
Hackers Used Fake Job Offer to Hack and Steal $540 Million from Axie Infinity
11.7.22 Incindent Thehackernews
The $540 million hack of Axie Infinity's Ronin Bridge in late March 2022 was the consequence of one of its former employees getting tricked by a fraudulent job offer on LinkedIn, it has emerged.
According to a report from The Block published last week citing two people familiar with the matter, a senior engineer at the company was duped into applying for a job at a non-existent company, causing the individual to download a fake offer document disguised as a PDF.
"After what one source described as multiple rounds of interviews, a Sky Mavis engineer was offered a job with an extremely generous compensation package," the Block reported.
The offer document subsequently acted as a conduit to deploy malware designed to breach Ronin's network, ultimately facilitating one of the crypto sector's biggest hacks to date.
"Sky Mavis employees are under constant advanced spear-phishing attacks on various social channels and one employee was compromised," the company said in a post-mortem analysis in April.
"This employee no longer works at Sky Mavis. The attacker managed to leverage that access to penetrate Sky Mavis IT infrastructure and gain access to the validator nodes."
In April 2022, the U.S. Treasury Department implicated the North Korea-backed Lazarus Group in the incident, calling out the adversarial collective's history of attacks targeting the cryptocurrency sector to gather funds for the hermit kingdom.
Bogus job offers have been long employed by the advanced persistent threat as a social engineering lure, dating back as early as August 2020 to a campaign dubbed by Israeli cybersecurity firm ClearSky as "Operation Dream Job."
In its T1 Threat Report for 2022, ESET noted how actors operating under the Lazarus umbrella have employed fake job offers through social media like LinkedIn as its strategy for striking defense contractors and aerospace companies.
While Ronin's Ethereum bridge was relaunched in June, three months after the hack, the Lazarus Group is also suspected to be behind the recent $100 million altcoin theft from Harmony Horizon Bridge.
The findings also come as blockchain projects centered around Web 3.0 have lost more than $2 billion to hacks and exploits in the first six months this year, blockchain auditing and security company CertiK disclosed in a report last week.
HackerOne Employee Caught Stealing Vulnerability Reports for Personal Gains
5.7.22 Incindent Thehackernews
Vulnerability coordination and bug bounty platform HackerOne on Friday disclosed that a former employee at the firm improperly accessed security reports submitted to it for personal gain.
"The person anonymously disclosed this vulnerability information outside the HackerOne platform with the goal of claiming additional bounties," it said. "In under 24 hours, we worked quickly to contain the incident by identifying the then-employee and cutting off access to data."
The employee, who had access to HackerOne systems between April 4 and June 23, 2022, for triaging vulnerability disclosures associated with different customer programs, has since been terminated by the San Francisco-headquartered company as of June 30.
Calling the incident as a "clear violation" of its values, culture, policies, and employment contracts, HackerOne said it was alerted to the breach on June 22 by an unnamed customer, which asked it to "investigate a suspicious vulnerability disclosure" through an off-platform communication from an individual with the handle "rzlr" using "aggressive" and "intimidating" language.
Subsequently, analysis of internal log data used to monitor employee access to customer disclosures traced the exposure to a rogue insider, whose goal, it noted, was to re-submit duplicate vulnerability reports to the same customers using the platform to receive monetary payouts.
"The threat actor created a HackerOne sockpuppet account and had received bounties in a handful of disclosures," HackerOne detailed in a post-mortem incident report, adding seven of its customers received direct communication from the threat actor.
"Following the money trail, we received confirmation that the threat actor's bounty was linked to an account that financially benefited a then-HackerOne employee. Analysis of the threat actor's network traffic provided supplemental evidence connecting the threat actor's primary and sockpuppet accounts."
HackerOne further said it has individually notified customers about the exact bug reports that were accessed by the malicious party along with the time of access, while emphasizing it found no evidence of vulnerability data having been misused or other customer information accessed.
On top of that, the company noted it aims to implement additional logging mechanisms to improve incident response, isolate data to reduce the "blast radius," and enhance processes in place to identify anomalous access and proactively detect insider threats.
Nearly 100,000 NPM Users' Credentials Stolen in GitHub OAuth Breach
28.5.22 Incindent Thehackernews
Cloud-based repository hosting service GitHub on Friday shared additional details into the theft of its integration OAuth tokens last month, noting that the attacker was able to access internal NPM data and its customer information.
"Using stolen OAuth user tokens originating from two third-party integrators, Heroku and Travis CI, the attacker was able to escalate access to NPM infrastructure," Greg Ose said, adding the attacker then managed to obtain a number of files -
A database backup of skimdb.npmjs.com consisting of data as of April 7, 2021, including an archive of user information from 2015 and all private NPM package manifests and package metadata. The archive contained NPM usernames, password hashes, and email addresses for roughly 100,000 users
A set of CSV files encompassing an archive of all names and version numbers of published versions of all NPM private packages as of April 10, 2022, and
A "small subset" of private packages from two organizations
As a consequence, GitHub is taking the step of resetting the passwords of impacted users. It's also expected to directly notify users with exposed private package manifests, metadata, and private package names and versions over the next couple of days.
The attack chain, as detailed by GitHub, involved the attacker abusing the OAuth tokens to exfiltrate private NPM repositories containing AWS access keys, and subsequently leveraging them to gain unauthorized access to the registry's infrastructure.
That said, none of the packages published to the registry are believed to have been modified by the adversary nor were any new versions of existing packages uploaded to the repository.
Additionally, the company said the investigation into the OAuth token attack revealed an unrelated issue that involved the discovery of an unspecified "number of plaintext user credentials for the npm registry that were captured in internal logs following the integration of npm into GitHub logging systems."
GitHub noted that it mitigated the problem prior to the discovery of the attack campaign and that it had purged the logs containing the plaintext credentials.
The OAuth theft, which GitHub uncovered on April 12, concerned an unidentified actor taking advantage of stolen OAuth user tokens issued to two third-party OAuth integrators, Heroku and Travis CI, to download data from dozens of organizations, including NPM.
The Microsoft-owned subsidiary, earlier this month, called the campaign "highly targeted" in nature, adding "the attacker was only listing organizations in order to identify accounts to selectively target for listing and downloading private repositories."
Heroku has since acknowledged that the theft of GitHub integration OAuth tokens further involved unauthorized access to an internal customer database, prompting the company to reset all user passwords.
Heroku Forces User Password Resets Following GitHub OAuth Token Theft
7.5.22 Incindent Thehackernews
Salesforce-owned subsidiary Heroku on Thursday acknowledged that the theft of GitHub integration OAuth tokens further involved unauthorized access to an internal customer database.
The company, in an updated notification, revealed that a compromised token was abused to breach the database and "exfiltrate the hashed and salted passwords for customers' user accounts."
As a consequence, Salesforce said it's resetting all Heroku user passwords and ensuring that potentially affected credentials are refreshed. It also emphasized that internal Heroku credentials were rotated and extra detections have been put in place.
The attack campaign, which GitHub discovered on April 12, related to an unidentified actor leveraging stolen OAuth user tokens issued to two third-party OAuth integrators, Heroku and Travis-CI, to download data from dozens of organizations, including NPM.
The timeline of events as shared by the cloud platform is as follows -
April 7, 2022 - Threat actor obtains access to a Heroku database and downloads stored customer OAuth access tokens used for GitHub integration.
April 8, 2022 - Attacker enumerates metadata about customer repositories using the stolen tokens.
April 9, 2022 - Attacker downloads a subset of Heroku private repositories from GitHub
GitHub, last week, characterized the attack as highly targeted, adding the adversary was "only listing organizations in order to identify accounts to selectively target for listing and downloading private repositories."
Heroku has since revoked all the access tokens and removed support for deploying apps from GitHub through the Heroku Dashboard to ascertain that "the integration is secure before we re-enable this functionality."
Thousands of Borrowers' Data Exposed from ENCollect Debt Collection Service
7.5.22 Incindent Thehackernews
An ElasticSearch server instance that was left open on the Internet without a password contained sensitive financial information about loans from Indian and African financial services.
The leak, which was discovered by researchers from information security company UpGuard, amounted to 5.8GB and consisted of a total of 1,686,363 records.
"Those records included personal information like name, loan amount, date of birth, account number, and more," UpGuard said in a report shared with The Hacker News. "A total of 48,043 unique email addresses were in the collection, some of which were for the product administrators, corporate clients, and collection agents assigned to each case."
The exposed instance, used as data storage for a debt collection platform called ENCollect, was detected on February 16, 2022. The leaky server has since been rendered non-accessible to the public as of February 28 following intervention from the Indian Computer Emergency Response Team team (CERT-In).
ENCollect is billed as the "world's best collector's app," allowing collection agents to track loan payments, initiate legal actions as well as offer methods for delinquency management, settlements, and repossession.

UpGuard said the loans originated from lending services such as Lendingkart, IndiaLends, Shubh Loans (MyShubhLife), Centrum, Rosabo, and Accion, with the leaked information also incorporating personal details associated with the borrowers.
Furthermore, the dataset encompassed 114,747 mailing addresses, 105,974 phone numbers, and 157,403 loan amounts. A subset of these records also revealed additional information such as contact details of co-applicants, family members, and other personal references.
"Some records contained overdue amounts, the type and length of the loan, and internal notes left by collection agency staff regarding loan repayments," UpGuard said.
Although the misconfigured server has been secured, there are always chances that anyone with malicious intent may likely use the information to target users as part of scams or extortion schemes and even masquerade as loan collectors to target borrowers.
"The digitization of financial services provides many opportunities for efficiencies in processes like debt collection, but also creates unexpected risks in the supply chain," the researchers said. "Vendor solutions also create the risk for multiparty exposures when their data sets are sourced from several clients, as in this case."
Okta Says Security Breach by Lapsus$ Hackers Impacted Only Two of Its Customers
21.4.22 Incindent Thehackernews
Identity and access management provider Okta on Tuesday said it concluded its probe into the breach of a third-party vendor in late January 2022 by the LAPSUS$ extortionist gang and that it was far more limited in scope.
Stating that the "impact of the incident was significantly less than the maximum potential impact" the company had previously shared last month, Okta said the intrusion impacted only two customer tenants, down from 366 as was initially assumed.
The security event took place on January 21 when the LAPSUS$ hacking group gained unauthorized remote access to a workstation belonging to a Sitel support engineer. But it only became public knowledge nearly two months later when the adversary posted screenshots of Okta's internal systems on their Telegram channel.
In addition to accessing two active customer tenants within the SuperUser application — which is used to perform basic management functions — the hacker group is said to have viewed limited additional information in other applications like Slack and Jira, corroborating prior reports.
"Control lasted for 25 consecutive minutes on January 21, 2022," David Bradbury, Okta's chief security officer, said. "The threat actor was unable to successfully perform any configuration changes, MFA or password resets, or customer support 'impersonation' events."
"The threat actor was unable to authenticate directly to any Okta accounts," Bradbury added.
Okta, which has faced criticism for its delayed disclosure and its handling of the incident, said it has terminated its relationship with Sitel and that it's making changes to its customer support tool to "restrictively limit what information a technical support engineer can view."
GitHub Says Hackers Breached Dozens of Organizations Using Stolen OAuth Access Tokens
17.4.22 Incindent Thehackernews
Cloud-based repository hosting service GitHub on Friday revealed that it discovered evidence of an unnamed adversary capitalizing on stolen OAuth user tokens to unauthorizedly download private data from several organizations.
"An attacker abused stolen OAuth user tokens issued to two third-party OAuth integrators, Heroku and Travis-CI, to download data from dozens of organizations, including NPM," GitHub's Mike Hanley disclosed in a report.
OAuth access tokens are often used by apps and services to authorize access to specific parts of a user's data and communicate with each other without having to share the actual credentials. It's one of the most common methods used to pass authorization from a single sign-on (SSO) service to another application.
As of April 15, 2022, the list of affected OAuth applications is as follows -
Heroku Dashboard (ID: 145909)
Heroku Dashboard (ID: 628778)
Heroku Dashboard – Preview (ID: 313468)
Heroku Dashboard – Classic (ID: 363831), and
Travis CI (ID: 9216)
The OAuth tokens are not said to have been obtained via a breach of GitHub or its systems, the company said, as it doesn't store the tokens in their original, usable formats.
Additionally, GitHub warned that the threat actor may be analyzing the downloaded private repository contents from victim entities using these third-party OAuth apps to glean additional secrets that could then be leveraged to pivot to other parts of their infrastructure.
The Microsoft-owned platform noted it found early evidence of the attack campaign on April 12 when it encountered unauthorized access to its NPM production environment using a compromised AWS API key.
This AWS API key is believed to have been obtained by downloading a set of unspecified private NPM repositories using the stolen OAuth token from one of the two affected OAuth applications. GitHub said it has since revoked the access tokens associated with the affected apps.
"At this point, we assess that the attacker did not modify any packages or gain access to any user account data or credentials," the company said, adding it's still investigating to ascertain if the attacker viewed or downloaded private packages.
GitHub also said it's currently working to identify and notify all of the known-affected victim users and organizations that may be impacted as a result of this incident over the next 72 hours.
Twitch Suffers Massive 125GB Data and Source Code Leak Due to Server Misconfiguration
9.10.21 Incindent Thehackernews
Interactive livestreaming platform Twitch acknowledged a "breach" after an anonymous poster on the 4chan messaging board leaked its source code, an unreleased Steam competitor from Amazon Game Studios, details of creator payouts, proprietary software development kits, and other internal tools.
The Amazon-owned service said it's "working with urgency to understand the extent of this," adding the data was exposed "due to an error in a Twitch server configuration change that was subsequently accessed by a malicious third party."
"At this time, we have no indication that login credentials have been exposed," Twitch noted in a post published late Wednesday. "Additionally, full credit card numbers are not stored by Twitch, so full credit card numbers were not exposed."
The forum user claimed the hack is designed to "foster more disruption and competition in the online video streaming space" because "their community is a disgusting toxic cesspool." The development was first reported by Video Games Chronicle, which said Twitch was internally "aware" of the leak on October 4. The leak has also been labeled as "part one," suggesting that there could be more on the way.
The massive trove, which comes in the form of a 125GB Torrent, allegedly includes —
The entirety of Twitch's source code with commit history "going back to its early beginnings"
Proprietary software development kits and internal AWS services used by Twitch
An unreleased Steam competitor, codenamed Vapor, from Amazon Game Studios
Information on other Twitch properties like IGDB and CurseForge
Creator revenue reports from 2019 to 2021
Mobile, desktop and console Twitch clients, and
Cache of internal "red teaming" tools designed to improve security
The leak of internal source code poses a serious security risk in that it allows interested parties to search for vulnerabilities in the source code. While the data doesn't include password related details, users are advised to change their credentials as a precautionary measure and turn on two-factor authentication for additional security.
Poorly Configured Apache Airflow Instances Leak Credentials for Popular Services
9.10.21 Incindent Thehackernews
Cybersecurity researchers on Monday discovered misconfigurations across older versions of Apache Airflow instances belonging to a number of high-profile companies across various sectors, resulting in the exposure of sensitive credentials for popular platforms and services such as Amazon Web Services (AWS), Binance, Google Cloud Platform (GCP), PayPal, Slack, and Stripe.
"These unsecured instances expose sensitive information of companies across the media, finance, manufacturing, information technology (IT), biotech, e-commerce, health, energy, cybersecurity, and transportation industries," Intezer said in a report shared with The Hacker News.
Originally launched in June 2015, Apache Airflow is an open-source workflow management platform that enables programmatic scheduling and monitoring of workflows on AWS, GCP, Microsoft Azure, and other third-party services. It's also one of the most popular task orchestration tools, followed by Luigi, Kubeflow, and MLflow.
It's worth stressing that the findings from Intezer concern exposed Apache Airflow managed by individuals and organizations, causing a leak of credentials associated with different applications and services, and doesn't indicate a weakness in the platforms themselves.
Some of the most common insecure coding practices uncovered by Intezer include the use of hard-coded database passwords in Python code for orchestrating workflows as well as in a feature called Variables, plaintext credentials in the "Extra" field of Connections, and cleartext keys in publicly-accessible configuration files (airflow.cfg).
Chief among the concerns associated with misconfigured Airflow instances is the leakage of credentials, making them ideal candidates for exploitation by threat actors, who can abuse the information to spread laterally and gain access to accounts and databases, thus leading to violation of data protection laws and giving the attackers an insight into the organizations' tools and packages, which could later be exploited to stage supply-chain attacks.
"If a large number of passwords are visible, a threat actor can also use this data to detect patterns and common words to infer other passwords," Intezer researchers said. "These can be leveraged in dictionary or brute-force-style attacks against other platforms."
Even more concerning is also the possibility that malware can be launched on the exposed production environments by leveraging the Variables feature to modify the container image variables to point to a different image laced with unauthorized code.
Apache Airflow, for its part, has remediated a lot of security issues with version 2.0.0 that was released in December 2020, making it critical that users of the software update to the latest version and adopt secure coding practices to prevent passwords from being exposed.
Colombian Real Estate Agency Leak Exposes Records of Over 100,000 Buyers
6.10.21 Incindent Thehackernews
More than one terabyte of data containing 5.5 million files has been left exposed, leaking personal information of over 100,000 customers of a Colombian real estate firm, according to cybersecurity company WizCase.
The breach was discovered by Ata Hakçıl and his team in a database owned by Coninsa Ramon H, a company that specializes in architecture, engineering, construction, and real estate services. "There was no need for a password or login credentials to see this information, and the data was not encrypted," the researchers said in an exclusive report shared with The Hacker News.
The data exposure is the result of a misconfigured Amazon Web Services (AWS) Simple Storage Service (S3) bucket, causing sensitive information such as clients' names, photos, and addresses to be disclosed. The details stored in the bucket range from invoices and income documents to quotes and account statements dating between 2014 and 2021. The complete list of information contained in the documents is as follows -
Full names
Phone numbers
Email addresses
Residential addresses
Amounts paid for estates, and
Asset values
In addition, the bucket is also said to contain a database backup that includes additional information such as profile pictures, usernames, and hashed passwords. Troublingly, the researchers said they also found malicious, backdoor code in the bucket that could be exploited to gain persistent access to the website and redirect unsuspecting visitors to fraudulent pages.
It's not immediately clear if these files were put to use by bad actors in any campaign. Coninsa Ramon H did not respond to inquiries from The Hacker News sent via email regarding the vulnerability.
"Based on viewing a sample of the documents, […] the misconfiguration revealed $140 to $200 billion in transactions, or an annual transaction history of at least $46 billion," the researchers said. "For perspective, that's roughly 14% of Colombia's total economy."
The highly confidential nature of the data contained within the database makes it highly susceptible to exploitation by cybercriminals to mount phishing attacks and conduct a variety of fraud or scam activities, including tricking users into making additional payments and worse, reveal more personally identifiable information by tampering with the website's backend infrastructure.
Hackers Leak VPN Account Passwords From 87,000 Fortinet FortiGate Devices
10.9.21 Incindent Thehackernews
Network security solutions provider Fortinet confirmed that a malicious actor had unauthorizedly disclosed VPN login names and passwords associated with 87,000 FortiGate SSL-VPN devices.
"These credentials were obtained from systems that remained unpatched against CVE-2018-13379 at the time of the actor's scan. While they may have since been patched, if the passwords were not reset, they remain vulnerable," the company said in a statement on Wednesday.
The disclosure comes after the threat actor leaked a list of Fortinet credentials for free on a new Russian-speaking forum called RAMP that launched in July 2021 as well as on Groove ransomware's data leak site, with Advanced Intel noting that the "breach list contains raw access to the top companies" spanning across 74 countries, including India, Taiwan, Italy, France, and Israel. "2,959 out of 22,500 victims are U.S. entities," the researchers said.
CVE-2018-13379 relates to a path traversal vulnerability in the FortiOS SSL VPN web portal, which allows unauthenticated attackers to read arbitrary system files, including the session file, which contains usernames and passwords stored in plaintext.
Although the bug was rectified in May 2019, the security weakness has been repeatedly exploited by multiple adversaries to deploy an array of malicious payloads on unpatched devices, prompting Fortinet to issue a series of advisories in August 2019, July 2020, April 2021, and again in June 2021, urging customers to upgrade affected appliances.
CVE-2018-13379 also emerged as one of the top most exploited flaws in 2020, according to a list compiled by intelligence agencies in Australia, the U.K., and the U.S. earlier this year.
In light of the leak, Fortinet is recommending companies to immediately disable all VPNs, upgrade the devices to FortiOS 5.4.13, 5.6.14, 6.0.11, or 6.2.8 and above followed by initiating an organization-wide password reset, warning that "you may remain vulnerable post-upgrade if your users' credentials were previously compromised."
38 Million Records Exposed from Microsoft Power Apps of Dozens of Organisations
25.8.21 Incindent Thehackernews
More than 38 million records from 47 different entities that rely on Microsoft's Power Apps portals platform were inadvertently left exposed online, bringing into sharp focus a "new vector of data exposure."
"The types of data varied between portals, including personal information used for COVID-19 contact tracing, COVID-19 vaccination appointments, social security numbers for job applicants, employee IDs, and millions of names and email addresses," UpGuard Research team said in a disclosure made public on Monday.
Governmental bodies like Indiana, Maryland, and New York City, and private companies such as American Airlines, Ford, J.B. Hunt, and Microsoft are said to have been impacted. Among the most sensitive information that was left in the open were 332,000 email addresses and employee IDs used by Microsoft's own global payroll services, as well as more than 85,000 records related to Business Tools Support and Mixed Reality portals.
Power Apps is a Microsoft-powered development platform for building low-code custom business apps that work across mobile and the web using prebuilt templates, in addition to offering APIs to enable access to data by other applications, including options to retrieve and store information. The company describes the service as a "suite of apps, services, and connectors, as well as a data platform, that provides a rapid development environment to build custom apps for your business needs."
But a misconfiguration in the way a portal could share and store data could lead to a scenario wherein sensitive data is made publicly accessible, resulting in a potential data leak.
"Power Apps portals have options built in for sharing data, but they also have built in data types that are inherently sensitive," the researchers said. "In cases like registration pages for COVID-19 vaccinations, there are data types that should be public, like the locations of vaccination sites and available appointment times, and sensitive data that should be private, like the personally identifying information of the people being vaccinated."
UpGuard said it notified Microsoft of the data leakage in June 24, 2021, only for the company to initially close the case, citing the behavior was "by design" but subsequently take actions to alert its government cloud customers of the issue in the wake of an abuse report filed by the security firm on July 15.
Additionally, Microsoft has released a tool called Portal Checker to diagnose any potential exposure arising out of misconfiguration reasons and has made updates so that "newly created portals will have table permissions enforced for all forms and lists irrespective of the Enable Table Permissions setting."
"While we understand (and agree with) Microsoft's position that the issue here is not strictly a software vulnerability, it is a platform issue that requires code changes to the product, and thus should go in the same workstream as vulnerabilities," the researchers noted.
"It is a better resolution to change the product in response to observed user behaviors than to label systemic loss of data confidentiality an end user misconfiguration, allowing the problem to persist and exposing end users to the cybersecurity risk of a data breach."
MobiKwik Suffers Major Breach — KYC Data of 3.5 Million Users Exposed
30.3.2021 Incindent Thehackernews
Popular Indian mobile payments service MobiKwik on Monday came under fire after 8.2 terabytes (TB) of data belonging to millions of its users began circulating on the dark web in the aftermath of a major data breach that came to light earlier this month.
The leaked data includes sensitive personal information such as:
customer names,
hashed passwords,
email addresses,
residential addresses,
GPS locations,
list of installed apps,
partially-masked credit card numbers,
connected bank accounts and associated account numbers,
and even know your customer (KYC) documents of 3.5 million users.
Even worse, the leak also shows that MobiKwik does not delete the card information from its servers even after a user has removed them, in what's likely a breach of government regulations.
New guidelines issued by India's apex banking institution, the Reserve Bank of India, prohibit online merchants, e-commerce websites, and payment aggregators from storing card details of a customer online. The rules are set to come into effect starting July 2021.
As of July 2020, MobiKwik serves 120 million users and 3 million retailers across the country.
The data leak site, which is accessible via Tor browser and boasts of 36,099,759 records, came online after the digital wallet company vehemently denied the incident on March 4 following a report by an independent security researcher Rajshekhar Rajaharia.
"A media-crazed so-called security researcher has repeatedly over the last week presented concocted files wasting precious time of our organization while desperately trying to grab media attention," MobiKwik tweeted. "We thoroughly investigated his allegations and did not find any security lapses. The various sample text files that he has been showcasing prove nothing. Anyone can create such text files to falsely harass any company."
However, multiple users have confirmed to the contrary, finding their personal details in the "MobiKwik India data leak" site, lending credence to the breach.
"Never *ever* behave like @MobiKwik has in this thread from 25 days ago," Troy Hunt, security researcher and creator of breach notification tool Have I Been Pwned, said in a tweet, calling out the company MobiKwik's handling of the situation.
According to sources close to the incident, the compromise was originally advertised in a database leaking forum on February 24, with a hacker claiming access to 6TB data from an unnamed Paytm competitor.
Interestingly, it appears that after Rajaharia disclosed the leak, outed the company's identity, and warned MobiKwik over email, the firm simultaneously took measures to stop the hacker from downloading the data.
"We [...] lost access to main company servers, not surprising though... Cant download anything new," the hacker said in a forum post a day later, adding that partial download might have been corrupted.
"We never wanted any money anyway, so not sad. But one of the biggest hacks of KYC ever shit!!! OR SO WE THOUGHT. :( So, I guess I grow old saying I used to hack and shit. Rather than actually hacking and shit. Exciting 1 month though!!!," the hacker said, implying that the hack dated back to January, echoing Rajaharia's tweets from March 4.
But a month later, in a separate listing on March 27, the hacker claimed, "we recovered all data and it's up for sale," offering up what is alleged to be 8TB of their data for 1.5 bitcoin ($85,684.65).
However, in an interesting turn of events, plans to put the data on sale appear to have been suspended until further notice. "Only sell this to company after due verification that we are dealing with company," the hacker said in an update, implying an extortion scheme.
It's not immediately clear how the threat actor managed to gain unauthorized access to MobiKwik's servers, but the hacker said, "it'll be embarrassing for the company. story for someother time.." (sic)
The Hacker News has reached out to MobiKwik, and we will update the story if we receive a response.
30 million Americans affected by the Astoria Company data breach
26.3.2021 Incindent Securityaffairs
Researchers discovered the availability in the DarK Web of 30M of records of Americans affected by the Astoria Company data breach
Astoria Company LLC is a lead generation company that leverages on a network of websites to collect information on a person that may be looking for discounted car loans, different medical insurance, or even payday loans.
Collected data si shared with a number of partner sites (such as insurance or loan agencies), that pay per lead referral.
DATABASE SALE ON DARKWEB MARKETS
On January 26, 2021, threat intelligence team at Nightlion Security became aware of several new breached databases being sold on the Dark0de market by the popular hacking group Shiny Hunters.
The data listed for sale included 400 million Facebook users, a database allegedly containing Instagram users, and a dump allegedly containing 300 million user database from Astoria Company. The details of the Astoria Company data sale included, most notably, 40 million U.S. social security numbers (these numbers were later proven to be inflated).
Exposed records include the following fields:
Name
Email address
Date of Birth
Mobile Phone
Physical Address
IP Address
while other lead types exposed in the leak included additional information such as social security numbers, full bank account information, and even medical history. The leaked Astoria data also contained email transaction logs showing sensitive user information being transferred, unencrypted, via email.
Night Lion analysis of the data revealed the presence of:
10 million people with social security numbers, bank accounts, and drivers license numbers
10 million+ people with other exposed fields, such as credit history, medical data, home, and vehicle information.
A week later, these databases were published for sale on the Dark0de forum by user ShinyHunters.

