28.6.22 Android Thehackernews

A previously unknown Android banking trojan has been discovered in the wild, targeting users of the Spanish financial services company BBVA.
OS 2024 2023 2022 2020 ANDROID 2022 2021 2020
Microsoft Warns About Evolving Capabilities of Toll Fraud Android Malware Apps
2.7.22 Android Thehackernews
Microsoft has detailed the evolving capabilities of toll fraud malware apps on Android, pointing out its "complex multi-step attack flow" and an improved mechanism to evade security analysis.
Toll fraud belongs to a category of billing fraud wherein malicious mobile applications come with hidden subscription fees, roping in unsuspecting users to premium content without their knowledge or consent.
It's also different from other fleeceware threats in that the malicious functions are only carried out when a compromised device is connected to one of its target network operators.
"It also, by default, uses cellular connection for its activities and forces devices to connect to the mobile network even if a Wi-Fi connection is available," Dimitrios Valsamaras and Sang Shin Jung of the Microsoft 365 Defender Research Team said in an exhaustive analysis.
"Once the connection to a target network is confirmed, it stealthily initiates a fraudulent subscription and confirms it without the user's consent, in some cases even intercepting the one-time password (OTP) to do so."
Such apps are also known to suppress SMS notifications related to the subscription to prevent the victims from becoming aware of the fraudulent transaction and unsubscribing from the service.
At its core, toll fraud takes advantage of the payment method which enables consumers to subscribe to paid services from websites that support the Wireless Application Protocol (WAP). This subscription fee gets charged directly to the users' mobile phone bills, thus obviating the need for setting up a credit or debit card or entering a username and password.
"If the user connects to the internet through mobile data, the mobile network operator can identify him/her by IP address," Kaspersky noted in a 2017 report about WAP billing trojan clickers. "Mobile network operators charge users only if they are successfully identified."
Optionally, some providers can also require OTPs as a second layer of confirmation of the subscription prior to activating the service.
"In the case of toll fraud, the malware performs the subscription on behalf of the user in a way that the overall process isn't perceivable," the researchers said. "The malware will communicate with a [command-and-control] server to retrieve a list of offered services."
It achieves this by first turning off Wi-Fi and turning on mobile data, followed by making use of JavaScript to stealthily subscribe to the service, and intercepting and sending the OTP code (if applicable) to complete the process.
The JavaScript code, for its part, is designed to click on HTML elements that contain keywords such as "confirm," "click," and "continue" to programmatically initiate the subscription.
Upon a successful fraudulent subscription, the malware either conceals the subscription notification messages or abuses its SMS permissions to delete incoming text messages containing information about the subscribed service from the mobile network operator.
Toll fraud malware is also known to cloak its malicious behavior by means of dynamic code loading, a feature in Android that allows apps to pull additional modules from a remote server during runtime, making it ripe for abuse by malicious actors.
From a security standpoint, this also means that a malware author can fashion an app such that the rogue functionality is only loaded when certain prerequisites are met, effectively defeating static code analysis checks.
"If an app allows dynamic code loading and the dynamically loaded code is extracting text messages, it will be classified as a backdoor malware," Google lays out in its developer documentation about potentially harmful applications (PHAs).
With an install rate of 0.022%, toll fraud apps accounted for 34.8% of all PHAs installed from the Android app marketplace in the first quarter 2022, ranking second below spyware. Most of the installations originated from India, Russia, Mexico, Indonesia, and Turkey.
To mitigate the threat of toll fraud malware, it's recommended that users install applications only from the Google Play Store or other trusted sources, avoid granting excessive permissions to apps, and consider upgrading to a new device should it stop receiving software updates.
New Android Banking Trojan 'Revive' Targeting Users of Spanish Financial Services
28.6.22 Android Thehackernews 
A previously unknown Android banking trojan has been discovered in the wild, targeting users of the Spanish financial services company BBVA.
Said to be in its early stages of development, the malware — dubbed Revive by Italian cybersecurity firm Cleafy — was first observed on June 15, 2022 and distributed by means of phishing campaigns.
"The name Revive has been chosen since one of the functionality of the malware (called by the [threat actors] precisely 'revive') is restarting in case the malware stops working, Cleafy researchers Federico Valentini and Francesco Iubatti said in a Monday write-up.
Available for download from rogue phishing pages ("bbva.appsecureguide[.]com" or "bbva.european2fa[.]com") as a lure to trick users into downloading the app, the malware impersonates the bank's two-factor authentication (2FA) app and is said to be inspired from open-source spyware called Teardroid, with the authors tweaking the original source code to incorporate new features.
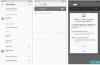
Unlike other banking malware that are known to target a wide range of financial apps, Revive is tailored for a specific target, in this case, the BBVA bank. That said, it's no different from its counterparts in that it leverages Android's accessibility services API to meet its operational objectives.
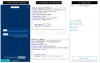
Revive is mainly engineered to harvest the bank's login credentials through the use of lookalike pages and facilitate account takeover attacks. It also incorporates a keylogger module to capture keystrokes and the ability to intercept SMS messages received on the infected devices, primarily one-time passwords and 2FA codes sent by the bank.
"When the victim opens the malicious app for the first time, Revive asks to accept two permissions related to the SMS and phone calls," the researchers said. "After that, a clone page (of the targeted bank) appears to the user and if the login credentials are inserted, they are sent to the [command-and-control server] of the TAs."
The findings once again underscore the need to exercise caution when it comes to downloading apps from third-party untrusted sources. The abuse of sideloading has not gone unnoticed by Google, which has implemented a new feature in Android 13 that blocks such apps from using accessibility APIs.
BRATA Android Malware Gains Advanced Mobile Threat Capabilities
21.6.22 Android Thehackernews
The operators behind BRATA have once again added more capabilities to the Android mobile malware in an attempt to make their attacks against financial apps more stealthy.
"In fact, the modus operandi now fits into an Advanced Persistent Threat (APT) activity pattern," Italian cybersecurity firm Cleafy said in a report last week. "This term is used to describe an attack campaign in which criminals establish a long-term presence on a targeted network to steal sensitive information."
An acronym for "Brazilian Remote Access Tool Android," BRATA was first detected in the wild in Brazil in late 2018, before making its first appearance in Europe last April, while masquerading as antivirus software and other common productivity tools to trick users into downloading them.
