
The malicious app purports to uninstall after download. Credit: Cisco Talos
Android Articles - H 1 2 3 2020 Android List - H 2021 2020 2019 2018 2017 2016
Firestarter Android Malware Abuses Google Firebase Cloud Messaging
31.10.20 Android Threatpost
The DoNot APT threat group is leveraging the legitimate Google Firebase Cloud Messaging server as a command-and-control (C2) communication mechanism.
An APT group is starting fires with a new Android malware loader, which uses a legitimate Google messaging service to bypass detection.
The malware, dubbed “Firestarter,” is used by an APT threat group called “DoNot.” DoNot uses Firebase Cloud Messaging (FCM), which is a cross-platform cloud solution for messages and notifications for Android, iOS and web applications. The service is provided by Firebase, a subsidiary of Google, and has been previously leveraged by cybercriminals.
In this case, the loader uses it as a communication mechanism to connect with DoNot’s command-and-control (C2) servers, helping the group’s activities avoid detection.
“Our research revealed that DoNot has been experimenting with new techniques to keep a foothold on their victim machines,” according to researchers with Cisco Talos in a Thursday analysis. “These experiments, substantiated in the Firestarter loader, are a sign of how determined they are to keep their operations despite being exposed, which makes them a particularly dangerous actor operating in the espionage area.”
The DoNot team continues to focus on India and Pakistan, and is known for targeting Pakistani government officials and Kashmiri non-profit organizations (Kashmiris are a Dardic ethnic group native to the disputed Kashmir Valley).
Users are lured to install a malicious app on their mobile device, likely done via direct messages that utilize social engineering, researchers said. The filename of these Android applications (kashmir_sample.apk or Kashmir_Voice_v4.8.apk) show continued interest in India, Pakistan and the Kashmir crisis.
Once the app — which purports to be a chat platform — is downloaded and opened, users receive a message that chats are continually loading, and that the application is not supported, and that uninstallation is in progress. This is a lure to make the victim believe that there was no malicious install, researchers said. Once the message of uninstallation is shown, the icon is removed from the user interface (though it still shows in the application list in the phone’s settings).

The malicious app purports to uninstall after download. Credit: Cisco Talos
In the background, however, the malicious app is attempting to download a payload using FCM.
According to Firebase, an FCM implementation includes two main components for sending and receiving messages. These include an app server on which to build, target and send messages; and an iOS, Android, or web (JavaScript) client app that receives messages via the corresponding platform-specific transport service.
In this case, the app sends the C2 server a Google FCM token with various device info – including the geographic location, IP address, IMEI and email address from the victims – which then allows operators to decide whether the victim should receive the payload. This ensures that only very specific devices are delivered the malicious payload, researchers said.
The C2 then sends a Google FCM message containing the URL for the malware to download the payload. When the malware receives this message, it checks if it contains a key called “link,” and if that exists, it checks if it starts with “https.” It then uses the link to download the payload from a hosting server.
Of note, researchers said that the Google FCM communication channel is encrypted and mixed among other communications performed by Android OS using the Google infrastructure, which helps it escape notice.
“DoNot team is hiding part of their traffic among legitimate traffic,” said researchers. “Even though the malicious actors still need a [C2] infrastructure, the hardcoded one is only needed at installation time, afterwards it can be discarded and easily replaced by another one. Thus, if their C2 is taken down by law enforcement or deemed malicious, they can still access the victim’s device and instruct it to contact a new C2.”

DoNot’s Firestarter malware attack vector. Credit: Cisco Talos
The final payload, meanwhile, is not embedded in the Android application, making it impossible for analysts to dissect it.
“This approach also makes detection more difficult,” they said. “The application is a loader with a fake user interface that manipulates the target after installing it.”
Wroba Mobile Banking Trojan Spreads to the U.S. via Texts
31.10.20 Android Threatpost
The Roaming Mantis group is targeting the States with a malware that can steal information, harvest financial data and send texts to self-propagate.
The Wroba mobile banking trojan has made a major pivot, targeting people in the U.S. for the first time.
According to researchers at Kaspersky, a wave of attacks are taking aim at U.S. Android and iPhone users in an effort that started on Thursday. The campaign uses text messages to spread, using fake notifications for “package deliveries” as a lure.
The message inside the SMS contains a link and reads, “Your parcel has been sent out. Please check and accept it,” noted researchers from Kaspersky, in an emailed alert on Friday.
If users click on the link, the next thing that happens depends on which operating system is used by the device. A click takes Android users to a malicious site, which in turn surfaces an alert to users saying that the browser is out-of-date and needs to be updated. If the user clicks ‘OK’, next the downloading of a trojanized browser package with the malicious application begins.
But where Android users are served up the full Wroba download, according to researchers, the executable doesn’t work on iPhone. For iOS users the Wroba operators instead engineer a redirect to a phishing page. The page mimics the Apple ID login page in an effort to harvest credentials from Apple aficionados, but no malware is installed.
Apple had more than half of the total U.S. smartphone market share as of May.
Wroba has been around for years, but previously mainly targeted users in APAC. It was first developed as an Android-specific mobile banking trojan, capable of stealing files related to financial transactions, but has since expanded its functionality. Researchers believe the operator behind Wroba are China-based and known as “Roaming Mantis.”
This latest iteration of Wroba can send SMS messages, check which apps are installed, open web pages, harvest any files related to financial transactions, steal contact lists, call specified numbers and show fake phishing pages to steal victim’s credentials, researchers said.
Once it has infected a device, Wroba uses some of its functionality – stolen contact lists and the SMS capability – to propagate, using infected devices to spread further by sending SMS with malicious links, purporting to come from the host.
“Wroba shows how delivering malware to a device can enable longer-term gain for the attack,” according to Hank Schless, senior manager of security solutions at Lookout, which has been tracking Wroba as well.
“A credential-harvesting link only targets you for one purpose, such as when you receive an SMS saying your bank account has been compromised and the intent is to phishing your banking credentials,” he told Threatpost.
“Wroba, on the other hand, can sit silently in the background and deliver credential harvesting pages to your browser at will,” he said. “As long as it goes unnoticed, it can attempt to grab your login data for even your most private accounts.”
The malware has targeted users worldwide since the start of the year, researchers said, mainly in China, Japan and the Russian Federation.
“The USA is currently not at the top of the list but it seems that cybercriminals are heading to this region and the number of users seeing Wroba will increase,” according to Kaspersky. “The wave was detected on 29th of October and targeted users in different states of USA (judging by the phone numbers that were the targets of this campaign).”
The firm added, “Previously seen campaigns targeted users from APAC, so it is interesting to see how cybercriminals expand their targets.”
In 2018, Wroba saw a major reboot when it began targeting Europe and the Middle East in addition to Asian countries. According to Kaspersky researchers at the time, it also expanded its capabilities to include cryptomining as well as the iOS phishing tactic mentioned previously. At that point, it was spreading via DNS hijacking, which redirected users to a malicious webpage that, as in the current campaign distributed a trojanized application (at that time, it was pretending to be either Facebook or Chrome).
Roaming Mantis has swarmed into the U.S. in the past, it should be noted. This summer, it was spotted trotting out a different SMS phishing campaign that spread the FakeSpy infostealer. The malware, which was disguised as legitimate global postal-service apps, also steals SMS messages, financial data and more from the victims’ devices. It started by going after South Korean and Japanese speakers, but then expanded that targeting to China, Taiwan, France, Switzerland, Germany, the United Kingdom and the United States.
Schless told Threatpost that according to Lookout data, 88 percent of U.S. consumer phishing attacks so far in 2020 were attempts to deliver malware to the mobile device.
