
The tool is available on GitHub.
Security 2024 2023 2022 2021 2020
HackerOne announces first bug hunter to earn more than $2M in bug bounties
28.12.2020
Security
Securityaffairs
White hat hacker could be a profitable profession, Cosmin Iordache earned more
than $2M reporting flaws through the bug bounty program HackerOne.
Iordache
is the first bug bounty hunter to earn more than $2,000,000 in bounty awards
through the vulnerability coordination and bug bounty program HackerOne.
HackerOne announced that the bug bounty hunter Cosmin Iordache (@inhibitor181) was the first to earn more than $2,000,000 in bounty awards. According to HackerOne, in March 2019 the first hacker that become a millionaire was Santiago Lopez (19).
In august 2019, HackerOne announced that five more hackers have become millionaires thanks to their contributes to the bug bounty programs managed by the platform.
In June 2020, the platform announced that the bug bounty hacker @mayonaise is the ninth hacker to earn $1 Million hacking for good on the HackerOne platform.
The list of millionaire hackers today includes:
Santiago Lopez (@try_to_hack)
from Argentina;
Cosmin Iordache (@inhibitor181) from Germany;
Mark
Litchfield (@mlitchfield) from the U.K.;
Nathaniel Wakelam (@nnwakelam)
from Australia;
FransRosen (@fransrosen) from Sweden;
Ron Chan
(@ngalog) from Hong Kong;
Tommy DeVoss (@dawgyg) from the U.S;
Eric
(@todayisnew) from Canada;
Jon Colston (@mayonaise) from the U.S;
Cosmin
has already submitted 468 vulnerabilities through bug bounty programs, he
reported security flaws in systems and services of prominent organizations
including Verizon Media, PayPal, Dropbox, Facebook, Spotify, AT&T, TikTok,
Twitter, Uber, and GitHub, The Romanian white hat hacker also reported multiple
flaws to the U.S. Dept Of Defense.
“He was able to get to the 7-figure payout mark by bringing in roughly $300,000 in bounties over just 90 days.” reported Bleeping Computer.
In May, HackerOne announced that it has paid a total of $100,000,000 in rewards to bug bounty hackers as of May 26, 2020.
According to the HackerOne bug bounty platform, around 12% of hackers earn over $20,000 each year in bug bounties, while 1,1% will earn rewards worth over $350,000 annually and 3% over $100,000 per year.
In the last two years, seven white hat hackers earned more than $1 million.
CrowdStrike releases free Azure tool to review assigned privileges
26.12.2020
Security
Securityaffairs
CrowdStrike released a free Azure security tool after it was notified by
Microsoft of a failed attack leveraging compromised Azure credentials.
While
investigating the impact of the recent SolarWind hack, on December 15th
Microsoft reported to CrowdStrike that threat actors attempted to read
CrowdStrike’s emails by using a compromised Microsoft Azure reseller’s account.
“Specifically, they identified a reseller’s Microsoft Azure account used for managing CrowdStrike’s Microsoft Office licenses was observed making abnormal calls to Microsoft cloud APIs during a 17-hour period several months ago.” reads the post published by Crowdstrike. “There was an attempt to read email, which failed as confirmed by Microsoft. As part of our secure IT architecture, CrowdStrike does not use Office 365 email.”
“CrowdStrike, which does not use SolarWinds, said it had found no impact from the intrusion attempt and declined to name the reseller.” reads the article published by Reuters.
“They got in through the reseller’s access and tried to enable mail ‘read’ privileges,” one of the people familiar with the investigation told Reuters. “If it had been using Office 365 for email, it would have been game over.”
The attempt was made months ago, but it failed because CrowdStrike does not use Office 365.
“Our investigation of recent attacks has found incidents involving abuse of credentials to gain access, which can come in several forms,” said Microsoft senior Director Jeff Jones. “We have not identified any vulnerabilities or compromise of Microsoft product or cloud services.”
CrowdStrike experts decided to create their own tool because they face difficulties in using Azure’s administrative tools to enumerate privileges assigned to third-party resellers and partners in their Azure tenant.
“CrowdStrike launches CrowdStrike Reporting Tool for Azure (CRT), a free community tool that will help organizations quickly and easily review excessive permissions in their Azure AD environments, help determine configuration weaknesses, and provide advice to mitigate risk.” states the security firm.
“Throughout our analysis, we experienced first hand the difficulties customers face in managing Azure’s administrative tools to know what relationships and permissions exist within Azure tenants, particularly with third-party partner/resellers, and how to quickly enumerate them. We found it particularly challenging that many of the steps required to investigate are not documented, there was an inability to audit via API, and there is the requirement for global admin rights to view important information which we found to be excessive. Key information should be easily accessible.”
The CrowdStrike Reporting Tool for Azure (CRT) tool could be used by administrators to analyze their Microsoft Azure environment and review the privileges assigned to third-party resellers and partners.

The tool is available on GitHub.
Google Explains YouTube, Gmail, Cloud Service Outage
22.12.2020
Security
Securityweek
Google has blamed a bug in its global authentication system for last week's outage that affected Gmail, Calendar, YouTube, Meet and multiple other Google services.
The 47-minute outage last Monday, which severely affected operations at workplaces and schools globally, was caused by a bug in an automated quota management system that powers the Google User ID Service.
In a root cause incident report, Google explained that the Google User ID Service maintains a unique identifier for every account and handles authentication credentials for OAuth tokens and cookies. This account data is stored in a distributed database, which uses Paxos protocols to coordinate updates.
For security reasons, this service is programmed to reject requests when it detects outdated data.
Google said one of its automated tools used to manage the quota of various resources allocated for services contained a bug that caused error in authentication results, leading to the service outage.
"As part of an ongoing migration of the User ID Service to a new quota system, a change was made in October to register the User ID Service with the new quota system, but parts of the previous quota system were left in place which incorrectly reported the usage for the User ID Service as 0. An existing grace period on enforcing quota restrictions delayed the impact, which eventually expired, triggering automated quota systems to decrease the quota allowed for the User ID service and triggering this incident," the company explained.
"Existing safety checks exist to prevent many unintended quota changes, but at the time they did not cover the scenario of zero reported load for a single service," Google added.
The problem "was immediately clear as the new quotas took effect." At the height of the incident, Google could not verify that user requests were authenticated and the company confirmed it was seeing 5xx errors on virtually all authenticated traffic.
"The majority of authenticated services experienced similar control plane impact: elevated error rates across all Google Cloud Platform and Google Workspace APIs and Consoles, the company said.
Cloud is King: 9 Software Security Trends to Watch in 2021
19.12.2020
Security
Threatpost
Researchers predict software security will continue to struggle to keep up with cloud and IoT in the new year.
IT security professionals have largely spent the year managing a once-in-a-generation workforce shift from office to home in 2020. With the initial push over, experts predict that 2021 will be focused on shoring up the cloud and re-imagining organizational workflows under this new normal. Software security will be critical in this environment.
That’s according to researchers from Checkmarx, which just published its 2021 Software Security Predictions report. It envisions a new era for software-development teams, including a focus on better application security tools, scaling on-premise security tools to the cloud and better protecting internet-of-things (IoT) devices.
Adapt to the Cloud
Checkmarx advises software-development teams they will
need to keep apace with the development of applications in the cloud going
forward.
2020 Reader Survey: Share Your Feedback to Help Us Improve
“You can’t push code and then roll back to fix vulnerabilities, as it presents an opportunity for malicious actors to infiltrate your systems,” Maty Siman, Checkmarx CTO said in the report. “In 2021, the tools used for application security that integrate into the tool chain must work much more rapidly, scale to cloud environments and present actionable findings in a format that developers can understand and use to make quick fixes.”
The message comes as cloud applications and environments are increasingly in the sights of attackers. This week for instance the National Security Agency issued a warning that threat actors have developed techniques to leverage vulnerabilities in on-premises network access to compromise the cloud.
“Malicious cyber-actors are abusing trust in federated authentication environments to access protected data,” the advisory read. “The exploitation occurs after the actors have gained initial access to a victim’s on-premises network. The actors leverage privileged access in the on-premises environment to subvert the mechanisms that the organization uses to grant access to cloud and on-premises resources and/or to compromise administrator credentials with the ability to manage cloud resources.”
Open-Source Vulnerabilities
Meanwhile, open source will continue to attract
attacks.
“Rarely does a week go by without a discovery of malicious open-source packages,” Siman wrote. “Yes, organizations understand they need to secure the open-source components they’re using, and existing solutions help them in removing packages that are mistakenly vulnerable (where a developer accidentally puts a vulnerability into the package). But they are still blind to instances where adversaries maliciously push tainted code into packages. This needs to change in 2021.”
He warned to stay away from new contributions and stick with more “mature,” well-known open-source components.
Infrastructure as Code
Developers have been feverishly building applications
using new infrastructure-as-code environments, which, Siman said, has left major
gaps in security. Going forward, that will drive additional training in IaC
security.
“I expect to see malicious attackers exploit developers’ missteps in these flexible environments. To combat this, we will see a major concentration around cloud security training, IaC best practices, and additional spend allocated toward software and application security to support the demand of a remote workforce and more complex software ecosystems,” he added.
Security will Report to Development
Diva developers are a fact of life, and
in order to drive security throughout the software-development process, security
teams will have to orient themselves within development teams to increase
collaboration, Sima explained.
“Developers are opinionated and increasingly influential, and you cannot force them to do or use something they don’t buy into,” he wrote. “To foster collaboration between security and development, security in 2021 will need to integrate into the development tool chain in a manner that the latter is most comfortable with.”
Holistic View of Security
Increasingly, Siman said, teams will need a
comprehensive view of their security postures across the entire organization,
driving a need for tools which provide that full ecosystem view.
When it comes to the security of open source in particular, more comprehensive views will allow organizations not only to know if they are consuming a vulnerable package, but also, and more importantly, whether or not the way that the application consumes it makes an attack or vulnerability possible.
Cloud-Native Security
Cloud-native security is currently underutilized and
not fully understood within the security community, but 2021 will see a push
toward prioritizing locking down cloud environments, according to the report’s
co-author and Checkmarx director of security research, Erez Yalon.
“If 2020 was the year of the API, 2021 will be the year where cloud-native security steals the spotlight,” Yalon wrote in the report. “APIs play a major role in cloud-native security, but the focus will turn to how cloud-based technologies continue to proliferate and increase in adoption across organizations. Securing the resulting ecosystems of interconnected cloud-based solutions will become a priority.”
Vulnerable APIs
Which brings Yalon to his next ominous prediction, that
those unsecured API’s will be the easiest place for attackers to breach systems.
“As malicious actors continue to ramp up their API-targeted attacks and organizations play catch-up in their understanding of how these programs can be exploited, adversaries will capitalize on this gap in the near-term, forcing developers to quickly identify ways to better secure API authentication and authorization processes,” he said.
Legacy Devices Vulnerable
Yalon added that old IoT devices, which are often
forgotten about while quietly operating in the background, will continue to be
juicy targets for threat actors in 2021.
“As these gadgets grow older but remain in use, many manufacturers have stopped supporting them with software updates and patches as they prioritize newer models, making older models prime targets for malicious actors looking for easy access points,” Yalon wrote. “As time moves on, vulnerabilities in these now outdated products will be discovered and exploited.”
Dovetailing with this, industrial, factory and medical gear were reported by Artemis to have been left largely unpatched to protect against URGENT/11 and CDPwn groups of malware, despite fixes being delivered. The researchers looked and found 97 percent of the OT devices impacted by URGENT/11 weren’t patched, for instance.
Slow Progress on IoT Security
The passage of the recent IoT Cybersecurity
Improvement Act in the U.S. last month was step in the right direction,
according to Yalon, but there is still much work to do.
The bipartisan legislation requires federal devices to meet a minimum standard security requirement. But Yalon added that no real progress can be made without intense pressure from consumers.
“Until consumers put real pressure on governments and manufacturers for improved security for IoT devices, or manufacturers take place a great emphasis for IoT security, this will be a continuing cause for concern,” he said.
The story of the year: remote work
11.12.2020
Security
Securelist
The coronavirus pandemic
has caused sudden, sweeping change around the world. The necessary social
distancing measures are having an impact on all of us. One large part of society
that has been affected by these measures more than others is the employed. While
direct customer facing businesses like restaurants and retailers have had to
change their opening hours, adapt their business models or close their doors
entirely, there are still millions of jobs that can be done at home, outside of
the usual office working environment.
Organizations need to adapt to meet employee needs and ensure they stay productive, motivated and secure. With so many of us being asked to work in new ways in order to stay connected to our colleagues and customers, it is important to remember both the professional and personal challenges working from home on a permanent basis can bring. Quite obviously, this situation has brought a lot of issues into our lives. A survey conducted in April 2020, as things were changing rapidly, revealed that around half (46%) of respondents had never worked from home before and therefore, were not entirely ready for such changes.
There is a lot to be said about social and productivity issues caused by the new rhythm of work, but in fact, things were not that bad, because remote work in some cases helped people to have a better work-life balance and even be more productive.
