In Q1 2020, Kaspersky’s mobile products and technologies detected 1,152,662 malicious installation packages, or 171,669 more than in the previous quarter.
IT threat evolution Q1 2020. Statistics
20.5.2020 Securelist Analysis
These statistics are based on detection verdicts for Kaspersky products received from users who consented to providing statistical data.
Quarterly figures
According to Kaspersky Security Network,
Kaspersky solutions blocked 726,536,269 attacks launched from online resources in 203 countries across the globe.
A total of 442,039,230 unique URLs were recognized as malicious by Web Anti-Virus components.
Attempted infections by malware designed to steal money via online access to bank accounts were logged on the computers of 249,748 unique users.
Ransomware attacks were defeated on the computers of 178,922 unique users.
Our File Anti-Virus detected 164,653,290 unique malicious and potentially unwanted objects.
Kaspersky products for mobile devices detected:
1,152,662 malicious installation packages
42,115 installation packages for mobile banking trojans
4339 installation packages for mobile ransomware trojans
Mobile threats
Quarter events
Q1 2020 will be remembered primarily for the coronavirus pandemic and cybercriminals’ exploitation of the topic. In particular, the creators of a new modification of the Ginp banking trojan renamed their malware Coronavirus Finder and then began offering it for €0.75 disguised as an app supposedly capable of detecting nearby people infected with COVID-19. Thus, the cybercriminals tried not only to scam users by exploiting hot topics, but to gain access to their bank card details. And, because the trojan remains on the device after stealing this data, the cybercriminals could intercept text messages containing two-factor authorization codes and use the stolen data without the victim’s knowledge.
Another interesting find this quarter was Cookiethief, a trojan designed to steal cookies from mobile browsers and the Facebook app. In the event of a successful attack, the malware provided its handler with access to the victim’s account, including the ability to perform various actions in their name, such as liking, reposting, etc. To prevent the service from spotting any abnormal activity in the hijacked profile, the trojan contains a proxy module through which the attackers issue commands.
The third piece of malware that caught our attention this reporting quarter was trojan-Dropper.AndroidOS.Shopper.a. It is designed to help cybercriminals to leave fake reviews and drive up ratings on Google Play. The attackers’ goals here are obvious: to increase the changes of their apps getting published and recommended, and to lull the vigilance of potential victims. Note that to rate apps and write reviews, the trojan uses Accessibility Services to gain full control over the other app: in this case, the official Google Play client.
Mobile threat statistics
In Q1 2020, Kaspersky’s mobile products and technologies detected 1,152,662 malicious installation packages, or 171,669 more than in the previous quarter.
Number of malicious installation packages detected, Q1 2019 – Q1 2020 (download)
Starting in Q2 2019, we have seen a steady rise in the number of mobile threats detected. Although it is too early to sound the alarm (2019 saw the lowest number of new threats in recent years), the trend is concerning.
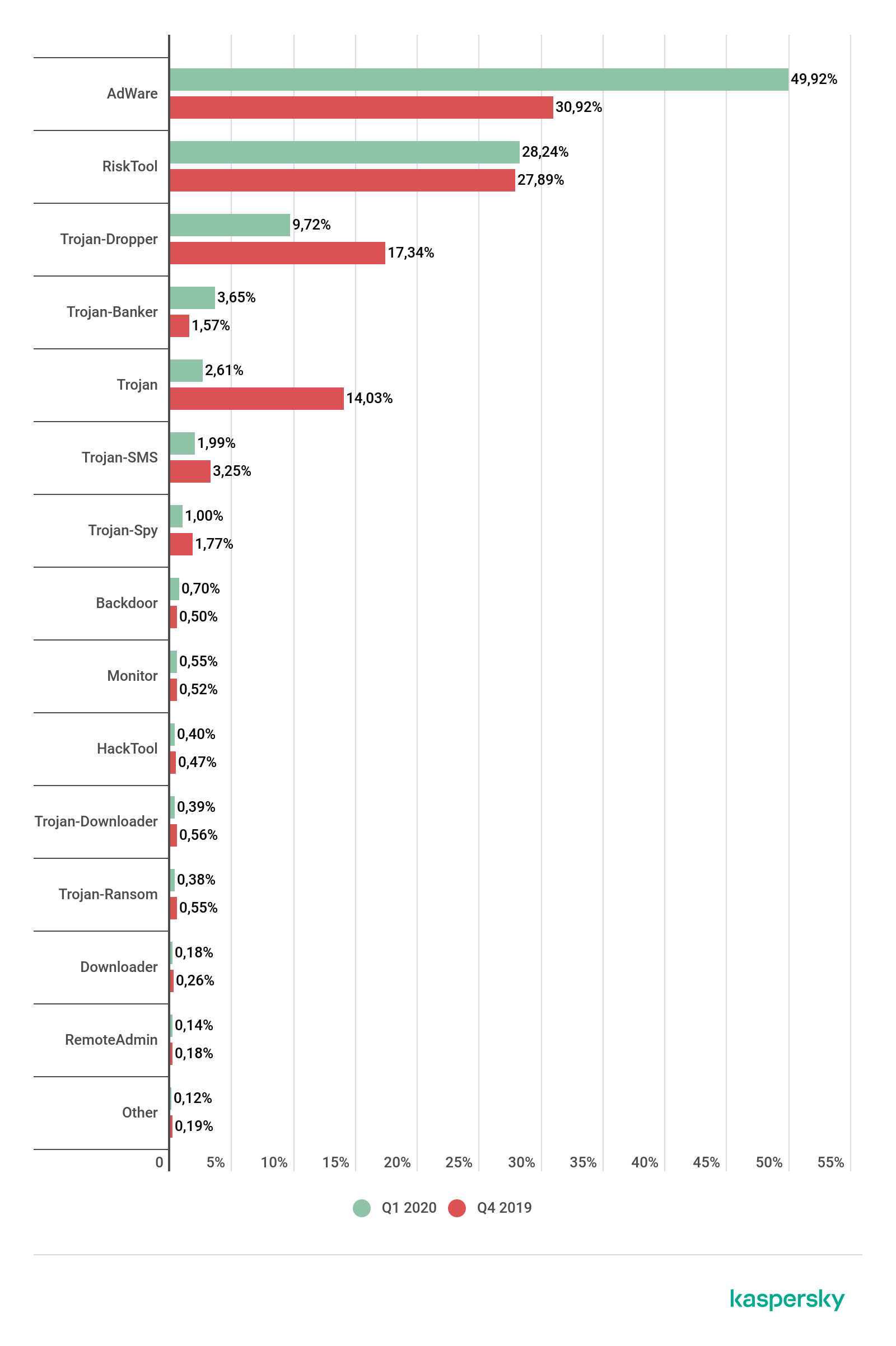
Distribution of detected mobile apps by type
Distribution of newly detected mobile programs by type, Q1 2020 and Q4 2019 (download)
Of all the threats detected in Q1, half were unwanted adware apps (49.9%), their share having increased by 19 p.p. compared to the previous quarter. Most often, we detected members of the HiddenAd and Ewind families, with a combined slice of 40% of all detected adware threats, as well as the FakeAdBlocker family (12%).
Potentially unwanted RiskTool apps (28.24%) took second place; the share of this type of threat remained almost unchanged. The Smsreg (49% of all detected threats of this class), Agent (17%) and Dnotua (11%) families were the biggest contributors. Note that in Q1, the number of detected members of the Smsreg family increased by more than 50 percent.
In third place were Trojan-Dropper-type threats (9.72%). Although their share decreased by 7.63 p.p. against the previous quarter, droppers remain one of the most common classes of mobile threats. Ingopack emerged as Q1’s leading family with a massive 71% of all Trojan-Dropper threats, followed by Waponor (12%) and Hqwar (8%) far behind.
It is worth noting that mobile droppers are most often used for installing financial malware, although some financial threats can spread without their help. The share of these self-sufficient threats is quite substantial: in particular, the share of Trojan-Banker in Q1 increased by 2.1 p.p. to 3.65%.
