
OS 2024 2023 2022 2020 ANDROID 2022 2021 2020
Cyberpunk 2077 Headaches Grow: New Spyware Found in Fake Android Download
19.12.2020 Android Threatpost
Threat actors impersonate Google Play store in scam as Sony pulls the game off the PlayStation store due to myriad performance issues.
Threat actors continue to take advantage of the hype surrounding the release of the videogame Cyberpunk 2077 in a variety of ways. The latest twist is ransomware targeting Android devices disguised as a legitimate download of the new open-world game.
Kaspersky researcher Tatyana Shishkova discovered the malware earlier this week, and in a tweet described the sample as a type of CoderWare ransomware, more specifically of the “Black Kingdom” family. She noted that the malware code was being promoted as a download of Cyberpunk 2077 from a fake version of the Google Play mobile app marketplace.
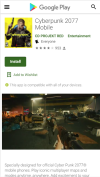
The listing for the game, which is named “Cyberpunk 2077 Mobile (Beta),” even had reviews from users so as to appear legitimate – as seen on one of several screenshots of the scam that Shishkova posted on Twitter.
If users click on the download and execute the binary, they received a message informing them that they’ve been infected with CoderWare ransomware. Next, victims are advised, via the ransomware note, to take a screenshot of the message, which contains information for decryption. Hackers request that victims pay $500 in Bitcoin to obtain the key for unlocking decrypted files.
Shishkova, however, noted that CoderWare ransomware uses a hardcoded key, which means that paying the ransom may not be necessary if someone falls victim to the scam.
“RC4 algorithm with hardcoded key (in this example – ‘21983453453435435738912738921’) is used for encryption,” she tweeted. “That means that if you got your files encrypted by this #ransomware, it is possible to decrypt them without paying the ransom.”
CoderWare: A Magnet for Cyber Punks
CoderWare has been linked to Cyberpunk 2077 in the past. The Malware Hunter team tweeted in November that they had discovered a version of the ransomware for Python disguised as a Windows Cyberpunk 2077 installer, according to a report in BleepingComputer. Both that version of CoderWare and the one discovered by Shishkova appear to be variants of the Black Kingdom ransomware, which was seen earlier this year in attacks on Pulse Secure VPNs.
The hotly anticipated Cyberpunk 2077 lets players create a character called “V” who lives in Night City and even features a digital Keanu Reeves as a major character. Before the game was even released, threat actors were exploiting its popularity with scams offering “free copies” of the game while stealing personal information, something researchers at Kaspersky also uncovered.
The latest scam is similar but with a twist, as the game is already available for purchase and download for PC, PlayStation 4, Xbox One and Stadia, with compatibility with PS5 and Xbox Series X for a price tag of $60.
Rocky Release of Cyberpunk 2077
As if cyber threats surrounding the game aren’t enough to turn game enthusiasts off, there are myriad other issues with Cyberpunk 2077 that gamers have reported with the initial release of the title, including poor performance and numerous bugs and glitches that make the user experience less than pleasant.
It’s gotten so bad that Sony even pulled the game from the PlayStation store, offering those who purchased it already a full refund. To make matters even worse, some users seeking refunds then experienced problems with downloading the form to register for that refund, something Sony said it would fix as soon as possible.
“What a mess!” tweeted James Webber, a writer and director who already downloaded and played Cyberpunk 77—expressing what is likely a similar sentiment among early adopters. “Despite quite enjoying the game so far, I’ve encountered almost too many bugs to count. Hoping for a patch asap.”
Fake mobile version of Cyberpunk 2077 spreads ransomware
19.12.2020 Android Securityaffairs
A threat actor is spreading ransomware dubbed CoderWare that masquerades as Windows and Android versions of the recent Cyberpunk 2077.
Crooks are spreading fake Windows and Android versions of installers for the new Cyberpunk 2077 video game that is delivering the CoderWare ransomware. Cyberpunk 2077 is a 2020 action role-playing video game developed and published by CD Projekt, it was one of the most
It is not the first time that threat actors attempt to exploit the interest of the gamers into new video games like has happened with mobile versions of the popular Fortnite back in 2028.
The fake version of the Cyberpunk 2077 game was discovered by Kaspersky researcher Tatyana Shishkova and reported by BleepingComputer.
Shishkova has discovered a fake Android version of the game that was being distributed from a website impersonating the legitimate Google Play Store.

The good news is that the CoderWare ransomware uses a RC4 algorithm with hardcoded key, this means that victims can decrypt their files without paying the ransom.
Bleeping Computer pointed out that a Windows version of Cyberpunk 2017 installer was spotted in November by malware researchers at MalwareHunterTeam. The malware employed in the attack was calling itself CoderWare, but the researchers reported that it is a variant of the BlackKingdom ransomware that was appending the ,DEMON extension to the filenames of the encrypted files.
Google Patches Critical Wi-Fi and Audio Bugs in Android Handsets
9.12.2020 Android Threatpost
Google updates its mobile OS, fixing ten critical bugs, including one remote code execution flaw.
Google patched ten critical bugs as part of its December Android Security Bulletin. The worst of the bugs was tied to the Android media framework component and gives attacker remote control of vulnerable handsets.
Google did not reveal the technical specifics of the critical flaw, tracked as CVE-2020-0458, and will likely not until a majority of handsets are patched. The other nine critical bugs plugged this month by Google are tied to the underlying Qualcomm chipsets and accompanying firmware, common on most Android phones.
The critical Qualcomm bugs fixed were each rated 9.8 out of 10 in severity, using the standard CVSS score. Eight of these flaws were tied to the vendor’s subsystem software that controls audio. Another bug, tracked as CVE-2020-11225, is tied to the Qualcomm Wi-Fi radio’s WLAN host communication component.
Bug descriptions are available via Qualcomm’s own December 2020 Security Bulletin, posted Monday. Several of these critical flaws were identified as buffer-overflow bugs and buffer over-read vulnerabilities.
One the audio flaws, tracked as CVE-2020-11137, is identified as a “buffer over-read issue in audio” that could be exploited remotely, according to Qualcomm. It wrote, an attacker can create conditions for an “integer multiplication overflow resulting in lower buffer size allocation than expected [which] causes memory access out of bounds resulting in possible device instability.”