Astoria’s data were later offered for sale on other darkweb forums by a seller that goes online with the name “Seller13.”
Nightlion researchers reported a recent blog post that claims Seller13 is a member of ShinyHunters. The experts believe that Seller 13 is “Yousef” the original broker of nearly 400 million stolen Facebook accounts.
“At this time it is unclear whether Seller13 is using the ShinyHunters name as a type of misdirection, or if the two actors are actually working together. Our conversations with Seller13 seem to indicate that he and ShinyHunters are working together.” reported Night Lion.
Investigating the alleged breach experts found a list of more than 400 domains registered to Astoria Company, LLC.
The researchers spotted several web shells and malicious scripts on Astoria’s MortgageLeads.loans domain, including Corex.php and Adminer.php.
Attackers deployed the Corex web shell URL and used a number of other exploit tools that were left on the system, including the adminer.php script. Adminer is a full-featured database management tool written in PHP. that easily allows managing any online database type, including MySQL, SQLite, MS SQL, and PostgreSQL.
“Given ShinyHunters’ tendency to hack sites using leaked credentials, our next step was to use the HiddenWWW search engine to look for publicly accessible code with potentially leaked credentials or AWS keys. The HiddenWWW search engine returned a list of potentially vulnerable URLs across a number of different Astoria domains. We then leveraged an OSINT telegram bot to ping each of the URLs and return a list of any that were valid.” continues the experts.
Night Lion’s counterintelligence team contacted Seller13, who explained to them how they were able to access Astoria’s database.
“Visiting the http://mortgageleads.loans/adminer.php URL, we noticed immediately that the admin credentials for user “adminastoria” were pre-saved, allowing anyone complete access to the database from a public URL — no authentication needed.” continues the experts.
Night Lion Security’s CEO, Vinny Troia, reported to Astoria Company the flaw in their database on January 29, 2021 and the availability of their data on Dark Web.
The company investigated the issue and discovered that a “former developer from India” was most likely responsible for intentionally, saving the credentials to the site.
The Astoria Company identified and confirmed the presence of the malicious scripts on its website and took them offline.
Experts found a total of 19 Astoria-owned domains using the same Adminer script that were taken offline after the Night Lion report to Astoria.
Billions of FBS Records Exposed in Online Trading Broker Data Leak
25.3.2021 Incindent Securityaffairs
Ata Hakcil led the team of white hat hackers from WizCase in identifying a major data leak on online trading broker FBS’ websites.
The data from FBS.com and FBS.eu comprised millions of confidential records including names, passwords, email addresses, passport numbers, national IDs, credit cards, financial transactions and more.
Were such detailed personally identifiable information (PII) to fall in the wrong hands, it could have been used in the execution of a wide range of cyber threats. The data leak was unearthed as part of WizCase’s ongoing research project that randomly scans for unsecured servers and seeks to establish who are the owners of these servers. We notified FBS of the breach so they could take appropriate action to secure the data. They got back to us a few days later and secured the server within 30 minutes.
What’s Going On
Forex, a portmanteau of foreign currency and exchange, is the process of converting one currency into another for a wide range of reasons including finance, commerce, trading and tourism. The forex trading market averages more than US$5 trillion in daily trading volume. Forex trading may be dominated by banks and global financial services but, thanks to the Internet, the average person can today dabble directly in forex, securities and commodities trading.
In the rush toward online trading though, users have entrusted terabytes of confidential data to online forex trading platforms. With financial transactions being at the core of forex trading, the nature of user data held in these trading databases is highly sensitive. This has made online trading sites a lucrative target for cybercriminals.
FBS, a major online forex trading site, left an unsecured ElasticSearch server containing almost 20TB of data and over 16 billion records. Despite containing very sensitive financial data, the server was left open without any password protection or encryption. The WizCase team found that the FBS information was accessible to anyone. The breach is a danger to both FBS and its customers. User information on online trading platforms should be well secured to prevent similar data leaks.
Who is FBS
Founded in 2009, FBS is an international online forex broker with more than 400,000 partners and 16 million traders spanning over 190 countries. It is one of the most popular online trading brokers in the world. The FBS app for the Android OS has been downloaded more than one million times on Google Play Store as of January 2021.
So large is the number of traders on FBS that every 20 seconds, an FBS client submits a request to withdraw their profit. An official trading partner of soccer giants FC Barcelona, FBS clients rake in half a billion dollars in profit each year. While FBS operates worldwide through its platforms FBS.com and FBS.eu, the company’s primary offices are in Belize and in Limassol, Cyprus.
What Was Leaked?
Nearly 20TB of data was leaked comprising more than 16 billion records. Millions of FBS users spread across the world were affected. Leaked information included the following:
PIIs such as
Names and surnames
Email addresses
Phone numbers
Billing addresses
Country
Time zone
IP addresses
Coordinates
Passport numbers
Mobile device models
Operating system
Email sent to FBS users
Social media IDs including GoogleIDs and FacebookIDs
Files uploaded by users for verification including personal photos, national ID cards, drivers licenses, birth certificates, bank account statements, utility bills and unredacted credit cards
User ID and Credit Card Photo Uploads
FBS user ID
FBS account creation date
Unencrypted passwords encoded in base64
Password reset links
Login history
Loyalty data including loyalty level, level points, prize points, total money deposited, active days, active clients, points earned and points spent
A German User’s Account
An Australian User’s Account

Plain Text (base64) Passwords
Financial details such as
User transaction details including deposited money, currency, payment system, transaction IDs, account IDs, transaction dates, number of times money was deposited, last deposit amount, last deposit date, total deposit, credit, balance, last month’s balance, interest rate, taxes, equity and margin free. Some of the transactions are really large.
A $500,000 Transaction

Each data set would on its own provide valuable information for an attacker but combining all of them makes the threat much more formidable.
What Does This Mean for FBS and Its Users?
The primary threats for FBS and its users include the following:
1. Identity Theft and Fraud
The personal identifiable information (PII) exposed by the leak could be used in fraudulent authentication across other platforms. The names, email addresses, physical address, passport numbers, driver’s license numbers, national ID numbers, phone numbers, social media IDs, credit cards, photos, financial records, and more could allow bad actors to impersonate the owner.
2. Scams, Phishing and Malware
Leaked contact information may be used to launch scam, phishing and malware attacks against FBS users. The data could be the basis for establishing trust in order to encourage clicks, malware downloads and the availing of more confidential information. Armed with the sensitive authentic data, a cybercriminal will sound more credible when they request for information over the phone or email.
3. Credit Card Fraud
To complete a card payment, FBS asks users to upload a photo of both sides of their credit/debit card. With the images accessible to bad actors, it is not difficult for the information to be used to commit credit card fraud.
4. Blackmailing
With email addresses, physical addresses, social media IDs and financial records accessible, bad actors could target for extortion users who move relatively large amounts.
5. Personal Safety
With cyber criminals having access to not just your financial transactions on FBS but also your physical address and phone number, you or your home could be the target of a robbery or burglary. Your transactions may give criminals a hint of your financial status.
6. Business Espionage
With FBS user email addresses and phone numbers readily accessible, competitors could extract this information and use it to target and lure users to their own online trading platforms. Stolen source code and information on the site’s structure also makes it easier for third parties to clone the FBS website then make minor adjustments in accordance to their needs.
7. Account Takeover
The leak exposed password reset links. With access to such sensitive information, an attacker could easily take over the account of any FBS user as long as they knew the user’s email address. Also, with the plaintext password (encoded in base64) and knowing that many people reuse passwords across platforms, cybercriminals could attempt to use the password on other platforms and take over.
This list does not cover all the risks users and organizations are exposed to from the FBS breach. Cybercriminals are continuously exploring new ways of using confidential information for nefarious ends.
As an FBS User, What Should You Do?
Air Charter Firm Solairus Aviation Suffers Data Breach
25.3.2021 Incindent Securityweek
Private aviation services provider Solairus Aviation on Tuesday announced that some employee and customer data was compromised in a security incident at third-party vendor Avianis.
In a data breach announcement on March 23, Solairus said aviation business management platform provider Avianis provided notification last December about an intrusion into Avianis' Microsoft Azure cloud platform, which hosts Solairus flight scheduling and tracking system.
An investigation into the incident has revealed that some of Solairus’ data that was hosted on that environment was indeed accessed by an unknown party.
Solairus data stored in that environment possibly includes employee and client names, along with information such as dates of birth, Social Security numbers, driver's license numbers, passport numbers, and financial account numbers, the company says.
The private aviation services provider says it has already informed some of the affected individuals, but claims that it does not have the “current addresses for all such individuals.”
The company also notes that both employees and clients should remain vigilant for any sign of unauthorized activity and to review their financial account statements for any unauthorized charges or activity. If any suspicious activity is identified, the affected individuals should immediately contact their financial institution.
“Solairus regrets the inconvenience or concern this incident may cause you. Every member of the Solairus community is important, and Solairus values your security and privacy,” the aviation services provider notes.
MangaDex Site Offline Following Hacking Incident
24.3.2021 Incindent Threatpost
A cyberattacker taunted the site about open security vulnerabilities, prompting a code review.
MangaDex, the online repository of manga animation comics, will be closed until further notice following a hacking incident.
Last week, the site reported that a cyberattacker had gained access to an administrative account, “through the reuse of a session token found in an old database leak through faulty configuration of session management.”
After remediating the issue by clearing all sessions globally, the site’s builders took a look at the code that runs MangaDex, trying to patch any vulnerabilities they came across as they went along. However, while the code review was ongoing, the same adversary was then able to access one of MangaDex’s developer accounts, stealing the site’s version-three source code. The attacker’s likely motivation was to cause “maximum disruption” to the site, according to MangaDex.
“While the attacker gained access to information not typically visible from the context of a normal user, we have not been able to confirm a full host compromised, or an up-to-date database breach,” the site announced. “As a user, we will encourage that you would assume that your data has been breached, and take precautions immediately, such as changing the passwords of any accounts that might share the same password as your MangaDex account. As a generally good security practice, password managers are highly recommended to keep your online identity secure.”
Multiple Site Vulnerabilities
The attacker also taunted the site’s operators with knowledge of security bugs in the codebase, which is the main reason that MangaDex went offline, it said.
“The attacker had updated the git repository containing the source-code leak, claiming that we had successfully patched two out of three possible CVEs,” according to a website notice posted on Sunday. “Without any way to confirm the claims, we assumed the worst-case scenario and kept the site down to further investigate.”
Volunteer-run MangaDex plans to take the time it needs to complete a site re-write that will be based on version five of the source code. That could take as long as three weeks, it estimated.
MangaDex plans to expedite its return by going online once the basic functions of version five are ready: Namely, to allow readers to read and follow manga titles and to allow groups to upload “scanlations” of comics.
“Instead of keeping up a likely vulnerable website and wasting our time and efforts playing cat-and-mouse with constant attacks from [distributed denial of service] DDoS to hacking, we have decided to take this opportunity to refocus and expedite our planned rewrite of the site,” according to the notice. “Contrary to our original plans, however, we will be launching this v.5 as soon as the minimum essential features are ready.”
The site has in the meantime invited ethical hackers to help find the security vulnerabilities claimed by the attacker in the codebase, along with any other flaws.
Potential Bug-Bounty Program
While MangaDex is for now relying on volunteers to find and rectify security vulnerabilities – the site said these helpers have already identified “a good number” of bugs – a more formal program could be in the offing.
“We are still open to any suggestions or responsible disclosures of vulnerabilities found in the leaked v.3 source code,” according to the notice. “While we have found numerous at time of writing, and have moved to patch most of it, we appreciate all attempts at helping us to find more.”
Further, it said that once the new site is live, it may implement bounties for the finds.
“We sincerely intend to improve upon the security on existing and future infrastructure, and while some of our developers have experience in the security fields, we have decided that having some form of a bug-bounty program for v.5 will only prove to be beneficial to MangaDex,” according to the notice. “As means of backing that, we intend to consider payouts depending on the severity of reported bugs. More details to be released in the near future.”
Hobby Lobby Exposes Customer Data in Cloud Misconfiguration
24.3.2021 Incindent Threatpost
The arts-and-crafts retailer left 138GB of sensitive information open to the public internet.
Arts-and-crafts retailer Hobby Lobby has suffered a cloud-bucket misconfiguration, exposing a raft of customer information, according to a report.
An independent security researcher who goes by the handle “Boogeyman” uncovered the issue and reported it to Motherboard in an online chat, according to a Vice writeup.
The researcher said that customer names, partial payment-card details, phone numbers, and physical and email addresses were all caught up in the leak – along with source code for the company’s app, and employee names and email addresses.
Boogeyman offered screenshots verifying the exposure of the data, which totaled 138GB and impacted around 300,000 customers. It was housed in an Amazon Web Services (AWS) cloud database that was misconfigured to be publicly accessible. The issue is now resolved, but it’s unclear if any malicious actors tapped the information before the database was secure.
“We identified the access control involved and have taken steps to secure the system,” Hobby Lobby told Motherboard. Threatpost has reached out to Hobby Lobby to independently confirm the issue.
Cloud Misconfigurations: A Cyberthreat Attack Vector
Cloud misconfigurations are a common threat vector for organizations of all sizes. For instance, an analysis last fall found that 6 percent of all Google Cloud buckets are misconfigured and left open to the public internet, for anyone to access their contents.
“The Hobby Lobby incident is the latest example of why we need to take public cloud threat vectors so seriously,” said Douglas Murray, CEO at Valtix, told Threatpost. “In 2020, spend in public cloud exceeded spend in on-prem data centers for the first time. The hackers are doing their own version of ‘lift and shift’ and are aggressively moving to where the market is going. Just as concerning is that for every Hobby Lobby like leak that we learn about, there is another that goes undetected.”
Hank Schless, senior manager of security solutions at Lookout, noted that such misconfigurations are easy to do.
“Misconfigured cloud resources are frequently the cause of data breaches like this one,” he told Threatpost. “Organizations that have transitioned to the cloud have massive infrastructure that spans thousands of host servers and other services. Amazon’s S3 service is the base data storage offering for AWS, which means it’s simple to set up and integrate S3 buckets into cloud infrastructure. Unfortunately, that simplicity they offer and the speed at which organizations scale these services up and down oftentimes means the configuration of these buckets is overlooked and the data inside is left exposed.”
He added to mitigate the risk of a breach, organizations need to be sure they secure every aspect of their infrastructure from the individual endpoint all the way up to the cloud service itself.
“Advanced cloud access security broker (CASB) technology helps secure access to these resources,” he said. “Coupling CASB with a security posture management tool ensures secure access and configuration of cloud infrastructure. Cloud providers offer countless supporting services and integrations that help teams build a well-architected infrastructure. Leveraging these services should be done in tandem with security teams to ensure there aren’t any misconfigurations that leave data exposed or violate compliance policies.”
Shell Says Personal, Corporate Data Stolen in Accellion Security Incident
23.3.2021 Incindent Securityweek
Oil and gas giant Royal Dutch Shell (Shell) is the latest company to have confirmed impact from the December 2020 cyber-attack on Accellion’s File Transfer Appliance (FTA) file sharing service.
A legacy service designed to allow for the sharing of large files, Accellion’s FTA service fell victim to a cyber-attack in December 2020, when hackers exploited zero-day vulnerabilities to gain access to customer data.
The soon-to-be-retired service had roughly 300 customers at the time, with up to 25 of them suffering significant data compromise following the incident.
Some of those to have already confirmed impact include U.S.-based grocery and pharmacy chain Kroger, law firm Jones Day, information security and compliance solutions provider Qualys, Australian health and transport agencies, the Office of the Washington State Auditor (SAO), the Reserve Bank of New Zealand, and jet maker Bombardier.
In a data breach notification last week, Shell confirmed that it too was affected by the security incident.
Shell says that it worked with Accellion to immediately address the security holes, while also launching an investigation into the incident. To date, the investigation hasn’t revealed impact on Shell’s core IT systems – the FTA service is isolated from Shell’s infrastructure.
“The ongoing investigation has shown that an unauthorized party gained access to various files during a limited window of time. Some contained personal data and others included data from Shell companies and some of their stakeholders,” the company says.
Shell also notes that it is in contact with the individuals and stakeholders that have been affected, to address any possible risks associated with the data breach, but hasn’t disclosed the exact number of impacted entities. Regulators and authorities were also alerted on the matter.
“Cyber security and personal data privacy are important for Shell and we work continuously to improve our information risk management practices,” Shell also notes.
Data Breaches Tracker monitor unsecured ElasticSearch servers online
18.3.2021 Incindent Securityaffairs
Cybersecurity research at WizCase, an online security and privacy portal, built a tool to track accessible ElasticSearch servers on the internet.
Cybersecurity research at WizCase, an online security and privacy portal, developed a tool that allows track accessible ElasticSearch servers on the Internet.
The tool scans the web for accessible ElasticSearch servers and displays different variables such as the total number of running Elasticsearch instances, a breakdown of secure vs insecure servers and more.
More specifically – the tool is tracking the number of servers attacked by “Meow,” interestingly the experts noticed a quite significant rise in the number of servers wiped the first week of March. According to the experts over 2500 servers have been erased within a few days.
As it’s always hard to figure out the amount of data exposed due to misconfiguration, here the tool: https://www.wizcase.com/tools/data-breaches-tracker/.
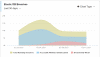
A recent scan performed on March 15th, 2021 provided the following results:
Total number of Servers Scanned 334,013
Total number of Running instances 9,202
Total number of Servers accessible without authorization 5,740
Total size of Servers accessible without authorization 9 TB
Total number of Records exposed in servers accessible without authorization17,830,145,680
Total number of Servers accessible without authorization hit by Meow 1,362
Breach Exposes Data of 200K Health System Staff, Patients
13.3.2021 Incindent Securityweek
A medical practice management firm that provides support to Tacoma-based MultiCare Health System has alerted over 200,000 patients, providers and staff that their personal information may have been exposed.
Woodcreek Provider Services announced Tuesday that after a ransomware attack of its tech vendor, the information was retrieved upon paying an undisclosed ransom, The News Tribune reported.
Woodcreek says an investigation by its vendor, Netgain Technology, determined the breach happened sometime between November 24 and December 3, 2020, although it’s possible that it happened as early as September.
“The server containing Woodcreek’s medical records system was untouched; however, scanned clinical and financial data and other business records on an archive server was stolen by the attackers,” the company said Tuesday.
The attack allowed access to personal information which for some includes Social Security numbers, dates of birth and other data.
On Feb. 17, counsel for Woodcreek notified the Washington state Attorney General’s Office that it would send notifications to more than 200,000 people whose information was potentially compromised.
In response to questions from The News Tribune on Tuesday about the breach, MultiCare noted the breach was isolated to Woodcreek’s server and said that Woodcreek manages “a small number of pediatric clinics in the Puget Sound region for Mary Bridge Children’s Hospital and Health Network.”
The health system said that it “deeply regrets that this breach has occurred on a vendor platform of one of our affiliated providers.”
Breach Exposes Verkada Security Camera Footage at Tesla, Cloudflare
11.3.2021 Incindent Threatpost
Surveillance footage from companies such as Tesla as well as hospitals, prisons, police departments and schools was accessed in the hack.
Hackers claim to have breached Silicon Valley startup Verkada to gain unauthorized access to live feeds of 150,000 security cameras. They claim, the hack gave them widespread access to surveillance footage within companies such as Tesla and Cloudflare, as well as hospitals, companies, law-enforcement departments, schools and prisons.
The group provided video footage from cameras managed by San Mateo, Calif.-based Verkada to Bloomberg to prove the success of their breach, according to a report published on the news outlet’s website. Verkada provides and manages a web-based network of security cameras to customers and claims to be a more secure and scalable alternative to on-premises solutions for video surveillance.
The breach represents a broad vision of the privacy and security violations that can occur if video surveillance footage falls into the wrong hands. It also is very likely to put Verkada in regulatory and legal hot water once investigations are complete, security experts said.
The hacker collective, which call themselves “Advanced Persistent Threat 69420,” claimed they accessed security cameras from inside Florida hospital Halifax Health, with some of the footage viewed by Bloomberg appearing to show eight hospital staffers tackling a man and then holding him down on a bed.
Other footage viewed by Bloomberg appeared to be inside a Tesla factory in Shanghai, showing workers on an assembly line. The hackers claimed they accessed 222 cameras displaying activity inside Tesla factories and warehouses.
Bloomberg said it also viewed surveillance footage from a police station in Stoughton, Massachusetts. Meanwhile, the hackers told the publication that they also gained access to the security cameras of Sandy Hook Elementary School in Newtown, Connecticut, where a gunman killed more than 20 people in 2012; 330 security cameras inside the Madison County Jail in Huntsville, Alabama; cameras of multiple locations of the luxury gym chain Equinox; surveillance footage from the ICU of Wadley Regional Medical Center, a hospital in Texarkana, Texas; and cameras at Tempe St. Luke’s Hospital, in Arizona, according to the report.
Tillie Kottmann, one of the hackers who claimed credit for the incident, told Bloomberg the group’s intention behind the breach was to demonstrate the extent to which video surveillance exists – but also how easy it is to break into these systems and expose sensitive and private footage.
Kottmann cited “lots of curiosity, fighting for freedom of information and against intellectual property, a huge dose of anti-capitalism, a hint of anarchism — and it’s also just too much fun not to do it” as reasons for hacking into Verkada, according to the report. Previous breaches for which the group claimed responsibility include incidents at Intel and Nissan.
The Hack: Gaining Admin Privileges
In this instance, the group gained access to Verkada through a “Super Admin” account, by using a username and password for an administrator account that was publicly exposed on the internet. This gave them access to the cameras of all of the company’s customers, Kottmann told Bloomberg. After the publication contacted Verkada, the hackers lost access to the video feeds and archives, the group said, according to the report.
This method shows the type of downstream impact of email-based attacks such as spear-phishing attacks, which use social engineering to fool a company’s employees to hand over credentials, one security expert observed.
“It’s very likely that this was done through a phishing attack that was made more convincing through social engineering,” said Hank Schless, senior manager of security solutions at Lookout in an email to Threatpost. “Attackers have also been known to target lower-level employees and phish their credentials, only to move laterally through the infrastructure once they have access.”
Ongoing Investigations into Verkada Breach
Verkada did not immediately return request for comment about the attack and the company’s mitigation efforts on Wednesday morning. A Verkada spokesperson told Bloomberg in a statement that the company disabled all internal administrator accounts to prevent any unauthorized access.
“Our internal security team and external security firm are investigating the scale and scope of this issue, and we have notified law enforcement,” the spokesperson said.
Verkada’s CISO, an internal team and an external security firm are currently investigating the incident, and the company is in the process of notifying customers and setting up a support line to field questions and requests for assistance, according to Bloomberg.
No matter what the company’s findings reveal, Verkada will surely face tough questions and scrutiny as well as regulatory investigations and potential lawsuits over the incident, which once again demonstrates the security issues with making sensitive data accessible on cloud-based networks, observed Rick Holland, CISO at security firm Digital Shadows.
“The Verkada intrusion is an example of the risks associated with outsourcing services to cloud providers,” he said in an email to Threatpost. “You don’t always get more secure when you outsource your security to a third party.”
Moreover, the Department of Health and Human Services (HHS) will probably launch an investigation into Verkada and the breach for HIPAA/HITECH violations, as surveillance footage can be considered protected health information, Holland said.
Other regulatory and legal trouble also might be on the way for the company, he added: “GDPR violations of personal data could have also occurred, and class action lawsuits could also be on the horizon,” Holland said.
White hat hackers gained access more than 150,000 surveillance cameras
11.3.2021 Incindent Securityaffairs
A group of hackers claimed to have compromised more than 150,000 surveillance cameras at banks, jails, schools, and prominent companies like Tesla and Equinox.
A group of US hackers claimed to have gained access to footage from 150,000 security cameras at banks, jails, schools, healthcare clinics, and prominent organizations. The news was first reported by Bloomberg News who reported its to Verkada.
Hackers also posted images captured from the hacked surveillance video on Twitter with an #OperationPanopticon hashtag.
The hacker also published a series of images as proof of the hack, some of them show that they have gained root shell access to the surveillance cameras used by Telsa and Cloudflare.

Tillie Kottmann’s Tweet
One of the members of the group, Tillie Kottmann, revealed that they have gained access to these surveillance cameras using a super admin account for the surveillance company Verkada.
According to BleepingComputer, Kottmann has performed reverse engineering of the firmware used by Verkada and discovered hardcoded credentials for a super admin account.
Once Verkada became aware of the hack, it has disabled all internal administrator accounts to prevent any unauthorised access.
“We have disabled all internal administrator accounts to prevent any unauthorised access.” a Verkada spokesperson told the BBC. “Our internal security team and external security firm are investigating the scale and scope of this issue, and we have notified law enforcement.”
“This afternoon we were alerted that the Verkada security camera system that monitors main entry points and main thoroughfares in a handful of Cloudflare offices may have been compromised.” Cloudflare spokesperson told the BBC:
“The cameras were located in a handful of offices that have been officially closed for several months.”
When asked about the motivation behind the hack, Kottmann explained that the reasons were, “lots of curiosity, fighting for freedom of information and against intellectual property, a huge dose of anti-capitalism, a hint of anarchism – and it’s also just too much fun not to do it”.
Hackers Breach Cameras at Banks, Jails, Tesla and More
11.3.2021 Incindent Securityweek
A US hacker collective on Tuesday claimed to have tapped into footage from 150,000 security cameras at banks, jails, schools, carmaker Tesla and other sites to expose "the surveillance state."
Images captured from hacked surveillance video were posted on Twitter with an #OperationPanopticon hashtag.
"What if we just absolutely ended surveillance capitalism in two days?" a purported member of a group called APT-69420 Arson Cats asked amid a string of tweeted images.
"This is the tip of the tip of the tip of the iceberg."
The hacker group claimed to have ferreted out credentials of an high level administrator account at Silicon Valley firm Verkada, which runs a platform operating security systems online.
"We have disabled all internal administrator accounts to prevent any unauthorized access," a Verkada spokesperson said in response to an AFP inquiry.
"Our internal security team and external security firm are investigating the scale and scope of this issue, and we have notified law enforcement."
Verkada added that it has notified companies that rely on its platform.
Surveillance camera imagery posted on Twitter included a jail cell block and a man wearing a fake beard dancing in a bank storage room.
The Verkada breach shows the risk of outsourcing security surveillance to companies in the internet cloud, according to Rick Holland, chief information security officer at Digital Shadows, a risk protection firm.
"Verkada positions itself as a 'more secure, scalable' alternative to on-premises network video recorders," Holland said.
"You don't always get more secure when you outsource your security to a third party."
He said he expected the breach to trigger investigations by privacy regulators in the US and Europe.
Hackers breached four prominent underground cybercrime forums
7.3.2021 Incindent Securityaffairs
A suspicious wave of attacks resulted in the hack of four cybercrime forums Verified, Crdclub, Exploit, and Maza since January.
Since January, a series of mysterious cyberattacks that resulted in the hack of popular Russian-language cybercrime forums.
Unknown threat actors hacked the Verified forum in January, Crdclub in February, and Exploit and Maza in March, the attackers also leaked stolen data and in some cases they offered it for sale.
“Since the beginning of the year, Intel 471 has observed four well-known cybercriminal forums dealing with a breach, including two since the beginning of March.” reads the post published by threat intelligence firm Intel 471. “Intel 471 does not know who is responsible for the hacks, but due to their public nature, we think it is unlikely that this is a law enforcement operation.”
The nature of the data breaches leads the experts into excluding that the hacks were the result of law enforcement operations.
In January, experts noticed on the popular Raid Forums an advertisement for the Verified’s database containing registered users’ data and their private messages, posts, and threads. The database was offered for sale for US $100,000. The attackers also managed to transfer $150,000 worth of cryptocurrency from Verified’s wallet to a wallet under his control.
In February, the administrator of the cybercrime forum Crdclub discloses a cyber attack that resulted in the hack of the administrator’s account.
“By doing so, the actor behind the attack was able to lure forum customers to use a money transfer service that was allegedly vouched for by the forum’s admins. That was a lie, and resulted in an unknown amount of money being diverted from the forum.” continues Intel 471. “The forum’s admins promised to reimburse those who were defrauded. No other information looked to be compromised in the attack.”
In March, the cybercrime forums Exploit and Maza were hacked, the attackers also gained secure shell (SSH) access to an Exploit proxy server destined for distributed denial-of-service (DDoS) protection, and also attempted to dump network traffic.
This week, the administrator of the Exploit cybercrime forum disclosed an unauthorized secure shell (SSH) access to a proxy server used for protection from distributed denial-of-service (DDoS) attacks, he also observed an attempt to dump network traffic.
This week also the Maza cybercrime forum was hacked, its members were redirected to a breach notification page upon signing in. The notice also included a PDF file allegedly containing data of forum users (i.e. usernames, partially obfuscated password hashes, email addresses). Intel 471 researchers confirmed that Maza’s database were breached by the attackers.

Source FlashPoint
The hack of the Maza cybercrime forum was also reported by researchers at Flashpoint.
“Flashpoint analysts successfully obtained the purported leaked data. While the compromised data appears to be extensive, it’s worth noting that the passwords have been hashed and most other data fields included in the dump have been hashed or further obfuscated.” reads Flashpoint. “The leaked Maza data includes the following:
User id
Username
email
Password (hashed and obfuscated)
Crt_filename
Crt_pass
Icq (when available)
Aim (when available)
Yahoo (when available)
Msn (when available)
Skype (when available)“
“Users on the Exploit forum are discussing moving away from using emails to register on forums as recent disruption efforts may have increased exposure of their online activities. Others are claiming that the database leaked by the attackers is either old or incomplete,” Flashpoint concludes.
Millions of travelers of several airlines impacted by SITA data breach
6.3.2021 Incindent Securityaffairs
SITA, a multinational IT company that provides services to the air transport industry was the victim of cyberattack that impacted multiple airlines.
SITA is a multinational information technology company providing IT and telecommunication services to the air transport industry. The company provides its services to around 400 members and 2,800 customers worldwide, which it claims is about 90% of the world’s airline business. Around the world, nearly every passenger flight relies on SITA technology.
This week the company announced it has suffered a highly sophisticated, hackers had access to certain passenger data stored on servers of SITA Passenger Service System (PSS). The total number of travelers impacted in the security breach is still unknown.
“Passenger Service System (US) Inc. (“SITA PSS”) operates passenger processing systems for airlines. After confirmation of the seriousness of the data security incident on February 24, 2021, SITA took immediate action to contact affected SITA PSS customers and all related organizations,” reads the company’s statement.
“SITA acted swiftly and initiated targeted containment measures. The matter remains under continued investigation by SITA’s Security Incident Response Team with the support of leading external experts in cyber-security.”