The change in the attack pattern, which scaled new highs in early April 2022, involves tailoring the malware to strike a specific financial institution at a time, switching to a different bank only after the victim begins implementing countermeasures against the threat.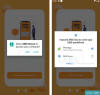
Also incorporated in the rogue apps are new features that enable it to impersonate the login page of the financial institution to harvest credentials, access SMS messages, and sideload a second-stage payload ("unrar.jar") from a remote server to log events on the compromised device.
"The combination of the phishing page with the possibility to receive and read the victim's sms could be used to perform a complete Account Takeover (ATO) attack," the researchers said.
Additionally, Cleafy said it found a separate Android app package sample ("SMSAppSicura.apk") that used the same command-and-control (C2) infrastructure as BRATA to siphon SMS messages, indicating that the threat actors are testing out different methods to expand their reach.
The SMS stealer app is said to be specifically singling out users in the U.K., Italy, and Spain, its goal being able to intercept and exfiltrate all incoming messages related to one-time passwords sent by banks.
"The first campaigns of malware were distributed through fake antivirus or other common apps, while during the campaigns the malware is taking the turn of an APT attack against the customer of a specific Italian bank," the researchers said.
"They usually focus on delivering malicious applications targeted to a specific bank for a couple of months, and then moving to another target."
Researchers Uncover 'Hermit' Android Spyware Used in Kazakhstan, Syria, and Italy
17.6.22 Android Thehackernews
An enterprise-grade surveillanceware dubbed Hermit has been put to use by entities operating from within Kazakhstan, Syria, and Italy over the years since 2019, new research has revealed.
Lookout attributed the spy software, which is equipped to target both Android and iOS, to an Italian company named RCS Lab S.p.A and Tykelab Srl, a telecom services provider which it suspects to be a front company. The San Francisco-based cybersecurity firm said it detected the campaign aimed at Kazakhstan in April 2022.
Hermit is modular and comes with myriad capabilities that allow it to "exploit a rooted device, record audio and make and redirect phone calls, as well as collect data such as call logs, contacts, photos, device location and SMS messages," Lookout researchers Justin Albrecht and Paul Shunk said in a new write-up.
The spyware is believed to be distributed via SMS messages that trick users into installing what are seemingly innocuous apps from Samsung, Vivo, and Oppo, which, when opened, loads a website from the impersonated company while stealthily activating the kill chain in the background.
Like other Android malware threats, Hermit is engineered to abuse its access to accessibility services and other core components of the operating system (i.e., contacts, camera, calendar, clipboard, etc.) for most of its malicious activities.
Android devices have been at the receiving end of spyware in the past. In November 2021, the threat actor tracked as APT-C-23 (aka Arid Viper) was linked to a wave of attacks targeting Middle East users with new variants of FrozenCell.
Then last month, Google's Threat Analysis Group (TAG) disclosed that at least government-backed actors located in Egypt, Armenia, Greece, Madagascar, Côte d'Ivoire, Serbia, Spain, and Indonesia are buying Android zero-day exploits for covert surveillance campaigns.
"RCS Lab, a known developer that has been active for over three decades, operates in the same market as Pegasus developer NSO Group Technologies and Gamma Group, which created FinFisher," the researchers noted.
"Collectively branded as 'lawful intercept' companies, they claim to only sell to customers with legitimate use for surveillanceware, such as intelligence and law enforcement agencies. In reality, such tools have often been abused under the guise of national security to spy on business executives, human rights activists, journalists, academics and government officials."
The findings come as the Israel-based NSO Group is said to be reportedly in talks to sell off its Pegasus technology to U.S. defense contractor L3Harris, the company that manufactures StingRay cellular phone trackers, prompting concerns that it could open the door for law enforcement's use of the controversial hacking tool.
The German maker behind FinFisher has been courting troubles of its own in the wake of raids conducted by investigating authorities in connection with suspected violations of foreign trading laws by way of selling its spyware in Turkey without obtaining the required license.
Earlier this March, it shut down its operations and filed for insolvency, Netzpolitik and Bloomberg reported, adding, "the office has been dissolved, the employees have been laid off, and business operations have ceased."
MaliBot: A New Android Banking Trojan Spotted in the Wild
15.6.22 Android Thehackernews
A new strain of Android malware has been spotted in the wild targeting online banking and cryptocurrency wallet customers in Spain and Italy, just weeks after a coordinated law enforcement operation dismantled FluBot.
The information stealing trojan, codenamed MaliBot by F5 Labs, is as feature-rich as its counterparts, allowing it to steal credentials and cookies, bypass multi-factor authentication (MFA) codes, and abuse Android's Accessibility Service to monitor the victim's device screen.
MaliBot is known to primarily disguise itself as cryptocurrency mining apps such as Mining X or The CryptoApp that are distributed via fraudulent websites designed to attract potential visitors into downloading them.
It also takes another leaf out of the mobile banking trojan playbook in that it employs smishing as a distribution vector to proliferate the malware by accessing an infected smartphone's contacts and sending SMS messages containing links to the malware.
"MaliBot's command-and-control (C2) is in Russia and appears to use the same servers that were used to distribute the Sality malware," F5 Labs researcher Dor Nizar said. "It is a heavily modified re-working of the SOVA malware, with different functionality, targets, C2 servers, domains, and packing schemes."
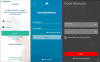
SOVA (meaning "Owl" in Russian), which was first detected in August 2021, is notable for its ability to conduct overlay attacks, which work by displaying a fraudulent page using WebView with a link provided by the C2 server should a victim open a banking app included in its active target list.
Some of the banks targeted by MaliBot using this approach include UniCredit, Santander, CaixaBank, and CartaBCC.
Accessibility Service is a background service running in Android devices to assist users with disabilities. It has long been leveraged by spyware and trojans to capture the device contents and intercept credentials entered by unsuspecting users on other apps.
Besides being able to siphon passwords and cookies of the victim's Google account, the malware is designed to swipe 2FA codes from the Google Authenticator app as well as exfiltrate sensitive information such as total balances and seed phrases from Binance and Trust Wallet apps.
What's more, Malibot is capable of weaponizing its access to the Accessibility API to defeat Google's two-factor authentication (2FA) methods, such as Google prompts, even in scenarios where an attempt is made to sign in to the accounts using the stolen credentials from a previously unknown device.
"The versatility of the malware and the control it gives attackers over the device mean that it could, in principle, be used for a wider range of attacks than stealing credentials and cryptocurrency," the researchers said.
