Ransom News |
Datum | Název | Obrázek | Popis |
| 22.6.19 | New [Locked] Ransomware |  | Michael Gillespie is looking for a new ransomware that appends the [LOCKED] extension and drops a ransom note named UNLOCK INSTRUCTIONS.txt. |
| 22.6.19 | New Hack Dharma Ransomware variant |  | Jakub Kroustek found a new Dharma Ransomware variant that appends the .HACK extension to encrypted files. |
| 22.6.19 | New 0day Dharma Ransomware variant |  | Michael Gillespie found a new Dharma Ransomware variant that appends the .0Day extension to encrypted files. |
| 22.6.19 | Stop Decryptor updated |  | Michael Gillespie updated his Stop Decryptor to support the offline key for the .vesad extension variant. |
| 22.6.19 | Release of GandCrab 5.2 Decryptor Ends a Bad Ransomware Story |  | In collaboration with law enforcement agencies around the world, Bitdefender has released an updated decryptor for the GandCrab Ransomware that can decrypt files encrypted by versions 1, 4, and 5 through 5.2. |
| 22.6.19 | New Horon STOP Djvu variant |  | Michael Gillespie found a new variant of STOP Djvu ransomware that appends the .horon extension to encrypted files. |
| 22.6.19 | New Orion version of Major Ransomware |  | Amigo-A found a new variant of the Major Ransomware that appends the .orion extension on encrypted files and drops a ransom note named READ_ME.orion. |
| 22.6.19 | WannaCash Decryptor updated |  | Alex Svirid updated his WannaCash Decryptor to support new variants. |
| 22.6.19 | New Middleman Ransomware |  | Michael Gillespie is looking for a new ransomware that appends the .middleman2020 extension and drops a ransom note named !INSTRUCTI0NS!.TXT. |
| 22.6.19 | New Copan DCRTR Ransomware |  | Amigo-A found a new variant of the DCRTR Ransomware that appends the .COPAN extension and drops ransom notes named HOW TO DECRYPT FILES.txt and HOW TO DECRYPT FILES.hta. |
| 22.6.19 | Ryuk Ransomware Adds IP and Computer Name Blacklisting |  | A new variant of the Ryuk Ransomware has been discovered that adds IP address and computer blacklisting so that matching computers will not be encrypted. |
| 22.6.19 | New Neras STOP Djvu variant |  | Michael Gillespie found a new variant of STOP Djvu ransomware that appends the .neras extension to encrypted files. |
| 22.6.19 | New Adage Phobos Ransomware variant |  | M. Shahpasandi found a new variant of the Phobos Ransomware that appends the .id[********-****].[helpteam38@protonmail.com].adage exemsion to encrypted files. |
| 22.6.19 | Florida city pays $600,000 to ransomware gang to have its data back |  | The city council for Riviera Beach, Florida, voted this week to pay more than $600,000 to a ransomware gang so city officials could recover data that has been locked and encrypted more than three weeks ago. |
| 22.6.19 | DanaBot Banking Trojan Upgraded with 'Non Ransomware' Module |  | A new malicious campaign is distributing an upgraded variant of DanaBot that comes with a new ransomware module used to target potential victims from Italy and Poland via phishing emails which deliver malware droppers. Checkpoint also released a decryptor for this ransomware. |
| 22.6.19 | Stop Decryptor updated |  | Michael Gillespie updated his Stop Decryptor to support the offline key for the .horon extension variant. |
| 22.6.19 | New Ransomnix Ransomware variant |  | Amigo-A found a new variant of the Ransomnix Ransomware that appends the .dmo extension and drops a ransom note named HOW_TO_RETURN_FILES.txt. |
| 22.6.19 | Sodinokibi Ransomware Spreads Wide via Hacked MSPs, Sites, and Spam |  | With the GandCrab Ransomware operation shutting down, affiliates are looking to fill the hole left behind with other ransomware. Such is the case with the Sodinokibi Ransomware, whose affiliates are using a wide range of tactics to distribute the ransomware and earn a commission. |
| 22.6.19 | New LooCipher Ransomware Spreads Its Evil Through Spam | 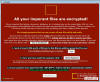 | A new ransomware called LooCipher has been discovered that is actively being used in the wild to infect users. While it is not known exactly how this ransomware is being distributed, based on some of the files that were found, we believe it is through a spam campaign. |
| 22.6.19 | New Truke STOP Djvu variant |  | Michael Gillespie found a new variant of STOP Djvu ransomware that appends the .truke extension to encrypted files. |
| 22.6.19 | New Bitch Ransomware | 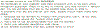 | MalwareHunterTeam found a new ransomware that calls itself "Bitch Ransomware". Nuff said. |
| 16.6.19 | New Myskle and Boston STOP Djvu Ransomware |  | Michael Gillespie found a new variants of the STOP Djvu Ransomware that append the .myskle or .boston extensions to encrypted files. |
| 16.6.19 | STOP Decryptor Updated |  | Michael Gillespie updated his STOP Decryptor to contain the offline key for the .heroset variant. |
| 16.6.19 | New Zoh Dharma Ransomware variant |  | Jakub Kroustek found a new variant of the Dharma Ransomware that appends the .zoh extension to encrypted files. |
| 16.6.19 | JSWorm Ransomware 3.1 Released |  | Amigo-A discovered JSWorm Ransomware 3.1 that uses a new ransom note named JSWORM-DECRYPT.hta. Still uses the .jsworm extension. |
| 16.6.19 | New Muslat STOP Djvu Ransomware |  | Michael Gillespie found a new variant of the STOP Djvu Ransomware that appends the .muslat extension to encrypted files. |
| 16.6.19 | Food Bank Hit By Ransomware, Needs Your Charity to Rebuild |  | Ransomware attacks hit indiscriminately and sometimes they may affect charitable organizations that can’t afford to surrender to the demand. Auburn Food Bank in King County, Washington, fell victim to a ransomware strain known as GlobeImposter 2.0, which encrypted all computers on their network. |
| 16.6.19 | How Cybercriminals Recruited Young Romanian Woman |  | In this excerpt from Kate Fazzini’s “Kingdom of Lies,” one former Romanian hacker tells how she got into the biz. |
| 16.6.19 | New Gerosan STOP Djvu Ransomware |  | Michael Gillespie found a new variant of the STOP Djvu Ransomware that appends the .gerosan extension to encrypted files. |
| 16.6.19 | New Html Dharma Ransomware variant |  | Jakub Kroustek found a new variant of the Dharma Ransomware that appends the .html extension to encrypted files. |
| 16.6.19 | Bisquilla Ransomware discovered |  | Jack found the Bisquilla Ransomware, which appears to be in dev as it does not encrypt. |
| 16.6.19 | New Cephalo Ransomware discovered |  | Daniel Gallagher discovered a ransomware being distributed through a LNK file that contains a PowerShell command. |
| 16.6.19 | Ransomware identification for the judicious analyst |  | Malware detection is a simple yes- or no-answer to the question: Is this file malicious?