The cyberattack impacted multiple airlines, including Singapore Airlines, Lufthansa, Malaysia Airlines, Cathay Pacific, SAS-Scandinavian Airlines, Finland’s Finnair, Jeju Air, and Air New Zealand.
Singapore Airlines disclosed the security breach this week, the airline confirmed that approximately 580,000 members of its KrisFlyer frequent flyer program have been impacted.
The airline notified its customers and informed them that it doesn’t use the SITA PSS, but at least one of the 26 Star Alliance member airlines use the PSS system, and SITA has access to some frequent flyer program data for all Star Alliance airlines.
“Star Alliance received a notification from SITA about the PSS breach on February 27. Star Alliance says that they were informed that not all its member carriers are affected, but it does not exclude this possibility.” reported BleepingComputer.
According to the impacted airlines, intruders have had access to some customers’ data, including name, tier status, and membership number. At the time of this writing, there is no indication that any sensitive or financial data compromised.
Multiple Airlines Impacted by Data Breach at Aviation IT Firm SITA
6.3.2021 Incindent Securityweek
SITA, a multinational company that specializes in air transport communications and IT, this week confirmed falling victim to a cyberattack that appears to have impacted multiple airlines around the world.
SITA said on Thursday that the attack, which it described as “highly sophisticated,” affected certain passenger data stored on servers of SITA Passenger Service System (PSS) Inc., which operates passenger processing systems for airlines.
“After confirmation of the seriousness of the data security incident on February 24, 2021, SITA took immediate action to contact affected SITA PSS customers and all related organizations,” the company said in a statement.
It added, “SITA acted swiftly and initiated targeted containment measures. The matter remains under continued investigation by SITA’s Security Incident Response Team with the support of leading external experts in cyber-security.”
Several airlines have confirmed being affected by the breach, including Singapore Airlines, Malaysia Airlines, Finland’s Finnair, Jeju Air in South Korean, and Air New Zealand.
Singapore Airlines told customers that it’s not a customer of the SITA PSS, but since at least one of the 26 Star Alliance member airlines is a PSS customer, SITA has access to some frequent flyer program data for all Star Alliance airlines. Star Alliance is the world’s largest global airline network.
“All Star Alliance member airlines provide a restricted set of frequent flyer programme data to the alliance, which is then sent on to other member airlines to reside in their respective passenger service systems. This data transfer is necessary to enable verification of the membership tier status, and to accord to member airlines’ customers the relevant benefits while travelling,” Singapore Airlines explained.
Singapore Airlines said roughly 580,000 members of its KrisFlyer and PPS programs are affected by the breach at SITA.
Based on the notifications sent by impacted airlines to their customers, only information such as name, tier status and membership number has been compromised. However, this type of information can still be useful for targeted phishing attacks. There is no indication at this time that passwords, payment card information, passport numbers, reservations, or contact information has been compromised.
According to its website, SITA has more than 2,500 customers and has a presence in over 1,000 airports across 200 countries and territories.
Someone Is Hacking Cybercrime Forums and Leaking User Data
6.3.2021 Incindent Securityweek
Since the beginning of this year, an unknown threat actor has been hacking cybercrime forums and leaking user data publicly or offering it for sale.
At least four such forums have been breached to date, namely Verified in January, Crdclub in February, and Exploit and Maza in March. All are predominantly Russian-language forums and saw their breaches publicly disclosed elsewhere.
Intelligence firm Intel 471, which has been closely following the hacks, says that, while the identity of the actor behind the attacks is unknown, the public nature of the attacks eliminates the possibility of a law enforcement operation.
In January, a threat actor announced on underground forum Raid Forums that they breached Verified, an established Russian-language cybercrime forum. The adversary said they had Verified’s entire database, containing details on all registered users, including private messages, posts, threads, and hashed passwords.
The hacker, who apparently was able to transfer $150,000 worth of cryptocurrency out of Verified’s wallet, was offering the database for $100,000.
In February, the administrator account of cybercrime forum Crdclub was hacked, which allowed the threat actor behind the compromise to lure forum customers into using a fraudulent money transfer service and divert an unknown amount of money from the forum.
This week, both the Exploit and Maza underground forums were hacked. The attacker apparently gained secure shell (SSH) access to an Exploit proxy server destined for distributed denial-of-service (DDoS) protection, and also attempted to dump network traffic.
“Users on the Exploit forum are discussing moving away from using emails to register on forums as recent disruption efforts may have increased exposure of their online activities. Others are claiming that the database leaked by the attackers is either old or incomplete,” threat intelligence company Flashpoint notes.
Maza, an invite-only cybercrime forum active since 2003, was displaying a data breach notification on March 3, most likely the work of the hacker who managed to take over the forum.
A PDF file accompanying the announcement contained over 3,000 rows, including usernames, email addresses, various contact details, and partially obfuscated password hashes.
“Our initial analysis found that a portion of the leaked data correlated with our previous research findings, which confirms that at least some of Maza’s databases was breached,” Intel 471 said.
To date, no one appears to have claimed responsibility for the breaches, but the perpetrator’s actions could provide security researchers with increased visibility into who is using these cybercrime forums.
Malaysia Air Downplays Frequent-Flyer Program Data Breach
4.3.2021 Incindent Threatpost
A third-party IT provider exposed valuable airline data that experts say could be a goldmine for cybercriminals.
Malaysia Airlines sent out an email to frequent flyer program members assuring them that there’s “no evidence” their personal data has been misused in the wake of a supply-chain attack via a third-party vendor.
However, experts think that’s unlikely. And, they say the repercussions could be significant.
Malaysia Airlines’ frequent flyer program, Enrich, was breached sometime around March 2010 — and remained exposed until June 2019, leaving thousands of members’ personal data, including name, date of birth, gender, contact information, ID number, status and tier level unprotected, an email sent out to members from the company said.
Malaysia Airlines hasn’t released a formal statement, but its official Twitter account @MAS offered some explanation in a Mar. 1 response to a user, linking to news of the breach.
“…The data security incident occurred at our third-party IT service provider and not Malaysia Airlines’ computer systems.” the airline’s account responded. “However, the airline is monitoring any suspicious activity concerning its members’ accounts and in constant contact with the affected IT service provider to secure Enrich members’ data and investigate the incident’s scope and causes.”
A subsequent tweet from the airline added, “Kindly note that Malaysia Airlines has no evidence that the incident affected any account passwords. We nevertheless encourage members to change their passwords as a precautionary measure.”
Threatpost’s requests for comment from Malaysia Air’s press and privacy offices have not yet received a response.
The Threat of Breached Malaysia Air Data
Stolen personal data collected from sources like loyalty programs can be pieced together with other details to create a full, incredibly detailed profile of a victim, which can be used in attacks ranging from socially engineered spear-phishing campaigns to straightforward fraud.
The attackers’ persistence demonstrates how much value they saw in the Malaysia Air data, Purandar Das, CEO of security firm Sotero, said — along with showcasing a lack of defenses.
“This stolen data forms a part of the consumer’s profile that is created by data stolen from many locations,” Das explained. “The fact that this breach happened over a long period of time without detection indicates the lack of security at the service provider.”
Das added the hackers likely wouldn’t have hung around if they weren’t using the stolen personal details for profit.
“It is also unlikely that this data was not used for wrong reasons if the breach lasted as long it did,” he said. “If the data was useless, the hackers would have moved on. It is time for organizations to take control of their data and its protection, even when it is in the hands of service providers.”
Airlines are an ideal target for bad actors trying to build these intricate consumer profiles.
“Airlines in general are a high-profile target, with loyalty data that can be easily monetized, and huge volumes of data, including often a large volume of payment data, as was seen in the British Airways breach,” Andrew Barratt, cybersecurity advisor with Coalfire, told Threatpost.
Why the Timeframe Matters
First, Barratt told Threatpost the nine-year window offered by Malaysia Air for the exposure tells him the service provider lacked any kind of regular security monitoring that would have helped pinpoint the attack timing.
He added that the airline could face regulatory repercussions too, since the high-profile 2014 disappearance of Malaysia Air 370 was within that timeframe.
“The question here is whether it happened within the nine-year period and they did not disclose until now or if it happened within the nine years and they just found out now,” Brandon Hoffman from Netenrich told Threatpost by email. “Based on the oddly specific, nine-year window, it seems likely that this issue persisted for all the nine years, or happened nine years ago, and they are just discovering it. If that turns out to be the case, then there is a whole different set of issues and that need to be addressed from a cyber-hygiene perspective.”
Third-Party Service Providers Are Easy Cyber-Targets
Malaysia Air is just the latest organization to fall prey to a supply chain attack of a third-party IT service provider.
“This seems like the inflection point of two themes at the moment – a continued assault on third-party service providers, that are then leveraged to gain access to other parties and high-profile businesses that perhaps don’t have the appropriate third-party review programs in place,” Barratt said.
In the recent attack on SolarWinds, threat actors used trojanized updates to access some of the most sensitive data available within the United States government. FTA, a file-sharing service from Accellion was meanwhile weaponized against its biggest customers starting last December, including law firm Jones Day, with more victims likely to surface in the months to come, according to experts.
Third-party service providers are and will continue to be a prime point of attack for cybercriminals.
“The reason is fairly simple. Service providers are less organized in terms of security,” Das said. “Their infrastructure is less secure and more easily penetrated. Hackers target them knowing that their access to potentially valuable data is easier [to crack]. ”
Basic due diligence, continuous monitoring and an increased focus on vendor security are critical to staving off this type of attack, Chris Clements from Cerberus Sentinel explained.
“One of the worst aspects of supply chain attack compromises is that it can be even harder to detect than a direct breach of an organization,” Clements said. “Now more than ever, businesses need to fully vet and actively manage vendors who may be able to access sensitive systems or data.”
Data Breach: Turkish legal advising company exposed over 15,000 clients
27.2.2021 Incindent Securityaffairs
Data Breach: WizCase team uncovered a massive data leak containing private information about Turkish Citizens through a misconfigured Amazon S3 bucket.
The server contained 55,000 court papers regarding over 15,000 legal cases, which affected hundreds of thousands of people.
What’s Going On?
Our online security team has uncovered a massive data breach originating from a misconfigured Amazon Bucket, which was operated by a Turkish Legal advising company, INOVA YÖNETIM & AKTÜERYAL DANIªMANLIK. Inova is an actuarial consultancy company, which means they compile statistical analysis and calculate insurance risks and premiums. Inova has been operating since 2012 and has handled thousands of cases since then.
While Amazon offers the necessary tools to secure their services, Inova has not implemented these measures properly.
Data leak discovered: 30.09.2020
Inova contacted: 01.10.2020
Amazon contacted: 06.10.2020
Turkish CERT contacted: 05.10.2020
Response received: –
Server secured: 12.10.2020
After further investigation, we have concluded that these documents belonged to people injured or deceased in traffic accidents. All court cases had several types of documents containing the following info regarding the victim:
PII’s such as:
Name and Surname
National ID number
Gender
Marital Status
Birthdate
Details about the insurance such as:
Insurance Company Details/Name
Dossier No
Policy Issuance date
Victim’s past and future expected salary
Accident details such as:
Accident’s/Death’s date
Report Date
Fault rate
Document included in every court case, showing personal information about the victim
Document showing victims salary before the accident as well as expected future salary prior to the accident
Some of the court cases had more information about the victim or involved other people. This included parties such as victims beneficiaries, other parties involved in the accident, police officers, prosecutors.
While investigating, we have also stumbled upon the following kinds of documents:
Documents sent to insurance companies containing:
Name and surname of involved parties
Vehicle license plates
Date of accident
Severity of the injuries
Incident reports taken at the accident site by the police officers containing:
Detailed information about how the accident took place
Vehicles involved and damages caused to them
Both parties insurance information
Drivers names, surnames, national ID’s, birthdates, phone numbers, driver’s license information
A summary of the accident in handwriting
Sketch of the accident
Information about the police officers who held the report
Photocopies of drivers licenses
Photocopies of vehicle licenses
Photocopies of alcohol breathalyzer tests
Police complaints post-accident containing:
Name surname of the complainant
Mothers and fathers names
Birthplace and birthplace
Residency address
Profession
Phone number
Education level
Marital Status
Gender
Signature of the complainant
Testimony of the other party containing:
Name surname
National identifier
Mother and father’s name
Birthdate and birthplace
Residency address
Profession
Workplace address
Email
Phone number
Education level
Marital status
Gender
Signature
Judicial committee reports containing:
Name, surname
Birthdate
National ID
Birthdate
Phone number
Medical history
Reports from multiple hospitals about the victim’s injuries and the condition
Symptoms
Administered drugs
Epicrisis report
Decisions like how long the victim will need care, how long they can’t work for
Doctors name
Hospital dossier no
Advance capital value reports containing how much money is owed by the insurance to the victim,
Documents sent to court in objection to court experts’ calculation of how much insurance companies owe each of the victims
Legal papers including
Name surname
Address
National identifier
Bank account details
Power of attorney information
Emails between lawyers and the clients

Data Breach - Police report containing accident details
Police report containing accident details, as well as involved parties phone numbers, driver’s license information, name-surname, and national identifier
Sketch of the accident from the police report

Document sent to the insurance company by the victim’s lawyer
Post-trauma health report about the accident
How Did the Data Breach Happen?
This breach originated from a misconfigured Amazon S3 bucket, which contained 55,000 crucial court documents Inova was involved with. These documents’ total size was more than 20GB, and it was accessible by anyone who found the S3 bucket. They required no authorization to access, meaning anyone could access this bucket and download massive amounts of personally identifying information about Inova’s clients.
Whose Data was Exposed and What Are the Consequences
Leaked data contained information about more than 15,000 clients of Inova, people who had accidents and hired Inova between the start of 2018 and end of summer 2020. If you had a traffic accident in the last 5 years, odds are Inova was involved with your court case at some point. Although your data may not have been found by anyone else, in case any ill-intentioned hacker discovered it, here are some of the risks people exposed could face:
Phishing Scams and Malware
People whose data might have been exposed need to be extra careful since they can run into scammers masquerading as law enforcement, prosecutors, or lawyers. Scammers like this are pretty common in Turkey. The leaked information also contained the amount of relief funds victims and their families received, so scammers could target people who recently received large amounts of money from the court.
Since these documents also leaked information about the court case that only lawyers, insurance companies, and other officials should have access to, like dossier number, accident details, client details, as well as phone numbers; always be sceptical about people calling you about your past court cases and asking for money or information.
Identity theft
With large amounts of identity information being leaked about the clients in this breach, criminals can use it for identity theft. With details like a client’s beneficiaries, national ID numbers of them and their beneficiaries, and phone numbers being leaked, some of the more elaborate identity theft cases could be executed. With some social engineering, bad actors or criminals could contact a GSM operator, masquerading as the victim, and verify all kinds of verification questions GSM operators would ask to clone a SIM card.
After having access to victims’ phone calls and SMS messages, bad actors could then try to do the same operation with clients’ insurance and bank.
Corporate Espionage
Some competitive corporations will be able to contact individuals whose court information was leaked and try to convince them to hire their company instead. This is made easier since competitors will have access information from Inova’s clients.
Blackmails and Threats
Leaked documents include information such as police officers who have kept the reports; documents sent to prosecutors from police officers; names and surnames of the judicial committee members. Personal information like this could cause these individuals to be harassed or blackmailed by people involved in such cases since their identities have been leaked.
Bribing
With the amount of sensitive information in these papers, people involved in one of these cases could attempt to find and track other people involved in the case. This will lead to a rise of attempts to bribe officers to make decisions favoring them, bribe them to suppress them, or change their statements.
What Can I Do to Protect My Data?
With cases such as these, it is unusually difficult to protect your own data because it is often in the hands of the company you are working with. Make sure to send only the necessary information they need and ask them what kind of security measures they are taking to keep your private data private. If you are a European citizen, contact the company that needs your private information and ask them what kind of measures they implemented to comply with GDPR laws.
In this particular case, Turkey has its own set of laws against the improper handling of personal data, named KVKK. We highly recommend people to reach out to Inova and make sure the leak is properly handled. In any case, never trust anyone asking for personal data over the phone, if you receive calls related to your accident, please inform your contact at Inova and make sure the request comes from them.
How and Why We Discovered the Breach
At Wizcase, we are constantly scanning random parts of the internet to find data breaches and to get the data secured before criminals can find and abuse it.
As this bucket was left public, without any configuration to protect the files, it could have been discovered and accessed by anyone with the URL. We’ve seen that this bucket also contained technical logs from the company infrastructure that was not accessible to us without proper authorization. Even though authorization mechanisms were there, they were not in place to adequately protect the important files that were found inside the bucket.
Who is Wizcase?
WizCase is one of the biggest international online security websites, with content translated to 30 different languages. We provide tools, tricks, and best practices for online safety and security. This includes detailed VPN reviews and tutorials.
Our online web security team of White Hat hackers have uncovered some of the most significant data breaches, including unsecured webcams and dating site scandals.
Not only do we release our reports to the public, but we disclose them to the company as well, allowing them to secure their serves and creating a more secure environment for everyone.
Author the author: Chase Williams
Original post: https://www.wizcase.com/blog/inova-breach-research/
Health Website Leaks 8 Million COVID-19 Test Results
26.2.2021 Incindent Threatpost
A teenaged ethical hacker discovered a flawed endpoint associated with a health-department website in the state of Bengal, which exposed personally identifiable information related to test results.
Yet another human-related error — this time a flaw in a health department website in the state of Bengal, India — has exposed the confidential results of COVID-19 tests as well as personally identifying information (PII) for an entire geographic region’s population.
Test results related to more than 8 million people potentially were exposed before the agency fixed the error, according to a security researcher.
Sourajeet Majumder, a teenaged ethical hacker in India, noticed a flaw in the structure of a URL in a text informing someone of their test result from Bengal health authorities. It included a pathway for finding other people’s test results, according to a report in BleepingComputer. The error was eventually traced back to a faulty endpoint at the Health and Family Welfare Department of the state of West Bengal, according to the report.
Specifically, the structure of a URL in the text of the message just before providing the test result comprised a base64-encoded report ID number, which a threat actor could decode to construct new sets of URLs that would enable access to other test results, Majumder told the publication. In the case of the example shown in the report, the text “The Covid-19 Test Result of [Name]” was followed by the text “SRF ID 193” before showing the result as “negative.”
Majumder did some investigating and realized that the base64 encoding applied to the numeric identifier was optional, so removing it did not impact the ability to retrieve reports. He said that by enumerating URLs, an attacker could retrieve millions of confidential COVID-19 test results, according to the report.
Each medical record contained information pertaining to the patient’s name, age, gender, partial home address, COVID-19 test result, date of the test, report identifier and even identifying details for the lab where the test was conducted, Majumder said.
“I have found an issue in an Indian government site which is resulting in the leakage of test reports of EVERYONE who took a COVID-19 test in a particular state,” he told the outlet. “These reports have sensitive information about the citizens in them, like name, age, date and time of sample testing, residence address, etc.”
A potential hack leading to the ability to view the information would have looked something like this, according to the report:
https://cpms.wbhealth.gov[.]in:8003/Covid19.aspx?SRFID=1931XXXXXX1
https://cpms.wbhealth.gov[.]in:8003/Covid19.aspx?SRFID=1931XXXXXX2
https://cpms.wbhealth.gov[.]in:8003/Covid19.aspx?SRFID=1931XXXXXX3
The researcher said he tried to contact the health department about the leak but did not reach them. Majumder also disclosed his finding to a regional newspaper in India, which published a report on Tuesday in which a North Bengal health, Dr. Sushant Roy, acknowledged the flaw and said it would be fixed immediately.
It has since been remediated and it’s no longer possible to access reports using the enumeration method, according to BleepingComputer.
COVID-19 Data-Leak Accidents Abound
Though there was no intention in this case to leak relevant COVID-19 data, it’s not the first inadvertent potential exposure of test results or other related sensitive information since the pandemic began.
In September, the Wales arm of the U.K.’s NHS admitted that it accidentally uploaded PII for Welsh residents who tested positive for COVID-19 to a public server that anyone could search, exposing the information of more than 16,000 people. The leak, which was fixed 24 hours later, was blamed on “individual human error.”
In November, a COVID-19 data-sharing platform used by healthcare workers in the Philippines was found to be exposing healthcare worker data and potentially could have leaked patient data due to multiple system flaws.
Not all the COVID-19-related breaches have been accidental, either, as threat actors have willfully sought ways to get their hands on sensitive pandemic-related data with targeted attacks. In December for example, threat actors broke into the server of the European Medicines Agency and accessed documentation about the vaccine from Pfizer and BioNTech — data that was later leaked online.
Tax Season Ushers in Quickbooks Data-Theft Spike
25.2.2021 Incindent Threatpost
Quickbooks malware targets tax data for attackers to sell and use in phishing scams.
Cybercriminals are ready for tax season with new malware designed to exfiltrate Quickbooks data and post it on the internet, according to a new report from ThreatLocker.
Attackers use email to deliver the malware, which the ThreatLocker’s CEO Danny Jenkins told Threatpost is a simple, 15-line piece of code. There are two specific methods attackers used to get the malware to targets: The first is to send a PowerShell command to exfiltrate the data; and the second is to use a Word document to deliver a link or macro to retrieve a file.
After that, the stolen files are sent to the internet, where they’re up for grabs.
“Once the executable or PowerShell command is running, it retrieves your most recently saved Quickbooks’ file location, points to your file share or local file, and proceeds to upload your file to the internet,” the report said.
Jump in PowerShell Access to Quickbooks
Jenkins added that ThreatLocker has seen a six- to seven-times increase in instances of PowerShell accessing QuickBooks in recent weeks. A QuickBooks default permissions setting makes things extra-easy for attackers, according to the firm.
“When Quickbooks is on a file server, you are required to use a Quickbooks Database Server Manager, the report said. “When carrying out a repair, file permissions are reset and the ‘everyone’ group is added to the permission. As a result, access to the database is left wide open and this is a major security concern. ”
Jenkins said he was able to reverse engineer the Quickbooks malware and traced Quickbooks data on the dark web. He found it to be up for sale at prices starting at 100 databases for $100, and “up to thousands of dollars,” for a clean database of financial information with passwords, he explained.
Besides selling the Quickbooks data for a profit, Jenkins said that he predicts the data will also likely be stored and used to power future spear-phishing campaigns, which rely on personal information to tailor social-engineering scams for maximum effect.
Quickbooks Default Permissions
To protect tax data, ThreatLocker recommended making sure the “everyone” group is not selected for Quickbooks permissions — the best idea is to limit access to a single user.
“If you are using a Database Server Manager, be sure to check the permissions after running a database repair and confirm they are locked down,” the report added.
Jenkins said that his company looks at wide trends in data the ThreatLocker solutions encounter across a variety of networks, and said he suspects that Quickbooks attacks are more visible because it’s one of the most-used accounting packages during tax season. He said other, similar software is also likely vulnerable to this type of malware.
Jenkins told Threatpost once attackers have a person’s data, they can use it whenever, wherever and however many times they want, amounting to what can feel like “seven years of bad luck,” following a breach. He added that when this kind of sensitive tax data is exfiltrated without alerting victims, coupled with the potential long-term fallout, it makes these types of attacks a “worst-case scenario.”
Hackers Leak Data Stolen From Jet Maker Bombardier
25.2.2021 Incindent Securityweek
Just as the cybercriminals behind the Clop ransomware operation made public information supposedly stolen from Canadian business jet manufacturer Bombardier, the company confirmed suffering a data breach.
In a Thursday statement, the jet maker revealed that an unauthorized party was able to access and steal data by exploiting a vulnerability in “a third-party file-transfer application.” While the company did not say which third-party software was compromised, the general characteristics of the incident suggest it was Accellion’s FTA service.
A 20-year-old file sharing service set to be retired on April 30, FTA was recently targeted in a cyber-attack that affected up to 100 Accellion customers, out of a total of 300 that were still using the application at the time of the attack.
These include Australian health and transport agencies, U.S.-based law firm Jones Day, and grocery and pharmacy chain Kroger. The attacks, security researchers with FireEye say, appear linked to the TA505 spin-off FIN11.
The threat actors behind the attack on Accellion’s software have been sending extortion emails to organizations affected by the incident, threatening to share the stolen data publicly on the “CL0P^_- LEAKS” Tor website.
With data pertaining to Bombardier emerging on the website and the company disclosing a data breach caused by a third-party application used for file transfer, it’s clear that Accellion’s FTA was responsible for this incident.
“Forensic analysis revealed that personal and other confidential information relating to employees, customers and suppliers was compromised. Approximately 130 employees located in Costa Rica were impacted,” Bombardier says.
The company also notes that it has launched an investigation into the incident and that law enforcement was informed on the issue. It also claims that only the “data stored on the specific servers” was affected, and that its network was not compromised.
“Manufacturing and customer support operations have not been impacted or interrupted. Bombardier can also confirm the company was not specifically targeted—the vulnerability impacted multiple organizations using the application,” Bombardier also says.
In addition to data taken from Bombardier, the attackers behind the Clop operation also leaked information supposedly stolen from Pentair and CSA Group. However, neither of these companies has confirmed a data breach yet.
VC Giant Sequoia Capital Informs Investors of Data Breach
24.2.2021 Incindent Securityweek
Silicon Valley-based venture capital giant Sequoia Capital informed investors last week that their information may have been compromised in a data breach.
Axios, which broke the news on Saturday, said investors were told that some of their personal and financial information may have been accessed after a Sequoia employee fell victim to an email phishing attack.
According to Axios, the VC firm told investors that it had been monitoring the dark web to see if the compromised information would surface — it had not at the time when investors were first notified.
Sequoia has since confirmed being hacked, saying that its security team responded promptly to what it described as a “cybersecurity incident.” The company said it hired an outside cybersecurity firm to “help remediate the issue and maintain the ongoing security of our systems.” Law enforcement has also been informed about the incident.
Sequoia has invested in many tech companies, including ones that provide apps and services, data and analytics, developer tools, hardware, infrastructure, marketing, networking, cybersecurity, and storage, as well as financial, gaming, healthcare, media, productivity, search and social firms.
Its website lists 300 U.S. companies — including tech giants Google, Apple and Cisco — as well as hundreds of others in China, India and Israel. Sequoia has invested in several cybersecurity companies, including Netskope, Salt Security, StackRox, Wiz, Skyhigh Networks, SentinelOne, FireEye and Palo Alto Networks.
NurseryCam daycare cam service shut down after security breach
23.2.2021 Incindent Securityaffairs
Daycare camera product NurseryCam was hacked last week, the company was forced to shut down its IoT camera service.
On Friday, The Register become aware of the compromise of the NurseryCam network. NurseryCam is produced by the companies FootfallCam Ltd and Meta Technologies Ltd.
In response to the incident, the company shut down its IoT camera service on Saturday and reported the security breach to the parents.
“On 17:18 Friday 19th February 2021, it has come to our attention of a cyber incident detected in our NurseryCam system.” reads the security noticed sent by the company to the parents.
NurseryCam is a webcam solution that allows parents to watch their children while at nursery school. The service was used by about 40 nurseries across the UK.

NurseryCam has also reported a possible data breach to the UK’s data watchdog, the Information Commissioner’s Office (ICO).
The attackers exploited a “loophole” in its systems to obtain data from parents’ viewing accounts, exposed data includes usernames, hashed passwords, names, email addresses.
“The person who identified the loophole has so far acted responsibly,” said Dr Melissa Kao, director of FootfallCam Ltd and Meta Technologies “He stated he has no intention to use this to do any harm [and] wants to see NurseryCam raise the overall standards of our security measures.”
According to El Reg the security breach impacted 12,000 NurseryCam users’ accounts, the attackers dumped them online.
The El Reg reported that a FootfallCam corporate customer that has used the devices has found some security issues and reported them to FootfallCam. The customer explained that he was able to browse “data for other customers” by simply manipulating URL parameters in his browser.
Another NurseryCam user told El Reg he had reported multiple flaws in the product to the vendor in 2020, but it had received an unsatisfactory response.
Chinese Hackers Cloned Equation Group Exploit Years Before Shadow Brokers Leak
23.2.2021 Incindent Securityweek
A Chinese threat actor known as APT31 likely acquired and cloned one of the Equation Group’s exploits three years before the targeted vulnerability was publicly exposed as part of Shadow Brokers’ “Lost in Translation” leak, cybersecurity firm Check Point says in a new report.
Tracked as CVE-2017-0005, the vulnerability was addressed by Microsoft in March 2017, after Lockheed Martin’s Computer Incident Response Team observed a possible attack against an American target and reported it to the Redmond-based tech giant.
Attributed to APT31, a Chinese hacking group also tracked as Zirconium, the exploit for this vulnerability is, in fact, the clone of an Equation Group exploit code-named “EpMe,” Check Point says.
Exploitation tools that the Equation Group had been using for years were made public in early 2017 by a mysterious group calling themselves Shadow Brokers. The Equation Group has been linked to the Tailored Access Operations (TAO) unit of the U.S. National Security Agency (NSA).
The Shadow Brokers, which some believe was backed by Russia, claimed at the time to have obtained the tools after an intrusion into Equation Group’s systems. They released several series of exploits for free, but also attempted to monetize the data.
In March 2017, Microsoft patched CVE-2017-0005, a Windows local privilege escalation (LPE) vulnerability that had been actively exploited by a Chinese threat actor. Called Jian and attributed to APT31, the exploit for this vulnerability is now believed to be the clone of an Equation Group exploit that targeted the same security hole.
Dated 2013, the original exploit is codenamed EpMe, and is one of the 4 different LPE exploits (ElEi, ErNi, EpMe, and EpMo) in the Equation Group’s DanderSpritz attack framework that was publicly disclosed in April 2017. These exploits, however, did not receive the same coverage as Eternal Blue (ETBL), Eternal Romance (ETRO), and other tools leaked by Shadow Brokers.
A dive into the DanderSpritz attack framework revealed that two of the targeted vulnerabilities are old (ElEi was targeting CVE-2011-3402, while ErNi aimed at CVE-2013-3128), that one of them has no CVE identifier, despite being patched in March 2017 (EpMo), and that the fourth had been cloned by APT31 approximately three years before patching (EpMe targeted CVE-2017-0005).
Check Point’s security researchers discovered that, following the release of a patch for CVE-2017-0005, both the EpMe and the Jian exploits stopped working. While having two adversaries targeting the same security bug could be a coincidence, a comparison between the two exploits revealed code similarities, shared constants, and a completely identical memory layout.
Further analysis has revealed that the exploits contain artefacts specific to the Equation Group tools, suggesting that EpMe was the original exploit for CVE-2017-0005, Check Point says. APT31 was apparently able to capture the exploit and clone it in 2014 (Jian), and started using it roughly the same year, until the 2017 patch was released.
“To our surprise, we found out that this APT31 exploit is in fact a reconstructed version of an Equation Group exploit called ‘EpMe’. This means that an Equation Group exploit was eventually used by a Chinese-affiliated group, probably against American targets,” Check Point notes.
Supermarket Chain Kroger Discloses Data Breach
23.2.2021 Incindent Securityweek
Grocery and pharmacy chain Kroger has started informing customers and associates of a data breach involving Accellion’s file transfer service FTA.
The Cincinnati-based retail company operates more than 2,900 locations across 35 states and the District of Columbia, including department stores, hypermarkets, jewelry stores, supermarkets, and superstores.
In a data breach notification on its website, the company says that a data security incident involving Accellion’s FTA service has resulted in unauthorized access to certain Kroger data.
According to Kroger, information that might have been affected by the incident includes associates’ HR data, pharmacy records, and money services records.
“No grocery store data or systems, credit or debit card (including digital wallet) information, or customer account passwords were impacted,” the company underlines.
Kroger said it was informed of the incident on January 23 and that it has since discontinued the use of FTA, launched an investigation into the incident, and also contacted federal law enforcement on the matter.
“Kroger has no indication of fraud or misuse of personal information as a result of this incident. However, Kroger is directly notifying potentially impacted customers and associates through mail notices,” the company says.
Meant to provide secure file transfers, the FTA service was found recently to be riddled with vulnerabilities that allowed adversaries to access certain information of Accellion’s customers.
Less than 50 organizations were using the file sharing service in mid-December, when the first vulnerabilities were discovered, but the number of affected individuals has at least seven figures.
Accellion has formally announced plans to retire FTA, a 20-year-old service, saying that it would honor ongoing license agreements past the end-of-life point, which has been set for April 30, 2021.
The Australian Securities and Investments Commission (ASIC), the Office of the Washington State Auditor (SAO), the Reserve Bank of New Zealand, and Singapore telecoms firm Singtel were among the organizations affected by the cyber-attack on FTA.
Prominent U.S.-based law firm Jones Day was also affected, and some of the information stolen from the organization was recently leaked online by the Clop ransomware gang, which is believed to be linked to the financially-motivated, Russian-speaking group known as TA505 and Hive0065.
Sequoia Capital Venture Capital firm discloses a data breach
21.2.2021 Incindent Securityaffairs
Sequoia Capital, one of the most prominent venture capital firms, told its investors that an unauthorized third party had access to their information.
Sequoia Capital, one of the most prominent venture capital firms that focus on the technology industry, discloses a data breach. The company informed its investors that an unauthorized third party had access to their personal and financial information. Sequoia’s portfolio includes Airbnb, DoorDash, and Robinhood, it also invested in major cybersecurity firms like FireEye and Carbon Black.
The intrusion is the result of a successful phishing attack against one of its employees.
“Sequoia Capital told its investors on Friday that some of their personal and financial information may have been accessed by a third party, after a Sequoia employee’s email was successfully phished, Axios has learned.” reported the security firm Axios.