"In fact, any application which makes use of WebView is liable to having the users' credentials and cookies stolen."
FluBot Android Spyware Taken Down in Global Law Enforcement Operation
3.6.22 Android Thehackernews
An international law enforcement operation involving 11 countries has culminated in the takedown of a notorious mobile malware threat called FluBot.
"This Android malware has been spreading aggressively through SMS, stealing passwords, online banking details and other sensitive information from infected smartphones across the world," Europol said in a statement.
The "complex investigation" included authorities from Australia, Belgium, Finland, Hungary, Ireland, Romania, Spain, Sweden, Switzerland, the Netherlands, and the U.S.
FluBot, also called Cabassous, emerged in the wild in December 2020, masking its insidious intent behind the veneer of seemingly innocuous package tracking applications such as FedEx, DHL, and Correos.
It primarily spreads via smishing (aka SMS-based phishing) messages that trick unsuspecting recipients into clicking on a link to download the malware-laced apps.

Once launched, the app would proceed to request access to Android's Accessibility Service to stealthily siphon bank account credentials and other sensitive information stored in cryptocurrency apps.
To make matters worse, the malware leveraged its access to contacts stored in the infected device to propagate the infection further by sending messages containing links to the FluBot malware.
FluBot campaigns, while primarily an Android malware, have also evolved to target iOS users in recent months, wherein users attempting to access the infected links are redirected to phishing sites and subscription scams.
"This FluBot infrastructure is now under the control of law enforcement, putting a stop to the destructive spiral," the agency noted, adding that the Dutch Police orchestrated the seizure last month.
According to ThreatFabric's mobile threat landscape report for H1 2022, FluBot was the second most active banking trojan behind Hydra, accounting for 20.9% of the samples observed between January and May.
"ThreatFabric has closely worked with law enforcement on the case," founder and CEO Han Sahin told The Hacker News.
"It's a great win considering FluBot threat actors have or had one of the most resilient strategies when it comes to distribution and hosting of their backends with DNS-tunneling through public DNS-over-HTTPS services. This backend resilience in C2 hosting and fronting is what makes the efforts of the Dutch digital crime unit very impressive."
The Dutch cybersecurity company also noted that unique malware samples developed by the operators of FluBot stopped after May 19, coinciding with the takedown, effectively slowing their "worming efforts."
"The overall impact [of the dismantling] on the mobile threat landscape is limited since FluBot is not the strongest Android banking trojan," Sahin added. "Exobot, Anatsa, Gustuff — those are a real problem to any user. The power behind FluBot has always been [its] infection numbers."
Latest Mobile Malware Report Suggests On-Device Fraud is on the Rise
1.6.22 Android Thehackernews
An analysis of the mobile threat landscape in 2022 shows that Spain and Turkey are the most targeted countries for malware campaigns, even as a mix of new and existing banking trojans are increasingly targeting Android devices to conduct on-device fraud (ODF).
Other frequently targeted countries include Poland, Australia, the U.S., Germany, the U.K., Italy, France, and Portugal.
"The most worrying leitmotif is the increasing attention to On-Device Fraud (ODF)," Dutch cybersecurity company ThreatFabric said in a report shared with The Hacker News.
"Just in the first five months of 2022 there has been an increase of more than 40% in malware families that abuse Android OS to perform fraud using the device itself, making it almost impossible to detect them using traditional fraud scoring engines."
Hydra, FluBot (aka Cabassous), Cerberus, Octo, and ERMAC accounted for the most active banking trojans based on the number of samples observed during the same period.

Accompanying this trend is the continued discovery of new dropper apps on Google Play Store that come under the guise of seemingly innocuous productivity and utility applications to distribute the malware -
Nano Cleaner (com.casualplay.leadbro)
QuickScan (com.zynksoftware.docuscanapp)
Chrome (com.talkleadihr)
Play Store (com.girltold85)
Pocket Screencaster (com.cutthousandjs)
Chrome (com.biyitunixiko.populolo)
Chrome (Mobile com.xifoforezuma.kebo)
BAWAG PSK Security (com.qjlpfydjb.bpycogkzm)
What's more, on-device fraud — which refers to a stealthy method of initiating bogus transactions from victims' devices — has made it feasible to use previously stolen credentials to login to banking applications and carry out financial transactions.
To make matters worse, the banking trojans have also been observed constantly updating their capabilities, with Octo devising an improved method to steal credentials from overlay screens even before they are submitted.

"This is done in order to be able to get the credentials even if [the] victim suspected something and closed the overlay without actually pressing the fake 'login' present in the overlay page," the researchers explained.
ERMAC, which emerged last September, has received noticeable upgrades of its own that allow it to siphon seed phrases from different cryptocurrency wallet apps in an automated fashion by taking advantage of Android's Accessibility Service.
Accessibility Service has been Android's Achilles' heel in recent years, allowing threat actors to leverage the legitimate API to serve unsuspecting users with fake overlay screens and capture sensitive information.
Last year, Google attempted to tackle the problem by ensuring that "only services that are designed to help people with disabilities access their device or otherwise overcome challenges stemming from their disabilities are eligible to declare that they are accessibility tools."

But the tech giant is going a step further in Android 13, which is currently in beta, by restricting API access for apps that the user has sideloaded from outside of an app store, effectively making it harder for potentially harmful apps to misuse the service.
That said, ThreatFabric noted it was able to bypass these restrictions trivially by means of a tweaked installation process, suggesting the need for a more stricter approach to counteract such threats.
It's recommended that users stick to downloading apps from the Google Play Store, avoid granting unusual permissions to apps that have no purpose asking for them (e.g., a calculator app asking to access contact lists), and watch out for any phishing attempts aimed at installing rogue apps.
"The openness of Android OS serves both good and bad as malware continues to abuse the legitimate features, whilst upcoming restrictions seem to hardly interfere with the malicious intentions of such apps," the researchers said.
Microsoft Finds Critical Bugs in Pre-Installed Apps on Millions of Android Devices
28.5.22 Android Thehackernews
Four high severity vulnerabilities have been disclosed in a framework used by pre-installed Android System apps with millions of downloads.
The issues, now fixed by its Israeli developer MCE Systems, could have potentially allowed threat actors to stage remote and local attacks or be abused as vectors to obtain sensitive information by taking advantage of their extensive system privileges.