Or in case of ransomware detection: Is this file ransomware? Identification on the other hand will provide an aswer to the question: Which malware or ransomware family is this? |
| 16.6.19 | Ransomware halts production for days at major airplane parts manufacturer |  | ASCO, one of the world's largest suppliers of airplane parts, has ceased production in factories across four countries due to a ransomware infection reported at its plant in Zaventem, Belgium. |
| 16.6.19 | New SD 1.1 Ransomware |  | A new ransomware called SD 1.1 was posted on the BleepingComputer forums and was identified by Amigo-A, The ransomware appends the .[Unlock11@protonmail.com].enc extension. |
| 16.6.19 | pyLocky Decryptor Released by French Authorities |  | A decryptor for pyLocky Ransomware versions 1 and 2 has been released by French authorities that allows victim to decrypt their files for free. |
| 16.6.19 | New Vesad STOP Djvu Ransomware |  | Michael Gillespie found a new variant of the STOP Djvu Ransomware that appends the .vesad extension to encrypted files. |
| 16.6.19 | STOP Decryptor Updated |  | Michael Gillespie updated his STOP Decryptor to contain the offline key for the .boston, .muslat, and .gerosan extension. |
| 16.6.19 | New Harma Dharma Ransomware variant |  | Jakub Kroustek found a new variant of the Dharma Ransomware that appends the .harma extension to encrypted files. |
| 16.6.19 | Armageddon Ransomware Discovered | 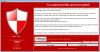 | S!Ri discovered the Armageddon Ransomware. This ransomware does not encrypt all files on the PC. |
| 16.6.19 | New Poop Ransomware? |  | Petrovic found a new ransomware that appends the .poop extension to encrypted files. It is quite ugly too. |
| 16.6.19 | GandCrab is covering up their tracks |  | CapsLo0ck noticed that the Gandcrab devs have asked Exploit.in to delete their posts on the site. |
| 9.6.19 | GandCrab Ransomware Shutting Down After Claiming to Earn $2.5 Billion |  | After almost a year and a half, the operators behind the GandCrab Ransomware are shutting down their operation and affiliates are being told to stop distributing the ransomware. |
| 9.6.19 | Dodger Ransomware discovered | 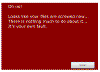 | MalwareHunterTeam discovered a new ransomware called Dodger that appends the .dodger extension and shows this not very nice screen. |
| 9.6.19 | New Lanset and Redmat Stop Ransomware variants |  | Michael Gillespie found new variants of the STOP Djvu Ransomware that appends the .lanset and .redmat extensions to encrypted files. |
| 9.6.19 | New BSC Dharma Ransomware variant |  | Jakub Kroustek found a new Dharma Ransomware variant that appends the .bsc extension to encrypted files. |
| 9.6.19 | Strange Bits: Sodinokibi Spam, CinaRAT, and Fake G DATA |  | Sodinokibi ransomware was known so far for being installed via Oracle WebLogic exploit (see Talos' article). A new campaign uses spam emails with attached MS Office Word document to download Sokinokibi to the target system. JamesWT found the first sample, Sculabs another one[1]. The email pretends to be a warning letter from the fee collection center of public-law broadcasting institutions in the Federal Public of Germany and demands 213.50 EUR payment. |
| 9.6.19 | Baltimore ransomware perp pinky-swears he didn’t use NSA exploit |  | Over the past few weeks, a Twitter account that has since been confirmed by researchers to be that of the operator of the ransomware that took down Baltimore City's networks May 4 has posted taunts of Baltimore City officials and documents demonstrating that at least some data was stolen from a city server. Those documents were posted in response to interactions I had with the ransomware operator in an attempt to confirm that the account was not a prank. |
| 9.6.19 | New Davda Stop Ransomware found |  | Michael Gillespie found a new variant of the STOP Djvu Ransomware that appends the .davda extension to encrypted files. |
| 9.6.19 | Baltimore’s bill for ransomware: Over $18 million, so far |  | It has been a month since the City of Baltimore's networks were brought to a standstill by ransomware. On Tuesday, Mayor Bernard "Jack" Young and his cabinet briefed press on the status of the cleanup, which the city's director of finance has estimated will cost Baltimore $10 million—not including $8 million lost because of deferred or lost revenue while the city was unable to process payments. The recovery remains in its early stages, with less than a third of city employees issued new log-in credentials thus far and many city business functions restricted to paper-based workarounds. |
| 9.6.19 | New Pidom and Poret Stop Ransomware variants |  | Michael Gillespie found new variants of the STOP Djvu Ransomware that appends the .pidom and .poret extensions to encrypted files. |
| 9.6.19 | New Kjh Dharma Ransomware variant |  | Michael Gillespie found a new variant of the Dharma Ransomware that appends the .kjh extension to encrypted files. |
| 9.6.19 | New Wannacash Ransomware variant |  | Alex Svirid found a new WannaCash Ransomware variant that changes an encrypted file's name to "файл зашифрован (original_filename) .punisher" |
| 9.6.19 | The RIG Exploit Kit is Now Pushing the Buran Ransomware |  | The RIG exploit kit is now infecting victim's computers with a new ransomware variant called Buran. This ransomware is a variant of the Vega ransomware that was previously being distributed through Russian malvertising campaigns. |
| 9.6.19 | New Heroset Stop Ransomware found |  | Michael Gillespie found a new variant of the STOP Djvu Ransomware that appends the .heroset extension to encrypted files. |
| 9.6.19 | STOP Djvu Decryptor udpated |  | Michael Gillespie has updated his STOP Djvu decrypter to include the offline keys for the .stone, .lanset, .davda, .poret, .pidon extensions. |
| 9.6.19 | New GlobeImposter 2 variant |  | Michael Gillespie found a new GlobeImposter 2 variant that appends the .{dresdent@protonmail.com}DDT extension to encrypted files. |
| 9.6.19 | New Euclid Ransomware |  | Michael Gillespie found a new ransomware called Euclid uploaded to ID Ransomware that appends the .euclid extension and drops a ransom note named how to recovery.txt. |
| 9.6.19 | Hackers Won’t Let Up in Their Attack on U.S. Cities |  | WSJ reports that there were two intrusions in Baltimore city networks; one by an actor that used EternalBlue to move around the network and the other was the one who installed RobbinHood and did not use EternalBlue."Local governments across the country are facing a growing threat of cyberattacks and escalating ransom demands, as an attack in this city has crippled thousands of computers for a month." |
| 2.6.19 | In-dev GottaCry Ransomware | 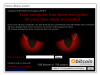 | MalwareHunterTeam found a new ransomware called GottaCry that is in-development. |
