
These controllers are used in multiple sectors, including heavy equipment, industrial manufacturing, transportation, power generation, and oil and gas.
Critical Flaws in Kepware Products Can Facilitate Attacks on Industrial Firms
23.12.2020 ICS Securityweek
Several critical vulnerabilities have been found by researchers in products from PTC-owned industrial automation solutions provider Kepware.
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) last week published two advisories describing vulnerabilities identified in Kepware products.
One of the advisories covers three flaws discovered by researchers at industrial cybersecurity firm Claroty. The security holes, two rated critical and one high severity, are described as a stack-based buffer overflow, a heap-based buffer overflow, and a use-after-free bug.
The critical vulnerabilities can be exploited to crash the server, leak data, and remotely execute arbitrary code by opening a specially crafted OPC UA message. The high-severity bug can allow an attacker to crash the server by creating and closing OPC UA connections at a high rate, CISA said in its advisory.
“The vulnerabilities were located in the KEPServerEX, ThingWorx and OPC-Aggregator OPC products,” Uri Katz, senior researcher at Claroty, told SecurityWeek. “In order to exploit these vulnerabilities, attackers would need to have network access to the OPC server. OPC servers are a central part in many OT networks, which makes them a lucrative target for attackers.”
Katz added, “In our research we were able to show that these vulnerabilities can be exploited remotely without any authentication needed and that successful exploitation of these vulnerabilities could lead to a server crashing, a denial-of-service condition, data leakage, or remote code execution.”
CISA noted that products from Rockwell Automation, GE Digital and Software Toolbox also use a vulnerable component, and advised the customers of these companies to check if their products are affected and apply available patches. Advisories released by Rockwell, GE and Software Toolbox only mention crashes (DoS) and data leaks in terms of impact. However, DoS attacks can have serious consequences in the case of industrial control systems (ICS).
The second advisory released last week by CISA describes one critical vulnerability found by a Cisco Talos researcher in Kepware LinkMaster, which is designed for exchanging data between OPC DA servers.
The vulnerability was found in the product’s default configuration and it allows a local attacker to execute arbitrary code with SYSTEM privileges. Talos published an advisory for this flaw on December 16, one day before CISA released its advisories.
“The vulnerabilities were raised and addressed through PTC's Coordinated Vulnerability Disclosure (CVD) program - an important piece of our product security strategy. We appreciate our partnership with security research firms like Claroty and Cisco Talos and their willingness to work with PTC through the CVD program. Working with CISA provides a vehicle for the disclosure of vulnerabilities in a responsible way,” PTC said in an emailed statement.
Critical Flaws in Kepware Products Can Facilitate Attacks on Industrial Firms
23.12.2020 ICS Securityweek
Several critical vulnerabilities have been found by researchers in products from PTC-owned industrial automation solutions provider Kepware.
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) last week published two advisories describing vulnerabilities identified in Kepware products.
One of the advisories covers three flaws discovered by researchers at industrial cybersecurity firm Claroty. The security holes, two rated critical and one high severity, are described as a stack-based buffer overflow, a heap-based buffer overflow, and a use-after-free bug.
The critical vulnerabilities can be exploited to crash the server, leak data, and remotely execute arbitrary code by opening a specially crafted OPC UA message. The high-severity bug can allow an attacker to crash the server by creating and closing OPC UA connections at a high rate, CISA said in its advisory.
“The vulnerabilities were located in the KEPServerEX, ThingWorx and OPC-Aggregator OPC products,” Uri Katz, senior researcher at Claroty, told SecurityWeek. “In order to exploit these vulnerabilities, attackers would need to have network access to the OPC server. OPC servers are a central part in many OT networks, which makes them a lucrative target for attackers.”
Katz added, “In our research we were able to show that these vulnerabilities can be exploited remotely without any authentication needed and that successful exploitation of these vulnerabilities could lead to a server crashing, a denial-of-service condition, data leakage, or remote code execution.”
CISA noted that products from Rockwell Automation, GE Digital and Software Toolbox also use a vulnerable component, and advised the customers of these companies to check if their products are affected and apply available patches. Advisories released by Rockwell, GE and Software Toolbox only mention crashes (DoS) and data leaks in terms of impact. However, DoS attacks can have serious consequences in the case of industrial control systems (ICS).
The second advisory released last week by CISA describes one critical vulnerability found by a Cisco Talos researcher in Kepware LinkMaster, which is designed for exchanging data between OPC DA servers.
The vulnerability was found in the product’s default configuration and it allows a local attacker to execute arbitrary code with SYSTEM privileges. Talos published an advisory for this flaw on December 16, one day before CISA released its advisories.
“The vulnerabilities were raised and addressed through PTC's Coordinated Vulnerability Disclosure (CVD) program - an important piece of our product security strategy. We appreciate our partnership with security research firms like Claroty and Cisco Talos and their willingness to work with PTC through the CVD program. Working with CISA provides a vehicle for the disclosure of vulnerabilities in a responsible way,” PTC said in an emailed statement.
Industrial Control Systems Ripe Targets for Ransomware Attacks
19.12.2020 ICS Securityweek
Security researchers at IBM Corp. and Dragos Inc. are warning that the industrial control systems that power manufacturing plants and utilities are prime targets for ransomware attackers.
In a report issued this week, the researchers noted that ransomware attacks against industrial entities jumped more than 500 percent over the last two years.
Interestingly, the increase in the ransomware incidents appears to coincide with the global COVID-19 pandemic. "Ransomware adversaries leveraged Coronavirus-themed phishing lures for initial access operations, preying on users’ concern for health and safety," the researchers noted.
In some cases, the IBM and Dragos report said adversaries are targeting cold storage facilities and biomedical, and pharmaceutical manufacturers researching and developing virus vaccines and distribution methods, which could disrupt the development and distribution of the vital drugs."
The analysis also found that ransomware operators are increasingly incorporating data theft and extortion operations into their attack techniques, potentially posing even greater impact from ransomware than disrupted operations through leaked intellectual property and other critical data.
According to the report (PDF), data stolen and leaked on publicly available websites could provide ICS targeting attackers with victim data that could inform or guide future ICS disruptive attacks.
To combat ransomware in ICS environments, the researchers suggest that asset owners and operators engage in effective defense-in-depth security strategies.
"Ensure an understanding of network interdependencies and conduct crown jewel analysis to identify potential weaknesses that could disrupt business continuity and production.
Over the summer, FireEye reported that a total of seven ransomware families have been found to target processes associated with operational technology (OT) software.
Flaws in Medtronic MyCareLink can allow attackers to take over implanted cardiac devices
16.12.2020 ICS Securityaffairs
Experts reported flaws in Medtronic ’s MyCareLink Smart 25000 Patient Reader product that could be exploited to take control of a paired cardiac device.
Experts from IoT security firm Sternum discovered vulnerabilities discovered in Medtronic’s MyCareLink Smart 25000 Patient Reader product that could be exploited to take control of a paired cardiac device.
MyCareLink Smart 25000 Patient Reader is a platform designed by Medtronic to gather data from patients ’ implanted cardiac devices and transfer it to Medtronic CareLink network.
The vulnerabilities ((CVE-2020-25183, CVE-2020-25187, CVE-2020-27252)) could be only exploited by an attacker within the Bluetooth range of the vulnerable product.
The experts found three flaws that could be exploited to modify or forge data that is received from the implanted cardiac devices. The flaws could also allow remote attackers to taking control of the paired cardiac device and execute arbitrary code on the MCL Smart Patient Reader.
The CVE-2020-25183 is an improper authentication issue that could be exploited by an attacker to bypass the authentication between the MCL Smart Patient Reader and the Medtronic MyCareLink Smart mobile app.
“This vulnerability enables an attacker to use another mobile device or malicious application on the patient’s smartphone to authenticate to the patient’s Medtronic Smart Reader, fooling the device into believing it is communicating with the original Medtronic smart phone application when executed within range of Bluetooth communication,” reads the advisory published by DHS CISA.
The second flaw, tracked as CVE-2020-25187, is a heap-based buffer overflow that could be exploited by an authenticated attacker to remotely execute code on the MCL Smart Patient Reader.
“The affected products are vulnerable when an authenticated attacker runs a debug command, which can be sent to the patient reader and cause a heap overflow event within the MCL Smart Patient Reader software stack. The heap overflow could allow an attacker to remotely execute code on the MCL Smart Patient Reader, potentially leading to control of the device” continues the advisory
The third vulnerability, tracked as CVE-2020-27252, is a race condition that could be leveraged to upload and execute unsigned firmware on the Patient Reader. The flaw could be exploited by an attacker to remotely execute code taking over the device.
“The affected products are vulnerable to a race condition in the MCL Smart Patient Reader software update system, which allows unsigned firmware to be uploaded and executed on the Patient Reader. If exploited, an attacker could remotely execute code on the MCL Smart Patient Reader device, leading to control of the device.” states the advisory.
Medtronic addressed the flaw with the release of a firmware update that can be applied via the MyCareLink Smart app through the associated mobile app store.
At the time of the advisory, Medtronic is not aware of attacks in the wild exploiting the above flaws.
“Medtronic is currently unaware of any cyberattack, privacy breach, or patient harm as a result of these vulnerabilities.” states the advisory.
Vulnerabilities in Medtronic Product Can Allow Hackers to Control Cardiac Devices
16.12.2020 ICS Securityweek
Vulnerabilities discovered in Medtronic’s MyCareLink Smart 25000 Patient Reader product could be exploited to take control of a paired cardiac device.
Designed to obtain information from a patient’s implanted cardiac device, the MCL Smart Patient Reader then sends the data to the Medtronic CareLink network, to facilitate care management, through the patient’s mobile device.
Three vulnerabilities discovered by researchers at IoT security firm Sternum in the MCL Smart Model 25000 Patient Reader could be exploited to modify or fabricate data that is transmitted from the implanted patient device to the CareLink network. Medtronic MyCareLink Smart vulnerabilities
Furthermore, they could allow an attacker to execute code remotely on the MCL Smart Patient Reader, essentially taking control of the paired cardiac device. Exploitation of the flaws, however, requires for the attacker to be within Bluetooth range of the vulnerable product.
Tracked as CVE-2020-25183 (CVSS score of 8.0), the first of the bugs is an authentication protocol issue that allows an attacker to bypass the method used to authenticate between the MCL Smart Patient Reader and the Medtronic MyCareLink Smart mobile app.
“This vulnerability enables an attacker to use another mobile device or malicious application on the patient’s smartphone to authenticate to the patient’s Medtronic Smart Reader, fooling the device into believing it is communicating with the original Medtronic smart phone application when executed within range of Bluetooth communication,” CISA notes in an advisory.
Tracked as CVE-2020-25187 and featuring a CVSS score of 8.8, the second flaw is triggered when an authenticated attacker runs a debug command sent to the patient reader. This could cause a heap overflow, resulting in remote code execution, potentially allowing the attacker to control the device.
Also with a CVSS score of 8.8, the third vulnerability (CVE-2020-27252) is a race condition that could be leveraged to upload and execute unsigned firmware on the Patient Reader. This could allow an attacker to remotely execute code, thus taking control of the device.
Medtronic has already released a firmware update to address the vulnerabilities, and it can be applied via the MyCareLink Smart app through the associated mobile app store. Updating the application (to version 5.2.0 or higher) also ensures that the Patient Reader is automatically updated on next use. The company has published step-by-step details on how to apply the update.
As additional mitigation steps, Medtronic has implemented Sternum’s enhanced integrity validation (EIV) technology and advanced detection system technology, which allow it to detect vulnerabilities and monitor for anomalous device activity.
“To date, no cyberattack, no unauthorized access to patient data, and no harm to patients has been observed with these vulnerabilities,” Medtronic explains.
Robotic Process Automation vendor UiPath discloses data breach
15.12.2020 ICS Securityaffairs
Last week, ZDnet reported in an exclusive that the tech unicorn UiPath admitted having accidentally exposed the personal details of some users.
UiPath is a leading Robotic Process Automation vendor providing a complete software platform to help organizations efficiently automate business processes.
The startup started reporting the security incident to its customers that had their data accidentally exposed online, only users who registered on its platform before or on March 17, 2020, were impacted.
“On December 1, 2020, UiPath became aware of an incident that resulted in unauthorized disclosure of a file containing limited personal information about users of UiPath Academy,” reads an email statement, seen by ZDNet. sent by the company to its users today.
Exposed accidentally users’ details include real names, email addresses, usernames, company name, country locations, and UiPath certification details for users who signed up for the Academy learning platform.
“We are aware of only one online source where the information was made available,” the company added. “For important security (and other related) reasons, UiPath is unable to name the source.”
The user details were contained in a file that appears to be an older backup.
The company pointed out that financial information either passwords were not exposed. The incident did not expose the company’s official products.
At the time of this writing, the software firm hasn’t disclosed the number of impacted users.
