
Mobil 2024 2023 2022 2021 2020
Cellebrite claims to be able to access Signal messages
23.12.2020 Mobil Securityaffairs
Israeli cyber security firm Cellebrite claims that it can decrypt messages from the popular Signal’s messaging app.
Israeli security firm Cellebrite has claimed that it can decrypt messages from the Signal highly secure messaging app.
The BBC reported the link to a blog on the company website that details the procedure to decrypt the Signal messages. The post was later changed and only reported that the Cellebrite Physical Analyzer allows lawful access to Signal app data, while the instructions have been removed.
“Signal keeps its database encrypted using SqlScipher, so reading it requires a key. We found that acquiring the key requires reading a value from the shared preferences file and decrypting it using a key called “AndroidSecretKey”, which is saved by an android feature called “Keystore”.” states the original version of the post. “Once the decrypted key is obtained, we needed to know how to decrypt the database. To do it, we used Signal’s open-source code and looked for any call to the database.” “After finding this, we simply ran SqlCipher on the database with the decrypted key and the values 4096 and 1 for page size and kdf iterations. By doing so we managed to decrypt the database.”
The creator of Signal, Moxie Marlinspike, defined the Cellebrite’announcement as being risible.
Highly encrypted messaging apps such as Signal and Telegram are widely adopted by those people that want to protect their privacy, unfortunately, it is widely adopted by ill-intentioned to protect their communications.
The Israeli mobile forensics firm Cellebrite is one of the leading companies in the world in the field of digital forensics, it works with law enforcement and intelligence agencies worldwide.
One of the most popular services provided by the company is the UFED (Universal Foresenic Extraction Device) which is used by law enforcement and intelligence agencies to unlock and access the data on mobile devices.
Despite the rumors about Cellebrite capabilities, Signal remains one of the most secure apps to communicate, the popular whistleblower Edward Snowden also endorsed it.
“Cellebrite seem to have been able to recover the decryption key, which seems extraordinary as they are usually very well protected on modern mobile devices.” Alan Woodward, a professor of computer science at Surrey University, told BBC.
“I suspect someone in authority told them to, or they realised they may have provided enough detail to allow others – who don’t just supply to law-enforcement agencies – to achieve the same result.”
Research: nearly all of your messaging apps are secure
23.12.2020 Mobil Securityaffairs
CyberNews Investigation team analyzed the 13 most popular messaging apps to see if the apps are really safe.
Source: https://cybernews.com/security/research-nearly-all-of-your-messaging-apps-are-secure/
In recent research, the CyberNews Investigation team discovered that a chat service, most likely based in China, had leaked more than 130,000 extremely NSFW images, video and audio recordings of their users. While this messaging service was connected to a company that offered a “private social network,” and therefore with a small user base, we wanted to see the security features of larger messaging apps.
For users of these bigger messaging apps, we have some good news: 86% of the apps (11 of 13) we looked at were secure by default. Only two apps – Telegram and Facebook Messenger – did not have these secure features enabled by default. These results are generally promising, as it signifies that the secure messaging industry is heading in the right direction.
We also found that most of the apps used variations of RSA and AES for encryption and key hashes – which are some of the most secure encryption algorithms available today.
In general, this is good not only for your “late night” messages (NSFW or not), but also for other important activities. We’ve covered before how important it is for people participating in protests around the world – whether Black Lives Matter in the US or anti-Lukashenko in Belarus – to use secure messaging services to coordinate activities and provide support. Our research shows that those users would be wise to use the top secure messaging apps like Signal, Wire, Cyber Dust and others on our list.
Key takeaways
Signal Wire Qtox
Wickr Me Viber Session
Messenger Cyber Dust Briar
WhatsApp iMessage Pryvate
Telegram
In order to perform our analysis, we looked at various aspects of 13 popular secure messaging apps:
Our analysis included the various apps’ transport and encryption standards, keys-exchange principles, and cryptographic primitives.
These are the key results of our analysis:
2 of the messaging apps were not secure by default, and users will have to turn on this security in the settings
4 of the secure messaging apps use the industry-trusted Signal Protocol for encryption
Only two of the apps use P2P for their transport mechanism
iMessage does not encrypt messages if they are sent through GSM (used for 2G and 3G)
3 out of 13 applications have paid plans that allow more users to access extra features
Most of the applications use RSA and AES, some of the most secure encryption algorithms available today, for encryption and key hashes
The nature of secure messaging apps
While most of the attention focuses on the most popular secure messaging apps, such as Signal, Messenger, Viber, Telegram and WhatsApp, we wanted to expand our analysis to understand the larger scope of the secure messaging industry. This includes looking at less-popular secure messaging services like Session, Briar, Wickr Me, Wire and Cyber Dust.
For the most part, we were not interested in ranking these apps in any way – rather, we wanted to investigate the applications’ encryption, transport and overall privacy.
What we found was largely positive: all but two of the apps offered security by default, and of those two apps, Telegram and Messenger, both could easily be made secure by changing user settings.
Four of the apps – Signal, Messenger, WhatsApp and Session – used the Signal protocol for end-to-end encryption. In end-to-end encryption, only the sender and the receiver will be able to view the messages, whereas without end-to-end encryption, the messaging app server that sits between the sender and receiver might be able to read the messages. The Signal protocol has become the industry standard for securing messaging, voice and video communications.
One interesting aspect of our analysis was that Apple’s iMessage, which is used in iPhone, iPad, Apple Watch and Mac, only uses encryption on HTTPS. When messages are sent through GSM – a protocol for 2G and 3G devices – they are not encrypted.
Only two apps – Briar and Qtox – use a peer-to-peer (P2P) transport mechanism. P2P here means that there is no server sitting in the middle between the sender and receiver: the messages go directly from one device to the next. While Briar offers other transfer mechanisms, Qtox only uses its TOX P2P, and therefore it has no privacy policy – it doesn’t need it, since it never touches the user’s data.
While nearly all of the messaging services we looked at are free or have a free version, only Wired requires a subscription. That’s because this messaging service is built for corporate use – something like Slack or Microsoft Teams, but with end-to-end encryption.
A caveat: what secure does and doesn’t mean in messaging apps
It’s important to note that there are some limitations when it comes to secure messaging services. This largely depends on what you want to do with the messaging service.
