
Trump Fires FBI Director Over Clinton Probe, Amid Russia Investigation
10.5.2017 thehackernews BigBrothers
President Donald Trump has abruptly fired James Comey, the director of the Federal Bureau of Investigation (FBI) who was leading an investigation into alleged links between Trump and Russia.
The White House announced on Tuesday that Comey was fired on the "clear recommendation" of Deputy Attorney General Rod Rosenstein and Attorney General Jeff Sessions, citing the reason that he was no longer able to lead the bureau effectively.
"While I greatly appreciate you informing me, on three separate occasions, that I am not under investigation, I nevertheless concur with the judgment of the Department of Justice that you are not able to effectively lead the Bureau," Trump wrote in a termination letter to Comey.
Later a memo from the US deputy attorney general Rod Rosenstein explained that Comey was fired as director of the FBI over mishandling of the inquiry into Hillary Clinton's emails, including his decision to close this investigation without prosecution.
However, the memo doesn't mention the FBI investigation into possible links between the Trump campaign and the Russian government.
Mr. Comey was delivering a speech in Los Angeles when he learned that Trump had fired him, and initially he thought it was a fairly funny prank.
Comey's Firing has Drawn Wide Criticism
The move stunned Washington and raised suspicions among Democrats, who called it a "Nixonian" move by the Trump.
Democrats quickly suggested that Comey's firing may have more to do with 'investigation into Trump's ties with Russia' than with the Hillary email scandal.
Last Wednesday, Comey testified before Congress about Russia's role in influencing the 2016 U.S. presidential election.
Tim Kaine, Senator from Virginia and former Democratic vice presidential nominee, made a series of tweets, saying the Comey's termination proved "how frightened the Admin is over Russia investigation," arguing that the firing was "part of a growing pattern by White House to cover-up the truth."
Here's a statement from American Civil Liberties Union (ACLU) Executive Director Anthony D. Romero:
"The independence of the FBI director is meant to ensure that the president does not operate above the law. For President Trump to fire the man responsible for investigating his own campaign’s ties to the Russians imperils that fundamental principle.
Regardless of how one judges the performance of James Comey in either the Hillary Clinton or Russia investigations, President Trump's dismissal of a sitting FBI director raises serious alarm bells for our system of checks and balances." Meanwhile, Senator Minority Leader Chuck Schumer called for an independent investigator to take over the Russia probe.
Even NSA whistleblower Edward Snowden condemn the termination despite Comey "has sought for years to jail me on account of my political activities," he tweeted.
"Set politics aside: every American should condemn such political interference in the bureau's work" — Edward Snowden.
Trump has appointed FBI Deputy Director Andrew McCabe to serve as an interim director unless they get someone to replace Comey, who was serving the FBI from last 27 years and appointed to the director's position by President Barack Obama in 2013.
Vulnerability Allowed Hackers to Steal iCloud Keychain Secrets
10.5.2017 securityweek Vulnerebility
Apple has recently patched a Keychain vulnerability that could have been exploited by man-in-the-middle (MitM) attackers to obtain sensitive user information. The details of the flaw were disclosed on Monday by the researcher who reported it to the vendor.
One of the many security holes patched by Apple in late March in iOS, macOS and other products is CVE-2017-2448, a Keychain weakness discovered by Alex Radocea of Longterm Security.
According to Radocea, the flaw affects the iCloud Keychain, which stores account names, passwords, credit card data, and Wi-Fi network information. The iCloud Keychain sync feature allows users to synchronize their keychain so that passwords and other data are accessible from all their Apple devices.
Apple designed the iCloud Keychain to be highly secure and it told customers that not even the NSA can access their secrets. The sync feature uses end-to-end encryption to exchange data — the encryption relies on a syncing identity key unique to each device, and the encryption keys are never exposed to iCloud.
Data is transmitted via the iCloud Key-Value Store (KVS), which applications use to synchronize the data of iCloud users. Communications between apps and the KVS are arbitrated by “syncdefaultsd” and other iCloud system services. The KVS is tied to each user’s account and accessing it requires the targeted account’s credentials or intercepted iCloud authentication tokens.
The vulnerability found by Radocea is related to Apple’s open source implementation of the Off-The-Record (OTR) messaging protocol. Devices can only transmit OTR data if they are part of a group of trust called “signed syncing circle,” which is signed with a syncing identity key associated with each device and a key derived from the user’s iCloud password. Joining the circle requires permission from an existing device and user interaction.
The researcher discovered that, due to improper error handling, the signature verification routine for OTR could have been bypassed, allowing an MitM attacker to negotiate an OTR session without needing the syncing identity key.
While an attacker cannot exploit this vulnerability to join a signing circle, it does allow them to impersonate other devices in the circle when keychain data is being synced, and intercept passwords and other secrets, the expert said.
“For an adversary to gain access to user Keychain secrets, an adversary could leverage this flaw with one of several capabilities to receive keychain secrets. First, assuming that two-factor authentication is not enabled for the user, an attacker with the victim’s iCloud password would be able to directly access and modify entries in the user’s iCloud KVS data,” Radocea said in a blog post this week.
“Second, a sophisticated adversary with backend access to iCloud KVS would also be able to modify entries to perform the attack,” the researcher added. “Third, the ‘syncdefaultsd’ service does not perform certificate pinning for TLS communications. Without key-pinning, a maliciously issued TLS certificate from any trusted system Certificate Authority could intercept TLS sessions to the iCloud KVS web servers and also perform the attack.”
Radocea has pointed out that it’s often easy for attackers to obtain iCloud passwords, especially since many people set weak passwords or use the same one across multiple online services.
Apple said it addressed the vulnerability through improved validation for the authenticity of OTR packets.
Microsoft Patch Tuesday updates for May 2017 fix Zero Days exploited by Russian APT groups
10.5.2017 securityaffairs Vulnerebility
Microsoft Patch Tuesday for May 2017 address tens security vulnerabilities, including a number of zero-day flaws exploited by Russian APT groups.
Microsoft Patch Tuesday updates for May 2017 fix more than 50 security flaws, including a number of zero-day vulnerabilities exploited by Russian APT groups.
Microsoft released security updates for Windows, Internet Explorer, Edge, Office, the .NET framework, and Flash Player on Tuesday.
Security experts at Microsoft worked with peers at ESET and FireEye to address the vulnerabilities affecting Encapsulated PostScript (EPS) filter in Office.
Russian APT groups
Researchers at FireEye investigated some attacks attributed to the Russian APT groups and also an unknown financially-motivated threat actor.
“At the end of March 2017, we detected another malicious document leveraging an unknown vulnerability in EPS and a recently patched vulnerability in Windows Graphics Device Interface (GDI) to drop malware. Following the April 2017 Patch Tuesday, in which Microsoft disabled EPS, FireEye detected a second unknown vulnerability in EPS.” reads the analysis shared by FireEye.
“FireEye believes that two actors – Turla and an unknown financially motivated actor – were using the first EPS zero-day (CVE-2017-0261), and APT28 was using the second EPS zero-day (CVE-2017-0262) along with a new Escalation of Privilege (EOP) zero-day (CVE-2017-0263). Turla and APT28 are Russian cyber espionage groups that have used these zero-days against European diplomatic and military entities. The unidentified financial group targeted regional and global banks with offices in the Middle East.”
The Turla group (aka Waterbug, KRYPTON, and Venomous Bear) has been exploiting an Office remote code execution (RCE) vulnerability (CVE-2017-0261) to spread the SHIRIME custom JavaScript malware.
A second group of financially motivated threat actors has been exploiting the same vulnerability to deliver a new variant of the NETWIRE malware.
The experts observed that The Turla APT also leveraged CVE-2017-0001 for privilege escalation, while the cyber crime gang the CVE-216-7255 for privilege escalation.
The experts from the two firms confirmed that the notorious APT28 group exploited a number of zero-day vulnerabilities in targeted attacks, including the CVE-2017-0262 Office RCE vulnerabilities and a Windows privilege escalation tracked as CVE-2017-0263.
The hackers leveraged the above exploits to deliver the GAMEFISH malware (Seduploader).
Microsoft announced that the security updates released this month have fixed vulnerabilities in Office (CVE-2017-0261 and CVE-2017-0262) exploited the Russian APT groups.
The list of flaws fixed by Microsoft on Tuesday includes also a memory corruption issue in Internet Explorer tracked as CVE-2017-0222, this memory corruption zero-day can be exploited by a remote attacker for code execution.
Adobe fixes critical and important flaws in Flash Player and Experience Manager
10.5.2017 securityaffairs Vulnerebility
Adobe has issued security updates to address critical and important security vulnerabilities in Flash Player and Experience Manager.
The last Flash Player release 25.0.0.171 addresses seven vulnerabilities that can be exploited to take over vulnerable systems.
According to the security advisory published by Adobe, the vulnerabilities include a use-after-free and other memory corruption flaws that can be exploited by attackers to execute arbitrary code.
“Adobe has released security updates for Adobe Flash Player for Windows, Macintosh, Linux and Chrome OS. These updates address critical vulnerabilities that could potentially allow an attacker to take control of the affected system. ” reads the security advisory.
“These updates resolve a use-after-free vulnerability that could lead to code execution (CVE-2017-3071).
These updates resolve memory corruption vulnerabilities that could lead to code execution (CVE-2017-3068, CVE-2017-3069, CVE-2017-3070, CVE-2017-3072, CVE-2017-3073, CVE-2017-3074).”
The company acknowledged Jihui Lu of Tencent KeenLab and Mateusz Jurczyk and Natalie Silvanovich of Google Project Zero for reporting the vulnerabilities.
Lu reported the following flaws:
CVE-2017-3069, CVE-2017-3070, CVE-2017-3071, CVE-2017-3072, CVE-2017-3073, CVE-2017-3074;
Jurczyk and Silvanovich reported the CVE-2017-3068 vulnerability.
According to Adobe, the vulnerabilities have not been exploited by threat actors in the wild.
Adobe Flash Player
A separate security advisory published by Adobe addresses an important information disclosure vulnerability in the Adobe Experience Manager Forms tracked as CVE-2017-3067.
“Adobe has released security updates for Adobe Experience Manager (AEM) Forms on Windows, Linux, Solaris and AIX. These updates resolve an important information disclosure vulnerability (CVE-2017-3067) resulting from abuse of the pre-population service in AEM Forms.” reads the advisory.”This issue was resolved by providing administrators with additional controls in the configuration manager to restrict the file paths and protocols used to pre-fill a form. Adobe recommends users apply the available updates using the instructions provided in the “Solution” section below.”
The vulnerability was discovered by Ruben Reusser and affects the Versions 6.0 through 6.2 are.
The flaw is related to the abuse of the pre-population service in Experience Manager Forms, also in this case, Adobe confirmed that there is no evidence of exploitation in the wild.
Spam v prvním čtvrtletí 2017: Největší botnet 5000krát menší
10.5.2017 SecurityWorld Spam
Největší spam botnet na světě, Necurs, podstatně snížil svou aktivitu. Vyplývá to z dat zprávy „Spam a phishing v prvním čtvrtletí 2017“ společnosti Kaspersky Lab. Zatímco v prosinci 2016 detekovala řešení Kaspersky Lab více než 35 milionů podvodných e-mailů, v březnu tohoto roku jich bylo pouhých sedm tisíc.
V roce 2016 analytici Kaspersky Lab zaznamenali prudký nárůst škodlivých spamových příloh obsahujících především šifrátory. Velká část těchto útoků pocházela od botnetu Necurs považovaného v současnosti za největšího spamového botneta na světě. Tato síť nicméně ke konci roku 2016 v podstatě přestala fungovat. V průběhu téměř celého prvního čtvrtletí tohoto roku se její aktivita držela na velmi nízké úrovni.
Zdá se, že se kyberzločinci zalekli zvýšené pozornosti, která je v současnosti šifrátorům věnována, a proto upustili od hromadného rozesílání e-mailů. Tento krok ale neznamená, že síť přestane fungovat.
V průběhu prvních tří měsíců tohoto roku se objevil nový trend v rozesílání nevyžádaných e‑mailů. Jeho cílem je různými způsoby znesnadnit detekci spamu. Kyberzločinci k tomu mimo jiné využívají rozesílání malwaru v zaheslovaných souborech. Oběť se snaží přinutit k otevření a uložení přílohy hned po jejím obdržení.
V takto podvržených e-mailech se vydávají za známé prodejce, přičemž uživatele nabádají k ověření platby nebo jim slibují finanční odměnu. Často také posílají e-maily jménem různých malých a středních společností, jejichž věrohodnost podporují kontaktními údaji či podpisy.
Jakmile oběť soubor otevře, aktivuje se škodlivý skript, který do počítače stáhne malware. Obsah malwaru je různý, zahrnuje zpravidla ransomware, spyware, backdoors nebo novou verzi známého trojského koně Zeus.
Moderní bezpečnostní řešení pro ochranu před e-mailovým spamem dokáží uživatele účinně chránit před spamem šířeným e-maily. Z toho důvodu se zločinci snaží najít nové kanály, díky nimž by tyto bariéry obešli. Nově se tak zaměřují na messengery a sociální sítě, jejichž prostřednictvím své podvodné nabídky šíří.
Obětem většinou přijde na mail upozornění, že jim byla doručena soukromá zpráva. V takových případech není předmět e-mailu nijak podezřelý, na rozdíl od obvyklých spamů. Spam je tak možné odhalit pouze analýzou těla e-mailu, což vyžaduje daleko větší úsilí. Detekce může být o to složitější, pokud zločinci vystupují jménem známé firmy, kterou oběť považuje za důvěryhodnou.
Microsoft Patches Zero-Days Exploited by Russia-Linked Hackers
10.5.2017 securityweek Vulnerebility
Microsoft’s Patch Tuesday updates for May 2017 address tens of vulnerabilities, including several zero-day flaws exploited by profit-driven cybercriminals and two notorious Russia-linked cyber espionage groups.
The company has resolved more than 50 security holes affecting Windows, Internet Explorer, Edge, Office, the .NET framework, and Flash Player, for which Adobe released an update on Tuesday.
A blog post published by Microsoft revealed that the company had worked with ESET and FireEye to protect customers against attacks leveraging vulnerabilities in the Encapsulated PostScript (EPS) filter in Office. Both ESET and FireEye have released reports on the attacks they have observed.
FireEye has spotted attacks launched by a couple of cyber espionage groups believed to be connected to the Russian government and an unknown financially-motivated threat actor.
According to the security firm, the group known as Turla, Waterbug, KRYPTON and Venomous Bear has been exploiting an Office remote code execution (RCE) vulnerability tracked as CVE-2017-0261 to deliver a custom JavaScript implant dubbed by FireEye “SHIRIME.” The same vulnerability has also been exploited by profit-driven cybercriminals to deliver a new variant of the NETWIRE malware, a threat used by multiple actors over the past years.
The Turla group’s attacks also leveraged CVE-2017-0001 for privilege escalation, while the cybercriminals used CVE-2016-7255 for privilege escalation.
Both FireEye and ESET have observed attacks involving zero-day vulnerabilities launched by the group known as APT28, Pawn Storm, Fancy Bear, Sofacy, Sednit and Strontium. This Russia-linked group, which some believe could be behind the recent election cyberattacks in France, has leveraged an Office RCE flaw (CVE-2017-0262) and a Windows privilege escalation (CVE-2017-0263). The malware delivered in these attacks is tracked by the security firms as Seduploader and GAMEFISH.
Microsoft pointed out that the Turla attacks were first spotted in March, and customers who had up-to-date systems had already been protected as CVE-2017-0001 was patched earlier that month. In April, the company also rolled out a defense-in-depth protection designed to prevent EPS attacks by disabling the EPS filter by default.
The updates released by the company this month patch the EPS-related vulnerabilities in Office (CVE-2017-0261 and CVE-2017-0262) to ensure that customers who need to use EPS filters are still protected.
Another zero-day patched by Microsoft on Tuesday is CVE-2017-0222, a memory corruption in Internet Explorer that can be exploited for remote code execution. No information has been shared on the attacks leveraging this security hole.
The tech giant has also addressed four vulnerabilities that have been publicly disclosed. The list includes an RCE flaw in the JavaScript engines used by web browsers (CVE-2017-0229), a SmartScreen filter-related browser spoofing vulnerability (CVE-2017-0231), a privilege escalation in Edge (CVE-2017-0241), and a Mixed Content warnings bypass in Internet Explorer (CVE-2017-0064).
New Persirai IoT Botnet Emerges
10.5.2017 securityweek IoT
Around 120,000 Internet Protocol (IP) Camera models based on various Original Equipment Manufacturer (OEM) products are vulnerable to a newly discovered Internet of Things (IoT) botnet, Trend Micro warns.
Dubbed Persirai, the new botnet’s development comes on the heels of Mirai, the IoT malware that became highly popular in late 2016, after being involved in multiple high-profile distributed denial of service (DDoS) attacks. Similar to the recent Hajime botnet, Mirai mainly targets Digital Video Recorders (DVRs) and CCTV cameras.
According to Trend Micro, the newly discovered Persirai is targeting over 1,000 IP Camera models, with most users unaware that their devices are exposed to Internet-based attacks. As a result, the researchers argue, attackers can easily gain access to the devices’ web-based interfaces via TCP Port 81.
Because IP Cameras typically use the Universal Plug and Play (UPnP) protocol, which allows devices to open a port on the router and act like a server, they are highly visible targets for IoT malware. By accessing the vulnerable interface of these devices, an attacker can perform command injections to force the device to connect to a site, and download and execute malicious shell scripts.
After Persirai has been executed on the vulnerable device, the malware deletes itself and continues to run only in memory. Further, it blocks the zero-day exploit it uses to prevent other attackers from hitting the same IP Camera. Because the malicious code runs in the memory, however, a reboot renders the device vulnerable to the exploit once again.
Affected IP Cameras were observed reporting to several command and control (C&C) servers (load.gtpnet.ir, ntp.gtpnet.ir, 185.62.189[.]232, and 95.85.38[.]103). Upon receiving commands from the server, infected devices automatically start attacking other IP Cameras by exploiting a public zero-day vulnerability, which allows attackers to get the password file from the user and perform command injections.
The botnet can launch DDoS attacks via User Datagram Protocol (UDP) floods and can perform these attacks with SSDP packets without spoofing IP address.
The security researchers managed to link the botnet to C&C servers that were using the .IR country code, which is managed by an Iranian research institute and is restricted to Iranians only. Furthermore, the malware’s code contains some special Persian characters.
Persirai appears built on Mirai’s source code, which was made publicly available in October last year. The malware targets even devices with the latest firmware versions installed, and can’t be slowed by the use of strong passwords because it abuses a password-stealing vulnerability. Thus, IP Camera owners should implement other security steps to ensure their devices are protected.
“The burden of IoT security does not rest on the user alone—it’s also dependent on the vendors themselves, as they should be the ones responsible for making sure that their devices are secure and always updated. In line with this, users should make sure that their devices are always updated with the latest firmware to minimize the chance of vulnerability exploits,” Trend Micro notes.
Trump Fires FBI Director James Comey
10.5.2017 securityweek BigBrothers
FBI Director James Comey
US President Donald Trump on Tuesday fired his FBI director James Comey, the man who leads the agency charged with investigating his campaign's ties with Russia -- a move that sent shockwaves through Washington.
The surprise dismissal of Comey, who played a controversial role in last year's presidential election, came as he was leading a probe into whether Trump's aides colluded with Moscow to sway the November vote.
Top Senate Democrat Chuck Schumer said he told Trump he was making a "big mistake" by dismissing Comey, a move that prompted parallels with a decision by a crisis-plagued Richard Nixon to fire his attorney general.
Trump "has accepted the recommendation of the attorney general and the deputy attorney general regarding the dismissal of the director of the Federal Bureau of Investigation," his spokesman Sean Spicer told reporters.
A search for a new FBI director was to begin "immediately," the White House said.
In a letter, Trump told Comey: "You are hereby terminated and removed from office, effective immediately."
"While I greatly appreciate you informing me, on three separate occasions, that I am not under investigation, I nevertheless concur with the judgment of the Department of Justice that you are not able to effectively lead the Bureau."
"It is essential that we find new leadership for the FBI that restores public trust and confidence in its vital law enforcement mission," Trump said.
The stated reason for Comey's dismissal -- according to a memo from Deputy Attorney General Rod Rosenstein that was circulated by the White House -- was for mishandling the probe into Democratic presidential hopeful Hillary Clinton's emails.
But his sacking raised immediate questions about Trump's motives.
FBI directors are appointed for a single 10-year term. The 56-year-old Comey, who is popular among rank-and-file agents, was appointed four years ago.
He played an outsized -- and controversial -- role on the American political stage over the past year, lobbing one bombshell after another that rankled both parties in Washington.
Clinton accused Comey of trashing her chances of becoming president by revealing an renewed investigation into her email use.
Comey told lawmakers last week he felt "mildly nauseous" at the thought that he had swayed the election -- but could not have acted any other way.
- 'Nothing less than Nixonian' -
Since the start of Trump's presidency, the FBI chief had increasingly appeared to be a thorn in the president's side.
He has confirmed that the agency is investigating Russian interference in last year's presidential election and notably Moscow's possible collusion with Trump's campaign.
Democrats -- already angry that Congressional inquiries into Russian meddling have been hamstrung by Republicans' willingness to defend Trump -- voiced sharp concerns that the FBI's investigation may now be in jeopardy too, with several calling for an independent commission to take over the probe.
"This is nothing less than Nixonian," charged Senator Patrick Leahy of Vermont, who called Trump's official justification for firing Comey "absurd."
"That fig leaf explanation seeks to cover the undeniable truth: The president has removed the sitting FBI director in the midst of one of the most critical national security investigations in the history of our country -- one that implicates senior officials in the Trump campaign and administration," he charged.
When Trump initially decided to keep Comey -- who was appointed by Barack Obama -- in his job, it raised eyebrows from critics who saw it as a tacit reward for his role in damaging Clinton's chances.
But within months, the FBI chief was back in the national spotlight -- this time taking aim at Trump.
During testimony to Congress last month, Comey flatly rejected Trump's explosive claim that he was wiretapped by his predecessor.
Comey's public testimony -- watched by millions around the world -- came as Trump sought to steer the news focus by calling the question of Russian election meddling "fake news."
But it had become increasingly clear that Comey had set his sights on the issue of Russia's election meddling, which has stalked Trump's presidency since he took office.
U.S. Alerted France to Russia Hack Targeting Macron: NSA
10.5.2017 securityweek BigBrothers
The head of America's National Security Agency said Tuesday that Russia was behind the 11th-hour hack of French President-elect Emmanuel Macron's campaign team, and that US officials had informed France a cyber-attack was underway.
The hacking attack on Macron's campaign, just hours ahead of Sunday's run-off vote that saw him elected, led to thousands of files being leaked online.
"We had become aware of Russian activity," Admiral Mike Rogers told a Senate Armed Services Committee hearing.
"We had talked to our French counterparts prior to the public announcements of the events that were publicly attributed this past weekend and gave them a heads up.
"'Look, we're watching the Russians, we're seeing them penetrate some of your infrastructure. Here's what we've seen, what can we do to try and assist?'" said Rogers, who also heads US Cyber Command.
The NSA chief did not specify what type of "infrastructure" has been compromised. He said that the agency was in contact with its counterparts in Britain and Germany ahead of elections in those countries later this year.
NSA LogoRogers drew comparisons between the hack targeting Macron and those of the US Democratic Party and a close aide to presidential candidate Hillary Clinton ahead of the November election won by Donald Trump.
Washington has officially accused Russia of being behind those hacks, saying Moscow was trying to boost Trump's chances of victory.
"The Russians appear to be assessing that some leaders might be more inclined to be supportive of their positions," Rogers told lawmakers.
"You saw that just play out in the French election where there clearly was a difference between these two candidates and their views of Russia," he said.
Thousands of emails and documents from Macron's campaign were dumped online by hackers shortly before midnight in France on Friday and were then relayed by anti-secrecy group WikiLeaks.
A statement from the 39-year-old Macron called it a "massive and coordinated" hack. Paris prosecutors have opened a probe into the attack, a source close to the investigation has said.
BitKangoroo Ransomware Deletes User Files
10.5.2017 securityweek Ransomware
A piece of ransomware currently in development is deleting users’ files if the ransom isn’t paid within a given period of time.
Dubbed BitKangoroo, the malware doesn’t appear to be the work of a skilled developer and can encrypt only files located in the Desktop folder at the moment, but could become a highly destructive threat because of code that erases users’ data.
Once a computer has been infected, the malware starts encrypting user’s files using AES-256 encryption, and appends the .bitkangoroo extension to each of the affected files. Once the process has been completed, the ransomware displays a window informing the victim that their files have been encrypted and that a 1 Bitcoin ransom should be paid to decrypt them.
The note warns that one file will be deleted every hour until the ransom has been paid, and also displays a countdown. When deleting the encrypted file, the malware also resets the timer to 60 minutes, BleepingComputer’s Lawrence Abrams reveals.
BitKangoroo isn’t the first ransomware family out there to delete user’s files if a payment wasn’t made, but previous threats did allow for a longer period of time before proceeding to such action, which would make more sense, considering that it could take days before being able to buy Bitcoin.
The good news is that security researcher Michael Gillespie has already managed to crack the malware’s encryption and has released a free decryption tool, called BitKangarooDecrypter.
Analysis of the malware also revealed code capable of deleting all of the encrypted files if the victim enters the wrong decryption key (a warning message is displayed when the user clicks on the Decrypt my files button). Fortunately, the code isn’t working and the ransomware can’t delete user’s files.
The BitKangoroo ransomware also provides the victim with a Bitcoin address they should send the ransom payment to, as well as the possibility to contact the malware author directly, via email. At the moment, the bitkangoroo@mailinator.com address is used.
Adobe Patches Flaws in Flash Player, Experience Manager
9.5.2017 securityweek Vulnerebility
Updates released by Adobe on Tuesday for Flash Player and Experience Manager patch several vulnerabilities classified as critical and important.
Flash Player 25.0.0.171 addresses a total of seven flaws which, according to the software giant, can be exploited to take control of vulnerable systems.
The security holes have been described as use-after-free and other memory corruption vulnerabilities that can lead to arbitrary code execution. A majority of the weaknesses were reported to Adobe by Jihui Lu of Tencent KeenLab, and one was discovered by Google Project Zero researchers.
The Flash Player vulnerabilities are tracked as CVE-2017-3068, CVE-2017-3069, CVE-2017-3070, CVE-2017-3071, CVE-2017-3072, CVE-2017-3073 and CVE-2017-3074. There is no evidence that they have been exploited in the wild.
Adobe has published a separate advisory for a flaw in the Forms feature of the Experience Manager enterprise content management solution. Versions 6.0 through 6.2 of the product are affected by an information disclosure vulnerability discovered by Ruben Reusser of headwire.com and tracked as CVE-2017-3067.
The flaw is related to the abuse of the pre-population service in Experience Manager Forms.
“This issue was resolved by providing administrators with additional controls in the configuration manager to restrict the file paths and protocols used to pre-fill a form,” Adobe said in its advisory.
Adobe has released hotfixes and cumulative fix packs for each affected version. The company has found no evidence of exploitation in the wild.
The number of vulnerabilities resolved this Patch Tuesday is small compared to last month, when Adobe addressed nearly 60 vulnerabilities, including ones disclosed at this year’s Pwn2Own hacking competition.
Jenkins patched a critical RCE flaw in its open source automation server
9.5.2017 securityaffairs Vulnerebility
Jenkins developers fixed a critical RCE vulnerability in the popular open source automation server along with many other issues.
Jenkins is the most popular open source automation server, it is maintained by CloudBees and the Jenkins community.
The automation server supports developers build, test and deploy their applications, it has more than 133,000 active installations worldwide with more than 1 million users.
The developers of the automation server recently patched several vulnerabilities, including a critical flaw that can be exploited by a remote attacker for arbitrary code execution.
A security researcher recently reported to the Beyond Security’s SecuriTeam Secure Disclosure program that the popular automation server is affected by a critical issue related to Java deserialization.

The vulnerability could be exploited by a remote unauthenticated attacker to execute arbitrary code on the target system, a hacker just needs to send two specially crafted requests to the affected server.
“CLI: Unauthenticated remote code execution
SECURITY-429 / CVE-2017-1000353
An unauthenticated remote code execution vulnerability allowed attackers to transfer a serialized Java SignedObject object to the remoting-based Jenkins CLI, that would be deserialized using a new ObjectInputStream, bypassing the existing blacklist-based protection mechanism.
SignedObject has been added to the remoting blacklist.” reads the security advisory published by Jenkins.
Jenkins developers admitted that the flaw “allowed attackers to transfer a serialized Java SignedObject object to the remoting-based Jenkins CLI, that would be deserialized using a new ObjectInputStream, bypassing the existing blacklist-based protection mechanism.”
The development team released the versions 2.57 and 2.46.2 (LTS) to address the issue. The security updates also fixed other problems, such as multiple high severity cross-site request forgery (CSRF) vulnerabilities and high severity cross-site request forgery (CSRF) vulnerabilities.
According to the development team, the CSRF flaws can be exploited by attackers to conduct several malicious activities such as restarting the server and installing plugins.
The security updates also fixed a Login command that allowed to impersonate any Jenkins user (SECURITY-466 / CVE-2017-1000354) and an XStream issue that could cause Java crash when trying to instantiate void/Void (SECURITY-503 / CVE-2017-1000355).
Microsoft Issues Emergency Patch For Critical RCE in Windows Malware Scanner
9.5.2017 thehackernews Vulnerebility
Microsoft's own antivirus software made Windows 7, 8.1, RT and 10 computers, as well as Windows Server 2016 more vulnerable.
Microsoft has just released an out-of-band security update to patch the crazy bad bug discovered by a pair of Google Project Zero researchers over the weekend.
Security researchers Tavis Ormandy announced on Twitter during the weekend that he and another Project Zero researcher Natalie Silvanovich discovered "the worst Windows remote code [execution vulnerability] in recent memory."
Natalie Silvanovich also published a proof-of-concept (PoC) exploit code that fits in a single tweet.
The reported RCE vulnerability, according to the duo, could work against default installations with "wormable" ability – capability to replicate itself on an infected computer and then spread to other PCs automatically.
According to an advisory released by Microsoft, the remotely exploitable security flaw (CVE-2017-0290) exists in Microsoft Malware Protection Engine (MMPE) – the company's own antivirus engine that could be used to fully compromise Windows PCs without any user interaction.
List of Affected Anti-Malware Software
Eventually, every anti-malware software that ship with the Microsoft's Malware Protection Engine are vulnerable to this flaw. The affected software includes:
Windows Defender
Windows Intune Endpoint Protection
Microsoft Security Essentials
Microsoft System Center Endpoint Protection
Microsoft Forefront Security for SharePoint
Microsoft Endpoint Protection
Microsoft Forefront Endpoint Protection
Microsoft's Defender security software comes enabled by default on Windows 7, 8.1, RT 8.1, and Windows 10, as well as Windows Server 2016. All are at risk of full remote system compromise.
Remote Code Execution Flaw in Microsoft's Malware Protection Engine
The flaw resides in the way the Microsoft Malware Protection Engine scan files. It is possible for an attacker to craft a malicious file that could lead to memory corruption on targeted systems.
Researchers have labeled the flaw as a "type confusion" vulnerability that exists in NScript, a "component of mpengine that evaluates any filesystem or network activity that looks like JavaScript," which fails to validate JavaScript inputs.
"To be clear, this is an unsandboxed and highly privileged JavaScript interpreter that is used to evaluate untrusted code, by default on all modern Windows systems. This is as surprising as it sounds," Google security researchers explained in a bug report posted on the Chromium forum.
Since antivirus programs have real-time scanning functionality enabled by default that automatically scans files when they are created, opened, copied or downloaded, the exploit gets triggered as soon as the malicious file is downloaded, infecting the target computer.
The vulnerability could be exploited by hackers in several ways, like sending emails, luring victims to sites that deliver malicious files, and instant messaging.
"On workstations, attackers can access mpengine by sending emails to users (reading the email or opening attachments is not necessary), visiting links in a web browser, instant messaging and so on," researchers explained.
"This level of accessibility is possible because MsMpEng uses a filesystem minifilter to intercept and inspect all system filesystem activity, so writing controlled contents to anywhere on disk (e.g. caches, temporary internet files, downloads (even unconfirmed downloads), attachments, etc.) is enough to access functionality in mpengine."
The injected malicious payload runs with elevated LocalSystem level privileges that would allow hackers to gain full control of the target system, and perform malicious tasks like installing spyware, stealing sensitive files, and login credentials, and much more.
Microsoft responded to the issue very quickly and comes up with a patch within just 3 days, which is very impressive. The patch is now available via Windows Update for Windows 7, 8.1, RT and 10.
The vulnerable version of Microsoft Malware Protection Engine (MMPE) is 1.1.13701.0, and the patched version is 1.1.13704.0.
By default, Windows PCs automatically install the latest definitions and updates for the engine. So, your system will install the emergency update automatically within 1-2 days, but you can also get it installed immediately by pressing 'Check Update' button in your settings.
Google Offers $20,000 to Join OSS-Fuzz Program
9.5.2017 securityweek IT
Five months ago, Google launched its free OSS-Fuzz service with the purpose to help open source developers locate bugs in their code. "It is important," said Google at the time, "that the open source foundation be stable, secure, and reliable, as cracks and weaknesses impact all who build on it."
Since then, the cloud service has attracted 47 open-source projects and has uncovered more than 1,000 bugs (264 of which are potential security vulnerabilities) while processing 10 trillion test inputs per day.
Google now wishes to attract more OSS projects to the initiative, and is offering a reward to do so. "We believe that user and internet security as a whole can benefit greatly if more open source projects include fuzzing in their development process," the company announced in a blog post yesterday. "To this end, we'd like to encourage more projects to participate and adopt the ideal integration guidelines that we've established."
Google is expanding its Patch Rewards program to include rewards for the integration of fuzz targets into OSS-Fuzz. It will pay projects $1,000 for the initial integration, and up to $20,000 (at its own discretion) for what it describes as an 'ideal integration'.
The $20,000 is broken into four chunks of up to $5,000 each. The first requires checking the fuzz targets into their upstream repository and integrating into the build system with sanitizer support.
The second $5,000 comes if the targets are efficient and provide more than 80% code coverage. The third part of the 'ideal' integration requires regression testing; that is the targets be maintained, run against old known crashers and the periodically updated corpora.
Google calls the final $5,000 a 'l33t' bonus, "that we may reward at our discretion for projects that we feel have gone the extra mile or done something really awesome."
The Patch Reward Program Rules have been expanded to include 'projects integrated into OSS-Fuzz'. Interested parties are invited to apply for OSS-Fuzz integration and subsequent awards via the adapted Patch Submission Form.
FCC Says Website Downtime Caused by DDoS Attacks
9.5.2017 securityweek Attack
The U.S. Federal Communications Commission (FCC) said its website was disrupted by distributed denial-of-service (DDoS) attacks on Sunday night, not due to a large number of attempts to submit comments on net neutrality.
“Last Week Tonight” host John Oliver revisited the subject of net neutrality on Sunday, urging people to leave comments on the FCC’s website. Oliver has criticized FCC Chairman Ajit Pai over the proposal to roll back net neutrality rules, and he even set up a domain, gofccyourself.com, which redirects users to a page on the FCC website where they can submit comments on the proposal. The FCC’s site became inaccessible shortly after.
The TV host made similar comments back in June 2014, when the FCC’s website crashed due to the large number of users that attempted to vent their frustration. While many believe the latest incident was also caused by too much traffic on the server hosting the site, the FCC has blamed the downtime on DDoS attacks.
“Beginning on Sunday night at midnight, our analysis reveals that the FCC was subject to multiple distributed denial-of-service attacks (DDos). These were deliberate attempts by external actors to bombard the FCC’s comment system with a high amount of traffic to our commercial cloud host,” the FCC stated.
“These actors were not attempting to file comments themselves; rather they made it difficult for legitimate commenters to access and file with the FCC. While the comment system remained up and running the entire time, these DDoS events tied up the servers and prevented them from responding to people attempting to submit comments.” it added.
Some people are still skeptical and believe the FCC may have mistaken the large volume of traffic for a DDoS attack. Other theories are that someone launched a DDoS attack on the FCC just for fun, or that entities opposing net neutrality rules launched the attacks to prevent consumers from complaining.
Digital rights group “Fight for the Future” believes the FCC is either intentionally misleading or someone did actually launch DDoS attacks to block comments from net neutrality supporters. The organization believes both scenarios are concerning and it has called on the FCC to release its logs to independent security analysts or the media, and guarantee that all comments will be counted.
“The public deserves to know [what happened], and the FCC has a responsibility to maintain a functioning website and ensure that every member of the public who wants to submit a comment about net neutrality has the ability to do so. Anything less is a subversion of our democracy,” Fight for the Future said in a blog post.
RedLock Emerges from Stealth With Cloud Security Platform
9.5.2017 securityweek Security
Cloud security startup RedLock emerged from stealth mode on Tuesday with a cloud infrastructure security offering and $12 million in funding from several high profile investors.
According to the company, its RedLock Cloud 360 platform is designed to help organizations manage security and compliance risks in their public cloud infrastructure without having a negative impact on DevOps.
The company says its product can help security teams identify risks in their cloud infrastructure by providing comprehensive visibility into workloads and the connections between user activity, network traffic, configurations, and threat intelligence data. The solution works across multiple public cloud services, such as Amazon Web Services (AWS), Microsoft Azure and Google Cloud Platform.
RedLock emerges from stealth mode
RedLock Cloud 360 uses machine learning and correlation with third-party data sources to establish a baseline for user and network behavior, which allows it to quickly identify anomalies. The product monitors new and existing cloud workloads for policy violations, including policies set by security teams and security best practices defined by NIST, CIS and PCI.
The solution continuously assigns a score to every workload based on risky attributes and behavior, which helps security personnel assess the risks and prioritize their response. Data provided by the product can also be integrated with third-party tools to speed up response.
RedLock Cloud 360 also includes forensics capabilities that allow organizations to go back to any point in time and identify threats. Users can also review a history of changes for each workload and determine the root cause of a security incident.
The platform also provides reporting features that allow organizations to compile reports for auditors, management and the board of directors.
RedLock has come out of stealth mode with $12 million in funding from Sierra Ventures, Storm Ventures, Dell Technologies Capital, and other investors.
While the company has only now announced the general availability of its cloud security platform, the product has already been used by several companies, including security firm Proofpoint. Pricing for RedLock Cloud 360 is subscription-based and it depends on the number of workloads deployed in the customer’s cloud environment.
Odemčení zabijákova iPhonu stálo přes 22 miliónů korun, přiznala senátorka
9.5.2017 Novinky/Bezpečnost Apple
Americký Federální úřad pro vyšetřování (FBI) zaplatil za odemčení iPhonu teroristy Syeda Farooka ze San Bernardina 900 tisíc dolarů, tedy v přepočtu něco málo přes 22 miliónů korun. Po uplynutí více než roku od celé kauzy, to potvrdila americká senátorka Dianne Feinsteinová.
Zástupci FBI doposud oficiálně nepotvrdili, jak vysokou částku zaplatili bezpečnostním expertům, aby se do smartphonu s logem nakousnutého jablka dostali. Šéf FBI James Comey se pouze nechal slyšet, že „opravdu hodně“.
„Je to víc, než si zvládnu u FBI vydělat do konce svého funkčního období. Tedy za sedm let a čtyři měsíce,“ přiblížil Comey.
Tehdy se spekulovalo, že vyšetřovatelé za odblokování iPhonu zaplatili zhruba 1,3 miliónu dolarů, podle tehdejšího kurzu více než 31 miliónů korun. Senátorka však nyní uvedla celou věc na pravou míru, když přiznala, že částka byla téměř o třetinu nižší.
Dokážou odemknout i další iPhony
I tak je ale částka 900 tisíc dolarů patrně jedna z největších, kterou FBI v podobných kauzách utratila. Suma byla tak vysoká, neboť vyšetřovatelé získali přístup nejen do zabijákova smartphonu, ale také do starších chytrých telefonů s logem nakousnutého jablka – získali univerzální nástroj k odemykání iPhonu 5C a starších modelů.
Jaká společnost pomohla vyšetřovatelům se do iPhonu dostat, oficiálně oznámeno nebylo. Podle dřívějších informací je to však práce společnosti Cellebrite se sídlem v Izraeli. Firma britské stanici BBC potvrdila, že s americkými vyšetřovateli spolupracuje, ale více nesdělila. Na svých internetových stránkách nicméně Cellebrite prohlašuje, že jeden z jejích nástrojů umí dekódovat a extrahovat data z iPhonu 5C.
„Máme nástroj, který však nepracuje na všech iPhonech,“ prohlásil již dříve Comey. Ani tehdy však žádné bližší informace nechtěl prozradit.
Spor o „zadní vrátka”
Vyšetřovatelé z FBI se do uzamčeného iPhonu islámského radikála nemohli dostat dlouhé dva měsíce. Jeho iPhone 5C byl nastaven tak, aby se po zadání deseti nesprávných kódů automaticky vymazal, s čímž si bezpečnostní experti z FBI původně nedokázali poradit.
Soud proto Applu v únoru nařídil, aby tuto funkci vypnula, což však není technicky možné. Proto vyšetřovatelé chtěli po americkém softwarovém gigantu vytvořit v operačním systému iOS „zadní vrátka“, což však vedení Applu odmítalo.
Vyšetřovatelům z FBI se nakonec podařilo do uzamčeného zařízení dostat právě díky nástroji vytvořenému na míru, který byl popsán výše.
Útok v San Bernardinu byl nejtragičtějším od teroristických útoků v zemi v září 2001. Zradikalizovaný muslim Syed Farook a jeho žena Tashfeen Maliková tam na počátku prosince zastřelili 14 lidí. Později byli zabiti při přestřelce s policií.
Útočníci hacknuli server oblíbené aplikace pro macOS. Získali přihlašovací údaje včetně správců hesel
9.5.2017 Živě.cz Apple
Pravděpodobně nejoblíbenějším nástrojem pro konverzi videa pro macOS je Handbrake. Ten se minulý týden stal terčem hackerů, kteří kompromitovali jeden ze serverů, který sloužil pro distribuci aplikace. Místo ní si uživatelé několik dní stahovali extrémně nebezpečný malware.
Hackeři se dostali k jednomu z dvojice serverů, které sloužily jako tzv. mirrory pro stažení programu a distribuci aktualizací existujícím uživatelům. V úterý zaměnili legitimní instalační soubory za malware, který je nazýván jako Proton, který navíc nebyl detekován žádným z dostupných antivirů.
Po spuštění aplikace (v domnění, že jde o instalaci Handbrake) si malware vyžádal zadání systémového hesla, které okamžitě společně s uživatelským jménem putovalo k útočníkům. Ti díky tomu získali přístup k většině obsahu uživatelského účtu, a především klíčence Keychain, kam macOS ukládá hesla a další údaje. Útočníci kromě hesel z Keychain vytěžili uložená data pro automatické vyplňování formulářů nebo hlavní hesla pro správce údajů jako je 1Password.
Handbrake ve verzi pro Windows
Kromě toho, že hackeři nechali stahovat uživatele malware místo instalačních souborů, rovněž jej distribuovali pomocí systému aktualizací. Ty totiž vývojáři neopatřili certifikátem, který by zamezoval instalaci neautorizovaných updatů a útočníci místo aktualizace aplikace rozeslali uživatelům malware.
Kensington má snímač otisků prstů do USB, který si rozumí s Windows Hello. Přihlásí vás i do mailu či na Facebook
Uživatelé, kteří v inkriminovaném období stahovali Handrake mají padesátiprocentní šanci, že je jejich stroj infikován. Mohou zkontrolovat kontrolní součet instalačního souboru, který nesmí odpovídat hodnotě 0935a43ca90c6c419a49e4f8f1d75e68cd70b274, za tou se skrývá malware Proton. Ten je podle webu Arstechnica mocným nástrojem, který se v rámci tržišť v Toru prodává za cenu kolem 63 tisíc dolarů, tedy asi 1,5 milionu korun.
Microsoft fixes Microsoft Malware Protection Engine RCE vulnerability CVE-2017-0290 found by Google
9.5.2017 securityaffairs Vulnerebility
Microsoft fixes the vulnerability in the Microsoft Malware Protection Engine (CVE-2017-0290) discovered just three days by Google experts.
Last week the researchers at the Google Project Zero team have discovered a new critical Windows RCE vulnerability, tracked as CVE-2017-0290, they defined the bug as the worst Windows RCE in recent memory.
Follow
Tavis Ormandy ✔ @taviso
I think @natashenka and I just discovered the worst Windows remote code exec in recent memory. This is crazy bad. Report on the way. 🔥🔥🔥
4:14 AM - 6 May 2017
2,542 2,542 Retweets 2,793 2,793 likes
The researchers only revealed the following information on the Windows RCE vulnerability:
The PoC exploit the Project Zero team has developed works against default Windows installations.
The Windows RCE vulnerability could be exploited by a remote attacker.
The attack is “wormable,” capability to spread itself.
It took Microsoft less than three days to fix the critical RCE flaw that affects the Microsoft Malware Protection Engine.
Follow
Tavis Ormandy ✔ @taviso
Still blown away at how quickly @msftsecurity responded to protect users, can't give enough kudos. Amazing.
3:14 AM - 9 May 2017
305 305 Retweets 855 855 likes
“Microsoft is releasing this security advisory to inform customers that an update to the Microsoft Malware Protection Engine addresses a security vulnerability that was reported to Microsoft.” reads the advisory published by Microsoft.
“The update addresses a vulnerability that could allow remote code execution if the Microsoft Malware Protection Engine scans a specially crafted file. An attacker who successfully exploited this vulnerability could execute arbitrary code in the security context of the LocalSystem account and take control of the system.
The Microsoft Malware Protection Engine ships with several Microsoft antimalware products.”
CVE-2017-0290 Windows RCE vulnerability
The Flaw affects the “MsMpEng” service, which runs unsandboxed with SYSTEM privileges and is accessible without authentication via Windows services such as Exchange and IIS.
The list of affected software includes Forefront Endpoint Protection, Endpoint Protection, Forefront Security for SharePoint Service Pack 3, System Center Endpoint Protection, Security Essentials, Windows Defender, and Windows Intune Endpoint Protection.
Google Project Zero has published the technical details and the proof-of-concept (PoC) exploit code for the CVE-2017-0290 flaw.
“MsMpEng is the Malware Protection service that is enabled by default on Windows 8, 8.1, 10, Windows Server 2012, and so on. Additionally, Microsoft Security Essentials, System Centre Endpoint Protection and various other Microsoft security products share the same core engine. MsMpEng runs as NT AUTHORITY\SYSTEM without sandboxing, and is remotely accessible without authentication via various Windows services, including Exchange, IIS, and so on.” reads the advisory published by the Google Project Zero Team.”
The Google Project Zero researchers said the vulnerability can be exploited via email – opening the malicious email is not necessary for exploitation – or by getting the targeted user to access a specially crafted link.
“Vulnerabilities in MsMpEng are among the most severe possible in Windows, due to the privilege, accessibility, and ubiquity of the service.” added Google.
“This level of accessibility is possible because MsMpEng uses a file system minifilter to intercept and inspect all system filesystem activity, so writing controlled contents to anywhere on disk (e.g. caches, temporary internet files, downloads (even unconfirmed downloads), attachments, etc) is enough to access functionality in mpengine,” the experts said in their advisory.
The experts highlighted that on workstations, attackers can access mpengine just by sending emails to users (reading the email or opening attachments is not necessary), visiting links in a web browser, instant messaging and so on.
According to Microsoft, the security fix should be sent out automatically to antimalware products that use the Microsoft Malware Protection Engine within 48 hours.
Malwaresearch – A command line tool to find malware on Openmalware.org
9.5.2017 securityaffairs Virus
Malwaresearch is a command line tool to find malware on Openmalware.org, it was developed to facilitate and speed up the process of finding and downloading malware samples.
The tool was developed to facilitate and speed up the process of finding and downloading malware samples via the command line interface.
We’ve made use of the API provided by the two major malware dump sites (openmalware.org and malwr.com) in a script that’s simple and pretty straightforward, which allows users to query information pertaining to malware, such as: Name, MD5, SHA-1, SHA-256, download the desired malware sample file, and even compare its digital signature (hash) with the ones present in the dumps in question.
Our next mission is to pull off the same deed, this time, however, using malwr.com, MalShare, MalwareBlacklist, Malware.lu’s AVCaesar from command line malware samples submission, to hash comparison and research.
Video:
Usage
Optional Arguments:
$ Malwaresearch.py [--h HELP] [-f FIND] [-w WRITE]
[-o OUTPUT] [-d DOWNLOAD] [-hash HASH
-h,HELP, --help Show this help message and exit
-f FIND, --find Enter your search via NAME, MD5, SHA1, SHA256 or an Common Signature name.
-w WRITE, --write Save this result on file
-o OUTPUT, --output Max numbers of malwares search
-d DOWNLOAD, --download Download your specific malware
Example to find rxbot samples:

Github: https://github.com/MalwareReverseBrasil/malwaresearc
Community: https://github.com/MalwareReverseBrasil
About the author: Ialle Teixeira
Information Security and Malware Researcher, Core of Malware Reverse Brazil( Articles and live reverse engineering and malware analysis classes)
#MacronLeaks metadata suggests Russian threat actors behind Macron’s hack
9.5.2017 securityaffairs BigBrothers
#MacronLeaks – Experts discovered evidence suggesting Russian threat actors behind the hack of French presidential candidate Macron.
Who are the hackers that attempted to subvert the final vote of French Presidential Election by targeting the Macron’s campaign?
Hackers leaked a 9GB batch of internal documents through the Magnet file-sharing service. The Macron data leakage has happened while candidates are banned from publicly discussing the campaign, clearly such kind of events can subvert the final result of the election.
Security experts and media blamed Russia for the attack, but the without referencing solid clues.
According to a report published by Trend Micro in April, the notorious APT 28 group spied on numerous high-profile targets, including the Macron’s campaign.
Now it seems that analysts have discovered evidence that suggests the involvement of Russia-linked threat actors.
The files stolen from Macron’s staff systems were initially distributed via links posted on 4Chan and then shared by WikiLeaks.
Forensic experts analyzed file metadata that seems to be linked to a Russian government contract employee, this person is suspected to have falsified some of the dumped documents for obvious reasons.
Wikileaks who was informed of the discovery acknowledged the presence of metadata pointed to a Russian company with ties to the government.
The experts discovered that the name of an employee for the Russian government security contractor Evrika appears 9 times in the metadata of the leaked dump.
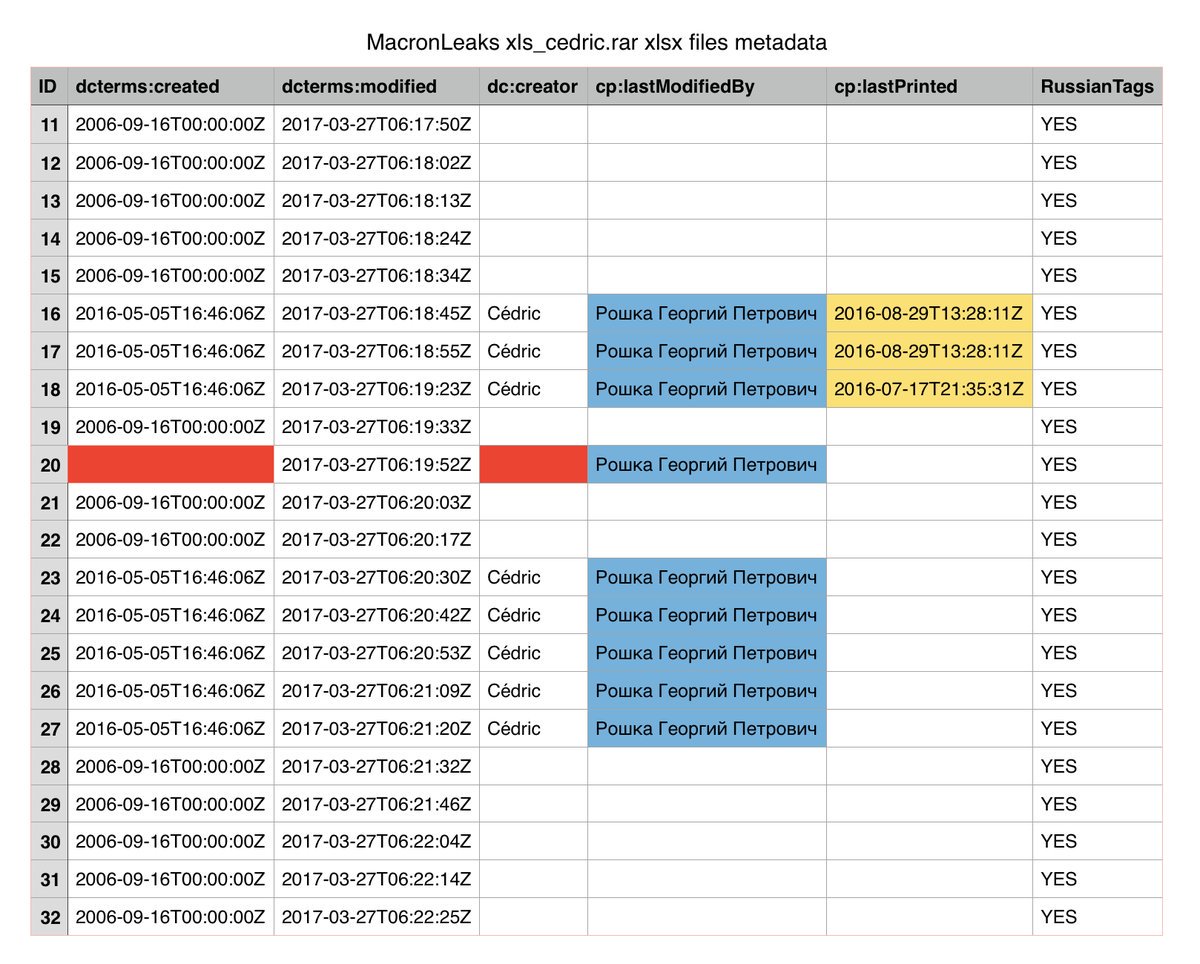
WikiLeaks ✔ @wikileaks
#MacronLeaks: name of employee for Russian govt security contractor Evrika appears 9 times in metadata for "xls_cendric.rar" leak archive
11:44 PM - 6 May 2017
2,853 2,853 Retweets 2,625 2,625 likes
Evrika (“Eureka”) ZAO is a Russian ICT firm based in St. Petersburg that is known for its collaboration with the Kremlin. The company also works for the Federal Security Service of the Russian Federation (FSB).
The metadata in some Microsoft Office files included in the dump shows that the last person to have edited the documents is “Roshka Georgiy Petrovich,” an Evrika ZAO employee.