NI CompactRIO controller flaw could allow disrupting production
13.12.2020 ICS Securityaffairs
A serious flaw in National Instruments CompactRIO controllers could allow remote attackers to disrupt production processes in an organization.
A high-severity vulnerability affecting CompactRIO controllers manufactured by the vendor National Instruments (NI) could allow remote attackers to disrupt production processes in an organization.
The National Instruments CompactRIO product, a rugged, real-time controller that provides high-performance processing capabilities, sensor-specific conditioned I/O, and a closely integrated software toolchain that makes them ideal for Industrial Internet of Things (IIoT), monitoring, and control applications.
These controllers are used in multiple sectors, including heavy equipment, industrial manufacturing, transportation, power generation, and oil and gas.
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) published a security advisory to warn organizations about the flaw.
The flaw, tracked as CVE-2020-25191, affects driver versions prior to 20.5.
“Incorrect permissions are set by default for an API entry-point of a specific service, allowing a non-authenticated user to trigger a function that could reboot the device remotely.” reads the security advisory published by CISA.
The vendor revealed that it is not aware of attacks in the wild that exploited this vulnerability.
An attacker could repeatedly trigger the flaw to reboot the device, causing a prolonged denial-of-service (DoS) condition and potentially disrupting industrial processes.
NI provided the following mitigations to prevent hackers from targeting this flaw in its products.
NI recommends the following steps for mitigation:
Download the NI CompactRIO 20.5 Driver.
Install the driver on host computer.
Update the firmware on CompactRIO controllers to v8.5 or higher. Refer to Upgrading Firmware on my NI Linux Real-Time Device for directions on how to update the firmware on current controllers. Updating the firmware patches the Safe Mode where defaults are loaded.
Format the target to apply the new safemode default permissions. Refer to How to Restore LabVIEW RT Target to Factory Default Configuration for directions on how to format and reinstall software on target.
Repeat Steps 3 and 4 for each affected CompactRIO target.
Open Source Tool Helps Secure Siemens PCS 7 Control Systems
3.12.2020 ICS Securityweek
Industrial cybersecurity company OTORIO has released an open source tool designed to help organizations harden Siemens’ SIMATIC PCS 7 distributed control systems (DCS).
The tool has been made available on GitHub as a PowerShell script, and OTORIO says it has been tested on Windows 7, Windows 10, Windows Server 2012 R2 and Windows Server 2016. Users only need to run the script as an administrator.
According to the cybersecurity firm, the script is designed to assess the security configuration of the SIMATIC PCS 7 OS client, OS server and engineering station.
It collects data from various sources, including the Windows registry, Windows Management Instrumentation (WMI), running services, PCS 7 Web Navigator and Information Server configuration files, RsoP (Resultant Set of Policy), and security policies related to passwords. The data is then analyzed based on OTORIO’s research into PCS 7 DCS and security recommendations from Siemens documentation.
Matan Dobrushin, OTORIO's head of research, told SecurityWeek that based on his team’s experience, it’s more cost-effective to start with server configurations when securing an environment. Additionally, it can be far more efficient compared to patching software vulnerabilities, considering that the process reduces risk to the entire operational project, unlike plugging a single security hole on a single asset.
“The control servers are the ones responsible for the complete operational process, making them the ‘crown jewels’ of the network,” Dobrushin explained. “Based on the knowledge gathered from studying previous attacks, we see that the number of vulnerabilities exploited is not high (in comparison to other security issues exploitation). From our experience, this is the case in a lot of modern attacks. So, if you have limited resources, and you always have limited resources, you should probably start mitigating the easy, and most cost-effective issues.”
Learn more about ICS security tools at SecurityWeek’s ICS Cyber Security Conference and SecurityWeek’s Security Summits virtual event series
The researcher believes it’s important that industrial organizations secure PCS 7 environments as this is one of the most commonly used DCS solutions in a number of verticals, particularly manufacturing.
“Once an attacker has a network with PCS 7 in his sights, he really does not have a better way to impact the network, other than to exploit the PCS 7 itself” he said.
Dobrushin told SecurityWeek that internally they have a tool that not only flags potential security issues but also fixes them.
“However, from the OT personnel perspective, fixing gaps automatically is something that may sound alarming to some, so we decided to only publish the tool for detecting those issues and allowing everyone to use their own mitigation tools,” he explained.
OTORIO plans on releasing other DCS and SCADA security tools in the near future, for products from Siemens and other prominent vendors.
“Some tools that are already in the pipeline are even more complex and check more configurations than just the Windows configurations,” Dobrushin said.
ICS threat predictions for 2021
2.12.2020 ICS Securelist
We present our vision of what challenges industrial cybersecurity will soon be (or already is) facing, and what to expect from cybercriminals in 2021.
Random infections
Infections will tend to be less random or have non-random follow-ups, as cybercriminals have spent the past several years profiling randomly infected computers that are connected to industrial networks or have periodic access to them. Access to such computers will be — and is perhaps already being — resold to more sophisticated groups with specific schemes for monetizing attacks on industrial facilities already in place.
For several years now, various groups have specialized in attacks against industrial enterprises with the express aim to steal money — through BEC schemes or advanced hacks to gain access to victims’ financial and accounting systems. Through years of criminal operations, they have come to understand the business processes of industrial enterprises and gained access to a large amount of technical information about network assets and operational technologies. We expect to see new and unconventional scenarios of attacks on OT/ICS and field devices, coupled with ingenious monetization schemes. Cybercriminals have had more than enough time and opportunities to develop them.
End of support for Windows 7 and Windows Server 2008, which are popular in ICS around the world, and, especially, the leak of the source code of Windows XP, which is still very common on industrial networks, pose a significant threat to the security of industrial enterprises. There is a high chance that a WannaCry-like scenario will be repeated in the very near future. And industrial enterprises may be among the hardest hit.
Ransomware attacks
Ransomware is becoming more technically advanced and sophisticated. Cybercriminals will continue to employ hacker and APT techniques, painstakingly exploring and probing the network of the target organization to locate the most valuable/vulnerable systems, hijack administrator accounts, and launch simultaneous blitz attacks using standard admin tools.
Cybercriminals have developed a fondness for industrial companies, because they tend to pay ransom. This means that the attacks will continue.
There will be hybrid attacks involving document theft with the threat to publish the documents or sell them on the darknet in case of refusal to pay up.
The ideas implemented in Snake for ransomware attacks targeting OT/ICS will gain traction.
It is highly likely that we will see attacks disguised as ransomware but pursuing completely different goals — a repeat of the ExPetr technique.
Cyberespionage
Cybercriminals will figure out (some already have) that inside the OT perimeter secrets are not guarded as well as in office networks and that OT networks may be even easier to break into, since they have their own perimeter and attack surface.
The flat network topology and other access control issues in OT networks can make them an attractive entry point into the intimate recesses of the corporate network and a springboard into other related organizations and facilities.
The desire of many countries for technological independence, alongside with global geopolitical and macroeconomic upheaval, means that attack targets will include not only traditional opponents, but also tactical and strategic partners — threats can come from any direction. We have already seen examples of such attacks.
APT
The number of APT groups will continue to grow — we will see more and more new actors, including ones that attack various industrial sectors.
The activity of these groups will correlate with local conflicts, including those in the hot phase, with cyberattacks on industrial enterprises and other facilities used as a warfare tool, alongside drones and media-driven misinformation.
In addition to data theft and other piecemeal operations, some group is likely to get down to more serious business in 2021, perhaps in the vein of Stuxnet, Black Energy, Industroyer and Triton.
COVID consequences
Against the backdrop of economic decline, lockdowns, slower growth and ruin for small businesses, the ranks of cybercriminals are sure to swell as skilled people seek alternative employment, and groups associated with national governments will strengthen as well.
The online presence of municipal services and utilities and the increased digitization of government and public services will make them more vulnerable to attacks of cybercriminals and create more opportunities for cross-agency attacks and assaults on central and local government functions and the systems that support and implement them. For example, a threat actor could use a governmental or municipal web service as an entry point, compromise the victim’s internal infrastructure and use the communication channels and supply chain connecting various governmental, municipal and even private organizations to reach their final target (such as shutting down transportation systems).
Restrictions on on-site work, which prevented new equipment from being installed and configured, have slowed down the efforts of many industrial enterprises to beef up their perimeter security. Together with the increasing number and variety of remote sessions, this may even reduce the level of perimeter protection of industrial networks. This being the case, the safety of industrial facilities will largely depend on the performance of endpoint solutions and the security awareness of employees. At the same time, cyberattacks aimed at industrial companies are maturing. As a result, despite the currently observed drop in attacks on OT/ICS computers, the number of serious incidents is not going to decrease.
The reduction in on-site personnel who are able to promptly transfer systems and installations to manual control in the event of a successful cyberattack on the industrial network could facilitate the wider spread of malware and lead to more severe consequences.
Flaws in Rockwell Automation Product Expose Engineering Workstations to Attacks
2.12.2020 ICS Securityweek
Vulnerabilities discovered by researchers in Rockwell Automation’s FactoryTalk Linx product can allow attackers to compromise engineering workstations in industrial environments.
FactoryTalk Linx, formerly known as RSLinx Enterprise, is a widely used product designed for connecting Allen Bradley programmable logic controllers (PLCs) to Rockwell applications, including for programming, data acquisition and HMI interaction.
Rockwell Automation and the U.S. Cybersecurity and Infrastructure Security Agency (CISA) last week published advisories to inform organizations using this product that researchers have identified three potentially serious vulnerabilities. Rockwell has released updates that should patch the flaws.FactoryTalk vulnerabilities
One of the vulnerabilities has been rated critical and described as a heap overflow bug that can allow a remote and unauthenticated attacker to execute arbitrary code by sending malicious port ranges.
Another vulnerability, rated high severity, affects the Ingress/Egress checks routine of FactoryTalk Linx, and it can be exploited by a remote, unauthenticated attacker for denial-of-service (DoS) attacks.
Learn more about vulnerabilities in industrial systems at SecurityWeek’s ICS Cyber Security Conference and SecurityWeek’s Security Summits virtual event series
The third security hole has been classified as medium severity and it can allow an unauthenticated attacker to obtain information that can be useful for bypassing the Address Space Layout Randomization (ASLR) memory protection feature.
The vulnerabilities were discovered by researchers at industrial cybersecurity firm Claroty. The company told SecurityWeek that the issues were reported to the vendor in April and they are related to a new CIP security feature of the FactoryTalk Linx solution.
“In order to exploit these vulnerabilities, attackers would need to have network access to the Engineering Workstation (EWS) machines. In many cases these machines are laptops, which means they are moving between networks and that makes them a good target for attackers,” Sharon Brizinov, research team lead at Claroty, said via email.
“In our research we were able to show how these three vulnerabilities could be linked together in order to achieve remote code execution while bypassing modern binary security mechanisms such as ASLR,” Brizinov explained. “By exploiting these vulnerabilities, attackers can completely take over the EWS where FactoryTalk Linx is installed. This is highly dangerous because attackers could affect and compromise the PLC program logic that is stored on the EWS before being transferred to the PLC.”
Exclusive: Experts from TIM’s Red Team Research (RTR) found 6 zero-days
1.12.2020 ICS Securityaffairs
TIM’s Red Team Research led by Massimiliano Brolli discovered 6 new zero-day vulnerabilities in Schneider Electric StruxureWare.
Today, TIM’s Red Team Research led by Massimiliano Brolli, discovered 6 new vulnerabilities in the StruxureWare product. The flaws have been addressed by the manufacturer Schneider Electric, between April and November 2020.
Schneider Electric is a vendor specialized in energy and automation products, like ICS, SCADA and IoT products. StruxureWare Building Operation is a software integrated with physical devices for integrated monitoring, control, and management of energy, lighting, fire safety, and HVAC.
Below the list of vulnerabilities discovered by the TIM’s Red Team Research team:
CVE Vulnerability Severity
CVE-2020-7569: Upload of File with Dangerous Type 8.8
CVE-2020-7572 Improper Restriction of XML External Entity Reference 8.8
CVE-2020-28209 Windows Unquoted Search Path 7.0
CVE-2020-7570 Cross-Site Scripting Stored 5.4
CVE-2020-7571 Cross-Site Scripting Reflected 5.4
CVE-2020-7573 Improper Access Control 6.5
The issues were discovered during laboratory tests, promptly managed in a CVD (Coordinated Vulnerability Disclosure) process with the vendor.
The laboratory has been active for less than a year (based on the CVE recorded on the national Vulnerability Database), the experts also discovered unknown vulnerabilities in various products, including NOKIA, Wowza, Selesta, Flexera, Oracle and Siemens.
The research team has identified a total of 31 published CVEs, an average of one CVE every 11 days and this is the result of a great job that TIM is doing, especially in the Bug Hunting activities, where the Italian cybersecurity community should do much more.
