
- Android -
Last update 04.10.2017 16:16:35
Introduction List Kategorie Subcategory 0 1 2 3 4 5 6 7 8
New KevDroid Android Backdoor Discovered
3.4.2018 securityweek Android
Security researchers have discovered a new Android Remote Access Trojan (RAT) that can steal a great deal of information from infected devices.
Dubbed KevDroid, the mobile threat can steal contacts, messages, and phone history, while also able to record phone calls, Talos reports. Two variants of the malware have been identified so far.
One of the variants exploits CVE-2015-3636 to gain root access, but both implement the same call recording capabilities, taken from an open-source project on GitHub.
Once it has infected a device, the first KevDroid variant can gather and siphon information such as installed applications, phone number, phone unique ID, location, stored contacts information, stored SMS, call logs, stored emails, and photos.
Large in size, the second variant of the malware was hosted at the same URL in February, and has been observed using SQLite databases to store data. It includes the same data gathering capabilities, along with camera recording, audio recording, web history stealing, file stealing, and the ability to gain root on the device.
An ELF file embedded in the APK attempts to exploit the CVE-2015-3636 vulnerability using code available on GitHub to obtain root permission. By gaining higher privileges, the malware can perform more in-depth actions, including stealing files from other applications.
“If an adversary were successful in obtaining some of the information KevDroid is capable of collecting, it could result in a multitude of issues for the victim. The social aspect of a mobile device results in a large amount of data residing on the device. This can be sensitive data, such as photographs, passwords, banking information or social engineering,” Talos notes.
Attackers could also blackmail victims using images or information deemed secret, could steal credentials and multi-factor tokens (SMS MFA), and could also engage in banking/financial fraud using their access to privileged information. Should the infected device be used in corporate environments, a KevDroid attack could lead to cyber espionage, Talos says.
While analyzing the threat, the security researchers also discovered a Windows-targeting RAT hosted on the same C&C server. They called the malware PubNubRAT, because of it uses the PubNub global data stream network (DSN) as a C&C and leverages PubNub API to send orders to the compromised systems.
“Using legitimate services is always challenging for defenders. It's hard to identify malicious communications hidden in legitimate network flows (especially if the requests use encryption via HTTPS),” Talos notes.
A RTF file attempting to exploit the CVE-2017-11882 vulnerability in Office using an embedded Microsoft Equation object is used for infection. The document is written in Korean and contains information on Bitcoin and China.
Once it has infected a system, the malware can steal files, download files, execute commands, kill processes, and take screenshots.
According to Talos, they started the investigation into these malware families because of a possible link to Group 123, but the evidence they discovered was too weak to identify a clear connection with the group.
“We do not have a strong link between the two malware samples and Group 123. The TTP overlaps are tenuous — using public cloud infrastructure as a C2 server is something other malware has used before as a technique, not just Group 123. Additionally, the C2 server is hosted in Korea, and this malware has been known to target Korean users. However, this information cannot lead us to a strong link,” Talos concludes.
New Monero-Mining Android Malware Discovered
3.4.2018 securityweek Android
A newly discovered malware family attempts to leverage the (limited) computing power of Android devices to mine for Monero crypto-currency, Trend Micro warns.
Dubbed HiddenMiner, the malware was developed with self-protection and persistence mechanisms that allow it to hide itself from the unwitting user and to abuse the Device Administrator feature to perform its nefarious activities.
The main issue with this threat, however, is the fact that it has no switch, controller, or optimizer in its code, meaning that it essentially continuously mines for Monero until all of the device’s resources are depleted. Because of that, the malware can cause the infected devices to overheat and potentially fail, Trend Micro's researchers point out.
HiddenMiner is used in an active campaign that has resulted in its operators already making several thousands of dollars as of last week (based on the known Monero mining pools and wallets connected to the malware).
HiddenMiner, Trend Micro says, is somehow similar to the Loapi Monero-mining Android malware, which has been previously observed causing a device’s battery to bloat. Furthermore, both Loapi and HiddenMiner use a similar technique to lock the device screen after revoking device administration permissions.
The new threat spreads via third-party application marketplaces and has been observed impacting only users in India and China so far. However, the security researchers say it might spread beyond these two countries as well.
The malware masquerades as a legitimate Google Play update application, featuring the Google Play icon and appearing on the Android device’s screen as com.google.android.provider. The miner then asks the user to activate it as a device administrator and continuously displays the pop-up window until the users grants it the requested permissions.
Once installed, HiddenMiner empties the app label and uses a transparent icon to hide itself from the user. As soon as the device administrator rights are enabled, it hides from the app launcher by calling setComponentEnableSetting() and starts the mining operation in the background.
The threat hides itself and automatically runs with administrator permissions until the next device boot, the same as the DoubleHidden Android adware does.
Furthermore, the malware includes anti-emulator capabilities that allow it to bypass detection and automated analysis. It leverages an Android emulator detector found on Github for that.
To prevent victims from removing the acquired device administrator privileges, HiddenMiner locks the device’s screen when the user attempts to perform this action. For that, it abuses a bug in Android releases prior to Android 7.0 Nougat, the security researchers say.
In newer Android releases, device admin applications can no longer lock the screen. This security improvement prevents other malware such as ransomware and information stealers from abusing the device admin privileges as well.
“HiddenMiner is yet another example of how cybercriminals are riding the cryptocurrency mining wave. For users and businesses, this reinforces the importance of practicing mobile security hygiene: download only from official app marketplaces, regularly update the device’s OS (or ask the original equipment manufacturer for their availability), and be more prudent with the permissions you grant to applications,” Trend Micro concludes.
TeleRAT, a new Android Trojan that uses Telegram for data exfiltration
22.3.2018 securityaffairs Android
Security experts at Palo Alto Networks discovered a new Android Trojan dubbed TeleRAT that uses Telegram Bot API to communicate with the command and control (C&C) server and to exfiltrate data.
TeleRAT appears to be originating from and/or to be targeting individuals in Iran, experts found similarities with another Android malware dubbed IRRAT Trojan, which also leverages Telegram’s bot API for C&C communication communications.
“Telegram Bots are special accounts that do not require an additional phone number to setup and are generally used to enrich Telegram chats with content from external services or to get customized notifications and news.” reads the analysis published by PaloAlto networks. “And while Android malware abusing Telegram’s Bot API to target Iranian users is not fresh news (the emergence of a Trojan using this method called IRRAT was discussed in June and July 2017), we set out to investigate how these Telegram Bots were being abused to command and control malicious Android applications.”
The IRRAT is able to steal contact information, a list of Google accounts registered on the devices, SMS history, it is also able to take a picture with the front-facing and back-facing cameras.
Stolen data are stored on a series of files on the phone’s SD card and then sent to an upload server. The IRRAT malware reports to a Telegram bot, hides its icon from the phone’s app menu and runs in the background waiting for commands.
The TeleRAT Android malware operates in a different way, it creates two files on the device, telerat2.txt containing device information (i.e. system bootloader version number, available memory, and a number of processor cores), and thisapk_slm.txt containing a Telegram channel and a list of commands.
Once installed, the malicious code informs attackers on this by sending a message to a Telegram bot via the Telegram bot API with the current date and time. The malware also starts a background service that listens for changes made to the clipboard, and finally, the app fetches updates from the Telegram bot API every 4.6 second listening for several commands written in Farsi (Persian).
The TeleRAT is able to receive commands to grab contacts, location, app list, or the content of the clipboard; receive charging information; get file list or root file list; download files, create contacts, set wallpaper, receive or send SMS; take photos; receive or make calls; turn phone to silent or loud; turn off the phone screen; delete apps; cause the phone to vibrate; and get photos from the gallery.
TeleRAT is also able of uploading exfiltrated data using Telegram’s sendDocument API method, in this way it evades network-based detection.
“TeleRAT is an upgrade from IRRAT in that it eliminates the possibility of network-based detection that is based on traffic to known upload servers, as all communication (including uploads) is done via the Telegram bot API.” continues the analysis.
“Aside from additional commands, this new family’s main differentiator to IRRAT is that it also uploads exfiltrated data using Telegram’s sendDocument API method”
The malware is able to get updates in two ways, namely the getUpdates method (which exposes a history of all the commands sent to the bot, including the usernames the commands originated from), and the use of a Webhook (bot updates can be redirected to a HTTPS URL specified by means of a Webhook).
The TeleRAT malware is distributed via seemingly legitimate applications in third-party Android app stores and also via both legitimate and nefarious Iranian Telegram channels. According to PaloAlto networks, a total of 2,293 users were apparently infected, most of them (82%) having Iranian phone numbers.

The campaign has a poor OPSEC, the experts have found an image of the botmaster testing out the malware, along with exfiltrated messages to confirm it. The analysis of the malicious code revealed that it contains the developer’s username in the code and reference to ‘vahidmail67’ Telegram channel that advertises applications to help users get likes and followers on Instagram, ransomware, and even the source code for an unnamed RAT.
“Aside from the Telegram channel, while looking for references to certain TeleRAT components we stumbled upon somethreads on an Iranian programmers’ forum advertising the sale of a Telegram bot control library. The forum is frequented by some of the developers whose code is heavily reused in a big portion of the TeleRAT samples we came across.” continues the analysis.
Experts pointed out that TeleRAT puts together code written by several developers, including freely available source code via Telegram channels and code offered for sale on several forums, making it difficult to attribute the malware to one single bad actor behind both IRRAT and TeleRAT.
The experts concluded that the malware could be the work of several actors possibly operating inside of Iran.
Android Trojan Leverages Telegram for Data Exfiltration
21.3.2018 securityweek Android
A newly discovered Android Trojan is abusing Telegram’s Bot API to communicate with the command and control (C&C) server and to exfiltrate data, Palo Alto Networks security researchers warn.
Dubbed TeleRAT, the malware appears to be originating from and/or to be targeting individuals in Iran. The threat is similar to the previously observed IRRAT Trojan, which uses Telegram’s bot API for C&C communication only.
Still active in the wild, IRRAT masquerades as applications supposedly informing users on the number of views their Telegram profile received (something that Telegram doesn’t actually allow for). After the app’s first launch, the malware creates and populates a series of files on the phone’s SD card, which it then sends to an upload server.
The files contain contact information, a list of Google accounts registered on the phone, SMS history, a picture taken with the front-facing camera, and a picture taken with back-facing camera. The malicious app reports to a Telegram bot, hides its icon from the phone’s app menu, and continues to run in the background, waiting for commands.
TeleRAT, on the other hand, creates two files on the device, one containing various device information (including system bootloader version number, available memory, and number of processor cores), and another containing a Telegram channel and a list of commands, Palo Alto Networks says.
After installation, the RAT informs attackers on this by sending a message to a Telegram bot via the Telegram bot API with the current date and time. It also starts a background service to listen for changes made to the clipboard, and fetches updates from the Telegram bot API every 4.6 seconds, listening for commands.
Based on the received commands, the malware can grab contacts, location, app list, or the content of the clipboard; receive charging information; get file list or root file list; download files, create contacts, set wallpaper, receive or send SMS; take photos; receive or make calls; turn phone to silent or loud; turn off the phone screen; delete apps; cause the phone to vibrate; and get photos from the gallery.
The new malware family is also capable of uploading exfiltrated data using Telegram’s sendDocument API method. By performing all communication via the Telegram bot API, it evades network-based detection.
The use of said API allows for getting updates in two manners, namely the getUpdates method (which exposes a history of all the commands sent to the bot, including the usernames the commands originated from), and the use of a Webhook (bot updates can be redirected to a HTTPS URL specified by means of a Webhook).
The researchers claim to have found an image of the botmaster testing out the RAT, along with exfiltrated messages to confirm it. The malware also appears to contain the developer’s username in the code, which lead researchers to the ‘vahidmail67’ Telegram channel, which advertises applications to help users get likes and followers on Instagram, ransomware, and even the source code for an unnamed RAT.
The researchers also found threads on an Iranian programmers’ forum advertising the sale of a Telegram bot control library and say that code from developers frequenting the forum was found in encountered TeleRAT samples. Although the forum claims all content is in accordance with Iran’s laws, the malicious use for some of the code advertised there is clear.
Because TeleRAT puts together code written by several developers, including freely available source code via Telegram channels and code sold on forums, this makes it difficult to point to one single actor commanding either IRRAT or TeleRAT. Thus, Palo Alto Networks says the malware could be the work of several actors possibly operating inside of Iran.
The malware is distributed via seemingly legitimate applications in third-party Android app stores and also distributed and shared via both legitimate and nefarious Iranian Telegram channels. A total of 2,293 users were apparently infected, based on the analyzed infrastructure, with 82% of the victims having Iranian phone numbers.
Pre-Installed Malware Found On 5 Million Popular Android Phones
17.3.2018 thehackernews Android
Security researchers have discovered a massive continuously growing malware campaign that has already infected nearly 5 million mobile devices worldwide.
