modules, simply because the code base itself is smaller, better documented and a lot less complex,” Paris explained. “Even without good documentation or tutorials, I managed to learn the basics of writing a PHP module within a day. If I (a novice C developer) can do it, the bad guys definitely can.
Paris’ PHP rootkit allows attackers to gain persistence on the hacked server without getting detected.
According to Paris, the use of PHP modules to hide rootkits is very effective for the following reasons:
Accessibility – Writing a rootkit as a PHP module is a lot easier than learning how to write kernel modules. Developers can use smaller portions of code, Paris explained that he has learned the basics of writing a PHP module in just one day.
Stability – Rootkits are designed to run in kernel space, this implies that poorly written malware can crash the entire system. Using PHP rootkits this problem is overwhelmed. A poorly written PHP rootkit can’t crash the entire system.
“In the worst-case scenario, a rootkit will cause a segmentation fault and just interrupt the current request (note: most web servers report this in their error log, so this could raise suspicion).” states Paris.
Detectability – PHP Rootkits are difficult to detect because of the lack of checks of PHP modules.
“Furthermore, kernel rootkits require you to hook system calls for every process rather than just one, this slows down your machine drastically, which might lead to more suspicion.” stated the developer.
Portability – PHP rootkits are cross-platform rootkits because PHP is (in most cases) platform-independent.
Luke Paris published on GitHub a Proof of concept PHP rootkit, it is an open-source project. The PoC code developed by Paris hooks into the PHP server’s “hash” and “sha1” functions, the rootkit is composed of only 80 lines of code, and it is quite easy for a hacker to hide it in legitimate modules.

To prevent attackers from using his code, Paris has omitted some of its parts, making compilation harder for non-expert PHP developers.
The post also includes a recommendation for administrators:
Keep a list of the module hashes after installing PHP. Administrators can use a cron job that tries to hash all files in the extension directory and compares them to the current hash. Paris also published a Python script that checks the SHA1 hashes of a user’s PHP modules.
Hacker pleaded guilty to stealing satellite data from US DoD
17.6.2017 securityaffairs Crime
The British hacker Sean Caffrey, 25, from Sutton Coldfield pleaded guilty to stealing satellite data from US Department of Defense (DoD).
The British hacker Sean Caffrey, 25, from Sutton Coldfield pleaded guilty to stealing user accounts from a U.S. military communications system.
According to the NCA, the man admitted in the Birmingham Crown Court to stealing information belonging to 800 users of a satellite communications system. Stolen data include ranks, usernames, and email addresses.
The hacker breached the US Department of Defense (DoD) on 15 June 2014, the officers from the NCA’s National Cyber Crime Unit (NCCU) and West Midlands Police arrested him in March 2015.

Caffrey also stole information associated with 30,000 satellite phones.
“A computer hacker has admitted stealing hundreds of user accounts from a US military communications system.” states the announcement published by the National Crime Agency.
Sean Caffrey, 25, of Sutton Coldfield, accessed and stole the ranks, usernames and email addresses of more than 800 users of a satellite communications system, as well as of about 30,000 satellite phones.
He pleaded guilty at Birmingham Crown Court today to an offence under the Computer Misuse Act.”
Just after the hack, Caffrey posted a message online threatening the notorious group Lizard Squad that made the headlines with the DDoS attack that shut down Sony PSN and XBox live networks.
“We smite the Lizards, LizardSquad your time is near. We’re in your bases, we control your satellites. Department of Defense has no Defenses,” the message, posted on Pastebin, said.
The NCA experts found the stolen data on the Caffrey’s hard drives, forensics investigation revealed the young man used his PC to operate with an online messaging account linked to the attack.
“Janey Young, investigations manager at the NCA, said: “After strong partnership working between the NCA, the FBI and the DoD’s Defense Criminal Investigative Service there was very clear, very compelling evidence against Sean Caffrey.” Janey Young, the investigations manager at the NCA, said.
“No one should think that cyber crime is victimless or that they can get away with it.
“The NCA has people with skills like Caffrey’s, but they’re doing the opposite to him in detecting cyber criminals and bringing them to justice.
“We’re working to keep the internet a safe space for people who use it legitimately.”
According to the DoD, it spent approximately $628,000 to fix the damage caused by the hacker’s intrusion.
Nmap 7.50 released with many significant improvements
17.6.2017 securityweek Safety
The Nmap project announced the release of Nmap 7.50, the first big release since last December that has hundreds of improvements.
Nmap 7.50 is the new release of the popular the Network Mapper, the previous release dates back December 2016 and the new one brings hundreds of improvements.
Nmap 7.50
Nmap 7.50 includes the Npcap packet capturing driver and library for Window, instead WinPcap that is no longer maintained. The Npcap a new set of APIs to improve performance and ensure software compatibility with most popular OSs, including Windows 10.
The new version includes loopback packet capture and injection and raw wireless sniffing.
“It is a replacement for WinPcap, which served us well for many years, but is no longer maintained. Npcap uses newer APIs for better performance and compatibility, including Windows 10 support. We also added loopback packet capture and injection, raw wireless sniffing for beacon frames and such, and extra security features such as requiring Administrator access.” states the Seclists.org.Nmap 7.50 also improved the Nmap Scripting Engine, maintainers released a detection script for the MS17-010 vulnerability exploited by the Wannacry ransomware and for the Sambacry flaw tracked as CVE 2017-7494.
The new release also includes more than 300 new service detection fingerprints and many other improvements.
You can download the Nmap 7.50 source code and binary packages for Linux, Windows, and Mac are available here.
Industry Reactions to 'CrashOverride' Malware: Feedback Friday
16.6.2017 securityweek Virus
ESET and Dragos this week published reports detailing a sophisticated piece of malware believed to have been used in the December 2016 attack aimed at Ukraine’s power grid.
Dubbed Industroyer and CrashOverride, this modular malware has several components: a backdoor, a launcher, a data wiper, DoS and port scanner tools, and at least four payloads.
The payloads allow the malware’s operators to control electric circuit breakers via industrial communication protocols, which suggests that at least some of the malware’s developers have a deep understanding of power grid operations and industrial network communications.
Industry reactions to CrashOverride Industroyer ICS malware
Researchers described some theoretical attack scenarios involving this malware and warned that the threat could be adapted for attacks on other countries, including the U.S., and other sectors.
Contacted by SecurityWeek, industry professionals shared some thoughts on the threat posed by CrashOverride/Industroyer, and provided recommendations on how organizations can protect their systems.

Phil Neray, VP of Industrial Cybersecurity, CyberX:
“Unlike in the first Ukrainian grid attack, where humans were required to remotely control the mouse on compromised SCADA workstations to open the breakers, this malware hijacks ICS devices by communicating directly with them in an automated way, using native ICS protocols such as OPC and IEC 101. We've only seen that once before, with Stuxnet. Another interesting way it's similar to Stuxnet is that it manipulates ICS systems to report back that everything's OK when in fact it isn't.
[...]
The malware is very modular and could easily be extended to support other protocols such as DNP3 that are commonly used in US electric utilities. But it could also be extended to attack other industries such as manufacturing, food processing, chemicals, and pharmaceuticals. We've already seen that nation-states and cybercriminal organizations commonly share advanced tools, so it's easy to imagine the same tools being used to lock down factories and hold companies up for a lot of ransomware. Another plausible scenario would be stealing corporate trade secrets by probing ICS devices for proprietary information about manufacturing processes and formulas, and then selling the sensitive IP to competitors or to the Chinese on the black market.”
Eric Cornelius, VP of Innovation, Cylance:
“Despite the fact that power grids around the world could be exploited by such a tool, the fear that our nation’s infrastructure will be attacked is largely unfounded. Simply because this weapon is made of code rather than lead doesn’t change the response that its use on our civilian infrastructure will provoke. Given our heightened sensitivity to cyberattacks due to the recent evidence of election tampering, it is easy to conclude that our power grid will be next. That being said, we can’t forget that it is the role of militaries around the world to develop, and test, weapons to use in the defense of their national interests. The existence of these weapons alone however, does not imply the intent to use them in acts of aggression and the concept of mutually assured destruction remains as true today as it did in the height of the cold war.
The takeaway from the discovery of this tool should be a firm reminder that the security of our critical infrastructure is on the minds of our adversaries and should remain at the top of ours. Whether or not there is an immediate intent to harm us, our way of life is inextricably linked to our aging infrastructure and the road to resiliency is long. The time to protect our future is now, yet our calls to action are all too often silenced by the uproar of the next big headline.”
Jalal Bouhdada, Founder and Principal ICS Security Consultant, Applied Risk:
“Industroyer seems to be just a communication driver which toggles commands to achieve undefined or abnormal behaviour, of course the platform is build with smart logic in mind to cause destruction. The modular design might be an indication that the malware will be used in different environments, possibly hitting the US as well, as (DNP protocol for example) modules can be added at the desire of the Industroyer creators. Adding more advanced modules seems to be a viable options for the attackers, allowing them to perform targeted attacks a la Stuxnet.
We can debate who is responsible for creating such malware however what matters the most is how easy to create such piece of malware (like PoC ransomware Scythe) which target industrial devices. Industroyer is attacking the principal design choices of industrial protocols. Moreover If authentication was used to secure the communications between SCADA application in field devices, we wouldn’t had to face the effects of this malware. As little requirements are needed to perform Industroyer-like attacks, a fair prediction would say that we will see such malware more often, targeting a variety of industries (One can literally use legitimate tools to recreate the effects of Industroyer).”
Learn More at SecurityWeek’s 2017 ICS Cyber Security Conference
Avi Chesla, CEO and Founder, empow:
The latest cyberthreat out of Russia – the CrashOverride malware – is particularly dangerous because it is capable of executing various malicious activities against different systems autonomously. Yes, it still may require control from the outside, but with developments in AI, hackers can develop ever-more sophisticated, “smarter” malware that can do an enormous amount of damage without human intervention. For example, they can independently identify patterns of different system types and vulnerabilities and decide how to exploit them.
So “self-sufficient” malware is the future of cyberattacks. The WannaCry attack demonstrated some initial basic capabilities – ransomware that can propagate inside the network – which make it more independent than most previous ransomware we’ve seen. In 2015, the Russian malware used to disrupt the power supply network in Ukraine required hackers to remotely manipulate control systems. But the definite trend is toward malware that does not require external activation, and can independently act and propagate inside its target organization.”
Patrick McBride, CMO, Claroty:
“Industrial control systems have been exposed to attack for quite some time. The combination of IT/ICS network convergence – providing poorly secured pathways to industrial control environments that were not designed with cybersecurity in mind – is a dangerous mix. Individual systems have varying, often lackluster security controls in place. While it is very simple to attack ICS networks and cause some level of damage/outage to processes, plants and the electric grid, it is harder to cause permanent damage because of safety systems and the unique system/environment knowledge required to build malware with a more permanently destructive payload. But the systems are dangerously unprotected and the level of sophistication required to cause outages and real damage has been lowered. You don’t need “nation state”-level expertise to copy or reuse existing malware like Industroyer or WannaCry to impact industrial systems.
It is unclear, at this time, whether Industroyer has been used beyond Ukraine. The concentration in Ukraine is plausibly rooted in the Russian/Ukraine conflict in general. Further, the adversary may also be leveraging the Ukraine grid as a test bed – enabling it to further refine its malware and methods and better understand how victims will respond.”
Alan Brill, Senior Managing Director, Cyber Security & Investigations, Kroll:
“The parts of an ICS “talk” to one another over data lines. In this case, an electric grid ICS could talk to a switch at a given substation and open or close it. Doing this to the right combination of switches can cause power to flow where it can cause damage to equipment and leave people in the dark with power outages. To avoid a utility being tied to only one vendor, the “languages” that these devices use to communicate became standardized across manufacturers. So once you understand how the language works, it’s going to work in a lot of power networks.
These systems were developed with the assumption that they weren’t connected to the Internet. Thus, commands could only come from the authorized users. Once the malware is in, it is able to transmit completely accurate and valid-appearing commands, and the language does not provide for positive authentication of the source.
Even more interesting, the “bad guys” realized that the authorized users could undo the damage they caused by issuing correcting commands. My understanding is that the malware also can wipe the software from the switch, so that undoing the unauthorized command takes manual intervention at the switch, which prolongs the problem.”
Barak Perelman, CEO, Indegy:
“This malware demonstrates why ICS control-plane protocols must be protected. These proprietary, vendor-specific protocols, which are used to communicate with control devices (e.g. PLCs, RTUs and DCS) in industrial networks, make it very difficult to monitor access and changes made to critical devices. This lack of visibility enables adversaries to effectively attack these systems while hiding in plain sight.
Detecting malicious activity requires a deep understanding of these native protocols which cannot be accomplished using traditional network monitoring tools or by looking for network anomalies. Monitoring activity performed over control-plane protocols would have immediately identified all the reconnaissance scans in the CRASHOVERRIDE attack and enabled operational staff to prevent the outage. This approach can also identify attempts to tamper with these devices in real-time so threats can be mitigated before any damage is done.”
“Nathan Wenzler, chief security strategist, AsTech:
“Incidents involving malware that target specific ICS systems, such as industroyer, are still relatively rare occurrences. However, because of their focus on disrupting power grids and other industrial systems, the amount of damage that can be caused can be incredibly significant. While malware of this nature targeting assets here in the U.S. as yet to reported publicly, it's incredibly likely that we will eventually face such a threat. Since malware like this is often backed by government groups, there is a lot of political motivation behind propagating this kind of attack to cause damage to infrastructure or other core services provided to large populations.
Industroyer is particularly interesting in that it is built in a modular fashion, which allows for multiple tools, exploit kits, or customized attack methods for different ICS targets to be added quickly and easily. This will make it trivial for whoever wrote this code to modify it for attacks against different targets or types of systems, allowing for a sort of morphing characteristic that will make it harder to detect and protect against as more and more variations are released into the wild. Add to this the fact that many vendors of ICS products don't often build security into their applications or provide quick upgrades, patches or hotfixes in response to identified vulnerabilities, it makes a malleable, flexible malware package like industroyer especially dangerous to defend against even if the variants are identified.”
John Bamabenek, Threat Research Manager, Fidelis Cybersecurity:
“In the realm of security, bigger nations picking on smaller nations is nothing new and it’s often done without consequence. If Russia is behind this latest attack, there isn't much Ukraine can do about it. If Ukraine did have sufficient deterrent capability, they'd have kicked Russia out of Crimea and Eastern Ukraine by now.
Picking on the US is another matter. Unlike Russia’s election information operations, the US has a wide variety of response strategies. The US can launch physical attacks and respond in-kind. After all, the US and allies created Stuxnet. It can always decide to put the band back together.
The fact that the US can retaliate does not mean we aren't at risk. As a nation, we have a wide variety of infrastructure that’s susceptible to attack. At the moment, our largest defense seems to be deterrence.”
Paul Edon, Director of International Customer Services, Tripwire:
“Historically Industrial networks have used airgap and diode based architecture to defend against the risks associated with corporate intranet and Internet communications. However, due to economic pressures i.e. increasing costs and decreasing numbers of skilled resources, it has become necessary for many organizations to centralize some of the management and control functions that would have previously been local to industrial plants, refineries, distribution facilities etc. This centralization has meant expanding the reach of the enterprise network into the industrial environment, and in doing so, exposing those industrial environments to levels of cyber risk for which they were neither secured nor designed.
Post design security is always a much greater challenge than the “security by design and default” that we would expect today. However, the majority of attacks can still be defended against by employing the same strategy as that used for the enterprise i.e. “Security Best Practise,” “Defence in Depth” and “ Foundational Controls.”
Kaspersky Lab:
“Malware with such functionality is pretty unique - although it shares ideas and approaches with other malware we have seen and attacks we have investigated. However, Kaspersky Lab and its ICS CERT have been warning for some time that cyber-attackers are increasingly willing and able to launch attacks on critical infrastructure, particularly industrial control systems connected to the Internet – while organizations and countries remain worryingly under-prepared.
In order to protect the ICS environment from possible cyber-attacks, Kaspersky Lab advises the following:
Conduct a security assessment to identify and remove security loopholes.
Request external intelligence: intelligence from reputable vendors helps organizations to predict future attacks on the company’s industrial infrastructure.
Train your personnel
Provide protection inside and outside the perimeter. A proper security strategy has to devote significant resources to attack detection and response, to block an attack before it reaches critically important objects.
Evaluate advanced methods of protection. A Default Deny scenario for SCADA systems, regular integrity checks for controllers, and specialized network monitoring to increase the overall security of a company will reduce the chances of a successful breach, even if some inherently vulnerable nodes cannot be patched or removed.”
Owen Connolly, VP of Services at IOActive:
“CrashOverride is a threat, certainly, and yet another wake up call for the industry. How large of a threat? It may impact lots of systems globally, but it is unlikely it will have widespread impacts to grid operations. The good news about attacking power grids is that it is hard. Not impossible, but certainly difficult. And requires insider equivalent information about systems across largely geographic areas. Also, given the mixture of digital, analog, and manual systems, widespread outages are unlikely from malware alone.
But, combining various cyber-physical techniques along with malware in a combined threat could certainly force multiply what CrashOverride can do now into a large scale grid event. That would require a lot of information about substation automation, what systems were in use, timing requirements between substations, interconnected systems across multiple utilities, and a myriad of other data. All obtainable, but certainly a large work effort to pull off.”
Joseph Carson, chief security scientist, Thycotic:
“It’s very likely we’ll see similar attacks in the US as most of the SCADA Control Systems and industrial control systems being used are the same. The major difference will be on how well those systems are being protected and what additional security controls are in place. For example, many of the incidents like that which occurred in Ukraine was a failure to even do the basic security controls that allowed the attackers to easily gain access and laterally move around the network undetected eventually carrying out the malicious activity. This highlights that cyber-criminals with sufficient technical knowledge, resources and time can plan an effective attack with potentially serious catastrophic results.”
Andrea Carcano, Co-founder and Chief Product Officer, Nozomi Networks:
“Organizations with Industrial Control Systems (ICS) should know that technology is available today that provides real-time cybersecurity visibility for SOCs (Security Operations Centers) and that detects and mitigates APTs on OT systems.
For example, such a solution will detect queries being made to devices to collect data that could be used to design and implement a critical systems attack. And, through a deep understanding of the process being run by the ICS, identify that process parameters are changing and could bring the system into a critical state.
Once alerts about both data collection communications and process variable changes are communicated to the SOC, staff can execute prevention and mitigation measures.”
Sven Schrecker, Chair, Industrial Internet Consortium Security Working Group:
“Attacks on critical infrastructure are becoming too common in the world today. Furthermore, the techniques being implemented by the bad guys are becoming more advanced in their capabilities. It is a grave concern that these threats may target US infrastructure and succeed in doing significant damage. We’ve seen such activity at a small scale in the past, and that should be a wake-up call that we must be proactive.
The methods for delivering the malware and attacking the systems is evolving at an ever increasing pace. Unfortunately, the legacy equipment that makes up the majority of the critical infrastructure base was never designed with cyber security in mind. The attackers are preying on this oversight. Fortunately, existing technology can be applied to critical infrastructure to mitigate some of the most egregious vulnerabilities and enable the critical infrastructure to continue to use the legacy protocols and processes with additional security in place.”
David Zahn, GM of Cybersecurity Business Unit, PAS:
“There seems an undercurrent of surprise or reactionary concern when we hear details on how bad actors are advancing sophisticated means to attack critical infrastructure. In power, we are in denial that a similar attack could happen in the US. We also get mired in misconceptions that we are well prepared because of regulation, or squirrels - yes squirrels - are more likely to bring down power than a hacker. The problem is that nation states have a plan, squirrels do not.
The latest news about Crash Override is one more wakeup call that we need to become better at the cybersecurity basics which most industrial companies struggle doing today - know what ICS cyber assets you have (from smart field instruments to controllers to workstations), identify and managing vulnerabilities, detect when an unauthorized change occurs, and ensure backups are available.”
Hacker Admits Stealing Satellite Data from DoD
16.6.2017 securityweek BigBrothers
A British man from Sutton Coldfield on Thursday pleaded guilty to stealing user accounts from a U.S. military communications system, the UK's National Crime Agency (NCA) announced.
Sean Caffrey, 25, admitted in court to accessing and stealing information pertaining to 800 users of a satellite communications system, including ranks, usernames and email addresses. Moreover, he stole information associated with 30,000 satellite phones, NCA says.
Caffrey pleaded guilty on Thursday at Birmingham Crown Court to an offense under the Computer Misuse Act: “Causing a computer to perform a function to secure unauthorized access to a program or data.”
Shortly after the hack, Caffrey posted a message online apparently condemning Lizard Squad, a known group of hackers previously associated with attacks on Microsoft and Sony and with various distributed denial of service incidents.
“We smite the Lizards, LizardSquad your time is near. We're in your bases, we control your satellites. Department of Defense has no Defenses,” the message, posted on Pastebin, said.
The hacker stole said data from the US Department of Defense (DoD) on June 15, 2014, but was arrested only in March 2015, after “intelligence showed the hack originated from his internet connection.” Officers from the NCA’s National Cyber Crime Unit (NCCU) and West Midlands Police made the arrest.
During forensic analysis of Caffrey’s computer, NCA officers found the stolen data on the hard drives, and also discovered that the PC was used to open and operate under a pseudonym an online messaging account linked to the attack.
“After strong partnership working between the NCA, the FBI and the DoD’s Defense Criminal Investigative Service there was very clear, very compelling evidence against Sean Caffrey. The NCA has people with skills like Caffrey’s, but they’re doing the opposite to him in detecting cyber criminals and bringing them to justice,” Janey Young, investigations manager at the NCA, said.
The financial damages incurred by the hacker’s intrusion amounted to approximately $628,000, the DoD said. Caffrey is scheduled for sentencing on August 14.
Senators Say Cybersecurity Should be Top Priority for Autonomous Vehicles
16.6.2017 securityweek Cyber
Self-Driving Cars Need Regulations, But Commercial Priorities May Prevail Over Consumer Privacy
The arrival of autonomous vehicles (AV, or self-driving vehicles) on the public highways is getting closer. Just this month (June 2017), Nutonomy announced a partnership with Lyft for R&D on its existing AV testing on the streets of Boston. Lyft announced yesterday that by 2025 it will provide "at least 1 billion rides per year using electric autonomous vehicles." Also this week, Japanese robotics firm ZMP announced its plan to have an AV taxi on the streets of Tokyo in time for the 2020 Olympics. The need for AV regulation is pressing.
The U.S. Senate Commerce, Science, and Transportation Committee responded Tuesday by releasing bipartisan principles for AV legislation ahead of a Wednesday hearing titled 'Paving the way for self-driving vehicles.' The authors of the principles, U.S. Sens. John Thune (R-S.D.), Gary Peters (D-Mich.), and Bill Nelson (D-Fla.), plan to introduce legislation, but have so far set neither a date nor deadline for this.
The principles focus on safety, promoting innovation, tech-neutral legislation, clarification over federal and state responsibilities, public education, and -- of course -- cybersecurity. The last is minimal. The document states that cybersecurity must be included 'from the very beginning of their development,' and that "Legislation must address the connectivity of self-driving vehicles and potential cybersecurity vulnerabilities before they compromise safety."
In short, it addresses cyber vulnerabilities, but not user privacy. The former is necessary. Researchers have shown for years that the onboard computer systems of existing non-autonomous vehicles are vulnerable to hacking, from the Vlasek/Miller research in 2010 to the Tesla hack late last year.
But user privacy is also important. In March this year, Sens Edward J. Markey (D-Mass.) and Richard Blumenthal (D-Conn.), members of the same committee, re-introduced their own SPY Car Act-- which specifically requires a dashboard to inform consumers "about the extent to which the motor vehicle protects the cybersecurity and privacy of motor vehicle owners, lessees, drivers, and passengers beyond the minimum requirements."
The lack of privacy conditions in this week's bipartisan principles would suggest two camps within the Commerce, Science, and Transportation Committee: one that seeks to prioritize the commercial value of AV, while the other seeks to also protect the privacy of AV users. The reality of modern business is that you cannot maximize both simultaneously.
The dearth of security priority in this week's approach also shows itself in the currently available details of Wednesday's hearing. The introductory remarks from Chairman John Thune talk about the expected benefits from AVs, but never once mention security nor privacy.
There are four published statements for the hearing: The Alliance of Automobile Manufacturers, The American Center for Mobility (ACM), Mothers Against Drunk Driving, and Nvidia. Three of these statements never mention security nor privacy.
Only ACM broaches these subjects, but specifically calls for 'voluntary standards'. "Additional voluntary standards are needed immediately to ensure that these new approaches in testing, validation, data collection, data-sharing, privacy, cybersecurity, and other areas are developed to ensure safety, while not inhibiting or stalling the technology development."
Most security professionals believe that voluntary privacy standards simply do not work -- they need to be backed by strict legislation with strong sanctions (see, for example, GDPR). ACM's declaration that it "will fully protect consumer and public privacy and security, and will take steps to ensure that any data or information sharing activities do not violate, hinder, or compromise integrity of any consumer privacy/security agreements or arrangements put in place by manufacturers, testers, agencies, public entities, or by ACM itself" is welcome, but simply continues the concept of self-regulation.
The size, reach and monetary value of the consumer data industry makes it unlikely that user privacy can be maintained voluntarily -- and it is improbable that many people fully understand the extent to which they are currently profiled. A new and detailed analysis (PDF) published this month by Cracked Labs (Vienna) analyzes 'how companies collect, combine, analyze, trade, and use personal data on billions.' It concludes, "we might soon end up in a society of pervasive digital social control, where privacy becomes -- if it remains at all -- a luxury commodity for the rich. The building blocks are already in place."
In the coming mass market of self-driving vehicles, only time will tell whether the privacy-protecting proposals of the CAR Spy Act, or the commerce promoting stance of this week's new proposals will prevail.
Industrial Companies Targeted by Nigerian Cybercriminals
16.6.2017 securityweek CyberCrime
Industrial companies from around the world have been targeted in phishing attacks believed to have been launched by cybercriminals located in Nigeria, Kaspersky Lab reported on Thursday.
In October 2016, Kaspersky’s Industrial Control Systems Cyber Emergency Response Team (ICS CERT) noticed a significant increase in malware infection attempts aimed at industrial organizations in the metallurgy, construction, electric power, engineering and other sectors. The security firm had observed attacks against 500 organizations in more than 50 countries.
The attacks started with spear phishing emails carrying documents set up to exploit an Office vulnerability (CVE-2015-1641) patched by Microsoft in April 2015. The phishing messages were well written and they purported to come from the victim’s suppliers, customers, or delivery services.
The malicious documents delivered a wide range of malware, including ZeuS, Pony, LokiBot, Luminosity RAT, NetWire RAT, HawkEye, ISR Stealer, and the iSpy keylogger. While the significant number of malware families used suggests that the emails could be part of multiple campaigns, there are some elements linking them together.
Researchers noticed that all malware samples delivered in the attacks were packed with VB and .NET packers. Furthermore, they all communicate with the same command and control (C&C) servers. This indicates that it’s either one group behind all attacks, or multiple threat actors are working together.
According to Kaspersky, many of the C&C domains mimicked the domains of industrial companies – the attackers either registered the same name on a different TLD or they registered a name that was very similar to the legitimate domain. In some cases, the cybercriminals breached the targeted organization’s website using stolen credentials and abused it to host malware and C&C servers.
Experts noted that a majority of the C&C domains used in these attacks were registered to residents of Nigeria.
The malware delivered in this campaign has helped the hackers steal data they can use for business email compromise (BEC) attacks, where attackers claim to represent a business partner or customer and trick the targeted organization’s employees into sending them significant amounts of money.
The FBI reported last year that losses caused by BEC scams exceeded $3.1 billion. Nigerian cybercriminals have been running these types of schemes for several years now, but Kaspersky researchers believe they recently came to realize that targeting larger companies can be more lucrative and last year they turned their attention to industrial organizations.
“Nigerian phishing attacks are particularly dangerous for industrial companies. In the event of a successful attack, the company making a purchase not only loses money but also fails to receive the goods they need on time,” said Kaspersky researchers. “This can be critical for industrial companies: if the goods are raw materials used in manufacturing or spare parts needed to repair equipment, their non-delivery can result in downtime or failure to perform scheduled maintenance or commissioning and start-up work.”
Furthermore, experts pointed out that the malware used in these attacks has stolen a wide range of data, including files apparently coming from the workstations of operators, engineers, architects and designers. While it’s unclear if the theft of such files has been monetized, researchers noted that this can pose a serious threat. Kaspersky has also warned that cybercriminals could use their access to make unauthorized changes to industrial control systems (ICS).
"FIN10" Cybercrime Group Extorts Canadian Firms
16.6.2017 securityweek CyberCrime
A profit-driven cybercrime group tracked as FIN10 has been running an extortion operation mainly targeting organizations in North America, security firm FireEye reported on Friday.
A majority of the FIN10 attacks observed by FireEye have been aimed at mining companies and casinos in Canada. The hackers breached the targeted organization’s systems, obtained valuable data, and threatened to make it public unless a ransom was paid. Victims that refused to pay up had their data published online and their systems disrupted.
FIN10 has been around since as early as 2013 and its activities have continued through at least 2016. The first phase of its attacks has, at least in some cases, involved spear-phishing emails carrying links to servers controlled by the cybercrooks. The phishing emails were apparently crafted using data obtained from LinkedIn and other sources.
The early stage tools used by the attackers included software such as Meterpreter, the Splinter remote access trojan (RAT), and PowerShell-based utilities, including ones written by the hackers themselves.
The attackers then used compromised credentials, the Windows RDP service and tools such as Splinter RAT, PowerShell Empire and Meterpreter to maintain persistence and move laterally within the victim’s network. Their goal was to steal corporate business data, including correspondence and customer PII, which they could use to extort the victim.
Organizations that refused to pay had their data leaked and their systems and networks were often disrupted via batch scripts designed to delete critical files.
Victims were asked to pay between 100 and 500 bitcoins, which are worth hundreds of thousands of dollars. FireEye told SecurityWeek that some of the victims gave in to the extortion demands.
FIN10 has carried out its attacks claiming to represent various hacker groups, particularly hacktivists. In one operation they claimed to be a Russian group called “Angels_Of_Truth” and told their victim that the attack was carried out in response to Canada’s economic sanctions on Russia. Researchers determined, however, that the posts in Russian were likely written using online translation tools and not by a native speaker.
DataBreaches.net reported in June 2015 that a group calling itself “Angels_Of_Truth,” claiming to be from Russia, breached the systems of Canada-based intermediate gold producer Detour Gold Corporation. At the time, the hackers leaked personal information of employees and customers, salary information, confidential deals, donation records, medical records, legal documents, invoices, performance reviews and other data.
In other attacks, the hackers claimed to represent “Tesla Team,” a Serbian hacktivist group. In one operation, the group introduced itself as Tesla Team, but later changed its name to “Anonymous Threat Agent.”
In order to increase their chances of making the victim pay the ransom, FIN10 sent emails to staff and board members of the targeted organization. The group also informed the media about its breaches, either to put pressure on the victim or to maximize the exposure of those who refused to pay, FireEye said.
Researchers believe that FIN10’s focus on North America could suggest the attacker’s familiarity with this region.
“The relative degree of operational success enjoyed by FIN10 makes it highly probable the group will continue to conduct similar extortion-based campaigns at least in the near term. Notably, we already have some evidence to suggest FIN10 has targeted additional victims beyond currently confirmed targets,” FireEye said in its report. “Furthermore, while FIN10 is predominantly financially motivated, as evidenced by its preferred monetization technique (i.e., extortion), it is plausible the group is also motivated, at least in part, by ego.”
New Code-injecting SOREBRECT Fileless Ransomware detected in the wild
16.6.2017 securityaffairs Ransomware
The number of fileless malware continues to increase, recently security researchers spotted a new Fileless Ransomware dubbed Sorebrect.
Sorebrect is able to inject malicious code into a legitimate system process (svchost.exe) on a targeted system and it terminates its binary to evade detection. It also make hard forensics analysis by deleting the affected system’s event logs using wevtutil.exe and shadow copies with vssadmin,and other artifacts such as files executed on the system.
SOREBRECT leveraged on Tor network to anonymize communications to command-and-control (C&C) server.
Unlike other ransomware, Sorebrect has been designed to specifically target enterprise’s systems in various industries (manufacturing, technology, and telecommunications), the malicious code it injects is tasked of file encryption on the local machine and connected network shares. The Sorebrect ransomware scans the local network for other connected systems with open shares and encrypts files stored on them.
“Extracting and analyzing the SOREBRECT samples revealed the unusual techniques it employs to encrypt its victim’s data. Its abuse of the PsExec utility is also notable; SOREBRECT’s operators apparently use it to leverage the ransomware’s code injection capability.” states the analysis shared by Trend Micro.
“While file encryption is SOREBRECT’s endgame, stealth is its mainstay. The ransomware’s self-destruct routine makes SOREBRECT a fileless threat. The ransomware does this by injecting code to a legitimate system process (which executes the encryption routine) before terminating its main binary.”

The experts noticed that the SOREBRECT fileless ransomware first compromises administrator credentials (i.e. by brute forcing attacks), then leverage Microsoft Sysinternals PsExec command-line utility to encrypt files.
“Why PsExec? While attackers can both use Remote Desktop Protocol (RDP) and PsExec to install SOREBRECT in the affected machine, its code injection capability makes the attack more effective. Compared to using RDP, utilizing PsExec is simpler and can take advantage of SOREBRECT’s fileless and code injection capabilities.” continues the analysis.
“PsExec can enable attackers to run remotely executed commands, instead of providing and using an entire interactive login session, or manually transferring the malware into a remote machine, like in RDPs,” Trend Micro says.
The fileless ransomware was first spotted in Middle Eastern countries like Kuwait and Lebanon, recently experts observed attacks against systems in Canada, China, Croatia, Italy, Japan, Mexico, Russia, Taiwan, and the U.S.
Below the best practices for securing systems and networks suggested by TrendMicro.
Restrict user write permissions.
Limit privilege for PsExec.
Back up files.
Keep the system and network updated.
Deploy multilayered security mechanisms.
A New malware dubbed dvmap for android was found and removed from play store
16.6.2017 securityaffairs Android
Kaspersky Lab had discovered a new malware dubbed dvmap for Android was found and removed from the official Google Play store
A New malware dubbed dvmap for Android was found and removed from the official Google Play store
Kaspersky Lab had discovered the new malware that is capable of obtaining root access on Android devices and is capable of taking over the system library with the execution of a code injection attack.
The malware named DVMAP was seen being distributed as a game called Colourblock and has a new feature in mobile malware.
“In April 2017 we started observing new rooting malware being distributed through the Google Play Store. Unlike other rooting malware, this Trojan not only installs its modules into the system, it also injects malicious code into the system runtime libraries. Kaspersky Lab products detect it as Trojan.AndroidOS.Dvmap.a.” states Kaspersky Lab.

The ability to deploy code injection is a new capability unseen until now and represents a dangerous evolution on Android menaces.
The malware tries to gain root access after the application installation and launches a file to verify the Android version and what library it will inject the code. Once successful the malware tries to connect to C&C server that keeps updating every process of the malware. DVMAP can also disable the user’s security settings to try gain root access over the device.
The creators of the malware were able to bypass Play Store security mechanisms by embedding it with a game, in a two-phase infection method. First, a game was uploaded to the Play Store free of malware, and then the application was substituted with the malware itself bypassing this way the security mechanisms of Google. Before its removal, the malware was able to infect at least 50,000 devices that downloaded the game application.
“This makes Dvmap the first Android malware that injects malicious code into the system libraries in runtime, and it has been downloaded from the Google Play Store more than 50,000 times. Kaspersky Lab reported the Trojan to Google, and it has now been removed from the store.” continues Kaspersky.
DVMAP can disable runtime libraries depending which version of Android is in use, so it can install other payloads linked to third parties that could compromise sensitive data as banking accounts. One of these payloads is “com.qualcmm.timeservices” The malware can also work on 32 and 64 bits of Android.
Until now there is no correction for the malware, but users can count on simple best practices of security do avoid or detain the infection. It is highly recommended that users download only from developer’s official site, maintain an up to date backup of data and always verify which privilege will be granted to the application that will be installed. A full factory reset also is highly recommended to users who have been infected and also maintaining up to date the definitions of antivirus.
CIA vyvinula „Třešňový květ,“ který obsadí třeba váš router a bude jej odposlouchávat
16.6.2017 Živě.cz BigBrother
Skupina Wikileaks zveřejnila další uniklé materiály z agentury CIA
Tentokrát popisují útoky na Wi-Fi routeru a AP body
Cherry Blossom je dokáže odposlouchávat
Skupina Wikileaks po dvou týdnech zveřejnila další balík úniků ze CIA. Zatímco na sklonku května se pochlubila materiály o kybernetické zbrani Pandemic, která mohla snadno napadnout podnikové sítě skrze protokoly SMB/CIFS, nový úlovek popisuje balík nástrojů Cherry Blossom – Třešňový květ.
Wikileaks zveřejnil detaily další kyberzbraně CIA. Jmenuje se Pandemic a mohla na přání zasáhnout celé podniky
A není to zrovna kvítek, který byste chtěli mít doma, tento Cherry Blassom totiž zaútočí třeba na váš Wi-Fi router. Tedy pokud se dostanete do hledáčku agentury, což asi nebude příliš pravděpodobné. CIA jej podle dokumentů Wikileaks vyvinula ve spolupráci s SRI International (Stanford Research Institute) a jedná se o typický útok MITM – man in the middle.
To v praxi znamená, že se program usadí přímo na routeru, respektive na něj nahraje vlastní upravený firmware. Útočník, v tomto případě agentura CIA, poté může na dálku router ovládat, ale hlavně odposlouchávat, co přes něj teče, a v případě, že se jedná o šifrovanou komunikaci (HTTPS), může se ji pokoušet oblafnout pomocí falešných certifikátů
Další várka úniků ze CIA. Wikileaks popisuje, jak se Američané údajně vydávají za Rusy, Číňany a další
Cherry Blossom se soustředí na ovládnutí těch síťových krabiček, které umožňují aktualizaci firmwaru z webu. Pakliže se to podaří, agentura může ovládnout router sledované osoby klidně ze svého ústředí pro kybernetické operace.
V rozsáhlém uživatelském manuálu (PDF) od SRI se dočtete třeba o tom, že se Cherry Blossom hodí na sběr používaných e-mailových adres, přezdívek z chatů, MAC adres a čísel pro VoIP. Útočník má ale v podstatě přístup k celé komunikaci, která přes router teče, stejně jako ji má i jeho majitel.
Skutečnost, že podobné nástroje CIA vlastní a používá, není s ohledem na její činnost nikterak překvapující, ve světle nedávné aféry WannaCry, však roste riziko potenciálních škod, které mohou nastat, pokud se podobný software dostane ven.
WannaCry totiž sám pro snadné šíření počítačovou sítí využíval kódu, který už dříve unikl na web a za kterým stála NSA. Ze serverů CIA se sice dostaly k veřejnosti jen manuály, útržky dokumentace a nejrůznějších technických zpráv – použitelné kódy naštěstí nikoliv –, už i to je však alarmující.
Pokud by se ven dostaly podobné aplikace jako Cherry Blossom nebo Pandemic, téměř jistě by brzy došlo k jejich implementaci do nejrůznějších malwarů. Přitom se vlastně nejedná o nic exotického a CIA a NSA, na rozdíl od hollywoodských filmů, nepoužívá jiné postupy, než třeba penetrační testovací linuxová distribuce Kali, která je všem zájemcům k dispozici, a ačkoliv je určená k testování zabezpečení počítačových systémů, je zároveň i oblíbenou hernou script kiddies.
New Fileless Ransomware with Code Injection Ability Detected in the Wild
16.6.2017 thehackernews Ransomware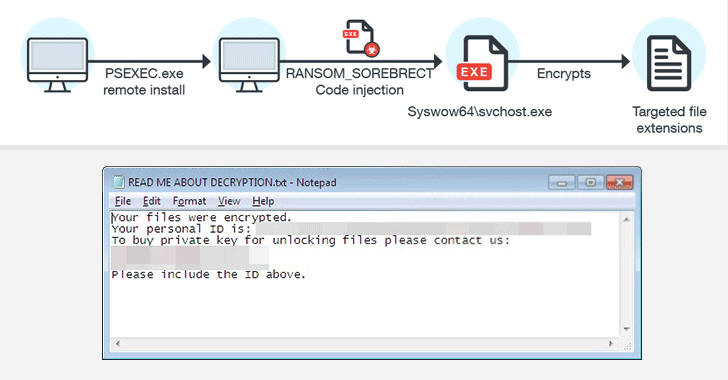
It is no secret that hackers and cybercriminals are becoming dramatically more adept, innovative, and stealthy with each passing day.
While new forms of cybercrime are on the rise, traditional activities seem to be shifting towards more clandestine techniques that come with limitless attack vectors with low detection rates.
Security researchers have recently discovered a new fileless ransomware, dubbed "Sorebrect," which injects malicious code into a legitimate system process (svchost.exe) on a targeted system and then self-destruct itself in order to evade detection.
Unlike traditional ransomware, Sorebrect has been designed to target enterprise's servers and endpoint. The injected code then initiates the file encryption process on the local machine and connected network shares.
This fileless ransomware first compromises administrator credentials by brute forcing or some other means and then uses Microsoft’s Sysinternals PsExec command-line utility to encrypt files.
"PsExec can enable attackers to run remotely executed commands, instead of providing and using an entire interactive login session, or manually transferring the malware into a remote machine, like in RDPs," Trend Micro says.
Sorebrect Also Encrypts Network Shares
Sorebrect also scans the local network for other connected computers with open shares and locks files available on them as well.
"If the share has been set up such that anyone connected to it has read-and-write access to it, the share will also be encrypted," researchers say.
The nasty ransomware then deletes all event logs (using wevtutil.exe) and shadow copies (using vssadmin) on the infected machine that could provide forensic evidence such as files executed on the system and their timestamps, which makes this threat hard-to-detect.
In addition, Sorebrect uses the Tor network protocol in an attempt to anonymize its communication with its command-and-control (C&C) server, just like almost every other malware.
Sorebrect Ransomware Spreads Worldwide
The Sorebrect fileless ransomware has been designed to target systems from various industries including manufacturing, technology, and telecommunications.
According to Trend Micro, Sorebrect was initially targeting Middle Eastern countries like Kuwait and Lebanon, but from last month, this threat has started infecting people in Canada, China, Croatia, Italy, Japan, Mexico, Russia, Taiwan, and the U.S.
"Given ransomware’s potential impact and profitability, it wouldn’t be a surprise if SOREBRECT turns up in other parts of the world, or even in the cybercriminal underground where it can be peddled as a service," the researchers note.
This is not the first time when researchers have come across Fileless malware. Two months ago, Talos researchers discovered a DNSMessenger attack that was completely Fileless and used DNS TXT messaging capabilities to compromise systems.
In February, Kaspersky researchers also discovered fileless malware that resided solely in the memory of the compromised computers, which was found targeting banks, telecommunication companies, and government organizations in 40 countries.
Ways to Protect Against Ransomware Attacks
Since the ransomware does not target individuals but organizations, sysadmins and information security professionals can protect themselves by:
Restricting user write permissions: a significant factor that exposes network shares to ransomware by giving users full permissions.
Limiting privilege for PsExec: Limit PsExec and provide permission to run them only to system administrators.
Keeping your system and network up-to-date: Always keep your operating system, software, and other applications updated.
Backing up your data regularly: To always have a tight grip on all your important files and documents, keep a good backup routine in place that makes their copies to an external storage device that is not always connected to your PC.
Adopting a cyber security-aware workforce: Educating your employees about malware, threat vectors and security measure always plays a major role in any organization.
25-Year-Old Hacker Pleads Guilty to Hacking U.S. Military Satellite Phone System
16.6.2017 thehackernews Crime
A British computer hacker who allegedly hacked a United States Department of Defense satellite system in 2014 and accessed the personal information of hundreds of military personnel has pleaded guilty on Thursday.
Sean Caffrey, a 25-year-old resident of Sutton Coldfield in the West Midlands, has admitted to breaking into a US military communications system in June 2014 and stealing usernames and email addresses of over 800 employees and data from 30,000 satellite phones, the UK's National Crime Agency announced on Thursday.
The UK authorities arrested Caffrey in March 2015 after they traced back the hack to his home IP address, which indicates the hacker did not use any anonymity service, such as VPN, proxy or Tor, to hide its track.
The NCA officials also discovered that an online messaging account linked to the Pentagon satellite system attack was opened and operated from Caffrey's computer.
After a forensic examination of his seized computers, the investigators discovered the stolen data related to the United States DoD satellite on the hard drives.
However, the U.S. government did not say exactly how Caffrey successfully carried out the hack.
According to the NCA's March 2014 press release, evidence of the DoD breach was shared on Pastebin (which is still online) along with a text message referencing Lizard Squad, a hacking group that's responsible for many high-profile attacks, including Xbox Live and PlayStation.
"ISIS WARRIORS UNVEIL - We smite the Lizards, LizardSquad your time is near. We're in your bases, we control your satellites," the Pastebin post read. "The missiles shall rein upon thy who claim alliance, watch your heads. TOP THE AIR-STRIKES OR WE WILL DO AS YOU DO! "
Caffrey pleaded guilty at Birmingham Crown Court Thursday to one offense under the Britain's anti-hacking law, the Computer Misuse Act.
According to the U.S. Defence Department, the breach cost the Pentagon about $628,000 to fix the damages caused by the Caffrey's intrusion.
"After strong partnership working between the NCA, the FBI and the DoD's Defense Criminal Investigative Service there was very clear, very compelling evidence against Sean Caffrey," said Janey Young, investigations manager at the NCA.
"No one should think that cyber crime is victimless or that they can get away with it. The NCA has people with skills like Caffrey's, but they're doing the opposite to him in detecting cyber criminals and bringing them to justice."
The FBI and the Department of Defense collaborated in the investigation with the UK officials.
Caffery is scheduled to appear before the judge for sentencing on 14 August.
False Flag Attack on Multi Stage Delivery of Malware to Italian Organisations
16.6.2017 securityaffairs Virus
Researchers at the security firm Yoroi have discovered a False Flag Attack on Multi-Stage Delivery of Malware to Italian Organisations.
Everything started from a well edited Italian language email (given to me from a colleague of mine, thank you Luca!) reaching out many Italian companies. The Italian language email had a weird attachment: ordine_065.js (it would be “Order Form” in English) which appeared “quite malicious” to me.
By editing the. js attachment it becomes clear that it is not an “order form” but contrary it turns out to be a downloader. The following image shows the .JS content. Our reverse adventure is going to start: we are facing a first stage of infection.

