Ne, Elon Musk lidem neposílá ethereum. Je to podvod
28.2.2018 Živě.cz Spam
Ne, Elon Musk lidem neposílá ethereum. Je to podvod
Podvodníci si zase našli způsob, jak z důvěřivých lidí vytáhnout peníze. Tentokrát k tomu použili osobu vizionáře Elona Muska, pod jehož jménem založili falešný účet na Twitteru a slíbili, že lidem rozdají ethereum v hodnotě 4 milionů dolarů. Stačí jen, když mu lidé pošlou nějaký malý obnos, aby získal adresu jejich peněženky. Samozřejmě je to nesmysl.
Skutečný Elon Musk ve středu na Twitteru informoval o plánovaném startu satelitů Starlink. Příspěvek byl relativně nadšený. Nějakého podvodníka tak napadlo, že toho využije a založil téměř totožný účet @elonhmusk, ve kterém na příspěvek navázal jednoduchým sdělením - k příležitosti úspěchu rozdá lidem 5000 kusů etherea. Pokud kryptoměnu lidé chtějí získat, mají poslat nějaký malý obnos, aby Musk získal adresu jejich peněženky.
Účet je už z Twitteru odstraněný, zpráva vypadala takto:
To celebrate this, I'm also giving awaу 5,000 ЕTH!
To identify your address, just sеnd 0.5-1.0 ЕTH to the address bеlow and gеt 5-10 ЕTH back to the address you used for the transaсtion. ЕТH Аddress: ...
If you are latе, yоur EТH will bе sent back.
— Еlon Мusk (@elonhmusk)
Zní to jako jasný podvod a podvod to také je. Už samotný princip nedává smysl, adresu peněženky stačí sdělit, není potřeba z ní něco posílat. Nicméně mnoho lidí se nachytalo a podle sledování v blockchainu je možné zjistit, že podvodníkovi už lidé poslali ethereum v hodnotě více než 16 tisíc dolarů.
Účet lze přitom velice jednoduše odhalit. Není verifikovaný a má jinou adresu. Hlavně je třeba říct, že i když je Elon Musk znám jako šílenec, určitě by jen tak lidem neposlal skoro 4,3 miliony dolarů. A určitě by nechtěl, aby mu lidé něco posílali.
Není to letos poprvé, co se něco podobného stalo. Twitter už musel zrušit účty @elonmus_ a @elonnmuusk, které se pokoušely o něco podobného.
Smart Life od Avastu ochrání IoT před malwarem. Pomůže mu A.I.
28.2.2018 Živě.cz IoT
Smart Life od Avastu ochrání IoT před malwarem. Pomůže mu A.I.Smart Life od Avastu ochrání IoT před malwarem. Pomůže mu A.I.Smart Life od Avastu ochrání IoT před malwarem. Pomůže mu A.I.Smart Life od Avastu ochrání IoT před malwarem. Pomůže mu A.I.Smart Life od Avastu ochrání IoT před malwarem. Pomůže mu A.I.
Avast zprvu před malwarem chránil počítače, pak přibral chytré telefony a nyní se pokusí dohlédnout i na malou firemní a domácí síť s chytrými krabičkami IoT. Novou bezpečnostní platformu pojmenoval Smart Life.
Jak to bude fungovat v praxi? Vedle běžné detekce malwaru bude platforma pracovat i s prvky strojového učení a odhalování podezřelé aktivity. Když se tedy třeba chytrý termostat zapne v netradiční dobu, která neodpovídá dosavadnímu charakteru používání, a zároveň začne komunikovat s podezřelými IP adresami, Smart Life aktivitu vyhodnotí jako útok, zabrání pokračování a upozorní správce domácí sítě.
Podobným způsobem by měl bezpečnostní systém odhalit třeba podezřelou aktivitu chytrých televizorů, webkamer, všemožných přehrávačů a dalších prvků v domácím LANu, nebo v síti malé firmy. Ostatně jak upozorňuje sám Avast, hromadu podobných zařízení lze zneužít útočníkem třeba k těžbě kryptoměny Monero, kterou lze při větším množství napadených krabiček smysluplně těžit i na slabších armových čipsetech.
