
- Android -
Last update 04.10.2017 16:16:35
Introduction List Kategorie Subcategory 0 1 2 3 4 5 6 7 8
Android Malware Developed in Kotlin Programming Language Found in Google Play
10.1.2018 securityweek Android
Security researchers at Trend Micro have discovered a malicious application in Google Play that was developed using the Kotlin programming language.
Detected as ANDROIDOS_BKOTKLIND.HRX, the malicious program was masquerading as Swift Cleaner, a utility designed to clean and optimize Android devices. The application had between 1,000 and 5,000 installs when discovered.
Kotlin, a first-class language for writing Android apps, was announced in May 2017. Coming from Google, it is open source and is already used by 17% of Android Studio projects. Some of the top applications to use the programming language include Twitter, Pinterest, and Netflix.
Developers using Kotlin can deliver safer applications, due to avoiding entire classes of errors, and can also ensure their software is interoperable by taking advantage of existing libraries for JVM, Android, and the browser. What’s yet uncertain is how malware developers can leverage the programming language when building nefarious code.
The discovered malicious application, Trend Micro says, can engage into a broad range of nefarious activities, including remote command execution. It is also capable of stealing users’ information, sending SMS messages, forwarding URLs, and performing click ad fraud. Furthermore, it has been designed to sign up users for premium SMS subscription services without their permission.
When first launched, the malware sends device information to a remote server and starts a background service to receive tasks from the command and control (C&C) server. Upon the initial infection, the malware also sends a message to a specified number provided by the C&C.
Upon receiving SMS commands, the remote server starts executing URL forwarding and click ad fraud operations on the infected device.
During the click ad fraud routine, the malware uses Wireless Application Protocol (WAP), a technical standard for accessing information over a mobile wireless network. Next, malicious JavaScript code is injected and regular expressions are replaced, so that the malicious actors can parse the ads’ HTML code in a specific search string.
“Subsequently, it will silently open the device’s mobile data, parse the image base64 code, crack the CAPTCHA, and send the finished task to the remote server,” Trend Micro explains.
The malicious program can send information on the service provider, login data, and CAPTCHA images to the C&C server. Once such information is uploaded, the C&C server automatically processes a premium SMS service subscription, which can cost the victim money.
To stay protected from such threats, both end users and enterprise customers are advised to install and maintain a security solution on their devices.
According to Trend Micro, Google was informed on the security risk the Swift Cleaner application poses and the company verified that Google Play Protect can keep users safe from this malware family.
Trend Micro spotted 36 malicious apps advertised as security tools spotted in Google Play
8.1.2018 securityaffairs Android
Researchers from Trend Micro have discovered 36 malicious apps on Google Play that are posing as security tools of major firms.
Once again crooks bypassed security checks implemented by Google, researchers from Trend Micro have discovered 36 malicious apps on Google Play that are posing as security tools.
Crooks advertised the apps as security tools as applications developed by major security firms, including Security Defender, Security Keeper, Smart Security, Advanced Boost.
The applications were developed to steal user information and flood them with ads.
“These apps posed as useful security tools under the names Security Defender, Security Keeper, Smart Security, Advanced Boost, and more. They also advertised a variety of capabilities: scanning, cleaning junk, saving battery, cooling the CPU, locking apps, as well as message security, WiFi security, and so on.” reads the blog post published Trend Micro.
“The apps were actually able to perform these simple tasks, but they also secretly harvested user data, tracked user location, and aggressively pushed advertisements.”
The apps collect information such as the user’s Android ID, Mac address, IMSI, OS data, brand and model of the device, device specifics, language, location information, and data on installed apps like Google Play and Facebook to sends to a remote server.
The malicious apps are also capable of uploading installed app information, attachments, user operational information, and data on activated events as well.
When the apps are launched for the first time, they will not appear on the device launcher’s list of applications, the shortcuts will also not appear on the device screen in this way victims will only be able to see notifications sent by the apps. The malicious apps typically push alarmist security warnings and pop-up windows to the victims.
Experts noticed that the apps implement a specific function called “hide” that will not allow the applications to run on specified devices including the Google Nexus 6P, Xiaomi MI 4LTE, ZTE N958St and LGE LG-H525n. Experts believe that the “hide” function was developed to avoid security checks implemented by Google Play.
The apps bombard the users with false security notifications and other messages like advertisements, examples of notifications are “10.0 GB files are being wasted” or “Fraud SMS Broadcast Vulnerability.”

If a user clicks the displayed button on the prompt, the fake security tools will show a simple animation notifying the resolution of the problem.
“The user is bombarded with ads with almost every action. It is clear that one of the main focuses of the app is ad display and click fraud.” continues the analysis.
“Users are actually asked to sign and agree to a EULA (end-user license agreement) which describes the information that will be gathered and used by the app,” researchers said in the report. “But we can still say that the app abuses privacy because the collection and transmission of personal data is unrelated to the functionality of the app.”
The game security tools were spotted in December 2017 and promptly removed.
Android Security Bulletin for January 2018, tech giant fixes multiple Critical flaws
4.1.2017 securityaffairs Android
Google patched five Critical bugs and 33 High severity flaws as part of the Android Security Bulletin for January 2018.
The tech giant addressed 38 Android security vulnerabilities, 20 as part of the 2018-01-01 security patch level and 18 in the 2018-01-05 security patch level.
The 2018-01-01 security patch level fixed four Critical remote code execution issue and 16 High risk elevation of privilege and denial of service flaws.
The most severe vulnerability in Android runtime, tracked as CVE-2017-13176, could be exploited by a remote attacker to bypass user interaction requirements in order to gain access to additional permissions.
A Critical remote code execution flaw was fixed in System, the company also addressed one High risk denial of service vulnerability and two High severity elevation of privilege vulnerabilities.
The security updates fixed 15 vulnerabilities issues in Media framework, the most severe one could be exploited by an attacker using a specially crafted malicious file to execute arbitrary code within the context of a privileged process.
The 2018-01-05 security patch level addressed just one Critical flaw in the Qualcomm components, it could allow a remote attacker using a specially crafted file to execute arbitrary code within the context of a privileged process.
The 2018-01-05 security patch level also fixed 1 Critical issue and 6 High severity vulnerabilities in Qualcomm closed-source components.
The patch level addressed High risk elevation of privilege flaws in LG components, MediaTek components, Media framework, and NVIDIA components.
The security patch level addressed one information disclosure bug in Kernel components, and three High severity elevation of privilege.
The tech giant also fixed resolved 46 vulnerabilities in Google devices as part of the Pixel / Nexus Security Bulletin—January 2018.
High severity flaws only affected older Android versions, meanwhile, most of the issues were rated Moderate severity.
The affected components included Framework (1 vulnerability), Media framework (16 vulnerabilities), System (1 flaw), Broadcom components (1 issue), HTC components (1 flaw), Kernel components (7 bugs), MediaTek components (1 issue), and Qualcomm components (18 vulnerabilities).
Google Patches Multiple Critical, High Risk Vulnerabilities in Android
4.1.2018 securityweek Android
Google patched several Critical and High severity vulnerabilities as part of its Android Security Bulletin for January 2018.
A total of 38 security flaws were resolved in the popular mobile OS this month, 20 as part of the 2018-01-01 security patch level and 18 in the 2018-01-05 security patch level. Five of the bugs were rated Critical and 33 were rated High risk.
Four of the vulnerabilities addressed with the 2018-01-01 security patch level were rated Critical, all of them remote code execution bugs. The remaining 16 issues resolved in this patch level were High risk elevation of privilege and denial of service vulnerabilities.