The Wi-Fi bug is triggered when the chip is forced to “buffer copy without checking size of input in WLAN”. The result are conditions ripe of a “classic buffer overflow” attack. This type of attack occurs when an adversary floods a program too much data. “The excess data corrupts nearby space in memory. If attackers know the memory layout of a program, they can intentionally feed input that the buffer cannot store, and overwrite areas that hold executable code, replacing it with their own code,” describes Imperva.
Qualcomm credited a number of researchers for discovering vulnerabilities including Haikuo Xie of Huawei Security and Ying Wang of Baidu Security Lab and Jun Yao (姚俊) (@_2freeman) and Guang Gong (@oldfresher) of 360 Alpha Lab working with 360 BugCloud. Other credited bug hunters included Ben Hawkes of Google Project Zero and researcher Nick Landers.
Rana Android Malware Updates Allow WhatsApp, Telegram IM Snooping
8.12.2020 Android Threatpost
The developers behind the Android malware have a new variant that spies on instant messages in WhatsApp, Telegram, Skype and more.
Researchers have discovered new samples of a previously discovered Android malware, which is believed to be linked to the APT39 Iranian cyberespionage threat group. The new variant comes with new surveillance capabilities – including the ability to snoop on victims’ Skype, Instagram and WhatsApp instant messages.
According to U.S. feds, the developers of this malware are allegedly operating under the guise of a front company, Rana Intelligence Computing Co., which has been linked to APT39 (also known as Chafer, Cadelspy, Remexi, and ITG07), as well as Iran’s Ministry of Intelligence and Security (MOIS). On Sept. 17, the U.S. Department of the Treasury’s Office of Foreign Assets Control placed sanctions on APT39, which has carried out various malware campaigns since 2014, targeting Iranian dissidents, journalists and international companies in the travel sector.
In tandem with the sanctions, the FBI released a public threat analysis report that investigated several tools used by Rana Corp. Researchers recently conducted further analysis of one of these malware samples (com.android.providers.optimizer) and found that its latest variant showcases several new commands that point to the threat actors sharpening their surveillance capabilities.
“It’s important to remember that there are many reasons that cause threat groups to turn their focus to specific targets,” said researchers with ReversingLabs in a Monday analysis. “Whether it’s political dissidents, opposition in countries under authoritarian regimes, or corporations the threat actors goal is to make gains monetarily or politically.”
It’s unclear what the initial infection point is for this malware. Threatpost has reached out to researchers for further details.
Instant Message Snooping
While previously, the malware had information stealing and remote access functionality, researchers found that the variant takes it a step further by utilizing mobile accessibility services in order to target victims’ instant messaging applications. Android’s Accessibility Service, which has previously been leveraged by cybercriminals in Android attacks, assists users with disabilities. They run in the background and receive callbacks by the system when “AccessibilityEvents” run. Bad actors have leveraged these services to gain the permissions necessary to snoop in on victims’ phones.
This particular malware uses accessibility services in order to monitor a full list of messages on communications applications, including the Android Instagram app, Skype, Telegram, Viber and WhatsApp.
“Looking at the monitored IM applications additionally proves that this malware is probably used for the surveillance of Iranian citizens,” explained researchers. “One of the monitored IM applications is a package named ‘org.ir.talaeii,’ which is described as ‘an unofficial Telegram client developed in Iran.'”
Other Commands
The malware also now includes various commands, such as the ability to receive commands from the command and control (C2) server that are sent by SMS: “In that case, the malware intercepts the received SMS and, if it starts with a predefined command header, the malware aborts further propagation of the SMS_RECEIVED Intent,” said researchers. “This prevents the received SMS from ending up in the default SMS application.”
The malware can also take photos and record audio on the victims’ phones – as well as automatically answer calls from specific phone numbers.
“The malware also enables scheduling a device boot at some specific moment, ensuring malware activation even when someone turns off the phone,” said researchers.
Another less-common Android command that the malware sports is the ability to add a custom Wi-Fi access point and to force the device to connect to it. Researchers believe this feature was introduced to avoid possible detection due to unusual data traffic usage on the target’s mobile account.
Android users continue to be hit by various mobile threats – including “undeletable” adware and Android banking trojans. Mobile phone users can avoid such mobile malware by knowing which apps have what permissions, and making sure that enterprises have a solid mobile management policy in place.
“What we can take away from this analysis is the importance of maintaining control over your device to reduce the risk of infection,” they said. “On an individual level this includes knowing which apps have access to microphones and sensitive information. If you are part of a government agency, or even a private corporation, it means having a solid BYOD policy, that includes application control, continually auditing the system setting, and malware scanning.”
ss
Iranian RANA Android Malware Also Spies On Instant Messengers
7.12.2020 Android BigBrothers Thehackernews
A team of researchers today unveiled previously undisclosed capabilities of an Android spyware implant—developed by a sanctioned Iranian threat actor—that could let attackers spy on private chats from popular instant messaging apps, force Wi-Fi connections, and auto-answer calls from specific numbers for purposes of eavesdropping on conversations.
In September, the US Department of the Treasury imposed sanctions on APT39 (aka Chafer, ITG07, or Remix Kitten) — an Iranian threat actor backed by the country's Ministry of Intelligence and Security (MOIS) — for carrying out malware campaigns targeting Iranian dissidents, journalists, and international companies in the telecom and travel sectors.
Coinciding with the sanctions, the Federal Bureau of Investigation (FBI) released a public threat analysis report describing several tools used by Rana Intelligence Computing Company, which operated as a front for the malicious cyber activities conducted by the APT39 group.
Formally linking the operations of APT39 to Rana, the FBI detailed eight separate and distinct sets of previously undisclosed malware used by the group to conduct their computer intrusion and reconnaissance activities, including an Android spyware app called "optimizer.apk" with information-stealing and remote access capabilities.
"The APK implant had information stealing and remote access functionality which gained root access on an Android device without the user's knowledge," the agency stated.
"The main capabilities include retrieving HTTP GET requests from the C2 server, obtaining device data, compressing and AES-encrypting the collected data, and sending it via HTTP POST requests to the malicious C2 server."
ReversingLabs, in a newly published report today, dug deeper into this implant ("com.android.providers.optimizer") using a previous unobfuscated version of the malware described in the FBI Flash report.
