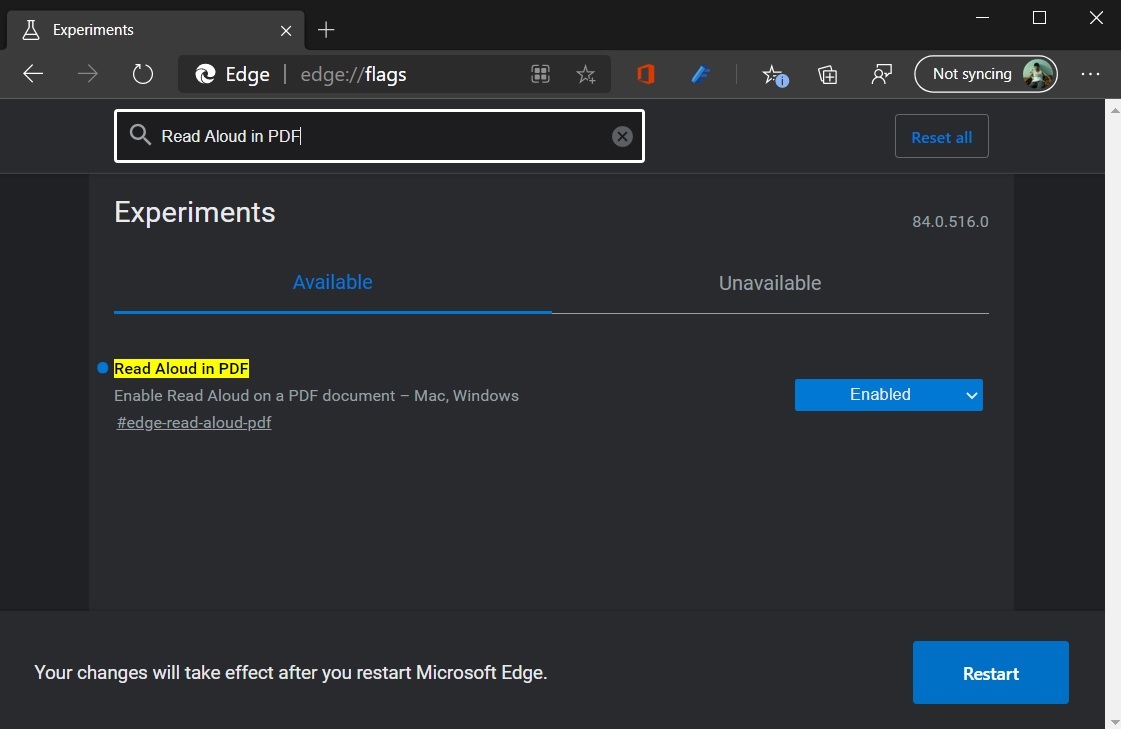
Search for Read Aloud in PDF in the flags menu.
OS Articles - H 2020 1 2 3 OS List - H 2021 2020 2019 2018 2017 2016 OS Blog OS Blog
Microsoft Edge Canary now lets you read aloud your PDF files
19.5.2020 Bleepingcomputer OS
Microsoft has been working on improvements for Chromium Edge's new cloud-powered Read Aloud feature, which was announced last year.
In latest Edge Canary, the company has finally added support for Read Aloud feature in PDFs.
If you use Microsoft Edge Canary, you should be able to add support for Read Aloud feature to PDF files by following these steps:
Update Microsoft Edge and launch Edge://flags menu.
Search for Read Aloud in PDF in the flags menu.
Select "Enabled" to turn on the feature.
Relaunch Edge.
Once enabled, you can use Read Aloud to read the entire PDF or selected text.
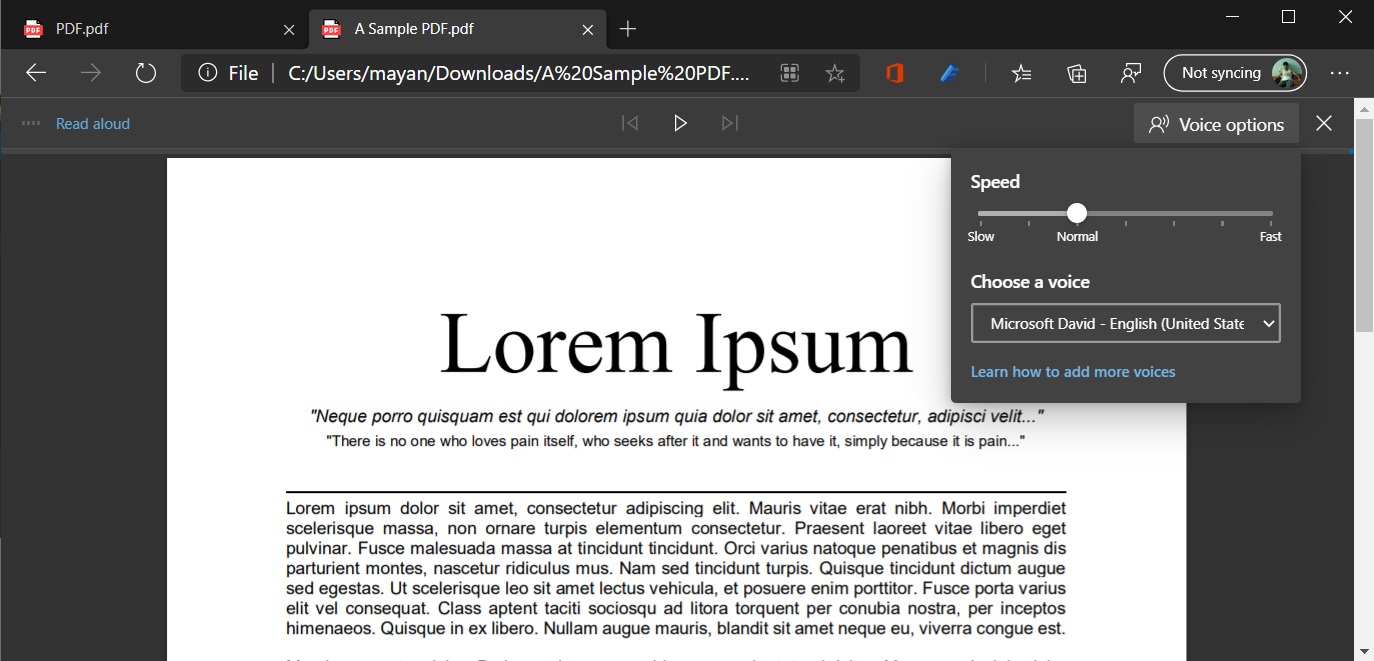
The cloud-powered voices are categorized into two styles:
Neural voices – Powered by deep neural networks, these voices are the most natural sounding voices.
Standard voices – These voices are the standard online voices offered by Microsoft Cognitive Services. Voices with “24kbps” in their title will sound clearer compared to other standard voices due to their improved audio bitrate.
The feature is currently available in Microsoft Edge Canary 84 and it could be released to everyone with Edge 84 update later this year.
What's new in Windows Subsystem for Linux 2.0, coming soon
19.5.2020 Bleepingcomputer OS
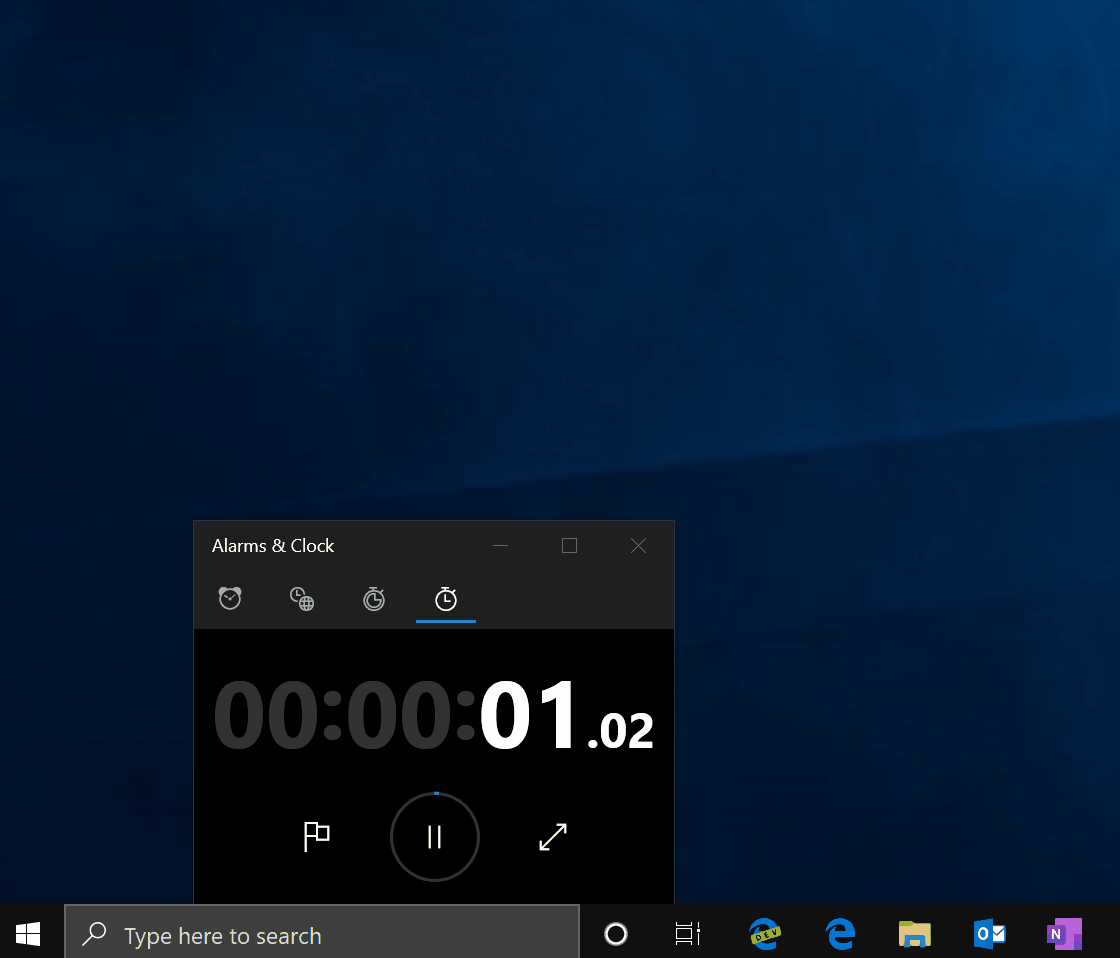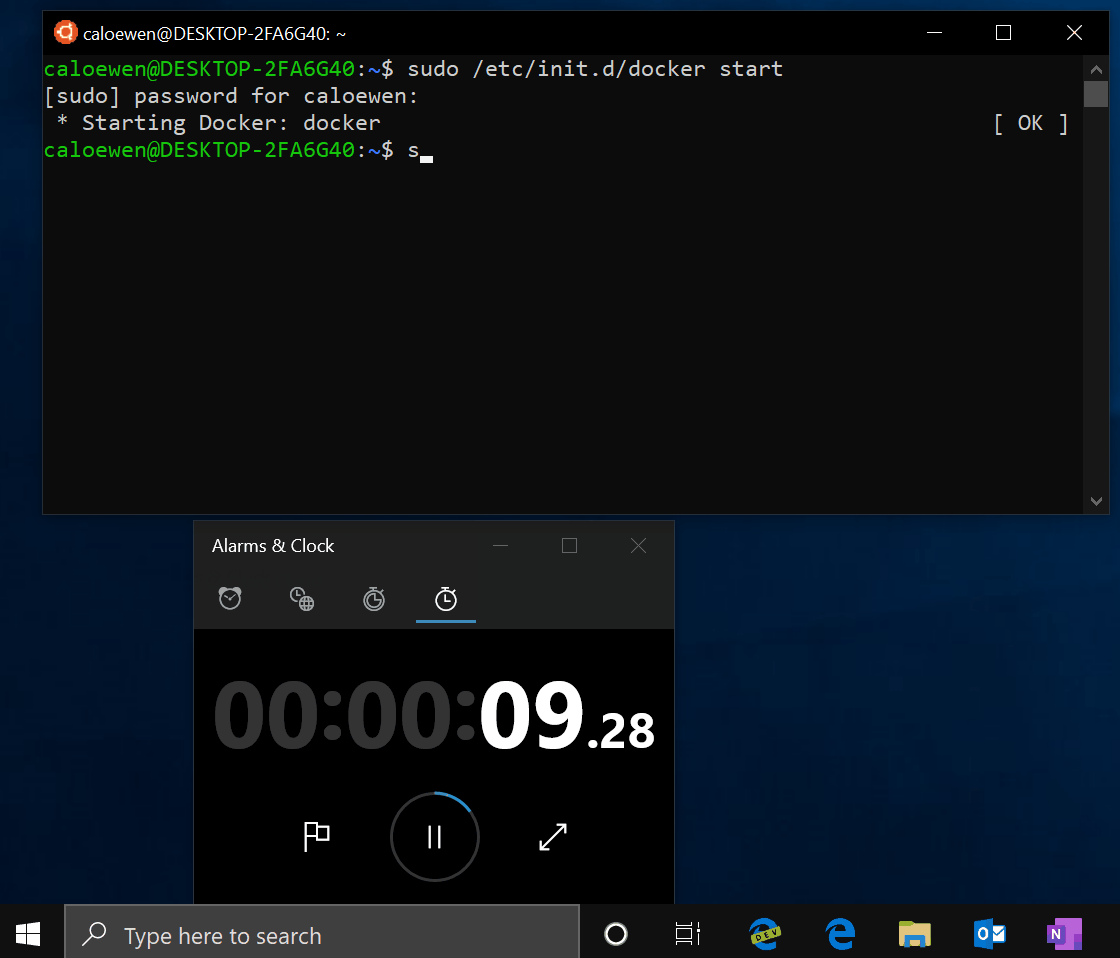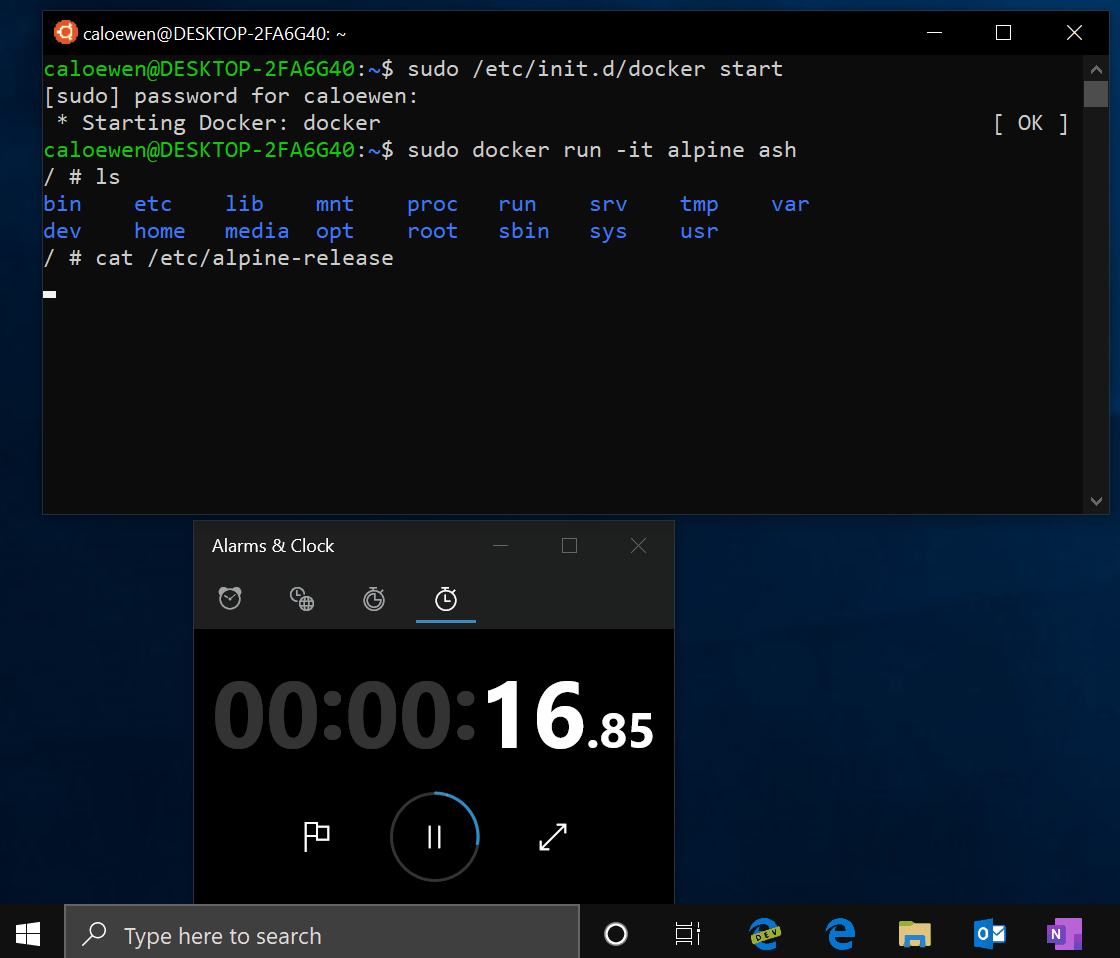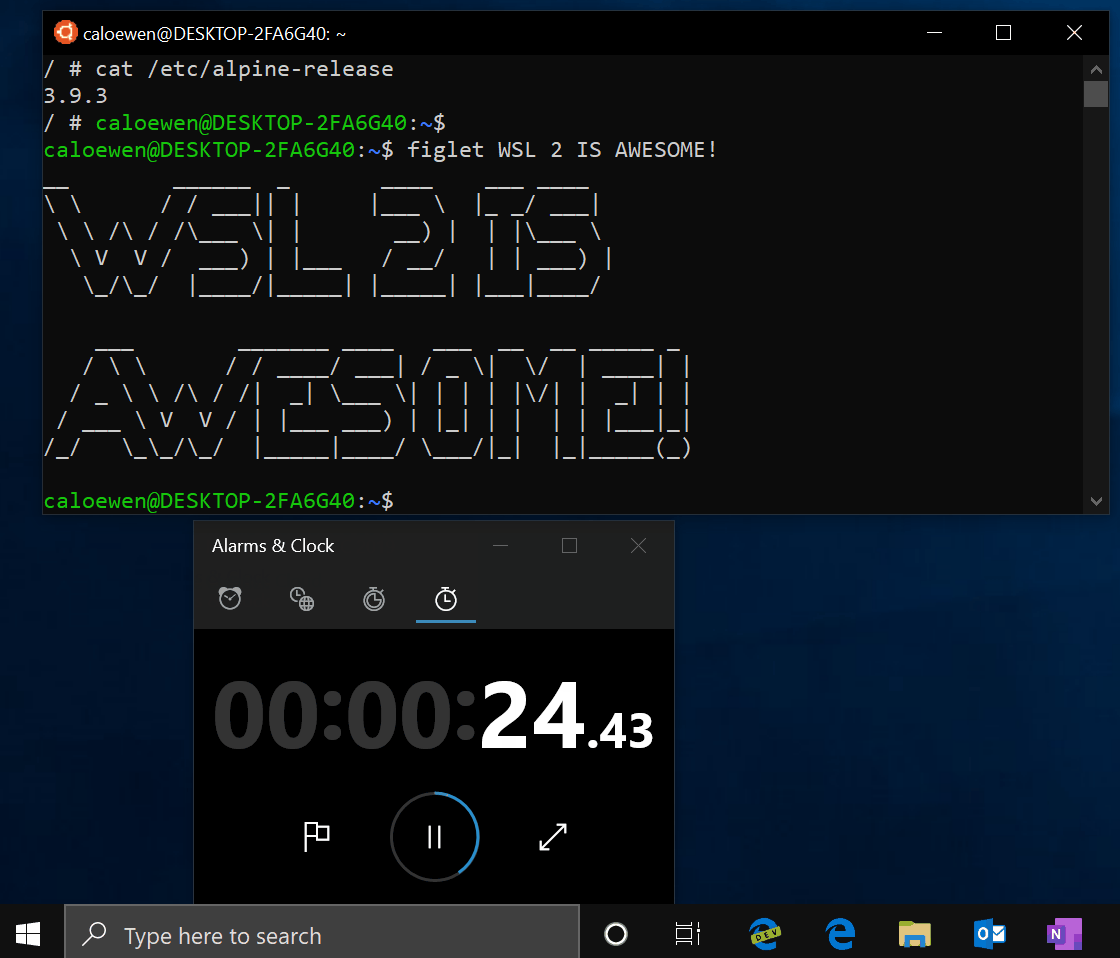
Windows Subsystem for Linux 2 (WSL2) is being released soon with the May 2020 Update (Windows 10 2004) and comes with new features and performance improvements.
The Windows Subsystem for Linux feature allows you to install and run Linux distributions within Windows 10.
WSL version 1 (WSL1), though, used a Linux-compatible kernel that translates Linux system calls so they could communicate and work with the Windows NT kernel. This decreased the performance and made it difficult, if not impossible, to run certain Linux applications.
In Windows 10 version 2004, Microsoft has been testing new features for Windows Subsystem for Linux, which uses in-house built Linux kernel and full system call compatibility to run more Linux apps.
Under-the-hood changes
According to Microsoft, WSL 2 includes a new architecture that changes how these Linux binaries interact with Windows and hardware. The updated WSL will still provide the same user experience as WSL 1.
Real Linux kernel
Windows 10 version 2004 introduces a real Linux kernel for Windows Subsystem for Linux that will make full system call compatibility possible.
This would be the first time a Linux kernel is shipped with Windows. The kernel is based on the source available at kernel.org and it has been specially tuned for WSL 2 with optimized size and performance.
Microsoft says it will update Linux kernel through Windows Updates, which means you don't have to manually download software or tool to patch Linux kernel with security fixes.
Microsoft says that WSL 2 uses virtualization technology to run the Linux kernel within a lightweight utility virtual machine, but it won't be a traditional VM experience with limited resources and reduced integration.
WSL 2 does not have traditional virtual machine limitations such as reduced performance and limited resources.
The new virtualization technology also promises better Windows and Linux integration, fast boot times, and it won't require VM configuration or management from your end.
WSL 2 is faster than WSL 1
In WSL 2, you will notice that file intensive operations like git clone, npm install, apt update, apt upgrade, and more would be "noticeably faster".
Microsoft claimed that WSL 2 is up to 20x faster compared to WSL 1 when unpacking a zipped tarball. Likewise, it is around 2-5x faster when using git clone, npm install and cmake.
