
Germany Bans Facebook From Collecting WhatsApp Data
27.9.2016 thehackernews Social
Just last month, the most popular messaging app WhatsApp updated its privacy policy and T&Cs to start sharing its user data with its parent company, and now both the companies are in trouble, at least in Germany and India.
Both Facebook, as well as WhatsApp, have been told to immediately stop collecting and storing data on roughly 35 Million WhatsApp users in Germany.
The Hamburg Commissioner for Data Protection and Freedom of Information Johannes Caspar even ordered Facebook on Tuesday to delete all data that has already been forwarded to WhatsApp since August.
Also in India, the Delhi High Court on September 23 ordered WhatsApp to delete all users’ data from its servers up until September 25 when the company’s new privacy policy came into effect.
When Facebook first acquired WhatsApp for $19 billion in cash in 2014, WhatsApp made a promise that its users’ data would not be shared between both companies.
But now apparently this has changed, which, according to Caspar, is not only "misleading" for their users and public, but also "constitutes an infringement of national data protection law" in Germany.
"Such an exchange is only admissible if both companies, the one that provides the data (WhatsApp) as well as the receiving company (Facebook) have established a legal basis for doing so." the press release [PDF] from the Commission reads.
"Facebook, however, neither has obtained an effective approval from the WhatsApp users nor does a legal basis for the data reception exist."
Apparently, the new measure was taken by the companies in favor of more targeted advertising on the largest social network and to fight spam.
In response to the privacy watchdog’s decision, Facebook released a statement that it complied with EU data protection law, saying: "We are open to working with the Hamburg DPA in an effort to address their questions and resolve any concerns."
According to the watchdog, since Facebook and WhatsApp are independent companies, they should process their users' data based on their own terms and conditions as well as data privacy policies.
However, WhatsApp users need not to worry about the content of their WhatsApp messages, like chats and images, as they are end-to-end encrypted, which means even the company cannot read them.
Google to Launch 'Andromeda OS' — An Android-Chrome OS Hybrid
27.9.2016 thehackernews Android
Google's long-rumored Android-Chrome hybrid operating system is expected to debut at the company's upcoming hardware event on October 4.
The company has been working to merge the two OSes for roughly 3 years with a release planned for 2017, but an "early version" to show things off to the world in 2016.
Android + Chrome = Andromeda
The hybrid OS, currently nicknamed 'Andromeda,' could be come on a new Pixel laptop as well as Huawei Nexus tablet from Google by Q3 2017, if not sooner, according to new leaks from 9to5Google and Android Police.
Android + Chrome = Andromeda
The laptop, officially codenamed "Bison" and nicknamed "Pixel 3," is a reference to the "Chromebook Pixel," but since this edition is not running Chrome operating system, one can not call it a "Chromebook" anymore.
Andromeda is separate from the company's Fuchsia OS, which is focused on Internet-of-Thing (IoT) devices. Moreover, the report also makes it clear that Andromeda "is [an entirely] distinct effort from Google's current campaign to bring Android apps to Chromebooks." So, don't get confused.
Rumored specs suggest Bison is expected to pack a 12.3-inch display with a 'tablet' mode and stylus and reportedly powered by an Intel M3 processor like Apple's 12-inch MacBook, or an Intel Core i5.
Bison is expected to have two models with 32GB or 128GB of internal storage, and 8GB or 16GB of RAM.
Other features could include two USB-C ports, a 3.5mm headphone jack, a fingerprint scanner, stereo speakers, a backlit keyboard, quad microphones, a glass trackpad, and a battery that lasts around 10 hours.
For more details about the new hybrid operating system, you need to wait for two more weeks for Google's October 4 event that is set to launch a Google's new hardware product line, including "Google Wi-Fi" router, Google Home, the refreshed 4K-capable Chromecast rumored to be called Chromecast Ultra, and a "Daydream" VR headset.
How much time does it take to create a malware that evades antimalware solutions? One or two minutes
27.9.2016 securityaffairs Android
A Group of the researchers from the Iswatlab team at the University of Sannio demonstrated how is easy to create new malware that eludes antimalware.
It’s not easy to ‘write’ a new malware that is able to evade the detection of antimalware and other defensive software, but it is easier to ‘produce’ a new malware that can evade the detection of antimalware solutions.
The difference between writing and producing is very subtle and stands in the fact that in the latter case the malware writer does not need to write any line of code, he just needs to press a button.
The researchers at the Iswatlab (www.iswatlab.eu) at the University of Sannio (Italy) realized an engine that applies eight transformations to a mobile malware code which alter the code’s shape, but not the behavior of the malware.
This tool used by the team is named the “Malware Washing Machine” for obvious reasons.
The transformation engine developed by the researcher for Android malware works by applying the following transformations:
Disassembling & Reassembling.
Repacking.
Changing package name.
Identifier Renaming.
Data Encoding.
Call indirections.
Code Reordering.
Junk Code Insertion.
Composite Transformations.
The Iswatlab crew tested the Malware Washing Machine against 57 well known commercial antimalware solutions.
They used their engine for changing 5560 malware that was identified and classified as malware by tall the 57 antimalware used in the test session.
Anyway, after the modification, the majority of antimalware is no more able to recognize a large subset of the malware.
“Are the actual signature based detection algorithms effective on mobile environments? We developed a framework which applies a set of transformations to Android
applications small code. We then transformed a real world malware data-set (available at: https://www.sec.cs.tu-bs.de/~danarp/drebin/index.html) and then we submitted the applications to the website www.virustotal.com, in order to evaluate the maliciousness before and after the transformations (we submitted every sample pre and post transformation process).” reads the report.
The test showed that there are some malware families that are recognized by some antimalware also after the transformations, but they were a very little part.
“In the following table, first column represents the Anti-Malware, the second the number of samples (without transformations) correctly detected by the antimalware while in the third column (in red) the number of correctly detected samples after transformation process.”

“The results is impressive: the antimalware is not able to recognize the transformed malware (given that it was able to recognize the original malware).
The transformation engine is released for the scientific community with the open source license at the following url: https://github.com/faber03/AndroidMalwareEvaluatingTools“
The details of the test conducted by the Iswatlab are included in the report titled “Evaluating malware obfuscation techniques against antimalware detection algorithms”
This test raises the discussion about the capability to limit the production of malware, the experts at the Iswatlab were able to create new malware without writing any line of new code, but just scrambling some old well-known threats.
Summing up, the producing a new-born malware, that is not detectable by defense solutions, just takes a few minutes. Take an old malware and put it into the Malware Washing Machine!
The Malware Washing Machine is available at https://github.com/faber03/AndroidMalwareEvaluatingTools
Fancy Bear Hackers use a new Mac Trojan against aerospace industry
27.9.2016 securityaffairs Virus
Researchers at Palo Alto spotted a new campaign of the Russian Fancy Bear APT using a new Mac OS X Trojan against companies in the aerospace industry.
In the last weeks, we have discussed a lot about a string of attacks that targeted the US Democratic National Committee (DNC), security experts collected evidence of the involvement of Russian nation-state actors.
In particular, security experts at threat intelligence firm ThreatConnect have conducted an analysis on the IP addresses listed in the flash alert issued in August by the FBI that warned about two cyber attacks against the election systems in two U.S. states.
The experts from ThreatConnect discovered some connections to a Russian threat actor alleged linked to the Government of Moscow. One of the domains hosting the phishing content was registered with an email address associated with a domain known to be used by the infamous APT28 group (aka Fancy Bear, Pawn Storm, Sednit, Sofacy).
Now the Fancy Bear is again in the headlines, according to the malware researchers at Palo Alto, the dreaded group is the behind a trojan targeting Mac OS X machines.
