Android Articles - H 1 2 3 | Android List - H 2021 2020 2019 2018 2017 2016
Lucy malware for Android adds file-encryption for ransomware ops
2.5.2020 Bleepingcomputer Android Ransomware
A threat actor focusing on Android systems has expanded their malware-as-a-service (MaaS) business with file-encrypting capabilities for ransomware operations.
Named Lucy Gang by researchers, the actor is a Russian-speaking team that made itself known two years ago with the Black Rose Lucy service, offering botnet and malware dropping capabilities for Android devices.
No cryptocurrency demand
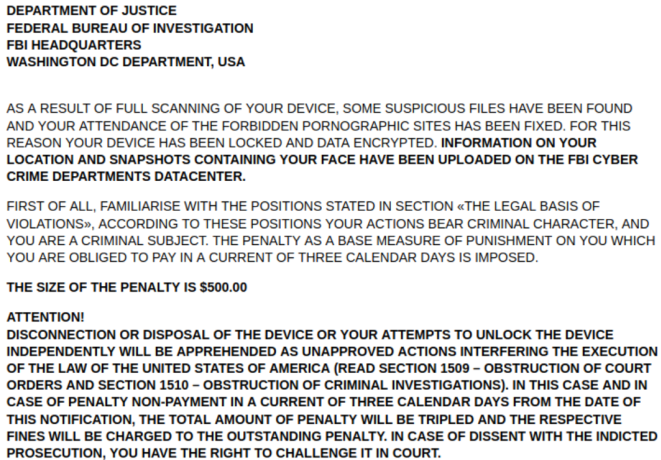
The new feature allows customers of the service to encrypt files on infected devices and show a ransom note in the browser window asking for $500. The message purports to be from the FBI and accuses the victim of storing adult content on the mobile device.
The purpose of the fake FBI note is to scare the victim into obeying the cybercriminals’ request. It is a clear extortion attempt preying on fear of legal consequences for visiting adult websites and storing lewd files.
Adding to the scare, the criminals say that a picture of the victim’s face had been taken and uploaded to FBI’s cyber crime data center along with location details. Payment is expected in three days from the notification, otherwise the fine triples, the message warns.
Interestingly, the attacker does not take cryptocurrency. Instead, they demand credit card information. This is unusual as ransomware operators are typically cashing in by making victims pay the ransom in cryptocurrency.
According to researchers from Check Point, who discovered the Black Rose Lucy malware family in September 2018, more than 80 samples of the new version have been distributed in the wild via instant messaging apps and social media.
One of the new samples was spotted by Tatyana Shishkova, an Android malware researcher at Kaspersky, who in February tweeted a list of four IP addresses used for command and control (C2).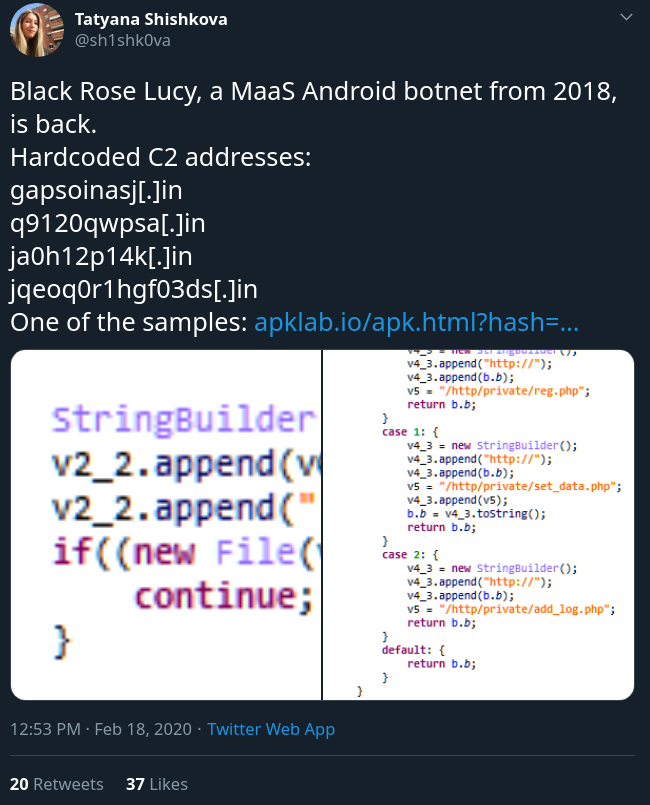
source: Tatyana Shishkova
Speaking to BleepingComputer, Check Point manager of mobile research Aviran Hazum said that the current campaign targets only victims in former Soviet states, for reasons unknown. This restriction is enforced upon malware initialization by checking the country code of the device.
Using an alert dialog, Lucy then tries to trick the victim into enabling the Accessibility Service, which is intended for users with disabilities to assist them with various tasks on behalf of installed apps.
The alert calls the user to turn on Streaming Video Optimization, which allegedly allows video to play on the phone. If the ruse works, the malware gets permission to use the accessibility service.
“Inside the MainActivity module, the application triggers the malicious service, which then registers a BroadcastReceiver that is called by the command action.SCREEN_ON and then calls itself. This is used to acquire the ‘WakeLock’ service, which keeps the device’s screen on, and ‘WifiLock’ service, which keeps the WIFI on” - Check Point
Encrypt, decrypt, and self-delete
As far as encryption goes, Lucy first tries to retrieve all the directories on the device. In case of failure, it looks for the “/storage” directory. If this also fails, the malware searches for the “/sdcard” folder.
In the next stage, it starts encrypting the data in the selected storage location and verifies the success of the operation when it completes. The procedure does not discriminate between files, Hazum told us, as long as they can be encrypted/decrypted.
“On this campaign, we have not observed a specific file-type targeting. All files were encrypted” - Aviran Hazum
As an interesting note, there is a false lead during the encryption process. A false key is generated using the AES algorithm with a constant seed of 0x100. This may be a trick from the malware developer or a mistake in the code.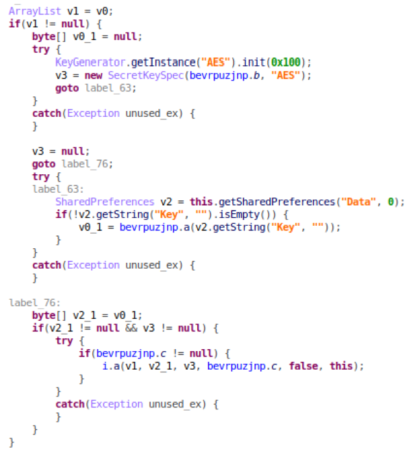
However, the real encryption key is made of data in the first segment of the ‘SecretKeySpec’ and the ‘Key’ string that is taken from SharedPreferences.