Stage 1: Downloader
The romantic dropper (code on the previous image) downloads and executes a PE file (let’s call it Second stage) from 31.148.99.254. The IP address seems to be hosted by a telecommunication company who sells cloud services such as: dedicated servers, colocation systems, and so on located in Ukraine. The used language in the current stage perfectly fits the dropping website language. Please keep in mind this language since later on, it would become a nice find.
By listing the http://31.148.99.254, we might appreciate a nice malware ‘implant’ where multiple files are in place, probably to serve multiple attack vectors (es: emails, or tag inclusions, or script inclusion into benevolent html files). My first analysis was on obf.txt (the following image shows a small piece of it) which woke up my curiosity.
Lateral Analysis: obf.txt
That piece of VB code, could be used to obfuscate VBScripts. Many pieces of code belonging to obf.txt are related to the Russian Script-Coding.com thread where dab00 published it on 2011. Another interesting file is the Certificate.js which shows the following code.
Lateral Analysis: Certificate.js
Quite an original technique to hide a Javascript File ! As you might see private and public keys are quoted by resulting a valid .js file which would be correctly interpreted by a js engine. Following this way, before getting into our real attack path represented by the set.tmp file, from Stage: 1 (ref. Image Stage: 1), the decision landed on performing some slow and intensive manual transformations in order to evaluate the result of GET “http://88.99.112.78/js/P8uph16W” (content in the following image). Certificate.js gets that data and evaluates it through the function: eval(“”+Cs+””)
Lateral Analysis: P8uph16W evaluated javascript
Once beautified it becomes easier to read:
Lateral Analysis: Fresh IoC on Dropper 2
Now, it’s obvious that it tries to: (i) download stat.exe from third party web sources, (ii) to rename the downloaded file using the Math.random().toString(36).substr(2, 9) + “.exe” and to (iii) launch it by using the var VTmBaOw = new ActiveXObject(“WScript.Shell”); This is super fun and interesting but I am getting far away from my original attack path.
So, let’s assume the downloaded file are the same (really they are not) and let’s get back to our original Stage 1 where a romantic .JS dropper downloads the “set.tmp” file and executes it (please refer to image Stage 1: Downloader).
The dropped file is: 00b42e2b18239585ed423e238705e501aa618dba which is actually evading SandBoxes and AntiVirus engines. It is a PE file which has been implemented in a valid .NET compiled source. Let’s call it Stage 2, since coming after the Stage 1 ;). Decompiling the “Second stage” some “ambiguous and oriental characters” appear as content in the “array” variable (please refer to the following code image).
Stage 2: Oriental Characters in array
By following those “interesting strings” (“interesting strings” by meaning to be faraway from the previous detected language) I landed on a “reflective function” which used a .NET Assembly.Load() to dynamically load the binary translation of the “array”-variable and an EntryPoin.Invoke() to dynamically run the binary. This is a well known .NET technique exploiting the .NET language ability to introspect its own runtime.
Stage 2: Assembly.Load and EntryPoint.Invoke
In order to get the dynamically generate binary “array”-variable I decided to patch the Sample code. The following picture shows how the .NET has been patched, in other words by simply forcing the control flow to saves the dynamically generated content on HD (the red breakpoint). In this specific case we are facing a third stage of infection composed by an additional PE file (Let’s have a look to HexEditor for the ‘MZ’ string). Let’s call it Stage 3.

Stage 3: Decrypted PE
In order to create the Stage 3, Stage 2 needed to decrypt the binary translation of “array” variable. Analysing the .NET code is not hard to figure out where Stage 2 decrypts the Stage 3. The Decryption loop has been implemented through a simple XOR-based encryption algorithm within a hardcoded key as shown in the following image.

Stage 2: decryption key
The decrypted new stage (named: Stage 3) happens to be an interpreted PE file as well! It is built over Microsoft VisualBasic technology (Do you remember the Lateral Analysis ??) and it’s hardly obfuscated (maybe from obf.txt ? … of course !). The following image shows the Third Stage structure.

Stage 3: Structure
The structure highlights three main modules as follows:
Anti Module. The aim of such a module is to implement various evasion techniques in order to weaponize the sample and block execution on VMs.
Service. The aim of such a module is to launch a background service.
RunPe. The aim of such a module is to launch an additional encrypted PE file placed in the resource folder.
Let’s try to investigate a little bit better what these modules do. The Anti Module tries to figure out if the analyzed sample lands on a controlled (emulated and/or simulated) environment in order to change its behaviour. The following images shows some of the performed checks. The sample tries to identify SanBoxie, fiddler and wireshark in order to dynamically change its own behaviour.

Stage 3: evasion checks
The service module tries to spawn a windows service and to disable many Windows features such as for example (but not limited to): EnableLUA, DisableCMD, DisableTaskMgr, etc… The following image shows some of the described actions.

Stage 3: Disabling Windows “Protections”
Finally the RunPE modules decrypts a further encrypted and embedded resource an tries to run it. The following images show the decryption loop following by the decrypted payload.

Stage 3: Decryption Loop
Stage 3: decrypted payload
On line 253 the Third Stage decrypts the resource and executes it. In the above picture you might appreciate the decrypted sequence: 0x4D, 0x5A, 0x90 which happens to be an additional windows PE. Let’s call it Stage: 4. The new stage appears to be a classic PE file written on C++, we’ll need a debugger to get into it. By analysing its dynamic behaviour (thanks to IDA Pro) it has been easy to catch the dropped files and to understand how that Sample uses them. The following image shows two dropped files (.nls and .bat) being saved on the HardDrive after the Stage 4 call.

Stage 4: dropping files (.nls and .bat)
The resulting .bat file tries to execute (through cmd.exe /c) %1 within the parameter %2 as shown in the next picture. If the file to be executed does not exist in HD it deletes the original file as well (itself).

Stage 4: file execution
%1 is an additional dropped PE File while %2 is a “random” value (key? unique id?).

Stage 4: Interesting “keys” passed to the .bat file.
Once the sample is run it performs external requests such the following ones, exfiltrating encrypted informations:
GET /htue503dt/images/uAsMyeumP3uQ/LlAgNzHCWo8/XespJetlxPFFIY/VWK7lnAXnqTCYVX_2BL6O/vcjvx6b8nqcXQKN3/J6ga_2FN2zw6Dv6/r5EUJoPCe
uwDIczvFL/kxAqCE1du/yzpHeaF3r0pY4KFUCyu0/jDoN_2BArkLgWaG/fFDxP.gif HTTP/1.1
POST /htue503dt/images/YtDKOb7fgj_2B10L/MN3zDY9V3IPW9vr/JSboSiHV4TAM_2BoCU/LocIRD_2B/MEDnB2QG_2Bf2dbtio8H/_2BLdLdN21RuRQj3xt2/SDWwjj
E2JeHnPcsubnBWMG/NJUCRhlTnTa9c/5Dzpqg92/AypuGS6etix2MQvl1C8/V.bmp HTTP/1.1
Conclusions:
Interesting to observe the sample complexity and how it is currently spread over Italian organisations. Interesting (at least on my personal point of view) how False flag attacks are developed in order to confuse the attack attribution (which is nowadays a huge technical issue) as well. Unfortunately nowadays through the information I have it is not possible to attribute that attack, the dropper has Russian strings on it, one of the payload has “oriental characters” on it, but again I am not able to say the attack is the result of a “joint venture” from Russia and China or it’s something hybrid or again it is borrowed or acquire from one to another, etc.. etc… For sure it’s not as it appears 😀 !
Index Of Compromise:
Following some of the most interesting Index Of Compromise.
http://88.99.112.78/
http://31.148.99.254/
http://mezzelune.com/arch/stat.exe
http://online.allscapelawnservices.com/arch/stat.exe
http://quotidianoannunci.it/arch/stat.exe
9b8251c21cf500dcb757f68b8dc4164ebbcbf6431282f0b0e114c415f8d84ad0
6456cd84f81b613e35b75ff47f4ccd4d83ec8634b5dcdf77f915fe7380106b28
5ab04878b630d1e0598fb6f74570f653a6bd0753dad9ef55ecf467bee7e618e1
4605dc8f1bc38075eacf526a1126636aa570fccbe78dca69781cc25edd1a1043
3fc092b52e6220713d2cb098c6d11a56575c241f
610df2672d7cae29e48118a27c4cb2a531e6399b
c304502aa7217399acc0162f41da00dc4add4105
magicians-blog.info
ozarkpatternconcrete.info
androidtutorials.info
executenet.pw
base.vuquoctrung.info/htue503dt
base.magicians-blog.info/htue503dt
base.ozarkpatternconcrete.info/htue503dt
base.androidtutorials.info/htue503dt
executenet.pw/htue503dt
Wikileaks revealed CIA Cherry Blossom framework for hacking Wireless devices
16.6.2017 securityaffairs BigBrothers
WikiLeaks released documents detailing the Cherry Blossom framework which is being used by the CIA cyber spies to hack into Wi-Fi devices.
WikiLeaks released a new batch of documents belonging to the Vault 7 leak, the files provide details related to the Cherry Blossom framework which is being used by the CIA cyber spies to hack into Wi-Fi devices.
The framework was developed by the CIA, along with experts at the Stanford Research Institute (SRI International), for hacking hundreds of home router models.
The Cherry Blossom framework was developed under the ‘Cherry Bomb’ project.
Cherry Blossom is a remotely controllable firmware-based implant for wireless networking devices, it could be used to compromise routers and wireless access points (APs) by triggering vulnerabilities to gain unauthorized access and load the custom Cherry Blossom firmware.
“The Cherry Blossom (CB) system provides a means of monitoring the internet
activity of and performing software exploits on targets of interest. In particular, CB is
focused on compromising wireless networking devices, such as wireless (802.11) routers
and access points (APs), to achieve these goals” states the user manual.
“An implanted device [called Flytrap] can then be used to monitor the internet activity of and deliver software exploits to targets of interest.” reads the CherryBlossom — Users Manual (CDRL-12).
“The wireless device itself is compromised by implanting a customized CherryBlossom firmware on it; some devices allow upgrading their firmware over a wireless link, so no physical access to the device is necessary for a successful infection,” WikiLeaks says.
The CherryBlossom is composed of four main components:
FlyTrap – beacon (compromised firmware) that runs on compromised device that communicates with the CherryTree C&C server.
CherryTree – C&C server that communicates with FlyTrap
CherryWeb – web-based admin panel running on CherryTree
Mission – a set of tasks sent by the C&C server to infected devices
CIA cyber spies use Cherry Blossom framework to compromise wireless networking devices on the targeted networks and then run man-in-the-middle attacks to eavesdrop and manipulate the Internet traffic of connected devices.
FlyTrap could perform the following malicious tasks:
Monitoring network traffic to gather data of interest such as email addresses, MAC addresses, VoIP numbers, and chat user names.
Hijack users to malicious websites.
Injecting malicious content into the data traffic to deliver malware.
Setting up VPN tunnels to access clients connected to Flytrap’s WLAN/LAN for further exploitation
According to the documents, the CherryTree C&C server must be located in a secure sponsored facility and deployed on Dell PowerEdge 1850 powered virtual servers, running Red Hat Fedora 9, with at least 4GB of RAM.
The documents include a list of more 200 router models that CherryBlossom can target, experts noticed that most of them are older models from various vendors, including Belkin, D-Link, Linksys, Aironet/Cisco, Apple AirPort Express, Allied Telesyn, Ambit, AMIT Inc, Accton, 3Com, Asustek Co, Breezecom, Cameo, Epigram, Gemtek, Global Sun, Hsing Tech, Orinoco, PLANET Technology, RPT Int, Senao, US Robotics and Z-Com.
For the full list of devices in included in a WikiLeaks document .

Below the list of release published by Wikileaks since March:
Cherry Blossom – 15 June, 2017
Pandemic – 1 June, 2017
Athena – 19 May, 2017
AfterMidnight – 12 May, 2017
Archimedes – 5 May, 2017
Scribbles – 28 April, 2017
Weeping Angel – 21 April, 2017
Hive – 14 April, 2017
Grasshopper – 7 April, 2017
Marble Framework – 31 March, 2017
Dark Matter – 23 March, 2017
První virtuální velvyslanectví bude v Lucembursku
16.6.2017 Novinky/Bezpečnost BigBrother
Estonsko se stane první zemí na světě, která soubor svých strategicky nejdůležitějších státních dokumentů uloží v elektronické podobě na bezpečném serveru v zahraničí. Oznámila to agentura Interfax. Virtuální velvyslanectví, jak Tallinn systém nazývá, bude umístěno v Lucembursku a bude mít všechny výsady skutečné diplomatické mise.
Podle estonské ministryně pro informační technologie Urve Palové budou lucemburské servery zajištěny mezinárodní imunitou a stanou se zárukou bezpečného uložení státních dokumentů pro případ jakýchkoli krizových situací.
Lucembursko bylo vybráno pro vysokou spolehlivost svých počítačových systémů, a také proto, že je dostatečně daleko od úložiště originálních dat. „Virtuální velvyslanectví bude mít naprosto stejné postavení, jako skutečné, reálné velvyslanectví Estonska v zahraničí," řekla novinářům Palová.
Premiéři Estonska a Lucemburska mají dohodu o digitálním úložišti podepsat příští úterý.
Bezpečnost internetového bankovnictví lidé podceňují, i když základní zásady znají
16.6.2017 Novinky/Bezpečnost Bezpečnost
Většina Čechů zná základní zásady, jak bezpečně využívat své internetové bankovnictví. Když ale dojde na uplatňování těchto zásad v praxi, jsou lidé liknaví. Používají jednoduchá hesla, mění je jen zřídka, a ještě větší mezery mají v zabezpečení svého mobilního telefonu. Vyplývá to z průzkumu ČSOB.
Tři čtvrtiny respondentů považují pravidelnou změnu hesla pro vstup do internetového bankovnictví za důležitou. Téměř 70 procent lidí neotevírá přílohy z e-mailů neznámých adresátů a přes 93 procent respondentů by nikomu prostřednictvím e-mailu neposkytlo důvěrné informace, jako je například číslo platební karty či heslo do internetového bankovnictví.
„To vše jsou pro nás velmi potěšující zjištění. Méně potěšující je, jak lidé tyto zásady dodržují v každodenním životě. Ukázalo se, že v mnoha případech upřednostňují pohodlí na úkor svého bezpečného pohybu na internetu,” uvedl člen představenstva ČSOB odpovědný za řízení rizik Tomáš Kořínek. Lidé si nepřipadají jako atraktivní terč pro hackera. To, že nemají na účtu milióny, ale podle něj neznamená, že jsou pro hackery nezajímaví.
Jednoduché heslo dává šanci hackerům
Podle 70 procent respondentů by se mělo heslo pro vstup do internetového bankovnictví měnit jednou nebo dvakrát za rok. Více než polovina dotázaných si svá hesla a PIN poznamenává na papír, který někteří nosí dokonce přímo v peněžence spolu s platební kartou. Ve věkové kategorii 55 až 85 let si hesla zapisují dokonce čtyři pětiny dotázaných. Lidé také často používají u různých služeb stejná nebo podobná hesla.
Jednoduché heslo dává hackerům zbytečně velkou šanci. Přitom se stačí jednou za čas pořádně zamyslet a vytvořit si silné heslo, které hackerovi vůbec nebude stát za to, aby se ho snažil prolomit, upozornil manažer bezpečnosti elektronických kanálů ČSOB Petr Vosála.
Falešné internetové bankovnictví
Jak ukázal nedávný experiment ČSOB s falešnou stránkou elektronického bankovnictví, klienti také často chybují v tom, že internetové bankovnictví navštěvují přes vyhledávače. Zde si pak v mnoha případech spletou falešný web se skutečnou stránkou internetového bankovnictví. V rámci této kampaně kliklo na falešný odkaz za měsíc více než 61 000 lidí, třetina z nich dokonce opakovaně.
Dalšímu riziku se lidé vystavují tím, že se k internetovému bankovnictví hlásí prostřednictvím nezabezpečené sítě. „Můžu mít zabezpečený počítač nejlepším antivirem, ale když se připojím k nezabezpečené Wi-Fi v kavárně nebo fastfoodu, je mi to k ničemu,” doplnil Vosála.
Millions of Devices Remain Exposed via SMB, Telnet Ports: Rapid7
16.6.2017 securityweek Safety
Despite being exploited in wide-spread malicious attacks, SMB, telnet, RDP, and other types of improperly exposed ports continue to put both enterprises and consumers at risk, a new Rapid7 report reveals.
Focused on providing an overview of the regional exposure to help Internet service providers (ISPs) worldwide address existing issues, Rapid7’s second National Exposure Index report (PDF) provides information on improperly exposed services and ports rendering systems and user data vulnerable to attacks. It includes data gathered through scanning the web for exposed services, including encrypted and unencrypted protocols, or those meant for public use.
Two of the improperly secured services that continue to make computers vulnerable to attacks are Server Message Block (SMB) and telnet. The former was recently associated with the massive WannaCry outbreak that hit over 160 countries, while the latter has been exploited by Internet of Things botnets such as Mirai, Persirai, or Hajime.
Apparently, there are 5.5 million machines with SMB port exposed, up from 4.7 million prior to May 2017, when WannaCry emerged. The ransomware managed to spread fast via a worm component leveraging the SMB-targeting EternalBlue exploit. Of the total endpoints exposing Microsoft file-sharing services (SMB, TCP port 445), 800,000 of them are confirmed Windows systems, Rapid7 says.
According to Shodan founder John Matherly, over 2 million machines with SMB appear in the device search engine, and most of them (90%) run SMB version 1. He also notes that, while Windows devices running SMB should have been already patched, given that Microsoft released security updates even for unsupported platform iterations, tens of thousands continue to be vulnerable.
Things aren’t better when it comes to devices with exposed telnet (port 23), as there are just under 10 million such devices out there at the moment. Granted, this is a great improvement when compared to the 14.8 million exposed devices discovered last year, but it also means that millions of devices can still fall victim to malware such as distributed denial of service (DDoS) botnets.
The 33% drop seen in the number of exposed telnet nodes is the result of two developments, Rapid7 says. On the one hand, ISPs might have taken stance and started closing port 23 following botnet attacks, while on the other hand the botnets themselves are taking nodes offline to protect themselves from rivals (except BrickerBot, which is only focused on rendering devices unusable).
However, there are other inappropriate services exposed to the Internet as well, including FTP (port 21), RDP (port 3389), PPTP (port 1723), rpcbind (port 111), MySQL (port 3306), and others more. Overall, Rapid7’s scan for these inappropriate services revealed over 90 million nodes.
The company’s report also reveals that Zimbabwe, Hong Kong SAR, Samoa, Republic of the Congo, Tajikistan, Romania, Ireland, Lithuania, Australia, and Estonia are the most exposed countries. When it comes to major cyber superpowers, China and the Russian Federation are among the top 50 most exposed nations, while the United States has “a relatively low exposure in relation to its enormous IPv4 address space.”
Rapid7 chose 30 service ports to scan for their report, but also had a look at two “canary” TCP ports, port 5 and port 61439, which have no well-known service associated with them, thus being unlikely to ever respond to port scanning. However, the company picked up responses from 3.2 million devices from these two ports, and discovered that over 2.3 million IPs (located in 133 countries) responded to both probes.
The report also points out that there are a series of services that have been specifically designed for public use, thus are expected to be exposed to the Internet, although some of them aren’t encrypted, such as HTTP. Many of these, however, are encrypted-by-default, including HTTPS, SSH, IMAPS, POP3S, SMTPS, and FTPS.
The good news, Rapid7 says, is that 3% more nodes are running fewer services compared to last year, partly because of a decrease in telnet exposure. However, the company also believes that “individuals and organizations are beginning to be more careful about what they expose to the world.”
“Server ransomware, ransomworm propagation, insecure Internet of Things, and dozens more headlines reminded us, almost monthly, that the internet is, indeed, a fragile ecosystem that needs deliberate care and attention. Being mindful of both what your organization deploys and how those services are deployed and maintained can have a significant impact on the health of the entire internet,” the company concludes.
U.K. Center of Security Excellence Hit by Ransomware
16.6.2017 securityweek Ransomware
One of the world's top ten universities, awarded the status of "centre of excellence in cyber-security research" by the UK's GCHQ, has been hit by a so-far unrecognized strain of ransomware. This comes just one month after many UK health trusts were struck by the global WannaCry ransomware.
In a statement originally issued yesterday and updated today, University College London (UCL) described the current and ongoing ransomware. "We are continuing to investigate the infection that is affecting UCL users. Our current hypothesis is that the malware infection occurred through users visiting a website that had been compromised rather than being spread via email attachments. However, this remains unconfirmed at the moment."
UCL believes it has now contained the outbreak by isolating the infected storage/devices, and does not expect any further infections. Twelve users had their local or shared drives infected and encrypted.
We believe, says UCL, "that the infection started as a result of UCL users visiting a website that had been compromised. Clicking on a popup or even just visiting a compromised site may have then introduced the malware to their device. The website could be one that they use regularly. We are still trying to confirm this and determine the site that may have caused the infection."
For now, UCL cannot confirm the type of ransomware that was used; but it seems to be Windows only. Its anti-virus defenses were, it says, up-to-date.
For now, UCL's comments ask as many questions as they answer. While there is no 100% secure defense against phishing (it will always catch someone), was this one person tricked and 12 users affected by the ransomware spreading through local shares; or twelve people tricked?
Or was there no phishing attack? Could this have been a watering hole attack -- hinted at by UCL's comment that the poisoned website could be one used regularly. Either way, was the user, or users, operating unpatched software? If the delivering exploit were a zero-day exploit, it wouldn't matter; but there is no immediate news of any widespread use of a zero-day elsewhere -- and it is unlikely that a criminal actor would waste a zero-day on a single UK university.
It is possible, then that this ransomware managed to get into UCL by just one user operating an unpatched browser. But whatever the infection vector, it seems that existing anti-malware failed to detect and stop it. "Clearly, we are seeing again that the old guard of AV isn't able to deal with evolving threats, even the obvious ransomware," comments Tony Rowan, security consultant at SentinelOne. "For each case of ransomware, we have to ask ourselves how many silent attacks are going unnoticed?"
Andrew Stuart, MD at Datto takes a similar view that AV alone is not enough against modern malware. "What this attack highlights," he claims, "is that anti-virus alone is simply not sufficient enough to prevent ransomware. Along with vulnerability patching, these AV tools might be capable of catching known strains of malware, but newer ones too often pass through defenses undetected." His own view is that regular back-up snapshots are the best solution. "If companies take regular snapshots of their systems, they are able to quickly spin-up systems to a 'healthy' point before the ransomware took hold."
Jason Allaway, VP at RES, sees the solution -- at least partly -- in education. "Everyone involved in a university needs to be prepared, as after all, lecturers and other staff members are just as weak a link in the security chain if they don't know what to look for. Organizations should provide informative materials and classes on the techniques of hackers, such as phishing emails, how to spot these and how to counter-act them."
Mike Viscuso, CTO at Carbon Black, agrees on all counts. "Organizations can better set themselves up to deal with ransomware attacks by consistently backing up critical files, educating employees on proper cybersecurity hygiene, and patching vulnerabilities in a timely manner. The fact this attack on UCL appears to have circumvented AV filters shows the inadequacy traditional AV protection provides."
Steven Malone, director of security product management at Mimecast, believes that UCL's problem is typical of organizations that do not sufficiently consider email as an attack vector. "UCL appears to be running 'naked' Office 365 for its email security gateway. This is case in point for why all organizations need to ask if they are happy to trade defense-in-depth strategies for single vendor reliance when moving to the cloud...
"The vast majority of ransomware attacks are spread by email yet many organizations have still not put any additional security controls in place. Real-time checks on links and converting all incoming attachments to safe formats seriously reduces the risk of infection."
The reality, however, is that we do not yet have enough information to know what went wrong, where or why. It is worth remembering that in a campus of almost 50,000 staff and students, UCL contained this outbreak to just 12 users.
Wikileaks Unveils 'Cherry Blossom' — CIA's Wireless Router Hacking Framework
15.6.2017 thehackernews BigBrothers
WikiLeaks has published a new batch of the ongoing Vault 7 leak, this time detailing a framework – which is being used by the CIA for monitoring the Internet activity of the targeted systems by exploiting vulnerabilities in Wi-Fi devices.
Dubbed "Cherry Blossom," the framework was allegedly designed by the Central Intelligence Agency (CIA) with the help of Stanford Research Institute (SRI International), an American nonprofit research institute, as part of its ‘Cherry Bomb’ project.
Cherry Blossom project focuses on developing implanted firmware for wireless networking devices, including routers and wireless access points (APs).
It exploits router vulnerabilities to gain unauthorized access to the targeted wireless devices and then replace its firmware with an implant called Flytrap.
"An implanted device [called Flytrap] can then be used to monitor the internet activity of and deliver software exploits to targets of interest." a leaked CIA manual reads.
"The wireless device itself is compromised by implanting a customized CherryBlossom firmware on it; some devices allow upgrading their firmware over a wireless link, so no physical access to the device is necessary for a successful infection," WikiLeaks says.
According to Wikileaks, CIA hackers use Cherry Blossom hacking tool to hijack wireless networking devices on the targeted networks, such as wireless routers and access points (APs) and then perform man-in-the-middle attacks to monitor or manipulate the Internet traffic of the connected users.
Once it takes full control on the wireless device, 'Flytrap' reports back to its command and control server referred to as 'CherryTree,' from where it receives instructions and accordingly perform malicious tasks, which include:
Monitoring network traffic to collect email addresses, chat user names, MAC addresses, and VoIP numbers
Redirecting connected users to malicious websites
Injecting malicious content into the data stream to fraudulently deliver malware and compromise the connected systems
Setting up VPN tunnels to access clients connected to Flytrap's WLAN/LAN for further exploitation
Copying of the full network traffic of a targeted device
According to an installation guide, the CherryTree C&C server must be located in a secure facility and installed on Dell PowerEdge 1850 powered virtual servers, running Red Hat Fedora 9, with at least 4GB of RAM.
CIA Can Hack Wi-Fi Devices From Wide-Range Of Vendors
Cherry Blossom can exploit vulnerabilities in hundreds of Wi-Fi devices (full list here) manufactured by the following vendors:
Belkin, D-Link, Linksys, Aironet/Cisco, Apple AirPort Express, Allied Telesyn, Ambit, AMIT Inc, Accton, 3Com, Asustek Co, Breezecom, Cameo, Epigram, Gemtek, Global Sun, Hsing Tech, Orinoco, PLANET Technology, RPT Int, Senao, US Robotics and Z-Com.
Previous Vault 7 CIA Leaks
Last week, WikiLeaks dumped an alleged CIA project, dubbed Pandemic, that allowed the agency to turn Windows file servers into covert attack machines that can silently infect other computers of interest inside a targeted network.
The tool is a persistent implant for Microsoft Windows machines that has been designed to infect networks of Windows computers through the Server Message Block (SMB) file sharing protocol by replacing application code on-the-fly with a trojanized version of the software.
Since March, the whistleblowing group has published 11 batches of "Vault 7" series, which includes the latest and last week leaks, along with the following batches:
Athena – a CIA's spyware framework that has been designed to take full control over the infected Windows PCs remotely, and works against every version of Microsoft's Windows operating systems, from Windows XP to Windows 10.
AfterMidnight and Assassin – two apparent CIA malware frameworks for the Microsoft Windows platform that has been designed to monitor and report back actions on the infected remote host computer and execute malicious actions.
Archimedes – a man-in-the-middle (MitM) attack tool allegedly created by the CIA to target computers inside a Local Area Network (LAN).
Scribbles – a piece of software allegedly designed to embed 'web beacons' into confidential documents, allowing the spying agency to track insiders and whistleblowers.
Grasshopper – reveal a framework which allowed the agency to easily create custom malware for breaking into Microsoft's Windows and bypassing antivirus protection.
Marble – revealed the source code of a secret anti-forensic framework, basically an obfuscator or a packer used by the CIA to hide the actual source of its malware.
Dark Matter – focused on hacking exploits the agency designed to target iPhones and Macs.
Weeping Angel – spying tool used by the agency to infiltrate smart TV's, transforming them into covert microphones.
Year Zero – dumped CIA hacking exploits for popular hardware and software.
High Severity Flaws Patched in Trihedral SCADA Software
15.6.2017 securityweek Vulnerebility
An update released by Trihedral for its VTScada product patches several vulnerabilities, including high severity weaknesses that can be exploited even by less skilled hackers.
VTScada, Trihedral’s flagship product, is a software suite designed for creating human-machine interfaces (HMI) for supervisory control and data acquisition (SCADA) systems. The product is used in various industries, mainly in North America and Europe.
Security researcher Karn Ganeshen discovered several vulnerabilities affecting VTScada versions prior to 11.2.26. The expert told SecurityWeek that a Shodan search showed a few systems running VTScada accessible from the Internet, but he believes there are more vulnerable instances that are exposed to attacks.
One of the flaws, tracked as CVE-2017-6043 and assigned a CVSS score of 7.5, is a denial-of-service (DoS) issue that exists due to the VTScada client’s failure to limit resource usage.
In an advisory published on his website, Ganeshen said an attacker with a non-privileged account can cause excessive CPU and RAM usage by submitting a large payload (up to roughly 80,000 characters) in the username field of the login window.
“Where a full-blown application (or multiple applications in production scenario) is deployed, i.e. with an operational/functional configuration, memory/CPU usage is notably higher than that of a test, blank application,” the expert said. “Repeatedly submitting such a large username input rapidly consumes available server memory resources leading to resource exhaustion. This forces a system reboot eventually.”
Another high severity flaw found by the researcher in VTScada is CVE-2017-6045, an information disclosure issue that exposes potentially sensitive configuration data to unauthenticated attackers.
Ganeshen also informed Trihedral of several cross-site scripting (XSS) vulnerabilities that can be exploited to execute arbitrary JavaScript code in the targeted user’s browser. These security holes are considered medium severity and they are tracked as CVE-2017-6053.
The flaws have been addressed by Trihedral with the release of VTScada 11.2.26. The researcher has confirmed that the resource exhaustion vulnerability has been properly patched.
In a brief statement published on Wednesday on its website, Trihedral pointed out that the vulnerabilities only affect “systems with unsecured internet connections with VTScada internet access enabled.” The company has advised customers to secure their connection and update the product to the latest version.
Ganeshen told SecurityWeek that he submitted two other VTScada vulnerability reports, which should soon be published by ICS-CERT.
Thailand: police raided massive click farms with more 500k SIM cards
15.6.2017 securityaffairs Crime
Thailand: Police raided massive click farms, the agents have seized nearly half a million SIM cards and hundreds of iPhones used to promote products online.
Police and army troops in Thailand has raided a massive click-fraud farm, the agents have seized nearly half a million SIM cards and hundreds of iPhones used to promote products online.
The authorities have raided to rented houses in Ban Mai Nong Sai in the Aranyaprathet District arresting three Chinese people, Wang Dong, 33, Niu Bang, 25, and Ni Wenjin, 32.
Tha amount of goods seized by the police is amazing, troop seized 474 5s, 5c and 4s iPhones and 347,200 SIM cards, as well as many electronic devices and computers.
The information obtained in the first raid allowed investigators to make a second raid that resulted in the seizure of another 100,000 SIM cards in a local house.

