
MongoDB Suffers Security Breach, Exposing Customer Data
17.12.23 Incindent The Hacker News
MongoDB on Saturday disclosed it's actively investigating a security incident that has led to unauthorized access to "certain" corporate systems, resulting in the exposure of customer account metadata and contact information.
The American database software company said it first detected anomalous activity on December 13, 2023, and that it immediately activated its incident response efforts.
It further noted that "this unauthorized access has been going on for some period of time before discovery," but emphasized it's not "aware of any exposure to the data that customers store in MongoDB Atlas." It did not disclose the exact time period of the compromise.
In light of the breach, MongoDB recommends that all customers be on the lookout for social engineering and phishing attacks, enforce phishing-resistant multi-factor authentication (MFA), as well as rotate their MongoDB Atlas passwords.
That's not all. The company said it's also experiencing elevated login attempts that are causing issues for customers attempting to log in to Atlas and its Support Portal. It, however, said the problem is unrelated to the security event.
When reached for comment, MongoDB told The Hacker News that the incident is a matter of ongoing investigation and that it will "provide updates as soon as we can."
(This is a developing story. Please check back for more updates.)
China's MIIT Introduces Color-Coded Action Plan for Data Security Incidents
16.12.23 Incindent The Hacker News
China's Ministry of Industry and Information Technology (MIIT) on Friday unveiled draft proposals detailing its plans to tackle data security events in the country using a color-coded system.
The effort is designed to "improve the comprehensive response capacity for data security incidents, to ensure timely and effective control, mitigation and elimination of hazards and losses caused by data security incidents, to protect the lawful rights and interests of individuals and organizations, and to safeguard national security and public interests, the department said.
The 25-page document encompasses all incidents in which data has been illegally accessed, leaked, destroyed, or tampered with, categorized them into four hierarchical tiers based on the scope and the degree of harm caused -
Red: Level I ("especially significant"), which applies to widespread shutdowns, substantial loss of business processing capability, interruptions arising due to serious anomalies lasting more than 24 hours, occurrence of major radio interference for more than 24 hours, economic losses 1 billion yuan, or affects the personal information of over 100 million people or sensitive personal information of more than 10 million people
Orange: Level II ("significant"), which applies to shutdowns and operational interruptions lasting more than 12 hours, occurrence of major radio interference for more than 12 hours,, economic losses between 100 million yuan and 1 billion yuan, or affects the personal information of over 10 million people or sensitive personal information of more than 1 million people
Yellow: Level III ("large"), which applies to operational interruptions lasting more than eight hours, occurrence of major radio interference for more than eight hours, economic losses between 50 million yuan and 100 million yuan, or affects the personal information of over 1 million people or sensitive personal information of more than 100,000 people
Blue: Level IV ("general"), which applies to minor events that cause operational interruptions lasting less than eight hours, economic losses of less than 50 million yuan, or affects the personal information of less than 1 million people or sensitive personal information of less than 100,000 people
The new rules also require affected companies to make an assessment to determine the severity of the incident, and if deemed serious, report it immediately to the local industry supervision department without omitting or concealing any facts, or providing any false information.
"If the local industry regulatory department initially determines that it is a particularly major or major data security incident, it should report it to the Mechanism Office in accordance with the requirements of '10 minutes by phone and 30 minutes in writing' after discovering the incident," the draft rules state.
Based on the response level activated – Red or Orange – the Mechanism Office is expected to report the matter to the MIIT. The draft rules are open for public comments until January 15, 2024.
Hackers Exploited ColdFusion Vulnerability to Breach Federal Agency Servers
7.12.23 Incindent The Hacker News
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) warned of active exploitation of a high-severity Adobe ColdFusion vulnerability by unidentified threat actors to gain initial access to government servers.
"The vulnerability in ColdFusion (CVE-2023-26360) presents as an improper access control issue and exploitation of this CVE can result in arbitrary code execution," CISA said, adding an unnamed federal agency was targeted between June and July 2023.
The shortcoming affects ColdFusion 2018 (Update 15 and earlier versions) and ColdFusion 2021 (Update 5 and earlier versions). It has been addressed in versions Update 16 and Update 6, released on March 14, 2023, respectively.