The full list of CVEs discovered by the researchers is available at the TIM Corporate websites:
https://www.gruppotim.it/redteam
TIM is a leading Italian telco carrier, it is one of the few Italian industrial realities that dedicate an important effort in conducting research of undocumented vulnerabilities, for this reason, I suggest you follow them.
A critical flaw in industrial automation systems opens to remote hack
30.11.20 ICS Securityaffairs
Experts found a critical flaw in Real-Time Automation’s (RTA) 499ES EtherNet/IP stack that could allow hacking industrial control systems.
Tracked as CVE-2020-25159, the flaw is rated 9.8 out of 10 in severity by the industry-standard Common Vulnerability Scoring System (CVSS) and impacts all versions of EtherNet/IP Adapter Source Code Stack prior to 2.28, which was released on November 21, 2012.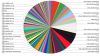
Security researchers from security company Claroty have discovered a critical flaw in Real-Time Automation’s (RTA) 499ES EtherNet/IP (ENIP) stack that could be exploited by a remote attacker to hack the industrial control systems.
“Claroty has privately disclosed details to Real Time Automation (RTA), informing the vendor of a critical vulnerability in its proprietary 499ES EtherNet/IP (ENIP) stack. The vulnerability could cause a denial-of-service situation, and depending on other conditions, could expose a device running older versions of the protocol to remote code execution.” reads the security advisory published by Claroty.
RTA’s ENIP stack is widely implemented in industrial automation systems.
The flaw, tracked as CVE-2020-25159, has received a CVSS score of 9.8 out of 10, it impacts all versions of EtherNet/IP Adapter Source Code Stack prior to 2.28.
Brizinov reported the stack overflow issue to the US agency CISA that published a security advisory.
“Successful exploitation of this vulnerability could cause a denial-of-service condition, and a buffer overflow may allow remote code execution,” reads the advisory published by the US cybersecurity and infrastructure agency (CISA). “The affected product is vulnerable to a stack-based buffer overflow, which may allow an attacker to send a specially crafted packet that may result in a denial-of-service condition or code execution.”
Experts used the search engines for Internet-connected devices, like Shodan.io, to search for ENIP-compatible internet-facing devices and discovered more than 8,000 systems exposed online.
Industrial Automation systems RTA-ENIP-BLOG-IMAGE-1-1024x580
Experts was that vendors may have bought vulnerable versions of this stack before the 2012 update and are still using it in their firmware.
“However, many vendors may have bought vulnerable versions of this stack prior to the 2012 update, starting in the early 2000s when it was first issued, and integrated it into their own firmware. This would leave many running in the wild still today.” continues the report.
“Claroty researchers were able to scan 290 unique ENIP-compatible devices, which identified 32 unique ENIP stacks. Eleven devices were found to be running RTA’s ENIP stack in products from six unique vendors.”
Operators have to update to current versions of the ENIP stack to address the vulnerability. CISA provided the following recommendations to minimize the risk of exploitation of this vulnerability:
Minimize network exposure for all control system devices and/or systems, and ensure that they are not accessible from the Internet.
Locate control system networks and remote devices behind firewalls, and isolate them from the business network.
When remote access is required, use secure methods, such as Virtual Private Networks (VPNs), recognizing that VPNs may have vulnerabilities and should be updated to the most current version available. Also recognize that VPN is only as secure as the connected devices.
Schneider Electric published a security advisory on Drovorub Linux Malware
15.11.20 ICS Securityaffairs
Schneider Electric is warning customers of the Drovorub Linux malware that was also analyzed recently by the NSA and the FBI.
Schneider Electric published a security bulletin to warn customers of the Drovorub Linux malware, the malware was analyzed in a joint alert published in August by NSA and the FBI.
According to the US agencies, the Linux malware was allegedly employed in attacks carried out by the Russia-linked cyber espionage group APT28.
The name comes from drovo [дрово], which translates to “firewood”, or “wood” and rub [руб], which translates to “to fell”, or “to chop.”
The FBI and NSA attribute the Drovorub malware to APT28 due to the reuse of the C2 infrastructure in different operations, including a past campaign targeting IoT devices in 2019.
Drovorub is a modular malware that includes the implant, a kernel module rootkit, a file transfer tool, a port-forwarding module, and a command-and-control (C2) server.
“Drovorub is a Linux malware toolset consisting of an implant coupled with a kernel module rootkit, a file transfer and port forwarding tool, and a Command and Control (C2) server. When deployed on a victim machine, the Drovorub implant (client) provides the capability for direct communications with actorcontrolled C2 infrastructure; file download and upload capabilities; execution of arbitrary commands as “root”; and port forwarding of network traffic to other hosts on the network.” reads the joint report. “A number of complementary detection techniques effectively identify Drovorub malware activity. However, the Drovorub-kernel module poses a challenge to large-scale detection on the host because it hides Drovorub artifacts from tools commonly used for live-response at scale.”
Drovorub could allow state-sponsored hackers to carry out a broad range of activities, such as stealing files, establishing backdoor access, remote controlling the target’s computer. The malware implements a sophisticated evasion technique, it leverages advanced ‘rootkit’ capabilities to remain under the radar.
The government agencies recommend that US organizations update any Linux system to a version running kernel version 3.7 or later to prevents Drovorub’s rootkit infections.
Drovorub targets systems running Linux kernel versions 3.7 or lower, the researchers pointed out that the malicious code cannot achieve persistence on systems that uses the UEFI secure boot in Full or Thorough mode.
Schneider Electric is urging customers to implement defense-in-depth recommendations to protect Trio Q Data Radio and Trio J Data Radio devices against Drovorub attacks.
The affected products are ethernet and serial data radios that provide long-range wireless data communications for SCADA and remote telemetry applications.
“Schneider Electric is aware of the recently published Drovorub malware. To further mitigate the effects of this malware, Schneider Electric recommends applying a defense in depth approach to protect their Q Data Radio and J Data Radio devices from malware being installed.” reads the security bulletin published by the vendor. “In addition, Schneider Electric recommends customers make use of the available features to reduce the risk of malware installation such as user access controls and the available secure protocols HTTPS and SSH.”
The company’s advisory states that once a device is infected, the malware could allow attackers to communicate with C2 infrastructure, download/upload files, execute arbitrary commands, port forward of network traffic to other hosts on the network, and implement hiding techniques to evade detection.
“Schneider Electric is establishing a remediation plan for all future versions of Trio J-Series Data Radios and Trio Q-Series Data Radios that will include a fix for the Drovorub vulnerability.” concludes the advisory. “We will update this document when the remediation is available. Until then, customers should immediately apply the following mitigations to reduce the risk of exploit. Enable Role-Based Access Control (RBAC).”
The good news is that the company is aware of attacks in the wild involving the Drovorub malware.
Schneider Electric Warns Customers of Drovorub Linux Malware
15.11.20 ICS Securityweek
One of the security bulletins released this week by Schneider Electric warns customers about Drovorub, a piece of Linux malware that was recently detailed by the NSA and the FBI.
The U.S. agencies issued a joint advisory in mid-August to warn organizations that the cyber-espionage group known as APT28, which has been linked to Russia’s General Staff Main Intelligence Directorate (GRU), has been using a piece of Linux malware named Drovorub.
Drovorub includes an implant, a kernel module rootkit, file transfer and port forwarding tools, and a C&C server. Once it has been deployed on a device, the malware allows its operators to download and upload files, execute commands with root privileges, and conduct port forwarding. It also has mechanisms for persistence and evading detection.
Drovorub impacts systems with Linux kernel versions 3.7 or lower (due to the lack of adequate kernel signing enforcement), and it cannot achieve persistence on systems where the UEFI secure boot is enabled in Full or Thorough mode.
Schneider Electric has advised customers to implement defense-in-depth recommendations in order to protect their Trio Q Data Radio and Trio J Data Radio devices against the malware.Schneider Trio Data Radio products vulnerable to Drovorub malware
These products are ethernet and serial data radios designed to provide long-range wireless data communications for SCADA and remote telemetry applications.
According to Schneider, installing the malware on these devices “could result in an attacker gaining direct communications capability with actor-controlled command and control infrastructure, file download and upload capabilities, execution of arbitrary commands, port forwarding of network traffic to other hosts on the network, and implement hiding techniques to evade detection.”
The French industrial giant told SecurityWeek that while Drovorub can pose a threat to its devices, it’s not actually aware of any incident involving the malware.
“When we learned how Drovorub worked, we looked to all of our Linux devices to see if they had the same vulnerabilities. Out of an abundance of caution, we elected to let our users know of the potential issue and offered a mitigation while a fix to the OS was prepared,” Andrew Kling, product security officer at Schneider Electric, said via email.
“By default, the Trio radios are not vulnerable because malware in this form cannot be loaded onto them without modification. A user would have to use unsecured protocols and fail to implement role-based access control to get the radios to be potentially vulnerable,” Kling added.
Learn more about threats to industrial systems at SecurityWeek’s ICS Cyber Security Conference and SecurityWeek’s Security Summits virtual event series
Schneider Electric has advised customers to apply recommended mitigations to reduce the risk of attacks and says it’s working on rolling out a fix that should further reduce the risk, but the company told SecurityWeek that it is not aware of any actual vulnerability that could be exploited by the malware so it does not expect to assign a CVE identifier.
Manufacturing Sector Targeted by Five ICS-Focused Threat Groups: Report
13.11.20 ICS Securityweek
A report published on Thursday by industrial cybersecurity firm Dragos reveals that the manufacturing sector has been attacked by five threat groups that have been known to target industrial environments.
According to Dragos, the manufacturing sector faces increasing risk of cyberattacks, including attacks whose goal may be to cause disruption to industrial processes and ones aimed at collecting valuable information. However, the firm says it has not observed any major or sophisticated incidents involving ICS-specific malware aimed at manufacturing operations.
The list of ICS-focused groups that Dragos spotted targeting organizations in this industry includes CHRYSENE, PARISITE, MAGNALLIUM, WASSONITE and XENOTIME.
MAGNALLIUM is an Iran-linked group that has been active since at least 2013. It’s known to have targeted companies in Europe, North America, South Korea and Saudi Arabia. MAGNALLIUM is not known to have any ICS-specific capability, but Dragos warns that the destructive wiper malware used by the hackers in IT environments could be used in control system networks as well. PARISITE is a separate group that helps MAGNALLIUM gain initial access to targeted systems.
WASSONITE is a group linked to North Korea that has targeted organizations in India, South Korea and Japan. It has been active since at least 2018, but it does not appear to have the capabilities needed to cause disruption or destruction in industrial environments.
The Iran-linked group CHRYSENE has been known to target industrial networks in the Middle East and the UK. It has been tied to OilRig and Greenbug, the threat actors believed to have been involved in the notorious Shamoon attacks. CHRYSENE has focused on penetrating networks and conducting ICS-specific reconnaissance.
XENOTIME, on the other hand, is the only group known to target the manufacturing industry which does have the capability to launch destructive ICS attacks, as demonstrated by its 2017 attack involving the Trisis/Triton malware. The malware has been linked to a Russian research institute.
If threat actors want to target ICS in manufacturing organizations, they have plenty of vulnerabilities that they can exploit to achieve their goals. According to Dragos, there are more than 260 vulnerabilities affecting equipment typically used in manufacturing environments, and many of them could have an impact on safety.
Dragos also reported seeing an increasing number of ransomware attacks aimed at ICS, and the company believes ransomware is “the most common threat to manufacturing.” There are several ransomware families capable of targeting processes associated with OT software.
Other major threats faced by the manufacturing sector are industrial espionage and theft of intellectual property, Dragos said.
“IP and theft of trade secrets related to process and automation functions can enable industrial organizations and interested states and governments to fast-track development of critical infrastructure, including manufacturing. It can also support state-sponsored espionage activities for political or national security efforts,” the company explained.
The complete report from Dragos, which also includes recommendations for manufacturing entities, is available for download in PDF format.
Bugs in Critical Infrastructure Gear Allow Sophisticated Cyberattacks
13.11.20 ICS Threatpost
Security problems in Schneider Electric programmable logic controllers allow compromise of the hardware, responsible for physical plant operations.
Two security vulnerabilities in Schneider Electric’s programmable logic controllers (PLCs) could allow attackers to compromise a PLC and move on to more sophisticated critical infrastructure attacks.
PLCs are key pieces of equipment in environments such as electric utilities and factories. They control the physical machinery footprint in factory assembly lines and other industrial environments, and are a key part of operational technology (OT) networks.
According to researchers at Trustwave, the issues are present in company’s EcoStruxure Machine Expert v1.0 PLC management software, and in the firmware for the M221 PLC, version 1.10.2.2, respectively.
CVEs and severity ratings are pending, and patches are available.
Breaking Password Encryption
The first vulnerability, a small-space seed vulnerability, allows the discovery of encryption keys used by EcoStruxure Machine-Expert Basic for application protection. There are two types of application protection available: Read protection protects the controller’s application from being read by any unauthorized personnel at the engineering workstation; and the write protection protects the controller’s application from unauthorized changes.