According to researcher Karlo Zanki, not only did the implant have permissions to record audio and take photos for government surveillance purposes, but it also contained a feature to add a custom Wi-Fi access point and force a compromised device to connect to it.
"This feature was probably introduced to avoid possible detection due to unusual data traffic usage on the target's mobile account," Zanki said in an analysis.
Also of note was the ability to automatically answer calls from specific phone numbers, thereby allowing the threat actor to tap on conversations on-demand.
Besides featuring support for receiving commands sent via SMS messages, the latest variant of "optimizer" malware referenced by the FBI abused accessibility services to access contents of instant messaging applications such as WhatsApp, Instagram, Telegram, Viber, Skype, and an unofficial Iran-based Telegram client called Talaeii.
It's worth noting that Telegram had previously issued "unsafe" warnings to users of Talaeii and Hotgram in December 2018 following disclosure from the Center for Human Rights in Iran (CHRI) citing security concerns.
"When targeting individuals, threat actors often want to monitor their communication and movement," Zanki concluded. "Mobile phones are most suitable for such goals because of the computing power contained in your pocket, and the fact that most people carry them all the time."
"Since the Android platform maintains the biggest part of the global smartphone market share, it follows that it is also the primary target of mobile malware."
Hundreds of millions of Android users exposed to hack due to CVE-2020-8913
5.12.2020 Android Securityaffairs
Hundreds of millions of Android users are potentially exposed to the risk of hack due to the use of Android Play Core Library versions vulnerable to CVE-2020-8913
The CVE-2020-8913 flaw is a local, arbitrary code execution vulnerability that resides exists in the SplitCompat.install endpoint in Android’s Play Core Library. The vulnerability is rated 8.8 out of 10.0 and impacts Android’s Play Core Library versions prior to 1.7.2.
A threat actor could create an apk to targets a specific application. Upon installing the apk, the attacker could perform a broad range of malicious activities, including execute code as the targeted application and access the targeted application’s data on the victims’ Android devices.
The bad news is that several popular Android apps are still using versions of Google’s app update library that are affected by the CVE-2020-8913 flaw, millions of users at potentially at risk of a cyber attack.
The list of vulnerable apps is long and includes OkCupid, MS Edge, Xrecorder, Yango Pro, and PowerDirector, are still vulnerable and can be hijacked to steal sensitive data, such as passwords, financial details, and e-mails.
The development teams behind some popular apps like Viber, Meetup, Cisco, Grindr, Moovit, Cisco Teams, and Booking.com have updated the library in their apps after being notified by Check Point.
Experts from Check Point Research discovered that many third-party app developers are yet to update the Play Core library into their apps despite Google addressed the CVE-2020-8913 in March.
“Since the vulnerability was patched in April, why is there cause for concern now? The answer is because the patch needs to be pushed by the developers into the application. Unlike server-side vulnerabilities, where the vulnerability is patched completely once the patch is applied to the server, for client-side vulnerabilities, each developer needs to grab the latest version of the library and insert it into the application.” reads the post published by Check Point.
The Play Core Library is the app’s runtime interface with the Google Play Store, it allows to download additional language resources, manage the delivery of feature modules, manage the delivery of asset packs, trigger in-app updates, request in-app reviews.
So, basically, the Google Play Core Library is a gateway for interacting with Google Play Services from within the application itself, starting from dynamic code loading (such as downloading additional levels only when needed), to delivering locale-specific resources, to interacting with Google Play’s review mechanisms.
The flaw was first documented by researchers from Oversecured.
“After further careful research, it emerged that the verified-splits folder contains verified apks with the current app’s signature, which are no longer verified in the future. When a file in that folder starts with a config. prefix, it will be added to the app’s runtime ClassLoader automatically.” reads the analysis published by Oversecured. “Using that weakness, the attacker can create a class implementing e.g. the Parcelable interface and containing malicious code and send their instances to the affected app, meaning the createFromParcel(…) method will be executed in their context during deserialization leading to local code execution.”
The impact and magnitude of successful exploitation of this flaw are very serious, attackers can trigger it injects code into banking applications to grab credentials, and at the same time have SMS permissions to steal the two-factor authentication (2FA) codes, to spy on chat apps, spy on users’ locations, and tamper with enterprise apps.
Researchers from Check Point reported that of the 13% of Google Play applications analyzed in the month of September 2020, 8% were running a vulnerable variant of the library.
The researchers also published a proof-of-concept that shows how to use a vulnerable version of the Google Chrome app to steal the bookmarks stored in the browser.
“We’re estimating that hundreds of millions of Android users are at security risk,” Check Point’s Manager of Mobile Research, Aviran Hazum, said. “Although Google implemented a patch, many apps are still using outdated Play Core libraries. The vulnerability CVE-2020-8913 is highly dangerous, [and] the attack possibilities here are only limited by a threat actor’s imagination.”
Many Android Apps Expose Users to Attacks Due to Failure to Patch Google Library
5.12.2020 Android Securityweek
A vulnerability in the Google Play Core Library continues to impact many applications several months after official patches were released.
The Google Play Core Library allows Android developers to deliver updates to their applications at runtime, via the Google API, without requiring interaction from the user.
The library can be used to download additional language resources, manage the manner in which feature modules and asset packs are delivered, trigger in-app updates, and more. Google Chrome, Facebook, Snapchat, and WhatsApp are only some of the apps that use this library.
Tracked as CVE-2020-8913 and addressed in March 2020, the vulnerability is a path traversal that could result in local code execution (LCE) “within the scope of any application that has the vulnerable version of the Google Play Core Library,” Check Point explains.
According to Oversecured, which provided technical details on this security bug in August, the flaw can allow an attacker to abuse the library to deliver executable modules to an application, essentially leading to arbitrary code execution within these modules.
“An attacker who had a malware app installed on the victim’s device could steal users’ login details, passwords, and financial details, and read their mail,” Oversecured notes.
In addition to the aforementioned path traversal, the attack relies on a combination of two features, one where all files that an application receives from Google Play are placed in a verified folder within the app’s sandbox, and another where other sources can push files into that sandbox.
