- Android -
Last update 04.10.2017 16:16:35
Introduction List Kategorie Subcategory 0 1 2 3 4 5 6 7 8
Expensive free apps
26.1.2017 Kaspersky Android
This post is the result of collaboration between Elevenpaths (Telefónica Cyber Security Unit) and Kaspersky Lab. Both companies have used their own expertise, researchers and tools, such as Tacyt (an innovative tool for the monitoring and analysis of mobile threats) and GReAT’s internal tools and resources.
Big Brother and Google Play
Fraudulent apps trying to send Premium SMS messages or trying to call to high rate phone numbers are not something new. Actually, it is easy to find them specially in Spain, Russia and some other european countries. Of course, it is much more interesting to talk about how certain groups bypass detection mechanisms such as those used by Google Play, since this has become difficult to achieve in the past few years.
Some years ago it was pretty easy to upload a dialer (or other similar fraudulent app) to Google Play [1] [2], but new detection mechanisms made attacker to focus on alternative markets, at least for a period of time.
Recently, we have found a Spanish group that successfully uploaded a non-official Big Brother (Gran Hermano) TV show app, which is one of the most popular TV shows in Spain even being on the air for 16 years now.
[Analysis:cdd254ee6310331a82e96f32901c67c74ae12425]
This was not a very sophisticated app, but they were able to upload it into Google Play using an old trick. First, they uploaded a clean an innocuous version that of course passed or the security controls from Google Play. Then, some days later, a new version was uploaded with a major features update, including subscription to paying services. This trick was extremely simple but successful, since the app was in the Google Play for around two months (from mid September to mid November 2015).
It seems this was not the first time this group tried to upload a Big Brother-like app. We have detected (via Tacyt [3]) at least another 4 similar applications that, regarding some particular logging messages we found in the code, could have the same origin:
com.granhermano.gh16_1; from 2015-09-15 to 2015-09-22;
com.granhermano162; from 2015-09-29 to 2015-11-14;
com.granhermanodieciseis; from 2015-09-29 to 2015-11-11
com.granh.gh16_3; from 2015-10-05 to 2015-10-15;
com.hisusdk; from 2015-09-16 to 2015-11-14 (the one analyzed).
As we said before, this group was found to be using a specific string “caca” as a logging tag, which is not something usual:
The word “caca” is a colloquial word in Spanish referring to an excrement (very similar to the word “poo” in English). We could find it in certain testing code, referring to lines of code that should be removed later, but it is unusual to find it in such similar applications and used in the same way. Because of that, it makes sense to think that those applications were developed by the same group. Other strings and function names used in the code make us conclude that those applications could be developer by native Spanish speakers.
This app is using several commercial third party services such as Parse.com for the first network communication. This first API call is used in order to get all the information necessary to run further actions (URLs, authentication, etc).
{“results”:[{“Funcionamiento”:” Ahora la única pestaña importante es la de VOT.”,”action1″:”http://tempuri.org/getPinCode”,”action2″:”http://tempuri.org/crearSubscripcion”,”activa”:”si”,”createdAt”:”2015-09-08T16:17:24.550Z”,”estado”:true,”id_categoria”:”2608″,”id_subscripcion”:”400″,”metodo1″:”getPinCode”,”metodo2″:”crearSubscripcion”,”namespace”:”http://tempuri.org/”,”nombreApp”:”GH16 – españa”,”numero_corto”:”795059″,”numero_sms”:”+34911067088″,”objectId”:”tNREzkEocZ”,”password”:”15xw7v7u”,”updatedAt”:”2015-11-27T10:28:00.406Z”,”url”:”http://ws.alertas.aplicacionesmonsan.net/WebSubscription.asmx?WSDL”,”urlcode”:”http://spamea.me/getcode.php?code=”,”usuario”:”yourmob”,”vot”:true}]}
As we can see above, it references to different URLs:
spamea.me is service that no longer exists at the time of writing, but that used to be hosted on 107.6.184.212, which seems a hosting service shared with many other websites.
ws.alertas.aplicacionesmonsan.net is legitimate service focused on mobile monetization, including SMS premium and direct carrier billing. It is used from the app in order to subscribe the user to a service called “yourmob.com”.
Of course, using paying services is not malicious itself, since it is legitimate that companies could bill for their services, but user should be clearly noticed about service cost and conditions beforehand.
Despite we found a reference to “Terms and Conditions” (in Spanish) poiting to the website servimob.com , we could not verify that this information is shown to users and, anyway, users don’t have the opportunity to reject the agreement and don’t be subscribed.
Presence outside Google Play
It make sense that if a group have included this kind of app in Google Play, They were going to try something similar using other app sources (thanks to Facundo J. Sánchez that spotted this).
Analysis: 9b47070e65f81d253c2452edc5a0eb9cd17447f4
This app worked slightly different. It uses other 3rd party services and it sends Premium SMSs for monetization. They got from the server what number to use, for how many seconds and if the screen should be on or off.
We found that they used very similar words for comments and method names (most of them in Spanish, including “caca”), same topic (Big Brother), references to “yourmob” and much more, so definitely we can link it with the Spanish group mentioned before.
One of the webservices used by this application (http://104.238.188.38/806/) exposed a control panel showing information about people using this app:
As you probably know, groups developing this kind of apps usually reuse their servers and supporting infrastructure for multiple apps, for example this one:
https://www.virustotal.com/en-gb/file/cc2895442fce0145731b8e448d57e343d17ca0d4491b7fd452e6b9aaa4c2508a/analysis/
It was using this vps as well http://vps237553.ovh.net. Some of the panels and services provided by the VPS were located here:
http://vps237553.ovh.net/nexmo/getcode.php?code=
http://vps237553.ovh.net/polonia/autodirect1.php
http://vps237553.ovh.net/polonia/autodirect2.php
http://vps237553.ovh.net/polonia/guardar_instalacion.php
http://vps237553.ovh.net/polonia/guardar_numero.php
http://vps237553.ovh.net/polonia/guardar_numero.php?androidID=
http://vps237553.ovh.net/polonia/guardar_sms.php
http://vps237553.ovh.net/polonia/push_recibido.php
http://vps237553.ovh.net/polonia/panel.php
http://vps237553.ovh.net/nexmo/
As we can see in their control panel, they have been quite successful in terms of spread, since there are registered phones from many different countries (Spain, Holland, Poland, etc).
In addition, an iterative search on terms such as IP addresses, unique paths, etc, has shown that other apps could be using the same supporting infrastructure that was shown above, including the following IP addresses and domain names:
104.238.188.38
45.32.236.127
51.255.199.164 (vps237553.ovh.net)
50.63.202.50
45.63.85.198
In particular, 45.32.236.127 was pointed by different domain names in the past months:
kongwholesaler.tk (2016-05-22)
acc-facebook.com (2016-04-11)
h-instagram.com (2016-04-11)
msg-vk.com (2016-04-11)
msg-google.ru (2016-04-10)
msg-mail.ru (2016-04-10)
iwantbitcoins.xyz (2015-11-04)
These domains have probably been used for fraudulent initiatives such as phishing attacks, since they are very similar to well-known and legitimate services.
Something that kept our attention was that “vps237553.ovh.net”, used from a sample and resolving to 51.255.199.164, was also used at some point (June 2016 regarding our passive DNS) by “servimob.com” domain (same domain referenced in the app from Google Play).
Back to Google Play
As you can imagine, they tried again to upload a new app to Google Play, following a similar philosophy and techniques that we have seen before.
e49faf379b827ee8d3a777e69f3f9bd3e559ba03
11a131c23e6427dd7e0e47280dd8f421febdc4f7
These apps were available in Google Play for a few weeks in September 2016, using similar techniques, especially to those applications that we found outside Google Play.
Conclusions
This Spanish group has been quite successful on uploading this kind of apps in Google Play, using interesting topics such as the Big Brother TV show. Spain and Poland have been two countries traditionally targeted by SMS scams and similar malware. However, we have never seen in the past few years any group that was able to upload apps to legitimate markets in such an easy way. Perhaps the key point is that they try to be close enough to the border between a legitimate business and a malicious one.
Android VPNs Introduce Security, Privacy Risks: Study
26.1.2017 Securityweek Android
Researchers have analyzed hundreds of virtual private network (VPN) applications for Android and determined that many of them introduce serious privacy and security risks.
A team of experts from the University of California, Berkeley, the Data 61 research unit at Australia’s Commonwealth Scientific and Industrial Organisation (CSIRO) and the University of New South Wales have analyzed 283 Google Play apps that request the BIND_VPN_SERVICE permission, which provides native support for VPN clients.
After running a series of passive and active tests, researchers determined that while 67% of the analyzed apps claim to enhance privacy and security, three-quarters of them include third-party tracking libraries and 82% of them request access to sensitive information, such as text messages and user accounts.
Experts discovered that more than one-third of these Android VPN apps, including ones that are highly popular, appear to include some malicious code when tested with Google’s VirusTotal service. Worryingly, only a small number of users have raised security or privacy concerns in the comments posted to Google Play when reviewing these applications.

Another problem identified during the study is that 18% of the applications do not provide any information on the entity hosting the VPN server, and 16% of them forward traffic through the devices of other users, which can pose serious trust, privacy and security issues. Furthermore, a small percentage of the apps implemented local proxies designed to inspect user traffic, mainly for filtering and security purposes.
VPN applications are supposed to provide anonymity and security, but researchers found that 18% of the ones from Google Play implement tunneling protocols without encryption, and many of them don’t tunnel IPv6 and DNS traffic.
A small number of Android VPN apps have been found to intercept TLS traffic and even inject JavaScript code for advertising and tracking purposes.
Researchers have contacted the developers of problematic apps and while some of them confirmed the findings and provided arguments in support of their methods, others did not respond.
“The ability of the BIND_VPN_SERVICE permission to break Android’s sandboxing and the naive perception that most users have about third-party VPN apps suggest that it is urging to re-consider Android’s VPN permission model to increase the control over VPN clients,” researchers wrote in their paper. “Our analysis of the user reviews and the ratings for VPN apps suggested that the vast majority of users remain unaware of such practices even when considering relatively popular apps.”
The complete paper, titled “An Analysis of the Privacy and Security Risks of Android VPN Permission-enabled Apps,” is available for download in PDF format.
Fake Netflix App Takes Control of Android Devices
25.1.2017 Securityweek Android
A recently spotted fake Netflix app is in fact installing a Remote Access Trojan (RAT) variant onto the victims’ devices, Zscaler security researchers have discovered.
Preying on the popularity of applications isn’t a new technique, with fake Super Mario Run games for Android recently used to distribute the Marcher and DroidJack Trojans. Now, it seems that the actors behind the SpyNote RAT have decided to use the same technique and leverage the enormous traction Netflix has among users looking to stream full movies and TV programs to their mobile devices.
Instead of a video streaming app, however, users end up with a RAT that can take advantage of their device in numerous ways, such as listening to live conversations by activating the microphone, executing arbitrary commands, sending files to a command and control (C&C) server, recording screen captures, viewing contacts, and reading SMS messages.
The fake Netflix app was supposedly created using an updated version of the SpyNote RAT builder, which leaked online last year, Zscaler reveals. Once installed, the app would display the icon that the legitimate Netflix app on Google Play has, but it should by no means be mistaken for it.
When the user clicks on the icon for the first time it disappears from the homescreen and nothing else seems to happen, a trick commonly used by mobile malware. In the background, however, the malware starts preparing its onslaught of attacks.
SpyNote RAT was found to use a free DNS service for C&C communication, as well as to leverage the Services, Broadcast Receivers, and Activities components of the Android platform to remain up and running on the infected device.
“Services can perform long-running operations in the background and does not need a user interface. Broadcast Receivers are Android components that can register themselves for particular events. Activities are key building blocks, central to an app’s navigation, for example,” Zscaler researchers note.
Additionally, the malware can uninstall apps from the infected device (such as antivirus protections), was designed to function only over Wi-Fi (to avoid raising suspicion), and can even click photos, the security researchers say. SpyNote RAT also collects the device’s location to identify the exact location of the victim, and packs various data exfiltration capabilities.
According to Zscaler, the SpyNote RAT builder was seen gaining popularity in the hacking community. It can be used to create various fake apps to masquerade the malware, such as WhatsApp, YouTube Video Downloader, Google Update, Instagram, Hack Wifi, AirDroid, WifiHacker, Facebook, Photoshop, SkyTV, Hotstar, Trump Dash, and Pokemon GO (the game was abused for malware distribution even before being launched on Android).
“Furthermore, we found that in just the first two weeks of 2017, there have been more than 120 such spyware variants already built using the same SpyNote Trojan builder as SpyNote RAT and roaming in the wild,” the security researchers say. A similar trend is usually observed after the source code of a piece of malware leaks online.
To stay protected, users should refrain from installing applications via third-party app stores or to side-load them, especially if they are games that haven’t yet been released on Android, such as Super Mario Run or Pokemon GO. “You should also avoid the temptation to play games from sources other than legitimate app stores; such games are not safe and may bring harm to your reputation and your bank account,” Zscaler concludes.
Charger Android Ransomware Infects Apps on Google Play
25.1.2017 Securityweek Android
A newly discovered piece of Android ransomware embedded in apps available on Google Play threatens to sell a victim's personal data on the black market if they don’t pay, Check Point security researchers warn.
Dubbed Charger, the threat was found embedded in an application called EnergyRescue, and had the ability to steal contacts and SMS messages, while also asking for admin permissions on the device. If permissions are granted, the ransomware locks the device and displays a message demanding payment.
While threatening to sell victim’s personal information on the black market, the malware authors also claim that all of the victim’s data has been already saved on an attacker-controlled server. The miscreants say that the stolen information includes social network details, bank accounts, credit cards, as well as all data about the victim’s “friends and family.”
The demanded ransom is 0.2 Bitcoins (around $180), which “is a much higher ransom demand than has been seen in mobile ransomware so far,” Check Point notes. Previously spotted mobile ransomware such as DataLust only demanded a $15 ransom. Charger victims are asked to send the payments to a specific Bitcoin account.
With Android ransomware inflicting direct harm to users, it’s clear that Charger is yet another attempt by mobile malware developers to catch up with the PC ransomware, which has been wreaking havoc for the past couple of years. Recently, even the Tordow Android banking Trojan was seen packing data collection capabilities and ransomware-like behavior.
Charger was observed checking the infected device’s location to ensure it doesn’t run on those located in Ukraine, Russia, or Belarus, supposedly in an attempt to avoid being prosecuted in their own countries or being extradited between countries.
While other malware in Google Play uses a dropper to download the malicious payload, Charger uses a heavy packing approach, which makes it harder for it to stay hidden. However, the ransomware authors did boost its evasion capabilities to ensure it can stay hidden in Google Play: the malware encodes strings into binary arrays to make it hard to inspect them, loads code from encrypted resources dynamically, and checks whether it runs in an emulator before running its routine.
According to Check Point, most detection engines cannot penetrate and inspect dynamically-loaded code, and the authors added an extra layer of protection by flooding the code with meaningless commands to mask the actual commands passing through. The researchers also point out that more and more mobile malware is running checks to avoid running in emulators and virtual machines, just as it happens in the PC malware landscape.
HummingWhale – HummingBad Android Malware returns even more dangerous than before
25.1.2017 securityaffairs Android
Last year, the HummingBad Android malware infected as many as 85 million devices, now it has returned under the new name of HummingWhale.
CERT-EU and other sources corroborated Check Point researchers’ findings which recently confirmed a new variant of the ad-fraud-big-money-making, HummingBad, is spreading rapidly on the Android marketplace Google Play. HummingBad was first seen and released almost a year ago in January/February 2016 by malware authors Yingmob, and racking upwards of approx. $300,000 USD per month for the better half of 2016. Approximately 10 million Android devices were infected in the firm part of the last year.
Now, dubbed by Check Point, “HummingWhale” is at large with better ad fraud capabilities and sophisticated techniques than HummingBad affecting several applications and has been downloaded several million times from the combined list of applications downloaded.
“Check Point researchers have found a new variant of the HummingBad malware hidden in more than 20 apps on Google Play. The infected apps in this campaign were downloaded several million times by unsuspecting users” reads the report published by CheckPoint security.

Check Point first came to know this when they uncovered something interesting with Trojan-riddled apps published under the “fake” names of developers of Chinese origin and the apps behavior at startup. In addition, the startup behavior, closing the application normally does not exit cleanly. Instead, it “minimizes” covertly and remains running in the virtual environment.
Moreover, the apps carried a payload of 1.3MB and disguised itself as an image called group.png however it is anything but. The payload contained is an executable apk file.
“This .apk operates as a dropper, used to download and execute additional apps, similar to the tactics employed by previous versions of HummingBad. However, this dropper went much further. It uses an Android plugin called DroidPlugin, originally developed by Qihoo 360, to upload fraudulent apps on a virtual machine.”, said Oren Koriat, Mobile Cyber Security Analyst @ Check Point
What makes HummingWhale unique from the original is that it runs the downloaded application without having to get root and or elevated privileges making the phone susceptible to further fraudulent applications or further deployment of remote access tools (RATs).
Further information is available in the report, including Indicators of Compromise (IoCs).
Nasty Android Malware that Infected Millions Returns to Google Play Store
24.1.2017 thehackernews Android
HummingBad – an Android-based malware that infected over 10 million Android devices around the world last year and made its gang an estimated US$300,000 per month at its peak – has made a comeback.
Security researchers have discovered a new variant of the HummingBad malware hiding in more than 20 Android apps on Google Play Store.
The infected apps were already downloaded by over 12 Million unsuspecting users before the Google Security team removed them from the Play Store.
Dubbed HummingWhale by researchers at security firm Check Point, the new malware utilizes new, cutting-edge techniques that allow the nasty software to conduct Ad fraud better than ever before and generate revenue for its developers.
The Check Point researchers said the HummingWhale-infected apps had been published under the name of fake Chinese developers on the Play Store with common name structure, com.[name].camera, but with suspicious startup behaviors.
"It registered several events on boot, such as TIME_TICK, SCREEN_OFF and INSTALL_REFERRER which [were] dubious in that context," Check Point researchers said in a blog post published Monday.
HummingWhale Runs Malicious Apps in a Virtual Machine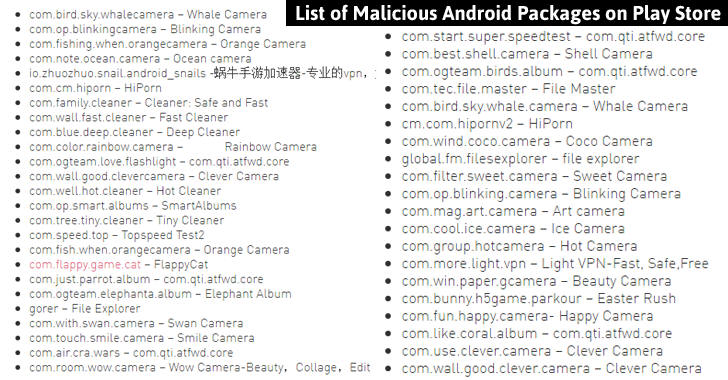
The HummingWhale malware is tricky than HummingBad, as it uses a disguised Android application package (APK) file that acts as a dropper which downloads and runs further apps on the victim's smartphone.
If the victim notices and closes its process, the APK file then drops itself into a virtual machine in an effort to make it harder to detect.
The dropper makes use of an Android plugin created by the popular Chinese security vendor Qihoo 360 to upload malicious apps to the virtual machine, allowing HummingWhale to further install other apps without having to elevate permissions, and disguises its malicious activity to get onto Google Play.
"This .apk operates as a dropper, used to download and execute additional apps, similar to the tactics employed by previous versions of HummingBad," researchers said. "However, this dropper went much further. It uses an Android plugin called DroidPlugin, originally developed by Qihoo 360, to upload fraudulent apps on a virtual machine."
HummingWhale Runs Without having to Root the Android Device
Thanks to the virtual machine (VM), the HummingWhale malware no longer needs to root Android devices unlike HummingBad and can install any number of malicious or fraudulent apps on the victim's devices without overloading their smartphones.
Once the victim gets infected, the command and control (C&C) server send fake ads and malicious apps to the user, which runs in a VM, generating a fake referrer ID used to spoof unique users for ad fraud purposes and generate revenue.
Alike the original HummingBad, the purpose of HummingWhale is to make lots of money through ad fraud and fake app installations.
Besides all these malicious capabilities, the HummingWhale malware also tries to raise its reputation on Google Play Store using fraudulent ratings and comments, the tactic similar to the one utilized by the Gooligan malware.
Millions Download HummingBad Variant via Google Play
24.1.2017 Securityweek Android
A newly discovered variant of the HummingBad Android malware has been downloaded millions of times after infecting 20 applications in Google Play, Check Point security researchers warn.
Discovered in early 2016, HummingBad already proved one of the most prolific Android malware families out there, accounting for over 72% of attacks in the first half of the year.
In a report published last July, Check Point suggested that around 10 million Android devices might have been compromised by HummingBad and that its rootkit capabilities allowed attackers take full control over the infected devices. The researchers also said that Yingmob, the group behind the malware, might have compromised over 85 million devices.
Dubbed HummingWhale, the newly discovered variant is said to include cutting edge techniques that allow it to perform its nefarious activities (ad fraud) better than before.
While HummingBad was spreading mainly through third-party app stores, the HummingWhale variant made its way into Google Play and infected 20 apps, all of which have been already removed by Google. The main giveaway feature, the researchers say was a 1.3MB encrypted file called ‘assets/group.png’ also found in some later HummingBad samples that were masquerading as an app called “file-explorer.”
Offending apps were found to register several events on boot, such as TIME_TICK, SCREEN_OFF and INSTALL_REFERRER, as well as to feature a common name structure – com.XXXXXXX.camera (e.g. com.bird.sky.whale.camera, com.color.rainbow.camera, com.fishing.when.orangecamera). Apps outside of the camera family were also identified.
The HummingWhale samples were also observed registering to certain events and packing some identical strings in their code and certificates when compared to the previous HummingBad variants. HummingWhale was also observed being promoted by several new HummingBad samples, Check Point says.
The new malware variant, researchers say, is heavily packed and has its main payload in the ‘group.png’ file, which is actually an .apk that operates as a dropper. This executable file can download additional apps, a functionality observed in previous versions of HummingBad as well. The new dropper, however, uses the DroidPlugin Android plugin to upload fraudulent apps on a virtual machine.
“First, the Command and Control server (C&C) provides fake ads and apps to the installed malware, which presents them to the user. Once the user tries to close the ad, the app, which was already downloaded by the malware, is uploaded to the virtual machine and run as if it is a real device. This action generates the fake referrer id, which the malware uses to generate revenues for the perpetrators,” the security researchers explain.
By using this method, the cybercriminals ensure that the malware installs apps without gaining elevated permissions first, and that the malicious activity is disguised, thus allowing the malware to infiltrate Google Play. What’s more, the embedded rootkit in the previous HummingBad variant is no longer needed, since the same results are achieved without it. On top of that, the malware can now install an infinite number of fraudulent apps without overloading the device.
“HummingWhale also conducted further malicious activities, like displaying illegitimate ads on a device, and hiding the original app after installation, a trait which was noticed by several users. As can be seen in the image below, HummingWhale also tries to raise its reputation in Google Play using fraudulent ratings and comments, similar to the Gooligan and CallJam malware before it,” the security researchers say.
Source Code for BankBot Android Trojan Leaks Online
24.1.2017 Securityweek Android
The source code of Android banking Trojan BankBot, along with instructions on how to use it, recently emerged on a hacker forum, Doctor Web security researchers have discovered.
The source code was published about a month ago, but Android malware based on the code was spotted last week. Once the malware gets admin privileges on an infected device, it removes its shortcut from the homescreen to hide itself and hinder removal. Next, it connects to a command and control (C&C) server to retrieve instructions.
The BankBot Trojan is distributed masquerading as benign applications. On the infected devices, it can request administrative privileges to display phishing pages to steal login credentials, intercept and send SMS messages, send USSD requests, retrieve contacts list, track the device, make calls, and receive an executable file containing a list of banking apps to attack.
Malicious programs that provide such capabilities are usually being sold as commercial products on underground forums. However, with the source code of this application leaked online, chances are that the number of attacks involving Android banking Trojans will register a significant increase soon, Dr.Web suggests.
The malware can track the launch of banking applications on the user’s device and overlay phishing dialogues to trick users into revealing their login information. The malware is targeting over three dozen such financial applications, including banking and payment system software.
The security researchers have discovered that the malware can also steal bank card information. For that, the Trojan tracks the launch of multiple popular applications on the device, including Facebook, Viber, Youtube, WhatsApp, Uber, Snapchat, WeChat, imo, Instagram, Twitter, and Play Store, to display a phishing dialog on top of them, tricking users into believing it is a Google Play purchase page.
“Information on found matches is sent to the C&C server. The Trojan receives a list of files to be monitored from execution. After one of them is launched, Android.BankBot.149.origin displays WebView on top of the attacked application with a fraudulent authentication form to access the user account. Then the entered information is sent to the server,” Dr.Web says.
BankBot was also designed to steal SMS messages. When an SMS arrives, the malware turns off sounds and vibrations and sends the content of the message to the cybercriminals, while also attempting to delete the original entry from the list of incoming SMS. This would result in users missing bank notifications about unplanned transactions that cybercriminals are performing.
Data stolen from the device, which includes information on the anti-virus applications installed on the infected device, is uploaded to the C&C server, making it accessible to the cybercriminals. What’s more, the security researchers say, an administration panel provides operators with control over the malicious app.
“In general, the possibilities of this Trojan are quite standard for modern Android bankers. However, as cybercriminals created it with publicly available information, one can anticipate that many Trojans similar to it will appear,” Doctor Web’s security researchers conclude.
“Dumping malware code is great way to allow others to contribute to the code and modify it to help evade detection. This tactic was very successful for distributing Zeus. When you have a larger group modifying the code, the number of variants increases rapidly, making it very hard for security products that rely on pattern matching to detect it,” Lamar Bailey, Senior Director of Security R&D for Tripwire, told SecurityWeek in an emailed comment.
Do web injections exist for Android?
23.1.2017 Kaspersky Android
Web injection attacks
There’s an entire class of attacks that targets browsers – so-called Man-in-the-Browser (MITB) attacks. These attacks can be implemented using various means, including malicious DLLs, rogue extensions, or more complicated malicious code injected into pages in the browser by spoofing proxy servers or other ways. The purpose of an MITB attack may vary from relatively innocuous ad spoofing on social networks or popular websites to stealing money from user accounts – the latter is what happened in the Lurk case.
A malicious app masquerades as a Kaspersky Lab product in an MITB attack
Web injection is used in most cases when an MITB-class attack targets online banking. This type of web injection attack involves malicious code being injected into an online banking service webpage to intercept the one-time SMS message, harvest information about the user, spoof banking details, etc. For example, our Brazilian colleagues have long reported about barcode spoofing attacks performed when users print out Boletos – popular banking documents issued by banks and all kind of businesses in Brazil.
Meanwhile, the prevalence of MITB attacks in Russia is decreasing – cybercriminals are opting for other methods and attack vectors to target banking clients. For the average cybercriminal, it is much easier to use readily available tools than develop and implement web injection tools.
Despite this, we’re often asked if there are any web injection attacks for Android devices. This is our attempt to investigate and give as full an answer as possible.
Web injection on Android
Despite the term ‘inject’ being used in connection with mobile banking Trojans (and sometimes used by cybercriminals to refer to their data-stealing technologies), Android malware is a whole different world. In order to achieve the same goals pursued by web injection tools on computers, the creators of mobile Trojans use two completely different technologies: overlaying other apps with a phishing window, and redirecting the user from a banking web page to a specially crafted phishing page.
Overlaying apps with phishing windows
This is the most popular technology with cybercriminals and is used in practically all banking Trojans. 2013 was when we first encountered a piece of malware overlaying other apps with its phishing window – that was Trojan-Banker.AndroidOS.Svpeng.
Today’s mobile banking Trojans most often overlay the Google Play Store app with their phishing window – this is done in order to steal the user’s bank card details.
The Marcher malware
Besides this, Trojans often overlay various social media and instant messaging apps and steal the passwords to them.
Do web injections exist for Android?
However, mobile banking Trojans typically target financial applications, mostly banking apps.
Three methods of MITB attacks for mobile OS can be singled out:
1. A special Trojan window, crafted beforehand by cybercriminals, is used to overlay another app’s window. This method was used, for example, by the Acecard family of mobile banking Trojans.
Acecard phishing windows
2. Apps are overlaid with a phishing web page located on a malicious server. This way, the cybercriminals can modify its contents any time they need to. This method is used by the Marcher family of banking Trojans.
Marcher phishing page
3. A template page is downloaded from a malicious server, to which the icon and the name of the attacked application is added. This is how one of the Trojan-Banker.AndroidOS.Faketoken modifications manages to attack over 2,000 financial apps.
FakeToken phishing page
It should be noted that starting from Android 6, for the above attack method to work, the FakeToken Trojan has to request the privilege of displaying its window on top of other app windows. It’s not alone though: as new versions of Android are gaining popularity, a growing number of mobile banking Trojans are beginning to request such privileges.
Redirecting the user from the bank’s page to a phishing page
We were only able to identify the use of this technology in the Trojan-Banker.AndroidOS.Marcher family. The earliest versions of the Trojan that redirected the user to a phishing page are dated late April 2016, and the latest are from the first half of November 2016.
Redirecting the user from a bank’s webpage to a phishing page works as follows. The Trojan subscribes to modify browser bookmarks, which includes changes in the current open page. This way the Trojan knows which webpage is currently open, and if it happens to be one of the targeted pages, the Trojan opens the corresponding phishing page in the same browser and redirects the user there. We were able to find over a hundred web pages belonging to financial organizations that were targeted by the Marcher family of Trojans.
However, two points need to be raised:
All new modifications of the Marcher Trojan that we were able to detect no longer use this technology.
Those modifications that used this technology also used a method of overlaying other apps with their phishing window.
Why then was the method of redirecting the user to a phishing page used by only one family of mobile banking Trojans, and why is this technology no longer used in newer modifications of the family? There are several reasons:
In Android 6 and later versions, this technology no longer works, meaning the number of potential victims is decreasing every day. For example, around 30% of those using Kaspersky Lab’s mobile security solutions now use Android 6 or a later version;
The technology only worked on a limited number of mobile browsers;
The user can easily spot that they are being redirected to a phishing site and they may also notice that the URL of the webpage has changed.
Attacks launched using root privileges
With superuser privileges, Trojans can perform any attack, including real malicious injections into browsers. Although we were unable to find a single case of this happening, the following should be noted:
Some modules of Backdoor.AndroidOS.Triada can substitute websites in certain browsers, using superuser privileges. All the attacks we found were launched with the purpose of making some money from advertising only, and did not result in the theft of banking information.
The banking Trojan Trojan-Banker.AndroidOS.Tordow, using superuser privileges, can steal passwords saved in browsers, which may include passwords to financial websites.
Conclusions
We can state that, despite all the available technical capabilities, cybercriminals that target banks do not make use of malicious web injections in mobile browsers or injections in mobile apps. Sometimes they use these technologies to spoof adverts, but even then that requires highly sophisticated malicious software.
So why do cybercriminals ignore the available opportunities? Most probably it is because of the diversity of mobile browsers and apps. Malware writers would have to adapt their creations to a long list of programs, which is rather costly, while simpler and more versatile attacks involving phishing windows do not require so much effort to target a larger number of users.
Nonetheless, the Triada and Tordow examples suggest that similar attacks may well take place in the future as malware creators gain more expertise.
Source Code for another Android Banking Malware Leaked
23.1.2017 thehackernews Android
Another bad news for Android users — Source code for another Android banking malware has been leaked online via an underground hacking forum.
This newly discovered banking Trojan is designed to steal money from bank accounts of Android devices' owners by gaining administrator privileges on their smartphones.
Apparently, it will attract the attention of many cyber criminals who can recompile the source code or can also use it to develop more customized and advanced variants of Android banking Trojans.
According to security researchers from Russian antivirus maker Dr. Web, the malware's source code was posted online, along with the information on how to use it, meaning Android devices are most likely to receive an increasing number of cyber attacks in upcoming days.
Leaked: Trojan Source Code + 'How to Use' Instructions
Dr. Web researchers said they have already discovered one banking trojan in the wild developed using this leaked source code, adding that the Trojan is distributed as popular apps either directly injected in APKs available online or in third-party app stores.
Dubbed BankBot, the trojan has the ability to get administrator privileges on infected devices. Once it gets full privileges, the malware trojan removes the app's icon from the phone's home screen in order to trick victims into believing it was removed.
However, the BankBot trojan remains active in the background, waiting for commands from attacker's command and control (C&C) server. It found targeting only users of Russian banks.
Also Read: GM Bot (Android Malware) Source Code Leaked Online
BankBot has the ability to perform a broad range of tasks, including send and intercept SMS messages, make calls, track devices, steal contacts, show phishing dialogs, and steal sensitive information, like banking and credit card details.
"Like many other Android bankers, [BankBot] steals confidential user information by tracking the launch of online banking apps and payment system software. One sample examined by Doctor Web's security researchers controls over three dozen such programs," the researchers explains.
"Once Android.BankBot.149.origin detects that any of the aforementioned applications have been launched, it loads the relevant phishing input form to access user bank account login and password information and displays it on top of the attacked application."
Why Should You Worry about BankBot?
The malware hides itself until the victim opens any mobile banking or social media app. Once the victim opens one such app, BankBot launches a phishing login overlays, tricking victims to re-authenticate or re-enter their payment card details.
The collected data is then sent back to online servers, where the attackers can access the stolen data.
BankBot can phish credentials for apps including Facebook, WhatsApp, Instagram, Twitter, Youtube, Snapchat, Viber, WeChat, imo, Uber, and the Google Play Store.
Besides this, the BankBot trojan can also intercept text messages, send them to the attackers, and then delete them from the victim's smartphone, which means bank notifications never reach the users.
How to Protect Yourself against such Attacks?
Now, this is just one piece of malware developed using the publicly available source code and discovered by researchers. There are chances that more such malware are out there targeting Android devices but not yet caught.
To prevent yourself against such attacks, as I previously recommended, you are advised to:
Always be super-careful when downloading APKs from third-party app stores. Go to Settings → Security and then Turn OFF "Allow installation of apps from sources other than the Play Store."
Never open attachments from unknown or suspicious sources.
Never click on links in SMS or MMS sent to your mobile phone. Even if the email looks legit, go directly to the website of origin and verify any possible updates.
Always keep your Anti-virus app up-to-date.
Keep your Wi-Fi turned OFF when not in use and Avoid unknown and unsecured Wi-Fi hotspots.
Analyzing a variant of the GM Bot Android malware
7.1.2017 securityaffairs Android
My friends at CyberBlog decided to analyze the GM Bot Android Malware as exercise aiming to receive feedback sand suggestions from the security community.
The sample explored is confirmed as a variant of the GM Bot Android malware – who’s source was released publicly in early 2016. The code appears to have been forked by a second author and has additions that target the Danske Bank MobilePay application and the popular Danish Nem ID two factor authentication (2FA) system.
This article shows the process of walking through Static and Dynamic analysis to unlock the packed source code for the malware.
We see how even with basic static analysis a full picture of the intent of the malware can be readily assembled, and with a little debugging we can quickly get to readable source code.
Background
As part of my journey into Cyber Security I thought it would be interesting to see how modern mobile malware operates. I chose the following sample at random based on an article here.
File Details
SHA256: 44ed4bbd5cdc13c28992c16e99a7dc58f5f95463e889dd494a433549754f7863
MD5: da88bdcb3d53d3ce7ab9f81d15be8497
A quick google search for these hashes will lead you to the file used if you would also like to explore this sample.
The article above demonstrates that the analyst has gone from sample to source code, but it is not clear how this is achieved. There are references to suggest that the code has been packed, but again no information on how it was unpacked for analysis.
This post will break down the process I used to analyse this sample, hopefully with enough detail to provide some tips and guidance for others wishing to attempt similar. The process I followed can be logically broken into the following stages:

Analysis Process
Public Analysis – What can we find out using existing public sources of information? What analysis has already been performed (automated or manual)?
Static Analysis – What can we determine from the sample without actually running it in an emulated environment?
Packer Debugging – Assuming the sample is packed (to frustrate analysis), how do we debug the unpacker to understand what is being loaded /run?
DEX Extraction and De-compilation – Once we have mapped out the function of the unpacker, how do we then recover the main code for the malware and reverse it?
Functional & Dynamic Analysis – once we have the extracted and reversed code, what do we see and how does this correlate with behavior in a safe emulated environment
Stage 1 – Public Analysis
First off let’s see what we can find about this in the public domain. Searching for the file hashes on Virus Total, where we see approximately 50% of AV products have identified it as malicious:

VirusTotal Results
However, we also note that all classify it heuristically as a generic strain of malware – either a Trojan, Dropper, Fake Installer etc. Nothing to suggest it is in fact GM Bot Android, or any specific type of malware. Other than this we don’t see much from google with either the SHA256, or MD5 hashes.
The original Security Intelligence article references IBM X-Force research, so this is the next stop – but again nothing immediately obvious with regards to this sample could be located.
A wider search of the internet reveals some history of GM bot, originally built and sold by Ganga Man on dark web forums. Following a dispute the source code for both client APK and C2 server were released publicly. A copy is hosted here on Github and will provide useful for cross referencing with this sample later in the analysis.
https://github.com/gbrindisi/malware/tree/master/android/gmbot
Stage 2 – Static Analysis
First up we are going to unpack the APK file using APK tool. This will unzip the contents, as well as providing a disassembly of the DEX code into Smali:
apktool d da88bdcb3d53d3ce7ab9f81d15be8497.apk
The results of this can be seen below and the tool has also provided a human readable version of the AndroidManifest.xml file.

Extracted APK files
First stop is to take a look at the Android Manifest file, that should provide an overview of the components of the application and permissions requested.
Manifest Analysis – AndroidManifest.xml
Android Manifest
Initial analysis shows a broad range of permissions that indicate malicious behavior including permissions to:
control all SMS messages (send, receive, read, write, delete)
list running applications
read the phone’s state, contacts, SD card data
request to be a device administrator enabling remote wiping of the device with no warning to the user
A summarized view of referenced class files for the main application, activities (15) and services (2) can be seen below:

Classes Declared in Manifest -Application, Activities and Services
In addition, we see 4 further classes mapped as Broadcast Receivers which will process event messages (Android system Intents) as shown below:

Broadcast Receiver Classes Declared in Manifest
From this we can see the application is capable of:
Executing code when the phone is powered on (starting the application automatically)
Receive notification when Device Admin is granted, requested or a request to disable admin is received (and hence interfere, or nag the user to enable it)
Receive notification of a new inbound SMS – with high priority flag to ensure the code can intercept it first and potentially stop any further alerts (can be used to steal 2FA tokens)
Before proceeding with any reverse engineering of the code, the next step is to explore the other files in the APK for clues.
Files of interest
The following files were noted as of interest:
File: assets/fytluah.dat
A binary file with no immediately obvious format. Possible code to be unencrypted / unpacked at run time?
File: res/values/strings.xml
English language strings for the application, as shown below:

File: res/values/strings.xml (English Language Resource File)
The strings clearly indicate that this malware is targeting capturing victims credit card information. It is interesting to note that:
The resource keys here are all in English, suggesting the original developer may be English speaking
There are specific strings that are in Danish, despite this resource file being intended for English language
In addition to English language strings we also see several other targeted countries:
Other Resource Files
File: res/values.xml
This file contains a list of country codes and specifically a group that are “non vbv”. This is understood to mean that they do not use the “Verified by Visa” process which is used to enforce additional verification checks during online purchases. It is likely that the attackers would seek to obtain additional VBV credentials via the malware in order to allow online purchases with the card details (or avoid these countries).

Verified By Visa Targeted Countries
Directory: res/drawable
Images and icons/logos including:
Sample photo of Danish “Nem Id” – https://en.wikipedia.org/wiki/NemID
Icon for Danske Bank mobile pay
Mastercard secure code
Icon for verified by visa
Google play
Flash icon (main application icon)
Whatsapp
Additionally there are png images prefixed “overlay_”, indicating a possible use in fraudulent overlay activity.
Decompiling to Java source code
Next we attempt to reverse engineer the DEX file back to original Java source code. For this we use dex2jar as follows to translate the DEX file (in the APK) into a Java Class file archive:
Dex2jar da88bdcb3d53d3ce7ab9f81d15be8497.apk
The resulting jar file can then be disassembled using JD-GUI as follows:
java -jar ../../jd-gui-1.4.0.jar da88bdcb3d53d3ce7ab9f81d15be8497_dex2jar.jar
The resulting java classes that we see in JD-GUI show that there are only 4 java classes contained in the application. This is in direct contrast to the 16 different classes we saw declared in the application manifest. This confirms that there must be additional code that is loaded dynamically at run time – it is most likely that these four classes are in fact an unpacker.

Unpacker Classes
Examining the code we see that it is heavily obfuscated and has been crafted in a way to prevent clean decompiling of the code. This aside, we can start to get an understanding of the function of these four classes by examining the system classes that are imported (and therefore used) when the application is first executed.
After exporting the java source from JD-GUI and unzipping to a new folder, we can extract the imported classes from these files:
find . -type f -exec grep "^import" {} \; | sort -u
The classes we find are shown below :
Class Imported Class
com.igcfse.enscbo.a com.igcfse.enscbo.b
com.igcfse.enscbo.a java.io.RandomAccessFile
com.igcfse.enscbo.a java.lang.reflect.Constructor
com.igcfse.enscbo.b android.app.Application
com.igcfse.enscbo.b android.content.Context
com.igcfse.enscbo.b com.igcfse.enscbo.a
com.igcfse.enscbo.b java.io.File
com.igcfse.enscbo.b java.lang.reflect.Field
com.igcfse.enscbo.b java.lang.reflect.Method
com.igcfse.enscbo.c android.content.Context
com.igcfse.enscbo.c com.igcfse.enscbo.b
com.igcfse.enscbo.c java.io.FileDescriptor
com.igcfse.enscbo.c java.io.IOException
com.igcfse.enscbo.c java.lang.reflect.Constructor
com.igcfse.enscbo.c java.util.Random
com.igcfse.enscbo.wieroel android.app.Application
com.igcfse.enscbo.wieroel android.content.Context
com.igcfse.enscbo.wieroel com.igcfse.enscbo.b
Essentially we have a very small set of libraries that are being imported and used. These consist of functionality for:
General Android application and context classes (expected and needed for all android apps)
File related classes (in red) – for access, reading and writing local files
Java reflection classes (in green) – for creating new classes and instances and invoking methods dynamically
This confirms the hypothesis that we are most likely dealing with an unpacker that unpacks it’s executable code from a local file resource (as opposed to pulling dynamically from network for example).
Stage 3 – Unpacker Debugging
As the Java code cannot be readily decompiled (due to protections injected by the malware author) we will instead debug the executable against the Smali assembly code. Smali is a disassembly of the DEX code used by the Dalvik Virtual Machine.
The Smali/Baksmali plugin for Android Studio is required, and then the output from Apktool is imported as a new project. We next set the breakpoints as required across the three classes that we are interested in (a,b,c):

Setting Breakpoints in Android Studio
We will initially debug the calls to interesting reflection methods identified, which are as below:
a.smali (a line that creates a new instance of a class based on a java.lang.reflect.Constructor instance)
![]()
b.smali (a line that invokes a method on an object via reflection)
![]()
c.smali (a line similar to that described above for a.smali)
![]()
Now we install the application to the emulator (via ADB to ensure it doesn’t start automatically as in some emulators).
To enable the debugger to connect to the application, we perform the following prior to starting the application:
Enable developer options by repeatedly clicking the build number in Settings > About device
In developer options, choose “Select debug app” and choose the malicious application – “Adobe Flash”
In developer options, enable the “wait for debugger”
Selecting Debug Application
Now start the application from the launcher, you will be prompted to attach the debugger:

Attaching Debugger
In Android Studio, attach the debugger using the icon. Choose the malicious application process. The debugger then stops at our first breakpoint as shown below:

First Breakpoint Reached
Note you should now set some variables to watch – as per above I have set v0 through v10 and p1 through p3. Our first breakpoint is hit and we see we are about to execute a method by reflection. Noting that we have not yet called newInstance() we can assume this is calling existing (loaded) classes – either one of the four loaded by the application, or some other Android framework classes.
Next we forces step into the method to see which method it is calling (the smali debugger seems a little buggy and we can’t at this point see the parameters being passed).