An elevation of privilege bug that Google patched in Android runtime could be exploited remotely to bypass user interaction requirements in order to gain access to additional permissions.
The most severe of the 15 vulnerabilities resolved in Media framework could allow an attacker using a specially crafted malicious file to execute arbitrary code within the context of a privileged process. These include 3 Critical remote code execution bugs, 4 High severity elevation of privilege issues, and 8 High risk denial of service flaws.
One other Critical remote code execution bug was patched in System, along with two High severity elevation of privilege flaws and one High risk denial of service vulnerability.
Only one of the flaws fixed with the 2018-01-05 security patch level was a Critical vulnerability. Along with 6 High severity flaws, it was affecting Qualcomm closed-source components.
The patch level also resolved a High risk denial of service issue in HTC components and High risk elevation of privilege bugs in LG components, Media framework, MediaTek components, and NVIDIA components (one in each).
The security patch level addressed three High severity elevation of privilege and one information disclosure bug in Kernel components, along with two High risk elevation of privilege vulnerabilities in Qualcomm components.
Google also resolved 46 vulnerabilities in Google devices as part of the Pixel / Nexus Security Bulletin—January 2018. Most of the flaws were rated Moderate severity, exception making issues addressed in Media framework (some were rated Low risk and others were rated High severity on older Android versions).
Impacted components included Framework (1 vulnerability), Media framework (16 vulnerabilities), System (1 flaw), Broadcom components (1 issue), HTC components (1 flaw), Kernel components (7 bugs), MediaTek components (1 issue), and Qualcomm components (18 vulnerabilities).
In addition to patching security flaws, the security bulletin also addressed functionality issues on Pixel devices. The update adjusted the handling of key upgrades in keystore and improved stability and performance after installing an OTA.
On Google devices, all of these issues are fixed as part of the security patch levels of 2018-01-05 or later.
Critical "Same Origin Policy" Bypass Flaw Found in Samsung Android Browser
30.12.2017 thehackernews Android
A critical vulnerability has been discovered in the browser app comes pre-installed on hundreds of millions of Samsung Android devices that could allow an attacker to steal data from browser tabs if the user visits an attacker-controlled site.
Identified as CVE-2017-17692, the vulnerability is Same Origin Policy (SOP) bypass issue that resides in the popular Samsung Internet Browser version 5.4.02.3 and earlier.
The Same Origin Policy or SOP is a security feature applied in modern browsers that is designed to make it possible for web pages from the same website to interact while preventing unrelated sites from interfering with each other.
In other words, the SOP makes sure that the JavaScript code from one origin should not be able to access the properties of a website on another origin.
The SOP bypass vulnerability in the Samsung Internet Browser, discovered by Dhiraj Mishra, could allow a malicious website to steal data, such as passwords or cookies, from the sites opened by the victim in different tabs.
"When the Samsung Internet browser opens a new tab in a given domain (say, google.com) through a Javascript action, that Javascript can come in after the fact and rewrite the contents of that page with whatever it wants," researchers from security firm Rapid7 explained.
"This is a no-no in browser design since it means that Javascript can violate the Same-Origin Policy, and can direct Javascript actions from one site (controlled by the attacker) to act in the context of another site (the one the attacker is interested in). Essentially, the attacker can insert custom Javascript into any domain, provided the victim user visits the attacker-controlled web page first."
Attackers can even snag a copy of your session cookie or hijack your session and read and write webmail on your behalf.
Mishra reported the vulnerability to Samsung, and the company replied that "the patch is already preloaded in our upcoming model Galaxy Note 8, and the application will be updated via Apps store update in October."
Meanwhile, Mishra, with the help of Tod Beardsley and Jeffrey Martin from Rapid7 team, also released an exploit for Metasploit Framework.
Rapid7 researchers have also published a video demonstrating the attack.
Since the Metasploit exploit code for the SOP bypass vulnerability in the Samsung Internet Browser is now publicly available, anyone with less technical knowledge can use and exploit the flaw on a large number of Samsung devices, most of which are still using the old Android Stock browser.
Samsung Android Browser is affected by a critical SOP bypass issue, a Metasploit exploit code is available
30.12.2017 securityaffairs Android
The browser app pre-installed on Samsung Android devices is affected by a critical SOP bypass issue, tracked as CVE-2017-17692.
The browser app pre-installed on Android devices is affected by a critical flaw, tracked as CVE-2017-17692, that could be exploited by an attacker to steal data from browser tabs if the user visits an attacker-controlled site.
The SOP bypass issue in the Samsung Internet Browser was discovered by the security researcher Dhiraj Mishra.
The CVE-2017-17692 vulnerability is a Same Origin Policy (SOP) bypass issue that affects the Samsung Internet Browser version 5.4.02.3 and earlier.
The Same Origin Policy is one of the most important security mechanisms implemented in modern browsers, the basic idea behind the SOP is the javaScript from one origin should not be able to access the properties of a website on another origin.
A SOP bypass occurs when a sitea.com is somehow able to access the properties of siteb.com such as cookies, location, response etc.
An attacker can copy victim’s session cookie or hijack his session and read and write webmail on your behalf.
Mishra developed a Metasploit Module for the exploitation of the SOP bypass issue and reported the flaw to the MITRE to assign CVE.
Mishra also reported the flaw to Samsung, who acknowledged it and confirmed that “the patch is already preloaded in our upcoming model Galaxy Note 8, and the application will be updated via Apps store update in October.“
Here is the Source Code for Bypassing Same Origin Policy in Samsung Internet Browser in Metasploit,
“When the Samsung Internet browser opens a new tab in a given domain (say, google.com) through a Javascript action, that Javascript can come in after the fact and rewrite the contents of that page with whatever it wants,” reads a blog post published by researchers from security firm Rapid7.
“This is a no-no in browser design since it means that Javascript can violate the Same-Origin Policy, and can direct Javascript actions from one site (controlled by the attacker) to act in the context of another site (the one the attacker is interested in). Essentially, the attacker can insert custom Javascript into any domain, provided the victim user visits the attacker-controlled web page first.”
The experts from Rapid7 have also published a video PoC of the attack.
The availability online of the Metasploit exploit code pose a serious risk to Android users that are still using the old Android Stock browser.
Three fake Bitcoin wallet apps were removed from the official Google Play
27.12.2017 securityaffairs Android
Researchers from the mobile security firm Lookout have discovered three fake Bitcoin wallet apps in the official Play store, Google promptly removed them.
Experts from mobile security firm Lookout have discovered three fake Bitcoin wallet apps in the official Play store. The fake Bitcoin wallet apps were removed by Google Play after security researchers reported their discovery to the tech giant.
The spike in Bitcoin prices is attracting crooks as never before, the number of attacks involving the cryptocurrency continues to increase.
The three fake applications tracked as PickBitPocket were developed to provide the attacker’s Bitcoin address instead of the seller’s one. The fake apps accounted for a total of up to 20,000 downloads before Google removed them from the Play store.
“Lookout has identified three Android apps disguised as bitcoin wallet apps, previously in the Google Play Store, that trick victims into sending bitcoin payments to attacker-specified bitcoin addresses.” reads the analysis published by Lookout.
“Google removed the apps immediately after Lookout notified the company. The apps collectively had up to 20,000 downloads at time of removal.”
The researchers explained that when users that installed the fake apps attempt to buy goods or services their payments are hijacked to the attacker’s wallet.