Dubbed RottenSys, the malware that disguised as a 'System Wi-Fi service' app came pre-installed on millions of brand new smartphones manufactured by Honor, Huawei, Xiaomi, OPPO, Vivo, Samsung and GIONEE—added somewhere along the supply chain.
All these affected devices were shipped through Tian Pai, a Hangzhou-based mobile phone distributor, but researchers are not sure if the company has direct involvement in this campaign.
According to Check Point Mobile Security Team, who uncovered this campaign, RottenSys is an advanced piece of malware that doesn't provide any secure Wi-Fi related service but takes almost all sensitive Android permissions to enable its malicious activities.
"According to our findings, the RottenSys malware began propagating in September 2016. By March 12, 2018, 4,964,460 devices were infected by RottenSys," researchers said.
To evade detection, the fake System Wi-Fi service app comes initially with no malicious component and doesn’t immediately start any malicious activity.
Instead, RottenSys has been designed to communicate with its command-and-control servers to get the list of required components, which contain the actual malicious code.
RottenSys then downloads and installs each of them accordingly, using the "DOWNLOAD_WITHOUT_NOTIFICATION" permission that does not require any user interaction.
Hackers Earned $115,000 in Just Last 10 Days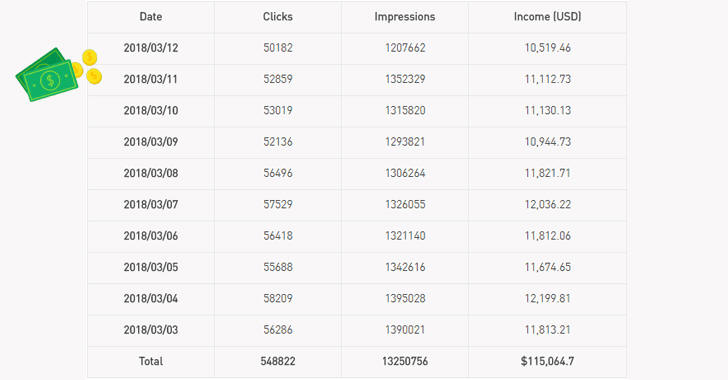
At this moment, the massive malware campaign pushes an adware component to all infected devices that aggressively displays advertisements on the device’s home screen, as pop-up windows or full-screen ads to generate fraudulent ad-revenues.
"RottenSys is an extremely aggressive ad network. In the past 10 days alone, it popped aggressive ads 13,250,756 times (called impressions in the ad industry), and 548,822 of which were translated into ad clicks," researchers said.
According to the CheckPoint researchers, the malware has made its authors more than $115,000 in the last 10 days alone, but the attackers are up to "something far more damaging than simply displaying uninvited advertisements."
Since RottenSys has been designed to download and install any new components from its C&C server, attackers can easily weaponize or take full control over millions of infected devices.
The investigation also disclosed some evidence that the RottenSys attackers have already started turning millions of those infected devices into a massive botnet network.
Some infected devices have been found installing a new RottenSys component that gives attackers more extensive abilities, including silently installing additional apps and UI automation.
"Interestingly, a part of the controlling mechanism of the botnet is implemented in Lua scripts. Without intervention, the attackers could re-use their existing malware distribution channel and soon grasp control over millions of devices," researchers noted.
This is not the first time when CheckPoint researchers found top-notch brands affected with the supply chain attack.
Last year, the firm found smartphone belonging to Samsung, LG, Xiaomi, Asus, Nexus, Oppo, and Lenovo, infected with two pieces of pre-installed malware (Loki Trojan and SLocker mobile ransomware) designed to spy on users.
How to Detect and Remove Android Malware?
To check if your device is being infected with this malware, go to Android system settings→ App Manager, and then look for the following possible malware package names:
com.android.yellowcalendarz (每日黄历)
com.changmi.launcher (畅米桌面)
com.android.services.securewifi (系统WIFI服务)
com.system.service.zdsgt
If any of above is in the list of your installed apps, simply uninstall it.
New “HenBox” Android Malware Discovered
15.3.2018 securityweek Android
A newly discovered Android malware family masquerades as various popular applications and can steal a broad range of information from infected devices, Palo Alto Networks warns.
Dubbed HenBox, the malware was observed installing the legitimate versions of apps it poses as to hide its presence on compromised devices. The threat is distributed via third-party app stores and mainly targets Uyghur, a minority Turkic ethnic group in the Xinjiang Uyghur Autonomous Region in North West China, and Xiaomi devices.
On the infected devices, HenBox can steal information from mainstream chat, communication, and social media apps. It gathers both personal and device information, can track the device’s location, can access the microphone and camera, and harvests outgoing phone numbers with an “86” prefix (the country code for the People’s Republic of China).
Palo Alto's researchers discovered nearly 200 HenBox samples, the oldest dating back to 2015, but activity occured in the second half of 2017. A small but consistent number of samples has been observed this year as well.
While analyzing the mobile threat, Palo Alto connected it to infrastructure used in targeted attacks in South East Asia that used malware such as PlugX, Zupdax, 9002, and Poison Ivy.
One of the apps HenBox was observed masquerading as (in May 2016) is DroidVPN, which promises increased security and privacy and the ability to bypass regional Internet restrictions. The software was distributed via uyghurapps[.]net, and the researchers believe a vulnerable Apache Web Server on a Windows 32-Bit operating system was exploited to replace the legitimate app.
The HenBox app had the look and feel of DroidVPN and also contained a legitimate version of the app within its APK package as an asset, to hide any malicious behaviors occurring in the background. The malware authors even embedded HenBox with the same version of the legitimate DroidVPN variant available for download on the third-party store.
DroidVPN, however, is only one example. Other apps were also found, some in other third-party stores. One was a Uyghur language keyboard app, while another was masquerading as Android’s Settings app.
A third app was called “Islamawazi,” which is the name of the Turkistan Islamic Party, formerly East Turkestan Islamic Party, a purportedly Islamic extremist separatist organization founded by Uyghur jihadists.
“These examples, together with the HenBox app placed on a very specific third-party app store, point clearly to at least some of the intended targets of these malicious apps being Uyghurs, specifically those with interest in or association with terrorist groups,” the researchers note.
The malware’s components are obfuscated in some way and are responsible for various functions, including handling decryption, network communications, gaining super-user privileges, monitoring system logs, loading additional Dalvik code files, tracking the device location, and more.
Once on a compromised device, HenBox is either executed by the victim – the app also checks whether it runs on a Xiaomi device with Xiaomi’s fork of Android and whether it runs in an emulator – or by using intents, broadcasts, and receivers – where the app is launched by another program.
Regardless of the execution method, a HenBox service is ultimately launched on the infected device, hidden from the user, and an ELF library is loaded to gather environmental information about the device, including running processes and apps, and device hardware information.
A customized super user tool is also loaded onto the device, to run privileged commands on the system. It can also steal messages and other data from popular messaging and social media apps, including Voxer Walkie Talkie Messenger and Tencent’s WeChat.
The HenBox infrastructure was found to be related to malware families used in targeted attacks against Windows users. “The overall image of these ties […] paints a picture of an adversary with at least 5 malware families in their toolbox dating back to at least 2015,” Palo Alto notes.
In addition to third-party stores, where the vetting process is not as thorough as in Google Play or other official stores, the malicious HenBox apps might also be distributed via forums and file-sharing sites, or could be delivered to the intended victims as email attachments. Either way, the malware appears mainly focused on spying on Uyghur language users.
“The targets and capabilities of HenBox, in addition to the ties to previous activity using four different Windows malware families with political-themed lures against several different South East Asian countries, indicates this activity likely represents an at least three-year-old espionage campaign,” Palo Alto Networks concludes.
Android's March 2018 Patches Fix Critical, High Risk Flaws
6.3.2018 securityweek Android
Google has released its March 2018 set of security updates for Android to address numerous Critical and High severity vulnerabilities in the popular mobile operating system.
The majority of the Critical vulnerabilities addressed this month could allow an attacker to execute code remotely on affected devices. Impacted components include media framework, system, and kernel, Nvidia, and Qualcomm components.
A total of 16 vulnerabilities were addressed as part of the 2018-03-01 security patch level: 8 rated Critical severity and 8 considered High risk. The most severe of these vulnerabilities could allow a remote attacker using a specially crafted file to run arbitrary code with high privileges.
Four of the Critical flaws (three remote code execution bugs and one elevation of privilege issue) and two High risk bugs (elevation of privilege) were addressed in media framework. The remaining four Critical vulnerabilities (all remote code execution) and six High risk issues (information disclosure bugs) were resolved in system.
The 2018-03-05 security patch level addressed 21 vulnerabilities, only three of which were rated Critical severity. All of the remaining bugs were assessed High risk, Google notes in an advisory.
The flaws affect Kernel components (two elevation of privilege and four information disclosure High risk issues), NVIDIA components (two High risk elevation of privilege bugs), Qualcomm components (two Critical – remote code execution – and nine High risk – six elevation of privilege, two information disclosure, and one denial of service – vulnerabilities), and Qualcomm closed-source components (one Critical and one High risk).
Google also addressed over 40 vulnerabilities impacting its Pixel / Nexus devices this month, most of them rated Moderate severity.
A Moderate risk elevation of privilege issue was patched in framework, 2 High severity denial of service bugs were resolved in Media framework, and 2 elevation of privilege and 2 information disclosure vulnerabilities were fixed in system, all four Medium risk.
Google also addressed 1 High risk information disclosure and 5 Moderate elevation of privilege issues in kernel components, 3 moderate information disclosure bugs in Nvidia components, and 18 elevation of privilege and 9 information disclosure issues in Qualcomm components (all Moderate severity).
Pixel 2 and Pixel 2 XL devices also received fixes for several functionality issues that were not related to the security of these devices. Instead, they improved screen wake performance with fingerprint unlock, audio performance when recording video, and crash reporting.
Mobile Banking Trojans Targeting Crypto-Currencies
6.3.2018 securityweek Mobil Android
Mobile malware is now targeting crypto-currencies with the intent of stealing victims’ funds, IBM says.
The immediate result of the massive increase in value that crypto-currencies have registered over the past year was the growth of malicious attacks attempting to steal coins from unsuspecting users. While most of these assaults involved PC malware so far, recent incidents have shown that mobile threats are picking up the pace as well.
Several weeks ago, IBM observed that the TrickBot Trojan was using webinjections to steal virtual coins from its victims by replacing legitimate addresses with those of the attacker. Working in a similar manner, mobile malware is now using screen overlays to trick victims into sending funds to the attacker instead, IBM's security researchers discovered.
According to IBM, mobile malware targeting crypto-coins usually leverages malicious miners to collect coins, but the practice isn’t that profitable, given the limited processing power a mobile device has. Furthermore, users are more likely to discover a mining operation on a mobile device when observing overheating, low performance and faster battery drain.
“Crooks operating mobile banking Trojans don’t install miners on the device. Rather, they typically steal existing coins from unsuspecting owners using mobile malware that creates the same effect as webinjections: cybercriminals trick users with fake on-screen information, steal their access credentials and take over accounts to empty coins into their own wallets,” IBM notes.
Some of the mobile malware families capable of detecting the application opened on a mobile device include ExoBot, BankBot, Marcher, and Mazar. Based on the launched application, these Trojans can display a hardcoded or dynamically fetched overlay and hide the legitimate app screen behind a fake one.
Thus, users end up revealing their credentials to the malware operators, which can then abuse them to access the victim’s account. If a second-factor authorization is required, the malware can hijack it from the compromised device without alerting the victim.
Usually employed in attacks targeting bank accounts, the method has been adapted for the theft of crypto-coins as well, the researchers discovered. Trojans such as BankBot and Marcher have been already packed with the necessary functionality to overlay a fake screen when the user opens relevant wallet apps.
The malware, IBM says, targets multiple virtual currencies, including Bitcoin, Bitcoin Cash, Ethereum, Litecoin, Monero, and other. Although basic-looking, the overlay screens are convincing and can trick users into unknowingly sending their access credentials to an attacker.
“The mobile malware arena already strives to emulate the success of PC banking Trojans and facilitate cross-channel fraud and identity theft. Cryptocurrency is just another target for malware operators looking to get in on the action. Given the rapid evolution of this threat, organizations should invest in mobile threat protection tools to minimize the risk posed by mobile banking Trojans,” IBM concludes.
Triada Trojan Pre-Installed on Low Cost Android Smartphones
5.3.2018 securityweek Android
Security researchers have discovered the sophisticated Triada Trojan in the firmware of more than 40 low-cost Android smartphone models.
Discovered in early 2016 and considered one of the most advanced mobile threats out there, Triada stands out in the crowd because it abuses the Zygote parent process to inject its code in the context of all software on the device. The Trojan uses root privileges to replace system files and resides mainly in the device’s RAM, which makes it difficult to detect.
In April last year, security researchers discovered that Triada had adopted sandbox technology in an attempt to boost its detection evasion capabilities. Specifically, the malware was using the open source sandbox DroidPlugin, which allowed it to dynamically load and run code going through the installation process.