What changed: guilty pleasures and life-work disbalance
Remote work is not an
entirely new phenomenon; its benefits have been discussed for years now. In some
industries, like IT, remote work has already been quite widespread. Last year,
Kaspersky analyzed some of the positives of remote work. This research
highlighted some of the most significant benefits of remote work, including
increased employees’ productivity, improved work-life balance and reduced
absenteeism. Situation in the world this year made it possible to verify such
assumptions.
At the same time, the massive move towards remote work was not particularly voluntary – employees who were forced to work from home did not always welcome this opportunity as they had to contend with new challenges. However, they have also uncovered some substantial benefits:
Comfort level: Employees became both more comfortable and uncomfortable. A study
by Kaspersky in April found that nearly a third of employees (32%) working from
home were struggling with back pain after being forced to use kitchen stools or
a sofa to work. However, by November, employees had begun to compensate for this
discomfort with certain “guilty pleasures”, such as “working in comfy clothes
all day” (with 48% wanting to have this option in the future) and even “working
without clothes”.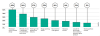
What lockdown/pandemic guilty pleasures would you like to keep?
Family issues: Being at home all day has, not surprisingly, had an effect on
people’s relationships with their loved ones, with 21% of respondents from the
same study in April admitting to experiencing family issues due to remote work.
Two drivers of this conflict are not having a separate room for every family
member who needs to work from home (26%) and arguments about how much children
should use the Internet (33%). But remote work is not all bad for families, as
recent study found that 47% were now able to spend more time with their
families, highlighting it as the key benefit of the whole work-from-home
situation.
What positive things have come out of the pandemic that you would like to keep?
Work-life balance: Staying at home has led to difficulties maintaining an
appropriate work-life balance, with nearly a third of respondents (31%) from the
same survey in April admitting that they were now working more, although 46%
admitted they were now spending more time pursuing personal activities. However,
by November, employee attitudes appear to have shifted in favor of remote work,
with nearly three-quarters (74%) saying they were happy to never return to at
least some of the traditional workplace dynamics.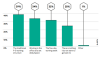
When thinking about the traditional, ‘old ways of working’ what do you not want to go back to?
Productivity levels: As previously mentioned, studies have indicated that
working remotely can actually lead to an increase in productivity. Kaspersky
found that a full 40% of employees noticed no change in their productivity
levels, with 29% admitting to being more productive. However, it is also
important to note employees are still missing some aspects of the traditional
workplace environment, chiefly seeing their colleagues face-to-face (34%).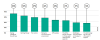
Over the past few months, what, if anything have you missed about work?
Security issues: old, new and refreshed
As shown above, questions regarding
remote work – good or bad, better or worse for employees, helpful or not for
businesses – are not as obvious as they might seem at first glance. However, in
this report, we will focus mainly on what remote work means for businesses and
employees from a security perspective. One of the most critical questions of
work-from-home security is related to employees’ awareness of the main concepts
of cybersecurity. As shown by the survey, by April, 73% of workers had not
received any IT security awareness training from their employer since they
transitioned to working from home, leading employees to feel unprepared for
facing cybersecurity issues that may arise when working remotely.
Moreover, our research showed that remote staff tended to overestimate the level of their knowledge of cybersecurity basics. In the early April of 2020, Kaspersky and Area9 Lyceum released an adaptive learning course for those transitioning to at-home working, covering the basics of secure remote operations. Analysis of anonymized learning results revealed that in 90% of the cases where learners selected an incorrect answer, they evaluated their feelings about the given response as “I know this” or “I think I know this”.
The most dangerous outcome of such a situation is “unconscious incompetence”, when a user is not even thinking about potential risks of some action, because it is habitual and seems to be appropriate.
Shadow IT
Meanwhile, the adoption of video conferencing, file storage
services, file sharing services and personal messaging apps are all on the rise
as we rely on the Internet for sharing information and keeping in touch for work
purposes. Some employees are not strictly using their business accounts for
work-related purposes.
Most common shadow IT in use
For example, 42% of workers say they are using personal email accounts for work and nearly half (49%) have admitted to increasing how often they do this. Additionally, 38% use personal messengers for work purposes, and 60% say they now do this more often because of working from home. File-sharing services that have not been approved by IT departments are also being used a lot, with 53% of respondents saying they are using these more often for work-related purposes. Using such services has great benefits for keeping staff connected but can come at a cost if one or more of them become a target for cybercriminals, as it can lead to both theft of corporate information and unauthorized access to internal resources of the company.
According to our telemetry, cybercriminals were actively trying to masquerade
their malware as popular messengers and online conference applications that were
used by remote workers to replace offline communications. Kaspersky detected
1.66 million unique malicious files spread under the guise of such applications.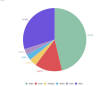
Applications used as lures, January – November 2020 (download)
Once installed, these files would primarily load Adware – programs that flooded victims’ devices with unwanted advertising and gathered their personal data for third-party use, but in particular cases the same spreading technique is used to download malicious implants for targeted espionage.
RDP attacks
Naturally, working from home requires employees to log in to
corporate resources remotely from their personal devices. One of the most common
tools used for this purpose is RDP, Microsoft’s proprietary protocol that
enables users to access Windows workstations or servers. Unfortunately, given
that many offices transitioned to remote work with little notice, many RDP
servers were not properly configured, something cybercriminals have sought to
take advantage of to gain unauthorized access to confidential corporate
resources.
The most common type of attack being used is brute-force, wherein criminals attempt to find the username and password for the RDP connection by trying different combinations until the correct one is discovered. Once it is found, the cybercriminals gain remote access to the target computer on the network.
Starting in the beginning of March, the number of Bruteforce.Generic.RDP attacks
skyrocketed, resulting in the total number of the attacks within the first
eleven months of 2020 reaching 3.3 billion. Within the same eleven-month period
in 2019, Kaspersky detected 969 million such attacks worldwide.
RDP attacks dynamics, January – November 2019 and 2020 (download)
Bring Your Own Device
A Kaspersky survey has found that a little more than
two-thirds of respondents are using a personal computer to work from home, and
nearly half have done so in the past. This kind of policy – Bring Your Own
Device – has long been disputed in the cybersecurity world, as it tends to make
corporate resources more vulnerable to attack. Even for those who have devices
provided by their employers (55%), most do not separate their work and personal
activities. In fact, a full 51% admit to watching adult content on the device
they use for work, content that is frequently targeted by cybercriminals.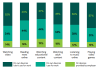
Activities workers are spending more of their time doing
Part of the problem with BYOD policies is that businesses that adopt them often do not accompany them with appropriate cybersecurity measures. The same survey that found that two-thirds of employees used their personal devices also found that half of companies with BYOD policies did not have policies in place to regulate their use – and only a third (32%) provided antivirus software for personal devices.
A virtual private network (VPN) allows for much more secure connections, but only 53% of workers are using one to access their corporate networks. This is particularly problematic if employees log in to corporate resources from unsecured public networks, say, in a coffee shop or restaurant. It is worth noting that, especially in smaller businesses, employees are storing documents with personally identifiable information. Should this information fall into the wrong hands, it would not only be problematic for the company, but would put the employer’s own privacy at risk.
In 2019, before remote work swept the world, Kaspersky found that over half (52%) of enterprises said that their breaches occurred as a result of employees’ inappropriate IT use. Working from home and using personal devices only compounds these risks, particularly when employees are not taught the appropriate cybersecurity policies or given the right tools.
Scam and phishing
One of the most common concerns for workers is related to
phishing scams. For instance, more than a quarter (27%) of survey respondents
say they have received malicious emails related to COVID-19 while working from
home, an activity Kaspersky’s experts are paying strong attention to during the
pandemic. Scammers may be trying to prey on worried workers who want to know
more about the coronavirus pandemic.
According to Kaspersky telemetry, the amount of scam related to social payments increased fivefold in 2020 compared to the same period in 2019. Fraud emails of this kind offer various financial assistance, surcharges, allowances and other types of payments.
In another scenario, victims, receive email, purportedly from their HR
departments, carrying important information about COVID-19 issued by the
government institution (CDC) as an attachment. It comes in the form of an IMG
file, which is just an enhanced carrier for malicious content capable of
bypassing email filters.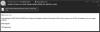
Another popular topic to exploit in times like these is money. Many people have
lost their jobs or are close to unemployment. In exploiting the need for money,
the attackers are offering reimbursement plans to individual employees. This
type of offers characteristically contains a URL that the recipient is asked to
follow or an attachment that needs to be opened.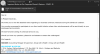
And of course, the attackers could not keep from exploiting the name of the WHO itself.
Using the WHO logo seems to be so effective that sometimes, it occupies half of
the email content, again spreading hope and false promises of a vaccine.
One fraudulent mailshot disguised as a WHO newsletter offered tips about staying safe from COVID-19
To get the information, the recipient had to click a link pointing to a fake WHO
website. The design was so close to the original that only the URL gave away the
scam. The cybercriminals were after login credentials for accounts on the
official WHO site. Whereas in the mailshots above, only a username and password
were asked for, in later ones, a phone number was also requested.
In addition, we detected several emails supposedly from the WHO, containing documents with malware. The recipient was asked to open the attachment in DOC or PDF format, which allegedly offered coronavirus prevention advice. For example, this message contained a copy of Backdoor.Win32.Androm.tvmf:
There were other, less elaborate mailshots with harmful attachments, including ones containing Trojan-Spy.Win32.Noon.gen:
APT groups
The COVID-19 topic was also abused in the world of APTs, where
multiple threat actors used it to create lures. This applies, for example, to
such threat actors as IronHusky and TransparentTribe.
IronHusky / ViciousPanda
Documents used by this APT group normally contain
VisualBasic macros or older exploits for Microsoft Office and, in the case of
successful infection, they present decoy content such as shown here: a document
in Mongolian, which looks like genuine correspondence between the Mongolian
Ministry of External Affairs and China. It mentions concerns about the spreading
epidemic in China and growing statistics in Asian countries.
TransparentTribe / MythicLeopard / APT36
This is another example of abusing
the COVID-19 topic, this time by another APT group known as TransparentTribe,
which reportedly has been active in South Asian countries, such as India and
Pakistan. This time, it is an Excel spreadsheet which does not really change the
medium of the attack from the previous case.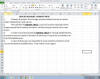
Ginp and tracking applications
Even those cybercriminals who were acting only
in the financial field adapted to the circumstances. A good example is Ginp, a
banking trojan for Android used in a campaign exploiting the COVID-19 topic.
After Ginp received a special command, it opened a web page titled “Coronavirus
Finder”. The page had a simple interface that showed the number of nearby people
infected with the coronavirus and urged the user to pay a small amount for
seeing their exact locations.
The web page offered the visitor to input bank card details to make the
transaction. Once the details were entered, they went directly to the criminals,
and nothing else would happen. The attackers did not even charge the victim the
small amount. And of course, they did not show any information about the people
infected with coronavirus, because they did not have any.
Home entertainment
Not all the threats are related to the work process
directly. Employees are spending more time at home, playing games, ordering food
and watching movies. Cybercriminals are aware of that and are doing their best
to exploit this situation.
Gaming threats
According to our telemetry, in April 2020, the daily amount of
attempts to visit malicious websites exploiting the gaming topic increased by
54% as compared to January. Interestingly, Minecraft was the most abused game,
followed by Counter Strike: Global Offensive and The Witcher 3.
One of the most popular gaming platforms, Steam, was also frequently imitated by cybercriminals: the number of notifications from fake Steam sites increased by 40% between February 2020 and April. Cybercriminals’ main goal as usual is to persuade users to visit fraudulent sites or download and install malware, which could be anything from keyloggers to ransomware and miners.
Online cinemas
Online cinemas and streaming services were also used to lure
users. Threat actors mimicked popular services, such as Netflix, Okko and IVI,
to trick users, or simply used the titles of popular TV shows to name malicious
files. The most popular TV shows among cybercriminals were Stranger Things, The
Witcher, Sex Education and Orange Is the New Black.
This is just more proof that it is vital to use only official streaming services for watching media content and always stay alert while doing something online. In 2019, we published an extensive report on how cybercriminals had disguised malware as episodes of top TV shows. The results of the year 2020 are still waiting to be studied.
Phishing in delivery
Another topic is delivery services. As ordering of food
and other products online grows in popularity, the number of scams abusing this
topic is growing, too. One of the most common targets is Amazon clients, and in
attempts to get them, phishers have used every trick they have: fake delivery
confirmations, fake alerts of suspicious activity in the Amazon account, gift
card fraud, etc. The names of other delivery services were also used in spam and
phishing emails, mostly to give victims malware or links to fraudulent clones of
well-known delivery websites.
Conclusion and recommendations
Overall, we have not seen anything
conceptually new in the way attacks are executed or the techniques used by the
attackers. Instead, we have seen them adapt to the current agenda and
environment.