To avoid becoming a victim of Wroba, or any other mobile malware, users should employ basic security hygiene, researchers stressed, such as only downloading applications from official stores; disabling the installation of applications from third-party sources in smartphone settings; and avoid clicking on suspicious links from unknown senders, or even suspicious links from known senders.
“People are still grasping to avoid phishing attacks by email,” Ray Kelly, principal security engineer at WhiteHat Security, told Threatpost. “Now, SMS messaging is complicating matters further. SMS should be treated the same as email, never click on links from unknown or suspicious senders.”
21 Malicious Apps Downloaded 8 Million Times From Google Play
28.10.20 Android Securityweek
Despite Google’s best efforts to keep Android users safe, malware does manage to slip into Google Play from time to time, and the 21 malicious apps that Avast identified recently are proof of that.
Catered for gamers, the apps were found to include adware that is part of the HiddenAds family. The offending applications appear to have been downloaded roughly 8 million times before being discovered.
The HiddenAds malware, Avast explains, poses as fun or useful apps but in reality delivers intrusive ads outside the application. Often, the malware would make detection difficult by hiding behind relevant-looking advertisements and would attempt to prevent removal by hiding icons.
In this case, the threat was disguised as games promising to provide users with highly engaging actions.
“Developers of adware are increasingly using social media channels, like regular marketers would. This time, users reported they were targeted with ads promoting the games on YouTube. In September, we saw adware spread via TikTok. The popularity of these social networks make them an attractive advertising platform, also for cybercriminals, to target a younger audience,” notes Jakub Vávra, threat analyst at Avast.
To stay protected, users are advised to always double-check any application they want to download and install on their devices, even those listed in Google Play.
Just as HiddenAds managed to bypass Google’s protections and enter the mobile app store, other malware families did and may continue to do so as well. Checking the app’s reviews, price, and ratings in the store and paying attention to the requested permissions should help users identify suspicious apps.
“Users need to be vigilant when downloading applications to their phones and are advised to check the applications’ profile, reviews and to be mindful of extensive device permission requests,” Vávra notes.
Avast also advises users to educate themselves to identify scammers in areas they most often visit, such as online social platforms, YouTube, and the like. Applying rules where children need an adult’s permission before downloading an app should also help keep scammers and malware away.
Google Removes 21 Malicious Android Apps from Play Store
27.10.20 Android Thehackernews
Google has stepped in to remove several Android applications from the official Play Store following the disclosure that the apps in question were found to serve intrusive ads.
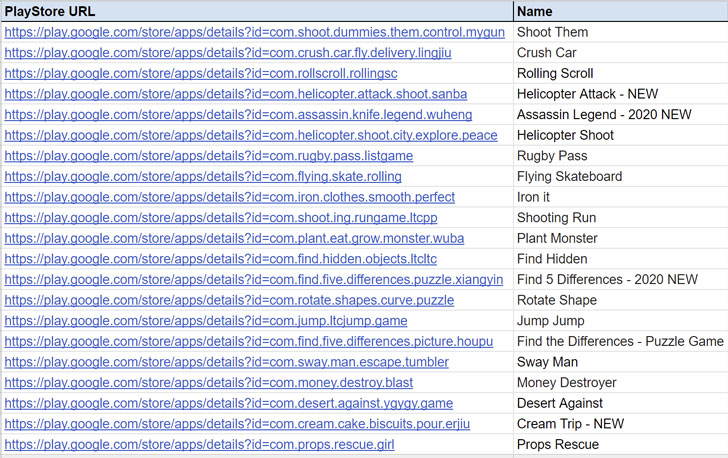
The findings were reported by the Czech cybersecurity firm Avast on Monday, which said the 21 malicious apps (list here) were downloaded nearly eight million times from Google's app marketplace.
The apps masqueraded as harmless gaming apps and came packed with HiddenAds malware, a notorious Trojan known for its capabilities to serve intrusive ads outside of the app. The group behind the operation relies on social media channels to lure users into downloading the apps.
Earlier this June, Avast discovered a similar HiddenAds campaign involving 47 gaming apps with over 15 million downloads that were leveraged to display device-wide intrusive ads.
"Developers of adware are increasingly using social media channels, like regular marketers would," Avast's Jakub Vávra said. "This time, users reported they were targeted with ads promoting the games on YouTube."
"In September, we saw adware spread via TikTok. The popularity of these social networks make them an attractive advertising platform, also for cybercriminals, to target a younger audience."
Once installed, the apps not only hide their icons to prevent deletion but also hide behind relevant-looking advertisements, making them hard to identify.
In addition, the apps also have the ability to draw over other apps to show timed ads that cannot be skipped, and in some cases, even open the browser to bombard users with ads.
Although such apps can be uninstalled through the app manager features of the device, it puts the onus on the users to search for the exact app that's the source of the ads and remove them.
Google, for its part, has been actively trying to stop rogue Android apps from infiltrating the Google Play Store. It has leveraged Google Play Protect as a means to screen potentially harmful applications and also forged an "App Defense Alliance" last year in partnership with cybersecurity firms ESET, Lookout, and Zimperium to reduce the risk of app-based malware.
If anything, the latest news is another reason why users need to scrutinize the reviews, developer details, and the list of requested permissions before installing any app.
Windows GravityRAT Malware Now Also Targets macOS and Android Devices
21.10.20 Android Thehackernews
A Windows-based remote access Trojan believed to be designed by Pakistani hacker groups to infiltrate computers and steal users' data has resurfaced after a two-year span with retooled capabilities to target Android and macOS devices.
According to cybersecurity firm Kaspersky, the malware — dubbed "GravityRAT" — now masquerades as legitimate Android and macOS apps to capture device data, contact lists, e-mail addresses, and call and text logs and transmit them to an attacker-controlled server.
First documented by the Indian Computer Emergency Response Team (CERT-In) in August 2017 and subsequently by Cisco Talos in April 2018, GravityRAT has been known to target Indian entities and organizations via malware-laced Microsoft Office Word documents at least since 2015.
Noting that the threat actor developed at least four different versions of the espionage tool, Cisco said, "the developer was clever enough to keep this infrastructure safe, and not have it blacklisted by a security vendor."
Then last year, it emerged that Pakistani spies used fake Facebook accounts to reach out to more than 98 officials from various defence forces and organizations, such as the Indian Army, Air Force, and Navy, and trick them into installing the malware disguised as a secure messaging app called Whisper.

But even as the latest evolution of GravityRAT goes beyond anti-malware evasion capabilities to gain multi-platform support — including Android and macOS — the overall modus operandi remains the same: sending targets links to booby-trapped Android (e.g., Travel Mate Pro) and macOS apps (Enigma, Titanium) to distribute the malware.
Kaspersky said it found over ten versions of GravityRAT that were being distributed under the guise of legitimate applications by cross-referencing the command-and-control (C2) addresses used by the Trojan.
In all, the trojanized applications spanned across travel, file sharing, media players, and adult comics categories, catering to users of Android, macOS, and Windows, thereby allowing the attackers to grab system information, documents with specific extensions, a list of running processes, record keystrokes and take screenshots, and even execute arbitrary Shell commands.
"Our investigation indicated that the actor behind GravityRAT is continuing to invest in its spying capacities," Kaspersky's Tatyana Shishkova said.
"Cunning disguise and an expanded OS portfolio not only allow us to say that we can expect more incidents with this malware in the APAC region, but this also supports the wider trend that malicious users are not necessarily focused on developing new malware, but developing proven ones instead, in an attempt to be as successful as possible."
RAINBOWMIX Apps in Google Play Serve Up Millions of Ad Fraud Victims
9.10.20 Android Threatpost
Collectively, 240 fraudulent Android apps — masquerading as retro game emulators — account for 14 million installs.
Researchers with White Ops have uncovered a scam to deliver millions of out-of-context (OOC) ads through a group of more than 240 Android applications on the official Google Play store, which the team said were collectively delivering more than 15 million impressions per day at their peak.