The three fake Bitcoin wallet apps discovered by Lookout are:
Bitcoin mining, which had between 1,000 and 5,000 installs at the time it was removed;
Blockchain Bitcoin Wallet – Fingerprint, which had between 5,000 and 10,000 installs;
Fast Bitcoin Wallet, which has between 1,000 and 5,000 installs.
“As Bitcoin captures broader interest, this means more people may be purchasing the cryptocurrency, or looking for mobile wallets to store their coins. Individuals should be vigilant in choosing a secure wallet and should also have a security solution in place to identify malicious activity on their device,” concluded Lookout.
Jack of all trades
22.12.2017 Kaspersky Android
Nowadays, it’s all too easy to end up with malicious apps on your smartphone, even if you’re using the official Google Play app store. The situation gets even worse when you go somewhere other than the official store – fake applications, limited security checks, and so on. However, the spread of malware targeting Android OS is not limited to unofficial stores – advertising, SMS-spam campaigns and other techniques are also used. Among this array of threats we found a rather interesting sample – Trojan.AndroidOS.Loapi. This Trojan boasts a complicated modular architecture that means it can conduct a variety of malicious activities: mine cryptocurrencies, annoy users with constant ads, launch DDoS attacks from the affected device and much more. We’ve never seen such a ‘jack of all trades’ before.
Distribution and infection
Samples of the Loapi family are distributed via advertising campaigns. Malicious files are downloaded after the user is redirected to the attackers’ malicious web resource. We found more than 20 such resources, whose domains refer to popular antivirus solutions and even a famous porn site. As we can see from the image below, Loapi mainly hides behind the mask of antivirus solutions or adult content apps:
After the installation process is finished, the application tries to obtain device administrator permissions, asking for them in a loop until the user agrees. Trojan.AndroidOS.Loapi also checks if the device is rooted, but never subsequently uses root privileges – no doubt they will be used in some new module in the future.
After acquiring admin privileges, the malicious app either hides its icon in the menu or simulates various antivirus activity, depending on the type of application it masquerades as:
Self-protection
Loapi aggressively fights any attempts to revoke device manager permissions. If the user tries to take away these permissions, the malicious app locks the screen and closes the window with device manager settings, executing the following code:
As well as this fairly standard technique to prevent removal, we also found an interesting feature in the self-protection mechanism. The Trojan is capable of receiving from its C&C server a list of apps that pose a danger. This list is used to monitor the installation and launch of those dangerous apps. If one of the apps is installed or launched, then the Trojan shows a fake message claiming it has detected some malware and, of course, prompts the user to delete it:
This message is shown in a loop, so even if the user rejects the offer, the message will be shown again and again until the user finally agrees and deletes the application.
Layered architecture
Let’s take a look at the Trojan’s architecture in more detail:
At the initial stage, the malicious app loads a file from the “assets” folder, decodes it using Base64 and afterwards decrypts it using XOR operations and the app signature hash as a key. A DEX file with payload, which was retrieved after these operations, is loaded with ClassLoader.
At the second stage, the malicious app sends JSON with information about the device to the central C&C server hxxps://api-profit.com:
A command in the following format is received as a response from the server:
Where “installs” is a list of module IDs that have to be downloaded and launched; “removes” is a list of module IDs that have to be deleted; “domains” is a list of domains to be used as C&C servers; “reservedDomains” is an additional reserved list of domains; “hic” is a flag that shows that the app icon should be hidden from the user; and “dangerousPackages” is a list of apps that must be prevented from launching and installing for self-protection purposes.
At the third stage, the modules are downloaded and initialized. All the malicious functionality is concealed inside them. Let’s take a closer look at the modules we received from the cybercriminals’ server.
Advertisement module
Purpose and functionality: this module is used for the aggressive display of advertisements on the user’s device. It can also be used for secretly boosting ratings. Functionality:
Display video ads and banners
Open specified URL
Create shortcuts on the device
Show notifications
Open pages in popular social networks, including Facebook, Instagram, VK
Download and install other applications
Example of task to show ads received from the server:
While handling this task, the application sends a hidden request with a specific User-Agent and Referrer to the web page hxxps://ronesio.xyz/advert/api/interim, which in turn redirects to a page with the ads.
SMS module
Purpose and functionality: this module is used for different manipulations with text messages. Periodically sends requests to the C&C server to obtain relevant settings and commands. Functionality:
Send inbox SMS messages to attackers’ server
Reply to incoming messages according to specified masks (masks are received from C&C server)
Send SMS messages with specified text to specified number (all information is received from C&C server)
Delete SMS messages from inbox and sent folder according to specified masks (masks are received from C&C server)
Execute requests to URL and run specified Javascript code in the page received as a response (legacy functionality that was later moved to a separate module)
Web crawling module
Purpose and functionality: this module is used for hidden Javascript code execution on web pages with WAP billing in order to subscribe the user to various services. Sometimes mobile operators send a text message asking for confirmation of a subscription. In such cases the Trojan uses SMS module functionality to send a reply with the required text. Also, this module can be used for web page crawling. An example of a web page crawling task received from the server is shown below:
This module together with the advertisement module tried to open about 28,000 unique URLs on one device during our 24-hour experiment.
Proxy module
Purpose and functionality: this module is an implementation of an HTTP proxy server that allows the attackers to send HTTP requests from the victim’s device. This can be used to organize DDoS attacks against specified resources. This module can also change the internet connection type on a device (from mobile traffic to Wi-Fi and vice versa).
Mining Monero
Purpose and functionality: this module uses the Android version of minerd to perform Monero (XMR) cryptocurrency mining. Mining is initiated using the code below:
The code uses the following arguments:
url – mining pool address, “stratum+tcp://xmr.pool.minergate.com:45560”
this.user – username, value randomly selected from the following list: “lukasjeromemi@gmail.com”, “jjopajopaa@gmail.com”, “grishaobskyy@mail.ru”, “kimzheng@yandex.ru”, “hirt.brown@gmx.de”, “swiftjobs@rambler.ru”, “highboot1@mail333.com”, “jahram.abdi@yandex.com”, “goodearglen@inbox.ru”, girlfool@bk.ru
password – constant value, “qwe”
Old ties
During our investigation we found a potential connection between Loapi and Trojan.AndroidOS.Podec. We gathered some evidence to support this theory:
Matching C&C server IP addresses. The current address of the active Loapi C&C server is resolved with DNS to 5.101.40.6 and 5.101.40.7. But if we take a look at the history, we can see other IP addresses to which this URL resolved before:
At first, this URL was resolved to the IP address 91.202.62.38. If we analyze the history of DNS records that resolved to this address, we see the following:
As we can see from the records, in 2015 (when Podec was active), this IP address was resolved from various generated domains, and many of them were used in Podec (for example, obiparujudyritow.biz, in the 0AF37F5F07BBF85AFC9D3502C45B81F2 sample).
Matching unique fields at the initial information collection stage. Both Trojans collect information with similar structure and content and send it in JSON format to the attackers’ server during the initial stage. Both JSON objects have the fields “Param1”, “Param2” and “PseudoId”. We performed a search in our internal ElasticSearch clusters – where we store information about clean and malicious applications – and found these fields were only used in Podec and Loapi.
Similar obfuscation.
Similar ways of detecting SU on a device.
Similar functionality (both can subscribe users to paid services).
None of these arguments can be considered conclusive proof of our theory, but taken together they suggest there’s a high probability that the malicious applications Podec and Loapi were created by the same group of cybercriminals.