Several months later, in July 2017, Doctor Web reported that Triada was present in the firmware of several low-cost Android smartphones. At the time, the list of infected device models included Leagoo M5 Plus, Leagoo M8, Nomu S10, and Nomu S20.
Now, the security firm reveals that the Trojan comes pre-installed on a larger number of Android smartphone models, even on devices that were launched in December 2017. Overall, over 40 device models were found to be impacted, the security researchers say.
The specific malware variant found on these devices is detected as Android.Triada.231 and includes all of the capabilities a member of the Triada family comes with: it injects its module in the Zygote process to penetrate all running applications on the device.
This allows the Trojan to carry out a broad range of malicious activities without user interaction, such as covertly downloading and launching applications. Designed with a modular architecture, Triada can redirect financial SMS transactions to buy additional content or steal money from the user.
Because the malware authors managed to inject Android.Triada.231 into the libandroid_runtime.so system library, they are able to compromise a device’s firmware during the manufacturing process, and users end up receiving smartphones that have been already infected.
Doctor Web says they notified manufacturers who produced infected devices of the compromise last year, but infected models continue to be produced. One of these is the Leagoo M9 smartphone, which was announced in December 2017.
“Additionally, our analysts’ research showed that the Trojan’s penetration into firmware happened at request of the Leagoo partner, the software developer from Shanghai. This company provided Leagoo with one of its applications to be included into an image of the mobile operating system, as well as with an instruction to add third-party code into the system libraries before their compilation,” Doctor Web says.
Despite this controversial request, the manufacturer didn’t become suspicious and the Trojan ended up on the new smartphone model without any obstacles.
The security researchers also discovered that the malicious application was signed with the same certificate as Android.MulDrop.924, a Trojan discovered in 2016. This suggests that the developer requesting the addition of the code into the mobile operating system image might be involved in the distribution of Triada.
Doctor Web published a list of the 40 device models infected with Triada, but warns that the list might not be comprehensive, as other compromised smartphones could exist out there. Impacted manufacturers include Leagoo, ARK, Zopo, Doogee, Vertex, Advan, Cubot, Prestigio, Pelitt, and more.
“Such widespread distribution of Android.Triada.231 shows that many Android device manufacturers pay little attention to security questions and penetration of the Trojan code into system components. This can be due to error or malicious intent and is likely common practice,” the researchers point out.
Over 40 models of low-cost Android devices shipped with Triada banking Trojan
4.3.2018 securityaffairs Android
Security researchers at Dr.Web have discovered over 40 models of low-cost Android smartphones are shipped with the dreaded Android Triada banking malware.
Security researchers at Antivirus firm Dr.Web have discovered that 42 models of low-cost Android smartphones are shipped with the Android.Triada.231 banking malware.
“In the middle of 2017, Doctor Web analysts discovered a new Trojan Android.Triada.231 in the firmware of some cheap models of Android devices. Since this detection, the list of infected devices has been constantly increasing.” reads the blog post published by Dr-Web. “At the moment, the list contains over 40 models. Doctor Web specialists have monitored the Trojan’s activity and now we can publish the results of this investigation.”
The Triada Trojan was spotted for the first time in 2016 by researchers at Kaspersky Lab that considered it the most advanced mobile threat seen to the date of the discovery.
Triada was designed with the specific intent to implement financial frauds, typically hijacking the financial SMS transactions. The most interesting characteristic of the Triada Trojan apart is its modular architecture, which gives it theoretically a wide range of abilities.
The Triada Trojan makes use of the Zygote parent process to implement its code in the context of all software on the device, this means that the threat is able to run in each application.
The only way to remove the threat is to wipe the smartphone and reinstall the OS.
Researchers at Dr.Web discovered the Triada Trojan pre-installed on newly shipped devices several minor brands, including Advan, Cherry Mobile, Doogee, and Leagoo.
This isn’t the first time the company discovered a pre-installed malware on Android device, back in in July 2017 Dr..Web researchers discovered the many smartphone models were shipped with the dreaded Triada trojan such as Leagoo M5 Plus, Leagoo M8, Nomu S10, and Nomu S20.
Triada Trojan Android pre-installed malware
The researchers at Dr.Web who investigated the issue discovered that a software developer from Shanghai was responsible for the infection.
“For example, it was detected on the Leagoo M9 smartphone that was announced in December 2017. Additionally, our analysts’ research showed that the Trojan’s penetration into firmware happened at request of the Leagoo partner, the software developer from Shanghai.” continues the blog post.
“This company provided Leagoo with one of its applications to be included into an image of the mobile operating system, as well as with an instruction to add third-party code into the system libraries before their compilation. Unfortunately, this controversial request did not evoke any suspicions from the manufacturer. Ultimately, Android.Triada.231 got to the smartphones without any obstacles.”
The infected app found on the device was developed by a Chinese firm, the experts highlighted that the code was signed with the same certificate that was observed in 2016 infections.
“The analysis of this application showed it is signed with the same certificate as Android.MulDrop.924. Doctor Web previously wrote about this Trojan in 2016. We can presume the developer that requested adding the additional program into the mobile operating system image can be connected expressly or implicitly with the distribution of Android.Triada.231.” continues Dr.Web.
At the moment, the experts confirmed to have detected the Android.Triada.231 in the firmware of the following Android device models:
Leagoo M5
Leagoo M5 Plus
Leagoo M5 Edge
Leagoo M8
Leagoo M8 Pro
Leagoo Z5C
Leagoo T1 Plus
Leagoo Z3C
Leagoo Z1C
Leagoo M9
ARK Benefit M8
Zopo Speed 7 Plus
UHANS A101
Doogee X5 Max
Doogee X5 Max Pro
Doogee Shoot 1
Doogee Shoot 2
Tecno W2
Homtom HT16
Umi London
Kiano Elegance 5.1
iLife Fivo Lite
Mito A39
Vertex Impress InTouch 4G
Vertex Impress Genius
myPhone Hammer Energy
Advan S5E NXT
Advan S4Z
Advan i5E
STF AERIAL PLUS
STF JOY PRO
Tesla SP6.2
Cubot Rainbow
EXTREME 7
Haier T51
Cherry Mobile Flare S5
Cherry Mobile Flare J2S
Cherry Mobile Flare P1
NOA H6
Pelitt T1 PLUS
Prestigio Grace M5 LTE
BQ 5510
Unfortunately, the number of infected smartphones models could be much bigger.
"RedDrop" Mobile Malware Records Ambient Audio
1.3.2018 securityweek Android
A newly detailed mobile malware can do more than steal data from infected devices: it can also record ambient audio and send the recordings to cloud storage accounts controlled by attackers.
Dubbed RedDrop, the malware can also inflict financial costs on victims by sending SMS messages to premium services, security firm Wandera says. The U.K.-based company has discovered 53 malware-ridden apps that are exfiltrating sensitive data from infected devices.
RedDrop-infected applications are being distributed through a network of more than 4,000 domains and range from tools such as image editors and calculators to recreational apps. Every observed application offers the expected functionality, thus hiding the malicious content stored within.
Once the user installs an application from the RedDrop family, invasive permissions are requested, so that the next steps of the attack would be performed without additional user interaction, the security researchers reveal. The malware even asks for permissions that allow it to persist between reboots and to continuously communicate with its command and control (C&C) servers.
To lure victims to their malicious network, the attackers even display ads on the popular Chinese search engine Baidu. One such ad would take the user to huxiawang.cn, the primary distribution site for the attack, which encourages users to download one of the 53 malicious apps.
Once the user installs a RedDrop-infected application, 7 additional APKs are silently downloaded and executed on the device, each meant to enable additional malicious functionality. The downloaded components are stored dynamically into the device’s memory.
One of the observed applications (CuteActress) was designed to send an SMS message to a premium service each time the user would touch the screen to interact with the app’s legitimate functionality. The threat would also delete all of these messages, thus erasing any evidence of these premium SMS.
The RedDrop malware family also includes a set of spyware tools capable of extracting valuable and damaging data from the victim’s device. The Wandera researchers associated encrypted and unencrypted data, encoded data and TCP streams to RedDrop’s exfiltration activities.
Stolen data includes locally saved files (such as photos and contacts), device-related information (IMEI, IMSI, etc), SIM info (MNC, MCC, etc), application data, and information on nearby Wi-Fi networks. More disturbing is the fact that RedDrop can also record an audio of device’s surroundings.
According to Wandera, RedDrop is one of the most sophisticated Android malware families, given the range of functioning malicious applications it hides behind and its complex distribution network. The malware is expected to remain active even after the applications are flagged as malicious, and new variants are expected to emerge in the coming months.
“This multifaceted hybrid attack is entirely unique. The malicious actor cleverly uses a seemingly helpful app to front an incredibly complex operation with malicious intent. This is one of the more persistent malware variants we’ve seen,” Dr Michael Covington, VP of Product Strategy at Wandera, says.
According to Craig Young, computer security researcher for Tripwire, this is not the first time Android malware that includes such extensive spyware capabilities has been discovered and the research appears exaggerated.
“This looks more like a very amateur trial run of Android malware rather than “one of the most sophisticated pieces of Android malware” as claimed by Wandera,” Young told SecurityWeek in an emailed comment.
He also pointed out that the malware’s ability to record and upload calls “provides minimal value outside of targeted attacks and potentially makes the malware more apparent by draining a victim’s battery quickly.”
Young recommends paying extra attention to the permissions applications may request, as this is a great means to stay safe from infections.
“With Android 6 (released 2015), apps will request permissions at runtime which should make it abundantly obvious when a malicious app wants to do something like sending SMS or recording audio. Users of older Android releases must rely instead on reviewing the requested permissions at install time to confirm that they are appropriate for the app,” Young concluded.
RedDrop, a new Android Malware records ambient Audio and exfiltrate user’s data
1.3.2018 securityaffairs Android
RedDrop malware is a recently discovered mobile threat that can steal data from infected devices and also record ambient audio.
Security researchers at Wandera have spotted a new sophisticated family of mobile malware dubbed RedDrop that can steal data, record audio, and intercept SMS. All data stolen from infected systems is uploaded to remote file storage systems.
The malicious code was found in dozens of apparently innocuous apps, the researchers discovered RedDrop hidden in 53 Android applications, including image editors, calculators, language learning apps and space exploration apps.
The applications work as expected and the RedDrop malware is executed in the background.
“The latest zero-day threat to be discovered by Wandera’s mobile threat research team is RedDrop, a family of mobile malware inflicting financial cost and critical data loss on infected devices.” reads the analysis published by Wandera. “The most worrying part? The 53 malware-ridden apps are exfiltrating sensitive data – including ambient audio recordings – and dumping it in the attackers’ Dropbox accounts to prepare for further attacks and extortion purposes.”
Once an infected app is installed, it downloads at least seven more Android Application Packages (APKs) from a different command and control server, each of them implements a malicious functionality. The APKs are stored in the memory of the device, this trick allows to execute them without including the feature in the original malware sample.
The RedDrop malware could also send SMS message to a premium service and then instantly deletes the message to avoid detection by the user.
The researchers discovered that the malicious Apps are distributed from a complex network composed of more than 4,000 domains registered to the same underground group that might be operating out of China.
“Wandera’s machine learning detections first uncovered one of the RedDrop apps when a user clicked on an ad displaying on popular Chinese search engine Baidu.” continues the analysis. “The user was then taken to huxiawang.cn, the primary distribution site for the attack. The landing pages that follow host various content to encourage and incite the user to download one of the 53 apps within the RedDrop family of malicious apps.”
One of the applications observed by the researchers (CuteActress) was designed to send an SMS message to a premium service every time the user would use a functionality of the app. The threat would also delete all of these messages, thus erasing any evidence of these premium SMS.

Currently, most of the infections were observed are in China, followed by Europe and America.
Android users that download apps from third-party sources and websites are most exposed to this threat, no instance of the RedDrop malware have been yet found on the Google Play store neither other official stores.
Android P Will Block Background Apps from Accessing Your Camera, Microphone
27.2.2018 thehackernews Android
Yes, your smartphone is spying on you. But, the real question is, should you care?
We have published thousands of articles on The Hacker News, warning how any mobile app can turn your smartphone into a bugging device—'Facebook is listening to your conversations', 'Stealing Passwords Using SmartPhone Sensors', 'Your Headphones Can Spy On You' and 'Android Malware Found Spying Military Personnel' to name a few.
All these stories have different objectives and targets but have one thing in common, i.e., apps running in the background covertly abuse ‘permissions’ without notifying users.
Installing a single malicious app unknowingly could allow remote attackers to covertly record audio, video, and taking photos in the background.
But, not anymore!
In a boost to user privacy, the next version of Google's mobile operating system, Android P, will apparently block apps idling in the background from accessing your smartphone's camera and microphone.
According to the Android Open Source Project (AOSP) commit, Google is working on two built-in features in Android P to protect its users from malicious apps spying on them using smartphones’ camera or microphone.
First spotted by XDA developers, the source code commit for both the camera and microphone changes notes that apps that are "idle" (aka running in the background) "for more than a certain amount of time" without specifying themselves will not be able to use the microphone or camera.