| 2.6.19 | SysFrog Ransomware discovered |  | Michael Gillespie spotted a ransomware that appends the .sysfrog extension to encrypted files and drops a ransom note named how_to_decrypt.txt. |
| 2.6.19 | New QBX Dharma Ransomware variant |  | Michael Gillespie spotted a new Dharma Ransomware variant that appends the .qbx extension to encrypted files. |
| 2.6.19 | New Mogera STOP Djvu variant |  | Michael Gillespie found a new STOP Djvu Ransomware variant that appends the .mogera extension to encrypted files. |
| 2.6.19 | New ZOH Dharma Ransomware variant |  | Michael Gillespie spotted a new Dharma Ransomware variant that appends the .zoh extension to encrypted files. |
| 2.6.19 | New BEETS Dharma Ransomware variant |  | Jakub Kroustek spotted a new Dharma Ransomware variant that appends the .beets extension to encrypted files. |
| 2.6.19 | New Rezuc STOP Djvu variant |  | Michael Gillespie found a new STOP Djvu Ransomware variant that appends the .rezuc extension to encrypted files. |
| 2.6.19 | New Eric Ransomware |  | Michael Gillespie spotted a new ransomware that appends the .ERIS extension and drops a ransom note named @ READ ME TO RECOVER FILES @.txt. |
| 2.6.19 | New GlobeImposter variant |  | GrujaRS found a new GlobeImposter variant that appends the .LotR extension and drops a ransom note named NEW_WAVE.html. |
| 2.6.19 | MBR-based NMoreira Boot Ransomware |  | Dave Logue found a variant of the NMoreira Ransomware that appears to be targeting the MBR. |
| 2.6.19 | Fake WannaCry Ransomware | 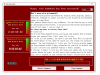 | MalwareHunterTeam found a fake WannaCry Ransomware that looks like it was made a joke, school assignment, or for "fun". |
| 2.6.19 | New Harma Dharma Ransomware variant |  | Michael Gillespie spotted a new Dharma Ransomware variant that appends the .harma extension to encrypted files. |
| 2.6.19 | STOP Ransomware Decryptor updated |  | Michael Gillespie updated his STOP Djvu Ransomware decryptor to support the offline keys for the .skymap, .mogera, and .rezuc variants. |
| 2.6.19 | New Buran Ransomware spotted |  | Michael Gillespie spotted a new ransomware on ID-Ransomware that utilizes what looks like a GUID for the extension. For example, .3674AD9F-5958-4F2A-5CB7-F0F56A8885EA. It also drops a ransom note named !!! YOUR FILES ARE ENCRYPTED !!!.TXT. |
| 2.6.19 | Sodinokibi Ransomware Pushed via Foreclosure Warning Spam | 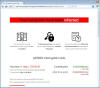 | A malspam campaign targeting potential German victims is actively distributing Sodinokibi ransomware via spam emails disguised as foreclosure notifications with malicious attachments which pose as foreclosure notifications. |
| 2.6.19 | Maze Ransomware Says Computer Type Determines Ransom Amount |  | A variant of the Maze Ransomware, otherwise known as the ChaCha Ransomware, has been spotted being distributed by the Fallout exploit kit. An interesting feature of this ransomware is that it says the ransom amount will be different depending on whether the victim is a home computer, server, or workstation. |
| 2.6.19 | New Stone STOP Djvu variant |  | Michael Gillespie found a new STOP Djvu Ransomware variant that appends the .stone extension to encrypted files. |
| 2.6.19 | New RotorCrypt Ransomware variant |  | Michael Gillespie found a new RotorCrypt Ransomware variant that appends the !__prontos@cumallover.me__.bak extension. |
26.5.19 | New ransomware discovered |  | Michael Gillespie found a new ransomware that appends the .[epta.mcold@gmail.com] and drops a ransom note named !INSTRUCTI0NS!.TXT, |
| 26.5.19 | New in-dev EZDZ Ransomware |  | MalwareHunterTeam found a new in-dev ransomware called EZDZ that utilizes the .EZDZ extension and drops a ransom note named HELP_PC.EZDZ-REMOVE.txt. |
| 26.5.19 | New Radman STOP Djvu Ransomware variant |  | Michael Gillespie found a new STOP Djvu Ransomware variant that appends the .radman extension. |
| 26.5.19 | New Ferosas STOP Djvu Ransomware variant |  | Michael Gillespie found a new STOP Djvu Ransomware variant that appends the .ferosas extension. |
| 26.5.19 | New TOR13 Dharma variant |  | Jakub Kroustek found a new Dharma Ransomware variant that appends the .TOR13 extension to encrypted files. |
26.5.19 | Cryptocurrent scam pushing ransomware |  | Frost found an Ether scam distributing a new ransomware. |
| 26.5.19 | JSWorm 2.0 Ransomware Decryptor Gets Your Files Back For Free |  | A decryptor for the JSWorm 2.0 Ransomware has been released by Emsisoft this week that allows victims to decrypt their files for free. If you become infected with JSWorm 2.0, do not pay the ransom and instead follow the instructions below. |
| 26.5.19 | Louisville Regional Airport Authority hit by 'ransomware' attack |  | WDRB reports: "The Louisville Regional Airport Authority said it fell victim to ransomware Monday morning." |
| 26.5.19 | GetCrypt Ransomware Brute Forces Credentials, Decryptor Released |  | A new ransomware called GetCrypt is being installed through malvertising campaigns that redirect victims to the RIG exploit kit. Once installed, GetCrypt will encrypt all of the files on a computer and then demand a ransom payment to decrypt the files. |
| 26.5.19 | Hackers Are Holding Baltimore Hostage: How They Struck and What’s Next |  | A NY Times article by Niraj Chokshi covering Baltimore being hit by the RobbinHood ransomware. Also includes a quote from your favorite ransomware information site :) |
26.5.19 | New Rectot STOP Djvu Ransomware variant |  | Michael Gillespie found a new STOP Djvu Ransomware variant that appends the .rectot extension. |
| 26.5.19 | New Les Scarab Ransomware variant |  | Michael Gillespie found a new Scarab Ransomware variant that appends the .les# extension and drops a ransom note named как расшифровать файлы les#.TXT. |
| 26.5.19 | Wiper disguised as ransomware distributed via email |  | honkone found an email pushing a malicious executable. Bart analyzed and determined it was a ransomware, but Michael Gillespie stated it was actually a wiper. The fun of malware. |
| 26.5.19 | STOP Djvu Decryptor updated |  | Michael Gillespie updated the STOP Djvu decryptor to support the offline IDs for .ferosas, .rectot, and .INFOWAIT variants. |
| 26.5.19 | Sodinokibi Ransomware Poised to Impact Larger Enterprises |  | Coveware states:"Given the sophisticated attack vector and the investment the developers of Sodinokibi have made to their payment TOR site, this variant seems to be poised to become a popular choice among ransomware distributors." |
| 26.5.19 | New Good Dharma variant |  | Jakub Kroustek found a new Dharma Ransomware variant that appends the .GOOD extension to encrypted files. |
| 26.5.19 | NordFox Ransomware discovered |  | GrujaRS discovered the NordFox Ransomware, which appends the .legacy extension to encrypted files and drops a ransom note named READ_ME.txt. |
