
Exploiting the weaknesses could not only allow a malicious actor to seize control of the target PLC device, but also download a rogue project to a PLC and execute arbitrary code.
Critical Security Flaws Identified in CODESYS ICS Automation Software
27.6.22 ICS Thehackernews
CODESYS has released patches to address as many as 11 security flaws that, if successfully exploited, could result in information disclosure and a denial-of-service (DoS) condition, among others.
"These vulnerabilities are simple to exploit, and they can be successfully exploited to cause consequences such as sensitive information leakage, PLCs entering a severe fault state, and arbitrary code execution," Chinese cybersecurity firm NSFOCUS said. "In combination with industrial scenarios on the field, these vulnerabilities could expose industrial production to stagnation, equipment damage, etc."
CODESYS is a software suite used by automation specialists as a development environment for programmable logic controller applications (PLCs).
Following responsible disclosure between September 2021 and January 2022, fixes were shipped by the German software company last week on June 23, 2022. Two of the bugs are rated as Critical, seven as High, and two as Medium in severity. The issues collectively affect the following products -
CODESYS Development System prior to version V2.3.9.69
CODESYS Gateway Client prior to version V2.3.9.38
CODESYS Gateway Server prior to version V2.3.9.38
CODESYS Web server prior to version V1.1.9.23
CODESYS SP Realtime NT prior to version V2.3.7.30
CODESYS PLCWinNT prior to version V2.4.7.57, and
CODESYS Runtime Toolkit 32 bit full prior to version V2.4.7.57
Chief among the flaws are CVE-2022-31805 and CVE-2022-31806 (CVSS scores: 9.8), which relate to the cleartext use of passwords used to authenticate before carrying out operations on the PLCs and a failure to enable password protection by default in the CODESYS Control runtime system respectively.

Exploiting the weaknesses could not only allow a malicious actor to seize control of the target PLC device, but also download a rogue project to a PLC and execute arbitrary code.
A majority of the other vulnerabilities (from CVE-2022-32136 to CVE-2022-32142) could be weaponized by a previously authenticated attacker on the controller to lead to a denial-of-service condition.
In a separate advisory published on June 23, CODESYS said it also remediated three other flaws in CODESYS Gateway Server (CVE-2022-31802, CVE-2022-31803, and CVE-2022-31804) that could be leveraged to send crafted requests to bypass authentication and crash the server.
Besides applying patches in a timely fashion, it's recommended to "locate the affected products behind the security protection devices and perform a defense-in-depth strategy for network security."
Over a Dozen Flaws Found in Siemens' Industrial Network Management System
18.6.22 ICS Thehackernews
Cybersecurity researchers have disclosed details about 15 security flaws in Siemens SINEC network management system (NMS), some of which could be chained by an attacker to achieve remote code execution on affected systems.
"The vulnerabilities, if exploited, pose a number of risks to Siemens devices on the network including denial-of-service attacks, credential leaks, and remote code execution in certain circumstances," industrial security company Claroty said in a new report.
The shortcomings in question — tracked from CVE-2021-33722 through CVE-2021-33736 — were addressed by Siemens in version V1.0 SP2 Update 1 as part of updates shipped on October 12, 2021.
"The most severe could allow an authenticated remote attacker to execute arbitrary code on the system, with system privileges, under certain conditions," Siemens noted in an advisory at the time.
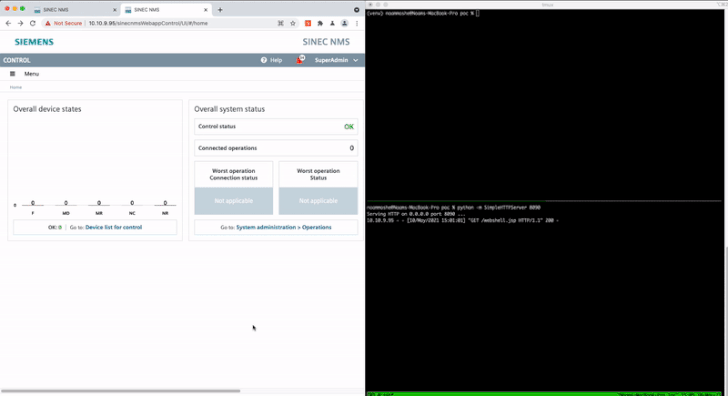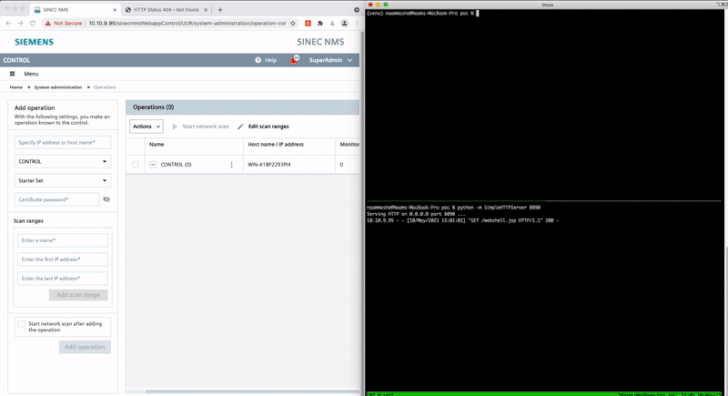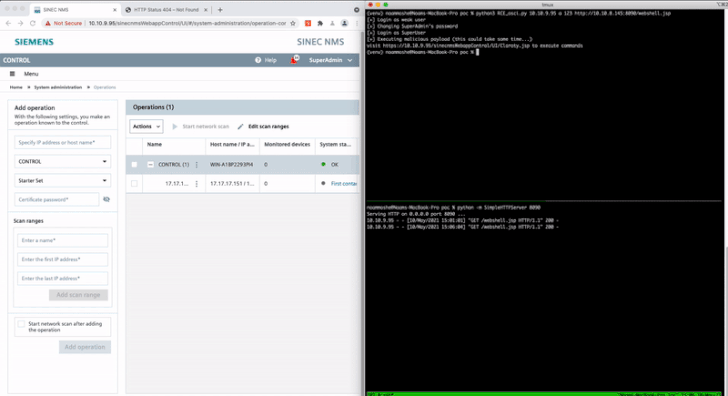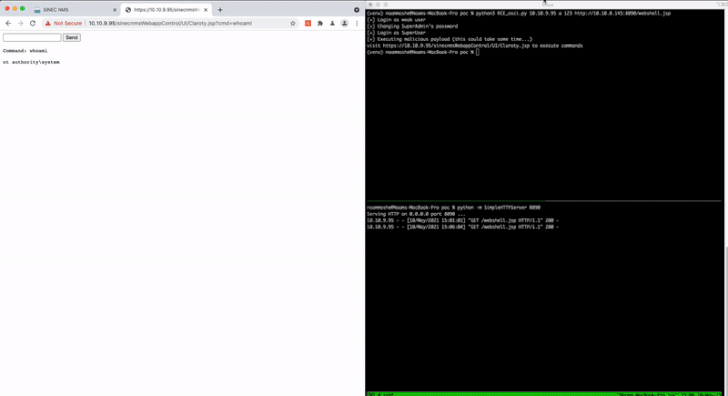
Chief among the weaknesses is CVE-2021-33723 (CVSS score: 8.8), which allows for privilege escalation to an administrator account and could be combined with CVE-2021-33722 (CVSS score: 7.2), a path traversal flaw, to execute arbitrary code remotely.
Another notable flaw relates to a case of SQL injection (CVE-2021-33729, CVSS score: 8.8) that could be exploited by an authenticated attacker to execute arbitrary commands in the local database.
"SINEC is in a powerful central position within the network topology because it requires access to the credentials, cryptographic keys, and other secrets granting it administrator access in order to manage devices in the network," Claroty's Noam Moshe said.
"From an attacker's perspective carrying out a living-off-the-land type of attack where legitimate credentials and network tools are abused to carry out malicious activity, access to, and control of, SINEC puts an attacker in prime position for: reconnaissance, lateral movement, and privilege escalation."
Researchers Disclose Critical Flaws in Industrial Access Control System from Carrier
11.6.22 ICS Thehackernews
As many as eight zero-day vulnerabilities have been disclosed in Carrier's LenelS2 HID Mercury access control system that's used widely in healthcare, education, transportation, and government facilities.
"The vulnerabilities uncovered allowed us to demonstrate the ability to remotely unlock and lock doors, subvert alarms and undermine logging and notification systems," Trellix security researchers Steve Povolny and Sam Quinn said in a report shared with The Hacker News.
The issues, in a nutshell, could be weaponized by a malicious actor to gain full system control, including the ability to manipulate door locks. One of the bugs (CVE-2022-31481) includes an unauthenticated remote execution flaw that's rated 10 out of 10 for severity on the CVSS scoring system.
Other shortcomings could lead to command injection (CVE-2022-31479, CVE-2022-31486), denial-of-service (CVE-2022-31480, CVE-2022-31482), user modification (CVE-2022-31484), and information spoofing (CVE-2022-31485) as well as achieve arbitrary file write (CVE-2022-31483).
LenelS2 is employed in environments to grant physical access to privileged facilities and integrate with more complex building automation deployments. The following HID Mercury access panels sold by LenelS2 are impacted -
LNL-X2210
LNL-X2220
LNL-X3300
LNL-X4420
LNL-4420
S2-LP-1501
S2-LP-1502
S2-LP-2500, and
S2-LP-4502
Trellix noted that by chaining two of the aforementioned weaknesses, it was able to gain root-level privileges on the device remotely and unlock and control the doors, effectively subverting the system monitoring protections.
Coinciding with the public disclosure is an industrial control systems (ICS) advisory from the U.S. Cybersecurity and Infrastructure Security Agency (CISA), urging users to update the access panels to the latest firmware version (CARR-PSA-006-0622).
"Successful exploitation of these vulnerabilities could allow an attacker access to the device, allowing monitoring of all communications sent to and from the device, modification of onboard relays, changing of configuration files, device instability, and a denial-of-service condition," the agency said in an alert.
U.S. Warns of APT Hackers Targeting ICS/SCADA Systems with Specialized Malware
15.4.22 ICS Thehackernews
The U.S. government on Wednesday warned of nation-state actors deploying specialized malware to maintain access to industrial control systems (ICS) and supervisory control and data acquisition (SCADA) devices.
"The APT actors have developed custom-made tools for targeting ICS/SCADA devices," multiple U.S. agencies said in an alert. "The tools enable them to scan for, compromise, and control affected devices once they have established initial access to the operational technology (OT) network."
The joint federal advisory comes courtesy of the U.S. Department of Energy (DoE), the Cybersecurity and Infrastructure Security Agency (CISA), the National Security Agency (NSA), and the Federal Bureau of Investigation (FBI).
The custom-made tools are specifically designed to single out Schneider Electric programmable logic controllers (PLCs), OMRON Sysmac NEX PLCs, and Open Platform Communications Unified Architecture (OPC UA) servers.
On top of that, the unnamed actors are said to possess capabilities to infiltrate Windows-based engineering workstations across IT and OT networks by making use of an exploit that compromises an ASRock-signed motherboard driver (AsrDrv103.sys) with known vulnerabilities (CVE-2020-15368) to execute malicious code in the Windows kernel.