In the B2B sector, this manifested itself either in targeted attacks imitating email from specialized organizations, such as lures using the WHO logo and name, or attempting to take advantage of the fact that companies rapidly transitioned to remote work – often without having the time to ensure that proper security measures were in place. For example, brute-force attacks on RDP are not knew, but never before have so many employees used these protocols. That is likely the reason why they became the primary focus for attackers this year, as did instant messaging applications, with criminals increasingly spreading “fake” applications that mimicked popular ones used by businesses for remote collaboration.
While corporate and perimeter security remains important, the recent mass transition to remote work has shown all too clearly that even the best corporate security cannot compensate for a lack of user awareness. Especially with 60% of companies allowing employees to use their own devices for work, businesses must train their staff in cybersecurity best practices, so that they are aware of the risks and understand how to work securely with corporate resources. This cyberhygiene training must also be accompanied by changes in IT administration. IT needs to provide additional support to employees, making sure updates are applied on time and issues with connecting remotely are fixed promptly.
For many businesses, remote work is not a temporary solution. Many have already announced that, even after the pandemic subsides, work-from-home options and a hybrid model will become a permanent fixture of the employee experience. That means now is the time to reflect on the lessons of 2020 and begin creating a security strategy that protects you and your employees.
Moving forward, businesses will need to rethink the way their corporate networks are organized. Since all machines are not located in the office and hence, not connected to the corporate network, adjustments need to be made to ensure endpoints stay secure and corporate resources are protected. For example, for those with a corporate VPN, they need to take steps to ensure nothing illicit can be downloaded.
The world has been becoming more digital for years, but, in 2020, our entire lives moved online. Even self-described luddites had no choice but to use digital services: for shopping, business meetings, classes. And yes – cybercriminals were ready to jump on this opportunity. Attackers attempted to exploit the COVID-19 topic in every way possible, and they were, quite often, successful.
Part of the problem is that, when we teach good Internet safety practices, we are typically speaking to active internet users. But the pandemic forced everyone to become an active internet user even those who did not want to – and they were, naturally, more vulnerable to attack.
COVID-19 will not be the last crisis, nor will it be the last one attackers exploit for personal gain. Cybercriminals will always be ready to take advantage of disruptive current events. Moving forward, no matter who you are – whether you are a novice Internet user or an experienced one, whether you spend five hours a day online or thirty minutes – you need to be ready for the unexpected in cyberspace. The year 2020 has proven that. Fortunately, staying protected against an evolving set of cyber risks does not require any high tech or advanced programming skills. It just requires a little knowledge of basic cybersafety rules.
Here are some tips to help employers and businesses stay on top of any potential IT security issues and remain productive while staff are working from home:
Ensure your employees have all they need to securely work from home and know who
to contact if they face an IT or security issue.
Schedule basic security
awareness training for your employees. This can be done online and cover
essential practices, such as account and password management, email security,
endpoint security and web browsing. Kaspersky and Area9 Lyceum have prepared a
free course to help staff work safely from home.
Take key data protection
measures including switching on password protection, encrypting work devices and
ensuring data is backed up.
Ensure devices, software, applications and
services are kept updated with the latest patches.
Install proven protection
software, such as Kaspersky Endpoint Security Cloud, on all endpoints, including
mobile devices, and switch on firewalls.
Ensure you have access to the latest
threat intelligence to bolster your protection solution. For example, Kaspersky
offers a free COVID-19-related threat data feed.
Double-check the protection
available on mobile devices. For example, it should enable anti-theft
capabilities such as remote device location, locking and wiping of data, screen
locking, passwords and biometric security features like Face ID or Touch ID, as
well as enable application controls to ensure only approved applications are
used by employees.
In addition to physical endpoints, it is important to
protect cloud workloads and virtual desktop infrastructure. As such, Kaspersky
Hybrid Cloud Security protects hybrid infrastructure of physical and virtual
endpoints, as well as cloud workloads whether running on-premise, in a
datacenter or in a public cloud. It supports integration with major cloud
platforms, such as VMware, Citrix or Microsoft, and facilitates migration from
physical to virtual desktops.
While there is a lot of responsibility on
employers to keep corporate devices and networks secure, Kaspersky is also
offering the following recommendations for consumers and workers during their
time at home:
Ensure your router supports and works smoothly when transmitting Wi-Fi to
several devices simultaneously, even when multiple workers are online and there
is heavy traffic (as is the case when using video conferencing).
Regularly
update your router to avoid potential security issues.
Set up strong
passwords for your router and Wi-Fi network.
If you can, only do work on
devices provided by your employer. Putting corporate information on your
personal devices could lead to potential security and confidentiality issues.
Do not share your work account details with anybody else, even if it seems a
good idea at the time.
Always feel able to speak to your employer’s IT or IT
security team if you have any concerns or issues while working from home.
Follow the rules of cyberhygiene: use strong passwords for all accounts, do not
open suspicious links from emails and IMs, never install software from
third-party markets, be alert and use reliable security solution such as
Kaspersky Security Cloud.
Microsoft Details Plans to Improve Security of Internet Routing
11.12.2020
Security
Securityweek
Microsoft this week shared details on the steps it will take in an effort to ensure improved security for Internet routing.
The Border Gateway Protocol (BGP) routing protocol, on which the Internet runs, relies on autonomous systems (AS) to exchange routing and reachability information. This allows for fast updates, but misconfigurations or malicious intent could lead to outages or traffic interception.
Over the past couple of years, numerous routing incidents, including route hijacking and leaks, have resulted in large-scale distributed denial of service (DDoS), data theft, reputational damage, financial loss, and more.
To help improve routing security, Microsoft last year joined the Mutually Agreed Norms for Routing Security (MANRS) initiative. The company now says it has already implemented the existing MANRS framework in its operations, and has been working with the Internet Society, the Cybersecurity Tech Accord, and others to find ways to improve routing security.
One of the first actions the company takes in strengthening routing security is RPKI (Resource Public Key Infrastructure) origin validation. Used to secure BGP route origin information, the RPKI is public key infrastructure framework that has enjoyed wide adoption recently.
With BGP routes announced by its Autonomous System Number (ASN) already signed, Microsoft is now working on implementing RPKI filtering, which should be completed by mid-2021.
The company also says it will use the public Internet Routing Registries (IRR) databases for route validation, and revealed that it has already built a global Route Anomaly Detection and Remediation (RADAR) system, an internal tool meant to detect route hijacks and route leaks in its own network. Route leaks on the Internet are detected as well.
RADAR, the tech giant says, ensures that traffic is routed via preferred paths even when signs of malicious activity are identified.
Customers working with internet exchange partners (IXPs), internet service providers (ISPs), and software-defined cloud interconnect (SDCI) providers enrolled in the Azure Peering Service, Microsoft says, can register to RADAR and receive data on detected route anomalies.
“Microsoft interconnects with thousands of networks via more than 170 edge points of presence locations. We will work with all peer networks to protect traffic over the Internet,” the company announced.
RPKI and route object information is already included in Microsoft’s peering portal, allowing peer networks to access RPKI, route object, and network path information and address routes in respective registries, and the company plans on making it easier for its peers and for ISPs to manage route objects.
“Internet routing security will require constant updates to standards. There is no single standard which can address the issues faced on the Internet today and we need to update routing security standards as and when we see new threats emerging,” Microsoft notes.
Record Levels of Software Bugs Plague Short-Staffed IT Teams in 2020
10.12.2020 Security Threatpost
As just one symptom, 83 percent of the Top 30 U.S. retailers have vulnerabilities which pose an “imminent” cyber-threat, including Amazon, Costco, Kroger and Walmart.
2020 is shaping up to be a banner year for software vulnerabilities, leaving security professionals drowning in a veritable sea of patching, reporting and looming attacks, many of which they can’t even see.
A trio of recent reports tracking software vulnerabilities over the past year underscore the challenges of patch management and keeping attacks at bay.
“Based on vulnerability data, the state of software security remains pretty dismal,” Brian Martin, vice president of vulnerability intelligence with Risk Based Security (RBS), told Threatpost.
Threatpost Webinar Promo Bug Bounty
Click to register.
The year didn’t start out that way. The VulnDB team at RBS saw a massive drop in disclosures during the first three quarters of 2020. Then COVID-19 hit, creating a juicy opportunity for malicious actors to exploit the chaos.
“At the end of Q1 this year, we saw what appeared to be a sharp decline in vulnerability disclosures as compared to 2019, dropping by 19.2 percent,” Martin wrote in the third-quarter report. “Statistically that is huge. However, as 2020 continues, we are starting to see just how large an impact the pandemic has had on vulnerability disclosures.”
Software Vuln Perfect Storm
Now, RBS reported that the number of
vulnerabilities disclosed will possibly exceed 2019’s numbers, but as the year
comes to a close, there’s still much uncertainty about the impact COVID will
have into 2021.
“With the pandemic seeing a resurgence in most of the world even as we enter the holiday season, it is difficult to predict the exact influence COVID-19 will have on the vulnerability-disclosure landscape,” the RBS report concluded.
Prior to the pandemic, IT teams were already under tremendous pressure to keep up with patching due to what RBS has dubbed “vulnerability Fujiwara events.” The term “Fujiwara,” according to RBS researchers, describes the confluence of two hurricanes, which they liken to days like Jan. 14, April 14 and July 14 this year, when 13 major vendors, including Microsoft and Oracle, all released patches at the same time. RBS said these three vulnerability Fujiwara events in 2020 put massive stress on security teams.
Meanwhile some major vendors’ regular Patch Tuesday events are starting to create a type of rolling Vulnerability Fujiwara Effect year-round, RBS added, since the number of patches for each of them have ramped up. With December’s Patch Tuesday, for instance, Microsoft’s patch tally totals 1,250 for the year – well beyond 2019’s 840.
In fact, Microsoft and Oracle lead the Top 50 vendors in the number of reported security vulnerabilities, according to the latest analysis from Comparitech.
Security researchers looked at CVE details across the Top 50 software vendors and found that since 1999, Microsoft is the hands-down leader with 6,700 reported, followed by Oracle with 5,500 and IBM with 4,600.
“New software is being released at a faster rate than old software is being deprecated or discontinued,” Comparitech’s Paul Bischoff told Threatpost. “Given that, I think more software vulnerabilities are inevitable. Most of those vulnerabilities are identified and patched before they’re ever exploited in the wild, but more zero days are inevitable as well. Zero days are a much bigger concern than vulnerabilities in general.”
Online v. Desktop Software Vulnerabilities
The real growth area in software
security flaws has been in third-party online software, according to Cyberpion,
which has developed a tool to evaluate security holes in entire online
ecosystems. Their findings include the startling statistic that 83 percent of
the Top 30 U.S. retailers have vulnerabilities which pose an “imminent”
cyber-threat, including Amazon, Costco, Kroger and Walmart.
“Software developed for the desktop is fundamentally different than software developed for online,” Cyberpion’s CRO Ran Nahmias told Threatpost. “Desktop software code needs to be secured against a virus for rewriting the code (and the attack occurs on one desktop at a time). Online software has a strong dependency on the infrastructure that hosts, operates and distributes it.
This creates a massive attack surface, including not just the code itself, but the infrastructure behind it.
“These online infrastructures can get complex, and one misconfiguration anywhere could lead to the code being compromised or modified,” Nahmias said. “Additionally, because the software is centrally located and then serves many customers, a single breach can affect many companies and people (as opposed to the desktop software being infected by a virus which would impact one user).”
What organizations really need to guard their systems appropriately is well-trained professionals. Unfortunately, as Bischoff added, they are in increasingly short supply.
“Aside from the increasing volume of software, the lack of qualified cybersecurity staff contributes to the rise in software vulnerabilities,” he said. “In almost every sector of the economy, cybersecurity personnel are in high demand.”
Meanwhile, software bugs aren’t going anywhere.
“Despite more organizations taking secure development more seriously, and despite more tools available to help find and eliminate vulnerabilities, the amount of disclosed vulnerabilities suggest it hasn’t tipped the scale yet,” Martin added. “We’re hopeful that as more and more news of organizations being breached are taken seriously, and organizations and developers better understand the severity of vulnerable code, that they will make the extra effort to ensure more auditing is done before releasing [software].”
OpenSSF Launches Open Source Tool for Evaluating SAST Products
10.12.2020
Security
Securityweek
The Open Source Security Foundation (OpenSSF) announced on Wednesday at the Black Hat Europe conference the availability of an open source tool designed for evaluating the ability of static analysis security testing (SAST) products to detect vulnerabilities.
The new tool, named OpenSSF CVE Benchmark, provides vulnerable code and metadata related to 218 known JavaScript and TypeScript vulnerabilities.
The tool can be integrated with ESLint, CodeQL and NodeJsScan, but its creators hope the community will help build integrations with more security tools and help expand the dataset. The developers pointed out that less than 200 lines of code are typically required to create a new security tool integration, and they believe it can be easily integrated with not only open source tools, but also commercial products.