For general usage, it’s important that the messaging service you use has encryption enabled – preferably by default. For the NSFW media files we discovered on an unsecured Amazon bucket, the files were not encrypted, and so that messaging service simply was not a secure choice.
But beyond that, there are users who want as much security as possible – which means near or total anonymity: to not have their messages readable by others, to not be tracked by others, to not be named or connected to communications by others. In this light, most of these messaging services have failed or will fail. And that’s simply the nature of software – all programs have bugs, some more serious than others.
One famous example is WhatsApp, which has had numerous vulnerabilities throughout the years. This includes Israeli spyware that could install surveillance software on a target’s phone by simply calling them through WhatsApp. Messenger had its share of problems too, where attackers could see who you’ve been messaging with.
Even Signal, probably the messaging app most recommended by cybersecurity professionals, was victim to a rather complex attack where someone could listen in on your surroundings by making a sort of ghost call – calling you through Signal and then pressing mute without the call being seen, to eavesdrop on your conversations.
And that’s just usage by cybercriminals to attack individuals. Law enforcement has been using various methods throughout the years to spy on groups of people. In Hong Kong, a Telegram bug was reportedly exploited by the Chinese government to leak users’ phone numbers. German researchers also discovered that WhatsApp, Signal and Telegram were exposing users’ personal data via contact discovery.
Suffice it to say: none of these apps offer absolute security, and none ever will, since there will always be a workaround by a person or a group with enough time and resources. Even if an app were absolutely secure in and of itself, it wouldn’t be able to mitigate your mistakes. As Telegram’s FAQ nicely puts it:
“We cannot protect you from your own mother if she takes your unlocked phone without a passcode. Or from your IT-department if they access your computer at work. Or from any other people that get physical or root access to your phones or computers running Telegram.”
If you behave unsecurely, no secure messaging app will save you.
Summary table
In the table below, you’ll find all the details about the 13 messaging apps we looked at:
Messaging app Transfer Protocols Default security? Encryption Keys- Exchange and Cryptographic primitives
Signal Https / SIP over WebSockets Yes Signal protocol (X3DH + Double ratchet + AES-256) pre-keys + Curve25519, HMAC-SHA256
Wickr Me Https Yes Wickr Secure Messaging Protocol HKDF, SHA-256
Messenger Https No Signal protocol (X3DH + Double ratchet + AES-256) pre-keys + Curve25519, HMAC-SHA256
WhatsApp Https Yes AES-256, AES-256 IV Pre-keys, HMAC-SHA256
Telegram Https / SIP over WebSockets No MTProto 2.0 (AES-256, AES IGE IV 256) Persistent shared key generated via DH, KDF, Double SHA-256
Wire Https / SRTP Yes Axolotl/Double Ratchet pre-keys + Curve25519, HMAC-SHA256, ChaCha20, AES-GCM-256
Viber Http/Https – RTP(SRTP) Yes Double ratchet pre-keys + Curve25519, SHA256, HMAC_SHA256, ECDH
Cyber Dust Https, hsts, websocket Yes + RAM- based message storage AES-128 RSA-2048
iMessage Https / GSM Yes (if Http is used) Double AES-128 RSA
Pryvate Https Yes AES-256 RSA-4096, DH key exchange
Qtox TOX p2p Yes NaCl via libsodium Curve25519, xsalsa20, poly1305
Session TOR Onion Http Yes Modified Signal protocol pre-keys, AES, 4 DH
Briar Bluetooth/ Http/Tor onion Http Yes BTP pseudo random function BLAKE2b,authenticated cipher, random numbers
Infographic for the table above:
Vulnerabilities in Standalone 5G Networks Expose Users to Attacks
17.12.2020 Mobil Securityweek
Vulnerabilities in the protocols used by standalone 5G network implementations could expose users to information theft, impersonation, and other types of attacks, Positive Technologies warned on Wednesday.
Current 5G networks are non-standalone implementations that are based on the existing 4G LTE infrastructure, but wireless carriers are expected to invest heavily into transitioning to standalone implementations in the next few years.
And while the non-standalone 5G networks are prone to attacks targeting flaws in the Diameter and GTP protocols, standalone 5G networks can be attacked through vulnerabilities in the HTTP/2 and PFCP protocols, Positive Technologies notes in a newly published report.
Possible attacks would target subscribers and the operator’s network, and may originate from the operator’s network, the international roaming network, or from partner networks offering access to services.
The Packet Forwarding Control Protocol (PFCP), which makes subscriber connections, contains security issues that could lead to denial of service or traffic redirection, allowing the attacker to downlink the data of a subscriber.
An attacker could send session deletion request packages (containing the subscriber session identifier) or a session modification request to cause denial of service. A session modification request can also be used to redirect the subscriber to the attacker.
According to Positive Technologies, such vulnerabilities can be avoided if operators apply the proper configuration, given that the interface is internal.
Responsible for vital network functions, the HTTP/2 protocol is plagued by issues that could allow an attacker to impersonate a network service or delete network function profiles.
Attackers could attempt to register new network functions. They might cause disruptions if the functions exist, or access subscriber data if they end up serving subscribers through the attacker-controlled function.
By obtaining the profile of a network function, the attacker could impersonate a network service or access further data. If certain operations are not restricted, an attacker able to obtain network function profiles may delete these profiles, thus causing denial of service for the network’s subscribers.
Positive Technologies notes that other vulnerabilities also impact standalone 5G networks, including some related to subscriber authentication, the disclosure of subscriber profiles, or the creation of sessions impersonating existing subscribers.
“There is a risk that attackers will take advantage of standalone 5G networks while they are being established and operators are getting to grips with potential vulnerabilities. Therefore, security considerations must be addressed by operators from the offset,” Dmitry Kurbatov, CTO at Positive Technologies, said.
New 5G Network Flaws Let Attackers Track Users' Locations and Steal Data
17.12.2020 Mobil Thehackernews
As 5G networks are being gradually rolled out in major cities across the world, an analysis of its network architecture has revealed a number of potential weaknesses that could be exploited to carry out a slew of cyber assaults, including denial-of-service (DoS) attacks to deprive subscribers of Internet access and intercept data traffic.