The intent, the agencies said, is to leverage the access to ICS systems to elevate privileges, move laterally within the networks, and sabotage mission-critical functions in liquified natural gas (LNG) and electric power environments.
Industrial cybersecurity company Dragos, which has been tracking the malware under the name "PIPEDREAM" since early 2022, described it as a "modular ICS attack framework that an adversary could leverage to cause disruption, degradation, and possibly even destruction depending on targets and the environment."
Dragos CEO Robert M. Lee attributed the malware to a state actor dubbed CHERNOVITE, assessing with high confidence that the destructive toolkit has yet to be employed in real-world attacks, making it possibly the first time "an industrial cyber capability has been found *prior* to its deployment for intended effects."
PIPEDREAM features an array of five components to accomplish its goals, enabling it to conduct reconnaissance, hijack target devices, tamper with the execution logic of controllers, and disrupt PLCs, effectively leading to "loss of safety, availability, and control of an industrial environment."
Boasting of a wide range of functionality, PIPEDREAM allows for highly automated exploits against targeted devices, with the modules supporting the ability to upload malicious configuration to the controllers, back up or restore device contents, and modify device parameters.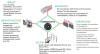
The versatile malware is also known to take advantage of CODESYS, a third-party development environment for programming controller applications and which has been uncovered to contain as many as 17 different security vulnerabilities in the past year alone.
"Capabilities to reprogram and potentially disable safety controllers and other machine automation controllers could then be leveraged to disable the emergency shutdown system and subsequently manipulate the operational environment to unsafe conditions," Dragos cautioned.
Coinciding with the disclosure is another report from threat intelligence firm Mandiant, which characterized PIPEDREAM as a "set of novel industrial control system (ICS)-oriented attack tools" aimed at machine automation devices from Schneider Electric and Omron.
The state-sponsored malware, which it has named INCONTROLLER, is designed to "interact with specific industrial equipment embedded in different types of machinery leveraged across multiple industries" by means of industrial network protocols such as OPC UA, Modbus, and CODESYS.
Schneider Electric, in an independent security notification, said it has not identified any weakness or vulnerability being exploited and that it's not aware of any confirmed targets that have been victimized by the PIPEDREAM attack toolset.
However, the company forewarned that "the framework poses a critical risk to organizations using the targeted devices," adding it "has capabilities related to disruption, sabotage, and potentially physical destruction."
That said, it's unclear as yet how the government agencies as well as Dragos and Mandiant found the malware. The findings come a day after Slovak cybersecurity company ESET detailed the use of an upgraded version of the Industroyer malware in a failed cyberattack directed against an unnamed energy provider in Ukraine last week.
The discovery of PIPEDREAM makes it the seventh publicly-known ICS-specific malware orchestrated to tamper with industrial processes, following Stuxnet, Havex, Industroyer (aka CrashOverride), Triton (aka Crisis), BlackEnergy2, and Industroyer2.
"INCONTROLLER [aka PIPEDREAM] represents an exceptionally rare and dangerous cyber attack capability," Mandiant said. "It is comparable to Triton, which attempted to disable an industrial safety system in 2017; Industroyer, which caused a power outage in Ukraine in 2016; and Stuxnet, which sabotaged the Iranian nuclear program around 2010."
To mitigate potential threats and secure ICS and SCADA devices, the agencies are commending organizations to enforce multi-factor authentication for remote access, periodically change passwords, and continuously be on the lookout for malicious indicators and behaviors.
Flaws in Ovarro TBox RTUs Could Open Industrial Systems to Remote Attacks
30.3.2021 ICS Thehackernews
As many as five vulnerabilities have been uncovered in Ovarro's TBox remote terminal units (RTUs) that, if left unpatched, could open the door for escalating attacks against critical infrastructures, like remote code execution and denial-of-service.
"Successful exploitation of these vulnerabilities could result in remote code execution, which may cause a denial-of-service condition," the U.S. Cybersecurity and Infrastructure Security Agency (CISA) said in an advisory published on March 23.
TBox is an "all-in-one" solution for automation and control systems for supervisory control and data acquisition (SCADA) applications, with its telemetry software used for remote control and monitoring of assets in a number of critical infrastructure sectors, such as water, power, oil and gas, transportation, and process industries. TBox devices can be programmed using a software suite called TWinSoft, which allows for the creation of interactive web pages, where users will be able to monitor and control their site assets.
The flaws were detected and reported to CISA by Uri Katz, a security researcher for operational technology security company Claroty. They affect multiple products, including TBox LT2, TBox MS-CPU32, TBox MS-CPU32-S2, TBox MS-RM2, TBox TG2, and all versions of TWinSoft prior to 12.4 and TBox Firmware before 1.46.
Claroty found that of all the internet-accessible TBox RTUs that were found online, nearly 62.5% of the devices required no authentication, thus potentially enabling attackers to exploit the HTTP service and take control of the units. Most of the devices are said to be located in Canada, Germany, Thailand, and the U.S.
Further investigation into the remote terminal units revealed multiple vulnerabilities in its proprietary Modbus protocol used for communications that could be leveraged to run malicious code in TBox (CVE-2021-22646), crash a TBox system (CVE-2021-22642), and even decrypt the login password (CVE-2021-22640) by capturing the network traffic between the RTU and the software.
A fourth flaw discovered in Modbus file access functions granted an attacker elevated permissions to read, alter, or delete a configuration file (CVE-2021-22648), while CVE-2021-22644 made it possible to extract the hard-coded cryptographic key.
As a proof-of-concept, the researchers chained three of the above flaws — CVE-2021-22648, CVE-2021-22644, and CVE-2021-22646 — to access the configuration file, extract and decode the hard-coded key, and ultimately deploy a malicious update package in the RTU.
Given the prevalence of TBox RTUs in critical infrastructure, the research demonstrates the dangers involved in exposing such devices directly on the Internet, thereby posing a threat to the integrity of automation processes and public safety alike.
"Connecting unprotected critical infrastructure components to the internet carries with it unacceptable risks that industrial enterprises must make themselves aware of," Claroty's Katz and Sharon Brizinov noted.
"That may sound like an obvious statement, but it's becoming increasingly clear that many organizations aren't heeding the warnings from researchers about exposing misconfigured web-based interfaces online and mitigating control system software and firmware vulnerabilities in a timely fashion."
Kaspersky Sees Rise in Ransomware Attacks on ICS Devices in Developed Countries
27.3.2021 ICS Securityweek
Cybersecurity firm Kaspersky observed a drop in ransomware attacks on industrial control system (ICS) computers in the second half of 2020, but it saw an increase in these types of attacks in developed countries.
According to the company’s Industrial Control System Threat Landscape report for H2 2020, globally, the percentage of ICS computers targeted with ransomware dropped from 0.63% in the first half of the year to 0.49% in the second half of 2020. However, there has been an increase in the United States and Canada (+0.25 percentage points), Australia (+0.23 percentage points) and Western Europe (+0.13 percentage points).
“We believe that these curious dynamics could indicate the response of threat actors to the economic consequences of the pandemic. In those countries where the ‘creditworthiness’ of organizations decreased as a result of the pandemic, the number of attacks on industrial enterprises also fell (and so did the percentage of attacked ICS computers),” Kaspersky said.
“At the same time, in countries where industrial organizations were generally more financially stable and were still able to pay ransom, the activity of attackers increased (and the percentage of attacked ICS computers surged). It can be hypothesized that the changes that we observed were due, among other things, to a shift in some groups’ focus when choosing victims towards organizations in more economically stable countries,” it added.
This data is collected by Kaspersky from ICS-related Windows devices protected by its solutions, including HMIs, SCADA systems, historians, data gateways, engineering workstations, computers used for the administration of industrial networks, and devices used to develop software for industrial systems.
In 2020, ransomware infection attempts were blocked on 0.77% of ICS devices protected by Kaspersky products.
The percentage of ICS computers targeted by malicious actors was slightly bigger in Asia compared to the rest of the world.
The only European country in the top 15 — based on percentage of ransomware-targeted ICS computers — is Hungary, which made the list for the first time.
Globally, roughly 38% of ICS computers protected by Kaspersky products were attacked in 2020 — with any type of malware, not just ransomware. On these devices, the company’s products blocked malware belonging to more than 5,000 families.
There has been a downward trend in the percentage of targeted ICS devices since the second half of 2019, but in the second half of 2020 that downward trend stopped and there was an 0.85% increase compared to the first half.
Vulnerabilities Can Allow Attackers to Remotely Gain Control of Weintek HMIs
27.3.2021 ICS Securityweek
A cybersecurity researcher who specializes in industrial control systems (ICS) has identified three types of critical vulnerabilities in products made by human-machine interface (HMI) manufacturer Weintek.
The Taiwan-based vendor’s products are used worldwide. The company has posted a technical advisory instructing customers to install available patches and take steps to mitigate risks. It noted that the risk of exploitation is more significant if the devices are connected to an open network.
Weintek HMI vulnerabilitiesThe vulnerabilities were discovered by Marcin Dudek, a senior ICS/OT security researcher at Poland’s CERT Polska. The security holes have been found to impact the EasyWeb web-based configuration interface available for Weintek cMT products. Affected products include HMIs (including screenless HMIs), programmable logic controllers (PLCs), and gateways.
The vulnerabilities can be exploited by a remote, unauthenticated attacker for code execution with root privileges (CVE-2021-27446), to remotely access sensitive information and conduct actions on behalf of an admin (CVE-2021-27444), and to execute malicious JavaScript code via a stored XSS flaw (CVE-2021-27442).
Dudek noted on Twitter that there are more than 170 cMT HMIs connected directly to the internet, including systems located in Europe, Asia and North America.
The researcher told SecurityWeek that an attacker could exploit the first two vulnerabilities with a single request sent to the targeted device. In the case of CVE-2021-27444, an attacker could leverage it to obtain the administrator password hash.
In the worst case scenario, an attacker can exploit the vulnerabilities to take complete control of the targeted device with root privileges, which in a real world environment could have serious consequences.
“Having such high privileges, an attacker can have unlimited access to all functions of the HMI,” Dudek explained. “It could also be used as a proxy to get access to the internal network of an organization, or to have direct access to other industrial devices in the same network, such as PLCs.
Dudek said he worked well with the vendor during the disclosure process. He said it took roughly two months to release all patches, but most of the fixes were ready one month after he reported his findings.
Remotely accessible HMIs can pose a serious threat to organizations in critical infrastructure sectors. Some of the high-profile incidents that came to light recently involve attacks on the water sector.
According to the U.S. Cybersecurity and Infrastructure Security Agency (CISA), which issued an advisory for the Weintek cMT vulnerabilities this week, the impacted products are mostly used in the water and commercial facilities sectors.