The venture capital firm told investors that it’s been monitoring the dark web, at the time of this writing it is not aware of threat actors trading the compromised data.
“We recently experienced a cybersecurity incident. Our security team responded promptly to investigate, and we contacted law enforcement and engaged leading outside cybersecurity experts to help remediate the issue and maintain the ongoing security of our systems.” a Sequoia spokesperson told Axios. “We regret that this incident has occurred and have notified affected individuals. We have made considerable investments in security and will continue to do so as we work to address constantly evolving cyber threats.”
Inside the Battle to Control Enterprise Security Data Lakes
20.2.2021 Incindent Securityweek
NEWS ANALYSIS: The strategic positioning to own and control the massive data lakes powering enterprise security programs took another expensive turn with CrowdStrike announcing it would shell out $400 million to buy early-stage log analytics start-up Humio.
The $400 million cash-and-equity deal represents a massive exit for Humio, a company that raised just $32 million in two funding rounds led by Dell Technologies Capital. Humio has about 70 employees in the U.S., London and Denmark and has found a niche as an affordable -- but powerful -- alternative to bigger vendors in the lucrative log analytics space.
The CrowdStrike/Humio marriage signals a continuation of the trend by anti-malware vendors to beef up data logging and indexing capabilities to cash in on “proactively-collect-and-store-everything” policies at larger enterprises.
Elastic (the company behind ElasticSearch and Elastic Stack) kicked off the push with the 2019 acquisition of Endgame ($234 million price tag) and SentinelOne followed up earlier this month with its $155 million purchase of Scalyr.
That’s $789 million in just three deals combining anti-malware capabilities with the always-on log analytics tools required to parse through terabytes of data per data to find signs of malware and other malicious activities.
Yet, that figure is peanuts compared to the $10 billion a year figure floated by Microsoft as its cybersecurity-specific revenue haul or the $3.5 billion that Palo Alto Networks rakes in from its security product lines.
Microsoft has emerged as the elephant in the room, having cleverly positioned itself as the data lake for customers in its Windows/Azure/Defender ecosystem.
It’s yet to be seen how these mergers affect the larger SIEM (Security Information and Event Management) category, where big-ticket products jostle to provide real-time analysis of security alerts generated by applications and network hardware.
Network defenders and security analysts expect the deals to immediately shake up pricing models at big-name log analytics and SIEM vendors. The pay-per-usage model can be incredibly expensive for defenders ingesting, logging and indexing terabytes of data per day.
This led to a sharp shift with the emergence of startups like Chronicle (now folded back into Google Cloud) and Humio pushing flat-rate pricing and unlimited indexing to snap up market share from the likes of Splunk, Sumo Logic and Datadog.
CrowdStrike claims it already processes around five trillion security-related events per week and, with the Humio technology added to its stack, gives it some room in what Gartner is describing as “eXtended Detection and Response (XDR)” category.
The great promise of XDR is to match all the endpoint data with network telemetry from other sources to provide more visibility into hidden attack surfaces. With the Humio tech, CrowdStrike can now market a complete suite to ingest and correlate data from any log, application or feed to deliver actionable insights and real-time protection.
CrowdStrike chief executive George Kurtz said the company did a “thorough market review of existing solutions” before making the decision to buy Humio’s technology architecture and ability to deliver at scale.
Assuming the integration goes smoothly, CrowdStrike expects to eventually market a platform that spans endpoints, identities, the network edge, and the cloud, offering that “unified data layer” to help enterprise security and IT operations.
Microsoft: SolarWinds Hackers Attempted to Access Our Systems Until January 2021
20.2.2021 Incindent Securityweek
Microsoft said on Thursday that it has completed its internal investigation into the activities conducted by the hackers that breached Texas-based IT management firm SolarWinds.
The tech giant previously admitted that the hackers had managed to access some internal source code, but said they did not compromise or modify its software.
The company on Thursday confirmed that some source code was accessed, but claimed impact was limited.
“There was no case where all repositories related to any single product or service was accessed. There was no access to the vast majority of source code. For nearly all of code repositories accessed, only a few individual files were viewed as a result of a repository search,” it said.
Microsoft said the attackers apparently first accessed source code in late November, but their attempts did not stop after the breach was discovered and resolved in December. They continued making attempts until January 2021, but none of these attempts were successful.
The company said the attackers downloaded source code from repositories storing “a small subset” of Azure (service, security and identity), Intune, and Exchange components.
Microsoft also determined — based on the search terms used by the hackers — that they were attempting to find “secrets” in the source code they accessed.
“Our development policy prohibits secrets in code and we run automated tools to verify compliance. Because of the detected activity, we immediately initiated a verification process for current and historical branches of the repositories. We have confirmed that the repositories complied and did not contain any live, production credentials,” the company said.
Microsoft also reiterated that it had found no evidence that production services or customer data were compromised, or that its own systems were used to attack others.
“Because of our defense-in-depth protections, the actor was also not able to gain access to privileged credentials or leverage the SAML techniques against our corporate domains,” Microsoft said.
Last month, Microsoft released a report detailing the methods and activities of the threat actor behind the SolarWinds attack, including operational security (OPSEC), anti-forensic behavior, and malware delivery methods.
Microsoft and others have claimed that more than 1,000 hackers may have been involved in the SolarWinds attack, but some cybersecurity professionals have questioned the claims.
SolarWinds was apparently targeted by two unrelated threat groups: one linked to Russia that compromised its systems and delivered trojanized updates to thousands of customers, and one linked to China that did not breach SolarWinds systems and instead exploited a zero-day vulnerability and delivered a piece of malware after gaining access to victims’ systems.
SolarWinds released patches in response to both attacks, but many of its customers have failed to secure their systems, according to a report from risk assessment firm RiskRecon.
mHealth Apps Expose Millions to Cyberattacks
13.2.2021 Incindent Threatpost
Researcher testing of 30 mobile health apps for clinicians found that all of them had vulnerable APIs.
Some 23 million mobile health (mHealth) application users are exposed to application programming interface (API) attacks that could expose sensitive information, according to researchers.
Generally speaking, APIs are an intermediary between applications that defines how they can talk to one another and allowing them to swap information. Researcher Alissa Knight with Approov tried to break into the APIs of 30 different mHealth app vendors, with the agreement she wouldn’t ID the vulnerable ones. Turns out, they were all vulnerable to one degree or another.
The average number of downloads for each app tested was 772,619.
According to the resulting report from Approov, out of 30 popular mHealth apps analyzed, 77 percent of them contained hardcoded API keys, which would allow an attacker to intercept that exchange of information — some of which don’t expire. Seven percent of these belonged to third-party payment processors that explicitly warn against hard-coding their secret keys in plain text.
Another 7 percent contained hardcoded usernames and passwords.
But that’s not all: More than a quarter (27 percent) of mobile apps tested didn’t have code-obfuscation protections against reverse engineering; and all of them without exception lacked certificate pinning, which prevents man (or woman) in the middle (MITM) attacks, for intercepting communications to observe and manipulate records.
Also, a full 50 percent of the APIs tested did not authenticate requests with tokens.
And finally, if one patient’s records can be accessed, often many others can be accessed indiscriminately: 100 percent of API endpoints tested were vulnerable to Broken Object Level Authorization (BOLA) attacks, which allowed the researcher to view the personal health information (PHI) and personally identifiable information (PII) for patients that were not assigned to the researcher’s clinician account.
For context, the report said there are more than 318,000 apps available in major app stores.
Medical Records Attract Cybercriminals
The pandemic has pushed hospitals and healthcare providers to rely increasingly on mHealth apps. But the analysis reveals they’re are often vulnerable to attackers, leaving critical and valuable health information sitting there just waiting to get ripped off.
What’s been exacerbating the security posture of mobile health apps is the mad rush to innovate first, secure second, Knight explained to Threatpost. And now is the time for security to catch up before a big breach happens, she added.
Threat actors meanwhile have a big financial incentive to target these mHealth APIs. Knight pointed out that while the going rate among cybercriminals for a Social Security number is $1 and a credit-card number sells for about $110, the big money is in full medical records, which fetch about $1,000 apiece.
“This growing attack surface is quickly drawing the attention of transnational crime syndicates wanting to lock-and-leak it in order to extort payments from its data owners and sell it to the highest bidder,” Knight wrote in the report.
What is the Top mHealth App Threat?
BOLA (a.k.a. Insecure Direct Object Reference, or IDOR) is the most common abuse vector for mHealth APIs, Knight said, pointing out it’s no coincidence that OWASP’s recently published list of top API threats put these types of vulns at the top.
“Simply put, a BOLA vulnerability enables an adversary to substitute the ID of a resource with the ID of another,” Knight explained. “When the object ID can be directly called in the URI, it opens the endpoint up to ID enumeration that allows an adversary the ability to read objects that don’t belong to them. These exposed references to internal implementation objects can point to anything, whether it’s a file, directory, database record or key.”
In-the-lab BOLA attacks conducted by Knight cracked 100 percent of the apps she tested, giving her theoretical access to downloadable full patient records, including lab results, x-ray images, blood work, family history, birth dates, Social Security numbers and more.
API Authorization Versus Authentication
Knight explained to Threatpost that when it comes to APIs, CISOs and security teams need to think about the distinction between authentication and authorization.
Knight used the analogy of security at a nightclub.
In an authorization-only scenario the bouncer (the authorizer) checks IDs and determines who is allowed inside the bar. So that inside, anyone who walks up the bar and orders a drink, the bartender can just assume, is legal to consume alcohol.
But in an authentication scenario there are two checks.
The bouncer checks IDs and issues wrist bands to those allowed to drink. Once at the bar, the bartender (the authenticator) looks for a wristband as an added layer of scrutiny. The bartender double-check confirms the person isn’t just authorized to be in the bar, but it also ensures their identity is authenticated to make sure they’re both allowed inside and allowed to consume alcohol.
APIs work much the same way, Knight explained. Half of the mHealth APIs she tested for this report didn’t authenticate requests with tokens.
“Types of authentication in APIs include API keys, a long string of random numbers and characters generated by the API endpoint that grants access to whomever passes it in the authorization header of the request; Basic Auth where a username and password are used to authenticate an individual; JSON Web Tokens (JWTs) and OAuth, which uses tokens instead of sharing credentials; OAuth2, which exchanges a username and password for a token; SMART, which is increasingly becoming an implementation of OAuth in healthcare; and OpenID Connect,” Knight said. “There are also other methods of authentication, such as implementing multifactor authentication through third-party solutions.”
Implementing Better mHealth Cybersecurity
David Stewart, founder and CEO of Approov, explained that existing security standards aren’t adequate to address rising security threats to mobile health applications. Companies need to do more.
“These findings are disappointing but not at all surprising,” Stewart said. “The fact is that leading developers and their corporate and organizational customers consistently fail to recognize that APIs servicing remote clients such as mobile apps need a new and dedicated security paradigm. ”
Heathcare entities must understand that APIs are an open door for malicious actors, particularly in the lucrative PHI market, he underlined.
“Because so few organizations deploy protections for APIs that ensure only genuine mobile app instances can connect to backend servers, these APIs are an open door for threat actors and present a real nightmare for vulnerable organizations and their patients,” Stewart said.
Yandex Data Breach Exposes 4K+ Email Accounts
13.2.2021 Incindent Threatpost
In a security notice, Yandex said an employee had been providing unauthorized access to users’ email accounts “for personal gain.”
Yandex – one of Europe’s largest internet companies – is warning of a data breach that compromised 4,887 email accounts. The breach stems from an insider threat.
Yandex is the most-used search engine in Russia – and the fifth most-popular search engine worldwide. Beyond its search engine, Yandex’s internet product lineup includes email services, online advertising, app analytics and more.
The company found that a Yandex employee had been providing unauthorized access to users’ mailboxes “for personal gain.” This employee was one of three system administrators, who had the access privileges to provide technical support for mailboxes, said Yandex.
“A thorough internal investigation of the incident is under way, and Yandex will be making changes to administrative access procedures,” said Yandex’s Friday security advisory. “This will help minimize the potential for individuals to compromise the security of user data in future. The company has also contacted law enforcement.”
Yandex Internally Discovers Data Breach
Threatpost has reached out to Yandex for further comment on the timeline of the data breach – including when the unauthorized access to email accounts began, when the breach was discovered, and who was able to access the compromised accounts.
The company discovered the breach during a routine screening by its security team. Yandex stressed, no payment details were compromised, and it has already blocked the unauthorized access to the compromised mailboxes.
“We have contacted the mailbox owners to alert them about the breach and they have been informed of the need to change their account passwords,” the company said.
What is a Cybersecurity Insider Threat?
The data breach is reflective of an insider threat. This is a type of threat that comes from within an organization – whether it’s an employee, former employee, contractor or otherwise. Insider threats can be non-malicious – such as a mistake by an employee (like a cloud misconfiguration) that leads personal data being exposed, for instance. Or, as in this incident, they can be malicious, where an employee purposefully gives access (or is persuaded to give access) to internal systems or records.
According to Verizon’s 2020 Data Breach Investigations Report (DBIR), internal actors were behind 30 percent of breaches (with the majority, or 70 percent, coming from external actors
Insider Threats Have Plagued ADT, Cisco and Amazon
An insider threat could leave companies spiraling from financial or brand damage – but also a lack of subsequent trust from customers.
In a recent January case, for instance, a former ADT employee was caught adding his personal email address to the accounts of attractive women, so he could have around-the-clock access to their most private moments.
In December, a former Cisco Systems employee was sentenced to two years in jail, after hacking into the networking company’s cloud infrastructure and deleting 16,000 Webex Teams accounts in 2018. And in October, Amazon fired an employee who shared customers’ names and email addresses with a third party.
Brandon Hoffman, chief information security officer at Netenrich, said this incident highlights the ongoing concern related to insider threats.
“Employees are always a prime target for adversaries, whether it is targeting them to leverage their machine or identity or recruiting them actively on a closed source (dark web) forum,” said Hoffman. “There has been several cases where we have seen a disgruntled employee posting messages on the dark web aiming to make a contact where they can ‘cash out’ their leverage as an employee. Considering this happened in Russia, a known hotspot (or even the primary hub) of cybercrime, the fact that it was an intentional insider is not all that surprising.”
Is your small- to medium-sized business an easy mark for attackers?
Yandex Employee Caught Selling Access to Users' Email Inboxes
13.2.2021 Incindent Thehackernews
Russian Dutch-domiciled search engine, ride-hailing and email service provider Yandex on Friday disclosed a data breach that compromised 4,887 email accounts of its users.
The company blamed the incident on an unnamed employee who had been providing unauthorized access to the users' mailboxes for personal gain.
"The employee was one of three system administrators with the necessary access rights to provide technical support for the service," Yandex said in a statement.
The company said the security breach was identified during a routine audit of its systems by its security team. It also said there was no evidence that user payment details were compromised during the incident and that it had notified affected mailbox owners to change their passwords.
It's not immediately clear when the breach occurred or when the employee began offering unauthorized access to third-parties.
"A thorough internal investigation of the incident is under way, and Yandex will be making changes to administrative access procedures," the company said. "This will help minimize the potential for individuals to compromise the security of user data in future. The company has also contacted law enforcement."
Insider Threats Continue to Hit Companies
This is not the first time insider threats have plagued tech companies and resulted in financial or reputational damage.
Last month, Telesforo Aviles, a 35-year-old former Dallas-based ADT technician, pled guilty to computer fraud and invasive visual recording for repeatedly breaking into cameras he installed and viewed customers engaging in sex and other intimate acts. He was terminated from the firm in April 2020.
In December, former Cisco engineer Sudhish Kasaba Ramesh, 31, was sentenced to 24 months in prison for deleting 16,000 Webex accounts without authorization, costing the company more than $2.4 million, with $1,400,000 in employee time and $1,000,000 in customer refunds.
In October last year, Amazon fired an employee for sharing customers' names and email addresses with a third-party.
And in November 2019, cybersecurity firm Trend Micro revealed that a rogue employee sold the data of 68,000 customers to malicious cybercriminals, who then used that data to target customers with scam calls by posing as Trend Micro support personnel.
Mobile Health Apps Found to Expose Records of Millions of Users
11.2.2021 Incindent Securityweek
An analysis of 30 popular mobile health (mHealth) applications has revealed that all of them expose the full patient records of millions of people.
Research conducted by Alissa Knight, partner at marketing agency Knight Ink, on behalf of mobile API threat protection firm Approov showed that the applications are vulnerable to API attacks that unauthorized parties could leverage to access protected health information (PHI) and personally identifiable information (PII).
With people increasingly relying on mHealth apps during the COVID-19 pandemic, researchers observed that such apps are now generating more user activities compared to other mobile apps.
The research study, All That We Let In - Hacking 30 Mobile Health Apps and APIs, is based on the analysis of 30 popular mHealth apps, with an average number of downloads of approximately 772,000. Thus, these apps had an estimated user base of roughly 23 million.
The number of affected users, however, is likely much higher, considering that there are over 300,000 mHealth apps available at the moment on major app stores, the researcher says.
None of the analyzed applications had certificate pinning implemented, thus allowing for man-in-the-middle (MitM) attacks, while 77% of them contained hardcoded API keys, tokens, and credentials. Half of the APIs did not authenticate requests with tokens and one quarter of the apps (27%) were not secured against reverse engineering.
During analysis, Knight discovered 114 hardcoded API keys and tokens that allowed for authenticating with the mHealth company and third-party APIs. Exposed secrets were identified for Branch.io, Cisco Umbrella, Google, Microsoft App Center, Stripe, AWS, AppsFlyer, Facebook, Sales Force, and more.
Half of the records that these applications exposed contained names, addresses, birthdates, social security numbers, allergies, medication data, and other sensitive information.
All of the tested API endpoints, the researcher says, were vulnerable to broken object level authorization (BOLA) attacks, thus providing access to PII and PHI even for patients not assigned to the clinician account. Half of the tested APIs provided access to pathology, X-rays, and clinical results of other patients.
The report also provides recommendations for mobile app developers to adopt a series of steps to ensure the protection of customer data and sensitive resources, such as ensuring the security of both the app and APIs, secure the development process and harden apps, implement certificate pinning to protect against MitM attacks, monitor implemented controls, and perform penetration testing.
Hacker Sets Alleged Auction for Witcher 3 Source Code
11.2.2021 Incindent Threatpost
The ransomware gang behind the hack of CD Projekt Red may be asking for $1 million opening bids for the company’s valuable data.
The ransomware gang behind an attack on videogame developer CD Projekt Red may have made good on its promise to auction off the company’s data – including source code for Cyberpunk 2077 and an unreleased version of the Witcher 3.
Or it may not have.
The Twitter account @vxunderground, which bills itself as “the largest collection of malware source code, samples and papers on the internet,” put out a notice on Wednesday that the purported stolen data was being put up for sale on the well-known Russian-language underground forum “Exploit,” and it provided alleged screenshots.
“This is the source code to ‘Gwent’ card game,” according to the tweets. “Witcher 3, CyberPunk 2077, etc. is being auctioned today on EXPLOIT forums…The ransomware authors said they will not be auctioning data anywhere else – any other location other than EXPLOIT is fake.”
@vxunderground also said that the information had a starting bid of $1 million, but they whole cache could be bought outright for $7 million.
When asked to independently verify the claim, Austin Merritt, cyber-threat intelligence analyst at Digital Shadows, told Threatpost that the auction posting did indeed exist. An Exploit user named “redengine” created a thread in the auctions section of the site, entitled “Auction date for CD Projekt RED” when translated from the Russian.
“The user claimed to have full source codes for various games including Thronebreaker, Cyberpunk 2077, Witcher 3 and the undeclared Witcher 3 RTX (a version of Witcher with raytracing),” Merritt said. “The user also claimed to have dumps of internal documents and files related to CD Projekt RED ‘offenses.'”
As for cost and timing, Merritt said that the poster set the auction to start Thursday, Feb. 11 at 13:00 Moscow time (5 a.m. ET), and that bidders would be required to make a 0.1 BTC deposit (around $44,900 at press time) to enter.
“The user started the auction at $1 million, however, users have not yet expressed any interest in purchasing this information,” Merritt told Threatpost. “At the time of writing, there have been six replies to the original post. Users that have replied have largely questioned the legitimacy of the post, alleging that user ‘redengine’ does not have an established reputation on the forum.”
Thus, it’s unclear if what the user is offering is legitimate, or if the posting is from an opportunist trying to take advantage of the buzz around the stolen data that percolated up this week in media accounts.
Merritt gave Threatpost a screenshot of the alleged Gwent data files:
CD Projekt Red has not responded to a request for comment or verification.
CD Projekt Red Ransomware Strike
The Warsaw-based videogame company tweeted out a notice on Tuesday, warning of “a targeted cyberattack in which some of our systems have become compromised.”
The attackers – believed to be part of the “Hello Kitty” ransomware gang, as Threatpost previously reported — acknowledged that the ransomware itself would likely not be a problem for the company, which had backups in place to quickly remediate the attack. More concerningly, the attackers threated to dump troves of stolen company data online – including game source code.
“We have encrypted all of your servers, but we understand that you can most likely recover from backups,” according to the ransom note shared by CD Projekt Red. However, “source codes will be sold or leaked online, and your documents will be sent to our contacts in gaming journalism.”
It went on to say that not paying up would have an impact on the company’s public image, stock price and investor confidence (CD Projekt Red is traded in over-the-counter markets). The attackers also claimed that the information will expose how terribly the company is run.
Release of the source code would allow fans to develop game hacks and perform all kinds of “modding” (i.e., development of custom features) and jailbreaks; and would be a gift to competitors.
Anti-malware firm Emsisoft accidentally exposes internal DB
11.2.2021 Incindent Securityaffairs
Antivirus firm Emsisoft discloses a data breach, a third-party had access to a publicly exposed database containing technical logs.
The anti-malware solutions provider Emsisoft disclosed last week a data breach. The company revealed that a third-party had accessed a publicly exposed database containing technical logs.
The root cause of the incident was a misconfiguration of a database, used in a test environment, that was exposed to the Internet. The company confirmed that the database was accidentally exposed online from January 18, 2021, to February 3, when it was discovered.
The misconfigured system was used to evaluate and benchmark possible solutions for the storage and the management of the log data generated by Emsisoft products and services.
The analysis of the exposed database revealed that the logs stored in the archive contained no personal information, except for 14 customer email addresses of 7 different organizations. The experts pointed out that these 14 customer email addresses were included in scan logs due to detections of malicious emails stored in the users’ email clients.
“Immediately after becoming aware of the breach, we took the affected system offline and started an investigation. We determined that the logged information contained no personal information whatsoever, except for 14 customer email addresses of 7 different organizations.” reads the data breach notification published by the company. “While this number is small, we still believe it is the right thing to inform all our customers about the incident, how exactly it happened, and what we are planning to do in order to prevent similar incidents in the future.”
Emsisoft experts believe that the attack was an automated attack and was not the result of a targeted campaign.
The company added that one of the databases set up for testing and benchmarking purposes remained accessible to third parties, Emsisoft confirmed that at least one individual accessed this database.
“We have reason to believe that at least one individual accessed some or all of the data contained within that database.” continues the notification.
“The stolen data in question consists of technical logs produced by our endpoint protection software during normal usage, such as update protocols, and generally does not contain any personal information like passwords, password hashes, user account names, billing information, addresses, or anything similar.”
Emsisoft explained that only parts of the affected database were accessed and not the entire database, but it is impossible to determine the specific exposed records.
The company already notified the affected users and implemented additional security measures to prevent similar incidents in the future.
Antivirus Firm Emsisoft Discloses Data Breach
10.2.2021 Incindent Securityweek
Antivirus solutions provider Emsisoft revealed last week that a third-party had accessed a publicly exposed database containing technical logs.
The issue, Emsisoft said, was a misconfiguration that resulted in a database from a test system becoming exposed to the Internet. The database was initially exposed on January 18, 2021, and remained so until the data breach was identified, on February 3.
The affected system was used for evaluation and benchmarking of the storage and management of log data generated from Emsisoft products and services.
Emsisoft said it immediately took the system offline and launched an investigation into the matter. As a result, it discovered that the only personal information in the database involved 14 email addresses from 7 different organizations.
The affected system, along with several others, was set up for the evaluation of storage options for log and event data, and was seeded with log records from production. One of the databases was made accessible to unauthorized third parties, and at least one “individual accessed some or all of the data contained within that database.”
“The stolen data in question consists of technical logs produced by our endpoint protection software during normal usage, such as update protocols, and generally does not contain any personal information like passwords, password hashes, user account names, billing information, addresses, or anything similar,” Emsisoft said.
The 14 customer email addresses that were stored in the database, the antivirus firm said, were included in the scan logs because malicious emails were detected in the users’ email clients.
According to Emsisoft, the attack was automated and not specifically targeted at the company.
“Also, our traffic logs indicate that only parts of the affected database were accessed and not the entire database. However, due to technical limitations it’s impossible to determine exactly which data rows were accessed,” the antivirus provider revealed.
Emsisoft said the exposed system did not provide access to production systems or databases and that the affected users were notified of the incident. The company also noted that it took additional security measures to ensure similar incidents won’t happen.
Hackers attempted to poison the water supply of a US city
9.2.2021 Incindent Securityaffairs
Pinellas Sheriff revealed that attackers tried to raise levels of sodium hydroxide, by a factor of more than 100, in the Oldsmar’s water supply.
The scenario described by Pinellas Sheriff Bob Gualtieri is disconcerting, an attacker attempted to raise levels of sodium hydroxide, also known as lye, by a factor of more than 100, in Oldsmar’s water supply.
The ingestion of water with high level of sodium hydroxide can be fatal.
The incident took place on Friday and local authorities, along with the FBI and the Secret Service, are still investigating the hack. The attackers gained access to the city’s water treatment system and altered the amount of sodium hydroxide, also known as lye.
The city’s water supply was not affected because a remote supervisor noticed the anomalous change in the concentration of the chemical substance and reverted it. Gualtieri pointed out that the water supply chain is also protected by other safeguards that prevent any manipulation and they’ve disabled the remote-access system used in the attack.
“Someone remotely accessed a computer for the city’s water treatment system and briefly increased the amount of sodium hydroxide, also known as lye, by a factor of more than 100, Gualtieri said at a news conference Monday. The chemical is used in small amounts to control the acidity of water but it’s also a corrosive compound commonly found in household cleaning supplies such as liquid drain cleaners.” reported the Tampa Bay Times.
“The city’s water supply was not affected. A supervisor working remotely saw the concentration being changed on his computer screen and immediately reverted it, Gualtieri said. City officials on Monday emphasized that several other safeguards are in place to prevent contaminated water from entering the water supply and said they’ve disabled the remote-access system used in the attack.”
The Pinellas County Sheriff’s Office is investigating, along with the FBI and the Secret Service, Gualtieri said.
It is not clear why attackers have chosen the City of Oldsmar, but authorities have already alerted other municipalities of the risk of similar attacks on water treatment systems and other critical infrastructure.
An operator at the water facility noticed access to the control systems about 8 a.m. Friday, but it did not throw an alert because the supervisor remotely accessed the system regularly.
But at about 1:30 p.m. something strange has happened, someone accessed the system, took control of the mouse, and used the software that controls water treatment for three to five minutes. The intruder increased the amount of sodium hydroxide from 100 parts per million to 11,100 parts per million.
The plant operator noticed the manipulation and reverted it immediately.
“Importantly, the public was never in danger.” sheriff added.
“The protocols that we have in place, monitoring protocols, they work — that’s the good news,” said Oldsmar Mayor Eric Seidel. “Even had they not caught them, there’s redundancies in the system that would have caught the change in the pH level.“
“The important thing is to put everyone on notice,” he said. “There’s a bad actor out there.”
Remote Hacker Caught Poisoning Florida City Water Supply
9.2.2021 Incindent Securityweek
Hacker Remotely Increased Sodium Hydroxide Levels in Florida City’s Water from 100 Parts Per Million to 11,100 Parts Per Million.
U.S. law enforcement agencies are investigating a remote compromise of a Florida city's water plant, warning that the hackers tried to poison the water supply serving approximately 15,000 residents.
The hack was spotted on February 5th -- and neutralized -- in real time by staff at the plant that supplies water to Oldsmar, a small city close to Tampa, Florida.
Local Sheriff Bob Gualtieri said an unknown adversary hacked into the plant remotely and attempted to elevate levels of levels of sodium hydroxide by a factor of more than 100.
Sodium hydroxide, also known as lye, controls the acidity in potable water but elevated levels maliciously added to water supply can cause physical harm to the public.
Details of the compromise are scarce but local officials made it clear the city's water supply was never affected.
During an explanation on Monday, Sheriff Gualtieri said the hack was first spotted in real time earlier in the morning by a staffer who noticed the remote connection to the plant.
The Sheriff said the remote access itself wasn't unusual but just after lunch on the same day Sheriff Gualtieri said the attacker returned and the plant operators watched as the hackers took control of the mouse and started operating the computer system.
The attacker spent about three to five minutes in the control software and jacked up the amount of lye from 100 parts per million to 11,100 parts per million.
Once the attacker left, the plant operators immediately reverted the change. “At no time was there a significant adverse effect on the water being treated. The public was never in danger,” he claimed.
Cybersecurity experts have long warned that hackers could cause serious damage to organizations by targeting exposed human-machine interfaces (HMIs), and the incident in Oldsmar is another reminder of how vulnerable such systems across the nation's critical infrastructure can be.
In early 2020, the Israeli government issued an alert to organizations in the water sector following a series of cyberattacks aimed at water facilities, and advised water and energy firms to immediately change the passwords of internet-accessible control systems, reduce internet exposure, and ensure that all control system software is up to date. Just weeks later, a group of Iranian hackers posted a video showing how they managed to access an industrial control system at a water facility in Israel.
SecurityWeek will be update this article as more information becomes available.
Web Developer Hub SitePoint Discloses Data Breach
9.2.2021 Incindent Securityweek
Web development resources provider SitePoint has notified users of a data breach that resulted in some of their information being stolen.
Based in Melbourne, Australia, and established more than two decades ago, SitePoint provides users with access to tutorials and books that can help them learn the basics of web development.
Last week, the company started informing users that some data was accessed by a third-party during a cyber-attack that was “recently confirmed.”
The culprit, SitePoint said, is a third-party tool that it uses to monitor its GitHub account, “which was compromised by malicious parties.”
While it did not provide further information on the compromised tool, SitePoint said that hackers abused it to access its systems and codebase. The Waydev GitHub application was previously abused in similar attacks.
In addition to removing the tool, the company rotated API keys and changed passwords.
“As a precautionary measure, while we continue to investigate, we have reset passwords on all accounts and increased our required length to 10 characters,” the company told users.
Information that was likely compromised during the incident includes names, usernames, hashed passwords, email addresses, and IP addresses. Although the passwords are stored hashed and salted, users are advised to change them, to ensure the security of their account.
“Your browser will remain logged in if you have used our service recently. However, you can still create a new password manually by clicking on the ‘Account > Profile & Settings’ option and entering your details in the ‘Change your password’ section,” SitePoint said.
Users who log into SitePoint with Google, Facebook, or similar social services won’t have to change their passwords.
The company also notes that it has no evidence that customers’ financial information was accessed during the data breach, as it does not store credit card data, but uses a third party service for credit card processing.
The company also said it is currently “performing a full assessment of the data breach,” as well as of its infrastructure and security posture.
SitePoint did not provide information on the number of affected users, but BleepingComputer suggests that over one million might have been affected, based on information that emerged in December 2020. The company was apparently warned of the incident at the time.
“This breach, and the fact that they were warned months earlier, serves as a lesson that organizations need to have a process in place to deal with reports of potential data leakage and must take them seriously. It is critical for organizations to deal with these issues quickly and transparently to allow those impacted to protect themselves,” Erich Kron, security awareness advocate at KnowBe4, said in an emailed comment.
“These types of breaches are a reason that individuals should be taught not to use the same login credentials across multiple services. In the event the attackers are able to crack the encryption, they are likely to try the credentials on other websites, especially banking sites and shopping sites, in the hope that they are reused there,” Kron added.
COMB breach: 3.2B email and password pairs leaked online
8.2.2021 Incindent Securityaffairs
The Largest compilation of emails and passwords (COMB), more than 3.2 billion login credentials, has been leaked on a popular hacking forum.
More than 3.2 billion unique pairs of cleartext emails and passwords have been leaked on a popular hacking forum, the collection aggregates data from past leaks, such as Netflix, LinkedIn, Exploit.in, Bitcoin, and more.
This breach was dubbed “Compilation of Many Breaches” (COMB), the data is archived in an encrypted, password-protected container.