The findings form the basis of a new "5G Standalone core security research" published by London-based cybersecurity firm Positive Technologies today, exactly six months after the company released its "Vulnerabilities in LTE and 5G Networks 2020" report in June detailing high impact flaws in LTE and 5G protocols.
"Key elements of network security include proper configuration of equipment, as well as authentication and authorization of network elements," Positive Technologies said.
"In the absence of these elements, the network becomes vulnerable [to] subscriber denial of service due to exploitation of vulnerabilities in the PFCP protocol," and other shortcomings that could lead to the disclosure of unique subscriber identifiers and profile information, and even use Internet services at a user's expense without their knowledge.
Security Benefits of 5G
One of the key security benefits offered by 5G is protection from stingray surveillance and encryption of International Mobile Subscriber Identity (IMSI) numbers — unique identifiers that come with every SIM card for the purpose of identifying users of a cellular network.
The 5G Core (5GC) also updates the IT protocol stack by using Transmission Control Protocol (TCP) as the transport layer protocol in place of Stream Control Transmission Protocol (SCTP), HTTP/2 as a substitute for Diameter protocol for application layer security, and an added TLS layer for encrypted communication between all network functions.
Deployed either in standalone or non-standalone modes depending on their reliance on 4G Evolved Packet Core (EPC) technology, the 5G mobile network is a framework consisting of as many as nine network functions (NFs) that are responsible for registering subscribers, managing sessions and subscriber profiles, storing subscriber data, and connecting the users (UE or user equipment) to the internet via a base station (gNB).
But the researchers say this very stack of technologies potentially opens the door to attacks on subscribers and the operator's network that could be exploited to stage man-in-the-middle and DoS attacks.
DoS and MitM Attacks
A problematic aspect of the system architecture is the interface devoted to session management (Session Management Function or SMF) via a protocol called Packet Forwarding Control Protocol (PFCP).
A bad actor can choose to send a session deletion or modification request PFCP packet, causing a DoS condition that, in turn, leads to disruption of internet access (CVSS score 6.1) and even interception of web traffic (CVSS score 8.3).
Positive Technologies also found issues with the part of the 5G standard that governs Network Repository Function (NRF), which enables registration and discovery of NFs in the control plane, noting that the adversaries could add an already existing network function in the repository to serve subscribers via an NF under their control and access user data (CVSS score 8.2).
In a different scenario, the lack of authorization in NRF could be abused to deregister critical components by deleting their corresponding NF profiles from the store, resulting in loss of service to subscribers.
Secretly Spy on Subscribers' Location
Also of note are a pair of subscriber authentication vulnerabilities that can be leveraged to disclose the Subscription Permanent Identifier (SUPI) allocated to each subscriber and serve the end-user using the leaked authentication information by spoofing a base station.
Separately, a design quirk in the User Data Management (UDM) module that manages subscriber profile data could permit an adversary with "access to the relevant interface [...] connect to the UDM directly or by impersonating a network service, and then extract all the necessary information," including location data (CVSS score 7.4).
"Access to such data would severely jeopardize security: it allows the attacker to secretly spy on the subscriber, while the latter will never know what is going on," the researchers said.
Last but not least, an attacker can impersonate the Access and Mobility Management Function (AMF) module that takes care of subscriber registration on the network by using a subscriber's identification information to create new stealthy internet sessions for which the subscriber will be billed (CVSS score 8.2).
The Need for Assessment, Monitoring, and Protection
There's no doubting the security advances offered by 5G, but it's also essential that the 5G standard is adequately scrutinized as the number of 5G network users continue to grow each year.
"Operators frequently make errors in equipment configuration with consequences for security," the researchers concluded. "An important role is played by equipment vendors, which are responsible for the technical implementation of all the architected network protection features.
"To prevent the consequences of such attacks, operators must employ timely protection measures, such as proper configuration of equipment, use of firewalls on the network edge, and security monitoring," the researchers said.
Data Broker X-Mode Being Booted From Mobile Apps
10.12.2020 Mobil Securityweek
Google on Wednesday confirmed it is banning location tracking software developed by data collection firm X-Mode Social from apps on Android-powered mobile devices, which dominate the global market.
Apple is also barring X-Mode from its coveted iOS devices, according to a Wall Street Journal report.
US-based X-Mode has been the subject of recent media scrutiny for its links to the country's defense sector, particularly for selling data to government contractors involved in national security, counterterrorism and even coronavirus response.
Vice News reported last November that X-Mode was collecting the location data of people using apps intended for Muslim audiences, particularly the dating platform Muslim Mingle.
Google sent developers a warning giving them seven days to rid their apps of X-Mode software or request more time if doing so is technically complex, according to a spokesperson.
"If X-Mode is still present in the app after the timeframe, the app will be removed from Play," the Google spokesperson said, referring to the internet giant's online shop for mobile apps and digital content.
Apple did not immediately return a request for comment.
However, according to the Journal, it also gave developers a warning that X-Mode tracking software must be removed from smartphone apps which otherwise risk being blocked.
Apple's iOS and Google's Android operating systems dominate the world smartphone market.
The two tech giants reported their decisions on X-Mode to a team working for US Senator Ron Wyden, a Democrat from Oregon, whose office is investigating the sale of location data to government agencies, the Journal said.
X-Mode did not respond to AFP's request for comment.
Cybercriminals Already Targeting, Selling Leaked GO SMS Pro Data
1.12.2020 Mobil Securityweek
Cybercriminals have been observed targeting a recently disclosed vulnerability in the GO SMS Pro messaging application to steal user data.
The issue, Trustwave revealed a couple of weeks ago, is that users’ media messages are stored insecurely on a publicly accessible server, exposing them to unauthenticated attackers.
Whenever a user attempts to send a media file, Trustwave’s SpiderLabs security researchers discovered, the application would generate a URL that can be easily guessed and which does not require authentication to access the shared media.
Minor scripting can be used to target the unprotected media files and exfiltrate them, and Trustwave now says that threat actors are publicly sharing tools and scripts exploiting the bug.
“Several popular tools are updating daily and on their third or fourth revision. We've also seen underground forums sharing images downloaded from GO SMS servers directly,” Trustwave says.
Not all media can be linked to specific users, but some of the shared images and videos do include people’s faces, names, and other identifying characteristics, thus representing a major privacy breach.
