28.12.23 OS The Hacker News

The Operation Triangulation spyware attacks targeting Apple iOS devices leveraged never-before-seen exploits that made it possible to even bypass pivotal hardware-based security protections erected by the company.
OS 2024 2023 2022 2020 ANDROID 2022 2021 2020
Most Sophisticated iPhone Hack Ever Exploited Apple's Hidden Hardware Feature
28.12.23 OS The Hacker News
The Operation Triangulation spyware attacks targeting Apple iOS devices leveraged never-before-seen exploits that made it possible to even bypass pivotal hardware-based security protections erected by the company.
Russian cybersecurity firm Kaspersky, which discovered the campaign at the beginning of 2023 after becoming one of the targets, described it as the "most sophisticated attack chain" it has ever observed to date. The campaign is believed to have been active since 2019.
The exploitation activity involved the use of four zero-day flaws that were fashioned into a chain to obtain an unprecedented level of access and backdoor target devices running iOS versions up to iOS 16.2 with the ultimate goal of gathering sensitive information.
The starting point of the zero-click attack is an iMessage bearing a malicious attachment, which is automatically processed sans any user interaction to ultimately obtain elevated permissions and deploy a spyware module. Specifically, it involves the weaponization of the following vulnerabilities -
CVE-2023-41990 - A flaw in the FontParser component that could lead to arbitrary code execution when processing a specially crafted font file, which is sent via iMessage. (Addressed in iOS 15.7.8 and iOS 16.3)
CVE-2023-32434 - An integer overflow vulnerability in the Kernel that could be exploited by a malicious app to execute arbitrary code with kernel privileges. (Addressed in iOS 15.7.7, iOS 15.8, and iOS 16.5.1 )
CVE-2023-32435 - A memory corruption vulnerability in WebKit that could lead to arbitrary code execution when processing specially crafted web content. (Addressed in iOS 15.7.7 and iOS 16.5.1)
CVE-2023-38606 - An issue in the kernel that permits a malicious app to modify sensitive kernel state. (Addressed in iOS 16.6)
It's worth noting that patches for CVE-2023-41990 were released by Apple in January 2023, although details about the exploitation were only made public by the company on September 8, 2023, the same day it shipped iOS 16.6.1 to resolve two other flaws (CVE-2023-41061 and CVE-2023-41064) that were actively abused in connection with a Pegasus spyware campaign.
This also brings the tally of the number of actively exploited zero-days resolved by Apple since the start of the year to 20.
Of the four vulnerabilities, CVE-2023-38606 deserves a special mention as it facilitates a bypass of hardware-based security protection for sensitive regions of the kernel memory by leveraging memory-mapped I/O (MMIO) registers, a feature that was never known or documented until now.
The exploit, in particular, targets Apple A12-A16 Bionic SoCs, singling out unknown MMIO blocks of registers that belong to the GPU coprocessor. It's currently not known how the mysterious threat actors behind the operation learned about its existence. Also unclear is whether it was developed by Apple or it's a third-party component like ARM CoreSight.
To put it in another way, CVE-2023-38606 is the crucial link in the exploit chain that's closely intertwined with the success of the Operation Triangulation campaign, given the fact that it permits the threat actor to gain total control of the compromised system.
"Our guess is that this unknown hardware feature was most likely intended to be used for debugging or testing purposes by Apple engineers or the factory, or that it was included by mistake," security researcher Boris Larin said. "Because this feature is not used by the firmware, we have no idea how attackers would know how to use it."
"Hardware security very often relies on 'security through obscurity,' and it is much more difficult to reverse-engineer than software, but this is a flawed approach, because sooner or later, all secrets are revealed. Systems that rely on "security through obscurity" can never be truly secure."
The development comes as the Washington Post reported that Apple's warnings in late October about how Indian journalists and opposition politicians may have been targeted by state-sponsored spyware attacks prompted the government to question the veracity of the claims and describe them as a case of "algorithmic malfunction" within the tech giant's systems.
In addition, senior administration officials demanded that the company soften the political impact of the warnings and pressed the company to provide alternative explanations as to why the warnings may have been sent. So far, India has neither confirmed nor denied using spyware such as those by NSO Group's Pegasus.
Citing people with knowledge of the matter, the Washington Post noted that "Indian officials asked Apple to withdraw the warnings and say it had made a mistake," and that "Apple India's corporate communications executives began privately asking Indian technology journalists to emphasize in their stories that Apple's warnings could be false alarms" to shift the spotlight away from the government.
New Sneaky Xamalicious Android Malware Hits Over 327,000 Devices
27.12.23 OS The Hacker News
A new Android backdoor has been discovered with potent capabilities to carry out a range of malicious actions on infected devices.
Dubbed Xamalicious by the McAfee Mobile Research Team, the malware is so named for the fact that it's developed using an open-source mobile app framework called Xamarin and abuses the operating system's accessibility permissions to fulfill its objectives.
It's also capable of gathering metadata about the compromised device and contacting a command-and-control (C2) server to fetch a second-stage payload, but only after determining if it fits the bill.
The second stage is "dynamically injected as an assembly DLL at runtime level to take full control of the device and potentially perform fraudulent actions such as clicking on ads, installing apps, among other actions financially motivated without user consent," security researcher Fernando Ruiz said.
The cybersecurity firm said it identified 25 apps that come with this active threat, some of which were distributed on the official Google Play Store since mid-2020. The apps are estimated to have been installed at least 327,000 times.
A majority of the infections have been reported in Brazil, Argentina, the U.K., Australia, the U.S., Mexico, and other parts of Europe and the Americas. Some of the apps are listed below -
Essential Horoscope for Android (com.anomenforyou.essentialhoroscope)
3D Skin Editor for PE Minecraft (com.littleray.skineditorforpeminecraft)
Logo Maker Pro (com.vyblystudio.dotslinkpuzzles)
Auto Click Repeater (com.autoclickrepeater.free)
Count Easy Calorie Calculator (com.lakhinstudio.counteasycaloriecalculator)
Sound Volume Extender (com.muranogames.easyworkoutsathome)
LetterLink (com.regaliusgames.llinkgame)
NUMEROLOGY: PERSONAL HOROSCOPE &NUMBER PREDICTIONS (com.Ushak.NPHOROSCOPENUMBER)
Step Keeper: Easy Pedometer (com.browgames.stepkeepereasymeter)
Track Your Sleep (com.shvetsStudio.trackYourSleep)
Sound Volume Booster (com.devapps.soundvolumebooster)
Astrological Navigator: Daily Horoscope & Tarot (com.Osinko.HoroscopeTaro)
Universal Calculator (com.Potap64.universalcalculator)
Xamalicious, which typically masquerades as health, games, horoscope, and productivity apps, is the latest in a long list of malware families that abuse Android's accessibility services, requesting users' access to it upon installation to carry out its tasks.
"To evade analysis and detection, malware authors encrypted all communication and data transmitted between the C2 and the infected device, not only protected by HTTPS, it's encrypted as a JSON Web Encryption (JWE) token using RSA-OAEP with a 128CBC-HS256 algorithm," Ruiz noted.
Even more troublingly, the first-stage dropper contains functions to self-update the main Android package (APK) file, meaning it can be weaponized to act as spyware or banking trojan without any user interaction.
McAfee said it identified a link between Xamalicious and an ad-fraud app named Cash Magnet, which facilitates app download and automated clicker activity to illicitly earn revenue by clicking on ads.
"Android applications written in non-java code with frameworks such as Flutter, react native and Xamarin can provide an additional layer of obfuscation to malware authors that intentionally pick these tools to avoid detection and try to stay under the radar of security vendors and keep their presence on apps markets," Ruiz said.

Android Phishing Campaign Targets India With Banker Malware#
The disclosure comes as the cybersecurity company detailed a phishing campaign that employs social messaging apps like WhatsApp to distribute rogue APK files that impersonate legitimate banks such as the State Bank of India (SBI) and prompt the user to install them to complete a mandatory Know Your Customer (KYC) procedure.
Once installed, the app asks the user to grant it SMS-related permissions and redirects to a fake page that only captures the victim's credentials but also their account, credit/debit card, and national identity information.
The harvested data, alongside the intercepted SMS messages, are forwarded to an actor-controlled server, thereby allowing the adversary to complete unauthorized transactions.
It's worth noting that Microsoft last month warned of a similar campaign that utilizes WhatsApp and Telegram as distribution vectors to target Indian online banking users.
"India underscores the acute threat posed by this banking malware within the country's digital landscape, with a few hits found elsewhere in the world, possibly from Indian SBI users living in other countries," researchers Neil Tyagi and Ruiz said.
Chameleon Android Banking Trojan Variant Bypasses Biometric Authentication
23.12.23 OS The Hacker News
Cybersecurity researchers have discovered an updated version of an Android banking malware called Chameleon that has expanded its targeting to include users in the U.K. and Italy.
"Representing a restructured and enhanced iteration of its predecessor, this evolved Chameleon variant excels in executing Device Takeover (DTO) using the accessibility service, all while expanding its targeted region," Dutch mobile security firm ThreatFabric said in a report shared with The Hacker News.
Chameleon was previously documented by Cyble in April 2023, noting that it had been used to single out users in Australia and Poland since at least January. Like other banking malware, it's known to abuse its permissions to Android's accessibility service to harvest sensitive data and conduct overlay attacks.
The rogue apps containing the earlier version were hosted on phishing pages and found to impersonate genuine institutions in the countries, such as the Australian Taxation Office (ATO) and a cryptocurrency trading platform called CoinSpot, in an attempt to lend them a veil of credibility.
The latest findings from ThreatFabric show that the banking trojan is now being delivered via Zombinder, an off-the-shelf dropper-as-a-service (DaaS) that's sold to other threat actors and which can be used to "bind" malicious payloads to legitimate apps.
Although the offering was suspected to have been shut down earlier this year, it resurfaced last month, advertising capabilities to bypass the 'Restricted Settings' feature in Android to install malware on devices and obtain access to the accessibility service.
Both the malicious artifacts distributing Chameleon masquerade as the Google Chrome web browser. Their package names are listed below -
Z72645c414ce232f45.Z35aad4dde2ff09b48
com.busy.lady
A notable feature of the enhanced variant is its ability to conduct Device Takeover (DTO) fraud, which leverages the accessibility service to perform unauthorized actions on the victim's behalf.

But in order to trick users into enabling the setting, the malware checks the Android version on the installed device and if it's found to be Android 13 or later, prompts the user to turn it on.
"Upon receiving confirmation of Android 13 Restricted Settings being present on the infected device, the banking trojan initiates the loading of an HTML page," ThreatFabric explained. "The page is guiding users through a manual step-by-step process to enable the accessibility service on Android 13 and higher."
Another new addition is the use of Android APIs to disrupt the biometric operations of the targeted device by covertly transitioning the lock screen authentication mechanism to a PIN so as to allow the malware to "unlock the device at will" using the accessibility service.
"The emergence of the new Chameleon banking trojan is another example of the sophisticated and adaptive threat landscape within the Android ecosystem," the company said. "Evolving from its earlier iteration, this variant demonstrates increased resilience and advanced new features."
The development comes as Zimperium revealed that 29 malware families – 10 of them new – targeted 1,800 banking applications across 61 countries over the past year. The new active families include Nexus, Godfather, PixPirate, Saderat, Hook, PixBankBot, Xenomorph v3, Vultur, BrasDex, and GoatRAT.
The U.S. top countries targeted comprise the U.S. (109 bank apps), the U.K. (48), Italy (44), Australia (34), Turkey (32), France (30), Spain (29), Portugal (27), Germany (23), Canada (17), and Brazil (11). The most targeted financial services apps are PhonePe (India), WeChat, Bank of America, Well Fargo, (U.S.), Binance (Malta), Barclays (U.K.), QNB Finansbank (Turkey), and CaixaBank (Spain).
"Traditional banking applications remain the prime target, with a staggering 1103 apps – accounting for 61% of the targets – while the emerging FinTech and Trading apps are now in the crosshairs, making up the remaining 39%," the company said.
Google Using Clang Sanitizers to Protect Android Against Cellular Baseband Vulnerabilities
13.12.23 OS The Hacker News
Google is highlighting the role played by Clang sanitizers in hardening the security of the cellular baseband in the Android operating system and preventing specific kinds of vulnerabilities.
This comprises Integer Overflow Sanitizer (IntSan) and BoundsSanitizer (BoundSan), both of which are part of UndefinedBehaviorSanitizer (UBSan), a tool designed to catch various kinds of undefined behavior during program execution.
"They are architecture agnostic, suitable for bare-metal deployment, and should be enabled in existing C/C++ code bases to mitigate unknown vulnerabilities," Ivan Lozano and Roger Piqueras Jover said in a Tuesday post.
The development comes months after the tech giant said it's working with ecosystem partners to increase the security of firmware that interacts with Android, thereby making it difficult for threat actors to achieve remote code execution within the Wi-Fi SoC or the cellular baseband.
IntSan and BoundSan are two of the compiler-based sanitizers that Google has enabled as an exploit mitigation measure to detect arithmetic overflows and perform bounds checks around array accesses, respectively.
Google acknowledged that while both BoundSan and IntSan incur a substantial performance overhead, it has enabled it in security-critical attack surfaces ahead of a full-fledged rollout over the entire codebase. This covers -
Functions parsing messages delivered over the air in 2G, 3G, 4G, and 5G
Libraries encoding/decoding complex formats (e.g., ASN.1, XML, DNS, etc.)
IMS, TCP, and IP stacks, and
Messaging functions (SMS, MMS)
"In the particular case of 2G, the best strategy is to disable the stack altogether by supporting Android's '2G toggle,'" the researchers said. "However, 2G is still a necessary mobile access technology in certain parts of the world and some users might need to have this legacy protocol enabled."
It's worth noting that the "tangible" benefits arising out of deploying sanitizers notwithstanding, they do not address other classes of vulnerabilities, such as those related to memory safety, necessitating a transition of the codebase to a memory-safe language like Rust.
In early October 2023, Google announced that it had rewritten the Android Virtualization Framework's (AVF) protected VM (pVM) firmware in Rust to provide a memory-safe foundation for the pVM root of trust.
"As the high-level operating system becomes a more difficult target for attackers to successfully exploit, we expect that lower level components such as the baseband will attract more attention," the researchers concluded.
"By using modern toolchains and deploying exploit mitigation technologies, the bar for attacking the baseband can be raised as well."
Apple Releases Security Updates to Patch Critical iOS and macOS Security Flaws
12.12.23 OS The Hacker News
Apple on Monday released security patches for iOS, iPadOS, macOS, tvOS, watchOS, and Safari web browser to address multiple security flaws, in addition to backporting fixes for two recently disclosed zero-days to older devices.
This includes updates for 12 security vulnerabilities in iOS and iPadOS spanning AVEVideoEncoder, ExtensionKit, Find My, ImageIO, Kernel, Safari Private Browsing, and WebKit. macOS Sonoma 14.2, for its part, resolves 39 shortcomings, counting six bugs impacting the ncurses library.
Notable among the flaws is CVE-2023-45866, a critical security issue in Bluetooth that could allow an attacker in a privileged network position to inject keystrokes by spoofing a keyboard.
The vulnerability was disclosed by SkySafe security researcher Marc Newlin last week. It has been remediated in iOS 17.2, iPadOS 17.2, and macOS Sonoma 14.2 with improved checks, the iPhone maker said.
Also released by Apple is Safari 17.2, containing fixes for two WebKit flaws – CVE-2023-42890 and CVE-2023-42883 – that could lead to arbitrary code execution and a denial-of-service (DoS) condition. The update is available for Macs running macOS Monterey and macOS Ventura.
iOS 17.2 and iPadOS 17.2, besides addressing a Siri bug that could allow an adversary with physical access to obtain sensitive data, packs in a security upgrade in the form of Contact Key Verification, which ensures privacy of iMessage conversations by enabling users to verify the contacts they are communicating with.
"iMessage Contact Key Verification advances the state of the art of Key Transparency deployments by having user devices themselves verify consistency proofs and ensure consistency of the KT system across all user devices for an account," Apple noted in a technical explainer in October 2023.
"These improvements protect against key directory compromise as well as compromise of the transparency service itself, and can detect split views presented by both services."
Coinciding with the updates, Apple has also released iOS 16.7.3 and iPadOS 16.7.3 to close out as many as eight security issues, two of which relate to WebKit (CVE-2023-42916 and CVE-2023-42917) and were disclosed by Redmond as having been actively exploited in the wild earlier this month.
Both the vulnerabilities have been patched in tvOS 17.2 and watchOS 10.2 as well. No additional details are available as yet regarding the nature of the exploitation and the threat actors that may be using them.
SpyNote: Beware of This Android Trojan that Records Audio and Phone Calls
16.10.23 OS The Hacker News
The Android banking trojan known as SpyNote has been dissected to reveal its diverse information-gathering features.
Typically spread via SMS phishing campaigns, attack chains involving the spyware trick potential victims into installing the app by clicking on the embedded link, according to F-Secure.
Besides requesting invasive permissions to access call logs, camera, SMS messages, and external storage, SpyNote is known for hiding its presence from the Android home screen and the Recents screen in a bid to make it difficult to avoid detection.
"The SpyNote malware app can be launched via an external trigger," F-Secure researcher Amit Tambe said in an analysis published last week. "Upon receiving the intent, the malware app launches the main activity."
But most importantly, it seeks accessibility permissions, subsequently leveraging it to grant itself additional permissions to record audio and phone calls, log keystrokes, as well as capture screenshots of the phone via the MediaProjection API.
A closer examination of the malware has revealed the presence of what are called diehard services that aim to resist attempts, either made by the victims or by the operating system, at terminating it.

This is accomplished by registering a broadcast receiver that's designed to restart it automatically whenever it is about to be shut down. What's more, users who attempt to uninstall the malicious app by navigating to Settings are prevented from doing so by closing the menu screen via its abuse of the accessibility APIs.
"The SpyNote sample is spyware that logs and steals a variety of information, including key strokes, call logs, information on installed applications, and so on," Tambe said. "It stays hidden on the victim's device making it challenging to notice. It also makes uninstallation extremely tricky."
"The victim is eventually left only with the option of performing a factory reset, losing all data, thereby, in the process."
The disclosure comes as the Finnish cybersecurity firm detailed a bogus Android app that masquerades as an operating system update to entice targets into granting it accessibility services permissions and exfiltrate SMS and bank data.
New 5G Modem Flaws Affect iOS Devices and Android Models from Major Brands
9.12.23 OS The Hacker News
A collection of security flaws in the firmware implementation of 5G mobile network modems from major chipset vendors such as MediaTek and Qualcomm impact USB and IoT modems as well as hundreds of smartphone models running Android and iOS.
Of the 14 flaws – collectively called 5Ghoul (a combination of "5G" and "Ghoul") – 10 affect 5G modems from the two companies, out of which three have been classified as high-severity vulnerabilities.
"5Ghoul vulnerabilities may be exploited to continuously launch attacks to drop the connections, freeze the connection that involve manual reboot or downgrade the 5G connectivity to 4G," the researchers said in a study published today.
As many as 714 smartphones from 24 brands are impacted, including those from Vivo, Xiaomi, OPPO, Samsung, Honor, Motorola, realme, OnePlus, Huawei, ZTE, Asus, Sony, Meizu, Nokia, Apple, and Google.