In the first home, the police found 112,200 SIM cards from Advanced Info Service, 131,000 from True Move and 104,000 from Total Access Communication (DTAC) telco companies.
“Police are investigating how almost half a million unused Thai SIM cards got into the hands of three Chinese people allegedly operating in Thailand the business of generating fake page views and engagement online” states the Bangkokpost. “Police found about 100,000 SIM cards, many computers and other electronic equipment at a shophouse in Ratchata Withi Road in Muang Aranyaprathet district of Sa Kaeo Monday afternoon. They searched the place following the statement of the three men arrested in the northeastern province on Sunday, allegedly for operating an illicit business.”
According to Benjaphol Rodsawasdi, immigration chief of Sa Kaeo, the three suspects admitted they were being paid 150,000 baht (US$4,423/£3,473) a month by a company in China to promote products in the Middle Kingdom, they didn’t reveal the name of the business.
They were tasked to ramp up sellers’ online ratings by giving them positive feedback on product listings. With this technique, they were able to increase the reputation of the sellers and gear up search result rankings, with a significant effect on the sales.
The suspects were hired to spam the Chinese social media platform WeChat with bogus page views, ratings, likes and shares.
The choice of the Thailand is not casual, over there mobile charges are very low compared to other countries, including China.
It is still unclear how the men have obtained a so large number of SIM cards without raising suspicion of telco companies.
The authorities are still investigating searching for other click farms established in the country.
The suspects were charged with working illegally Thailand and illegitimately importing the electronic devices.
Similar techniques are also used by threat actors in the wild to pump out fake news in disinformation campaigns.
Threat Hunting Sqrrl Raises $12.3 Million for Global Expansion
15.6.2017 securityweek Security
Cambridge, Mass-based Sqrrl -- one of the new breed of threat hunters -- has raised $12.3 million in Series C funding. This follows $7 million Series B funding in February 2015, and raises the total investment in the firm to $28.5 million.
Announced this week, the latest investment is led by Boston-based Spring Lake Equity Partners, which will now take a seat on Sqrrl's board. Existing investors Matrix Partners, Rally Ventures and Accomplice also took part. It follows Sqrrl's impressive growth rate of doubling revenue every year for the last four years. The new money will be used to expand Sqrrl's marketing reach, and this is expected to include expansion into Europe.
Sqrrl LogoThe company currently employs about 50 people, mostly in Cambridge. It hopes to expand to about 75 worldwide employees before the end of the year.
"Spring Lake invests in companies with technology platforms that have both a proven track record of customer success and high growth potential," said Jeff Williams, Spring Lake Partner. "Sqrrl's Threat Hunting Platform is enabling Fortune 2000 companies and government agencies to detect and investigate threats that have evaded detection. We are very impressed with their pioneering technology and their leading position in the rapidly growing threat hunting market space."
Threat hunting is considered de rigueur for today's SOCs. Traditional defenses are failing to stop advanced attackers -- who, by definition, are difficult to detect. Threat hunting systems don't wait for the inevitable breach but actively seek out the hidden and subtle indications of an attacker's presence. Threat hunting brings advanced analytics and queries to network data, and is part of the rapidly-evolving machine-learning security revolution.
"Threat hunting has become a top-level initiative in organizations with modern security operations, and those organizations have realized the significant advantages that threat hunting offers to reduce their overall security risk." explains Sqrrl CEO Mark Terenzoni. "Sqrrl makes it feasible for any organization to start threat hunting, and we are excited to use this funding to enable even more organizations to move their security operations from a reactive to proactive security posture."
Sqrrl was formed in 2012, evolving from an NSA database project known as Accumulo. Accumulo was open-sourced in 2011 and became Apache Accumulo. Six of the seven original members of the Sqrrl had worked for the NSA. Sqrrl's platform is built on top of Accumulo.
Hundreds of Fake Android Antivirus Apps Deliver Malware
15.6.2017 securityweek Android
There are thousands of Android applications containing the label “antivirus,” but a big chunk of them are dangerous programs designed to infect devices of unsuspecting users with malware, RiskIQ warns.
After the WannaCry ransomware outbreak last month, numerous fake programs claiming to keep Android users safe from the threat began to emerge, despite the fact that Android wasn’t targeted by the malware. RiskIQ decided to have a closer look at the many antivirus apps for Android and discovered that these fake apps aren’t limited to the WannaCry theme.
What’s more, the security company discovered, was that while some of the programs are worthless, others are straight up malicious, being designed to spread adware, Trojans, and other type of malware, instead of protecting users from such threats.
According to RiskIQ, there are 6,295 total Android apps, past and present, claiming to either be an antivirus solution, review antivirus solutions or be associated with antivirus software in some way. RiskIQ discovered that 707 of the apps triggered blacklist detections in VirusTotal. 655 of these “antivirus” apps are in Google Play, and 131 of them triggered blacklist detections.
Furthermore, 4,292 of these apps are active today, including 525 of those that triggered blacklist detections in VirusTotal. 508 of the apps are in Google Play, yet only 55 of them triggered blacklist detections.
Overall, while 11% of total antivirus apps lived in the Google Play store, only 12.2% of active antivirus apps are available through the portal. However, 20% of total blacklisted antivirus apps live in the store, although only 10.8% of the active blacklisted antivirus apps are present there, RiskIQ found.
RiskIQ also points out that, while not all of the blacklist hits from VirusTotal point to malicious applications, there are many malicious antivirus apps that are not blacklisted at all. However, as soon as one application is flagged by a well-known vendor, or by more of them, it may be worth further review.
“When it comes to the safety of your mobile devices, it is always best to be diligent. Be careful about inviting the bad guys in and giving them access to everything when choosing an antivirus app,” RiskIQ’s Forrest Gueterman notes.
To stay protected, users should pay close attention when choosing a mobile antivirus solution, and should download such apps only from official stores, as they tend to remove malicious apps faster than unofficial portals.
Reviewing the permissions requested by these apps is also very important, and users are also advised to have a close look at the developer email address (to avoid those using a free email service like Gmail or Hotmail) and at the app description (it could point to a fake app if riddled with grammatical errors). Checking the app against known blacklists can also keep devices protected.
'Kasperagent' Spyware Delivered via Palestine-Themed Documents
15.6.2017 securityweek Virus
Researchers spotted a new cyber espionage campaign involving Kasperagent, and while it’s unclear who the target was, the decoy documents used to deliver the malware focused on Palestine.
The first report describing this threat group’s activities was published in March by Chinese security firm Qihoo 360, which tracks the actor as APT-C-23 and Two-Tailed Scorpion. In early April, Palo Alto Networks and ClearSky also made public the results of a joint investigation into this group.
The group uses Windows malware dubbed Kasperagent and Micropsia, and Android malware called SecureUpdate and Vamp in attacks aimed mainly at Palestine. Some infections have also been observed in Israel, Egypt and the United States.
Researchers at threat intelligence firm ThreatConnect recently came across tens of Kasperagent samples that had been compiled in April and May.
These samples dropped various decoy documents associated with the Palestinian Authority, the governing body of the emerging Palestinian autonomous regions of the West Bank and Gaza Strip. The documents referenced subjects such as the assassination of Hamas military leader Mazen Fuqaha, and banning of the Palestinian political party Fatah from Gaza.
Kasperagent has mainly been used as a reconnaissance tool and downloader, but some newer samples include additional capabilities that allow attackers to steal passwords from browsers, take screenshots, log keystrokes, execute arbitrary commands, and exfiltrate files.
While the malware samples found by ThreatConnect were similar to ones analyzed by Palo Alto Networks and ClearSky a few months ago, the command and control (C&C) server they contacted was different.
An analysis of the C&C infrastructure showed that the domain contacted by the malware was hosted on an IP address that stored four domains, including two registered by a freelance web developer from Gaza.
“Just like we can’t make a definitive determination as to who conducted this campaign, we do not know for sure who it was intended to target. What we do know is that several of the malicious files were submitted to a public malware analysis site from the Palestinian Territories. This tells us that it is possible either the threat actors or at least one of the targets is located in that area,” ThreatConnect said in a blog post.
Experts believe the attack may have been aimed at Hamas, Israel or the Fatah party, whose members include the prime minister and president of the Palestinian Authority.
The attacks were carried out shortly after Hamas created a parallel institution to run local ministries in Gaza, which caused further tension between Hamas and the Palestinian Authority, and just before the Palestinian Authority held elections in the West Bank.
Fake News: Methods, Motivations and Countermeasures
15.6.2017 securityweek Cyber
Fake news is not new -- it is probably as old as humanity. It has long been rife in politics (manifestos announced but never kept), and commerce ("marketing is no longer about the stuff you make, but the stories you tell" -- Seth Godin, marketer). But most of all, it is rife and active on the internet following the US presidential campaign last year and the new administration this year.
Security firm Trend Micro has been considering how the internet fake news market operates, and finds that it is remarkably organized and effective: The Fake News Machine: How Propagandists Abuse the Internet and Manipulate the Public (PDF). For effective fake news via the internet, it finds that campaigns need three elements which it terms the Fake News Triangle: motivation; tools and services; and social networks.
The tools and services are available on the underground internet. Often, for a fee, these services generate the fake news itself as well as promote it via social media.
The social networks are used to spread the fire of fake news, using social engineering techniques: "the fake news posts are crafted to appeal to its readers' psychological desires," says the report; "confirming biases, the hierarchy of needs, etc."
Today, the most common motivation is political; but, warns Trend, "It is inevitable that other motivations -- such as profit -- will come to the forefront in later years."
Means
Today, fake news promoters can choose between underground tools and legitimate gray-area promotional tools. State-sponsored campaigns may choose to use their own resources; but market tools offer an additional layer of anonymity.
The Chinese fake news underground largely caters for its own market. It includes the generation and placement of advertorials disguised as news stories, large-scale commenting on news and blog sites, vote manipulation and click farms, and the use of social media to influence public opinion. It also offers the opposite -- the removal of content. Methods are known to include bribing website administrators and actual hacking and deletion.
The Russian marketplace, says Trend, "can be likened to a onestop shop for creating, promoting, and manipulating stories and events, news, and profiles -- real or imagined -- that favor the clientele's motive."
One feature of the Russian market is the use of crowdsourcing. VTope, for example, with 2,000,000 mostly real members, implements tasks that "incentivizes users with points, which they can resell or use for self-promotion." Other organizations, including SMOFast, Kwoki, like4u, TopSoc, and ZiSMO, offer similar or variations on this service.
Voter manipulation to influence public opinion is also available. "Siguldin," says the report, "markets itself to be capable of manipulating almost any voting system in the Internet and bypassing security checks such as source IP address, Captcha, and authentication mechanisms in social media, SMS, and email as well as on-site registration among others."
Such offerings are not the only option -- there are also DIY kits for automated social media spamming, which become particularly effective when used with a botnet.
The Middle East market, suggests Trend, is new but growing -- especially in generating social media followers. Interestingly, CoulSouk will promote content for a fee, but prohibits the promotion of racist, pornographic, and illegal content. Dr.Followers is a similar service provider.
The English-speaking world hosts numerous services designed to increase followers or YouTube viewers. These include BeSoEasy, Quick Follow Now, and 100kfollowers. Other sites, such as Break Your Own News and ClassTool's Breaking News Generator, allow users to generate their own fake news. "While these types of websites are only meant for personal recreation and must be taken with a grain of salt," comments Trend, "when combined with these underground services, they can be very effective in manipulating a story and leading the public into believing it's actually authentic."
Methods
The key to getting fake news accepted is in the headline. Modern society is an instant-gratification society -- and this applies to news consumption as much as anything else. More people read headlines than the actual article; and Twitter comments show that many people believe they know the content based on just 140 characters in a tweet. In fake news, that headline or tweet is designed to be attention-grabbing and something that reinforces extreme views.
"In the realm of political opinion manipulation," explains Trend, "this tends to be in the form of highly partisan content. Political fake news tends to align with the extremes of the political spectrum; "moderate" fake news does not really exist."
Spreading fake news is largely achieved by Twitter and Facebook. One Twitter method is to use Twitter bots to saturate Twitter searches with relevant and timely keywords plus a link to the fake news site. Alternatively, the Twitter bots might generate the same message, but mention different users and/or include the hashtags of unrelated but trending topics to increase their reach.
The intent is similar, but the method slightly different on Facebook. Facebook's algorithm is likely to promote news stories that receive large numbers of likes. Here the social engineering capability of a dramatic or tantalizing headline with a brief text expansion seeks the combined effect of garnering likes and sending readers to the fake news site.
A completely different method is the tampered data leak. "Let us suppose," postulates Trend, "a leak occurs and 99% of the documents are legitimate, but 1% was tampered to help the leaker's agenda. The victim organization will have a hard time proving that any tampering did occur, let alone which documents were modified. The very fact that a leak occurred also undermines the target's security and credibility." It is believed that just such an event occurred with the Fancy Bear hack and data leak of the World Anti-Doping Agency (WADA) in 2016.
Motivations
Trend Micro sees three current major motivations behind fake news: political, financial gain, and character assassination. Political propaganda is designed to get people to change their mind about their political beliefs or some other opinion. Fake news has a similar intent, but will use falsehoods to manipulate public opinion faster and across a wider audience. Rather than delivering arguments to persuade people to turn towards a new belief, it can use false events to turn people away from an existing belief.
The most obvious financial motivation could be advertising. Social media manipulation can be -- and already is -- used to drive traffic to a particular site, in what is already called clickbait. However, Trend also see a danger of using fake news to manipulate share prices. There are already many examples of how tweets have affected shares -- most notably, perhaps, in 2013 when the Syrian Electronic Army hacked the Associated Press Twitter account and claimed that Obama had been injured by a bomb at the White House. Stock markets plunged instantly.
"It's no big stretch of the imagination," claims Trend, "to think that fake news could be used to influence stock prices. This is particularly true for stocks with low prices and those that are infrequently traded, which makes their price easier to manipulate. For more established companies, a campaign could lower the image and reputation of a target company, affecting their earnings and stock price."
Character assassination by fake news could have many targets. The most obvious one is the politician. But private individuals are also at risk. For example, Mexican journalists are routinely harassed by Twitter bots under the control of drug cartels. In one recent example, a 'death threat' was delivered by promoting the fake news that a particular journalist had died in the recent Manchester terror attack.
Trend Micro's research describes and costs several potential fake news campaigns. These include: create a celebrity with 300,000 followers in just a month, $2,600; help instigate a street protest, $200,000; discredit a journalist, $55,000; and manipulate a decisive course of action, $400,000.
Countermeasures
Trend sees three approaches to countering the growing problem of fake news: legal, action from the social networking services, and increased reader awareness. In Germany, a new bill seeks to curb the spread of fake news and threatens to fine social networks as much as EUR 50 million where they fail to comply with rules.
"Google," comments Trend, "rolled out a feature where fact check can be tagged on the blurbs or snippets of news articles posted on its News search page. It is one of Google's many strategies for ridding its services of fake content -- including rewriting the algorithm of its search engine." Meanwhile, Facebook has suspended 30,000 fake news sites in France; and Twitter regularly shuts down abusive and bot accounts.
The ultimate arbiter, however, has to be the reader. "In a post-truth era where news is easy to manufacture but challenging to verify," says Trend, "it's essentially up to the users to better discern the veracity of the stories they read and prevent fake news from further proliferating."
Hundreds of Fake Android Antivirus Apps Deliver Malware
15.6.2017 securityweek Android
There are thousands of Android applications containing the label “antivirus,” but a big chunk of them are dangerous programs designed to infect devices of unsuspecting users with malware, RiskIQ warns.
After the WannaCry ransomware outbreak last month, numerous fake programs claiming to keep Android users safe from the threat began to emerge, despite the fact that Android wasn’t targeted by the malware. RiskIQ decided to have a closer look at the many antivirus apps for Android and discovered that these fake apps aren’t limited to the WannaCry theme.
What’s more, the security company discovered, was that while some of the programs are worthless, others are straight up malicious, being designed to spread adware, Trojans, and other type of malware, instead of protecting users from such threats.
According to RiskIQ, there are 6,295 total Android apps, past and present, claiming to either be an antivirus solution, review antivirus solutions or be associated with antivirus software in some way. RiskIQ discovered that 707 of the apps triggered blacklist detections in VirusTotal. 655 of these “antivirus” apps are in Google Play, and 131 of them triggered blacklist detections.
Furthermore, 4,292 of these apps are active today, including 525 of those that triggered blacklist detections in VirusTotal. 508 of the apps are in Google Play, yet only 55 of them triggered blacklist detections.
Overall, while 11% of total antivirus apps lived in the Google Play store, only 12.2% of active antivirus apps are available through the portal. However, 20% of total blacklisted antivirus apps live in the store, although only 10.8% of the active blacklisted antivirus apps are present there, RiskIQ found.
RiskIQ also points out that, while not all of the blacklist hits from VirusTotal point to malicious applications, there are many malicious antivirus apps that are not blacklisted at all. However, as soon as one application is flagged by a well-known vendor, or by more of them, it may be worth further review.
“When it comes to the safety of your mobile devices, it is always best to be diligent. Be careful about inviting the bad guys in and giving them access to everything when choosing an antivirus app,” RiskIQ’s Forrest Gueterman notes.
To stay protected, users should pay close attention when choosing a mobile antivirus solution, and should download such apps only from official stores, as they tend to remove malicious apps faster than unofficial portals.
Reviewing the permissions requested by these apps is also very important, and users are also advised to have a close look at the developer email address (to avoid those using a free email service like Gmail or Hotmail) and at the app description (it could point to a fake app if riddled with grammatical errors). Checking the app against known blacklists can also keep devices protected.
Centrify Launches Bug Bounty Program
15.6.2017 securityweek Safety
Centrify, a Santa Clara, Calif.-based provider of identity and access management (IAM) solutions, has teamed up with Bugcrowd for a public bug bounty program that offers researchers up to $3,000 per vulnerability.
Centrify has been running a private bug bounty program for the past two years, but it has now decided to allow all the 50,000 hackers on the Bugcrowd platform to find and report vulnerabilities.
The program covers the company’s main website, centrify.com, and its Identity Service and Privilege Service products.
The products are built on a cloud platform for which bug bounty hunters will have to register their own tenants for testing. The focus areas include web applications and the underlying REST API, and clients and installable agents.
Centrify said only its centrify.com website is in scope and bounty hunters have been instructed to focus on vulnerabilities exploitable in current web browsers and user authentication flaws. Subdomains or related hosts are not covered, but centrify.force.com/partners, centrify.force.com/support and partners.centrify.com can be tested for privilege escalation.
Researchers can earn the top rewards – $3,000 for flaws in the Identity and Privilege products and $1,500 for flaws in the corporate website – if they find vulnerabilities that have a P1 priority rating. This includes critical server misconfigurations, server-side injections, broken authentication and session management, sensitive data exposure, and cryptographic issues.
The least serious vulnerabilities affecting Centrify products can earn researchers $200, or $100 if they affect the company’s website.
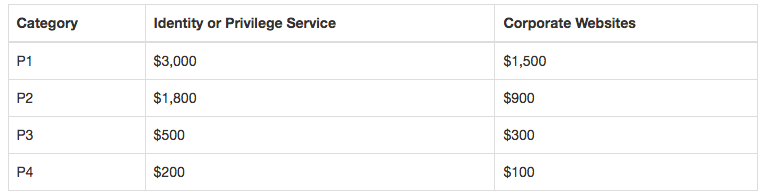
“As a leader in identity services, it is incumbent upon us to fully vet the security on our platform to ensure that each user’s access to apps and infrastructure is secure and that we continue to deliver the best solutions,” said Raun Nohavitza, Senior Director of IT at Centrify. “Bugcrowd’s platform, organization, experience with triage and relationship with the security community make their bounty program very attractive. With Bugcrowd we’re not only doing the right thing for our security offerings in the best way possible, but we’re also getting consistent administration and management for our ongoing program.”
Most SharePoint Installations Vulnerable to XSS Attacks
15.6.2017 securityweek Attack
One of the vulnerabilities patched by Microsoft this week with its monthly security updates is a potentially serious cross-site scripting (XSS) flaw believed to affect most SharePoint 2016 installations.
Microsoft SharePoint is a collaboration platform that allows users to share and manage content and applications with other people in their organization. Microsoft says the product is used by more than 200,000 organizations and 190 million people.
The security hole, discovered by researcher Ashar Javed and tracked as CVE-2017-8514, affects SharePoint’s Follow feature, which allows users to follow sites that interest them.
Users can follow a site by clicking on the “Follow” button in the top right corner of a page. The feature is also available in the emails users receive when someone shares a site with them via SharePoint.
Javed noticed that the request associated with the “Follow” link included in emails has a parameter named “SiteName” whose value is not properly sanitized, allowing malicious actors to abuse it for XSS attacks.
In order to exploit the vulnerability, an attacker needs to convince the targeted user to click on a link that looks something like this, where the part after “SiteName=” is the XSS payload:
http[s]://<SHAREPOINT URL>?FollowSite=0&SiteName='-confirm(document.domain)-'
In its advisory for CVE-2017-8514, Microsoft said this reflected XSS flaw can be exploited to run a malicious script in the context of the current user.
“These attacks could allow the attacker to read content that the attacker is not authorized to read, use the victim's identity to take actions on the SharePoint site on behalf of the victim, such as change permissions, delete content, steal sensitive information (such as browser cookies) and inject malicious content in the browser of the victim,” Microsoft said.
A Google search conducted by Javed showed more than 19,000 vulnerable SharePoint sites, including ones belonging to government organizations and universities from around the world. The expert believes nearly all SharePoint installations – both on-premises and online – are affected.
Microsoft was informed about this vulnerability on February 20 and confirmed it roughly one week later. The company has paid out a $2,500 reward for the security hole.
This is not the only SharePoint XSS flaw found by Javed and patched by Microsoft this month. The researcher also discovered a stored XSS vulnerability (CVE-2017-8551) affecting the Project Web App component of SharePoint 2013. Javed told SecurityWeek that he received a $1,500 bounty for the second XSS he reported.
Microsoft informed customers that this month’s security updates also include defense-in-depth measures for SharePoint Enterprise Server 2013 and 2016. These measures are designed to prevent remote code execution.
Authorities Disrupt International Payment Card Fraud Operation
15.6.2017 securityweek Crime
Approximately 3,000 European Union citizens fell victim to an international criminal network of payment card fraudsters before law enforcement agencies managed to take it down.
The takedown operation resulted in the arrest of 31 suspects, (21 in Spain, 9 in Bulgaria and one in the Czech Republic), and in 48 house searches (14 in Spain and 34 in Bulgaria). Equipment used to forge payment cards, payment card data readers-recorders, skimmers, micro cameras, devices designed to manipulate ATMs, cash, and numerous counterfeit cards were found in suspects’ possession.
The operation was carried out by Central Investigating Judge number 5, the Public Prosecution Office at the Audiencia Nacional and National Police of Spain, and the General Directorate Combating Organized Crime in Bulgaria, with the support of Eurojust and Europol’s European Cybercrime Centre (EC3).
As part of their fraudulent activity, the criminals installed skimming devices on an average of 400 ATMs every year, between 2014 and 2017, which allowed them to copy and clone bank cards, Europol says. The fake cards were then used to perform illegal transactions outside the European Union.
The criminals used the cards in 200 ATMs located mainly in the USA, the Dominican Republic, Malaysia, Indonesia, Vietnam, Peru, the Philippines and Costa Rica. Around 3,000 people were affected by the fraudulent activity, which resulted in total losses of at least 500,000 Euro.
During the investigation, Eurojust provided coordination among authorities in Spain and Bulgaria, while Europol offered tailored intelligence analysis and expertise and also deployed mobile offices on the spot in both countries. Eurojust and Europol also assisted the joint investigation team (JIT) that was set up between the cooperating countries.
“This successful operation confirms Eurojust’s commitment to protect the assets of EU citizens from falling into the hands of cyber fraudsters. An entire criminal network was taken down and, as a result, is no longer able to defraud innocent victims, thanks to the joint efforts of the Spanish and Bulgarian prosecuting authorities, and the valuable support provided by their National Desks at Eurojust,” Francisco Jiménez-Villarejo, National Member for Spain at Eurojust, said.
CashCrate Cash-for-Surveys Site breached, 6 Million accounts stolen
15.6.2017 securityaffairs Incindent
According to the data breach notification site LeakBase hackers have stolen 6 million accounts for the CashCrate Cash-for-Surveys Site.
Another day another data breach, this time hackers have stolen 6 million accounts for CashCrate, a site where users can be paid to complete online surveys. The news was reported by Motherboard who obtained the database and confirmed that records include user email addresses, passwords, names, and physical addresses.
The data breach notification site LeakBase provided Motherboard with a copy of the CashCrate archive.
CashCrate allows companies to pay users that test their products and services, or that participate in daily surveys.
The analysis of the database revealed that the earliest accounts date back to 2006, and the bad news is that accounts registered from 2010 have MD5 hashed passwords.
“Accounts from mid 2010 onwards appear to have passwords hashed with the notoriously weak MD5 algorithm, meaning that hackers may be able to crack the hashes and obtain the real login credentials.” states Motherboard.

Motherboard has verified that the accounts are legitimate, it also noticed it its post that CashCrate does not use basic web encryption on its website.
The company is notifying all its users about the security breach.
“We’re in the process of notifying all our members about the breach. While we’re still investigating the cause, at this point it appears that our third-party forum software was compromised, which led to the breach. We’ve deactivated it until we’re confident it’s secure,” a CashCrate spokesperson told Motherboard in an email.
“We have also confirmed that any users who have logged in since October 2013 have passwords that are fully hashed and salted, and we’re looking into why some inactive accounts have plaintext passwords. Those will be hashed and salted immediately,” the spokesperson added.
If you are a CashCrate user change your password now and in case you shared same login credentials on other websites you must change the passwords also for them.
Victims of Jaff Ransomware now can decrypt their locked files for free thanks to Kaspersky
15.6.2017 securityaffairs Ransomware
Victims of the Jaff ransomware can use an updated version of the Kaspersky Labs’s RakhniDecryptor tool to decrypt their encrypted files.
Security researchers at Kaspersky Lab have discovered a weakness in the Jaff ransomware that allowed the researchers creating of decryption keys to unlock files encrypted by the malware.
Once the victims were infected by the Jaff ransomware, crooks then demanded a ransom of between 0.5 to 2 Bitcoin (approximately $1,500 – $5,000, based on current exchange rates).
That weakness can be exploited by a free tool that has been included in the list of free ransomware decryptors shared by Kaspersky Lab. The tools allow recovering files encrypted by the ransomware like Rannoh and CoinVault.
“We have found a vulnerability in Jaff’s code for all the variants to date. Thanks to this, it is now possible to recover users’ files (encrypted with the .jaff, .wlu, or .sVn extensions) for free,” Kaspersky Lab said in a statement announcing the availability of the decryption keys.
The free decryption tool for unlocking files has been added to the RakhniDecryptor (version 1.21.2.1).
The Jaff ransomware was first spotted in May while it was being distributed by Necurs botnet previously used to spread the Locky and Dridex malware.
A few days ago, security researchers at Heimdal Security who were investigating a new strain of Jaff ransomware discovered that the malware is sharing the backend infrastructure with a black market offering for sale stolen card data and account information.
The Jaff ransomware has been recently discovered, it was involved in a number of large-scale email campaigns each using a PDF attachment with an embedded Microsoft Word document embedding macros that download and execute the malicious code.

According to Kaspersky Lab, top countries impacted by the ransomware are China, India, Russia, Egypt, and Germany.
Let me suggest giving a look at the numerous decryption utilities published by Kaspersky Lab under the No Ransom Project.
Kaspersky is very active in the fight against ransomware, one year ago it launched, along with the Europol and other security firms, the ‘NO More Ransom’ initiative.
European police target anti-malware detection services and their customers
15.6.2017 securityaffairs BigBrothers
An international operation conducted by the European police targeted customers of counter antivirus and crypter services: 6 arrested and tens of interviewed
The Germany’s Kriminalinspektion Mayen along with the Europol’s European Cybercrime Centre (EC3) have arrested six individuals and interviewed dozens of suspects as part of an international law enforcement operation targeting the users of two tools designed to help malware evade detection by security software.
“Between 5 and 9 June, 6 suspects were arrested and 36 were interviewed during an internationally coordinated operation in 6 European countries.” states the announcement published by the Europol. “The targets are all suspected customers of a counter anti-virus platform and crypter service – two cybercriminal tools used for testing and clouding of malware samples to prevent security software solutions from recognising them as malicious.”
The authorities seized hundreds of desktop and laptop devices, smartphones, and storage devices.
The first phase of the police operation, codenamed Neuland, took place in April 2016 and targeted the operators of two anti-malware detection services, and their customers based in Germany.
“The first phase of the operation, also supported by Europol, was executed on 5 April 2016 and targeted the suspects behind a counter anti-virus and a crypter service , as well as the German customers of the two tools, through a large-scale coordinated action in all state criminal police offices in Germany.” continues the report.
The police arrested a 22-year-old individual and searched the homes of 170 other from Germany, law enforcement also searched home other countries, including France, the Netherlands, and Canada.
It is interesting to note that the average age of the suspects was 23-
On Wednesday, the Europol announced the second phase of the operation that took place last week when the police targeted the international customers of the two anti-malware detection services.
“The second phase of this operation, from 5 to 9 June 2017, specifically targeted the international customers of the same two services. The following countries participated in this phase: Cyprus, Italy, the Netherlands, Norway, and the United Kingdom. Police officers searched 20 houses and 6 suspects were arrested, while 36 additional suspects have been interviewed so far. A large number of devices have also been seized. ” states the Europol.
A joint operation conducted by police in Cyprus, Norway, the Netherlands, Italy and the UK resulted in the arrest six people, a and questioned 36 other suspects. Police searched 20 houses and also in this case they seized electronics equipment and devices.
This isn’t the first time, police targets operators on anti-malware detection services, in November 2015 the police in the United Kingdom arrested two individuals. arrested.
Jaff Ransomware Decryption Tool Released – Don't Pay, Unlock Files for Free
15.6.2017 thehackernews Ransomware
Hit by Jaff Ransomware? Don't pay the Ransom. You can unlock your files for Free!
Kaspersky Labs has released an updated version 1.21.2.1 of its free ransomware decryption tool, RakhniDecryptor, which can now also decrypt files locked by the Jaff ransomware.
Security researchers at Kaspersky Labs have discovered a weakness in the Jaff ransomware code that makes it possible for victims to unlock their Jaff-infected files for free.
First identified last month, Jaff is relatively new ransomware that's being distributed with the help of 'Necurs botnet' that currently controls over 6 million infected computers worldwide.
Necurs botnet is the same botnet – army of compromised internet connected devices – that was used to distribute Dridex Banking Trojan and Locky ransomware, which also infects users’ machines, encrypt files and then demand a ransom before unlocking them.
Jaff ransomware (Trojan-Ransom.Win32.Jaff) attack is primarily carried out by sending spam emails to millions of users with an attached PDF, which if clicked, opens up an embedded Word document with a malicious macro script to downloads and execute the ransomware.
Once victims download and enable a Word macro associated with the .PDF, the Jaff ransomware gets downloaded onto their computer, encrypting victims files and then demanding a ransom of between 0.5 to 2 Bitcoin (~$1,500 to $5,000 today).
The Jaff attack started on May 12 – the same day when the devastating WannaCry ransomware debuted – by sending spam emails at the speed of 5 Million emails per hour.
How to Use RakhniDecryptor
Kaspersky RakhniDecryptor tool is a lightweight and portable piece of software designed to decrypt files encrypted by several variants of ransomware including Lobzik, Rakhni, Mircop, Crusis and 17 others.
RakhniDecryptor is very easy to use and doesn't require any technical knowledge. Here's the list of simple steps to use this tool:
Download RakhniDecryptor 1.21.2.1
Run the RakhniDecryptor.exe file on the infected computer
Click 'Change parameters' to select the objects to scan (hard drives/removable drives/network drives)
Click the 'Start Scan' button and then choose the specify path to one of the encrypted files
The RakhniDecryptor utility will then recover the decryption password to unlock files
How to Protect Yourself From Ransomware Attacks
Whether it's Jaff, Locky, CoinVault, TeslaCrypt, or any other ransomware, the protection measures are standard.
To safeguard against ransomware infections, you should always be suspicious of uninvited documents sent in an email and never click on links inside those documents unless verifying their source.
Check if macros are disabled in your MS Office apps. If not, block macros from running in MS Office files from the Internet. In enterprises, your system administrators can set the default setting for macros.
In order to always have a tight grip on all your important documents, keep a good backup routine in place that makes copies of your files to an external storage device which is not always connected to your PC.
Moreover, make sure that you run an active anti-virus security suite of tools on your system and keep them up-to-date, and most importantly, always browse the Internet safely.
Chytré mobily chrání před viry jen polovina Čechů
15.6.2017 Novinky/Bezpečnost Mobilní
Chytré mobilní telefony chrání před útoky škodlivých programů jen zhruba polovina českých uživatelů, u notebooků a PC přesahuje podíl chráněných zařízení 90 procent. Vyplývá to ze statistik antivirové firmy Eset.
Chytrý mobil je přitom podle posledního průzkumu Esetu nejčastěji používaným zařízením pro přístup k internetu. Využití mobilního připojení k internetu prostřednictvím smartphonu deklaruje 79 procent respondentů, přes notebook k internetu přistupuje 71 procent Čechů a na stolním počítači 59 procent.
„Je to vůbec poprvé, co nám v průzkumu vyšlo, že se nejvíce lidí připojuje k internetu přes mobil. Z hlediska ochrany přitom stále platí, že zatímco desktopová zařízení jsou většinou chráněna antivirem, mobilní zařízení chrání jen zhruba polovina uživatelů," uvedl technický ředitel Esetu Miroslav Dvořák.
Počet kybernetických hrozeb roste
Malý podíl chráněných mobilů ostře kontrastuje s růstem kybernetických hrozeb zacílených na tablety a chytré mobilní telefony. Jde například o vyděračské aplikace zaměřené na operační systém Android.
Tři čtvrtiny uživatelů používají některý ze způsobů uzamčení displeje mobilního telefonu. Nejčastěji jde o PIN (32 procent respondentů) nebo gesto (22 procent). Otisk prstu využívá k autentizaci pětina Čechů, snímek sítnice a jiný druh identifikace dvě procenta.
Plná čtvrtina respondentů přiznala, že svůj telefon nezabezpečuje. Obdobně jsou na tom Češi i se zabezpečením externích záznamových zařízení. Nejoblíbenější USB flash disky používá 81 procent respondentů, ale jen 27 procent chrání jejich obsah šifrováním, heslem nebo klíčem.
Největší hrozby pro chytré telefony
15.6.2017 SecurityWorld Mobilní
IT týmům a bezpečnostním profesionálům mohou mobilní telefony leckdy připadat jako tikající bomba – obzvlášť v rukou neopatrných uživatelů. V době, kdy je stále častější, že si zaměstnanec kupuje své vlastní zařízení (nebo např. s přispěním zaměstnavatele), riziko ještě vzrůstá.
A ve chvíli, kdy má uživatel na svém přístroji vše – od soukromých informací přes internetové bankovnictví po pracovní dokumenty – je jakákoli hrozba, např. ve formě malwaru nebo ransomwaru, ještě znásobena.
Chris Crowley, instruktor institutu SANS, představuje pět největších mobilních bezpečnostních hrozeb současnosti.
1. Nedůvěryhodná zařízení
Ač se to může zdát pro mnohé překvapivé, chyba je často už v samotném přístroji, kdy do něj někdy během procesu prodeje byl vložen malware. Crowley uvádí příklad: CheckPoint našel na začátku letošního roku 36 zařízení s Androidem ve velké telekomunikační společnosti. Ani v jediném případě však za únik dat z mobilů nemohl uživatel: přístroje malware (v podobě závadných aplikací) obsahovaly již ve chvíli, kdy je pracovníci teprve dostávali do rukou.
„Škodlivé aplikace nebyly součástí oficiální verze operačního systému dodavatele, přidány byly až později u následného dodavatelského řetězce,“ dodává.
2. Závadné aplikace
CheckPoint například našel malware v oblíbeném obchodu s aplikacemi Google Play. Autoklikací adware „Judy“ vyvinutý korejskou společností. „Malware využívá nakažená zařízení ke generování velkého množství automatických kliknutí na reklamy, což je zdrojem příjmů pro autory. Tento konkrétní malware ve formě aplikací dosáhl téměř neuvěřitelného počtu mezi 4,5 až 18,5 miliony stažení,“ popisuje CheckPoint.
3. Užitečné aplikace, jež odvádí data.
Stará pohádka, ale zůstává stále u vrcholku žebříčku. Nainstalované aplikace, které tvrdí, že dělají jednu věc a často ji dokonce zvládají, ale k tomu potajmu odvádí data a telefon činí zranitelným, nejsou raritou; i proto, že je lze poměrně těžko odhalit.
4. Bankovní malware
Jeden z nejnebezpečnějších druhů malwaru. Analytik malwaru z laboratoří Kaspersky Roman Uchunek vidí bankovní malwarem jako v současnosti rostoucí mobilní hrozbu. Phishing se momentálně specializuje na překrývání bankovních aplikací vlastními okny a následnou krádež vepsaných informací. Kybernetičtí kriminálníci umí ukrást i data z jiných aplikací, odhalit detaily o kreditní kartě a získat mohou také autorizační číslo příchozí mobilní transakce (mTans) nebo přesměrovávat hovory.
5. Ransomware
Soutěž o „nejpopulárnější IT hrozbu současnosti“ by, s trochou nadsázky, ransomware pravděpodobně vyhrál. Rozhodně není hrozbou jen pro uživatele stolních počítačů a laptopů: napadá i mobilní telefony. Vyskakující tabulka, která zablokuje uživateli přístup k datům v systému a následně požaduje po uživateli zaplatit za dešifrování souboru, v letošním roce nepřestává děsit prosté uživatele ani IT týmy.
Ransomware se samozřejmě dále vyvíjí. Dalším logickým krokem je to, co se prozatím nazývá „ransomworm“. Tedy ransom-červ, ransomware připojený k síťovému červu.
„Po infikování jednoho stroje by se neúnavně kopíroval do všech počítačů na lokální síti,“ popisuje Corey Nachreiner z WatchGuard Technologies. „Ať už si umíte takový scénář představit nebo ne – zločinci o něm již jistě přemýšlí.“
WannaCry už hrozbu nepředstavuje. Kvůli lajdácké práci počítačových pirátů
15.6.2017 Novinky/Bezpečnost Viry
Vyděračský virus WannaCry na začátku května vyděsil takřka celý svět. Tento škodlivý kód totiž za pouhých pár hodin stihl infikovat více než 300 000 počítačů ve 150 zemích světa. Jak však nyní ukázala detailní analýza tohoto nezvaného návštěvníka, počítačoví piráti při programování WannaCry odvedli lajdáckou práci. Udělali několik zásadních chyb, díky kterým je možné napadené soubory vrátit zpět.
Analýzu vyděračského viru WannaCry provedli bezpečnostní experti z antivirové společnosti Kaspersky Lab. Právě ti upozornili na to, že autoři tohoto malwaru při jeho vývoji udělali několik chyb, díky kterým je možné napadené soubory vrátit zpět.
Zmiňované chyby v kódu umožňují podle nich snadné obnovení zašifrovaných dat. To je možné pomocí volně dostupných nástrojů, jako je například WannaKey, o kterém Novinky.cz informovaly již dříve.
Lajdácká práce počítačových pirátů se ale ukázala na napadených strojích ještě daleko více. „Při procesu zpracování ‚read-only‘ souborů chyba vůbec neumožňuje tyto soubory zašifrovat. Místo toho malware vytvoří zašifrované kopie souborů, zatímco jejich originály zůstanou netknuté a jsou pouze skryté, což jde však snadno vrátit zpět. Jednoduše řečeno, malwaru se nepodaří originály smazat,“ popsal jednu z hlavních chyb ve WannaCry Anton Ivanov, bezpečnostní odborník společnosti Kaspersky Lab.
„S podobnými chybami jsme se už v minulosti několikrát setkali – autoři ransomwaru často dělají závažné chyby, které následně umožňují bezpečnostním systémům úspěšně navrátit napadené soubory. A právě to je i případ WannaCry – přinejmenším první a zároveň nejrozšířenější verze této ransomwarské rodiny. Pokud jím byl uživatelův počítač napaden, existuje velká šance na obnovu většiny souborů,” doplnil Ivanov.
Jak probíhá útok viru WannaCry
WannaCry – první i vylepšená druhá generace – útočí úplně stejně jako ostatní vyděračské viry, které jsou označovány souhrnným názvem ransomware. Nejprve tedy škodlivý kód pronikne do počítače, pak jej uzamkne a zašifruje všechna data. Za jejich zpřístupnění následně počítačoví piráti požadují výkupné.
Je však nutné zdůraznit, že ani po zaplacení výkupného uživatelé nemají jistotu, že se k datům dostanou.
WannaCry se začal internetem šířit v polovině května. Za pouhých pár hodin stihl nakazit více než 300 000 počítačů ve více než 150 zemích světa. Takřka polovina všech zachycených detekcí (45,07 %) připadá na Rusko. Je to dáno tím, že především v tamních chudých lokalitách ještě uživatelé hojně používají zastaralý operační systém Windows XP, který byl škodlivým kódem WannaCry nejvíce zranitelný.
Druhou a třetí příčku pak zaujaly Ukrajina (11,88 %) a Tchaj-wan (11,55 %). Ostatní státy, které se dostaly v žebříčku nejpostiženějších zemí do první desítky, měly podíl tak v řádech jednotek procent. Šlo například o Egypt, Indii či Filipíny.
Česká republika zasažena jen okrajově
Česká republika skončila v přehledu s podílem 0,15 % až na 52. místě. Sluší se nicméně podotknout, že spodní příčky měly velmi podobný podíl až prakticky do konce žebříčku, který obsahovat 150 států. Například sousední Slovensko ale na tom bylo hůře – virus WannaCry tam měl podíl 0,26 %.
V Česku byly přitom infikovány stovky strojů. „Podle našich údajů počet infekcí překonal číslo 620,“ uvedl již dříve na dotaz Novinek Pavel Bašta, bezpečnostní analytik Národního bezpečnostního týmu CSIRT.CZ.
Ani kontrolní systém Applu není dokonalý. Podvodníci za falešnou aplikaci vyinkasovali téměř 2 miliony
15.6.2017 Živě.cz Apple
Podvodníci nabízeli falešný antivir, který ale nic nedělal
Za odstranění neexistujícího malwaru si účtovali tisíce
K dvoumilionovému výdělku stačilo 200 podvedených
Ani kontrolní systém Applu není dokonalý. Podvodníci za falešnou aplikaci vyinkasovali téměř 2 miliony5 FOTOGRAFIÍ
zobrazit galerii
Drtivou většinu nebezpečných aplikací pro systém iOS odfiltruje schvalovací systému Applu, kterým si každá aplikace i její aktualizace musí projít před zveřejněním v App Store. Ať už se jedná o podvody nebo malware, k uživatelům proklouzne jen minimální množství škodlivých aplikací. Pokud se tak ale stane, vývojáři si takovým jednáním mohou přijít na velké peníze. Jeden ze způsobů nyní popsal Johny Lin na webu Medium.
Podvodníci v několika zdokumentovaných případech zneužívají nákupeů přímo v aplikacích, které mohou být potvrzeny velmi snadno a rychle a méně pozorný uživatel může nechtěně dokoupit draze placený obsah. V případě legitimních aplikací je takový proces v pořádku, tady si ale uživatelé připlatili 400 dolarů měsíčně za službu, která neexistuje.
Falešný antivir
Johny Lin si všimnul podezřelé aplikace v seznamu těch nejvýdělečnějších za poslední měsíc. Mezi zaběhnutými a notoricky známými aplikacemi se totiž na desáté místo v žebříčku dostala ta s názvem Mobile protection :Clean & Security VPN. A to včetně chyb v názvu. Pokud potom porovnal data s odhadnutým výdělkem, zjistil, že si vývojáři přišli na 80 tisíc dolarů (asi 1,8 milionu korun) za měsíc.
Trik podvodníků samozřejmě zneužíval neznalost a strach méně zkušených uživatelů – nabídnul falešný antivir, který v telefonu objevil škodlivý obsah a za odstranění si uživatel samozřejmě musel zaplatit. Nebyla to však nijak skromná částka – pomocí předplatného totiž vývojáři požadovali 100 dolarů za týden, přičemž uživatel pomocí Touch ID potvrdil jak jednorázovou platbu, tak dlouhodobé předplatné. Při pohledu na tuto částku už není tak nepochopitelné, jak si podvodníci mohli přijít na 80 tisíc dolarů za měsíc. Stačilo totiž takto oklamat pouhých 200 uživatelů.
Otázkou však je nejen to, jak se taková aplikace dostala do App Store, kde zkrátka mohl selhat lidský faktor při schvalování. Vážnějším problémem je spíše fakt, že mohla nepoužitelná aplikace bez legitimního fungování vyrůst napříč App Storem tak, aby ji stáhlo dostatek uživatelů. V tomto případě to bylo přes 50 000 lidí. Odpovědí jsou reklamy, které Apple ve virtuálním obchodě začal používat minulý rok – na hledání v obchodě se uživatelům může ještě před samotným seznamem vyhledaných aplikací objevit jedna inzerovaná. Ta samozřejmě musí odpovídat klíčovým slovům, která očividně volili podvodníci velmi dobře. Z obrovského množství stažených aplikací jim tak stačila konverze pouhých 0,4 % k téměř dvoumilionovému výdělku za měsíc.
Děravý systém reklam
Johny Lin upozorňuje na to, že tahle aplikace není jediná, která takového podvodu zneužívala – našel minimálně tři další, které byly postaveny na stejném principu falešné bezpečnostní aplikace a obřích předplatných.
Apple by měl zapracovat hned na několika vylepšeních, které by takové podvody ztížily nebo zcela znemožnily. Je to například zřetelnější dialog, kterým uživatelé pomocí Touch ID potvrzují platbu. V tomto případě totiž podvodníci nechali své oběti kliknout na tlačítko Free Trial a následně po nich požadovali sto dolarů za týden. Zlepšit by se také měly možnosti pro nahlášení závadných aplikací a jejich promtní odstranění z App Store. Ale tím hlavním zádrhelem v tomto případě je reklamní systém. Aplikace, u nichž vývojáři platí za inzertní kampaň musí projít ještě pečlivější kontrolou a rovněž by reklamní aplikace měly být více zvýrazněny. V aktuální podobě totiž uživatelé často netuší, že klikají na reklamu.
Microsoft opět vydal záplatu pro Windows XP. Je to chyba, XPčka patří do koše
15.6.2017 Živě.cz Zranitelnosti
Rozšířená podpora Windows XP skončila už před třemi lety
A Microsoft od té doby vydal už několik klíčových záplat
Tím zdánlivě prodlužuje životnost XP a to je chyba
Windows XP, prostředí Luna a tapeta BlissBSOD: Jedna z nejméně oblíbených funkcí Windows XPLegendární tapeta Bliss z Windows XPWindows XP a prohlížečAlternativní nabídka Start is back a téma Windows XP na Windows 1021 FOTOGRAFIÍ
8. dubna 2014 dorazila na Windows XP poslední várka záplat a legendární, nicméně už tehdy přes všechny servisní balíčky notně zastaralý, systém se konečně odporoučel alespoň do formálních věčných lovišť.
Ne, tak tomu bohužel nebylo. To už teď víme všichni.
Tak skončila podpora Windows XP, nebo ne?
Na sklonku dubna totiž postrašila komunitu kritická chyba napříč tehdejšími verzemi Internet Exploreru, a Microsoft tak nakonec porušil pravidlo a hned první květnový den vydal záplatu i pro Windows XP. Stalo se tak poprvé v jeho historii, kdy se věnoval operačnímu systému po definitivním konci jeho podpory. Domnívám se, že to byla chyba, která jen zpomalila přechod domácích uživatelů i firem na novější verzi Windows, mnozí totiž nabyli dojmu, že když se objeví nějaký další průšvih, Microsoft jej chtě nechtě stejně zase opraví.
Klepněte pro větší obrázek
Windows XP patří na staré počítače z doby předfacebookové a ne na ty současné a připojené k internetu
Jedna záplata přitom neřeší problém starého operačního systému jako takového, což potvrdila na podzim téhož roku analýza AVG, podle které patřily XPčka k nejnakažlivějším tržně-relevantním systémům té doby. Patrně je tomu dodnes.
Adrienne Hallová z Microsoftu v každém případě hned po vydání záplaty pro Windows XP v blogu upozorňovala uživatele, že se jedná o naprostou výjimku a firma se rozhodla opravit IE pro XPčka pouze z toho důvodu, že jejich podpora skončila teprve před pár týdny.
Bude se to opakovat i u Windows 7?
Již brzy bude Microsoft řešit stejná dilemata i v souvislosti s Windows 7, pomalu se totiž blíží i konec jejich rozšířené podpory. Ta základní skončila dokonce už před dvěma lety. Stárnutí Windows 7 jsme se věnovali v naší diskuzi.
Po třech letech zasáhl svět WannaCry a Microsoft opět porušil vlastní pravidla hry
Následující tři roky uplynuly jako voda, základna uživatelů Windows XP pozvolna klesla na 5,7 % (NetMarketShare, květen 2017) a v Česku dokonce až na 4,1 % (Rankings, květen 2017), načež počítačový svět v plné síle zasáhla aféra ransomwaru WannaCry, jehož autoři zneužili zranitelnost, která unikla z americké Bezpečnostní agentury NSA.
Ačkoliv se mělo za to, že WannaCry největší silou zasáhne právě XPčka, ta byla nakonec natolik technologicky zastaralá, že po spuštění malwaru často havarovala a namísto zašifrování souborů se naštěstí zobrazil BSOD – modrá obrazovka smrti, která mnohé zachránila. Ach ty počítačové paradoxy.
I z tohoto důvodu nakonec vládly žebříčkům nejpostiženějších systémů Windows 7. I to je paradoxní, oprava, která by zamezila masivnímu šíření WannaCry právě na Sedmičkách totiž byla k dispozici už nějaký měsíc.
Microsoft nicméně opět porušil pravidlo a vydal speciální bugfix pro Windows XP, jenž měl zalátat díry, kterými se do systému hodlal dostat právě WannaCry. I tentokrát redmondští manažeři hájili krok jako naprosto výjimečný, který odpovídal závažnosti problému.
Jak však píše Peter Bright z Ars Techniky: „There will always be one more emergency.“ Jinými slovy, XPčka nebudou nikdy dostatečně zabezpečená a stejně tak nehrozí, že bychom se snad měli v dohledné době dočkat okamžiku, kdy útočníci všeho druhu přestanou psát malware. Dělají to přeci posledních třicet let a jejich aktivita je přímo úměrná velikosti globálního počítačového ekosystému počínaje vašim mobilním telefonem a konče třeba superpočítačem NASA Pleiades v Mountain View.
Měsíc poté Microsoft opět opravuje XPčka a paradoxně tak prodlužuje jejich životnost
A skutečně, měsíc po útoku WannaCry Microsoft v rámci svého Patch Tuesday opět udělal výjimku, ze které se už pomalu stává samozřejmost, a opět vydal záplaty pro Windows XP a další již nepodporované verze; třeba Server 2003. Je jich celá hromada, na rozdíl od automatického aktualizačního systému je musí případní majitelé těchto muzejních softwarů nainstalovat ručně a mají opravit další související zranitelnosti, kterých by mohly zneužít v rámci kybernetického boje a špionáže nejrůznější státní agentury (Microsoft zjevně míří na Rusko a Čínu).
Klepněte pro větší obrázek
Aby byly podniky lépe chráněné třeba proti kybernetické špionáži, Microsoft jim vydal záplatu pro tři roky nepodporovaný operační systém. To není zrovna nelichotivější vizitka pro zainteresované firmy a možná i státní úřady.
Ano, obrana před potenciální průmyslovou špionáží a útoky ze strany Ruska a Číny je pro americké podniky klíčová – ostatně mnozí se domnívají, že i stopy v případě WannaCry směřují na východ –, ale možná by bylo mnohem lepší ochranou, než vydávat záplaty na 16 let starý operační systém (!), prostě sakra konečně přejít na nový.
Ačkoliv je totiž globální podíl Windows XP zdánlivě zanedbatelný, faktem zůstává, že i nadále přežívá v nejednom podniku, čímž si ostatně vydání opravdu, ale opravdu výjimečného bugfixu ospravedlňuje i Microsoft.
Začarovaný kruh
A tak tu máme začarovaný kruh. Mnohé firmy se stále nezbavují Windows XP, protože když bude nejhůře, Redmond tu záplatu prostě vydá a basta. A Redmond tu záplatu nakonec opravdu uvolní, protože některé podniky nejsou schopny, nebo ochotny ani tři roky po ukončení rozšířené podpory Windows XP přejít na modernější alternativu – ať už je jakákoliv. Tímto přístupem přitom zvyšují riziko na celém internetu.
Zároveň, jak už bylo řečeno, oprava jednoho problému nikterak nezvyšuje bezpečnost Windows XP jako celku. XPéčka jsou děravá a zastaralá už z principu. Mít nějaká v naší brněnské podnikové síti, útočil bych na ně z dlouhé chvíle s Kali na USB klíčence i já.
OSIsoft Patches Flaws in PI Server, Web API Products
15.6.2017 securityweek Vulnerebility
California-based operational intelligence firm OSIsoft has released updates for its PI Web API and PI Server products to address several vulnerabilities, including ones rated high severity.
ICS-CERT has published two advisories this week to inform organizations about three remotely exploitable flaws affecting the OSIsoft products.
One advisory describes two improper authentication vulnerabilities affecting PI Server, a real-time data storage and distribution engine that powers the company’s PI System data management product.
The most serious of the flaws, rated high severity and tracked as CVE-2017-7930, is a protocol weakness in the PI Data Archive component that can be exploited to access clear text data and spoof a server.
The second flaw, rated medium severity and identified as CVE-2017-7934, affects the PI Network Manager and it allows a malicious user to authenticate on the server and cause the vulnerable component to behave unexpectedly.
These weaknesses affect systems with PI Data Archive versions prior to 2017, and they were patched roughly one month ago with the release of security updates.
Another advisory published by ICS-CERT describes a high severity cross-site request forgery (CSRF) vulnerability affecting PI Web API, a suite of REST services and APIs designed to provide web and mobile programmatic access to PI System data.
“The vulnerability allowed for Cross-Site Request Forgery (CSRF) attacks to occur when an otherwise-unauthorized cross-site request was sent from a browser the server had previously authenticated,” ICS-CERT and OSIsoft wrote in their advisories.
The flaw (CVE-2017-7926) impacts all websites using versions of PI Web API prior to 2017 (1.9.0) as the data access layer. A patch was released in May.
All flaws were discovered by OSIsoft itself and there is no evidence of exploits in the wild. The vendor has also provided a series of recommendations for preventing potential attacks exploiting these flaws.
OSIsoft products are used around the world in several industries, including oil and gas, power and utilities, chemicals and petrochemicals, pulp and paper, pharmaceutical, critical facilities, IT, and federal sectors.
MACSPY – Remote Access Trojan as a service on Dark web
15.6.2017 securityaffairs Apple
Reporters for the online service “Bleeping Computer” have uncovered a new threat to Apple being offered on the dark web, it is the MACSPY RAT.
Reporters for the online service “Bleeping Computer” have uncovered a new threat to Apple being offered on the dark web. Thru their efforts the researchers for AlienVault were able to obtain a copy of the new “MacSpy” program, described as the most sophisticated malware for Mac OS-x operating system to date.
The hackers offering MacSpy on the dark net are not selling it but in fact – giving it away at no cost. The software combines with a provided TOR portal to enable users to hack into and obtain surveillance information from targeted MAC computers.
The authors of the malware claim that they created it because Apple products have grown so popular. It is this popularity of Apple products that appears to have driven their desire to create the remote access Trojan (RAT) program. The free version of the MacSpy malware is designed to monitor Apple users, record data on the Mac system and then covertly spin it back to the controller who launched the attacks. MacSpy is can capture screen image and has an embedded keylogger. In addition, MacSpy can also capture ICloud synced data such as photos, provide voice recording surveillance, extract clipboard contents and download browser information.
Much like contemporary software providers; the MacSpy developers offers a “paid” version with enhanced features for customers. The paid version of MacSpy has many similar features seen inside programs developed by the CIA as shown in the Wikileaks Vault 7 releases. The remote controller can update the Trojan silently, extract any file, encrypt whole user directories, deliver scheduled dumps of an entire infected system, and extract social media and email data for surveillance.