In version 2004 of Windows 10, Linux binaries use system calls execute functions such as accessing files, requesting memory, creating processes, etc.
With its own Linux kernel support, WSL 2 has access to full system call compatibility and it offers a whole new set of apps that you can run inside the container.
These improvements make WSL 2 much more powerful for you to run Linux apps.
Other improvements
WSL also comes with a long set of other improvements and bug fixes. Here's a list of all changes and fixes in the new WSL update:
Fix issue with handling of some Unicode characters
Fix rare cases where distros could be unregistered if launched immediately after a build-to-build upgrade.
Fix minor issue with wsl.exe --shutdown where instance idle timers were not cancelled.
Improve memory performance of WSL utility VM. Memory that is no longer in use will be freed back to the host.
Fix input relay to handle cases where stdin is a pipe handle that is not closed [GH 4424]
Make the check for \\wsl$ case-insensitive.
Use cache=mmap as the default for 9p mounts to fix dotnet apps
Fixes for localhost relay [GH 4340]
Introduce a cross-distro shared tmpfs mount for sharing state between distros
Fix restoring persistent network drive for \\wsl$
Update Linux kernel to 4.19.81
Change the default permission of /dev/net/tun to 0666 [GH 4629]
Tweak default amount of memory assigned to Linux VM to be 80% of host memory
Fix interop server to handle requests with a timeout so bad callers cannot hang the server
Clear the signal mask before launching the processes
Handle creation of /etc/resolv.conf symlink when the symlink is non-relative
Use a memory cgroup to limit the amount of memory used by install and conversion operations [GH 4669]
Make wsl.exe present when the Windows Subsystem for Linux optional component is not enabled to improve feature discoverability.
Change wsl.exe to print help text if the WSL optional component is not installed
Fix race condition when creating instances
Create wslclient.dll that contains all command line functionality
Prevent crash during LxssManagerUser service stop
Fix wslapi.dll fast fail when distroName parameter is NULL
Windows 10 quietly got a built-in network sniffer, how to use
19.5.2020 Bleepingcomputer OS
Microsoft has quietly added a built-in network packet sniffer to the Windows 10 October 2018 Update, and it has gone unnoticed since its release.
A packet sniffer, or network sniffer, is a program that monitors the network activity flowing over a computer down to an individual packet level.
This can be used by network administrators to diagnose networking issues, see what types of programs are being used on a network, or even listen in on network conversations sent via clear text.
While Linux users always had the tcpdump tool to perform network sniffing, Windows users have had to install third-party programs such as the Microsoft Network Monitor and Wireshark.
This all changed when Microsoft released the October 2018 Update as now Windows 10 comes with a new "Packet Monitor" program called pktmon.exe.
Built-in packet sniffer comes to Windows 10
With the release of the Windows 10 October 2018 Update, Microsoft quietly added a new network diagnostic and packet monitoring program called C:\Windows\system32\pktmon.exe.
This program has a description of "Monitor internal packet propagation and packet drop reports", which indicates it is designed for diagnosing network problems.
Similar to the Windows 'netsh trace' command, it can be used to perform full packet inspection of data being sent over the computer.
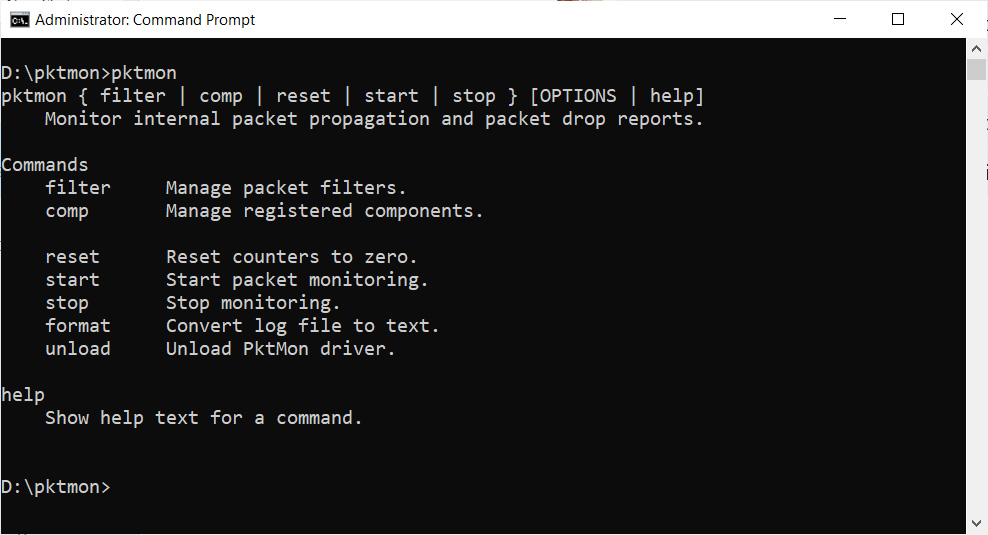
Pktmon Help
This program has no mention on Microsoft's site that we could find, and we had to learn how to use it by playing with the program.
Thankfully it includes a fairly extensive help system that can be used by typing 'pktmon [command] help'.