Top 20 mobile malware programs
Note that this malware rankings do not include potentially dangerous or unwanted programs such as RiskTool or adware.
Verdict %*
1 DangerousObject.Multi.Generic 44.89
2 Trojan.AndroidOS.Boogr.gsh 9.09
3 DangerousObject.AndroidOS.GenericML 7.08
4 Trojan-Downloader.AndroidOS.Necro.d 4.52
5 Trojan.AndroidOS.Hiddapp.ch 2.73
6 Trojan-Downloader.AndroidOS.Helper.a 2.45
7 Trojan.AndroidOS.Handda.san 2.31
8 Trojan-Dropper.AndroidOS.Necro.z 2.30
9 Trojan.AndroidOS.Necro.a 2.19
10 Trojan-Downloader.AndroidOS.Necro.b 1.94
11 Trojan-Dropper.AndroidOS.Hqwar.gen 1.82
12 Trojan-Dropper.AndroidOS.Helper.l 1.50
13 Exploit.AndroidOS.Lotoor.be 1.46
14 Trojan-Dropper.AndroidOS.Lezok.p 1.46
15 Trojan-Banker.AndroidOS.Rotexy.e 1.43
16 Trojan-Dropper.AndroidOS.Penguin.e 1.42
17 Trojan-SMS.AndroidOS.Prizmes.a 1.39
18 Trojan.AndroidOS.Dvmap.a 1.24
19 Trojan.AndroidOS.Agent.rt 1.21
20 Trojan.AndroidOS.Vdloader.a 1.18
* Unique users attacked by this malware as a percentage of all users of Kaspersky mobile products that were attacked.
First place in our Top 20 as ever went to DangerousObject.Multi.Generic (44.89%), the verdict we use for malware detected using cloud technology. They are triggered when the antivirus databases still lack the data for detecting a malicious program, but the Kaspersky Security Network cloud already contains information about the object. This is basically how the latest malware is detected.
Second and third places were claimed by Trojan.AndroidOS.Boogr.gsh (9.09%) and DangerousObject.AndroidOS.GenericML (7,08%) respectively. These verdicts are assigned to files that are recognized as malicious by our machine-learning systems.
In fourth (Trojan-Downloader.AndroidOS.Necro.d, 4.52%) and tenth (Trojan-Downloader.AndroidOS.Necro.b, 1.94%) places are members of the Necro family, whose main task is to download and install modules from cybercriminal servers. Eighth-placed Trojan-Dropper.AndroidOS.Necro.z (2.30%) acts in a similar way, extracting from itself only those modules that it needs. As for Trojan.AndroidOS.Necro.a, which took ninth place (2.19%), cybercriminals assigned it a different task: the trojan follows advertising links and clicks banner ads in the victim’s name.
Trojan.AndroidOS.Hiddapp.ch (2.73%) claimed fifth spot. As soon as it runs, the malware hides its icon on the list of apps and continues to operate in the background. The trojan’s payload can be other trojan programs or adware apps.
Sixth place went to Trojan-Downloader.AndroidOS.Helper.a (2.45%), which is what Trojan-Downloader.AndroidOS.Necro usually delivers. Helper.a is tasked with downloading arbitrary code from the cybercriminals’ server and running it.
The verdict Trojan.AndroidOS.Handda.san (2.31%) in seventh place is a group of diverse trojans that hide their icons, gain Device Admin rights on the device, and use packers to evade detection.
Trojan-Banker.AndroidOS.Rotexy.e (1.43%) and Trojan-Dropper.AndroidOS.Penguin.e (1.42%) warrant a special mention. The former is the only banking trojan in the top 20 this past quarter. The Rotexy family is all of six years old, and its members have the functionality to steal bank card details and intercept two-factor payment authorization messages. In turn, the first member of the Penguin dropper family was only detected last July and had gained significant popularity by Q1 2020.
Geography of mobile threats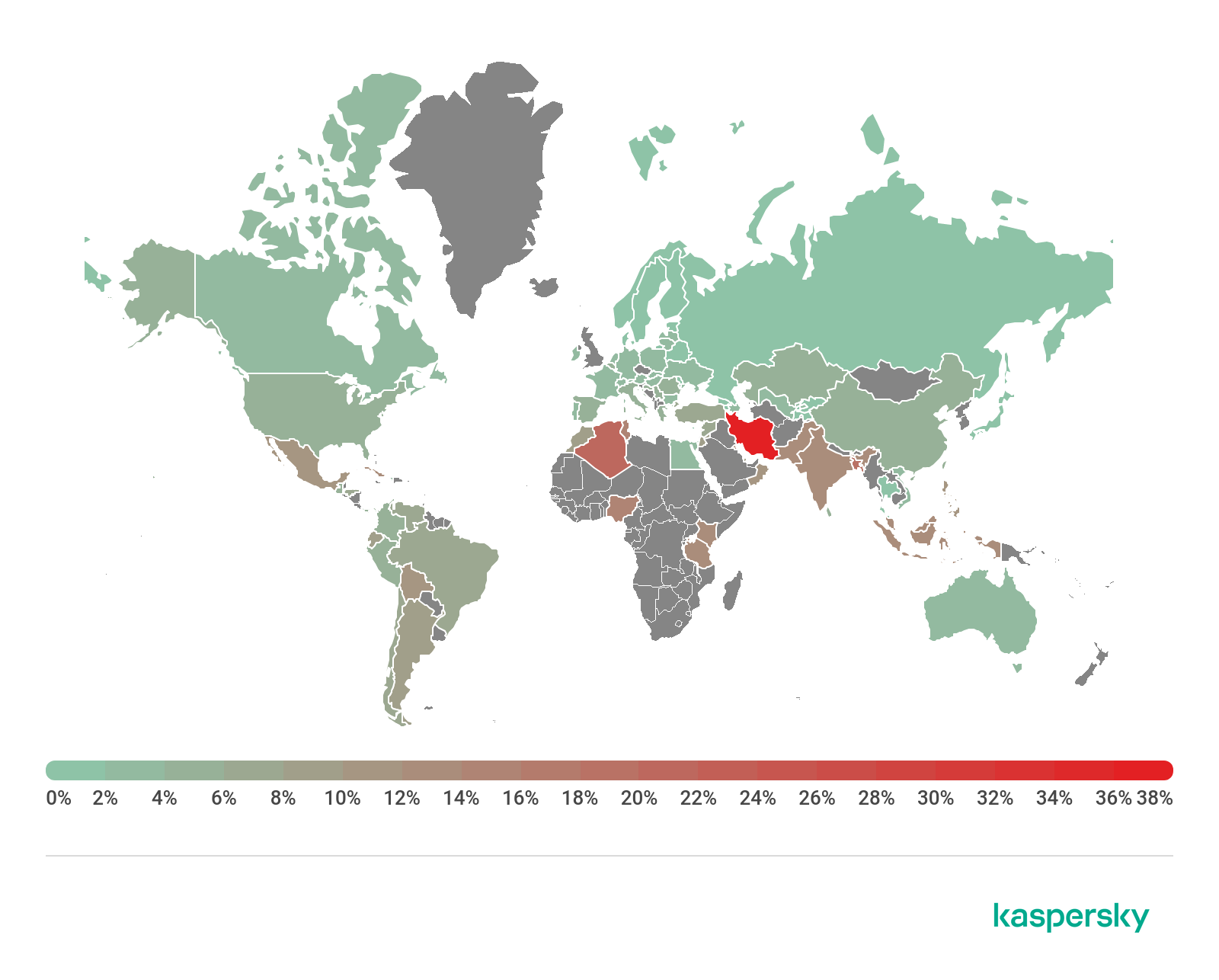
Map of infection attempts by mobile malware, Q1 2020 (download)
Top 10 countries by share of users attacked by mobile threats
Country* %**
1 Iran 39.56
2 Algeria 21.44
3 Bangladesh 18.58
4 Nigeria 15.58
5 Lebanon 15.28
6 Tunisia 14.94
7 Pakistan 13.99
8 Kuwait 13.91
9 Indonesia 13.81
10 Cuba 13.62
* Excluded from the rankings are countries with relatively few users of Kaspersky mobile products (under 10,000).