The function responsible for processing the files uses these with the chosen file directory and a boolean variable that switches between the encryption and the decryption mode.
Lucy stores the decryption key on the device, in the SharedPreferences variable, Hazum says, adding that “in order to access other application’s data, the device needs to be rooted, which we do not suggest doing.”
Check Point’s analysis reveals that the malware sends logs following the decryption process, to inform that all files were processed and then runs a command to delete itself.
A look into the commands sent from the C2 shows that Lucy can make calls, export a list of installed apps, delete the encryption keys, or run a remote shell on the device. A set of commands from the C2 that the malware recognizes is available below: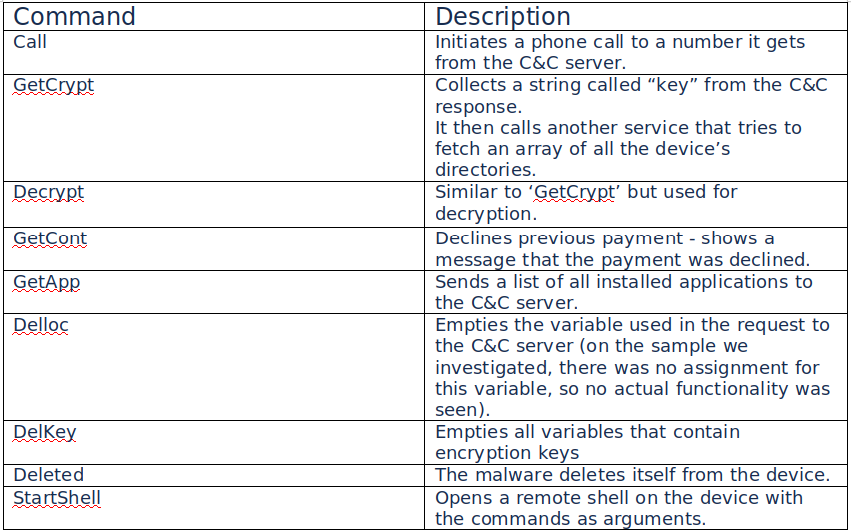
Google Play Protect Miserably Fails Android Protection Tests
14.3.2020 Bleepingcomputer Android
Google's Play Protect Android mobile threat protection system failed German antivirus testing lab AV-Test real-world tests, scoring zero out of a maximum of six points after very weak malware detection performance.
The Google Play Protect built-in malware protection for Android was introduced three years ago, during the Google I/O 2017 in May 2017, with Google starting full deployment to all Android devices during July 2017.
Today, Google's Play Protect is deployed on over 2.5 billion active Android devices as shown by the Android security center.
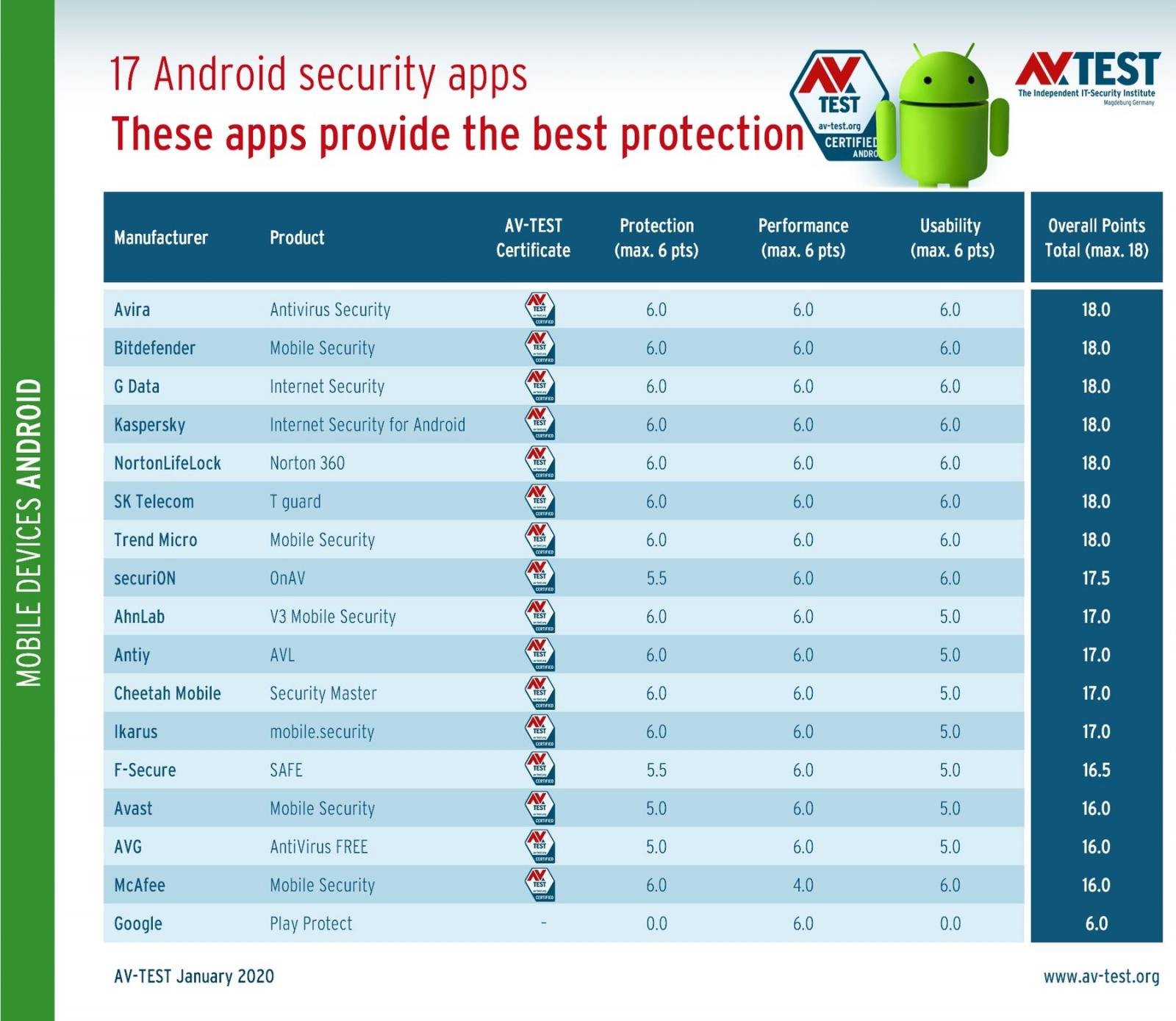
Android security app final rankings (AV-Test)
Anything else but Google Play Protect
According to AV-Test's results, Google Play Protect was able to detect a little over one-third of the roughly 6,700 malware samples the testing lab used throughout the tests which means that more than 4,000 of them were able to infect the test devices.