It was added by CISA to the Known Exploited Vulnerabilities (KEV) catalog a day later, citing evidence of active exploitation in the wild. Adobe, in an advisory released around that time, said it's aware of the flaw being "exploited in the wild in very limited attacks."
The agency noted that at least two public-facing servers were compromised using the flaw, both of which were running outdated versions of the software.
"Additionally, various commands were initiated by the threat actors on the compromised web servers; the exploited vulnerability allowed the threat actors to drop malware using HTTP POST commands to the directory path associated with ColdFusion," CISA noted.
There is evidence to suggest that the malicious activity is a reconnaissance effort carried out to map the broader network, although no lateral movement or data exfiltration has been observed.
In one of the incidents, the adversary was observed traversing the filesystem and uploading various artifacts to the web server, including binaries that are capable of exporting web browser cookies as well as malware designed to decrypt passwords for ColdFusion data sources.
A second event recorded in early June 2023 entailed the deployment of a remote access trojan that's a modified version of the ByPassGodzilla web shell and "utilizes a JavaScript loader to infect the device and requires communication with the actor-controlled server to perform actions."
Also undertaken by the adversary were attempts to exfiltrate the Windows Registry files as well as unsuccessfully download data from a command-and-control (C2) server.
"During this incident, analysis strongly suggests that the threat actors likely viewed the data contained in the ColdFusion seed.properties file via the web shell interface," CISA said.
"The seed.properties file contains the seed value and encryption method used to encrypt passwords. The seed values can also be used to decrypt passwords. No malicious code was found on the victim system to indicate the threat actors attempted to decode any passwords using the values found in seed.properties file."
Okta Discloses Broader Impact Linked to October 2023 Support System Breach
29.11.23 Incindent The Hacker News
Identity services provider Okta has disclosed that it detected "additional threat actor activity" in connection with the October 2023 breach of its support case management system.
"The threat actor downloaded the names and email addresses of all Okta customer support system users," the company said in a statement shared with The Hacker News.
"All Okta Workforce Identity Cloud (WIC) and Customer Identity Solution (CIS) customers are impacted except customers in our FedRamp High and DoD IL4 environments (these environments use a separate support system NOT accessed by the threat actor). The Auth0/CIC support case management system was not impacted by this incident."
News of the expanded scope of the breach was first reported by Bloomberg.
The company also told the publication that while it does not have any evidence of the stolen information being actively misused, it has taken the step of notifying all customers of potential phishing and social engineering risks.
It also stated that it "pushed new security features to our platforms and provided customers with specific recommendations to defend against potential targeted attacks against their Okta administrators."
Okta, which has enlisted the help of a digital forensics firm to support its investigation, further said it "will also notify individuals that have had their information downloaded."
The development comes more than three weeks after the identity and authentication management provider said the breach, which took place between September 28 to October 17, 2023, affected 1% – i.e., 134 – of its 18,400 customers.
The identity of the threat actors behind the attack against Okta's systems is currently not known, although a notorious cybercrime group called Scattered Spider has targeted the company as recently as August 2023 to obtain elevated administrator permissions by pulling off sophisticated social engineering attacks.
According to a report published by ReliaQuest last week, Scattered Spider infiltrated an unnamed company and gained access to an IT administrator's account via Okta single sign-on (SSO), followed by laterally moving from the identity-as-a-service (IDaaS) provider to their on-premises assets in less than one hour.
The formidable and nimble adversary, in recent months, has also evolved into an affiliate for the BlackCat ransomware operation, infiltrating cloud and on-premises environments to deploy file-encrypting malware for generating illicit profits.
"The group's ongoing activity is a testament to the capabilities of a highly skilled threat actor or group having an intricate understanding of cloud and on-premises environments, enabling them to navigate with sophistication," ReliaQuest researcher James Xiang said.
Kubernetes Secrets of Fortune 500 Companies Exposed in Public Repositories
24.11.23 Incindent The Hacker News
Cybersecurity researchers are warning of publicly exposed Kubernetes configuration secrets that could put organizations at risk of supply chain attacks.