The apps have since been purged from Google Play, but users should delete them off their phones as well. The full list is available here.
The apps worked the way they were supposed to, for the most part, making them all the more effective at hiding in plain sight. Most were simple retro games like Nintendo NES emulators, and used “packer” software to bypass protections. The apps would then deliver OOC ads disguised to appear as if they were from reputable sources like Chrome and YouTube, according to the White Ops team.
“The main tool in the adware developer’s arsenal are the packers,” Gabriel Cirlig, principal threat intelligence analyst for White Ops, told Threatpost. “They cloak and allow a threat to exist under the guise of intellectual property protection. However, once they passed any antivirus [protections] a user might have, the OOC ads were able to stay undetected for a period of time by pretending to be coming from popular applications and social-media platforms, such as YouTube and Chrome. Because of this, users think the ads are coming from legitimate platforms and do not get suspicious.”
The White Ops team of researchers, including Cirling, Michael Gethers, Lisa Gansky and Dina Haines, — who named the investigation “RAINBOWMIX,” inspired by the 8-16 bit color palate running throughout the retro game apps — found that these fraudulent apps were downloaded more than 14 million times by unsuspecting users.
How RAINBOWMIX Infiltrated User Devices
The various applications’ reviews show there wasn’t a lot of attention being paid to the RAINBOWMIX group.
“Most of the RAINBOWMIX apps have a “C-shaped rating distribution curve (with primarily one- and five-star reviews, which is common with suspect apps),” the team reported.
All of the RAINBOWMIX apps were loaded with the Tencent Legu packer, they add, noting that some did give clues to their nefarious intent, if you looked hard enough.
“It is worth noting that even while packed, these apps exhibit some potentially suspicious behavior corresponding to the interstitial component of the ad SDKs, which are renamed with labels that point to well-known apps,” the researchers said.
How RAINBOWMIX Fooled the System
The team also noticed triggers for services and receivers inside the apps’ manifests which shouldn’t have been there, including upon system boot, during connection changes, when a charging chord is plugged in or out, and during app installations. The assessment is that these were used to “confuse analysts and trick static-analysis engines,” the report read.
The analysts were able to pinpoint that the trigger for OOC ads “resides in the service com.timuz.a,” adding it was present in every one of the RAINBOWMIX group of applications.
“The receiver com.google.android.gms.common.license.a is a simple wrapper that tries to keep the service com.timuz.a running and sets up the out-of-context ad loop. It is contained in all bundles in the appendix,” the report said.
The service com.timuz.a gets its orders from a command-and-control server (C2), the researchers were able to discover, despite the C2 URL being buried behind base64 coding. After that connection with the C2 is established, another service takes over (com.ironsource.sdk.handlers.a.a), and attempts to deliver an OOC ad every 10 minutes, according to the report findings.
“It is important to note that while com.ironsource.sdk.handlers.a.a is a legit SDK, ironSource is unlikely involved or aware of the abuse,” researchers said.
The C2 domain (api[.]pythonexample[.]com) meanwhile has been identified by the group as a “likely hacked website.” Research showed that the site was posted with a question on an online forum two years ago, but now it defaults to a Ngnix page.
Once the C2 connection is made, a secondary URL (hxxp://api[.]pythonexample[.]com/xyyx?pn=com.androidapk.gbaemulator) is contacted and a JSON payload downloaded. After that, researchers could see ads being played on a compromised device, with nothing from than a small icon to alert the user was getting data from another app than the one they were running.
“This is used as the C2 of the ad SDK, which determines which ad network to use as well as the interstitials frequency,” the report read. “The same C2 architecture is used across all of the RAINBOWMIX apps identified in this investigation.”
The RAINBOWMIX apps were also able to boost their ad-delivery counts by monitoring when users turned their screen on and off, the analysts also discovered. “The code responsible for detecting screen on/off events was placed inside a fake Unity class ‘com.unity.b.’,” they explained.
The Impact of RAINBOWMIX & OOC Ads
Outside of the nuisance factor for users, delivering OOC ads damages every legit advertiser out there relying on consumers to trust the messages they consume online, White Ops pointed out.
“Alongside the usual fraudulent aspect of delivering ads that don’t have the same impact as a legitimate ones with users dismissing them on the spot, they also lower brand trust by masquerading as legitimate applications that would never spam the user in such as manner as the one presented,” Cirlig said.
The team found the majority (nearly 21 percent) of traffic came from Brazil, followed closely by Indonesia and Vietnam. The U.S. represented 7.7 percent of the traffic to RAINBOWMIX OOC ads.
Keywords: Out of Context ads, OOC ads, malware, RAINBOWMIX, White Ops, Google Play, emulator, Nintendo, retro games, 8-16 bit color palate, android, google play, malicious ads, ad fraud, white ops
Android's October 2020 Security Update Patches 48 Vulnerabilities
8.10.20 Android Securityweek
The October 2020 security updates for Android patch a total of 48 vulnerabilities, including critical-severity flaws that affect Qualcomm closed-source components.
Twenty of the vulnerabilities described in the latest Android Security Bulletin were patched as part of the 2020-10-01 security patch level, the most important of which is a high-risk bug in System that could allow a remote attacker to gain additional permissions.
A total of ten issues were fixed in Android System this month, all rated high severity. Two of these are elevation of privilege bugs, while the remaining eight are information disclosure vulnerabilities.
Other impacted components include Android runtime (a high-risk elevation of privilege bug that could allow attackers to run arbitrary code), Framework (two elevation of privilege bugs and three information disclosure issues, all high severity), and Media Framework (three high-risk information disclosure and one medium-severity elevation of privilege).
The second part of this month’s update arrives on devices as the 2020-10-05 security patch level and addresses 28 bugs in Kernel (one flaw), MediaTek components (five issues), Qualcomm components (four vulnerabilities), and Qualcomm closed-source components (18 flaws).
While 22 of these bugs have a severity rating of high, six of the vulnerabilities in Qualcomm closed-source components were rated critical.
Devices that run a patch level of October 5 include fixes for all of the vulnerabilities mentioned above, as well as those addressed in previous monthly updates.
Pixel devices are automatically updated to the 2020-10-05 security patch level. No security patches specific to Pixel devices were released this month.
Last month, Google started rolling out Android 11, which arrived with various new security improvements, including many designed specifically for the work profile that has been present on the operating system since 2014.
Beware: New Android Spyware Found Posing as Telegram and Threema Apps
1.10.20 Android Thehackernews
A hacking group known for its attacks in the Middle East, at least since 2017, has recently been found impersonating legitimate messaging apps such as Telegram and Threema to infect Android devices with a new, previously undocumented malware.
"Compared to the versions documented in 2017, Android/SpyC23.A has extended spying functionality, including reading notifications from messaging apps, call recording and screen recording, and new stealth features, such as dismissing notifications from built-in Android security apps," cybersecurity firm ESET said in a Wednesday analysis.
First detailed by Qihoo 360 in 2017 under the moniker Two-tailed Scorpion (aka APT-C-23 or Desert Scorpion), the mobile malware has been deemed "surveillanceware" for its abilities to spy on the devices of targeted individuals, exfiltrating call logs, contacts, location, messages, photos, and other sensitive documents in the process.
In 2018, Symantec discovered a newer variant of the campaign that employed a malicious media player as a lure to grab information from the device and trick victims into installing additional malware.
Then earlier this year, Check Point Research detailed fresh signs of APT-C-23 activity when Hamas operators posed as young teenage girls on Facebook, Instagram, and Telegram to lure Israeli soldiers into installing malware-infected apps on their phones.
