11.9.24 Attack The Hacker News

Attack 2024 2023 2022 2021 2020
New PIXHELL Attack Exploits LCD Screen Noise to Exfiltrate Data from Air-Gapped Computers
11.9.24 Attack The Hacker News
A new side-channel attack dubbed PIXHELL could be abused to target air-gapped computers by breaching the "audio gap" and exfiltrating sensitive information by taking advantage of the noise generated by pixels on an LCD screen.
"Malware in the air-gap and audio-gap computers generates crafted pixel patterns that produce noise in the frequency range of 0 - 22 kHz," Dr. Mordechai Guri, the head of the Offensive Cyber Research Lab in the Department of Software and Information Systems Engineering at the Ben Gurion University of the Negev in Israel, said in a newly published paper.
"The malicious code exploits the sound generated by coils and capacitors to control the frequencies emanating from the screen. Acoustic signals can encode and transmit sensitive information."
The attack is notable in that it doesn't require any specialized audio hardware, loudspeaker, or internal speaker on the compromised computer, instead relying on the LCD screen to generate acoustic signals.
Air-gapping is a crucial security measure that's designed to safeguard mission-critical environments against potentially security threats by physically and logically isolating them from external networks (i.e., internet). This is typically accomplished by disconnecting network cables, disabling wireless interfaces, and disabling USB connections.
That said, such defenses could be circumvented by means of rogue insider or a compromise of the hardware or software supply chain. Another scenario could involve an unsuspecting employee plugging in an infected USB drive to deploy malware capable of triggering a covert data exfiltration channel.
"Phishing, malicious insiders, or other social engineering techniques may be employed to trick individuals with access to the air-gapped system into taking actions that compromise security, such as clicking on malicious links or downloading infected files," Dr. Guri said.
"Attackers may also use software supply chain attacks by targeting software application dependencies or third-party libraries. By compromising these dependencies, they can introduce vulnerabilities or malicious code that may go unnoticed during development and testing."
Like the recently demonstrated RAMBO attack, PIXHELL makes use of the malware deployed on the compromised host to create an acoustic channel for leaking information from audio-gapped systems.
This is made possible by the fact that LCD screens contain inductors and capacitors as part of their internal components and power supply, causing them to vibrate at an audible frequency that produces a high-pitched noise when electricity is passed through the coils, a phenomenon called coil whine.
Specifically, changes in power consumption can induce mechanical vibrations or piezoelectric effects in capacitors, producing audible noise. A crucial aspect that affects the consumption pattern is the number of pixels that are lit and their distribution across the screen, as white pixels require more power to display than dark pixels.
"Also, when alternating current (AC) passes through the screen capacitors, they vibrate at specific frequencies," Dr. Guri said. "The acoustic emanates are generated by the internal electric part of the LCD screen. Its characteristics are affected by the actual bitmap, pattern, and intensity of pixels projected on the screen."
"By carefully controlling the pixel patterns shown on our screen, our technique generates certain acoustic waves at specific frequencies from LCD screens."
An attacker could therefore leverage the technique to exfiltrate the data in the form of acoustic signals that are then modulated and transmitted to a nearby Windows or Android device, which can subsequently demodulate the packets and extract the information.
That having said, it bears noting that the power and quality of the emanated acoustic signal depends on the specific screen structure, its internal power supply, and coil and capacitor locations, among other factors.
Another important thing to highlight is that the PIXHELL attack, by default, is visible to users looking at the LCD screen, given that it involves displaying a bitmap pattern comprising alternate black-and-white rows.
"To remain covert, attackers may use a strategy that transmits while the user is absent," Dr. Guri said. "For example, a so-called 'overnight attack' on the covert channels is maintained during the off-hours, reducing the risk of being revealed and exposed."
The attack, however, could be transformed into a stealthy one during working hours by reducing the pixel colors to very low values prior to transmission -- i.e., using RGB levels of (1,1,1), (3,3,3), (7,7,7), and (15,15,15) -- thereby giving the impression to the user that the screen is black.
But doing so has the side effect of "significantly" bringing down the sound production levels. Nor is the approach foolproof, as a user can still make out anomalous patterns if they look "carefully" at the screen.