Google Play Protect detected 37% of 3,300 newly discovered samples — not more than 2 to 24 hours old — in the real-time testing phase, and 33.1% in the reference set test that used 3,300 malware samples that have been circulating for up to 4 weeks.
As can be seen in the below screenshot, both results are the last in the rankings, with all other mobile antivirus security solutions having detection rates above 98% in both protection tests.
Google Play Protect also had issues with false alarms as it mistakenly tagged about 30 harmless applications as being a threat to the test devices.
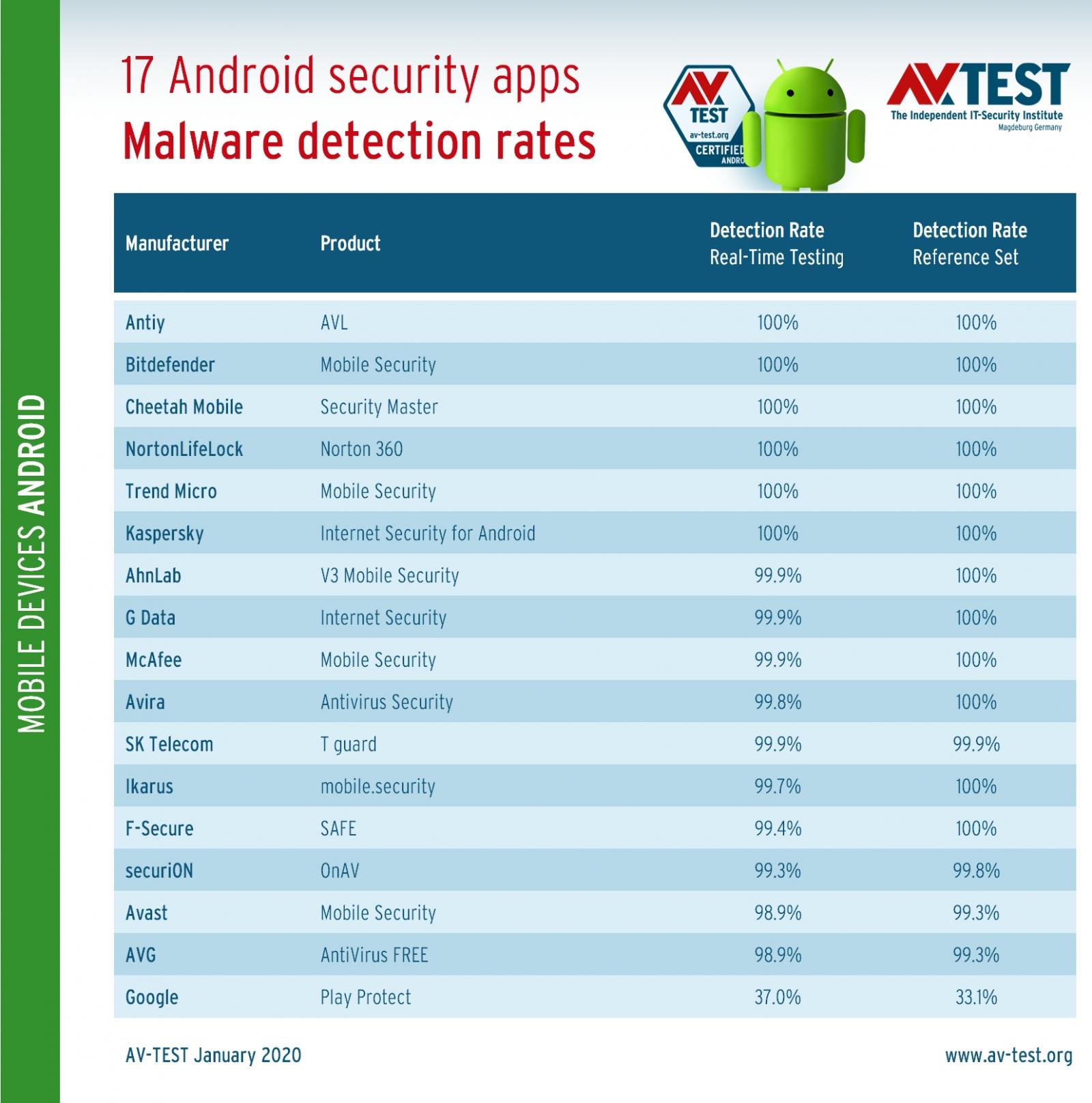
Android malware detection rates (AV-Test)
Actually, out of all mobile security suites, Antiy, Bitdefender, Cheetah Mobile, NortonLifeLock, Trend Micro, and Kaspersky hit a perfect 100% detection rate.
"With Play Protect, Google promises protection against infected programs," AV-Test says. "That's why the tool runs automatically on every newer Android system, scanning available apps."
"The current test indicates, however, that Android users should not rely solely on Play Protect," the testing lab adds.
"As the detection rates of Google Play Protect are really quite poor, the use of a good security app is highly recommended."
AV-Test's comparison only evaluated Android security apps for consumers, with the lab to test enterprise security apps and release the results in April 2020.
This is not the first time Android's built-in security app failed AV-Test's examination given that Google Play Protect was also at the bottom of the protection rankings far beyond the other mobile security tools in October 2017, right after its release.
100 billion apps scanned every day
According to Google, Play Protect scans over 100 billion apps for malware each day, up 50 billion when compared to 2018 and it provides Android users with information regarding potential security issues and the actions needed to keep their devices secure.
Last year, Google joined efforts with ESET, Lookout, and Zimperium through the App Defense Alliance to improve malicious Android app detection on submission and block such apps before getting published on the Play Store.
