Analysis Articles - H 1 2 Analysis List - H 2021 2020 2019 2018 2017 2016
IT threat evolution Q3 2020 Mobile statistics
20.11.20 Analysis Securelist
The statistics presented here draw on detection verdicts returned by Kaspersky products and received from users who consented to providing statistical data.
Quarterly figures
According to Kaspersky Security Network, the third quarter saw:
1,189 797 detected malicious installers, of which
39,051 packages were related to mobile banking trojans;
6063 packages proved to be mobile ransomware trojans.
A total of 16,440,264 attacks on mobile devices were blocked.
Quarterly highlights
In Q3 2020, Kaspersky mobile protective solutions blocked 16,440,264 attacks on mobile devices, an increase of 2.2 million on Q2 2020.

Number of attacks on mobile devices, Q1 2019 – Q3 2020 (download)
It is too early for conclusions now – we need to wait for the year’s results – but comparing Q3 2020 with Q3 2019 reveals a substantial difference: the number of attacks dropped by more that 2.7 million. One may conclude cybercriminals have not reached last year’s volume of attacks yet.
It is worth noting that in Q3 2020, the share of users attacked by malware increased, whereas the number of users who encountered adware and grayware decreased.

Proportions of users who encountered various threat classes in the total number of attacked users, Q3 2020 (download)
In Q3 2020, the share of users who encountered adware according to our data decreased by four percentage points. Notably, the complexity of these applications is no lower than that of malware. For instance, some samples of adware detected iin Q3 2020 use the KingRoot tool for obtaining superuser privileges on the device. This bodes no good for the user: not only does the device’s overall level of security is compromised – the ads are impossible to remove with the stock tools available on the device.
The third quarter reinforced the trend for the number of mobile users encountering stalkerware to drop.

Number of devices running Kaspersky Internet Security for Android on which stalkerware was detected in 2019 – 2020 (download)
The decrease is harder to explain this time around. It was probably caused by self-isolation in Q1 and Q2. Although big cities did not fully restore their levels of activity in Q3, people increasingly began to leave their homes and hence, to interest the users of stalker applications.
Mobile threat statistics
In Q3 2020, Kaspersky solutions detected 1,189,797 malicious installation packages, 56,097 more than in the previous quarter.

Number of detected malicious installers, Q2 2019 – Q3 2020 (download)
For the first time in a year, the number of detected mobile threats dropped when compared to the previous period. This was no ordinary year, though. A lot hinges on the level of activity of cybercriminals behind the threat family, so it is too early to call this a changing trend.
Distribution of detected mobile applications across types

Distribution of newly detected mobile applications across types, Q2 and Q3 2020 (download)
The share of adware (44.82%) has declined for a second consecutive quarter, but the pace of the decline is not strong enough to declare this type of threat as losing its relevance.
The Ewind adware family (48% of all adware detected) was most common in Q3, followed by the FakeAdBlocker family with 32% and HiddenAd with 6%.
The only class of threats that displayed significant growth in Q3 2020 was grayware, i.e. RiskTool (33.54%), with its share rising by more than 13 percentage points. The greatest contributor to this was the Robtes family with 45% of the total detected grayware programs. It was followed by Skymoby and SMSreg, with 15% and 13%, respectively.
The share of trojan-clickers rose by one percentage point in Q3 2020 on account of the Simpo family with its 96% share of all clickers detected.
Twenty most common mobile malware programs
Note that the malware rankings below exclude riskware or grayware, such as RiskTool or adware.
Verdict %*
1 DangerousObject.Multi.Generic 36.22
2 Trojan.AndroidOS.Boogr.gsh 8.26
3 DangerousObject.AndroidOS.GenericML 6.05
4 Trojan-SMS.AndroidOS.Agent.ado 5.89
5 Trojan-Dropper.AndroidOS.Hqwar.cf 5.15
6 Trojan.AndroidOS.Hiddad.fi 4.65
7 Trojan.AndroidOS.Piom.agcb 4.28
8 Trojan-Downloader.AndroidOS.Necro.d 4.10
9 Trojan.AndroidOS.Agent.vz 3.90
10 Trojan-Downloader.AndroidOS.Helper.a 3.42
11 Trojan.AndroidOS.MobOk.v 2.83
12 Trojan-Downloader.AndroidOS.Agent.hy 2.52
13 Trojan-SMS.AndroidOS.Agent.adp 2.20
14 Trojan.AndroidOS.Hiddad.fw 1.81
15 Trojan-Downloader.AndroidOS.Agent.ic 1.75
16 Trojan.AndroidOS.Handda.san 1.72
17 Trojan-Dropper.AndroidOS.Hqwar.gen 1.55
18 Trojan.AndroidOS.LockScreen.ar 1.48
19 Trojan-Downloader.AndroidOS.Malota.a 1.28
20 Trojan-Dropper.AndroidOS.Agent.rb 1.14
* Unique users attacked by this malware as a percentage of all users of Kaspersky solutions who were attacked.
As usual, first place in the Q3 rankings went to DangerousObject.Multi.Generic (36.22%), the verdict we use for malware detected with cloud technology. The technology is triggered when antivirus databases do not yet contain data for detecting the malware at hand, but the anti-malware company’s cloud already contains information about the object. This is essentially how the latest malicious programs are detected.
Second and third places went to trojan.AndroidOS.Boogr.gsh (8.26%) and DangerousObject.AndroidOS.GenericML (6,05%), respectively. These two verdicts are assigned to files recognized as malicious by our systems Powered by machine learning.
Fourth and thirteenth places went to the Agent family of SMS trojans. Around 95% of users attacked by these trojans were located in Russia, which is unusual, as we have always found the popularity of SMS trojans as a threat class to be very low, especially in Russia. The names of the detected files often allude to games and popular applications.
Fifth and seventeenth places were taken by members of the Trojan-Dropper.AndroidOS.Hqwar family. This was the most numerous family in its class in Q3 2020, with 40% of the total detected droppers. It was followed by Agent (32%) and Wapnor (22%).
Sixth and fourteenth positions in the rankings were occupied by the Trojan.AndroidOS.Hiddad malware, which displays ad banners.
Interestingly enough, our rankings of mobile threats for Q3 2020 include five different families of the Trojan-Downloader class. Two malware varieties, Trojan-Downloader.AndroidOS.Necro.d (4.10%) and Trojan-Downloader.AndroidOS.Helper.a (3.42%) belong to one infection chain, so it is little wonder their shares are so close. Both trojans are associated with spreading of aggressive adware. Two others, Trojan-Downloader.AndroidOS.Agent.hy (2.52%) and Trojan-Downloader.AndroidOS.Agent.ic (1.75%), were discovered back in 2019 and are members of one family. The final trojan, Trojan-Downloader.AndroidOS.Malota.a (1.28%), has been known since 2019 and appears unremarkable. All of the listed trojans serve the main purpose of downloading and running executable code.
Eleventh position belongs to Trojan.AndroidOS.MobOk.v (2.83%), a member of the MobOk family. This malware can auto-subscribe the target to paid services. It attempted to attack mobile users in Russia more frequently than residents of other countries.
Trojan.AndroidOS.LockScreen.ar (1.48%), in eighteenth place, is worth a separate mention. This primitive device-locking trojan was first seen in 2017. We have since repeatedly detected it with mobile users, 95% of these in Russia. The early versions of the trojan displayed an insulting political message in a mixture of Russian and poor English. Entering “0800” unlocked the device, and the trojan could then be removed with stock Android tools. LockScreen.ar carried no other malicious functions besides locking the device. However, it was accompanied by two Windows executables.
Both files are malicious, detected as Trojan-Ransom.Win32.Petr.a and Trojan-Ransom.Win32.Wanna.b, the most infamous among Windows ransomware trojans. Neither poses any threat to Android, and LockScreen.ar does not use them in any way. In other words, a mobile device infected with LockScreen.ar cannot infect a Windows workstation, so the presence of these two executables has no rational explanation.
In recent versions of LockScreen, the cybercriminals changed the lock screen design.
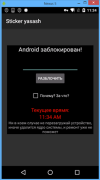
The unlock code changed, too, to 775. The trojan’s capabilities were unchanged, and the Windows executables were removed from the package.
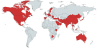
Geography of mobile threats
 M
M
ap of infection attempts by mobile malware, Q3 2020 (download)
Ten countries with the largest shares of users attacked by mobile malware
Country* %**
1 Iran 30.29
2 Bangladesh 17.18
3 Algeria 16.28
4 Yemen 14.40
5 China 14.01
6 Nigeria 13.31
7 Saudi Arabia 11.91
8 Morocco 11.12
9 India 11.02
10 Kuwait 10.45
* Excluded from the rankings are countries with relatively few users of Kaspersky Security for Mobile (under 10,000).
** Share of unique users attacked in the country as a percentage of all users of Kaspersky Security for Mobile in the country.
The three countries where mobile threats were detected on Kaspersky users’ devices most frequently remained unchanged. Bangladesh and Algeria exchanged positions, with the former rising to second place with 17.18% and the latter dropping to third place with 16.28%. Iran retained its leadership even as it lost 12.33 percentage points: 30.29% of users in that country encountered mobile threats in Q3 2020.
The AdWare.AndroidOS.Notifyer adware was the most frequent one. Members of this family accounted for nearly ten of the most widespread threats in Iran.
Frequently encountered in Algeria was the Trojan-SMS.AndroidOS.Agent.adp trojan, which occupied third place in that country, as well as AdWare.AndroidOS.BrowserAd family malware (fourth place) and the Trojan-Spy.AndroidOS.SmsThief.oz spyware trojan (fifth place).
The most widespread adware in Bangladesh was the HiddenAd family which hides itself on the application list, and members of the AdWare.AndroidOS.Loead and AdWare.AndroidOS.BrowserAd families, which occupied fourth and fifth places, respectively, in that country.
Mobile web threats
The statistics presented here are based on detection verdicts returned by the Web Anti-Virus module that were received from users of Kaspersky products who consented to providing statistical data.
In Q3 2020, we continued to assess the risks posed by web pages employed by hackers for attacking Kaspersky Security for Mobile users.
Geography of the countries with the highest risk of infection via web resources, Q3 2020 (download)
Ten countries with the highest risk of infection
Country* % of attacked users**
Ecuador 6.33
Morocco 4.51
Algeria 4.27
India 4.11
Saudi Arabia 3.78
Singapore 3.69
Kuwait 3.66
Malaysia 3.49
South Africa 3.31
UAE 3.12
* Excluded are countries with relatively few users of Kaspersky mobile products (under 10,000).
** Unique users targeted by all types of web attacks as a percentage of all unique users of Kaspersky mobile products in the country.
As in Q2 2020, residents of Ecuador (6.33%), Marocco (4.51%) and Algeria (4.27%) encountered various web-based threats most frequently during the reporting period.
Countries where mobile web threats originated
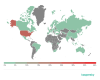
Geography of countries where mobile attacks originated, Q3 2020 (download)
Ten countries where the largest numbers of mobile attacks originated
Country* %*
Netherlands 37.77
Dominican Republic 26.33
USA 24.56
Germany 4.60
Singapore 3.32
Bulgaria 0.88
Ireland 0.52
Russia 0.50
Romania 0.49
Poland 0.21
* Share of sources in the country out of the total number of sources.
As in Q2 2020, the Netherlands was the biggest source of mobile attacks with 37.77%. It was followed by the Dominican Republic (26.3%), which pushed the United States (24.56%) to third place.
Mobile banking trojans
During the reporting period, we found 39,051 mobile banking trojan installers, only 100 fewer than in Q2 2020.
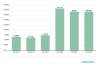
Number of mobile banking trojan installers detected by Kaspersky, Q2 2019 – Q3 2020 (download)
The biggest contributions to our statistics for Q3 2020 came from the creators of the Trojan-Banker.AndroidOS.Agent family trojans: 71.27% of all banker trojans detected. The Trojan-Banker.AndroidOS.Rotexy family (9.23%) came second, far behind the leader, and immediately followed by Trojan-Banker.AndroidOS.Wroba (4.91%).
Ten most commonly detected bankers
Verdict %*
1 Agent 71.27
2 Rotexy 9.23
3 Wroba 4.91
4 Gustuff 4.40
5 Faketoken 2.10
6 Anubis 1.79
7 Knobot 1.23
8 Cebruser 1.21
9 Asacub 0.82
10 Hqwar 0.67
* Unique users attacked by mobile bankers as a percentage of all Kaspersky Security for Mobile users who faced banking threats.
Speaking of specific samples of mobile bankers, Trojan-Banker.AndroidOS.Agent.eq (11.26%) rose to first place in Q3 2020. Last quarter’s leader, Trojan-Banker.AndroidOS.Svpeng.q (11.20%), came second, followed by Trojan-Banker.AndroidOS.Rotexy.e (10.68%).
Ten most common mobile bankers
Verdict %*
1 Trojan-Banker.AndroidOS.Agent.eq 11.26
2 Trojan-Banker.AndroidOS.Svpeng.q 11.20
3 Trojan-Banker.AndroidOS.Rotexy.e 10.68
4 Trojan-Banker.AndroidOS.Asacub.ce 6.82
5 Trojan-Banker.AndroidOS.Asacub.snt 6.60
6 Trojan-Banker.AndroidOS.Anubis.n 4.66
7 Trojan-Banker.AndroidOS.Hqwar.t 4.08
8 Trojan-Banker.AndroidOS.Agent.ep 3.67
9 Trojan-Banker.AndroidOS.Knobot.h 3.31
10 Trojan-Banker.AndroidOS.Asacub.a 3.04
* Unique users attacked by this malware as a percentage of all Kaspersky Security for Mobile users who encountered banking threats.
It is worth noting that the Agent.eq banker has a lot in common with the Asacub trojan whose varieties occupied three out of the ten positions in our rankings.

Geography of mobile banking threats, Q3 2020 (download)
Ten countries with the largest shares of users attacked by mobile banking trojans
Country* %**
1 Japan 1.89
2 Taiwan Province, China 0.48
3 Turkey 0.33
4 Italy 0.31
5 Spain 0.22
6 Korea 0.17
7 Tajikistan 0.16
8 Russia 0.12
9 Australia 0.10
10 China 0.09
* Excluded from the rankings are countries with relatively few users of Kaspersky Security for Mobile (under 10,000).
** Unique users attacked by mobile banking trojans as a percentage of all Kaspersky Security for Mobile users in the country.
The geographical distribution of financial mobile threats underwent a significant change in Q3 2020. The largest share (1.89%) of detections were registered in Japan, with the prevalent malware variety, which attacked 99% of users, being Trojan-Banker.AndroidOS.Agent.eq. Taiwan (0.48%) presented the exact same situation.
Turkey, which was third with 0.33%, had a slightly different picture. The most frequently encountered malware varieties in that countries were Trojan-Banker.AndroidOS.Cebruser.pac (56.29%), followed by Trojan-Banker.AndroidOS.Anubis.q (7.75%) and Trojan-Banker.AndroidOS.Agent.ep (6.06%).
Mobile ransomware trojans
In Q3 2020, we detected 6063 installation packages of mobile ransomware trojans, a fifty-percent increase on Q2 2020.
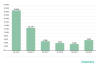
Number of mobile ransomware installers detected by Kaspersky, Q2 2019 – Q3 2020 (download)
It appears that it is too early to write off mobile ransomware trojans just yet. This class of threats is still popular with hackers who generated a sufficiently large number of installation packages in Q3 2020.
Judging by KSN statistics, the number of users who encountered mobile ransomware increased as well.

Number of users who encountered mobile ransomware, Q2 2019 – Q3 2020 (download)
Top 10 mobile ransomware varieties
Verdict %*
1 Trojan-Ransom.AndroidOS.Small.as 13.31
2 Trojan-Ransom.AndroidOS.Small.o 5.29
3 Trojan-Ransom.AndroidOS.Piom.ly 5.21
4 Trojan-Ransom.AndroidOS.Agent.bq 4.58
5 Trojan-Ransom.AndroidOS.Rkor.z 4.45
6 Trojan-Ransom.AndroidOS.Congur.y 3.80
7 Trojan-Ransom.AndroidOS.Small.ce 3.62
8 Trojan-Ransom.AndroidOS.Congur.am 2.84
9 Trojan-Ransom.AndroidOS.Soobek.a 2.79
10 Trojan-Ransom.AndroidOS.Rkor.x 2.72
* Unique users attacked by the malware as a percentage of all Kaspersky Mobile Antivirus users attacked by ransomware trojans.
Trojan-Ransom.AndroidOS.Small.as (13.31%) retained its leadership in Q3 2020. It was followed by Trojan-Ransom.AndroidOS.Small.o (5.29%), a member of the same family.
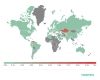
Geography of mobile ransomware trojans, Q3 2020 (download)
The ten countries with the largest shares of users attacked by mobile ransomware trojans
Country* %**
1 Kazakhstan 0.57
2 Kyrgyzstan 0.14
3 China 0.09
4 Saudi Arabia 0.08
5 Yemen 0.05
6 USA 0.05
7 UAE 0.03
8 Indonesia 0.03
9 Kuwait 0.03
10 Algeria 0.03
* Excluded from the rankings are countries with relatively few users of Kaspersky Security for Mobile (under 10,000).
** Unique users attacked by ransomware trojans as a percentage of all Kaspersky Security for Mobile users in the country.
Kazakhstan (0.57%) Kyrgyzstan (0.14%) and China (0.10%) saw the largest shares of users attacked by mobile ransomware trojans.
Stalkerware
This section uses statistics collected by Kaspersky Internet Security for Android.
Stalkerware was encountered less frequently in Q3 2020 than in Q3 2019. The same can be said of the entire year 2020, though. This must be another effect of the COVID-19 pandemic: users started spending much more time at home due to the restrictions, and following their family members and housemates did not require stalkerware. Those who took an interest in their coworkers’ lives had a much harder time gaining physical access to their targets’ devices amid self-isolation. Besides, the cybersecurity industry, not without our contribution, zeroed in on stalkerware, with protective solutions starting to warn users explicitly.

Number of devices running Kaspersky Internet Security for Android on which stalkerware was detected in 2019 – 2020 (download)
Developers of stalkerware have not gone anywhere. They create new designs quarter after quarter. In Q3 2020, we discovered seven hitherto-unknown stalkerware samples, which we singled out as separate families:
AndroidOS.CallRec.a
AndroidOS.Dromon.a
AndroidOS.Hovermon.a
AndroidOS.InterceptaSpy.a
AndroidOS.Manamon.a
AndroidOS.Spydev.a
AndroidOS.Tesmon.a
Ten most common stalkerware varieties
Verdict %*
1 Monitor.AndroidOS.Cerberus.a 13.38
2 Monitor.AndroidOS.Anlost.a 7.67
3 Monitor.AndroidOS.MobileTracker.c 6.85
4 Monitor.AndroidOS.Agent.af 5.59
5 Monitor.AndroidOS.Nidb.a 4.06
6 Monitor.AndroidOS.PhoneSpy.b 3.68
7 Monitor.AndroidOS.Reptilic.a 2.99
8 Monitor.AndroidOS.SecretCam.a 2.45
9 Monitor.AndroidOS.Traca.a 2.35
10 Monitor.AndroidOS.Alltracker.a 2.33
* Share of unique users whose mobile devices were found to contain stalkerware as a percentage of all Kaspersky Internet Security for Android users attacked by stalkerware
Cerberus (13.38%) has topped our stalkerware rankings for a second quarter in a row. The other nine contenders are well-known spyware programs that have been in the market for a long time.
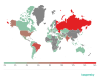
Geography of stalkerware distribution, Q3 2020 (download)
Country* Number of users
Russia 15.57%
Brazil 12.04%
India 9.90%
USA 8.02%
Germany 3.80%
Mexico 3.17%
Italy 2.50%
Iran 2.36%
Saudi Arabia 2.19%
Great Britain 1.83%
A decrease in the number of users who encountered stalkerware in Q3 2020 is typical both globally and for the three leaders.
IT threat evolution Q3 2020
20.11.20 Analysis Securelist
Targeted attacks
MATA: Lazarus’s multi-platform targeted malware framework
The more sophisticated threat actors are continually developing their TTPs (Tactics, Techniques and Procedures) and the toolsets they use to compromise the systems of their targets. However, malicious toolsets used to target multiple platforms are rare, because they required significant investment to develop and maintain them. In July, we reported the use of an advanced, multi-purpose malware framework developed by the Lazarus group.
We discovered the first artefacts relating to this framework, dubbed ‘MATA’ (the authors named their infrastructure ‘MataNet’) in April 2018. Since then, Lazarus has further developed MATA; and there are now versions for Windows, Linux and macOS operating systems.
The MATA framework consists of several components, including a loader, an orchestrator (which manages and coordinates the processes once a device is infected) a C&C server and various plugins.

Lazarus has used MATA to infiltrate the networks of organizations around the world and steal data from customer databases; and, in at least one case, the group has used it to spread ransomware – you can read more about this in the next section. The victims have included software developers, Internet providers and e-commerce sites; and we detected traces of the group’s activities in Poland, Germany, Turkey, Korea, Japan, and India.
You can read more about MATA here.
Lazarus on the hunt for big game
Targeted ransomware has been on the increase in recent years. Typically, such attacks are carried out by criminal groups, who license ‘as-a-service’ ransomware from third-party malware developers and then distribute it by piggy-backing established botnets.
However, earlier this year we discovered a new ransomware family linked to the Lazarus APT group. The VHD ransomware operates much like other ransomware – it encrypts files on drives connected to the victim’s computer and deletes System Volume Information (used as part of the Windows restore point feature) to prevent recovery of data. The malware also suspends processes that could potentially lock important files, such as Microsoft Exchange or SQL Server. However, the delivery mechanism is more reminiscent of APT campaigns. The spreading utility contains a list of administrative credentials and IP addresses specific to the victim, which is uses to brute-force the SMB service on every discovered computer. Whenever it makes a successful connection, a network share is mounted and the VHD ransomware is copied and executed through WMI calls.
While investigating a second incident, we were able to uncover the full infection chain. The malware gained access to a victim’s system by exploiting a vulnerable VPN gateway and then obtained administrative rights on the compromised machines. It used these to install a backdoor and take control of the Active Directory server. Then all computers were infected with the VHD ransomware using a loader created specifically for this task.
Further analysis revealed the backdoor to be part of the MATA framework described above.
WastedLocker
Garmin, the GPS and aviation specialist, was the victim of a cyber-attack in July that resulted in the encryption of some of its systems. The malware used in the attack was the WastedLocker and you can read our technical analysis of this ransomware here.
This ransomware, the use of which has increased this year, has several noteworthy features. It includes a command line interface that attackers can use to control the way it operates – specifying directories to target and setting a priority of which files to encrypt first; and controlling the encryption of files on specified network resources. WastedLocker also features a bypass for UAC (User Account Control) on Windows computers that allows the malware to silently elevate its privileges using a known bypass technique.
WastedLocker uses a combination of AES and RSA algorithms to encrypt files, which is a standard for ransomware families. Files are encrypted using a single public RSA key. This would be a weakness if this ransomware were to be distributed in mass attacks, since a decryptor from one victim would have to contain the only private RSA key that could be used to decrypt the files of all victims. However, since WastedLocker is used in attacks targeted at a specific organization, this decryption approach is worthless in real-world scenarios. Encrypted files are given the extension garminwasted_info, he added – and unusually, a new info file is created for each of the victim’s encrypted files.
CactusPete’s updated Bisonal backdoor
CactusPete is a Chinese-speaking APT threat actor that has been active since 2013. The group has typically targeted military, diplomatic and infrastructure victims in Japan, South Korea, Taiwan and the U.S. However, more recently the group has shifted its focus more towards other Asian and Eastern European organizations.
This group, which we would characterize as having medium level technical capabilities, seems to have acquired greater support and has access to more complex code such as ShadowPad, which CactusPete deployed earlier this year against government, defence, energy, mining and telecoms organizations.
Nevertheless, the group continues to use less sophisticated tools. We recently reported the group’s use of a new variant of the Bisonal backdoor to steal information, execute code on target computers and perform lateral movement within the network. Our research began with a single sample, but using the Kaspersky Threat Attribution Engine (KTAE) we discovered more than 300 almost identical samples. All of these appeared between March 2019 and April this year – so the group has developed more than 20 samples per month! Bisonal is not advanced, relying instead on social engineering in the form of spear-phishing e-mails.
Operation PowerFall
Earlier this year our technologies prevented an attack on a South Korean company. Our investigation uncovered two zero-day vulnerabilities: a remote code execution exploit for Internet Explorer and an elevation of privilege exploit for Windows. The exploits targeted the latest builds of Windows 10 and our tests demonstrated reliable exploitation of Internet Explorer 11 and Windows 10 build 18363 x64.
The exploits operated in tandem. The victim was first targeted with a malicious script that, because of the vulnerability, was able to run in Internet Explorer. Then a flaw in the system service further escalated the privileges of the malicious process. As a result, the attackers were able to move laterally across the target network.
We reported our discoveries to Microsoft, who confirmed the vulnerabilities. At the time of our report, the security team at Microsoft had already prepared a patch for the elevation of privilege vulnerability (CVE-2020-0986): although, before our discovery, Microsoft hadn’t considered exploitation of this vulnerability to be likely. The patch for this vulnerability was released on 9 June. The patch for the remote code vulnerability (CVE-2020-1380) was released on 11 August.

We named this malicious campaign Operation PowerFall. While we have been unable to find a clear link to known threat actors, we believe that DarkHotel might be behind it. You can read more about it here and here.
The latest activities of Transparent Tribe
Transparent Tribe, a prolific threat actor that has been active since at least 2013, specializes in cyber-espionage. The group’s main malware is a custom .NET Remote Access Trojan (RAT) called Crimson RAT, spread by means of spear-phishing e-mails containing malicious Microsoft Office documents.
During our investigation into the activities of Transparent Tribe, we found around 200 Crimson RAT samples. Kaspersky Security Network (KSN) telemetry indicates that there were more than a thousand victims in the year following June 2019. The main targets were diplomatic and military organizations in India and Pakistan.
Crimson RAT includes a range of functions for harvesting data from infected computers. The latest additions include a server-side component used to manage infected client machines and a USB worm component developed for stealing files from removable drives, spreading across systems by infecting removable media and downloading and executing a thin-client version of Crimson RAT from a remote server.

We also discovered a new Android implant used by Transparent Tribe to spy on mobile devices. The threat actor used social engineering to distribute the malware, disguised as a fake porn video player and a fake version of the Aarogya Setu COVID-19 tracking app developed by the government of India.
The app is a modified version of the AhMyth Android RAT, open source malware, downloadable from GitHub and built by binding a malicious payload inside legitimate apps. The malware is designed to collect information from the victim’s device and send it to the attackers.
DeathStalker: mercenary cybercrime group
In August, we reported the activities of a cybercrime group that specializes in stealing trade secrets – mainly from fintech companies, law firms, and financial advisors, although we’ve also seen an attack on a diplomatic entity. The choice of targets suggests that this group, which we have named DeathStalker, is either looking for specific information to sell, or is a mercenary group offering an ‘attack on demand’ service. The group has been active since at least 2018; but it’s possible that the group’s activities could go back further, to 2012, and may be linked to the Janicab and Evilnum malware families.
We have seen Powersing-related activities in Argentina, China, Cyprus, Israel, Lebanon, Switzerland, Taiwan, Turkey, the UK and the UAE. We also located Evilnum victims in Cyprus, India, Lebanon, Russia, Jordan and the UAE.
The group’s use of a PowerShell implant called Powersing first brought DeathStalker to our attention. The operation starts with spear-phishing e-mails with attached archives containing a malicious LNK file. If the victim clicks on the archive, it starts a convoluted sequence resulting in the execution of arbitrary code on the computer

Powersing periodically takes screenshots on the victim’s computer and sends them to the C2 (Command and Control) server. It also executes additional PowerShell scripts that are downloaded from the C2 server. So Powersing is designed to provide the attackers with an initial point of presence on the infected computer from which to install additional malware.
DeathStalker camouflages communication between infected computers and the C2 server by using public services as dead drop resolvers: these services allow the attackers to store data at a fixed URL through public posts, comments, user profiles, content descriptions, etc.

DeathStalker offers a good example of what small groups or even skilled individuals can achieve, without the need for innovative tricks or sophisticated methods. DeathStalker should serve as a baseline of what organizations in the private sector should be able to defend against, since groups of this sort represent the type of cyber-threat companies today are most likely to face. We advise defenders to pay close attention to any process creation related to native Windows interpreters for scripting languages, such as powershell.exe and cscript.exe: wherever possible, these utilities should be made unavailable. Security awareness training and security product assessments should also include infection chains based on LNK files.
You can read more about DeathStalkers here.
Other malware
The Tetrade: Brazilian banking malware goes global
Brazil has a well-established criminal underground and local malware developers have created many banking Trojans over the years. Typically, this malware is used to target customers of local banks. However, Brazilian cybercriminals are starting to expand their attacks and operations abroad, targeting other countries and banks. The Tetrade is our designation for four large banking Trojan families that have been created, developed and spread by Brazilian criminals, but which are now being used at a global level. The four malware families are Guildma, Javali, Melcoz and Grandoreiro.
We have seen attempts to do this before, with limited success using very basic Trojans. The situation is now different. Brazilian banking Trojans have evolved greatly, with hackers adopting techniques for bypassing detection, creating highly modular and obfuscated malware and using a very complex execution flow – making analysis more difficult. Notwithstanding the banking industry’s adoption of technologies aimed at protecting customers, including the deployment of plugins, tokens, e-tokens, two-factor authentication, CHIP and PIN credit, fraud continues to increase because Brazil still lacks proper cybercrime legislation.
Brazilian criminals are benefiting from the fact that many banks operating in Brazil also have operations elsewhere in Latin America and in Europe, making it easy to extend their attacks to customers of these financial institutions. They are also rapidly creating an ecosystem of affiliates, recruiting cybercriminals to work with in other countries, adopting MaaS (Malware-as-a-Service) and quickly adding new techniques to their malware as a way to keep it relevant and financially attractive to their partners.
The banking Trojan families are seeking to innovate by using DGA (Domain Generation Algorithm), encrypted payloads, process hollowing, DLL hijacking, a lot of LoLBins, fileless infections and other tricks to obstruct analysis and detection. We believe that these threats will evolve to target more banks in more countries.
We recommend that financial institutions monitor these threats closely, while improving their authentication processes, boosting anti-fraud technology and threat intelligence data to understand and mitigate such risks. Further information on these threats, along with IoCs, YARA rules and hashes, are available to customers of our Financial Threat Intelligence services.
The dangers of streaming
Home entertainment is changing as the adoption of streaming TV services increases. The global market for streaming services is estimated to reach $688.7 billion by 2024. For cybercriminals, the widespread adoption of streaming services offers new, potentially lucrative attack vector. For example, just hours after Disney + was launched last November, thousands of accounts were hacked and people’s passwords and email details were changed. The criminals sold the compromised accounts online for between $3 and $11.
Even established services, such as Netflix and Hulu, are prime targets for distributing malware, stealing passwords and launching spam and phishing attacks. The spike in the number of subscribers in the wake of the COVID-19 pandemic has provided cybercriminals with an even bigger pool of potential victims. In the first quarter of this year, Netflix added fifteen million subscribers—more than double what had been anticipated.
We took an in-depth look at the threat landscape as it relates to streaming services. Unsurprisingly, phishing is one of the approaches taken by cybercriminals, as they seek to trick people into disclosing login credentials or payment information.