Stepping into Reflected Method Call
An initial call to get the current context object -presumably to start retrieving local resources from the APK. We now allow the debugger to continue, and repeat this exercise several times to build up a flow of the reflected method calls:
Context android.context.ContextWrapper.getBaseContext()
//expected 2 arguments, got 1 – error in malware code, or to throw off debugging?
//Several more of these not shown
IllegalArgumentException java.lang.IllegalArgumentException(String s)
void Java.lang.reflect.setAccessible(boolean flag)
File android.app.getDataDir()
// returns /data/user/0/com.kzcaxog.mgmxluwswb/app_ydtjq
java.io.File.getAbsolutePath()
ContextImpl android.app.getImpl(Context context)
//filename is fytluah.dat
InputStream android.content.res.AssetManager.open(String fileName)
Pausing here, we can see the code is attempting to load the file that we had previously flagged as of interest in the static analysis section. Continuing we see the file is read, presumably decrypted and then written out again as a jar file:
int android.content.res.AssetManager.read(byte[] b)
//className = java.io.File
Class java.lang.Class.forName(String className)
//args = String “/data/user/0/com.kzcaxog.mgmxluwswb/app_ydtjq/gpyjzmose.jar”
T Java.lang.reflect.Constructor.newInstance(Object.. args)
void java.io.FileOutputStream.write(byte[] b) #25
void java.io.FileOutputStream.close()
Finally a DexClassLoader is invoked to load the additional code into the system:
ClassLoader java.lang.Class.getClassLoader()
//className is dalvik.system.DexClassLoader
java.lang.Class.forName(String className)
Looking at the API for the DexClassLoader we can see that it takes two arguments – the location of the file to load, and a writeable area that it will use to re-write an optimised version of the code for the specific machine architecture – eg the Android Run Time (ART). Further information on this can be seen in the Android API documentation:
https://developer.android.com/reference/dalvik/system/DexClassLoader.html
Stage 4 – DEX Extraction and Decompiling
We can see the exact location of the jar file in the debugger below, and the next step is to recover this file via ADB command line.

Debugging the Call to the DEXClassLoader
After execution of the classloader, connecting via ADB shell we see the two files, the original and the DEX optimised code:

Extracting the Payload Code
We copy these files to /sdcard/Download (+chmod) and then pull the .jar file to local machine for further analysis with adb pull.

Examining the files
Extracting the jar file we find the classes.dex file.
Repeating the steps to convert this to a jar file using dex2jar and decompiling with JD-GUI, we confirm we now have the full (un-obfuscated) source code for this malware sample.

Decompiled Source Code
Stage 5 – Dynamic and Functional Analysis
First Installation
Upon initial analysis we can see the codebase bear remarkable similarities with the leaked source identified in the static analysis. However there are significant differences, and the code has been customised to specifically target the Danske Bank MobilePay application.
As the code is basically un-obfuscated, I’ll now briefly walk through the key functionality of this malware, starting from first installation.

First Installation Process Overview
Upon first installation and execution the application will perform two primary functions. It will initially harvest a range of the users data, including phone contacts, all SMS messages and other key data and send this to the C&C server. The C&C server then returns a unique installation identifier that is then used for all future communication to uniquely identify the compromised device.
Secondly the malware will then nag the user to accept the software as a device administrator. If the user declines the request is re-triggered, making it very difficult for most users to escape this screen without accepting. With this permission in place, the malware achieves two objectives:
The application cannot be un-installed by the user easily, without de-activating the device administrator. Attempting to do this will trigger the launching of overlays that prevent removing the device admin
At some point in the future, once further data has been stolen from the phone, the C2 server can issue a command to wipe the device, removing evidence of the infection and restoring the device to a factory state
Ongoing Operations – including after each reboot
Command and Control Process Flows
The malware maintains a regular heartbeat to the C2 server, which provides a mechanism for the attacker to issue specific commands to the device. Each hearbeat contains the installation ID and the current screen status. It is hypothesised that the attacker would ideally choose to execute malicious activities when the screen was off, and the user was not watching the phone.
Firstly we see the ability to “lock” and “unlock” the phone. This simulates an Android software update screen, and effectively hides any other activity that is occurring behind the screen overlay (such as sending, receiving or deleting SMS messages). Additionally this could be used to disable the user, and prevent them from using the phone whilst their accounts or cards are being compromised in real time.
Next we see another function that is intended to intercept and forward SMS messages to the C2 server, and specifically trying to remove evidence that they ever existed by deleting them. This is used to steal 2FA credentials.
Next from a C2 server perspective we see two “reset” commands. The first, a “soft” reset, is used to reset the internal flag to re-attempt stealing Nem ID credentials. The second is the “hard” reset that performs and immediate wipe of the device data.
Finally, we see the ability to send an arbitrary SMS message to a mobile defined by the attacker and a function to launch a customised push notification to another application on the device. It was not clear what this could be used for.
SMS Remote Control
SMS Remote Control – “Admining Mode”
By listening for incoming SMS messages the malware could also trigger a fake Android update screen that would then harvest, forward and attempt to delete messages as they arrived on the phone. This mode could be enabled and disabled by customised SMS command messages delivered to the phone via SMS.
Automating Data Theft
Decompiled Code Showing Targeted Applications
As per the original article and many of the indicators from the static analysis, the primary purpose of the application is to steal data by performing overlays on top of legitimate applications. The malware targets three specific classes of applications:
Danske Bank’s MobilePay application, with specific intent to steal Nem ID credentials
Applications that trigger an attempt to steal credit card details via a custom overlay
Applications that trigger an attempt to steal the users mobile phone number (possibly for triggering the “admining” mode described above)
Danske Bank MobilePay
Danske Bank MobilePay Overlay Process
Upon launching the MobilePay application the overlay attempts to steal the users CPR number (unique social security type id), mobile number and Nem pass code. It then asks the user to take a photo of their Nem ID passbook, containing one time use codes which can be used by the attacker to then log into MobilePay (and other Danish systems) and issue payments.
Stealing Credit Card Details
Credit Card Overlay Process
Upon launching one of the targeted applications, a credit card overlay is displayed with a configurable icon depending on the application launched. After basic card details are collected, the application then attempts to recover the Verified by Visa password for the user. These details are then forwarded to the C2 server.
Stealing Phone Numbers
Phone Number Overlay Process
Finally we see the functionality that is targeted to capture the user’s phone number, presumably to enable further abuse of the victims account via abuse of text message 2FA.
Summary
The sample appears to be a specifically customised variant that is being used in a campaign to target the Danske Bank MobilePay application. We see evidence that it is probably not the original GM Bot authors work – the coding style compared with the public source code is different, and the mix of languages in the resource files implies the sample has been adapted in a “quick and dirty” fashion to achieve the objectives.
This is a good example of how once released, complex code can be quickly and easily forked by less skilled authors and a pattern we also see today with the release of the Mirai botnet code. Quickly we see a spread of variants of the codebase that become harder to trace and detect and importantly attribute to any individual or group.
As ever, the best advice to prevent becoming a victim of such malware is to ensure that your phone is not configured to install 3rd party applications, and always review requests for permissions carefully – eg, are they aligned with the expected purpose of the application?
Open Questions
Due to time constraints there are a few further areas I would have liked to explore. I may pick these up in a subsequent post, but for the record they are:
The unpacked code contains included super user functionality from Chainfire’s SuperSu application. It’s not clear how or where this is used, no apparent attempt at rooting the device was seen in the unpacked code.
The debugger failed to return from the call to unpack the payload code. It is not clear if any further reflected actions were performed beyond this.
Given key indicators in the codebase, is it possible to search / locate other similar samples, or perhaps identify further C2 infrastructure
Any constructive feedback or comments most welcome.
About the author, the owner of the CyberBlog
I am an experienced IT consultant with a broad range of experience across different disciplines from development to large-scale Project Management. I have a passion for all things Cyber related but do not currently work in a Cyber related industry or role. I welcome and encourage all feedback!
A fake Super Mario Run for Android is serving the Marcher Banking Trojan
6.1.2017 securityaffairs Android
Zscaler experts have found in the wild a fake version of the Super Mario Run Android App that could install the Android Marcher banking trojan.
Bad news for mobile gamers, security experts at Zscaler have spotted a strain of the Android Marcher Trojan masqueraded as the recently released Super Mario Run mobile game for Apple’s iOS.
Marcher is a sophisticated banking trojan that was used by cyber criminals to steal financial data from the victims.
“Marcher is a sophisticated banking malware strain that targets a wide variety of banking and financial apps and credit cards by presenting fake overlay pages. Once the user’s mobile device has been infected, the malware waits for victims to open one of its targeted apps and then presents the fake overlay page asking for banking details.” states the analysis published by Zscaler.
Super Mario Run mobile game for iOS device is one of the most interesting projects of the Nintendo, the company developed for Apple devices the notorious game. Anyway, Super Mario Run is still not available for Android, and crooks are taking advantage of this to spread their malicious variant.
The malicious code found by Zscaler installs the Marcher Trojan instead a legitimate version of Super Mario Run for Android.
“In this new strain, the Marcher malware is disguised as the Super Mario Run app for Android. Knowing that Android users are eagerly awaiting this game, the malware will attempt to present a fake web page promoting its release.” continues the blog post published by Zscaler.
The experts also shared the following details related to the threat:
Name : Super Mario Run
Package Name : uiq.pizfbwzbvxmtkmtbhnijdsrhdixqwd
MD5 : d332560f1fc3e6dc58d94d6fa0dab748
Detections : 12/55(at time of analysis)
When victims try to install the app it asks for multiple permissions including administrative rights.

The current Marcher version targets account management apps and major banks.
The researchers explained that also this Marcher variant presents fake credit card pages when the victims open the Google Play store. The trojan locks out Google Play until the victims supply the credit card information.
Researchers suspect the malware is still under development, they observed the banking overlay pages served by the C&C were not functioning properly at the time of the analysis.
“In the current variant, we have observed a new obfuscation technique, in which all important string characters are delimited with ‘<<zB5>>‘ as shown below.” continues the analysis.
Crooks always try to take advantage of gamers’ euphoria that coincides with the presentation of new games.
The same has happened last year when the Pokemon GO application was presented. Experts from ProofPoint spotted in the wild a backdoored version of the popular Pokemon GO Android App that could allow attackers to gain control over victims’ devices.
Switcher: Android joins the ‘attack-the-router’ club
1.1.2017 Kaspersky Android
Recently, in our never-ending quest to protect the world from malware, we found a misbehaving Android trojan. Although malware targeting the Android OS stopped being a novelty quite some time ago, this trojan is quite unique. Instead of attacking a user, it attacks the Wi-Fi network the user is connected to, or, to be precise, the wireless router that serves the network. The trojan, dubbed Trojan.AndroidOS.Switcher, performs a brute-force password guessing attack on the router’s admin web interface. If the attack succeeds, the malware changes the addresses of the DNS servers in the router’s settings, thereby rerouting all DNS queries from devices in the attacked Wi-Fi network to the servers of the cybercriminals (such an attack is also known as DNS-hijacking). So, let us explain in detail how Switcher performs its brute-force attacks, gets into the routers and undertakes its DNS-hijack.
Clever little fakes
To date, we have seen two versions of the trojan:
acdb7bfebf04affd227c93c97df536cf; package name – com.baidu.com
64490fbecefa3fcdacd41995887fe510; package name – com.snda.wifi
The first version (com.baidu.com), disguises itself as a mobile client for the Chinese search engine Baidu, simply opening a URL http://m.baidu.com inside the application. The second version is a well-made fake version of a popular Chinese app (http://www.coolapk.com/apk/com.snda.wifilocating) for sharing information about Wi-Fi networks (including the security password) between users of the app. Such information is used, for example, by business travelers to connect to a public Wi-Fi network for which they don’t know the password. It is a good place to hide malware targeting routers, because users of such apps usually connect with many Wi-Fi networks, thus spreading the infection.
The cybercriminals even created a website (though badly made) to advertise and distribute the aforementioned fake version of com.snda.wifilocating. The web server that hosts the site is also used by the malware authors as the command-and-control (C&C) server.
The infection process
The trojan performs the following actions:
Gets the BSSID of the network and informs the C&C that the trojan is being activated in a network with this BSSID
Tries to get the name of the ISP (Internet Service Provider) and uses that to determine which rogue DNS server will be used for DNS-hijacking. There are three possible DNS servers – 101.200.147.153, 112.33.13.11 and 120.76.249.59; with 101.200.147.153 being the default choice, while the others will be chosen only for specific ISPs
Launches a brute-force attack with the following predefined dictionary of logins and passwords:
admin:00000000
admin:admin
admin:123456
admin:12345678
admin:123456789
admin:1234567890
admin:66668888
admin:1111111
admin:88888888
admin:666666
admin:87654321
admin:147258369
admin:987654321
admin:66666666
admin:112233
admin:888888
admin:000000
admin:5201314
admin:789456123
admin:123123
admin:789456123
admin:0123456789
admin:123456789a
admin:11223344
admin:123123123
The trojan gets the default gateway address and then tries to access it in the embedded browser. With the help of JavaScript it tries to login using different combinations of logins and passwords. Judging by the hardcoded names of input fields and the structures of the HTML documents that the trojan tries to access, the JavaScript code used will work only on web interfaces of TP-LINK Wi-Fi routers
If the attempt to get access to the admin interface is successful, the trojan navigates to the WAN settings and exchanges the primary DNS server for a rogue DNS controlled by the cybercriminals, and a secondary DNS with 8.8.8.8 (the Google DNS, to ensure ongoing stability if the rogue DNS goes down). The code that performs these actions is a complete mess, because it was designed to work on a wide range of routers and works in asynchronous mode. Nevertheless, I will show how it works, using a screenshot of the web interface and by placing the right parts of the code successively.
If the manipulation with DNS addresses was successful, the trojan report its success to the C&C
So, why it is bad?
To appreciate the impact of such actions it is crucial to understand the basic principles of how DNS works. The DNS is used for resolving a human-readable name of the network resource (e.g. website) into an IP address that is used for actual communications in the computer network. For example, the name “google.com” will be resolved into IP address 87.245.200.153. In general, a normal DNS query is performed in the following way:
When using DNS-hijacking, the cybercriminals change the victim’s (which in our case is the router) TCP/IP settings to force it to make DNS queries to a DNS server controlled by them – a rogue DNS server. So, the scheme will change into this:
As you can see, instead of communicating with the real google.com, the victim will be fooled into communicating with a completely different network resource. This could be a fake google.com, saving all your search requests and sending them to the cybercriminals, or it could just be a random website with a bunch of pop-up ads or malware. Or anything else. The attackers gain almost full control over the network traffic that uses the name-resolving system (which includes, for example, all web traffic).
You may ask – why does it matter: routers don’t browse websites, so where’s the risk? Unfortunately, the most common configuration for Wi-Fi routers involves making the DNS settings of the devices connected to it the same as its own, thus forcing all devices in the network use the same rogue DNS. So, after gaining access to a router’s DNS settings one can control almost all the traffic in the network served by this router.
The cybercriminals were not cautious enough and left their internal infection statistics in the open part of the C&C website.
According to them, they successfully infiltrated 1,280 Wi-Fi networks. If this is true, traffic of all the users of these networks is susceptible to redirection.
Conclusion
The Trojan.AndroidOS.Switcher does not attack users directly. Instead, it targets the entire network, exposing all its users to a wide range of attacks – from phishing to secondary infection. The main danger of such tampering with routers’ setting is that the new settings will survive even a reboot of the router, and it is very difficult to find out that the DNS has been hijacked. Even if the rogue DNS servers are disabled for some time, the secondary DNS which was set to 8.8.8.8 will be used, so users and/or IT will not be alerted.
We recommend that all users check their DNS settings and search for the following rogue DNS servers:
101.200.147.153
112.33.13.11
120.76.249.59
If you have one of these servers in your DNS settings, contact your ISP support or alert the owner of the Wi-Fi network. Kaspersky Lab also strongly advises users to change the default login and password to the admin web interface of your router to prevent such attacks in the future.
New Android Malware Hijacks Router DNS from Smartphone
29.12.2016 thehackernews Android
android-dns-malware
Another day, another creepy malware for Android users!
Security Researchers have uncovered a new Android malware targeting your devices, but this time instead of attacking the device directly, the malware takes control over the WiFi router to which your device is connected to and then hijacks the web traffic passing through it.
Dubbed "Switcher," the new Android malware, discovered by researchers at Kaspersky Lab, hacks the wireless routers and changes their DNS settings to redirect traffic to malicious websites.
Over a week ago, Proofpoint researchers discovered similar attack targeting PCs, but instead of infecting the target's machines, the Stegano exploit kit takes control over the local WiFi routers the infected device is connected to.
Switcher Malware carries out Brute-Force attack against Routers
Hackers are currently distributing the Switcher trojan by disguising itself as an Android app for the Chinese search engine Baidu (com.baidu.com), and as a Chinese app for sharing public and private Wi-Fi network details (com.snda.wifilocating).
Once victim installs one of these malicious apps, the Switcher malware attempts to log in to the WiFi router the victim's Android device is connected to by carrying out a brute-force attack on the router's admin web interface with a set of a predefined dictionary (list) of usernames and passwords.
"With the help of JavaScript [Switcher] tries to login using different combinations of logins and passwords," mobile security expert Nikita Buchka of Kaspersky Lab says in a blog post published today.
"Judging by the hard coded names of input fields and the structures of the HTML documents that the trojan tries to access, the JavaScript code used will work only on web interfaces of TP-LINK Wi-Fi routers."
Switcher Malware Infects Routers via DNS Hijacking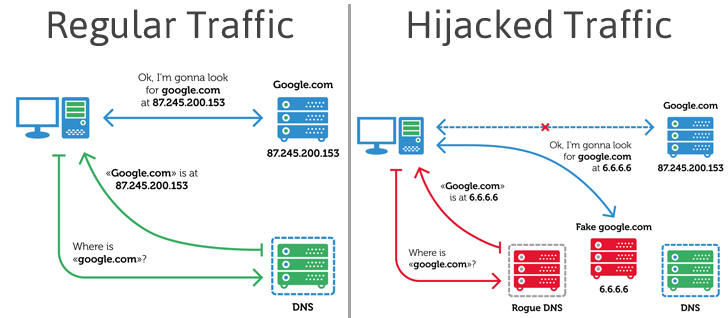
Once accessed web administration interface, the Switcher trojan replaces the router's primary and secondary DNS servers with IP addresses pointing to malicious DNS servers controlled by the attackers.
Researchers said Switcher had used three different IP addresses – 101.200.147.153, 112.33.13.11 and 120.76.249.59 – as the primary DNS record, one is the default one while the other two are set for specific internet service providers.
Due to change in router's DNS settings, all the traffic gets redirected to malicious websites hosted on attackers own servers, instead of the legitimate site the victim is trying to access.
"The Trojan targets the entire network, exposing all its users, whether individuals or businesses, to a wide range of attacks – from phishing to secondary infection," the post reads.
"A successful attack can be hard to detect and even harder to shift: the new settings can survive a router reboot, and even if the rogue DNS is disabled, the secondary DNS server is on hand to carry on."
Researchers were able to access the attacker’s command and control servers and found that the Switcher malware Trojan has compromised almost 1,300 routers, mainly in China and hijacked traffic within those networks.
The Bottom Line
Android users are required to download applications only from official Google's Play Store.
While downloading apps from third parties do not always end up with malware or viruses, it certainly ups the risk. So, it is the best way to avoid any malware compromising your device and the networks it accesses.
You can also go to Settings → Security and make sure "Unknown sources" option is turned off.
Moreover, Android users should also change their router's default login and passwords so that nasty malware like Switcher or Mirai, can not compromise their routers using a brute-force attack.
Did You Install Super Mario Run APK for Android? That's Malware
28.12.2016 thehackernews Android
After the success of Pokémon Go, Nintendo's "Super Mario Run" has become the hottest game to hit the market with enormous popularity and massive social impact. The game has taken the world by storm since its launch for iOS devices over a week ago.
Can you believe — it was downloaded more than 40 million times worldwide in its first four days of release.
But if you have downloaded a Super Mario Run APK for your Android device, Beware! That's definitely a malware.
Since Super Mario Run has currently been released only for iOS devices and is not on Google Play, it caused a lot of disappointment among Android users.
So, eventually, many Android device owners who love Mario games and can not wait to play Super Mario Run ended up downloading APKs outside of the Google Play Store.
But those tons of phony copycat unofficial Super Mario apps on many third-party Android app stores turn out to be malware or viruses that attempt to look like the legitimate Super Mario Run app.
Super Mario can Take Full Control of your Android Device
To download the third party APK, users are required to "side-load" the malicious app by modifying their Android core security settings, allowing their device's operating system to install apps from "untrusted sources."
Some of these malicious apps can even take full control of your Android device, as the apps request privileges to edit, read, receive and send text messages, take photos and record videos and track your location using GPS.
However, one of the apps titled "Super Mario" creates additional icons, displays pop-up and banner ads, installs other malicious apps onto victim's smartphone, and performs other intrusive activities without any users interaction, according to Tokyo-based Trend Micro antivirus firm, which detected malicious Super Mario apps 90,000 times this year.
"Clicking on these ads or icons will direct users to either adult sites or malicious sites. In either case, the goal is to get users to install various apps," researchers at Trend Micro writes.
"While some of these apps are perfectly legitimate, some are suspicious apps distributed by third-party app stores, including more malicious apps that even request for administrator rights."
Another app, also titled "Super Mario" and discovered by the security firm, prompts users first to install an app called 9Apps, which then asks for more permissions, including recording audio, reading modifying the calendar and even access to complete SD-card.
Here's How to Prevent Yourself
So, instead of downloading applications from unknown third party stores, Android users are required to wait for the official Google Play release.
Downloading apps from third parties do not always end up with malware or viruses, but it certainly ups the risk. So, it's the best way to wait to avoid compromising your device and the networks it accesses.
You can also go to Settings → Security and make sure "Unknown sources" option is turned off.
Faketoken, the Android ransomware banker that encrypted files
20.12.2016 securityaffairs Android
The banker Android ransomware Faketoken that steals financial informaton and sensitive data now also implements file-encrypting abilities.
Security experts from Kaspersky Lab have spotted a strain of known Android malware that now implements also ransomware-like abilities.According to the researchers, Vxers are adding file-encrypting capabilities to traditional mobile banking trojans, the result is a malware that is able both to steal sensitive data and lock user files on the phone’s SD card.This malware with hybrid capabilities is also called ransomware banker.The ransomware functionality in mobile banking Trojans is considered an exception, the Svpeng malware discovered in 2014 is one of the first malware with this ability. The modern mobile ransomware doesn’t limit their actions to block the screen, but it also encrypts user files.The trojan discovered by Kaspersky is dubbed Faketoken, the name suggests its primary feature is to steal login credentials by generating fake login screens for more than 2,000 financial applications. Faketoken is also able to steal credit card information by displaying victims displays phishing pages.
Researchers noticed that file-encrypting capabilities were implemented in Faketoken since July and have since released thousands of versions that include new features.
“We have managed to detect several thousand Faketoken installation packages capable of encrypting data, the earliest of which dates back to July 2016.” reads a blog post published by Kaspersky.
Trojan-Banker.AndroidOS.Faketoken is distributed under the guise of various programs and games, often imitating Adobe Flash Player.”
The researchers confirmed the number of the victims exceeds 16,000 users, they observed infections in 27 countries, mostly in Russia, Ukraine, Germany, and Thailand.
Faketoken uses an AES symmetric encryption algorithm to encrypt the files, this is a good news for the victims that have a chance of decrypting them without paying a ransom.
“The Trojan receives the encryption key and the initialization vector from the C&C server. The encrypted files include both media files (pictures, music, videos) and documents. The Trojan changes the extension of the encrypted files to .cat.” continues the analysis.
The researchers highlighted the fact that file encryptions are not popular with the mobile malware developers because most files stored on a mobile device are usually copied to the cloud.
For more in on Faketoken give a look at the technical analysis published by Kaspersky.
Infected firmware spotted in well-known low-cost Android devices
14.12.2016 securityaffairs Android
Experts from Doctor Web spotted new Trojans into the firmware of several dozens of low-cost Android smartphones and tablets.
Again problems with low-cost Android smartphones and tablets, once again experts discovered certain mobile devices shipped with malicious firmware.
According to malware researchers from antivirus firm Dr.Web, the firmware of a large number of popular Android devices operating on the MediaTek platform was compromised with at least two types of downloader Trojans.
These low-cost Android smartphones and tablets are mostly marketed in Russia.
“Doctor Web’s security researchers found new Trojans incorporated into firmwares of several dozens of Android mobile devices. Found malware programs are stored in system catalogs and covertly download and install programs.” states the blog post published by Dr.Web.
“One of these Trojans, dubbed Android.DownLoader.473.origin, was found in firmwares of a large number of popular Android devices operating on the MTK platform.”
Both malware found in low-cost Android mobile devices, detected as Android.DownLoader.473.origin and Android.Sprovider.7 are able to collect users’ data, displays advertisements on top of running applications and downloads unwanted apps.
Researchers found the malicious code on the following 26 models of low-cost Android mobile devices:
Lenovo A319, Lenovo A6000, MegaFon Login 4 LTE, Bravis NB85, Bravis NB105, Irbis TZ85, Irbis TX97, Irbis TZ43, Irbis tz56, Pixus Touch 7.85 3G, SUPRA M72KG, SUPRA M729G, SUPRA V2N10, Itell K3300, Digma Plane 9.7 3G, General Satellite GS700, Nomi C07000, Optima 10.1 3G TT1040MG, Marshal ME-711, 7 MID, Explay Imperium 8, Perfeo 9032_3G, Prestigio MultiPad Wize 3021 3G, Prestigio MultiPad PMT5001 3G, Ritmix RMD-1121, Oysters T72HM 3G, Irbis tz70, and Jeka JK103.
Android.DownLoader.473.origin is a downloader Trojan which is executed every time a mobile device is turned on, it can be used by crooks to download both benign apps and also malware and unwanted applications.
“It is known that cybercriminals generate their income by increasing application download statistics and by distributing advertising software,” the researchers pointed out. “Therefore, [both Trojans] were incorporated into Android firmware because dishonest outsourcers who took part in creation of Android system images decided to make money on users.” continues the report.
The Android.Sprovider.7 Trojan was spotted in the firmware of Lenovo A319 and Lenovo A6000 smartphones. Below the list of abilities observed by the researchers for this specific malware.:
Download, install and run APK files.
Open the specified link in a browser.
Make phone calls to certain numbers by using a standard system application.
Run a standard system phone application in which a specified number is already dialed.
Show advertisement on top of all apps.
Also, display advertisements in the status bar.
Create a shortcut on the home screen.
Update a major malicious module.
Unfortunately, the number of similar cases is increasing, last month, security researchers from Kryptowire discovered a backdoor in the firmware installed on low-cost Android phones. The backdoor affects mobile phones from BLU Products that are available for sale on both Amazon and Best Buy.
A few days later, researchers from Anubis Networks discovered that a third-party firmware included in more than 2.8 million low-cost Android devices could be exploited to compromise the smartphones Over-the-Air (OTA) updates and gain root privileges.
The firmware affected by the backdoor is developed by the Chinese company Ragentek Group. The problem resides in the lack of encryption for the OTA mechanisms that expose users to MITM attacks. The analysis revealed that the Ragentek firmware running on the smartphone implements an insecure Over-the-Air update mechanism that establishes an unprotected connection to remote servers via an unencrypted communications channel.
More Firmware Backdoor Found In Cheap Android Phones
13.12.2016 thehackernews Android
Here's some bad news for Android users again.
Certain low-cost Android smartphones and tablets are shipped with malicious firmware, which covertly gathers data about the infected devices, displays advertisements on top of running applications and downloads unwanted APK files on the victim's devices.
Security researchers from Russian antivirus vendor Dr.Web have discovered two types of downloader Trojans that have been incorporated in the firmware of a large number of popular Android devices operating on the MediaTek platform, which are mostly marketed in Russia.
The Trojans, detected as Android.DownLoader.473.origin and Android.Sprovider.7, are capable of collecting data about the infected devices, contacting their command-and-control servers, automatically updating themselves, covertly downloading and installing other apps based on the instructions it receives from their server, and running each time the device is restarted or turned on.
The list of Android device models that are affected by the malicious firmware includes:
Lenovo A319, Lenovo A6000, MegaFon Login 4 LTE, Bravis NB85, Bravis NB105, Irbis TZ85, Irbis TX97, Irbis TZ43, Irbis tz56, Pixus Touch 7.85 3G, SUPRA M72KG, SUPRA M729G, SUPRA V2N10, Itell K3300, Digma Plane 9.7 3G, General Satellite GS700, Nomi C07000, Optima 10.1 3G TT1040MG, Marshal ME-711, 7 MID, Explay Imperium 8, Perfeo 9032_3G, Prestigio MultiPad Wize 3021 3G, Prestigio MultiPad PMT5001 3G, Ritmix RMD-1121, Oysters T72HM 3G, Irbis tz70, and Jeka JK103.
"It is known that cybercriminals generate their income by increasing application download statistics and by distributing advertising software," the researchers pointed out. "Therefore, [both Trojans] were incorporated into Android firmware because dishonest outsourcers who took part in creation of Android system images decided to make money on users."
More Firmware Backdoor Found In Cheap Android Phones
Android.Sprovider.7 Trojan was discovered in the firmware of Lenovo A319 and Lenovo A6000 smartphones. The Trojan is capable of doing a lot of things including:
Download, install and run APK files.
Open the specified link in a browser.
Make phone calls to certain numbers by using a standard system application.
Run a standard system phone application in which a specified number is already dialed.
Show advertisement on top of all apps.
Also, display advertisements in the status bar.
Create a shortcut on the home screen.
Update a major malicious module.
On the other hand, Android.DownLoader.473.origin found in the remaining devices, which downloads and installs other malware programs and unwanted apps, including an advertising program called H5GameCenter.
H5GameCenter app displays a small box image on top of all running applications, and there is no option to disable it. Even if the infected users remove this app, the firmware Trojan reinstalls the app.
Last month, security researchers from Kryptowire discovered hidden backdoor in the firmware of many budget Android smartphones sold in the US, which also covertly gathers data on phone owners and sends it to a Chinese server without users knowledge.
The backdoored firmware software was developed by China-based company Shanghai AdUps Technology, which claims that its software runs updates for more than 700 Million devices worldwide.
In separate research last month, security rating firm BitSight discovered a flaw in the Ragentek firmware used by certain low-cost Android devices that allowed attackers to remotely execute malicious code with root privileges, turning over full control of the devices to hackers.
50 Million installations potentially impacted by AirDroid issues
3.12.2016 securityaffairs Android
At least 10 million Android users are exposed to cyber attacks due to multiple vulnerabilities affecting the popular AirDroid app.
According to experts from the firm Zimperium, multiple vulnerabilities in the Android remote management tool AirDroid could expose more than 50 million devices
The flaws could be exploited to abuse built-in features and use them against the application’s users.
Experts highlight that AirDroid uses insecure communication channels allowing attackers to power Man-in-the-Middle (MitM) attacks and other types of attacks.
Researchers from Zimperium discovered that communication channels used to send authentication data to the statistics server are not properly protected because the encryption key is hardcoded inside the application.
An attacker that shares the same network with the victim could run MitM attacks to capture authentication credentials from the first HTTP request the application performs, and use them to act on behalf of the user.
“A malicious party could perform a MITM network attack and grab the device authentication information as shown in the “Details” section from the very first HTTP request the application performs.” reads the blog post published by Zimperium. “This HTTP request can be decrypted at runtime using the 890jklms key hardcoded inside the application and the authentication fields parsed from the resulting JSON.
Having this information, the attacker can now impersonate the victim’s device and perform various HTTP or HTTPS requests on its behalf to the AirDroid API endpoints.
For instance, a payload like the following ( encrypted in DES with the same exact key ) can be sent to the https://id4.airdroid.com/p14//user/getuserinfoviadeviceid.html endpoint :”
Tha attacker could craft a payload encrypted in DES with the same key to trick the server into revealing user information, including the email and password hash.

The attacker could power a MitM attack alto to redirect HTTP traffic to a malicious transparent proxy that allows him to modify the response for the /phone/vncupgraderequest. In this way the attacker could inject a fake update or could execute malicious code remotely.
“Moreover, an attacker performing a MITM attack and redirecting HTTP traffic to a malicious transparent proxy, could modify the response for the /phone/vncupgrade request which is normally used by the application to check for addons updates:
GET /p14/phone/vncupgrade/?q=[DES ENCRYPTED PAYLOAD]&ver=20151 HTTP/1.1
Host: srv3.airdroid.com
Connection: close
User-Agent: Apache-HttpClient/UNAVAILABLE (java 1.4)
Injecting a new update, thus remotely executing custom code on the target device, is just a matter of modifying this response:”
In order to fix these issues, the AirDroid should use only secure communication channels (HTTPS), should implement key pinning to avoid SSL MitM, should use safe key exchange mechanisms, and should leverage and digital verify the update files.
More than 1 Million Google accounts hacked by Gooligan Android Malware
1.12.2016 securityaffairs Android
Experts from the security firm CheckPoint discovered a new Android malware dubbed Gooligan that has already compromised more than a million Google Accounts.
Another malware, dubbed Gooligan, is threatening Android users. The Android malware has already compromised more than 1 Million Google accounts.
The Gooligan Android malware roots vulnerable Android devices in the attempt of stealing email addresses and authentication tokens stored on them.
The stolen information are used by crooks to hijack victims’ Google account and access sensitive data from Google apps including Gmail, Google Photos, Google Docs, Google Play, Google Drive, and G Suite.
“The attack campaign, named Gooligan, breached the security of over one million Google accounts. The number continues to rise at an additional 13,000 breached devices each day.” reported CheckPoint.
“Our research exposes how the malware roots infected devices and steals authentication tokens that can be used to access data from Google Play, Gmail, Google Photos, Google Docs, G Suite, Google Drive, and more.”
Experts from the security firm CheckPoint have discovered dozens of legitimate-looking Android apps containing the Gooligan malware. These mobile apps were available for the download on third-party stores, but experts also highlighted that the malware could be downloaded users directly by tapping malicious links embedded in malicious messages.

Once the malware is installed it start sending device information and stolen data to the C&C server.
“Gooligan then downloads a rootkit from the C&C server that takes advantage of multiple Android 4 and 5 exploits including the well-known VROOT (CVE-2013-6282) and Towelroot (CVE-2014-3153),” added the researcher.
“These exploits still plague many devices today because security patches that fix them may not be available for some versions of Android, or the patches were never installed by the user. If rooting is successful, the attacker has full control of the device and can execute privileged commands remotely. If rooting is successful, the attacker has full control of the device and can execute privileged commands remotely.”
Experts from CheckPoint security confirmed that older versions of the Android operating system are affected by the issue, including Android 4.x (Jelly Bean, KitKat) and 5.x, (Lollipop) (roughly 74% of Android devices currently in use).

The crooks could rapidly monetize their efforts because Gooligan generates revenues by fraudulently buying and installing apps from the official Google Play Store and rating them and writing reviews on behalf of the phone’s owner. The malicious code also installs adware on the victims’ mobile devices.
If you fear being one of the victims of the Gooligan malware be free to use an online tool published by Check Point, the Gooligan Checker, that allows users to check if the Android device has been infected. It is very simple, just open the ‘Gooligan Checker’ and enter your Google email address.
If your device is infected you need to Re-Flash your device running a clean installation of Android OS.
Over 1 Million Google Accounts Hacked by 'Gooligan' Android Malware
30.11.2016 thehacknews Android
If you own an Android smartphone, Beware! A new Android malware that has already breached more than 1 Million Google accounts is infecting around 13,000 devices every day.
Dubbed Gooligan, the malware roots vulnerable Android devices to steal email addresses and authentication tokens stored on them.
With this information in hands, the attackers are able to hijack your Google account and access your sensitive information from Google apps including Gmail, Google Photos, Google Docs, Google Play, Google Drive, and G Suite.
Researchers found traces of Gooligan code in dozens of legitimate-looking Android apps on 3rd-party app stores, which if downloaded and installed by an Android user, malware starts sending your device’s information and stolen data to its Command and Control (C&C) server.
"Gooligan then downloads a rootkit from the C&C server that takes advantage of multiple Android 4 and 5 exploits including the well-known VROOT (CVE-2013-6282) and Towelroot (CVE-2014-3153)," researchers said in a blog post.
"If rooting is successful, the attacker has full control of the device and can execute privileged commands remotely."
According to CheckPoint security researchers, who uncovered the malware, anyone running an older version of the Android operating system, including Android 4.x (Jelly Bean, KitKat) and 5.x, (Lollipop) is most at risk, which represents nearly 74% of Android devices in use today.
"These exploits still plague many devices today because security patches that fix them may not be available for some versions of Android, or the patches were never installed by the user," researchers added.
Once hack into any Android device, Gooligan also generates revenues for the cyber criminals by fraudulently buying and installing apps from Google Play Store and rating them and writing reviews on behalf of the phone's owner. The malware also installs adware to generate revenue.
How to check if your Google account has been compromised with this malware?
Check Point has published an online tool to check if your Android device has been infected with the Gooligan malware. Just open ‘Gooligan Checker’ and enter your Google email address to find out if you've been hacked.
If you found yourself infected, Adrian Ludwig, Google's director of Android security, has recommended you to run a clean installation of the operating system on your Android device.
This process is called 'Flashing,' which is quite a complicated process. So, the company recommends you to power off your device and approach a certified technician or your mobile service provider in order to re-flash your device.
An Android Spyware revealed the existence of a new Italian surveillance firm
21.11.2016 securityaffairs Android
A strain of Android spyware recently analyzed by security experts from RedNaga Security team points to an another Italian company.
A new strain of Android malware reveals the existence of a new Italian player in the surveillance landscape. The Android spyware was analyzed by researchers from the RedNaga Security team, that is a first time investigated the possibility of a new threat developed by the notorious surveillance firm Hacking Team. The analysis revealed that another Italian company developed the dangerous Android spyware.
The Researcher Tim Strazzere and his colleagues analyzed a sample of the malware that infected a machine of an anonymous target, likely a government organization.
The Android implants implements the common functionalities of most spyware:
Automatically remove itself from the launcher after the first execution
Kick start it’s own MainService and set an alarm to keep it persistent
Stop processing commands from the C2 or doing work if the user is present
Mute all audio on the device
Turn GPS on or off
Query internal phone URIs for data and write to external media for later exfiltration
Create screenshots or record the screen
Record video and audio
Respond to specifically configured SMS numbers that include 873451679TRW68IO and reply or forward messages with device information
Execute code (“actions”) from downloaded .dex files (mainly for rooting different devices)
Asks for practically every permission
Can hide itself from the launcher, ensure persistence, mute all audio on the device, turn the GPS on and off, take screenshots or record what can be seen on the screen, record video and audio, reply to or forward messages, lay low while the user is using the device, executed code, exfiltrate data, and so on.
Likely masquerades as an update for a Google service, as the target is shown phrases such as “Servizi Google” (Google Service) and “Aggiornamento effettuato con successo” (Successful Update).
The experts noticed that the Android spyware was contacting two IP addresses belonging to the address space used in the past by the HackingTeam. This circumstance, alongside with the use of Italian string in the code suggests the involvement of an Italian threat actor.
The code was examined by two former Hacking Team employees and Citizen Lab researcher Bill Marczak and both groups excluded the HT authorship.
“The sample has nothing to do with Hacking Team,” another source told Lorenzo Bicchierai from Motherboard. “It’s structurally different from the ones attributed to Hacking Team and doesn’t share any part of the code.”
Segui
Guido Landi @k_sOSe
It doesn't really look like an HT implant.. https://twitter.com/timstrazz/status/798351533192511488 …
06:11 - 15 Nov 2016
Retweet 2 2 Mi piace
Who developed the Android Spyware?
A reference in the SSL certificate used by one of the servers contains a string that might point to the author of the malware, “Raxir”.

Raxir is the name of an Italian company launched in 2013 and located at the incubator “Citta’ Della Scienza” in Naples, Italy.
The company develops software for investigations and works with Italian law enforcement providing forensic services.
Marczak scanned the Internet for evidence of Raxir infections and related traces and found another server that exposes a digital certificate containing the string: “ProcuraNapoliRaxirSrv.”
“The Procura” is the office of the prosecutor and Napoli is a popular city in the South of Italy. It is likely that this office is one of the customers of the Raxir firm.
Let me close with the opinion of the cyber security expert Antonio Cocomazzi who reviewed the portion of codes reported in the analysis published by the Rednaga Security Team.