“We are able to run an exhaustive key search to identify the encryption key that is used to encrypt the hashed password used to protect the application on the PLC,” Trustwave researchers explained, in a posting on Thursday. “The malicious actor can use this encryption key to decrypt the encrypted hash password that is sent to the controller to unlock read/write protection.”
The brute-force effort was made possible thanks to two flaws, researchers noted: First, the random nonce and secret key used in the encryption process are exchanged in cleartext.
“Hence, we are able to intercept and obtain the secret key from the network packets,” they said.
And secondly, the seed that is used to generate the keys is only two bytes long. This means that there are only 65,535 possible combinations of seed.
“Once we have obtained the seed, we can use this seed and the nonce that we have extracted from the network packet to generate the encryption key,” researchers said. “This encryption key can be used to decrypt the encrypted hashed password that we have extracted from the network packet using XOR algorithm.”
More Sophisticated Attacks
The second bug is a security bypass problem for the application-protection mechanism that can open the door to much bigger attacks. Researchers discovered an alternate channel to bypass the read protection feature on the controller.
“This read protection feature is meant to protect the application that is deployed on the controller from being downloaded by unauthorized personnel,” according to the firm. “[The bypass] can be used by a malicious actor to bypass the protection and download the application from the M221 controller.”
The alternate channel is the ability to send requests for application data as a third-party directly to the controller.
“These payloads can be consumed by the controller successfully without any authentication, thereby bypassing any read protection in place,” according to Trustwave. “In our analysis, we also realized that the application data in transit will be sent in clear instead of being encrypted.”
This in turn would allow an attacker to perform reconnaissance on the M221’s core application, paving the way for more sophisticated, follow-on attacks, Trustwave researchers said. That’s because the application contains the control logic that is deployed on the controller. This logic uses what’s known as “tags” in industrial control systems (ICS), to communicate across an operational technology (OT) network.
“It’s not a trivial task to understand the function of these tags on the network,” according to Trustwave. “In order for an attacker to conduct a targeted attack, he will need to figure out the context of the tags that are used in the control logic. One way to make this process easier is to download the control logic from the controller and read the tags that are set to gain a complete understanding of the process that is deployed on the controller.”
Schneider Electric recommends patching the engineering software, updating the firmware of the controller and blocking ports on the firewall. Trustwave added that customers should also use two different complex passwords for different application protections, and take steps to ensure only the engineering workstation and authorized clients can communicate to the PLC directly.
ICS in the Spotlight
ICS is snagging an increased spotlight from security researchers and the federal government. For instance, critical infrastructure has become a main focus for the Department of Homeland Security’s Cybersecurity and Infrastructure Security Agency (CISA) this year, it announced.
And indeed, more and more bugs have been uncovered in ICS gear as that focus ramps up. Hacking competitions like Pwn2Own for instance have started to focus on ICS.
The efforts are bearing fruit: In March, critical bugs affecting PLCs and physical access-control systems from Rockwell Automation and Johnson Controls were found.
And in July, on the heels of a dire warning from CISA about impending critical infrastructure attacks, ICS-CERT issued an advisory on a critical security bug in the Schneider Electric Triconex TriStation and Tricon Communication Module. These safety instrumented system (SIS) controllers are responsible for shutting down plant operations in the event of a problem and act as an automated safety defense for industrial facilities, designed to prevent equipment failure and catastrophic incidents such as explosions or fire.
They’ve been targeted in the past, in the TRITON attack of 2017.
Encryption Vulnerabilities Allow Hackers to Take Control of Schneider Electric PLCs
13.11.20 ICS Securityweek
Schneider Electric this week released advisories for vulnerabilities impacting various products, including flaws that can be exploited to take control of Modicon M221 programmable logic controllers (PLCs).
A total of four vulnerabilities were discovered in Modicon M221 PLCs by researchers at industrial cybersecurity firm Claroty. Three of them were identified independently by employees of cybersecurity company Trustwave. Both Trustwave and Claroty have published blog posts detailing their findings.
The security holes, three of which have been rated high severity by Schneider, are related to encryption and authentication. The French industrial giant has shared some recommendations that customers can implement to reduce the risk of attacks.
Karl Sigler, senior threat intelligence manager at Trustwave, told SecurityWeek that an attacker needs to have a foothold on the OT network in order to exploit any of the vulnerabilities.
“By bypassing authentication protections and having direct access to manipulate the PLC, an attacker could take over complete control of the PLC actions, which could be catastrophic depending what type of OT environment the PLC is deployed,” Sigler explained. “This could potentially lead to complete failure of the control systems or hazardous situations where the safety of the systems is compromised.”
Yehuda Anikster, senior researcher at Claroty, told SecurityWeek that exploitation of the vulnerabilities requires capturing traffic between the EcoStruxure Machine engineering software and the targeted PLC.
“The attackers would then need to wait for an engineer or technician to connect and enter a password or perform download/upload operations to the M221 using the engineering software,” Anikster said. “At this stage, the attackers have all they need and can now extract the encryption key from the captured network traffic in order to decrypt the read/write passwords from the traffic.”
“After the attackers have obtained the read/write passwords, they can do anything they wish to the M221 PLC as if they were the engineers themselves. This includes uploading the M221's program, downloading (and overwriting) a program to the M221, changing the read/write passwords, stopping/starting the M221, and more,” the researcher added. “For example, attackers can extract all the code running on the M221s, stealing the company’s control process logic. Another potential scenario is of attackers deleting all the code and changing all passwords on the M221s, blocking all access to the devices and rendering the PLCs unusable in a denial-of-service attack. Furthermore, sly attackers could perform a Stuxnet-like attack and slightly change the code on the M221s to wreak havoc on the company’s devices.”
Schneider Electric also informed customers this week of critical and high-severity vulnerabilities affecting its PLC Simulator product, including ones that can be exploited for arbitrary command execution and DoS attacks.
It also warned of a critical flaw in the Easergy T300 RTU, which can allow command execution and DoS attacks, and several high-severity remote code execution vulnerabilities affecting the Interactive Graphical SCADA System (IGSS) product.
The vendor also advised customers to apply defense-in-depth measures to protect Q Data Radio and J Data Radio devices against Drovorub, a Russia-linked malware that was recently detailed by the NSA and the FBI.
Flaws in PcVue SCADA Product Can Facilitate Attacks on Industrial Organizations
10.11.20 ICS Securityweek
Researchers found several potentially serious vulnerabilities in the PcVue SCADA/HMI solution developed by France-based ARC Informatique, including flaws that can allow an attacker to take control of industrial processes or cause disruption.
The PcVue product was analyzed by researchers from Kaspersky, who identified a total of three vulnerabilities. The vendor has patched the security holes with the release of version 12.0.17 and it has also shared some mitigations and workarounds to help customers prevent attacks.
Andrey Muravitsky, senior security researcher at Kaspersky and one of the people credited for finding the PcVue issues, told SecurityWeek that ARC Informatique “did an awesome job” and patched all vulnerabilities 5 months after being notified — it often takes industrial solutions providers much longer to fix vulnerabilities.
Learn more about vulnerabilities in industrial systems at SecurityWeek’s ICS Cyber Security Conference and SecurityWeek’s Security Summits virtual event series
The most serious of the flaws, rated critical, is related to unsafe deserialization of messages received in the interface and it can lead to remote code execution. The other two vulnerabilities have been rated high severity — one can be leveraged for DoS attacks, while the other is an information disclosure issue that allows an attacker to access session data of legitimate users.
Kaspersky, which published advisories for these vulnerabilities in October, says exploitation is easy and it does not require any user interaction. The U.S. Cybersecurity and Infrastructure Security Agency (CISA) published an advisory last week to warn organizations of the risks posed by these flaws.
Muravitsky said the vulnerabilities can be exploited by an attacker who has network access to TCP port 8090, and they can achieve arbitrary code execution on the web and mobile backend server. The expert says remote exploitation from the internet may also be possible if the vulnerable component is exposed to the web.
“The attacker could execute commands on the computer connected to the OT network and expand the attack surface,” Muravitsky said via email. “And in some cases the attacker can take control of industrial processes and cause disruption.”
Attacks on industrial enterprises using RMS and TeamViewer: new data
5.11.20 ICS Securelist
In summer 2019, Kaspersky ICS CERT identified a new wave of phishing emails containing various malicious attachments. The emails target companies and organizations from different sectors of the economy that are associated with industrial production in one way or another.
We reported these attacks in 2018 in an article entitled “Attacks on industrial enterprises using RMS and TeamViewer“, but recent data shows that the attackers have modified their attack techniques and that the number of enterprises facing the threat of infection is growing.
Before publishing this report, we waited for the vendor of the RMS software to make changes to its services to ensure that the results of this research could not be used to exploit vulnerabilities.
This report in a nutshell:
From 2018 to at least the early fall of 2020, attackers sent phishing emails laced with malware.
The attacks make use of social engineering techniques and legitimate documents, such as memos and documents detailing equipment settings or other industrial process information, which have apparently been stolen from the company under attack or its business partners.
The attacks still use remote administration utilities. The graphical user interface of these utilities is hidden by the malware, enabling the attackers to control infected systems without their users’ knowledge.
In the new version of the malware, the attackers changed the notification channel used after infecting a new system: instead of malware command-and-control servers, they use the web interface of the RMS remote administration utility’s cloud infrastructure.
Stealing money from the organization under attack remains the main objective of the attackers.
During an ongoing attack, the cybercriminals use spyware and the Mimikatz utility to steal authentication credentials that are subsequently used to infect other systems on the enterprise network.
The full article is available on Kaspersky Threat Intelligence.
For more information please contact: ics-cert@kaspersky.com.
Technical Analysis
Since we described the technical details of this series of attacks in our previous report, Attacks on industrial enterprises using RMS and TeamViewer, in this document we only list the main stages of an attack and describe the changes to the attackers’ tactics and toolset that have been implemented since the publication of the previous report.
Spreading
Phishing emails used in this attack are in most cases disguised as business correspondence between organizations. Specifically, the attackers send claim letters on behalf of a large industrial company.
Phishing email disguised as a claim letter
In the earlier attack series, the attackers used a sender email address with a domain name that was similar to the official website address of the organization on whose behalf their phishing emails were sent. Now they use public email services to send their phishing emails and they use a different technique to mislead message recipients and persuade them to open a malicious attachment: they pretend to be a real business partner or to represent a real subsidiary of the company under attack and ask the recipient to view the documents attached by the deadline specified in the email, explaining the request by the approaching end of a purchase tender, possible penalties or the need to review equipment configuration data as soon as possible.
It should also be emphasized that the phishing emails are individually crafted for each specific company that is attacked. This is demonstrated by the fact that the name of the company under attack is mentioned in the email text, as well as by the documents used by the attackers as attachments (descriptions of the documents are provided below). In some of the cases identified earlier, the attackers also addressed the recipient by his or her full name.
Phishing email sent on behalf of a contractor
Attachments used in phishing emails are password-protected archives, with the password provided in the message body. The attackers explain this method of sending information by referring to confidentiality considerations in the message body, but in reality password protection prevents files stored in the archive from being scanned with antivirus tools.
Malware Features
The archive attached to a phishing email contains several malicious obfuscated JS scripts that have an identical functionality but slightly different structure due to different code obfuscation techniques being used. The script names are usually disguised as document names.
If a user runs one of these scripts, two files are unpacked and opened: a malicious program detected as HEUR:Backdoor.Win32.Generic, and a legitimate PDF file. Some JS script variants found in phishing emails download these files from a remote server rather than extracting them from the script’s body.
In earlier attacks, to ensure that the user didn’t have questions regarding the absence of the documents mentioned in the message body and to distract the user while installing the malware, the attackers opened a damaged PDF document or image or launched a legitimate software installer.
Image opened by the malware in earlier attacks
In their later attacks, the threat actor began to use actual documents related to the attacked organization’s area of work. A document can look like one created by a business partner or even the attacked organization itself. Specifically, documents used in attacks include scan copies of memos, letters to subsidiaries and contractors, as well as procurement documentation forms that were apparently stolen earlier.
PDF document containing instructions for subsidiaries, used by the attackers
A fact of particular interest is that in some cases, the attackers used documents containing industrial equipment configuration data and other information related to the industrial process.
Specifically, screenshots from the DIGSI application have been used. The application is designed to configure relay systems manufactured by Siemens.
DIGSI software screenshot 1
DIGSI is used by electric power facilities, such as substations, to configure their relay protection systems.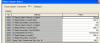
Screenshot of a relay system’s configuration matrix. List of setpoints
We also found screenshots with transformer oscillograms in documents used by the attackers: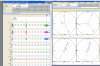
Vector diagrams with oscillograms
It is worth noting that the last screenshot shows oscillograms for a system at the moment of an accident.
Phishing emails with such screenshots do not call for the settings shown in attached documents to be implemented. It is most likely that the attackers use documents with the above screenshots to distract the personnel while the malware is being installed. Since the data mentioned above can provide a relay protection expert with information on standard settings used at the facility, the fact that the attackers have such screenshots at their disposal is cause for concern.