For example, pktmon filter help, will give you the help screen for the filter command.
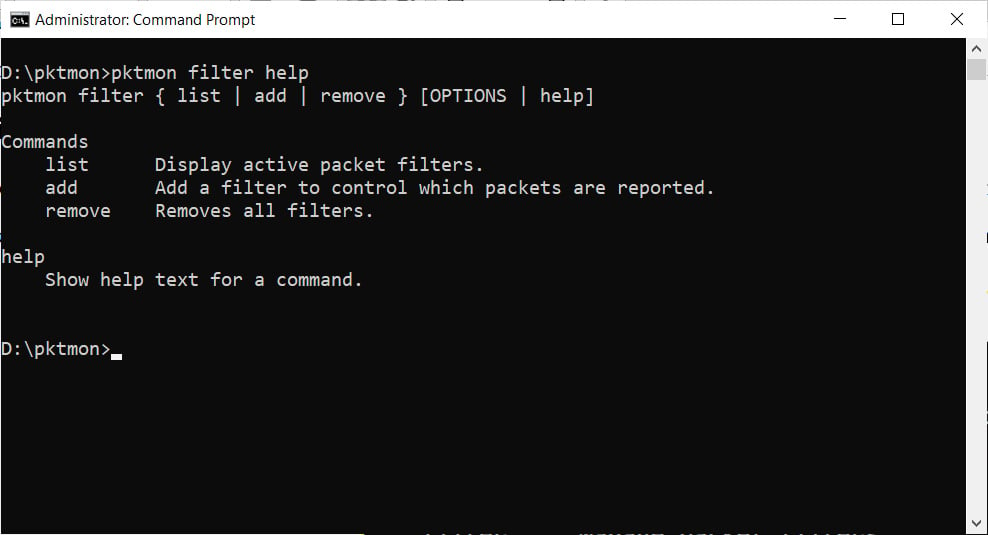
Filter command help screen
To learn how to use Pktmon, I strongly suggest you read through the help documentation and play around with the program. We have also provided an example in the next section to help you get started.
Using Pktmon to monitor network traffic
Unfortunately, diving into the full feature set of Pktmon is outside of the scope of this article, but we wanted to show you a basic example of how you can use the tool.
For our example, we will use Pktmon to monitor FTP traffic from the computer it is run on.
To do this, we first need to launch a Windows 10 elevated command prompt as Pktmon requires administrator privileges.
We then need to create two packet filters that tell Pktmon what traffic to monitor, which in our example will be the traffic on TCP ports 20 and 21.
These filters can be created by using the pktmon filter add -p [port] command for each port we want to monitor.
pktmon filter add -p 20
pktmon filter add -p 21
You can then use the pktmon filter list command to see the packet filters we just created.
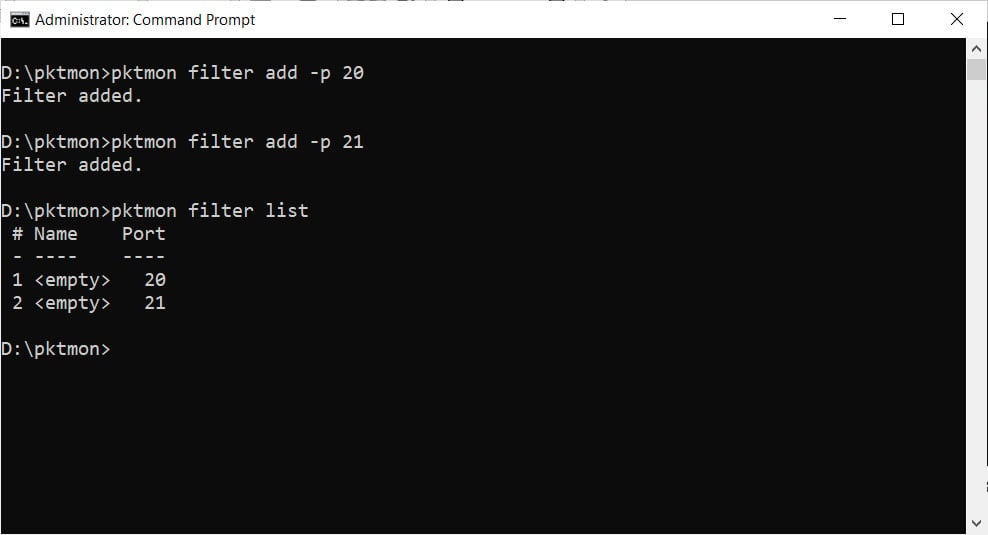
Configured packet filters
To start monitoring for packets communicating with TCP ports 20 and 21, we need to use the pktmon start --etw command.
Once executed, pktmon will log all packets on ALL network interfaces on the device to a file called PktMon.etl and only record the first 128 bytes of a packet.
To make it log the entire packet and only from a specific ethernet device, you can use the -p 0 (capture entire packet) and -c 13 (capture only from the adapter with ID 13) arguments.
To determine what ID your adapters are, you can run the command pktmon comp list command
When we combine all the arguments, we get a final command of:
pktmon start --etw -p 0 -c 13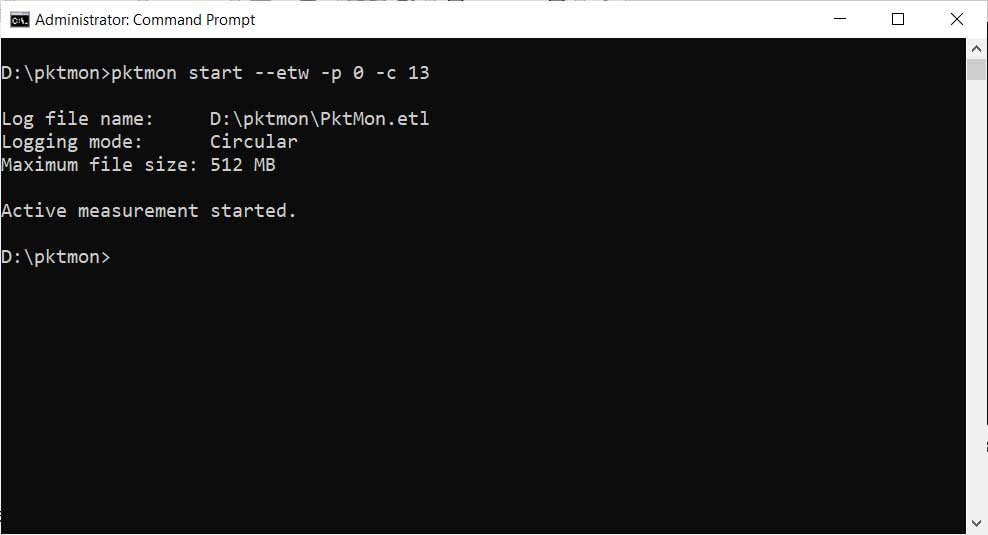
Capturing packets
Pktmon will now quietly run while capturing all packets that match our inputted filters.
To stop capturing packets, enter the pktmon stop command, and a log file called PktMon.etl will have been created in the same folder that contains the raw captured data.
This data in this file is not directly usable, so you need to convert it to a human-readable text format with the following command:
pktmon format PktMon.etl -o ftp.txt
Even converted into text, it is not going to give you the full packets, but only a summary of the network traffic as shown below.
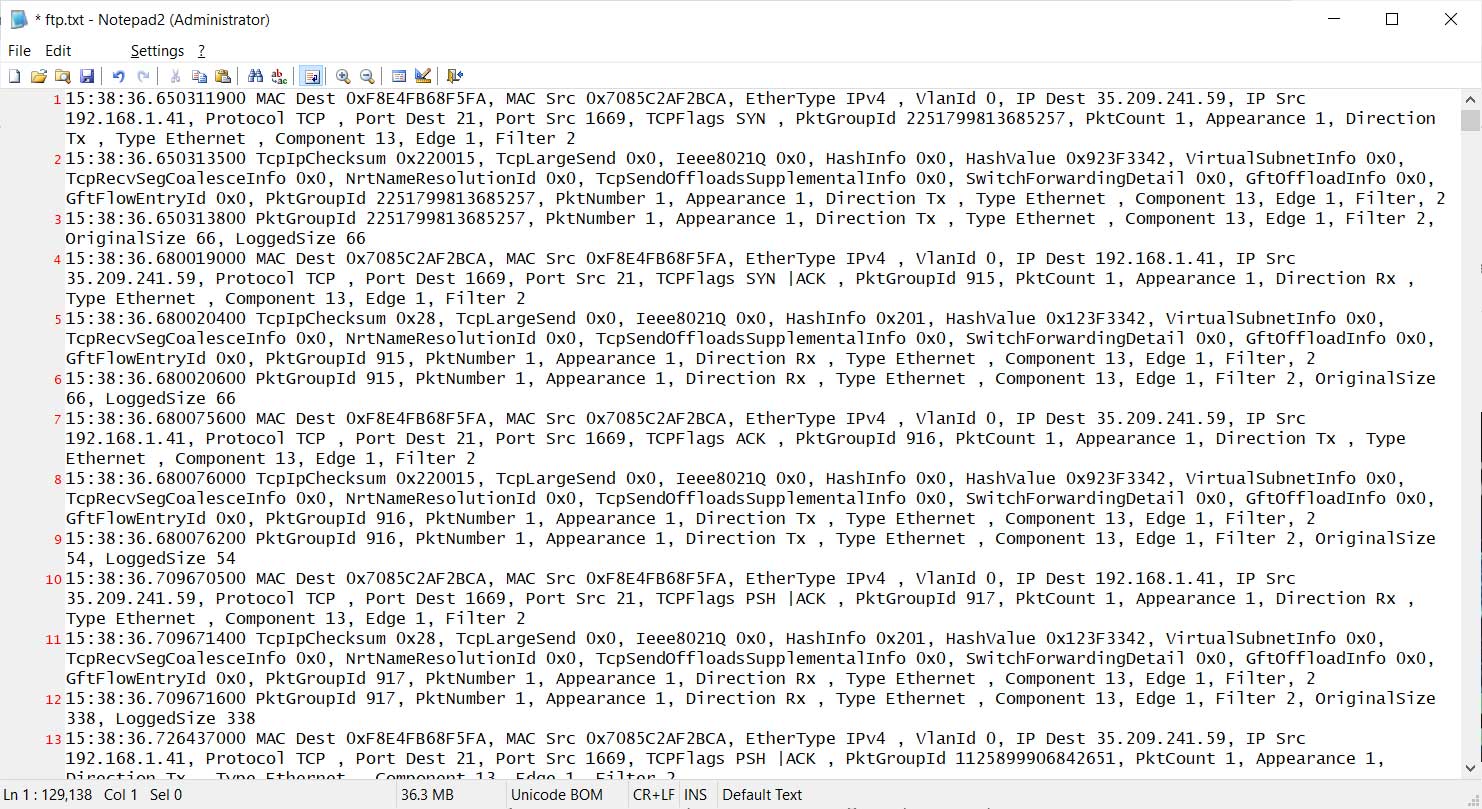
Converted into a text format
To benefit from the captured data, I suggest you download and install the Microsoft Network Monitor and use it to view the ETL file.
Using Network Monitor, you can see the full packet that was sent, including any clear-text information.
For example, below you can see a packet containing the clear-text password we entered when logging into this FTP test site.
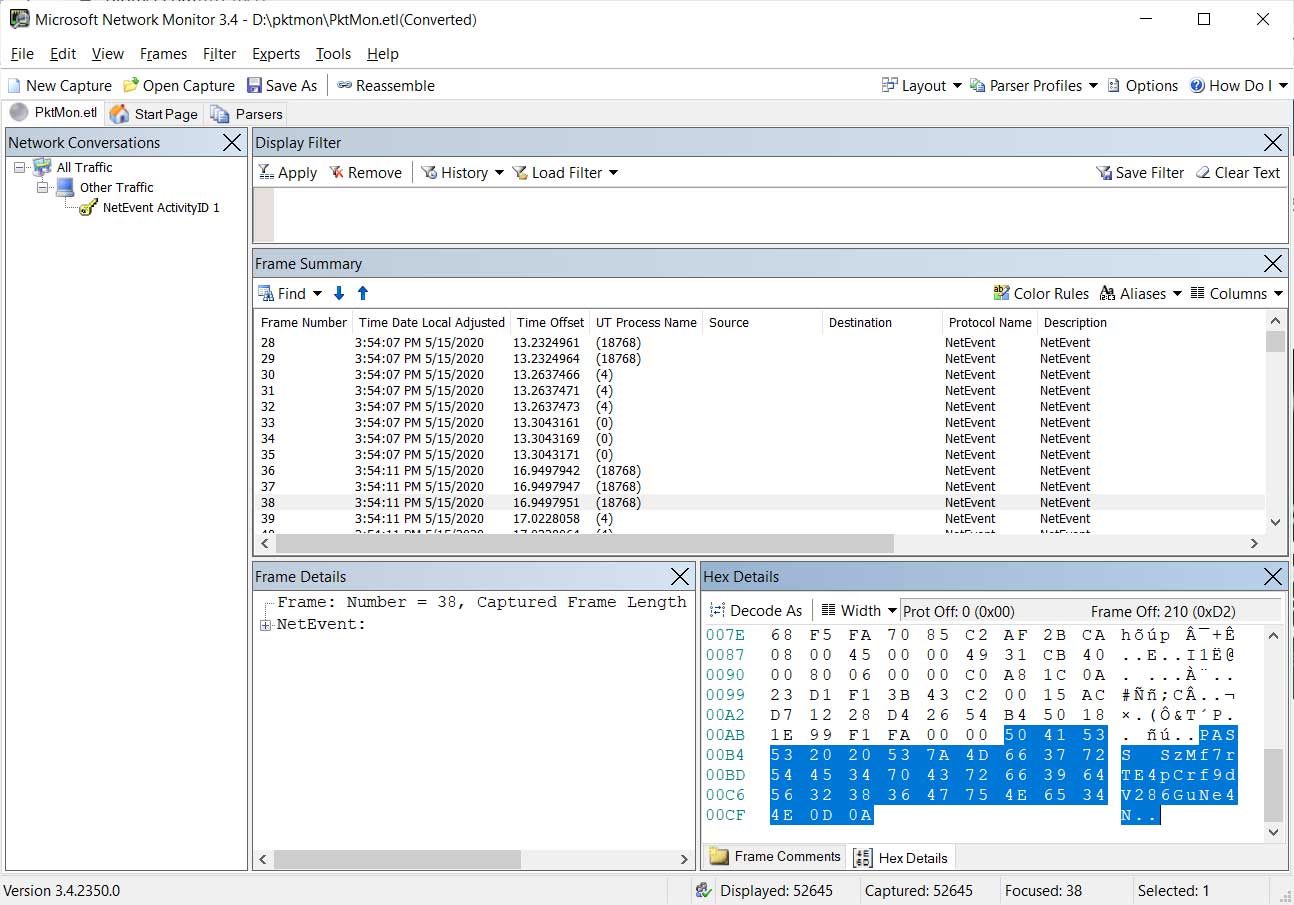
Network monitor showing clear-text FTP password
When done using the Pktmon program, you can remove all created filters using the command:
pktmon filter remove
Real-time monitoring and pcapng support coming soon
With the upcoming release of the Windows 10 May 2020 Update (Windows 10 2004), Microsoft has updated the Pktmon tool to allow you to display monitored packets in real-time and to convert ETL files to the PCAPNG format.