According to the AlienVault, the MacSpy program is currently “completely undetected by various AV companies and products”. The program also includes a feature to disable the ability of users to analyze, debug and understand its operation. The anti-analysis designs include a series of hardware checks against the CPU chips to ensure the program is not being executed in a virtual mode or on a minimal “sand-box” system to be examined. It also calls the Apple “ptrace” function with the proper options to prevent debuggers from attaching to the process itself.
Once the system has passed the anti-analysis features it installs itself, deletes the installation files for stealth and links up to a TOR proxy in order to begin the process of data surveillance. MacSpy does attach itself to start up files so the system will re-establish a link to the TOR proxy at the beginning of each reboot.
MacSpy transmits the data it collects by sending a POST request through the TOR proxy, and then repeatedly sends POST commands for the selected data that the malware has stolen from the infected target system. Once it has completed its download the malware deletes the temporary files containing the data it sent.
There are some bright sides to the MacSpy story. The developers appear to have copied much of their code from the Stack Overflow website for programmers. In addition, the MacSpy payload is not digitally signed and may trigger an alert on properly configured Mac OS systems.
However, according to AlienVault, the MacSpy malware is a sign that there is a dark future for Apple users.
“People generally assume when they are using Macs they are relatively safe from malware,” notes AlienVault in its dissection of the MacSpy Trojan.
“This has been a generally true statement, but this belief is becoming less and less true by the day, as evidenced by the increasing diversity in mac malware along with this name family.”
ISPs Should Block ‘The Pirate Bay’ Torrent Site: Top European Court Rules
14.6.2017 thehackernews Hacking
The Pirate Bay — a widely popular file-sharing website predominantly used to share copyrighted material free of charge — is once again in trouble, this time in Europe.
The European Union Court of Justice (ECJ) ruled today that Dutch ISPs can block access to The Pirate Bay, as the Swedish file-hosting website facilitates an "act of communication" by allowing users to post and obtain torrents for pirated films, TV shows and music for free.
Dutch anti-piracy group Stichting Brein (BREIN) in 2009 filed a case against local Internet Service Providers (ISPs) Ziggo and XS4ALL, and in 2012, the District Court of The Hague ruled that the ISPs must block users from accessing The Pirate Bay.
However, Ziggo and XS4ALL, ISPs successfully overturned the decision two years later with the court ruling against BREIN and concluding that the blockade restricted the internet providers entrepreneurial freedoms.
BREIN group then took the same case to the Supreme Court, who eventually referred the case to the European Court of Justice for seeking further clarification and assistance on the technicalities of the issue.
The Court of Justice closely reviewed the whole case and today ruled that The Pirate Bay website can be blocked, as the operators of the site "play an essential role in making those works [torrent links to the pirated content] available," court explains.
The court accepted the fact that the Pirate Bay does not physically host any illegal content on their servers, but it did say the platform, which knowingly allows its users to share, search, and locate copyright-protected works for download, "may constitute an infringement of copyright."
The today’s ruling would not immediately affect the Pirate Bay, as the Dutch Supreme Court will take the final decision about blocking the website in upcoming months.
The final decision may also affect court orders in other countries, including Austria, Italy, Belgium, Finland, and its hometown Sweden, where The Pirate Bay and other torrent websites are already blocked.
Surprisingly, the operators of the Pirate Bay do not seem to be worried about the latest ruling as they believe the "blockades will eventually help users to get around censorship efforts, which are not restricted to TPB," one of the Pirate Bay moderators told the TorrentFreak.
The Pirate Bay has fought many legal battles since its launch in 2003, even after losing its primary .SE domain last year, but the site remains well-functioning by moving itself to different Web domains, and still is one of the popular torrent sites on the Internet.
US Warns of 'DeltaCharlie' – A North Korean DDoS Botnet Malware
14.6.2017 thehackernews BigBrothers
The United States government has released a rare alert about an ongoing, eight-year-long North Korean state-sponsored hacking operation.
The joint report from the FBI and U.S. Department of Homeland Security (DHS) provided details on "DeltaCharlie," a malware variant used by "Hidden Cobra" hacking group to infect hundreds of thousands of computers globally as part of its DDoS botnet network.
According to the report, the Hidden Cobra group of hackers are believed to be backed by the North Korean government and are known to launch cyber attacks against global institutions, including media organizations, aerospace and financial sectors, and critical infrastructure.
While the US government has labeled the North Korean hacking group Hidden Cobra, it is often known as Lazarus Group and Guardians of Peace – the one allegedly linked to the devastating WannaCry ransomware menace that shut down hospitals and businesses worldwide.
DeltaCharlie – DDoS Botnet Malware
The agencies identified IP addresses with "high confidence" associated with "DeltaCharlie" – a DDoS tool which the DHS and FBI believe North Korea uses to launch distributed denial-of-service (DDoS) attacks against its targets.
DeltaCharlie is capable of launching a variety of DDoS attacks on its targets, including Domain Name System (DNS) attacks, Network Time Protocol (NTP) attacks, and Character Generation Protocol (CGP) attacks.
The botnet malware is capable of downloading executables on the infected systems, updating its own binaries, changing its own configuration in real-time, terminating its processes, and activating and terminating DDoS attacks.
However, the DeltaCharlie DDoS malware is not new.
DeltaCharlie was initially reported by Novetta in their 2016 Operation Blockbuster Malware Report [PDF], which described this as the third botnet malware from the North Korean hacking group, after DeltaAlpha and DeltaBravo.
Other malware used by Hidden Cobra include Destover, Wild Positron or Duuzer, and Hangman with sophisticated capabilities, including DDoS botnets, keyloggers, remote access tools (RATs), and wiper malware.
Hidden Cobra's Favorite Vulnerabilities
Operating since 2009, Hidden Cobra typically targets systems running older, unsupported versions of Microsoft operating systems, and commonly exploits vulnerabilities in Adobe Flash Player to gain an initial entry point into victim's machine.
These are the known vulnerabilities affecting various applications usually exploited by Hidden Cobra:
Hangul Word Processor bug (CVE-2015-6585)
Microsoft Silverlight flaw (CVE-2015-8651)
Adobe Flash Player 18.0.0.324 and 19.x vulnerability (CVE-2016-0034)
Adobe Flash Player 21.0.0.197 Vulnerability (CVE-2016-1019)
Adobe Flash Player 21.0.0.226 Vulnerability (CVE-2016-4117)
The simplest way to defend against such attacks is always to keep your operating system and installed software and applications up-to-date, and protect your network assets behind a firewall.
Since Adobe Flash Player is prone to many attacks and just today the company patched nine vulnerability in Player, you are advised to update or remove it completely from your computer.
The FBI and DHS have provided numerous indicators of compromise (IOCs), malware descriptions, network signatures, as well as host-based rules (YARA rules) in an attempt to help defenders detect activity conducted by the North Korean state-sponsored hacking group.
"If users or administrators detect the custom tools indicative of HIDDEN COBRA, these tools should be immediately flagged, reported to the DHS National Cybersecurity Communications and Integration Center (NCCIC) or the FBI Cyber Watch (CyWatch), and given highest priority for enhanced mitigation," the alert reads.
Besides this, the agencies have also provided a long list of mitigations for users and network administrators, which you can follow here.
Hackerské útoky na volební systémy v USA zaznamenali v 39 státech
14.6.2017 Novinky/Bezpečnost BigBrother
Hackerské útoky proti elektronickým volebním systémům v rámci loňských prezidentských voleb v USA byly mnohem rozsáhlejší, než se dosud uvádělo. S takovou zprávou přišla v úterý agentura Bloomberg odvolávající se na tři zdroje blízké vyšetřování. Bloomberg informoval, že útoky byly vedeny v 39 federálních státech a stojí za nimi Rusové. Situace prý byla natolik vážná, že si administrativa tehdejšího prezidenta Baracka Obamy prostřednictvím horké linky přímo stěžovala Moskvě.
Hackeři se podle zprávy pokoušeli proniknout do voličských seznamů a dalších softwareových systémů. V Illinois se měli pokusit vymazat nebo změnit voličská data. Pronikli také do softwaru pro volební průzkum a v nejméně jednom státu se ve volební den dostali do finanční databáze volebního štábu.
Rozsah útoků a jejich důmyslnost podle Bloombergu Američany vyděsily natolik, že si Obamova vláda prostřednictvím horké linky stěžovala v Moskvě, což je bezprecedentní.
V říjnu, tedy měsíc před volbami, měl pak Bílý dům prostřednictvím diplomatických kanálů Kremlu nabídnout podrobné dokumenty o ruských zásazích do voleb a varovat Moskvu, že takové vměšování by mohlo přerůst ve větší konflikt. Obama následně v prosinci vyhostil ze Spojených států ruské diplomaty a vysvětlil to právě ruským zasahováním do voleb. Jeho nástupce Donald Trump, který během kampaně prosazoval smíření a spolupráci s Ruskem, tento krok odsoudil, ale zatím ho oficiálně nezvrátil.
Možná vlastenci
Rusko hackerské útoky popírá, prezident Vladimir Putin však nedávno nevyloučil, že by za nimi nějací ruští občané stát mohli. V tom případě by se podle něj jednalo jen o „zapálené vlastence“ jednající na vlastní pěst.
Podle Bloombergu je otázka, jak to, že se ruská rozvědka nepokusila volby narušit, když byly prolomeny americké volební systémy na státní i místní úrovni. Odpovědí by podle agentury mohla být buď skutečnost, že Obamovo varování zabralo, anebo pravděpodobněji to, že hackeři neuspěli natolik, aby ovládli tisíce systémů, které jsou v USA rozličné kvůli specifikům volebních pravidel v různých státech.
Anti-Detection Tool Users Targeted in International Police Operation
14.6.2017 securityweek BigBrothers
Six individuals have been arrested and dozens have been interviewed as part of an international law enforcement operation targeting the users of two tools designed to help malware evade detection by security software, Europol announced on Wednesday.
The operation, codenamed Neuland, was led by Germany’s Kriminalinspektion Mayen and supported by Europol’s European Cybercrime Centre (EC3).
The first phase of this action took place in April 2016 and it targeted the operators of counter antivirus and crypter services, and their Germany-based customers. One 22-year-old individual was arrested and 170 other suspects from all regions of Germany had their homes and offices searched. Searches were also carried out at the time in France, the Netherlands and Canada.
Hundreds of desktop computers, laptops, smartphones, and storage devices were seized in the first part of the campaign. German authorities said at the time that the average age of the suspects was 23.
The second phase of the operation, announced by Europol on Wednesday, took place last week and it targeted the international customers of the same two anti-malware detection services. Police in Cyprus, Norway, the Netherlands, Italy and the United Kingdom arrested six people and questioned 36 other suspects. Officers searched 20 houses and seized a large number of devices.
At around the time of the first phase of the law enforcement operation, a report from Dell SecureWorks on underground hacker markets revealed that the price of crypters, which provide a layer of defense for the malicious core of malware, had reached $80-$440, a significant increase from 2014, when they had been sold for only up to $150.
Two individuals suspected of running similar services were also targeted by law enforcement in the United Kingdom in November 2015. A man and a woman believed to be the operators of a counter antivirus service called reFUD.me and a crypter named Cryptex Reborn were arrested.
Report Highlights Business Risks Drawn From Geopolitical Flashpoints
14.6.2017 securityweek BigBrothers
Geopolitical Cyber Risks
Flashpoint's mid-year Business Risk Intelligence Report analyzes data from geopolitics and the deep and dark web to show how threat actors and their motivations have evolved over the first six months of 2017, and to provide insight into what new threats might appear in the coming months. It comprises sections covering both the primary nation-states and the main threat sub-sections.
Russia
The report notes the continuing Russian effort to interfere with western elections; especially during the approach to the German national elections in September 2017.
The Shadow Brokers (TSB) have re-emerged from dormancy, and are generally considered to be tied to the Russian state. Internally, Russia is tightening control over dissidents and internet usage. Ruslan Stoyanov was arrested over un-specified charges relating to 'treason'. From prison, he warned the regime against "the consequences of partnering with domestic 'patriot-thieves' (cybercriminals).
"Moscow is moving quickly towards establishing an unprecedented level of information control within the country's borders" warns Flashpoint, "...cementing the state's authority over online activities."
China
Chinese state-sponsored activity has remained low following the Xi-Obama agreement made in September 2015. Nevertheless, there has been some activity. In early March, a DHS report described activity under the 'Pleasantly Surprised' campaign spear-phishing commercial entities in the financial, retail and technology sectors. APT10 was also linked to a campaign targeting the National Foreign Trade Council around the time of the US/China summit in early April. Other probable Chinese activities included attacks against MSSPs and attempts to compromise South Korea's Terminal High Altitude Area Defense (THAAD) anti-ballistic missile system.
Flashpoint notes that China remains a potent cyber force, but seems to have turned the focus of its attention to Asian and geographically nearby targets. Internally it continues to increase control over cyber activities with new regulations on data flows and VPNs.
Five Eyes
The Five Eyes group of nations is described as the "pinnacle of cyber capabilities of all actors in cyberspace" -- but one that is not considered a 'threat actor' to other western nations. However, the NSA continues to be embarrassed by the TSB leaks, while the CIA has been embarrassed by WikiLeaks' Vault7 leaks. However, "Despite the synchronicity between the ShadowBrokers releases and the Wikileaks dump, there is no known connection between the two," says Flashpoint.
Iran
Iran is described as a 'moderately-capable threat actor in cyberspace', and one that has concentrated on exploiting vulnerabilities in critical infrastructure systems. While it has been relatively quiet in recent months, Flashpoint warns that any attempt by the US Administration to dismantle the Iranian nuclear accord is likely "to be accompanied by renewed Iranian eff orts in the cyber domain." However, for the moment, it believes that the "re-election of Iranian President Hassan Rouhani is likely to have a stabilizing effect on Iranian cyber activities."
North Korea
North Korea is considered to be a potent threat, but one that has been relatively quiet this year following China's apparent withdrawal of political support. Nevertheless, there have been at least two spear-phishing campaigns: one against South Korean research organizations, and the other against North Korean defectors.
The report notes the suggested links of the WannaCry ransomware to the North Korean Lazarus Group. Its own findings suggest a Chinese-speaking author; but adds these two findings are not mutually exclusive.
Geopolitically, the Trump administration has said, the "era of strategic patience is over." Flashpoint concludes, "The North's current apparent quiescence in cyberspace may come to a swift end in the event that the United States reacts strongly to the country's sixth nuclear test, for which many analysts believe that Pyongyang is preparing."
Just this week, US-CERT released a technical alert on behalf of the DHS and the FBI to warn organizations of North Korea’s “Hidden Cobra” activities, particularly distributed denial-of-service (DDoS) attacks.
Disruptive and Attention-Seeking Actors
Such actors have been quieter than usual during the first half of 2017. Flashpoint believes it may be because they are starved of publicity due to the media's current focus on the new administration and the FBI/Russia probe. Other reasons may be industry's improving security stance and, for example, the increased awareness among police departments of SWATTING techniques.
Cybercriminals
Cybercriminals are continuing to innovate and evolve. The switch from targeting individuals to targeting organizations continues, and the focus on targeting healthcare remains. "Flashpoint has observed a variety of actors such as "svako," "hackworld," "covrig3500," and more targeting healthcare clinics across the United States in efforts to monetize the stolen data."
Business Email Compromise (BEC) is growing. In April, Google and Facebook became victims in a scam that netted $100 million for the scammers.
Hacktivists
Flashpoint notes a decline in western hacktivism. "Thus far in 2017," it says, "the hacktivist landscape has been dominated by a small subset of largely-ineffectual hacktivist operations linked to the Anonymous collective, as well as activity emanating out of Turkey and China in particular."
Jihadi Actors
Jihadi actors have shown little growth in technical skill over the first half of 2017. "Due to the lack of technical acumen within most jihadi hacker groups, their victims tend to be poorly-defended or smaller, low-hanging-fruit websites." The most active hacker group is the United Cyber Caliphate (UCC) which has called for all pro-ISIS hackers to unite under one banner, including the newly-created "Caliphate Cyber Terrorism Army (CCTA)." There is, however, no evidence that the group is directed or supported by ISIS itself. It has also suffered from the loss of at least three of its leaders to US airstrikes -- the most recent being Osed Agha in March 2017, and the most notable being Junaid Hussain, or "TriCk" of TeaMp0isoN.
The physical threat to western nations has, however, increased. As the strength of the Isis Caliphate has dwindled, it has turned to recruiting and encouraging the "lone mujahid in the West." Although not mentioned by Flashpoint as part of this report, this has led to increasing demands from western governments to curb end-to-end encryption, and for the social media giants to co-operate more closely with government.
Flashpoint believes that a deeper understanding of geopolitics and the interaction with cyber threats can help business better prepare for both current and future threats.
Microsoft Issues Updates for 96 Vulnerabilities You Need to Patch this Month
14.6.017 thehackernews Vulnerebility
As part of June's Patch Tuesday, Microsoft has released security patches for a total of 96 security vulnerabilities across its products, including fixes for two vulnerabilities being actively exploited in the wild.
This month's patch release also includes emergency patches for unsupported versions of Windows platform the company no longer officially supports to fix three Windows hacking exploits leaked by the Shadow Brokers in the April's data dump of NSA hacking arsenal.
The June 2017 Patch Tuesday brings patches for several remote code execution flaws in Windows, Office, and Edge, which could be exploited remotely by hackers to take complete control over vulnerable machines with little or no interaction from the user.
While two of the vulnerabilities have been exploited in live attacks, another three flaws have publicly available proof-of-concept (POC) exploits that anyone could use to target Windows users.
Vulnerabilities Under Active Attack
The two vulnerabilities currently under active attack include a Windows Search Remote Code Execution flaw (CVE-2017-8543) and an LNK Remote Code Execution bug (CVE-2017-8464).
The more critical of the two is the Windows Search RCE vulnerability which is present in most versions of Windows and resides in the Windows Search Services (WSS) — a feature that allows users to search across multiple Windows services and clients.
The vulnerability, which already has publicly disclosed POC exploit code since early February, could allow a remote code execution in the Windows operating system, enabling an attacker to take over the target machine remotely via a network connection.
"To exploit the vulnerability, the attacker could send specially crafted SMB messages to the Windows Search service. An attacker with access to a target computer could exploit this vulnerability to elevate privileges and take control of the computer," Microsoft explains in its advisory.
"Additionally, in an enterprise scenario, a remote unauthenticated attacker could remotely trigger the vulnerability through an SMB connection and then take control of a target computer."
The SMB vulnerabilities can be extremely dangerous, and the best example of it is the WannaCry ransomware that exploited an SMB flaw within a network to replicate itself to all unpatched machines very quickly.
Windows Server 2016, 2012, 2008 along with desktop systems such as Windows 10, 7 and 8.1 are all affected by this vulnerability.
Shares Striking Resemblance with Stuxnet Malware
Another critical flaw under active exploitation is LNK RCE vulnerability resides in the way Windows handles LNK desktop shortcuts, which could allow remote code execution if the icon of a specially crafted shortcut is displayed to a user.
"The attacker could present to the user a removable drive, or remote share, that contains a malicious .LNK file and an associated malicious binary," Microsoft explains.
"When the user opens this drive(or remote share) in Windows Explorer, or any other application that parses the .LNK file, the malicious binary will execute code of the attacker’s choice, on the target system."
According to the Zero Day Initiative (ZDI), the active attack exploiting the LNK vulnerability carries some resemblance to the way the dangerous Stuxnet malware infiltrated and sabotaged critical industrial control systems while carrying out its attacks.
"If you're experiencing déjà vu reading the bug title, it is certainly understandable," ZDI says in its blog post. "This type of vulnerability was used by the Stuxnet malware, then found again several years later through a ZDI program submission."
Another three vulnerabilities that have publicly available proof-of-concept exploits include three flaws in the Edge browser, two of which (CVE-2017-8530 and CVE-2017-8523) could allow security feature bypass, while the third (CVE-2017-8498) allows for information disclosure.
Besides this, the Edge browser also receives patches for three more flaws (CVE-2017-8496, CVE-2017-8497, and CVE-2017-8499) that would enable attackers to carry out remote code execution on vulnerable users.
Other patches include fixes for nine of its own remote code execution flaws in Office that could be targeted via DLL files, email messages, a website, and a PowerPoint file.
Adobe June 2017 Patch Updates
Meanwhile, Adobe has also issued security fixes for its most vulnerable software offerings, Flash Player and Shockwave Player.
The company addresses nine critical bugs in its Flash Player that could allow remote code execution, five of which are due to memory corruption and four are use-after-free conditions in the software.
Users running Chrome, Edge, and Internet Explorer 11 and later will get the update automatically from Google and Microsoft's security teams, while other users should download the patches directly from Adobe.
Shockwave Player received a patch for a single remote code execution vulnerability in the Windows version of its software. Users should download version Shockwave Player 12.2.9.199 in order to protect themselves.
Microsoft Releases Patches for 3 Remaining NSA Windows Exploits
14.6.017 thehackernews Vulnerebility
Did you know… last month's widespread WannaCry ransomware attack forced Microsoft to release security updates against EternalBlue SMB exploit for unsupported versions of Windows, but the company left other three Windows zero-day exploits unpatched?
For those unaware, EternalBlue is a Windows SMB flaw that was leaked by the Shadow Brokers in April and then abused by the WannaCry ransomware to infect nearly 300,000 computers in more than 150 countries within just 72 hours on 12th of May.
Shortly after WannaCry outbreak, we reported that three unpatched Windows exploits, codenamed "EsteemAudit," "ExplodingCan," and "EnglishmanDentist," were also being exploited by individuals and state-sponsored hackers in the wild.
Specially EsteemAudit, one of the dangerous Windows hacking tool that targets remote desktop protocol (RDP) service on Microsoft Windows Server 2003 and Windows XP machines, while ExplodingCan exploits bugs in IIS 6.0 and EnglishmanDentist exploits Microsoft Exchange servers.
But now Microsoft has released free security updates for unsupported versions of its products, including Windows XP and Server 2003, to patch all the three cyber-weapons and block next wave of "destructive cyberattacks" similar to WannaCry.
According to the recent Microsoft blog post, the critical down-level patches for three Windows exploits were prompted by an "elevated risk of destructive cyberattacks" by government organizations, referred to as "nation-state actors or other copycat organizations."
The security patches for Windows XP, Vista, and Server 2003 contain fixes or mitigations for three alleged NSA-developed exploits — EsteemAudit, ExplodingCan, and EnglishmanDentist — though none of these exploits works on supported Windows platform.
Unlike regular Patch Tuesday releases that delivered automatically through the Windows Update mechanism to your devices, these down-level patches must be downloaded and installed manually.
These updates are available in the Microsoft Download Center or, in the Update Catalog, or you can find download links at the bottom of Security Advisory 4025685.
No doubt, this move by Microsoft to protect its customers by releasing security updates for end-of-support products is commendable, but this could also motivate users to stick to 14-years-old unsupported and risky versions of Windows OS that are exposed to all manner of potential threats.
And since Microsoft is fixing known vulnerabilities in Windows XP and Server 2003 that weren't fixed before, the job of migrating away from unsupported versions just got a whole lot harder than before.
However, Eric Doerr, general manager of the company's Security Response Center, said in a separate blog post that the move was only meant to fix flaws that are at "heightened risk of exploitation due to past nation-state activity and disclosures."
"Our decision today to release these security updates for platforms not in extended support should not be viewed as a departure from our standard servicing policies," Doerr said. "Based on an assessment of the current threat landscape by our security engineers, we made the decision to make updates available more broadly."
However, Doerr urged users to adopt new, supported versions of Microsoft products, which are significantly more secured and resistant to exploits, and warned them not to expect regular security updates for out-of-date platforms in the future.
Meanwhile as part of its regular Patch Tuesday, Microsoft has released security updates to patch nearly a hundred flaws in its various Windows operating systems and software, two of which have actively been exploited in the wild.
All the regular releases are delivered automatically through the Windows Update mechanism to users running supported versions of Windows OS, including Windows 10, 8.1, 7, and post-2008 Windows Server releases, on their devices.
The notorious hacking group, Shadow Brokers, who claimed to have stolen a bunch of hacking tools from the NSA's elite hacking team Equation Group, had also promised to leak more zero-days and exploits starting this month.
U.S. Warns of North Korea's 'Hidden Cobra' Attacks
14.6.017 securityweek BigBrothers
The United States Computer Emergency Readiness Team (US-CERT) released a technical alert on Tuesday on behalf of the DHS and the FBI to warn organizations of North Korea’s “Hidden Cobra” activities, particularly distributed denial-of-service (DDoS) attacks.
The threat actor dubbed by the U.S. government “Hidden Cobra” is better known in the infosec community as Lazarus Group, which is believed to be behind several high-profile attacks, including the ones targeting Sony Pictures, Bangladesh’s central bank, and financial organizations in Poland. Links have also been found between the threat actor and the recent WannaCry ransomware attacks, but some experts are skeptical.
The joint alert from the FBI and the DHS provides indicators of compromise (IoC) associated with a botnet known as “DeltaCharlie.” The North Korean government has allegedly used DeltaCharlie, which has been detailed in Novetta’s “Operation Blockbuster” report, to launch DDoS attacks.US warns of North Korea's Hidden Cobra attacks
“DeltaCharlie is a DDoS tool capable of launching Domain Name System (DNS) attacks, Network Time Protocol (NTP) attacks, and Character Generation Protocol attacks,” US-CERT said. “The malware operates on victims’ systems as a svchost-based service and is capable of downloading executables, changing its own configuration, updating its own binaries, terminating its own processes, and activating and terminating denial-of-service attacks.”
US-CERT has shared information on exploits, malware, IP addresses, file hashes, network signatures, and YARA rules associated with Hidden Cobra in an effort to help defenders detect the group’s attacks. However, it noted that “further research is needed to understand the full breadth of this group’s cyber capabilities.”
The agency warned that, in some cases, the DDoS malware was present on victims’ networks for a significant period of time.
Network administrators have been advised to follow a series of recommendations for mitigating attacks and responding to unauthorized network access.
While North Korea is believed to be responsible for several major cyberattacks, experts have also observed sophisticated attacks aimed at the country. Last month, Cylance reported seeing a new fileless attack that seemed to have Chinese origins, and Cisco detailed a RAT used to spy on organizations linked to North Korea.
Bizarní cirkus pokračuje. Microsoft nabízí další záplaty i pro Windows XP a Vista
14.6.017 CNEWS.cz Zranitelnosti
„Žádné další záplaty pro Windows XP nevydáme“. Tak určitě.
Červnové záplatovací úterý není tak výjimečné jako dubnové, které nabídlo oficiálně poslední záplaty pro Windows Vista a současně zahájilo širokou distribuci nové hlavní verze Desítek.
Je ale výjimečné tím, že opět nabízí aktualizace pro nepodporované verze Windows, tj. zejména XP a Vista. K výjimečnému vydání aktualizace pro Ikspéčka došlo podruhé v historii nedávno, a to v souvislosti s ransomwarem WannaCry.
Další mimořádné záplaty pro Windows XP a Vista
Včera uvolněné opravy jsou třetím případem mimořádné aktualizace vydané po skončení podpory Windows XP a druhé v případě Windows Vista. Microsoft tak učinil, protože zaznamenal konkrétní rizika spojená s organizacemi, které by mohly podlehnout kybernetickým útokům. Jako projev dobré vůle příslušné díry opravuje i ve dvou zmíněných nepodporovaných systémech (plus ve Windows 8 a Windows Server 2003), viz MSA 4025685.
Proč? Určitě se jedná o výbornou zákaznickou podporu. Možná si chce firma přihřát polívčičku po útoku obávaného WannaCry, který se stal mediálním trhákem. Stále však platí, co jsem už kdysi zmínil.
Komentář: Vyhýbáte se aktualizacím? Jste nezodpovědní a ohrožujete společnost
Z novinářů a novinářek, kteří seznamují uživatelstvo s tím, že by nepodporovaný systém nemělo používat a že žádné další aktualizace neobdrží, činí lháře a lhářky. Sám pak vystupuje jako pokrytec a shazuje rozhodnutí těch, kdo se kvůli bezpečnosti rozhodli přejít na podporované verze Windows. Navíc tím vytváří pocit falešného bezpečí – někdo si to může vyložit tak, že i nepodporovaný systém je zabezpečený.
Záplaty pro Ikspéčka nebo Vistu tak nejsou automaticky přínosem. Navíc si sám Microsoft stěžoval na organizace, které neaktualizují. Právě neaktualizované počítače byly hlavní příčinou, proč je WannaCry napadl. Navíc některé vládní organizace hledají díry v systémech a Microsoftu o nich neříkají, aby je sami mohly zneužívat. (Exploit využitý ransomwarem WannaCry pochází od NSA.) Vládám pak Microsoft na oplátku ošetří záplatami počítače s nepodporovanými systémy. Je to vlastně bizarní situace.
Souhrnné informace
Jinak můžete skrze Windows Update stáhnout nové aktualizace pro podporované verze Windows, záplat se dočkaly také kancelářské balíky Microsoft Office. Přehledné reporty o záplatách Microsoft zrušil, místo nich nabízí tyto méně přehledné a méně detailní přehledy, další informace pak naleznete v tomto přehledu. (Děkujeme, tohle přehlednosti rozhodně nepomohlo.) Celkem pro své softwarové produkty vydal Microsoft patnáct záplat.
Opravné balíčky formou kumulativních aktualizací neminuly ani Desítky, Osmičky a Sedmičky:
aktualizace KB4022725 pro Windows 10 v1703 zvedá číslo sestavení na 15063.413 či 15063.414,
aktualizace KB4022715 pro Windows 10 v1607 zvedá číslo sestavení na 14393.1358,
aktualizace KB4022714 pro Windows 10 v1511 zvedá číslo sestavení na 10586.962,
aktualizace KB4022727 pro Windows 10 v1507 zvedá číslo sestavení na 10240.17443,
aktualizace KB4022726 pro Windows 8.1 přináší všechny opravy,
aktualizace KB4022717 pro Windows 8.1 přináší jen záplaty,
aktualizace KB4022719 pro Windows 7 přináší všechny opravy,
aktualizace KB4022722 pro Windows 7 přináší jen záplaty.
Všechny aktualizace, které jsou pro vaše zařízení dostupné, získáte prostřednictvím služby Windows Update. Abych byl přesný, v novější verzích Windows může Office využívat vlastní aktualizační mechanismus.
Microsoft patches two critical remote code execution (RCE) flaws that have been exploited in attacks
14.6.2017 Securityaffairs Vulnerebility
Microsoft released the June 2017 Patch Tuesday to address more than 90 security flaws, including two critical RCE that have been exploited in attacks.
Microsoft released June Patch Tuesday updates that address more than 90 vulnerabilities, including two critical remote code execution (RCE) vulnerabilities that have been exploited in attacks.
The first vulnerability, tracked as CVE-2017-8464, is a LNK remote code execution flaw in Windows that could be triggered by tricking victims into displaying the icon of a specially crafted shortcut file.
“A remote code execution exists in Microsoft Windows that could allow remote code execution if the icon of a specially crafted shortcut is displayed. An attacker who successfully exploited this vulnerability could gain the same user rights as the local user. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights.” states the advisory published by Microsoft. “The attacker could present to the user a removable drive that contains a malicious shortcut file and an associated malicious binary. When the user opens this drive in Windows Explorer or any other application that parses the icon of the shortcut, the malicious binary will execute code of the attacker’s choice on the target system,”
Windows RCE vulnerability
According to the experts at the Zero Day Initiative (ZDI), the flaw is similar to one exploited by the Stuxnet worm. The exploit code for the CVE-2017-8464 may affect different components of the code.
In the case of Stuxnet, the remote code execution occurs if a specially crafted shortcut is displayed with a USB thumb drive, but the LNK could also be hosted on a remote drive viewable by the target.
“This type of vulnerability was used by the Stuxnet malware, then found again several years later through a ZDI program submission. While this latest patch may touch different parts of code, the exploit vector remains the same – remote code execution can occur if a specially crafted shortcut is displayed.” states the ZeroDay report. “In the case of Stuxnet, this was done with a USB thumb drive, but the LNK could also be hosted on a remote drive viewable by the target. If there is a positive note here, the exploit only allows for code execution at the logged-on user level – another reminder not to use administrative privileges for daily tasks. Interestingly, there have been reports that the Stuxnet LNK attacks were still prevalent as recently as April 2017, however these appear to be unrelated to this bug.
The good news is that flaw could be exploited to execute code only at the logged-on user level, so for users that don’t have administrator rights in low.
The second RCE vulnerability tracked as CVE-2017-8543, is a remote code execution vulnerability affecting Windows Search.
“A remote code execution vulnerability exists when Windows Search handles objects in memory. An attacker who successfully exploited this vulnerability could take control of the affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights.” states the advisory published by Microsoft.
“To exploit the vulnerability, the attacker could send specially crafted SMB messages to the Windows Search service. An attacker with access to a target computer could exploit this vulnerability to elevate privileges and take control of the computer. Additionally, in an enterprise scenario, a remote unauthenticated attacker could remotely trigger the vulnerability through an SMB connection and then take control of a target computer.”
Microsoft addressed three security feature bypass and information disclosure issues in the Edge web browser.
Microsoft also fixed 18 critical flaws, the last security updates also patch some of the vulnerabilities disclosed at Pwn2Own hacking competition.
Adobe patches tens of vulnerabilities in Flash Player, Shockwave Player, Captivate and Digital Editions
14.6.2017 Securityaffairs Vulnerebility
On Tuesday, Adobe released updates for Flash Player, Shockwave Player, Captivate and Digital Editions addressing a total of 20 vulnerabilities.
Some vulnerabilities fixed by Adobe are critical remote code execution issue, the last release, version 26.0.0.126, addressed nine flaws in Flash Player.
The vulnerabilities were tracked as CVE-2017-3075, CVE-2017-3081, CVE-2017-3083, CVE-2017-3084, CVE-2017-3076, CVE-2017-3077, CVE-2017-3078, CVE-2017-3079, and CVE-2017-3082.
“Adobe has released security updates for Adobe Flash Player for Windows, Macintosh, Linux and Chrome OS. These updates address critical vulnerabilities that could potentially allow an attacker to take control of the affected system. ” states the security advisory.
The vulnerabilities in Adobe are classified as critical use-after-free and memory corruption flaws that can be exploited by attackers to remote code execution.
adobe flaws
The flaws have been reported by the researchers bee13oy of CloverSec Labs, Jihui Lu of Tencent KeenLab, and researchers from Google Project Zero reported the issues to Adobe.
Adobe also fixed nine vulnerabilities in the Digital Editions ebook reader, four of which are critical memory corruptions that can be exploited for remote code execution. The remaining vulnerabilities, classified as important, that can lead to privilege escalation and memory address disclosure.
These flaws were reported to Adobe by experts from Tencent, Fortinet, CTU Security and Japan-based researcher Yuji Tounai.
“Adobe has released a security update for Adobe Digital Editions for Windows, Macintosh, iOS and Android. This update resolves critical memory corruption vulnerabilities that could lead to code execution, three vulnerabilities rated important that could lead to escalation of privilege and two memory corruption vulnerabilities rated important that could lead to disclosure of memory addresses.” states the advisory.
Adobe fixed an important information disclosure flaw in the Windows and Macintosh versions of Adobe Captivate, a smart authoring platform to create responsive eLearning content.
“Adobe has released security updates for Adobe Captivate for Windows and Macintosh. These updates resolve an important information disclosure vulnerability (CVE-2017-3087) resulting from abuse of the quiz reporting feature in Captivate. ” states the advisory.
The last issue was reported by Fortinet, it is a remote code execution vulnerability in Shockwave Player for Windows.
“Adobe has released a security update for Adobe Shockwave Player for Windows. This update addresses a critical memory corruption vulnerability that could lead to code execution. ” states the advisory.
Windows XP Receives Patches for More 'Shadow Brokers' Exploits
14.6.2017 securityweek Vulnerebility
Microsoft has released patches for Windows XP and other outdated versions of the operating system to fix several critical vulnerabilities that are at heightened risk of being exploited by state-sponsored actors and other threat groups.
The tech giant informed customers in mid-April that a series of exploits leaked by the group known as Shadow Brokers, which allegedly obtained the files from the NSA-linked Equation Group, had been patched in supported versions of Windows with the March security updates. According to some reports, the NSA itself disclosed these flaws to Microsoft following the Shadow Brokers leaks.
Roughly one month later, following the WannaCry ransomware attacks that hit hundreds of thousands of systems across the world, Microsoft decided to fix the SMB vulnerability leveraged by WannaCry in Windows platforms under custom support agreements.
The company has now decided to release more patches for these versions, including Windows XP, Windows Vista, Windows 8 and Windows Server 2003, to address other vulnerabilities that are at elevated risk of exploitation “due to past nation-state activity and disclosures.”
The list of patched flaws includes ones leveraged by three other exploits leaked by Shadow Brokers, namely EnglishmanDentist (CVE-2017-8487), EsteemAudit (CVE-2017-0176) and ExplodingCan (CVE-2017-7269).
Both supported and unsupported versions of Windows also received patches on Tuesday for two vulnerabilities, CVE-2017-8464 and CVE-2017-8543, that have been exploited in attacks by unnamed threat actors.
The list of older vulnerabilities that have now been fixed in outdated versions of Windows also includes remote code executions described in the MS17-013 bulletin, an Internet Explorer memory corruption (CVE-2017-0222), several Windows SMB flaws (CVE-2017-0267 - CVE-2017-0280), an actively exploited IIS buffer overflow (CVE-2017-7269), a Windows privilege escalation issue (CVE-2017-8552), and an actively exploited Windows olecnv32.dll RCE (CVE-2017-8487).
“Our decision today to release these security updates for platforms not in extended support should not be viewed as a departure from our standard servicing policies. Based on an assessment of the current threat landscape by our security engineers, we made the decision to make updates available more broadly,” said Eric Doerr, General Manager of the Microsoft Security Response Center.
“As always, we recommend customers upgrade to the latest platforms. The best protection is to be on a modern, up-to-date system that incorporates the latest defense-in-depth innovations. Older systems, even if fully up-to-date, lack the latest security features and advancements,” Doerr added.
Microsoft Patches Windows Flaws Exploited in Attacks
14.6.2017 securityweek Vulnerebility
Microsoft released patches for more than 90 vulnerabilities on Tuesday, including two critical remote code execution flaws that have been exploited in attacks and several weaknesses whose details have already been disclosed.
One of the actively exploited vulnerabilities is CVE-2017-8464, a LNK remote code execution flaw in Windows that is triggered when the icon of a specially crafted shortcut file is displayed.
“The attacker could present to the user a removable drive that contains a malicious shortcut file and an associated malicious binary. When the user opens this drive in Windows Explorer, or any other application that parses the icon of the shortcut, the malicious binary will execute code of the attacker’s choice on the target system,” Microsoft said in an advisory.
Researchers at the Zero Day Initiative (ZDI) pointed out that this vulnerability is similar to one exploited by the notorious Stuxnet worm, although they pointed out that CVE-2017-8464 may affect different parts of the code. In addition to the removable drive scenario described by Microsoft, ZDI said an attacker could also plant the malicious file in a remote location that is accessible to the targeted user.
Microsoft noted that the impact of this flaw is less severe if the targeted user does not have administrator rights.
Another vulnerability that has been actively exploited is CVE-2017-8543, a remote code execution bug affecting Windows Search.
“To exploit the vulnerability, the attacker could send specially crafted SMB messages to the Windows Search service. An attacker with access to a target computer could exploit this vulnerability to elevate privileges and take control of the computer,” Microsoft warned. “Additionally, in an enterprise scenario, a remote unauthenticated attacker could remotely trigger the vulnerability through an SMB connection and then take control of a target computer.”
Three of the vulnerabilities patched today by Microsoft – all of them affecting the Edge web browser – have already been publicly disclosed. They have been described as security feature bypass and information disclosure issues, but none of them has been rated critical.
A total of 18 flaws have been rated critical, while the rest are considered important. ZDI pointed out that the latest updates also patch vulnerabilities disclosed at Pwn2Own, but some bugs reported at the hacking competition still haven’t been addressed.
Adobe has also released updates on Tuesday to patch 20 vulnerabilities in Flash Player, Shockwave Player, Captivate and Digital Editions. Microsoft has included the Flash Player patches in its security updates.
SAP Releases 18 Security Notes in June 2017 Patch Day
14.6.2017 securityweek Vulnerebility
SAP this week released its June 2017 set of security patches to address various bugs across its products, including a denial of service vulnerability that potentially impacts over 3,400 services exposed to the Internet.
SAP included 18 security notes in its latest SAP Security Patch Day. Updates to previously released notes and 11 security notes being released after the second Tuesday of the previous month and before the second Tuesday of this month make for a total of 29 security notes being part of the June Patch Day (21 SAP Security Patch Day Notes and 8 Support Package Notes).
Five of the release notes had a High priority rating with two of the vulnerabilities featuring a CVSS score of 7.5. 23 of the issues had a Medium risk rating, and one was considered Low severity, ERPScan, a company that specializes in securing SAP and Oracle products, points out.
The most common vulnerability type addressed this month is Cross-Site Scripting (XSS), at 8 bugs, followed by denial of service (DoS) and information disclosure at 4, XML external entity at 3, missing authorization checks at 2, and cross-site request forgery, SQL injection, authentication bypass, and open redirect at 1 each.
The most important of the addressed issues were DoS bugs in SAP NetWeaver Instance Agent Service, and in BILaunchPad and Central Management Console, featuring a CVSS base score of 7.5 each. By terminating the process of the vulnerable component, an attacker could prevent access to the service.
“One of two Notes assessed at High priority is a DoS vulnerability in SAP Host Agent Service identified by our researchers. The vulnerability is remotely exploitable without authentication. We have also conducted a custom scanning that revealed that there are about 3,400 potentially vulnerable such services available online,” ERPScan’s Darya Maenkova told SecurityWeek in an email.
The issue, ERPScan says, was reported to SAP in November 2016, and could cause response delays and service interruptions, with direct impact on availability. Most of the vulnerable services exposed to the Internet are located in the United States (780), India (691), China (216), Korea (126), and Mexico (114).
Other High priority flaws that SAP addressed this month include a Cross-Site Scripting vulnerability (CVSS Base Score: 7.1) in SAP BusinessObjects Web Intelligence HTML interface and a Missing certificate verification vulnerability (CVSS Base Score: 7) in SAP CommonCryptoLib (a bug related to HTTPS certificates validation).
Another High risk security note is an update to a note released in March 2017: Improved security for outgoing HTTPS connections in SAP NetWeaver (CVSS Base Score: 7.4). As Onapsis explains, this note “includes more information on how to properly configure HTTPS connections securely.”
Eset objevil Industroyer, vážnou hrozbu pro průmyslové řídící systémy
14.6.2017 SecurityWorld ICS
Tento malware hrozí narušením kritických průmyslových procesů a představuje největší riziko od Stuxnetu.
Analytici společnosti Eset objevili vzorky malwaru schopného napadat infrastrukturu elektrického napájení. Malware, který Eset detekuje jako Win32/Industroyer, byl s největší pravděpodobností zapojen do útoku na energetickou síť Ukrajiny, během něhož byla v prosinci 2016 část ukrajinského hlavního města Kyjeva na hodinu odstavena od elektrické energie.
„Nedávný útok na ukrajinskou rozvodnou síť by měl sloužit jako výzva pro všechny, co jsou zodpovědní za bezpečnost kritických systémů na celém světě,“ varuje Anton Cherepanov, Senior Malware Researcher ve společnosti Eset.
Analytici společnosti Eset zjistili, že Industroyer je schopen přímo ovládat spínače a jističe elektrické sítě. Používá k tomu protokoly průmyslové komunikace, které jsou po celém světě běžné pro infrastruktury napájení, systémy řízení dopravy a jiné kritické infrastruktury. Potenciální dopad této hrozby se může pohybovat v rozmezí od jednoduchého vypnutí rozvodu elektrické energie přes kaskádovité poruchy až po vážnější poškození zařízení.
„Schopnost škodlivého kódu Industroyer přetrvávat v systému a přímo zasahovat do provozu průmyslového hardwaru z něj činí největší hrozbu od Stuxnetu, který v roce 2010 úspěšně napadl íránský jaderný program. Aktuálně jde o nejnebezpečnější škodlivý software zaměřený na průmyslové řídící systémy,“ uzavírá Anton Cherepanov.
Adobe Patches 20 Flaws in Flash Player, Other Products
13.6.2017 securityweek Vulnerebility
Updates released by Adobe on Tuesday for Flash Player, Shockwave Player, Captivate and Digital Editions address a total of 20 vulnerabilities, including critical weaknesses that can be exploited for remote code execution.
Nine vulnerabilities have been patched in Flash Player with the release of version 26.0.0.126. The security holes have been described as critical use-after-free and memory corruption flaws that can lead to remote code execution.
bee13oy of CloverSec Labs, Jihui Lu of Tencent KeenLab, and researchers from Google Project Zero reported the issues to Adobe. The flaws have been assigned the following CVE identifiers: CVE-2017-3075, CVE-2017-3081, CVE-2017-3083, CVE-2017-3084, CVE-2017-3076, CVE-2017-3077, CVE-2017-3078, CVE-2017-3079 and CVE-2017-3082.
Nine flaws have also been fixed by Adobe in the Digital Editions ebook reader. However, these bugs have a lower priority rating and only four memory corruptions that can be exploited for remote code execution are considered critical.
The other vulnerabilities, classified as important, can lead to privilege escalation and memory address disclosure. These flaws were reported to Adobe by experts from Tencent, Fortinet, CTU Security and Japan-based researcher Yuji Tounai.
Fortinet employees also informed Adobe of a remote code execution vulnerability in Shockwave Player for Windows. The problem is considered critical, but it has been assigned a priority rating of “2,” which means it’s less likely to be exploited.
One important information disclosure flaw has been fixed in the Windows and Macintosh versions of Adobe Captivate, an authoring tool that is used for creating e-learning content.
Weaponize a Mouse with WHID Injector for Fun & W00t
13.6.2017 securityaffairs Hacking
Researcher Luca Bongiorni has detailed the procedure to weaponize a new mouse with WHID Injector to show you how to create malicious HID devices.
Hello there! Finally, I had some spare time to Weaponize a new Mouse, in order to show you how easy is possible to create malicious HID devices.
Materials Needed:
WHID Injector [x1]
Mini USB HUB [x1]
Wired USB Mouse [1]
Soldering Kit (Iron, Flux, etc.)
Wires
Rubber Tape
Bit of Hot Glue
First of all let’s start ripping a part one mini USB HUB.
Usually, I do use one of these two:
Mini USB Mouse from Aliexpress
NanoHub USB from Tindie
For this project, I have used the first one, since was cheaper and already available in my lab.
Next step is to desolder all those wires while keeping notes of its pinouts (i.e. GND, D+, D-, Vcc) since we will have to match the USB pinouts with the WHID Injector.
Afterward, we will have to solder the wires to the WHID Injector as explained in its Wiki.