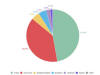
The criminals also capitalize on the growing interest in streaming services to distribute malware and adware. Typically, backdoors and other Trojans are downloaded when people attempt to gain access through unofficial means – by purchasing discounted accounts, obtaining a ‘hack’ to keep their free trial going, or attempting to access a free subscription. The chart below shows the number of people that encountered various threats containing the names of popular streaming platforms while trying to access these platforms through unofficial means between January 2019 and 8 April 2020:

The chart below shows the mix of malicious programs disguised under the name of popular streaming platforms between January 2019 and 8 April 2020:
You can read the full report here, including our guidance on how to avoid phishing scams and malware related to streaming services.
Threats facing digital education
Online learning became the norm in the wake of the COVID-19 pandemic, as classrooms and lecture theatres were forced to close. Unfortunately, many educational institutions did not have proper cyber-security measures in place, putting online classrooms at increased risks of cyber-attacks. On 17 June, Microsoft Security Intelligence reported that the education industry accounted for 61 percent of the 7.7 million malware encounters by enterprises in the previous 30 days – more than any other sector. In addition to malware, educational institutions also faced an increased risk of data breaches and violations of student privacy.
We recently published an overview of the threats facing schools and universities, including phishing related to online learning platforms and video conferencing applications, threats camouflaged as applications related to online learning and DDoS (Distributed Denial of Service) attacks affecting education.
In the first half of 2020, 168,550 people encountered various threats disguised as popular online learning platforms – a massive increase compared to just 820 in the same period the previous year.
The platform used most frequently as a lure was Zoom, with 99.5 per cent of detections, no surprise given the popularity of this platform.
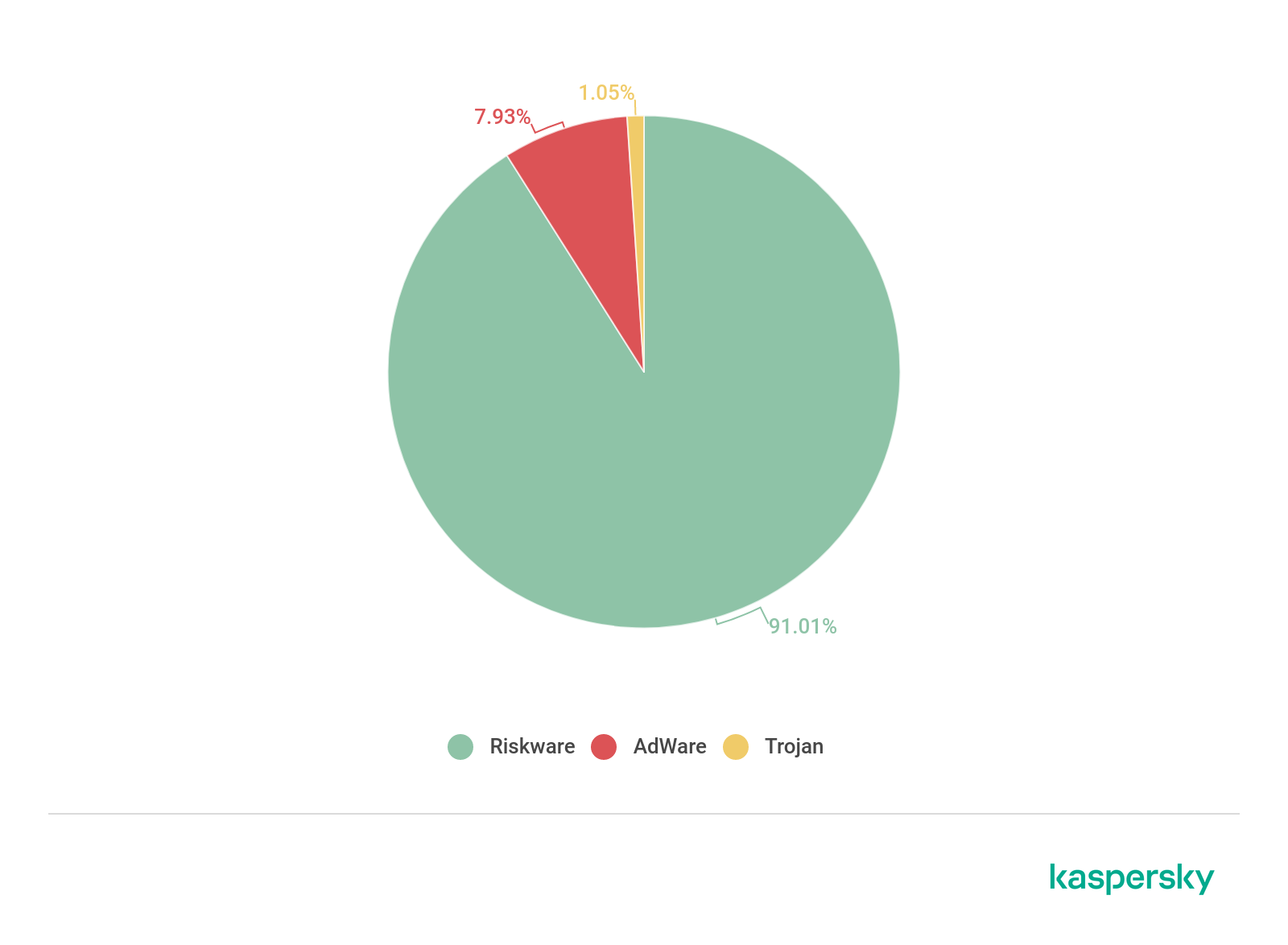
The overwhelming majority of threats distributed under the guise of legitimate video conferencing and online learning platforms were riskware and adware. Adware bombards users with unwanted adverts, while riskware consists of various files – including browser bars, download managers and remote administration tools – that may carry out various actions without consent.
In Q1 2020, the total number of DDoS attacks increased globally by 80 per cent when compared to the same period in 2019: and a large proportion of this increase can be attributed to attacks on distance e-learning services.
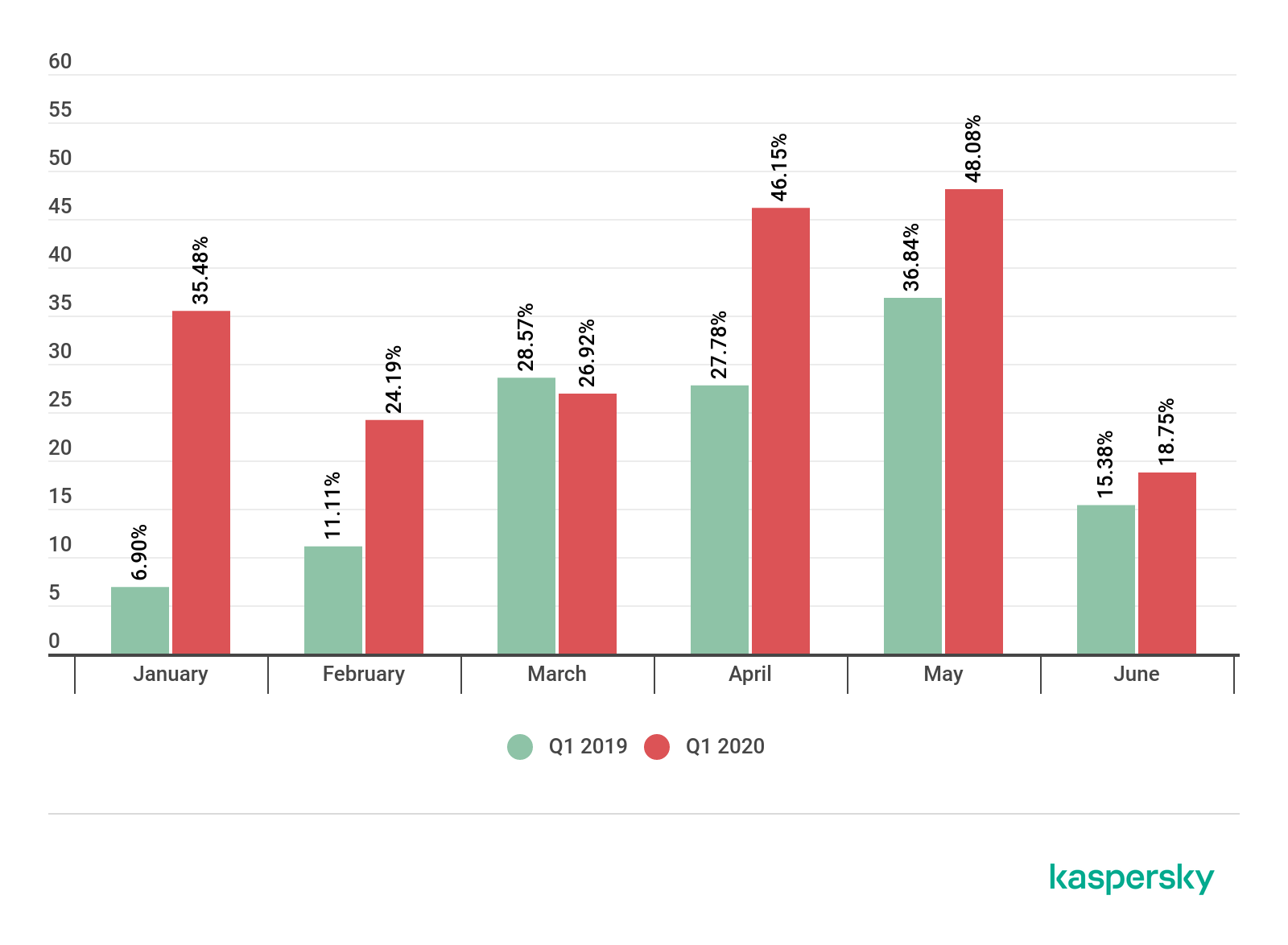
The number of DDoS attacks affecting educational resources that occurred between January and June this year increased by at least 350 per cent when compared to the same period in 2019.
It’s likely that online learning will continue to grow in the future and cybercriminals will seek to exploit this. So it’s vital that educational institutions review their cyber-security policy and adopt appropriate measures to secure their online learning environments and resources.
You can read our full report here.
Undeletable adware on smartphones
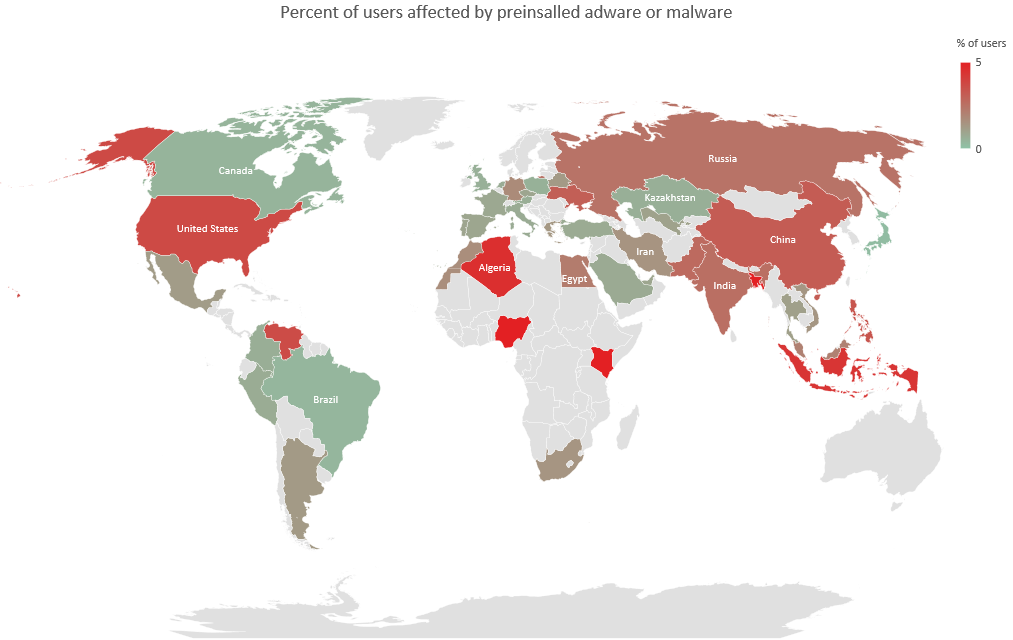
We’ve highlighted the issue of intrusive advertisements on smartphones a number of times in the past (you can find recent posts here and here). While it can be straightforward to remove adware, there are situations where it’s much more difficult because the adware is installed in the system partition. In such cases, trying to remove it can cause the device to fail. In addition, ads can be embedded in undeletable system apps and libraries at the code level. According to our data, 14.8 per cent of all users attacked by malware or adware in the last year suffered an infection of the system partition.
We have observed two main strategies for introducing undeletable adware onto a device. First, the malware obtains root access and installs adware in the system partition. Second, the code for displaying ads (or its loader) gets into the firmware of the device even before reaches the consumer. Our data indicates that between one and 5 per cent people running our mobile security solutions have encountered this. In the main, these are owners of smartphones and tablets of certain brands in the lower price segment. For some popular vendors offering low-cost devices, this figure reaches 27 per cent.
Since the Android security model assumes that anti-virus is a normal app, it is unable to do anything adware or malware in system directories, making this a serious problem.
Our investigations show that the focus of some mobile device suppliers is on maximizing profits through all kinds of advertising tools, even if such tools cause inconvenience to device owners. If advertising networks are ready to pay for views, clicks, and installations regardless of their source, it makes sense for them to embed ad modules into devices to increase the profit from each device sold.
IT threat evolution Q3 2020. Non-mobile statistics
20.11.20 Analysis Securelist
These statistics are based on detection verdicts of Kaspersky products received from users who consented to provide statistical data.
Quarterly figures
According to Kaspersky Security Network, in Q3:
Kaspersky solutions blocked 1,416,295,227 attacks launched from online resources across the globe.
456,573,467 unique URLs were recognized as malicious by Web Anti-Virus components.
Attempts to run malware for stealing money from online bank accounts were stopped on the computers of 146,761 unique users.
Ransomware attacks were defeated on the computers of 121,579 unique users.
Our File Anti-Virus detected 87,941,334 unique malicious and potentially unwanted objects.
Financial threats
Financial threat statistics
In Q3 2020, Kaspersky solutions blocked attempts to launch one or more types of malware designed to steal money from bank accounts on the computers of 146,761 users.

Number of unique users attacked by financial malware, Q3 2020 (download)
Attack geography
To evaluate and compare the risk of being infected by banking Trojans and ATM/POS malware worldwide, for each country we calculated the share of users of Kaspersky products who faced this threat during the reporting period as a percentage of all users of our products in that country.

Geography of financial malware attacks, Q3 2020 (download)
Top 10 countries by share of attacked users
Country* %**
1 Costa Rica 6.6
2 Turkmenistan 5.9
3 Tajikistan 4.7
4 Uzbekistan 4.6
5 Afghanistan 3.4
6 Syria 1.7
7 Iran 1.6
8 Yemen 1.6
9 Kazakhstan 1.5
10 Venezuela 1.5
* Excluded are countries with relatively few Kaspersky product users (under 10,000).
** Unique users whose computers were targeted by financial malware as a percentage of all unique users of Kaspersky products in the country.
First among the banker families, as in the previous quarter, is Zbot (19.7%), despite its share dropping 5.1 p.p. It is followed by Emotet (16.1%) — as we predicted, this malware renewed its activity, climbing by 9.5 p.p. as a result. Meanwhile, the share of another banker family, RTM, decreased by 11.2 p.p., falling from second position to fifth with a score of 7.4%.
Top 10 banking malware families
Name Verdicts %*
1 Zbot Trojan.Win32.Zbot 19.7
2 Emotet Backdoor.Win32.Emotet 16.1
3 CliptoShuffler Trojan-Banker.Win32.CliptoShuffler 12.2
4 Trickster Trojan.Win32.Trickster 8.8
5 RTM Trojan-Banker.Win32.RTM 7.4
6 Neurevt Trojan.Win32.Neurevt 5.4
7 Nimnul Virus.Win32.Nimnul 4.4
8 SpyEye Trojan-Spy.Win32.SpyEye 3.5
9 Danabot Trojan-Banker.Win32.Danabot 3.1
10 Gozi Trojan-Banker.Win32.Gozi 1.9
** Unique users who encountered this malware family as a percentage of all users attacked by financial malware.
Ransomware programs
Quarterly trends and highlights
Q3 2020 saw many high-profile ransomware attacks on organizations in various fields: education, healthcare, governance, energy, finance, IT, telecommunications and many others. Such cybercriminal activity is understandable: a successful attack on a major organization can command a ransom in the millions of dollars, which is several orders of magnitude higher than the typical sum for mass ransomware.
Campaigns of this type can be viewed as advanced persistent threats (APTs), and Kaspersky researchers detected the involvement of the Lazarus group in the distribution of one of these ransomware programs.
Distributors of these Trojans also began to cooperate with the aim of carrying out more effective and destructive attacks. At the start of the quarter, word leaked out that Maze operators had joined forces with distributors of LockBit, and later RagnarLocker, to form a ransomware cartel. The cybercriminals used shared infrastructure to publish stolen confidential data. Also observed was the pooling of expertise in countering security solutions.
Of the more heartening events, Q3 will be remembered for the arrest of one of the operators of the GandCrab ransomware. Law enforcement agencies in Belarus, Romania and the UK teamed up to catch the distributor of the malware, which had reportedly infected more than 1,000 computers.
Number of new modifications
In Q3 2020, we detected four new ransomware families and 6,720 new modifications of this malware type.

Number of new ransomware modifications, Q3 2019 – Q3 2020 (download)
Number of users attacked by ransomware Trojans
In Q3 2020, Kaspersky products and technologies protected 121,579 users against ransomware attacks.

Number of unique users attacked by ransomware Trojans, Q3 2020 (download)
Attack geography

Geography of attacks by ransomware Trojans, Q3 2020 (download)
Top 10 countries attacked by ransomware Trojans
Country* %**
1 Bangladesh 2.37
2 Mozambique 1.10
3 Ethiopia 1.02
4 Afghanistan 0.87
5 Uzbekistan 0.79
6 Egypt 0.71
7 China 0.65
8 Pakistan 0.52
9 Vietnam 0.50
10 Myanmar 0.46
* Excluded are countries with relatively few Kaspersky users (under 50,000).
** Unique users attacked by ransomware Trojans as a percentage of all unique users of Kaspersky products in the country.
Top 10 most common families of ransomware Trojans
Name Verdicts %*
1 WannaCry Trojan-Ransom.Win32.Wanna 18.77
2 (generic verdict) Trojan-Ransom.Win32.Gen 10.37
3 (generic verdict) Trojan-Ransom.Win32.Encoder 9.58
4 (generic verdict) Trojan-Ransom.Win32.Generic 8.55
5 (generic verdict) Trojan-Ransom.Win32.Phny 6.37
6 Stop Trojan-Ransom.Win32.Stop 5.89
7 (generic verdict) Trojan-Ransom.Win32.Crypren 4.12
8 PolyRansom/VirLock Virus.Win32.PolyRansom 3.14
9 Crysis/Dharma Trojan-Ransom.Win32.Crusis 2.44
10 (generic verdict) Trojan-Ransom.Win32.Crypmod 1.69
* Unique Kaspersky users attacked by this family of ransomware Trojans as a percentage of all users attacked by such malware.
Miners
Number of new modifications
In Q3 2020, Kaspersky solutions detected 3,722 new modifications of miners.

Number of new miner modifications, Q3 2020 (download)
Number of users attacked by miners
In Q3, we detected attacks using miners on the computers of 440,041 unique users of Kaspersky products worldwide. If in the previous quarter the number of attacked users decreased, in this reporting period the situation was reversed: from July we saw a gradual rise in activity.

Number of unique users attacked by miners, Q3 2020 (download)
Attack geography
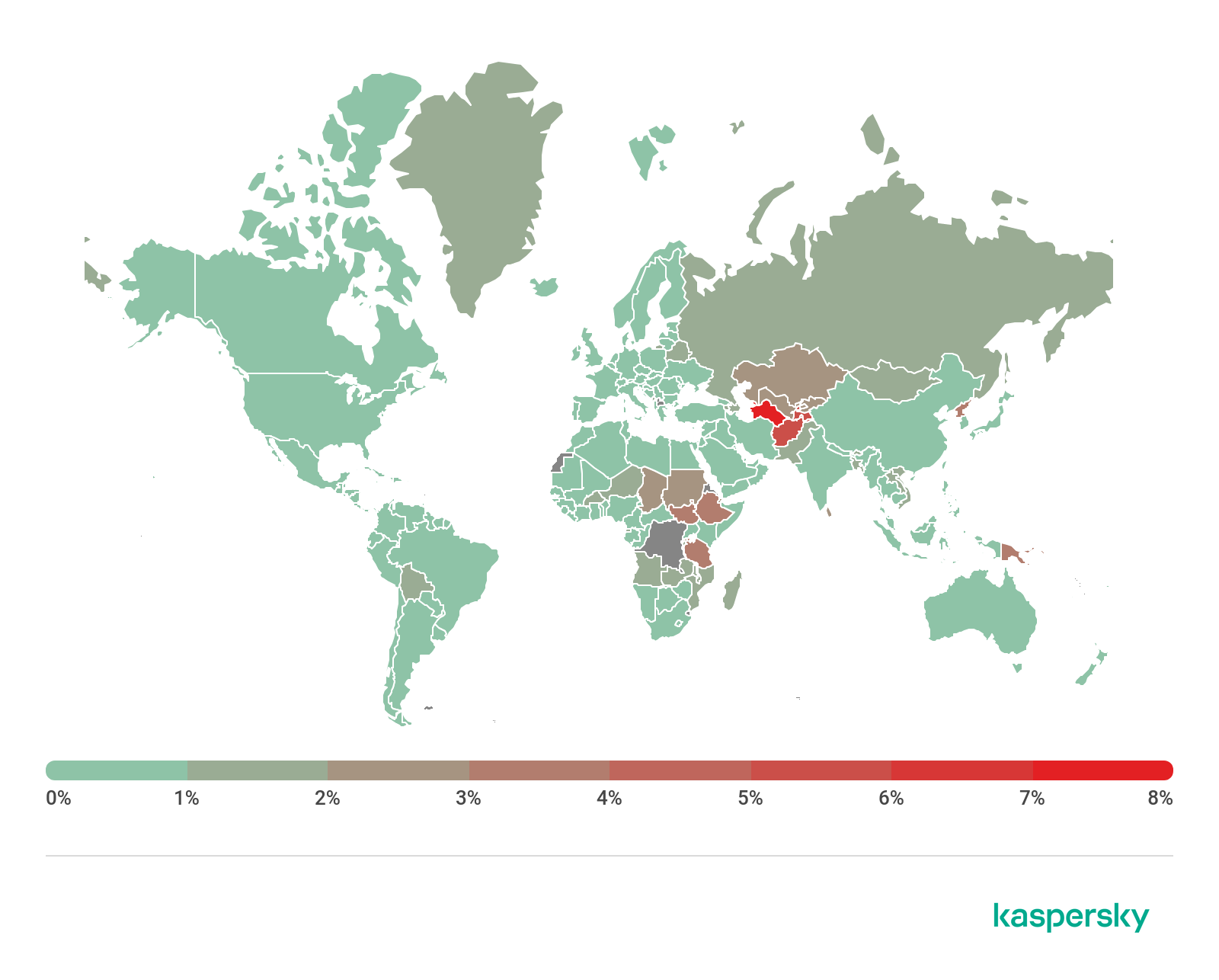
Geography of miner attacks, Q3 2020 (download)
Top 10 countries attacked by miners
Country* %**
1 Afghanistan 5.53
2 Ethiopia 3.94
3 Tanzania 3.06
4 Rwanda 2.58
5 Uzbekistan 2.46
6 Sri Lanka 2.30
7 Kazakhstan 2.26
8 Vietnam 1.95
9 Mozambique 1.76
10 Pakistan 1.57
* Excluded are countries with relatively few users of Kaspersky products (under 50,000).
** Unique users attacked by miners as a percentage of all unique users of Kaspersky products in the country.
Vulnerable applications used by cybercriminals during cyberattacks
According to our statistics, vulnerabilities in the Microsoft Office suite continue to lead: in Q3, their share amounted to 71% of all identified vulnerabilities. Users worldwide are in no rush to update the package, putting their computers at risk of infection. Although our products protect against the exploitation of vulnerabilities, we strongly recommend the timely installation of patches, especially security updates.
First place in this category of vulnerabilities goes to CVE-2017-8570, which can embed a malicious script in an OLE object placed inside an Office document. Almost on a par in terms of popularity is the vulnerability CVE-2017-11882, exploits for which use a stack overflow error in the Equation Editor component. CVE-2017-0199 and CVE-2018-0802 likewise remain popular.
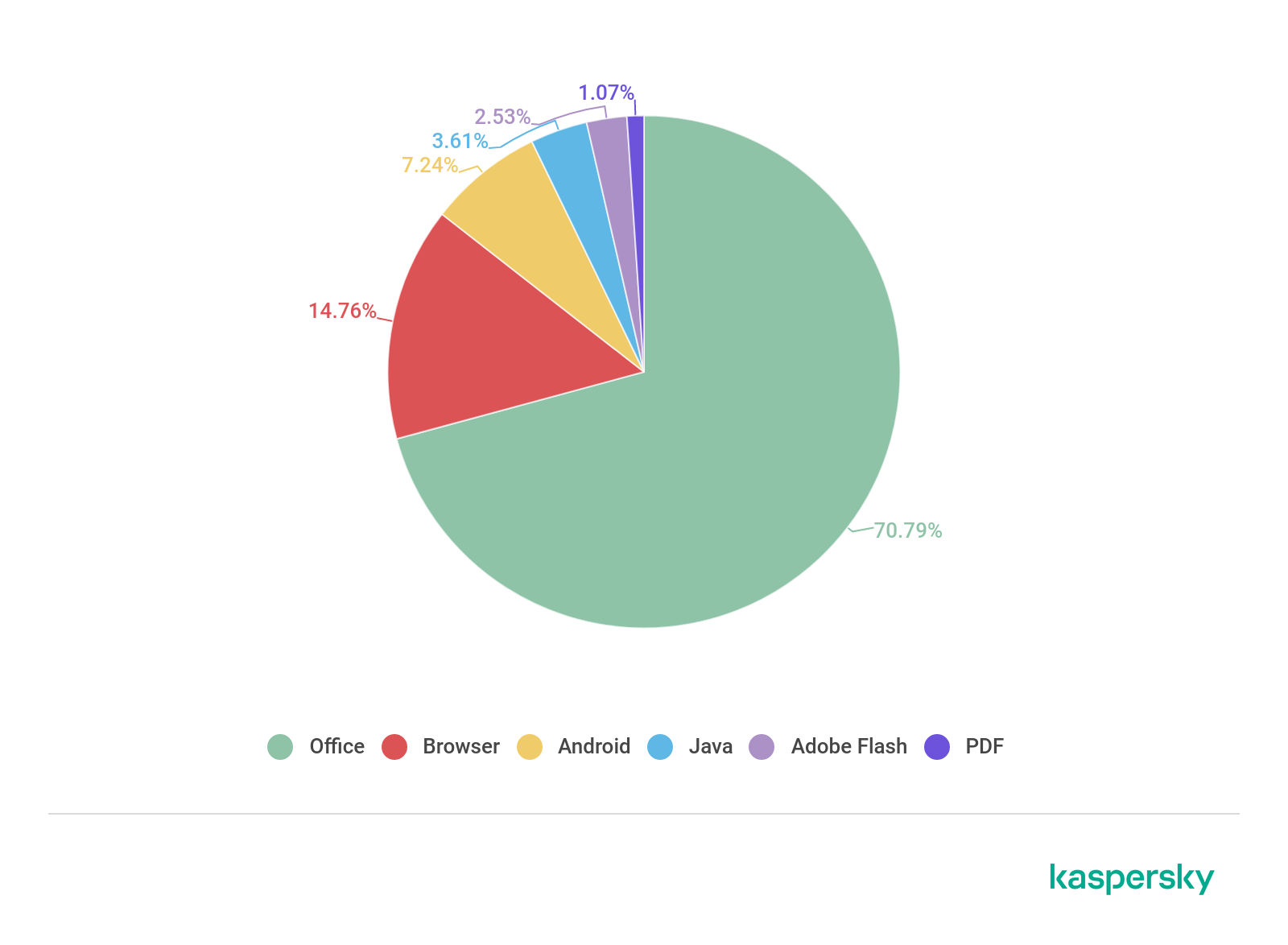
Distribution of exploits used by cybercriminals, by type of attacked application, Q3 2020 (download)
The share of vulnerabilities in Internet browsers increased by 3 p.p. this quarter to 15%. One of the most-talked-about browser vulnerabilities was CVE-2020-1380 — a use-after-free error in the jscript9.dll library of the current version of the Internet Explorer 9+ scripting engine. This same vulnerability was spotted in the Operation PowerFall targeted attack.
Also in Q3, researchers discovered the critical vulnerability CVE-2020-6492 in the WebGL component of Google Chrome. Theoretically, it can be used to execute arbitrary code in the context of a program. The similar vulnerability CVE-2020-6542 was later found in the same component. Use-after-free vulnerabilities were detected in other components too: Task Scheduler (CVE-2020-6543), Media (CVE-2020-6544) and Audio (CVE-2020-6545).
In another browser, Mozilla Firefox, three critical vulnerabilities, CVE-2020-15675, CVE-2020-15674 and CVE-2020-15673, related to incorrect memory handling, were detected, also potentially leading to arbitrary code execution in the system.
In the reporting quarter, the vulnerability CVE-2020-1464, used to bypass scans on malicious files delivered to user systems, was discovered in Microsoft Windows. An error in the cryptographic code made it possible for an attacker to insert a malicious JAR archive inside a correctly signed MSI file, circumvent security mechanisms, and compromise the system. Also detected were vulnerabilities that could potentially be used to compromise a system with different levels of privileges:
CVE-2020-1554, CVE-2020-1492, CVE-2020-1379, CVE-2020-1477 and CVE-2020-1525 in the Windows Media Foundation component;
CVE-2020-1046, detected in the .NET platform, can be used to run malicious code with administrator privileges;
CVE-2020-1472, a vulnerability in the code for processing Netlogon Remote Protocol requests that could allow an attacker to change any user credentials.
Among network-based attacks, those involving EternalBlue exploits and other vulnerabilities from the Shadow Brokers suite remain popular. Also common are brute-force attacks on Remote Desktop Services and Microsoft SQL Server, and via the SMB protocol. In addition, the already mentioned critical vulnerability CVE-2020-1472, also known as Zerologon, is network-based. This error allows an intruder in the corporate network to impersonate any computer and change its password in Active Directory.
Attacks on macOS
Perhaps this quarter’s most interesting find was EvilQuest, also known as Virus.OSX.ThifQseut.a. It is a self-replicating piece of ransomware, that is, a full-fledged virus. The last such malware for macOS was detected 13 years ago, since which time this class of threats has been considered irrelevant for this platform.
Top 20 threats for macOS
Verdict %*
1 Monitor.OSX.HistGrabber.b 14.11
2 AdWare.OSX.Pirrit.j 9.21
3 AdWare.OSX.Bnodlero.at 9.06
4 Trojan-Downloader.OSX.Shlayer.a 8.98
5 AdWare.OSX.Bnodlero.ay 6.78
6 AdWare.OSX.Pirrit.ac 5.78
7 AdWare.OSX.Ketin.h 5.71
8 AdWare.OSX.Pirrit.o 5.47
9 AdWare.OSX.Cimpli.k 4.79
10 AdWare.OSX.Ketin.m 4.45
11 Hoax.OSX.Amc.d 4.38
12 Trojan-Downloader.OSX.Agent.j 3.98
13 Trojan-Downloader.OSX.Agent.h 3.58
14 AdWare.OSX.Pirrit.gen 3.52
15 AdWare.OSX.Spc.a 3.18
16 AdWare.OSX.Amc.c 2.97
17 AdWare.OSX.Pirrit.aa 2.94
18 AdWare.OSX.Pirrit.x 2.81
19 AdWare.OSX.Cimpli.l 2.78
20 AdWare.OSX.Bnodlero.x 2.64
* Unique users who encountered this malware as a percentage of all users of Kaspersky security solutions for macOS who were attacked.
Among the adware modules and their Trojan downloaders in the macOS threat rating for Q3 2020 was Hoax.OSX.Amc.d. Known as Advanced Mac Cleaner, this is a typical representative of the class of programs that first intimidate the user with system errors or other issues on the computer, and then ask for money to fix them.
Threat geography

Geography of threats for macOS, Q3 2020 (download)
Top 10 countries by share of attacked users
Country* %**
1 Spain 6.20%
2 France 6.13%
3 India 5.59%
4 Canada 5.31%
5 Brazil 5.23%
6 USA 5.19%
7 Mexico 4.98%
8 Great Britain 4.37%
9 China 4.25%
10 Italy 4.19%
* Excluded from the rating are countries with relatively few users of Kaspersky security solutions for macOS (under 5000)
** Unique users attacked as a percentage of all users of Kaspersky security solutions for macOS in the country.
Spain (6.29%) and France (6.13%) were the leaders by share of attacked users. They were followed by India (5.59%) in third place, up from fifth in the last quarter. As for detected macOS threats, the Shlayer Trojan consistently holds a leading position in countries in this Top 10 list.
IoT attacks
IoT threat statistics
In Q3 2020, the share of devices whose IP addresses were used for Telnet attacks on Kaspersky traps increased by 4.5 p.p.
Telnet 85.34%
SSH 14.66%
Distribution of attacked services by number of unique IP addresses of devices that carried out attacks, Q3 2020
However, the distribution of sessions from these same IPs in Q3 did not change significantly: the share of operations using the SSH protocol rose by 2.8 p.p.
Telnet 68.69%
SSH 31.31%
Distribution of cybercriminal working sessions with Kaspersky traps, Q3 2020
Nevertheless, Telnet still dominates both by number of attacks from unique IPs and in terms of further communication with the trap by the attacking party.

Geography of IP addresses of devices from which attempts were made to attack Kaspersky Telnet traps, Q3 2020 (download)
Top 10 countries by location of devices from which attacks were carried out on Kaspersky Telnet traps
Country %*
India 19.99
China 15.46
Egypt 9.77
Brazil 7.66
Taiwan, Province of China 3.91
Russia 3.84
USA 3.14
Iran 3.09
Vietnam 2.83
Greece 2.52
* Devices from which attacks were carried out in the given country as a percentage of the total number of devices in that country.
In Q3, India (19.99%) was the location of the highest number of devices that attacked Telnet traps. China (15.46%), having ranked first in the previous quarter, moved down a notch, despite its share increasing by 2.71 p.p. Egypt (9.77%) took third place, up by 1.45 p.p.

Geography of IP addresses of devices from which attempts were made to attack Kaspersky SSH traps, Q3 2020 (download)
Top 10 countries by location of devices from which attacks were made on Kaspersky SSH traps
Country %*
China 28.56
USA 14.75
Germany 4.67
Brazil 4.44
France 4.03
India 3.48
Russia 3.19
Singapore 3.16
Vietnam 3.14
South Korea 2.29
* Devices from which attacks were carried out in the given country as a percentage of the total number of devices in that country.
In Q3, as before, China (28.56%) topped the leaderboard. Likewise, the US (14.75%) retained second place. Vietnam (3.14%), however, having taken bronze in the previous quarter, fell to ninth, ceding its Top 3 position to Germany (4.67%).
Threats loaded into traps
Verdict %*
Backdoor.Linux.Mirai.b 38.59
Trojan-Downloader.Linux.NyaDrop.b 24.78
Backdoor.Linux.Mirai.ba 11.40
Backdoor.Linux.Gafgyt.a 9.71
Backdoor.Linux.Mirai.cw 2.51
Trojan-Downloader.Shell.Agent.p 1.25
Backdoor.Linux.Gafgyt.bj 1.24
Backdoor.Linux.Mirai.ad 0.93
Backdoor.Linux.Mirai.cn 0.81
Backdoor.Linux.Mirai.c 0.61
* Share of malware type in the total number of malicious programs downloaded to IoT devices following a successful attack.
Attacks via web resources
The statistics in this section are based on Web Anti-Virus, which protects users when malicious objects are downloaded from malicious/infected web pages. Cybercriminals create such sites on purpose; web resources with user-created content (for example, forums), as well as hacked legitimate resources, can be infected.
Countries that are sources of web-based attacks: Top 10
The following statistics show the distribution by country of the sources of Internet attacks blocked by Kaspersky products on user computers (web pages with redirects to exploits, sites containing exploits and other malicious programs, botnet C&C centers, etc.). Any unique host could be the source of one or more web-based attacks.
To determine the geographical source of web-based attacks, domain names are matched against their actual domain IP addresses, and then the geographical location of a specific IP address (GEOIP) is established.
In Q3 2020, Kaspersky solutions blocked 1,416,295,227 attacks launched from online resources located across the globe. 456,573,467 unique URLs were recognized as malicious by Web Anti-Virus.
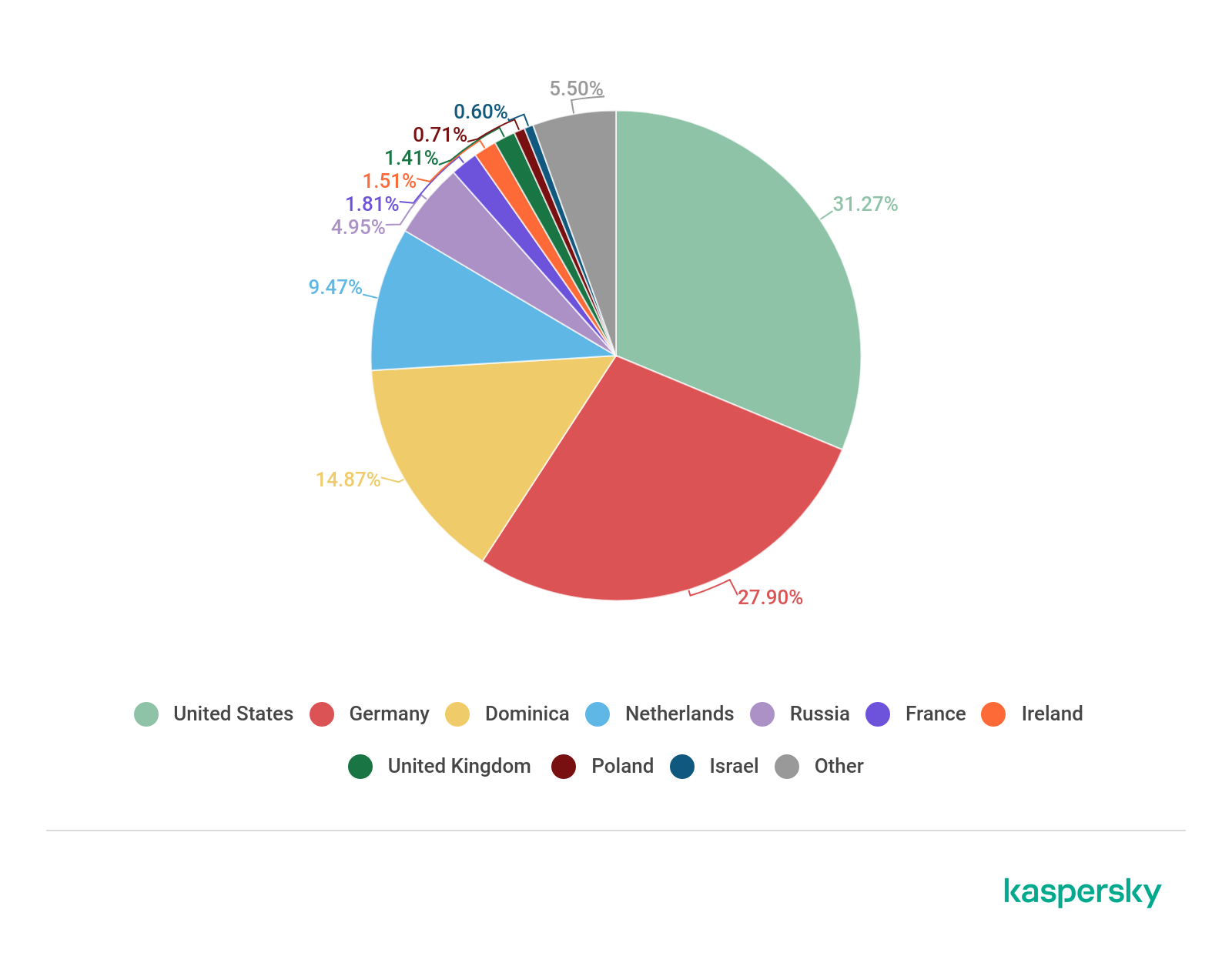
Distribution of web attack sources by country, Q3 2020 (download)
Countries where users faced the greatest risk of online infection
To assess the risk of online infection faced by users in different countries, for each country we calculated the share of Kaspersky users on whose computers Web Anti-Virus was triggered during the quarter. The resulting data provides an indication of the aggressiveness of the environment in which computers operate in different countries.
This rating only includes attacks by malicious programs that fall under the Malware class; it does not include Web Anti-Virus detections of potentially dangerous or unwanted programs such as RiskTool or adware.
Country* % of attacked users**
1 Vietnam 8.69
2 Bangladesh 7.34
3 Latvia 7.32
4 Mongolia 6.83
5 France 6.71
6 Moldova 6.64
7 Algeria 6.22
8 Madagascar 6.15
9 Georgia 6.06
10 UAE 5.98
11 Nepal 5.98
12 Spain 5.92
13 Serbia 5.87
14 Montenegro 5.86
15 Estonia 5.84
16 Qatar 5.83
17 Tunisia 5.81
18 Belarus 5.78
19 Uzbekistan 5.68
20 Myanmar 5.55
* Excluded are countries with relatively few Kaspersky users (under 10,000).
** Unique users targeted by Malware-class attacks as a percentage of all unique users of Kaspersky products in the country.
These statistics are based on detection verdicts by the Web Anti-Virus module that were received from users of Kaspersky products who consented to provide statistical data.
On average, 4.58% of Internet user computers worldwide experienced at least one Malware-class attack.

