"Whereas a message may stay unanswered for a while, calling the user increases the chances of getting the code. A phone call is also an opportunity to try and produce the desired effect on the victim with the tone of voice."
Security 2024 2023 2022 2021 2020
Mozilla Faces Privacy Complaint for Enabling Tracking in Firefox Without User Consent
25.9.24 Security The Hacker News
Vienna-based privacy non-profit noyb (short for None Of Your Business) has filed a complaint with the Austrian data protection authority (DPA) against Firefox maker Mozilla for enabling a new feature called Privacy Preserving Attribution (PPA) without explicitly seeking users' consent.
"Contrary to its reassuring name, this technology allows Firefox to track user behavior on websites," noyb said. "In essence, the browser is now controlling the tracking, rather than individual websites."
Noyb also called out Mozilla for allegedly taking a leaf out of Google's playbook by "secretly" enabling the feature by default without informing users.
PPA, which is currently enabled in Firefox version 128 as an experimental feature, has its parallels in Google's Privacy Sandbox project in Chrome.
The initiative, now abandoned by Google, sought to replace third-party tracking cookies with a set of APIs baked into the web browser that advertisers can talk to in order to determine users' interests and serve targeted ads.
Put differently, the web browser acts as a middleman that stores information about the different categories that users can be slotted into based on their internet browsing patterns.
PPA, per Mozilla, is a way for sites to "understand how their ads perform without collecting data about individual people," describing it as a "non-invasive alternative to cross-site tracking."
It's also similar to Apple's Privacy Preserving Ad Click Attribution, which allows advertisers to measure the effectiveness of their ad campaigns on the web without compromising on user privacy.
The way PPA works is as follows: Websites that serve ads can ask Firefox to remember the ads in the form of an impression that includes details about the ads themselves, such as the destination website.
If a Firefox user ends up visiting the destination website and performs an action that's deemed valuable by the business – e.g., making an online purchase by clicking on the ad, also called "conversion" – that website can prompt the browser to generate a report.
The generated report is encrypted and submitted anonymously using the Distributed Aggregation Protocol (DAP) to an "aggregation service," after which the results are combined with other similar reports to create a summary such that it makes it impossible to learn too much about any individual.
This, in turn, is made possible by a mathematical framework called differential privacy that enables the sharing of aggregate information about users in a privacy-preserving manner by adding random noise to the results to prevent re-identification attacks.
"PPA is enabled in Firefox starting in version 128," Mozilla notes in a support document. "A small number of sites are going to test this and provide feedback to inform our standardization plans, and help us understand if this is likely to gain traction."
"PPA does not involve sending information about your browsing activities to anyone. Advertisers only receive aggregate information that answers basic questions about the effectiveness of their advertising."
It's this aspect that noyb has found fault with, as it's in violation of the European Union's (E.U.) stringent data protection regulations by enabling PPA by default without seeking users' permissions.
"While this may be less invasive than unlimited tracking, which is still the norm in the US, it still interferes with user rights under the E.U.'s GDPR," the advocacy group said. "In reality, this tracking option doesn't replace cookies either, but is simply an alternative - additional - way for websites to target advertising."
It further noted that a Mozilla developer justified the move by claiming that users cannot make an informed decision and that "explaining a system like PPA would be a difficult task."
"It's a shame that an organization like Mozilla believes that users are too dumb to say yes or no," Felix Mikolasch, data protection lawyer at noyb, said. "Users should be able to make a choice and the feature should have been turned off by default."
Kaspersky Exits U.S., Automatically Replaces Software With UltraAV, Raising Concerns
24.9.24 Security The Hacker News
Antivirus vendor Kaspersky has formally begun pulling back its offerings in the U.S., migrating existing users to UltraAV, effective September 19, 2024, ahead of its formal exit at the end of the month.
"Kaspersky antivirus customers received a software update facilitating the transition to UltraAV," the company said in a post announcing the move on September 21.
"This update ensured that users would not experience a gap in protection upon Kaspersky's exit from the market."
The Russian company, which was banned from selling its software in the U.S. due to national security concerns, said it "worked closely" with UltraAV to ensure that the standards of security and privacy were maintained after the switch.
However, some users who experienced the update have taken to Kaspersky's forums and Reddit, stating that Kaspersky's software was automatically deleted and replaced by UltraAV without any prior notice.
UltraAV, in an FAQ, said "all Kaspersky U.S. users with a valid email address associated with their accounts received email communication detailing the transition process" starting September 5.
However, it appears that the notice reportedly failed to explicitly state that the switch of software in user systems would be an automatic process.
"I was using Kaspersky, didn't realize they'd be shuffling us off to some rando [antivirus] in September," one user wrote in a post on Reddit. "Nearly had a heart attack when I started my PC today and found a program I didn't download."