Conclusion
Loapi is an interesting representative from the world of malicious Android apps. It’s creators have implemented almost the entire spectrum of techniques for attacking devices: the Trojan can subscribe users to paid services, send SMS messages to any number, generate traffic and make money from showing advertisements, use the computing power of a device to mine cryptocurrencies, as well as perform a variety of actions on the internet on behalf of the user/device. The only thing missing is user espionage, but the modular architecture of this Trojan means it’s possible to add this sort of functionality at any time.
P.S.
As part of our dynamic malware analysis we installed the malicious application on a test device. The images below show what happened to it after two days:
Because of the constant load caused by the mining module and generated traffic, the battery bulged and deformed the phone cover.
C&C
ronesio.xyz (advertisement module)
api-profit.com:5210 (SMS module and mining module)
mnfioew.info (web crawler)
mp-app.info (proxy module)
Domains
List of web resources from which the malicious application was downloaded:
Domain IP
a2017-security.com 91.202.62.45
alert.com–securitynotice.us 104.18.47.240,104.18.46.240
alibabadownload.org 91.202.62.45
antivirus-out.net 91.202.62.45
antivirus360.ru 91.202.62.45,31.31.204.59,95.213.165.247,
194.58.56.226,194.58.56.50
clean-application.com 91.202.62.45
defenderdevicebiz.biz 104.27.178.88,104.27.179.88
fixdevice.biz 104.18.45.199,104.18.44.199
highspeard.eu 91.202.62.45
hoxdownload.eu 91.202.62.45
lilybrook.ru 104.24.113.21,104.24.112.21
nootracks.eu 91.202.62.45
noxrow.eu 91.202.62.45
s4.pornolub.xyz 91.202.62.45
sidsidebottom.com 9.56.163.55,104.27.128.72
titangelx.com 104.27.171.112,104.27.170.112
trust.com-mobilehealth.biz 04.27.157.60,104.27.156.60
trust.com-securitynotice.biz 104.31.68.110,104.31.69.110
violetataylor.ru 104.31.88.236,104.31.89.236
Fake Bitcoin Wallet Apps Removed from Google Play
21.12.2017 securityweek Android
Three fake Bitcoin applications were recently removed from Google Play after security researchers discovered they were tricking users into sending funds to their developers, mobile security firm Lookout has discovered.
The impressive increase in Bitcoin value over the past several months has stirred interest from individuals worldwide, including cybercriminals. The number of attacks involving the cryptocurrency has increased recently, and it appears that they moved to mobile as well.
Detected as PickBitPocket, the rogue applications in Google Play were designed in such a way that they provide the attacker’s Bitcoin address instead of the seller’s. The malicious programs registered a total of up to 20,000 downloads before Google removed them from the application storefront.
Basically, when attempting to buy goods or services from an Android device where a PickBitPocket wallet app is installed, the user ends up routing the Bitcoin payment to the attacker.
The three fake Bitcoin apps, Lookout reports, included Bitcoin mining, which had between 1,000 and 5,000 installs at the time it was removed, Blockchain Bitcoin Wallet – Fingerprint, which had between 5,000 and 10,000 installs, and Fast Bitcoin Wallet, with between 1,000 and 5,000 installs.
“As Bitcoin captures broader interest, this means more people may be purchasing the cryptocurrency, or looking for mobile wallets to store their coins. Individuals should be vigilant in choosing a secure wallet and should also have a security solution in place to identify malicious activity on their device,” Lookout concludes.
Loapi Android malware can destroy your battery mining Monero
20.12.2017 securityaffairs Android
Experts from Kaspersky have spotted an Android malware dubbed Loapi that includes a so aggressive mining component that it can destroy your battery.
Researchers from security firm Kaspersky Lab have spotted a new strain of Android malware dubbed Loapi lurking in fake anti-virus and porn applications, that implements many features, including cryptocurrency mining.
Loapi can be used to perform a wide range of malicious activities, thanks to a modular architecture it can be used to take part in a DDoS botnet or bombard infected handsets with advertisements.
The strain of malware analyzed by Kaspersky when running a few days to mine the Monero cryptocurrency physically damaged the device due to the load caused by the activity.
“Because of the constant load caused by the mining module and generated traffic, the battery bulged and deformed the phone cover.” reads the analysis published by Kaspersky.

According to the researchers, the Loapi malware is able to destroy an Android device in just 2 days.

The Loapi malware communicates with the following command and control servers:
ronesio.xyz (advertisement module) – A module used for the aggressive display of advertisements on the infected handset.
api-profit.com:5210 (SMS module and mining module) – A module used for the manipulations of text messages. It periodically sends requests to the C&C server to obtain relevant settings and commands.
mnfioew.info (web crawler); A module used for hidden Javascript code execution on web pages with WAP billing in order to subscribe the user to various services
mp-app.info (proxy module) – A module that implements an HTTP proxy server that allows the attackers to send HTTP requests from the device. It is the component used to power DDoS attacks.
Experts believe the gang behind the Loapi malware is the same responsible for the 2015 Android malware Podec.
The Loapi malware was distributed through third-party app stores and advertising campaigns.
“Malicious files are downloaded after the user is redirected to the attackers’ malicious web resource. We found more than 20 such resources, whose domains refer to popular antivirus solutions and even a famous porn site. As we can see from the image below, Loapi mainly hides behind the mask of antivirus solutions or adult content apps” continues the analysis.

Once installed, the Loapi malware tries to obtain ‘device administrator’ permissions by looping a pop-up until a victim clicks yes.
The sample analyzed by Kaspersky checks if the device is rooted, but never subsequently uses root privileges, experts believe cybercriminals will use them in some new module in the future for example to implements spyware features.
Researchers pointed out that the Android malware “aggressively fights any attempts to revoke device manager permissions” by locking the screen and closing phone windows by itself.
Loapi Android Trojan Does All Sorts of Bad
19.12.2017 securityweek Android
A recently discovered Android malware features a modular architecture that allows it to perform a broad range of nefarious activities, Kaspersky Lab researchers warn.
Detected by Kaspersky as Trojan.AndroidOS.Loapi, the malicious program was found masquerading as antivirus solutions or adult content apps. Its capabilities, the security researchers say, range from mining for cryptocurrencies to displaying a constant stream of ads and to launching distributed denial of service (DDoS) attacks, among others.
The mobile threat was observed distributed via advertising campaigns that redirected users to the attackers’ malicious websites. After installation, the malware attempts to gain device administrator rights, continuously requesting them in a loop. Although it checks whether the device is rooted, the Trojan doesn’t use root privileges.
If the user gives in and grants the malicious app admin privileges, Loapi either hides its icon in the menu or simulates antivirus activity. The displayed behavior depends on the type of application it masquerades as, Kaspersky has discovered.
The Trojan can prevent users from revoking its device manager permissions by locking the screen and closing the window with device manager settings. Moreover, the malware receives from the command and control (C&C) server a list of apps that could pose a danger and uses it to monitor the installation and launch of those apps.
When such an app is installed or launched, the Trojan displays a fake message claiming it has detected malware, prompting the user to delete it. The message is displayed in a loop, thus preventing the user from dismissing it until the application is deleted.
At installation, Loapi receives from the C&C lists of modules to install or remove, a list of domains that serve as C&C, an additional reserved list of domains, the list of “dangerous” apps, and a flag whether to hide its app icon. At a third stage during the process, the necessary modules are downloaded and initialized.