** Unique users attacked as a percentage of all users of Kaspersky mobile products in the country.
In Q1 2020, the leader by share of attacked users was Iran (39.56%). Inhabitants of this country most frequently encountered adware apps from the Notifyer family, as well as Telegram clone apps. In second place was Algeria (21.44%), where adware apps were also distributed, but this time it was the HiddenAd and FakeAdBlocker families. Third place was taken by Bangladesh (18.58%), where half of the top 10 mobile threats consisted of adware in the HiddenAd family.
Mobile banking trojans
During the reporting period, we detected 42,115 installation packages of mobile banking trojans. This is the highest value in the past 18 months, and more than 2.5 times higher than in Q4 2019. The largest contributions to the statistics came from the Trojan-Banker.AndroidOS.Agent (42.79% of all installation packages detected), Trojan-Banker.AndroidOS.Wroba (16.61%), and Trojan-Banker.AndroidOS.Svpeng (13.66%) families.
Number of installation packages of mobile banking trojans detected by Kaspersky, Q1 2019 – Q1 2020 (download)
Top 10 mobile banking trojans
Verdict %*
1 Trojan-Banker.AndroidOS.Rotexy.e 13.11
2 Trojan-Banker.AndroidOS.Svpeng.q 10.25
3 Trojan-Banker.AndroidOS.Asacub.snt 7.64
4 Trojan-Banker.AndroidOS.Asacub.ce 6.31
5 Trojan-Banker.AndroidOS.Agent.eq 5.70
6 Trojan-Banker.AndroidOS.Anubis.san 4.68
7 Trojan-Banker.AndroidOS.Agent.ep 3.65
8 Trojan-Banker.AndroidOS.Asacub.a 3.50
9 Trojan-Banker.AndroidOS.Asacub.ar 3.00
10 Trojan-Banker.AndroidOS.Agent.cf 2.70
* Unique users attacked by this malware as a percentage of all users of Kaspersky mobile products who were attacked by banking threats.
First and second places in our top 10 were claimed by trojans targeted at Russian-speaking mobile users: Trojan-Banker.AndroidOS.Rotexy.e (13.11%) and Trojan-Banker.AndroidOS.Svpeng.q (10.25%).
Third, fourth, eighth, and ninth positions in the top 10 mobile banking threats went to members of the Asacub family. The cybercriminals behind this trojan stopped creating new samples, but its distribution channels were still active in Q1.
Geography of mobile banking threats, Q1 2020 (download)
Top 10 countries by share of users attacked by mobile banking trojans
Country* %**
1 Japan 0.57
2 Spain 0.48
3 Italy 0.26
4 Bolivia 0.18
5 Russia 0.17
6 Turkey 0.13
7 Tajikistan 0.13
8 Brazil 0.11
9 Cuba 0.11
10 China 0.10
* Excluded from the rankings are countries with relatively few users of Kaspersky mobile products (under 10,000).
** Unique users attacked by mobile banking trojans as a percentage of all users of Kaspersky mobile products in the country.
In Q1 2020, Japan (0.57%) had the largest share of users attacked by mobile bankers; the vast majority of cases involved Trojan-Banker.AndroidOS.Agent.eq.
In second place came Spain (0.48%), where in more than half of all cases, we detected malware from the Trojan-Banker.AndroidOS.Cebruser family, and another quarter of detections were members of the Trojan-Banker.AndroidOS.Ginp family.
Third place belonged to Italy (0.26%), where, as in Spain, the Trojan-Banker.AndroidOS.Cebruser family was the most widespread with almost two-thirds of detections.
It is worth saying a bit more about the Cebruser family. Its creators were among the first to exploit the coronavirus topic to spread the malware.

When it runs, the trojan immediately gets down to business: it requests access to Accessibility Services to obtain Device Admin permissions, and then tries to get hold of card details.
The malware is distributed under the Malware-as-a-Service model; its set of functions is standard for such threats, but with one interesting detail — the use of a step-counter for activation so as to bypass dynamic analysis tools (sandbox). Cebruser targets the mobile apps of banks in various countries and popular non-financial apps; its main weapons are phishing windows and interception of two-factor authorization. In addition, the malware can block the screen using a ransomware tool and intercept keystrokes on the virtual keyboard.
Mobile ransomware trojans
In Q2 2020, we detected 4,339 installation packages of mobile trojan ransomware, 1,067 fewer than in the previous quarter.
Number of installation packages of mobile ransomware trojans detected by Kaspersky, Q1 2019 – Q1 2020 (download)
Top 10 mobile ransomware trojans
Verdict %*
1 Trojan-Ransom.AndroidOS.Svpeng.aj 17.08
2 Trojan-Ransom.AndroidOS.Congur.e 12.70
3 Trojan-Ransom.AndroidOS.Small.as 11.41
4 Trojan-Ransom.AndroidOS.Rkor.k 9.88
5 Trojan-Ransom.AndroidOS.Small.as 7.32
6 Trojan-Ransom.AndroidOS.Small.o 4.79
7 Trojan-Ransom.AndroidOS.Svpeng.aj 3.62
8 Trojan-Ransom.AndroidOS.Svpeng.ah 3.55
9 Trojan-Ransom.AndroidOS.Congur.e 3.32
10 Trojan-Ransom.AndroidOS.Fusob.h 3.17
* Unique users attacked by this malware as a percentage of all users of Kaspersky mobile products who were attacked by ransomware trojans.
Over the past few quarters, the number of ransomware trojans detected has been gradually decreasing; all the same, we continue to detect quite a few infection attempts by this class of threats. The main contributors to the statistics were the Svpeng, Congur, and Small ransomware families.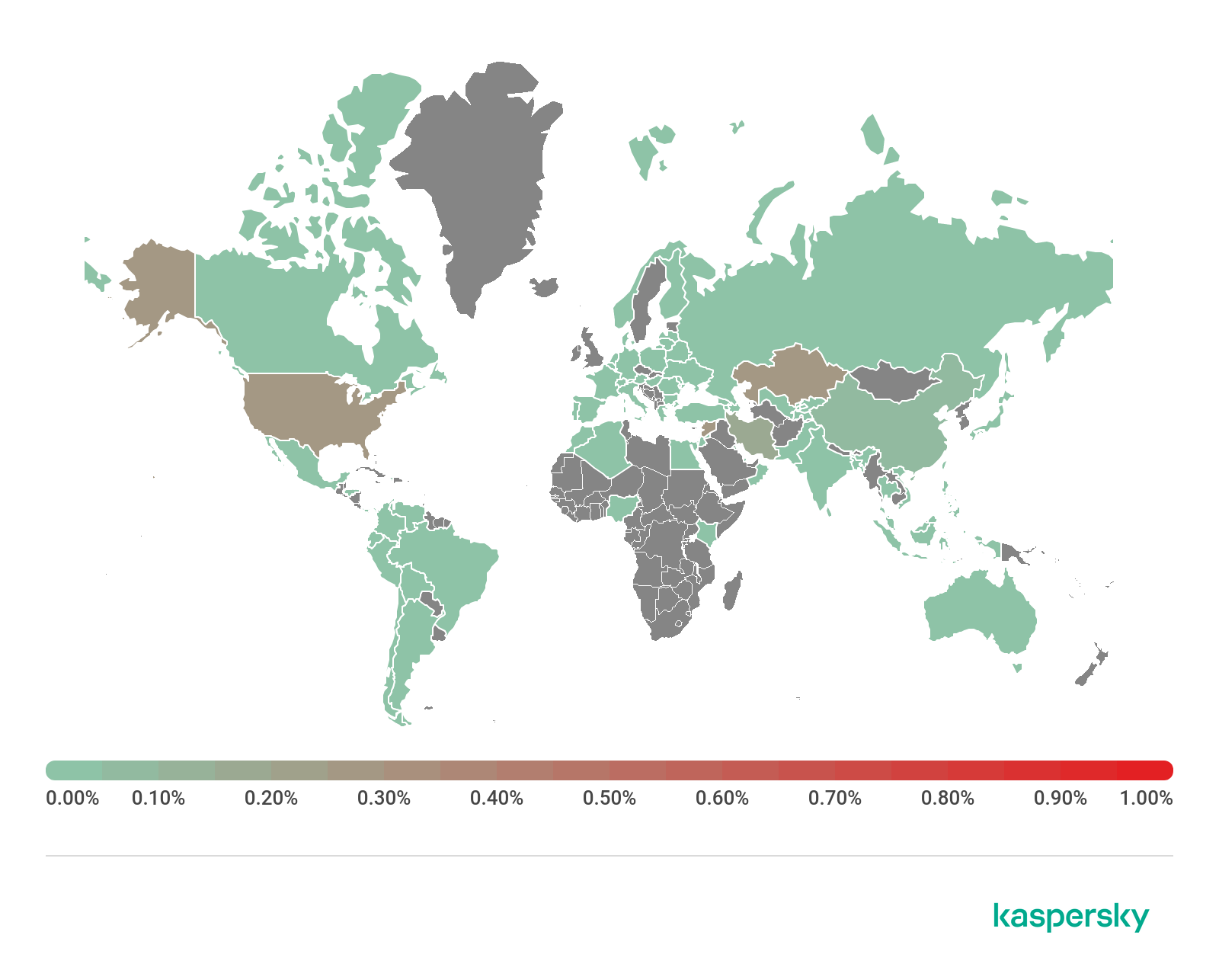
Geography of mobile ransomware trojans, Q1 2020 (download)
Top 10 countries by share of users attacked by mobile ransomware trojans:
Country* %**
1 USA 0.26
2 Kazakhstan 0.25
3 Iran 0.16
4 China 0.09
5 Saudi Arabia 0.08
6 Italy 0.03
7 Mexico 0.03
8 Canada 0.03
9 Indonesia 0.03
10 Switzerland 0.03
* Excluded from the rankings are countries with relatively few users of Kaspersky mobile products (under 10,000).