At this point, we need to solder back the wires in the USB HUB and connect WHID_Injector to it.
In my case the colors were:
Here below how it looks like once everything is assembled:
Now the tricky part is to put everything back into the plastic case… and voila’ the final result!
Now we test if everything works properly and start thinking of which payloads we can deploy, on-demand and remotely, into the targeted machines. 😎 P.S. These payloads are available at: Scammers Are Using Fake Apple In-App Subscriptions to Make Lot of Money MacSpy Malware Offered as Free Service 13.6.2017 securityweek Apple Virus Dubbed MacSpy and claiming to be the "most sophisticated Mac spyware ever”, the threat was built out of a “need of such programs on MacOS,” the malware’s author claims. The developers advertise the malware as free and advanced, but don’t appear to have set a specific price for the latter. The free variant includes support for anonymous communication over the TOR network, can capture screenshots, log keystrokes, record voice, retrieve clipboard content and browser data, and grab iCloud photos during the syncing process. Moreover, it is advertised as being completely untraceable courtesy of low memory and CPU usage, AlienVault discovered. The paid variant supposedly also allows users to adjust capture and recording intervals remotely, and can retrieve any files and data from the Mac, encrypt the entire user directory within seconds, and disguise the malware as a legitimate file format. Further, it supports daily archive of collected files, access to emails and social network accounts, and benefits from updates and code signing. The MaaS, however, doesn’t appear polished, as wannabe criminals can’t automatically sign up for the service, but need to email the author with the preferred username and password instead. After creating the account, the author sends a zipped file to the new user, along with unzipping instructions. Users can apparently infect machines by placing MacSpy’s unzipped folder onto a USB drive and manually executing a 64-bit executable called 'updated' when needed. The executable isn’t signed and doesn’t seem to be detected by the various AV companies on VirusTotal. In addition to the 'updated' file, the archive contains a 64-bit executable 'webkitproxy', a 64-bit dynamically linked shared library 'libevent-2.0.5.dylib', and a config file. Given that webkitproxy and libevent-2.0.5.dylib are signed by TOR, the researchers concluded they are related to the function of Tor Onion routing. The malware also includes anti-analysis capabilities, such as debugger and virtualization checks (CPU code count, amount of memory on the host). It also checks if it runs on a Mac, the same as MacRansom. For persistency, the threat creates a launch entry in ~/Library/LaunchAgents/com.apple.webkit.plist, ensuring it runs at every start up. After execution, the malware copies itself and associated files to “~/Library/.DS_Stores/” and deletes the original folder. Next, it uses the curl command to contact the command and control (C&C) server, and sends collected data to it using POST requests through the TOR proxy. It also deletes the temporary files it uses to collect data. The web portal is a “very bare bones directory listing containing a folder labeled the most recent date of the malware executing on a system in the YYYYMM format, followed by a folder in the DD format.” The folder includes directories resembling the directory naming on the victim system and containing the data collected from the victim. MacSpy, AlienVault notes, shows an increased focus on MacOS, which has been generally considered relatively safe from malware. “While this piece of Mac malware may not be the stealthiest program, it is feature rich and it goes to show that as OS X continues to grow in market share, we can expect malware authors to invest greater amounts of time in producing malware for this platform,” the security researchers conclude. IBM Adds New Service to Cloud Identity Offering 13.6.2017 securityweek Security IBM Cloud Identity Connect is a new Identity-as-a-Service (IDaaS) that provides quick and secure access to popular cloud applications using single sign-on (SSO) from any device, both from the cloud and on-premises. According to IBM, the new product aims to address the challenges of managing and securing multiple identities in hybrid cloud environments, which Gartner believes will be the most popular type of cloud. The new service, expected to become available in the IBM Cloud Marketplace on June 15, can be tested for 30 days for free. Customers of IBM Cloud applications such as Verse and Connections Cloud can use Cloud Identity Connect as a free one-year subscription for up to five apps. “Businesses need to infuse identity everywhere. Cloud Identity Connect makes it easier than ever before for customers to inspire productivity and efficiency – while ensuring their enterprise is securely managed and can effectively transition to the cloud,” said Jason Keenaghan, Director of Strategy and Offering Management, IAM and Fraud, IBM Security. “Regardless of where an organization is in that transition process, IBM is now positioned to scale on-premise and cloud offerings to meet the unique needs of nearly any business at any time.” IBM’s Cloud Identity offering also includes Cloud Identity Service, a comprehensive suite of identity and access management (IAM) capabilities designed to make it easier for organizations to move their IAM program to the cloud, and MaaS360 UEM, which is advertised as ideal for organizations that need unified endpoint management (UEM) for mobile devices. Emerging Matrix Banker Trojan is targeting banks in Latin America “Initially, we’ve called it “Matrix Banker” based on its command and control (C2) login panel, but it seems that “Matrix Admin” is a template available for the Bootstrap web framework. Proofpoint calls it “Win32/RediModiUpd” based on a debugging string from an earlier sample.” states Arbor Networks. The initial loader for Matrix Banker Trojan gains persistence through Registry Run, it extracts and injects a DLL into most popular Internet Browser, including Chrome, Firefox, Internet Explorer or Edge. The main DLL is injected in a browser to hook browser functions and run a Man-In-the-Browser attack. “Once the main DLL is injected in a browser, it starts by hooking the appropriate browser functions (e.g. PR_Read and PR_Write for Firefox) to setup a “man-in-the-browser” (MitB).” states the report. “It then phones home to its C2 server to get the webinject config. The request looks like this:” The malware then contacts the C&C server to get the webinject config. Matrix Banker is the first malware that encodes the and encrypts response from the C&C server with the Salsa20 crypto algorithm. Salsa20 is an unpatented stream cipher developed by Daniel Bernstein, it is the same algorithm used by the Petya ransomware to encrypt victims’ Master File Table. “While functional, the webinject format looks to be under construction.” state the report. “Earlier samples use a different, simpler format and there is plenty of work to do to catch up with the industry standard Zeus webinjects.” Experts noticed the malware uses a very difficult and effective redirection to a phishing page that looks like a perfect copy of the targeted bank’s login page.” Researchers believe it is not possible in this phase to predict the impact of the malware on a large-scale, the unique certainty is that the threat is actively being developed and targeting financial institutions in the wild. Americká kybernetická válka proti Islámskému státu selhala 13.6.2017 Novinky/Bezpečnost BigBrother Efektivita kybernetických zbraní podle něj narazila na své limity, když se pokusil zabránit tomu, aby Islámský stát přestal na internetu masově šířit svou propagandu a verbovat bojovníky i používat šifrované kanály pro komunikaci. Globální síť IS je většinou navzdory územním ztrátám v Sýrii a Iráku nedotčená, řekl na jaře Nicholas Rasmussen z Národního protiteroristického centra. Skupina pokračuje v publikování tisíců propagandistických děl a používá aplikace na síti, aby organizovala své příznivce a inspirovala je k útokům. Jsme schopni je oslepit Úspěch je krátkodobý Dým stoupající ze čtvrti Mišláb na jihovýchodě Rakky Internet je semeniště radikální ideologie Kybernetické velitelství narušuje nepřátelské velení během našich ofenzivních operací V poli se vede lépe „Jsme schopni je oslepit,“ řekl generál Jeffrey Harrigian, který velí spojeneckému letectvu v oblasti. „Jsou tu věci, které děláme spolu s kosmickým a kybernetickým velitelstvím a jsme schopni je synchronizovat, abychom dosáhli velkých výsledků dokonce i v Mosulu a Rakce.“ Další generál Sean MacFalrand, který velel v Iráku, naznačil, jak vše funguje: „Kybernetické velitelství narušuje nepřátelské velení během našich ofenzivních operací a tato podpora se zlepšila během doby, co jsem velel.“ Také se využívá údajů o poloze získaných z mobilních telefonů k útokům dronů na propagandisty IS. Eset nejspíše odhalil nebezpečnou ruskou kyberzbraň. Možná nás všechny odpojí od elektřiny Říkají mu Crash Override/Industroyer Specialisté z Esetu nejspíše zachytili ruskou zbraň pro kybernetickou válku Specialisté ze slovenského Esetu a společnosti Dragos, která se orientuje na bezpečnost průmyslových systémů, nyní přišli se zjištěním, ze kterého zamrazí. Anebo by mělo – přinejmenším správcům nejedné elektrické sítě po celém světě. Zatímco během útoků z roku 2015 se nejspíše jednalo pouze o hrubou sílu uplatněnou na ukrajinské počítačové systémy, loňský útok po důkladné analýze všechny překvapil svoji sofistikovaností, až příliš totiž připomíná třeba nechvalně proslulý Stuxnet. Mnohem nebezpečnější než někdejší Stuxnet Malware Stuxnet, za kterým pravděpodobně stály USA a Izrael, měl cíleně útočit na íránské průmyslové systémy a zkomplikovat tak tamní jaderné ambice. To bychom sice mohli na jednu stranu považovat za chvályhodné, ovšem už tehdy si mnozí kladli otázku, kdy někdo podobným způsobem zaútočí i na nás. Bezpečnost Malware útočí přímo na systémy rozvodné sítě Analytici, kteří zachytili jeho kód, přišli na to, že jakmile pronikne firewallem do nitra správy elektrické sítě a zneužije třeba nejrůznějších chyb v systémech od Siemensu, použije následně přímo průmyslové ovládací protokoly jednotlivých komponent. Jinými slovy, nezahltí hrubou silou třeba nějaký vedlejší webový systém, kvůli jehož havárii pak nemohou operátoři pracovat, ale vyšle do střediska rozvodné sítě přímý příkaz, aby ovládací mašina odpojila nějaký úsek. A co je nejhorší, Crash Override/Industroyer se umí i maskovat, takže operátor špatně zabezpečeného systému bude chvíli tápat, než pochopí, která bije. Industroyer nakonec může nestandardními chování stroje i poničit. Kód malwaru zároveň napověděl, že není určen pouze k útokům na jednu konkrétní – ukrajinskou – elektrickou síť, ale rozumí hned několika počítačovým systémům rozvodných sítí, a tak by mohl způsobit pohromu i v dalších zemích. Ostatně, analytici se domnívají, že útok z loňského prosince byl jen zkouškou (proof of concept) a cílem může být ve skutečnosti někdo jiný. Zbraně pro případný kybernetický válečný konflikt budoucnosti se tedy rok od roku zlepšují a ve svém zásahu se už vyrovnávají konvenčním zbraním. Pokud totiž dokážeme v roce 2017 odpojit v cíli elektřinu, sic třeba kvůli neadekvátně zabezpečené infrastruktuře, proč bychom rozvodnou síť ničili konvenčním útokem? Beware! Over 800 Android Apps on Google Play Store Contain 'Xavier' Malware Latvian Man Extradited to U.S. Over Scareware Operation 13.6.2017 securityweek Hacking The suspect, who made his first court appearance in Minneapolis on Monday, has been charged with wire fraud, computer fraud and conspiracy. Sahurovs and Marina Maslobojeva were arrested in Latvia in 2011 as a result of an international law enforcement operation dubbed “Trident Tribunal.” The operation targeted two massive scareware campaigns believed to have caused more than $74 million in losses to over one million people.Peteris Sahurovs Sahurovs, known online as "Piotrek," Piotrek89" and "Sagade," was released shortly after his arrest and he fled. He was arrested once again by law enforcement authorities in Poland in November 2016 and now he has been extradited to the U.S. The man was at one point the FBI’s fifth most wanted cybercriminal – the agency had offered a reward of up to $50,000 for information leading to his arrest. According to authorities, the suspect and other members of the conspiracy approached the Minneapolis Star Tribune’s news website, startribune.com, on behalf of a fake advertising agency that allegedly represented an American hotel chain. They purchased online advertising space from the news website and modified the initial ads with malicious code designed to deliver scareware to the site’s visitors. The scareware delivered by the group informed victims that their computers were infected with malware and instructed them to pay nearly $50 for a so-called antivirus software that would allegedly address the problem. While the Star Tribune is the only victim named in the indictment, the FBI said the cybercriminals used similar tactics against numerous other online businesses. Authorities said the scheme generated more than $2 million for the cybercriminals. Qualys Launches Container Security Product 13.6.2017 securityweek Security Qualys Container Security, which the company expects to become available in beta starting in July 2017, aims to help organizations proactively integrate security into container deployments and DevOps processes by extending visibility, vulnerability detection and policy compliance checks. One of the main features of the initial release will allow users to discover containers and track changes in real time. Organizations can visualize assets and relationships, enabling them to identify and isolate exposed elements.Qualys The product also provides vulnerability analysis capabilities for images, registries and containers. These capabilities can be integrated via the Qualys API into an organization’s Continuous Integration (CI) and Continuous Development (CD) tool chains, allowing DevOps and security teams to scan container images for known flaws before they are widely distributed. “Containers are core to the IT fabric powering digital transformation,” said Philippe Courtot, chairman and CEO of Qualys. “Our new solution for containers enables customers on that journey to incorporate 2-second visibility and continuous security as a critical part of their agile development.” In addition to Container Security, Qualys has announced a new add-on for the company’s Vulnerability Management product. The add-on, named Security Configuration Assessment (SCA), provides cloud-based tools for automating configuration assessment of IT assets using Center for Internet Security (CIS) benchmarks. The SCA add-on allows companies to scan their systems and assess, monitor and remediate security-related issues introduced by improper configurations. The product is already available for an annual subscription whose price depends on number of IPs. “Recent global cyber-attacks have served as a reminder that companies must take a proactive stance in securing the infrastructure and operations underpinning their digital transformation,” Courtot said. “Qualys SCA helps customers automate the security best practices behind leading benchmarks, and integrate them with DevSecOps for a more proactive approach towards securing today’s digital business.” Experts spotted Industroyer ICS Malware and linked it to Ukraine Power Outage Researchers at antivirus firm ESET have discovered a new strain of malware, dubbed Industroyer, that appears to have been designed to target power grids. “Win32/Industroyer is a sophisticated piece of malware designed to disrupt the working processes of industrial control systems (ICS), specifically industrial control systems used in electrical substations. ESET shared some data with ICS security firm Dragos that tracked the malware as CRASHOVERRIDE and the threat actor responsible for the campaign as ELECTRUM. Industroyer is the fourth malware specifically designed to target ICS systems, threats previously discovered by security experts are Stuxnet, BlackEnergy, and Havex. Industroyer is a sophisticated modular malware that includes several components such as a backdoor, a launcher, a data wiper, at least four payloads, and many other tools. The experts focused their analysis on the payloads (IEC 60870-5-101 (aka IEC 101), IEC 60870-5-104 (aka IEC 104), IEC 61850, OLE for Process Control Data Access (OPC DA)) the core components of the malware in the attacks that allow controlling electric circuit breakers. The Industroyer backdoor allows attackers to execute various commands on the targeted system, the C&C server is hidden in the Tor network and it can be programmed to be active only at specified times, making hard its detection. The backdoor installs the launcher component, which initiates the wiper and the payloads, it also drops a second backdoor disguised as a trojanized version of the Windows Notepad application. The wiper component is used in the final stage of the attack to hide tracks and make difficult to restore the targeted systems. The payloads allow the malware to control circuit breakers, it implements industrial communication protocols. Researchers at ESET believe the malware’s developers have a deep knowledge of power grid operations and industrial network communications. “In addition to all that, the malware authors also wrote a tool that implements a denial-of-service (DoS) attack against a particular family of protection relays, specifically the Siemens SIPROTEC range” continues ESET. “The capabilities of this malware are significant. When compared to the Both ESET and Dragos collected evidence that suggests Industroyer/CRASHOVERRIDE was involved in the 2016 power outages in Kiev region, which was attributed to Russia state-sponsored hackers. Researchers at Dragos believes the ELECTRUM APT group is directly linked to the Sandworm APT group, ESET highlighted that while there are no code similarities between the malware used in the 2015 and 2016 attacks in Ukraine, some components are similar in concept. “The CRASHOVERRIDE malware impacted a single transmission level substation in Ukraine on December 17th, 2016. Many elements of the attack appear to have been more of a proof of concept than what was fully capable in the malware. The most important thing to understand though from the evolution of tradecraft is the codification and scalability in the malware towards what has been learned through past attacks” states the report published by Dragos. Researchers at Dragos published the description of theoretical attacks, hackers used the Industroyer malware to open closed breakers in an infinite loop, causing the substation to de-energize. “The command then begins an infinite loop and continues to set addresses to this value effectively opening closed breakers. If a system operator tries to issue a close command on their HMI the sequence loop will continue to re-open the breaker. This loop maintaining open breakers will effectively de-energize the substation line(s) preventing system operators from managing the breakers and re-energize the line(s).” states the Dragos report. The operators of the targeted facility cannot close the breakers from the HMI, in order to restore the situation they need to interrupt communications with the substation and manually fix the problem. In another possible attack scenario, hackers initiate an infinite loop where breakers continually open and close, which can trigger protections and cause the substation to shut down. ICS Companies Are Worried About Cybersecurity, But Are They Worried About the Right Things? Companies operating Industrial Control Systems (ICS) have a special set of challenges to deal with. Which is the state of the art? Israeli Intelligence Discovered IS Plans for Laptop Bomb: Report 13.6.2017 securityweek BigBrothers Israeli government spies hacked into the operations of Islamic State bombmakers to discover they were developing a laptop computer bomb to blow up a commercial aircraft, the New York Times reported Monday. The Times said the work by Israeli cyber operators was a rare success of western intelligence against the constantly evolving, encryption-protected and social-media-driven cyber operations of the extremist group. It said the Israeli hackers penetrated the small Syria-based cell of bombmakers months ago, an effort that led to the March 21 ban on carry-on laptops and other electronics larger than cellphones on direct flights to the United States from 10 airports in Turkey, the Middle East and North Africa. The Israeli cyber-penetration "was how the United States learned that the terrorist group was working to make explosives that fooled airport X-ray machines and other screening by looking exactly like batteries for laptop computers," the Times said. The intelligence was so good that the detonation method for the bombs was understood, the Times said, citing two US officials familiar with the operation. Following the US laptop ban, Britain announced a similar prohibition for flights originating from six countries. Israel's contribution to the intelligence on the laptop bombs became public after President Donald Trump revealed details on it to Russian Foreign Minister Sergei Lavrov in a May 10 White House meeting. Trump's disclosure "infuriated" Israeli officials, according to the Times. New "Matrix Banker" Trojan Targets Latin America 12.6.2017 securityweek Virus In a quick analysis, serving more as early notification of its existence than a detailed technical analysis, Arbor Networks has posted a new report on a version compiled as recently as May 26, 2017. The initial loader for Matrix Banker sets persistence through Registry Run, and extracts and injects a DLL into Chrome, Firefox, Internet Explorer or Edge. The DLL hooks the relevant browser functions to establish the man-in-the-browser (MitB). The malware then phones home to its C2 server to get the webinject config. "Responses from the C2 are hex encoded and encrypted using the Salsa20 crypto algorithm," notes Dennis Schwarz, Sr. malware research analyst at Arbor. "This is the first malware family that we've seen that uses this algorithm." Salsa20 is an unpatented stream cipher developed by Daniel Bernstein. The Petya ransomware has always used Salsa20 to encrypt its victims' Master File Table. The Matrix Banker author's willingness and ability to employ unusual encryption contrasts with the current state of the malware's webinject. "While functional, the webinject format looks to be under construction," comments Schwarz. "Earlier samples use a different, simpler format and there is plenty of work to do to catch up with the industry standard Zeus webinjects." At the same time, the malware uses the more difficult but more recent and potentially more effective method of redirection to a phishing page. It was reported that the established and technically competent Gootkit banking trojan only moved to the redirection approach earlier this year. The ultimate success or failure of the redirect approach depends on the 'quality' of the false landing page. The better it is, the more likely is the user to enter his bank credentials. With Matrix Banker, Schwarz told SecurityWeek, "Visually, it looks like an exact copy of the targeted financial institution's login page." It is contradictions like these within the code that makes Arbor Networks believe the malware is still under development, and that it is too early yet to predict whether Matrix Banker will last the course. Nevertheless, it is in the wild and being used to target banks in Mexico and Peru. In the sample analyzed for this report, HTML and JavaScript code is used to redirect the user from the malware's targeted financial institution to the developer's copycat page hosted on "llinea[.]com". "Hoping the victim doesn't notice the redirect," says the report, "the threat actor will harvest the victim's banking credentials." Distribution is currently by botnet. "So far, we can trace it back to being dropped by another malware known as Beta Bot, which has been around for a long time," said Schwarz. "The associated Beta Bot samples are also being distributed via what looks like legitimate, but hacked sites with files like: Estado_Cuenta 29-05-2017.exe and CFE_Factura 30-05-2017.exe." "It is too soon to assess how active and widespread this new family will become," says Arbor, "but it is actively being developed and targeting financial institutions in the wild." 'Industroyer' ICS Malware Linked to Ukraine Power Grid Attack 12.6.2017 securityweek ICS Researchers have conducted a detailed analysis of a piece of malware that appears to have been specially designed for cyberattacks targeting power grids. The malware is believed to have been used in the December 2016 attack aimed at an electrical substation in Ukraine. The malware was discovered by ESET, which has dubbed it Industroyer. The company has also shared some data with ICS cybersecurity company Dragos, which tracks it as CRASHOVERRIDE and the threat actor that uses it as ELECTRUM. Links to Ukraine power grid attacks Malware designed to specifically target industrial control systems (ICS) is rare – Industroyer is only the fourth such threat known to the cybersecurity community. The other ICS-tailored malware families are Stuxnet, used in the 2010 attack targeting Iranian nuclear facilities, BlackEnergy, used in the December 2015 Ukraine power grid attacks, and Havex, used mainly against organizations in Europe. While they could not confirm that Industroyer/CRASHOVERRIDE was the direct cause of the 2016 power outages in Ukraine’s Kiev region, which are believed by many to be the work of Russia, both ESET and Dragos – based on compilation dates and other data – are fairly confident that this is the malware used in the attack. Dragos believes the ELECTRUM actor has direct ties to the BlackEnergy (Sandworm) group, and ESET pointed out that while there are no code similarities between the malware used in the 2015 and 2016 Ukraine attacks, some components are similar in concept. Attack scenarios Industroyer has been described as a sophisticated modular malware that has several components: a backdoor, a launcher, a data wiper, various tools, and at least four payloads. These payloads are the most interesting component as they allow the malware’s operators to control electric circuit breakers. In one theoretical attack scenario described by Dragos in its report, malicious actors use the malware to open closed breakers in an infinite loop, causing the substation to de-energize. By executing commands in an infinite loop, the attackers ensure that operators of the targeted facility cannot close the breakers from the HMI. This can require operators to interrupt communications with the substation and manually address the issue, which could result in an outage that lasts for a few hours. In another scenario described by researchers, the attackers initiate an infinite loop where breakers continually open and close, which can trigger protections and cause the substation to go offline. Experts believe that launching such an attack in a coordinated fashion against multiple sites could result in outages that last for a few days. Industroyer/CRASHOVERRIDE components The malware’s main backdoor component allows attackers to execute various commands on the infected system. It communicates with its command and control (C&C) servers over the Tor network and it can be programmed to be active only at specified times, which are likely mechanisms for avoiding detection. This component also deploys a secondary backdoor disguised as a trojanized version of the Windows Notepad application. The main backdoor is also responsible for installing the launcher component, which initiates the wiper and the payloads. The wiper is apparently designed for the final stages of the attack to help the attackers hide their tracks and make it more difficult to restore affected systems. This includes clearing registry keys, and overwriting ICS configuration and Windows files. The payloads, which allow attackers to control circuit breakers, leverage industrial communication protocols. This suggests that at least some of the malware’s developers have a deep understanding of power grid operations and industrial network communications. Other tools tied to the Industroyer malware include a custom-built port scanner and a denial-of-service (DoS) tool that exploits CVE-2015-5374 to cause Siemens SIPROTEC relays to become unresponsive. While the samples analyzed by ESET and Dragos can be used to target other energy organizations in Europe and some parts of the Middle East, the malware could also be adapted for attacks targeting the North American grid. Researchers at Dragos pointed out that while CRASHOVERRIDE appears to be designed to specifically target the energy sector, attackers could create new modules for other types of targets. Dangerous Malware Discovered that Can Take Down Electric Power Grids 12.6.2017 thehackernews Virus GameStop Confirms Payment Card Breach 12.6.2017 securityweek Incindent Video game and electronics retailer GameStop has started warning customers that their personal details and payment card data may have been stolen by cybercriminals. Security blogger Brian Krebs reported on April 7 that the GameStop.com website had apparently been breached. Krebs learned at the time from his sources in the financial industry that hackers had stolen names, addresses and card data entered on the site between mid-September 2016 and early February 2017. The company confirmed at the time that it had launched an investigation, but it only started notifying each impacted customer last week, specifying which of their payment cards may have been compromised. “Although the investigation did not identify evidence of unauthorized access to payment card data, we determined on April 18, 2017 that the potential for that to have occurred existed for certain transactions,” the company wrote in a letter mailed to customers. It turns out that hackers had access to the company’s website between August 10, 2016, and February 9, 2017. During this time, the cybercriminals may have stolen information provided when an order was placed, including names, addresses, card numbers, card expiration dates, and CVV codes. Payments made in stores do not appear to have been impacted. The company has not shared any information on how many of its customers have been affected by the breach. GameStop has provided some recommendations on how impacted customers can protect themselves, but it has not offered to pay for any specialized fraud protection services. The company has promised to enhance the security of its network to prevent future incidents. SambaCry Flaw Exploited to Deliver Cryptocurrency Miner 12.6.2017 securityweek Exploit These attacks, observed by both Kaspersky and Cyphort, were launched shortly after the existence of the security hole was brought to light and proof-of-concept (PoC) exploits were made available. The vulnerability, tracked as CVE-2017-7494, affects all versions of Samba since 3.5.0 and it has been addressed with the release of versions 4.6.4, 4.5.10 and 4.4.14. The flaw allows a malicious client to upload a shared library to a writable share, and cause the server to execute the file. In the attacks spotted by researchers, cybercriminals attempted to deliver files with a random name and a .so extension (e.g. GJZjrflB.so, INAebsGB.so, cblRWuoCc.so). The attackers first identified writable shares to which they could deliver their payload. In earlier attacks, the cybercriminals attempted to guess the local path needed to exploit the vulnerability, but Cyphort noticed that they later turned to using the NetShareGetInfo method, which provides information about a particular shared resource on a server. The first file delivered is a backdoor that provides the attackers a reverse shell they can leverage to remotely execute commands. Experts pointed out that this part of the attack is based on the Metasploit module released shortly after CVE-2017-7494 was disclosed. The backdoor is used to download and execute a popular open-source cryptocurrency miner named cpuminer (miderd). The miner is configured to abuse compromised systems to mine Monero (XMR) and send it to a wallet whose address is hardcoded. Kaspersky analyzed the wallet and found that, as of June 8, the attackers had obtained nearly 100 Monero, which is currently worth roughly $5,500. The domain from which the mining utility is downloaded was registered on April 29 and the attackers’ wallet started receiving Monero the next day. During the first two weeks the wallet received only one Monero per day, but the amount increased following the disclosure of CVE-2017-7494, and recently the attackers have been earning roughly 5 Monero each day. “The attacked machine turns into a workhorse on a large farm, mining crypto-currency for the attackers,” Kaspersky researchers said in a blog post. “In addition, through the reverse-shell left in the system, the attackers can change the configuration of a miner already running or infect the victim’s computer with other types of malware.” The Samba vulnerability has been found to affect many networking devices, including Cisco, Netgear, QNAP, Synology, Varitas and NetApp products. MacRansom: The first Mac ransomware offered as a RaaS Service The malware is available with Ransomware-as-a-service (RaaS) model through a hidden service in the TOR network. Experts believe this is the first time a Mac ransomware is offered as RaaS. “Just recently, we here at FortiGuard Labs discovered a Ransomware-as-a-service (RaaS) that uses a web portal hosted in a TOR network which has become a trend nowadays. However, in this case it was rather interesting to see cybercriminals attack an operating system other than Windows. And this could be the first time to see RaaS that targets Mac OS.” states the analysis published by Fortinet. Despite the threat is not sophisticated like other similar threats it could cause serious problems to the victims because it encrypts victim’s files. The availability of MacRansom as RaaS makes it easy to arranges ransomware campaign to crooks that have no specific skills. MacRansom variant is not readily available through the Tor portal, would-be crooks can contact the author of the ransomware in order to receive their version of the threat. “This MacRansom variant is not readily available through the portal. It is necessary to contact the author directly to build the ransomware. At first, we thought of it as a scam since there was no sample but to verify this we dropped the author an email and unexpectedly received a response.” continues the analysis. MacRansom implements symmetric encryption with a hard-coded key and the ransomware only encrypts a maximum of 128 files, it demands 0.25 bitcoin (around $700) for decryption keys. Researchers found two sets of symmetric keys used by the ransomware: ReadmeKey: 0x3127DE5F0F9BA796 The malicious code implements anti-analysis activity, the first thing the ransomware does is to check if the sample is being run in a non-Mac environment or if it is running in debugged environment. The author gives 30 per cent to the Bitcoin address of the customer once the victim has paid the ransom. Customers just have to spread the threat, for example delivering it via spam emails on through drive-by download attacks. The author discourages drive-by download attacks or other approaches that involve uploading customized versions of MacRansom. “It is not every day that we see new ransomware specifically targeting Mac OS platform. Even if it is far inferior from most current ransomware targeting Windows, it doesn’t fail to encrypt victim’s files or prevent access to important files, thereby causing real damage.” concluded Fortinet. “Last but not the least, this MacRansom variant is potentially being brewed by copycats as we saw quite a lot of similar code and ideas taken from previous OSX ransomware. Even though it utilizes anti-analysis tricks, which differs from previous OSX ransomware, these are well-known techniques widely deployed by many malware authors. MacRansom is yet another example of the prevalence of the ransomware threat, regardless of the OS platform being run.” Nový způsob distribuce malwaru. Na odkaz v prezentaci není nutné ani klepnout 12.6.2017 CNEWS.cz Viry Jak se může počítač nakazit malwarem? K typickým případům patří hypertextový odkaz v nevyžádané či podvodné zprávě, který otevřete. Stáhnete soubor, spustíte jej a dílo je dokonáno. Distribuce může být ovšem také automatická, takže o ní nemusíte vědět. Vraťme se k prvnímu případu – zdá se, že už na vložené odkazy nemusíte nutně klepat myší. Čerstvý výskyt jednoho trojského koně odhalil novinku. Odkaz se škodlivým kódem je vložený do prezentace pro PowerPoint. Kupodivu stačí, když nad něj najedete ukazatelem myši – infekce se tedy obejde bez klepnutí. Jak je to možné? Tentokrát se útočnictvo nespoléhá na klasické „hity“ jako makra nebo (Java)skripty. Při tomto útoku je zneužit Windows PowerShell. Podvratné je, že k vykonání příkazu stačí jen posunout ukazatel nad hypertextový odkaz. V šířené prezentaci z pohledu uživatele či uživatelky vidíte informační hlášku s tím, že dochází k načítání. Vy pak nad odkaz zamíříte a k jistému načtená skutečně dojde, jen to pro váš počítač nebude mít dobré důsledky. V tomto ohledu jsou nebezpečné především starší verze Microsoft Office. Novější totiž zobrazují bezpečnostní upozornění a nechají vás příkaz schválit. Novější verze PowerPointu vás upozorní, že chce prezentace provést příkaz Více o upravených prezentacích, které dokáží distribuovat malware bez klepnutí na odkaz, se dočtete na blogu Dodge This Security. V Linuxu byla objevena díra. V systému je už sedm let a hackeři ji teď aktivně využívají Kritická zranitelnost v populárním síťovém řešení Samba byla odhalena na konci května, přičemž postihuje všechny verze od 3.5.0, která byla uvolněna už v roce 2010. Uvedená chyba umožňuje získání plné kontroly nad ohroženým počítačem nebo serverem. Napadené systémy těží kryptoměnu Vývojáři Samby už chybu opravili. Záplaty byly průběžně zveřejněny také pro různé linuxové distribuce a díru je možné zacelit dokonce jen jediným řádkem v konfiguračním souboru. Přesto jsou útočníci úspěšní a našli dostatek neopravených systémů, které jim teď vytvářejí zisk. Bezpečnostní experti ze společnosti Kaspersky Lab zachytili krátce po zveřejnění detailů o zranitelnosti první útok, který ji dokázal úspěšně zneužít. V první fázi získali přístup do zranitelného linuxového systému, ve kterém experimentálně vytvořili textový soubor složený z osmi náhodných symbolů. Pokud byl pokus úspěšný, znamenalo to, že hackeři mají potřebné povolení a nic jim nestojí v cestě. Následně proběhla samotná infekce složená z dvojice modulů. "CblRWuoCc.so" vytvořil komplexní zadní vrátka, které mimo jiné obsahují i software CPUminer určený pro generování kryptoměn. "INAebsGB.so" je reverzní příkazový řádek poskytující vzdálený přístup k infikovanému systému. Prostřednictvím něj lze do počítače nainstalovat další malware, provádět jiné záškodnické aktivity nebo jen kontrolovat a měnit nastavení těžebního softwaru. Jak vydělat šest tisíc za den Jelikož je generování kryptoměn velmi náročné na výpočetní výkon, není překvapením, že různé organizované skupiny využívají množství zranitelných systémů právě pro tento účel. Za vše hovoří úvodní zisk autorů této kampaně. V době analýzy bylo na kontě útočníků celkově 98 XMR (alternativní kryptoměna, po přepočtu cca 125 tisíc korun), přičemž denní zisk činil cca 6 tisíc korun a stále průběžně stoupal. Zranitelnost byla opravena ve verzích 4.6.4, 4.5.10, 4.4.14 a v novějších. Pro verze 4.6.3, 4.5.9 a 4.4.13 byla uvolněna odpovídající záplata. Opravené verze zpřístupnili i tvůrci jednotlivých linuxových distribucí. V případě, že nemůžete přejít na nejnovější verzi, respektive nainstalovat záplatu, stačí do konfiguračního souboru softwaru Samba (smb.conf) vložit následující řádek: nt pipe support = no Chyba ve FreeRADIUS umožňuje připojení k Wi-Fi bez hesla Ve frameworku EAP se používají následující pojmy: supplicant (žadatel) – zařízení či příslušná část softwaru na zařízení, které se chce připojit do sítě, Protokol PEAP definuje dvě fáze autentizace. V první se vytvoří šifrovaný tunel dle standardu TLS. Součástí je autentizace serveru, tj. kontrola jména a certifikátu serveru. Ve druhé fázi se ověřuje supplicant/zařízení. Posílá se reálné uživatelské jméno, pro ověření správného hesla se obvykle používá protokol MS-CHAPv2. Komunikace probíhá uvnitř vytvořeného TLS tunelu. Po úspěšné autentizaci RADIUS server pošle autentizátoru zprávu Access-Accept, která obsahuje podklady k domluvení klíčů na zašifrování komunikace mezi zařízením a přístupovým bodem. Následuje tzv. 4-way handshake, který je popsán např. v článku „Odposlouchávání a prolamování Wi-Fi sítí zabezpečených pomocí WPA2“. Ve schématu není vyjádřena EAP fragmentace – certifikáty serveru se nevejdou do jedné EAP zprávy a proto nutně dochází k rozdělení do více EAP zpráv a každá z nich se potvrzuje. Při úspěšné autentizaci si zařízení s našim RADIUS serverem vymění obvykle 11 zpráv. Již od SSLv3 je součástí TLS podpora obnovení spojení (session resumption, viz RFC5246 sec 7.4.1.2). Nejdříve proběhne úplná TLS výměna a na jejím konci si obě strany uloží vygenerované session ID a bezpečnostní parametry včetně hlavního tajemství (master secret). Při vytváření následného spojení klient pošle session ID a pokud je platné, tak si obě strany obnoví uložený stav. Obnovení spojení výrazně zkracuje úvodní TLS výměnu, neboť není potřeba posílat certifikáty či se domlouvat na bezpečnostních parametrech. V protokolu PEAP je definováno rychlé obnovení spojení (Fast Reconnect), které zahrnuje obnovení TLS spojení a též přeskočení autentizace a autorizace klienta ve druhé fázi. Při rychlém obnovení spojení obvykle postačuje vyměnit 4 zprávy s RADIUS serverem. Snižuje se i zatížení serveru, neboť nemusí ověřovat heslo vůči databázi či LDAP serveru. Připojení protokolem EAP-TTLS má velmi podobný průběh. Pro rychlé obnovení spojení používá označení session resumption. FreeRADIUS rychlé obnovení spojení podporuje od verze 2.1.x. Ve verzi 3.0.x je již povoleno ve výchozí konfiguraci. Údaje o sezení si ukládá do paměti či na disk, údaje jsou platné 24 hodin. Odhalení zranitelnosti Zavolali jsme mu a shodli se na tom, že někomu pomáhal nastavovat připojení do eduroam na mobilu. A protože dotyčný neznal své heslo, tak kolega použil své přístupové údaje. Po telefonátu si kolega změnil své heslo do eduroam a tím jsme problém považovali za vyřízený. Druhý den kolega dorazil do práce a v průběhu dne jsme tak mezi řečí odbočili i k této záležitosti. Podívali jsme se do logů – a i tento den se stejné zařízení přihlásilo do eduroam pod účtem kolegy. Donutili jsme kolegu změnit si znovu heslo. Po změně hesla se notebook kolegy do WiFi nepřihlásil, dokud si na něm nenastavil nové heslo. Po víkendu jsme se vrátili do práce – neznámé zařízení se opět přihlásilo pod účtem kolegy. To již začalo být podezřelé. První nás napadla chyba v konfiguraci RADIUS serveru. Prošel jsem všechny konfigurační soubory, spustil několik testovacích skriptů, ale nic jsem nenašel. V detailních logách požadavků a odpovědí vypadal průběh komunikace takto: Time |Direction, Type | UserName |Calling-station-id Apr 12 09:57:25 2017| --> Acesss-Request |user@vse.cz|"7C-11-BE-5B-xx-xx" Při debugování jsme zjistili, že první komunikace skončí na začátku druhé fáze PEAP autentizace, kdy supplicant neodpoví na MS CHAPv2 Challenge. Zařízení následně zruší asociaci s přístupovým bodem, připojí se k jinému přístupovému bodu bezdrátové sítě a poté zkusí rychlé obnovení spojení (Fast Reconnect). To je úspěšné, čímž se úplně obejde autentizaci i autorizaci. Z analýzy zdrojových kódů vyplynulo, že FreeRADIUSu ukládá údaje o spojení ihned po vytvoření TLS tunelu s předpokladem budoucí úspěšné autentizace. Pokud autentizace a autorizace ve druhé fázi není úspěšná (EAP Failure), tak se údaje spojení z cache vymažou. Autoři FreeRADIUSu neošetřili předčasné ukončení komunikace ve druhé fázi autentizace. O ověření zranitelnosti jsem požádal Pavla Kaňkovského z MFF UK, kterému velmi děkuji, že se začal problému intenzivně věnovat. Analyzoval zdrojové kódy a následně upravil testovací aplikaci eapol_test na otestování zranitelnosti. Též nahlásil zranitelnost autorovi FreeRADIUSu a spolupracoval s ním na jejím odstranění. 26. května vyšel FreeRADIUS verze 3.0.14, který chybu opravuje. Zranitelnost má přiděleno označení CVE-2017–9148. Zajímavostí je, že zranitelnost byla nahlášena již dříve. První pokus o opravu z února 2017 se příliš nezdařil, verze 3.0.13 je stále děravá. Na řešení se velkou měrou podílel i správce národní eduroam federace Jan Tomášek z CESNETu, který o zranitelnosti informoval správce z připojených institucí i správce z jiných zemí. Do monitorovacího systému české federace eduroam doplnil pravidelné testování zranitelnosti u jednotlivých členů. Zneužívá se zranitelnost v praxi? V logách z FreeRADIUSu jsme našli 22 zařízení, která se do eduroam přihlásila s využitím uvedené zranitelnosti. 16 zařízení je od firmy Apple, v některých případech se takto přihlašují do eduroam již přes 4 měsíce. Některá z nich se takto připojují téměř každý den. Někteří vlastníci těchto mobilů si stěžovali, že s připojením do eduroam mají problémy – občas se jim mobil nepřipojí. V logách jsem našel případ jednoho zařízení, které se v průběhu dne snažilo připojit v 11:18, 11:53, 12:20, 12:40, 13:27,13:52 a 14:07. Teprve při posledním pokusu použilo fintu se zneužitím popisované zranitelnosti. Na zapůjčeném iPhone 4S jsme byli schopni nasimulovat autentizaci bez ověření hesla. Obvykle stačí se jednou úspěšně přihlásit. Po změně hesla se zařízení dále „přihlašuje“ bez nutnosti zadat na něm nové heslo. Na iPhone se neobjeví dotaz na nové heslo. Na iPhone 6 s novější verzí IOS se nám zneužití zranitelnosti nasimulovat nepodařilo. 6 zařízení má nainstalováno některou verzi systému Android, nejstarší je 4.1.2, nejnovější 6.0.1. Zařízení jsou od čtyř různých výrobců: Samsung, Lenovo, Motorola, Huawei. Využití zranitelnosti není spojeno se změnou hesla. Zařízení se úspěšné autentizuje pomocí hesla, poté se několik dní nepřipojí, největší nalezená přestávka je 15 dní. A poté se připojí s využitím uvedené zranitelnosti, tj. první pokus se v průběhu druhé fáze PEAP autentizace přeruší a poté následuje autentizace s obnovením spojení. V následující dny se připojují s ověřením hesla. Vzhledem k počtu výskytů jsem schopen uvěřit tomu, že přerušení při prvním pokusu o autentizaci je způsobené výpadky na síti. Řešení je snadné Nenarazili jsme na upravený software na zařízeních, který by tuto zranitelnost aktivně využíval. Starší zařízení firmy Apple nejspíše neúmyslně využívají chybu k obcházení bezpečnostní politiky. Pokud nastavím nové heslo, tak očekávám, že se zařízení s uloženým starým heslem již znovu nepřihlásí. Náhodně mohou chybu použít i další zařízení k připojení do sítě. Řešení je poměrně jednoduché: vypnout ve FreeRADIUSu cachování TLS session. Ve verzi 3.0.x to znamená nastavit „enabled = no” v sekci cache souboru raddb/mods-enabled-eap. SambaCry Flaw Exploited to Deliver Cryptocurrency Miner 12.6.2017 securityweek Exploit These attacks, observed by both Kaspersky and Cyphort, were launched shortly after the existence of the security hole was brought to light and proof-of-concept (PoC) exploits were made available. The vulnerability, tracked as CVE-2017-7494, affects all versions of Samba since 3.5.0 and it has been addressed with the release of versions 4.6.4, 4.5.10 and 4.4.14. The flaw allows a malicious client to upload a shared library to a writable share, and cause the server to execute the file. In the attacks spotted by researchers, cybercriminals attempted to deliver files with a random name and a .so extension (e.g. GJZjrflB.so, INAebsGB.so, cblRWuoCc.so). The attackers first identified writable shares to which they could deliver their payload. In earlier attacks, the cybercriminals attempted to guess the local path needed to exploit the vulnerability, but Cyphort noticed that they later turned to using the NetShareGetInfo method, which provides information about a particular shared resource on a server. The first file delivered is a backdoor that provides the attackers a reverse shell they can leverage to remotely execute commands. Experts pointed out that this part of the attack is based on the Metasploit module released shortly after CVE-2017-7494 was disclosed. The backdoor is used to download and execute a popular open-source cryptocurrency miner named cpuminer (miderd). The miner is configured to abuse compromised systems to mine Monero (XMR) and send it to a wallet whose address is hardcoded. Kaspersky analyzed the wallet and found that, as of June 8, the attackers had obtained nearly 100 Monero, which is currently worth roughly $5,500. The domain from which the mining utility is downloaded was registered on April 29 and the attackers’ wallet started receiving Monero the next day. During the first two weeks the wallet received only one Monero per day, but the amount increased following the disclosure of CVE-2017-7494, and recently the attackers have been earning roughly 5 Monero each day. “The attacked machine turns into a workhorse on a large farm, mining crypto-currency for the attackers,” Kaspersky researchers said in a blog post. “In addition, through the reverse-shell left in the system, the attackers can change the configuration of a miner already running or infect the victim’s computer with other types of malware.” The Samba vulnerability has been found to affect many networking devices, including Cisco, Netgear, QNAP, Synology, Varitas and NetApp products. Egypt blocks dozens of websites including ‘Medium’ without any official announcement Recently Egyptian Government blocked several news websites, including MadaMasr, Daily News Egypt, Al Borsa, Al Jazeera, Huffington Post Arabic and others, for supporting terrorism and Muslim Brotherhood. From 24 May to 11 June, several websites that are licensed to work in Egypt have been blocked, a measured that is considered a violation of the Article 57 stipulating the freedom of media and public’s right to know and to access information. Officially the Medium service was up & running, the there is no official report about blockage in the last 24 hours across the world, it is likely that the website has been blocked only in Egypt. Below a screenshot of the error page displayed to the users while trying to access Medium.com from Egypt. Below the tweet sent by the Radio Sawa Washington Correspondent, Zaid Benjamin about the alleged blockage. Follow “Al Bedaiah and El Badil news sites have been blocked on Sunday raising the number of blocked websites to 57, according to the Association of Freedom of Thought and Expression (AFTE). In a span of 3 weeks, an unknown body gradually blocked news websites including independent news website “Mada Masr” and the privately-owned Daily News Egypt.” According to AFTEs report. test conducted by the researchers suggest that Internet monitoring is operated through the Vodafone network, During blocking tests, it was indicated that there might be Internet monitoring through Vodafone network, according to AFTEs report. “AFTE has tested the accessibility of blocked sites through a variety of Internet service providers in Egypt (TE Data, Vodafone, Orange, Etisalat, LINKdotNET, NOOR). The association has used the Tor browser, various proxy services and websites, and VPN service to make sure that the sites work outside of Egypt.” states the report. “During OONI blocking tests, the (HTTP Invalid Request Line) test showed data that might indicate Internet monitoring on Vodafone network. The result shows that, based on the technique used in this test, the use of three spy software (BlueCoat, Squid, Privoxy) in 11 different countries, was detected.” Several members of the press syndicate expressed their opposition to the ban decision. French Police Seize 6 Tor Relay Servers in WannaCry Investigation Analyzing the attack landscape of the Dark Web. There is no honor among thieves. The research aims to analyze how crooks target platforms run by other criminal organizations or individuals. The honeypots used by the experts consisted of: A black market that only trades between a close circle of invited members. “To this end, we simulated a cybercriminal installation in Tor using several honeypots. Each honeypot exposes one or more vulnerabilities that would allow an attacker to take ownership of the installation. Upon infection we automatically recorded all logs and restored the environment to a clean state.” reads the analysis published by Trend Micro. The following chart shows the average number of daily attack attempts, as measured by the number of POST requests, in just one month, the number of attacks spiked to 160 per day, most of them successful. The first discovery made by the researchers is that many attacks were originated from Tor proxies like Tor2web that allows reaching hidden services from the clear web. “Tor proxies like Tor2web made Tor hidden services reachable without requiring any additional configuration from the public internet. Our honeypot was automatically made available to traditional search engines, and implicitly dangled as a target for automated exploitation scripts,” states the report. The analysis of the attacks revealed that most of them installed web shells on the server to gain control over it, in the majority of the cases attackers used the machine to power DDoS attacks and to run spam campaigns. In order to analyze only attacks from within the Dark Web, researchers filtering the traffic from Tor proxies, then observed the number of attacks drastically decreased. A second point emerged from the analysis is that while the attacks from Tor proxies were performed with automated tools, attacks from within the Dark Web were most manually conducted. “Attackers from the open internet tended to use automated attack tools, while Dark Web attackers tended to carry out manual attacks as they were generally more cautious and took their time. For example, once they gained access to a system via a web shell, they would gather information about the server first by listing directories, checking the contents of databases, and retrieving configuration/system files.” continues the report. “These manual attackers often deleted any files they placed into our honeypot; some even went ahead and left messages for us (including ‘Welcome to the honeypot!’), indicating that they had identified our honeypot.” The results of the study confirm that organizations operating in the Dark Web seem to be attacking each other. Hackers from within the Dark Web carried out the following attacks: Defacements aimed at subverting the business of our honeypot and aimed at promoting a competitor web site, possibly run by the attackers. “Apparently, there is no honor among thieves.” Police seized two Tor relays investigating WannaCry attack, others disappeared in the same period France’s cyber-crime investigation unit OCLCTIC seized one server running two Tor Relays Investigating the WannaCry attack. The server was operated by the French activist Aeris that reported the police’s action through the Tor Project mailing on May 15 asking other Tor operators to revoke trust in the two seized relays. The server was seized by France’s cyber-crime investigation unit OCLCTIC (L’Office Central de Lutte contre la Criminalité liée aux Technologies de l’Information et de la Communication). According to Aeris, the police seized the server hosted at hosting company Online SAS, because the traffic associated with WannaCry ransomware that infected a big French company on May 12 was pointing the two Tor relays. The WannaCry samples that infected the company were communicating with a command and control server hosted on the Tor Network, and it is likely that the server were used as a first hop of the Tor traffic. “Most Tor servers are configured to log very few details, such as uptime and status metrics, so to safeguard the privacy of its users. Unless Aeris made customizations to default configs, French police have no chance of finding any useful information on the seized servers.” reported Catalin Cimpanu from Bleepingcomputer.com. Aeris confirmed that tens of other Tor nodes in France disappeared just after the WannaCry attack, he provided Bleeping Computer a list of 30 servers he is currently investigating. “We have confirmation of 6 Tor nodes seizures [from 5 operators],” the activist told Bleeping Computers. ” A seized relay is not of this list because of hosted on another provider.”
Critical kernel command line injection flaw found in Motorola handsets MOTO G4, G5 Security experts have discovered a critical kernel command line injection vulnerability in the Motorola handsets Moto G4 and Moto G5. The flaw affects also handsets running the latest Motorola Android bootloader and could be exploited by a local malicious application to execute arbitrary code on the mobile device. The experts were able to exploit the vulnerability on the Motorola handsets by abusing the Motorola bootloader download functionality in order to force loading their malicious initramfs image (initial RAM file system) at a known physical address, named SCRATCH_ADDR. “Vulnerable versions of the Motorola Android Bootloader (ABOOT) allow for kernel command-line injection. We can inject a parameter, named initrd, which allows us to force the Linux kernel to populate initramfs into rootfs from a specified physical address.” reads the advisory published by the researchers. “We can abuse the ABOOT download functionality in order to place our own malicious initramfs at a known physical address, named SCRATCH_ADDR (0x11000000 for Nexus 6). Exploiting the vulnerability allows the adversary to gain an unrestricted root shell. (And more!)” Earlier this year, the security experts at Aleph Research have found the same flaw, tracked as CVE-2016-10277, in the Nexus 6 Motorola bootloader, Google fixed it last month. A local attacker could break the secure/verified boot mechanism to gain unrestricted root privileges and load a tampered or malicious initramfs image. “By exploiting the vulnerability, a physical adversary or one with authorized-ADB/fastboot USB access to the (bootloader-locked) device (such as PC malware awaiting for an ADB-authorized developer’s device to be hooked via USB) could break the Secure/Verified Boot mechanism, allowing him to gain unrestricted root privileges, and completely own the user space (which may also lead much more), by loading a tampered or malicious initramfs image. Moreover, exploitation does not lead to a factory reset hence user data remains intact (and still encrypted). It should be noted that we do not demonstrate an untethered attack.” the researchers wrote when discovered the flaw in the Nexus 6. The experts suggested the Kernel Command-line Injection issue in the Nexus devices could affect also devices from other vendors, so they decided to focus their tests on Motorola handsets. US Defense is working on new multifactor authentication systems DARPA is currently developing a multifactor authentication system that will replace the current common access card (CAC). DARPA is currently developing a multifactor authentication system that aims to replace the current common access card (CAC) which leverages two-factor authentication. The solution will verify the identity of the person using biometrics and behavioral analysis. Behavioral analysis is based on the concept of “patterns of life,” an individual is identified by analyzing his actions and comparing them to a database of habits. “The new system will employ behavioral analysis and biometrics to ensure that the identity of the person using the network is verified. This probably would feature “patterns of life,” in which a person’s actions are compared to their established habits, Gen. Lynn relates.” states Americansecuritytoday.com. biometrics authentication The Department of Defense (DoD) plans to adopt multi-factor authentication solutions including biometrics and other “patterns of life” technologies to replace access cards in the next months. In April, Alfred Rivera, Defense Information Systems Agency’s (DISA) director at that time, confirmed that the agency was analyzing different solutions from several vendors and that was searching for innovative technologies. Lt. Gen. Alan R. Lynn, who lead DISA and Joint Force Headquarters, Department of Defense Information Network (JFHQ-DODIN), announced that both agencies are searching for any solutions that could help to stay ahead of cyber adversaries “The cyber battlefield is growing, it’s unending and it’s 24/7, and we have to keep a constant eye on it, and any tools that industry can bring, we’re interested in,” said Gen. Alan R. Lynn. “If there is some technology that would allow us to provide more bandwidth, more capability, we’re interested in that as well.” DISA representatives will discuss new cyber tools for the creation of safe and secure cyber-physical systems at the AFCEA International’s Defensive Cyber Operations Symposium, to be held June 13-15 at the Baltimore Convention Center. SambaCry is reality, crooks are abusing CVE-2017-7494 to spread miners Security experts from Kaspersky confirmed that threat actors in the wild are exploiting the SambaCry vulnerability CVE-2017-7494 to spread a miner. The flaw, dubbed SambaCry, can be easily exploited, just a line of could be used for the hack under specific conditions: make file- and printer-sharing port 445 reachable on the Internet, “All versions of Samba from 3.5.0 onwards are vulnerable to a remote code execution vulnerability, allowing a malicious client to upload a shared library to a writable share, and then cause the server to load and execute it.” reads the security advisory issued by Samba. http://www.samba.org/samba/security/ Sysadmins have to patch their versions as soon as possible, if it is not possible for any reason a workaround can be implemented by the adding the line nt pipe support = no The change will limit clients from accessing some network computers. “Additionally, Samba 4.6.4, 4.5.10 and 4.4.14 have been issued as security releases to correct the defect. Patches against older Samba versions are available at http://samba.org/samba/patches/. Samba vendors and administrators running affected versions are advised to upgrade or apply the patch as soon as possible.” The Samba bug appears to be a network wormable issue that could be exploited by a malicious code to self-replicate from vulnerable machine to vulnerable machine without requiring user interaction. Security researcher speculated that a rapid increase in the number of cyber attacks leveraging the SambaCry issue, just like WannaCry attacks. Researchers at Kaspersky Lab set up honeypots to detect SambaCry attacks in the wild. The experts have spotted a malware campaign that is exploiting SambaCry vulnerability to infect Linux systems and install a cryptocurrency miner. The independent security researcher Omri Ben Bassat also observed the same campaign that he dubbed “EternalMiner.” The expert confirmed threat actors started exploiting the SambaCry flaw just a week after its discovery to hijack Linux PCs and to install an upgraded version of “CPUminer,” a Monero miner. INAebsGB.so — A simple reverse shell that allows a remote attacker to access the target system. According to Kaspersky, threat actors behind this campaign have already earned 98 XMR, which worth USD 5,380 today. The experts believe that crooks could earn much more with the increase in the number of compromised Linux systems. “The mining utility is downloaded from the domain registered on April 29th 2017. According to the log of the transactions, the attackers received their first crypto-coins on the very next day, on April 30th. During the first day they gained about 1 XMR (about $55 according to the currency exchange rate for 08.06.2017), but during the last week they gained about 5 XMR per day. This means that the botnet of devices working for the profit of the attackers is growing.,” the researchers say. Warning! Hackers Started Using "SambaCry Flaw" to Hack Linux Systems Two Tickets as Bait Naturally, there have been no promotions to give away airline tickets. Users were addressed by fraudsters who assumed the names of the largest airlines in order to subscribe their victims to paid mobile services, collect personal data, install malware, and increase traffic to websites with advertisements and dubious content. To do this, fraudsters have been registering a multitude of domains, where they host content on behalf of well-known brands. At the mentioned resources, users are congratulated on winning two airline tickets. Then, they’re asked to perform a series of actions to receive the gift. As a result, the victim ends up on another website that belongs to fraudsters, which monetizes their “work” and spreads information about the nonexistent campaign on a social network. An example of a social-network post with a link to a fraudulent website This is by no means the first case where users themselves have started spreading fraudulent content on social networks. We have previously about a fake petition in defense of Suarez, which was distributed by Facebook users, fake donations, and pornware. All of the incidents have one thing in common: the threats are distributed over social networks, which users themselves often participate in. The attack model Let us return to the most recent case and examine it a bit closer. By following the link from a social network news feed, a user navigates to a fraudulent website. We have found a series of domains that belong to fraudsters: deltagiveaway.com, vvxwx9.us, aeroflot-com.us, aeroflot-ticket.us, qq3mz9.us, emiratesnow.us, emiratesgo.us, com-beforeitsends.us, emirates.iwelltrip.us, and many others. Some examples of fraudulent websites that make use of famous airline brands Since the fraudulent schemes only varied by logo, language, and color scheme, depending on the brand, let’s take one website out of the many and discuss it. The website that claims to belong to American Airlines contains information about a promotional giveaway of two tickets to respondents who must answer three questions. An example of a fraudulent website that uses American Airlines branding. After completing the survey, the victim is asked to take two more steps. First, the victim is asked to post the promotional information on his or her page on a social network and thank the airline in the comment. Secondly, the victim has to click the “Like” button. It should be noted that the web page shows what appear to be Facebook comments from users who have already won tickets. An investigation showed that the comments are actually fake. We can even leave our own comment, but it will disappear after the page is refreshed. All of this is directed at coaxing a victim into believing that the page is legitimate. We would like to note that most comments are posted in various languages by the same people, andthe messages are similar in content and most likely are translated using machine translation. After performing all of the necessary actions, the website redirects the user to various web pages by using the geolocation feature. In some cases, we were redirected to the websites shown below. Each time all of the same aforementioned actions are performed and the same survey is completed, the website does something different and may redirect users to various web pages. We have found websites with a variety of dubious content, including lotteries, advertisements, new surveys with giveaways, links to suspicious files that can be downloaded, and so on. Among other things, some websites suggests users download a certain useful file and at the same time urge them to install a potentially dangerous extension for a browser. The extension obtains permission to read all of the data in a browser, potentially allowing fraudsters to get a hold of passwords, logins, credit-card data, and other confidential information entered by the user. Aside from that, later on, the extension may continue spreading links that redirect users to the extension itself on Facebook but on behalf of the user and among his or her friends. This is exactly the threat that was carried out by an attack that we discussed previously. At the moment of publication, this indicated extension alone had been installed on the systems of over 5,000 users, according to the statistics of the web apps store. The number of victims and their location Most resources that utilize the fraudulent scheme contain links to external services that collect statistics for website traffic. These data show that the attack was widely distributed and was mostly directed at smartphone users. For example, here are some impressive statistics for only two of all the domains that we discovered. Statistics for the aeroflot-ticket.us website Statistics for the aeroflot-ticket.us website Statistics for the emirateswow.us website Unfortunately, numerous users took the bait of the fraudsters. These users tried their luck and did not pay attention to a multitude of signs that are typical for a scam, which resulted in spreading potentially dangerous content among friends over a social network. Some examples of published posts with links to fraudulent websites Thus, fraudulent web resources and a plethora of their counterparts across the Internet gained huge popularity in a matter of hours. Some examples of published posts with links to fraudulent websites Finally, here are a few pieces of advice. You should be sensibly skeptical about similar “promotions”. Before navigating to suspicious links and entering your personal data on a web resource, you should contact a representative of the company that is supposedly running the promotion and confirm the information. SambaCry is coming Not long ago, news appeared online of a younger sibling for the sensational vulnerability EternalBlue. The story was about a new vulnerability for *nix-based systems – EternalRed (aka SambaCry). This vulnerability (CVE-2017-7494) relates to all versions of Samba, starting from 3.5.0, which was released in 2010, and was patched only in the latest versions of the package (4.6.4/4.5.10/4.4.14). On May 30th our honeypots captured the first attack to make use of this particular vulnerability, but the payload in this exploit had nothing in common with the Trojan-Crypt that was EternalBlue and WannaCry. Surprisingly, it was a cryptocurrency mining utility! Vulnerability exploitation In order to check that an unauthorized user has permissions to write to the network drive, the attackers first try to write a text file, consisting of 8 random symbols. If the attempt is successful they delete the file. Writing and deleting the text file After this check, it is time for the exploit’s payload (it is assembled as a Samba plugin). After successful exploitation of the vulnerability, this runs with super-user privileges, although first the attackers have to guess the full path to the dropped file with their payload, starting from the root directory of the drive. We can see such attempts in the traffic captured on our honeypot. They are just brute-forcing the most obvious paths (specified in different manuals, etc.), where