Another issue that Trustwave underlined was the app developer’s unwillingness to cooperate with its researchers to address the security hole.
However, it appears that the developer did attempt to address the issue, an application version uploaded to Google Play on November 23 reveals. However, analysis of the app showed that a complete fix hasn’t been deployed yet.
The developer initially disabled the option to send media files using the app. Soon after, the capability was re-enabled, although the media did not appear to be delivered to the recipient.
“Despite these half fixes, we can confirm that older media used to verify the original vulnerability is still available. That includes quite a bit of sensitive data like driver's licenses, health insurance account numbers, legal documents, and of course, pictures of a more 'romantic' nature,” Trustwave says.
SecurityWeek has once again attempted to contact GO SMS Pro’s developer for an official comment on the matter but received no reply as of yet.
Incomplete 'Go SMS Pro' Patch Left Millions of Users' Data Still Exposed Online
1.12.2020 Mobil Thehackernews
A week after cybersecurity researchers disclosed a flaw in the popular GO SMS Pro messaging app, it appears the developers of the app are silently taking steps to fix the issue from behind the scenes.
The security misstep made it possible for an attacker to come up with a trivial script to access media files transferred between users, including private voice messages, photos, and videos, stored on an unauthenticated, publicly accessible server.
Although the behavior was observed on version 7.91 of GO SMS Pro for Android, the app makers have since released three subsequent updates, two of which (v7.93 and v7.94) were pushed to the Google Play Store after public disclosure of the flaw and Google's removal of the app from the marketplace.
Google reinstated the app back to the Play Store on November 23.
Now following an analysis of the updated versions, Trustwave researchers said, "GOMO is attempting to fix the issue, but a complete fix is still not available in the app."
v7.93 of the app saw the developers completely turning off the ability to send media files, while the next update (v7.94) has brought back the functionality, albeit in a broken form.
"In v7.94, they are not blocking the ability to upload media in the app, but the media does not appear to go anywhere," the researchers said. "The recipient does not receive any actual text either with or without attached media. So it appears they are in the process of trying to fix the root problem."
What's more, Trustwave confirmed that older media shared prior to the advisory are still accessible, including a cache of sensitive information like driver's licenses, health insurance account numbers, legal documents, and photos of a more "romantic" nature.
Troublingly, not only tools and exploits leveraging this vulnerability have been released on Pastebin and Github; underground forums appear to be sharing images downloaded from GO SMS servers directly.
Given the lack of communication from the app developers and the fact that old data is being actively leaked, it is recommended to refrain from using the app until the issues are fully patched.
"We also think it would be a good idea for Google to take this app back down," the researchers said.
A flaw in GO SMS Pro App allows accessing media messages
20.11.20 Mobil Securityaffairs
An unpatched security flaw in GO SMS Pro, a popular messaging app for Android with over 100 million installs, exposes media messages.
GO SMS Pro is a popular Android messaging app with over 100 million installs, that has been found to be affected by an unpatched security flaw that publicly exposes media transferred between users.
An unauthenticated attacker could exploit the flaw to access any sensitive media shared between users of the app, including private voice messages, photos, and videos.
The flaw was discovered by researchers from Trustwave, it impacts version 7.91 of the app. The vulnerable version was uploaded to the Google Play Store on February 18, 2020.
“The GO SMS Pro application is a popular messenger app with over 100 million downloads and was discovered to publicly expose media transferred between users of the app.” reads the post published by Trustwave. “This exposure includes private voice messages, video messages, and photos.”
The experts noticed that if the recipient does not have the GO SMS Pro app installed, the app sends to the recipient an URL that points to media file via SMS. The recipient could then access the media file via a browser by clicking on the link.
SpiderLabs experts discovered that it is possible to access the link without any authentication or authorization, they also discovered that the URL link was sequential (hexadecimal) and predictable.
“Furthermore, when sharing media files, a link will be generated regardless of the recipient having the app installed. As a result, a malicious user could potentially access any media files sent via this service and also any that are sent in the future. This obviously impacts the confidentiality of media content sent via this application.” continues the report.
An attacker can exploit the bug to generate a list of URLs and access user data without their knowledge.
The researchers also wrote a simple bash script to generate a sample list of URLs and demonstrate how an attacker could easily access masses of user data.
#!/bin/bash
(echo obase=16; seq 1 $((echo ibase=16; echo FF) | bc)) | bc > 1
for i in $(cat 1); do echo "http://gs.3g.cn/D/dd1a$i /w"; done | tr -d " "
The cybersecurity firm attempted to contact the app developers multiple times since August 18, 2020, but received no reply.
Since then GO SMS Pro received two updates, but they still did not fix the flaw.
Below the timeline for the vulnerability:
08/18/2020 – Vendor contacted with no response
09/15/2020 – Vendor contacted with no response
10/14/2020 – Vendor contacted with no response
11/16/2020 – Vendor contacted with no response
11/19/2020 – Advisory published
WARNING: Unpatched Bug in GO SMS Pro App Exposes Millions of Media Messages
19.11.20 Mobil Thehackernews
GO SMS Pro, a popular messaging app for Android with over 100 million installs, has been found to have an unpatched security flaw that publicly exposes media transferred between users, including private voice messages, photos, and videos.
"This means any sensitive media shared between users of this messenger app is at risk of being compromised by an unauthenticated attacker or curious user," Trustwave Senior Security Consultant Richard Tan said in a report shared with The Hacker News.
According to Trustwave SpiderLabs, the shortcoming was spotted in version 7.91 of the app, which was released on the Google Play Store on February 18, 2020.
The cybersecurity firm said it attempted to contact the app makers multiple times since August 18, 2020, without receiving a response.
But checking the app's changelog, GO SMS Pro received an update (v7.92) on September 29, followed by another subsequent update, which was published yesterday. The latest updates to the app, however, still doesn't address the weakness mentioned above.
The vulnerability stems from the manner media content is displayed when recipients don't have the GO SMS Pro app installed on their devices, leading to potential exposure.
"If the recipient has the GO SMS Pro app on their device, the media would be displayed automatically within the app," Tan said. "However, if the recipient does not have the GO SMS Pro app installed, the media file is sent to the recipient as a URL via SMS. The user could then click on the link and view the media file via a browser."