"These encoded Kubernetes configuration secrets were uploaded to public repositories," Aqua security researchers Yakir Kadkoda and Assaf Morag said in a new research published earlier this week.
Some of those impacted include two top blockchain companies and various other fortune-500 companies, according to the cloud security firm, which leveraged the GitHub API to fetch all entries containing .dockerconfigjson and .dockercfg, which store credentials for accessing a container image registry.
Of the 438 records that potentially held valid credentials for registries, 203 records – about 46% – contained valid credentials that provided access to the respective registries. Ninety-three of the passwords were manually set by individuals, as opposed to the 345 that were computer-generated.
"In the majority of cases, these credentials allowed for both pulling and pushing privileges," the researchers noted. "Moreover, we often discovered private container images within most of these registries."
Furthermore, nearly 50% of the 93 passwords were deemed weak. This comprised password, test123456, windows12, ChangeMe, and dockerhub, among others.

"This underscores the critical need for organizational password policies that enforce strict password creation rules to prevent the use of such vulnerable passwords," the researchers added.
Aqua said it also found instances where organizations fail to remove secrets from the files that are committed to public repositories on GitHub, leading to inadvertent exposure.
But on a positive note, all the credentials associated with AWS and Google Container Registry (GCR) were found to be temporary and expired, making access impossible. In a similar vein, the GitHub Container Registry required two-factor authentication (2FA) as an added layer against unauthorized access.
"In some cases, the keys were encrypted and thus there was nothing to do with the key," the researchers said. "In some cases, while the key was valid it had minimal privileges, often just to pull or download a specific artifact or image."
According to Red Hat's State of Kubernetes Security Report released earlier this year, vulnerabilities and misconfigurations emerged as top security concerns with container environments, with 37% of the total 600 respondents identifying revenue/customer loss as a result of a container and Kubernetes security incident.
A Data Exfiltration Attack Scenario: The Porsche Experience
28.7.23 Incindent The Hacker News
As part of Checkmarx's mission to help organizations develop and deploy secure software, the Security Research team started looking at the security posture of major car manufacturers. Porsche has a well-established Vulnerability Reporting Policy (Disclosure Policy)[1], it was considered in scope for our research, so we decided to start there, and see what we could find.
What we found is an attack scenario that results from chaining security issues found on different Porsche's assets, a website and a GraphQL API, that could lead to data exfiltration. Data exfiltration is an attack technique that can impact businesses and organizations, regardless of size. When malicious users breach a company's or organization's systems and exfiltrate data, it can be a jarring and business-critical moment.
Porsche has a diverse online presence - deploying several microsites, websites, and web applications. The Porsche Experience [2] is one website that allows registered users to manage a virtual garage, book experiences (such as track days), as well as manage bookings and invoices. From a technical perspective this website is a single-page application (SPA) backed by a GraphQL API (https://experience.porsche.com/graphql) used to fetch data and perform operations such as user authentication, user profile updates, book events, etc.
While initially exploring the website, the team noticed some interesting API requests. More specifically the jwtToken cookie and the Appauthorization HTTP request header both had the same value.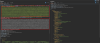
The image above shows the original API request issued by the website front-end to retrieve the user profile after a successful login attempt. On the left (Request) you can see the duplicate value.
This was enough to produce a hypothetical Cross-site Request Forgery (CSRF) [3] attack scenario, leading us to wonder whether the API would look for the authentication token in the jwtToken cookie if the custom HTTP request header Appauthorization was missing.
Including API auth tokens in a request header, rather than Cookie, are a game changer for Cross-Site Request Forgery (CSRF). Web browsers, unlike cookies, do not include such headers automatically, which must be done by some front-end custom logic (JavaScript).
To answer our question, we replayed the original request without including the Appauthorization request header. When we received the same response back from the API server, we confirmed our theory: the API retrieves the auth token from cookies when the custom request header is not present.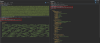
We had another question in mind that also needed to be answered: would the API server allow requests from origins other than porsche.com?
The answer to this question was also a resounding "yes."