About the section “Android Manifest”
As the author said, this manifesto has a really suspicious import of the permissions like READ_CONTACTS, CAMERA, SEND_SMS, RECEIVE_SMS, etc. that is common to a malware behavior.
The most interesting Observable is that the malware author tries to trick also the reverse engineer calling the activity label “Aggiornamento software” that is “Software update” in Italian.
About the section “String Encryption”
xor.py
1
2
3
4
5
6
7
8
9
10
11
def decrypt(encrypted, mod):
if not encrypted or not mod:
return ”
mod = mod – 0x5
out = ”
for char in list(encrypted):
out = ‘%s%s’ % (out, unichr(ord(char) ^ (mod & 0x5F)))
mod = (mod – 0xB)
return out.encode(‘ascii’, ‘replace’).encode(‘UTF-32’)
To decrypt the strings embedded into the apk they use a classic XOR Cipher with a little variant: a modifier passed as an argument.
Of course, if the malware contains a function do decrypt the strings, it means that strings were encrypted into the malware to complicate the reverse engineer analysis.
How is used that modifier?
This is a function that can decrypt the data with a dynamic XOR key (thanks to modifier passed as an argument).
That means, most probably, the xor encryption of the string is done with a dynamic XOR key.
This complicate the reverse engineer analysis because in that way the malware writer doesn’t hardcode the xor key in a statical way and, for example, he can let the malware download from a C2 Server.
Anyway, this key could be bruteforced, in fact the author of this article wrote a IDA Pro script to automate the key bruteforcing process, it’s called decryptor.py that you can find in the section below.
Dig deep into the code we can see that function accept 2 arguments: “encrypted”, the encrypted string to decrypt and the “mod”, in order to generate at every run of the malware different XORing encryption.
After a first check of the arguments (line 2), then it modifies the modifier subtracting a constant value 0x5 (5 in decimal).
In the line 7, it loops through every character of the encrypted string, in that cycle, it performs the decryption steps of every character.
This is done in the line 8 appending each new decrypted char to the variable “out” (that will be the final decrypted string).
The encryption of the char is represented by the following formula: “unichr(ord(char) ^ (mod & 0x5F))” so the ord() function returns an integer if you pass as argument a Unicode char, the result of that computation will be XORed (^ operator) with the modifier ANDed (& operator) with a constant value 0x5F (95 decimal).
The result of that computation will be an integer number, so it needs to cast it back to a Unicode char. This is done with the unichr() function.
Before the loop cycle continue, it changes the modifier subtracting 0xB (11 in decimal) from it.
In the end (line 10) it sets the right string encoding to the variable “out”.
About the section “Appendix: Captured C2 Interactions”
Looking at the appendix captured C2 interactions we can immediately realize that the server answer for some action requested by the client (the infected phone).
Unfortunately, we don’t have a .pcap file containing all the request done through Internet, but as we can guess, maybe the malware asks for the malicious action to perform (RequestActionsToExecute) in order to exfiltrate data and the server should answer. That answer should be handled by the malware in order to perform all the steps to grap the data.
Surprisingly, it seems the malware author manages also a way to receive the confirmation if the malware received the action correctly. (AckRequestedActions)
The request to UploadService page is a concrete data exfiltration action in which the malware compresses the data (with PKZip) and send it to the server.
We can guess, thanks to the parameter passed through the POST request “encrypted blob” that file will be stored in a database field instead of implementing a module to upload the file physically on the server.
The NotifyLog request seems to be a way to manage and debug strange behaviors generated by the infected device.
Conclusion
Below a few considerations:
The Italian “Procura” offices investigate crimes and it is strange that the sample of the Raxis Android spyware infected the mobile device of a Government representative.
Did the malware go out of control?
It seems very strange.
Another possibility is that for some reason, the malware was used by a different government entity.
Special Thanks to Odisseus who supported me in the analysis of the events.
Odisseus is an Independent Security Researcher involved in Italy and worldwide in topics related to hacking, penetration testing, and development.
Experts spotted a secret backdoor in Android phones that sends data to China
18.11.2016 securityaffairs Android
Experts at Kryptowire discovered a mobile phone firmware that transmitted personally identifiable information without user consent due to a backdoor.
Security experts from Kryptowire firm have discovered a backdoor in the firmware installed on low-cost Android phones. The backdoor affects mobile phones from BLU Products that are available for sale on both Amazon and Best Buy.
The backdoor resides in the commercial Firmware Over The Air (FOTA) update software that is installed on BLU Android devices provided as a service to BLU by AdUps.
The impact is worrisome if we consider that the backdoor could be exploited by threat actors to collect personal data about the phones and the owners’ activities and send it back to servers located in China. The servers appear to be owned by a firmware update software provider, the Shanghai AdUps Technologies.
“Kryptowire has identified several models of Android mobile devices that contained firmware that collected sensitive personal data about their users and transmitted this sensitive data to third-party servers without disclosure or the users’ consent. These devices were available through major US-based online retailers (Amazon, BestBuy, for example) and included popular smartphones such as the BLU R1 HD.” reads the analysis published by Kryptowire.”These devices actively transmitted user and device information including the full-body of text messages, contact lists, call history with full telephone numbers, unique device identifiers including the International Mobile Subscriber Identity (IMSI) and the International Mobile Equipment Identity (IMEI). “

Experts discovered that the data gathered by the backdoor include phone number, location data, the content of text messages, calls made, and applications installed and used.
Why such kind of backdoor?
It seems that the Shanghai AdUps Technologies firm has inserted a backdoor in its firmware for advertising and commercial purposes, its main goal is to collect data on users’ behavior.
The company also provides firmware updates for Chinese tech giants, including Huawei and ZTE, accounting for more than 700 million devices worldwide.
A legal representative of the company told The New York Times that the company is not gathering information for the Government of Beijing.
“This is a private company that made a mistake,” said Lily Lim, a lawyer who represents Adups.
“For many years, the Chinese government has used a variety of methods to filter and track internet use and monitor online conversations. It requires technology companies that operate in China to follow strict rules. Ms. Lim said Adups was not affiliated with the Chinese government.” reported the NYT.
Kryptowire who discovered the backdoor reported it to Google, BLU, AdUps, and Amazon.
Over 300,000 Android Devices Hacked Using Chrome Browser Vulnerability
9.11.2016 thehackernews Android
A vulnerability in Chrome for Android is actively being exploited in the wild that allows hackers to quietly download banking trojan apps (.apk) onto victim's’ device without their confirmation.
You might have encountered a pop-up advertisement that appears out of nowhere and surprise you that your mobile device has been infected with a dangerous virus and instructs you to install a security app to remove it immediately.
This malicious advertising web page automatically downloads an Android app installation (.apk) file to your device without requiring any approval.
Citing malware threats on your mobile device, attackers trick you to change your device's settings to allow installation of the third-party apps from stores other than Google Play Store and install the banking trojan app on your device.
Kaspersky researchers Mikhail Kuzin and Nikita Buchka discovered one such widespread malicious advertising campaign across Russian news sites and popular websites.
Since this August, the Trojan has infected over 318,000 Android devices across the world — thanks to Google AdSense advertisements that was being abused to spread malicious mobile banking trojan, dubbed Svpeng.
"When an APK file is broken down into pieces and handed over to the save function via Blob() class, there is no check for the type of the content being saved, so the browser saves the APK file without notifying the user," the duo explains in a blog post.
Google has acknowledged the issue, blocked the malicious ads and planned to patch it, although it is unclear when the next Android Chrome version will be released.
However, if Google sticks to its six-week release cycle, users can expect an update on 3rd December 2016. So, malicious actors have over three weeks to exploit the flaw.
"[The] next time they (criminals) push their adverts on AdSense they may well choose to attack users in other countries; we have seen similar cases in the past; After all, what could be more convenient than exploiting the most popular advertising platform to download their malicious creations to hundreds of thousands of mobile devices?" the pair say.
Even if the Google patch this issue with its next software update, attackers still have an evergreen technique to trick users into downloading malicious apps by exploiting vulnerabilities in popular websites.
For example, a recently disclosed XSS (Cross-Site Scripting) flaw, discovered by Indian security researcher Jitendra Jaiswal, on WhatsApp's official websites could allow attackers to trick users into downloading malware applications.
So, it is always a good idea to install apps from official Google Play Store as well as not to change default Android settings that prevent the installation of third-party apps.
So, the best recommendation for users is to think twice before installing any app (no matter how legitimate it looks) from untrusted sources or clicking on suspicious-looking links.
How to Exploit Belkin WEMO gear to hack Android devices
6.11.2016 securityaffairs Android
Belkin’s WeMo home automation firmware that’s in use in several IoT devices has recently been found vulnerable to an SQL injection.
Belkin’s WeMo home automation firmware that’s in use in its light bulbs, switches, security cameras, coffee makers and room heaters has recently been found vulnerable to an SQL injection.
The hack allows root privileges to a third party, which already has access to the devices’ local network.
Researchers at Virginia based Invincea Labs discovered the vulnerability and also warned of a related knock on exploit path which allows for compromise of the Android device used to control the Belkin home automation systems.
The flaw exploits a weakness in field validation by allowing a threat actor to inject malicious JavaScript via the device name field.
Scott Tenaglia, Research Director at Invincea stated that the flaws were previously unknown and not linked to earlier flaws in the WeMo home automation products.
Invincea Labs privately disclosed the flaws on Thursday the 11th of August with Belkin publicly announcing the vulnerability the next day.
On September the 1st, Belkin released a patch, which remedied the code injection vulnerability on the Android app. A further patch was released by Belkin to fix the WeMo appliances on November the 1st
It’s unknown how many WeMo products are vulnerable to this particular weakness, however, in 2015 it was reported that Belkin WeMo had approximately 1.5 million products in use.
Researchers at Invincea stated that every one of their devices that allow for remote control or administration is vulnerable to the attack.
In order to exploit this particular set of vulnerabilities, a malicious actor would first have to gain access to the local network where the smart devices were located. They would then have to leverage the shared network infrastructure in order to move the malicious code from their entry point to the vulnerable devices.
According to Tenaglia “The goal of the attacker is to hop from one device – a PC that can be later disinfected – to another device that can’t be protected – such as an IoT device,”. He then went on to explain, “Once the attacker has access to the IoT device they can do whatever they want from downloading Mirai-type malware for creating a botnet or just control the device in question. They can also infect or re-infect any PC on the same network with malware of their choice.”
Invincea Labs tested their concept by infecting a WeMo device with a malicious PowerShell script and from there open a telnet connection on the device and have it supply a root shell to requesters.
Tenaglia also stated that once infected the device could be configured to deny requests to patch the system and default setting reset attempts unless patched with the recently released firmware update.
Once the access had been granted the researchers found that the attack could progress to target Android devices running the WeMo app used to control the home automation devices.
“This is the first time anyone has discovered a way for IoT devices to hack your phone”, according to Tenaglia.

The vulnerability affects devices by placing unsanitized JavaScript into the name fields of the device, instead of only being recognized as a string the malicious code is executed instead.
“Every WeMo device can be assigned a name. What we found is you can set the name property in the device to a malicious string. The malicious string contains JavaScript code. And when the Android app requests the name of the devices it needs to connect to, it will download the malicious JavaScript code that is the name of the device, and execute the code,”
Utilizing the hack in the lab environment Tenaglia reported that they were able to both access the photo gallery on the phone as well as activate the GPS beaconing system, allowing third parties to track and locate the device.
“All this hack allows us to do is run code in the context of the WeMo app. We do not have root access to the phone,” Tenaglia said. Furthermore, access to the Android device is limited to only when the app is active or running in memory on the phone. Once the WeMo remote app is shut down, access is terminated. “What we have is an in-memory infection. The code does not persist on the phone when you force quit the app. However the name of the device is still that malicious string. So when you connect to that device again the reinfection occurs,”
Commercial Exaspy spyware used to target high-level executives
6.11.2016 securityaffairs Android
Security researchers at Skycure have discovered a new commodity Android Spyware, dubbed Exaspy, targeting high-level executives.
While in many countries the number of Smartphone and Tables is greater of desktop PC, new threats are targeting mobile devices.
Researchers at Skycure have discovered a new strain of Android spyware, dubbed Exaspy, that has been used in targeted attacks against high-level executives.
Researchers from Skycure discovered an instance of the Exaspy malware that was installed on an Android 6.0.1 device owned by a Vice President at an unnamed company.
One of the most interesting aspects of this Android malware is that it requires manual installation on the target device, this implies that attackers have to physical access the smartphone.
Below the analysis provided by Skycure, it is interesting to note that the Exaspy malware needs admin rights for its execution and a license number.
“Interestingly, this malware actually requires an end user to perform the initial installation steps, meaning physical access to the device is required at installation time. Here is how the app installs itself when it runs for the first time:
Malware requests access to device admin rights
Asks (nicely) for a licence number
Hides itself
Requests access to root (if the device is rooted and managed through popular rooting apps). Once granted, it installs itself as a system package to make its uninstallation process harder.”
Once the malware is installed on the device, it is able to access the victim’s chats and messages (SMS, MMS, Facebook Messenger, Google Hangouts, Skype, Gmail, native email client, Viber, WhatsApp, etc.).
On the infected device, the app runs under the name of Google Services leveraging the package name “com.android.protect,” this allows it masquerading the legitimate Google Play Services.
The Exaspy malware is able to record surrounding audio and victim’s calls, it can access photos on the device, it can take screenshots, and access many other user data, including the browser history and call logs.
The malware tries to transfer stolen data to C&C in presence of connectivity and waits for commands.
“The CNC (command and control) server is able to perform requests of its own, which include:
Monitor and transmit local files, such as photos and videos taken.
Execute shell commands, or spawn a reverse shell, which allows the app to elevate its privileges using exploits that are not included in the basic package.”
The spyware communicates with a server at hxxps://api.andr0idservices.com hosted in Google Cloud, it can download updates from the hard-coded URL hxxp://www.exaspy.com/a.apk.
Mobile malware is a privileged instrument for hackers that attempt targeting high-profile individuals, recently experts discovered another commercial spyware called Pegasus that was developed by the Israeli firm NSO Group.
I have forgotten to tell you that the Exaspy spyware is being sold as a $15-a-month turnkey service online.
What is the next commercial spyware?
One oAuth 2.0 hack, 1 Billion Android App Accounts potentially exposed
5.11.2016 securityaffairs Android
Security researchers demonstrated that a Wrong oAuth 2.0 implementation allows a remote simple hack that exposes more than 1 Billion Android App Accounts.
A remote simple hack devised by a group of security researchers threatens an amazing number of Android and iOS apps. An attacker can use the technique to sign into any victim’s mobile app account without any knowledge of the legitimate user.
The research team from the Chinese University of Hong Kong is composed of Ronghai Yang, Wing Cheong Lau, and Tianyu Liu. The experts discovered that the vast majority of popular mobile apps that use the single sign-on (SSO) service doesn’t properly implement the OAuth 2.0 protocol.
The OAuth 2.0 authentication protocol is widely used on social networking sites, every day billion of users access their profiles on Facebook and Google+ using it.
Using the OAuth 2.0, users can sign in for third-party services by verifying existing identity through their accounts on popular web services such as Google, Facebook, or Sina.
Once authenticated, the users haven’t to provide their credentials to access other services implementing the OAuth 2.0 protocol.
This process enables users to sign-in to any service without providing additional usernames or passwords. This magic is possible because when a user logs into a third party app via OAuth, the app checks with the ID provider (i.e. Facebook, Google).
The ID providers, in turn, provide the Access Token to the server of that mobile app that uses it to request the user’s authentication information from the ID provider (i.e. Facebook). In this way, it is able to check user’s identity with data provided by the ID provider and authorize the login.
Below an image from the slides presented by the Team at the Black Hat Europe.
The Chinese researchers discovered that a large number of Android apps did not properly check the validity of the information passed by the ID provider.
The experts explained that the server app instead of verifying the OAuth information included in the Access Token to authenticate the user, the app server would only check if the information is passed by a legitimate ID provider.
This implementation opens the doors to the attackers that can install the flawed app on their mobile devices, log in to their own account and then simply by changing their username to the victim’s one by setting up a server to modify the data sent from Facebook, Google or other ID providers.
With this technique, the attacker can access data used by the flawed app potentially exposing sensitive information or use the app acting on behalf of the victims.
“The problem is a pretty basic mistake,” Lau told Forbes.
“The impact, he said, could be severe. For instance, if the hacker broke into a travel app, they could learn the full itinerary of an individual. For a hotel booking app, they could book a room and have the victim pay for it. Or they could simply steal personal data, like addresses or bank details.” wrote Thomas Fox-Brewster from Forbes.
“A lot of third party developers are ma and pa shops, they don’t have the capability. Most of the time they’re using Google and Facebook recommendations, but if they don’t do it correctly, their apps will be wide open.” .
The experts have found hundreds of popular US and Chinese Android apps that support SSO service. The number of downloads is huge, the researchers explained that a total of over 2.4 Billion downloads are vulnerable to this attack.
The experts estimated that over a Billion different mobile app accounts are at risk of being hijacked with their attack.

The researchers did not perform any test on iOS devices, but they believed that the attack would work also on Apple apps
“Although our current attack is demonstrated over the Android platform, the exploit itself is platform-agnostic: any iOS or Android user of the vulnerable mobile app is affected as long as he/ she has used the OAuth2.0-based SSO service with the app before,” the researchers said.
WhatsApp Video Calling is Now Available for Android – Download Beta Version Now!
25.10.2016 thehackernews Android
WhatsApp is, no doubt, the largest end-to-end encrypted messaging network that allows over billion of its users to send messages, photos, videos, voice messages, documents, and calls that are secure from falling into the wrong hands.
And now it seems like WhatsApp is rolling out a much-awaited feature for the new beta versions of its Android app: Video Calling.
New beta version 2.16.318 of WhatsApp brings the ability for users to conduct video calls.
In order to activate video calls, you simply need to pull up a contact in the WhatsApp app, tap on the call icon and choose "Video Call." You can also go direct to the Calls tab to begin with the option.
The Video calls will only work if both the caller as well as the receiver have the same beta build of WhatsApp that supports the feature. If not, you will be notified with an error message that your contacts needs to update their app.
Download the latest build for WhatsApp Android from APKMirror now and give it a try.
For now, the Video calling feature is limited to WhatsApp's recent beta builds, reported Android Police, which first spotted the feature. So, you either need to download the APK link mentioned above or sign up to become a beta tester and update to WhatsApp (Beta) straight from the Google Play Store.
However, even if the feature doesn't work, there is a possible trick that you can try in order to activate the WhatsApp Video Calling feature.
Possible Trick to Activate WhatsApp Video Calling Feature
You simply need to follow these steps:
Backup all your chats,
Wipe WhatsApp data,
Log in again on WhatsApp.
You can try the above trick that had helped some users activate the video calling feature, but make sure you successfully backup your chats first.
Reportedly, WhatsApp Video Calling feature also provides an option to mute the call. You can even switch between the front and rear camera on your phone, just like any other video calling apps. Your app's call history list now displays both video and voice calls.
With its release in a stable version for over 1 Billion users in the coming weeks, the WhatsApp Video Calling feature could effectively ruin the market for Google's video calling app Duo, which has been released just few month ago.
Millions of Android smartphones exposed to new Drammer Android attack
25.10.2016 securityaffairs Android
A new method of attack dubbed DRAMMER could be exploited to gain ‘root’ access to millions of Android smartphones and take control of affected devices.
Earlier last year, security researchers from Google’s Project Zero outlined a way to hijack the computers running Linux by abusing a design flaw in the memory and gaining higher kernel privileges on the system.
Now, the same previously found designing weakness has been exploited to gain unfettered “root” access to millions of Android smartphones, allowing potentially anyone to take control of the affected devices.
Experts from the VUSec Lab at Vrije Universiteit Amsterdam have discovered a vulnerability that could be exploited to gain “root” access to millions of Android smartphones targeting the device’s dynamic random access memory (DRAM). using an attack called
The attack called Rowhammer, is not new, but this is the first time it was successfully used against target mobile devices.
On March 2015, security researchers at Google’s Project Zero team demonstrated how to hijack the Intel-compatible PCs running Linux by exploiting the physical weaknesses in certain varieties of DDR DRAM (double data rate dynamic random-access memory) chips.
By exploiting the rowhammer technique the hackers can obtain higher kernel privileges on the target system. Rowhammer is classified as a problem affecting some recent DRAM devices in which repeatedly accessing a row of memory can cause bit flips in adjacent rows, this means that theoretically an attacker can change any value of the bit in the memory.
The Rowhammer attack for mobile device involves a malicious application that once in execution repeatedly accesses the same “row” of transistors on a memory chip in a tiny fraction of a second (Hammering process)
Hammering a specific portion of memory can electrically interfere with neighboring row. This interference can cause the row to leak electricity into the next row, which eventually causes a bit to flip and consequent data modification.
An attacker can exploit these modifications to execute its code and gain control of the device.
In short, Rowhammer is an issue with new generation DRAM chips in which repeatedly accessing a row of memory can cause “bit flipping” in an adjacent row that could allow anyone to change the value of contents stored in the memory.
The researchers created a proof-of-concept exploit, dubbed DRAMMER, to test mobile the Rowhammer attack on mobile devices.
Details on the DRAMMER attack are included in a paper published by the experts and on this page.
To test the Rowhammer attack on mobile phones, the researchers created a new proof-of-concept exploit, dubbed DRAMMER. The hack could modify crucial bits of data allowing attacker to root Android devices from major vendors, including Samsung, OnePlus, LG, and Motorola.
The experts exploited the Android mechanism known as the ION memory allocator to give an app a direct access to the dynamic random access memory (DRAM). The ION memory allocator also allows the attackers to identify adjacent rows on the DRAM, which is essential to power the Rowhammer attack by generating bit flips.
The ability allowed the researchers to achieve root access on the victim’s device, giving them full control of the mobile device.
“On a high level, our technique works by exhausting available memory chunks of different sizes to drive the physical memory allocator into a state in which it has to start serving memory from regions that we can reliably predict,” states the paper.
“We then force the allocator to place the target security-sensitive data, i.e., a page table, at a position in physical memory which is vulnerable to bit flips and which we can hammer from adjacent parts of memory under our control.”

“Drammer is a new attack that exploits the Rowhammer hardware vulnerability on Android devices. It allows attackers to take control over your mobile device by hiding it in a malicious app that requires no permissions. Practically all devices are possibly vulnerable and must wait for a fix from Google in order to be patched. Drammer has the potential to put millions of users at risk, especially when combined with existing attack vectors like Stagefright or BAndroid.” states a blog post published by the researchers.
The experts successfully rooted Android handsets including Google’s Nexus 4 and Nexus 5; LG’s G4; Samsung Galaxy S4 and Galaxy S5, Motorola’s Moto G models from 2013 and 2014; and OnePlus One.

“Not only does our [DRAMMER] attack show that practical, deterministic Rowhammer attacks are a real threat to billions of mobile users, but it is also the first effort to show that Rowhammer is…(reliably exploitable) on any platform other than x86 and with a much more limited software feature set than existing solutions,” reads a paper published by the experts.
The DRAMMER app is able to take over the victim’s mobile within minutes and doesn’t request user’s interaction.
The researchers published two following proof-of-concept videos that demonstrate DRAMMER attack in action against an unrooted LG Nexus 5.
In the first video, the phone is running Android 6.0.1 with security patches Google released on October 5, while in the second one the researchers show how the DRAMMER attack can be combined with Stagefright bug that is still unpatched in many older Android devices.
The researchers have released on GitHub the source code of the DRAMMER app in order to allow users to test their mobile device and anonymously share their results.
The experts reported the issue to Google in July, and the tech giant recognized it as a “critical” vulnerability and awarded the researchers $4,000 under its bug bounty program.
The issue is expected to be partially solved with the upcoming November security bulletin, in this way it will be more difficult for attacker to launch a DRAMMER attack.
The problem is that some software features that DRAMMER exploits are so essential to any OS, it is not possible to remove or modify them without a significant impact on the overall design of the device.
New Drammer Android Hack lets Apps take Full control (root) of your Phone
24.10.2016 thehackernews Android
Earlier last year, security researchers from Google's Project Zero outlined a way to hijack the computers running Linux by abusing a design flaw in the memory and gaining higher kernel privileges on the system.
Now, the same previously found designing weakness has been exploited to gain unfettered "root" access to millions of Android smartphones, allowing potentially anyone to take control of affected devices.
Researchers in the VUSec Lab at Vrije Universiteit Amsterdam have discovered a vulnerability that targets a device's dynamic random access memory (DRAM) using an attack called Rowhammer.
Although we are already aware of the Rowhammer attack, this is the very first time when researchers have successfully used this attack to target mobile devices.
What is DRAM Rowhammer Attack?
The Rowhammer attack against mobile devices is equally dangerous because it potentially puts all critical data on millions of Android phones at risk, at least until a security patch is available.
The Rowhammer attack involves executing a malicious application that repeatedly accesses the same "row" of transistors on a memory chip in a tiny fraction of a second in a process called "Hammering."
As a result, hammering a memory region can disturb neighboring row, causing the row to leak electricity into the next row which eventually causes a bit to flip. And since bits encode data, this small change modifies that data, creating a way to gain control over the device.
In short, Rowhammer is an issue with new generation DRAM chips in which repeatedly accessing a row of memory can cause "bit flipping" in an adjacent row that could allow anyone to change the value of contents stored in the memory.
Is Your Android Phone Vulnerable?
To test the Rowhammer attack on mobile phones, the researchers created a new proof-of-concept exploit, dubbed DRAMMER, and found their exploit successfully altered crucial bits of data in a way that completely roots big brand Android devices from Samsung, OnePlus, LG, Motorola, and possibly other manufacturers.
The researchers successfully rooted Android handsets including Google's Nexus 4 and Nexus 5; LG's G4; Samsung Galaxy S4 and Galaxy S5, Motorola's Moto G models from 2013 and 2014; and OnePlus One.
"Not only does our [DRAMMER] attack show that practical, deterministic Rowhammer attacks are a real threat to billions of mobile users, but it is also the first effort to show that Rowhammer is...(reliably exploitable) on any platform other than x86 and with a much more limited software feature set than existing solutions," the researchers wrote in their paper [PDF] titled, "Drammer: Deterministic Rowhammer Attacks on Mobile Platforms."
How does the DRAMMER Attack Work? (Exploit Source Code)
The researchers created an app — containing their rooting exploit — that requires no special user permissions in order to avoid raising suspicion. The DRAMMER attack would then need a victim to download the app laced with malware (researchers' exploit code) to execute the hack.
The researchers took advantage of an Android mechanism called the ION memory allocator to gain direct access to the dynamic random access memory (DRAM).
Besides giving every app direct access to the DRAM, the ION memory allocator also allows identifying adjacent rows on the DRAM, which is an important factor for generating targeted bit flips.
Knowing this, the researchers then had to figure out how to use the bit flipping to achieve root access on the victim's device, giving them full control of the target phone and the ability to do anything from accessing data to taking photos.
"On a high level, our technique works by exhausting available memory chunks of different sizes to drive the physical memory allocator into a state in which it has to start serving memory from regions that we can reliably predict," the paper reads.
"We then force the allocator to place the target security-sensitive data, i.e., a page table, at a position in physical memory which is vulnerable to bit flips and which we can hammer from adjacent parts of memory under our control."
Once you download this malicious app, the DRAMMER exploit takes over your phone within minutes – or even seconds – and runs without your interaction. The attack continues to run even if you interact with the app or put your phone in "sleep" mode.
The researchers expect to soon publish an app [source code available here] that will let you test your Android smartphone yourself and anonymously include your results in a running tally, which will help researchers track the list of vulnerable devices.
DRAMMER Has No Quick Fix
The group of researchers privately disclosed its findings to Google in July, and the company designated the flaw as "critical," awarding the researchers $4,000 under its bug bounty program.
Google says the company has informed its manufacturing partners of the issue earlier this month and has developed a mitigation which it will include in its upcoming November security bulletin to make the DRAMMER attack much harder to execute.
However, the researchers warned that one could not replace the memory chip in Android smartphones that have already been shipped.
And even some software features that DRAMMER exploits are so fundamental and essential to any OS that they are difficult to remove or modify without impacting the user experience.
In short, the attack is not easy to patch in the next generation of Android phones.
Video Demonstration of DRUMMER Attack on Android 6.0.1
The researchers have also published two proof-of-concept videos that demonstrate DRAMMER attack in action against an unrooted LG Nexus 5.
In the first video, the phone is running Android 6.0.1 with security patches Google released on October 5.
In the second video, the researchers show how the DRAMMER attack can be combined with Stagefright bug that remains unpatched in many older Android handsets.
The Stagefright exploit gives the researchers an advanced shell, and by running the DRAMMER exploit, the shell gains root access.
The researcher's exploit can target the majority of the world's Android phones.
"Our research shows that practical large-scale Rowhammer attacks are a serious threat and while the response to the Rowhammer has been relatively slow from vendors, we hope our work will accelerate mitigation efforts both in industry and academia," the researchers concluded.
The group research focuses on Android rather than iOS because the researchers are intimately familiar with the Google's mobile OS which is based on Linux. But the group says it would theoretically be possible to replicate the same attack in an iPhone with additional research.
For more detailed information, you can head on to this informational page about DRAMMER and this paper published early this morning.
Android Banking Trojan Tricks Victims into Submitting Selfie Holding their ID Card
15.10.2016 thehackernews Android
Advanced Android Banking Trojan Tricks Victims to Submit a Selfie Holding Their ID Card
While some payment card companies like Mastercard have switched to selfies as an alternative to passwords when verifying IDs for online payments, hackers have already started taking advantage of this new security verification methods.
Researchers have discovered a new Android banking Trojan that masquerades primarily as a video plugin, like Adobe Flash Player, pornographic app, or video codec, and asks victims to send a selfie holding their ID card, according to a blog post published by McAfee.
The Trojan is the most recent version of Acecard that has been labeled as one of the most dangerous Android banking Trojans known today, according to Kaspersky Lab Anti-malware Research Team.
Once successfully installed, the trojan asks users for a number of device's permissions to execute the malicious code and then waits for victims to open apps, specifically those where it would make sense to request payment card information.
Acecard Steals your Payment Card and Real ID details
android-banking-malware
The banking trojan then overlays itself on top of the legitimate app where it proceeds to ask users for their payment card number and card details such as card holder's name, expiration date, and CVV number.
"It displays its own window over the legitimate app, asking for your credit card details," explains McAfee researcher Bruce Snell. "After validating the card number, it goes on to ask for additional information such as the 4-digit number on the back."
Once this is done, the trojan then looks to obtain users' personal information, including their name, date of birth, mailing address, for "verification purposes," and even requests a photo of the front and back sides of their ID card.
After this, the Trojan also prompts to ask users to hold their ID card in their hand, underneath their face, and take a selfie.
Hackers can make illegal Transfers and Take Over your Online Accounts
All these pieces of information are more than enough for an attacker to verify illegal banking transactions and steal access to victims' social media accounts by confirming the stolen identities.
So far this version of Acecard Android banking Trojan has impacted users in Singapore and Hong Kong.
This social engineering trick of Trojan obviously is not new, and any tech-savvy users would quickly catch this malicious behavior as there is no reason for Google to ask for your ID card. But the trick still works with non and less technical users.
Since all of these fake apps have been distributed outside of Google Play Store, users are strongly advised to avoid downloading and installing apps from untrusted sources. Besides this, users should pay attention to the permissions apps are asking for.
Most importantly: No app needs a photo of you holding your ID card except perhaps a mobile banking service. So, always be cautious before doing that.
Android Acecard banking trojan asks users for selfie with an ID card
16.10.2016 securityaffairs Android
Experts discovered a new variant of the Android Acecard banking trojan that asks victims to take a selfie while they are holding an ID card.
The inventiveness of the criminals is a never ending pit. Recently, a number of organizations announced a new authentication method based on the selfies. For example, HSBC customers can open new bank accounts using a selfie, such as the Bank of Scotland and many other financial organizations and Mastercard.
Crooks have already started taking advantage of this new method of biometric authentication, experts at McAfee discovered a new Android banking Trojan, dubbed Acecard, that pretends to be an adult video app or a codec/plug-in necessary to see a specific video.
“Recently the McAfee Labs Mobile Research Team found a new variant of the well-known Android banking Trojan Acecard (aka Torec, due to the use of Tor to communicate with the control server) that goes far beyond just asking for financial information.” reads a blog post published by McAfee. “In addition to requesting credit card information and second-factor authentication, the malicious application asks for a selfie with your identity document—very useful for a cybercriminal to confirm a victim’s identity and access not only to banking accounts, but probably also even social networks.”
The fake video plugin appears like an Adobe Flash Player, a pornographic app, or video codec.
When it is running in the background, the Acecard banking Trojan monitors the opening of specific apps usually associated with payment transactions. When the victim will open one of these apps the malware will present him a main phishing overlay, pretending to be Google Play and asking for a credit card number, that requests the submission of the card details and more personal and financial data (i.e. Cardholder name, date of birth, phone number, credit card expiration date, and CCV)
After collecting credit card and personal information from the victim, the Acecard banking Trojan the malware asks victims to complete a fake “identity confirmation” composed of three steps. In the first two steps the app requests the victim to upload a clean and readable photo of the front and back side of his identity document (national ID, passport, driver’s license):

In the final step, the malicious app asks victims to take a selfie while holding their ID card.
“After collecting credit card and personal information from the victim, the malware offers a fake “identity confirmation” that consists of three steps. The first two steps ask the user to upload a clean and readable photo of the front and back side of the victim’s identity document (national ID, passport, driver’s license).” continues the post. “The final step asks for a selfie with the identity document.”
The information collected by the Acecard banking Trojan allows attackers to perform several illegal activities that would result in the victim’s identity theft.
According to the experts, this variant of the Acecard banking Trojan has impacted users in Singapore and Hong Kong.
As usual, let me suggest avoid download from untrusted app stores and carefully review the permissions apps are asking for … and of course don’t take selfies while holding your ID card.
How much time does it take to create a malware that evades antimalware solutions? One or two minutes
27.9.2016 securityaffairs Android
A Group of the researchers from the Iswatlab team at the University of Sannio demonstrated how is easy to create new malware that eludes antimalware.
It’s not easy to ‘write’ a new malware that is able to evade the detection of antimalware and other defensive software, but it is easier to ‘produce’ a new malware that can evade the detection of antimalware solutions.
The difference between writing and producing is very subtle and stands in the fact that in the latter case the malware writer does not need to write any line of code, he just needs to press a button.
The researchers at the Iswatlab (www.iswatlab.eu) at the University of Sannio (Italy) realized an engine that applies eight transformations to a mobile malware code which alter the code’s shape, but not the behavior of the malware.
This tool used by the team is named the “Malware Washing Machine” for obvious reasons.
The transformation engine developed by the researcher for Android malware works by applying the following transformations:
Disassembling & Reassembling.
Repacking.
Changing package name.
Identifier Renaming.
Data Encoding.
Call indirections.
Code Reordering.
Junk Code Insertion.
Composite Transformations.
The Iswatlab crew tested the Malware Washing Machine against 57 well known commercial antimalware solutions.
They used their engine for changing 5560 malware that was identified and classified as malware by tall the 57 antimalware used in the test session.
Anyway, after the modification, the majority of antimalware is no more able to recognize a large subset of the malware.
“Are the actual signature based detection algorithms effective on mobile environments? We developed a framework which applies a set of transformations to Android
applications small code. We then transformed a real world malware data-set (available at: https://www.sec.cs.tu-bs.de/~danarp/drebin/index.html) and then we submitted the applications to the website www.virustotal.com, in order to evaluate the maliciousness before and after the transformations (we submitted every sample pre and post transformation process).” reads the report.
The test showed that there are some malware families that are recognized by some antimalware also after the transformations, but they were a very little part.
“In the following table, first column represents the Anti-Malware, the second the number of samples (without transformations) correctly detected by the antimalware while in the third column (in red) the number of correctly detected samples after transformation process.”

“The results is impressive: the antimalware is not able to recognize the transformed malware (given that it was able to recognize the original malware).
The transformation engine is released for the scientific community with the open source license at the following url: https://github.com/faber03/AndroidMalwareEvaluatingTools“
The details of the test conducted by the Iswatlab are included in the report titled “Evaluating malware obfuscation techniques against antimalware detection algorithms”
This test raises the discussion about the capability to limit the production of malware, the experts at the Iswatlab were able to create new malware without writing any line of new code, but just scrambling some old well-known threats.
Summing up, the producing a new-born malware, that is not detectable by defense solutions, just takes a few minutes. Take an old malware and put it into the Malware Washing Machine!
The Malware Washing Machine is available at https://github.com/faber03/AndroidMalwareEvaluatingTools
Google to Launch 'Andromeda OS' — An Android-Chrome OS Hybrid
27.9.2016 thehackernews Android
Google's long-rumored Android-Chrome hybrid operating system is expected to debut at the company's upcoming hardware event on October 4.
The company has been working to merge the two OSes for roughly 3 years with a release planned for 2017, but an "early version" to show things off to the world in 2016.
Android + Chrome = Andromeda
The hybrid OS, currently nicknamed 'Andromeda,' could be come on a new Pixel laptop as well as Huawei Nexus tablet from Google by Q3 2017, if not sooner, according to new leaks from 9to5Google and Android Police.
Android + Chrome = Andromeda
The laptop, officially codenamed "Bison" and nicknamed "Pixel 3," is a reference to the "Chromebook Pixel," but since this edition is not running Chrome operating system, one can not call it a "Chromebook" anymore.
Andromeda is separate from the company's Fuchsia OS, which is focused on Internet-of-Thing (IoT) devices. Moreover, the report also makes it clear that Andromeda "is [an entirely] distinct effort from Google's current campaign to bring Android apps to Chromebooks." So, don't get confused.
Rumored specs suggest Bison is expected to pack a 12.3-inch display with a 'tablet' mode and stylus and reportedly powered by an Intel M3 processor like Apple's 12-inch MacBook, or an Intel Core i5.
Bison is expected to have two models with 32GB or 128GB of internal storage, and 8GB or 16GB of RAM.
Other features could include two USB-C ports, a 3.5mm headphone jack, a fingerprint scanner, stereo speakers, a backlit keyboard, quad microphones, a glass trackpad, and a battery that lasts around 10 hours.
For more details about the new hybrid operating system, you need to wait for two more weeks for Google's October 4 event that is set to launch a Google's new hardware product line, including "Google Wi-Fi" router, Google Home, the refreshed 4K-capable Chromecast rumored to be called Chromecast Ultra, and a "Daydream" VR headset.
Rooting Pokémons in Google Play Store
16.9.2016 Kaspersky Android
A few days ago we reported to Google the existence of a new malicious app in the Google Play Store. The Trojan presented itself as the “Guide for Pokémon Go”. According to the Google Play Store it has been downloaded more than 500,000 times. Our data suggests there have been at least 6,000 successful infections, including in Russia, India and Indonesia. However, since the app is oriented towards English-speaking users, people in such geographies, and more, are also likely to have been hit.
Analysis reveals that the app contains a malicious piece of code that downloads rooting malware – malware capable of gaining access to the core Android operating system, in this case for the purposes of unsolicited app install and adware.
Kaspersky Lab products detect the Trojan as HEUR:Trojan.AndroidOS.Ztorg.ad.
At least one other version of this particular app was available through Google Play in July 2016. Further, we have tracked back at least nine other apps infected with this Trojan and available on Google Play Store at different times since December 2015.
Trojan characteristics
The Trojan has many layers of defense in place to help it bypass detection. This includes a commercial packer that decrypts the original executable file to make it harder to analyze. The unpacked executable file contains useful code related to the malicious Pokémon Go guide, and one small and obfuscated module.
Process of infection
This small module doesn’t start when the user launches the app. Instead, it waits for the user to install or uninstall another app, then checks to see if that app runs on a real device or on a virtual machine. If it turns out that it’s dealing with a device, the Trojan will wait for a further two hours before starting its malicious activity.
The first thing it does is connect to its command-and-control (CnC) server and upload data about the device, including country, language, device model and OS version.
If the server wants the Trojan to continue it will respond with an ID string. Only if the Trojan receives this ID string will it make its next request to the CnC. If it doesn’t receive anything, it will wait for two hours and then resubmit the first request. This feature is included so that the control server can stop the attack from proceeding if it wants to – skipping those users it does not wish to target, or those which it suspects are a sandbox/virtual machine, for example. Among other things, this provides an additional layer of protection for the malware.
Upon receiving the second request, the CnC server will send the Trojan a JSON file containing a URL. The Trojan downloads file from the specified URL, decrypts it and executes. In our case the Trojan downloaded a file detected as HEUR:Trojan.AndroidOS.Ztorg.a. This file is obfuscated too.
After execution, the Trojan will drop and download some more files. All downloaded files are encrypted and most of them are local root exploit packs for vulnerabilities dating from 2012 to 2015, including one that was previously used by Hacking Team.
These other files represent additional modules of the Trojan and are detected by Kaspersky Lab as:
HEUR:Backdoor.AndroidOS.Ztorg.c, HEUR:Trojan.AndroidOS.Muetan.b, HEUR:Trojan.AndroidOS.Ztorg.ad, HEUR:Backdoor.AndroidOS.Ztorg.h, HEUR:Backdoor.AndroidOS.Ztorg.j, HEUR:Trojan-Dropper.AndroidOS.Agent.cv, HEUR:Trojan.AndroidOS.Hiddad.c. And a few clean tools like busybox and chattr.
Using these exploit packs the Trojan will gain root access rights to the device. After gaining root access, the Trojan will install its modules into the system folders, silently installing and uninstalling other apps and displaying unsolicited ads to the user.
Most of the other apps with this Trojan module available in Google Play had about 10,000 downloads (according to Google Play), but one – “Digital Clock” had more than 100,000 downloads.
MD5 of Malicious Files Mentioned in Article
8CB3A269E50CA1F9E958F685AE4A073C
0235CE101595DD0C594D0117BB64C8C3
How to hack Google FR by exploiting a cross-site scripting flaw
15.9.2016 securityaffairs Android
The security expert Issam Rabhi (@issam_rabhi) has discovered a cross-site scripting vulnerability in Google France. The giant already fixed it.
A security expert from French security outfit Sysdream, Issam Rabhi (@issam_rabhi), discovered a cross-site scripting vulnerability in Google France. Yes, you‘ve got it right, the website of the IT giant was affected by one of the most common vulnerabilities. According to the OWASP Top Ten, the cross-site scripting is the third most popular issue affecting web applications.