According to Palo Alto researcher Ryan Olson, Fancy Bear has used the Komplex trojan to target organizations in the aerospace sector that were using the MacKeeper antivirus software.
“The Sofacy group, also known as APT28, Pawn Storm, Fancy Bear, and Sednit, continues to add to the variety of tools they use in attacks; in this case, targeting individuals in the aerospace industry running the OS X operating system. During our analysis, we determined that Komplex was used in a previous attack campaign targeting individuals running OS X that exploited a vulnerability in the MacKeeper antivirus application to deliver Komplex as a payload.” reads the analysis published by PaloAlto. “Komplex shares a significant amount of functionality and traits with another tool used by Sofacy – the Carberp variant that Sofacy had used in previous attack campaigns on systems running Windows. In addition to shared code and functionality, we also discovered Komplex command and control (C2) domains that overlapped with previously identified phishing campaign infrastructures associated with the Sofacy group.”
The experts observed the Komplex malware in a previous attack campaign targeting individuals running OS X that exploited a vulnerability in the MacKeeper antivirus application.
“The Sofacy group created the Komplex trojan to use in attack campaigns targeting the OS X operating system – a move that showcases their continued evolution toward multi-platform attacks,” Olsen says. “The tool is capable of downloading additional files to the system, executing and deleting files, as well as directly interacting with the system shell. While detailed targeting information is not currently available, we believe Komplex has been used in attacks on individuals related to the aerospace industry, as well as attacks leveraging an exploit in MacKeeper to deliver the Trojan”
The Komplex malware has numerous similarities with the Carberp trojan, it was improved to gain access on PC and OS X systems and use the same command-and-control server.
The researchers noticed that Komplex’s C2 domain appleupdate[.]org was not used in the past by the group, while both the apple-iclouds[.]net and itunes-helper[.]net domains have direct ties to the activity of Fancy Bear.
A close look at the malicious payload used by the ATP revealed that it begins the infection process by conducting an anti-debugging check to see if it is being debuggedby detection software. This function was borrowed by Fancy Bear by an official Apple guide created in 2004 titled “Detecting the Debugger”.
“This is not the first time the Sofacy group’s malware authors have obtained techniques from publicly available sources, as demonstrated in the use of the Office Test Persistence Method that they obtained from a blog posted in 2014.” continues the analysis.
The malware implements classic RAT features, it gathers information on the victim’s machine including running processes, user identities, and of course it is able to remotely control it.
The malicious code is delivered within a PDF decoy on Russian space projects that executes the malware.

Největší DDoS útok v historii, internet věcí útočí
27.9.2016 SecurityWorld Počítačový útok
Soustředit se na zabezpečení internetu věcí by se nyní mělo stát prioritou; pro jeden z největších distribuovaných DoS útoků v historii útočník využil botnet až milionu infikovaných počítačů a zařízení internetu věcí.
Botnet obřích rozměrů, tvořený hacknutými, k internetu připojenými chytrými zařízeními typu kamery, žárovky a termostaty, zaútočil na účet bezpečnostního bloggera, spadajícího pod velkou americkou IT firmu Akamai. Ta mu nakonec musela účet zrušit, neboť jeho obrana zabrala příliš mnoho zdrojů.
Nebylo to tak, že by se firma nepokoušela útoku bránit – tři dny tak činila – ale nakonec se vlivem vysokých finančních nákladů vzdala a zákazníkovi musela účet zrušit, popisuje Andy Ellis, hlavní bezpečnostní manažer firmy.
Akamai tedy zrušila ochranu blogu Briana Krebse „Krebs on Security“, který zůstává nedostupný. Provoz v době útoků činil 665 Gb/s a web zcela zahltil. Velikost útoku je téměř dvojnásobná oproti jakémukoli jinému, který kdy firma zažila.
Analýza botnetu internetu věcí generujícího takový datový provoz podle Ellise zabere určitý čas, ale mohl by vést k lepším obranným nástrojům na zmírnění následků útoku.
Dopad je podobný jako v roce 2010, kdy Anonymous útočili pomocí open-source programu LOIC nebo jako v roce 2014, kdy DDoS útoky dočasně poškodily servery hostingových služeb Joomla a Wordpress.
Lekce pro podniky dle Ellise spočívá v tom, že současné formy ochrany proti DDoS útokům se musí zlepšit, aby se weby zvládly ubránit i vyšším objemům dat.
Internet věcí musí zapracovat na zabezpečení
Podle firmy Akamai stojí za útokem na web Briana Krebse velký botnet, složený primárně ze zařízení internetu věcí. Použito dokonce bylo takové množství zařízení, že útočník ani nemusel využívat běžné taktiky, využívané na zvýšení efektivity jednotlivých přístrojů, sdělil Ellis.
Přesný počet zařízení zneužitých k útoku zatím není znám, ale mohl by snadno dosahovat jednoho milionu.
„Stále se snažíme odhadnout velikost,“ říká Ellis. „Myslíme si, že jde o přehnaný odhad, ale nakonec se může ukázat, že není daleko od pravdy.“
S předpokládaným množstvím zařízení internetu věcí dosahujícího 21 miliard v roce 2020 by velikost botnetů, tvořených těmito relativně nechráněnými přístroji, mohla dosáhnout gigantických rozměrů, myslí si Dave Lewis, významný bezpečnostní odborník Akamai. Sdělil to během čtvrteční konference Security of Things Forum v Cambridgi v Massachussetts.
„Co když útočník do zařízení vpraví kód, aby vytvořil Fitbit botnet?“ Naráží na slavné fitness náramky Lewis. Výzkumníci prokázali, že bezdrátově nahrát do Fitbitu malware jde do 10 sekund, takže nejde o přehánění. Zabezpečení zařízení internetu věcí je skutečně chabé, pokud vůbec existuje.
Některé z přístrojů zjištěné během útoku využívaly klienty, které standardně běží na kamerách.
„Možná jde o podvod, ale možná do útoku opravdu zasáhly kamery,“ věří Lewis. „Jsou tu náznaky, že se v botnetu nacházela zařízení internetu věcí, a ne v malém množství.“
Útočník ani nevyužil klasické metody zesílení distribuovaného DoS útoku typu odražení, takže šlo o legitimní http requesty, potvrdil Ellis.
Mnoho informací o útoku je stále nejasných nebo neznámých. Kdo útočil nebo jaké metody útočník použil k ovládnutí jednotlivých zombie, se lze jen domnívat.
Akamai kontaktovali i jiní poskytovatelé, kteří zažili podobné útoky v menším rozsahu. Z části šlo o herní stránky, o útocích na něž Krebs psal; dle Ellise zde může existovat souvislost.
Firma útok zanalyzuje a vyvine nástroje pro boj s podobnými útoky, dodává.
Poškozený blogger Krebs po útoku o vynuceném smazání jeho účtu tweetnul:
„Nemohu Akamai vinit z jejich rozhodnutí. Asi jsem je dnes stál hodně peněz. Sbohem všichni. Bylo to fajn.“
Podnikovou síť ochrání NetShield
27.9.2016 SecurityWorld Zabezpečení
Produkt NetShield společnosti SnoopWall, který podle dodavatele poskytuje zabezpečení vnitřní sítě, jež nejsou schopné nabídnout současné firewally a antivirové programy, uvedl na náš trh VUMS Datacom.
NetShield představuje novou generaci řešení pro řízení přístupu mobilních i pevných zařízení. Firma pomocí něj získá přehled a kontrolu nad nedůvěryhodnými síťovými aktivitami prostřednictvím dynamického řízení pevných, mobilních a virtuálních koncových zařízení.