| 26.5.19 | New Skymap STOP Djvu Ransomware variant |  | Michael Gillespie found a new STOP Djvu Ransomware variant that appends the .skymap extension. |
18.5.19 | New STOP Djvu variant discovered |  | Michael Gillespie found a new STOP Djvu variant that adds the .codnat extension to encrypted files. |
| 18.5.19 | New Dharma variants released |  | Jakub Kroustek found new variants of the Dharma Ransomware that append the .qbtex and the .yG extension to encrypted files. |
| 18.5.19 | New STOP Djvu variant discovered |  | Michael Gillespie found a new STOP Djvu variant that adds the .codnat1 extension to encrypted files. |
| 18.5.19 | WannaCry still present on 1.7 million machines |  | 2 years after WannaCry and there’s still 1.7M machines with SMB exposed to the Internet! |
| 18.5.19 | New DrWeb Dharma variant released |  | Jakub Kroustek found a new variant of the Dharma Ransomware that appends the .drweb extension to encrypted files. |
| 18.5.19 | New STOP Djvu variant discovered |  | Michael Gillespie found a new STOP Djvu variant that adds the .bufas extension to encrypted files. |
| 18.5.19 | Wesker Encrypter discovered | 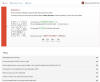 | Michael Gillespie found the Wesker Encrypter that does not add an extension but drops ransom notes name !!!INSTRUCTION_RNSMW!!!.txt. |
18.5.19 | New ChaCha Ransomware variant |  | Michael Gillespie found a new ChaCha Ransomware variant that appends a random 6-7 char extension and drops a ransom note named DECRYPT-FILES.html. |
| 18.5.19 | Non Ransomware discovered |  | GrujaRS found the Non Ransomware that appends the .non extension and drops a ransom note named HowToBackFiles.txt. Possibly in-dev as the ransom note does not include an email address. |
| 18.5.19 | New Dharma variants released |  | Jakub Kroustek found new variants of the Dharma Ransomware that append the .jack and .PLUT extensions to encrypted files. |
| 18.5.19 | JSWorm Ransomware sends a shoutout to researchers | 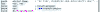 | The JSWorm Ransomware sent a shoutout in its code to MalwareHunterTeam, S!Ri, and Amigo-A. |
| 18.5.19 | Possible new Desktop Ransomware variant | 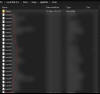 | GrujaRS found a new ransomware that could be a variant of the Desktop Ransomware. This ransomware prepends the Locked. string to encrypted file's names. |
| 18.5.19 | THE TRADE SECRET: Firms That Promised High-Tech Ransomware Solutions Almost Always Just Pay the Hackers |  | As ransomware attacks crippled businesses and law enforcement agencies, two U.S. data recovery firms claimed to offer an ethical way out. Instead, they typically paid the ransom and charged victims extra. |
| 18.5.19 | New DDOS Dharma variant released |  | Jakub Kroustek found a new variant of the Dharma Ransomware that appends the .DDOS extension to encrypted files. |
18.5.19 | New Oops Scarab Ransomware variant |  | Amigo-A found a new Scarab Ransomware variant that appends the .Oops extension and drops a ransom note named HOW TO RECOVER ENCRYPTED FILES.TXT. |
| 18.5.19 | New Mamba Phobos Ransomware variant |  | GrujaRS found a new Phobos Ransomware variant that appends the .mamba extension to encrypted files. |
| 18.5.19 | New Cry Dharma variant released |  | Jakub Kroustek found a new variant of the Dharma Ransomware that appends the .cry extension to encrypted files. |
| 18.5.19 | New STOP Djvu variant discovered |  | Michael Gillespie found a new STOP Djvu variant that adds the .dotmap extension to encrypted files. |
| 18.5.19 | The Reality Of Ransomware |  | "About 1.5 million ransomware attacks occur annually, putting individuals and corporations in a no-win situation. ProPublica technology reporter Renee Dudley joins host Krys Boyd to explain how these attacks work, how firms can sometimes recover the stolen data, and how sometimes the solution is just to pay up.Her recent story on the topic is a joint investigation with The Guardian." |
| 18.5.19 | New Ge0l0Gic Ransomware |  | GrujaRS found the Ge0l0Gic Ransomware that appends the .ge0l0gic extension and drops a ransom note named .ge0l0gic_readme.txt. |
| 18.5.19 | ZQ Ransomware decryptor updated |  | Emsisoft has updated their ZQ Ransomware decryptor to support the w_unblock24@qq.com].ws variant. |
| 18.5.19 | New 4k Dharma variant released |  | Jakub Kroustek found a variant of the Dharma Ransomware that appends the .4k extension to encrypted files. |
| 18.5.19 | Baltimore Ransomware still affecting city services |  | Catalin Cimpanu states "A list of what's still down, almost 2 weeks after the attack:" |
| 18.5.19 | STOP Djvu Decrypter updated |  | Michael Gillespie released an update for his STOP Decrypter to support the offline IDs for the .shadow, .fordan, .codnat, and .dotmap extensions. |
11.5.19 | New MegaCortex Ransomware Found Targeting Business Networks | 
| A new ransomware has been discovered called MegaCortex that is targeting corporate networks and the workstations on them. Once a network is penetrated, the attackers infect the entire network by distributing the ransomware using Windows domain controllers. |
11.5.19 | New STOP Ransomware variant | 
| Amigo-A found a new STOP Djvu Ransomware variant that appends the .sarut extension to encrypted files. |
11.5.19 | New Navi Scarab Ransomware variant | 
| Alex Svirid found a new Scarab Ransomware variant that appends the .Navi extension to encrypted files. |
11.5.19 | New BAT Dharma variant | 
| Jakub Kroustek found a new Dharma ransomware variant that appends the .bat extension to encrypted files. |
11.5.19 | New Scarab Ransomware variant | 
| Amigo-A found a new Scarab Ransomware variant that appends the kes$ extension and drops a ransom nte named Инструкция по расшифровке.TXT. |
11.5.19 | New Scarab Ransomware variant | 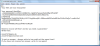
| Amigo-A found a new Scarab Ransomware variant that appends the .zoro extension and drops a ransom nte named !!! RESTORE DATA !!!.TXT. |
11.5.19 | New Dharma variants | 
| Jakub Kroustek found a bunch of new Dharma ransomware variants that append the ,qbix, .aa1, and .wal extension to encrypted files. |
11.5.19 | Yara rules created for the MegaCortex Ransomware | 
| Marc Rivero López created Yara rules to detect the MegaCortex ransomware and the Rietspoof loader. This MegaCortex rule is posted here and the Rietspoof rule is here. |
11.5.19 | New STOP Ransomware variant | 
| Amigo-A found a new STOP Djvu Ransomware variant that appends the .fedasot extension to encrypted files and drops a ransom note named _readme.txt. |
11.5.19 | New KBK GlobeImposter 2.0 variant | 
| Michael Gillespie found a new GlobeImposter 2.0 Ransomware variant that appends the .{Killback@protonmail.com}KBK extension. |