Not only is this link (e.g. "https://gs.3g.cn/D/dd1efd/w") accessible to anyone without prior authentication, the URL is generated irrespective of whether the recipient has the app installed, thereby allowing a malicious actor to access any media files sent via the app.
Specifically, by incrementing the sequential hexadecimal values in the URL (e.g., "https://gs.3g.cn/D/e3a6b4/w"), the flaw makes it possible to view or listen to other media messages shared between other users. An attacker can leverage this technique to generate a list of URLs and steal user data without their knowledge.
It's likely that the flaw impacts the iOS version of GO SMS Pro as well, but until there's a fix in place, it is highly recommended to avoid sending media files using the affected messenger app.
We have reached out to the developers of GO SMS Pro, and we will update the story if we hear back.
Boom in Demand for Friendly Hackers as 5G Approaches
18.11.20 Mobil Securityweek
As the number of online devices surges and superfast 5G connections roll out, record numbers of companies are offering handsome rewards to ethical hackers who successfully attack their cybersecurity systems.
The fast-expanding field of internet-connected devices, known as the "internet of things" (IoT) which includes smart televisions and home appliances, are set to become more widespread once 5G becomes more available -- posing one of the most serious threats to digital security in future.
At a conference hosted by Nokia last week, "friendly hacker" Keren Elazari said that co-opting hackers -- many of whom are amateurs -- to hunt for vulnerabilities "was looked at as a trendy Silicon Valley thing six to eight years ago".
But "bug bounty programmes" are now offered by organisations ranging from the Pentagon and banks such as Goldman Sachs to airlines, tech giants and thousands of smaller businesses.
The largest bug-bounty platform, HackerOne, has 800,000 hackers on its books and said its organisations paid out a record $44 million (38.2 million euros) in cash rewards this year, up 87 percent on the previous 12 months.
"Employing just one full-time security engineer in London might cost a company 80,000 pounds (89,000 euros, $106,000) a year, whereas we open companies up to this global community of hundreds of thousands of hackers with a huge diversity in skills," Prash Somaiya, security solutions architect at HackerOne, told AFP.
"We're starting to see an uptick in IoT providers taking hacking power seriously," Somaiya said, adding that HackerOne now regularly ships internet-connected toys, thermostats, scooters and cars out to its hackers for them to try to breach.
"We already know from what has happened in the past five years that the criminals find very clever ways to utilise digital devices," Elazari told AFP.
A sobering example was the 2016 "Mirai" cyberattack, during which attackers took control of 300,000 unsecured devices, including printers, webcams and TV recorders, and directed them to flood and disable websites of media, companies and governments around the world.
"In the future of 5G we're talking about every possible device having high-bandwidth connections, it's not just your computer or your phone," Elazari warned.
In October Nokia announced it had detected a 100 percent increase in malware infections on IoT devices in the previous year, noting in its threat report that each new application of 5G offers criminals "more opportunities for inflicting damage and extracting ransom".
- Breaker mindset -
The rewards for hackers can be high: 200 of HackerOne's bug-hunters have now claimed more than $100,000 in prizes, while nine have breached the million-dollar earnings mark.
Apple, which advertises its own bug bounty programme, increased its maximum reward to more than $1 million at the end of last year, for a hacker able to demonstrate "zero click" weaknesses that would allow someone to access a device without any action by the user.
"A big driver is of course the financial incentive, but there's this element of a breaker mindset, to figure out how something is built so you can break it and tear it apart," Somaiya said.
"Being one individual who's able to hack multibillion-dollar companies is a real thrill, there's a buzz to it."
The rush of companies shifting to remote working during the pandemic has also led to "a surge in hacktivity", HackerOne said, with a 59 percent increase in hackers signing up and a one-third increase in rewards paid out.
The French and UK governments are among those to have opened up coronavirus tracing apps to friendly hackers, Somaiya added.
- Incentive to act -
While 5G internet systems will have new security features built into the network infrastructure -- something absent before -- the new technology is vastly more complex than its predecessors, leaving more potential for human error.
"I see a lot of risk for misconfiguration and improper access control, these glitches are one of the main risks," Silke Holtmanns, head of 5G security research for cybersecurity firm AdaptiveMobile, told AFP.
But companies are being motivated to act as security moves up the agenda, Holtmanns believes.
The EU, along with governments around the world, has begun tightening cybersecurity demands on organisations, and fines for data breaches have been increasing.
"Before now it's been hard for companies to justify higher investment in security," Holtmanns, who sits on the EU cybersecurity advisory group Enisa, said.
But she added, "If they can say: 'With that security level we can attract a higher level of customer, or lower insurance premiums,' people start thinking in this direction, which is a good thing."
'Find My Mobile' Vulnerabilities Exposed Samsung Galaxy Phones to Attacks
11.8.20 Mobil Securityweek
A series of vulnerabilities affecting Samsung’s Find My Mobile could have been chained to perform various types of activities on a compromised smartphone, a researcher from Portugal-based cybersecurity services provider Char49 revealed at the DEF CON conference on Friday.
Find My Mobile is designed to help users find lost Samsung phones. It can also be used to remotely lock a device, block access to Samsung Pay, and completely wipe the phone if it “falls into the wrong hands.”Samsung Find My Mobile Vulnerabilities
According to Char49, there were a total of four vulnerabilities in Find My Mobile components and they could have been exploited by a malicious app installed on the targeted device.
Pedro Umbelino, the Char49 researcher who found the flaws, told SecurityWeek that the malicious app would only require access to the device’s SD card in order to exploit the first vulnerability in the chain and create a file that allows the attacker to intercept communications with backend servers.
Successful exploitation of the vulnerabilities would have allowed a malicious app to perform any action that the Find My Mobile app could perform, including force a factory reset, wipe data, track the device’s location in real time, retrieve phone calls and messages, and lock and unlock the phone.
The exploit was successfully reproduced on Samsung Galaxy S7, S8 and S9+ devices before the vendor released a patch.
Char49 told SecurityWeek that the vulnerabilities were found more than a year ago, but Samsung only patched them in late October 2019, and the security company wanted to wait for 9 months before making details public.