Threat landscape for industrial automation systems. Statistics for H2 2020
26.3.2021 ICS Securelist
Threat landscape for industrial automation systems Statistics for H2 2020
Global percentage of attacked ICS computers 32.6% 33.42% 38.55%
Percentage of attacked ICS computers by region
Northern Europe 10.1% 11.5% 12.3%
Western Europe 15.1% 14.8% 17.6%
Australia 16.3% 17.0% 18.9%
United States and Canada 17.2% 16.5% 19.6%
Eastern Europe 26.4% 28.0% 30.5%
Southern Europe 27.6% 29.6% 33.1%
Latin America 33.6% 34.3% 38.8%
Russia 32.2% 34.6% 39.5%
Middle East 34.0% 34.6% 40.2%
South Asia 38.8% 41.3% 47.0%
East Asia 42.9% 41.8% 46.3%
Central Asia 43.7% 43.9% 48.8%
Africa 45.6% 46.4% 51.2%
Southeast Asia 49.8% 47.5% 53.9%
Main threat sources globally
Internet 16.7% 16.7% 20.5%
Removable media 5.8% 5.4% 7.0%
Email clients 3.4% 4.1% 4.4%
Traits
There is no longer a downward trend in the percentage of ICS computers on which malicious objects were blocked.
Starting with the second half (H2) of 2019, we observed a decline in the percentages of ICS computers on which malicious objects were blocked. This was observed in industrial control systems (ICS) as well as in corporate and personal computing environments. This downward trend was not observed in the second half of 2020.
Globally, the percentage of attacked ICS computers in the second half of the year was 33.4%, which was 0.85 percentage points (p.p.) higher than the first half (H1) of the year.
Percentage of ICS computers on which malicious objects were blocked, by half-year, 2017 – 2020 (download)
The percentage of attacked ICS computers increased in 62% of countries.
In H2 2020, the percentage of ICS computers on which malicious objects were blocked increased in relation to H1 in 62% of countries. In comparison, this trend was observed in 7% of countries in 2019, and the same was seen in H1 2020 compared to H2 2019.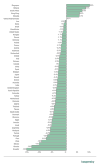
Change in the percentage of attacked computers in countries of the world (p.p.) in H2 compared to H1, 2019 vs 2020 (download 1, 2)
The maximum growth of this indicator in a country was 8.2 p.p. (in Saudi Arabia), while most countries observed no more than a 4 p.p. increase. Therefore, the global average change over the half-year was insignificant.
The seasonal fluctuations typical of past years were not observed this year
In previous years, the percentage of ICS computers on which malicious objects were blocked was at its maximum in March/April and October, while this indicator sagged between those months.In 2020, this indicator behaved differently. It reached its maximum in February and dropped almost to its minimum in May. In the first two months of summer, it grew to its near-maximum in July. In October, the percentage of attacked ICS computers was one of the lowest.
Percentage of ICS computers on which malicious objects were blocked, by month, 2018 – 2020 (download)
The percentage of ICS computers on which malicious email attachments were blocked increased
Globally, in H2 2020, the percentage of ICS computers on which malicious email attachments were blocked increased by 0.7 p.p. compared to H1.
Percentage of ICS computers on which malicious email attachments were blocked (download)
This indicator increased in all regions except East Asia, the US and Canada, Western Europe, and Russia.
In 73.4% of all countries in H2 2020, the percentage of ICS computers on which malicious email attachments were blocked increased compared to H1 2020.This is three times larger than the equivalent indicator for 2019 (23.6%).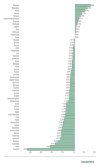
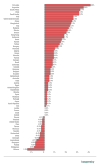
Change in the percentage of ICS computers (p.p.) on which malicious email attachments were blocked in H2 compared to H1, countries and territories, 2019 vs 2020 (download 1, 2)
There was a rise in the percentage of ICS computers on which threats distributed over the internet and email, and spyware and miners were blocked
Malicious objects from the internet – web resources involved in the distribution or management of malware (+2.5 p.p.), and malicious scripts and redirects on web resources (JS and HTML) (+1.6 p.p.).
Typical threats distributed by email (+1.2 p.p.). – malicious MS Office and PDF documents (+1.2 p.p.).
Spyware (+1.4 p.p.) – Trojans, backdoors, and keyloggers.
Miners (+0.7 p.p.) – executable files for Windows.
For all these threats, the indicators of H2 2020 exceeded the equivalent results of not only H1 2020 but also H2 2019.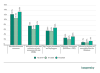
Percentage of ICS computers on which various types of malicious objects were blocked, H2 2019 – H2 2020 (download)
In developed countries, the percentage of ICS computers attacked by ransomware increased
Globally, the percentage of ICS computers on which ransomware was blocked decreased from 0.63% in H1 to 0.49% in H2.At the same time, this indicator increased in regions with developed countries:
+0.25 p.p. in the US and Canada
+0.23 p.p. in Australia
+0.13 p.p. in Western Europe
Change in the percentage of ICS computers (p.p.) on which ransomware was blocked in H2 2020 compared to H1 (download)
Impact of the COVID-19 pandemic
In our H1 2020 report, we wrote about the impact of the COVID-19 pandemic on the changes that we observed in the attack surface and threat landscape for industrial enterprises and industrial automation systems. In H2 2020, we continued our observations and identified a number of trends that could, in our opinion, be due to circumstances connected with the pandemic in one way or another, as well as the reaction of governments, organizations and people to these circumstances.
Changes in seasonal fluctuations in the percentage of attacked computers
It can be seen in the ‘Percentage of ICS computers on which malicious objects were blocked’ diagram that in the past years the percentage of attacked ICS computers significantly decreased in summer months and in December. It is likely that this decrease was associated with traditional vacation periods: an infected USB drive cannot transfer malware from one computer to another all by itself, nor can an engineering workstation click on a link leading to a phishing website when the engineer is not there.
However, there was a noticeable change in the situation in 2020: we saw no significant seasonal fluctuations in the percentage of attacked computers. It is likely that this was due to changes in employee vacation schedules, since many people decided to go without vacations in the time of lockdown, travel restrictions, and closed borders.
Attacks on RDP remote connection services
Another effect of the pandemic was a noticeable increase in the percentage of ICS computers that could be accessed remotely via the RDP protocol.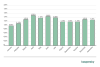
Percentage of ICS computers accessible via RDP, by months of 2020 (download)
It can be seen in the diagram above that the percentage grew continuously from January to April – the time when many organizations were dealing with the challenges of organizing work under an impending and actual lockdown. Then, after some fluctuations, the percentage decreased somewhat and stabilized at a slightly higher level than before the pandemic.
We do not have sufficient data to make conclusions as to what proportion of these computers could only be accessed from the industrial network of the enterprise, what part could be accessed from the corporate segment of the network and what percentage was available even outside the organization’s perimeter. However, we can state with confidence that the increase in the availability of ICS computers certainly affected the attack surface. Threat actors clearly took advantage of that – this is obvious from the following diagram, which shows the percentages of ICS computers on which brute force attacks on credentials used to access the RDP service were detected and blocked: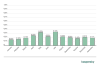
Percentage of ICS computers on which attempts to brute force RDP passwords were detected, by months of 2020 (download)
It is easy to notice a certain synchronism in the changes occurring in these two parameters: the percentage of attacked RDP connections follows the percentage of UCS computers available via RDP almost all through the year (from January to October) with a delay of approximately one month, catching up (i.e., the changes are synchronized) in October and November.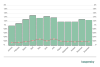
Percentage of ICS computers on which brute force attacks on RDP passwords were detected and percentage of ICS computers available via RDP (download)
We can only guess whether the one-month ‘delay’ in changes occurring in the percentage of attacked computers had to do with the speed with which attacks propagated on the enterprise network or the speed with which threat actors responded to changes in the opportunity landscape (attack surface).
Changes in ransomware priorities
One more potential consequence of the pandemic can be identified by analyzing the dynamics of ransomware attacks on industrial enterprises in different regions, which can be indirectly assessed based on the percentage of ICS computers attacked by ransomware. It can be seen in the ‘Change in the percentage of ICS computers (p.p.) on which ransomware was blocked’ diagram, as well as the diagram below that this percentage decreased in H2 2020 in all regions of the world except North America, Western Europe and Australia, where it did not just fail to decrease but increased several times over!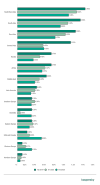
Percentage of ICS computers on which ransomware was blocked, H2 2019 – H2 2020 (download)
We believe that these curious dynamics could indicate the response of threat actors to the economic consequences of the pandemic. In those countries where the ‘creditworthiness’ of organizations decreased as a result of the pandemic, the number of attacks on industrial enterprises also fell (and so did the percentage of attacked ICS computers). At the same time, in countries where industrial organizations were generally more financially stable and were still able to pay ransom, the activity of attackers increased (and the percentage of attacked ICS computers surged). It can be hypothesized that the changes that we observed were due, among other things, to a shift in some groups’ focus when choosing victims towards organizations in more economically stable countries.
Vulnerabilities in TBox RTUs Can Expose Industrial Organizations to Remote Attacks
25.3.2021 ICS Securityweek
UK-based industrial automation company Ovarro recently patched a series of vulnerabilities in its TBox remote terminal units (RTUs). Cybersecurity experts say these flaws could pose a serious risk to organizations.
Ovarro’s TBox RTUs are described by the vendor as a remote telemetry solution for remote automation and monitoring of critical assets. These devices are used worldwide, including in the water, oil and gas, power, transportation and process industries.
Tbox RTU vulnerabilitiesResearchers at industrial cybersecurity firm Claroty discovered last year that the TBox RTUs, as well as the associated TWinSoft engineering software, are affected by five types of vulnerabilities.
Information about the vulnerabilities — all of which have been rated “high severity” — is available in a blog post published by Claroty and advisories released by the U.S. Cybersecurity and Infrastructure Security Agency (CISA) and Ovarro.
The vulnerabilities can allow an attacker to bypass protection features, cause a denial-of-service (DoS) condition, and execute arbitrary code on a targeted device.
“The risks associated with these flaws threaten not only the integrity of automation processes, but also, in some cases public safety,” Claroty said in its blog post. “Using these security shortcomings, we were able to find web-based interfaces, similar to HMIs, that monitor process levels and other industrial activity. We’ve seen in the past what could go wrong when such an interface is exposed to the internet without security; the fact such interfaces are exposed online removes many barriers to entry for adversaries of all types.”
The company has conducted a search for TBox RTUs and discovered that more than 62% of the systems exposed to the internet did not require authentication.
Claroty reported last month that the number of vulnerabilities discovered in industrial control system (ICS) products in 2020 increased significantly compared to previous years. The company said nearly 900 flaws were disclosed last year.
Which is the Threat landscape for the ICS sector in 2020?
23.3.2021 ICS Securityaffairs
The Kaspersky ICS CERT published a report that provided details about the threat landscape for computers in the ICS engineering and integration sector in 2020.
Kaspersky ICS CERT published a report that provided details about the threat landscape for ICS engineering and integration sector in 2020.
The experts gathered data related to the cyberthreats that were blocked on computers used to manage industrial control equipment and targeting software used in ICS engineering and integration industry, including human-machine interface (HMI), OPC gateway, engineering, control, and data acquisition software.
“A key aspect in which of the ICS engineering sector is different from other industries is that an ICS engineering computer often has direct and indirect connections to various industrial control systems, some of which may even belong to other industrial enterprises. And while an ICS engineering computer has more access rights and fewer restrictions (such as application control, device control, etc.) than the average ICS computer, it also has a wider attack surface.” reads the report published by Kaspersky.