Source: CyberNews
The database includes a script named count_total.sh, which was also included in 2017’s Breach Compilation. COMB also includes the query.sh script for querying emails and the sorter.sh script for sorting the data.
Experts at CyberNews added the new COMB emails to their Personal Data Leak Checker.
This does not appear to be a new breach, but rather the largest compilation of multiple breaches. Much like 2017’s Breach Compilation, COMB’s data is organized by alphabetical order in a tree-like structure, and it contains the same scripts for querying emails and passwords.
At the time of this writing, it is not clear what previously leaked databases are included in the COMB breach.
“This current leaked database appears to build on 2017’s Breach Compilation. In that leak, intelligence analysts at 4iQ discovered a single file database with 1.4 billion email and password pairs, all in plaintext.” reads the post published by CyberNews.
“At the time, this was considered the largest credential breach exposure, almost two times larger than the previous largest credential exposure from Exploit.in which had nearly 800 million records.”
The analysis of data included in the COMB breach revealed that “14% of exposed username/passwords pairs had not previously been decrypted by the community and are now available in clear text.”
Experts from the intelligence security firm 4iQ who discovered the Breach Compilation, verified the tested credential worked.
“The intelligence analysts state that they found the 41GB dump on December 5, 2017, with the latest data updated on November 29, 2017.” continues the post.
They also remarked that the leak was not just a list, but rather an “interactive database” that allowed for “fast (one second response) searches and new breach imports. Given the fact that people reuse passwords across their email, social media, e-commerce, banking and work accounts, hackers can automate account hijacking or account takeover.”
Experts warn of the impact to consumers and businesses of this new breach that may be unprecedented due to the bad habit of reusing login credentials.
Web developers SitePoint discloses a data breach
8.2.2021 Incindent Securityaffairs
The website, and publisher of books, courses and articles for web developers, SitePoint discloses a data breach that impacted 1M users.
SitePoint is an Australian-based website, and publisher of books, courses and articles for web developers. The company has disclosed a data breach and notified its users via email.
Threat actors offered for sale an archive containing user details for one million SitePoint users on a cybercrime forum.
In December, security experts from Bleeping Computer reported that a threat actor was selling user records allegedly stolen from twenty-six companies on a hacker forum.
The total volume of data available for sale is composed of 368.8 million stolen user records, 1 million records belong to SitePoint.
“We have recently confirmed that SitePoint’s infrastructure was breached by a third party and some non-sensitive customer data was accessed as part of this attack.” reads the data breach notification share by El Reg.
“As a precautionary measure, while we continue to investigate, we have reset passwords on all accounts and increased our required length to 10 characters. Next time you login to SitePoint you will need to create a new password.”
The company revealed that threat actors compromised an unnamed “third party tool we used to monitor our GitHub account.”
“This allowed access through our codebase into our systems. This tool has since been removed, all of our API keys rotated and passwords changed,” the company said.
Data accessed by the threat actors could be exploited to access users’ codebase and system, the good news is that no financial information was exposed because it was not stored on the company system.
Both ZDNet and Bleeping computer speculate that the third-party tool compromised by attackers is the Waydev app.
In response to the security breach, the company has reset user passwords for all its users.
The company pointed out that passwords were hashed with the bcrypt algorithm and salted, which is considered secure and makes it hard to crack passwords.
Spotify Suffers Second Credential-Stuffing Cyberattack in 3 Months
5.2.2021 Incindent Threatpost
As many as 100,000 of the music streaming service’s customers could face account takeover.
Spotify streaming music aficionados are in the crosshairs of yet another credential-stuffing cyberattack, just three months after the last one. The service has forced password resets for impacted users.
Cybercriminals carrying out credential-stuffing take advantage of people who reuse the same passwords across multiple online accounts. Attackers simply build automated scripts that systematically try stolen IDs and passwords (either gleaned from a breach of another company or website, or purchased online) against various types of accounts.
Cybercriminals have successfully leveraged the approach to steal data from various popular companies’ customers, including big names like the North Face, Dunkin Donuts (which was also hit twice in three months) and popular chicken-dinner chain Nando’s. And last year, FC Barcelona’s official Twitter account was hacked in an apparent credential-stuffing attack.
Replay: A Second Credential-Stuffing Attack for Spotify
Back in November, cybercriminals attacked hundreds of thousands of Spotify users utilizing this approach, prompting the streaming music service to issue password-reset notices.
Researcher Bob Diachenko tweeted about the new Spotify attack on Thursday: “I have uncovered a malicious #Spotify logger database, with 100K+ account details (leaked elsewhere online) being misused and compromised as part of a credential stuffing attack.”
He also posted a Spotify statement on the incident that confirmed the attack.
“We recently protected some of our users against [a credential-stuffing attack],” the notice read. “Once we became aware of the situation, we issued password resets to all impacted users, which rendered the public credentials invalid.”
The company also noted that the attacks were carried out using an ill-gotten set of data: “We worked to have the fraudulent database taken down by the ISP hosting it.”
Cybercriminals Misconfigure the Cloud Too
In the first Spotify incident in November, researchers found a misconfigured and open Elasticsearch cloud database containing more than 380 million individual records, including login credentials and countries of residence for various people, all being actively being validated against Spotify accounts. The database was owned by a malicious third party, researchers said at the time.
This second attack is very similar, with the log-in data also exposed in a public Elasticsearch instance.
“There are similarities but this one looks different, like coming from a rival group,” Diachenko tweeted. He told Threatpost via Twitter DM that the data sets were unique to this attack.
“Originally this data was exposed inside a misconfigured (thus publicly reachable) Elasticsearch cluster – most likely operated by the malicious actors themselves,” he said. “It contained entire logs of their operations, plus email/password pairs they used [for the attack].”
The data once again also was likely gleaned from prior breaches.
“I suppose that login pairs came from previously reported breaches or collections of data, so they just re-use them against Spotify accounts to become part of this automated process,” Diachenko said.
What Are the Dangers of Credential-Stuffing?
On the surface, a cybercriminal being able to log into someone’s Spotify account would seem to be more of a nuisance than anything else. Setting up rogue playlists, deleting saved songs or straight-up hijacking the ability to listen to music are some of the potential headaches.
However, there’s more to think about, Diachenko noted: For those who do reuse passwords, a validated Spotify log-in combo can simply be used to infiltrate other, higher-value accounts.
“Technically, it is not that dangerous if somebody breaks into your Spotify account (apart from moral part of course),” he said. “However, the worst-case scenario is that your details would be traded underground or even publicly (I know there are many eBay resellers to do that).”
Compromised accounts could contain credit-card information, loyalty points that could be stolen or used, or physical shipping addresses. And, accounts can also contain information like birthdays, preferences (those Spotify playlists, for example) and other data that is ripe for abuse when it comes to developing social-engineering tricks for phishing attacks.
To protect themselves from credential-stuffing attacks, users should enable multi-factor authentication (MFA) on their accounts and avoid using passwords more than once.
Hackers accessed Stormshield data, including source code of ANSSI certified products
5.2.2021 Incindent Securityaffairs
The provider of network security products Stormshield discloses data breach, threat actors stole information on some of its clients.
Stormshield is a major provider of network security products to the French government, some approved to be used on sensitive networks.
Stormshield is a French publisher of software specialized in computer security, its products are certified and qualified by ANSSI (Agence Nationale de la Sécurité des Systèmes d’Information).
Attackers breached one of the customer support portals and stole information on some of its clients.
The company also admitted that threat actors managed to steal the source code for the Stormshield Network Security (SNS) firewall, which is one of the products certified by the ANSSI to be used in sensitive French government environments.
“Recently, the Stormshield teams detected a security incident that resulted in an unauthorized access to a technical portal used, in particular, by our customers and partners for the management of their support tickets on our products.” reads the data breach notification published the vendor.
“Personal data and technical exchanges associated with certain accounts may have been consulted.”
The company reported the incident to the authorities and launched an investigation with the support of the ANSSI agency.
In response to the intrusion, as a precaution, the Stormshild experts reset the passwords of all accounts and enhanced the security measures to protect the portal. The IT staff reviewed all the support tickets and technical exchanges in the impacted accounts and shared the results with the customers.
At the time of this writing, it is not clear the impact of the security breach on government networks.
“Further investigations in the context of this incident have revealed the leakage of some parts of the SNS (Stormshield Network Security) source code.” continues Stormshield.
“As of today, the in-depth analysis carried out with the support of the relevant authorities has not identified any evidence of illegitimate modification in the code, nor have any of the Stormshield products in operation been compromised.”
The ANSSI announced to have put Stormshield SNS and SNI products “under observation” for the duration of the investigation.
“Although the incident has no immediate operational impact for its customers, Stormshield has published an update that we recommend that you apply as a precaution.” reads a press release published by the ANSSI.
“Furthermore, for the duration of the investigations and also as a precautionary measure, ANSSI has decided to place the qualifications and approvals of SNS and SNI products under observation.”

The French security provider announced to have anticipated the replacement of the trusted certificate that signs and ensures the integrity of the SNS (Stormshield Network Security) releases and updates. This measure was necessary to prevent supply chain attacks that could employ the update mechanisms to deliver tained updates.
The company released updates to customers and partners to deploy new certificates.
The company also reset passwords for the accounts registered on the Stormshield Institute portal, which is used for customer training courses.
Airbus CyberSecurity Subsidiary Stormshield Discloses Data Breach
5.2.2021 Incindent Securityweek
Stormshield, a wholly-owned subsidiary of France-based cybersecurity company Airbus CyberSecurity, has disclosed a data breach that resulted in source code and customer information getting compromised.
Stormshield provides network security, endpoint security and data security solutions. The company describes itself as a “European leader in digital infrastructure security” and claims to have a presence in more than 40 countries.
In a security incident notice posted on its website, Stormshield said it recently detected unauthorized access to a technical portal used by customers and partners for managing support tickets related to the company’s products. The attackers may have gained access to “personal data and technical exchanges.”
The company has determined that the hackers may have also obtained some source code for the Stormshield Network Security (SNS) product, but there is no evidence that code has been modified or that the products used by customers have been compromised.
In response to the incident, Stormshield notified authorities and impacted customers, and it decided to reset passwords for the impacted portal, implement additional security mechanisms, and replace a certificate used to sign releases and updates for the SNS product. Updates have been released to ensure that existing deployments work with the new certificate.
The company said its operations were not impacted.
“Companies like Stormshield, that provide cybersecurity solutions against the explosion of cyberthreats, would appear to be a new target for highly prepared and experienced attackers,” Stormshield said.
The French National Agency for the Security of Information Systems (ANSSI), which assisted Stormshield in its investigation, has also issued a statement in response to the incident. The agency said the attackers apparently also exfiltrated source code for the company’s Stormshield Network Security Industrial Firewall (SNI).
“Although the incident has no immediate operational impact for its customers, Stormshield has published an update that we recommend that you apply as a precaution. Furthermore, for the duration of the investigations and also as a precautionary measure, ANSSI has decided to place the qualifications and approvals of SNS and SNI products under observation,” reads a translation of ANSSI's statement.
Magento Web Skimmers Piggyback in Ongoing Costway Website Compromise
3.2.2021 Incindent Threatpost
An e-commerce credit-card skimmer is being used by a second skimmer to steal payment data – and both are on Costway’s website.
Two web skimmers have been discovered on the payment webpages of Costway, one of the top retailers in North America and Europe, which sells appliances, furniture and more. The skimmers are targeting consumers’ credit-card payment details.
In a twist, researchers say one of these web skimmers is piggybacking on top of the other, to take over the fake forms that had previously been injected onto Costway’s site. The tactic gives the cybercriminals behind the piggybacking skimmer an easy way to harvest credit-card details – without doing the heavy lifting, said researchers.
The website under attack runs on the no-longer-maintained Magento 1 e-commerce software branch. Magento is an e-commerce platform for online merchants that’s built on open-source technology. Support for Magento 1 ended last June, with the thousands of retailers worldwide operating on the platform being urged to update to the more mobile-friendly Magento 2 iteration.
“A large number of Magento 1 sites have been hacked but yet are not necessarily being monetized,” said researchers with Malwarebytes on Tuesday. “Other threat actors that want access will undoubtedly attempt to inject their own malicious code. When that happens, we see criminals trying to access the same resources and sometimes fighting with one another.”
Researchers first discovered a skimmer that had injected a fake payment form directly onto the checkout page for costway[.]fr, the merchant’s French website. The payment form was harvesting visitors’ payment-card details as they input them.
“Our crawlers identified that the websites for Costway France, U.K., Germany and Spain, which run the Magento 1 software, had been compromised around the same time frame,” said researchers.
Costway site already hacked with Magento 1 skimmer. Credit: Malwarebytes
The potential threat to victims here is massive, with Costway’s French portal (costway[.]fr) attracting about 180K visitors just in December, said researchers.
Upon further investigation, researchers were surprised to discover another skimmer present on the site. This skimmer was loaded externally from securityxx[.]top.
Researchers believe that the second skimmer may not have had the same foothold or access to the webpage as the first skimmer. In this scenario it would make sense for attackers to simply inject code on top of the first skimmer and grab credentials from the first skimmer’s fake form.
“It’s possible that the threat actors’ level of access to e-commerce sites differs,” they explained. “The former exploit a core vulnerability that grants them root access, while perhaps the latter can only perform specific types of injections. If that is the case, this would explain why they simply leave the fake form alone and grab credentials from it.”
An Ongoing Attack
Researchers said that cybercriminals also continue to actively re-inject Costway’s website, even after they notified the retailer of the compromise.
“We informed Costway during our investigation but also witnessed their site getting re-infected,” said researchers. “The costway[.]top domain was discarded in favor of securityxx[.]top where threat actors customized the skimmer specifically for them.”
It’s unclear if this particular attack is the work of Magecart — a conglomeration of threat groups that specialize in compromising vulnerable e-commerce stores to inject payment-card skimmers. But researchers have reported that they have seen an uptick in the number of e-commerce sites that are being attacked by Magecart and related groups that utilize web skimming. In September for instance, one of the largest known Magecart campaigns to date occurred, with nearly 2,000 e-commerce sites hacked in an automated campaign that may be linked to a zero-day exploit.
Hackers stole personnel records of software developer Wind River
3.2.2021 Incindent Securityaffairs
The global leader of embedded system software Wind River Systems discloses a data breach that resulted in the theft of customers’ personal information.
Wind River Systems, a global leader in delivering software for smart connected systems, discloses a data breach.
The company claims its technology is found in more than 2 billion products, it develops run-time software, middleware, development and simulation platforms.
The security breach took place on or around September 29, 2020, attackers accessed the personal information of its employees.
“Our outside experts recently determined that some of your personal information would have been available within one or more files that were downloaded from our network on or about September 29, 2020,” reads the data breach notification letter sent by the company to its employees.
The company is not aware of misuse of the information contained within the downloaded files, it also added that it has not found the stolen files online.
Personnel records accessed by the attackers could include birth dates, driver’s license numbers, national identification numbers, social insurance numbers, social security numbers, passport or visa numbers, health details, and/or financial account information.
At the time of this writing, Wind River hasn’t provided information on how attackers breached the company either the number of affected employees.
Police Exam Database Exposes 500K Indian Citizens ’ PII
3.2.2021 Incindent Securityaffairs
CloudSEK has discovered a post on a well-known database sharing forum advertising the PII of 500,000 Indian citizens.
While the threat actor does not mention the name of an organization, the data provided in the sample is clearly associated with a police exam conducted on 22 Dec 2019.
Discovery of the leak
CloudSEK’s proprietary risk monitoring tool XVigil discovered a post on a popular surface web forum on 29 January 2021. The actor claims to have 500,000 records and has shared a sample of the leak that contains the data of 10,000 users. For more records, the threat actor has to be reached via email or Telegram.
Contents of the leak
The sample CSV file, shared over a file hosting link, contains 10,452 records. Each record includes the following fields:
transactionid
first_name
middle_name
last_name
name
father_name
mother_name
husband_name
mobileNumber
email address
sex
dob
marrital_status
nationality
identity_type
identification_mark
community
jk_domiciled
hno
street
village postoffice
district state
pincode
correspondance_address
hno1
street1 village1
postoffice1
district1
state1
pincode1
ffw
exman govt_emp_service
debarment
fir_case
fir_case_pending
arrested
criminal_case_acquitted
good_behavior_bond
preference1
preference2
preference3
is_duplicate
wedistrict
weexamcode
wedistrictcode
wecentrecode
werollno
wedate wecentre
attendence
attendence1
attendence_scaning
attendence_scaning_remarks
omr_remark
Data verification and validation
On analysing the sample, CloudSEK researchers identified that the common denominators of a significant amount of the sample data are Bihar (“wedistrict”) and 22 December 2019 (“wedate”). This points to the candidates of the preliminary examination conducted by Bihar Police Subordinate Services Commission (BPSSC) for the post of Sub Inspector/ Sergeant/ Assistant Superintendent Jail / Assistant Superintendent Jail, on 22 December 2019.