As you can see in the image above, the request was made from a different website, which is reflected in the Access-Control-Allow-Origin [4] response header, indicating that the response can be shared with the requesting code from the given origin. Moreover, the API server also tells browsers to expose the response to the front-end JavaScript code when the request's credentials mode is include [5].
Typically, to be able to perpetrate a CSRF attack from an attacker's-controlled website the victims' web browsers must automatically include the jwtToken cookie in the API requests. That was not the case for Porsche Experience: the jwtToken cookie SameSite attribute was set to Lax.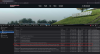
The SameSite attribute [6] controls whether a cookie should be sent with cross-site requests providing some protection against CSRF attacks. Lax means that the cookie is not sent on cross-site requests[7], and it is the default value when not specified at the time the cookie is set. We would not be able to make request to GraphQL API from a website controlled by us, but the definition of "Site" and "Same Site" [8] still leaves us an opportunity.
Any website served from a subdomain of porsche.com using HTTPS is considered "Same Site", and the jwtToken is automatically included by web browsers in requests to the API. Then, all we need to exfiltrate data from the API is to find a way to lead a Porsche website to issue API requests to our target API, sending the response to a server controlled by us. We should not expect to find such a feature on a Porsche website, but a Cross-Site Scripting (XSS) vulnerability [9] would allow us to do it.
The initial reconnaissance process gave us a comprehensive list of Porsche websites which we considered in our research. campaigns.porsche.com was a vulnerable website and the most credible to be included in a "marketing campaign" phishing email.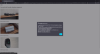
The /charging/WebAjaxGet endpoint of the vulnerable website (campaigns.porsche.com) did not properly sanitize nor encode query string parameter values before including them in the HTML server response. Bad actors could have exploited this issue to inject arbitrary code into the server response, which would end up being executed by the web browser into the victims' session context. Below is the special crafted URL that triggered the alert dialog box in the image above:
To exfiltrate data from the API to a remote server, controlled by us, we needed a more complex JavaScript logic. We ended up exploiting the Reflected XSS vulnerability to load a JavaScript script from our remote server. This is how the payload looks like:
The snippet simply creates a script element, setting the src attribute with the address where our malicious script should be fetched from. When appending it to the Document Object Model (DOM) the script is then downloaded and executed. To avoid encoding issues, the JavaScript payload was encoded base64, and appended to the URL as an argument of the atob JavaScript function, whose output is passed to the eval function. This is how the final crafted URL looks like:
The next step was to write the malicious exfiltrate.js script, downloaded and executed by our XSS payload. For victims, with an active session on experience.porsche.com, the jwtToken auth cookie is automatically included in requests to the API. All we need is to trigger the request with the appropriate GraphQL query and send the response to our remote server. To make the attack a bit sturdier, after that we will redirect the browser to the Porsche Experience website.
With everything in place, and working properly, malicious actors would need to deliver the final malicious URL to victims, enticing them to click it. Email phishing is certainly the most common way attackers do it. The image below illustrates such a phishing email: instead of trying to hide the URL, attacker may have taken advantage of the fact that it starts with HTTPS, and it is an actual porsche.com website.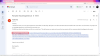
This attack scenario is not theoretical, and you can watch the proof-of-concept video provided to Porsche on YouTube [10].
Although this proof-of-concept focuses on profile data exfiltration the loaded JavaScript script could include other logic to retrieve additional data from the GraphQL API (e.g., invoices) or perform actions on victims' behalf (e.g., booking or cancel events).
Some quick security tips:
To prevent XSS [11] always encode unsafe data, according to the context to which it will be written to. On the APIs side, always establish a proper Cross-Origin Resource Sharing (CORS) policy [12] that restricts what hosts are allowed to interact with it. Also properly set cookies' options, and whenever possible, avoid using cookies to exchange auth tokens between clients and the API server.
It was a pleasure to collaborate with Porsche who took ownership and were professional throughout the disclosure and remediation process. For this reason, and a great researcher experience, we're granting Porsche the Checkmarx Seal of Approval.
And, as always, our security research team will continue to focus on ways to improve application security practices everywhere.