The vulnerabilities were disclosed by a team of researchers from the ASSET (Automated Systems SEcuriTy) Research Group at the Singapore University of Technology and Design (SUTD), who also previously uncovered BrakTooth in September 2021 and SweynTooth in February 2020.
The attacks, in a nutshell, attempt to deceive a smartphone or a 5G-enabled device to connect a rogue base station (gNB), resulting in unintended consequences. "The attacker does not need to be aware of any secret information of the target UE e.g., UE's SIM card details, to complete the NAS network registration," the researchers explained. "The attacker only needs to impersonate the legitimate gNB using the known Cell Tower connection parameters." A threat actor can accomplish this by using apps like Cellular-Pro to determine the Relative Signal Strength Indicator (RSSI) readings and trick the user equipment to connect to the adversarial station (i.e., a software-defined radio) as well as an inexpensive mini PC. Notable among the 14 flaws is CVE-2023-33042, which can permit an attacker within radio range to trigger a 5G connectivity downgrade or a denial-of-service (DoS) within Qualcomm's X55/X60 modem firmware by sending malformed Radio Resource Control (RRC) frame to the target 5G device from a nearby malicious gNB. Cybersecurity Patches have been released by both MediaTek and Qualcomm for 12 of the 14 flaws. Details of the two other vulnerabilities have been withheld due to confidentiality reasons and are expected to be disclosed in the future. "Finding issues in the implementation of the 5G modem vendor heavily impacts product vendors downstream," the researchers said, adding that "it can often take six or more months for 5G security patches to finally reach the end-user via an OTA update." "This is because the software dependency of product vendors on the Modem / Chipset Vendor adds complexity and hence delays to the process of producing and distributing patches to the end-user."
Successful exploitation of the other DoS vulnerabilities could require a manual reboot of the device to restore 5G connectivity.
Mac Users Beware: New Trojan-Proxy Malware Spreading via Pirated Software
9.12.23 OS The Hacker News
Unauthorized websites distributing trojanized versions of cracked software have been found to infect Apple macOS users with a new Trojan-Proxy malware.
"Attackers can use this type of malware to gain money by building a proxy server network or to perform criminal acts on behalf of the victim: to launch attacks on websites, companies and individuals, buy guns, drugs, and other illicit goods," Kaspersky security researcher Sergey Puzan said.
The Russian cybersecurity firm said it found evidence indicating that the malware is a cross-platform threat, owing to artifacts unearthed for Windows and Android that piggybacked on pirated tools.
The macOS variants propagate under the guise of legitimate multimedia, image editing, data recovery, and productivity tools. This suggests that users searching for pirated software are the targets of the campaign.
Unlike their genuine, unaltered counterparts, which are offered as disk image (.DMG) files, the rogue versions are delivered in the form of .PKG installers, which come equipped with a post-install script that activates the malicious behavior post installation.
"As an installer often requests administrator permissions to function, the script run by the installer process inherits those," Puzan noted.
The end goal of the campaign is to launch the Trojan-Proxy, which masks itself as the WindowServer process on macOS to evade detection. WindowServer is a core system process responsible for window management and rendering the graphical user interface (GUI) of applications.
Upon start, it attempts to obtain the IP address of the command-and-control (C2) server to connect to via DNS-over-HTTPS (DoH) by encrypting the DNS requests and responses using the HTTPS protocol.
Trojan-Proxy subsequently establishes contact with the C2 server and awaits further instructions, including processing incoming messages to parse the IP address to connect to, the protocol to use, and the message to send, signaling that its ability to act as a proxy via TCP or UDP to redirect traffic through the infected host.
Kaspersky said it found samples of the malware uploaded to the VirusTotal scanning engine as early as April 28, 2023. To mitigate such threats, users are recommended to avoid downloading software from untrusted sources.
Warning for iPhone Users: Experts Warn of Sneaky Fake Lockdown Mode Attack
6.12.23 OS The Hacker News
A new "post-exploitation tampering technique" can be abused by malicious actors to visually deceive a target into believing that their Apple iPhone is running in Lockdown Mode when it's actually not and carry out covert attacks.
The novel method, detailed by Jamf Threat Labs in a report shared with The Hacker News, "shows that if a hacker has already infiltrated your device, they can cause Lockdown Mode to be 'bypassed' when you trigger its activation."
In other words, the goal is to implement Fake Lockdown Mode on a device that's compromised by an attacker through other means, such as unpatched security flaws that can trigger execution of arbitrary code.
Lockdown Mode, introduced by Apple last year with iOS 16, is an enhanced security measure that aims to safeguard high-risk individuals from sophisticated digital threats such as mercenary spyware by minimizing the attack surface.
What it doesn't do is prevent the execution of malicious payloads on a compromised device, thereby allowing a trojan deployed on it to manipulate Lockdown Mode and give users an illusion of security.
"In the case of an infected phone, there are no safeguards in place to stop the malware from running in the background, whether the user activates Lockdown Mode or not," security researchers Hu Ke and Nir Avraham said.

The fake Lockdown Mode is accomplished by hooking functions – e.g., setLockdownModeGloballyEnabled, lockdownModeEnabled, and isLockdownModeEnabledForSafari – that are triggered upon activating the setting so as to create a file called "/fakelockdownmode_on" and initiate a userspace reboot, which terminates all processes and restarts the system without touching the kernel.
This also means that a piece of malware implanted on the device sans any persistence mechanism will continue to exist even after a reboot of this kind and surreptitiously spy on its users.
What's more, an adversary could alter the Lockdown Mode on the Safari web browser to make it possible to view PDF files, which are otherwise blocked when the setting is turned on.
"Since iOS 17, Apple has elevated Lockdown Mode to kernel level," the researchers said. "This strategic move is a great step in enhancing security, as changes made by Lockdown Mode in the kernel typically cannot be undone without undergoing a system reboot, thanks to existing security mitigations."
The disclosure from Jamf arrives nearly four months after it demonstrated another novel method on iOS 16 that could be abused to fly under the radar and maintain access to an Apple device by tricking the victim into thinking their device's Airplane Mode is enabled.
New FjordPhantom Android Malware Targets Banking Apps in Southeast Asia
1.12.23 OS The Hacker News
Cybersecurity researchers have disclosed a new sophisticated Android malware called FjordPhantom that has been observed targeting users in Southeast Asian countries like Indonesia, Thailand, and Vietnam since early September 2023.
"Spreading primarily through messaging services, it combines app-based malware with social engineering to defraud banking customers," Oslo-based mobile app security firm Promon said in an analysis published Thursday.
Propagated mainly via email, SMS, and messaging apps, attack chains trick recipients into downloading a purported banking app that comes fitted with legitimate features but also incorporates rogue components.
Victims are then subjected to a social engineering technique akin to telephone-oriented attack delivery (TOAD), which involves calling a bogus call center to receive step-by-step instructions for running the app.
A key characteristic of the malware that sets it apart from other banking trojans of its kind is the use of virtualization to run malicious code in a container and fly under the radar.
The sneaky method, Promon said, breaks Android's sandbox protections as it allows different apps to be run on the same sandbox, enabling the malware to access sensitive data without requiring root access.
"Virtualization solutions like the one used by the malware can also be used to inject code into an application because the virtualization solution first loads its own code (and everything else found in its app) into a new process and then loads the code of the hosted application," security researcher Benjamin Adolphi said.
In the case of FjordPhantom, the host app downloaded includes a malicious module and the virtualization element that's then used to install and launch the embedded app of the targeted bank in a virtual container.
In other words, the bogus app is engineered to load the bank's legitimate app in a virtual container while also employing a hooking framework within the environment to alter the behavior of key APIs to grab sensitive information from the application's screen programmatically and close dialog boxes used to warn malicious activity on users' devices.
"FjordPhantom itself is written in a modular way to attack different banking apps," Adolphi said. "Depending on which banking app is embedded into the malware, it will perform various attacks on these apps."
Zero-Day Alert: Apple Rolls Out iOS, macOS, and Safari Patches for 2 Actively Exploited Flaws
1.12.23 OS The Hacker News
Apple has released software updates for iOS, iPadOS, macOS, and Safari web browser to address two security flaws that it said have come under active exploitation in the wild on older versions of its software.
The vulnerabilities, both of which reside in the WebKit web browser engine, are described below -
CVE-2023-42916 - An out-of-bounds read issue that could be exploited to leak sensitive information when processing web content.
CVE-2023-42917 - A memory corruption bug that could result in arbitrary code execution when processing web content.
Apple said it's aware of reports exploiting the shortcomings "against versions of iOS before iOS 16.7.1," which was released on October 10, 2023. Clément Lecigne of Google's Threat Analysis Group (TAG) has been credited with discovering and reporting the twin flaws.
The iPhone maker did not provide additional information regarding ongoing exploitation, but previously disclosed zero-days in iOS have been used to deliver mercenary spyware targeting high-risk individuals, such as activists, dissidents, journalists, and politicians.
It's worth pointing out here that every third-party web browser that's available for iOS and iPadOS, including Google Chrome, Mozilla Firefox, and Microsoft Edge, and others, are powered by the WebKit rendering engine due to restrictions imposed by Apple, making it a lucrative and broad attack surface.
The updates are available for the following devices and operating systems -
iOS 17.1.2 and iPadOS 17.1.2 - iPhone XS and later, iPad Pro 12.9-inch 2nd generation and later, iPad Pro 10.5-inch, iPad Pro 11-inch 1st generation and later, iPad Air 3rd generation and later, iPad 6th generation and later, and iPad mini 5th generation and later
macOS Sonoma 14.1.2 - Macs running macOS Sonoma
Safari 17.1.2 - Macs running macOS Monterey and macOS Ventura
With the latest security fixes, Apple has remediated as many as 19 actively exploited zero-days since the start of 2023. It also comes days after Google shipped fixes for a high-severity flaw in Chrome (CVE-2023-6345) that has also come under real-world attacks, making it the seventh zero-day to be patched by the company this year.
200+ Malicious Android Apps Targeting Iranian Banks: Experts Warn
29.11.23 OS The Hacker News
An Android malware campaign targeting Iranian banks has expanded its capabilities and incorporated additional evasion tactics to fly under the radar.
That's according to a new report from Zimperium, which discovered more than 200 malicious apps associated with the malicious operation, with the threat actor also observed carrying out phishing attacks against the targeted financial institutions.
The campaign first came to light in late July 2023 when Sophos detailed a cluster of 40 credential-harvesting apps targeting customers of Bank Mellat, Bank Saderat, Resalat Bank, and Central Bank of Iran.
The primary goal of the bogus apps is to trick victims into granting them extensive permissions as well as harvest banking login credentials and credit card details by abusing Android's accessibility services.
"The corresponding legitimate versions of the malicious apps are available at Cafe Bazaar, an Iranian Android marketplace, and have millions of downloads," Sophos researcher Pankaj Kohli said at the time.
"The malicious imitations, on the other hand, were available to download from a large number of relatively new domains, some of which the threat actors also employed as C2 servers."
Interestingly, some of these domains have also been observed to serve HTML phishing pages designed to steal credentials from mobile users.
The latest findings from Zimperium illustrate continued evolution of the threat, not only in terms of a broader set of targeted banks and cryptocurrency wallet apps, but also incorporating previously undocumented features that make it more potent.
This includes the use of the accessibility service to grant it additional permissions to intercept SMS messages, prevent uninstallation, and click on user interface elements.
Some variants of the malware have also been found to access a README file within GitHub repositories to extract a Base64-encoded version of the command-and-control (C2) server and phishing URLs.
"This allows attackers to quickly respond to phishing sites being taken down by updating the GitHub repository, ensuring that malicious apps are always getting the latest active phishing site," Zimperium researchers Aazim Yaswant and Vishnu Pratapagiri said.
Another noteworthy tactic is the use of intermediate C2 servers to host text files that contain the encoded strings pointing to the phishing sites.
While the campaign has so far trained its eyes on Android, there is evidence that Apple's iOS operating system is also a potential target based on the fact that the phishing sites verify if the page is opened by an iOS device, and if so, direct the victim to a website mimicking the iOS version of the Bank Saderat Iran app.
It's currently not clear if the iOS campaign is under development stages, or if the apps are distributed through an, as of yet, unidentified source.
The phishing campaigns are no less sophisticated, impersonating the actual websites to exfiltrate credentials, account numbers, device models, and IP addresses to two actor-controlled Telegram channels.
"It is evident that modern malware is becoming more sophisticated, and targets are expanding, so runtime visibility and protection are crucial for mobile applications," the researchers said.
The development comes a little over a month after Fingerprint demonstrated a method by which malicious Android apps can stealthily access and copy clipboard data by leveraging the SYSTEM_ALERT_WINDOW permission to obscure the toast notification that's displayed when a particular app is reading clipboard data.
"It's possible to overdraw a toast either with a different toast or with any other view, completely hiding the original toast can prevent the user from being notified of clipboard actions," Fingerprint said. "Any application with the SYSTEM_ALERT_WINDOW permission can read clipboard data without notifying the user."
N. Korean Hackers 'Mixing' macOS Malware Tactics to Evade Detection
28.11.23 OS The Hacker News
The North Korean threat actors behind macOS malware strains such as RustBucket and KANDYKORN have been observed "mixing and matching" different elements of the two disparate attack chains, leveraging RustBucket droppers to deliver KANDYKORN.
The findings come from cybersecurity firm SentinelOne, which also tied a third macOS-specific malware called ObjCShellz to the RustBucket campaign.
RustBucket refers to an activity cluster linked to the Lazarus Group in which a backdoored version of a PDF reader app, dubbed SwiftLoader, is used as a conduit to load a next-stage malware written in Rust upon viewing a specially crafted lure document.
The KANDYKORN campaign, on the other hand, refers to a malicious cyber operation in which blockchain engineers of an unnamed crypto exchange platform were targeted via Discord to initiate a sophisticated multi-stage attack sequence that led to the deployment of the eponymous full-featured memory resident remote access trojan.
The third piece of the attack puzzle is ObjCShellz, which Jamf Threat Labs revealed earlier this month as a later-stage payload that acts as a remote shell that executes shell commands sent from the attacker server.
Further analysis of these campaigns by SentinelOne has now shown that the Lazarus Group is utilizing SwiftLoader to distribute KANDYKORN, corroborating a recent report from Google-owned Mandiant about how different hacker groups from North Korea are increasingly borrowing each other's tactics and tools.
"The DPRK's cyber landscape has evolved to a streamlined organization with shared tooling and targeting efforts," Mandiant noted. "This flexible approach to tasking makes it difficult for defenders to track, attribute, and thwart malicious activities, while enabling this now collaborative adversary to move stealthily with greater speed and adaptability."
This includes the use of new variants of the SwiftLoader stager that purports to be an executable named EdoneViewer but, in reality, contacts an actor-controlled domain to likely retrieve the KANDYKORN RAT based on overlaps in infrastructure and the tactics employed.
The disclosure comes as the AhnLab Security Emergency Response Center (ASEC) implicated Andariel – a subgroup within Lazarus – to cyber attacks exploiting a security flaw in Apache ActiveMQ (CVE-2023-46604, CVSS score: 10.0) to install NukeSped and TigerRAT backdoors.
ClearFake Campaign Expands to Deliver Atomic Stealer on Macs Systems
22.11.23 OS The Hacker News
The macOS information stealer known as Atomic is now being delivered to target via a bogus web browser update chain tracked as ClearFake.
"This may very well be the first time we see one of the main social engineering campaigns, previously reserved for Windows, branch out not only in terms of geolocation but also operating system," Malwarebytes' Jérôme Segura said in a Tuesday analysis.
Atomic Stealer (aka AMOS), first documented in April 2023, is a commercial stealer malware family that's sold on a subscription basis for $1,000 per month. It comes with capabilities to siphon data from web browsers and cryptocurrency wallets.
Then in September 2023, Malwarebytes detailed an Atomic Stealer campaign that takes advantage of malicious Google ads, tricking macOS users searching for a financial charting platform known as TradingView into downloading the malware.
ClearFake, on the other hand, is a nascent malware distribution operation that employs compromised WordPress sites to serve fraudulent web browser update notices in hopes of deploying stealers and other malware.
It's the latest addition to a larger pool of threat actors such as TA569 (aka SocGholish), RogueRaticate (FakeSG), ZPHP (SmartApeSG), and EtherHiding that are known to use themes related to fake browser updates for this purpose.
As of November 2023, the ClearFake campaign has been expanded to target macOS systems with a near-identical infection chain, leveraging hacked websites to deliver Atomic Stealer in the form of a DMG file.
The development is a sign that stealer malware continues to rely on fake or poisoned installer files for legitimate software via malicious advertisements, search engine redirects to malicious websites, drive-by downloads, phishing, and SEO poisoning for propagation.
"The popularity of stealers such as AMOS makes it quite easy to adapt the payload to different victims, with minor adjustments," Segura said.
Lumma Stealer Claims to Find a Way to Extract Persistent Google Cookies#
The disclosure also follows updates to the LummaC2 stealer that utilizes a novel trigonometry-based anti-sandbox technique that forces the malware to wait until "human" behavior is detected in the infected machine.
The operators of the malware have also been promoting a new feature that they claim can be used to gather Google Account cookies from compromised computers that will not expire or get revoked even if the owner changes the password.
"This will result in a major shift in the cybercrime world, enabling hackers to infiltrate even more accounts and perform significant attacks," Alon Gal, co-founder and CTO at Hudson Rock, said in a set of posts on LinkedIn.
"The bottom line is that these cookies seem more persistent and could lead to an influx of Google services used by people being hacked, and if the claim that a password change doesn't invalidate the session is true, we're looking at much bigger problems."
Malicious Apps Disguised as Banks and Government Agencies Targeting Indian Android Users
21.11.23 OS The Hacker News
Android smartphone users in India are the target of a new malware campaign that employs social engineering lures to install fraudulent apps that are capable of harvesting sensitive data.
"Using social media platforms like WhatsApp and Telegram, attackers are sending messages designed to lure users into installing a malicious app on their mobile device by impersonating legitimate organizations, such as banks, government services, and utilities," Microsoft threat intelligence researchers Abhishek Pustakala, Harshita Tripathi, and Shivang Desai said in a Monday analysis.
The ultimate goal of the operation is to capture banking details, payment card information, account credentials, and other personal data.
The attack chains involve sharing malicious APK files via social media messages sent on WhatsApp and Telegram by falsely presenting them as banking apps and inducing a sense of urgency by claiming that the targets' bank accounts will be blocked unless they update their permanent account number (PAN) issued by the Indian Income Tax Department through the bogus app.
Upon installation, the app urges the victim to enter their bank account information, debit card PIN, PAN card numbers, and online banking credentials, which are subsequently transmitted to an actor-controlled command-and-control (C2) server and a hard-coded phone number.
"Once all the requested details are submitted, a suspicious note appears stating that the details are being verified to update KYC," the researchers said.
"The user is instructed to wait 30 minutes and not to delete or uninstall the app. Additionally, the app has the functionality to hide its icon, causing it to disappear from the user's device home screen while still running in the background."
Another notable aspect of the malware is that it requests the user to grant it permission to read and send SMS messages, thereby enabling it to intercept one-time passwords (OTPs) and send the victims' messages to the threat actor's phone number via SMS.