This is not the first time audio-gap restrictions have been surmounted in an experimental setup. Prior studies undertaken by Dr. Guri and others have employed sounds generated by computer fans (Fansmitter), hard disk drives (Diskfiltration), CD/DVD drives (CD-LEAK), power supply units (POWER-SUPPLaY), and inkjet printers (Inkfiltration).
As countermeasures, it's recommended to use an acoustic jammer to neutralize the transmission, monitor the audio spectrum for unusual or uncommon signals, limit physical access to authorized personnel, prohibit the use of smartphones, and use an external camera for detecting unusual modulated screen patterns.
New RAMBO Attack Uses RAM Radio Signals to Steal Data from Air-Gapped Networks
11.9.24 Attack The Hacker News
A novel side-channel attack has been found to leverage radio signals emanated by a device's random access memory (RAM) as a data exfiltration mechanism, posing a threat to air-gapped networks.
The technique has been codenamed RAMBO (short for "Radiation of Air-gapped Memory Bus for Offense") by Dr. Mordechai Guri, the head of the Offensive Cyber Research Lab in the Department of Software and Information Systems Engineering at the Ben Gurion University of the Negev in Israel.
"Using software-generated radio signals, malware can encode sensitive information such as files, images, keylogging, biometric information, and encryption keys," Dr. Guri said in a newly published research paper.
"With software-defined radio (SDR) hardware, and a simple off-the-shelf antenna, an attacker can intercept transmitted raw radio signals from a distance. The signals can then be decoded and translated back into binary information."
Over the years, Dr. Guri has concocted various mechanisms to extract confidential data from offline networks by taking advantage of Serial ATA cables (SATAn), MEMS gyroscope (GAIROSCOPE), LEDs on network interface cards (ETHERLED), and dynamic power consumption (COVID-bit).
Some of the other unconventional approaches devised by the researcher entail leaking data from air-gapped networks via covert acoustic signals generated by graphics processing unit (GPU) fans (GPU-FAN), (ultra)sonic waves produced by built-in motherboard buzzers (EL-GRILLO), and even printer display panels and status LEDs (PrinterLeak).
Last year, Dr. Guri also demonstrated AirKeyLogger, a hardwareless radio frequency keylogging attack that weaponizes radio emissions from a computer's power supply to exfiltrate real-time keystroke data to a remote attacker.
"To leak confidential data, the processor's working frequencies are manipulated to generate a pattern of electromagnetic emissions from the power unit modulated by keystrokes," Dr. Guri noted in the study. "The keystroke information can be received at distances of several meters away via an RF receiver or a smartphone with a simple antenna."
As always with attacks of this kind, it requires the air-gapped network to be first compromised through other means – such as a rogue insider, poisoned USB drives, or a supply chain attack – thereby allowing the malware to trigger the covert data exfiltration channel.
RAMBO is no exception in that the malware is used to manipulate RAM such that it can generate radio signals at clock frequencies, which are then encoded using Manchester encoding and transmitted so as to be received from a distance away.
The encoded data can include keystrokes, documents, and biometric information. An attacker on the other end can then leverage SDR to receive the electromagnetic signals, demodulate and decode the data, and retrieve the exfiltrated information.
"The malware utilizes electromagnetic emissions from the RAM to modulate the information and transmit it outward," Dr. Guri said. "A remote attacker with a radio receiver and antenna can receive the information, demodulate it, and decode it into its original binary or textual representation."
The technique could be used to leak data from air-gapped computers running Intel i7 3.6GHz CPUs and 16 GB RAM at 1,000 bits per second, the research found, with keystrokes being exfiltrated in real-time with 16 bits per key.
"A 4096-bit RSA encryption key can be exfiltrated at 41.96 sec at a low speed and 4.096 bits at a high speed," Dr. Guri said. "Biometric information, small files (.jpg), and small documents (.txt and .docx) require 400 seconds at the low speed to a few seconds at the fast speeds."
"This indicates that the RAMBO covert channel can be used to leak relatively brief information over a short period."
Countermeasures to block the attack include enforcing "red-black" zone restrictions for information transfer, using an intrusion detection system (IDS), monitoring hypervisor-level memory access, using radio jammers to block wireless communications, and using a Faraday cage.