[1]: https://www.porsche.com/international/product-security/
[2]: https://experience.porsche.com
[3]: https://owasp.org/www-community/attacks/csrf
[4]: https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/Access-Control-Allow-Origin
[5]: https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/Access-Control-Allow-Credentials
[6]: https://owasp.org/www-community/SameSite
[7]: https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/Set-Cookie#lax
[8]: https://developer.mozilla.org/en-US/docs/Glossary/Site
[9]: https://owasp.org/www-community/attacks/xss/
[10]: https://youtu.be/if0Lmw-tJWo
[11]: https://cheatsheetseries.owasp.org/cheatsheets/Cross_Site_Scripting_Prevention_Cheat_Sheet.html
[12]: https://cheatsheetseries.owasp.org/cheatsheets/Cross-Site_Request_Forgery_Prevention_Cheat_Sheet.html
Cybersecurity Agencies Warn Against IDOR Bugs Exploited for Data Breaches
28.7.23 Incindent The Hacker News
Cybersecurity agencies in Australia and the U.S. have published a joint cybersecurity advisory warning against security flaws in web applications that could be exploited by malicious actors to orchestrate data breach incidents and steal confidential data.
This includes a specific class of bugs called Insecure Direct Object Reference (IDOR), a type of access control flaw that occurs when an application utilizes user-supplied input or an identifier for direct access to an internal resource, such as a database record, without any additional validations.
A typical example of an IDOR flaw is the ability of a user to trivially change the URL (e.g., https://example[.]site/details.php?id=12345) to obtain unauthorized data of another transaction (i.e., https://example[.]site/details.php?id=67890).
"IDOR vulnerabilities are access control vulnerabilities enabling malicious actors to modify or delete data or access sensitive data by issuing requests to a website or a web application programming interface (API) specifying the user identifier of other, valid users," the agencies said. "These requests succeed where there is a failure to perform adequate authentication and authorization checks."
The authoring entities – the Australian Signals Directorate's Australian Cyber Security Centre (ACSC), the U.S. Cybersecurity and Infrastructure Security Agency (CISA), and the U.S. National Security Agency (NSA) – noted that such flaws are being abused by adversaries to compromise the personal, financial, and health information of millions of users and consumers.
To mitigate such threats, it's recommended that vendors, designers, and developers adopt secure-by-design and -default principles and ensure software performs authentication and authorization checks for every request that modifies, deletes, and accesses sensitive data.
The development comes days after CISA released its analysis of data gathered from risk and vulnerability assessments (RVAs) conducted across multiple federal civilian executive branch (FCEB) as well as high-priority private and public sector critical infrastructure operators.
The study found that "Valid Accounts were the most common successful attack technique, responsible for 54% of successful attempts," followed by spear-phishing links (33.8%), spear-phishing attachments (3.3%), external remote services (2.9%), and drive-by compromises (1.9%).
Legitimate accounts, which could either be former employee accounts that have not been removed from the active directory or default administrator accounts, have also emerged as the top vector for establishing persistence in a compromised network (56.1%), escalating privileges (42.9%), and defense evasion (17.5%).
"To guard against the successful Valid Accounts technique, critical infrastructure entities must implement strong password policies, such as phishing-resistant [multi-factor authentication], and monitor access logs and network communication logs to detect abnormal access," CISA said.
VirusTotal Data Leak Exposes Some Registered Customers' Details
18.7.23 Incindent The Hacker News
Data associated with a subset of registered customers of VirusTotal, including their names and email addresses, were exposed after an employee inadvertently uploaded the information to the malware scanning platform.
The security incident, which comprises a database of 5,600 names in a 313KB file, was first disclosed by Der Spiegel and Der Standard yesterday.
Launched in 2004, VirusTotal is a popular service that analyzes suspicious files and URLs to detect types of malware and malicious content using antivirus engines and website scanners. It was acquired by Google in 2012 and became a subsidiary of Google Cloud's Chronicle unit in 2018.
When reached for comment, Google confirmed the leak and said it took immediate steps to remove the data.
"We are aware of the unintentional distribution of a small segment of customer group administrator emails and organization names by one of our employees on the VirusTotal platform," a Google Cloud spokesperson told The Hacker News.