"As it is with many of pre-installed or default applications that most Android devices come with these days, some of the affected apps cannot be fully uninstalled or disabled without gaining root access to the device," the Microsoft 365 Defender Research Team said in a report published Friday.
The weaknesses, which range from command-injection to local privilege escalation, have been assigned the identifiers CVE-2021-42598, CVE-2021-42599, CVE-2021-42600, and CVE-2021-42601, with CVSS scores between 7.0 and 8.9.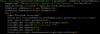
Command injection proof-of-concept (POC) exploit code

The vulnerabilities were discovered and reported in September 2021 and there is no evidence that the shortcomings are being exploited in the wild.
Microsoft didn't disclose the complete list of apps that use the vulnerable framework in question, which is designed to offer self-diagnostic mechanisms to identify and fix issues impacting an Android device.
This also meant that the framework had broad access permissions, including that of audio, camera, power, location, sensor data, and storage, to carry out its functions. Coupled with the issues identified in the service, Microsoft said it could permit an attacker to implant persistent backdoors and take over control.
Some of the affected apps are from large international mobile service providers such as Telus, AT&T, Rogers, Freedom Mobile, and Bell Canada -
Mobile Klinik Device Checkup (com.telus.checkup)
Device Help (com.att.dh)
MyRogers (com.fivemobile.myaccount)
Freedom Device Care (com.freedom.mlp.uat), and
Device Content Transfer (com.ca.bell.contenttransfer)
Additionally, Microsoft is recommending users to look out for the app package "com.mce.mceiotraceagent" — an app that may have been installed by mobile phone repair shops — and remove it from the phones, if found.
The susceptible apps, although pre-installed by the phone providers, are also available on the Google Play Store and are said to have passed the app storefront's automatic safety checks without raising any red flags because the process was not engineered to look out for these issues, something that has since been rectified.
Cytrox's Predator Spyware Targeted Android Users with Zero-Day Exploits
20.5.22 Android Thehackernews
Google's Threat Analysis Group (TAG) on Thursday pointed fingers at a North Macedonian spyware developer named Cytrox for developing exploits against five zero-day (aka 0-day) flaws, four in Chrome and one in Android, to target Android users.
"The 0-day exploits were used alongside n-day exploits as the developers took advantage of the time difference between when some critical bugs were patched but not flagged as security issues and when these patches were fully deployed across the Android ecosystem," TAG researchers Clement Lecigne and Christian Resell said.
Cytrox is alleged to have packaged the exploits and sold them to different government-backed actors located in Egypt, Armenia, Greece, Madagascar, Côte d'Ivoire, Serbia, Spain, and Indonesia, who, in turn, weaponized the bugs in at least three different campaigns.
The commercial surveillance company is the maker of Predator, an implant analogous to that of NSO Group's Pegasus, and is known to have developed tools that enables its clients to penetrate iOS and Android devices.
In December 2021, Meta Platforms (formerly Facebook) disclosed that it had acted to remove roughly 300 accounts on Facebook and Instagram that the company used as part of its compromise campaigns.
The list of the five exploited zero-day flaws in Chrome and Android is below -
CVE-2021-37973 - Use-after-free in Portals API
CVE-2021-37976 - Information leak in core
CVE-2021-38000 - Insufficient validation of untrusted input in Intents (root cause analysis)
CVE-2021-38003 - Inappropriate implementation in V8, and
CVE-2021-1048 - Use-after-free in Android kernel (root cause analysis)
According to TAG, all the three campaigns in question commenced with a spear-phishing email that contained one-time links mimicking URL shortener services that, once clicked, redirected the targets to a rogue domain that dropped the exploits before taking the victim to a legitimate site.
"The campaigns were limited — in each case, we assess the number of targets was in the tens of users," Lecigne and Resell noted. "If the link was not active, the user was redirected directly to a legitimate website."
The ultimate goal of the operation, the researchers assessed, was to distribute a malware dubbed Alien, which acts as a precursor for loading Predator onto infected Android devices.
The "simple" malware, which receives commands from Predator over an inter process communication (IPC) mechanism, is engineered to record audio, add CA certificates, and hide apps to evade detection.
The first of the three campaigns took place in August 2021. It used Google Chrome as a jumping off point on a Samsung Galaxy S21 device to force the browser to load another URL in the Samsung Internet browser without requiring user interaction by exploiting CVE-2021-38000.
Another intrusion, which occurred a month later and was delivered to an up-to-date Samsung Galaxy S10, involved an exploit chain using CVE-2021-37973 and CVE-2021-37976 to escape the Chrome sandbox (not to be confused with Privacy Sandbox), leveraging it to drop a second exploit to escalate privileges and deploy the backdoor.
The third campaign — a full Android 0-day exploit — was detected in October 2021 on an up-to-date Samsung phone running the then latest version of Chrome. It strung together two flaws, CVE-2021-38003 and CVE-2021-1048, to escape the sandbox and compromise the system by injecting malicious code into privileged processes.
Google TAG pointed out that while CVE-2021-1048 was fixed in the Linux kernel in September 2020, it wasn't backported to Android until last year as the fix was not marked as a security issue.
"Attackers are actively looking for and profiting from such slowly-fixed vulnerabilities," the researchers said.
"Tackling the harmful practices of the commercial surveillance industry will require a robust, comprehensive approach that includes cooperation among threat intelligence teams, network defenders, academic researchers and technology platforms."
Over 200 Apps on Play Store Caught Spying on Android Users Using Facestealer
17.5.22 Android Thehackernews
More than 200 Android apps masquerading as fitness, photo editing, and puzzle apps have been observed distributing spyware called Facestealer to siphon user credentials and other valuable information.
"Similar to Joker, another piece of mobile malware, Facestealer changes its code frequently, thus spawning many variants," Trend Micro analysts Cifer Fang, Ford Quin, and Zhengyu Dong said in a new report. "Since its discovery, the spyware has continuously beleaguered Google Play."
Facestealer, first documented by Doctor Web in July 2021, refers to a group of fraudulent apps that invade the official app marketplace for Android with the goal of plundering sensitive data such as Facebook login credentials.
Of the 200 apps, 42 are VPN services, followed by a camera (20) and photo editing applications (13). In addition to harvesting credentials, the apps are also designed to collect Facebook cookies and personally identifiable information associated with a victim's account.
Additionally, Trend Micro disclosed that it uncovered over 40 rogue cryptocurrency miner apps that target users interested in virtual coins with malware designed to trick users into watching ads and paying for subscription services.