A U.S. company, UltraAV is part of Pango Group, which also offers several other VPN apps like UltraVPN, OVPN, and VPN360. It touts more than 25 million active users across its brands, and over 650 million lifetime users.
CrowdStrike Reveals Root Cause of Global System Outages
7.8.24 Security The Hacker News
Cybersecurity company CrowdStrike has published its root cause analysis detailing the Falcon Sensor software update crash that crippled millions of Windows devices globally.
The "Channel File 291" incident, as originally highlighted in its Preliminary Post Incident Review (PIR), has been traced back to a content validation issue that arose after it introduced a new Template Type to enable visibility into and detection of novel attack techniques that abuse named pipes and other Windows interprocess communication (IPC) mechanisms.
Specifically, it's related to a problematic content update deployed over the cloud, with the company describing it as a "confluence" of several shortcomings that led to a crash – the most prominent of them is a mismatch between the 21 inputs passed to the Content Validator via the IPC Template Type as opposed to the 20 supplied to the Content Interpreter.
CrowdStrike said the parameter mismatch was not discovered during "multiple layers" of the testing process, in part due to the use of wildcard matching criteria for the 21st input during testing and in the initial IPC Template Instances that were delivered between March and April 2024.
In other words, the new version of Channel File 291 pushed on July 19, 2024, was the first IPC Template Instance to make use of the 21st input parameter field. The lack of a specific test case for non-wildcard matching criteria in the 21st field meant that this was not flagged until after the Rapid Response Content was shipped to the sensors.
"Sensors that received the new version of Channel File 291 carrying the problematic content were exposed to a latent out-of-bounds read issue in the Content Interpreter," the company said.
"At the next IPC notification from the operating system, the new IPC Template Instances were evaluated, specifying a comparison against the 21st input value. The Content Interpreter expected only 20 values. Therefore, the attempt to access the 21st value produced an out-of-bounds memory read beyond the end of the input data array and resulted in a system crash."
Besides validating the number of input fields in the Template Type at sensor compile time to address the issue, CrowdStrike said it also added runtime input array bounds checks to the Content Interpreter to prevent out-of-bounds memory reads and corrected the number of inputs provided by the IPC Template Type.
"The added bounds check prevents the Content Interpreter from performing an out-of-bounds access of the input array and crashing the system," it noted. "The additional check adds an extra layer of runtime validation that the size of the input array matches the number of inputs expected by the Rapid Response Content."
On top of that, CrowdStrike said it plans to increase test coverage during Template Type development to include test cases for non-wildcard matching criteria for each field in all (future) Template Types.
Some of the sensor updates are also expected to resolve the following gaps -
The Content Validator is being modified to add new checks to ensure that content in Template Instances does not include matching criteria that match over more fields than are being provided as input to the Content Interpreter
The Content Validator is being modified to only allow wildcard matching criteria in the 21st field, which prevents the out-of-bounds access in the sensors that only provide 20 inputs
The Content Configuration System has been updated with new test procedures to ensure that every new Template Instance is tested, regardless of the fact that the initial Template Instance is tested with the Template Type at creation
The Content Configuration System has been updated with additional deployment layers and acceptance checks
The Falcon platform has been updated to provide customers with increased control over the delivery of Rapid Response Content
Last but not least, CrowdStrike said it has engaged two independent third-party software security vendors to conduct further review of the Falcon sensor code for both security and quality assurance. It's also carrying out an independent review of the end-to-end quality process from development through deployment.
It has further pledged to work with Microsoft as Windows introduces new ways to perform security functions in user space as opposed to relying on a kernel driver.
"CrowdStrike's kernel driver is loaded from an early phase of system boot to allow the sensor to observe and defend against malware that launches prior to user mode processes starting," it said.
"Providing up-to-date security content (e.g., CrowdStrike's Rapid Response Content) to these kernel capabilities enables the sensor to defend systems against a rapidly evolving threat landscape without making changes to kernel code. Rapid Response Content is configuration data; it is not code or a kernel driver."
The release of the root cause analysis comes as Delta Air Lines said it has "no choice" but to seek damages from CrowdStrike and Microsoft for causing massive disruptions and costing it an estimated $500 million in lost revenue and extra costs related to thousands of canceled flights.
Both CrowdStrike and Microsoft have since responded to the criticism, stating they are not to blame for the days-long outage and that Delta declined their offers for on-site assistance, indicating that the carrier's problems could run a lot deeper than its Windows machines going down as a result of the faulty security update.
CrowdStrike Explains Friday Incident Crashing Millions of Windows Devices
25.7.24 Security The Hacker News
Cybersecurity firm CrowdStrike on Wednesday blamed an issue in its validation system for causing millions of Windows devices to crash as part of a widespread outage late last week.