Normally, the pushed files are placed into a 'non-verified' folder and not handled by the library, but said path traversal allowed an attacker to supply a path within their malicious application so that their nefarious file would be written to the 'verified' folder.
Thus, not only is the file automatically loaded and executed by the Google Play Core library, but it is no longer verified in the future, given the folder it is stored into.
The main concern regarding this flaw is that, although a patch was released months ago, many software developers have yet to implement it in their applications. An analysis performed by Check Point revealed that 13% of Google Play applications used the library, and that 8% of them had a vulnerable version.
Some of the apps found to be vulnerable included Viber, Booking, Cisco Teams, Moovit, Grindr, and OKCupid, all of which were patched after Check Point contacted the developers to inform them on the issue. However, apps such as Edge, PowerDirector, Xrecorder, and Yango Pro (Taximeter) remain vulnerable.
Google Play Apps Remain Vulnerable to High-Severity Flaw
4.12.2020 Android Threatpost
Patches for a flaw (CVE-2020-8913) in the Google Play Core Library have not been implemented by several popular Google Play apps, including Edge.
UPDATE
Researchers are warning that several popular Google Play applications – including mobile browser app Edge – have yet to push out an important update addressing a high-severity vulnerability in the Google Play Core Library.
The vulnerability exists in Google Play Core Library, which is utilized by various popular applications like Google Chrome, Facebook and Instagram. This is essentially a gateway for interacting with Google Play services from within the application itself, allowing developers to carry out various processes like dynamic code loading, delivering locale-specific resources and interacting with Google Play’s review mechanisms.
The vulnerability (CVE-2020-8913) in the Google Play Core Library is a local, arbitrary code execution issue in the SplitCompat.install endpoint in of Android’s Play Core Library (in versions prior to 1.7.2). The flaw, which ranks 8.8 out of 10 on the CVSS v3 scale, making it high severity, was previously disclosed in late August. Google patched the flaw on April 6, 2020. However, in a report issued Thursday by Check Point researchers warned that the patch still needs to be pushed out by developers for several applications – and potentially still impacts hundreds of millions of Android users.
“Unlike server-side vulnerabilities, where the vulnerability is patched completely once the patch is applied to the server, for client-side vulnerabilities, each developer needs to grab the latest version of the library and insert it into the application,” said Aviran Hazum and Jonathan Shimonovich, security researchers with Check Point Research on Thursday.
In fact, as of September 2020, researchers found that 13 percent of Google Play applications used the Google Play Core Library – and 8 percent of those apps had a vulnerable version. These include several popular apps, such as social app Viber, travel app Booking, business app Cisco Teams, navigation apps Yango Pro and Movit, dating apps Grindr, OKCupid and Bumble, mobile browser app Edge and utility apps Xrecorder and PowerDirector.
“Prior to this publication, we have notified all Apps about the vulnerability and the need to update the version of the library, in order not to be affected,” said researchers. “Further tests show Viber and Booking updated to the patched versions after our notification.”
As of Dec. 2, Cisco has also addressed this vulnerability in the latest version of Cisco Webex Teams, released in the Google Play Store, a Cisco spokesperson told Threatpost.
The Flaw
In order to exploit the flaw, an attacker would need to convince a victim to install malicious application. The malicious app would then exploit one of the applications with a vulnerable version of the Google Play Core Library. The library handles the payload, loads it and executes the attack; the payload can then access all of the resources available in the hosting application.
This flaw “is extremely easy to exploit,” said researchers. “All you need to do is to create a ‘hello world’ application that calls the exported intent in the vulnerable app to push a file into the verified files folder with the file-traversal path. Then sit back and watch the magic happen.”
Meanwhile, the potential impact of an exploit could be serious, researchers said. If a malicious application exploits this vulnerability, it can execute code inside popular applications and have the same access as the vulnerable application, they warned. That could create a number of malicious situations, including attackers injecting code into banking applications to steal credentials and steal two-factor authentication (2FA) codes, injecting code into enterprise applications to access sensitive corporate resources, or injecting code into instant-messaging apps to view – and even send – messages on the victim’s behalf.
Researchers said they reached out to Google with their findings. Google responded in a statement: “The relevant vulnerability CVE-2020-8913 does not exist in up-to-date Play Core versions.” Application developers are urged to update to Android’s Play Core Library version 1.7.2.
This article was updated on Dec. 3 at 1pm ET to reflect that Cisco has updated its Android app to address the flaw.
Several Unpatched Popular Android Apps Put Millions of Users at Risk of Hacking
3.12.2020 Android Thehackernews
A number of high-profile Android apps are still using an unpatched version of Google's widely-used app update library, potentially putting the personal data of hundreds of millions of smartphone users at risk of hacking.
Many popular apps, including Grindr, Bumble, OkCupid, Cisco Teams, Moovit, Yango Pro, Microsoft Edge, Xrecorder, and PowerDirector, are still vulnerable and can be hijacked to steal sensitive data, such as passwords, financial details, and e-mails.
The bug, tracked as CVE-2020-8913, is rated 8.8 out of 10.0 for severity and impacts Android's Play Core Library versions prior to 1.7.2.
Although Google addressed the vulnerability in March, new findings from Check Point Research show that many third-party app developers are yet to integrate the new Play Core library into their apps to mitigate the threat fully.
"Unlike server-side vulnerabilities, where the vulnerability is patched completely once the patch is applied to the server, for client-side vulnerabilities, each developer needs to grab the latest version of the library and insert it into the application," the cybersecurity firm said in a report.
Play Core Library is a popular Android library that allows developers to manage the delivery of new feature modules effectively, trigger in-app updates at runtime, and download additional language packs.
First reported in late August by researchers at app security startup Oversecured, the issue allows a threat actor to inject malicious executables to any app relying on the library, thus granting the attacker full access to all the resources as that of the compromised application.
The flaw stems from a path traversal vulnerability in the library that could be exploited to load and execute malicious code (e.g., an APK file) onto a target app to steal users' login details, passwords, financial details, and other sensitive information stored in it.
The consequences of successful exploitation of this flaw are enormous. It can be used to "inject code into banking applications to grab credentials, and at the same time have SMS permissions to steal the two-factor authentication (2FA) codes," grab messages from chat apps, spy on users' locations, and even gain access to corporate resources by tampering with enterprise apps.
