17.3.24 Virus The Hacker News
Hackers Using Cracked Software on GitHub to Spread RisePro Info Stealer
17.3.24 Virus The Hacker News
Cybersecurity researchers have found a number of GitHub repositories offering cracked software that are used to deliver an information stealer called RisePro.
The campaign, codenamed gitgub, includes 17 repositories associated with 11 different accounts, according to G DATA. The repositories in question have since been taken down by the Microsoft-owned subsidiary.
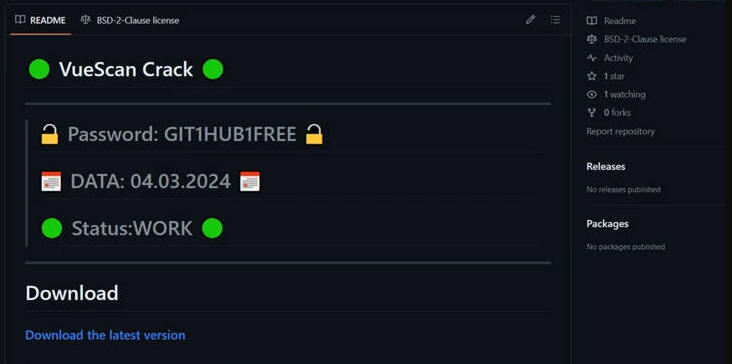
"The repositories look similar, featuring a README.md file with the promise of free cracked software," the German cybersecurity company said.
"Green and red circles are commonly used on Github to display the status of automatic builds. Gitgub threat actors added four green Unicode circles to their README.md that pretend to display a status alongside a current date and provide a sense of legitimacy and recency."
The list of repositories is as follows, with each of them pointing to a download link ("digitalxnetwork[.]com") containing a RAR archive file -
andreastanaj/AVAST
andreastanaj/Sound-Booster
aymenkort1990/fabfilter
BenWebsite/-IObit-Smart-Defrag-Crack
Faharnaqvi/VueScan-Crack
javisolis123/Voicemod
lolusuary/AOMEI-Backupper
lolusuary/Daemon-Tools
lolusuary/EaseUS-Partition-Master
lolusuary/SOOTHE-2
mostofakamaljoy/ccleaner
rik0v/ManyCam
Roccinhu/Tenorshare-Reiboot
Roccinhu/Tenorshare-iCareFone
True-Oblivion/AOMEI-Partition-Assistant
vaibhavshiledar/droidkit
vaibhavshiledar/TOON-BOOM-HARMONY
The RAR archive, which requires the victims to supply a password mentioned in the repository's README.md file, contains an installer file, which unpacks the next-stage payload, an executable file that's inflated to 699 MB in an effort to crash analysis tools like IDA Pro.
The actual contents of the file – amounting to a mere 3.43 MB – act as a loader to inject RisePro (version 1.6) into either AppLaunch.exe or RegAsm.exe.
RisePro burst into the spotlight in late 2022 when it was distributed using a pay-per-install (PPI) malware downloader service known as PrivateLoader.
Written in C++, it's designed to gather sensitive information from infected hosts and exfiltrate it to two Telegram channels, which are often used by threat actors to extract victims' data. Interestingly, recent research from Checkmarx showed that it's possible to infiltrate and forward messages from an attacker's bot to another Telegram account.
The development comes as Splunk detailed the tactics and techniques adopted by Snake Keylogger, describing it as a stealer malware that "employs a multifaceted approach to data exfiltration."
"The use of FTP facilitates the secure transfer of files, while SMTP enables the sending of emails containing sensitive information," Splunk said. "Additionally, integration with Telegram offers a real-time communication platform, allowing for immediate transmission of stolen data."
Stealer malware have become increasingly popular, often becoming the primary vector for ransomware and other high impact data breaches. According to a report from Specops published this week, RedLine, Vidar, and Raccoon have emerged as the most widely-used stealers, with RedLine alone accounting for the theft of more than 170.3 million passwords in the last six months.
"The current rise of information-stealing malware is a stark reminder of constantly evolving digital threats," Flashpoint noted in January 2024. "While the motivations behind its use is almost always rooted in financial gain, stealers are continually adapting while being more accessible and easier to use."