** Unique users attacked by mobile ransomware trojans as a percentage of all users of Kaspersky mobile products in the country.
The leaders by number of users attacked by mobile ransomware trojans are Syria (0.28%), the United States (0.26%) and Kazakhstan (0.25%)
Attacks on Apple macOS
In Q1 2020, we detected not only new versions of common threats, but one new backdoor family, whose first member was Backdoor.OSX.Capip.a. The malware’s operating principle is simple: it calls the C&C for a shell script, which it then downloads and executes.
Top 20 threats to macOS
Verdict %*
1 Trojan-Downloader.OSX.Shlayer.a 19.27
2 AdWare.OSX.Pirrit.j 10.34
3 AdWare.OSX.Cimpli.k 6.69
4 AdWare.OSX.Ketin.h 6.27
5 AdWare.OSX.Pirrit.aa 5.75
6 AdWare.OSX.Pirrit.o 5.74
7 AdWare.OSX.Pirrit.x 5.18
8 AdWare.OSX.Spc.a 4.56
9 AdWare.OSX.Cimpli.f 4.25
10 AdWare.OSX.Bnodlero.t 4.08
11 AdWare.OSX.Bnodlero.x 3.74
12 Hoax.OSX.SuperClean.gen 3.71
13 AdWare.OSX.Cimpli.h 3.37
14 AdWare.OSX.Pirrit.v 3.30
15 AdWare.OSX.Amc.c 2.98
16 AdWare.OSX.MacSearch.d 2.85
17 RiskTool.OSX.Spigot.a 2.84
18 AdWare.OSX.Pirrit.s 2.80
19 AdWare.OSX.Ketin.d 2.76
20 AdWare.OSX.Bnodlero.aq 2.70
* Unique users attacked by this malware as a percentage of all users of Kaspersky security solutions for macOS who were attacked
The top 20 threats for macOS did not undergo any major changes in Q1 2020. The adware trojan Shlayer.a (19.27%) still tops the leaderboard, followed by objects that Shlayer itself loads into the infected system, in particular, numerous adware apps from the Pirrit family.
Interestingly, the unwanted program Hoax.OSX.SuperClean.gen landed in 12th place on the list. Like other Hoax-type programs, it is distributed under the guise of a system cleanup app, and immediately after installation, scares the user with problems purportedly found in the system, such as gigabytes of trash on the hard drive.
Threat geography
Country* %**
1 Spain 7.14
2 France 6.94
3 Italy 5.94
4 Canada 5.58
5 USA 5.49
6 Russia 5.10
7 India 4.88
8 Mexico 4.78
9 Brazil 4.65
10 Belgium 4.65
* Excluded from the rankings are countries with relatively few users of Kaspersky security solutions for macOS (under 5,000)
** Unique users who encountered macOS threats as a percentage of all users of Kaspersky security solutions for macOS in the country.
The leading countries, as in previous quarters, were Spain (7.14%), France (6.94%) and Italy (5.94%). The main contributors to the number of detections in these countries were the familiar Shlayer trojan and adware apps from the Pirrit family.
IoT attacks
IoT threat statistics
In Q1 2020, the share of IP addresses from which attempts were made to attack Kaspersky telnet traps increased significantly. Their share amounted to 81.1% of all IP addresses from which attacks were carried out, while SSH traps accounted for slightly less than 19%.
SSH 18.9%
Telnet 81.1%
Distribution of attacked services by number of unique IP addresses of devices that carried out attacks, Q1 2020
It was a similar situation with control sessions: attackers often controlled infected traps via telnet.
SSH 39.62%
Telnet 60.38%
Distribution of cybercriminal working sessions with Kaspersky traps, Q1 2020
Telnet-based attacks
Geography of device IP addresses where attacks at Kaspersky telnet traps originated, Q1 2020 (download)
Top 10 countries by location of devices from which attacks were carried out on Kaspersky telnet traps.
Country* %
China 13.04
Egypt 11.65
Brazil 11.33
Vietnam 7.38
Taiwan 6.18
Russia 4.38
Iran 3.96
India 3.14
Turkey 3.00
USA 2.57
For several quarters in a row, the leading country by number of attacking bots has been China: in Q1 2020 its share stood at 13.04%. As before, it is followed by Egypt (11.65%) and Brazil (11.33%).
SSH-based attacks
Geography of device IP addresses where attacks at Kaspersky SSH traps originated, Q1 2020 (download)
Top 10 countries by location of devices from which attacks were made on Kaspersky SSH traps.
Country* %
China 14.87
Vietnam 11.58
USA 7.03
Egypt 6.82
Brazil 5.79
Russia 4.66
India 4.16
Germany 3.64
Thailand 3.44
France 2.83
In Q1 2020, China (14.87%), Vietnam (11.58%) and the US (7.03%) made up the top three countries by number of unique IPs from which attacks on SSH traps originated.
Threats loaded into honeypots
Verdict %*
Trojan-Downloader.Linux.NyaDrop.b 64.35
Backdoor.Linux.Mirai.b 16.75
Backdoor.Linux.Mirai.ba 6.47
Backdoor.Linux.Gafgyt.a 4.36
Backdoor.Linux.Gafgyt.bj 1.30
Trojan-Downloader.Shell.Agent.p 0.68
Backdoor.Linux.Mirai.c 0.64
Backdoor.Linux.Hajime.b 0.46
Backdoor.Linux.Mirai.h 0.40
Backdoor.Linux.Gafgyt.av 0.35
* Share of malware type in the total amount of malware downloaded to IoT devices following a successful attack.
In Q1 2020, attackers most often downloaded the minimalistic trojan loader NyaDrop (64.35%), whose executable file does not exceed 500 KB. Threats from the Mirai family traditionally dominated: its members claimed four places in our top 10. These malicious programs will continue to rule the world of IoT threats for a long time to come, at least until the appearance of a more advanced (and publicly available) DDoS bot.