Smart Life je nicméně pouze software, takže aby mohl neustále skenovat vaši síť, musí běžet na nějakém železe. Tím bude buď přímo výkonnější Wi-Fi router některého ze smluvních partnerů, anebo dedikovaná krabička – sniffer – připojená do LANu. „Sniffer je v podstatě takové lepší Raspberry Pi postavené přímo pro nás,“ řekl nám bezpečnostní expert Avastu Filip Chytrý.
Internet věcí
Domácí IoT může vypadat všelijak počínaje komerčními krabičkami a konče DIY. Třeba takto, když si jej složíte a naprogramujete sami. Bezpečnostní a meteorologický systém autora článku obsahuje kameru s rybím okem, infračervený a mikrovlnný detektor pohybu, teploměr, vlhkoměr, tlakoměr, luxmetr, síť vnitřních i venkovních dálkových bezdrátových sond (868 MHz, LoRa), senzor CO2 a nakonec automatické spínání světel v bytě. Vše je postavené na Raspberry Pi Zero W, které může být také napadnutelné útočníky.

Bezpečnostní a meteorologická centrála postavená na Raspberry Pi Zero W
Samozřejmě jsme se Avastu zeptali i na to, jestli bude moci zkušenější uživatel nahodit celý systém i na některou z otevřených platforem – třeba na router s OpenWrt, kam patří i populární český router Turris. Ačkoliv se tomu Avast výhledově nebrání, zatím se bude soustředit pouze na železo od partnerů.
Pro Avast není Smart Life úplnou novinkou, podle Chytrého se totiž v podstatě jedná o evoluci platformy Chime, kterou vyvíjí AVG. No a AVG dnes patří pod křídla Avastu.
Siemens Releases BIOS Updates to Patch Intel Chip Flaws
28.2.2018 securityweek Vulnerebility
Siemens has released BIOS updates for several of its industrial devices to patch vulnerabilities discovered recently in Intel chips, including Meltdown, Spectre and flaws affecting the company’s Management Engine technology.
Following the disclosure of the Meltdown and Spectre attack methods, industrial control systems (ICS) manufacturers immediately started analyzing the impact of the flaws on their products. Advisories have been published by companies such as Siemens, Rockwell Automation, Schneider Electric, ABB, and Pepperl+Fuchs.
Siemens has determined that the security holes expose many of its product lines to attacks, including RUGGEDCOM, SIMATIC, SIMOTION, SINEMA, and SINUMERIK.
The company informed customers recently that it has started releasing BIOS updates for some of its impacted products, including SIMATIC industrial PCs, SIMATIC field PG rugged laptops, SIMATIC industrial tablet PCs (ITP), and SINUMERIK panel control units (PCU). In addition to firmware patches, users have been advised to install operating system updates, which should mitigate the Meltdown flaw and one variant of Spectre.
The BIOS updates released by the company for the aforementioned SIMATIC and SINUMERIK devices also patch several vulnerabilities discovered last year by researchers in Intel’s Management Engine (ME), Server Platform Services (SPS), and Trusted Execution Engine (TXE) technologies.
The flaws impacting these Intel products can be exploited – in most cases locally, but at least one bug is remotely exploitable – for arbitrary code execution, privilege escalation, and denial-of-service (DoS) attacks.
The firmware updates from Siemens also fix a vulnerability affecting the Trusted Platform Module (TPM) in chips made by German semiconductor manufacturer Infineon.
The flaw, CVE-2017-15361, is related to the RSA library in TPM and it could allow a remote attacker who knows the public key to obtain the private RSA key. The security hole affects the products of several major tech firms, including Microsoft, Google, HP, Lenovo and Fujitsu.
Siemens has published separate advisories to inform users about the availability of patches for Meltdown/Spectre, Intel ME, and Infineon TPM vulnerabilities. ICS-CERT has so far published an advisory only for the Infineon issue.