Matt Suiche ✔ @msuiche
Dropping files after appending metadata to Microsoft Offices files such as "Автор" or "Область_печати" Why? #attribution H/T @voulnet
9:45 AM - 6 May 2017
204 204 Retweets 155 155 likes
The metadata related to the upload of the Macron files to archive.org also includes an e-mail address (frankmacher1@gmx.de) for the person who made the operation:
6 May
Pwn All The Things @pwnallthethings
What kind of monster does their mandatory training on time without being reminded? You want a guy who employs folks like that as President?
Follow
Pwn All The Things @pwnallthethings
Well this is fun pic.twitter.com/oXsH83snCS
3:41 AM - 6 May 2017
View image on Twitter
130 130 Retweets 196 196 likes
The e-mail address frankmacher1@gmx.de is registered with a German free webmail provider that was used in past operation by the APT28 group for phishing campaigns against the US DNC and the German Chancellor Angela Merkel’s political party.
Experts believe that the APT28 edited the documents and spread them via social media as part of a PSYOPs operation, like the one conducted against Clinton’s party during 2016 Presidential Election.
I have reached my colleague Emanuele Gentili (@emgent) Director of Cyber Intelligence of the Italian Security Firm TS-WAY who shared with me this interesting document:

The Supply chain of the HandBrake Mac software compromised to spread Proton malware
9.5.2017 securityaffairs Virus
Maintainers of the HandBrake video transcoder are warning Mac users who recently downloaded the software that they may have been infected with malware.
Maintainers of the open-source HandBrake video transcoder are warning Mac users who recently downloaded the application that they may have been infected with malware.Mac users who downloaded and installed the program from May 2 to May 6 need to check their computers for malware.
The handlers of the project urge users to verify the SHA1 or SHA256 sum of the file before running it.
SHA1: 0935a43ca90c6c419a49e4f8f1d75e68cd70b274
SHA256: 013623e5e50449bbdf6943549d8224a122aa6c42bd3300a1bd2b743b01ae6793
The attackers broke into a download mirror server hosted under download.handbrake.fr for HandBrake and compromised it to distribute a macOS version of the software packaged with a malware.The primary download server was not compromised by hackers, for this reason, users who downloaded HandBrake-1.0.7.dmg have a 50/50 chance of having installed a trojanized version of the applications.The users of HandBrake 1.0 and later who upgraded their version to version 1.0.7 using the built-in update feature shouldn’t be affected because the updater verifies the checksum of the package.Users of version 0.10.5 and earlier who used the built-in updater during those five days might be affected.
“Anyone who has downloaded HandBrake on Mac between [02/May/2017 14:30 UTC] and [06/May/2017 11:00 UTC] needs to verify the SHA1 / 256 sum of the file before running it.” reads a security warning published on the HandBrake forum.
“Anyone who has installed HandBrake for Mac needs to verify their system is not infected with a Trojan. You have 50/50 chance if you’ve downloaded HandBrake during this period.”

The software contained a new strain of the Proton malware for MacOS that is a remote access tool (RAT) available for sale on some cybercrime forums.
The Proton RAT first appeared in the threat landscape last year, the variant recently advertised on hacking forums includes many features such as the ability to execute console commands, access the user’s webcam, log keystrokes, capture screenshots and open SSH/VNC remote connections. The malicious code is also able to inject malicious code in the user’s browser to display popups asking victims’ information such as credit card numbers, login credentials, and others.
In order to obtain admin privileges, the rogue HandBrake installer asked Mac users for their password under the guise of installing additional video codecs.
According to the security expert Patrick Wardle, the Proton variant used in this attack was not detected by antimalware engines on VirusTotal.
The advisory published on the HandBrake forum also provides manual removal instructions. Mac users who have found the malware on their Macs must change all the passwords stored in their macOS keychains or browsers.
Crooks have used similar tactics in the past to spread malware, the macOS version of the popular Transmission BitTorrent client was found distributing Mac malware two times.
Microsoft Fixes Antimalware Engine Flaw Found by Google Experts
9.5.2017 securityweek Vulnerebility
It took Microsoft less than three days to patch a critical remote code execution vulnerability found by Google Project Zero researchers in the company’s Malware Protection Engine. Most users don’t need to take any action as the affected products should be updated automatically.
The existence of the flaw was disclosed by Google Project Zero researchers Tavis Ormandy and Natalie Silvanovich on Friday. Ormandy described the weakness as “the worst Windows remote code exec [vulnerability] in recent memory.”
The expert said the vulnerability was “wormable,” it affected default Windows installations, and exploitation did not require access to the victim’s network.
Microsoft announced a patch for the vulnerability and published an advisory on Monday. While Ormandy initially described it as a Windows vulnerability, the security hole actually affects the Microsoft Malware Protection Engine, which is shipped with several of the company’s Windows antimalware products.
The list of impacted software includes Forefront Endpoint Protection, Endpoint Protection, Forefront Security for SharePoint Service Pack 3, System Center Endpoint Protection, Security Essentials, Windows Defender, and Windows Intune Endpoint Protection.
Follow
Tavis Ormandy ✔ @taviso
Still blown away at how quickly @msftsecurity responded to protect users, can't give enough kudos. Amazing.
3:14 AM - 9 May 2017
313 313 Retweets 880 880 likes
According to Ormandy and Silvanovich, the vulnerability, tracked as CVE-2017-0290, affects the “MsMpEng” service, which runs unsandboxed with SYSTEM privileges and is accessible without authentication via Windows services such as Exchange and IIS.
The Google Project Zero researchers said the vulnerability can be exploited via email – opening the malicious email is not necessary for exploitation – or by getting the targeted user to access a specially crafted link.
“This level of accessibility is possible because MsMpEng uses a filesystem minifilter to intercept and inspect all system filesystem activity, so writing controlled contents to anywhere on disk (e.g. caches, temporary internet files, downloads (even unconfirmed downloads), attachments, etc) is enough to access functionality in mpengine,” the experts said in their advisory.
The researchers believe that vulnerabilities in the Microsoft Malware Protection Engine “are among the most severe possible in Windows, due to the privilege, accessibility, and ubiquity of the service.”
Google Project Zero has made public technical details and proof-of-concept (PoC) exploit code.
Microsoft pointed out that the patch should be sent out automatically to antimalware products that use the Malware Protection Engine within 48 hours. However, the company has advised users to check their software to ensure that the automatic deployment of updates and malware definitions is working properly.
Thousands of Devices Hacked by Rakos Botnet
9.5.2017 securityweek BotNet
Thousands of devices have been hacked by a Linux malware named Rakos, and while researchers have yet to see any actual malicious activity involving the botnet, they believe it could be used for powerful distributed denial-of-service (DDoS) attacks.
Rakos, whose existence was brought to light in December 2016 by ESET, targets Linux systems by launching brute-force attacks via SSH. The security firm reported at the time that the compromised machines had not been leveraged for DDoS attacks or spam campaigns, as one might expect.
Brazil-based Morphus Labs recently deployed some high interaction honeypots that were quickly targeted by Rakos. A closer analysis revealed that the botnet had ensnared roughly 8,300 devices per day across 178 countries.
Rakos consists of bots and command and control (C&C) servers, but since it’s a peer-to-peer botnet some infected machines may play both these roles. Rakos bots obtain a list of IP addresses from a C&C server and attack those hosts via SSH. Each compromised device will in turn target other devices.
The botnet has been described as “transient” due to the fact that the infection is not persistent after a reboot of the hacked device.
Morphus Labs researchers analyzed the botnet by using crawlers and by injecting fake nodes to act as sensors. Data collected over the course of 72 hours revealed the existence of just over 25,000 unique infected devices, or roughly 8,300 per day. This includes nearly 300 machines that served as C&C servers.
The country with the highest number of nodes was China (3,300), followed by Vietnam, Taiwan, Thailand, Russia, India, Brazil and the United States, which had just under 1,000 unique infections.
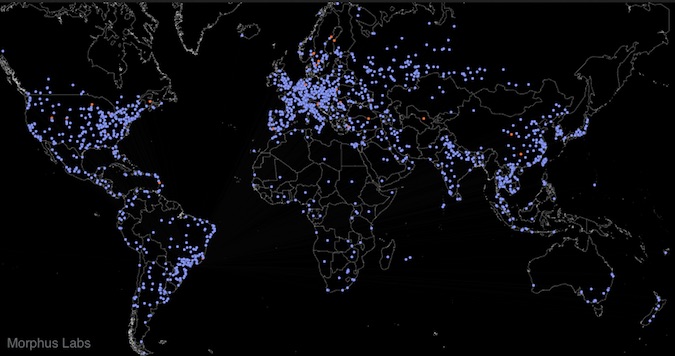
Experts determined that more than 45 percent of the compromised devices were Raspberry Pis, followed by Open Embedded Linux Entertainment Center (OpenELEC) systems, which also typically run on Raspberry Pi. Unsurprisingly, the third most targeted systems are wireless access points from Ubiquiti Networks, which are often targeted by cybercriminals.
The Rakos botnet can hack devices because their owners have neglected to set strong passwords, but researchers pointed out that, in some cases, such as OpenELEC, default SSH passwords cannot be changed by users.
While 8,000 bots might not seem much, Morphus noted that a new Mirai variant recently used a similar number of compromised devices to launch a significant DDoS attack on a U.S. college. The attack lasted for 54 hours and peaked at 37,000 requests per second (RPS).
However, there is currently no evidence of malicious activity coming from Rakos, except for the brute-force SSH attacks.
“It seems that someone is preparing it to be sold or to offer ‘services’ using it when it gets in the right size,” explained Renato Marinho, director of research at Morphus Labs. “Thinking this way, the innocuous-looking may be a strategy to fly under the radar.”
Yahoo Paid Out $2 Million in Bug Bounty Program
9.5.2017 securityweek Security
Yahoo reported on Monday that between the launch of its bug bounty program in 2013 and December 2016 it had paid out a total of more than $2 million.
A comparison to the previous report shows that the Internet giant awarded bounty hunters roughly $400,000 in 2016.
Since the launch of its program three years ago, Yahoo has worked with more than 2,000 researchers from 80 countries, and its HackerOne page lists a total of 3,500 resolved vulnerability reports. The company said it rewarded nearly 200 researchers last year.
“Yes, this all comes with a degree of vulnerability. After all, we’re asking some of the world’s best hackers to seek out soft spots in our defenses,” said Andrew Rios, security engineer at Yahoo. “But it’s acceptable risk. The right incentives combined with some hackers who actually want to do some good has resulted in a diverse and growing global community of contributors to our security.”
Yahoo did not want to share any information on its largest single payout, but pointed to a post that explains how the company evaluates each vulnerability report. The blog post published by the company on Monday references a recent Flickr account hijacking exploit that earned a researcher $7,000.
“Most bounties accounted for less impactful vulnerabilities, but some were more substantial,” Rios said.
In comparison, Facebook has paid out more than $5 million since the launch of its program in 2011, while Google has awarded experts $9 million since 2010.
Google’s biggest single reward last year was $100,000 (of a total of $3 million). Facebook is also known to award significant bounties – the largest payout to date was $40,000 for a remote code execution vulnerability introduced by the ImageMagick image processing suite.
What Can be Expected in Trump's Cybersecurity Executive Order?
9.5.2017 securityweek BigBrothers
Executive Order - Cybersecurity
The latest draft of President Trump's much anticipated cybersecurity executive order was posted to the internet last week by security consultant Paul Rosenzweig. It is not the first and may not be the last draft that gets public scrutiny before the final version is formally published. Although it is currently a draft, it provides detailed insight into what can be expected.
The draft Trump Cybersecurity executive order (EO) follows the recent trend in legislation and regulation to take responsibility for cybersecurity away from the practitioners (CIOs and CISOs) and force it to the top of an organization. Agency Heads will be responsible for security and will be required to report regularly to the OMB and DHS (or the Secretary of Defense and the Director of National Intelligence for national security systems).
The latest draft cybersecurity EO displays semantic rather than substantive changes over the previous leaked version -- although with a new section on security workforce development that includes monitoring the workforce development of potential adversaries. The limited changes could suggest that this EO is close to being issued; however, with no federal CISO to replace Gregory Touhill (who resigned Jan. 17) yet announced, it is equally likely there will yet be some delay.
Touhill publicly announced his resignation on LinkedIn. He said, "Frankly, we don't need more policies, we need to execute the ones we have and eliminate the ones that no longer are aligned with contemporary best practices."
Nevertheless, he went on to describe what lies at the heart of Trump's draft EO: "We need a better architecture focused on shared services capabilities rather than one built on organization charts. We need accountability and ownership built into our culture. We need to intelligently leverage cloud computing and mobility solutions that produce effective, efficient, and secure results. We need to do regular risk assessments across each department and agency. We need to better train and regularly exercise our personnel."
The draft EO does indeed focus on a better and updated architecture, and a risk management approach to securing federal systems. It notes, for example, "The executive branch has for too long accepted antiquated and difficult–to-defend IT." Not everyone agrees, however, that updating systems should be the priority -- with suggestions that securing new and complex systems will be no easier than securing older, more simple systems.
There is no explicit definition of an 'antiquated' IT system, although the draft does call out 'known but unmitigated vulnerabilities'. These include "using operating systems or hardware beyond the vendor's support lifecycle..." Antiquated may effectively mean 'no longer supported'; although it is worth noting that on 12 April 2017, Frank Konkel wrote in NextGov, "The U.S. nuclear arsenal is coordinated by the 54-year-old Strategic Automated Command and Control System, run on 1970s-era IBM mainframes that still use 8-inch floppy disks."
Risk management is specified and required. "Agency Heads will be held accountable by the President for implementing risk management measures commensurate with the risk and magnitude of the harm that would result from unauthorized access, use, disclosure, disruption, modification, or destruction of IT and data. They will also be held accountable by the President for ensuring that cybersecurity risk management processes are aligned with strategic, operational, and budgetary planning processes, in accordance with chapter 35, subchapter II of title 44, United States Code."
Risk management is specifically tied to "The Framework for Improving Critical Infrastructure Cybersecurity (the Framework), or any successor document, developed by the National Institute of Standards and Technology to manage the agency's cybersecurity risk."
Protecting the critical infrastructure (CI) is another area of focus. Indeed, the executive order is titled, 'Strengthening the Cybersecurity of Federal Networks and Critical Infrastructure'. The CI is defined as comprising those "entities identified pursuant to section 9 of Executive Order 13636 of February 12, 2013 (Improving Critical Infrastructure Cybersecurity)." The current list identified by the DHS comprises 16 CI sectors, including energy, communications, finance, healthcare, defense and emergency services.
These sectors will be examined to see if federal agencies can provide additional security support in their risk management efforts, and whether there are any obstacles in doing so. There is some criticism, however, that in specifying section 9, 13636 sectors for special treatment, other critical areas (such as water purification and on-line voting) might suffer.
One area that does cover the wider private sector is the desire to promote resilience against botnets and other automated, distributed threats. Here, "The Secretary of Commerce and the Secretary of Homeland Security shall jointly lead an open and transparent process to identify and promote action by appropriate stakeholders to improve the resilience of the Internet and communications ecosystem and to encourage collaboration with the goal of dramatically reducing threats perpetrated by automated and distributed attacks (e.g., botnets)."
It is perhaps disappointing that there is no specific reference here to the internet of things (IoT); nor indeed any reference to the IoT anywhere in the draft EO. Many security experts fear a dire future of distributed denial of service attacks from IoT-based botnets (such as Mirai); and a more specific targeting of intrinsic IoT insecurity would benefit the entire internet.
The section of the executive order that specifies 'cybersecurity for the nation' is limited to broad brush strokes. The 'policy' is to "promote an open, interoperable, reliable, and secure Internet that fosters efficiency, innovation, communication, and economic prosperity, while respecting privacy and guarding against disruption, fraud, and theft." Subsections talk about deterrence and protection (demanding "options for deterring adversaries and better protecting the American people from cyber threats"); international cooperation (requesting "an engagement strategy for international cooperation in cybersecurity"); and workforce development (including, for example, an assessment of "the scope and sufficiency of U.S. efforts to ensure U.S. national security-related cyber capability advantage").
It would not be possible for a single short document on cybersecurity to satisfy everyone -- and there are indeed both strong and weak points in this document. For example, there are fifteen separate reports required by the draft EO, which must be delivered in timescales ranging from 45 days to 240 days from the date of the order. The effect of these reports could be to delay actual implementation of important security policies. It is tempting to refer to the words former federal CISO Gregory Touhill: "We don't need more policies, we need to execute the ones we have..."
One very strong point, however, is that the policy outlined by this executive order (albeit just a draft for now) builds on the cybersecurity efforts already achieved by the previous administration. This will promote an invaluable bi-partisan approach to the future of federal and critical infrastructure security.
Google Tightens OAuth Rules to Combat Phishing
9.5.2017 securityweek Phishing
Following last week’s phishing attack against Gmail users, Google is planning tightened OAuth rules to prevent similar incidents from occurring.
Phishing emails, which impersonate a trusted source to trick the recipient into opening a malicious attachment or clicking a suspicious link, have long been a favorite tool for attackers. Google’s email service blocks millions of phishing emails each day, but last week’s incident proved that the system isn’t invincible.
The phishing attack tricked users into granting access to their contact information to a third-party application cleverly named “Google Docs.” The incident resulted in the attacker gaining access to all of the affected users’ email content, as well as in the phishing attack immediately propagating to all of the victim’s contacts.
The phishing emails, which appeared to arrive from someone in the victim’s contact list, claimed to contain a link to Google Docs content that the sender wanted to share with the recipient. Once the user clicked on the link, they were taken to a legitimate Google sign-in page, where they were asked to authorize an app called “Google Docs,” thus allowing it to read, send, delete, and manage emails and contacts.
Google was able to spot and block the attack fast, but the incident meant that immediate actions that users might have taken, such as changing passwords, had no effect. Because OAuth was used, the attackers still had access to the account, and only removing permissions for the offending app could solve the issue.
“We have taken action to protect users against an email impersonating Google Docs, and have disabled offending accounts. We've removed the fake pages, pushed updates through Safe Browsing, and our abuse team is working to prevent this kind of spoofing from happening again,” Google said after the incident.
Now, the company reveals that it is updating its policies and enforcement on OAuth applications to prevent similar attacks from happening in the future. Moreover, updates to Google’s anti-spam systems should help prevent similar campaigns, and augmented monitoring of suspicious third-party apps that request information from users should add an extra layer of security.
“We’re committed to keeping your Google Account safe, and have layers of defense in place to guard against sophisticated attacks of all types, from anti-hijacking systems detecting unusual behavior, to machine learning models that block malicious content, to protection measures in Chrome and through Safe Browsing that guard against visiting suspicious sites,” Google says.
What should be noted is that the concept of launching such an attack isn’t new. It was first presented in 2011 by André DeMarre, and then thoroughly detailed by Greg Carson in February 2017.
In fact, the cyber espionage group known as Pawn Storm (aka Fancy Bear, APT28) was observed using the very same technique in the past. Trend Micro recently revealed that this actor’s phishing scheme employed an application dubbed Google Defender, while abusing “the same legitimate OAuth connection to exploit the user’s lack of knowledge of available services.”
In an emailed statement to SecurityWeek, Jaime Blasco, Chief Scientist at AlienVault, shared a similar point of view: “This is similar to what APT28 (the group behind the DNS hack, France election groups attacks, etc) was using a while back. I don't believe they are behind this though because this is way too widespread. Many people/organizations have received similar attempts so this is probably something massive and less targeted.”
According to Google, less than 0.1% of Gmail users were impacted by last week’s “Google Docs” incident, but, as Talos’ Sean Baird and Nick Biasini point out, this proof-of-concept did reveal that a convincing Google phish via OAuth is possible.
To further protect users from such attacks, Google also announced anti-phishing security checks for Gmail for Android. Thus, users will be warned when clicking on suspicious links they receive via email, which should help prevent them from disclosing financial and personal information.
Důmyslný phishing zaútočil na uživatele Google Docs
9.5.2017 SecurityWorld Phishing
Google potvrdil, že zneškodnil phishingový email, který byl doručen zhruba milionu jeho uživatelů.
Podvodný email se tvářil jako zpráva z Google Docs, přičemž uživatelé, kteří se jí nechali oklamat, se vystavili riziku, že hackeři proniknou do jejich emailových účtů. Dle vyjádření Googlu se mu šíření emailu podařilo zastavit během jediné hodiny, i tak však byl doručen přibližně milionu lidí, což je podle Googlu méně než 0,1 % registrovaných uživatelů.
„Naše vyšetřování ukázalo, že hackeři se dostali ke kontaktním informacím postižených uživatelů, další data však ohrožena nebyla,“ uvádí Google. „Uživatelé tak nemusí podnikat žádné další kroky. Ti, kteří by přece jen chtěli zkontrolovat aplikace třetích stran, které mají se svým účtem propojené, tak mohou učinit prostřednictvím Google Security Checkup.“
Zpráva odeslaná z adresy hhhhhhhhhhhhhhhh@mailinator.com měla podobu pozvánky k editaci googlovského dokumentu. V případě, že ji uživatel otevřel, byl přesměrován na webovou stránku, kde byl službou tvářící se jako Google Docs požádán o přístup k emailovému účtu. Jestliže jej uživatel poskytl, sdílel jej tak s hackery, kteří se k účtu mohli přihlásit, respektive rozšířit malware na další kontakty z účtu.
Podle odborníků se jednalo o sofistikovanější útok, než jaký představuje běžný phishing, jelikož hackerům se podařilo vydávat za vysoce renomovanou společnost, čehož dosáhli vytvořením aplikace simulující postupy Googlu.
Hackeři využili chyby v mobilní sítí O2 Telefónica, získali ověřovací SMS a vybrali lidem bankovní účty
8.5.2017 Živě.cz Mobilní
Hackeři využili dlouho známou chybu mobilních sítí k získání SMS
Útok proběhl na německé mobilní síti O2 Telefónica
Po získání údajů k přihlášení do internetového bankovnictví už dokázali „vyluxovat“ bankovní účty
Hackerům se podařilo zneužít chyby v technologii SS7, kterou používají mobilní sítě ke komunikaci a získali přístup k SMS napadených uživatelů. Ve spojení s e-mailovým phishingem tak byli schopni za posledních několik měsíců v rámci německé mobilní sítě O2 Telefónica získat ověřovací SMS pro přihlášení i provedení platby a doslova vysát peníze z bankovních účtů napadených uživatelů. Kvůli přesměrování neměl daný majitel účtu celou dobu o ničem ani ponětí.
Stačí telefonní číslo a hacker vás bude odposlouchávat lépe než NSA
Je celkem překvapením, že nebezpečná zneužitelná chyba (je jich víc), která se nachází v komunikační technologii SS7 (Signal System No. 7), kterou mezi sebou ke komunikaci používají telefonní operátoři po celém světě, je už tři roky zveřejněná a stále je neopravená. Důvodem je především to, že celý komunikační systém, na kterém se sítě propojují, vychází z hodně zastaralých technologií (SS7 je z devadesátých let minulého století), které se upgradují jen velmi pozvolna a opravit chyby není jednoduché.
Problém ale je, že už začíná přituhovat. Ve starším článku jsme informovali o tom, že bylo možné pomocí jedné z chyb odposlouchávat a sledovat polohu takřka jakéhokoli telefonu – stačí znát číslo. Jak ale ukázaly čerstvé případy v Německu, chyby lze využít i pro získání peněz z cizího bankovního účtu.
Jak probíhal útok
Hackeři využili k získání peněz z bankovního účtu několik „ověřených“ metod, které fungují i pro jiné případy. Cílem bylo získat dvě věci – přihlašovací údaje k elektronickému bankovnictví a telefonní číslo.
K tomu využili dvě metody – klasický malware nainstalovaný na počítač, který získal přístupové údaje k bankovnictví například skrze snímání stisknutých kláves a také pomocí phishingových e-mailů. Ty lze velmi dobře použít nejen pro získání telefonního čísla napadeného (typicky „Využijte akce xxx zadejte nám telefonní číslo a pošleme Vám xxx“ a tak podobně), tak i jeho přihlašovacích údajů třeba přes podvrženou stránku, která se vydává za skutečnou banku.
Jakmile měli hackeři obě části, mohli využít chyby v SS7, přesměrovat SMS uživatele a přihlásit se k bankovnímu účtu i přes to, že jste měli zapnuté dvoufaktorové ověřování. Na telefon napadeného žádné SMS nechodily, takže celou dobu vůbec nevěděl, že se něco děje. Hackerům přišel ověřovací kód pro přihlášení k internetovému bankovnictví a jakmile byli přihlášení, mohli začít odesílat peníze v dostupných dávkách, obvykle dle denního omezení daného bankovního účtu.
Peníze se poté přesunuly na připravené speciální bankovní účty, ze kterých poté probíhá další přesun, aby bylo možné peníze „vyprat“ a nějakou formou vybrat tak, aby to bylo nedohledatelné. Obvykle tento proces zajišťují jiní „specialisté“ než samotní hackeři, kteří řeší jen samotný útok a odeslání peněz.
Buďte na pozoru
Jak je vidět, dvoufaktorové ověřování rozhodně není všespásné a proto je nutné i s ním dodržovat všechna bezpečnostní pravidla, která minimalizují nebezpečí podobného útoku. Některé banky už podporují ověřování v rámci jejich mobilní aplikace, kterou máte nainstalovanou v mobilním telefonu. A pokud do mobilního telefonu neinstalujete aplikace mimo oficiální obchody (App Store, Google Play) a máte nejnovější verzi operačního systému, měli byste být v relativním bezpečí proti útoku.
V případě e-mailů a podvržených stránek je nutné dávat pozor, na co klikáte a zda údaje zadáváte do pravé webové stránky vaší banky – zelený pruh s „https“ v horní řádce by měl být samozřejmostí. Pokud kdokoli, kdo se vydává, že je z banky či podobných institucí a volá vám, nikdy ale opravdu nikdy mu nesdělujte své osobní údaje. Pouze pokud voláte vy do banky či jinam a víte, na jaké číslo voláte a s kým jste ve spojení.
Google 0-Day Hunters Find 'Crazy Bad' Windows RCE Flaw
8.5.2017 thehackernews Vulnerebility
Google Project Zero's security researchers have discovered another critical remote code execution (RCE) vulnerability in Microsoft’s Windows operating system, claiming that it is something truly bad.
Tavis Ormandy announced during the weekend that he and another Project Zero researcher Natalie Silvanovich discovered "the worst Windows remote code [execution vulnerability] in recent memory. This is crazy bad. Report on the way."
Ormandy did not provide any further details of the Windows RCE bug, as Google gives a 90-day security disclosure deadline to all software vendors to patch their products and disclose it to the public.
This means the details of the new RCE vulnerability in Windows will likely be disclosed in 90 days from now even if Microsoft fails to patch the issue.
However, Ormandy later revealed some details of the Windows RCE flaw, clarifying that:
The vulnerability they claimed to have discovered works against default Windows installations.
The attacker does not need to be on the same local area network (LAN) as the victim, which means vulnerable Windows computers can be hacked remotely.
The attack is "wormable," capability to spread itself.
Despite not even releasing any technical details on the RCE flaw, some IT professionals working for corporates have criticized the Google Project Zero researcher for making the existence of the vulnerability public, while Twitter's infosec community is happy with the work.
"If a tweet is causing panic or confusion in your organization, the problem isn't the tweet, the problem is your organization," Project Zero researcher Natalie Silvanovich tweeted.
This is not the first time when Google's security researchers have discovered flaws in Microsoft’s products. Most recently in February, Google researchers disclosed the details of an unpatched vulnerability impacting Microsoft's Edge and Internet Explorer browsers.
Microsoft released a patch as part of its next Patch Tuesday but criticized Google for making all details public, exposing millions of its Windows users at risk of being hacked.
Microsoft has not yet responded to the latest claims, but the company has its May 2017 Patch Tuesday scheduled tomorrow, May 9, so hopefully, it will include a security patch to resolve this issue.
Website of Popular Mac Software Hacked to Spread Malware
8.5.2017 thehackernews Apple
If you have recently downloaded the popular open source video transcoder app HandBrake on your Mac, there are chances that your computer is infected with a notorious Remote Access Trojan (RAT).
The HandBrake team issued a security alert on Saturday, warning Mac users that one of its mirror servers to download the software has been compromised by hackers.
In case you aren't aware, HandBrake is an open source video transcoder app that allows Mac users to convert multimedia files from one format to another.
According to the HandBrake team, an unknown hacker or group of hackers compromised the download mirror server (download.handbrake.fr) and then replaced the Mac version of the HandBrake client (HandBrake-1.0.7.dmg) with a malicious version infected with a new variant of Proton.
Originally discovered in February on a Russian underground hacking forum, Proton is a Mac-based remote access trojan that gives attackers root access privileges to the infected system.
The affected server has been shut down for investigation, but the HandBrake team is warning that anyone who has downloaded HandBrake for Mac from the server between May 2 and May 6, 2017, has a "50/50 chance" of getting their Mac infected by Proton.
How to Check if You're Infected?
The HandBrake team has provided instructions for less technical folks, who can check if they've been infected.
Head on to the OSX Activity Monitor application, and if you see a process called "Activity_agent" there, you are infected with the trojan.
You can also check for hashes to verify if the software you have downloaded is corrupted or malicious. The infected app is signed with the following hashes:
SHA1: 0935a43ca90c6c419a49e4f8f1d75e68cd70b274
SHA256: 013623e5e50449bbdf6943549d8224a122aa6c42bd3300a1bd2b743b01ae6793
If you have installed a HandBrake.dmg with the above checksums, you are infected with the trojan.
How to Remove the Proton RAT?
The HandBrake developers have also included removal instructions for Mac users who have been compromised.
Follow the following instructions to remove the Proton Rat from your Mac:
Step 1: Open up the "Terminal" application and run the following command:
launchctl unload ~/Library/LaunchAgents/fr.handbrake.activity_agent.plist
rm -rf ~/Library/RenderFiles/activity_agent.app
Step 2: If ~/Library/VideoFrameworks/ includes proton.zip, remove the folder.
Step 3: once done, you should remove any installations of Handbrake.app you may find.
However, instead of stopping here; head on to your settings and change all the passwords that are stored in your OS X KeyChain or any browser password stores, as an extra security measure.
Meanwhile, Mac users who have updated to HandBrake version 1.0 or later are not affected by the issue, as it uses DSA signatures to verify the downloaded files, so malware-tainted version reportedly would not pass the DSA verification process.
Critical Flaw Patched in Jenkins Automation Server
8.5.2017 securityweek Vulnerebility
The developers of Jenkins recently patched several vulnerabilities, including a critical weakness that can be exploited by a remote attacker for arbitrary code execution.
Jenkins is the most popular open source automation server, with over 133,000 installations and more than 1 million users worldwide. The product, maintained by CloudBees and the Jenkins community, is designed to help developers build, test and deploy their software.
An independent security researcher recently informed Beyond Security’s SecuriTeam Secure Disclosure program that Jenkins is affected by a serious vulnerability related to Java deserialization.
According to experts, the flaw allows an unauthenticated attacker to execute arbitrary code by sending two specially crafted requests to the vulnerable server. Technical details for the security hole, tracked as CVE-2017-1000353, were published by Beyond Security earlier this month.
In a security advisory published in late April, Jenkins developers said this critical vulnerability “allowed attackers to transfer a serialized Java SignedObject object to the remoting-based Jenkins CLI, that would be deserialized using a new ObjectInputStream, bypassing the existing blacklist-based protection mechanism.”
The flaw has been patched with the release of Jenkins 2.57 and 2.46.2 (LTS), which also address several other types of problems. This includes multiple high severity cross-site request forgery (CSRF) vulnerabilities that can be exploited by an attacker to perform administrative actions by getting targeted users to open a specially crafted webpage.
Jenkins developers said the CSRF flaws can be exploited to restart the server, downgrade Jenkins, install plugins, change users’ API tokens, modify configurations, and create administrator accounts.
Another high severity weakness, tracked as CVE-2017-1000354, allowed an attacker to impersonate Jenkins users. The flaw was related to the “login” command, which stored the encrypted username of successfully authenticated users in a cache file.
The update also fixes a medium severity issue related to the XStream library. This third-party component, which is used by Jenkins for serializing and deserializing XML, is affected by a flaw that can be leveraged to crash the Java process.
Google Researchers Find "Worst" Windows RCE Flaw
8.5.2017 securityweek Vulnerebility
Google Project Zero researchers Tavis Ormandy and Natalie Silvanovich claim to have found a critical vulnerability in Windows. The details of the flaw will likely be disclosed in 90 days from now even if a patch is not available.
Ormandy announced over the weekend on Twitter that he and Silvanovich had discovered “the worst Windows remote code exec [vulnerability] in recent memory.”
The expert has not shared any details, but he has clarified that the exploit they created works against default Windows installations, and the attacker does not need to be on the same local area network as the victim. He also said the attack is “wormable.”
Despite not releasing any technical details on the vulnerability, some members of the industry have criticized the Google Project Zero researchers for making the existence of the flaw public.
Follow
Natalie Silvanovich @natashenka
If a tweet is causing panic or confusion in your organization, the problem isn't the tweet, the problem is your organization
7:58 PM - 6 May 2017
330 330 Retweets 781 781 likes
SecurityWeek has reached out to Microsoft for comment and will update this article if the company responds.
Google typically gives companies 90 days to patch vulnerabilities found by its researchers before making their details public, but the deadline is only 7 days if the weakness has been exploited in attacks.
In November, Project Zero disclosed the details of an actively exploited zero-day affecting the Windows kernel after Microsoft failed to release a fix.
More recently, in February, Google researcher Ivan Fratric made public the details and proof-of-concept (PoC) code for a potentially serious vulnerability affecting the Edge and Internet Explorer browsers. Microsoft patched the vulnerability a few weeks later.
In the past years, Google disclosed the details of several Windows vulnerabilities after 90 days. The search giant made some changes to its disclosure policy in February 2015 due to criticism from Microsoft and members of the industry, but the company continues to strictly apply its 90-day deadline.
Exploitable Details of Intel's 'Apocalyptic' AMT Firmware Vulnerability Disclosed
8.5.2017 securityweek Exploit
Details of the Intel AMT firmware vulnerability announced on May 1, 2017 are now public knowledge; and the suggestion that 'this is somewhere between nightmarish and apocalyptic' has been proven correct.
One day after Intel's alert, Embedi (the firm that discovered the vulnerability back in February this year) published a brief note. One particular sentence stood out to researchers at Tenable: "With 100 percent certainty it is not an RCE but rather a logical vulnerability."
This persuaded Tenable to look at 'authentication' as the possible basis for a logical flaw that allows remote access. Within one day it discovered the flaw by trial and error -- and experience.
"Drawing on past experience," explains Carlos Perez, Tenable's director of reverse engineering in a blog post last Friday, "when we reported an authentication-related vulnerability in which the length of credential comparison is controlled by the attacker (memcmp(attacker_passwd, correct_passwd, attacker_pwd_len)), we tested out a case in which only a portion of the correct response hash is sent to the AMT web server. To our surprise, authentication succeeded!"
Further tests showed that a NULL/empty response hash (response="" in the HTTP Authorization header) still worked. "We had discovered a complete bypass of the authentication scheme."
Tenable asked Intel if this was the flaw in question. Intel said it was, and asked Tenable to delay publication until the end of the day on Thursday Pacific time (effectively Friday). This gave Embedi (the original finder of the flaw) time to simultaneously publish its own findings on Friday.
If Tenable could find the flaw within a single day, blackhats could do the same. The time for obfuscation had passed. While Tenable had found the flaw, Embedi's whitepaper (PDF), also published Friday, explains it.
Embedi had been looking into AMT and its admin account that is present by default and always uses digest authentication. By reverse engineering the firmware it discovered, "The value of the computed response, which is the first argument, is being tested against the one that is provided by user, which is the second argument, while the third argument is the length of the response. It seems quite obvious that the third argument of strncmp() should be the length of computed_response, but the address of the stack variable response_length, from where the length is to be loaded, actually points to the length of the user_response!"
In short, it explains, "Given an empty string the strncmp() evaluates to zero thus accepting an invalid response as a valid one."
Armed with this knowledge, any attacker could get admin control over AMT. It is the power of AMT that makes the vulnerability so severe. "First of all," explains Embedi, "you should remember that Intel AMT provides the ability to remotely control the computer system even if it's powered off (but connected to the electricity mains and network)." Furthermore, it is completely independent of the installed operating system. No traditional security defense could even see, let own prevent, anything done through AMT.
Embedi describes some of the possible attack scenarios. These include, remote load and install of any file onto the target system; read any file; remotely change the boot device to some other virtual image; remotely power on/power off/reboot/reset and do other actions; and even edit the BIOS setup.
The situation now is that any business PC that uses AMT, ISM or SBT that has not received the Intel firmware patch, is vulnerable to a silent, unpreventable, major attack -- and details of how to perform the attack are public knowledge. Several PC vendors have started rolling out the new Intel firmware (Dell, HP, Lenovo, Fujitsu) -- but some older and boutique PCs may never receive the patch.
On Friday, May 5, 2017, Intel issued an update to its original alert. It reiterates its original recommendations. Intel users should first determine whether they are vulnerable (that is, if the devices incorporate AMT, ISM or SBT), and then take the mitigation steps already published. But note, it adds, "capabilities and features provided by AMT, ISM and SBT will be made unavailable by these mitigations."
Intel has also released a discovery tool, which will analyze systems to see if the vulnerability is present.
What is clear, however, is that this flaw (which has existed for more than 9 years) truly is somewhere between nightmarish and apocalyptic. Taking no action is not an option.
Software Download Mirror Distributes Mac Malware
8.5.2017 securityweek Apple
A download mirror server for the video converting tool HandBrake was recently compromised and configured to distribute a remote administration Trojan (RAT) for Mac computers.
The company has posted a security alert on its website, informing Mac users that from Tuesday to Saturday of last week they might have downloaded a Trojanized version of the application. According to HandBrake, while not all users might have been affected, all of them should verify the downloaded file before running it.
“Anyone who has downloaded HandBrake on Mac between [02/May/2017 14:30 UTC] and [06/May/2017 11:00 UTC] needs to verify the SHA1 / 256 sum of the file before running it. Anyone who has installed HandBrake for Mac needs to verify their system is not infected with a Trojan. You have 50/50 chance if you've downloaded HandBrake during this period,” the company says.
The company notes that its primary download mirror and website were unaffected. Only the download mirror at download.handbrake.fr has been compromised, but it has been already shut down for investigation. Further, HandBrake says it is rebuilding the download mirror server, a move that might affect performance and the availability of old versions of HandBrake.
Related: High-Profile Targets Attacked via Software Update Mechanism
While downloads via the application’s built-in updater with 1.0 and later are unaffected, those via the application’s built-in updater with 0.10.5 and earlier are not verified by a DSA Signature, and users should check their systems for malicious versions.
HandBrake also detailed a series of steps users should perform to clean up their systems in the event of infection. They also note that impacted users should also “change all the passwords that may reside in [their] OSX KeyChain or any browser password stores.”
To check whether they are affected or not, users should look for a process called “Activity_agent” in the OSX Activity Monitor application. If it is present, it means that they were infected with malware.
The actors who managed to compromise the download mirror replaced the legitimate HandBrake file on the server with one packing a new variant of OSX.Proton RAT that was detailed in March this year. The threat was discovered on a closed Russian cybercrime message board, where it was offered at 2 Bitcoins (around $2,500) for single installations.
At the time, the malware was being advertised as “a professional FUD surveillance and control solution” that included root-access privileges and features. The RAT was said to provide operators with full control over the infected machines and to allow them to monitor keystrokes, take screenshots, and even execute commands.
According to objective-see.com, the variant of Proton being distributed though the compromised HandBrake mirror is almost identical to the initial version, except for the screenshot taking capabilities, which are missing now.
The malware has a very low detection rate on VirusTotal, but Apple has already released an XProtect signature for it, which should help keep users protected.
Android’s Vampire Bat Apps are listening to your life through ultrasonic beacons
8.5.2017 securityaffairs Android
Researchers at Technische Universitat Braunschweig published a study on 200+ Android mobile apps that are listening to your life through ultrasonic beacons.
Researchers at Technische Universitat Braunschweig in Germany recently published a finding that over 200 Android mobile applications are listening to your life through ultrasonic beacons.
Like digital electronic vampire bats, these apps are checking for ultrasonic beacons and the data is then used to track users and then serve them with targeted advertising.
Basically, software developers have combined with advertisers to have your phone pick up broadcast sounds inside stores, on TV and via the Internet. The ultrasonic beacon sounds vibrate at 18,000 to 20,000 times a second which is well above the hearing of most people. These beacon sounds are monitored covertly by the android phone applications which then transmit the results to the developer who in turn sells the information that you were in a specific store, or watching the tagged ad on TV or the Internet.
The process is relatively simple by programming standards. The covert surveillance software is embedded into popular programs such as coupon offers, games or text message systems offered for free by various organizations. The first time you run the program – it embeds an endless loop called a “service” so the surveillance portion is always running even when you are not using the app or have restarted your phone. The surveillance software is also keyed to listen for specific frequencies of sound and will transmit that information when it detects that sound via a hidden internet link.
The technology and design employed by the app developers is similar in format to that used by the US Central Intelligence Agency (CIA) for surveillance as revealed by Wikileaks in their VAULT7 publications. Companies caught using these apps so far include the Philippines versions of the McDonald’s and Krispy Kreme. The German researchers also found four local retail stores also had ultrasonic beacons installed designed to trigger any listening cell phone.
“It was really interesting to find beacons at the entrance of some stores in two German cities,” says Erwin Quiring, a privacy researcher who worked on the study. “It affects all of us if there’s some kind of privacy invasive technique we don’t know about and which runs silently on phones.”
The applications, most of which are available on the Google Play Store, have not informed customers that they are being monitored and may continue to monitor them even after the app is uninstalled. The app developers, companies and advertisers involved are clearly in violation of the privacy agreement to post on Google Play which requires developers to “comprehensively disclose how an app collects, uses and shares user data, including the types of parties with whom it’s shared.”
Google has not commented publically if they intend to pursue the developers for their privacy violations. Under Google policy – the developers and the advertising corporations may be prohibited from using the Play store but a similar privacy violation by Uber against Apple only resulted in a quiet scolding and an apology. It is unlikely that Google will banish large corporations such as McDonalds for breaking privacy requirements with surveillance apps distributed by the Play Store.
The researchers were able to focus their attention on one particular provider named Silverpush which now claims that it has disabled the tracking features in its applications. However, the data shows that tracking apps developed with the Silverpush implanted covert surveillance technology have been downloaded more that 2 million times from Google Play.
Phone owners have few options when it comes to defending against this surveillance. The most effective is to closely inspect your applications using the SETTINGS menu. Each application has a permissions list which will show if they are allowed to record audio.
A hint to newbie users here – if you download a free flashlight app and it has audio recording permissions – it is doing more than turn on or off your cellphone light.

To demonstrate how easy it is to develop and use such a surveillance system we put together a card game program that has a secret listener hidden inside it. The demonstration Black Jack program does not perform the “service” installation and only records 1 time after the game is started and stops when a player selects the “HIT” option. The output is written to a file in MP4 format and stored openly on the external SD card under the name “BJ(date/time).mp4”. The source code and signed Android APK run file are included in a zip file with a SHA256 check at:
https://www.softwar.net/blackjack.html
The differences between the demonstration program and the operational ultrasonic surveillance app systems are:
1 – Game demo does not install as a “SERVICE” so only runs when app is in use.
2 – Game demo does not have a special listener to detect ultrasonic beacon sounds.
3 – Game demo does not have a transmit feature to send data back to a controller.
4 – Game demo stores the recorded sound locally in a mp4 file so you can examine it.
However, as the demonstrator quickly shows, a surveillance application designed to pick up sound does not limit itself to just ultrasonic beacons but can pick up all sounds. The ultrasonic beacon detection has to be programmed into the system to filter out other sounds. While companies that employ this kind of targeting state they did not listen to conversations – the potential is there to re-transmit your conversations to a controller just as the CIA versions do.
All that is required is to remove the code filtering out the ultrasonic beacon sound, and insert a routine to transmit all the sounds that are picked up. The end program would resemble a hidden one-way ISP phone service with everything within detection being relayed in real-time, or stored for later downloading if the phone is outside the range of an internet connection.
In addition, other information such as your phone number, GPS location and even proximity to the nearest beacons can be pinpointed, by advertisers who then market to you as if they were a salesman in your pocket, or by others who can abuse this technology. When combined with GPS location and even video surveillance your cell phone not only becomes a major threat to privacy but to your personal security as well.
The question for phone makers, owners, and government officials is exactly what are we all going to do about this? Phone makers can do a better job showing what powers each application is using and how the consumer can limit them. Owners can actually take the time to be more cautious; observing that Caveat emptor – “Let the buyer beware” – applies to free downloaded applications. Finally, government officials may want to consider new regulations on the use of such surveillance technology for marketing purposes.
Operation WilySupply – Software remote update channel of the supply chain exploited as attack vector
8.5.2017 securityaffairs Hacking
Microsoft has recently uncovered an attack dubbed Operation WilySupply that leveraged the update mechanism of an unnamed software editing tool to compromise targets.
The attackers mostly targeted organizations in the finance and payment industries.
“An unknown attacker was taking advantage of a silent yet effective attack vector: the compromised update mechanism or software supply chain for a third-party editing tool.” wrote Elia Florio, senior security software engineer, with Windows Defender ATP Research Team. “The software vendor that develops the editing tool was unaware of the issue. In fact, while their software supply chain served as a channel for attacking other organizations, they themselves were also under attack.”
Microsoft confirmed that attackers were financially motivated and conducted surgical attacks, but did not provide data on the number of targets.
“We believe that the activity group behind Operation WilySupply is motivated by financial gain. They compromise third-party software packages delivered through updaters and other channels to reach victims who are mostly in the finance and payment industries.” added Florio.
Experts at Microsoft discovered the insidious attack vector after a number of machines using the updater were flagged by Windows ATP.
“Windows Defender ATP initially called our attention to alerts flagging suspicious PowerShell scripts, self-deletion of executables, and other suspect activities,” added Florio.
The analysis of the Temp Folder on one of the infected systems revealed the legitimate third-party updater running as service, anyway, the updater also downloaded an unsigned, low-prevalence executable just before the malicious activity was observed.
“The downloaded executable turned out to be a malicious binary that launched PowerShell scripts bundled with the Meterpreter reverse shell, which granted the remote attacker silent control. The binary is detected by Microsoft as Rivit.”