Variants of the banking trojan discovered by Microsoft have also been found to steal credit card details along with personally identifiable information (PII) and incoming SMS messages, exposing unsuspecting users to financial fraud.
However, it's worth noting that for these attacks to be successful, users will have to enable the option to install apps from unknown sources outside of the Google Play Store.
"Mobile banking trojan infections can pose significant risks to users' personal information, privacy, device integrity, and financial security," the researchers said. "These threats can often disguise themselves as legitimate apps and deploy social engineering tactics to achieve their goals and steal users' sensitive data and financial assets."
The development comes as the Android ecosystem has also come under attack from the SpyNote trojan, which has targeted Roblox users under the guise of a mod to siphon sensitive information.
In another instance, fake adult websites are being used as lures to entice users into downloading an Android malware called Enchant that specifically focuses on pilfering data from cryptocurrency wallets.
"Enchant malware uses the accessibility service feature to target specific cryptocurrency wallets, including imToken, OKX, Bitpie Wallet, and TokenPocket wallet," Cyble said in a recent report.
"Its primary objective is to steal critical information such as wallet addresses, mnemonic phrases, wallet asset details, wallet passwords, and private keys from compromised devices."
Last month, Doctor Web uncovered several malicious apps on the Google Play Store that displayed intrusive ads (HiddenAds), subscribed users to premium services without their knowledge or consent (Joker), and promoted investment scams by masquerading as trading software (FakeApp).
The onslaught of Android malware has prompted Google to announce new security features such as real-time code-level scanning for newly encountered apps. It also launched restricted settings with Android 13 that prohibits apps from obtaining access to critical device settings (e.g., accessibility) unless it's explicitly enabled by the user.
It's not just Google. Samsung, in late October 2023, unveiled a new Auto Blocker option that prevents app installations from sources other than Google Play Store and Galaxy Store, and blocks harmful commands and software installations through the USB port.
To avoid downloading malicious software from Google Play and other trusted sources, users are advised to check the legitimacy of the app developers, scrutinize reviews, and vet the permissions requested by the apps.
Microsoft Warns of Fake Skills Assessment Portals Targeting IT Job Seekers
12.11.23 OS The Hacker News
A sub-cluster within the infamous Lazarus Group has established new infrastructure that impersonates skills assessment portals as part of its social engineering campaigns.
Microsoft attributed the activity to a threat actor it calls Sapphire Sleet, describing it as a "shift in the persistent actor's tactics."
Sapphire Sleet, also called APT38, BlueNoroff, CageyChameleon, and CryptoCore, has a track record of orchestrating cryptocurrency theft via social engineering.
Earlier this week, Jamf Threat Labs implicated the threat actor to a new macOS malware family called ObjCShellz that's assessed to be a late-stage payload delivered in connection with another macOS malware known as RustBucket.
"Sapphire Sleet typically finds targets on platforms like LinkedIn and uses lures related to skills assessment," the Microsoft Threat Intelligence team said in a series of posts on X (formerly Twitter).
"The threat actor then moves successful communications with targets to other platforms."
The tech giant said past campaigns mounted by the hacking crew involved sending malicious attachments directly or embedding links to pages hosted on legitimate websites like GitHub.
However, the swift detection and deletion of these payloads may have forced Sapphire Sleet to flesh out its own network of websites for malware distribution.
"Several malicious domains and subdomains host these websites, which entice recruiters to register for an account," the company added. "The websites are password-protected to impede analysis."
New Android Malware CherryBlos Utilizing OCR to Steal Sensitive Data
30.7.23 Android The Hacker News
A new Android malware strain called CherryBlos has been observed making use of optical character recognition (OCR) techniques to gather sensitive data stored in pictures.
CherryBlos, per Trend Micro, is distributed via bogus posts on social media platforms and comes with capabilities to steal cryptocurrency wallet-related credentials and act as a clipper to substitute wallet addresses when a victim copies a string matching a predefined format is copied to the clipboard.
Once installed, the apps seek users' permissions to grant it accessibility permissions, which allows it to automatically grant itself additional permissions as required. As a defense evasion measure, users attempting to kill or uninstall the app by entering the Settings app are redirected back to the home screen.
Besides displaying fake overlays on top of legitimate crypto wallet apps to steal credentials and make fraudulent fund transfers to an attacker-controlled address, CherryBlos utilizes OCR to recognize potential mnemonic phrases from images and photos stored on the device, the results of which are periodically uploaded to a remote server.
The success of the campaign banks on the possibility that users tend to take screenshots of the wallet recovery phrases on their devices.
Trend Micro said it also found an app developed by the CherryBlos threat actors on the Google Play Store but without the malware embedded into it. The app, named Synthnet, has since been taken down by Google.
The threat actors also appear to share overlaps with another activity set involving 31 scam money-earning apps, dubbed FakeTrade, hosted on the official app marketplace based on the use of shared network infrastructure and app certificates.
Most of the apps were uploaded to the Play Store in 2021 and have been found to target Android users in Malaysia, Vietnam, Indonesia, Philippines, Uganda, and Mexico.
"These apps claim to be e-commerce platforms that promise increased income for users via referrals and top-ups," Trend Micro said. "However, users will be unable withdraw their funds when they attempt to do so."
The disclosure comes as McAfee detailed a SMS phishing campaign against Japanese Android users that masquerades as a power and water infrastructure company to infect the devices with malware called SpyNote. The campaign took place in early June 2023.
"After launching the malware, the app opens a fake settings screen and prompts the user to enable the Accessibility feature," McAfee researcher Yukihiro Okutomi said last week.
"By allowing the Accessibility service, the malware disables battery optimization so that it can run in the background and automatically grants unknown source installation permission to install another malware without the user's knowledge."

It's no surprise that malware authors constantly seek new approaches to lure victims and steal sensitive data in the ever-evolving cyber threat landscape.
Google, last year, began taking steps to curb the misuse of accessibility APIs by rogue Android apps to covertly gather information from compromised devices by blocking sideloaded apps from using accessibility features altogether.
But stealers and clippers just represent one of the many kinds of malware – such as spyware and stalkerware – that are used to track targets and gather information of interest, posing severe threats to personal privacy and security.
New research published this week found that a surveillance app called SpyHide is stealthily collecting private phone data from nearly 60,000 Android devices around the world since at least 2016.
"Some of the users (operators) have multiple devices connected to their account, with some having as much as 30 devices they've been watching over a course of multiple years, spying on everyone in their lives," a security researcher, who goes by the name maia arson crimew, said.
It's therefore crucial for users to remain vigilant when downloading apps from unverified sources, verify developer information, and scrutinize app reviews to mitigate potential risks.
The fact that there is nothing stopping threat actors from creating bogus developer accounts on the Play Store to distribute malware hasn't gone unnoticed by Google.
Earlier this month, the search giant announced that it will require all new developer accounts registering as an organization to provide a valid D-U-N-S number assigned by Dun & Bradstreet before submitting apps in an effort to build user trust. The change goes into effect on August 31, 2023.
Apple Sets New Rules for Developers to Prevent Fingerprinting and Data Misuse
30.7.23 Apple The Hacker News
Apple has announced plans to require developers to submit reasons to use certain APIs in their apps starting later this year with the release of iOS 17, iPadOS 17, macOS Sonoma, tvOS 17, and watchOS 10 to prevent their abuse for data collection.
"This will help ensure that apps only use these APIs for their intended purpose," the company said in a statement. "As part of this process, you'll need to select one or more approved reasons that accurately reflect how your app uses the API, and your app can only use the API for the reasons you've selected."
The APIs that require reasons for use relate to the following -
File timestamp APIs
System boot time APIs
Disk space APIs
Active keyboard APIs, and
User defaults APIs
The iPhone maker said it's making the move to ensure that such APIs are not abused by app developers to collect device signals to carry out fingerprinting, which could be employed to uniquely identify users across different apps and websites for other purposes such as targeted advertising.
The policy enforcement, which goes live in Fall 2023 and also extends to visionOS, will require developers submitting new apps or app updates to declare the reasons for using these "required reason APIs" in their app's privacy manifest. Starting Spring 2024, apps that don't describe their use of the APIs in their privacy manifest file will be rejected.
"Regardless of whether a user gives your app permission to track, fingerprinting is not allowed," Apple explicitly cautions in its developer documentation. "Your app or third-party SDK must declare one or more approved reasons that accurately reflect your use of each of these APIs and the data derived from their use."
"You may use these APIs and the data derived from their use for the declared reasons only. These declared reasons must be consistent with your app's functionality as presented to users, and you may not use the APIs or derived data for tracking."
macOS Under Attack: Examining the Growing Threat and User Perspectives
25.7.23 Apple The Hacker News
As the number of people using macOS keeps going up, so does the desire of hackers to take advantage of flaws in Apple's operating system.
What Are the Rising Threats to macOS?#
There is a common misconception among macOS fans that Apple devices are immune to hacking and malware infection. However, users have been facing more and more dangers recently. Inventive attackers are specifically targeting Mac systems, as seen with the "Geacon" Cobalt Strike tool attack. This tool enables them to perform malicious actions such as data theft, privilege elevation, and remote device control, placing the security and privacy of Mac users at grave risk.
Earlier this year, researchers also uncovered the MacStealer malware, which also stole sensitive data from Apple users. Documents, iCloud keychain data, browser cookies, credit card credentials – nothing is safe from the prying eyes.
But that's not all. CloudMensis is malicious software that specifically targets macOS systems, spreading through email attachments and compromising device security. It can steal sensitive information and grant unauthorized access to users' systems. JockerSpy, on the other hand, can infiltrate a system through deceptive websites or bundled with seemingly harmless software. Once installed, it can monitor users' activities, capture keystrokes, and access personal data.
Even state-sponsored hacking organizations, like the North Korean Lazarus Group, have started targeting Apple Macs. Do you think this was a wake-up call for many Apple users who thought their devices were immune to getting attacked?
Mac Security Survey 2023: User Awareness and Behavior#
To understand the state of cybersecurity on the Mac, the Moonlock team, a dedicated group of MacPaw's researchers and engineers focused on the cybersecurity needs of Mac users, conducted a survey. From their fears and concerns to their behaviors and misconceptions, here's how Mac users are navigating the increasingly complex security landscape:
Cybersecurity Myths are Still Alive#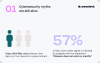
Despite the growing risks, many Mac users still take their cybersecurity lightly. Just think about it, Moonlock's Mac Security Survey 2023 reveals that every third Mac user believes their data is of no interest to cybercriminals. 57% of Mac users either agree or hesitate to disagree with the statement, "Malware does not exist on macOS."
Awareness is High, but Risky Behaviors Abound#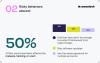
The truth is many Mac users have already fallen victim to attacks. More than 50% of respondents have experienced malware, hacking, or fraud personally or in their closest environment. 69% of them have personally faced at least one of these threats:
Malware, viruses
Hacking accounts, stealing passwords
Scam
Collection of personal data from browsers and social networks
Breach of personal data
Phishing
Violation of online payment security
Identity theft (including SSN theft)
Access to correspondence and private files.
This shows how vulnerable macOS is and highlights the need for stronger security.
Despite threats, 22% of Mac users have the same password for multiple accounts, and 31% skip software updates. At the same time, 45% feel that they don't do enough to protect themselves from cyber threats.
There's a Lack of Clarity About Security Tools#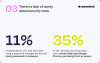
When it comes to digital security, there seems to be a lack of clarity around the use of security tools. Did you know that 11% of respondents who say they use a password manager actually store their passwords in their browsers? And interestingly, 35% of self-reported secure browser users consider Safari and Google Chrome to be safe options.
There's Also a Lack of Reliable Info #
According to Moonlock's research, 52% of Mac users actually want to talk to experts about how to stay safe online. However, 30% of users struggle to find reliable sources of information on the topic.
It is critical that Mac users remain vigilant, make cybersecurity a priority, and stay informed about the evolving threat landscape. By raising awareness and promoting proactive security measures, we can strengthen the protection of our Mac systems and safeguard our digital lives.
Apple Rolls Out Urgent Patches for Zero-Day Flaws Impacting iPhones, iPads and Macs
25.7.23 Apple The Hacker News
Apple has rolled out security updates to iOS, iPadOS, macOS, tvOS, watchOS, and Safari to address several security vulnerabilities, including one actively exploited zero-day bug in the wild.
Tracked as CVE-2023-38606, the shortcoming resides in the kernel and permits a malicious app to modify sensitive kernel state potentially. The company said it was addressed with improved state management.
"Apple is aware of a report that this issue may have been actively exploited against versions of iOS released before iOS 15.7.1," the tech giant noted in its advisory.
It's worth noting that CVE-2023-38606 is the third security vulnerability discovered in connection with Operation Triangulation, a sophisticated mobile cyber espionage campaign targeting iOS devices since 2019 using a zero-click exploit chain. The other two zero-days, CVE-2023-32434 and CVE-2023-32435, were patched by Apple last month.
Kaspersky researchers Valentin Pashkov, Mikhail Vinogradov, Georgy Kucherin, Leonid Bezvershenko, and Boris Larin have been credited with discovering and reporting the flaw.
The updates are available for the following devices and operating systems -
iOS 16.6 and iPadOS 16.6 - iPhone 8 and later, iPad Pro (all models), iPad Air 3rd generation and later, iPad 5th generation and later, and iPad mini 5th generation and later
iOS 15.7.8 and iPadOS 15.7.8 - iPhone 6s (all models), iPhone 7 (all models), iPhone SE (1st generation), iPad Air 2, iPad mini (4th generation), and iPod touch (7th generation)
macOS Ventura 13.5, macOS Monterey 12.6.8, and macOS Big Sur 11.7.9
tvOS 16.6 - Apple TV 4K (all models) and Apple TV HD, and
watchOS 9.6 - Apple Watch Series 4 and later
With the latest round of patches, Apple has resolved a total of 11 zero-days impacting its software since the start of 2023. It also comes two weeks after the company published emergency fixes for a remote code execution bug in WebKit that could lead to arbitrary code execution (CVE-2023-37450).
Apple Threatens to Pull iMessage and FaceTime from U.K. Amid Surveillance Demands
22.7.23 Apple The Hacker News
Apple has warned that it would rather stop offering iMessage and FaceTime services in the U.K. than bowing down to government pressure in response to new proposals that seek to expand digital surveillance powers available to state intelligence agencies.
The development, first reported by BBC News, makes the iPhone maker the latest to join the chorus of voices protesting against forthcoming legislative changes to the Investigatory Powers Act (IPA) 2016 in a manner that would effectively render encryption protections ineffective.
Specifically, the Online Safety Bill requires companies to install technology to scan for child sex exploitation and abuse (CSEA) material and terrorism content in encrypted messaging apps and other services. It also mandates that messaging services clear security features with the Home Office before releasing them and take immediate action to disable them if required without informing the public.
While the fact does not explicitly call out for the removal of end-to-end encryption, it would de facto amount to weakening it as the companies offering the services would have to scan all messages to flag and take them down. This has been viewed as a disproportionate step that allows the government to enforce bulk interception and surveillance.
Apple told the British broadcaster that such a provision would "constitute a serious and direct threat to data security and information privacy."
Earlier this April, a number of messaging apps that currently offer encrypted chats, such as Element, Signal, Threema, Viber, Meta-owned WhatsApp, and Wire, published an open letter, urging the U.K. government to rethink its approach and "encourage companies to offer more privacy and security to its residents."
"The Bill provides no explicit protection for encryption, and if implemented as written, could empower OFCOM to try to force the proactive scanning of private messages on end-to-end encrypted communication services – nullifying the purpose of end-to-end encryption as a result and compromising the privacy of all users," the letter read.
Apple, which previously announced its own plans to flag potentially problematic and abusive content in iCloud Photos, abandoned it last year after receiving pushback from digital rights groups over worries that the capability could be abused to undermine users' privacy and security.
This is not the first time the tussle between end-to-end encryption vis-à-vis the need to tackle serious crimes online has cropped up.
In May 2021, WhatsApp sued the Indian government to block internet regulations that would compel the messaging app to break encryption by incorporating a traceability mechanism to identify the "first originator of information" or risk facing criminal penalties. The case is still pending.
Apple's refusal to play ball is in line with its public stance on privacy, one that allows it to position itself as a "privacy hero" among other companies that thrive on collecting user data to serve targeted ads.
But it also rings hollow when considering the fact that every message sent to or received from a non-Apple device is unencrypted – SMS does not support end-to-end encryption – and could potentially open the door for government surveillance.
Apple Issues Urgent Patch for Zero-Day Flaw Targeting iOS, iPadOS, macOS, and Safari
11.7.23 Apple The Hacker News
Apple has released Rapid Security Response updates for iOS, iPadOS, macOS, and Safari web browser to address a zero-day flaw that it said has been actively exploited in the wild.
The WebKit bug, cataloged as CVE-2023-37450, could allow threat actors to achieve arbitrary code execution when processing specially crafted web content. The iPhone maker said it addressed the issue with improved checks.
Credited with discovering and reporting the flaw is an anonymous researcher. As with most cases like this, there are scant details about the nature and the scale of the attacks and the identity of the threat actor behind them.
But Apple noted in a terse advisory that it's "aware of a report that this issue may have been actively exploited."
UPCOMING WEBINAR
🔐 PAM Security – Expert Solutions to Secure Your Sensitive Accounts
This expert-led webinar will equip you with the knowledge and strategies you need to transform your privileged access security strategy.
Claim Your Spot
The updates, iOS 16.5.1 (a), iPadOS 16.5.1 (a), macOS Ventura 13.4.1 (a), and Safari 16.5.2, are available for devices running the following operating system versions:
iOS 16.5.1 and iPadOS 16.5.1
macOS Ventura 13.4.1
macOS Big Sur and macOS Monterey
Apple has addressed 10 zero-day vulnerabilities in its software since the start of 2023. It also arrives weeks after the company rolled out patches to fix three zero-days, two of which have been weaponized by unidentified actors in connection with an espionage campaign called Operation Triangulation.
Update#
Apple has pulled the software update after reports emerged that installing the patches caused certain websites like Facebook, Instagram, and Zoom to throw an "Unsupported Browser" error on Safari.
Two Spyware Apps on Google Play with 1.5 Million Users Sending Data to China
8.7.23 Android The Hacker News
Two file management apps on the Google Play Store have been discovered to be spyware, putting the privacy and security of up to 1.5 million Android users at risk. These apps engage in deceptive behaviour and secretly send sensitive user data to malicious servers in China.
Pradeo, a leading mobile security company, has uncovered this alarming infiltration. The report shows that both spyware apps, namely File Recovery and Data Recovery (com.spot.music.filedate) with over 1 million installs, and File Manager (com.file.box.master.gkd) with over 500,000 installs, are developed by the same group. These seemingly harmless Android apps use similar malicious tactics and automatically launch when the device reboots without user input.
Contrary to what they claim on the Google Play Store, where both apps assure users that no data is collected, Pradeo's analytics engine has found that various personal information is collected without users' knowledge. Stolen data includes contact lists, media files (images, audio files and videos), real-time location, mobile country code, network provider details, SIM provider network code, operating system version, device brand, and model.
What is particularly alarming is the large amount of data transferred by these spyware apps. Each app performs more than a hundred transmissions, a considerable amount for malicious activities. Once the data is collected, it is sent to multiple servers in China, which are deemed malicious by security experts.