The mobile numbers provided in the sample have been validated against the candidate’s name.
Impact
The entire leaked database consists of ~500K records. Since the database includes sensitive data, i.e. name, mobile number, and PII, it makes the victims vulnerable to phishing campaigns, scams, and even identity theft.
Embedded Software Developer Wind River Discloses Data Breach
3.2.2021 Incindent Securityweek
Embedded system software provider Wind River Systems has started informing employees of a data breach that resulted in their personal information being stolen by a third party.
The Alameda, California-based wholly owned subsidiary of TPG Capital develops run-time software, middleware, industry-specific software, development tools, and simulation technology. Its product portfolio includes the Wind River Linux operating system and the VxWorks real-time operating system.
A copy of the data breach notification that the company has filed with California’s Attorney General reveals that the newly disclosed security incident took place on or around September 29, 2020.
“Our outside experts recently determined that some of your personal information would have been available within one or more files that were downloaded from our network on or about September 29, 2020,” the letter sent to employees reads.
The company also says it has no indication that the information contained within those files might have been misused, and that it did not find these files being shared online.
Wind River says that the type of personal information compromised might vary, and would include the information stored in the company’s personnel records.
Thus, compromised employee data could include birth dates, driver’s license numbers, national identification numbers, social security numbers, social insurance numbers, passport or visa numbers, health details, and/or financial account information.
Wind River hasn’t provided information on the number of affected employees, or how the attackers were able to compromise its systems.
SecurityWeek has reached out to Wind River for additional information on the security incident and will update this article as soon as a reply arrives.
Over 1 Million Impacted by Data Breach at Washington State Auditor
3.2.2021 Incindent Securityweek
The Office of the Washington State Auditor (SAO) has disclosed a cybersecurity incident in which the personal information of more than 1 million individuals might have been stolen.
At the heart of the incident, SAO says, was Accellion software used for file transfers. Hackers exploited a security flaw in the file sharing service and gained access to restricted files.
Called FTA (File Transfer Application), Accellion’s service in mid-December received a patch for a critical vulnerability impacting less than 50 customers. The fix was sent to all affected organizations.
Despite that, the vulnerable service has been exploited by hackers to breach the systems of other Accellion customers as well, namely the Reserve Bank of New Zealand and the Australian Securities and Investments Commission (ASIC).
In its breach notification this week, SAO revealed that some of the files that were compromised in the incident contained “personal information of Washington state residents who filed unemployment insurance claims in 2020.”
Other Washington residents might have been affected as well, as their information was in state agency or local government files that SAO was reviewing.
While SAO did not provide details on the number of impacted users, the Employment Security Department (ESD) issued an alert on the incident, revealing that more than one million individuals might have been affected.
The affected data can include names, bank account numbers, bank routing numbers, social security numbers, driver’s license/state identification numbers, and places of employment.
When “other information from state agencies and local governments” is added, the figure rises to approximately 1.6 million unemployment claims that might have been affected in the incident, ESD says.
SAO also said that the intrusion happened in late December 2020, but that Accellion only confirmed the incident on January 25, 2021.
As part of the investigation launched into the matter, SAO attempted to identify which files from state agencies and local governments were affected, as well as the individuals who might have had their personal information stolen.
Data Breach Exposes 1.6 Million Jobless Claims Filed in the Washington State
3.2.2021 Incindent Thehackernews
The Office of the Washington State Auditor (SAO) on Monday said it's investigating a security incident that resulted in the compromise of personal information of more than 1.6 million people who filed for unemployment claims in the state in 2020.
The SAO blamed the breach on a software vulnerability in Accellion's File Transfer Appliance (FTA) service, which allows organizations to share sensitive documents with users outside their organization securely.
"During the week of January 25, 2021, Accellion confirmed that an unauthorized person gained access to SAO files by exploiting a vulnerability in Accellion's file transfer service," the SAO said in a statement.
password auditor
The accessed information is said to have contained personal details of Washington state residents who filed unemployment insurance claims in 2020, as well as other data from local governments and state agencies.
The exact information that may have been compromised include:
Full name
Social security number
Driver's license
State identification number
Bank account number and bank routing number, and
Place of employment
The unauthorized access incident is believed to have occurred in late December of last year, although it appears the full scope of the intrusion wasn't made aware until Accellion disclosed earlier this month that its file transfer application was the "target of a sophisticated cyberattack."
The Palo Alto-based cloud solutions company said on January 11 that it was made aware of a vulnerability in its legacy FTA software in mid-December, following which it claimed it addressed the issue and released a patch "within 72 hours" to the less than 50 customers affected.
Accellion also said it's contracting with an "industry-leading cybersecurity forensics firm" to investigate the incident.
Given that the compromised information can be abused to carry out identity theft or fraud, the SAO said it's in the process of arranging measures to protect the identities of those whose information may have been contained within SAO's files.
In the meanwhile, the agency recommends reviewing account statements and credit reports, notifying financial institutions of any suspicious activity, and reporting any suspected incidents of identity theft to law enforcement.
It's worth noting that Accellion's FTA software was used as an attack vector to strike two other organizations, including the Australian Securities and Investments Commission (ASIC) and the Reserve Bank of New Zealand (RBNZ), in recent weeks.
UScellular data breach: attackers ported customer phone numbers
31.1.2021 Incindent Securityaffairs
US wireless carrier UScellular discloses data breach, personal information of customers may have been exposed and their phone numbers ported.
US wireless carrier UScellular discloses a data breach that exposed personal information of its customers.
United States Cellular Corporation, is the fourth-largest wireless carrier in the United States, with over 4.9 million customers in 426 markets in 23 states as of the second quarter of 2020.
The company detected the security breach on January 6, 2021, and determined that the intrusion took place early this year, on January 4th, 2021.
Then threat actors tricked UScellular employees working in retail stores into downloading and installing malicious software.
The malware allowed the attackers to access the CRM using the employee’s accounts and then access personal information, including phone numbers, of the company customers.
“On January 6, 2021, we detected a data security incident in which unauth0rized individuals may have gained access to your wireless customer account and wireless phone number. A few employees in retail stores were successfully scammed by unauthorized individuals and downloaded software onto a store computer.” reads the USCellular data breach notification.
“Since the employee was already logged into the customer retail management (“CRM”) system, the downloaded software allowed the unauthorized individual to remotely access the store computer and enter the CRM system under the employee’s credentials.”
The attackers accessed the customer accounts and ported their wireless number to another carrier.
UScellular reported the incident to law enforcement as well as certain state agencies.
Exposed customer details include names, addresses, PIN codes, phone numbers, and information on wireless services, usage, and billing statements (CPNI). The company added that even if the social security numbers and payment card information are present in the CRM, they likely haven’t been exposed because they are “masked”
The news was confirmed in a data breach notification that was initially published by the US mobile carrier on its website, but at the time of this writing is no more available.
“On January 6, 2021, we detected a data security incident in which unauthorized individuals may have gained access to your wireless customer account and wireless phone number.” reads the notice. “After accessing your account, a wireless number on your account was ported to another carrier by the unauthorized individuals.” – USCellular
In response to the incident, the company removed the malicious software from the computers at the retail store and reset passwords for the impacted employees. UScellular also changed users’ and user Authorized Contacts’ PIN and security question/answer.
“We also have worked with those who had a number ported to provide a new temporary number while working to retrieve the fraudulently ported number or provide a new number at the customer’s choice. When a number is ported, the unauthorized individuals do not obtain access to information contained on the customer’s mobile device such as contacts or applications,” the company added. “Nevertheless, we advised these customers to be diligent about monitoring and reviewing their online accounts and financial statements for unauthorized access and transactions and recommend changing the usernames and passwords of online accounts.”
UScellular Breach Allowed Hackers to Port Customer Phone Numbers
30.1.2021 Incindent Securityweek
Chicago-based wireless carrier UScellular started informing customers last week that their personal information may have been accessed and their phone numbers ported as a result of a cybersecurity breach.
UScellular is one of the largest wireless carriers in the United States — it claims to have nearly 5 million customers across 20 states. However, it’s unclear how many were affected by the data breach. SecurityWeek has reached out to the company for more information.
The carrier said it detected the breach on January 6, 2021, and its investigation so far suggests that the attackers first gained access to its systems two days earlier. The hackers used an undisclosed method to trick UScellular employees working in retail stores into downloading malicious software.
This malware then allowed the attacker to remotely access compromised store computers and the customer retail management (CRM) system running on them. Since employees were already logged into the CRM system, the attackers were able to access the CRM with the employee credentials and access wireless customer accounts and phone numbers.
“After accessing your account, a wireless number on your account was ported to another carrier by the unauthorized individuals,” the company told customers in a data breach notice posted on its website.
UScellular said the attackers may have gained access to names, addresses, PIN codes, phone numbers, and information on wireless services, usage, and billing statements (CPNI). Social security numbers and payment card information are entered into the CRM, but they are “masked” so they likely haven’t been exposed.
“At this time, we have no indication that there has been unauthorized access to your UScellular online user account (My Account),” customers were told.
In response to the incident, UScellular has removed infected computers from stores, changed compromised employee credentials, and modified the PIN and security question/answer of customers and their authorized contacts. Law enforcement has also been notified.
“We also have worked with those who had a number ported to provide a new temporary number while working to retrieve the fraudulently ported number or provide a new number at the customer’s choice. When a number is ported, the unauthorized individuals do not obtain access to information contained on the customer’s mobile device such as contacts or applications,” the company said. “Nevertheless, we advised these customers to be diligent about monitoring and reviewing their online accounts and financial statements for unauthorized access and transactions and recommend changing the usernames and passwords of online accounts.”
It’s unclear why the attackers ported phone numbers, but taking control of someone’s phone number can be highly useful to cybercriminals in some cases, particularly if they want to access an account protected with SMS-based two-factor authentication (2FA). If they have the targeted user’s username and password, having control of their phone number ensures that the 2FA code is sent to them when they try to log in.
Deep Analysis of More than 60,000 Breach Reports Over Three Years
30.1.2021 Incindent Securityweek
Hackers Are Winning Battles, While Victims are Gaming the Notification Laws
Threat intelligence platform provider HackNotice has analyzed more than 60,000 breach reports over the last three years, and finds some disturbing results ‒ including the rate of increase in breaches and a relative decline in the number of official breach notifications.
In its analysis, shared exclusively with SecurityWeek, the company examined 67,529 breaches that were publicly reported from 2018 to 2020. The source of the reports is as follows:
Leak reports containing data from a breached company as disclosed by hackers (41,030).
News; that is, a breach report first announced by an online news service (15,219).
With 2.7 times more breaches first being disclosed by hackers rather than a news service, the implication is that companies monitoring the news for their own or suppliers’ compromise would be better served by monitoring the dark web.
Ransomware, being data leaked by hackers when a victim refuses to pay the ransom (988).
This is not an indication of the number of successful ransomware attacks, but merely the number of companies that were breached but refused to pay the ransom in an increasingly frequent double extortion attack. The first of such breach announcements occurred in April 2020, but the number grew to almost 1,000 by January 1, 2021. The implication is that double extortion ransomware attacks are increasing and will likely continue to increase through 2021 and beyond.
Defacement, where a website has been breached and content changed by the hacker as proof (2,243).
Hacktivism
Website defacements have long been popular with hacktivists wishing to make a point ‒ usually political and/or ethical. A decade ago they were commonplace, but seemed to lose popularity in recent years. However, according to HackNotice they began to increase again in July 2019, and then dramatically from April 2020. This is perhaps not surprising given the tumultuous state of geopolitics in recent years.
It is difficult to predict whether this will continue, but it will most likely reflect the state of national and international geopolitics. Companies working in either politically or ethically sensitive areas should take extra care in protecting their websites from defacement attacks.
Official disclosure, where a data breach was reported to official sources and disclosed ‒ such as state level DOJ websites and HHS (9131).
The interesting point here is the relatively small number of breaches, around 13.5% of the total, that are reported through official channels. This has fallen from 25% at the beginning of the period analyzed.
HackNotice, a startup headquartered in Austin, Texas, was founded in 2018. CEO and co-founder Steve Thomas told SecurityWeek, “We collect hack notices (data breaches, defacements, ransomware, etc.) from hundreds of sources, scraping official data breach disclosure sites, ransomware disclosure sites, APIs, twitter accounts and hashtags throughout the day. All those events go into a queue, where each one is reviewed by a security researcher. We remove all the noise, identify the companies being broken into, and add those events to our system. We use machine learning to analyze each event’s disclosure statement to identify what data was exposed.”
Two elements of the new analysis of breaches occurring in 2018 to 2020 are particularly interesting: the steady growth in hacker successes and the decline in the percentage of breaches disclosed through official channels.
In 2018, HackNotice discovered 29,562 reported breaches. By December 2019, the total discovered had risen to 44,863 ‒ a 51.7% increase over the year. By December 2020, the total had risen to 67,529 ‒ a 50.5% over the year. In absolute terms, these figures show an increase from 15,301 in 2019 to 22,666 in2020.
The obvious question is why have the hackers become more successful at a time when we have increased security budgets, and more and supposedly superior security products?
Thomas believes it is because companies concentrate defenses in the wrong areas. “Hackers are winning the cyberwar,” he said, “largely because they don’t target the infrastructure, but they target people. Phishing, credential stuffing, account takeover of personal accounts to get into business accounts… All the major attack vectors rely on the fact that average employees are not informed as to how exposed they are, and they value security much less than the security team does.”
Other security experts have similar views. Josh Angell, application security Consultant at Falls Church, Virginia-based nVisium, suggests, “Human error still accounts for the vast majority of breaches, making tools and secure coding practices obsolete if the people who maintain these networks and systems, and have access to company emails and sensitive client data, are not compliant with industry best practices.”
“Several factors play into the increase in breaches,” explains Brandon Hoffman, CISO at San Jose, Calif.-based Netenrich. “Some of it is indeed related to the ingenuity of the adversary but much of it seems related to the deviation from foundational security. Security tooling has advanced significantly yet the focus of security as a discipline seems to be more on the use of advanced tooling. The challenge this creates is time and resources.”
Alec Alvarado, threat intelligence team lead at San Francisco-based Digital Shadows, summarizes this viewpoint, “The bad guys are winning the war simply because they are sticking to ways that work and have proven effective. The most robust security team with the most extensive cybersecurity practices and a multi-million dollar cybersecurity budget will fail with the single click of a well-crafted phishing email or a weak password.”
The implication is clear. While hackers are becoming more sophisticated, defenders are perhaps spending too much time and effort on shiny new toys rather than getting the basics of security right.
The second notable discovery from the HackNotice research is the decline in the number of breaches that are disclosed through official channels. This seems surprising considering the growing number of national and international breach notification laws that now exist. HackNotice CEO Thomas puts the apparent anomaly down to the number of state breach laws that allow 30 days or more before notification is required.
“There is no federal breach notification law in the US, so you have to go by the states,” he told SecurityWeek. “However, each state writes its law different and the laws allow the breached company 30 days or even more before they have to disclose. News outlets, ransomware and defacement gangs end up disclosing before the official notice, so we are seeing market share being taken away from official disclosures.”
Delaying breach disclosure until the last possible moment almost seems like gaming the system. Netenrich’s Hoffman agrees with this. “We, the security industry, also suspect there is in fact flouting of the notification law or that the notification period is being abused to the maximum extent possible to provide a rosier picture for investors and the public,” he said. “To phrase it differently if an organization is breached and their notification window by law is 90 days, they will not announce it until they have used 89 days to perform maximum triage and cleanup effort so that when they do announce they can claim it has all been addressed.”
“Breach notification laws do not guarantee that companies will be willing to sacrifice investor confidence or risk lawsuits to disclose a breach every time there is one,” adds nVisium’s Angell.
Digital Shadows’ Alverado has an interesting addendum to this. He accepts that current notification laws give companies wiggle room to avoid damage to stock value and brand image, but adds, “We often hear of a company announcing that ‘there was a cybersecurity incident, but there was no indication that data was exfiltrated.’ This should raise eyebrows for most as it does not fit the typical motive of a threat actor to sit on a network and not pull data or find a way to monetize on that access.” It may be that whenever we hear ‘incident’ we should automatically suspect ‘probable breach’.
The HackNotice analysis of 60,000 breaches over the last three years provides extensive data on where things are going wrong, and highlights trends on what is likely in the future. Importantly, it shows that the criminals are winning. It is likely that at least a partial solution might be for companies to do better basic security rather just throw money at the newest and most shiny product.
It also shows that if knowing what is going on is important, a more accurate picture will be obtained from monitoring the dark web though threat intelligence rather than monitoring the news feeds. And it also shows that current breach notification laws are not truly fit for purpose.
Cypriot National Admits in U.S. Court to Extorting Website Owners
28.1.2021 Incindent Securityweek
A Cypriot national has admitted in a United States court to hacking websites based in the U.S., stealing user data, and demanding ransom payments from the site owners to keep the data private.
The man, Joshua Polloso Epifaniou, 21, of Nicosia, Cyprus, the first Cypriot national to be extradited to the U.S., perpetrated the scheme between at least October 2014 and November 2016, the U.S. Department of Justice says.
According to court documents, during the scheme, Epifaniou was a teenage hacker. He would find potential targets by looking at website traffic rankings, and then steal personally identifiable information (PII) from them, with the help of co-conspirators.
The hacker targeted both user and customer databases, harvesting data of interest through exploiting security vulnerabilities or by obtaining the data from co-conspirators.
Once in possession of the PII, Epifaniou emailed the victim websites, threatening to make the stolen data public and demanding a ransom payment be made in crypto-currency.
Some of the hacker’s victims include an online sports news website in Atlanta, Georgia; a free online game publisher in Irvine, California; a hardware company in New York, New York; an online employment website in Innsbrook, Virginia; and Phoenix, Arizona-based Ripoff Report (ROR).
Prior to pleading guilty, Epifaniou paid approximately $600,000 in restitution to the victims. In the plea agreement, he agreed to forfeit $389,113 and roughly 70,000 euros to the government.
Epifaniou was indicted on September 19, 2017, on multiple counts of wire fraud conspiracy, wire fraud, computer fraud conspiracy, and extortion. He was also charged in a 24-count indictment transferred from the District of Arizona, and pleaded guilty to one count of computer fraud.
The hacker is scheduled for sentencing for March 3, 2021.
23M Gamer Records Exposed in VIPGames Leak
27.1.2021 Incindent Threatpost
The personal data of 66,000 users was left wide open on a misconfigured Elasticsearch server, joining a growing list of companies with leaky clouds.
VIPGames.com, a free platform with a total of 56 available classic board and card games like Hearts, Crazy Eights, Euchre, Dominoes, Backgammon and others, has exposed the personal data of tens of thousands of users.
In all, more than 23 million records for more than 66,000 users were left exposed thanks to a cloud misconfiguration, according to a new report from WizCase. Aside from its desktop users, VIPGames has mobile players too, including via an app that’s been downloaded from the Google Play store more than 100,000 times alone.
The site joins a growing list of companies caught without properly configurated clouds which can lead to disastrous results for customers.
The WizCase research team, led by Ata Hackl, regularly scans the internet for open servers and found the sensitive personal information exposed and available to any cybercriminal who happened to stumble across it.
Online gaming represents a particularly desirable set of personal details for cybercriminals, the report explained.
Leaky Gamer Clouds Particularly Dangerous
“Online gaming brings together user personal information, transaction details and gaming habits. This fusion of confidential information creates a lucrative environment for cybercriminals to exploit,” the WizCase report explained. “Gaming platforms routinely experience multiple attacks from hackers, sabotage from competing platforms, intra-platform attacks by players targeting the Internet connections of rival users, and more.”
In this case, the site’s unprotected server leaked more than 30GB of data containing 23 million individual records, including usernames, emails, IP addresses, hashed passwords, Facebook, Twitter and Google IDs, bets and even data on players who were banned from the platform, WizCase said.
“Each of these data sets is not just valuable on its own but can also be used to map out other information,” the report explained. “For example, from the player IDs, it’s possible for an attacker to locate the player’s email address, IP address and hashed password, which is particularly relevant for the banned players.”
The report added that the VIPGames.com Terms of Use explains players can be blocked from the platform for bad behavior or cheating, and that the exposed records included the dirty details of each infraction.
“Some of these included potential pedophilia and exhibitionism,” WizCase said, adding potential blackmail to the list of threats the exposed data posed to users, in addition to identity theft, password breaches, phishing scams, malware and more.
Threatpost reached out to VIPGames.com for comment but hasn’t received a response.
And while this breach is alarming, it is part of a wider trend of companies failing to lock down their data in the cloud.
Misconfigured Clouds Are Everywhere
Last September high-end gaming gear company Razer left the personal data of about 100,000 users exposed on a similar Elasticsearch cloud cluster.
That same month, a group of 70 different adult dating sites was also discovered to be storing sensitive personal data — like sexual preferences — on an unsecured Elasticsearch server, leaking more than 320 million individual records.
In April, the Key Ring digital wallet app exposed 44 million customer records including IDs, charge cards, loyalty cards, gift cards and membership cards left open on an Amazon Web Services S3 server. And last summer, Joomla exposed the data of 2,700 people signed up for the Joomla Resources Directory community forum in an unsecured Amazon Web Services cloud storage bucket.
Palo Alto Networks’ Unit 42 estimates about 60 percent of breaches occur because of misconfigured public clouds.
Ryan Olson, vice president of threat intelligence with the Unit 42 team, explained that while 86 percent of companies deploy cloud apps, only 34 percent have “single sign-on (SSO) solutions in place, demonstrating a massive gap in cloud adoption and necessary cloud-security solutions.”
As for users, experts agree basic best practices for online security are always a good idea — be careful about what you share, avoid clicking on suspicious emails or links and proper password hygiene are important, WizCase advised. The firm also suggested using a VPN service to keep location data secure and install good antivirus software while the industry struggles to keep up.
“The use of the cloud enables organizations to reach their goals and scale with ease,” Anurag Kahol, CTO at Bitglass, said via email. “As more organizations adopt cloud-based tools to obtain a competitive advantage, the rate of cloud-application usage increases in tandem. However, most organizations are not equipped to handle the security demands of the cloud.”
Criminal, Domestic Violence Case Info Exposed in Cook County Leak
27.1.2021 Incindent Threatpost
Cook County, Ill., home to Chicago, has left a database exposed since at least September that contained sensitive criminal and family-court records.
A non-password protected database, belonging to a county in Illinois, exposed 323,000 court records for at least four months, according to researchers. The database exposed the names of various people involved in sensitive criminal, domestic-abuse or child-custody court cases.
Researchers from Website Planet (in conjunction with security researcher Jeremiah Fowler) alleged the database was owned by Cook County, home to the city of Chicago and which has 5.1 million residents (making it t second most populous county in the U.S., behind Los Angeles county).
The researchers discovered the database on Sept. 26, and notified the Cook County CTO of the exposure soon after. However, the database remained publicly exposed until this week on Monday, when it was secured and public access was restricted.
“Nearly every record contained some form of personally identifiable information (PII) such as full names, home addresses, email addresses, case numbers and private details about the cases,” said researchers with Website Planet on Tuesday. “Based on the potentially sensitive PII exposed, it was clear that this data was not meant to be public.”
The database appeared to be an internal record-management system, which was comprised of detailed data about the status of, or issues with, various cases.
A redacted view of the database. Credit: Website Planet
It’s unclear which specific part of the county managed the database (Threatpost has reached out to Website Planet for further comment). Cook County’s website lists the Clerk of the Circuit Court as being in charge of court records and archives, child-support assistance, divorce records and court eFilings.
The exposed court records, which were dated between 2012 to 2020, exposed both case plaintiffs and defendants “in a tone that was clearly aimed for internal use only and should not have been publicly exposed,” said researchers.
Wrapped up in the database were files labeled “IMM,” that researchers believed to be various immigration court records; including various email addresses (related to USCIS accounts, which are used for citizenship and immigration services) and various court records that included names, case numbers, and case notes about the status or progress of the case (for instance, if the client needed a translator).
Researchers said they presume these court documents were part of a specialized department or case workers within the Cook County courts who assisted those who did not speak English or who needed some type of help from the court.
Also part of the database were various criminal-court records (labeled CRI) and family-court cases (labeled FAM). These could include cases pertaining to divorce (including child custody and visitation), domestic violence, the Child Protection Division (which handles protecting minors from abuse) and the Juvenile Justice Division (which handles crimes by minors).
Verdict: Big Cyberattacks Possible
Researchers said that if accessed by malicious actors, this database would be “a gold mine” for spear-phishing and phishing campaigns, blackmail, identity theft and other nefarious activities.
For instance, scammers could target immigrants whose PII was part of the database, threatening deportation unless a ransom is paid. They could also blackmail families that they would leak their private information – relating to divorce or domestic abuse –if a ransom were not paid.
Unprotected databases continue to expose various types of sensitive information across the internet. Earlier in January, a misconfigured ElasticSearch database exposed more than 400GB of public and private profile data for 214 million social-media users from around the world – including details for celebrities and social-media influencers in the U.S. and elsewhere. And in September, a cloud misconfiguration at gaming-gear merchant Razer potentially exposed 100,000 customers to phishing and fraud.
Threatpost has reached out to Cook County for comment.
Norway to Fine Dating App Grindr $11.7M Over Privacy Breach
27.1.2021 Incindent Securityweek
Gay dating app Grindr faces a fine of more than $10 million from Norwegian regulators for failing to get consent from users before sharing their personal information with advertising companies, in breach of stringent European Union privacy rules.
The Norwegian data privacy watchdog said Tuesday that it notified Grindr LLC of its draft decision to issue a fine for 100 million Norwegian krone ($11.7 million), equal to 10% of the U.S. company’s global revenue.
The Data Protection Authority took action following a complaint by the Norwegian Consumer Council alleging personal data was shared unlawfully for marketing purposes. The council had detailed in a report last year how Grindr and other dating apps leaked personal information to advertising technology companies for targeted ads in ways the council said violated the EU’s tough GDPR privacy rules.
Norway isn’t a member of the EU but closely mirrors the bloc’s rules and regulations.
“The Norwegian Data Protection Authority considers that this is a serious case,” said Director-General Bjorn Erik Thon. “Users were not able to exercise real and effective control over the sharing of their data.”
The company has until Feb. 15 to give feedback, which the watchdog will take into account for its final decision.
Grindr said it looked forward to holding a “productive dialogue” with Norwegian regulators about the allegations, which it said date back to 2018 and don’t reflect current privacy policy or practices.
The app’s privacy approach includes “detailed consent flows, transparency, and control” provided to all users, the company said, adding it has “retained valid legal consent” from all its European users “on multiple occasions.”
“We continually enhance our privacy practices in consideration of evolving privacy laws and regulations,” the company said in a statement.
The watchdog’s preliminary conclusion is that Grindr shared user data with a number of third parties without legal basis. The data included GPS location, user profile information as well as the fact that users are on Grindr, which could indicate their sexual orientation.
Sharing such information could put someone at risk of being targeted, the authority said in its notice to Grindr.
The fact that a person “is a Grindr user may lead to prejudice and discrimination even without revealing their specific sexual orientation,” it said.
The Data Protection Authority said the way Grindr asked users for permission to use their information went against GDPR’s requirements for “valid consent.” Users weren’t given the chance to opt out of sharing data with third parties and were forced to accept Grindr’s privacy policy in its entirety, it said, adding that users weren’t properly informed about the data sharing.
The watchdog is still investigating five “ad tech” companies that received data from Grindr, including Twitter’s mobile app advertising platform, MoPub, which has more than 160 partners.
The Norwegian Consumer Council welcomed the fine.
“We hope that this marks the starting point for many similar decisions against companies that engage in buying and selling personal data,” said the group’s director of digital policy, Finn Myrstad.
Australian Corporate Regulator Discloses Breach Involving Accellion Software
27.1.2021 Incindent Securityweek
The Australian Securities and Investments Commission (ASIC) on Monday disclosed a security incident that involved Accellion software.
An independent commission of the Australian government, ASIC is the national corporate regulator, overseeing enterprise and financial services and also tasked with the enforcement of laws designed to protect consumers, creditors, and investors in Australia.
The newly disclosed incident, ASIC says, was identified on January 15, 2021, and resulted in unauthorized access to one of its servers, on which documents related to recent Australian credit license applications were stored.
“This incident is related to Accellion software used by ASIC to transfer files and attachments,” the Australian regulator says.
The watchdog says that there’s no evidence that license application forms or attachments were accessed or downloaded, but notes that “there is some risk that some limited information may have been viewed by the threat actor.”
Access to the affected server has been disabled, to contain the incident, and an investigation into the matter has been launched. Furthermore, ASIC and Accellion are working on notifying the impacted parties, the Commission says.
Responding to a SecurityWeek inquiry, ASIC stressed on the fact that, while the investigation continues, no data appears to have been accessed or downloaded.
“While we are still checking the underlying context, with others, the credit licence process was immediately addressed. The site was deactivated, taken down, and in the process of being returned to service,” ASIC said.
The regulator did not say what Accellion software was involved in the incident, but chances are that the FTA (File Transfer Application) file sharing service was the culprit.
A legacy product, FTA was recently revealed to have been at the heart of a similar security incident, involving the Reserve Bank of New Zealand – Te Pūtea Matua.
In December 2020, Accellion, a provider of cloud solutions designed to secure file sharing and collaboration, addressed a critical vulnerability in FTA, and that issue is suspected to have been abused by hackers to target affected customers (less than 50 in total).
SecurityWeek has reached out to Accellion for a comment on the matter, but the company only pointed to a press release published earlier this month.
2.28M MeetMindful Daters Compromised in Data Breach
26.1.2021 Incindent Threatpost
The ShinyHunters hacking group offer a raft of information, from location and contact info to dating preferences and bodily descriptions, as a free download.
More than 2.28 million members of the online dating site MeetMindful have reportedly been caught up in a wide-ranging data breach that exposes everything from Facebook tokens to physical characteristics.
The ShinyHunters hacking group has stolen and published the personally identifiable (PII) data of MeetMindful users, according to a report from ZDNet. The data has been made available as a free download on a “publicly accessible hacking forum known for its trade in hacked databases,” according to a security researcher speaking anonymously to the outlet.
In total the data makes up a 1.2 GB file, which has 1,500 views in the public forum. How many times it has been downloaded is unknown.
MeetMindful combines a dating platform with a focus on wellness, life-coach articles, “intentional living” tips and musings on spirituality.
The file collects the information together that MeetMindful users provided when they registered to use the service and set up their profiles. Thus, it includes names; emails; city, state and ZIP codes; dating preferences; birth dates; marital status; IP addresses; and Bcrypt-protected account passwords, according to the researcher’s findings. However, other potentially more sensitive information is also included for some users, like dating preferences; “body details”; and even latitude and longitude. To boot, Facebook user IDs and authentication tokens are part of the harvest as well.
Threatpost reached out to MeetMindful for confirmation and comment, but has received no response as of press time.
Numerous Attacks Possible
Security researchers noted that dating apps in particular represent a highly attractive target for cybercriminals.
“Cyberattackers are increasingly targeting individuals on dating platforms across both mobile and desktop,” Hank Schless, senior manager of Security Solutions at Lookout, told Threatpost. “They’re doing this because these apps are a treasure trove of personal data that require lots of device permissions such as location, access to the camera and access to contacts in order to work.”
This particular breach comes on the tail of Interpol’s warning of financial scams being carried out in dating apps, he noted.
“Each of these incidents shows that there’s no one way that attackers seek to attack dating app users,” he said. “Both app developers and users need to be wary of the risks involved with trusting so much personal data to mobile apps. App developers need to embed security into their mobile apps and keep their infrastructure security up to date as malicious tactics evolve. App users should be careful about how they interact with people on dating apps and have a mobile security app installed that keeps them safe. Social-engineering is a common tactic to phish users, get them to share personal information, or convince them to download a malicious app.”
There’s also a sextortion trend of leveraging sexual preferences and other highly personal information found in dating platforms against the user.
“Attackers realize that individuals may be willing to pay a high price to keep these personal details from being widely distributed,” Schless said. “Lookout recently discovered a sextortion campaign called Goontact that targeted users of illicit sites, typically offering escort services, to steal personal data from their mobile phone.”
Dirk Schrader, global vice president at New Net Technologies (NNT), noted that a number of attacks are possible using this level of information.
“This combination of data points included in the data is nothing less than toxic. The simplest of approaches is to set up some filters in the data, such as marital status and try some extortion on the results using email,” he told Threatpost. “A more sinister one is to use the different data points to lure people into phishing attempts at their work place. However, as Big Data is not unknown to hackers it will require just a little more research about the Facebook accounts and email addresses.”
ShinyHunters Strikes Again
The site’s data was released by a well-known steal-and-leak actor known as ShinyHunters. The group made a splash last May, allegedly compromising 73.2 million user records from more than 11 companies worldwide, including online delivery services like Homechef, photo-print service ChatBooks, and Chronicle.com, a news source for higher education.
The largest ShinyHunters heist involved stealing log-in data for 91 million users of Indonesia’s largest e-commerce platform, Tokopedia, and then selling it on the dark web for $5,000.
The group also last year claimed that it broke into Microsoft’s GitHub account and stole 500 GB of data from the tech giant’s own private repositories on the developer platform.
Last week, the group leaked details 12.8 million Teespring users, a web portal that lets users create and sell custom-printed apparel. They offered the data for free, in what researchers said was a likely sabotage of another data broker’s deal.
Cloud Environments in Hacker Crosshairs
It’s unclear how ShinyHunters were able to access the site’s data, but cybersecurity expert and CTO of Cymulate Avihai Ben-Yossef suspects a cloud misconfiguration.
“The attacker ShinyHunters…has a penchant for going after cloud-first companies — those who put their infrastructure in the cloud from the outset,” he said via email. “There is much to be done to shore up cloud hygiene – multifactor authentication, good certificate and identity store management, better configuration and account control, better segmentation of the workloads, etc.; alongside continuous security assessment.”
Schrader noted, “Little seems to be known about the attack itself, but it should not come as a surprise if they missed out on all basic security control about vulnerabilities, patching, change control and File Integrity Monitoring.”
Clothing Brand Bonobos Notifies Users of Data Breach
26.1.2021 Incindent Securityweek
Menswear brand Bonobos has started informing customers of a data breach that may have resulted in their personal information getting compromised.
Founded in 2007, Bonobos started as an online retailer of men's clothing, but it began opening physical retail locations in 2012. In 2017, Walmart bought the retailer for $310 million, incorporating it as a subsidiary of its fashion department.
Over the weekend, the company started informing users of a data breach that may have resulted in their personal information being stolen.
“We believe an unauthorized third party may have been able to view some of your account details, including your contact information and encrypted password. Your encrypted password was protected so your actual password was not visible,” the data breach notification sent to users reads.
The company also told users that no payment card information was affected in the incident.
Bonobos has decided to reset users’ passwords; they have been logged out of their accounts and they will have to set up a new password the next time they try to log in.
While the company did not provide specific details on the type of data that might have been compromised, its privacy policy reveals that personal information it collects may include names, addresses, phone numbers, email addresses, system information, national identification numbers, driver’s license numbers, age and date of birth, gender, nationality, purchase history information, location information, credit and debit card numbers, and other information.
The retailer appears to have been hacked by a threat actor known as ShinyHunters, which is known for conducting similar attacks, and which has apparently already shared all of the stolen data on a hacker forum.
The information was contained in a 70 GB SQL file and included user data such as addresses and phone numbers for roughly 7 million users, account information for nearly 2 million registered users, and partial numbers of 3.5 million payment cards, BleepingComputer reports.
While the stolen passwords were hashed, it appears that at least one hacker was able to crack some of the passwords.
Contacted by SecurityWeek, Bonbos said they were still investigating the matter, but so far had not found any evidence of unauthorized parties gaining access to its internal systems.
"What we have discovered is an unauthorized third party was able to view a backup file hosted in an external cloud environment. We contacted the host provider to resolve this issue as soon as we became aware of it,” Bonobos told SecurityWeek.
“Also, we have taken additional precautionary steps, including turning off access points, invalidating account passwords and requiring password resets, to further secure customer accounts. We emailed customers to notify them that their contact information and encrypted passwords may have been viewed by an unauthorized third party. Payment information was not affected by this issue. We’ll continue to share updates with customers as they become available,” the retailer added.
*Updated with response from Bonobos
Illinois Court Exposes More Than 323,000 Sensitive Records
26.1.2021 Incindent Securityweek
Unsecured Server Exposed Records Containing Sensitive Personal Data and Case Notes From Cook County Court
On September 26, 2020, researchers discovered an unsecured Elasticsearch server exposing more than 323,277 Cook County court related records containing highly sensitive personal data. Cook County, Illinois, is the second most populous county in the U.S., with a population in excess of 5 million people.
The records contained PII such as full names, home addresses, email addresses, and court case numbers, WebsitePlanet together with researcher Jeremiah Fowler, said. More worryingly, they also contained notes on the status of both the case and the individuals concerned. The case type seems to have been categorized by indicators such as IMM (probably ‘immigration’), FAM (probably ‘family’), and CRI (probably ‘criminal’). The data was in plaintext, and internet access had no restrictions. The content could be accessed, downloaded, altered or deleted by anyone with an internet connection.
On the day of discovery, a Saturday, WebsitePlanet informed the Cook County CTO about the exposure. Early the following Monday, the database was secured and public access restricted. It was exposed for at least the best part of two days, but there is no indication on how long the database may have been available online prior to WebsitePlanet’s discovery.
The researchers received no response from the Cook County CTO, so there is no guarantee that the database actually belonged to Cook County. However, the timing of disclosure and remediation makes it highly likely. Similarly, with no response from Cook County, there is no way to determine whether the database had been accessed by people with criminal intent. However, it is worth assuming that if researchers can discover a misconfigured database, so can hackers. Criminals who may have accessed the database would have found a treasure trove of actionable information.
WebsitePlanet postulates that the database may have belonged to a specialist Cook County department of case workers working with people who needed additional help. Almost by definition, everybody included within the database could be classified as ‘vulnerable’ and a prime target for scammers. The information contained would provide numerous approaches to such attacks.
Attacks could range from identity theft to blackmail. The latter would have been facilitated by the detailed case notes in the records. One, for example, reads, “I-30 (petition for Alien Relative) is approved through child\ she needs to marry in order to proceed with waiver\ Husband. However, Husband was accused of sexual assault against a minor. Need to wait to see Dispo of that charge to ensure eligibility - we will wait.” This was coupled with the name of the individual concerned and the case number in plaintext.
The family court records ‒ most likely those delimited with the FAM epithet ‒ are similarly open to abuse by blackmail. The family court deals with matters including divorce, child custody, visitation, domestic violence, protecting minors from abuse or neglect, and crimes by minors. Sensitive data in the wrong hands could be used for extortion by threatening to release the data to other family members, employers or just generally.
It is worth noting that many of the details exposed by this database are far more explicit than the details published in the public court proceedings, where personal details of vulnerable people are left vague or excluded.
Interestingly, WebsitePlanet contacted the Cook County CTO via his Major Scale Technology Management ‒ a firm that specializes in management consulting on IT strategy ‒ email address. According to the researchers, this CTO had founded Major Scale Technology Management several years earlier, and it had contracts with Cook County. The speed with which the database was subsequently secured led Website Planet to comment, “We can only assume that our data exposure notice made it to the right person who was responsible for this dataset. Although the data was clearly internal court records it is still not entirely clear what role Major Scale plays currently in Cook County’s IT infrastructure or the separation between the CTO and Major Scale.”
In reality, these are only assumptions. WebsitePlanet has never received confirmation of its database exposure disclosure, and has found no record of Cook County publicly confirming a possible breach. Nor is it known whether the County contacted the individuals contained in the database to warn them their personal data may have been exposed.
Tesla sues former employee for allegedly stealing sensitive docs
25.1.2021 Incindent Securityaffairs
Tesla has accused a former employee, a software engineer, of downloading about 26,000 sensitive files and transferring them on his personal Dropbox
On Saturday, Tesla sued the former employee Alex Khatilov for allegedly stealing 26,000 confidential documents, including trade secrets. The software engineer transferred the sensitive files to his personal Dropbox account.
Khatilov stole files from the internal network of the carmaker, the documents were related to the Warp Drive software. The Warp Drive is a proprietary back-end software system used to automate business processes.
According to the complaint, the former employee started stealing the company files a few days after he was hired.
“The complaint says he began working for Tesla on December 28, 2020, and almost immediately began uploading files and scripts (written in a programming language called Python) to his Dropbox account. Tesla confronted him about his alleged theft on January 6th.” states CNBC.
The defendant claimed that he “forgot” he had downloaded the files and was not able to explain the reason for his downloads.
“The Tesla Trade Secrets are extremely valuable to Tesla, and would be to a competitor. Access to the scripts would enable engineers at other companies to reverse engineer Tesla’s automated processes to create a similar automated system in a fraction of the time and with a fraction of the expense it took Tesla to build it.” states the complaint. “Third-party engineers could not compose these scripts based on public information, especially with such minimal time and effort. The scripts also would inform competitors of which systems Tesla believes are important and valuable to automate and how to automate them – providing a roadmap to copy Tesla’s innovation.”
Khatilov told to New York Post that he had unintentionally moved the files to Dropbox.
“I’ve been working for, like, 20 years in this industry, and I know what sensitive documents are about, and I never, ever tried to access any of those, or steal it” said Khatilov. “I didn’t know that there was 26,000 files there.”
The company has a different opinion, it accused the former employee of trying to cover his tracks.
“Even worse, it became apparent that Defendant had brazenly attempted to destroy the evidence by hurriedly deleting the Dropbox client and other files during the beginning of the interview when investigators were attempting to remotely access his computer.” states the complaint.
Hacker leaks data of 2.28M users of dating site MeetMindful
25.1.2021 Incindent Securityaffairs
A well-known threat actor has leaked data belonging to 2.28 million users registered on the dating website MeetMindful.
ZDNet first reported that the well-known threat actor ShinyHunters has leaked the data of more than 2.28 million users registered on the dating site MeetMindful,
The threat actor leaked the data for free download on a publicly accessible hacking forum.
“The leaked data, a 1.2 GB file, appears to be a dump of the site’s users database.” reported ZDNet.
Leaked data included real names, email addresses, city, state, and ZIP details, body details, dating preferences, marital status, birth dates, latitude and longitude, IP addresses, bcrypt-hashed account passwords, Facebook user IDs, and Facebook authentication tokens.
The availability of such data expose users of the dating site to several cybercriminals activities, including sextortion and scams.
ZDNet pointed out that the leaked dump doesn’t include the messages exchanged by the registered users.
MeetMindful has yet to confirm the alleged data breach.
Thousands of users of the hacker forum have viewed the thread where the MeetMindful data was shared, this means that it is already circulating in the hacking community.
Early this week, ShinyHunters leaked the details of millions of users registered on Teespring, and in November he leaked data of the Pluto TV service.
In July, ShinyHunters offered on a hacker forum a collection of databases stolen from eighteen companies, over 386 million user records available online.
Chipmaker Intel reveals that an internal error caused a data leak
25.1.2021 Incindent Securityaffairs
The chipmaker Intel Corp. revealed that an internal error it the root cause of a data leak, it confirmed that corporate network was not impacted.
The computer chipmaker Intel Corp. confirmed that an internal error is the cause of a data leak that prompted it to release a quarterly earnings report early.
Intel chief financial officer, George Davis, told The Financial Times that the chipmaker believed a threat actor stole financially sensitive information from its site and for this reason, it anticipated the release of a quarterly earnings report to avoid that attackers could use this data for operations on the stock market.
The company confirmed that attackers did not compromise the corporate network.
““An infographic was hacked off of our PR newsroom site,” the newspaper quoted Davis as saying. It quoted an unnamed company spokesperson as saying Intel was notified that the graphic was circulating outside the company.” reported the Associated Press.
Now the company excluded the hack, and confirmed the incident was caused by an internal error, below the statement issued by the company:
“the URL of our earnings infographic was inadvertently made publicly accessible before publication of our earnings and accessed by third parties.” reads the Intel’s statement. “Once we became aware of the situation we promptly issued our earnings announcement. Intel’s network was not compromised and we have adjusted our process to prevent this in the future.”
ADT employee pleads guilty for accessing cameras installed by the company
24.1.2021 Incindent Securityaffairs
A former ADT employee pleads guilty for accessing the cameras he installed at the home of the company’s customers in the Dallas area.
Telesforo Aviles (35) is a former ADT employee that pleaded for accessing the cameras he installed at the home of the company’s customers.
Every time the man worked at the home of a customer in the Dallas area where an attractive woman was living, he added his personal email address to customers’ “ADT Pulse” accounts, to have real-time access to the video feeds from the cameras.
“This defendant, entrusted with safeguarding customers’ homes, instead intruded on their most intimate moments,” said Acting U.S. Attorney Prerak Shah. “We are glad to hold him accountable for this disgusting betrayal of trust.”