According to Check Point Research, of the 13% of Google Play applications analyzed in the month of September 2020, 8% of those apps had a vulnerable version.

After the cybersecurity firm responsibly disclosed their findings, Viber, Meetup, and Booking.com updated their apps to the patched version of the library.
The researchers also demonstrated a proof-of-concept that used a vulnerable version of the Google Chrome app to siphon the bookmarks stored in the browser through a dedicated payload.
"We're estimating that hundreds of millions of Android users are at security risk," Check Point's Manager of Mobile Research, Aviran Hazum, said. "Although Google implemented a patch, many apps are still using outdated Play Core libraries. The vulnerability CVE-2020-8913 is highly dangerous, [and] the attack possibilities here are only limited by a threat actor's imagination."
Android Messenger App Still Leaking Photos, Videos
2.12.2020 Android Threatpost
The GO SMS Pro app has been downloaded 100 million times; now, underground forums are actively sharing images stolen from GO SMS servers.
The GO SMS Pro Android app has published two new versions on Google Play since a major security weakness was disclosed in November – but neither fixes the original issue, leaving 100 million users at risk for privacy violations, researchers said.
Meanwhile, a raft of exploitation tools have been released in the wild for the bug.
That’s according to Trustwave SpiderLabs, which originally discovered a security issue that can be exploited to publicly expose private voicemails, video missives and photos sent using the popular messenger app.
With GO SMS Pro, when a user sends a multimedia message, the recipient can receive it even if they don’t themselves have the app installed. In that case, the media file is sent to the recipient as a URL via SMS, so the person can click on the link to view the media file in a browser window. The issue is that there’s no authentication required to view the content, so anyone with the link (and links can be guessable) can click through to the content.
“With some very minor scripting, it is trivial to throw a wide net around that content,” according to Trustwave. “While it’s not directly possible to link the media to specific users, those media files with faces, names, or other identifying characteristics do that for you.”
Some of the available-to-be-hacked content. Source: Trustwave.
A new version of the app was uploaded to the Play Store the day before the original Trustwave advisory on Nov. 19; followed quickly by a second updated version on Nov. 23. Trustwave has now tested both versions, specifically v7.93 and v7.94.
“We can confirm that older media used to verify the original vulnerability is still available,” researchers explained in a Tuesday posting. In other words, past messages that have been sent are still accessible. “That includes quite a bit of sensitive data like driver’s licenses, health insurance account numbers, legal documents, and of course, pictures of a more ‘romantic’ nature.”
Unfortunately, cybercrooks have been quick to exploit the problem, with “more tools and scripts released to exploit this on sites like Pastebin and Github than you can shake a stick at,” according to Trustwave. “Several popular tools are updating daily and on their third or fourth revision. We’ve also seen underground forums sharing images downloaded from GO SMS servers directly.”
As for the new versions, “It seems like [the developer] is attempting to fix the issue, but a complete fix is still not available in the app,” researchers explained. “For v7.93, it appears that they disabled the ability to send media files completely. We were not even able to attach files to an MMS message. In v7.94, they are not blocking the ability to upload media in the app, but the media does not appear to go anywhere…the recipient does not receive any actual text either with or without attached media. So, it appears they are in the process of trying to fix the root problem.”
Trustwave said that it still has had no contact from the GO SMS Pro team.
“Our only avenue is public education to keep users from continuing to risk their sensitive photos, videos and voice messages,” researchers said. “Given that old data is still at risk and being actively leaked, in addition to the lack of communication or full fixes, we also think it would be a good idea for Google to take this app back down.”
GO SMS Pro did not immediately return a request for comment.
‘Minecraft Mods’ Attack More Than 1 Million Android Devices
25.11.20 Android Threatpost
Fake Minecraft Modpacks on Google Play deliver millions of abusive ads and make normal phone use impossible.
Scammers are taking advantage of the Minecraft sandbox video game’s wild success by developing Google Play apps which appear to be Minecraft modpacks, but instead deliver abusive ads, according to researchers.
Since July, Kaspersky researchers have found more than 20 of these apps and determined that they have been downloaded on more than a million Android devices.
Minecraft is a problem-solving game aimed at kids and teens where players create their own worlds. Its original version, called Java Edition, was first released by Mojang Studios in 2009. The skills players build playing Minecraft have been touted by parents and educators as beneficial for kids, which has likely contributed to the game’s success. According to PC Games, more than 200 million copies of Minecraft were sold as of May.
Because Minecraft was designed in Java, it was easy for third-party developers to create compatible applications or “modpacks” to enhance and customize the gaming experience for players. Gamepedia said that today, there are more than 15,000 modpacks for Minecraft available.
Among those 15,000 Minecraft mods lurk at least 20 that Kaspersky researchers were able to identify as malicious. Google Play has removed all but five of the malicious titles, Kaspersky said: Zone Modding Minecraft, Textures for Minecraft ACPE, Seeded for Minecraft ACPE, Mods for Minecraft ACPE and Darcy Minecraft Mod are still up and available.
Google has not responded to Threatpost’s request for comment.
Malicious Modpacks
Of the list of 20 malicious mods, the most popular had more than 1 million installs. Even the least popular was downloaded 500 times, the report said.
Once the modpack malware is installed on the Android device, it only allows itself to be opened once, according to Kaspersky. And once opened, the app is glitchy and useless — exactly how it’s intended to work.
Fake app ratings. Source: Kaspersky.
“The frustrated user closes the app, which promptly vanishes. More precisely, its icon disappears from the smartphone’s menu,” the report said. “Because the ‘modpack’ seemed glitchy from the start, most users, especially kids and teens, won’t waste time looking for it.”
Forgotten, the app still runs in the background, working overtime to deliver ads.
“The sample we examined automatically opened a browser window with ads every two minutes, greatly interfering with normal smartphone use,” the report continued. “In addition to the browser, the apps can open Google Play and Facebook or play YouTube videos, depending on the [command-and-control] server’s orders. Whatever the case, the constant stream of full-screen ads makes the phone practically unusable.”
Getting Rid of Mod Malware
Researchers said reinstalling the browser or messing with the settings would be the next likely troubleshoot, but that won’t get rid of the malware either. First the user needs to identify the malicious app. The device will display a full list of apps under settings, (Settings → Apps and notifications → Show all apps). Delete the app from this list and the malware should be gone.