To make matters worse, the developers of these spyware apps have used sneaky techniques to appear more legitimate and make it difficult to uninstall them. Hackers artificially increased the number of downloads of apps with install Farms or mobile device emulators, creating a false sense of trustworthiness. Moreover, both apps have advanced permissions that allow them to hide their icons on the home screen, making it difficult for unsuspecting users to uninstall them.
Pradeo provides security recommendations for individuals and businesses in light of this disturbing discovery. Individuals should be cautious when downloading apps, especially those without ratings if they claim a large user base. It is extremely critical to read and understand app permissions before accepting them to prevent breaches like this.
Organizations should prioritize educating their employees about mobile threats and setting up automated mobile detection and response systems to protect against potential attacks.
This incident highlights the ongoing battle between cybersecurity experts and malicious actors exploiting unsuspecting users. Malware and spyware attacks are constantly evolving and finding new ways to infiltrate trusted platforms like the Google Play Store. As a user, it is imperative to stay vigilant, exercise caution when downloading apps, and rely on reputable sources for software.
Google Releases Android Patch Update for 3 Actively Exploited Vulnerabilities
7.7.23 Android The Hacker News
Google has released its monthly security updates for the Android operating system, addressing 46 new software vulnerabilities. Among these, three vulnerabilities have been identified as actively exploited in targeted attacks.
One of the vulnerabilities tracked as CVE-2023-26083 is a memory leak flaw affecting the Arm Mali GPU driver for Bifrost, Avalon, and Valhall chips. This particular vulnerability was exploited in a previous attack that enabled spyware infiltration on Samsung devices in December 2022.
This vulnerability was regarded as serious enough to prompt the Cybersecurity and Infrastructure Security Agency (CISA) to issue a patching order for federal agencies in April 2023.
Another significant vulnerability, identified as CVE-2021-29256, is a high-severity issue that affects specific versions of the Bifrost and Midgard Arm Mali GPU kernel drivers. This flaw permits an unprivileged user to gain unauthorized access to sensitive data and escalate privileges to the root level.
The third exploited vulnerability, CVE-2023-2136, is a critical-severity bug discovered in Skia, Google's open-source multi-platform 2D graphics library. It was initially disclosed as a zero-day vulnerability in the Chrome browser and allows a remote attacker who has taken over the renderer process to perform a sandbox escape and implement remote code on Android devices.
Besides these, Google's July Android security bulletin highlights another critical vulnerability, CVE-2023-21250, affecting the Android System component. This issue can cause remote code execution without user interaction or additional execution privileges, making it particularly precarious.
These security updates are rolled out in two patch levels. The initial patch level, made available on July 1, focuses on core Android components, addressing 22 security defects in the Framework and System components.
The second patch level, released on July 5, targets kernel and closed source components, tackling 20 vulnerabilities in Kernel, Arm, Imagination Technologies, MediaTek, and Qualcomm components.
It's important to note that the impact of the addressed vulnerabilities may extend beyond the supported Android versions (11, 12, and 13), potentially affecting older OS versions no longer receive official support.
Google has further launched particular security patches for its Pixel devices, dealing with 14 vulnerabilities in Kernel, Pixel, and Qualcomm components. Two of these critical weaknesses could result in privilege elevation and denial-of-service attacks.
Iranian Hackers' Sophisticated Malware Targets Windows and macOS Users
7.7.23 Apple The Hacker News
The Iranian nation-state actor known as TA453 has been linked to a new set of spear-phishing attacks that infect both Windows and macOS operating systems with malware.
"TA453 eventually used a variety of cloud hosting providers to deliver a novel infection chain that deploys the newly identified PowerShell backdoor GorjolEcho," Proofpoint said in a new report.
"When given the opportunity, TA453 ported its malware and attempted to launch an Apple flavored infection chain dubbed NokNok. TA453 also employed multi-persona impersonation in its unending espionage quest."
TA453, also known by the names APT35, Charming Kitten, Mint Sandstorm, and Yellow Garuda, is a threat group linked to Iran's Islamic Revolutionary Guard Corps (IRGC) that has been active since at least 2011. Most recently, Volexity highlighted the adversary's use of an updated version of a Powershell implant called CharmPower (aka GhostEcho or POWERSTAR).
In the attack sequence discovered by the enterprise security firm in mid-May 2023, the hacking crew sent phishing emails to a nuclear security expert at a U.S.-based think tank focused on foreign affairs that delivered a malicious link to a Google Script macro that would redirect the target to a Dropbox URL hosting a RAR archive.
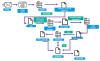
Present within the file is an LNK dropper that kicks off a multi-stage procedure to ultimately deploy GorjolEcho, which, in turn, displays a decoy PDF document, while covertly awaiting next-stage payloads from a remote server.
But upon realizing that the target is using an Apple computer, TA453 is said to have tweaked its modus operandi to send a second email with a ZIP archive embedding a Mach-O binary that masquerades as a VPN application, but in reality, is an AppleScript that reaches out to a remote server to download a Bash script-based backdoor called NokNok.
NokNok, for its part, fetches as many as four modules that are capable of gathering running processes, installed applications, and system metadata as well as setting persistence using LaunchAgents.
The modules "mirror a majority of the functionality" of the modules associated with CharmPower, with NokNok sharing some source code overlaps with macOS malware previously attributed to the group in 2017.
Also put to use by the actor is a bogus file-sharing website that likely functions to fingerprint visitors and act as a mechanism to track successful victims.
"TA453 continues to adapt its malware arsenal, deploying novel file types, and targeting new operating systems," the researchers said, adding the actor "continues to work toward its same end goals of intrusive and unauthorized reconnaissance" while simultaneously complicating detection efforts.
Mexico-Based Hacker Targets Global Banks with Android Malware
4.7.23 Android The Hacker News
An e-crime actor of Mexican provenance has been linked to an Android mobile malware campaign targeting financial institutions globally, but with a specific focus on Spanish and Chilean banks, from June 2021 to April 2023.
The activity is being attributed to an actor codenamed Neo_Net, according to security researcher Pol Thill. The findings were published by SentinelOne following a Malware Research Challenge in collaboration with vx-underground.
"Despite using relatively unsophisticated tools, Neo_Net has achieved a high success rate by tailoring their infrastructure to specific targets, resulting in the theft of over 350,000 EUR from victims' bank accounts and compromising Personally Identifiable Information (PII) of thousands of victims," Thill said.
Some of the major targets include banks such as Santander, BBVA, CaixaBank, Deutsche Bank, Crédit Agricole, and ING.
Neo_Net, linked to a Spanish-speaking actor residing in Mexico, has established themselves as a seasoned cybercriminal, engaging in the sales of phishing panels, compromised victim data to third-parties, and a smishing-as-a-service offering called Ankarex that's designed to target a number of countries across the world.
The initial entry point for the multi-stage attack is SMS phishing, in which the threat actor employs various scare tactics to trick unwitting recipients into clicking on bogus landing pages to harvest and exfiltrate their credentials via a Telegram bot.
"The phishing pages were meticulously set up using Neo_Net's panels, PRIV8, and implemented multiple defense measures, including blocking requests from non-mobile user agents and concealing the pages from bots and network scanners," Thill explained.
"These pages were designed to closely resemble genuine banking applications, complete with animations to create a convincing façade."
The threat actors have also been observed duping bank customers into installing rogue Android apps under the guise of security software that, once installed, requests SMS permissions to capture SMS-based two-factor authentication (2FA) codes sent by the bank.
The Ankarex platform, for its part, has been active since May 2022. It's actively promoted on a Telegram channel that has about 1,700 subscribers.
"The service itself is accessible at ankarex[.]net, and once registered, users can upload funds using cryptocurrency transfers and launch their own Smishing campaigns by specifying the SMS content and target phone numbers," Thill said.
The development comes as ThreatFabric detailed a new Anatsa (aka TeaBot) banking trojan campaign that has been targeting banking customers in the U.S., U.K., Germany, Austria, and Switzerland since the start of March 2023.
Beware: New 'Rustbucket' Malware Variant Targeting macOS Users
1.7.23 Apple The Hacker News
Researchers have pulled back the curtain on an updated version of an Apple macOS malware called Rustbucket that comes with improved capabilities to establish persistence and avoid detection by security software.
"This variant of Rustbucket, a malware family that targets macOS systems, adds persistence capabilities not previously observed," Elastic Security Labs researchers said in a report published this week, adding it's "leveraging a dynamic network infrastructure methodology for command-and-control."
RustBucket is the work of a North Korean threat actor known as BlueNoroff, which is part of a larger intrusion set tracked under the name Lazarus Group, an elite hacking unit supervised by the Reconnaissance General Bureau (RGB), the country's primary intelligence agency.
The malware came to light in April 2023, when Jamf Threat Labs described it as an AppleScript-based backdoor capable of retrieving a second-stage payload from a remote server. Elastic is monitoring the activity as REF9135.
The second-stage malware, compiled in Swift, is designed to download from the command-and-control (C2) server the main malware, a Rust-based binary with features to gather extensive information as well as fetch and run additional Mach-O binaries or shell scripts on the compromised system.
It's the first instance of BlueNoroff malware specifically targeting macOS users, although a .NET version of RustBucket has since surfaced in the wild with a similar set of features.
"This recent Bluenoroff activity illustrates how intrusion sets turn to cross-platform language in their malware development efforts, further expanding their capabilities highly likely to broaden their victimology," French cybersecurity company Sekoia said in an analysis of the RustBucket campaign in late May 2023.
The infection chain consists of a macOS installer file that installs a backdoored, yet functional, PDF reader. A significant aspect of the attacks is that the malicious activity is triggered only when a weaponized PDF file is launched using the rogue PDF reader. Initial intrusion vector includes phishing emails, as well as employing bogus personas on social networks such as LinkedIn.
The observed attacks are highly targeted and focused on finance-related institutions in Asia, Europe, and the U.S., suggesting that the activity is geared towards illicit revenue generation to evade sanctions.
What makes the newly identified version notable is its unusual persistence mechanism and the use of dynamic DNS domain (docsend.linkpc[.]net) for command-and-control, alongside incorporating measures focused on remaining under the radar.
"In the case of this updated RUSTBUCKET sample, it establishes its own persistence by adding a plist file at the path /Users/<user>/Library/LaunchAgents/com.apple.systemupdate.plist, and it copies the malware's binary to the following path /Users/<user>/Library/Metadata/System Update," the researchers said.
Fluhorse: Flutter-Based Android Malware Targets Credit Cards and 2FA Codes
30.6.23 Android The Hacker News
Cybersecurity researchers have shared the inner workings of an Android malware family called Fluhorse.
The malware "represents a significant shift as it incorporates the malicious components directly within the Flutter code," Fortinet FortiGuard Labs researcher Axelle Apvrille said in a report published last week.
Fluhorse was first documented by Check Point in early May 2023, detailing its attacks on users located in East Asia through rogue apps masquerading as ETC and VPBank Neo, which are popular in Taiwan and Vietnam. The initial intrusion vector for the malware is phishing.
The ultimate goal of the app is to steal credentials, credit card details, and two-factor authentication (2FA) codes received as SMS to a remote server under the control of the threat actors.
The latest findings from Fortinet, which reverse-engineered a Fluhorse sample uploaded to VirusTotal on June 11, 2023, suggest that the malware has evolved, incorporating additional sophistication by concealing the encrypted payload in a packer.
"Decryption is performed at the native level (to harden reverse engineering) using OpenSSL's EVP cryptographic API," Apvrille explained. The encryption algorithm is AES-128-CBC, and its implementation uses the same hard-coded string for the key and initialization vector (IV)."
The decrypted payload, a ZIP file, contains within it a Dalvik executable file (.dex), which is then installed on the device to listen to incoming SMS messages and exfiltrate them to the remote server.
"Reversing Flutter applications statically is a breakthrough for anti-virus researchers, as, unfortunately, more malicious Flutter apps are expected to be released in the future," Apvrille said.
Android Spy App LetMeSpy Suffers Major Data Breach, Exposing Users' Personal Data
30.6.23 Android The Hacker News
Android-based phone monitoring app LetMeSpy has disclosed a security breach that allowed an unauthorized third-party to steal sensitive data associated with thousands of Android users.
"As a result of the attack, the criminals gained access to email addresses, telephone numbers and the content of messages collected on accounts," LetMeSpy said in an announcement on its website, noting the incident took place on June 21, 2023.
Following the discovery of the hack, LetMeSpy said it notified law enforcement and data protection authorities. It's also taking steps to suspend all account-related functions until further notice. The identity of the threat actor and their motives are currently unknown.
The work of a Polish company named Radeal, LetMeSpy is offered as a monthly subscription ($6 for Standard or $12 for Pro), allowing its customers to snoop on others simply by installing the software on their devices. An Internet Archive snapshot from December 2013 shows that it's billed as a tool for parental or employee control.
LetMeSpy comes with a wide range of features to collect call logs, SMS messages, and geolocations, all of which can be accessed from the website. In an attempt to evade detection and removal, the app's icon can be hidden from the device's home screen launcher.
As of January 2023, the stalkerware app has been used to track 236,322 phones across the world, harvesting over 63.5 million text messages, 39.7 million call logs, and 43.2 million locations.
Polish security research blog Niebezpiecznik, which first reported the breach and analyzed a dump of the stolen data, said it includes about 26,000 email addresses, 16,000 SMS messages, and a database of victims' locations.
A further review of the leaked information by TechCrunch has revealed that the data goes all the way back to 2013, when LetMeSpy became operational. The records also contain data from at least 13,000 compromised devices. A majority of the victims are located in the U.S., India, and parts of Africa.
Zero-Day Alert: Apple Releases Patches for Actively Exploited Flaws in iOS, macOS, and Safari
22.6.23 Apple The Hacker News
Apple on Wednesday released a slew of updates for iOS, iPadOS, macOS, watchOS, and Safari browser to address a set of flaws it said were actively exploited in the wild.
This includes a pair of zero-days that have been weaponized in a mobile surveillance campaign called Operation Triangulation that has been active since 2019. The exact threat actor behind the campaign is not known.
CVE-2023-32434 - An integer overflow vulnerability in the Kernel that could be exploited by a malicious app to execute arbitrary code with kernel privileges.
CVE-2023-32435 - A memory corruption vulnerability in WebKit that could lead to arbitrary code execution when processing specially crafted web content.
The iPhone maker said it's aware that the two issues "may have been actively exploited against versions of iOS released before iOS 15.7," crediting Kaspersky researchers Georgy Kucherin, Leonid Bezvershenko, and Boris Larin for reporting them.
The advisory comes as the Russian cybersecurity vendor dissected the spyware implant used in the zero-click attack campaign targeting iOS devices via iMessages carrying an attachment embedded with an exploit for a remote code execution (RCE) vulnerability.
The exploit code is also engineered to download additional components to obtain root privileges on the target device, after which the backdoor is deployed in memory and the initial iMessage is deleted to conceal the infection trail.
The sophisticated implant, called TriangleDB, operates solely in the memory, leaving no traces of the activity following a device reboot. It also comes with diverse data collection and tracking capabilities.
This includes "interacting with the device's file system (including file creation, modification, exfiltration, and removal), managing processes (listing and termination), extracting keychain items to gather victim credentials, and monitoring the victim's geolocation, among others."
Also patched by Apple is a third zero-day CVE-2023-32439, which has been reported anonymously and could result in arbitrary code execution when processing malicious web content.
The actively exploited flaw, described as a type confusion issue, has been addressed with improved checks. The updates are available for the following platforms -
iOS 16.5.1 and iPadOS 16.5.1 - iPhone 8 and later, iPad Pro (all models), iPad Air 3rd generation and later, iPad 5th generation and later, and iPad mini 5th generation and later
iOS 15.7.7 and iPadOS 15.7.7 - iPhone 6s (all models), iPhone 7 (all models), iPhone SE (1st generation), iPad Air 2, iPad mini (4th generation), and iPod touch (7th generation)
macOS Ventura 13.4.1, macOS Monterey 12.6.7, and macOS Big Sur 11.7.8
watchOS 9.5.2 - Apple Watch Series 4 and later
watchOS 8.8.1 - Apple Watch Series 3, Series 4, Series 5, Series 6, Series 7, and SE, and
Safari 16.5.1 - Macs running macOS Monterey
With the latest round of fixes, Apple has resolved a total of nine zero-day flaws in its products since the start of the year.
In February, the company plugged a WebKit flaw (CVE-2023-23529) that could lead to remote code execution. In April, it released updates for two bugs (CVE-2023-28205 and CVE-2023-28206) that allowed for code execution with elevated privileges.
Subsequently, in May, it shipped patches for three more vulnerabilities in WebKit (CVE-2023-32409, CVE-2023-28204, and CVE-2023-32373) that could permit a threat actor to escape sandbox protection, access sensitive data, and execute arbitrary code.
New Report Exposes Operation Triangulation's Spyware Implant Targeting iOS Devices
22.6.23 Apple The Hacker News
More details have emerged about the spyware implant that's delivered to iOS devices as part of a campaign called Operation Triangulation.
Kaspersky, which discovered the operation after becoming one of the targets at the start of the year, said the malware has a lifespan of 30 days, after which it gets automatically uninstalled unless the time period is extended by the attackers.
The Russian cybersecurity company has codenamed the backdoor TriangleDB.
"The implant is deployed after the attackers obtain root privileges on the target iOS device by exploiting a kernel vulnerability," Kaspersky researchers said in a new report published today.
"It is deployed in memory, meaning that all traces of the implant are lost when the device gets rebooted. Therefore, if the victim reboots their device, the attackers have to reinfect it by sending an iMessage with a malicious attachment, thus launching the whole exploitation chain again."
Operation Triangulation entails the use of zero-click exploits via the iMessage platform, thereby allowing the spyware to complete control over the device and user data.
"The attack is carried out using an invisible iMessage with a malicious attachment, which, using a number of vulnerabilities in the iOS operating system, is executed on a device and installs spyware," Eugene Kaspersky, CEO of Kaspersky, said earlier this month.
"The deployment of the spyware is completely hidden and requires no action from the user."
TriangleDB, written in Objective-C, forms the crux of the covert framework. It's designed to establish encrypted connections with a command-and-control (C2) server and periodically send a heartbeat beacon containing the device metadata.
The server, for its part, responds to the heartbeat messages with one of 24 commands that make it possible to dump iCloud Keychain data and load additional Mach-O modules in memory to harvest sensitive data.
This includes file contents, geolocation, installed iOS applications, and running processes, among others. The attack chains culminate with the erasure of the initial message to cover up the tracks.
A closer examination of the source code has revealed some unusual aspects where the malware authors refers to string decryption as "unmunging" and assign names from database terminology to files (record), processes (schema), C2 server (DB Server), and geolocation information (DB Status).
Another notable aspect is the presence of the routine "populateWithFieldsMacOSOnly." While this method is nowhere called in the iOS implant, the naming convention raises the possibility that TriangleDB could also be weaponized to target macOS devices.
"The implant requests multiple entitlements (permissions) from the operating system," Kaspersky researchers said.
"Some of them are not used in the code, such as access to camera, microphone and address book, or interaction with devices via Bluetooth. Thus, functionalities granted by these entitlements may be implemented in modules."
It's currently not known who is behind the campaign and what their ultimate objectives are. Apple, in a previous statement shared with The Hacker News, said it has "never worked with any government to insert a backdoor into any Apple product and never will."