“This flaw, after setup, can be easily exploited and with severe implications for the user and with a potentially catastrophic impact: permanent denial of service via phone lock, complete data loss with factory reset (sdcard included), serious privacy implication via IMEI and location tracking as well as call and SMS log access,” the company explained in a technical report describing each of the vulnerabilities.
It added, “The [Find My Mobile] application should not have arbitrary components publicly available and in an exported state. If absolutely necessary, for example if other packages call these components, then they should be protected with proper permissions. Testing code that relies on the existence of files in public places should be eliminated.”
Operators rethinking security while making rapid progress toward 5G
28.5.2020 Net-Security Mobil
Mobile service providers say they are making substantial progress toward ushering in a new generation of 5G networks that will enable ultra-high-speed mobile connectivity and a wide variety of new applications and smart infrastructure use cases.
progress 5G
Progress includes steady work toward virtualizing core network functions and a reexamination of the security investments they will need to protect their networks and customers.
COVID-19 is not expected to significantly delay the progress of 5G deployments, according to a global study report, developed by the Business Performance Innovation (BPI) Network, in partnership with A10 Networks.
The percentage of mobile service providers who say their companies are “moving rapidly toward commercial deployment” has increased significantly in the past year, climbing from 26 percent in a survey announced in early 2019 to 45 percent in the new survey. Virtually all respondents say improved security is a critical network requirement and top concern in the 5G era.
Adding standalone 5G
Early 5G networks are being designed in accordance with the already-approved non-standalone 5G standard. However, 30 percent of respondents say they are already proactively planning to add standalone 5G, and another 9 percent say their companies will move directly to standalone.
Standalone 5G will require a whole new network core utilizing a cloud-native, virtualized, service-based architecture. Many respondents, in fact, say they are making significant progress toward network virtualization.
“Our latest study indicates that major mobile carriers around the world are on track with their 5G plans, and more expect to begin commercial build-outs in the coming months,” said Dave Murray, director of thought leadership with the BPI Network.
“While COVID-19 may result in some short-term delays for operators, the pandemic ultimately demonstrates a global need for higher speed, higher capacity 5G networks and the applications and use case they enable.”
Key findings
81% say industry progress toward 5G is moving rapidly, mostly in major markets, or is at least in line with expectations.
71% expect to begin 5G network build-outs within 18 months, including one-third who have already begun or will do so in 2020.
95% percent say virtualizing network functions is important to their 5G plans, and some three-quarters say their companies are either well on their way or making good progress toward virtualization.
99% view deployment of mobile edge clouds as an important aspect of 5G networks, with 65% saying they expect edge clouds on their 5G networks within 18 months.
“Mobile operators globally need to proactively prepare for the demands of a new virtualized and secure 5G world,” said Gunter Reiss, worldwide vice president of A10 Networks, a provider of secure application services for mobile operators worldwide.
“That means boosting security at key protection points like the mobile edge, deploying a cloud-native infrastructure, consolidating network functions, leveraging new CI/CD integrations and DevOps automation tools, and moving to an agile and hyperscale service-based architecture as much as possible.
“All of these improvements will pay dividends immediately with existing networks and move carriers closer to their ultimate goals for broader 5G adoption and the roll-out of new and innovative ultra-reliable low-latency use cases.”
Challenges: The security mandate
The industry’s top 5G challenges:
Heavy cost of build-outs (59%)
Security of network (57%)
Need for new technical skills (55%)
Lack of 5G enabled devices (42%)
Importance of security to 5G:
99% rate security as important to their 5G planning, higher than even network reach and coverage or network capacity and throughput
97% say increased traffic, connected devices and mission-critical use case significantly increase security and reliability concerns for 5G
93% say their security investments are already being affected (52%) or are under review (41%) due to 5G requirements
Top use cases expected to power 5G adoption
Next two years:
Ultra-high-speed connectivity (81%)
Industrial automation & smart manufacturing (62%)
Smart cities (54%)
Connected vehicles
Next 5 to 6 years:
Smart cities (62%)
Ultra-high-speed connectivity (59%)
Connected Vehicles (57%)
Industrial automation & smart manufacturing (42%)
“Mobile operators globally need to be proactively preparing for the demands of a new 5G world,” Reiss said.
Samsung Unveils New Security Chip for Mobile Devices
27.5.2020 Securityweek Mobil
Samsung on Tuesday unveiled a new security solution — composed of a secure element (SE) chip and security software — designed to enhance data protection on mobile devices.
Samsung has described it as a “standalone turnkey security solution” that provides protection for the booting process, isolated storage, mobile payments and other applications. The SE chip is named S3FV9RR and it’s Common Criteria Evaluation Assurance Level (CC EAL) 6+ certified, which Samsung says is the highest level for a mobile component.
The announcement comes after Samsung announced S3K250AF in February. That security chip was CC EAL 5+ certified.
According to Samsung, the latest security solution supports hardware-based root of trust (RoT), device authentication, and secure boot, which improve protection against attacks and malicious software updates.
The tech giant says the new solution’s security capabilities work independently from the ones of the device’s primary processor, which significantly enhances the security of mobile and Internet of Things (IoT) devices.
S3FV9RR is expected to become available in the third quarter of 2020.
“In this era of mobility and contact-less interactions, we expect our connected devices, such as smartphones or tablets, to be highly secure so as to protect personal data and enable fintech activities such as mobile banking, stock trading and cryptocurrency transactions,” said Dongho Shin, senior vice president of System LSI marketing at Samsung Electronics.
“With the new standalone security element solution (S3FV9RR), Samsung is mounting a powerful deadbolt on smart devices to safeguard private information,” Shin added.
Hangzhou could permanently adopt COVID-19 contact-tracing app
26.5.2020 Securityaffairs Mobil Privacy
The City of Hangzhou is planning to make a contact tracing system developed to fight the COVID-19 pandemic permanent for its citizens.
Hangzhou, one of the major tech hubs in China, is planning to permanently use the tracking system developed to fight the COVID-19 outbreak.
The city’s health commission declared that the permanent version of the contact tracing system would be a “‘firewall’ to enhance people’s health and immunity” after the COVID-19 pandemic.
The contact tracing app was developed by Tencent and Alibaba and is mandatory, it implements a “triage” system based on the travel history of the citizen.