Such kind of flaw could be exploited by a malicious attacker for various attacks, including defacements and traffic hijacking.
“XSS flaws occur whenever an application takes untrusted data and sends it to a web browser without proper validation or escaping. XSS allows attackers to execute scripts in the victim’s browser which can hijack user sessions, deface web sites, or redirect the user to malicious sites.” reads the description provided by the OWASP TOP 10.
The experts reported the cross-site scripting vulnerability to Google on August 5th and the experts of the company fixed the vulnerability in just four days.
Rabhi published a Proof-of-concept for the attack on his website, below the exploitation step by step:
First we need to click the link below using Firefox browser:
https://www.google.fr/#q=Olympiade&mie=oly%2C%5B%22%2Fm%2F03tnk7%22%2C1%2C%22r%22%2C1%2Cnull%2Cnull%2Cnull%2Cnull%2Cnull%2Cnull%2Cnull%2Cnull%2Cnull%2Cnull%2Cnull%2Cnull%2Cnull%2Cnull%2Cnull%2C0%5D
Then, to insert the following payload in the input field related to search:
<svg onload=alert(document.domain)>
Finally, the alert message box will pop up on the screen.
The expert did not submit the bug under the Google bug bounty program, anyway he received kudos from his colleagues.
Banking Trojan, Gugi, evolves to bypass Android 6 protection
9.9.2016 Kaspersky Android
Almost every Android OS update includes new security features designed to make cybercriminals’ life harder. And, of course, the cybercriminals always try to bypass them.
We have found a new modification of the mobile banking Trojan, Trojan-Banker.AndroidOS.Gugi.c that can bypass two new security features added in Android 6: permission-based app overlays and a dynamic permission requirement for dangerous in-app activities such as SMS or calls. The modification does not use any vulnerabilities, just social engineering.
Initial infection
The Gugi Trojan is spread mainly by SMS spam that takes users to phishing webpages with the text “Dear user, you receive MMS-photo! You can look at it by clicking on the following link”.
Clicking on the link initiates the download of the Gugi Trojan onto the user’s Android device.
Circumventing the security features
To help protect users from the impact of phishing and ransomware attacks, Android 6 introduced a requirement for apps to request permission to superimpose their windows/views over other apps. In earlier versions of the OS they were able to automatically overlay other apps.
The Trojan’s ultimate goal is to overlay banking apps with phishing windows in order to steal user credentials for mobile banking. It also overlays the Google Play Store app to steal credit card details.
The Trojan-Banker.AndroidOS.Gugi.c modification gets the overlay permission it needs by forcing users to grant this permission. It then uses that to block the screen while demanding ever more dangerous access.
The first thing an infected user is presented with is a window with the text “Additional rights needed to work with graphics and windows” and one button: “provide.”
After clicking on this button, the user will see a dialog box that authorizes the app overlay (“drawing over other apps”).
System request to permit Trojan-Banker.AndroidOS.Gugi.c to overlay other apps
But as soon as the user gives Gugi this permission, the Trojan will block the device and show its window over any other windows/dialogs.
Trojan-Banker.AndroidOS.Gugi.c window that blocks the infected device until it receives all the necessary rights
It gives the user no option, presenting a window that contains only one button: “Activate”. Once the user presses this button they will receive a continuous series of requests for all the rights the Trojan is looking for. They won’t get back to the main menu until they have agreed to everything.
For example, following the first click of the button, the Trojan will ask for Device Administrator rights. It needs this for self-defense because it makes it much harder for the user to uninstall the app.
After successfully becoming the Device Administrator, the Trojan produces the next request. This one asks the user for permission to send and view SMS and to make calls.
It is interesting that Android 6 has introduced dynamic request capability as a new security features
Earlier versions of the OS only show app permissions at installation; but, starting from Android 6, the system will ask users for permission to execute dangerous actions like sending SMS or making calls the first time they are attempted, or allows apps to ask at any other time – so that is what the modified Gugi Trojan does.
TSystem request for dynamic permission
The Trojan will continue to ask the user for each permission until they agree. Should the user deny permission, subsequent requests will offer them the option of closing the request. If the Trojan does not receive all the permissions it wants, it will completely block the infected device. In such a case the user’s only option is to reboot the device in safe mode and try to uninstall the Trojan.
TRepeating system request for dynamic permission
A standard banking Trojan
With the exception of its ability to bypass Android 6 security features, and its use of the Websocket protocol, Gugi is a typical banking Trojan. It overlays apps with phishing windows to steal credentials for mobile banking or credit card details. It also steals SMS, contacts, makes USSD requests and can send SMS by command from the CnC.
The Trojan-Banker.AndroidOS.Gugi family has been known about since December 2015, with the modification Trojan-Banker.AndroidOS.Gugi.c first discovered in June 2016.
Victim profile
The Gugi Trojan mainly attacks users in Russia: more than 93% of attacked users to date are based in that country. Right now it is a trending Trojan – in the first half of August 2016 there were ten times as many victims as in April 2016.
TUnique number users attacked by Trojan-Banker.AndroidOS.Gugi.
We will shortly be publishing a detailed report into the Trojan-Banker.AndroidOS.Gugi malware family, its functionality and its use of the Websocket protocol.
All Kaspersky Lab products detect all modifications of the Trojan-Banker.AndroidOS.Gugi malware family.
How Trojans manipulate Google Play
1.9.2016 Kaspersky Android
For malware writers, Google Play is the promised land of sorts. Once there, a malicious application gains access to a wide audience, gains the trust of that audience and experiences a degree of leniency from the security systems built into operating systems. On mobile devices, users typically cannot install applications coming from sources other than the official store, meaning this is a serious barrier for an app with malicious intent. However, it is far from easy for the app to get into Google Play: one of the main conditions for it is to pass a rigorous check for unwanted behavior by different analysis systems, both automatic and manual.
Some malware writers have given up on their efforts to push their malicious creations past security checks, and instead learned how to use the store’s client app for their unscrupulous gains. Lately, we have seen many Trojans use the Google Play app during promotion campaigns to download, install and launch apps on smartphones without the owners’ knowledge, as well as leave comments and rate apps. The apps installed by the Trojan do not typically cause direct damage to the user, but the victim may have to pay for the created excessive traffic. In addition, the Trojans may download and install paid apps as if they were free ones, further adding to the users’ bills.
Let us look into the methods how such manipulations with Google Play happen.
Level 1. N00b
The first method is to make the official Google Play app store undertake the actions the cybercriminal wants. The idea is to use the Trojan to launch the client, open the page of the required app in it, then search for and use special code to interact with the interface elements (buttons) to cause download, installation and launch of the application. The misused interface elements are outlined with red boxes in the screenshots below:
The exact methods of interaction with the interface vary. In general, the following techniques may be identified:
Use of the Accessibility services of the operating system (used by modules in Trojan.AndroidOS.Ztorg).
Imitation of user input (used by Trojan-Clicker.AndroidOS.Gopl.c).
Code injection into the process of Google Play client to modify its operation (used by Trojan.AndroidOS.Iop).
To see how such Trojans operate. Let us look at the example of Trojan.AndroidOS.Ztorg.n. This malicious program uses Accessibility services originally intended to create applications to help people with disabilities, such as GUI voice control apps. The Trojan receives a job from the command and control server (C&C) which contains a link to the required application, opens it in Google Play, and then launches the following code:
This code is needed to detect when the required interface element appears on the screen, and to emulate the click on it. This way, the following buttons are clicked in a sequence: “BUY” (the price is shown in the button), “ACCEPT” and “CONTINUE”. This is sufficient to purchase the app, if the user has a credit card with sufficient balance connected to his/her Google account.
Level 2. Pro
Some malware writers take roads less traveled. Instead of using the easy and reliable way described above, they create their own client for the app store using HTTPS API.
The difficult part about this approach is that the operation of the self-made client requires information (e.g. user credentials and authentication tokens) which is not available to a regular app. However, the cybercriminals are very fortunate that all required data are stored on the device in clear text, in the convenient SQLite format. Access to the data is limited by the Android security model, however apps may abuse it e.g. by rooting the device and thus gaining unlimited access.
For example, some versions of the Trojan.AndroidOS.Guerrilla.a have their own client for Google Play, which is distributed with the help of the rooter Leech. This client successfully fulfils the task of downloading and installing free and paid apps, and is capable of rating apps and leaving comments in the Google store.
After launch, Guerrilla starts to collect the following required information:
The credentials to the user’s Google Play account.
Activities in Google Play require special tokens that are generated when the user logs in. When the user is already logged in to Google Play, the Trojan can use the locally cached tokens. They can be located through a simple search through the database located at /data/system/users/0/accounts.db:
With the help of the code below, the Trojan checks if there are ready tokens on the infected device, i.e. if the user has logged on and can do activities in Google Play:
If no such tokens are available, the Trojan obtains the user’s username and hashed password, and authenticates via OAuth:
Android_id is the device’s unique ID.
Google Service Framework ID is the device’s identifier across Google services.
First, the Trojans attempts to obtain this ID using regular methods. If these fail for whatever reason, it executes the following code:
Google Advertising ID is the unique advertising ID provided by Google Play services.
Guerrilla obtains it as follows:
In a similar way, the Trojan obtains hashed data about the device from the file “/data/data/com.google.android.gms/shared_prefs/Checkin.xml“.
When the Trojan has collected the above data, it begins to receive tasks to download and install apps. Below is the structure of one such task:
The Trojan downloads the application by sending POST requests using the links below:
https://android.clients.google.com/fdfe/search: a search is undertaken for the request sent by the cybercriminals. This request is needed to simulate the user’s interaction with the Google Play client. (The main scenario of installing apps from the official client presupposes that the user first does the search request and only then visits the app’s page).
https://android.clients.google.com/fdfe/details: with this request, additional information needed to download the app is collected.
https://android.clients.google.com/fdfe/purchase: the token and purchase details are downloaded, used in the next request.
https://android.clients.google.com/fdfe/delivery: the Trojan receives the URL and the cookie-files required to download the Android application package (APK) file.
https://android.clients.google.com/fdfe/log: the download is confirmed (so the download counter is incremented.)
https://android.clients.google.com/fdfe/addReview: the app is rated and a comment is added.
When creating the requests, the cybercriminals attempted to simulate most accurately the equivalent requests sent by the official client. For example, the below set of HTTP headers is used in each request:
After the request is executed, the app may (optionally) get downloaded, installed (using the command ‘pm install -r’ which allows for installation of applications without the user’s consent) and launched.
Conclusion
The Trojans that use the Google Play app to download, install and launch apps from the store to a smartphone without the device owner’s consent are typically distributed by rooters – malicious programs which have already gained the highest possible privileges on the device. It is this particular fact that allows them to launch such attacks on the Google Play client app.
This type of malicious program pose a serious threat: in Q2 2016, different rooters occupied more than a half of the Top 20 of mobile malware. All the more so, rooters can download not only malicious programs that compromise the Android ecosystem and spend the user’s money on purchasing unnecessary paid apps, but other malware as well.
Warning! Over 900 Million Android Phones Vulnerable to New 'QuadRooter' Attack
8.8.2016 Android
Android has Fallen! Yet another set of Android security vulnerabilities has been discovered in Qualcomm chipsets that affect more than 900 Million Android smartphones and tablets worldwide.
What's even worse: Most of those affected Android devices will probably never be patched.
Dubbed "Quadrooter," the set of four vulnerabilities discovered in devices running Android Marshmallow and earlier that ship with Qualcomm chip could allow an attacker to gain root-level access to any Qualcomm device.
The chip, according to the latest statistics, is found in more than 900 Million Android tablets and smartphones.
That's a very big number.
The vulnerabilities have been disclosed by a team of Check Point researchers at the DEF CON 24 security conference in Las Vegas.
Critical Quadrooter Vulnerabilities:
The four security vulnerabilities are:
CVE-2016-2503 discovered in Qualcomm's GPU driver and fixed in Google's Android Security Bulletin for July 2016.
CVE-2016-2504 found in Qualcomm GPU driver and fixed in Google's Android Security Bulletin for August 2016.
CVE-2016-2059 found in Qualcomm kernel module and fixed in April, though patch status is unknown.
CVE-2016-5340 presented in Qualcomm GPU driver and fixed, but patch status unknown.
Qualcomm is the world's leading designer of LTE (Long Term Evolution) chipsets with a 65% share of the LTE modem baseband market. If any one of the four flaws is exploited, an attacker can trigger privilege escalations for gaining root access to an affected device.
All an attacker needs is to write a piece of malware and send it to the victim. When installed, the malware offers the attacker privilege escalation on the affected devices.
According to the researchers, the attack can also be conducted through a malicious app. An attacker needs to trick a user into installing a malicious app that, unlike other malware, would execute without requiring any special permission checks.
"Such an app would require no special permissions to take advantage of these vulnerabilities, alleviating any suspicion users may have when installing," Check Point researchers write in a blog post.
If any of the four vulnerabilities are successfully exploited, an attacker could gain root access to an affected device, giving the attacker full access to the device, including its data, camera and microphone.
List of Affected Devices (Popular)
More than 900 Million Android devices that ship with Qualcomm chip are vulnerable to the flaws.
Here's the list of some of the popular affected devices, though there are far more devices that are impacted by one or more Quadrooter vulnerabilities.
Samsung Galaxy S7 and Samsung S7 Edge
Sony Xperia Z Ultra
OnePlus One, OnePlus 2 and OnePlus 3
Google Nexus 5X, Nexus 6 and Nexus 6P
Blackphone 1 and Blackphone 2
HTC One, HTC M9 and HTC 10
LG G4, LG G5, and LG V10
New Moto X by Motorola
BlackBerry Priv
How to Check if Your Device is Vulnerable?
You can check if your smartphone or tablet is vulnerable to Quadrooter attack using Check Point's free app.
Since the vulnerable software drivers, which control communication between Qualcomm chipset components, come pre-installed on these devices at the time of manufacturing, they can only be fixed by installing a patch from the devices' distributors or carriers after receiving fixed driver packs from Qualcomm.
"This situation highlights the inherent risks in the Android security model," the researchers say. "Critical security updates must pass through the entire supply chain before they can be made available to end users."
Three of the four vulnerabilities have already been fixed in Google's latest set of monthly security updates, and a patch for the remaining flaw will be rolled out in the upcoming September update.
Since Qualcomm has already released the code, the phone manufacturers could be able to issue patches to the individual devices as soon as possible.
Android Nexus devices are already patched via the over-the-air updates, but other smartphone models will need to wait until their lazy phone manufacturers integrate the fixes into their own custom Android ROMs.
Android Instant Apps — Run Apps Quickly Without Installation
19.5.2016 Android
Downloading an app is a real pain sometimes when you don't want to install the complete app on your smartphone just for booking a movie ticket, or buying something online. Isn't that?
Now, Imagine the world where you can use any Android app without actually the need to download or even install it on your smartphone.
This is exactly what Google has intended to offer you with its all new Instant Apps feature.
Announced at Google I/O event Wednesday, Android Instant Apps will break down the walls between websites and Android apps by allowing people to tap on a URL and open an Android app instantly, without even having to install it.
As a live demonstration, Google's presenter on stage showed how just clicking a Buzzfeed Video link, which has a dedicated app, opened the relevant part of an app — all in just 2 seconds.
In another demonstration, the presenter showed a link to buy a camera bag at B&H Photo and complete the purchasing process instantly through the shopping cart inside the company's touchscreen-friendly Android app, without even installing the whole app.
For Developers:
Android Instant Apps
Developers who want to provide Instant Apps will have to modularize their already existing apps that can start within a few seconds and users don't have to install the whole app just to use some of its features.
According to Google, some developers with basic apps could even implement Instant Apps support to their apps in as little as a day.
Additionally, alongside with their Instant apps, developers can provide "call to action" links to encourage users to download and install their complete apps if users find them particularly useful.
For Users:
When users click on a Web URL and if that URL has an associated Instant App, users will get a tiny version of that app instead of the website. Once tap, the smartphone fetches some part of the app that users want to use, allowing the app to instantly and seamlessly install.
The user experience with Android Instant Apps is as fast as loading up a web page with the same functionality. So, just don’t bother about Loading…
Instant Apps will run in a secure sandbox and once released, Android Instant Apps feature will work on all smartphones running Android 4.2 (Jelly Bean) or later.
The company will make the feature available via an update to the Google Play Services software coming "later this year."
Malware-Laced Porn Apps Behind Wave of Android Lockscreen Attacks
14.5.2016 Android
Incidents of Android lockscreen malware masquerading as porn apps are a growing concern to security analysts who are forecasting an uptick in attacks. Once infected, Android users bitten by this malware appear to be locked out of their device and are forced to undergo a complex extraction of the app to win back control of their phone or tablet. The warning comes from Dell SonicWALL Threats Research Team that said this yet-to-be-named variant of lockscreen malware is immature, but potent. “We have found over a 100 different apps that contain this malware and suspect that the authors behind the apps are gearing up for a much larger more deadly assault,” said Alex Dubrovsky, director of software engineering and threat research at Dell. Unlike other lockscreen malware such as ICE, Jisut and Cyber.Police that locks the user’s screen and asks them to pay a ransom, the lockscreen malware that Dell found does not appear to be financially motivated, yet. The malware is closely tied to porn websites. Users are enticed to download porn-themed apps via links or SMS message requests that link users to third-party Android app stores. Once a target downloads the advertised malicious porn app, it requests for Device Administrator privileges. When users click the application or open the System Settings app a screen, what appears to be the ransom or lockscreen message appears. But that lockscreen can be easily circumvented by clicking the Home or Recent Apps buttons, according to a SonicWALL team research blog about the discovery posted Thursday. At this time, Dubrovsky said, attackers are not employing a command and control backend to manipulate the device. Neither are attackers executing remote code or taking control over a user’s Android device. However, “once the application starts running, encoded data is transmitted to multiple domains in the background,” SonicWALL reports. Dubrovsky said his team is still dissecting the malware and at this time he suspects that data transmitted from the phone could possibly be personal in nature, but couldn’t be sure. “This is clearly beta software that attackers are refining in real time. Many of the obvious features you’d expect with malware are just not feature complete.” One thing is certain about this strain of lockscreen malware is it is hard to remove. “If an Android device gets infected with a malware with Device Administrator privileges it becomes difficult to remove it as the uninstall button gets greyed out,” write Dell’s SonicWALL security team. Dell said that the obvious solution of running your Android device in Safe Mode to remove app doesn’t work in this instance. Once in Safe Mode the malicious app starts blocking the System Settings after a few moments making it impossible to uninstall. The alternative is to disable the running app via Android Debug Bridge, a software developer’s tool. The other option for non-technical users is simply, reset your Android device. “Overall it looks like this campaign is in its early days as the lockscreen does not work as expected and it is easy to come out of the ‘lock’ state,” Dell wrote. “Considering the volume of malicious apps that are part of this campaign it can be said that this campaign might grow bigger in the near future with updated components.” Dubrovsky said his researchers are bracing for more mature variants of this lockscreen malware that will be much more technically adept at demanding a ransom in some form from mobile porn surfers and apps that have a broader non-adult themed appeal.
How to Use Apple's iMessage on Android Phone
9.5.2016 Android
If you wish to send iMessages from your Android smartphone to a friend who owns an iPhone, it's possible now, at least for those who own MacBooks and iMacs.
A developer has come up with a smart solution to bring Apple's iPhone messaging platform to Android phones. Though the solution is not practical for most people, technical people and nerds can use it to send end-to-end encrypted iMessages.
The solution is a smart hack, but the best part is: PieMessage totally works.
Developed by Eric Chee, PieMessage needs an OS X client as a server to route messages to an Android device, enabling iMessage support on Android devices. So, it's the Mac that handles the entire workload.
"Basically, what the Android client does is send the text to a MacBook," Chee said. "And uses the Mac's Messages app to send off the notification. When the Mac detects an incoming message, it will pass it back to the Android. So yes, there is both software you need to run on a Mac and Android. I have an old 2007 MacBook that is just always on connected at home that serves as its client…"
Here's How PieMessage Works:
PieMessage uses an AppleScript to capture iMessages as they arrive on your Mac system.
A Java app scoops up those messages from the script.
Then the Java app forwards them to a custom messaging app on an Android phone to display and respond to those iMessages.
Chee has also presented a proof-of-concept video demonstration that shows the PieMessage app in work.
He also released the PieMessage code open source on GitHub.
There are some limitations to PieMessage:
You can reply to one-to-one messages from your Android device but currently can't send group messages; instead you can just receive them.
Also, you can not send images and can not see when someone is typing — though the author plans to add more functionality in future updates.
Currently, PieMessage identifies different iMessage conversations by phone numbers or email addresses instead of names.
Since Apple could block this type of functionality in the future due to security risks to its platform, there are other good alternatives for sending and receiving end-to-end encrypted messages, like WhatsApp and Facebook Messenger, with cross-platform support.
New Android Gmobi adware found in firmware and popular apps
18.3.2016 Android
Malware researchers at the Dr Web firm have found an Android malware named Gmobi specifically designed to spread as a software development kit (SDK).
Malware researchers at security firm Dr.Web have detected a new strain of malware that was specifically designed to spread as a software development kit (SDK) used by software developers and mobile device manufacturers. The malware, named Android.Gmobi.1, has been found in several legitimate applications developed by well-known companies, as well as in firmware for nearly 40 mobile devices.
“This Trojan, which was named Android.Gmobi.1, is designed as a specialized program package (the SDK platform) usually used either by mobile device manufacturers or by software developers to expand functionality of Android applications. In particular, this module is able to remotely update the operating system, collect information, display notifications (including advertising ones), and make mobile payments.” states the analysis published by the company.
The malware acts as an information stealer, it collects user and device data and send them back to the C&C server. Gmobi collects user emails, device info, roaming availability status, GPS or mobile network coordinates, whether the Google Play app that installed on the device.
Gmobi collects the following information and sends it to the C&C server: user emails, device info, roaming availability status, device location and mobile network coordinates, whether the presence of a Google Play application on the device.
The malware belongs to the adware category, once the C&C server has received the data from the device it can instruct the Gmobi in showing ads in specific positions of the device. The bad news is that operators behind Gmobi can also instruct the malware to download and install malicious APK files using a standard system dialog.

The experts highlighted that the Gmobi adware can install the APK files in a covert way only if the malware has the necessary privileges.
The server replies with an encrypted JSON (Java Script Object Notification) object that can contain the following commands:
Update the database with information about the advertisement to display.
Create an advertising shortcut on the home screen.
Display an advertising notification.
Display a notification tapping which will result in launch of an installed application.
Automatically download and install APK files using a standard system dialog. A covert installation of these files is performed only if the Trojan has necessary privileges.
The researchers have detected Gmobi in Trend Micro’s Dr. Safety and Dr. Booster apps, and the ASUS WebStorage apps. The Gmobi variant that was discovered in the software of the Trend Micro firm only collected information from the Android devices and sent it to a remote server.
Dr.Web reported the issue to all the impacted companies, Trend Micro has promptly released a new version of the infected apps.
“If your device’s firmware is infected by this Trojan, the malware cannot be removed by the anti-virus without root privileges. However, even if root privileges are gained, there is a high risk of making the device non-operational because the Trojan can be incorporated into some critical system application. Therefore, the safest solution for victims ofAndroid.Gmobi.1 is to contact the manufacturer of the device and ask them to release a firmware update without the Trojan.” concludes Dr Web.
Android Stagefright Exploit, Millions devices open to 10-seconds hack
18.3.2016 Android
Millions of Android devices are open to hacking attacks due to the newly disclosed Android Stagefright Exploit that hack a smartphone in 10 seconds.
New problems for Android users, security experts at software research firm NorthBit have developed an exploit for a Stagefright vulnerability affecting Google’s operating system.
Millions of Android devices are open to hacking attacks due to the newly disclosed Android Stagefright Exploit that could allow attackers to hack a smartphone in 10 seconds.
The attacker just needs to trick users into visiting a specifically crafted web page that includes a malicious multimedia file.
The researchers at NorthBit have dubbed the Android Stagefright Exploit Metaphor, they published a detailed analysis of the attack in a paper entitled “Metaphor A (real) reallife Stagefright exploit.”
The researchers have published a proof-of-concept video that shows how they hacked an Android Nexus 5 device using their Metaphor exploit in just 10 seconds. They also demonstrated that the Android Stagefright Exploit Metaphor works against other mobile devices, including Samsung Galaxy S5, LG G3 and HTC One smartphones.
“Although the bug exists in many versions (nearly a 1,000,000,000 devices) it was claimed impractical to exploit inthewild, mainly due to the implementation of exploit mitigations in newer Android versions, specifically ASLR.” states the paper.
The Android Stagefright Exploit works on Android versions 2.2 to 4.0 and 5.0 to 5.1 while bypassing ASLR on Android versions 5.0 to 5.1, as version 2.2 to version 4.0 do not implement ASLR. Other Android versions are not affected by the new Stagefright exploit.
The Stagefright was first discovered in July 2015, experts at security firm Zimperium announced the flaw is the worst Android vulnerability flaw in the mobile OS history.
The Stagefright flaw affects a media library app that is used for by Android to process Stagefright media files. According to the experts at Zimperium the media library is affected by several vulnerabilities.
Joshua Drake from Zimperium discovered seven critical vulnerabilities in the native media playback engine called Stagefright, the expert defined the Stagefright flaw the “Mother of all Android Vulnerabilities.”
The attackers can exploit the vulnerability by sending a single multimedia text message to an unpatched Android device. Despite Google has already issued a patch and has sent out to it to the company’s partners, but most manufacturers haven’t already distributed the patch to their customers exposing them to cyber attack.
In September 2015, experts at Zimperium released a Stagefright exploit, demonstrating how to trigger the Remote Code Execution (RCE). The researchers implemented the Stagefright Exploit in python by creating an MP4 exploiting the ‘stsc’ vulnerability, aka Stagefright vulnerability.
Stagefright Exploit
In October 2015, experts at Zimperium discovered that a billion Android phones were vulnerable to new Stagefright vulnerabilities, dubbed Stagefright 2.0 that could allow attackers to execute malicious code on the targeted device.
The researchers discovered two bugs that are triggered when processing specially crafted MP3 audio or MP4 video files.
The hacking procedure described by the researchers at NorthBit is composed of the following steps:
Tricking a victim into visiting a malicious page containing a video file that crashes the media server to reset its internal state.
Once the media server restarts, the JavaScript hosted on the web page sends information about the device to the attacker’s server.
The server reply with a custom generated video file to the affected device, exploiting the Stagefright bug to reveal more info about the device’s internal state.
This information is also sent back to the attacker’s server to craft another video file that embeds a malicious payload that allows gaining the control of the mobile device.
New Exploit to 'Hack Android Phones Remotely' threatens Millions of Devices
17.3.2016 Android
Millions of Android devices are vulnerable to hackers and intelligence agencies once again – Thanks to a newly disclosed Android Stagefright Exploit.
Yes, Android Stagefright vulnerability is Back…
…and this time, the Stagefright exploit allows an attacker to hack Android smartphones in 10 seconds just by tricking users into visiting a hacker's web page that contains a malicious multimedia file.
A group of security researchers from Israel-based research firm NorthBit claimed it had successfully exploited the Stagefright bug that was emerged in Android last year and described as the "worst ever discovered".
The new Stagefright exploit, dubbed Metaphor, is detailed in a research paper [PDF] that guides bad guy, good guy as well as government spying agencies to build the Stagefright exploit for themselves.
Just yesterday, we reported about critical vulnerabilities in Qualcomm Snapdragon chip that could be exploited by any malicious application to gain root access on a vulnerable Android device, leaving more than a Billion Android devices at risk.
Video Demonstration — Exploit to Hack Android Phone in 10 Seconds
The researchers have also provided a proof-of-concept video demonstration that shows how they successfully hacked an Android Nexus 5 device using their Metaphor exploit in just 10 seconds. They also successfully tested Metaphor on a Samsung Galaxy S5, LG G3 and HTC One smartphones.
According to the researchers, Millions of unpatched Android devices are vulnerable to their exploit that successfully bypasses security defenses offered by Android operating system.
What is StageFright Bug and Why You have to Worry about it?
Stagefright is a multimedia playback library, written in C++, built inside the Android operating system to process, record and play multimedia files such as videos.
However, what Zimperium researchers discovered last year was that this core Android component can be remotely exploited to hijack 95 percent of Android devices with just a simple booby-trapped message or web page.
Another critical vulnerability discovered last October in Stagefright exploited flaws in MP3 and MP4 files, which when opened were capable of remotely executing malicious code on Android devices, and was dubbed Stagefright 2.0.
However, to tackle this serious issue, Google released a security update that patches the critical bug as well as promised regular security updates for Android smartphones following the seriousness of the Stagefright bugs.
Here's How the New Stagefright Exploit Works
Researchers described the following process to successfully hijack any vulnerable Android smartphone or tablet:
Step 1: Tricking a victim into visiting a malicious web page containing a video file that crashes the Android's mediaserver software to reset its internal state.
Step 2: Once the mediaserver gets a restart, JavaScript on the web page sends information about the victim's device over the Internet to the attacker's server.
Step 3: The attacker's server then sends a custom generated video file to the affected device, exploiting the Stagefright bug to reveal more info about the device's internal state.
Step 4: This information is also sent back to the attacker's server to craft another video file that embeds a payload of malware in it, which when processed by Stagefright starts executing on the victim's smartphone with all the privileges it needs to spy on its owner.
The researchers also claim that their exploit specifically attacks the CVE-2015-3864 vulnerability in a way that bypasses Address Space Layout Randomisation (ASLR), a memory protection process.
"It was claimed [the Stagefright bug] was impractical to exploit in the wild, mainly due to the implementation of exploit mitigations in [latest] Android versions, specifically ASLR," the research paper reads.
The team's exploit works on Android versions 2.2 to 4.0 and 5.0 to 5.1 while bypassing ASLR on Android versions 5.0 to 5.1, as version 2.2 to version 4.0 do not implement ASLR. Other Android versions are not affected by the new Stagefright exploit.
You can go through the full research paper [PDF] that provides enough details to create a fully working and successful exploit.
Russia Rejects Google's Appeal and Orders to Stop Pre-Installing its own Android Apps
16.3.2016 Android
The Giant search engine Google has lost an anti-monopoly appeal in Russia against ruling related to its Android mobile OS
The Moscow Arbitration Court on Monday ruled that Google had violated its dominant position with the help of its free open source mobile platform "Android" by forcing its own apps and services like Youtube, Google Map, and others, on users — reducing competition.
The complaint was brought against Google last February by competing search engine Yandex — Russian Counterpart of Google — which had argued that Google broke competition rules by requiring handset manufacturers to pre-install its apps on Android phones and tablets.
Yandex-1, Google-0
According to the survey conducted by Liveinternet data in September 2013, Yandex accounted 57.4% of the Russian search market, while Google shared 34.9%. This stats reflected in the share market, as their shares were 62.2 and 26 percent respectively.
These statistical analyzes really worried Google about its operations in the Russian Cyberspace and soon it rolled out its Plan B to gain widespread popularity in the Russian Markets by shipping Android smartphones with Google Play Store as bloatware.
This, however, gained a pony monopoly among the Russian Markets. But soon, Yandex noticed that millions of smartphones in Russia shipped with the Android platform that uses Google as the default search engine.
As Yandex ranked as the 4th largest search engine worldwide, the popularity of Android in Russia had already reflected the changes in the Russian Stock Market, forcing Yandex to proceed with a lawsuit against Google in February 2015.
No Pre-installed Google Apps for Russians
The original ruling was then handed down by the country's privacy watchdog, the Federal Antimonopoly Service (FAS), last September over the pre-installed Google apps on Android and blocking other service providers.
Google appealed the ruling and filed an antitrust to adhere their business in the Russian Markets last year.
However, yesterday (Tuesday) the Moscow Arbitration Court rejected the company's appeal — upholding FAS' judgment that Google's practices broke Russian law by leading to the 'prohibition of pre-installation of apps of other producers.'
To regain its dominance over foreign search engines, FAS had already passed the case in favor of Yandex, the native search engine.
FAS adjourned that the default Android would not be coming with any pre-installed Google apps on Android smartphones and tablets in Russia.
Google will now be required to amend its contract with OEMs in Russia to comply with the ruling. The company now faces having to instruct its contracts with manufacturers and paying a penalty based on its local earnings.
Is Yandex - An Unsung Hero?
There is already a buzz in the cyber chat rooms that Yandex was a cloned product of Google, which is evident from many social discussion sites.
Yandex had already developed a unique method to search the whole Bible and Russian Literatures at its infancy stage, which was adopted by Google later.
These are some of the hidden facts about Yandex:
Yandex launched as a search engine in 1997, a year earlier than Google.
Yandex also launched maps in 2004, Google a year later in 2005.
Yandex was the first to launch news search in 2000, Google in 2002.
Blog search came out of Russia in 2004, but out of California only in 2006.
Yandex had already launched an RSS aggregator in 2005, Google followed in 2006.
Even Though Google had implemented many new ideas as time progressed with the help of its think tanks, yet Yandex was behind the implementations of classic times.
Let's look what would be the next roll out from Yandex after the Thumbs Up Rule from FAS.
More than a Billion Snapdragon-based Android Phones Vulnerable to Hacking
16.3.2016 Android
More than a Billion of Android devices are at risk of a severe vulnerability in Qualcomm Snapdragon chip that could be exploited by any malicious application to gain root access on the device.
Security experts at Trend Micro are warning Android users of some severe programming blunders in Qualcomm's kernel-level Snapdragon code that if exploited, can be used by attackers for gaining root access and taking full control of your device.
Gaining root access on a device is a matter of concern, as it grants attackers access to admin level capabilities, allowing them to turn your device against you to snap your pictures, and snoop on your personal data including accounts’ passwords, emails, messages and photos.
The company’s own website notes that Qualcomm Snapdragon SoCs (systems on a chip) power more than a Billion smart devices, including many Internet of Things (IoTs) as of today. Thus, the issue puts many people at risk of being attacked.
Although Google has pushed out updates after Trend Micro privately reported the issues that now prevents attackers from gaining root access with a specially crafted app, users will not be getting updates anytime soon.
The security update rolls out to your device through a long chain:
Qualcomm → Google → Your device's manufacturer → Your network carrier → Your handheld over the air
"Given that many of these devices are either no longer being patched or never received any patches in the first place," said Trend engineer Wish Wu, "they would essentially be left in an insecure state without any patch forthcoming."
Unfortunately, what’s more concerning is the fact that the same vulnerable chips are used in a large number of IoT devices, which are no longer in line for security updates. This makes it possible for hackers to gain root access to these connected devices, which is more worrying.
"Smartphones aren't the only problem here," said Trend's Noah Gamer. "Qualcomm also sells their SoCs to vendors producing devices considered part of the Internet of Things, meaning these gadgets are just as at risk."
"If IoT is going to be as widespread as many experts predict, there needs to be some sort of system in place ensuring these devices are safe for public use. Security updates are an absolute necessity these days, and users of these connected devices need to know what they're dealing with."
Whatever be the reason: if security patches are not available for your device model or take too long to arrive, in both the cases it gives miscreants time to exploit the security holes to gain control of your device.
However, some users are lucky to choose Google’s handsets that get their patches direct from the tech giant automatically, making them safe from the vulnerabilities. The handsets include Nexus 5X, Nexus 6P, Nexus 6, Nexus 5, Nexus 4, Nexus 7, Nexus 9, and Nexus 10.
All of the smart devices using the Qualcomm Snapdragon 800 series, including the 800, 805 and 810 and running a 3.10-version kernel are affected by the vulnerabilities.
The vulnerable code is present in Android version 4 to version 6. In the tests, researchers found Nexus 5, 6 and 6P, and Samsung Galaxy Note Edge using vulnerable versions of Qualy's code.
Though the researchers do not have access to every Android handset and tablet to test, the list of vulnerable devices is non-exhaustive.
Since the researchers have not disclosed full details about the flaws, the short brief about the vulnerabilities is as follows:
1. Qualcomm-related flaw (CVE-2016-0819): The vulnerability has been described by the researchers as a logic bug that allows a small section of kernel memory to be tampered with after it is freed, causing an information leakage and a Use After Free issue in Android.
2. The flaw (CVE-2016-0805) is in Qualcomm chipset kernel function get_krait_evtinfo: The get_krait_evtinfo function returns an index into an array used by other kernel functions. With the help of carefully crafted input data, it is possible to generate a malicious index, leading to a buffer overflow.
3. Gaining root access: Using both the flaws together on vulnerable devices, attackers can gain root access on the device.
The researchers will disclose the full details of exactly how to leverage the bugs at the upcoming Hack In The Box security conference in the Netherlands to be held in late May 2016.
More than a billion Android devices are easy to hack
9.3.2016 Android
A large percentage of Android devices is affected by security vulnerabilities that could be exploited by attackers to easily gain a Root Access.
According to experts at TrendMicro a large percentage of Android devices in use today is affected by security vulnerabilities that could be exploited by attackers to easily gain a root access.
The attack allows an ill-intentioned to escalate the privileges of any code that is executed on a target device, however, this attack scenario sees an attacker having installed his malicious code onto the device in the first place. Android users need to be very careful of installing any mobile apps from untrusted sources.
Below the description provided by TrendMicro for the CVE-2016-0819 and CVE-2016-0805 flaws discovered by its experts:
CVE-2016-0819
We discovered this particular vulnerability, which is described as a logic bug when an object within the kernel is freed. A node is deleted twice before it is freed. This causes an information leakage and a Use After Free issue in Android. (UAF issues are well-known for being at the heart of exploits, particularly in Internet Explorer.)
CVE-2016-0805
This particular vulnerability lies in the function get_krait_evtinfo. (Krait refers to the processor core used by several Snapdragon processors). The function returns an index for an array; however, the validation of the inputs of this function are not sufficient. As a result, when the array krait_functionsis accessed by the functions krait_clearpmu and krait_evt_setup, an out-of-bounds access results. This can be useful as part of a multiple exploit attack.

The problem affects the Qualcomm Snapdragon systems on a chip, more than a billion devices is at risk. The root access to a mobile device allows an attacker to conduct a number of malicious activities, from surveillance to financial frauds.
The vulnerability could be exploited by simply running a malicious app on snapdragon-powered Android devices. Experts at TrendMicro privately reported the security holes to Google that fixed them.
As usually happen in these cases, the high fragmentation of the Android market complicates the patch management process. Many users are still vulnerable to the attack waiting for a security patch.
“As the number of embedded SoCs in devices explode with the IoT growth, we anticipate that these kinds of vulnerabilities will become a bigger problem that will challenge the overall security posture of Internet of Things.” continues the post published by TrendMicro.
Going into technical details, the flaws could be exploited in every mobile and IoT devices that could allow the invocation of the system call perf_event_open. Fortunately, many vendors can have customized the kernel and SELinux policies in order to avoid the call.
According to the Nexus Security Bulletin – February 2016, the CVE-2016-0805 vulnerability affects versions earlier than 4.4.4 to 6.0.1, this means that Nexus 5, Nexus 6, Nexus 6P, Samsung Galaxy Note Edge are vulnerable to the attack.
“We believe that any Snapdragon-powered Android device with a 3.10-version kernel is potentially at risk of this attack. As mentioned earlier, given that many of these devices are either no longer being patched or never received any patches in the first place, they would essentially be left in an insecure state without any patch forthcoming.” conclude TrendMicro.
How to Steal Secret Encryption Keys from Android and iOS SmartPhones
4.3.2016 Android iOS
Unlike desktops, your mobile devices carry all sorts of information from your personal emails to your sensitive financial details. And due to this, the hackers have shifted their interest to the mobile platform.
Every week new exploits are discovered for iOS and Android platform, most of the times separately, but the recently discovered exploit targets both Android as well as iOS devices.
A team of security researchers from Tel Aviv University, Technion and The University of Adelaide has devised an attack to steal cryptographic keys used to protect Bitcoin wallets, Apple Pay accounts, and other highly sensitive services from Android and iOS devices.
The team is the same group of researchers who had experimented a number of different hacks to extract data from computers. Last month, the team demonstrated how to steal sensitive data from a target air-gapped computer located in another room.
Past years, the team also demonstrated how to extract secret decryption keys from computers using just a radio receiver and a piece of pita bread, and how to extract the cryptographic key just by solely touching the chassis of the computer.
Side-Channel Attacks
According to the researchers, the recent exploit is a non-invasive Side-Channel Attack: Attack that extracts the secret crypto key from a system by analyzing the pattern of memory utilization or the electromagnetic outputs of the device that are emitted during the decryption process.
The exploit works against the Elliptic Curve Digital Signature Algorithm (ECDSA), a standard digital signature algorithm that is most widely used in many applications like Bitcoin wallets and Apple Pay and is faster than several other cryptosystems.
How to Steal Secret Encryption Keys?
how-to-hack-android-story
During the experimental hack, the researchers placed a $2 magnetic probe near an iPhone 4 when the phone was performing cryptographic operations.
While performing cryptographic operations, the security researchers measured enough electromagnetic emanations and were able to fully extract the secret key used to authenticate the end user's sensitive data and financial transactions.
The same hack can be performed using an improvised USB adapter connected to the phone's USB cable, and a USB sound card to capture the signal.
"Using such measurements, we were able to fully extract secret signing keys from OpenSSL and CoreBitcoin running on iOS devices," the researchers wrote in a blog post published Wednesday. "We also showed partial key leakage from OpenSSL running on Android and from iOS's CommonCrypto."
The researchers also experimented their exploit on a Sony-Ericsson Xperia X10 Phone running Android and said they believe such an attack is feasible.
The security researchers also cited a recent independent research by a separate team of security researchers that discovered a similar Side-Channel flaw in Android's version of the BouncyCastle crypto library, making the device vulnerable to intrusive electromagnetic key extraction attacks.
Currently, the hack requires an attacker to have physical control of, or, at least, a probe or cable in proximity to, a vulnerable mobile device as long as it performed enough tasks to measure a few thousand of ECDSA signatures.
Affected Devices
Older iOS versions 7.1.2 through 8.3 are vulnerable to the side-channel attack. The current iOS 9.x version includes defenses against side-channel attacks, so are unaffected.
However, nothing can save iPhone and iPad users even running current iOS versions if they are using vulnerable apps. One such vulnerable iOS app is CoreBitcoin that is used to protect Bitcoin wallets on iPhones and iPads.
Developers of CoreBitcoin told the security researchers that they are planning to replace their current crypto library with one that is not susceptible to the key extraction attack. Meanwhile, the recent version of Bitcoin Core is not vulnerable.
Both OpenSSL versions 1.0.x and 1.1.x are vulnerable except when compiled for x86-64 processors with the non-default option enabled or when running a special option available for ARM CPUs.
The team has already reported the vulnerability to the maintainers of OpenSSL, who said that hardware side-channel attacks are not a part of their threat model.
For in-depth technical details, you can read the full research paper [PDF].
How To Keep Your Android Phone Secure
26.2.2016 Android
As the number of threats is on the rise, Android platform is no longer safe, which isn't a surprise to anyone.
Most of us are usually worried more about the security of our desktops or laptops and forget to think about the consequences our smartphones can make if compromised or stolen.
Unlike desktops, your smartphones and tablets carry all sorts of information from your personal photographs, important emails, messages to your sensitive financial details. And due to rise in mobile usage, the hackers have shifted their interest from desktops to the mobile platform.
Nowadays, nearly all possible threats that were previously attacking desktop platform are now targeting smartphone users.
Ransomware, Phishing, Spams, Spyware, Botnets, Banking Malware, OS and Software vulnerabilities, just to name a few examples, but users don't understand the potential threat when it comes to mobile devices.
Additionally, your smartphones and tablets are also subjectable more threats like, Smartphone Thefts and unnecessary app permissions that allow even legitimate & reputed companies to spy on you.
However, there are a number of solutions to solve all the above issues, but for that, you generally need to install multiple cumbersome and untrusted applications to your mobile devices.
Like a good antivirus to resolve malware and virus issues, an app to manage Android app permissions, a device tracking application in case your device is lost or stolen and lots more and installing all these apps consume lots of space, RAM, the battery of your device.
I frequently receive these types of queries from my readers who ask me for some good solution that could solve most of the security and privacy issues in one go.
So I headed to Google Play Store and started searching for an app that offers a full suite of security and privacy tools. I came across some reputed apps, but they resolve few issues and some apps that address several issues but originate from some vendor I can’t trust.
Then I came across , which comes from one of the reputed antivirus vendors, that is offering protection for all the threats we discussed above.
Anti-Virus Feature with 99.9% Detection Rate
best-mobile-antivirus-app
As its primary role, ESET offers the best antivirus scanning for your smartphone devices with up-to-date threat database and clean mobile app interface.
According to the latest test and review conducted by AV-TEST, an independent lab, ESET mobile security antivirus detects 99.9% of latest threats with the protection and usability score 6 out of 6.
After installing and registering my account, the app's Anti-Virus feature offered me options to have my smartphone scanned periodically:
At specific times, when I’m not using my phone, or
When I plugged in my smartphone for charging
Moving further, I found 3 different levels of scanning available in the software: Quick Scan, Smart Scan, and Deep Scan. So, one can choose to perform any of the options one's feel suitable. I chose Deep Scan that scanned every data and files available on my phone.
ESET Mobile Security also allows to access scan logs easily, and one can also have a look at quarantined items (suspicious files or malware) detected by the anti-virus.
Moreover, the anti-virus feature is also offering a series of advanced antivirus options, including support for ESET Live Grid, detection of potentially unwanted or harmful applications and real-time protection.
Anti-Theft (Remote Lock / Remote Wipe / Locate)
android-anti-theft-app
It is always unfortunate when our expensive mobile device is lost or stolen. Many apps in the market offer device recovery feature via GPS-based tracking, but many times these apps are unable to locate the device. Even if an attacker somehow gets access to the device, it is easy for him/her to uninstall the tracking app.
But, I liked the way works. It is designed to help you easily track your lost or stolen device, and password protects your app so that no one can uninstall it, except you.
All you need to do is:
Set a trusted SIM card within the app.
Provide a trusted number in case of emergency
In the case of lost or stolen, you can log into your ESET account at my.eset.com and track your devices through an easy-to-use web interface and ensure that all your data remains protected from unauthorized users.
As soon as you mark your device as 'Missing' on the online portal, the location of your stolen or lost device will be displayed on a real-time map so that you can easily trace it. You can even view a list of IP addresses that your lost device was connected to.
Bonus — 'Selfies' of Phone Thieves: Marked as Missing devices will automatically capture photographs with its back and front cameras, and then send them to the online portal, which helps you find the location of a missing device easier.
But, What if your stolen device is not connected to the Internet?
Here's How you can Protect Your Smartphone:
Like other apps, ESET Anti-Theft feature lets you send an SMS message command from a trusted number to remotely lock or erase your smartphone data immediately, as well as ringing it in case it has been lost somewhere nearby.
On the top of that, ESET Anti-Theft functionality provides a series of new features, like even if an unauthorized SIM card has been inserted in your stolen smartphone, you can send remote commands to it.
Even if someone tries a wrong PIN or pattern on your smartphone, or insert an unauthorized SIM, your device will be able to take preventive actions on its own in an effort to ensure that your data remains protected.
Device Monitoring and Application Audit:
android-security-app
These features are something that most of us ignore while searching for a good mobile security solution.
Today many apps, even legitimate, request for unnecessary app permissions. Some of your apps can make phone calls, track your location, read your browsing history, contacts, SMS, photos and calendar, and even share this data with third-party advertising companies without your knowledge.
And since I'm security conscious, I always make sure which app is requesting what permissions and for this I found ESET Mobile Security best fit for me.
ESET Mobile Security offers 'Application Audit' feature to help you know what permissions various apps installed on your smartphone or tablet have.
You can click on any app listed in the Application Audit interface, which will land you to your smartphone’s settings menu, from where you can easily restrict unnecessary app permissions or even uninstall it.
Besides this, the app offers you 'Device Monitoring' feature that will help you inform any necessary settings you haven't set correct that could compromise your security.
Anti-Phishing and SMS/MMS/Call Blocker
android-anti-phishing-app
Phishing emails, messages and even contacts are common these days. Hackers or malicious attackers can trick you handing over your sensitive accounts like banking, email or social media accounts access to them.
So, it has become important for us to keep an eye on every email and message that we receive every day, but it’s not as easy as it sounds.
This app resolves the above hurdle as well. ESET's Anti-Phishing feature offers an additional level of protection when you browse the web from your smartphone or tablet.
Though the app doesn't support all browsers currently, you can choose the one that is present on the list of supported browsers to navigate the web.
Besides all the above tools, ESET Mobile Security also offers text messages (SMS), and multimedia messages (MMS) and phone calls blocking capabilities to Android users.
So you can easily opt to simply block calls and messages from all unknown numbers, or more interestingly, all or specific known numbers — with options for both incoming and outgoing blocks.
android-antivirus-security-app
In short, I found ESET Mobile Security a package of security and privacy tools bundled into a single app.
The app is fast, provides a user-friendly interface, keeps you safe from malware, protects against phishing attacks, with numerous other tools to keep your smartphone safe even when it's out of your hands.
However, ESET Mobile Security app doesn't provide any Encrypted Cloud-based Backups, device encryption, which I will like to see in-built in the future.
Overall, ESET Mobile Security for Android is a solid choice for protecting your smartphone or tablet with its top-notch malware protection and huge array of anti-theft and privacy-protection features.
You can download and install app for FREE for a lifetime from the Google Play Store if you are seeking for basic protection capabilities.
However, those seeking for Advanced security and privacy protection on their smartphones should upgrade to a premium subscription, via in-app purchase.
GM Bot (Android Malware) Source Code Leaked Online
22.2.2016 Android
The source code of a recently discovered Android banking Trojan that has the capability to gain administrator access on your smartphone and completely erase your phone's storage has been LEAKED online.
The banking Trojan family is known by several names; Security researchers from FireEye dubbed it SlemBunk, Symantec dubbed it Bankosy, and last week when Heimdal Security uncovered it, they dubbed it MazarBot.
All the above wave of Android banking Trojans originated from a common threat family, dubbed GM Bot, which IBM has been tracking since 2014.
GM Bot emerged on the Russian cybercrime underground forums, sold for $500 / €450, but it appears someone who bought the code leaked it on a forum in December 2015, the IBM X-Force team reported.
What is GM Bot and Why Should You Worry about it?
The recent version of GM Bot (dubbed MazarBOT) has the capability to display phishing pages on the top of mobile banking applications in an effort to trick Android users into handing over their financial credentials to the fraudsters.
Besides this, the banking trojan is also capable of forwarding phone calls and intercepting SMS messages to help fraudsters bypass an additional layer of bank security mechanisms, and locking a device’s screen.
Cyber criminals could also use the malware to:
Spy on victims
Delete data from the infected device
Gain boot persistence to help survive device restart
Send and Read your SMS message
Make Calls to your contacts
Read the phone's state
Plague phone's control keys
Infect your Chrome browser
Change phone settings
Force the phone into sleep mode
Query the network status
Access the Internet
Wipe your device's storage (the most critical capabilities of the malware)
However, someone leaked the malware source code only to boost his/her reputation on an underground forum, according to the researchers.
GM Bot Android Malware Source Code for FREE
Yes, the source code for GM Bot and its control panel is now accessible to cybercriminals and fraudsters for FREE.
Here’s the Cherry on the Top:
Besides the source code, the leader also posted a tutorial and instructions for server-side installation, which means cybercriminals can create their own versions of the malware strain to conduct online banking frauds.
Though the archive file containing the source code and its control panel is password protected, the leader is offering the password only to active forum members who is approaching him.
"Those who received the password, in turn, passed it on to other, unintended users, so the actual distribution of the code went well beyond that discussion board’s member list," IBM cyber security evangelist Limor Kessem wrote in a blog post.
Online users had started sharing the password to the archive among their friends, and in no time, the GM Bot source code was all over the hacking underground forums.
GM Bot is one of the most dangerous banking trojan in the Android ecosystem and after its source code gets leaked, users are recommended to beware while banking online.
How to Protect Yourself?
As I previously mentioned, online users are advised to follow these steps in order to protect themselves against this kind of threat:
Never open attachments from unknown sources.
Never click on links in SMS or MMS messages sent to your phone.
Even if the email looks legit, go directly to the source website and verify any possible updates.
Go to Settings → Security → Turn OFF "Allow installation of apps from sources other than the Play Store" option.
Always keep an up-to-date Anti-virus app on your Android devices.
Avoid unknown and unsecured Wi-Fi hotspots and Keep your Wi-Fi turned OFF when not in use.
Source code of the Android GM Bot malware was leaked online
22.2.2016 Android
The experts at the IBM X-Force threat intelligence have discovered that the source code for Android malware GM Bot was leaked online.
Bad news for the Android community, the experts at IBM X-Force threat intelligence have discovered that the source code for Android malware GM Bot was leaked on an underground. The source code was leaked in December 2015, it include the bot component and the control panel.
It seems that one of GM Bot’s buyers decided to leak the code online to enhance credibility in the underground boards.
He leaked the code in an encrypted archive, then he indicated he would give the password only to active forum members who contacted him.
Of course, the code rapidly spread within the criminal ecosystem, it is now free and online is available a tutorial and the instructions for the server-side installation.
The availability online of the source code of a malware represents a crucial moment in the life cycle of malicious codes. Once the code is leaked online, cyber criminal organizations can work on it to create new variants that could be offered for sale or rent.
The original creator of the Android malware has sold the rights to distribute GM Bot v1 (aka MazarBot) to other cyber criminal organizations that is offering it for $500.
“According to X-Force threat intelligence, the code’s author moved on to working on a new version dubbed GM Bot v2.0, which is sold in financial fraud-themed underground boards.” states a blog post published by the X-Force threat intelligence.
GM Bot appeared in the wild in 2014, it was offered in the Russian underground as a powerful instrument for mobile phishing.
“This Android malware’s differentiating capability is its deployment of overlay screens on top of running banking applications, with the goal of tricking users into entering their access credentials into a fake window that will grab and forward them to a remote attacker.” continues the post.
The malware implements a number of features to target Android users, including intercepting SMS messages. The malware allows attackers to gain control of the targeted device, including the customization of fake screens.
In short, mobile banking Trojans such as GM Bot are a one-stop fraud shop for criminals:
They launch fake overlay windows that mimic bank applications to steal user credentials and payment card details.
They control the device’s SMS relay to eavesdrop, intercept and send out SMS messages.
They can forward phone calls to a remote attacker.
They have spyware features and can control the device via remote commands.
The experts at the IBM have analyzed only the control panel because many other organizations and security firms already produced a detailed analysis of malware.
The most interesting feature discovered by the experts in the GM Bot’s botnet administration panel is the possibility to create and deploy new injections to infected user devices.