The latest version of the spyware detailed by ESET expands on these features, including the ability to collect information from social media and messaging apps via screen recording and screenshots, and even capture incoming and outgoing calls in WhatsApp and read the text of notifications from social media apps, including WhatsApp, Viber, Facebook, Skype, and Messenger.
The infection begins when a victim visits a fake Android app store called "DigitalApps," and downloads apps such as Telegram, Threema, and weMessage, suggesting that the group's motivation behind impersonating messaging apps is to "justify the various permissions requested by the malware."
In addition to requesting invasive permissions to read notifications, turn off Google Play Protect, and record a user's screen under the guise of security and privacy features, the malware communicates with its command-and-control (C2) server to register the newly infected victim and transmit the device information.
The C2 servers, which typically masquerade as websites under maintenance, are also responsible for relaying the commands to the compromised phone, which can be used to record audio, restart Wi-Fi, uninstall any app installed on the device, among others.
What's more, it also comes equipped with a new feature that allows it to stealthily make a call while creating a black screen overlay to mask the call activity.
"Our research shows that the APT-C-23 group is still active, enhancing its mobile toolset and running new operations. Android/SpyC32.A – the group's newest spyware version — features several improvements making it more dangerous to victims," ESET said.
Apps downloaded from fraudulent third-party app stores has been a conduit for Android malware in recent years. It's always essential to stick to official sources to limit risk, and scrutinize permissions requested by apps before installing them on the device.
Joker Trojans Flood the Android Ecosystem
29.9.20 Android Threatpost
September saw dozens of Joker malware variants hitting Google Play and third-party app stores.
More variants of the Joker Android malware are cropping up in Google Play as well as third-party app stores, in a trend that researchers say points to a relentless targeting of the Android mobile platform.
Researchers at Zscaler have found 17 different samples of Joker being regularly uploaded to Google Play during September. Collectively, these have accounted for 120,000 downloads, the firm said.
Meanwhile, Zimperium analysts said that they’re finding malicious applications on user devices every day, mostly arriving through third-party stores, sideloaded applications and malicious websites that trick users into downloading and installing apps. In all, they’ve identified 64 new variants of Joker during September alone.
The Joker malware has been around since 2017 – it’s a mobile trojan that carries out a type of billing fraud that researchers categorize the malware as “fleeceware”. The Joker apps advertise themselves as legitimate apps (like games, wallpapers, messengers, translators and photo editors). Once installed, they simulate clicks and intercept SMS messages to subscribe victims to unwanted, paid premium services. The apps also steal SMS messages, contact lists and device information.
Malicious Joker apps are commonly found outside of the official Google Play store, as Zimperium noted, but Joker apps have continued to skirt Google Play’s protections since 2019 too. That’s mostly because the malware’s author keeps making small changes to its attack methodology.
“[Joker] keeps finding its way into Google’s official application market by employing changes in its code, execution methods or payload-retrieving techniques,” said researchers with Zscaler, in a recent blog. The 17 apps they flagged in Google Play have been removed, they added.
New Variants: Technical Details
Joker’s main functionality is carried out by loading a DEX file, according to a technical analysis from Zimperium. DEX files are executable files saved in a format that contains compiled code written for Android. Multiple DEX files are typically zipped into a single .APK package, which serves as a final Android application file for most programs.
In Joker’s case, an application, once installed, connects to a URL to receive a payload DEX file, which is “almost the same among all the Jokers, except that some use a POST request while others use a GET request,” according to Zimperium.
“The Joker trojans pose a higher risk to Android users as the user interface is designed to look very normal and covertly perform the malicious activity,” according to Zimperium researchers. “The trojan displays the screen…with a progress bar and ‘Loading data…’ but is meanwhile connecting to the first-stage URL and downloading the payload.”
Joker apps also use code-injection techniques to hide among commonly used package names like org.junit.internal, com.google.android.gms.dynamite or com.unity3d.player.UnityProvider, Zimperium analysts noted.
“The purpose of this is to make it harder for the malware analyst to spot the malicious code, as third-party libraries usually contain a lot of code and the presence of additional obfuscation can make the task of spotting the injected classes even harder, they explained in a blog posting on Monday. “Furthermore, using legit package names defeats naïve blacklisting attempts.”
Recent variants exhibited some new tricks, such as the use of AES encryption, and code injection into Android’s “content provider” function.
“In an attempt to hide the interesting strings related to the maliciousness of Jokers, the trojan retrieves the encrypted strings from resources (/resources/values/strings.xml) which is decrypted using ‘AES/ECB,'” said Zimperium researchers. “The decryption mechanism in Jokers is usually a plain AES or DES encryption that has evolved in an attempt to not raise suspicion with the encrypted strings by obfuscating them.”
Meanwhile, the new variants also insert code into functions of the content provider, which is an Android component used to handle databases and information through functions like query() and delete(), researchers said.
In all, it’s clear that Joker continues to be a scourge for Android users.
“Every day, Zimperium’s researchers find malware installed on user devices,” the firm concluded. “Malware that is not supposed to be there, but that is. The samples reported in this blog post are just a subset of them – the tip of the iceberg.”
Google removes 17 Joker -infected apps from the Play Store
28.9.20 Android Securityaffairs
Google removed this week 17 Android apps from its Play Store because they were infected with the Joker (aka Bread) malware, Zscaler revealed.
Security researchers from Zscaler spotter 17 apps in the Play Store that were infected with the Joker (Bread) malware.
The Joker malware is a malicious code camouflaged as a system app and allows attackers to perform a broad range of malicious operations, including disable the Google Play Protect service, install malicious apps, generate fake reviews, and show ads.
The spyware is able to steal SMS messages, contact lists and device information along with to sign victims up for premium service subscriptions.
In October, Google has removed from Google Play 24 apps because they were infected with Joker malware, the 24 malicious apps had a total of 472,000 installs.
In January, Google successfully removed more than 1,700 apps from the Play Store over the past three years that had been infected with the Joker malware.
In February, the infamous Joker malware has found a way to bypass the security checks to be published in the official Play Store, Check Point researchers discovered a new clicker.
In July, Google removed another batch of apps infected with the Joker malware that was discovered by security researchers from Anquanke, the malicious applications had been active since March and allegedly infected millions of devices.
Early September Google removed another six apps that have been spotted by security researchers from Pradeo.
Now Google removed 17 new Android apps, which were reported by ZScaler, from the Play Store.
“Our Zscaler ThreatLabZ research team has been constantly monitoring the Joker malware. Recently, we have seen regular uploads of it onto the Google Play store.” reads the post published by ZScaler. “Once notified by us, the Google Android Security team took prompt action to remove the suspicious apps (listed below) from the Google Play store.”
According to the experts the 17 different samples were uploaded to Google Play in September 2020 and they had a total of 120,000 downloads.
Below the list of the infected apps discovered on the Google Play store:
All Good PDF Scanner
Mint Leaf Message-Your Private Message
Unique Keyboard – Fancy Fonts & Free Emoticons
Tangram App Lock
Direct Messenger
Private SMS
One Sentence Translator – Multifunctional Translator
Style Photo Collage
Meticulous Scanner
Desire Translate
Talent Photo Editor – Blur focus
Care Message
Part Message
Paper Doc Scanner
Blue Scanner
Hummingbird PDF Converter – Photo to PDF
All Good PDF Scanner
The analysis published by ZScaler includes details about the tactics used by the Joker malware author to bypass the Google Play vetting process.
In a first attack scenario detailed by the experts, for some of the Joker variants, the final payload was delivered via a direct URL received from the C2 server. In this variant, the C&C address was hidden in the code itself with string obfuscation.
In a second download scenario, some infected apps used a stager payload to retrieve the final payload. In this case, the stager payload URL encoded in the code itself was encrypted using Advanced Encryption Standard (AES).