Windows Downgrade Attack Risks Exposing Patched Systems to Old Vulnerabilities
8.8.24 Attack The Hacker News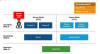
Microsoft said it is developing security updates to address two loopholes that it said could be abused to stage downgrade attacks against the Windows update architecture and replace current versions of the operating system files with older versions.
The vulnerabilities are listed below -
CVE-2024-38202 (CVSS score: 7.3) - Windows Update Stack Elevation of Privilege Vulnerability
CVE-2024-21302 (CVSS score: 6.7) - Windows Secure Kernel Mode Elevation of Privilege Vulnerability
Credited with discovering and reporting the flaws is SafeBreach Labs researcher Alon Leviev, who presented the findings at Black Hat USA 2024 and DEF CON 32.
CVE-2024-38202, which is rooted in the Windows Backup component, allows an "attacker with basic user privileges to reintroduce previously mitigated vulnerabilities or circumvent some features of Virtualization Based Security (VBS)," the tech giant said.
It, however, noted that an attacker attempting to leverage the flaw would have to convince an Administrator or a user with delegated permissions to perform a system restore which inadvertently triggers the vulnerability.
The second vulnerability also concerns a case of privilege escalation in Windows systems that support VBS, effectively allowing an adversary to replace current versions of Windows system files with outdated versions.
The consequences of CVE-2024-21302 are that it could be weaponized to reintroduce previously addressed security flaws, bypass some features of VBS, and exfiltrate data protected by VBS.

Leviev, who detailed a tool dubbed Windows Downdate, said it could be used to turn a "fully patched Windows machine susceptible to thousands of past vulnerabilities, turning fixed vulnerabilities into zero-days and making the term 'fully patched' meaningless on any Windows machine in the world."
The tool, Leviev added, could "take over the Windows Update process to craft fully undetectable, invisible, persistent, and irreversible downgrades on critical OS components—that allowed me to elevate privileges and bypass security features."
Furthermore, Windows Downdate is capable of bypassing verification steps, such as integrity verification and Trusted Installer enforcement, effectively making it possible to downgrade critical operating system components, including dynamic link libraries (DLLs), drivers, and NT kernel.
The issues, on top of that, could be exploited to downgrade Credential Guard's Isolated User Mode Process, Secure Kernel, and Hyper-V's hypervisor to expose past privilege escalation vulnerabilities, as well as disable VBS, alongside features like Hypervisor-Protected Code integrity (HVCI).
The net result is that a completely patched Windows system could be rendered susceptible to thousands of past vulnerabilities and turn fixed shortcomings into zero-days.
These downgrades have an added impact in that the operating system reports that the system is fully updated, while simultaneously preventing the installation of future updates and inhibiting detection by recovery and scanning tools.
"The downgrade attack I was able to achieve on the virtualization stack within Windows was possible due to a design flaw that permitted less privileged virtual trust levels/rings to update components residing in more privileged virtual trust levels/rings," Leviev said.
"This was very surprising, given Microsoft's VBS features were announced in 2015, meaning the downgrade attack surface I discovered has existed for almost a decade."
RADIUS Protocol Vulnerability Exposes Networks to MitM Attacks
9.7.24 Attack The Hacker News
Cybersecurity researchers have discovered a security vulnerability in the RADIUS network authentication protocol called BlastRADIUS that could be exploited by an attacker to stage Mallory-in-the-middle (MitM) attacks and bypass integrity checks under certain circumstances.
"The RADIUS protocol allows certain Access-Request messages to have no integrity or authentication checks," InkBridge Networks CEO Alan DeKok, who is the creator of the FreeRADIUS Project, said in a statement.
"As a result, an attacker can modify these packets without detection. The attacker would be able to force any user to authenticate, and to give any authorization (VLAN, etc.) to that user."
RADIUS, short for Remote Authentication Dial-In User Service, is a client/server protocol that provides centralized authentication, authorization, and accounting (AAA) management for users who connect and use a network service.
The security of RADIUS is reliant on a hash that's derived using the MD5 algorithm, which has been deemed cryptographically broken as of December 2008 owing to the risk of collision attacks.
This means that the Access-Request packets can be subjected to what's called a chosen prefix attack that makes it possible to modify the response packet such that it passes all of the integrity checks for the original response.