Fake ionCube Malware Hits Hundreds of Sites
28.2.2018 securityweek Virus
Hundreds of websites have been infected with malware that masquerades as legitimate ionCube-encoded files, SiteLock warns.
The malicious files were initially discovered in core directories of a WordPress site, featuring naming patterns usually associated with malware, namely “diff98.php” and “wrgcduzk.php.” Because the obfuscated files appear as if they had been encoded with ionCube, the researchers named the threat ionCube malware.
ionCube is an old and powerful PHP obfuscation technology that can be used to scramble text-based PHP files to hide the intellectual property. Due to licensing costs, ionCube isn’t usually used for malicious purposes.
Malicious attackers, however, found a way to pack their malware in a manner that resembles that of ionCube-encoded files, and started targeting various websites. Although the infection was initially spotted on a WordPress site, SiteLock's researchers discovered that Joomla and CodeIgniter sites have been infected as well.
According to SiteLock, the malware is likely to run on any web server running PHP, and could hide in plain sight by using filenames such as “inc.php” and “menu.php.” Overall, the researchers discovered over 7,000 infected files and say that over 700 sites were compromised.
Once decoded, the fake ionCube files turn into the malware itself, which still contains some obfuscation, along with some sort of access control, researchers discovered.
“While there’s still some degree of obfuscation, the presence of the $_POST and $_COOKIE superglobals and the eval request at the end of the file reveal its true purpose: to accept and execute remotely supplied code. It looks like the remote code supplied to this file is further obfuscated and there may be some sort of access control implemented, judging by the GUID-formatted string present,” SiteLock says.
Site administrators who haven’t specifically and intentionally installed ionCube-encoded files but do find such files on their servers were likely infected. If an infection is detected, the scanning of the entire site is recommended, to completely eliminate the threat.
According to SiteLock, differentiating between the fake and legitimate files can be very difficult as well, given the large number of malware variations out there. The researchers say it is common to see up to 100 slightly different variants of the malware on a single site.
Talos experts shared details of a remote code execution flaw in Adobe Acrobat Reader DC
28.2.2018 securityweek Vulnerebility
Security experts at Cisco Talos disclosed details of a remote code execution flaw that affects Adobe Acrobat Reader DC versions 2018.009.20050 and 2017.011.30070 and earlier.
Security experts at Cisco Talos shared details of a remote code execution vulnerability tracked as CVE-2018-4901, that affects Adobe Acrobat Reader DC.
A remote attacker can exploit the vulnerability tricking the victim into opening a malicious file or visiting a specially crafted webpage.
The flaw affects Adobe Acrobat Reader versions 2018.009.20050 and 2017.011.30070 and earlier. The vulnerability was disclosed on Dec. 7 and Adobe addressed it a few days ago, on February 13.
“Adobe Acrobat Reader is the most popular and most feature-rich PDF reader. It has a big user base, is usually a default PDF reader on systems and integrates into web browsers as a plugin for rendering PDFs. As such, tricking a user into visiting a malicious web page or sending a specially crafted email attachment can be enough to trigger this vulnerability.” reads the analysis published by the Talos team.
Adobe classified the flaw with a “priority 2” level that equals to “important”, this means that there is an “elevated risk” of exploitation. The good news is that there are currently no known exploits in the wild.
The researchers explained that the flaw could be used by attackers to embed a malicious JavaScript code in a PDF file to use document ID to perform unauthorized operations to trigger a stack-based buffer overflow when opening a specially crafted PDF document.
“A specific Javascript script embedded in a PDF file can cause the document ID field to be used in an unbounded copy operation leading to stack-based buffer overflow when opening a specially crafted PDF document in Adobe Acrobat Reader,” continues Talos.
Researchers at Talos also released Snort rules 45102-3 that could be used by administrators to detect exploitation attempts.