In a third scenario, some groups of infected Google Play store apps were using two-stager payload downloads to retrieve the final payload. The Google Play infected app downloads the stage one payload, which in turn downloads the stage two payload, which finally loads the end Joker payload.
Unlike previous two scenarios, the infected app contacts the C&C server for stage one payload URL, which hides it in response location header.
Additional technical details, including Indicators of Compromise (IoCs), are included in the report published by ZScaler.
“We recommend paying close attention to the permission list in the apps that you install on your Android device. Always watch out for the risky permissions related to SMS, call logs, contacts, and more. Reading the comment or reviews on the app page aslo helps identify compromised apps.” concludes the report.
Alien Android banking Trojan, the powerful successor of the Cerberus malware
25.9.20 Android Securityaffairs
Security researchers spotted a new strain of Android malware, dubbed Alien, that implements multiple features allowing it to steal credentials from 226 apps.
Researchers from ThreatFabric have discovered and analyzed a new strain of Android malware, tracked as Alien, that implements multiple features allowing it to steal credentials from 226 applications.
Alien first appeared in the threat landscape early this year, its model of sale is Malware-as-a-Service (MaaS) and is advertised on several underground hacking forums.
According to researchers, Alien borrows portions of the source code from the Cerberus malware.
ThreatFabric pointed out that Cerberus operators attempted to sell their project because several issues in the malware remained unsolved for a long time due to shortcomings of the development team in the criminal gang. The delay in addressing the problems allowed Google Play Protect to detect the threat on all infected devices.
Alien is not affected by the same issues and this is the reason of the success of its MaaS model
Alien is considered a next-generation banking trojan that also implements remote-access features into their codebases.
The list of features implemented in Alien is:
Overlaying: Dynamic (Local injects obtained from C2)
Keylogging
Remote access
SMS harvesting: SMS listing
SMS harvesting: SMS forwarding
Device info collection
Contact list collection
Application listing
Location collection
Overlaying: Targets list update
SMS: Sending
Calls: USSD request making
Calls: Call forwarding
Remote actions: App installing
Remote actions: App starting
Remote actions: App removal
Remote actions: Showing arbitrary web pages
Remote actions: Screen-locking
Notifications: Push notifications
C2 Resilience: Auxiliary C2 list
Self-protection: Hiding the App icon
Self-protection: Preventing removal
Self-protection: Emulation-detection
Architecture: Modular
This banking Trojan is an optimal choice for crooks behind multiple fraudulent operations.
Experts discovered that Alien is able to show fake login pages for 226 other Android applications that allow its operators to intercept credentials.
“In the case of Alien, advanced features such as the authenticator-code stealer and notifications-sniffer aside, the features of the Trojan are quite common. As for many Trojans, the target list can be extended dynamically by the renter and applied to all bots enrolled to the botnet. The targeted applications in the appendix of the article are the concatenated list of targets observed in samples found in the wild, growing to over 226 targeted applications so far.” reads the report published by the researchers.
“Although it is hard to predict the next steps of the Alien authors, it would be logical for them to improve the RAT, which is currently based on TeamViewer (and therefore visible when installed and executed on the device).”
Alien is also able to target other apps including Gmail, Facebook, Telegram, Twitter, Snapchat, WhatsApp, as well as cryptocurrency apps
Experts reported that most of the apps targeted by Alien were used by financial institutions mostly in Spain, Turkey, Germany, the US, Italy, France, Poland, Australia, and the UK.
Additional technical details, including Indicators of Compromise (IoCs) are included in the report published by ThreatFabric.
Android Malware Bypasses 2FA And Targets Telegram, Gmail Passwords
22.9.20 Android Threatpost
A new Android malware strain has been uncovered, part of the Rampant Kitten threat group’s widespread surveillance campaign that targets Telegram credentials and more.
Researchers have uncovered a threat group launching surveillance campaigns that target victims’ personal device data, browser credentials and Telegram messaging application files. One notable tool in the group’s arsenal is an Android malware that collects all two-factor authentication (2FA) security codes sent to devices, sniffs out Telegram credentials and launches Google account phishing attacks.
Researchers found the threat group, dubbed Rampant Kitten, has targeted Iranian entities with surveillance campaigns for at least six years. It specifically targets Iranian minorities and anti-regime organizations, including the Association of Families of Camp Ashraf and Liberty Residents (AFALR); and the Azerbaijan National Resistance Organization.
The threat group has relied on a wide array of tools for carrying out their attacks, including four Windows info-stealer variants used for pilfering Telegram and KeePass account information; phishing pages that impersonate Telegram to steal passwords; and the aforementioned Android backdoor that extracts 2FA codes from SMS messages and records the phone’s voice surroundings.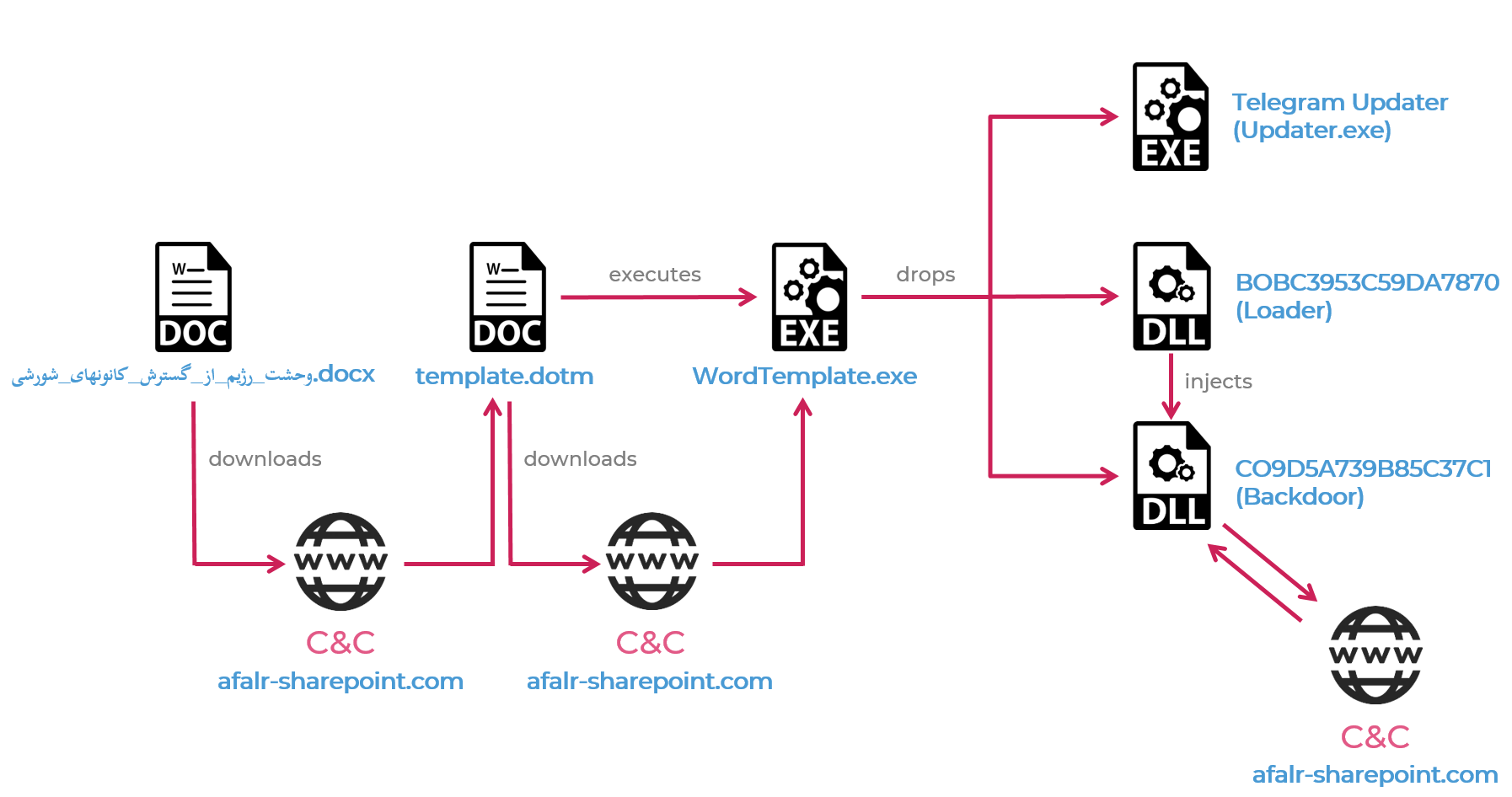
“Following the tracks of this attack revealed a large-scale operation that has largely managed to remain under the radar for at least six years,” said researchers with Check Point Research, in a Friday analysis. “According to the evidence we gathered, the threat actors, who appear to be operating from Iran, take advantage of multiple attack vectors to spy on their victims, attacking victims’ personal computers and mobile devices.”