Attackers used the Meterpreter to power in-memory or fileless attacks through in-memory DLL injections.
This isn’t the first time that hackers exploit software remote update channel of the supply chain as an attack vector.
Experts at Microsoft confirmed that the technique was observed in the past in cyber attacks against high-profile targets.
“This generic technique of targeting self-updating software and their infrastructure has played a part in a series of high-profile attacks, such as unrelated incidents targeting Altair Technologies’ EvLog update process, the auto-update mechanism for South Korean software SimDisk, and the update server used by ESTsoft’s ALZip compression application.” continues the post.
Back to the present, experts observed recon activities, including machine enumeration, using standard commands, such as NET, IPCONFIG, NETSTAT, NLTEST, and WHOAMI. Hackers also used common tools like Mimikatz and Kerberoast to dump hashes and lateral movement leveraging the Windows Management Instrumentation (WMI).
European law enforcement takes down Darknet marketplace
8.5.2017 securityaffairs CyberCrime
Europol supported the Slovak NAKA crime unit in an operation that resulted in the seizure of the Bloomsfield darknet marketplace.
Another success of the European police, last week Europol supported the Slovak NAKA crime unit in the arrest of a Slovak national believed to operate the Bloomsfield darknet marketplace dealing in drugs and arms.
“Bloomsfield started its marketplace around two years ago, but remained throughout its shelf life a rather small market with few listings and users.” reported website darkweb.world.
The police took into custody the suspect and several of his premises have been searched.
“Europol has supported the Slovak authorities in their investigation into a Slovak national who had been trading firearms, ammunition, and drugs on the Darknet.” reads the statement published by the Europol.

“In one of the locations searched, Slovak authorities discovered and seized five firearms and approximately 600 rounds of ammunition of different calibers. The investigators also found a sophisticated indoor cannabis plantation, 58 cannabis plants and a Bitcoin wallet containing bitcoins worth EUR 203 000, which is thought to have been obtained from illegal online activities.”
The law enforcement has seized the server running the darknet marketplace, experts are analyzing it searching for evidence and other information useful for the investigation.
“The server used by the suspect to host the Darknet marketplace was also seized during the raids and is currently being forensically analysed. Slovak authorities and Europol have extended the investigation into the users and vendors who utilised the marketplace.” states Europol
Bloomsfield was launched around two years ago but is considered a very small market with few listings and users. It started as the vendor shop of the vendor ‘Biocanna‘ and later other vendors have joined the darknet market.
Biocanna has shared a portion of a conversation on Twitter concerning the ‘owner of the failing Bloomsfield market.’

C @2ctfm
Best I've ever seen
7:37 PM - 4 May 2017
Retweets likes
It the above claims are correct the Europol will have no difficulties to track the other operators of the black market.
“Europol supported Slovakia throughout the entire investigation by providing its analytical and financial intelligence capabilities.” reads the Europol’s announcement. “Also, across-check performed during the house searches generated a hit on Europol’s databases which helped investigators identify a Darknet vendor living in another EU country. The individual was suspected of supplying one of the firearms found during the house searches in Bratislava.”
Darknet marker places are important facilitators of criminal activities, the monitoring of this ecosystem is crucial for law enforcement.
Fatboy Ransomware as a Service sets the ransom based on the victims’ location
8.5.2017 securityaffairs Ransomware
Recently discovered Fatboy ransomware implements a dynamic method of setting the ransom amount based on the geographic location of the victims.
Ransomware continues to monopolize the threat landscape, recently security experts have observed numerous evolution of this specific family of malware.
A newly discovered ransomware-as-a-service (RaaS), dubbed Fatboy, implements a dynamic method of setting the ransom amount based on the geographic location of the victims.

According to threat intelligence firm Recorded Future, the Fatboy ransomware was first discovered on March 24 on a top-tier Russian cyber-criminal forum.
The alleged malware author that goes online with the moniker “polnowz” was advertising the threat on the forum as a partnership, offering support and guidance through Jabber. A few days later, a reputable member of the forum offered to assist the author with translation in the product.
The most interesting feature of this ransomware is the payment scheme based on The Economist’s Big Mac Index, this implies that victims will pay a different ransom depending on the cost of living of their region.
“The Fatboy ransomware is dynamic in the way it targets its victims; the amount of ransom demanded is determined by the victim’s location.” reads the analysis published by Recorded Future.
“According to polnowz, Fatboy uses a payment scheme based on The Economist’s Big Mac Index (cited as the “McDonald’s Index” in the product description), meaning that victims in areas with a higher cost of living will be charged more to have their data decrypted.”

Crooks that intend to be partners of the author can benefit from instant payments when the victim pays the ransom.
Since February 7, 2017, the author of the Fatboy ransomware supposedly earned at least $5,321 USD from his ransomware campaigns.
On infected computers, the ransomware displays a ransom note that warns victims that their files would be completely lost if the ransom isn’t paid within a specific period.
Fatboy ransomware is written in C++ and works on all Windows OS versions for both x86 and x64 architectures.
The malware target more than 5000 file extensions and it uses AES-256 encryption and a key for each victim that is encrypted with RSA-2048.
Below the product description shared by Recorded Future:
Base load 15.6 kB, written in C++
Active cryptolocker development and support
Works on all Windows OS x86/x64
Multi-language user interface (12 languages)
Encrypts every file with AES-256 with individual keys, then, all keys are encrypted with RSA-2048
Comfortable partner panel with full statistics by country and time
Detailed information on each individual client is in the partner panel
Scans all disks and network folders
New Bitcoin wallet number for each client
Software deletes after payment
Instant transfer of funds to the partner after the victim pays for decryption
Automatic file decryption after payment
Support for more than 5000 file extensions
Automatic price adjustment depending on the country’s living standards (McDonald’s Index)
Extended help with step-by-step instructions for payment
The FatBoy RaaS implements a user-friendly partner panel that includes statistics by country and time, and of course detailed information related to each infected machine.
“The level of transparency in the Fatboy RaaS partnership may be a strategy to quickly gain the trust of potential buyers. Additionally, the automatic price adjustment feature shows an interest in customizing malware based on the targeted victim.” concludes Recorded Future.
“Organizations should be aware of the adaptability of Fatboy, as well as other ransomware products, and continuously update their cyber security strategies as these threats evolve.”
High-Profile Targets Attacked via Software Update Mechanism
8.5.2017 securityweek Hacking
A recently discovered cyber-attack targeting high-profile technology and financial organizations is using a compromised software update mechanism for malware delivery, Microsoft security researchers reveal.
This type of attack isn’t new, as it has been previously used in incidents involving Altair Technologies’ EvLog update process, South Korean software SimDisk’s auto-update mechanism, and the update server used by ESTsoft’s ALZip. The new campaign, however, also employed a series of commodity tools and simple malware, the researchers say.
Through compromising the update mechanism or software supply chain for a third-party editing tool, the actors were able to deploy a piece of malware Microsoft detects as Rivit. This malicious executable would launch PowerShell scripts bundled with the Meterpreter reverse shell, which provided remote attackers with silent control over the compromised machines.
Dubbed Operation WilySupply, this cyber-espionage campaign was discovered in its early stages, before it could do actual harm, Microsoft says. The company has notified the affected parties and the third-party software vendor and worked with them to mitigate potential risks. The well-planned, finely orchestrated cyberattack was so stealth that even the developer of the third-party tool was completely unaware of the issue.
“Although it did not utilize a zero-day exploit, this cyberattack effectively compromised an asset. It took advantage of the common trust relationship with software supply chains and the fact that the attacker has already gained control of the remote update channel,” Elia Florio, Windows Defender Advanced Threat Protection (Windows Defender ATP) Research Team, explains.
Interestingly, only certain machines were affected, while a majority of the possible targets were ignored. This, however, is an indicative of the actors’ intent to focus on the most valuable targets and to keep a low profile.
The commodity tools used in these attacks are typically employed in penetration testing exercises, and allow attackers to evade attribution. The malware binary, named ue.exe, was a small piece of code focused only on launching a Meterpreter shell from a Base64/Gzip encoded blob downloaded using PowerShell.
For network exploration, credential dumping, and lateral movement, the attackers used either native system commands or scripted tools executed only in memory through PowerShell, a technique that has become increasingly popular among cybercriminals.
The techniques, tactics, and procedures (TTPs) observed during the attack included non-persistent, self-destructing initial binary; memory-only payloads; recon activities such as machine enumeration; migration into long-living processes; use of common tools like Mimikatz and Kerberoast to dump hashes; lateral movement using Windows Management Instrumentation (WMI); and persistence through scheduled tasks.
As part of this operation, the attackers used the following network addresses to perform initial network scanning, lateral movement, and command-and-control (C&C) communication: hXXp://5.39.218.205/logo.png and hXXp://176.53.118.131/logo.png. The same addresses were used to download Meterpreter-based payloads as well.
“We believe that the activity group behind Operation WilySupply is motivated by financial gain. They compromise third-party software packages delivered through updaters and other channels to reach victims who are mostly in the finance and payment industries,” Florio notes.
Top Obama Officials to Testify on Russian Election Interference
8.5.2017 securityweek BigBrothers
The scandal over Russian meddling in last year's US presidential election returns to the forefront of Washington politics after weeks of quiet on Monday, when two top officials from the Obama administration are set to testify in Congress.
Sally Yates -- acting attorney general in the Trump administration for 10 days before being fired -- could bring new pressure on the White House over what it knew about former national security adviser Michael Flynn's communications with Russian officials.
Obama's director of national intelligence James Clapper is also set to testify, after repeatedly warning of the need to get to the bottom of how the Russians interfered in the election, and whether anyone on President Donald Trump's team colluded with Moscow.
The case simmered for weeks as attention focused on what keynote legislation the president could push through in his first 100 days, a milestone reached last week.
Congressional investigations into Russian meddling have also been held up by infighting between Democrats and Republicans over how aggressively to pursue a matter that continues to cast a cloud over Trump's election win.
Dianne Feinstein, the top Democrat on the Senate Intelligence Committee, which also is investigating Russia's role in the election, said she is eager to hear Yates's testimony.
"Sally Yates is very much respected. She's a professional. She's not a politician. She's spent a lot of time in the department," Feinstein told NBC News's "Meet the Press" program.
"She apparently has some information as to who knew what when that she is willing to share -- and that would be what she knew about Michael Flynn's connections to Russia," said Feinstein.
- Trump: Russia story is 'phony' -
Trump last week repeated his dismissal of US intelligence chiefs' conclusion that Moscow had sought to boost his campaign over his Democratic rival Hillary Clinton's in an effort overseen by Russian President Vladimir Putin.
In an interview with CBS's "Face the Nation" program marking his 100 days, Trump last week again rejected the official view that Russians hacked Democratic Party computers and communications.
"(It) could have been China, could have been a lot of different groups," he said.
On Tuesday, he again branded the whole story as fake. "The phony Trump/Russia story was an excuse used by the Democrats as justification for losing the election," he said on Twitter.
Trump's dismissals notwithstanding, the Senate Judiciary Committee -- where Yates and Clapper are to appear on Monday -- and the House and Senate intelligence committees are stepping up their probes, calling numerous current and former government witnesses to testify, mostly behind closed doors.
And the FBI is continuing its own investigation into possible collusion.
The country's top intelligence officials say they have no doubt that Moscow tried to swing the election against Clinton last year through hacking and disinformation.
Nor do they doubt that people closely associated with the Trump campaign -- including Flynn, onetime foreign affairs adviser Carter Page and former campaign chairman Paul Manafort -- all had ongoing contacts with Russians.
But whether those contacts resulted in any collusion with Moscow remains unproved.
Asked on CNN last week if she had yet seen evidence of collusion in private intelligence briefings, Feinstein responded: "Not at this time."
In Monday's open hearing, Yates -- an Obama deputy attorney general who was fired by Trump for refusing to support his immigration ban -- reportedly could testify that she warned the incoming administration in January that Flynn's discussions with Russia's US ambassador left Flynn vulnerable to blackmail.
A former military intelligence chief, Flynn was Trump's national security adviser for 24 days before he was fired for lying about the substance of the calls.
Clapper, still bound by secrecy requirements of his former job, might not add more than what the intelligence community has already said publicly about the scandal.
- Subpoena warnings -
The more serious investigative action in the coming weeks will take place out of the public eye. The House and Senate intelligence committees are holding interviews with current intelligence and Trump campaign officials behind closed doors.
The Senate side has warned possible witnesses, including Flynn, Page and Manafort, that they could be subpoenaed to testify if they do not voluntarily cooperate, according to the New York Times.
In a statement Friday, the top senators of the Senate committee specifically warned Page, a former Moscow-based investment banker, to meet their week-old request for specific documents.
"Should Mr. Page choose to not provide the material requested" by specified dates, they said, "the committee will consider its next steps."
"Fatboy" Ransomware-as-a-Service Sets Ransom Based on Victim Location
8.5.2017 securityweek Ransomware
A newly discovered ransomware-as-a-service (RaaS) has a dynamic method of setting the ransom amount based on the victim’s location, Recorded Future reports.
Dubbed Fatboy, the malware was first spotted on March 24 on a top-tier Russian cyber-criminal forum, where a member started advertising it as a partnership, while also promising support and guidance through Jabber. Two days later, a reputable member of the forum offered to assist the malware author with translation in the product.
The ransomware’s author claims that a payment scheme based on The Economist’s Big Mac Index is used, “meaning that victims in areas with a higher cost of living will be charged more to have their data decrypted,” Recorded Future’s Diana Granger explains.
Wannabe criminals interested in the Fatboy RaaS would partner directly with the author, without going through a third-party vendor. They are also promised instant payments when the victim pays the ransom, which would supposedly add an extra level of transparency to the partnership.
While not a large sum, the Fatboy author supposedly earned more than $5,000 using this malware since February 7, 2017.
On infected computers, the ransomware displays a message explaining to the user that their files have been encrypted. The message also informs the victim what ransom amount has been set and warns them not to interfere with the malware’s activities. The message also claims that user’s files would be completely lost if the ransom isn’t paid within a specific period of time.
In their description of the Fatboy RaaS, the author claims the malware was written in C++, and works on all Windows versions (x86/x64). Additionally, cryptolocker development and support are included in the partnership, and a multi-language user interface with support for 12 languages is available. The author also says that the threat can scan all disks and network folders and that it can encrypt every file with AES-256 with an individual key and that all keys are encrypted with RSA-2048.
The author claims they use a new Bitcoin wallet number for each client, that the malware automatically decrypts files and deletes itself after payment, and that it can target more than 5000 file extensions. The partner panel, they say, offers full statistics by country and time, along with detailed information on each individual client.
“The level of transparency in the Fatboy RaaS partnership may be a strategy to quickly gain the trust of potential buyers. Additionally, the automatic price adjustment feature shows an interest in customizing malware based on the targeted victim. Organizations should be aware of the adaptability of Fatboy, as well as other ransomware products, and continuously update their cyber security strategies as these threats evolve,” Granger notes.
Za hackerským útokem na Macrona je možná Rusko, tvrdí Wikileaks
7.5.2017 Novinky/Bezpečnost BigBrother
Portál WikiLeaks, který se zaměřuje na zveřejňování tajných informací, naznačil možnou ruskou stopu za únikem dokumentů ze štábu francouzského prezidentského kandidáta Emmanuela Macrona. V metadatech k uniklým materiálům se podle serveru objevuje jméno pracovníka bezpečnostní společnosti spojené s ruskou vládou. Ukradené e-maily, snímky, faktury a další dokumenty se objevily na internetu dva dny před nedělním rozhodujícím kolem francouzských prezidentských voleb.
WikiLeaks v noci na neděli na twitteru zveřejnil tabulku s metadaty, v nichž je devětkrát uvedeno v azbuce jméno Georgij Petrovič Roška. Podle serveru jde o zaměstnance společnosti Evrika, která smluvně pracuje pro ruskou vládu.
Informaci zaznamenala ruská agentura RIA Novosti, podle níž WikiLeaks neupřesnil, o jakou společnost Evrika konkrétně jde. Nicméně WikiLeaks v následujícím tweetu s odkazem na článek portálu lenizdat.ru dodal, že se jedná o společnost, která získala od ruské tajné služby FSB licence k činnosti zaměřené na ochranu státního tajemství.

WikiLeaks ✔ @wikileaks
#MacronLeaks: name of employee for Russian govt security contractor Evrika appears 9 times in metadata for "xls_cendric.rar" leak archive
11:44 PM - 6 May 2017
2,238 2,238 Retweets 2,093 2,093 likes
RIA Novosti k tomu poznamenala, že mezi ruskými firmami v oblasti IT je skutečně společnost Evrika, která na oficiálním webu uvádí své stálé klienty. Jsou mezi nimi například ruská ministerstva zahraničí a zdravotnictví. Reakci společnosti se zatím získat nepodařilo.
Na internetu se v pátek večer objevil velký balík dokumentů patřících štábu prezidentského kandidáta Macrona, jehož volebním protivníkem je nacionalistka Marine Le Penová. Zástupci Macronovy kampaně následně potvrdili, že jde o výsledek masivního a koordinovaného hackerského útoku, jehož obětí se stali před několika týdny.
Kvůli zákazu politické agitace, který platí s ukončením kampaně od půlnoci z pátku na neděli až do konce hlasování v neděli ve 20:00, zakázaly úřady sdělovacím prostředkům zveřejňovat podrobnosti o uniklých dokumentech.
Business email compromise (BEC), the 5 billion dollar scam
7.5.2017 securityaffairs Spam
The Federal Bureau of Investigation report reveals that Business email compromise scams caused losses to businesses for 5 billion dollars over four years.
Business email compromise (BEC) continues to be a profitable attack technique for crooks and a serious threat to businesses.
The FBI has published data related to this specific criminal practice, and financial figures are astonishing.
The fraud scheme is very simple, busy employees receive a request to transfer funds by representatives of high management of their company.
The request could be sent by an attacker that either compromises a company’s email accounts or sets up a phishing message that submits a fake invoice to the victim from someone posing as a contractor or business partner.
It is clear that businesses and personnel using open source e-mail are most targeted by Business Email Compromise, in many cases the criminals spoofed e-mails of individuals within enterprises who are entitled to submit such payment requests.
Individuals responsible for handling wire transfers within specific companies are privileged targets of criminals which compose well-worded e-mail requests for a wire transfer.
The attacker behind Business Email Compromise scams shows a deep knowledge of their victims, their requests are proportional to the economic capabilities of the target and of the specific individual used as the sender of the request. The criminals sent e-mails concurrently with business travel dates for executives whose e-mails were spoofed.
The statement issued by the FBI in 2015 reported three different versions of the Business Email Compromise based on complaints received since 2009:
Version 1
A business, which often has a long standing relationship with a supplier, is asked to wire funds for invoice payment to an alternate, fraudulent account. This particular version has also been referred to as “The Bogus Invoice Scheme,” “The Supplier Swindle,” and “Invoice Modification Scheme.”
Version 2
The e-mail accounts of high-level business executives (CFO, CTO, etc) are compromised. The account may be spoofed or hacked. A request for a wire transfer from the compromised account is made to a second employee within the company who is normally responsible for processing these requests. This particular version has also been referred to as “CEO Fraud,” “Business Executive Scam,” “Masquerading,” and “Financial Industry Wire Frauds.”
Version 3
An employee of a business has his/her personal e-mail hacked. Requests for invoice payments to fraudster-controlled bank accounts are sent from this employee’s personal e-mail to multiple vendors identified from this employee’s contact list. The business may not become aware of the fraudulent requests until they are contacted by their vendors to follow up on the status of their invoice payment.
Data provided by the FBI is related to BEC crimes occurred between 2013 and December 2016, cyber criminals have earned $5,302,890,448 from 40,203 cases involving US and international businesses.
The FBI also confirmed that BEC scams continue to increase, 2,370 percent over the past year.
The FBI set up a reporting site for BEC scams and observed that between June and December of last year, US businesses reported losses of $346,160,957 in 3,044 attacks.
In the same period, non-US businesses reported losses of $448,464,415, but the overall number of BEC scams was much lower: 774. These data confirm that BEC scams are an emergency for US firms.
“The BEC/EAC scam continues to grow, evolve, and target small, medium, and large businesses. Between January 2015 and December 2016, there was a 2,370% increase in identified exposed losses. The scam has been reported in all 50 states and in 131 countries. Victim complaints filed with the IC3 and financial sources indicate fraudulent transfers have been sent to 103 countries.” states the Alert published by the FBI.
Based on the financial data, Asian banks located in China and Hong Kong remain the primary destinations of fraudulent funds; however, financial institutions in the United Kingdom have also been identified as prominent destinations.”

Stolen funds were mostly diverted to Asian banks located in China and Hong Kong, but Feds also confirmed that the use of British banks is on the rise.
The FBI report highlights that many recent attacks were preceded by a malware-based attack, mainly ransomware, likely because the crooks evaluate the ability of the firm to pay.
The FBI confirmed an increase of Real estate scams (+480 percent respect 2016).
The report also suggests company further security measures to prevent Business Email Compromise attacks, including the implementation of a two-step verification process. For example:
Out-of-Band Communication: Establish other communication channels, such as telephone calls, to verify significant transactions. Arrange this two-factor authentication early in the relationship and outside the e-mail environment to avoid interception by a hacker.
Digital Signatures: Both entities on EACh side of a transaction should utilize digital signatures. This will not work with web-based e-mail accounts. Additionally, some countries ban or limit the use of encryption.
Give a look at the report, it is full of interesting data.
UK Government’s secret programme for mass surveillance on internet and phones leaked
7.5.2017 securityaffairs BigBrothers
According to a draft document leaked online, UK Government is assigning itself more powers to spy on live communications and use malware for surveillance.
While the NSA is announcing it will stop surveillance activities on emails, texts, and other internet communications, the UK government has secretly drawn up more details of its new bulk surveillance powers. – awarding itself the ability to monitor Brits’ live
The UK Government is assigning itself more powers to spy on live communications and use malware for surveillance purposes.
UK gov surveillance draft
In the draft technical capability notices paper, the UK Government requests communications companies to provide real-time access to the full content of any named individual within one working day, along with “secondary data” relating to that person.
The draft document was obtained by the Open Rights Group, which leaked it.
“To provide and maintain the capability to carry out the interception of, or the obtaining of secondary data from, communications transmitted by means of a postal service and to disclose anything obtained under the warrant to the person to whom the warrant is addressed or any person acting on that person’s behalf within one working day, or such longer period as may be specified in the technical capability notice, of the postal operator being informed that the warrant has been issued.” states the draft. “To provide and maintain the capability to disclose secondary data in a form specified in the technical capability notice. “
The UK Government intends to have the ability to spy also on encrypted communications, this means that it will request every company operating communication services to not implementing end-to-end encryption or to insert a backdoor.
The authorities will request communication providers to allow bulk surveillance by deploying real-time interception systems that will allow spying on 1 in 10,000 their customers.
The live surveillance if any individual has to be authorized from secretaries of state and overseen by a judge appointed by the prime minister.
The worrying aspect of the draft is that the document has only been provided to a select number of ISPs and telcos companies for a four-week consultation.
The draft reports that is content has already passed through the UK’s Technical Advisory Board currently composed by telco companies (O2, BT, BSkyB, Cable and Wireless, Vodafone and Virgin Media) and six representatives from the government’s intercepting agencies.
The rules will have to be approved by the two houses of Parliament before becoming law.
Spam and phishing in Q1 2017
6.5.2017 Kaspersky Spam
We wrote earlier about a sharp increase in the amount of spam with malicious attachments, mainly Trojan encryptors. Most of that spam was coming from the Necurs botnet, which is currently considered the world’s largest spam botnet. However, in late December 2016, the network’s activity almost ceased completely and, as time showed, it wasn’t just a break for the festive season. The volume of spam sent from this botnet remained at an extremely low level for almost the entire first quarter of 2017.
In Q1 2017, the percentage of spam in email traffic amounted to 55.9%.
Tweet
Why has Necurs stopped distributing spam? We know that the botnet is active and the bots are waiting for commands. Perhaps the criminals behind the botnet got scared by all the fuss made about encryptors and decided to temporarily suspend their mass mailings.
We still continue to register malicious mass mailings from what is presumably the Necurs botnet, though their volume is a fraction of the amount recorded in December:
The number of malicious messages caught by our traps that were presumably sent by the Necurs botnet
As before, the emails usually imitate various types of bills and other official documents:
The email above contained an attached MSWord document with macros that downloaded the Rack family encryptor (detected as Trojan.NSIS.Sod.jov) to the victim machine.
In addition to malicious mailings from the botnet, we came across a mass mailing about pump-and-dump stock schemes:
As a rule, mass mailings exploiting this subject are distributed in huge volumes over a very short period of time. This is because the fraudsters have to pump and dump shares quickly, before their scams are discovered on the stock exchange. This type of stock fraud is against the law, so cybercriminals try to wind up the affair within a couple of days. The Necurs botnet is ideal for this sort of scam due to its size – according to estimates, it currently exceeds 200,000 bots.
The average share of spam in Russia’s email traffic in Q1 2017 was 61.6%.
Tweet
Does this sharp drop mean we have reached peak crypto-spam mass mailing and it’s about to disappear? Unfortunately, no.
The total volume of malware detected in email decreased, but not that dramatically – 2.4 times less than the previous quarter.
The number of email antivirus detections, Q4 2016 vs Q1 2017
Malicious mass mailings are still being sent out and, although their volume has decreased, cybercriminals are using a variety of techniques to deceive both security solutions and users.
Malicious emails with password-protected archives
In the first quarter we observed a trend towards packing malware into password-protected archives to complicate detection of malicious emails.
All the classic tricks were used to make potential victims open the archives: fake notifications about orders from large stores, various bills, money transfers, resumes, or the promise of lots of money.
The attached archives usually contained office documents with macros or JavaScript scripts. When launched, the files downloaded other malicious programs on the user’s computer. Interestingly, after the decline in Necurs botnet activity, the harmful “payload” that spread via spam became much more diverse. The cybercriminals sent out ransomware and spyware, backdoors and a new modification of the infamous Zeus Trojan.
The attachments above contain Microsoft Word documents with macros that download several different modifications of a Trojan encryptor belonging to the Cerber family from onion domains in different zones. This malicious program selectively encrypts data on the user’s computer and demands a ransom for decrypting it via a site on the Tor network.
The archive in the message above contains the Richard-CV.doc file with macros that downloads representatives of the Fareit spyware family from the onion.nu domain. These malicious programs collect confidential information about the user and send it to the remote server.
There was yet another case involving downloadable spyware, this time from the Pinch family. The Trojan collects passwords, email addresses, information about the system configuration and registry settings. Among other things, it harvests information from instant messaging services and mail clients. The obtained data is encrypted and sent to the criminals by email. According to our information received from KSN, the program is most widespread in Russia, India and Iran.
Most email antivirus detections occurred in China – 18% of all spam.
Tweet
It’s worth pointing out that this spyware was spread using fake business correspondence. Emails were sent out using the names of real small and medium businesses with all the relevant signatures and contacts, rather than using the name of some made-up organization.
Unlike other emails, the example above does not contain a password-protected archive. The request to enter a password is just a trick: the fraudsters want the user to enable Microsoft Word macros to run the malicious script.
The contents of the email above include a password-protected document with a script in Visual Basic that downloads the Andromeda bot on the victim machine. The latter establishes a connection with the command center and waits for commands from the owners. It has broad functionality and can download other malicious programs on the user’s computer.
This fake notification from an e-store contains a malicious script. On entering the password and launching the malicious content, the Receipt_320124.lnk file is created in the %TEMP% catalogue. It, in turn, downloads a Trojan-banker of the Sphinx family, which is a modification of the older and infamous Zeus, on the victim computer.
As we can see, very different mass mailings with malicious attachments now contain files packed in a password-protected archive. Most likely, this trend will continue: a password-protected document is likely to appear more trustworthy to the user, while causing problems for security solutions.
Spam via legal services
Modern virtual platforms for communication (messengers, social networks) are also actively used by spammers to spread advertising and fraudulent offers. Cybercriminals register special accounts for spamming in social networks and to make their messages look more authentic they use techniques similar to those used in traditional mass mailings (for example, the personal data from the account and that sent in the email are the same). The same type of spam, for example, ‘Nigerian letters’, offering earnings, etc. can be distributed via email traffic and social networks. A notification about a message is usually sent to the recipient’s email address; in this case, the technical header of the email is legitimate, and it is only possible to detect the spam by the contents of the message. Spam distributed directly via email, can be easily detected by technical headers. The same cannot be said for messages sent via legitimate services, especially if the address of the service is added to the user’s list of trusted addresses.
Today’s email spam filters can cope effectively with the task of detecting spam that is sent in the traditional way, so spammers are forced to look for new methods to bypass filters.
Holidays and spam
The first quarter of 2017 saw festive spam dedicated to New Year, St. Patrick’s Day, Easter and Valentine’s Day. Small and medium-sized businesses advertised their services and products and offered holiday discounts. Offers from Chinese factories were timed to coincide with the Chinese New Year, which was celebrated in mid-February.
Spammers also sent out numerous offers to participate in a survey and get coupons or gift cards from major online stores, hoping to collect the recipients’ personal information and contact details.
Burst of B2B spam
In the first three months of 2017, we also recorded a large number of mass mailings containing offers to buy company databases from specific industries. This type of spam remains popular with spammers and primarily targets companies or individual representatives of large businesses rather than ordinary users. Therefore, these messages are sent mainly to people or companies from a list of contacts or addresses for a particular business segment that is obtained, as a rule, in the same way – via spam.
The offers are sent on behalf of firms or their representatives, but they are often completely impersonal.
Spammers have databases of companies for any business segment, as well as the contact details of participants at major exhibitions, seminars, forums and other events. To make recipients interested in their offers, spammers often send several free contacts from their collections.
Statistics
Proportion of spam in email traffic
Percentage of spam in global email traffic, Q4 2016 and Q1 2017
Compared to Q4 2016, there was a decline in the overall proportion of spam in global email traffic in the first three months of 2017. In January, the proportion fell to 55.05%, while in February the share was even lower – 53.4%. However, in March the level of spam showed an upward trend, rising to 56.9%. As a result, the average share of spam in global email traffic for the first quarter of 2017 was 55.9%.
Percentage of spam in Russia’s email traffic, Q4 2016 and Q1 2017
The spam situation in the Russian segment of the Internet was somewhat different from the global one. In January 2017, the proportion of junk email increased to almost 63% and stayed in the 60-63% range until the end of the quarter. In February, as was the case with overall global traffic, there was a decline – to 60.35% – followed by an increase to 61.65% in March. The average share of spam in Russian email traffic in the first quarter of 2017 was 61.66%.
Sources of spam by country
Sources of spam by country, Q1 2017
In the first quarter of 2017, the US remained the leading source of spam – its share accounted for 18.75%. Representatives from the Asia-Pacific region – Vietnam (7.86%) and China (7.77%) – came second and third.
Trojan-Downloader.JS.Agent remained the most popular malware family spread via email.
Tweet
Germany was the fourth biggest source, responsible for 5.37% of world spam, followed by India (5.16%). Russia, in sixth place, accounted for 4.93% of total spam.
The top 10 biggest sources also included France (4.41%), Brazil (3.44%), Poland (1.90%) and the Netherlands (1.85%).
Spam email size
Breakdown of spam emails by size, Q4 2016 and Q1 2017
In Q1 2017, the share of small emails (up to 2 KB) in spam traffic decreased considerably and averaged 29.17%, which is 12.93 p.p. less than in the fourth quarter of 2016. The proportion of emails sized 2–5 KB (3.74%) and 5–10 KB (7.83%) also continued to decline.
Meanwhile, the proportion of emails sized 10-20 KB (25.61%) and 20-50 KB (28.04%) increased. Last year’s trend of fewer super-short spam emails and more average-sized emails has continued into 2017.
Malicious attachments in email
Top 10 malware families
Trojan-Downloader.JS.Agent (6.14%) once again topped the rating of the most popular malware families. Trojan-Downloader.JS.SLoad (3.79%) came second, while Trojan-PSW.Win32.Fareit (3.10%) completed the top three.
TOP 10 malware families in Q1 2017
The Backdoor.Java.Adwind family (2.36%) in fifth place is a cross-platform multifunctional backdoor written in Java and sold on DarkNet as malware-as-a-service (MaaS). It is also known under the names of AlienSpy, Frutas, Unrecom, Sockrat, JSocket, and jRat. It is typically distributed via email as a JAR attachment.
A newcomer – Trojan-Downloader.MSWord.Cryptoload (1.27%) – occupied ninth place. It’s a JS script containing malware, which it installs and runs on the computer.
Trojan-Downloader.VBS.Agent (1.26%) rounded off the Top 10.
Countries targeted by malicious mailshots
Distribution of email antivirus verdicts by country, Q1 2017
In Q1 2017, China (18.23%) was the country targeted most by malicious mailshots. Germany, last year’s leader, came second (11.86%), followed by the UK (8.16%) in third.
Italy (7.87%), Brazil (6.04%) and Japan (4.04%) came next, with Russia occupying seventh place with a share of 3.93%. The US was in ninth place with (2.46%), while Vietnam (1.94%) completed the Top 10.
Phishing
In the first quarter of 2017, the Anti-Phishing system was triggered 51,321,809 times on the computers of Kaspersky Lab users. Overall, 9.31% of unique users of Kaspersky Lab products worldwide were attacked by phishers in Q1 2017.
Geography of attacks
China (20.88%) remained the country where the largest percentage of users is affected by phishing attacks, although its share decreased by 1.67 p.p.
Geography of phishing attacks*, Q1 2017
* Number of users on whose computers the Anti-Phishing system was triggered as a percentage of the total number of Kaspersky Lab users in the country
The percentage of attacked users in Brazil decreased by 0.8 p.p. and amounted to 19.16%, placing the country second in this ranking. Macao added 0.91 p.p. to the previous quarter’s figure and came third with 11.94%. Russia came fourth with 11.29% (+0.73 p.p.), followed by and Australia on 10.73% (-0.37p.p).
TOP 10 countries by percentage of users attacked
Country %
China 20.87%
Brazil 19.16%
Macao 11.94%
Russia 11.29%
Australia 10.73%
Argentina 10.42%
New Zealand 10.18%
Qatar 9.87%
Kazakhstan 9.61%
Taiwan 9.27%
Argentina (10.42%, +1.78 p.p.), New Zealand (10.18%), Qatar (9.87%), Kazakhstan (9.61%) and Taiwan (9.27%) completed the top 10.
Organizations under attack
Rating the categories of organizations attacked by phishers
The rating of attacks by phishers on different categories of organizations is based on detections of Kaspersky Lab’s heuristic anti-phishing component. It is activated every time a user attempts to open a phishing page while information about it has not yet been included in Kaspersky Lab’s databases. It does not matter how the user attempts to open the page – by clicking a link in a phishing email or in a message on a social network or, for example, as a result of malware activity. After the security system is activated, a banner is displayed in the browser warning the user about a potential threat.
In Q1 2017, the ‘Banks’ (25.82%, -0.53 p.p.), ‘Payment systems’ (13.6%, +2.23 p.p.) and ‘Online stores’ (10.89%, +0.48 p.p.) categories accounted for more than half of all registered attacks. The total share of ‘Financial organizations’ was a little over 50% of all phishing attack
Distribution of organizations affected by phishing attacks by category, Q1 2017
In addition to financial organizations, phishers most often targeted ‘Global Internet portals’ (19.1%), although their share decreased by 5.25 p.p. from the previous quarter. ‘Social networking sites’ (9.56%) and ‘Telecommunication companies’ (5.93%) also saw their shares fall by 0.32 p.p. and 0.83 p.p. respectively. The percentage of the ‘Online games’ category accounted for 1.65% while the figure for ‘Instant messaging’ was 1.53%.
TOP 3 attacked organizations
Fraudsters continue to focus most of their attention on the most popular brands, enhancing their chances of a successful phishing attack. More than half of all detections of Kaspersky Lab’s heuristic anti-phishing component are for phishing pages using the names of fewer than 15 companies.
In Q1 2017, Kaspersky Lab products blocked 51 million attempts to open a phishing page.
Tweet
The TOP 3 organizations attacked most frequently by phishers remained unchanged for the second quarter in a row. Yahoo! was once again the organization whose brand was mentioned most often on phishing pages (7.57%, – 1.16 p.p.). Facebook (7.24%), whose share fell by 0.13 p.p., was second, while Microsoft (5.39%, -0.83 p.p.) came third.
Organization % of detected phishing links
Yahoo! 7.57
Facebook 7.24
Microsoft Corporation 5.39
In order to reach the widest possible audience with one attack, scammers often mention a variety of brands expecting the victims to react to at least one of them. This is facilitated by authentication with existing accounts, which many Internet services use trying to make life easier for their users. Therefore, a page offering to use different accounts to enter a site does not arouse suspicions. This allows fraudsters to steal user data from several different resources using just one phishing page.
Phishing page prompting the user to login via the accounts of other web resources to access a file
This phishing page uses a similar trick under the pretext of accessing the Google Drive service
Hot topics this quarter
Payment systems
In the first quarter Q1 2017, 13.6% of detections of Kaspersky Lab’s heuristic anti-phishing component fell under the ‘Payment Systems’ category. It means that every eighth attack targeted this category, which has been popular with phishers for several quarters now.
PayPal (28.25%) came first on the list of attacked payment systems, followed by Visa (25.78%) and American Express (24.38%).
Organization %*
PayPal 28.25
Visa Inc. 25.78
American Express 24.38
MasterCard International 16.66
Others 4.94
* The percentage of attacks on an organization as a total of all attacks on organizations from the ‘Payment Systems’ category
The goal of phishers attacking customers of popular payment systems is to get personal and payment data, login details for accounts, etc. Criminals often place fraudulent content on reputable resources in order to gain the trust of the user and bypass blacklisting. For example, we came across a fake PayPal support page located on the Google Sites service (the primary domain is google.com). After clicking on the banner, the user is redirected to a phishing page, where they are asked to enter their account data for the payment system.
Phishing page using the PayPal brand located on the Google domain
Another trick used by phishers is to place phishing content on the servers of government agencies. This is possible because a significant number of government agencies do not pay much attention to the security of their web resources.
Phishing page using the PayPal brand located on a server belonging to Sri Lankan government
Phishing page using the PayPal brand located on a server belonging to the Bangladesh government
Emails threatening to block an account or asking to update data in a payment system were used as bait.
Online stores
Every tenth phishing attack targeted users of online stores. In Q1 2017, Amazon (39.13%) was the most popular brand with phishers.
Organization %
Amazon.com: Online Shopping 39.13
Apple 15.43
Steam 6.5
eBay 5.15
Alibaba Group 2.87
Taobao 2.54
Other targets 28.38
By using the Amazon brand, cybercriminals are trying not only to steal login data but also all the personal information of the user, including their bank card details. Also, they often place fake pages on domains that have a good reputation (for example, on a domain owned by Vodafone).
Phishing page using the Amazon brand located on the Vodafone domain
Earning money with anti-phishing
In addition to standard phishing emails and pages, we often come across other methods of tricking users. Scammers often exploit people’s desire to make easy money by offering cash to view advertising, automatic stock trading programs and much more.
Spam emails offering quick money on the Internet
In the first quarter of 2017, we saw a rather interesting fraudulent resource which claimed to be combating phishing sites. All you had to do if you wanted to make some quick cash was to register and perform several tasks, the essence of which was to evaluate web pages using the following options: malicious, safe, does not load. Only the content of the page was evaluated, while its address was not displayed.
After checking 31 sites, it turned out that $7 needed to be paid to withdraw the money that was earned
For each ‘checked’ site, the user earned about $3. To withdraw that money, they had to transfer $7 to the owners of the resource as confirmation that they were an adult and financially solvent. Of course, no ‘earnings’ were ever received after that.
Conclusion
Although the beginning of Q1 2017 was marked by a decline in the amount of spam in overall global email traffic, in March the situation became more stable, and the average share of spam for the quarter amounted to 55.9%. The US (18.75%) remained the biggest source of spam, followed by Vietnam (7.86%) and China (7.77%).
The first quarter of 2017 was also notable for the decrease in the volume of malicious spam sent from the Necurs botnet: the number of such mass mailings decreased significantly compared to the previous reporting period. However, the lull may be temporary: the attackers may have decided to suspend mass mailings until all the hype about encryptors subsides.
Trojan-Downloader.JS.Agent (6.14%) once again topped the rating of the most popular malware families detected in email. Trojan-Downloader.JS.SLoad (3.79%) came second, while Trojan-PSW.Win32.Fareit (3.10%) completed the top three.
In Q1 2017, the Anti-Phishing system was triggered 51,321,809 times on the computers of Kaspersky Lab users. China (20.88%) topped the rating of countries most often attacked by phishers. Financial organizations remained the main target for phishers, and we expect this trend to continue in the future.
'Macronleaks': Hackers Find Flaw in French Cyber-Fortress
6.5.2017 securityweek CyberSpy
They knew months ago that top-of-the-range hackers had been targeting them. They believe their security measures, too, had been nothing short of top-rate. But, in the end, French presidential candidate Emmanuel Macron's team got hacked.
And on Friday night, just an hour before the end of official campaigning, thousands of documents including emails and accounts belonging to his En Marche! (On the Move!) movement were dumped online.
"It's just incredible what's happening," said Belgian researcher Nicolas Vanderbiest, a specialist on online rumours, whose map showing how the "Macron Leak" propagated on Twitter has Wikileaks at the centre.
Macron's campaign team says it put in place servers protected by sophisticated software filters, recommended the use of several encrypted messaging and cellphone networks, and required double and triple authentication to access emails.
It says it stored its information in multiple-partitioned cells, with databases separated like fortresses, accessible by passwords that were complex and regularly changed.
But a squad of shadowy hackers seem to have found the back door.
"In this kind of organisation the real potential faultline is the human element," the head of computer services for En Marche! recently told AFP, requesting anonymity.
Because security procedures can become long and cumbersome, some people can be tempted to get around them by using personal email services which are little or badly protected.
- 'en-nnarche.com' -
On April 25, a report by Japanese cyber-security company Trend Micro, blamed a so-called "phishing" attack targetting the Macron campaign on Russian hacking group Pawn Storm, also known as Fancy Bears, Tsar Team and APT28.
The group, suspected of close links to the Russian security services, is also accused of having targetted the Democratic Party during last year's US presidential election, in which Republican-backed Donald Trump defeated Democrat Hillary Clinton.
In this kind of attack, which does not require sophisticated resources, hackers can open up security gaps in software, for example during an update or through a so-called mirror site.
This would be something like "en-nnarche.com", hoping that a user when reading quickly would mistake the "nn" for an "m" and fall into the trap, revealing access codes.
The principle of phishing, a classic arm in the hackers' arsenal, is to send a large number of fake emails often containing infected attachments, hoping that a distracted recipient will click on one, creating a breach in the targetted system.
The gap is unlikely to show up immediately, and the loophole it generates may be exploited weeks or months later.
The Macron campaign reacted swiftly to Friday night's data dump, saying it would take all measures necessary to shed light on the "unprecedented" incident.
But it did not seem overly worried by the substance of what had been leaked.
"Throughout the campaign, En Marche! has constantly been the party the most targeted by such attempts, in an intense and repeated fashion," it said in a lengthy statement.
"The aim of those behind this leak is, all evidence suggests, to hurt the En Marche! party. Clearly, the documents arising from the hacking are all lawful and show the normal functioning of a presidential campaign."
Senator Bazira Khiari, a national delegate for En Marche!, told AFP Saturday morning: "We were informed last night... We were just told to change our passwords".
French Authorities Warn Against Spreading Leaked Macron Data
6.5.2017 securityweek CyberSpy
French electoral authorities took a hard line Saturday on a hacking attack targeting presidential frontrunner Emmanuel Macron's campaign, saying anyone who circulates the leaked information could be committing a "criminal offence".
The electoral commission met following the announcement Friday by the pro-EU centrist's team that his campaign had been the target of a "massive and coordinated hacking attack" after a flood of internal documents were released online a day before the election.
"The dissemination of such data, which have been fraudulently obtained and in all likelihood may have been mingled with false information, is liable to be classified as a criminal offence," a commission statement said.
The documents spread on social media just before midnight on Friday -- when 39-year-old Macron and his far-right rival Marine Le Pen officially wrapped up campaigning for Sunday's decisive run-off vote -- with his aides calling the leak "unprecedented in a French electoral campaign".
Macron's team said the files were stolen weeks ago when several officials from his En Marche party had their personal and work emails hacked -- one of "an intense and repeated" series of cyber-attacks against Macron since the launch of the campaign.
"On the eve of the most important election for our institutions, the commission calls on all those on websites and social media... not to spread this information," the statement said.
Cisco fixes a critical flaw in CISCO CVR100W Wireless-N VPN Small Business Routers
6.5.2017 securityaffairs Vulnerebility
Cisco released a firmware update to fix a critical buffer overflow vulnerability in CISCO CVR100W Wireless-N VPN Small Business Routers.
Cisco has released a firmware update to fix a critical vulnerability in its CVR100W Wireless-N VPN routers.
The flaw, tracked as CVE-2017-3882, can be exploited by attackers to trigger a denial-of-service (DoS) condition and execute arbitrary code with root privileges.
The CVE-2017-3882 vulnerability was discovered by researchers from the Chinese GeekPwn hacker group. The company said there was no evidence of malicious exploitation.

The good news is that CISCO revealed that there was no evidence of exploitation of the flaw in the wild.
“A vulnerability in the Universal Plug-and-Play (UPnP) implementation in the Cisco CVR100W Wireless-N VPN Router could allow an unauthenticated, Layer 2–adjacent attacker to execute arbitrary code or cause a denial of service (DoS) condition. The remote code execution could occur with root privileges.” reads the CISCO security advisory.
The vulnerability resides in the Universal Plug and Play (UPnP) implementation of the CVR100W Wireless-N VPN routers.
The exploitation of the flaw is quite simple, an attacker can trigger the vulnerability by sending a specially crafted request to the UPnP listening port of the router.
“The vulnerability is due to incomplete range checks of the UPnP input data, which could result in a buffer overflow. An attacker could exploit this vulnerability by sending a malicious request to the UPnP listening port of the targeted device. An exploit could allow the attacker to cause the device to reload or potentially execute arbitrary code with root privileges.” continues the analysis.
The flaw affects CVR100W Wireless-N VPN routers running a version of the firmware prior to 1.0.1.22, no other small business routers are affected.
Administrators can determine which firmware release is running on their routers by logging in to the web interface using the http(s)://system-ip access URL.
Below there is an example included in the advisory, in this the router is running Firmware Release 1.0.1.21.
Cisco Small Business
CVR100W Wireless-N VPN Router
Version 1.0.1.21
The CVR100W Wireless-N VPN routers are also affected by a medium severity bug that can be exploited by an unauthenticated attacker to bypass the remote management ACL. This flaw was fixed with the release of version 1.0.1.24.
The Bondnet botnet- From China with Love
6.5.2017 securityaffairs BotNet
The new Bondnet botnet “Bond007.01” recently discovered coming out of China and it has infected an estimated 15,000 Windows server computers world-wide.
There’s a new botnet in town and it’s named after the spy with a license to kill – James Bond. The new Bondnet botnet “Bond007.01” was discovered coming out of China by researchers at Guardicore Labs and it has infected an estimated 15,000 Windows server computers worldwide. The infected systems make up a wide variety of government, corporate, university, city and hospital computers.
So far the Bondnet botnet has not been weaponized but instead seems to be focused on using the thousands of slaved computers to mine a variety of cryptocurrencies such as ZCash, RieConin, and what appears to be its primary target, Monero.
“Operating under the name Bond007.01, the attacker can then take full control of the servers to exfiltrate data, hold it for ransom, use the server to stage further attacks and more. Active since December 2016, Bondent primarily mines Monero. Bond007.01 is financially motivated, earning around a thousand dollars a day.” states the report published by Guardicore.
Crypto-currency mining is a mechanism used to introduce more currency into the system. Miners are often paid a small transaction fee as well as a “subsidy” of newly created electronic coins. Crypto-currency mining is a very computer resource intensive effort and can consume the availability of infected machines to the point of making them useless to the owners.
The Bondnet botnet, which has been reportedly in operation since late 2016, produces over $1,000 a day in mined currency.
The prime targets for the Bondnet attacks seem to be Windows 2008 servers equipped with MySQL however, the creators have a wide variety of targets and exploits they employ to infect a targeted system. The primary attack surface appears to be Windows RDP combined with brute force attacks against weak credentials.