"On Friday, July 19, 2024 at 04:09 UTC, as part of regular operations, CrowdStrike released a content configuration update for the Windows sensor to gather telemetry on possible novel threat techniques," the company said in its Preliminary Post Incident Review (PIR).
"These updates are a regular part of the dynamic protection mechanisms of the Falcon platform. The problematic Rapid Response Content configuration update resulted in a Windows system crash."
The incident impacted Windows hosts running sensor version 7.11 and above that was online between July 19, 2024, 04:09 UTC and 05:27 UTC and received the update. Apple macOS and Linux systems were not affected.
CrowdStrike said it delivers security content configuration updates in two ways, one via Sensor Content that's shipped with Falcon Sensor and another through Rapid Response Content that allows it to flag novel threats using various behavioral pattern-matching techniques.
The crash is said to have been the result of a Rapid Response Content update containing a previously undetected error. It's worth noting that such updates are delivered in the form of Template Instances corresponding to specific behaviors – each of which is mapped to a unique Template Type – for enabling new telemetry and detection.
The Template Instances, in turn, are created using a Content Configuration System, after which they are deployed to the sensor over the cloud through a mechanism dubbed Channel Files, which are ultimately written to disk on the Windows machine. The system also encompasses a Content Validator component that carries out validation checks on the content before it is published.
"Rapid Response Content provides visibility and detections on the sensor without requiring sensor code changes," it explained.
"This capability is used by threat detection engineers to gather telemetry, identify indicators of adversary behavior and perform detections and preventions. Rapid Response Content is behavioral heuristics, separate and distinct from CrowdStrike's on-sensor AI prevention and detection capabilities."
These updates are then parsed by the Falcon sensor's Content Interpreter, which then allows the Sensor Detection Engine to detect or prevent malicious activity, depending on the customer's policy configuration.
While each new Template Type is stress tested for different parameters like resource utilization and performance impact, the root cause of the problem, per CrowdStrike, could be traced back to the rollout of the Interprocess Communication (IPC) Template Type on February 28, 2024, that was introduced to flag attacks that abuse named pipes.
The timeline of events is as follows -
February 28, 2024 - CrowdStrike releases sensor 7.11 to customers with new IPC Template Type
March 5, 2024 - The IPC Template Type passes the stress test and is validated for use
March 5, 2024 - The IPC Template Instance is released to production via Channel File 291
April 8 - 24, 2024 - Three more IPC Template Instances are deployed in production
July 19, 2024 - Two additional IPC Template Instances are deployed, one of which passes validation despite having problematic content data
"Based on the testing performed before the initial deployment of the Template Type (on March 05, 2024), trust in the checks performed in the Content Validator, and previous successful IPC Template Instance deployments, these instances were deployed into production," CrowdStrike said.
"When received by the sensor and loaded into the Content Interpreter, problematic content in Channel File 291 resulted in an out-of-bounds memory read triggering an exception. This unexpected exception could not be gracefully handled, resulting in a Windows operating system crash (BSoD)."
In response to the sweeping disruptions caused by the crash and preventing them from happening again, the Texas-based company said it has improved its testing processes and enhanced its error handling mechanism in the Content Interpreter. It's also planning to implement a staggered deployment strategy for Rapid Response Content.
Google Abandons Plan to Phase Out Third-Party Cookies in Chrome
23.7.24 Security The Hacker News
Google on Monday abandoned plans to phase out third-party tracking cookies in its Chrome web browser more than four years after it introduced the option as part of a larger set of a controversial proposal called the Privacy Sandbox.
"Instead of deprecating third-party cookies, we would introduce a new experience in Chrome that lets people make an informed choice that applies across their web browsing, and they'd be able to adjust that choice at any time," Anthony Chavez, vice president of the initiative, said.
"We're discussing this new path with regulators, and will engage with the industry as we roll this out."
The significant policy reversal comes nearly three months following the company's announcement that it intends to eliminate third-party cookies starting early next year after repeated delays, underscoring the project's tumultuous history.
While Apple Safari and Mozilla Firefox no longer support third-party cookies as of early 2020, Google has had a tougher time turning it off owing to its own prominent role as a web browser vendor and an advertising platform.
The company's idea of balancing online privacy vis-à-vis an ad-supported internet using Privacy Sandbox has courted scrutiny from regulators, advertisers, and privacy advocates, prompting it to redraw the contours of the cookie-replacement technology several times over the past few years.
Last month, Austrian privacy non-profit noyb (none of your business) said it merely shifts the control from a third-party to Google and that it can still be used to track users without giving them an option to consent in an informed and transparent manner.
Apple, which has introduced advanced tracking and fingerprinting protections in Safari, has been critical of Topics API, a crucial aspect of Privacy Sandbox that sorts users' interests into an ever-evolving list of predefined topics based on their browsing histories in order to serve personalized ads.