Aviles faces up to five years in federal prison for having illegally accessed roughly 200 accounts more than 9,600 times, in a period of more than four years.
Mr. Aviles admitted having regularly added his own email address to customers’ ADT Pulse accounts to watch women naked and couples engaged in sexual activity for his own sexual gratification, they said.
“The defendant used his position of employment to illegally breach the privacy of numerous people. The FBI works with our law enforcement partners to thoroughly investigate all cyber intrusions and hold criminals accountable for their actions,” said FBI Dallas Special Agent in Charge Matthew J. DeSarno.
ADT discovered Aviles’s activity on April 23 when a customer informed the company of the presence of an unauthorized email on their ADT account.
In April 2020, ADT terminated Aviles and reported him to law enforcement.
“Recently, a customer called to let us know there was an unauthorized email on their ADT account. The security and privacy of our customers is our top priority, and we immediately began an internal investigation.” reads a statement published by the company. “Unfortunately, our investigation revealed that during a service visit, one of our Dallas-area technicians had added his personal email address to this customer’s account to gain unauthorized access, and he had done the same thing during service visits with other customers in the Dallas area.”
The company contacted the impacted customers and apologized to them.
“We apologize to the customers affected by the actions of this former employee and deeply regret this incident,” ADT’s statement said. “The ADT mission is to help protect and connect people with the things they love most. Fully earning this trust back may take time, but nothing is more important to us and to those who have served our customers under the ADT banner for the last 145 years.”
Chipmaker Intel Corp. Blames Internal Error on Data Leak
24.1.2021 Incindent Securityweek
The computer chipmaker Intel Corp. on Friday blamed an internal error for a data leak that prompted it to release a quarterly earnings report early. It said its corporate network was not compromised.
The company’s chief financial officer, George Davis, had earlier told The Financial Times that Intel published its earnings ahead of the stock market’s close on Thursday because it believed a hacker stole financially sensitive information from the site.
The company’s quarterly results were originally scheduled to be published hours later after the close of trading on Wall Street Thursday.
“An infographic was hacked off of our PR newsroom site,” the newspaper quoted Davis as saying. It quoted an unnamed company spokesperson as saying Intel was notified that the graphic was circulating outside the company.
Early access to such information could benefit a stock trader.
On Friday, Intel issued a statement saying it had determined that no hack occurred.
It said “the URL of our earnings infographic was inadvertently made publicly accessible before publication of our earnings and accessed by third parties. Once we became aware of the situation we promptly issued our earnings announcement. Intel’s network was not compromised and we have adjusted our process to prevent this in the future.”
The company’s stock price closed down more than 9% Friday.
Data of 2 million MyFreeCams users sold on a hacker forum
23.1.2021 Incindent Securityaffairs
A threat actor was offering for sale on a hacker forum data from 2 million users allegedly stolen from the adult streaming site MyFreeCams.
A threat actor was offering for sale on a hacker forum a database containing user records allegedly stolen from the adult streaming site MyFreeCams.
MyFreeCams it’s one of the top adult streaming websites thta has nearly 70 million visitors each month.
The seller claims that the data related MyFreeCams was stolen in December 2020 through an SQL injection attack. Stolen records belong to 2 million user records of MyFreeCams Premium members, they include usernames, email addresses, MyFreeCams Token (MFC Token) amounts, and passwords in plain text.
At the time of this writing, the threat actor has deleted its post, as well as its account, and emptied the cryptocurrency wallet used for the sale. According to CyberNews that reported the news, the threat actor collected ~$22,400 worth of Bitcoin from the sale of the data across 49 transactions.
“The author of the forum post is asking for $1500 in Bitcoin per 10,000 user records and claims that a single batch would net the buyers at least $10,000, which they could make by selling premium accounts with MFC Token (MyFreeCams’ virtual currency) balances on the black market.” reported CyberNews.

CyberNews contacted MyFreeCams which confirmed the authenticity of the data and notified affected users. In response to the incident, MyFreeCams reset the passwords of impacted users. The investigation conducted by MyFreeCams revealed that data were stolen in “a security incident that occurred more than ten years ago in June 2010.” The company added that it has secured its infrastructure shortly after the attack occurred fixing the issue exploited by the threat actors.
The company pointed out that no financial data was stolen in the attack and added that it did not have evidence that user data was actually compromised as part of the incident.
“To see if any of your online accounts were leaked, use our personal data leak checker with a library of 15+ billion breached records.” continues CyberNews.
It is impossible to determine how many accounts were accessed by using the data available for sale before the passwords were reset.
Data stolen by the threat actors could be used to conduct a broad range of malicious activities, such as blackmailing and extorting money from MyFreeCams users, stealing their MFC Tokens to sell them on the black market, conducting credential stuffing attacks, launch phishing and spam campaigns.
Einstein Healthcare Network Announces August Breach
22.1.2021 Incindent Threatpost
Einstein is in violation of the the HHS 60-day breach notification rule, but unlikely to face penalty.
Einstein Health Network, a Pennsylvania-based company operating medical rehab, outpatient and primary care centers, announced a breach of its employee email system, which exposed patient personal and medical information.
The company waited more than five months to make the compromise public.
Einstein said its email system was compromised by an “unauthorized person” on Aug. 5, according to the statement, and persisted through Aug. 17. Einstein added it wasn’t able to figure out whether the contents of patient-related emails were stolen but is taking steps to alert patients who might have had everything from their name, date of birth and even diagnoses and prescriptions exposed to criminals.
2020 Reader Survey: Share Your Feedback to Help Us Improve
Einstein said it has known about suspicious activity in employee email accounts since Aug. 10.
“While this review is ongoing, we have identified emails and/or attachments in the accounts that contained patient information, which may have included some patients’ names, dates of birth, medical record or patient account numbers, and/or treatment or clinical information, such as diagnoses, medications, providers, types of treatment, or treatment locations,” Einstein said. “In some instances, patients’ health insurance information and/or Social Security numbers were also included in the accounts.”
Einstein Broke HHS Breach Notification Rule
Einstein emphasized the breach didn’t affect all patients, just those contained within employee email accounts.
The company has opened a helpline and is offering one year of credit monitoring for patients whose Social Security Numbers were compromised.
But why did the company wait five months after the breach to notify their patients that their most sensitive data was potentially in the wrong hands? The statement said “we are mailing letters,” so presumably malicious actors have had a hefty head start on any potential mitigation efforts.
Threatpost contacted Einstein Healthcare Network for comment but has not yet heard back.
The five-month lag in reporting the attack puts Einstein Health Network in clear violation of the Health and Human Services HIPPA Breach Notification Rule, which mandates individuals be notified “without unreasonable delay and in no case later than 60 days following the discovery of a breach and must include, to the extent possible, a brief description of the breach, a description of the types of information that were involved in the breach, the steps affected individuals should take to protect themselves from potential harm, a brief description of what the covered entity is doing to investigate the breach, mitigate the harm, and prevent further breaches, as well as contact information for the covered entity (or business associate, as applicable).”
Lack of Enforcement
While the violation is clear, Ben Pick, senior application security consultant at nVisium told Threatpost penalties levied against the healthcare organization are likely to be light.
“The end result against the company may only be minor penalties, such as credit monitoring or similar services for those impacted,” Pick said.
Pick explained a lack of tough enforcement of healthcare security could be behind the decision Einstein’s delay in reporting.
“As for why Einstein Healthcare failed to notify its end users within a reasonable time period, that was likely a business decision to be further removed from the time of the incident. Without more serious penalties, there is not a strong incentive to report these breaches,” he said.
Healthcare has come under increased attack from cybercriminals as entire hospital systems are strained to their limits trying to combat the pandemic.
Dirk Schrader, global vice president of New Net Technologies agrees Einstein isn’t likely to get more than a warning.
“Whether the HHS will lecture Einstein about the 60 days notification period mandated in HIPAA is one thing,” Schrader said. “Drastic fines will most likely not be imposed.”
Google Searches Expose Stolen Corporate Credentials
22.1.2021 Incindent Threatpost
A phishing campaign spoofs Xerox notifications to lure victims into clicking on malicious HTML attachments.
Attackers behind a recently discovered phishing campaign have unintentionally left more than 1,000 stolen credentials available online via simple Google searches, researchers have found.
The campaign, which began in August 2020, used e-mails that spoof notifications from Xerox scans to lure victims into clicking on malicious HTML attachments, according to a report from Check Point Research released Thursday.
Check Point worked with security firm Otorio to uncover the campaign, which managed to bypass Microsoft Office 365 Advanced Threat Protection (ATP) filtering to steal more than 1,000 corporate credentials, researchers said.
2020 Reader Survey: Share Your Feedback to Help Us Improve
While this is and of itself is not atypical of phishing campaigns, attackers made a “simple mistake in their attack chain” that left the credentials they’d stolen exposed to the “public Internet, across dozens of drop-zone servers used by the attackers,” researchers said.
Usually credentials are the crown jewels of an attack, something threat actors keep for themselves so they can sell them on the dark web for profit or use them for their own nefarious purposes.
However, in this campaign, “with a simple Google search, anyone could have found the password to one of the compromised, stolen email addresses: a gift to every opportunistic attackers,” researchers wrote.
This is because the attackers stored the stolen credentials in designated webpages on compromised servers, said Lotem Finkelsteen, head of threat intelligence for Check Point Software. However, because Google constantly indexes the internet, the search engine also indexed these pages, making them available to anyone who queried Google for a stolen email address.
“The attackers didn’t think that if they are able to scan the internet for those pages — Google can too,” Finkelsteen said in an e-mailed statement. “This was a clear operation security failure for the attackers.”
Organizations targeted in the campaign spanned a number of industries—including retail, manufacturing, healthcare and IT–with a special interest in energy and construction companies, researchers noted. There also was evidence that the campaign is not the attackers’ first rodeo, as emails and JavaScript encoding used in the attacks correlated to a phishing campaign from May of the same year, they said.
The campaign started with an email using one of several phishing templates imitating a Xerox notification with the target’s first name or company title in the subject line. The email included an HTML file that, once clicked on, would prompt the user with a lookalike login page for Xerox.
“After the HTML file was launched, a JavaScript code would then run in the background of the document,” researchers wrote. “The code was responsible for simple password checks, sending the data to the attackers’ drop-zone server, and redirecting the user to a legitimate Office 365 login page.”
Drop-zone servers used by the campaign were dozens of WordPress websites that hosted malicious PHP pages and would process all incoming credentials from the phishing victims, researchers said.
“While using a specialized infrastructure, the server would run for roughly two months with dozens of XYZ domains,” they noted. “These registered domains were used in the phishing attacks.”
The campaign also not only evaded Microsoft 365 ATP but also most anti-virus protections through its simple use of compromised servers. Attackers also continuously polished and refined their code to create “a more realistic experience so the victims were less likely to have their suspicions aroused, and more likely to provide their login credentials,” researchers noted.
Researchers provided the usual advice to people to avoid getting duped by phishing campaigns, such as reminding them to check domains carefully, be skeptical of unknown senders, think twice before accepting a “special offer,” and use different passwords for different online accounts. Indeed, that last point in particular is still a common mistake that even the most savvy of internet user makes, research has found.
Malwarebytes Hit by SolarWinds Attackers
21.1.2021 Incindent Threatpost
The attack vector was not the Orion platform but rather an email-protection application for Microsoft 365.
Malwarebytes is the latest discovered victim of the SolarWinds hackers, the security company said – except that it wasn’t targeted through the SolarWinds platform.
“While Malwarebytes does not use SolarWinds, we, like many other companies were recently targeted by the same threat actor,” it disclosed in a Tuesday web posting.
Instead of using the SolarWinds Orion network-management system, the advanced persistent threat (APT) abused “applications with privileged access to Microsoft Office 365 and Azure environments,” the security firm said — specifically, an email-protection application.
“What started out as the SolarWinds attack is slowly turning out to be perhaps the most sophisticated and wide-reaching cyber-campaign we have ever seen,” Ami Luttwak, CTO and co-founder of Wiz, said via email. “It encompasses multiple companies used as backdoors to other companies, numerous tools and novel attack methods. This is far more than SolarWinds.”
Suspicious Microsoft 365 API Calls
The Microsoft Security Response Center flagged suspicious activity from a third-party email-security application used with Malwarebytes’ Microsoft Office 365 hosted service on Dec. 15. The activity was visible in the application’s API calls. After that, the company and Microsoft kicked off an “extensive” investigation.
“A newly released CISA report reveals how threat actors may have obtained initial access by password guessing or password spraying in addition to exploiting administrative or service credentials,” according to Malwarebytes. “In our particular instance, the threat actor added a self-signed certificate with credentials to the service principal account. From there, they can authenticate using the key and make API calls to request emails via MSGraph.”
While the tactics, techniques and procedures (TTPs) turned out to be consistent with those used by the SolarWinds APT, in this case the espionage effort only affected a “limited subset of internal company emails,” the firm noted. “We found no evidence of unauthorized access or compromise in any of our internal on-premises and production environments….We do not use Azure cloud services in our production environments.”
A thorough investigation of all Malwarebytes source code, build and delivery processes showed no evidence of unauthorized access or compromise, it added.
A Malwarebytes spokesperson noted only, “This was a nation-state attack against many vectors, including multiple security vendors.” The company declined to provide additional information on the TTPs linking this attack to the SolarWinds attackers.
“Why are the SolarWinds hackers going after security companies? When you piece together the puzzle it becomes scary,” Luttwak said. “They are trying to feed the beast, the more power they have, it gives them more tools and capabilities to attack more companies and get their capabilities as well. If we think about how this all started, they were after the FireEye tools… it’s like a game, they are attacking whoever has additional skills they can get.”
He added, “What does a company like Malwarebytes… have? Well… endless capabilities. Every sensitive computer out there runs a security agent, most of them even have a cloud portal that allows to run privileged commands on any computer directly.”
Other Attack Vectors Beyond SolarWinds
The SolarWinds espionage attack, which has affected several U.S. government agencies, tech companies like Microsoft and FireEye, and many others, began with a poisoned software update that delivered the Sunburst backdoor to around 18,000 organizations last spring. After that broad-brush attack, the threat actors (believed to have links to Russia) selected specific targets to further infiltrate, which they did over the course of several months. The compromises were discovered in December.
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) announced earlier in January that the adversary did not only rely on the SolarWinds supply-chain attack but also used additional means to compromise high-value targets by exploiting administrative or service credentials.
“While we have learned a lot of information in a relatively short period of time, there is much more yet to be discovered about this long and active campaign that has impacted so many high-profile targets,” according to Malwarebytes. “It is imperative that security companies continue to share information that can help the greater industry in times like these, particularly with such new and complex attacks often associated with nation-state actors.”
Malwarebytes Targeted by SolarWinds Hackers
21.1.2021 Incindent Securityweek
Cybersecurity firm Malwarebytes on Tuesday revealed that it too was targeted by the hackers who breached the systems of Texas-based IT management company SolarWinds as part of a sophisticated supply chain attack.
Malwarebytes says it has not used any SolarWinds products, but its investigation revealed that the threat actor gained access to some of its systems by abusing applications with privileged access to Microsoft 365 and Azure environments.
“After an extensive investigation, we determined the attacker only gained access to a limited subset of internal company emails. We found no evidence of unauthorized access or compromise in any of our internal on-premises and production environments,” said Marcin Kleczynski, CEO and co-founder of Malwarebytes.
According to Kleczynski, his company discovered the breach after being notified by Microsoft on December 15 about suspicious activity possibly conducted by the SolarWinds hackers. An investigation conducted with assistance from Microsoft revealed that the attackers abused a dormant email protection product within the company’s Microsoft 365 tenant, which gave them access to “a limited subset of internal company emails.”
Malwarebytes does not use Azure in its production environment and a thorough analysis of its source code and build and delivery processes uncovered no evidence of compromise. “Our software remains safe to use,” Kleczynski said.
FireEye on Tuesday released a detailed white paper on the techniques and tactics used by the SolarWinds hackers to target Microsoft 365 environments. The paper offers remediation guidance to targeted organizations, hardening guidance for those not impacted, as well as detection guidance.
The cybersecurity firm also released an open source tool designed to check Microsoft 365 tenants for the use of techniques associated with the SolarWinds hackers. Similar tools were also made available recently by CISA and CrowdStrike.
Earlier this month, email security company Mimecast revealed that a sophisticated threat actor had obtained a certificate provided to certain customers, and some have speculated that the incident may be related to the SolarWinds breach.
Cybersecurity researchers continue to analyze the tools and tactics used by the SolarWinds hackers. Symantec on Tuesday reported spotting yet another piece of malware used by the threat actor, namely a loader named Raindrop, which has been used for lateral movement and for deploying additional payloads.
OpenWrt Informs Users of Forum Breach
20.1.2021 Incindent Securityweek
The OpenWrt Project, the developer of the open source Linux operating system for embedded devices, informed users on Monday that someone had breached its forum over the weekend.
In a security notice posted on the OpenWrt forum, users were told that the hacker gained access to the account of an administrator on January 16. It’s unclear how the account became compromised — it had a “good password,” but two-factor authentication was not enabled.
According to the OpenWrt Project, the attacker downloaded user information, including email addresses, handles, and statistical data related to forum users.
While there is no indication that the forum database has been downloaded, the decision has been made to reset all passwords and flush API keys.
Users have been instructed to manually reset their password using the “get a new password” feature on the OpenWrt forum. Since email addresses and usernames have been exposed, impacted individuals have been warned that they may receive phishing emails. GitHub logins or OAuth keys should also be reset.
“OpenWrt forum credentials are entirely independent of the OpenWrt Wiki. There is no reason to believe there has been any compromise to the Wiki credentials,” the security notice reads.
The OpenWrt Project has promised to provide updates if more information comes to light.
SolarWinds Hackers Also Breached Malwarebytes Cybersecurity Firm
20.1.2021 Incindent Thehackernews
Malwarebytes on Tuesday said it was breached by the same group who broke into SolarWinds to access some of its internal emails, making it the fourth major cybersecurity vendor to be targeted after FireEye, Microsoft, and CrowdStrike.
The company said its intrusion was not the result of a SolarWinds compromise, but rather due to a separate initial access vector that works by "abusing applications with privileged access to Microsoft Office 365 and Azure environments."
The discovery was made after Microsoft notified Malwarebytes of suspicious activity from a dormant email protection app within its Office 365 tenant on December 15, following which it performed a detailed investigation into the incident.
"While Malwarebytes does not use SolarWinds, we, like many other companies were recently targeted by the same threat actor," the company's CEO Marcin Kleczynski said in a post. "We found no evidence of unauthorized access or compromise in any of our internal on-premises and production environments."
The fact that initial vectors beyond SolarWinds software were used adds another missing piece to the wide-ranging espionage campaign, now believed to be carried out by a threat actor named UNC2452 (or Dark Halo), likely from Russia.
Indeed, the US Cybersecurity and Infrastructure Security Agency (CISA) said earlier this month it found evidence of initial infection vectors using flaws other than the SolarWinds Orion platform, including password guessing, password spraying, and inappropriately secured administrative credentials accessible via external remote access services.
"We believe our tenant was accessed using one of the TTPs that were published in the CISA alert," Kleczynski explained in a Reddit thread.
Malwarebytes said the threat actor added a self-signed certificate with credentials to the principal service account, subsequently using it to make API calls to request emails via Microsoft Graph.
The news comes on the heels of a fourth malware strain called Raindrop that was found deployed on select victim networks, widening the arsenal of tools used by the threat actor in the sprawling SolarWinds supply chain attack.
FireEye, for its part, has also published a detailed rundown of the tactics adopted by the Dark Halo actor, noting that the attackers leveraged a combination of as many as four techniques to move laterally to the Microsoft 365 cloud.
Steal the Active Directory Federation Services (AD FS) token-signing certificate and use it to forge tokens for arbitrary users
Modify or add trusted domains in Azure AD to add a new federated Identity Provider (IdP) that the attacker controls.
Compromise the credentials of on-premises user accounts that are synchronized to Microsoft 365 that have high privileged directory roles, and
Backdoor an existing Microsoft 365 application by adding a new application
The Mandiant-owned firm has also published an auditing script, called Azure AD Investigator, that it said can help companies check their Microsoft 365 tenants for indicators of some of the techniques used by the SolarWinds hackers.
500K+ records of C-level people from Capital Economics leaked online
19.1.2021 Incindent Securityaffairs
Experts from Cyble recently found a leak of 500K+ records of C-level people from Capital Economics on a Russian-speaking forum.
During a routine Darkweb monitoring, researchers from Cyble found a leak of 500K+ records of C-level people from Capital Economics on a Russian-speaking forum.
CapitalEconomics.com is one of the leading independent economic research companies in the world that provides macroeconomic, financial market and sectoral forecasts and consultancy.