Another interesting component of the Botnet is the “Search and Stats” section that allows operators to analyze their database that includes stolen information, credit card details, lists of apps installed on infected devices, bank accounts the victims and other info.
Let me suggest to give a look to the interesting analysis published by IBM that also includes the indicators of compromise.
This Android Malware Can Root Your Device And Erase Everything
15.2.2016 Android
A new Android malware has been making waves recently that have the capability to gain root access on your smartphone and completely erase your phone's storage.
Dubbed Mazar BOT, the serious malware program is loaded with so many hidden capabilities that security researchers are calling it a dangerous malware that can turn your smartphone into a zombie inside hacker's botnet.
Mazar BOT was discovered by Heimdal Security while the researchers at the firm were analyzing an SMS message sent to random mobile numbers and locations.
How Mazar BOT Works
Despite other Android malware that distributes itself by tricking users into installing an app from third-party app stores, Mazar spreads via a spam SMS or MMS messages that carry a link to a malicious APK (Android app file).
Once the user clicks the given link, he/she'll be ending up downloading the APK file on their Android devices, which when run, prompts the user to install a new application.
This new Android app has a generic name, MMS Messaging, that asks for admin level privileges. Most of the users end up giving the root access to the malicious app due to its common name.
What Makes Mazar BOT So Nasty
Once gaining root access on the victim's device, Mazar BOT can do variety of nasty stuff on your Android devices, like:
Gain boot persistence to help survive device restarts
Send and Read your SMS messages
Make Calls to your contacts
Read the phone's state
Plague phone's control keys
Infect your Chrome browser
Change phone settings
Force the phone into sleep mode
Query the network status
Access the Internet
Wipe your device's storage (the most critical capabilities of all)
Mazar BOT Browses Internet Anonymously Using TOR
Besides these tasks, Mazar BOT can also download a legitimate TOR (The Onion Router) Android app on your smartphone and install it too, even without your consent or permission.
Using TOR app, the malware would be able to surf the Internet anonymously via the Tor network.
Once the malware installs TOR on victim's phone, Mazar BOT sends a "Thank you" message to an Iranian phone number (9876543210), along with the device's location.
In some instances, Mazar BOT also installs an Android app called Polipo Proxy that establishes a proxy on the device, allowing the malware's author to spy on victim's Web traffic and carry out Man-in-the-Middle (MitM) attacks.
Who is Behind This Awful Malware?
Mazar BOT is believed to be distributed by a Russia-based group of cyber-criminals.
One clue to this assumption is: Mazar BOT cannot be installed on Android smartphones in Russia, as its source code includes instructions on how to stop the malware installation process on phone configured with the Russian language.
Another clue is: There is an unwritten law in Russia that says "if cyber criminals don't go after Russians, Russian authorities will not go after them." Moreover, there is no such indication yet that this Mazar BOT campaign has affected anyone in Russia.
Until now, Mazar BOT for Android has been advertised for sale on several Russian underground (Dark Web) forums, but this is the first time this creepy code has been abused in active attacks.
How to Protect Yourself from Mazar BOT
There are standard protection measures you need to follow to remain unaffected:
NEVER click on links in SMS or MMS messages sent to your phone.
Go to Settings → Security → Turn OFF "Allow installation of apps from sources other than the Play Store" option.
Always keep an up-to-date Anti-virus app on your Android devices.
Avoid unknown and unsecured Wi-Fi hotspots and Keep your Wi-Fi turned OFF when not in use.
Apple Could Offer iMessage App for Android
9.2.2016 Android
Although Apple has its own operating system for both desktop (Mac OS X) and iPhone (iOS), the com pany has always tried to port its in-house applications to other OS platforms.
Apple debuted on its rival mobile OS platform last year with the launch of Apple Music on Android. However, iTunes and Safari has already been made available for both Windows as well as Mac.
Now, the company will soon move more of its mobile applications to Android if comments made by Chief Executive Tim Cook at the recent company-wide event for Apple employees are to be believed.
iMessage App for Android Platform
Cook reportedly told his staff that sooner Apple may bring other apps and exclusive services to the Android Systems, and added that bringing Apple Music to Android in November was "a way of testing the waters for growing its services division through other platforms," reports 9to5Mac.
So, you could see iMessage, the company's encrypted messaging application, expanded to Android.
iMessage is one of the most famous Apple's apps that allows Apple users to send and receive messages, photos, and videos to their fellow Apple users as long as the device has a data connection.
How Apple Can Read End-to-End Encrypted iMessages
What many of us know is iMessage uses end-to-end encryption that even Apple or anyone else can not access or read your messages, but what we don’t know is backed up messages to Apple's iCloud service are vulnerable to federal warrants.
With iCloud Backup enabled, the copies of all your messages, photographs and every important data stored on your iPhone or iPad are encrypted on iCloud using a key controlled by Apple, and not you.
This would allow Apple and hence, anyone who breaks into your account, to read your messages and see your personal and confidential data.
List of Apple Apps you Might See on Android
Besides iMessages, the list of Apple apps that you could see expanded to Android may include iTunes, Music Memos, Apple Maps, and iCloud.
In September, the company released its first-ever Android application, known as Move to iOS, designed to help Android users transfer their content quickly and safely from an Android device to an iOS device.
Although it is yet unclear when Apple will make the move, if this happens anytime soon, Which one of your favorite Apple apps you want to see on your Android devices?
Let me know in the comments below.
Android1
Nasty Android Malware that Infected Millions Returns to Google Play Store
24.1.2017 thehackernews Android
HummingBad – an Android-based malware that infected over 10 million Android devices around the world last year and made its gang an estimated US$300,000 per month at its peak – has made a comeback.
Security researchers have discovered a new variant of the HummingBad malware hiding in more than 20 Android apps on Google Play Store.
The infected apps were already downloaded by over 12 Million unsuspecting users before the Google Security team removed them from the Play Store.
Dubbed HummingWhale by researchers at security firm Check Point, the new malware utilizes new, cutting-edge techniques that allow the nasty software to conduct Ad fraud better than ever before and generate revenue for its developers.
The Check Point researchers said the HummingWhale-infected apps had been published under the name of fake Chinese developers on the Play Store with common name structure, com.[name].camera, but with suspicious startup behaviors.
"It registered several events on boot, such as TIME_TICK, SCREEN_OFF and INSTALL_REFERRER which [were] dubious in that context," Check Point researchers said in a blog post published Monday.
HummingWhale Runs Malicious Apps in a Virtual Machine
The HummingWhale malware is tricky than HummingBad, as it uses a disguised Android application package (APK) file that acts as a dropper which downloads and runs further apps on the victim's smartphone.
If the victim notices and closes its process, the APK file then drops itself into a virtual machine in an effort to make it harder to detect.
The dropper makes use of an Android plugin created by the popular Chinese security vendor Qihoo 360 to upload malicious apps to the virtual machine, allowing HummingWhale to further install other apps without having to elevate permissions, and disguises its malicious activity to get onto Google Play.
"This .apk operates as a dropper, used to download and execute additional apps, similar to the tactics employed by previous versions of HummingBad," researchers said. "However, this dropper went much further. It uses an Android plugin called DroidPlugin, originally developed by Qihoo 360, to upload fraudulent apps on a virtual machine."
HummingWhale Runs Without having to Root the Android Device
Thanks to the virtual machine (VM), the HummingWhale malware no longer needs to root Android devices unlike HummingBad and can install any number of malicious or fraudulent apps on the victim's devices without overloading their smartphones.
Once the victim gets infected, the command and control (C&C) server send fake ads and malicious apps to the user, which runs in a VM, generating a fake referrer ID used to spoof unique users for ad fraud purposes and generate revenue.
Alike the original HummingBad, the purpose of HummingWhale is to make lots of money through ad fraud and fake app installations.
Besides all these malicious capabilities, the HummingWhale malware also tries to raise its reputation on Google Play Store using fraudulent ratings and comments, the tactic similar to the one utilized by the Gooligan malware.
Millions Download HummingBad Variant via Google Play
24.1.2017 Securityweek Android
A newly discovered variant of the HummingBad Android malware has been downloaded millions of times after infecting 20 applications in Google Play, Check Point security researchers warn.
Discovered in early 2016, HummingBad already proved one of the most prolific Android malware families out there, accounting for over 72% of attacks in the first half of the year.
In a report published last July, Check Point suggested that around 10 million Android devices might have been compromised by HummingBad and that its rootkit capabilities allowed attackers take full control over the infected devices. The researchers also said that Yingmob, the group behind the malware, might have compromised over 85 million devices.
Dubbed HummingWhale, the newly discovered variant is said to include cutting edge techniques that allow it to perform its nefarious activities (ad fraud) better than before.
While HummingBad was spreading mainly through third-party app stores, the HummingWhale variant made its way into Google Play and infected 20 apps, all of which have been already removed by Google. The main giveaway feature, the researchers say was a 1.3MB encrypted file called ‘assets/group.png’ also found in some later HummingBad samples that were masquerading as an app called “file-explorer.”
Offending apps were found to register several events on boot, such as TIME_TICK, SCREEN_OFF and INSTALL_REFERRER, as well as to feature a common name structure – com.XXXXXXX.camera (e.g. com.bird.sky.whale.camera, com.color.rainbow.camera, com.fishing.when.orangecamera). Apps outside of the camera family were also identified.
The HummingWhale samples were also observed registering to certain events and packing some identical strings in their code and certificates when compared to the previous HummingBad variants. HummingWhale was also observed being promoted by several new HummingBad samples, Check Point says.
The new malware variant, researchers say, is heavily packed and has its main payload in the ‘group.png’ file, which is actually an .apk that operates as a dropper. This executable file can download additional apps, a functionality observed in previous versions of HummingBad as well. The new dropper, however, uses the DroidPlugin Android plugin to upload fraudulent apps on a virtual machine.
“First, the Command and Control server (C&C) provides fake ads and apps to the installed malware, which presents them to the user. Once the user tries to close the ad, the app, which was already downloaded by the malware, is uploaded to the virtual machine and run as if it is a real device. This action generates the fake referrer id, which the malware uses to generate revenues for the perpetrators,” the security researchers explain.
By using this method, the cybercriminals ensure that the malware installs apps without gaining elevated permissions first, and that the malicious activity is disguised, thus allowing the malware to infiltrate Google Play. What’s more, the embedded rootkit in the previous HummingBad variant is no longer needed, since the same results are achieved without it. On top of that, the malware can now install an infinite number of fraudulent apps without overloading the device.
“HummingWhale also conducted further malicious activities, like displaying illegitimate ads on a device, and hiding the original app after installation, a trait which was noticed by several users. As can be seen in the image below, HummingWhale also tries to raise its reputation in Google Play using fraudulent ratings and comments, similar to the Gooligan and CallJam malware before it,” the security researchers say.
Source Code for BankBot Android Trojan Leaks Online
24.1.2017 Securityweek Android
The source code of Android banking Trojan BankBot, along with instructions on how to use it, recently emerged on a hacker forum, Doctor Web security researchers have discovered.
The source code was published about a month ago, but Android malware based on the code was spotted last week. Once the malware gets admin privileges on an infected device, it removes its shortcut from the homescreen to hide itself and hinder removal. Next, it connects to a command and control (C&C) server to retrieve instructions.
The BankBot Trojan is distributed masquerading as benign applications. On the infected devices, it can request administrative privileges to display phishing pages to steal login credentials, intercept and send SMS messages, send USSD requests, retrieve contacts list, track the device, make calls, and receive an executable file containing a list of banking apps to attack.
Malicious programs that provide such capabilities are usually being sold as commercial products on underground forums. However, with the source code of this application leaked online, chances are that the number of attacks involving Android banking Trojans will register a significant increase soon, Dr.Web suggests.
The malware can track the launch of banking applications on the user’s device and overlay phishing dialogues to trick users into revealing their login information. The malware is targeting over three dozen such financial applications, including banking and payment system software.
The security researchers have discovered that the malware can also steal bank card information. For that, the Trojan tracks the launch of multiple popular applications on the device, including Facebook, Viber, Youtube, WhatsApp, Uber, Snapchat, WeChat, imo, Instagram, Twitter, and Play Store, to display a phishing dialog on top of them, tricking users into believing it is a Google Play purchase page.
“Information on found matches is sent to the C&C server. The Trojan receives a list of files to be monitored from execution. After one of them is launched, Android.BankBot.149.origin displays WebView on top of the attacked application with a fraudulent authentication form to access the user account. Then the entered information is sent to the server,” Dr.Web says.
BankBot was also designed to steal SMS messages. When an SMS arrives, the malware turns off sounds and vibrations and sends the content of the message to the cybercriminals, while also attempting to delete the original entry from the list of incoming SMS. This would result in users missing bank notifications about unplanned transactions that cybercriminals are performing.
Data stolen from the device, which includes information on the anti-virus applications installed on the infected device, is uploaded to the C&C server, making it accessible to the cybercriminals. What’s more, the security researchers say, an administration panel provides operators with control over the malicious app.
“In general, the possibilities of this Trojan are quite standard for modern Android bankers. However, as cybercriminals created it with publicly available information, one can anticipate that many Trojans similar to it will appear,” Doctor Web’s security researchers conclude.
“Dumping malware code is great way to allow others to contribute to the code and modify it to help evade detection. This tactic was very successful for distributing Zeus. When you have a larger group modifying the code, the number of variants increases rapidly, making it very hard for security products that rely on pattern matching to detect it,” Lamar Bailey, Senior Director of Security R&D for Tripwire, told SecurityWeek in an emailed comment.
Do web injections exist for Android?
23.1.2017 Kaspersky Android
Web injection attacks
There’s an entire class of attacks that targets browsers – so-called Man-in-the-Browser (MITB) attacks. These attacks can be implemented using various means, including malicious DLLs, rogue extensions, or more complicated malicious code injected into pages in the browser by spoofing proxy servers or other ways. The purpose of an MITB attack may vary from relatively innocuous ad spoofing on social networks or popular websites to stealing money from user accounts – the latter is what happened in the Lurk case.
A malicious app masquerades as a Kaspersky Lab product in an MITB attack
Web injection is used in most cases when an MITB-class attack targets online banking. This type of web injection attack involves malicious code being injected into an online banking service webpage to intercept the one-time SMS message, harvest information about the user, spoof banking details, etc. For example, our Brazilian colleagues have long reported about barcode spoofing attacks performed when users print out Boletos – popular banking documents issued by banks and all kind of businesses in Brazil.
Meanwhile, the prevalence of MITB attacks in Russia is decreasing – cybercriminals are opting for other methods and attack vectors to target banking clients. For the average cybercriminal, it is much easier to use readily available tools than develop and implement web injection tools.
Despite this, we’re often asked if there are any web injection attacks for Android devices. This is our attempt to investigate and give as full an answer as possible.
Web injection on Android
Despite the term ‘inject’ being used in connection with mobile banking Trojans (and sometimes used by cybercriminals to refer to their data-stealing technologies), Android malware is a whole different world. In order to achieve the same goals pursued by web injection tools on computers, the creators of mobile Trojans use two completely different technologies: overlaying other apps with a phishing window, and redirecting the user from a banking web page to a specially crafted phishing page.
Overlaying apps with phishing windows
This is the most popular technology with cybercriminals and is used in practically all banking Trojans. 2013 was when we first encountered a piece of malware overlaying other apps with its phishing window – that was Trojan-Banker.AndroidOS.Svpeng.
Today’s mobile banking Trojans most often overlay the Google Play Store app with their phishing window – this is done in order to steal the user’s bank card details.
The Marcher malware
Besides this, Trojans often overlay various social media and instant messaging apps and steal the passwords to them.
Do web injections exist for Android?
However, mobile banking Trojans typically target financial applications, mostly banking apps.
Three methods of MITB attacks for mobile OS can be singled out:
1. A special Trojan window, crafted beforehand by cybercriminals, is used to overlay another app’s window. This method was used, for example, by the Acecard family of mobile banking Trojans.
Acecard phishing windows
2. Apps are overlaid with a phishing web page located on a malicious server. This way, the cybercriminals can modify its contents any time they need to. This method is used by the Marcher family of banking Trojans.
Marcher phishing page
3. A template page is downloaded from a malicious server, to which the icon and the name of the attacked application is added. This is how one of the Trojan-Banker.AndroidOS.Faketoken modifications manages to attack over 2,000 financial apps.
FakeToken phishing page
It should be noted that starting from Android 6, for the above attack method to work, the FakeToken Trojan has to request the privilege of displaying its window on top of other app windows. It’s not alone though: as new versions of Android are gaining popularity, a growing number of mobile banking Trojans are beginning to request such privileges.
Redirecting the user from the bank’s page to a phishing page
We were only able to identify the use of this technology in the Trojan-Banker.AndroidOS.Marcher family. The earliest versions of the Trojan that redirected the user to a phishing page are dated late April 2016, and the latest are from the first half of November 2016.
Redirecting the user from a bank’s webpage to a phishing page works as follows. The Trojan subscribes to modify browser bookmarks, which includes changes in the current open page. This way the Trojan knows which webpage is currently open, and if it happens to be one of the targeted pages, the Trojan opens the corresponding phishing page in the same browser and redirects the user there. We were able to find over a hundred web pages belonging to financial organizations that were targeted by the Marcher family of Trojans.
However, two points need to be raised:
All new modifications of the Marcher Trojan that we were able to detect no longer use this technology.
Those modifications that used this technology also used a method of overlaying other apps with their phishing window.
Why then was the method of redirecting the user to a phishing page used by only one family of mobile banking Trojans, and why is this technology no longer used in newer modifications of the family? There are several reasons:
In Android 6 and later versions, this technology no longer works, meaning the number of potential victims is decreasing every day. For example, around 30% of those using Kaspersky Lab’s mobile security solutions now use Android 6 or a later version;
The technology only worked on a limited number of mobile browsers;
The user can easily spot that they are being redirected to a phishing site and they may also notice that the URL of the webpage has changed.
Attacks launched using root privileges
With superuser privileges, Trojans can perform any attack, including real malicious injections into browsers. Although we were unable to find a single case of this happening, the following should be noted:
Some modules of Backdoor.AndroidOS.Triada can substitute websites in certain browsers, using superuser privileges. All the attacks we found were launched with the purpose of making some money from advertising only, and did not result in the theft of banking information.
The banking Trojan Trojan-Banker.AndroidOS.Tordow, using superuser privileges, can steal passwords saved in browsers, which may include passwords to financial websites.
Conclusions
We can state that, despite all the available technical capabilities, cybercriminals that target banks do not make use of malicious web injections in mobile browsers or injections in mobile apps. Sometimes they use these technologies to spoof adverts, but even then that requires highly sophisticated malicious software.
So why do cybercriminals ignore the available opportunities? Most probably it is because of the diversity of mobile browsers and apps. Malware writers would have to adapt their creations to a long list of programs, which is rather costly, while simpler and more versatile attacks involving phishing windows do not require so much effort to target a larger number of users.
Nonetheless, the Triada and Tordow examples suggest that similar attacks may well take place in the future as malware creators gain more expertise.
Source Code for another Android Banking Malware Leaked
23.1.2017 thehackernews Android
Another bad news for Android users — Source code for another Android banking malware has been leaked online via an underground hacking forum.
This newly discovered banking Trojan is designed to steal money from bank accounts of Android devices' owners by gaining administrator privileges on their smartphones.
Apparently, it will attract the attention of many cyber criminals who can recompile the source code or can also use it to develop more customized and advanced variants of Android banking Trojans.
According to security researchers from Russian antivirus maker Dr. Web, the malware's source code was posted online, along with the information on how to use it, meaning Android devices are most likely to receive an increasing number of cyber attacks in upcoming days.
Leaked: Trojan Source Code + 'How to Use' Instructions
Dr. Web researchers said they have already discovered one banking trojan in the wild developed using this leaked source code, adding that the Trojan is distributed as popular apps either directly injected in APKs available online or in third-party app stores.
Dubbed BankBot, the trojan has the ability to get administrator privileges on infected devices. Once it gets full privileges, the malware trojan removes the app's icon from the phone's home screen in order to trick victims into believing it was removed.
However, the BankBot trojan remains active in the background, waiting for commands from attacker's command and control (C&C) server. It found targeting only users of Russian banks.
Also Read: GM Bot (Android Malware) Source Code Leaked Online
BankBot has the ability to perform a broad range of tasks, including send and intercept SMS messages, make calls, track devices, steal contacts, show phishing dialogs, and steal sensitive information, like banking and credit card details.
"Like many other Android bankers, [BankBot] steals confidential user information by tracking the launch of online banking apps and payment system software. One sample examined by Doctor Web's security researchers controls over three dozen such programs," the researchers explains.
"Once Android.BankBot.149.origin detects that any of the aforementioned applications have been launched, it loads the relevant phishing input form to access user bank account login and password information and displays it on top of the attacked application."
Why Should You Worry about BankBot?
The malware hides itself until the victim opens any mobile banking or social media app. Once the victim opens one such app, BankBot launches a phishing login overlays, tricking victims to re-authenticate or re-enter their payment card details.
The collected data is then sent back to online servers, where the attackers can access the stolen data.
BankBot can phish credentials for apps including Facebook, WhatsApp, Instagram, Twitter, Youtube, Snapchat, Viber, WeChat, imo, Uber, and the Google Play Store.
Besides this, the BankBot trojan can also intercept text messages, send them to the attackers, and then delete them from the victim's smartphone, which means bank notifications never reach the users.
How to Protect Yourself against such Attacks?
Now, this is just one piece of malware developed using the publicly available source code and discovered by researchers. There are chances that more such malware are out there targeting Android devices but not yet caught.
To prevent yourself against such attacks, as I previously recommended, you are advised to:
Always be super-careful when downloading APKs from third-party app stores. Go to Settings → Security and then Turn OFF "Allow installation of apps from sources other than the Play Store."
Never open attachments from unknown or suspicious sources.
Never click on links in SMS or MMS sent to your mobile phone. Even if the email looks legit, go directly to the website of origin and verify any possible updates.
Always keep your Anti-virus app up-to-date.
Keep your Wi-Fi turned OFF when not in use and Avoid unknown and unsecured Wi-Fi hotspots.
Analyzing a variant of the GM Bot Android malware
7.1.2017 securityaffairs Android
My friends at CyberBlog decided to analyze the GM Bot Android Malware as exercise aiming to receive feedback sand suggestions from the security community.
The sample explored is confirmed as a variant of the GM Bot Android malware – who’s source was released publicly in early 2016. The code appears to have been forked by a second author and has additions that target the Danske Bank MobilePay application and the popular Danish Nem ID two factor authentication (2FA) system.
This article shows the process of walking through Static and Dynamic analysis to unlock the packed source code for the malware.
We see how even with basic static analysis a full picture of the intent of the malware can be readily assembled, and with a little debugging we can quickly get to readable source code.
Background
As part of my journey into Cyber Security I thought it would be interesting to see how modern mobile malware operates. I chose the following sample at random based on an article here.
File Details
SHA256: 44ed4bbd5cdc13c28992c16e99a7dc58f5f95463e889dd494a433549754f7863
MD5: da88bdcb3d53d3ce7ab9f81d15be8497
A quick google search for these hashes will lead you to the file used if you would also like to explore this sample.
The article above demonstrates that the analyst has gone from sample to source code, but it is not clear how this is achieved. There are references to suggest that the code has been packed, but again no information on how it was unpacked for analysis.
This post will break down the process I used to analyse this sample, hopefully with enough detail to provide some tips and guidance for others wishing to attempt similar. The process I followed can be logically broken into the following stages:

Analysis Process
Public Analysis – What can we find out using existing public sources of information? What analysis has already been performed (automated or manual)?
Static Analysis – What can we determine from the sample without actually running it in an emulated environment?
Packer Debugging – Assuming the sample is packed (to frustrate analysis), how do we debug the unpacker to understand what is being loaded /run?
DEX Extraction and De-compilation – Once we have mapped out the function of the unpacker, how do we then recover the main code for the malware and reverse it?
Functional & Dynamic Analysis – once we have the extracted and reversed code, what do we see and how does this correlate with behavior in a safe emulated environment
Stage 1 – Public Analysis
First off let’s see what we can find about this in the public domain. Searching for the file hashes on Virus Total, where we see approximately 50% of AV products have identified it as malicious:

VirusTotal Results
However, we also note that all classify it heuristically as a generic strain of malware – either a Trojan, Dropper, Fake Installer etc. Nothing to suggest it is in fact GM Bot Android, or any specific type of malware. Other than this we don’t see much from google with either the SHA256, or MD5 hashes.
The original Security Intelligence article references IBM X-Force research, so this is the next stop – but again nothing immediately obvious with regards to this sample could be located.
A wider search of the internet reveals some history of GM bot, originally built and sold by Ganga Man on dark web forums. Following a dispute the source code for both client APK and C2 server were released publicly. A copy is hosted here on Github and will provide useful for cross referencing with this sample later in the analysis.
https://github.com/gbrindisi/malware/tree/master/android/gmbot
Stage 2 – Static Analysis
First up we are going to unpack the APK file using APK tool. This will unzip the contents, as well as providing a disassembly of the DEX code into Smali:
apktool d da88bdcb3d53d3ce7ab9f81d15be8497.apk
The results of this can be seen below and the tool has also provided a human readable version of the AndroidManifest.xml file.

Extracted APK files
First stop is to take a look at the Android Manifest file, that should provide an overview of the components of the application and permissions requested.
Manifest Analysis – AndroidManifest.xml
Android Manifest
Initial analysis shows a broad range of permissions that indicate malicious behavior including permissions to:
control all SMS messages (send, receive, read, write, delete)
list running applications
read the phone’s state, contacts, SD card data
request to be a device administrator enabling remote wiping of the device with no warning to the user
A summarized view of referenced class files for the main application, activities (15) and services (2) can be seen below:

Classes Declared in Manifest -Application, Activities and Services
In addition, we see 4 further classes mapped as Broadcast Receivers which will process event messages (Android system Intents) as shown below:

Broadcast Receiver Classes Declared in Manifest
From this we can see the application is capable of:
Executing code when the phone is powered on (starting the application automatically)
Receive notification when Device Admin is granted, requested or a request to disable admin is received (and hence interfere, or nag the user to enable it)
Receive notification of a new inbound SMS – with high priority flag to ensure the code can intercept it first and potentially stop any further alerts (can be used to steal 2FA tokens)
Before proceeding with any reverse engineering of the code, the next step is to explore the other files in the APK for clues.
Files of interest
The following files were noted as of interest:
File: assets/fytluah.dat
A binary file with no immediately obvious format. Possible code to be unencrypted / unpacked at run time?
File: res/values/strings.xml
English language strings for the application, as shown below:

File: res/values/strings.xml (English Language Resource File)
The strings clearly indicate that this malware is targeting capturing victims credit card information. It is interesting to note that:
The resource keys here are all in English, suggesting the original developer may be English speaking
There are specific strings that are in Danish, despite this resource file being intended for English language
In addition to English language strings we also see several other targeted countries:
Other Resource Files
File: res/values.xml
This file contains a list of country codes and specifically a group that are “non vbv”. This is understood to mean that they do not use the “Verified by Visa” process which is used to enforce additional verification checks during online purchases. It is likely that the attackers would seek to obtain additional VBV credentials via the malware in order to allow online purchases with the card details (or avoid these countries).

Verified By Visa Targeted Countries
Directory: res/drawable
Images and icons/logos including:
Sample photo of Danish “Nem Id” – https://en.wikipedia.org/wiki/NemID
Icon for Danske Bank mobile pay
Mastercard secure code
Icon for verified by visa
Google play
Flash icon (main application icon)
Whatsapp
Additionally there are png images prefixed “overlay_”, indicating a possible use in fraudulent overlay activity.
Decompiling to Java source code
Next we attempt to reverse engineer the DEX file back to original Java source code. For this we use dex2jar as follows to translate the DEX file (in the APK) into a Java Class file archive:
Dex2jar da88bdcb3d53d3ce7ab9f81d15be8497.apk
The resulting jar file can then be disassembled using JD-GUI as follows:
java -jar ../../jd-gui-1.4.0.jar da88bdcb3d53d3ce7ab9f81d15be8497_dex2jar.jar
The resulting java classes that we see in JD-GUI show that there are only 4 java classes contained in the application. This is in direct contrast to the 16 different classes we saw declared in the application manifest. This confirms that there must be additional code that is loaded dynamically at run time – it is most likely that these four classes are in fact an unpacker.

Unpacker Classes
Examining the code we see that it is heavily obfuscated and has been crafted in a way to prevent clean decompiling of the code. This aside, we can start to get an understanding of the function of these four classes by examining the system classes that are imported (and therefore used) when the application is first executed.
After exporting the java source from JD-GUI and unzipping to a new folder, we can extract the imported classes from these files:
find . -type f -exec grep "^import" {} \; | sort -u
The classes we find are shown below :
Class Imported Class
com.igcfse.enscbo.a com.igcfse.enscbo.b
com.igcfse.enscbo.a java.io.RandomAccessFile
com.igcfse.enscbo.a java.lang.reflect.Constructor
com.igcfse.enscbo.b android.app.Application
com.igcfse.enscbo.b android.content.Context
com.igcfse.enscbo.b com.igcfse.enscbo.a
com.igcfse.enscbo.b java.io.File
com.igcfse.enscbo.b java.lang.reflect.Field
com.igcfse.enscbo.b java.lang.reflect.Method
com.igcfse.enscbo.c android.content.Context
com.igcfse.enscbo.c com.igcfse.enscbo.b
com.igcfse.enscbo.c java.io.FileDescriptor
com.igcfse.enscbo.c java.io.IOException
com.igcfse.enscbo.c java.lang.reflect.Constructor
com.igcfse.enscbo.c java.util.Random
com.igcfse.enscbo.wieroel android.app.Application
com.igcfse.enscbo.wieroel android.content.Context
com.igcfse.enscbo.wieroel com.igcfse.enscbo.b
Essentially we have a very small set of libraries that are being imported and used. These consist of functionality for:
General Android application and context classes (expected and needed for all android apps)
File related classes (in red) – for access, reading and writing local files
Java reflection classes (in green) – for creating new classes and instances and invoking methods dynamically
This confirms the hypothesis that we are most likely dealing with an unpacker that unpacks it’s executable code from a local file resource (as opposed to pulling dynamically from network for example).
Stage 3 – Unpacker Debugging
As the Java code cannot be readily decompiled (due to protections injected by the malware author) we will instead debug the executable against the Smali assembly code. Smali is a disassembly of the DEX code used by the Dalvik Virtual Machine.
The Smali/Baksmali plugin for Android Studio is required, and then the output from Apktool is imported as a new project. We next set the breakpoints as required across the three classes that we are interested in (a,b,c):

Setting Breakpoints in Android Studio
We will initially debug the calls to interesting reflection methods identified, which are as below:
a.smali (a line that creates a new instance of a class based on a java.lang.reflect.Constructor instance)
![]()
b.smali (a line that invokes a method on an object via reflection)
![]()
c.smali (a line similar to that described above for a.smali)
![]()
Now we install the application to the emulator (via ADB to ensure it doesn’t start automatically as in some emulators).
To enable the debugger to connect to the application, we perform the following prior to starting the application:
Enable developer options by repeatedly clicking the build number in Settings > About device
In developer options, choose “Select debug app” and choose the malicious application – “Adobe Flash”
In developer options, enable the “wait for debugger”
Selecting Debug Application
Now start the application from the launcher, you will be prompted to attach the debugger:

Attaching Debugger
In Android Studio, attach the debugger using the icon. Choose the malicious application process. The debugger then stops at our first breakpoint as shown below:

First Breakpoint Reached
Note you should now set some variables to watch – as per above I have set v0 through v10 and p1 through p3. Our first breakpoint is hit and we see we are about to execute a method by reflection. Noting that we have not yet called newInstance() we can assume this is calling existing (loaded) classes – either one of the four loaded by the application, or some other Android framework classes.
Next we forces step into the method to see which method it is calling (the smali debugger seems a little buggy and we can’t at this point see the parameters being passed).

Stepping into Reflected Method Call
An initial call to get the current context object -presumably to start retrieving local resources from the APK. We now allow the debugger to continue, and repeat this exercise several times to build up a flow of the reflected method calls:
Context android.context.ContextWrapper.getBaseContext()
//expected 2 arguments, got 1 – error in malware code, or to throw off debugging?
//Several more of these not shown
IllegalArgumentException java.lang.IllegalArgumentException(String s)
void Java.lang.reflect.setAccessible(boolean flag)
File android.app.getDataDir()
// returns /data/user/0/com.kzcaxog.mgmxluwswb/app_ydtjq
java.io.File.getAbsolutePath()
ContextImpl android.app.getImpl(Context context)
//filename is fytluah.dat
InputStream android.content.res.AssetManager.open(String fileName)
Pausing here, we can see the code is attempting to load the file that we had previously flagged as of interest in the static analysis section. Continuing we see the file is read, presumably decrypted and then written out again as a jar file:
int android.content.res.AssetManager.read(byte[] b)
//className = java.io.File
Class java.lang.Class.forName(String className)
//args = String “/data/user/0/com.kzcaxog.mgmxluwswb/app_ydtjq/gpyjzmose.jar”
T Java.lang.reflect.Constructor.newInstance(Object.. args)
void java.io.FileOutputStream.write(byte[] b) #25
void java.io.FileOutputStream.close()
Finally a DexClassLoader is invoked to load the additional code into the system:
ClassLoader java.lang.Class.getClassLoader()
//className is dalvik.system.DexClassLoader
java.lang.Class.forName(String className)
Looking at the API for the DexClassLoader we can see that it takes two arguments – the location of the file to load, and a writeable area that it will use to re-write an optimised version of the code for the specific machine architecture – eg the Android Run Time (ART). Further information on this can be seen in the Android API documentation:
https://developer.android.com/reference/dalvik/system/DexClassLoader.html
Stage 4 – DEX Extraction and Decompiling
We can see the exact location of the jar file in the debugger below, and the next step is to recover this file via ADB command line.

Debugging the Call to the DEXClassLoader
After execution of the classloader, connecting via ADB shell we see the two files, the original and the DEX optimised code:

Extracting the Payload Code
We copy these files to /sdcard/Download (+chmod) and then pull the .jar file to local machine for further analysis with adb pull.

Examining the files
Extracting the jar file we find the classes.dex file.
Repeating the steps to convert this to a jar file using dex2jar and decompiling with JD-GUI, we confirm we now have the full (un-obfuscated) source code for this malware sample.

Decompiled Source Code
Stage 5 – Dynamic and Functional Analysis
First Installation
Upon initial analysis we can see the codebase bear remarkable similarities with the leaked source identified in the static analysis. However there are significant differences, and the code has been customised to specifically target the Danske Bank MobilePay application.
As the code is basically un-obfuscated, I’ll now briefly walk through the key functionality of this malware, starting from first installation.

First Installation Process Overview
Upon first installation and execution the application will perform two primary functions. It will initially harvest a range of the users data, including phone contacts, all SMS messages and other key data and send this to the C&C server. The C&C server then returns a unique installation identifier that is then used for all future communication to uniquely identify the compromised device.
Secondly the malware will then nag the user to accept the software as a device administrator. If the user declines the request is re-triggered, making it very difficult for most users to escape this screen without accepting. With this permission in place, the malware achieves two objectives:
The application cannot be un-installed by the user easily, without de-activating the device administrator. Attempting to do this will trigger the launching of overlays that prevent removing the device admin
At some point in the future, once further data has been stolen from the phone, the C2 server can issue a command to wipe the device, removing evidence of the infection and restoring the device to a factory state
Ongoing Operations – including after each reboot
Command and Control Process Flows
The malware maintains a regular heartbeat to the C2 server, which provides a mechanism for the attacker to issue specific commands to the device. Each hearbeat contains the installation ID and the current screen status. It is hypothesised that the attacker would ideally choose to execute malicious activities when the screen was off, and the user was not watching the phone.
Firstly we see the ability to “lock” and “unlock” the phone. This simulates an Android software update screen, and effectively hides any other activity that is occurring behind the screen overlay (such as sending, receiving or deleting SMS messages). Additionally this could be used to disable the user, and prevent them from using the phone whilst their accounts or cards are being compromised in real time.
Next we see another function that is intended to intercept and forward SMS messages to the C2 server, and specifically trying to remove evidence that they ever existed by deleting them. This is used to steal 2FA credentials.
Next from a C2 server perspective we see two “reset” commands. The first, a “soft” reset, is used to reset the internal flag to re-attempt stealing Nem ID credentials. The second is the “hard” reset that performs and immediate wipe of the device data.
Finally, we see the ability to send an arbitrary SMS message to a mobile defined by the attacker and a function to launch a customised push notification to another application on the device. It was not clear what this could be used for.
SMS Remote Control
SMS Remote Control – “Admining Mode”
By listening for incoming SMS messages the malware could also trigger a fake Android update screen that would then harvest, forward and attempt to delete messages as they arrived on the phone. This mode could be enabled and disabled by customised SMS command messages delivered to the phone via SMS.
Automating Data Theft
Decompiled Code Showing Targeted Applications
As per the original article and many of the indicators from the static analysis, the primary purpose of the application is to steal data by performing overlays on top of legitimate applications. The malware targets three specific classes of applications:
Danske Bank’s MobilePay application, with specific intent to steal Nem ID credentials
Applications that trigger an attempt to steal credit card details via a custom overlay
Applications that trigger an attempt to steal the users mobile phone number (possibly for triggering the “admining” mode described above)
Danske Bank MobilePay
Danske Bank MobilePay Overlay Process
Upon launching the MobilePay application the overlay attempts to steal the users CPR number (unique social security type id), mobile number and Nem pass code. It then asks the user to take a photo of their Nem ID passbook, containing one time use codes which can be used by the attacker to then log into MobilePay (and other Danish systems) and issue payments.
Stealing Credit Card Details
Credit Card Overlay Process
Upon launching one of the targeted applications, a credit card overlay is displayed with a configurable icon depending on the application launched. After basic card details are collected, the application then attempts to recover the Verified by Visa password for the user. These details are then forwarded to the C2 server.
Stealing Phone Numbers
Phone Number Overlay Process
Finally we see the functionality that is targeted to capture the user’s phone number, presumably to enable further abuse of the victims account via abuse of text message 2FA.
Summary
The sample appears to be a specifically customised variant that is being used in a campaign to target the Danske Bank MobilePay application. We see evidence that it is probably not the original GM Bot authors work – the coding style compared with the public source code is different, and the mix of languages in the resource files implies the sample has been adapted in a “quick and dirty” fashion to achieve the objectives.
This is a good example of how once released, complex code can be quickly and easily forked by less skilled authors and a pattern we also see today with the release of the Mirai botnet code. Quickly we see a spread of variants of the codebase that become harder to trace and detect and importantly attribute to any individual or group.
As ever, the best advice to prevent becoming a victim of such malware is to ensure that your phone is not configured to install 3rd party applications, and always review requests for permissions carefully – eg, are they aligned with the expected purpose of the application?
Open Questions
Due to time constraints there are a few further areas I would have liked to explore. I may pick these up in a subsequent post, but for the record they are:
The unpacked code contains included super user functionality from Chainfire’s SuperSu application. It’s not clear how or where this is used, no apparent attempt at rooting the device was seen in the unpacked code.
The debugger failed to return from the call to unpack the payload code. It is not clear if any further reflected actions were performed beyond this.
Given key indicators in the codebase, is it possible to search / locate other similar samples, or perhaps identify further C2 infrastructure
Any constructive feedback or comments most welcome.
About the author, the owner of the CyberBlog
I am an experienced IT consultant with a broad range of experience across different disciplines from development to large-scale Project Management. I have a passion for all things Cyber related but do not currently work in a Cyber related industry or role. I welcome and encourage all feedback!
A fake Super Mario Run for Android is serving the Marcher Banking Trojan
6.1.2017 securityaffairs Android
Zscaler experts have found in the wild a fake version of the Super Mario Run Android App that could install the Android Marcher banking trojan.
Bad news for mobile gamers, security experts at Zscaler have spotted a strain of the Android Marcher Trojan masqueraded as the recently released Super Mario Run mobile game for Apple’s iOS.
Marcher is a sophisticated banking trojan that was used by cyber criminals to steal financial data from the victims.
“Marcher is a sophisticated banking malware strain that targets a wide variety of banking and financial apps and credit cards by presenting fake overlay pages. Once the user’s mobile device has been infected, the malware waits for victims to open one of its targeted apps and then presents the fake overlay page asking for banking details.” states the analysis published by Zscaler.
Super Mario Run mobile game for iOS device is one of the most interesting projects of the Nintendo, the company developed for Apple devices the notorious game. Anyway, Super Mario Run is still not available for Android, and crooks are taking advantage of this to spread their malicious variant.
The malicious code found by Zscaler installs the Marcher Trojan instead a legitimate version of Super Mario Run for Android.
“In this new strain, the Marcher malware is disguised as the Super Mario Run app for Android. Knowing that Android users are eagerly awaiting this game, the malware will attempt to present a fake web page promoting its release.” continues the blog post published by Zscaler.
The experts also shared the following details related to the threat:
Name : Super Mario Run
Package Name : uiq.pizfbwzbvxmtkmtbhnijdsrhdixqwd
MD5 : d332560f1fc3e6dc58d94d6fa0dab748
Detections : 12/55(at time of analysis)
When victims try to install the app it asks for multiple permissions including administrative rights.