"The user doesn't get told upfront which topics Chrome has tagged them with or which topics it exposes to which parties," Apple's John Wilander said, noting how it can be used to fingerprint and re-identify users as well as profile their cross-site activity.
Specifically, it pointed out implementation loopholes that could potentially allow a data broker embedded in websites to capture a user's changing interests over time by periodically querying the Topics API and creating a permanent profile by combining it with other data points.
"Now imagine what advanced machine learning and artificial intelligence can deduce about you based on various combinations of interest signals," Wilander said. "What patterns will emerge when data brokers and trackers can compare and contrast across large portions of the population?"
"We think the web should not expose such information across websites and we don't think the browser, i.e. the user agent, should facilitate any such data collection or use."
Privacy Sandbox has also faced regulatory hurdles over concerns that the technology could give Google an unfair advantage in the digital advertising market and limit competition, complicating the rollout process further.
The development is an admission from Google that gaining industry-wide consensus around a single solution is more challenging than it sounds. A pivot from cookies "requires significant work by many participants and will have an impact on publishers, advertisers, and everyone involved in online advertising," it said.
The U.K. Competition and Markets Authority (CMA), which is closely overseeing the changes being made by the search giant, said it's evaluating the impact of the new announcement.
"Instead of removing third-party cookies from Chrome, it will be introducing a user-choice prompt, which will allow users to choose whether to retain third-party cookies," the CMA said. "The CMA will now work closely with the [Information Commissioner's Office] to carefully consider Google's new approach to Privacy Sandbox."
Faulty CrowdStrike Update Crashes Windows Systems, Impacting Businesses Worldwide
19.7.24 Security The Hacker News
Businesses across the world have been hit by widespread disruptions to their Windows workstations stemming from a faulty update pushed out by cybersecurity company CrowdStrike.
"CrowdStrike is actively working with customers impacted by a defect found in a single content update for Windows hosts," the company's CEO George Kurtz said in a statement. "Mac and Linux hosts are not impacted. This is not a security incident or cyberattack."
The company, which acknowledged "reports of [Blue Screens of Death] on Windows hosts," further said it has identified the issue and a fix has been deployed for its Falcon Sensor product, urging customers to refer to the support portal for the latest updates.
For systems that have been already impacted by the problem, the mitigation instructions are listed below -
Boot Windows in Safe Mode or Windows Recovery Environment
Navigate to the C:\Windows\System32\drivers\CrowdStrike directory
Find the file named "C-00000291*.sys" and delete it
Restart the computer or server normally
It's worth noting that the outage has also impacted Google Cloud Compute Engine, causing Windows virtual machines using Crowdstrike's csagent.sys to crash and go into an unexpected reboot state.
"After having automatically received a defective patch from Cloudstrike, Windows VMs crash and will not be able to reboot," it said. "Windows VMs that are currently up and running should no longer be impacted."
Security researcher Kevin Beaumont said "I have obtained the Crowdstrike driver they pushed via auto update. I don't know how it happened, but the file isn't a validly formatted driver and causes Windows to crash every time."
"Crowdstrike is the top tier EDR product, and is on everything from point of sale to ATMs etc – this will be the biggest 'cyber' incident worldwide ever in terms of impact, most likely."
Airlines, financial institutions, food and retail chains, hospitals, hotels, news organizations, railway networks, and telecom firms are among the many businesses affected. Shares of CrowdStrike have tanked 15% in U.S. premarket trading.
"The current event appears – even in July – that it will be one of the most significant cyber issues of 2024," Omer Grossman, Chief Information Officer (CIO) at CyberArk, said in a statement shared with The Hacker News. "The damage to business processes at the global level is dramatic. The glitch is due to a software update of CrowdStrike's EDR product."
"This is a product that runs with high privileges that protects endpoints. A malfunction in this can, as we are seeing in the current incident, cause the operating system to crash."
The recovery is expected to take days as the problem needs to be solved manually, endpoint by endpoint, by starting them in Safe Mode and removing the buggy driver, Grossman pointed out, adding the root cause behind the malfunction will be of the "utmost interest."
Jake Moore, global security advisor at Slovakian cybersecurity company ESET, told The Hacker News that the incident serves to highlight the need for implementing multiple "fail safes" in place and diversification of IT infrastructure.
"Upgrades and maintenance to systems and networks can unintentionally include small errors, which can have wide-reaching consequences as experienced today by Crowdstrike's customers," Moore said.
"Another aspect of this incident relates to 'diversity' in the use of large-scale IT infrastructure. This applies to critical systems like operating systems (OSes), cybersecurity products, and other globally deployed (scaled) applications. Where diversity is low, a single technical incident, not to mention a security issue, can lead to global-scale outages with subsequent knock-on effects."
