Mobil Articles - H 2020 1 Mobil List - H 2021 2020 2019 2018 2017 2016
Xiaomi tracks private browser and phone usage, defends behavior
3.5.2020 Bleepingcomputer Mobil
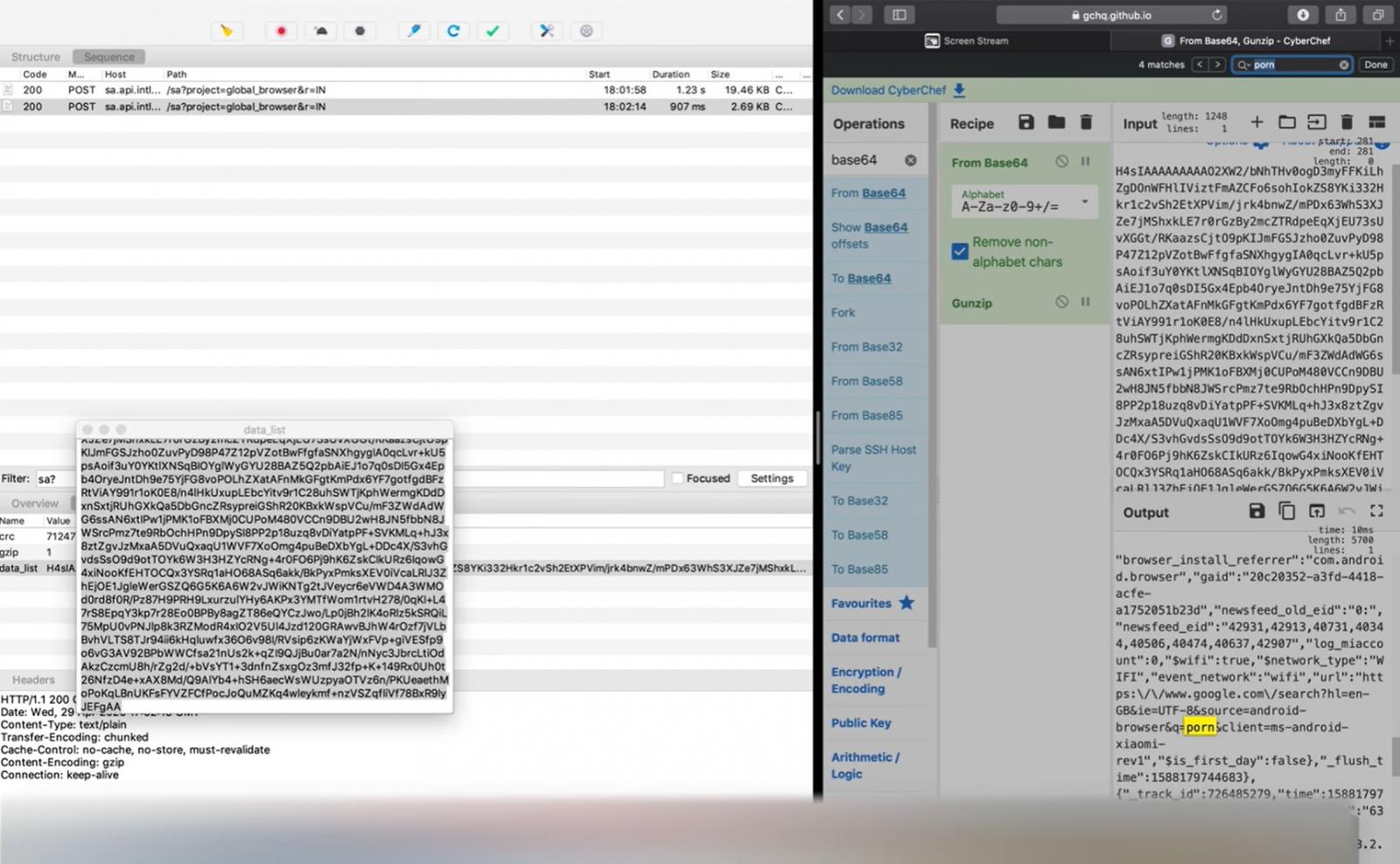
New research claims that China-based Xiaomi is tracking sensitive information and sending it to their servers if you use the Mi browser, which is bundled with all Redmi and Mi phones.
In a report by Forbes, security research Gabi Cirlig states that Xiaomi's Mi Browser app sends your internet searches, including incognito mode sessions, to Xiaomi servers in Singapore and Russia.
Even more concerning is that Cirlig states that the data being set can easily be associated with a particular user allowing the company to single out users they wish to track.
“My main concern for privacy is that the data sent to their servers can be very easily correlated with a specific user,” Cirlig told Forbes.
While all of this data is uploaded to remote servers in Singapore and Russia, the domains themselves are registered to an organization in Beijing.
Additionally, the researcher noticed that Xiaomi phones record the folders a user opens, the screens a user views, and configured settings.
Xiaomi's music player app was also recording what and when the user played songs.
Xiaomi's Mint Browser is also recording data
At Forbes' request, cybersecurity researcher Andrew Tierney also investigated the findings, and he reportedly found that the Mi Browser Pro and the Mint Browser collected the same data.