The JS script then launches the malware, which installs a version of TeamViewer, a remote administration tool (RAT), modified by the attackers. As in earlier attacks, the attackers use a malicious DLL library to hide the graphical user interface in order to control the infected system without the user’s knowledge.
If additional information needs to be collected, the attackers download an additional set of malware selected specifically for each victim. This can be spyware designed to collect credentials for a variety of programs and services, including email clients, browsers, SSH/FTP/Telnet clients, as well as recording keypresses and making screenshots. In some cases, the Mimikatz utility is used to collect account credentials for Windows accounts entered on the compromised system. The use of Mimikatz poses a particular danger, because it can provide the attackers with access to a large number of systems on the enterprise’s network.
In most cases, the attackers disguise malware components as Windows components to hide traces of malicious activity on the system.
Infrastructure
While analyzing the new series of attacks, we noticed two ways in which the infrastructure is organized differently from that used in earlier attacks.
First, the attackers use resources disguised as websites of existing Russian-speaking companies to store files downloaded by malicious JS scripts at the system infection stage.
The second and more important difference is that the attackers no longer use a malware command-and-control server in their communication with infected systems.
The main reason for having a malware command-and-control server in this type of attack was the need to get the infected machine’s ID in the TeamViewer system. The attackers already had any other information they needed (the password required to connect was provided in a special configuration file). In the new series of attacks, the attackers sent the infected machine’s TeamViewer ID using the legitimate infrastructure of the RMS remote administration system.
This was possible because the RMS remote administration infrastructure has a dedicated web service designed to notify the administrator that an RMS distribution package has been installed on a remote system. To send the notification, the RMS server generates an email message that contains the machine’s ID in the RMS system in the message body. For the message to be generated, it is sufficient for the RMS client to send an HTTP POST request to the dedicated web page, providing the following data: product name, ID of the language pack used in the system, user name, computer name, email address to which the notification should be delivered, and the machine’s ID in the RMS system assigned after installing the program.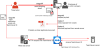
Attack kill chain
The underlying mechanism of the web service contained a vulnerability: it did not use any kind of authorization procedure. The malicious DLL responsible for hiding the TeamViewer graphic interface included code for sending the request described above to the RMS server. However, it sent the machine’s ID in the TeamViewer system instead of its ID in the RMS system. The ID length in the TeamViewer system is different from the ID length in the RMS system; however, since there is no verification of the contents of fields sent to the server in the HTTP POST request, a notification message with information on a newly infected machine was successfully delivered to the attacker’s address.
Kaspersky ICS CERT has notified RMS developers that their infrastructure is being used for criminal purposes, providing them with all the technical details needed to close the vulnerability. To date, the vulnerability has not been closed by the developers, but a workaround, filtration based on an address whitelist, has been implemented.
In other words, the functionality still works, but notification emails are only sent to email addresses included in a special list of customers ‘verified’ by RMS developers.
For technical details about this vulnerability please contact: ics-cert@kaspersky.com
Victims
As mentioned above, the vast majority of attacked systems are industrial enterprises in Russia representing various sectors of the economy. We identified attacks on companies from the following industries:
Manufacturing
Oil and gas
Metal industry
Engineering
Energy
Construction
Mining
Logistics
Consequently, this is not a case of an attack narrowly targeting one specific industry; however, since most legitimate documents used in the attacks are from the energy sector, it can be assumed that the attackers have a particular interest in the sector.
Attribution
We are convinced that a Russian-speaking group is behind these attacks.
The main arguments in favor of this theory were offered in our previous report, “Attacks on industrial enterprises using RMS and TeamViewer“.
Note also that the code used to send requests to the RMS server, which was identified in the process of analyzing the new version of the malicious DLL, contains a language ID for the Russian localization of the operating system.
According to available information, the main objective of the criminals is to steal money from victim organizations’ accounts. This means that the attackers must have a good understanding of the financial workflow, which differs in some of its aspects from country to country, and support the appropriate infrastructure for cash withdrawal.
The group does not use any sophisticated tactics or technologies, but it carefully prepares each attack and expertly uses social engineering techniques, as well as technologies that are already known from attacks staged by other criminal groups.
We believe that the group includes people responsible for the technical aspect of infecting victims’ systems, as well as people responsible for financial operations, i.e., for stealing money from the group’s victims.
Conclusions
The threat actor continues to attack industrial enterprises successfully using relatively simple techniques, but its methods are evolving. To persuade users of the legitimacy of phishing emails, criminals have begun to use documents that were apparently stolen during earlier attacks. It is worth noting that some of the documents used for this purpose contain information on industrial equipment settings and industrial process parameters. This is one more reason to believe that these attacks specifically target industrial enterprises.
The main technical change in the attacks is that the attackers have discarded the most vulnerable stage in data collection and transmission – that is, malware command-and-control servers, which can be disconnected by the hosting provider or blocked by information security systems. Instead, new system infection notifications are delivered via the legitimate web interface of the RMS remote administration utility’s cloud infrastructure. Resources disguised as legitimate websites of existing organizations are used to store malware samples.
The attackers have full control of an infected system from the moment it becomes infected. Stealing money from the organization’s accounts remains their main objective. When the attackers connect to a victim’s computer, they look for financial and accounting software (1C accounting software, bank-client, etc.). In addition, they find and analyze procurement-related accounting documents and peruse the email correspondence of the enterprise’s employees. After that, the attackers look for various ways in which they can commit financial fraud. We believe that the criminals are able to substitute the bank details used to pay invoices.
Clearly, the attackers’ remote access to infected systems also poses other threats, such as the organization’s sensitive data being leaked, systems being put out of operation, etc. As the latest events have shown, the attackers use documents that were probably stolen from organizations to carry out subsequent attacks, including attacks on victim companies’ partners.
If you have encountered an attack of this kind, you can report it to us through a form on our website.
Recommendations
Train employees at enterprises in using email securely and, specifically, in identifying phishing messages
Restrict the ability of programs to gain SeDebugPrivilege privileges (wherever possible)
Install antivirus software with support for centrally managing the security policy on all systems; keep the antivirus databases and program modules of security solutions up to date
Use accounts with domain administrator privileges only when necessary. After using such accounts, restart the system on which the authentication was performed
Implement a password policy with password strength and regular password change requirements
If it is suspected that some systems are infected: remove all third-party remote administration utilities, scan these systems with antivirus software and force a change of passwords for all accounts that have been used to log on to compromised systems
Monitor network connections for any traces of remote administration utilities installed without proper authorization. Make a special emphasis on the use of RMS and TeamViewer utilities
Use network activity filtration systems to block connections to servers and IP addresses listed in Appendix I – Indicators of Compromise
Never use obsolete versions of the TeamViewer utility (versions 6.0 and earlier). To discover any instances of obsolete versions of TeamViewer being used, the YARA rule provided in Appendix I – Indicators of Compromise can be used
It should be noted that, since the attack uses legitimate remote administration software, that software can remain on the victim’s computer and continue operating even when the malicious downloader has been removed. If remote administration software has been identified at the stage of scanning corporate systems, it should be determined in each case whether it was installed legitimately
For more information please contact: ics-cert@kaspersky.com
Appendix I – Indicators of Compromise
File Hashes (malicious documents, malware, emails etc.)
386a1594a0add346b8fbbebcf1547e77
203e341cf850d7a05e44fafc628aeaf1
3b79aacdc33593e8c8f560e4ab1c02c6
ea1440202beb02cbb49b5bef1ec013c0
1091941264757dc7e3da0a086f69e4bb
72f206e3a281248a3d5ca0b2c5208f5f
da4dff233ffbac362fee3ae08c4efa53
d768a65335e6ca715ab5ceb487f6862f
9219e22809a1dff78aac5fff7c80933c
86e14db0bcf5654a01c1b000d75b0324
File Names
Акт.js
Запрос 17782-09-1.js
Перечень документов.js
спецификация на оборудование xls.js
tv.dll
tv.ini
Some malware modules installed on the system have randomly generated names that follow a specific format. The following regular expression can be used to search for such files:
%TEMP%\\[a-z]{2,3}[0-9]{2}.exe
These files are saved in the temporary file directory (%TEMP%); the first part of the file name consists of two or three Roman characters; the second is a two-digit number followed by the extension .exe
Domains and IPs
timkasprot.temp.swtest[.]ru (RemoteAdmin.Win32.RemoteManipulator.vpj)
77.222.56[.]169 (RemoteAdmin.Win32.RemoteManipulator.vpj)
z-wavehome[.]ru (RemoteAdmin.Win32.RemoteManipulator.vpj)
dncars[.]ru (RemoteAdmin.Win32.RemoteManipulator.vpj)
Yara Rules
The attackers use outdated versions of the TeamViewer client that contain a vulnerability enabling them to hide the utility’s graphic interface. This YARA rule can be used to determine whether there are outdated versions of the TeamViewer software installed on the system. Checking whether any such software found was installed legitimately is a first-priority task.
If instances of outdated versions of the TeamViewer client being used legitimately are identified, it is recommended that the software in question be updated to the latest version.
Registry keys
Key:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnce\rundll32
Value:
rundll32.exe shell32.dll,ShellExec_RunDLL
“%AppData%\Roaming\TeamViewer\5\TeamViewer.exe”
Key:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnce\CCFTray
Value:
rundll32.exe shell32.dll,ShellExec_RunDLL “%temp%\TeamViewer.exe”
Threat actors’ email addresses
timkas@protonmail.com
smoollsrv@gmail.com
nataly@z-wavehome.ru
info@dncars.ru
Appendix II – MITRE ATT&CK Mapping
Tactic Technique/Subtechnique Description
Initial Access T1566.001 Phishing: Spearphishing Attachment
The attackers use phishing emails with archives containing malicious scripts
Execution T1204.002 User Execution: Malicious File
Malicious software is executed when the user opens the file
T1059.007 Command and Scripting Interpreter: JavaScript/Jscript
Used to execute malicious PE and open bait PDF files
Persistence T1547.001 Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder
The malware creates a registry value to run automatically after system restart
Defense Evasion T1027.002 Obfuscated Files or Information: Software Packing
To make analysis more difficult, files of the malware are packed and its code is obfuscated
T1564.001 Hide Artifacts: Hidden Files and Directories
The attributes “hidden” and “system” are assigned to malware files
T1574.001 Hijack Execution Flow: DLL Search Order Hijacking
To hide the GUI of the TeamViewer remote administration utility, a malicious program is loaded into the process instead of a system library
T1036.005 Masquerading: Match Legitimate Name or Location
In most cases, attackers disguise malware components as Windows operating system components to hide the traces of malicious activity in the system
Credential Access T1003.001 OS Credential Dumping: LSASS Memory
The attackers use the Mimikatz utility in cases where they need authentication credentials to infect other systems in an organization
T1056.001 Input Capture: Keylogging
In some cases, malware (class: Spyware) designed to collect logins and passwords for various different programs and services, record keypresses and capture screenshots is downloaded to an infected system
Discovery T1057 Process Discovery
The malware collects information on antivirus software running on the system
T1018 Remote System Discovery
The attackers explore the organization’s other systems to which they can gain access over the network
T1518 Software Discovery
The attackers take notes on which software associated with financial operations is installed on an infected system
Lateral Movement T1021.001 Remote Services: Remote Desktop Protocol
RDP connections with account credentials obtained earlier using the Mimikatz utility are used for lateral movement
Collection T1005 Data from Local System
The attackers analyze documents found on infected systems; these documents can be used in subsequent attacks
T1114.001 Email Collection: Local Email Collection
The attackers analyze the business correspondence of the organization under attack in order to use it for subsequent attacks on the victim’s business partners
T1056.001, T1113 Input Capture: Keylogging and Screen Capture
In some cases, malware (class: Spyware) designed to collect logins and passwords for various different programs and services, record keypresses and capture screenshots is downloaded to an infected system
Command And Control T1071.001 Application Layer Protocol: Web Protocols
To send the TeamViewer ID, an HTTP POST request is sent to the RMS server
T1071.003 Application Layer Protocol: Mail Protocols
The RMS server sends an email to an address controlled by the attackers. The email contains the infected machine’s TeamViewer ID
T1219 Remote Access Software
The attackers use the TeamViewer remote administration utility to connect to the infected system
Exfiltration T1020 Automated Exfiltration
The attackers use malware to receive information collected on the infected system
Impact T1565.001 Data Manipulation: Stored Data Manipulation
Substitution of bank details in payment forms
Over 12% of ICS Security Incidents Attributed to Nation-State Hackers: Survey
3.11.20 ICS Securityweek
The Control System Cyber Security Association International (CS)2AI and KPMG on Monday announced their first annual cybersecurity report focusing on industrial control systems (ICS) and operational technology (OT).