The App Defense Alliance couldn't have come sooner seeing that that malware has managed to infiltrate Google's app ecosystem quite often despite the company's efforts to stop it. (1, 2, 3)
Google also enhanced the machine-learning detection systems used by Google Play Protect to analyze Android app code, metadata, and user engagement signals for suspicious content and behavior.
BleepingComputer has reached out to Google for comment but had not heard back at the time of this publication.
Cerberus Android Malware Can Bypass 2FA, Unlock Devices Remotely
24.2.2020 Bleepingcomputer Android
The Cerberus banking Trojan has been upgraded with RAT functionality and is now capable of stealing victims' Google Authenticator two-factor authentication (2FA) codes used as an extra layer of security when logging into online accounts.
Google Authenticator is Google's alternative to SMS-based 2FA that uses a data connection to send one-time passcode (OTP) via text messages, something that the search giant frowns upon seeing that they can be intercepted because they're sent using an external carrier network.
While using an app to generate 2FA codes locally is seen as a more secure alternative to SMS-delivered ones, security researchers at mobile threat intelligence firm ThreatFabric have discovered an upgraded Cerberus banking Trojan sample that can now also log and steal information from Google Authenticator.
This might get app-based 2FA on the same level of security as SMS-based 2FA in the near future seeing that the codes can now be stolen in both cases.
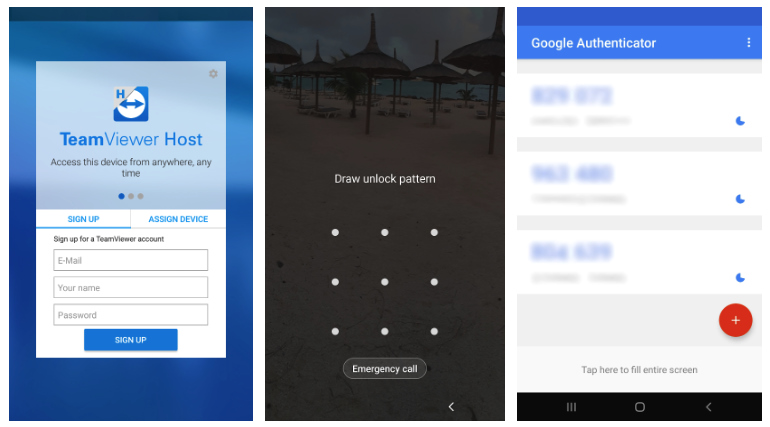
New Cerberus capabilities (ThreatFabric)
Abusing Google's Authenticator
The Android malware that was first spotted in June 2019 as a run-of-the-mill banking Trojan now steals Google Authenticator 2FA codes by abusing Android Accessibility privileges.
"When the app is running, the Trojan can get the content of the interface and can send it to the C2 server," the report adds. "Once again, we can deduce that this functionality will be used to bypass authentication services that rely on OTP codes."
These stolen codes can be used to bypass the additional 2FA security layer on online services such as banks, email services, messaging apps, and social media networks to name just a few.
Cerberus' 2FA code theft module is not the first one spotted in the wild so far, with previous cases of malware capable of this stunt being discovered by ESET and Symantec. However, those strains were targeting SMS-based two-factor authentication to bypass 2FA protection.
Fully operational RAT module
As the ThreatFabric security researchers also discovered, Cerberus now has TeamViewer-based remote access Trojan (RAT) capabilities designed to provide its operators with full RAT functionality.
"The RAT service is able to traverse the file system of the device and download its contents. On top of that, it can also launch TeamViewer and setup connections to it, providing threat actors full remote access of the device," ThreatFabric says.
This new RAT module can be used by Cerberus' operators to manage apps on infected Android devices, change a device's settings, as well as use any of the apps installed just like the device's owner.
The Android malware sample they analyzed also comes with a screen-lock grabbing feature that uses overlays, making it possible for the attackers to use the built-in RAT to unlock their victims' Android devices remotely.
"From the implementation of the RAT we can conclude that this screen-lock credential theft was built in order for the actors to be able to remotely unlock the device in order to perform fraud when the victim is not using the device," ThreatFabric adds. "This once more shows the creativity of criminals to build the right tools to be successful."
#Malware challenge :
Try finding the relation between these screenshots...
The answer: They represent latest changes in the #Cerberus #Android banking #Trojan, first spotted mid January, still under development pic.twitter.com/QRFdiWYpLe
— ThreatFabric (@ThreatFabric) February 20, 2020
Until the report was published, ThreatFabric has seen no attempts to advertise these new capabilities on underground forums or YouTube channels Cerberus is being peddled on.
This hints at the upgraded malware still going through a testing phase at the moment, although the researchers thin that it "might be released soon."
"Having an exhaustive target list including institutions from all over the world, combined with its new RAT capability, Cerberus is a critical risk for financials offering online banking services," ThreatFabric adds.
The full-report available here also provides updated information on the Gustuff, the Hydra, the Ginp, and the Anubis Android banking malware, together with a list of indicators of compromise (IOCs) for all the analyzed malware samples.
PayPal Users Hit With Fraudulent 'Target' Charges via Google Pay
24.2.2020 Bleepingcomputer Android
Hackers are using an unknown method to make fraudulent charges on PayPal accounts linked via GooglePay. These transactions are being charged through Target stores or Starbucks in the United States even though the account holders are in Germany.
Starting on February 22nd, numerous people in Germany began reporting [1, 2, 3, 4, 5, 6] that their PayPal accounts linked to Google Pay were being charged with fraudulent transactions ranging from €1,73 to over €1800.