The Attacks
Researchers first discovered Rampant Kitten’s campaign through a document, the title of which translates to “The Regime Fears the Spread of the Revolutionary Cannons.docx.” It’s unclear how this document is spread (via spear phishing or otherwise), but it purports to describe the ongoing struggle between the Iranian regime and the Revolutionary Cannons, an anti-regime, Mujahedin-e Khalq movement.
The document when opened loads a document template from a remote server (afalr-sharepoint[.]com), which impersonates a website for a non-profit that aids Iranian dissidents.
rampant kitten cyberattack
The attack vector. Credit: Check Point Research
It then downloads malicious macro code, which executes a batch script to download and execute a next-stage payload. This payload then checks if the popular Telegram messenger service is installed on the victims’ system. If so, it extracts three executables from its resources.
These executables include an information stealer, which lifts Telegram files from victim’s computer, steals information from the KeePass password-management application, uploads any file it can find which ends with a set of pre-defined extensions, and logs clipboard data and takes desktop screenshots.
Researchers were able to track multiple variants of this payload dating back to 2014. These include the TelB (used in June and July 2020) and TelAndExt variants (May 2019 to February 2020), which focus on Telegram; a Python infostealer (February 2018 to January 2020) that is focused on stealing data from Telegram, Chrome, Firefox and Edge; and a HookInjEx variant (December 2014 to May 2020), an infostealer that targets browsers, device audio, keylogging and clipboard data.
Android Backdoor
During their investigation, researchers also uncovered a malicious Android application tied to the same threat actors. The application was purporting to be a service to help Persian speakers in Sweden get their driver’s license.
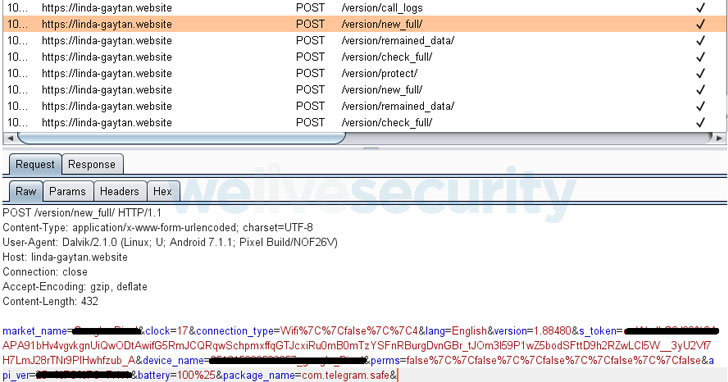
Instead, once victims download the application, the backdoor steals their SMS messages and bypasses 2FA by forwarding all SMS messages containing 2FA codes to an attacker-controlled phone number.
“One of the unique functionalities in this malicious application is forwarding any SMS starting with the prefix G- (The prefix of Google two-factor authentication codes) to a phone number that it receives from the C2 server,” said researchers. “Furthermore, all incoming SMS messages from Telegram, and other social network apps, are also automatically sent to the attackers’ phone number.”
Of note, the application also launches a phishing attack targeting victims’ Google account (Gmail) credentials. The user is presented with a legitimate Google login page, inside Android’s WebView. In reality, attackers have used Android’s JavascriptInterface to steal typed-in credentials, as well as a timer which periodically retrieves the information from the username and password input fields.
It also retrieves personal data (like contacts and account details) and records the phone’s surroundings.
“We have located two different variants of the same application, one which appears to be compiled for testing purposes, and the other is the release version, to be deployed on a target’s device,” said researchers.
Researchers also warned of websites owned by the threat actors that were phishing pages impersonating Telegram. A Telegram bot was sending phishing messages warning recipients that they were making improper use of Telegram’s services, and that their account will be blocked if they do not enter the phishing link.
“Since most of the targets we identified are Iranians, it appears that similarly to other attacks attributed to the Islamic Republic, this might be yet another case in which Iranian threat actors are collecting intelligence on potential opponents to the regime,” said researchers.
Rampant Kitten ‘s arsenal includes Android malware that bypasses 2FA
19.9.20 Android Securityaffairs
Security researchers discovered Android malware capable of bypassing 2FA that was developed by an Iran-linked group dubbed Rampant Kitten
Security researchers from Check Point discovered an Android malware, developed by an Iran-linked group dubbed Rampant Kitten, that is able to bypass 2FA.
Rampant Kitten has been active at least since 2014 and was involved in ongoing surveillance operations against Iranian minorities, anti-regime organizations, and resistance movements.
Some of the organizations targeted by the group are:
Association of Families of Camp Ashraf and Liberty Residents (AFALR)
Azerbaijan National Resistance Organization
Balochistan people
The arsenal of the group included several strains of malware, including an Android backdoor disguised inside malicious apps and four variants of Windows infostealers that were also able to access victims’ Telegram Desktop and KeePass account information.
The report states that among the different attack vectors they have found there are:
Four variants of Windows infostealers intended to steal the victim’s personal documents as well as access to their Telegram Desktop and KeePass account information
Android backdoor that extracts two-factor authentication codes from SMS messages, records the phone’s voice surroundings and more
Telegram phishing pages, distributed using fake Telegram service accounts
Rampant Kitten also developed an Android backdoor that could steal the victim’s contacts list and SMS messages, record surroundings via the microphone, and show phishing pages.
In order to silently turn on the microphone in a real-time manner, the app needs to have its service running in the background, but this implies that a specific notification is displayed to the users to alert him.
The authors of the malware chose to display the user with a fake notification of “Google protect is enabled“ to circumvent this issue.
Experts discovered that the Android backdoor implements the forwarding of any SMS starting with the prefix
G-
(The prefix of Google two-factor authentication codes), to a phone number that it receives from the C&C server.
The feature is also able to automatically send all incoming SMS messages from Telegram, and other social network apps, to a phone number under the control of the attackers.
According to the experts, this feature could be used by Rampant Kitten to show a Google phishing page and steal user’s account credentials to access the victim’s account.
If the victim had 2FA enabled, the malware is also able to intercept 2FA SMS and send them to the attackers.
“Following the tracks of this attack revealed a large-scale operation that has largely managed to remain under the radar for at least six years. According to the evidence we gathered, the threat actors, who appear to be operating from Iran, take advantage of multiple attack vectors to spy on their victims, attacking victims’ personal computers and mobile devices.” concludes the report that also includes Indicators of Compromise (IoCs). “Since most of the targets we identified are Iranians, it appears that similarly to other attacks attributed to the Islamic Republic, this might be yet another case in which Iranian threat actors are collecting intelligence on potential opponents to the regiment.”
Google Play Bans Stalkerware and ‘Misrepresentation’
18.9.20 Android Threatpost
The official app store is taking on spy- and surveillance-ware, along with apps that could be used to mount political-influence campaigns.