"We removed the list from the platform within an hour of its posting and we are looking at our internal processes and technical controls to improve our operations in the future."
Included among the data are accounts linked to official U.S. bodies such as the Cyber Command, Department of Justice, Federal Bureau of Investigation (FBI), and the National Security Agency (NSA). Other accounts belong to government agencies in Germany, the Netherlands, Taiwan, and the U.K.
Last year, Germany's Federal Office for Information Security (BSI) warned against automating uploading of suspicious email attachments, noting that doing so could lead to the exposure of sensitive information.
JumpCloud Blames 'Sophisticated Nation-State' Actor for Security Breach
18.7.23 Incindent The Hacker News
A little over a week after JumpCloud reset API keys of customers impacted by a security incident, the company said the intrusion was the work of a sophisticated nation-state actor.
The adversary "gained unauthorized access to our systems to target a small and specific set of our customers," Bob Phan, chief information security officer (CISO) at JumpCloud, said in a post-mortem report. "The attack vector used by the threat actor has been mitigated."
The U.S. enterprise software firm said it identified anomalous activity on June 27, 2023, on an internal orchestration system, which it traced back to a spear-phishing campaign mounted by the attacker on June 22.
While JumpCloud said it took security steps to shield its network by rotating credentials and rebuilding its systems, it wasn't until July 5 when it detected "unusual activity" in the commands framework for a small set of customers, prompting a forced-rotation of all admin API keys. The number of affected customers was not disclosed.
Further analysis of the breach, per the company's disclosure, unearthed the attack vector, which it described as a "data injection into the commands framework." It also said the attacks were highly targeted.
JumpCloud, however, did not explain how the phishing attack it spotted in June is connected to the data injection. It's currently not clear if the phishing emails led to the deployment of malware that facilitated the attack.
Additional indicators of compromise (IoCs) associated with the attack shows that the adversary leveraged domains named nomadpkg[.]com and nomadpkgs[.]com, a likely reference to the Go-based workload orchestrator used to deploy and manage containers.
"These are sophisticated and persistent adversaries with advanced capabilities," Phan said. JumpCloud has yet to reveal the name and the origins of the group allegedly responsible for the incident.
Hackers Steal $20 Million by Exploiting Flaw in Revolut's Payment Systems
10.7.23 Incindent The Hacker News
Malicious actors exploited an unknown flaw in Revolut's payment systems to steal more than $20 million of the company's funds in early 2022.
The development was reported by the Financial Times, citing multiple unnamed sources with knowledge of the incident. The breach has not been disclosed publicly.
The fault stemmed from discrepancies between Revolut's U.S. and European systems, causing funds to be erroneously refunded using its own money when some transactions were declined.
The problem was first detected in late 2021. But before it could be closed, the report said organized criminal groups leveraged the loophole by "encouraging individuals to try to make expensive purchases that would go on to be declined." The refunded amounts would then be withdrawn from ATMs.
The exact technical details associated with the flaw are currently unclear.
About $23 million was stolen in total, with some funds recovered by pursuing those who had withdrawn cash. The mass fraud scheme is said to have resulted in a net loss of about $20 million for the neobank and fintech firm.
The disclosure arrives less than a week after Interpol announced the arrest of a suspected senior member of a French-speaking hacking crew known as OPERA1ER, which has been linked to attacks aimed at financial institutions and mobile banking services with malware, phishing campaigns, and large-scale Business Email Compromise (BEC) scams.
JumpCloud Resets API Keys Amid Ongoing Cybersecurity Incident
7.7.23 Incindent The Hacker News
JumpCloud, a provider of cloud-based identity and access management solutions, has swiftly reacted to an ongoing cybersecurity incident that impacted some of its clients.
As part of its damage control efforts, JumpCloud has reset the application programming interface (API) keys of all customers affected by this event, aiming to protect their valuable data.
The company has informed the concerned clients about the critical nature of this move, reinforcing its commitment to safeguarding their operations and organizations. This API key reset will, however, disrupt certain functionalities like AD import, HRIS integrations, JumpCloud PowerShell modules, JumpCloud Slack apps, Directory Insights Serverless apps, ADMU, third-party zero-touch MDM packages, Command Triggers, Okta SCIM integration, Azure AD SCIM integration, Workato, Aquera, Tray, and more.