The goal of the tool, whose source code is available on GitHub, is to make it easier for security teams to evaluate various SAST tools. Specifically, it helps determine if a security tool can detect a vulnerability or if it produces a false negative, and whether it can recognize a validated patch or it produces a false positive
“The benchmark addresses two problems that security teams face today when assessing security tools. First, rather than using synthetic test code, the OpenSSF CVE Benchmark uses real life CVEs that have been validated and fixed in open source projects. Using this approach, security tools are tested on real codebases that contain validated real vulnerabilities,” the developers explained.
“Second, by also analyzing the patched versions of the same codebases, false positive rates of these tools can be measured more accurately and based on real validated fixes,” they added.
Launched in August 2020 and hosted by the Linux Foundation, OpenSSF aims to improve the security of open source software by building a community, best practices and targeted initiatives. Its members include GitHub, IBM, Google, VMware, Microsoft, NCC Group, OWASP, JPMorgan Chase, Red Hat, Intel, HackerOne, Uber, GitLab, Okta and others.
Dox, steal, reveal. Where does your personal data end up?
1.12.2020
Security
Securelist
The technological shift
that we have been experiencing for the last few decades is astounding, not least
because of its social implications. Every year the online and offline spheres
have become more and more connected and are now completely intertwined, leading
to online actions having real consequences in the physical realm — both good and
bad.
One of the most affected areas in this regard is communication and sharing of information, especially personal. Posting something on the internet is not like speaking to a select club of like-minded tech enthusiasts anymore — it is more akin to shouting on a crowded square. This gives rise to many unique threats, from cyberbullying and simple financial scams to spear phishing and social engineering attacks on business executives and government officials. And while awareness of privacy issues is increasing, much of the general public still only have a basic understanding of why privacy matters.
Unfortunately, even if we take good care of how and with whom we share our personal data, we are not immune from being doxed. The abusers may be motivated enough to go beyond gathering data available in the public domain and turn to the black market in the hope of finding personal information that will do real harm, for instance, gaining access to social media accounts. In this report, we will dig deeper into two major consequences of (willing and unwilling) sharing personal data in public — doxing (the public de-anonymization of a person online) and the selling of personal data on the dark web — and try to untangle the connection between the two. We’ll’ also look at how these phenomena affect our lives and what challenges these conditions present to users.
Key findings
Doxing is not something that only vulnerable groups or people with specific
professions, such as journalists or sex workers, can be affected by. Anyone who
voices an opinion online may potentially become a victim of doxing.
Almost
any public data can be abused for the purpose of doxing or cyberbullying with an
unlimited number of ways users can be harmed by their own data.
With
increasing digitization of most aspects of our everyday lives, even more data is
now shared with organizations and may end up in the hands of criminals. This now
includes personal medical records and selfies with personal identification
documents.
Access to personal data can start from as low as US$0.50 for an
ID, depending on the depth and breadth of the data offered.
Some personal
information is as mch in demand as it was almost a decade ago – primarily credit
card data and access to banking and e-payment services. The cost of this type of
data has not fallen over time and that is unlikely to change.
Data sold on
dark market websites can be used for extortion, executing scams and phishing
schemes and direct stealing of money. Certain types of data, such as access to
personal accounts or password databases, can be abused not just for financial
gain but also for reputational harm and other types of social damage including
doxing.
Unwanted spotlight: doxing
The increasing political and social
division of recent years combined with a perceived anonymity exacerbates some of
the corresponding social dangers on the internet, such as trolling and
cyberbullying. And at the intersection with privacy threats there is the issue
of doxing.
What is doxing?
Historically, doxing (also spelled doxxing) meant
de-anonymizing a person on the internet, especially in early hacker culture,
where people preferred to be known by their nickname (online handle). The
meaning has evolved, however, to have a broader sense.
Doxing is, in a way, a method of cyberbullying. It occurs when a person shares some private information about another person without their consent to embarrass, hurt or otherwise put the target in danger. This can include sharing:
embarrassing photos or videos;
parts of private correspondence, probably
taken out of context;
a person’s physical address, phone number, private
email address and other private contacts;
occupation and job details;
medical or financial data, criminal records.
EXAMPLE: An example of a threat
of doxing in this classic sense is the story of the anonymous blogger Slate Star
Codex, who claimed that a New York Times journalist insisted on publishing his
real name in a piece about him. This prompted the blogger to delete his blog.
Luckily, the newspaper seems to have abandoned the idea.
Doxing also includes cases when data about the victim is already publicly available, but a perpetrator gathers and compiles it into an actionable “report”, especially if also inciting other people to act on it. For example, if a person voices an opinion on a divisive issue in a post on a social network, throwing in their phone number in the comments and suggesting people should call them at night with threats is still doxing, even if the phone number is available online in some database or on some other social network.
EXAMPLE: A journalist from Pitchfork, a US music outlet, received numerous threats on Twitter including suggestions to “burn her house” after her phone number and home address were published by Taylor Swift fans who were unhappy about a review of the singer’s latest album that wasn’t positive enough.
Why is doxing dangerous?
Compared to the physical world, information on the
internet can spread very quickly and is almost impossible to remove once posted
online. This makes doxing even more harmful.
The most common goal of doxing is to cause a feeling of stress, fear, embarrassment and helplessness. If you are caught in a heated argument on Twitter, and somebody posts your home address and suggests that people should hurt you, it naturally causes anxiety. Threats can also be directed at your relatives. The real danger, however, comes if someone decides to actually carry out the threats, which means doxing also threatens your physical safety — something that happens more often than you would think.
Besides posting your information online for everyone to see, attackers can share it in a targeted way with your relatives, friends or employer, especially if it is embarrassing. This can harm the victim’s relationships with their loved ones, as well as their career prospects.
EXAMPLE: After a service for finding people using only a photo gained popularity in VK, a popular social network in Russia, it was used to de-anonymize women who starred in porn movies or worked in the sex industry. The perpetrators specifically suggested sharing this information with their relatives. One of the victims was a school teacher who eventually lost her job.
Doxing scenarios
How can you be doxed? These are some common scenarios and
how they can harm the victim:
Identifying the user and sharing information directly with their employer, which
results in the person getting fired due to social pressure;
Leaking intimate
photo and video content of a user to the public — an activity that is often
called ‘revenge porn’ is a widespread method of attacking one’s privacy with
malicious intent that can have significant consequences for the victim;
Revealing the identity of anonymous bloggers, internet users, opinion leaders
and creators, which can lead to real danger if the victim is in a hostile
environment, for instance, opposition bloggers in certain countries or a person
who supports unconventional views;
Outing the person and providing their
personal details in the media when this information does not serve the public
interest and may directly harm the person;
Gathering and sharing information
about the account of a specific person (the potential victim) featured in
sensitive or questionable content with hostile groups or accounts that may
engage in online or even offline violence against that person.
Social impact
Doxing is a very pressing matter in times of increasing social and political
division. Doxing, as well as the threat of doxing, hampers freedom of speech and
produces a chilling effect. It prevents people from voicing their opinions,
which is harmful to democracy and healthy social debate.
Some people are more likely to be victims of doxing. Journalists, bloggers, activists, lawyers, sex industry workers, law enforcement officers all run a higher risk of being doxed. For women, doxing goes hand in hand with sexualized verbal abuse and threats. For law enforcement officers, it also means direct danger for their physical safety, especially for undercover officers. This can lead people to abandon their jobs.
High-profile internet personas are more at risk than average users. It doesn’t mean that “ordinary” people are safe from doxing. Having said something online or done something on camera that “upsets” a large group of people can randomly attract excessive attention from online crowds and turn your life into a nightmare — even if you never actually said or did it in the first place.
EXAMPLE: Tuhina Singh, a CEO of a Singapore company was doxed: her phone number and private email address were published online, resulting in insults and threats. Reason? She was misidentified as a woman from a viral video, refusing to put on a mask amidst the coronavirus pandemic.
The darknet database. How much do you cost?
Doxing is the result of abusing
information that is available in the public domain and not used for financial
gain. However, the threats to personal data and, hence, personal safety, do not
end there. Aside from the publicly available data that we freely share and that
can be gathered by anyone and used for malicious purposes, the organizations we
share our data with don’t always handle it responsibly.
By definition, we do not expect this information to leak out into the public and even if it does, do not anticipate that it might harm us. According to recent research by Kaspersky, 37% of millennials think they are too boring to be the victim of cybercrime. The number of massive data leaks hit a new high this year and we no longer get surprised by yet another company being hacked and their customers’ data being leaked or used in ransom demands.
Efforts to better protect personal data are being made in a variety of countries, with governments imposing new directives to ensure protection and penalize irresponsible management of citizens’ data. New personal information protection directives such as the General Data Protection Regulation (GDPR) in the EU and Brazilian General Data Protection Act (LGPD), as well as increasing customer scrutiny towards data handling practices, have forced organizations to improve their security and take the data leakage threat more seriously.
However, that doesn’t mean the data is safe. In some cases, stolen data is used for ransom practices, in others it is published out in the open. Sometimes it is a mix of both: threat actors who employed the Maze ransomware published stolen data if they did not succeed in getting the ransom money. But most of it ends up on the dark web as a commodity, and a very accessible one. Darknet forums and markets, essentially marketplaces for illegal physical and digital goods, are used by cybercriminals to sell services and products, from malware to personal data.
Our experts, who specialize in understanding what goes on in the dark web, researched the current state of data as a commodity on such platforms to find out what kind of personal data is in demand, what it is used for and how much it costs.
Methodology
For the purposes of this research we analyzed active offers on 10
international darknet forums and marketplaces that operate in English or
Russian. The sample included posts that were shared during the third quarter of
2020 and that are still relevant.
Research findings – how much do you cost?
Covering all types of personal data
offers on the dark web would turn this report into a short book, so it focuses
on just some of the most popular categories available on dark markets. However,
it is important to mention that the types of databases leaked and then sold on
the dark web vary, which is unsurprising considering they are stolen from
different institutions and organizations. Leaked databases can be
cross-referenced and this way made even more valuable, as they present a fuller
picture of a subject’s personal details. With that in mind, let’s dig into what
is out there in the shadows that cybercrooks might have on you:
ID card data: $0.5 – $10
Identity documents or ID cards are the main means of identification in most
countries, including the US and throughout Europe. Usually they are tied to the
most important services, especially state services and contain sensitive
information such as social security number (SSN) in the US. Though important,
the cost of these documents on the black market is not that high and depends on
how full the information is. For instance, information with a full name and
insurance number will cost as little as $0.50 per person, while the price for a
‘full pack’ including ID number, full name, SSN, date of birth (DOB), email and
mobile phone can reach up to $10 per person. The price also varies depending on
the size of the purchase – data sold in bulk is cheaper per unit.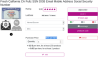
Purchasing 150 ID cards will cost as little as 50 cents per unit
Data from identity documents can be used for a variety of scams, filling out
applications for specific services and gaining access to other sensitive
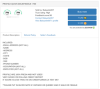
information that can later be used for criminal purposes.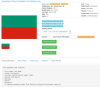
Sometimes the leaked databases contain much more than just ID info
Passport scans: $6 – $15
Passports are another type of identification document that are popular with cybercriminals. In some countries such as Russia, Ukraine and other former Soviet states they are used instead of IDs and are required to receive pretty much any government-related or financial service – from filing a complaint in a shop to taking out a loan. In other countries, passports can also be used for identification on international platforms such as cryptocurrency exchanges – or for international fraud.
This is the reason passport scans go around the web quite often – think of how many times you have uploaded a copy of your passport to some service, sent it to an organization or allowed them to scan it themselves.
Passport scans are more expensive than identification details with prices
varying from $6 to $15 depending on the quality of the scan and the country of
origin. Typically, there are two types of passport scans sold – a scan of the
first page which, understandably, is cheaper than a scan of a full passport.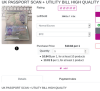
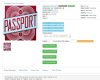
Passport copies for purchase can be selected by gender if required
Driver’s license scans: $5 – $25
Driver’s licenses are another type of identification document that is in demand
in the shadows, primarily due to the growing number of services that one can
register for using a driver’s ID. Typically, the information sold on forums
includes a scan of the license with full information. Varying in price from $5
to $25, these can be used by cybercriminals for car rental, as an ID for local
services or insurance fraud.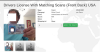
Selfie with documents: $40 – $60
Have you ever taken a selfie with your passport or ID? User identification is taken more seriously these days with organizations adhering to so-called know-your-customer (KYC) programs that require identity verification for various operations. For instance, cryptocurrency exchanges employ this practice to prevent money laundering by getting people extracting funds to confirm they are who they say they are. Social networks require selfies with documents when users need to recover access to their account and bank employees take pictures like these when delivering credit cards to clients’ homes.