Google is taking the step of prohibiting “stalkerware” in Google Play, along with apps that could be used in political-influence campaigns.
Effective October 1, apps that would allow someone to surreptitiously track the location or online activity of another person will be removed from the internet giant’s official online store.
According to Google, stalkerware is defined as “code that transmits personal information off the device without adequate notice or consent and doesn’t display a persistent notification that this is happening.” This includes apps that can be used to monitor texts, phone calls or browsing history; or GPS trackers specifically marketed to spy or track someone without their consent.
Abusers can use such apps for the purposes of harassment, surveillance, stalking and they can even lead to domestic violence, critics say.
Google also specified that any consent-based tracking-related apps distributed on the Play Store (telemetry apps used by enterprises to keep tabs on employee activity) must comply with certain parameters. For instance, they can’t market themselves as spying or secret-surveillance solutions (such as apps that go with surveillance cameras, stealth audio recorders, dash cams, nanny cams and the like).
Apps also can’t hide or cloak tracking behavior or attempt to mislead users about such functionality, and they have to present users with a “persistent notification and unique icon that clearly identifies the app,” according to a Wednesday website notice.
The new rules also include a clause meant to close down developer loopholes: “Apps and app listings on Google Play must not provide any means to activate or access functionality that violate these terms, such as linking to a non-compliant APK hosted outside Google Play.”
There is, however, a significant exemption from these rules: Services designed for parents to track or monitor their underage children.
“Acceptable forms of these apps can be used by parents to track their children,” according to Google. “However, these apps cannot be used to track a person (a spouse, for example) without their knowledge or permission unless a persistent notification is displayed while the data is being transmitted.”
Stalkerware companies in the past have sold apps that purport to help parents track their young children – even though their capabilities could be used for other purposes. That was the case with three Retina-X apps, which last October were barred by the Federal Trade Commission (FTC): MobileSpy, PhoneSheriff and TeenShield. While these three apps were marketed for monitoring mobile devices used by children, or for monitoring employees, the FTC determined that “these apps were designed to run surreptitiously in the background and are uniquely suited to illegal and dangerous uses.”
Another example is an app called “Monitor Minor,” which researchers flagged as problematic in March. The Android version of the app gives stalkers near absolute control of targeted devices, going so far as allowing them to capture the unlock pattern or unlock code of phones; and, it gives users the ability to creep on a target’s missives swapped via Instagram, Skype and Snapchat, researchers said.
Loophole aside, Google has been addressing stalkerware since the summer, when it prohibited “the promotion of products or services that are marketed or targeted with the express purpose of tracking or monitoring another person or their activities without their authorization” as part of updated advertising policies.
Earlier this year, Kaspersky stats showed that the number of stalkerware attacks on mobile devices increased 50 percent in 2019, showing an upward and continued trend in the emerging threat.
Influence Campaign Apps
Besides stalkerware, Google also addressed what it terms “misrepresentation,” in an effort to put a crimp in influence campaigns and coordinated political activity.
Specifically, Google will prohibit apps or developer accounts that “impersonate any person or organization, or that misrepresent or conceal their ownership or primary purpose,” starting Oct. 21.
“This includes, but isn’t limited to, apps or developer accounts that misrepresent or conceal their country of origin and that direct content at users in another country,” according to its announcement, “[or those that] coordinate with other apps, sites, developers or other accounts to conceal or misrepresent developer or app identity or other material details, where app content relates to politics, social issues or matters of public concern.”
Coordinated activity (i.e. the use of ads in cooperation with other sites or accounts to create viral content and an artificial echo chamber) has been seen as a hallmark of disinformation and fake-news influence campaigns. Social media platforms have cracked down periodically on fake accounts ever since such operations were discovered to be widespread during the 2016 presidential election. Leading up to the 2020 election, researchers have flagged these kinds of campaigns as one of the biggest cyber-threats to the democratic process.
This Google Play move follows, like with stalkerware, previous changes to Google’s advertising policies.
In August, it updated its Google Ads Misrepresentation Policy to prevent coordinated activity around politics, social issues or “matters of public concern,” by requiring advertisers to provide transparency about who they are. As of Sept. 1, this means big penalties for “concealing or misrepresenting your identity or other material details about yourself,” and violations will be considered “egregious.”
“If we find violations of this policy, we will suspend your Google Ads accounts upon detection and without prior warning, and you will not be allowed to advertise with us again,” according to Google.
Google Squashes Critical Android Media Framework Bug
10.9.20 Android Threatpost
The September Android security bulletin addressed critical- and high-severity flaws tied to 53 CVEs overall.
Google patched a critical vulnerability in the Media Framework of its Android operating system, which if exploited could lead to remote code execution attacks on vulnerable devices.
Overall, Google fixed flaws tied to 53 CVEs as part of its September security updates for the Android operating system, released on Tuesday. As part of this, Qualcomm, whose chips are used in Android devices, patched a mix of high and critical-severity vulnerabilities tied to 22 CVEs.
“The most severe of these issues is a critical security vulnerability in the Media Framework component that could enable a remote attacker using a specially crafted file to execute arbitrary code within the context of a privileged process,” according to the Android security update.
Threatpost Webinar Promo Bug Bounty
Click to Register
Android Media Framework includes support for playing a variety of common media types, so users can easily utilize audio, video and images. The flaw (CVE-2020-0245) allows RCE in Android versions 8.0, 8.1 and 9 – but that severity is lowered to “high” and the impact instead is information disclosure for Android version 10.
Beyond this critical-severity glitch, the Android Media Framework also includes five other high-severity information disclosure flaws (CVE-2020-0381, CVE-2020-0383, CVE-2020-0384, CVE-2020-0385, CVE-2020-0393) and an elevation of privilege issue (CVE-2020-0392).
Two other critical vulnerabilities were patched, existing in the Android System area. These included an RCE flaw (CVE-2020-0380) and information disclosure flaw (CVE-2020-0396) that both affect Android versions 8.0, 8.1, 9 and 10.
These flaws could allow “a remote attacker using a specially crafted transmission to execute arbitrary code within the context of a privileged process,” according to Google. The System also includes two high-severity elevation of privilege errors (CVE-2020-0386, CVE-2020-0394) and an information disclosure (CVE-2020-0379) hole.
Ten high-severity vulnerabilities also exist in the Android Framework, which is a set of APIs – consisting of system tools and user interface design tools – that allow developers to quickly and easily write apps for Android phones. These include four elevation of privilege flaws (CVE-2020-0074, CVE-2020-0388, CVE-2020-0391, CVE-2020-0401) and six information disclosure errors (CVE-2020-0382, CVE-2020-0389, CVE-2020-0390, CVE-2020-0395, CVE-2020-0397, CVE-2020-0399).
Component Vulnerabilities
Google also rolled out patches for flaws in various third-party components in its Android ecosystem. These include four high severity flaws affecting MediaTek components (MediaTek and Google collaborate on Android TV’s Ultra HD TV platform) – including issues affecting the sound driver of Android TV.
Three high-severity flaws in the Android kernel, meanwhile, include an elevation of privileges flaw in the storage subsystem (CVE-2020-0402) and one in the USB driver (CVE-2020-0404), as well as an information disclosure flaw (CVE-2020-0407). Finally, 22 high- and critical-severity flaws were fixed in Qualcomm components, including five flaws in the kernel. The remaining Qualcomm flaws were in closed-source components.
Manufacturers of Android devices typically push out their own patches to address updates in tandem with or after the monthly security bulletin. Samsung said in a September security release that it is releasing several of the Android security bulletin patches to major Samsung models. And, according to a bulletin, a security update for Pixel devices, which run on Google’s Android operating system, is “coming soon.”