Experts warn Memcached DDoS attacks could be soon a dangerous threat
28.2.2018 securityweek Attack
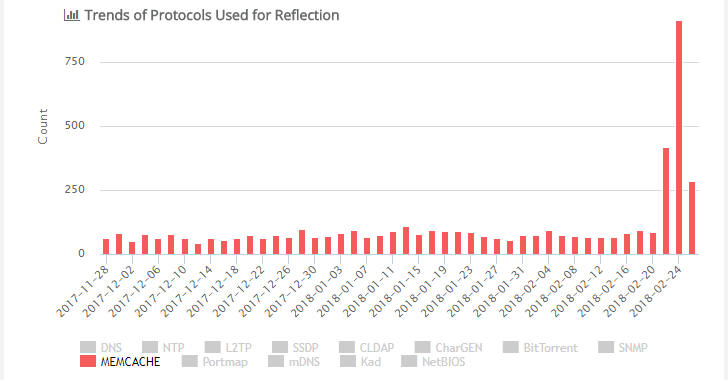
Security experts started observing a dangerous trend in DDoS amplification technique, Memcached DDoS Attacks.
Security experts from some security firms have reported that threat actors have started abusing the memcached protocol to power distributed denial-of-service (DDoS) Attacks, so-called memcached DDoS attacks.
Memcached is a free and open source, high-performance, distributed memory caching system designed to speed up dynamic web applications by alleviating database load.
Clients communicate with memcached servers via TCP or UDP on port 11211.
Researchers from Cloudflare, Arbor Networks and security firm Qihoo 360 discovered that recently attackers are abusing the memcached for DDoS amplification attacks.
Chinese experts warned about abuses of memcached DDoS attacks in November.
Experts at Cloudflare dubbed this type of attack Memcrashed.
“Over last couple of days we’ve seen a big increase in an obscure amplification attack vector – using the memcached protocol, coming from UDP port 11211.” reads the analysis published by Cloudflare.
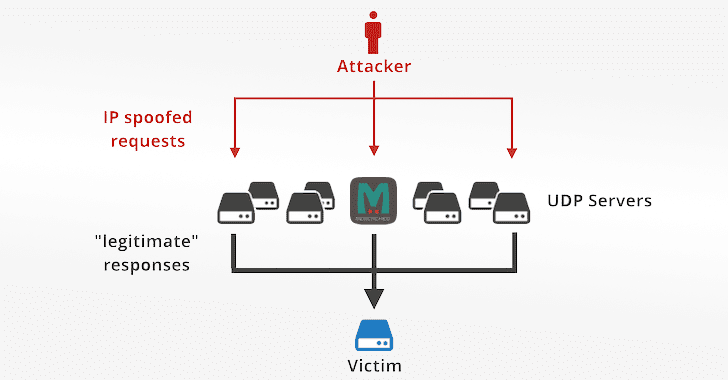
“An IP-spoofing capable attacker sends forged requests to a vulnerable UDP server. The UDP server, not knowing the request is forged, politely prepares the response. The problem happens when thousands of responses are delivered to an unsuspecting target host, overwhelming its resources – most typically the network itself.“
The involvement of memcached servers in DDoS Attacks is quite simple, the attacker sends a request to the targeted server on port 11211 spoofing the IP address of the victim. In a memcached DDoS attack, the request sent to the server is composed of a few bytes, while the response can be tens of thousands of times bigger, resulting in an amplification attack.

The researchers at Cloudflare observed a memcached DDoS attack that peaked at 260 Gbps while Arbor Networks reported observing attacks that peaked at 500 Gbps and even more.
“We have observed a considerable uptick in memcached reflection/amplification attacks ranging in size from a few hundred mb/sec up to 500gb/sec and larger. The amplified attack traffic is sourced from UDP/11211, with a packet size of 1428 bytes (1442 bytes with layer-2 Ethernet framing included), and no fragmentation (memcached segments large responses at layer-7, as does ntp).” reads the analysis published by Arbor Networks. “The attacker typically ‘primes’ a given set of memcached reflectors/amplifiers with arbitrary-length key/value pairs, and then issues memcached queries for those key/value pairs, spoofing the IP addresses of targeted hosts/networks.”
Researchers at Arbor Networks added that attackers can also send queries at TCP port 11211, but since TCP queries cannot be reliably spoofed, the hackers opted for UDP.