Despite the potential disruptions, JumpCloud maintains that the key reset is for the greater good of its clients. For those needing assistance with resetting or re-establishing their API keys, the company stands ready to provide support.
The company urges affected clients to promptly reset their API keys to enhance their systems' security. To aid in this, JumpCloud has made available a detailed guide and an interactive simulation.
This recent event has highlighted the importance of API security, demonstrating the need for robust protective measures. It is crucial for businesses to adequately secure their APIs to avert potential security breaches.
JumpCloud's cloud-based Active Directory (AD) services are utilized by over 180,000 organizations globally. A multitude of software vendors and cloud service providers have integrated their systems with JumpCloud's suite of identity, access, and device management services.
Details regarding the specifics or scale of the incident are not available at this moment, but JumpCloud is actively addressing the situation. It is yet to be ascertained whether the company's network was compromised or the precise cause of the issue.
JumpCloud's communication has drawn some criticism for not being fully transparent.
Clients of JumpCloud affected by this event are advised to expedite their API key resets and stay tuned for further developments or announcements related to this incident.
Western Digital Confirms Customer Data Stolen by Hackers in March Breach
8.5.23 Incindent The Hacker News
Digital storage giant Western Digital confirmed that an "unauthorized third party" gained access to its systems and stole personal information belonging to the company's online store customers.
"This information included customer names, billing and shipping addresses, email addresses and telephone numbers," the San Jose-based company said in a disclosure last week.
"In addition, the database contained, in encrypted format, hashed and salted passwords and partial credit card numbers. We will communicate directly with impacted customers."
The development comes a little over a month after Western Digital divulged a "network security incident" on March 26, 2023, prompting the company to take its cloud services offline.
A subsequent report from TechCrunch last month revealed that the threat actors behind the attack were allegedly in possession of "around 10 terabytes of data," and were negotiating with Western Digital for a ransom of a "minimum 8 figures" to avoid leaking the information.
While the identity of the extortionists was unknown at the time, ALPHV (aka BlackCat) ransomware actors have since taken credit for the theft, issuing an ultimatum on April 18, 2023, to make the payment or risk the release of "important documents" and "priceless artifacts."
The actors have also published various screenshots on their dark web portal, displaying what appears to be video calls, emails, and documents related to Western Digital's incident response efforts in an attempt to indicate continued access to the company's systems even after the hack came to light.
Western Digital said it's aware of the publication of "other alleged Western Digital information," that it's "investigating the validity of this data," and that it has "control over our digital certificate infrastructure."
It has also taken the step of taking its online store offline, which it said is expected to be restored the week of May 15, 2023. Access to My Cloud service was restored on April 13, 2023.
Kodi Confirms Data Breach: 400K User Records and Private Messages Stolen
14.4.23 Incindent The Hacker News
Open source media player software provider Kodi has confirmed a data breach after threat actors stole the company's MyBB forum database containing user data and private messages.
What's more, the unknown threat actors attempted to sell the data dump comprising 400,635 Kodi users on the now-defunct BreachForums cybercrime marketplace.
"MyBB admin logs show the account of a trusted but currently inactive member of the forum admin team was used to access the web-based MyBB admin console twice: on 16 February and again on 21 February," Kodi said in an advisory.
The threat actors then abused the account to create database backups that were then downloaded and deleted. Also downloaded were existing nightly full backups of the database. The account in question has now been disabled.
The nightly backups contained all public forum posts, team forum posts, messages sent through the user-to-user messaging system, and user information such as forum username, email address used for notifications, and an encrypted (hashed and salted) password generated by the MyBB software.
Kodi said there is no evidence threat actors managed to obtain unauthorized access to the underlying server hosting the MyBB software. It further emphasized that the legitimate account owner did not perform malicious actions on the admin console, suggesting credential theft.
Out of an abundance of caution, the maintainers said work is underway to initiate a global password reset. Users are recommended to change their passwords on other sites if the same password has been used.