As seen below, when visiting a site, the browser will send the URL being visited back to a remote host. This URL is not obfuscated in any way.

According to the Play Store, the browser has more than 15 million downloads.
Xiaomi refuted these claims
In response to these claims, China-based Xiaomi published a lengthy blog post and stated, "the research claims are untrue" and that it "strictly follows and is fully compliant with local laws and regulations on user data privacy matters."
“Xiaomi was disappointed to read the recent article from Forbes. We feel they have misunderstood what we communicated regarding our data privacy principles and policy. Our user’s privacy and internet security is of top priority at Xiaomi; we are confident that we strictly follow and are fully compliant with local laws and regulations. We have reached out to Forbes to offer clarity on this unfortunate misinterpretation.”
Xiaomi said that the collected data is anonymized and the company's spokesperson denied that Mi Browser records browsing data while users are in incognito mode.
Xiaomi's statement was shown not to be the case after security researcher Cirlig created a video proving that Mi Browser search results are sent to remote servers even when the browser is in "incognito" mode.
Forbes provided Xiaomi with that video, but the company defended its privacy protocols.
Xiaomi doesn't think its users should feel worried as the video "shows the collection of anonymous browsing data" and that it "is one of the most common solutions adopted by internet companies."
Manu Kumar Jain, Vice President of Xiaomi India and Managing Director, also responded to the security allegations in a video.
Xiaomi India head noted that privacy and security are their top priority:
“A news report claims that Mi Browser collects unnecessary information while browsing and sends the user data to other countries. This is incorrect and not true,” Manu Jain, Vice President and Managing Director, Xiaomi India, said in a statement.
In a Twitter post, Tierney showed how he and others could prove for themselves that the Mint browser upload usage data to Xiaomi's servers.
Well, unsurprisingly, Xiaomi are saying that we're wrong that their browsers send all your data in Incognito mode.
So here's the evidence.
The app first downloaded was the "Mint Browser". It was obtained from the Play Store direct, yesterday.https://t.co/GJedDen5B1 pic.twitter.com/lYzQdCzAwX
— Cybergibbons (@cybergibbons) April 30, 2020
Xiaomi has not responded to the latest information posted on Twitter.
Opening 100 tabs in Google Chrome Mobile gets you a smiley face
3.5.2020 Bleepingcomputer Mobil
Today I learned something new; Google Chrome Mobile has an Easter egg that turns the tab count into a smiley face when you have over 100 tabs.
For the past couple of weeks, my Chrome Mobile's tab count has been showing a smiley face rather than the normal tab count.
In between other things, I poked around the settings to figure out what causes it, but never really made an effort to look into it. That is until today when my son said: "Cool, you have a smiley face in your browser!"
:) Easter egg
It turns out that Chrome Mobile has had an Easter egg for years that causes a smiley face to display instead of the tab count if you have over 100 tabs.
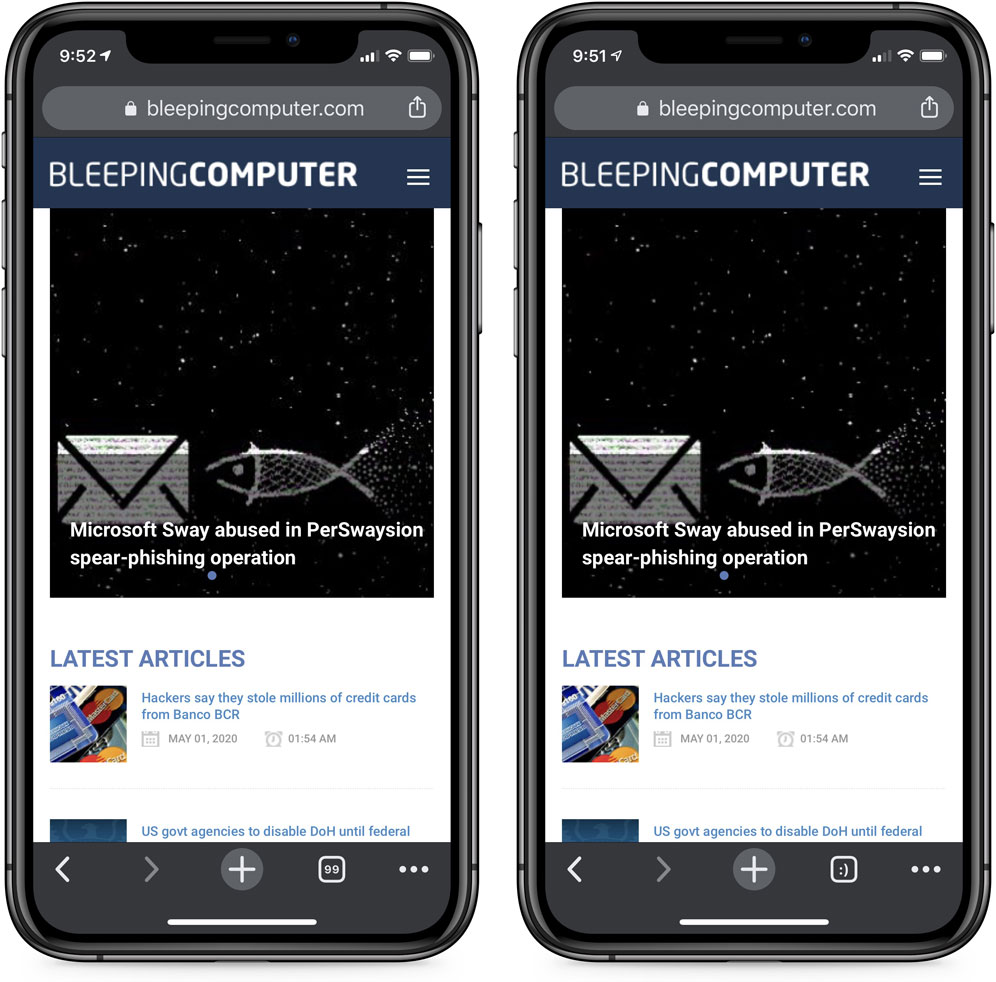
Before and after 100 tabs open
(Look at bottom right)
While it would be fun to think that the smiley face is shown because you are feeding the browser so much memory, the more likely reason is that the Google developers didn't want to increase the size of the tab count box to display 3 characters.