Geography of web-based malware attacks, Q3 2020 (download)
Local threats
In this section, we analyze statistical data obtained from the OAS and ODS modules in Kaspersky products. It takes into account malicious programs that were found directly on users’ computers or removable media connected to them (flash drives, camera memory cards, phones, external hard drives), or which initially made their way onto the computer in non-open form (for example, programs in complex installers, encrypted files, etc.).
In Q3 2020, our File Anti-Virus detected 87,941,334 malicious and potentially unwanted objects.
Countries where users faced the highest risk of local infection
For each country, we calculated the percentage of Kaspersky product users on whose computers File Anti-Virus was triggered during the reporting period. These statistics reflect the level of personal computer infection in different countries.
Note that this rating only includes attacks by malicious programs that fall under the Malware class; it does not include File Anti-Virus triggers in response to potentially dangerous or unwanted programs, such as RiskTool or adware.
Country* % of attacked users**
1 Afghanistan 49.27
2 Turkmenistan 45.07
3 Myanmar 42.76
4 Tajikistan 41.16
5 Ethiopia 41.15
6 Bangladesh 39.90
7 Burkina Faso 37.63
8 Laos 37.26
9 South Sudan 36.67
10 Uzbekistan 36.58
11 Benin 36.54
12 China 35.56
13 Sudan 34.74
14 Rwanda 34.40
15 Guinea 33.87
16 Vietnam 33.79
17 Mauritania 33.67
18 Tanzania 33.65
19 Chad 33.58
20 Burundi 33.49
* Excluded are countries with relatively few Kaspersky users (under 10,000).
** Unique users on whose computers Malware-class local threats were blocked, as a percentage of all unique users of Kaspersky products in the country.

Geography of local infection attempts, Q3 2020 (download)
Overall, 16.40% of user computers globally faced at least one Malware-class local threat during Q3.
The figure for Russia was 18.21%.
ENISA Threat Landscape Report 2020
22.10.20 Analysis Securityaffairs
According to the ENISA Threat Landscape Report 2020, cyberattacks are becoming more sophisticated, targeted, and in many cases undetected.
I’m proud to present the ENISA Threat Landscape Report 2020, the annual report published by the ENISA that provides insights on the evolution of cyber threats for the period January 2019-April 2020.
The 8th annual ENISA Threat Landscape (ETL) report was compiled by the European Union Agency for Cybersecurity (ENISA), with the support of the European Commission, EU Member States and the CTI Stakeholders Group.
It is an amazing work that identifies and evaluates the top cyber threats for the period January 2019-April 2020.
This year the report has a different format that could allow the readers to focus on the threat of interest. The publication is divided into 22 different reports, which are available in both pdf form and ebook form.
The report provides details on threats that characterized the period of the analysis and highlights the major change from the 2018 threat landscape as the COVID-19-led transformation of the digital environment.
“During the pandemic, cyber criminals have been seen advancing their capabilities, adapting quickly and targeting relevant victim groups more effectively. (Infographic – Threat Landscape Mapping during COVID-19). states the report.
ENISA Threat Landscape Report 2020
The ETL report provides strategic and technical analysis of the events, it was created to provide relevant information to both technical and non-technical readers.
For a better understanding of how the ETL is structured, we recommend the initial reading of “The Year in Review” report, the following table could help readers to focus on the section of their interest included in the publication.

The report highlights the importance of cyber threat intelligence to respond to increasingly automated attacks leveraging automated tools and skills.
Another element of concern is the diffusion of IoT devices, in many cases, smart objects are exposed online without protection.
Below the main trends reported in the document:
Attack surface in cybersecurity continues to expand as we are entering a new phase of the digital transformation.
There will be a new social and economic norm after the COVID-19 pandemic even more dependent on a secure and reliable cyberspace.
The use of social media platforms in targeted attacks is a serious trend and reaches different domains and types of threats.
Finely targeted and persistent attacks on highvalue data (e.g. intellectual property and state secrets) are being meticulously planned and executed by state-sponsored actors.
Massively distributed attacks with a short duration and wide impact are used with multiple objectives such as credential theft.
The motivation behind the majority of cyberattacks is still financial.
Ransomware remains widespread with costly consequences to many organisations.
Still many cybersecurity incidents go unnoticed or take a long time to be detected.
With more security automation, organisations will be invest more in preparedness using Cyber Threat Intelligence as its main capability.
The number of phishing victims continues to grow since it exploits the human dimension being the weakest link.
Let me close with the Top Threats 2020, for each threat the report includes detailed information on trends and observed evolution.

Enjoy it!
IT threat evolution Q2 2020
3.9.20 Analysis Securelist
IT threat evolution Q2 2020. PC statistics
IT threat evolution Q2 2020. Mobile statistics
Targeted attacks
PhantomLance: hiding in plain sight
In April, we reported the results of our investigation into a mobile spyware campaign that we call ‘PhantomLance’. The campaign involved a backdoor Trojan that the attackers distributed via dozens of apps in Google Play and elsewhere.

Dr Web first reported the malware in July 2019, but we decided to investigate because the Trojan was more sophisticated than most malware for stealing money or displaying ads. The spyware is able to gather geo-location data, call logs and contacts; and can monitor SMS activity. The malware can also collect information about the device and the apps installed on it.
The earliest registered PhantomLance domain we found dates back to December 2015. We found dozens of related samples that had been appearing in the wild since 2016 and one of the latest samples was published in November last year. We informed Google about the malware, and Google removed it soon after. We observed around 300 attacks targeting specific Android devices, mainly in Southeast Asia.
During our investigation, we discovered various overlaps with reported OceanLotus APT campaigns, including code similarities with a previous Android campaign, as well as macOS backdoors, infrastructure overlaps with Windows backdoors and a few cross-platform characteristics.
Naikon’s Aria
The Naikon APT is a well-established threat actor in the APAC region. Kaspersky first reported and then fully described the group in 2015. Even when the group shut down much of its successful offensive activity, Naikon maintained several splinter campaigns.
Researchers at Check Point recently published their write-up on Naikon resources and activities related to “Aria-Body”, which we detected in 2017 and reported in 2018. To supplement their research findings, we published a summary of our June 2018 report, “Naikon’s New AR Backdoor Deployment to Southeast Asia“, which aligns with the Check Point report.
AR is a set of backdoors with compilation dates between January 2017 and February 2018. Much of this code operates in memory, injected by other loader components without touching disk, making it very difficult to detect. We trace portions of this codebase back to “xsFunction” EXE and DLL modules used in Naikon operations going back to 2012. It’s probably that the new backdoor, and related activity, is an extension of, or a merger with, the group’s “Paradir Operation”. In the past, the group targeted communications and sensitive information from executive and legislative offices, law enforcement, government administrative, military and intelligence organizations within Southeast Asia. In many cases we have seen that these systems also were targeted previously with PlugX and other malware.
The group has evolved since 2015, although it continues to focus on the same targets. We identified at least a half a dozen individual variants from 2017 and 2018.
You can read our report here.
COMpfun authors spoof visa application with HTTP status-based Trojan
Last October, we observed malware that we call Reductor, with strong code similarities to COMpfun, which infected files on the fly to compromise TLS traffic. The attackers behind Reductor have continued to develop their code. More recently, the Kaspersky Threat Attribution Engine revealed a new Trojan with strong code similarities to COMpfun.
The new malware, like its predecessor, targeted diplomatic bodies in Europe. To lure their victims, the attackers used spoofed visa applications that contain malware that acts as a first-stage dropper. This in turn downloads the main payload, which logs the target’s location, gathers host- and network-related data, performs keylogging and takes screenshots. The Trojan also monitors USB devices and can infect them in order to spread further, and receives commands from the C2 server in the form of HTTP status codes.
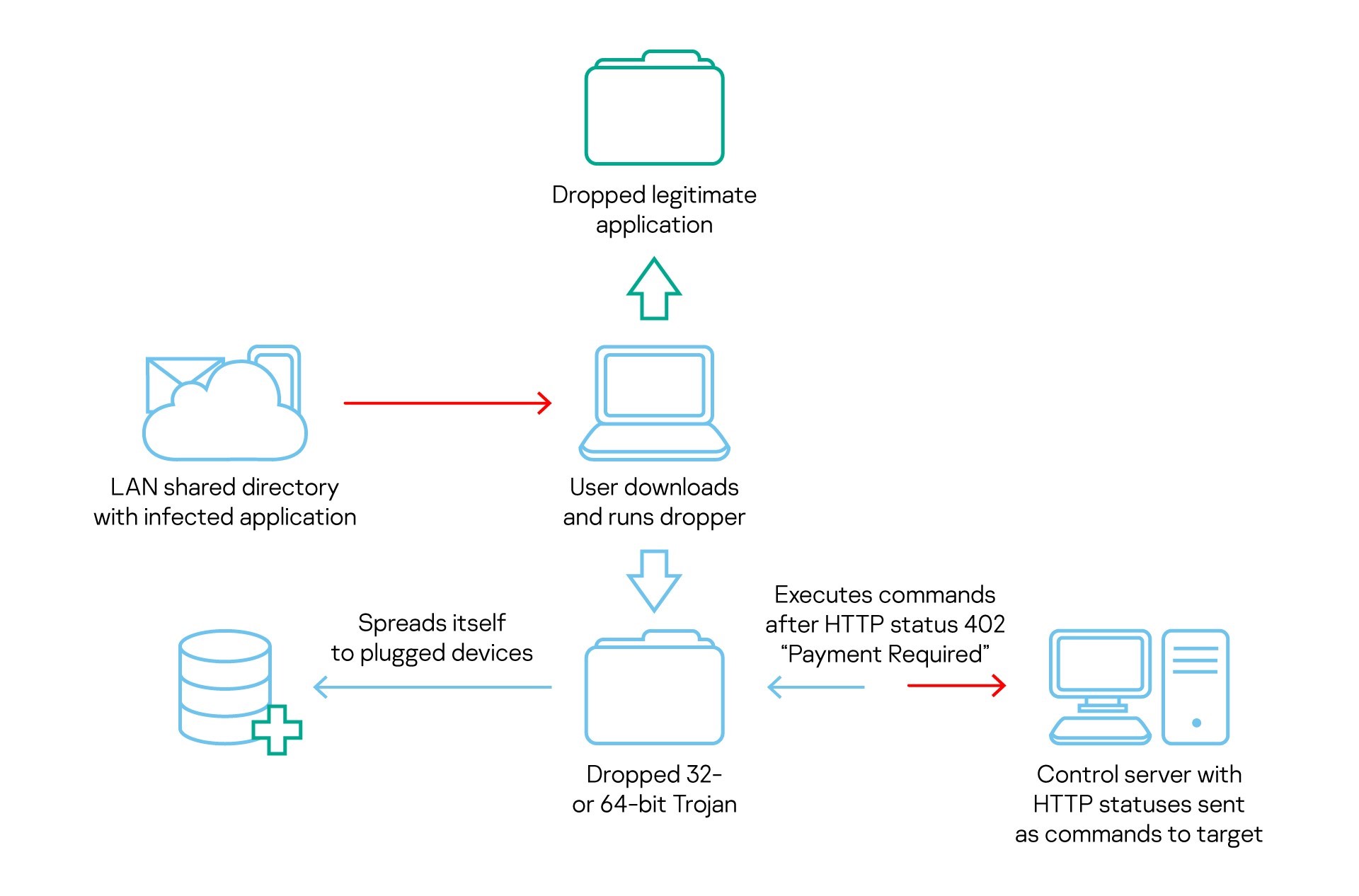
It’s not entirely clear which threat actor is behind COMpfun. However, based mostly on the victims targeted by the malware, we associate it, with medium-to-low confidence, with the Turla APT.
Mind the [air] gap
In June, we published our report on the latest tools and TTPs (Tactics Techniques and Procedures) of Cycldek (aka Goblin Panda, APT 27 and Conimes), a threat actor that has targeted governments in Southeast Asia since 2013.
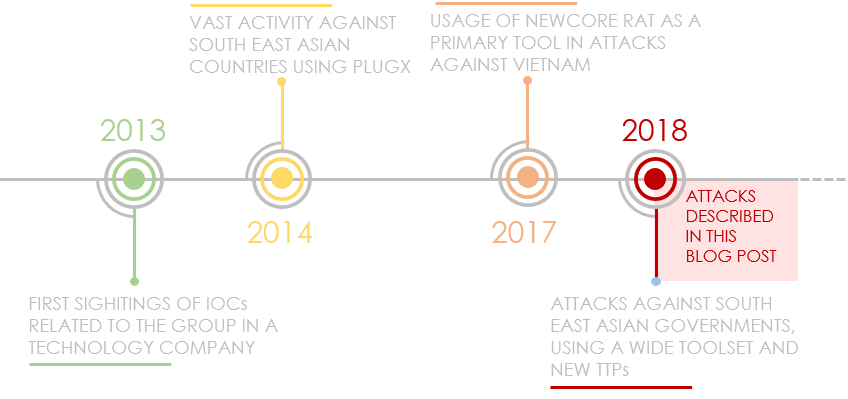
Most of the attacks we have seen since 2018 start with phishing emails that contain politically themed, booby-trapped RTF documents that exploit known vulnerabilities. Once the target computer has been compromised, the attackers install malware called NewCore RAT. There are two variants. The first, BlueCore, appears to have been deployed against diplomatic and government targets in Vietnam; while the second, RedCore, was first deployed in Vietnam before being found in Laos.
Bot variants download additional tools, including a custom backdoor, a tool for stealing cookies and a tool that steals passwords from Chromium-based browser databases. The most striking of these tools is USBCulprit, which relies on USB media to exfiltrate data from victims’ computers. This may suggest that Cycldek is trying to reach air-gapped networks in compromised environments or relies on a physical presence for the same purpose. The malware is implanted as a side-loaded DLL of legitimate, signed applications.
Looking at big threats using code similarity
In June, we announced the release of KTAE (Kaspersky Threat Attribution Engine). KTAE was initially developed as an internal threat hunting tool by the Global Research and Analysis Team at Kaspersky and was instrumental in our investigations into the LightSpy, TajMahal, Dtrack, ShadowHammer and ShadowPad campaigns.
Here’s how it works in a nutshell. We extract from a suspicious file something that we call ‘genotypes’ – short fragments of code selected using our proprietary algorithm – and compare it with more than 60,000 objects of targeted attacks from our database, using a wide range of characteristics. Based on the code similarities, KTAE calculates a reputational score and highlights the possible origin and author, with a short description and links to both private and public resources, outlining the previous campaigns.
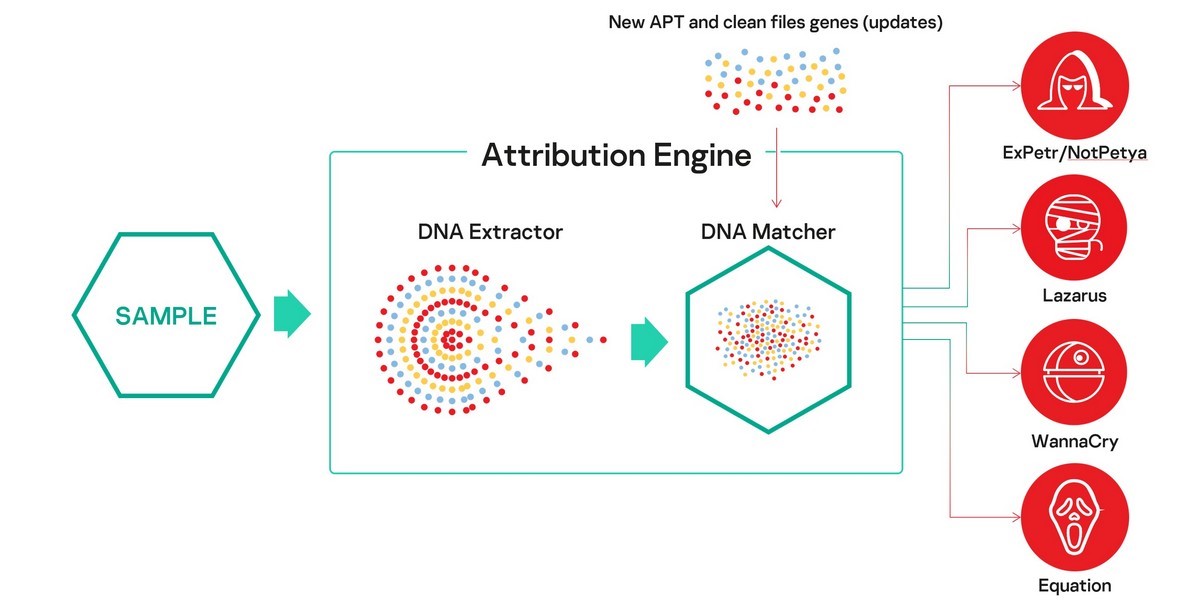
Subscribers to our APT intelligence reports can see a dedicated report on the TTPs used by the identified threat actor, as well as further response steps.
KTAE is designed to be deployed on a customer’s network, with updates provided via USB, to ensure confidentiality. In addition to the threat intelligence available ‘out of the box’, customers can create their own database and fill it with malware samples found by in-house analysts. In this way, KTAE will learn to attribute malware analogous to those in the customer’s database while keeping this information confidential. There’s also an API (application programming interface) to connect the engine to other systems, including a third-party SOC (security operations center).
Code similarity can only provide pointers; and attackers can set false flags that can trick even the most advanced threat hunting tools – the ‘attribution hell’ surrounding Olympic Destroyer provided an object lesson in how this can happen. The purpose of tools such as KTAE is to point experts in the right direction and to test likely scenarios.
You can find out more about the development of KTAE in this post by Costin Raiu, Director of the Global Research and Analysis Team and this product demonstration.
SixLittleMonkeys
Earlier this year, we observed a Trojan injected into the spooler system process memory of a computer belonging to a diplomatic body. The malware is implemented like an API using an enterprise-grade programming style – something that is quite rare and is mostly used by advanced threat actors. We attribute this campaign to a threat actor called SixLittleMonkeys (aka Microcin) because of the re-use of C2 infrastructure, code similarities and focus on diplomatic targets in Central Asia.
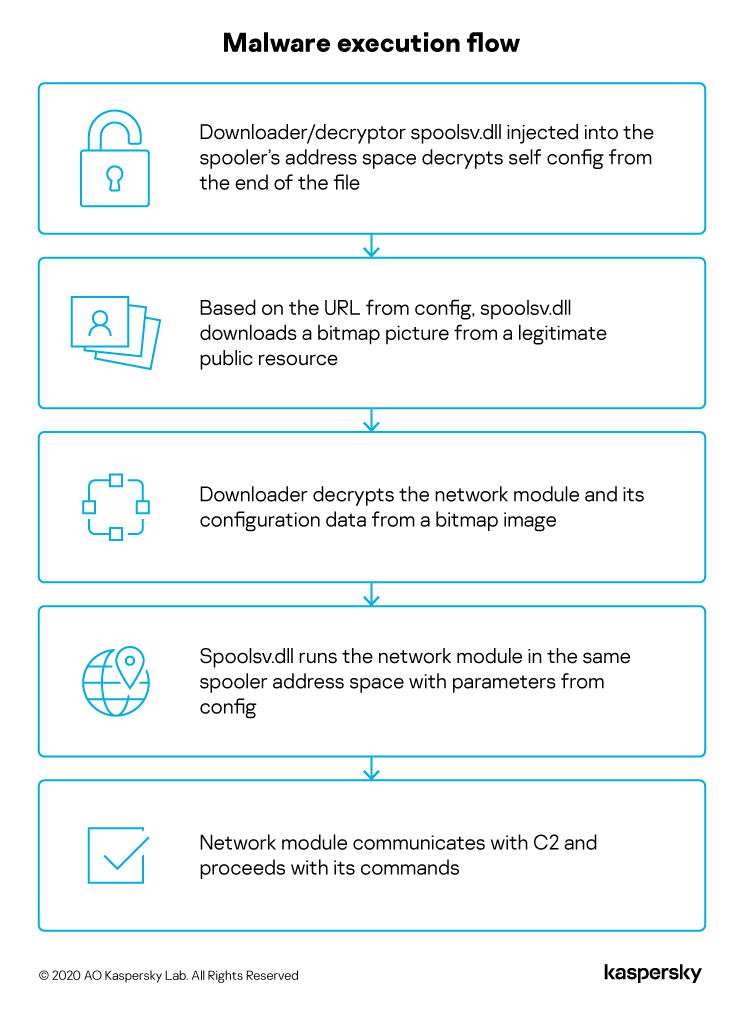
This threat actor uses steganography to deliver malicious modules and configuration data from a legitimate public resource, in this case from the legitimate public image hosting service cloudinary.com:

You can read our full report here.
Other malware
Loncom packer: from backdoors to Cobalt Strike
In March, we reported the distribution of Mokes and Buerak malware under the guise of a security certificate update. Following publication of that report, we conducted a detailed analysis of the malware associated with this campaign. All of the malware uses legitimate NSIS software for packing and loading shellcode, and the Microsoft Crypto API for decrypting the final payload.
Besides Mokes and Buerak, which we mentioned in the previous article, we noticed packed specimens of DarkVNC and Sodin (aka REvil and Sodinokibi). The former is a backdoor used to control an infected machine via the VNC protocol; the latter is a ransomware family. However, the most striking find was the Cobalt Strike utility, which is used both by legal pen-testers and by various APT groups. The command center of the sample that contained Cobalt Strike had previously been seen distributing CactusTorch, a utility for running shellcode present in Cobalt Strike modules, and the same Cobalt Strike packed with a different packer.
xHelper: the Trojan matryoshka
The xHelper Trojan remains as active as ever. The most notable feature of this Trojan is its persistence on an Android device: once it gets onto a phone, it’s able to survive even if it’s deleted or the device is restored to factory settings.
The architecture of the latest version resembles a Russian nesting doll (or ‘matryoshka’). The infection starts by tricking a victim into downloading a fake app – in the case of the version we analyzed, an app that masquerades as a popular cleaner and speed-up utility. Following installation, it is listed as an installed app in the system settings, but otherwise disappears from the victim’s view – there’s no icon and it doesn’t show up in search results. The payload, which is decrypted in the background, fingerprints the victim’s phone and sends the data to a remote server. It then unpacks a dropper-within-a-dropper-within-a-dropper (hence the matryoshka analogy). The malicious files are stored sequentially in the app’s data folder, to which other programs do not have access. This mechanism allows the malware authors to obscure the trail and use malicious modules that are known to security solutions.
The final downloader in the sequence, called Leech, is responsible for installing the Triada Trojan, whose chief feature is a set of exploits for obtaining root privileges on the victim’s device. This allows the Trojan to install malicious files directly in the system partition. Normally this is mounted at system startup and is read-only. However, once the Trojan has obtained root access, it remounts the system partition in write mode and modifies the system such that the user is unable to remove the malicious files, even after a factory reset.
Simply deleting xHelper isn’t enough to clean the device. If you have ‘recovery’ mode set up on the device, you can try to extract the ‘libc.so’ file from the original firmware and replace the infected one with it, before removing all malware from the system partition. However, it’s simpler and more reliable to completely re-flash the phone. If the firmware of the device contains pre-installed malware capable of downloading and installing programs, even re-flashing will be pointless. In that case, it’s worth considering an alternative firmware for the device.
Spike in RDP brute-force attacks
The huge increase in remote working due to the COVID-19 pandemic has had a direct impact on cybersecurity and the threat landscape. Alongside the higher volume of corporate traffic, the use of third-party services for data exchange and employees working on home computers (, IT security teams also have to grapple with the increased use of remote access tools, including the Microsoft RDP (Remote Desktop Protocol).
RDP, used to connect remotely to someone else’s desktop, is used by telecommuters and IT support staff to troubleshoot problems. A successful RDP attack provides a cybercriminal with remote access to the target computer with the same permissions enjoyed by the person whose computer it is.
In the two months prior to our report (i.e. March and April), we observed a huge increase in attempts to brute-force passwords for RDP accounts. The numbers rose from 100,000 to 150,000 per day in January and February to nearly a million per day at the beginning of March.
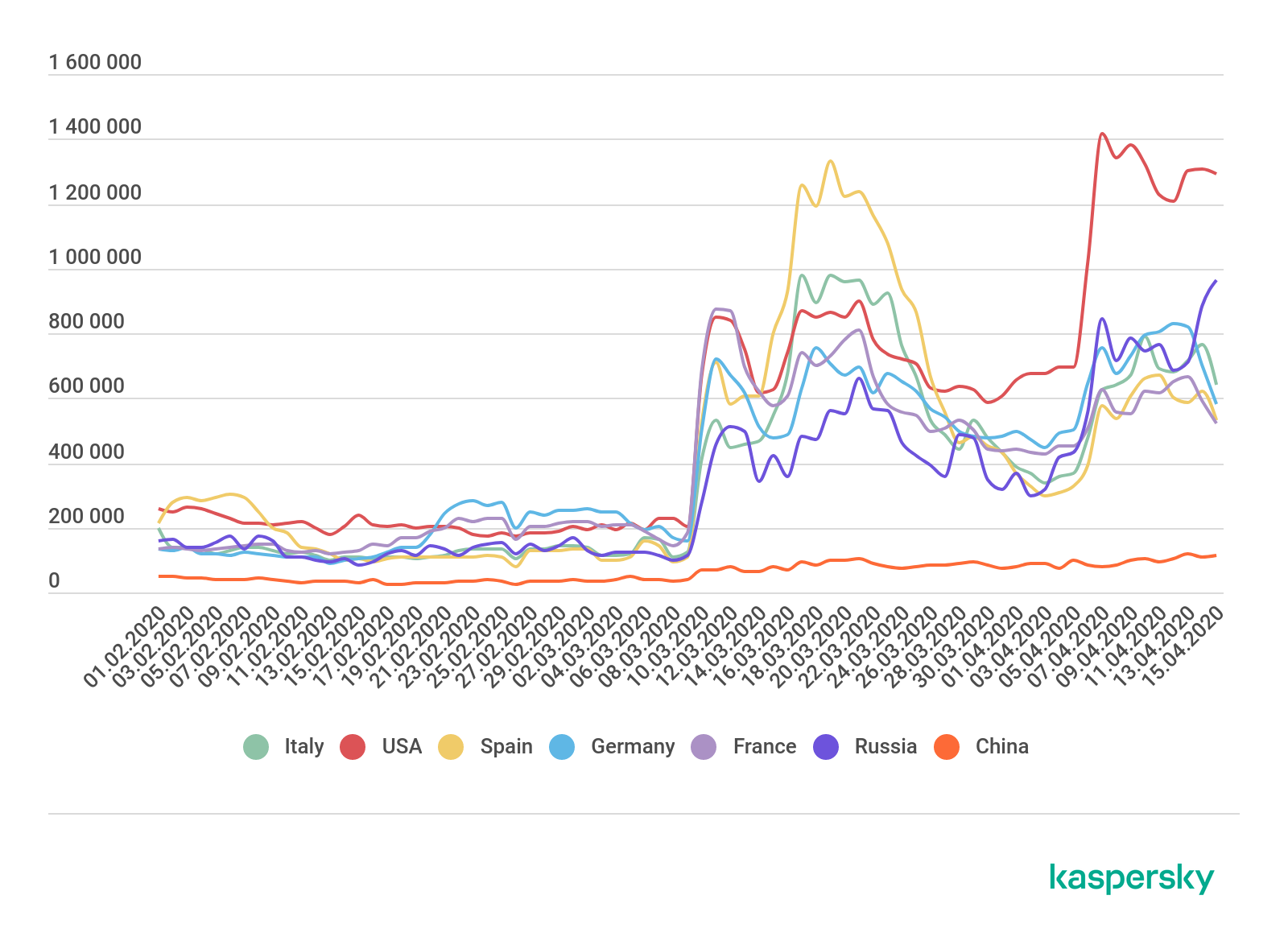
Growth in the number of attacks by the Bruteforce.Generic.RDP family, February–April 2019 (download)
Since attacks on remote infrastructure will undoubtedly continue, it’s important for anyone using RDP to protect their systems. This includes the following.
Use strong passwords.
Make RDP available only through a corporate VPN.
Use NLA (Network Level Authentication).
Enable two-factor authentication.
If you don’t use RDP, disable it and close port 3389.
Use a reliable security solution.
Even if you use a different remote access protocol, you shouldn’t relax. At the end of last year, Kaspersky experts found 37 vulnerabilities in various clients that connected via the VNC protocol, which, like RDP, is used for remote access.
Gaming during the COVID-19 pandemic
Online gamers face various threats, including malware in pirated copies, mods and cheats, phishing and other scams when buying or exchanging in-game items and dangers associated with buying accounts.
The COVID-19 pandemic has led to a marked increase in player activity. For one thing, the sales of games have increased:
Growth in game sales in the week of March 16-22. Source: gamesindustry.biz (download)
The amount of time spent playing has also increased:

Growth in game sales in the week of March 16-22. Source: gamesindustry.biz (download)
This hasn’t gone unnoticed by cybercriminals. With the connection of work computers to home networks, and, conversely, the entry of home devices into work networks that are often poorly prepared for this, attacks on players are becoming not only a way to get to an individual user’s wallet but also a way to access the corporate infrastructure. Cybercriminals are actively hunting for vulnerabilities that they can exploit to compromise systems. For example, in the first five months of this year alone, the number of vulnerabilities discovered on Steam exceeded those discovered in any of the previous years.

Vulnerabilities discovered in Steam. Source: cve.mitre.org (download)
Of course, cybercriminals also exploit human vulnerabilities – hence the increase in phishing scams:
An increase in the number of hits on phishing Steam-related topics relative to February 2020. Source: KSN (download)
And the increase in detections on sites with names exploiting the theme of games:
The number of web attacks using game subjects during the period from January to May 2020. Source: KSN (download)
Data from KSN (Kaspersky Security Network) indicate that attackers focus most on Minecraft, followed by CS: GO and Witcher:
The number of attacks using the theme of an online game, January-May 2020. Source: KSN (download)
You can read more about this in our full report.
Rovnix bootkit back in business
In mid-April, our threat monitoring systems detected an attempt by cybercriminals to exploit the COVID-19 pandemic to distribute the Rovnix bootkit. The infected file, which has an EXE or RAR extension, is called (in Russian) ‘on the new initiative of the World Bank in connection with the coronavirus pandemic’. The file is a self-extracting archive that contains ‘easymule.exe’ and ‘1211.doc’.