Bez-agentová podoba ochrany usnadňuje integraci do stávající podnikové infrastruktury, a navíc je řešení prý snadno spravovatelné, flexibilní, nákladově efektivní a škálovatelné. Navíc se může připojit kdekoliv -- a odhalit či zajistit problém odkudkoliv.
NetShield přináší sadu funkcí Network Access Control (NAC). Implementovaná funkce Pre-Cognition Engine zajišťuje, aby karanténa koncového bodu předcházela infekci. Tento mechanismus tak podle dodavatele zajišťuje umístění do karantény s nulovým výskytem false-positive chyb.
Vlastnosti řešení NetShield podle výrobce:
NAC – aby se ke korporátním sítím připojily pouze důvěryhodné zdroje
Zero-hour malware a phishing karanténa – prevence ransomwaru s nulovou false positive chybou
Vulnerability assessment a patch management
Vykazování shody s bezpečnostními standardy
TLD blokování & Detekce MAC spoof
Microsoft removed Windows Journal from its OSs due to security flaws
27.9.2016 securityaffairs Vulnerebility
Microsoft encourages Windows users to remove the Windows Journal application by following the steps found in Microsoft update KB3161102.
Microsoft has removed the Windows Journal application from its OSs due to the presence of multiple security flaws that can be exploited by hackers through specially crafted Journal files (.jnt) which are used to store notes and drawings created with the app.
The presence of the flaws affecting Windows Journal is known since a long ago, bug hunters have discovered several denial-of-service (DoS) and remote code execution flaws in the application.
In the last months, Microsoft solved two memory corruption flaws, the CVE-2016-0182 reported by the researchers Jason Kratzer and Bingchang Liu, and the CVE-2016-0038 discovered by Rohit Mothe.
In August, the security researcher Honggang Ren from the security firm Fortinet identifies a heap overflow that could be exploited by attackers to crash the application. Fortinet published a blog post last week detailing the vulnerability.
Microsoft promptly decided to remove Windows Journal through the security update KB3161102.
Microsoft suggests its customers the migration to OneNote, anyway, users who need to use Windows Journal can decide to install it separately after they apply the update KB3161102. Windows will show them a security alert whenever they attempt to open Journal Note (JNT) or Journal Template (JTP) files.
“Last month, Fortinet researcher Honggang Ren discovered a heap overflow vulnerability in Windows Journal and reported it to Microsoft. This month, Microsoft released update KB3161102 and removed the Journal component from all versions of Windows because the file format used by Journal has been demonstrated to be susceptible to a number of security exploits. Microsoft recommends that all users install this update immediately. On the Microsoft Acknowledgments web page, Microsoft labeled the title of this vulnerability as “Defense-in-depth”.” reads a blog post published by Fortinet.

“Windows Journal is a note-taking application that was first introduced in Windows XP Tablet PC Edition. It’s currently a component of all supported client versions of Windows through Windows 10 Version 1511. The file format that’s used by Windows Journal (Journal Note File, or JNT) has been demonstrated to be susceptible to many security exploits. Therefore, Windows Journal will be removed from all versions of Microsoft Windows soon. ” Microsoft explained in the security update.
The Libyan Scorpions group is behind a cyber espionage campaign in Lybia
26.9.2016 securityaffairs Cyber
The Cyberkov Security Incident Response team spotted a cyber espionage campaign in Lybia conducted by a group named Libyan Scorpions.
Thinking of Libya we have in mind a non-stable political country where various forces fight for the control of strategic territories and oil productions. but only a few experts know about cyber malicious activities in the area.
Evidently, something is changing, for the first time experts at the Cyberkov Security Incident Response team (CSIRT) collected evidence of a cyber espionage campaign operating in different areas in Libya especially in Tripoli and Benghazi.
On 6 August 2016, the Cyberkov Security Incident Response team (CSIRT) spotted numerous samples of Android malware targeting entities in Libya.
The experts noticed that the Android malware spreading very fast through the popular Telegram messaging application and targeting high-profile Libyan influential and political figures.
According to the CSIRT, the malware was first spotted after it has compromised a highly Libyan influential Telegram account via web Telegram using IP address from Spain.
Once the attackers compromised the mobile device of the above account they used is to target all his contacts. The experts at the Cyberkov Security Incident Response team linked the cyber espionage campaign to a group named Libyan Scorpions.
“Libyan Scorpions is believed to be a political motivated group targeting a high-level influential and political figures in multiple cities within Libya. Libyan Scorpions first compromised a personal Telegram account for a Libyan influential person with unknown vector. The victim received a push notification from his Telegram app that someone from Spain is logged into his account” reads the report published by the CSIRT titled “Hunting Libyan Scorpions”

“The victim mistakenly deleted Telegram application from his phone thinking that this is going to stop the attacker(s). Second day, the attacker used the victim phone number to spear phish his contacts in Telegram by pretending that the real person is sending a voice message while the file is actually a malicious APK (Android Package) file.”
Threat actors abused it to spread an Android malware bound with legitimate Android application pretending it is an important voice message (misspelled it by “VoiceMassege.apk”) which indicates a non-english (maybe an Arabic) attacker.
The experts have found the legitimate application in the official App store, this means that the Libyan Scorpions group took an instance of the APK and trojanized it.
“This APK file targets only Android-based smartphones. Once the new victim click on the APK file, the application installs itself in the device without any problem and is fully functional. The icon of the application appears in the Apps menu named (URL Shortener).” continues the report.
With this technique, the threat actors spread the malware that used the same technique to infect via telegram other victims of the network of contacts.
Further investigations revealed that the malware has been active at least since September 2015.
The so-called Libyan Scorpions is a politically motivated group intent in gathering intelligence and spying on influentials and political figures within Libya. The group used different malware in his campaigns, the malicious code were designed to target Android and Windows machines.
The researchers made a reverse engineering of the malicious code and discovered a configuration files containing information of the Command and Control (C2) infrastructure. The sample of malware analyzed in the report presents many similarities with popular spyware like the AlienSpy RAT.
“Resolving the hostname gives: 41.208.110.46 which is a static Libyan IP address owned by Libya Telecom and Technology Backbone.” reads the analysis. “Cyberkov discovered that the malware has not been uploaded to VirusTotal before and the first sample of this malware has been uploaded by us. However, 8 out of 54 AntiVirus engines detect it which is a very low detection rate (15%). Most and major American top Gartner Antivirus companies did not detect it!!”
Libyan Scorpions doesn’t have highly technical skills anyway it was able to use a set of methods to hide and operate their malware, the cyber espionage operation leverage on good social engineering and phishing tactics.
“Libyan Scorpions threat actors used a set of methods to hide and operate their malwares. They appear not to have highly technical skills but a good social engineering and phishing tricks. The threat actors are not particularly sophisticated, but it is well-understood that such attacks don’t need to be sophisticated in order to be effective. ” reads the report published by the Cyberkov Security Incident Response team. “Using malwares as weapon in an active warzone such as Libya, make the victims easy targets for assassination or kidnapping by tracking their physical locations and monitoring them day and night. “
I suggest you read the report that also includes Indicators of Compromise (IoCs)
A nation-state actor is testing methods for a massive takedown of the Internet
26.9.2016 securityaffairs Attack
According to the popular cyber security experts an unknown nation state actor may be running tests for taking down the entire internet infrastructure.
What happens if someone shuts down the Internet? Is it possible?
Our society heavily depends on technology and the Internet is the privileged vector of the information today. Blocking the Internet could paralyze countless services in almost any industry, from finance to transportation.
Early September the popular cyber security expert Bruce Schneier published an interesting post titled “Someone Is Learning How to Take Down the Internet” that reveals an escalation of cyber attacks against service providers and companies responsible for the basic infrastructure of the Internet.