However, for the attack to succeed, the adversary has to be able to modify RADIUS packets in transit between the RADIUS client and server. This also means that organizations that send packets over the internet are at risk of the flaw.
Other mitigation factors that prevent the attack from being potent stem from the use of TLS to transmit RADIUS traffic over the internet and increased packet security via the Message-Authenticator attribute.
BlastRADIUS is the result of a fundamental design flaw and is said to impact all standards-compliant RADIUS clients and servers, making it imperative that internet service providers (ISPs) and organizations that use the protocol update to the latest version.
"Specifically, PAP, CHAP, and MS-CHAPv2 authentication methods are the most vulnerable," DeKok said. "ISPs will have to upgrade their RADIUS servers and networking equipment."
"Anyone using MAC address authentication, or RADIUS for administrator logins to switches is vulnerable. Using TLS or IPSec prevents the attack, and 802.1X (EAP) is not vulnerable."
For enterprises, the attacker would already need to have access to the management virtual local area network (VLAN). What's more, ISPs can be susceptible if they send RADIUS traffic over intermediate networks, such as third-party outsourcers, or the wider internet.
It's worth noting that the vulnerability, which carries a CVSS score of 9.0, particularly affects networks that send RADIUS/UDP traffic over the internet given that "most RADIUS traffic is sent 'in the clear.'" There is no evidence that it's being exploited in the wild.
"This attack is the result of the security of the RADIUS protocol being neglected for a very long time," DeKok said.
"While the standards have long suggested protections which would have prevented the attack, those protections were not made mandatory. In addition, many vendors did not even implement the suggested protections."
New Intel CPU Vulnerability 'Indirector' Exposes Sensitive Data
2.7.24 Attack The Hacker News
Modern CPUs from Intel, including Raptor Lake and Alder Lake, have been found vulnerable to a new side-channel attack that could be exploited to leak sensitive information from the processors.
The attack, codenamed Indirector by security researchers Luyi Li, Hosein Yavarzadeh, and Dean Tullsen, leverages shortcomings identified in Indirect Branch Predictor (IBP) and the Branch Target Buffer (BTB) to bypass existing defenses and compromise the security of the CPUs.
"The Indirect Branch Predictor (IBP) is a hardware component in modern CPUs that predicts the target addresses of indirect branches," the researchers noted.
"Indirect branches are control flow instructions whose target address is computed at runtime, making them challenging to predict accurately. The IBP uses a combination of global history and branch address to predict the target address of indirect branches."
Cybersecurity
The idea, at its core, is to identify vulnerabilities in IBP to launch precise Branch Target Injection (BTI) attacks – aka Spectre v2 (CVE-2017-5715) – which target a processor's indirect branch predictor to result in unauthorized disclosure of information to an attacker with local user access via a side-channel.
This is accomplished by means of a custom tool called iBranch Locator that's used to locate any indirect branch, followed by carrying out precision targeted IBP and BTP injections to perform speculative execution.
Intel, which was made aware of the findings in February 2024, has since informed other affected hardware/software vendors about the issue.
As mitigations, it's recommended to make use of the Indirect Branch Predictor Barrier (IBPB) more aggressively and harden the Branch Prediction Unit (BPU) design by incorporating more complex tags, encryption, and randomization.
The research comes as Arm CPUs have been found susceptible to a speculative execution attack of their own called TIKTAG that targets the Memory Tagging Extension (MTE) to leak data with over a 95% success rate in less than four seconds.
The study "identifies new TikTag gadgets capable of leaking the MTE tags from arbitrary memory addresses through speculative execution," researchers Juhee Kim, Jinbum Park, Sihyeon Roh, Jaeyoung Chung, Youngjoo Lee, Taesoo Kim, and Byoungyoung Lee said.
Cybersecurity
"With TikTag gadgets, attackers can bypass the probabilistic defense of MTE, increasing the attack success rate by close to 100%."
In response to the disclosure, Arm said "MTE can provide a limited set of deterministic first line defenses, and a broader set of probabilistic first line defenses, against specific classes of exploits."
"However, the probabilistic properties are not designed to be a full solution against an interactive adversary that is able to brute force, leak, or craft arbitrary Address Tags."