An advertisement module is used to aggressively display ads on the device, but can also be used to open URLs, create shortcuts, show notifications, open pages in popular social network apps (including Facebook, Instagram, VK), and download and install other applications.
An SMS module can perform various text message manipulation operations. Based on C&C commands, it can send inbox SMS messages to attackers’ server, reply to incoming messages, send SMS messages with specified text to specified number, delete SMS messages from inbox and sent folder, and execute requests to URL and run specified JavaScript code in the page received as response.
A Web crawling module can subscribe users to services by covertly executing JavaScript code on web pages with WAP billing, in addition to performing web page crawling. Should operators send text messages asking for confirmation, the SMS module is employed to reply with the required text. Together with the ad module, it was observed attempting to open 28,000 unique URLs on a single device during a 24-hour experiment.
The Trojan also packs a proxy module that allows attackers to send HTTP requests from the victims’ devices via an HTTP proxy server. This feature allows the malware authors to organize DDoS attacks against specified resources or to change the Internet connection type on a device, the security researchers warn.
Another module uses the Android version of minerd to mine for the Monero (XMR) cryptocurrency.
According to Kaspersky, Loapi might be related to the Podec malware (Trojan.AndroidOS.Podec), as both threats use the same C&C server IP address, both use the same obfuscation, and feature similar ways of detecting superuser on the device. Moreover, both collect information with similar structure and content and send it in JSON format to the C&C during the initial stage.
“Loapi is an interesting representative from the world of malicious Android apps. Its creators have implemented almost the entire spectrum of techniques for attacking devices […]. The only thing missing is user espionage, but the modular architecture of this Trojan means it’s possible to add this sort of functionality at any time,” Kaspersky concludes.
This New Android Malware Can Physically Damage Your Phone
19.12.2017 thehackernews Android

Due to the recent surge in cryptocurrency prices, not only hackers but also legitimate website administrators are increasingly using JavaScript-based cryptocurrency miners to monetize by levying the CPU power of your PC to mine Bitcoin or other cryptocurrencies.
Just last week, researchers from AdGuard discovered that some popular video streaming and ripper sites including openload, Streamango, Rapidvideo, and OnlineVideoConverter hijacks CPU cycles from their over hundreds of millions of visitors for mining Monero cryptocurrency.
Now, researchers from Moscow-based cyber security firm Kaspersky Lab have uncovered a new strain of Android malware lurking in fake anti-virus and porn applications, which is capable of performing a plethora of nefarious activities—from mining cryptocurrencies to launching Distributed Denial of Service (DDoS) attacks.
Dubbed Loapi, the new Android Trojan can perform so many more malicious activities at a time that can exploit a handset to the extent that within just two days of infection it can cause the phone's battery to bulge out of its cover.
Described as a "jack-of-all-trades" by the researchers, Loapi has a modular architecture that lets it conduct a variety of malicious activities, including mining the Monero cryptocurrency, launching DDoS attacks, bombarding infected users with constant ads, redirecting web traffic, sending text messages, and downloading and installing other apps.
Loapi Destroyed An Android Phone In Just 2 Days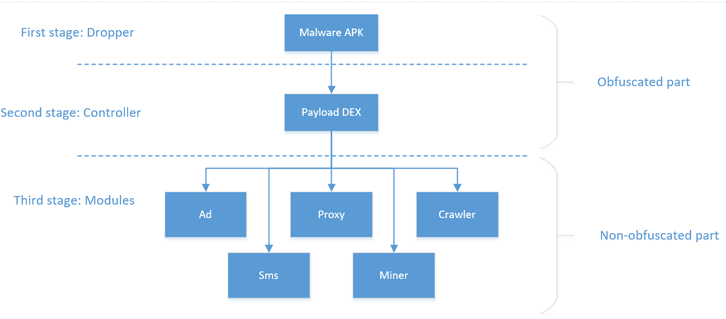
When analyzed a Loapi sample, Kaspersky's researchers discovered that the malware mines the Monero cryptocurrency so intensely that it destroyed an Android phone after two days of testing, causing the battery to bulge and deforming the phone cover.
According to researchers, the cybercriminals behind Loapi are the same responsible for the 2015 Android malware Podec. They are distributing the malware through third-party app stores and online advertisements that pose as apps for "popular antivirus solutions and even a famous porn site."
A screenshot in the Kaspersky blog suggests that Loapi impersonates as at least 20 variations of adult-content apps and legitimate antivirus software from AVG, Psafe DFNDR, Kaspersky Lab, Norton, Avira, Dr. Web and CM Security, among others.
Upon installation, Loapi forces the user to grant it 'device administrator' permissions by looping a pop-up until a victim clicks yes, which gives the malicious app the same power over your smartphone that you have.
This highest level privilege on a device would also make the Loapi malware ideal for user espionage, though this capability is not yet present in the malware, the Kaspersky researchers think this can be included in the future.
Loapi Malware Aggressively Fights to Protect Itself
Researchers also said the malware "aggressively fights any attempts to revoke device manager permissions" by locking the screen and closing phone windows by itself.
Loapi communicates with the module-specific command and control (C&C) servers, including advertisement module, SMS module and mining module, web crawler, and proxy module, for different functions to be performed on the infected device.
By connecting with one of the above-mentioned C&C servers, Loapi sends a list of legitimate antivirus apps that pose it danger and claims the real app as malware and urges the user to delete it by showing the pop-up in a loop until the user finally deletes the app.
"Loapi is an interesting representative from the world of malicious Android apps. It’s creators have implemented almost the entire spectrum of techniques for attacking devices: the Trojan can subscribe users to paid services, send SMS messages to any number, generate traffic and make money from showing advertisements, use the computing power of a device to mine cryptocurrencies, as well as perform a variety of actions on the internet on behalf of the user/device," the researchers concluded.
Fortunately, Loapi failed to make its ways to Google Play Store, so users who stick to downloads from the official app store are not affected by the malware. But you are advised to remain vigilant even when downloading apps from Play Store as malware often makes its ways to infect Android users.
Golduck Malware Infects Classic Android Games
13.12.2017 securityweek Android
Several classic game applications in Google Play have been silently downloading and installing a malicious APK file onto Android devices, Appthority reports.
The malicious code was downloaded from a "Golduck" server and installed on devices using a technique called Java reflection. The offending applications, the security company says, were also observed running shell commands and sending SMS messages.
Appthority describes the malicious applications as high quality classic games, including Tank and Bomber. Rated high on Google Play, the games had up to 10.5 million downloads when their nefarious behavior was exposed.
The extra APK was being fetched from hxxp://golduck.info/pluginapk/gp.apk, after which the original game app would load the downloaded code via the /system/bin/dex2oat command.
Appthority's security researchers discovered three folders inside the loaded gp.apk file, each featuring seemly benign names, such as “google.android”, “startapp.android.unity.ads,” and “unity.ads.” The malicious code was hidden inside the google.android folder.
By analyzing the content of the folders, Appthority found code (PackageUtils.class) designed to silently install applications using system permissions.
“These malicious apps seem to be at their initial stage and the code is not obfuscated,” the company notes.
The downloaded payload also contains code for sending SMS messages to users’ contacts. These messages contained game information, thus potentially increasing the chances that the malware would spread to other users.
The Golduck malware, the security company says, could allow attackers to completely compromise the infected device, especially if root is available. The threat also sets the stage for adware-related attacks.
Appthority found two Golduck-infected applications in Google Play and informed Google on the matter on Nov. 20, 2017. All of the offending applications have been taken down by the Android Security team.