Financial threats
Financial threat statistics
In Q1 2020, Kaspersky solutions blocked attempts to launch one or several types of malware designed to steal money from bank accounts on the computers of 249,748 users.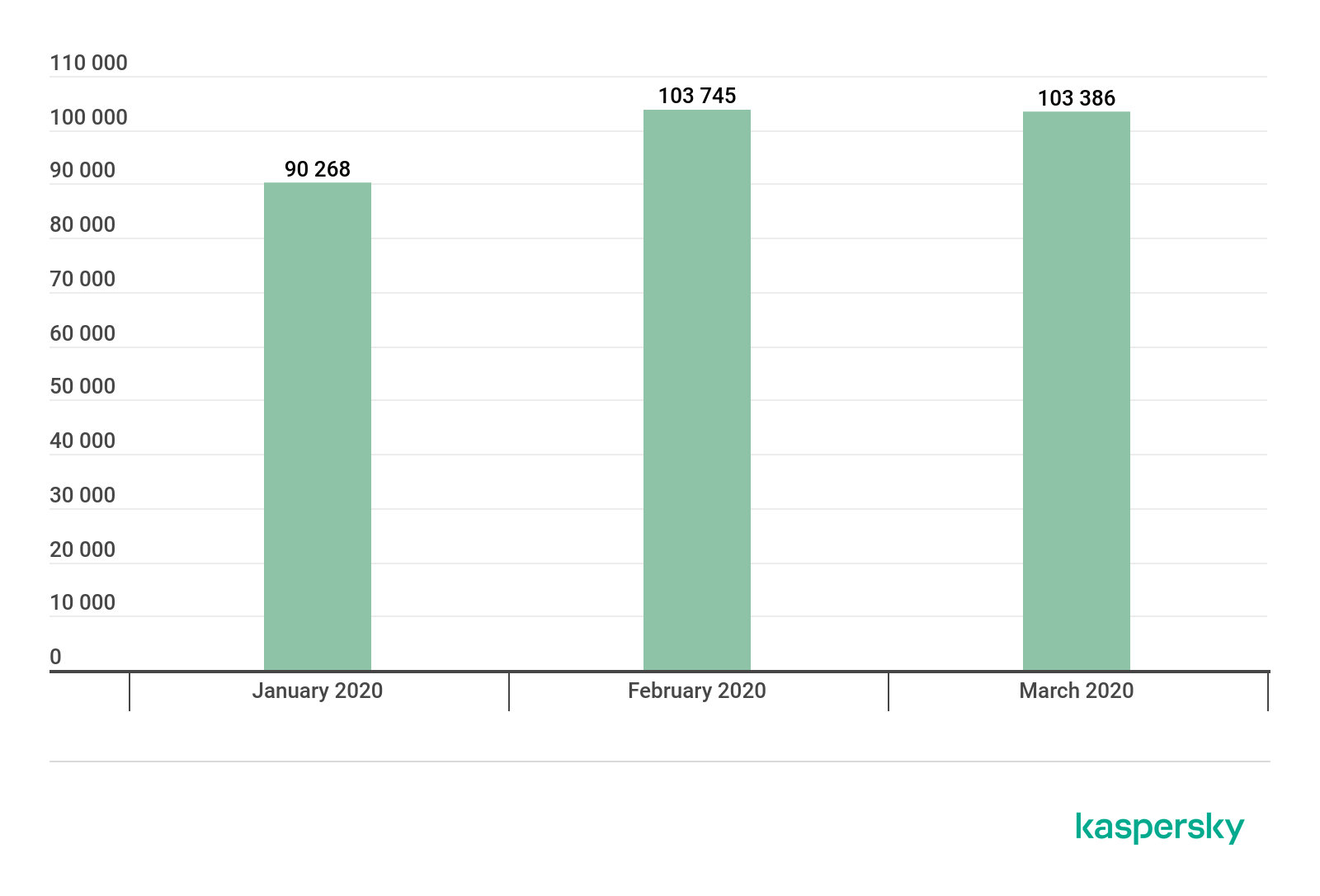
Number of unique users attacked by financial malware, Q1 2020 (download)
Attack geography
To assess and compare the risk of being infected by banking trojans and ATM/POS malware in various countries, for each country we calculated the share of users of Kaspersky products that faced this threat during the reporting period out of all users of our products in that country.
Geography of banking malware attacks, Q1 2020 (download)
Top 10 countries by share of attacked users
Country* %**
1 Uzbekistan 10.5
2 Tajikistan 6.9
3 Turkmenistan 5.5
4 Afghanistan 5.1
5 Yemen 3.1
6 Kazakhstan 3.0
7 Guatemala 2.8
8 Syria 2.4
9 Sudan 2.1
10 Kyrgyzstan 2.1
* Excluded are countries with relatively few Kaspersky product users (under 10,000).
** Unique users whose computers were targeted by financial malware as a percentage of all unique users of Kaspersky products in the country.
Top 10 banking malware families
Name Verdicts %*
1 Emotet Backdoor.Win32.Emotet 21.3
2 Zbot Trojan.Win32.Zbot 20.8
3 CliptoShuffler Trojan-Banker.Win32.CliptoShuffler 17.2
4 RTM Trojan-Banker.Win32.RTM 12.3
5 Nimnul Virus.Win32.Nimnul 3.6
6 Trickster Trojan.Win32.Trickster 3.6
7 Neurevt Trojan.Win32.Neurevt 3.3
8 SpyEye Trojan-Spy.Win32.SpyEye 2.3
9 Danabot Trojan-Banker.Win32.Danabot 2.0
10 Nymaim Trojan.Win32.Nymaim 1.9
** Unique users attacked by this malware family as a percentage of all users attacked by financial malware.
Ransomware programs
Quarterly highlights
Ransomware attacks on organizations, as well as on city and municipal networks, did not ease off. Given how lucrative they are for cybercriminals, there is no reason why this trend of several years should cease.
More and more ransomware is starting to supplement encryption with data theft. To date, this tactic has been adopted by distributors of ransomware families, including Maze, REvil/Sodinokibi, DoppelPaymer and JSWorm/Nemty/Nefilim. If the victim refuses to pay the ransom for decryption (because, say, the data was recovered from a backup copy), the attackers threaten to put the stolen confidential information in the public domain. Such threats are sometimes empty, but not always: the authors of several ransomware programs have set up websites that do indeed publish the data of victim organizations.