The current Marcher version targets account management apps and major banks.
The researchers explained that also this Marcher variant presents fake credit card pages when the victims open the Google Play store. The trojan locks out Google Play until the victims supply the credit card information.
Researchers suspect the malware is still under development, they observed the banking overlay pages served by the C&C were not functioning properly at the time of the analysis.
“In the current variant, we have observed a new obfuscation technique, in which all important string characters are delimited with ‘<<zB5>>‘ as shown below.” continues the analysis.
Crooks always try to take advantage of gamers’ euphoria that coincides with the presentation of new games.
The same has happened last year when the Pokemon GO application was presented. Experts from ProofPoint spotted in the wild a backdoored version of the popular Pokemon GO Android App that could allow attackers to gain control over victims’ devices.
Switcher: Android joins the ‘attack-the-router’ club
1.1.2017 Kaspersky Android
Recently, in our never-ending quest to protect the world from malware, we found a misbehaving Android trojan. Although malware targeting the Android OS stopped being a novelty quite some time ago, this trojan is quite unique. Instead of attacking a user, it attacks the Wi-Fi network the user is connected to, or, to be precise, the wireless router that serves the network. The trojan, dubbed Trojan.AndroidOS.Switcher, performs a brute-force password guessing attack on the router’s admin web interface. If the attack succeeds, the malware changes the addresses of the DNS servers in the router’s settings, thereby rerouting all DNS queries from devices in the attacked Wi-Fi network to the servers of the cybercriminals (such an attack is also known as DNS-hijacking). So, let us explain in detail how Switcher performs its brute-force attacks, gets into the routers and undertakes its DNS-hijack.
Clever little fakes
To date, we have seen two versions of the trojan:
acdb7bfebf04affd227c93c97df536cf; package name – com.baidu.com
64490fbecefa3fcdacd41995887fe510; package name – com.snda.wifi
The first version (com.baidu.com), disguises itself as a mobile client for the Chinese search engine Baidu, simply opening a URL http://m.baidu.com inside the application. The second version is a well-made fake version of a popular Chinese app (http://www.coolapk.com/apk/com.snda.wifilocating) for sharing information about Wi-Fi networks (including the security password) between users of the app. Such information is used, for example, by business travelers to connect to a public Wi-Fi network for which they don’t know the password. It is a good place to hide malware targeting routers, because users of such apps usually connect with many Wi-Fi networks, thus spreading the infection.
The cybercriminals even created a website (though badly made) to advertise and distribute the aforementioned fake version of com.snda.wifilocating. The web server that hosts the site is also used by the malware authors as the command-and-control (C&C) server.
The infection process
The trojan performs the following actions:
Gets the BSSID of the network and informs the C&C that the trojan is being activated in a network with this BSSID
Tries to get the name of the ISP (Internet Service Provider) and uses that to determine which rogue DNS server will be used for DNS-hijacking. There are three possible DNS servers – 101.200.147.153, 112.33.13.11 and 120.76.249.59; with 101.200.147.153 being the default choice, while the others will be chosen only for specific ISPs
Launches a brute-force attack with the following predefined dictionary of logins and passwords:
admin:00000000
admin:admin
admin:123456
admin:12345678
admin:123456789
admin:1234567890
admin:66668888
admin:1111111
admin:88888888
admin:666666
admin:87654321
admin:147258369
admin:987654321
admin:66666666
admin:112233
admin:888888
admin:000000
admin:5201314
admin:789456123
admin:123123
admin:789456123
admin:0123456789
admin:123456789a
admin:11223344
admin:123123123
The trojan gets the default gateway address and then tries to access it in the embedded browser. With the help of JavaScript it tries to login using different combinations of logins and passwords. Judging by the hardcoded names of input fields and the structures of the HTML documents that the trojan tries to access, the JavaScript code used will work only on web interfaces of TP-LINK Wi-Fi routers
If the attempt to get access to the admin interface is successful, the trojan navigates to the WAN settings and exchanges the primary DNS server for a rogue DNS controlled by the cybercriminals, and a secondary DNS with 8.8.8.8 (the Google DNS, to ensure ongoing stability if the rogue DNS goes down). The code that performs these actions is a complete mess, because it was designed to work on a wide range of routers and works in asynchronous mode. Nevertheless, I will show how it works, using a screenshot of the web interface and by placing the right parts of the code successively.
If the manipulation with DNS addresses was successful, the trojan report its success to the C&C
So, why it is bad?
To appreciate the impact of such actions it is crucial to understand the basic principles of how DNS works. The DNS is used for resolving a human-readable name of the network resource (e.g. website) into an IP address that is used for actual communications in the computer network. For example, the name “google.com” will be resolved into IP address 87.245.200.153. In general, a normal DNS query is performed in the following way:
When using DNS-hijacking, the cybercriminals change the victim’s (which in our case is the router) TCP/IP settings to force it to make DNS queries to a DNS server controlled by them – a rogue DNS server. So, the scheme will change into this:
As you can see, instead of communicating with the real google.com, the victim will be fooled into communicating with a completely different network resource. This could be a fake google.com, saving all your search requests and sending them to the cybercriminals, or it could just be a random website with a bunch of pop-up ads or malware. Or anything else. The attackers gain almost full control over the network traffic that uses the name-resolving system (which includes, for example, all web traffic).
You may ask – why does it matter: routers don’t browse websites, so where’s the risk? Unfortunately, the most common configuration for Wi-Fi routers involves making the DNS settings of the devices connected to it the same as its own, thus forcing all devices in the network use the same rogue DNS. So, after gaining access to a router’s DNS settings one can control almost all the traffic in the network served by this router.
The cybercriminals were not cautious enough and left their internal infection statistics in the open part of the C&C website.
According to them, they successfully infiltrated 1,280 Wi-Fi networks. If this is true, traffic of all the users of these networks is susceptible to redirection.
Conclusion
The Trojan.AndroidOS.Switcher does not attack users directly. Instead, it targets the entire network, exposing all its users to a wide range of attacks – from phishing to secondary infection. The main danger of such tampering with routers’ setting is that the new settings will survive even a reboot of the router, and it is very difficult to find out that the DNS has been hijacked. Even if the rogue DNS servers are disabled for some time, the secondary DNS which was set to 8.8.8.8 will be used, so users and/or IT will not be alerted.
We recommend that all users check their DNS settings and search for the following rogue DNS servers:
101.200.147.153
112.33.13.11
120.76.249.59
If you have one of these servers in your DNS settings, contact your ISP support or alert the owner of the Wi-Fi network. Kaspersky Lab also strongly advises users to change the default login and password to the admin web interface of your router to prevent such attacks in the future.
New Android Malware Hijacks Router DNS from Smartphone
29.12.2016 thehackernews Android
android-dns-malware
Another day, another creepy malware for Android users!
Security Researchers have uncovered a new Android malware targeting your devices, but this time instead of attacking the device directly, the malware takes control over the WiFi router to which your device is connected to and then hijacks the web traffic passing through it.
Dubbed "Switcher," the new Android malware, discovered by researchers at Kaspersky Lab, hacks the wireless routers and changes their DNS settings to redirect traffic to malicious websites.
Over a week ago, Proofpoint researchers discovered similar attack targeting PCs, but instead of infecting the target's machines, the Stegano exploit kit takes control over the local WiFi routers the infected device is connected to.
Switcher Malware carries out Brute-Force attack against Routers
Hackers are currently distributing the Switcher trojan by disguising itself as an Android app for the Chinese search engine Baidu (com.baidu.com), and as a Chinese app for sharing public and private Wi-Fi network details (com.snda.wifilocating).
Once victim installs one of these malicious apps, the Switcher malware attempts to log in to the WiFi router the victim's Android device is connected to by carrying out a brute-force attack on the router's admin web interface with a set of a predefined dictionary (list) of usernames and passwords.
"With the help of JavaScript [Switcher] tries to login using different combinations of logins and passwords," mobile security expert Nikita Buchka of Kaspersky Lab says in a blog post published today.
"Judging by the hard coded names of input fields and the structures of the HTML documents that the trojan tries to access, the JavaScript code used will work only on web interfaces of TP-LINK Wi-Fi routers."
Switcher Malware Infects Routers via DNS Hijacking
Once accessed web administration interface, the Switcher trojan replaces the router's primary and secondary DNS servers with IP addresses pointing to malicious DNS servers controlled by the attackers.
Researchers said Switcher had used three different IP addresses – 101.200.147.153, 112.33.13.11 and 120.76.249.59 – as the primary DNS record, one is the default one while the other two are set for specific internet service providers.
Due to change in router's DNS settings, all the traffic gets redirected to malicious websites hosted on attackers own servers, instead of the legitimate site the victim is trying to access.
"The Trojan targets the entire network, exposing all its users, whether individuals or businesses, to a wide range of attacks – from phishing to secondary infection," the post reads.
"A successful attack can be hard to detect and even harder to shift: the new settings can survive a router reboot, and even if the rogue DNS is disabled, the secondary DNS server is on hand to carry on."
Researchers were able to access the attacker’s command and control servers and found that the Switcher malware Trojan has compromised almost 1,300 routers, mainly in China and hijacked traffic within those networks.
The Bottom Line
Android users are required to download applications only from official Google's Play Store.
While downloading apps from third parties do not always end up with malware or viruses, it certainly ups the risk. So, it is the best way to avoid any malware compromising your device and the networks it accesses.
You can also go to Settings → Security and make sure "Unknown sources" option is turned off.
Moreover, Android users should also change their router's default login and passwords so that nasty malware like Switcher or Mirai, can not compromise their routers using a brute-force attack.
Did You Install Super Mario Run APK for Android? That's Malware
28.12.2016 thehackernews Android
After the success of Pokémon Go, Nintendo's "Super Mario Run" has become the hottest game to hit the market with enormous popularity and massive social impact. The game has taken the world by storm since its launch for iOS devices over a week ago.
Can you believe — it was downloaded more than 40 million times worldwide in its first four days of release.
But if you have downloaded a Super Mario Run APK for your Android device, Beware! That's definitely a malware.
Since Super Mario Run has currently been released only for iOS devices and is not on Google Play, it caused a lot of disappointment among Android users.
So, eventually, many Android device owners who love Mario games and can not wait to play Super Mario Run ended up downloading APKs outside of the Google Play Store.
But those tons of phony copycat unofficial Super Mario apps on many third-party Android app stores turn out to be malware or viruses that attempt to look like the legitimate Super Mario Run app.
Super Mario can Take Full Control of your Android Device
To download the third party APK, users are required to "side-load" the malicious app by modifying their Android core security settings, allowing their device's operating system to install apps from "untrusted sources."
Some of these malicious apps can even take full control of your Android device, as the apps request privileges to edit, read, receive and send text messages, take photos and record videos and track your location using GPS.
However, one of the apps titled "Super Mario" creates additional icons, displays pop-up and banner ads, installs other malicious apps onto victim's smartphone, and performs other intrusive activities without any users interaction, according to Tokyo-based Trend Micro antivirus firm, which detected malicious Super Mario apps 90,000 times this year.
"Clicking on these ads or icons will direct users to either adult sites or malicious sites. In either case, the goal is to get users to install various apps," researchers at Trend Micro writes.
"While some of these apps are perfectly legitimate, some are suspicious apps distributed by third-party app stores, including more malicious apps that even request for administrator rights."
Another app, also titled "Super Mario" and discovered by the security firm, prompts users first to install an app called 9Apps, which then asks for more permissions, including recording audio, reading modifying the calendar and even access to complete SD-card.
Here's How to Prevent Yourself
So, instead of downloading applications from unknown third party stores, Android users are required to wait for the official Google Play release.
Downloading apps from third parties do not always end up with malware or viruses, but it certainly ups the risk. So, it's the best way to wait to avoid compromising your device and the networks it accesses.
You can also go to Settings → Security and make sure "Unknown sources" option is turned off.
Faketoken, the Android ransomware banker that encrypted files
20.12.2016 securityaffairs Android
The banker Android ransomware Faketoken that steals financial informaton and sensitive data now also implements file-encrypting abilities.
Security experts from Kaspersky Lab have spotted a strain of known Android malware that now implements also ransomware-like abilities.According to the researchers, Vxers are adding file-encrypting capabilities to traditional mobile banking trojans, the result is a malware that is able both to steal sensitive data and lock user files on the phone’s SD card.This malware with hybrid capabilities is also called ransomware banker.The ransomware functionality in mobile banking Trojans is considered an exception, the Svpeng malware discovered in 2014 is one of the first malware with this ability. The modern mobile ransomware doesn’t limit their actions to block the screen, but it also encrypts user files.The trojan discovered by Kaspersky is dubbed Faketoken, the name suggests its primary feature is to steal login credentials by generating fake login screens for more than 2,000 financial applications. Faketoken is also able to steal credit card information by displaying victims displays phishing pages.
Researchers noticed that file-encrypting capabilities were implemented in Faketoken since July and have since released thousands of versions that include new features.
“We have managed to detect several thousand Faketoken installation packages capable of encrypting data, the earliest of which dates back to July 2016.” reads a blog post published by Kaspersky.
Trojan-Banker.AndroidOS.Faketoken is distributed under the guise of various programs and games, often imitating Adobe Flash Player.”
The researchers confirmed the number of the victims exceeds 16,000 users, they observed infections in 27 countries, mostly in Russia, Ukraine, Germany, and Thailand.
Faketoken uses an AES symmetric encryption algorithm to encrypt the files, this is a good news for the victims that have a chance of decrypting them without paying a ransom.
“The Trojan receives the encryption key and the initialization vector from the C&C server. The encrypted files include both media files (pictures, music, videos) and documents. The Trojan changes the extension of the encrypted files to .cat.” continues the analysis.
The researchers highlighted the fact that file encryptions are not popular with the mobile malware developers because most files stored on a mobile device are usually copied to the cloud.
For more in on Faketoken give a look at the technical analysis published by Kaspersky.
Infected firmware spotted in well-known low-cost Android devices
14.12.2016 securityaffairs Android
Experts from Doctor Web spotted new Trojans into the firmware of several dozens of low-cost Android smartphones and tablets.
Again problems with low-cost Android smartphones and tablets, once again experts discovered certain mobile devices shipped with malicious firmware.
According to malware researchers from antivirus firm Dr.Web, the firmware of a large number of popular Android devices operating on the MediaTek platform was compromised with at least two types of downloader Trojans.
These low-cost Android smartphones and tablets are mostly marketed in Russia.
“Doctor Web’s security researchers found new Trojans incorporated into firmwares of several dozens of Android mobile devices. Found malware programs are stored in system catalogs and covertly download and install programs.” states the blog post published by Dr.Web.
“One of these Trojans, dubbed Android.DownLoader.473.origin, was found in firmwares of a large number of popular Android devices operating on the MTK platform.”
Both malware found in low-cost Android mobile devices, detected as Android.DownLoader.473.origin and Android.Sprovider.7 are able to collect users’ data, displays advertisements on top of running applications and downloads unwanted apps.
Researchers found the malicious code on the following 26 models of low-cost Android mobile devices:
Lenovo A319, Lenovo A6000, MegaFon Login 4 LTE, Bravis NB85, Bravis NB105, Irbis TZ85, Irbis TX97, Irbis TZ43, Irbis tz56, Pixus Touch 7.85 3G, SUPRA M72KG, SUPRA M729G, SUPRA V2N10, Itell K3300, Digma Plane 9.7 3G, General Satellite GS700, Nomi C07000, Optima 10.1 3G TT1040MG, Marshal ME-711, 7 MID, Explay Imperium 8, Perfeo 9032_3G, Prestigio MultiPad Wize 3021 3G, Prestigio MultiPad PMT5001 3G, Ritmix RMD-1121, Oysters T72HM 3G, Irbis tz70, and Jeka JK103.
Android.DownLoader.473.origin is a downloader Trojan which is executed every time a mobile device is turned on, it can be used by crooks to download both benign apps and also malware and unwanted applications.
“It is known that cybercriminals generate their income by increasing application download statistics and by distributing advertising software,” the researchers pointed out. “Therefore, [both Trojans] were incorporated into Android firmware because dishonest outsourcers who took part in creation of Android system images decided to make money on users.” continues the report.
The Android.Sprovider.7 Trojan was spotted in the firmware of Lenovo A319 and Lenovo A6000 smartphones. Below the list of abilities observed by the researchers for this specific malware.:
Download, install and run APK files.
Open the specified link in a browser.
Make phone calls to certain numbers by using a standard system application.
Run a standard system phone application in which a specified number is already dialed.
Show advertisement on top of all apps.
Also, display advertisements in the status bar.
Create a shortcut on the home screen.
Update a major malicious module.
Unfortunately, the number of similar cases is increasing, last month, security researchers from Kryptowire discovered a backdoor in the firmware installed on low-cost Android phones. The backdoor affects mobile phones from BLU Products that are available for sale on both Amazon and Best Buy.
A few days later, researchers from Anubis Networks discovered that a third-party firmware included in more than 2.8 million low-cost Android devices could be exploited to compromise the smartphones Over-the-Air (OTA) updates and gain root privileges.
The firmware affected by the backdoor is developed by the Chinese company Ragentek Group. The problem resides in the lack of encryption for the OTA mechanisms that expose users to MITM attacks. The analysis revealed that the Ragentek firmware running on the smartphone implements an insecure Over-the-Air update mechanism that establishes an unprotected connection to remote servers via an unencrypted communications channel.
More Firmware Backdoor Found In Cheap Android Phones
13.12.2016 thehackernews Android
Here's some bad news for Android users again.
Certain low-cost Android smartphones and tablets are shipped with malicious firmware, which covertly gathers data about the infected devices, displays advertisements on top of running applications and downloads unwanted APK files on the victim's devices.
Security researchers from Russian antivirus vendor Dr.Web have discovered two types of downloader Trojans that have been incorporated in the firmware of a large number of popular Android devices operating on the MediaTek platform, which are mostly marketed in Russia.
The Trojans, detected as Android.DownLoader.473.origin and Android.Sprovider.7, are capable of collecting data about the infected devices, contacting their command-and-control servers, automatically updating themselves, covertly downloading and installing other apps based on the instructions it receives from their server, and running each time the device is restarted or turned on.
The list of Android device models that are affected by the malicious firmware includes:
Lenovo A319, Lenovo A6000, MegaFon Login 4 LTE, Bravis NB85, Bravis NB105, Irbis TZ85, Irbis TX97, Irbis TZ43, Irbis tz56, Pixus Touch 7.85 3G, SUPRA M72KG, SUPRA M729G, SUPRA V2N10, Itell K3300, Digma Plane 9.7 3G, General Satellite GS700, Nomi C07000, Optima 10.1 3G TT1040MG, Marshal ME-711, 7 MID, Explay Imperium 8, Perfeo 9032_3G, Prestigio MultiPad Wize 3021 3G, Prestigio MultiPad PMT5001 3G, Ritmix RMD-1121, Oysters T72HM 3G, Irbis tz70, and Jeka JK103.
"It is known that cybercriminals generate their income by increasing application download statistics and by distributing advertising software," the researchers pointed out. "Therefore, [both Trojans] were incorporated into Android firmware because dishonest outsourcers who took part in creation of Android system images decided to make money on users."
More Firmware Backdoor Found In Cheap Android Phones
Android.Sprovider.7 Trojan was discovered in the firmware of Lenovo A319 and Lenovo A6000 smartphones. The Trojan is capable of doing a lot of things including:
Download, install and run APK files.
Open the specified link in a browser.
Make phone calls to certain numbers by using a standard system application.
Run a standard system phone application in which a specified number is already dialed.
Show advertisement on top of all apps.
Also, display advertisements in the status bar.
Create a shortcut on the home screen.
Update a major malicious module.
On the other hand, Android.DownLoader.473.origin found in the remaining devices, which downloads and installs other malware programs and unwanted apps, including an advertising program called H5GameCenter.
H5GameCenter app displays a small box image on top of all running applications, and there is no option to disable it. Even if the infected users remove this app, the firmware Trojan reinstalls the app.
Last month, security researchers from Kryptowire discovered hidden backdoor in the firmware of many budget Android smartphones sold in the US, which also covertly gathers data on phone owners and sends it to a Chinese server without users knowledge.
The backdoored firmware software was developed by China-based company Shanghai AdUps Technology, which claims that its software runs updates for more than 700 Million devices worldwide.
In separate research last month, security rating firm BitSight discovered a flaw in the Ragentek firmware used by certain low-cost Android devices that allowed attackers to remotely execute malicious code with root privileges, turning over full control of the devices to hackers.
50 Million installations potentially impacted by AirDroid issues
3.12.2016 securityaffairs Android
At least 10 million Android users are exposed to cyber attacks due to multiple vulnerabilities affecting the popular AirDroid app.
According to experts from the firm Zimperium, multiple vulnerabilities in the Android remote management tool AirDroid could expose more than 50 million devices
The flaws could be exploited to abuse built-in features and use them against the application’s users.
Experts highlight that AirDroid uses insecure communication channels allowing attackers to power Man-in-the-Middle (MitM) attacks and other types of attacks.
Researchers from Zimperium discovered that communication channels used to send authentication data to the statistics server are not properly protected because the encryption key is hardcoded inside the application.
An attacker that shares the same network with the victim could run MitM attacks to capture authentication credentials from the first HTTP request the application performs, and use them to act on behalf of the user.
“A malicious party could perform a MITM network attack and grab the device authentication information as shown in the “Details” section from the very first HTTP request the application performs.” reads the blog post published by Zimperium. “This HTTP request can be decrypted at runtime using the 890jklms key hardcoded inside the application and the authentication fields parsed from the resulting JSON.
Having this information, the attacker can now impersonate the victim’s device and perform various HTTP or HTTPS requests on its behalf to the AirDroid API endpoints.
For instance, a payload like the following ( encrypted in DES with the same exact key ) can be sent to the https://id4.airdroid.com/p14//user/getuserinfoviadeviceid.html endpoint :”
Tha attacker could craft a payload encrypted in DES with the same key to trick the server into revealing user information, including the email and password hash.

The attacker could power a MitM attack alto to redirect HTTP traffic to a malicious transparent proxy that allows him to modify the response for the /phone/vncupgraderequest. In this way the attacker could inject a fake update or could execute malicious code remotely.
“Moreover, an attacker performing a MITM attack and redirecting HTTP traffic to a malicious transparent proxy, could modify the response for the /phone/vncupgrade request which is normally used by the application to check for addons updates:
GET /p14/phone/vncupgrade/?q=[DES ENCRYPTED PAYLOAD]&ver=20151 HTTP/1.1
Host: srv3.airdroid.com
Connection: close
User-Agent: Apache-HttpClient/UNAVAILABLE (java 1.4)
Injecting a new update, thus remotely executing custom code on the target device, is just a matter of modifying this response:”
In order to fix these issues, the AirDroid should use only secure communication channels (HTTPS), should implement key pinning to avoid SSL MitM, should use safe key exchange mechanisms, and should leverage and digital verify the update files.
More than 1 Million Google accounts hacked by Gooligan Android Malware
1.12.2016 securityaffairs Android
Experts from the security firm CheckPoint discovered a new Android malware dubbed Gooligan that has already compromised more than a million Google Accounts.
Another malware, dubbed Gooligan, is threatening Android users. The Android malware has already compromised more than 1 Million Google accounts.
The Gooligan Android malware roots vulnerable Android devices in the attempt of stealing email addresses and authentication tokens stored on them.
The stolen information are used by crooks to hijack victims’ Google account and access sensitive data from Google apps including Gmail, Google Photos, Google Docs, Google Play, Google Drive, and G Suite.
“The attack campaign, named Gooligan, breached the security of over one million Google accounts. The number continues to rise at an additional 13,000 breached devices each day.” reported CheckPoint.
“Our research exposes how the malware roots infected devices and steals authentication tokens that can be used to access data from Google Play, Gmail, Google Photos, Google Docs, G Suite, Google Drive, and more.”
Experts from the security firm CheckPoint have discovered dozens of legitimate-looking Android apps containing the Gooligan malware. These mobile apps were available for the download on third-party stores, but experts also highlighted that the malware could be downloaded users directly by tapping malicious links embedded in malicious messages.

Once the malware is installed it start sending device information and stolen data to the C&C server.
“Gooligan then downloads a rootkit from the C&C server that takes advantage of multiple Android 4 and 5 exploits including the well-known VROOT (CVE-2013-6282) and Towelroot (CVE-2014-3153),” added the researcher.
“These exploits still plague many devices today because security patches that fix them may not be available for some versions of Android, or the patches were never installed by the user. If rooting is successful, the attacker has full control of the device and can execute privileged commands remotely. If rooting is successful, the attacker has full control of the device and can execute privileged commands remotely.”
Experts from CheckPoint security confirmed that older versions of the Android operating system are affected by the issue, including Android 4.x (Jelly Bean, KitKat) and 5.x, (Lollipop) (roughly 74% of Android devices currently in use).

The crooks could rapidly monetize their efforts because Gooligan generates revenues by fraudulently buying and installing apps from the official Google Play Store and rating them and writing reviews on behalf of the phone’s owner. The malicious code also installs adware on the victims’ mobile devices.
If you fear being one of the victims of the Gooligan malware be free to use an online tool published by Check Point, the Gooligan Checker, that allows users to check if the Android device has been infected. It is very simple, just open the ‘Gooligan Checker’ and enter your Google email address.
If your device is infected you need to Re-Flash your device running a clean installation of Android OS.
Over 1 Million Google Accounts Hacked by 'Gooligan' Android Malware
30.11.2016 thehacknews Android
If you own an Android smartphone, Beware! A new Android malware that has already breached more than 1 Million Google accounts is infecting around 13,000 devices every day.
Dubbed Gooligan, the malware roots vulnerable Android devices to steal email addresses and authentication tokens stored on them.
With this information in hands, the attackers are able to hijack your Google account and access your sensitive information from Google apps including Gmail, Google Photos, Google Docs, Google Play, Google Drive, and G Suite.
Researchers found traces of Gooligan code in dozens of legitimate-looking Android apps on 3rd-party app stores, which if downloaded and installed by an Android user, malware starts sending your device’s information and stolen data to its Command and Control (C&C) server.
"Gooligan then downloads a rootkit from the C&C server that takes advantage of multiple Android 4 and 5 exploits including the well-known VROOT (CVE-2013-6282) and Towelroot (CVE-2014-3153)," researchers said in a blog post.
"If rooting is successful, the attacker has full control of the device and can execute privileged commands remotely."
According to CheckPoint security researchers, who uncovered the malware, anyone running an older version of the Android operating system, including Android 4.x (Jelly Bean, KitKat) and 5.x, (Lollipop) is most at risk, which represents nearly 74% of Android devices in use today.
"These exploits still plague many devices today because security patches that fix them may not be available for some versions of Android, or the patches were never installed by the user," researchers added.
Once hack into any Android device, Gooligan also generates revenues for the cyber criminals by fraudulently buying and installing apps from Google Play Store and rating them and writing reviews on behalf of the phone's owner. The malware also installs adware to generate revenue.
How to check if your Google account has been compromised with this malware?
Check Point has published an online tool to check if your Android device has been infected with the Gooligan malware. Just open ‘Gooligan Checker’ and enter your Google email address to find out if you've been hacked.
If you found yourself infected, Adrian Ludwig, Google's director of Android security, has recommended you to run a clean installation of the operating system on your Android device.
This process is called 'Flashing,' which is quite a complicated process. So, the company recommends you to power off your device and approach a certified technician or your mobile service provider in order to re-flash your device.
An Android Spyware revealed the existence of a new Italian surveillance firm
21.11.2016 securityaffairs Android
A strain of Android spyware recently analyzed by security experts from RedNaga Security team points to an another Italian company.
A new strain of Android malware reveals the existence of a new Italian player in the surveillance landscape. The Android spyware was analyzed by researchers from the RedNaga Security team, that is a first time investigated the possibility of a new threat developed by the notorious surveillance firm Hacking Team. The analysis revealed that another Italian company developed the dangerous Android spyware.
The Researcher Tim Strazzere and his colleagues analyzed a sample of the malware that infected a machine of an anonymous target, likely a government organization.
The Android implants implements the common functionalities of most spyware:
Automatically remove itself from the launcher after the first execution
Kick start it’s own MainService and set an alarm to keep it persistent
Stop processing commands from the C2 or doing work if the user is present
Mute all audio on the device
Turn GPS on or off
Query internal phone URIs for data and write to external media for later exfiltration
Create screenshots or record the screen
Record video and audio
Respond to specifically configured SMS numbers that include 873451679TRW68IO and reply or forward messages with device information
Execute code (“actions”) from downloaded .dex files (mainly for rooting different devices)
Asks for practically every permission
Can hide itself from the launcher, ensure persistence, mute all audio on the device, turn the GPS on and off, take screenshots or record what can be seen on the screen, record video and audio, reply to or forward messages, lay low while the user is using the device, executed code, exfiltrate data, and so on.
Likely masquerades as an update for a Google service, as the target is shown phrases such as “Servizi Google” (Google Service) and “Aggiornamento effettuato con successo” (Successful Update).
The experts noticed that the Android spyware was contacting two IP addresses belonging to the address space used in the past by the HackingTeam. This circumstance, alongside with the use of Italian string in the code suggests the involvement of an Italian threat actor.
The code was examined by two former Hacking Team employees and Citizen Lab researcher Bill Marczak and both groups excluded the HT authorship.
“The sample has nothing to do with Hacking Team,” another source told Lorenzo Bicchierai from Motherboard. “It’s structurally different from the ones attributed to Hacking Team and doesn’t share any part of the code.”
Segui
Guido Landi @k_sOSe
It doesn't really look like an HT implant.. https://twitter.com/timstrazz/status/798351533192511488 …
06:11 - 15 Nov 2016
Retweet 2 2 Mi piace
Who developed the Android Spyware?
A reference in the SSL certificate used by one of the servers contains a string that might point to the author of the malware, “Raxir”.

Raxir is the name of an Italian company launched in 2013 and located at the incubator “Citta’ Della Scienza” in Naples, Italy.
The company develops software for investigations and works with Italian law enforcement providing forensic services.
Marczak scanned the Internet for evidence of Raxir infections and related traces and found another server that exposes a digital certificate containing the string: “ProcuraNapoliRaxirSrv.”
“The Procura” is the office of the prosecutor and Napoli is a popular city in the South of Italy. It is likely that this office is one of the customers of the Raxir firm.
Let me close with the opinion of the cyber security expert Antonio Cocomazzi who reviewed the portion of codes reported in the analysis published by the Rednaga Security Team.

About the section “Android Manifest”
As the author said, this manifesto has a really suspicious import of the permissions like READ_CONTACTS, CAMERA, SEND_SMS, RECEIVE_SMS, etc. that is common to a malware behavior.
The most interesting Observable is that the malware author tries to trick also the reverse engineer calling the activity label “Aggiornamento software” that is “Software update” in Italian.
About the section “String Encryption”
xor.py
1
2
3
4
5
6
7
8
9
10
11
def decrypt(encrypted, mod):
if not encrypted or not mod:
return ”
mod = mod – 0x5
out = ”
for char in list(encrypted):
out = ‘%s%s’ % (out, unichr(ord(char) ^ (mod & 0x5F)))
mod = (mod – 0xB)
return out.encode(‘ascii’, ‘replace’).encode(‘UTF-32’)
To decrypt the strings embedded into the apk they use a classic XOR Cipher with a little variant: a modifier passed as an argument.
Of course, if the malware contains a function do decrypt the strings, it means that strings were encrypted into the malware to complicate the reverse engineer analysis.
How is used that modifier?
This is a function that can decrypt the data with a dynamic XOR key (thanks to modifier passed as an argument).
That means, most probably, the xor encryption of the string is done with a dynamic XOR key.
This complicate the reverse engineer analysis because in that way the malware writer doesn’t hardcode the xor key in a statical way and, for example, he can let the malware download from a C2 Server.
Anyway, this key could be bruteforced, in fact the author of this article wrote a IDA Pro script to automate the key bruteforcing process, it’s called decryptor.py that you can find in the section below.
Dig deep into the code we can see that function accept 2 arguments: “encrypted”, the encrypted string to decrypt and the “mod”, in order to generate at every run of the malware different XORing encryption.
After a first check of the arguments (line 2), then it modifies the modifier subtracting a constant value 0x5 (5 in decimal).
In the line 7, it loops through every character of the encrypted string, in that cycle, it performs the decryption steps of every character.
This is done in the line 8 appending each new decrypted char to the variable “out” (that will be the final decrypted string).
The encryption of the char is represented by the following formula: “unichr(ord(char) ^ (mod & 0x5F))” so the ord() function returns an integer if you pass as argument a Unicode char, the result of that computation will be XORed (^ operator) with the modifier ANDed (& operator) with a constant value 0x5F (95 decimal).
The result of that computation will be an integer number, so it needs to cast it back to a Unicode char. This is done with the unichr() function.
Before the loop cycle continue, it changes the modifier subtracting 0xB (11 in decimal) from it.
In the end (line 10) it sets the right string encoding to the variable “out”.
About the section “Appendix: Captured C2 Interactions”
Looking at the appendix captured C2 interactions we can immediately realize that the server answer for some action requested by the client (the infected phone).
Unfortunately, we don’t have a .pcap file containing all the request done through Internet, but as we can guess, maybe the malware asks for the malicious action to perform (RequestActionsToExecute) in order to exfiltrate data and the server should answer. That answer should be handled by the malware in order to perform all the steps to grap the data.
Surprisingly, it seems the malware author manages also a way to receive the confirmation if the malware received the action correctly. (AckRequestedActions)
The request to UploadService page is a concrete data exfiltration action in which the malware compresses the data (with PKZip) and send it to the server.
We can guess, thanks to the parameter passed through the POST request “encrypted blob” that file will be stored in a database field instead of implementing a module to upload the file physically on the server.
The NotifyLog request seems to be a way to manage and debug strange behaviors generated by the infected device.
Conclusion
Below a few considerations:
The Italian “Procura” offices investigate crimes and it is strange that the sample of the Raxis Android spyware infected the mobile device of a Government representative.
Did the malware go out of control?
It seems very strange.
Another possibility is that for some reason, the malware was used by a different government entity.
Special Thanks to Odisseus who supported me in the analysis of the events.
Odisseus is an Independent Security Researcher involved in Italy and worldwide in topics related to hacking, penetration testing, and development.
Experts spotted a secret backdoor in Android phones that sends data to China
18.11.2016 securityaffairs Android
Experts at Kryptowire discovered a mobile phone firmware that transmitted personally identifiable information without user consent due to a backdoor.
Security experts from Kryptowire firm have discovered a backdoor in the firmware installed on low-cost Android phones. The backdoor affects mobile phones from BLU Products that are available for sale on both Amazon and Best Buy.
The backdoor resides in the commercial Firmware Over The Air (FOTA) update software that is installed on BLU Android devices provided as a service to BLU by AdUps.
The impact is worrisome if we consider that the backdoor could be exploited by threat actors to collect personal data about the phones and the owners’ activities and send it back to servers located in China. The servers appear to be owned by a firmware update software provider, the Shanghai AdUps Technologies.
“Kryptowire has identified several models of Android mobile devices that contained firmware that collected sensitive personal data about their users and transmitted this sensitive data to third-party servers without disclosure or the users’ consent. These devices were available through major US-based online retailers (Amazon, BestBuy, for example) and included popular smartphones such as the BLU R1 HD.” reads the analysis published by Kryptowire.”These devices actively transmitted user and device information including the full-body of text messages, contact lists, call history with full telephone numbers, unique device identifiers including the International Mobile Subscriber Identity (IMSI) and the International Mobile Equipment Identity (IMEI). “

Experts discovered that the data gathered by the backdoor include phone number, location data, the content of text messages, calls made, and applications installed and used.
Why such kind of backdoor?
It seems that the Shanghai AdUps Technologies firm has inserted a backdoor in its firmware for advertising and commercial purposes, its main goal is to collect data on users’ behavior.
The company also provides firmware updates for Chinese tech giants, including Huawei and ZTE, accounting for more than 700 million devices worldwide.
A legal representative of the company told The New York Times that the company is not gathering information for the Government of Beijing.
“This is a private company that made a mistake,” said Lily Lim, a lawyer who represents Adups.
“For many years, the Chinese government has used a variety of methods to filter and track internet use and monitor online conversations. It requires technology companies that operate in China to follow strict rules. Ms. Lim said Adups was not affiliated with the Chinese government.” reported the NYT.
Kryptowire who discovered the backdoor reported it to Google, BLU, AdUps, and Amazon.
Over 300,000 Android Devices Hacked Using Chrome Browser Vulnerability
9.11.2016 thehackernews Android
A vulnerability in Chrome for Android is actively being exploited in the wild that allows hackers to quietly download banking trojan apps (.apk) onto victim's’ device without their confirmation.
You might have encountered a pop-up advertisement that appears out of nowhere and surprise you that your mobile device has been infected with a dangerous virus and instructs you to install a security app to remove it immediately.
This malicious advertising web page automatically downloads an Android app installation (.apk) file to your device without requiring any approval.
Citing malware threats on your mobile device, attackers trick you to change your device's settings to allow installation of the third-party apps from stores other than Google Play Store and install the banking trojan app on your device.
Kaspersky researchers Mikhail Kuzin and Nikita Buchka discovered one such widespread malicious advertising campaign across Russian news sites and popular websites.
Since this August, the Trojan has infected over 318,000 Android devices across the world — thanks to Google AdSense advertisements that was being abused to spread malicious mobile banking trojan, dubbed Svpeng.
"When an APK file is broken down into pieces and handed over to the save function via Blob() class, there is no check for the type of the content being saved, so the browser saves the APK file without notifying the user," the duo explains in a blog post.
Google has acknowledged the issue, blocked the malicious ads and planned to patch it, although it is unclear when the next Android Chrome version will be released.
However, if Google sticks to its six-week release cycle, users can expect an update on 3rd December 2016. So, malicious actors have over three weeks to exploit the flaw.
"[The] next time they (criminals) push their adverts on AdSense they may well choose to attack users in other countries; we have seen similar cases in the past; After all, what could be more convenient than exploiting the most popular advertising platform to download their malicious creations to hundreds of thousands of mobile devices?" the pair say.
Even if the Google patch this issue with its next software update, attackers still have an evergreen technique to trick users into downloading malicious apps by exploiting vulnerabilities in popular websites.
For example, a recently disclosed XSS (Cross-Site Scripting) flaw, discovered by Indian security researcher Jitendra Jaiswal, on WhatsApp's official websites could allow attackers to trick users into downloading malware applications.
So, it is always a good idea to install apps from official Google Play Store as well as not to change default Android settings that prevent the installation of third-party apps.
So, the best recommendation for users is to think twice before installing any app (no matter how legitimate it looks) from untrusted sources or clicking on suspicious-looking links.
How to Exploit Belkin WEMO gear to hack Android devices
6.11.2016 securityaffairs Android
Belkin’s WeMo home automation firmware that’s in use in several IoT devices has recently been found vulnerable to an SQL injection.
Belkin’s WeMo home automation firmware that’s in use in its light bulbs, switches, security cameras, coffee makers and room heaters has recently been found vulnerable to an SQL injection.
The hack allows root privileges to a third party, which already has access to the devices’ local network.
Researchers at Virginia based Invincea Labs discovered the vulnerability and also warned of a related knock on exploit path which allows for compromise of the Android device used to control the Belkin home automation systems.
The flaw exploits a weakness in field validation by allowing a threat actor to inject malicious JavaScript via the device name field.
Scott Tenaglia, Research Director at Invincea stated that the flaws were previously unknown and not linked to earlier flaws in the WeMo home automation products.
Invincea Labs privately disclosed the flaws on Thursday the 11th of August with Belkin publicly announcing the vulnerability the next day.
On September the 1st, Belkin released a patch, which remedied the code injection vulnerability on the Android app. A further patch was released by Belkin to fix the WeMo appliances on November the 1st
It’s unknown how many WeMo products are vulnerable to this particular weakness, however, in 2015 it was reported that Belkin WeMo had approximately 1.5 million products in use.
Researchers at Invincea stated that every one of their devices that allow for remote control or administration is vulnerable to the attack.
In order to exploit this particular set of vulnerabilities, a malicious actor would first have to gain access to the local network where the smart devices were located. They would then have to leverage the shared network infrastructure in order to move the malicious code from their entry point to the vulnerable devices.
According to Tenaglia “The goal of the attacker is to hop from one device – a PC that can be later disinfected – to another device that can’t be protected – such as an IoT device,”. He then went on to explain, “Once the attacker has access to the IoT device they can do whatever they want from downloading Mirai-type malware for creating a botnet or just control the device in question. They can also infect or re-infect any PC on the same network with malware of their choice.”
Invincea Labs tested their concept by infecting a WeMo device with a malicious PowerShell script and from there open a telnet connection on the device and have it supply a root shell to requesters.
Tenaglia also stated that once infected the device could be configured to deny requests to patch the system and default setting reset attempts unless patched with the recently released firmware update.
Once the access had been granted the researchers found that the attack could progress to target Android devices running the WeMo app used to control the home automation devices.
“This is the first time anyone has discovered a way for IoT devices to hack your phone”, according to Tenaglia.