“I was surprised to learn that memcached does UDP, but there you go! The protocol specification shows that it’s one of the best protocols to use for amplification ever! There are absolutely zero checks, and the data WILL be delivered to the client, with blazing speed! Furthermore, the request can be tiny and the response huge (up to 1MB).” continues the analysis published by Cloudflare.
“Launching such an attack is easy. First the attacker implants a large payload on an exposed memcached server. Then, the attacker spoofs the “get” request message with target Source IP.”
According to Cloudflare, most of the memchached DDoS Attacks were launched from servers in North America and Europe, the majority of them is hosted by OVH, DigitalOcean, and Sakura.

The experts observed attacks from roughly 5,700 unique IPs associated with memcached servers.
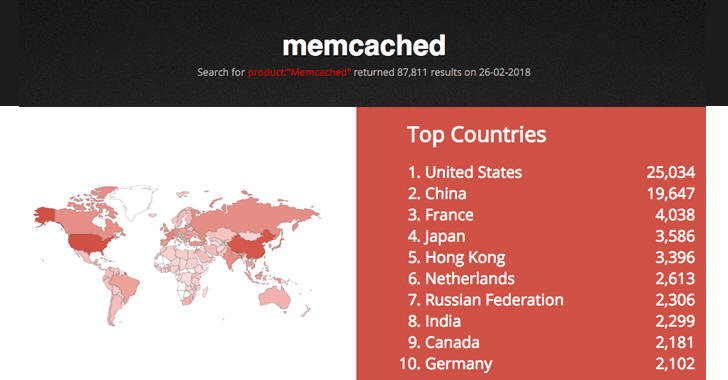
The situation can rapidly get worse because the result of a simple Shodan query shows nearly 88,000 unsecured memchached servers, most of them in the United States, China and France.

Cloudflare recommends disabling UDP support unless it’s needed and isolating memcached servers from the Internet. Internet service providers have to fix vulnerable protocols and prevent IP spoofing.
“Internet Service Providers – In order to defeat such attacks in future, we need to fix vulnerable protocols and also IP spoofing. As long as IP spoofing is permissible on the internet, we’ll be in trouble.” concluded Cloudflare.
“Developers – Please please please: Stop using UDP. If you must, please don’t enable it by default. If you do not know what an amplification attack is I hereby forbid you from ever typing
SOCK_DGRAM
into your editor.”
Memcached Servers Abused for Massive Amplification DDoS Attacks
28.2.2018 thehackernews Attack
Cybercriminals have figured out a way to abuse widely-used Memcached servers to launch over 51,000 times powerful DDoS attacks than their original strength, which could result in knocking down of major websites and Internet infrastructure.
In recent days, security researchers at Cloudflare, Arbor Networks, and Chinese security firm Qihoo 360 noticed that hackers are now abusing "Memcached" to amplify their DDoS attacks by an unprecedented factor of 51,200.
Memcached is a popular open-source and easily deployable distributed caching system that allows objects to be stored in memory and has been designed to work with a large number of open connections. Memcached server runs over TCP or UDP port 11211.
The Memcached application has been designed to speed up dynamic web applications by reducing stress on the database that helps administrators to increase performance and scale web applications. It's widely used by thousands of websites, including Facebook, Flickr, Twitter, Reddit, YouTube, and Github.
Dubbed Memcrashed by Cloudflare, the attack apparently abuses unprotected Memcached servers that have UDP enabled in order to deliver DDoS attacks 51,200 times their original strength, making it the most prominent amplification method ever used in the wild so far.
How Memcrashed DDoS Amplification Attack Works?
Like other amplification methods where hackers send a small request from a spoofed IP address to get a much larger response in return, Memcrashed amplification attack also works by sending a forged request to the targeted server (vulnerable UDP server) on port 11211 using a spoofed IP address that matches the victim's IP.
According to the researchers, just a few bytes of the request sent to the vulnerable server can trigger the response of tens of thousands of times bigger.
"15 bytes of request triggered 134KB of response. This is amplification factor of 10,000x! In practice we've seen a 15-byte request result in a 750kB response (that's a 51,200x amplification)," Cloudflare says.