The development comes as Microsoft is recovering from a separate outage of its own that caused issues with Microsoft 365 apps and services, including Defender, Intune, OneNote, OneDrive for Business, SharePoint Online, Windows 365, Viva Engage, and Purview.
"A configuration change in a portion of our Azure backend workloads, caused interruption between storage and compute resources which resulted in connectivity failures that affected downstream Microsoft 365 services dependent on these connections," the tech giant said.
Singapore Banks to Phase Out OTPs for Online Logins Within 3 Months
15.7.24 Security The Hacker News
Retail banking institutions in Singapore have three months to phase out the use of one-time passwords (OTPs) for authentication purposes when signing into online accounts to mitigate the risk of phishing attacks.
The decision was announced by the Monetary Authority of Singapore (MAS) and The Association of Banks in Singapore (ABS) on July 9, 2024.
"Customers who have activated their digital token on their mobile device will have to use their digital tokens for bank account logins via the browser or the mobile banking app," the MAS said.
"The digital token will authenticate customers' login without the need for an OTP that scammers can steal, or trick customers into disclosing."
The MAS is also urging customers to activate their digital tokens to safeguard against attacks that are designed to steal credentials and hijack their accounts for conducting financial fraud.
"This measure provides customers with further protection against unauthorized access to their bank accounts," Ong-Ang Ai Boon, director of ABS, said in a statement. "While they may give rise to some inconvenience, such measures are necessary to help prevent scams and protect customers."
While OTPs were originally introduced as a form of second-factor authentication (2FA) to bolster account security, cybercriminals have devised banking trojans, OTP bots, and phishing kits that are capable of harvesting such codes using lookalike sites.
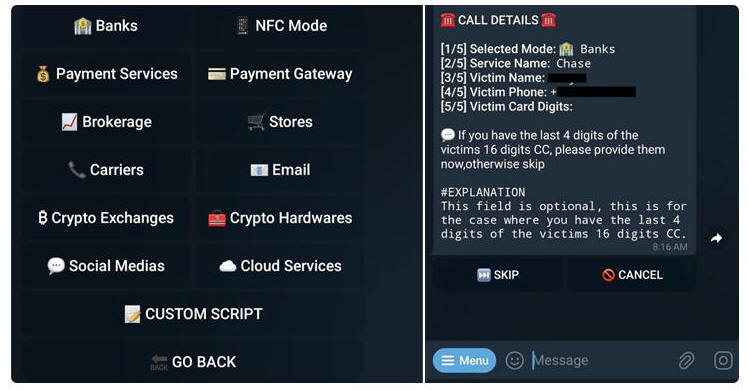
OTP bots, accessible via Telegram and advertised for anywhere between $100 and $420, take social engineering to the next level by calling users and convincing them to enter the 2FA code on their phones to help bypass account protections.
It's important to mention that such bots are mainly designed to plunder a victim's OTP code, necessitating that scammers obtain valid credentials through other means such as data breaches, datasets available for sale on the dark web, and credential harvesting web pages.
"The OTP bot's key task is to call the victim. It is calls that scammers count on, as verification codes are only valid for a limited time," Kaspersky threat researcher Olga Svistunova said in a recent report.

"Whereas a message may stay unanswered for a while, calling the user increases the chances of getting the code. A phone call is also an opportunity to try and produce the desired effect on the victim with the tone of voice."
Last week, SlashNext disclosed details of an "end-to-end" phishing toolkit dubbed FishXProxy that, while ostensibly meant for "educational purposes only," lowers the technical bar for aspiring threat actors looking to mount phishing campaigns at scale while skirting defenses.
"FishXProxy equips cybercriminals with a formidable arsenal for multi-layered email phishing attacks," the company noted. "Campaigns begin with uniquely generated links or dynamic attachments, bypassing initial scrutiny."
"Victims then face advanced antibot systems using Cloudflare's CAPTCHA, filtering out security tools. A clever redirection system obscures true destinations, while page expiration settings hinder analysis and aid campaign management."
Another noteworthy addition to FishXProxy is the use of a cookie-based tracking system that allows attackers to identify and track users across different phishing projects or campaigns. It can also create malicious file attachments using HTML smuggling techniques that make it possible to evade sidestep detection.
"HTML smuggling is quite effective in bypassing perimeter security controls such as email gateways and web proxies for two main reasons: It abuses the legitimate features of HTML5 and JavaScript, and it leverages different forms of encoding and encryption," Cisco Talos said.
The rise of mobile malware over the years has since also prompted Google to unveil a new pilot program in Singapore that aims to prevent users from sideloading certain apps that abuse Android app permissions to read OTPs and gather sensitive data.
Google Postpones Third-Party Cookie Deprecation Amid U.K. Regulatory Scrutiny
27.4.24 Security The Hacker News
Google has once again pushed its plans to deprecate third-party tracking cookies in its Chrome web browser as it works to address outstanding competition concerns from U.K. regulators over its Privacy Sandbox initiative.