In H2 2020, 39.3% of computers in the ICS engineering and integration sector protected by Kaspersky were targeted by malware, an increase compared with detections for H1 2020 (31.5%). Building automation, automotive manufacturing, energy and oil & gas, suffered major increases in the ICS engineering sector.
Experts pointed out that the threat landscape for computers in the ICS engineering and integration sector varies depending on multiple factors, including the geographical location, the ability to access external networks and services, and user behavior.
Latin America, the Middle East, Asia and North America were the regions with the highest number infections attempts blocked by the security solutions in H2 2020. On the other end, the number of blocked malware attacks in Africa, Russia and Europe decreased in H2 2020 compared to H1 2020.
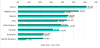
The highest percentage increase in H2 2020 (22.8%) was observed in North America, the majority of the attacks observed by the experts involved crypto-currency miners. The second region with the highest increase was the Middle East due to an outbreak of Fast-Load AutoLISP modules that spread within infected AutoCAD projects and other self-propagating worms that spread via USB.
European ICS engineering organizations were mainly targeted by phishing campaigns attempting to deliver spyware and cryptominers.
Experts reported that the majority of computers in the ICS engineering sector are represented by desktop systems, but laptops remain more exposed to attacks via the internet, removable media devices, and email.
Computers that use VPN software are less exposed to online threats, but unfortunately, they represent only 15% of the total.
“From time to time, the various viruses and worms that have been spreading for a decade between computers in ICS environments via USB devices or network folders hit the computers of ICS engineers. Such threats were blocked more often on computers with VPN software.” continues the report.
Computers with remote access software (64.6% of the total) are less exposed to internet threats, especially when VPN software is used, but these systems are exposed to attacks leveraging network services, such as SMB, MS SQL and RDP.
“The majority of these attacks are due to worm outbreaks in a subnet (physical or virtual). Those worms use Mimikatz and spread over the network by abusing stolen credentials, exploiting an RCE vulnerability or by successfully running brute-force attacks on a network service.” states the report.
The report also provides the following recommendations to protect ICS systems:
Ensure that ICS engineering computers and especially laptops are well protected from network attacks, web-based threats and phishing campaigns, including targeted attacks. To achieve this, consider using modern threat detection technologies – both at the network perimeter and on all endpoints inside and outside the perimeter.
Install all OS and application software updates in a timely fashion, with particular emphasis on security updates, or apply workaround protection measures when installing updates is not an option.
Regularly train employees to recognize suspicious behavior by a computer or application, as well as fraudulent emails and instant messages.
If possible, restrict the use of any unnecessary but dangerous and/or vulnerable software that widens the attack surface, including remote access software, office solutions, PowerShell, Windows Script Host, etc.
Monitor the execution of files in the organization and use application control with Default Deny to limit the use of applications to only those apps that are allowed.
Restrict the use of USB devices to only those that are trusted and encrypted. The implementation of such restrictions should be monitored. Many modern host protection tools include the necessary functionality.
Use different accounts for different users. Manage the rights of user and service accounts in such a way as to prevent an infection from spreading across the enterprise if an account is compromised. Log and monitor the use of administrator functions.
Restrict the rights of users on their systems, as well as corporate service access rights, leaving the minimal set of rights required for specific employees to perform their work.
Maximize granular access control. Limit the use of privileged accounts. When possible, admins should use accounts with local administration privileges or with administration rights to specific services and avoid using accounts with domain administration rights.
Audit the use of privileged accounts and regularly review access rights.
Use group policies that require users to change their passwords on a regular basis. Introduce password strength requirements.
Configure the OS to always show file extensions for all file types in order to see files with double extensions (a tactic used to trick users).
Here's How Security Flaws in GE Relays Could Be Exploited in Real World Attacks
20.3.2021 ICS Securityweek
Organizations using Universal Relay (UR) products made by GE’s Grid Solutions have been informed this week that many of the devices in this product line are affected by nearly a dozen vulnerabilities.
Grid Solutions is a GE Renewable Energy business that provides electricity management solutions for the energy sector, including oil and gas, as well as industry and infrastructure organizations.
Advisories published this week by the U.S. Cybersecurity and Infrastructure Security Agency (CISA) and GE Grid Solutions (account required) inform customers that more than a dozen UR protection and control relays are impacted by a series of vulnerabilities to which 10 different CVE identifiers have been assigned. The vendor has released firmware updates that should patch the vulnerabilities.
GE grid relay vulnerabilitiesThe flaws are related to inadequate encryption of communications, exposure of potentially sensitive information, cross-site scripting (XSS) attacks, denial-of-service (DoS) attacks, unauthorized firmware uploading, the inability to disable a factory service mode, and the presence of hardcoded credentials in the bootloader. More than half of the vulnerabilities have a severity rating of high or critical.
Researchers from SCADA-X, Verve Industrial, VuMetric and the Department of Energy’s Cyber Testing for Resilient Industrial Control Systems (CyTRICS) program have been credited for finding the security holes.
Ron Brash, director of cyber security insights at ICS management and cybersecurity provider Verve Industrial Protection, told SecurityWeek that he has identified two or possibly three of the vulnerabilities — he says it’s difficult to say exactly due to multiple disclosures and some likely overlap. These include flaws that can be exploited to upload malicious firmware to the device, obtain potentially sensitive information, and access a device or disrupt it.
According to Brash, exploitation of these vulnerabilities requires direct or network access to the targeted system.
“Generally these devices are not found on the Internet directly unless someone has not applied any secure deployment strategies, or has inadvertently misconfigured various network infrastructure devices/security apparatuses,” he explained.
In terms of impact, the expert pointed out that while the vulnerable relays are used within the energy industry, they are not limited to the “grid.”
“For example, a mine may be generating power, and these types of devices might be present,” Brash explained. “This can mean that the results or motivations of what ‘an attacker could do’ might be situationally dependent, or require specific contexts. Therefore, in continuation of the example, if your mine needs energy to keep liquids unfrozen (e.g., washes, effluent management systems, etc), and the mine is located in Canada’s North, then you might have a BIG problem during winter. Secondly, if you can get access to these devices, and upload your own logic or firmware, then you can effectively brick them, upload malicious functionality, and the consequences will be highly negative.”
He added, “I don’t wish to speculate as to the motives, or what could be accomplished by an attacker, but if exploited at scale (which by the way, takes a great level of skill, budget, and organization) – nothing positive would result.”
Contacted by SecurityWeek, GE said it’s currently not aware of any attacks exploiting these vulnerabilities.
“GE was made aware of vulnerabilities related to GE’s Grid Solutions’ Universal Relay (UR) family products and immediately worked to assess any potential impact and remediate the reported vulnerabilities. GE’s UR firmware Version 8.10 and greater resolve the identified vulnerabilities, and we encourage our customers to visit the Grid Solutions customer portal and/or the CISA Advisory for additional information and mitigation recommendations,” said a GE spokesperson.
Critical Security Hole Can Knock Smart Meters Offline
13.3.2021 ICS Threatpost
Unpatched Schneider Electric PowerLogic ION/PM smart meters are open to dangerous attacks.
Critical security vulnerabilities in Schneider Electric smart meters could allow an attacker a path to remote code execution (RCE), or to reboot the meter causing a denial-of-service (DoS) condition on the device.
Schneider Electric’s PowerLogic ION/PM smart meter product line, like other smart meters, is used by consumers in their homes, but also by utility companies that deploy these meters in order to monitor and bill customers for their services. They’re also used by industrial companies, data centers and healthcare companies.
Two vulnerabilities were disclosed this week, present in numerous versions of the products. According to Claroty, which originally found the flaws, they stem from the fact that the smart meters communicate using a proprietary ION protocol over TCP port 7700, and packets received by the device are parsed by a state machine function.
“We found that it is possible to trigger [a pre-authentication integer-overflow vulnerability] during the packet-parsing process by the main state machine function by sending a crafted request,” researchers said, in a blog posting this week. “This can be done without authentication because the request is fully parsed before it is handled or authentication is checked.”
The function that parses the incoming packet reads the number of items or characters in the string or array and the buffer, which is a fixed size, researchers explained. They discovered that they were able to fully control the size of the buffer with a DWORD that is read from the request.
The Schneider Electric PM5000 series.
A DWORD, which is short for “double word,” is a data type definition is an unsigned, 32-bit unit of data that is specific to Microsoft Windows. It can contain an integer value in the range 0 through 4,294,967,295.
“We discovered a bug in the function that is responsible for advancing the parsing buffer, we named this function advance_buffer,” according to Claroty’s analysis. “We found that the advance_buffer function always returns true, regardless of other inner functions failing and returning false. Therefore, providing any large packet size will always pass the advance_buffer function without triggering an error message or exception. Thus, Claroty researchers were able to bypass buffer checks and reach exploitation.”
Two Exploitation Paths, Two Bugs
While researching the different firmware for the smart meters, researchers found that there are two different exploitation paths that arise from improper restriction of operations within a memory buffer, depending on the specific architecture. They reported these as two different vulnerabilities.
The bug tracked as CVE-2021-22714 rates 9.8 out of 10 on the CVSS vulnerability-severity scale.
“This vulnerability [is a] critical integer-overflow vulnerability that could enable an attacker to send a specially crafted TCP packet to the device to either cause it to reboot the meter or remotely run code of their choice, depending on the architecture of the targeted device,” according to the advisory.
Schneider Electric said the affected products include:
ION7400 (prior to V3.0.0)
ION9000 (prior to V3.0.0)
PM8000 (prior to V3.0.0)
The bug tracked as CVE-2021-22713 exists in a number of versions of the PowerLogic ION line of meters, but was assessed a CVSS score of 7.5 because successful exploitation of the versions does not enable remote code execution, and enables only an attacker to force the meter to reboot.
The list of affected products includes:
ION8650 (prior to V4.40.1)
ION8800 (prior to V372)
ION7650 Hardware rev. 4 or earlier (prior to V376)
ION7650 Hardware rev. 5 (prior to V416)
ION7700/73xx (all versions)
ION83xx/84xx/8600 (all versions)
The vulnerability was addressed in updates released in January and March, and users are urged to move to the patched versions:
ION8650 users should update to V4.40.1, released on Jan. 4
ION8800 users should update to V372, released on March 3
ION7650 Hardware rev. 4 or earlier should update to V376, released on March 3
ION7650 Hardware rev. 5 should update to V416, released on March 3
Serious Vulnerabilities Found in Schneider Electric Power Meters
12.3.2021 ICS Securityweek
Industrial cybersecurity firm Claroty this week disclosed technical details for two potentially serious vulnerabilities affecting PowerLogic smart meters made by Schneider Electric.
PowerLogic is a line of revenue and power quality meters that are used not only by utilities, but also industrial companies, healthcare organizations, and data centers for monitoring electrical networks.
Researchers at Claroty discovered that some of the PowerLogic ION and PM series smart meters are affected by vulnerabilities that can be exploited remotely by an unauthenticated attacker by sending specially crafted TCP packets to the targeted device.
Vulnerabilities found in Schneider Electric PowerLogic power meters“These smart meters communicate using a proprietary ION protocol over TCP port 7700, and packets received by the device are parsed by a state machine function,” Claroty explained in a blog post. “We found that It is possible to trigger the flaw during the packet-parsing process by the main state machine function by sending a crafted request. This can be done without authentication because the request is fully parsed before it is handled or authentication is checked.”