Using stolen passport or ID selfies allows fraudsters to bypass KYC guidelines
and continue to launder money. These documents can also be used for a whole
variety of services – from car rentals to getting micro-loans or manipulating
insurance companies. Such documents allow cybercriminals to enter the cache or
execute their schemes, and even blackmail the people identified in these
documents. As a result, this data is very valuable, varying from $40 to $60 per
person.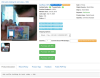
Selfies with identification documents can be used to bypass a service’s security procedures
Medical records – $1 – $30
The world is becoming more digitized along with certain aspects of our lives that we never thought would go online. Take medical records, for instance – cybercriminals have laid their hands on them too. Looking back to 2012, when we analyzed different types of data available in the darknet, medical data was not even a thing. Now, however, this data is in demand as it can be used for a whole variety of fraudulent activities from obtaining health insurance services to purchasing regulated drugs. It can also be used to demand ransom. Recently, for instance, Vastaamo, a Finnish mental health organization, was hacked and the data of their patients, including children, stolen and later exposed on dark web markets, with at least two thousand patients affected. The hackers initially demanded a ransom payment to delete the information, but then switched their attention directly to the patients.
Leaks of medical information can become very unpleasant as they put the victims
who are already vulnerable into an even more vulnerable position. The type of
data shared on the darknet varies from a medical form with a full name, email,
insurance number, and the name of the medical organization to a full medical
record of a patient – with their medical history, prescriptions and more.
Medical records sold on darknet forums can vary from full information about a person to forms from medical institutions
Credit card details: $6 – $20
Credit card details fall under the category of most basic information stolen and used by cybercriminals. Full credit card information including the name, number and CVV code can be used to withdraw funds or purchase goods online and is valued from $6 to $20 per unit. Back in 2012, our evaluation put the price at $10. On average, the cost is more or less the same. The price for such data is dictated by the country of origin, the bank and more importantly, on how large the purchase is, with ‘better’ value with larger volume purchases. Of course, new anti-fraud banking systems are making life harder for cybercriminals, forcing them to constantly come up with new ways to cash out. Nevertheless, with credit card details being the starting point for most of these schemes, they are nowhere near becoming outdated.
Online banking and PayPal accounts: $50 – $500
Another type of financial data is online banking access and PayPal account information. Both provide direct access to the funds of the victims with PayPal being a sweet spot for the cybercriminals who want to launder their money and withdraw it without any security checks. Access to online banking is generally valued at between one and 10 percent of the funds available in the account, while PayPal accounts cost from $50 to $500 depending on the available credit and previous user operations.
Subscription services: $0.50 – $8
In the world of subscription-based entertainment, access to popular streaming, gaming or content platforms is in high demand. While little personal information is given away, losing access to one’s account on Netflix, Twitch or PornHub is not something that anyone would enjoy. Stolen subscription service credentials are not only sold on only in the dark web – they can be found in some shady regular forums too. The dark web usually has offers to purchase access details in bulk, which can later be sold individually to multiple customers. The price for access to such services varies from 50 cents to $8.
How much does your data cost?
Credit card details: $6 – $20
Driver’s
license scans: $5 – $25
Passport scans: $6 – $15
Subscription services:
$0.50 – $8
ID (full name, SSN, DOB, email, mobile): $0.50 – $10
Selfie
with documents (passport, driver’s license): $40 – $60
Medical records: $1 –
$30
Online banking account: 1-10% of value
PayPal accounts: $50 – $500
Password databases
Leaks of password databases are among the most widespread data leaks. From
retail loyalty cards to logins for banks, such databases have been appearing on
the dark web and even on the normal web for years, and they have a tendency to
be leaked into the public domain, requiring very small payments to access them,
or sometimes access to the data is entirely free. While these databases are
outdated for the most part, they still represent a real danger. Users tend to
use the same passwords across a number of platforms and accounts, often tying
them all to the same email. Picking up the right password for a specific account
is often a matter of time and effort, and as a result, users are at risk of
having more of their data compromised – from their social network accounts to
their personal email or private accounts on adult websites. Access to other
accounts can later be resold (as in the case of subscription services) or used
for blackmail or scam.
Certain services aggregate leaked passwords and enable paid subscription-based or single time access to their databases as shown on the screenshot. The service on the screenshot allows one database check for 30 coins
Unauthorized access to email and social media: $400 – $800
With so much personal data available for sale, one may wonder whether purchasing
access to someone’s email or social network account is also as easy as obtaining
IDs. The darknet operators do indeed offer to hack into specific accounts or
emails, charging from $400 per account. However, the methods employed by those
who offer such services are rather basic – they can only go as far as trying to
guess the password or checking the account against existing leaked databases or
executing social engineering attacks to get the user to reveal their password.
Increased security of social media and email services has also made these
practices less successful with double authentication and various other security
measures protecting users better than before. As a result, most of these kinds
of offers on dark markets are, ironically enough, actually scams against other
cybercriminals.
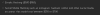
Examples of forum advertisements offering to hack social media accounts and emails
Nevertheless, this doesn’t rule out the possibility of real targeted account hacking – more covert, technically complex methods are employed by experienced actors and these services usually cost a lot. For instance, the actor may identify a specific email of the potential victim, send a spear-phishing email prompting the target to download malware that will be able to collect information about the passwords and ultimately gain access to the targeted accounts. These services, however, are extremely expensive, time consuming and are usually executed by advanced threat actors against priority targets.
Key takeaways
In the course of this research we have witnessed a number of
trends relating to stolen and repurposed personal data. Some personal
information remains as much in demand as it was almost a decade ago – primarily
credit card data and access to banking and e-payment services. The cost of this
type of data has not fallen over time and that is unlikely to change.
Another big change is the type of data now available for sale. With the digitization of medical institutions, personal medical records traditionally categorized as very sensitive information became available for the public and cybercriminals to use and abuse for financial gain. The current development and spread of telemedicine in the world is unlikely to decrease this trend, although, we hope that after recent cases such as the Vastaamo hack, medical organizations will approach data collection and security with greater responsibility.
The growth in the number of photos of people with documents in their hand and various schemes exploiting them also reflects a trend in the cybergoods game and indicates that any data shared, even with organizations, can potentially end up in the hands of cybercrooks and abused for the purposes of financial gain. The repercussions of such data abuse are very real for the victims as they will have to deal with the loans taken out in their name or services used on the basis of their identity.
At the same time, there is some good news when it comes to the safety of personal accounts and gaining access to specific emails and social media accounts. With improved security measures employed at the industry level, targeting and hijacking a specific individual’s account is very costly, and in most cases, not doable. In this sphere there is evidence of an interesting dynamic of cybercriminals scamming each other, with most cybercrooks unable to deliver what they advertise. That does not, however, eliminate the threat entirely: provided they have the funds and their order is big enough, the criminals may still be able to buy what they want.
The overview of the types of data available on dark markets suggests that at least some of the offers might be of interest to especially determined doxers. While we believe that such cases are unlikely due to their cost right now, things might change depending largely on the determination of the abusers to dox an individual.
Protecting your data and yourself
With our ever-growing online presence and
footprint, it is almost impossible to be completely anonymous online. A
determined person with some computer skills, especially if they have access to
privileged information (say, a private investigator or a law enforcement
officer), will find at least some data about you given enough time.
EXAMPLE: Kevin Mitnick shares a story in his book “The Art of Invisibility” about how he managed to find out the SSN, city of birth and the mother’s maiden name of a reporter who thought she had a very minimal online presence (he did it with her consent). To do so, he used his access to a specialized web resource for private investigators. People who usually enjoy privacy can also be tracked to their homes if you have specific data: a geolocation dataset from a marketing company obtained by the New York Times in 2019 showed the GPS location over time of senior US government officials, policemen and even acquaintances of Johnny Depp and Arnold Schwarzenegger.
This means that online privacy is almost always about assessing the risks that you face and taking appropriate measures to mitigate them. If you think you might anger a few low-caliber online trolls with a tweet, it is enough to hide your email address from your social network profile. If you are a political reporter covering extremist movements, you need more control of your digital footprint. Below, we describe a few basic steps that will be sufficient against doxing for an average internet user.
Know what they know
The first thing to do if you want to protect yourself
against doxing is to research what the Internet knows about you. Try googling
your name, combine it with some other data about you such as your place of
residence or year of birth to narrow down the results. Try searching for your
online handles and emails as well. If your name is not very popular, you can
even subscribe to notificationы from Google in case it pops up somewhere on the
web.
Apart from Google, there are so-called people search engines such as BeenVerified that allow background checks to be conducted on people using open web data or government records. Publishing this kind of information online might be illegal depending on the country, so availability of such websites differs in various jurisdictions.
If you have public social media profiles, review the posts. Check if they contain geotags with places that you frequent, such as your home or office, or photos that can reveal their location. Of course, not all photos are dangerous, but the more specific they are, the more risk they carry. Scout your older posts for some more private data, such as names of your family members. If you have a private profile, check if you actually know all the people in your friend list.
Remember that, besides social networks per se, there are many other applications that have a social component and can reveal information about you, ranging from languages that you learn to your level of sexual activity. Pay special attention to apps that record some sort of geodata, such as fitness tracking applications. Check that your account in such apps is private.
EXAMPLE: In 2018, a security researcher noted that there were spots with a high level of activity in a dataset of user activity in Strava, a fitness app, in the Middle East. These spots, cross-referenced with Google Maps, gave away the location of US military bases in the region.
Finally, check if your data was leaked in data breaches. Leak monitoring is usually built into password managers and web browsers, but you can also use a dedicated service like HaveIBeenPwned. If your email is found in a leak, you can assume that any other information from the breached info is available somewhere (e.g. your home address if the breached service is a web store, or your favorite running routes if it is a fitness tracker).
Remove what you can
If you think that the information about you on the
internet can be used against you, try to get rid of it. In the case of social
networks, it is usually relatively easy: you either remove the posts with
private data or make your profile private.
With other websites, check if you can just remove or disable your account. Otherwise, check if the website has a complaint or information removal form and use it. If not, try to contact the administrators directly. If your jurisdiction has strict data privacy laws, such as GDPR or CCPA, it is easier for a service to just remove your data than face a regulator and the threat of huge fines.
If some information is impossible to remove from the source, you can ask the search engine to remove links to websites containing your private data from search results by exercising the so-called right to be forgotten. Whether you can do so depends on the search engine and jurisdiction.
EXAMPLE: One of our researchers uses a smart watch with an application that traces his physical activity and helps him monitor his progress when jogging. One day he was approached by another runner that he didn’t know. Turns out the guy knew his name and where he runs – all thanks to this application, which did not only tracked his data but also shared it in its internal social network. While this strange occurrence didn’t result in any harm and the intention of the application was to help fellow runners meet each other, it is clear how knowledge of someone’s location and regular jogging route could be used against them – possibly by less friendly strangers.
Protect yourself
Doxing is most devastating when the data being published is
private, i.e., cannot be found on the internet. An adversary can obtain this
data by hacking into the accounts and services that you use. To minimize the
risks of being hacked, follow these simple rules:
Never reuse your passwords across accounts. Use a unique password for each
account and a password manager to store them.
Protect your devices with
fingerprint/face scan or with a PIN or password.
Use two-factor
authentication. Remember that using an application that generates one-time codes
is more secure than receiving the second factor via SMS. If you need additional
security, invest in a hardware 2FA key.
Beware of phishing email and
websites.
If you are ready to invest a bit more effort into protecting your
privacy, here are some additional ways to protect your personal information or
check if your passwords or data have become compromised without your knowledge:
Think twice before you post on social media channels. Could there be unforseen
consequences of making your views or information public? Could content be used
against you or to your detriment now or in the future?
To make sure people
close to home, including family, friends or colleagues, can’t access your
devices or accounts without your consent, never share passwords even if it seems
like a good idea or convenient to do so. Writing them on a sticky note next to
your screen might be helpful for you, but it may also help others to access
things you don’t want them to.
Ensure you always check permission settings on
the apps you use, to minimize the likelihood of your data being shared or stored
by third parties – and beyond – without your knowledge. You might end up giving
consent by default, so it is always worth double-checking before you start using
an app or service.
There is no substitute for strong and robust passwords.
Use a reliable security solution like Kaspersky Password Manager to generate and
secure unique passwords for every account, and resist the temptation to re-use
the same one over and over again.
Password managers also allow personal data
to be stored in an encrypted private vault where you can upload your driver’s
licenses, passports/IDs, bank cards, insurance files and other valuable
documents and manage them securely.
To find out if any of the passwords you
use to access your online accounts have been compromised, use a tool such as
Kaspersky Security Cloud. Its Account Check feature allows users to inspect
their accounts for potential data leaks. If a leak is detected, Kaspersky
Security Cloud provides information about the categories of data that may be
publicly accessible so that the individual affected can take appropriate action.
When it is too late
If you have fallen victim to doxing, you can try to
contact the moderators of the website where your data was leaked or flag the
posts with your data on the social network to have it removed before the
information spreads.
Note that usually the goal of doxers is to cause the victim stress and psychological discomfort. Do not engage with trolls, make your accounts private and seek comfort with your friends, relatives and offline activities. It takes a short time for an online mob to give up on their victim and move on if you do not give them additional reasons to attack you.
However, if you receive threats or fear for your physical safety, you might want to contact law enforcement. In this case, remember to document what is going on, for example screenshot the threats, to provide law enforcement officers with additional evidence.