In the version of Pktmon coming in the next feature update, you can enable real-time monitoring using the -l real-time argument.
This will cause the captured packets to be displayed directly to the screen while also saving it to the ETL file.
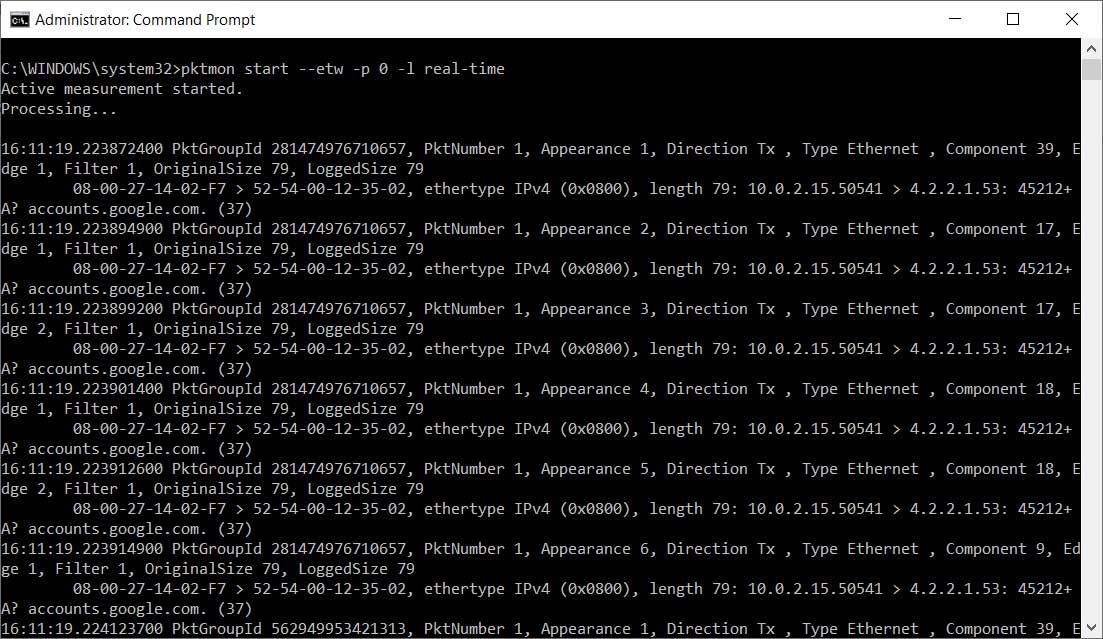
Real-time monitoring of DNS packets
Microsoft is also adding the ability to convert ETL files to the PCAPNG format so that they can be used in programs like Wireshark.
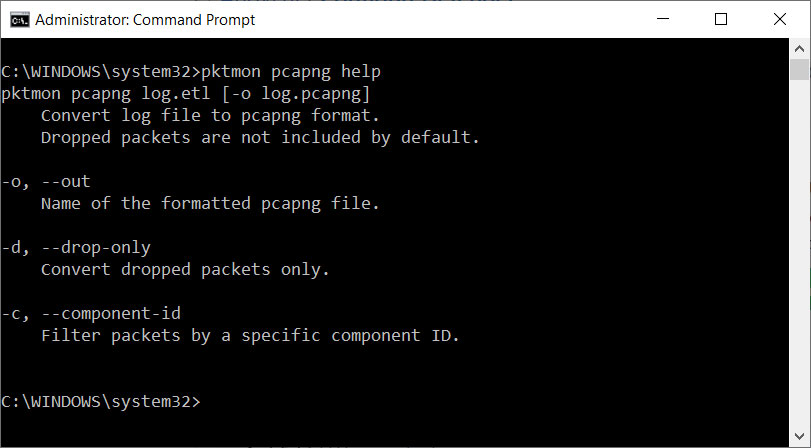
Convert ETL files into PCAPNG format
Once the file has been converted into the PCAPNG format, they can be opened into Wireshark so you can view the network communication better.
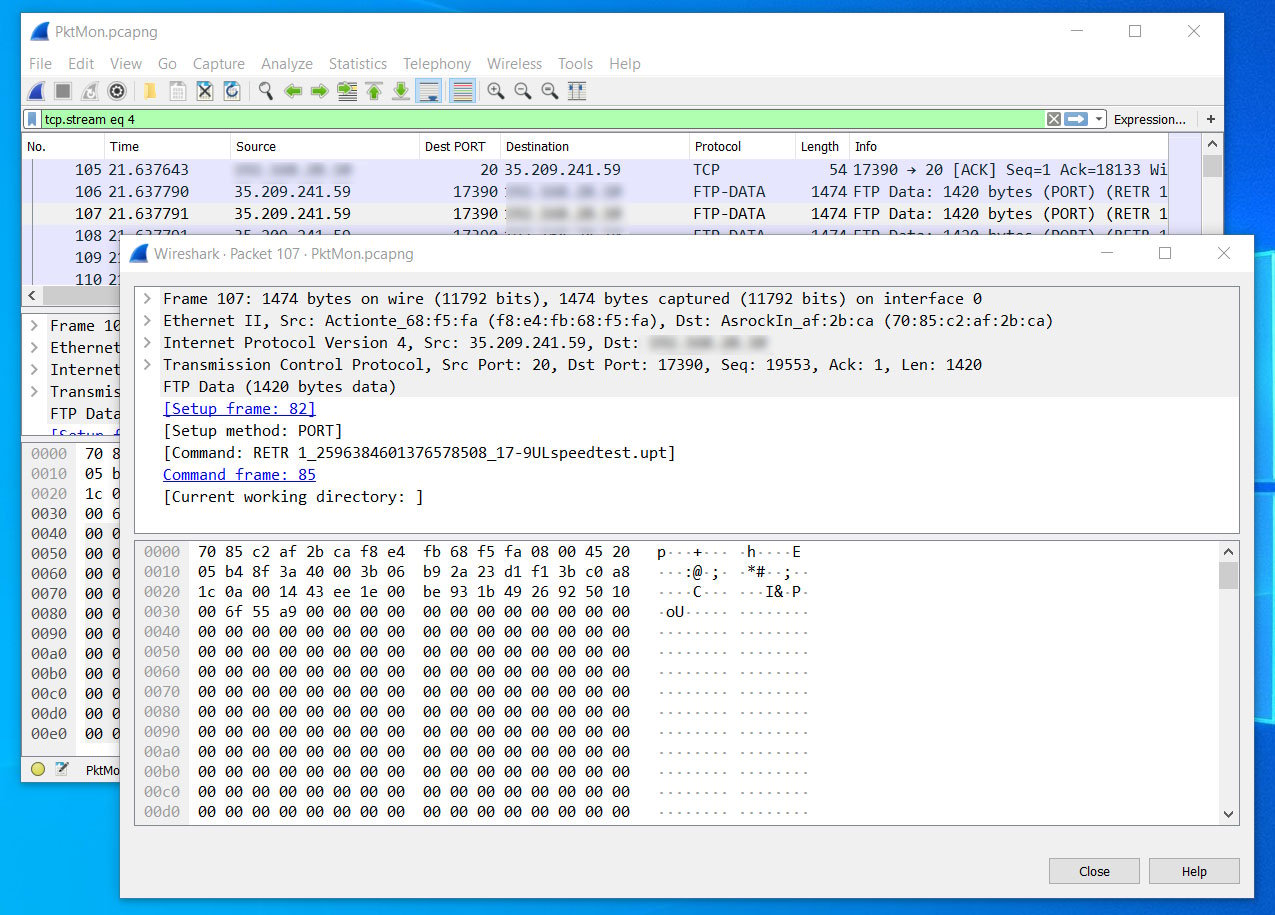
Viewing traffic in Wireshark
Once again, these features are not available in Windows 10 1903/1909, and will be coming to Windows 10 2004 when it's released at the end of the month.
Update 5/16/20: Added other new features coming with Windows 10 2004
RIP: Microsoft to drop support for Windows 10 on 32-bit systems
17.5.2020 Bleepingcomputer OS
Microsoft has stated that future versions of Windows 10, starting with the May 2020 Update, will no longer be available as 32-bit builds on new OEM computers.
An update to the Windows 10 Minimum hardware requirements document, Microsoft states that starting with Windows 10 2004, new OEM computers will be required to use 64-bit builds of the operating system.
"Beginning with Windows 10, version 2004, all new Windows 10 systems will be required to use 64-bit builds and Microsoft will no longer release 32-bit builds for OEM distribution. This does not impact 32-bit customer systems that are manufactured with earlier versions of Windows 10; Microsoft remains committed to providing feature and security updates on these devices, including continued 32-bit media availability in non-OEM channels to support various upgrade installation scenarios."
This change does not mean that Microsoft is no longer supporting 32-bit builds, as they will continue to do so in a limited manner.
Microsoft states that they will are still committed to supporting users running older hardware and will continue to make 32-bit media available in non-OEM channels.
Furthermore, Microsoft will continue to offer feature updates and security updates for versions of Windows running on 32-bit hardware.
Few still use Windows 10 32-bit
Microsoft does not offer statistics on the number of devices continuing to use Windows 10 32-bit, but the Steam Hardware & Software Survey: April 2020 shows that it is in limited use.
According to Steam's hardware survey, only 0.20% use Windows 10 32-bit while 86.08% use Windows 10 64-bit.
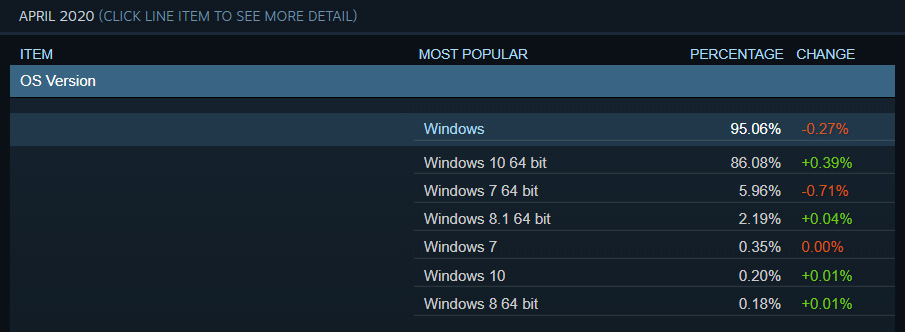
While Steam's statistics focus on gamers who are likely running on newer equipment, it does give us an indication that the amount of people continuing to use Windows 32-bit is small.
With few users using continuing to use Windows 10 32-bit and almost all new equipment having 64-bit support, this change eliminates a whole range of potential issues and development conflicts that may arise by supporting both architectures.
This change by Microsoft, though, is essentially killing off 32-bit Windows as older versions reach end of support, and new versions are released.
Windows 10 gets DNS over HTTPS support, how to test
17.5.2020 Bleepingcomputer OS
Microsoft announced that initial support for DNS over HTTPS (DoH) is now available in Windows 10 Insider Preview Build 19628 for Windows Insiders in the Fast ring.
The DoH protocol addition in a future Windows 10 release was advertised by Redmond in November 2018, with the inclusion of DNS over TLS (DoT) to also stay on the table.
DoH enables DNS resolution over encrypted HTTPS connections, while DoT is designed to encrypt DNS queries via the Transport Layer Security (TLS) protocol, instead of using clear text DNS lookups.
Thorugh the inclusion of DoH support to the Windows 10 Core Networking, Microsoft boosts its customers' security and privacy on the Internet by encrypting their DNS queries and automatically removing the plain-text domain names normally present in unsecured web traffic.
"If you haven’t been waiting for it, and are wondering what DoH is all about, then be aware this feature will change how your device connects to the Internet and is in an early testing stage so only proceed if you’re sure you’re ready," Microsoft explains.
How to test DoH right now
Although DoH support is included in the Windows 10 Insider Preview Build 19628 release, the feature is not enabled by default, and Insiders who want Windows to use encryption when making DNS queries will have to opt-in.
If you are a Windows Insider and you want to start testing DoH on your Windows 10 device right away, you will first have to make sure that you are in the Fast ring and that you are running Windows 10 Build 19628 or higher.