The file includes the Rovnix bootkit.
Rovnix is well-known and the source code published some time ago. And there’s nothing new about cybercriminals exploiting the current pandemic to distribute malware. However, Rovnix has been updated with a UAC (User Account Control) bypass tool, allowing the malware to escalate its privileges without displaying a UAC request. It also uses DLL hijacking to camouflage itself in the system.
This version also delivers a loader that is unusual for this malware. Once the malware is installed, the C2 can send commands to control the infected computer, including recording sound from the microphone and sending the audio file to the cybercriminals, turning off or restarting the computer.
Our analysis of this version makes it clear that even well-known threats like Rovnix can throw up surprises when the source code goes public. Freed from the need to develop their own protection-bypassing tools from scratch, cybercriminals can pay more attention to the capabilities of their own malware and add their own ‘goodies’ to the source code – in this case, UAC bypass.
You can read our full analysis here.
Web skimming with Google Analytics
Web skimming is a common method of stealing the data of online shoppers. Cybercriminals inject malicious code into a target website to harvest the data entered by consumers. They gain access to the compromised site by brute-forcing an administrator account password, exploiting vulnerabilities in the CMS (content management system) or one of its third-party plugins, or by injecting malicious code into an incorrectly coded input form.
One way to prevent this is to try to block the exfiltration of the harvested data using a Content Security Policy (CSP) – a technical header that lists all services with the right to collect information on a particular site or page. If the service used by the cybercriminals is not listed in the header, they will not be able to withdraw any information they harvest.
Some attackers are using Google Analytics to work around this. Most online providers today carefully monitor visitor statistics; and the most convenient tool for doing this is Google Analytics. The service, which allows data collection based on many parameters, is currently used by around 29 million sites. So, there’s a strong likelihood that data transfer to Google Analytics is allowed in the CSP header of an online store. To collect website statistics, all you have to do is configure tracking parameters and add a tracking code to your pages. As far as the service is concerned, if you are able to add this code, you are the legitimate owner of the site. So, the malicious script injected by the attacker can collect user data and then, using their own tracking code, send it through the Google Analytics Measurement Protocol directly to their account.
To prevent these issues, webmasters should do the following:
Adopt a strict CMS access policy that restricts user rights to a minimum.
Install CMS components from trusted sources only.
Create strong passwords for all administrator accounts.
Apply updates to all software.
Filter user-entered data and query parameters, to prevent third-party code injection.
For e-commerce sites, use PCI DSS-compliant payment gateways.
Consumers should use a reliable security solution – one that detects malicious scripts on payment sites.
You can read more about this method here.
The Magnitude Exploit Kit
Exploit kits are not as widespread as they used to be. In the past, they sought to exploit vulnerabilities that had already been patched. However, newer and more secure web browsers with automatic updates simply prevent this. The decline in the use of Adobe Flash Player has also reduced the opportunities for cybercriminals. Adobe Flash Player is a browser plug-in: so even if the browser was up-to-date, there was a possibility that Adobe Flash was still vulnerable to known exploits. The end of life date for Adobe Flash is fast approaching. It is disabled by default in all web browsers and has pretty much been replaced with open standards such as HTML5, WebGL, and WebAssembly.
Nevertheless, exploit kits have not disappeared completely. They have adapted and switched to target people running Internet Explorer that haven’t installed the latest security updates.
Although Edge replaced Internet Explorer as the default web browser with the release of Windows 10, Internet Explorer is still installed for backward compatibility on machines running Windows 10; and has remained the default web browser for Windows 7, 8 and 8.1. The switch to Microsoft Edge development also meant that Internet Explorer would no longer be actively developed and would only receive vulnerability patches without general security improvements. Notwithstanding this, Internet Explorer remains a relatively popular web browser. According to NetMarketShare, as of April 2020, Internet Explorer is used on 5.45% of desktop computers (for comparison, Firefox accounts for 7.25%, Safari 3.94% and Edge 7.76%).
Despite the security of Internet Explorer being five years behind that of its modern counterparts, it supports a number of legacy script engines. CVE-2018-8174 is a vulnerability in a legacy VBScript engine that was originally discovered in the wild as an exploited zero-day. The majority of exploit kits quickly adopted it as their primary exploit. Since its discovery, a few more vulnerabilities for Internet Explorer have been discovered as in-the-wild zero-days – CVE-2018-8653, CVE-2019-1367, CVE-2019-1429 and CVE-2020-0674. All of them exploited another legacy component of Internet Explorer – a JScript engine. It felt like it was just a matter of time until exploit kits adopted these new exploits.
Exploit kits still play a role in today’s threat landscape and continue to evolve. We recently analyzed the evolution of one of the most sophisticated exploit kits out there – the Magnitude Exploit Kit – for a whole year. We discovered that this exploit kit continues to deliver ransomware to Asia Pacific (APAC) countries via malvertising. Study of the exploit kit’s activity over a period of 12 months showed that the Magnitude Exploit Kit is actively maintained and undergoes continuous development. In February this year, the exploit kit switched to an exploit for the most recent vulnerability in Internet Explorer – CVE-2019-1367 – originally discovered as an exploited zero-day in the wild. Magnitude Exploit Kit also uses a previously unknown elevation of privilege exploit for CVE-2018-8641, developed by a prolific exploit writer.
You can read more about our findings here.
While the total volume of attacks performed using exploit kits has decreased, it’s clear that they still exist, remain active, and continue to pose a threat. Magnitude is not the only active exploit kit and we see other exploit kits that are also switching to newer exploits for Internet Explorer. We recommend that people install security updates, migrate to a supported operating system (and make sure you stay up-to-date with Windows 10 builds) and also replace Internet Explorer as their web browser.
IT threat evolution Q2 2020. PC statistics
3.9.20 Analysis Securelist
IT threat evolution Q2 2020. Review
IT threat evolution Q2 2020. Mobile statistics
These statistics are based on detection verdicts of Kaspersky products received from users who consented to provide statistical data.
Quarterly figures
According to Kaspersky Security Network, in Q2:
Kaspersky solutions blocked 899,744,810 attacks launched from online resources in 191 countries across the globe.
As many as 286,229,445 unique URLs triggered Web Anti-Virus components.
Attempted infections by malware designed to steal money via online access to bank accounts were logged on the computers of 181,725 unique users.
Ransomware attacks were defeated on the computers of 154,720 unique users.
Our File Anti-Virus detected 80,993,511 unique malware and potentially unwanted objects.
Financial threats
Financial threat statistics
In Q2 2020, Kaspersky solutions blocked attempts to launch one or more types of malware designed to steal money from bank accounts on the computers of 181,725 users.

Number of unique users attacked by financial malware, Q2 2020 (download)
Geography of attacks
To evaluate and compare the risk of being infected by banking Trojans and ATM/POS malware worldwide, for each country we calculated the share of users of Kaspersky products that faced this threat during the reporting period out of all users of our products in that country.

Geography of financial malware attacks, Q2 2020 (download)
Top 10 countries by share of attacked users
Country* %**
1 Turkmenistan 7.5
2 Uzbekistan 5.7
3 Tajikistan 5.6
4 Afghanistan 2.6
5 Macedonia 2.6
6 Yemen 2.2
7 Syria 1.9
8 Kazakhstan 1.7
9 Cyprus 1.7
10 Iran 1.5
* Excluded are countries with relatively few Kaspersky product users (under 10,000).
** Unique users of Kaspersky products whose computers were targeted by financial malware as a share of all unique users of Kaspersky products in the country.
Among the banking Trojan families, the share of Backdoor.Win32.Emotet decreased markedly from 21.3% to 6.6%. This botnet’s activity decreased at the end of Q1 2020, but the results only became clear in the second quarter. However, as we prepared this report, we noticed that Emotet was gradually recovering.
Top 10 banking malware families
Name Verdicts %*
1 Zbot Trojan.Win32.Zbot 24.8
2 RTM Trojan-Banker.Win32.RTM 18.6
3 CliptoShuffler Trojan-Banker.Win32.CliptoShuffler 15.4
4 Emotet Backdoor.Win32.Emotet 6.6
5 Trickster Trojan.Win32.Trickster 4.7
6 Nimnul Virus.Win32.Nimnul 4.3
7 Danabot Trojan-Banker.Win32.Danabot 3.4
8 SpyEye Trojan-Spy.Win32.SpyEye 3.0
9 Nymaim Trojan.Win32.Nymaim 2.5
10 Neurevt Trojan.Win32.Neurevt 1.4
** Unique users attacked by this malware family as a percentage of all users attacked by financial malware.
Ransomware programs
Quarterly trend highlights
The attackers behind the Shade ransomware announced that they had ceased to distribute the Trojan. In addition, they published keys to decrypt files affected by all of its versions. The number of keys that had been accumulated over the years exceeded 750,000, and we updated our ShadeDecryptor utility to help Shade victims to regain access to their data.
Ransomware written in Go began surfacing more often than before. Examples of recently discovered Trojans include Sorena, Smaug, Hydra, Satan/M0rphine, etc. What is this: hackers showing an interest in new technology, ease of development or an attempt at making researchers’ work harder? No one knows for sure.
Number of new modifications
We detected five new ransomware families and 4,406 new modifications of these malware programs in Q2 2020.

Number of new ransomware modifications detected, Q2 2019 – Q1 2020 (download)
Number of users attacked by ransomware Trojans
Kaspersky products and technologies protected 154,720 users from ransomware attacks in Q2 2020.
Number of unique users attacked by ransomware Trojans, Q2 2020 (download)
Geography of attacks

Geography of attacks by ransomware Trojans, Q2 2020 (download)
Top 10 countries attacked by ransomware Trojans
Country* %**
1 Bangladesh 1.69%
2 Mozambique 1.16%
3 Uzbekistan 1.14%
4 Egypt 0.97%
5 Ethiopia 0.94%
6 China 0.74%
7 Afghanistan 0.67%
8 Pakistan 0.57%
9 Vietnam 0.55%
10 Mongolia 0.49%
* Excluded are countries with relatively few Kaspersky users (under 50,000).
** Unique users whose computers were attacked by Trojan encryptors as a share of all unique users of Kaspersky products in the country.
Top 10 most common families of ransomware Trojans
Name Verdicts %*
1 WannaCry Trojan-Ransom.Win32.Wanna 14.74%
2 (generic verdict) Trojan-Ransom.Win32.Gen 9.42%
3 (generic verdict) Trojan-Ransom.Win32.Generic 7.47%
4 (generic verdict) Trojan-Ransom.Win32.Encoder 7.11%
5 Stop Trojan-Ransom.Win32.Stop 7.06%
6 GandCrab Trojan-Ransom.Win32.GandCrypt 4.68%
7 (generic verdict) Trojan-Ransom.Win32.Crypren 4.28%
8 (generic verdict) Trojan-Ransom.Win32.Phny 3.29%
9 Cerber Trojan-Ransom.Win32.Zerber 2.19%
10 Crysis/Dharma Trojan-Ransom.Win32.Crusis 2.16%
* Unique Kaspersky users attacked by the specified family of ransomware Trojans as a percentage of all users attacked by ransomware Trojans.
Miners
Number of new modifications
Kaspersky solutions detected 3,672 new miner modifications in Q2 2020, which is several dozen times fewer than in the previous quarter.

Number of new miner modifications, Q2 2020 (download)
The difference can be explained by thousands of modifications of one miner family, which were detected in the first quarter. In the quarter under review, that miner’s activity dwindled, which is reflected in the statistics.
Number of users attacked by miners
We detected miner attacks on the computers of 440,095 unique Kaspersky users worldwide in Q2 2020. This type of threats shows a clear downward trend.

Number of unique users attacked by miners, Q2 2020 (download)
Geography of attacks
Geography of miner attacks, Q2 2020 (download)
Top 10 countries attacked by miners
Country* %**
1 Afghanistan 4.08%
2 Ethiopia 4.04%
3 Uzbekistan 2.68%
4 Tanzania 2.57%
5 Vietnam 2.17%
6 Rwanda 2.11%
7 Kazakhstan 2.08%
8 Sri Lanka 1.97%
9 Mozambique 1.78%
10 Belarus 1.41%
* Excluded are countries with relatively few Kaspersky product users (under 50,000).
** Unique users whose computers were attacked by miners as a share of all unique users of Kaspersky products in the country.
Vulnerable applications used by cybercriminals during cyberattacks
Exploit distribution statistics for Q2 2020, as before, show that vulnerabilities in the Microsoft Office suite are the most common ones. However, their share decreased to 72% in the last quarter. The same vulnerabilities we had seen before still topped the list. CVE-2017-8570, which allows inserting a malicious script into an OLE object placed inside an Office document, was the most commonly exploited vulnerability. It was followed by the Q1 favorite, CVE-2017-11882. This vulnerability exploits a stack overflow error in the Equation Editor component of the Office suite. CVE-2017-8570, a vulnerability similar to CVE-2017-0199, came third. The remaining positions on the TOP 5 list were occupied by CVE-2018-0802 and CVE-2017-8759.
The second category (exploits for popular browsers) accounted for about 12% in Q2, its share increasing slightly when compared to the previous period. During the reporting period, cybercriminals attacked Firefox using the CVE-2020-6819 vulnerability, which allows malicious code to be executed when an HTTP header is parsed incorrectly. Exploits that use the vulnerabilities in the ReadableStream interface, such as CVE-2020-6820, have been observed as well. No major vulnerability exploited to spread malware was observed during the reporting period for any of the other popular browsers: Google Chrome, Microsoft Edge, or Internet Explorer. However, fixes for a number of vulnerabilities that could potentially have been used for creating exploits, but were detected by researchers in time, were announced to software manufacturers.

Distribution of exploits used by cybercriminals, by type of attacked application, Q2 2020 (download)
The first quarter set a trend for researching font and other graphic primitives subsystems in Windows. In Q2, two vulnerabilities were discovered in Windows Codecs Library, assigned CVE-2020-1425 and CVE-2020-1457 codes. Both were fixed, and neither is known to have been exploited in the wild. Another interesting vulnerability fixed in the last quarter is CVE-2020-1300. It allows for remote execution of code due to incorrect processing of Cabinet files, for example, if the user is trying to run a malicious CAB file pretending to be a printer driver. Notably, the CVE-2020-1299 vulnerability allowed the attacker to execute arbitrary code with the user’s privileges by generating a specially formatted LNK file.
The trend for brute-forcing of Remote Desktop Services, Microsoft SQL Services and SMB access passwords persisted in Q2 2020. No full-on network attacks that exploited new vulnerabilities in network exchange protocols were detected. However, software developers did discover and fix several vulnerabilities in popular network services. Among the most interesting ones were CVE-2020-1301 for SMBv1, which allowed the attacker to execute code remotely on a target system. CVE-2020-0796 (SmbGhost), a popular SMBv3 vulnerability among researchers, received unexpected follow-up in the form of an exploit that allowed compromising the system without interacting with the user. The same protocol version was found to contain an error, designated as CVE-2020-1206 and known as the SMBleed vulnerability, which allowed the attacker to get a portion of the Windows kernel memory. The researchers even published several exploit versions that used a bundle of SMBleed and SMBGhost to execute the code with system privileges. In that mode, the attacker can install any software and access any information on the computer.
Attacks on Apple macOS
In Q2 2020, we discovered new versions of previously known threats and one new backdoor, which received the verdict of Backdoor.OSX.Lador.a. The malware is notable for being written in Go, a language gaining popularity as a means to create malware aimed at the macOS platform. If you compare the size of the Lador file with any backdoor created in Objective C, the difference will be very significant: the size of a Lador file is 5.5 megabytes, i.e. many times larger. And all this for the sake of remote access to the infected machine and execution of arbitrary code downloaded from the control center.
Top 20 threats for macOS
Verdict %*
1 Monitor.OSX.HistGrabber.b 17.39
2 Trojan-Downloader.OSX.Shlayer.a 12.07
3 AdWare.OSX.Pirrit.j 9.10
4 AdWare.OSX.Bnodlero.at 8.21
5 AdWare.OSX.Cimpli.k 7.32
6 AdWare.OSX.Pirrit.o 5.57
7 Trojan-Downloader.OSX.Agent.h 4.19
8 AdWare.OSX.Ketin.h 4.03
9 AdWare.OSX.Pirrit.x 4.00
10 AdWare.OSX.Spc.a 3.98
11 AdWare.OSX.Amc.c 3.97
12 Backdoor.OSX.Lador.a 3.91
13 AdWare.OSX.Pirrit.v 3.22
14 RiskTool.OSX.Spigot.a 2.89
15 AdWare.OSX.Bnodlero.t 2.87
16 AdWare.OSX.Cimpli.f 2.85
17 AdWare.OSX.Adload.g 2.60
18 AdWare.OSX.Pirrit.aa 2.54
19 AdWare.OSX.MacSearch.d 2.44
20 AdWare.OSX.Adload.h 2.35
* Unique users attacked by this malware as a percentage of all users of Kaspersky security solutions for macOS that were attacked.
The rankings of the most common threats for the macOS platform has not changed much compared to the previous quarter and is still largely made up of adware. As in Q1 2020, Shlayer (12.07%) was the most common Trojan. That malware loads adware from the Pirrit, Bnodlero and Cimpli families, which populate our TOP 20.
The Lador.a backdoor, which we mentioned above, entered the rankings along with adware.
Finally, in Q2 2020, a group of potentially unwanted programs collectively detected as HistGrabber.b joined the rankings. The main purpose of such software is to unpack archives, but HistGrabber.b also quietly uploaded the user’s browsing history to the developer’s servers. This is nothing new: all applications that steal browsing history have long been withdrawn from the App Store, and servers that could receive the data, disabled. Nevertheless, we deem it necessary to inform users of any such software discovered on their devices.
Threat geography

Threat geography for the macOS platform, Q2 2020 (download)
TOP 10 countries
Country* %**
1 Spain 9.82%
2 France 7.73%
3 Mexico 6.70%
4 Italy 6.54%
5 India 6.47%
6 Canada 6.34%
7 Brazil 6.25%
8 USA 5.99%
9 United Kingdom 5.90%
10 Russia 5.77%
* Excluded from the rating are countries with relatively few users of Kaspersky security solutions for MacOS (under 5,000).
** Unique users attacked in the country as a percentage of all users of Kaspersky security solutions for MacOS in the same country.
The most common threats in all the countries on the list without exception bundled various adware with the Shlayer Trojan.
IoT attacks
IoT threat statistics
Q2 2020 saw no dramatic change in cybercriminal activity targeting IoT devices: attackers most frequently ran Telnet login and password brute-force campaigns.
Telnet 80.83%
SSH 19.17%
Distribution of attacked services by number of unique IP addresses of attacking devices, Q2 2020
Further communication with IoT devices that pretended to be infected (and actually traps), was much more often conducted via Telnet.
Telnet 71.52%
SSH 28.48%
Distribution of cybercriminals’ working sessions with Kaspersky traps, Q2 2020

Geography of IP addresses of device from which attacks on Kaspersky Telnet traps originated, Q2 2020 (download)
TOP 10 countries by location of devices from which Telnet-based attacks were carried out on Kaspersky traps
Country %*
China 12.75%
Brazil 11.88%
Egypt 8.32%
Taiwan 6.58%
Iran 5.17%
India 4.84%
Russia 4.76%
Vietnam 3.59%
Greece 3.22%
USA 2.94%
* Share of devices from which attacks were carried out in the country out of the total number of devices
The three countries with the most devices that launched attacks on Kaspersky Telnet traps remained virtually unchanged. China (12.75%) was first, while Brazil (11.88%) and Egypt (8.32%) swapped positions.

Geography of IP addresses of device from which attacks on Kaspersky SSH traps originated, Q2 2020 (download)
TOP 10 countries by location of devices from which SSH-based attacks were carried out on Kaspersky traps
Country %*
China 22.12%
USA 10.91%
Vietnam 8.20%
Brazil 5.34%
Germany 4.68%
Russia 4.44%
France 3.42%
India 3.01%
Egypt 2.77%
Singapore 2.59%
* Share of devices from which attacks were carried out in the country out of the total number of devices
As with Telnet, the three countries where the most attacks on SSH traps originated remained unchanged from Q1 2020: China (22.12%), U.S. (10.91%) and Vietnam (8.20%).
Threats loaded into traps
Verdict %*
Trojan-Downloader.Linux.NyaDrop.b 32.78
Backdoor.Linux.Mirai.b 17.47
HEUR:Backdoor.Linux.Mirai.b 12.72
HEUR:Backdoor.Linux.Gafgyt.a 9.76
Backdoor.Linux.Mirai.ba 7.99
HEUR:Backdoor.Linux.Mirai.ba 4.49
Backdoor.Linux.Gafgyt.bj 2.23
HEUR:Trojan-Downloader.Shell.Agent.p 1.66
Backdoor.Linux.Mirai.cn 1.26
HEUR:Backdoor.Linux.Mirai.c 0.73
* Share of the malware type in the total amount of malware downloaded to IoT devices following a successful attack.
As in the first quarter, the NyaDrop Trojan led by the number of loads onto traps. The Mirai Trojan family retained its relevance in Q2 2020, occupying half of our IoT threat rankings.
Attacks via web resources
The statistics in this section are based on Web Anti-Virus, which protects users when malicious objects are downloaded from malicious/infected web pages. Malicious websites are specially created by cybercriminals; web resources with user-created content (for example, forums), as well as hacked legitimate resources, can be infected.
Countries that are sources of web-based attacks: TOP 10
The following statistics show the distribution by country of the sources of Internet attacks blocked by Kaspersky products on user computers (web pages with redirects to exploits, sites containing exploits and other malicious programs, botnet C2 centers, etc.). Any unique host could be the source of one or more web-based attacks.
To determine the geographical source of web-based attacks, domain names are matched against their actual domain IP addresses, and then the geographical location of a specific IP address (GEOIP) is established.
In Q2 2020, Kaspersky solutions defeated 899,744,810 attacks launched from online resources located in 191 countries across the globe. A total of 286,229,445 unique URLs were recognized as malicious by Web Anti-Virus components.

Distribution of web-based attack sources by country, Q2 2020 (download)
Countries where users faced the greatest risk of online infection
To assess the risk of online infection faced by users in different countries, for each country we calculated the share of Kaspersky users on whose computers Web Anti-Virus was triggered during the quarter. The resulting data provides an indication of the aggressiveness of the environment in which computers operate in different countries.
This rating only includes attacks by malicious objects that fall under the Malware class; it does not include Web Anti-Virus triggers in response to potentially dangerous or unwanted programs, such as RiskTool or adware.
Country* % of attacked users**
1 Algeria 11.2052
2 Mongolia 11.0337
3 Albania 9.8699
4 France 9.8668
5 Tunisia 9.6513
6 Bulgaria 9.5252
7 Libya 8.5995
8 Morocco 8.4784
9 Greece 8.3735
10 Vietnam 8.2298
11 Somalia 8.0938
12 Georgia 7.9888
13 Malaysia 7.9866
14 Latvia 7.8978
15 UAE 7.8675
16 Qatar 7.6820
17 Angola 7.5147
18 Réunion 7.4958
19 Laos 7.4757
20 Mozambique 7.4702
* Excluded are countries with relatively few Kaspersky users (under 10,000).
** Unique users targeted by Malware-class attacks as a share of all unique Kaspersky users in the country.
These statistics are based on detection verdicts returned by the Web Anti-Virus module that were received from users of Kaspersky products who consented to provide statistical data.
On average, 5.73% of Internet user computers worldwide experienced at least one Malware-class attack.
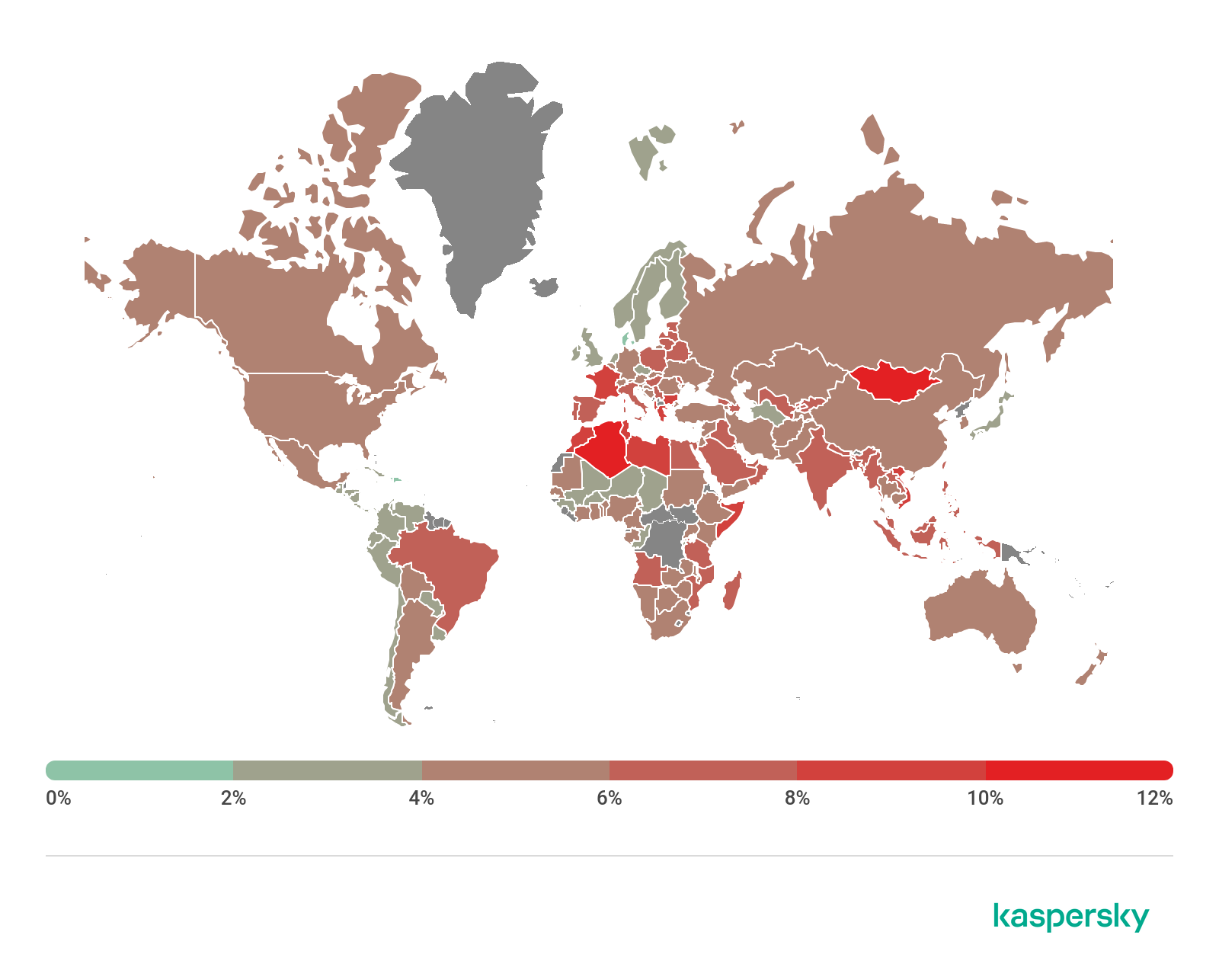
Geography of malicious web-based attacks, Q2 2020 (download)
Local threats
In this section, we analyze statistical data obtained from the OAS and ODS modules in Kaspersky products. It takes into account malicious programs that were found directly on users’ computers or removable media connected to computers (flash drives, camera memory cards, phones, external hard drives), or which initially made their way onto the computer in non-open form (for example, programs included in complex installers, encrypted files, etc.).
In Q2 2020, our File Anti-Virus detected 80,993,511 malware and potentially unwanted objects.
Countries where users faced the highest risk of local infection
For each country, we calculated the percentage of Kaspersky users on whose computers File Anti-Virus was triggered during the reporting period. These statistics reflect the level of personal computer infection in different countries.
Note that the rating includes only Malware-class attacks; it does not include File Anti-Virus triggers in response to potentially dangerous or unwanted programs, such as RiskTool or adware.
Country* % of attacked users**
1 Turkmenistan 48.0224
2 Uzbekistan 42.2632
3 Tajikistan 42.1279
4 Ethiopia 41.7213
5 Afghanistan 40.6278
6 Myanmar 39.1377
7 Burkina Faso 37.4560
8 Benin 37.4390
9 China 36.7346
10 Kyrgyzstan 36.0847
11 Vietnam 35.4327
12 Mauritania 34.2613
13 Laos 34.0350
14 Mongolia 33.6261
15 Burundi 33.4323
16 Belarus 33.0937
17 Guinea 33.0097
18 Mali 32.9902
19 Togo 32.6962
20 Cameroon 32.6347
* Excluded are countries with relatively few Kaspersky users (under 10,000).
** Unique users on whose computers Malware-class local threats were blocked, as a share of all unique users of Kaspersky products in the country.
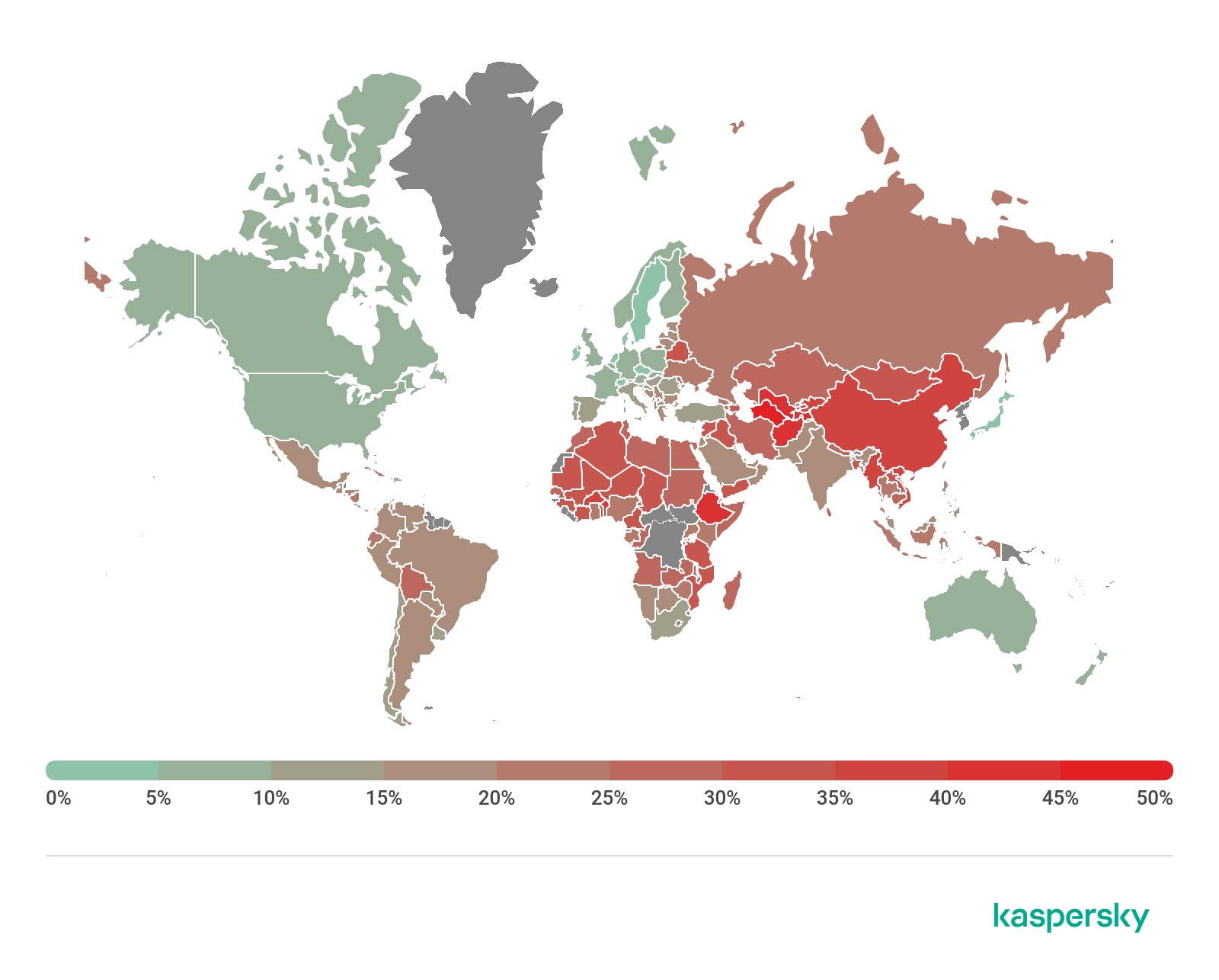
Geography of local infection attempts, Q2 2020 (download)
Overall, 17.05% of user computers globally faced at least one Malware-class local threat during Q2 2020.
IT threat evolution Q2 2020. Mobile statistics
3.9.20 Analysis Securelist
IT threat evolution Q2 2020. Review
IT threat evolution Q2 2020. PC statistics
These statistics are based on detection verdicts of Kaspersky products received from users who consented to provide statistical data.
Quarterly figures
According to Kaspersky Security Network, the second quarter saw:
1,245,894 detected malicious installers, of which
38,951 packages were related to mobile banking trojans
3,805 packages proved to be mobile ransomware trojans
A total of 14,204,345 attacks on mobile devices were blocked
Quarterly highlights
In summing up the results of the second quarter, we will begin with the number of attacks that targeted mobile devices. In Q2 2019, we thwarted 15,137,884 attacks, but one year later, the number decreased insignificantly, to 14,204,345.
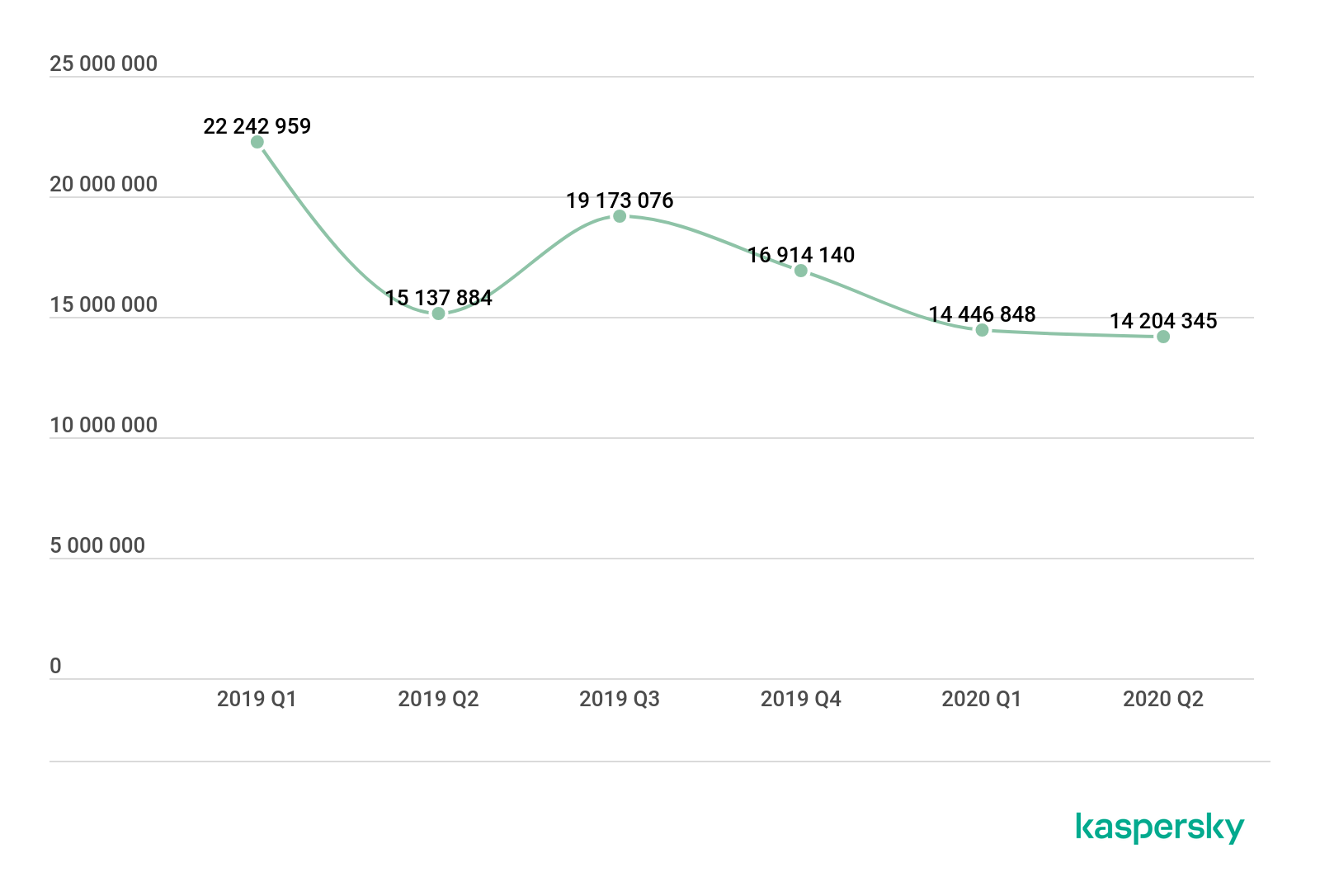
Number of attacks on mobile devices, Q1 2019 – Q2 2020 (download)
The absence of significant changes indicates that malware developers kept up their activities in the face of the coronavirus pandemic. At the same time, this shows that we are not going through an epidemic caused by any particular family or class of mobile threats. In other words, no one reached the level of Asacub in yet another quarter, which is good news.
Nevertheless, mobile security users encountered malicious files more often than adware or potentially unwanted apps.