To sum up: take good care of yourself and your data
The digital world
provides us with endless opportunities to express our individuality and share
our stories, but we need to make sure it is a safe place to express ourselves.
As this research shows, our data is valuable not only to us but to many other
users with malicious intentions – ranging from an expression of dissatisfaction
with your actions to cybercriminals who thrive on profiting off personal data.
That’s why it’s crucial to know how to protect it.
An important point to remember here is that cybercriminals are not the only ones who can use our data to cause harm – with new phenomena such as doxing, users need to be aware that they can never know how someone can capitalize on their data. Approaching personal data sharing with responsibility is a must-have skill nowadays that will help keep us safer in the storms of the digital world.
TurkeyBombing Puts New Twist on Zoom Abuse
28.11.20
Security
Threatpost
Threat actors already stole nearly 4,000 credentials before the holiday was even over, according to report.
Millions of family and friends, forced to spend Thanksgiving socially distant, are being targeted by cybercriminals as they turn to video platforms like Zoom to virtually be together. In this ongoing attack, cybersecurity experts warn, victims are targeted with a Zoom-related and Thanksgiving-specific hook reminiscent to ZoomBoming — call it TurkeyBombing.
On Thursday, a security researcher warned that a major phishing campaign kicked off over the Thanksgiving long weekend and is aimed at stealing Microsoft credentials. Attackers have already successfully pried credentials out of thousands of users, according to the researcher who goes by the handle TheAnalyst. According to the researcher, quoted in a BleepingComputer report, the attack is ongoing and forecast to continue.
The Turkey-Day themed email ploy leverages the juggernaut popularity of the Zoom Video Communications platform. Bogus messages are being sent en masse and falsely tell recipients, “You received a video conference invitation,” according to TheAnalyst. Messages, naturally, included a link to review the malicious invitation.
The link leads victims to a fake Microsoft login page hosted on a Google domain, Appspot.com. The domain is used primarily by developers to host web applications in the Google-managed data center.
According to the report when a victim is brought to the phishing page, their email address pre-populates the login field of the landing page. Next, they are prompted to enter their associated Microsoft account password.
If someone takes the bait, the phishing page not only records the victims’ email addresses and passwords, but also their IP addresses and geographic location. If it is determined the credentials successfully allow access to a privileged account, the attackers attempted to breach the account via Internet Message Access Protocol (IMAP) credential verification.
IMAP is a type of protocol used by companies and email services to offer direct access to emails on a email server.
Millions Targeted, Thousands Fall Victim
As of the time of the original
report, attackers had stolen more than 3,600 unique email credentials. Given the
that millions will likely connected with loved ones virtually to celebrate
Thanksgiving this year, that number could be much higher, the expert said.
Indeed, the day after Thanksgiving, Twitter was abuzz with tweets not only about people’s various Zoom meetings with family and friends, but also about numerous special events hosted on Zoom to celebrate the holiday.
Anticipating the Thanksgiving usage surge, the company had even removed the usual 40-minute limit on meetings for all of its free user accounts from midnight ET on Thursday, Nov. 26, through 6 a.m. ET Friday, Nov. 27, “so your family gatherings don’t get cut short,” the company said in a blog post.
Zoom Marketing Blitz, Ideal for TurkeyBombing
Zoom Phishing Attack Targets
Thanksgiving Conference CallsSince its rise in popularity that started in March
at the beginning of the pandemic when many aspects of every-day life moved
online, Zoom has been plagued with security issues.
ZoomBombing became the initial way hackers would break into video conferences, using the ease with which they could access links to Zoom conferences and jump on calls uninvited to disrupt them with pornography, hate speech or even physical threats to users.
Zoom eventually made a tweak to its user interface by removing meeting ID numbers from the title bar of its client interface to mitigate the attacks from threat actors. Before the tweak, anyone could join a Zoom meeting if they knew the meeting link, which many users would send via social-media channels.
A raft of other security threats emerged soon after, forcing Zoom to take various actions to mitigate and eliminate these threats. Among these moves include patching zero-day flaws in its MacOS client that could give local, unprivileged attackers root privilege allowing access to victims’ microphone and camera.
Zoom also eliminated a feature called LinkedIn Sales Navigator that came under fire for “undisclosed data mining” of users’ names and email addresses, which the service used to match them with their LinkedIn profiles.
Changing Employee Security Behavior Takes More Than Simple Awareness
27.11.20 Security Threatpost
Designing a behavioral change program requires an audit of existing security practices and where the sticking points are.
Security awareness rarely leads to sustained behavior change on its own, according to a recent analysis – meaning that organizations need to proactively develop a robust “human-centered” security program to reduce the number of security incidents associated with poor security behavior.
According to the Information Security Forum (ISF), the information security
industry is playing catch-up when it comes to positively influencing behavior –
the proliferation of remote-working arrangements, exacerbated by the stress
associated with the pandemic, has underlined the importance of strengthening the
human elements of security.
In its digest released this week, entitled “Human-Centered Security: Positively Influencing Security Behavior,” the ISF laid out four elements that can move the needle on security behavior:
Understanding the key factors that influence employees’ security choices
Delivering impactful security education, training, and awareness
Designing
systems, applications, processes, and the physical environment to account for
user behavior
Developing metrics to measure behavior change and demonstrate
return on investment
How to shift to a human-centered approach. Source: ISF.
“Errors and acts of negligence can cause significant financial and reputational damage to an organization, with many security incidents and data breaches originating from a human source,” said Daniel Norman, senior solutions analyst at the ISF, and author of the report. “A human-centered security program helps organizations to understand their people and carefully craft initiatives that are targeted at behavior change, reducing the number of security incidents related to human error and negligence.”
A successful program leverages cross-departmental collaboration to fully grasp
the current state of security behavior, which subsequently enables organizations
to target investment to mitigate the identified risks.
Top elements influencing security behavior. Source: ISF
Lisa Plaggemier, chief strategy officer at MediaPro, noted that in large organizations, where there are multiple reviews before awareness can go out to employees, there are a few specific issues to consider in this regard.
“The security team lets corporate communications or human resources have too much veto power,” she said via email. “I frequently talk to very talented training and awareness professionals that would like to push the envelope and do something creative that gets people’s attention, and their good ideas get shot down or watered down to the point of no longer being engaging. I know of one large company that wanted to move from one hour once a year training, to shorter trainings over the course of the year. This is considered the norm for any mature security awareness program, but even that was shot down by corporate administrative functions (like HR) that have no responsibility for securing the organization. If the security team is responsible and accountable, we also have to be empowered to run the program.”
Some top pitfalls to avoid, according to Plaggemeir, include:
Letting perfection be the enemy of good. It’s better to do something, even if
it’s imperfect, than to do nothing or spend too much time in limbo in corporate
reviews and sign offs.
Under-communicating. Don’t assume everyone is reading
everything you put out.
Poor writing and bad design. No one wants to read
verbose security newsletters in 10 point font with no graphics.
An example of successful security behavior redesign. Source: ISF
“If the ‘brand’ of your security team isn’t to be approachable, helpful and add value, you won’t be included in projects where you really do need a seat at the table,” she said. “Your training and awareness program is the most visible thing your security team does, so use it to show that you want to work with the business, not against it, and that you’re friendly and approachable.”
Lookalike domains and how to outfox them
25.11.20
Security
Securityaffairs
Our colleagues
already delved into how cybercriminals attack companies through compromised
email addresses of employees, and how to protect against such attacks using SPF,
DKIM and DMARC technologies. But despite the obvious pluses of these solutions,
there is a way to bypass them that we want to discuss.
But let’s start from a different angle: how relevant is email these days? After
all, this year saw a sharp rise in the popularity of video-conferencing tools,
preceded by several years of healthy growth in the use of instant messengers, in
particular, WhatsApp and Telegram. Nevertheless, email is still the main means
of online communication, at least in the business world. Indirect confirmation
of this is the increase in the number and quality of Business Email Compromise
(BEC) attacks. According to data from the US Internet Crime Complaint Center
(IC3), the financial damage from such attacks has risen sevenfold in the past
five years.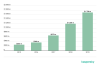
Financial damage from BEC attacks, 2015–2019 (download)
Data for 2020 has not yet been published, but given the COVID-19 pandemic and the mass shift of employees to remote working, it is safe to assume that the number of BEC attacks will only grow. Initial threat landscape studies also point to this.
Lookalike domains in BEC
A feature of BEC is the emphasis not on the
technical side (cybercriminals’ options are rather limited when it comes to
email), but on social engineering. Typically, attacks of this kind combine
technical and social techniques to achieve greater efficiency. The three
protection technologies mentioned above cope with most combinations well enough.
But there is one exception: lookalike-domain attacks. The method is simple in
essence: the cybercriminals register a domain that looks very similar to that of
the target company or a partner firm. Messages sent from this domain sail
through Sender Policy Framework (SPF) authentication, possess a DomainKeys
Identified Mail (DKIM) cryptographic signature, and generally do not arouse the
suspicions of security systems. The snag is that these emails are phishing. And
if written believably enough — with a corporate template, stressing the urgency
of the matter, etc. — they will likely fool the victim.
Here are some examples of fake domain names:
Original domain Fake domain
netflix.com netffix.com
kaspersky.com
kapersky.com
uralairlines.ru uralairilnes.ru
As you can see, the fake
differs from the original by only one letter added (or removed) so that a closer
look is required to spot it. Incidentally, the last example of a fake Morgan
Stanley domain is real — we prevented this very attack at the end of 2019.
For an overview of the use of fake domains, we compiled statistics on lookalike
spoofing for Q3 2020. Having analyzed the data, we concluded that this year’s
pandemic has significantly changed the direction of cybercriminal activity.
Whereas before, the focus of such attacks was the financial sector, now the
service sector is in the firing line, including various e-commerce services:
food delivery, online shopping, buying air tickets, etc. Domains related to this
sector accounted for 34.7% of the total number of attacks in Q3.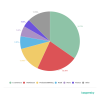
Distribution of detected lookalike domains by category, Q3 2020 (download)
Also note the rise in the IT sector’s share in 2020: up from 17.9% in Q1 to 22.2% in Q3. This is to be expected, since the mass transition to remote working was bound to impact the overall situation.
A word about lookalikes
Unlike spam mailings, which tend to be large in both
scale and duration, attacks involving lookalike domains, like any BEC attack,
target a specific victim (or group of victims). Consequently, emails are few and
well thought out, and the domains are extremely short lived. We see that half of
all fake domains are used only once, and in 73% of cases the domain is only
active for just one day. This renders traditional signature-based anti-spam
solutions (detect an attack, create a rule) effectively useless, thus the need
arises for proactive protection. There are two common and at the same time
simple methods available to companies keen to guard at least in some measure
against lookalike and other such attacks.
The first is for the company itself to register domains with typos, and set up redirects to its official domain. This reduces cybercriminals’ ability to register a plausible fake, but does not nullify it completely or prevent counterfeiting of domains belonging to partners, contractors and other organizations which the company deals with.
The second is to compile lists of plausible fake names for both the company’s domain and those of partners and contractors. Next, the list is loaded into the anti-spam solution, which preemptively blocks all messages arriving from the fakes. The main drawback of this method is the same as before: it is impossible to cover all possible fake domains, especially if the company works with many counterparties. Plus, there is the ever-present human factor — one typo in the list of tens or hundreds of domain names can lead to a security breach or the filtering out of emails from a legitimate domain instead of a fake one, causing additional headaches for business units.
When simple solutions no longer suited our clients, they came to us for something more complex. The result was a method that requires no user interaction. In a nutshell, it automatically compiles a global list of legitimate domains that could potentially be faked, on which basis it analyzes and blocks messages from lookalike domains. In essence, it is proactive.
How it works
Protection against lookalike-domain attacks is three-pronged:
client-side processing; domain reputation check in Kaspersky Security Network;
infrastructure-side processing. The general principle is shown schematically
below:
In practice, it goes as follows. On receiving an email, the technology forwards the sender domain to Kaspersky Security Network (KSN), which matches it against the list of lookalike domains already known to us. If the sender domain is found, the message is instantly blocked (steps 1 to 3). If there is no information about it, the email is quarantined for a short fixed period (step 4). This gives time for the technology to check the domain according to the set algorithm, and, if it recognizes it as fake, to add it to the list of lookalike domains in KSN. After the email leaves quarantine, it is rescanned (step 9) and blocked, since by then the list of lookalike domains has been updated.
Let’s take a look at how sender verification works and how the list of lookalike domains gets updated. Information about quarantined messages is sent to the KSN database together with additional metadata, including the sender domain (step 5). At the first stage of analysis, the domain undergoes a “suspiciousness” check based on a wide range of criteria, such as Whois data, DNS records, certificates, and so on; the purpose of this stage is to quickly sift out domains that are clearly legitimate, but not yet known to our system. Henceforth, emails from these domains are no longer quarantined, because KSN now has information about them. At the second stage, the system compares the similarity of suspicious domains and addresses in our global list of legitimate domains (step 7), which includes the domains of our clients and their counterparties. This list is generated automatically based on an assessment of the frequency with which legitimate messages are sent from the domain and the uniformity of the mail flow over time. The extent to which the overall picture matches the behavior of employees in terms of business correspondence determines the reputation of the domain (step 6). If the resemblance of the scammer’s domain to a legitimate address is high, the sender domain too is added to the list of lookalike domains and all messages sent from it are blocked.