files can be stored on the drive. Bruteforcing the pathto the payload After the path to the file is found, it can be loaded and executed in the context of the Samba-server process, using the SambaCry vulnerability. Afterwards the file is deleted in order to hide the traces. From this moment it exists and runs only in the virtual memory. In our case two files were uploaded and executed in such a way: INAebsGB.so (349d84b3b176bbc9834230351ef3bc2a – Backdoor.Linux.Agent.an) and cblRWuoCc.so (2009af3fed2a4704c224694dfc4b31dc – Trojan-Downloader.Linux.EternalMiner.a). INAebsGB.so This file stores the simplest reverse-shell. It connects to the particular port of the IP-address specified by its owner, giving him remote access to the shell (/bin/sh). As a result, the attackers have an ability to execute remotely any shell-commands. They can literally do anything they want, from downloading and running any programs from the Internet, to deleting all the data from the victim’s computer. Listing of INAebsGB.so It’s worth noting that a similar payload can be found in the implementation of the SambaCry exploit in Metasploit. cblRWuoCc.so The main functionality of this file is to download and execute one of the most popular open-source cryptocurrency mining utilities – cpuminer (miderd). It is done by the hardcoded shell-command, shown on the screenshot below. The main functionality of cblRWuoCc.so The file minerd64_s (8d8bdb58c5e57c565542040ed1988af9 — RiskTool.Linux.BitCoinMiner.a) downloaded in such a way is stored in /tmp/m on the victim’s system. Cpuminer and what it actually mines The interesting part is that the version of cpuminer used is “upgraded”, so it can be launched without any parameters to mine currency directly to the hardcoded attackers’ wallet. We obviously became interested in this wallet, so we decided to investigate a bit and uncover the balance of the attackers account. Along with the attackers’ wallet number, the pool address (xmr.crypto-pool.fr:3333) can be found in the body of the miner. This pool is created for mining the open-source cryptocurrency – monero. Using all this data we managed to check out the balance on the attackers’ wallet and the full log of transactions. Let’s have a look: Balance of the attackers’ account on 08.06.2017 Log of transactions with all the attackers’ cryptocurrency income The mining utility is downloaded from the domain registered on April 29th 2017. According to the log of the transactions, the attackers received their first crypto-coins on the very next day, on April 30th. During the first day they gained about 1 XMR (about $55 according to the currency exchange rate for 08.06.2017), but during the last week they gained about 5 XMR per day. This means that the botnet of devices working for the profit of the attackers is growing. Considering that the world discovered the EternalRed vulnerability only at the end of May, and the attackers had already adopted it, the rate of growth in the number of infected machines has significantly increased. After about a month of mining, the attackers gained 98 XMR, which means they earned about $5,500 according to the currency exchange rate at the time of writing. Conclusion As a result, the attacked machine turns into a workhorse on a large farm, mining crypto-currency for the attackers. In addition, through the reverse-shell left in the system, the attackers can change the configuration of a miner already running or infect the victim’s computer with other types of malware. At the moment we don’t have any information about the actual scale of the attack. However, this is a great reason for system administrators and ordinary Linux users to update their Samba software to the latest version immediately to prevent future problems. Hackers Are Using An Effective Way to Spread Fake News From Verified Accounts Gamestop hacked. Financial data of online shoppers were accessed by crooks The company sent postal letters to its customers, the company confirmed that an undisclosed number of online customers had their credit card or bankcard data stolen. Hackers accessed card numbers, expiration dates, names, addresses and also the three-digit card verification values (CVV2). Customers are questioning the company about the delay of the breach notification, customers that were not promptly informed had their financial data exposed for months. “GameStop recently identified and addressed a security incident that may have involved your payment card information. We are providing this notice to inform you of the incident and to call your attention to some steps you can take to protect yourself. At GameStop, we value our customers and understand the importance of protecting customer personal information. We sincerely apologize for any inconvenience or concern this incident may cause.” reads the letter sent to the customers. “After receiving a report that data from payment cards used on www.GameStop.com may have been obtained by unauthorized individuals, we immediately began an investigation and hired a leading cybersecurity firm to assist us. Although the investigation did not identify evidence of unauthorized access to payment card data, we determined on April 18, 2017 that the potential for that to have occurred existed for certain transactions.” In April, the popular investigator Brian Krebs reported that GameStop had received an alert from a credit card processor stating that the company website was hacked and financial data exposed. “GameStop recently received notification from a third party that it believed payment card data from cards used on the GameStop.com website was being offered for sale on a website.” reads a statement published by GameStop. The company operates 7,500 retail stores and it owns online game sites GameStop.com, Kongregate.com and online retailer ThinkGeek. No retail customers were impacted by the breach, according to the company. According to the company, retail customers were not impacted by the security breach, the PoS systems ar the company stores were not infected. At the time I was writing there in no information about the extension of the breach or the hacking techniques used by attackers. Thousands of IP Cameras Hijacked by Persirai, Other IoT Botnets 10.6.2017 securityweek IoT The Persirai backdoor is designed to target more than 1,000 IP camera models, and researchers said there had been roughly 120,000 devices vulnerable to this malware at the time of its discovery several weeks ago. The malware, which uses a recently disclosed zero-day vulnerability to spread from one hacked IP camera to another, allows its operators to execute arbitrary code on the targeted device and launch distributed denial-of-service (DDoS) attacks. Trend Micro has determined that of a total of 4,400 IP cameras it tracks in the United States, just over half have been infected with malware. The percentage of infected cameras spotted by the security firm in Japan is nearly 65 percent. According to the company, more than 64 percent of the total number of 3,675 compromised devices located in the United States, Japan, Taiwan and South Korea have been infected with Persirai. However, Persirai is not the only IoT malware targeting IP cameras. Trend Micro says there are three other malware families: Mirai, DvrHelper and TheMoon. Mirai made a lot of headlines recently due to the significant number of devices it infected all around the world. Data from Trend Micro shows that of the hijacked devices it is monitoring in the U.S., Japan, Taiwan and Korea, Mirai accounts for more than a quarter of infections. DvrHelper is based on Mirai, but its authors have implemented some interesting features, including additional DDoS modules and a mechanism for bypassing anti-bot solutions, including JavaScript-based challenges and Google’s reCAPTCHA system. Another threat targeting IP cameras is TheMoon. This is actually the oldest IoT malware, but its authors have continued to improve it. DvrHelper and TheMoon account for 6.8 percent and 1.4 percent of the infections seen by Trend Micro in the U.S. and the aforementioned East Asian countries. Researchers pointed out that since the number of potential victims for these malware families is limited, some of them are designed to “lock the door” behind them after they infect a device. For example, Persirai attempts to patch the zero-day vulnerability it exploits to prevent other malware from infecting the device. However, since the malware resides only in memory and the changes it makes are not persistent, the threat will be removed and the camera will become vulnerable once again after it’s restarted. TheMoon also tries to keep other malware out. It does this by importing specific iptables firewall rules to the device. Mouseover PowerPoint attack exploited to deliver the Gootkit Trojan Experts at Trend Micro observed a spam campaign leveraging the PowerPoint ‘Mouseover’ attack to deliver the Gootkit banking Trojan. Researchers Rubio Wu and Marshall Chen observed the campaign targeting specific organizations in the U.K., Poland, Netherlands, and Sweden. “This technique is employed by a Trojan downloader (detected by Trend Micro as TROJ_POWHOV.A and P2KM_POWHOV.A), which we’ve uncovered in a recent spam email campaign in the EMEA region, especially organizations in the U.K., Poland, Netherlands, and Sweden. Affected industries include manufacturing, device fabrication, education, logistics, and pyrotechnics.” reads the report published by TrendLabs. Malicious messages are disguised as an invoice or purchase order, they have a subject comprising a finance-related word followed by a number. “In some of the spam emails we saw, the subject lines had a pattern—using a financial or transaction-related word (or phrase), such as “fee”, or “purchase orders”, then followed by a serial number. The pattern we saw is “[fee] #__NUM__”, indicating that the operator, or the service provider that sends the spam email on behalf of the operator, are tracking the spam messages they send.” continues the report. The emails have a malicious PowerPoint Show file attached that opens the document directly in presentation mode. The malicious content will attempt to run as soon as the user moves the mouse over the presentation, but it is intercepted by the Microsoft Protected View mechanism and needs the user’s interaction to enable the macros. “Once the would-be victim downloads and opens the file, user interaction is needed—hovering over the text or picture embedded with a malicious link (which triggers a mouseover action), and choosing to enable the content to run when prompted by a security notice pop-up. Microsoft disables the content of suspicious files by default—via Protected View for later versions of Office—to mitigate the execution of malicious routines that abuse features in Microsoft Office, such as macros and Object Linking and Embedding (OLE).” states the analysis published by Trend Micro.”Hence, a key ingredient in the infection chain is social engineering—luring the victim into opening the file and enabling the malware-laced content to run on the system.” Once the macro is executed by the user, the document runs an embedded malicious PowerShell script that downloads another downloader (JS_NEMUCOD.ELDSAUGH) in the form of a JScript Encoded File (JSE). The downloader is tasked to retrieves the final payload, the OTLARD banking Trojan (aka Gootkit), from a command-and-control server. The experts noticed that the number of malicious messages is limited, a circumstance that suggests this campaign may be followed by large-scale attacks leveraging the ‘mouseover’ technique. “And while the numbers aren’t impressive, it can also be construed as a dry run for future campaigns, given the technique’s seeming novelty. It wouldn’t be far-fetched for other malware like ransomware to follow suit, for instance, considering the notoriety of OTLARD/Gootkit’s operators for spreading other threats in their payloads, as well as ransomware’s history with using malware-laced Office documents.” states Trend Micro. The researchers highlighted that this tactic is typical of the Gootkit operators that use to run small campaigns focused on a limited number of countries, before larger attacks. In order to prevent these attacks, users must ensure that Microsoft’s Protected View is enforced and have to be vigilant of the mail that they receive refusing to enable macros. Hundred of thousands of IP Cameras Hijacked by Persirai and other thingbots Thousands of IP cameras have been hijacked by the Persirai IoT botnet that targets more than 1,000 IP camera models, but it isn’t the only one. “C&C (Command and Control) servers we discovered were found to be using the .IR country code. This specific country code is managed by an Iranian research institute which restricts it to Iranians only. We also found some special Persian characters which the malware author used,” stated Trend Micro in its discovery release posted online. IP Camera users have also encountered the malware attack and noted its point of origin appears to be Iran. The Persirai attack is disturbing on a number of fronts. It’s based on the open-source Mirai strike shows that the freely available source code will be modified by attackers to strike again in different forms. Persirai is also very stealthy, leaving most camera owners unaware that their systems are infected. Yet, the worst feature is that the command and control computers used to run the malicious bot-net are using the country code of IR or Iran. Infected IP cameras report to command servers at: load.gtpnet.ir Persirai blocks other zero-day exploits from gaining access to a targeted IP Camera by pointing ftpupdate.sh and ftpupload.sh to /dev/null, preventing other attacks. This feature may be an effort to prevent duplicate attacks by Persirai as much as to prevent other bot-net attackers from gaining control of the now captured IP Camera. The fact that Persirai is running in memory does mean it is also eliminated once the IP Camera is rebooted but, unless the user takes counter-measures, the targeted system will still be vulnerable to the exploit. The Persirai attack is based on the previously successful Mirai IOT strike against IP cameras that was used to disrupt the Internet with a giant Denial of Service (DOS) attack in 2016. However, while over 120,000 IP camera systems appear to be infected, over 30% of the Persirai targets are inside China with only small fraction located outside of the PRC; in Italy (3%), the UK (3%) and the USA (8%). Trend Micro provided data related to the impact and distribution of the Persirai botnet. The researchers have determined that of a total of 4,403 IP cameras they counted in the United States, 51,37% have been infected with the backdoor, in Japan on a total of 661 cameras 64,85 percent have been infected. The Persirai backdoor is not the only IoT malware targeting IP cameras, experts at Trend Micro are monitoring three other malware families: Mirai, DvrHelper, and TheMoon. “Finally, TheMoon (detected by Trend Micro as ELF_THEMOON.B) is the oldest malware targeting IoT devices. The family was first discovered by SANS ICS in 2014 and it continues to upgrade attack methods and target new vulnerabilities.” DvrHelper and TheMoon account for 6.8 percent and 1.4 percent of the infections detected by Trend Micro are in the U.S. and Japan, Taiwan and Korea. Researchers highlighted the “lock the door” mechanisms implemented by these threats to avoid that other malware will infect the device they have compromised. “We find that there are four different malware families which all focus on IP cameras. Each one has its own unique features, but since the pool of targets is finite they all compete for territory and build defenses to block rival malware.” states the report Čtyři dobré důvody, proč neplatit při útoku ransomwaru 10.6.2017 SecurityWorld Viry Když se v důležitém systému objeví požadavek na zaplacení peněz, máte jen krátký čas na rozhodnutí, zda zareagovat na útok ransomwaru. On-line vydírání je na vzestupu, protože zločinci používají různé útočné vektory včetně sad exploitů, škodlivých souborů a odkazů ve spamových zprávách, aby infikovali systémy pomocí ransomwaru. Jakmile jsou všechny soubory zašifrované, může se oběť buď sama pokusit obnovit soubory, nebo zaplatit výkupné. Přestože existují určité výjimky, oběti jen zřídka dokážou prolomit šifrování a obnovit přístup. Mnohem častěji vyvolá úspěšný útok ransomwaru úplné smazání dotčených systémů a rychlé obnovení všeho z čistých záloh. Ať už organizace zaplatí, nebo ne, výkupné není bezpečnostním rozhodnutím. Je to rozhodnutí obchodní. Placení totiž podporuje zločince v tom, aby příště znovu zaútočili. Nezaplacení znamená ušlý zisk při čekání na obnovení souborů personálem IT. Není to snadná volba, ale čtěte dál o důvodech, proč je dobré výkupnéne zaplatit. 1. Stanete se větším cílem Jak se říká: Nekrmte trolly, jinak budou provokovat, aby vyvolaly reakci. Ransomware je trochu podobný. Platba výkupného jen útočníky povzbudí. Zločinci spolu mluví. Řeknou ostatním, kdo zaplatil výkupné a kdo ne. Jakmile se zjistí, že oběť platí, nic nezabrání dalším, aby se také nepokusili získat nějaké výkupné. Další nebezpečí: Stejní útočníci se mohou vrátit. Když jste zaplatili jednou, proč byste nezaplatili znovu? 2. Zločincům nelze věřit Spoléhat na zločince, že dodrží své slovo, je riskantní pokus. Vypadá to jako jednoduchá výměna – peníze za dešifrovací klíč. Neexistuje však žádný způsob, jak zjistit, zda lze vyděračskému gangu věřit, že dodrží svou část dohody. Mnoho obětí zaplatilo výkupné a zpět přístup ke svým souborům nezískalo. Platí to oběma směry: Proč platit, když nelze očekávat, že získáte svá data zpět? Na pověsti záleží, a to i ve světě zločinu. Gang CryptoWall je dobře známý pro své vynikající služby zákazníkům, jako jsou poskytnutí prodloužené lhůty pro získání výkupného, poskytování informací, jak získat bitcoiny (preferovaná metoda platby) či rychlé dešifrování souborů po zaplacení. Ostatní rodiny malwaru, jako TeslaCrypt, Reveton a CTB-Locker, mají horší pověst. Komu lze skutečně věřit? Zjišťovat odpověď zaplacením není nejlepší strategie. 3. Vaše příští výkupné bude vyšší Vyděrači obvykle nepožadují přehnané částky. Průměrné výkupné je mezi 300 až 1 000 dolary. Jak podléhá více organizací, zločincům roste sebevědomí a požadují vyšší částky. Je těžké stanovit tržní cenu dat, když oběti skutečně potřebují získat své soubory zpět. Například zdravotnické zařízení Hollywood Presbyterian Medical Center zaplatilo 17 tisíc dolarů za obnovení přístupu ke svým systémům s elektronickými lékařskými záznamy. To je doslova almužna ve srovnání s potenciální ztrátou obratu cca 534 tisíc dolarů v době, kdy se oddělení IT snažilo obnovit data a pacienti museli cestovat do jiných nemocnic, uvádí hrubý odhad Andrew Hay, ředitel zabezpečení informací ve společnosti DataGravity. Nyní to bylo 17 tisíc, ale tento gang by snadno mohl příští týden požadovat 50 tisíc dolarů atd. Je to jednoduchá ekonomika. Prodávající nastaví cenu na základě toho, co je kupující ochoten zaplatit. Pokud oběti odmítají platit, útočníci nemají důvod zvyšovat částky výkupného. 4. Povzbuzujete zločince Vezměte to z dlouhodobého hlediska. Zaplacení výkupného umožní organizaci obnovit data, ale tyto peníze nepochybně podpoří další kriminální aktivitu. Útočníci mají více peněz na vývoj pokročilejších verzí ransomwaru a důmyslnějších mechanismů dodávek. Mnoho gangů kyberzločinu funguje jako legitimní společnosti s více zdroji obratu a různými produktovými řadami. Peníze ze schémat ransomwaru lze použít k financování dalších útočných kampaní. „Vždy je zde kus odpovědnosti za to, na co se peníze použijí,“ uvedl William Noonan, zástupce zvláštního agenta kybernetických operací tajné služby USA na přednášce Verizon RISK Team během nedávné konference RSA v San Francisku. Placení výkupného problém přiživuje. Jeden důvod zaplatit Všechny argumenty uvedené výše jsou naprosto platné. Existuje však pádný důvod, proč mnoho obětí nakonec zaplatí: Potřebují své soubory zpět. A nemají na výběr. Když ransomware zasáhne všechny spisy na policejním oddělení, není čas čekat na někoho, kdo by se pokusil prolomit šifrování a soubory obnovil. Když probíhá aktivní vyšetřování, může obnovení ze záloh trvat příliš dlouho. Pomiňme příslovečné coby, kdyby. Když organizace nemá zavedenou dostatečně robustní zálohovací strategii pro obnovení souborů (nebo jsou zálohy poškozené též), je kázání o důležitosti prevence mimořádně neužitečné. Mnoho obětí se může také rozhodnout zaplatit ze strachu, že pokud tak neučiní, může útočník způsobit v rámci odvety ještě větší škody. Organizace, které se rozhodnou platit, nejsou samy. V nedávné studii Bitdefenderu polovina obětí ransomwaru uvedla, že zaplatily, a dvě pětiny respondentů uvedly, že by zaplatily, kdyby se do takové situace někdy dostaly. Oborové odhady naznačují, že gang CryptoWall od června 2014 vymohl od svých obětí více než 325 milionů dolarů. Pár gramů prevence... Nelze dostatečně zdůraznit, že nepřetržité zálohy usnadňují organizacím obnovu po infikování ransomwarem bez nutnosti platit zločincům. Dobrá strategie zálohování obsahuje platformy Linux, Mac OS X i Windows. Není to totiž jen záležitost systému Windows, protože došlo ke zjištění ransomwaru pro všechny tři operační systémy. A ani mobilní zařízení nejsou imunní. Přemýšlejte holisticky a nezávisle na platformách. Pravidelně zálohujte a udržujte nedávnou záložní kopii mimo lokalitu a off-line. Zálohování na sdílené svazky nefunguje, pokud jsou připojené místně k počítači – ransomware dokáže k těmto souborům přistupovat také. Po vytvoření zálohy odpojte USB disk, aby ransomware nemohl infikovat dané úložné zařízení. Pravidelně testujte zálohování, abyste zajistili, že jsou soubory archivované správně. Období následující po infekci ransomwarem není časem pro zjišťování, že kritické soubory nebyly uložené a úlohy nebyly spuštěné včas. Mnoho útoků ransomwaru spoléhá na škodlivé přílohy e-mailů a na odkazy ve spamových e-mailech. Zajistěte, aby všichni, od řadových zaměstnanců přes IT personál až po nejvyšší manažery, znali základy: Neklikat na odkazy bez ověření, že jde o legitimní e-mail. Dobré je také ověřit zprávu před otevřením přílohy, a pokud dokument požaduje povolení maker, tak to neumožnit. Mohl by být dobrý nápad nainstalovat prohlížeče dokumentů Microsoft Office, aby bylo možné zkontrolovat soubory bez jejich otevření v aplikacích Word a Excel – ztíží to tak spouštění škodlivého kódu. Udržujte veškerý software v aktuálním stavu. Mnoho kitů pro tvorbu exploitů spoléhá na neopravené zranitelnosti v populárních aplikacích, jako jsou Microsoft Office, Internet Explorer a Adobe Flash. Nainstalujte tyto aktualizace, jakmile to bude možné. Pro útočníky zvyšte obtížnost instalace ransomwaru do počítače prostřednictvím útoku typu drive-by-download. Microsoft vydal novinkami nejnapěchovanější Windows 10 Insider Preview za dlouhou dobu 9.6.2017 CNEWS.cz Aktualizace Na pokračování programu Windows Insider jsme si museli počkat celé tři týdny. Čekání za to stálo, protože nové sestavení přináší spoustu novinek. Připomínám, že původně chtěl Microsoft nové vydání Windows 10 Insider Preview nabídnout v minulém týdnu, jenže se něco nepovedlo a k počítačům a mobilům zamířilo interní sestavení 16212. Toto fiasko nám aspoň pomohlo odhalit kousek budoucnosti. Včera večer na počítače a tablety zamířil Windows 10 Insider Preview build 16215, na smartphony pak Windows 10 Mobile Insider Preview build 15222. Obě sestavení jsou dostupná pouze prostřednictvím Fast ringu. Nový design a další vylepšení Centra akcí a nabídky Start Nejviditelnější novinku představuje předělání dalších prvků do designu Fluent. Proto pokud máte aktivní průhlednost, bude nabídka Start průsvitná ve stylu nového designu. Start se plynuleji přepíná do tabletového režimu, především ale v neceloobrazovkovém režimu poskytuje více možností, jak změnit její velikost. Pryč je úprava velikostí ve vybraných stupních, navíc lze měnit velikost úhlopříčně. Zaplňování děr v Edgi Co Microsoft nezmiňuje? Adresní řádek je vždy bílý, nikoli šedivý. Osobně jsem volal také po celoobrazovkovém režimu, který vyvoláte mj. klávesovou zkratkou F11. Trvalo to jen dva roky a tato banální funkce je v Edgi konečně dostupná. (Tedy, pro většinu lidí bude dostupná až během podzimu.) Prohlížeč se dále zlepšil v práci s e-knihami. V těch si teď zvýrazníte důležité pasáže – k dispozici jsou čtyři barvy, dále podtrhování i komentáře. Více zvýrazňovačů je k ruce i při práci s dokumenty v PDF. Ruční psaní Mnoho novinek je spojených s ručním psaním. Ty ovšem využije minorita uživatelů a uživatelek – tablet s Windows není zdaleka tak běžný jako počítač s Windows, natož pak tablet s digitálním perem. Psát můžete do nového panelu, který automaticky uvolňuje místo pro další text a nechá vás psaním opravovat chyby v textu převedeném do digitální podoby. Můžete také hledat ztracené pero podobně ztracený počítač. Novinek je více, dočtete se o nich na blogu Windows Experience. Klávesnice Microsoft se věnoval také psaní pomocí klasické hardwarové klávesnice. I s ní se snadno otevřete nabídku emoji, stačí zmáčknout klávesy Win+. nebo Win+;. Pomocí klávesnice lze pohodlně ovládat kompletní proces výběru a vložení emoji. Jen zatím platí, že tato novinka není dostupná na klávesnici v jiných jazycích, jen v americké angličtině. Jak předeslalo omylem uvolněné sestavení 16212, Microsoft pracoval na nové softwarové klávesnici. Jedná se o klávesnici vycházející ze SwiftKey, takže nabízí možnost psát pohybem prstu. Tento koncept už dříve nabízel v mobilní edici Windows, nově je ale stejná možnost dostupná také na počítačích a tabletech. Další novinky Seznam novinek je dnes skoro nekonečně dlouhý, takže dál to vezmeme zkratkovitě: Sdílení se dočkalo dalšího rozšíření. Nyní nabízí ke zkopírování odkaz, pokud tedy hodláte sdílet webovou stránku či aplikaci ze Storu. First-Ever Data Stealing Malware Found Using Intel AMT Tool to Bypass Firewall The Platinum hacking group has been using zero-day exploits, hot patching technique and other advanced tactics to penetrate in their target systems and networks in South Asian countries, but this is the first time someone is abusing legitimate management tools to evade detection. New Tor Browser 7.0 implements multiprocess mode, content sandbox, and Unix domain sockets The Tor network implements an anonymous communication system that leverages on more than 7,000 relays set up by volunteers worldwide. The project aims to protect user’s anonymity online by concealing the users’ location and implementing algorithms to avoid dragnet surveillance or traffic eavesdropping. “The Tor Browser Team is proud to announce the first stable release in the 7.0 series. This release is available from the Tor Browser Project page and also from our distribution directory.” reads the official announcement. Tor Browser 7.0 The Tor Browser is built on top of Mozilla’s Firefox Extended Support Release (ESR), a version designed for groups who deploy and maintain the desktop environment in large organizations such as universities and other schools, county or city governments, and businesses. The Tor Browser 7.0 is based on Firefox 52 ESR and implements two major features: multiprocess mode; Mac and Linux users can improve the security of their Tor Browser by using only Unix domain sockets for communication through the Tor network. “Most notably we hope having Mozilla’s multiprocess mode (e10s) and content sandbox enabled will be one of the major new features in the Tor Browser 7.0 series, both security- and performance-wise.” states the announcement. “While we are still working on the sandboxing part for Windows (the e10s part is ready), both Linux and macOS have e10s and content sandboxing enabled by default in Tor Browser 7.0. In addition to that, Linux and macOS users have the option to further harden their Tor Browser setup by using only Unix Domain sockets for communication with tor.” The switch to ESR 52 introduces new system requirements for Windows and macOS users: On Windows Tor Browser 7.0 won’t run on non-SSE2 capable machines anymore. On Apple systems, the minimum system requirement is OS X 10.9. The Tor Browser 7.0 also improves the resilience to tracking and fingerprinting attacks. “cookies, view-source requests and the Permissions API are isolated to the first party URL bar domain now to enhance our tracking related defenses. On the fingerprinting side we disabled and/or patched several new features, among them WebGL2, the WebAudio, Social, SpeechSynthesis, and Touch APIs, and the MediaError.message property.” states the announcement. CISCO Prime Data Center Network Manager affected by two critical flaws Cisco èiblished two security advisories to warn customers of the presence of two critical vulnerabilities in the CISCO Prime Data Center Network Manager, A remote, unauthenticated attacker can exploit the flaw by connecting to the debugging tool via TCP. “A vulnerability in the role-based access control (RBAC) functionality of Cisco Prime Data Center Network Manager (DCNM) could allow an unauthenticated, remote attacker to access sensitive information or execute arbitrary code with root privileges on an affected system.” states the advisory published by CISCO. “The vulnerability is due to the lack of authentication and authorization mechanisms for a debugging tool that was inadvertently enabled in the affected software. An attacker could exploit this vulnerability by remotely connecting to the debugging tool via TCP. A successful exploit could allow the attacker to access sensitive information about the affected software or execute arbitrary code with root privileges on the affected system.” Affected versions are the Cisco Prime DCNM releases 10.1(1) and 10.1(2) for Windows, Linux and virtual appliances. The second vulnerability in CISCO Prime Data Center Network Manager (DCNM) tracked as CVE-2017-6640, exists due to a presence of a default user account protected by a static password. A remote attacker can connect to the affected system and use this account to gain privileged access to the server’s administration interface. Affected versions are the Prime DCNM running software version 10.2(1) for Windows, Linux and virtual appliances. “A vulnerability in Cisco Prime Data Center Network Manager (DCNM) Software could allow an unauthenticated, remote attacker to log in to the administrative console of a DCNM server by using an account that has a default, static password. The account could be granted root- or system-level privileges.” states the advisory. “The vulnerability exists because the affected software has a default user account that has a default, static password. The user account is created automatically when the software is installed.” Both flaws were reported to Cisco by Antonius Mulder of Commonwealth Bank of Australia, the good news is that there is no evidence that they have been exploited in attacks the wild. Cisco patched the flaws with the release of version 10.2(1), the company informs that no workarounds are not available. Default Account, Debug Tool Expose Cisco Prime Users to Attacks 9.6.2017 securityweek Vulnerebility One of the flaws, tracked as CVE-2017-6639, is related to the lack of authentication and authorization for a debugging tool that was inadvertently left enabled. A remote, unauthenticated attacker can exploit the vulnerability to access sensitive information or execute arbitrary code with root privileges by connecting to the debugging tool via TCP. The security hole affects Cisco Prime DCNM releases 10.1(1) and 10.1(2) for Windows, Linux and virtual appliances. The second Prime DCNM vulnerability, identified as CVE-2017-6640, exists due to a default user account protected by a static password. An attacker who can remotely connect to the affected system can use this account to gain privileged access to the server’s administration interface. The networking giant said this flaw only affects Prime DCNM running software version 10.2(1) for Windows, Linux and virtual appliances. Both DCNM vulnerabilities were disclosed to Cisco by Antonius Mulder of Commonwealth Bank of Australia and there is no evidence that they have been exploited in the wild. The flaws have been patched with the release of version 10.2(1), but workarounds are not available. Cisco has also published an advisory for a high severity local privilege escalation vulnerability affecting AnyConnect Secure Mobility Client for Windows versions prior to 4.4.02034. The security hole, reported by Felix Wilhelm of ERNW, allows a local attacker to install and execute a file with SYSTEM privileges. Another advisory describes a high severity denial-of-service (DoS) vulnerability in the Session Initiation Protocol (SIP) of the Cisco TelePresence Codec (TC) and Collaboration Endpoint (CE) software. A remote, unauthenticated attacker can exploit this flaw to cause a DoS condition by sending a flood of SIP INVITE packets to the vulnerable device. The weakness, reported to Cisco by Knud Hojgaard of F-Secure, affects several TelePresence MX, Profile, SX, System Profile MXP, System EX, and Integrator C series products. Two Collaboration Desk Endpoint DX series devices are also impacted. Mouseover Macro Campaign Delivers Gootkit Trojan Via PowerPoint 9.6.2017 securityweek Virus TrendLabs researchers Rubio Wu and Marshall Chen suggest that although the recent campaign was limited (which in itself is not unusual as attackers try to avoid detection), it could be considered a dry run for future campaigns. The campaign was targeted particularly and organizations in the U.K., Poland, Netherlands, and Sweden. Similar to the earlier analysis, it used emails with a subject comprising a finance-related word followed by a number. "The pattern we saw," notes the TrendLabs report "is '[fee] #__NUM__', indicating that the operator, or the service provider that sends the spam email on behalf of the operator, are tracking the spam messages they send." The email is disguised as an invoice or purchase order and has a malicious PowerPoint Show file attached. This opens directly in presentation mode. The malicious macro will attempt to run as soon as the mouse is moved over the presentation; but is generally prevented by Microsoft's Protected View until and unless the user 'enables' macros. "Hence," say the researchers, "a key ingredient in the infection chain is social engineering -- luring the victim into opening the file and enabling the malware-laced content to run on the system." The report does not elaborate on this, merely pointing out that, "A socially engineered email and mouse hover -- and possibly a click if the latter is disabled -- are all it would take to infect the victim." Once the macro runs, an embedded malicious PowerShell script is executed to download another downloader (JS_NEMUCOD.ELDSAUGH) in the form of a JScript Encoded File (JSE). It is this that retrieves the final payload from a command-and-control (C&C) server. The payload detected by TrendLabs is a variant of the OTLARD banking Trojan, also known as Gootkit. This is well-known in Europe for stealing credentials and bank account information. TrendLabs suggests the detected campaign may be the precursor of wider use. "It wouldn't be far-fetched for other malware like ransomware to follow suit," say the researchers; "for instance, considering the notoriety of OTLARD/Gootkit's operators for spreading other threats in their payloads, as well as ransomware's history with using malware-laced Office documents." This behavior is typical of the Gootkit operators: small campaigns focused on a limited number of countries -- but with innovative and advanced operators. Earlier this year, the Gootkit malware evolved from web-injection to redirection which is a more difficult but potentially more successful way of deceiving users. The danger inherent in this type of macro-based mouseover attack is that it can be entirely invisible to the victim. Ensuring that Microsoft's Protected View is enforced will at least prevent the malicious macro from running automatically -- but that will still require the user to be aware and to refuse to enable macros. Locking down and adopting best practices for using tools and services like PowerShell will also help. The bottom-line, however, is that security awareness is the best defense against this new breed of macro-based attacks. "Given that social engineering is vital in these attacks," say the researchers, "fostering a culture of cybersecurity among employees helps mitigate a weakness for which there is no silver bullet -- the human psyche."
Here below I recorded a couple of PoCs about some useful payloads I was using during engagements. Enjoy!
You will see how WHID can easily help pen testers to exfiltrate domain credentials with both Phishing Technique and Mimikatz (FUDed) In-Memory.
https://github.com/whid-injector/WHID/tree/master/payloads
13.6.2017 thehackernews Apple
In this year's annual event, Apple announced that the company had paid out $70 Billion to developers in the App Store's lifetime and that $21 Billion of the amount was paid in the last year alone.
But has all this money gone to the legitimate app developers?
Probably not, as app developer Johnny Lin last week analyzed the Apple's App Store and discovered that most of the trending apps on the app store are completely fake and are earning their makers hundreds of thousands of dollars through in-app purchases and subscriptions.
Scammers Use 'Search Ads' Platform to Boost App Ranking
Shady developers are abusing Apple's relatively new and immature App Store Search Ads, which was launched at last year's Worldwide Developers Conference (WWDC), to promote their app in the store by using a few strategically chosen search ads and a bit of SEO.
"They're taking advantage of the fact that there's no filtering or approval process for ads, and that ads look almost indistinguishable from real results, and some ads take up the entire search result's first page," Lin wrote in his lengthy Medium post.
"I dug deeper to find that unfortunately, these aren't isolated incidents, they're fairly common in the app store's top grossing lists. And this isn't just happening with security related keywords. It seems like scammers are bidding on many other keywords."
Watch Out, Don't fall for Fake Apple In-App Subscriptions
One of the top earning apps Lin found was named "Mobile Protection: Clean & Security VPN" that tricked users into signing up for a $99.99 per week subscription for a complete garbage service by just laying their thumb on the Touch ID.
According to Lin, this app alone has earned its developer an estimated $80,000 per month, according to data from marketing firm Sensor Tower.
With spell and grammatical errors and fake reviews, 'Mobile Protection: Clean & Security VPN' claimed to be a Virus scanner, prompting users to "Instantly use full of smart anti-virus" by offering them a "FREE TRIAL."
But as soon as a victim tapped on the free trial, Touch ID screen appeared that read:
"Use Touch ID to start your free trial to Full Virus, Malware Scanner? You will pay $99.99 for a 7-day subscription starting June 9, 2017."
Usually, users who landed on the Touch ID screen making their mind for a free trial accidentally pressed their thumb on the Touch ID, which netted nearly $400 per month from just one user.
Therefore, the shady app developer needed just 200 people to be tricked into paying for the junk service to earn them $80,000 per month, which means $960,000 annually, according to Lin's calculations.
Lin explained how shady developers are abusing the App Store Search Ads service and "taking advantage of the fact that there's no filtering or approval process for ads, and that ads look almost indistinguishable from real results."
Though Apple removed the app, and several other apps that Lin highlighted in his post, but its App Store is still full of shady apps that use in-app purchases and misleading descriptions to trick users into spending lots of money on garbage.
Affected? Here's How to Cancel App Subscriptions
However, if you, unfortunately, downloaded any of the shady apps in question and paid for an expensive subscription, you can follow these steps to cancel all future payments:
Open Settings app and go to iTunes & App Store → Apple ID → View Apple ID.
Enter your Apple ID password or press against Touch ID when prompted.
Click on Subscriptions and then tap on the subscriptions you want to cancel, and tap Confirm.
Now once your current subscription period ends, you'll not charge.
Lin has also provided a long list of recommendation for Apple to implement to make its App Store safe for users, which includes steps to make better UI on Touch ID subscriptions, stricter Review of subscriptions, easier cancellation of subscriptions, fraud- and abuse-proof Search Ads, and remove scams and refund users.
Just days after MacRansom Ransomware-as-a-service (RaaS) was uncovered, the first malware-as-a-service (MaaS) targeting Mac users was discovered on an undground forum available for free, AlienVault reveals.
IBM Security announced on Tuesday that a new product designed to help organizations manage how their employees access business applications has been added to the company’s Cloud Identity offering. 
13.6.2017 securityaffairs Virus
Security Experts at Arbor Networks have spotted a new banking trojan, initially called ‘Matrix Banker’, that is targeting Latin America.
Malware researchers at Arbor Networks have spotted a new banking trojan, initially called ‘Matrix Banker’, that is targeting Latin America.
The malicious code seems to be still under development, most of the victims were located in Mexico and Perù. 
Snahy americké armády a bezpečnostních služeb narušit internetovou komunikaci Islámského státu (IS) přinesly většinou jen velká zklamání, napsal list The New York Times s odvoláním na experty a bývalé velitele. Islámský stát nadále bez problémů šíří svou propagandu a verbuje lidi.
„Obecně tu panuje pocit rozčarování ohledně schopnosti uštědřit velký úder IS pomoci kybernetických operací,“ řekl Joshua Geltzer, bývalý ředitel protiteroristických operací Národní bezpečnostní rady, kde působil do letošního března. „V praxi je to mnohem těžší, než si lidé myslí. Nikdy to není tak snadné jako se dostat do systému a myslet si – teď uvidíte, jak věci nadobro zmizí.“
Generál Jeffrey Harrigian, velitel spojeneckého letectva v Iráku
Islámský stát je tvrdým protivníkem v oblasti kybernetické války. Džihádisté nepoužívají internet a sociální sítě při vývoji a testech nových zbraní, ale k šíření propagandy a rekrutování bojovníků i k získávání prostředků a koordinování útoků. Takové aktivity nejsou spojeny s jedním určitým místem, jako byly íránské centrifugy, které Spojené státy vyřadily z provozu za pomoci Izraelců. Radikálové navíc mohou využít výhody pokročilých levných šifrovacích zařízení, jako je systém pro posílání vzkazů Telegram.
Zatím nejrozsáhlejší útok vedený proti IS z USA byla loni v listopadu operace Glowing Symphony. Americké velitelství získalo přístupová hesla k několika účtům islamistů a s jejich pomocí vymazalo nebo zablokovalo propagandistický obsah některých serverů. Zpočátku to vypadalo, že je operace úspěšná, protože videa z bojů zmizela, leč úspěch byl jen dočasný. Američtí představitelé záhy zjistili, že se materiál radikálům podařilo obnovit nebo byl přesunut na jiné servery. Důvodem také je, že často mají uložený materiál zašifrovaný v cloudu, takže ho jen znovu stáhnou a nahrají.
Kybernetické operace pomáhají i v operaci proti Islámskému státu v Rakce.
Protože jsou bojovníci mobilní a jejich vybavení je celkem běžné, mohou se přesunout a pracovat z jiného místa. Veterány kybernetických operací to nepřekvapuje, podle nich nejsou kybernetické zbraně na internetu dokonalým řešením.
I britská premiérka Theresa Mayová si stěžovala po útoku na London Bridge, že na internetu vznikl bezpečný přístav pro radikální ideologie a že „velké společnosti, které poskytují internetové služby, by se se měly plně zapojit do boje proti radikalismu”. List The New York Times ale upozorňuje, že v USA je to těžší, protože by to mohlo být v rozporu s prvním dodatkem ústavy, který garantuje svobodu projevu.
Generál Sean MacFalrand, bývalý velitel v Iráku
Zklamání z nedostatečné účinnosti elektronického boje vedlo už vládu Baracka Obamy k pokusům sesadit ředitele Národní agentury pro bezpečnost (NSA) Michaela Rogerse, píše The New York Times. Byl kritizován, že se soustředil na tradiční špionáž a vysoce sofistikované údery proti jednotlivým místům.
Situace se podle amerického listu v poslední době zlepšila alespoň při operacích přímo na bojišti. Kybernetické útoky armáda v Iráku synchronizuje s pozemními operacemi, zlepšuje se vybavení i kvalita „kybernetických zbraní”. Mazání účtů nebo blokování islamistické komunikace během útoků bezpilotními aparáty je už dnes v Iráku standardní operační postup, napsal The New York Times.
13.6.2017 Živě.cz BigBrother
Je to možná nejpokročilejší virus, který útočí na elektrickou síť
Loni v prosinci odpojil od elektřiny Kyjev
Schéma uzlu elektrické sítě napojeného na internet a vhodného pro útok, pokud není dostatečně zabezpečenýÚtočníci pronikli do uzlu ukrajinské elektrické sítě z internetuSchéma malwaru, který měl několik různých jištění, aby s ním operátor neztratil kontaktAnalytici ze společnosti Dragos popsali útok v detailní zprávěKyjevské domácnosti se na sklonku loňského roku ponořily do tmy. Pravděpodobně ruští hackeři zde totiž testovali svůj malware.5 FOTOGRAFIÍ
zobrazit galerii
Loni 17. prosince se v hlavním ukrajinském městě krátce před půlnoci odporoučela elektrická síť a tisíce domácností se ponořily do tmy. Nebyl to ojedinělý případ, podivné výpadky totiž trápily energetiky už od 6. prosince a vypořádali se s nimi až krátce před Vánocemi.
Teprve později se přišlo na to, že se s největší pravděpodobností jednalo o útok neznámých hackerů. Kyjev tehdy obvinil Rusko, nebezpečná situace totiž až příliš připomínala podobný kybernetický útok z prosince 2015, během kterého přišlo o elektřinu více než 200 000 Ukrajinců.
A tak se nakonec i stalo – loni na Ukrajině, která opět viní Rusko, jenž se skutečně nabízí, má k tomu totiž kvůli letitému vzájemnému sporu dostatek motivů. A hlavně kapitál. Nejen finanční, ale i znalostní, malware Crash Override/Industroyer se totiž od mnoha ostatních liší v tom, že na stroje elektrické sítě útočí přímo.
Analytici varují, že malware jednoduše zneužívá základních vlastností podobných průmyslových strojů, jejichž ovládací protokoly nepočítaly s přílišnou bezpečností, protože pocházejí z dob, kdy nebyla centra rozvodné elektrické sítě napojená na internet.
13.6.2017 thehackernews Android
Over 800 different Android apps that have been downloaded millions of times from Google Play Store found to be infected with malicious ad library that silently collects sensitive user data and can perform dangerous operations.
Dubbed "Xavier," the malicious ad library, initially emerged in September 2016, is a member of AdDown malware family, potentially posing a severe threat to millions of Android users.
Since 90 percent of Android apps are free for anyone to download, advertising on them is a key revenue source for their developers. For this, they integrate Android SDK Ads Library in their apps, which usually doesn't affect an app's core functionality.
According to security researchers at Trend Micro, the malicious ad library comes pre-installed on a wide range of Android applications, including photo editors, wallpapers and ringtone changers, Phone tracking, Volume Booster, Ram Optimizer and music-video player.
Features of Xavier Info-Stealing Malware
The previous variant of Xavier Ad library was a simple adware with an ability to install other APKs silently on the targeted devices, but in the latest release, the malware author has replaced those features with more sophisticated ones, including:
Evade Detection: Xavier is smart enough to escape from being analyzed, from both static and dynamic malware analysis, by checking if it is being running in a controlled environment (Emulator), and using data and communication encryptions.
Remote Code Execution: The malware has been designed to download codes from a remote Command & Control (C&C) server, allowing hackers to remotely execute any malicious code on the targeted device.
Info-Stealing Module: Xavier is configured to steal devices and user related information, which includes user’ email address, Device id, model, OS version, country, manufacturer, sim card operator, resolution, and Installed apps.
According to the researchers, the highest number of infected users are from Southeast countries in Asia such as Vietnam, Philippines, and Indonesia, with a fewer number of downloads are from the United States and Europe.
Here is a list of 75 infected Android apps that Google has already removed from its Play Store, and if you have installed any of these apps on your device, you are advised to remove it immediately.
Android malware continues to evolve with more sophisticated and never-seen-before capabilities with every passing day. Just last week, we saw first Android malware with code injecting capabilities making rounds on Google Play Store.
How to Protect Yourself
The easiest way to prevent yourself from being targeted by a clever malware like Xavier, always beware of fishy applications, even when downloading them from official Play Store and try to stick to the trusted brands only.
Moreover, always look at the reviews below left by other users who have downloaded the app and verify app permissions before installing any app and grant those permissions that have are relevant for the app's purpose.
Last but not the least, you are strongly advised to always keep a good antivirus application on your device that can detect and block such malware before they can infect your device, and keep your device and apps up-to-date.
Peteris Sahurovs, a 28-year-old Latvian national suspected of being part of a group that caused losses of millions of dollars through a scareware scheme, has been extradited to the United States. 
Cloud-based security and compliance solutions provider Qualys on Monday announced a new product designed for securing containers across cloud and on-premises deployments.
13.6.2017 securityaffairs ICS
The experts published a detailed analysis of the malware, they speculated the malicious code has been involved in the December 2016 attack on an electrical substation in Ukraine.
Those behind the Win32/Industroyer malware have a deep knowledge and understanding of industrial control systems and, specifically, the industrial protocols used in electric power systems” states the report published by ESET. 
toolset used by threat actors in the 2015 attacks against the Ukrainian power grid which culminated in a black out on December 23, 2015 (BlackEnergy, KillDisk, and other components, including legitimate
remote access software) the gang behind Industroyer are more advanced, since they went to great lengths to create malware capable of directly controlling switches and circuit breakers”
13.6.2017 securityaffairs ICS
The equipment was expected to be installed and left alone for a long time. Pressures to reduce operating costs led to this equipment being connected, and the easiest networking equipment to find was designed for convenience in a corporate environment — not security in an ICS environment. Once connected, companies discovered the value of data that comes from industrial systems and additional pressures arose to connect isolated Control Networks to relatively open Corporate Networks. This has led to the current situation where malware designed to compromise corporate systems can impact ICS equipment and have tragic impacts in the real world.
Kaspersky Lab recently conducted a survey of 359 industrial cybersecurity practitioners and uncovered some discrepancies between the perception and reality of ICS cybersecurity incidents.
83% of respondents feel prepared to handle an ICS cybersecurity incident, which is fortunate because over 50% had at least one cybersecurity incident to deal with in the past year — so they are getting a lot of practice.
The media talks at length about skilled attacks against ICS assets coming from nation states, hacktivists, competitors — often against 3rd party contractors up the supply chain. Survey takers seem to agree as 74% are expecting to see an attack against their industrial infrastructure in the coming year. But this is an interesting discrepancy as the top concern is conventional malware affecting control systems. How many companies are preparing to defend against the few, skilled attackers when they are most likely to be impacted by run-of-the-mill malware being sprayed across the Internet?
Inline image 3
ICS vendors’ traditional development model didn’t accommodate regular patches and updates so it is quite likely that companies with ICS equipment are forced to consider other security tools. According to the survey, companies are responding to the threats with antimalware, network monitoring and device access controls. Over half of the respondents aren’t considering vulnerability scanning and patch management.
Based on the stats above, it seems likely that there will be many cybersecurity incidents in the coming months. What should industrial organizations prepare for? The survey highlights the top three concerns as:
– damage to product and service quality,
– loss of proprietary or confidential information, and
– reduction or loss of production at a site
On average these impacts added up to $497,000 per incident last year. So we have a likely probability and a quantifiable impact to base risk decisions upon. Now, these companies need to figure out how to make the right decisions.
Given that these companies are responsible for large scale industrial equipment, security incidents could have much bigger impacts in the real world than most. The challenges of an ICS environment are different than traditional, stand-alone control systems and highly connected corporate networks. The successful companies will be the ones with a unique plan to address the unique risks.
“The growing interconnectedness of IT and OT systems raises new security challenges and requires a good deal of preparedness from board members, engineers, and IT security teams. They need a solid understanding of the threat landscape, well-considered protection means and they need to ensure employee awareness.” said Andrey Suvorov, Head of Critical Infrastructure Protection, Kaspersky Lab. “With cyber threats on the ICS shop floor, it is better to be prepared. Security incident mitigation will be much easier for those who have leveraged the benefits of a tailored security solution built with ICS needs in mind”.
A new banking trojan, initially called 'Matrix Banker', has been spotted currently targeting Latin America -- or more specifically, Mexico and Peru. It seems to be still under development, and for now the jury is out over whether it will become a long-term threat.
Industroyer/CRASHOVERRIDE malware targets electrical substations - Photo Credit: Idaho National Laboratory 
Last December, a cyber attack on Ukrainian Electric power grid caused the power outage in the northern part of Kiev — the country's capital — and surrounding areas, causing a blackout for tens of thousands of citizens for an hour and fifteen minutes around midnight.
Now, security researchers have discovered the culprit behind those cyber attacks on the Ukrainian industrial control systems.
Slovakia-based security software maker ESET and US critical infrastructure security firm Dragos Inc. say they have discovered a new dangerous piece of malware in the wild that targets critical industrial control systems and is capable of causing blackouts.
Dubbed "Industroyer" or "CrashOverRide," the grid-sabotaging malware was likely to be used in the December 2016 cyber attack against Ukrainian electric utility Ukrenergo, which the security firms say represents a dangerous advancement in critical infrastructure hacking.
According to the researchers, CrashOverRide is the biggest threat designed to disrupt industrial control systems, after Stuxnet — the first malware allegedly developed by the US and Israel to sabotage the Iranian nuclear facilities in 2009.
This Malware Does Not Exploit Any Software Flaw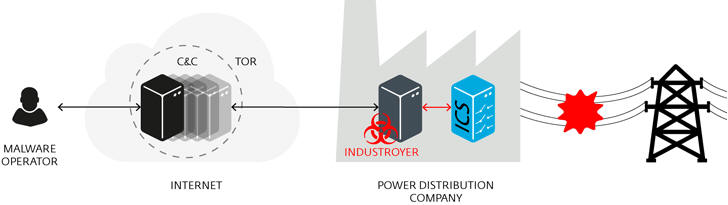
Unlike Stuxnet worm, the CrashOverRide malware does not exploit any "zero-day" software vulnerabilities to do its malicious activities; instead, it relies on four industrial communication protocols used worldwide in power supply infrastructure, transportation control systems, and other critical infrastructure systems.
The CrashOverRide malware can control electricity substation' switches and circuit breakers, designed decades ago, allowing an attacker to simply turning off power distribution, cascading failures and causing more severe damage to equipment.
Industroyer malware is a backdoor that first installs four payload components to take control of switches and circuit breakers; and then connects to a remote command-and-control server to receive commands from the attackers.
"Industroyer payloads show the authors' in-depth knowledge and understanding of industrial control systems." ESET researchers explain.
"The malware contains a few more features that are designed to enable it to remain under the radar, to ensure the malware's persistence, and to wipe all traces of itself after it has done its job."
Since there have been four malware discovered in the wild to date that target industrial control systems, including Stuxnet, Havex, BlackEnergy, and CrashOverRide; Stuxnet and CrashOverRide were designed only for sabotage, while BlackEnergy and Havex were meant for conducting espionage.
"The functionality in the CRASHOVERRIDE framework serves no espionage purpose and the only real feature of the malware is for attacks which would lead to electric outages," reads Dragos analysis [PDF] of the malware.
Malware Can Cause Wider and Longer-Lasting Blackouts
The analysis of the malware suggests CrashOverRide could cause power outages far more widespread, sophisticated and longer lasting than the one Ukraine suffered last December.
Dragos CEO Robert M. Lee said the CrashOverRide malware is capable of causing power outages that can last up to a few days in portions of a country's electric grid, but it is not capable enough to bring down the entire grid of a nation.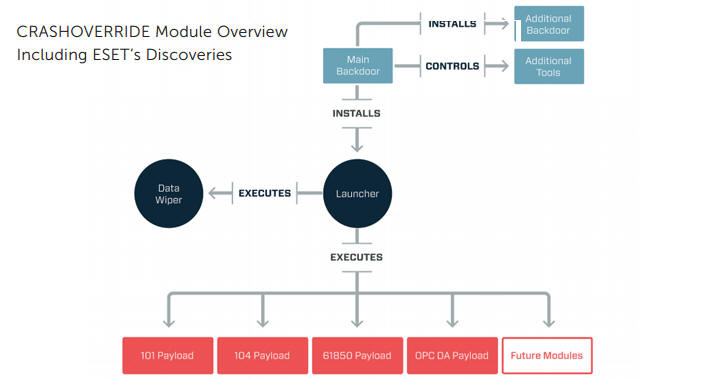
The malware includes interchangeable, plug-in components that could allow CrashOverRide to be altered to different electric power utilities or even launched simultaneous attacks on multiple targets.
"CrashOverRide is not unique to any particular vendor or configuration and instead leverages knowledge of grid operations and network communications to cause impact; in that way, it can be immediately re-purposed in Europe and portions of the Middle East and Asia," Dragos' paper reads.
"CrashOverRide is extensible and with a small amount of tailoring such as the inclusion of a DNP3 [Distributed Network Protocol 3] protocol stack would also be effective in the North American grid."
According to the researchers, the malware can be modified to target other types of critical infrastructure, like transportation, gas lines, or water facilities, as well with additional protocol modules.
The security firms have already alerted government authorities and power grid companies about the dangerous threat, along with some advises that could help them to defend against this threat.
The security firms already argued that the 2016 power outage was likely caused by the same group of hackers who caused 2015 blackout — Sandworm, a state-sponsored hacking group believed to be from Russia.
Dragos tracked the perpetrators behind CrashOverRide as Electrum and assessed "with high confidence through confidential sources that Electrum has direct ties to the Sandworm team."
The security firms have already alerted government authorities and power grid companies about the dangerous threat, along with some advises that could help them to defend against this threat.
GameStop Admits Hackers Had Access to Its Website for Six Months
A recently patched Samba flaw known as EternalRed and SambaCry has been exploited in the wild to deliver a cryptocurrency miner to vulnerable machines, researchers warned.
12.6.2017 securityaffairs Ransomware Apple
Malware researchers at security firm Fortinet have spotted MacRansom, it is the first Mac ransomware offered as a RaaS Service.
Malware researchers at security firm Fortinet have spotted a new strain of ransomware dubbed MacRansom that targets Mac machines. 
TargetFileKey: 0x39A622DDB50B49E9
The ReadmeKey is used to decrypt ._README_ file that contains the ransom notes and instructions, while the TargetFileKey is used to encrypt and decrypt the victim’s files.
Rady typu „neklepejte na odkazy v nedůvěryhodných prezentacích“ už nemusí být dostatečné. 
Novější verze PowerPointu vás upozorní, že chce prezentace provést příkaz (Foto: Dodge This Security)
Nedělám si ovšem iluze, že by tento dialog byl nezkušenému jedinci srozumitelný. Upozornění je dle mého názoru snadné přejít a automatický klepnout na Povolit. Co si ze situace odnést? Nestahujte prezentace z nedůvěryhodných zdrojů, zvlášť ne ty šířené hromadnými e-maily. Jindy bych uvedl, že nemáte klepat na nedůvěryhodné odkazy v prezentacích, ale to je v tomto případě zbytečná rada. Aspoň používejte novější verze Office, které před akcemi v prezentacích varují. Tato upozornění pak pečlivě analyzujte.
12.6.2017 Živě.cz Zranitelnosti
Hackeři začali zneužívat zranitelnosti operačního systému Linux, která byla zveřejněna před pár týdny a týká se síťového řešení Samba. Zranitelné systémy přeměňují na těžební stroje generující kryptoměny. Bližší informace o hrozbě zveřejnil web Bleeping Computer.
Stav konta útočníků (zdroj: Kaspersky lab)
Nakonec službu "smbd" restartujte a váš systém bude před uvedenou chybou chráněný.
12.6.2017 Root.cz Zranitelnosti
V dubnu se nám podařilo objevit zranitelnost v autentizačním serveru FreeRADIUS, která umožňuje připojovat se do sítě bez znalosti hesla. Některá zařízení zranitelnost nejspíše neúmyslně využívají pro své připojení do sítě.
Autentizace uživatelů v podnikových bezdrátových sítích
Nalezená zranitelnost se týká podnikových bezdrátových sítí, které pro ověřování používají metodu Protected Extensible Authentication Protocol (PEAP) či EAP-TTLS. Obě metody rozšiřují autentizační framework EAP, v obou se vytváří zašifrovaný TLS tunel. Údaje potřebné pro autentizaci uživatele se posílají uvnitř tohoto tunelu, většinou se kontroluje znalost hesla s využitím protokolu MS-CHAPv2. Studenti a učitelé z Vysoké školy ekonomické v Praze se takto ověřují v síti eduroam.
authenticator (autentizátor) – přístupový bod (Access Point) či přepínač, ke kterému se zařízení připojuje,
authentication server (autentizační server) – aplikace, která povoluje či zamítá přístup do sítě. Při komunikaci mezi autentizátorem a serverem se obvykle používá protokol RADIUS, do kterého se zapouzdřují EAP zprávy.
Při autentizaci se zařízení (např. mobil) nejdříve připojí k nejbližšímu přístupovému bodu. Následuje zahájení EAP autentizace, kdy supplicant odešle vnější jméno a domluví se EAP protokol mezi zařízením a autentizačním serverem. Tato část komunikace není zašifrována a proto se jako vnější jméno někdy nastavuje anonymní identita. 
Přibližně v polovině dubna jsme dokončili aplikaci, která uživatelům zobrazí logy z RADIUS serverů včetně přibližné lokalizace. Správci bezdrátové sítě si mohou zobrazit údaje pro jednotlivé účty či MAC adresy zařízení. Náš vedoucí začal aplikaci testovat a mimo jiné zadal vyhledání údajů za kolegu, který ten den nebyl v Praze. K našemu překvapení se vypsalo, že se ráno přibližně v 8:15 přihlásil do eduroam v budově na Žižkově. A poté znovu v době oběda.
---------------------------------------------------------------------------
Apr 12 09:57:05 2017| --> Acesss-Request |user@vse.cz|"7C-11-BE-5B-xx-xx"
Apr 12 09:57:05 2017| <-- Acesss-Challenge |user@vse.cz|"7C-11-BE-5B-xx-xx"
Apr 12 09:57:05 2017| --> Acesss-Request |user@vse.cz|"7C-11-BE-5B-xx-xx"
Apr 12 09:57:05 2017| <-- Acesss-Challenge |user@vse.cz|"7C-11-BE-5B-xx-xx"
Apr 12 09:57:05 2017| --> Acesss-Request |user@vse.cz|"7C-11-BE-5B-xx-xx"
Apr 12 09:57:05 2017| <-- Acesss-Challenge |user@vse.cz|"7C-11-BE-5B-xx-xx"
Apr 12 09:57:05 2017| --> Acesss-Request |user@vse.cz|"7C-11-BE-5B-xx-xx"
Apr 12 09:57:05 2017| <-- Acesss-Challenge |user@vse.cz|"7C-11-BE-5B-xx-xx"
Apr 12 09:57:05 2017| --> Acesss-Request |user@vse.cz|"7C-11-BE-5B-xx-xx"
Apr 12 09:57:05 2017| <-- Acesss-Challenge |user@vse.cz|"7C-11-BE-5B-xx-xx"
Apr 12 09:57:05 2017| --> Acesss-Request |user@vse.cz|"7C-11-BE-5B-xx-xx"
Apr 12 09:57:05 2017| <-- Acesss-Challenge |user@vse.cz|"7C-11-BE-5B-xx-xx"
Apr 12 09:57:05 2017| --> Acesss-Request |user@vse.cz|"7C-11-BE-5B-xx-xx"
Apr 12 09:57:05 2017| <-- Acesss-Challenge |user@vse.cz|"7C-11-BE-5B-xx-xx"
Apr 12 09:57:05 2017| --> Acesss-Request |user@vse.cz|"7C-11-BE-5B-xx-xx"
Apr 12 09:57:05 2017| <-- Acesss-Challenge |user@vse.cz|"7C-11-BE-5B-xx-xx"
Apr 12 09:57:25 2017| <-- Acesss-Challenge |user@vse.cz|"7C-11-BE-5B-xx-xx"
Apr 12 09:57:25 2017| --> Acesss-Request |user@vse.cz|"7C-11-BE-5B-xx-xx"
Apr 12 09:57:25 2017| <-- Acesss-Challenge |user@vse.cz|"7C-11-BE-5B-xx-xx"
Apr 12 09:57:25 2017| --> Acesss-Request |user@vse.cz|"7C-11-BE-5B-xx-xx"
Apr 12 09:57:25 2017| <-- Acesss-Challenge |user@vse.cz|"7C-11-BE-5B-xx-xx"
Apr 12 09:57:25 2017| --> Acesss-Request |user@vse.cz|"7C-11-BE-5B-xx-xx"
Apr 12 09:57:25 2017| <-- Acesss-Accept |user@vse.cz|"7C-11-BE-5B-xx-xx"
Tj. na začátku přišlo 8 Access-Request požadavků, které nejsou ukončeny povolením (Access-Accept) či zamítnutím (Access-Reject) přístupu. Po 20 vteřinách začne nové ověřování, kde k úspěšné autentizaci stačí poslat čtyři požadavky Access-Request.
Zařízení, na kterém jsme si všimli nestandardní autentizace do eduroam, byl iPhone od firmy Apple. Používá ho výše postavený pracovník školy a sledování jeho komunikace by pro některé kruhy mohlo mít větší finanční smysl. Na mobilu nebyl jailbreak, ani nebyly nainstalovány nějaké neobvyklé aplikace. Začali jsme monitorovat jeho síťový provoz, po měsíci vyhodnocování si nemyslíme, že by někdo cizí mobil ovládal.
Popisovaná zranitelnost FreeRADIUSu je spojena s ověřováním zařízení (supplicant) pomocí protokolu PEAP či EAP-TTLS. Týká se i ověřování v drátových sítích pomocí 802.1X.
upgradovat na FreeRADIUS 3.0.14.
A recently patched Samba flaw known as EternalRed and SambaCry has been exploited in the wild to deliver a cryptocurrency miner to vulnerable machines, researchers warned.
12.6.2017 securityaffairs BigBrothers
The Egyptian government blocked a number of websites in Egypt, including the publishing platform Medium, without any official announcement.
Egyptians users of the online publishing platform, Medium were not able to access the service from their country. Readers and bloggers using both desktop and mobile app suffered access problems, the reason of the blackout is still unclear but privacy advocates fear Government censorship. 
medium blockage egypt
Zaid Benjamin ✔ @zaidbenjamin
Reports of #Egypt blocking Medium, online publishing platform, which is used by pro-Muslim Brotherhood websites to bypass government block.
1:11 AM - 11 Jun 2017
23 23 Retweets 14 14 likes
Twitter Ads info and privacy
Medium Bloggers and readers in Egypt expressed frustration over the blockage operated by the Government.
Follow
hossam bahgat @hossambahgat
So today #Egypt also blocked @Medium bringing the number of sites blocked this month to 41 including @MadaMasr
9:26 PM - 10 Jun 2017
162 162 Retweets 38 38 likes
Twitter Ads info and privacy
“Blocking of websites in Egypt has continued with the ban of the online publishing platform “Medium” on Saturday.” states the Egyptianstreets.com.
12.6.2017 thehackernews Ransomware
WannaCry, the biggest ransomware attack in the history, gained prominence very rapidly in the media globally after the ransomware infected more than 300,000 computers in over 150 countries within just 72 hours.
Governments, Intelligence agencies and law enforcement around the world have already started their investigations and are working closely with affected companies to track down hackers responsible for the global cyber attack launched on Friday, 12th May.
Some researchers traced back WannaCry to a state-sponsored hacking group in North Korea, while other believed the perpetrators might be Chinese.
If you have been following WannaCry coverage on The Hacker News, you should be aware of that the WannaCry ransomware uses Tor hidden service to communicate with its command-and-control server.
Just yesterday, we came to know that French authorities had seized at least 6 Tor's entry guard node servers, hosted on France-based hosting providers, just two days after the outbreak of ransomware attack while investigating the WannaCry incident.
On 15th May, a French hacktivist, who uses online moniker ‘Aeris,’ informed Tor community that the official from Central Office for Combating Crime Related to Information and Communication Technologies (OCLCTIC) raided the Online.net hosting provider and have seized his "kitten1" and "kitten2" (torguard and fallback directory) servers on 14th May.
"Cops raided OVH, Online.net and FirstHeberg hosting providers on the basis of a complaint filed by French Renault company that was one of the victims of the WannaCry infection," Aeris told The Hacker News.
"I went to court to have access to information about the seizer of my servers, but it refused to provide me with any information, and even the providers are under gag order."
Aeris told THN that he is aware of the seizer of total 6 Tor relays, operated by 5 operators.
Perhaps nobody was aware of the takedown of these servers in question until the author of Deepdotweb first reported about this incident on Saturday.
Aeris also claimed that the French authorities had taken this action after a victim company (possibly Renault, a France-based multinational automobile manufacturer) contacted the agency for help and provided network traffic logs to assist the investigation.
Since the Tor nodes have been securely implemented to protect the privacy of Tor users and no actual data had been retained on them, the law enforcement authorities would hardly find any evidence related to the WannaCry gang.
"Private key are under encrypted volume and may be protected, but please revoke immediately kitten1 & kitten2 tor node. Those nodes are also fallback directory." Aeris warned.
WannaCry epidemic that hit victims worldwide was using self-spreading capabilities to infect vulnerable Windows computers, particularly those using older versions of the operating system.
While most of the affected organisations have now returned to normal, law enforcement agencies across the world are still on the hunt.
12.6.2017 securityaffairs Cyber
Security researchers at Trend Micro used Tor honeypots to conduct a six-months study of the attack landscape of the Dark Web,
Security experts at Trend Micro have conducted a six-months study of the attack landscape of the Dark Web, researchers operated a honeypot setup simulating several underground services on the Dark Web in order to analyze the way they were targeted.
A blog offering customized services and solutions for the Dark Web.
An underground forum that only allows registered members to log in. In addition, vouching is needed to become a member.
A private file server for sensitive documents offering File Transfer Protocol (FTP) and Secure Shell (SSH) logins.