Share of users who encountered various threat classes, Q2 2020 (download)
The number of users whose devices were found to contain adware is almost half the number of those whose devices were infected with various classes of malware. At the same time, adware is a clear leader by number of objects detected, both in the second quarter and in previous ones. What is peculiar about adware and applications with an integrated advertising module is that they are extremely difficult for the user to identify or remove. The applications themselves naturally give no warning that they will pop up half-screen or even full-screen advertisements, and telling which application is being displayed if the user did not run it is impossible without special tools.
This kind of applications can be found in the official Google Play store, too, and to our utter regret, some developers are not making a conscious effort to remove questionable advertisements from their products.
Further good news from Q2 2020 is a decrease in the number of devices that were found to contain stalkerware. Several possible explanations exist as to the cause of the significant decline that we have seen since Q4 2019 – we shall talk about these in the appropriate section.
Mobile threat statistics
In Q2 2020, Kaspersky detected 1,245,894 malicious installers, an increase of 93,232 over the previous quarter.
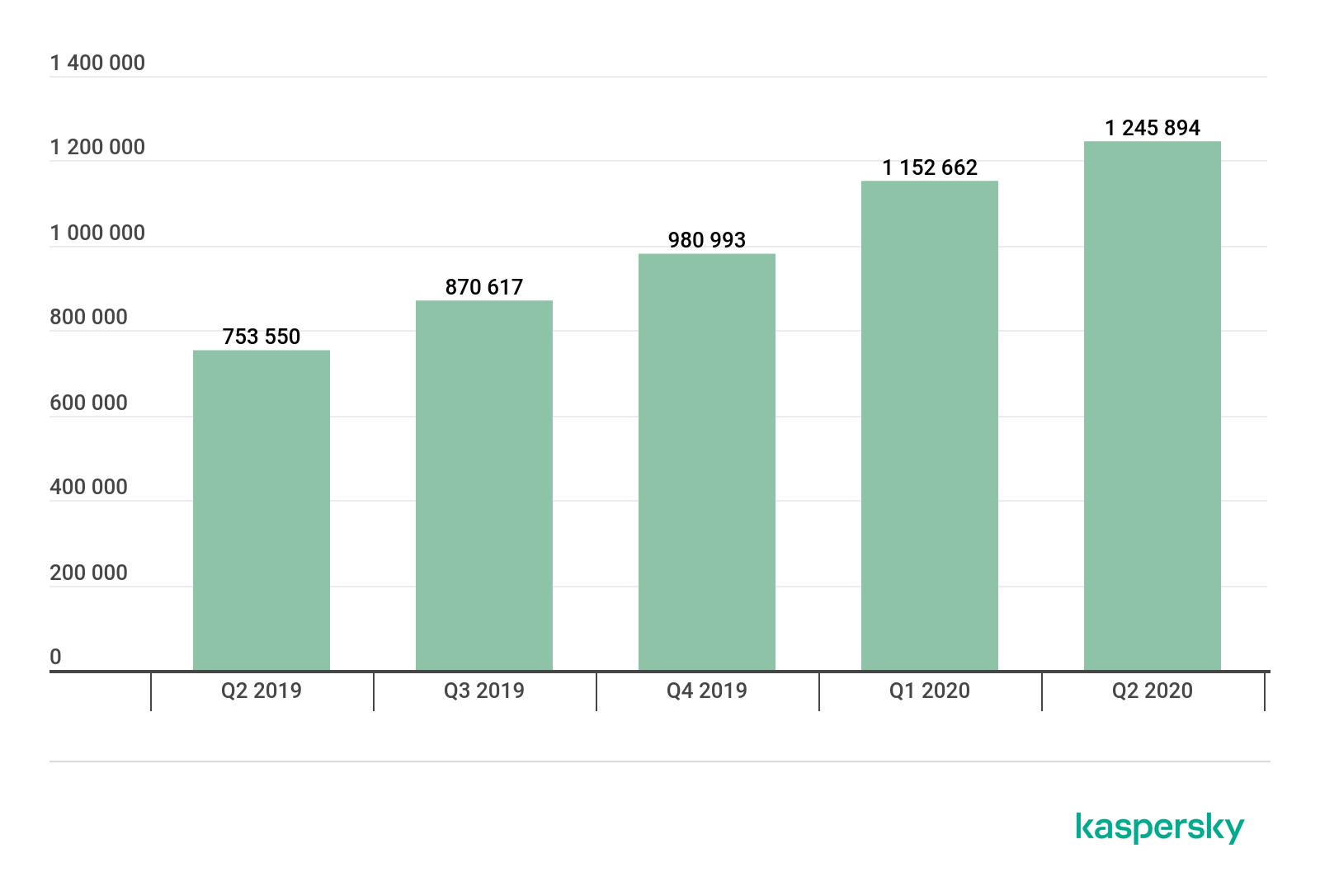
Number of detected malicious installation packages, Q2 2019 – Q2 2020 (download)
Over the past few quarters, we have seen an increase in the number of detected objects. Early 2018 saw a similar situation, when a great number of trojan droppers and potentially unwanted software was discovered.
Distribution of detected mobile apps by type

Distribution of newly detected mobile apps by type, Q1 and Q2 2020 (download)
Adware topped the list with 48%, a decrease of one percentage point from the previous quarter. The Ewind adware family (60.53% of all adware detected) was most common in Q2, followed by the FakeAdBlocker family with 13.14% and Inoco with 10.17%.
RiskTool-type potentially unwanted software ranked second among all detected threat classes. Its share was 20%, which is eight percentage points smaller than in Q1 2020 and 21 p.p. smaller than in Q2 2019.
Most of the detected RiskTool variants were SMSreg (44.6% of all detected potentially unwanted software), Resharer (12.63%) and Dnotua (11.94%) families.
SMS trojans hold third place among all detected threats with 7.59%. This threat class is believed to be dying out, as a mobile carrier account is a far less tempting target for criminals than a bank account, and both can be controlled from a mobile device. Agent (33.74%), Fakeinst (26.80%) and Opfake (26.33%) were the largest of the detected families of SMS trojans. All the three families were more common with Russian users, which is typical of the entire SMS trojan threat class. Users from Iran followed, far behind the Russians. The Opfake and Fakeinst families are also the leaders in the number of detections on end-user devices, each accounting for 23% of the total number of unique users attacked by SMS trojans. The Prizmes family (21%) and the Agent family (16%) followed in third and fourth place, respectively.
The Opfake and Fakeinst families are among the oldest mobile threats known to Kaspersky. It is safe to say that their discovery in the wild is more of an echo of past large-scale distribution campaigns. This is supported by the fact that most of the malware detected no longer had functioning control centers. Since the main means of distributing these trojans are fake application websites, one can assume that during lockdown users are more likely to turn to such resources in search of free content and thus provide the malware families with a statistical boost.
Top 20 mobile malware programs
Note that this malware rating does not include potentially dangerous or unwanted programs, such as RiskTool or AdWare.
Verdict %*
1 DangerousObject.Multi.Generic 40.29
2 Trojan.AndroidOS.Boogr.gsh 9.02
3 DangerousObject.AndroidOS.GenericML 6.17
4 Trojan-Downloader.AndroidOS.Necro.d 4.86
5 Trojan-Dropper.AndroidOS.Hqwar.cf 3.63
6 Trojan.AndroidOS.Hiddad.fi 3.19
7 Trojan-Downloader.AndroidOS.Helper.a 2.84
8 Trojan-Downloader.AndroidOS.Agent.hy 2.64
9 Trojan.AndroidOS.Agent.vz 2.32
10 Trojan-Downloader.AndroidOS.Agent.ik 2.06
11 Trojan.AndroidOS.Handda.san 2.04
12 Trojan.AndroidOS.MobOk.v 1.89
13 Trojan-Downloader.AndroidOS.Agent.ic 1.84
14 Trojan.AndroidOS.MobOk.x 1.67
15 Trojan-Dropper.AndroidOS.Hqwar.gen 1.54
16 Trojan-Dropper.AndroidOS.Helper.n 1.45
17 Trojan-Banker.AndroidOS.Rotexy.e 1.36
18 Trojan-Downloader.AndroidOS.Malota.a 1.29
19 Trojan-Dropper.AndroidOS.Penguin.e 1.24
20 Trojan.AndroidOS.Dvmap.a 1.13
* Unique users attacked by this malware as a percentage of all users of Kaspersky mobile antivirus that were attacked.
As per tradition, first place in our Top 20 for Q2 went to the DangerousObject.Multi.Generic verdict (40.29%), which we use for malware detected using cloud technologies. Cloud technologies are deployed when the antivirus databases lack data for detecting a piece of malware, but the company’s cloud already contains information about the object. This is basically how the latest malicious programs are detected.
Second and third places were claimed by Trojan.AndroidOS.Boogr.gsh (9.02%) and DangerousObject.AndroidOS.GenericML (6.17%). These verdicts are assigned to files recognized as malicious by our machine-learning systems.
In fourth place, as in the last quarter, is Trojan-Downloader.AndroidOS.Necro.d (4.86%). This Trojan family is closely associated with various classes of Triada group of complex threats, as well as the xHelper Trojan family, whose members took the seventh and sixteenth positions in the rankings, respectively. A distinctive feature of Necro trojans, which leads to serious problems for its victims, is their ability to take root on the device by escalating access rights. Having obtained root privileges, such trojans can write themselves to the device’s read-only memory, preventing the user from removing the malware with built-in tools.
Fifth and fifteenth places in the rankings were taken by representatives of the Trojan-Dropper.AndroidOS.Hqwar family. This is the most popular dropper in the wild: if you look at the number of detected droppers from various families, you will find Hqwar in second position, immediately after the Agent generalized verdict. In Q2 2020, the share of the Hqwar family among all detected droppers increased markedly to 30.12% from 8% in Q1 2020.
TOP 3 detected droppers
Verdict %
Agent 30.38%
Hqwar 30.32%
Wapnor 30.12%
The sixth position in the rankings went to Trojan.AndroidOS.Hiddad.fi (3.19%), whose capabilities include displaying advertising banners and concealing its activities.
Members of Trojan-Downloader.AndroidOS.Agent took the eighth, tenth and thirteenth positions. These trojans have the simple task of downloading modules from the C2 and running these. The downloaded modules are often adware, but we have seen trojan payloads as well.
Trojan.AndroidOS.vz (2.32%) took the ninth place. Apparently, this Trojan served as a payload for a different type of malware, with Agent.vz’s task coming down to downloading executable code as well. This suggests that the malware is only an intermediate link in the infection chain.
In the eleventh place, we find the Trojan.AndroidOS.Handda.san trojan (2.04%). This verdict covers a whole group of malware, which includes a variety of trojans united by common capabilities: hiding their icons, obtaining Device Admin rights and using packers to counteract detection.
The twelfth and fourteenth places went to members of the Trojan.AndroidOS.MobOk family. These trojans are a link in infection chains and most commonly have been detected with mobile users from Russia.
As in Q1 2020, the twenty most common threats included the bank trojan Rotexy (1.36%). It is worth noting that this is likely not the only widespread banker, as more popular Hqwar droppers often conceal financial malware.
In the eighteenth place we see Trojan-Downloader.AndroidOS.Malota.a (1.29%). We have known this trojan since October 2019. Its main task is to download executable code from the C2 to the infected device.
Geography of mobile threats

Map of mobile malware infection attempts, Q2 2020 (download)
Top 10 countries by share of users attacked by mobile malware
Country* %**
1 Iran 43.62
2 Algeria 21.97
3 Bangladesh 19.30
4 Morocco 17.57
5 Nigeria 15.12
6 India 13.54
7 Saudi Arabia 13.52
8 Kenya 12.61
9 Indonesia 12.17
10 Pakistan 12.16
* Excluded from the rating are countries with relatively few users of Kaspersky mobile security solutions (under 10000).
** Unique users attacked in the country as a share of all users of Kaspersky mobile security solutions in the country.
The TOP 3 countries with the largest user shares remained unchanged in Q2: Iran (43.62%) followed by Algeria (21.97%) and Bangladesh (19.30%).
Most commonly detected in Iran were AdWare.AndroidOS.Notifyer-family adware, alternate Telegram clients (RiskTool.AndroidOS.FakGram.d, for instance, is one of the ten most commonly detected threats in Iran), and Trojan.AndroidOS.Hiddap-family trojans. The latter have a variety of tools and one common feature: the tendency to hide their icons from the app manager screen.
HiddenAd and FakeAdBlocker adware was most common in Algeria, a similar situation to Q1 2020.
In Bangladesh, the leader is HiddenAd-family adware, which conceals their carrier application. AdWare.AndroidOS.Outad.c (fifth place within the country) and AdWare.AndroidOS.Loead (sixth place) adware types were common as well.
Mobile web threats
The statistics presented here are based on detection verdicts returned by the Web Anti-Virus module that were received from users of Kaspersky products who consented to provide statistical data.
Hackers use a variety of techniques to attract potential victims to malicious landing pages, from rogue SEO for displaying their sites in top ten results for certain search queries to redirect chains that will quickly and discreetly take the user from a legitimate site to a malicious one. We decided to calculate the countries where mobile users were most likely to encounter malicious websites while browsing the Web and where these sites are located.
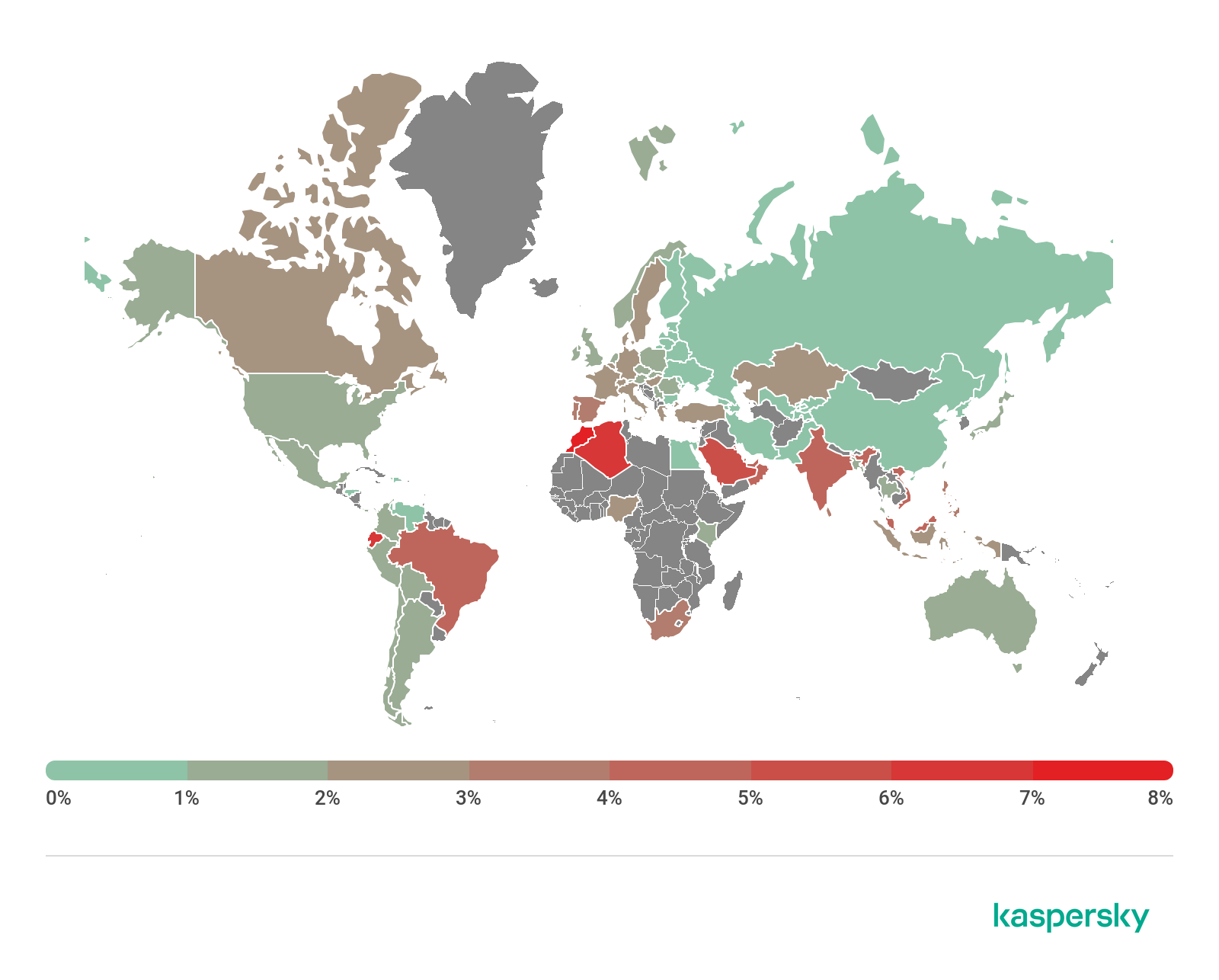
Ten countries with the highest risk of infection
Country* % of attacked users**
Morocco 7.08
Algeria 6.25
Ecuador 6.05
Saudi Arabia 5.24
Oman 4.98
India 4.93
Vietnam 4.63
Kuwait 4.47
UAE 4.27
Brazil 4.25
* Excluded are countries with relatively few Kaspersky mobile product users (under 10,000).
** Unique users targeted by all types of web attacks as a share of all unique users of Kaspersky mobile products in the country.
Countries where mobile web threats are based

Geography of countries where mobile attacks are based, Q2 2020 (download)
TOP 10 countries where the largest numbers of mobile attacks are based
Country %*
Netherlands 51.17
USA 32.87
Dominican Republic 8.36
Singapore 3.64
Germany 1.53
Russian Federation 1.00
Luxembourg 0.44
Ireland 0.32
France 0.19
India 0.05
* Share of mobile threat sources in the country out of the total number of such sources
The Netherlands and the United States topped the list of web threat sources in Q2 2020. The Netherlands accounted for more than half of all attacks, typically engaging advertising-related websites. The United States were the other most common source of a similar type of threats.
Mobile banking Trojans
During the reporting period, we detected 38,951 mobile banking trojan installer packages, 3,164 fewer than in Q1 2020.
TOP 10 detected bankers
1 Agent 58.7%
2 Wroba 8.3%
3 Zitmo 8.2%
4 Rotexy 6.5%
5 Knobot 4.4%
6 Anubis 3.8%
7 Faketoken 3.0%
8 Cebruser 2.4%
9 Asacub 1.0%
10 Ginp 0.9%
The Trojan-Banker.AndroidOS.Agent family made the largest contribution to the number of packages detected: 58.7% of all discovered banking trojans. The Trojan-Banker.AndroidOS.Wroba family (8.3%) was second, far behind the leader, and immediately followed by Trojan-Banker.AndroidOS.Zitmo (8.2%).
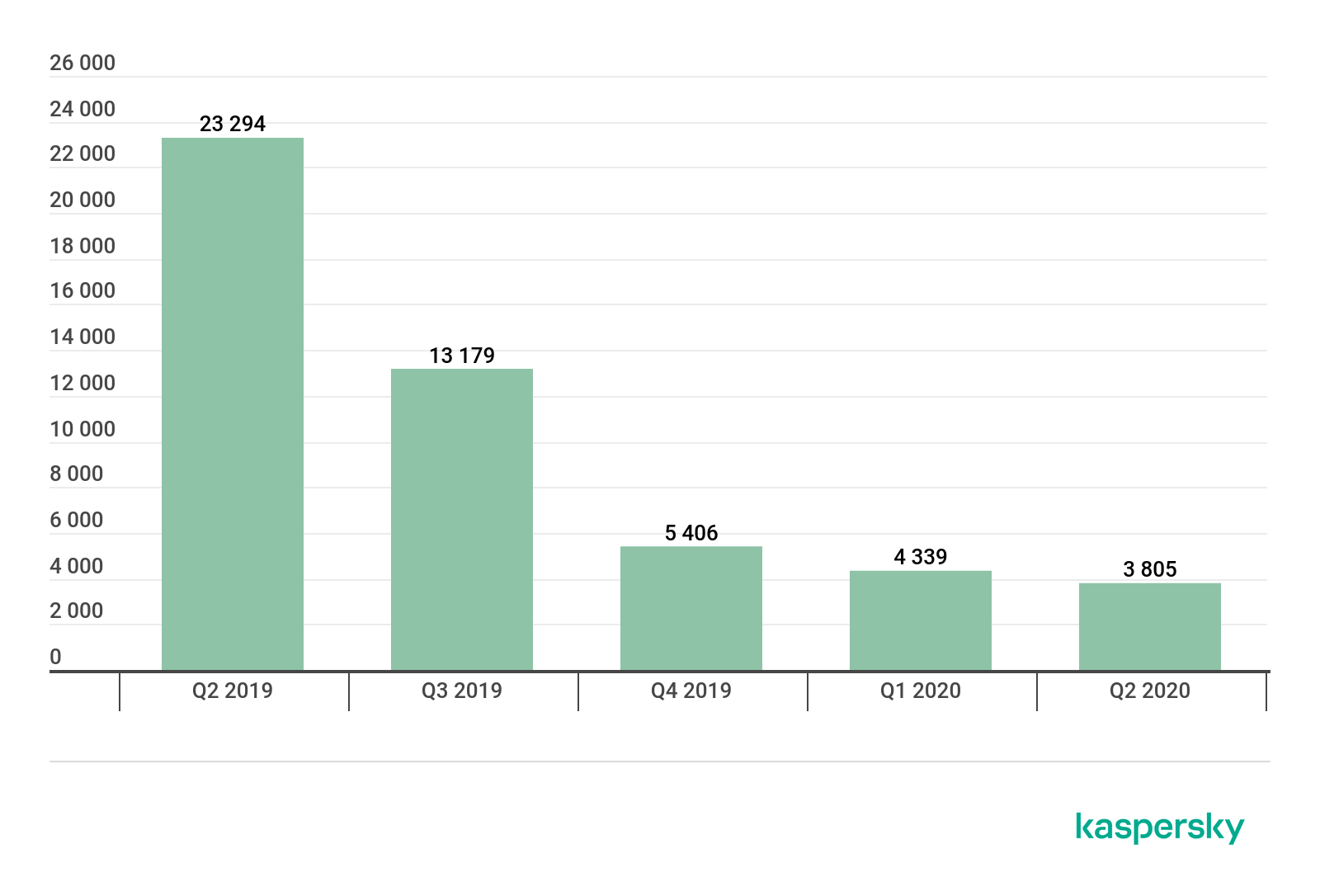
Number of installation packages for mobile banking Trojans detected by Kaspersky, Q2 2019 – Q2 2020 (download)
TOP 10 mobile bankers
Verdict %*
1 Trojan-Banker.AndroidOS.Rotexy.e 13.29
2 Trojan-Banker.AndroidOS.Svpeng.q 9.66
3 Trojan-Banker.AndroidOS.Agent.eq 6.48
4 Trojan-Banker.AndroidOS.Asacub.snt 6.45
5 Trojan-Banker.AndroidOS.Asacub.ce 5.59
6 Trojan-Banker.AndroidOS.Anubis.san 5.49
7 Trojan-Banker.AndroidOS.Faketoken.snt 4.34
8 Trojan-Banker.AndroidOS.Anubis.n 3.49
9 Trojan-Banker.AndroidOS.Hqwar.t 3.14
10 Trojan-Banker.AndroidOS.Asacub.a 3.09
* Unique users attacked by this malware as a share of all Kaspersky mobile security solution users attacked by banking threats.
The first and second places on our list went to mobile bankers that targeted mobile users from Russia: Trojan-Banker.AndroidOS.Rotexy.e (13.29%) and Trojan-Banker.AndroidOS.Svpeng.q (9.66%).
Various members of the Asacub family took three positions out of ten on the TOP 10 for mobile financial threats. Although this threat family is not particularly numerous, it is very popular with attackers.
The Anubis banker family gained popularity in Q2 2020, with its members occupying the sixth and eighth positions. We believe that these versions of the trojan were built from source code leaked onto the Internet.
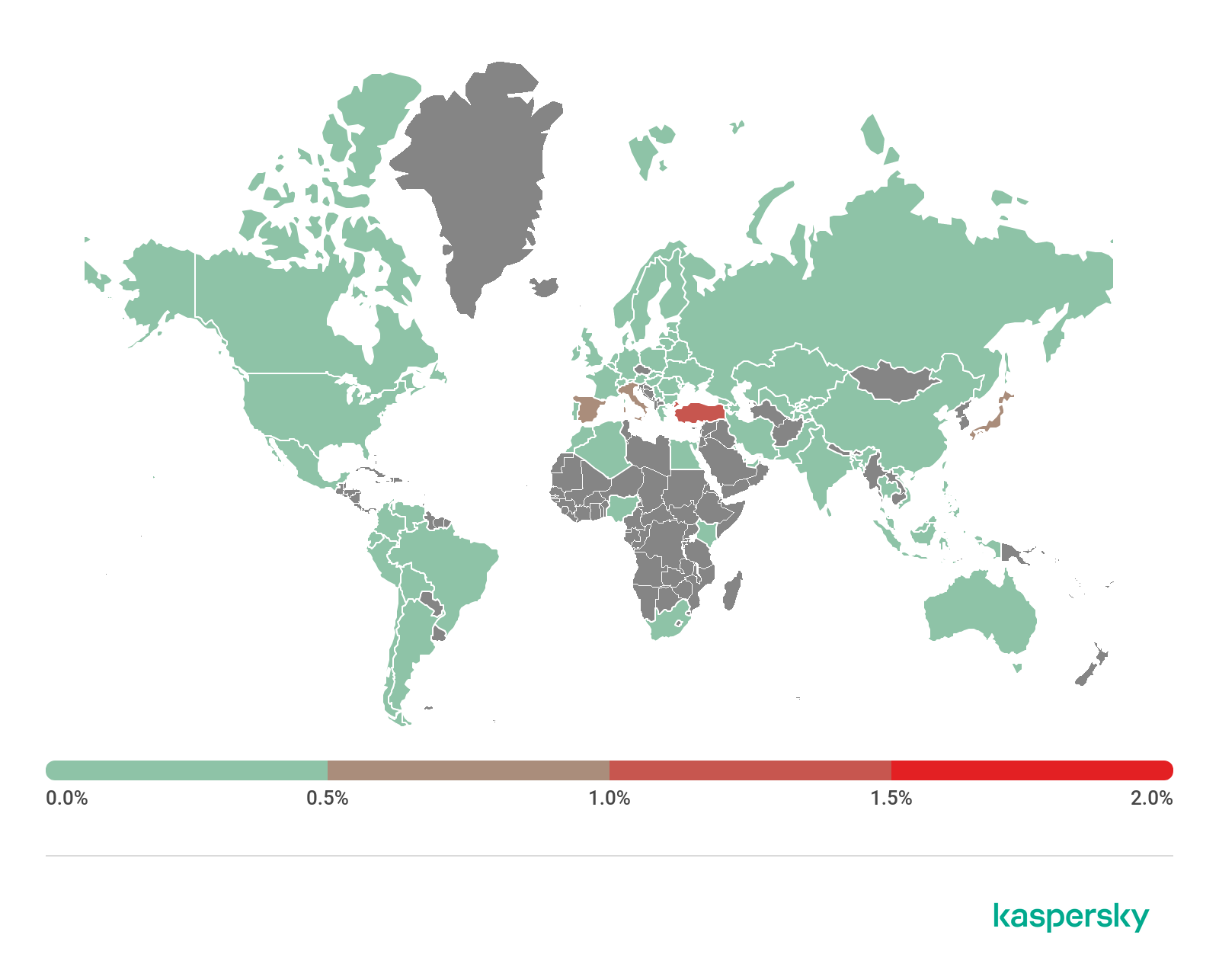
Geography of mobile banking threats, Q2 2020 (download)
TOP 10 countries by share of users attacked by mobile banking Trojans
Country* %**
1 Turkey 1.29%
2 Japan 0.90%
3 Spain 0.71%
4 Italy 0.65%
5 Taiwan 0.49%
6 China 0.19%
7 Tajikistan 0.16%
8 Korea 0.14%
9 Russia 0.14%
10 Poland 0.13%
* Excluded from the rating are countries with relatively few users of Kaspersky mobile security solutions (under 10,000).
** Unique users attacked by mobile banking Trojans as a share of all users of Kaspersky mobile security solutions in the country.
Turkey had the largest share of unique users attacked by mobile financial threats in Q2 2020, 1.29%. Members of the Trojan-Banker.AndroidOS.Cebruser family were most commonly detected there.
Turkey was followed by Spain with 0.71%. The rankings of mobile financial threats in this country were as follows:
Verdict %
Trojan-Banker.AndroidOS.Ginp.snt 36.60%
Trojan-Banker.AndroidOS.Cebruser.san 25.57%
Trojan-Banker.AndroidOS.Cebruser.pac 22.43%
Trojan-Banker.AndroidOS.Knobot.g 5.19%
Trojan-Banker.AndroidOS.Knobot.pac 4.89%
Trojan-Banker.AndroidOS.Knobot.c 3.73%
Trojan-Banker.AndroidOS.Knobot.h 3.43%
Trojan-Banker.AndroidOS.Agent.eq 2.99%
Trojan-Banker.AndroidOS.Knobot.c 2.63%
Trojan-Banker.AndroidOS.Cebruser.b 2.12%
Unlike the Ginp and Cebruser mobile bankers, which we have mentioned in the past, Knobot is a relatively new player on the market for threats that target financial data. Along with phishing windows and interception of 2FA verification messages, the trojan has several tools that are uncharacteristic of financial threats. An example of these is hijacking device PINs through exploitation of Accessibility Services. The attackers probably require the PIN in case they need to control the device manually in real time.
Mobile ransomware Trojans
In Q2 2020, we detected 3,805 installation packages for mobile Trojan ransomware, which is 534 fewer than last quarter.
The number of detected objects has been decreasing from quarter to quarter. We believe that there are two main causes:
It is much harder to extort cash from users than to steal the bank account data right away. At the same time, the device needs to be previously infected in either case, so with the costs being equal, cybercriminals will choose the path of least resistance, i.e. theft.
A ransomware trojan is a threat the user will likely want to fight to get the device back to a functional state. The user is likely to win, too, even if by factory-resetting the device. Cybercriminals, in their turn, try to keep their malware undetected on the device as long as possible, which runs counter to the whole idea of mobile ransomware.

Number of installation packages for mobile ransomware Trojans detected by Kaspersky, Q2 2019 – Q2 2020 (download)
Attacks reveal a similar pattern: the number of users attacked by ransomware trojans in Q2 2020 fell threefold compared to Q2 2019.
Verdict %*
1 Trojan-Ransom.AndroidOS.Small.as 14.27
2 Trojan-Ransom.AndroidOS.Agent.bq 8.46
3 Trojan-Ransom.AndroidOS.Svpeng.aj 7.67
4 Trojan-Ransom.AndroidOS.Small.o 5.77
5 Trojan-Ransom.AndroidOS.Rkor.k 5.37
6 Trojan-Ransom.AndroidOS.Agent.bo 5.01
7 Trojan-Ransom.AndroidOS.Congur.am 4.32
8 Trojan-Ransom.AndroidOS.Small.ce 3.65
9 Trojan-Ransom.AndroidOS.Fusob.h 3.42
10 Trojan-Ransom.AndroidOS.Soobek.a 3.01
* Unique users attacked by this malware as a share of all Kaspersky mobile antivirus users attacked by ransomware trojans.
The list TOP 10 ransomware trojans detected in Q2 2020 contains only two new species: Trojan-Ransom.AndroidOS.Agent.bq (8,46%) and Trojan-Ransom.AndroidOS.Agent.bo (5.01%). All the rest were originally developed in 2017–2019 and have been kept relevant by their creators through minor code changes.
The aforementioned Agent.bq and Agent.bo, like various other trojan classes, notably contain code that exploits Accessibility Services. In the case of these two, however, the code is used for screen locking and delete protection, literally leaving the victim no chances to remove the trojan without an external utility, such as ADB. However, ADB cannot always be used for removing the ransomware either: developer mode, which it requires, is deactivated on an overwhelming majority of devices.