By showing a smiley face instead of 100, the user interface does not need to be changed and they can continue to display two characters in the same sized box.
Still, it's a fun little Easter egg, and if you see it, you now know that you have 100+ tabs open and maybe it's time to do a little pruning.
UK's ICO Says Mobile Tracking is Legal During COVID-19 Crisis
4.4.2020 Bleepingcomputer Mobil
UK's Information Commissioner's Office (ICO) has announced over the weekend that the government can use anonymized mobile phone tracking data to help fight the current coronavirus pandemic.
ICO’s Deputy Commissioner Steve Wood said in a statement that as long as the government anonymizes the mobile phone tracking data, it has the green light to do so as no individuals can be identified and privacy laws aren't breached.
"Generalised location data trend analysis is helping to tackle the coronavirus crisis," Wood said. "Where this data is properly anonymised and aggregated, it does not fall under data protection law because no individual is identified."
"In these circumstances, privacy laws are not breached as long as the appropriate safeguards are in place."
Since the start of this pandemic, Singapore, South Korea and China have already made us of mobile phone tracking to fight the spread of the SARS-CoV-2 virus, while Israel and the US both want to make use of similar data collection practices to keep track of how the virus spreads.
Secure data store for tracking pandemic-related info
On the same day, UK's Department of Health and Social Care said that the NHS, Britain's publicly funded healthcare system, needs accurate real-time information to be able to fight this pandemic for an"operating picture of the virus, how it’s spreading, where it might spread next and how that will affect the NHS and social care services."
All this information will be collected with the help of Palantir, Amazon, and Google within a secure, central data store controlled by NHS England and NHS Improvement on Microsoft’s Azure cloud platform, and it will either be destroyed or returned once the current public health emergency will end.
For the time being, mobile tracking data is not among the info that will be centralized in this data store, as only 111 online/call center data and COVID-19 test result data are being assembled at the moment.
"All the data in the data store is anonymous, subject to strict controls that meet the requirements of data protection legislation and ensure that individuals cannot be re-identified," the department said.
"The controls include removing identifiers such as name and address and replacing these with a pseudonym. GDPR principles will be followed, for example, the data will only be used for Covid-19 and not for any other purpose and only relevant information will be collected."
Data collection can help in public health threat situations
"The ICO has provided advice about how data protection law can continue to apply flexibly to protect lives and data. The safety and security of the public remains our primary concern," Wood concluded.
"We will continue to work alongside Government to provide advice about the application of data protection law during these unprecedented times.”
The British privacy watchdog previously said in a statement on data protection and coronavirus that data protection and electronic communication laws do not stop the government, the NHS, health professionals, and public bodies from requiring "additional collection and sharing of personal data to protect against serious threats to public health."
"Regarding compliance with data protection, we will take into account the compelling public interest in the current health emergency," the ICO added. "The safety and security of the public remains our primary concern."
An information hub was also set up by the ICO to help organizations and individuals alike to navigate data protection during the coronavirus pandemic.
Ginp Mobile Banker Targets Spain with "Coronavirus Finder" Lure
28.3.2020 Bleepingcomputer Mobil
In today's deluge of malicious campaigns exploiting the COVID-19 topic, handlers of the Android banking trojan Ginp stand out with operation Coronavirus Finder.
They prey on the anxiety generated by the massive spread of the virus and launch on infected devices a page claiming to show the location infected people nearby for a small fee.
The purpose is to make victims provide payment card data in the hope of learning how close they are to infected individuals.
It's a particularly heinous campaign because it targets users in Spain, a country that's been hit hard by the new coronavirus: close to 3,000 people died from the virus and almost 40,000 are infected.
A loathsome lure
Ginp started in June 2019 as an SMS stealer and quickly evolved to a banking trojan, with code borrowed from Anubis, that targeted banks in Spain and the U.K.
In a recent version, the malware used the Accessibility feature in Android fake push notifications to make victims open apps for which Ginp had an overlay ready that asked for payment card data.
Researchers at Kaspersky are now seeing that Ginp operators are sending the malware a special command that opens a webpage called Coronavirus Finder.