The tech giant said it's working closely with the U.K. Competition and Markets Authority (CMA) and hopes to achieve an agreement by the end of the year.
As part of the new timeline, it aims to start phasing out third-party cookies early next year, making it the third such extension since the tech giant announced the plans in 2020, postponing it from early 2022 to late 2023, and again to the second half of 2024.
Privacy Sandbox refers to a set of initiatives that offers privacy-preserving alternatives to tracking cookies and cross-app identifiers in order to serve tailored ads to users.
While Google has since enabled the features to a subset of Chrome browser users as of last year, the U.K. watchdog, alongside the Information Commissioner's Office (ICO), has been keeping a close eye on the implementation to ensure that Privacy Sandbox benefits consumers and doesn't favor Google's own advertising tech.
Both Apple and Mozilla have discontinued support for third-party cookies in their respective web browsers as of early 2020.
"We recognize that there are ongoing challenges related to reconciling divergent feedback from the industry, regulators and developers, and will continue to engage closely with the entire ecosystem," Google said in an update.
"It's also critical that the CMA has sufficient time to review all evidence including results from industry tests, which the CMA has asked market participants to provide by the end of June."
In a setback for Google, a draft report from the ICO revealed that the company's proposed replacements have gaps that advertisers could exploit to identify users, effectively undermining the privacy and anonymity objectives, according to the Wall Street Journal last week.
The development comes as Google said it's updating client-side encrypted (CSE) Google Meet calls to include support for inviting external participants, including those without a Google account.
OpenJS Foundation Targeted in Potential JavaScript Project Takeover Attempt
16.4.24 Security The Hacker News
Security researchers have uncovered a "credible" takeover attempt targeting the OpenJS Foundation in a manner that evokes similarities to the recently uncovered incident aimed at the open-source XZ Utils project.
"The OpenJS Foundation Cross Project Council received a suspicious series of emails with similar messages, bearing different names and overlapping GitHub-associated emails," OpenJS Foundation and Open Source Security Foundation (OpenSSF) said in a joint alert.
According to Robin Bender Ginn, executive director of OpenJS Foundation, and Omkhar Arasaratnam, general manager at OpenSSF, the email messages urged OpenJS to take action to update one of its popular JavaScript projects to remediate critical vulnerabilities without providing any specifics.
The email author(s) also called on OpenJS to designate them as a new maintainer of the project despite having little prior involvement. Two other popular JavaScript projects not hosted by OpenJS are also said to have been at the receiving end of similar activity.
That said, none of the people who contacted OpenJS were granted privileged access to the OpenJS-hosted project.
The incident brings into sharp focus the method by which the lone maintainer of XZ Utils was targeted by fictitious personas that were expressly created for what's believed to be a social engineering-cum-pressure campaign designed to make Jia Tan (aka JiaT75) a co-maintainer of the project.
This has raised the possibility that the attempt to sabotage XZ Utils may not be an isolated incident and that it's part of a broader campaign to undermine the security of various projects, the two open source groups said. The names of the JavaScript projects were not disclosed.
Jia Tan, as it stands, has no other digital footprints outside of their contributions, indicating that the account was invented for the sole purpose of gaining the credibility of the open-source development community over years and ultimately push a stealthy backdoor into XZ Utils.
It also serves to pinpoint the sophistication and patience that has gone behind planning and executing the campaign by targeting an open-source, volunteer-run project that's used in many Linux distributions, putting organizations and users at risk of supply chain attacks.
The XZ Utils backdoor incident also highlights the "fragility" of the open-source ecosystem and the risks created by maintainer burnout, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) said last week.
"The burden of security shouldn't fall on an individual open-source maintainer — as it did in this case to near-disastrous effect," CISA officials Jack Cable and Aeva Black said.
"Every technology manufacturer that profits from open source software must do their part by being responsible consumers of and sustainable contributors to the open source packages they depend on."
The agency is recommending that technology manufacturers and system operators that incorporate open-source components should either directly or support the maintainers in periodically auditing the source code, eliminating entire classes of vulnerabilities, and implementing other secure by design principles.
"These social engineering attacks are exploiting the sense of duty that maintainers have with their project and community in order to manipulate them," Bender Ginn and Arasaratnam said.
"Pay attention to how interactions make you feel. Interactions that create self-doubt, feelings of inadequacy, of not doing enough for the project, etc. might be part of a social engineering attack."
AWS, Google, and Azure CLI Tools Could Leak Credentials in Build Logs
16.4.24 Security The Hacker News
New cybersecurity research has found that command-line interface (CLI) tools from Amazon Web Services (AWS) and Google Cloud can expose sensitive credentials in build logs, posing significant risks to organizations.
The vulnerability has been codenamed LeakyCLI by cloud security firm Orca.