To activate the built-in DoH client, you will have to follow the following procedure:
• Open the Registry Editor
• Navigate to the HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Dnscache\Parameters registry key
• Create a new DWORD value named “EnableAutoDoh”
• Set its value to 2
Enable the DoH client
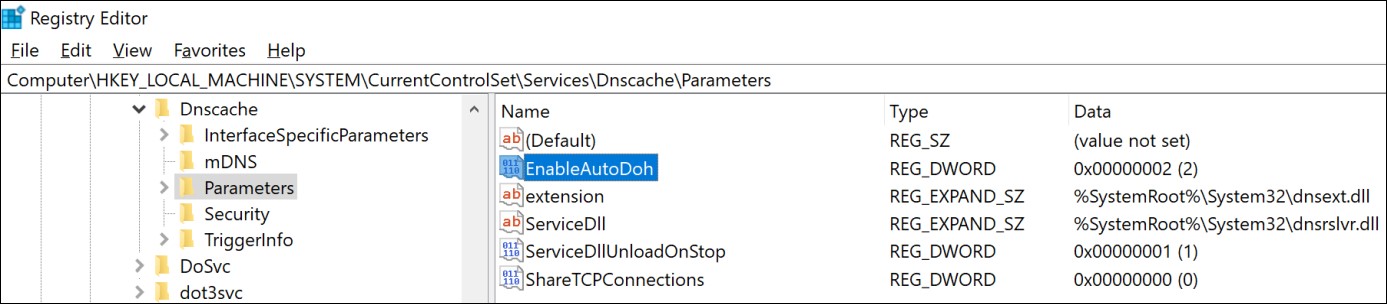
Adding the EnableAutoDoh reg key (Microsoft)
After you activate the Windows 10 DoH client, Windows will automatically start encrypting your DNS queries if you are using one of this DoH-enabled DNS servers:
Server Owner Server IP addresses
Cloudflare 1.1.1.1
1.0.0.1
2606:4700:4700::1111
2606:4700:4700::1001
Google 8.8.8.8
8.8.4.4
2001:4860:4860::8888
2001:4860:4860::8844
Quad9 9.9.9.9
149.112.112.112
2620:fe::fe
2620:fe::fe:9
"You can configure Windows to use any of these IP addresses as a DNS server through the Control Panel or the Settings app," Microsoft further explains.
"The next time the DNS service restarts, we’ll start using DoH to talk to these servers instead of classic DNS over port 53. The easiest way to trigger a DNS service restart is by rebooting the computer."
To add your own custom DNS servers using the Windows Control Panel, use the following steps:
• Go to Network and Internet -> Network and Sharing Center -> Change adapter settings.
• Right click on the connection you want to add a DNS server to and select Properties.
• Select either “Internet Protocol Version 4 (TCP/IPv4)” or “Internet Protocol Version 6 (TCP/IPv6)” and click Properties.
• Ensure the “Use the following DNS server addresses” radio button is selected and add the DNS server address into the fields below.
How to test if DoH is working
To check if the Windows DoH client is doing its job, you can use the PacketMon utility to check the traffic going out to the web over port 53 — once DoH is enabled, there should be little to no traffic.
To do that, open a Command Prompt or a PowerShell window and run the following commands to reset PacketMon network traffic filters, add a traffic filter for port 53 (the port used for unencrypted DNS queries), and to start real-time traffic logging:
pktmon filter remove
pktmon filter add -p 53
pktmon start --etw -l real-time
Microsoft also provides instructions on how to test the DoH client by manually adding DNS servers with DoH support that aren't in the default auto-promotion list.
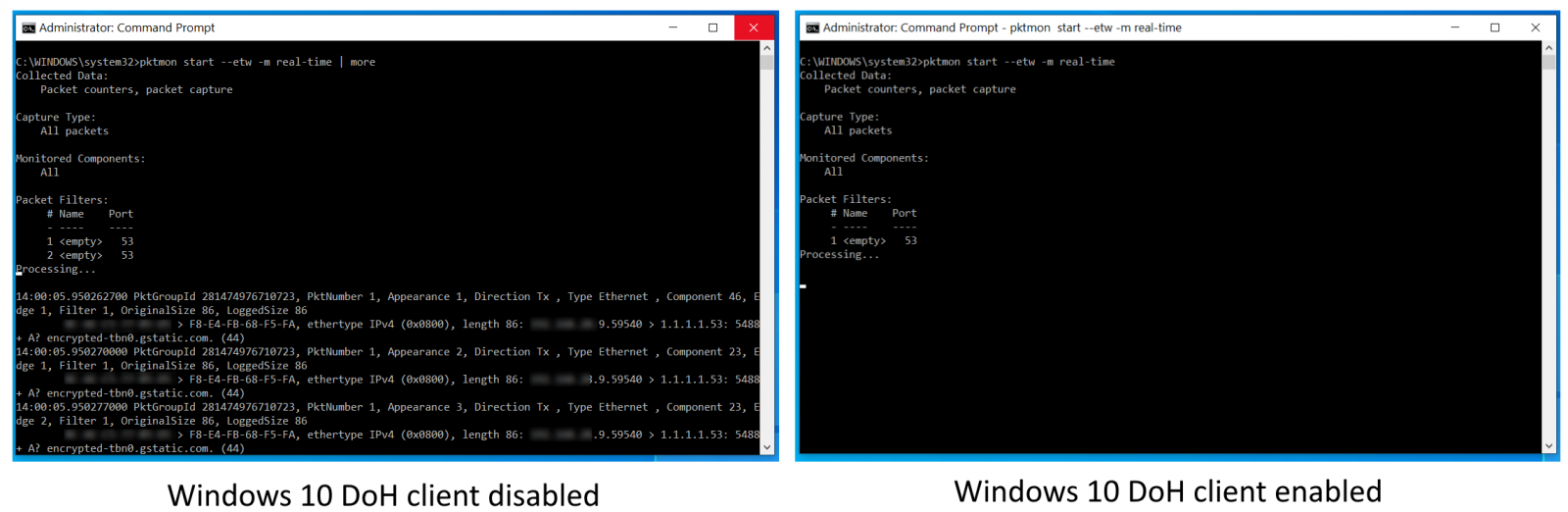
Monitoring Windows 10 plain text DNS traffic
DoH adoption, trials, and future plans
Mozilla already rolled out DNS-over-HTTPS by default to all US-based Firefox users starting February 25, 2020, by enabling Cloudflare's DNS provider and allowing users to switch to NextDNS or another custom provider from the browser's network options.
Google is also currently running a limited DoH trial on all platforms (besides Linux and iOS) starting with the release of Chrome 79.
However, unlike Mozilla, Google will not automatically change the DNS provider but, instead, they will only upgrade Chrome's DNS resolution protocol only when the default DNS provider has DoH support.
US government agencies' CIOs were also advised last month to disable third-party encrypted DNS services until an official federal DNS resolution service with DNS over HTTPS (DoH) and DNS over TLS (DoT) support is ready.
Windows 10 2004 improves potentially unwanted app protection
16.5.2020 Bleepingcomputer OS
In the soon to be released Windows 10 2004, otherwise known as the May 2020 Update, Microsoft is finally making it easy to detect potentially unwanted programs and tightly integrating it into the operating system.
Potentially unwanted applications, otherwise known as PUAs or PUPs, are programs that are not quite malware but pretty close to it.
While legal entities create these programs, they skirt the boundaries of respectable software, and in most cases, they are ultimately detrimental to users in some manner.
Previously had to be enabled via PowerShell
For years, Microsoft Defender has been able to detect and remove PUAs, but only after the feature was manually enabled via PowerShell or through Group Policies.
To enable PUA Protection, users would need to enter the following command in a PowerShell Administrator console:
Set-MpPreference -PUAProtection Enabled
To disable it, users can enter the command:
Set-MpPreference -PUAProtection Disabled
To see if the setting is enabled, you can use following command and check if the setting was set to 1, as illustrated in the image below.
Get-MpPreference | findstr PUAProtection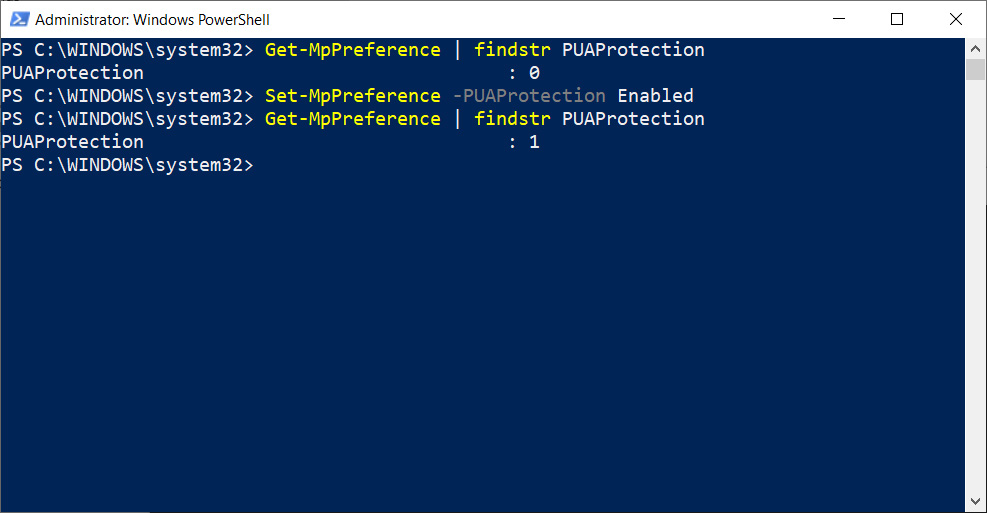
Checking status and enabling PUA Protection
May 2020 Update adds a new PUA setting
With the release of the May 2020 Update, Microsoft is adding a new settings section to Windows Security called 'Reputation-based protection'.
This new section combines all the detection settings that are based on the reputation of a particular web site, download, or application.
To access this section, Windows users need to click on Settings > Update & Security > Windows Security > App & browser control, and they will see a new section titled 'Reputation-based protection'.
If you wish to turn on all of the reputation-based protection at once, you can click on the 'Turn on' button.
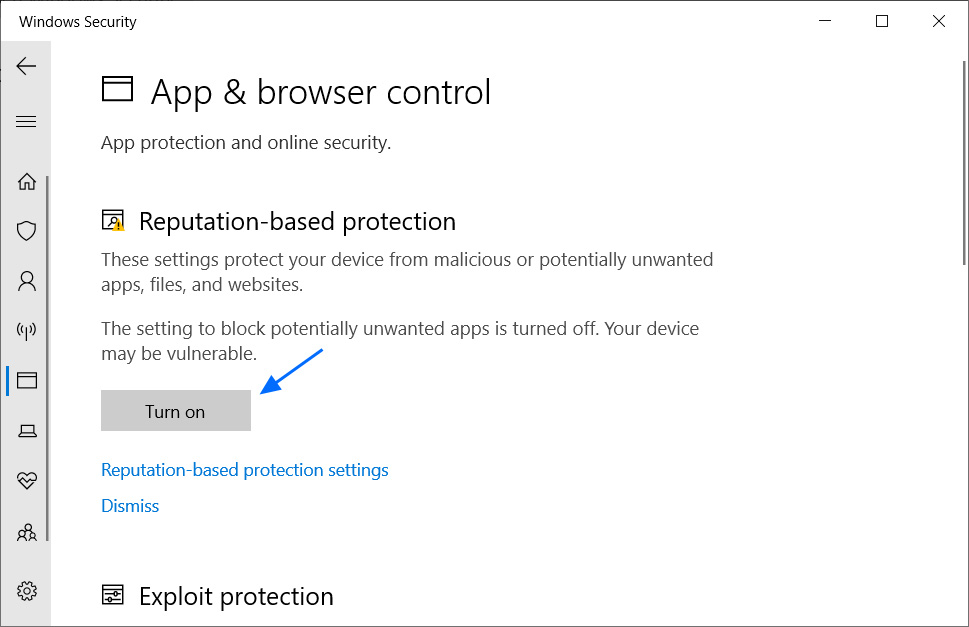
Reputation-based protection setting
For more granular controls, you can click on the 'Reputation-based protection settings' link, which brings you to a list of all of Windows 10's prior SmartScreen protections.
These settings include the 'Check apps and files', and 'SmartScreen for Microsoft Edge', and 'SmartScreen for Microsoft Store apps' settings.
With the release of the May 2020 Update, Microsoft has now added a 'Potentially unwanted app blocking' setting that allows you to enable protection against PUAs and PUPs.
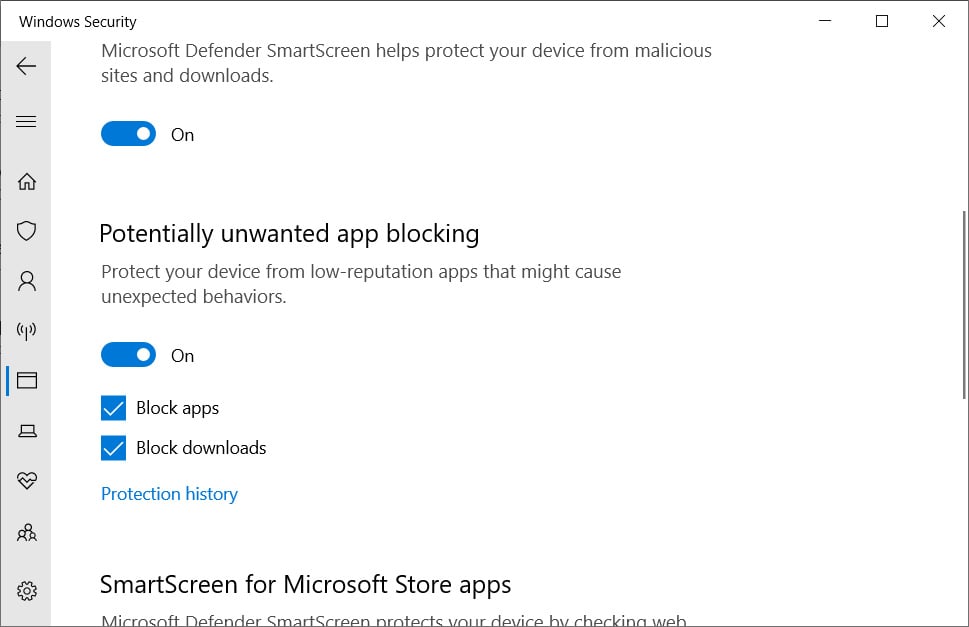
Potentially unwanted app blocking settings
As you can see from the above image, the new PUA blocking setting has two options that you can enable.