11.5.19 | Ransomware hunt for the Recry Ransomware | 
| Michael Gillespie is looking for a ransomware that appends the .recry1 extension and drops a ransom note named decryption_help.txt. |
11.5.19 | New STOP Ransomware variants | 
| Michael Gillespie found new STOP Djvu Ransomware variants that appends the .forasom or .berost extensions to encrypted files. |
11.5.19 | Local Authorities in Texas and Maryland Hit by Ransomware | 
| The servers of Baltimore City Hall and Amarillo, TX, Potter County were hit by ransomware attacks, with the former having shut down most servers while the latter already got some of its computing systems back online. |
11.5.19 | STOP Decryptor offline keys updated | 
| Michael Gillespie updated STOP Decryptor with the offline keys for .roldat, .dutan, .sarut, .berost, and .forasom. |
11.5.19 | Dharma Ransomware Uses Legit Antivirus Tool To Distract Victims | 
| A new Dharma ransomware strain is using ESET AV Remover installations as a "smoke screen" technique designed to distract victims while their files are encrypted in the background as detailed by Trend Micro. |
11.5.19 | New MERS Dharma variant | 
| Jakub Kroustek found a new Dharma ransomware variant that appends the .MERS extension to encrypted files. |
11.5.19 | New Blitzkrieg Ransomware | 
| Amigo-A found the new Blitzkrieg Ransomware that appends the .bkc extension and drops a ransom note named HowToBackFiles.txt. |
11.5.19 | Imperial County officials to invest in rebuilding network following cyber attack | 
| The hacker made a ransom demand of $1.2 million dollars in bitcoin to restore the network, a demand Imperial County decided not to pay. |
11.5.19 | Jokeroo Ransomware as a Service Pulls an Exit Scam | 
| Since May 7th, 2019, the Tor sites for the Jokeroo Ransomware as a Service (RaaS) have started displaying a notice stating that their server was seized by the Royal Thai Police in conjunction with the Dutch National Police and Europol. It turns out that this notice is fake and the RaaS is performing an exit scam. |
11.5.19 | New BKC GlobeImposter 2.0 variant | 
| Michael Gillespie found a new GlobeImposter 2.0 Ransomware variant that appends the [blellockr@godzym.me].bkc extension. |
| 11.5.19 | New STOP Ransomware variant |  | Michael Gillespie found a new STOP Djvu Ransomware variant that appends the .fordan extension to encrypted files. |
| 11.5.19 | MegaCortex, deconstructed: mysteries mount as analysis continues |  | It’s been a week since we published our initial research on the ransomware calling itself MegaCortex. Our initial post was written over about a day and a half, as we started to observe an early outbreak on May 1. We have a lot of new information to share today. |
| 11.5.19 | New Matrix Ransomware variant |  | Michael Gillespie found a new Matrix Ransomware variant that appends the .QH24 extension and drops a ransom note named !QH24_INFO!.rtf. |
| 11.5.19 | New FLKR Ransomware variant |  | Alex Svirid found a new FLKR Ransomware variant that appends the .+jabber-theone@safetyjabber.com extension to encrypted files. |
| 4.5.19 | Russian Legion Ransomware found |  | MalwareHunterTeam found a new HiddenTear variant called Russian Legion |
| 4.5.19 | Sodinokibi Ransomware found |  | GrujaRS found the Sodinokibi Ransomware that assigned a random extension to each victim. |
| 4.5.19 | BellevueInject Ransomware |  | MalwareHunterTeam found the BellevueInject CryptoWire variant that appears to target Bellevue College. Looks in-dev. |
| 4.5.19 | STOP Djvu Decryptor updated |  | Michael Gillespie updated the STOP Djvu decryptor to include the offline IDs for .etols, .guvara, .norvas, .moresa, .verasto, and .hrosas. |
| 4.5.19 | New Fredd Dharma variant |  | Michael Gillespie spotted a new Dharma Ransomware variant that appends the .FREDD extension. |
| 4.5.19 | BigBobRoss Ransomware decrypted updated |  | Emsisoft has updated their decryptor for the BigBobRoss Ransomware to support the .cheetah variant. |
| 4.5.19 | New Prodecryptor Ransomware |  | GrujaRS found a new ransomware named Prodecryptor that appends the .Prodecryptor extension and drops a ransom note named ReadME-Prodecryptor@gmail.com.txt. |
| 4.5.19 | New STOP Djvu variant |  | Michael Gillespie found a new STOP Djvu variant that appends the .todarius extension to encrypted files. |
| 4.5.19 | LockerGoga Ransomware Family Used in Targeted Attacks |  | Once again, we have seen a significant new ransomware family in the news. LockerGoga, which adds new features to the tried and true formula of encrypting victims’ files and asking for payment to decrypt them, has gained notoriety for the targets it has affected. |
| 4.5.19 | Sodinokibi Ransomware Being Installed on Exploited WebLogic Servers |  | Attackers are exploiting a recently disclosed WebLogic vulnerability to install a new ransomware called Sodinokibi. As this vulnerability is trivial to exploit, it is important that server admins install the patch immediately in order to prevent infections or unauthorized access. |
| 4.5.19 | GitHub-Hosted Malware Targets Accountants With Ransomware |  | Threat actors ran a malvertising campaign on the Russian Yandex.Direct advertising network starting October 2018 to disseminate a malware cocktail designed to encrypt victims' data and steal cryptocurrency. |
| 4.5.19 | New STOP Djvu ransomware variants |  | Michael Gillespie has found new STOP Djvu variants that append the .roldat or .hofos extensions to encrypted files. |
| 4.5.19 | New .TXT Dharma Variant |  | Michael Gillespie has spotted a new variant of the Dharma ransomware that uses the .txt extension for encrypted files. This going to confuse as a lot of people. |
| 4.5.19 | Windows Server hosting provider still down a week after ransomware attack |  | A ransomware infection has crippled the operations of a US-based web hosting provider for almost eight days now, several of the company's disgruntled customers have told ZDNet today. |
| 4.5.19 | New Video Dharma variant |  | Jakub Kroustek found a new variant of the Dharma ransomware that appends the .video extension to encrypted files. |
| 4.5.19 | New Zeropadypt Ransomware |  | Amigo_A_ found a new ransomware that fills "files with zeros". |
| 4.5.19 | Emsisoft releases a decryptor for the ZQ Ransomware |  | Emsisoft has released a decryptor for the ZQ Ransomware. |
| 4.5.19 | New WannaOof Ransomware |  | MalwareHunterTeam found a new ransomware called WannaOof that appends the .oof extension to encrypted files. |
| 4.5.19 | STOP decryptor updated with further offline keys |  | Michael Gillespie has updated his STOP decryptor with the offline keys for .kiratos and .todarius. |
| 4.5.19 | Decryptor for MegaLocker and NamPoHyu Virus Ransomware Released |  | Emsisoft has released a decryptor for the MegaLocker and NamPoHyu Virus ransomware that has been targeting exposed Samba servers. Victims can now use this decryptor to recover their files for free. |