Many reported that their accounts were first hit with a small transaction ranging between €0,01 to €4,00, which were most likely used as a test. Soon after they were hit with numerous charges from Target stores in the USA, with most being located in New York and North Carolina.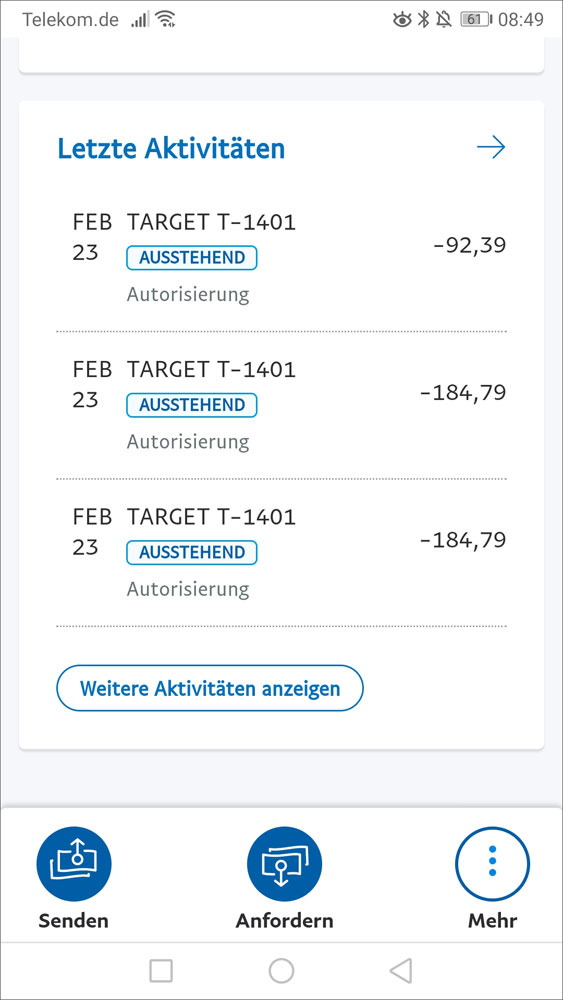
Fraudulent Transactions
The list of known Target stores involved with these fraudulent transactions can be seen below.
Target Store ID
Target Address
T-0762
9531 South Blvd Charlotte, NC 28273
T-1087
7860 Rea Rd Charlotte, NC 28277
T-1150
13505 20th Ave, College Point, NY 11356
T-1401
519 Gateway Dr, Brooklyn, NY 11239
T-1429
1230 S Longmore Mesa, AZ 85202
T-2069
8210 Renaissance Pkwy Durham, NC 27713
T-2132
12830 Walker Branch Rd Charlotte, NC 28273
T-2212
1598 Flatbush Ave, Brooklyn, NY 11210
T-2451
4024 College Point Blvd f600, Flushing, NY 11354
T-2475
700 Exterior Street, The Bronx, NY 10451
T-2811
815 Hutchinson River Pkwy, The Bronx, NY 10465
T-2850
445 Albee Square W, Brooklyn, NY 11201
T-3243
1715 E 13th St, Brooklyn, NY 11229
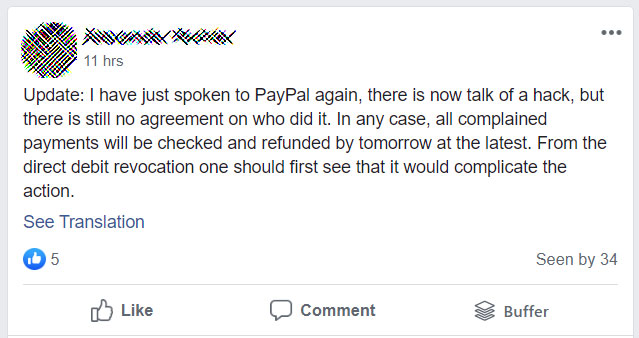
When users first started reporting the issues, they were having difficulty getting refunds from PayPal.
Today, users in a German 'Google Pay / Paypal / Target Hack 2020 victims' Facebook Group have stated that PayPal has begun refunding these fraudulent charges.
"Some others and I have already received emails from PayPal that the reported payments will be credited to the linked bank account," one user posted to the Facebook account.
Another user was told by PayPal that they are investigating the issue and that they would be refunding all affected users.
PayPal told BleepingComputer in a statement that they are have addressed and fixed the issue, but declined to explain how the attackers were able to make the fraudulent charges.
"The security of customer accounts is a top priority for the company. We quickly addressed and fixed this issue, which affected a small number of PayPal customers using Google Pay in Germany," PayPal told BleepingComputer.
When we asked how PayPal victims can receive a refund for this attack, we were told that users should contact customer service.
"We are establishing a process for refunding customers. Anyone potentially impacted should (re)contact our customer service teams," PayPal told us.
Google also issued a statement to BleepingComputer confirming that the issue was on PayPal's side and has been fixed.
"We understand the frustration of our users when any type of fraudulent activity occurs on their accounts. We’re glad that PayPal took swift action to address the issue. Security has always been the center of our approach with Google Pay. Payments fraud is a complex challenge, and the team remains committed to supporting our partners in making sure users are protected," a Google spokesperson told BleepingComputer.
Possible link to a reported Paypal vulnerability
After German media started reporting about these fraudulent transactions, a security researcher known as 'iblue' tweeted that this may be related to a vulnerability they reported to PayPal a year ago.
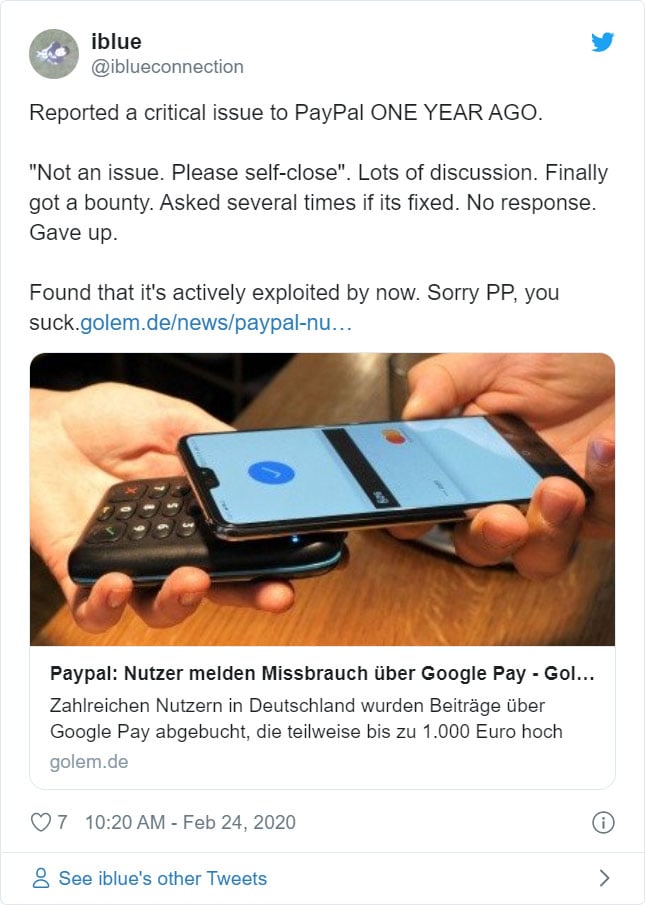
According to iblue, you can link PayPal accounts to Google Pay to make contactless payments through a virtual credit card. The vulnerability iblue reported allowed nearby mobile users to read the virtual credit card and make through that are deducted from the associated PayPal account.