The services running on the honeypots were deliberately affected by a number of vulnerabilities to allow attackers to hack them. The researchers automatically recorded all logs after every successful attack and restored the environment to a clean state each day. 
Attempts to hijack and spy on the communications originating to and from our honeypot
Theft of confidential data from our disguised FTP file server
Monitoring of IRC conversations via logins to our simulated chat platform
Manual attacks against the custom application running the underground forum
Let me close with the following statement included in the report:
11.6.2017 securityaffairs Ransomware
A few days after the massive WannaCry attack the French authorities seized a server running two Tor relays in connection to the ransomware campaign, both relays were also working as Tor entry guard nodes, key components of Tor routing when users connect the anonymizing network. 
11.6.2017 securityaffairs Mobil
Security researchers from Aleph Research Motorola have discovered a critical kernel command line injection flaw in the Motorola handset Moto G4 and Moto G5 models. 
11.6.2017 securityaffairs BigBrothers
According to a report published by American Security Today, the DARPA High-Assurance Cyber Military Systems (HACMS) program is designing technology for the creation of safe and secure cyber-physical systems.
11.6.2017 securityaffairs Vulnerebility
At the end of May, a seven-year-old remote code execution vulnerability affecting all versions of the Samba software since 3.5.0 was patched by the development team of the project. An attacker can exploit the CVE-2017-7494 RCE to upload a shared library to a writable share, and then cause the server to load and execute it.
SambaCry allows a remote hacker to take full control of a vulnerable Linux and Unix system.
configure shared files to have write privileges.
use known or guessable server paths for those files.
When the above conditions are satisfied, remote attackers can upload any code of their choosing and cause the server to execute it, possibly with unfettered root privileges, depending on the vulnerable platform.
The announcement published by Samba informed users that a patch addressing this remote code execution vulnerability tracked as CVE-2017-7494 was available at the following URL:
to their Samba configuration file and restarting the network’s SMB daemon.
When SambaCry was discovered, nearly 485,000 Samba-enabled computers were found to be exposed on the Internet. 
“On May 30th our honeypots captured the first attack to make use of this particular vulnerability, but the payload in this exploit had nothing in common with the Trojan-Crypt that was EternalBlue and WannaCry. Surprisingly, it was a cryptocurrency mining utility!” reported Kaspersky. 
Omri Ben Bassat @omri9741
Cryptocurrency miner #EternalMiner using #SambaCry #CVE_2017_7494 to infect Linux servers. brand new sample @malwrhunterteam.
10:25 AM - 8 Jun 2017
52 52 Retweets 34 34 likes
Twitter Ads info and privacy
Once compromised a Linux Machine exploiting the SambaCry vulnerability, attackers execute two different payloads on the targeted systems:
cblRWuoCc.so — A backdoor that includes cryptocurrency mining utilities – CPUminer.
“the attacked machine turns into a workhorse on a large farm, mining crypto-currency for the attackers. In addition, through the reverse-shell left in the system, the attackers can change the configuration of a miner already running or infect the victim’s computer with other types of malware” Kaspersky researchers say.
10.6.2017 thehackernews Ransomware
Remember SambaCry?
Two weeks ago we reported about a 7-year-old critical remote code execution vulnerability in Samba networking software (re-implementation of SMB networking protocol) that allows a remote hacker to take full control of a vulnerable Linux and Unix machines.
To know more about the SambaCry vulnerability (CVE-2017-7494) and how it works, you can read our previous article.
At that time, nearly 485,000 Samba-enabled computers were found to be exposed on the Internet, and researchers predicted that the SambaCry-based attacks also have potential to spread just like WannaCry ransomware widely.
The prediction came out to be quite accurate, as honeypots set up by the team of researchers from Kaspersky Lab have captured a malware campaign that is exploiting SambaCry vulnerability to infect Linux computers with cryptocurrency mining software.
Another security researcher, Omri Ben Bassat, independently discovered the same campaign and named it "EternalMiner."
According to the researchers, an unknown group of hackers has started hijacking Linux PCs just a week after the Samba flaw was disclosed publicly and installing an upgraded version of "CPUminer," a cryptocurrency mining software that mines "Monero" digital currency.
After compromising the vulnerable machines using SambaCry vulnerability, attackers execute two payloads on the targeted systems:
INAebsGB.so — A reverse-shell that provides remote access to the attackers.
cblRWuoCc.so — A backdoor that includes cryptocurrency mining utilities – CPUminer.
"Through the reverse-shell left in the system, the attackers can change the configuration of a miner already running or infect the victim’s computer with other types of malware," Kaspersky researchers say.
Mining cryptocurrencies can be a costly investment as it requires an enormous amount of computing power, but such cryptocurrency-mining malware makes it easier for cybercriminals by allowing them to utilise computing resources of compromised systems to make the profit.
If you have been following The Hacker News regularly, you must be aware of Adylkuzz, a cryptocurrency-mining malware that was using Windows SMB vulnerability at least two weeks before the outbreak of WannaCry ransomware attacks.
The Adylkuzz malware was also mining Monero by utilizing the enormous amount of computing resources of the compromised Windows systems.
The attackers behind SambaCry-based CPUminer attack have already earned 98 XMR, which worth 5,380 today and this figure is continuously rising with the increase in the number of compromised Linux systems.
"During the first day they gained about 1 XMR (about $55 according to the currency exchange rate for 08.06.2017), but during the last week they gained about 5 XMR per day," the researchers say.
The maintainers of Samba has already patched the issue in their new Samba versions 4.6.4/4.5.10/4.4.14, and are urging those using a vulnerable version of Samba to install the patch as soon as possible.
10.6.2017 Kaspersky Social
Over the previous weekend, social networks were hit with a wave of posts that falsely claimed that major airlines were giving away tickets for free. Users from all over the world became involved in this: they published posts that mentioned Emirates, Air France, Aeroflot, S7 Airline, Eva Air, Turkish Airlines, Air Asia, Air India, and other companies. We cannot rule out that similar posts mentioning other brands may appear in the nearest future as well.
The possibilities of social networks are endless when it comes to spreading information across the globe. These fraudsters only confirm this fact.
A scrupulous examination of a web resource’s address will help identify fraud. It may be a good idea to verify whether the domain belongs to the company indicated on the website or not. Services that provide whois data about domains may prove helpful in that endeavor.
Be responsible when posting content from your account on a social network. In order to avoid becoming involved in a fraudulent scheme, do not spread information with questionable authenticity.
Do not install suspicious browser extensions. Upon detection of an installed extension that seems suspicious or whose purpose you do not remember, delete the extension immediately in the settings section of your browser and change the passwords of websites that you visit, especially those dealing with online banking.
Use security solutions that protect users from phishing, such as Internet Security-level solutions and higher. They will block any attempts to navigate your browser to fraudulent websites.
10.6.2017 Kaspersky Ransomware
10.6.2017 thehackernews Social
Social media networks are no doubt a quick and powerful way to share information and ideas, but not everything shared on Facebook or Twitter is true.
Misinformation, or "Fake News," has emerged as a primary issue for social media platforms, seeking to influence millions of people with wrong propaganda and falsehoods.
In past years, we have seen how political parties and other groups have used spoofed social media profiles of influencers or leaders to spread misinformation, and most of the time such techniques work to successfully convince people into believing that the information is true.
Although social media services like Facebook, Twitter, and Google, offers account verification (verified accounts with blue tick) for public figures, we have seen hackers hijacking verified accounts to spread fake news from legitimate account to their millions of followers.
Now, researchers have uncovered a new, cunning attack technique currently being used by hackers to take over verified Twitter accounts and rename them to influential people in order to spread fake news.
Dubbed DoubleSwitch, the attack begins with a simple account takeover, but then the hackers change the username and display name with the one having a large influence on social media.
According to a new report from digital rights group Access Now, hackers are targeting Twitter accounts of journalists, activists, and human rights defenders in Venezuela, Bahrain, and Myanmar, some of them were verified with a large number of followers.
This attack was discovered when two journalists — Milagros Socorro and Miguel Pizarro, a member of Venezuela's parliament — were hacked and then renamed.
What's creepy? The hacker then registered a new account, resembling with their original profiles, under the original usernames (Twitter handles), but using the attacker's controlled email addresses.
This means, every time victims try to recover their accounts using regular password reset option, the confirmation emails will be sent to the hijacker, who pretends that the issue has been resolved, making it almost impossible for the victims to recover their account.
Hackers then use hijacked verified accounts, but renamed to another influence, to feed fake news to the millions of followers of the original accounts.
While it's unclear how the hackers managed to hijack the verified users at the first place, it is believed that the attack begins with malware or phishing attacks.
How DoubleSwitch Attack Works (Illustrated Example)
To illustrate how effective DoubleSwitch technique is, we have prepared an example below:
Let's say, a hacker somehow managed to hijack The Hacker News’ Twitter account (@thehackersnews), which is verified with 368,000 followers, where most of the are influencers in Infosec community.
Original @thehackersnews Twitter Account
And then the "DoubleSwitch" begins.
Original Tim Cook Twitter Profile
The First Switch: Once hacked, the hacker first changes the password and associated email id, along with the username, let's say @tim__cook, spoofing the Apple's CEO who is on Twitter with @tim_cook (single underscore).
Hijacked @thehackersnews Account (Impersonates Tim Cook)
Now, the hacker holds a verified account with the name of Apple CEO Tim Cook and can feed misinformation to nearly 370,000 influential followers from the tech industry, and many of them will believe without realising the account is hijacked and the tweets from it are fake.
The Second Switch: The hacker creates a new Twitter account with the original username @thehackersnews, which will be available, as once a Twitter account is deactivated, the handle for that account is freed for others to use.
But mind it, this new Twitter account registered with our Twitter handle (@thehackersnews) will not be verified with zero followers.
Locking the Legitimate Account Owner Out of its Account
In order to get our account back, if we use password reset option, Twitter will send the confirmation email only to the attacker' email id that he used to register the new account.
So any attempt by the victim to regain access to its account fails, as the attacker can simply notify Twitter that the issue has been resolved, locking out the legitimate account holder.
Fortunately, Twitter also offers an alternative way, an online form, to report account hacking incidents directly to the Twitter team, which then they review and investigate the issue accordingly to help victims recover their accounts.
Using this method, Access Now helped the journalists regain access to their accounts, but by the time they regained access, some of the original account holder’s tweets were deleted, and the accounts were used to spread the fake news about events in Venezuela, confusing followers and damaging their reputations in the process.
Access Now says the attack can be conducted over Facebook and Instagram as well, but users can protect themselves by enabling two-factor authentication feature offered by the services.
Two-factor authentication uses two different methods in an attempt to verify a user's identity — a password and a one-time passcode (OTP) sent to the user's mobile phone — which makes it much harder for hackers to compromise an account in the first place.
However, two-factor verification is not an actual solution for the journalists, activists and human rights defenders in countries like Venezuela, as they do not associate their personally-identifiable information like phone numbers with their online accounts in fear of getting spied on.
10.6.2017 securityaffairs Hacking
Personal and financial information about Gamestop online shoppers could have been compromised in a breach occurred between Aug. 10, 2016 to Feb. 9, 2017
GameStop is the last victim of a data breach, customers received a security breach notification warnings this week. Personal and financial information could have been compromised in a breach occurred between Aug. 10, 2016 to Feb. 9, 2017, the company publicly acknowledged the breach in April. 
Thousands of IP cameras have been hijacked by Internet of Things (IoT) botnets and data from Trend Micro shows that the recently launched Persirai malware is responsible for a large percentage of infections.
10.6.2017 securityaffairs Virus
Earlier this week, the security expert Ruben Daniel Dodge published an interesting post on a new technique to deliver malware through PowerPoint files leveraging on mouseover events. Now experts at Trend Micro revealed details of a spam campaign they detected in late May leveraging the technique. 
10.6.2017 securityaffairs Hacking
Thousands of IP cameras have been hijacked by the Persirai IoT botnet that targets more than 1,000 IP camera models.
Early May, the researchers at Trend Micro discovered a new attack on internet-based IP cameras and recorders. The new Internet of Things (IOT) attack called ELF_PERSIRAI has also been back-tracked to an Iranian research institute which restricts its use to Iranians only, indicating a possible state-sponsored cyber strike by Tehran.
ntp.gtpnet.ir
185.62.189.232
95.85.38.103
The Persirai attack installs itself and then deletes the installation files to hide its presence on the target camera, running in memory only. It then proceeds to download and install additional control software and blocking software. Once communications are established with the command and control network server, the infected camera is then ordered to search for other cameras and infect them as well. 