Geography of mobile ransomware Trojans, Q2 2020 (download)
Top 10 countries by share of users attacked by mobile ransomware Trojans:
Country* %**
1 Kazakhstan 0.41
2 Malaysia 0.10
3 USA 0.10
4 Iran 0.09
5 Indonesia 0.07
6 Saudi Arabia 0.04
7 Vietnam 0.03
8 Italy 0.02
9 Algeria 0.02
10 Romania 0.02
* Excluded from the rating are countries with relatively few Kaspersky mobile antivirus users (under 10000).
** Unique users attacked by mobile ransomware Trojans in the country as a percentage of all users of Kaspersky mobile solutions in the same country.
Kazakhstan (0.41%), Malaysia (0.10%) and the United States (0.10%) saw the largest shares of users attacked by mobile ransomware trojans.
Stalkerware
This section uses statistics collected by Kaspersky Mobile Antivirus security solution.
The past second quarter of 2020 seems not to have been the most successful one for stalkerware developers. Many of the countries were this type of spyware enjoyed popularity went on a lockdown or imposed self-isolation requirements, which resulted in stalkerware users finding themselves locked up for a long period of time with those they intended to spy on. One can assume this led to a decrease in the number of mobile devices on which we detected stalkerware. At the same time, we discovered ten previously unknown families of stalker software in Q2 2020:
AndroidOS.Andropol.a
AndroidOS.AndTrace.a
AndroidOS.Basmon.a
AndroidOS.Flashlog.a
AndroidOS.Floatspy.a
AndroidOS.FoneSpy.a
AndroidOS.GmSpy.a
AndroidOS.Spytm.a
AndroidOS.UniqSpy.a
AndroidOS.Xnspy.a
It would hence be incorrect to assume that developers have lost interest in creating this type of programs. We will continue to monitor new samples, as none of the families listed above were popular enough in Q2 2020 to get on the list of the ten most common stalkerware types.
TOP 10 stalkerware
Verdicts %
1 Monitor.AndroidOS.Cerberus.a 14.21%
2 Monitor.AndroidOS.Nidb.a 13.66%
3 Monitor.AndroidOS.MobileTracker.c 5.56%
4 Monitor.AndroidOS.Agent.af 5.07%
5 Monitor.AndroidOS.Anlost.a 4.20%
6 Monitor.AndroidOS.PhoneSpy.b 3.39%
7 Monitor.AndroidOS.Agent.a 2.56%
8 Monitor.AndroidOS.Agent.hb 2.37%
9 Monitor.AndroidOS.SecretCam.a 2.27%
10 Monitor.AndroidOS.Traca.a 2.25%
11 Monitor.AndroidOS.Alltracker.a 2.22%
12 Monitor.AndroidOS.Agent.al 2.15%
13 Monitor.AndroidOS.SpyHuman.c 2.10%
14 Monitor.AndroidOS.Wspy.a 1.91%
15 Monitor.AndroidOS.Agent.gt 1.73%
16 Monitor.AndroidOS.MonitorMinor.e 1.62%
17 Monitor.AndroidOS.Reptilic.a 1.49%
18 Monitor.AndroidOS.Agent.he 1.43%
19 Monitor.AndroidOS.Anfur.a 1.39%
20 Monitor.AndroidOS.Talkw.a 1.25%
The rankings include long-standing, widely used commercial stalkerware families, among others, MonitorMinor, which we wrote about in the first quarter of this year.
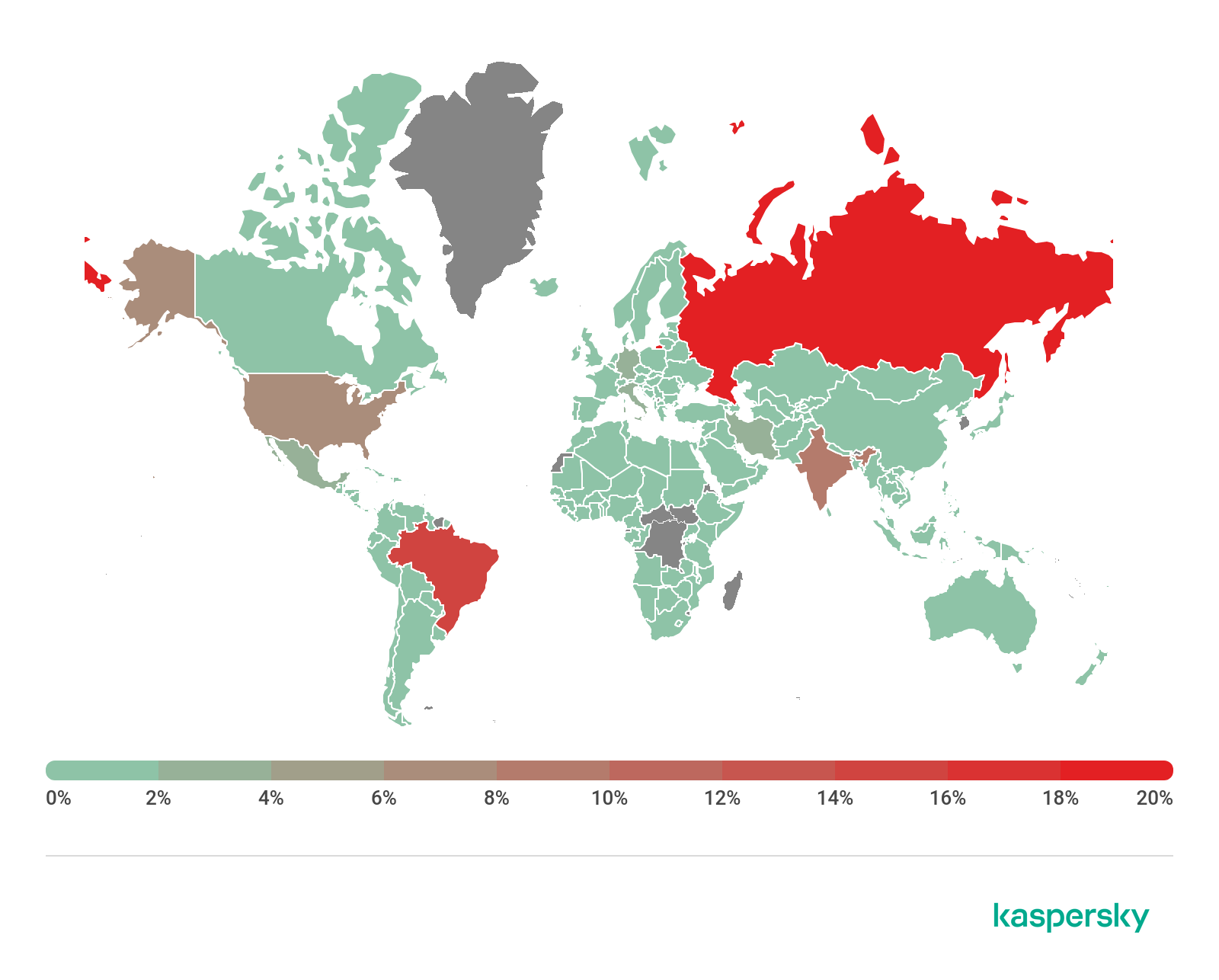
Geography of stalkerware distribution, Q2 2020 (download)
Russia had the largest number of users whose devices were found to contain stalkerware in Q2 2020. It was followed closely by Brazil. India came third, having half of Russia’s number of users that had encountered stalkerware.
Both Russia and Brazil notably showed an encouraging trend, with the number of devices containing stalkerware dropping significantly in the second quarter.

Number of devices with stalkerware in Russia, Q1 2019 – Q2 2020 (download)

Number of devices with stalkerware in Brazil, Q1 2019 – Q2 2020 (download)
As for India, its statistics remained relatively unchanged in the second quarter of the year.

Number of devices with stalkerware in India, Q1 2019 – Q2 2020 (download)
Spam and phishing in Q1 2020
26.5.2020 Securelist Analysis Spam Phishing
Quarterly highlights
Don’t get burned
Burning Man is one of the most eagerly awaited events among fans of spectacular performance and installation art. The main obstacle to attending is the price of admission: a standard ticket will set you back $475, the number is limited, and the buying process is a challenge all by itself (there are several stages, registration data must be entered at a specific time, and if something goes wrong you might not get a second chance). Therefore, half-price fake tickets make for excellent bait.
Scammers tried to make their website as close as possible to the original — even the page with the ticket description looked genuine.
There were just three major differences from the original: only the main page and the ticket purchase section were actually operational, tickets were “sold” without prior registration, and the price was a steal ($225 versus $475).
Oscar-winning scammers
February 2020 saw the 92nd Academy Awards ceremony. Even before the big night, websites were popping up offering free viewings of all the nominated films. Fraudsters targeted users eager to see the short-listed movies before the presentation of the awards.
To promote these sites, Twitter accounts were created — one for each nominated film.
Curious users were invited to visit the resource, where they were shown the first few minutes before being asked to register to continue watching.
During registration, the victim was prompted to enter their bank card details, allegedly to confirm their region of residence. Unsurprisingly, a short while later a certain amount of money disappeared from their account, and the movie did not resume.
Users should be alert to the use of short links in posts on social networks. Scammers often use them because it’s impossible to see where a shortened URL points without actually following it.
There are special services that let you check what lies behind such links, often with an additional bonus in the form of a verdict on the safety of the website content. It is important to do a proper check on links from untrusted sources.
ID for hire
US companies that leak customer data can be heavily fined by the Federal Trade Commission (FTC). For example, in 2019 Facebook was slapped with a $5 billion penalty; however, users whose data got stolen do not receive any compensation. This is what scammers decided to exploit by sending a fake e-mail offering compensation from the non-existent Personal Data Protection Fund, created by the equally fictitious US Trading Commission.
Inspired by the idea of services for checking accounts for leaks, the cybercriminals decided to create their own. Visitors were invited to check whether their account details had been stolen, and if so (the answer was “yes” even if the input was gibberish), they were promised compensation “for the leakage of personal data.”
To receive “compensation,” the victim’s citizenship was of no consequence — what mattered was their first name, last name, phone number, and social network accounts. For extra authenticity, a warning message about the serious consequences of using other people’s data to claim compensation popped up obsessively on the page.
To receive the payment, US citizens were asked to enter their Social Security Number (SSN). Everyone else had to check the box next to the words “I’am don’t have SSN” (the mistakes are a good indicator of a fake), whereupon they were invited to “rent” an SSN for $9. Interestingly, even if the user already had an SSN, they were still pestered to get another one.
After that, the potential victim was redirected to a payment page with the amount and currency based on the user’s location. For instance, users in Russia were asked to pay in rubles.
The scam deployed the conventional scheme (especially common in the Runet) of asking the victim to pay a small commission or down payment for the promise of something much bigger. In Q1, 14,725,643 attempts to redirect users to such websites were blocked.
Disaster and pandemic
Fires in Australia
The natural disaster that hit the Australian continent was another get-rich opportunity for scammers. For example, one “Nigerian prince”-style e-mail scam reported that a millionaire dying of cancer was ready to donate her money to save the Australian forests. The victim was asked to help withdraw the funds from the dying woman’s account by paying a fee or making a small contribution to pay for the services of a lawyer, for which they would be rewarded handsomely at a later date.
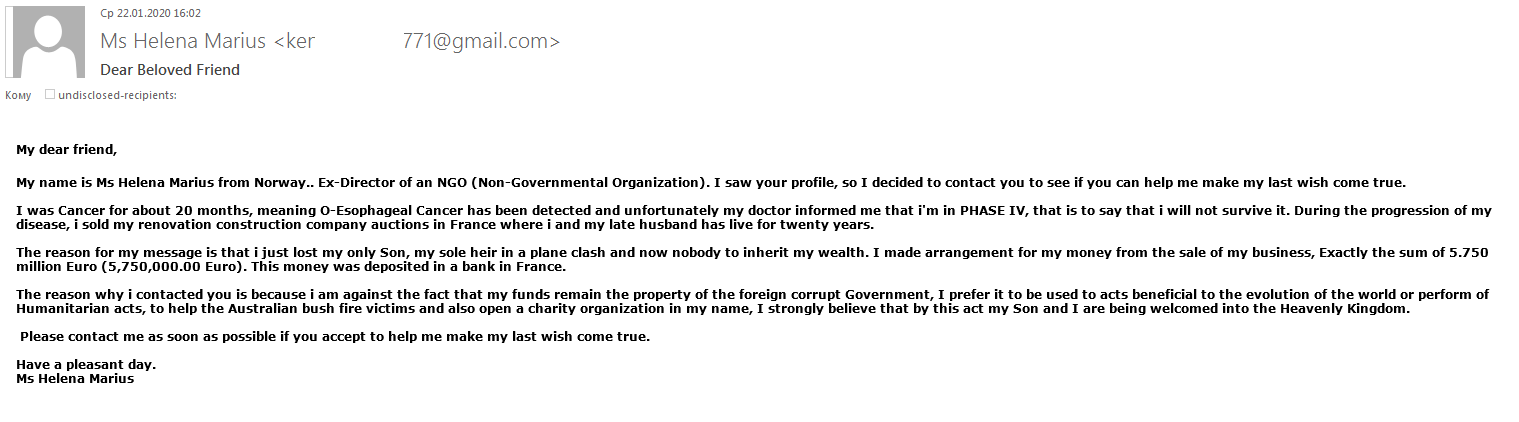
Besides the fictional millionaire, other “nature lovers” were keen to help out — their e-mails were more concise, but the scheme was essentially the same.

COVID-19
“Nigerian prince” scheme
COVID-19 was (and continues to be) a boon to scammers: non-existent philanthropists and dying millionaires are popping up everywhere offering rewards for help to withdraw funds supposedly for humanitarian purpsoses. Some recipients were even invited to help finance the production of a miracle vaccine, or take part in a charity lottery, the proceeds of which, it was said, would be distributed to poor people affected by the pandemic.
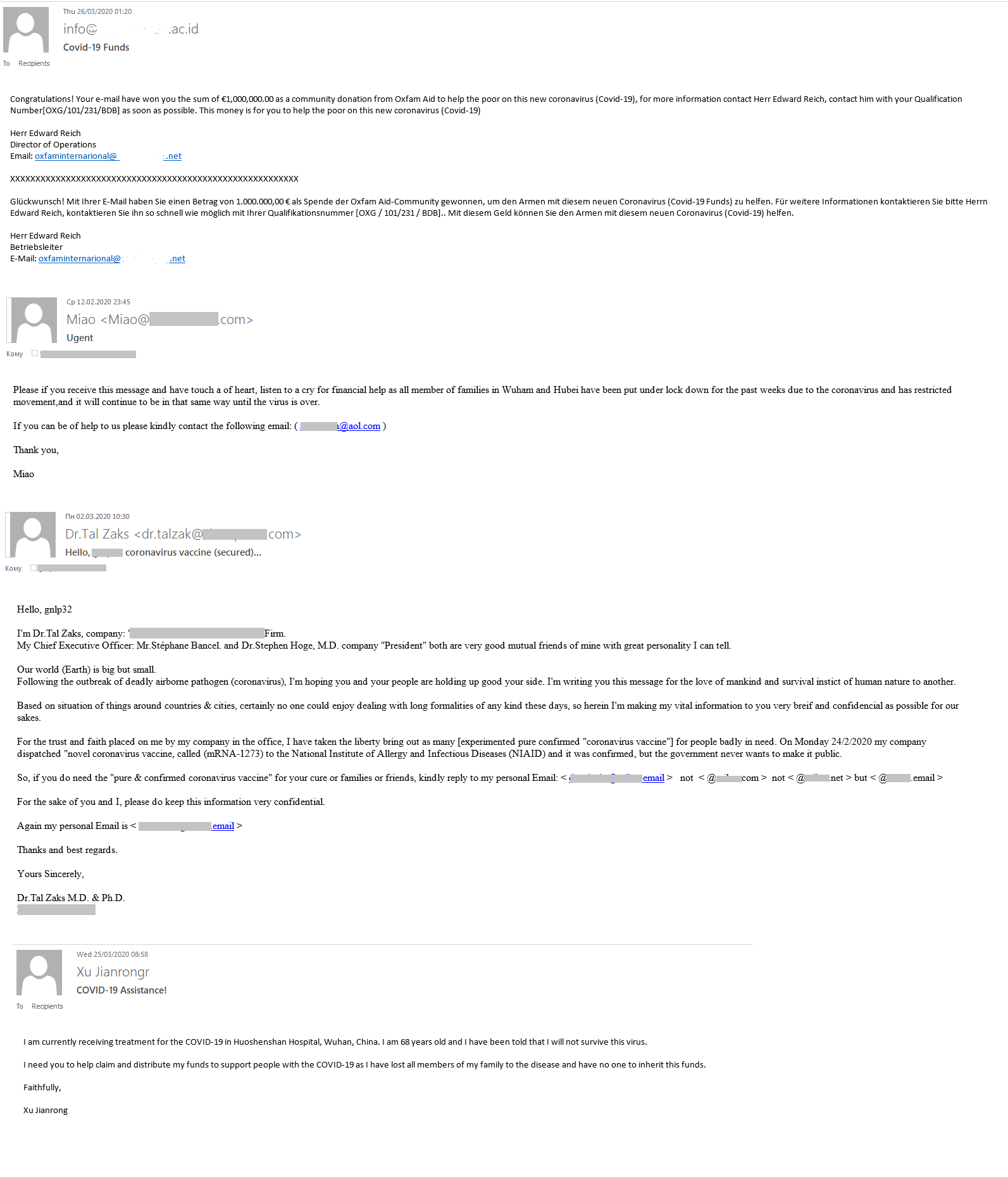
Bitcoin for coronavirus
Having introduced themselves as members of a healthcare organization, the scammers appealed to the victim to transfer a certain sum to the Bitcoin wallet specified in the message. The donation would allegedly go toward fighting the coronavirus outbreak and developing a vaccine, as well as helping victims of the pandemic.
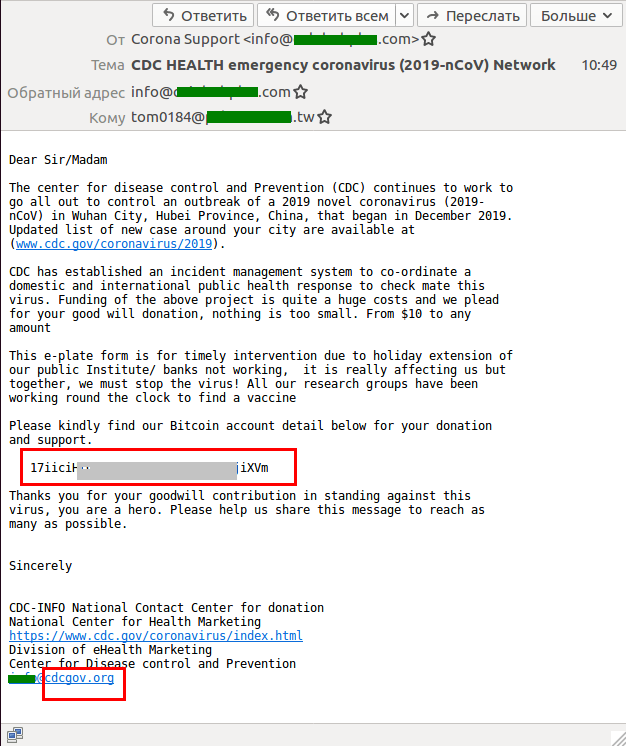
In one e-mail, the attackers played on people’s fear of contracting COVID-19: the message was from an unnamed “neighbor” claiming to be dying from the virus and threatening to infect the recipient unless the latter paid a ransom (which, it was said, would help provide a comfortable old age for the ransomer’s parents).
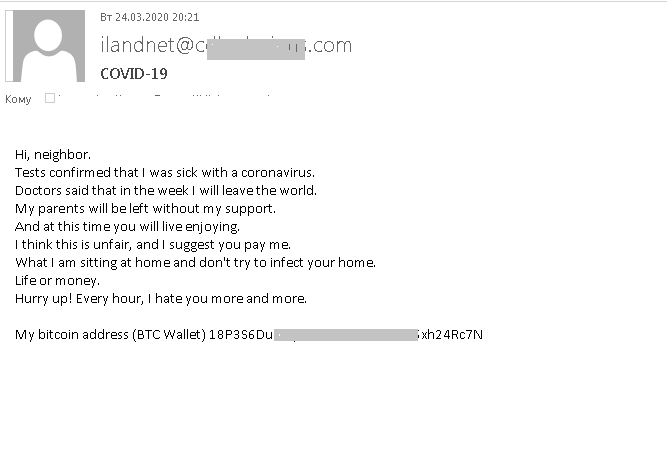
Dangerous advice from the WHO
One fraudulent mailing disguised as a WHO newsletter offered tips about staying safe from COVID-19.
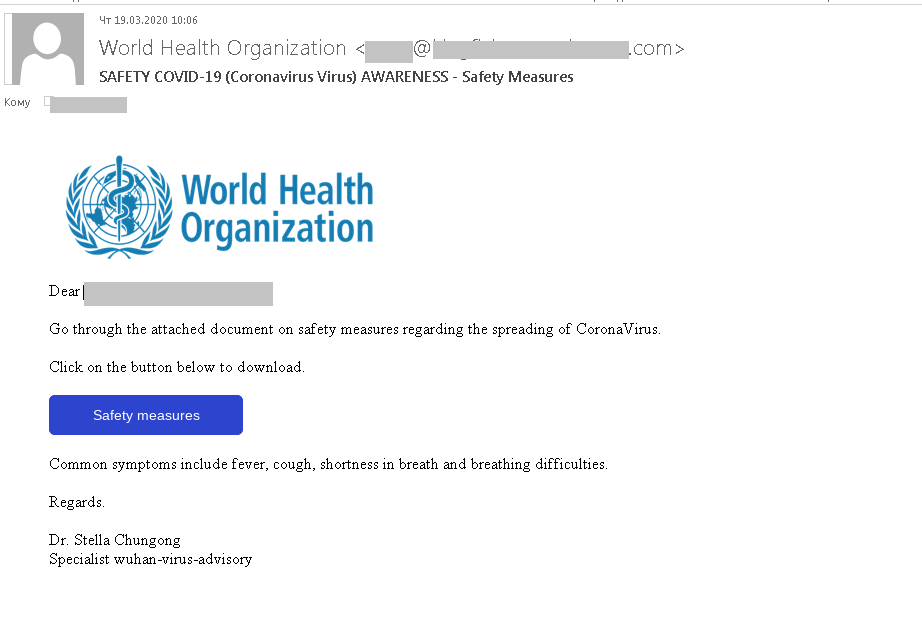
To get the information, the recipient had to click a link pointing to a fake WHO website. The design was so close to the original that only the URL gave away the scam. The cybercriminals were after login credentials for accounts on the official WHO site. Whereas in the first mailings only a username and password were asked for, in later ones a phone number was also requested.
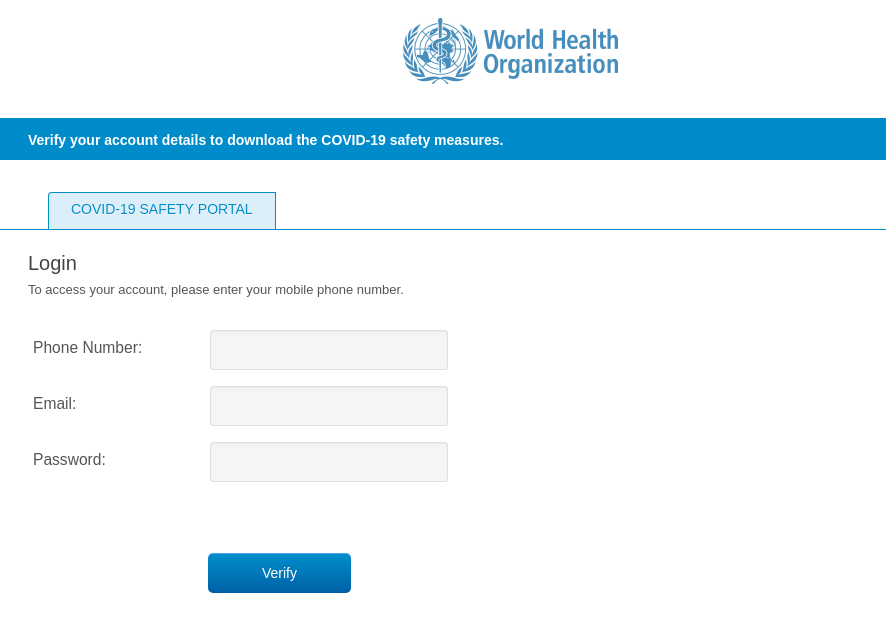
In addition, we detected several e-mails supposedly from the WHO containing documents with malware. The recipient was asked to open the attachment (in DOC or PDF format), which allegedly offered coronavirus prevention advice. For example, this message contained Backdoor.Win32.Androm.tvmf:

There were other, less elaborate mailings with harmful attachments, including ones containing Trojan-Spy.Win32.Noon.gen:
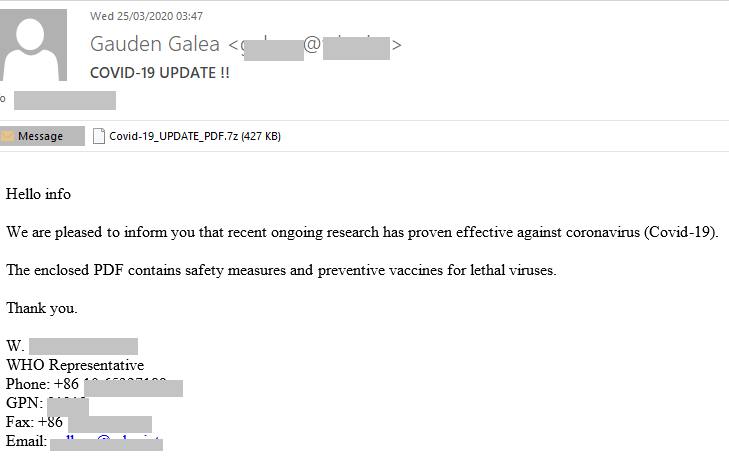
Corporate segment
The coronavirus topic was also exploited in attacks on the corporate sector. For example, COVID-19 was cited in fraudulent e-mails as a reason for delayed shipments or the need to reorder. The authors marked the e-mails as urgent and required to check attached files immediately.
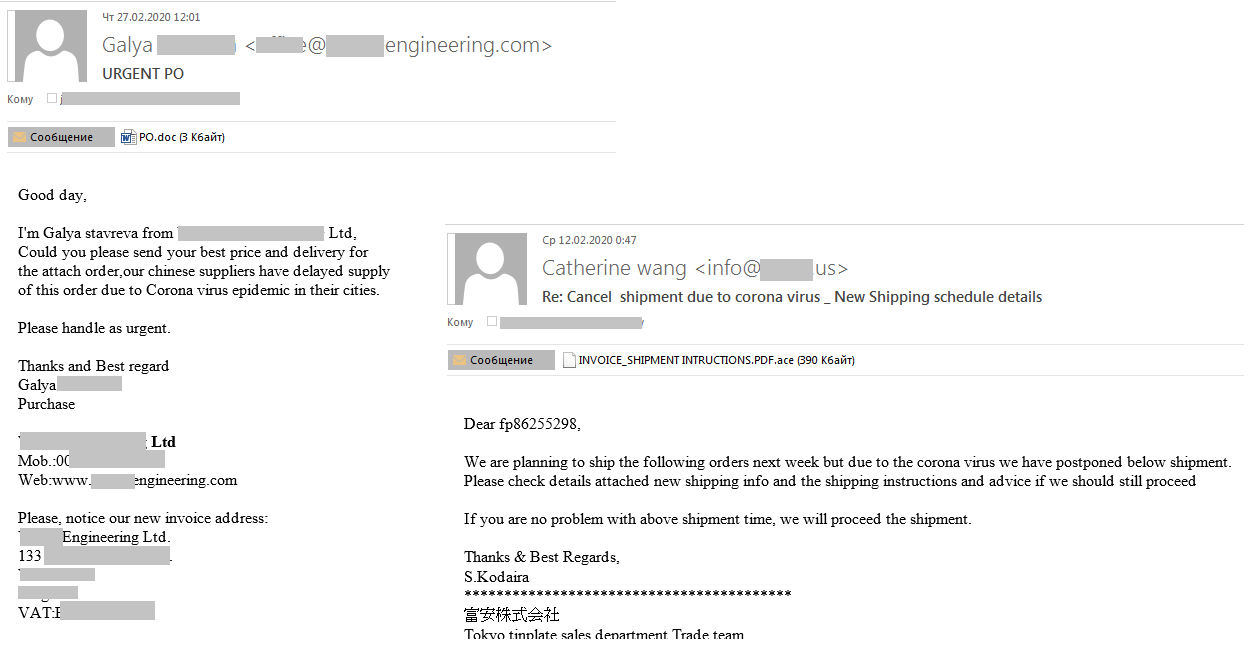
Another mailing prompted recipients to check whether their company was in a list of firms whose activities were suspended due to the pandemic. After which it asked for a form to be filled out, otherwise the company could be shut down. Both the list of companies and the form were allegedly in the archives attached to the message. In actual fact, the attachments contained Trojan-PSW.MSIL.Agensla.a:
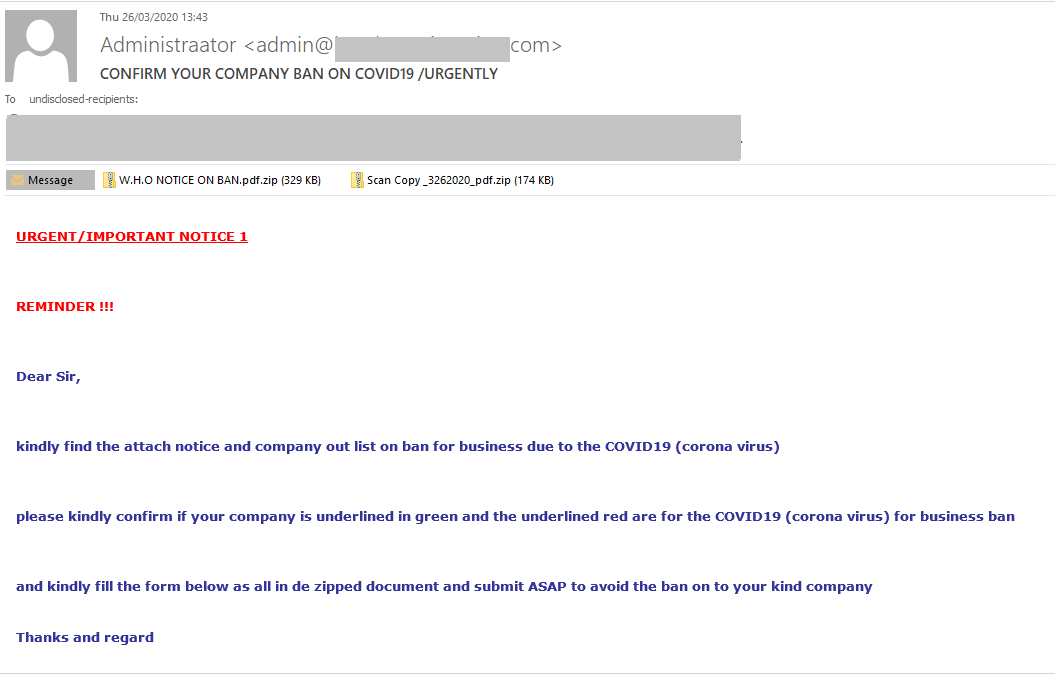
We also registered a phishing attack on corporate users. On a fake page, visitors were invited to monitor the coronavirus situation across the world using a special resource, for which the username and password of the victim’s corporate mail account were required.
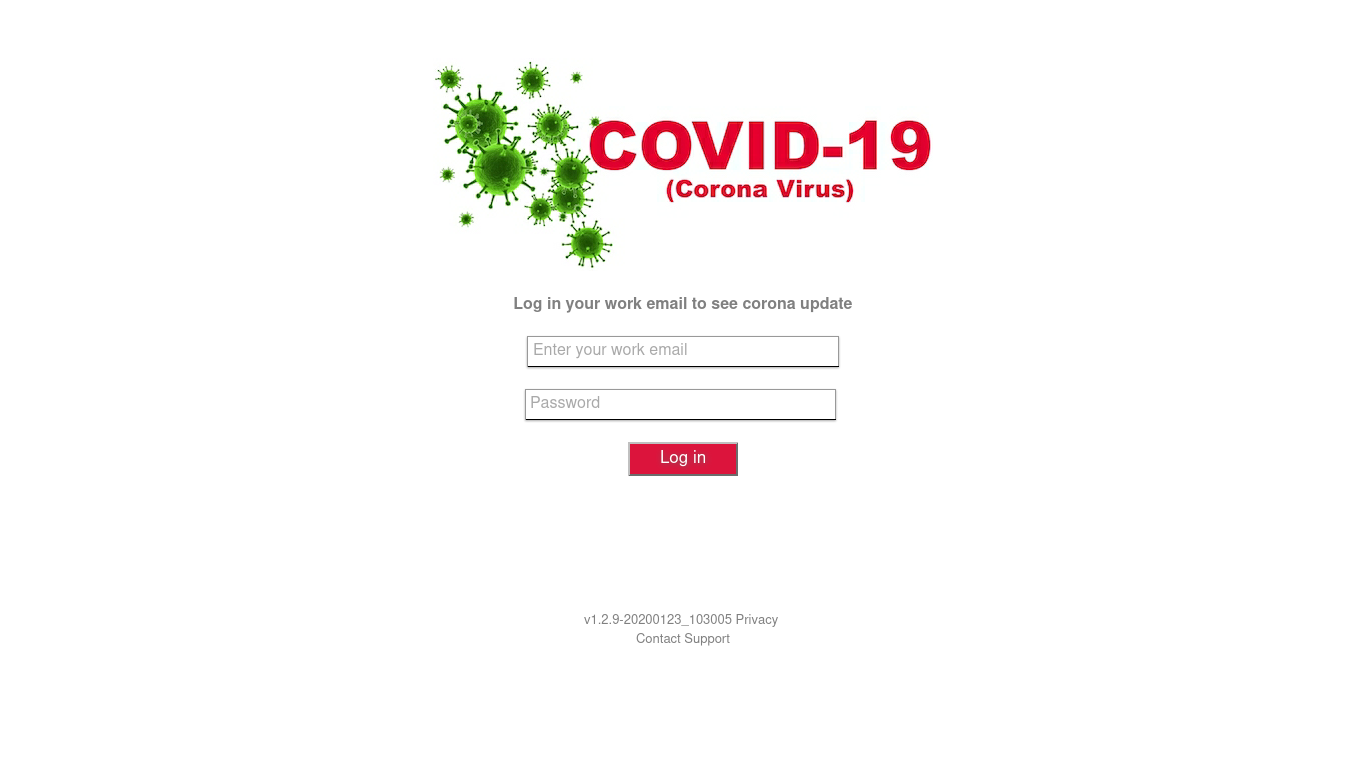
Government compensation
The introduction of measures to counter the pandemic put many people in a difficult financial situation. Forced downtime in many industries has had a negative impact on financial well-being. In this climate, websites offering compensation from the government pose a particular danger.
One such popular scheme was highlighted by a colleague of ours from Brazil. A WhatsApp messages about financial or food assistance were sent that appeared to come from a supermarket, bank, or government department. To receive the aid, the victim had to fill out the attached form and share the message with a certain number of contacts. After the form was filled out, the data was sent to the cybercriminals, while the victim got redirected to a page with advertising, a phishing site, a site offering a paid SMS subscription, or similar.
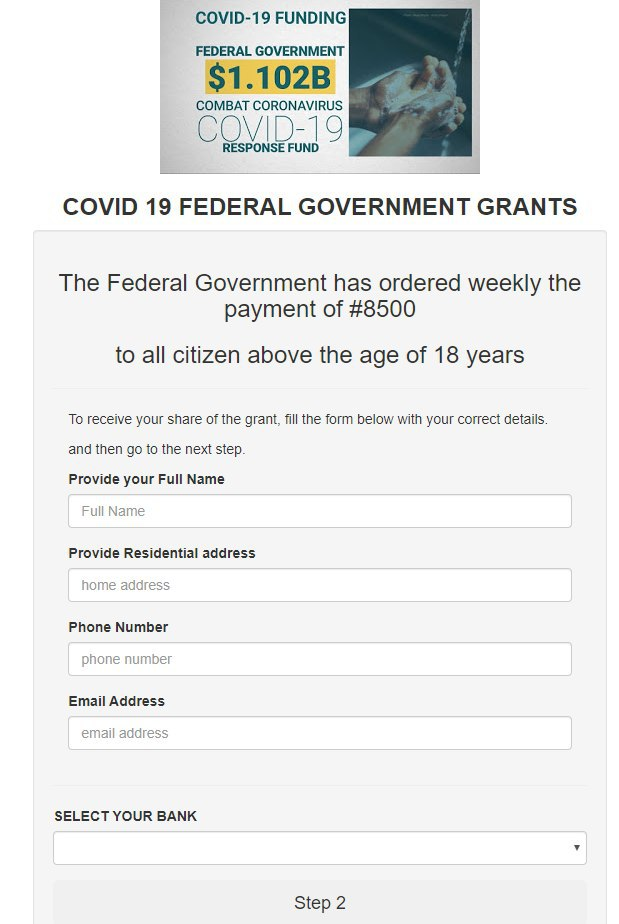

Given that the number of fake sites offering government handouts seems likely only to increase, we urge caution when it comes to promises of compensation or material assistance.
Anti-coronavirus protection with home delivery
Due to the pandemic, demand for antiseptics and antiviral agents has spiked. We registered a large number of mailings with offers to buy antibacterial masks.
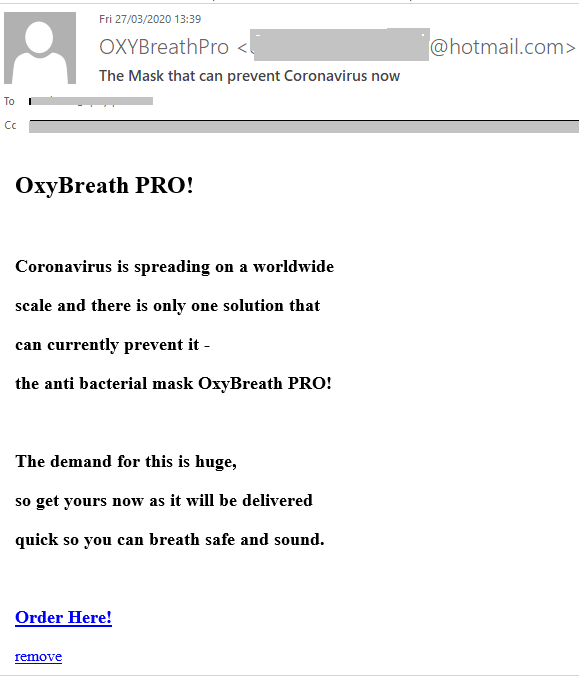
In Latin America, WhatsApp mass messages were used to invite people to take part in a prize draw for hand sanitizer products from the brewing company Ambev. The company has indeed started making antiseptics and hand gel, but exclusively for public hospitals, so the giveaway was evidently the work of fraudsters.