The app is currently mandatory and assigns users green, yellow, or red status. Residents who visited COVID-19 hot spots or that were in contact with infected individuals, would be given a red code and be asked to quarantine for 14 days. Residents in good health status and had no contact with infected individuals cases are given a green code and could move without any restriction around the city.

The app is already used by one billion people and the codes it generates have been scanned more than nine billion times.
“According to Qiu Yuepeng, vice president of Tencent and President of Tencent Cloud, since the official version of the health code was launched on February 9, Tencent’s health code has covered more than 20 provinces and more than 400 cities and counties in the country, covering more than 1 billion people.” reads the post published by Tencent. “The total number of visits exceeded 26 billion, and the cumulative number of code visits exceeded 9 billion.”
The Hangzhou’s Health Commission aims to permanently use the system that would assign users a health score ranging from 0 to 100 based on different factors, such as their medical records, physical examinations, and habits (e.g. steps they walk, or hours they sleep or make sport daily).
Clearly privacy advocates fear that the contact tracing system could improve the dragnet surveillance implemented by the Chinese government to monitor its citizens.
Facial recognition technology is widely adopted in China where the government already uses the social credit system to monitor citizen’s online behaviour and assigns a “citizen score.”
70 Percent of Mobile, Desktop Apps Contain Open-Source Bugs
26.5.2020 Threatpost Mobil
A lack of awareness about where and how open-source libraries are being used is problematic, researchers say.
A full 70 percent of applications being used today have at least one security flaw stemming from the use of an open-source library.
According to Veracode’s annual State of Software Security report, these open-source libraries – free, centralized code repositories that provide ready-made application “building blocks” for developers – are not only ubiquitous but also risky.
The analysis examined 351,000 external libraries in 85,000 applications, and found that open-source libraries are extremely, extremely common. For instance, most JavaScript applications contain hundreds of open-source libraries – some have more than 1,000 different libraries. In addition, most languages feature the same set of core libraries.
“JavaScript and PHP in particular have several core libraries that are in just about every application,” according to the report.
These libraries, like other software, have bugs. The issue is that thanks to code re-use, a single bug can affect hundreds of applications.
“Prominent in almost every application today, open-source libraries allow developers to move faster by quickly adding basic functionality,” according to Veracode. “In fact, it would be nearly impossible to innovate with software without these libraries. However, lack of awareness about where and how open source libraries are being used and their risk factors is a problematic practice.”
Four main libraries represent the majority of the open-source bugs found in applications: Swift, .NET, Go and PHP.
Swift has specialized use in the Apple ecosystem, and has the highest density of flaws, according to Veracode. However, it also has an overall low percentage of flawed libraries in terms of volume.
.NET meanwhile has the lowest percentage of flawed libraries out of the four, and on a population that is more than 17 times larger than Swift.
Go has a high percentage of libraries with flaws, but an overall low number of flaws per individual library. And PHP has a higher rate of flawed libraries than Go – but more double the density of flaws in a given library.
The firm also found that cross-site scripting (XSS) is the most common vulnerability category found in open-source libraries – present in 30 percent of them. This is followed by insecure deserialization (23.5 percent) and broken access control (20.3 percent).
“We found insecure deserialization was a relatively rare flaw among in-house applications (ranking eighth out of 10),” according to the report. “Having such a high ranking when looking at libraries is troubling as this category of flaws can result in unexpected code paths being executed, which means that portions of libraries that we are not even intending to use may be inserted into the execution path of their hosting applications through use of this flaw.”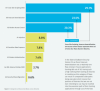
Percentage of bug types found stemming from open-source. Click to enlarge.
The data also showed that most flawed libraries end up in code indirectly – thanks to cascading interdependencies. Developers might use one library – but unbeknownst to them, the library that they’re using has pulled in code from an entirely different open-source library to underpin it.
“Forty-seven percent of the flawed libraries in applications are transitive – in other words, they are not pulled in directly by developers, but are being pulled in by the first library (42 percent are pulled in directly, 12 percent are both). This means that developers are introducing much more code, and often flawed code, than they might be anticipating.”
The good news is that addressing security flaws in these libraries is not a huge lift.
“Most library-introduced flaws (nearly 75 percent) in applications can be addressed with only a minor version update; major library upgrades are not usually required,” according to the Veracode report. “This data point suggests that this problem is one of discovery and tracking, not huge refactoring of code.”
Signal PINs Allow Users to Recover Data When Switching Phones
22.5.2020 Securityweek Mobil
Encrypted messaging service Signal has announced the introduction of a new feature that allows users to recover their data if they switch to a new device.
Offering end-to-end encrypted conversations, Signal was built by default in such a manner that users’ information is always kept private and never sent to a server. What this means is that, if a user’s phone is lost or stolen, the data cannot be retrieved.
The new feature, Signal PINs, is based on Secure Value Recovery, which the company introduced in December, and is meant to help users import data such as profile, settings, and blocked users when switching to a new device.
Signal has been working on adding new features recently, such as the ability to chat with contacts that aren’t saved in an address book, and some of the data might be lost forever.
With the introduction of PINs, Signal wants to change that, to help users transfer some data to a new device if needed, and to facilitate new addressing that isn’t based on phone numbers (users will no longer rely solely on the address book to maintain a network of contacts).
The Signal PINs will be at least 4 digits, with longer PINs and alphanumeric codes also supported.
“Because Signal doesn’t have access to your keys – or your data – your PIN isn’t recoverable if you forget it, so our apps help you remember your PIN with periodic reminders. Don’t worry, these reminders get less frequent over time,” Signal says.
This week, Signal also addressed a vulnerability in its service, which could have allowed attackers to identify a user’s DNS server by ringing their Signal number.
Tracked as CVE-2020–5753, the issue exists because WebRTC is doing DNS requests, and does not reside in the Signal code itself, meaning that other messaging applications might be impacted as well, Tenable security researcher David Wells, who discovered the bug, explains.
What he discovered was that, although Signal does not share users’ IP addresses, WebRTC’s use of “signaling” to identify a valid connection path for communication between peers could be abused to force a DNS lookup when the target’s phone is ringed, before the Signal user answers the call.
The vulnerability was addressed with the release of version 4.59.11 of Signal Messenger for Android, and version 3.8.4 of Signal for iOS.