Some of the fake crypto apps, such as Cryptomining Farm Your own Coin, take it one step further by also attempting to steal private keys and mnemonic phrases (or seed phrases) that are used to recover access to a cryptocurrency wallet.
To avoid falling victim to such scam apps, it's recommended that users check negative reviews, verify the legitimacy of the developers, and avoid downloading apps from third-party app stores.
New study analyzes malicious Android apps installed in the wild
The findings come as researchers from NortonLifeLock and Boston University published what they called the "largest on-device study" of potentially harmful apps (PHAs) on Android-based on 8.8 million PHAs installed on over 11.7 million devices between 2019 and 2020.

"PHAs persist on Google Play for 77 days on average and 34 days on third-party marketplaces," the study noted, pointing out the delay between when PHAs are identified and when they are removed, adding 3,553 apps exhibited inter-market migration after being taken down.
On top of that, the research also shows that PHAs linger for a much longer period on average when users switch devices and automatically install the apps when restoring from a backup.
As many as 14,000 PHAs are said to have been transferred to 35,500 new Samsung devices by using the Samsung Smart Switch mobile app, with the apps lasting on the phones for a period of approximately 93 days.
"The Android security model severely limits what mobile security products can do when detecting a malicious app, allowing PHAs to persist for many days on victim devices," the academics said. "The current warning system employed by mobile security programs is not effective in convincing users to promptly uninstall PHAs."
Android and Chrome Users Can Soon Generate Virtual Credit Cards to Protect Real Ones
14.5.22 Android Thehackernews
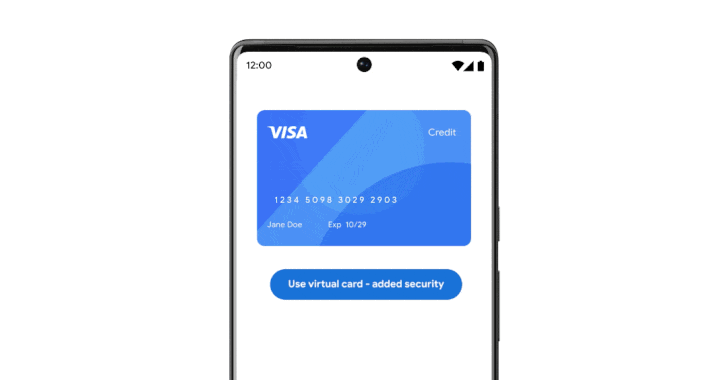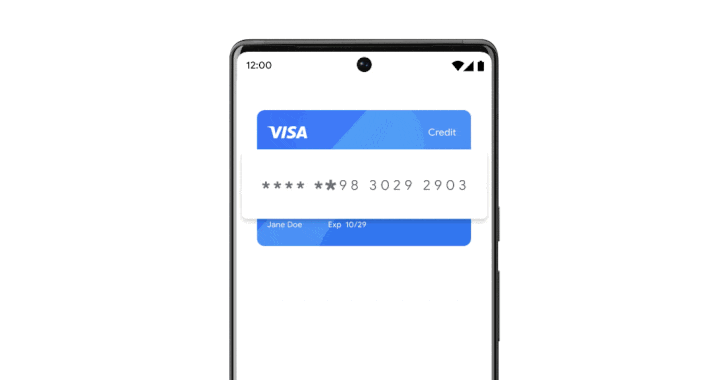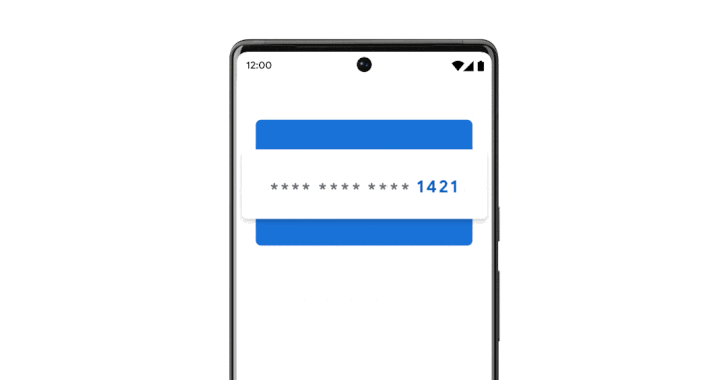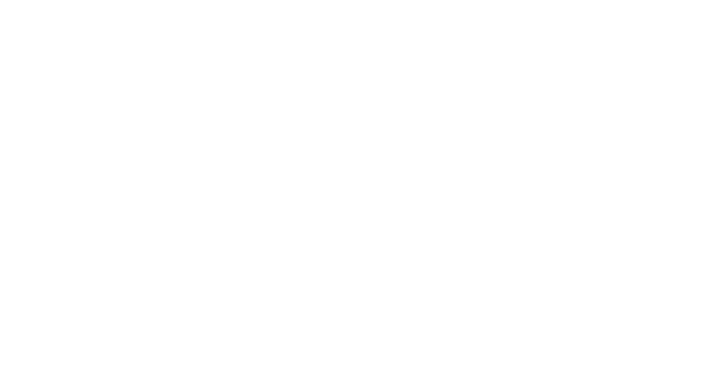
Google on Wednesday took to its annual developer conference to announce a host of privacy and security updates, including support for virtual credit cards on Android and Chrome.
"When you use autofill to enter your payment details at checkout, virtual cards will add an additional layer of security by replacing your actual card number with a distinct, virtual number," Google's Jen Fitzpatrick said in a statement.
The goal, the search giant, said to keep payment information safe and secure during online shopping and protect users from skimming attacks wherein threat actors inject malicious JavaScript code to plunder credit card numbers and sell them on the black market.
The feature is expected to roll out in the U.S. for Visa, American Express, Mastercard, and Capital One cards starting this summer.
Interestingly, while Apple offers an option to mask email addresses via Hide My Email, which enables users to create unique, random email addresses to use with apps and websites, it's yet to offer a similar functionality for creating virtual credit cards.
The development comes a week after Google, Apple, and Microsoft banded together to accelerate support for a common passwordless sign-in standard that allows "websites and apps to offer consistent, secure, and easy passwordless sign-ins to consumers across devices and platforms."