Number of new modifications
In Q1 2020, we detected five new ransomware families and 5,225 new modifications of these malware programs.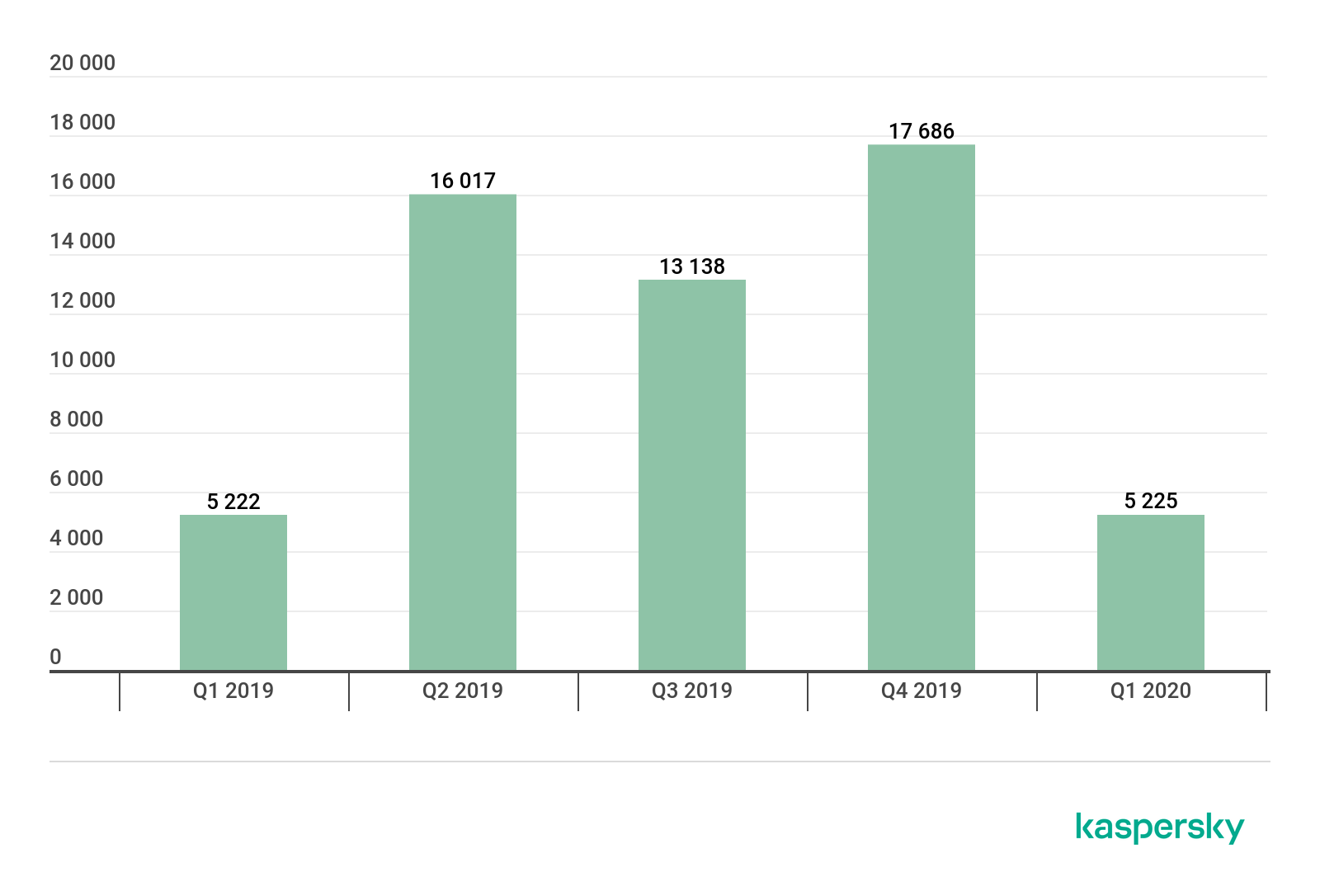
Number of new ransomware modifications detected, Q1 2019 – Q1 2020 (download)
Number of users attacked by ransomware trojans
In Q1 2020, Kaspersky products and technologies protected 178,922 users from ransomware attacks.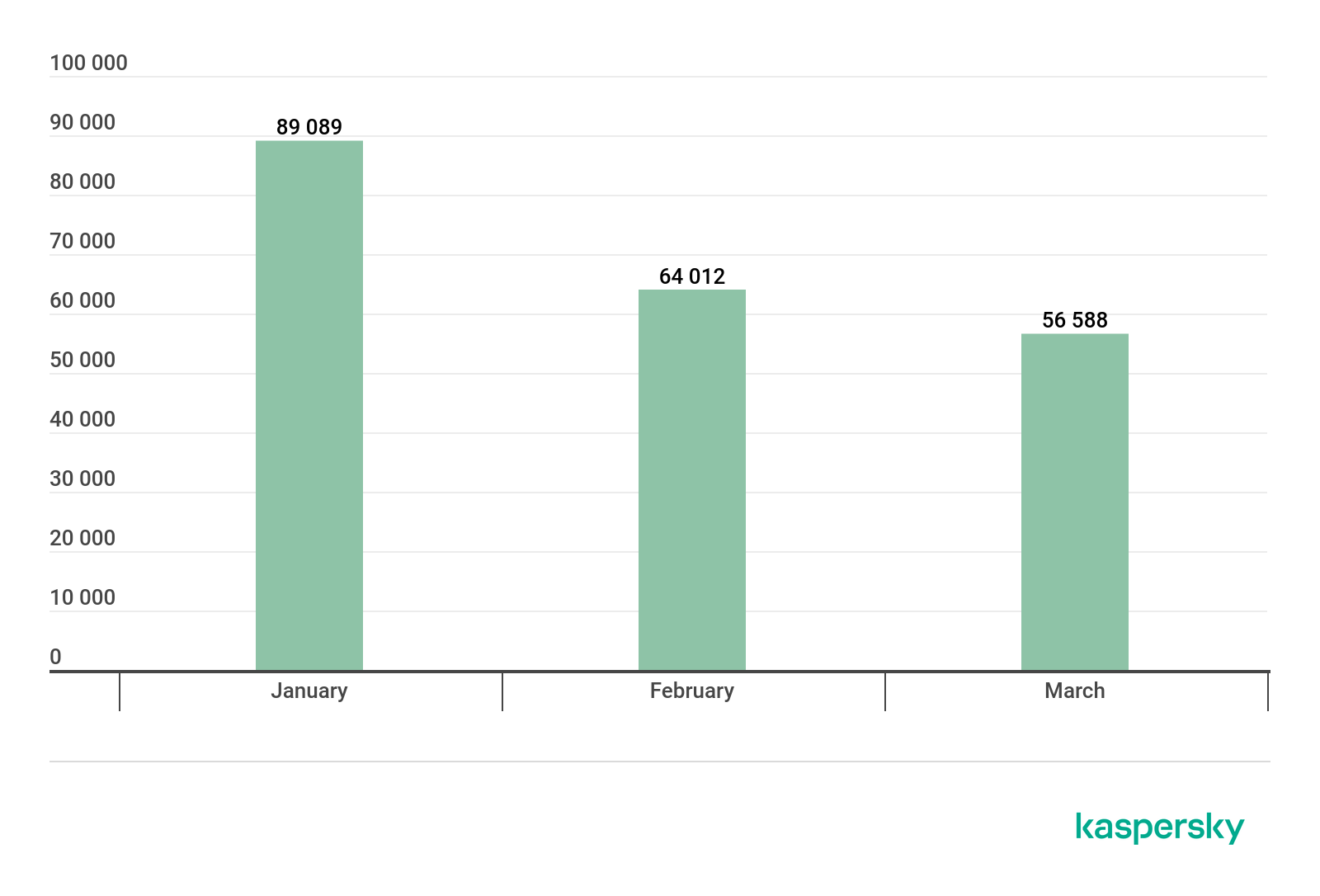
Number of unique users attacked by ransomware trojans, Q1 2020 (download)
Attack geography
Geography of attacks by ransomware trojans, Q1 2020 (download)
Top 10 countries attacked by ransomware trojans
Country* %**
1 Bangladesh 6.64
2 Uzbekistan 1.98
3 Mozambique 1.77
4 Ethiopia 1.67
5 Nepal 1.34
6 Afghanistan 1.31
7 Egypt 1.21
8 Ghana 0.83
9 Azerbaijan 0.81
10 Serbia 0.74
* Excluded are countries with relatively few Kaspersky users (under 50,000).
** Unique users whose computers were attacked by ransomware trojans as a percentage of all unique users of Kaspersky products in the country.
Top 10 most common families of ransomware trojans
Name Verdicts %*
1 WannaCry Trojan-Ransom.Win32.Wanna 19.03
2 (generic verdict) Trojan-Ransom.Win32.Gen 16.71
3 (generic verdict) Trojan-Ransom.Win32.Phny 16.22
4 GandCrab Trojan-Ransom.Win32.GandCrypt 7.73
5 Stop Trojan-Ransom.Win32.Stop 6.62
6 (generic verdict) Trojan-Ransom.Win32.Encoder 4.28
7 (generic verdict) Trojan-Ransom.Win32.Crypren 4.15
8 PolyRansom/VirLock Virus.Win32.PolyRansom,
Trojan-Ransom.Win32.PolyRansom
2.96
9 Crysis/Dharma Trojan-Ransom.Win32.Crusis 2.02
10 (generic verdict) Trojan-Ransom.Win32.Generic 1.56
* Unique Kaspersky users attacked by the specified family of ransomware trojans as a percentage of all users attacked by ransomware trojans.