| 4.5.19 | New Wal Dharma variant |  | Michael Gillespie has found a new Dharma variant that appends the .wal extension to encrypted files. |
| 4.5.19 | New STOP Djvu ransomware variant |  | Michael Gillespie has found a new STOP Djvu variant that append the .dutan extension to encrypted files. |
| 4.5.19 | “MegaCortex” ransomware wants to be The One |  | A new ransomware that calls itself MegaCortex got a jolt of life on Wednesday as we detected a spike in the number of attacks against Sophos customers around the world, including in Italy, the United States, Canada, the Netherlands, Ireland, and France. The attackers delivering this new malware campaign employed sophisticated techiques in the attempt to infect victims. |
| 27.4.19 | New STOP Djvu Ransomware variant |  | Michael Gillespie found a new STOP Djvu ransomware variant that appends the .moresa extension to encrypted files. |
| 27.4.19 | New Scarab Ransomware variant |  | Michael Gillespie found a new variant of the Scarab Ransomware that appends the .croc and drops a ransom note named HELP_BY_CROC.TXT. |
| 27.4.19 | New Paradise Ransomware variant |  | Michael Gillespie found a new Paradise Ransomware variant that appends the .sambo extension and drops a ransom note named Instructions with your files.txt. |
| 27.4.19 | New LDPR Dharma variant |  | Michael Gillespie found a new Dharma Ransomware that appends the .LDPR extension to encrypted files. |
| 27.4.19 | Someone made a payment to a WannaCry Ransomware wallet |  | Someone just paid 0.0584 BTC ($309.26 USD) to a bitcoin wallet tied to #WannaCry ransomware. |
| 27.4.19 | New Colorit Ransomware |  | Michael Gillespie spotted a new ransomware that appends the .COLORIT on ID Ransomware. |
| 27.4.19 | ST04: Ransomware Trends with Raj Samani and John Fokker |  | Raj Samani, Chief Scientist and McAfee Fellow, and John Fokker, Head of Cyber Investigations for McAfee Advanced Threat Research, discuss various ransomware attacks and how it’s evolving. |
| 27.4.19 | New STOP Djvu Ransomware variant |  | Michael Gillespie found a new version of the STOP Djvu ransomware that appends the .verasto extension to encrypted files. |
| 27.4.19 | New Scarab Ransomware variant |  | Amigo-A found a new variant of the Scarab Ransomware that appends the .vally extension. |
| 27.4.19 | New Major Ransomware variant |  | Michael Gillespie found a new variant of the Major Ransomware that appends the .mars extesion and drops a ransom note named READ_ME.mars. |
| 27.4.19 | Over 500% Increase in Ransomware Attacks Against Businesses |  | Cybercriminals have started focusing their efforts on businesses during Q1 2019, with consumer threat detections decreasing by roughly 24% year over year while businesses have seen a 235% increase in the number of cyber attacks against their computing systems. |
| 27.4.19 | New BigBobRoss Ransomware variant |  | Michael Gillespie found a new BigBobRoss variant that appends the .cheetah extension that drops a ransom note named How to recover your files.txt. |
| 27.4.19 | New STOP Djvu Ransomware variant |  | Michael Gillespie found a new STOP Djvu Ransomware variant that appends the .hrosas extension to encrypted files. |
| 27.4.19 | New Scarab Ransomware variant |  | Michael Gillespie found a new Scarab Ransomware variant that appends the .[zoro4747@gmx.de].zoro and drops a ransom note named !!! RESTORE DATA !!!.TXT. |
| 27.4.19 | New JSWorm variant discovered with a message for ID-Ransomware |  | S!Ri found a new variant of the JSWorm that has a message for ID Ransomware. |
| 27.4.19 | New GlobeImposter variant |  | GrujaRS found a new GlobeImposter variant that appends the .DOCM and drops a ransom note named Restore-My-Files.txt. |
| 27.4.19 | Vulnerable Confluence Servers Get Infected with Ransomware, Trojans |  | A critical Atlassian Confluence Server vulnerability is being remotely exploited by attackers to compromise both Linux and Windows servers, allowing them to drop GandCrab ransomware and the Dofloo (aka AES.DDoS, Mr. Black) Trojan. |
| 27.4.19 | Snatch Ransomware discovered |  | GrujaRS found the Snatch Ransomware that appends the .hceem extension and drops a ransom note named RESTORE_HCEEM_DATA.txt. |
| 27.4.19 | Signed Hermes Ransomware variant spotted |  | MalwareHunterTeam found a signed Hermes Ransomware variant. |
| 27.4.19 | New Kiratos Stop Djvu Ransomware variant |  | Amigo-A found a new STOP Djvu ransomware variant that appends the .kiratos extension to encrypted files. |
| 27.4.19 | A Closer Look at the RobbinHood Ransomware |  | The RobbinHood Ransomware is the latest player in the ransomware scene that is targeting companies and the computers on their network. This ransomware is not being distributed through spam but rather through other methods, which could include hacked remote desktop services or other Trojans that provide access to the attackers. |
| 20.4.19 | RobbinHood Ransomware Claims It's Protecting Your Privacy |  | A new ransomware is in play called RobbinHood that is targeting entire networks and then encrypting all computers that they can gain access to. They then request a certain amount of bitcoins to decrypt a single computer or a larger amount to decrypt the entire network. |
| 20.4.19 | New Locked Ransomware | 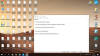 | Petrovic found a new ransomware that appends the .locked extension and drops a ransom note named README[number].txt. Below is an image supplied by GrujaRS of this infection. |
| 20.4.19 | New Proyecto X Ransomware |  | MalwareHunterTeam found a ransomware called Proyecto X that appends the .robinhood extension to encrypted files. |
| 20.4.19 | Android Sauron Locker Ransomware discovered |  | Lukas Stefanko found a new Android ransomware called Sauron Locker that locks device and replaces background wallpaper for ransom note. |
| 20.4.19 | Ransom amounts rise 90% in Q1 as Ryuk increases |  | Coveware's Q1 Ransomware Marketplace report aggregates anonymized ransomware data from cases handled and resolved by Coveware’s Incident Response Team. Unlike surveys, which rely on sentiment, this report is created solely from a standardized set of data collected from every case. By aggregating and sharing this data we believe large and small enterprises can better protect themselves from the persistent and ever-evolving ransomware threat. |
| 20.4.19 | 'NamPoHyu Virus' Ransomware Targets Remote Samba Servers |  | A new ransomware family called NamPoHyu Virus or MegaLocker Virus is targeting victims a bit differently than other ransomware. Instead of an executable running on a victim's computer, the attacker is running the ransomware locally and having it remotely encrypt accessible Samba servers. |