"Issue: PayPal allows contactless payments via Google Pay. If you have set it up, you can read the card details of a virtual credit card from the mobile, if the mobiles device is enabled. No auth.
So basically anyone near your mobile phone has a virtual credit card which deducts money from your PayPal account. Its not limited in validity or amount."
It is not known if this is the exploit being used in current fraudulent charges, and if it is, why the nearby virtual cards in Germany would be hit with charges out of Targets in the USA.
Update 2/25/20 9:36 AM EST: Updated article with statement from PayPal and Google.
Android Malware: Joker Still Fools Google's Defense, New Clicker Found
24.2.2020 Bleepingcomputer Android
Joker malware that subscribes Android users to premium services without consent is giving Google a hard time as new samples constantly bypass scrutiny and end up in Play Store.
The malware is under constant development and new samples found in the official Android repository seem to be created specifically to avoid Google's detection mechanisms.
Also known as Bread, the malware is a spyware and premium dialer that can access notifications, read and send SMS texts. These capabilities are used to invisibly subscribe victims to premium services.
Joker avoids US and Canada
Researchers at Check Point discovered four new samples in Play Store recently, in apps with a cumulative installation count higher than 130,000. The malware was hidden in camera, wallpaper, SMS, and photo editing software:
com.app.reyflow.phote
com.race.mely.wpaper
com.landscape.camera.plus
com.vailsmsplus
To conceal malicious functionality in infected apps, a simple XOR encryption with a static key is applied to relevant strings that check for the presence of an initial payload; if non-existent, it is downloaded from a command and control (C2) server.
The malware does not target devices from the U.S. and Canada, as Check Point discovered a function that reads the operator information specifically to filter out these regions.
If conditions are met, Joker contacts its C2 server to load a configuration file containing a URL for another payload that is executed immediately after download.
"With access to the notification listener, and the ability to send SMS, the payload listens for incoming SMS and extract the premium service confirmation code (2FA) and sends it to the “Offer Page”, to subscribe the user to that premium service" - Check Point
The subscription process is invisible to the user as the URLs for the premium services, which are present in the configuration file, are opened in a hidden webview.
Joker's developer frequently adapts the code to remain undetected. Google says that many of the samples observed in the wild appear to be specifically created for distribution via Play Store as they were not seen elsewhere.
Since Google started tracking Joker in early 2017, the company removed about 1,700 infected Play Store apps. This did not deter the malware author, though, who "used just about every cloaking and obfuscation technique under the sun in an attempt to go undetected."
"At different times, we have seen three or more active variants using different approaches or targeting different carriers. [..] At peak times of activity, we have seen up to 23 different apps from this family submitted to Play in one day" - Google
New Joker samples emerge almost every day in Google's Play Store, says Aviran Hazum, mobile security researcher at Check Point.
Tatyana Shishkova, Android malware analyst at Kaspersky, has been tweeting about apps with Joker code since October, 2019. She listed over 70 compromised apps that made it into Play Store, many having at least 5,000 installations and a few with more than 50,000.
Almost all of them have been removed from the repository. At least, three totaling more than 21,000 installations, are still present, as Shishkova shows with a tweet today:
Tatyana Shishkova
@sh1shk0va
#Joker Trojans on Google Playhttps://play.google.com/store/apps/details?id=com.swecamet.sweet … Feb 18, 10,000+ installshttps://play.google.com/store/apps/details?id=com.messaging.snaptextrasmsmanager … Feb 19, 1,000+ installshttps://play.google.com/store/apps/details?id=com.bittersweet.collagephoto.maker … Feb 20, 10,000+ installs
View image on TwitterView image on TwitterView image on Twitter
14
10:40 AM - Feb 21, 2020
Twitter Ads info and privacy
See Tatyana Shishkova's other Tweets
The three apps are Sweet Cam, Photo Collage Editor, and Snap Message. They are listed under different developer names and very few reviews averaging a score of three stars.
New clicker in Play Store
The same Check Point researchers, Ohad Mana, Israel Wernik, and Bogdan Melnykov led by Aviran Hazum, discovered a new clicker malware family in eight apps on Play Store that seemed to be benign. Collectively, they have more than 50,000 installations.
The purpose of a clicker is ad fraud by mimicking user clicks on advertisements. Mobile ad fraud is a constant challenge these days as it can take many forms. For this offense Google announced yesterday that it removed nearly 600 apps from the official Android store and also banned them from its ad monetization platforms, Google AdMob and Google Ad Manager.
Named Haken, the new clicker malware relies on native code and injection into Facebook and AdMob libraries and gets the configuration from a remote server after it gets past Google's verification process.
The malware was present in applications that provide the advertised functionality, such as a compass app. One flag indicating malicious intent is asking for permissions that the compromised app does not need, such as running code when the device boots.
Once it gets the necessary permissions, Haken achieves its goal by loading a native library ('kagu-lib') and registering two workers and a timer.
"One worker communicates with the C&C server to download a new configuration and process it, while the other is triggered by the timer, checks for requirements and injects code into the Ad-related Activity classes of well-known Ad-SDK’s like Google’s AdMob and Facebook" - Check Point
Native code, injecting into legitimate Ad-SDKs (software development kit), and backdooring apps already in the Play Store allowed Haken to keep a low profile and generate revenue from fraudulent ad campaigns.
It is unclear how long the malware survived and the revenue it made but the low installation count suggests a small figure. If still present on their devices, users are advised to remove the following apps:
Kids Coloring - com.faber.kids.coloring
Compass - com.haken.compass
qrcode - com.haken.qrcode
Fruits Coloring Book - com.vimotech.fruits.coloring.book
Soccer Coloring Book - com.vimotech.soccer.coloring.book
Fruit Jump Tower - mobi.game.fruit.jump.tower
Ball Number Shooter - mobi.game.ball.number.shooter
Inongdan - com.vimotech.inongdan
Check Point reported to Google the 12 malicious apps found on Play Store and they are no longer available in the repository.