Additionally, Google said it's expanding phishing protections in Google Workspace to Docs, Slides and Sheets, and that it plans to debut a new "My Ad Center" later this year to give users more control over personalized ads on YouTube, Search, and Discover feed.
What's more, users would be able to request personally identifiable information such as email, phone number, or home address to be removed from search results through a new tool that will be accessible from the Google App.
Also coming is a new Account Safety Status setting that will "feature a simple yellow alert icon on your profile picture that will flag actions you should take to secure your account."
Other key privacy and security features unveiled at Google I/O 2022 include support for end-to-end encryption for group conversations in the Messages app for Android and the availability of on-device encryption for Google Password Manager.
Another Set of Joker Trojan-Laced Android Apps Resurfaces on Google Play Store
10.5.22 Android Thehackernews
A new set of trojanized apps spread via the Google Play Store has been observed distributing the notorious Joker malware on compromised Android devices.
Joker, a repeat offender, refers to a class of harmful apps that are used for billing and SMS fraud, while also performing a number of actions of a malicious hacker's choice, such as stealing text messages, contact lists, and device information.
Despite continued attempts on the part of Google to scale up its defenses, the apps have been continually iterated to search for gaps and slip into the app store undetected.
"They're usually spread on Google Play, where scammers download legitimate apps from the store, add malicious code to them and re-upload them to the store under a different name," Kaspersky researcher Igor Golovin said in a report published last week.
The trojanized apps, taking the place of their removed counterparts, often appear as messaging, health tracking, and PDF scanner apps that, once installed, request permissions to access text messages and notifications, abusing them to subscribe users to premium services.
A sneaky trick used by Joker to bypass the Google Play vetting process is to render its malicious payload "dormant" and only activate its functions after the apps have gone live on the Play Store.
Three of the Joker-infected apps detected by Kaspersky through the end of February 2022 are listed below. Although they have been purged from Google Play, they continue to be available from third-party app providers.
Style Message (com.stylelacat.messagearound),
Blood Pressure App (blood.maodig.raise.bloodrate.monitorapp.plus.tracker.tool.health), and
Camera PDF Scanner (com.jiao.hdcam.docscanner)
This is not the first time subscription trojans have been uncovered on app marketplaces. Last year, apps for the APKPure app Store and a widely-used WhatsApp mod were found compromised with a malware called Triada.
Then in September 2021, Zimperium took the wraps off an aggressive money-making scheme called GriftHorse, following it up with yet another case of premium service abuse called Dark Herring earlier this January.
"Subscription trojans can bypass bot detection on websites for paid services, and sometimes they subscribe users to scammers' own non-existent services," Golovin said.
"To avoid unwanted subscriptions, avoid installing apps from unofficial sources, which is the most frequent source of malware."
Even when downloading apps from official app stores, users are advised to read the reviews, check the legitimacy of the developers, the terms of use, and only grant permissions that are essential to perform the intended functions.
Google Releases Android Update to Patch Actively Exploited Vulnerability
7.5.22 Android Thehackernews
Google has released monthly security patches for Android with fixes for 37 flaws across different components, one of which is a fix for an actively exploited Linux kernel vulnerability that came to light earlier this year.
Tracked as CVE-2021-22600 (CVSS score: 7.8), the vulnerability is ranked "High" for severity and could be exploited by a local user to escalate privileges or deny service.
The issue relates to a double-free vulnerability residing in the Packet network protocol implementation in the Linux kernel that could cause memory corruption, potentially leading to denial-of-service or execution of arbitrary code.
Patches were released by different Linux distributions, including Debian, Red Hat, SUSE, and Ubuntu in January 2022.
"There are indications that CVE-2021-22600 may be under limited, targeted exploitation," Google noted in its Android Security Bulletin for May 2022. Specifics about the nature of the attacks are unknown as yet.
It's worth noting that the vulnerability has also been added by the U.S. Cybersecurity and Infrastructure Security Agency (CISA) to its Known Exploited Vulnerabilities Catalog as of last month based on evidence of active exploitation.
Also fixed as part of this month's patches are three other bugs in the kernel as well as 18 high-severity and one critical-severity flaw in MediaTek and Qualcomm components.
Google to Add Passwordless Authentication Support to Android and Chrome
7.5.22 Android Thehackernews
Google today announced plans to implement support for passwordless logins in Android and the Chrome web browser to allow users to seamlessly and securely sign in across different devices and websites irrespective of the platform.
"This will simplify sign-ins across devices, websites, and applications no matter the platform — without the need for a single password," Google said.
Apple and Microsoft are also expected to extend the support to iOS, macOS, and Windows operating systems as well as Safari and Edge browsers.
The common Fast IDentity Online (FIDO) sign-in system does away with passwords entirely in favor of displaying a prompt asking a user to unlock the phone when signing into a website or an application.
This is made possible by storing a cryptographically-secured FIDO credential called a passkey on the phone that's used to log in to the online account after unlocking the device.
"Once you've done this, you won't need your phone again and you can sign-in by just unlocking your computer," Google said.
"Even if you lose your phone, your passkeys will securely sync to your new phone from cloud backup, allowing you to pick up right where your old device left off."
With passkeys, the goal is to enable sign in from any device regardless of the platform or browser the device is running. "For example, users can sign in on a Google Chrome browser that's running on Microsoft Windows, using a passkey on an Apple device," Microsoft's Vasu Jakkal said.
The new passwordless sign-in capabilities are expected to become available across Apple, Google, and Microsoft platforms over the course of the coming year.
"Users will sign in through the same action that they take multiple times each day to unlock their devices, such as a simple verification of their fingerprint or face, or a device PIN," the FIDO alliance said.
"This new approach protects against phishing and sign-in will be radically more secure when compared to passwords and legacy multi-factor technologies such as one-time passcodes sent over SMS."
In a way, the method can be viewed as an extension of its own Google prompts for logging into accounts secured with two-factor authentication (aka 2-Step Verification).
The development comes as code hosting platform GitHub announced that it will "require all users who contribute code on GitHub.com to enable one or more forms of two-factor authentication (2FA) by the end of 2023" to prevent account takeover attacks.
Google Releases First Developer Preview of Privacy Sandbox on Android 13
3.5.22 Android Thehackernews
Google has officially released the first developer preview for the Privacy Sandbox on Android 13, offering an "early look" at the SDK Runtime and Topics API to boost users' privacy online.
"The Privacy Sandbox on Android Developer Preview program will run over the course of 2022, with a beta release planned by the end of the year," the search giant said in an overview.