The attackers also used a wide range of attacks against other web server software including JBoss, Oracle web apps, MSSQL and Apache Tomcat. Researchers have confirmed the Bondnet attacks seen so far are limited to Windows based server systems with 2008 and 2012 releases facing the brunt of the assault.
Once the Bondnet intruder has broken through into the Windows system it then installs a series of Visual Basic programs, DLLs and Windows management programs to act as a Remote Access Trojan (RAT) and the crypto-currency mining system. The RAT allows back door access for the Bondnet controllers and the mining system reports back with its results so the controllers can profit from the stolen computer usage.
While the Bondnet botnet creators are stealing computer time and resources to obtain their digital bounty, there are darker forces that can be unleashed. The Bondnet botnet is managed and controlled remotely by the unknown users and thus can also be weaponized to form a DOS attack network, a ransomware net or be used for simple passive surveillance.
Guardicore and other researchers have not seen any indication that the Bondnet operators are interested in data stored on the infected systems. Instead, they are concentrating their efforts on stealing the computer time for the crypto-currency mining operations. The speculation is that the amount of money earned by the Bondnet stealthy mining techniques exceeds what could be obtained via extortion by ransomware or DOS attacks.
However, the added usage and power consumption inflicted by Bondnet botnet reportedly costs victims as much as $2,000 a month and the potential of the Bondnet to be weaponized into something more sinister shows just how dangerous it is.
“While organisations can treat this as an issue of increased electric bills which can annually result in additional costs of 1000-2000$ per server, this may only be the beginning.” warns the analysis. “With relatively simple modifications the Bondnet can use its complete control over compromised organization servers, many of which contain sensitive information, to spread evil and perform other illegal actions. Today’s mining may easily become a ransomware campaign, data exfiltration or lateral movement inside the victim’s network.”
Owners of Windows server based systems are advised to monitor usage carefully, update their software to the latest versions to close security holes, raise the level of their password and credential employment and run a complete check for the Bondnet using AV security products.
Guardicore has released a full technical report on the Bondnet, a removal tool and an analysis of its operations at.
Macron Blasts Huge Hacking Attack Just Before French Vote
6.5.2017 securityweek CyberSpy
French presidential candidate Emmanuel Macron's team blasted a "massive and coordinated hacking attack" against his campaign after a flood of internal documents were released online barely 24 hours before the election.
The centrist candidate's furious staff said the release late Friday of thousands of emails, accounting documents and other files was an attempt at "democratic destabilisation, like that seen during the last presidential campaign in the United States".
The documents spread on social media just before midnight on Friday -- when 39-year-old Macron and his far-right rival Marine Le Pen officially wrapped up campaigning for Sunday's decisive run-off vote -- with his aides calling the leak "unprecedented in a French electoral campaign".
Hillary Clinton has alleged Russian hacking of her campaign's emails was partly to blame for her defeat in last year's US presidential election to Donald Trump.
The leak, posted by someone calling themselves EMLEAKS, came as an 11th-hour twist in what has proved to be one of the most drama-packed elections in French history.
Macron's team said the files were stolen weeks ago when several officials from his En Marche party had their personal and work emails hacked -- one of "an intense and repeated" series of cyber-attacks against Macron since the launch of the campaign.
"Clearly, the documents arising from the hacking are all lawful and show the normal functioning of a presidential campaign," aides said in a statement.
But they warned that whoever was behind the leak had mixed fake documents with real ones "in order to sow doubt and disinformation".
The WikiLeaks website posted a link on Twitter to the trove of documents, saying it was not responsible for the leak but that it was "examining" parts of the cache, amounting to around nine gigabytes of data in total.
Last month cybersecurity research group Trend Micro said Russian hackers called Pawn Storm had targeted Macron's campaign, using "phishing" techniques to try to steal personal data.
Senior Le Pen aide Florian Philippot suggested on Twitter that the leak might contain information that the media had deliberately suppressed.
France's presidential election commission advised media not to publish details of the documents, warning that publication could lead to criminal charges and that some of the documents were probably fake. The commission is due to meet later Saturday to discuss the hack.
- Security jitters -
The upset came at the end of a frantic final day of campaigning and as fresh security concerns emerged following the arrest of a suspected extremist.
Polls released earlier Friday had showed Macron gaining momentum, forecasting victory for the pro-European, pro-business former banker with around 62 percent to 38 percent for Le Pen.
He and Le Pen -- who is hoping to ride a global wave of anti-establishment anger to the Elysee Palace -- have offered starkly different visions for France during a campaign that has been closely watched in Europe and around the world.
After a policeman was shot dead in an Islamic State-claimed attack on Paris's Champs-Elysees three days before the first election round last month, jitters rose again when police arrested a suspected extremist near a military airbase on Friday.
Guns were discovered as well as a pledge of allegiance to IS and several of the group's flags, sources close to the case told AFP after the arrest in Evreux, north of Paris.
The suspect, a 34-year-old Muslim convert, was arrested early Friday after police found his car near the base.
In another major security incident on Friday, Greenpeace activists partially scaled the Eiffel Tower to hang a giant anti-Le Pen banner saying "Liberty, Equality, Fraternity" and "#resist".
Paris police said the stunt exposed "flaws" in the security surrounding the world-famous monument, and city authorities announced immediate measures to reinforce patrols at the site.
- Polar opposites -
Le Pen has tried to portray Macron as being soft on security and Islamic fundamentalism, playing to the concerns of many of her supporters after a string of terror attacks in France that have killed more than 230 people since 2015.
She has said she wants to copy Britain's example and hold a referendum on France's EU membership, sending alarm bells ringing in capitals across the bloc.
In the first round of the election, she finished second behind Macron on 21.3 percent after softening the FN's image over the past six years -- but without fully removing doubts about the party's core beliefs.
A former economy minister under Socialist President Francois Hollande, Macron quit the government last August to concentrate on his new political movement En Marche, which has drawn 250,000 members in 12 months.
He won high-profile backing from former US president Barack Obama on Thursday, who said in a video that Macron "appeals to people's hopes and not their fears".
French Authorities Warn Against Spreading Leaked Macron Data
6.5.2017 securityweek CyberSpy
French electoral authorities took a hard line Saturday on a hacking attack targeting presidential frontrunner Emmanuel Macron's campaign, saying anyone who circulates the leaked information could be committing a "criminal offence".
The electoral commission met following the announcement Friday by the pro-EU centrist's team that his campaign had been the target of a "massive and coordinated hacking attack" after a flood of internal documents were released online a day before the election.
"The dissemination of such data, which have been fraudulently obtained and in all likelihood may have been mingled with false information, is liable to be classified as a criminal offence," a commission statement said.
The documents spread on social media just before midnight on Friday -- when 39-year-old Macron and his far-right rival Marine Le Pen officially wrapped up campaigning for Sunday's decisive run-off vote -- with his aides calling the leak "unprecedented in a French electoral campaign".
Macron's team said the files were stolen weeks ago when several officials from his En Marche party had their personal and work emails hacked -- one of "an intense and repeated" series of cyber-attacks against Macron since the launch of the campaign.
"On the eve of the most important election for our institutions, the commission calls on all those on websites and social media... not to spread this information," the statement said.
Growth in Cyber Fraud Attacks Outpacing Growth of Transactions: Report
6.5.2017 securityweek CyberCrime
Cybercrime in 2017
The United States is the world's primary target for cyber fraud attacks. Europe has emerged as the major source of attacks, now accounting for 50% more attacks than the US. The growth in attacks is outpacing the growth of transactions; and in a 90-day period, 130 million fraud attacks were detected.
These details come from the ThreatMetrix Cybercrime Report Q1 2017 (PDF). The report shows that strong economies tend to attack other strong economies, with the USA primarily targeting the USA, Canada and the UK; Germany targeting the USA, the UK and Germany; and the UK targeting the USA, the UK and Ireland. The UK is now one of the world's largest attack originators.
While this concentration on North America and Europe is partly driven by the expectation of richer targets, it is probably also affected by attackers concentrating on areas where they already understand the local banking and finance methodologies.
The figures come from ThreatMetrix's analysis of 'high-risk' transactions found among the nearly 2 billion transactions it monitors every month. It shows a growth in mobile transactions, a growth in the sophistication of attacks, and an increase of around 23% in the figures from the same period in 2016.
"The complexity and speed of evolving attack vectors continues to take us by surprise," commented Vanita Pandey, vice president of product marketing at ThreatMetrix. "Fraudsters are operating within a much broader cybercrime landscape; one that shares knowledge, tools and exploits; trades information, tests and refines and constantly analyzes the market for new opportunities."
Partly this is being driven by the availability of huge volumes of user credentials stolen over the last few years and now readily available on the internet. Although breached organizations are quick to claim that their stolen data was encrypted or hashed, "what is clear," says the report, "is that identity data is the critical currency in global cybercrime, as fraudsters piece together full and convincing identities which are then used to perpetrate large-scale attacks."
"Cybercrime," it adds, "is becoming increasingly automated, sophisticated and is scaling exponentially through well organized crime rings with access to large-scale networks of infected devices available at their disposal to inundate online systems with large volumes of fraudulent transactions. They also use scripts (often in conjunction with bots) to perpetrate such transactions."
Fintech, unsurprisingly, is a major target. This is set against a background of increasing mobility, digital wallets and online remittances. Digital wallet transactions grew by 80% year-on-year, with a 180% increase in associated bot attacks. "Loan stacking and bustout scenarios are common attack vectors," explains ThreatMetrix, "where fraudsters capitalize on time delays inherent in reporting loan agreements to credit bureaus. Stolen identity credentials and device spoofing techniques allow cybercriminals to bypass even complex application procedures."
The company warns that attackers have a wide range of attack vectors and tools at their disposal. "Fraudsters have a gamut of threat vectors at their disposal to perpetrate fraud, including Malware, remote access Trojans (RATs), Man-in-the-Middle attacks and automated bot attacks. These are often used in combination to perform mass identity testing attacks (via an advanced bot), and then take over a trusted user account via a Man-in-the-Middle attack and/or RAT."
Pandey comments, "We saw a number of high-profile global breaches over the last year. Identities are being bought, sold, traded and augmented by criminals seeking to improve the success of their increasingly complex attacks. All of this points to one thing: Identities are the critical currency in cybercrime this year and it is up to businesses to look beyond static data to check that users are who they say they are."
ThreatMetrix has raised more than $90 million in funding, including $20 million in Series E funding in March 2014, and $30 million in growth funding from Silicon Valley Bank in October 2016.
Wikileaks Unveils CIA's Man-in-the-Middle Attack Tool
6.5.2017 thehackernews BigBrothers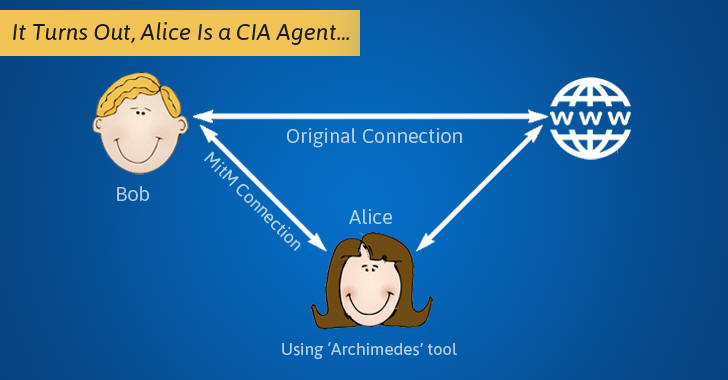
Wikileaks has published a new batch of the Vault 7 leak, detailing a man-in-the-middle (MitM) attack tool allegedly created by the United States Central Intelligence Agency (CIA) to target local networks.
Since March, WikiLeaks has published thousands of documents and other secret tools that the whistleblower group claims came from the CIA.
This latest batch is the 7th release in the whistleblowing organization's 'Vault 7' series.
Dubbed Archimedes, the newly released CIA tool, dumped on Friday, purportedly used to attack computers inside a Local Area Network (LAN).
According to the leaked documents, this MitM tool was previously named 'Fulcrum' but later was renamed to 'Archimedes' with several improvements on the previous version, like providing a way to "gracefully shutting down the tool on demand," and adding "support for a new HTTP injection method based on using a hidden iFrame."
The leaked documents describe Archimedes as a tool that lets users redirect LAN traffic from a targeted computer through a malware-infected computer controlled by the CIA before the traffic is passed on to the gateway, which is known as man-in-the-middle (MitM) attack.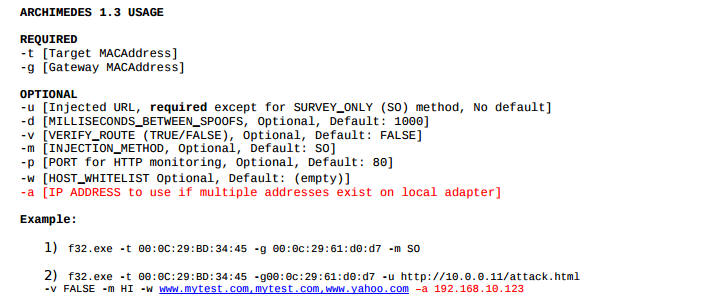
The tool in itself is very simple without any extraordinary capabilities, as there are many MitM tools available on the Internet that anyone can be download and use it to target users on the local network.
Rendition Infosec founder Jake Williams also pointed out that the tool is not even originally developed by the CIA, rather appears to be a repackaged version of Ettercap – an open source toolkit for MitM attacks.
Williams also noted that the potential CIA targets could even use the leaked information to see whether their computers had been targeted by the agency.
Last week, WikiLeaks dumped source code for a more interesting CIA tool known as "Scribbles," a piece of software allegedly designed to embed 'web beacons' into confidential documents, allowing the spying agency to track insiders and whistleblowers.
Since March the Whistleblowing website has published 7 batches of "Vault 7" series, which includes the latest and last week leaks, along with the following batches:
"Year Zero" – dumped CIA hacking exploits for popular hardware and software.
"Weeping Angel" – spying tool used by the agency to infiltrate smart TV's, transforming them into covert microphones.
"Dark Matter" – focused on hacking exploits the agency designed to target iPhones and Macs.
"Marble" – revealed the source code of a secret anti-forensic framework, basically an obfuscator or a packer used by the CIA to hide the actual source of its malware.
"Grasshopper" – reveal a framework which allowed the agency to easily create custom malware for breaking into Microsoft's Windows and bypassing antivirus protection.
Clash of Greed
6.5.2017 Kaspersky Incindent
In 2015, the game Clash of Clans was bringing in about 1.5 million dollars per day for its developer, Supercell. Later on, the company launched a new project, Clash Royale, after addressing the flaws of their first game and implementing battles with real players into the new game, which shares the same characters and the same cartoonish design as the first project. Yet, the more popular game is, the higher the probability that fraudsters will be looking to make a fortune on that popularity by, for example, organizing phishing attacks on the player base.
The money-making model for both of the games has been thoroughly thought-out: anyone can play without investing real money. But this would mean putting a lot of effort into the games and losing more often to other players who basically purchase and upgrade either rare and strong cards with extremely low drop rates or battle units and building levels (when talking about Clash of Clans). In this regard, the majority of the game’s players do not have much money but are full of ambition. These players often seek not-so-legal ways to procure and upgrade rare cards to put less effort into winning battles and ranking up to play in the premier leagues.
This has been exploited by fraudsters, who subtly abuse human foibles such as cupidity, love for freebies, and the desire to be the top player. Phishing attacks, though always quite similar in their nature, are very competently planned. Phishing websites are designed with holidays in mind (either New Year’s Eve or Christmas) or are linked to game updates that include additions to the game or changes in the game’s mechanics (new cards, units, balancing, etc.).
Here, for example, is the headline of a phishing website targeted at Clash of Clans players. It was designed specially for New Year’s Eve, and, according to the published description, the developer of the game supposedly gives out New Year’s gifts to players, including game currency, building level upgrades, etc.
The address of the website contains the phrase “eventchristmasandnewyear”, which makes the website look even more credible.
Victims can choose what they want from a list that includes gold, crystals, resources, and building upgrades.
The intention of the fraudsters becomes obvious as early as at the next step, where victims are prompted fill out a form by entering the credentials of their Google and Facebook accounts. After that, these credentials are passed on to the fraudster and the victims are robbed of both of their accounts.
The form created by the fraudsters offers “authorization” with Google and Facebook credentials
Also, fraudsters reacted quickly to the release of the latest updates, which included new battle arenas and legendary cards. On behalf of Supercell, players were offered their choice of one of the “legendaries”, as well as gold and crystals. Of course, in order to obtain these, Google and Facebook credentials were required.
One of their recent releases was “a gift from the developers”, which gives the player the option of selecting their desired hero or resources
Input fields for credentials
After sending the credentials, the victim receives a message to confirm their registration. It can be assumed that the evildoers may need this to ascertain the authenticity of the user-specified credentials.
To avoid falling victim to this fraudulent scheme, it is a good idea to follow these simple rules: do not use any links from social network groups, especially if the groups are not official, or from e-mail messages received from unknown users, even though they may promise you progress in the game or imminent profit. It certainly couldn’t hurt to install good security software that features anti-phishing functionality with database updates on malicious and phishing links that cover every subject. If the “free lunch” being offered proves to be too tempting, then go to the game developer’s official website and verify whether the holiday offer is genuine.
Macron Blasts Huge Hacking Attack Just Before French Vote
6.5.2017 securityweek CyberSpy
French presidential candidate Emmanuel Macron's team blasted a "massive and coordinated hacking attack" against his campaign after a flood of internal documents were released online late Friday, barely 24 hours before the election.
The centrist candidate's furious staff said the release of thousands of emails, accounting documents and other files was an attempt at "democratic destabilisation, like that seen during the last presidential campaign in the United States".
The documents spread on social media just before midnight on Friday -- when 39-year-old Macron and his far-right rival Marine Le Pen officially wrapped up campaigning for Sunday's election -- with his aides calling the leak "unprecedented in a French electoral campaign".
Hillary Clinton has alleged Russian hacking of her campaign's emails was partly to blame for her defeat in last year's US presidential election to Donald Trump.
The leak, posted by someone calling themselves EMLEAKS, came as an 11th-hour twist in what has proved to be one of the most drama-packed elections in French history.
Macron's team said the files were stolen weeks ago when several officials from his En Marche party had their personal and work emails hacked -- one of "an intense and repeated" series of cyber-attacks against Macron since the launch of the campaign.
"Clearly, the documents arising from the hacking are all lawful and show the normal functioning of a presidential campaign," aides said in a statement.
The WikiLeaks website posted a link on Twitter to the trove of documents, saying it was not responsible for the leak but that it was "examining" parts of the cache, amounting to around 9 gigabytes of data in total.
The hashtag #MacronLeaks swiftly began trending worldwide on Twitter.
Last month a cybersecurity research group said Russian hackers called Pawn Storm had targeted Macron's campaign.
Japan-based Trend Micro said the group had used "phishing" techniques to try to steal personal data from Macron and members of his campaign.
- Security jitters -
The upset came at the end of a frantic final day of campaigning and as fresh security concerns emerged following the arrest of a suspected extremist.
Polls released earlier Friday had showed Macron gaining momentum, forecasting victory for the pro-European, pro-business former banker with around 62 percent to 38 percent for Le Pen.
He and Le Pen -- who is hoping to ride a global wave of anti-establishment anger to the Elysee Palace -- have offered starkly different visions for France during a campaign that has been closely watched in Europe and around the world.
After a policeman was shot dead in an Islamic State-claimed attack on Paris's Champs-Elysees three days before the first election round last month, jitters rose again as police had arrested a suspected extremist near a military airbase.
Guns were discovered as well as a pledge of allegiance to IS and several of the group's flags, sources close to the case told AFP after the arrest in Evreux, north of Paris.
The suspect, a 34-year-old Muslim convert, was arrested early Friday after police found his car near the base.
In a major security breach, meanwhile, Greenpeace activists had partially scaled the Eiffel Tower to hang a giant anti-Le Pen banner saying "Liberty, Equality, Fraternity" and "#resist".
Paris police said the incident exposed "flaws" in the security surrounding the world-famous monument, and city authorities announced immediate measures to reinforce patrols at the site.
- Polar opposites -
Le Pen has tried to portray Macron as being soft on security and Islamic fundamentalism, playing to the concerns of many of her supporters after a string of terror attacks in France that have killed more than 230 people since 2015.
She has said she wants to copy Britain's example and hold a referendum on France's EU membership, sending alarm bells ringing in capitals across the bloc.
In the first round of the election, she finished second behind Macron on 21.3 percent after softening the FN's image over the past six years -- but without fully removing doubt about the party's core beliefs.
A former economy minister under Socialist President Francois Hollande, Macron is a pro-EU, pro-business and pro-trade reformer who quit the government last August to concentrate on his new political movement En Marche, which has drawn 250,000 members in 12 months.
He won high-profile backing from former US president Barack Obama on Thursday, who said in a video that Macron "appeals to people's hopes and not their fears".
WikiLeaks Details MitM Attack Tool Used by CIA
6.5.2017 securityweek BigBrothers
WikiLeaks has released documents detailing a man-in-the-middle (MitM) attack tool allegedly used by the U.S. Central Intelligence Agency (CIA) to target local networks.
The tool, initially called Fulcrum and later renamed Archimedes by its developers, can be used to conduct MitM attacks within a local area network (LAN). The leaked documents, dated between 2011 and 2014, describe it as a tool that allows the user to redirect LAN traffic from a targeted computer through an attacker-controlled machine before it’s passed on to the gateway.
“This enables the tool to inject a forged web-server response that will redirect the target’s web browser to an arbitrary location. This technique is typically used to redirect the target to an exploitation server while providing the appearance of a normal browsing session,” developers wrote in the tool’s user guide.
Jake Williams, founder of Rendition Infosec and SANS instructor, analyzed the leaked documents and determined that the tool appears to be a repackaged version of Ettercap, a popular MitM tool.
While the tool’s capabilities are not impressive, Williams pointed out that potential targets of the CIA can use the leaked information to see if their systems had been targeted by the agency.
23h
Jake Williams @MalwareJake
.@wikileaks In short, nothing to get excited about media peeps. I was talking about this capability to an entry level hacking class Wed night 5/n
Follow
Jake Williams @MalwareJake
.@wikileaks Honestly I'm more interested in how WikiLeaks tries to spin this than I am in the tool itself. 6/6
12:41 PM - 5 May 2017
Retweets 3 3 likes
A more interesting tool, including its source code, was published by WikiLeaks last week. The project, dubbed Scribbles, is designed for inserting special watermarks into documents that may be copied by insiders and whistleblowers.
The first major version of the Scribbles tool was released in March 2016 and it may have been developed by the CIA to identify people such as Edward Snowden, who in 2013 leaked a massive amount of information on the NSA’s surveillance capabilities.
WikiLeaks has already released numerous documents as part of its “Vault 7” dump. In the past weeks, the whistleblower organization has made public documents describing various tools, including ones for hacking Samsung smart TVs, a framework used to make attribution and analysis of malware more difficult, and a platform designed for creating custom malware installers.
Many of the tools are outdated and the vulnerabilities they leverage have already been patched. However, the leaked information can be very useful for entities that may have been targeted with these exploits.
In fact, researchers at Symantec and Kaspersky have found links between the tools exposed by Wikileaks and the malware used by a cyber espionage group tracked as Longhorn and The Lamberts.
Neverquest Trojan Ceases Operations
6.5.2017 securityweek Virus
Despite being the most active malware in its category last year, the Neverquest banking Trojan has disappeared from the threat landscape over the past few months, in what could be a permanent departure, IBM security researchers say.
Also known as Vawtrak, Neverquest apparently took a dive after 32-year-old Russian national Stanislav Lisov, supposedly the malware’s author, was detained in January 2017. Even so, IBM argues that this alone shouldn’t have caused the Trojan’s disappearance from the threat landscape, given that Gozi and Dridex remained active even after their developers got arrested.
Neverquest was the second most active banking Trojan in 2015, when Dyre was at the top of financial malware charts, and took the leading position last year after Dyre disappeared. In late 2016, however, new Zeus variants that were rising in underground forums managed to push Neverquest down to second rank.
After starting 2017 in second place on the financial malware chart, the Trojan ended the first quarter last on the top 10 list, after its activity dropped rapidly. Neverquest’s modus operandi and the cybergang’s composition for committing fraud, coupled with the January arrest, influenced the recent drop in activity, IBM suggests.
First discovered in 2014 as a Gozi Trojan variation that had to battle Dridex and Dyre, Neverquest is linked to organized cybercrime groups such as 76 Service and the HangUp Team, IBM asserts.
Focused on business banking and investment banking, the malware’s platform is believed to have supported geo-specific operators, with the malware calling home immediately after an infection with a specific ID to identify its campaign. This approach meant that the botnet was segmented into different campaigns, each with its specific configuration instructions.
“Neverquest, unlike the GootKit gang for example, is not one close-knit gang; it’s a service to the cybercrime elite. The minute Neverquest’s dubious collaborators saw law enforcement reach one of their trusted parties, they realized the FBI was already too close for comfort and dropped it like it was hot: campaigns delivering the Neverquest Trojan dropped considerably on Jan. 19, 2017, just a few days after Lisov’s arrest in Spain,” IBM’s Limor Kessem explains.
What remains to be seen, however, is whether Neverquest is gone for good or just taking a vacation of sorts, given its connection to longstanding cybercrime groups dating back to the year 2000. One possibility, IBM says, is that the group has decided to shift away from this malware to evade the attention from law enforcement. However, they could also consider reactivating it, modifying it, or even selling it to a different group.
One threat to keep an eye on at the moment, IBM says, is the Sphinx Trojan, which has been rising rapidly and is expected to grow further before year’s end. Apparently, Neverquest was outsourcing distribution to the Moskalvzapoe Network, which switched to dropping Zeus Sphinx Trojan via Terdot in January.
Netrepser Cyber espionage campaign compromised hundreds of Government organizations worldwide
6.5.2017 securityaffairs CyberSpy
Experts from Bitdefender have uncovered the Netrepser Cyber espionage campaign that compromised more than 500 Government organizations worldwide.
Security experts at Bitdefender uncovered a cyber espionage campaign that leverages a strain of malware dubbed Netrepser to target government organizations.
Netrepser Trojan samples were first discovered by the Bitdefender in May 2016, according to experts the analysis of the command and control (C&C) servers confirms that the malware had infected more than 500 computers, mainly government agencies.
The malware researchers haven’t found any evidence linking this cyber campaign to threat actors previously analyzed.
The Netrepser Trojan allows attackers to collect system information on the target system, record keystrokes, and to steal email and instant messaging passwords, session cookies and passwords from web browsers.
“Paired with advanced spear phishing techniques and the malware’s primary focus to collect intelligence and exfiltrate it systematically, we presume that this attack is part of a high-level cyber-espionage campaign,” states the report published by Bitdefender. “The piece of malware we look at in this report comes with quite an array of methods to steal information, ranging from keylogging to password and cookie theft. “

The malware used in the campaign was built around a legitimate recovery toolkit provided by Nirsoft, the malicious code leverages the Nirsoft email and instant messaging password recovery tools to steal email and IM passwords. The Netrepser Trojan also uses another Nirsoft utility to steal passwords stored in browsers.
The malware used other legitimate tools such as the Sysinternal SDelete utility to delete files to prevent the recovery of forensic evidence and WinRAR to compress stolen data before sending it to the C&C.
The threat actors delivered the malware via spear-phishing emails that use weaponized documents. The documents embed macros to deliver the final payload in the form of JavaScript or JavaScript Encoded files.
One of the decoy documents was titled “Russia Partners Drafting guidelines (for directors’ discussion),” researchers also observed messages using files with Russian names that translated to “installation” and “Ural.”
“The message purportedly comes from a Donald Spencer, who, according to this LinkedIn profile, is currently the Managing Director of Siguler Guff, Siguler Guff is a multi-strategy private equity investment firm which, by their own account, has over $11 billion of assets under management. Their real-estate portfolio spans from Mumbai to Moscow, where Drew Guff actually gave a speech at St. Petersburg International Economic Forum in June ‘16.” reads the analysis. “The headers reveal that the email originates from an inbox called piskulov@rp.co.ru. Attached to the message is a DOC file containing a Visual Basic macro. If opened, the document would ask the user to enable macros in order to execute the dynamic content which would subsequently drop a JavaScript or JavaScript Encoded file to act as final payload. “
Bitdefender hasn’t made any hypothesis about the threat actor behind the campaign, the experts only highlighted that some file paths used by the Trojan are also written in Cyrillic script.
“Because of the nature of these attacks, attribution is impossible unless we dig into the realm of speculation. Our technical analysis, however, has revealed that some documents and file paths this campaign is using are written in Cyrillic” concluded Bitdefender.
WikiLeaks leaked documents that detail the Archimedes tool used by the CIA in MitM attacks
6.5.2017 securityaffairs BigBrothers
WikiLeaks has released a news batch of documents detailing the Archimedes tool, a MitM attack tool allegedly used by the CIA to target LAN networks.
WikiLeaks has released a news batch of documents detailing a man-in-the-middle (MitM) attack tool dubbed Archimedes allegedly used by the CIA to target local networks.
The leaked documents, dated between 2011 and 2014, provide details about a tool initially codenamed Fulcrum and later renamed Archimedes by the development team.

The CIA hacking tool that allows the operators to redirect LAN traffic from a targeted computer through a machine controlled by the attackers before it is routed to the gateway.
“Archimedes is an update to Fulcrum 0.6.1.” reads the Archimedes Tool Documentation. “Archimedes is used to redirect LAN traffic from a target’s computer through an attacker controlled computer before it is passed to the gateway. This enables the tool to inject a forged webserver response that will redirect the target’s web browser to an arbitrary location. This technique is typically used to redirect the target to an exploitation server while providing the appearance of a normal browsing session. For more tool information please refer to the original Fulcrum 0.6.1 documentation.”
According to the SANS instructor Jake Williams who analyzed the leaked documents, the Archimedes tool seems to be a repackaged version of popular MitM tool Ettercap.
Follow
Jake Williams @MalwareJake
The new dump by @wikileaks, FULCRUM, appears to be nothing more than a repackaged ettercap. Honestly nothing to write home about 1/n
12:34 PM - 5 May 2017
5 5 Retweets 3 3 likes
CIA alleged targets can use the leaked information about the Archimedes tool to check if their systems had been compromised by the US Intelligence.
Potential victims can search for these hashes on their systems.

Archimedes introduced several improvements respect the Fulcrum tool such as:
Support disabling the route verification check that occurs prior to exploitation.
Add support for a new HTTP injection method based on using a hidden IFRAME.
Modify the DLLs to support the Fire and Forget specification (version 2).
Provide a method of gracefully shutting down the tool on demand.
Removes the most alerting strings from the release binaries.
The tool itself is not sophisticated, it could be interesting to understand how CIA agents did use it in targeted attacks.
Beware! Don't Fall for FireFox "HoeflerText Font Wasn't Found" Banking Malware Scam
5.5.2017 thehackernews Virus
The malicious scam campaign, "The 'HoeflerText' font wasn't found," is back, which was previously targeting Google Chrome users to trick them into installing Spora ransomware on their computers.
This time the campaign has been re-designed to target Mozilla Firefox users with a banking trojan, called Zeus Panda.
Interestingly, the attackers behind this new campaign are so stupid that they forgot to change the name of the font, i.e. HoeflerText, due to which it was easily caught by Kafeine, a security researcher at Proofpoint.
As I previously warned — Next time when you accidentally land up on a suspicious website with jumbled content prompting to update the Firefox or Chrome font pack by downloading a missing text font to read the article… Just don't download it. It's obviously a trap.
Just like the previous one, the latest Firefox 'HoeflerText font wasn't found scam is also very convincing and easy to fall for.
The attack initiates with an alert message, which states that "The 'HoeflerText' font was not found," asking Firefox users to update their "Mozilla Font Pack."
Once clicked, it downloads a ZIP file (Mozilla_Font_v7.87.zip) on the victim’s system, containing a JavaScript file. Meanwhile, the screen will display a set of instructions, asking victims to run the JS file in order to install the missing "Mozilla Font Pack."
If the victims turned out to be so stupid that they run the JS file themselves, as instructed, the program will download the malware payload (.exe) from a remote server and then runs it automatically, injecting the Zeus Panda banking Trojan into the infected systems.
Panda is an online banking trojan that was initially found to be targeting banks in Europe and North America early last year and then started spreading itself to Brazil through at least three different exploit kits, including Angler, Nuclear, and Neutrino.
Once it infects a system, the Zeus Panda banking trojan contacts its command and control (C&C) server to send the infected device information, including a list of installed antivirus and firewall products.
Panda focuses on stealing banking credentials from users, as well as those of bitcoin exchanges, payment card services and online payments providers, prepaid cards, airline loyalty programs and online betting accounts, to name a few.
To protect yourself from such scams, always exercise caution when downloading anything from the Internet onto your computers. Moreover, keep your antivirus up-to-date and do not ever fall for scam asking you to update your Mozilla or Chrome font pack, as it already comes with everything you need.
Unpatched Wordpress Flaw Could Allow Hackers To Reset Admin Password
5.5.2017 thehackernews Vulnerebility
WordPress, the most popular CMS in the world, is vulnerable to a logical vulnerability that could allow a remote attacker to reset targeted users’ password under certain circumstances.
The vulnerability (CVE-2017-8295) becomes even more dangerous after knowing that it affects all versions of WordPress — including the latest 4.7.4 version.
The WordPress flaw was discovered by Polish security researcher Dawid Golunski of Legal Hackers last year in July and reported it to the WordPress security team, who decided to ignore this issue, leaving millions of websites vulnerable.
"This issue has been reported to WordPress security team multiple times with the first report sent back in July 2016. It was reported both directly via security contact email, as well as via HackerOne website," Golunski wrote in an advisory published today. "As there has been no progress, in this case, this advisory is finally released to the public without an official patch."
Golunski is the same researcher who discovered a critical vulnerability in the popular open source PHPMailer libraries that allowed malicious actors to remotely execute arbitrary code in the context of the web server and compromise the target web application.
The vulnerability lies in the way WordPress processes the password reset request, for the user it has been initiated.
In general, when a user requests to reset his/her password through forgot password option, WordPress immediately generates a unique secret code and sends it to user’s email ID already stored in the database.
What's the Vulnerability?
While sending this email, WordPress uses a variable called SERVER_NAME to obtain the hostname of a server to set values of the From/Return-Path fields.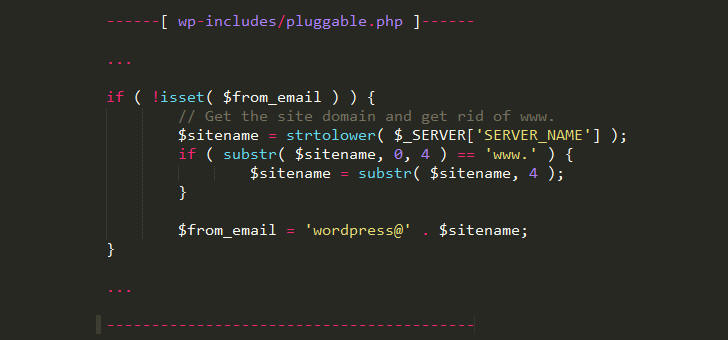
Here, "From" refers to the email address of the sender and "Return-Path" refers to the email address where 'bounce-back' emails should be delivered in the case of failure in the delivery for some reason.
According to Golunski, an attacker can send a spoofed HTTP request with a predefined custom hostname value (for example attacker-mxserver.com), while initiating password reset process for a targeted admin user.
Since the hostname in the malicious HTTP request is an attacker-controlled domain, the From and Return-Path fields in the password reset email will be modified to include an email ID associated with the attacker's domain, i.e. wordpress@attacker-mxserver.com, instead of wordpress@victim-domain.com.
"Because of the modified HOST header, the SERVER_NAME will be set to the hostname of attacker's choice. As a result, Wordpress will pass the following headers and email body to the /usr/bin/sendmail wrapper," Golunski says.
Don't get confused here: You should note that the password reset email will be delivered to victim's email address only, but since the From and Return-Path fields now point to attacker's email ID, the attacker can also receive reset code under following scenarios:
If, in case, the victim replies to that email, it will be delivered to attacker email ID (mentioned in 'From' field), containing a password reset link in the message history.
If, for some reason, victim's email server is down, the password reset email will automatically bounce-back to the email address mentioned in "Return-Path" field, which points to the attacker's inbox.
In another possible scenario, to forcefully retrieve bounce-back email, the attacker can perform a DDoS attack against the victim's email server or send a large number of emails, so that the victim's email account can no longer receive any email.
"The CVE-2017-8295 attack could potentially be carried out both with user interaction (the user hitting the 'reply' button scenario), or without user interaction (spam victim's mailbox to exceed their storage quota)," Golunski told The Hacker News in an email.
For obvious reason, this is not a sure shot method, but in the case of targeted attacks, sophisticated hackers can manage to exploit this flaw successfully.
Another notable fact on which successful exploitation of this flaw depends is that, even if WordPress website is flawed, not all web servers allow an attacker to modify hostname via SERVER_NAME header, including WordPress hosted on any shared servers.
"SERVER_NAME server header can be manipulated on default configurations of Apache Web server (most common WordPress deployment) via HOST header of an HTTP request," Golunski says.
Since the vulnerability has now been publically disclosed with no patch available from the popular CMS company, WordPress admins are advised to update their server configuration to enable UseCanonicalName to enforce static/predefined SERVER_NAME value.
An Army of Thousands of Hacked Servers Found Mining Cryptocurrencies
5.5.2017 thehackernews BotNet
A new botnet consisting of more than 15,000 compromised servers has been used to mine various cryptocurrencies, earning its master around $25,000 per month.
Mining cryptocurrencies can be a costly investment, as it requires an enormous amount of computing power, but cybercriminals have found an easy money-making solution.
Dubbed BondNet, the botnet was first spotted in December 2016 by GuardiCore researchers, who traced back the botnet malware developer, using online handle Bond007.01, to China.
According to the GuardiCore researchers, Bond007.01 is currently using BondNet for mining cryptocurrencies — primarily Monero, but also ByteCoin, RieCoin, and ZCash — but they warn that the hacker could easily take full control of compromised servers for malicious purposes, like mounting Mirai-style DDoS attacks.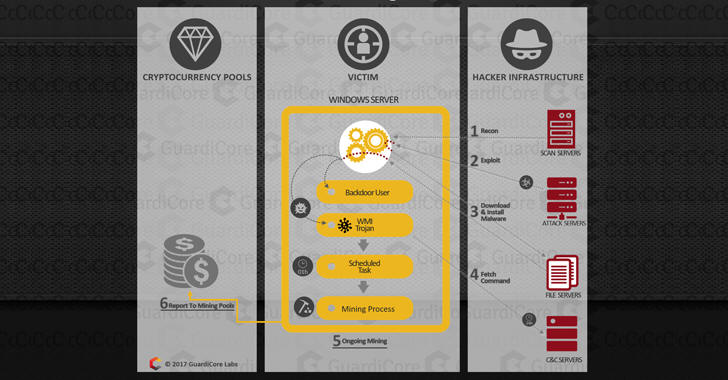
BondNet Attacks only Windows Server Machines
Since mining cryptocurrencies require large amounts of CPU/GPU power, the botnet master goes after Windows Server machines; instead of consumer IoT devices.
However, in order to compromise Windows Server machines, the botnet master relies on different attack techniques. Researchers say the hacker uses a combination of old vulnerabilities and weak user/password combinations to attack mostly old and unsupported Windows Server machines.
The most common flaws exploited by the botnet operator include known phpMyAdmin configuration flaws, exploits in JBoss, and bugs in Oracle Web Application Testing Suite, MSSQL servers, ElasticSearch, Apache Tomcat, Oracle Weblogic, and other services.
Once the hacker gain access to a Windows Server machine, he deploys Visual Basic files to gather information about the infected system and then install a Remote Access Trojan (RAT) and a cryptocurrency miner to make a huge profit from the hacked servers.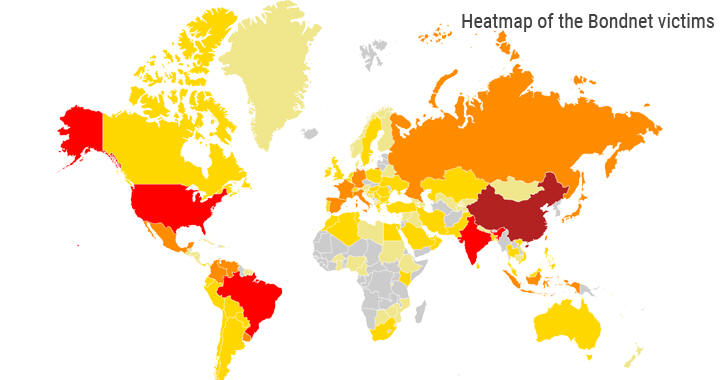
BondNet's Botnet Infrastructure
One thing that's worth noticing is that the botnet operator does not use all infected machines for mining cryptocurrencies. The operator has built its botnet infrastructure of compromised servers with various roles:
1. Some infected machines serve as scanning servers to check for vulnerable systems on the Internet by going through a list of IP addresses with open ports that have been compiled with the WinEggDrop TCP port scanner.
2. Some servers are used as file servers to host the mining software.
3. Other infected servers are turned into command-and-control (C&C) servers after they have been equipped with a fork of goup — a small open source HTTP server written in Golang.
"Building an attack infrastructure on top of victim machines helps conceal the attacker’s true identity and origin of the attack," the GuardiCore researchers explained in their report published Thursday.
"It also provides high availability infrastructure, which is very helpful when relying on compromised servers, providing infinite backup options in case one of the servers fails or loses connectivity to the internet."
BondNet has already infected more than 15,000 server machines at major institutions around the world, including high-profile global companies, universities, and city councils, while the majority of them runs Windows Server 2008 R2.
Additionally, the BondNet botnet adds around 500 new machines to its network each day, and an approximately the same number of servers are delisted.
Here's How to Detect the Threat and How to Mitigate:
To prevent your machines from getting hacked, server admins are advised to secure their systems by regularly applying security patches for all software, updating the firmware, and employing stronger passwords.
Meanwhile, GuardiCore has also provided network and file indicators of compromise systems to help server administrators check whether their machines are among compromised ones.
The researchers have also released a detection & cleanup tool (registration is required to download it) to help admins find and remove BondNet bots from their servers, as well as instructions on how to clean the system manually, without using the script.
The Snake APT Group is preparing its offensive against high-profile Mac users
5.5.2017 securityaffairs APT
According to experts from the Fox-IT firm, the notorious Russian Snake APT group is ready to target also Mac users with a new variant of its malicious code.
The sophisticated Russian Snake APT group is back and is leveraging on new malware to target Mac users.The Snake APT group, also known as Turla or Uroburos, has ported its Windows backdoor to macOS.
The cyber espionage crew has been active since at least 2007, the hackers launched several high-profile attacks against targets worldwide, including the ones aimed at Swiss defense firm RUAG and the U.S. Central Command.