The 'Block apps' setting will enable the Microsoft Defender 'PUAProtection' setting that was previously only enabled via PowerShell and Group Policies. This setting will detect PUAs/PUPs after they have already been downloaded.
The 'Block downloads' setting will control whether the 'Block potentially unwanted apps' setting is enabled in the new Microsoft Edge browser. When enabled, SmartScreen will block PUAs and PUPs as they are downloaded.
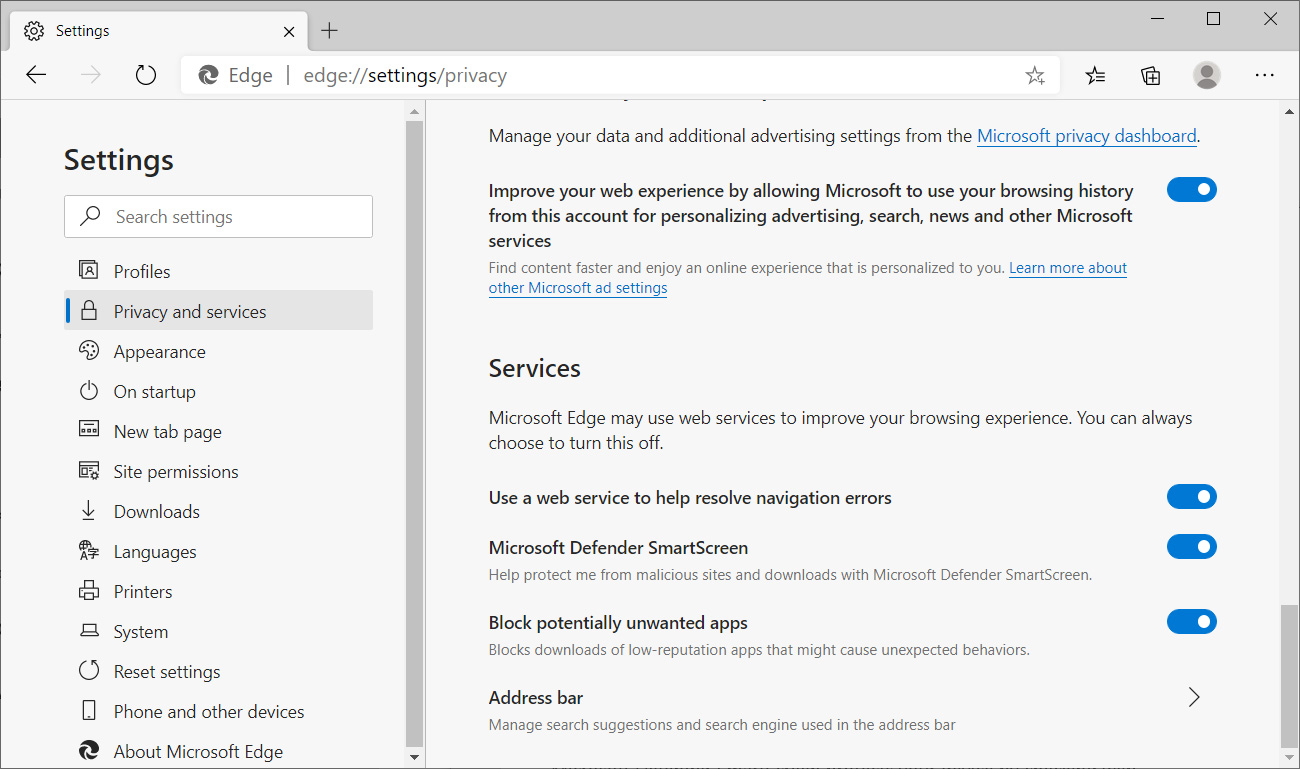
PUA protection in Microsoft Edge
These Windows Security settings are synchronized with both Microsoft Defender and Microsoft Edge. This means disabling a setting via Edge, PowerShell, or other methods will synchronize it with the Windows Security settings.
It also illustrates how the new Microsoft Edge is not just a stand-alone web browser but is tightly integrated into Windows 10 2004 and now an essential part of the overall security of the operating system.
Windows 10 2004 is almost here, what developers need to know
16.5.2020 Bleepingcomputer OS
The Windows Developer Team today detailed the new Windows 10 SDK additions developers should be aware of with the impending release of Windows 10, version 2004 (20H1), now known as Windows 10 May 2020 Update.
"The Windows 10 SDK for Windows 10, version 2004 is now available with a go-live license," as Microsoft said in a blog post published today.
"A Go-Live license gives developers and organizations authorization to begin deployment of their applications using pre-RTM code," Microsoft explained.
New APIs and features
The new Windows 10 SDK version comes with new APIs, with a full list of what's new for Windows 10 apps, the build process, MSIX, packaging, and deployment, as well as in the Windows UI Library (WinUI) available in the Windows Dev Center.
A full list of new and updated API namespaces available to developers in Windows 10 build 19041 (including links to documentation for each API) is available here.
Out of all the changes for developers in Windows 10 build 19041, Microsoft highlights the following updates to app model, MSIX and the Windows Subsystem for Linux (WSL):
Windows Subsystem for Linux: The Windows Subsystem for Linux 2 is the latest and greatest version of WSL. It has significantly faster file IO performance (up to 20x faster) with full system call compatibility, meaning you can run more of the Linux apps you love (like Docker).
Hosted App Model: Applications can now declare themselves as a host for other applications via the new HostRuntime extension. These hosted apps look and behave like independent apps and can have deep Windows integration, even though they get their main executable from the host app. This technology powers PWAs on Microsoft Edge.
Sparse Signed Packages: Applications can now include a signed MSIX package in their existing installers and have their installers register it. This allows applications to keep their existing installers but still assign themselves identities. An identity makes the app known to Windows and allows for a more deeply integrated experience by enabling the app to call Windows APIs that require identities such as Tiles, Toasts, Notifications and BackgroundTasks.
Updating your development environment
Updating to the new Windows 10 SDK is just a matter of deploying the Windows 10 May 2020 Update that should roll out later this month using the WIP (Windows Insider Program) Release Preview Ring to download it.
To enroll in the Release Preview Ring of the Windows Insider Program, you can use the detailed step-by-step procedure on how to get the May 2020 Update laid out by the Insider team in this blog post.
Windows 10 Insider Release Preview Ring
After enrolling, "go into Visual Studio 2017 or 2019 and grab the new SDK, and you’ll be good to go," Microsoft explains. "Once version 2004 goes to general availability in May, the SDK will become the default SDK inside Visual Studio."
To start using the latest Windows 10 SDK right away with Windows 10 WIP, you should:
1. Run the Visual Studio installer or go to https://www.visualstudio.com/downloads/ and download it
2. Go to "Individual Components", go to "SDKs, libraries, and frameworks" section, check "Windows 10 SDK (10.0.19041)"
3. Click "Install"
After Windows 10 2004 rolls out, you can switch to Universal Windows Platform development:
1. Run the Visual Studio installer or go to https://www.visualstudio.com/downloads/ and download it
2. Select “Universal Windows Platform development” under Workloads, Windows 10 SDK (10.0.19041) will be included by default
3. Click “Install”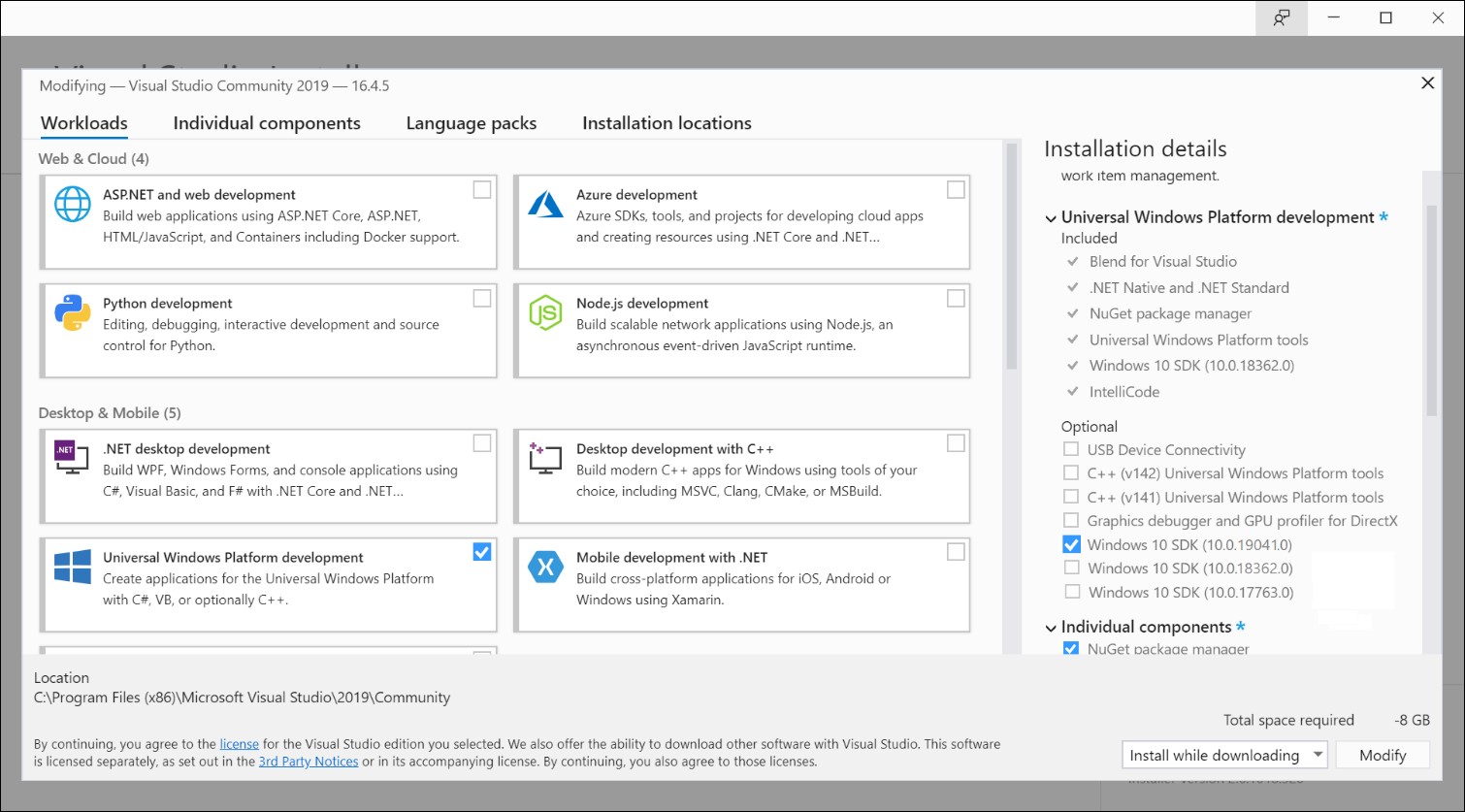
Visual Studio 2019 (Microsoft)
Depending on the type of tools you need, you can choose between C++ Universal Windows Platform tools in the UWP Workload section or desktop development with C++ Workload and the Windows SDK 10 (10.0.19041).
Microsoft is pushing Windows 10 2004 (20H1) to Windows Insiders on the Slow and Release Preview rings with the latest KB4517389 cumulative update just released earlier today.
Windows 10 2004 was also made available by Redmond to IT administrators as a Windows Server Update Service (WSUS) option.
If you are interested in the user side of things for the Windows 10 May 2020 Update, we have already covered the list of new features to be rolled out as part of the Windows 10 2004 update, with a focus on those that should make a difference for regular users.
May 2020 Patch Tuesday: Microsoft fixes 111 vulnerabilities, 13 Critical
16.5.2020 Bleepingcomputer OS
Today is Microsoft's May 2020 Patch Tuesday, and as many system administrators are working remotely, so please be patient as they may not be able to respond quickly.
With the release of the May 2020 Patch Tuesday security updates, Microsoft has released fixes for 111 vulnerabilities in Microsoft products. Of these vulnerabilities, 13 are classified as Critical, 91 as Important, 3 as Moderate, and 4 as Low.
This month there are no zero-day or unpatched vulnerabilities.
Users should install these security updates as soon as possible to protect Windows from known security risks.
For information about the non-security Windows updates, you can read about today's Windows 10 Cumulative Updates KB4556799 & KB4551853 Released.
Vulnerabilities of interest
Three Critical Microsoft Edge vulnerabilities were patched by Microsoft this month that could allow an attacker to perform remote code execution by tricking a user into visiting a maliciously crafted web site.
CVE-2020-1056 - Microsoft Edge Elevation of Privilege Vulnerability
CVE-2020-1059 - Microsoft Edge Spoofing Vulnerability
CVE-2020-1096 - Microsoft Edge PDF Remote Code Execution Vulnerability
If exploited, these vulnerabilities could allow the attacker to execute commands on the computer with full user rights.
Another critical vulnerability exists in the Color Management Module (ICM32.dll) that allows attackers to perform remote code execution by tricking a user into visiting a malicious web site.
CVE-2020-1117 | Microsoft Color Management Remote Code Execution Vulnerability
Recent security updates from other companies
Other vendors who released security updates recently include:
Adobe released security updates today for Acrobat, Reader, and DNG SDK.
SAP also released their monthly security updates today, with six having a CVSS score of 9 or higher.
vBulletin released a security update this week for their vBulletin forum software versions 5.5.6, 5.6.0, and 5.6.1.