We are referring to coordinated attacks that experts consider a sort of tests to evaluate the resilience of most critical nodes of the global Internet. The attacks experienced by the companies request a significant effort and huge resources, a circumstance that suggests the involvement of a persistent attacker like a government, and China is the first suspect.
“Recently, some of the major companies that provide the basic infrastructure that makes the Internet work have seen an increase in DDoS attacks against them. Moreover, they have seen a certain profile of attacks. These attacks are significantly larger than the ones they’re used to seeing. They last longer. They’re more sophisticated. And they look like probing.” wrote Schneier.
“I am unable to give details, because these companies spoke with me under a condition of anonymity. But this all is consistent with what Verisign is reporting. Verisign is the registrar for many popular top-level Internet domains, like .com and .net. If it goes down, there’s a global blackout of all websites and e-mail addresses in the most common top-level domains. Every quarter, Verisign publishes a DDoS trends report. While its publication doesn’t have the level of detail I heard from the companies I spoke with, the trends are the same: “in Q2 2016, attacks continued to become more frequent, persistent, and complex.”
It is clear that attackers aim to cause a global blackout of the most common top-level domains paralyzing a large portion of the Internet.
Schneier, who has spoken with companies that faced the attacks, pointed out powerful DDoS attacks that attacks that stand out of the ordinary for their methodically escalating nature.
The attacks start with a certain power that increases as time goes by forcing the victims to deploy all its countermeasures to mitigate the threat.
The report mentioned by Schneier, titled “VERISIGN-OBSERVED DDoS ATTACK TRENDS: Q2 2016” confirms that companies are experiencing a wave of DDoS attacks even more sophisticated.

“DDoS Attacks Become More Sophisticated and Persistent DDoS attacks are a reality for today’s web-reliant organizations. In Q2 2016, DDoS attacks continued to become more frequent, persistent and complex.” states the report.
Schneier also reported other types of attacks against the Internet infrastructure, such as numerous attempts to tamper with Internet addresses and routing.
“One company told me about a variety of probing attacks in addition to the DDoS attacks: testing the ability to manipulate Internet addresses and routes, seeing how long it takes the defenders to respond, and so on. Someone is extensively testing the core defensive capabilities of the companies that provide critical Internet services.” continues Schneier.
Who is behind the attacks?
Schneier believes that the attacks are launched by someone with cyber capabilities of a government, and he seems to exclude the efforts of hacktivists or cyber criminals, and I agree.
“It doesn’t seem like something an activist, criminal, or researcher would do. Profiling core infrastructure is common practice in espionage and intelligence gathering. It’s not normal for companies to do that. Furthermore, the size and scale of these probes — and especially their persistence — points to state actors.” explains Schneier.
The attribution of the attacks is very difficult by data suggests that China is behind them, let me add also that Russia has similar cyber abilities and is able to hide its operations online. Both countries are largely investing in building infrastructures that would be resilient to such kind of mass attacks.
“We don’t know where the attacks come from. The data I see suggests China, an assessment shared by the people I spoke with. On the other hand, it’s possible to disguise the country of origin for these sorts of attacks.”
Security firm Sucuri analyzed tens of thousands of compromised websites
26.9.2016 securityaffairs Vulnerebility
Security firm Sucuri published a detailed study, titled Hacked Website Report for 2016/Q2, on compromised websites on the Internet.
According to the security expert Daniel Cid from Sucuri, at least 15,769 WordPress websites have been compromised this year.
Sucuri has published a report, titled Hacked Website Report for 2016/Q2, related compromised websites on the web.
The experts analyzed 21,821 sites, 3099 of which were running the Joomla! CMS, 15,769 WordPress, and the remaining Magento, Drupal, vBulletin, and Modx.

The researchers focused their research on out-of-date software found on compromised websites discovering that WordPress installations were out-of-date 55% of the time while Joomla! (86%), Drupal (84%), and Magento (96%).
The vast majority of the website (roughly 75 percent) were backdoored by crooks that used them to deliver malware, target visitors, control botnets, and run further attacks.
Google has already blacklisted 52 per cent of the total compromised sites analyzed by the Sucuri, but 48 percent went undetected demonstrating that the backdoors used by crooks are hard to detect.
The experts added that Norton Safeweb was able to detect only 38 percent of compromised websites, while McAfee SiteAdvisor detected 11 percent of them.
“Per our data, 18% of the infected websites we analyzed were blacklisted, which means that 82% of the infected websites we worked on were not flagged. The most prominent blacklist was Google Safe Browsing with 52% of blacklisted sites. Here is a more complete distribution of the blacklist APIs we monitored:” reported the Sucuri report.
Sucuri also highlighted that most websites were hacked due to vulnerable or poorly configured extensions.
Below key findings of the Sucuri Report:
Some quick takeaways that you might find interesting:
WordPress continues to lead the infected websites we worked on (at 74%), and the top three plugins affecting that platform are still Gravity Forms, TimThumb, and RevSlider.
WordPress saw a 1% decrease in out-of-date core software and infected websites, while Drupal had a 3% increase. Joomla! and Magento website deployments continue to show the most out of date instances of any platform.
New data points show that on average, WordPress installations have 12 plugins, and the report provides a list of the most popular plugins within our set of compromised sites.
New data points were introduced showing what percentage of infected websites were blacklisted. Only 18% were blacklisted, and Google made up 52% of that grouping (or 10% of the total infected sites).
Analyzing the malware families showed that SEO spam continues to be on the rise, increasing to 38% this quarter (a 6% increase) and backdoors rose to 71%of compromised sites.
Australian Police warns of malware-laden USB drives left in letterboxes
26.9.2016 securityaffairs Virus
The Police in the Australian State of Victoria issued a warning to the local population of malware-laden USB drives left in letterboxes.
USB drives are a privileged vector of attack, security experts have demonstrated that it is possible to hide malicious code in memory stick that could compromise almost every computer.
We are aware that found USB drives in a parking work could be exploited by attackers to deliver cyber threats, but the number of victims is still high due to the lack of awareness.
This summer, at Black Hat USA 2016, the security researcher Elie Bursztein demonstrated the dangers of found USB drive and explained how to create a realistic one.
The expert dropped 297 USB drives on the University of Illinois Urbana-Champaign campus in six different locations, the devices were able to take over the PC of the unaware user that will find the key.
“Despite the dangers of hackers, viruses and other bad things, almost half of those who found one of our flash drives plugged it into a computer,” explained Bursztein.
Bursztein demonstrated that a smart attacker can camouflage a malicious USB drive outfitted with a Teensy development board that could be used to hack a target’s computer in a few seconds.
48 percent of USB drives were picked up by passers and plugged into a computer, and the unaware users also tried to open the file within.

This week the Police in the Australian State of Victoria issued a warning to the local population of malware-laden USB sticks left in letterboxes.
The authorities are asking residents in Pakenham to not trust un-marked USB sticks that appear in their letterboxes.
“The USB drives are believed to be extremely harmful and members of the public are urged to avoid plugging them into their computers or other devices.”
“Upon inserting the USB drives into their computers victims have experienced fraudulent media streaming service offers, as well as other serious issues.” reads the warning.
“The USB drives are believed to be extremely harmful and members of the public are urged to avoid plugging them into their computers or other devices. Below is an image of USB drives similar to those believed to be involved in the scam.”

Unfortunately, similar attackers in the wild could use a similar technique to spread their malware, watch out USB drives left unattended in public places of during meetings and conferences.
At the time of the warning, only the suburb of Pakenham in Victoria’s capital Melbourne has experienced the malicious USB sticks drop, but we cannot underestimate the problem.