New ZenHammer Attack Bypasses RowHammer Defenses on AMD CPUs
29.3.24 Attack The Hacker News
Cybersecurity researchers from ETH Zurich have developed a new variant of the RowHammer DRAM (dynamic random-access memory) attack that, for the first time, successfully works against AMD Zen 2 and Zen 3 systems despite mitigations such as Target Row Refresh (TRR).
"This result proves that AMD systems are equally vulnerable to Rowhammer as Intel systems, which greatly increases the attack surface, considering today's AMD market share of around 36% on x86 desktop CPUs," the researchers said.
The technique has been codenamed ZenHammer, which can also trigger RowHammer bit flips on DDR5 devices for the first time.
RowHammer, first publicly disclosed in 2014, is a well-known attack that exploits DRAM's memory cell architecture to alter data by repeatedly accessing a specific row (aka hammering) to cause the electrical charge of a cell to leak to adjacent cells.
This can induce random bit flips in neighboring memory rows (from 0 to 1, or vice versa), which can alter the memory contents and potentially facilitate privilege escalation, compromising confidentiality, integrity, and availability of a system.
The attacks take advantage of the physical proximity of these cells within the memory array, a problem that's likely to worsen as the DRAM technology scaling continues and the storage density increases.
"As DRAM continues to scale, RowHammer bit flips can occur at smaller activation counts and thus a benign workload's DRAM row activation rates can approach or even exceed the RowHammer threshold," ETH Zurich researchers noted in a paper published in November 2022.
"Thus, a system may experience bit flips or frequently trigger RowHammer defense mechanisms even without a malicious party performing a RowHammer attack in the system, leading to data corruption or significant performance degradation."
One of the crucial mitigations implemented by DRAM manufacturers against RowHammer is TRR, which is an umbrella term used for mechanisms that refresh target rows that are determined to be accessed frequently.
In doing so, the idea is to generate more memory refresh operations so that victim rows will either be refreshed before bits are flipped or be corrected after bits are flipped due to RowHammer attacks.
ZenHammer, like TRRespass and SMASH, bypasses TRR guardrails by reverse engineering the secret DRAM address functions in AMD systems and adopting improved refresh synchronization and scheduling of flushing and fencing instructions to trigger bit flips on seven out of 10 sample Zen 2 devices and six out of 10 Zen 3 devices.
The study also arrived at an optimal hammering instruction sequence to improve row activation rates in order to facilitate more effective hammering.
"Our results showed that regular loads (MOV) with CLFLUSHOPT for flushing aggressors from the cache, issued immediately after accessing an aggressor ('scatter' style), is optimal," the researchers said.
ZenHammer has the distinction of being the very first method that can trigger bit flips on systems equipped with DDR5 chips on AMD's Zen 4 microarchitectural platform. That said, it only works on one of the 10 tested devices (Ryzen 7 7700X).
It's worth noting that DDR5 DRAM modules were previously considered immune to RowHammer attacks owing to them replacing TRR with a new kind of protection called refresh management.
"The changes in DDR5 such as improved RowHammer mitigations, on-die error correction code (ECC), and a higher refresh rate (32 ms) make it harder to trigger bit flip," the researchers said.
"Given the lack of bit flips on nine of 10 DDR5 devices, more work is needed to better understand the potentially new RowHammer mitigations and their security guarantees."
AMD, in a security bulletin, said it's assessing RowHammer bit flips on DDR5 devices, and that it will provide an update following its completion.
"AMD microprocessor products include memory controllers designed to meet industry-standard DDR specifications," it added. "Susceptibility to RowHammer attacks varies based on the DRAM device, vendor, technology, and system settings."
New 'Loop DoS' Attack Impacts Hundreds of Thousands of Systems
21.3.24 Attack The Hacker News
A novel denial-of-service (DoS) attack vector has been found to target application-layer protocols based on User Datagram Protocol (UDP), putting hundreds of thousands of hosts likely at risk.
Called Loop DoS attacks, the approach pairs "servers of these protocols in such a way that they communicate with each other indefinitely," researchers from the CISPA Helmholtz-Center for Information Security said.
UDP, by design, is a connectionless protocol that does not validate source IP addresses, making it susceptible to IP spoofing.
Thus, when attackers forge several UDP packets to include a victim IP address, the destination server responds to the victim (as opposed to the threat actor), creating a reflected denial-of-service (DoS) attack.