Claroty said its researchers identified two different exploitation paths — depending on the architecture of the targeted device — and two different CVE identifiers have been assigned.
One of them, CVE-2021-22714, is considered critical as it allows an attacker to cause the targeted meter to reboot (i.e. DoS condition) and possibly even to execute arbitrary code. The other one, CVE-2021-22713, can only be exploited to force the device to reboot and it has been assigned a high severity rating.
The vulnerabilities impact several PowerLogic ION device models and one PM model. Security updates for some of the impacted devices were released in July 2020, while others were patched in January and March 2021. Some of the impacted power meters will not receive patches as they are no longer supported.
Users of the affected Schneider Electric products should apply the patches or mitigations to prevent potential attacks, particularly since information about the flaws has been made public.
Additional details about the patches and mitigations are available in the advisories (CVE-2021-22714 and CVE-2021-22713) released this week by Schneider Electric.
UPDATED: the penultimate paragraph initially mentioned risk to consumer and utilities, but the reference was removed due to PowerLogic meters being part of a B2B offer and not used by consumers
Siemens Releases Several Advisories for Vulnerabilities in Third-Party Components
10.3.2021 ICS Securityweek
Siemens on Tuesday published 12 new security advisories to inform customers about nearly two dozen vulnerabilities affecting its products.
Half of the new advisories cover vulnerabilities in third-party components. One of these advisories is related to AMNESIA:33, a collection of vulnerabilities discovered recently in open source TCP/IP stacks. Siemens has been publishing advisories to describe the impact of these flaws on its products, and the latest advisory focuses on the impact of two AMNESIA:33 denial-of-service (DoS) flaws on SENTRON 3VA and PAC Meter products.
Two advisories are related to NUMBER:JACK, a set of TCP/IP stack vulnerabilities that were discovered even more recently. The advisories describe the impact of some NUMBER:JACK issues, ones that allow session hijacking, on the SIMATIC MV400 optical readers and PLUSCONTROL products used in the energy sector.
Siemens also informed customers that its SIMATIC NET CM 1542-1 and SCALANCE SC600 devices are affected by a DoS vulnerability that exists in libcurl, a multiprotocol file transfer library.
Another advisory describes five vulnerabilities affecting Luxion’s 3D rendering and animation software KeyShot. The security holes are related to the processing of specially crafted files and they can be exploited for arbitrary code execution.
The company has released yet another advisory for file parsing vulnerabilities in product development solutions — these types of advisories were also released in January and February.
Siemens also issued an advisory for an account takeover vulnerability affecting the Mendix Forgot Password Appstore module. The German industrial giant acquired the Mendix low-code platform in 2018.
The remaining advisories address a high-severity DoS vulnerability in SCALANCE and RUGGEDCOM devices, high-severity unauthorized access issues in SINEMA Remote Connect Server, a DoS vulnerability in LOGO! 8 BM, and DoS flaws in SIMATIC S7-PLCSIM.
Siemens has released or plans on releasing updates for many of these vulnerabilities, but in some cases the company has advised customers to implement mitigations or workarounds to protect their systems or devices against potential attacks.
Experts found a critical authentication bypass flaw in Rockwell Automation software
28.2.2021 ICS Securityaffairs
A critical authentication bypass vulnerability could be exploited by remote attackers to Rockwell Automation programmable logic controllers (PLCs).
A critical authentication bypass vulnerability, tracked as CVE-2021-22681, can be exploited by remote attackers to compromise programmable logic controllers (PLCs) manufactured by Rockwell Automation.
The vulnerability was independently reported to Rockwell by researchers at the Soonchunhyang University in South Korea, Claroty, and Kaspersky.
“Successful exploitation of this vulnerability could allow a remote unauthenticated attacker to bypass the verification mechanism and connect with Logix controllers.” reads the advisory published by CISA. “Additionally, this vulnerability could enable an unauthorized third-party tool to alter the controller’s configuration and/or application code.”
The CVE-2021-22681 flaw has received a CVSS score of 10, it affects the following products:
Rockwell software versions:
RSLogix 5000: Versions 16 through 20
Studio 5000 Logix Designer: Versions 21 and later
Rockwell Logix Controllers:
CompactLogix 1768
CompactLogix 1769
CompactLogix 5370
CompactLogix 5380
CompactLogix 5480
ControlLogix 5550
ControlLogix 5560
ControlLogix 5570
ControlLogix 5580
DriveLogix 5560
DriveLogix 5730
DriveLogix 1794-L34
Compact GuardLogix 5370
Compact GuardLogix 5380
GuardLogix 5570
GuardLogix 5580
SoftLogix 5800
The issue resides in the Logix Designer software that uses a poorly protected private cryptographic key to verify communications with controllers.
“This key is not sufficiently protected, allowing a remote, unauthenticated attacker to bypass the verification mechanism and connect to the controller by mimicking an engineering workstation.” reads the post published by Claroty. “An attacker who is able to extract the secret key would be able to authenticate to any Rockwell Logix controller.”
The secret keys are used to digitally sign all communication with the Rockwell PLCs, then PLCs verify the signature and authenticate the company engineering software. An attacker that obtained the key impersonate the engineering software and control the PLC.
Claroty privately reported the vulnerability to Rockwell in 2019.
Rockwell provided a list of risk mitigation and recommended user actions for its projects.
Four Additional Threat Groups Seen Targeting Industrial Organizations in 2020
25.2.2021 ICS Securityweek
A total of 15 threat groups have been observed targeting industrial organizations, according to industrial cybersecurity firm Dragos.
Dragos on Wednesday released its ICS Cybersecurity Year in Review report for 2020, which covers the industrial control systems (ICS) threat landscape and vulnerabilities disclosed last year. It also shares insights from the lessons learned by Dragos as a result of its work in 2020, and provides recommendations for industrial organizations on securing their networks.
In 2018, Dragos reported seeing five groups that had either attacked ICS directly or had shown an interest in gathering information on these types of systems. The next year, the company reported that the number had grown to nine, and now there are a total of 15 activity groups.
Dragos said it added four new groups to the list in 2020. These threat actors have shown an interest in targeting operational technology (OT) systems. In addition, the previously described 11 groups remained active.
The company told SecurityWeek that the newly added groups “have the potential to disrupt control systems, but have not been seen exclusively targeting control systems.”
Hacker groups targeting ICSOne of the new groups is tracked by Dragos as STIBNITE and it has been observed targeting electric energy companies — specifically wind turbines — in Azerbaijan. While there is an ongoing conflict between Armenia and Azerbaijan, the cybersecurity firm said there is “only a loose correlation between the conflict and STIBNITE operations, and the Dragos team is not making an assessment on who may be responsible for the targeting.”
STIBNITE, which has been seen using PoetRAT malware to gather information from victims, may have targeted the supplier and maintainer of the wind farms, which are based in Ukraine.
Another new group is tracked by Dragos as VANADINITE, which has been observed targeting the energy, manufacturing and transportation sectors in North America, Asia, Europe and Australia. The hackers have focused on harvesting information, including related to ICS processes and design, which experts believe could enable its sponsor to develop ICS-targeting capabilities.
Dragos believes VANADINITE could be behind the ransomware known as ColdLock, which has been used to target Taiwan, including state-owned industrial companies whose operations were indirectly disrupted by the ransomware.
VANADINITE has been linked to Winnti — which has been around for over a decade and is believed to have Chinese origins — and a Winnti-related activity group tracked as LEAD.
The third new group has been named TALONITE and it appears to focus on initial access to organizations in the U.S. electric sector. The hackers have been conducting phishing campaigns that leverage power grid-related themes. They have been known for the use of malware such as LookBack, a remote access trojan (RAT) that emerged in 2019 when it was used to target U.S. utilities, and FlowCloud, a RAT analyzed by researchers in 2020.
Dragos also started tracking a threat group dubbed KAMACITE, which also targeted U.S. energy companies. KAMACITE’s operations have overlapped with the activities of Sandworm (ELECTRUM), a notorious Russia-linked group that is believed to have launched disruptive attacks against Ukraine’s power grid. Despite the overlaps, Dragos believes KAMACITE is a distinct group that should be tracked separately.
The company believes KAMACITE is an “access-enablement team” that aids other teams specializing in disruptive operations.
“These types of events, where adversaries gain access to ICS networks but do not have the intention of currently disrupting them, are much more common than is publicly reported,” Dragos said. “The threats are learning ICS. Although not every compromise will relate to an impact today, many may inform the attacks of the future.”
It added, “Threats are growing at a rate three times faster than they are going dormant. This is likely due to the increased investment made by adversaries in targeting ICS over the last five to 10 years, and whose investment will continue to accelerate the ICS threat environment.”
Siemens Patches 21 More File Parsing Vulnerabilities in PLM Products
11.2.2021 ICS Securityweek
Siemens this week released nine new security advisories describing vulnerabilities affecting the company’s products.
The biggest advisory covers 21 security holes affecting JT2Go, a 3D viewing tool for JT data (ISO-standardized 3D data format), and Teamcenter Visualization, which provides organizations visualization solutions for documents, 2D drawings and 3D models. These products are made by Siemens Digital Industries Software, which specializes in product lifecycle management (PLM) solutions.
All of these vulnerabilities are related to how certain types of files are parsed by these products. An attacker can exploit them for arbitrary code execution, data extraction and DoS attacks if they can trick the targeted user into opening a malicious file. Many of the issues affect the Siemens products due to their use of the Open Design Alliance (ODA) Drawings SDK. The ODA has published its own advisory for the flaws.
Last month, Siemens informed customers about 18 similar file parsing vulnerabilities in JT2Go and Teamcenter Visualization.
Will Dormann from the CERT Coordination Center (CERT/CC) at Carnegie Mellon University informed Siemens about a serious privilege escalation issue affecting the Totally Integrated Administrator (TIA) portal. An advisory for this vulnerability has also been published on the CERT/CC website.
A high-severity privilege escalation vulnerability was also discovered in DIGSI 4, the operation and configuration software for SIPROTEC 4 and SIPROTEC Compact protection devices.
The German industrial giant also informed customers about a high-severity “Zip-Slip” vulnerability affecting SINEC and SINEMA network management products. The flaw allows an authenticated attacker to upload files or modify existing ones and possibly achieve arbitrary code execution.
Customers were also informed about six medium- and high-severity DoS issues affecting RUGGEDCOM products. The flaws are related to IPsec and they impact the Network Security Services (NSS) and Libreswan components.
Siemens also issued an advisory for CVE-2020-28388, one of the nine TCP/IP stack vulnerabilities disclosed this week by cybersecurity firm Forescout. The flaws, tracked collectively as NUMBER:JACK, allow attackers to hijack or spoof TCP connections.
Patches from Schneider Electric
Schneider Electric only released one new advisory this Patch Tuesday to inform customers about the existence of three vulnerabilities affecting some of its PowerLogic power metering products.
Two of the vulnerabilities, rated high severity, can allow a man-in-the-middle attacker to obtain credentials when intercepting Telnet and HTTP traffic between a user and a device. The third issue is a medium-severity CSRF bug that can be exploited to perform actions on behalf of a legitimate user.