To do so, the Android P mobile operating system would target something known as an app's User ID (UID)—a unique ID assigned to an app when a user downloads it on his/her Android device that cannot be altered and are permanent until the app is uninstalled.
Android P would keep an eye on the app’s UID and block it from accessing the camera and microphone in any way whenever that UID is idle. Repeated attempts of requesting access to the camera would generate errors.
However, microphone-using apps will not be cut off from the microphone, but will "report empty data (all zeros in the byte array), and once the process goes in an active state, we report the real mic data."
It should also be noted that users talking on the smartphone while using other apps will not have to worry about these new features because the dialer application went into the background while active.
Imposing such limitations on apps would surely alleviate spying fears for Android users as of today when advertisers misuse such features to listen in on app users and Android malware capable of capturing audio, video, and images in the background are out there, for example, Skygofree and Lipizzan.
Android P is still in development and is not yet named. The company seems to release the next major version of Android in this year's Google I/O developer conference that will take place from May 8 to May 10 at the Shoreline Amphitheatre in Mountain View, California.
3 Million New Android Malware Samples Discovered in 2017
20.2.2018 securityweek Android
More than 3 million new malware samples targeting the Android operating system were discovered in 2017, marking a slight decrease from the previous year, G Data reports.
The security firm counted 3,002,482 new Android malware samples during 2017, at an average of 8,225 per day, or 343 new malware samples every hour. Although the number is slightly lower when compared to 2016 (when 3,246,284 samples were discovered), the decrease isn’t significant.
In late January, Google revealed that it took down over 700,000 bad apps from Google Play during 2017, a 70% increase compared to the previous year. Many of these programs were copycats – they were either apps packing unacceptable content or malware posing as legitimate apps.
With Android being the most popular mobile operating system out there, it’s no wonder cybercriminals are focused on bypassing Google’s protection mechanisms in their attempt to push malware into the official app store.
This also shows that users should not rely solely on Google’s security features to protect their devices and data. A third-party security program should also be installed and maintained, to detect applications with malicious functions in due time.
Despite the large number of new Android malware samples and that of malicious programs slipping through Google’s protections, the overall security of the operating system appears to be improving, especially with the Internet giant stepping up the platform update process.
Previously, the update process involved multiple steps: the Android team published the open source code, processor providers adapted it to their specific hardware, smartphone providers worked on customizations for the software, network operators also added their own modifications, and only then could an update finally be released.
“Frequently, these concatenated processes take a very long time, so users do not receive the updates until months after they were released by the Android team,” G Data notes.
Lately, Google has been trying to have updates available for all users faster, and initiatives like Project Treble helps in this direction. Through it, a so-called vendor interface is provided, bridging the Android OS framework and the provider’s modifications and making relevant hardware-specific information readily available. Thus, manufacturers can deliver Android updates quickly.
Last year, developers and researchers discovered a total of 841 vulnerabilities among the various versions of Android, making the platform a clear forerunner when it comes to security issues. As a recent Risk Based Security report revealed, the Android-based Pixel/Nexus devices had the most (354) vulnerabilities featuring CSSv2 Scores 9.0 - 10.0 last year.
This leading position could be explained by Android’s open source nature, which provides more people with the opportunity of researching it.
“However, the problem is not only vulnerabilities in the software, but specifically holes in the hardware. Meltdown and Spectre, the serious security holes in processors, which are also present in mobile devices, have again demonstrated how important a speedy security process is so that users receive new updates quickly,” G Data points out.
Android Security Bulletin – Google fixed several Critical Code Execution vulnerabilities
15.2.2018 securityaffairs Android
Android Security Bulletin for February 2018 – Google has fixed tens of vulnerabilities for Android OS, including several critical remote code execution (RCE) flaws.
The Android Security Bulletin for February 2018 addresses 26 vulnerabilities in the mobile operating system, most of which are elevation of privilege flaws.
The 2018-02-01 security patch level fixed 7 vulnerabilities, 6 in Media Framework and one issue affecting the System component.
The tech giant has fixed two critical RCE vulnerabilities in Media Framework. The first issue is the CVE-2017-13228 that affects Android 6.0 and newer, the second one, tracked as CVE-2017-13230, impacts Android 5.1.1 and later.

Google also fixed other vulnerabilities in Media Framework, including an information disclosure vulnerability, an elevation of privilege bug, and several denial-of-service flaws.
“The most severe of these issues is a critical security vulnerability in Media framework that could enable a remote attacker using a specially crafted file to execute arbitrary code within the context of a privileged process.” states the advisory.
The most severe of these vulnerabilities is tracked as CVE-2017-13236, it is a System issue that could be exploited by an attacker to achieve remote code execution in the context of a privileged process. The attacker can trigger the flaw via email, web browsing, and MMS when processing media files.
The 2018-02-05 security patch level includes fixes for 19 vulnerabilities in HTC, Kernel, NVIDIA, Qualcomm, and Qualcomm closed-source components.
The most severe flaws included in the 2018-02-05 security patch level are two remote code execution vulnerabilities in Qualcomm components tracked as CVE-2017-15817 and CVE-2017-17760.
Google also released the Pixel / Nexus Security Bulletin that addresses 29 vulnerabilities in Google devices.
“The Pixel / Nexus Security Bulletin contains details of security vulnerabilities and functional improvements affecting supported Google Pixel and Nexus devices (Google devices). For Google devices, security patch levels of 2018-02-05 or later address all issues in this bulletin and all issues in the February 2018 Android Security Bulletin.” states Google.
“All supported Google devices will receive an update to the 2018-02-05 patch level. We encourage all customers to accept these updates to their devices.”
Critical Code Execution Flaws Patched in Android
14.2.2018 securityweek Android
Google this month addressed several critical severity remote code execution (RCE) vulnerabilities in the Android operating system.
Split in two parts, the Android Security Bulletin for February 2018 resolves only 26 vulnerabilities in the mobile operating system, most of which are rated high severity. The vast majority of the security issues are elevation of privilege (EoP) bugs.
A total of 7 issues were addressed with the 2018-02-01 security patch level, including 6 flaws in Media Framework and one vulnerability in the System component.
This month, Google addressed two critical RCE bugs in Media Framework: CVE-2017-13228, which impacts Android 6.0 and newer, and CVE-2017-13230, which impacts Android 5.1.1 and later (it is considered a high risk denial-of-service (DoS) flaw on Android 7.0 and newer).
Other issues addressed in Media Framework included an information disclosure vulnerability, an elevation of privilege bug, and several denial-of-service flaws.
By successfully exploiting the most severe of these vulnerabilities, an attacker could achieve remote code execution in the context of a privileged process. The issues could be abused via email, web browsing, and MMS when processing media files.
The vulnerability addressed in System (CVE-2017-13236) was an EoP bug that could allow a local malicious application to execute commands normally limited to privileged processes, Google explained in an advisory.
The 2018-02-05 security patch level includes fixes for 19 vulnerabilities in HTC, Kernel, NVIDIA, Qualcomm, and Qualcomm closed-source components.
The most severe of these issues are two remote code execution vulnerabilities in Qualcomm components (CVE-2017-15817 and CVE-2017-17760).
Except for an information disclosure in HTC components (bootloader) and an undisclosed bug type on Qualcomm closed-source components, the remaining issues were elevation of privilege vulnerabilities impacting components such as Media Framework, WLan, Graphics, Kernel, and Bootloader.
Google also released a separate set of patches to address 29 vulnerabilities as part of the Pixel / Nexus Security Bulletin for February 2018.
While most of these bugs were rated moderate severity, one critical remote code execution bug and one high risk denial-of-service issue (both only on Android 5.1.1, 6.0, and 6.0.1 releases and medium severity on Android 7.0 and up) slipped among them.
Impacted components included Media Framework, System, Kernel and Qualcomm. Most of the bugs were elevation of privilege and information disclosure vulnerabilities.
In addition to these security patches, Google included a series of functional improvements in the software updates for the Pixel devices.
A new variant of the dreaded AndroRAT malware appeared in threat landscape
14.2.2018 securityaffairs Android
Security researchers from Trend Micro detected a new variant of the popular AndroRAT Android RAT in the criminal ecosystem.
Security experts from Trend Micro reported the availability of a new variant of the popular AndroRAT.
The malware was first born in 2012 as a university project, designed as an open-source client/server application to offer remote control of a device. Unfortunately, hackers noticed the capabilities of the threat and started using it.
The new version includes the code to trigger the CVE-2015-1805, it is a local elevation of privilege flaw that affects the kernel of the Android OS of certain devices.
The vulnerability is ranked as critical and can be exploited by rooting applications that users have installed on their devices to elevate privileges and run arbitrary code on the vulnerable device.
The security flaw is very old, it was discovered in the upstream Linux kernel years ago and fixed in April 2014. Unfortunately, the flaw was underestimated until last early 2016 when the C0RE Team reported to Google that it was possible to exploit it to target the Android OS.
All unpatched Android devices running OS based on kernel versions 3.4, 3.10 and 3.14, including all Nexus devices are vulnerable to the CVE-2015-1805 vulnerability.
“Trend Micro detected a new variant of Android Remote Access Tool (AndroRAT) (identified as ANDROIDOS_ANDRORAT.HRXC) that has the ability to inject root exploits to perform malicious tasks such as silent installation, shell command execution, WiFi password collection, and screen capture.” states the analysis published by Trend Micro.
The new AndroRAT variant masquerades as a utility app called TrashCleaner that is likely delivered from a malicious URL. Once launched, the TrashCleaner will prompt the user to install a Chinese-labeled calculator app, hide its icon from the device’s UI, and activates the RAT in the background.

The new variant included the following additional features:
Theft of mobile network information, storage capacity, rooted or not
Theft of list of installed applications
Theft of web browsing history from pre-installed browsers
Theft of calendar events
Record calls
Upload files to victim device
Use front camera to capture high resolution photos
Delete and send forged SMS
Screen capture
Shell command execution
Theft of WiFi passwords
Enabling accessibility services for a key logger silently
Experts recommend downloading apps only from official stores and keeping updated the OS and the apps.
CSE CybSec ZLAB Malware Analysis Report: Dark Caracal and the Pallas malware family
12.2.2018 securityaffairs Android
Dark Caracal APT – The Pallas Family
Researchers from CSE ZLAB malware Analysis Laboratory analyzed a set of samples of the Pallas malware family used by the Dark Caracal APT in its hacking operations.
The malware researchers from ZLab analyzed a collection of samples related to a new APT tracked as Dark Caracal, which was discovered by Electronic Frontier Foundation in collaboration with Lookout Mobile Security.
Dark Caracal has been active at least since 2012, but only recently it was identified as a powerful threat actor in the cyber arena.
The first analysis of the APT linked it to Lebanese General Directorate of General Security.
Dark Caracal is behind a number of stealth hacking campaigns that in the last six years, aimed to steal text messages, call logs, and files from journalists, military staff, corporations, and other targets in 21 countries worldwide.
One of their most powerful campaigns started in the first months of last year, using a series of trojanized Android applications to steal sensitive data from the victim’s mobile device. The trojan injected in these applications is known in the threat landscape with the name Pallas.
Threat actors use the “repackaging” technique to generate its samples, they start from a legitimate application and inject the malicious code before rebuilding the apk.
The target applications belongs to specific categories, such as social chat app (Whatsapp, Telegram, Primo), secure chat app (Signal, Threema), or software related to secure navigation (Orbot, Psiphon).
The attackers used social engineering techniques to trick victims into installing the malware. Attackers use SMS, a Facebook message or a Facebook post, which invites the victim to download a new version of the popular app through from a specific URL
http://secureandroid[.]info,
All the trojanized app are hosted at the same URL.

Figure 1 – Dark Caracal Repository – Malicious site
This malware is able to collect a large amount of data and to send it to a C&C through an encrypted URL that is decrypted at runtime. The capabilities of the trojan are:
Read SMS
Send SMS
Record calls
Read calls log
Retrieve account and contacts information
Gather all stored media and send them to C2C
Download and install other malicious software
Display a phishing window in order to try to steal credentials
Retrieve the list of all devices connected to the same network
Further details are included in the complete report published by CSE.
Watch Out! New Cryptocurrency-Mining Android Malware is Spreading Rapidly
8.2.2018 thehahckernews Android CoinMine
Due to the recent surge in cryptocurrency prices, threat actors are increasingly targeting every platform, including IoT, Android, and Windows, with malware that leverages the CPU power of victims' devices to mine cryptocurrency.
Just last month, Kaspersky researchers spotted fake antivirus and porn Android apps infected with malware that mines Monero cryptocurrency, launches DDoS attacks, and performs several other malicious tasks, causing the phone's battery to bulge out of its cover.
Now, security researchers at Chinese IT security firm Qihoo 360 Netlab discovered a new piece of wormable Android malware, dubbed ADB.Miner, that scans wide-range of IP addresses to find vulnerable devices and infect them to mine digital cryptocurrency.