To stay protected from the Golduck malware, users are advised to keep an eye on unusual activity on their mobile devices, such as the availability of root access without their intent. SMS charges from unknown sources would also indicate possible infection.
Users are also advised to avoid installing applications from unknown developers and from unofficial app stores.
The applications Appthority has found infected with Golduck include Classic Block Puzzle, Classic Bomber, and Classic Tank vs Super Bomber. Users are advised to uninstall these as soon as possible.
Millions Impacted by Credential-Stealers in Google Play
13.12.2017 securityweek Android
During October and November 2017, Kaspersky Lab researchers discovered 85 applications in Google Play that were designed to steal credentials for Russian social network VK.com. One of the malicious applications had more than a million downloads.
While most of the applications were listed in the marketplace in October and gathered fewer than 1,000 installations, some were uploaded in July and proved to be highly popular among users. Seven of the apps had between 10,000 and 100,000 downloads, while nine had between 1,000 and 10,000 installations.
The most popular of the apps masqueraded as a game. It was submitted to Google Play in April 2017 without malicious code in it, but an update in October 2017 added the information stealing capabilities. The game gathered more than 1 million downloads in the seven months it was active on Google Play.
Most of the offending applications were designed to look like apps for the VK.com social platform, supposedly allowing users to listen to music or monitor user page visits. Because apps of this type normally ask for the user to log into their account, they didn’t raise suspicion. Some of the programs were game apps.
The campaign was targeted at VK users only. The platform is highly popular in CIS countries, and the malicious apps first checked the device language and only asked for login credentials if Russian, Ukrainian, Kazakh, Armenian, Azerbaijani, Belarusian, Kyrgyz, Romanian, Tajik, and Uzbek were in use, Kaspersky has discovered.
The actors behind these apps had been publishing their malicious applications in Google Play for over two years, so they had to modify their code to bypass detection, Kaspersky's researchers say.
The recently observed apps used a modified VK SDK with tricky code, which served the standard login page to the user, relied on malicious JS code to steal credentials from the login page and pass them back to the app. The stolen credentials were encrypted and then uploaded to a remote server.
Most of the malicious apps had the described functionality, but some were slightly different: they also used malicious JS code from the OnPageFinished method for extracting credentials and for uploading them.
“We think that cybercriminals use stolen credentials mostly for promoting groups in VK.com. They silently add users to promote various groups and increase their popularity by doing so. We have reason to think so because there were complaints from some infected users that their accounts had been silently added to such groups,” Kaspersky says.
The researchers also note that other Google Play apps submitted by these miscreants were published as unofficial clients for popular messaging app Telegram. Built using an open source Telegram SDK, these apps would work just as any other such software, but they would also add users to promoted groups/chats (based on a list received from the server).
The credential-stealing apps are detected as Trojan-PSW.AndroidOS.MyVk.o. Kaspersky reported 72 of the apps to Google, all of which were removed (13 apps had been removed before). The malicious Telegram clients are detected as not-a-virus:HEUR:RiskTool.AndroidOS.Hcatam.a. They too were removed from Google Play.
A banking Trojan targeting the Polish banks was found in Google Play
13.12.2017 securityaffairs Android
It has happened again, several banking Trojan samples have been found on Google Play, this time the malicious code targeted a number of Polish banks.
The malware was disguised as seemingly legitimate apps “Crypto Monitor”, a cryptocurrency price tracking app, and “StorySaver”, a third-party tool for downloading stories from Instagram.
The malicious code is able to display fake notifications and login forms on the infected device to harvest login credentials used to access legitimate banking applications. The code is also able to intercept SMS messages to bypass two-factor authentication used by the financial institutions.
The same malware was discovered by experts at security firm RiskIQ in November.
According to researchers from ESET, the “Crypto Monitor” app was uploaded to the Play store on November 25 by the developer walltestudio, while the “StorySaver” app was uploaded by the developer kirillsamsonov45 on November 29.
“Together, the apps had reached between 1000 and 5000 downloads at the time we reported them to Google on December 4. Both apps have since been removed from the store.” states the analysis published by ESET.
When the user launches the malicious apps, they compare the apps installed on the infected device against a list of fourteen apps used by Polish banks and once found one of them, the malicious code can display fake login forms imitating those of the targeted legitimate apps.
App name Package name
Alior Mobile com.comarch.mobile
BZWBK24 mobile pl.bzwbk.bzwbk24
Getin Mobile com.getingroup.mobilebanking
IKO pl.pkobp.iko
Moje ING mobile pl.ing.mojeing
Bank Millennium wit.android.bcpBankingApp.millenniumPL
mBank PL pl.mbank
BusinessPro pl.bph
Nest Bank pl.fmbank.smart
Bank Pekao eu.eleader.mobilebanking.pekao
PekaoBiznes24 eu.eleader.mobilebanking.pekao.firm
plusbank24 eu.eleader.mobilebanking.invest
Mobile Bank eu.eleader.mobilebanking.raiffeisen
Citi Handlowy com.konylabs.cbplpat
In some cases the fake login form is displayed to the user only after he clicks on a fake notification presented by the malware imitated the ones used by the targeted bank app.
“ESET’s security systems detect the threat as Android/Spy.Banker.QL and prevent it from getting installed.” states ESET.
“ESET telemetry shows that 96% of the detections come from Poland (the remaining 4% from Austria), apparently due to local social engineering campaigns propagating the malicious apps.”
The experts noticed that it is very easy to remove the malicious apps by going to Settings > (General) > Application manager/Apps, searching for the malicious apps and uninstalling them.
“To avoid falling prey to mobile malware in the future, make sure to always check app ratings and reviews, pay attention to what permissions you grant to apps, and use a reputable mobile security solution to detect and block latest threats.” concluded ESET.
ESET, who credited Witold Precikowski for the discovery, included the IoCs for this specific threat in its report.
Still Stealing
12.12.2017 Kaspersky Android
Two years ago in October 2015 we published a blogpost about a popular malware that was being distributed from the Google Play Store. Over the next two years we detected several similar apps on Google Play, but in October and November 2017 we found 85 new malicious apps on Google Play that are stealing credentials for VK.com. All of them have been detected by Kaspersky Lab products as Trojan-PSW.AndroidOS.MyVk.o. We reported 72 of them to Google and they deleted these malicious apps from Google Play Store, 13 other apps were already deleted. Furthermore, we reported these apps with technical details to VK.com. One of these apps was masquerading as a game and was installed more than a million times according to Google Play Store.
One of the apps detected as Trojan-PSW.AndroidOS.MyVk.o was distributed as a game.
There were some other popular apps among them too – seven apps had 10,000-100,000 installations from Google Play and nine apps had 1,000-10,000 installation. All other apps had fewer than 1,000 installations.
App detected as Trojan-PSW.AndroidOS.MyVk.o on Google Play Store
Most of these apps were uploaded to Google Play in October 2017, but several of them were uploaded in July 2017, so they were being distributed for as long as 3 months. Moreover, the most popular app was initially uploaded to the Google Play Store on March 2017, but without any malicious code—it was just a game. Cybercriminals updated this app with a malicious version only in October 2017, having waited more than 7 months to do so!
Most of these apps looked like apps for VK.com – for listening to music or for monitoring user page visits.
App detected as Trojan-PSW.AndroidOS.MyVk.o on Google Play Store
Sure, such apps need a user to login into an account – that’s why they didn’t look suspicious. The only apps whose functionality was not VK-related were game apps. Because VK is popular mostly in CIS countries, cybercriminals checked the device language and asked for VK credentials only from users with certain languages – Russian, Ukrainian, Kazakh, Armenian, Azerbaijani, Belarusian, Kyrgyz, Romanian, Tajik, and Uzbek.