A "multi-year effort," Privacy Sandbox on Android aims to create technologies that's both privacy-preserving as well as keep online content and services free without having to resort to opaque methods of digital advertising.
The idea is to limit sharing of user data with third-parties and operate without cross-app identifiers, including advertising ID, a unique, user-resettable string of letters and digits that can be used to track users as they move between apps.
Google originally announced its plans to bring Privacy Sandbox to Android earlier this February, following the footsteps of Apple's App Tracking Transparency (ATT) framework.
Integral to the proposed initiative are two key solutions —
SDK Runtime, which runs third-party code in mobile apps such as software development kits (SDKs), including those for ads and analytics, in a dedicated sandbox, and
Topics API, which gleans "coarse-grained" interest signals on-device based on a user's app usage that are then shared with advertisers to serve tailored ads without cross-site and cross-app tracking
To address criticisms that the model could possibly give Google an unfair advantage, the tech behemoth noted that the privacy-oriented systems will be developed as part of the Android Open Source Project (AOSP) to ensure transparency into the design and implementation of these solutions.
"Android will collaborate with the entire industry and app ecosystem on the journey to a more privacy-first mobile platform, and one which supports a rich diversity of value-exchange that benefits users, developers, and advertisers," the company said.
Critical Chipset Bugs Open Millions of Android Devices to Remote Spying
23.4.22 Android Thehackernews
Three security vulnerabilities have been disclosed in the audio decoders of Qualcomm and MediaTek chips that, if left unresolved, could allow an adversary to remotely gain access to media and audio conversations from affected mobile devices.
According to Israeli cybersecurity company Check Point, the issues could be used as a launchpad to carry out remote code execution (RCE) attacks simply by sending a specially crafted audio file.
"The impact of an RCE vulnerability can range from malware execution to an attacker gaining control over a user's multimedia data, including streaming from a compromised machine's camera," the researchers said in a report shared with The Hacker News.
"In addition, an unprivileged Android app could use these vulnerabilities to escalate its privileges and gain access to media data and user conversations."
The vulnerabilities, dubbed ALHACK, are rooted in an audio coding format originally developed and open-sourced by Apple in 2011. Called the Apple Lossless Audio Codec (ALAC) or Apple Lossless, the audio codec format is used for lossless data compression of digital music.
Since then, several third-party vendors, including Qualcomm and MediaTek, have incorporated the Apple-supplied reference audio codec implementation as the basis for their own audio decoders.
And while Apple has consistently patched and remediated security flaws in its proprietary version of ALAC, the open-sourced variant of the codec has not received a single update since it was uploaded to GitHub 11 years ago on October 27, 2011.
The vulnerabilities discovered by Check Point relate to this ported ALAC code, two of which have been identified in MediaTek processors and one in Qualcomm chipsets -
CVE-2021-0674 (CVSS score: 5.5, MediaTek) - A case of improper input validation in ALAC decoder leading to information disclosure without any user interaction
CVE-2021-0675 (CVSS score: 7.8, MediaTek) - A local privilege escalation flaw in ALAC decoder stemming from out-of-bounds write
CVE-2021-30351 (CVSS score: 9.8, Qualcomm) - An out-of-bound memory access due to improper validation of number of frames being passed during music playback
In a proof-of-concept exploit devised by Check Point, the vulnerabilities made it possible to "steal the phone's camera stream," said security researcher Slava Makkaveev, who is credited with discovering the flaws alongside Netanel Ben Simon.
Following responsible disclosure, all the three vulnerabilities were closed by the respective chipset manufacturers in December 2021.
"The vulnerabilities were easily exploitable," Makkaveev explained. "A threat actor could have sent a song (media file) and when played by a potential victim, it could have injected code in the privileged media service. The threat actor could have seen what the mobile phone user sees on their phone."
New Octo Banking Trojan Spreading via Fake Apps on Google Play Store
9.4.22 Android Thehackernews
A number of rogue Android apps that have been cumulatively installed from the official Google Play Store more than 50,000 times are being used to target banks and other financial entities.
The rental banking trojan, dubbed Octo, is said to be a rebrand of another Android malware called ExobotCompact, which, in turn, is a "lite" replacement for its Exobot predecessor, Dutch mobile security firm ThreatFabric said in a report shared with The Hacker News.
Exobot is also likely said to have paved the way for a separate descendant called Coper, that was initially discovered targeting Colombian users around July 2021, with newer infections targeting Android users in different European Countries.
"Coper malware apps are modular in design and include a multi-stage infection method and many defensive tactics to survive removal attempts," Cybersecurity company Cyble noted in an analysis of the malware last month.
Like other Android banking trojans, the rogue apps are nothing more than droppers, whose primary function is to deploy the malicious payload embedded within them. The list of Octo and Coper droppers used by multiple threat actors is below -
Pocket Screencaster (com.moh.screen)
Fast Cleaner 2021 (vizeeva.fast.cleaner)
Play Store (com.restthe71)
Postbank Security (com.carbuildz)
Pocket Screencaster (com.cutthousandjs)
BAWAG PSK Security (com.frontwonder2), and
Play Store app install (com.theseeye5)
These apps, which pose as Play Store app installer, screen recording, and financial apps, are "powered by inventive distribution schemes," distributing them through the Google Play store and via fraudulent landing pages that purportedly alert users to download a browser update.

The droppers, once installed, act as a conduit to launch the trojans, but not before requesting users to enable the Accessibility Services that allow it a wide breadth of capabilities to exfiltrate sensitive information from the compromised phones.
Octo, the revised version of ExobotCompact, is also equipped to perform on-device fraud by gaining remote control over the devices by taking advantage of the accessibility permissions as well as Android's MediaProjection API to capture screen contents in real-time.
The ultimate goal, ThreatFabric said, is to trigger the "automatic initiation of fraudulent transactions and its authorization without manual efforts from the operator, thus allowing fraud on a significantly larger scale."
Other notable features of Octo include logging keystrokes, carrying out overlay attacks on banking apps to capture credentials, harvesting contact information, and persistence measures to prevent uninstallation and evade antivirus engines.
"Rebranding to Octo erases previous ties to the Exobot source code leak, inviting multiple threat actors looking for opportunity to rent an allegedly new and original trojan," ThreatFabric noted.