Update [02/21/2020]: Article updated with information of new apps containing the Joker trojan that are currently available from the Play Store
Google Cleans Play Store of Nearly 600 Apps for Ad Policy Violation
24.2.2020 Bleepingcomputer Android
Google reacted severely against nearly 600 Android apps in Play Store that were violating two ad-related policies by kicking them out of the repository.
The penalty went further with banning the apps from the company's ad monetization platforms (Google AdMob and Google Ad Manager), essentially cutting authors any hope of getting revenue from their apps through Google.
Ad-serving principles
In an announcement today, the company explains that offensive apps featured advertisements in a way that was in contrast with the disruptive ads and disallowed interstitial policies.
The two principles infringed ensure smooth user experience and help combat mobile the many forms of ad fraud, including harmless apps that disobey the rules.
When referring to disruptive ads, Google describes them as displayed in a way that could cause the user to click them unintentionally.
"Forcing a user to click an ad or submit personal information for advertising purposes before they can fully use an app is prohibited," reads the policy.
These unruly promotions can appear in-app but a form that's becoming more popular is when an ill-intended developer serves ads on a mobile device when the user is not active in their app.
Also known as "out-of-context ads," they can be displayed in full screen at an inconvenient time, e.g. using the phone for a different task, unlocking it.
"Malicious developers continue to become more savvy in deploying and masking disruptive ads, but we’ve developed new technologies of our own to protect against this behavior" - Google
Using machine learning, Google is now able to detect when apps display out-out-of-context ads. This method helped find the apps that have been removed from the Play Store.
The company says that nurturing technologies that detect and prevent new threats that can generate invalid traffic is the plan for the future, along with adjusting the platform and the policies in a way that protects both users and advertisers from malicious intent in apps.
Google Play Protect Blocked 1.9 Billion Malware Installs in 2019
16.2.2020 Bleepingcomputer Android
Google's Play Protect mobile threat protection service blocked the installation of over 1.9 billion malicious apps downloaded from non-Play Store sources in 2019.
During 2017 and 2018, Google Play Protect has also prevented the installation of another 3.2 billion Potentially Harmful Application (PHAs) — as Google refers to malicious apps — from outside of the Play Store per Android Year in Review security reports.
The stats go as far as the beginning of 2017 because that's when Google Play Protect was introduced, during the Google I/O 2017 on May 17, 2017, with Google starting full deployment of the built-in malware protection to all Android devices during July 2017.
Today, Google Play Protect is deployed on over 2.5 billion active Android devices as described in the Android security center.
Backed by Google’s machine learning, it’s always adapting and improving. Every day, it automatically scans all of the apps on Android phones and works to prevent harmful apps from ever reaching them, making it the most widely deployed mobile threat protection service in the world.
100 billion apps scanned every day
Google Play Protect scans over 100 billion apps for malware every day, up 50 billion compared to 2018 and providing users with info about potential security issues and providing details on actions needed to keep their devices secure.
In 2019, Google worked on strengthening policies to better protect families and children and joined efforts with ESET, Lookout, and Zimperium through the App Defense Alliance to improve malicious Android app detection on submission blocking them before they get published on the Play Store.
The App Defense Alliance couldn't have come sooner given that malware managed to infiltrate Google's app ecosystem more and more often notwithstanding the company's efforts to stop this evolving trend. (1, 2, 3)
Google also improved the developer approval process last year and enhanced the machine-learning detection systems used by Google Play Protect to examine Android app code, metadata, and user engagement signals for suspicious behavior and content.
Google working to improve Play Store's safety
All these efforts made the Play Store a much cleaner app distribution market seeing that Google's vetting team was able to stop more than 790,000 policy-violating app submissions before being published.
Google is also committed to investing more to protect the security of Android devices by strengthening app safety policies designed to protect users' privacy, by blocking repeat offenders and detecting bad actors faster, as well as identifying and removing Android apps featuring harmful content and behaviors.
"Such a thriving ecosystem can only be achieved and sustained when trust and safety is one of its key foundations," Google Play & Android App Safety product manager Andrew Ahn said.
"Over the last few years we’ve made the trust and safety of Google Play a top priority, and have continued our investments and improvements in our abuse detection systems, policies, and teams to fight against bad apps and malicious actors."
Critical Android Bluetooth Flaw Exploitable without User Interaction
9.2.2020 Bleepingcomputer Android
Android users are urged to apply the latest security patches released for the operating system on Monday that address a critical vulnerability in the Bluetooth subsystem.
An attacker could leverage the security flaw, now identified as CVE-2020-0022 without user participation to run arbitrary code on the device with the elevated privileges of the Bluetooth daemon when the wireless module is active.
Short-distance worm
Discovered and reported by Jan Ruge at the Technische Universität Darmstadt, Secure Mobile Networking Lab, the bug is considered critical on Android Oreo (8.0 and 8.1) and Pie (9) because exploiting it leads to code execution.
According to Ruge, attackers could use this security fault to spread malware from one vulnerable device to another, like a worm. However, the transmission is limited to the short distance covered by Bluetooth.
The Android security bulletin notes that CVE-2020-0022 "could enable a remote attacker using a specially crafted transmission to execute arbitrary code within the context of a privileged process."
The only prerequisite for taking advantage of the issue is knowing the Bluetooth MAC address. This is not difficult to find, though.
"For some devices, the Bluetooth MAC address can be deduced from the WiFi MAC address," says the researcher on the the blog site of German IT security consultant ERNW.
On Android 10, the severity rating drops to moderate since it all it does is crash the Bluetooth daemon, the researcher says. Android versions earlier than 8.0 may also be affected but the impact on them has not been assessed.
Technical details, PoC to be published
The severity of the issue is what keeps the researcher from disclosing technical details and proof of concept (PoC) code demonstrating the findings.
Despite a patch being available, OEM vendors and mobile carriers also have to push it to user terminals. For devices still under support, it can take weeks until the update rolls out.
If a patch does not become available, Ruge recommends enabling Bluetooth only "if strictly necessary." If you need to activate it, consider keeping the device non-discoverable, a feature that hides it from other gadgets looking for a pair.
Ruge says that a technical report will be available for this vulnerability "as soon as we are confident that patches have reached the end users."
Phishing Attack Disables Google Play Protect, Drops Anubis Trojan
9.2.2020 Bleepingcomputer Android Phishing
Android users are targeted in a phishing campaign that will infect their devices with the Anubis banking Trojan that can steal financial information from more than 250 banking and shopping applications.