“Upon analysis of the data, Cyble discovered that there are 500K+ lines of record containing various prominent user profiles.” reads the post published by Cyble.
Leaked records include email IDs, password hashes, addresses, etc.
Cyble experts informed its clients about this leak, it pointed out that the availability of corporate email IDs could allow threat actors to carry out a broad range of malicious activities.
Cyble recommends people to:
Never share personal information, including financial information over phone, email or SMSes.
Use strong passwords and enforce multi-factor authentication wherever possible.
Regularly monitor your financial transactions, and if you notice any suspicious activity, contact your bank immediately.
Turn on the automatic software update feature on your computer, mobile and other connected devices wherever possible and pragmatic.
Use a reputed anti-virus and Internet security software package on your connected devices including PC, laptop, and mobile.
People who are concerned about their exposure in the Darkweb can register at AmiBreached.com to ascertain their exposure.
Refrain from opening untrusted links and email attachments without verifying their authenticity.
Mimecast Discloses Certificate Incident Possibly Related to SolarWinds Hack
14.1.2021 Incindent Securityweek
Email security company Mimecast on Tuesday revealed that a sophisticated threat actor had obtained a certificate provided to certain customers.
According to Mimecast, it learned from Microsoft that hackers had compromised a certificate used to authenticate Mimecast Continuity Monitor, Internal Email Protect (IEP), and Sync and Recover products with Microsoft 365 Exchange Web Services.
“As a precaution, we are asking the subset of Mimecast customers using this certificate-based connection to immediately delete the existing connection within their M365 tenant and re-establish a new certificate-based connection using the new certificate we’ve made available,” Mimecast said in a statement. “Taking this action does not impact inbound or outbound mail flow or associated security scanning.”
The company has not shared any details about the attacks abusing the compromised certificate, but some experts have speculated that the certificate may have allowed the hackers to intercept Mimecast customers’ communications.
Mimecast did say that roughly 10 percent of its customers used the impacted connection. The company claims to have over 36,000 customers across more than 100 countries, but the incident is believed to have impacted only “a low single digit number” of its customers’ Microsoft 365 tenants.
Mimecast said affected customers have been alerted and a third-party forensics firm has been called in to help investigate the incident.
According to Reuters, people with knowledge of the situation believe this incident may be related to the recently disclosed supply chain attack involving Texas-based IT management solutions provider SolarWinds.
The SolarWinds attack resulted in trojanized software updates being delivered to roughly 18,000 of the company’s customers. The attackers then delivered other payloads to a few hundred government and private organizations that presented an interest.
The attack on SolarWinds is believed to be the work of Russian cyberspies. The U.S. government said Russia is likely behind the attack and the malware used in the SolarWinds attack has been connected to a known Russian cyberspy group.
Data Breach at ‘Resident Evil’ Gaming Company Widens
13.1.2021 Incindent Threatpost
Capcom, the game developer behind Resident Evil, Street Fighter and Dark Stalkers, now says its recent attack compromised the personal data of up to 400,000 gamers.
A ransomware attack launched against gaming company Capcom last November keeps getting worse. The company now says that the personal data of up to 400,000 of its customers was compromised in the attack — 40,000 more than the company originally thought.
Capcom is a Japan-based publisher of blockbuster games like Resident Evil, Street Fighter and Dark Stalkers. The breach was first detected on Nov. 2.. On Nov. 19, Capcom said its personal as well as corporate data was compromised. This is the third update from Capcom on the incident.
“As an update to its ongoing investigation, the company has verified that the personal information of an additional 16,406 people has been compromised, making the cumulative number since this investigation began 16,415 people, the latest update dated Jan. 12 said. “Further, the company has also ascertained that the potential maximum number of customers, business partners and other external parties etc., whose personal information may have been compromised in the attack is approximately 390,000 people (an increase of approximately 40,000 people from the previous report).”
The announcement added an investigation is ongoing and that new evidence of additional compromise could still come.
“Capcom offers its sincerest apologies for any complications and concerns that this may bring to its potentially impacted customers as well as to its many stakeholders,” the statement said.
Ragnar Locker
The Ragnar Locker ransomware group is the most likely culprit. The ransom note, accessed by Bleeping Computer at the time the incident was first revealed, said the Ragnar Locker group claimed responsibility and said they had downloaded more than 1TB of corporate data, including banking details, contracts, proprietary data, emails and more.
Gaming is increasingly becoming a target for all types of cyberattacks. Over the past several months, along with Capcom, popular games like Among Us, Minecraft, Roblox and Animal Jam all reported breaches or hacks, while publishers like Ubisoft have also found themselves in the crosshairs. And in October, the REvil ransomware gang threatened a “big hit” on gaming.
Leading gaming companies are attractive to cybercriminals that aim to turn a profit by selling leaked insider-credentials. Recently, more than 500,000 stolen credentials tied to the top 25 gaming firms were found on caches of breached data online and up for sale at criminal marketplaces, according to researchers at Kela.
Boris Cipot, senior sales engineer with Synopsys, said that player accounts often link to payment details, making them attractive to criminals.
Gaming a Target
“The gaming industry is a common target for attacks, be it data theft or ransomware attacks,” Cipot said. “An interesting observation within the gaming industry is that player accounts are often high-value assets due to in-app purchases, or rewards from leveling up. In other words, gaming accounts are often seen as items for sale — at least accounts owned by adults spending money.”
The good news for Capcom customers is that the company doesn’t think any customer credit-card data was exfiltrated during the breach. The company goes onto reassure players it’s currently safe to play and purchase the company’s games online.
“None of the at-risk data contains credit card information,” the update said. “All online transactions etc. are handled by a third-party service provider, and as such Capcom does not maintain any such information internally,” Capcom advised. “Additionally, the areas that were impacted in this attack are unrelated to those systems used when connecting to the internet to play or purchase the company’s games online, which have continued to utilize either an external third-party server or an external server.”
For those Capcom customers who have been impacted, the company is reaching out to discuss next steps. The company said its continuing efforts to investigate the matter with law enforcement and IT security specialists, adding its systems have largely recovered and the company will provide any additional updates.
“Capcom would once again like to reiterate its deepest apologies for any complications or concerns caused by this incident,” the statement said. “As a company that handles digital content, it is regarding this incident with the utmost seriousness. In order to prevent the reoccurrence of such an event, it will endeavor to further strengthen its management structure while pursing legal options regarding criminal acts such as unauthorized access of its networks.”
Ethical Hackers Breach U.N., Access 100,000 Private Records
13.1.2021 Incindent Threatpost
Researchers informed organization of a flaw that exposed GitHub credentials through the organization’s vulnerability disclosure program.
Security researchers successfully hacked the United Nations, accessing user credentials and personally identifiable information (PII)–including more than 100,000 private employee and project records—before informing the U.N. about the problem through the organization’s vulnerability disclosure program.
Ethical hackers from the research group Sakura Samurai used a vulnerability in a GitHub directory that exposed WordPress DB and GitHub credentials, allowing access to numerous private records from the U.N.’s Environment Program (UNEP).
Researchers Jackson Henry, Nick Sahler, John Jackson and Aubrey Cottle discovered the vulnerability after the team decided to take a crack at finding an entry for the U.N.’s Vulnerability Disclosure Program and Hall of Fame and eventually identified an endpoint that exposed the credentials, researchers wrote in a blog post.
“The credentials gave us the ability to download the Git repositories, identifying a ton of user credentials and PII,” they wrote. “In total, we identified over 100K+ private employee records. We also discovered multiple exposed .git directories on U.N.-owned web servers [ilo.org], the .git contents could then be exfiltrated with various tools such as ‘git-dumper’.”
Researchers were able to access a significant amount of sensitive U.N. information in their breach, including 102,000 travel records; more than 7,000 records of human resources nationality demographics; more than 1,000 generalized employee records; more than 4,000 project and funding-source records; and evaluation reports of 283 projects.
Data revealed in the records included the names, ID numbers, nationalities, genders, pay grades and a raft of other personal information pertaining to U.N. employees, as well as identification numbers, locations and financing amounts for various UNEP projects, as well as funding sources and other specific details.
In addition to accessing records through the Git-related flaw, researchers “on the lesser side of severity” took over an SQL Database and a Survey Management program belonging to the International Labor Organization (ILO). However, the vulnerabilities “were of little prominence” and the database and platform were “fairly abandoned in nature,” they wrote.
“Nonetheless, a database takeover and admin account takeover on a platform are still critical vulnerabilities,” researchers observed.
Accessing the SQL database also was significant in it was a gateway into the discovery of the GitHub credentials and eventual trove of records, researchers explained in their post. They began their exploration initially by performing subdomain enumeration of all of the domains in scope for the U.N.’s disclosure program, they said.
“During our research, we began to fuzz multiple endpoints with tooling and initially discovered that an ilo.org subdomain had an exposed .git contents,” they wrote. “Utilizing git-dumper [https[://]github[.]com/arthaud/git-dumper] we were able to dump the project folders hosted on the web application, resulting in the takeover of a MySQL database and of survey management platform due to exposed credentials within the code.”
After researchers took over the ILO MySQL database and subsequently performed account takeover on the survey management platform, they began to enumerate other domains/subdomains, they said.
“Eventually, we found a subdomain on the United Nations Environment Programme [sic] that allowed us to discover GitHub credentials after a bit of fuzzing,” researchers wrote.
Ultimately, once they discovered the GitHub credentials, researchers could download a lot of private password-protected GitHub projects and found within them multiple sets of database and application credentials for the UNEP production environment, they said.
“In total, we found seven additional credential-pairs which could have resulted in unauthorized access of multiple databases,” researchers wrote. At that point they decided to stop their work and report the vulnerability.
The U.N. is no stranger to intrusion by hackers, and not merely ethical ones. Last July, hackers breached the U.N. by exploiting a Microsoft SharePoint vulnerability in an apparent espionage operation, reportedly giving the attackers access to an estimated 400 GB of sensitive data. The hack was not disclosed until about six months later.
Then, almost a year ago to the date of the Sakura Samurai disclosure, the operators behind the Emotet malware targeted U.N. personnel in an attack aimed at delivering the TrickBot trojan.
EMA: Some of Pfizer/BioNTech COVID-19 vaccine data was leaked online
13.1.2021 Incindent Securityaffairs
The European Medicines Agency (EMA) revealed that some of the Pfizer/BioNTech COVID-19 vaccine data were stolen from its servers.
In December, a cyber attack hit the European Medicines Agency (EMA). At the time, the EMA did not provide technical details about the attack, nor whether it will have an impact on its operations while it is evaluating and approving COVID-19 vaccines.
The European agency plays a crucial role in the evaluation of COVID-19 vaccines across the EU, it has access to sensitive and confidential information, including quality, safety, and effectivity data resulting from trials.
After the attack, Pfizer and BioNTech issued a joint statement that confirms that some documents related to their COVID-19 submissions were accessed by the threat actors.
“Today, we were informed by the European Medicines Agency (EMA) that the agency has been subject to a cyberattack and that some documents relating to the regulatory submission for Pfizer and BioNTech’s COVID-19 vaccine candidate, BNT162b2, which has been stored on an EMA server, had been unlawfully accessed,” Pfizer’s and BioNTech’s joint statement read.
Today, the European Medicines Agency (EMA) revealed threat actors have stolen some of the Pfizer/BioNTech COVID-19 vaccine data and leaked it leaked online.
“The ongoing investigation of the cyberattack on EMA revealed that some of the unlawfully accessed documents related to COVID-19 medicines and vaccines belonging to third parties have been leaked on the internet. Necessary action is being taken by the law enforcement authorities.” reads the update published by the agency.
“The Agency continues to fully support the criminal investigation into the data breach and to notify any additional entities and individuals whose documents and personal data may have been subject to unauthorised access.”
The agency added that the European medicines regulatory network is fully functional and that the cyber attack had no impact on COVID-19 evaluation and approval timelines.
At the end of December, security experts from threat intelligence firm Cyble have found several documents relating to the Covid-19 vaccine allegedly stolen from the European Medicines Agency (EMA) leaked in the Darkweb.
Cyble started tracking documents being shared on one of the Russian-speaking forums. The links to the documents have been shared by a newly created profile which was used only for the alleged data leak.
The documents also include the alleged assessment report of COVID-19 vaccine along with the summary report of drug release and stability.
Nation-state actors consider organizations involved in the research of the vaccine a strategic target to gather intelligence on the ongoing response of the government to the pandemic. At the end of November, the Reuters agency revealed in an exclusive that the COVID vaccine maker AstraZeneca was targeted by alleged North Korea-linked hackers.
Healthcare organizations like Johnson & Johnson are observing a surge of cyber attacks carried by state-sponsored hackers during COVID-19 pandemic.
In December, IBM X-Force experts warned of threat actors actively targeting organizations associated with the COVID-19 vaccine cold chain.
Ubiquiti Tells Users to Change Passwords After Breach at Cloud Provider
13.1.2021 Incindent Securityweek
American technology company Ubiquiti this week revealed that one of its third-party cloud providers suffered a data breach.
Founded in 2005, the New York City-based company manufactures wired and wireless data communication products for both corporate and home users, including routers, security cameras, network video recorders, and other Internet of Things devices.
“We recently became aware of unauthorized access to certain of our information technology systems hosted by a third party cloud provider. We have no indication that there has been unauthorized activity with respect to any user’s account,” Ubiquiti said in a notification published on Monday.
An investigation into the incident hasn’t revealed evidence that the adversary managed to access databases that host user data. However, Ubiquiti says, it’s still possible that user data might have been exposed in the breach.
Such data, if exposed, may include names and email addresses, along with encrypted passwords to accounts (the company stores passwords hashed and salted), along with addresses and phone numbers.
Ubiquiti encourages users to change their passwords, as a precautionary measure.
“We recommend that you also change your password on any website where you use the same user ID or password. Finally, we recommend that you enable two-factor authentication on your Ubiquiti accounts if you have not already done so,” the company says.
Hackers Steal Mimecast Certificate Used to Securely Connect with Microsoft 365
13.1.2021 Incindent Thehackernews
Mimecast said on Tuesday that "a sophisticated threat actor" had compromised a digital certificate it provided to certain customers to securely connect its products to Microsoft 365 (M365) Exchange.
The discovery was made after the breach was notified by Microsoft, the London-based company said in an alert posted on its website, adding it's reached out to the impacted organizations to remediate the issue.
The company didn't elaborate on what type of certificate was compromised, but Mimecast offers seven different digital certificates based on the geographical location that must be uploaded to M365 to create a server Connection in Mimecast.
"Approximately 10 percent of our customers use this connection," the company said. "Of those that do, there are indications that a low single digit number of our customers' M365 tenants were targeted."
Mimecast is a cloud-based email management service for Microsoft Exchange and Microsoft Office 365, offers users email security and continuity platform to safeguard them from spam, malware, phishing, and targeted attacks.
The compromised certificate is used to verify and authenticate Mimecast Sync and Recover, Continuity Monitor, and Internal Email Protect (IEP) products to M365 Exchange Web Services.
A consequence of such a breach could result in a man-in-the-middle (MitM) attack, where an adversary could potentially take over the connection and intercept email traffic, and even steal sensitive information.
As a precaution to prevent future abuse, the company said it's asked its customers to delete the existing connection within their M365 tenant with immediate effect and re-establish a new certificate-based connection using the new certificate that it has made available.
"Taking this action does not impact inbound or outbound mail flow or associated security scanning," Mimecast stated in its advisory.
An investigation into the incident is ongoing, with the company noting that it will work closely with Microsoft and law enforcement as appropriate.
The development comes as Reuters, citing sources, said the hackers who compromised Mimecast were the same group that breached U.S. software maker SolarWinds and a host of sensitive U.S. government agencies.
We have reached out to Mimecast for more information, and we'll update the story if we hear back.
Millions of Social Profiles Leaked by Chinese Data-Scrapers
12.1.2021 Incindent Threatpost
A cloud misconfig by SocialArks exposed 318 million records gleaned from Facebook, Instagram and LinkedIn.
More than 400GB of public and private profile data for 214 million social-media users from around the world has been exposed to the internet – including details for celebrities and social-media influencers in the U.S. and elsewhere.
The leak stems from a misconfigured ElasticSearch database owned by Chinese social-media management company SocialArks, which contained personally identifiable information (PII) from users of Facebook, Instagram, LinkedIn and other platforms, according to researchers at Safety Detectives.
The server was found to be publicly exposed without password protection or encryption during routine IP-address checks on potentially unsecured databases, researchers said. It contained more than 318 million records in total.
2020 Reader Survey: Share Your Feedback to Help Us Improve
SocialArks’ data-management platform is used for programmatic advertising and marketing. It bills itself as a “cross-border social-media management company dedicated to solving the current problems of brand building, marketing, marketing, social customer management in China’s foreign trade industry.”
The data included reams of North American users’ information. Source: Security Detectives.
The affected server, hosted by Tencent, was segmented into indices in order to store data obtained from each social-media source, which allowed researchers to look into the data further.
“Our research team was able to determine that the entirety of the leaked data was ‘scraped’ from social-media platforms, which is both unethical and a violation of Facebook’s, Instagram’s and LinkedIn’s terms of service,” researchers said, in a Monday blog post.
The scraped profiles included 11,651,162 Instagram user profiles; 66,117,839 LinkedIn user profiles; 81,551,567 Facebook user profiles; and 55,300,000 Facebook profiles that were deleted within a few hours after the open server was discovered.
The public profile data included biographies, profile pictures, follower totals, location settings, contact details such as email addresses and phone numbers, number of followers, number of comments, frequently used hashtags, company names, employment position and more.
“Social media data scraped for marketing purposes will inevitably include sensitive information,” Jack Mannino, CEO at nVisium, told Threatpost. “For every privacy-conscious person using social media, there is an exponentially greater number of people publicly sharing intimate details about their private lives. To protect yourself, restrict public access to your profile and media assets, be sensible about what you post online, and be careful what permissions you grant to applications that may abuse, misuse or steal your information.”
However, in addition to the collating of publicly available data, the database also included, inexplicably, private data for social-media users.
“SocialArks’ database stored personal data for Instagram and LinkedIn users such as private phone numbers and email addresses for users that did not divulge such information publicly on their accounts,” researchers said. “How SocialArks could possibly have access to such data in the first place remains unknown…It remains unclear how the company managed to obtain private data from multiple secure sources…Moreover, the company’s server had insufficient security and was left completely unsecured.”
Threatpost has reached out to SocialArks for more information.
The database was secured by SocialArks the same day that Security Detectives alerted the company to the issue.
SocialArks suffered a similar data breach in August, which affected 66 million LinkedIn users, 11.6 million Instagram accounts and 81.5 million Facebook accounts – about 150 million in all. The information exposed also consisted of scraped, publicly available data such as full names, country of residence, place of work, position, subscriber data and contact information, as well as direct links to profiles.
Having a central repository for such information opens the door to high-volume, automated social-engineering attacks, experts warned.
“Most data scraping is completely innocuous and carried out by web developers, business intelligence analysts, honest businesses such as travel booker sites, as well as being done for market research purposes online,” the researchers said. “However, even if such data is obtained legally – if it is stored without adequate cybersecurity, large leaks affecting millions of people can occur. When private information including phone numbers, email addresses and birth information is extracted and/or leaked, criminals are empowered to commit heinous acts including identity theft and financial fraud.”
Dirk Schrader, global vice president at New Net Technologies, said that the fact the scraping took place at all – public or private information – is in itself of interest.
“Public profiles have been scraped before and the giants in that space usually try to block mass scraping attempts as the intention behind is to get access to their ‘oil,'” he told Threatpost. “Why it hasn’t worked in this case would be an interesting fact to know. As a likely affected LinkedIn user, my choices are limited. Either I accept that scraping will happen, or I can reduce my profile which limits my ability to make business connections to a certain extent. How much information a user provides is their choice. Scraping itself, especially when the data collected is so badly secured, increases the likelihood to be targeted with specific attacks and unwanted emails.”
Ubiquiti discloses a data breach
12.1.2021 Incindent Securityaffairs
American technology company Ubiquiti Networks is disclosed a data breach and is notifying its customers via email.
American technology vendor Ubiquiti Networks suffered a data breach and is sending out notification emails to its customers asking them to change their passwords and enable 2FA for their accounts.
The company discovered unauthorized access to some of its systems managed by a third-party cloud provider.
The company is not aware of any access to any databases that were containing user data.
“We recently became aware of unauthorized access to certain of our information technology systems hosted by a third party cloud provider. We have no indication that there has been unauthorized activity with respect to any user’s account” reads the data breach notification sent to the customers.
“We are not currently aware of evidence of access to any databases that host user data, but we cannot be certain that user data has not been exposed. This data may include your name, email address, and the one-way encrypted password to your account (in technical terms, the passwords are hashed and salted). The data may also include your address and phone number if you have provided that to us.”
The attackers have had access to the servers containing information related to the user accounts for the web portal ui.com, exposed records include names, email addresses, and salted and hashed passwords.
For some users also home addresses and phone numbers may have also been exposed.
The company did not provide additional details about the data breach, including how many users have been impacted.
Experts found gained access to the Git Repositories of the United Nations
12.1.2021 Incindent Securityaffairs
Researchers obtained gained access to the Git Repositories belonging to the United Nations, exposing staff records and credentials.
The research group Sakura Samurai was able to access the repositories of the United Nations as part of the Vulnerability Disclosure Program and a Hall of Fame operated by the organization.
The group, composed of Jackson Henry, Nick Sahler, John Jackson, and Aubrey Cottle, has identified an endpoint that exposed Git Credentials. Then the group used the credentials to access the Git Repositories and download their content, including 100K+ private records for the United Nations Environmental Programme (UNEP) employees.
“The credentials gave us the ability to download the Git Repositories, identifying a ton of user credentials and PII. In total, we identified over 100K+ private employee records. We also discovered multiple exposed .git directories on UN owned web servers [ilo.org], the .git contents could then be exfiltrated with various tools such as “git-dumper”.” reads the post published by the experts.
The list of exposed PII includes:
Travel Records [Two Documents: 102,000+ Records]
HR Nationality Demographics [Two Documents: 7,000+ Records]
Generalized Employee Records [One document: 1,000+ Records]
Project and Funding Source Records [One Document: 4,000+ Records]
Evaluation Reports [One Document: 283 Projects]
The team of experts also performed subdomain enumeration of the United Nations domains covered by the program. Probing multiple endpoints with fuzzing tools the team discovered that an ilo.org subdomain had an exposed .git contents. Then they used the git-dumper to dump the project folders hosted on the web application.
“During our research, we began to fuzz multiple endpoints with tooling and initially discovered that an ilo.org subdomain had an exposed .git contents. Utilizing git-dumper [https://github.com/arthaud/git-dumper] we were able to dump the project folders hosted on the web application, resulting in the takeover of a MySQL database and of survey management platform due to exposed credentials within the code.” continues the research team.
The experts took over one of the International Labour Organization’s MySQL Databases and performed an account takeover on the survey management platform, then they enumerated the domains/subdomains.
The team found a subdomain on the United Nations Environment Programme and using a fuzzing technique they discovered the github credentials.
Once discovered the GitHub credentials, they downloaded the projects in the repositories, some of them were containing multiple sets of database and application credentials for the UNEP production environment.
“In total, we found 7 additional credential-pairs which could have resulted in unauthorized access of multiple databases. We decided to stop and report this vulnerability once we were able to access PII that was exposed via Database backups that were in the private projects.” conclude the experts.
In January 2020, an internal confidential report from the United Nations that was leaked to The New Humanitarian revealed that dozens of servers of the organization were “compromised” at offices in Geneva and Vienna. One of the offices that were hit by a sophisticated cyber attack is the U.N. human rights office, the hackers were able to compromise active directory and access a staff list and details like e-mail addresses. According to the report, attackers did not access passwords.
United Nations Environment Programme Exposed 100,000 Employee Records
12.1.2021 Incindent Securityweek
Security researchers with Sakura Samurai identified exposed GitHub credentials on a United Nations Environment Programme (UNEP) subdomain, which allowed them to access a trove of data, including more than 100,000 employee records.
While researching security flaws in assets within the scope of The United Nations’ vulnerability disclosure program, the Sakura Samurai researchers discovered an ilo.org subdomain that exposed .git contents.
This allowed them to take over an SQL database, as well as perform account takeover on a Survey Management Platform belonging to the International Labour Organization. However, although these are critical vulnerabilities, both resources were found to be abandoned, thus containing little data of use.
Further fuzzing, however, led the researchers to a UNEP subdomain that leaked GitHub credentials, thus enabling them to access and download “a lot of private password-protected GitHub projects.”
These projects, Sakura Samurai says, contained multiple databases, as well as application credentials for the UNEP production environment. A total of 7 credential pairs were identified, providing unauthorized access to more databases.
In one of these, two documents containing over 102,000 travel records of employees were identified. These records included names, employee ID numbers, employee groups, justification of travel, start and end dates of travel, approval status, length of stay, and destination.
The researchers also found two documents containing over 7,000 HR nationality demographics records: employee names and groups, ID numbers, nationality and gender of employee, employee pay grade, and organization work unit identification number and unit text tags.
Over 1,000 generalized employee records were found in another document: index numbers, employee names and emails, and employee work subareas.
Another document exposed in excess of 4,000 project and funding source records, including affected areas, grant and co-financing amounts, funding sources, project identification numbers, implementing agencies, countries, period of the project, and approval status.
A document containing evaluation reports contained information on 283 projects, including overall description of the evaluations and reports, periods when the evaluation was conducted, and links to the report.
Source code for malware that targets Qiui Cellmate device was leaked online
11.1.2021 Incindent Securityaffairs
The source code for the ChastityLock ransomware that was used in attacks aimed at the users of the Qiui Cellmate adult toy is now publicly available.
Recently a family of ransomware was observed targeting the users of the Bluetooth-controlled Qiui Cellmate chastity device.
Qiui Cellmate made the headlines in October when the researchers at Pen Test Partners published a report that provides details about security vulnerabilities affecting them.
Crooks were threatening the victims of locking indefinitely the device if they did not pay the ransom.
Security expert AX Sharma reported the discovery of a GitHub repository containing the ransomware code that could take over Cellmate IoT devices and control them via the smartphone app to receive a ransom amount in Bitcoins.
Qiui Cellmate app
Ransomware operators were demanding a 0.02 BTC ransom amount (approx. $678) to the victims, the requests were sent to the victims via the Cellmate mobile app.
The availability of the ransomware code was first reported in a tweet by the user @vx-underground.
“Security Report has observed the exposed piece of code contains instructions to communicate with QIUI’s API endpoints to enumerate user’s info, send messages to the victim’s app, add friends, request a ransom amount, and perform other tasks.” wrote Ax Sharma on Security Report.
The leaked code includes information to send commands to the devices through the QIUI’s API endpoints.
The malicious code also includes a function to enumerate a list of available QIUI devices they could be targeted.
At the time Ax Sharma reported the new, the API endpoints were returning an error message (“The specified key does not exist”).
The expert warns of threat actors that could use the code to launch a cyberattack against Cellmate devices.
Whether this source code is functional or not remains debatable, but the next iteration of a copycat attack targeting your Cellmate device remains a possibility.
“However, the malware source code does reference terms like memberCode, binding, and friend requests which line up with what was in Pen Test Partners‘ original disclosure of security vulnerabilities in QIUI devices.” concludes the post.
“Whether this source code is functional or not remains debatable, but the next iteration of a copycat attack targeting your Cellmate device remains a possibility.”
The good news is that Qiui addressed the vulnerabilities exploited by the malware, users have to install the latest version of the app.
Unsecured Git server exposed Nissan North America
9.1.2021 Incindent Securityaffairs
A misconfigured Git server is the root cause for the leak of source code of mobile apps and internal tools belonging to Nissan North America.
A misconfigured Git server has caused the leak of the source code of mobile apps and internal software used by Nissan North America.
The situation is embarrassing because the software engineer Tillie Kottmann was informed by an anonymous source that the Git server was exposed online and accessible to anyone using the default login credentials admin/admin.
The news was first reported by ZDNet which was contacted by Kottmann.
RELEASE: Nissan North America Source Code Dump
A COMPLETE dump of all git repositories from Nissan NA, most notably including sources for:
– the Nissan NA Mobile apps
– some parts of the ASIST diagnostics tool
– the Dealer Business Systems / Dealer Portal
(1/n) pic.twitter.com/ltDvg9blTB
— tillie, doer of crime 💛🤍💜🖤 (@antiproprietary) January 4, 2021
– Nissan internal core mobile library
– Nissan/Infiniti NCAR/ICAR services
– client acquisition and retention tools
– sale / market research tools + data
– various marketing tools
– the vehicle logistics portal
(2/n)
— tillie, doer of crime 💛🤍💜🖤 (@antiproprietary) January 4, 2021
The engineers analyzed the content of the repository and confirmed the presence of the source code for:
Nissan NA Mobile apps
some parts of the Nissan ASIST diagnostics tool
the Dealer Business Systems / Dealer Portal
Nissan internal core mobile library
Nissan/Infiniti NCAR/ICAR services
client acquisition and retention tools
sale / market research tools + data
various marketing tools
the vehicle logistics portal
vehicle connected services / Nissan connect things
and various other backends and internal tools
In a series of tweets, the researchers also provided insights related to the code such as the password handling routine implemented in the ASIST/NNA_MNS_PartsServices_IMS-ASISTUserAuthentication process.
If you look at ASIST/NNA_MNS_PartsServices_IMS-ASISTUserAuthentication, you can see that this is how password handling in ASIST works.
oh no.
(5/n) pic.twitter.com/qM1GqMq6FL
— tillie, doer of crime 💛🤍💜🖤 (@antiproprietary) January 4, 2021
The car maker shut down the Git server after the public disclosure of the leak.
The leaked data are already circulating in the hacking underground, experts reported the availability of torrent links to the leaked material on hacking forums and Telegram channels.
A company spokesperson told ZDNet that the company launched an investigation into the incident and promptly secured the impacted server.
“Nissan conducted an immediate investigation regarding improper access to proprietary company source code. We take this matter seriously and are confident that no personal data from consumers, dealers or employees was accessible with this security incident.” states the spokesperson. “The affected system has been secured, and we are confident that there is no information in the exposed source code that would put consumers or their vehicles at risk.”
The researcher found a similar data leak in May 2020 that impacted Mercedes Benz.
Data from August Breach of Amazon Partner Juspay Dumped Online
6.1.2021 Incindent Threatpost
Researcher discovered info of 35 million credit-card users from an attack on the Indian startup, which handles payments for numerous online marketplaces.
Data from a breach that occurred five months ago involving Juspay, which handles payments for Amazon and other online retailers in India, has been dumped online, a researcher has found.
Security researcher Rajshekhar Rajaharia discovered data of 35 million Indian credit-card holders from a breach of a Juspay server that occurred on Aug. 18, he revealed on Twitter. The data included sensitive information such as the name, mobile number and bank name of customers whose payment info went through the company’s service, Rajaharia said in the tweet, which included an edited screenshot of some of the data.
Juspay is a Bengaluru, India-based start-up that partners with leading online retailers to make payment transactions—upwards of 650,000 per day–in India. Merchants with payments going through the service include Amazon, Swiggy, MakeMyTrip, Yatra, Freecharge, BookMyShow and Snapdeal.Juspay discovered the breach during the early morning-hours of Aug. 18, alerted by unauthorized activity in one of the data stores, according to a detailed statement on the company’s website posted Monday and updated Tuesday in response to reports of the incident. Threat actors used an old, unrecycled Amazon Web Services (AWS) access key to gain unauthorized access to the server, which triggered an automatic system alert due to the sudden boost in system resources by the data store, the company said.
Juspay responded immediately to the incident and stopped the intrusion, terminated the server used in the attack, and sealed its entry point, according to the statement.
“Within the same day, a system audit was done to make sure the entire category of such issues is prevented, the company said. “Our merchants were informed of the cyberattack on the same day and we worked with them to take various precautionary measures to safeguard information.”
Those mitigation steps included refreshing API keys and invalidating the old keys; enforcing 2 Factor Authentication for all of its tools; and moving away from AWS key-based automation, according to the statement. Juspay also has added threat-monitoring tools to its security profile to prevent further attacks.
While breaches and subsequent data dumps like this are commonplace these days, what’s worrying in this case is the time lag between the breach and Juspay’s public acknowledgment of it. While the company may have already informed partners, it did not reveal the breach publicly until this week, after Rajaharia’s discovery of the dumped data.
“Perhaps the biggest concern is the dwell time,” acknowledged Saryu Nayyar, CEO of unified security and risk analytic firm Gurucul. “The breach happening mid-August 2020 and only being reported now, indicates there may have been some gaps in Juspay’s security stack or their security operations process.”
Indeed, in its statement Juspay appeared to downplay the breach, saying the threat actors didn’t access sensitive data. The company said threat actors breached about 35 million records with “masked card data and card fingerprint (which is non-sensitive information).”
“The masked card data is used for display purposes on merchant UI and cannot be used for completing a transaction,” according to the statement.
However, Juspay did acknowledge the compromise of some data records containing non-anonymized, plain-text email and phone numbers, as well as anonymous metadata for 100 million processed transactions, a subset of which contained email and mobile information.
Juspay’s delayed approach to revealing the breach has some, including Rajaharia, calling for the company to be investigated by Indian authorities on Twitter for its lack of immediate disclosure.
T-Mobile Faces Yet Another Data Breach
5.1.2021 Incindent Threatpost
The cyberattack incident is the wireless carrier’s fourth in three years.
T-Mobile USA has reported a data breach – its fourth in three years.
The wireless carrier disclosed the breach last week via its website, saying that it detected and shut down “malicious, unauthorized access to some information” related to T-Mobile accounts. Specifically, that data consisted of customer proprietary network information (CPNI) – a data set that the FCC calls “some of the most sensitive personal information that carriers and providers have about their customers.”
CPNI includes records of which phone numbers users called; the frequency, duration, and timing of such calls; and any services purchased by the consumer, such as call waiting. T-Mobile said that the thieves in this case lifted phone numbers, number of lines subscribed to on accounts, “and, in some cases, call-related information.”
2020 Reader Survey: Share Your Feedback to Help Us ImproveThe good news is that the data accessed did not include names on the account, physical or email addresses, financial data, credit-card information, Social Security numbers, tax ID, passwords or PINs, the wireless company said in the notice.
T-Mobile said it is investigating the incident with help from law enforcement and a security firm, and it told outlets that 0.2 percent of customers (around 200,000 people) were affected.
While the attackers weren’t able to collect any highly sensitive personal data, there is still risk posed to those whose phone numbers were stolen in the breach, Hank Schless, senior manager for security solutions at Lookout, told Threatpost.
“An area code is all an attacker needs to carry out a socially engineered mobile phishing attack,” he said. “The attacker can pretend to be T-Mobile support over voice or text in order to get customers to share their login credentials. Since customers know there was a recent security incident, they may not think twice before engaging with an individual who claims they can help. If this were successful and the attacker made their way into the customer’s account, they could have access to sensitive information associated with the account.”
Lookout discovered a mobile phishing campaign in February that associated area codes with popular banks in the area to try to phish mobile banking login credentials.
“Mobile phishing represents one of the biggest security blind spots for individuals and enterprise security teams alike,” Schless said.
4th Incident in 3 Years
T-Mobile previously reported breaches in August 2018, November 2019 and most recently in March.
The 2018 incident impacted 2.3 million subscribers, exposing customers’ names, billing ZIP codes, phone numbers, email addresses, account numbers and account types (prepaid or postpaid).
In 2019, about 1.26 million of T-Mobile’s prepaid were affected by a breach that included names, billing addresses (if provided), phone numbers, account numbers and CPNI.
The 2020 breach meanwhile impacted both employees and customers (it’s unclear how many were affected). Cybercriminals accessed employee email accounts, some of which contained account information for T-Mobile customers, including names and addresses, phone numbers, account numbers and more.
In all three of those cases, as with the most recent incident, financial and Social Security data was not impacted.
Sprint meanwhile, which merged with T-Mobile in 2020, had two of its own in 2019.
“The volume of attacks and successful attacks against wireless carriers continues to rise,” Brandon Hoffman, CISO at Netenrich, told Threatpost. “In this particular case, one has to wonder if it is related to the merging of two titans. Sprint had a series of issues last year and this is a another in a list of success attacks on T-Mobile.”
He added, “in our industry, when issues continue regardless of impact, we usually go back to the drawing board. It feels like there is an opportunity here to review the foundations of cyber relative to the merged entity and find out where quick wins can be had to shore up defenses. With the volume of successful attacks that we are seeing, either they are suffering from consistent advanced persistent threats or there is something easily exploited that is being overlooked.”
It should be noted that T-Mobile and Sprint were also impacted by an incident in December 2019, where hundreds of thousands of mobile phone bills for AT&T, Verizon and T-Mobile subscribers were laid open to anyone with an internet connection, thanks to the oversight of a contractor working with Sprint.
According to a media investigation, the contractor misconfigured a cloud storage bucket on Amazon Web Services (AWS), in which more than 261,300 documents were stored – mainly cell phone bills from Sprint customers who switched from other carriers.
Cell phone bills are a treasure trove of data, and include names, addresses and phone numbers along with spending histories and in many cases, call and text message records. In this case, some of the bills dated back to 2015; it’s unclear how long the bucket was exposed.
Threat actor is selling 368.8 million records from 26 data breaches
1.1.2021 Incindent Securityaffairs
A data breach broker is selling user records allegedly from twenty-six data breaches on a hacker forum.
Security experts from Bleeping Computer reported that a threat actor is selling user records allegedly stolen from twenty-six companies on a hacker forum.
The total volume of data available for sale is composed of 368.8 million stolen user records.
“Last Friday, a data broker began selling the combined total of 368.8 million stolen user records for twenty-six companies on a hacker forum.” reported Bleeping Computer.
For some of these companies, the data breaches have not been previously disclosed, including Teespring.com, MyON.com, Chqbook.com, Anyvan.com, Eventials.com, Wahoofitness.com, Sitepoint.com, and ClickIndia.com.
Below the list of affected companies published by Bleeping Computer, which attempted to notify them.
Company User Records Known?
Teespring.com 8.2 million No
MyON.com 13 million No
Chqbook.com 1 million No
Anyvan.com 4.1 million No
Eventials.com 1.4 million No
Wahoofitness.com 1.7 million No
Sitepoint.com 1 million No
Clickindia.com 8 million No
Juspay.in 100 million Yes
Knockcrm.com 6 million Yes
Mindful.org 1.7 million Yes
Bigbasket.com 20 million Yes
Reddoorz.com 5.8 million Yes
Hybris.com (SAP.com) 4 million SAP client data
Wedmegood.com 1.3 million Yes
Wongnai.com 4.3 million Yes
Geekie.com.br 8.1 million Yes
Accuradio.com 2.2 million Yes
Everything5pounds.com 2.9 million Yes
Cermati.com 2.9 million Yes
Netlog.com (Twoo.com) 53 million Yes
Reverbnation.com 7.8 million Yes
Fotolog.com 33 million Yes
Pizap.com 60 million Yes
ModaOperandi.com 1.2 million Yes
Singlesnet.com 16 million Yes
Some of the companies confirmed the incident to BleepingComputer, others such as Chqbook.com claims that they haven’t suffered a security breach.
“There has been no data breach and no information belonging to our customers has been compromised. Data security is a key priority area for us and we conduct periodic security audits to ensure the safety of our customers’ information,” Chqbook told BleepingComputer.
For now, if you have an account at any of the sites listed above, it is strongly suggested that you change your password to a strong and unique one used only at that site.
Users of the above services are recommended to change their password and use unique credentials for each service they access.