Let me remind you the attempted cyberespionage plot relied on USB drives planted in company parking of the Dutch chemical giant DSM in 2012.
The USB drives used in that case were containing a keylogger designed to exfiltrate sensitive data from the company.
OVH hosting hit by 1Tbps DDoS attack, the largest one ever seen
26.9.2016 securityaffairs Attack
The hosting company OVH was the victim of a 1 Tbps DDoS attack that hit its servers, this is the largest one ever seen on the Internet.
The hosting provider OVH faced 1Tbps DDoS attack last week, likely the largest offensive ever seen.
The OVH founder and CTO Octave Klaba reported the 1Tbps DDoS attack on Twitter sharing an image that lists the multiple sources of the attack.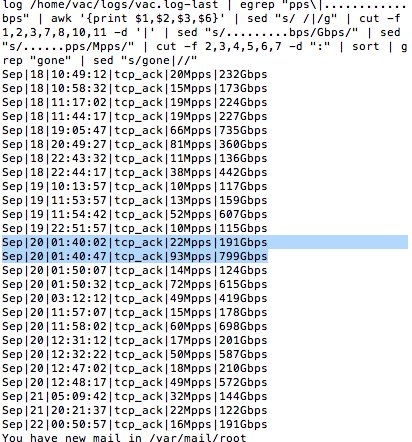
Visualizza l'immagine su Twitter
Segui
Octave Klaba / Oles @olesovhcom
Last days, we got lot of huge DDoS. Here, the list of "bigger that 100Gbps" only. You can see the
simultaneous DDoS are close to 1Tbps !
07:37 - 22 Set 2016
394 394 Retweet 325 325 Mi piace
Klaba explained that the servers of its company were hit by multiple attacks exceeding 100 Gbps simultaneously concurring at 1 Tbps DDoS attack. The severest single attack that was documented by OVH reached 93 MMps and 799 Gbps.
One of the attacks documented by the OVH reached 93 MMps and 799 Gbps.

According to Klaba, the attackers used an IoT botnet composed also of compromised CCTV cameras.
22 Set
Octave Klaba / Oles @olesovhcom
Last days, we got lot of huge DDoS. Here, the list of "bigger that 100Gbps" only. You can see the
simultaneous DDoS are close to 1Tbps ! pic.twitter.com/XmlwAU9JZ6
Segui
Octave Klaba / Oles @olesovhcom
This botnet with 145607 cameras/dvr (1-30Mbps per IP) is able to send >1.5Tbps DDoS. Type: tcp/ack, tcp/ack+psh, tcp/syn.
14:31 - 23 Set 2016
427 427 Retweet 267 267 Mi piace
22 Set
Octave Klaba / Oles @olesovhcom
Last days, we got lot of huge DDoS. Here, the list of "bigger that 100Gbps" only. You can see the
simultaneous DDoS are close to 1Tbps ! pic.twitter.com/XmlwAU9JZ6
Segui
Octave Klaba / Oles @olesovhcom
This botnet with 145607 cameras/dvr (1-30Mbps per IP) is able to send >1.5Tbps DDoS. Type: tcp/ack, tcp/ack+psh, tcp/syn.
14:31 - 23 Set 2016
427 427 Retweet 267 267 Mi piace
Unfortunately, this is not a novelty, in June 2016 security experts from Sucuri firm have discovered a large botnet of compromised CCTV devices used by crooks to launch DDoS attacks in the wild.
Earlier this week, the website of the popular cyber security expert Brian Krebs was targeted by a DDoS attack of 665 Gbps. Experts speculate the attackers hit Krebs in response to his blog post in which he exposed a the operators behind the vDOS DDoS service.
IoT devices, including CCTV, often lack proper configuration, it is easy for hackers to locate on the Internet systems with weak or default login credentials.
Recently security experts reported several Linux malware targeting IoT devices such as Luabot and Bashlite.
Earlier September, experts from Level 3 and Flashpoint confirmed the overall number of devices infected by the BASHLITE malware is more than 1 million.
The number includes compromised devices belonging to several botnets, according to the experts, almost every infected device are digital video recorders (DVRs) or cameras (95%), the remaining is composed of routers (4%), and Linux servers (1%).
“Of the identifiable devices participating in these botnets, almost 96 percent were IoT devices (of which 95 percent were cameras and DVRs), roughly 4 percent were home routers and less than 1 percent were compromised Linux servers. This represents a drastic shift in the composition of botnets compared to the compromised server- and home router-based DDoS botnets we’ve seen in the past.” states a blog post published by Level 3 firm.
The researchers have been tracking more than 200 C&C worldwide used by the BASHLITE botnets. Fortunately, the IP addresses of the C&C servers were found hardcoded in the instance of malware detected in the wild making easy for experts to shut them down.
Back to the case of the 1Tbps DDoS attack against the OVH firms, at the time I was writing the servers were back online.
Internetová bezpečnost: Flash vs. HTML5
25.9.2016 SecurityWorld Bezpečnost
Jste už znechuceni z bezpečnostních děr v řešeních postavených na technologii Flash? Pak vězte, že i HTML5 má své zranitelnosti.
Technologie HTML5 se propagovala jako přirozený a na standardech založený nástupce proprietárních modulů plug-in, jako jsou například přehrávače Adobe Flash Player, pro poskytování bohatých multimediálních služeb na webu. Pokud však jde o bezpečnost, která je jednou z hlavních slabin technologie Flash, ani HTML5 není všelékem.
Ve skutečnosti má HTML5 své vlastní bezpečnostní problémy. Julien Bellanger, výkonný ředitel společnosti Prevoty, která se zabývá monitorováním zabezpečení aplikací, prohlašuje že HTML5 složitost zabezpečení nesnižuje, ale naopak zvyšuje. Upozorňuje, že nad bezpečností HTML5 visel mnoho let otazník a za tu dobu se situace nijak nezlepšila.
Bellanger uvádí následující rizika přinášená technologií HTML5:
Exploity vykreslování obrazu pozadí (canvas image), které mohou způsobit přetečení zásobníku využitelné hackerem k injektáži kódu do relace.
Skriptování mezi weby (XSS), při němž mohou narušitelé ukrást informace z relace v prohlížeči.
SQL injection – záškodnický dotaz se v prohlížeči použije k získání informací z databáze.
CSRF nebo také XSRF (Cross-Site Request Forgeries) s převzetím tokenu uživatele a jeho následným použitím k vydávání se za dotyčného uživatele na webu.
Použití HTML5 také odhaluje více toho, co je k dispozici v počítači či mobilním zařízení, jako jsou například místní úložiště a poloha zařízení. „Aplikace HTML5 mohou přistupovat k těmto platformám, existuje zde možnost zneužití,“ upozorňuje Dan Cornell, technologický ředitel společnosti Denim Group, která poskytuje poradenství v oblasti kybernetické bezpečnosti.
Nezabezpečené prohlížeče
„Problém spočívá v tom, že prohlížeče jsou ve své podstatě nezabezpečené,“ vysvětluje Kevin Johnson, výkonný ředitel konzultační firmy Secure Ideas. Poznamenává, že HTML5 například neposkytuje žádnou ochranu prostřednictvím tzv. sandboxu, jako může poskytnout Flash v prohlížeči Chrome.
„Dalším problémem je, že do HTML5 přidáváme významnou složitost, aniž přidáváme stejnou úroveň kontroly pro uživatele,“ upozorňuje Johnson. Flash si alespoň mohou uživatelé vypnout. HTML5 ale vypnout nelze.