The number of fake sites offering folk remedies for the treatment of coronavirus, drugs to strengthen the immune system, and non-contact thermometers and test kits has also risen sharply. Most of the products on offer have no kind of certification whatsoever.
On average, the daily share of e-mails mentioning COVID-19 in Q1 amounted to around 6% of all junk traffic. More than 50% of coronavirus-related spam was in the English language. We anticipate that the number of phishing sites and pandemic-related scams will only increase, and that cybercriminals will use new attack schemes and strategies.
Statistics: spam
Proportion of spam in mail traffic
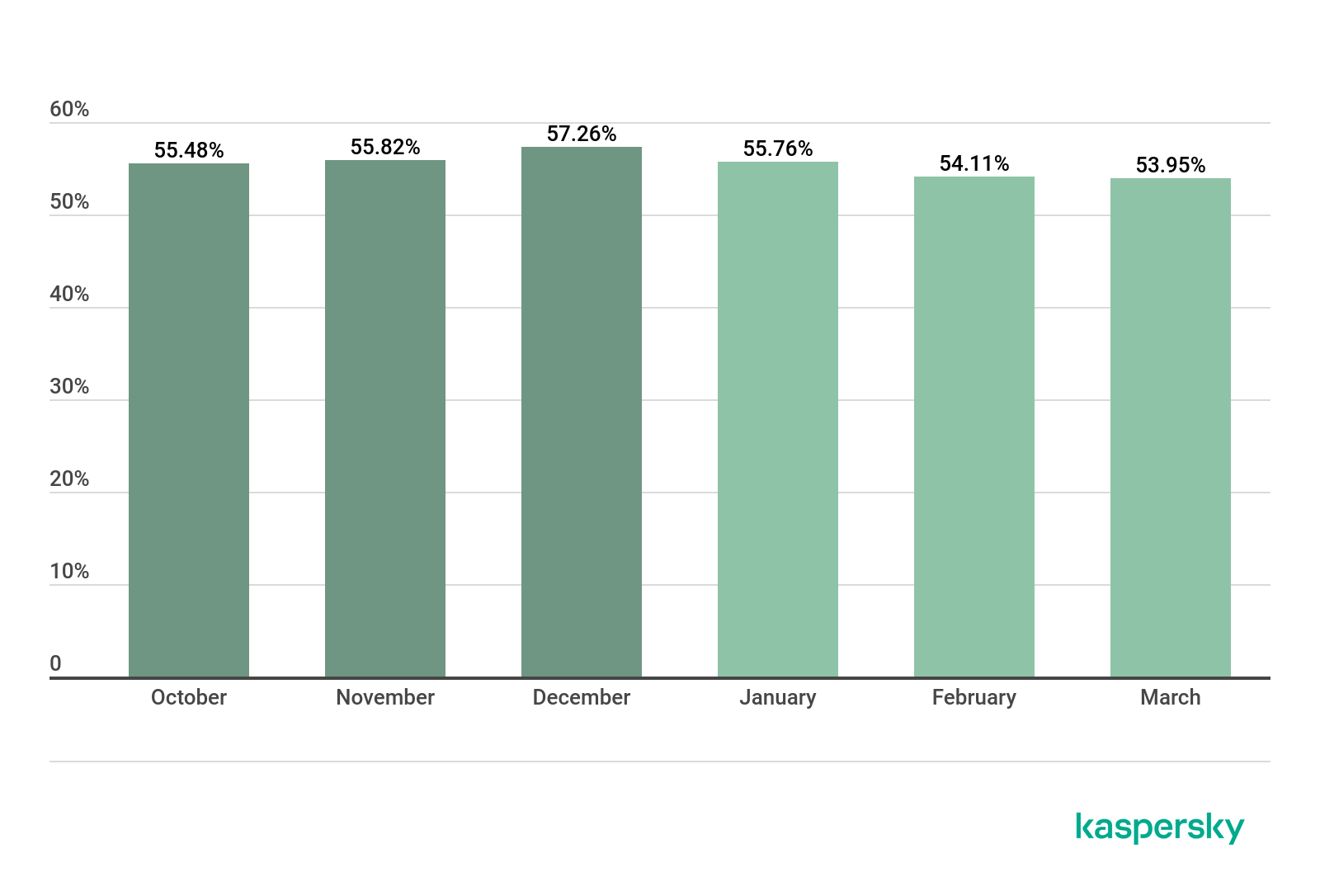
Proportion of spam in global mail traffic, Q4 2019 – Q1 2020 (download)
In Q1 2020, the largest share of spam was recorded in January (55.76%). The average percentage of spam in global mail traffic was 54.61%, down 1.58 p.p. against the previous reporting period.
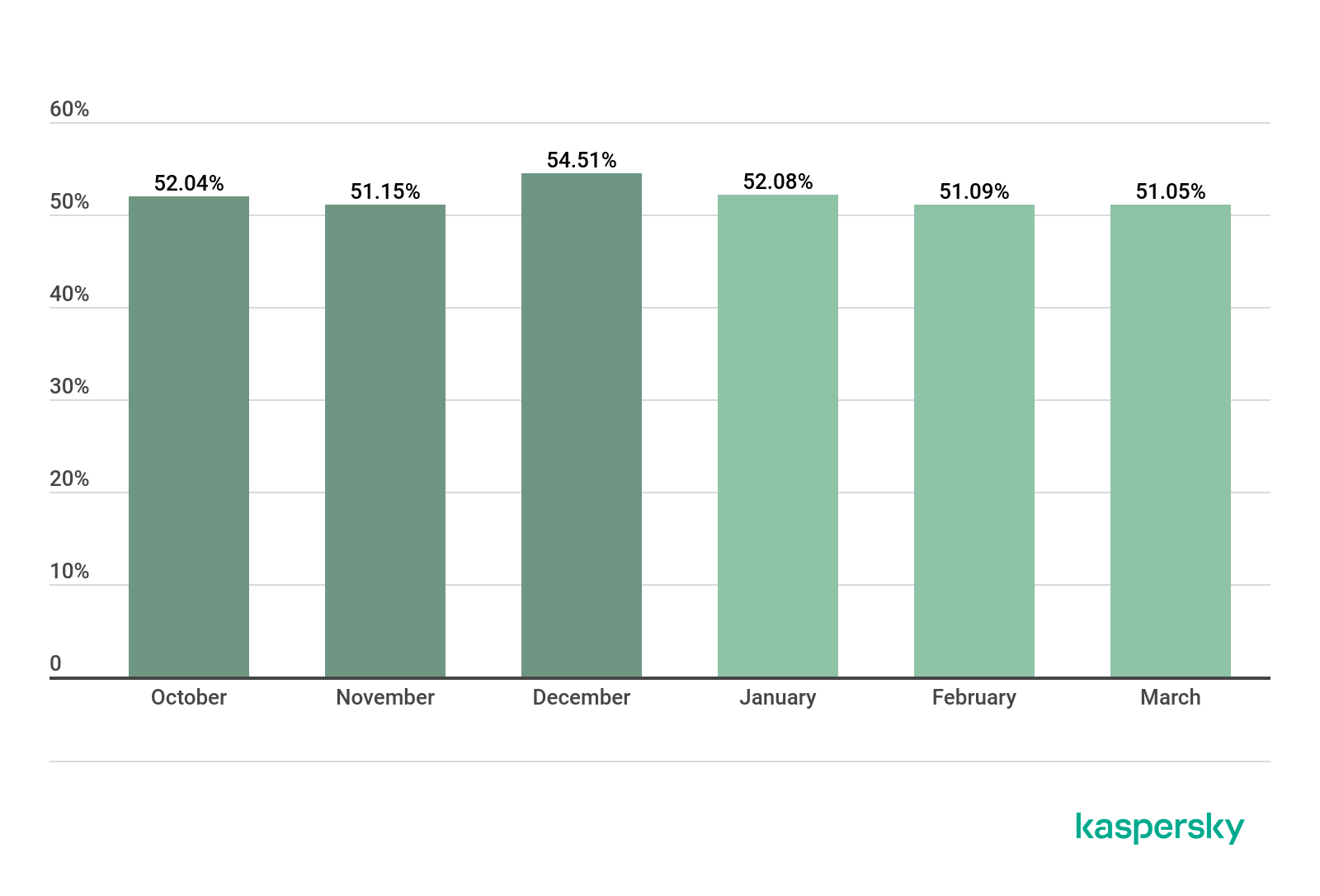
Proportion of spam in Runet mail traffic, Q4 2019 – Q1 2020 (download)
In Q1, the share of spam in Runet traffic (the Russian segment of the Internet) likewise peaked in January (52.08%). At the same time, the average indicator, as in Q4 2019, remains slightly lower than the global average (by 3.20 p.p.).
Sources of spam by country
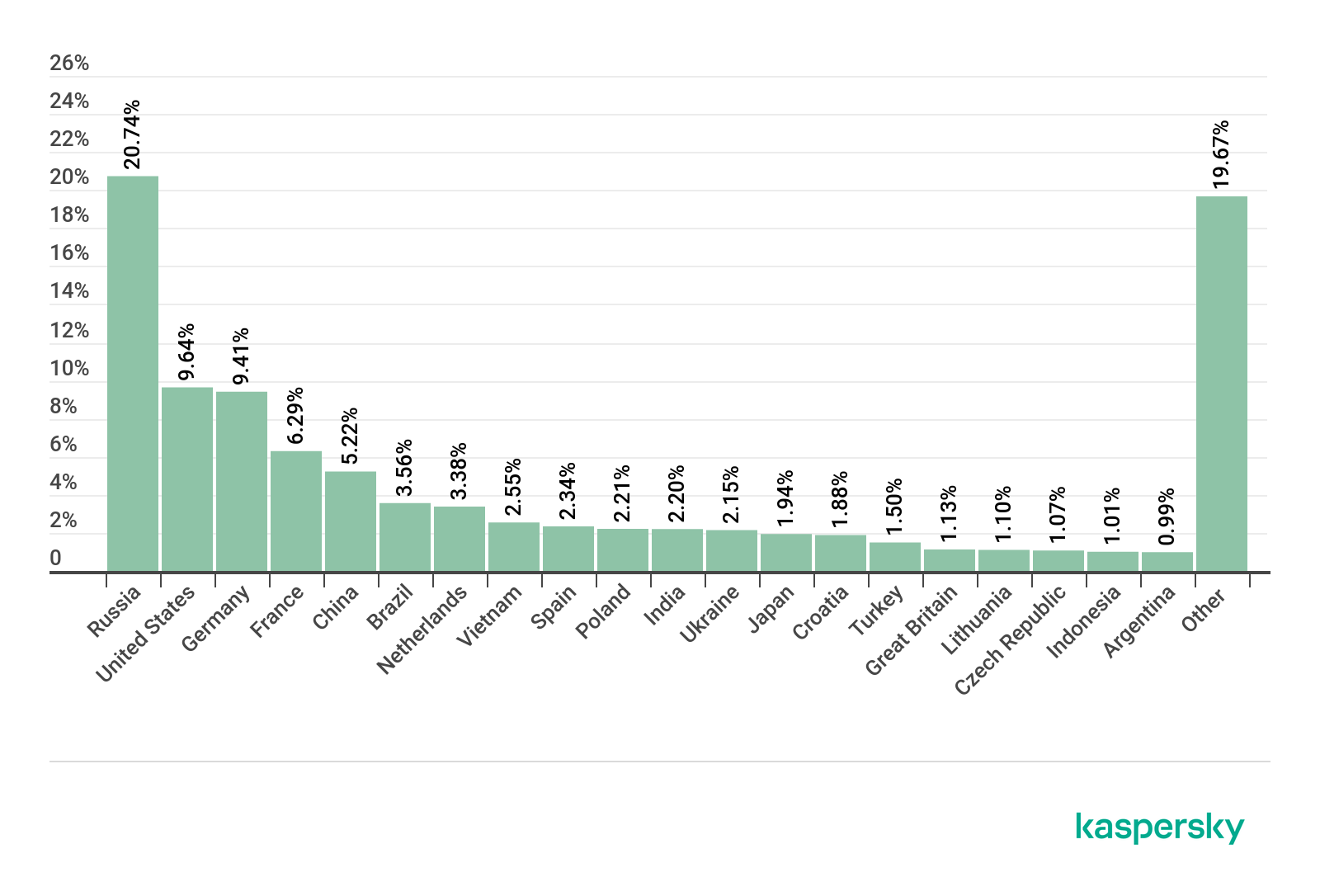
Sources of spam by country, Q1 2020 (download)
In Q1 2020, Russia led the TOP 5 countries by amount of outgoing spam. It accounted for 20.74% of all junk traffic. In second place came the US (9.64%), followed by Germany (9.41%) just 0.23 p.p. behind. Fourth place goes to France (6.29%) and fifth to China (5.22%), which is usually a TOP 3 spam source.
Brazil (3.56%) and the Netherlands (3.38%) took sixth and seventh positions, respectively, followed by Vietnam (2.55%), with Spain (2.34%) and Poland (2.21%) close on its heels in ninth and tenth.
Spam e-mail size
Spam e-mail size, Q4 2019 – Q1 2020 (download)
Compared to Q4 2019, the share of very small e-mails (up to 2 KB) in Q1 2020 fell by more than 6 p.p. and amounted to 59.90%. The proportion of e-mails sized 5-10 KB grew slightly (by 0.72 p.p.) against the previous quarter to 5.56%.
Meanwhile, the share of 10-20 KB e-mails climbed by 3.32 p.p. to 6.36%. The number of large e-mails (100–200 KB) also posted growth (+2.70 p.p.). Their slice in Q1 2020 was 4.50%.
Malicious attachments in e-mail
Number of Mail Anti-Virus triggerings, Q4 2019 – Q1 2020 (download)
In Q1 2020, our security solutions detected a total of 49,562,670 malicious e-mail attachments, which is almost identical to the figure for the last reporting period (there were just 314,862 more malicious attachments detected in Q4 2019).
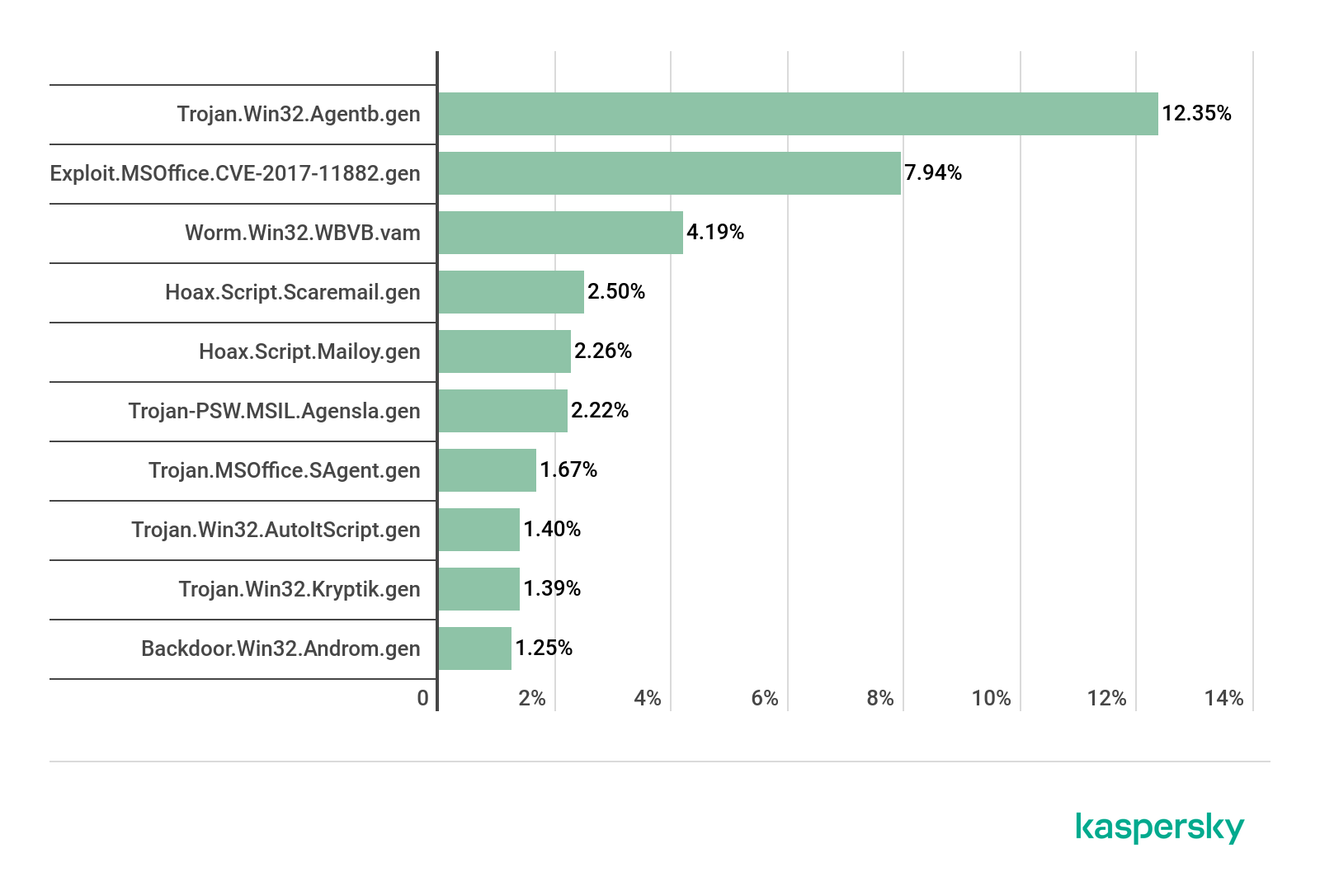
TOP 10 malicious attachments in mail traffic, Q1 2020 (download)
In Q1, first place in terms of prevalence in mail traffic went to Trojan.Win32.Agentb.gen (12.35%), followed by Exploit.MSOffice.CVE-2017-11882.gen (7.94%) in second and Worm.Win32.WBVB.vam (4.19%) in third.
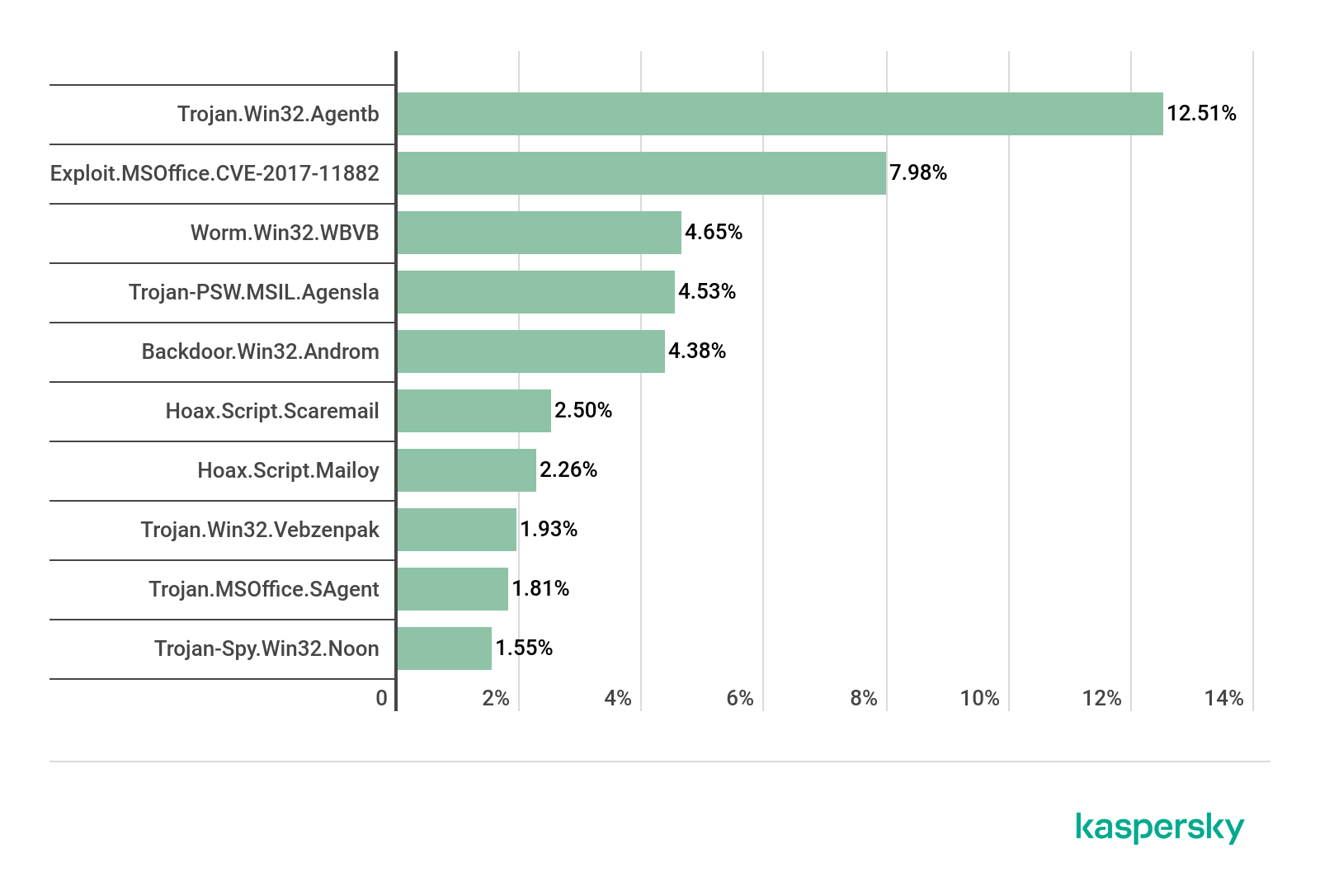
TOP 10 malicious families in mail traffic, Q1 2020 (download)
As regards malware families, the most widespread this quarter was Trojan.Win32.Agentb (12.51%), with Exploit.MSOffice.CVE-2017-11882 (7.98%), whose members exploit a vulnerability in Microsoft Equation Editor, in second place and Worm.Win32.wbvb (4.65%) in third.
Countries targeted by malicious mailshots
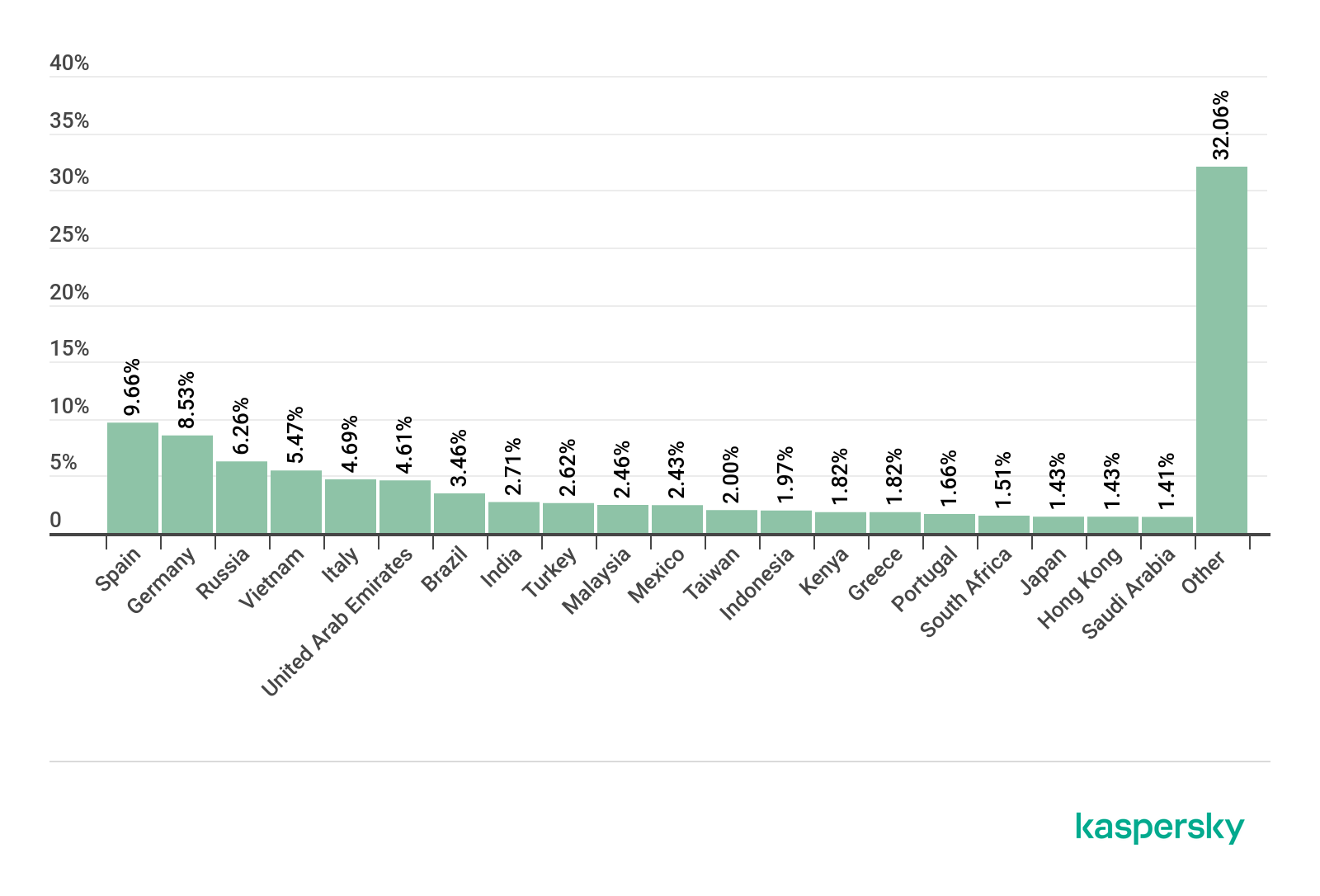
Distribution of Mail Anti-Virus triggerings by country, Q1 2020 (download)
First place by number of Mail Anti-Virus triggerings in Q1 2020 was claimed by Spain. This country accounted for 9.66% of all users of Kaspersky security solutions who encountered e-mail malware worldwide. Second place went to Germany (8.53%), and Russia (6.26%) took bronze.
Statistics: phishing
In Q1 2020, the Anti-Phishing system prevented 119,115,577 attempts to redirect users to scam websites. The percentage of unique attacked users was 8.80% of the total number of users of Kaspersky products in the world.
Attack geography
The country with the largest proportion of users attacked by phishers, not for the first time, was Venezuela (20.53%).
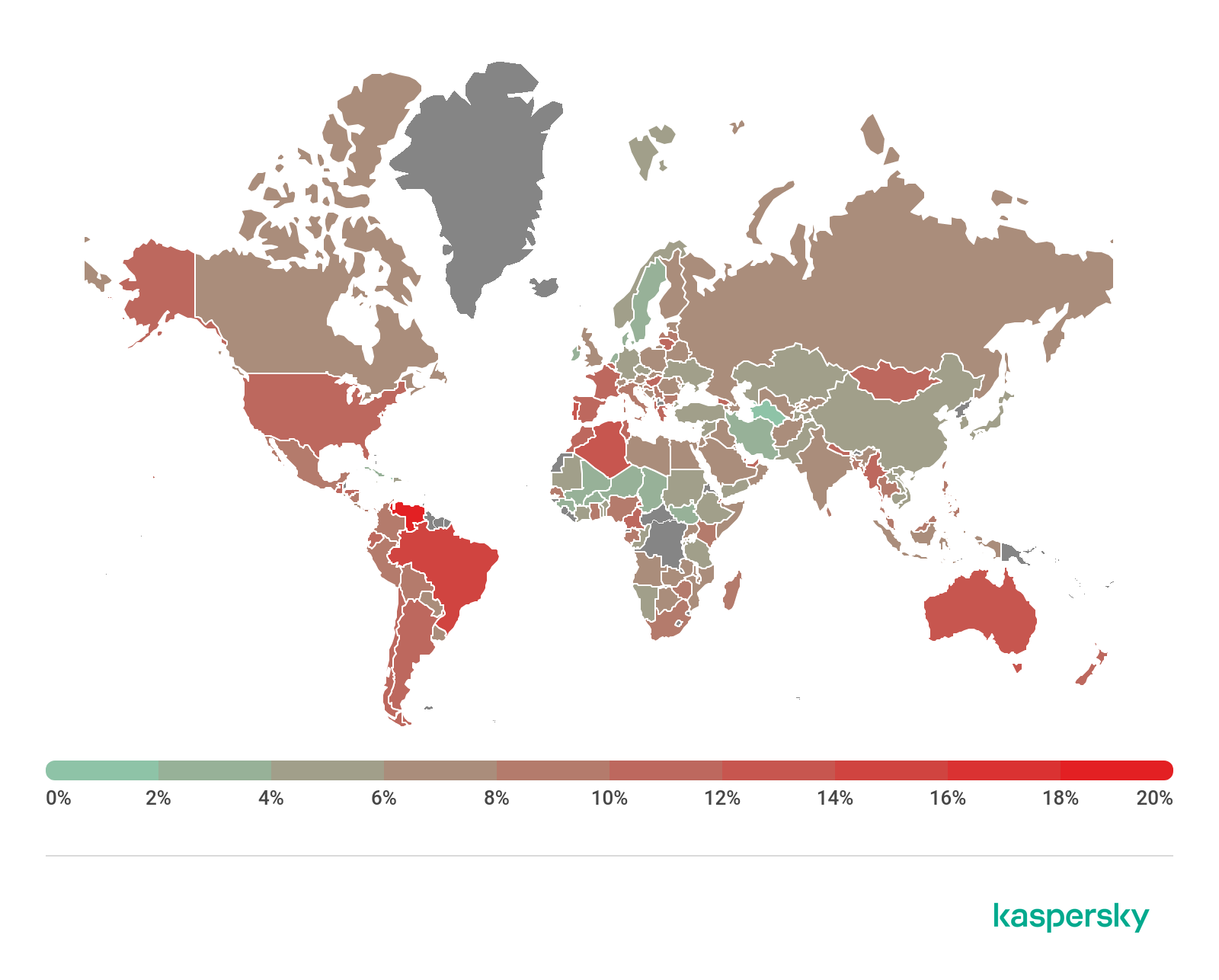
Geography of phishing attacks, Q1 2020 (download)
In second place, by a margin of 5.58 p.p., was Brazil (14.95%), another country that is no stranger to the TOP 3. Next came Australia (13.71%), trailing by just 1.24 p.p.
Country %*
Venezuela 20.53%
Brazil 14.95%
Australia 13.71%
Portugal 12.98%
Algeria 12.12%
France 11.71%
Honduras 11.62%
Greece 11.58%
Myanmar 11.54%
Tunisia 11.53%
* Share of users on whose computers Anti-Phishing was triggered out of all Kaspersky users in the country
Organizations under attack
The rating of attacks by phishers on different categories of organizations is based on detections by Kaspersky products Anti-Phishing component. This component detects pages with phishing content that the user gets redirected to. It does not matter whether the redirect is the result of clicking a link in a phishing e-mail or in a message on a social network, or the result of a malicious program activity. When the component is triggered, a banner is displayed in the browser warning the user about a potential threat.
The largest share of phishing attacks in Q1 2020 fell to the Online Stores category (18.12%). Second place went to Global Internet Portals (16.44%), while Social Networks (13.07%) came in third.
Distribution of organizations affected by phishing attacks by category, Q1 2020 (download)
As for the Banks category, a TOP 3 veteran, this time it placed fourth with 10.95%.
Conclusion
Glancing at the results of Q1 2020, we anticipate that the COVID-19 topic will continue to be actively used by cybercriminals for the foreseeable future. To attract potential victims, the pandemic will be mentioned even on “standard” fake pages and in spam mailings.
The topic is also used extensively in fraudulent schemes offering compensation and material assistance.
It is highly likely that this type of fraud will become more frequent.
The average share of spam in global mail traffic (54.61%) this quarter decreased by 1.58 p.p. against the previous reporting period, while the number of attempted redirects totaled nearly 120 million.
Top of this quarter’s list of spam-source countries is Russia, with a share of 20.74%. Our security solutions blocked 49,562,670 malicious mail attachments, while the most common mail-based malware family, with a 12.35% share of mail traffic, was Trojan.Win32.Agentb.gen.
IT threat evolution Q1 2020
20.5.2020 Securelist Analysis
Targeted attacks and malware campaigns
Operation AppleJeus: the sequel
In 2018, we published a report on Operation AppleJeus, one of the more notable campaigns of the threat actor Lazarus, currently one of the most active and prolific APT groups. One notable feature of this campaign was that it marked the first time Lazarus had targeted macOS targets, with the group inventing a fake company in order to deliver its manipulated application and exploit the high level of trust among potential victims.
Our follow-up research revealed significant changes to the group’s attack methodology. To attack macOS victims, Lazarus has developed homemade macOS malware and added an authentication mechanism to deliver the next stage payload very carefully, as well as loading the next-stage payload without touching the disk. In addition, to attack Windows victims, the group has elaborated a multi-stage infection procedure and made significant changes to the final payload. We believe Lazarus has been more careful in its attacks since the release of Operation AppleJeus and has employed a number of methods to avoid detection.
We identified several victims as part of our ongoing research, in the UK, Poland, Russia and China. Moreover, we were able to confirm that several of the victims are linked to cryptocurrency business organizations.
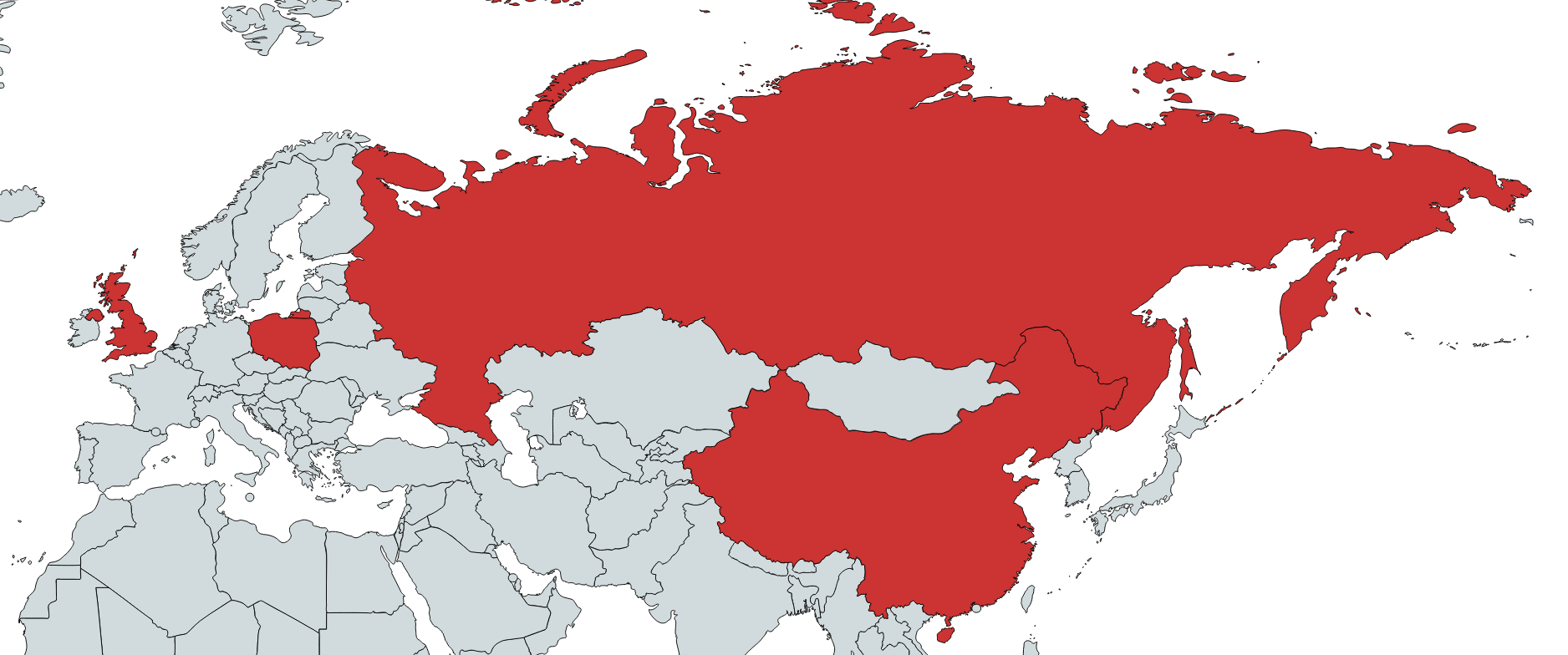
Roaming Mantis turns to SMiShing and enhances anti-researcher techniques
Kaspersky continues to track the Roaming Mantis campaign. This threat actor was first reported in 2017, when it used SMS to distribute its malware to Android devices in just one country – South Korea. Since then, the scope of the group’s activities has widened considerably. Roaming Mantis now supports 27 languages, targets iOS as well as Android and includes cryptocurrency mining for PCs in its arsenal.
Roaming Mantis is strongly motivated by financial gain and is continuously looking for new targets. The group has also put a lot of effort into evading tracking by researchers, including implementing obfuscation techniques and using whitelisting to avoid infecting researchers who navigate to the malicious landing page. While the group is currently applying whitelisting only to Korean pages, we think it is only a matter of time before Roaming Mantis implements this for other languages.
Roaming Mantis has also added new malware families, including Fakecop and Wroba.j. The actor is still very active in using ‘SMiShing‘ for Android malware distribution. This is particularly alarming, because it means that the attackers could combine infected mobile devices into a botnet for malware delivery, SMiShing, and so on. In one of the more recent methods used by the group, a downloaded malicious APK file contains an icon that impersonates a major courier company brand: the spoofed brand icon is customized for the country it targets – for example, Sagawa Express for Japan, Yamato Transport and FedEx for Taiwan, CJ Logistics for South Korea and Econt Express for Russia.
WildPressure on industrial networks in the Middle East
In March, we reported a targeted campaign to distribute Milum, a Trojan designed to gain remote control of devices in target organizations, some of which operate in the industrial sector. We detected the first signs of this operation, which we have dubbed WildPressure, in August 2019; and the campaign remains active.
The Milum samples that we have seen so far do not share any code similarities with any known APT campaigns. All of them allow the attackers to control infected devices remotely: letting them download and execute commands, collect information from the compromised computer and send it to the C2 server and install upgrades to the malware.
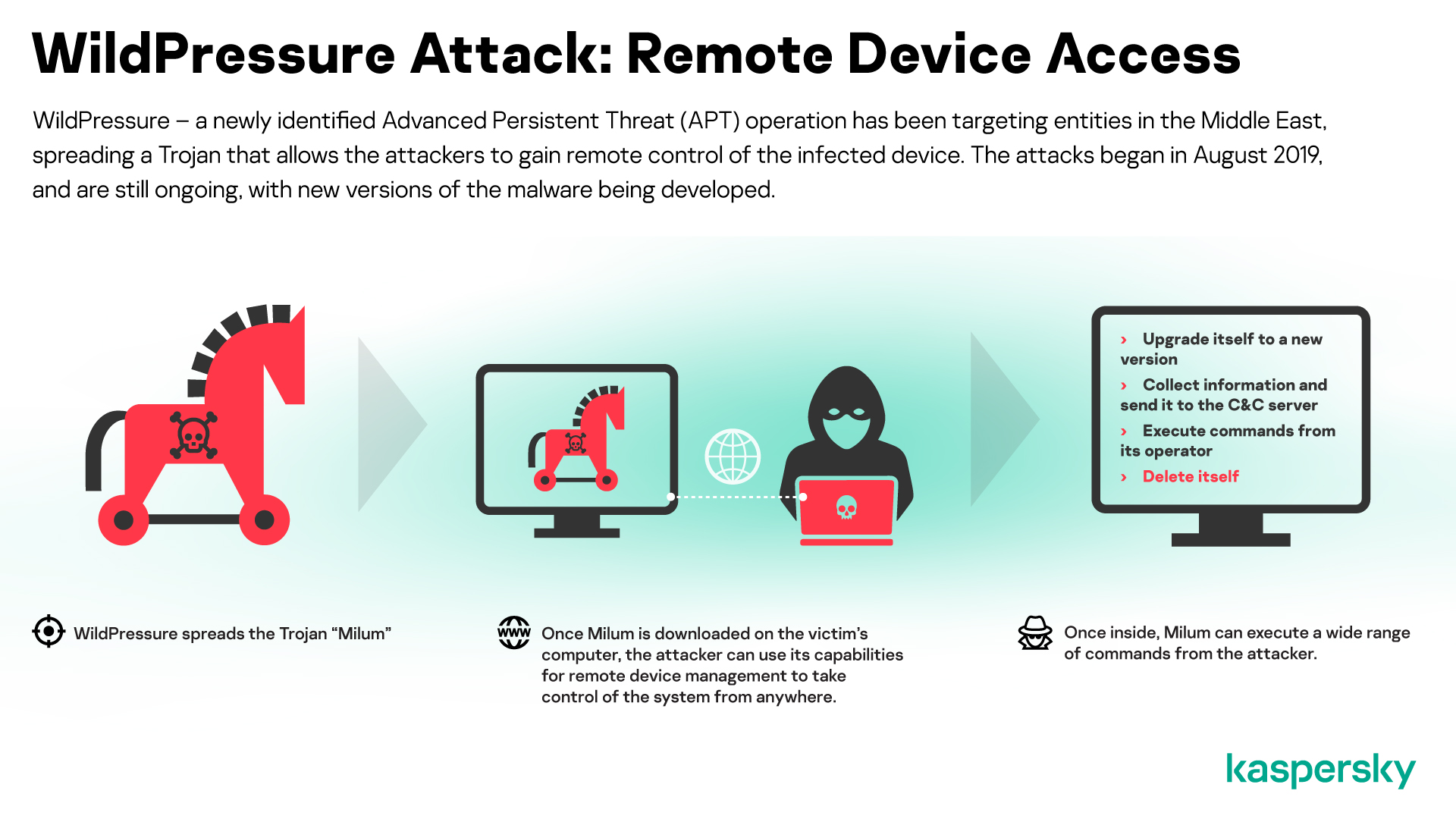
Attacks on industrial targets can be particularly devastating. So far, we haven’t seen evidence that the threat actor behind WildPressure is trying to do anything beyond gathering data from infected networks. However, the campaign is still in development, so we don’t yet know what other functionality might be added.
To avoid becoming a victim of this and other targeted attacks, organizations should do the following.
Update all software regularly, especially when a new patch becomes available.
Deploy a security solution with a proven track record, such as Kaspersky Endpoint Security, that is equipped with behavior-based protection against known and unknown threats, including exploits.
On top of endpoint protection, implement a corporate-grade security solution designed to detect advanced threats against the network, such as Kaspersky Anti Targeted Attack Platform.
Ensure staff understand social engineering and other methods used by attackers and develop a security culture within in the organization.
Provide your security team with access to comprehensive cyberthreat intelligence, such as Kaspersky APT Intelligence Reporting.
TwoSail Junk
On January 10, we discovered a watering-hole attack that utilized a full remote iOS exploit chain to deploy a feature-rich implant named LightSpy. Judging by the content of the landing page, the site appears to have been designed to target users in Hong Kong.
Since then, we have released two private reports on LightSpy, available to customers of Kaspersky Intelligence Reporting (please contact intelreports@kaspersky.com for further information).
We are temporarily calling the APT group behind this implant TwoSail Junk. Currently, we have hints from known backdoor callbacks to infrastructure about clustering this campaign with previous activity. We are also working with fellow researchers to tie LightSpy to prior activity from a well-established Chinese-speaking APT group, previously reported (here and here) as Spring Dragon (aka Lotus Blossom and Billburg(Thrip)), known for its Lotus Elise and Evora backdoors.
As this LightSpy activity was disclosed publicly by fellow researchers from Trend Micro, we wanted to contribute missing information to the story without duplicating content. In addition, in our quest to secure technologies for a better future, we have reported this malware and activity to Apple and other relevant companies.
Our report includes information about the Android implant, including its deployment, spread and support infrastructure.
A sprinkling of Holy Water in Asia
In December, we discovered watering-hole websites that were compromised to selectively trigger a drive-by download attack with fake Adobe Flash update warnings.
This campaign, which has been active since at least May 2019, targets an Asian religious and ethnic group. The threat actor’s unsophisticated but creative toolset, which has evolved greatly and may still be in development, makes use of Sojson obfuscation, NSIS installer, Python, open-source code, GitHub distribution, Go language and Google Drive-based C2 channels.
The threat actor’s operational target is unclear because we haven’t been able to observe many live operations. We have also been unable to identify any overlap with known APT groups.
Threat hunting with Bitscout
In February, Vitaly Kamluk, from the Global Research and Analysis Team at Kaspersky, reported on a new version of Bitscout, based on the upcoming release of Ubuntu 20.04 (scheduled for release in April 2020).
Bitscout is a remote digital forensics tool that we open-sourced about two and a half years ago, when Vitaly was located in the Digital Forensics Lab at INTERPOL. Bitscout has helped us in many cyber-investigations. Based on the widely popular Ubuntu Linux distribution, it incorporates forensics and malware analysis tools created by a large number of excellent developers around the world.
Here’s a summary of the approach we use in Bitscout
Bitscout is completely FREE, thereby reducing your forensics budget.
It is designed to work remotely, saving time and money that would otherwise be spent on travel. Of course, you can use the same techniques locally.
The true value lies not in the toolkit itself, but in the power of all the forensic tools that are included.
There’s a steep learning curve involved in mastering Bitscout, which ultimately reinforces the technical foundations of your experts.
Bitscout records remote forensics sessions internally, making it perfect for replaying and learning from more experienced practitioners or using as evidential proof of discovery.
It is fully open source, so you don’t need to wait for the vendor to implement a patch or feature for you: you are free to reverse-engineer and modify any part of it.
We have launched a project website, bitscout-forensics.info, as the go-to destination for those looking for tips and tricks on remote forensics using Bitscout.
Hunting APTs with YARA
In recent years, we have shared our knowledge and experience of using YARA as a threat hunting tool, mainly through our training course, ‘Hunting APTs with YARA like a GReAT ninja’, delivered during our Security Analyst Summit. However, the COVID-19 pandemic has forced us to postpone the forthcoming SAS.
Meanwhile, we have received many requests to make our YARA hands-on training available to more people. This is something we are working on and hope to be able to provide soon as an online training experience. Look out for updates on this by following us on Twitter – @craiu, @kaspersky.
With so many people working from home, and spending even more time online, it is also likely the number of threats and attacks will increase. Therefore, we decided to share some of the YARA experience we have accumulated in recent years, in the hope that all of you will find it useful for keeping threats at bay.
If you weren’t able to join the live presentation, on March 31, you can find the recording here.