The hackers targeted government entities, embassies, military organizations, research and academic institutions, large corporations and also intelligence agencies.
“Researchers who have previously analyzed compromises where Snake was used have attributed the attacks to Russia. Compared to other prolific attackers with alleged ties to Russia, such as APT28 (Fancy Bear) and APT29 (Cozy Bear), Snake’s code is significantly more sophisticated, it’s infrastructure more complex and targets more carefully selected.” reads the analysis published by the security firm Fox-IT.
“The framework has traditionally focused on the Windows operating system, but in 2014 the first Linux variant was observed. Now, Fox-IT has identified a version of Snake targeting Mac OS X.”
According to the experts, the malicious code used by the Snake APT group is more sophisticated than the ones used by other Russian threat actors, including the notorious APT 28 and APT29.
“Compared to other prolific attackers with alleged ties to Russia, such as APT28 (Fancy Bear) and APT29 (Cozy Bear), Snake’s code is significantly more sophisticated, it’s infrastructure more complex and targets more carefully selected,” said the researchers.
The Snake malware was originally developed to target Windows systems, later in 2014, malware experts from Kaspersky Lab spotted a Linux variant of the malicious code.
The Fox-IT researchers recently spotted a macOS version of the Snake malware that still included artefacts referencing Microsoft’s Internet Explorer in the code, a circumstance that confirms it is a porting from the Windows version. The Russian hackers are improving their arsenal to target Apple users.
The researchers believe the malware is in a testing phase because they haven’t seen the macOS sample being distributed in the wild.
“Several strings found throughout the binary indicate that this version is in fact a debug build”
The Snake macOS sample discovered by the malware researchers at Fox-IT masquerades as a Flash Player installer and is signed with a legitimate Apple code signing certificate, likely stolen by the APT. It obtains persistence via Apple’s LaunchDaemon service.
“The Snake binary comes inside of a ZIP archive named Adobe Flash Player.app.zip which is a backdoored version of Adobe’s Flash Player installer.” continues the analysis.
Fox-IT reported its discovery to the Apple security team.
Carbanak Hackers Use Shims for Process Injection, Persistence
5.5.2017 securityweek Virus
Recent attacks associated with the financially-motivated threat group FIN7 were using an application shim database to achieve persistence on systems, FireEye security researchers discovered.
The actor, also referred to as the “Carbanak Group,” has been active since 2015, and was associated with multiple incidents in 2017, in some of which the Carbanak backdoor was used. The group is believed to have hit hundreds of financial organizations worldwide, and to have stolen upwards of $1 billion.
Earlier this year, FIN7 was observed using a new PowerShell backdoor dubbed POWERSOURCE in a series of fileless attacks that were eventually associated with an attack framework used by other cybercriminals. Last month, the group was said to have adopted new phishing techniques.
FireEye now says that the group is using a "shim" to inject a malicious in-memory patch into the Services Control Manager (“services.exe”) process, and then spawn a Carbanak backdoor process. The same technique is used to install a payment card harvesting utility for persistent access, the security firm said.
Shims are small patches that application developers can create through the Windows Application Compatibility Infrastructure, and are mainly used for compatibility purposes for legacy applications. Designed for legitimate use, shims can intercept APIs (via hooking), change the parameters passed, handle the operation itself, or redirect the operation elsewhere, and can be abused for malicious purposes.
As part of their attack, the FIN7 hackers used a custom Base64 encoded PowerShell script to run the sdbinst.exe utility and register a custom shim database file (SDB) containing a patch. Next, they wrote an “.sdb” file to the 64-bit shim database default directory, and create specific registry keys for the shim database, which had the description “Microsoft KB2832077.”
The SDB file could patch both the 32-bit and the 64-bit versions of “services.exe” with the Carbanak payload when the process was executed at startup and contained shellcode for the first stage loader. This linked to a second stage shellcode that launched the Carbanak DLL, which spawned an instance of Service Host (svchost.exe) and injected itself into it.
To stay protected, organizations are advised to monitor their environments for new shim database files created in the default shim database directories (C:\Windows\AppPatch\Custom and C:\Windows\AppPatch\Custom\Custom64) and for registry key creation and/or modification events for HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\AppCompatFlags\Custom and HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\AppCompatFlags\InstalledSDB. They should also monitor process execution events and command line arguments for malicious use of the sdbinst.exe utility, FireEye said.
Authorities Take Down Darknet Marketplace
5.5.2017 securityweek CyberCrime
Europol announced Thursday that it had assisted the Slovak NAKA crime unit in the arrest of a Slovak national believed to operate a small darknet marketplace dealing in drugs and arms. The individual is in police custody, and several of his premises have been searched.
"In one of the locations searched," says the Europol statement, "Slovak authorities discovered and seized five firearms and approximately 600 rounds of ammunition of different calibres. The investigators also found a sophisticated indoor cannabis plantation, 58 cannabis plants and a Bitcoin wallet containing bitcoins worth EUR 203 000, which is thought to have been obtained from illegal online activities."
An associated video shows armed Slovak NAKA personnel dragging an individual from a motor vehicle, and subsequently searching premises. Several of the individual's premises have been searched. The server used to run the marketplace has been seized and is being forensically examined. "Slovak authorities and Europol have extended the investigation into the users and vendors who utilised the marketplace," states Europol.
There are some suggestions on Twitter that the marketplace concerned is Bloomsfield. Darknet Markets describes Bloomsfield as a "Market started as the vendor shop of the vendor 'Biocanna' and later expanded to server other vendors. Offers Multisig transactions and low fees. The site itself does not look that poor, it is built to look clean and easy to navigate, but the lack of any added security measures and limited range of products to choose from makes it look like a bad place to do business on."
Deep.dot.web currently reports Bloomsfield as "Down from unknown reason – Market started as the vendor shop of the vendor 'Biocanna' / Thcsupport (Note – Using Bitwasp) and later expanded to server other vendors. Offers Multisig transactions and low fees."
It seems that Biocanna was originally a cannabis supplier on the Silk Road who later established his own marketplace; not apparently very successfully. 'C' has posted a conversation snippet on Twitter concerning the 'owner of the failing Bloomsfield market.'
It includes, "It is obvious you have no clue about security or cryptography or even basic understanding of the linux gpg package. Oh wait, you also expose all your users and their pgp keys by allowing anyone to download the public key ring..."
If it is indeed the Bloomsfield server that has been seized and is being analyzed, and its security is lax as that suggested, it is likely to lead Europol to other illegal product suppliers. Europol's announcement already comments, "a crosscheck performed during the house searches generated a hit on Europol's databases which helped investigators identify a Darknet vendor living in another EU country. The individual was suspected of supplying one of the firearms found during the house searches in Bratislava."
Europol notes that "The online trade in illegal firearms has expanded to the extent that nowadays it is considered a key facilitator for firearms trafficking." Its Serious and Organized Threat Assessment 2017 report (PDF) explains, "There is a shift from sales on the surface web to sales on the Darknet, typically when the status of a product or substance changes from being legal to illegal. For example, the sales of gun parts or de-activated firearms is legal in certain jurisdictions and therefore available on the surface web, but when the gun is assembled or re-activated it is illegal and will be sold on the Darknet."
Europol's concern is that darknet trade in illegal firearms can fuel real world terrorist activity in Europe.
Blackmoon Banking Trojan Continues to Target South Korea
5.5.2017 securityweek Virus
Cybercriminals have continued to use the Blackmoon banking Trojan to target individuals in South Korea, and the malware is now being delivered via a new framework that helps evade detection.
Blackmoon, also known as KRBanker and Banbra, has been around since at least 2014 and its main goal is to steal online banking credentials from users in South Korea. Just over one year ago, Fortinet researchers reported that the malware had infected the systems of more than 100,000 of the country’s users.
Fidelis Cybersecurity reported on Thursday that it had observed two separate Blackmoon campaigns since late 2016, and they relied on a new framework that researchers have named the Blackmoon Downloader Framework.
The framework is designed to download several components over three stages, and it ensures that the malware is only delivered to users in South Korea.
According to experts, the attack starts with an initial downloader that is under 10 Kb in size. This downloader can execute any code on the infected machine, essentially creating a backdoor, but it serves a simple purpose – downloading and executing a bytecode downloader.
In the second stage, the bytecode downloader fetches a PE file disguised as a harmless JPG image. This fake image file, dubbed by Fidelis “KRDownloader,” is responsible for downloading the actual Blackmoon payload. The KRDownloader component is also designed to ensure that the infected system’s language is set to Korean. If the language is not Korean, the bot terminates.
“The framework is tightly coupled and designed to operate in sequence to facilitate multiple objectives, including evasion as well as geolocation targeting,” Fidelis said in a blog post. “The multistage downloader serves a practical purpose: It is another tactic used presumably to avoid detection, as functionality is distributed between these separate (but related) components.”
Blackmoon is designed to target a long list of websites, including ones belonging to top financial organizations in South Korea, such as Citibank Korea, Hana Bank, KB, Shinhan Bank, Woori Bank, Standard Chartered and Samsung Card.
The malware uses a technique known as “pharming” to gather valuable data. When victims access one of the targeted sites from an infected machine, they are redirected to a fake website where they are instructed to provide their credentials and other information.
Security firms previously reported that cybercriminals had used various methods to deliver the Blackmoon Trojan, including adware and exploit kits.
Government Organizations Targeted in "Netrepser" Attacks
5.5.2017 securityweek CyberSpy
A report published by Bitdefender on Friday details a previously undocumented cyber espionage campaign that leverages a piece of malware dubbed “Netrepser” to target government organizations.
The first Netrepser malware samples were discovered by the security firm in May 2016. No information has been shared on the location of the targets, but researchers determined, based on data from the threat’s command and control (C&C) infrastructure, that the malware had infected more than 500 machines. Most of the victims are government agencies.
Bitdefender told SecurityWeek that the attacks are ongoing, and the company has not found any evidence linking this campaign to other threat actors.
The Netrepser Trojan is mainly designed for intelligence gathering, and it allows attackers to collect system information, email and instant messaging passwords, session cookies and passwords from web browsers, and keystrokes.
“Paired with advanced spear phishing techniques and the malware’s primary focus to collect intelligence and exfiltrate it systematically, we presume that this attack is part of a high-level cyber-espionage campaign,” Bitdefender said in its report.
Researchers pointed out that while the attack is complex, the Netrepser malware relies heavily on free tools to carry out various tasks. Experts determined that much of its functionality is provided by a controversial recovery toolkit from Nirsoft, which many antimalware vendors have flagged due to the fact that it can easily be abused for malicious purposes.
For example, Nirsoft email and instant messaging password recovery tools are used by the Netrepser malware to steal email and IM passwords. Another Nirsoft utility is used by the Trojan to steal passwords stored in browsers.
The list of legitimate tools abused by Netrepser also includes WinRAR, used to compress stolen data before exfiltration, and SDelete from Sysinternals, which is used to delete files likely in an effort to prevent the recovery of forensic evidence. Researchers noted that nearly all third-party tools used in these attacks are packed with what appears to be a custom packer.
According to Bitdefender, the Netrepser malware is delivered via spear-phishing emails that carry malicious documents.
One of the documents was titled “Russia Partners Drafting guidelines (for directors’ discussion),” but researchers also found files with Russian names that translated to “installation” and “Ural.” The malicious documents leverage macros to deliver the final payload in the form of JavaScript or JavaScript Encoded files.
The English-language document appeared to have been sent by Donald Spencer, a managing director of private equity investment firm Siguler Guff. One of the company’s founding partners, Drew Guff, gave a speech last year at the St. Petersburg International Economic Forum.
While Bitdefender has refrained from making any statement on attribution, the company pointed out that, in addition to documents, some file paths used by the malware are also written in Cyrillic script.
Podvodníci se snaží napálit klienty Komerční banky
5.5.2017 Novinky/Bezpečnost Phishing
Na pozoru by se měli mít uživatelé internetového bankovnictví od Komerční banky. Zaměřili se na ně totiž počítačoví piráti, kteří se z nich prostřednictvím nevyžádaných e-mailů snaží vylákat jejich přihlašovací údaje. Před novým podvodem varovali zástupci banky.
„V současné době pozorujeme zvýšený výskyt podvodných e‑mailů,“ uvedli zástupci Komerční banky.
Podle nich se podvodníci snaží v příjemcích podvodné zprávy vzbudit dojem, že jde o oficiální komunikaci banky. „Útočník vystupuje jménem ředitele společnosti a kontaktuje pracovníka firmy, který má přístup k firemním financím a oprávnění provádět bankovní převody,“ přiblížili jednání počítačových pirátů bankéři.
„Nejprve se dotáže na stav účtu a pak předá pokyn k urgentnímu proplacení částky do zahraničí. Na závěr se ujistí o výsledku zpracování. V e‑mailu je použita nekorektní čeština a může být použit popis platby Administrativní seminár,“ konstatovali pracovníci banky.
Podobné e-maily raději ignorovat
Podvod tedy pozornější uživatelé mohou rozpoznat na první pohled, jednoduše podle toho, že není napsán správně česky. Není nicméně vyloučeno, že se v další vlně objeví podvodné zprávy, ve kterých již budou mít kyberzločinci všechny chyby vychytané.
Vhodné je tak všechny podobné nabídky ignorovat, a pokud si uživatel není jistý, tak raději svou banku kontaktovat napřímo – buď osobně, nebo telefonicky.
„V případě, že jste podezřelý e‑mail obdrželi, neprodleně kontaktujte naši telefonní linku internetového bankovnictví +420 955 551 552 nebo nám napište na mojebanka@kb.cz,“ uzavřeli zástupci banky.
Podobně by měli uživatelé postupovat také v případě, že jim podezřelá zpráva přijde pod hlavičkou úplně jiné banky či nějaké finanční instituce.
Threat actors leverage the KONNI Malware to target organizations linked to North Korea
5.5.2017 securityaffairs Virus
Cisco Talos team discovered a RAT dubbed KONNI malware that target organizations linked to North Korea. Here you are an analysis of its evolution.
Security researchers at Cisco Talos team have discovered a remote access Trojan (RAT) that target organizations linked to North Korea.
The malware, dubbed by researchers “KONNI,” was undetected for more than 3 years and was used in highly targeted attacks. It was able to avoid detection due to a continuous evolution, the recent versions capable of executing arbitrary code on the target systems and stealing data.
“Talos has discovered an unknown Remote Administration Tool that we believe has been in use for over 3 years. During this time it has managed to avoid scrutiny by the security community. The current version of the malware allows the operator to steal files, keystrokes, perform screenshots, and execute arbitrary code on the infected host. Talos has named this malware KONNI. ” states the analysis published by Talos.
According to Talos, several campaigns leveraged the KONNI malware this piece of malware over the past years. The first attacks observed by Talos are likely launched in September 2014, threat actors used an SRC file as a dropper for two other files: a picture that served as a decoy and the KONNI executable.
The 2014 campaign involved a variant of the KONNI malware that was designed to be executed only once and steal information from the targets (i.e. keystrokes, clipboard content, and data associated with the Chrome, Firefox and Opera web browsers).
Another campaign associated with the malware was observed in 2016. In this case, attackers involved an SRC file, but this time it dropped two office documents.
The dropped library was compiled in 2014 and was observed by Talos in August 2015, a circumstance that indicates that the library was probably used in another campaign.
“The .src file contains 2 Office documents. The first document was in English and a second in Russian. In the sample only the English version can be displayed to the user (that is hardcoded in the sample)” continues the analysis.
The decoy documents, titled “N. Korean hydrogen bomb can wipe out Manhattan: propaganda outlet,” referenced the tension between North Korea and the US, and they were titled “N. Korean hydrogen bomb can wipe out Manhattan: propaganda outlet.”
The 2016 attacks used a malware with a different architecture and implemented a new set of features that allowed attackers to upload and download files, and execute arbitrary commands on the infected system.
The KONNI malware was also used in at least two campaigns in 2017. Threat actors used a decoy document titled “Pyongyang e-mail lists – April 2017” and it contained the email addresses and phone numbers of individuals working at organizations such as the United Nations, UNICEF and embassies linked to North Korea.
Hackers also used a second decoy document, titled “Inter Agency List and Phonebook – April 2017” contained names and contact information for members of agencies, embassies and other organizations linked to North Korea.
“The last identified campaign where KONNI was used was named Inter Agency List and Phonebook – April 2017 RC_Office_Coordination_Associate.src. This file drops exactly the same files than the previous campaign but the decoy document is different:”

“This document contains the name, phone number and email address of members of agencies, embassies and organizations linked to North Korea.”
The variant of the malware used in the last campaign added further features, such as the ability to collect system information and to capture screenshots. The author has developed a 64-bit version of the malware. The latest campaign leveraging the KONNI malware is still ongoing.
It is interesting to note that 3 of the 4 campaigns analyzed by Cisco Talos were aimed at organizations linked to North Korea, this circumstance suggests the state was the first target of the threat actors.
Hackers are stealing money from Bank accounts in Germany by exploiting flaws in #SS7 protocol
5.5.2017 securityaffairs Mobil
The company O2-Telefonica in Germany has confirmed to Süddeutsche Zeitung agency that some of its customers suffered cyber heists exploiting the SS7 flaws.
Security experts have been warning for years about security vulnerabilities affecting the SS7 protocol widely adopted in mobile communications.
SS7, aka Signalling System No. 7, is a set of protocols used in telecommunications ever since the late 1970s, enabling smooth transportation of data without any breaches.
The flaws could be used by hackers to spy on targets by redirecting incoming calls, to track a phone’s location, and text messages to their devices.
Attacks exploiting vulnerabilities in the SS7 protocols could allow attackers to bypass any authentication process of principal web services (e.g. Facebook, WhatsApp) that leveraging on SMSs to identify the users.
In December 2014, a group of German researchers at the Chaos Communication Hacker Congress revealed the existence of serious security issues in the protocol used by a large number of carriers of mobile telephony. Despite the huge investment in security made by telco companies, the adoption of flawed protocols exposes customers to serious privacy and security risks.
“It’s like you secure the front door of the house, but the back door is wide open,” said Tobias Engel, one of the German researchers.

Figure 1 – Tobias Engel Slides presented at CCC Berlin
What does the network know about your location?
Tobias explained that the network knows the location of the cell tower that could be used to have a pretty good approximation of a user’s location. Despite the access to the information managed by operators is restricted to the technical operation of the network, voice calls, and short messages can be initiated to your phone number from almost anywhere in the global SS7 network.

Figure 2 – Tobias Engel Slides presented at CCC Berlin
Attacks relying on these security issues already happened in the past, one of the major incidents was registered by the NKRZI (which is the National Commission for the State Regulation of Communications and Informatization in Ukraine) and involved Russian addresses back in April 2014.
The expert noticed that many Ukrainian mobile phone holders have been targeted by SS7 packets sent from Russia to track them and steal information from the mobile devices.
Back to the present, security experts are observing the first massive hacking campaign exploiting the design flaws in the SS7 protocol to drain bank accounts. Multiple sources confirmed that hackers used this technique in the past few months.
The company O2-Telefonica in Germany has confirmed to Süddeutsche Zeitung agency that some of its customers suffered cyber heists exploiting the SS7 flaws to bypass SFA authentication mechanisms.
Hackers exploited the vulnerabilities in the SS7 protocol to intercept authentication code sent by the banking services to the customers using the two-factor authentication process.
Hackers exploited a two-factor authentication system of transaction authentication numbers used by sine German banks. The attackers first conducted a spam campaign to deliver a malware on the bank customers PC in order to collect financial information (the bank account balance, login credentials, and the mobile number).
Then hackers purchased access to a rogue telecommunications provider and set up a redirect for the victim’s mobile phone number to a handset controlled by the attackers.
At night time crooks logged into victims’ bank accounts and drained them exploiting the SS7 flaws to access the account and authorize the fraudulent transactions.
This is the first publicly confirmed attack exploiting the design flaws in the SS7 protocol in Europe.
Which is a possible solution?
Telco experts propose a replacement for SS7 on 5G networks, dubbed the Diameter protocol, unfortunately also this protocol is affected by critical security holes.
Security researchers discovered that Diameter is also affected by security issues, one of them is the lack of mandatory implementation of the Internet Protocol Security (IPsec) protocol.
According to researchers from Nokia Bell Labs and Aalto University in Finland, this means that Diameter could be hacked with the same techniques that are effective against SS7.
Last year, the team of experts made several tests to evaluate attacks against users connected to the LTE network. They simulated the attacks on a test network set up by an unnamed global mobile operator. In the tests, they powered a cyber attack against UK subscribers from Finland and discovered several methods of disrupting service to users.
The researchers were able to temporarily and permanently shut down users connections, they were also able to target entire regions.
Security researcher disclosed a WordPress Password Reset Vulnerability
5.5.2017 securityaffairs Vulnerebility
A researcher reported a WordPress Password Reset vulnerability, tracked as CVE-2017-8295, and detailed it in a security advisory.
On Wednesday, the popular security experts Dawid Golunski reported a WordPress Password Reset vulnerability, tracked as CVE-2017-8295, and detailed it in a security advisory.
Golunski classified the flaw as a “medium/high severity,” he explained that the issue is caused by the fact that WordPress uses a variable named SERVER_NAME to obtain the hostname of a server when setting the From/Return-Path header in password reset emails sent to users.
The value of the SERVER_NAME variable is often set using the hostname supplied by the client via the HTTP_HOST header, Golunski discovered that an attacker can inject an arbitrary domain by sending a specially crafted request to the targeted WordPress website.
“WordPress is using SERVER_NAME variable to get the hostname of the server in order to create a From/Return-Path header of the outgoing password reset email. However, major web servers such as Apache by default set the SERVER_NAME variable using the hostname supplied by the client (within the HTTP_HOST header): https://httpd.apache.org/docs/2.4/mod/core.html#usecanonicalname” reads the security advisory.
“Because SERVER_NAME can be modified, an attacker could set it to an arbitrary domain of his choice e.g: attackers-mxserver.com which would result in WordPress setting the $from_email to wordpress@attackers-mxserver.com and thus result in an outgoing email with From/Return-Path set to this malicious address.”
Summarizing, an attacker can force a password reset by sending a specially crafted request to the targeted WordPress site, the request will include as the hostname the name of a domain controlled by the attacker, meanwhile the From and Return-Path fields in the password reset email sent to the victim will specify an email address on the attacker’s domain.
Once the targeted user receives the password reset link, there are several methods the attacker can use to obtain it now that the From and Return-Path fields point to their domain.
The attacker can make the victim’s email account unusable, for example via an attack on its DNS server or by sending it large files until to saturate its capacity.
When the victim’s email account stop receiving messages, the password reset email is returned to the sender’s recipient) the attacker’s email account as it is specified in the From and Return-Path fields.
In the case an autoresponder is enabled on the victim’s email account, the attacker will easily obtain a copy of the password reset email includes in the automatic reply.
Another option is to send a large number of password reset emails to the victim, hoping the victim will reply one of them with an email that likely includes the password reset link.
Below the three scenarios described by Golunski:
Attacker can perform a prior DoS attack on the victim’s email account/server (e.g by sending multiple large files to exceed user’s disk quota, attacking the DNS server etc) in order to prevent the password reset email from reaching the victim’s account and bounce back to the malicious sender address that is pointed at the attacker (no user interaction required).
Some autoresponders might attach a copy of the email sent in the body of the auto-replied message (no user interaction required)
Sending multiple password reset emails to force the user to reply to the message to inquiry explanation for endless password reset emails. The reply containing the password link would then be sent to attacker. (user interaction required)
The Password Reset vulnerability affects all versions of WordPress, including the 4.7.4 version released a couple of weeks ago.
Golunski reported the flaw hole to WordPress several times since July 2016, but in an absence of a concrete action, he decided to disclose it.
Golunski has suggested a temporary solution to enable UseCanonicalName to enforce a static SERVER_NAME value https://httpd.apache.org/docs/2.4/mod/core.html#usecanonicalname
On a specific thread on Reddit users discussed possible temporary countermeasures, such as the use of as a utility that notifies users when users reset passwords.
Turla Cyberspies Developing Mac OS X Malware
5.5.207 securityweek Apple
The Russia-linked cyberespionage group known as Turla has been working on developing a Mac OS X version of its Snake malware framework, researchers at Fox-IT revealed this week.
Turla is also known as Waterbug, KRYPTON and Venomous Bear. Snake, also tracked as Turla and Uroburos, is one of its primary tools. The group is believed to have been active since at least 2006, but experts recently linked it to one of the earliest known state-sponsored cyberespionage operations carried out in the ‘90s.
The threat actor initially focused on targeting Windows systems, but in late 2014 Kaspersky Lab reported uncovering a piece of malware designed to work on Linux.
Now, Fox-IT has identified what it believes to be a Mac OS X version of Turla’s Snake malware. According to researchers, the sample they found contained debug functionality and it was signed on February 21, which indicates that it’s still under development.
An analysis of the Mac malware, delivered by the attackers as an Adobe Flash Player installer, showed that it had actually been ported from the Windows version. Its code included references to the “explorer” process, the Internet Explorer web browser and named pipes.
Once deployed, the malware maintains persistence by abusing Apple’s LaunchDaemon service. In order to bypass the GateKeeper security feature, the malware has been signed with a valid developer certificate that was likely stolen by the cyberspies. Fox-IT has notified Apple about the compromised certificate.
Experts noticed that the malware’s developers likely speak Russian, based on the use of the KOI8-R character encoding, which covers the Cyrillic alphabet.
“This indicates that the developers tested with Russian command output (encoded using the KOI8-R codepage). On systems where the command output is displayed in another language (and another codepage), text would be incorrectly represented in Cyrillic characters,” Fox-IT researchers said in a blog post.
The security firm has yet to see any attacks leveraging the OS X version of the Snake malware.
The Turla group is believed to be responsible for attacks on many organizations around the world, and despite having its operations exposed by the cybersecurity community on several occasions, the threat actor has continued to launch attacks and improve its tools.
In recent weeks, researchers reported seeing a new JavaScript malware used to profile victims, and an improved version of the second-stage backdoor tracked as Carbon and Pfinet.
Hackers Exploit SS7 Flaws to Loot Bank Accounts
5.5.207 securityweek Mobil
SS7 flaws exploited in cybercrime operations
Cybercriminals have exploited vulnerabilities in the SS7 protocol to bypass security mechanisms and steal money from bank accounts. Researchers have warned about the threat for years and these types of attacks have recently become a reality.
SS7, which stands for Signalling System No. 7, is a telephony signaling protocol used by telecommunications providers worldwide. It allows the customers of different networks to communicate with one another and ensures that calls are not interrupted when users are traveling over longer distances.
SS7 was developed back in 1975 and it does not include any protection or authentication, making it easy for third-parties to connect to the SS7 network.
The fact that SS7 has serious weaknesses has been known for years and researchers have often warned that malicious actors could leverage them to locate subscribers, intercept calls and SMS messages, and conduct fraud.
The first case of malicious actors exploiting SS7 flaws to make a profit has now come to light. German newspaper Süddeutsche Zeitung reported on Wednesday that cybercriminals had relied on SS7 attacks to bypass two-factor authentication (2FA) systems and conduct unauthorized wire transfers.
Attackers first obtained bank account information from the victims, which can be done either via phishing or malware, and then launched an SS7 attack to obtain the mobile transaction authentication number (mTAN) sent by the bank via SMS. mTANs are one-time passwords used by banks to confirm financial transactions.
According to Süddeutsche Zeitung, the attackers forwarded the SMS messages containing the mTAN to a number they controlled, allowing them to complete the wire transfers they had initiated from victims’ accounts.
Telecommunications firm O2-Telefonica confirmed for the newspaper that some of its customers in Germany had been targeted is such attacks via the network of a foreign mobile operator in mid-January. The company said it had blocked the offending provider and notified affected customers.
Experts told the German newspaper that access to SS7 networks can be acquired for under €1,000.
Jean Gottschalk, SS7 mobile network security consultant at Las Vegas-based Telecom Defense, has confirmed for SecurityWeek that access to the SS7 network can be obtained for roughly €1,000 per month, but the expert pointed out that this is not enough to conduct attacks.
Attackers also need an identity on the network, known as a global title (GT), which can be obtained from legitimate mobile operators. Normally, these identities are not handed out to anyone, but attackers could obtain them by bribing individuals working for mobile operators in less developed countries. The only condition is that the company needs to have a roaming agreement with the country whose citizens are targeted by the cybercriminals.
Gottschalk said attackers might pay another €1,000 per month for the GT, or their accomplice may want a share of the profit.
Another way to obtain access is via third-parties that rent global titles for SMS delivery and other types of services, the expert said.
Gottschalk told SecurityWeek that he had been aware of malicious operations targeting Germany, and the attacks were traced back to a former Soviet Union country.
The expert pointed out that malicious traffic has been seen on SS7 networks for many years, but it had mainly been used for geolocation purposes.
As for the United States, Gottschalk said attacks such as the ones in Germany are less likely to take place as banks typically don’t use SMS-based tokens for wire transfers. On the other hand, the expert warned that attackers can use the technique to hijack WhatsApp and Signal accounts, and bypass 2FA on services such as Gmail. Due to the risks, NIST and industry professionals have proposed replacing SMS-based 2FA with more secure alternatives.
Last year, researchers demonstrated the risks associated with SS7 when they managed to eavesdrop on U.S. Representative Ted Lieu knowing only his phone number. The official has now once again called for action.
“Both the FCC and telecom industry have been aware that hackers can acquire our text messages and phone conversations just knowing our cell phone number,” Lieu stated on Wednesday. “It is unacceptable the FCC and telecom industry have not acted sooner to protect our privacy and financial security. I urge the Republican-controlled Congress to hold immediate hearings on this issue.”
Until the issues are addressed on a wide scale, mobile operators can turn to specialized security firms such as Telecom Defense, which conduct security audits and help companies implement signaling firewalls.
Consent Control and eDiscovery: Devils in GDPR Detail
5.5.207 securityweek Privacy
The European General Data Protection Regulation will be in force in just over 12 months: May 25, 2018. This is the date by which all EU nations must have enacted the regulation. Gartner predicts that "by the end of 2018, more than 50 percent of companies affected by the GDPR will not be in full compliance with its requirements."
GDPR will affect all EU-based companies, and all US companies that have any trade with the EU. Despite the threat of hefty non-compliance fines, Gartner is not alone in finding a lack of preparatory urgency among organizations.
"The Gartner data aligns with a survey Imperva recently conducted of IT security professionals at RSA," Imperva's chief product strategist Terry Ray told SecurityWeek. "Our data showed an overall lack of urgency among the IT professionals surveyed, with only 43 percent of respondents indicating that they are evaluating or implementing change in preparation for GDPR."
An April 2017 NetApp survey that queried 750 CIOs, IT Managers and C-suite executives in France, Germany and the UK, found that around 10% of companies have yet to begin preparations. Seventy-three percent of respondents have some concern over meeting the GDPR deadline.
A new report (PDF) published Wednesday by Pierre Audoin Consultants (PAC) and sponsored by Reliance acsn also supports the idea that companies do not understand the urgent need for GDPR compliance. Paul Fisher, a research analyst and cyber security lead at PAC, suggests, "The fact that compliance and more especially, GDPR, has such a low priority among our respondents is worrying. I do not believe that they are burying their hands in the sand, more that the implications and complexity of GDPR compliance have not yet fully sunk in."
It is tempting to believe the lack of preparedness is due to a misunderstanding of the nature of the regulation -- a belief that so long as personal data is kept safe, compliance will be assured. This is not true with GDPR. "The big change is that organizations will be financially punished for violations of record keeping and privacy impact assessment obligations, and not just actual data breaches," explains the PAC analysis.
"The increasingly empowered position of individual data subjects tilts the business case for compliance and should cause decision makers to re-evaluate measures to safely process personal data," warns Gartner.
It is this data subject empowerment that particularly makes GDPR different and complex. Simply installing new layers of security will not ensure compliance.
Gartner suggests organizations should focus on "five high-priority changes to help them to get up to speed with GDPR requirements." These are:
Check for GDPR applicability
Appoint a data protection officer (DPO)
Demonstrate accountability in all processing activities
Check cross-border data flows
Prepare for data subjects exercising their rights
The devil is in the detail of that final recommendation. In full, Gartner says, "Data subjects have extended rights under the GDPR. These include the right to be forgotten, to data portability and to be informed (e.g., in case of a data breach). If a business is not yet prepared to adequately handle data breach incidents and subjects exercising their rights, now is the time to start implementing additional controls." An additional right is the data subject's right to withdraw consent for personal data processing.
Compliance and security officers need to consider the effect of data subjects exercising their rights -- and in particular the two issues of withdrawal of consent and the right to be forgotten.
The first issue involves the provision and withdrawal of the data subject's consent. Implied consent and implied cessation are no longer sufficient -- consent must explicit. Being able to prove that consent was given and continues (that is, has not been withdrawn) is new and will require completely new procedures. Gartner says, "A clear and express action is needed that will require organizations to implement streamlined techniques to obtain and document consent and consent withdrawal." One option could be the Consent Receipt Specification being developed by the Kantara Initiative -- but whatever solution is adopted, maintaining the status quo is not an option.
The second issue -- the right to be forgotten -- requires that an organization should have absolute knowledge of where all EU personal data is stored, and be able to remove it. That is no simple task in the age of cloud and mobility.
The PAC report notes, "Compliance with GDPR will only be legally registered if an organization is able to identify exactly where data is, whether in its own data centres, in the cloud or with a third party. The data controller will be held responsible for data at all times."
This requirement is little different to eDiscovery; but the reality is that few organizations currently have fully effective eDiscovery. Historically, the primary motivation has been litigation and the threat of litigation -- with the implication that if you don't get sued, you don't need eDiscovery.
This will no longer be realistic. Any one of the European data subjects can request -- effectively on a whim -- that all data you hold on them be removed. Organizations will not merely be required to do that, they will need to be able to demonstrate that they can do that. A combination of data classification and eDiscovery needs to be in place by May of next year.
"One of the huge holes for GDPR compliance," Skyhigh's privacy spokesperson Nigel Hawthorn told SecurityWeek, "is third party data handling. Most organizations aren't sure how many third parties process data for them, whether that's an outsourcer or a cloud provider being used to crunch or collaborate on data. The Data Controller is ultimately responsible for data handling of all of their third-party data processors and needs to ensure that the data processor's data handling procedures are robust -- I am sure this will catch out a lot of people."
The message from Gartner, reinforced by many other surveys, is that the task is more complex, and the available time much less, than many organizations realize. Hawthorn adds, "Gartner's prediction that by the end of 2018 less than 50% of organizations will be in full compliance reminds everyone we need to accelerate our efforts now -- as the regulation will be been in force for over 6 months by the end of 2018 and the risks of non-compliance can be huge."
His advice is that "Organizations need to take an holistic approach to GDPR compliance involving teams from multiple departments, led by senior management. The Governance, Risk and Compliance teams need to lead the project but involve IT risk and security along with other teams that are heavy users of data, such as marketing and HR. Sadly, marketing, the team most likely to break the regulations, is rarely involved in the discussions."
Cisco Patches Critical Flaw in Small Business Router
5.5.207 securityweek Vulnerebility
Cisco has released a firmware update for one of its small business routers to address a critical vulnerability that can be exploited for denial-of-service (DoS) attacks and arbitrary code execution.
The vulnerability, discovered by researchers from GeekPwn, a China-based IoT-focused hacking competition, affects CVR100W Wireless-N VPN routers. The company said there was no evidence of malicious exploitation.
The flaw, tracked as CVE-2017-3882 and described as a buffer overflow, affects the device’s Universal Plug and Play (UPnP) implementation and it can allow an unauthenticated, layer 2-adjacent attacker to execute arbitrary code with root privileges or cause vulnerable routers to reload.Cisco CVR routers vulnerable to hacker attacks

The security hole can be exploited by sending a specially crafted request to the UPnP listening port of the targeted router.
The flaw affects CVR100W Wireless-N VPN routers running a version of the firmware prior to 1.0.1.22. Cisco said no other small business routers are affected. Users can determine which firmware version is running on their device from the product’s web interface.
The same router model is also affected by a medium severity bug that can be exploited by an unauthenticated attacker to bypass the remote management ACL. This security hole has been addressed with the release of version 1.0.1.24.
Cisco on Wednesday also published three other advisories describing high severity vulnerabilities affecting various products.
The networking giant informed customers that several of its Aironet access points are affected by a PnP-related vulnerability that can be exploited for arbitrary code execution with root privileges. While the security hole has been classified “high severity,” Cisco pointed out that there is only a small window for exploitation and the attacker needs to have network access.
The other two flaws, affecting IOS XR and TelePresence Collaboration Endpoint (CE) software, allow a remote, unauthenticated attacker to cause devices to enter a DoS condition.
Patches are available for all vulnerabilities and Cisco says it’s not aware of any in-the-wild attacks where these weaknesses have been exploited.
Botnet of Thousands of Servers Mines for Crypto-Currency
5.5.207 securityweek BotNet
A botnet comprised of more than 15,000 servers is currently being used for mining crypto-currency, but attackers could easily take full control of the compromised machines if they choose, GuardiCore warns.
Dubbed BondNet, the botnet appears to have been active since December 2016 and is mainly focused on mining Monero, a crypto-currency highly popular among cybercriminals. The botnet’s operator is estimated to be earning around $1,000 a day, or more than $25,000 a month, the security researchers say.
To breach servers, the attackers use a variety of public exploits, after which they install a Windows Management Interface (WMI) backdoor to establish communication with the command and control (C&C) server. This also allows attackers to take full control of the servers and steal data on them, hold it for ransom, or stage further attacks.
The security firm determined that BondNet has penetrated more than 15,000 machines to date and says that around 2,000 of the compromised servers report to the C&C each day. Additionally, the botnet adds around 500 new machines to the network daily, while delisting around the same number of servers. The oldest server breached has an uptime of over 7.5 years.
The botnet operators use a mix of vulnerabilities and weak credentials to breach Windows Server machines, including known phpMyAdmin configuration bugs, exploits in JBoss, Oracle Web Application Testing Suite, ElasticSearch, MSSQL servers, Apache Tomcat, Oracle Weblogic and other common services.
Common to all attacks is the use of Visual Basic files to download and install a remote access Trojan (RAT) and a crypto-currency miner. The compromised machines are then used to expand the botnet infrastructure, to conduct attacks, or serve up malware files such as miner executables. Other machines would host the C&C servers, the researchers say.
Although the crooks appear focused on mining Monero, miners such as ByteCoin, RieCoin or ZCash (all convertible to USD) are also dropped in some cases. Up-to-date versions of the mining programs are downloaded and installed, and scheduled task, triggered hourly, ensure that the miner process can survive reboots.
The backdoor used by the botnet is a WMI RAT downloaded from an Amazon S3 bucket (mytest01234), and is installed using a known MOF file method. Set to run every night at 11PM, the backdoor defines a new WMI provider class, which allows the attacker to execute code as a result of a WMI event and to hide the activity behind the WMI service process.
The backdoor enables the Guest account and resets its password, so that the attacker can remotely connect using Remote Desktop Protocol (RDP), Server Message Block (SMB), or Microsoft Remote Procedure Call (RPC).
Next, it collects information about the machine, including computer name, RDP port, guest username, OS version, number of active processors, uptime measured in hours, original infection vector, whether the victim is running a Chinese version of Windows, OS language, and CPU architecture (x86/x64), and sends it to the C&C encoded, over HTTP. The malware also downloads a command file and executes it (the commands are obfuscated Visual Basic code and are executed “in memory”).
On victim-turned-C&C servers, the attackers install a fork of goup, which is a small open source HTTP server written in Golang. The attackers’ webserver can track victims and encrypt files on disk using AES. The use of .asp and .zip extensions for the files served by the C&C server allows the attackers to avoid auditing and firewall alerts.
The attackers deploy new command and control instances manually by connecting over RDP to the victim machine and copying a ZIP file that contains the server, an open source service manager (nssm), and command files. The server is installed using an included batch script, is named w3wp, the same as the Microsoft IIS host process, and runs at startup. Because the attackers sometimes forget to save all.asp, some C&C servers don’t save the information the Trojans send.
The botnet’s infrastructure is built of compromised servers with various roles: C&C servers, file servers, scanning servers etc. The attackers use the TCP port scanner WinEggDrop to scan the Internet for new targets. The scanning servers also check for public, unpatched vulnerabilities in different frameworks, and store those IPs for attack servers to attempt to compromise.
Many of the victims are used as file servers to serve up mining software, and they have the same web server as the C&Cs. The WMI Trojan files, however, are hosted on an Amazon S3 bucket.
“While organizations can treat this as a minor issue of increased electric bills, with relatively simple modifications this backdoor is capable of taking complete control of thousands of victim machines, many of which contain sensitive information like mail servers. Today's mining may easily become a ransomware campaign, data exfiltration or lateral movement inside the victim's network,” GuardiCore concludes.
Gmail čelil největšímu hackerskému útoku. V ohrožení byla miliarda účtů
4.5.2017 Novinky/Bezpečnost Phishing
V noci ze středy na čtvrtek čelila e-mailová služba Gmail, kterou provozuje společnost Google, obřímu hackerskému útoku. Počítačoví piráti tak mohli získat podle serveru NBC News přístup až k miliardě uživatelských účtů, napadnout se jich ale nakonec podařilo zhruba jen milión. V každém případě jde o největší zaznamenaný hackerský útok na Gmail v celé historii této služby.
Zatím neznámým útočníkům se podařilo obejít prakticky všechny důležité bezpečnostní systémy společnosti Google. Díky tomu mohli do služby Google Docs, která slouží k práci s textovými a dalšími dokumenty, propašovat škodlivý virus.
Právě v tom byl kámen celého úrazu. Uživatelé se tedy mohli snadno nakazit pouze tím, že rozklikli na první pohled neškodný dokument, jenž jim přišel do jejich schránky. Následně byli uživatelé vyzváni k zadání přihlašovacích údajů. To přitom není nijak neobvyklé, protože služby Googlu skutečně zadání hesel v některých konkrétních krocích vyžadují.
Pokud však uživatelé své přihlašovací údaje vyplnili, předali počítačovým pirátům úplnou kontrolu nad celým svým účtem.
22h
Zeynep Tufekci ✔ @zeynep
Phishing (or malware) Google Doc links that appear to come from people you may know are going around. DELETE THE EMAIL. DON'T CLICK. pic.twitter.com/fSZcS7ljhu
Follow
Zach Latta @zachlatta
@zeynep Just got this as well. Super sophisticated. pic.twitter.com/l6c1ljSFIX
8:52 PM - 3 May 2017
2,043 2,043 Retweets 1,303 1,303 likes
Takto vypadal podvodný e-mail s infikovaným dokumentem.
Mohli číst i mazat e-maily
Ti pak mohli snadno číst cizí poštu, mazat obsah elektronických poštovních schránek nebo odesílat jakékoliv e-maily pod jménem napadeného účtu. A právě poslední možnost kyberzločinci podle prvních zpráv využívali nejčastěji.
Prostřednictvím napadených účtů a kontaktů v nich uložených totiž rozesílali infikované dokumenty na další a další účty. Mohlo se tedy klidně stát, že infikovaný soubor přišel uživateli od jeho skutečného známého. I proto se škodlivý kód v prostředí Gmailu tak snadno šířil – uživatelé jednoduše nerozpoznali, že jde o podvod.
Touto cestou se podle vyjádření Googlu podařilo počítačovým pirátům nakonec napadnout „méně než 0,1 procenta uživatelských účtů“. S ohledem na popularitu Gmailu jde však zhruba o milión poštovních schránek, podotkl server NBC News.
Je však nutné zdůraznit, že podvodné e-maily se šířily výhradně v anglickém jazyce. Je tedy krajně nepravděpodobné, že by se touto cestou mohli nechat napálit i tuzemští uživatelé. I tak je vhodné zkontrolovat v nastavení svého účtu přístupy, odkud se uživatelé ke svému Gmailu připojovali. Právě tak zjistí, zda k jejich schránce nepřistupoval někdo jiný.
Follow
St George Police @sgcitypubsafety
Do you Goole? Or use GMAIL? Watch out for this scam & spread the word (not the virus!) https://www.reddit.com/r/google/comments/692cr4/new_google_docs_phishing_scam_almost_undetectable/ …
10:50 PM - 3 May 2017
Photo published for New Google Docs phishing scam, almost undetectable • r/google
New Google Docs phishing scam, almost undetectable • r/google
I received a phishing email today, and very nearly fell for it. I'll go through the steps here: 1. I [received an...
reddit.com
2 2 Retweets 3 3 likes
Před podvodnými e-maily varovala i americká policie.
Raději změnit heslo
Googlu se podařilo útok zastavit až po několika hodinách po nahlášení celého incidentu. Teprve pak byly účty, prostřednictvím kterých byly podvodné e-maily rozesílány, zablokovány.
„Zatímco kontaktní informace byly v této kampani zneužity, naše vyšetřování ukázalo, že žádná další data nebyla hackerům vystavena,“ uvedl mluvčí Googlu s tím, že podnik již pracuje na takových krocích, aby hackeři nemohli podobnou aktivitu zopakovat.
Uživatelé nicméně nezkazí nic tím, pokud si z preventivních důvodů změní své heslo. A platí to i v případě, že stejné přihlašovací údaje používají na dalších internetových službách.
Real-World SS7 Attack — Hackers Are Stealing Money From Bank Accounts
4.5.2017 thehackernews Mobil
Security researchers have been warning for years about critical security holes in the Signaling System 7 (SS7) that could allow hackers to listen in private phone calls and read text messages on a potentially vast scale, despite the most advanced encryption used by cellular networks.
Cellular networks, on the other hand, have consistently been ignoring this serious issue, saying that it is a very low risk for most people, as the exploitation of the SS7 flaws requires significant technical and financial investment.
But some unknown hackers have just proved them wrong by recently exploiting the design flaws in the SS7 to drain victims' bank accounts, according to a report published Wednesday by German-based newspaper Süddeutsche Zeitung.
SS7 is a telephony signaling protocol created in the 1980s by telcos and powered more than 800 telecom operators across the world, including AT&T and Verizon, to interconnect and exchange data, like routing calls and texts with one another, enabling roaming, and other services.
Real-World SS7 Attack Scenarios
The global telecom network SS7 is vulnerable to several design flaws that could allow hackers to listen to phone calls and intercept text messages on a potentially massive scale, despite the most advanced encryption used by cellular network operators.
The designing flaws in SS7 have been in circulation since 2014 when a team of researchers at German Security Research Labs alerted the world to it.
So, the privacy concerns regarding the SS7 protocol is not new.
Here's the real-world evidence that cyber-criminals are using long-known SS7 vulnerability to drain Bank accounts.
CLICK TO TWEET
Last year, Karsten Nohl of German Security Research Labs demonstrated the SS7 attack on US Congressman Ted Lieu's phone number (with his permission) at TV program 60 Minutes and successfully intercepted his iPhone, recorded call, and tracked his precise location in real-time just by using his cell phone number and access to an SS7 network.
In a separate demonstration, the researchers from Positive Technologies last year also gave a demonstration on the WhatsApp, Telegram, and Facebook hacks using the same designing flaws in SS7 to bypass two-factor authentication used by the services.
Thieves Using SS7 Flaw to Steal Money From Bank Accounts
Now, Germany's O2 Telefonica has confirmed that the same SS7 weaknesses have recently been exploited by cybercriminals to bypass two-factor authentication (2FA) banks used to prevent unauthorized withdrawals from users bank accounts.
"Criminals carried out an attack from a network of a foreign mobile network operator in the middle of January," an O2 Telefonica representative told Süddeutsche Zeitung. "The attack redirected incoming SMS messages for selected German customers to the attackers."
In short, cyber criminals exploited SS7 flaws to intercept two-factor authentication codes (one-time passcode, or OTP) sent to online banking customers and drained their bank accounts.
Here's How:
The attackers first spammed out traditional bank-fraud trojans to infect account holders' computers and steal passwords used to log into bank accounts, view accounts balance, along with their mobile number.
But what prevented the attackers from making money transfers is the one-time password the bank sent via a text message to its online banking customers in order to authorize the transfer of funds between accounts.
To overcome this issue, the cyber crooks then purchased the access to a fake telecom provider and set-up a redirect for the victim's phone number to a handset controlled by them. Specifically, they used SS7 to redirect the SMSes containing OTPs sent by the bank.
Next, the attackers logged into victims' online bank accounts and transferred money out, because as soon as the authorization codes were sent by the bank, instead of designated account holders, they were routed to numbers controlled by the attackers, who finalized the transaction.
Can You Avoid this Hack?
This latest SS7 attack once again shed light on the insecurity by design and lack of privacy in the global telephone network protocol, making it clear that real-world SS7 attacks are possible. And since the SS7 network is used worldwide, the issue puts billions of users in danger.
The incident also underscores the risks of relying on SMS-based two-factor authentication.
Although the network operators are unable to patch the hole anytime soon, there is little the smartphone users can do. Avoid using two-factor authentication via SMS texts for receiving OTP codes. Instead, rely on cryptographically-based security keys as a second authentication factor.
Hundreds of Apps Using Ultrasonic Signals to Silently Track Smartphone Users
4.5.2017 thehackernews Mobil
Your smartphone may have some apps that are continuously listening inaudible, high-frequency ultrasonic sounds from your surroundings and they know where you go, what you like and dislike — all without your knowledge.
Ultrasonic Cross-Device Tracking is a new technology that some marketers and advertising companies are currently using to track users across multiple devices and have access to more information than ever before for ad targeting.
For example, retail stores you visit, a commercial on TV or an advertisement on a web page can emit a unique "ultrasonic audio beacon" that can be picked up by your device’s mobile application containing a receiver.
This information helps advertisers to create your personalized profile and collect your interests by figuring out that both devices probably belongs to you, allowing them to target you with interest-based advertisements.
More & More Apps Have Started Using Ultrasonic Tracking Technology
In fact, while presenting research last week at the IEEE European Symposium on Security and Privacy, security researchers said they discovered 234 Android applications that ask permission to access your smartphone’s microphone to incorporate a particular type ultrasonic beacon to track consumers.
Moreover, the researchers found that 4 of the 35 retail stores they visited in Germany have ultrasonic beacons installed at the entrance.
According to investigators, SilverPush, Lisnr, and Shopkick are three SDKs that use ultrasonic beacons to send messages to the mobile device. While SilverPush allows developers to track users across multiple devices, Lisnr and Shopkick perform location tracking.
The researchers analyzed millions of Android apps and discovered few that were using the Shopkick and Lisnr SDKs, but there were much more that were using the SilverPush SDK.
Serious Privacy Concerns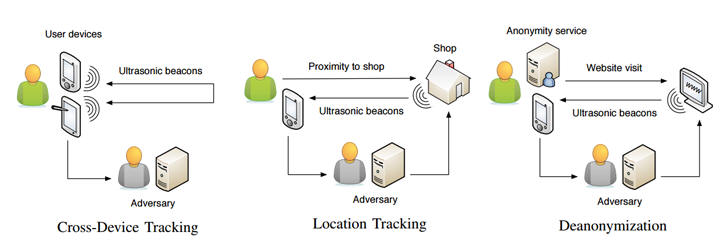
Although cross-device user tracking technologies are currently being used for the legitimate purposes, it has already raised some serious privacy concerns.
Since an app requires no mobile data nor Wi-Fi connection, but only microphone access to listen to beacons, tracking works even when you have disconnected your phone from the Internet.
In fact, a team of researchers last year demonstrated that how ultrasonic sounds emitted by ads on a web page accessed through Tor can be used to deanonymize Tor users by making nearby phones or computers send identification information, such as location and IP, back to advertisers.
"The case of SilverPush emphasizes that the step between spying and legitimately tracking is rather small. SilverPush and Lisnr share essential similarities in their communication protocol and signal processing. While the user is aware of Lisnr location tracking, SilverPush does not reveal the application names with the tracking functionality," research paper reads.
In 2014, Snowden revelations disclosed that how spying agencies were tracking foreign travelers’ movements across the city by capturing their device’ unique MAC address at the airport and then comparing it with the data collected by free WiFi hotspots installed in various coffee shops, restaurants, and retail stores.
This incident could also be another great example, showcasing how intelligence agency could use this ultrasonic cross-device tracking technology to track your movements across the country.
How can You Protect Yourself?
Since you can not stop ultrasonic beacons from emitting sound frequencies around you, the best way to reduce the chance of your smartphone listening for beacons and feed data to a third party is to simply restrict unnecessary permissions you have granted to the apps installed on your device.
In other words, use your common sense.
For example, Skype wants microphone access? Fair enough, as it is necessary for Skype to work as intended. But what about if an app for beauty or clothing store wants microphone access? No way.
To revoke such unnecessary app permissions, some Android phone manufacturers, like One Plus provide a feature called Privacy Guard that allowed its users to block unnecessary app permissions of certain apps on a smartphone that do not have anything to do with the primary function of the apps.
Navigate to Settings → Personal → Privacy → Privacy Guard. Now select any from the list of apps and edit unnecessary permissions you have granted it.
A similar feature has been included in Android 7. Navigate to Settings → Apps → App Permissions. Now edit the privileges you’ve granted each app.
For iOS 10 users: Go to Settings → Privacy → Microphone to see which apps have requested access to it, and which apps you have granted it to.
Warning! Don't Click that Google Docs Link You Just Received in Your Email
4.5.2017 thehackernews Phishing
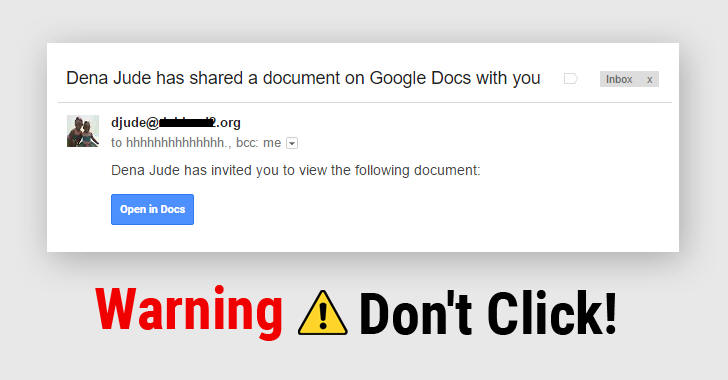
Did someone just share a random Google Doc with you?
First of all — Do not click on that Google Doc link you might have just received in your email and delete it immediately — even if it's from someone you know.
I, my colleagues at The Hacker News, and even people all around the Internet, especially journalists, are receiving a very convincing OAuth phishing email, which says that the person [sender] "has shared a document on Google Docs with you."
Once you clicked the link, you will be redirected to a page which says, "Google Docs would like to read, send and delete emails, as well access to your contacts," asking your permission to "allow" access.
If you allow the access, the hackers would immediately get permission to manage your Gmail account with access to all your emails and contacts, without requiring your Gmail password.
Beware! New GoogleDocs Phishing Email Scam Spreading Across the World — Here's Everything You Need to Know
CLICK TO TWEET
But How? The "Google Docs" app that requests permissions to access your account is fake and malicious, which is created and controlled by the attacker.
You should know that the real Google Docs invitation links do not require your permission to access your Gmail account.
Anything Linked to Compromised Gmail Accounts is at Risk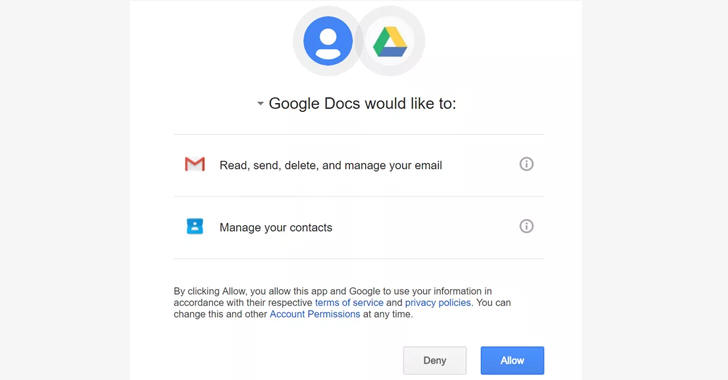
Once the app controlled by the attacker receives permissions to manage your email, it automatically sends same Google Docs phishing email to everyone on your contact list on your behalf.
Since your personal and business email accounts are commonly being used as the recovery email for many online accounts, there are possibilities that hackers could potentially get control over those online accounts, including Apple, Facebook, and Twitter.
In short, anything linked to a compromised Gmail account is potentially at risk and even if you enabled two factor authentication, it would not prevent hackers to access your data.
Meanwhile, Google has also started blacklisting malicious apps being used in the active phishing campaign.
"We are investigating a phishing email that appears as Google Docs. We encourage you to not click through & report as phishing within Gmail," Google tweeted.
This Google Docs phishing scheme is spreading incredibly quickly, hitting employees at multiple organizations and media outlets that use Google for email, as well as thousands of individual Gmail users who are reporting the same scam at the same time.
If by anyhow you have clicked on the phishing link and granted permissions, you can remove permissions for the fraudulent "Google Docs" app from your Google account. Here’s how you can remove permissions:
Go to your Gmail accounts permissions settings at https://myaccount.google.com and Sign-in.
Go to Security and Connected Apps.
Search for "Google Docs" from the list of connected apps and Remove it. It's not the real Google Docs.
Stay tuned to our Facebook Page for more updates ! Stay Safe!
Travel Tech Giant Sabre suffered a Data Breach, traveler data potentially at risk
4.5.2017 securityaffairs Incindent
Travel giant Sabre investigating a data breach that could have exposed payment and customer data tied to bookings processed through its reservations system.
Another day, another data breach, this time the victim is the Travel Tech Giant Sabre that in a SEC filing confirmed it is “investigating an incident involving unauthorized access to payment information contained in a subset of hotel reservations processed through the Sabre Hospitality Solutions SynXis Central Reservation system.”
In its SEC filing, Sabre confirmed that the attackers had been locked out of its systems, anyway we cannot exclude that crooks had accessed personally identifiable information (PII), payment card data, and other information managed by the firm.
“The unauthorized access has been shut off and there is no evidence of continued unauthorized activity,” reads a statement that Sabre sent to affected properties today. “There is no reason to believe that any other Sabre systems beyond SynXis Central Reservations have been affected.”
The impact of the incident could be severe, the SynXis Central Reservation product is a rate and inventory management SaaS application that is currently used by more than 32,000 hotels worldwide.
According to the popular expert Brian Krebs, the company Sabre notified the incident to law enforcement and hired the firm Mandiant to investigate the case.
“Today, travel industry giant Sabre Corp. disclosed what could be a significant breach of payment and customer data tied to bookings processed through a reservations system that serves more than 32,000 hotels and other lodging establishments.” wrote Krebs.