The number of ICS flaws in 2020 was 24,72% higher compared to 2019
8.2.2021 ICS Securityaffairs
The number of vulnerabilities discovered in industrial control system (ICS) products surged in 2020, security firm Claroty reports.
According to a report published by the industrial cybersecurity firm Claroty that focuses on the second half of 2020, the number of flaws discovered in industrial control system (ICS) products in 2020 (893 flaws) was 24,72% higher compared to 2019.
Experts reported that 449 vulnerabilities were disclosed affecting ICS products from 59 vendors during 2H 2020. More than 70% of the issues
were rated as high or critical Common Vulnerability Scoring System (CVSS) scores, down from more than 75% in 1H 2020.
“The number of ICS vulnerabilities disclosed in 2020 increased by 32.89% compared to 2018 and 24.72% compared to 2019. The primary factors for the increase are likely heightened awareness of the risks posed by ICS vulnerabilities and increased focus from researchers and vendors on identifying and remediating such vulnerabilities as effectively and efficiently as possible.” reads the report published by Claroty.
The data doesn’t surprise Claroty because researchers and vendors have spent a significant effort in searching for vulnerabilities in industrial products. Most of the vulnerabilities discovered in ICS systems (71.49%) are exploited through a network attack vector (i.e. remotely exploitable), and 89.98% of them don’t require special conditions to exploit.
60.8% of vulnerabilities were reported by third-party experts.
“Among all third-party companies, there were 22 that reported their first disclosures, further evidence of growth in the ICS vulnerability research market. continues the report.
The analysis of the impact of ICS flaw by infrastructure sector revealed that in the second half of 2020 critical manufacturing (194 vulnerabilities), energy (186), water and wastewater (111), and commercial facilities (108) were most impacted industries.
The majority of the products with disclosed and patched flaws in the 2H of 2020 belong to Schneider, Mitsubishi, and Siemens.
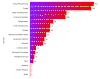
“Compounding the risk is the fact that attacks against ICS devices and OT networks tend to be targeted. While ICS and SCADA vulnerability research is maturing, there are still many decades-old security issues yet uncovered.” concludes the report. “For the time being, attackers may have an edge in exploiting them, because defenders are often hamstrung by uptime requirements and an increasing need for detection capabilities against exploitable flaws that could lead to process interruption or manipulation.”
Let me suggest to read with attention the report because it provides a clear picture of the security of ICS systems.
Industrial Networks See Sharp Uptick in Hackable Security Holes
6.2.2021 ICS Threatpost
Claroty reports that adversaries, CISOs and researchers have all turned their attention to finding critical security bugs in ICS networks.
It’s on: Adversaries, CISOs and researchers are all simultaneously involved in a frantic race to find cybersecurity vulnerabilities hiding within industrial networks, according to the latest Biannual ICS Risk and Vulnerability report from Claroty.
The report analyzed all publicly disclosed vulnerabilities in ICS networks in the second half of 2020 and found a nearly 33 percent increase in ICS disclosures over 2018, both from organizations like Claroty and from independent researchers.
Industries with the most disclosures include vital infrastructure components like critical manufacturing, energy, water, wastewater and commercial facilities.
Worse yet, more than 71 percent of the bugs were remotely exploitable, and every disclosure in the second half of 2020 ranked highly on MITRE’s 2020 CWE Top 25 Most Dangerous Software Weaknesses list because they were easy to exploit and potentially catastrophic, the report said.
ICS Cybersecurity Attracts Researchers
During the second half of 2020, Claroty counted 449 vulnerabilities reported across 59 ICS vendors; and there were 893 for the whole year. To put that in perspective, in 2018, the total number of disclosed ICS bugs for the entire year was 672, and in 2019 the year’s count was 716, Claroty reported.
Increasingly, those reports are from independent researchers, the report said. In fact, Claroty found that 50 new researchers published disclosures in the second half of 2020, who hadn’t published in the two previous years.
“There has been a shift towards ICS research with strong growth in security research groups for this second biannual report, as more organizations try and understand the new attack landscape,” Amir Preminger, vice president of research at Claroty, explained to Threatpost. “With this increase in the amount of players coming into the market and focusing on ICS security, there will naturally be an increase in vulnerabilities [that are found].”
Adversaries Turn Attention Toward Industrial Bugs
Adversaries are also ratcheting up their pressure on industrial networks. For instance, Claroty observed the addition of industrial processes into the Snake ransomware kill list.
“The ICS environment has become a more attractive target for cybercriminals and this incentive is not just about what will cause the most damage, but also what equipment they can get their hands on,” Preminger said. “Attacks will grow increasingly sophisticated and targeted, so it is important that organizations use different walls of detection and practice security in depth.”
Legacy systems with long shelf lives are also weak spots.
“While ICS and SCADA vulnerability research is maturing, there are still many decades-old security issues yet uncovered,” the report explained. “For the time being, attackers may have an edge in exploiting them, because defenders are often hamstrung by uptime requirements and an increasing need for detection capabilities against exploitable flaws that could lead to process interruption or manipulation.”
ICS CISOs & SolarWinds PTSD
The report added that headlines about the SolarWinds attack have made CISOs in every industry think twice about the sheer scope of their networks and who might want to attack them.
“Nation-state actors are clearly looking at many aspects of the network perimeter to exploit, and cybercriminals are also focusing specifically on ICS processes, which emphasizes the need for security technologies such as network-based detection and secure remote access in industrial environments,” Preminger added.
The good news is that the industry is starting to react.
“It is heartening to see a growing interest in ICS within the security research community, as we must shine a brighter light on these vulnerabilities in order to keep threats at arm’s length,” Preminger said. “More vulnerabilities identified means the industry is more secure, so it is reassuring to see the security community take this seriously.
Open Source Tool Helps Organizations Secure GE CIMPLICITY HMI/SCADA Systems
6.2.2021 ICS Securityweek
Industrial cybersecurity firm OTORIO this week announced the availability of a new open source tool designed to help organizations secure their GE CIMPLICITY systems.
GE Digital’s CIMPLICITY is a highly popular human-machine interface (HMI) and supervisory control and data acquisition (SCADA) product that the company says is used by some of the world’s largest organizations.
OTORIO has worked with GE Digital to develop a free and open source tool that can be used to harden CIMPLICITY systems by ensuring that they are configured in accordance with the vendor’s guidelines for security best practices.Open source security tool for GE CIMPLICITY
The tool is a PowerShell script and it has been tested on systems running Windows 7, 10, Server 2008 R2, Server 2012 R2 and Server 2016. It’s designed to collect data from the Windows registry, Windows Management Instrumentation (WMI), security policies, Netstat, DirList, and the Net and Netsh commands.
The CYMPLICITY hardening tool checks the system to ensure that passwords need to be long and complex and are not stored in clear text, that accounts are protected against brute-force attacks, that users who don’t need them don’t have elevated privileges, that unnecessary ports are not open, that shared resources are protected, that only admins have debugging privileges, that communications are encrypted, that CIMPLICITY files are not exposed, and that RDP does not expose the system to remote attacks.
“The new tool designed by OTORIO is simple to use and requires no cyber expertise. Cybersecurity experts are seldom present on the production floor. Therefore, we designed the tool with the system integrators who install these systems and OT security personnel within the plants as its primary users. The tool is as simple as a ‘double click’ of a PowerShell script, making it easy to run even for non-technical personnel,” said Yuval Ardon, one of the OTORIO researchers involved in the development of the tool.
This is the second open source ICS security tool released by OTORIO. In December, the company announced the availability of a tool designed to help organizations harden Siemens SIMATIC PCS 7 distributed control systems (DCS).
When it released the tool for the Siemens DCS, OTORIO told SecurityWeek that, when trying to secure an environment, it’s more cost effective to start with server configurations.
It’s worth pointing out that both the Siemens and GE tools inform customers about identified issues, but are not designed to automatically address them.
Number of ICS Vulnerabilities Continued to Increase in 2020: Report
5.2.2021 ICS Securityweek
The number of vulnerabilities discovered in industrial control system (ICS) products in 2020 increased significantly compared to previous years, according to a report released on Thursday by industrial cybersecurity firm Claroty.
According to Claroty, the number of ICS vulnerabilities disclosed in 2020 (893 vulnerabilities) was nearly 25% higher compared to 2019 and close to 33% higher than in 2018. The company believes this increase is likely the result of heightened awareness of the risks posed by vulnerabilities in industrial products, as well as researchers and vendors putting more effort into identifying and patching security holes.
The company said 61% of vulnerabilities were discovered by third-party researchers, many of them employed by cybersecurity companies.
Claroty’s report, which focuses on the second half of 2020, reveals that, similar to the first half of the year, roughly 70% of the identified flaws can be exploited remotely. Also similar to the first half, the security holes were found in the products of more than 50 vendors. More than 70% of the bugs disclosed in H2 were rated critical or high severity, down from over 75% in H1.
In terms of industries, Claroty said the most impacted in the second half of 2020 were critical manufacturing (194 vulnerabilities), energy (186), water and wastewater (111), and commercial facilities (108).
“The steady growth of reported ICS vulnerabilities is noteworthy in terms of maturation, but currently, it’s also largely limited to three vendors: Schneider, Mitsubishi, and Siemens. A large majority of the products with disclosed and patched vulnerabilities in the 2H of 2020 belong to those three leading vendors; the remaining vendors had combined relatively fewer products affected by vulnerabilities,” Claroty said in its report.
It added, “Does this mean that the smaller number of vendors we looked at have cleaner, more secure products? Likely, no. Instead, it’s more of an issue of accessibility to equipment for a growing number of researchers; market leaders have an abundance of equipment inside organizations that can be assessed for security flaws. Some of this gear that has been retired can also be purchased on eBay and other platforms for research purposes.”
Siemens Releases Patches to Prevent Remote Takeover of SIMATIC HMI Panels
4.2.2021 ICS Securityweek
Siemens has released patches for some of its SIMATIC human-machine interface (HMI) panels to address a high-severity vulnerability that can be exploited remotely to take full control of a device.
SIMATIC HMI panels are designed for operator control and the monitoring of machines and plants.Siemens SIMATIC HMI vulnerability
Ta-Lun Yen, a researcher at TXOne Networks, an IIoT security-focused joint venture between Trend Micro and Moxa, discovered that these products are affected by a missing authentication issue related to the Telnet service. Affected devices that have Telnet enabled do not require any authentication, allowing a remote attacker to gain full access to a device, Siemens said.
The German industrial giant said the vulnerability (CVE-2020-15798) impacts SIMATIC HMI Comfort Panels, including SIPLUS products designed for extreme conditions, and SIMATIC HMI KTP Mobile Panels. Patches are included in v16 update 3a and later. All previous versions are affected.
In addition to installing the available patches, organizations can disable Telnet to prevent potential attacks exploiting this vulnerability. Siemens pointed out that Telnet is not enabled by default on the impacted devices.
TXOne’s Yen told SecurityWeek that he has not identified many devices that can be targeted from the internet, but noted that there may be some configurations that make them reachable over the intranet.
According to the researcher, an attacker could exploit the vulnerability to use the HMI as a foothold in the targeted network — the devices run Windows CE and he says there is no endpoint protection available.