We track the activities of hundreds of APT threat actors and regularly highlight the more interesting findings here. However, if you want to know more, please reach out to us at intelreports@kaspersky.com
Other security news
Shlayer Trojan attacks macOS users
Although many people consider macOS to be safe, there are cybercriminals who seek to exploit those who use this operating system. One malicious program stands out – the Shlayer Trojan. In 2019, Kaspersky macOS products blocked this Trojan on every tenth device, making this the most widespread threat to people who use macOS.
Shlayer is a smart malware distribution system that spreads via a partner network, entertainment websites and even Wikipedia. This Trojan specializes in the installation of adware – programs that feed victims illicit ads, intercepting and gathering their browser queries and modifying search results to distribute even more advertising messages.
Shlayer accounted for almost one-third of all attacks on macOS devices registered by Kaspersky products between January and November last year – and nearly all other top 10 macOS threats were adware programs that Shlayer installs.
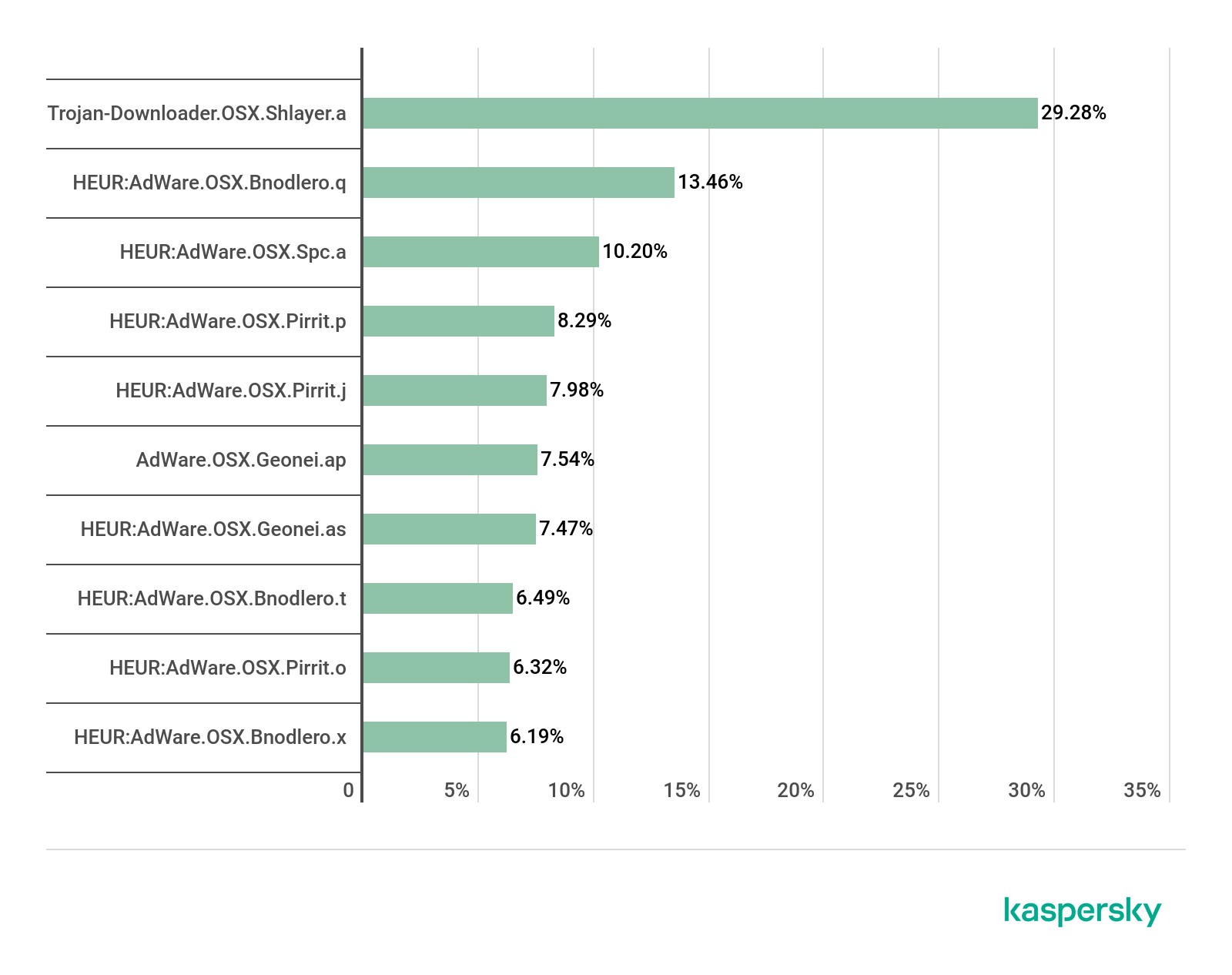
The infection starts with an unwitting victim downloading the malicious program. The criminals behind Shlayer set up a malware distribution system with a number of channels leading their victims to download the malware. Shlayer is offered as a way to monetize websites in a number of file partner programs, with relatively high payment for each malware installation made by users in the US, prompting over 1,000 ‘partner sites’ to distribute Shlayer. This scheme works as follows: a user looks for a TV series episode or a football match, and advertising landing pages redirect them to fake Flash Player update pages. From here, the victim downloads the malware; and for each installation, the partner who distributed links to the malware receives a pay-per-install payment.
Other schemes that we saw led to a fake Adobe Flash update page that redirected victims from various large online services with multi-million audiences, including YouTube, where links to the malicious website were included in video descriptions, and Wikipedia, where such links were hidden in article references. People that clicked on these links would also be redirected to the Shlayer download landing pages. Kaspersky researchers found 700 domains containing malicious content, with links to them on a variety of legitimate websites.
Almost all the websites that led to a fake Flash Player contained content in English. This corresponds to the countries where we have seen most infections – the US (31%), Germany (14%), France (10%) and the UK (10%).
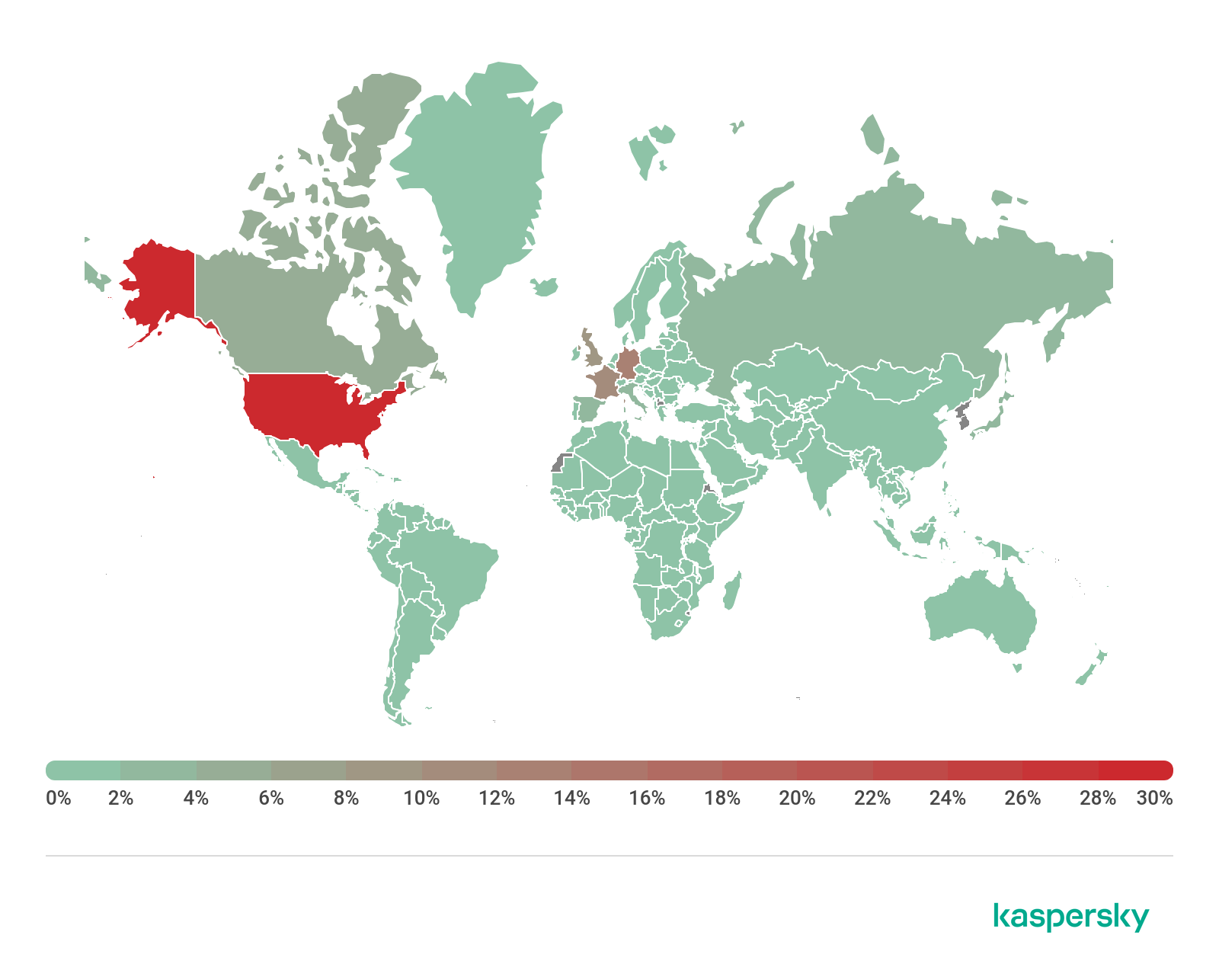
Blast from the past
Although many people still use the term “virus” to mean any malicious program, it actually refers specifically to self-replicating code, i.e., malicious code that copies itself from file to file on the same computer. Viruses, which used to dominate the threat landscape, are now rare. However, there are some interesting exceptions to this trend and we came across one recently – the first real virus we’ve seen in the wild for some time.
The virus, called KBOT, infects the victim’s computer via the internet, a local network, or infected external media. After the infected file is launched, the malware gains a foothold in the system, writing itself to Startup and the Task Scheduler, and then deploys web injects to try to steal the victim’s bank and personal data. KBOT can also download additional stealer modules that harvest and send to the Command-and-Control (C2) server comprehensive information about the victim, including passwords/logins, crypto-wallet data, lists of files and installed applications, and so on. The malware stores all its files and stolen data in a virtual file system, encrypted using the RC6 algorithm, making it hard to detect.
Cybercriminals exploiting fears about data breaches
Phishers are always on the lookout for hot topics that they can use to hook their victims, including sport, politics, romance, shopping, banking, natural disasters and anything else that might entice someone into clicking on a link or malicious file attachment.
Recently, cybercriminals have exploited the theme of data leaks to try to defraud people. Data breaches, and the fines imposed for failing to safeguard data, are now a staple feature of the news. The scammers posed as an organization called the “Personal Data Protection Fund” and claim that the “US Trading Commission” had set up a fund to compensate people whose personal data had been exposed.
However, in order to get the compensation, the victims are asked to provide a social security number. The scammers offer to sell a temporary SSN to those who don’t have one.
Even if the potential victim enters a valid SSN, they are still directed to a page asking them to purchase a temporary SSN.
You can read the full story here.
… and coronavirus
The bigger the hook, the bigger the pool of potential victims. So it’s no surprise that cybercriminals are exploiting the COVID-19 pandemic. We have found malicious PDF, MP4 and DOCX files disguised as information about the coronavirus. The names of the files suggest they contain video instructions on how to protect yourself, updates on the threat and even virus detection procedures. In fact, these files are capable of destroying, blocking, modifying or copying data, as well as interfering with the operation of the computer.
The cybercriminals behind the Ginp banking Trojan recently developed a new campaign related to COVID-19. After receiving a special command, the Trojan opens a web page called Coronavirus Finder. This provides a simple interface that claims to show the number of people nearby who are infected with the virus and asks you to pay a small sum to see their location.
The Trojan then provides a payment form.
Then … nothing else happens – apart from the criminals taking your money. Data from the Kaspersky Security Network suggests that most users who have encountered Ginp are located in Spain. However, this is a new version of Ginp that is tagged “flash-2”, while previous versions were tagged “flash-es12”. So perhaps the lack of “es” in the tag of the newer version means the cybercriminals are planning to expand their campaign beyond Spain.
We have also seen a number of phishing scams where cybercriminals pose as bona fide organizations to trick people into clicking on links to fake sites where the scammers capture their personal information, or even ask them to donate money.
If you’ve ever wanted to know why it’s so easy for phishers to create spoof emails, and what efforts have been made to make it harder for them, you can find a good overview of the problems and potential solutions here.
Cybercriminals are also taking the opportunity to attack the information infrastructure of medical facilities, clearly hoping that the overload on IT services will provide them with an opportunity to break into hospital networks, or are attempting to extort money from clinical research companies. In an effort to ensure that IT security isn’t something that medical teams have to worry about, we’re offering medical institutions free six-month licenses for our core solutions.
AZORult campaign abuses popular VPN service to steal crypto-currency
In February, we reported an unusual malware campaign in which cybercriminals were spreading the AZORult Trojan as a fake installer for ProtonVPN.
The aim of the campaign is to steal personal information and crypto-currency from the victims.
The attackers created a spoof copy a VPN service’s website, which looks like the original but has a different domain name. The criminals spread links to the domain through advertisements using different banner networks – a practice known as malvertizing. When someone visits a phishing website, they are prompted to download a free VPN installer for Windows. Once launched, this drops a copy of the AZORult botnet implant. This collects the infected device’s environment information and reports it to the server. Finally, the attackers steal crypto-currency from locally available wallets (Electrum, Bitcoin, Etherium and others), FTP logins, and passwords from FileZilla, email credentials, information from locally installed browsers (including cookies), credentials from WinSCP, Pidgin messenger and others.
AZORult is one of the most commonly bought and sold stealers on Russian forums due to its wide range of capabilities. The Trojan is able to harvest a good deal of data, including browser history, login credentials, cookies, files and crypto-wallet files; and can also be used as a loader to download other malware.
Distributing malware under the guise of security certificates
Distributing malware under the guise of legitimate software updates is not new. Typically, cybercriminals invite potential victims to install a new version of a browser or Adobe Flash Player. However, we recently discovered a new approach: visitors to infected sites were informed that some kind of security certificate had expired.
They were offered an update that infected them with malware – specifically the Buerak downloader and Mokes backdoor.
We detected the infection on variously themed websites – from a zoo to a store selling auto parts. The earliest infections that we found date back to January 16.
Mobile malware sending offensive messages
We have seen many mobile malware apps re-invent themselves, adding new layers of functionality over time. The Faketoken Trojan offers a good example of this. Over the last six years, it has developed from an app designed to capture one-time passcodes, to a fully-fledged mobile banking Trojan, to ransomware. By 2017, Faketoken was able to mimic many different apps, including mobile banking apps, e-wallets, taxi service apps and apps used to pay fines and penalties – all in order to steal bank account data.
Recently, we observed 5,000 Android smartphones infected by Faketoken sending offensive text messages. SMS capability is a standard feature of many mobile malware apps, many of which spread by sending links to their victims’ contacts; and banking Trojans typically try to make themselves the default SMS application, in order to intercept one-time passcodes. However, we had not seen one become a mass texting tool.
The messages sent by Faketoken are charged to the owner of the device; and since many of the infected smartphones we saw were texting a foreign number, the cost was quite high. Before sending any messages, the Trojan checks to see if there are sufficient funds in the victim’s bank account. If there are, Faketoken tops up the mobile account sending any messages.
We don’t yet know whether this is a one-off campaign or the start of a trend. To avoid becoming a victim of Faketoken, download apps only from Google Play, disable the downloading of apps from other sources, don’t follow links from messages and protect your device with a reputable mobile security product.
The use and abuse of the Android AccessibilityService
In January, we reported that cybercriminals were using malware to boost the rating of specific apps, to increase the number of installations.
The Shopper.a Trojan also displays advertising messages on infected devices, creates shortcuts to advertising sites and more.
The Trojan opens Google Play (or other app store), installs several programs and writes fake user reviews about them. To prevent the victim noticing, the Trojan conceals the installation window behind an ‘invisible’ window. Shopper.a gives itself the necessary permissions using the Android AccessibilityService. This service is intended to help people with disabilities use a smartphone, but if a malicious app obtains permission to use it, the malware has almost limitless possibilities for interacting with the system interface and apps – including intercepting data displayed on the screen, clicking buttons and emulating user gestures.
Shopper.a was most widespread in Russia, Brazil and India.
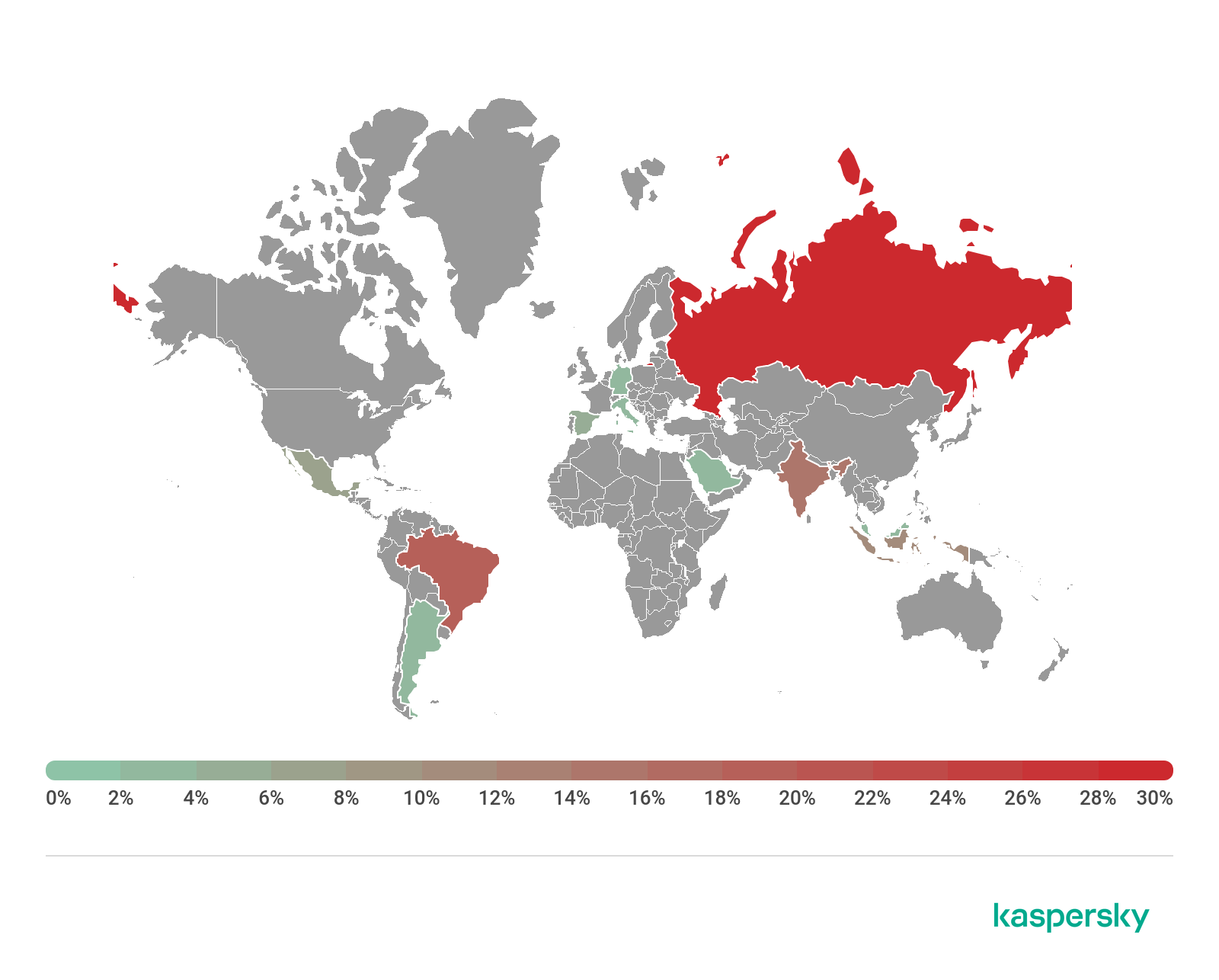
You should be wary if an app requests access to the AccessibilityService but doesn’t need it. Even if the only danger posed by such apps comes from automatically written reviews, there is no guarantee that its creators will not change the payload later.
Everyone loves cookies – including cybercriminals
We recently discovered a new malicious Android Trojan, dubbed Cookiethief, designed to acquire root permissions on the victim’s device and transfer cookies used by the browser and the Facebook app to the cybercriminals’ C2 server. Using the stolen cookies, the criminals can gain access to the unique session IDs that websites and online services use to identify someone, thereby allowing the criminals to assume someone’s identity and gain access to online accounts without the need for a login and password.
On the C2 server, we found a page advertising services for distributing spam on social networks and messengers, which we think is the underlying motive in stealing cookies.
From the C2 server addresses and encryption keys used, we were able to link Cookiethief to widespread Trojans such as Sivu, Triada, and Ztorg. Usually, such malware is either planted in the device firmware before purchase, or it gets into system folders through vulnerabilities in the operating system and then downloads various applications onto the system.
Stalkerware: no place to hide
We recently discovered a new sample of stalkerware – commercial software typically used by those who want to monitor a partner, colleague or others – that contains functionality beyond anything we have seen before. You can find more information on stalkerware here and here.
MonitorMinor, goes beyond other stalkerware programs. Primitive stalkerware uses geo-fencing technology, enabling the operator to track the victim’s location, and in most cases intercept SMS and call data. MonitorMinor goes a few steps further: recognizing the importance of messengers as a means of data collection, this app aims to get access to data from all the popular modern communication tools.
Normally, the Android sandbox prevents direct communication between apps. However, if a superuser app has been installed, which grants root access to the system, it overrides the security mechanisms of the device. The developers of MonitorMinor use this to enable full access to data on a variety of popular social media and messaging applications, including Hangouts, Instagram, Skype and Snapchat. They also use root privileges to access screen unlock patterns, enabling the stalkerware operator to unlock the device when it is nearby or when they next have physical access to the device. Kaspersky has not previously seen this feature in any other mobile threat.
Even without root access, the stalkerware can operate effectively by abusing the AccessibilityService API, which is designed to make devices friendly for users with disabilities. Using this API, the stalkerware is able to intercept any events in the applications and broadcast live audio.
Our telemetry indicates that the countries with the largest share of installations of MonitorMinor are India, Mexico, Germany, Saudi Arabia and the UK.
We recommend the following tips to reduce the risk of falling victim to a stalker:
Block the installation of apps from unknown sources in your smartphone settings.
Never disclose the password or passcode to your mobile device, even with someone you trust.
If you are ending a relationship, change security settings on your mobile device, such as passwords and app location access settings.
Keep a check on the apps installed on your device, to see if any suspicious apps have been installed without your consent
Use a reliable security solution that notifies you about the presence of commercial spyware programs aimed at invading your privacy, such as Kaspersky Internet Security.
If you think you are being stalked, reach out to a professional organization for advice.
For further guidance, contact the Coalition against Stalkerware
There are resources that can assist victims of domestic violence, dating violence, stalking and sexual violence. If you need further help, please contact the Coalition against Stalkerware.



















































































































