In the interim, the company has taken down the Kodi forum and noted that it's in the process of commissioning a new server, an activity that's expected to last "several days." It's also planning to redeploy the forum on the latest version of MyBB software.
As additional security measures, Kodi is hardening access to the MyBB admin console, revising admin roles to limit privileges, and improving audit logging and backup processes.
Western Digital Hit by Network Security Breach - Critical Services Disrupted!
4.4.23 Incindent The Hacker News
Data storage devices maker Western Digital on Monday disclosed a "network security incident" that involved unauthorized access to its systems.
The breach is said to have occurred on March 26, 2023, enabling an unnamed third party to gain access to a "number of the company's systems."
Following the discovery of the hack, Western Digital said it has initiated incident response efforts and enlisted the help of cybersecurity and forensic experts to conduct an investigation.
It also said it's coordinating with law enforcement agencies on the matter, adding the probe is in its initial stages.
The company has taken several of its services offline, noting that the threat actor may have obtained "certain data from its systems" and that it's working on estimating the nature and scope of the data accessed.
While Western Digital did not reveal the exact services that are impacted, the My Cloud status page shows that cloud, proxy, web, authentication, emails, and push notification services are down.
"Western Digital is currently experiencing a service outage impacting the following products: My Cloud, My Cloud Home, My Cloud Home Duo, My Cloud OS5, SanDisk ibi, SanDisk Ixpand Wireless Charger," the company said in a message posted on April 2.
Update#
Western Digital, in a message shared on April 3, said that it's "currently experiencing a service interruption that is preventing customers from accessing the My Cloud, My Cloud Home, My Cloud Home Duo, My Cloud OS 5, SanDisk ibi, SanDisk Ixpand Wireless Charger service."
It also noted that it's "working urgently to resolve the issue and restore access as soon as possible."
OpenAI Reveals Redis Bug Behind ChatGPT User Data Exposure Incident
25.3.23 Incindent The Hacker News
OpenAI on Friday disclosed that a bug in the Redis open source library was responsible for the exposure of other users' personal information and chat titles in the upstart's ChatGPT service earlier this week.
The glitch, which came to light on March 20, 2023, enabled certain users to view brief descriptions of other users' conversations from the chat history sidebar, prompting the company to temporarily shut down the chatbot.
"It's also possible that the first message of a newly-created conversation was visible in someone else's chat history if both users were active around the same time," the company said.
The bug, it further added, originated in the redis-py library, leading to a scenario where canceled requests could cause connections to be corrupted and return unexpected data from the database cache, in this case, information belonging to an unrelated user.
To make matters worse, the San Francisco-based AI research company said it introduced a server-side change by mistake that led to a surge in request cancellations, thereby upping the error rate.
While the problem has since been addressed, OpenAI noted that the issue may have had more implications elsewhere, potentially revealing payment-related information of 1.2% of the ChatGPT Plus subscribers on March 20 between 1-10 a.m. PT.
This included another active user's first and last name, email address, payment address, the last four digits (only) of a credit card number, and credit card expiration date. It emphasized that full credit card numbers were not exposed.
The company said it has reached out to affected users to notify them of the inadvertent leak. It also said it "added redundant checks to ensure the data returned by our Redis cache matches the requesting user."
OpenAI Fixes Critical Account Takeover Flaw#
In another caching-related issue, the company also addressed a critical account takeover vulnerability that could be exploited to seize control of another user's account, view their chat history, and access billing information without their knowledge.
The flaw, which was discovered by security researcher Gal Nagli, bypasses protections put in place by OpenAI on chat.openai[.]com to read a victim's sensitive data.
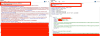
This is achieved by first creating a specially crafted link that appends a .CSS resource to the "chat.openai[.]com/api/auth/session/" endpoint and tricking a victim to click on the link, causing the response containing a JSON object with the accessToken string to be cached in Cloudflare's CDN.
The cached response to the CSS resource (which has the CF-Cache-Status header value set to HIT) is then abused by the attacker to harvest the target's JSON Web Token (JWT) credentials and take over the account.
Nagli said the bug was fixed by OpenAI within two hours of responsible disclosure, indicative of the severity of the issue.