"Its capabilities put at risk not only explicitly targeted applications that are targeted by overlay attack, but any application installed on the infected device as ExobotCompact/Octo is able to read content of any app displayed on the screen and provide the actor with sufficient information to remotely interact with it and perform on-device fraud (ODF)."
The findings come close on the heels of the discovery of a distinct Android bankbot named GodFather — sharing overlaps with the Cereberus and Medusa banking trojans — that has been observed targeting banking users in Europe under the guise of the default Settings app to transfer funds and steal SMS messages, among others.
On top of that, a new analysis published by AppCensus found 11 apps with more than 46 million installations that were implanted with a third-party SDK named Coelib that made it possible to capture clipboard content, GPS data, email addresses, phone numbers, and even the user's modem router MAC address and network SSID.
SharkBot Banking Trojan Resurfaces On Google Play Store Hidden Behind 7 New Apps
9.4.22 Android Thehackernews
As many as seven malicious Android apps discovered on the Google Play Store masqueraded as antivirus solutions to deploy a banking trojan called SharkBot.
"SharkBot steals credentials and banking information," Check Point researchers Alex Shamshur and Raman Ladutska said in a report shared with The Hacker News. "This malware implements a geofencing feature and evasion techniques, which makes it stand out from the rest of malwares."
Particularly, the malware is designed to ignore users from China, India, Romania, Russia, Ukraine, and Belarus. The rogue apps are said to have been installed more than 15,000 times prior to their removal, with most of the victims located in Italy and the U.K.
The report complements previous findings from NCC Group, which found the bankbot posing as antivirus apps to carry out unauthorized transactions via Automatic Transfer Systems (ATS).
SharkBot takes advantage of Android's Accessibility Services permissions to present fake overlay windows on top of legitimate banking apps. Thus when unsuspecting users enter their usernames and passwords in the windows that mimic benign credential input forms, the captured data is sent to a malicious server.
One new notable feature of SharkBot is its ability to auto reply to notifications from Facebook Messenger and WhatsApp to distribute a phishing link to the antivirus app, thus propagating the malware in a worm-like fashion. A similar feature was incorporated in FluBot earlier this February.
"What's also noteworthy here is that the threat actors push messages to victims containing malicious links, which leads to widespread adoption," Alexander Chailytko, cyber security, research and innovation manager at Check Point Software, said.
"All in all, the use of push-messages by the threat actors requesting an answer from users is an unusual spreading technique."
The latest findings come as Google took steps to banish 11 apps from the Play Store on March 25 after they were caught incorporating an invasive SDK to discreetly harvest user data, including precise location information, email and phone numbers, nearby devices, and passwords.
Researchers Uncover New Android Spyware With C2 Server Linked to Turla Hackers
5.4.22 Android Thehackernews
An Android spyware application has been spotted masquerading as a "Process Manager" service to stealthily siphon sensitive information stored in the infected devices.
Interestingly, the app — that has the package name "com.remote.app" — establishes contact with a remote command-and-control server, 82.146.35[.]240, which has been previously identified as infrastructure belonging to the Russia-based hacking group known as Turla.
"When the application is run, a warning appears about the permissions granted to the application," Lab52 researchers said. "These include screen unlock attempts, lock the screen, set the device global proxy, set screen lock password expiration, set storage encryption and disable cameras."
Once the app is "activated," the malware removes its gear-shaped icon from the home screen and runs in the background, abusing its wide permissions to access the device's contacts and call logs, track its location, send and read messages, access external storage, snap pictures, and record audio.

The gathered information is captured in a JSON format and subsequently transmitted to the aforementioned remote server. Despite the overlap in the C2 server used, Lab52 said it doesn't have enough evidence to definitively attribute the malware to the Turla group.
Also unknown at this stage is the exact initial access vector employed for distributing the spyware and intended targets of the campaign.
That said, the rogue Android app also attempts to download a legitimate application called Roz Dhan (meaning "Daily Wealth" in Hindi) that has over 10 million installations and allows users to earn cash rewards for completing surveys and questionnaires.
"The application, [which] is on Google Play and is used to earn money, has a referral system that is abused by the malware," the researchers said. "The attacker installs it on the device and makes a profit."
New Android Malware Targeting Brazil's Itaú Unibanco Bank Customers
1.1.2022 Android Thehackernews
Researchers have discovered a new Android banking malware that targets Brazil's Itaú Unibanco with the help of lookalike Google Play Store pages to carry out fraudulent financial transactions on victim devices without their knowledge.
"This application has a similar icon and name that could trick users into thinking it is a legitimate app related to Itaú Unibanco," Cyble researchers said in a report published last week. "The [threat actor] has created a fake Google Play Store page and hosted the malware that targets Itaú Unibanco on it under the name 'sincronizador.apk.'"
The tactic of leveraging fake app store pages as a lure is not new. In March, Meta (previously Facebook) disclosed details of an attack campaign that used its platform as part of a broader operation to spy on Uyghur Muslims using rogue third-party websites that used replica domains for popular news portals and websites designed to resemble third-party Android app stores, where attackers put fake keyboard, prayer, and dictionary apps that might appeal to the targets.

In the latest instance observed by Cyble, the fake URL not only impersonates the official Android app marketplace, but also hosts the malware-laced Itaú Unibanco application, in addition to claiming that the app has had 1,895,897 downloads.
Users who install and launch the imposter app from the supposed Google Play Store page are subsequently prompted to enable accessibility services as well as other intrusive permissions that allow the malware to access notifications, retrieve window content, and perform tap and swipe gestures.
The goal of the trojan, per the researchers, is to perform fraudulent financial transactions on the legitimate Itaú Unibanco application by tampering with the user's input fields, joining a long list of banking malware that abuse the accessibility API. Google, for its part, has begun imposing new limitations to restrict the use of such permissions that allow apps to capture sensitive information from Android devices.
This is far from the first time the Sao Paulo-based financial services company has come under the radar of financially-motivated threat groups. Earlier this April, ESET revealed a new banking trojan dubbed Janeleiro that was observed striking corporate users in Brazil at least since 2019 across various sectors such as engineering, healthcare, retail, manufacturing, finance, transportation, and government.
"Threat Actors constantly adapt their methods to avoid detection and find new ways to target users through increasingly sophisticated techniques. Such malicious applications often masquerade as legitimate applications to trick users into installing them," the researchers said.
"Users should install applications only after verifying their authenticity and install them exclusively from the official Google Play Store and other trusted portals to avoid such attacks."