The latest study found that certain implementations of the UDP protocol, such as DNS, NTP, TFTP, Active Users, Daytime, Echo, Chargen, QOTD, and Time, can be weaponized to create a self-perpetuating attack loop.
"It pairs two network services in such a way that they keep responding to one another's messages indefinitely," the researchers said. "In doing so, they create large volumes of traffic that result in a denial-of-service for involved systems or networks. Once a trigger is injected and the loop set in motion, even the attackers are unable to stop the attack."
Put simply, given two application servers running a vulnerable version of the protocol, a threat actor can initiate communication with the first server by spoofing the address of the second server, causing the first server to respond to the victim (i.e., the second server) with an error message.
The victim, in turn, will also exhibit similar behavior, sending back another error message to the first server, effectively exhausting each other's resources and making either of the services unresponsive.
"If an error as input creates an error as output, and a second system behaves the same, these two systems will keep sending error messages back and forth indefinitely," Yepeng Pan and Christian Rossow explained.
CISPA said an estimated 300,000 hosts and their networks can be abused to carry out Loop DoS attacks.
While there is currently no evidence that the attack has been weaponized in the wild, the researchers warned that exploitation is trivial and that multiple products from Broadcom, Cisco, Honeywell, Microsoft, MikroTik, and Zyxel are affected.
"Attackers need a single spoofing-capable host to trigger loops," the researchers noted. "As such, it is important to keep up initiatives to filter spoofed traffic, such as BCP38."
Hacked WordPress Sites Abusing Visitors' Browsers for Distributed Brute-Force Attacks
7.3.24 Attack The Hacker News
Threat actors are conducting brute-force attacks against WordPress sites by leveraging malicious JavaScript injections, new findings from Sucuri reveal.
The attacks, which take the form of distributed brute-force attacks, "target WordPress websites from the browsers of completely innocent and unsuspecting site visitors," security researcher Denis Sinegubko said.
The activity is part of a previously documented attack wave in which compromised WordPress sites were used to inject crypto drainers such as Angel Drainer directly or redirect site visitors to Web3 phishing sites containing drainer malware.
The latest iteration is notable for the fact that the injections – found on over 700 sites to date – don't load a drainer but rather use a list of common and leaked passwords to brute-force other WordPress sites.
The attack unfolds over five stages, enabling a threat actor to take advantage of already compromised websites to launch distributed brute-force attacks against other potential victim sites -
Obtaining a list of target WordPress sites
Extracting real usernames of authors that post on those domains
Inject the malicious JavaScript code to already infected WordPress sites
Launching a distributed brute-force attack on the target sites via the browser when visitors land on the hacked sites
Gaining unauthorized access to the target sites
"For every password in the list, the visitor's browser sends the wp.uploadFile XML-RPC API request to upload a file with encrypted credentials that were used to authenticate this specific request," Sinegubko explained. "If authentication succeeds, a small text file with valid credentials is created in the WordPress uploads directory."
It's currently not known what prompted the threat actors to switch from crypto drainers to distributed brute-force attack, although it's believed that the change may have been driven by profit motives, as compromised WordPress sites could be monetized in various ways.
That said, crypto wallet drainers have led to losses amounting to hundreds of millions in digital assets in 2023, according to data from Scam Sniffer. The Web3 anti-scam solution provider has since revealed that drainers are exploiting the normalization process in the wallet's EIP-712 encoding procedure to bypass security alerts.
The development comes as the DFIR report revealed that threat actors are exploiting a critical flaw in a WordPress plugin named 3DPrint Lite (CVE-2021-4436, CVSS score: 9.8) to deploy the Godzilla web shell for persistent remote access.
It also follows a new SocGholish (aka FakeUpdates) campaign targeting WordPress websites in which the JavaScript malware is distributed via modified versions of legitimate plugins that are installed by taking advantage of compromised admin credentials.
"Although there have been a variety of maliciously modified plugins and several different fake-browser update campaigns, the goal of course is always the same: To trick unsuspecting website visitors into downloading remote access trojans that will later be used as the initial point of entry for a ransomware attack," security researcher Ben Martin said.