The page claims that 12 people infected with the new coronavirus are in the vicinity of the victim and promises to show their location for 0.75 EUR.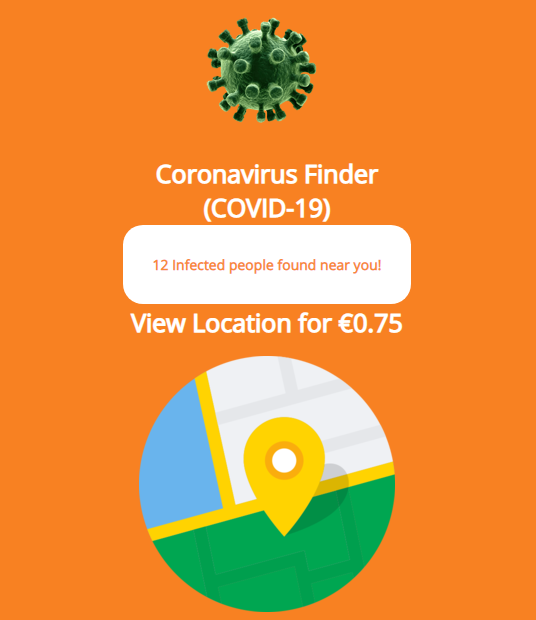
This is just to lure the victim into providing their payment card data, which is delivered to the cybercriminals. Once the info is provided, nothing happens.
"They don’t even charge you this small sum (and why would they, now that they have all the funds from the card at their command?)," writes Alexander Eremin, malware analyst at Kaspersky, in a blog post today.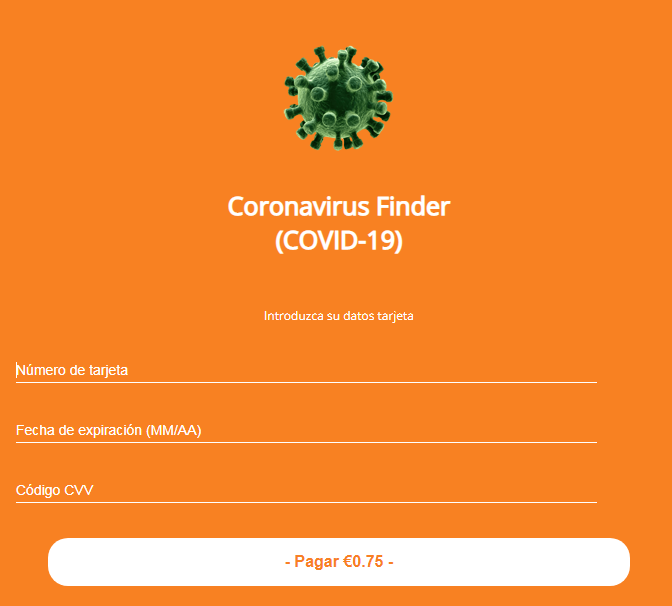
The source of inspiration for this lure may be the "Shield" mobile app recently released by the Israeli Ministry of Health, which alerts users if they've been at a location at the same time as a known Coronavirus carrier.
Telemetry data from Kaspersky shows that Ginp's main targets for this campaign are users in Spain. However, they warn that this operation may expand beyond Spain's territory.
"However, this is a new version of Ginp that is tagged “flash-2”, while previous versions were tagged “flash-es12”. Maybe the lack of “es” in the tag of the newer version means that cybercriminals plan to expand the campaign beyond Spain" - Alexander Eremin
These days, it is easy to render the new Ginp campaign ineffective: staying home ensures that you're at safe distance from people carrying COVID-19 (check here for guidelines from WHO).
Also, in this time of public health crisis, governments are the only entities with the most accurate information about the spread of the new coronavirus. If they make such an app available, they would not charge users for details on the current situation.
For mobile malware that does not use COVID-19 lures, following standard security recommendations should be enough to keep you safe:
install a reliable security solution
download apps from official sources
do not give apps other than antivirus permission to use the Accessibility feature
don't click on links from suspicious sources
don't provide sensitive information (access codes, logins, payment details) to forms that look suspicious
Europol Dismantles SIM Swap Criminal Groups That Stole Millions
15.3.2020 Bleepingcomputer CyberCrime Mobil
Europol arrested suspects part of two SIM swapping criminal groups in collaboration with local law enforcement agencies from Spain, Austria, and Romania following two recent investigations.
SIM swap fraud (also known as SIM hijacking) happens when a scammer takes control over a target's phone number via social engineering or by bribing mobile phone operator employees to port the number to a SIM controlled by the fraudster.
Subsequently, the attacker will receive all messages and calls delivered to the victim onto his own phone, thus being able to bypass SMS-based multi-factor authentication (MFA) by gaining access to one-time password (OTP) codes, to steal credentials, and to take control of online service accounts.
Successful SIM hijacking attacks allow criminals to log in to their victims' bank accounts and steal money, take over their email or social media accounts, as well as change account passwords and locking victims out of their accounts.
"Fraudsters are always coming up with new ways to steal money from the accounts of unsuspecting victims," acting Head of Europol’s European Cybercrime Centre Fernando Ruiz said.