Our approach is more complex than simply registering lookalike domains to the company and enables real-time blocking of attacks that use such domains as soon as they appear. In addition, the human factor is eliminated, and the global list of legitimate domains stays current thanks to automatic updates.
Study Finds New Employees Immediately Given Access to Millions of Files
18.11.20
Security
Securityweek
A new report demonstrates that the size of the problem for financial services created by the COVID-related switch to remote working can only be solved by automation.
Data protection firm Varonis analyzed a dataset of 4 billion files in 56 financial services companies. It found that all new employees immediately had access to an average of 10 million files -- which was nearer 20 million in the larger companies. This is a security issue in itself -- but one that is made worse by the dramatic and forced switch to working from home by international pandemic lockdowns. All companies -- not just financial services -- were required to step into the cloud without adequate preparation.
"Mobilizing without proper security controls," warns Varonis in its latest study on financial services, "exponentially increases the risk posed by insiders, malware, and ransomware attacks, and opens companies up to possible non-compliance with regulations such as SOX, GDPR, and PCI."
Detailed analysis of the files available to staff working remotely or from home shows home workers have unrestricted freedom to view, copy, move and change data to almost 20% of all files containing sensitive employee and customer data. On average, Varonis finds that every financial services organization has approximately 20,000 folders exposed to every employee per terabyte of stored data.
"It takes IT professionals an estimated 6–8 hours per folder to locate and manually remove global access, meaning it would take years to remediate these folders manually," says Varonis -- something that is impossibly tedious and time-consuming without automation.
The current inadequately secured global access results in a series of threats to financial services organizations. A single successful phishing attack against an employee could result in a corporate compromise. According to the IBM Cost of a Data Breach Report 2020, "The average time to identify and contain a data breach, or the 'breach lifecycle', was 280 days in 2020." This, warns Varonis, is ample time for adversaries to severely damage reputation, revenue and customer faith.
Ransomware is of course a major threat. In October 2020, a G7 advisory warned that the threat was increasing and possibly involved state actors. "The financial services sector has become an attractive target for ransomware attacks," warned the G7, "and financial institutions have reported increased sophistication in malicious cyber-enabled attacks in recent months. Some prominent strains of ransomware have been linked to groups that are vulnerable to influence by state actors."
The growth of 'double extortion' ransomware is not the only non-compliance threat faced by the financial services sector. The Varonis study found that more than 64% of the companies have more than 1,000 sensitive files open to every employee. This puts them at risk of non-compliance with regulations like the EU General Data Protection Regulation (GDPR), Sarbanes-Oxley (SOX) and California Consumer Privacy Act (CCPA) -- which all require strict controls on sensitive information. Violators could face prison and (in the case of GDPR) up to €20 million in fines.
These threats are exacerbated by the common but rarely cured habit of poor password hygiene. Varonis found that 59% of financial services companies have over 500 passwords that never expire and 71% have folders with unresolved SIDs. Finding these vulnerabilities takes time and internal collaboration across teams -- and again is best achieved through automation.
The stakes are high for the financial services industry. It is one of the most attacked sectors by both financial criminals and nation state actors, while the cost of a data breach is amongst the highest at an average of $5.8 million. "As financial services take to remote work via Office 365," warns Varonis (PDF), "having guardrails in place to enforce controls and manage the increased risk is taking priority. Proving regulatory compliance in this environment can be tricky, so clear audit trails and reporting mechanisms are must-haves."
Mozilla Boosts Security in Firefox With HTTPS-Only Mode
18.11.20
Security
Securityweek
Firefox 83 has been released to the stable channel with a new feature meant to improve the security of its users, namely HTTPS-Only Mode.
The new feature is designed to prevent eavesdropping, especially when it comes to websites containing sensitive information, such as emails, financial data, or medical details.
With HTTPS-Only Mode enabled, Firefox attempts to establish a fully secure connection for each and every site the user accesses, and also asks for the user’s permission before connecting to a site that lacks support for secure connections.
Hypertext Transfer Protocol (HTTP) over TLS (HTTPS) was meant to address the security shortcomings of HTTP through encrypting the connection between the browser and the visited website.
While most websites do include support for HTTPS, and those that don’t are fewer by the day, many sites do fall back to the unsecure HTTP protocol.
On top of that, Mozilla notes, millions of legacy HTTP links pointing to insecure versions of websites still exist, meaning that, when the user clicks on them, the browser traditionally connects using the insecure HTTP protocol.
“In light of the very high availability of HTTPS, we believe that it is time to let our users choose to always use HTTPS. That’s why we have created HTTPS-Only Mode, which ensures that Firefox doesn’t make any insecure connections without your permission,” Mozilla says.
Once HTTPS-Only Mode has been enabled, Firefox will attempt to always establish a fully secure connection to the visited website, and even if the user clicks on an HTTP link or manually enters it, the browser will still use HTTPS instead.
The new feature can be enabled from the “Preferences” menu, in the “Privacy & Security” section. There, after scrolling down to “HTTPS-Only Mode,” users need to select the “Enable HTTPS-Only Mode in all windows” option.
“Once HTTPS-Only Mode is turned on, you can browse the web as you always do, with confidence that Firefox will upgrade web connections to be secure whenever possible, and keep you safe by default,” Mozilla notes.
When encountering a website that doesn’t include support for HTTPS, Firefox will deliver an error message, providing the user with the option to connect using HTTP.
For websites that do support HTTPS but serve resources such as images or videos over insecure connections, some pages might malfunction, and users will be provided with the option to temporarily disable HTTPS-Only Mode for that site.
Mozilla expects for HTTP connections to be deprecated once HTTPS is more widely supported and even required for all websites. HTTPS-Only Mode, the browser maker says, is the future of the Internet.
“At-Risk Meeting Notifier Zoom” feature alerts meeting organizers of Zoombombing
risk
17.11.20
Security
Securityaffairs
The popular video conferencing application Zoom implemented the new “At-Risk
Meeting Notifier” feature to warn of Zoombombing threat.
Zoom announced the
launch a new feature dubbed “At-Risk Meeting Notifier” to warn conference
organizers of potential Zoombombing attacks.
The feature scans the web for links to Zoom meetings that have been posted online and warn organizers of the risk of Zoombombing attack.
“The At Risk Meeting Notifier scans public posts on social media sites and other public online resources for Zoom meeting links. When it finds publicly posted meeting information that indicates a given meeting may be at high risk of being disrupted, we notify account owners and admins by email.” reads the Zoom’s announcement.
The idea behind the “At-Risk Meeting Notifier” feature is that threat actors use to arrange Zoombombing attacks by sharing links to the targeted meeting on public posts on social media and other public sites.
When At-Risk Meeting Notifier finds a Zoom meeting URL, it sends an email to the organizers with a warning that attackers may disrupt their meeting.
The number of Zoombombing attacks surged with the increased popularity of the video conferencing platform since the beginning of COVID-19 pandemic.
The FBI and Spokane police recently announced an investigation into the hack of
Gonzaga University Black Student Union. The hackers broke into a Zoom meeting
and bombarded participants with racial and homophobic slurs.
Media reported
numerous Zoombombing attacks that disrupted the meeting by hurling insults,
playing pornographic content, or threatening other participants.
Organizers that will receive the alert from the At Risk Meeting Notifier should take the following actions to make their future meetings private:
Remove or report the public post.
Delete the existing meeting.
Schedule a
new meeting.
Enable these security settings:
Meeting password/passcode
Waiting room
Meeting registration
Send the new meeting information only to
people that you know.
Organizers that would like to keep their meeting public
are recommended to convert their meeting to a webinar, because a webinar will
them control over who participates with video, audio, chat, and screen sharing.
Crooks use software skimmer that pretends to be a security firm
17.11.20
Security
Securityaffairs
Security experts from Sucuri analyzing a software skimmer that is abusing its
brand name in order to evade detection.
Researchers at Sucuri analyzed a
software skimmer that is using their brand name in order to evade detection. The
e-skimmer is a base64-encoded JavaScript blob that attackers inject into target
webpages.
During a routine investigation, the researchers found the web skimmer that pretends to be related to Sucuri, the malicious code was injected into the database of a Magento site.
The analysis of the software skimmer revealed that the first 109 lines in its code don’t contain any content, while line #110 contains a base64-encoded Javascript ( eval(atob(… ). With this trick, attackers likely attempted to avoid detection.
software skimmer magento
The skimmer is added to the onclick event of the
checkout button and onunload event of the web page.
Upon execution, the code
gathers any data from form fields, such as credit card and billing details, and
exfiltrates it to a remote gateway using a GET request with plaintext
parameters.
“The payment data exfiltration takes place via an <img> tag whose
src parameter is changed to
hxxps://terminal4.veeblehosting[.]com/~sucurrin/i/gate.php, with relevant GET
parameters such as card number, CVV, and expiration date stored in plain text.”
reads the analysis published by Sucuri.
“terminal4.veeblehosting[.]com is neither a malicious site nor a hacked site. It’s a host name of some shared servers (108.170.55.202, 108.170.55.203) belonging to the Dutch hosting provider Veeble.”
This gateway is hosted on Dutch hosting provider Veeble and operated under the
account name “sucurrin.”
The skimmer works on a site that belongs to the
“sucurrin” Veeble account that resembles the name of Sucuri. Experts noticed
that terminal4.veeblehosting[.]com/~sucurrin/ redirected to the legitimate
Sucuri website (https://sucuri.net/) to avoid raising suspicion.
According to X-Force Threat Intelligence, the same software skimmer was injected into at least three website belonging to Harley-Davidson Military, Nappy Land National Childcare Supplier, and Soccer4All.
At the time it not clear if the skimmers are still active on this site.
“To filter out bad actors masquerading as known brand and mitigate the risk of malicious credit card skimmers, consider employing integrity control and security monitoring on your website to mitigate an attack. A good website firewall can help to minimize the risk of infection in the first place.” concluded Sucuri.
Mozilla Says Intermediate CA Preloading Reduces Connection Errors in Firefox
16.11.20
Security
Securityweek
Courtesy of the recently added Intermediate Certificate Authority (CA) Preloading feature, Firefox is handling secure connections better and users are experiencing fewer errors, Mozilla says.
The technique essentially consists of the browser pre-downloading all trusted Web Public Key Infrastructure (PKI) intermediate CA certificates through Mozilla’s Remote Settings infrastructure.
Thus, Firefox users won’t see an error page when the proper intermediate CA certificates are not specified, which, according to Mozilla, is one of the most commonly encountered issues when it comes to configuring TLS security.
For Intermediate CA Preloading, Mozilla enumerates all of the intermediate CA certificates in the trusted Web PKI, with the relevant ones available through the multi-browser Common CA Database (CCADB) reporting mechanisms.
“As a result of Mozilla’s leadership in the CA community, each CA in Mozilla’s Root Store Policy is required to disclose these intermediate CA certificates” to the CCADB, the browser maker explains.
Mozilla periodically synthesizes a list of intermediate CA certificates and then places the list into Remote Settings, with more than two thousand entries currently included in that list.
When first receiving the list, or when updates are made, Firefox downloads the necessary intermediate CA certificates in the background. With changes made to the list at a slow pace, keeping it updated is an easy task.
“Certificates provided via Intermediate CA Preloading are added to a local cache and are not imbued with trust. Trust is still derived from the standard Web PKI algorithms,” Mozilla explains.
According to the company, Intermediate CA Preloading in Firefox 68 has resulted in a lower number of unknown errors when a TLS handshake is performed.
“While there are other factors that affect the relative prevalence of this error, this data supports the conclusion that Intermediate CA Preloading is achieving the goal of avoiding these connection errors for Firefox users,” the company says.
While Intermediate CA Preloading is currently available for desktop users only, Mozilla plans on rolling it out for mobile users as well, to ensure they too encounter fewer secure connection errors.
Apple Unveils Security Features in New M1 Chip
16.11.20
Security
Securityweek
Apple this week unveiled its new M1 chip and the company has provided a brief description of its security features.
The tech giant told SecurityWeek that it will detail the M1’s security features in the coming weeks. For now, it has only shared limited information, but it was still enough for experts to share some thoughts.
Apple says the M1 is the first system-on-chip (SoC) designed specifically for the Mac. The chip uses 5nm technology, it has 16 billion transistors, and it includes an 8-core CPU, as well as an 8-core GPU, which the company says deliver high performance without consuming a lot of power.
In terms of security features, Apple says the M1 chip includes the latest generation Secure Enclave, a high-performance storage controller with AES encryption hardware, and hardware‑verified secure boot. The company says it has built new security protections “deep into the code execution architecture of M1.”