This isn’t the first time Sabre suffered a cyber attack, in August 2015, the travel tech giant notified a cyber attack allegedly powered by a Chinese threat actor.
In December 2016, the notorious hackers Karsten Nohl and Nemanja Nikodijevic have demonstrated that the current travel booking systems are deeply insecure, they lack cyber security by design.
The experts explained that it is quite easy to modify any passenger’s reservation, cancel their flight bookings, and even use the refunds to book tickets for themselves.
New insidious Google Docs phishing scheme is rapidly spreading on the web
4.5.2017 securityaffairs Phishing
Don’t click Google Docs link! A Google Docs phishing scheme is quickly spreading across the Internet targeting a large number of users.
Did you receive an unsolicited Google Doc from someone?
First, do not click on that Google Doc link embedded in the email you have received and delete the message, even if it’s from someone you know.
A Google Docs phishing scheme is quickly spreading across the Internet targeting a large number of users and employees at multiple media outlets and organizations that Gmail.
Some of the websites associated with this campaign appear to have been shut down.
A large number of users are receiving a very insidious OAuth phishing email, which informs the recipient that sender “has shared a document on Google Docs” with the,
Once the recipient clicked the link, he will be redirected to a page which says, “Google Docs would like to read, send and delete emails, as well access to your contacts,” asking the victim’s permission to “allow” access.

If the user will allow the access, the attackers would get access to the recipient’s Gmail account without providing any Gmail password.
At this point, the attackers have the key of your kingdom and anything linked to the compromised Gmail Accounts is at risk.
Once the victim gives the attacker’s applications the permissions to manage his email account, it automatically sends same Google Docs phishing email to everyone on the contact list on behalf of the victim.
The attack technique used in this Google Docs phishing scheme was also associated recently with and Pawn Storm ongoing espionage campaign. The cyber spies are abusing OAuth, presenting a legitimate Google dialogue box requesting authorization, then asks permission for access to “view and manage your e-mail” and “view and manage the files in your Google Drive.”
Google also already started blocking any malicious apps leveraging this subtle trick.
Follow
Google Docs ✔ @googledocs
We are investigating a phishing email that appears as Google Docs. We encourage you to not click through & report as phishing within Gmail.
10:08 PM - 3 May 2017
4,378 4,378 Retweets 2,325 2,325 likes
“We have taken action to protect users against an email impersonating Google Docs, and have disabled offending accounts,” said a Google spokesperson in an email.
“We’ve removed the fake pages, pushed updates through Safe Browsing, and our abuse team is working to prevent this kind of spoofing from happening again. We encourage users to report phishing emails in Gmail.”
“There’s a very clever phishing scam going around at the moment – originally thought to be targeting journalists given the sheer number of them mentioning it on their Twitter feeds, it’s also been slinging its way across unrelated mailboxes – from orgs to schools / campuses,” explained Christopher Boyd, malware intelligence analyst at Malwarebytes, today.
“This doesn’t mean it didn’t begin with a popped journo mailbox and spread its way out from there, or that someone didn’t intentionally send it to a number of journalists of course – but either way, this one has gone viral and not in a ‘look at the cute cat pic’ fashion.”
If you have already clicked on the phishing link and granted permissions you can remove them for the bogus “Google Docs” app directly from your Google account.
Below the procedure to remove permissions:
Go to your Gmail accounts permissions settings at https://myaccount.google.com and Sign-in.
Go to Security and Connected Apps.
Search for “Google Docs” from the list of connected apps and Remove it.
Carbanak gang makes the headlines again, hackers refined intrusion tactics
4.5.2017 securityaffairs Virus
The notorious cyber crime gang Carbanak is back and it is continuing to refine its techniques and tactics and developed new tools for its attacks.
The cyber crime gang Carbanak continues to refine its techniques and tactics. According to a new analysis conducted by the security firm Trustwave, the group has refined its intrusion strategy and developed new tools for its arsenal.
The Carbanak gang was first discovered by Kaspersky Lab in 2015. the group has stolen at least $300 million from 100 financial institutions.
In early 2016, the Carbanak gang target banks and financial institutions, mainly in the US and the Middle East.
In November last year, experts at Trustwave uncovered a new campaign launched by the group targeting organizations in the hospitality sector.
In January, the Carbanak gang started using Google services for command and control (C&C) communication.
The crooks used the “ggldr” script to send and receive commands to and from Google Apps Script, Google Sheets, and Google Forms services.
Hackers used to create a unique Google Sheets spreadsheet for each infected user, in this way they attempted to avoid detection.
Back to the present, researchers at Trustwave observed the group using new social engineering techniques. The hackers are sending a malicious Word or RTF document to employees of organizations in the hospitality sector, and then call to ask whether the document was opened and would follow up with another call after 30 minutes.
The actors claim that the sender faced problems with the online ordering system, or that the document referred to a lawsuit caused by a member of the group getting sick after having a meal at one of the targeted organization’s restaurants.
“This social engineering scam is augmented with a personal phone call from the attacker, encouraging the intended victim to open the email attachment and click inside it. The attacker then calls back 30 minutes later to check if the document was opened and hangs up as soon as the employee says yes.” reads the analysis from Trustwave.
The researchers analyzed one of the infected RTF documents used by the hackers that dropped two VBS and one PS1 file onto the targeted system. The malware gain persistence by using scheduled task to run the main malware file every 25 minutes.
The researchers also observed the C&C malware creator script dropping additional malware and support files in a different folder, including another PS1 file, four more VBS scripts, and INI and TXT files.
The experts discovered that the INI file was used to issue commands to the compromised machine and to reflect the status of previous commands.
“The INI processing script parses and processes the contents of the INI file, providing the following commands:”
Screenshot (save screenshot as screenshot.png)
Runvbs
Runexe
Runps
Update
Delete
Below the information sent by the malware back to the C&C:
OS Name, Version, Service Pack, OS Manufacturer, Windows Directory, Locale
Available Physical Memory, Total Virtual Memory, Available Virtual Memory
OS Name, System Name, System Manufacturer, System Model, Time Zone
Total Physical Memory, Processor System Type, Processor, BIOS Version
Microsoft Office Apps, Computer name, Domain, User name
The attackers no longer used user accounts and passwords for lateral movement. Instead, the malware would bypass authentication on the remote system and use SMB commands to locate vulnerable hosts and compromise them.
Unlike previous campaigns, where Carbanak hackers leveraged Mimikatz or some other credential stealer for lateral movement, the malware bypasses authentication on the remote system and uses SMB commands (including TreeConnect and Open/Write AndX) to locate a vulnerable host.
“Instead, the malware bypasses authentication on the remote system and uses SMB commands (including TreeConnect and Open/Write AndX) to locate a vulnerable host by checking the ability to write data to the C:\Windows\Temp folder on a potential victim system.” reads the analysis.
Trustwave also reported that the Carbanak malware authors used several techniques to hide the activity of the malicious code.
Below a list of useful suggestions provided by Trustwave experts to organizations that need to protect their systems from Carbanak attacks.
Regular security awareness training for all employees, paying particular attention to spear phishing.
Spear phishing exercises where employees are sent a ‘phishing’ email that points to a site controlled by IT (Trustwave SpiderLabs also offers this service).
An email server or appliance that can assist with malware detection, such as scanning incoming email attachments for base64 strings.
Macros disabled by default on all Office applications (although a user can still re-enable them).
A SIEM or other log-and-event aggregation system that allows aggregated network traffic to be examined by an expert security team before, during, and after an attack.
Ensuring that IDS rules are able to detect metasploit modules.
Threat intelligence driven software restriction policies, such as preventing program execution from C:\Windows\Temp.
Whitelist PowerShell scripts and VBS scripts used by the organization and blacklist all others.
Continuous DNS monitoring with threshold alerts for systems issuing excessive DNS queries in a given period of time.
Restrict DNS traffic so that internal systems are only able to query your DNS servers.
NSA Cyber Weapons installed in High Profile Targets in Greece
4.5.2017 securityaffairs BigBrothers
The installation of monitoring software has been conducted either by NSA highly sophisticated hacking team or by hackers who leveraged the tools leaked by the Shadow Brokers.
Last week, a collection of spy tools allegedly used by the National Security Agency for operations against global targets of interest was leaked online by the underground hacking group, Shadow Brokers.
The tools were released online in the following form and were accessible to anyone:

NSA’s cyber-weapons include many exploits for Microsoft Windows, Lotus Notes, MDaemon Webadmin, IIS, Solaris systems and Microsoft Exchange, as well as additional Python-based tools.

These tools (Fuzzbunch, Eternalblue, Doublepulsar, Danderspritz) are part of the powerful NSA hacking toolset (also known as NSA Metasploit) exploited by the intelligence organization for hacking operations against governments, companies, and organizations.

THE RESEARCH
SecNews researchers conducted a thorough study of the Shadow Brokers leak, mainly focusing on its effects. As it has been known, the NSA backdoor has already been installed on thousands of computers and servers around the world. A map of the affected countries is presented below:

The purpose of SecNews research, considering the importance of the leaked data, was to identify companies or networks exclusively from the Greek Territory that have been targeted by malicious activities related to NSA’s cyber weapons.
After analyzing the leaked NSA toolkit and taking into consideration its particular digital features, we conducted an investigation as to detect which IP addresses in Greece are affected by the NSA cyber weapons!
The assessment procedure was carried out in the following steps:
Firstly, we scanned the Greek Internet for publicly exposed SMB (Port 445) & Remote Desktop (RDP Port 3389) services.
We detected 1086 IP addresses with SMB enabled online
We detected 4263 IP addresses with Remote Desktop enabled online
Then, using properly parameterized scripts like Mass-scan, detect_doublepulsar_rdp & smb (Python) and in conjuction with the NSA-leaked files, we detected where the cyber weapon is installed.
The final findings/results are shown in the table below. For security reasons, the IP addresses are hidden, as to protect the targeted companies/organizations. Thus, it is not possible for a malicious user to use the mentioned cyber-weapon for his own benefit.

CONCLUSIONS
According to the findings, the NSA remote access software was installed:
Within the network (AIA-Cust3-Infr) of Athens International Airport “Eleftherios Venizelos”. We are not in a position to know whether the network is related to the airport’s infrastructure or to a third party company in which the airport provides backbone access.
On a web server (accessible via the internet) belonging to SKAI TV, one of the largest media groups in Greece.
On a server belonging to Vodafone (or an affiliated company).
On a server / part of the Internal Network Management system of Interworks Cloud (interworks.biz, webserve.gr). It is worth mentioning that the Business marketplace of the telecommunications company Wind (windbusiness.com.gr) is located in the same IP class.
On a PC with DSL / VDSL connection (OTE/Cosmote) but it’s not known whether it is a corporate customer or a home user. In every case, it does not seem to have any correlation with OTE / Cosmote ‘s critical infrastructure.
Within a server of SYKARIS (possibly a graphic arts company).
Within a server of MELKA (possibly a construction company).
On a terminal / server of the Civil Engineering Department of The Aristotle University of Thessaloniki.
On a terminal / server of the Technological Educational Institute of Epirus, in the VLAN management system.
On a terminal at the University of Thessaly (possibly a remote DSL connection).
According to our research, all of the aforementioned systems were infected with the “Doublepulsar” exploit. Doublepulsar allows an attacker to install malicious software of choice, that can not be tracked as a DLL.
“It must be mentioned that we can not know whether the installation of the cyber weapons was conducted by the NSA or third-party hackers who leveraged the tools leaked by the ShadowBrokers. One think is sure, however, that the affected companies/organizations should immediately test and evaluate their systems security (and especially if the affected systems are related to internal networks).”
The same procedure that we’ve applied during our research to the Greek Public Internet, can be also implemented on internal servers, in order to check if the cyber-monitoring software is installed. The aforementioned targets are ought to conduct digital analysis and security audits as to get an objective analysis of the affected servers.
SecNews researchers are at the disposal of administrators or legal representatives of the affected companies, organizations, and entities, as to provide them with any additional information needed. Details on the assessment procedure or οn how security audits can be performed on an internal network can be also provided, after the detection of a related infection by the administrators and the identification of its extent.
Cyberspies Use KONNI Malware to Target North Korea
4.5.2017 securityweek BigBrothers
A remote access Trojan (RAT) that managed to stay under the radar for more than 3 years has been used by cyberspies to target organizations linked to North Korea, Cisco’s Talos research and intelligence group reported on Wednesday.
The malware, dubbed by researchers “KONNI,” has evaded detection likely due to the fact that it has only been used in highly targeted attacks. The malware has evolved over the years, with recent versions capable of stealing data and executing arbitrary code on infected systems.
Talos is aware of several campaigns using this piece of malware over the past years. The first, likely launched in September 2014, involved an SRC file acting as a dropper for two other files: a picture that served as a decoy and the KONNI executable.
In this attack, the KONNI malware was designed to be executed only once and steal information from the infected device, including keystrokes, clipboard content, and data associated with the Chrome, Firefox and Opera web browsers.
The second campaign, observed last year, also involved an SRC file, but this time it dropped two office documents. These documents, one written in English and one in Russian, referenced the tension between North Korea and the U.S., and they were titled “N. Korean hydrogen bomb can wipe out Manhattan: propaganda outlet.”
The 2016 attacks leveraged malware that had a different architecture, and introduced new features that also allowed attackers to upload and download files, and execute arbitrary commands. While analyzing this campaign, researchers found evidence suggesting that an operation also took place in 2015.
Experts have already spotted two KONNI campaigns this year. One of the decoy documents was titled “Pyongyang e-mail lists - April 2017” and it contained the email addresses and phone numbers of individuals working at organizations such as the United Nations, UNICEF and embassies linked to North Korea.
Another decoy document, titled “Inter Agency List and Phonebook - April 2017” contained names and contact information for members of agencies, embassies and other public organizations connected to North Korea. Researchers said it’s unclear if these are legitimate files that have been stolen by the cyberspies or if the attackers created the documents themselves.
Compared to previous versions, the latest malware samples are also capable of collecting system information and capturing screenshots. The threat actor has also created 64-bit versions of the malware.
The fact that 3 of the 4 campaigns analyzed by Cisco were aimed at organizations linked to North Korea has led researchers to believe that the threat group behind KONNI has a real interest in this country. The latest attack started a few days ago and it’s still active.
Carbanak Hackers Refine Intrusion Tactics
4.5.2017 securityweek Virus
The prolific Carbanak crime group has refined its intrusion strategy and expanded its arsenal of tools used in attacks, a new Trustwave report reveals.
The Carbanak group, also known as Anunak, was exposed in 2015 after it managed to steal an estimated $1 billion from more than 100 banks across 30 countries. In early 2016, the group continued to target banks, mainly in the Middle East and U.S.
In November last year, Trustwave observed a campaign targeting organizations in the hospitality sector where Carbanak hackers would call customer service saying they couldn’t make a reservation and requested to send information via email.
Earlier this year, the Carbanak malware was seen using Google services for command and control (C&C) communication, and security researchers revealed that the group would deploy a large number of tools as part of their attacks.
The most recent attacks associated with the group continue to employ a variety of tools, but have switched to new social engineering techniques. The attackers now send a malicious Word or RTF document to employees of organizations in the hospitality sector, and then call to ask whether the document was opened and would follow up with another call 30 minutes later.
The actors claim that the sender had trouble with the online ordering system, or that the document referred to a lawsuit caused by a member of the group getting sick after having a meal at one of the targeted organization's restaurants. The phone calls were meant to ensure the victim opened the malicious document, the security researchers say.
One of the analyzed infected RTF documents dropped two VBS and one PS1 file onto the targeted system. To achieve persistence, a scheduled task to run the main malware file every 25 minutes was created. On top of that, the C&C malware creator script was observed dropping additional malware and support files in a different folder, including another PS1 file, four more VBS scripts, and INI and TXT files.
The INI file in this campaign is used to issue commands to the compromised machine and to reflect the status of previous commands. The INI processing script, which parses and processes the INI file, provides commands such as Screenshot (save screenshot as screenshot.png), Runvbs, Runexe, Runps, Update, and Delete.
The INI file also contains information on whether the malware has transmitted the victim's system information to the attacker. The sent information includes OS name and version, available physical memory, total physical and virtual memory, time zone, computer name, a list of processes, user name, and processor and BIOS information.
The attackers no longer used user accounts and passwords for lateral movement. Instead, the malware would bypass authentication on the remote system and use SMB commands to locate vulnerable hosts and compromise them.
Trustwave also notes that the Carbanak malware writers have used various methods to hide the functionality of their malicious programs: PowerShell script file created from base64 encoded string hidden in malicious Word document; three levels of decoding for the final PowerShell script; a base64 encoded string in this script; alphanumeric shellcode and encoded payload obtained via DNS TXT records; and more.
To stay protected, organization are advised to perform regular security awareness training for all employees and pay particular attention to spear phishing, do spear phishing exercises, use an email server or appliance that can assist with malware detection, disable macros by default on all Office applications, use a SIEM or other log-and-event aggregation system so that aggregated network traffic can be examined, ensure IDS rules are able to detect metasploit modules, blacklist all PowerShell scripts and VBS scripts not used by the organization, perform continuous DNS monitoring, and restrict DNS traffic.
Europol Probing IS Setting Up of Social Network
4.5.2017 securityweek Social
The Hague - European police are probing whether the Islamic State group and other extremists are setting up a social network to spread propaganda, gain funding and avoid security crackdowns, an official said Wednesday.
"We are investigating the possibility that IS and other terror groups are setting up a social media platform," said Jan Op Gen Oorth, communications officer for the Europol policing agency.
"We are still working on identifying the full details of the account, including who has set it up and for what purpose," Oorth told AFP, but added that it showed likely links to IS and other extremists.
The investigation comes as Europe's policing agency struck out at online radical groups last week in a two-day operation.
Together with officers from Belgium, Greece, Poland, Portugal and the United States, Europol assessed more than 2,000 pieces of online content last Tuesday and Wednesday as "harmful and illegal" and referred them to online service providers for removal, the agency said in a statement.
"This coordinated hit against online terrorist propaganda focused mainly on the online production of terrorist materials by IS and Al-Qaeda affiliated media outlets," Europol said.
Among the items referred were propaganda videos and publications glorifying or supporting terrorism and extremism, it said.
Europol added that "efforts made by numerous online platforms to remove inappropriate content have driven supporters of terrorist groups to simultaneously use multiple platforms to promote terrorism and incite violence".
"They have also been searching for new service providers to make sure their messages reach potential supporters, while a growing interest for platforms that do not require identification can be witnessed," the agency said.
Google Docs Phishing Scam Doused After Catching Fire
4.5.2017 securityweek Phishing
A phishing scam that tricked people with what appeared to be Google Docs links was doused by the internet giant after spreading wildly on Wednesday.
The purpose of the scam, and the culprits behind it, remained unknown late in the day.
"We have taken action to protect users against an email impersonating Google Docs, and have disabled offending accounts," a Google spokesperson said in an email response to an AFP inquiry.
"We've removed the fake pages, pushed updates through Safe Browsing, and our abuse team is working to prevent this kind of spoofing from happening again."
The scam combined "a phishing attack and a worm," using a deceptive email to get people to open the door to malicious code that wriggled into their messaging programs to spread itself to others, according to Electronic Frontier Foundation staff technologist Cooper Quintin.
Email sent from a known contact's real address would arrive containing a link it claimed led to a file to be shared at Google Docs online service, according to a rundown of the chicanery.
Clicking the link led to a real Google web address and asked for authorization to run an application the attacker had cleverly called 'Google Docs.'
Permissions granted to the application included allowing it to read or send email on a person's behalf.
"It doesn't immediately look like a phishing email," Quintin said.
"When you authorize the app, the very next thing it does is send the same emails to everyone in your contacts."
The application, along with online domains it was connecting to, were disabled within hours of it starting to spread wildly, according to Quintin.
"I suspect that it was far more successful than whoever released it into the world hoped or expected, and was maybe undone by its own success," he said.
"The domains went down pretty quickly. Google disabled the app, so it is no longer a threat."
Unpatched WordPress Password Reset Flaw Disclosed
4.5.2017 securityweek Vulnerebility
A researcher has disclosed the details of a WordPress vulnerability that can be exploited by an unauthenticated attacker to reset a targeted user’s password. The flaw was reported to WordPress months ago, but it still has not been patched.
Security researcher Dawid Golunski, known for finding serious vulnerabilities in MySQL and some popular email-sending PHP libraries, published an advisory on Wednesday detailing a weakness in the WordPress password reset feature.
Successful exploitation of the vulnerability allows an unauthenticated attacker to obtain the password reset link for a targeted WordPress account and change its password. The issue, tracked as CVE-2017-8295, has been classified by Golunski as “medium/high severity.”
The problem, according to the expert, is related to the fact that WordPress uses a variable named SERVER_NAME to obtain the hostname of a server when setting the From/Return-Path header in password reset emails sent to users.
Since the value of this variable is often set using the hostname supplied by the client via the HTTP_HOST header, an attacker can inject an arbitrary domain by sending a specially crafted request to the targeted WordPress website.
In an attack scenario described by Golunski, the attacker sends a specially crafted request to the targeted WordPress site in order to trigger a password reset. Since the hostname in the request is an attacker-controlled domain, the From and Return-Path fields in the password reset email sent to the victim will specify an email address on the attacker’s domain.
Once the targeted user receives the password reset link, there are several methods the attacker can use to obtain it now that the From and Return-Path fields point to their domain.
One possibility, said Golunski, is to get the victim’s email account to stop accepting emails, either via an attack on its DNS server or by sending it large files until the mailbox quota is exceeded. If the email account can no longer receive emails, the password reset email is returned to its sender, which in this case is the attacker’s email account as it is specified in the From and Return-Path fields.
If an autoresponder is enabled on the victim’s email account, the attacker could easily obtain a copy of the password reset email as some autoresponders include a copy of the original message in the automatic reply.
Another option is to send a large number of password reset emails to the victim, which could get them to reply in an effort to find out why they are getting so many messages. The reply, which likely includes the password reset link, goes to the attacker.
According to Golunski, the vulnerability affects all versions of WordPress, including 4.7.4, released two weeks ago. The researcher said he reported the security hole to WordPress’ security team several times since July 2016, and decided to make his findings public after no progress was made.
Until a patch is released, Golunski has proposed a temporary solution. Users have also discussed possible mitigations and workarounds on Reddit.
SecurityWeek has reached out to WordPress for comment and will update this article if they respond. It’s possible that WordPress developers see this as a low risk issue given that an attack would not work against websites hosted on shared servers, and considering that obtaining the password reset link may not be easy.
eDiscovery - An Enterprise Issue That Can't be Ignored
4.5.2017 securityweek Privacy
eDiscovery for Enterprises
eDiscovery is a concept born from litigation. It describes the need to find and retain electronic data that might be required in litigation ― whether for the plaintiff, the defendant or a third party. In recent years, eDiscovery has become considerably more complex. Business is increasingly litigious; legal obligations such as freedom of information (FoIA) laws and Europe’s General Data Protection Regulation (GDPR) are generating new demands; and the sheer volume and diversity of corporate electronically stored information (ESI) is expanding dramatically.
E-discovery Requirements
For Litigation
In its original sense, eDiscovery is the process of fulfilling the legal requirement to locate and present documents pertinent to a legal case; that is, litigation support. It goes beyond simple discovery to include the concept of ‘litigation hold’; that is, the safe preservation of such documents.
The need to do this is growing. A recent paper compiled by Osterman Research questioned nearly 150 decision makers from medium and large companies in North America ― and found that 60% of the respondents were somewhat or very worried that their organizations would be sued. The research also indicated that 75% of the organizations had received an average of 12 requests during the past 12 months.
The primary source of litigation obligation in the US comes from the 1938 Federal Rules of Civil Procedure. This was updated in 2006, and again in 2015. It now places greater focus on the preservation of ESI, and makes the failure to produce required documents potentially more expensive. There is effectively no source of ESI that is exempt, whether that is in the cloud, on social media, or stored on employees’ personal devices.
“In short,” notes Osterman, “any electronic information that contains a business record, regardless of the tool that was used to create it or the venue in which it is stored, will potentially be subject to eDiscovery. The amendments to the FRCP in 2006 and 2015 have, for all intents and purposes, made anything from any source potentially subject to eDiscovery.”
For FoIA
While litigation eDiscovery is governed by the Federal Rules, FoIA requests are governed directly by the Freedom of Information Act. The FoIA establishes a statutory right of public access to Executive Branch information in the federal government.
In litigation, only those parties involved can demand eDiscovery, and can only demand eDiscovery of litigation-pertinent ESI. FoIA requests, however, can be from anyone for anything, and there are no relevancy requirements. So, while FoIA targets may be fewer (limited to government), the source of requests is much greater and can include just about anything.
For GDPR
GDPR is a new type of eDiscovery driver that applies only to companies operating in, or with operations in (such as trading with) the European Union. It includes facets of both litigation discovery and FoIA discovery. Like FoIA, it does not require litigation, but it does require relevancy (that is, a customer or customer’s representative).
GDPR is a user-centric privacy law. It gives users greater control over how their personal information is used by commerce; with potentially huge sanctions on companies that break the law. Two example requirements will demonstrate the need for efficient eDiscovery: the so-called right-to-be-forgotten; and the requirement for unambiguous and revocable informed consent from the user to the company collecting and using personal data.
The only way an organization can comply with either is if it can ‘discover’ all instances of personal data that it needs to forget (remove), and can prove that it has removed those records. Similarly, to demonstrate that it has revoked consent, it will need a record of the initial consent that is now revoked.
The Scope of the Difficulty
“eDiscovery is a term that seems simple in conversation ― but no one is truly ready for what it really means,” warns Drew Koenig, security solutions architect at Magenic. “Off the record, I’ve seen a 200% increase in the last 3 years with Lit Holds and eDiscovery involved cases,” commented a CISO who did not wish to be named.
There are two primary categories to the eDiscovery problem: data and organization. The data issue comprises volume, variety of data types, and physical location of that data. The organization problem is one of ownership. Who owns responsibility for eDiscovery?
Volume
The sheer volume of ESI stored by corporations is staggering. Without specific procedures able to find relevant documents, the time and cost involved would be enormous. Part of the volume problem is data classification ― the need to know what data might be relevant.
Variety
eDiscovery draws no distinction over how data is stored. It could be in structured databases and spreadsheets, or unstructured email, voicemail, documents, presentations or CRM data. It simply needs to be stored.
Location
eDiscovery draws no distinction over where data is stored. It could be on in-house servers, in the cloud, on employees’ personal devices, on websites or in social media accounts ― or with a service provider.
Responsibility
eDiscovery involves multiple departments. IT is responsible for the infrastructure that holds ESI; Security is responsible for protecting it; Compliance is involved through regulations such as GDPR; and Legal is responsible for litigation aspects of discovery. With no single owner to take responsibility of eDiscovery, the danger is that no-one does.
The combination and interaction of these difficulties is a huge problem for many organizations. “Depending on legal requirements a business may have to reach out into social networks, personal home computers (BYOD), cloud services, IoT/mobile devices in addition to corporate assets,” warns Koenig.
“The ever-changing data flows makes a consistent model and applying control sets near impossible. The infrastructure to store and process is usually under-estimated. Most clients, in my experience, begin but collapse under the immense weight of data they realize they truly have. There is a growing compliance need for this, but no security tool will tell you how to be secure or how to classify data. That's up to the business to solve, then find the tools to solve them. eDiscovery is another example that security is a business problem not a technology problem. Without business security processes around data classification and use, no tool will help you fully.”
Solutions in Practice
Despite these difficulties, eDiscovery is a legal requirement that cannot be shirked. Adequate preparation is the key, so that when a discovery request or right-to-be-forgotten demand is made, it can be actioned efficiently.
“Lack of preparation for eDiscovery can expose a business to serious legal and financial risks if the organization can’t find the complete set of information requested,” warns Mike Pagani, chief evangelist at Smarsh, a provider of cloud-based information archiving solutions. “If the information wasn’t retained in an organized way for easy retrieval, or if it was altered in any significant way, that creates significant eDiscovery problems.”
The first task is that of ownership; and there is no single solution. Much will depend on the type and size of the organization.
For Samsung Research America, eDiscovery is owned by Security. Steve Lentz, CSO, explains. “Security is responsible here for anything to do with security, including eDiscovery. We work with the relevant departments, such as IT, Legal, HR, Lab, etc, to gather the data… Bottom line,” he adds, “is that you need to communicate and collaborate with the responsible departments.”
This is a good working model ― effectively a committee of relevant department heads that meets regularly, but with a specific chairman. In this organization, it is Security; in others that might be subject to a high rate of litigation, it could be Legal.
“The answer to the question,” suggests Brian Kelly, chief information security leader at Quinnipiac University, “like many legal questions, is ‘it depends’. The size of the organization is the key. In my role, I see the Information Security function as a ‘support agency’ to both Legal and Compliance (depending on the case being investigated). While I was at a health insurance company, it was part of Internal Audit. Ultimately, I think it’s a combination that works best with Legal directing and Information Security or IT completing tasks.”
The very largest corporations may require something different. “There was a prediction made not long ago,” says Martin Zinaich, information security officer at the city of Tampa, “that a new position would start to appear in larger organizations ― Chief Information Governance Officer ― a combination of Information Security and Governance. If that ever does happen, eDiscovery will have found its home.”
Technology
The volume of ESI, the diversity of data types, and its physical distribution combine to create a problem that for most companies can only be solved by technology. “eDiscovery systems are plentiful, from cloud hosted to on-site,” says Zinaich ― but choice is important. “The reality is most of the cloud based system are more record processing. They help identify, preserve, collect, review and process. The real trick is making sure everything relevant is in the eDiscovery system. On-site packages often tackle the collection of data from disparate systems and the processing of that data.”
Pagani believes the solution is in the cloud. “Modern comprehensive archiving technology can enable eDiscovery for blog posts, social media feeds, instant messages, text messages and much more, all in one platform,” he claims. The single platform is important to avoid multiple separate silos of discoverable EIS. “Furthermore,” he adds, “comprehensive archiving platforms that retain non-email electronic communications in their native, proper context (e.g. a Tweet as a Tweet and not an email representation of a Tweet) should be implemented to prevent material alteration of messages.”
The cloud becomes important, he suggests, “because it offers the scalability needed to keep up with the rapidly expanding volume of information created each day.” But technology alone is not enough ― especially where eDiscovery is based on separate silos of archived EIS.
Manual Processes
“From a pure legal standpoint,” comments Zinaich, “it is advantageous to keep records only as long as they are relevant or legally required. Yet, often that determination is based on the type of data.” An email archive, he explains, “is likely holding spam, solicitations, birthday announcements and other transitory data. Unless each email is categorized, the IT department is stuck with keeping everything, and they are not sure how long they have to keep everything.”
“Keeping track of where everything is, or could be, is daunting. In most cases email is the primary ‘place’ for evidence,” says Kelly. “Microsoft has some great Lit Hold and eDiscovery tools built in to Exchange and Office 365 (email, OneDrive, SharePoint). Collecting and searching can be done through automation and there is a host of vendors and tools out there.” But, he warns, “Making sense of the results is still a manual process that either staff lawyers, legal assistants or IT workers at counsel have the unenviable job of sifting through.”
“Another challenge is redaction,” adds Zinaich. “When information is gathered from all points, it has to be reviewed and appropriately redacted to keep security information, investigation information, intellectual property and other exempt data safe. While there are systems that help with a bit of AI, it is largely a very costly manual process.”
eDiscovery going Forward
eDiscovery is already a complex issue, involving multiple departments and a mix of business and technology processes. It is going to get worse. Both business and society are increasingly litigious; regulations such as the FoIA and GDPR are likely to increase; and both the volume and location of EIS are expanding.
There is one other emerging area that will make matters worse: the internet of things (IoT). It is already here in some areas, and will emerge in others. Consider a company connected car. If it is involved in an accident, access to the vehicle’s logs will be required either to make or defend a claim.
But it goes further, and even beyond business. “The IoT will move eDiscovery from the Boardroom to the Livingroom,” warns Kelly. “Every divorce lawyer will be looking for logs from NEST thermostats, webcams and maybe even the refrigerator.” Much of that could just as easily apply to the office.
Large Companies Lack Clear Vision on Industrial IoT
4.5.2017 securityweek IoT
Interest in the internet of things (IoT) and the industrial internet of things (IIoT) continues to grow; but actual activity lags behind interest. Security remains industry's biggest concern.
A recent survey and report from the Business Performance Innovation (BPI) network and the CMO Council, sponsored by The Nerdery, indicates that 55% of all executives say IIoT is gaining adoption within their industries, including both pilots and larger-scale adoption. But only 1.5% of executives at large companies say they have a "clear vision with implementation well underway".
Cyber security and data privacy are the top concerns, with cost and complexity and staff issues following. Although security and privacy are separate issues, the report places greater emphasis on privacy than security -- which is perhaps not surprising given the CMO Council's involvement.
Patrick Theimer, Director of Marketing Technologies at Kennametal, sees the IoT revolutionizing both productivity and sales. But he also sees a conflict between the demands of IT and marketing.
"You need to design to prevent data breaches because the customer now has much more access to your organization, but you also need to ensure it is done in such a way that they don't keep you from having the response levels you need," Theimer said. "I think we will see a lot of struggles over this balance between the CIO and the CMO, with CMOs rightly focused on the need to respond quicker and be more agile and with CIOs focused more on security and protection. In larger organizations, this is a significant challenge."
Arjan de Jong, a senior business developer at Nuon, the Dutch subsidiary of Vattenfall (which works with renewable energy and smart homes) doesn't see security as the biggest problem. His concern is over standards. "We have an example of a smart lighting producer that wants to do business with us, but we have been unable to partner with them because of different standards; their products do not really integrate with popular solutions, such as Apple Home."
Nevertheless, he does see privacy as an issue. In the Netherlands, he believes that the privacy issue is hyped by activists who 'leverage fear'. "We did some testing, and we found that about a third of the Dutch population is deeply concerned or even paranoid about privacy -- they do not want to share anything. Another third wants to share data, especially if it makes their life easier. The other third is prepared to share their data if they profit from it, so they want to sell us their data. Data security is the same as regular security. There will always be a risk, but also potentially a great opportunity."
CMO and head of strategy at Philips Lighting, Bill Bien, suggests that customers are not yet aware of the advantages that can accrue from IoT. "I think the biggest issue for us is to educate customers about the benefits and opportunities of connectivity and how lighting technology has changed by developing use cases that demonstrate significant value gains," he explains.
For security professionals and researchers, a big concern with this report will be the relative lack of interest in cyber security and data privacy. It is discussed as a concern, but with no solutions beyond educating customers to the benefits of data sharing.
Despite this, both security and privacy are likely to play major parts in the evolution of the IoT. The General Data Protection Regulation (GDPR) will force vendors to be more open about the data collected and how it is used, and to protect that data from cyber criminals.
In the US, recent months have seen increased activity from lawmakers who now seem to accept the need to impose security by legislation. Two developments in particular are designed to force cyber security responsibility into the boardroom: the New York State Department of Financial Services regulation and the Cybersecurity Disclosure Act of 2017.
There is even a new bill aimed specifically at the IoT: the California SB 327 Information privacy: connected devices. It proposes: "A manufacturer that sells or offers to sell a connected device in this state shall equip the device with reasonable security features appropriate to the nature of the device and the information it may collect, contain, or transmit, that protect the device and any information contained therein from unauthorized access, destruction, use, modification, or disclosure."
It also proposes, "A manufacturer that sells or offers to sell a connected device in this state shall design the device to obtain consumer consent before it collects or transmits information beyond what is necessary in order to fulfill a consumer transaction or for the stated functionality of the connected device."
While industry might be viewing the IoT in terms of competitiveness and commercial opportunity, it simply cannot and must not ignore cyber security and data privacy.
Se Shodanem proti malwaru
4.5.2017 SecurityWorld Viry
Nový nástroj Malware Hunter, spolupracující s vyhledávacím enginem Shodan, už odhalil téměř šest tisíc zákeřných RAT serverů.
Společnost Recorded Future představila nový nástroj pro boj s malwarem, určený především do podnikového prostředí. Na jeho vývoji spolupracovala s autory Shodanu, vyhledávacího enginu určeného pro vyhledávání nikoliv stránek, ale počítačů a dalších elektronických zařízení připojených k internetu.
Jejich společné dílo má prostý název Malware Hunter. Jeho úkolem je nepřetržité skenování sítě a nacházení kontrolních bodů spjatých s více než desítkou různých RAT trojských koňů, včetně programů Gh0st RAT, DarkComet, njRAT, ZeroAccess nebo XtremeRAT. Ty všechny spadají do kategorie komerčních malwarových nástrojů sehnatelných za peníze na pochybných hackerských fórech.
K odhalení jejich centrálních uzlů Malware Hunter navazuje spojení s veřejnými IP adresami a odesílá data tvářící se jako ta, která by vzdálenému serveru odesílal trojan. Zatím se mu takto podařilo nalézt více než 5700 RAT serverů, z nichž se víc než 4000 nacházelo na území Spojených států. Nejrozšířenější mezi nimi byl Gh0st RAT, malware čínského původu používaný od roku 2009.
Výstupem práce Malware Hunteru je v reálném čase aktualizovaný seznam centrálních uzlů malwaru, s nímž mohou bezpečnostní, ale i jiné firmy či nezávislí vývojáři pracovat a škodlivý přenos dat blokovat. Tím tak brání útočníkům ve zneužívání zasažených počítačů nebo kradení dat. Teoreticky jde o rychlejší řešení, než čekat na to, až bezpečnostní společnosti odhalí nové typy nebezpečných RAT programů a škodné servery ve svém sofwaru zablokují.
Chinese TA459 APT exploits CVE-2017-0199 flaw to target Financial firms
3.5.2017 securityaffairs APT
Malware researchers at security firm ProofPoint reported the Chinese TA459 APT has exploited the CVE-2017-0199 vulnerability to target Financial firms.
The notorious cyber espionage group tracked as TA459 APT has targeted analysts working at major financial firms using the recently patched CVE-2017-0199 Microsoft Office vulnerability.
Experts at Proofpoint published a detailed analysis of the espionage campaign conducted by the TA459 APT group against military and aerospace organizations in Russia and Belarus.
“Proofpoint is tracking this attacker, believed to operate out of China, as TA459. The actor typically targets Central Asian countries, Russia, Belarus, Mongolia, and others.” reads the analysis published by Proofpoint. “TA549 possesses a diverse malware arsenal including PlugX, NetTraveler, and ZeroT”
The TA459 APT group has been active since at least 2013, the hackers leveraged several malware in their campaign, including NetTraveler , PlugX, Saker, Netbot, DarkStRat, and ZeroT. The hackers most focused their efforts on spying on organizations in Russia and neighboring countries.
The attacks conducted by the TA459 APT group were apparently aimed at analysts covering the telecommunications industry, Proofpoint researchers speculate this latest campaign is likely a continuation of the campaign they uncovered in the summer of 2015.
“Proofpoint researchers recently observed a campaign targeting telecom and military in Russia. Beginning in July 2015 (and possibly earlier), the attack continued into August” wrote Proofpoint.
The TA459 APT leveraged spear-phishing emails using weaponized Word document that trigger the CVE-2017-0199 flaw. The hackers started exploiting the Office flaw just a few days after Microsoft released a fix.
When victims open the decoy document, an HTML application (HTA) file disguised as an RTF document is downloaded. The attack exploits PowerShell to download and executes a script that fetches and runs the ZeroT downloader.

Proofpoint noticed some improvements in the last ZeroT version such as the use of a legitimate McAfee utility for sideloading instead of a Norman Safeground utility.
“The attack group has made incremental changes to ZeroT since our last analysis. While they still use RAR SFX format for the initial payloads, ZeroT now uses a the legitimate McAfee utility named mcut.exe instead of the Norman Safeground AS for sideloading as they have in the past. The encrypted ZeroT payload, named Mctl.mui, is decoded in memory revealing a similarly tampered PE header and only slightly modified code when compared to ZeroT payloads we analyzed previously.” continues the analysis.
Proofpoint reported that the TA459 APT group used both PlugX and a Trojan tracked as PCrat/Gh0st in the last wave of attacks.
The experts invite multinational organizations to stay vigilant about state-sponsored actors that use sophisticated malware in their cyber espionage campaigns.
“Ongoing activity from attack groups like TA459 who consistently target individuals specializing in particular areas of research and expertise further complicate an already difficult security situation for organizations dealing with more traditional malware threats, phishing campaigns, and socially engineered threats every day.” concluded Proofpoint.
[adrotate banner=”9″]
Industrial Robots Vulnerable to Remote Hacker Attacks
3.5.2017 securityweek Vulnerebility
Researchers have conducted an in-depth analysis of industrial robots in an effort to determine how easy it would be for malicious actors to remotely take control of such machines.
Robots are increasingly present in industrial environments, including in critical sectors, and they are often connected to the outside world, which could make them an easy target for hacker attacks.
On Wednesday, researchers at Trend Micro and the Polytechnic University of Milan released a paper focusing on the cybersecurity risks associated with industrial robots.
During their analysis, experts discovered that a growing number of industrial robots include remote access features designed for monitoring and maintenance. While these features can be useful for operators, they can also introduce serious security risks.
Internet scans conducted using the Shodan, Censys and ZoomEye services showed that some robots are exposed to the Internet via their FTP servers. Experts identified more than two dozen exposed robots in Europe, the United States, East and Southeast Asia, and Australia.
Robots can also be exposed to attacks from the Internet through industrial routers. Researchers discovered more than 80,000 industrial routers, mostly from vendors such as Sierra Wireless (50,000), Moxa (12,000), eWON (6,000) and Westermo (6,000). A majority of these devices are located in the United States, followed by Canada and several European countries.
The problem is that these routers are often misconfigured or affected by vulnerabilities. The security holes identified by experts include outdated software, device information leaks, default credentials or poor authentication, weak transport encryption, and insecure web interfaces.
While the actual robots can cost tens of thousands of dollars and some vendors only provide software and firmware to customers, researchers pointed out that software and firmware is often publicly available, and some manufacturers provide simulators that can be leveraged by hackers to test their attacks.
Researchers described several possible attack scenarios, including ones where the attacker alters the control system or changes calibration to cause the robot to move inaccurately or unexpectedly. An attacker could also tamper with the production logic, manipulate robot status information to trick the operator, and modify the machine’s state.
Robots can be targeted in a wide range of attacks, including to inject faults and microdefects into a product, take control of a machine to cause physical damage or to injure people, cause damage to the production line, and exfiltrate sensitive data. Ransomware attacks are also possible, where the attacker stealthily introduces microdefects in the production chain and then asks for a ransom to reveal which product lots are affected.
Researchers created a setup to demonstrate an actual attack using an IRB140 industrial robot from ABB Robotics:
Trend Micro has notified affected robot and router vendors, but some of them did not seem interested in the company’s findings. The security firm named ABB, eWON and Moxa as the companies that were open to suggestions for making security improvements.
Trend Micro’s research comes shortly after IOActive published a paper describing vulnerabilities in home, business and industrial robots.
Mozilla Tells Symantec to Accept Google's CA Proposal
3.5.2017 securityweek Safety
Mozilla has shared details about its own position in the debate between Symantec and Google regarding improper issuance of digital certificates. The organization advised Symantec to accept Google’s offer, but it has also described alternative action it may take if an agreement is not reached.
Google announced in March its intent to stop trusting all Symantec-issued digital certificates due to the certificate authority’s failure to play by the rules. Symantec, its subsidiaries and its partners had been accused of making too many exceptions from Baseline Requirements (BR) in favor of their customers.
The developer of the Chrome web browser initially proposed the reduction of the validity period for newly issued Symantec certificates to nine months or less, gradual distrust and replacement of all existent certificates, and the removal of extended validation (EV) status for Symantec certificates.
Symantec called Google’s statements “exaggerated and misleading,” and pointed out that the changes could have a serious impact for its customers.
After some debate, Google made a second proposal that involves Symantec partnering with one or more existing CAs and using their infrastructure and validation process. Symantec would still handle business relations with customers and all CAs would be cross-signed by the company.
“It's worth noting that this proposal minimizes any impact to Symantec customers, existing or new,” said Ryan Sleevi, a software engineer on the Google Chrome team. “It provides a graceful transition path that does not negatively impact existing customers who have special needs - such as those of pinning or certain roots. It does not prohibit Symantec from continuing to use and operate its existing infrastructure for non-Web cases, but eliminates the security risk from doing so.”
Last week, Symantec came forward with its own proposal for restoring trust. The cybersecurity giant’s proposal includes auditing of all active certificates by a third-party auditor, more transparency, shorter validity for certificates, and several operational improvements.
Google is still not satisfied with the steps Symantec has offered to take, and it plans on continuing public discussions on the matter.
Mozilla, which has been conducting its own investigation into Symantec’s CA business, also has some concerns regarding Symantec’s proposal. The browser vendor says some of the proposed actions either don’t make any difference or they are simply not enough for regaining trust.
Mozilla has advised Symantec to accept Google’s second proposal and said it’s open to discussing its implementation. However, if Symantec refuses, Mozilla may take alternative action to “reduce the risk from potential past and future mis-issuances by Symantec, and to ensure future compliance with the BRs and with other root program requirements.”
Mozilla’s proposal requires Symantec to clean up its public key infrastructure (PKI) and cut off parts that are not compliant with BR. The organization could also limit the validity of newly-issued certificates to 13 months, and progressively reduce the lifetime of existing certificates to the same period.
Google Patches More Critical Flaws in Android Mediaserver
3.5.2017 securityweek Android
Google this week announced the contents of the May 2017 Android security patches, revealing that six Critical Remote Code Execution (RCE) flaws were addressed in the Mediaserver component.
Over the past couple of years, Mediaserver emerged as one of the most vulnerable Android components, after a Critical RCE bug dubbed Stagefright was said to affect 950 million devices. Detailed in July 2015, the vulnerability encouraged Google to issue monthly security updates for Android.
A second Stagefright flaw was resolved only months later, and Google addressed numerous other vulnerabilities in Mediaserver over the nearly two years of regular patches. The company even decided to re-architect Mediaserver with the release of Android 7.0 Nougat in August last year, but security researchers continue to find vulnerabilities in the component.
Published on Monday, Google’s Android Security Bulletin for May 2017 was divided into two patch levels: the 2017-05-01 partial security patch level string, which addresses 20 flaws, and the 2017-05-05 complete security patch level string, which addresses 98 issues. None of the vulnerabilities has been exploited or abused in live attacks, Google’s advisory reveals.
The six Critical issues in Mediaserver, resolved in the 2017-05-01 patch level string, could enable remote code execution on affected devices through multiple methods, including email, web browsing, and MMS when processing media files. The bugs impact numerous platform versions, including Android 4.4.4, 5.0.2, 5.1.1, 6.0, 6.0.1, 7.0, 7.1.1, and 7.1.2.
The patch level also addresses three High-risk Elevation of privilege (EoP) and four Denial of service (DoS) (two High, one Moderate, and one Low severity) vulnerabilities in the Mediaserver component.
The remaining 7 issues include two High risk bugs in Framework APIs (one EoP and one Information disclosure), a High severity EoP in Audioserver, a Medium risk EoP in Bluetooth, and three Moderate severity Information disclosure vulnerabilities (in File-Based Encryption, Bluetooth, and OpenSSL & BoringSSL).
The 2017-05-05 security patch string resolves 23 Critical bugs, 59 High severity issues, and 16 Moderate risk flaws. All of the vulnerabilities addressed in the previous strings are also resolved in this patch level, Google notes.
The 23 Critical bugs included an RCE in GIFLIB, 8 EoPs in MediaTek touchscreen driver, Qualcomm bootloader, kernel sound subsystem, Motorola bootloader, NVIDIA video driver, Qualcomm power driver, kernel trace subsystem, and 14 various vulnerabilities in Qualcomm components.
Of the 59 High severity issues, 14 were various bugs in Qualcomm components; one RCE in libxml2; 40 EoPs in MediaTek drivers, Qualcomm drivers, kernel subsystems (performance and networking), Goodix touchscreen driver, and HTC bootloader; 3 Information disclosure flaws in MediaTek command queue driver and Qualcomm Wi-Fi and crypto engine drivers; and one DoS in Qualcomm Wi-Fi driver.
All of the 16 Moderate severity vulnerabilities were Information disclosure bugs, affecting kernel UVC driver and kernel trace subsystem, Qualcomm drivers (video, power, LED, shared memory, sound codec, camera, sound, SPCom), Broadcom Wi-Fi driver, and Synaptics touchscreen driver.
“The most interesting piece of the May Android patches is that Google fixed six issues affecting Mediaserver, all with critical severity indicating the potential for remote code execution. What is not clearly stated is whether the mitigations added into the Android 7.0 release might actually prevent an attacker from exploiting the bugs,” Craig Young, computer security researcher for Tripwire’s Vulnerability and Exposures Research Team (VERT), told SecurityWeek in an emailed comment.
“With Android 7.0, Google has revamped the Mediaserver component by moving risky parsing code into unprivileged sandboxes and by enabling Undefined Behavior Sanitizer (UBSAN) to prevent exploitation of the most common bug classes found in this component. It would be nice to see Google release more detailed bulletins indicating the impact of various vulnerabilities specifically to the different Android versions.
“It is also good to see that Google’s telemetry through SafetyNet did not reveal any active customer exploitation of any flaws fixed in the May update,” Young concluded.
New Cerber Ransomware Variant Emerges
3.5.2017 securityweek Ransomware
A new variant of the Cerber ransomware has emerged over the past month, featuring multipart arrival vectors and refashioned file encryption routines, TrendMicro security researchers warn.
An active threat for over a year, Cerber managed to climb at the top of ransomware charts earlier this year, accounting for 87% of attacks in the first quarter of 2017. The rise was fueled mainly by a major decrease in Locky attacks, but Cerber’s popularity among cybercriminals also helped.
Cerber distribution campaigns leverage various methods to increase the rate of infection, including spam email, exploit kits, or newly discovered vulnerabilities, such as the Apache Struts 2 flaw. The malware itself has received numerous improvements, including the ability to evade machine learning security.
Distributed using a ransomware-as-a-service business model, Cerber reached version 6 in April 2017 and is believed to be generating millions of dollars in annual revenue for its operators and developers. The new threat variant packs not only new encryption routines, but also additional defense mechanisms, such as anti-sandbox and anti-AV techniques.
The new variant is being distributed through spam emails containing a zipped attachment with a malicious JavaScript (JS) file inside. After analyzing multiple JS files, TrendMicro found that all have a three-pronged approach: directly download and execute the payload, create a scheduled task to run the malware after two minutes, or run an embedded PowerShell script.
The use of delayed execution allows the ransomware to elude traditional sandbox defenses that feature time-out mechanisms or which wait for the final execution of the malware. The use of PowerShell for Cerber’s delivery isn’t surprising, given the popularity this technique has seen over the past months.
Cerber 6 no longer has a routine for terminating processes, a feature added around October 2016 to terminate database software-related processes to ensure encryption of files. The new threat variant also added another check on file extensions it’s not supposed to encrypt.
“This harks back to how we saw Cerber exhibiting behaviors that foreshadowed its shift to stealth-focused techniques. In February this year, certain variants started checking if the affected system had any firewall, antivirus, and antispyware products installed, ensuring that their associated files aren’t encrypted,” the security researchers say.
Cerber 6 can now be configured to have Windows firewall rules added to block the outbound traffic of executables of firewalls, antivirus, and antispyware products installed in the system, in an attempt to restrict their detection and mitigation capabilities.
The ransomware now uses Cryptographic Application Programming Interface (CryptoAPI) for encryption, and has a separate function that reads and encrypts the contents of the file. Detailed in the beginning of this year, the Spora ransomware also leverages Windows CryptoAPI for encryption.
“Cerber’s developers are noted to implement their own encryption; the abuse of Windows’s CryptoAPI and separation of encryption function for Cerber 6 denote constant efforts from the malware authors to streamline their operations,” TrendMicro notes.
WordPress Attacks Powered by Router Botnet Drop Rapidly
3.5.2017 securityweek BotNet
A botnet powered by compromised home routers has been apparently shut down. It is unclear if the botnet operators decided to pull the plug on their operation or if the disruption was caused by law enforcement.
Security firm Wordfence warned last month that tens of thousands of vulnerable routers from dozens of ISPs worldwide had been abused for brute-force and other types of attacks aimed at WordPress websites.
Researchers said the attackers may have hijacked the devices by exploiting some known vulnerabilities that users and ISPs had failed to patch, including the flaw dubbed “Misfortune Cookie.”
However, on Tuesday, Wordfence reported that the volume of attacks had started to drop significantly over the weekend, particularly on Sunday night, Pacific time. By Monday evening, the 30,000 or 40,000 attack attempts coming every hour from some ISPs had dropped to less than 5,000, and the frequency of the attacks continued to decrease.
Wordfence has not been able to determine what caused the apparent shut down of the botnet and it’s unclear if the situation is permanent or just temporary. However, the company believes we might know exactly in the next few weeks.
One possible scenario is that the attackers themselves decided to end their operation for some reason. Another possibility is that law enforcement or other entities managed to take down the command and control (C&C) servers used by the botnet.
Law enforcement agencies have been very busy targeting cybercriminal operations in recent weeks. In April, U.S. authorities announced efforts to disrupt and dismantle the Kelihos botnet. Two weeks later, Interpol reported that authorities in the ASEAN region worked with private companies to identify nearly 9,000 C&C servers and hundreds of compromised websites.
The recent attacks originating from routers had caused Wordfence and organizations such as Spamhaus to blacklist the offending IP addresses, which resulted in users being unable to access certain online services.
“By reducing these attacks, this ensures those ISP customers have full internet access again,” said Wordfence’s Mark Maunder.
Number of WordPress Attacks powered by compromised routers is rapidly dropping
3.5.2017 securityaffairs Vulnerebility
Experts from security firm WordFence reported a rapid reduction of WordPress attacks originating from hundreds of ISPs worldwide.
Experts at the security firm Wordfence a few weeks ago reported that tens of thousands of flawed routers from dozens of ISPs worldwide were recruited in a botnet used to power several types of attacks against WordPress websites.
Hackers exploited the CVE-2014-9222 flaw, also known as ‘Misfortune Cookie,‘ to hack thousands of home routers and abuse them for WordPress attacks.
According to a new analysis published by WordFence, the volume of the attacks had started to drop significantly over the weekend, by Monday evening, the 30,000 or 40,000 attack attempts coming every hour from some ISPs had dropped to less than 5,000. and the frequency of the attacks continued to decrease.
According to the researchers, this frequency is continuing to decrease.
“Yesterday morning we noticed that there was a rapid drop-off in attacks from the ISPs we identified 3 weeks ago, that had targeted WordPress websites.” reads the analysis published by WordFence.
“This is what the change in activity looked like from the top 50 ISPs from where these attacks were originating during a 72 hour period ending yesterday (Monday) evening. Click the chart for a larger version.”
“As you can see, starting at around midnight on Sunday night (April 30th) Pacific time, the number of attacks we are seeing from ISPs where we found vulnerable routers have dropped from peaks of 40,000 in some cases to peaks of just above 5,000 attacks per hour. In many cases the attacks drop to much lower levels and continue to decrease.”