New Silver SAML Attack Evades Golden SAML Defenses in Identity Systems
1.3.24 Attack The Hacker News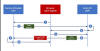
Cybersecurity researchers have disclosed a new attack technique called Silver SAML that can be successful even in cases where mitigations have been applied against Golden SAML attacks.
Silver SAML "enables the exploitation of SAML to launch attacks from an identity provider like Entra ID against applications configured to use it for authentication, such as Salesforce," Semperis researchers Tomer Nahum and Eric Woodruff said in a report shared with The Hacker News.
Golden SAML (short for Security Assertion Markup Language) was first documented by CyberArk in 2017. The attack vector, in a nutshell, entails the abuse of the interoperable authentication standard to impersonate almost any identity in an organization.
It's also similar to the Golden Ticket attack in that it grants attackers the ability to gain unauthorized access to any service in a federation with any privileges and to stay persistent in this environment in a stealthy manner.
"Golden SAML introduces to a federation the advantages that golden ticket offers in a Kerberos environment – from gaining any type of access to stealthily maintaining persistency," security researcher Shaked Reiner noted at the time.
Real-world attacks leveraging the method have been rare, the first recorded use being the compromise of SolarWinds infrastructure to gain administrative access by forging SAML tokens using compromised SAML token signing certificates.
Golden SAML has also been weaponized by an Iranian threat actor codenamed Peach Sandstorm in a March 2023 intrusion to access an unnamed target's cloud resources sans requiring any password, Microsoft revealed in September 2023.
The latest approach is a spin on Golden SAML that works with an identity provider (IdP) like Microsoft Entra ID (formerly Azure Active Directory) and doesn't require access to the Active Directory Federation Services (AD FS). It has been assessed as a moderate-severity threat to organizations.
"Within Entra ID, Microsoft provides a self-signed certificate for SAML response signing," the researchers said. "Alternatively, organizations can choose to use an externally generated certificate such as those from Okta. However, that option introduces a security risk."
"Any attacker that obtains the private key of an externally generated certificate can forge any SAML response they want and sign that response with the same private key that Entra ID holds. With this type of forged SAML response, the attacker can then access the application — as any user."
Following responsible disclosure to Microsoft on January 2, 2024, the company said the issue does not meet its bar for immediate servicing, but noted it will take appropriate action as needed to safeguard customers.
While there is no evidence that Silver SAML has been exploited in the wild, organizations are required to use only Entra ID self-signed certificates for SAML signing purposes. Semperis has also made available a proof-of-concept (PoC) dubbed SilverSAMLForger to create custom SAML responses.
"Organizations can monitor Entra ID audit logs for changes to PreferredTokenSigningKeyThumbprint under ApplicationManagement," the researchers said.
"You will need to correlate those events to Add service principal credential events that relate to the service principal. The rotation of expired certificates is a common process, so you will need to determine whether the audit events are legitimate. Implementing change control processes to document the rotation can help to minimize confusion during rotation events."
Mandiant's X Account Was Hacked Using Brute-Force Attack
11.1.24 Attack The Hacker News
The compromise of Mandiant's X (formerly Twitter) account last week was likely the result of a "brute-force password attack," attributing the hack to a drainer-as-a-service (DaaS) group.
"Normally, [two-factor authentication] would have mitigated this, but due to some team transitions and a change in X's 2FA policy, we were not adequately protected," the threat intelligence firm said in a post shared on X.
The attack, which took place on January 3, 2023, enabled the threat actor to take control of the company's X account and distribute links to a phishing page hosting a cryptocurrency drainer tracked as CLINKSINK.
Drainers refer to malicious scripts and smart contracts that facilitate the theft of digital assets from the victim's wallets after they are tricked into approving the transactions.
According to the Google-owned subsidiary, multiple threat actors are believed to have leveraged CLINKSINK since December 2023 to siphon funds and tokens from Solana (SOL) cryptocurrency users.
As observed in the case of other drainers like Angel Drainer and Inferno Drainer, affiliates are roped in by the DaaS operators to conduct the attacks in exchange for a cut (typically 20%) of the stolen assets.
The identified activity cluster involves at least 35 affiliate IDs and 42 unique Solana wallet addresses, collectively netting the actors no less than $900,000 in illegal profits.
The attack chains involve the use of social media and chat applications such as X and Discord to distribute cryptocurrency-themed phishing pages that encourage the targets to connect their wallets to claim a bogus token airdrop.