He also believes an attacker could use the compromised HMI device to reach other systems, such as sensors and PLCs, or to disable them by sending them “weird values.” An attacker could also display inaccurate information in the HMI to avoid raising suspicion while they conduct other malicious activities that could cause damage to an industrial organization.
Yen said the vulnerability can also be leveraged to brick a device and temporarily prevent the operator from interacting with factory processes. It’s also possible to abuse the HMI for cryptocurrency mining, but this scenario is unlikely as it’s economically unfeasible, the researcher noted.
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has also published an advisory to warn industrial organizations about the risk posed by this flaw. Trend Micro’s Zero Day Initiative (ZDI), which along with CISA helped coordinate disclosure, will also publish an advisory for this vulnerability in the upcoming period.
Industrial Gear at Risk from Fuji Code-Execution Bugs
30.1.2021 ICS Threatpost
Fuji Electric’s Tellus Lite V-Simulator and V-Server Lite can allow attackers to take advantage of operational technology (OT)-IT convergence on factory floors, at utility plants and more.
Industrial control software (ICS) from Fuji Electric is vulnerable to several high-severity arbitrary code-execution security bugs, according to a federal warning. Authorities are warning the flaws could allow physical attacks on factory and critical-infrastructure equipment.
Fuji Electric’s Tellus Lite V-Simulator and V-Server Lite are both affected by the vulnerabilities, which all carry a CVSS severity rating of 7.8. The two make up a comprehensive human-machine interface (HMI) system, used to remotely monitor and collect production data in real time, and control a variety of industrial and critical-infrastructure gear. It can be used to interface with various manufacturers’ programmable logic controllers (PLCs), temperature controllers, inverters and so on.
“Successful exploitation of these vulnerabilities could allow an attacker to execute code under the privileges of the application,” CISA explained.
The security bugs require “low skill level to exploit,” according to an advisory from the Cybersecurity and Infrastructure Security Agency (CISA) this week. They’re not exploitable remotely, so non-local attackers would have to gain initial access to the user’s computer before carrying out any malicious activities. However, Saryu Nayyar, CEO at Gurucul, told Threatpost that this is not too large of a hurdle.
“The most likely attack vector is through compromising a user’s desktop through any of a myriad of common methods, or otherwise gaining access to the environment and access to the affected platforms,” she said. “A malicious actor would then upload a file to the system which would take advantage of the exploit and enable them to compromise the server.”
Real-World Attack Scenarios
While best practice in industrial environments is to keep the physical equipment operating in an isolated environment (the operational technology or OT environment), increasingly platforms like the Tellus Lite V-Simulator and V-Server Lite connect IT resources to that formerly isolated footprint. That in turn opens up ICS to potentially physical attacks.
“One of the biggest challenges facing ICS and SCADA systems is that they are no longer on isolated networks – they are basically connected to the internet, although typically ‘firewalled’ off, explained Christian Espinosa, managing director at Cerberus Sentinel, speaking to Threatpost. “This greatly increases risk associated with a vulnerability.”
Nayyar said that in this case, the worst-case scenario would be an attacker executing a file that could cause extensive damage to manufacturing equipment on the line. But, “a more likely scenario is production slowdowns and the loss of valuable data about what is happening on the production lines,” she said.
The vulnerabilities could accomplish a couple of other primary objectives, according to Espinosa.
“Attackers could alter the data displayed on the HMI monitoring systems, so the humans monitoring the systems would be blind to an attack on the remote equipment,” he explained. He used the analogy of putting a loop in a camera feed that is monitored by a security guard, so that a criminal can carry out an intrusion without the guard noticing.
“Or, they could create a stimulus on the monitoring display designed to drive a prescriptive response,” he added, noting that this is akin to setting off fire alarms, causing the person monitoring the system to turn on sprinklers to extinguish the fire, while destroying equipment.
“Stuxnet actually took advantage of a similar vulnerability,” he said. “One of the exploits in Stuxnet was designed to make everything look okay on the HMI, so the operator would not be alerted to the fact that the centrifuges were spinning at an extremely high rate, causing them to break.”

Five different kinds of security vulnerabilities exist in vulnerable versions of the Fuji Electric Tellus Lite V-Simulator and V-Server Lite. In all cases they were identified in the way the application processes project files, allowing an attacker to craft a special project file that may allow arbitrary code execution.
The bugs are:
Multiple stack-based buffer overflow issues, collectively tracked as CVE-2021-22637;
Multiple out-of-bounds read issues, collectively tracked as CVE-2021-22655;
Multiple out-of-bounds write issues, collectively tracked as CVE-2021-22653;
An uninitialized-pointer issue has been identified (CVE-2021-22639);
And a heap-based buffer overflow issue also exists (CVE-2021-22641).
The platform is vulnerable in versions prior to v4.0.10.0. CISA said that so far, no known public exploits specifically target these vulnerabilities, but administrators should apply a patch as soon as possible.
“This attack is a specific exploit against a specific platform, and patches already exist – which is the first step in mitigating the attack,” Nayyar said. “In a more general sense, keeping systems patched is always a best practice. Manufacturing equipment should be operated in as isolated an environment as practical, in order to reduce exposure; and, control systems need to be protected with policy, process and technical cybersecurity safeguards that reduce the risk of unauthorized access.”
Kimiya, Khangkito – Tran Van Khang of VinCSS and an anonymous researcher, working with Trend Micro’s Zero Day Initiative, were credited with reporting the vulnerabilities to CISA.
CISA warns of high-severity flaws in Fuji Electric Tellus Lite V-Simulator and Server Lite
28.1.2021 ICS Securityaffairs
The U.S. CISA published a security advisory for High-Severity flaws in some SCADA/HMI products made by Japanese company Fuji Electric.
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) issued a security advisory to warn industrial organizations of some high severity flaws in SCADA/HMI products made by Japanese electrical equipment company Fuji Electric.
The vulnerabilities affect the Tellus Lite V-Simulator (Versions prior to v4.0.10.0) and Server Lite (Versions prior to v4.0.10.0).
Telus and V-Server SCADA/HMI allow organizations to remotely monitor and control equipment in a factory, they are widely adopted in the critical manufacturing sector.
The vulnerabilities included in the advisory are Stack-based Buffer Overflow, Out-of-Bounds Read, Out-of-Bounds Write, Access of Uninitialized Pointer, and Heap-based Buffer Overflow issues that can be exploited by an attacker to execute arbitrary code on vulnerable installs. An attacker can trigger the flaws by tricking the target user into opening a malicious project file.
“Successful exploitation of these vulnerabilities could allow an attacker to execute code under the privileges of the application.” reads the CISA advisory.
The flaws were reported to the Japanese vendor Kimiya, by Khangkito – Tran Van Khang of VinCSS (Member of Vingroup), and an anonymous researcher through Trend Micro’s Zero Day Initiative (ZDI) and CISA,
All the flaws, tracked CVE-2021-22637, CVE-2021-22655, CVE-2021-22653, CVE-2021-22639, CVE-2021-22641 respectively, received a CVSS v3 base score of 7.8.
According to the advisory published by the Zero Day Initiative, the issue results from the lack of proper validation of user-supplied data, which can trigger a buffer overflow and consequent arbitrary code execution.
The issue has been disclosed publicly because the vendor did not address it in accordance with the ZDI 120 day deadline
CISA Issues Advisory for High-Severity Vulnerabilities in Fuji Electric HMI Products
28.1.2021 ICS Securityweek
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) this week released an advisory to inform industrial organizations that some SCADA/HMI products made by Japanese electrical equipment company Fuji Electric are affected by potentially serious vulnerabilities.
The impacted products are Tellus Lite V-Simulator and V-Server Lite. Telus and V-Server SCADA/HMI products are designed to help users monitor and operate their plants, including remote locations. CISA says the products are used worldwide, particularly in the critical manufacturing sector.
The vulnerabilities, reported to Fuji Electric by various researchers through Trend Micro’s Zero Day Initiative (ZDI) and CISA, have been described as buffer overflow, out-of-bounds read/write and uninitialized pointer issues that can be exploited for arbitrary code execution. An attacker could exploit the vulnerabilities by tricking the targeted user into opening a malicious project file.
According to CISA, the vulnerabilities affect Tellus Lite V-Simulator and V-Server Lite versions prior to 4.0.10.0, which should patch the flaws. This update was apparently released in October 2020.
It’s worth noting that ZDI published advisories for some of these vulnerabilities in September 2020, after the vendor failed to release patches within a 120-day deadline. The advisories were published at the time with a “0day” status. ZDI will likely soon also make public the advisories describing the remaining vulnerabilities.
The public ZDI advisories reveal that the vulnerabilities are caused by “the lack of proper validation of user-supplied data,” which results in memory corruption, and can ultimately lead to remote code execution.
Hundreds of Industrial Organizations Received Sunburst Malware in SolarWinds Attack
28.1.2021 ICS Securityweek
Hundreds of industrial organizations have apparently received a piece of malware named Sunburst as part of the supply chain attack that hit IT management and monitoring firm SolarWinds last year, Kaspersky’s ICS CERT unit reported on Tuesday.
SolarWinds’ analysis of the attack revealed that up to 18,000 of its customers may have received trojanized updates for its Orion monitoring product. These updates contained the Sunburst backdoor, which gave the attackers access to victims’ systems, allowing them to deploy other payloads to organizations that represented an interest.
An analysis of command and control (C&C) mechanisms used by the Sunburst malware, specifically DNS responses, has allowed researchers to determine which organizations may have received Sunburst and which might have been breached further by the SolarWinds hackers.
Kaspersky’s industrial cybersecurity researchers analyzed a list of nearly 2,000 domains impacted by Sunburst and estimated that roughly 32% of them were associated with industrial organizations.
A majority of them are organizations in the manufacturing sector, followed by utilities, construction, transportation and logistics, oil and gas, mining, and energy. Kaspersky says they are located in various countries in the Americas, Europe, Asia and Africa, including the U.S., Canada, Iran, the Netherlands, Russia, Saudi Arabia and Uganda.
The cybersecurity firm has determined that roughly 200 of its customers received the malicious SolarWinds updates, including more than 20 in industrial sectors.
“The SolarWinds software is highly integrated into many systems around the globe in different industries and, as a result, the scale of the Sunburst attack is unparalleled – a lot of organizations that had been affected might have not been of interest to the attackers initially,” said Maria Garnaeva, senior security researcher at Kaspersky.
“While we do not have evidence of a second-stage attack among these victims, we should not rule out the possibility that it may come in the future. Therefore, it is crucial for organizations that may be victims of the attack to rule out the infection and make sure they have the right incident response procedures in place,” Garnaeva added.
Three cybersecurity firms confirmed this week that they were impacted to some extent by the activities of the SolarWinds hackers, including Mimecast, Qualys, and Fidelis Cybersecurity.
Industrial Firms Informed About Serious Vulnerabilities in Matrikon OPC Product
26.1.2021 ICS Securityweek
Industrial organizations have been informed about the existence of several potentially serious vulnerabilities affecting an OPC UA product made by Honeywell subsidiary Matrikon.