“Fortunately, the misbehaving modpacks get removed entirely with deletion and do not try to restore themselves.”
Signs of Malicious Apps
Avoiding malicious apps can be easier if parents and kids know where to look. For instance, Kaspersky researchers pointed out that although two of the malicious modpacks have different publishers, the descriptions are identical, “down to the typos.”
The app ratings also offer a clue something is fishy. Kaspersky pointed out that the average rating was in the three-star neighborhood, but that’s because there were extreme reviews on either end of the spectrum, one-star or five-stars.
“That kind of spread suggests that bots are leaving rave reviews, but real users are very unhappy,” the report added. “Unfortunately, in this case, the cybercriminals are targeting kids and teenagers, who may not pay attention to ratings and reviews before installing an app.”
Popular kids games have been attracting the attention of scammers in general over the past few months.
Minecraft players were also targeted on Google Play earlier this month by fraudsters offering premium skins, mods and wallpapers under a free “trial period,” which quickly ends and starts racking up charges on the victims’ phone bills.
The same week, the company behind the popular kids’ game Animal Jam announced a breach of a third-party server that exposed more than 46 million account records, which were then put up for sale on the dark web.
Baidu's Android Apps Caught Collecting and Leaking Sensitive User Data
25.11.20 Android Thehackernews
Two popular Android apps from Chinese tech giant Baidu have been removed from the Google Play Store in October after they were caught collecting sensitive user details.
The two apps in question—Baidu Maps and Baidu Search Box—were found to collect device identifiers, such as the International Mobile Subscriber Identity (IMSI) number or MAC address, without users' knowledge, thus making them potentially trackable online.
The discovery was made by network security firm Palo Alto Networks, who notified both Baidu and Google of their findings, after which the search company pulled the apps on October 28, citing "unspecified violations."
As of writing, a compliant version of Baidu Search Box has been restored to the Play Store on November 19, while Baidu Maps remains unavailable until the unresolved issues highlighted by Google are fixed.
A separate app named Homestyler was also found to collect private information from users' Android devices.
According to Palo Alto researchers, the full list of data collected by the apps include:
Phone model
Screen resolution
Phone MAC address
Carrier (Telecom Provider)
Network (Wi-Fi, 2G, 3G, 4G, 5G)
Android ID
IMSI number
International Mobile Equipment Identity (IMEI) number
Using a machine learning-based algorithm designed to detect anomalous spyware traffic, the origin of the data leak was traced to Baidu's Push SDK as well as ShareSDK from the Chinese vendor MobTech, the latter of which supports 37,500 apps, including more than 40 social media platforms.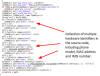
While Google has taken steps to secure the Play store and stop the malicious activity, bad actors are still finding ways to infiltrate the app marketplace and leverage the platform for their gain.
Indeed, an academic study published by researchers from NortonLifeLock earlier this month found the Play Store to be the primary source of malware installs (about 67.5%) on Android devices based on an analysis of app installations on 12 million handsets over a four-month period between June and September 2019, fueled in part due to the wide popularity of the platform.
However, its vector detection ratio — the ratio of unwanted apps installed through that vector overall apps installed through that vector — was found to be only 0.6% when compared to alternative third-party app stores (3.2%).
"Thus, the Play market defenses against unwanted apps work, but still significant amounts of unwanted apps are able to bypass them, making it the main distribution vector for unwanted apps," the researchers said.
If anything, the incident is yet another reminder that no app, even if developed by a legitimate third-party, can be taken for granted.
This also means the usual safeguards such as scrutinizing app reviews, developer details, and the list of requested permissions may not offer enough protection, thus making it difficult to ascertain if a permission is misused by cybercriminals to steal private data.
"In mobile devices, it is typical to ask a user to grant a list of permissions upon installation of an application or to prompt a user to allow or deny a permission while the application is running," Palo Alto researchers concluded.
"Disallowing permissions can often result in a non-working application, which leads to a bad user experience and might tempt a user to click on 'allow' just to be able to use an application. Even if a certain permission is
Google Launches Strong Encryption for Android Messages
20.11.20 Android Securityweek
Google said Thursday it will be rolling out end-to-end encryption for Android users, making it harder for anyone -- including law enforcement -- to read the content of messages.
"End-to-end encryption ensures that no one, including Google and third parties, can read the content of your messages as they travel between your phone and the phone of the person you're messaging," said Google product lead Drew Rowny in announcing the rollout.
Google's move is part of an upgrade from SMS to the Rich Communication Services (RCS) standard with additional features for images and videos.
It will be available for people communicating using Android-powered devices.
The move brings additional privacy and security to Google's messaging application, but comes amid rising complaints from law enforcement agencies around the world that strong encryption may enable criminals to hide their tracks.
Digital rights activists have long supported strong encryption to allow users to avoid snooping by governments and cybercriminals. But some governments have warned the technology could hinder criminal investigations.
End-to-end encryption is already available on some services such as Facebook-owned WhatsApp, but the company has been facing resistance over its plan to bring full encryption to its Messenger app.
Last year, US Attorney General William Barr joined with British and Australian counterparts in urging Facebook to abandon its encryption, claiming the plan court hurt investigations into child exploitation.
Civil liberties groups countered that a lack of encryption or privileged access for law enforcement could hurt privacy and security for all internet users, creating holes that could be exploited by bad actors.
Minecraft Apps on Google Play Fleece Players Out of Big Money
12.11.20 Android Threatpost
Seven mobile apps for Android sneakily charge fans of Minecraft and Roblox hundreds of dollars per month.
Fans of the popular Minecraft video game are in the crosshairs of cybercriminals, who have loaded up Google Play with scam apps bent on fleecing players out of cash.
According to researchers, the mobile apps for Android fool users into spending hundreds of dollars per month, by offering skins, wallpapers and game mods for Minecraft and other games at super-premium prices. These “fleeceware” offerings start with a “free trial” period but then automatically and quietly start charging up to $30 per week after that. The charges show up on victims’ phone bills, where they may or may not be noticed. Users can easily find themselves paying hundreds of dollars for the app over time, researchers noted.