The Russian government, however, has pointed fingers at the U.S., accusing it of breaking into "several thousand" Apple devices belonging to domestic subscribers and foreign diplomats as part of what it claimed to be a reconnaissance operation.
Rogue Android Apps Target Pakistani Individuals in Sophisticated Espionage Campaign
20.6.23 Android The Hacker News
Individuals in the Pakistan region have been targeted using two rogue Android apps available on the Google Play Store as part of a new targeted campaign.
Cybersecurity firm Cyfirma attributed the campaign with moderate confidence to a threat actor known as DoNot Team, which is also tracked as APT-C-35 and Viceroy Tiger.
The espionage activity involves duping Android smartphone owners into downloading a program that's used to extract contact and location data from unwitting victims.
"The motive behind the attack is to gather information via the stager payload and use the gathered information for the second-stage attack, using malware with more destructive features," the company said.
DoNot Team is a suspected India-nexus threat actor that has a reputation for carrying out attacks against various countries in South Asia. It has been active since at least 2016.
While an October 2021 report from Amnesty International linked the group's attack infrastructure to an Indian cybersecurity company called Innefu Labs, Group-IB, in February 2023, said it identified overlaps between DoNot Team and SideWinder, another suspected Indian hacking crew.
Attack chains mounted by the group leverage spear-phishing emails containing decoy documents and files as lures to spread malware. In addition, the threat actor is known to use malicious Android apps that masquerade as legitimate utilities in their target attacks.
These apps, once installed, activate trojan behavior in the background and can remotely control the victim's system, besides pilfering confidential information from the infected devices.
The latest set of applications discovered by Cyfirma originate from a developer named "SecurITY Industry" and pass off as VPN and chat apps, with the latter still available for download from the Play Store -
iKHfaa VPN (com.securityapps.ikhfaavpn) - 10+ downloads
nSure Chat (com.nSureChat.application) - 100+ downloads
The VPN app, which reuses source code taken from the genuine Liberty VPN product, is no longer hosted on the official app storefront, although evidence shows that it was available as recently as June 12, 2023.
The low download counts is an indication that the apps are being used as part of a highly targeted operation, a hallmark of nation-state actors. Both apps are configured to trick the victims into granting them invasive permissions to access their contact lists and precise locations.
Little is known about the victims targeted using the rogue apps barring the fact that they are based in Pakistan. It's believed that users may have been approached via messages on Telegram and WhatsApp to lure them into installing the apps.
By utilizing the Google Play Store as a malware distribution vector, the approach abuses the implicit trust placed by users on the online app marketplace and lends it an air of legitimacy. It's, therefore, essential that apps are carefully scrutinized prior to downloading them.
"It appears that this Android malware was specifically designed for information gathering," Cyfirma said. "By gaining access to victims' contact lists and locations, the threat actor can strategize future attacks and employ Android malware with advanced features to target and exploit the victims."
Researchers Discover New Sophisticated Toolkit Targeting Apple macOS Systems
19.6.23 Apple The Hacker News
Cybersecurity researchers have uncovered a set of malicious artifacts that they say is part of a sophisticated toolkit targeting Apple macOS systems.
"As of now, these samples are still largely undetected and very little information is available about any of them," Bitdefender researchers Andrei Lapusneanu and Bogdan Botezatu said in a preliminary report published on Friday.
The Romanian firm's analysis is based on an examination of four samples that were uploaded to VirusTotal by an unnamed victim. The earliest sample dates back to April 18, 2023.
Two of the three malicious programs are said to be generic Python-based backdoors that are designed to target Windows, Linux, and macOS systems. The payloads have been collectively dubbed JokerSpy.
The first constituent is shared.dat, which, once launched, runs an operating system check (0 for Windows, 1 for macOS, and 2 for Linux) and establishes contact with a remote server to fetch additional instructions for execution.
This includes gathering system information, running commands, downloading and executing files on the victim machine, and terminating itself.
On devices running macOS, Base64-encoded content retrieved from the server is written to a file named "/Users/Shared/AppleAccount.tgz" that's subsequently unpacked and launched as the "/Users/Shared/TempUser/AppleAccountAssistant.app" application.
The same routine, on Linux hosts, validates the operating system distribution by checking the "/etc/os-release" file. It then proceeds to write C code to a temporary file "tmp.c," which is compiled to a file called "/tmp/.ICE-unix/git" using the cc command on Fedora and gcc on Debian.
Bitdefender said it also found a "more potent backdoor" among the samples, a file labeled "sh.py" that comes with an extensive set of capabilities to gather system metadata, enumerate files, delete files, execute commands and files, and exfiltrate encoded data in batches.
The third component is a FAT binary known as xcc that's written in Swift and targets macOS Monterey (version 12) and newer. The file houses two Mach-O files for the twin CPU architectures, x86 Intel and ARM M1.
"Its primary purpose is apparently to check permissions before using a potential spyware component (probably to capture the screen) but does not include the spyware component itself," the researchers said.
"This leads us to believe that these files are part of a more complex attack and that several files are missing from the system we investigated."
xcc's spyware connections stem from a path identified within the file content, "/Users/joker/Downloads/Spy/XProtectCheck/" and the fact that it checks for permissions such as Disk Access, Screen Recording, and Accessibility.
The identity of the threat actors behind the activity is unknown as yet. It's currently also not clear how initial access is obtained, and if it involves an element of social engineering or spear-phishing.
The disclosure comes a little over two weeks after Russian cybersecurity company Kaspersky disclosed that iOS devices have been targeted as part of a sophisticated and long-running mobile campaign dubbed Operation Triangulation that began in 2019.
Apple's Safari Private Browsing Now Automatically Removes Tracking Parameters in URLs
12.6.23 Apple The Hacker News
Apple is introducing major updates to Safari Private Browsing, offering users better protections against third-party trackers as they browse the web.
"Advanced tracking and fingerprinting protections go even further to help prevent websites from using the latest techniques to track or identify a user's device," the iPhone maker said.
"Private Browsing now locks when not in use, allowing a user to keep tabs open even when stepping away from the device."
The privacy improvements were previewed at Apple's annual Worldwide Developers Conference (WWDC) last week. They are expected to be rolled out to users as part of iOS 17, iPadOS 17, and macOS Sonoma later this year.
Another key change includes Link Tracking Protection in Mail, Messages, and Safari's private mode to automatically remove tracking parameters in URLs, which are often used to track information about a click.
"Safari has been a somewhat unheralded pioneer of private browsing, and so many privacy and security features, and this year it's just a tour de force," Apple's Craig Federighi was quoted as saying to Fast Company. "Browsing the internet is one of the major privacy threat vectors."
Also coming to iOS is a new embedded Photos picker that allows users to share specific photos with other apps while keeping the rest of their library private.
Apple is further improving Communication Safety, which warns children when receiving or sending explicit images in Messages, to encompass video content. On top of that, the feature is being extended to AirDrop, FaceTime video messages, and the Photos picker.
The privacy-preserving technology that underpins Communication Safety is also expected to power Sensitive Content Warning, an optional setting that helps adult users avoid receiving unsolicited nude images and videos via Messages, AirDrop, or FaceTime video messages.
Users will also be able to share a set of passwords and passkeys securely with others over iCloud Keychain by creating a group. Every individual in the group can add and edit passwords to ensure that they are up to date.
Lastly, Apple is bringing new capabilities to Lockdown Mode, including "safer wireless connectivity defaults, media handling, media sharing defaults, sandboxing, and network security optimizations." The enhanced security setting is also being expanded to support watchOS.
"Turning on Lockdown Mode further hardens device defenses and strictly limits certain functionalities, sharply reducing the attack surface for those who need additional protections," Apple said.
"Lockdown Mode expands to provide even more protections for those who may be targeted by mercenary spyware because of who they are or what they do."
Over 60K Adware Apps Posing as Cracked Versions of Popular Apps Target Android Devices
7.6.23 Android The Hacker News
Thousands of adware apps for Android have been found to masquerade as cracks or modded versions of popular applications to serve unwanted ads to users as part of a campaign ongoing since October 2022.
"The campaign is designed to aggressively push adware to Android devices with the purpose to drive revenue," Bitdefender said in a technical report shared with The Hacker News. "However, the threat actors involved can easily switch tactics to redirect users to other types of malware such as banking Trojans to steal credentials and financial information or ransomware."
The Romanian cybersecurity company said it has discovered 60,000 unique apps carrying the adware, with a majority of the detections located in the U.S., South Korea, Brazil, Germany, the U.K., France, Kazakhstan, Romania, and Italy.
It's worth pointing out that none of the apps are distributed through the official Google Play Store. Instead, users searching for apps like Netflix, PDF viewers, security software, and cracked versions of YouTube on a search engine are redirected to an ad page hosting the malware.
The apps, once installed, have no icons or names in a bid to evade detection. What's more, users launching an app for the first time after installation are displayed the message "Application is unavailable in your region from where the app serves. Tap OK to uninstall," while stealthily activating the malicious activity in the background.
The modus operandi is another area of note wherein the adware behavior remains dormant for the first few days, after which it's awakened when the victim unlocks the phone in order to serve a full-screen ad using Android WebView.
The findings come as cybersecurity firm CloudSEK disclosed it had identified the rogue SpinOK SDK – which was revealed by Doctor Web last month – in 193 apps on the Google Play Store that have been downloaded 30 million times.
On the surface, the SpinOk module is designed to maintain users' interest in apps with the help of mini-games and tasks to win alleged rewards. But peer inside, the trojan harbors functionalities to steal files and replace clipboard contents.
In a related development, the SonicWall Capture Labs Threat research team also unearthed another strain of Android malware that impersonates legitimate apps to harvest a wide range of information from compromised handsets by abusing the operating system's accessibility services.

"These features allow the attacker to access and steal valuable information from the victim's device, which can lead to various types of fraud, including financial fraud, and identity theft," SonicWall said.
New Zero-Click Hack Targets iOS Users with Stealthy Root-Privilege Malware
1.6.23 Apple The Hacker News
A previously unknown advanced persistent threat (APT) is targeting iOS devices as part of a sophisticated and long-running mobile campaign dubbed Operation Triangulation that began in 2019.
"The targets are infected using zero-click exploits via the iMessage platform, and the malware runs with root privileges, gaining complete control over the device and user data," Kaspersky said.
The Russian cybersecurity company said it discovered traces of compromise after creating offline backups of the targeted devices.
The attack chain begins with the iOS device receiving a message via iMessage that contains an attachment bearing the exploit.
The exploit is said to be zero-click, meaning the receipt of the message triggers the vulnerability without requiring any user interaction in order to achieve code execution.
It's also configured to retrieve additional payloads for privilege escalation and drop a final stage malware from a remote server that Kaspersky described as a "fully-featured APT platform."
The implant, which runs with root privileges, is capable of harvesting sensitive information and equipped to run code downloaded as plugin modules from the server.
"Further, the spyware also quietly transmits private information to remote servers: microphone recordings, photos from instant messengers, geolocation and data about a number of other activities of the owner of the infected device," Kaspersky researchers said.
In the final phase, both the initial message and the exploit in the attachment are deleted to erase any traces of the infection.
"The malicious toolset does not support persistence, most likely due to the limitations of the [operating system]," Kaspersky said. "The timelines of multiple devices indicate that they may be reinfected after rebooting."
The exact scale and scope of the campaign remains unclear, but the company said the attacks are ongoing, with successful infections penetrating devices running iOS 15.7, which was released on September 12, 2022.
It's currently also not known if the attacks are taking advantage of a zero-day vulnerability – i.e., a flaw discovered by attackers before it's known to the software vendor – in iOS. The latest version of iOS is 16.5, although Apple also shipped an 15.7.6 update last month.
Kremlin Accuses U.S. of Hacking Thousands of Apple Devices#
Coinciding with Kaspersky's report, Russia's Federal Security Service (FSB) released an advisory accusing U.S. intelligence agencies of hacking "several thousand" Apple devices belonging to domestic subscribers and foreign diplomats via hitherto unknown pathways as part of a "reconnaissance operation."
The FSB also claimed the efforts showed "close cooperation" between Apple and the National Security Agency (NSA). No other technical details were provided. Apple, in a statement shared with The Hacker News, said it has "never worked with any government to insert a backdoor into any Apple product and never will."
"The U.S. intelligence services have been using IT giants for decades to collect internet users' personal data without their knowledge," the Russian Ministry of Foreign Affairs said in a statement. "In this instance, they used the software vulnerabilities of U.S.-made smartphones."
Kaspersky researcher Ivan Kwiatkowski has since acknowledged the "two sets of activities are in fact related," citing overlaps in the indicators of compromise (IoCs) released by RU-CERT.
The antimalware vendor further described Operation Triangulation as an "extremely complex, professional targeted cyberattack," noting it targeted "several dozen iPhones of senior employees." The real exposure of the espionage campaign is yet to be ascertained.
(The story has been updated after publication to reflect additional information about the attacks and the targets involved.)
Microsoft Details Critical Apple macOS Vulnerability Allowing SIP Protection Bypass
31.5.23 Apple The Hacker News
Microsoft has shared details of a now-patched flaw in Apple macOS that could be abused by threat actors with root access to bypass security enforcements and perform arbitrary actions on affected devices.
Specifically, the flaw – dubbed Migraine and tracked as CVE-2023-32369 – could be abused to get around a key security measure called System Integrity Protection (SIP), or "rootless," which limits the actions the root user can perform on protected files and folders.
"The most straight-forward implication of a SIP bypass is that [...] an attacker can create files that are protected by SIP and therefore undeletable by ordinary means," Microsoft researchers Jonathan Bar Or, Michael Pearse, and Anurag Bohra said.
Even worse, it could be exploited to gain arbitrary kernel code execution and even access sensitive data by replacing databases that manage Transparency, Consent, and Control (TCC) policies.
The bypass is made possible by leveraging a built-in macOS tool called Migration Assistant to activate the migration process via an AppleScript that's designed to ultimately launch an arbitrary payload.
This, in turn, stems from the fact that systemmigrationd – the daemon used to handle device transfer – comes with the com.apple.rootless.install.heritable entitlement, allowing all its child processes, including bash and perl, to bypass SIP checks.
As a result, a threat actor already with code execution capabilities as root could trigger systemmigrationd to run perl, which could then be used to run a malicious shell script as the migration process is underway.
Following responsible disclosure, the vulnerability was addressed by Apple as part of updates (macOS Ventura 13.4, macOS Monterey 12.6.6, and macOS Big Sur 11.7.7) shipped on May 18, 2023.
The iPhone maker described CVE-2023-32369 as a logic issue that could allow a malicious app to modify protected parts of the file system.
Migraine is the latest addition to the list of macOS security bypasses that have been documented under the names Shrootless (CVE-2021-30892, CVSS score: 5.5), powerdir (CVE-2021-30970, CVSS score: 5.5), and Achilles (CVE-2022-42821, CVSS score: 5.5).
"The implications of arbitrary SIP bypasses are serious, as the potential for malware authors is significant," the researchers said.
"Bypassing SIP could lead to serious consequences, such as increasing the potential for attackers and malware authors to successfully install rootkits, create persistent malware, and expand the attack surface for additional techniques and exploits."
The findings come as Jamf Threat Labs disclosed details of a type confusion flaw in the macOS kernel that could be weaponized by a rogue app installed on the device to execute arbitrary code with kernel privileges.
Labeled ColdInvite (aka CVE-2023-27930), the flaw "can be exploited to leverage the co-processor in order to obtain read/write privileges to the kernel, allowing a bad actor to get closer to realizing their ultimate goal of fully compromising the device."
Predator Android Spyware: Researchers Uncover New Data Theft Capabilities
28.5.23 Android The Hacker News
Security researchers have detailed the inner workings of the commercial Android spyware called Predator, which is marketed by the Israeli company Intellexa (previously Cytrox).
Predator was first documented by Google's Threat Analysis Group (TAG) in May 2022 as part of attacks leveraging five different zero-day flaws in the Chrome web browser and Android.
The spyware, which is delivered by means of another loader component called Alien, is equipped to record audio from phone calls and VoIP-based apps as well as gather contacts and messages, including from Signal, WhatsApp, and Telegram.
Its other functionalities allow it to hide applications and prevent applications from being executed upon rebooting the handset.
"A deep dive into both spyware components indicates that Alien is more than just a loader for Predator and actively sets up the low-level capabilities needed for Predator to spy on its victims," Cisco Talos said in a technical report.
Spyware like Predator and NSO Group's Pegasus are carefully delivered as part of highly-targeted attacks by weaponizing what are called zero-click exploit chains that typically require no interaction from the victims and allow for code execution and privilege escalation.
"Predator is an interesting piece of mercenary spyware that has been around since at least 2019, designed to be flexible so that new Python-based modules can be delivered without the need for repeated exploitation, thus making it especially versatile and dangerous," Talos explained.
Both Predator and Alien are designed to get around security guardrails in Android, with the latter loaded into a core Android process called Zygote to download and launch other spyware modules, counting Predator, from an external server.
It's currently not clear how Alien is activated on an infected device in the first place. However, it's suspected to be loaded from shellcode that's executed by taking advantage of initial-stage exploits.
"Alien is not just a loader but also an executor — its multiple threads will keep reading commands coming from Predator and executing them, providing the spyware with the means to bypass some of the Android framework security features," the company said.
The various Python modules associated with Predator make it possible to accomplish a wide array of tasks such as information theft, surveillance, remote access, and arbitrary code execution.
The spyware, which arrives as an ELF binary before setting up a Python runtime environment, can also add certificates to the store and enumerate the contents of various directories on disk if it's running on a device manufactured by Samsung, Huawei, Oppo, or Xiaomi.
That said, there are still many missing pieces that could help complete the attack puzzle. This comprises a main module called tcore and a privilege escalation mechanism dubbed kmem, both of which have remained elusive to obtain thus far.
Cisco Talos theorized that tcore could have implemented other features like geolocation tracking, camera access, and simulating a shutdown to covertly spy on victims.
The findings come as threat actors' use of commercial spyware has witnessed a surge in recent years just as the number of cyber mercenary companies supplying these services are on an upward trajectory.
While these sophisticated tools are intended for exclusive use by governments to counter serious crime and combat national security threats, they have also been abused by customers to surveil on dissidents, human rights activists, journalists, and other members of the civil society.
As a case in point, digital rights group Access Now said that it uncovered evidence of Pegasus targeting a dozen people in Armenia – including an NGO worker, two journalists, a United Nations official, and a human rights ombudsperson in Armenia. One of the victims was hacked at least 27 times between October 2020 and July 2021.
"This is the first documented evidence of the use of Pegasus spyware in an international war context," Access Now said, adding it began an investigation after Apple sent notifications to the individuals in question that they may have been a victim of state-sponsored spyware attacks in November 2021.
There are no conclusive links that connect the spyware use to a specific government agency in either Armenia or Azerbaijan. It's worth noting that Armenia was outed as a customer of Intellexa by Meta in December 2021 in attacks aimed at politicians and journalists in the nation.
What's more, cybersecurity company Check Point earlier this year disclosed that various Armenian entities have been infected with a Windows backdoor referred to as OxtaRAT as part of an espionage campaign aligned with Azerbaijani interests.