Android released their May 2020 security updates last week.
Mozilla released Firefox 76.0 last week along with security fixes.
Google Chrome 81.0.4044.138 was released on May 5th, with three security fixes.
VMWare released a security update for VMware vRealize Operations Manager on May 8th.
The May 2020 Patch Tuesday Security Updates
Below is the full list of resolved vulnerabilities and released advisories in the May 2020 Patch Tuesday updates. To access the full description of each vulnerability and the systems that it affects, you can view the full report here.
Tag CVE ID CVE Title Severity
.NET Core CVE-2020-1161 ASP.NET Core Denial of Service Vulnerability Important
.NET Core CVE-2020-1108 .NET Core & .NET Framework Denial of Service Vulnerability Important
.NET Framework CVE-2020-1066 .NET Framework Elevation of Privilege Vulnerability Important
Active Directory CVE-2020-1055 Microsoft Active Directory Federation Services Cross-Site Scripting Vulnerability Important
Common Log File System Driver CVE-2020-1154 Windows Common Log File System Driver Elevation of Privilege Vulnerability Important
Internet Explorer CVE-2020-1092 Internet Explorer Memory Corruption Vulnerability Low
Internet Explorer CVE-2020-1064 MSHTML Engine Remote Code Execution Vulnerability Moderate
Internet Explorer CVE-2020-1062 Internet Explorer Memory Corruption Vulnerability Moderate
Internet Explorer CVE-2020-1093 VBScript Remote Code Execution Vulnerability Moderate
Microsoft Dynamics CVE-2020-1063 Microsoft Dynamics 365 (On-Premise) Cross Site Scripting Vulnerability Important
Microsoft Edge CVE-2020-1059 Microsoft Edge Spoofing Vulnerability Important
Microsoft Edge CVE-2020-1056 Microsoft Edge Elevation of Privilege Vulnerability Critical
Microsoft Edge CVE-2020-1096 Microsoft Edge PDF Remote Code Execution Vulnerability Important
Microsoft Graphics Component CVE-2020-1145 Windows GDI Information Disclosure Vulnerability Important
Microsoft Graphics Component CVE-2020-1135 Windows Graphics Component Elevation of Privilege Vulnerability Important
Microsoft Graphics Component CVE-2020-1179 Windows GDI Information Disclosure Vulnerability Important
Microsoft Graphics Component CVE-2020-1153 Microsoft Graphics Components Remote Code Execution Vulnerability Critical
Microsoft Graphics Component CVE-2020-1140 DirectX Elevation of Privilege Vulnerability Important
Microsoft Graphics Component CVE-2020-0963 Windows GDI Information Disclosure Vulnerability Important
Microsoft Graphics Component CVE-2020-1054 Win32k Elevation of Privilege Vulnerability Important
Microsoft Graphics Component CVE-2020-1142 Windows GDI Elevation of Privilege Vulnerability Important
Microsoft Graphics Component CVE-2020-1117 Microsoft Color Management Remote Code Execution Vulnerability Critical
Microsoft Graphics Component CVE-2020-1141 Windows GDI Information Disclosure Vulnerability Important
Microsoft JET Database Engine CVE-2020-1176 Jet Database Engine Remote Code Execution Vulnerability Important
Microsoft JET Database Engine CVE-2020-1051 Jet Database Engine Remote Code Execution Vulnerability Important
Microsoft JET Database Engine CVE-2020-1175 Jet Database Engine Remote Code Execution Vulnerability Important
Microsoft JET Database Engine CVE-2020-1174 Jet Database Engine Remote Code Execution Vulnerability Important
Microsoft Office CVE-2020-0901 Microsoft Excel Remote Code Execution Vulnerability Important
Microsoft Office SharePoint CVE-2020-1069 Microsoft SharePoint Server Remote Code Execution Vulnerability Critical
Microsoft Office SharePoint CVE-2020-1100 Microsoft Office SharePoint XSS Vulnerability Important
Microsoft Office SharePoint CVE-2020-1105 Microsoft SharePoint Spoofing Vulnerability Important
Microsoft Office SharePoint CVE-2020-1102 Microsoft SharePoint Remote Code Execution Vulnerability Critical
Microsoft Office SharePoint CVE-2020-1024 Microsoft SharePoint Remote Code Execution Vulnerability Critical
Microsoft Office SharePoint CVE-2020-1023 Microsoft SharePoint Remote Code Execution Vulnerability Critical
Microsoft Office SharePoint CVE-2020-1104 Microsoft SharePoint Spoofing Vulnerability Important
Microsoft Office SharePoint CVE-2020-1101 Microsoft Office SharePoint XSS Vulnerability Important
Microsoft Office SharePoint CVE-2020-1099 Microsoft Office SharePoint XSS Vulnerability Important
Microsoft Office SharePoint CVE-2020-1103 Microsoft SharePoint Information Disclosure Vulnerability Important
Microsoft Office SharePoint CVE-2020-1107 Microsoft SharePoint Spoofing Vulnerability Important
Microsoft Office SharePoint CVE-2020-1106 Microsoft Office SharePoint XSS Vulnerability Important
Microsoft Scripting Engine CVE-2020-1060 VBScript Remote Code Execution Vulnerability Low
Microsoft Scripting Engine CVE-2020-1065 Scripting Engine Memory Corruption Vulnerability Critical
Microsoft Scripting Engine CVE-2020-1037 Chakra Scripting Engine Memory Corruption Vulnerability Critical
Microsoft Scripting Engine CVE-2020-1035 VBScript Remote Code Execution Vulnerability Low
Microsoft Scripting Engine CVE-2020-1058 VBScript Remote Code Execution Vulnerability Low
Microsoft Windows CVE-2020-1111 Windows Clipboard Service Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-1112 Windows Background Intelligent Transfer Service Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-1082 Windows Error Reporting Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-1086 Windows Runtime Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-1048 Windows Print Spooler Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-1090 Windows Runtime Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-1088 Windows Error Reporting Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-1166 Windows Clipboard Service Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-1021 Windows Error Reporting Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-1164 Windows Runtime Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-1165 Windows Clipboard Service Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-1184 Windows State Repository Service Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-1188 Windows State Repository Service Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-1191 Windows State Repository Service Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-1185 Windows State Repository Service Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-1187 Windows State Repository Service Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-1125 Windows Runtime Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-1131 Windows State Repository Service Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-1121 Windows Clipboard Service Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-1123 Connected User Experiences and Telemetry Service Denial of Service Vulnerability Important
Microsoft Windows CVE-2020-1132 Windows Error Reporting Manager Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-1010 Microsoft Windows Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-1028 Media Foundation Memory Corruption Vulnerability Critical
Microsoft Windows CVE-2020-1136 Media Foundation Memory Corruption Vulnerability Critical
Microsoft Windows CVE-2020-1139 Windows Runtime Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-1144 Windows State Repository Service Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-1149 Windows Runtime Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-1076 Windows Denial of Service Vulnerability Important
Microsoft Windows CVE-2020-1143 Win32k Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-1071 Windows Remote Access Common Dialog Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-1155 Windows Runtime Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-1150 Media Foundation Memory Corruption Vulnerability Important
Microsoft Windows CVE-2020-1151 Windows Runtime Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-1138 Windows Storage Service Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-1118 Microsoft Windows Transport Layer Security Denial of Service Vulnerability Important
Microsoft Windows CVE-2020-1124 Windows State Repository Service Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-1084 Connected User Experiences and Telemetry Service Denial of Service Vulnerability Important
Microsoft Windows CVE-2020-1116 Windows CSRSS Information Disclosure Vulnerability Important
Microsoft Windows CVE-2020-1078 Windows Installer Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-1137 Windows Push Notification Service Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-1126 Media Foundation Memory Corruption Vulnerability Critical
Microsoft Windows CVE-2020-1134 Windows State Repository Service Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-1070 Windows Print Spooler Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-1068 Microsoft Windows Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-1067 Windows Remote Code Execution Vulnerability Important
Microsoft Windows CVE-2020-1072 Windows Kernel Information Disclosure Vulnerability Important
Microsoft Windows CVE-2020-1081 Windows Printer Service Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-1079 Microsoft Windows Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-1077 Windows Runtime Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-1190 Windows State Repository Service Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-1158 Windows Runtime Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-1157 Windows Runtime Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-1186 Windows State Repository Service Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-1156 Windows Runtime Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-1189 Windows State Repository Service Elevation of Privilege Vulnerability Important
Power BI CVE-2020-1173 Microsoft Power BI Report Server Spoofing Vulnerability Important
Visual Studio CVE-2020-1192 Visual Studio Code Python Extension Remote Code Execution Vulnerability Critical
Visual Studio CVE-2020-1171 Visual Studio Code Python Extension Remote Code Execution Vulnerability Important
Windows Hyper-V CVE-2020-0909 Windows Hyper-V Denial of Service Vulnerability Important
Windows Kernel CVE-2020-1114 Windows Kernel Elevation of Privilege Vulnerability Important
Windows Kernel CVE-2020-1087 Windows Kernel Elevation of Privilege Vulnerability Important
Windows Scripting CVE-2020-1061 Microsoft Script Runtime Remote Code Execution Vulnerability Important
Windows Subsystem for Linux CVE-2020-1075 Windows Subsystem for Linux Information Disclosure Vulnerability Important
Windows Task Scheduler CVE-2020-1113 Windows Task Scheduler Security Feature Bypass Vulnerability Important
Windows Update Stack CVE-2020-1109 Windows Update Stack Elevation of Privilege Vulnerability Important
Windows Update Stack CVE-2020-1110 Windows Update Stack Elevation of Privilege Vulnerability Important
Windows 10 Cumulative Updates KB4556799 & KB4551853 Released
16.5.2020 Bleepingcomputer OS
Patch Tuesday updates are now rolling out to all supported versions of Windows 10. Like every Patch Tuesday release, the cumulative update comes with security fixes and is rolling out to PCs with November 2019 Update, May 2019 Update and October 2018 Update.
In the latest cumulative update for Windows 10 version 1909, 1903, and version 1809, there are only security enhancements for Internet Explorer, Edge browser, Xbox app, core components and other basic functions.
Here's a list of all new updates for Windows 10:
Windows 10 version 1507 — KB4556826 (OS Build 10240.18575)
Windows 10 version 1607 — KB4556813 (OS Build 14393.3686)
Windows 10 version 1703 — KB4556804 (OS Build 15063.2375)
Windows 10 version 1709 — KB4556812 (OS Build 16299.1868)
Windows 10 version 1803 — KB4556807 (OS Build 17134.1488)
Windows 10 version 1809 — KB4551853 (OS Build 17763.1217)
Windows 10 version 1903/1909 — KB4556799 (OS Builds 18362.836 and 18363.836)
Like every Windows Update, you can open the Settings app and click on the Windows Update option to install the patches. If you own multiple PCs or if you would like to patch the PCs manually, you can learn more about it here.
Build 18362.836 and 18363.836 for Windows 10
KB 4556799 for Windows 10 version 1909 and version 1903 (November 2019 Update / May 2019 Update) contains the following improvements and fixes:
Updates to improve security when using Internet Explorer and Microsoft Edge.
Updates to improve security when using input devices such as a mouse, keyboard, or stylus.
Updates for verifying usernames and passwords.
Updates to improve security when using Microsoft Xbox.
Updates to improve security when Windows performs basic operations.
Updates for storing and managing files.
Updates to improve security when using Microsoft Office products.
Updates the 2020 start date for daylight saving time (DST) in the Kingdom of Morocco.
Security updates to Internet Explorer, the Microsoft Scripting Engine, Windows App Platform and Frameworks, Microsoft Graphics Component, Windows Input and Composition, Windows Media, Windows Shell, Microsoft Xbox, Microsoft Edge, Windows Fundamentals, Windows Cryptography, Windows Authentication, Windows Kernel, Windows Linux, Windows Update Stack, Windows Network Security and Containers, Windows Active Directory, Windows Storage and Filesystems, and the Microsoft JET Database Engine.
Microsoft says the company is not aware of any issues with this update.
Build 17763.1217 for October 2018 Update
Build 17763.1217 for Windows 10 October 2018 Update comes with the following changes:
Updates the 2020 start date for daylight saving time (DST) in the Kingdom of Morocco.
Adds Shell Launcher v2 to improve reliability and usability. Shell launcher v2 allows you to specify a Universal Windows Platform (UWP) app as the replacement shell. For more information, see Use Shell Launcher to create a Windows 10 kiosk.
Addresses an issue that prevents a call to NCryptGetProperty() from returning the correct pbOutput value when pszProperty is set to "Algorithm Group" and you are using a Trusted Platform Module (TPM) 1.2 device.
Security updates to Internet Explorer, the Microsoft Scripting Engine, Windows App Platform and Frameworks, Microsoft Graphics Component, Windows Input and Composition, Windows Media, Windows Shell, Microsoft Xbox, Microsoft Edge, Windows Fundamentals, Windows Cryptography, Windows Authentication, Windows Kernel, Windows Linux, Windows Update Stack, Windows Core Networking, Internet Information Services, Windows Network Security and Containers, Windows Active Directory, Windows Storage and Filesystems, and the Microsoft JET Database Engine.
Known issues in this update
Symptom Workaround
After installing KB4493509, devices with some Asian language packs installed may receive the error, "0x800f0982 - PSFX_E_MATCHING_COMPONENT_NOT_FOUND."
Uninstall and reinstall any recently added language packs. For instructions, see Manage the input and display language settings in Windows 10.
Select Check for Updates and install the April 2019 Cumulative Update. For instructions, see Update Windows 10.
Note If reinstalling the language pack does not mitigate the issue, reset your PC as follows:
Go to the Settings app > Recovery.
Select Get Started under the Reset this PC recovery option.
Select Keep my Files.
Microsoft is working on a resolution and will provide an update in an upcoming release.