“Fraudsters expect the user to forget about the installed application and its short trial, or fail to notice the real subscription cost,” Avast researchers explained, in a posting on Tuesday. “Scams of this nature take advantage of those who don’t always read the fine print details of every app they download. In this case, young children are particularly at risk because they may think they are innocently downloading a Minecraft accessory, but not understand or may not pay attention to the details of the service to which they are subscribing.”
Avast found and reported seven apps to Google, but as of Wednesday, they were all still active. Five of them have more than a million downloads each, and the other two have more than 100,000 installs. Google did not immediately respond to a request for comment.
Ondrej David, malware analysis team lead at Avast, noted: “We urge our customers to remain vigilant when downloading any app from unknown developers and to always carefully research user reviews and billing agreements before subscribing.”
In the case of the seven most recent apps, the reviews tend to be either a one- or five-star, with nothing in-between, and most have a low-star rating overall, according to the firm.
The offending apps, all likely the work of the same author, are: Mods, Maps for Minecraft PE; Skins for Roblox; Live Wallpapers HD & 3D Background; MasterCraft for Minecraft; Master for Minecraft; Boys and Girls Skins; and Maps Skins and Mods for Minecraft.
Google has made a concerted effort to try to eliminate bad apps for its Android mobile platform on the Google Play store – but fleeceware often sneaks past Google’s radar in significant numbers, according to security researchers.
A Sophos report earlier this year found that these type of apps have been installed nearly 600 million times on 100 million plus devices.
“As we saw last fall, there were a wide variety of entertainment or utility apps, including fortune tellers, instant messengers, video editors and beauty apps,” researchers wrote at the time. “And just like last time, user reviews reveal serious complaints about overcharging, and that many of these apps are substandard, and don’t work as expected.”
And Google is not alone in being plagued by this type of scam. In April, Sophos researchers found more than 30 examples of fleeceware apps for iPhone on Apple’s App Store.
These were mainly image editors, horoscope apps, QR code or barcode scanners, and face filter apps targeted at younger generations, researchers said. Each racked up between 500,000 downloads (Selfie Art – Photo Editor) to 1 million downloads (mSpy Lite Phone Family Tracker), they noted. And one of these apps, Zodiac Master Plus, was listed as the 11th-highest revenue-generating app on Apple’s App Store at the time.
Tetrade hackers target 112 financial apps with Ghimob banking Trojan
11.11.20 Android Securityaffairs
Researchers from Kaspersky Lab spotted a new Android banking Trojan, dubbed Ghimob, that is able to steal data from 112 financial Apps
Ghimob is a new Android banking Trojan discovered by Kaspersky that is able to steal data from 112 financial apps.
In July, cybersecurity researchers from Kaspersky Lab have detailed four different families of Brazilian banking trojans, tracked as Tetrade, that have targeted financial institutions in Brazil, Latin America, and Europe.
The four malware families are named Guildma, Javali, Melcoz, and Grandoreiro, experts believe are the result of a Brazilian banking group/operation that is evolving its capabilities targeting banking users abroad.
The Brazilian cybercrime underground is recognized as the most focuses on the development and commercialization of banking trojans.
Now the experts from Kaspersky’s Global Research and Analysis Team (GReAT) gathered further evidence that demonstrates that malware operators behind Tetrade, tracked as Guildma, have expanded their tactics to infect mobile devices with spyware.
Ghimob was designed to target financial apps from banks, fintech companies, exchanges, and cryptocurrencies in Brazil, Paraguay, Peru, Portugal, Germany, Angola, and Mozambique.
“Ghimob is a full-fledged spy in your pocket: once infection is completed, the hacker can access the infected device remotely, completing the fraudulent transaction with the victim’s smartphone, so as to avoid machine identification, security measures implemented by financial institutions and all their anti-fraud behavioral systems,” reads the report published by Kaspersky.
Ghimob Trojan is able to record a screen lock pattern in place and later replay it to unlock the device. When the attackers have to perform the transaction, they can display a black screen as an overlay or open some website in full screen, to trick the victim into looking at that screen while performing the transaction in the background by using one of the financial apps running on the victim’s device that the user has opened or logged in to.
Experts noticed that Ghimob shares the C2 infrastructure as that of Guildma, threat actors use the same TTPs continuing to launch phishing emails to spread the malware. The messages were devised to trick unsuspecting users into clicking malicious URLs that downloads the Ghimob APK installer.

Ghimob is also interesting in the way it uses C2s with fallback protected by Cloudflare, hiding the real C2 with DGA and employing several other tricks. Compared to other BRATA or Basbanke, Ghimob is far more advanced and implements a wide range of features.
The Trojan supports common functions similar to other mobile RATs, such us the capability to mask its presence by hiding the icon from the app drawer and abuses Android’s accessibility features.
“While monitoring a Guildma Windows malware campaign, we were able to find malicious URLs used for distributing both ZIP files for Windows boxes and APK files, all from the same URL. If the user-agent that clicked the malicious link is an Android-based browser, the file downloaded will be the Ghimob APK installer.” continues the analysis.
“The APKs thus distributed are posing as installers of popular apps; they are not on Google Play but rather hosted in several malicious domains registered by Guildma operators. Once installed on the phone, the app will abuse Accessibility Mode to gain persistence, disable manual uninstallation and allow the banking trojan to capture data, manipulate screen content and provide full remote control to the fraudster: a very typical mobile RAT.”
Ghimob is the first Brazilian mobile banking trojan ready to target financial institutions and their customers in many other countries worldwide.
“The Trojan is well prepared to steal credentials from banks, fintechs, exchanges, crypto-exchanges, and credit cards from financial institutions operating in many countries.” concludes the report.
“Ghimob is the first Brazilian mobile banking trojan ready to expand and target financial institutions and their customers living in other countries. The Trojan is well prepared to steal credentials from banks, fintechs, exchanges, crypto-exchanges, and credit cards from financial institutions operating in many countries.”
Let’s Encrypt Warns Some Android Users of Compatibility Issues
10.11.20 Android Securityweek
Let’s Encrypt has warned users whose devices are running older versions of Android that they may start getting errors next year when visiting websites secured by its certificates.