According to the researchers, ADB.Miner is the first Android worm to reuse the scanning code programmed in Mirai—the infamous IoT botnet malware that knocked major Internet companies offline last year by launching massive DDoS attacks against Dyndns.
ADB.Miner scans for Android devices—including smartphones, smart TVs, and TV set-top boxes—with publicly accessible ADB debug interface running over port 5555 and then infects them with a malware that mines Monero cryptocurrency for its operators.
Android Debug Bridge (ADB) is a command-line tool that helps developers debug Android code on the emulator and grants access to some of the operating system’s most sensitive features.
It should be noted that almost all Android devices by default come with the ADB port disabled, so botnet would target only those devices that have manually been configured to enable port 5555.
Besides mining Monero cryptocurrency, ADB.Miner installed on an infected device also attempts to propagate itself by scanning for more targets on the Internet.
Researchers did not reveal exactly how or by exploiting which ADB flaw hackers are installing malware onto Android devices.
However, the researchers believed hackers are not exploiting any vulnerability that targets any specific device vendor since they found devices from a wide range of manufacturers impacted.
According to the researchers, the infection started on January 21, and the number of attacks has increased recently. As of Sunday, the researchers detected 7,400 unique IP addresses using the Monero mining code—that's more than 5,000 impacted devices in just 24 hours.
Based on the scanning IP addresses, the highest number of infection has been noticed in China (40%) and South Korea (31%), the researchers estimated.
In order to fight against such malware Android users are advised not to install unnecessary and untrusted applications from the app store, even from Google Play Store, and keep your devices behind a firewall or a VPN.
Crypto-mining Botnet Targets Android Devices
6.2.2018 securityweek Android
A new crypto-mining botnet has been growing and targeting Android devices with an open ADB port, Qihoo 360's NetLab researchers reveal.
The attacks started last week, targeting port 5555, which is the working port for the adb debug interface on Android devices. While this port should be normally closed on all devices, sometimes it could remain open, thus allowing devices to be compromised.
Courtesy of scanning code borrowed from the infamous Mirai botnet – which targets Internet of Things (IoT) devices – the new threat can spread as a worm, NetLab reports. Each of the infected bots would continue to scan for open 5555 adb ports to spread further.
This is the first time the Mirai code has been reused to target Android devices, the researchers point out.
The infection appears to have started on January 21, 2018, and the researchers say that the number of attacks has increased recently.
As of February 4, between 2,700 and 5,500 devices had been affected by the botnet, with most of them located in China (40%) and South Korea (31%) – based on the scanning IP addresses targeted devices include smartphones and smart TVs (TV set-top boxes), the security researchers say.
It appears that the botnet isn’t targeting vulnerabilities affecting only specific devices, mainly because models from a broad range of manufacturers have been already impacted. However, the security firm hasn’t provided details on the impacted device models.
The purpose of the newly created botnet, NetLab reports, is to mine for the Monero crypto-currency. The malware’s configuration shows the use of two mining pools, but both groups of devices are using the same wallet address.
The researchers revealed that no payment had been made to the used wallet by the time of their report, but also said they would continue watching and analyzing the threat to provide additional details.
700,000 Bad Android Apps Removed From Google Play in 2017
31.1.2018 securityweek Android
Google took down over 700,000 Android applications from the official software marketplace last year, 70% more than were removed from the store in 2016.
Additonally, Google improved its ability to identify bad applications earlier, and 99% of apps featuring abusive contents were rejected before reaching users, the company claims.
According to Andrew Ahn, Product Manager, Google Play, this was possible because of new machine learning models and techniques that power Google’s abuse detection abilities (including impersonation, inappropriate content, or malware).
Furthermore, the company focused on identifying repeat offenders and abusive developer networks, which resulted in taking down 100,000 bad developers in 2017. It also “made it more difficult for bad actors to create new accounts and attempt to publish yet another set of bad apps,” Ahn says.
Last year, Google took action against copycat apps, or those programs attempting to deceive users by posing as popular programs. Because famous programs get massive search traffic for particular keywords, the bad actors attempt to take advantage of this by publishing impersonating apps to Google Play Store.
Some of the methods employed include the use of confusable Unicode characters or the hiding of impersonating app icons in a different locale. Google says it took down over a quarter of a million such applications last year.
Applications that contain or promote inappropriate content (pornography, extreme violence, hate, and illegal activities) aren’t accepted in the app store either, and Google removed tens of thousands of such programs from the Android marketplace last year.
Potentially Harmful Applications (PHAs) – malware that performs SMS fraud, acts as Trojans, or phishes user's information – can harm people or their devices despite going to lengths to appear as legitimate programs. According to Ahn, Google Play Protect helped the Internet giant reduce the annual PHA installs rates on Google Play by 50% last year.
“Despite the new and enhanced detection capabilities that led to a record-high takedowns of bad apps and malicious developers, we know a few still manage to evade and trick our layers of defense. We take these extremely seriously, and will continue to innovate our capabilities to better detect and protect against abusive apps and the malicious actors behind them,” Ahn says.
Three Sonic apps in the Google Play are leaking data to uncertified servers
23.1.2018 securityaffairs Android
According to a researcher from security firm Predeo, three Sonic apps in the Google Play published by SEGA leak users’ data to uncertified servers.
According to a researcher from security firm Predeo, some game applications in the Google Play published by SEGA leak users’ data to uncertified servers.
The Android apps are Sonic Dash, Sonic the Hedgehog™ Classic, and Sonic Dash 2: Sonic Boom, that have been totally downloaded millions of times.
The expert discovered that the apps are leaking users’ geolocation and device data to suspicious servers, thereby posing a privacy threat to mobile gamers, according to researchers.
“Pradeo’s Lab discovered that some game applications in the Google Play published by SEGA, the famous video games developer and publisher, access and leak users’ geolocation and device data. Hundreds of millions of users are concerned by these data privacy violations.” states the blog post published by Pradeo.

The Sonic apps send data to an average of 11 distant servers, three of which are not certified. Most of the servers obviously collect data for marketing purposes, but the expert observed that two of the three uncertified servers are linked to a potential unwanted library app dubbed Android/Inmobi.D,
Android.InMobi is classified as an advertisement library that is bundled with certain Android applications.
The expert discovered that the Sonic apps also leak mobile network information, including the service provider name, network type, and device information (i.e. manufacturer, commercial name, battery level, the maximum level of the battery, and operating system version number).
The researchers at Pradeo also conducted a vulnerability assessment for the three Sonic App and discovered an average of 15 OWASP (Open Web Application Security Project) flaws.
Experts discovered two critical flaws, X.509TrustManager and PotentiallyByPassSslConnection, that could be exploited by hackers to power man-in-the-middle attacks due to the lack of validation for SSL certificate errors.
“Unsafe implementation of the interface X509TrustManager. Specifically, the implementation ignores all SSL certificate validation errors when establishing an HTTPS connection to a remote host, thereby making your app vulnerable to man-in-the-middle attacks. An attacker could read transmitted data (such as login credentials) and even change the data transmitted on the HTTPS connection.” reads the description for the X.509TRUSTMANAGER flaw, while the POTENTIALLY_BYPASS SSL_CONNECTION is described as:
“The implementation bypasses all SSL certificate validation errors when establishing an HTTPS connection to a remote host, thereby making your app vulnerable to man-in-the-middle attacks. An attacker could read transmitted data (such as login credentials) and even change the data transmitted on the HTTPS connection.”
I suggest you read the post to discover the remaining issues and the risks they posed to the users.
Google awarded Chinese hacker record $112,500 for Android exploit chain
22.1.2018 securityaffairs Android
Google has awarded a record $112,500 to a security researcher for reporting an exploit chain that could be used to hack Pixel smartphones.
Last week the Google disclosed the technical details of the exploit chain that was devised in August 2017 by the Guang Gong from Alpha Team at Qihoo 360 Technology. The exploit chain triggers two vulnerabilities, CVE-2017-5116 and CVE-2017-14904, researchers submitted it through the Android Security Rewards (ASR) program.
“The exploit chain includes two bugs, CVE-2017-5116 and CVE-2017-14904. CVE-2017-5116 is a V8 engine bug that is used to get remote code execution in sandboxed Chrome render process. CVE-2017-14904 is a bug in Android’s libgralloc module that is used to escape from Chrome’s sandbox. Together, this exploit chain can be used to inject arbitrary code into system_server by accessing a malicious URL in Chrome.” reads the analysis published by Google.

Chaining the vulnerabilities the attackers can remotely inject arbitrary code into the system_server process when a malicious URL in Chrome is accessed.
In an attack scenario, the victims can be tricked into clicking on such a URL by hackers that can fully compromise their mobile device.
Gong was awarded $105,000 for this exploit chain, he received also an additional award of $7500 through the Chrome Rewards program.
Google addressed the flaws as part of Google Android ‘s December security bulletin that addressed a total of 42 bugs.
Pixel mobile devices and partner devices using A/B updates will automatically install the security updates that fixed the flaws.
“The Android security team responded quickly to our report and included the fix for these two bugs in the December 2017 Security Update. Supported Google device and devices with the security patch level of 2017-12-05 or later address these issues.” concluded Google.
The overall ASR payout rewards is over $1.5 million to date, with the top research team earning $300,000 for 118 vulnerability reports.
Researchers Uncover Government-Sponsored Mobile Hacking Group Operating Since 2012
19.1.2018 thehackernews Android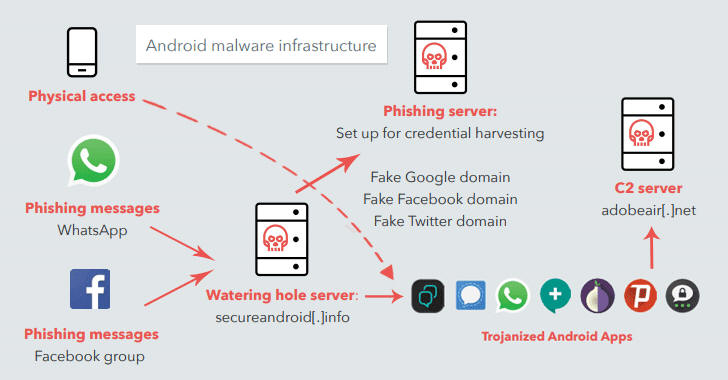
A global mobile espionage campaign collecting a trove of sensitive personal information from victims since at least 2012 has accidentally revealed itself—thanks to an exposed server on the open internet.
It's one of the first known examples of a successful large-scale hacking operation of mobile phones rather than computers.
The advanced persistent threat (APT) group, dubbed Dark Caracal, has claimed to have stolen hundreds of gigabytes of data, including personally identifiable information and intellectual property, from thousands of victims in more than 21 different countries, according to a new report from the Electronic Frontier Foundation (EFF) and security firm Lookout.
After mistakenly leaking some of its files to the internet, the shadowy hacking group is traced back to a building owned by the Lebanese General Directorate of General Security (GDGS), one of the country's intelligence agencies, in Beirut.
"Based on the available evidence, it's likely that the GDGS is associated with or directly supporting the actors behind Dark Caracal," the report reads.
According to the 51-page-long report [PDF], the APT group targeted "entities that a nation-state might attack," including governments, military personnel, utilities, financial institutions, manufacturing companies, defence contractors, medical practitioners, education professionals, academics, and civilians from numerous other fields.
Researchers also identified at least four different personas associated with Dark Caracal's infrastructure — i.e. Nancy Razzouk, Hassan Ward, Hadi Mazeh, and Rami Jabbour — with the help of email address op13@mail[.]com.
"The contact details for Nancy present in WHOIS information matched the public listing for a Beirut-based individual by that name. When we looked at the phone number associated with Nancy in the WHOIS information, we discovered the same number listed in exfiltrated content and being used by an individual with the name Hassan Ward."
"During July 2017, Dark Caracal’s internet service provider took the adobeair[.]net command and control server offline. Within a matter of days, we observed it being re-registered to the email address op13@mail[.]com with the name Nancy Razzouk. This allowed us to identify several other domains listed under the same WHOIS email address information, running similar server components. "
Multi-Platform Cyber Espionage Campaign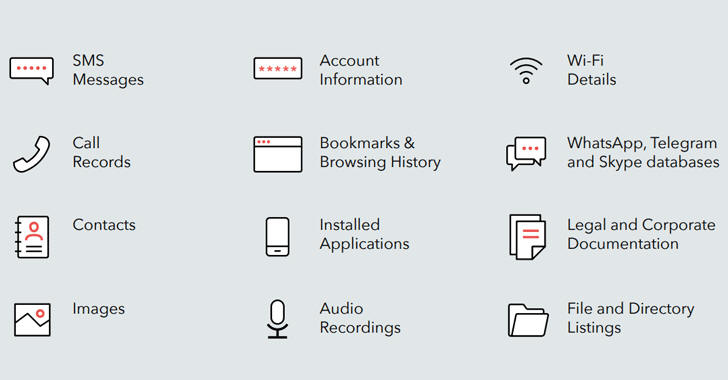
Dark Caracal has been conducting multi-platform cyber-espionage campaigns and linked to 90 indicators of compromise (IOCs), including 11 Android malware IOCs, 26 desktop malware IOCs across Windows, Mac, and Linux, and 60 domain/IP based IOCs.