Stále slibující
Navzdory chmurným vyhlídkám nabízí HTML5 naději pro lepší bezpečnost, pokud tvůrci prohlížečů udělají správnou věc, tvrdí Cornell z Denim Group. „Dodavatelé browserů musejí přemýšlet o svých plánech podpory HTML5 a integrovat zabezpečení do svých implementací již od začátku,“ vysvětluje Cornell.
Podle něj mnoho nových funkcí představených v jazyce HTML5 aplikacím poskytuje přístup k citlivému vybavení, takže je potřebné to odpovídajícím způsobem ošetřit.“
A Johnson dodává, že dodavatelé prohlížečů by měli poskytnout uživatelům možnost vypínat funkce, které nechtějí nebo jim nevěří.
Počet používaných prohlížečů také přináší určitou bezpečnost, protože zranitelnosti přítomné v jednom prohlížeči nemusejí existovat v ostatních browserech, uvádí Cornell. To snižuje riziko univerzálně zneužitelné chyby, jaké existuje v případě technologie Flash.
Vývojáři prohlížečů rovněž pracují na celkovém zlepšení zabezpečení, tvrdí Richard Barnes, vedoucí zabezpečení Firefoxu v Mozille. Konkurence mezi Googlem, Microsoftem, Mozillou a Applem znamená ohrožení jejich pověsti v případě problémů se zabezpečením. Všichni hlavní tvůrci prohlížečů proto mají silné bezpečnostní týmy, poznamenává Barnes.
Existuje také celooborové úsilí s cílem zlepšit zabezpečení pro všechny, zmiňuje Barnes. Například ve vývoji je univerzální metoda šifrování a tvůrci prohlížečů se snaží poskytovat uživatelům více informací a kontroly nad tím, co o nich web ví.
Na cestě je také pomoc standardizačního orgánu. Konsorcium W3C (World Wide Web Consortium), které dohlíželo na vývoj HTML5, má svůj návrh specifikace CSP (Content Security Policy, zásady zabezpečení obsahu).
Wendy Seltzerová z W3C uvádí, že nabízí jazyk zásad pro autory webů k omezení aktivního obsahu na jejich webech a ochranu proti injektáži skriptů. Existuje také snaha o vytvoření specifikace bezpečného obsahu (Secure Content), která by měla zajistit, aby výkonné webové funkce pracovaly jen v zabezpečených a ověřených kontextech.
Bezpečnost však nakonec musejí zajistit zejména aplikace, ať už běží v prohlížeči nebo v operačním systému. Bellanger ze společnosti Prevoty doporučuje, aby vývojáři používali návod vytvořený Microsoftem pro životní cyklus bezpečného vývoje, který je určený k zesílení odolnosti aplikací vůči narušením.
„Vývoj aplikace, tak aby byla co nejbezpečnější, je stále odpovědností samotných vývojářů,“ uzavírá Bellanger.
Ardit Ferizi, the hacker who helped ISIS to share a Kill List of US Military Personnel has been sentenced to 20 years in prison
25.9.2016 securityaffairs Hacking
The hacker Ardit Ferizi, aka Th3Dir3ctorY, who helped ISIS to share a Kill List of US Military Personnel has been sentenced to 20 years in a US prison
Months ago, I reported you the story of Ardit Ferizi, aka Th3Dir3ctorY, who is the hacker that supported the ISIS organization by handing over data for 1,351 US government and military personnel.
Ferizi is the first man charged with cyber terrorism that was extradited to the US early this year.
He was charged with hacking crimes and providing support to a terrorist organization. The 20-year-old man was accused of supporting the ISIS terrorist organization, he was the subject of extradition from the Malaysian government, where he lived. The man of Kosovar origin was studying computer science in Malaysia.
He was arrested in Malaysia in September 2015 and transferred to the US to face trial.
Now Ardit Ferizi has been sentenced to 20 years in a U.S. prison. According to the US investigators, he provided the data to the popular IS militant Junaid Hussain, which disclosed it on the web. The collaboration between the IS hackers Hussain and Ferizi started in April 2015, according to the US authorities.
The details of the Ferizi’s case are described in the court filings [PDF].
Leaked data included names, e-mail addresses, passwords, locations and phone numbers of 1,351 U.S. military and other government personnel.

Ardit Ferizi cyber terrorism ISIS invites to Kill US military personnel
The stolen data included names, physical addresses, phone numbers, email addresses, and passwords.
Ardit Ferizi, aka Th3Dir3ctorY, from Kosovo was sentenced in federal court in Alexandria, for “providing material support to the Islamic State of Iraq and the Levant (ISIL) and accessing a protected computer without authorization and obtaining information in order to provide material support to ISIL,” the Department of Justice announced on Friday.
The 21-year-old ISIS-linked hacker obtained the data by hacking into the US web hosting company’s servers on June 13, 2015.
The US authorities suspected that Ferizi is a member of a Kosovan hacking team known as KHS, he used the pseudonym of “Th3Dir3ctorY”. The KHS breached a database of a US retailer was able to identify the records belonging to military and government personnel.
The Kosova Hacker’s Security (KHS) hit numerous organizations across the world, including Serbian Government websites, Israeli websites under the #OpIsrael campaign, The Interpol, IBM Research, Hotmail, US National Weather Service Website and numerous targets in Ukraine.

I wrote about Ferizi in October 2015, when the man was arrested by Malaysian authorities because for the first time ever the US Justice Department has charged a suspect for terrorism and hacking (cyber terrorism).
Ferizi was pleaded guilty on June 15, 2016, the faced a sentence of up to 35 years in prison, but the sentence was reduced to a maximum of 25 years in jail after agreeing to plead guilty.
However, the Ferizi’s defense lawyers sustained that his client had no real intention of put militaries in danger, then he asked for a six-year sentence.
Pippa Middleton private photos stolen in an Apple iCloud hack
25.9.2016 securityaffairs Apple
In what could be another serious celebrity hack, 3,000 photos have been stolen from Pippa Middleton ’s account and they are being offered for sale.
The UK Police is investigating the Pippa Middleton iCloud hack and consequent theft of private photos.
According to The Sun newspaper the stolen photos were offered for sale, it seems that someone had contacted the newspaper asking for £50,000 within 48 hours. The images included shots of the duchess’s children, Prince George and Princess Charlotte.
“Pippa was horrified last night after a crook tried to sell intimate photos said to have been hacked from her phone.” reported The Sun.
The man contacted The Sun claiming to have 3,000 images of the Duchess of Cambridge’s sister, 33. He said snaps included her at a wedding dress fitting and ones of her fiancé nude.”
The Met Police confirmed that inquiries were ongoing and that the authorities haven’t arrested ant suspects until now.
“Police have received a report concerning the alleged hacking of a personal iCloud account. Specialist officers are now investigating.” explained a Met Police spokesman.
The hacker, calling himself “Crafty Cockney”, claimed to be in possession of private photographs of Pippa Middleton, including her being fitted in a wedding dress and naked snaps of her millionaire fiance James Matthews. In order to prove the authenticity of his claims, the hacker sent via email two photos via email.
The stolen photos also include shots of the Duchess of Cambridge Kate, and brother-in-law Prince William.
The Sun also confirmed that an anonymous person has reportedly tried to sell the stolen photos them via encrypted messaging service WhatsApp.

The Sun confirmed that it had no intention of entering into a deal with the hacker and reported the issue to Pippa Middleton.
“Thank you very much for drawing this to the family’s attention.” said a spokesman for Miss Middleton cited by The Sun. “I can confirm that not only have the lawyers been informed but the police are about to be involved as well.”
Pippa Middleton is the last celebrity in order of time that was the victim of an “iCloud hack,” a long list of VIPs have had images stolen from their iCloud accounts in the Fappening saga.
As usual, it is strongly suggested to use a second factor of authentication for all the services that implement it.