In a more unusual turn of events, The New York Times and The Washington Post reported this week that the Mexican government may be spying on itself by using Pegasus against a senior official in charge of investigating alleged military abuses.
Mexico is also the first and most prolific user of Pegasus, despite its promises to cease the illegal use of the notorious spyware.
Data Stealing Malware Discovered in Popular Android Screen Recorder App
24.5.23 Android The Hacker News
Google has removed a screen recording app named "iRecorder - Screen Recorder" from the Play Store after it was found to sneak in information stealing capabilities nearly a year after the app was published as an innocuous app.
The app (APK package name "com.tsoft.app.iscreenrecorder"), which accrued over 50,000 installations, was first uploaded on September 19, 2021. The malicious functionality is believed to have been introduced in version 1.3.8, which was released on August 24, 2022.
"It is rare for a developer to upload a legitimate app, wait almost a year, and then update it with malicious code," ESET security researcher Lukáš Štefanko said in a technical report.
"The malicious code that was added to the clean version of iRecorder is based on the open source AhMyth Android RAT (remote access trojan) and has been customized into what we named AhRat."
iRecorder was first flagged as harboring the AhMyth trojan on October 28, 2022, by Kaspersky security analyst Igor Golovin, indicating that the app managed to stay accessible all this time and even received a new update as recently as February 26, 2023.
The application's malicious behavior specially involves extracting microphone recordings and harvesting files with specific extensions, with ESET describing AhRat as a lightweight version of AhMyth.
The data gathering characteristic points to a possible espionage motive, although there is no evidence to link the activity to any known threat actor. However, AhMyth has been previously employed by Transparent Tribe in attacks targeting South Asia.
iRecorder is the work of a developer named Coffeeholic Dev, who has also released several other apps over the years. None of them are accessible as of writing -
iBlock (com.tsoft.app.iblock.ad)
iCleaner (com.isolar.icleaner)
iEmail (com.tsoft.app.email)
iLock (com.tsoft.app.ilock)
iVideoDownload (com.tsoft.app.ivideodownload)
iVPN (com.ivpn.speed)
File speaker (com.teasoft.filespeaker)
QR Saver (com.teasoft.qrsaver)
Tin nóng tin lạnh (read: Hot news and cold news in Vietnamese) (com.teasoft.news)
This development is just the latest example of malware adopting a technique called versioning, which refers to uploading a clean version of the app to the Play Store to build trust among users and then adding malicious code at a later stage via app updates, in a bid to slip through the app review process.
"The AhRat research case serves as a good example of how an initially legitimate application can transform into a malicious one, even after many months, spying on its users and compromising their privacy," Štefanko said.
WebKit Under Attack: Apple Issues Emergence Patches for 3 New Zero-Day Vulnerabilities
19.5.23 Apple The Hacker News
Apple on Thursday rolled out security updates to iOS, iPadOS, macOS, tvOS, watchOS, and the Safari web browser to address three new zero-day flaws that it said are being actively exploited in the wild.
The three security shortcomings are listed below -
CVE-2023-32409 - A WebKit flaw that could be exploited by a malicious actor to break out of the Web Content sandbox. It was addressed with improved bounds checks.
CVE-2023-28204 - An out-of-bounds read issue in WebKit that could be abused to disclose sensitive information when processing web content. It was addressed with improved input validation.
CVE-2023-32373 - A use-after free bug in WebKit that could lead to arbitrary code execution when processing maliciously crafted web content. It was addressed with improved memory management.
The iPhone maker credited Clément Lecigne of Google's Threat Analysis Group (TAG) and Donncha Ó Cearbhaill of Amnesty International's Security Lab for reporting CVE-2023-32409. An anonymous researcher has been acknowledged for reporting the other two issues.
It's worth noting that both CVE-2023-28204 and CVE-2023-32373 were patched as part of Rapid Security Response updates – iOS 16.4.1 (a) and iPadOS 16.4.1 (a) – the company released at the start of the month.
There are currently no additional technical specifics about the flaws, the nature of the attacks, or the identity of the threat actors that may be exploiting them.
That said, such weaknesses have been historically leveraged as part of highly-targeted intrusions to deploy mercenary spyware on the devices of dissidents, journalists, and human rights activists, among others.
The latest updates are available for the following devices and operating systems -
iOS 16.5 and iPadOS 16.5 - iPhone 8 and later, iPad Pro (all models), iPad Air 3rd generation and later, iPad 5th generation and later, and iPad mini 5th generation and later
iOS 15.7.6 and iPadOS 15.7.6 - iPhone 6s (all models), iPhone 7 (all models), iPhone SE (1st generation), iPad Air 2, iPad mini (4th generation), and iPod touch (7th generation)
macOS Ventura 13.4 - macOS Ventura
tvOS 16.5 - Apple TV 4K (all models) and Apple TV HD
watchOS 9.5 - Apple Watch Series 4 and later
Safari 16.5 - macOS Big Sur and macOS Monterey
Apple has so far remediated a total of six actively exploited zero-days since the start of 2023. Earlier this February, the company plugged a WebKit flaw (CVE-2023-23529) that could lead to remote code execution.
Then last month, it shipped fixes for a pair of vulnerabilities (CVE-2023-28205 and CVE-2023-28206) that allowed for code execution with elevated privileges. Lecigne and Ó Cearbhaill were credited with reporting the security defects.
This Cybercrime Syndicate Pre-Infected Over 8.9 Million Android Phones Worldwide
19.5.23 Android The Hacker News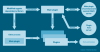
A cybercrime enterprise known as Lemon Group is leveraging millions of pre-infected Android smartphones worldwide to carry out their malicious operations, posing significant supply chain risks.
"The infection turns these devices into mobile proxies, tools for stealing and selling SMS messages, social media and online messaging accounts and monetization via advertisements and click fraud," cybersecurity firm Trend Micro said.
The activity encompasses no fewer than 8.9 million compromised Android devices, particularly budget phones, with the highest concentration of the infections discovered in the U.S., Mexico, Indonesia, Thailand, Russia, South Africa, India, Angola, the Philippines, and Argentina.
The findings were presented by researchers Fyodor Yarochkin, Zhengyu Dong, Vladimir Kropotov, and Paul Pajares at the Black Hat Asia conference held in Singapore last week.
Describing it as a continuously evolving problem, the cybersecurity firm said the threat actors are branching out to other Android-based IoT devices such as Smart TVs, Android TV boxes, entertainment systems, and even children's watches.
The infections are globally spread across in over 180 countries, with over 50 brands of mobile devices compromised by a malware strain called Guerilla.
"Following our timeline estimates, the threat actor has spread this malware over the last five years," the researchers said. "A compromise on any significant critical infrastructure with this infection can likely yield a significant profit for Lemon Group in the long run at the expense of legitimate users."
Guerilla was first documented by Sophos in 2018 when it discovered 15 apps uploaded on the Play Store that harbored functionality to engage in click fraud and act as a backdoor.
The malware also attracted attention in early 2022 for its ability to intercept SMS messages that match predefined characteristics such as one-time passwords (OTPs) associated with various online platforms, shortly after which the threat actor changed the name of the undertaking from Lemon to Durian Cloud SMS.
The goal, per Trend Micro, is to bypass SMS-based verification and advertise bulk virtual phone numbers – which belong to unsuspecting users of the infected Android handsets – for sale to create online accounts.

While such services have a privacy benefit, allowing users to sign up for services using temporary or disposable phone numbers, they can also be abused to create spam accounts on a large scale and conduct fraud.
The latest findings from the cybersecurity company illustrate that the SMS grabbing feature is just one of the many plugins associated with a downloader component (aka the main plugin) that's loaded into a zygote process by means of a tampered library.
It's worth noting that the same technique of modifying the zygote process has also been adopted by another mobile trojan called Triada.
"With this, every time other app processes are forked from the zygote, it would also be tampered," the researchers said. "The main plugin will load other plugins with the current process being the target, and the other plugins will try to control the current app via a hook."
Each of the Guerilla plugins serves a particular business function and a monetization opportunity for the Lemon Group actors. Some of them are listed below -
Proxy plugin to setup reverse proxy from an infected phone and allow other actors to rent out access to the network resources of the affected mobile device
Cookie plugin to harvest users' Facebook cookies and other profile information
WhatsApp plugin to hijack sessions and send unwanted messages
Splash plugin to serve unwarranted ads when launching certain apps, and
Silent plugin to stealthily install an APK file and launch the app
Further investigation into the sprawling operation has unraveled infrastructure overlaps Lemon Group and Triada, suggesting that the two groups may have collaborated at some point.
The unauthorized firmware modifications are believed to have occurred via an unnamed third-party vendor that "produces the firmware components for mobile phones" and which also manufactures similar components for Android Auto.
That said, Trend Micro did not reveal the exact modus operandi of how the devices are infected with the trojanized firmware containing Guerilla, how they are sold in the market, and what brands are impacted.
The disclosure comes as Microsoft security researcher Dimitrios Valsamaras detailed a new attack method dubbed Dirty Stream that turns Android share targets into a vector for distributing malicious payloads and capturing sensitive data from other apps installed on a device.
"The concept is similar to a file upload vulnerability of a web application," Valsamaras said. "More specifically, a malicious app uses a specially crafted content provider to bear a payload that it sends to the target application."
"As the sender controls the content but also the name of the stream, the receiver may overwrite critical files with malicious content in case it doesn't perform some necessary security checks. Additionally, when certain conditions apply, the receiver may also be forced to copy protected files to a public directory, setting the user's private data at risk."
Apple Thwarts $2 Billion in App Store Fraud, Rejects 1.7 Million App Submissions
18.5.23 Apple The Hacker News
Apple has announced that it prevented over $2 billion in potentially fraudulent transactions and rejected roughly 1.7 million app submissions for privacy and security violations in 2022.
The computing giant said it terminated 428,000 developer accounts for potential fraudulent activity, blocked 105,000 fake developer account creations, and deactivated 282 million bogus customer accounts. It further noted that it thwarted 198 million attempted fraudulent new accounts prior to their creation.
In contrast, Apple is estimated to have booted out 802,000 developer accounts in 2021. The company attributed the decline to new App Store "methods and protocols" that prevent the creation of such accounts in the first place.
"In 2022, Apple protected users from nearly 57,000 untrustworthy apps from illegitimate storefronts," the company emphasized. "These unauthorized marketplaces distribute harmful software that can imitate popular apps or alter them without the consent of their developers."
It also touted its App Review process as having been able to flag apps using malicious code designed to steal users' credentials from third-party services as well as those that impersonated legitimate financial management platforms. A total of 6.1 million app submissions were reviewed.
"Over 153,000 app submissions rejected from the App Store last year were found to be spam, copycats, or misleading, and nearly 29,000 submissions were rejected for containing hidden or undocumented features," Apple said. "Upward of 400,000 app submissions were rejected for privacy violations."
On a related note, more than 147 million fraudulent ratings and reviews in the App Store were detected and blocked in 2022, with Apple intercepting close to 3.9 million attempts to install or launch apps distributed illicitly through its Developer Enterprise Program over the past 30 days alone.
Last but not least, Cupertino highlighted that it also blocked nearly 3.9 million stolen credit cards from being used to make fraudulent purchases, and banned 714,000 accounts from transacting again. In all, $2.09 billion in fraudulent transactions on the App Store were blocked in 2022.
The numbers come amid speculations that Apple may soon enable sideloading and allow third-party app stores on iOS devices to comply with the European Union's Digital Markets Act (DMA), which went into effect on November 1, 2022.
The disclosure also arrives close on the heels of a similar report from Google, which said it dismantled 173,000 bad accounts and blocked 1.43 million harmful apps from being published to the Play Store in 2022. It also fended off more than $2 billion in fraudulent and abusive transactions.
Despite these ongoing efforts by Apple and Google, threat actors have found a variety of ways to bypass security protections and publish their apps on the official app stores, often submitting innocuous apps to get past the vetting process and subsequently updating them with malicious functionality.
Earlier this February, app development company Mysk uncovered sketchy two-factor authentication (2FA) apps – one of them ranking at number five for "authenticator app" in the US App Store – that trick users into subscribing to a weekly or annual plan. Similar scam apps were reported in 2022.
"As bad actors evolve their dishonest tactics and methods of deception, Apple supplements its anti-fraud initiatives with feedback gleaned from a myriad of channels — from news stories to social media to AppleCare calls — and will continue to develop new approaches and tools designed to prevent fraud from harming App Store users and developers," the company said.
OilAlpha: Emerging Houthi-linked Cyber Threat Targets Arabian Android Users
18.5.23 Android The Hacker News
A hacking group dubbed OilAlpha with suspected ties to Yemen's Houthi movement has been linked to a cyber espionage campaign targeting development, humanitarian, media, and non-governmental organizations in the Arabian peninsula.
"OilAlpha used encrypted chat messengers like WhatsApp to launch social engineering attacks against its targets," cybersecurity company Recorded Future said in a technical report published Tuesday.
"It has also used URL link shorteners. Per victimology assessment, it appears a majority of the targeted entities were Arabic-language speakers and operated Android devices."
OilAlpha is the new cryptonym given by Recorded Future to two overlapping clusters previously tracked by the company under the names TAG-41 and TAG-62 since April 2022. TAG-XX (short for Threat Activity Group) is the temporary moniker assigned to emerging threat groups.
The assessment that the adversary is acting in the interest of the Houthi movement is based on the fact that the infrastructure used in the attacks is almost exclusively associated with Public Telecommunication Corporation (PTC), a Yemeni telecom service provider subjected to Houthi's control.
That having said, the persistent use of PTC assets doesn't exclude the possibility of a compromise by an unknown third-party. Recorded Future, however, noted that it did not find any evidence to back up this line of reasoning.
Another factor is the use of malicious Android-based applications to likely surveil delegates associated with Saudi Arabian government-led negotiations. These apps mimicked entities tied to the Saudi Arabian government and a humanitarian organization in the U.A.E.

The attack chains commence with potential targets – political representatives, media personalities, and journalists – receiving the APK files directly from WhatsApp accounts using Saudi Arabian telephone numbers by masquerading the apps as belonging to UNICEF, NGOs, and other relief organizations.
The apps, for their part, act as a conduit to drop a remote access trojan called SpyNote (aka SpyMax) that comes with a plethora of features to capture sensitive information from infected devices.
"OilAlpha's focus in targeting Android devices is not surprising due to the high saturation of Android devices in the Arabian Peninsula region," Recorded Future said.
The cybersecurity company said it also observed njRAT (aka Bladabindi) samples communicating with command-and-control (C2) servers associated with the group, indicating that it's simultaneously making use of desktop malware in its operations.
"OilAlpha launched its attacks at the behest of a sponsoring entity, namely Yemen's Houthis," it theorized. "OilAlpha could be directly affiliated to its sponsoring entity, or could also be operating like a contracting party."
"While OilAlpha's activity is pro-Houthi, there is insufficient evidence to suggest that Yemeni operatives are responsible for this threat activity. External threat actors like Lebanese or Iraqi Hezbollah, or even Iranian operators supporting the IRGC, may have led this threat activity."
Hackers Using Golang Variant of Cobalt Strike to Target Apple macOS Systems
16.5.23 Apple The Hacker News
A Golang implementation of Cobalt Strike called Geacon is likely to garner the attention of threat actors looking to target Apple macOS systems.
The findings come from SentinelOne, which observed an uptick in the number of Geacon payloads appearing on VirusTotal in recent months.
"While some of these are likely red-team operations, others bear the characteristics of genuine malicious attacks," security researchers Phil Stokes and Dinesh Devadoss said in a report.
Cobalt Strike is a well-known red teaming and adversary simulation tool developed by Fortra. Owing to its myriad post-exploitation capabilities, illegally cracked versions of the software have been abused by threat actors over the years.
While post-exploitation activity associated with Cobalt Strike has primarily singled out Windows, such attacks against macOS are something of a rarity.
In May 2022, software supply chain firm Sonatype disclosed details of a rogue Python package called "pymafka" that was designed to drop a Cobalt Strike Beacon onto compromised Windows, macOS, and Linux hosts.
That may, however, change with the emergence of Geacon artifacts in the wild. Geacon is a Go variant of Cobalt Strike that has been available on GitHub since February 2020.
Further analysis of two new VirusTotal samples that were uploaded in April 2023 has traced their origins to two Geacon variants (geacon_plus and geacon_pro) that were developed in late October by two anonymous Chinese developers z3ratu1 and H4de5.
The geacon_pro project is no longer accessible on GitHub, but an Internet Archive snapshot captured on March 6, 2023, reveals its ability to bypass antivirus engines such as Microsoft Defender, Kaspersky, and Qihoo 360 360 Core Crystal.
H4de5, the developer behind geacon_pro, claims the tool is mainly designed to support CobaltStrike versions 4.1 and later, while geacon_plus supports CobaltStrike version 4.0. The current version of the software is 4.8.
Xu Yiqing's Resume_20230320.app, one of the artifacts discovered by SentinelOne, employs a run-only AppleScript to reach out to a remote server and download a Geacon payload. It's compatible with both Apple silicon and Intel architectures.
"The unsigned Geacon payload is retrieved from an IP address in China," the researchers said. "Before it begins its beaconing activity, the user is presented with a two-page decoy document embedded in the Geacon binary. A PDF is opened displaying a resume for an individual named 'Xu Yiqing.'"
The Geacon binary, compiled from the geacon_plus source code, packs a multitude of functions that allows it to download next-stage payloads and exfiltrate data, and facilitate network communications.
The second sample, per the cybersecurity firm, is embedded within a trojanized app that masquerades as the SecureLink remote support app (SecureLink.app) and mainly targets Intel devices.
The barebones, unsigned application requests for users' permission to access contacts, photos, reminders, as well as the device's camera and microphone. Its main component is a Geacon payload built from the geacon_pro project that connects to a known command-and-control (C2) server in Japan.
The development comes as the macOS ecosystem is being targeted by a wide variety of threat actors, including state-sponsored groups, to deploy backdoors and information stealers.
"The uptick in Geacon samples over the last few months suggests that security teams should be paying attention to this tool and ensuring that they have protections in place," the researchers said.
New Android Malware 'FluHorse' Targeting East Asian Markets with Deceptive Tactics
6.5.23 Android The Hacker News
Various sectors in East Asian markets have been subjected to a new email phishing campaign that distributes a previously undocumented strain of Android malware called FluHorse that abuses the Flutter software development framework.
"The malware features several malicious Android applications that mimic legitimate applications, most of which have more than 1,000,000 installs," Check Point said in a technical report. "These malicious apps steal the victims' credentials and two-factor authentication (2FA) codes."
The malicious apps have been found to imitate popular apps like ETC and VPBank Neo, which are widely used in Taiwan and Vietnam. Evidence gathered so far shows that the activity has been active since at least May 2022.
The phishing scheme in itself is fairly straightforward, wherein victims are lured with emails that contain links to a bogus website that hosts malicious APK files. Also added to the website are checks that aim to screen victims and deliver the app only if their browser User-Agent string matches that of Android.
Once installed, the malware requests for SMS permissions and prompts the user to input their credentials and credit card information, all of which is subsequently exfiltrated to a remote server in the background while the victim is asked to wait for several minutes.
The threat actors also abuse their access to SMS messages to intercept all incoming 2FA codes and redirect them to the command-and-control server.