The root cause of this drop is still unclear, researchers at WordFence believe the situation will be more clear in the next week.
A possible cause is that the attackers ended their operation for some reason, otherwise law enforcement along security firms have tracked the botnet and took down the command and control (C&C) servers.
A few weeks ago, US authorities announced have dismantled the infamous Kelihos botnet. In the same period, the Interpol located and shut down nearly 9,000 Command and control servers located in Asia and hacked with a WordPress plug-in exploit.
This reduction of WordPress attacks originating from hundreds of ISPs worldwide is a good news. The experts were able to track the WordPress attacks originating from these ISPs and ban IP addresses involved in the botnet.
“The attacks originating from these ISPs were also resulting in their IP addresses being blacklisted by Wordfence and other services like SpamHaus. That resulted in the customers of those ISPs suffering because certain websites and services would block them. By reducing these attacks, this ensures those ISP customers have full internet access again.” concluded WordFence.
Information Security Practices of Aadhaar – 135 Million Indian government payment card details leaked
3.5.2017 securityaffairs Incindent
A CIS study estimated number of Aadhaar numbers leaked through 4 gov portals could be around 135 million and 100M bank account numbers.
The Aadhaar is the world’s largest biometric ID system, with over 1.123 billion enrolled members as of 28 February 2017.
The role of the system is crucial for both authenticating and authorizing transactions and is a pillar of the Indian UID (unique identification database).
Every problem with a similar system represents a disaster as explained in a report recently published by the Indian Centre for Internet and Society (CIS) titled “Information Security Practices of Aadhaar (or lack thereof): A documentation of public availability of Aadhaar Numbers with sensitive personal financial information“
The report highlighted the high security implemented by the Aahdaar itself, rather warn of possible data leaks caused by other government agencies accessing the system.
The research paper focus on four government-operated projects: Andhra Pradesh’s Mahatma Gandhi National Rural Employment Scheme; Chandranna Bima; the National Social Assistance Program; and an Andhra Pradesh portal of Daily “Online Payment Reports under NREGA” maintained by the National Informatics Centre.
Aadhaar system
The CIS examined numerous databases used by government offices, many of which included “numerous instances” of Aadhaar Numbers, associated with personal information.
“Actually, Aadhaar has a very strong privacy regulation built into it… But the area we are working on is enforcement,” Aruna Sundararajan, Secretary, Union Electronics and Information Technology Ministry, told The Hindu.
“People are not aware that so a large number of government agencies are making available all this sensitive data. So now, the process is to educate them so that they become aware that Aadhaar data is not meant to be published like this freely,”
According to the report, 135 million Aadhaar numbers and 100 million bank account numbers could have leaked from official portals dealing with government programs of pensions and rural employment.
The leaks represent a significant and “potentially irreversible privacy harm”, they potentially expose citizens to numerous illegal purposes.
Sundararajan confirmed that security and privacy issued will be addressed in the legislative amendments to the country’s IT legislation.
“Other major schemes, who have also used Aadhaar for direct benefit transfer [DBT] could have leaked PII similarly due to lack of information security practices. Over 23 crore beneficiaries have been brought under Aadhaar programme for DBT and if a significant number of schemes have mishandled data in a similar way, we could be looking at a data leak closer to that number,” concluded the report.
Trojský kůň Chromex se Českem šíří jako lavina, varovali bezpečnostní odborníci
3.5.2017 Novinky/Bezpečnost Viry
Doslova jako lavina se Českem šíří škodlivý kód Chromex. Tento trojský kůň představoval v dubnu každou pátou zachycenou hrozbu. Upozornili na to bezpečnostní odborníci z antivirové společnosti Eset.
Trojskému koni Chromex, jehož celý název zní JS/Chromex.Submelius, patří aktuálně druhá příčka v žebříčku nejrozšířenějších počítačových hrozeb. „Uživatel na něj může narazit například při sledování filmů nebo seriálů prostřednictvím některé neplacené a neoficiální streamovací stránky,“ uvedl Miroslav Dvořák, technický ředitel společnosti Eset.
„Ty totiž pro spuštění videa vyžadují několikeré kliknutí na náhled videa, které otevírá nová okna prohlížeče a zobrazuje v nich reklamy. Tyto weby v některých případech fungují na doménách .cz a .sk a obsahují nabídky instalace škodlivých pluginů,“ doplnil Dvořák.
Uživatel vpustí záškodníka sám do PC
Chromex může přesměrovat prohlížeč na konkrétní adresu URL se škodlivým softwarem. Ten je obvykle vložen do HTML a může zobrazovat falešná chybová hlášení typu „Chcete-li pokračovat v práci s prohlížečem, měli byste si nainstalovat rozšíření“.
Pokud uživatelé budou na tuto výzvu reagovat, nevědomky vpustí do svého počítače nezvaného návštěvníka – trojského koně.
Chromex nicméně není jedinou hrozbou, která dělá aktuálně bezpečnostním expertům vrásky na čele. Již několik měsíců varují také před škodlivým kódem zvaným Danger. Tento virus otevírá zadní vrátka do operačního systému. Útočníci pak díky němu mohou propašovat do napadeného počítače další škodlivé kódy, nejčastěji tak šíří vyděračské viry z rodiny ransomware.
Zašifrují data a chtějí výkupné
Tyto škodlivé kódy začnou šifrovat obsah počítače a uživateli zobrazí oznámení, že za dešifrování počítače musí zaplatit, jinak se ke svým datům údajně již nikdy nedostane.
Ani po zaplacení výkupného navíc nemají uživatelé jistotu, že se ke svým datům skutečně dostanou. Virus je nutné z počítače odinstalovat a data následně pomocí speciálního programu odšifrovat. V některých případech to ale není možné.
Přehled deseti nejrozšířenějších virových hrozeb za měsíc duben naleznete v tabulce níže:
Top 10 hrozeb v České republice za duben 2017:
1. JS/Danger.ScriptAttachment (21,33 %)
2. JS/Chromex.Submeliux (19,22 %)
3. Win32/Adware.ELEX (3,78 %)
4. JS/TrojanDownloader.Nemucod (3,73 %)
5. Java/GRat (2,89 %)
6. VBA/TrojanDownloader.Agent.CZT (2,38 %)
7. Java/Kryptik.AP (2,28 %)
8. PowerSheil/TrojanDownloader.Agent.MY (1,88 %)
9. Java/Adwind (1,47 %)
10. Win32/Packed.VMProtect.ABO (1,37 %)
Zdroj: Eset
Google Patches 6 Critical Android Mediaserver Bugs in May Security Update
3.5.2017 thehackernews Vulnerebility
Google has released its monthly security patches for Android this week, addressing 17 critical vulnerabilities, 6 of which affect Android Mediaserver component that could be used to execute malicious code remotely.
Besides patches for Mediaserver, Google also fixed 4 critical vulnerabilities related to Qualcomm components discovered in Android handsets, including Google's Nexus 6P, Pixel XL, and Nexus 9 devices.
According to the Google security bulletin for Android published Monday, this month's security update is one of the largest security fixes the company ever compiled in a single month.
Google has split Android's monthly security bulletin into security "patch levels":
Partial security patch level (2017-05-01) covers patches for vulnerabilities that are common to all Android devices.
Complete security patch level (2017-05-05) includes additional fixes for hardware drivers as well as kernel components that are present only in some devices.
Critical RCE Flaw in Android Mediaserver
The most severe vulnerability exists in Mediaserver – an Android component that handles the processing of image and video files and has been a source of many issues over the past few years, including the critical Stagefright vulnerabilities.
According to the search engine giant, the Mediaserver vulnerability "could enable remote code execution on an affected device through multiple methods such as email, web browsing, and MMS when processing media files."
In other words, attackers could exploit the Mediaserver vulnerability by tricking users into downloading a specially crafted multimedia file on their devices, or sharing the media file via email or other messaging apps and remotely execute arbitrary code.
Interestingly, this vulnerability could be triggered while you sleep, as it’s not even necessary for you to open the file because as soon as your device receives the media file, the file system will cause Mediaserver to process it.
The vulnerability was discovered in early January and affects Android versions 4.4.4 KitKat through 7.1.2 Nougat.
Kernel-level Vulnerabilities in Qualcomm
Google has also patched four critical vulnerabilities that stemmed from Qualcomm components and could allow an attacker to gain high-level (root) privileges on an Android device.
Two critical vulnerabilities (CVE-2016-10275 and CVE-2016-10276) in Qualcomm bootloader create conditions ripe for an elevation of privilege attacks, enabling "a local malicious application to execute arbitrary code within the context of the kernel," according to the bulletin.
Another critical Qualcomm bug (CVE-2017-0604) in power driver could also allow a local malicious application to execute malicious code on the device within the context of the kernel, which is the most privileged area of the OS.
No Evidence of Flaws Being Exploited in the Wild
Six of the 17 critical patches are addressed with the 2017-05-01 partial security patches, while the remaining 11 critical security flaws affecting various drivers, libraries and bootloaders are patched in the 2017-05-05 complete patch level.
Good news is that Google assured its users that there are no reports of any of the security vulnerabilities being exploited in the wild.
Google says, having two patch levels "provide Android partners with the flexibility to more quickly fix a subset of vulnerabilities that are similar across all Android devices."
So, users are strongly advised to download the most recent Android security update to keep their devices protected against any potential attack.
Nexus and Pixel devices will receive the complete patch in an over-the-air update in the coming days, or the owners can download it directly from Google's developer site.
It's also worth noting that Google revealed last week that the Nexus 6 and Nexus 9, which were released in November 2014, would no longer be "guaranteed" to receive security updates after October 2017.
A similar timeline has been offered for newer Pixel and Pixel XL handsets of October 2019. After that, the tech giant will only push necessary security fixes to those devices.
Travel Tech Giant Sabre Investigating Data Breach
3.5.2017 securityweek Security
Travel technology giant Sabre revealed that it has launched an investigation after detecting unauthorized access to sensitive information processed through one of its systems.
Southlake, Texas-based Sabre said in an SEC filing this week that it’s “investigating an incident involving unauthorized access to payment information contained in a subset of hotel reservations processed through the Sabre Hospitality Solutions SynXis Central Reservation system.”
The SynXis Central Reservation product is a rate and inventory management SaaS application used by more than 32,000 hotels worldwide.
The company has notified law enforcement and hired third-party experts to help investigate the incident. Security blogger Brian Krebs reported that Sabre hired Mandiant to assist its investigation.
In its SEC filing, Sabre said the attackers had been locked out of its systems. However, the company believes the investigation may reveal that the hackers had accessed personally identifiable information (PII), payment card data, and other information.
“While we don’t know the specifics of who had unauthorized access to the information and what tactics were used, we’ve seen from similar attacks that hackers gain access with co-opted credentials of someone with too much access,” Ken Spinner, VP of Field Engineering at Varonis Systems, told SecurityWeek.
“A breach of this magnitude underscores the need for SaaS services, especially those hosted on cloud providers, to increase their security posture capabilities at a faster rate,” said John Martinez, VP of Solutions at Evident.io. “Not all cloud-borne vulnerabilities are covered by traditional security tools; These threats require security tooling and services that are born in, and optimized for the cloud.”
This is not the first time Sabre has publicly admitted being targeted by hackers. Back in August 2015, the company confirmed investigating a cybersecurity incident following reports that it had been targeted by a China-linked threat actor.
Late last year, researchers warned that global distribution systems (GDS) from some of the world’s top service providers, including Sabre, were affected by vulnerabilities that could have been exploited by fraudsters to steal travel tickets.
The OSX.Dok dropper spotted installing the new Bella backdoor
3.5.2017 securityaffairs Apple
Bad news for Mac users, a new variant of the OSX.Dok dropper was discovered by researchers at Malwarebytes, it was spotted installing a new payload dubbed Bella backdoor.
Once the DOK malware infects a macOS system, it gains administrative privileges and installs a new root certificate. The root certificate allows the malicious code to intercept all victim’s communications, including SSL encrypted traffic.
Today the Malwarebytes malware researcher Adam Thomas has discovered found a variant of the OSX.Dok dropper works in a different way respect the first one and installs a different payload, dubbed Bella.
“Adam Thomas, a Malwarebytes researcher, found a variant of the OSX.Dok dropper that behaves altogether differently and installs a completely different payload.” states the analysis published by Malwarebytes.
The new Bella malware is delivered using the same technique of the DOK malware, it leverages a zipped app named Dokument.app masquerading as a document.
The malicious code is signed with the same digital certificate as the OSX.Dok dropper and it was first uploaded to VirusTotal around the same time.
Apple now revoked the certificate in order to neutralize the threat.
Bella, such as DOK, copies itself to /Users/Shared/AppStore.app, then it creates a window on top of all other windows, displaying a message claiming that a security problem has been detected in the operating system and an update is available, it requests victims to enter his password.
Bella displays the fake “OS X Updates Available” window, covering the entire screen, then after a minute it simply closes and deletes itself.

Bella is an open-source backdoor that was developed by a coder that goes online with the GitHub handle “Noah.”
“Noah first joined GitHub back in 2015 but was not active there until August of 2016, when he began creating Python scripts to attack various macOS data, such as stealing iCloud authorization tokens, or password and credit card information from Chrome.” continues the analysis.
“In February of this year, he published the code for Bella, a Python script with some frightening capabilities, including:
Exfiltration of iMessage and SMS chat transcripts
Location of devices via Find My iPhone and Find My Friends
Phishing of passwords
Exfiltration of the keychain
Capture of data from the microphone and webcam
Creation and exfiltration of screenshots
Remote shell and screen sharing”
The Bella payload includes the capability to escalate to root privileges by exploiting flaws in the OS, this feature only works on macOS 10.12.1 and earlier, or phishing to obtain an admin credential.
Bella is customizable with a script named BUILDER , below an example related to a Bella sample that is controlled by a C&C server with the following characteristics:
host = ‘185.68.93.74’ #Command and Control IP (listener will run on)
port = 4545 #What port Bella will operate over
This above address is owned by a hosting company located in Moscow, Russia.
The malware has also been set to install the script, database, and launch agent files in the following locations:
~/Library/Containers/.bella/Bella
~/Library/Containers/.bella/bella.db
~/Library/LaunchAgents/com.apple.iTunes.plist
If the malware gains the root access, it will be placed in the corresponding locations in the root library folder, rather than the user’s library folder.
Experts speculate the Bella backdoor will be used by other threat actors in the future due to a modular structure.
“Of course, since the code signing certificate on the Dokument.app dropper for this malware has been revoked, no one can be newly-infected by this particular variant of this malware at this point. However, since Bella is open-source and surprisingly powerful for a Python script, it’s quite likely it will be dropped by other malicious installers in the future.” concluded MalwareBytes.
Malware Hunter, the project developed by Shodan and Recorded Future to find C&C Servers
3.5.2017 securityaffairs Virus
Shodan and security firm Recorded Future launched Malware Hunter, a service that allows scanning the Internet to identify botnet C&C servers.
Malware researchers have a new powerful weapon in their arsenal, a joint project from Shodan and security firm Recorded Future dubbed Malware Hunter allow them to scan the Internet to identify botnet C&C servers.
The malware Hunter it able to identify botnet command and control (C&C) servers for various malware and botnets.
The results of the scan conducted with the Malware Hunter have been integrated into Shodan.
The researchers have designed specialized crawlers, to scan the Internet looking for computers and devices configured to function as a botnet C&C server by pretending to be infected computer that is reporting back to the command and control server.
The crawlers report to the maintainers of the project every IP address discovered during the scan that provides a response usually associated with a RAT.
“Port scanning tools are often used to identify and count specific services available to the public Internet, and using these same tools to identify and profile RATs is advantageous both for law enforcement and operational defenders.”
“RATs return specific responses (strings) when a proper request is presented on the RAT controller’s listener port,” state the report published by Recorded Future.
“In some cases, even a basic TCP three-way handshake is sufficient to elicit a RAT controller response. The unique response is a fingerprint indicating that a RAT controller (control panel) is running on the computer in question.”
According to the researchers, the Malware Hunter service has already found more than 5,700 Malicious C&C Servers, 18 of them located in my country, Italy.
To see Malware Hunter results, log in the Shodan service and search for ‘category:malware‘.

According to current results obtained by the Malware Hunter service, top 3 countries hosting command and control servers are United States (72%), Hong Kong (12%) and China (5.2%).
Most common Remote Access Trojan (RAT) that are widely used are Gh0st RAT (93.5%), DarkComet (3.7%).
“Shodan’s signatures also include RATs, specifically Black Shades, Dark Comet, njRAT, XtremeRAT, Poison Ivy, and Net Bus. Thus Shodan is a valuable and useful originating intelligence source for identifying live RAT controllers. While the number of results varies, Shodan typically identifies between 400 and 600 individual RAT controllers on any given day. The results from September 18, 2015, can be downloaded from Recorded Future’s GitHub page” continues the report.
Netgear Patches RCE Flaws in Routers, Switches
2.5.2017 securityweek Vulnerebility
Netgear recently informed customers that it has released firmware updates for some of its routers and switches to address remote code execution and other types of vulnerabilities.
Netgear announced the launch of a bug bounty program in early January and the company has been regularly publishing security advisories and notifications over the past months. The firm has been offering between $150 and $15,000 for responsibly disclosed vulnerabilities, and it already claims to have rewarded more than 150 bug reports.
In the most recent advisories, Netgear informed users about the existence of CVE-2017-6862, a buffer overflow vulnerability that can be exploited by a remote attacker to bypass authentication and execute arbitrary commands.
The flaw, discovered by Maxime Peterlin of ON-X, affects WNR2000v3, WNR2000v4, WNR2000v5 and R2000 routers. Firmware updates that patch the vulnerability are available for all impacted models.
Netgear said the weakness can only be exploited by an attacker with access to the network hosting the device, or if the router has the remote management feature enabled. This feature is disabled by default.
A different advisory describes a vulnerability affecting some of the company’s smart and managed switches. The flaw allows an unauthenticated attacker to access a debugging URL from where they can execute arbitrary commands, including for resetting and rebooting the switch.
An attack can be launched remotely if the switch is remotely accessible, but Netgear believes most users have firewalls in place that should prevent exploitation.
The security hole affects nearly three dozen switches, including FS, GS, M, S and XS models. Firmware updates that patch the flaw are available for most of the impacted devices.
Another recent advisory warns users of a vulnerability affecting CM700 high speed cable modems. The bug does not pose any risk to data, but it can allow an attacker to disrupt a targeted user’s network connection. No workarounds or patches are available.
Fuze Collaboration Platform Allowed Anyone to Download Recorded Meetings
2.5.2017 securityweek IT
As globalization and mobility both advance, organizations are turning to web-based unified communications systems as a means of improving collaboration and reducing costs. Fuze is one such service. It offers voice (with conferencing), video (with conferencing) and messaging, all from anywhere at any time and any device.
The security of web-based third-party service providers is a major concern for business, where security audits are difficult and expensive. It often comes down to reputation: if other major businesses are using a particular service, it must be good.
Fuze has a number of major clients, including Associated Press, USAuto Sales and ThoughtWorks. But reputation does not equal security, as Rapid7 researcher Samuel Huckins discovered in February 2017 and disclosed today. Huckins discovered 'improper access control' of Fuze meetings.
More specifically, he notes, "Meetings recorded on the Fuze collaboration platform did not have sufficient controls to ensure that the recordings were kept private (CWE-284)." Recorded Fuze meetings are saved to the cloud hosting service, from where they could be accessed via an URL with the format /browser.fuzemeeting.com/?replayID=7digitnum.
'7digitnum' is a seven-digit number that increments over time. The problem, according to Rapid7, is that the 7 digit number is insufficient to resist brute-forcing. Specific meeting recordings could be downloaded by third-parties simply by guessing a replay ID reasonably close to the target and iterating through possible 7-digit numbers. The format also allows a third-party to use a search engine to find available recordings.
The threat is clear. Meetings are used to discuss plans, share and collaborate on intellectual property, and generally conduct international business. The potential is for sensitive data to fall into the wrong hands.
Rapid7 reported the issue to Fuze on Monday, February 27, 2017. Two days later, March 1, 2017, Fuze disabled public access via the earlier URL format. In a statement, it commented, "Security is a top priority for Fuze and we appreciate Rapid7 identifying this issue and bringing it to our attention. When we were informed by the Rapid7 team of the issue, we took immediate action and have resolved the problem."
"As of Mar 10, 2017," reports Rapid7, "all meeting recordings now appear to require password authentication in order to be viewed from Fuze's cloud-hosted web application via direct browsing or from the Fuze desktop and mobile clients. This authentication control is configurable by the user via the client applications as of version 4.3.1 (released on Mar 10, 2017). Fuze users are encouraged to update their Fuze client applications in order to take advantage of new access controls."
It was a silly security issue easily solved -- but one that could have had serious consequences for Fuze's clients. It highlights the need for all cloud usage to be signed off by an organization's security team rather than simply rubber-stamped by the IT department. A security professional might have seen at the outset that URL-based access control is simply not good enough -- but similarly, Fuze should never have designed its system like that in the first place.
Evolution and Escalation: Two Key Cyber Threat Trends
2.5.2017 securityweek CyberCrime
Existing threats escalated and new threats emerged in a turbulent 2016. Ransomware spiked, IoT-based DDoS threatened the internet, political subversion and sabotage grew, and hackers moved towards non-malware based attacks -- or 'living off the land'. These and more threats are highlighted in Symantec's new Internet Security Threat Report (ISTR).
Ransomware continued its rise throughout 2016. "The number of new ransomware families uncovered during 2016 more than tripled to 101 and Symantec logged a 36 percent increase in ransomware infections." The ransom demands also escalated, "with the average ransom demand in 2016 rising to $1,077, up from $294 a year earlier," notes the report (PDF).
In fact, the threat is now so severe that earlier this week, F-Secure security advisor Sean Sullivan warned governments need to find some way of curtailing the use of bitcoins for ransom payments. "If the U.S. pursues all the forms of potentially illegal payments, ransomware's growth could be abated. Otherwise, we expect to see the new ransomware families we discovered in 2017 at least double." He explained to SecurityWeek, "My point is about Bitcoin exchanges and brokers that trade euros/pounds/dollars for Bitcoin – like a bank... Regulations don't need to require identification – they only need to limit easy access to accounts by victims. That adds overhead, and that decreases profits for the cybercriminals."
The cyber threat from insecure internet of things (IoT) devices has been a talking point for several years. That threat became fact in 2016 with the emergence of the Mirai botnet. Mirai comprises hundreds of thousands of compromised IoT devices, such as routers and security cameras, that can be used to target massive DDoS attacks. In October, it was used against DNS company Dyn, and disrupted many of the world's leading websites, including Netflix, Twitter, and PayPal. In September, Mirai delivered the largest ever DDoS against French hosting company OVH, peaking at 1 Tbps.
"With Gartner predicting that there will be more than 20 billion IoT devices in the world by 2020, it's important that security problems be addressed or campaigns like Mirai could be seen on an even larger scale," warns Symantec.
The emergence of cyber-based political subversion was one of the more startling developments over the year. Cyberattacks against the Democratic Party and the subsequent leak of information are believed to have been an attempt to influence the 2016 US presidential election. "With the US Intelligence Community attributing the attacks to Russia and concluding the campaign would have been judged a success," warns Symantec, "it is likely these tactics will be reused in efforts to influence politics and sow discord in other countries."
This is already happening, with both France and Germany warning that Russian actors might attempt to influence their own elections. In the UK, GCHQ has written to the major political parties with advice on how to protect their networks -- although there has been no public suggestion of interference in the Brexit referendum of 2016.
"The ongoing conflict in Ukraine, the US election, and the Olympics were all affected by campaigns designed to steal and leak data in order to influence public opinion, create an atmosphere of distrust, and possibly influence political outcomes," notes Symantec.
The potential for cyber-based political sabotage has been evident since the Stuxnet attacks against the Iranian nuclear program in 2010. It was also evident in Shamoon disk wiping attacks on Saudi oil company Aramco in 2012. Shamoon has now reappeared with further attacks against multiple Saudi organizations, while a similar disk wiping trojan (KillDisk) was used against power facilities in the Ukraine. This brings the threat of destructive attacks against western critical infrastructures very much to the fore.
'Living off the land' is the term used by Symantec to describe the growing practice of hackers avoiding the use of malware in their attacks. Other companies use the term 'fileless', while Carbon Black has used the term 'non-malware attacks'. "Zero-day vulnerabilities have become less important and some adversaries are no longer as reliant on malware, increasingly 'living off the land' -- making use of the resources to hand including legitimate administrative and penetration testing tools to carry out attacks," notes Symantec.
The purpose of the fileless attack is to deposit no or minimal files onto the compromised network. With no new file to detect, it becomes harder for anti-virus defenses to detect the presence of an intruder. The approach comes in two distinct varieties, both starting with breaching the network without using malware. Spear-phishing is the preferred method, since it can gain legitimate access credentials that won't raise a red-flag when used. Sometimes, this is all that is needed; for example, if the attack is specifically seeking access to the target's emails.
At other times, the phishing email will carry an MS Office document carrying weaponized macros. If the target can be pursuaded to open the document and allow macros to run, the macro might load a script into something like PowerShell. Symantec notes that a version of this method was used to spread Shamoon.
"If the file was opened, a macro ran a PowerShell script that provided remote access and performed basic reconnaissance of the compromised computer. If a computer was of interest, they then installed malware (Backdoor.Mhretriev).
"From there, the attackers used a cornucopia of legitimate administrative and penetration testing tools to traverse the target's network and identify computers for infection." If the purpose of the attack is destructive or ransom, then malware can be dropped to trigger immediately -- in theory the malware could be detected, but it may be too late for the defenders to do anything.
If the purpose of the attack is to exfiltrate data, then 'living off the land' can complete the task without ever depositing any malware.
Two fundamental developments in cyber threats come from the Symantec ISTR: evolution and escalation. Attackers are continually refining their methods -- as shown in living off the land and harnessing the IoT for DDoS attacks. Escalation is best seen in the purpose of the attacks. In traditional attacks, there has been a distinct growth in attacks against banks and financial systems (such as SWIFT), where previously the majority of attacks were against bank customers. It can also be seen in the size of DDoS attacks now possible, and in the physical sabotage attacks and the attempts to influence public opinion in entire geopolitical regions. "New sophistication and innovation are the nature of the threat landscape, but this year Symantec has identified seismic shifts in motivation and focus," said Kevin Haley, director at Symantec Security Response.
Intel Warns of Critical Vulnerability in Processor Firmware
2.5.2017 securityweek Vulnerebility
Nine-Year-Old Critical Vulnerability Affects Intel Active Management Technology
Intel issued a critical alert Monday concerning an escalation of privilege vulnerability affecting Intel Active Management Technology (AMT), Intel Small Business Technology (SBT), and Intel Standard Manageability. Firmware updates are available in all cases -- but that's not the end of the story.
While the Intel alert states, "This vulnerability does not exist on Intel-based consumer PCs," security commentators such as Charlie Demerjian suggest "there is literally no Intel box made in the last 9+ years that isn't at risk. This is somewhere between nightmarish and apocalyptic." The vulnerability affects every Intel system from Nehalem in 2008 to Kaby Lake in 2017.
According to Intel, the vulnerability (CVE-2017-5689) can be accessed in two ways. Where AMT and ISM have been provisioned, an unprivileged network attacker could gain system privileges. Where not provisioned, a local attacker could provision them and gain local system privileges on AMT, ISM and SBT. Intel gives no details on the vulnerability itself.
The three main issues for business are the extent of the damage that could be done through this vulnerability; the difficulty in knowing what systems are vulnerable; and the lack of control over the availability of Intel's firmware updates.
AMT is intended to give IT departments a means to manage client systems. When enabled, packets sent to ports 16992 or 16993 are redirected through Intel's Management Engine (a small, separate processor independent of the main CPU) and passed to AMT. The operating system never sees these packets. AMT can be used to install media, reboot the machine and more, remotely. It requires a password for access; but this vulnerability suggests that the password can be bypassed.
Understanding the extent of the risk could also be difficult. "What about embedded devices that are increasingly PC based?" asks Demerjian. "Digital signage perhaps? Industrial controls. HVAC. Security systems. Flight controls. Air traffic controls. Medical devices. I could go on but all of these are likely PC based and anything infrastructure related is likely networked."
SANS' Richard Porter suggests, "Get a good, complete hardware inventory together, and get a good software inventory -- know what's in your organization and on your network, and know what's running on that gear. This includes elevator controls, industrial presses, MRI machines, point of sale stuff, TVs, DVRs and photocopiers -- all of it! Without knowing what's on your network, the best you'll do is to get a reasonable percentage of affected systems -- you'll never patch the machines you don't know about."
The third issue is patching. While it is Intel's responsibility to develop the patches (which it has done), it is not Intel's responsibility to deliver them. That's down to the device manufacturers and OEMs; and it is generally thought that not all will do so.
Demerjian warns, "If you have a white-box PC or one from a sketchy vendor, chances are they won't bother with a firmware update. Security is a cost center and most OEMs run on margins too thin to bother with security patches even if they cared. Most simply don't care." Put bluntly, many systems will likely never be patched.
This raises two further issues: what should be done when you have little or no control over whether or even if you will receive patches; and secondly, how urgent is this issue? The latter takes us into conjecture. The Intel alert makes no statement over whether the company is aware of any current exploitation of the vulnerability -- the alert neither confirms nor denies it.
Researchers have been warning Intel for years. In 2012, Demerjian wrote, "Intel doesn't understand security, but they are not shy about shouting it from the rooftops. They took a good idea, vPro [which includes AMT], and turned it into a remote exploit and security risk that prevents a compromised machine from being repaired."
Demerjian in particular wonders, 'why now?'; adding "SemiAccurate strongly suspects this vulnerability is being exploited in the wild as we speak." It is conjecture, but it could be true (and all the while we don't know whether Shadow Brokers has any further exploits to announce).
The implication is clear: business cannot wait for a solution to be handed to it; it needs to be proactive and mitigate the vulnerability as soon as possible. Luckily, Intel has published separate documents that should help.
How To Find Intel® vPro™ Technology Based PCs will help to determine whether a system is AMT, SBA or ISM capable. If it is not, then no mitigation is required.
INTEL-SA-00075 Detection Guide steps through the process of using Intel's System Discovery utility to determine the firmware version and whether it is vulnerable.
INTEL-SA-00075 Mitigation Guide provides "instructions on how to implement mitigations on Intel's manageability SKU systems that are vulnerable to a known privilege escalation issue."
All three documents are useful; but business is advised to employ mitigations where necessary as soon as possible. The mitigation document provides details on removing the supporting code in Windows. "What it boils down to," says SANS' Porter, "is you want to stop and disable the LMS Service (Local Management Service), then delete LMS.exe."
A critical RCE flaw in Intel Management Engine affects Intel enterprise PCs dates back 9 years
2.5.2017 securityaffairs Vulnerebility
A critical remote code execution vulnerability tracked as CVE-2017-5689 in Intel Management Engine affects Intel enterprise PCs dates back 9 years.
A critical remote code execution (RCE) vulnerability tracked as CVE-2017-5689 has been discovered in the remote management features implemented on computers shipped with Intel Chipset in past 9 years.
The vulnerability affects the Intel Management Engine (ME) technologies such as Active Management Technology (AMT), Small Business Technology (SBT), and Intel Standard Manageability (ISM) and could be exploited by hackers to remotely take over the vulnerable systems.
The remote management features allow system administrators to remotely manage computers over an enterprise network. Such kind of features are implemented only in enterprise solutions and doesn’t affect chips running on Intel-based consumer PCs.
“There is an escalation of privilege vulnerability in Intel® Active Management Technology (AMT), Intel® Standard Manageability (ISM), and Intel® Small Business Technology versions firmware versions 6.x, 7.x, 8.x 9.x, 10.x, 11.0, 11.5, and 11.6 that can allow an unprivileged attacker to gain control of the manageability features provided by these products. This vulnerability does not exist on Intel-based consumer PCs. ” reads the advisory published by Intel.
The vulnerability rated by Intel as highly critical, could be exploited in two ways:
An unprivileged network attacker could gain system privileges to provisioned Intel manageability SKUs: Intel® Active Management Technology (AMT) and Intel® Standard Manageability (ISM).
CVSSv3 9.8 Critical /AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
An unprivileged local attacker could provision manageability features gaining unprivileged network or local system privileges on Intel manageability SKUs: Intel® Active Management Technology (AMT), Intel® Standard Manageability (ISM), and Intel® Small Business Technology (SBT).
CVSSv3 8.4 High /AV:L/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
An attacker can exploit the vulnerability to remotely access the vulnerable machine and perform in a stealth way malicious activities, including to deliver a malware.
The flaw was first reported in March by the security expert Maksim Malyutin of Embedi.
These flawed remote management features have been implemented in many Intel chipsets for nine years, starting from Nehalem Core i7 in 2008. Modern Apple Macs do not ship with the AMT software, so they are not affected.
This kind of flaw is very insidious because any countermeasure implemented at the operating system level is not able to detect malicious operation because AMT has direct access to the computer’s network hardware. Malicious traffic is routed directly to the Management Engine and passed on to AMT, but the local OS never sees it.
According to Intel, the remote code execution vulnerability affects Intel manageability firmware versions 6.x, 7.x, 8.x 9.x, 10.x, 11.0, 11.5, and 11.6 for Intel’s AMT, ISM, and SBT platforms. Versions before 6 or after 11.6 are not impacted.
Intel promptly released new firmware versions along with a detection guide to check if a system is vulnerable. The company also shared a mitigation guide that is essential for those organizations that can not immediately install updates.
The chipmaker is recommending vulnerable customers install a firmware patch as soon as possible.
"Malware Hunter" Helps Researchers Find C&C Servers
2.5.2017 securityweek Virus
C&C Discovery Service Launched by Shodan and Recorded Future
Recorded Future and Shodan announced on Tuesday the launch of Malware Hunter, a new crawler that allows security researchers to identify devices that act as botnet command and control (C&C) servers.
The free service has been in the works since 2015 and it initially focused on C&C servers used by remote access Trojans (RATs). While a majority of the malware families tracked by Malware Hunter are still classified as RATs, the project has been expanded to cover all types of threats.
Malware Hunter conducts Internet-wide port scans in an effort to identify servers, routers, webcams and other devices that may be communicating with RATs or other malware. Unlike traditional honeypots, which are more passive, the crawler pretends to be an infected client that wants to report back to its C&C server. It reports back to every IP on the Web as if it’s a C&C in an effort to identify malicious systems.
The service takes information from Shodan and feeds it into Recorded Future’s API in order to provide a comprehensive analysis that can help defenders identify threats and quickly shut down malicious operations.
According to Shodan, Malware Hunter has so far been used to identify more than 3,000 C&C servers leveraged by over 10 RAT families, including Dark Comet, njRAT, Poison Ivy and Gh0st RAT.
“This methodology is the first to use Shodan to locate RAT controllers before the malware samples are found,” explained Levi Gundert, vice president of intelligence and strategy at Recorded Future. “By doing it this way — signature scans for RAT controller IP addresses, observing malware through our API and cross-correlating it with a variety of sources — we are able to locate RAT controllers before the associated malware begins spreading or compromising targeted victims”
Kaspersky Lab APT Trends report, Q1 2017 – From Lazarus APT to StoneDrill
2.5.2017 securityaffairs APT
Kaspersky is currently monitoring the activities of more than 100 threat actors, from the From Lazarus APT to StoneDrill.
According to the experts from KasperskyLab, the infamous Lazarus APT group, aka BlueNoroff, is the most dangerous threat against financial institutions worldwide.
The activity of the Lazarus Group surged in 2014 and 2015, its members used mostly custom-tailored malware in their attacks and experts that investigated on the crew consider it highly sophisticated.
This threat actor has been active since at least 2009, possibly as early as 2007, and it was involved in both cyber espionage campaigns and sabotage activities aimed to destroy data and disrupt systems.
Experts at Symantec collected evidence demonstrating the Lazarus APT group was behind the campaign that leveraged on a “loader” software used to stage attacks by installing other malicious programs.
Both US and South Korea governments are blaming Pyongyang for the attacks, but the North Korean government has denied allegations it was behind the hacks.
The Lazarus APT has been associated with numerous cyber attacks against high-profile targets, including the 2014 Sony Pictures hack, the Bangladesh cyberheist at the New York Federal Reserve Bank and the recent attack against banks in Poland.
According to Kaspersky Lab, the hacking campaign against banks worldwide is still ongoing, recently the experts detected new malware samples linked to the group’s activity.
Below the findings of an ATP trends report recently published by Kaspersky Lab:
We believe BlueNoroff is one of the most active groups in terms of attacks against financial institutions and is trying to actively infect different victims in several regions.
We think their operations are still ongoing, and in fact, their most recent malware samples were found in March 2017.
At the moment we believe BlueNoroff is probably the most serious threat against banks.
Kaspersky is currently monitoring the activities of more than 100 threat actors, APT groups and financially motivated cybercrime gangs, that are targeting almost any industry across over 80 countries.
Other APT groups tracked by Kaspersky that were most active in the first quarter of 2017 were Shamoon and StoneDrill APTs. According to the researchers, the groups are distinct, but they share the same two separate likely they are working together to compromise Saudi targets with high sophisticated wiper malware.
The experts linked the StoneDrill malware to Shamoon 2 attacks and Charming Kitten campaign (aka Newscaster and NewsBeef).
The malware was used by threat actors against entities in Saudi Arabia and at least one organization in Europe.