Code where a Trojan checks the device language.
These cybercriminals were publishing their malicious apps on Google Play Store for more than two years, so they had to modify their code to bypass detection. In these apps they used a modified VK SDK with tricky code–users logged on to the standard page, but the cybercriminals used malicious JS code to get the credentials from the login page and pass them back to the app.
Malicious code where a Trojan executes JS code to get VK credentials.
Then the credentials are encrypted and uploaded to the malicious website.
Code where a Trojan decrypts a malicious URL, encrypts stolen credentials and uploads them.
The interesting thing is that although most of these malicious apps had a described functionality, a few of them were slightly different—they also used malicious JS code from the OnPageFinished method, but not only for extracting credentials but for uploading them too.
Malicious code where a Trojan executes JS code to get and upload VK credentials
We think that cybercriminals use stolen credentials mostly for promoting groups in VK.com. They silently add users to promote various groups and increase their popularity by doing so. We have reason to think so because there were complaints from some infected users that their accounts had been silently added to such groups.
Another reason to think so is that we were able to find several other apps on Google Play that were published by the same cybercriminals responsible for Trojan-PSW.AndroidOS.MyVk.o. They were published as unofficial clients for Telegram, a popular messaging app. All of them were detected by Kaspersky Lab products as not-a-virus:HEUR:RiskTool.AndroidOS.Hcatam.a. We notified Google about these apps too and they deleted them from Google Play Store.
App infected with not-a-virus:HEUR:RiskTool.AndroidOS.Hcatam.a on Google Play Store
These apps were not only masquerading as Telegram apps, they were actually built using an open source Telegram SDK and work almost like every other such app. Except one thing – they added users to promoted groups/chats. These apps receive a list with groups/chats from their server. What’s more, they can add users to groups anytime – to do so they steal a GCM token which allows cybercriminals to send commands 24/7.
We also discovered an interesting thing about the malicious website extensionsapiversion.space. According to KSN statistics, in some cases it was used for mining cryptocurrencies by using an API from http://coinhive.com.
CNC
space
guest-stat.com
APPS
Package name MD5
com.parmrp.rump F5F8DF1F35A942F9092BDE9F277B7120
com.weeclient.clientold 6B55AF8C4FB6968082CA2C88745043A1
com.anocat.stelth C70DCF9F0441E3230F2F338467CD9CB7
com.xclient.old 6D6B0B97FACAA2E6D4E985FA5E3332A1
com.junglebeat.musicplayer.offmus 238B6B7069815D0187C7F39E1114C38
com.yourmusicoff.yourmusickoff 1A623B3784256105333962DDCA50785F
com.sharp.playerru 1A7B22616C3B8223116B542D5AFD5C05
com.musicould.close 053E2CF49A5D818663D9010344AA3329
com.prostie.dvijenija 2B39B22EF2384F0AA529705AF68B1192
com.appoffline.musicplayer 6974770565C5F0FFDD52FC74F1BCA732
com.planeplane.paperplane 6CBC63CBE753B2E4CB6B9A8505775389
Millions Impacted by Credential-Stealers in Google Play
12.12.2017 securityweek Android
During October and November 2017, Kaspersky Lab researchers discovered 85 applications in Google Play that were designed to steal credentials for Russian social network VK.com. One of the malicious applications had more than a million downloads.
While most of the applications were listed in the marketplace in October and gathered fewer than 1,000 installations, some were uploaded in July and proved to be highly popular among users. Seven of the apps had between 10,000 and 100,000 downloads, while nine had between 1,000 and 10,000 installations.
The most popular of the apps masqueraded as a game. It was submitted to Google Play in April 2017 without malicious code in it, but an update in October 2017 added the information stealing capabilities. The game gathered more than 1 million downloads in the seven months it was active on Google Play.
Most of the offending applications were designed to look like apps for the VK.com social platform, supposedly allowing users to listen to music or monitor user page visits. Because apps of this type normally ask for the user to log into their account, they didn’t raise suspicion. Some of the programs were game apps.
The campaign was targeted at VK users only. The platform is highly popular in CIS countries, and the malicious apps first checked the device language and only asked for login credentials if Russian, Ukrainian, Kazakh, Armenian, Azerbaijani, Belarusian, Kyrgyz, Romanian, Tajik, and Uzbek were in use, Kaspersky has discovered.
The actors behind these apps had been publishing their malicious applications in Google Play for over two years, so they had to modify their code to bypass detection, Kaspersky's researchers say.
The recently observed apps used a modified VK SDK with tricky code, which served the standard login page to the user, relied on malicious JS code to steal credentials from the login page and pass them back to the app. The stolen credentials were encrypted and then uploaded to a remote server.
Most of the malicious apps had the described functionality, but some were slightly different: they also used malicious JS code from the OnPageFinished method for extracting credentials and for uploading them.
“We think that cybercriminals use stolen credentials mostly for promoting groups in VK.com. They silently add users to promote various groups and increase their popularity by doing so. We have reason to think so because there were complaints from some infected users that their accounts had been silently added to such groups,” Kaspersky says.
The researchers also note that other Google Play apps submitted by these miscreants were published as unofficial clients for popular messaging app Telegram. Built using an open source Telegram SDK, these apps would work just as any other such software, but they would also add users to promoted groups/chats (based on a list received from the server).
The credential-stealing apps are detected as Trojan-PSW.AndroidOS.MyVk.o. Kaspersky reported 72 of the apps to Google, all of which were removed (13 apps had been removed before). The malicious Telegram clients are detected as not-a-virus:HEUR:RiskTool.AndroidOS.Hcatam.a. They too were removed from Google Play.
Golduck Malware Infects Classic Android Games
12.12.2017 securityweek Android
Several classic game applications in Google Play have been silently downloading and installing a malicious APK file onto Android devices, Appthority reports.
The malicious code was downloaded from a "Golduck" server and installed on devices using a technique called Java reflection. The offending applications, the security company says, were also observed running shell commands and sending SMS messages.
Appthority describes the malicious applications as high quality classic games, including Tank and Bomber. Rated high on Google Play, the games had up to 10.5 million downloads when their nefarious behavior was exposed.
The extra APK was being fetched from hxxp://golduck.info/pluginapk/gp.apk, after which the original game app would load the downloaded code via the /system/bin/dex2oat command.
Appthority's security researchers discovered three folders inside the loaded gp.apk file, each featuring seemly benign names, such as “google.android”, “startapp.android.unity.ads,” and “unity.ads.” The malicious code was hidden inside the google.android folder.
By analyzing the content of the folders, Appthority found code (PackageUtils.class) designed to silently install applications using system permissions.
“These malicious apps seem to be at their initial stage and the code is not obfuscated,” the company notes.
The downloaded payload also contains code for sending SMS messages to users’ contacts. These messages contained game information, thus potentially increasing the chances that the malware would spread to other users.
The Golduck malware, the security company says, could allow attackers to completely compromise the infected device, especially if root is available. The threat also sets the stage for adware-related attacks.
Appthority found two Golduck-infected applications in Google Play and informed Google on the matter on Nov. 20, 2017. All of the offending applications have been taken down by the Android Security team.
To stay protected from the Golduck malware, users are advised to keep an eye on unusual activity on their mobile devices, such as the availability of root access without their intent. SMS charges from unknown sources would also indicate possible infection.