The Israeli cybersecurity firm said it further identified a dating app that redirected Chinese-speaking users to rogue landing pages that are designed to capture credit card information.
Several high-profile organizations are said to be among the recipients of these phishing emails, including employees of the government sector and large industrial companies, with new infrastructure and fraudulent applications showing up every month.
Interestingly, the malicious functionality is implemented with Flutter, an open source UI software development kit that can be used to develop cross-platform apps from a single codebase.
While threat actors are known to use a variety of tricks like evasion techniques, obfuscation, and long delays before execution to resist analysis and get around virtual environments, the use of Flutter marks a new level of sophistication.
"The malware developers did not put much effort into the programming, instead relying on Flutter as a developing platform," the researchers concluded.
"This approach allowed them to create dangerous and mostly undetected malicious applications. One of the benefits of using Flutter is that its hard-to-analyze nature renders many contemporary security solutions worthless."
Fleckpe Android Malware Sneaks onto Google Play Store with Over 620,000 Downloads
5.5.23 Android The Hacker News
A new Android subscription malware named Fleckpe has been unearthed on the Google Play Store, amassing more than 620,000 downloads in total since 2022.
Kaspersky, which identified 11 apps on the official app storefront, said the malware masqueraded as legitimate photo editing apps, camera, and smartphone wallpaper packs. The apps have since been taken down.
The operation primarily targets users from Thailand, although telemetry data gathered by the Russian cybersecurity firm has revealed victims in Poland, Malaysia, Indonesia, and Singapore.
The apps further offer the promised functionality to avoid raising red flags, but conceal their real purpose under the hood. The list of the offending apps is as follows -
Beauty Camera Plus (com.beauty.camera.plus.photoeditor)
Beauty Photo Camera (com.apps.camera.photos)
Beauty Slimming Photo Editor (com.beauty.slimming.pro)
Fingertip Graffiti (com.draw.graffiti)
GIF Camera Editor (com.gif.camera.editor)
HD 4K Wallpaper (com.hd.h4ks.wallpaper)
Impressionism Pro Camera (com.impressionism.prozs.app)
Microclip Video Editor (com.microclip.vodeoeditor)
Night Mode Camera Pro (com.urox.opixe.nightcamreapro)
Photo Camera Editor (com.toolbox.photoeditor)
Photo Effect Editor (com.picture.pictureframe)
"When the app starts, it loads a heavily obfuscated native library containing a malicious dropper that decrypts and runs a payload from the app assets," Kaspersky researcher Dmitry Kalinin said.
The payload, for its part, is designed to contact a remote server and transmit information about the compromised device (e.g., Mobile Country Code and Mobile Network Code), following which the server responds back with a paid subscription page.
The malware subsequently opens the page in an invisible web browser window and attempts to subscribe on the user's behalf by abusing its permissions to access notifications and obtain the confirmation code required to complete the step.
In a sign that Fleckpe is being actively developed, recent versions of the malware have moved most of the malicious functionality to the native library in a bid to evade detection by security tools.
"The payload now only intercepts notifications and views web pages, acting as a bridge between the native code and the Android components required for purchasing a subscription," Kalinin noted.
"Unlike the native library, the payload has next to no evasion capabilities, although the malicious actors did add some code obfuscation to the latest version."
This is not the first time subscription malware has been found on the Google Play Store. Fleckpe joins other fleeceware families like Joker (aka Bread or Jocker) and Harly, which subscribe infected devices to unwanted premium services and conduct billing fraud.
While such apps are not as dangerous as spyware or financial trojans, they can still incur unauthorized charges and be repurposed by its operators to harvest a wide range of sensitive information and serve as entry points for more nefarious malware.
If anything, the findings are yet another indication that threat actors are continuing to discover new ways to sneak their apps onto official app marketplaces to scale their campaigns, requiring that users exercise caution when downloading apps and granting permissions to them.
"Growing complexity of the trojans has allowed them to successfully bypass many anti-malware checks implemented by the marketplaces, remaining undetected for long periods of time," Kalinin said.
BouldSpy Android Spyware: Iranian Government's Alleged Tool for Spying on Minority Groups
3.5.23 Android The Hacker News
A new Android surveillanceware possibly used by the Iranian government has been used to spy on over 300 individuals belonging to minority groups.
The malware, dubbed BouldSpy, has been attributed with moderate confidence to the Law Enforcement Command of the Islamic Republic of Iran (FARAJA). Targeted victims include Iranian Kurds, Baluchis, Azeris, and Armenian Christian groups.
"The spyware may also have been used in efforts to counter and monitor illegal trafficking activity related to arms, drugs, and alcohol," Lookout said, based on exfiltrated data that contained photos of drugs, firearms, and official documents issued by FARAJA.
BouldSpy, like other Android malware families, abuses its access to Android's accessibility services and other intrusive permissions to harvest sensitive data such as web browser history, photos, contact lists, SMS logs, keystrokes, screenshots, clipboard content, microphone audio, and video call recordings.
It's worth pointing out that BouldSpy refers to the same Android malware that Cyble codenamed DAAM in its own analysis last month.

Evidence gathered so far points to BouldSpy being installed on targets' devices via physical access, potentially confiscated after detention. This theory is bolstered by the fact that the first locations gathered from victim devices are mostly concentrated around Iranian law enforcement establishments and border control posts.
The malware comes alongside a command-and-control (C2) panel to manage victim devices, not to mention create new malicious apps that masquerade as seemingly innocuous apps like benchmarking tools, currency converters, interest calculators, and the Psiphon censorship circumvention utility.
Other noteworthy features comprise its ability to run additional code sent from the C2 server, receive commands through SMS messages, and even disable battery management features to prevent the device from terminating the spyware.
It further incorporates an "unused and nonfunctional" ransomware component that borrows its implementation from an open source project called CryDroid, raising the possibility that it's being actively developed or is a false flag planted by the threat actor.
"Once installed, the spyware will seek to establish a network connection to its C2 server and exfiltrate any cached data from the victim's device to the server," Lookout researchers said. "BouldSpy represents yet another surveillance tool taking advantage of the personal nature of mobile devices."
Google Blocks 1.43 Million Malicious Apps, Bans 173,000 Bad Accounts in 2022
1.5.23 Android The Hacker News
Google disclosed that its improved security features and app review processes helped it block 1.43 million bad apps from being published to the Play Store in 2022.
In addition, the company said it banned 173,000 bad accounts and fended off over $2 billion in fraudulent and abusive transactions through developer-facing features like Voided Purchases API, Obfuscated Account ID, and Play Integrity API.
The addition of identity verification methods such as phone number and email address to join Google Play contributed to a reduction in accounts used to publish apps that go against its policies, Google pointed out.
The search behemoth further said it "prevented about 500K submitted apps from unnecessarily accessing sensitive permissions over the past 3 years."
"In 2022, the App Security Improvements program helped developers fix ~500K security weaknesses affecting ~300K apps with a combined install base of approximately 250B installs," it noted.
In contrast, Google blocked 1.2 million policy-violating apps from being published and banned 190,000 bad accounts in 2021.
The development comes weeks after Google enacted a new data deletion policy that requires app developers to offer a "readily discoverable option" to users from both within an app and outside of it.
Despite these efforts from Google, cybercriminals are continuing to find ways around the app storefront's security protections and publish malicious and adware apps.
Case in point, McAfee's Mobile Research Team discovered 38 games masquerading as Minecraft and which have been installed by no less than 35 million users worldwide, primarily located in the U.S., Canada, South Korea, and Brazil.
Android Security
These gaming apps, while offering the promised functionality, have been found to incorporate the HiddenAds malware to stealthily load ads in the background to generate illicit revenue for its operators.
Some of the most downloaded apps are as follows -
Block Box Master Diamond (com.good.robo.game.builder.craft.block)
Craft Sword Mini Fun (com.craft.world.fairy.fun.everyday.block)
Block Box Skyland Sword (com.skyland.pet.realm.block.rain.craft)
Craft Monster Crazy Sword (com.skyland.fun.block.game.monster.craft)
Block Pro Forrest Diamond (com.monster.craft.block.fun.robo.fairy)
"One of the most accessible content for young people using mobile devices is games," McAfee said. "Malware authors are also aware of this and try to hide their malicious features inside games."
Complicating the problem is the surge in Android banking malware that can be weaponized by threat actors to gain access to victim devices and harvest personal information.
Another emerging trend is the use of binding services to trojanize legitimate applications and conceal a rogue APK payload. This technique has been adopted by bad actors to distribute an Android botnet dubbed DAAM, Cyble said.
The malware, once installed, establishes connections with a remote server to perform a wide range of nefarious actions, including acting as ransomware by encrypting files stored in the devices using a password retrieved from the server.
DAAM also abuses Android's accessibility services to monitor users' activity, thereby allowing it to log keystrokes, record VoIP calls from instant messaging apps, collect browser history, call logs, photos, screenshots, and SMS messages, run arbitrary code, and open phishing URLs.
"Malware authors often leverage genuine applications to distribute malicious code to avoid suspicion," the cybersecurity firm said in an analysis published last month.
Android Security
The findings also follow an advisory from CloudSEK, which discovered that several popular Android applications like Canva, LinkedIn, Strava, Telegram, and WhatsApp do not invalidate or revalidate session cookies after app data is transferred from one device to another.
While this attack scenario requires an adversary to have physical access to a target's phone, it could allow for account takeover and grant an adversary unauthorized access to confidential data.
To mitigate such threats, it's advised to enable two-factor authentication (2FA) to add an extra layer of account protection, scrutinize app permissions, secure devices with a password, and avoid leaving them unattended in public places.
New Atomic macOS Malware Steals Keychain Passwords and Crypto Wallets
28.4.23 Apple The Hacker News
Threat actors are advertising a new information stealer for the Apple macOS operating system called Atomic macOS Stealer (or AMOS) on Telegram for $1,000 per month, joining the likes of MacStealer.
"The Atomic macOS Stealer can steal various types of information from the victim's machine, including Keychain passwords, complete system information, files from the desktop and documents folder, and even the macOS password," Cyble researchers said in a technical report.
Among other features include its ability to extract data from web browsers and cryptocurrency wallets like Atomic, Binance, Coinomi, Electrum, and Exodus. Threat actors who purchase the stealer from its developers are also provided a ready-to-use web panel for managing the victims.
The malware takes the form of an unsigned disk image file (Setup.dmg) that, when executed, urges the victim to enter their system password on a bogus prompt to escalate privileges and carry out its malicious activities -- a technique also adopted by MacStealer.
The initial intrusion vector used to deliver the malware is immediately not clear, although it's possible that users are manipulated into downloading and executing it under the guise of legitimate software.
The Atomic stealer artifact, submitted to VirusTotal on April 24, 2023, also bears the name "Notion-7.0.6.dmg," suggesting that it's being propagated as the popular note-taking app. Other samples unearthed by the MalwareHunterTeam are distributed as "Photoshop CC 2023.dmg" and "Tor Browser.dmg."
"Malware such as the Atomic macOS Stealer could be installed by exploiting vulnerabilities or hosting on phishing websites," Cyble noted.
Atomic then proceeds to harvest system metadata, files, iCloud Keychain, as well as information stored in web browsers (e.g., passwords, autofill, cookies, credit card data) and crypto wallet extensions, all of which are compressed into a ZIP archive and sent to a remote server. The ZIP file of the compiled information is then sent to pre-configured Telegram channels.
The development is another sign that macOS is increasingly becoming a lucrative target beyond nation-state hacking groups to deploy stealer malware, making it imperative that users only download and install software from trusted sources, enable two-factor authentication, review app permissions, and refrain from opening suspicious links received via emails or SMS messages.
NSO Group Used 3 Zero-Click iPhone Exploits Against Human Rights Defenders
20.4.23 Apple The Hacker News
Israeli spyware maker NSO Group deployed at least three novel "zero-click" exploits against iPhones in 2022 to infiltrate defenses erected by Apple and deploy Pegasus, according to the latest findings from Citizen Lab.
"NSO Group customers widely deployed at least three iOS 15 and iOS 16 zero-click exploit chains against civil society targets around the world," the interdisciplinary laboratory based at the University of Toronto said.
NSO Group is the manufacturer of Pegasus, a sophisticated cyber weapon that's capable of extracting sensitive information stored in a device – e.g., messages, locations, photos, and call logs, among others — in real-time. It's typically delivered to targeted iPhones using zero-click and/or zero-day exploits.
While it has been pitched as a tool for law enforcement agencies to combat serious crimes such as child sexual abuse and terrorism, it has also been deployed illegally by authoritarian governments to spy on human rights defenders, democracy advocates, journalists, dissidents, and others.
The misuse of Pegasus prompted the U.S. government to add NSO Group to its trade blocklist in late 2021, with Apple filing a lawsuit of its own against the company for targeting its users.
In July 2022, it emerged that the spyware was used against Thai activists involved in the country's pro-democracy protests between October 2020 and November 2021 using two zero-click exploits named KISMET and FORCEDENTRY.
Two of the targets of the latest campaign unearthed by Citizen Lab include human rights defenders from Centro PRODH, which represents victims of the Mexican Army's extrajudicial killings and disappearances. The intrusions occurred in June 2022.
This entailed the use of three disparate exploit chains dubbed LATENTIMAGE, FINDMYPWN, and PWNYOURHOME that weaponized various flaws in iOS 15 and iOS 16 as zero-days to penetrate the devices and ultimately launch Pegasus -
LATENTIMAGE (iOS version 15.1.1, detected in January 2022) - An exploit that's suspected to involve the iPhone's Find My feature and SpringBoard
FINDMYPWN (iOS versions 15.5 and 15.6, detected in June 2022) - A two-phase exploit that makes use of the Find My service and iMessage
PWNYOURHOME (iOS version 16.0.3, detected in October 2022) - A two-phase exploit that combines the HomeKit functionality built into iPhones and iMessage to bypass BlastDoor protections
In an encouraging sign, Citizen Lab said it found evidence of Lockdown Mode stepping in to thwart an attempted PWNYOURHOME attack, warning users that it blocked unknown parties with Gmail and Yahoo! accounts from trying to "access a Home."
The development marks the first publicly documented instance where Lockdown Mode, which is specifically designed to reduce the iPhone's attack surface, has successfully protected an individual from a compromise.
Zero-Click iPhone
That said, Citizen Lab pointed out that NSO Group "may have figured out a way to correct the notification issue, such as by fingerprinting Lockdown Mode." Apple has since shipped several security improvements to HomeKit in iOS 16.3.1 and sent out notifications to targeted victims in November and December 2022, and March 2023.
The findings are the latest example of NSO's evolving attack techniques to break into iPhones without requiring any targets to take any action to trigger the infection.
They also coincide with a new investigation from the New York Times uncovering Mexico's use of Pegasus to target human rights defenders in recent months, detailing how the country became the first and most prolific user of the spyware.
In yet another indication of the pervasive nature of such campaigns, Jamf Threat Labs uncovered evidence of a human rights activist based in the Middle East as well as a Hungarian journalist being targeted with spyware. Their names were not disclosed.
The attack targeting the journalist's iPhone is also significant for the fact that the device was an iPhone 6s, which is no longer compatible with the latest iOS version, indicating threat actors' penchant for exploiting known and unknown vulnerabilities to meet their goals.
While Apple does back-port fixes for critical flaws to older devices (the current version supported by iPhone 6s is iOS 15.7.5), it's important to note that not all vulnerabilities are addressed for legacy devices.
"As a result, threat actors can continue to exploit unpatched vulnerabilities that have been patched on newer supported devices, potentially giving attackers more time and more information to gain remote access to targeted devices," Jamf said.
To safeguard against spyware attacks, it's recommended to apply the latest operating system updates, upgrade outdated devices to newer iPhone or iPad models, and consider enabling Lockdown Mode.
The U.K. National Cyber Security Centre (NCSC), in an advisory released on April 19, 2023, cautioned the "proliferation of commercial cyber tools will pose a growing threat to organizations and individuals globally."
"The commercial proliferation of cyber tools and services lowers the barrier to entry to state and non-state actors in obtaining capability and intelligence that they would not otherwise be able to develop or acquire," the agency said.
Goldoson Android Malware Infects Over 100 Million Google Play Store Downloads
18.4.23 Android The Hacker News
A new Android malware strain named Goldoson has been detected in the official Google Play Store spanning more than 60 legitimate apps that collectively have over 100 million downloads.
An additional eight million installations have been tracked through ONE store, a leading third-party app storefront in South Korea.
The rogue component is part of a third-party software library used by the apps in question and is capable of gathering information about installed apps, Wi-Fi and Bluetooth-connected devices, and GPS locations.
"Moreover, the library is armed with the functionality to perform ad fraud by clicking advertisements in the background without the user's consent," McAfee security researcher SangRyol Ryu said in a report published last week.
What's more, it includes the ability to stealthily load web pages, a feature that could be abused to load ads for financial profit. It achieves this by loading HTML code in a hidden WebView and driving traffic to the URLs.
Following responsible disclosure to Google, 36 of the 63 offending apps have been pulled from the Google Play Store. The remaining 27 apps have been updated to remove the malicious library.
Some of the prominent apps include -
L.POINT with L.PAY
Swipe Brick Breaker (removed)
Money Manager Expense & Budget
TMAP - 대리,주차,전기차 충전,킥보드를 티맵에서!
롯데시네마
지니뮤직 - genie
컬쳐랜드[컬쳐캐쉬]
GOM Player
메가박스 (removed), and
LIVE Score, Real-Time Score
The findings highlight the need for app developers to be transparent about the dependencies used in their software, not to mention take adequate steps to safeguard users' information against such abuse.
"Attackers are becoming more sophisticated in their attempts to infect otherwise legitimate applications across platforms," Kern Smith, vice president of sales engineering for the Americas at Zimperium, said.
"The use of third-party SDKs and code, and their potential to introduce malicious code into otherwise legitimate applications is only continuing to grow as attackers start to target the software supply chain to gain the largest footprint possible."
The development comes as Cyble took the wraps off a new Android banking trojan dubbed Chameleon that has been active since January 2023 and is targeting users in Australia and Poland.
The trojan is no different from other banking malware spotted in the wild owing to its abuse of Android's accessibility services to harvest credentials and cookies, log keystrokes, prevent its uninstallation, and perform other nefarious activities.
It's also designed to display rogue overlays on top of a specific list of apps, intercept SMS messages, and even comprises an unused functionality that allows it to download and execute another payload.
Chameleon, true to its name, has a penchant for evasion by incorporating anti-emulation checks to detect if the device is rooted or it's being executed in a debugging environment, and if so, terminate itself.
To mitigate such threats, users are recommended to only download apps from trusted sources, scrutinize app permissions, use strong passwords, enable multi-factor authentication, and exercise caution when receiving SMS or emails from unknown senders.
Severe Android and Novi Survey Vulnerabilities Under Active Exploitation
14.4.23 Android The Hacker News
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added two vulnerabilities to its Known Exploited Vulnerabilities (KEV) catalog, based on evidence of active exploitation.
The two flaws are listed below -
CVE-2023-20963 (CVSS score: 7.8) - Android Framework Privilege Escalation Vulnerability
CVE-2023-29492 (CVSS score: TBD) - Novi Survey Insecure Deserialization Vulnerability
"Android Framework contains an unspecified vulnerability that allows for privilege escalation after updating an app to a higher Target SDK with no additional execution privileges needed," CISA said in an advisory for CVE-2023-20963.