"Although seemingly innocuous, SIM swapping robs victims of more than just their phones: SIM hijackers can empty your bank account in a matter of hours," he added. "Law enforcement is gearing up against this threat, with coordinated actions happening across Europe."
Millions of euros stolen from victims
12 individuals suspected to be part of a hacking ring which was able to steal more than €3 million in several SIM swapping attacks were arrested in Spain by the Spanish National Police (Policía Nacional) in collaboration with Europol and the Civil Guard (Guardia Civil), during 'Operation Quinientos Dusim.'
"Composed of nationals between the ages of 22-52 years old from Italy, Romania, Colombia and Spain, this criminal gang struck over 100 times, stealing between €6,000 and €137,000 from bank accounts of unsuspecting victims per attack," Europol said.
"The criminals managed the obtain the online banking credentials from the victims of the different banks by means of hacking techniques such as the use of banking Trojans or other types of malware. Once they had these credentials, the suspects would apply for a duplicate of the SIM cards of the victims, providing fake documents to the mobile service providers.
"With these duplicates in their possession, they would receive directly to their phones the second-factor authentication codes the banks would send to confirm transfers."
As Europol explains, once they gained access to their victims' bank accounts, the suspects made transfers to mule accounts within a time frame of two hours so that their victims weren't able to realize that something was wrong with their phones.
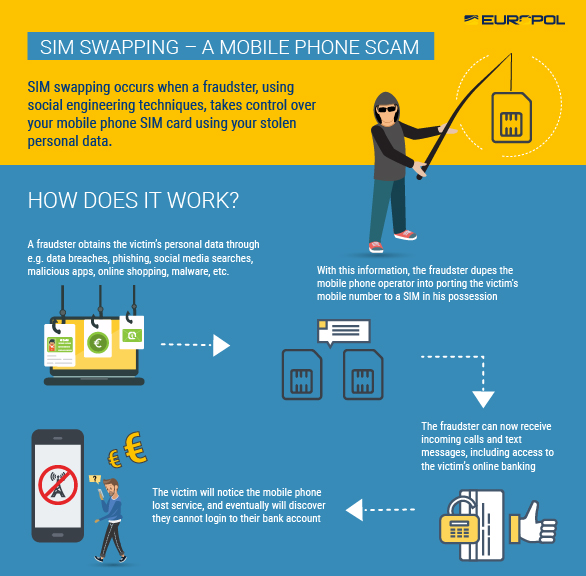
Image: Europol
Another 14 members of a SIM hijacking gang were also arrested as part of 'Operation Smart Cash' following an investigation led by the Romanian National Police (Poliția Românã) and the Austrian Criminal Intelligence Service (Bundeskriminalamt), in collaboration with the Europol.
"The thefts, which netted dozens of victims in Austria, were perpetrated by the gang in the spring of 2019 in a series of SIM swapping attacks," Europol said.
"Once having gained control over a victim’s phone number, this particular gang would then use stolen banking credentials to log onto a mobile banking application to generate a withdraw transaction which they then validated with a one-time password sent by the bank via SMS allowing them to withdraw money at cardless ATMs."
This crime group was able to steal more than €500,000 from dozens of Austrian during the spring of 2019 and until they were arrested at their homes in Romania during early February.
Defending against SIM swapping attacks
Europol also shared measures you can take if you want to prevent SIM hijackers from stealing your credentials and locking out of your accounts.
To make sure that SIM swapping doesn't affect you, Europol recommends the following:
• Keep your devices’ software up to date
• Do not click on links or download attachments that come with unexpected emails
• Do not reply to suspicious emails or engage over the phone with callers that request your personal information
• Limit the amount of personal data you share online
• Try to use two-factor authentication for your online services, rather than having an authentication code sent over SMS
• When possible, do not associate your phone number with sensitive online accounts
• Set up your own PIN to restrict access to the SIM card. Do not share this PIN with anyone.
If you lose mobile connectivity where you normally have no issues, you should immediately contact your provider and the bank if you spot any suspicious activity on your bank account.
Depending on what your mobile provider says, you might have to quickly change passwords for your online accounts to avoid further compromise in case scammers got your SIM ported to an attacker-controlled device.
The Federal Bureau of Investigation (FBI) also issued a SIM swapping alert last year with guidance on defending against such attacks after observing an increase in the number of SIM jacking attacks.
The FTC provides detailed info on how to secure personal information on your phone and on how to keep personal information secure online.
Ring Forces 2FA On All Users to Secure Cameras from Hackers
22.2.2020 Bleepingcomputer Hacking Mobil
Ring announced today the roll-out of mandatory two-factor authentication (2FA) to all user accounts, as well as the inclusion of additional security and privacy controls over third-party service providers, and the choice to opt-out of personalized advertising.
"While we already offered two-factor authentication to customers, starting today we’re making a second layer of verification mandatory for all users when they log into their Ring accounts," Ring President Leila Rouhi said.
"This added authentication helps prevent unauthorized users from gaining access to your Ring account, even if they have your username and password."
This change comes after attackers terrified homeowners after taunting them or speaking to their children over their Ring devices' speakers following a series of hacks targeting Ring cameras.