| 20.4.19 | New Phoenix Phobos Ransomware variant | 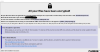 | GrujaRS found a new variant of the Phobos Ransomware that appends the .phoenix extension to encrypted files and drops a ransom note named info.txt. |
| 20.4.19 | New Exploit Paradise Ransomware variant |  | Amigo-A found a new Paradise Ransomware variant that appends the .exploit extension to encrypted files. |
| 20.4.19 | New Burn Scarab Ransomware variant |  | Michael Gillespie found a new Scarab Ransomware variant that appends the .burn extension to encrypted files. |
| 20.4.19 | Cube Ransomware Hunt |  | Michael Gillespie is looking for a new ransomware that appends the .cube extension and drops a ransom note named READ_ME.cube. |
| 20.4.19 | New CRABSLKT Scarab Ransomware variant |  | Amigo-A found a new Scarab Ransomware variant that appends the .CRABSLKT and drops a ransom note named HOW TO RECOVER ENCRYPTED FILES.TXT. |
| 20.4.19 | Cyber-security firm Verint hit by ransomware |  | The Israel offices of US cyber-security firm Verint have been hit by ransomware, according to a screenshot taken by a Verint employee that started circulating online earlier today. |
| 20.4.19 | DLL Cryptomix Ransomware Variant Installed Via Remote Desktop |  | The CryptoMix ransomware is still alive and kicking as a new variant has been spotted being spread in the wild. This new version appends the .DLL extension to encrypted files and is said to be installed through hacked remote desktop services. |
| 20.4.19 | New norvas STOP Djvu Ransomware |  | Michael Gillespie found a new STOP Djvu Ransomware variant that appends the .norvas extension to encrypted files. |
| 20.4.19 | Weekly Ransomware Market Share from Coveware | 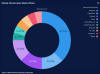 | Coveware notes that Ryuk attacks have continued to decline in prevalence since last week. New Variants of Dharma and Phobos continue to hit smaller enterprises via RDP in the US. A slew of GandCrab attacks hit enterprises in Western Europe via CVE’s that allow remote code execution |
| 20.4.19 | Jokeroo jokers modify a GandCrab executable? |  | Jakub Kroustek discovered an unpacked GandCrab 5.3 executable that contains strings from the Jokeroo RaaS. It is not known if it's the GandCrab devleopers poking fun at another ransomware developers or the jokers behind Jokeroo playing with GandCrab. |
| 13.4.19 | Genesee County, Michigan Recovering from Ransomware Attack |  | Genesee County, Michigan was hit with a ransomware attack on Tuesday and the county has been working non-stop to get their systems back online. Unfortunately, this process turned out to be more difficult than expected and system are still down. |
| 13.4.19 | Pick-Six: Intercepting a FIN6 Intrusion, an Actor Recently Tied to Ryuk and LockerGoga Ransomware |  | Recently, FireEye Managed Defense detected and responded to a FIN6 intrusion at a customer within the engineering industry, which seemed out of character due to FIN6’s historical targeting of payment card data. The intent of the intrusion was initially unclear because the customer did not have or process payment card data. Fortunately, every investigation conducted by Managed Defense or Mandiant includes analysts from our FireEye Advanced Practices team who help correlate activity observed in our hundreds of investigations and voluminous threat intelligence holdings. Our team quickly linked this activity with some recent Mandiant investigations and enabled us to determine that FIN6 has expanded their criminal enterprise to deploy ransomware in an attempt to further monetize their access to compromised entities. |
| 13.4.19 | New .btix Dharma variant |  | Jakub Kroustek discovered a new variant of the Dharma ransomware that appends the .btix extension to encrypted files. |
| 13.4.19 | New raldug STOP Djvu variant |  | Amigo-A found a new variant of the STOP Djvu ransomware that appends the .raldug extension to encrypted file names. |
| 13.4.19 | AsuraHTTP Bot with Ransomware capabilities |  | MalwareHunterTeam discovered a LiteHTTP Bot renamed as AsuraHTTP with some Ransomware code added to it. |
| 13.4.19 | Planetary Ransomware Decryptor Gets Your Files Back For Free |  | A decryptor for the Planetary Ransomware family was released by Emsisoft this week that allows victims to decrypt their files for free. This ransomware family is named Planetary because it commonly uses the names of planets for the extensions added to encrypted file's names. |
| 13.4.19 | Anubis Android Trojan Spotted with Almost Functional Ransomware Module |  | An Android application which steals PayPal credentials, encrypts files from the device's external storage, and locks the screen using a black screen was spotted in the Google Play Store by ESET malware researcher Lukas Stefanko. |
| 13.4.19 | GET YOUR DATA BACK WITHOUT PAYING RANSOM |  | "We reached out to three battle-weary ransomware knights — Wosar (whose day job is at Emsisoft), Lawrence Abrams from Bleeping Computer (a computer help site started in 2004) and Michael Gillespie, who founded the free ID Ransomware service three years ago — for tips on how individuals and businesses can thwart the thievery. They all had surprisingly similar advice" |
| 13.4.19 | Turkish Aurora offline variant |  | MalwareHunterTeam discovered a new Turkish Aurora offline variant that adds the .cryptoid extension to encrypted files. |
| 13.4.19 | GoRansom pushed by maldoc |  | enSilo found a ransomware written in Go that is being pushed by a malicious Word document. Appears to be a research project. |
| 13.4.19 | Distributor of the Reveton Police Ransomware Jailed by UK's NCA |  | A key member of a crime group behind the notorious Reveton Police Trojan that locked users out of Windows unless they paid a ransom has now found himself locked up in jail. |
| 13.4.19 | How did a teenager become the UK’s biggest cyber criminal? |  | BBC radio discusses:
Zain Qaiser made hundreds of thousands blackmailing porn users from his parents’ house. |
| 13.4.19 | STOP Djvu Decryptor updated |  | Michael Gillespie updated his STOP Djvu decryptor to support the offline IDs for the .grovat, .raldug, and .roland variants. |
| 13.4.19 | New Extortion Email Threatens to Install WannaCry and DDoS Your Network |  | A new extortion email scam campaign is underway that states that your computer was hacked and that it was discovered you were hiding your taxes. The alleged hackers then demand 2 bitcoins or they will notify the "Tax Department", DDoS your network, and then install the WannaCry ransomware. |