Signal fixes location-revealing flaw, introduces Signal PINs
22.5.2020 Net-security Mobil
Signal has fixed a vulnerability affecting its popular eponymous secure communications app that allowed bad actors to discover and track a user’s location.
The non profit organization has also announced on Tuesday a new mechanism – Signal PINs – that will, eventually, allow users not to use their phone number as their user ID.
About the vulnerability
The vulnerability, discovered by Tenable researcher David Wells, stems from the fact that the WebRTC fork used by Signal for voice and video communication must discover a valid connection path for the local (the calling party) and remote peer (the called party) to communicate.
While doing that, it makes a DNS request and reveals the DNS server the phone automatically connects to.
While the DNS server information cannot tell the caller where exactly the callee is located as it offers just coarse location data, according to Wells, “in instances such as Google Public DNS (8.8.8.8/8.8.4.4) and others, this attack can narrow the location down to the Signal user’s city due to usage of EDNS Client Subnet.”
Most importantly, the information can be gleaned even if the called party does not answer the call, meaning that the called party can’t prevent a threat actor from placing the call, hanging up before they answer, and collect the DNS server info.
Doing so many times during the day and for weeks would allow the threat actor to build a profile of frequent DNS servers the app uses as the called party moves from home, to work, to a coffee shop, and so on.
While this may not be a problem for average users, one can see how certain users like journalists, activists, dissidents, or even victims of stalkers could be affected by malicious actors being able to know, at any time, their general location.
Luckily, Signal has already pushed out updated versions of Signal for Android (v4.59.11) and iOS (3.8.4) that fix the problem, so users can update their apps immediately.
If updating is impossible, Wells advises using a mobile VPN app that tunnels DNS traffic.
About Signal PINs
By setting up and using a Signal PIN, users will be able to save (backup) important data (e.g., profile, account settings, contacts, block list) that they might lose if their phones get lost, stolen or destroyed. This will also allow users to easily migrate their Signal data when they switch phones.
The data will be encrypted and saved on Signal’s servers, but won’t be accessible to Signal because they don’t know the users’ PIN.
It’s also important to point out that the saved data does not include Signal conversations.
Signal PINs can also serve as an optional “registration lock” – an additional protection against Signal account hijacking.
Finally, as this mechanism “will also help facilitate new features like addressing that isn’t based exclusively on phone numbers, since the system address book will no longer be a viable way to maintain your network of contacts.”
Users can change their PIN and switch on the Registration Lock through the app’s privacy settings. More information about Signal PINs can be found here.
Security and the rapidly growing importance of mobile apps
18.5.2020 Net-security Mobil
Organizations are under more pressure than ever before to rapidly produce both new apps and updates to existing apps, not only because it’s essentially the only way they can interact with their customers, but also because there will be a flood of new users who previously relied on physical locations to conduct their business. Continuous mobile development is now more critical than ever, and organizations must provide error-free, engaging user experiences.
In the rush to deliver intuitive apps that will capture customer attention and loyalty, it’s likely that security will take a backseat to features and functionality. According to the Verizon Mobile Security Index 2020, 43% of organizations said they knowingly cut corners on mobile security in 2019 to “get the job done.” And that was before the global pandemic.
Features trump security – until they don’t
It’s not hard to understand why developers would make this choice. Mobile users rarely look into security as a reason to use an app; features and functionality rule the roost. Plus, implementing security is time consuming and expensive. Getting first to market is a huge competitive advantage, so no one wants to delay their delivery schedules. Even worse, iOS and Android security specialists are scarce and in high demand. Development teams may lack the skills to secure their apps properly.
But developers will find that, eventually, skimping on security will come back to bite them. Features will always trump security – until they don’t. And with the pandemic causing a spike in usage, all these new users will likely shine a light on security flaws that cybercriminals and hackers will exploit.
For example, when Zoom rapidly became the de facto conferencing app for businesses and educational institutions around the world, the sudden crush of millions of new users exposed security flaws that had previously gone unnoticed and unaddressed. To their credit, Zoom acknowledged the problems and took quick action to address them, but their experience should serve as a warning for all organizations.
Security flaws can contribute to far more dire consequences. For example, there’s little doubt that Travelex, which bill itself as the world’s largest retail currency dealer, was seriously damaged by a ransomware attack on New Year’s Eve, which forced it to take down its website in at least 30 countries. The company is now reportedly preparing for bankruptcy and seeking a buyer.
Organizations cannot afford for consumers to doubt the security of a mobile app when that app is, in some cases, the only revenue generation engine they have left. Brands today no longer have the luxury of putting features above security.
Implementing app security in a fast-paced digital world
So, what should businesses do? If development teams opt to take on the task of security themselves, they should at the very least make sure they are addressing each of the OWASP Mobile Top Ten vulnerabilities. This will be a struggle for many organizations unless they have mobile security professionals embedded in their development teams, and as I mentioned earlier, mobile security professionals are in short supply.
Other development teams will look to integrate security software development kits (SDKs) into their apps that provide security. This is a much more efficient option than manually coding security into an app, but it’s still not a trivial exercise to manually integrate an SDK. Plus, it’s critical to vet the SDKs a team uses, as rogue and vulnerable SDKs are a serious problem in the mobile app industry.
For example, Tushu and Twoshu SDKs infected hundreds of apps on Google Play last year, enabling cyber criminals to mount mobile ad fraud schemes. Other SDKs introduced vulnerabilities, such as Adobe’s Mobile SDK. If organizations go this route, it’s a good idea to hire a security consultant to vet the security SDKs for potential flaws and to evaluate their ability to protect an app.
Finally, organizations are increasingly turning to security automation through artificial intelligence to harden and protect their apps. This option has the advantage of being very fast, as AI can implement security in minutes without needing source code at all, and it’s inexpensive when compared to manual coding.
As an additional benefit, automation always builds security in the same way, which provides brands with an auditable guarantee that the security posture was implemented according to the requirements of the organization, unlike manual implementations.
The pandemic and associated lockdown have accelerated the move toward mobile as the primary way customers interact with businesses, so time is of the essence. The winners in this new digital world will be the app makers and security providers who can quickly and reliably deliver apps that delight the customer while also remaining safe and trustworthy.