The experts discovered many similarities between malware styles and malware components in Shamoon, StoneDrill, and NewsBeef.
Malware researchers highlighted that APT groups leverage on the use of generic tools in attacks making hacked the attribution of the attacks.
“Rather than creating and having their own tools, these use generic tools that are good enough to complete an operation, and provide an evident economic advantage, with the added value of making both analysis of the incident and attribution to a particular actor more difficult.” states the report.
“Nowadays there is a large number of different frameworks providing cyber-actors with many options, especially for lateral movement. This category includes Nishang, Empire, Powercat, Meterpreter, etc. Interestingly, most of these are based on Powershell, and allow the use of fileless backdoors.”
Bezpečnostní experti bijí na poplach. Nebezpečný virus Locky je opět na scéně
2.5.2017 Novinky/Bezpečnost Viry
Locky patřil v loňském roce k těm nejrozšířenějším vyděračským virům, které kolují internetem. I když se mohlo zkraje letošního roku zdát, že je na ústupu, opak je pravdou. Výzkumníci z týmu Cisco Talos upozornili, že jej kyberzločinci nasazují znovu.
„Po většinu roku 2016 patřil Locky mezi nejrozšířenější vyděračské softwary. Ke svému šíření využíval e-mailové kampaně s infikovanými přílohami. Ransomware Locky byl rozesílán prostřednictvím botnetu (internetový robot zasílající spamy, pozn. red.) Necurs,“ připomněli bezpečnostní experti.
Ti zároveň zdůraznili, že s koncem roku 2016 šíření tohoto vyděračského viru z rodiny ransomwarů bylo výrazně utlumeno.
Zlom nastal až s příchodem jara. „Před několika týdny se Necurs opět probudil a začal posílat spamy nabízející výhodný nákup akcií. Dne 21. dubna zaznamenal bezpečnostní tým Cisco Talos první velkou kampaň ransomwaru Locky prostřednictvím botnetu Necurs za posledních několik měsíců,“ upozornili bezpečnostní experti.
Dešifrovací algoritmus zatím není znám
Podle nich je aktuálně probíhající kampaň velmi intenzivní. Za pouhých pár hodin se jim totiž podařilo zajistit přes 35 tisíc odeslaných e-mailů, ve kterých se nezvaný návštěvník ukrýval.
Samotný útok tedy probíhá úplně stejně, jako tomu bylo u Lockyho již v loňském roce. Po spuštění přílohy v nevyžádaném e-mailu se do PC nahraje vyděračský virus, který dále škodí. Zašifruje data a za jejich zpřístupnění požaduje výkupné.
Dešifrovací algoritmus zaručující obnovu dat po útoku Lockyho zatím není bohužel znám.
PCs with Intel Server Chipsets, Launched in Past 9-Years, Can be Hacked Remotely
2.5.2017 thehackernews Hacking
A critical remote code execution (RCE) vulnerability has been discovered in the remote management features on computers shipped with Intel processors for nearly a decade, which could allow attackers to take control of the computers remotely.
The RCE flaw (CVE-2017-5689) resides in the Intel's Management Engine (ME) technologies such as Active Management Technology (AMT), Small Business Technology (SBT), and Intel Standard Manageability (ISM), according to an advisory published Monday by Intel.
These features allow a systems administrator to remotely manage large fleets of computers over a network (via ports 16992 or 16993) in an organization or an enterprise.
Since these functions are present only in enterprise solutions, and mostly in server chipsets, the vulnerability doesn't affect chips running on Intel-based consumer PCs.
According to the Intel advisory, this critical security vulnerability was discovered and reported in March by security researcher Maksim Malyutin of Embedi, and could be exploited in two ways:
An unprivileged network attacker could gain system privileges to provisioned Intel manageability SKUs: Intel AMT and ISM. However, Intel SBT is not vulnerable to this issue.
An unprivileged local attacker could provision manageability features gaining unprivileged network or local system privileges on Intel manageability SKUs: Intel AMT, ISM, and SBT.
How Bad is this Vulnerability
In short, a potential attacker can log into a vulnerable machine's hardware and silently perform malicious activities, like tampering with the machine, installing virtually undetectable malware, using AMT's features.
The PC's operating system never knows what's going around because AMT has direct access to the computer's network hardware. When AMT is enabled, any packet sent to the PC's wired network port will be redirected to the Management Engine and passed on to AMT – the OS never sees those packets.
These insecure management features have been made available in various, but not all, Intel chipsets for nearly a decade, starting from Nehalem Core i7 in 2008 to this year's Kaby Lake Core, with a higher degree of a flaw for users on Intel vPro systems.
Fortunately, none of these Management Engine features come enabled by default, and system administrators must first enable the services on their local network. So, basically if you are using a computer with ME features enabled, you are at risk.
Despite using Intel chips, modern Apple Mac computers do not ship with the AMT software and are thus not affected by the flaw.
Affected Firmware Versions & How to Patch
The security flaw affects Intel manageability firmware versions 6.x, 7.x, 8.x 9.x, 10.x, 11.0, 11.5, and 11.6 for Intel's AMT, ISM, and SBT platforms. However, versions before 6 or after 11.6 are not impacted.
Intel has rated the vulnerability as highly critical and released new firmware versions, instructions to detect if any workstation runs AMT, ISM, or SBT, a detection guide to check if your system is vulnerable, and a mitigation guide for those organizations that can not immediately install updates.
The chipmaker is recommending vulnerable customers install a firmware patch as soon as possible.
"Fixing this requires a system firmware update in order to provide new ME [management engine] firmware (including an updated copy of the AMT code). Many of the affected machines are no longer receiving firmware updates from their manufacturers, and so will probably never get a fix," CoreOS security engineer Matthew Garrett explained in a blog post. "Anyone who ever enables AMT on one of these devices will be vulnerable."
"That's ignoring the fact that firmware updates are rarely flagged as security critical (they don't generally come via Windows Update), so even when updates are made available, users probably won't know about them or install them."
You can head on to Intel advisory for further details.
China-Linked Spies Use Recent Zero-Day to Target Financial Firms
2.5.2017 securityweek BigBrothers
A cyber espionage group has targeted analysts working at major financial firms using a recently patched Microsoft Office vulnerability, Proofpoint reported last week.
The threat actor, tracked by the security firm as TA459, has been active since at least 2013 and it’s believed to be operating out of China. The cyberspies have been known for using malware such as NetTraveler (aka TravNet), PlugX, Saker, Netbot, DarkStRat, and ZeroT in attacks aimed at organizations in Russia and neighboring countries.
Proofpoint recently detailed a series of attacks launched by the group against military and aerospace organizations in Russia and Belarus.
On April 20, researchers spotted a campaign aimed at global financial firms operating in Russia and neighboring countries. Given that the attacks were apparently aimed at analysts covering the telecommunications industry, experts believe this latest operation is likely a continuation of a similar campaign first analyzed in the summer of 2015.
In the recent attacks, TA459 sent out spear-phishing emails containing a Word document set up to exploit a recently patched remote code execution vulnerability tracked as CVE-2017-0199. The attackers started leveraging this flaw just days after Microsoft released a fix.
When the malicious document is opened, an HTML application (HTA) file disguised as an RTF document is downloaded. PowerShell is then used to download and execute a script that fetches and runs the ZeroT downloader.
ZeroT was analyzed by Proofpoint when it investigated the recent attacks aimed at military and aerospace organizations, but some changes and improvements have been made in the latest version. One of the changes is the use of a legitimate McAfee utility for sideloading instead of a Norman Safeground utility.
While ZeroT is the threat actor’s most common first stage payload, the second payload includes various pieces of malware. In recent attacks, Proofpoint noticed both PlugX and a Trojan tracked as PCrat/Gh0st, which is used less often by the group.
“Multinational organizations like the financial services firms targeted here must be acutely aware of the threats from state-sponsored actors working with sophisticated malware to compromise users and networks,” Proofpoint researchers explained. “Ongoing activity from attack groups like TA459 who consistently target individuals specializing in particular areas of research and expertise further complicate an already difficult security situation for organizations dealing with more traditional malware threats, phishing campaigns, and socially engineered threats every day.”
The fact that the threat actor has used CVE-2017-0199 in its operation is not surprising. The flaw had been exploited by several groups before Microsoft released a patch for it, and others, including Iranian hackers, started using it shortly after its existence came to light.
Unity Game Engine Forum Hacked
2.5.2017 securityweek Hacking
Over the weekend, hackers breached the official forum of the Unity cross-platform game engine developed by Unity Technologies. The attackers claim to have stolen user data, but the company has denied that any sensitive information has been compromised.
The hacker group calling itself OurMine has defaced the Unity forum and abused it to send out emails to registered users via a built-in mass email feature. In their message, the hackers informed recipients that they had gained access to a database containing the details of 2 million users, and advised everyone to change their passwords.
In a blog post published on Monday, Unity confirmed the breach and blamed it on “poorly implemented password routines.” However, the company claims the hackers only accessed “a limited set of data,” and assured users that no passwords, payment information or other Unity services had been compromised.
“No passwords were lost in the breach, but we still recommend a password change due to possibility of the group having emails and passwords from another source, which could be used to access their account,” Unity representatives said.
The company says it does not store passwords in clear text, and it plans on rolling out additional account protections in the next few weeks, including two-factor authentication, alerts for logins from unrecognized devices, and new password policies.
The forum was taken offline following the hack, but it has now been restored. Some posts may have been lost as the forum was restored using a backup timestamped April 30, 14:01 CEST.
Gaming-related forums have often been targeted by cybercriminals. The list of breached websites includes ones dedicated to Bohemia Interactive’s DayZ, Epic Games’ Unreal Engine and Unreal Tournament, and Valve’s Dota 2.
OurMine, which describes itself as a group that provides security services, has targeted numerous high profile social media accounts in the past months.
The hackers have taken over the online accounts of Sony Music Entertainment, Facebook CEO Mark Zuckerberg, Google CEO Sundar Pichai, Spotify founder Daniel Ek, and many others. The group recently also hijacked several high profile YouTube accounts.
TrickBot is a rising threat, the banking Trojan now targets Private Banking
2.5.2017 securityaffairs Virus
According to a new analysis conducted by the IBM’s X-Force security team, a new wave of attacks powered by the TrickBot banking Trojan have been targeting private banks in the UK, Australia, and Germany.
The researchers observed new redirection attacks focused on new brands, including private banks, private wealth management firms, investment banking, and a retirement insurance and annuity company.
“operators of the infamous Trojan have been adding new redirection attacks focused on a list of brands that I had never seen in the past.” states the analysis published by IBM.
“Curious about this addition to the TrickBot prime target roster, I went on to examine each URL, only to find out that the operators have been doing a lot of homework. The current configuration files are replete with private banks, private wealth management firms, investment banking, and even a retirement insurance and annuity company. One of the new targets is among the oldest banks in the world, located in the U.K.”
TrickBot was initially observed in September 2016 by the researchers at security firm Fidelis Cybersecurity, that linked it to the Dyre banking trojan.
The security firm first spotted the TrickBot malware in September while it was used by crooks to target the customers of Australian banks (ANZ, Westpac, St. George and NAB).
The first TrickBot samples analyzed by the experts were implementing a single data stealer module, but a few weeks later, the researchers discovered a new sample including webinjects that appear to be in the testing phase.
In September 2016, Fidelis Cybersecurity was alerted to a new malware bot calling itself TrickBot that we believe has a strong connection to the Dyre banking trojan. From first glance at the loader, called TrickLoader, there are some striking similarities between it and the loader that Dyre commonly used. It isn’t until you decode out the bot, however, that the similarities become staggering.” reads the analysis published by Fidelis Cybersecurity.
“This would suggest, but is far from conclusive, that some individuals related to the development of Dyre have found their way into resuming criminal operations.”
TrickBot and Dyre have many similarities, the code of the new banking trojan seems to have been rewritten with a different coding style, but maintaining many functionalities.
The malware was used in a number of attacks at the end of 2016 targeting banks in the UK and Australia, and Asian financial institutions.
Back to the present, TrickBot was used to target 20 new private banking brands, eight building societies in the UK, two Swiss banks, private banking platforms in Germany, and four investment banking firms in the U.S.
“Looking at the configuration, in the U.K., TrickBot has added 20 new private banking brands to its regular attack roster, as well as eight building societies. Also added were two Swiss banks, a few regular expressions for private banking platforms in Germany and four investment banking firms in the U.S. The complete set of targets includes over 300 unique URLs and regular expressions.” continues the analysis.
Among the novelties, the configuration shows crooks started targeting a Sharia law-compliant bank.
Trickbot is a rising threat, the researchers are observing to a significant intensification of the campaign leveraging the threat, in particular in Australia, New Zealand, and the UK.

“In terms of its attack types, TrickBot is quite similar to Dyre. Its signature moves are browser manipulation techniques that enable the malware to implement server-side web injections and redirection attacks,” IBM says.
Experts from IBM believe TrickBot would climb up the global chart of financial malware families, reaching the same level of threats like Dridex and Ramnit in the next months.
Yahoo awarded $7,000 a bug hunter for Flickr account hijacking vulnerability
2.5.2017 securityaffairs Vulnerebility
Yahoo awarded $7,000 to the bug hunter Michael Reizelman, aka mishre, for Flickr account hijacking vulnerability.
Reizelman was a popular bug hunter that discovered vulnerabilities in many web services, including Badoo, Dropbox, GitHub, Google, Imgur, Slack, Twitter, and Uber.
The expert has discovered three vulnerabilities in the company’s image and video hosting service that could have been chained together to take over Flickr accounts.
Reizelman discovered that every time a user logs in to his Flickr.com account, it is redirected to the login.yahoo.com domain used for the authentication.
Below the URL used to redirect the user:
https://login.yahoo.com/config/login?.src=flickrsignin&.pc=8190&.scrumb=0&.pd=c%3DH6T9XcS72e4mRnW3NpTAiU8ZkA--&.intl=il&.lang=en&mg=1&.done=https%3A%2F%2Flogin.yahoo.com%2Fconfig%2Fvalidate%3F.src%3Dflickrsignin%26.pc%3D8190%26.scrumb%3D0%26.pd%3Dc%253DJvVF95K62e6PzdPu7MBv2V8-%26.intl%3Dil%26.done%3Dhttps%253A%252F%252Fwww.flickr.com%252Fsignin%252Fyahoo%252F%253Fredir%253Dhttps%25253A%25252F%25252Fwww.flickr.com%25252F
The user provides his credentials and if they are valid, he is redirected back to Flickr.com and authenticated with the following URL:
https://www.flickr.com/signin/yahoo/?redir=https%3A%2F%2Fwww.flickr.com%2F&.data={first-token-value}&.ys={second-token-value}
The researcher also observed that the user is redirected in the background to login.yahoo.com if he is already logged in,
The request to login.yahoo.com is used to obtain an access token for the user.
Reizelman discovered that is possible to manipulate a parameter named ‘.done’ that is used to control where the login token is sent.
Yahoo just checks that the token could only be sent to the flickr.com domain.
“The first thing I have noticed is that the second .done parameter can be manipulated. This parameter actually controls where the login tokens are sent. It appears that Yahoo’s servers only verify that it starts with https://www.flickr.com/signin/yahoo/ but we can still append ../ so if we append ../../test to the .done original value the .ys and .data tokens will be sent to https://www.flickr.com/test endpoint.” explained the researcher in a blog post.

Initially, Reizelman searched for an open redirect vulnerability on flickr.com to exploit the vulnerability, but he had no success. Anyway, the expert devised another method to exploit the issue by embedding an image from an attacker-controlled server into a Flickr.com page using the <img> tag.
The expert found a method to bypass Yahoo checks, he was able to embed an external image into comments posted on flickr.com/help/forum/en-us/, which did not have a Content Security Policy (CSP).
Then he pointed the .done parameter to a malicious image embedded into a post on the Flickr help forum, with this mechanism an attacker could send the access tokens to his server.
In the attack scenario, a hacker has to trick the user into clicking on a specially crafted link to obtain his access token and take over the victim’s Flickr account.
The researcher reported the vulnerabilities to Yahoo on April 2, he was awarded a $7,000 bounty. The company operates a bug bounty program through HackerOne.
Below the Timeline of the Flickr Account Hijacking flaw:
Apr 2nd 2017 – Initial Report via Hackerone
Apr 3rd 2017 – Report Triaged
Apr 10th 2017 – Report Resolved
Apr 21st 2017 – 7K$ Bounty Rewarded
Yahoo fixed the problem by only allowing the .done parameter to point to flickr.com/signin/yahoo, adding CSP to the Flickr forum, the experts also neutralized the image embedding bypass method.
NSA announces it will stop surveillance activities on emails, texts and other internet communications
2.5.2017 securityaffairs BigBrothers
NSA announces a change in its surveillance activities, it will no longer spy on citizens’ emails, texts, and other Internet communications.
It is official, the US NSA announced it will no longer spy on emails, texts and other internet communications that mention targets of surveillance.The NSA issued the official statement last week, announcing a historical change of tactic about surveillance activities on specific foreign targets located outside the United States.
“Since 2008, the National Security Agency (NSA) and other members of the U.S. Intelligence Community have relied on Section 702 of the Foreign Intelligence Surveillance Act (FISA) to conduct surveillance on specific foreign targets located outside the United States to acquire critical intelligence on issues ranging from international terrorism to cybersecurity.” reads the NSA’s statement.”After a comprehensive review of mission needs, current technological constraints, United States person privacy interests, and certain difficulties in implementation, NSA has decided to stop some of its activities conducted under Section 702.”

In the past NSA cyber spies were flagging any communication where a foreign surveillance target was mentioned, even when the target wasn’t involved in the conversation.
The NSA reform will involve upstream surveillance collection and not other surveillance activities such as the PRISM program.
“After considerable evaluation of the program and available technology, NSA has decided that its Section 702 foreign intelligence surveillance activities will no longer include any upstream internet communications that are solely “about” a foreign intelligence target.” continue the statement.”Instead, this surveillance will now be limited to only those communications that are directly “to” or “from” a foreign intelligence target. These changes are designed to retain the upstream collection that provides the greatest value to national security while reducing the likelihood that NSA will acquire communications of U.S. persons or others who are not in direct contact with one of the Agency’s foreign intelligence targets.”
The NSA will delete most of the data collected during its surveillance activity.Officially the NSA decided to stop conducting surveillance activities because of technological difficulties and to respect the privacy of the US citizens.In many cases, the US intelligence has inadvertently collected citizens’ communications while conducting its surveillance activities.Of course, the NSA statement represents an important success for Privacy advocates.https://twitter.com/Snowden/status/858021773425729543
Edward Snowden defined this reforms the most substantive of the post-2013 NSA reforms.
APT Trends report, Q1 2017
2.5.2017 Kaspersky APT
APT FILELESS MALWARE INTERNET BANKING LAZARUS TARGETED ATTACKS WIPER
Kaspersky Lab is currently tracking more than a hundred threat actors and sophisticated malicious operations targeting commercial and government organizations in over 80 countries. During the first quarter of 2017, there were 33 private reports released to subscribers of our Intelligence Services, with Indicators of Compromise (IOC) data and YARA rules to assist in forensics and malware-hunting.
We continue to observe a sharp rise in the sophistication of attacks with nation-state backing and a merger of tactics, techniques, and procedures (TTPs) between APT actors and financially motivated cybercriminals. We have witnessed the Middle East becoming one of the major cyber battlefields. At the same time, during Q1 2017, the discovery of a new Wiper victim in Europe raised eyebrows and suggested that these kinds of destructive attacks have now spread beyond the Middle East.
In this report, we discuss the targeted attack highlights from the first quarter of 2017, and discuss some emerging trends that demand immediate attention.
Highlights in targeted attacks
Evolution of Wipers: a new weapon for APT actors
During the last few months a new wave of wiper attacks, mainly focused against Saudi interests, raised a red flag for many companies, and for a good reason. The new wave of Shamoon attacks apparently relied on stolen credentials from Active Directory for their internal distribution stage. The investigation of these attacks lead us to the discovery of a new wiper we called StoneDrill.
We believe both Shamoon and StoneDrill groups are aligned in their interests, but are two separate actors, which might also indicate two different groups working together.
Our technical analysis of StoneDrill lead to the discovery of old samples (2014) in our collection that share their base code with the new StoneDrill samples. Interestingly, these old samples were attributed to the NewsBeef (Charming Kitten) group. The similarities between samples include sharing the same credentials (username and password) for C2 communications, which establish a very strong link between them.
Figure 1. Credentials used for C2 communication both in StoneDrill and NewsBeef samples
We believe that StoneDrill might be a more recent version of NewsBeef artifacts, effectively relating the known APT actor with this new wave of wiper attacks.
In addition, and related to the Shamoon attacks, we have collected different artifacts that might have been used by the actor during the first stages of attack. This first stage is critical, as credentials need to be stolen for the subsequent distribution of the malware at the victim’s premises.
Ismdoor is a backdoor found to be related to the Shamoon attacks, and might serve well for the attackers’ purposes. This tool was found mainly in Saudi Arabia and belongs to the oil and energy industry. The analysis revealed very interesting details about additional tools used by the attackers for lateral movement, which were mainly based in Powershell-based exploitation frameworks, following the trend of using fileless generic malware explained later in this report.
Finally, it is remarkable that we have detected the first victim of StoneDrill in Europe. The victim belongs to the energy industry, something which might be an indicator that this actor is spreading out of the Middle East. After attributing this wiper with what we believe might be a government-sponsored actor, this fact is highly worrying, as it might indicate a geopolitically-motivated spread of cyber-sabotage operations. This last assumption is yet to be confirmed.
Summary:
Wipers are now extending their geography
Wipers are now a part of the arsenal of APT groups. They can be used in destructive operations, as well as for deleting traces after a cyberespionage operation.
One of the modules used in the last Shamoon wave of attacks had ransomware capabilities, which might be considered another form of not-so-obvious wiping.
The fact that these destructive operations against energy companies might be related to some government sponsored APT actors is definitely worrying, and surpasses typical espionage operations.
BlueNoroff/Lazarus: bank robbery, evolved
A massive waterhole attack targeting Polish banks was publicly disclosed on 3 February, 2017. The attack leveraged the webserver of a Polish financial sector regulatory body, the Polish Financial Supervision Authority (www.knf.gov.pl), which was hacked and used to redirect users to an exploit kit. A very similar technique was used against the Mexican financial authority at the same time, and even if no other victims of this group were made public, it is very likely that more banks were also similarly affected.
Our analysis linked the attack with the BlueNoroff/Lazarus group, which has been responsible for multiple other bank attacks, including the famous Bangladesh bank heist. This waterhole attack revealed, for the first time, one of the strategies used by BlueNoroff for gaining a foothold in its target organizations. Although the attack didn’t use any zero days, the Flash Player and Silverlight exploit appeared to be enough to compromise a large number of banks, which were running on outdated software.
Indeed, we started tracking the BlueNoroff actor a long time ago. We originally saw this actor trying to infect banks in the South-East Asian region. BlueNoroff has developed a characteristic set of tools for lateral movement inside targeted organizations, and in several cases attempted tampering with SWIFT software for cashing out. This technique showed its enormous potential with the Bangladesh central bank heists, where attackers attempted to steal more than 900 million USD. In the February “Polish case”, we saw the group reusing these known lateral movements tools repackaged for their new wave of victims. This provided us with a high degree of confidence in attributing the attack to this actor.
Interestingly, the BlueNoroff group planted Russian words within the code, to derail investigators and avoid attribution. The code contained grammar errors a native Russian speaker wouldn’t make, and sentences were likely translated using online tools.
Summary:
We believe BlueNoroff is one of the most active groups in terms of attacks against financial institutions and is trying to actively infect different victims in several regions.
We think their operations are still ongoing, and in fact, their most recent malware samples were found in March 2017.
At the moment we believe BlueNoroff is probably the most serious threat against banks.
Fileless malware: enough for the job with no attribution
Avoiding attribution is one of the key goals for many APT actors, especially since a large number of operations have been exposed in recent last years. For the most sophisticated groups, the problem is that they already have their well established procedures, specially crafted tools and training, that do not always allow them to stay unnoticed.
But that is not the case for the not-so-big actors or cybercriminals. Rather than creating and having their own tools, these use generic tools that are good enough to complete an operation, and provide an evident economic advantage, with the added value of making both analysis of the incident and attribution to a particular actor more difficult.
Nowadays there is a large number of different frameworks providing cyber-actors with many options, especially for lateral movement. This category includes Nishang, Empire, Powercat, Meterpreter, etc. Interestingly, most of these are based on Powershell, and allow the use of fileless backdoors.
We have seen such techniques being widely adopted in the last few months. We find examples in the lateral movement tools used in Shamoon attacks, in attacks against Eastern European banks, and used by different APT actors such as CloudComputating, Lungen or HiddenGecko, as well as in the evolution of old backdoors like Hikit, which evolved to new fileless versions.
This trend makes traditional forensic analysis harder, traditional IOCs such as file hashes obsolete, application whitelisting more difficult, and antivirus evasion easier. It also helps to evade most of the log activity.
On the other hand, attackers usually need to escalate privileges or steal administrator credentials, they don´t usually have a reboot survival mechanism in the machines they want to infect, and they rely on accessing them when they are reconnected to the infected network. The use of standard tools in the victim environment might also limit their options. This new paradigm is still unfolding and the best practices from a defense perspective are currently not totally clear. However, we offer our recommendations in the final section of this document.
Summary:
No malware samples are needed for the successful exfiltration of data from a network.
The use of standard and open source utilities, combined with different tricks, makes detection and attribution almost impossible.
The determination of attackers to hide their activity and make detection and incident response increasingly difficult explains the latest trend of anti-forensic techniques and memory-based malware. That is why memory forensics is becoming critical to the analysis of malware and its functions.
Incident response in cases like this is key.
How to keep yourself protected
Exploiting vulnerabilities remains a key approach to infecting systems, therefore timely patching is of utmost importance – which, being one of the most tedious IT maintenance tasks, works much better with good automation. Kaspersky Endpoint Security for Business Advanced and Kaspersky Total Security include Vulnerability & Patch management components, offering convenient tools for making patching much easier, and much less time-consuming for IT staff.
Given the trend of using Powershell-based techniques, including bodiless malware scenarios, you need to make sure that your security solution is aware of such specifics. All tiers of Kaspersky Security Endpoint Security for Business as well as Kaspersky Security for Virtualization possess the broadest range of machine learning-powered detection techniques including those specifically taking care of malware using Powershell. Our behavioral System Watcher technology is also aware of specific Wiper activities like mass file deletion; after blocking the malware, its Rollback feature brings important user files back from their deleted state.
Still, it is necessary to understand that targeted attacks are dangerous not only because of their sophistication (which sometimes is not the case), but because they are usually well-prepared, and try to leverage security gaps unobvious to their targets.
Therefore, it is highly recommended that you arm yourself not only with prevention (such as endpoint protection) but also with detection capabilities, specifically with a solution that can detect anomalies in the whole network’s ongoing activities, and scrutinize suspicious files at a much deeper level than it is possible on users’ endpoints. Kaspersky Anti Targeted Attack is an intellectual detection platform that matches events coming from different infrastructure levels, discerns anomalies and aggregates them into incidents, while also studying related artifacts in a safe environment of a sandbox. As with most Kaspersky products, Kaspersky Anti Targeted Attack is powered by HuMachine Intelligence, which is backed by on premise and in lab-running machine learning processes coupled with real-time analyst expertise and our understanding of threat intelligence big data.
And the best way to prevent the attackers from finding and leveraging security holes is getting rid of them all, including those involving improper system configurations or errors in proprietary applications. For this, Kaspersky Penetration Testing and Application Security Assessment services can become a convenient and highly effective solution, providing not only data on found vulnerabilities, but also advising on how to fix it, further strengthening corporate security.
Cloud-Hosted Botnet Controllers on the Rise: Report
2.5.2017 securityweek BotNet
The number of botnet controllers hosted in the cloud has spiked in recent months, data from international nonprofit organization Spamhaus reveals.
Cloud computing has become highly popular lately, and it appears that cybercriminals are also adopting it for their nefarious operations. Because of advantages such as low-cost and scalability, an increasing number of malicious actors are abusing legitimate services to deploy botnet command and control (C&C) servers, researchers say.
Starting in January 2017, several large botnet operators were found using cloud services from Amazon AWS (Amazon Web Services), with Google Compute Engine becoming increasingly popular as well.
A chart provided by Spamhaus shows that the uptick in the use of Amazon AWS for the hosting of botnet controllers started in November 2016 and reached its peak in January 2017. While the number of newly detected botnet controllers on these platforms has decreased, more and more instances of C&C servers hosted on Google Compute Engine have started to emerge.
Spamhaus has been considering only botnet controllers for the creation of the said chart, but warns that other fraudulent infrastructure, including payment sites for ransomware (TorrentLocker, Locky, Cerber etc) or malware distribution sites are also increasingly abusing Amazon and Google services.
“Neither Amazon nor Google are handling abuse reports about botnet controllers, malware distribution sites, and other types of criminal activity on their clouds in a timely manner. Both allow botnet controllers to remain online for weeks at a time, despite multiple abuse reports and reminders,” Spamhaus’ Thomas Morrison notes.
He also notes that Spamhaus has reached out repeatedly to both Amazon and Google to report these abuse issues, but that “no relevant response from either” has been received so far. The researcher also speculates that the root cause of this problem might be a weak or non-existent customer verification process. A weak Acceptable Use Policy, or a corporate culture and management not supporting of Abuse Desk policy enforcement might also contribute to the issue, Morrison notes.
Currently, the Spamhaus Block List (SBL), which is “a database of IP addresses from which Spamhaus does not recommend the acceptance of electronic mail,” contains 159 items for Amazon.com and 53 addresses for Google.com.
“We encourage Amazon and Google to take the appropriate actions to stop all outstanding abuse problems on their networks, just as all responsible hosting networks must do. In addition, Amazon and Google must take necessary and appropriate steps to prevent further abuse of all types from being generated on their network. That includes reacting to abuse reports from many sources including, but not limited to, SBL listings, and effectively prohibiting all services to spammers and other abusive users,” the researcher notes.
Contacted by SecurityWeek, a Google spokesperson provided the following statement: "Google Cloud Platform has many precautions in place to prevent, detect, and stop abusive behavior. A team of engineers is dedicated to investigating and addressing potential security and abuse incidents 24/7, and we suspend activity that violates our Acceptable Use Policy. Our team identifies the vast majority of abuse before we are notified. When third parties notify us of potential abuse, we investigate claims to verify them before taking action. Potential abuse on Google Cloud Platform can be reported here."
TrickerBot Trojan Targets Private Banking
2.5.2017 securityweek Virus
Recent attacks associated with the TrickBot banking Trojan have been targeting private banks, and the threat is also sharpening its focus on business banking, IBM's X-Force security team warns.
Campaigns observed in the UK, Australia, and Germany were showing new redirection attacks focused on new brands, including private banks, private wealth management firms, investment banking, and a retirement insurance and annuity company. The Trojan also added some new brands to its list of targeted business banks, the security researchers say.
TrickBot was initially observed in October last year, when Fidelis Cybersecurity researchers determined that the treat had a strong connection to the Dyre gang. Before the end of 2016, the new Trojan was observed in a series of attacks targeting banks in the UK and Australia, as well as in campaigns aimed at financial institutions in Asia.
IBM has since discovered that the malware is targeting 20 new private banking brands and eight building societies in the UK, in addition to the usual set of targets. The Trojan also added two Swiss banks to the list, a few regular expressions for private banking platforms in Germany, and four investment banking firms in the U.S.
One of the newly acquired targets, the security researchers explain, is a Sharia law-compliant bank, which hasn’t been observed as a target in the past eight years. The “banking activity consistent with the principles of Sharia law prohibits certain exchanges such as interest fees and investment in business types unacceptable in Islam,” the researchers explain.
Overall, the malware now has over 300 unique URLs and regular expressions in its list of targets, IBM says. At the moment, the malware is increasingly active in Australia, New Zealand and the UK. It has grown from one to three major campaigns per month to five campaigns in April and might increase activity in an attempt to infect more endpoints.
“In terms of its attack types, TrickBot is quite similar to Dyre. Its signature moves are browser manipulation techniques that enable the malware to implement server-side web injections and redirection attacks,” IBM says.
The security researchers expect TrickBot to become one of the most prevalent financial malware families worldwide, capable of reaching a similar magnitude as Dridex and even outnumbering Dridex attacks by year’s end.
Flaws Found in Evoko Meeting Room Management Devices
1.5.2017 securityweek Vulnerebility
Meeting room management devices from Evoko have flaws that can be exploited by malicious actors in attacks aimed at enterprises that use the product, researchers warned.
The Evoko Liso product allows the employees of an organization to book meeting rooms from their calendar or by using the touchscreen interface of the device installed at each meeting room’s door. The system is managed, configured and updated via the Evoko Home software.
The product is used by thousands of organizations worldwide, including the U.S. Senate, Microsoft, Verizon, HP, Atos, Coca Cola, Siemens, DHL, Ernst & Young, Philips and McDonald’s.

Researchers at TrueSec performed a three-day analysis of the solution for a client and discovered that it’s affected by many potentially serious vulnerabilities, including ones that can be exploited to remotely hijack the device.Evoko Liso vulnerabilities
One of the flaws allows an attacker who has physical access to the device to boot a custom Linux system from a USB drive and install a backdoor that remains active even after a firmware update. The flaw can be exploited to access sensitive information, including passwords, and to create a reverse shell on the device.
Researchers determined that the device’s firmware upgrade process is also vulnerable. They discovered that while firmware images are encrypted, the encryption key is derived from a hardcoded password, and the firmware update functionality does not include integrity and authenticity checks. The firmware update process is also vulnerable to man-in-the-middle (MitM) attacks.
Malicious actors could also manipulate firmware metadata and file content to exploit an arbitrary file write vulnerability that allows the execution of arbitrary code with root privileges.
An attacker who has access to the device can also break out of the kiosk mode and launch a Chrome browser that is running with root privileges. Once they have access to the browser, a hacker can access sensitive information and execute arbitrary shell commands with root privileges from a JavaScript loaded in the browser.
Experts said hackers can also execute shell commands as root by abusing the device’s Wi-Fi connection menu.
As for the Evoko Home software, researchers determined that an attacker with network access to the application can exploit various flaws to create new admin accounts, send out emails, cause a denial-of-service (DoS) condition, and read arbitrary files on the system.
Experts also said the DDP remote procedure call used between Liso and Home allows unauthenticated connections, which can be exploited by attackers to obtain sensitive information, trigger firmware updates, and send emails.
TrueSec reported its findings to Evoko in late January. The vendor told researchers that most of the issues they reported have been patched in recent releases of its firmware, and steps have been taken to mitigate remaining issues. TrueSec said it could not confirm these claims as the company no longer has access to the tested Evoko Liso devices.
SecurityWeek has reached out to the vendor for comment last week, but the company has not responded.
“The Evoko Liso device is a typical example of embedded equipment that will be connected to a corporate network. These devices contain a full Linux system, but corporate IT admins have very little control over them (due to their encapsulated design and limited interfaces). This leaves most of the security decisions to the device vendors – for application code, operating system and third party libraries,” TrueSec’s Emil Kvarnhammar said in a blog post. “It is crucial that IoT vendors build secure and robust systems, and that the systems can be updated remotely in a secure fashion when new vulnerabilities are discovered.”
Hackers Threaten Media Firms After Stealing Unreleased TV Shows
1.5.2017 securityweek Hacking
A group of hackers has threatened to leak unreleased TV shows and movies belonging to Netflix and various television networks after breaching the systems of a production company. The incident once again underscores the security risks posed by third-party vendors.
The hacker group calling itself “TheDarkOverlord” has leaked several unreleased episodes from season 5 of Netflix’s “Orange is the new black” TV show. They obtained the files after reportedly breaching the systems of Larson Studios, an audio post-production company in Hollywood.
The hackers told DataBreaches.net that after they breached Larson Studios in December, the company had agreed to pay them 50 bitcoins to avoid having the stolen movies leaked to the public. TheDarkOverlord said Larson later changed its mind about giving in to the extortion demand.
The hackers recently changed their strategy and started targeting the companies whose movies they obtained. The first was Netflix, from which they demanded an undisclosed amount of money. The streaming giant refused to pay up, which led to the hackers leaking “Orange is the new black” episodes.
Netflix has confirmed that a production vendor used by several major studios had its systems compromised. The company said law enforcement authorities are aware of the incident and they have launched an investigation.
TheDarkOverlord claims to have obtained 37 TV shows and movies belonging to various networks, either one of which could be targeted next.
Follow
thedarkoverlord @tdohack3r
Who is next on the list? FOX, IFC, NAT GEO, and ABC. Oh, what fun we're all going to have. We're not playing any games anymore.
4:54 AM - 29 Apr 2017
146 146 Retweets 251 251 likes
In the past months, the group breached the systems of several organizations, particularly ones in the healthcare sector.
This incident once again shows the risks posed by third-party vendors that fail to protect their customers’ data.
"What this highlights is the very real fact that managing risk at third-party vendors isn’t limited to regulated industries like Banking and Healthcare. Outsourcing critical services has become a way of life for companies in all industries, making the need to manage third-party risk a universal requirement. The debate over whether to pay ransom demands shouldn’t divert attention from the need to proactively manage all of the risks presented from outsourcing,” said Brad Keller, senior director of 3rd party strategy at Prevalent, a firm that develops third-party vendor management solutions.
“In addition to customer data and access to sensitive systems, those risks include: protecting all forms of intellectual property, merger and acquisition information, litigation strategies, and any other information a company wants/needs to protect,” Keller added. “While this was a hard lesson learned for Netflix, hopefully it will cause other companies to take a closer look at what they may have at risk at their vendors."
Brian Vecci, technical evangelist at data protection firm Varonis, believes organizations should avoid doing business with vendors not capable of demonstrating that only the right users have access to sensitive data, and that they have mechanisms in place for detecting compromised users and systems.
“If you haven’t already, it’s time to make sure the third parties with whom you share data aren’t a weak link in your security chain. Vendors are hired for their expertise, and because of that they have access to and store an immense amount of their client’s data. More and more breaches start from a compromised third party, and this will have an impact on how future organizations and vendors conduct business together,” Vecci said.
IBM Supply Chain Breached as Storwize USBs Ship With Malware
1.5.2017 securityweek Virus
The need to maintain security over the supply chain has been confirmed by alerts issued at the end of last week by both IBM and Lenovo. IBM has been shipping malware-infected initialization USBs for its Storwize storage systems which are used by Lenovo.
"IBM has detected that some USB flash drives containing the initialization tool shipped with the IBM Storwize V3500, V3700 and V5000 Gen 1 systems contain a file that has been infected with malicious code," warns IBM in its alert.
Lenovo published a similar alert: "Some USB flash drives containing the initialization tool shipped with the IBM Storwize for Lenovo V3500, V3700 and V5000 Gen 1 storage systems manufactured by IBM contain a file that has been infected with malicious code. The malicious file does not in any way affect the integrity or performance of the storage systems."
The last statement is only true so long as the infected file is not manually executed by the user. Launching the initialization copies the malware and the initialization tool to a temporary folder, but does not execute the malware itself.
This malware is not new. Detected variously as Win32/Pondre, VirTool:Win32/Injector.EG, W32.Faedevour!inf and others by different AV engines, it was detected by 57 out of 61 AV engines on Virus Total at the end of March 2017. It follows that most mainstream anti-virus products would immediately detect its presence.
USB drive models V3500-2071, V3700-2072, V5000-2077 and V5000-2078 may be infected. "IBM Storwize Systems with serial numbers starting with the characters 78D2 are not affected," says IBM.
Lenovo recommends that users should destroy the affected drives. Users who have already used the drive should first check that their AV system has effectively quarantined or removed the malware. If it hasn't, it can be manually removed by deleting the Windows directory %TMP%\initTool or the Mac or Linux directory /tmp/initTool; taking care to delete the directory rather than simply moving it to the Recycle Bin.
There are two primary aspects to this incident. The first is a serious embarrassment to IBM; but the most worrying aspect is that the supply chain of a company as large and prestigious as IBM can be affected. The malware itself seems to be neither difficult to detect, nor difficult to remove -- but the supply chain has become a major attack vector. Both IBM and Lenovo can consider themselves lucky that it wasn't more sophisticated new malware.
North Korea-Linked Hacker Group Poses Serious Threat to Banks: Kaspersky
1.5.2017 securityweek BigBrothers
A North Korea-linked hacking group responsible for multiple financial and destructive attacks is believed to be the most serious threat against banks, security firm Kaspersky Lab says.
The group, referred to as BlueNoroff or Lazarus, has been associated with numerous high profile attacks over the past several years, including the devastating attack against Sony Pictures in late 2014. Last year’s $81 million cyber heist from Bangladesh's account at the New York Federal Reserve Bank has been attributed to this group as well.
The actor is also believed to have orchestrated an attack aimed at banks in Poland earlier this year, where the website of the Polish Financial Supervision Authority (knf.gov.pl) was hijacked and abused to deliver malware. The hackers inserted Russian words as decoy in the malware used in this attack, security researchers discovered.
Active since 2009 or earlier, Lazarus is believed to have been conducting a large campaign aimed at financial institutions worldwide. The operation is ongoing, with the most recent malware samples found in March. Kaspersky Lab says that currently the group “is probably the most serious threat against banks.”
BlueNoroff/Lazarus is, however, only one of the more than 100 threat actors and sophisticated malicious operations that Kaspersky Labs is monitoring at the moment. The attacks target commercial and government organizations in over 80 countries and show an evolution of these actors, with both Advanced Persistent Threat (APT) actors and financially motivated cybercriminals using the same tactics, techniques, and procedures (TTPs).
Other APT groups that were active during the first quarter of the year were Shamoon and StoneDrill, two separate actors that have aligned interests and which might be working together. Aimed at Saudi targets, the two malware families pack disk-wiping capabilities, which makes them extremely destructive.
According to Kaspersky, StoneDrill appears to have been around since 2014, with old samples attributed to the NewsBeef (Charming Kitten) group. The samples share the same credentials (username and password) for command and control (C&C) communications, and the security researchers suggest that StoneDrill might be a more recent version of NewsBeef artifacts.
Recently, StoneDrill was also used in attacks against targets in the energy industry in Europe, which suggests that the actor is expanding its reach outside of the Middle East, the security researchers suggest.
Another piece of malware related to the Shamoon attacks is Ismdoor, a backdoor used in Saudi Arabia to target the oil and energy industry. The attackers were also found to have used mainly Powershell-based tools for lateral movement, and to have adopted the trend of using fileless generic malware for nefarious operations.
The use of generic tools in attacks has been generally associated mainly with “not-so-big actors or cybercriminals,” who wouldn’t create their own set of malicious programs. Some of the available frameworks that offer many options, especially for lateral movement, include Nishang, Empire, Powercat, and Meterpreter, all of which are based on Powershell and allow the use of fileless backdoors.
“We have seen such techniques being widely adopted in the last few months. We find examples in the lateral movement tools used in Shamoon attacks, in attacks against Eastern European banks, and used by different APT actors such as CloudComputating, Lungen or HiddenGecko, as well as in the evolution of old backdoors like Hikit, which evolved to new fileless versions,” Kaspersky Lab explains.
Researchers Expose Huge Ad Scam Operation
1.5.2017 securityweek Spam
Researchers from security frim RiskIQ recently discovered a large ad scam operation where cybercriminals employed advanced automation techniques to deliver scam ads from millions of different domain names.
Dubbed NoTrove, the threat actor managed to stay ahead of detection and takedown efforts, while also building a network that generated huge amounts of traffic. The group was first observed a year ago, but the security researchers believe that it has been operating since at least 2010.
NoTrove was mainly focused on getting as much web traffic as possible, for monetary gain, and RiskIQ associated the group to 78 campaigns, including scam survey rewards, fake software downloads, and redirections to PUPs (Potentially Unwanted Programs). Although the used domains were short-lived, the generated traffic from scam ad deliveries was so large that it even pushed one of them to a 517 ranking on the Alexa top 10,000 web sites.
The actor was observed switching between 2,000 randomly generated domains and more than 3,000 IP addresses, operating across millions of Fully Qualified Domain Names (FQDNs). An FQDN is a complete web address, typically including subdomains for ad scammers, RiskIQ security researchers explain in their report (PDF).
The NoTrove FQDNs show high-entropy (they are highly random hosts), which shows that automation was used when creating them. Next to the high-entropy hosts, the researchers identified campaign-specific middle hosts, which appear to label the type of scam employed in the campaign, along with high-entropy or randomly worded domains, also generated using automation.
“With high-entropy domains and always-shifting hosting, we’ve seen NoTrove burn through just under 2,000 domains and over 3,000 IPs. Combined with the 78 variations of campaign-specific middle word variants and randomized hostnames, we’ve seen NoTrove operate across millions of FQDNs. Typically, one IP used by NoTrove will house a set of domains, but each campaign-specific *.domain.tld campaign variant will be hosted on its own IP, usually a Choopa or Linode droplet,” the researchers say.
“NoTrove harms not only visiting users, but also legitimate advertisers, adversely affecting those reliant on the credibility of the digital advertising ecosystem such as online retailers, service providers and media outlets. Constantly shifting infrastructure means simply blocking domains and IPs isn't enough. We must now begin utilizing machine learning to leverage human security teams who increasingly depend on accurate, automated scam detection,” RiskIQ threat researcher William MacArthur said.
Hackers Threaten Media Firms After Stealing Unreleased TV Shows
1.5.2017 securityweek Hacking
A group of hackers has threatened to leak unreleased TV shows and movies belonging to Netflix and various television networks after breaching the systems of a production company. The incident once again underscores the security risks posed by third-party vendors.
The hacker group calling itself “TheDarkOverlord” has leaked several unreleased episodes from season 5 of Netflix’s “Orange is the new black” TV show. They obtained the files after reportedly breaching the systems of Larson Studios, an audio post-production company in Hollywood.
The hackers told DataBreaches.net that after they breached Larson Studios in December, the company had agreed to pay them 50 bitcoins to avoid having the stolen movies leaked to the public. TheDarkOverlord said Larson later changed its mind about giving in to the extortion demand.
The hackers recently changed their strategy and started targeting the companies whose movies they obtained. The first was Netflix, from which they demanded an undisclosed amount of money. The streaming giant refused to pay up, which led to the hackers leaking “Orange is the new black” episodes.
Netflix has confirmed that a production vendor used by several major studios had its systems compromised. The company said law enforcement authorities are aware of the incident and they have launched an investigation.
TheDarkOverlord claims to have obtained 37 TV shows and movies belonging to various networks, either one of which could be targeted next.
Follow
thedarkoverlord @tdohack3r
Who is next on the list? FOX, IFC, NAT GEO, and ABC. Oh, what fun we're all going to have. We're not playing any games anymore.
4:54 AM - 29 Apr 2017
138 138 Retweets 234 234 likes
In the past months, the group breached the systems of several organizations, particularly ones in the healthcare sector.
This incident once again shows the risks posed by third-party vendors that fail to protect their customers’ data.
"What this highlights is the very real fact that managing risk at third-party vendors isn’t limited to regulated industries like Banking and Healthcare. Outsourcing critical services has become a way of life for companies in all industries, making the need to manage third-party risk a universal requirement. The debate over whether to pay ransom demands shouldn’t divert attention from the need to proactively manage all of the risks presented from outsourcing,” said Brad Keller, senior director of 3rd party strategy at Prevalent, a firm that develops third-party vendor management solutions.
“In addition to customer data and access to sensitive systems, those risks include: protecting all forms of intellectual property, merger and acquisition information, litigation strategies, and any other information a company wants/needs to protect,” Keller added. “While this was a hard lesson learned for Netflix, hopefully it will cause other companies to take a closer look at what they may have at risk at their vendors."
Brian Vecci, technical evangelist at data protection firm Varonis, believes organizations should avoid doing business with vendors not capable of demonstrating that only the right users have access to sensitive data, and that they have mechanisms in place for detecting compromised users and systems.
“If you haven’t already, it’s time to make sure the third parties with whom you share data aren’t a weak link in your security chain. Vendors are hired for their expertise, and because of that they have access to and store an immense amount of their client’s data. More and more breaches start from a compromised third party, and this will have an impact on how future organizations and vendors conduct business together,” Vecci said.
Yahoo Awards $7,000 for Flickr Account Hijacking Flaws
1.5.2017 securityweek Vulnerebility
A bug bounty hunter has earned $7,000 from Yahoo for finding vulnerabilities in the company’s image and video hosting service Flickr.
Michael Reizelman, aka mishre, said he uncovered three minor flaws that could have been chained together to take control of Flickr accounts.
According to the researcher, when users log in to their Flickr.com account, they are redirected to the login.yahoo.com domain, where their credentials are entered and verified. If the credentials are valid, the user is taken back to Flickr.com and authenticated. The redirect to login.yahoo.com also occurs if the user is already logged in, but it takes place in the background.
The request to login.yahoo.com is used to obtain an access token for the user. Reizelman noticed that a parameter named .done, which controls where the login token is sent, could have been manipulated. However, Yahoo made sure that the token could only be sent to the flickr.com domain.
While finding an open redirect vulnerability on flickr.com could have allowed him to exploit the vulnerability, the expert could not find such weaknesses. He did however discover another method that involved embedding an image from an attacker-controlled server into a Flickr.com page using the <img> tag.
Yahoo had been manipulating this type of code to prevent abuse, but the expert discovered a bypass method.
Reizelman noticed that he could embed an external image into comments posted on flickr.com/help/forum/en-us/, which did not have a Content Security Policy (CSP). By pointing the .done parameter to a malicious image embedded into a post on the Flickr help forum, an attacker could have ensured that the access tokens were sent to their server.
An attacker simply needed to trick the targeted user into clicking on a specially crafted link. Once the token was in their possession, they could have easily accessed the victim’s Flickr account.
The researcher reported the vulnerabilities to Yahoo on April 2 via the tech giant’s HackerOne bug bounty program. The vendor addressed the issue roughly one week later and awarded the expert a $7,000 bounty.
Yahoo addressed the security hole by only allowing the .done parameter to point to flickr.com/signin/yahoo, adding CSP to the Flickr forum, and ensuring that the expert’s image embedding bypass method no longer works.
Reizelman has also earned bounties for reporting vulnerabilities to Uber, GitHub, Dropbox, Twitter, Google, Slack, Badoo and Imgur.
New "Dok" Mac OSX Malware Steals Sensitive Data
1.5.2017 securityweek Apple
New malware able to spy on OSX users' internet traffic, including https traffic, has been found targeting European users. The malware was previously not stopped by Apple's Gatekeeper, and when discovered was not detected by anti-malware signature engines.
Called "Dok" (OSX/Dok) by Check Point, the malware combines phishing techniques and a valid developer certificate to effect a MITM attack capable of eavesdropping on all of the victim's internet traffic.
The attack starts with a phishing email. In the example given by Check Point, a sample sent to a user in Germany was baited with supposed inconsistencies in the user's tax returns. The email included an attachment, Dokument.zip, containing the malware bundle signed on April 21, 2017 by Seven Muller and called Truesteer.AppStore.
If activated, the malware copies itself to the /Users/Shared folder and executes. A pop-up message tells the user that the expected bundle was damaged and could not be opened; but the malware itself replaces any loginitem named 'AppStore' in order to gain persistence.
Further social engineering is then used to obtain the user's password in order to complete the malware installation. It uses localization to pop-up a window in either English or German. The window overlays all other windows and claims that a security issue has been identified.
The user is asked to enter his or her password in order to obtain the necessary updates. This window persists, and the user is unable to do anything but comply. Even if the computer is restarted, the window will reappear. However, once the he or she enters the password, the malware obtains administrator privileges and installs the Homebrew command-line installation system. This is then used to download and install a Tor client and SOCAT.
OSX/Dok then uses its user-granted privileges to suppress further password prompts. It proceeds to install a new root certificate and alter the system's network settings, redirecting traffic through a server hidden in Tor. This allows the hacker to intercept and read all outgoing traffic, even when legitimately encrypted with SSL. Because the server is located in Tor, the hacker remains anonymous.
The potential is serious. For consumers, login details for any accessed online service can be seen and stolen -- including bank details.
It is potentially more harmful for businesses. Thomas Reed, director of Mac offerings at Malwarebytes, comments: "The impact on business could be much more severe, as it could expose information that could allow an attacker to gain access to company resources. For example, consider the potential damage if, while infected, you visited an internal company page that provided instructions for how to connect to the company VPN and access internal company services. The malware would have sent all that information to the malicious proxy server."
Apple has reacted swiftly. It revoked the developer certificate on April 28. Installation of this particular version should now be stopped by Gatekeeper. It has also pushed out silent updates that protect OSX users against two variants of the malware, OSX.Dok.A and OSX.Dok.B, and also against a new version of the intrusive adware known as OSX.Genieo.F.
While there should now be no new infections of this version of OSX/Dok, Reed warns that complete removal for anyone already infected is not simple. The malware makes many changes to the system, and even though its activity can be stopped, other changes could cause ongoing problems. "For people who don't know their way around in the Terminal and the arcane corners of the system," he suggests, "it would be wise to seek the assistance of an expert, or erase the hard drive and restore the system from a backup made prior to infection."
For businesses, he suggests, "If you have been infected by this malware in a business environment, you should consult with your IT department, so they can be aware of the risks and begin to mitigate them."
Cloudflare Launches Service to Protect IoT Devices
1.5.2017 securityweek IoT
Cloudflare has launched a new service that aims to address one of the most wide-spread issues in today’s connected world: the poor security of Internet of Things (IoT) devices.
Dubbed Orbit, the new service is designed to keep devices safe from vulnerabilities, weak authentication, and other types of threats, the security company claims. Orbit adds an extra layer of security between the device and the Internet, meaning that even devices that can no longer receive security patches can be protected from exploits.
The issue of improperly secured IoT devices has been a hot subject over the past couple of years, fueled mainly by the emergence of IoT botnets such as Mirai and Bashlite. Other IoT threats include Hajime, which hasn’t revealed its true purpose as of now, and the destructive BrickerBot, which permanently disables devices.
While these threats abuse a single vulnerability type, namely the use of hardcoded or easily-guessable login credentials, other IoT malware families attempt to exploit different issues with these devices. Attacks can often result in entire networks being compromised, and patching could prove problematic sometimes, and it either requires massive recalls or isn’t performed in due time by the users themselves.
According to Cloudflare, the newly announced service can address all of these issues at once. Should a vulnerability be discovered, the impacted company wouldn’t have to attempt to patch each of the affected devices immediately, but could resolve it through setting specific rules in Cloudflare's firewall, thus restricting access to the impacted devices. Devices protected by Cloudflare Orbit can still access the Internet, but only after malicious requests are filtered by the service.
“Orbit sits one layer before the device and provides a shield of security, so even if the device is running past its operating system’s expiration date, Cloudflare protects it from exploits. And while devices may be seldom patched, the Cloudflare security team is shipping code every day, adding new firewall rules to Cloudflare’s edge,” the company explains.
Orbit has been built in collaboration with a number of IoT vendors, and already protects over 120 million IoT devices, Cloudflare says. It allows IoT companies to write logic on Cloudflare’s edge and create firewall rules that are immediately updated to the Cloudflare Orbit layer for all devices, without having to write and ship a patch.
Alongside Orbit, Cloudflare announced Enterprise domains TLS Client Authentication, which attempts to address the issue of authenticating IoT devices while disseminating between authorized company devices and bots only pretending to be. The Client Authentication is a TLS handshake where the client authenticates the server’s certificate but also has a certificate that the server authenticates.
“With Client Authentication on Cloudflare, Cloudflare’s edge handles the load of the TLS handshakes, validating the device client certificates and only sending the IoT infrastructure traffic from authorized devices,” the company says.