| 13.4.19 | How to Save Ransomware Encrypted Files for Decryption |  | Coveware writes: When ransomware strikes and restoring from backups is not an option, a victim often feels that paying the ransom is the only option. Often, victims realize that they can indeed live without the data that has been encrypted, and are able to wait for a potential free decryption solution to be published. Given how unpredictable the release of free decryptor tools is, how should ransomware victims plan their recovery? What can they do to increase their chances of a full recovery? |
| 13.4.19 | New Bitcoin666 Ransomware |  | MalwareHunterTeam found a new ransomware that appends the .bitcoin666@cock.li.word extension to encrypted files. |
| 13.4.19 | New .gate Dharma variant |  | Michael Gillespie spotted a new Dharma variant that uses the .gate extension. |
| 13.4.19 | New langolier Scarab variant |  | Amigo-A found a new Scarab variant that appends the .langolier extension to encrypted files and drops a ransom note named HOW TO RECOVER ENCRYPTED FILES.TXT. |
| 13.4.19 | New guvara and etols STOP Djvu Ransomware variants |  | Michael Gillespie found new variants of the STOP Djvu Ransomware that append the .guvara and .etols extensions. |
| 13.4.19 | Emsisoft released a decryptor for the CryptoPokemon |  | Emsisoft released a decryptor for the CryptoPokemon Ransomware that appends the .CRYPTOPOKEMON extension. |
| 13.4.19 | New fuchsia Scarab Ransomware variant |  | Amigo-A found a new Scarab variant that appends the .fuchsia extension and drops a ransom note named DECRYPT FILES.TXT. |
| 13.4.19 | New Love Dharma variant |  | Jakub Kroustek found a new variant of the Dharma ransomware that appends the .LOVE extension. |
| 13.4.19 | New Tokog Scarab Ransomware variant |  | Amigo-A found a new Scarab variant that appends the .tokog extension and drops a ransom note named HOW TO RECOVER ENCRYPTED FILES.TXT. |
| 13.4.19 | SadComputer Ransomware discovered |  | MalwareHunterTeam found the SadComputer ransomware which appends the .sad extension and drops a ransom note named sadcomputer_note.txt. |
| 13.4.19 | Weekly Ransomware Market Share from Coveware | 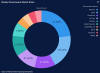 | According to Coveware, Ryuk cases have slowed a bit, though are still a substantial portion of new cases. GandCrab v5.2 has picked up slightly in April. Phobos and Dharma continue to hold the largest share of attacks affecting enterprises. |
| 13.4.19 | New browec STOP Djvu Ransomware variants |  | Michael Gillespie found a new variant of the STOP Djvu Ransomware that appends the .browec extension. |
6.4.19 | New Plant Matrix Ransomware variant |  | Stephen DeLucia discovered a new Matrix Ransomware variant that appends the .Plant extension. |
6.4.19 | RobLocker X discovered | 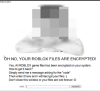 | GrujaRS found a new ransomware called RobLocker X. |
6.4.19 | vxCrypter Is the First Ransomware to Delete Duplicate Files |  | The vxCrypter Ransomware could be the first ransomware infection that not only encrypts a victim's data, but also tidy's up their computer by deleting duplicate files. |
6.4.19 | New York Albany Capital Hit by Ransomware Attack |  | The City of Albany, the capital of the U.S. state of New York, was hit by a ransomware attack on March 30, with city officials working over the weekend to respond to the incident. |
6.4.19 | Mira Ransomware decryptor released |  | F-secure released a decryptor for the Planetary ransomware variant that appends the .Mira extension. |
6.4.19 | Pacman Ransomware | 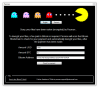 | MalwareHunterTeam found a new ransomware called.... Pacman. This ransomware prepends encrypted before the original extension. |
6.4.19 | Aurora decryptor released |  | Emsisoft released a decryptor for the Aurora ransomware. |
6.4.19 | New STOP Djvu variant |  | Michael Gillespie found a new variant of the STOP Djvu Ransomware that appends the .grovat extension to encrypted files. |
6.4.19 | Cyber Criminals Increasingly Target Small and Midsize Businesses |  | A report by Chubbs "examines the emergence of new #ransomware and #malware strains, including Emotet, Ryuk, and Credential Stuffing". |
6.4.19 | Norsk Hydro releases a documentary-like video on their LockerGoga cyberattack |  | In a unprecedented move, Norsk Hydro created a documentary-like video about the employees who discovered they were infected by LockerGoga. |
6.4.19 | New STOP Djvu variant |  | Michael Gillespie found a new variant of the STOP Djvu Ransomware that appends the .roland extension to encrypted files. |
6.4.19 | Arizona Beverages knocked offline by ransomware attack |  | Arizona Beverages, one of the largest beverage suppliers in the U.S., is recovering after a massive ransomware attack last month, TechCrunch has learned. |
6.4.19 | MR.Z3B1 Jigsaw variant | 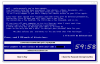 | MalwareHunterTeam found a new Jigsaw Ransomware variant that appends the Contact onlineservices1@usa.com Hacked by Z3b1 your ID [MI0985547KE] .locked extension to encrypted files. |
6.4.19 | New hunt for Ransomware that appends ._Crypted |  | Michael Gillespie is looking for a ransomware sample that appends the ._Crypted extension and drops a ransom note named _CRYPTED_README.html. |
6.4.19 | Seon Ransoware ver 0.2 found |  | JAMESWT found a new variant of the Seon Ransomware that brings it to "ver 0.2" and appends the .FIXT extension. |
6.4.19 | New ms13 Dharma variant |  | safety found a new variant of the Dharma ransomware that appends the .ms13 extension to encrypted files. |
6.4.19 | New Xwo Web Scanner Helps MongoLock Ransomware Find Victims |  | Code and infrastructure from two known malware families have been observed with a new threat named Xwo, which helps operators of the MongoLock ransomware discover unprotected web services reachable over the internet. |
6.4.19 | Planetary Ransomware decryptor released |  | Emsisoft has released a new decryptor for the Planetary Ransomware. This decryptor will target ransomware variants that append the .mira, .yum, .Neptune, or .Pluto extension. |
6.4.19 | New ransomware hunt |  | Michael Gillespie is looking for ransomware samples that append the .bmps@tutanota.com.major or .bmps@tutanota.com.major extension. |
6.4.19 | New STOP Djvu variant |  | Michael Gillespie found a new variant of the STOP Djvu Ransomware that appends the .refols extension to encrypted files. |
6.4.19 | FIN6 Group Diversifies Activity, Uses LockerGoga and Ryuk Ransomware |  | FIN6 cybercrime group has taken a step toward increased monetization of their intrusions and added ransomware to its portfolio, choosing LockerGoga and Ryuk file encryption malware for the extortion jobs. |
6.4.19 | New Phobos Ransomware variant |  | Michael Gillespie found a new Phobos variant that appends the .phoenix extension. |
| 6.4.19 | New .carcn Dharma variant |  | Jakub Kroustek found a new variant of the Dharma ransomware that appends the .carcn extension. |
| | | |












![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()






