A statement released by Ring at the time said that the attackers were gaining access to the cameras through credential stuffing attacks and that no unauthorized access to Ring's systems or networks was detected.
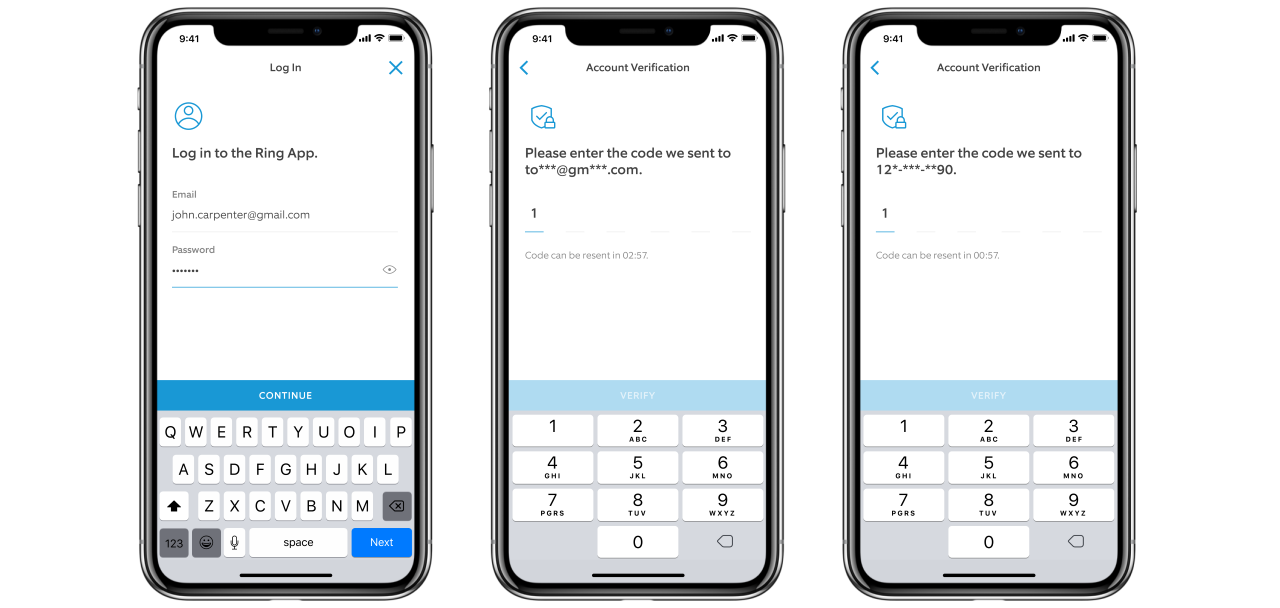
Ring log in (Ring)
2FA for extra account security
This means that starting today when Ring users will log in to their accounts on their mobile phone or computer, they will receive one-time and randomly generated six-digit codes designed to verify their login attempts, a code that will have to be entered in addition to their username and password.
"You can choose to receive this one-time passcode via the email address you have listed on your Ring account or on your phone as a text message (SMS)," Rouhi added.
Enabling 2FA for their accounts will allow users to add an extra security layer that a password is not able to provide on its own. 2FA will thus block someone else that might have gained access to their password from logging into their account if they don't also have access to the trusted device used to receive the 2FA codes.
"Requiring this code will help ensure that the person trying to log into your account is you. This mandatory second layer of verification will begin rolling out to users today," Rouhi further explained.
While 2FA was always an option available to Ring users, the company made the drastic decision to enforce it for all accounts as a defense measure against attacks such as the ones we reported about in December. 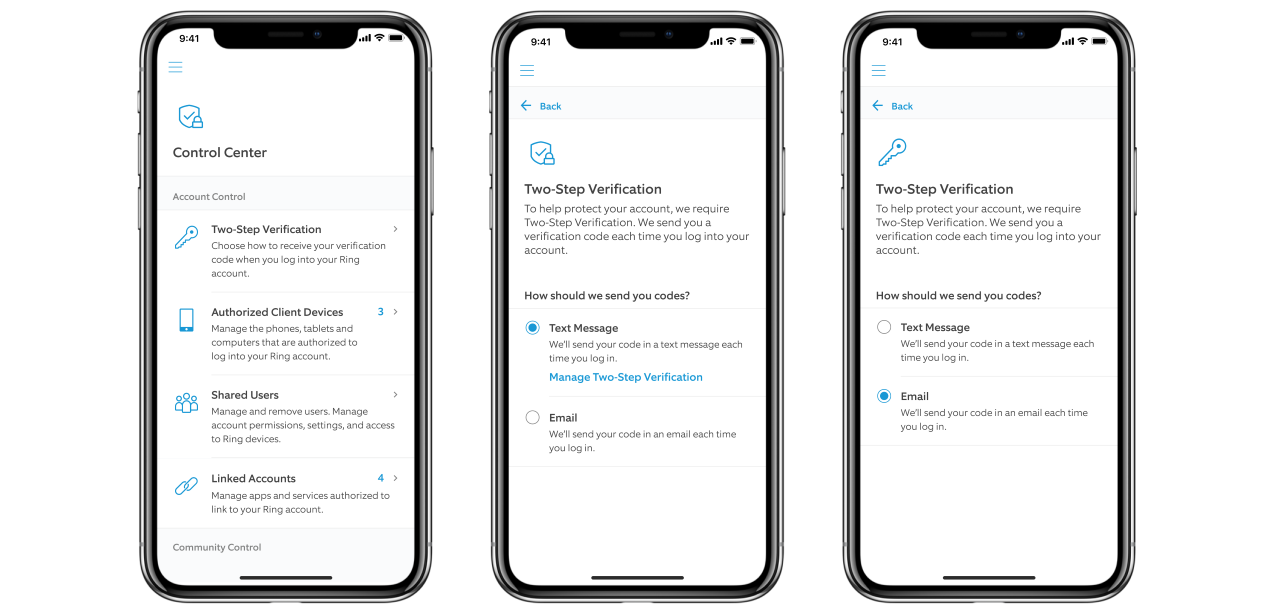
Control Center 2SV (Ring)
Ring users that won't log out and re-login to have 2FA toggled on for their accounts will be alerted when someone logs into their accounts via the login notifications feature added last December.