“A newer version of Mirai, DvrHelper (detected by Trend Micro as ELF_MIRAI.AU ) also learned from its predecessor. Since Mirai triggered such a response from companies and industries all over the world, DDoS prevention solutions have been surfacing. To match the increase in security, DvrHelper has eight more DDoS attack modules. It is also the first malware designed to bypass an anti-DDoS solution.” states Trend Micro.
Útoky ransomwaru jsou, jak se zdá, stále na vzestupu. Zde jsou čtyři dobré důvody, proč byste neměli za získání vašich dat zpět platit, a také jeden důvod, proč to lidé dělají.
Na co se můžete těšit? Více nového designu, zase zajímavější Edge a pak na milion drobností. 
Centrum akcí je přehlednější a zapadá do nového designového stylu (Foto: Microsoft)
Co se estetiky týče, výrazně upraveno bylo Centrum akcí. Kromě toho, že je rovněž přepracováno do nového designu, na pohled jiným způsobem prezentuje zmeškaná oznámení. Seskupuje je podle aplikace nebo typu zařízení. První zkušenost napovídá, že je to změna k lepšímu a že bude Centrum přehlednější, ale na velká hodnocení je zatím brzy.
Prohlížeč nastupující Internet Explorer není špatný, ale stále není dostatečně dobrý, abychom jej doporučovali pro náročnější použití. Microsoft do něj v této verzi konečně přidává možnost připnout weby na hlavní panel. To uměl už Internet Explorer a patřil jsem k těm, kteří poslední dva roky volali po tom, aby se připínání naučil také Edge. 
Kdo pracuje s poznámkovým aparátem, bude s Edgem o kousek spokojenější (Foto: Microsoft)
Z malých novinek ještě zbývá zmínit možnost zavřít okno prohlížeče i ve chvíli, kdy je zobrazen nějaký javascriptový dialog. Z kontextové nabídky panelů můžete přidat aktuálně otevřené stránky k oblíbeným položkám (do nové složky). Animace otevření a zavření panelu jsou plynulejší, obnova relace je chytřejší. Když se prohlížeč spouští kvůli otevření odkazu, přepne vás rovnou na nový odkaz. 
Nová klávesnice mj. nabízí chytřejší návrhy (Foto: Microsoft)
Klávesnice dále slibuje chytřejší návrhy slov (zatím ale jen pro americkou angličtinu) a pohodlnější vkládání emoji. Dále vznikla malá verze klávesnice vhodná pro psaní jednou rukou. Dokonce je k dispozici diktování, takže bude text automaticky přepisován. Ani tato funkce není dostupná v českém prostředí.
Univerzální aplikace jako Groove nebo Fotografie už nebudou ignorovat lokálně uložené soubory. Při prohledání úložiště vám relevantní soubory nabídnou k importu.
Byla zlepšena spolehlivost a pár drobností ve funkci My People.
Po ručním vypnutí či zapnutí Nočního osvětlení dojde k rychlejšímu barevnému přechodu. Totéž platí pro restart zařízení.
Byly přidány nové možnosti nastavení přehrávání videí, včetně určení, zda preferujete kvalitu, nebo raději delší běh na akumulátor.
V Nastavení můžete změnit asociovat podle programu. To dosud šlo jen v Ovládacích panelech. V Nastavení jste mohli měnit asociace s jednotlivými příponami.
Nastavení profilu sítě (veřejná či soukromá) je viditelnější.
Přehled bezdrátových sítí obsahuje kontextovou nabídku, odkud můžete rychle pracovat se sítěmi.
Windows Update vám umožní sledovat stav instalace jednotlivých aktualizací a aplikovaných zásad.
Pár vylepšení se dotklo herního panelu (lze snímat obrazovku v režimu HDR).
Došlo i na vylepšení pro vývojářskou komunitu.
Jako vždy byly zlepšeny funkce pro handicapované. (Přibyly i barevné filtry obrazu, které značně rozšiřují původní režim vysokého kontrastu.)
V tomto sestavení opět funguje stahování jazykových balíčků, zato nefunguje stahování funkcí, které můžete dodatečně zapnout. To se týká např. frameworku .NET nebo aktivace vývojářského režimu. Pokud cokoli podobného požadujete, proveďte instalaci před upgradem na sestavení 16215. Kompletní seznam novinek, oprav a známých chyb naleznete na blogu Windows Experience. (Mobily opět čeká jen pár oprav.)
9.6.2017 thehackernews Vulnerebility
It's not hard for a well-funded state-sponsored hacking group to break into corporate networks and compromise systems with malware, but what's challenging for them is to keep that backdoor and its communication undetectable from a firewall and other network monitoring applications.
However, a cyber-espionage group known as "Platinum," that is actively targeting governmental organisations, defense institutes, and telecommunication providers since at least 2009, has found a way to hide its malicious activities from host-based protection mechanisms.
Microsoft has recently discovered that the cyber-espionage group is now leveraging Intel's Active Management Technology (AMT) Serial-over-LAN (SOL) channel as a file-transfer tool to steal data from the targeted computers without detection.
Intel-based chip sets come with an embedded technology, called AMT, which is designed to allow IT administrators to remotely manage and repair PCs, workstations, and servers of their organisations.
The Intel AMT technology operates independently of the operating system and works even when the system is turned off, as long as the platform is connected to a line power and a network cable.
That means, when AMT is enabled, any packet sent to the PC's wired network port will be redirected to the Management Engine and passed on to AMT – the operating system, as well as network monitoring applications installed on a system, never knows what's going around.
Moreover, Linux systems with Intel's chips and AMT enabled may also be exposed to Platinum's malware.
"As this embedded processor is separate from the primary Intel processor, it can execute even when the main processor is powered off and is, therefore, able to provide out-of-band (OOB) remote administration capabilities such as remote power-cycling and keyboard, video, and mouse control (KVM)," Microsoft said.
"Furthermore, as the SOL traffic bypasses the host networking stack, it cannot be blocked by firewall applications running on the host device. To enable SOL functionality, the device AMT must be provisioned."
Unlike the remote authentication flaw discovered last month that enabled hackers to take over full control of a system by using AMT features without the need of any password, Platinum does not exploit any flaw in AMT, instead, requires AMT to be enabled on infected systems.
Microsoft notes that SOL session requires a username and password, so either the hacking group is using stolen credentials to make its malware remotely communicate with the C&C servers, or "during the provisioning process, PLATINUM could select whichever username and password they wish."
Microsoft said it has already updated its own Windows Defender Advanced Threat Protection software that will alert network administrators of any malicious attempts at using AMT SOL, but only for systems running Windows operating system.
9.6.2017 securityaffairs Safety
The Tor Project Team has announced the release of Tor Browser 7.0, it comes with multiprocess mode, content sandbox, and Unix domain sockets.
The Tor Project has released the stable release of Tor Browser 7.0 that includes many security features and according to the development team, it also improved performance.
content sandbox;
The Development team enabled both features by default on macOS and Linux, unfortunately, it is still working on the sandboxing for Windows systems.
9.6.2017 securityaffairs Vulnerebility
Cisco warns its customers of the presence of two critical vulnerabilities in the CISCO Prime Data Center Network Manager (DCNM) that can be exploited by remote attackers for code execution and to access the administrative console.
The first flaw tracked as CVE-2017-6639, is related to the lack of authentication and authorization for a debugging tool that was left enabled in the product. 
Cisco informed customers this week that its Prime Data Center Network Manager (DCNM) is affected by two critical vulnerabilities that can be exploited for remote code execution and to access the product’s administrative console.
Earlier this week, a researcher analyzed a newly detected technique for delivering malware involving PowerPoint files and mouseover events. Today, Trend Micro has published details on a spam campaign it detected in late May using the same technique.