"Some commands on Azure CLI, AWS CLI, and Google Cloud CLI can expose sensitive information in the form of environment variables, which can be collected by adversaries when published by tools such as GitHub Actions," security researcher Roi Nisimi said in a report shared with The Hacker News.
Microsoft has since addressed the issue as part of security updates released in November 2023, assigned it the CVE identifier CVE-2023-36052 (CVSS score: 8.6).
The idea, in a nutshell, has to do with how the CLI commands such as could be used to show (pre-)defined environment variables and output to Continuous Integration and Continuous Deployment (CI/CD) logs. A list of such commands spanning AWS and Google Cloud is below 0
aws lambda get-function-configuration
aws lambda get-function
aws lambda update-function-configuration
aws lambda update-function-code
aws lambda publish-version
gcloud functions deploy <func> --set-env-vars
gcloud functions deploy <func> --update-env-vars
gcloud functions deploy <func> --remove-env-vars
Orca said it found several projects on GitHub that inadvertently leaked access tokens and other sensitive data via Github Actions, CircleCI, TravisCI, and Cloud Build logs.
Unlike Microsoft, however, both Amazon and Google consider this to be expected behavior, requiring that organizations take steps to avoid storing secrets in environment variables and instead use a dedicated secrets store service like AWS Secrets Manager or Google Cloud Secret Manager.
Google also recommends the use of the "--no-user-output-enabled" option to suppress the printing of command output to standard output and standard error in the terminal.
"If bad actors get their hands on these environment variables, this could potentially lead to view sensitive information including credentials, such as passwords, user names, and keys, which could allow them to access any resources that the repository owners can," Nisimi said.
"CLI commands are by default assumed to be running in a secure environment, but coupled with CI/CD pipelines, they may pose a security threat."
Google to Delete Billions of Browsing Records in 'Incognito Mode' Privacy Lawsuit Settlement
2.4.24 Security The Hacker News
Google has agreed to purge billions of data records reflecting users' browsing activities to settle a class action lawsuit that claimed the search giant tracked them without their knowledge or consent in its Chrome browser.
The class action, filed in 2020, alleged the company misled users by tracking their internet browsing activity who thought that it remained private when using the "incognito" or "private" mode on web browsers like Chrome.
In late December 2023, it emerged that the company had consented to settle the lawsuit. The deal is currently pending approval by the U.S. District Judge Yvonne Gonzalez Rogers.
"The settlement provides broad relief regardless of any challenges presented by Google's limited record keeping," a court filing on April 1, 2024, said.
"Much of the private browsing data in these logs will be deleted in their entirety, including billions of event level data records that reflect class members' private browsing activities."
As part of the data remediation process, Google is also required to delete information that makes private browsing data identifiable by redacting data points like IP addresses, generalizing User-Agent strings, and remove detailed URLs within a specific website (i.e., retain only domain-level portion of the URL).
In addition, it has been asked to delete the so-called X-Client-Data header field, which Google described as a Chrome-Variations header that captures the "state of the installation of Chrome itself, including active variations, as well as server-side experiments that may affect the installation."
This header is generated from a randomized seed value, making it potentially unique enough to identify specific Chrome users.
Other settlement terms require Google to block third-party cookies within Chrome's Incognito Mode for five years, a setting the company has already implemented for all users. The tech company has separately announced plans to eliminate tracking cookies by default by the end of the year.
Google has since also updated the wording of Incognito Mode as of January 2024 to clarify that the setting will not change "how data is collected by websites you visit and the services they use, including Google."
The lawsuit extracted admissions from Google employees that characterized the browser's Incognito browsing mode as a "confusing mess," "effectively a lie," and a "problem of professional ethics and basic honesty."
It further laid bare internal exchanges in which executives argued Incognito Mode shouldn't be called "private" because it risked "exacerbating known misconceptions."
The development comes as Google said it has started automatically blocking bulk senders in Gmail that don't meet its Email sender guidelines in an attempt to cut down on spam and phishing attacks.
The new requirements make it mandatory for email senders who push out more than 5,000 messages per day to Gmail accounts to provide a one-click unsubscribe option and respond to unsubscription requests within two days.
Google Introduces Enhanced Real-Time URL Protection for Chrome Users
15.3.24 Security The Hacker News
Google on Thursday announced an enhanced version of Safe Browsing to provide real-time, privacy-preserving URL protection and safeguard users from visiting potentially malicious sites.
"The Standard protection mode for Chrome on desktop and iOS will check sites against Google's server-side list of known bad sites in real-time," Google's Jonathan Li and Jasika Bawa said.
"If we suspect a site poses a risk to you or your device, you'll see a warning with more information. By checking sites in real time, we expect to block 25% more phishing attempts."