In August, Google released patches addressing a high-severity issue in its Framework component, which if exploited could enable remote code execution (RCE) on Android mobile devices. Overall, 54 high-severity flaws were patched as part of Google’s August security updates.
Joker Spyware Plagues More Google Play Apps
3.9.20 Android Threatpost
The six malicious apps have been removed from Google Play, but could still threaten 200,000 installs.
Google has deleted six apps from its Google Play marketplace that were infecting users with the Joker malware (a.k.a. Bread).
Together, the apps – which tout functionalities ranging from text messaging to emoji wallpaper – account for nearly 200,000 installs, researchers with Pradeo said in a post this week. As of Wednesday, Google confirmed with Threatpost that all infected applications have been removed from Google Play, but researchers said that they are still installed on the devices of their users, and urged users to immediately delete the apps.
“Most apps embedding Joker malware are programmed to load and execute external code after being published on the store,” Roxane Suau, with Pradeo, told Threatpost. “First, these apps are riddled with permission requests and submitted to Google Play by their developers. They get approved, published and installed by users. Once running on users’ devices, they automatically download malicious code. Then, they leverage their numerous permissions to execute the malicious code.”
The apps found with malware are: Convenient Scanner 2 (with 100,000 installs), Separate Doc Scanner (with 50,000 installs), Safety AppLock (with 10,000 installs), Push Message-Texting & SMS (with 10,000 installs), Emoji Wallpaper (with 10,000 installs) and Fingertip GameBox (with 1,000 installs). More information on these apps can be found here.
The apps were expressly developed by individuals who programmed them to act maliciously, Suau told Threatpost. Suau said that looking at the apps’ ratings revealed several red flags, including reviews that say the apps are fake (see graphic, below).

Credit: Pradeo
Joker is a billing-fraud family of malware (which researchers categorize as “fleeceware”) that emerged in 2017 but began to ramp up in 2019.
It advertises itself as a legitimate app, but once installed, simulates clicks and intercepts SMS messages to subscribe victims to unwanted, paid premium services (unbeknownst to them), researchers said.
Malicious apps spreading the Joker have continued to skirt Google Play’s protections since 2019, because the malware’s author kept making small changes to its code.
“By using as little code as possible and thoroughly hiding it, Joker generates a very discreet footprint that can be tricky to detect,” Suau said.
In 2020, the Joker malware has continued to thrive on Google Play. In July, Google removed 11 malicious Android apps from the store that were spreading the malware, and in January, researchers revealed that Google had removed 17,000 Android apps at that point that had been conduits for the Joker malware.
Hank Schless, senior manager for Security Solutions at Lookout, said that researchers continue to see Joker popping up in Android apps — and now with workforces going remote due to the current, ongoing pandemic, the threat of Joker being spread via productivity apps is increasing.
“Because of how frequently Joker and other discreet malware appear in a wide variety of apps, mobile users need to leverage mobile security in order to keep themselves and their organizations safe,” he said via email. “Especially in a time of global remote work, mobile devices and tablets are used for both work and personal reasons. If you download an app infected with Joker or other malware, you’re giving the threat actor access to your personal data as well as any company data you access from that device.”
The re-emergence of Joker malware in the Google Play Store also highlights the fundamental challenge of how users can know if a piece of software is reasonably secure, Jonathan Knudsen, senior security strategist with Synopsys said.
“In an app store, it’s impractical to understand the development processes for every app, so the store must rely on security testing to assess submitted apps,” he said. “For many organizations, however, the procurement process offers untapped opportunities to assess how vendors build software, to perform rigorous testing, and to make informed decisions based on risk.”
Google removed malicious Terracotta apps from the Play Store
1.9.20 Android BotNet Securityaffairs
Researchers from White Ops discovers several Android apps in the official Play store which installed on users’ mobile devices the Terracotta ad fraud malware.
Researchers from security firm White Ops discovered several Android apps in the official Play Store that installed a hidden browser to load pages containing ad and commit ad fraud.
The company shared its findings with Google which has quickly removed an undisclosed number of Android apps from the Google Play Store.
According to Google, the apps were part of an ad fraud botnet tracked as Terracotta.
The White Ops Satori Threat Intelligence & Research team has been actively tracking the Terracotta botnet since late 2019.
Terracotta operators uploaded apps on the Google Play Store, they promised users free goods (i.e. coupons, shoes, tickets) if they installed the applications on their devices.
“The TERRACOTTA malware offered Android users free goods in exchange for downloading the app—including shoes, coupons, and concert tickets—which users never received.” reads the report published by WhiteOps. “Once the app was installed and the malware activated, the malware used the device to generate non-human advertising impressions purporting to be ads shown in legitimate Android apps.”
In a single week in June 2020, the campaign generated more than two billion fraudulent bid requests, the malware has infected upwards of 65,000 devices, and spoofed more than 5,000 apps.
Users were tricked into waiting two weeks before receiving the free products, while the app installed on their devices was operating in the background.
The malicious apps downloaded and executed a modified version of WebView browser in stealth way. The browser was used to perform ad fraud by loading ads and gaining revenue from non-human generated advertising impressions.

According to WhiteOps researchers, the Terracotta botnet used advanced techniques to avoid detection.
Experts pointed out that Google has removed multiple apps from the Play Store, but some devices still appearing to be infected. Google also disabled malicious apps on all users’ devices.
“Due to our collaboration with White Ops investigating the TERRACOTTA ad fraud operation, their critical findings helped us connect the case to a previously-found set of mobile apps and to identify additional bad apps. This allowed us to move quickly to protect users, advertisers and the broader ecosystem – when we determine policy violations, we take action,” a Google spokesperson said.
The list of all identified TERRACOTTA apps is available here.
Google removed malicious Terracotta apps from the Play Store
1.9.20 Android BotNet Securityaffairs
Researchers from White Ops discovers several Android apps in the official Play store which installed on users’ mobile devices the Terracotta ad fraud malware.
Researchers from security firm White Ops discovered several Android apps in the official Play Store that installed a hidden browser to load pages containing ad and commit ad fraud.
The company shared its findings with Google which has quickly removed an undisclosed number of Android apps from the Google Play Store.
According to Google, the apps were part of an ad fraud botnet tracked as Terracotta.
The White Ops Satori Threat Intelligence & Research team has been actively tracking the Terracotta botnet since late 2019.
Terracotta operators uploaded apps on the Google Play Store, they promised users free goods (i.e. coupons, shoes, tickets) if they installed the applications on their devices.
“The TERRACOTTA malware offered Android users free goods in exchange for downloading the app—including shoes, coupons, and concert tickets—which users never received.” reads the report published by WhiteOps. “Once the app was installed and the malware activated, the malware used the device to generate non-human advertising impressions purporting to be ads shown in legitimate Android apps.”
In a single week in June 2020, the campaign generated more than two billion fraudulent bid requests, the malware has infected upwards of 65,000 devices, and spoofed more than 5,000 apps.
Users were tricked into waiting two weeks before receiving the free products, while the app installed on their devices was operating in the background.
The malicious apps downloaded and executed a modified version of WebView browser in stealth way. The browser was used to perform ad fraud by loading ads and gaining revenue from non-human generated advertising impressions.

According to WhiteOps researchers, the Terracotta botnet used advanced techniques to avoid detection.
Experts pointed out that Google has removed multiple apps from the Play Store, but some devices still appearing to be infected. Google also disabled malicious apps on all users’ devices.
“Due to our collaboration with White Ops investigating the TERRACOTTA ad fraud operation, their critical findings helped us connect the case to a previously-found set of mobile apps and to identify additional bad apps. This allowed us to move quickly to protect users, advertisers and the broader ecosystem – when we determine policy violations, we take action,” a Google spokesperson said.
The list of all identified TERRACOTTA apps is available here.