(CS)2AI, a non-profit organization, has more than 16,000 members worldwide and the report is based on information provided by 600 of them. Respondents represent all continents — although nearly half of them are from North America — and a wide range of industries and organization sizes. More than 80% of respondents are decision makers when it comes to OT security expenditure.
(CS)2AI released a preview of the report last year at SecurityWeek’s ICS Cyber Security Conference in Atlanta. The organization revealed at the time that some respondents claimed to have experienced ICS security incidents that resulted in injury and even loss of life.
The final version of the report covers a wide range of topics, including control system cybersecurity prioritization, budgets, staffing, awareness training, vulnerabilities, organizational plans, managed services, assessments, network monitoring, frameworks and technologies, and incidents.
Of the incidents observed by respondents in the year prior to taking part in the survey, a majority involved an email-based attack vector (32%) or an infected removable media drive (35%). Nearly 46% of attacks have been attributed to negligent insiders (i.e. individuals with trusted access who unwittingly facilitate or cause a breach), but some were also attributed to scammers (16%), cybercriminals (14%), nation-state actors (12%) and malicious insiders (11%).
Learn more at SecurityWeek’s 2020 ICS Cyber Security Conference and SecurityWeek’s Security Summits virtual event series
Much of the data in the report is presented separately for organizations with a more mature cybersecurity program and organizations with a less mature program.
(CS)2AI noted that organizations with a mature program are more likely to detect the involvement of social engineering in an attack (12% for those with a mature program vs 4% for less mature program), or nation-state actors (20% vs 13%).
(CS)2AI has highlighted some interesting differences between organizations with a mature cybersecurity program and ones with a less mature program.
For instance, 47% of organizations with a mature program use managed services for ICS cybersecurity, compared to only 5% of companies with a less mature program. Additionally, those with a mature program conduct end-to-end security assessments more frequently (53% vs 36%).
The report also shows that companies with a mature program are much more likely to replace vulnerable hardware or software after an assessment (63% for mature programs vs 34% for less mature programs).
Derek Harp, founder and chairman of (CS)2AI, told SecurityWeek that they will continue to collect data, which will enable the organization to regularly identify trends in this area.
FDA Approves Use of New Tool for Medical Device Vulnerability Scoring
23.10.20 ICS Securityweek
The U.S. Food and Drug Administration (FDA) this week announced that it has approved the use of a new rubric specifically designed by the MITRE Corporation for assigning CVSS scores to vulnerabilities found in medical devices.
The Common Vulnerability Scoring System (CVSS) was originally designed to convey the severity of vulnerabilities found in IT systems, and it may not be as relevant in some areas, such as industrial control systems (ICS) or medical devices.
That is why the FDA contracted MITRE to create a special rubric for assigning CVSS scores to medical device vulnerabilities. MITRE developed the new rubric last year and the FDA announced this week that it has qualified as a Medical Device Development Tool (MDDT).
The MDDT program enables the organization to qualify tools that can be used in the development and evaluation of medical devices. In order for a tool to qualify, it must be evaluated by the FDA, which must agree that it “produces scientifically-plausible measurements and works as intended within the specified context of use.”
The FDA believes that using MITRE’s rubric for applying CVSS to medical devices, together with CVSS v3.0, “allows a common framework for risk evaluation and communication between all parties involved in a security vulnerability disclosure, particularly when discussing its severity and urgency.”
The FDA’s approval of the tool means “that vendors can communicate measurements from the rubric about their devices with the FDA for pre-market security and risk assessments,” Elad Luz, head of research at New York-based healthcare cybersecurity firm CyberMDX, told SecurityWeek.
CyberMDX has identified more than ten vulnerabilities in medical devices over the past year and it has seen first hand how misleading CVSS can be if it’s not adapted. For instance, a vulnerability it discovered last year in some of GE Healthcare’s hospital anesthesia devices was assigned a CVSS score of only 5.3 but, as the vendor itself admitted, exploitation of the flaw posed a direct risk to patients, which made it highly serious.
“[The vulnerability] was not scored as high severity because you could not execute remote code, or remotely access information, just remotely alter limited specific functionality,” Luz explained. “The problem is — when you look at the medical aspect of this — those remote functions altered might just be the most severe thing to compromise on this device, so this must be expressed for anyone doing a risk assessment for it.”
Luz says the new rubric addresses these and other issues. The expert says the new guidelines are clear and easy to use, with real-world examples taken from medical devices used worldwide.
“When doing disclosures there are many disagreements regarding the interpretation of CVSS because it was not always clear how one should project those measurements that were meant for computers/mobiles software to medical devices,” he explained. “The rubric goes through all CVSS measurements and clears them out in the form of a Q&A flowchart. This makes things much more clear and will hopefully spare much of the arguments.”
Luz also pointed out that the new rubric gives the environmental metric group “the place it deserves.”
“When people get exposed to CVSS scores they mostly consume the ‘base metric group’. This is unfortunate because the base score only gives a general impression of the risk,” he said. “The ‘environmental metric group’ is another group on CVSS that adjusts the score to your specific case. The environment where the device is deployed and used greatly affects the actual risk and this must be taken into account. Almost half of the rubric talks about this environmental group and finally it gets the right attention it deserves.”
Talos experts disclosed unpatched DoS flaws in Allen-Bradley adapter
15.10.20 ICS Securityaffairs
Cisco Talos found several remotely exploitable denial-of-service (DoS) vulnerabilities in a Rockwell Automation industrial automation product.
A researcher from Cisco Talos released technical details of several remotely exploitable denial-of-service (DoS) vulnerabilities in an industrial automation product made by Rockwell Automation.
The product affected by the flaw is the Allen-Bradley 1794-AENT Flex I/O series B adapter, the issue resides in the Ethernet/IP request path port/data/logical segment functionality.
Cisco Talos researcher has found five high-severity buffer overflow vulnerabilities that impact Allen-Bradley devices running versions 4.003 and earlier.
“The Allen-Bradley Flex input/output system contains multiple denial-of-service vulnerabilities in its ENIP request path data segment. These bugs exist specifically in the 1794-AENT FLEX I/O modular platform. It provides many I/O operations and servers as a smaller physical device compared to other similar hardware.” reads the Cisco Advisory.
An attacker could exploit the above vulnerabilities by sending a specially crafted, malicious packet to the vulnerable device, this will causing a loss of communication between the victim’s network and the device resulting in denial-of-service.
Talos reported the flaws to Rockwell Automation in February and for two times the vendor requested disclosure extensions. When Rockwell Automation requested a third extension, Talos decided to disclose the issues on October 12 regardless of whether or not the vendor has released security updates.
Rockwell Automation published a security advisory for its registered customers on October 12 that includes general recommendations to prevent attacks exploiting the above flaws.
The vendor recommends configuring the devices to accept CIP connections only from trusted sources on port 44818. The company also suggests implementing network segmentation and security controls to minimize exposure of affected devices. Other recommendations include the use of firewalls, VPNs and other network infrastructure controls.
Remotely Exploitable DoS Vulnerabilities Found in Allen-Bradley Adapter
14.10.20 ICS Securityweek
Cisco Talos this week released the details of several remotely exploitable denial-of-service (DoS) vulnerabilities found by one of its researchers in an industrial automation product made by Rockwell Automation.
The affected product is the Allen-Bradley 1794-AENT Flex I/O series B adapter, specifically the device’s Ethernet/IP request path port/data/logical segment functionality.
Cisco Talos and Rockwell Automation say a total of five high-severity buffer overflow vulnerabilities have been identified. They impact adapters running versions 4.003 and earlier.DoS vulnerabilities in Allen-Bradley adapters
A remote, unauthenticated attacker can exploit these flaws to cause the targeted device to enter a DoS condition by sending it specially crafted packets.
Cisco noted in its advisories that “all remote communications with the device are stopped and a physical power cycle is required to regain functionality.”
The vulnerabilities were reported to Rockwell Automation in February and the vendor requested two disclosure extensions, but when it asked for a third extension, Talos informed it that the vulnerabilities would be disclosed on October 12 regardless of whether or not a patch is available.
Learn more about vulnerabilities in industrial systems at SecurityWeek’s 2020 ICS Cyber Security Conference and SecurityWeek’s Security Summits virtual event series
Rockwell Automation also published an advisory (account required) for these vulnerabilities on October 12 and while a patch does not appear to be available, the company has provided specific and general recommendations to prevent attacks.
Specific recommendations include only accepting CIP connections from trusted sources on port 44818, employing network segmentation and security controls to minimize exposure of affected devices, and the use of firewalls, VPNs and other network infrastructure controls.
Flaws in leading industrial remote access systems allow disruption of operations
1.10.20 ICS Securityaffairs
Experts found critical security flaws in two popular industrial remote access systems that could be exploited by threat actors for malicious purposes.
Security researchers from Israeli firm OTORIO found critical vulnerabilities in leading industrial remote access systems that could be exploited by attackers to ban access to industrial production floors, hack into company networks, tamper with data, and even steal sensitive business secrets.
Remote access has crucial in the modern industry, especially due to the increased demands of industrial remote access systems sustained during the ongoing COVID-19 pandemic.
The issues affect the popular industrial remote access systems B&R Automation’s SiteManager and GateManager broadly used in multiple sectors, including in automotive, energy, oil & gas, and metal.
The experts found six vulnerabilities in B&R Automation’s SiteManager and GateManager (CVE-2020-11641, CVE-2020-11642, CVE-2020-11643, CVE-2020-11644, CVE-2020-11645, CVE-2020-11646) that could potentially disrupt operations.
“Exploiting the 6 new vulnerabilities, an attacker who has gained authorized access to the solution could view sensitive information about other users, their assets and their processes (even when they belong to an external organization).” reads the advisory published by the company. “Additionally, hackers can fool users to malicious foreign sites through fictive system messages and alerts, and trigger a repeated restart of both the GateManager and the SiteManager, leading eventually to a loss of availability, and halt production.”
“Leveraging all three vulnerabilities would have enabled attackers to devise a worst-case scenario to an operations floor which relied on remote access employees.”
The US CISA agency also published a security advisory to warn of risks associated with the successful exploitation of the flaws in the B&R Automation systems. The Agency confirmed that an authenticated attacker with access to the solution via a general license could exploit the flaws to trigger a DoS condition or to achieve arbitrary information disclosure and data manipulation.
The vulnerabilities impact all versions of SiteManager prior to v9.2.620236042, GateManager 4260, and 9250 before v9.0.20262, and GateManager 8250 prior to v9.2.620236042.
Experts also found security vulnerabilities in mymbCONNECT24 and mbCONNECT24 that could be exploited by authenticated attackers to access arbitrary information via SQL injection, steal session details by carrying out a cross-site request forgery (CSRF).
The vulnerabilities, tracked as (CVE-2020-24569, CVE-2020-24568, CVE-2020-24570), impact mymbCONNECT24 and mbCONNECT24 versions v2.6.1 and prior.
The most severe issue is an IMPROPER NEUTRALIZATION OF SPECIAL ELEMENTS USED IN A COMMAND (‘COMMAND INJECTION’) vulnerability that received a CVSS score of 9.8.
CISA also published a security advisory for these vulnerabilities, the US agency provided the following recommendations to the users:
Minimize network exposure for all control system devices and/or systems, and ensure that they are not accessible from the Internet.
Locate control system networks and remote devices behind firewalls, and isolate them from the business network.
When remote access is required, use secure methods, such as Virtual Private Networks (VPNs), recognizing that VPNs may have vulnerabilities and should be updated to the most current version available. Also recognize that VPN is only as secure as the connected devices.
Critical Flaws Discovered in Popular Industrial Remote Access Systems
1.10.20 ICS Thehackernews
Cybersecurity researchers have found critical security flaws in two popular industrial remote access systems that can be exploited to ban access to industrial production floors, hack into company networks, tamper with data, and even steal sensitive business secrets.
The flaws, discovered by Tel Aviv-based OTORIO, were identified in B&R Automation's SiteManager and GateManager, and MB Connect Line's mbCONNECT24, two of the popular remote maintenance tools used in automotive, energy, oil & gas, metal, and packaging sectors to connect to industrial assets from anywhere across the world.
Six Flaws in B&R Automation's SiteManager and GateManager
According to an advisory published by the US Cybersecurity and infrastructure Security Agency (CISA) on Wednesday, successful exploitation of the B&R Automation vulnerabilities could allow for "arbitrary information disclosure, manipulation, and a denial-of-service condition."
The flaws, ranging from path traversal to improper authentication, impact all versions of SiteManager prior to v9.2.620236042, GateManager 4260, and 9250 before v9.0.20262, and GateManager 8250 prior to v9.2.620236042.
OTORIO's Nikolay Sokolik and Hay Mizrachi found that by exploiting these six vulnerabilities (CVE-2020-11641 through CVE-2020-11646), an authenticated attacker with access to the solution via a general license could view sensitive information about other users, their assets, and their processes, even when they belong to a different organization from that of the adversary.