Google also forcibly enabled 2FA for all Nest accounts a week ago to block automated credential stuffing and dictionary attacks targeting Nest users.
More privacy controls and advertising opt-out
Ring also announced today that users will have more control of the info they share with third-party service providers and will be able to opt-out of personalized advertising.
"When a user opts out via Control Center, Ring will not share their information with third parties to serve them personalized Ring ads," Ring says.
These measures are part of a move to provide users with more transparency and to protect their privacy as requested by Ring customers in the past.
"Beginning immediately, we are temporarily pausing the use of most third-party analytics services in the Ring apps and website while we work on providing users with more abilities to opt-out in Control Center," according to Rouhi.
"In early Spring, we will provide you with additional options to limit sharing information with third-party service providers."
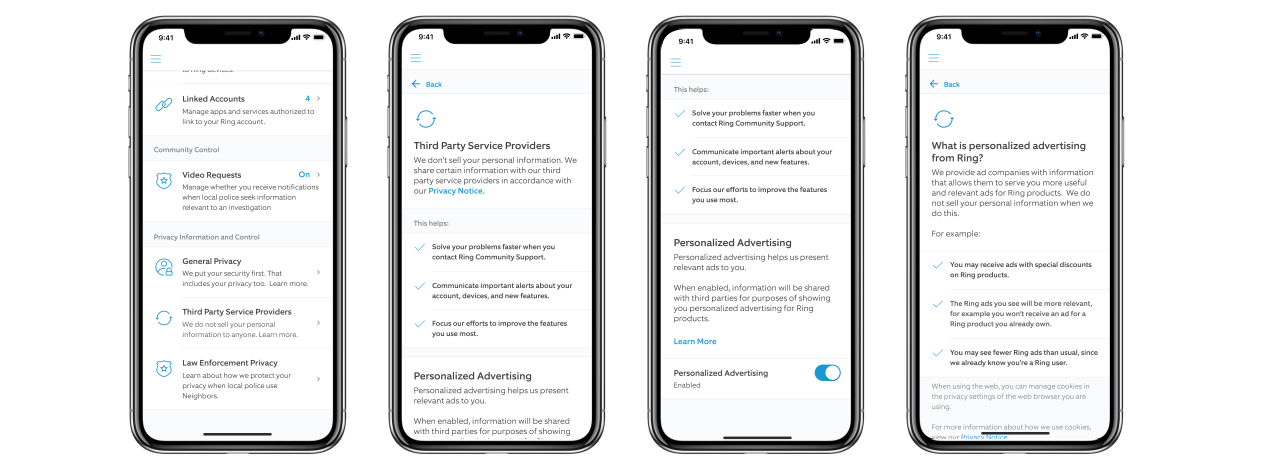
Third-party privacy controls (Ring)
"You can now opt out of sharing your information with third-party service providers for the purpose of receiving personalized ads," she added.
"If you opt-out, Ring will not share the information required to serve you personalized ads, though you may still see non-personalized Ring ads from time to time.
"Although we believe personalized advertising can deliver a better customer experience, beginning this week we will provide you with a choice to opt-out in Control Center."
Mobile Phishing Campaign Uses over 200 Pages to Spoof Bank Sites
16.2.2020 Bleepingcomputer Mobil Phishing
A phishing campaign focused on mobile banking used over 200 pages to impersonate legitimate websites for well-known banks in the U.S. and Canada.
Thousands of victims were lured to the fake sites with short messages delivered through an automated tool in the phishing kit.
Major banks targeted
In an effort to capture banking credentials, the cybercriminals spoofed login pages for at least a dozen banks, say in a report today security researchers at mobile security company Lookout.
The list of targeted banks includes major players on the market like Scotiabank, CIBC, RBC, UNI, HSBC, Tangerine, TD, Meridian, Laurentian, Manulife, BNC, and Chase.
According to the research, the phishing pages were created specifically for mobile, mimicking the layout and sizing. In their attempt to trick victims, the crooks also used links such as "Mobile Banking Security and Privacy" and "Activate Mobile Banking."