In 2014, Apple introduced a “two-step verification” mechanism to protect iCloud users from such kind of hack. The mechanism leverages on a four-digit code that is either texted to the users’ mobile phone number or sent via Apple’s Find My iPhone app.
Don’t waste time, enable the two-step verification!
Dějiny psané rootkity
24.9.2016 SecurityWorld Viry
Rootkity představují noční můru všech bezpečnostních specialistů. Jde o aplikace, které nahrazují standardní administrátorské nástroje a umožňují skrývat své aktivity před legitimním uživatelem/správcem. A jejich odhalení je proto velmi komplikované.
Složitost detekce rootkitů je způsobená mimo jiné tím, že když už si někdo dá s vytvořením a instalací rootkitu práci, zpravidla mu na průniku do systému a následném skrytí svých aktivit docela záleží – jak o tom svědčí případ v lednu 2015 uvězněného IT specialisty Eddieho Raymonda Tiptona (51), který býval ředitelem informační bezpečnosti v Multi-State Lottery Association.
Tipton využil své znalosti fungování loterií a ochranných mechanismů k tomu, aby získal přístup k počítači, na kterém se losovala vítězná čísla. Ten je pochopitelně přísně střežený a není napojený na internet. Tipton však dokázal ostrahu obejít přeprogramováním monitorovacích kamer – a do počítače následně skrze Flash disk instaloval právě rootkit, který zajistil vylosování „těch správných“ čísel.
Když se tak stalo, rootkit sám sebe smazal. Tipton podal výpověď a vybral si výhru (což byla právě ona chyba, protože jako bývalý zaměstnanec společnosti byl ihned v hledáčku bezpečnostních procesů – kdyby použil nějakého „bílého koně“, dost možná by se na jeho podvod nikdy nepřišlo).
Název rootkitů je odvozen od „root“ (základ) – což je označení superuživatele na unixové rodině operačních systémů. Rootkit je pak označení programů, které slouží útočníkům k získávání nejvyšších práv v operačním systému (resp. jsou jim v mnoha případech dokonce nadřazené).
Operační systém zajišťuje pro počítač celou řadu základních úkonů počínaje otevíráním souborů až třeba po síťová připojení. Jde o rozhraní API (Application Programmer Interface).
Jak funguje rootkit
Rootkit je přitom aplikace, která nekompromisně zasahuje do této vlastnosti operačního systému a nahrazuje specifické API funkce, takže jejich volání je modifikované. Jinými slovy: rootkit mění způsob, jakým operační systém pracuje.
Uveďme si to na velmi zjednodušeném příkladu. Máme v počítači dvě zcela samostatné aplikace. Dejme tomu, že jedna z nich je textový editor, druhá špionážní program (spyware) zaznamenávající stisknuté klávesy.
Za normálních okolností spustíte textový editor a píšete. Pokud ale do počítače dokáže proniknout útočník, může na spuštění textového editoru navázat právě spuštění druhého programu. V praxi tedy spouštíte textový editor, na úrovni operačního systému je ale zavolaný spyware a následně se kontrola znovu vrátí textovému editoru.
Že to není nic zvláštního? Že něco podobného lze udělat i bez rootkitu? To samozřejmě jde, ale s jedním velkým omezením: pokud modifikujete registry nebo spouštíte spyware, jste zpravidla varovaní antivirovým programem.
Ovšem při použití rootkitu tomu tak není – tato aplikace totiž dokáže onen mezistupeň skrýt (pokud chce). Prostě pro všechny nástroje na nižších úrovních (souborové editory, antivirové programy aj.) žádný mezistupeň není.
Rootkit postavený na nejvyšší úrovni zkrátka „ukazuje“ ostatním aplikacím jen to, co jim chce ukázat. A ty nemají možnost si podávané informace jakkoliv ověřit právě proto, že rootkit hlídá poskytování informací.
Takže i v případě vznesení dotazu to jde přes operační systém (a tedy i přes rootkit), čili opět je vidět jen to, co chce autor rootkitu. Dnešní bezpečnostní aplikace jsou zkrátka založeny na tom, že informace podávané na úrovni operačního systému jsou důvěryhodné. Rootkit ale zcela mění způsob, jakým celý operační systém pracuje.
Rootkit tak může skrýt sám sebe, může se navázat na určité funkce, může skrýt další aplikace, soubory, adresáře, registry, procesy apod. S trochou nadsázky lze říci, že o čem rootkit prohlásí, že neexistuje – tak navenek opravdu neexistuje. Ve skutečnosti to je ale samozřejmě reálné, jen rootkit ví, kde.
Jak šel čas
Rootkity byly teoreticky rozpracované v roce 1983, kdy Ken Thompson z Bell Labs (mj. jeden z tvůrců Unixu) představil koncept modifikovaného kompilátoru, který akceptoval nejen regulérní heslo, ale také heslo „tajného administrátora“. To se nedalo běžnými prostředky zjistit – stejně jako jeho prostá existence.
Trvalo ale několik let, než se celá myšlenka dočkala praktické realizace. Stalo se tak v roce 1990, kdy Lane Davis a Steven Dake vytvořili rootkit pro SunOS Unix. V devadesátých letech byly rootkity používané jako administrátorské nástroje – i jako prostředky k pronikání do systémů. Až v roce 1999 vstoupily na novou půdu, kdy vznikl první rootkitový malware: NTRootkit pro Windows NT (uživatelé Mac OS X si museli ještě deset let počkat).
Největší slávu – byť pochybnou – si rootkity „užily“ v roce 2005, kdy začala společnost Sony BMG chránit některá svá CD protikopírovací ochranou XCP. Po prvním vložení CD s hudbou do počítače se zobrazila EULA.
Do počítače se pak instaloval speciální program, který umožňoval vypálení pouze určitého množství záložních kopií (pro osobní potřebu) a blokoval třeba spouštění hudby přes jiné přehrávače než přes přehrávač dodávaný od firmy Sony.
Problém byl v tom, že docházelo do počítače k instalaci nejen avizovaného softwaru, ale i rootkitu, který jej skryl. A potíž tkvěla i v tom, že tento rootkit bylo možné zneužít k dalším útokům: objeven byl například také v počítačích amerického Pentagonu.
Hacker Who Helped ISIS to Build 'Hit List' Of US Military Personnel Jailed for 20 Years
24.9.2016 thehackernews Hacking
A computer hacker who allegedly helped the terrorist organization ISIS by handing over data for 1,351 US government and military personnel has been sentenced to 20 years in a U.S. prison.
Ardit Ferizi, aka Th3Dir3ctorY, from Kosovo was sentenced in federal court in Alexandria, for "providing material support to the Islamic State of Iraq and the Levant (ISIL) and accessing a protected computer without authorization and obtaining information in order to provide material support to ISIL," the Department of Justice announced on Friday.
The 21-year-old ISIS-linked hacker obtained the data by hacking into the US web hosting company's servers on June 13, 2015.
Ferizi then filtered out over 1,300 US military and government employees' information from the stolen data and then handed them over to Junaid Hussain, according to court filings [PDF].
The stolen data contains personally identifiable information (PII), which includes names, email addresses, passwords, locations and phone numbers of US military service members and government workers.
Junaid Hussain, who was a British jihadi and believed to be the then leader and creator of a group of ISIS hackers called the Islamic State Hacking Division (ISHD), posted the names and personal data of 100 US service member's families online.
The Hussain's statements included:
"We are in your emails and computer systems, watching and recording your every move, we have your names and addresses, we are in your emails and social media accounts, we are extracting confidential data and passing on your personal information to the soldiers of the Khilafah, who soon with the permission of Allah will strike at your necks in your own lands!"