Windows 10 May 2020 Update Insider Preview
For those on May 2020 Update, a new cumulative update Build 19041.264 (KB4556803) is also available with these improvements:
We have fixed a performance issue in Windows Mixed Reality (WMR) that prevents it from working correctly for many users.
We fixed an issue that prevents cleaning tools, such as Disk Cleanup, from removing previously installed updates.
We have updated the 2020 start date for daylight saving time (DST) in the Kingdom of Morocco. For more information, see KB4557900.
Security updates to Internet Explorer, the Microsoft Scripting Engine, Windows App Platform and Frameworks, Microsoft Graphics Component, Windows Input and Composition, Windows Media, Windows Shell, Microsoft Xbox, Microsoft Edge, Windows Fundamentals, Windows Cryptography, Windows Authentication, Windows Kernel, Windows Virtualization, Windows Update Stack, Windows Core Networking, Internet Information Services, Windows Network Security and Containers, Windows Active Directory, Windows Server, and the Microsoft JET Database Engine.
Microsoft Edge rolls out in Windows 10 2004 via Windows Update
16.5.2020 Bleepingcomputer OS
Microsoft has started to push out an update to Windows Insiders in the Release preview ring that replaces Microsoft Edge Legacy with the new Chromium-based Microsoft Edge browser.
Windows Insiders on the Release preview ring are currently using Windows 10 2004 build 19041.264, which Microsoft expects to be the final release that will be delivered as the May 2020 Update.
Starting around May 8th, 2020, Microsoft began rolling out a new '2020-05 Microsoft Edge Update for Windows 10 Version 2004 for x64-based Systems (KB4559309)' update to Windows Insiders in the Release preview ring.
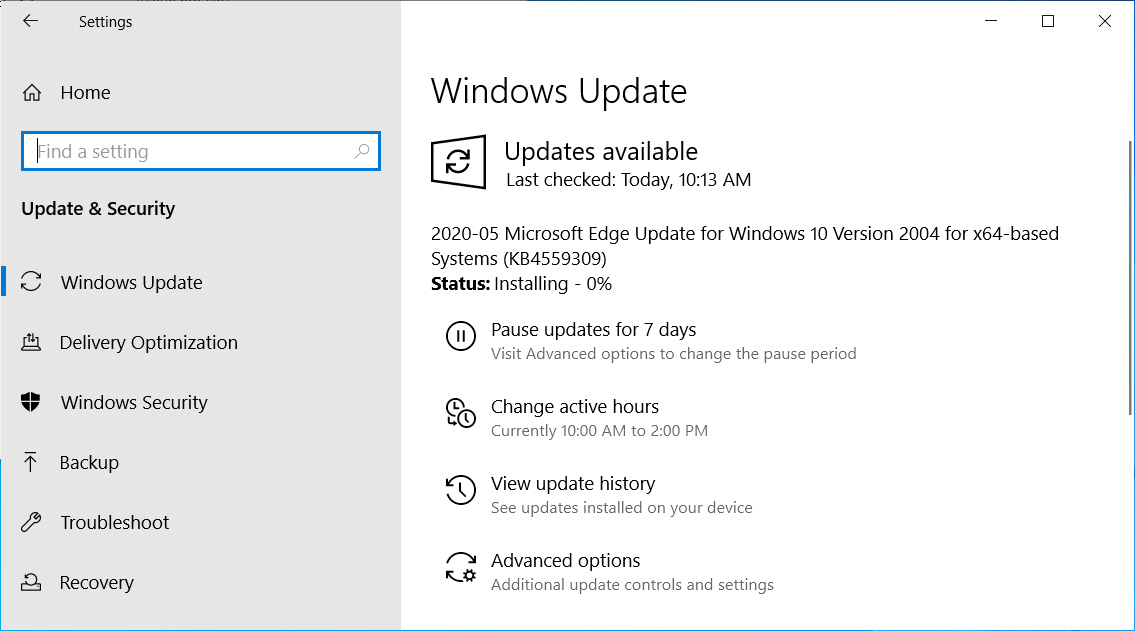
Windows Update rolling out new Microsoft Edge
After the update is installed, users will be prompted to restart Windows. During this restart process, Microsoft Edge Legacy will be removed and replaced with the current version of Microsoft Edge.
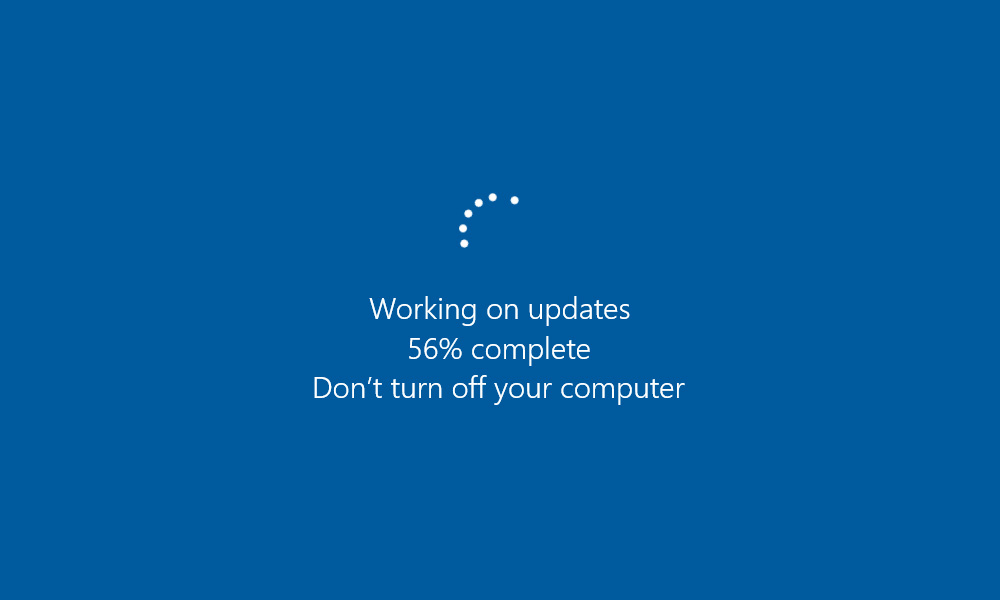
Windows Update replacing Microsoft Edge
At the time of this writing, the version of Microsoft Edge being installed is 81.0.416.72, and once installed will walk users through a short guided setup wizard. 
New Microsoft Edge setup wizard
The rollout of the new Microsoft Edge is going to be extremely beneficial to Windows users, especially those who do not install other browsers on the computer.
As the new Microsoft Edge is based on Chromium, which is the most widely supported browser, users will be able to take advantage of a reliable browser right out of the box.
The new Microsoft edge also includes new features such as QR Code web site sharing, Collections, and vertical tabs.
Office 365 to let regular users revoke encrypted messages
15.5.2020 OS
Microsoft is working on expanding the capability to revoke encrypted email messages sent using the Office 365 Message Encryption (OME) service to regular users as part of a larger effort to prevent data leaks and enterprise data theft.
OME is built on Microsoft Azure Rights Management (Azure RMS) and it combines rights management with email encryption capabilities.
It allows Office 365 customers to send and receive encrypted emails using Outlook.com, Yahoo!, Gmail, and several other email services with support for encryption, authorization, and identity policies.
Encrypted email revocation for end-users
"As part of Office 365 Advance Message Encryption, we are extending the email revocation capabilities to the end user," Microsoft explains on the new feature's entry on the Microsoft 365 roadmap.
"Previously, you had to be an admin to revoke an already sent message; with this update, end users will have this capability as well."
This new capability will only be available to users whose organization's Office 365 subscription with Advanced Message Encryption support such as Microsoft 365 Enterprise E5, Office 365 E5, Microsoft 365 E5 (Nonprofit Staff Pricing), Office 365 Enterprise E5 (Nonprofit Staff Pricing), and Office 365 Education A5.
While Microsoft doesn't explain what will happen with the revoked encrypted messages, according to its support site, when admins revoke such emails, the recipients receive 'The message has been revoked by the sender' errors on trying to access the encrypted emails through the Office 365 Message Encryption portal.
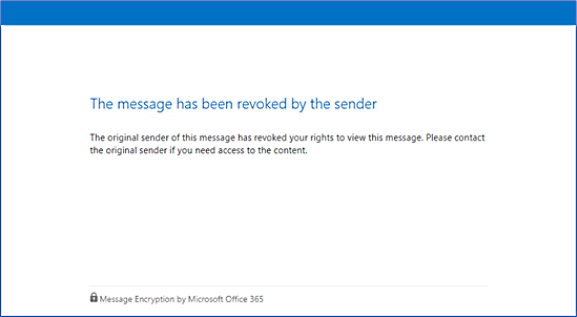
Revoked encrypted email error (Microsoft)
The Microsoft Exchange team is planning to roll out this new OME capability expansion during Q4 2020 and it will be generally available on a worldwide basis for standard multi-tenant environments.
As part of its larger effort to put a stop to enterprise data theft, Microsoft is also planning to disable Office 365's email forwarding to external recipients by default starting with the fourth quarter of 2020.
The company is also in the process of adding improved external email forwarding controls which will allow Office 365 admins to enable the feature only to select employees in their organizations.
More OME enhancements
Redmond has also recently added several other new capabilities to the Office 365 Message Encryption service in December 2019, including support for Shared Mailboxes and PDF attachments, and Mac pre-licensing.
Microsoft is also working on improving the way emails sent using the OME service are recognized by mail servers so that they are less likely to be sent to the Trash folder after being marked as spam.
They are also expected to roll out support for sending one-time passcode (OTP) emails from an organization's Office 365 domain later this year.
A quick overview of the Office Message Encryption capability in Office 365 with instructions on sending protected emails to almost anyone inside and outside your organization is available here.
Microsoft's Family Safety parental control app opens for testing
15.5.2020 OS
Microsoft has announced today that users can signup to preview their Family Safety parental control app on Android and iOS devices.
Family Safety features have always been a part of Windows 10 and Xbox and these tools are finally available on mobile devices, which should allow users to manage their family safety features on the go.
With the Microsoft Family Safety app for Android and iOS, you can get information about your family’s activity including what your kids are doing online across Windows and Xbox devices.
For example, you can use Family Safety tools to learn more about your kid's view screen time, top websites visited, and the terms they are searching for online.
Screen time limits
The app will allow you to set screen time limits across Windows and Xbox devices. You can set limits for a specific app or game and activities such as learning online. The kids can also ask you for additional screen time if they run out of screen time set by you.
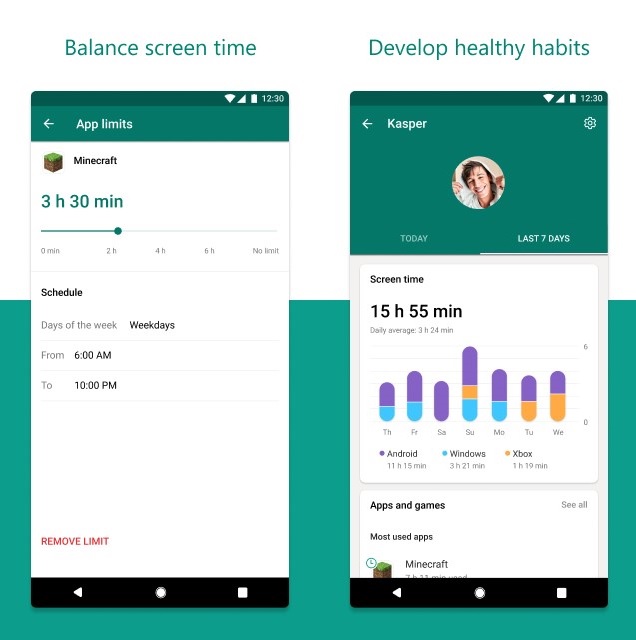
You have the choice to customize the experience based on what is right for your family.
Create a safe space
Another feature will allow you to create a safe space for kids to explore the Internet. You can use web and safety filters to block mature content and you can also set browsing to kid-friendly websites on Microsoft Edge across your devices.
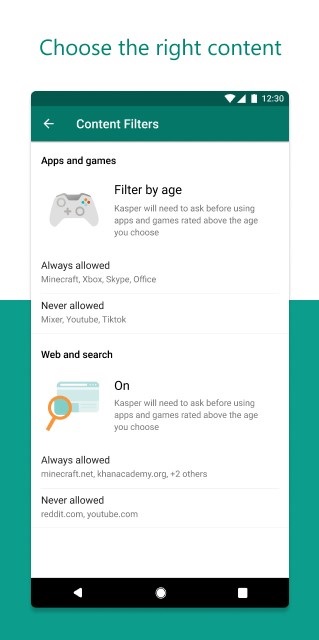
You will also get a notification when your kids try to download a more mature app or game from the Microsoft Store.
Location sharing
The third key feature of the Microsoft Family Safety app lets you track the location of your loved ones.
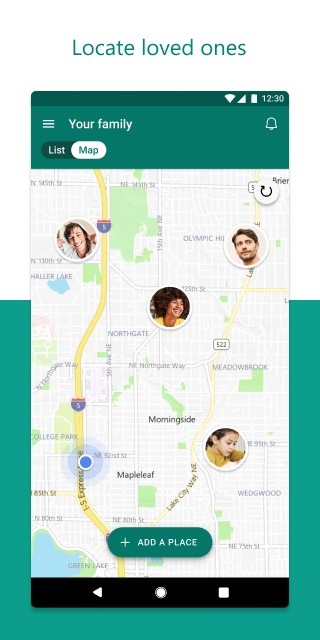
With the location sharing feature, you can even save the places they visit the most, like home, work, or school
Join the preview
Microsoft says the app is available in the limited preview and Microsoft will be first reaching out to those have expressed interest in these tools for their Android and iOS devices.
"We have limited availability for additional users on Android and iOS and invite you to sign up. As a participant in the preview, you gain early access to the app and get to help shape the product by sharing feedback about your experience," Microsoft said.
You can register for the preview from here.