Miners
Number of new modifications
In Q1 2020, Kaspersky solutions detected 192,036 new miner modifications.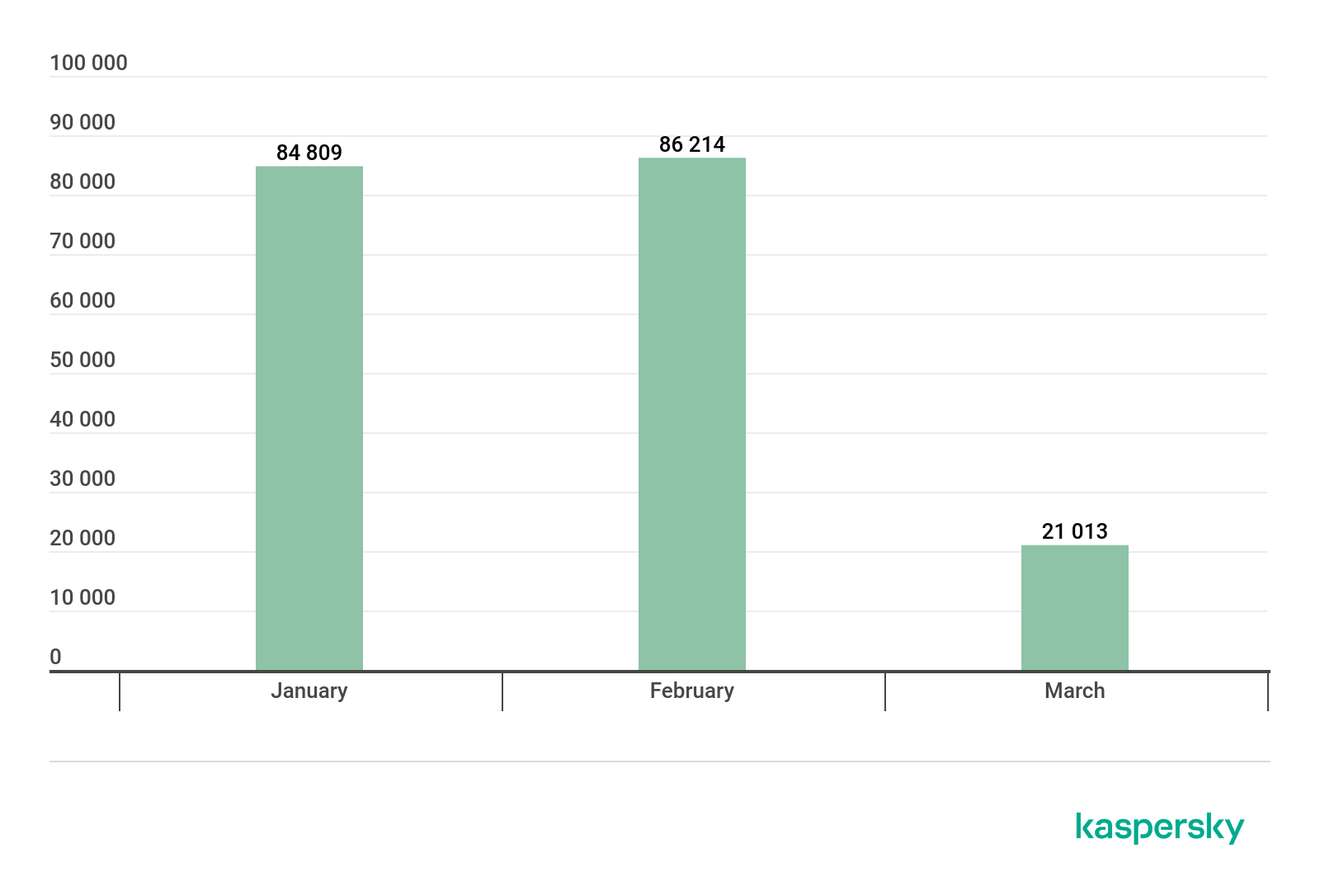
Number of new miner modifications, Q1 2020 (download)
Number of users attacked by miners
In Q1, we detected attacks using miners on the computers of 518,857 unique users of Kaspersky Lab products worldwide.
Number of unique users attacked by miners, Q1 2020 (download)
Attack geography
Geography of miner attacks, Q1 2020 (download)
Top 10 countries attacked by miners
Country* %**
1 Afghanistan 6.72
2 Ethiopia 4.90
3 Tanzania 3.26
4 Sri Lanka 3.22
5 Uzbekistan 3.10
6 Rwanda 2.56
7 Vietnam 2.54
8 Kazakhstan 2.45
9 Mozambique 1.96
10 Pakistan 1.67
* Excluded are countries with relatively few users of Kaspersky products (under 50,000).
** Unique users whose computers were attacked by miners as a percentage of all unique users of Kaspersky products in the country.
Vulnerable applications used by cybercriminals during cyberattacks
We already noted that Microsoft Office vulnerabilities are the most common ones. Q1 2020 was no exception: the share of exploits for these vulnerabilities grew to 74.83%. The most popular vulnerability in Microsoft Office was CVE-2017-11882, which is related to a stack overflow error in the Equation Editor component. Hard on its heels was CVE-2017-8570, which is used to embed a malicious script in an OLE object inside an Office document. Several other vulnerabilities, such as CVE-2018-0802 and CVE-2017-8759, were also popular with attackers. In the absence of security updates for Microsoft Office, these vulnerabilities are successfully exploited and the user’s system becomes infected.
In second place were exploits for vulnerabilities in Internet browsers (11.06%). In Q1, cybercriminals attacked a whole host of browsers, including Microsoft Internet Explorer, Google Chrome, and Mozilla Firefox. What’s more, some of the vulnerabilities were used in APT attacks, such as CVE-2020-0674, which is associated with the incorrect handling of objects in memory in an outdated version of the JScript scripting engine in Internet Explorer, leading to code execution. Another example is the previously identified CVE-2019-17026, a data type mismatch vulnerability in Mozilla Firefox’s JIT compiler, which also leads to remote code execution. In the event of a successful attack, both browser exploits cause a malware infection. The researchers also detected a targeted attack against Google Chrome exploiting the RCE vulnerability CVE-2020-6418 in the JavaScript engine; in addition, the dangerous RCE vulnerability CVE-2020-0767 was detected in a component of the ChakraCore scripting engine used by Microsoft Edge. Although modern browsers have their own protection mechanisms, cybercriminals are forever finding ways around them, very often using chains of exploits to do so. Therefore, it is vital to keep the operating system and software up to date at all times.
Distribution of exploits used in attacks by type of application attacked, Q1 2020 (download)
This quarter, a wide range of critical vulnerabilities were detected in operating systems and their components.
CVE-2020-0601 is a vulnerability that exploits an error in the core cryptographic library of Windows, in a certificate validation algorithm that uses elliptic curves. This vulnerability enables the use of fake certificates that the system recognizes as legitimate.
CVE-2020-0729 is a vulnerability in processing LNK files in Windows, which allows remote code execution if the user opens a malicious shortcut.
CVE-2020-0688 is the result of a default configuration error in Microsoft Exchange Server, whereby the same cryptographic keys are used to sign and encrypt serialized ASP.NET ViewState data, enabling attackers to execute their own code on the server side with system rights.
Various network attacks on system services and network protocols were as popular as ever with attackers. We continue to detect attempts at exploiting vulnerabilities in the SMB protocol using EternalBlue, EternalRomance and similar sets of exploits. In Q1 2020, the new vulnerability CVE-2020-0796 (SMBGhost) was detected in the SMBv3 network protocol, leading to remote code execution, in which regard the attacker does not even need to know the username/password combination (since the error occurs before the authentication stage); however, it is present only in Windows 10. In Remote Desktop Gateway there were found two critical vulnerabilities (CVE-2020-0609 and CVE-2020-0610) enabling an unauthorized user to execute remote code in the target system. In addition, there were more frequent attempts to brute-force passwords to Remote Desktop Services and Microsoft SQL Server via the SMB protocol as well.