The campaign uses a devious method to get the potential victims to install the malware on their devices: it asks them to enable Google Play Protect while actually disabling it after being granted permissions on the device.
To deliver the malware, the attackers use a malicious link embedded within the phishing email that will download an APK file camouflaged as an invoice as Cofense found.
After being asked if he wants to use Google Play Protect and installing the downloaded APK, the victim's device will be infected with the Anubis Trojan.
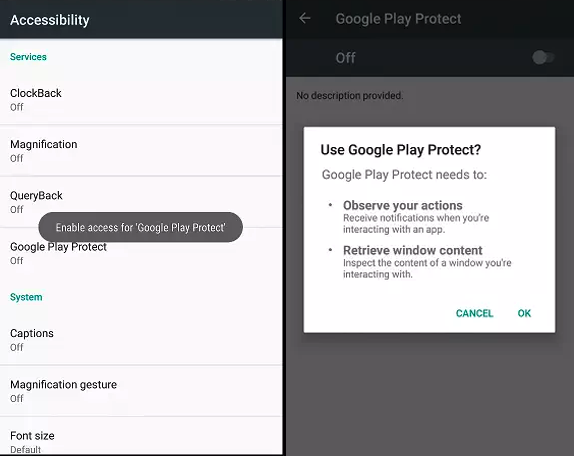
Google Play Protect used as cover (Cofense)
Targets over 250 financial applications
Cofense discovered that, once the Android smartphone or tablet is compromised, Anubis will start harvesting "a list of installed applications to compare the results against a list of targeted applications.
The malware mainly targets banking and financial applications, but also looks for popular shopping apps such as eBay or Amazon.
Once an application has been identified, Anubis overlays the original application with a fake login page to capture the user’s credentials."
After analyzing the malware's source code, Cofense found that the banking Trojan has a wide range of capabilities included but not limited to:
• capturing screenshots
• toggling off and altering administration settings
• disabling Google's Play Protect built-in malware protection for Android
• recording audio
• making calls and sending SMS
• stealing the contact list
• stealing the contacts from the addressbook
• receiving commands from its operators via Telegram and Twitter
• controlling the device over a VNC
• opening URLs
• locking device screen
• and collecting device and location information
The malware also comes with a keylogger module that can capture keystrokes from every app installed on the compromised Android device.
However, this keylogging module has to be specifically enabled by the attackers via a command sent through Anubis' command and control (C2) server.
Also comes with a ransomware module
On top of all of these, Anubis is also capable of encrypting files on the internal storage and from external drives using the RC4 stream cipher with the help of a dedicated ransomware module, adding the .AnubisCrypt extension to the encrypted files and sending it to the C2 server.
Anubis Trojan samples with ransomware capabilities are not new, as Sophos previously discovered Anubis-infected apps in the Play Store in August 2018 that also added the .AnubisCrypt file extension to the encrypted files.
"Remember, this runs on a phone, which is even less likely to be backed up than a laptop or desktop, and more likely to have personal photos or other valuable data," Sophos said at the time.
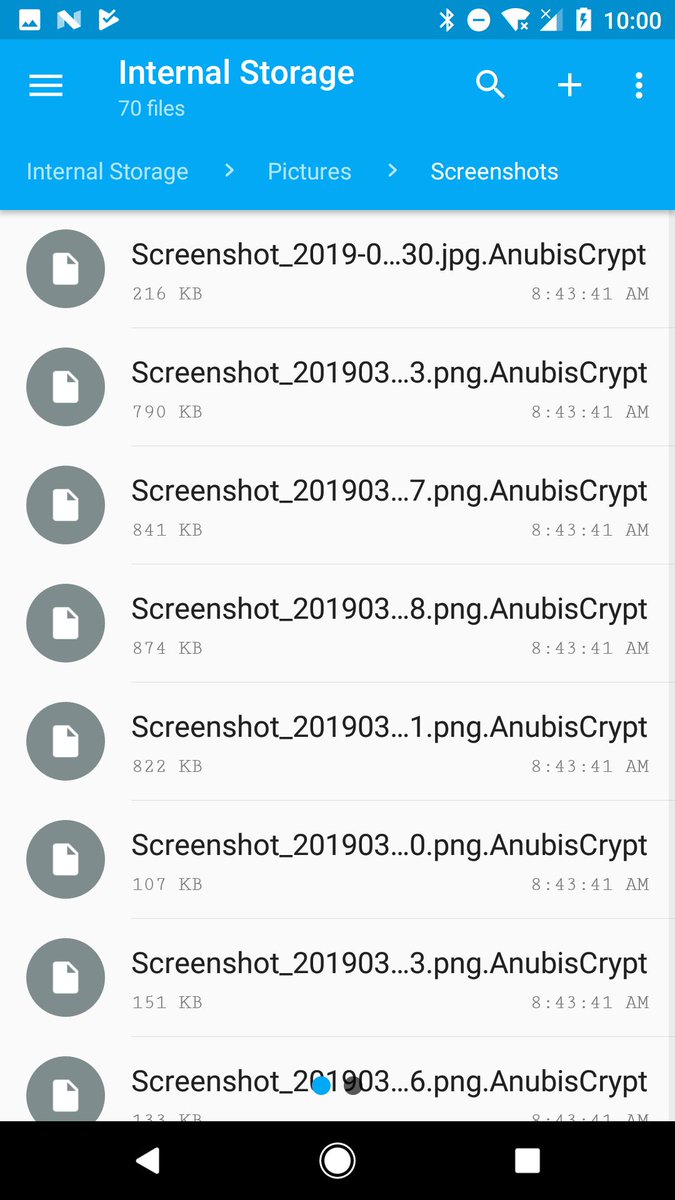
AnubisCrypt encrypted files
According to the Cofense report, "this version of Anubis is built to run on several iterations of the Android operating system, dating back to version 4.0.3, which was released in 2012."
Trend Micro's researchers also found in January 2019 that the Anubis Trojan was used in a campaign that targeted 377 bank apps from 93 countries all over the globe, with banks like Santander, Citibank, RBS, and Natwest, as well as shopping apps such as Amazon, eBay, and PayPal being listed as targets.
An extensive list of indicators of compromised (IOCs) including hashes of the malicious APK installer used in the campaign, associated URLs, and all application IDs for the apps targeted by this Anubis sample is available at the end of Cofense's report.