However, since at least 2012, the group has run more than ten hacking campaigns aimed mainly at Android users in at least 21 countries, including North America, Europe, the Middle East and Asia.
The data stolen by Dark Caracal on its targets include documents, call records, text messages, audio recordings, secure messaging client content, browsing history, contact information, photos, and location data—basically every information that allows the APT group to identify the person and have an intimate look at his/her life.
To get its job done, Dark Caracal did not rely on any "zero-day exploits," nor did it has to get the malware to the Google Play Store. Instead, the group used basic social engineering via posts on Facebook groups and WhatsApp messages, encouraging users to visit a website controlled by the hackers and application permissions.
"One of the interesting things about this ongoing attack is that it doesn’t require a sophisticated or expensive exploit. Instead, all Dark Caracal needed was application permissions that users themselves granted when they downloaded the apps, not realizing that they contained malware," said EFF Staff Technologist Cooper Quintin.
"This research shows it’s not difficult to create a strategy allowing people and governments to spy on targets around the world."
Here's How Dark Caracal Group Infects Android Users
Once tricked into landing on the malicious websites, the victims were served fake updates to secure messenger apps, including WhatsApp, Signal, Threema Telegram, and Orbot (an open source Tor client for Android), which eventually downloaded the Dark Caracal malware, dubbed Pallas, on targets' mobile devices.
Pallas is a piece of surveillance malware that's capable of taking photographs, stealing data, spying on communications apps, recording video and audio, acquiring location data, and stealing text messages, including two-factor authentication codes, from victims' devices.
"Pallas samples primarily rely on the permissions granted at the installation in order to access sensitive user data. However, there is functionality that allows an attacker to instruct an infected device to download and install additional applications or updates." report says.
"Theoretically, this means it’s possible for the operators behind Pallas to push specific exploit modules to compromised devices in order to gain complete access."
Besides its own custom malware, Dark Caracal also used FinFisher—a highly secret surveillance tool that is often marketed to law enforcement and government agencies—and a newly discovered desktop spyware tool, dubbed CrossRAT, which can infect Windows, Linux, and OS X operating systems.
"Citizen Lab previously flagged the General Directorate of General Security in a 2015 report as one of two Lebanese government organizations using the FinFisher spyware5." report says.
According to the researchers, though Dark Caracal targeted macOS and Windows devices in various campaigns, at least six distinct Android campaigns were found linked to one of its servers that were left open for analysis, revealing 48GB was stolen from around 500 Android phones.
Overall, Dark Caracal successfully managed to steal more than 252,000 contacts, 485,000 text messages and 150,000 call records from infected Android devices. Sensitive data such as personal photos, bank passwords and PIN numbers were also stolen.
The best way to protect yourself from such Android-based malware attacks is to always download applications from the official Google Play Store market rather than from any third-party website.
Skygofree: Following in the footsteps of HackingTeam
19.1.2018 Kaspersky Android
Skygofree Appendix — Indicators of Compromise (PDF)
At the beginning of October 2017, we discovered new Android spyware with several features previously unseen in the wild. In the course of further research, we found a number of related samples that point to a long-term development process. We believe the initial versions of this malware were created at least three years ago – at the end of 2014. Since then, the implant’s functionality has been improving and remarkable new features implemented, such as the ability to record audio surroundings via the microphone when an infected device is in a specified location; the stealing of WhatsApp messages via Accessibility Services; and the ability to connect an infected device to Wi-Fi networks controlled by cybercriminals.
We observed many web landing pages that mimic the sites of mobile operators and which are used to spread the Android implants. These domains have been registered by the attackers since 2015. According to our telemetry, that was the year the distribution campaign was at its most active. The activities continue: the most recently observed domain was registered on October 31, 2017. Based on our KSN statistics, there are several infected individuals, exclusively in Italy.
Moreover, as we dived deeper into the investigation, we discovered several spyware tools for Windows that form an implant for exfiltrating sensitive data on a targeted machine. The version we found was built at the beginning of 2017, and at the moment we are not sure whether this implant has been used in the wild.
We named the malware Skygofree, because we found the word in one of the domains*.
Malware Features
Android
According to the observed samples and their signatures, early versions of this Android malware were developed by the end of 2014 and the campaign has remained active ever since.
Signature of one of the earliest versions
The code and functionality have changed numerous times; from simple unobfuscated malware at the beginning to sophisticated multi-stage spyware that gives attackers full remote control of the infected device. We have examined all the detected versions, including the latest one that is signed by a certificate valid from September 14, 2017.
The implant provides the ability to grab a lot of exfiltrated data, like call records, text messages, geolocation, surrounding audio, calendar events, and other memory information stored on the device.
After manual launch, it shows a fake welcome notification to the user:
Dear Customer, we’re updating your configuration and it will be ready as soon as possible.
At the same time, it hides an icon and starts background services to hide further actions from the user.
Service Name Purpose
AndroidAlarmManager Uploading last recorded .amr audio
AndroidSystemService Audio recording
AndroidSystemQueues Location tracking with movement detection
ClearSystems GSM tracking (CID, LAC, PSC)
ClipService Clipboard stealing
AndroidFileManager Uploading all exfiltrated data
AndroidPush XMPP С&C protocol (url.plus:5223)
RegistrationService Registration on C&C via HTTP (url.plus/app/pro/)
Interestingly, a self-protection feature was implemented in almost every service. Since in Android 8.0 (SDK API 26) the system is able to kill idle services, this code raises a fake update notification to prevent it:
Cybercriminals have the ability to control the implant via HTTP, XMPP, binary SMS and FirebaseCloudMessaging (or GoogleCloudMessaging in older versions) protocols. Such a diversity of protocols gives the attackers more flexible control. In the latest implant versions there are 48 different commands. You can find a full list with short descriptions in the Appendix. Here are some of the most notable:
‘geofence’ – this command adds a specified location to the implant’s internal database and when it matches a device’s current location the malware triggers and begins to record surrounding audio.
”social” – this command that starts the ‘AndroidMDMSupport’ service – this allows the files of any other installed application to be grabbed. The service name makes it clear that by applications the attackers mean MDM solutions that are business-specific tools. The operator can specify a path with the database of any targeted application and server-side PHP script name for uploading.
Several hardcoded applications targeted by the MDM-grabbing command
‘wifi’ – this command creates a new Wi-Fi connection with specified configurations from the command and enable Wi-Fi if it is disabled. So, when a device connects to the established network, this process will be in silent and automatic mode. This command is used to connect the victim to a Wi-Fi network controlled by the cybercriminals to perform traffic sniffing and man-in-the-middle (MitM) attacks.
addWifiConfig method code fragments
‘camera’ – this command records a video/capture a photo using the front-facing camera when someone next unlocks the device.
Some versions of the Skygofree feature the self-protection ability exclusively for Huawei devices. There is a ‘protected apps’ list in this brand’s smartphones, related to a battery-saving concept. Apps not selected as protected apps stop working once the screen is off and await re-activation, so the implant is able to determine that it is running on a Huawei device and add itself to this list. Due to this feature, it is clear that the developers paid special attention to the work of the implant on Huawei devices.
Also, we found a debug version of the implant (70a937b2504b3ad6c623581424c7e53d) that contains interesting constants, including the version of the spyware.
Debug BuildConfig with the version
After a deep analysis of all discovered versions of Skygofree, we made an approximate timeline of the implant’s evolution.
Mobile implant evolution timeline
However, some facts indicate that the APK samples from stage two can also be used separately as the first step of the infection. Below is a list of the payloads used by the Skygofree implant in the second and third stages.
Reverse shell payload
The reverse shell module is an external ELF file compiled by the attackers to run on Android. The choice of a particular payload is determined by the implant’s version, and it can be downloaded from the command and control (C&C) server soon after the implant starts, or after a specific command. In the most recent case, the choice of the payload zip file depends on the device process architecture. For now, we observe only one payload version for following the ARM CPUs: arm64-v8a, armeabi, armeabi-v7a.
Note that in almost all cases, this payload file, contained in zip archives, is named ‘setting’ or ‘setting.o’.
The main purpose of this module is providing reverse shell features on the device by connecting with the C&C server’s socket.
Reverse shell payload
The payload is started by the main module with a specified host and port as a parameter that is hardcoded to ‘54.67.109.199’ and ‘30010’ in some versions:
Alternatively, they could be hardcoded directly into the payload code:
We also observed variants that were equipped with similar reverse shell payloads directly in the main APK /lib/ path.
Equipped reverse shell payload with specific string
After an in-depth look, we found that some versions of the reverse shell payload code share similarities with PRISM – a stealth reverse shell backdoor that is available on Github.
Reverse shell payload from update_dev.zip
Exploit payload
At the same time, we found an important payload binary that is trying to exploit several known vulnerabilities and escalate privileges. According to several timestamps, this payload is used by implant versions created since 2016. It can also be downloaded by a specific command. The exploit payload contains following file components:
Component name Description
run_root_shell/arrs_put_user.o/arrs_put_user/poc Exploit ELF
db Sqlite3 tool ELF
device.db Sqlite3 database with supported devices and their constants needed for privilege escalation
‘device.db’ is a database used by the exploit. It contains two tables – ‘supported_devices’ and ‘device_address’. The first table contains 205 devices with some Linux properties; the second contains the specific memory addresses associated with them that are needed for successful exploitation. You can find a full list of targeted models in the Appendix.
Fragment of the database with targeted devices and specific memory addresses
If the infected device is not listed in this database, the exploit tries to discover these addresses programmatically.
After downloading and unpacking, the main module executes the exploit binary file. Once executed, the module attempts to get root privileges on the device by exploiting the following vulnerabilities:
CVE-2013-2094
CVE-2013-2595
CVE-2013-6282
CVE-2014-3153 (futex aka TowelRoot)
CVE-2015-3636
Exploitation process
After an in-depth look, we found that the exploit payload code shares several similarities with the public project android-rooting-tools.
Decompiled exploit function code fragment
run_with_mmap function from the android-rooting-tools project
As can be seen from the comparison, there are similar strings and also a unique comment in Italian, so it looks like the attackers created this exploit payload based on android-rooting-tools project source code.
Busybox payload
Busybox is public software that provides several Linux tools in a single ELF file. In earlier versions, it operated with shell commands like this:
Stealing WhatsApp encryption key with Busybox
Social payload
Actually, this is not a standalone payload file – in all the observed versions its code was compiled with exploit payload in one file (‘poc_perm’, ‘arrs_put_user’, ‘arrs_put_user.o’). This is due to the fact that the implant needs to escalate privileges before performing social payload actions. This payload is also used by the earlier versions of the implant. It has similar functionality to the ‘AndroidMDMSupport’ command from the current versions – stealing data belonging to other installed applications. The payload will execute shell code to steal data from various applications. The example below steals Facebook data:
All the other hardcoded applications targeted by the payload:
Package name Name
jp.naver.line.android LINE: Free Calls & Messages
com.facebook.orca Facebook messenger
com.facebook.katana Facebook
com.whatsapp WhatsApp
com.viber.voip Viber
Parser payload
Upon receiving a specific command, the implant can download a special payload to grab sensitive information from external applications. The case where we observed this involved WhatsApp.
In the examined version, it was downloaded from:
hxxp://url[.]plus/Updates/tt/parser.apk
The payload can be a .dex or .apk file which is a Java-compiled Android executable. After downloading, it will be loaded by the main module via DexClassLoader api:
As mentioned, we observed a payload that exclusively targets the WhatsApp messenger and it does so in an original way. The payload uses the Android Accessibility Service to get information directly from the displayed elements on the screen, so it waits for the targeted application to be launched and then parses all nodes to find text messages:
Note that the implant needs special permission to use the Accessibility Service API, but there is a command that performs a request with a phishing text displayed to the user to obtain such permission.
Windows
We have found multiple components that form an entire spyware system for the Windows platform.
Name MD5 Purpose
msconf.exe 55fb01048b6287eadcbd9a0f86d21adf Main module, reverse shell
network.exe f673bb1d519138ced7659484c0b66c5b Sending exfiltrated data
system.exe d3baa45ed342fbc5a56d974d36d5f73f Surrounding sound recording by mic
update.exe 395f9f87df728134b5e3c1ca4d48e9fa Keylogging
wow.exe 16311b16fd48c1c87c6476a455093e7a Screenshot capturing
skype_sync2.exe 6bcc3559d7405f25ea403317353d905f Skype call recording to MP3
All modules, except skype_sync2.exe, are written in Python and packed to binary files via the Py2exe tool. This sort of conversion allows Python code to be run in a Windows environment without pre-installed Python binaries.
msconf.exe is the main module that provides control of the implant and reverse shell feature. It opens a socket on the victim’s machine and connects with a server-side component of the implant located at 54.67.109.199:6500. Before connecting with the socket, it creates a malware environment in ‘APPDATA/myupd’ and creates a sqlite3 database there – ‘myupd_tmp\\mng.db’:
CREATE TABLE MANAGE(ID INT PRIMARY KEY NOT NULL,Send INT NOT NULL, Keylogg INT NOT NULL,Screenshot INT NOT NULL,Audio INT NOT NULL);
INSERT INTO MANAGE (ID,Send,Keylogg,Screenshot,Audio) VALUES (1, 1, 1, 1, 0 )
Finally, the malware modifies the ‘Software\Microsoft\Windows\CurrentVersion\Run’ registry key to enable autostart of the main module.