Security researcher Daniel Gruss told SecurityWeek that the M1 chip does not appear to contain any breakthroughs in terms of security.
Nevertheless, Gruss said, “The M1 is a very interesting and cutting-edge piece of hardware with state-of-the-art security techniques based on the information that has become public so far.”
Gruss is a researcher at the Graz University of Technology in Austria. He is one of the researchers involved in the discovery of Meltdown, Specter and several other significant processor vulnerabilities, including the recently disclosed PLATYPUS attack, which can be used to obtain sensitive data by monitoring a processor’s power consumption.
Jesse Michael, principal researcher at hardware security company Eclypsium, explained that by adding its own AES encryption hardware to the storage controller, Apple doesn’t have to depend on possibly-broken encryption in the SSD itself and it prevents the main CPU from being bogged down due to encryption duties.
“Intel added AES-NI instructions a number of years ago to speed up encryption because dedicated hardware to do the AES operations is faster than doing it only using general-purpose instructions,” Michael told SecurityWeek.
As for hardware-verified secure boot, which is designed to ensure that only Apple-signed code can run on a device (even if an attacker has physical access), the expert pointed out that similar features have been available on Apple’s phones for a while and “it makes sense for them to add those to their laptops and other devices.”
“Many other vendors have been working on adding a hardware-based root of trust for secure boot,” Michael said. “Intel has the BootGuard feature to verify even the first parts of the code that are read out of the SPI flash and close one of the secure boot gaps in Intel platforms, but it's not deployed everywhere yet. BootGuard is most likely to show up in enterprise laptops, I think.”
As for the Secure Enclave, which is designed to protect highly sensitive information even if the operating system has been compromised, the researcher noted that it’s similar to Intel’s SGX technology, but “Intel's version is a little more general-purpose than the Apple Secure Enclave.”
5 Components of the Kubernetes Control Plane that Demand Special Attention in
Your Security Strategy
31.10.20
Security
Securityaffairs
Organizations and security incidents in Kubernetes environments, these are 5 key
components of the control plane that demand special attention
Organizations
are no strangers to security incidents in their Kubernetes environments. In its
State of Container and Kubernetes Security Fall 2020 survey, StackRox found that
90% of respondents had suffered a security incident in their Kubernetes
deployments in the last year. Two-thirds of respondents explained that they had
weathered a misconfiguration incident, followed by vulnerability cases, runtime
events and failed audits at 22%, 17% and 16%, respectively.
Misconfiguration incidents are so prolific because they can appear in many different aspects of an organization’s Kubernetes environment. For instance, they can affect the Kubernetes control plane. This section of a Kubernetes deployment is responsible for making global decisions about a cluster as well as for detecting and responding to events affecting the cluster, notes Kubernetes.
This raises an important question: how can organizations harden the Kubernetes control plane against digital attacks?
To answer that question, this blog post will discuss five components within the Kubernetes control plane that require special attention within organizations’ security strategy. These are the kube-apiserver, etcd, kube-scheduler, kube-controller-manager and cloud-controller-manager. It will then provide recommendations on how organizations can secure each of these components.
kube-apiserver
What it is
Per Kubernetes’ documentation, kube-apiserver is
the front end for the Kubernetes control plane. It functions as the main
implementation of a Kubernetes API server. Organizations can scale
kube-apiserver horizontally by deploying more instances.
Why it needs to be secured
The Container Journal noted that attackers are
committed to scanning the web for publicly accessible API servers. Acknowledging
that reality, organizations need to make sure they don’t leave their
kube-apiserver instances publicly exposed. If they do, they could provide
attackers with an opening for compromising a Kubernetes cluster.
How to secure it
Administrators can follow the Container Journal’s advice by
configuring their API servers to allow cluster API access only via the internal
network or a corporate VPN. Once they’ve implemented that security measure, they
can use RBAC authorization to further limit who has access to the cluster. They
can enable this feature specifically via the kube-apiserver.
etcd
What it is
Kubernetes uses etcd as key value backing store for
cluster data. In order to use etcd, organizations need to have a backup plan for
the highly sensitive configuration data that they’d like to protect with this
store.
Why it needs to be secured
As with kube-apiserver, organizations might
accidentally leave etcd exposed to the Internet. The New Stack covered the work
of one software developer who conducted a search on Shodan to look for exposed
etcd servers. This investigation uncovered 2,284 etcd servers that malicious
actors could access through the Internet.
How to secure it
Kubernetes notes in its cluster administration resources
that etcd is equivalent to root permission in the cluster. In response,
administrators should grant permission to only the nodes that require access to
etcd clusters. They should also use firewall rules as well as the feature’s
inherent security features, notably peer.key/peer.cert and
client.key/client.cert, to secure communications between etcd members as well as
between etcd and its clients.
kube-scheduler
What it is
The kube-scheduler is a component within the
control plane that watches for the creation of new pods with no assigned node.
If it detects such a pod, it selects a node for them to run on. It makes these
decisions by taking individual and collective resource requirements, data
locality and other considerations into consideration, per Kubernetes’ website.
Why it needs to be secured
Any compromise involving the kube-scheduler could
affect the performance and availability of a cluster’s pods, explains Packt.
Such an event could thereby cause disruptions in an organization’s Kubernetes
environment that undermines business productivity.
How to secure it
Administrators can follow Packt’s advise to secure the
kube-scheduler by disabling profiling, a feature which exposes system details.
They can do this by setting the “–profiling” setting to “false.” Additionally,
they can disable external connections to kube-scheduler using the
“AllowExtTrafficLocalEndpoints” configuration to prevent outside attackers from
gaining access to this control plane component.
kube-controller-manager
What it is
This particular component lives up to
its name in that it runs controller processes. Each of those processes,
including those run by the node controller, replication controller and others,
are separate processes. However, the kube-controller-manager compiles all of
those processes and runs them together.
Why it needs to be secured
A security issue in the kube-controller-manager
could negatively affect the scalability and resilience of applications that are
running in the cluster. Such an event could thus have an effect on the
organization’s business.
How to secure it
Organizations can secure the kube-controller-manager by
monitoring the number of instances that they have of this feature deployed in
their environments. They can also follow the recommendations that StackRox made
in September 2020 by restricting the feature’s file permissions, configuring to
serve only HTTPs, binding it to a localhost interfact and using Kubernetes RBAC
to allow access to individual service accounts per controller.
cloud-controller-manager
What is it?
Last but not least, the
cloud-controller-manager enables administrators to link their cluster into their
Cloud Service Provider’s (CSP’s) API. They can then use that feature to separate
out elements that interact with the CSP’s cloud platform from those that
interact with the cluster. Per Kubernetes’ documentation,
cloud-controller-manager functions similarly to kube-controller-manager in its
ability to compile multiple processes into one. The difference is that the
cloud-controller-manager runs controllers that are specific to an organization’s
CSP only.
Why it needs to be secured
Issues involving the cloud-controller-manager pose
a similar threat to organizations as those that affect the
kube-controller-manager.
How to secure it
Acknowledging the similarities between
kube-controller-managers and cloud-controller-managers, organizations can use
the same measures to secure both.
The Security Work Doesn’t End There
The five control plane components
discussed above all demand attention as part of an organization’s overall
Kubernetes security efforts. Even so, organizations’ work to secure their
Kubernetes architecture doesn’t end there. There are also the Node components.
Bug-Bounty Awards Spike 26% in 2020
30.10.20 Security Threatpost
The most-rewarded flaw is XSS, which is among those that are relatively cheap for organizations to identify.
Cross-site scripting (XSS) remained the most impactful vulnerability and thus the one reaping the highest rewards for ethical hackers in 2020 for a second year running, according to a list of top 10 vulnerabilities released on Thursday by HackerOne.
The vulnerability — which enables attackers to inject client-side scripts into web pages viewed by other users — earned hackers $4.2 million in total bug-bounty awards in the last year, a 26-percent increase from what was paid out in 2019 for finding XSS flaws, according to the report.
Following XSS on the ethical hacking company’s list of “Top 10 Most Impactful and Rewarded Vulnerability Types of 2020” are: Improper access control, information disclosure, server-side request forgery (SSRF), insecure direct object reference (IDOR), privilege escalation, SQL injection, improper authentication, code injection and cross-site request forgery (CSRF).
In total, organizations paid ethical hackers $23.5 million in bug bounties for all of these flaws this year, according to HackerOne, which maintains a database of 200,000 vulnerabilities found by hackers.
Attackers use XSS vulnerabilities to gain control of an online user’s account and steal personal information such as passwords, bank account numbers, credit card info, personally identifiable information (PII), Social Security numbers and the like. While they account for 18 percent of all reported vulnerabilities, ethical hackers are actually underpaid for finding them, according to HackerOne.
A bug-bounty award for an XSS flaw is about $501, well below the $3,650 average award for a critical flaw, allowing organizations to mitigate the common bug on the cheap, researchers noted.
Indeed, researchers found that the more common a vulnerability is, the less ethical hackers are paid — and thus the less that organizations pay out — to locate and mitigate it, observed HackerOne senior director of product management, Miju Han.
“Finding the most common vulnerability types is inexpensive,” he said in a press statement, noting that only three of the top 10 vulnerabilities on the list — improper access control, server-side request forgery (SSRF) and information disclosure — saw their average bounty awards rise more than 10 percent over the course of the year.
This demonstrates that using ethical hackers to sniff out bugs potentially can be a more cost-effective value proposition for organizations than implementing “traditional security tools and methods, which become more expensive and cumbersome as goals change and attack surface expands,” Han said.
Of the vulnerabilities that saw their stock rise in 2020, improper access control rose from ninth place to second, and information disclosure, which held steady in third place for commonality, became more valuable on the bug-bounty market, researchers noted.
Awards for improper access control increased 134 percent year over year to slightly more than $4 million, while bug bounties for information disclosure rose 63 percent year over year.
Because access-control design decisions have to be made by humans, not technology, the potential for errors is high, researchers said. These flaws also are nearly impossible to detect using automated tools, which makes an ethical hacker’s ability to identify them more valuable, they said.
Indeed, even large tech companies who were historically resistant to being transparent about their product’s security protocols have warmed to the idea of awarding ethical hackers for their work. Both Apple and ByteDance’s TikTok rolled out public, award-based bug-bounty programs in the last 12 months.
Han noted that the boost in interest in ethical hacking in 2020 also has come due to the increased digitalization of organizations’ products and services due to the COVID-19 pandemic and its stay-at-home orders.
“Businesses scrambled to find new revenue streams, creating digital offerings for customers whose lifestyles had dramatically changed,” he said in the statement. “Tens of millions of workers started working remotely whether or not they were ready.”
This “accelerated pace of digital transformation” gave security leaders a new perspective on using ethical hacking to augment existing security resources, making them more willing to support a pay-for-results-based
Amazon Fires Employee Who Leaked Customer Names, Emails
28.10.20
Security
Threatpost
Amazon notified customers and law enforcement of the insider-threat incident this week.
Amazon has fired an employee who shared customers’ names and email addresses with a third party.
An Amazon spokesperson told Threatpost that it has systems in place to limit and control access to information, and processes in place for identifying and investigating suspicious behavior. These systems notified Amazon of “suspicious behavior.” After the company investigated the incident, it fired the employee, referred them to law enforcement and is working with law enforcement in their criminal prosecution.
“No other information related to your account was shared,” according to the note, shared on Twitter by several Amazon customers. “This is not a result of anything you have done and there is no need for you to take any action. We apologize for this incident.”
Amazon did not comment on an inquiry from Threatpost asking how many customers
were impacted, and what the role of the Amazon employee was.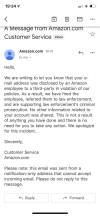
“It is critical for businesses to recognize that threats from legitimate users have always been more elusive and harder to detect or prevent than traditional external threats,” said Orion Cassetto, director of product marketing at Exabeam, in an emailed statement. “Though the extent of the leak is currently unknown, a number of Amazon customers have been notified that their email addresses have been passed on to a third-party by an employee, which has resulted in their termination. Organizations must be armed with the tools to prevent threats from within their walls from launching attacks.”
Researchers for their part say that a combination of training, organizational alignment and technology can help companies prevent insider threats. Behavioral analytics tools are one type preventative technology that tracks, collects and analyzes user data to detect threats, said Cassetto.
“This is typically done by collecting data over a period of time to understand what normal user behavior looks like, then flagging behavior that does not fit that pattern,” said Cassetto. “It can often spot unusual online behaviors – credential abuse, unusual access patterns, large data uploads – that are telltale signs of insider threats. More importantly, it can often spot these unusual behaviors among compromised insiders long before criminals have gained access to critical systems.”
Insider threats continue to plague tech companies. Last year, Trend Micro said that a rogue employee sold the data of 68,000 customers to a malicious third party, who then used that data to target customers with scam calls. In May 2019, a report outlined how Snap employees were abusing their access to private user data – which includes location data, saved Snaps and phone numbers. And a report in 2018 found that Facebook had fired an employee who allegedly abused access privileges to data to stalk women.