Up until now, the Chrome browser used a locally-stored list of known unsafe sites that's updated every 30 to 60 minutes, and then leveraging a hash-based approach to compare every site visited against the database.
Google first revealed its plans to switch to real-time server-side checks without sharing users' browsing history with the company in September 2023.
The reason for the change, the search giant said, is motivated by the fact that the list of harmful websites is growing at a rapid pace and that 60% of the phishing domains exist for less than 10 minutes, making them difficult to block.
"Not all devices have the resources necessary to maintain this growing list, nor are they always able to receive and apply updates to the list at the frequency necessary to benefit from full protection," it added.
Thus, with the new architecture, every time a user attempts to visit a website, the URL is checked against the browser's global and local caches containing known safe URLs and the results of previous Safe Browsing checks in order to determine the site's status.
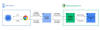
Should the visited URL be absent from the caches, a real-time check is performed by obfuscating the URL into 32-byte full hashes, which are then truncated into 4-byte long hash prefixes, encrypted, and sent to a privacy server.
"The privacy server removes potential user identifiers and forwards the encrypted hash prefixes to the Safe Browsing server via a TLS connection that mixes requests with many other Chrome users," Google explained.
The Safe Browsing server subsequently decrypts the hash prefixes and matches them against the server-side database to return full hashes of all unsafe URLs that match one of the hash prefixes sent by the browser.
Finally, on the client side, the full hashes are compared against the full hashes of the visited URL, and a warning message is displayed if a match is found.
Google also confirmed that the privacy server is nothing but an Oblivious HTTP (OHTTP) relay operated by Fastly that sits between Chrome and the Safe Browsing server to prevent the latter from access users' IP addresses, thereby preventing it from correlating the URL checks with a user's internet browsing history.
"Ultimately, Safe Browsing sees the hash prefixes of your URL but not your IP address, and the privacy server sees your IP address but not the hash prefixes," the company emphasized. "No single party has access to both your identity and the hash prefixes. As such, your browsing activity remains private."
GitHub Rolls Out Default Secret Scanning Push Protection for Public Repositories
1.3.24 Security The Hacker News
GitHub on Thursday announced that it's enabling secret scanning push protection by default for all pushes to public repositories.
"This means that when a supported secret is detected in any push to a public repository, you will have the option to remove the secret from your commits or, if you deem the secret safe, bypass the block," Eric Tooley and Courtney Claessens said.
Push protection was first piloted as an opt-in feature in August 2023, although it has been under testing since April 2022. It became generally available in May 2023.
The secret scanning feature is designed to identify over 200 token types and patterns from more than 180 service providers in order to prevent their fraudulent use by malicious actors.
The development comes nearly five months after the Microsoft subsidiary expanded secret scanning to include validity checks for popular services such as Amazon Web Services (AWS), Microsoft, Google, and Slack.
It also follows the discovery of an ongoing "repo confusion" attack targeting GitHub that's inundating the source code hosting platform with thousands of repositories containing obfuscated malware capable of stealing passwords and cryptocurrency from developer devices.
The attacks represent another wave of the same malware distribution campaign that was disclosed by Phylum and Trend Micro last year, leveraging bogus Python packages hosted on the cloned, trojanized repositories to deliver a stealer malware called BlackCap Grabber.
"Repo confusion attacks simply rely on humans to mistakenly pick the malicious version over the real one, sometimes employing social engineering techniques as well," Apiiro said in a report this week.
Google Settles $5 Billion Privacy Lawsuit Over Tracking Users in 'Incognito Mode'
3.1.24 Security The Hacker News
Google has agreed to settle a lawsuit filed in June 2020 that alleged that the company misled users by tracking their surfing activity who thought that their internet use remained private when using the "incognito" or "private" mode on web browsers.
The class-action lawsuit sought at least $5 billion in damages. The settlement terms were not disclosed.
The plaintiffs had alleged that Google violated federal wiretap laws and tracked users' activity using Google Analytics to collect information when in private mode.
They said this allowed the company to collect an "unaccountable trove of information" about users who assumed they had taken adequate steps to protect their privacy online.
Google subsequently attempted to get the lawsuit dismissed, pointing out the message it displayed when users turned on Chrome's incognito mode, which informs users that their activity might still be visible to websites you visit, employer or school, or their internet service provider.
It's worth noting here at this point that enabling incognito or private mode in a web browser only gives users the choice to search the internet without their activity being locally saved to the browser.
That said, websites using advertising technologies and analytics APIs can still continue to track users within that incognito session and can further correlate that activity by, for example, matching their IP addresses.
"Google's motion hinges on the idea that plaintiffs consented to Google collecting their data while they were browsing in private mode," U.S. District Judge Yvonne Gonzalez Rogers ruled.
"Because Google never explicitly told users that it does so, the Court cannot find as a matter of law that users explicitly consented to the at-issue data collection."