Attacks via web resources
The statistics in this section are based on Web Anti-Virus, which protects users when malicious objects are downloaded from malicious/infected web pages. Malicious websites are specially created by cybercriminals; web resources with user-created content (for example, forums), as well as hacked legitimate resources, can be infected.
Countries that are sources of web-based attacks: Top 10
The following statistics show the distribution by country of the sources of Internet attacks blocked by Kaspersky products on user computers (web pages with redirects to exploits, sites containing exploits and other malicious programs, botnet C&C centers, etc.). Any unique host could be the source of one or more web-based attacks.
To determine the geographical source of web-based attacks, domain names are matched against their actual domain IP addresses, and then the geographical location of a specific IP address (GEOIP) is established.
In Q1 2020, Kaspersky solutions defeated 726,536,269 attacks launched from online resources located in 203 countries worldwide. As many as 442,039,230 unique URLs were recognized as malicious by Web Anti-Virus components.
Distribution of web-based attack sources by country, Q1 2020 (download)
Countries where users faced the greatest risk of online infection
To assess the risk of online infection faced by users in different countries, for each country, we calculated the percentage of Kaspersky users on whose computers Web Anti-Virus was triggered during the quarter. The resulting data provides an indication of the aggressiveness of the environment in which computers operate in different countries.
This rating only includes attacks by malicious programs that fall under the Malware class; it does not include Web Anti-Virus detections of potentially dangerous or unwanted programs such as RiskTool or adware.
Country* % of attacked users**
1 Bulgaria 13.89
2 Tunisia 13.63
3 Algeria 13.15
4 Libya 12.05
5 Bangladesh 9.79
6 Greece 9.66
7 Latvia 9.64
8 Somalia 9.20
9 Philippines 9.11
10 Morocco 9.10
11 Albania 9.09
12 Taiwan, Province of China 9.04
13 Mongolia 9.02
14 Nepal 8.69
15 Indonesia 8.62
16 Egypt 8.61
17 Georgia 8.47
18 France 8.44
19 Palestine 8.34
20 Qatar 8.30
* Excluded are countries with relatively few Kaspersky users (under 10,000).
** Unique users targeted by Malware-class attacks as a percentage of all unique users of Kaspersky products in the country.
These statistics are based on detection verdicts returned by the Web Anti-Virus module that were received from users of Kaspersky products who consented to providing statistical data.
On average, 6.56% of Internet user’ computers worldwide experienced at least one Malware-class attack.
Geography of malicious web-based attacks, Q1 2020 (download)
Local threats
In this section, we analyze statistical data obtained from the OAS and ODS modules in Kaspersky products. It takes into account malicious programs that were found directly on users’ computers or removable media connected to computers (flash drives, camera memory cards, phones, external hard drives), or which initially made their way onto the computer in non-open form (for example, programs in complex installers, encrypted files, etc.).
In Q1 2020, our File Anti-Virus registered 164,653,290 malicious and potentially unwanted objects.
Countries where users faced the highest risk of local infection
For each country, we calculated the percentage of Kaspersky product users on whose computers File Anti-Virus was triggered during the reporting period. These statistics reflect the level of personal-computer infection in different countries.
Note that this rating only includes attacks by malicious programs that fall under the Malware class; it does not include File Anti-Virus triggers in response to potentially dangerous or unwanted programs, such as RiskTool or adware.
Country* % of attacked users**
1 Afghanistan 52.20
2 Tajikistan 47.14
3 Uzbekistan 45.16
4 Ethiopia 45.06
5 Myanmar 43.14
6 Bangladesh 42.14
7 Kyrgyzstan 41.52
8 Yemen 40.88
9 China 40.67
10 Benin 40.21
11 Mongolia 39.58
12 Algeria 39.55
13 Laos 39.21
14 Burkina Faso 39.09
15 Malawi 38.42
16 Sudan 38.34
17 Rwanda 37.84
18 Iraq 37.82
19 Vietnam 37.42
20 Mauritania 37.26
* Excluded are countries with relatively few Kaspersky users (under 10,000).
** Unique users on whose computers Malware-class local threats were blocked as a percentage of all unique users of Kaspersky products in the country.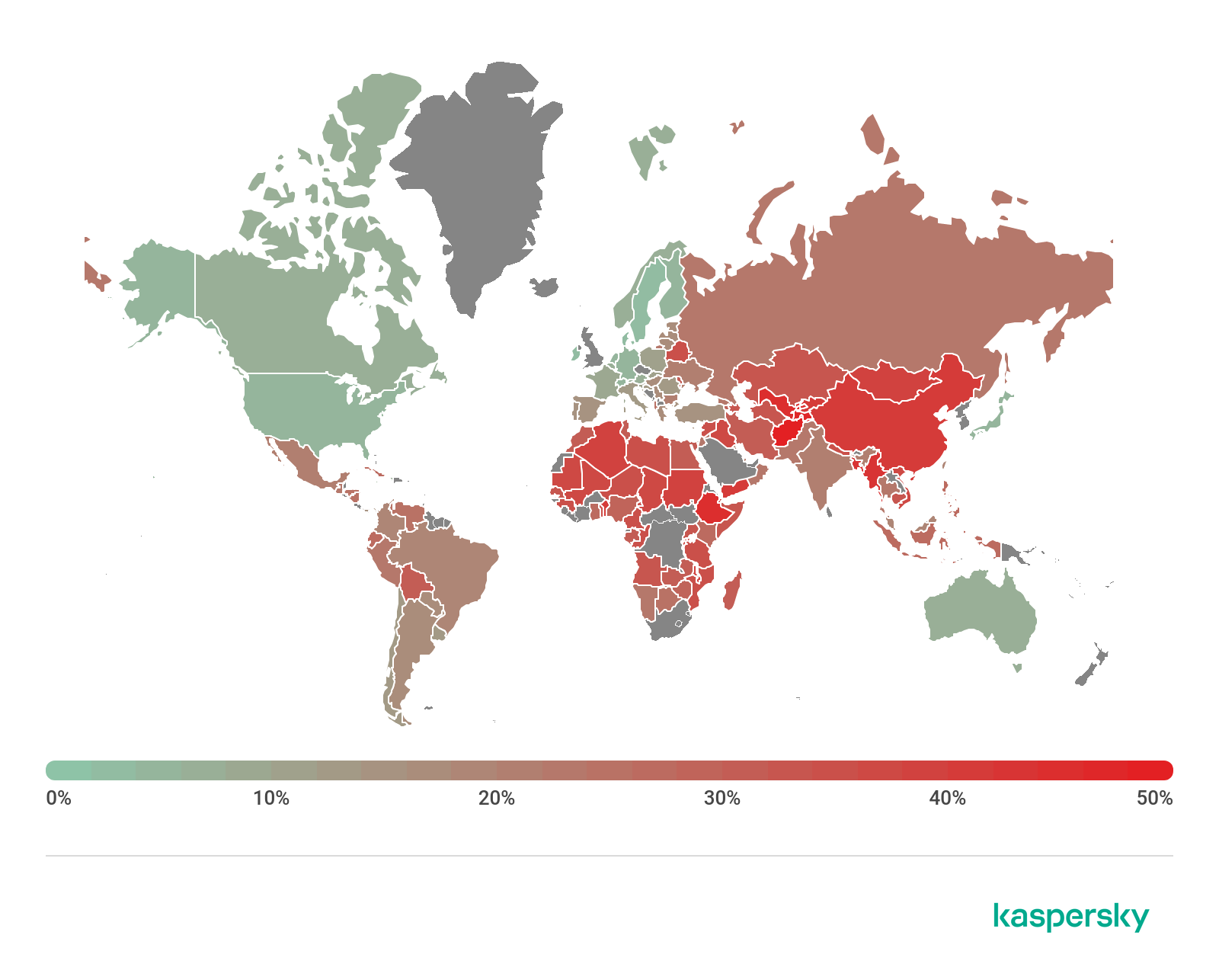
Geography of local infection attempts, Q1 2020 (download)
Overall, 19.16% of user computers globally faced at least one Malware-class local threat during Q1.