Hussain, who was also known as Abu Hussain Al-Britani and used the moniker TriCk, was later killed in a US drone strike in Syria in August last year.
The US authorities also tracked down Ferizi to Malaysia, where he was arrested by the local authorities on October 6, 2015, while trying to catch a flight back to Kosovo.
Before helping ISIS, Ferizi had served as an alleged leader of the Kosova Hacker's Security (KHS) hacking group and hacked into a number of government sites belonging to the Presidency of Macedonia, the Greek Ministry of Education, the Greek Decentralized Administration of Macedonia and Thrace (DAMT), Lifelong Learning and Religion. He also stole data from IBM and Greek mobile telecoms firm OTE.
Ferizi was pleaded guilty on June 15, 2016, and faced a sentence of up to 35 years in prison, but the sentence was reduced to a maximum of 25 years after agreeing to plead guilty. However, defense lawyers said he meant no real harm and asked for a six-year sentence.
Cyber crooks focus on the future as ATM Biometric Skimmers go on Sale
24.9.2016 securityaffairs Cyber
Kaspersky Lab presented an investigation on the future of ATM Biometric Skimmers and how cybercriminals could exploit them.
A recent investigation by Kaspersky Labs reports that a number of underground sellers are offering skimmers, which have the capability of stealing users biometric data such as fingerprints. A number of others are researching iris scanning and palm vein recognition systems.
With a number of banks looking to introduce fingerprint-reading technology into their ATMs, Cyber Criminals are looking to stay ahead of the curve by cashing in on exploiting these systems before they make it to general release.
With the inherent weaknesses in PIN and password based authentication, biometrics looks to take over as the most prominent authentication type in the near future.
Biometric skimmers first made their appearance in September of last year, however, due to a number of technical limitations and bugs including the slow data transfer rates of biometric over GSM impacting the functionality, progress was quickly stalled.
This generation of the technology, however, is proving to be more effective and faster.
“The problem with biometrics is that unlike passwords or pin codes, which can be easily modified in the event of compromise, it is impossible to change your fingerprint or iris image. Thus, if your data is compromised once, it won’t be safe to use that authentication method again. That is why it is extremely important to keep such data secure and transmit it in a secure way.” explained Olga Kochetova, a security expert at Kaspersky Labs.
“Biometric data is also recorded in modern passports – called e-passports – and visas. So, if an attacker steals an e-passport, they don’t just possess the document, but also that person’s biometric data. They have stolen a person’s identity.”

Discussions have also been seen online where would be scammers are looking into mobile applications that use masks worn over they would be criminals face in order to fool facial recognition systems.
Although these techniques are more advanced than the current malware and ransomware attacks that are so prevalent against today’s Internet banking technologies, Kaspersky Labs also commented that it did not expect to see many of the more traditional methods abates.
Below a video PoC of an ATM attack.
It’s expected that exploiting biometric authentication will just be added to the banking scammers arsenal.
Enjoy the report “FUTURE ATTACK SCENARIOS AGAINST AUTHENTICATION SYSTEMS, COMMUNICATING WITH ATMS”
Cracking Apple iOS 10 Backup Encryption is now 2,500 times faster
24.9.2016 securityaffairs iOS
Experts from Elcomsoft discovered a new vector of attack to access password-protected local backups produced by iOS 10 devices.
According to security experts from the computer forensics company Elcomsoft, Apple has weakened the backup security protection of its recently-issued iOS 10 skipping certain security checks. This means that hackers could easily crack password protection used to protect the backups of iOS devices that are stored on Macs and PCs.
“We discovered a major security flaw in the iOS 10 backup protection mechanism. This security flaw allowed us developing a new attack that is able to bypass certain security checks when enumerating passwords protecting local (iTunes) backups made by iOS 10 devices.” reads a blog post published by Elcomsoft.
ios-10
The researchers reported the presence of a security hole that opens the door for a new type of iOS brute-force password attack.
“We looked into it, and found out that the new mechanism (in iOS 10) skips certain security checks, allowing us to try passwords approximately 2,500 times faster compared to the old mechanism used in iOS 9 and older,” continues the post.
Apple has downgraded the hashing algorithm for iOS 10 from “PBKDF2 SHA-1 with 10,000 iterations” to“plain SHA256 with a single iteration.” With this premise, an attacker can brute-force the password via a standard desktop computer processor faster.
PBKDF2 (Password-Based Key Derivation Function) leverages on a SHA-1 hash with thousands of password iterations, making it hard the password cracking.
In iOS 9 and prior versions back to iOS 4, Apple was using the PBKDF2 function to generate the final crypto key using a pseudorandom function (PRF) 10,000 times (password iterations).
In a real attack scenario, hackers need to have a local or remote access to the machine where the Apple backup is stored, then crack it by running a brute-force attack.
The experts explained that the new security checks implemented by Apple allow 2,500 times faster brute force attacks compared to the old one that was used in iOS 9 backups.
Below data related to brute-force attacks reported by Elcomsoft:
iOS 9 (CPU): 2,400 passwords per second (Intel i5)
iOS 9 (GPU): 150,000 passwords per second (NVIDIA GTX 1080)
iOS 10 (CPU): 6,000,000 passwords per second (Intel i5)
Elcomsoft confirmed that the password hole could be exploited to gain access to Apple Keychain. iOS 10 backups allow a hacker to extract and decrypt Keychain data.
“Keychain contains information such as saved passwords or authentication tokens to applications requesting secure storage for authentication credentials, Safari logins and passwords, credit card information, Wi-Fi network information, and any data that third-party app developer consider worthy of extra protection.” states the post about the Keychain.
Users can download the Elcomsoft Phone Breaker 6.10 that comes with 6 million passwords per second (CPU only) for iOS 10 backups.
Leaked NSA Hacking Tools Were 'Mistakenly' Left By An Agent On A Remote Server
23.9.2016 thehackernews BigBrothers
NSA's private zero-day exploits, malware and hacking tools
If you are a hacker, you might have enjoyed the NSA's private zero-day exploits, malware and hacking tools that were leaked last month.
But the question is: How these hacking tools ended up into the hands of hackers?
It has been found that the NSA itself was not directly hacked, but a former NSA employee carelessly left those hacking tools on a remote server three years ago after an operation and a group of Russian hackers found them, sources close to the investigation told Reuters.
The leaked hacking tools, which enable hackers to exploit vulnerabilities in systems from big vendors like Cisco Systems, Juniper, and Fortinet, were dumped publicly online by the group calling itself "The Shadow Brokers."
NSA officials have also admitted to the FBI that their careless employee acknowledged the error shortly afterward, and hence the agency was aware of its operative's mistake from last three years.
But instead of warning the affected companies that their customers were at risk, the NSA maintained the silence.
"After the discovery, the NSA tuned its sensors to detect [the] use of any of the tools by other parties, especially foreign adversaries with strong cyber espionage operations, such as China and Russia," Reuters reports.
Well, that's Bullshit! If they call it a 'tactic.'
Shortly after the public release of NSA cyber weapons, firewall vendors Cisco and Fortinet confirmed that the leaked zero-day vulnerabilities were legitimate and issued out patches to fix those exploits.
We are still waiting for the comments from the NSA, the FBI and the Office of the Director of National Intelligence about the matter.
Since the initial leak of NSA's hacking tools last month and confirmation of the leaked vulnerabilities being legitimate by Cisco and Fortinet, the intelligence agency and online community has been finding out the working exploits in the data dump that are still unknown and used in the wild.
Just recently, Cisco revealed a new zero-day vulnerability from the leaked data dump that had been used by hackers to target some of its customers, which indicates that hackers would likely continue to take advantage of the now-exposed exploits to conduct cyber attacks.