The vulnerability affects devices by placing unsanitized JavaScript into the name fields of the device, instead of only being recognized as a string the malicious code is executed instead.
“Every WeMo device can be assigned a name. What we found is you can set the name property in the device to a malicious string. The malicious string contains JavaScript code. And when the Android app requests the name of the devices it needs to connect to, it will download the malicious JavaScript code that is the name of the device, and execute the code,”
Utilizing the hack in the lab environment Tenaglia reported that they were able to both access the photo gallery on the phone as well as activate the GPS beaconing system, allowing third parties to track and locate the device.
“All this hack allows us to do is run code in the context of the WeMo app. We do not have root access to the phone,” Tenaglia said. Furthermore, access to the Android device is limited to only when the app is active or running in memory on the phone. Once the WeMo remote app is shut down, access is terminated. “What we have is an in-memory infection. The code does not persist on the phone when you force quit the app. However the name of the device is still that malicious string. So when you connect to that device again the reinfection occurs,”
Commercial Exaspy spyware used to target high-level executives
6.11.2016 securityaffairs Android
Security researchers at Skycure have discovered a new commodity Android Spyware, dubbed Exaspy, targeting high-level executives.
While in many countries the number of Smartphone and Tables is greater of desktop PC, new threats are targeting mobile devices.
Researchers at Skycure have discovered a new strain of Android spyware, dubbed Exaspy, that has been used in targeted attacks against high-level executives.
Researchers from Skycure discovered an instance of the Exaspy malware that was installed on an Android 6.0.1 device owned by a Vice President at an unnamed company.
One of the most interesting aspects of this Android malware is that it requires manual installation on the target device, this implies that attackers have to physical access the smartphone.
Below the analysis provided by Skycure, it is interesting to note that the Exaspy malware needs admin rights for its execution and a license number.
“Interestingly, this malware actually requires an end user to perform the initial installation steps, meaning physical access to the device is required at installation time. Here is how the app installs itself when it runs for the first time:
Malware requests access to device admin rights
Asks (nicely) for a licence number
Hides itself
Requests access to root (if the device is rooted and managed through popular rooting apps). Once granted, it installs itself as a system package to make its uninstallation process harder.”
Once the malware is installed on the device, it is able to access the victim’s chats and messages (SMS, MMS, Facebook Messenger, Google Hangouts, Skype, Gmail, native email client, Viber, WhatsApp, etc.).
On the infected device, the app runs under the name of Google Services leveraging the package name “com.android.protect,” this allows it masquerading the legitimate Google Play Services.
The Exaspy malware is able to record surrounding audio and victim’s calls, it can access photos on the device, it can take screenshots, and access many other user data, including the browser history and call logs.
The malware tries to transfer stolen data to C&C in presence of connectivity and waits for commands.
“The CNC (command and control) server is able to perform requests of its own, which include:
Monitor and transmit local files, such as photos and videos taken.
Execute shell commands, or spawn a reverse shell, which allows the app to elevate its privileges using exploits that are not included in the basic package.”
The spyware communicates with a server at hxxps://api.andr0idservices.com hosted in Google Cloud, it can download updates from the hard-coded URL hxxp://www.exaspy.com/a.apk.
Mobile malware is a privileged instrument for hackers that attempt targeting high-profile individuals, recently experts discovered another commercial spyware called Pegasus that was developed by the Israeli firm NSO Group.
I have forgotten to tell you that the Exaspy spyware is being sold as a $15-a-month turnkey service online.
What is the next commercial spyware?
One oAuth 2.0 hack, 1 Billion Android App Accounts potentially exposed
5.11.2016 securityaffairs Android
Security researchers demonstrated that a Wrong oAuth 2.0 implementation allows a remote simple hack that exposes more than 1 Billion Android App Accounts.
A remote simple hack devised by a group of security researchers threatens an amazing number of Android and iOS apps. An attacker can use the technique to sign into any victim’s mobile app account without any knowledge of the legitimate user.
The research team from the Chinese University of Hong Kong is composed of Ronghai Yang, Wing Cheong Lau, and Tianyu Liu. The experts discovered that the vast majority of popular mobile apps that use the single sign-on (SSO) service doesn’t properly implement the OAuth 2.0 protocol.
The OAuth 2.0 authentication protocol is widely used on social networking sites, every day billion of users access their profiles on Facebook and Google+ using it.
Using the OAuth 2.0, users can sign in for third-party services by verifying existing identity through their accounts on popular web services such as Google, Facebook, or Sina.
Once authenticated, the users haven’t to provide their credentials to access other services implementing the OAuth 2.0 protocol.
This process enables users to sign-in to any service without providing additional usernames or passwords. This magic is possible because when a user logs into a third party app via OAuth, the app checks with the ID provider (i.e. Facebook, Google).
The ID providers, in turn, provide the Access Token to the server of that mobile app that uses it to request the user’s authentication information from the ID provider (i.e. Facebook). In this way, it is able to check user’s identity with data provided by the ID provider and authorize the login.
Below an image from the slides presented by the Team at the Black Hat Europe.
The Chinese researchers discovered that a large number of Android apps did not properly check the validity of the information passed by the ID provider.
The experts explained that the server app instead of verifying the OAuth information included in the Access Token to authenticate the user, the app server would only check if the information is passed by a legitimate ID provider.
This implementation opens the doors to the attackers that can install the flawed app on their mobile devices, log in to their own account and then simply by changing their username to the victim’s one by setting up a server to modify the data sent from Facebook, Google or other ID providers.
With this technique, the attacker can access data used by the flawed app potentially exposing sensitive information or use the app acting on behalf of the victims.
“The problem is a pretty basic mistake,” Lau told Forbes.
“The impact, he said, could be severe. For instance, if the hacker broke into a travel app, they could learn the full itinerary of an individual. For a hotel booking app, they could book a room and have the victim pay for it. Or they could simply steal personal data, like addresses or bank details.” wrote Thomas Fox-Brewster from Forbes.
“A lot of third party developers are ma and pa shops, they don’t have the capability. Most of the time they’re using Google and Facebook recommendations, but if they don’t do it correctly, their apps will be wide open.” .
The experts have found hundreds of popular US and Chinese Android apps that support SSO service. The number of downloads is huge, the researchers explained that a total of over 2.4 Billion downloads are vulnerable to this attack.
The experts estimated that over a Billion different mobile app accounts are at risk of being hijacked with their attack.

The researchers did not perform any test on iOS devices, but they believed that the attack would work also on Apple apps
“Although our current attack is demonstrated over the Android platform, the exploit itself is platform-agnostic: any iOS or Android user of the vulnerable mobile app is affected as long as he/ she has used the OAuth2.0-based SSO service with the app before,” the researchers said.
WhatsApp Video Calling is Now Available for Android – Download Beta Version Now!
25.10.2016 thehackernews Android
WhatsApp is, no doubt, the largest end-to-end encrypted messaging network that allows over billion of its users to send messages, photos, videos, voice messages, documents, and calls that are secure from falling into the wrong hands.
And now it seems like WhatsApp is rolling out a much-awaited feature for the new beta versions of its Android app: Video Calling.
New beta version 2.16.318 of WhatsApp brings the ability for users to conduct video calls.
In order to activate video calls, you simply need to pull up a contact in the WhatsApp app, tap on the call icon and choose "Video Call." You can also go direct to the Calls tab to begin with the option.
The Video calls will only work if both the caller as well as the receiver have the same beta build of WhatsApp that supports the feature. If not, you will be notified with an error message that your contacts needs to update their app.
Download the latest build for WhatsApp Android from APKMirror now and give it a try.
For now, the Video calling feature is limited to WhatsApp's recent beta builds, reported Android Police, which first spotted the feature. So, you either need to download the APK link mentioned above or sign up to become a beta tester and update to WhatsApp (Beta) straight from the Google Play Store.
However, even if the feature doesn't work, there is a possible trick that you can try in order to activate the WhatsApp Video Calling feature.
Possible Trick to Activate WhatsApp Video Calling Feature
You simply need to follow these steps:
Backup all your chats,
Wipe WhatsApp data,
Log in again on WhatsApp.
You can try the above trick that had helped some users activate the video calling feature, but make sure you successfully backup your chats first.
Reportedly, WhatsApp Video Calling feature also provides an option to mute the call. You can even switch between the front and rear camera on your phone, just like any other video calling apps. Your app's call history list now displays both video and voice calls.
With its release in a stable version for over 1 Billion users in the coming weeks, the WhatsApp Video Calling feature could effectively ruin the market for Google's video calling app Duo, which has been released just few month ago.
Millions of Android smartphones exposed to new Drammer Android attack
25.10.2016 securityaffairs Android
A new method of attack dubbed DRAMMER could be exploited to gain ‘root’ access to millions of Android smartphones and take control of affected devices.
Earlier last year, security researchers from Google’s Project Zero outlined a way to hijack the computers running Linux by abusing a design flaw in the memory and gaining higher kernel privileges on the system.
Now, the same previously found designing weakness has been exploited to gain unfettered “root” access to millions of Android smartphones, allowing potentially anyone to take control of the affected devices.
Experts from the VUSec Lab at Vrije Universiteit Amsterdam have discovered a vulnerability that could be exploited to gain “root” access to millions of Android smartphones targeting the device’s dynamic random access memory (DRAM). using an attack called
The attack called Rowhammer, is not new, but this is the first time it was successfully used against target mobile devices.
On March 2015, security researchers at Google’s Project Zero team demonstrated how to hijack the Intel-compatible PCs running Linux by exploiting the physical weaknesses in certain varieties of DDR DRAM (double data rate dynamic random-access memory) chips.
By exploiting the rowhammer technique the hackers can obtain higher kernel privileges on the target system. Rowhammer is classified as a problem affecting some recent DRAM devices in which repeatedly accessing a row of memory can cause bit flips in adjacent rows, this means that theoretically an attacker can change any value of the bit in the memory.
The Rowhammer attack for mobile device involves a malicious application that once in execution repeatedly accesses the same “row” of transistors on a memory chip in a tiny fraction of a second (Hammering process)
Hammering a specific portion of memory can electrically interfere with neighboring row. This interference can cause the row to leak electricity into the next row, which eventually causes a bit to flip and consequent data modification.
An attacker can exploit these modifications to execute its code and gain control of the device.
In short, Rowhammer is an issue with new generation DRAM chips in which repeatedly accessing a row of memory can cause “bit flipping” in an adjacent row that could allow anyone to change the value of contents stored in the memory.
The researchers created a proof-of-concept exploit, dubbed DRAMMER, to test mobile the Rowhammer attack on mobile devices.
Details on the DRAMMER attack are included in a paper published by the experts and on this page.
To test the Rowhammer attack on mobile phones, the researchers created a new proof-of-concept exploit, dubbed DRAMMER. The hack could modify crucial bits of data allowing attacker to root Android devices from major vendors, including Samsung, OnePlus, LG, and Motorola.
The experts exploited the Android mechanism known as the ION memory allocator to give an app a direct access to the dynamic random access memory (DRAM). The ION memory allocator also allows the attackers to identify adjacent rows on the DRAM, which is essential to power the Rowhammer attack by generating bit flips.
The ability allowed the researchers to achieve root access on the victim’s device, giving them full control of the mobile device.
“On a high level, our technique works by exhausting available memory chunks of different sizes to drive the physical memory allocator into a state in which it has to start serving memory from regions that we can reliably predict,” states the paper.
“We then force the allocator to place the target security-sensitive data, i.e., a page table, at a position in physical memory which is vulnerable to bit flips and which we can hammer from adjacent parts of memory under our control.”

“Drammer is a new attack that exploits the Rowhammer hardware vulnerability on Android devices. It allows attackers to take control over your mobile device by hiding it in a malicious app that requires no permissions. Practically all devices are possibly vulnerable and must wait for a fix from Google in order to be patched. Drammer has the potential to put millions of users at risk, especially when combined with existing attack vectors like Stagefright or BAndroid.” states a blog post published by the researchers.
The experts successfully rooted Android handsets including Google’s Nexus 4 and Nexus 5; LG’s G4; Samsung Galaxy S4 and Galaxy S5, Motorola’s Moto G models from 2013 and 2014; and OnePlus One.

“Not only does our [DRAMMER] attack show that practical, deterministic Rowhammer attacks are a real threat to billions of mobile users, but it is also the first effort to show that Rowhammer is…(reliably exploitable) on any platform other than x86 and with a much more limited software feature set than existing solutions,” reads a paper published by the experts.
The DRAMMER app is able to take over the victim’s mobile within minutes and doesn’t request user’s interaction.
The researchers published two following proof-of-concept videos that demonstrate DRAMMER attack in action against an unrooted LG Nexus 5.
In the first video, the phone is running Android 6.0.1 with security patches Google released on October 5, while in the second one the researchers show how the DRAMMER attack can be combined with Stagefright bug that is still unpatched in many older Android devices.
The researchers have released on GitHub the source code of the DRAMMER app in order to allow users to test their mobile device and anonymously share their results.
The experts reported the issue to Google in July, and the tech giant recognized it as a “critical” vulnerability and awarded the researchers $4,000 under its bug bounty program.
The issue is expected to be partially solved with the upcoming November security bulletin, in this way it will be more difficult for attacker to launch a DRAMMER attack.
The problem is that some software features that DRAMMER exploits are so essential to any OS, it is not possible to remove or modify them without a significant impact on the overall design of the device.
New Drammer Android Hack lets Apps take Full control (root) of your Phone
24.10.2016 thehackernews Android
Earlier last year, security researchers from Google's Project Zero outlined a way to hijack the computers running Linux by abusing a design flaw in the memory and gaining higher kernel privileges on the system.
Now, the same previously found designing weakness has been exploited to gain unfettered "root" access to millions of Android smartphones, allowing potentially anyone to take control of affected devices.
Researchers in the VUSec Lab at Vrije Universiteit Amsterdam have discovered a vulnerability that targets a device's dynamic random access memory (DRAM) using an attack called Rowhammer.
Although we are already aware of the Rowhammer attack, this is the very first time when researchers have successfully used this attack to target mobile devices.
What is DRAM Rowhammer Attack?
The Rowhammer attack against mobile devices is equally dangerous because it potentially puts all critical data on millions of Android phones at risk, at least until a security patch is available.
The Rowhammer attack involves executing a malicious application that repeatedly accesses the same "row" of transistors on a memory chip in a tiny fraction of a second in a process called "Hammering."
As a result, hammering a memory region can disturb neighboring row, causing the row to leak electricity into the next row which eventually causes a bit to flip. And since bits encode data, this small change modifies that data, creating a way to gain control over the device.
In short, Rowhammer is an issue with new generation DRAM chips in which repeatedly accessing a row of memory can cause "bit flipping" in an adjacent row that could allow anyone to change the value of contents stored in the memory.
Is Your Android Phone Vulnerable?
To test the Rowhammer attack on mobile phones, the researchers created a new proof-of-concept exploit, dubbed DRAMMER, and found their exploit successfully altered crucial bits of data in a way that completely roots big brand Android devices from Samsung, OnePlus, LG, Motorola, and possibly other manufacturers.
The researchers successfully rooted Android handsets including Google's Nexus 4 and Nexus 5; LG's G4; Samsung Galaxy S4 and Galaxy S5, Motorola's Moto G models from 2013 and 2014; and OnePlus One.
"Not only does our [DRAMMER] attack show that practical, deterministic Rowhammer attacks are a real threat to billions of mobile users, but it is also the first effort to show that Rowhammer is...(reliably exploitable) on any platform other than x86 and with a much more limited software feature set than existing solutions," the researchers wrote in their paper [PDF] titled, "Drammer: Deterministic Rowhammer Attacks on Mobile Platforms."
How does the DRAMMER Attack Work? (Exploit Source Code)
The researchers created an app — containing their rooting exploit — that requires no special user permissions in order to avoid raising suspicion. The DRAMMER attack would then need a victim to download the app laced with malware (researchers' exploit code) to execute the hack.
The researchers took advantage of an Android mechanism called the ION memory allocator to gain direct access to the dynamic random access memory (DRAM).
Besides giving every app direct access to the DRAM, the ION memory allocator also allows identifying adjacent rows on the DRAM, which is an important factor for generating targeted bit flips.
Knowing this, the researchers then had to figure out how to use the bit flipping to achieve root access on the victim's device, giving them full control of the target phone and the ability to do anything from accessing data to taking photos.
"On a high level, our technique works by exhausting available memory chunks of different sizes to drive the physical memory allocator into a state in which it has to start serving memory from regions that we can reliably predict," the paper reads.
"We then force the allocator to place the target security-sensitive data, i.e., a page table, at a position in physical memory which is vulnerable to bit flips and which we can hammer from adjacent parts of memory under our control."
Once you download this malicious app, the DRAMMER exploit takes over your phone within minutes – or even seconds – and runs without your interaction. The attack continues to run even if you interact with the app or put your phone in "sleep" mode.
The researchers expect to soon publish an app [source code available here] that will let you test your Android smartphone yourself and anonymously include your results in a running tally, which will help researchers track the list of vulnerable devices.
DRAMMER Has No Quick Fix
The group of researchers privately disclosed its findings to Google in July, and the company designated the flaw as "critical," awarding the researchers $4,000 under its bug bounty program.
Google says the company has informed its manufacturing partners of the issue earlier this month and has developed a mitigation which it will include in its upcoming November security bulletin to make the DRAMMER attack much harder to execute.
However, the researchers warned that one could not replace the memory chip in Android smartphones that have already been shipped.
And even some software features that DRAMMER exploits are so fundamental and essential to any OS that they are difficult to remove or modify without impacting the user experience.
In short, the attack is not easy to patch in the next generation of Android phones.
Video Demonstration of DRUMMER Attack on Android 6.0.1
The researchers have also published two proof-of-concept videos that demonstrate DRAMMER attack in action against an unrooted LG Nexus 5.
In the first video, the phone is running Android 6.0.1 with security patches Google released on October 5.
In the second video, the researchers show how the DRAMMER attack can be combined with Stagefright bug that remains unpatched in many older Android handsets.
The Stagefright exploit gives the researchers an advanced shell, and by running the DRAMMER exploit, the shell gains root access.
The researcher's exploit can target the majority of the world's Android phones.
"Our research shows that practical large-scale Rowhammer attacks are a serious threat and while the response to the Rowhammer has been relatively slow from vendors, we hope our work will accelerate mitigation efforts both in industry and academia," the researchers concluded.
The group research focuses on Android rather than iOS because the researchers are intimately familiar with the Google's mobile OS which is based on Linux. But the group says it would theoretically be possible to replicate the same attack in an iPhone with additional research.
For more detailed information, you can head on to this informational page about DRAMMER and this paper published early this morning.
Android Banking Trojan Tricks Victims into Submitting Selfie Holding their ID Card
15.10.2016 thehackernews Android
Advanced Android Banking Trojan Tricks Victims to Submit a Selfie Holding Their ID Card
While some payment card companies like Mastercard have switched to selfies as an alternative to passwords when verifying IDs for online payments, hackers have already started taking advantage of this new security verification methods.
Researchers have discovered a new Android banking Trojan that masquerades primarily as a video plugin, like Adobe Flash Player, pornographic app, or video codec, and asks victims to send a selfie holding their ID card, according to a blog post published by McAfee.
The Trojan is the most recent version of Acecard that has been labeled as one of the most dangerous Android banking Trojans known today, according to Kaspersky Lab Anti-malware Research Team.
Once successfully installed, the trojan asks users for a number of device's permissions to execute the malicious code and then waits for victims to open apps, specifically those where it would make sense to request payment card information.
Acecard Steals your Payment Card and Real ID details
android-banking-malware
The banking trojan then overlays itself on top of the legitimate app where it proceeds to ask users for their payment card number and card details such as card holder's name, expiration date, and CVV number.
"It displays its own window over the legitimate app, asking for your credit card details," explains McAfee researcher Bruce Snell. "After validating the card number, it goes on to ask for additional information such as the 4-digit number on the back."
Once this is done, the trojan then looks to obtain users' personal information, including their name, date of birth, mailing address, for "verification purposes," and even requests a photo of the front and back sides of their ID card.
After this, the Trojan also prompts to ask users to hold their ID card in their hand, underneath their face, and take a selfie.
Hackers can make illegal Transfers and Take Over your Online Accounts
All these pieces of information are more than enough for an attacker to verify illegal banking transactions and steal access to victims' social media accounts by confirming the stolen identities.
So far this version of Acecard Android banking Trojan has impacted users in Singapore and Hong Kong.
This social engineering trick of Trojan obviously is not new, and any tech-savvy users would quickly catch this malicious behavior as there is no reason for Google to ask for your ID card. But the trick still works with non and less technical users.
Since all of these fake apps have been distributed outside of Google Play Store, users are strongly advised to avoid downloading and installing apps from untrusted sources. Besides this, users should pay attention to the permissions apps are asking for.
Most importantly: No app needs a photo of you holding your ID card except perhaps a mobile banking service. So, always be cautious before doing that.
Android Acecard banking trojan asks users for selfie with an ID card
16.10.2016 securityaffairs Android
Experts discovered a new variant of the Android Acecard banking trojan that asks victims to take a selfie while they are holding an ID card.
The inventiveness of the criminals is a never ending pit. Recently, a number of organizations announced a new authentication method based on the selfies. For example, HSBC customers can open new bank accounts using a selfie, such as the Bank of Scotland and many other financial organizations and Mastercard.
Crooks have already started taking advantage of this new method of biometric authentication, experts at McAfee discovered a new Android banking Trojan, dubbed Acecard, that pretends to be an adult video app or a codec/plug-in necessary to see a specific video.
“Recently the McAfee Labs Mobile Research Team found a new variant of the well-known Android banking Trojan Acecard (aka Torec, due to the use of Tor to communicate with the control server) that goes far beyond just asking for financial information.” reads a blog post published by McAfee. “In addition to requesting credit card information and second-factor authentication, the malicious application asks for a selfie with your identity document—very useful for a cybercriminal to confirm a victim’s identity and access not only to banking accounts, but probably also even social networks.”
The fake video plugin appears like an Adobe Flash Player, a pornographic app, or video codec.
When it is running in the background, the Acecard banking Trojan monitors the opening of specific apps usually associated with payment transactions. When the victim will open one of these apps the malware will present him a main phishing overlay, pretending to be Google Play and asking for a credit card number, that requests the submission of the card details and more personal and financial data (i.e. Cardholder name, date of birth, phone number, credit card expiration date, and CCV)
After collecting credit card and personal information from the victim, the Acecard banking Trojan the malware asks victims to complete a fake “identity confirmation” composed of three steps. In the first two steps the app requests the victim to upload a clean and readable photo of the front and back side of his identity document (national ID, passport, driver’s license):

In the final step, the malicious app asks victims to take a selfie while holding their ID card.
“After collecting credit card and personal information from the victim, the malware offers a fake “identity confirmation” that consists of three steps. The first two steps ask the user to upload a clean and readable photo of the front and back side of the victim’s identity document (national ID, passport, driver’s license).” continues the post. “The final step asks for a selfie with the identity document.”
The information collected by the Acecard banking Trojan allows attackers to perform several illegal activities that would result in the victim’s identity theft.
According to the experts, this variant of the Acecard banking Trojan has impacted users in Singapore and Hong Kong.
As usual, let me suggest avoid download from untrusted app stores and carefully review the permissions apps are asking for … and of course don’t take selfies while holding your ID card.
How much time does it take to create a malware that evades antimalware solutions? One or two minutes
27.9.2016 securityaffairs Android
A Group of the researchers from the Iswatlab team at the University of Sannio demonstrated how is easy to create new malware that eludes antimalware.
It’s not easy to ‘write’ a new malware that is able to evade the detection of antimalware and other defensive software, but it is easier to ‘produce’ a new malware that can evade the detection of antimalware solutions.
The difference between writing and producing is very subtle and stands in the fact that in the latter case the malware writer does not need to write any line of code, he just needs to press a button.
The researchers at the Iswatlab (www.iswatlab.eu) at the University of Sannio (Italy) realized an engine that applies eight transformations to a mobile malware code which alter the code’s shape, but not the behavior of the malware.
This tool used by the team is named the “Malware Washing Machine” for obvious reasons.
The transformation engine developed by the researcher for Android malware works by applying the following transformations:
Disassembling & Reassembling.
Repacking.
Changing package name.
Identifier Renaming.
Data Encoding.
Call indirections.
Code Reordering.
Junk Code Insertion.
Composite Transformations.
The Iswatlab crew tested the Malware Washing Machine against 57 well known commercial antimalware solutions.
They used their engine for changing 5560 malware that was identified and classified as malware by tall the 57 antimalware used in the test session.
Anyway, after the modification, the majority of antimalware is no more able to recognize a large subset of the malware.
“Are the actual signature based detection algorithms effective on mobile environments? We developed a framework which applies a set of transformations to Android
applications small code. We then transformed a real world malware data-set (available at: https://www.sec.cs.tu-bs.de/~danarp/drebin/index.html) and then we submitted the applications to the website www.virustotal.com, in order to evaluate the maliciousness before and after the transformations (we submitted every sample pre and post transformation process).” reads the report.
The test showed that there are some malware families that are recognized by some antimalware also after the transformations, but they were a very little part.
“In the following table, first column represents the Anti-Malware, the second the number of samples (without transformations) correctly detected by the antimalware while in the third column (in red) the number of correctly detected samples after transformation process.”

“The results is impressive: the antimalware is not able to recognize the transformed malware (given that it was able to recognize the original malware).
The transformation engine is released for the scientific community with the open source license at the following url: https://github.com/faber03/AndroidMalwareEvaluatingTools“
The details of the test conducted by the Iswatlab are included in the report titled “Evaluating malware obfuscation techniques against antimalware detection algorithms”
This test raises the discussion about the capability to limit the production of malware, the experts at the Iswatlab were able to create new malware without writing any line of new code, but just scrambling some old well-known threats.
Summing up, the producing a new-born malware, that is not detectable by defense solutions, just takes a few minutes. Take an old malware and put it into the Malware Washing Machine!
The Malware Washing Machine is available at https://github.com/faber03/AndroidMalwareEvaluatingTools
Google to Launch 'Andromeda OS' — An Android-Chrome OS Hybrid
27.9.2016 thehackernews Android
Google's long-rumored Android-Chrome hybrid operating system is expected to debut at the company's upcoming hardware event on October 4.
The company has been working to merge the two OSes for roughly 3 years with a release planned for 2017, but an "early version" to show things off to the world in 2016.
Android + Chrome = Andromeda
The hybrid OS, currently nicknamed 'Andromeda,' could be come on a new Pixel laptop as well as Huawei Nexus tablet from Google by Q3 2017, if not sooner, according to new leaks from 9to5Google and Android Police.
Android + Chrome = Andromeda
The laptop, officially codenamed "Bison" and nicknamed "Pixel 3," is a reference to the "Chromebook Pixel," but since this edition is not running Chrome operating system, one can not call it a "Chromebook" anymore.
Andromeda is separate from the company's Fuchsia OS, which is focused on Internet-of-Thing (IoT) devices. Moreover, the report also makes it clear that Andromeda "is [an entirely] distinct effort from Google's current campaign to bring Android apps to Chromebooks." So, don't get confused.
Rumored specs suggest Bison is expected to pack a 12.3-inch display with a 'tablet' mode and stylus and reportedly powered by an Intel M3 processor like Apple's 12-inch MacBook, or an Intel Core i5.
Bison is expected to have two models with 32GB or 128GB of internal storage, and 8GB or 16GB of RAM.
Other features could include two USB-C ports, a 3.5mm headphone jack, a fingerprint scanner, stereo speakers, a backlit keyboard, quad microphones, a glass trackpad, and a battery that lasts around 10 hours.
For more details about the new hybrid operating system, you need to wait for two more weeks for Google's October 4 event that is set to launch a Google's new hardware product line, including "Google Wi-Fi" router, Google Home, the refreshed 4K-capable Chromecast rumored to be called Chromecast Ultra, and a "Daydream" VR headset.
Rooting Pokémons in Google Play Store
16.9.2016 Kaspersky Android
A few days ago we reported to Google the existence of a new malicious app in the Google Play Store. The Trojan presented itself as the “Guide for Pokémon Go”. According to the Google Play Store it has been downloaded more than 500,000 times. Our data suggests there have been at least 6,000 successful infections, including in Russia, India and Indonesia. However, since the app is oriented towards English-speaking users, people in such geographies, and more, are also likely to have been hit.
Analysis reveals that the app contains a malicious piece of code that downloads rooting malware – malware capable of gaining access to the core Android operating system, in this case for the purposes of unsolicited app install and adware.
Kaspersky Lab products detect the Trojan as HEUR:Trojan.AndroidOS.Ztorg.ad.
At least one other version of this particular app was available through Google Play in July 2016. Further, we have tracked back at least nine other apps infected with this Trojan and available on Google Play Store at different times since December 2015.
Trojan characteristics
The Trojan has many layers of defense in place to help it bypass detection. This includes a commercial packer that decrypts the original executable file to make it harder to analyze. The unpacked executable file contains useful code related to the malicious Pokémon Go guide, and one small and obfuscated module.
Process of infection
This small module doesn’t start when the user launches the app. Instead, it waits for the user to install or uninstall another app, then checks to see if that app runs on a real device or on a virtual machine. If it turns out that it’s dealing with a device, the Trojan will wait for a further two hours before starting its malicious activity.
The first thing it does is connect to its command-and-control (CnC) server and upload data about the device, including country, language, device model and OS version.
If the server wants the Trojan to continue it will respond with an ID string. Only if the Trojan receives this ID string will it make its next request to the CnC. If it doesn’t receive anything, it will wait for two hours and then resubmit the first request. This feature is included so that the control server can stop the attack from proceeding if it wants to – skipping those users it does not wish to target, or those which it suspects are a sandbox/virtual machine, for example. Among other things, this provides an additional layer of protection for the malware.
Upon receiving the second request, the CnC server will send the Trojan a JSON file containing a URL. The Trojan downloads file from the specified URL, decrypts it and executes. In our case the Trojan downloaded a file detected as HEUR:Trojan.AndroidOS.Ztorg.a. This file is obfuscated too.
After execution, the Trojan will drop and download some more files. All downloaded files are encrypted and most of them are local root exploit packs for vulnerabilities dating from 2012 to 2015, including one that was previously used by Hacking Team.
These other files represent additional modules of the Trojan and are detected by Kaspersky Lab as:
HEUR:Backdoor.AndroidOS.Ztorg.c, HEUR:Trojan.AndroidOS.Muetan.b, HEUR:Trojan.AndroidOS.Ztorg.ad, HEUR:Backdoor.AndroidOS.Ztorg.h, HEUR:Backdoor.AndroidOS.Ztorg.j, HEUR:Trojan-Dropper.AndroidOS.Agent.cv, HEUR:Trojan.AndroidOS.Hiddad.c. And a few clean tools like busybox and chattr.
Using these exploit packs the Trojan will gain root access rights to the device. After gaining root access, the Trojan will install its modules into the system folders, silently installing and uninstalling other apps and displaying unsolicited ads to the user.
Most of the other apps with this Trojan module available in Google Play had about 10,000 downloads (according to Google Play), but one – “Digital Clock” had more than 100,000 downloads.
MD5 of Malicious Files Mentioned in Article
8CB3A269E50CA1F9E958F685AE4A073C
0235CE101595DD0C594D0117BB64C8C3
How to hack Google FR by exploiting a cross-site scripting flaw
15.9.2016 securityaffairs Android
The security expert Issam Rabhi (@issam_rabhi) has discovered a cross-site scripting vulnerability in Google France. The giant already fixed it.
A security expert from French security outfit Sysdream, Issam Rabhi (@issam_rabhi), discovered a cross-site scripting vulnerability in Google France. Yes, you‘ve got it right, the website of the IT giant was affected by one of the most common vulnerabilities. According to the OWASP Top Ten, the cross-site scripting is the third most popular issue affecting web applications.

Such kind of flaw could be exploited by a malicious attacker for various attacks, including defacements and traffic hijacking.
“XSS flaws occur whenever an application takes untrusted data and sends it to a web browser without proper validation or escaping. XSS allows attackers to execute scripts in the victim’s browser which can hijack user sessions, deface web sites, or redirect the user to malicious sites.” reads the description provided by the OWASP TOP 10.
The experts reported the cross-site scripting vulnerability to Google on August 5th and the experts of the company fixed the vulnerability in just four days.
Rabhi published a Proof-of-concept for the attack on his website, below the exploitation step by step:
First we need to click the link below using Firefox browser:
https://www.google.fr/#q=Olympiade&mie=oly%2C%5B%22%2Fm%2F03tnk7%22%2C1%2C%22r%22%2C1%2Cnull%2Cnull%2Cnull%2Cnull%2Cnull%2Cnull%2Cnull%2Cnull%2Cnull%2Cnull%2Cnull%2Cnull%2Cnull%2Cnull%2Cnull%2C0%5D
Then, to insert the following payload in the input field related to search:
<svg onload=alert(document.domain)>
Finally, the alert message box will pop up on the screen.
The expert did not submit the bug under the Google bug bounty program, anyway he received kudos from his colleagues.
Banking Trojan, Gugi, evolves to bypass Android 6 protection
9.9.2016 Kaspersky Android
Almost every Android OS update includes new security features designed to make cybercriminals’ life harder. And, of course, the cybercriminals always try to bypass them.
We have found a new modification of the mobile banking Trojan, Trojan-Banker.AndroidOS.Gugi.c that can bypass two new security features added in Android 6: permission-based app overlays and a dynamic permission requirement for dangerous in-app activities such as SMS or calls. The modification does not use any vulnerabilities, just social engineering.
Initial infection
The Gugi Trojan is spread mainly by SMS spam that takes users to phishing webpages with the text “Dear user, you receive MMS-photo! You can look at it by clicking on the following link”.
Clicking on the link initiates the download of the Gugi Trojan onto the user’s Android device.
Circumventing the security features
To help protect users from the impact of phishing and ransomware attacks, Android 6 introduced a requirement for apps to request permission to superimpose their windows/views over other apps. In earlier versions of the OS they were able to automatically overlay other apps.
The Trojan’s ultimate goal is to overlay banking apps with phishing windows in order to steal user credentials for mobile banking. It also overlays the Google Play Store app to steal credit card details.
The Trojan-Banker.AndroidOS.Gugi.c modification gets the overlay permission it needs by forcing users to grant this permission. It then uses that to block the screen while demanding ever more dangerous access.
The first thing an infected user is presented with is a window with the text “Additional rights needed to work with graphics and windows” and one button: “provide.”
After clicking on this button, the user will see a dialog box that authorizes the app overlay (“drawing over other apps”).
System request to permit Trojan-Banker.AndroidOS.Gugi.c to overlay other apps
But as soon as the user gives Gugi this permission, the Trojan will block the device and show its window over any other windows/dialogs.
Trojan-Banker.AndroidOS.Gugi.c window that blocks the infected device until it receives all the necessary rights
It gives the user no option, presenting a window that contains only one button: “Activate”. Once the user presses this button they will receive a continuous series of requests for all the rights the Trojan is looking for. They won’t get back to the main menu until they have agreed to everything.
For example, following the first click of the button, the Trojan will ask for Device Administrator rights. It needs this for self-defense because it makes it much harder for the user to uninstall the app.
After successfully becoming the Device Administrator, the Trojan produces the next request. This one asks the user for permission to send and view SMS and to make calls.
It is interesting that Android 6 has introduced dynamic request capability as a new security features
Earlier versions of the OS only show app permissions at installation; but, starting from Android 6, the system will ask users for permission to execute dangerous actions like sending SMS or making calls the first time they are attempted, or allows apps to ask at any other time – so that is what the modified Gugi Trojan does.
TSystem request for dynamic permission
The Trojan will continue to ask the user for each permission until they agree. Should the user deny permission, subsequent requests will offer them the option of closing the request. If the Trojan does not receive all the permissions it wants, it will completely block the infected device. In such a case the user’s only option is to reboot the device in safe mode and try to uninstall the Trojan.
TRepeating system request for dynamic permission
A standard banking Trojan
With the exception of its ability to bypass Android 6 security features, and its use of the Websocket protocol, Gugi is a typical banking Trojan. It overlays apps with phishing windows to steal credentials for mobile banking or credit card details. It also steals SMS, contacts, makes USSD requests and can send SMS by command from the CnC.
The Trojan-Banker.AndroidOS.Gugi family has been known about since December 2015, with the modification Trojan-Banker.AndroidOS.Gugi.c first discovered in June 2016.
Victim profile
The Gugi Trojan mainly attacks users in Russia: more than 93% of attacked users to date are based in that country. Right now it is a trending Trojan – in the first half of August 2016 there were ten times as many victims as in April 2016.
TUnique number users attacked by Trojan-Banker.AndroidOS.Gugi.
We will shortly be publishing a detailed report into the Trojan-Banker.AndroidOS.Gugi malware family, its functionality and its use of the Websocket protocol.
All Kaspersky Lab products detect all modifications of the Trojan-Banker.AndroidOS.Gugi malware family.
How Trojans manipulate Google Play
1.9.2016 Kaspersky Android
For malware writers, Google Play is the promised land of sorts. Once there, a malicious application gains access to a wide audience, gains the trust of that audience and experiences a degree of leniency from the security systems built into operating systems. On mobile devices, users typically cannot install applications coming from sources other than the official store, meaning this is a serious barrier for an app with malicious intent. However, it is far from easy for the app to get into Google Play: one of the main conditions for it is to pass a rigorous check for unwanted behavior by different analysis systems, both automatic and manual.
Some malware writers have given up on their efforts to push their malicious creations past security checks, and instead learned how to use the store’s client app for their unscrupulous gains. Lately, we have seen many Trojans use the Google Play app during promotion campaigns to download, install and launch apps on smartphones without the owners’ knowledge, as well as leave comments and rate apps. The apps installed by the Trojan do not typically cause direct damage to the user, but the victim may have to pay for the created excessive traffic. In addition, the Trojans may download and install paid apps as if they were free ones, further adding to the users’ bills.
Let us look into the methods how such manipulations with Google Play happen.
Level 1. N00b
The first method is to make the official Google Play app store undertake the actions the cybercriminal wants. The idea is to use the Trojan to launch the client, open the page of the required app in it, then search for and use special code to interact with the interface elements (buttons) to cause download, installation and launch of the application. The misused interface elements are outlined with red boxes in the screenshots below:
The exact methods of interaction with the interface vary. In general, the following techniques may be identified:
Use of the Accessibility services of the operating system (used by modules in Trojan.AndroidOS.Ztorg).
Imitation of user input (used by Trojan-Clicker.AndroidOS.Gopl.c).
Code injection into the process of Google Play client to modify its operation (used by Trojan.AndroidOS.Iop).
To see how such Trojans operate. Let us look at the example of Trojan.AndroidOS.Ztorg.n. This malicious program uses Accessibility services originally intended to create applications to help people with disabilities, such as GUI voice control apps. The Trojan receives a job from the command and control server (C&C) which contains a link to the required application, opens it in Google Play, and then launches the following code:
This code is needed to detect when the required interface element appears on the screen, and to emulate the click on it. This way, the following buttons are clicked in a sequence: “BUY” (the price is shown in the button), “ACCEPT” and “CONTINUE”. This is sufficient to purchase the app, if the user has a credit card with sufficient balance connected to his/her Google account.
Level 2. Pro
Some malware writers take roads less traveled. Instead of using the easy and reliable way described above, they create their own client for the app store using HTTPS API.
The difficult part about this approach is that the operation of the self-made client requires information (e.g. user credentials and authentication tokens) which is not available to a regular app. However, the cybercriminals are very fortunate that all required data are stored on the device in clear text, in the convenient SQLite format. Access to the data is limited by the Android security model, however apps may abuse it e.g. by rooting the device and thus gaining unlimited access.
For example, some versions of the Trojan.AndroidOS.Guerrilla.a have their own client for Google Play, which is distributed with the help of the rooter Leech. This client successfully fulfils the task of downloading and installing free and paid apps, and is capable of rating apps and leaving comments in the Google store.
After launch, Guerrilla starts to collect the following required information:
The credentials to the user’s Google Play account.
Activities in Google Play require special tokens that are generated when the user logs in. When the user is already logged in to Google Play, the Trojan can use the locally cached tokens. They can be located through a simple search through the database located at /data/system/users/0/accounts.db:
With the help of the code below, the Trojan checks if there are ready tokens on the infected device, i.e. if the user has logged on and can do activities in Google Play:
If no such tokens are available, the Trojan obtains the user’s username and hashed password, and authenticates via OAuth:
Android_id is the device’s unique ID.
Google Service Framework ID is the device’s identifier across Google services.
First, the Trojans attempts to obtain this ID using regular methods. If these fail for whatever reason, it executes the following code:
Google Advertising ID is the unique advertising ID provided by Google Play services.
Guerrilla obtains it as follows:
In a similar way, the Trojan obtains hashed data about the device from the file “/data/data/com.google.android.gms/shared_prefs/Checkin.xml“.
When the Trojan has collected the above data, it begins to receive tasks to download and install apps. Below is the structure of one such task:
The Trojan downloads the application by sending POST requests using the links below:
https://android.clients.google.com/fdfe/search: a search is undertaken for the request sent by the cybercriminals. This request is needed to simulate the user’s interaction with the Google Play client. (The main scenario of installing apps from the official client presupposes that the user first does the search request and only then visits the app’s page).
https://android.clients.google.com/fdfe/details: with this request, additional information needed to download the app is collected.
https://android.clients.google.com/fdfe/purchase: the token and purchase details are downloaded, used in the next request.
https://android.clients.google.com/fdfe/delivery: the Trojan receives the URL and the cookie-files required to download the Android application package (APK) file.
https://android.clients.google.com/fdfe/log: the download is confirmed (so the download counter is incremented.)
https://android.clients.google.com/fdfe/addReview: the app is rated and a comment is added.
When creating the requests, the cybercriminals attempted to simulate most accurately the equivalent requests sent by the official client. For example, the below set of HTTP headers is used in each request:
After the request is executed, the app may (optionally) get downloaded, installed (using the command ‘pm install -r’ which allows for installation of applications without the user’s consent) and launched.
Conclusion
The Trojans that use the Google Play app to download, install and launch apps from the store to a smartphone without the device owner’s consent are typically distributed by rooters – malicious programs which have already gained the highest possible privileges on the device. It is this particular fact that allows them to launch such attacks on the Google Play client app.
This type of malicious program pose a serious threat: in Q2 2016, different rooters occupied more than a half of the Top 20 of mobile malware. All the more so, rooters can download not only malicious programs that compromise the Android ecosystem and spend the user’s money on purchasing unnecessary paid apps, but other malware as well.
Warning! Over 900 Million Android Phones Vulnerable to New 'QuadRooter' Attack
8.8.2016 Android
Android has Fallen! Yet another set of Android security vulnerabilities has been discovered in Qualcomm chipsets that affect more than 900 Million Android smartphones and tablets worldwide.
What's even worse: Most of those affected Android devices will probably never be patched.
Dubbed "Quadrooter," the set of four vulnerabilities discovered in devices running Android Marshmallow and earlier that ship with Qualcomm chip could allow an attacker to gain root-level access to any Qualcomm device.
The chip, according to the latest statistics, is found in more than 900 Million Android tablets and smartphones.
That's a very big number.
The vulnerabilities have been disclosed by a team of Check Point researchers at the DEF CON 24 security conference in Las Vegas.
Critical Quadrooter Vulnerabilities:
The four security vulnerabilities are:
CVE-2016-2503 discovered in Qualcomm's GPU driver and fixed in Google's Android Security Bulletin for July 2016.
CVE-2016-2504 found in Qualcomm GPU driver and fixed in Google's Android Security Bulletin for August 2016.
CVE-2016-2059 found in Qualcomm kernel module and fixed in April, though patch status is unknown.
CVE-2016-5340 presented in Qualcomm GPU driver and fixed, but patch status unknown.
Qualcomm is the world's leading designer of LTE (Long Term Evolution) chipsets with a 65% share of the LTE modem baseband market. If any one of the four flaws is exploited, an attacker can trigger privilege escalations for gaining root access to an affected device.
All an attacker needs is to write a piece of malware and send it to the victim. When installed, the malware offers the attacker privilege escalation on the affected devices.
According to the researchers, the attack can also be conducted through a malicious app. An attacker needs to trick a user into installing a malicious app that, unlike other malware, would execute without requiring any special permission checks.
"Such an app would require no special permissions to take advantage of these vulnerabilities, alleviating any suspicion users may have when installing," Check Point researchers write in a blog post.
If any of the four vulnerabilities are successfully exploited, an attacker could gain root access to an affected device, giving the attacker full access to the device, including its data, camera and microphone.
List of Affected Devices (Popular)
More than 900 Million Android devices that ship with Qualcomm chip are vulnerable to the flaws.
Here's the list of some of the popular affected devices, though there are far more devices that are impacted by one or more Quadrooter vulnerabilities.
Samsung Galaxy S7 and Samsung S7 Edge
Sony Xperia Z Ultra
OnePlus One, OnePlus 2 and OnePlus 3
Google Nexus 5X, Nexus 6 and Nexus 6P
Blackphone 1 and Blackphone 2
HTC One, HTC M9 and HTC 10
LG G4, LG G5, and LG V10
New Moto X by Motorola
BlackBerry Priv
How to Check if Your Device is Vulnerable?
You can check if your smartphone or tablet is vulnerable to Quadrooter attack using Check Point's free app.
Since the vulnerable software drivers, which control communication between Qualcomm chipset components, come pre-installed on these devices at the time of manufacturing, they can only be fixed by installing a patch from the devices' distributors or carriers after receiving fixed driver packs from Qualcomm.
"This situation highlights the inherent risks in the Android security model," the researchers say. "Critical security updates must pass through the entire supply chain before they can be made available to end users."
Three of the four vulnerabilities have already been fixed in Google's latest set of monthly security updates, and a patch for the remaining flaw will be rolled out in the upcoming September update.
Since Qualcomm has already released the code, the phone manufacturers could be able to issue patches to the individual devices as soon as possible.
Android Nexus devices are already patched via the over-the-air updates, but other smartphone models will need to wait until their lazy phone manufacturers integrate the fixes into their own custom Android ROMs.
Android Instant Apps — Run Apps Quickly Without Installation
19.5.2016 Android
Downloading an app is a real pain sometimes when you don't want to install the complete app on your smartphone just for booking a movie ticket, or buying something online. Isn't that?
Now, Imagine the world where you can use any Android app without actually the need to download or even install it on your smartphone.
This is exactly what Google has intended to offer you with its all new Instant Apps feature.
Announced at Google I/O event Wednesday, Android Instant Apps will break down the walls between websites and Android apps by allowing people to tap on a URL and open an Android app instantly, without even having to install it.
As a live demonstration, Google's presenter on stage showed how just clicking a Buzzfeed Video link, which has a dedicated app, opened the relevant part of an app — all in just 2 seconds.
In another demonstration, the presenter showed a link to buy a camera bag at B&H Photo and complete the purchasing process instantly through the shopping cart inside the company's touchscreen-friendly Android app, without even installing the whole app.
For Developers:
Android Instant Apps
Developers who want to provide Instant Apps will have to modularize their already existing apps that can start within a few seconds and users don't have to install the whole app just to use some of its features.
According to Google, some developers with basic apps could even implement Instant Apps support to their apps in as little as a day.
Additionally, alongside with their Instant apps, developers can provide "call to action" links to encourage users to download and install their complete apps if users find them particularly useful.
For Users:
When users click on a Web URL and if that URL has an associated Instant App, users will get a tiny version of that app instead of the website. Once tap, the smartphone fetches some part of the app that users want to use, allowing the app to instantly and seamlessly install.
The user experience with Android Instant Apps is as fast as loading up a web page with the same functionality. So, just don’t bother about Loading…
Instant Apps will run in a secure sandbox and once released, Android Instant Apps feature will work on all smartphones running Android 4.2 (Jelly Bean) or later.
The company will make the feature available via an update to the Google Play Services software coming "later this year."
Malware-Laced Porn Apps Behind Wave of Android Lockscreen Attacks
14.5.2016 Android
Incidents of Android lockscreen malware masquerading as porn apps are a growing concern to security analysts who are forecasting an uptick in attacks. Once infected, Android users bitten by this malware appear to be locked out of their device and are forced to undergo a complex extraction of the app to win back control of their phone or tablet. The warning comes from Dell SonicWALL Threats Research Team that said this yet-to-be-named variant of lockscreen malware is immature, but potent. “We have found over a 100 different apps that contain this malware and suspect that the authors behind the apps are gearing up for a much larger more deadly assault,” said Alex Dubrovsky, director of software engineering and threat research at Dell. Unlike other lockscreen malware such as ICE, Jisut and Cyber.Police that locks the user’s screen and asks them to pay a ransom, the lockscreen malware that Dell found does not appear to be financially motivated, yet. The malware is closely tied to porn websites. Users are enticed to download porn-themed apps via links or SMS message requests that link users to third-party Android app stores. Once a target downloads the advertised malicious porn app, it requests for Device Administrator privileges. When users click the application or open the System Settings app a screen, what appears to be the ransom or lockscreen message appears. But that lockscreen can be easily circumvented by clicking the Home or Recent Apps buttons, according to a SonicWALL team research blog about the discovery posted Thursday. At this time, Dubrovsky said, attackers are not employing a command and control backend to manipulate the device. Neither are attackers executing remote code or taking control over a user’s Android device. However, “once the application starts running, encoded data is transmitted to multiple domains in the background,” SonicWALL reports. Dubrovsky said his team is still dissecting the malware and at this time he suspects that data transmitted from the phone could possibly be personal in nature, but couldn’t be sure. “This is clearly beta software that attackers are refining in real time. Many of the obvious features you’d expect with malware are just not feature complete.” One thing is certain about this strain of lockscreen malware is it is hard to remove. “If an Android device gets infected with a malware with Device Administrator privileges it becomes difficult to remove it as the uninstall button gets greyed out,” write Dell’s SonicWALL security team. Dell said that the obvious solution of running your Android device in Safe Mode to remove app doesn’t work in this instance. Once in Safe Mode the malicious app starts blocking the System Settings after a few moments making it impossible to uninstall. The alternative is to disable the running app via Android Debug Bridge, a software developer’s tool. The other option for non-technical users is simply, reset your Android device. “Overall it looks like this campaign is in its early days as the lockscreen does not work as expected and it is easy to come out of the ‘lock’ state,” Dell wrote. “Considering the volume of malicious apps that are part of this campaign it can be said that this campaign might grow bigger in the near future with updated components.” Dubrovsky said his researchers are bracing for more mature variants of this lockscreen malware that will be much more technically adept at demanding a ransom in some form from mobile porn surfers and apps that have a broader non-adult themed appeal.
How to Use Apple's iMessage on Android Phone
9.5.2016 Android
If you wish to send iMessages from your Android smartphone to a friend who owns an iPhone, it's possible now, at least for those who own MacBooks and iMacs.
A developer has come up with a smart solution to bring Apple's iPhone messaging platform to Android phones. Though the solution is not practical for most people, technical people and nerds can use it to send end-to-end encrypted iMessages.
The solution is a smart hack, but the best part is: PieMessage totally works.
Developed by Eric Chee, PieMessage needs an OS X client as a server to route messages to an Android device, enabling iMessage support on Android devices. So, it's the Mac that handles the entire workload.
"Basically, what the Android client does is send the text to a MacBook," Chee said. "And uses the Mac's Messages app to send off the notification. When the Mac detects an incoming message, it will pass it back to the Android. So yes, there is both software you need to run on a Mac and Android. I have an old 2007 MacBook that is just always on connected at home that serves as its client…"
Here's How PieMessage Works:
PieMessage uses an AppleScript to capture iMessages as they arrive on your Mac system.
A Java app scoops up those messages from the script.
Then the Java app forwards them to a custom messaging app on an Android phone to display and respond to those iMessages.
Chee has also presented a proof-of-concept video demonstration that shows the PieMessage app in work.
He also released the PieMessage code open source on GitHub.
There are some limitations to PieMessage:
You can reply to one-to-one messages from your Android device but currently can't send group messages; instead you can just receive them.
Also, you can not send images and can not see when someone is typing — though the author plans to add more functionality in future updates.
Currently, PieMessage identifies different iMessage conversations by phone numbers or email addresses instead of names.
Since Apple could block this type of functionality in the future due to security risks to its platform, there are other good alternatives for sending and receiving end-to-end encrypted messages, like WhatsApp and Facebook Messenger, with cross-platform support.
New Android Gmobi adware found in firmware and popular apps
18.3.2016 Android
Malware researchers at the Dr Web firm have found an Android malware named Gmobi specifically designed to spread as a software development kit (SDK).
Malware researchers at security firm Dr.Web have detected a new strain of malware that was specifically designed to spread as a software development kit (SDK) used by software developers and mobile device manufacturers. The malware, named Android.Gmobi.1, has been found in several legitimate applications developed by well-known companies, as well as in firmware for nearly 40 mobile devices.
“This Trojan, which was named Android.Gmobi.1, is designed as a specialized program package (the SDK platform) usually used either by mobile device manufacturers or by software developers to expand functionality of Android applications. In particular, this module is able to remotely update the operating system, collect information, display notifications (including advertising ones), and make mobile payments.” states the analysis published by the company.
The malware acts as an information stealer, it collects user and device data and send them back to the C&C server. Gmobi collects user emails, device info, roaming availability status, GPS or mobile network coordinates, whether the Google Play app that installed on the device.
Gmobi collects the following information and sends it to the C&C server: user emails, device info, roaming availability status, device location and mobile network coordinates, whether the presence of a Google Play application on the device.
The malware belongs to the adware category, once the C&C server has received the data from the device it can instruct the Gmobi in showing ads in specific positions of the device. The bad news is that operators behind Gmobi can also instruct the malware to download and install malicious APK files using a standard system dialog.

