15.3.24 Security The Hacker News
Google Introduces Enhanced Real-Time URL Protection for Chrome Users
15.3.24 Security The Hacker News
Google on Thursday announced an enhanced version of Safe Browsing to provide real-time, privacy-preserving URL protection and safeguard users from visiting potentially malicious sites.
"The Standard protection mode for Chrome on desktop and iOS will check sites against Google's server-side list of known bad sites in real-time," Google's Jonathan Li and Jasika Bawa said.
"If we suspect a site poses a risk to you or your device, you'll see a warning with more information. By checking sites in real time, we expect to block 25% more phishing attempts."
Up until now, the Chrome browser used a locally-stored list of known unsafe sites that's updated every 30 to 60 minutes, and then leveraging a hash-based approach to compare every site visited against the database.
Google first revealed its plans to switch to real-time server-side checks without sharing users' browsing history with the company in September 2023.
The reason for the change, the search giant said, is motivated by the fact that the list of harmful websites is growing at a rapid pace and that 60% of the phishing domains exist for less than 10 minutes, making them difficult to block.
"Not all devices have the resources necessary to maintain this growing list, nor are they always able to receive and apply updates to the list at the frequency necessary to benefit from full protection," it added.
Thus, with the new architecture, every time a user attempts to visit a website, the URL is checked against the browser's global and local caches containing known safe URLs and the results of previous Safe Browsing checks in order to determine the site's status.
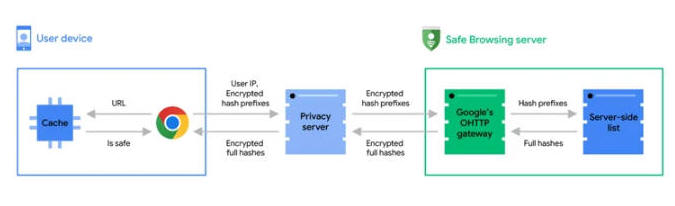
Should the visited URL be absent from the caches, a real-time check is performed by obfuscating the URL into 32-byte full hashes, which are then truncated into 4-byte long hash prefixes, encrypted, and sent to a privacy server.
"The privacy server removes potential user identifiers and forwards the encrypted hash prefixes to the Safe Browsing server via a TLS connection that mixes requests with many other Chrome users," Google explained.
The Safe Browsing server subsequently decrypts the hash prefixes and matches them against the server-side database to return full hashes of all unsafe URLs that match one of the hash prefixes sent by the browser.
Finally, on the client side, the full hashes are compared against the full hashes of the visited URL, and a warning message is displayed if a match is found.
Google also confirmed that the privacy server is nothing but an Oblivious HTTP (OHTTP) relay operated by Fastly that sits between Chrome and the Safe Browsing server to prevent the latter from access users' IP addresses, thereby preventing it from correlating the URL checks with a user's internet browsing history.
"Ultimately, Safe Browsing sees the hash prefixes of your URL but not your IP address, and the privacy server sees your IP address but not the hash prefixes," the company emphasized. "No single party has access to both your identity and the hash prefixes. As such, your browsing activity remains private."