"After connecting their wallet, the victim is then prompted to sign a transaction to the drainer service, which allows it to siphon funds from the victim," security researchers Zach Riddle, Joe Dobson, Lukasz Lamparski, and Stephen Eckels said.
CLINKSINK, a JavaScript drainer, is designed to open a pathway to the targeted wallets, check the current balance on the wallet, and ultimately pull off the theft after asking the victim to sign a fraudulent transaction. This also means that the attempted theft will not succeed if the victim rejects the transaction.
The drainer has also spawned several variants, including Chick Drainer (or Rainbow Drainer), raising the possibility that the source code is available to multiple threat actors, allowing them to mount independent draining campaigns.
"The wide availability and low cost of many drainers, combined with a relatively high potential for profit, likely makes them attractive operations for many financially motivated actors," Mandiant said.
"Given the increase in cryptocurrency values and the low barrier to entry for draining operations, we anticipate that financially motivated threat actors of varying levels of sophistication will continue to conduct drainer operations for the foreseeable future."
The development comes amid an uptick in attacks targeting legitimate X accounts to spread cryptocurrency scams.
Earlier this week, the X account associated with the U.S. Securities and Exchange Commission (SEC) was breached to falsely claim that the regulatory body had approved the "listing and trading of spot bitcoin exchange-traded products," causing bitcoin prices to spike briefly.
X has since revealed the hack was the result of "an unidentified individual obtaining control over a phone number associated with the @SECGov account through a third-party," and that the account did not have two-factor authentication enabled.
New Terrapin Flaw Could Let Attackers Downgrade SSH Protocol Security
1.1.24 Attack The Hacker News
Security researchers from Ruhr University Bochum have discovered a vulnerability in the Secure Shell (SSH) cryptographic network protocol that could allow an attacker to downgrade the connection's security by breaking the integrity of the secure channel.
Called Terrapin (CVE-2023-48795, CVSS score: 5.9), the exploit has been described as the "first ever practically exploitable prefix truncation attack."
"By carefully adjusting the sequence numbers during the handshake, an attacker can remove an arbitrary amount of messages sent by the client or server at the beginning of the secure channel without the client or server noticing it," researchers Fabian Bäumer, Marcus Brinkmann, and Jörg Schwenk said.
SSH is a method for securely sending commands to a computer over an unsecured network. It relies on cryptography to authenticate and encrypt connections between devices.
This is accomplished by means of a handshake in which a client and server agree upon cryptographic primitives and exchange keys required for setting up a secure channel that can provide confidentiality and integrity guarantees.
However, a bad actor in an active adversary-in-the-middle (AitM) position with the ability to intercept and modify the connection's traffic at the TCP/IP layer can downgrade the security of an SSH connection when using SSH extension negotiation.
"The attack can be performed in practice, allowing an attacker to downgrade the connection's security by truncating the extension negotiation message (RFC8308) from the transcript," the researchers explained.
"The truncation can lead to using less secure client authentication algorithms and deactivating specific countermeasures against keystroke timing attacks in OpenSSH 9.5."
Another crucial prerequisite necessary to pulling off the attack is the use of a vulnerable encryption mode such as ChaCha20-Poly1305 or CBC with Encrypt-then-MAC to secure the connection.
"In a real-world scenario, an attacker could exploit this vulnerability to intercept sensitive data or gain control over critical systems using administrator privileged access," Qualys said. "This risk is particularly acute for organizations with large, interconnected networks that provide access to privileged data."
The flaw impacts many SSH client and server implementations, such as OpenSSH, Paramiko, PuTTY, KiTTY, WinSCP, libssh, libssh2, AsyncSSH, FileZilla, and Dropbear, prompting the maintainers to release patches to mitigate potential risks.
"Because SSH servers and OpenSSH in particular are so commonly used throughout cloud-based enterprise application environments, it's imperative for companies to ensure they have taken appropriate measures to patch their servers," Yair Mizrahi, senior security researcher of security research at JFrog, told The Hacker News.
"However, a vulnerable client connecting to a patched server will still result in an vulnerable connection. Thus, companies must also take steps to identify every vulnerable occurrence across their entire infrastructure and apply a mitigation immediately."