Open Platform Communications (OPC) is a communications protocol for operational technology (OT) systems and it’s widely used to ensure interoperability between various types of industrial control systems (ICS). Matrikon, which Honeywell acquired in 2010 for roughly $140 million, specializes in vendor-neutral OPC UA (Unified Architecture) and OPC-based data interoperability products for industrial control automation.
As part of their analysis of OPC UA security, researchers at industrial cybersecurity firm Claroty discovered that Matrikon’s OPC UA Tunneller product, which is designed for integrating OPC UA clients and servers with OPC Classic architecture, is affected by four critical and high-severity vulnerabilities that can be exploited for remote code execution, DoS attacks, and for obtaining potentially valuable information. Most of them can be exploited to crash a server, and some, under certain conditions, can result in remote code execution.
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) last week published an ICS advisory to inform industrial organizations about these vulnerabilities.
Honeywell has released an update that should patch the flaws.
“We’ve taken the appropriate actions to remedy the situation, and have issued an update to the software. We strongly recommend that our customers upgrade to version 6.3.0.8233 immediately,” Honeywell told SecurityWeek in an emailed statement.
The most serious of the flaws found by Claroty in Matrikon OPC UA Tunneller — based on its CVSS score of 9.8 — is a heap buffer overflow bug that can allow an attacker to remotely execute arbitrary code or cause a DoS condition. Another vulnerability, rated high severity, can be exploited to obtain information that could be useful for conducting other activities on the targeted organization’s network.
“By exploiting these vulnerabilities, attackers can control the overwritten memory space outside the targeted buffer and can redirect a function pointer to their malicious code. In other words, attackers that exploit those vulnerabilities could also achieve remote code execution and take over the OPC server,” Claroty said in a blog post published on Monday.
The company told SecurityWeek that exploitation of the vulnerabilities requires network access to the targeted OPC server or OPC tunneller (depending on the OT network architecture), but authentication is not required.
“The flaws can be exploited remotely over the network. However, usually these systems are not directly facing the internet because they are used in closed OT networks. There are some cases where asset owners decide to open these OPC-related products to the web, but that’s uncommon,” Claroty said via email.
As part of its research into OPC security, Claroty also identified vulnerabilities in products made by industrial automation solutions providers Kepware and Softing Industrial Automation. The Kepware vulnerabilities were disclosed by CISA in December 2020, while the Softing product issues were disclosed in July 2020.
Claroty told SecurityWeek after the Kepware vulnerabilities were disclosed that they can be exploited by a remote, unauthenticated attacker with access to the OPC server for arbitrary code execution, data leakage, and DoS attacks.
The company has also pointed out that the vulnerabilities found by its researchers likely affect products from other vendors as well due to the use of third-party libraries such as one developed by Softing, and white label products made by Kepware.
“OPC is the communication hub of an OT network, centrally supporting communication between proprietary devices that otherwise could not exchange information. It’s deeply embedded in many product configurations and OPC-centered development and usage figures to continue,” Claroty said in its blog post on Monday.
“Also contributing to the expansive use of OPC is the fact that many vendors are already connecting parts of their networks that communicate using OPC to the cloud. This introduces industrial IOT devices into the equation, those that both receive and exchange device and process information,” it added.
Siemens fixed tens of flaws in Siemens Digital Industries Software products
17.1.2021 ICS Securityaffairs
Siemens has addressed tens of vulnerabilities in Siemens Digital Industries Software products that can allow arbitrary code execution.
Siemens has addressed 18 vulnerabilities affecting some products of Siemens Digital Industries Software which provides product lifecycle management (PLM) solutions.
The vulnerabilities affect Siemens JT2Go, a 3D viewing tool for JT data (ISO-standardized 3D data format) and the Teamcenter Visualization solution. JT2Go is a 3D JT viewing tool to allows its customers to view JT, PDF, Solid Edge, PLM XML with available JT, VFZ, CGM, and TIF data. Teamcenter Visualization software provides a comprehensive family of visualization solutions to access documents, 2D drawings and 3D models in a single environment.
“JT2Go and Teamcenter Visualization are affected by multiple vulnerabilities that could lead to arbitrary code execution or data extraction on the target host system. Siemens has released updates for both affected products and recommends to update to the latest versions.” states the advisory published by the vendor.
The company recommends limiting the opening of untrusted files in systems where JT2Go or Teamcenter Visualisation is installed to mitigate the risk of attacks exploiting these issues. It also suggests applying a Defense-in-Depth concept to reduce the probability that the untrusted code is run on the system.
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) also published an advisory related to these security flaws.
According to CISA, the addressed flaws include Type Confusion, Improper Restriction of XML External Entity Reference, Out-of-bounds Write, Heap-based Buffer Overflow, Stack-based Buffer Overflow, Untrusted Pointer Dereference, and Out-of-bounds Read.
The following products are affected by the vulnerabilities addressed by Siemens:
JT2Go: All versions prior to v13.1.0
JT2Go: Version 13.1.0. only affected by CVE-2020-26989, CVE-2020-26990, CVE-2020-26991
Teamcenter Visualization: All versions prior to V13.1.0
Teamcenter Visualization: Version 13.1.0 only affected by CVE-2020-26989, CVE-2020-26990, CVE-2020-26991
Several vulnerabilities addressed by the vendor received a CVSS v3 base score of 7.8, including:
ACCESS OF RESOURCE USING INCOMPATIBLE TYPE (‘TYPE CONFUSION’) CWE-843
OUT-OF-BOUNDS WRITE CWE-787
HEAP-BASED BUFFER OVERFLOW CWE-122
STACK-BASED BUFFER OVERFLOW CWE-121
ACCESS OF RESOURCE USING INCOMPATIBLE TYPE (‘TYPE CONFUSION’) CWE-843
UNTRUSTED POINTER DEREFERENCE CWE-822
OUT-OF-BOUNDS READ CWE-125
The flaws were reported by two researchers through Trend Micro’s Zero Day Initiative (ZDI) and the U.S. CISA.
Siemens also addressed six vulnerabilities in its Solid Edge solution that provides software tools for 3D design, simulation and manufacturing. The flaws could lead arbitrary code execution and information disclosure.
“Solid Edge is affected by multiple vulnerabilities that could allow arbitrary code execution on an affected system. Siemens has released an update for Solid Edge and recommends to update to the latest version.” reads the advisory.
Tens of Vulnerabilities in Siemens PLM Products Allow Code Execution
16.1.2021 ICS Securityweek
Siemens this week informed customers that some of its product development solutions are affected by a total of nearly two dozen vulnerabilities that can be exploited for arbitrary code execution using malicious files.
The security holes were discovered by a couple of researchers and their disclosure was coordinated through Trend Micro’s Zero Day Initiative (ZDI) and the U.S. Cybersecurity and Infrastructure Security Agency (CISA), which published their own advisories. The impacted products are all developed by Siemens Digital Industries Software, which specializes in product lifecycle management (PLM) solutions.
Siemens and CISA have published one advisory for 18 vulnerabilities affecting Siemens JT2Go, a 3D viewing tool for JT data (ISO-standardized 3D data format), and Teamcenter Visualization, which provides organizations visualization solutions for documents, 2D drawings and 3D models.
A second advisory was published for six vulnerabilities affecting Siemens Solid Edge, a solution that provides software tools for 3D design, simulation and manufacturing. A couple of the vulnerabilities described in each advisory overlap.
A vast majority of the vulnerabilities are high-severity issues that can result in arbitrary code execution in the context of the targeted process. One vulnerability can lead to information disclosure and it has been classified as medium severity.
The code execution flaws are related to improper validation of user-supplied data when parsing certain types of files, which leads to a memory corruption vulnerability. In order to conduct an attack, the attacker needs to convince the targeted user to open a specially crafted file.
The types of files that can be used to trigger the vulnerabilities include JT, CG4, CGM, PDF, RGB, TGA, PAR, ASM, PCX, SGI and DFT. Even though the description for all these bugs is similar, a separate CVE identifier has been assigned to each variant of a flaw.
Siemens has started releasing patches for the impacted products. The German industrial giant has shared workarounds for versions that have yet to receive fixes.
Siemens has also released a couple of advisories describing vulnerabilities found in its SCALANCE X industrial switches. These security holes, classified as critical and high severity, can expose the switches to DoS and man-in-the-middle attacks.
Schneider Electric this week released three new advisories. One of them describes the impact of a recently disclosed Treck vulnerability on its Sepam ACE850 multi-protocol communication interface.
The second advisory informs customers of a high-severity code execution vulnerability in Operator Terminal Expert (formerly Vijeo XD) and Pro-face BLUE products. The last advisory describes two high-severity code execution flaws in EcoStruxure Power Build - Rapsody when processing specially crafted SSD files.
DoS Vulnerabilities Found in Rockwell's FactoryTalk Linx and RSLinx Classic Products
9.1.2021 ICS Securityweek
Researchers have discovered vulnerabilities that expose Rockwell Automation’s FactoryTalk Linx and RSLinx Classic products to denial-of-service (DoS) attacks.
According to an advisory published by Rockwell late last month, researchers from cybersecurity firm Tenable discovered a total of four DoS vulnerabilities, three affecting FactoryTalk Linx and one impacting the FactoryTalk Services Platform.
FactoryTalk Linx, formerly RSLinx Enterprise, is a widely used product designed for connecting Allen Bradley PLCs to Rockwell applications, including for programming, data acquisition and HMI interaction.
Two of the security holes affecting FactoryTalk Linx are caused by an unhandled exception in a DLL file and they can allow a remote, unauthenticated attacker to cause a DoS condition by sending specially crafted packets that result in the termination of the RSLinxNG.exe process. These issues have been rated high severity and they are tracked as CVE-2020-5801 and CVE-2020-5802.
The other vulnerability affecting FactoryTalk Linx is a buffer overflow in a DLL file and it can also result in a DoS condition by sending malicious packets that cause the RSLinxNG.exe process to terminate. However, while exploitation does not require authentication, it does require local access, according to Rockwell’s advisory, which Tenable has confirmed for SecurityWeek that is accurate.
The flaw affecting the FactoryTalk Services Platform can be exploited for DoS attacks by convincing the targeted user to open a specially crafted log file.
“When the malicious log file is opened by a local user, it can cause a buffer overflow in the FactoryTalk Services Platform resulting in temporary denial-of-service conditions. Users can recover from the condition by reopening the impacted software,” the vendor explained (account required).
Rockwell Automation has not released patches for these vulnerabilities. It has, however, shared some risk mitigation recommendations, including network, software, social engineering and general mitigation strategies.
“A denial of service in the RSLinx component would not impact the operation of the PLC in most cases; however, it would prevent an Administrator from applying new configurations and changes to the PLC as well as lose visibility in the PLC's operation,” David Wells, staff research engineer at Tenable, told SecurityWeek.
Cisco Talos this week revealed that one of its researchers discovered a high-severity flaw that can allow an attacker to cause a DoS condition in Rockwell’s RSLinx Classic, a widely used communication server for industrial automation products. The issue, tracked as CVE-2020-13573, is related to the product’s Ethernet/IP server functionality and it can be exploited by sending specially crafted network requests.
Rockwell Automation told Talos that the issue was resolved in November, but it appears that the vendor has not released a security advisory. Talos has published an advisory explaining how the vulnerability can be exploited.