Google, in its monthly Android Security Bulletin for March 2023, acknowledged "there are indications that CVE-2023-20963 may be under limited, targeted exploitation."
The development comes as tech news site Ars Technica disclosed late last month that Android apps digitally signed by China's e-commerce company Pinduoduo weaponized the flaw to seize control of the devices and steal sensitive data, citing analysis from mobile security firm Lookout.
Chief among the capabilities of the malware-laced app includes inflating the number of Pinduoduo daily active users and monthly active users, uninstalling rival apps, accessing notifications and location information, and preventing itself from being uninstalled.
CNN, in a follow-up report published at the start of the month, said an analysis of the 6.49.0 version of the app revealed code designed to achieve privilege escalation and even track user activity on other shopping apps.
The exploits allowed the malicious app to access users' contacts, calendars, and photo albums without their consent and requested a "large number of permissions beyond the normal functions of a shopping app," the news channel said.
It's worth pointing out that Google suspended Pinduoduo's official app from the Play Store in March, citing malware identified in "off-Play versions" of the software.
That said, it's still not clear how these APK files were signed with the same key used to sign the legitimate Pinduoduo app. This either points to a key leak, the work of a rogue insider, a compromise of Pinduoduo's build pipeline, or a deliberate attempt by the Chinese company to distribute malware.
The second vulnerability added to the KEV catalog relates to an insecure deserialization vulnerability in Novi Survey software that allows remote attackers to execute code on the server in the context of the service account.
The issue, which impacts Novi Survey versions prior to 8.9.43676, was addressed by the Boston-based provider earlier this week on April 10, 2023. It's currently not known how the flaw is being abused in real-world attacks.
To counter the risks posed by the vulnerabilities, Federal Civilian Executive Branch (FCEB) agencies in the U.S. are advised to apply necessary patches by May 4, 2023.
Israel-based Spyware Firm QuaDream Targets High-Risk iPhones with Zero-Click Exploit
12.4.23 Apple The Hacker News
Threat actors using hacking tools from an Israeli surveillanceware vendor named QuaDream targeted at least five members of civil society in North America, Central Asia, Southeast Asia, Europe, and the Middle East.
According to findings from a group of researchers from the Citizen Lab, the spyware campaign was directed against journalists, political opposition figures, and an NGO worker in 2021. The names of the victims were not disclosed.
It's also suspected that the company abused a zero-click exploit dubbed ENDOFDAYS in iOS 14 to deploy spyware as a zero-day in version 14.4 and 14.4.2. There is no evidence that the exploit has been used after March 2021.
ENDOFDAYS "appears to make use of invisible iCloud calendar invitations sent from the spyware's operator to victims," the researchers said.
The Microsoft Threat Intelligence team is tracking QuaDream as DEV-0196, describing the cyber mercenary company as a private sector offensive actor (PSOA). While QuaDream is not directly involved in targeting, it is known to sell its "exploitation services and malware" to government customers, the tech giant assessed with high confidence.
The malware, named KingsPawn, contains a monitor agent and the primary malware agent, both of which are Mach-O files written in Objective-C and Go, respectively.
While the monitor agent is responsible for reducing the forensic footprint of the malware to evade detection, the main agent comes with capabilities to gather device information, cellular and Wi-Fi data, harvest files, access camera in the background, access location, call logs, and iOS Keychain, and even generate an iCloud time-based one-time password (TOTP).
Other samples support recording audio from phone calls and the microphone, running queries in SQL databases, and cleaning up forensic trails, such as deleting all calendar events from two years prior to the current time. The data is exfiltrated via HTTPS POST requests.
Internet scans carried out by the Citizen Lab reveal that QuaDream's customers operated 600 servers from several countries around the world between late 2021 and early 2023, including Bulgaria, Czech Republic, Hungary, Romania, Ghana, Israel, Mexico, Singapore, the U.A.E., and Uzbekistan.
Despite attempts made by the spyware to cover its tracks, the interdisciplinary laboratory said it was able to uncover unspecified traces of what it calls the "Ectoplasm Factor" that could be used to track QuaDream's toolset in the future.
This is not the first time QuaDream has attracted attention. In February 2022, Reuters reported that the company weaponized the FORCEDENTRY zero-click exploit in iMessage to deploy a spyware solution named REIGN.
Then in December 2022, Meta disclosed that it took down a network of 250 fake accounts on Facebook and Instagram controlled by QuaDream to infect Android and iOS devices and exfiltrate personal data.
If anything, the development is yet another indication that despite the notoriety attracted by NSO Group, commercial spyware firms continue to fly under the radar and develop sophisticated spyware products for use by government clients.
"Until the out-of-control proliferation of commercial spyware is successfully curtailed through systemic government regulations, the number of abuse cases is likely to continue to grow, fueled both by companies with recognizable names, as well as others still operating in the shadows," the Citizen Lab said.
Calling the growth of mercenary spyware companies as a threat to democracy and human rights, Microsoft said combating such offensive actors requires a "collective effort" and a "multistakeholder collaboration."
"Moreover, it is only a matter of time before the use of the tools and technologies they sell spread even further," Amy Hogan-Burney, the company's associate general counsel for cybersecurity policy and protection, said.
"This poses real risk to human rights online, but also to the security and stability of the broader online environment. The services they offer require cyber mercenaries to stockpile vulnerabilities and search for new ways to access networks without authorization."
Cybercriminals Turn to Android Loaders on Dark Web to Evade Google Play Security
11.4.23 Android The Hacker News
Malicious loader programs capable of trojanizing Android applications are being traded on the criminal underground for up to $20,000 as a way to evade Google Play Store defenses.
"The most popular application categories to hide malware and unwanted software include cryptocurrency trackers, financial apps, QR-code scanners, and even dating apps," Kaspersky said in a new report based on messages posted on online forums between 2019 and 2023.
Dropper apps are the primary means for threat actors looking to sneak malware via the Google Play Store. Such apps often masquerade as seemingly innocuous apps, with malicious updates introduced upon clearing the review process and the applications have amassed a significant user base.
This is achieved by using a loader program that's responsible for injecting malware into a clean app, which is then made available for download from the app marketplace. Users who install the tampered app are prompted to grant it intrusive permissions to facilitate malicious activities.
The apps, in some instances, also incorporate anti-analysis features to detect if they are being debugged or installed in a sandboxed environment, and if so, halt their operations on the compromised devices.
As another option, threat actors can purchase a Google Play developer account – either hacked or newly created by the sellers – for anywhere between $60 and $200, depending on the number of already published apps and download counts.
App developer accounts lacking in strong password or two-factor authentication (2FA) protections can be trivially cracked and put up for sale, thereby allowing other actors to upload malware to existing apps.
A third alternative is the use of APK binding services, which are responsible for hiding a malicious APK file in a legitimate application, for distributing the malware through phishing texts and dubious websites advertising cracked games and software.
Binding services, as opposed to loaders, cost less owing to the fact that the poisoned apps are not available via the Google Play Store. Notably, the technique has been used to deliver Android banking trojans like SOVA and Xenomorph in the past.
Some other illicit services offered for sale on cybercrime markets include malware obfuscation ($30), web injects ($25-$80), and virtual private servers ($300), the latter of which can be used to control infected devices or to redirect user traffic.
Furthermore, attackers can buy installs for their Android apps (legitimate or otherwise) through Google Ads for $0.5 on average. Installation costs vary based on the targeted country.
To mitigate risks posed by Android malware, users are recommended to refrain from installing apps from unknown sources, scrutinize app permissions, and keep their devices up-to-date.
Apple Releases Updates to Address Zero-Day Flaws in iOS, iPadOS, macOS, and Safari
8.4.23 Apple The Hacker News
Apple on Friday released security updates for iOS, iPadOS, macOS, and Safari web browser to address a pair of zero-day flaws that are being exploited in the wild.
The two vulnerabilities are as follows -
CVE-2023-28205 - A use after free issue in WebKit that could lead to arbitrary code execution when processing specially crafted web content.
CVE-2023-28206 - An out-of-bounds write issue in IOSurfaceAccelerator that could enable an app to execute arbitrary code with kernel privileges.
Apple said it addressed CVE-2023-28205 with improved memory management and the second with better input validation, adding it's aware the bugs "may have been actively exploited."
Credited with discovering and reporting the flaws are Clément Lecigne of Google's Threat Analysis Group (TAG) and Donncha Ó Cearbhaill of Amnesty International's Security Lab.
Details about the two vulnerabilities have been withheld in light of active exploitation and to prevent more threat actors from abusing them.
The updates are available in version iOS 16.4.1, iPadOS 16.4.1, macOS Ventura 13.3.1, and Safari 16.4.1. The fixes also span a wide range of devices -
iPhone 8 and later, iPad Pro (all models), iPad Air 3rd generation and later, iPad 5th generation and later, and iPad mini 5th generation and later
Macs running macOS Big Sur, Monterey, and Ventura
Apple has patched three zero-days since the start of the year. In February, Apple addressed another actively exploited zero-day (CVE-2023-23529) in WebKit that could result in arbitrary code execution.
The development also comes as Google TAG disclosed that commercial spyware vendors are leveraging zero-days in Android and iOS to infect mobile devices with surveillance malware.
Google Mandates Android Apps to Offer Easy Account Deletion In-App and Online
6.4.23 Android The Hacker News
Google is enacting a new data deletion policy for Android apps that allow account creation to also offer users with a setting to delete their accounts in an attempt to provide more transparency and control over their data.
"For apps that enable app account creation, developers will soon need to provide an option to initiate account and data deletion from within the app and online," Bethel Otuteye, senior director of product management for Android App Safety, said.
"This web requirement, which you will link in your Data safety form, is especially important so that a user can request account and data deletion without having to reinstall an app."
The goal, the search behemoth said, is to have a "readily discoverable option" to initiate an app account deletion process from both within an app and outside of it.
To that end, developers are to provide users with an in-app path as well as a web link resource to request app account deletion and associated data. Should users submit such a request, it's required of app developers to purge all data associated with that account.
In addition, users may be provided with alternatives to selectively delete only portions of the data (e.g., activity history, images, or videos) instead of entirely deleting their accounts.
Developers who wish to retain certain data for valid reasons such as security, fraud prevention, or regulatory compliance are mandated to disclose such data retention practices upfront.
"Temporary account deactivation, disabling, or 'freezing' the app account does not qualify as account deletion," Google explicitly spells out.
The new policy is expected to go into effect early next year, with developers having time till December 7, 2023, to submit answers to the data deletion questions in the app's Data safety form. Developers can file for an extension until May 31, 2024.
The development also puts Android in line with Apple's iOS and iPadOS operating systems, which instituted a similar policy starting June 30, 2022. It, however, doesn't require that users should be able to delete their accounts via the web as well.
That said, it remains to be seen if any enforcement actions will be taken if a developer fails to follow the rules. Earlier this year, Mozilla called out Google after discovering serious discrepancies between the top 20 most popular free apps' privacy policies and the information they self-reported in the Play Store.
In a related privacy measure, Google has also imposed additional guardrails that prohibit personal loan apps from accessing sensitive data, such as user contacts, photos, and locations, in an attempt to curb blackmail and extortion.
Spyware Vendors Caught Exploiting Zero-Day Vulnerabilities on Android and iOS Devices
29.3.23 OS The Hacker News
A number of zero-day vulnerabilities that were addressed last year were exploited by commercial spyware vendors to target Android and iOS devices, Google's Threat Analysis Group (TAG) has revealed.
The two distinct campaigns were both limited and highly targeted, taking advantage of the patch gap between the release of a fix and when it was actually deployed on the targeted devices.
"These vendors are enabling the proliferation of dangerous hacking tools, arming governments that would not be able to develop these capabilities in-house," TAG's Clement Lecigne said in a new report.
"While use of surveillance technologies may be legal under national or international laws, they are often found to be used by governments to target dissidents, journalists, human rights workers, and opposition party politicians."
The first of the two operations took place in November 2022 and involved sending shortened links over SMS messages to users located in Italy, Malaysia, and Kazakhstan.
Upon clicking, the URLs redirected the recipients to web pages hosting exploits for Android or iOS, before they were redirected again to legitimate news or shipment-tracking websites.
The iOS exploit chain leveraged multiple bugs, including CVE-2022-42856 (a then zero-day), CVE-2021-30900, and a pointer authentication code (PAC) bypass, to install an .IPA file onto the susceptible device.
The Android exploit chain comprised three exploits – CVE-2022-3723, CVE-2022-4135 (a zero-day at the time of abuse), and CVE-2022-38181 – to deliver an unspecified payload.
While CVE-2022-38181, a privilege escalation bug affecting Mali GPU Kernel Driver, was patched by Arm in August 2022, it's not known if the adversary was already in possession of an exploit for the flaw prior to the release of the patch.
Another point of note is that Android users who clicked on the link and opened it in Samsung Internet Browser were redirected to Chrome using a method called intent redirection.
The second campaign, observed in December 2022, consisted of several zero-days and n-days targeting the latest version of Samsung Internet Browser, with the exploits delivered as one-time links via SMS to devices located in the U.A.E.
The web page, similar to those that were used by Spanish spyware company Variston IT, ultimately implanted a C++-based malicious toolkit capable of harvesting data from chat and browser applications.
The flaws exploited constitute CVE-2022-4262, CVE-2022-3038, CVE-2022-22706, CVE-2023-0266, and CVE-2023-26083. The exploit chain is believed to have been used by a customer or partner of Variston IT.
That said, the scale of the two campaigns and the nature of the targets are currently unknown.
The revelations come just days after the U.S. government announced an executive order restricting federal agencies from using commercial spyware that presents a national security risk.
"These campaigns are a reminder that the commercial spyware industry continues to thrive," Lecigne said. "Even smaller surveillance vendors have access to zero-days, and vendors stockpiling and using zero-day vulnerabilities in secret pose a severe risk to the Internet."
"These campaigns may also indicate that exploits and techniques are being shared between surveillance vendors, enabling the proliferation of dangerous hacking tools."
Apple Issues Urgent Security Update for Older iOS and iPadOS Models
28.3.23 Apple The Hacker News
Apple on Monday backported fixes for an actively exploited security flaw to older iPhone and iPad models.
The issue, tracked as CVE-2023-23529, concerns a type confusion bug in the WebKit browser engine that could lead to arbitrary code execution.
It was originally addressed by the tech giant with improved checks as part of updates released on February 13, 2023. An anonymous researcher has been credited with reporting the bug.
"Processing maliciously crafted web content may lead to arbitrary code execution," Apple said in a new advisory, adding it's "aware of a report that this issue may have been actively exploited."
Details surrounding the exact nature of exploitation are currently not known, but withholding technical specifics is standard procedure as it helps prevent additional in-the-wild abuse targeting susceptible devices.
The update is available in versions iOS 15.7.4 and iPadOS 15.7.4 for iPhone 6s (all models), iPhone 7 (all models), iPhone SE (1st generation), iPad Air 2, iPad mini (4th generation), and iPod touch (7th generation).
The disclosure comes as Apple rolled out iOS 16.4, iPadOS 16.4, macOS Ventura 13.3, macOS Monterey 12.6.4, macOS Big Sur 11.7.5, tvOS 16.4, and watchOS 9.4 with numerous bug fixes.
New MacStealer macOS Malware Steals iCloud Keychain Data and Passwords
28.3.23 Apple The Hacker News
A new information-stealing malware has set its sights on Apple's macOS operating system to siphon sensitive information from compromised devices.
Dubbed MacStealer, it's the latest example of a threat that uses Telegram as a command-and-control (C2) platform to exfiltrate data. It primarily affects devices running macOS versions Catalina and later running on M1 and M2 CPUs.
"MacStealer has the ability to steal documents, cookies from the victim's browser, and login information," Uptycs researchers Shilpesh Trivedi and Pratik Jeware said in a new report.
First advertised on online hacking forums for $100 at the start of the month, it is still a work in progress, with the malware authors planning to add features to capture data from Apple's Safari browser and the Notes app.
In its current form, MacStealer is designed to extract iCloud Keychain data, passwords and credit card information from browsers like Google Chrome, Mozilla Firefox, and Brave. It also features support for harvesting Microsoft Office files, images, archives, and Python scripts.
The exact method used to deliver the malware is not known, but it is propagated as a DMG file (weed.dmg) that, when executed, opens a fake password prompt to harvest the passwords under the guise of seeking access to the System Settings app.
MacStealer is one of several info-stealers that have surfaced just over the past few months and adds to an already large number of similar tools currently in the wild.
This also includes another piece of new C#-based malware called HookSpoofer that's inspired by StormKitty and comes with keylogging and clipper abilities and transmits the stolen data to a Telegram bot.
Another browser cookie-stealing malware of note is Ducktail, which also uses a Telegram bot to exfiltrate data and re-emerged in mid-February 2023 with improved tactics to sidestep detection.
This involves "changing the initial infection from an archive containing a malicious executable to an archive containing a malicious LNK file that would start the infection chain," Deep Instinct researcher Simon Kenin said earlier this month.
Stealer malware is typically spread through different channels, including email attachments, bogus software downloads, and other social engineering techniques.
To mitigate such threats, it's recommended that users keep their operating system and security software up to date and avoid downloading files or clicking links from unknown sources.
"As Macs have become increasingly popular in the enterprise among leadership and development teams, the more important the data stored on them is to attackers," SentinelOne researcher Phil Stokes said last week.
Nexus: A New Rising Android Banking Trojan Targeting 450 Financial Apps
23.3.23 Android The Hacker News
An emerging Android banking trojan dubbed Nexus has already been adopted by several threat actors to target 450 financial applications and conduct fraud.
"Nexus appears to be in its early stages of development," Italian cybersecurity firm Cleafy said in a report published this week.
"Nexus provides all the main features to perform ATO attacks (Account Takeover) against banking portals and cryptocurrency services, such as credentials stealing and SMS interception."
The trojan, which appeared in various hacking forums at the start of the year, is advertised as a subscription service to its clientele for a monthly fee of $3,000. Details of the malware were first documented by Cyble earlier this month.
However, there are indications that the malware may have been used in real-world attacks as early as June 2022, at least six months before its official announcement on darknet portals.
It's also said to overlap with another banking trojan dubbed SOVA, reusing parts of its source code and incorporating a ransomware module that appears to be under active development.
A point worth mentioning here is that Nexus is the same malware that Cleafy initially classified as a new variant of SOVA (dubbed v5) in August 2022.
Interestingly, the Nexus authors have laid out explicit rules that prohibit the use of its malware in Azerbaijan, Armenia, Belarus, Kazakhstan, Kyrgyzstan, Moldova, Russia, Tajikistan, Uzbekistan, Ukraine, and Indonesia.
The malware, like other banking trojans, contains features to take over accounts related to banking and cryptocurrency services by performing overlay attacks and keylogging to steal users' credentials.
Furthermore, it's capable of reading two-factor authentication (2FA) codes from SMS messages and the Google Authenticator app through the abuse of Android's accessibility services.
Some new additions to the list of functionalities is its ability to remove received SMS messages, activate or stop the 2FA stealer module, and update itself by periodically pinging a command-and-control (C2) server.
"The [Malware-as-a-Service] model allows criminals to monetize their malware more efficiently by providing a ready-made infrastructure to their customers, who can then use the malware to attack their targets," the researchers said.