Users are also advised to avoid installing applications from unknown developers and from unofficial app stores.
The applications Appthority has found infected with Golduck include Classic Block Puzzle, Classic Bomber, and Classic Tank vs Super Bomber. Users are advised to uninstall these as soon as possible.
Vulnerability Allows Modification of Signed Android Apps
11.12.2017 securityweek Android
One of the vulnerabilities patched by Google as part of the December 2017 Android security patches is a High severity bug that could result in tampering with applications’ code without altering their signature.
Discovered by GuardSquare security researchers and tracked as CVE-2017-13156, the security flaw is created by the fact that “a file can be a valid APK file and a valid DEX file at the same time.” Because of that, the researchers called the bug the Janus vulnerability (after the Roman god of duality).
The issue, the researchers say, is that extra bytes can be added to APK files and to DEX files. As ZIP archives, APK files can contain arbitrary bytes at the start, between its ZIP entries, which are the only ones the JAR signature scheme takes into account when verifying the application's signature (any extra bytes are ignored). DEX files, on the other hand, can contain arbitrary bytes at the end.
Another issue is that the Dalvik/ART virtual machine can load and execute both APK and DEX files. In theory, it loads the APK then extracts the DEX and runs it. In practice, it looks at the file’s header and, depending on how it interprets the information there, loads the APK either as a DEX file or as an APK file containing a ZIP entry with a DEX file.
“An attacker can leverage this duality. He can prepend a malicious DEX file to an APK file, without affecting its signature. The Android runtime then accepts the APK file as a valid update of a legitimate earlier version of the app. However, the Dalvik VM loads the code from the injected DEX file,” the security researchers explain.
By exploiting the vulnerability, an attacker could have malicious code running on an Android device with the same permissions as the targeted application, provided they trick the user into downloading and installing a fake update.
“An attacker can replace a trusted application with high privileges (a system app, for instance) by a modified update to abuse its permissions. Depending on the targeted application, this could enable the hacker to access sensitive information stored on the device or even take over the device completely,” the security researchers note.
An attacker could clone sensitive applications (such as banking or messaging apps) and deliver them as fake updates of legitimate software. Thus, the cloned application could look and behave the same as the original but inject malicious behavior.
Attack scenarios would require for the user to accept the malicious update from a source outside Google Play, which would prove relatively easy to pull off in some cases, considering that the application would still look exactly like the original.
The Janus vulnerability was found in Android 5.0 and newer. Applications signed with APK signature scheme v2 and running on Android 7.0 and newer platforms, which support the latest signature scheme, are protected. Apps using DexGuard's tamper detection mechanism are better hardened against the attack.
“Unlike scheme v1, this scheme v2 considers all bytes in the APK file. Older versions of applications and newer applications running on older devices remain susceptible. Developers should at least always apply signature scheme v2,” GuardSquare says.
Google was informed on the vulnerability on July 31, 2017, but only released a patch to its partners in November. A fix was included in the Android Security Bulletin released on December 4, 2017.
Google May Allow Innovative Use of Android Accessibility Service
11.12.2017 securityweek Android
After getting complaints from many developers, Google is evaluating whether it should continue allowing Android applications to use accessibility services for purposes other than assisting people with disabilities.
Many Android adware and malware families that make it onto Google Play abuse the BIND_ACCESSIBILITY_SERVICE permission to obtain administrator privileges and for other unauthorized activities.
As a result, Google informed application developers last month that they had 30 days to either demonstrate that the accessibility service is actually needed to help users with disabilities or remove the use of the permission from their product. The Internet giant warned that those who fail to comply would risk having their apps pulled from the official store.
The developers of several popular applications that use the accessibility service for various features that may otherwise be difficult to implement complained on various forums and reached out to Google with their concerns. The list of impacted apps includes the LastPass password manager and the Tasker automation app – the latter is not designed specifically for people with disabilities, but it is used by them.
In response to complaints, Google told developers, “We’re evaluating responsible and innovative uses of accessibility services. While we complete this evaluation, we are pausing the 30 day notice we previously contacted you about.”
In the meantime, developers whose Android applications require the BIND_ACCESSIBILITY_SERVICE permission must clearly inform users of why the service is needed before asking them to enable it. Developers must also convince Google that their app uses the permission for responsible and innovative purposes.
“Your disclosure must meet the following requirements: In all cases, you must have a disclosure to explain why you need to observe user actions in general using the Accessibility Service API. For each accessibility capability declared, you must have an accompanying disclosure to describe the app functionality that the Accessibility Service permission is enabling for your app. (The default disclosure tells us ‘what’, but you must disclose to the user ‘why’),” Google told developers.
The information provided by application developers on how they use the service will help Google make a decision regarding the use of the accessibility service.
Dark Web – The median price range for Android ransomware kits hits $200
11.12.2017 Securityaffairs Android
According to the firm Carbon Black, Android ransomware kits are very popular in the dark web, and the median price range for them hits $200.
According to the firm Carbon Black, Android ransomware kits are very popular in the dark web, more than 5,000 Android ransomware kit listings have been discovered in 2017.
Even if most ransomware kits are still focused on targeting Windows systems, Android ransomware kits are expected to grow in volume and price.
The median price range for Android ransomware kits hits $200, 20 times higher than the $10 median price of Windows ransomware kits.
Researchers at Carbon Black found 1,683 Android ransomware kits out of a total of 5,050, their price ranges from $250 up to $850.
The experts explicitly mentioned the case of the DoubleLocker ransomware for Android that was spotted early this year by security researchers from cybersecurity firm ESET. DoubleLocker is the first-ever ransomware to abuse the Android accessibility feature that implements alternative ways to interact with a mobile device, it was a new malware that not only encrypts the Android mobile devices but also changes PIN lock.

Well, experts at Carbon Black reported a case of a cybercriminal that wanted $854 for the Locker Android ransomware kit.
“We are already seeing an uptick in Android Ransomware kits in underground markets, selling for a much higher price. In our research, we discovered that the median price of ransomware targeting Windows OS is $10, whereas Android-capable ransomware has a median range of $200.” reads a report published by Carbon Black.
Rick McElroy, a Carbon Black security strategist, explained that there is a significant difference between typical iOS users and Android ones. Apple users have a tendency to buy new devices everytime a new model is on the market and update their applications and operating systems on a regular basis.
Android users being remiss in updating their devices, giving much more opportunities to the attackers.
“One of the most surprising things was how many Android devices are out there that have not been updated for two years now, and probably never will,” McElroy says. “Updates are usually simple to conduct, but many users simply don’t do them.”
Crooks choose to target Android users because Android holds the largest OS marketshare worldwide for smartphones, roughly 86% in the first quarter of Q1.
Another factor that influences the median price higher for Android ransomware kits is the level of coding sophistication that is needed to create these tools compared to the efforts necessary to develop similar kits for Windows.
“This speaks a bit to how easy it is to get ransomware onto a Windows system versus other operation systems,” McElroy says. “The longer a developer has to spend to get his ransomware to work effectively at scale the higher the price will be.”
The last catalyst that is driving the median price higher for Android ransomware kits is the spike in the value of Bitcoin. Bitcoin is the currency used for payments of the ransom, “with Bitcoin value increasing so quickly, the expansion of this space will likely be connected closely to the value of BTC.”
“However, as those attacks become tougher, and crypto-currency, such as Bitcoin, gains popularity; we believe ransom-based attacks such as screen-lock and file-encryption will gain popularity going forward.” concludes the report.