According to the researchers, most of the Memcached servers being abused for amplification DDoS attacks are hosted at OVH, Digital Ocean, Sakura and other small hosting providers.
In total, researchers have seen only 5,729 unique source IP addresses associated with vulnerable Memcached servers, but they are "expecting to see much larger attacks in future, as Shodan reports 88,000 open Memcached servers." Cloudflare says.
"At peak we've seen 260Gbps of inbound UDP memcached traffic. This is massive for a new amplification vector. But the numbers don't lie. It's possible because all the reflected packets are very large," Cloudflare says.
Arbor Networks noted that the Memcached priming queries used in these attacks could also be directed towards TCP port 11211 on abusable Memcached servers.
But TCP is not currently considered a high-risk Memcached reflection/amplification vector because TCP queries cannot be reliably spoofed.
The popularly known DDoS amplification attack vectors that we reported in the past include poorly secured domain name system (DNS) resolution servers, which amplify volumes by about 50 times, and network time protocol (NTP), which increases traffic volumes by nearly 58 times.
Mitigation: How to Fix Memcached Servers?
One of the easiest ways to prevent your Memcached servers from being abused as reflectors is firewalling, blocking or rate-limiting UDP on source port 11211.
Since Memcached listens on INADDR_ANY and runs with UDP support enabled by default, administrators are advised to disable UDP support if they are not using it.
The attack size potentially created by Memcached reflection cannot be easily defended against by Internet Service Providers (ISPs), as long as IP spoofing is permissible on the internet.
Hacker Who Never Hacked Anyone Gets 33-Month Prison Sentence
28.2.2018 thehackernews Crime

A hacker who was arrested and pleaded guilty last year—not because he hacked someone, but for creating and selling a remote access trojan that helped cyber criminals—has finally been sentenced to serve almost three years in prison.
Taylor Huddleston, 26, of Hot Springs, Arkansas, pleaded guilty in July 2017 to one charge of aiding and abetting computer intrusions by building and intentionally selling a remote access trojan (RAT), called NanoCore, to hackers for $25.
Huddleston was arrested in March, almost two months before the FBI raided his house in Hot Springs, Arkansas and left with his computers after 90 minutes, only to return eight weeks later with handcuffs.
This case is a rare example of the US Department of Justice (DOJ) charging someone not for actively using malware to hack victims' computers, but for developing and selling it to other cybercriminals.
Huddleston admitted to the court that he created his software knowing it would be used by other cybercriminals to break the law.
He initially started developing NanoCore in late 2012 with a motive to offer a low-budget remote management software for schools, IT-conscious businesses, and parents who desired to monitor their children's activities on the web.
However, Huddleston marketed and sold the NanoCore RAT for $25 in underground hacking forums that were extremely popular with cybercriminals around the world from January 2014 to February 2016. He then sold ownership of NanoCore to a third-party in 2016.
NanoCore RAT happens to be popular among cybercriminals on underground hacking forums and has been linked to intrusions in at least ten countries. Among the victims was a high-profile assault on Middle Eastern energy firms in 2015.
Huddleston also agreed with prosecutors that NanoCore RAT and available third-party plugins offered a full set of features including:
Stealing sensitive information from victim computers, such as passwords, emails, and instant messages.
Remotely activating and controlling connected webcams on the victims' computers in order to spy on them.
Ability to view, delete, and download files.
Locking infected PCs and holding them to ransom.
Using infected PCs to launch distributed denial of service (DDoS) attacks on websites and similar services.
In July plea, Huddleston also took responsibility for creating and operating a software licensing system called "Net Seal" that was used by another suspect, Zachary Shames, to sell thousands of copies of Limitless keylogger.
Shames used Net Seal to infect 3,000 people that were, in turn, used it to infect 16,000 computers, according to the DoJ.
In his guilty plea, Huddleston admitted that he intended his products to be used maliciously.
Besides the 33-month prison sentence handed down by judges on Friday, Huddleston also gets two years of supervised release.