Let’s Encrypt, which earlier this year announced releasing over one billion certificates since its launch in 2015, initially relied on a cross-signature from IdenTrust. It can take a certificate authority (CA) years to get a new root certificate accepted by browsers and operating systems, and in order to be able to immediately start issuing certificates that are trusted by devices, a CA can get a cross-signature from a trusted CA.
Let’s Encrypt’s own root certificate is now mature and the initial certificate, which is set to expire on September 1, 2021, is no longer needed. While this will not impact most users, software that has not been updated since September 2016 and which does not trust Let’s Encrypt’s own root certificate will likely cause problems.
The CA believes one of the products most impacted by this will be Android, prior to version 7.1.1. The organization estimates that roughly one-third of Android devices are still running these older versions, which means their users will start getting certificate errors once the cross-signed certificate expires. Major integrators indicated that these users account for roughly 1-5% of their traffic.
While the situation might improve until next year when the certificate expires, Let’s Encrypt believes there will still be many impacted devices so it’s trying to raise awareness.
“What can we do about this? Well, while we’d love to improve the Android update situation, there’s not much we can do there. We also can’t afford to buy the world a new phone,” said Jacob Hoffman-Andrews, lead developer at Let’s Encrypt.
“Can we get another cross-signature? We’ve explored this option and it seems unlikely. It’s a big risk for a CA to cross-sign another CA’s certificate, since they become responsible for everything that CA does,” he added. “It’s important for us to be able to stand on our own. Also, the Android update problem doesn’t seem to be going away. If we commit ourselves to supporting old Android versions, we would commit ourselves to seeking cross-signatures from other CAs indefinitely.”
Let’s Encrypt has advised users who cannot upgrade their Android devices to install Firefox on their smartphone, as Firefox comes with its own list of trusted root certificates rather than using the list from the operating system.
The organization has also provided recommendations for website owners and users who get certificates from their hosting provider.
Let’s Encrypt’s goal is to make the internet safer by enabling website owners to easily obtain an SSL/TLS certificate at no cost. However, unsurprisingly, its services have also been abused by cybercriminals.
Watch Out! New Android Banking Trojan Steals From 112 Financial Apps
10.11.20 Android Thehackernews
Four months after security researchers uncovered a "Tetrade" of four Brazilian banking Trojans targeting financial institutions in Brazil, Latin America, and Europe, new findings show that the criminals behind the operation have expanded their tactics to infect mobile devices with spyware.
According to Kaspersky's Global Research and Analysis Team (GReAT), the Brazil-based threat group Guildma has deployed "Ghimob," an Android banking Trojan targeting financial apps from banks, fintech companies, exchanges, and cryptocurrencies in Brazil, Paraguay, Peru, Portugal, Germany, Angola, and Mozambique.
"Ghimob is a full-fledged spy in your pocket: once infection is completed, the hacker can access the infected device remotely, completing the fraudulent transaction with the victim's smartphone, so as to avoid machine identification, security measures implemented by financial institutions and all their anti-fraud behavioral systems," the cybersecurity firm said in a Monday analysis.
In addition to sharing the same infrastructure as that of Guildma, Ghimob continues the modus operandi of using phishing emails as a mechanism to distribute the malware, luring unsuspecting users into clicking malicious URLs that downloads the Ghimob APK installer.
The Trojan, once installed on the device, functions a lot similar to other mobile RATs in that it masks its presence by hiding the icon from the app drawer and abuses Android's accessibility features to gain persistence, disable manual uninstallation and allow the banking trojan to capture keystrokes, manipulate screen content and provide full remote control to the attacker.
"Even if the user has a screen lock pattern in place, Ghimob is able to record it and later replay it to unlock the device," the researchers said.
"When the cybercriminal is ready to perform the transaction, they can insert a black screen as an overlay or open some website in full screen, so while the user looks at that screen, the criminal performs the transaction in the background by using the financial app running on the victim's smartphone that the user has opened or logged in to."
What's more, Ghimob targets as many as 153 mobile apps, 112 of which are financial institutions based in Brazil, with cryptocurrency and banking apps in Germany, Portugal, Peru, Paraguay, Angola, and Mozambique accounting for the rest.
"Ghimob is the first Brazilian mobile banking trojan ready to expand and target financial institutions and their customers living in other countries," Kaspersky researchers concluded. "The Trojan is well prepared to steal credentials from banks, fintechs, exchanges, crypto-exchanges, and credit cards from financial institutions operating in many countries."
Google Patches 30 Vulnerabilities With November 2020 Android Updates
4.11.20 Android Securityweek
Google this week announced the availability of a new set of monthly patches for the Android operating system, containing fixes for a total of 30 vulnerabilities.
The first part of the update, the 2020-11-01 security patch level addresses a total of 17 vulnerabilities in the Android runtime, Framework, Media Framework, and System components.
The most serious of the flaws is CVE-2020-0449, a critical bug in System that could be exploited to execute code remotely. The issue impacts Android 8.0, 8.1, 9, 10, and 11.
“The most severe of these issues is a critical security vulnerability in the System component that could enable a proximal attacker using a specially crafted transmission to execute arbitrary code within the context of a privileged process,” Google explains.
System was the Android component that received patches for the largest number of vulnerabilities this month, at seven. Aside from the aforementioned critical flaw, the remaining issues were high severity: one elevation of privilege, four information disclosure, and one denial of service bug.
Framework comes in second most affected, with six vulnerabilities: two critical issues, both leading to denial of service, and four high-risk bugs, leading to elevation of privilege, information disclosure, and denial of service.
This month’s Android patches also address three vulnerabilities in Framework (leading to information disclosure, remote code execution, and elevation of privilege) and one in Android runtime (a high-risk bug leading to privilege escalation).
Fixes for a total of 13 vulnerabilities were included in the second part of this month’s set of patches, which arrives on devices as the 2020-11-05 security patch level.
These issues were identified in MediaTek components (three high-severity flaws) and Qualcomm closed-source components (one critical and nine high-risk bugs).
This week, Google also announced the availability of a separate set of patches for Pixel devices, containing fixes for four bugs in Qualcomm components and Qualcomm closed-source components. All issues are rated moderate severity and are addressed on devices that run a security patch level of 2020-11-05 or later.
This week, Google also released an update for the Chrome browser on Android, to patch a vulnerability already exploited in the wild.