Apart from increasing confidence in the page, these links might also be used to collect sensitive information by asking for the credentials when accessing them.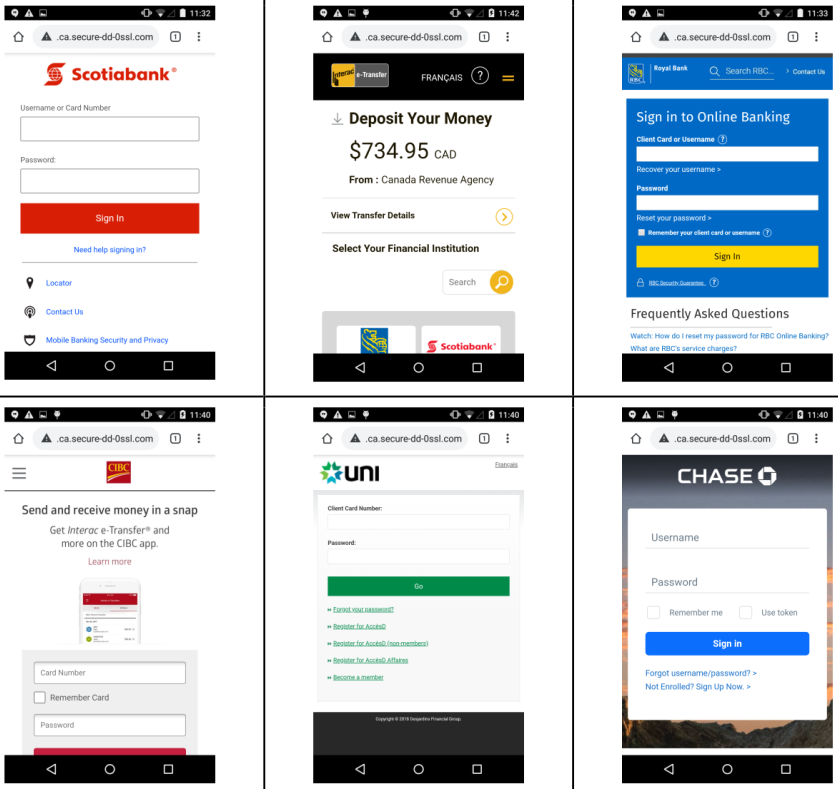
The cybercriminals behind this campaign used an automated SMS tool available in the phishing kit to deliver custom messages to numerous mobile phone numbers.
This suggests a mobile-first attack strategy, Lookout researchers say. It may also contribute to the success of the campaign since users expect bank communication via SMS.
"Many of the pages in this campaign appear legitimate through actions like taking the victim through a series of security questions, asking them to confirm their identity with a card’s expiration date or double-checking the account number" - Lookout
Spoofed pages accessed from thousands of IPs
Victims of this campaign spread all over the world, as researchers found on phishing pages lists of IP addresses belonging to devices that accessed the malicious link.
Additional details available included how far the victims went and if they were completely duped by the scam. From these statistical data, crooks could see what information was collected, such as account number and date of birth.
The security company identified more than 200 phishing pages that were created for this campaign. Since June 27, 2019, the malicious links were accessed from over 3,900 unique IP addresses, most of them in North America.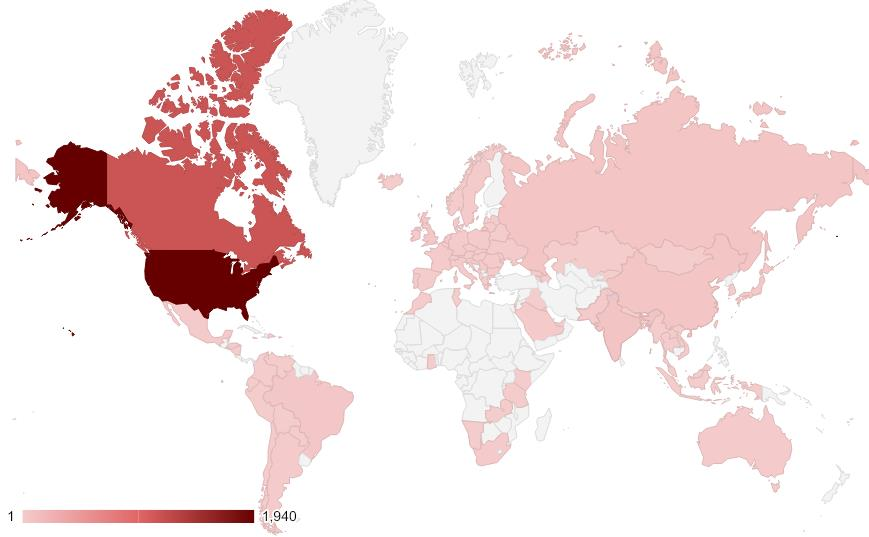
The campaign is no longer active and Lookout contacted all targeted banks about the impersonation attempts.
Avoiding these scams is more difficult on mobile than on a desktop computer because the limited space on the screen plays to the attacker's advantage.
However, there is a simple trick that can save you from becoming a victim of a mobile phishing attempt: instead of clicking on a link you get in a text message, type it yourself in a browser or launch the bank's app if you have it on the device.