The code contains multiple comments in Italian, here is the most noteworthy example:
“Receive commands from the remote server, here you can set the key commands to command the virus”
Here are the available commands:
Name Description
cd Change current directory to specified
quit Close the socket
nggexe Execute received command via Python’s subprocess.Popen() without outputs
ngguploads Upload specified file to the specified URL
nggdownloads Download content from the specified URLs and save to specified file
nggfilesystem Dump file structure of the C: path, save it to the file in json format and zip it
nggstart_screen
nggstop_screen Enable/disable screenshot module. When enabled, it makes a screenshot every 25 seconds
nggstart_key
nggstop_key Enable/disable keylogging module
nggstart_rec
nggstop_rec Enable/disable surrounding sounds recording module
ngg_status Send components status to the C&C socket
*any other* Execute received command via Python’s subprocess.Popen(), output result will be sent to the C&C socket.
All modules set hidden attributes to their files:
Module Paths Exfiltrated data format
msconf.exe %APPDATA%/myupd/gen/ %Y%m%d-%H%M%S_filesystem.zip (file structure dump)
system.exe %APPDATA%/myupd/aud/ %d%m%Y%H%M%S.wav (surrounding sounds)
update.exe %APPDATA%/myupd_tmp/txt/
%APPDATA%/myupd/txt/ %Y%m%d-%H%M%S.txt (keylogging)
wow.exe %APPDATA%/myupd/scr/ %Y%m%d-%H%M%S.jpg (screenshots)
skype_sync2.exe %APPDATA%/myupd_tmp/skype/
%APPDATA%/myupd/skype/ yyyyMMddHHmmss_in.mp3
yyyyMMddHHmmss_out.mp3
(skype calls records)
Moreover, we found one module written in .Net – skype_sync2.exe. The main purpose of this module is to exfiltrate Skype call recordings. Just like the previous modules, it contains multiple strings in Italian.
After launch, it downloads a codec for MP3 encoding directly from the C&C server:
http://54.67.109.199/skype_resource/libmp3lame.dll
The skype_sync2.exe module has a compilation timestamp – Feb 06 2017 and the following PDB string:
\\vmware-host\Shared
Folders\dati\Backup\Projects\REcodin_2\REcodin_2\obj\x86\Release\REcodin_2.pdb
network.exe is a module for submitting all exfiltrated data to the server. In the observed version of the implant it doesn’t have an interface to work with the skype_sync2.exe module.
network.exe submitting to the server code snippet
Code similarities
We found some code similarities between the implant for Windows and other public accessible projects.
https://github.com/El3ct71k/Keylogger/
It appears the developers have copied the functional part of the keylogger module from this project.
update.exe module and Keylogger by ‘El3ct71k’ code comparison
Xenotix Python Keylogger including specified mutex ‘mutex_var_xboz’.
update.exe module and Xenotix Python Keylogger code comparison
‘addStartup’ method from msconf.exe module
‘addStartup’ method from Xenotix Python Keylogger
Distribution
We found several landing pages that spread the Android implants.
Malicious URL Referrer Dates
http://217.194.13.133/tre/internet/Configuratore_3.apk http://217.194.13.133/tre/internet/ 2015-02-04 to
present time
http://217.194.13.133/appPro_AC.apk – 2015-07-01
http://217.194.13.133/190/configurazione/vodafone/smartphone/VODAFONE%20Configuratore%20v5_4_2.apk http://217.194.13.133/190/configurazione/vodafone/smartphone/index.html 2015-01-20 to
present time
http://217.194.13.133/190/configurazione/vodafone/smartphone/Vodafone%20Configuratore.apk http://217.194.13.133/190/configurazione/vodafone/smartphone/index.html currently active
http://vodafoneinfinity.sytes.net/tim/internet/Configuratore_TIM.apk http://vodafoneinfinity.sytes.net/tim/internet/ 2015-03-04
http://vodafoneinfinity.sytes.net/190/configurazione/vodafone/smartphone/VODAFONE%20Configuratore%20v5_4_2.apk http://vodafoneinfinity.sytes.net/190/configurazione/vodafone/smartphone/ 2015-01-14
http://windupdate.serveftp.com/wind/LTE/WIND%20Configuratore%20v5_4_2.apk http://windupdate.serveftp.com/wind/LTE/ 2015-03-31
http://119.network/lte/Internet-TIM-4G-LTE.apk http://119.network/lte/download.html 2015-02-04
2015-07-20
http://119.network/lte/Configuratore_TIM.apk 2015-07-08
Many of these domains are outdated, but almost all (except one – appPro_AC.apk) samples located on the 217.194.13.133 server are still accessible. All the observed landing pages mimic the mobile operators’ web pages through their domain name and web page content as well.
Landing web pages that mimic the Vodafone and Three mobile operator sites
NETWORK CONFIGURATION
** AGG. 2.3.2015 ***
Dear Customer, in order to avoid malfunctions to your internet connection, we encourage you to upgrade your configuration. Download the update now and keep on navigating at maximum speed!
DOWNLOAD NOW
Do you doubt how to configure your smartphone?
Follow the simple steps below and enter the Vodafone Fast Network.
Installation Guide
Download
Click on the DOWNLOAD button you will find on this page and download the application on your smartphone.
Set your Smartphone
Go to Settings-> Security for your device and put a check mark on Unknown Sources (some models are called Sources Unknown).
Install
Go to notifications on your device (or directly in the Downloads folder) and click Vodafone Configuration Update to install.
Try high speed
Restart your device and wait for confirmation sms. Your smartphone is now configured.
Further research of the attacker’s infrastructure revealed more related mimicking domains.
Unfortunately, for now we can’t say in what environment these landing pages were used in the wild, but according to all the information at our dsiposal, we can assume that they are perfect for exploitation using malicious redirects or man-in-the-middle attacks. For example, this could be when the victim’s device connects to a Wi-Fi access point that is infected or controlled by the attackers.
Artifacts
During the research, we found plenty of traces of the developers and those doing the maintaining.
As already stated in the ‘malware features’ part, there are multiple giveaways in the code. Here are just some of them:
ngglobal – FirebaseCloudMessaging topic name
Issuer: CN = negg – from several certificates
negg.ddns[.]net, negg1.ddns[.]net, negg2.ddns[.]net – C&C servers
NG SuperShell – string from the reverse shell payload
ngg – prefix in commands names of the implant for Windows
Signature with specific issuer
Whois records and IP relationships provide many interesting insights as well. There are a lot of other ‘Negg’ mentions in Whois records and references to it. For example:
Conclusions
The Skygofree Android implant is one of the most powerful spyware tools that we have ever seen for this platform. As a result of the long-term development process, there are multiple, exceptional capabilities: usage of multiple exploits for gaining root privileges, a complex payload structure, never-before-seen surveillance features such as recording surrounding audio in specified locations.
Given the many artifacts we discovered in the malware code, as well as infrastructure analysis, we are pretty confident that the developer of the Skygofree implants is an Italian IT company that works on surveillance solutions, just like HackingTeam.
Notes
*Skygofree has no connection to Sky, Sky Go or any other subsidiary of Sky, and does not affect the Sky Go service or app.
Skygofree — Powerful Android Spyware Discovered
17.1.2018 thehackernews Android
Security researchers have unveiled one of the most powerful and highly advanced Android spyware tools that give hackers full control of infected devices remotely.
Dubbed Skygofree, the Android spyware has been designed for targeted surveillance, and it is believed to have been targeting a large number of users for the past four years.
Since 2014, the Skygofree implant has gained several novel features previously unseen in the wild, according to a new report published by Russian cybersecurity firm Kaspersky Labs.
The 'remarkable new features' include location-based audio recording using device's microphone, the use of Android Accessibility Services to steal WhatsApp messages, and the ability to connect infected devices to malicious Wi-Fi networks controlled by attackers.
Skygofree is being distributed through fake web pages mimicking leading mobile network operators, most of which have been registered by the attackers since 2015—the year when the distribution campaign was most active, according to Kaspersky's telemetry data.
Italian IT Firm Behind Skygofree Spyware?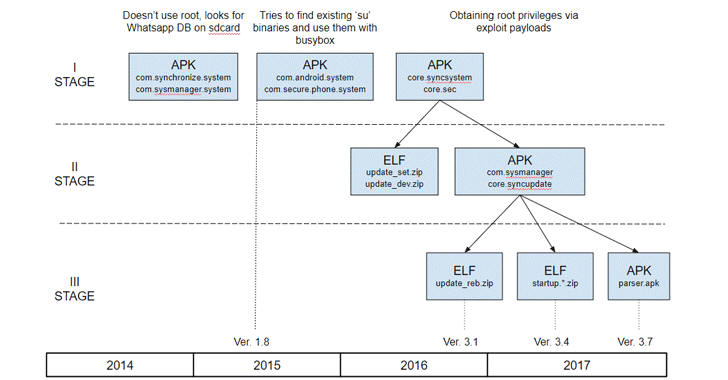
Researchers at Kaspersky Lab believe the hacker or hacking group behind this mobile surveillance tool has been active since 2014 and are based in Italy—the home for the infamous 'Hacking Team'—one of the world's bigger players in spyware trading.
"Given the many artifacts we discovered in the malware code, as well as infrastructure analysis, we are pretty confident that the developer of the Skygofree implants is an Italian IT company that works on surveillance solutions, just like HackingTeam," said the report.
Kaspersky found several Italian devices infected with Skygofree, which the firm described as one of the most powerful, advanced mobile implants it has ever seen.
Although the security firm has not confirmed the name of the Italian company behind this spyware, it found multiple references to Rome-based technology company "Negg" in the spyware's code. Negg is also specialised in developing and trading legal hacking tools.
Skygofree: Powerful Android Spyware Tool
Once installed, Skygofree hides its icon and starts background services to conceal further actions from the user. It also includes a self-protection feature, preventing services from being killed.
As of October last year, Skygofree became a sophisticated multi-stage spyware tool that gives attackers full remote control of the infected device using a reverse shell payload and a command and control (C&C) server architecture.
According to the technical details published by researchers, Skygofree includes multiple exploits to escalate privileges for root access, granting it ability to execute most sophisticated payloads on the infected Android devices.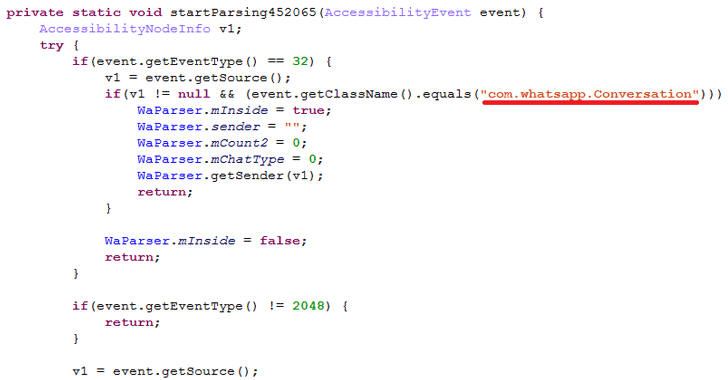
One such payload allows the implant to execute shellcode and steal data belonging to other applications installed on the targeted devices, including Facebook, WhatsApp, Line, and Viber.
"There are multiple, exceptional capabilities: usage of multiple exploits for gaining root privileges, a complex payload structure, [and] never-before-seen surveillance features," the researchers said.
Skygofree’s control (C&C) server also allows attackers to capture pictures and videos remotely, seize call records and SMS, as well as monitor the users' geolocation, calendar events and any information stored in the device's memory.
Besides this, Skygofree also can record audio via the microphone when the infected device was in a specified location and the ability to force the infected device to connect to compromised Wi-Fi networks controlled by the attacker, enabling man-in-the-middle attacks.
The spyware uses "the Android Accessibility Service to get information directly from the displayed elements on the screen, so it waits for the targeted application to be launched and then parses all nodes to find text messages," Kaspersky said.
Kaspersky researchers also found a variant of Skygofree targeting Windows users, suggesting the authors' next area of interest is the Windows platform.
The best way to prevent yourself from being a victim is to avoid downloading apps via third-party websites, app stores or links provided in SMS messages or emails.