"This information can be used by attackers to target other organizations and their industrial systems," OTORIO said.

"Additionally, hackers can fool users into malicious foreign sites through fake system messages and alerts. The attacker can also trigger a repeated restart of both the GateManager and the SiteManager, leading eventually to a loss of availability and halt production."
An RCE Flaw in mbCONNECT24
Likewise, mymbCONNECT24 and mbCONNECT24 versions v2.6.1 and prior have been found vulnerable to four different security issues that could make it possible for a logged-in attacker to access arbitrary information via SQL injection, steal session details by carrying out a cross-site request forgery (CSRF) attack with merely a specifically crafted link, and leverage outdated and unused third-party libraries bundled with the software to gain remote code execution.
The RCE vulnerability is the severest of all, with a CVSS score of 9.8 out of a maximum of 10.
Although these flaws have since been fixed, the development is another reminder of how weaknesses in remote access solutions can have destructive consequences on critical infrastructure.
For its part, CISA has recommended minimizing network exposure for all control system devices, in addition to putting control system networks and remote devices behind firewalls, and isolating them from the business network.
"When remote access is required, use secure methods, such as Virtual Private Networks (VPNs), recognizing that VPNs may have vulnerabilities and should be updated to the most current version available," the agency cautioned. Also, recognize that VPN is only as secure as the connected devices."
FireEye Proposes Converged Enterprise and ICS ATT&CK Matrix
29.9.20 ICS Securityweek
FireEye's Mandiant Threat Intelligence and MITRE have collaborated on developing a new visualization able to combine the two separate Enterprise ATT&CK and ICS ATT&CK threat knowledgebases into a single holistic view combining both IT and OT attack behaviors.
In developing its ICS ATT&CK matrix, MITRE stressed that it is necessary to understand both Enterprise ATT&CK and ICS ATT&CK to accurately track threat actor behaviors across OT incidents. But just as the historical divide between IT and OT can lead to loss of visibility between the two, so too can the separation of ATT&CK into Enterprise and ICS lead to a loss of visibility on attacker behaviors.
The problem is focused on what FireEye describes as 'intermediary systems'. These may structurally be part of OT, but nevertheless run on standard enterprise operating systems. They are used to control the ICS equipment, and consequently run non-enterprise software systems. Enterprise ATT&CK can map attacker behavior up to the intermediary systems, but loses visibility in the handover to ICS. The problem in providing a complete view of attack behavior is that most of a sophisticated attack's behavior is found within the intermediary systems.
"Over the past 5 to 10 years," Nathan Brubaker, senior manager at Mandiant Threat Intelligence told SecurityWeek, "every sophisticated ICS attack instance we have observed has passed through these intermediary systems on their way to impacting ICS. This includes malware like Stuxnet, Triton and most others. Ninety to ninety-five percent of threat actor activity occurs on these intermediary systems." So that's the most likely place you're going to find ICS attackers, and the best opportunity to stop them. Once they get beyond the intermediary systems and actually into the PLCs, there is little that can be done, and you're in trouble. While MITRE, he continued, "has highlighted that Enterprise and ICS should be used and viewed together, from our use case as a security vendor, we think it is more useful and practical to merge the two into one holistic view."
While you can map a lot of the attackers' intermediary activity in Enterprise, you will primarily see standard IT attacks -- like data theft. But you will not be able to map the attacks against ICS systems that start from here. For example, an HMI could be used to shut down an OT process and impact the ICS and you won't be able to map that in Enterprise.
To make matters worse, said Brubaker, "attackers are increasingly directly targeting the intermediary systems. One recent example was the attack on an Israeli water system in Spring 2020 that started with a direct attack against the intermediary systems. In this case it was a Windows machine running HMI software that was connected to the internet without authentication. Such things can easily be found in Shodan."
In a blog posted Wednesday, FireEye describes its work on a new single matrix visualization. "It takes into consideration MITRE's current work in progress aimed at creating a STIX representation of ATT&CK for ICS, incorporating ATT&CK for ICS into the ATT&CK Navigator tool, and representing the IT portions of ICS attacks in ATT&CK for Enterprise. As a result, this proposal focuses not only on data accuracy, but also on the tools and data formats available for users."
ICS ATT&CK contains details of TTPs that explain threats to ICS, such as PLCs and other embedded systems, but by design does not include the intermediary systems that run on standard enterprise operating systems. By the time the attacker reaches the PLCs, there is little that can be done -- it's pretty much game over. It is better, therefore, to be able to see the attack holistically from the IT network through the intermediary systems and into the ICS systems.
To achieve this holistic view of the full OT attack lifecycle, Mandiant Threat Intelligence has proposed a hybrid matrix comprising ICS/Enterprise overlap, ICS/Enterprise subtechnique overlap, ICS only, and Enterprise only techniques.
"It presents a holistic view of an incident involving both ICS and Enterprise tactics and techniques throughout the attack lifecycle," says Mandiant Threat Intelligence."
Such an holistic view is becoming increasingly important. While attacks against ICS systems specifically designed to cause physical damage remain relatively rare because of the difficulty, cost and resources to develop them (largely limiting them to nation-state attackers), common criminals are increasingly targeting ICS systems with ransomware to increase the likelihood of a substantial extortion return.
"The threat actors don't see two separate networks," explained Brubaker, "they just see networks and targets; and they don't really care how they get there. Consider financial threat actors," he added; "they're not necessarily targeting ICS, but the targets they are going after have ICS and they are interacting with those to get what they want -- for example by deploying ransomware in those systems to increase the ransom. By looking at it holistically, we can start to bridge that divide between Enterprise and ICS, and not drop the ball between the two. The hybrid model won't stop attacks against ICS, but will increase knowledge and understanding of how such attacks unfold; and will help defenders prepare against future attacks -- for example in writing rules for anomaly detection systems that will detect an attack in progress likely to impact ICS in time to stop it."
Industrial Cyberattacks Get Rarer but More Complex
26.9.20 ICS Threatpost
The first half of 2020 saw decreases in attacks on most ICS sectors, but oil/gas firms and building automation saw upticks.
Cyberattacks against the oil and gas industry inched up only slightly compared to the second half of 2019. Security experts say they are encouraged by the anemic growth, but at the same time are expressing concern that attacks are now becoming more potent, targeted and complex.
According to new research from Kaspersky, 37.8 percent of computers tied to the industrial control systems (ICS) segment suffered attacks in the first half of 2020, which represents only a 2 percentage increase.
Researchers found that ICS-related attacks on the oil and gas sector are one of the only increases found within the ICS sector. It also reported an almost-2 percent increase in attacked computers in the building automation space (39.9 percent of these weathered threats in the first half).
Threats in the form of computer worms were a particularly active area of development for oil-and-gas attackers. Researchers observed numerous new variants of standalone malware in the form of worms written in script languages, specifically Python and PowerShell, on computers used for design, maintain and automate industrial systems in that sector. The surge in these detections occurred from the end of March to mid-June 2020, mainly in China and the Middle East.
“All of the detected worm samples, both in Python and in PowerShell, are capable of collecting authentication credentials from the memory of system processes on the attacked machines in order to spread within the network,” according to the research. “In most cases, the malware uses different versions of Mimikatz to steal authentication credentials from memory. However, there were some PowerShell samples which used the comsvsc.dll system library (MS Windows) to save a memory dump of the system process in which the malware then searched for authentication credentials.”
Overall ICS attack volumes. Click to enlarge. Source: Kaspersky
Kaspersky also said that the slight increase in building-automation attacks in particular is cause for concern.
“Building-automation systems often belong to contractor organizations, and even when these systems have access to the client’s corporate network, they are not always controlled by the corporate information security team,” according to the report, issued Thursday. “Given that the decrease in mass attacks is offset by an increase in the number and complexity of targeted attacks where we see active utilization of various lateral movement tools, building automation systems might turn out to be even less secure than corporate systems within the same network.”
Overall though, the percentage of ICS computers that were attacked has decreased by 6.6 percentage points from the second half of 2019, to 32.6 percent, Kaspersky found. The volume of attacks varied by geography; Algeria still saw high numbers of them (58.1 percent), while Switzerland had just 12.7 percent of ICS computers in cyberattackers’ sights.
More Complex Attacks
Behind those positive numbers, Kaspersky identified a few key trends. For one, threats are becoming more targeted and more complex.
For instance, in March, the firm’s researchers discovered a previously unknown APT campaign called “WildPressure.” Targeting industrial firms and others, it used a trojan that was dubbed Milum. Milum has the capability to control devices remotely. It can download and execute commands and collect a variety of information from the target device. For their campaign infrastructure, the operators used rented OVH and Netzbetrieb virtual private servers (VPS) and a domain registered with the Domains by Proxy anonymization service.
“A code analysis of the new malware did not show any notable overlaps or similarities with any previously known APT campaign,” Kaspersky researchers noted.
Meanwhile, ransomware was almost a non-factor, found to target just 0.63 percent of ICS computers. However, when incidents happened, they were significant. For instance, Belgium’s Picanol Group, a large manufacturer of high-tech weaving machines, fell victim to a massive ransomware attack in January.
No information has been released on the ransomware itself, but “the attack seriously disrupted the operations of the company’s manufacturing plants in Belgium, Romania and China,” according to the report. “The attack was discovered during the night, when Picanol employees in China were unable to access the company’s IT systems. Similar issues also arose in Ypres in Belgium. The company’s operations were nearly completely paralyzed. Picanol’s 2,300 employees were out of work for over a week.”
Otherwise, “we are seeing noticeably more families of backdoors, spyware, Win32 exploits and malware built on the .Net platform,” according to the research. “The internet, removable media and email continue to be the main sources of threats in the ICS environment.”
COVID-19 Impact
The Kaspersky analysis also looked at the possible impact of COVID-19 and remote working on the cyberattack landscape for ICS, which it did by assessing the statistics of attacks on Remote Desktop Protocol on industrial computers.
RDP attack volumes. Click to enlarge. Source: Kaspersky.
Between February and May, there was a clear month-to-month growth (with a subsequent decrease in June) in the percentage of detected attempts to crack RDP passwords through brute-force attacks, according to the report.
“The increase in the percentage of attacked ICS computers on which attempts to brute force the RDP password were detected (and prevented) may seem insignificant, but it should be remembered that any such attack, if successful, would immediately have provided the attackers with remote access to engineering computers and ICS systems,” according to the report. “The danger posed by such attacks should not be underestimated.”
Otherwise, the firm was unable to identify any other abnormal surges in malicious activity that could be attributed to the pandemic’s consequences.
“We hope this was due to an actual absence of negative changes in the ICS threat landscape,” researchers said.
Pandemic Leads to Rise in Industrial Systems Targeted Via RDP: Report
25.9.20 ICS Securityweek
The COVID-19 pandemic has apparently resulted in industrial systems being increasingly targeted by malicious actors through brute-force attacks on the Remote Desktop Protocol (RDP), Kaspersky reported on Thursday.
Kaspersky’s report on the industrial threat landscape for the first half of 2020 reveals that the number of attacks aimed at RDP on industrial computers increased steadily between February and May.
The cybersecurity firm has seen brute-force attacks against RDP passwords on 0.16% of the industrial control systems (ICS) it protected in February and 0.33% in May. The percentage dropped slightly in June, but still remained at an above average level.
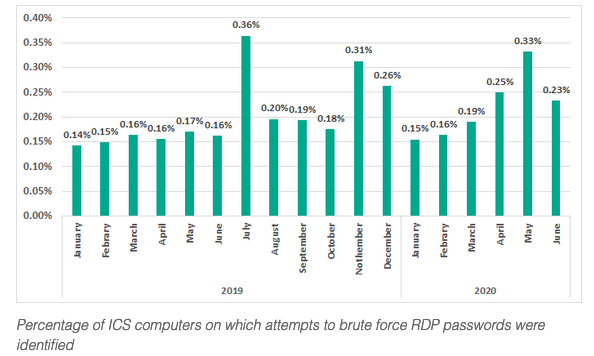
The higher number of attacks on RDP coincides with more industrial organizations using RDP during the COVID-19 pandemic to enable their employees to remotely access and manage resources.
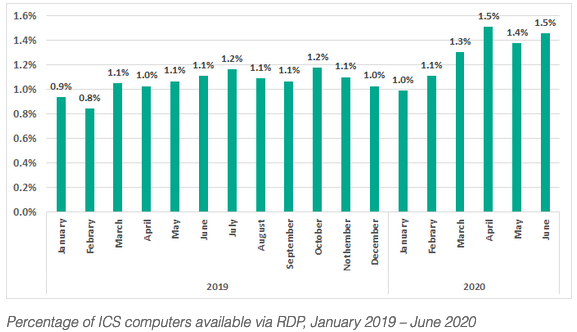
Kaspersky last year observed that the use of remote administration tools (RATs) by industrial organizations decreased steadily, until February 2020, when it started to stabilize, which experts believe could also be a result of the pandemic as organizations needed to maintain the ability to remotely access systems.