The experts highlighted that the Gmobi adware can install the APK files in a covert way only if the malware has the necessary privileges.
The server replies with an encrypted JSON (Java Script Object Notification) object that can contain the following commands:
Update the database with information about the advertisement to display.
Create an advertising shortcut on the home screen.
Display an advertising notification.
Display a notification tapping which will result in launch of an installed application.
Automatically download and install APK files using a standard system dialog. A covert installation of these files is performed only if the Trojan has necessary privileges.
The researchers have detected Gmobi in Trend Micro’s Dr. Safety and Dr. Booster apps, and the ASUS WebStorage apps. The Gmobi variant that was discovered in the software of the Trend Micro firm only collected information from the Android devices and sent it to a remote server.
Dr.Web reported the issue to all the impacted companies, Trend Micro has promptly released a new version of the infected apps.
“If your device’s firmware is infected by this Trojan, the malware cannot be removed by the anti-virus without root privileges. However, even if root privileges are gained, there is a high risk of making the device non-operational because the Trojan can be incorporated into some critical system application. Therefore, the safest solution for victims ofAndroid.Gmobi.1 is to contact the manufacturer of the device and ask them to release a firmware update without the Trojan.” concludes Dr Web.
Android Stagefright Exploit, Millions devices open to 10-seconds hack
18.3.2016 Android
Millions of Android devices are open to hacking attacks due to the newly disclosed Android Stagefright Exploit that hack a smartphone in 10 seconds.
New problems for Android users, security experts at software research firm NorthBit have developed an exploit for a Stagefright vulnerability affecting Google’s operating system.
Millions of Android devices are open to hacking attacks due to the newly disclosed Android Stagefright Exploit that could allow attackers to hack a smartphone in 10 seconds.
The attacker just needs to trick users into visiting a specifically crafted web page that includes a malicious multimedia file.
The researchers at NorthBit have dubbed the Android Stagefright Exploit Metaphor, they published a detailed analysis of the attack in a paper entitled “Metaphor A (real) reallife Stagefright exploit.”
The researchers have published a proof-of-concept video that shows how they hacked an Android Nexus 5 device using their Metaphor exploit in just 10 seconds. They also demonstrated that the Android Stagefright Exploit Metaphor works against other mobile devices, including Samsung Galaxy S5, LG G3 and HTC One smartphones.
“Although the bug exists in many versions (nearly a 1,000,000,000 devices) it was claimed impractical to exploit inthewild, mainly due to the implementation of exploit mitigations in newer Android versions, specifically ASLR.” states the paper.
The Android Stagefright Exploit works on Android versions 2.2 to 4.0 and 5.0 to 5.1 while bypassing ASLR on Android versions 5.0 to 5.1, as version 2.2 to version 4.0 do not implement ASLR. Other Android versions are not affected by the new Stagefright exploit.
The Stagefright was first discovered in July 2015, experts at security firm Zimperium announced the flaw is the worst Android vulnerability flaw in the mobile OS history.
The Stagefright flaw affects a media library app that is used for by Android to process Stagefright media files. According to the experts at Zimperium the media library is affected by several vulnerabilities.
Joshua Drake from Zimperium discovered seven critical vulnerabilities in the native media playback engine called Stagefright, the expert defined the Stagefright flaw the “Mother of all Android Vulnerabilities.”
The attackers can exploit the vulnerability by sending a single multimedia text message to an unpatched Android device. Despite Google has already issued a patch and has sent out to it to the company’s partners, but most manufacturers haven’t already distributed the patch to their customers exposing them to cyber attack.
In September 2015, experts at Zimperium released a Stagefright exploit, demonstrating how to trigger the Remote Code Execution (RCE). The researchers implemented the Stagefright Exploit in python by creating an MP4 exploiting the ‘stsc’ vulnerability, aka Stagefright vulnerability.
Stagefright Exploit
In October 2015, experts at Zimperium discovered that a billion Android phones were vulnerable to new Stagefright vulnerabilities, dubbed Stagefright 2.0 that could allow attackers to execute malicious code on the targeted device.
The researchers discovered two bugs that are triggered when processing specially crafted MP3 audio or MP4 video files.
The hacking procedure described by the researchers at NorthBit is composed of the following steps:
Tricking a victim into visiting a malicious page containing a video file that crashes the media server to reset its internal state.
Once the media server restarts, the JavaScript hosted on the web page sends information about the device to the attacker’s server.
The server reply with a custom generated video file to the affected device, exploiting the Stagefright bug to reveal more info about the device’s internal state.
This information is also sent back to the attacker’s server to craft another video file that embeds a malicious payload that allows gaining the control of the mobile device.
New Exploit to 'Hack Android Phones Remotely' threatens Millions of Devices
17.3.2016 Android
Millions of Android devices are vulnerable to hackers and intelligence agencies once again – Thanks to a newly disclosed Android Stagefright Exploit.
Yes, Android Stagefright vulnerability is Back…
…and this time, the Stagefright exploit allows an attacker to hack Android smartphones in 10 seconds just by tricking users into visiting a hacker's web page that contains a malicious multimedia file.
A group of security researchers from Israel-based research firm NorthBit claimed it had successfully exploited the Stagefright bug that was emerged in Android last year and described as the "worst ever discovered".
The new Stagefright exploit, dubbed Metaphor, is detailed in a research paper [PDF] that guides bad guy, good guy as well as government spying agencies to build the Stagefright exploit for themselves.
Just yesterday, we reported about critical vulnerabilities in Qualcomm Snapdragon chip that could be exploited by any malicious application to gain root access on a vulnerable Android device, leaving more than a Billion Android devices at risk.
Video Demonstration — Exploit to Hack Android Phone in 10 Seconds
The researchers have also provided a proof-of-concept video demonstration that shows how they successfully hacked an Android Nexus 5 device using their Metaphor exploit in just 10 seconds. They also successfully tested Metaphor on a Samsung Galaxy S5, LG G3 and HTC One smartphones.
According to the researchers, Millions of unpatched Android devices are vulnerable to their exploit that successfully bypasses security defenses offered by Android operating system.
What is StageFright Bug and Why You have to Worry about it?
Stagefright is a multimedia playback library, written in C++, built inside the Android operating system to process, record and play multimedia files such as videos.
However, what Zimperium researchers discovered last year was that this core Android component can be remotely exploited to hijack 95 percent of Android devices with just a simple booby-trapped message or web page.
Another critical vulnerability discovered last October in Stagefright exploited flaws in MP3 and MP4 files, which when opened were capable of remotely executing malicious code on Android devices, and was dubbed Stagefright 2.0.
However, to tackle this serious issue, Google released a security update that patches the critical bug as well as promised regular security updates for Android smartphones following the seriousness of the Stagefright bugs.
Here's How the New Stagefright Exploit Works
Researchers described the following process to successfully hijack any vulnerable Android smartphone or tablet:
Step 1: Tricking a victim into visiting a malicious web page containing a video file that crashes the Android's mediaserver software to reset its internal state.
Step 2: Once the mediaserver gets a restart, JavaScript on the web page sends information about the victim's device over the Internet to the attacker's server.
Step 3: The attacker's server then sends a custom generated video file to the affected device, exploiting the Stagefright bug to reveal more info about the device's internal state.
Step 4: This information is also sent back to the attacker's server to craft another video file that embeds a payload of malware in it, which when processed by Stagefright starts executing on the victim's smartphone with all the privileges it needs to spy on its owner.
The researchers also claim that their exploit specifically attacks the CVE-2015-3864 vulnerability in a way that bypasses Address Space Layout Randomisation (ASLR), a memory protection process.
"It was claimed [the Stagefright bug] was impractical to exploit in the wild, mainly due to the implementation of exploit mitigations in [latest] Android versions, specifically ASLR," the research paper reads.
The team's exploit works on Android versions 2.2 to 4.0 and 5.0 to 5.1 while bypassing ASLR on Android versions 5.0 to 5.1, as version 2.2 to version 4.0 do not implement ASLR. Other Android versions are not affected by the new Stagefright exploit.
You can go through the full research paper [PDF] that provides enough details to create a fully working and successful exploit.
Russia Rejects Google's Appeal and Orders to Stop Pre-Installing its own Android Apps
16.3.2016 Android
The Giant search engine Google has lost an anti-monopoly appeal in Russia against ruling related to its Android mobile OS
The Moscow Arbitration Court on Monday ruled that Google had violated its dominant position with the help of its free open source mobile platform "Android" by forcing its own apps and services like Youtube, Google Map, and others, on users — reducing competition.
The complaint was brought against Google last February by competing search engine Yandex — Russian Counterpart of Google — which had argued that Google broke competition rules by requiring handset manufacturers to pre-install its apps on Android phones and tablets.
Yandex-1, Google-0
According to the survey conducted by Liveinternet data in September 2013, Yandex accounted 57.4% of the Russian search market, while Google shared 34.9%. This stats reflected in the share market, as their shares were 62.2 and 26 percent respectively.
These statistical analyzes really worried Google about its operations in the Russian Cyberspace and soon it rolled out its Plan B to gain widespread popularity in the Russian Markets by shipping Android smartphones with Google Play Store as bloatware.
This, however, gained a pony monopoly among the Russian Markets. But soon, Yandex noticed that millions of smartphones in Russia shipped with the Android platform that uses Google as the default search engine.
As Yandex ranked as the 4th largest search engine worldwide, the popularity of Android in Russia had already reflected the changes in the Russian Stock Market, forcing Yandex to proceed with a lawsuit against Google in February 2015.
No Pre-installed Google Apps for Russians
The original ruling was then handed down by the country's privacy watchdog, the Federal Antimonopoly Service (FAS), last September over the pre-installed Google apps on Android and blocking other service providers.
Google appealed the ruling and filed an antitrust to adhere their business in the Russian Markets last year.
However, yesterday (Tuesday) the Moscow Arbitration Court rejected the company's appeal — upholding FAS' judgment that Google's practices broke Russian law by leading to the 'prohibition of pre-installation of apps of other producers.'
To regain its dominance over foreign search engines, FAS had already passed the case in favor of Yandex, the native search engine.
FAS adjourned that the default Android would not be coming with any pre-installed Google apps on Android smartphones and tablets in Russia.
Google will now be required to amend its contract with OEMs in Russia to comply with the ruling. The company now faces having to instruct its contracts with manufacturers and paying a penalty based on its local earnings.
Is Yandex - An Unsung Hero?
There is already a buzz in the cyber chat rooms that Yandex was a cloned product of Google, which is evident from many social discussion sites.
Yandex had already developed a unique method to search the whole Bible and Russian Literatures at its infancy stage, which was adopted by Google later.
These are some of the hidden facts about Yandex:
Yandex launched as a search engine in 1997, a year earlier than Google.
Yandex also launched maps in 2004, Google a year later in 2005.
Yandex was the first to launch news search in 2000, Google in 2002.
Blog search came out of Russia in 2004, but out of California only in 2006.
Yandex had already launched an RSS aggregator in 2005, Google followed in 2006.
Even Though Google had implemented many new ideas as time progressed with the help of its think tanks, yet Yandex was behind the implementations of classic times.
Let's look what would be the next roll out from Yandex after the Thumbs Up Rule from FAS.
More than a Billion Snapdragon-based Android Phones Vulnerable to Hacking
16.3.2016 Android
More than a Billion of Android devices are at risk of a severe vulnerability in Qualcomm Snapdragon chip that could be exploited by any malicious application to gain root access on the device.
Security experts at Trend Micro are warning Android users of some severe programming blunders in Qualcomm's kernel-level Snapdragon code that if exploited, can be used by attackers for gaining root access and taking full control of your device.
Gaining root access on a device is a matter of concern, as it grants attackers access to admin level capabilities, allowing them to turn your device against you to snap your pictures, and snoop on your personal data including accounts’ passwords, emails, messages and photos.
The company’s own website notes that Qualcomm Snapdragon SoCs (systems on a chip) power more than a Billion smart devices, including many Internet of Things (IoTs) as of today. Thus, the issue puts many people at risk of being attacked.
Although Google has pushed out updates after Trend Micro privately reported the issues that now prevents attackers from gaining root access with a specially crafted app, users will not be getting updates anytime soon.
The security update rolls out to your device through a long chain:
Qualcomm → Google → Your device's manufacturer → Your network carrier → Your handheld over the air
"Given that many of these devices are either no longer being patched or never received any patches in the first place," said Trend engineer Wish Wu, "they would essentially be left in an insecure state without any patch forthcoming."
Unfortunately, what’s more concerning is the fact that the same vulnerable chips are used in a large number of IoT devices, which are no longer in line for security updates. This makes it possible for hackers to gain root access to these connected devices, which is more worrying.
"Smartphones aren't the only problem here," said Trend's Noah Gamer. "Qualcomm also sells their SoCs to vendors producing devices considered part of the Internet of Things, meaning these gadgets are just as at risk."
"If IoT is going to be as widespread as many experts predict, there needs to be some sort of system in place ensuring these devices are safe for public use. Security updates are an absolute necessity these days, and users of these connected devices need to know what they're dealing with."
Whatever be the reason: if security patches are not available for your device model or take too long to arrive, in both the cases it gives miscreants time to exploit the security holes to gain control of your device.
However, some users are lucky to choose Google’s handsets that get their patches direct from the tech giant automatically, making them safe from the vulnerabilities. The handsets include Nexus 5X, Nexus 6P, Nexus 6, Nexus 5, Nexus 4, Nexus 7, Nexus 9, and Nexus 10.
All of the smart devices using the Qualcomm Snapdragon 800 series, including the 800, 805 and 810 and running a 3.10-version kernel are affected by the vulnerabilities.
The vulnerable code is present in Android version 4 to version 6. In the tests, researchers found Nexus 5, 6 and 6P, and Samsung Galaxy Note Edge using vulnerable versions of Qualy's code.
Though the researchers do not have access to every Android handset and tablet to test, the list of vulnerable devices is non-exhaustive.
Since the researchers have not disclosed full details about the flaws, the short brief about the vulnerabilities is as follows:
1. Qualcomm-related flaw (CVE-2016-0819): The vulnerability has been described by the researchers as a logic bug that allows a small section of kernel memory to be tampered with after it is freed, causing an information leakage and a Use After Free issue in Android.
2. The flaw (CVE-2016-0805) is in Qualcomm chipset kernel function get_krait_evtinfo: The get_krait_evtinfo function returns an index into an array used by other kernel functions. With the help of carefully crafted input data, it is possible to generate a malicious index, leading to a buffer overflow.
3. Gaining root access: Using both the flaws together on vulnerable devices, attackers can gain root access on the device.
The researchers will disclose the full details of exactly how to leverage the bugs at the upcoming Hack In The Box security conference in the Netherlands to be held in late May 2016.
More than a billion Android devices are easy to hack
9.3.2016 Android
A large percentage of Android devices is affected by security vulnerabilities that could be exploited by attackers to easily gain a Root Access.
According to experts at TrendMicro a large percentage of Android devices in use today is affected by security vulnerabilities that could be exploited by attackers to easily gain a root access.
The attack allows an ill-intentioned to escalate the privileges of any code that is executed on a target device, however, this attack scenario sees an attacker having installed his malicious code onto the device in the first place. Android users need to be very careful of installing any mobile apps from untrusted sources.
Below the description provided by TrendMicro for the CVE-2016-0819 and CVE-2016-0805 flaws discovered by its experts:
CVE-2016-0819
We discovered this particular vulnerability, which is described as a logic bug when an object within the kernel is freed. A node is deleted twice before it is freed. This causes an information leakage and a Use After Free issue in Android. (UAF issues are well-known for being at the heart of exploits, particularly in Internet Explorer.)
CVE-2016-0805
This particular vulnerability lies in the function get_krait_evtinfo. (Krait refers to the processor core used by several Snapdragon processors). The function returns an index for an array; however, the validation of the inputs of this function are not sufficient. As a result, when the array krait_functionsis accessed by the functions krait_clearpmu and krait_evt_setup, an out-of-bounds access results. This can be useful as part of a multiple exploit attack.

The problem affects the Qualcomm Snapdragon systems on a chip, more than a billion devices is at risk. The root access to a mobile device allows an attacker to conduct a number of malicious activities, from surveillance to financial frauds.
The vulnerability could be exploited by simply running a malicious app on snapdragon-powered Android devices. Experts at TrendMicro privately reported the security holes to Google that fixed them.
As usually happen in these cases, the high fragmentation of the Android market complicates the patch management process. Many users are still vulnerable to the attack waiting for a security patch.
“As the number of embedded SoCs in devices explode with the IoT growth, we anticipate that these kinds of vulnerabilities will become a bigger problem that will challenge the overall security posture of Internet of Things.” continues the post published by TrendMicro.
Going into technical details, the flaws could be exploited in every mobile and IoT devices that could allow the invocation of the system call perf_event_open. Fortunately, many vendors can have customized the kernel and SELinux policies in order to avoid the call.
According to the Nexus Security Bulletin – February 2016, the CVE-2016-0805 vulnerability affects versions earlier than 4.4.4 to 6.0.1, this means that Nexus 5, Nexus 6, Nexus 6P, Samsung Galaxy Note Edge are vulnerable to the attack.
“We believe that any Snapdragon-powered Android device with a 3.10-version kernel is potentially at risk of this attack. As mentioned earlier, given that many of these devices are either no longer being patched or never received any patches in the first place, they would essentially be left in an insecure state without any patch forthcoming.” conclude TrendMicro.
How to Steal Secret Encryption Keys from Android and iOS SmartPhones
4.3.2016 Android iOS
Unlike desktops, your mobile devices carry all sorts of information from your personal emails to your sensitive financial details. And due to this, the hackers have shifted their interest to the mobile platform.
Every week new exploits are discovered for iOS and Android platform, most of the times separately, but the recently discovered exploit targets both Android as well as iOS devices.
A team of security researchers from Tel Aviv University, Technion and The University of Adelaide has devised an attack to steal cryptographic keys used to protect Bitcoin wallets, Apple Pay accounts, and other highly sensitive services from Android and iOS devices.
The team is the same group of researchers who had experimented a number of different hacks to extract data from computers. Last month, the team demonstrated how to steal sensitive data from a target air-gapped computer located in another room.
Past years, the team also demonstrated how to extract secret decryption keys from computers using just a radio receiver and a piece of pita bread, and how to extract the cryptographic key just by solely touching the chassis of the computer.
Side-Channel Attacks
According to the researchers, the recent exploit is a non-invasive Side-Channel Attack: Attack that extracts the secret crypto key from a system by analyzing the pattern of memory utilization or the electromagnetic outputs of the device that are emitted during the decryption process.
The exploit works against the Elliptic Curve Digital Signature Algorithm (ECDSA), a standard digital signature algorithm that is most widely used in many applications like Bitcoin wallets and Apple Pay and is faster than several other cryptosystems.
How to Steal Secret Encryption Keys?
how-to-hack-android-story
During the experimental hack, the researchers placed a $2 magnetic probe near an iPhone 4 when the phone was performing cryptographic operations.
While performing cryptographic operations, the security researchers measured enough electromagnetic emanations and were able to fully extract the secret key used to authenticate the end user's sensitive data and financial transactions.
The same hack can be performed using an improvised USB adapter connected to the phone's USB cable, and a USB sound card to capture the signal.
"Using such measurements, we were able to fully extract secret signing keys from OpenSSL and CoreBitcoin running on iOS devices," the researchers wrote in a blog post published Wednesday. "We also showed partial key leakage from OpenSSL running on Android and from iOS's CommonCrypto."
The researchers also experimented their exploit on a Sony-Ericsson Xperia X10 Phone running Android and said they believe such an attack is feasible.
The security researchers also cited a recent independent research by a separate team of security researchers that discovered a similar Side-Channel flaw in Android's version of the BouncyCastle crypto library, making the device vulnerable to intrusive electromagnetic key extraction attacks.
Currently, the hack requires an attacker to have physical control of, or, at least, a probe or cable in proximity to, a vulnerable mobile device as long as it performed enough tasks to measure a few thousand of ECDSA signatures.
Affected Devices
Older iOS versions 7.1.2 through 8.3 are vulnerable to the side-channel attack. The current iOS 9.x version includes defenses against side-channel attacks, so are unaffected.
However, nothing can save iPhone and iPad users even running current iOS versions if they are using vulnerable apps. One such vulnerable iOS app is CoreBitcoin that is used to protect Bitcoin wallets on iPhones and iPads.
Developers of CoreBitcoin told the security researchers that they are planning to replace their current crypto library with one that is not susceptible to the key extraction attack. Meanwhile, the recent version of Bitcoin Core is not vulnerable.
Both OpenSSL versions 1.0.x and 1.1.x are vulnerable except when compiled for x86-64 processors with the non-default option enabled or when running a special option available for ARM CPUs.
The team has already reported the vulnerability to the maintainers of OpenSSL, who said that hardware side-channel attacks are not a part of their threat model.
For in-depth technical details, you can read the full research paper [PDF].
How To Keep Your Android Phone Secure
26.2.2016 Android
As the number of threats is on the rise, Android platform is no longer safe, which isn't a surprise to anyone.
Most of us are usually worried more about the security of our desktops or laptops and forget to think about the consequences our smartphones can make if compromised or stolen.
Unlike desktops, your smartphones and tablets carry all sorts of information from your personal photographs, important emails, messages to your sensitive financial details. And due to rise in mobile usage, the hackers have shifted their interest from desktops to the mobile platform.
Nowadays, nearly all possible threats that were previously attacking desktop platform are now targeting smartphone users.
Ransomware, Phishing, Spams, Spyware, Botnets, Banking Malware, OS and Software vulnerabilities, just to name a few examples, but users don't understand the potential threat when it comes to mobile devices.
Additionally, your smartphones and tablets are also subjectable more threats like, Smartphone Thefts and unnecessary app permissions that allow even legitimate & reputed companies to spy on you.
However, there are a number of solutions to solve all the above issues, but for that, you generally need to install multiple cumbersome and untrusted applications to your mobile devices.
Like a good antivirus to resolve malware and virus issues, an app to manage Android app permissions, a device tracking application in case your device is lost or stolen and lots more and installing all these apps consume lots of space, RAM, the battery of your device.
I frequently receive these types of queries from my readers who ask me for some good solution that could solve most of the security and privacy issues in one go.
So I headed to Google Play Store and started searching for an app that offers a full suite of security and privacy tools. I came across some reputed apps, but they resolve few issues and some apps that address several issues but originate from some vendor I can’t trust.
Then I came across , which comes from one of the reputed antivirus vendors, that is offering protection for all the threats we discussed above.
Anti-Virus Feature with 99.9% Detection Rate
best-mobile-antivirus-app
As its primary role, ESET offers the best antivirus scanning for your smartphone devices with up-to-date threat database and clean mobile app interface.
According to the latest test and review conducted by AV-TEST, an independent lab, ESET mobile security antivirus detects 99.9% of latest threats with the protection and usability score 6 out of 6.
After installing and registering my account, the app's Anti-Virus feature offered me options to have my smartphone scanned periodically:
At specific times, when I’m not using my phone, or
When I plugged in my smartphone for charging
Moving further, I found 3 different levels of scanning available in the software: Quick Scan, Smart Scan, and Deep Scan. So, one can choose to perform any of the options one's feel suitable. I chose Deep Scan that scanned every data and files available on my phone.
ESET Mobile Security also allows to access scan logs easily, and one can also have a look at quarantined items (suspicious files or malware) detected by the anti-virus.
Moreover, the anti-virus feature is also offering a series of advanced antivirus options, including support for ESET Live Grid, detection of potentially unwanted or harmful applications and real-time protection.
Anti-Theft (Remote Lock / Remote Wipe / Locate)
android-anti-theft-app
It is always unfortunate when our expensive mobile device is lost or stolen. Many apps in the market offer device recovery feature via GPS-based tracking, but many times these apps are unable to locate the device. Even if an attacker somehow gets access to the device, it is easy for him/her to uninstall the tracking app.
But, I liked the way works. It is designed to help you easily track your lost or stolen device, and password protects your app so that no one can uninstall it, except you.
All you need to do is:
Set a trusted SIM card within the app.
Provide a trusted number in case of emergency
In the case of lost or stolen, you can log into your ESET account at my.eset.com and track your devices through an easy-to-use web interface and ensure that all your data remains protected from unauthorized users.
As soon as you mark your device as 'Missing' on the online portal, the location of your stolen or lost device will be displayed on a real-time map so that you can easily trace it. You can even view a list of IP addresses that your lost device was connected to.
Bonus — 'Selfies' of Phone Thieves: Marked as Missing devices will automatically capture photographs with its back and front cameras, and then send them to the online portal, which helps you find the location of a missing device easier.
But, What if your stolen device is not connected to the Internet?
Here's How you can Protect Your Smartphone:
Like other apps, ESET Anti-Theft feature lets you send an SMS message command from a trusted number to remotely lock or erase your smartphone data immediately, as well as ringing it in case it has been lost somewhere nearby.
On the top of that, ESET Anti-Theft functionality provides a series of new features, like even if an unauthorized SIM card has been inserted in your stolen smartphone, you can send remote commands to it.
Even if someone tries a wrong PIN or pattern on your smartphone, or insert an unauthorized SIM, your device will be able to take preventive actions on its own in an effort to ensure that your data remains protected.
Device Monitoring and Application Audit:
android-security-app
These features are something that most of us ignore while searching for a good mobile security solution.
Today many apps, even legitimate, request for unnecessary app permissions. Some of your apps can make phone calls, track your location, read your browsing history, contacts, SMS, photos and calendar, and even share this data with third-party advertising companies without your knowledge.
And since I'm security conscious, I always make sure which app is requesting what permissions and for this I found ESET Mobile Security best fit for me.
ESET Mobile Security offers 'Application Audit' feature to help you know what permissions various apps installed on your smartphone or tablet have.
You can click on any app listed in the Application Audit interface, which will land you to your smartphone’s settings menu, from where you can easily restrict unnecessary app permissions or even uninstall it.
Besides this, the app offers you 'Device Monitoring' feature that will help you inform any necessary settings you haven't set correct that could compromise your security.
Anti-Phishing and SMS/MMS/Call Blocker
android-anti-phishing-app
Phishing emails, messages and even contacts are common these days. Hackers or malicious attackers can trick you handing over your sensitive accounts like banking, email or social media accounts access to them.
So, it has become important for us to keep an eye on every email and message that we receive every day, but it’s not as easy as it sounds.
This app resolves the above hurdle as well. ESET's Anti-Phishing feature offers an additional level of protection when you browse the web from your smartphone or tablet.
Though the app doesn't support all browsers currently, you can choose the one that is present on the list of supported browsers to navigate the web.
Besides all the above tools, ESET Mobile Security also offers text messages (SMS), and multimedia messages (MMS) and phone calls blocking capabilities to Android users.
So you can easily opt to simply block calls and messages from all unknown numbers, or more interestingly, all or specific known numbers — with options for both incoming and outgoing blocks.
android-antivirus-security-app
In short, I found ESET Mobile Security a package of security and privacy tools bundled into a single app.
The app is fast, provides a user-friendly interface, keeps you safe from malware, protects against phishing attacks, with numerous other tools to keep your smartphone safe even when it's out of your hands.
However, ESET Mobile Security app doesn't provide any Encrypted Cloud-based Backups, device encryption, which I will like to see in-built in the future.
Overall, ESET Mobile Security for Android is a solid choice for protecting your smartphone or tablet with its top-notch malware protection and huge array of anti-theft and privacy-protection features.
You can download and install app for FREE for a lifetime from the Google Play Store if you are seeking for basic protection capabilities.
However, those seeking for Advanced security and privacy protection on their smartphones should upgrade to a premium subscription, via in-app purchase.
GM Bot (Android Malware) Source Code Leaked Online
22.2.2016 Android
The source code of a recently discovered Android banking Trojan that has the capability to gain administrator access on your smartphone and completely erase your phone's storage has been LEAKED online.
The banking Trojan family is known by several names; Security researchers from FireEye dubbed it SlemBunk, Symantec dubbed it Bankosy, and last week when Heimdal Security uncovered it, they dubbed it MazarBot.
All the above wave of Android banking Trojans originated from a common threat family, dubbed GM Bot, which IBM has been tracking since 2014.
GM Bot emerged on the Russian cybercrime underground forums, sold for $500 / €450, but it appears someone who bought the code leaked it on a forum in December 2015, the IBM X-Force team reported.
What is GM Bot and Why Should You Worry about it?
The recent version of GM Bot (dubbed MazarBOT) has the capability to display phishing pages on the top of mobile banking applications in an effort to trick Android users into handing over their financial credentials to the fraudsters.
Besides this, the banking trojan is also capable of forwarding phone calls and intercepting SMS messages to help fraudsters bypass an additional layer of bank security mechanisms, and locking a device’s screen.
Cyber criminals could also use the malware to:
Spy on victims
Delete data from the infected device
Gain boot persistence to help survive device restart
Send and Read your SMS message
Make Calls to your contacts
Read the phone's state
Plague phone's control keys
Infect your Chrome browser
Change phone settings
Force the phone into sleep mode
Query the network status
Access the Internet
Wipe your device's storage (the most critical capabilities of the malware)
However, someone leaked the malware source code only to boost his/her reputation on an underground forum, according to the researchers.
GM Bot Android Malware Source Code for FREE
Yes, the source code for GM Bot and its control panel is now accessible to cybercriminals and fraudsters for FREE.
Here’s the Cherry on the Top:
Besides the source code, the leader also posted a tutorial and instructions for server-side installation, which means cybercriminals can create their own versions of the malware strain to conduct online banking frauds.
Though the archive file containing the source code and its control panel is password protected, the leader is offering the password only to active forum members who is approaching him.
"Those who received the password, in turn, passed it on to other, unintended users, so the actual distribution of the code went well beyond that discussion board’s member list," IBM cyber security evangelist Limor Kessem wrote in a blog post.
Online users had started sharing the password to the archive among their friends, and in no time, the GM Bot source code was all over the hacking underground forums.
GM Bot is one of the most dangerous banking trojan in the Android ecosystem and after its source code gets leaked, users are recommended to beware while banking online.
How to Protect Yourself?
As I previously mentioned, online users are advised to follow these steps in order to protect themselves against this kind of threat:
Never open attachments from unknown sources.
Never click on links in SMS or MMS messages sent to your phone.
Even if the email looks legit, go directly to the source website and verify any possible updates.
Go to Settings → Security → Turn OFF "Allow installation of apps from sources other than the Play Store" option.
Always keep an up-to-date Anti-virus app on your Android devices.
Avoid unknown and unsecured Wi-Fi hotspots and Keep your Wi-Fi turned OFF when not in use.
Source code of the Android GM Bot malware was leaked online
22.2.2016 Android
The experts at the IBM X-Force threat intelligence have discovered that the source code for Android malware GM Bot was leaked online.
Bad news for the Android community, the experts at IBM X-Force threat intelligence have discovered that the source code for Android malware GM Bot was leaked on an underground. The source code was leaked in December 2015, it include the bot component and the control panel.
It seems that one of GM Bot’s buyers decided to leak the code online to enhance credibility in the underground boards.
He leaked the code in an encrypted archive, then he indicated he would give the password only to active forum members who contacted him.
Of course, the code rapidly spread within the criminal ecosystem, it is now free and online is available a tutorial and the instructions for the server-side installation.
The availability online of the source code of a malware represents a crucial moment in the life cycle of malicious codes. Once the code is leaked online, cyber criminal organizations can work on it to create new variants that could be offered for sale or rent.
The original creator of the Android malware has sold the rights to distribute GM Bot v1 (aka MazarBot) to other cyber criminal organizations that is offering it for $500.
“According to X-Force threat intelligence, the code’s author moved on to working on a new version dubbed GM Bot v2.0, which is sold in financial fraud-themed underground boards.” states a blog post published by the X-Force threat intelligence.
GM Bot appeared in the wild in 2014, it was offered in the Russian underground as a powerful instrument for mobile phishing.
“This Android malware’s differentiating capability is its deployment of overlay screens on top of running banking applications, with the goal of tricking users into entering their access credentials into a fake window that will grab and forward them to a remote attacker.” continues the post.
The malware implements a number of features to target Android users, including intercepting SMS messages. The malware allows attackers to gain control of the targeted device, including the customization of fake screens.
In short, mobile banking Trojans such as GM Bot are a one-stop fraud shop for criminals:
They launch fake overlay windows that mimic bank applications to steal user credentials and payment card details.
They control the device’s SMS relay to eavesdrop, intercept and send out SMS messages.
They can forward phone calls to a remote attacker.
They have spyware features and can control the device via remote commands.
The experts at the IBM have analyzed only the control panel because many other organizations and security firms already produced a detailed analysis of malware.
The most interesting feature discovered by the experts in the GM Bot’s botnet administration panel is the possibility to create and deploy new injections to infected user devices.

Another interesting component of the Botnet is the “Search and Stats” section that allows operators to analyze their database that includes stolen information, credit card details, lists of apps installed on infected devices, bank accounts the victims and other info.
Let me suggest to give a look to the interesting analysis published by IBM that also includes the indicators of compromise.
This Android Malware Can Root Your Device And Erase Everything
15.2.2016 Android
A new Android malware has been making waves recently that have the capability to gain root access on your smartphone and completely erase your phone's storage.
Dubbed Mazar BOT, the serious malware program is loaded with so many hidden capabilities that security researchers are calling it a dangerous malware that can turn your smartphone into a zombie inside hacker's botnet.
Mazar BOT was discovered by Heimdal Security while the researchers at the firm were analyzing an SMS message sent to random mobile numbers and locations.
How Mazar BOT Works
Despite other Android malware that distributes itself by tricking users into installing an app from third-party app stores, Mazar spreads via a spam SMS or MMS messages that carry a link to a malicious APK (Android app file).
Once the user clicks the given link, he/she'll be ending up downloading the APK file on their Android devices, which when run, prompts the user to install a new application.
This new Android app has a generic name, MMS Messaging, that asks for admin level privileges. Most of the users end up giving the root access to the malicious app due to its common name.
What Makes Mazar BOT So Nasty
Once gaining root access on the victim's device, Mazar BOT can do variety of nasty stuff on your Android devices, like:
Gain boot persistence to help survive device restarts
Send and Read your SMS messages
Make Calls to your contacts
Read the phone's state
Plague phone's control keys
Infect your Chrome browser
Change phone settings
Force the phone into sleep mode
Query the network status
Access the Internet
Wipe your device's storage (the most critical capabilities of all)
Mazar BOT Browses Internet Anonymously Using TOR
Besides these tasks, Mazar BOT can also download a legitimate TOR (The Onion Router) Android app on your smartphone and install it too, even without your consent or permission.
Using TOR app, the malware would be able to surf the Internet anonymously via the Tor network.
Once the malware installs TOR on victim's phone, Mazar BOT sends a "Thank you" message to an Iranian phone number (9876543210), along with the device's location.
In some instances, Mazar BOT also installs an Android app called Polipo Proxy that establishes a proxy on the device, allowing the malware's author to spy on victim's Web traffic and carry out Man-in-the-Middle (MitM) attacks.
Who is Behind This Awful Malware?
Mazar BOT is believed to be distributed by a Russia-based group of cyber-criminals.
One clue to this assumption is: Mazar BOT cannot be installed on Android smartphones in Russia, as its source code includes instructions on how to stop the malware installation process on phone configured with the Russian language.
Another clue is: There is an unwritten law in Russia that says "if cyber criminals don't go after Russians, Russian authorities will not go after them." Moreover, there is no such indication yet that this Mazar BOT campaign has affected anyone in Russia.
Until now, Mazar BOT for Android has been advertised for sale on several Russian underground (Dark Web) forums, but this is the first time this creepy code has been abused in active attacks.
How to Protect Yourself from Mazar BOT
There are standard protection measures you need to follow to remain unaffected:
NEVER click on links in SMS or MMS messages sent to your phone.
Go to Settings → Security → Turn OFF "Allow installation of apps from sources other than the Play Store" option.
Always keep an up-to-date Anti-virus app on your Android devices.
Avoid unknown and unsecured Wi-Fi hotspots and Keep your Wi-Fi turned OFF when not in use.
Apple Could Offer iMessage App for Android
9.2.2016 Android
Although Apple has its own operating system for both desktop (Mac OS X) and iPhone (iOS), the com pany has always tried to port its in-house applications to other OS platforms.
Apple debuted on its rival mobile OS platform last year with the launch of Apple Music on Android. However, iTunes and Safari has already been made available for both Windows as well as Mac.
Now, the company will soon move more of its mobile applications to Android if comments made by Chief Executive Tim Cook at the recent company-wide event for Apple employees are to be believed.
iMessage App for Android Platform
Cook reportedly told his staff that sooner Apple may bring other apps and exclusive services to the Android Systems, and added that bringing Apple Music to Android in November was "a way of testing the waters for growing its services division through other platforms," reports 9to5Mac.
So, you could see iMessage, the company's encrypted messaging application, expanded to Android.
iMessage is one of the most famous Apple's apps that allows Apple users to send and receive messages, photos, and videos to their fellow Apple users as long as the device has a data connection.
How Apple Can Read End-to-End Encrypted iMessages
What many of us know is iMessage uses end-to-end encryption that even Apple or anyone else can not access or read your messages, but what we don’t know is backed up messages to Apple's iCloud service are vulnerable to federal warrants.
With iCloud Backup enabled, the copies of all your messages, photographs and every important data stored on your iPhone or iPad are encrypted on iCloud using a key controlled by Apple, and not you.
This would allow Apple and hence, anyone who breaks into your account, to read your messages and see your personal and confidential data.
List of Apple Apps you Might See on Android
Besides iMessages, the list of Apple apps that you could see expanded to Android may include iTunes, Music Memos, Apple Maps, and iCloud.
In September, the company released its first-ever Android application, known as Move to iOS, designed to help Android users transfer their content quickly and safely from an Android device to an iOS device.
Although it is yet unclear when Apple will make the move, if this happens anytime soon, Which one of your favorite Apple apps you want to see on your Android devices?
Let me know in the comments below.