Powerful Skygofree spyware was reported in November by Lukas Stefanko and first analyzed by CSE CybSec
17.1.2018 securityaffairs Android
The Skygofree spyware analyzed by Kaspersky today was first spotted by the researcher Lukas Stefanko and the first analysis was published last year by the CSE Cybsec ZLab.
Security researchers at Kaspersky Lab have made the headlines because they have spotted a new strain of a powerful Android spyware, dubbed Skygofree, that was used to gain full control of infected devices remotely.
Skygofree is an Android spyware that could be used in targeted attacks and according to the experts it has infected a large number of users for the past four years.
The name Skygofree is not linked to Sky Go, which is the subsidiary of Sky and does not affect its services.
The malware has been in the wild at least since 2014, and it was improved several times over the years.
“At the beginning of October 2017, we discovered new Android spyware with several features previously unseen in the wild. In the course of further research, we found a number of related samples that point to a long-term development process. We believe the initial versions of this malware were created at least three years ago – at the end of 2014.” reads the analysis published by Kaspersky.
“Since then, the implant’s functionality has been improving and remarkable new features implemented, such as the ability to record audio surroundings via the microphone when an infected device is in a specified location; the stealing of WhatsApp messages via Accessibility Services; and the ability to connect an infected device to Wi-Fi networks controlled by cybercriminals.”
In this post, I’ll show you that the malware was first found by the security researcher at ESET Lukas Stefanko and the first detailed analysis of the spyware (titled “Malware Analysis Report: Fake 3MobileUpdater“) was published by the experts at the CSE Cybsec ZLab.
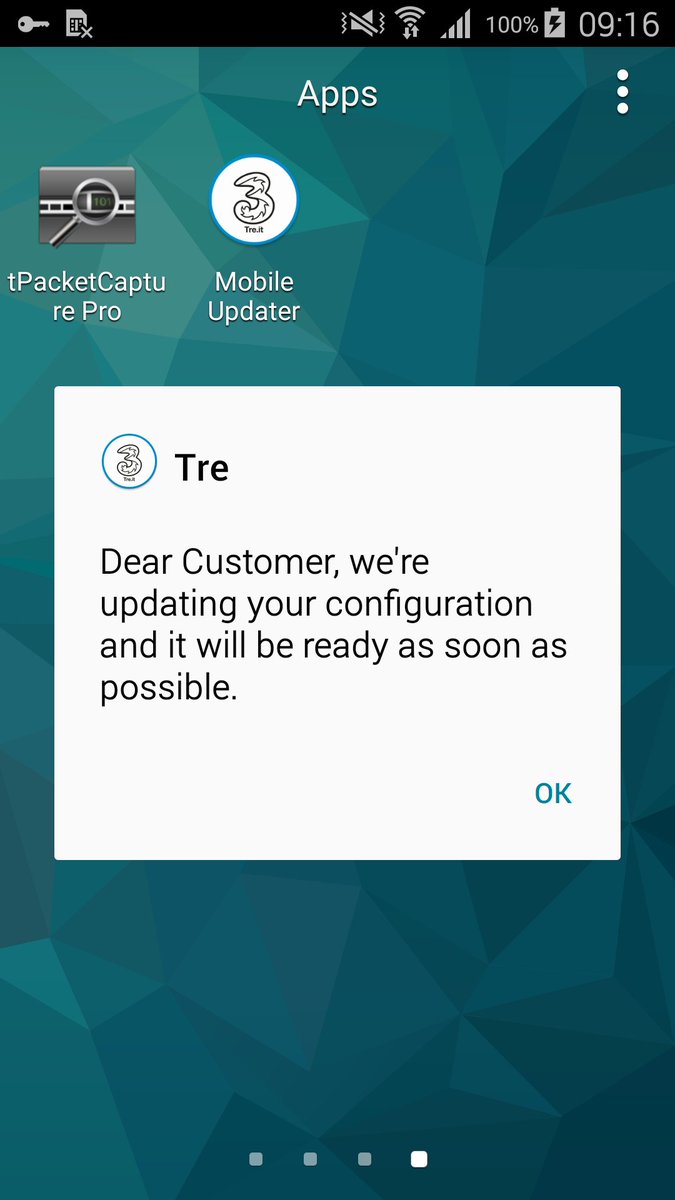
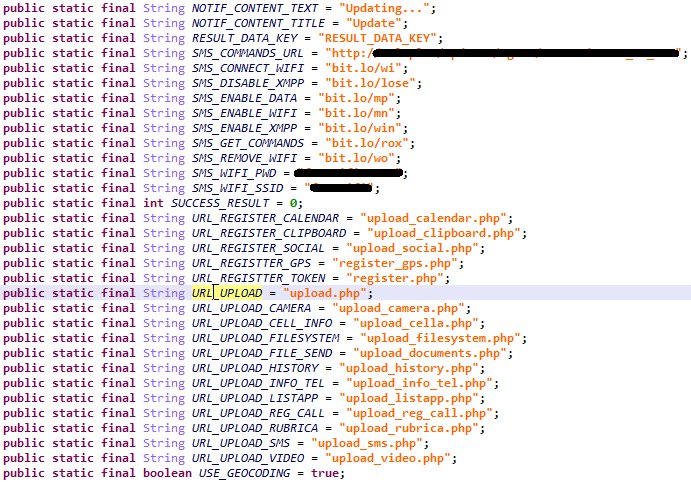
Lukas Stefanko
@LukasStefanko
The Android Italian Job 🇮🇹
Android Spy Trojan steals sensitive info from victims
Spreads in #Italy 🇮🇹 as fake telecommunication company @Tre_It
Remotely controlled, capable of: install apps, upload files, uses accessibility, take pics, record audio, get sms/location, XMPP...
10:02 AM - Nov 9, 2017
7 7 Replies 113 113 Retweets 110 110 likes
Twitter Ads info and privacy
According to Kaspersky, Skygofree has being distributed through fake web pages mimicking leading mobile network operators. The attackers registered some of the domains used in the attack since 2015.
The most recently observed domain was registered on October 31, 2017, according to Kaspersky data the malicious code was used against several infected individuals, exclusively in Italy.
The team of researchers at CSE CybSec ZLab analyzed in November a fake 3 Mobile Updater that was used pose itself as a legitimate application of the Italian Telco company, TRE Italia.
“The most classic and efficient method used to lure the users is to believe that the application does something good. This is just what 3 Mobile Updater does. In fact, this malicious Android application looks like a legitimate app used to retrieve mobile system update and it improperly uses the logo of the notorious Italian Telco company, TRE Italia, in order to trick victims into trusting it.” reads the report published by CSE CybSec.

The analysis conducted by Kaspersky suggests the involvement of an Italian firm due to the presence in the code of strings in Italian.
“As can be seen from the comparison, there are similar strings and also a unique comment in Italian, so it looks like the attackers created this exploit payload based on android-rooting-tools project source code.” states Kaspersky.
The CSE CybSec researchers arrived atthe same conclusion, below a portion of the code analyzed by the members of the ZLab.

“Moreover, both in the logcat messages and in the code, the malware writers used the Italian language. So, we can say with high confidence that this malicious app has been written by an Italian firm that intended to target users of the Italian telco company Tre.” CSE wrote in the analysis.
The artifacts analyzed by Kaspersky in the malware code and information gathered on the control infrastrucure suggest the developer of the Skygofree implants is an Italian IT company that works for surveillance solutions.

Kaspersky Lab has not confirmed the name of the Italian company behind this spyware, we at the CSE CybSec ZLab opted for the same decision in October due to the possible involvement of law enforcement or intelligence Agencies.
Unfortunately, the OPsec implemented by the firm is very poor. The name of the company is present in multiple reference of the code. Not only, one of the domains used to control registered by the attacker is linked to an Italian technology company.
“Although the security firm has not confirmed the name of the Italian company behind this spyware, it found multiple references to Rome-based technology company “Negg” in the spyware’s code. Negg is also specialized in developing and trading legal hacking tools.” states the blog post published by THN.
Once installed, Skygofree hides its icon and starts background services to conceal its malicious actions from the victim, one interesting feature implemented by the malicious code prevents its services from being killed.
“Interestingly, a self-protection feature was implemented in almost every service. Since in Android 8.0 (SDK API 26) the system is able to kill idle services, this code raises a fake update notification to prevent it” continues Kaspersky.
According to Kaspersky, the Skygofree malware was enhanced since October implementing a sophisticated multi-stage attack and using a reverse shell payload.
The malicious code includes multiple exploits to escalate privileges for root access used by attackers to execute sophisticated payloads, including a shellcode used to spy on popular applications such as Facebook, WhatsApp, Line, and Viber.
The same spying abilities were implemented in the app we analyzed at the CSE CybSec.
“The capabilities of this malicious app are enormous and include the information gathering from various sources, including the most popular social apps, including Whatsapp, Telegram, Skype, Instagram, Snapchat. It is able to steal picture from the gallery, SMS and calls registry apps. All this data is first stored in a local database, created by the malicious app, and later it is sent to the C2C.” reads the preliminary analysis published on SecurityAffairs.
“There are multiple, exceptional capabilities: usage of multiple exploits for gaining root privileges, a complex payload structure, [and] never-before-seen surveillance features,” the researchers said.
Skygofree is able to take pictures and videos remotely, monitor SMS, call records and calendar event, of course, it also able to gather target’ location and access any information stored on the mobile.
Skygofree also can record audio via the microphone, the attacker can also force the victim’s device to connect to compromised Wi-Fi networks it controls in order to conduct man-in-the-middle attacks.
Kaspersky also found a variant of Skygofree targeting Windows users, a circumstance that suggests the same company is also targeting machines running Windows OS.
The best way to prevent yourself from being a victim is to avoid downloading apps via third-party websites, app stores or links provided in SMS messages or emails.
Comparative analysis fake 3 Mobile Updater vs SkyGoFree
I asked my colleague Dr. Antonio Pirozzi, Director of the CSE CybSec ZLab, to compare the stubs of code shared by Kaspersky with the ones related to the code we analyzed back in November.
This is what has emerged:
These classes are identical:


The spyware we analyzed did not contain the Android exploits found by Kaspersky, as well as the reverse shell PRISM and the busy box.
The class used for parsing are similar;
The DNS used are the same;

The IoCs published by Kaspersky includes the URL of the C&C (url[.] plus) which was the same of the Spyware analyzed by CSE CybSec.
Conclusion
Many parts of the code are identical, both source codes include strings in Italian and the reference to the Italian firms are the same. The version analyzed by Kaspersky is a new version of the malware analyzed by CSE CybSec ZLab.
Kaspersky also shared the URL from which the spyware is downloaded and one of them was related to the version we analyzed (Fake 3 mobile updater).
The two version of the malware shared numerous classes, C&C server, Whois records and many other info. The sample analyzed by CSE was probably still under development.
Kaspersky Discovers Powerful Mobile Spyware
17.1.2018 securityweek Android
Kaspersky Lab has shared details of a sophisticated, multi-stage mobile spyware that gives attackers the ability to take over an infected Android device, with advanced features that have never been seen before in other mobile threats.
Named Skygofree, the mobile implant has been active since 2014 and has the ability to record nearby conversations and noise when an infected device enters a specified location.
Other advanced functions that have never been seen before include using Android’s Accessibility Services to access WhatsApp messages and the ability to connect an infected device to Wi-Fi networks controlled by the attackers.
“The implant carries multiple exploits for root access and is also capable of taking pictures and videos, seizing call records, SMS, geolocation, calendar events and business-related information stored in the device’s memory,” Kaspersky explained.
Furthermore, a special feature enables it to circumvent a battery-saving technique used on China-made Huawei devices by adding itself to the list of ‘protected apps’ so that it is not switched off automatically when the screen is off.
"Due to this feature, it is clear that the developers paid special attention to the work of the implant on Huawei devices," Kaspersky's researchers noted.
Designed for targeted cyber-surveillance, Kaspersky said the malware could be an offensive security product used for law enforcement purposes, similar to products offered by Hacking Team, a controversial Italy-based company that develops and sells surveillance technology to governments around the world.
Kaspersky did not provide statistics on the number of Android devices that may have been infected, but the number appears to be relatively small. There are “several infected individuals,” all located in Italy, Kaspersky said.
“Given the artefacts we discovered in the malware code and our analysis of the infrastructure, we have a high level of confidence that the developer behind the Skygofree implants is an Italian IT company that offers surveillance solutions, rather like HackingTeam,” said Alexey Firsh, Malware Analyst, Targeted Attacks Research, Kaspersky Lab.
The operators used spoofed landing pages that mimic the sites of mobile operators for spreading the implant, and Kaspersky’s researchers found 48 different commands that can be leveraged by the attackers.
Kaspersky provided technical analysis on Skygofree in an associated blog post, including an overview of the various commands, along with details on a number of modules that target computers running Microsoft Windows.
“High end mobile malware is very difficult to identify and block and the developers behind Skygofree have clearly used this to their advantage: creating and evolving an implant that can spy extensively on targets without arousing suspicion,” Firsh said.
The attacks are ongoing and the most recent domain was registered in October 2017.