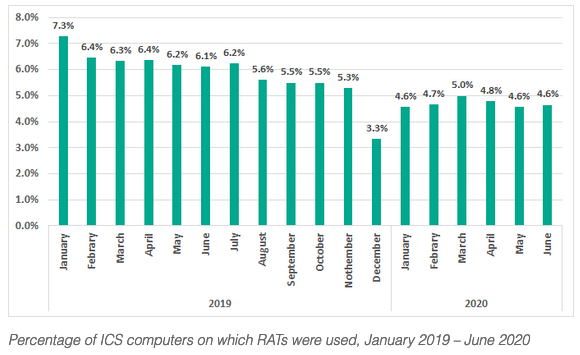
“We believe that the increase in the percentage of ICS computers on which RDP is used could be an indication that most new RDP sessions were authorized by IT and information security services. In fact, all other things being equal, it may be easier to configure and control the secure operation of RDP services than that of any other RAT applications. It would seem that allowing new RDP installations was a compromise caused by the objective need to perform production-related tasks remotely in a pandemic,” Kaspersky noted in its report.
Learn more about threats to industrial systems at SecurityWeek’s 2020 ICS Cyber Security Conference and SecurityWeek’s Security Summits virtual event series
It added, “The increase in the percentage of attacked ICS computers on which attempts to brute force the RDP password were detected (and prevented) may seem insignificant, but it should be remembered that any such attack, if successful, would immediately have provided the attackers with remote access to engineering computers and ICS systems. The danger posed by such attacks should not be underestimated.”
Kaspersky said it blocked attacks on 32.6% of the ICS devices it protected in the first half of 2020, a decrease of 6.6 percentage points compared to the second half of 2019.
Industrial systems from which the cybersecurity firm collected threat data include SCADA servers, historians, OPC systems, engineering and operator workstations, HMIs, computers used to manage industrial networks, and computers used to develop industrial automation software.
The company said its products blocked over 19,000 malware variants belonging to over 4,100 families. The main source of these threats was the internet, followed by removable devices and email.
As for regional statistics, Kaspersky said Asia and Africa saw the highest percentage of attacks. Australia, Europe, the US and Canada are at the other end of the chart.
ICS Vendors Release Advisories for CodeMeter Vulnerabilities
12.9.20 ICS Securityweek
Several major industrial control system (ICS) vendors have released security advisories in response to the recently disclosed vulnerabilities affecting the CodeMeter licensing and DRM solution made by Germany-based Wibu-Systems.
CodeMeter provides license management capabilities and it’s designed to protect software against piracy and reverse engineering. It’s used for a wide range of applications, including various types of industrial products.
Industrial cybersecurity firm Claroty reported earlier this week that CodeMeter is affected by six critical and high-severity vulnerabilities that can be exploited to launch attacks against industrial systems, including to deliver malware and exploits, and shut down devices or processes.
The company’s researchers showed how an attacker can launch attacks by setting up a malicious website and luring targeted users to it, or by creating their own CodeMeter API and client and sending commands to devices running CodeMeter.
Wibu-Systems was informed about the vulnerabilities and it has released patches (version 7.10), which vendors have been encouraged to apply to their products. The United States Cybersecurity and Infrastructure Security Agency (CISA) has also released an advisory and so have many of the major ICS vendors that are impacted. Schneider Electric is not on the list, but the company is also expected to release an advisory.
ABB
ABB says the vulnerabilities impact its AC 800PEC Tool, EXC Control Terminal (ECT), Control Terminal Management Studio (CTMS), and Traction Control Terminal (TCT). The company is analyzing the flaws, and while it has yet to release patches, it has provided mitigations and workarounds that customers can use to prevent attacks.
COPA-DATA
COPA-DATA says the vulnerabilities affect its zenon Editor, zenon Runtime, zenon Analyzer, zenon Web Server, zenon logic Workbench, and straton Workbench products. The company has provided mitigations for each of the flaws and it has advised customers to update CodeMeter.
Pepperl+Fuchs
Pepperl+Fuchs says its VMT MSS and VMT IS products are affected, but only if certain components are present. VMT MSS users have been advised to update CodeMeter to version 7.10, and VMT IS users have been advised to contact VMT, which is a subsidiary.
Phoenix Contact
Phoenix Contact says only three of the CodeMeter vulnerabilities impact its PC Worx Engineer, PLCnext Engineer, FL Network Manager, E-Mobility Charging Suite and IOL-CONF products. The company has released an Activation Wizard update that installs CodeMeter 7.10 and patches the vulnerabilities.
Pilz
Pilz has determined that the security holes affect its PAS4000, PASvisu, PASloto, PNOZsigma, Live Video Server and SafetyEYE products. The company has advised customers to update CodeMeter and use a local firewall to prevent unauthorized access to devices running CodeMeter.
Rockwell Automation
Rockwell Automation (advisory available only to registered customers) has shared a long list of products that use its FactoryTalk Activation (FTA) Manager, which uses CodeMeter. The company has released an FTA update that patches the vulnerabilities.
Siemens
Siemens says the flaws affect its SIMATIC, SIMIT, SINEC, SINEMA and SPPA products. The German industrial giant has already released updates for some of the affected products, and it has provided workarounds and mitigations for the others.
WAGO
WAGO says its e!COCKPIT engineering software installation bundles are impacted, but its controllers and IO devices are not. The company expects to release an e!COCKPIT update containing the latest CodeMeter version in the fourth quarter and in the meantime it has advised customers to manually update CodeMeter.
Critical Flaws in 3rd-Party Code Allow Takeover of Industrial Control Systems
10.9.20 ICS Threatpost
Researchers warn of critical vulnerabilities in a third-party industrial component used by top ICS vendors like Rockwell Automation and Siemens.
Six critical vulnerabilities have been discovered in a third-party software component powering various industrial systems. Remote, unauthenticated attackers can exploit the flaws to launch various malicious attacks – including deploying ransomware, and shutting down or even taking over critical systems.
The flaws exists in CodeMeter, owned by Wibu-Systems, which is a software management component that’s licensed by many of the top industrial control system (ICS) software vendors, including Rockwell Automation and Siemens. CodeMeter gives these companies tools to bolster security, help with licensing models, and protect against piracy or reverse-engineering.
Wibu-Systems made patches available for all of the flaws in version 7.10 of CodeMeter, on Aug. 11; however, the flaws were only recently disclosed by researchers on Tuesday. Many of the affected vendors have been notified and added – or are in the process of adding – fixes to their installers, said researchers with Claroty who discovered the glitches.
Threatpost Webinar Promo Bug Bounty
Click to Register
“Successful exploitation of these vulnerabilities could allow an attacker to alter and forge a license file, cause a denial-of-service condition, potentially attain remote code-execution, read heap data and prevent normal operation of third-party software dependent on the CodeMeter,” according to a Tuesday advisory published by ICS-CERT.
Researchers discovered a set of flaws in the CodeMeter WebSocket API (CVE-2020-14519) enabling management of licenses via JavaScript. To exploit the flaws, an attacker would first have to phish or socially-engineer victims to lure them to a site they control.
In one attack scenario, an attacker could target a specific group of engineers looking for advice on a forum dedicated to programmable logic controllers (PLCs), by hosting the malicious payload on a phony or compromised forum. Once the target visits the attacker-controlled website, the threat actors are able to use JavaScript to inject a malicious license of their own onto the target’s machine, researchers said.
“These flaws can be exploited via phishing campaigns or directly by attackers who would be able to fingerprint user environments in order to modify existing software licenses or inject malicious ones, causing devices and processes to crash,” according to Sharon Brizinov and Tal Keren, security researchers with Claroty, in a Tuesday analysis. “Serious encryption implementation issues, also discovered by Claroty, can be exploited to allow attackers to execute code remotely, and move laterally on [operational technology] (OT) networks.”
Another severe flaw (CVE-2020-14509) is a simple buffer-access error, in the packet parser mechanism used by CodeMeter, which does not verify length fields. This flaw has the highest CVSS v3 score possible (10 out of 10), making it critical.
“CVE-2020-14509 is a highly critical vulnerability that poses a great risk to products that are using the third-party component, CodeMeter,” Brizinov told Threatpost. “The vulnerability is a heap buffer overflow memory-corruption flaw, and it could be exploited to gain remote code execution without any prior knowledge of the target machine. All an attacker will need to do is be able to communicate with the target machine via TCP port 22350.”
Another serious bug (CVE-2020-14517) was found in the CodeMeter encryption implementation. This flaw could be leveraged to attack the CodeMeter communication protocol and internal API, in order to remotely communicate with, and send commands to, any machine running CodeMeter, researchers said.
A breakdown of the CodeMeter WebSocket vulnerability (click to enlarge). Credit: Claroty
The remaining three flaws include an improper input-validation error (CVE-2020-14513) that could force CodeMeter to shut down; an issue in the license-file signature-checking mechanism (CVE-2020-14515) that allows attackers to build arbitrary license files; and an improper-resource shutdown or release vulnerability (CVE-2020-16233).
“Chaining these… bugs allows an attacker to sign their own licenses and then inject them remotely,” said researchers. “Vulnerabilities related to input-validation errors (CVE-2020-14513) could also be exploited to cause industrial gear to crash and be unresponsive, leading to a denial-of-service condition.”
According to ICS-CERT, Wibu-Systems recommends that users update to the latest version of the CodeMeter Runtime (version 7.10). Affected vendors like Rockwell and Siemens have released their own security advisories, but researchers warn that, due to CodeMeter being integrated into many leading ICS products, users may be unaware this vulnerable third-party component is running in their environment.
“CodeMeter is a widely deployed third-party tool that is integrated into numerous products; organizations may not be aware their product has CodeMeter embedded, for example, or may not have a readily available update mechanism,” warned researchers.
Brizinov told Threatpost, researchers have not encountered any active campaigns using these exploits yet. Threatpost has reached out to Wibu-Systems for further comment.
Vulnerabilities in industrial gear has worried the security space due to the dire implications if a critical system is attacked. In July, the U.S. National Security Agency (NSA) and the Cybersecurity and Infrastructure Security Agency (CISA) issued an alert warning that adversaries could be targeting critical infrastructure across the U.S.
In March, security vulnerabilities requiring very little skill to exploit were discovered in ICS devices from Rockwell Automation and Johnson Controls. And in July, researchers warned that remote code-execution flaws in virtual private network (VPN) products could impact the physical functioning of critical infrastructure in the oil and gas, water and electric utilities space.
Vulnerabilities in CodeMeter Licensing Product Expose ICS to Remote Attacks
9.9.20 ICS Securityweek
Vulnerabilities affecting CodeMeter, a popular licensing and DRM solution made by Germany-based Wibu-Systems, can expose industrial systems to remote attacks, industrial cybersecurity company Claroty warned on Tuesday.
CodeMeter is designed to protect software against piracy and reverse engineering, it offers licensing management capabilities, and it includes security features that provide protection against tampering and other attacks.
CodeMeter can be used for a wide range of applications, but it’s often present in industrial products, including industrial PCs, IIoT devices, and controllers.
CodeMeter is the successor of WibuKey, a DRM solution that in the past was found to expose industrial products from Siemens and other vendors to attacks due to the existence of potentially serious vulnerabilities.
Researchers at Claroty have discovered six vulnerabilities in CodeMeter, some of which could be exploited to launch attacks against industrial control systems (ICS), including to shut down devices or processes, deliver ransomware or other malware, or to execute further exploits.
Two of the security holes have been classified as critical, while the rest are considered high severity.
Learn more about vulnerabilities in industrial systems at SecurityWeek’s 2020 ICS Cyber Security Conference and SecurityWeek’s Security Summits virtual event series
Claroty reported its findings to the vendor in February and April 2019, and updates released throughout 2019 patched some of the vulnerabilities. CodeMeter 7.10, which Claroty says patches all of the reported issues, was released in August 2020.
The industrial cybersecurity firm’s researchers found various types of flaws in CodeMeter, including memory corruption bugs and cryptographic flaws that can be leveraged to alter or forge license files. They showed how some of the vulnerabilities can be exploited remotely without authentication to launch denial-of-service (DoS) attacks or achieve arbitrary code execution.
In one attack scenario described by the researchers, an attacker sets up a website designed to push a malicious license to the devices of users lured to the site. The rogue license, when processed by CodeMeter, can generate a DoS condition or allow the attacker to execute arbitrary code.
In a different attack scenario, the experts achieved remote code execution by creating their own CodeMeter API and client, which enabled them to send commands to any device running CodeMeter.
Security advisories for the CodeMeter vulnerabilities found by Claroty have also been published by Wibu-Systems and the U.S. Cybersecurity and Infrastructure Security Agency (CISA).
Siemens and Rockwell Automation have also released advisories describing the impact of these vulnerabilities on their products.
Claroty has created an online tool that allows users to check if they are running a vulnerable version of CodeMeter. The company has also set up a GitHub page for this project.