
Attack 2024 2023 2022 2021 2020
New NTLM Relay Attack Lets Attackers Take Control Over Windows Domain
21.6.22 Attack Thehackernews
A new kind of Windows NTLM relay attack dubbed DFSCoerce has been uncovered that leverages the Distributed File System (DFS): Namespace Management Protocol (MS-DFSNM) to seize control of a domain.
"Spooler service disabled, RPC filters installed to prevent PetitPotam and File Server VSS Agent Service not installed but you still want to relay [Domain Controller authentication to [Active Directory Certificate Services]? Don't worry MS-DFSNM have (sic) your back," security researcher Filip Dragovic said in a tweet.
MS-DFSNM provides a remote procedure call (RPC) interface for administering distributed file system configurations.
The NTLM (NT Lan Manager) relay attack is a well-known method that exploits the challenge-response mechanism. It allows malicious parties to sit between clients and servers and intercept and relay validated authentication requests in order to gain unauthorized access to network resources, effectively gaining an initial foothold in Active Directory environments.
The discovery of DFSCoerce follows a similar method called PetitPotam that abuses Microsoft's Encrypting File System Remote Protocol (MS-EFSRPC) to coerce
Windows servers, including domain controllers, into authenticating with a relay under an attacker's control, letting threat actors potentially take over an entire domain.
"By relaying an NTLM authentication request from a domain controller to the Certificate Authority Web Enrollment or the Certificate Enrollment Web Service on an AD CS system, an attacker can obtain a certificate that can be used to obtain a Ticket Granting Ticket (TGT) from the domain controller," the CERT Coordination Center (CERT/CC) noted, detailing the attack chain.
To mitigate NTLM relay attacks, Microsoft recommends enabling protections like Extended Protection for Authentication (EPA), SMB signing, and turning off HTTP on AD CS servers.
New Hertzbleed Side-Channel Attack Affects All Modern AMD and Intel CPUs
15.6.22 Attack Thehackernews
A newly discovered security vulnerability in modern Intel and AMD processors could let remote attackers steal encryption keys via a power side channel attack.
Dubbed Hertzbleed by a group of researchers from the University of Texas, University of Illinois Urbana-Champaign, and the University of Washington, the issue is rooted in dynamic voltage and frequency scaling (DVFS), power and thermal management feature employed to conserve power and reduce the amount of heat generated by a chip.
"The cause is that, under certain circumstances, periodic CPU frequency adjustments depend on the current CPU power consumption, and these adjustments directly translate to execution time differences (as 1 hertz = 1 cycle per second)," the researchers said.
This can have significant security implications on cryptographic libraries even when implemented correctly as constant-time code to prevent timing-based side channels, effectively enabling an attacker to leverage the execution time variations to extract sensitive information such as cryptographic keys.
Both AMD (CVE-2022-23823) and Intel (CVE-2022-24436) have issued independent advisories in response to the findings, with the latter noting that all Intel processors are affected by Hertzbleed. No patches have been made available.
"As the vulnerability impacts a cryptographic algorithm having power analysis-based side channel leakages, developers can apply countermeasures on the software code of the algorithm. Either masking, hiding, or key-rotation may be used to mitigate the attack," AMD stated.
While no patches have been made available to address the weakness, Intel has recommended cryptographic developers follow its guidance to harden their libraries and applications against frequency throttling information disclosure.
This is not the first time novel methods have been uncovered to siphon data from Intel processors. In March 2021, two co-authors of Hertzbleed demonstrated an "on-chip, cross-core" side-channel attack targeting the ring interconnect used in Intel Coffee Lake and Skylake processors.
"The takeaway is that current cryptographic engineering practices for how to write constant-time code are no longer sufficient to guarantee constant time execution of software on modern, variable-frequency processors," the researchers concluded.
Cloudflare Saw Record-Breaking DDoS Attack Peaking at 26 Million Request Per Second
15.6.22 Attack Thehackernews
Cloudflare on Tuesday disclosed that it had acted to prevent a record-setting 26 million request per second (RPS) distributed denial-of-service (DDoS) attack last week, making it the largest HTTPS DDoS attack detected to date.
The web performance and security company said the attack was directed against an unnamed customer website using its Free plan and emanated from a "powerful" botnet of 5,067 devices, with each node generating approximately 5,200 RPS at peak.
The botnet is said to have created a flood of more than 212 million HTTPS requests within less than 30 seconds from over 1,500 networks in 121 countries, including Indonesia, the U.S., Brazil, Russia, and India. Roughly 3% of the attack came through Tor nodes.
The attack "originated mostly from Cloud Service Providers as opposed to Residential Internet Service Providers, indicating the use of hijacked virtual machines and powerful servers to generate the attack — as opposed to much weaker Internet of Things (IoT) devices," Cloudflare's Omer Yoachimik said.
Launching HTTPS-based DDoS attacks tend to be more expensive computationally owing to the higher cost associated with establishing a secure TLS encrypted connection.
This is the second such volumetric HTTPS DDoS attack to be thwarted by Cloudflare in as many months. In late April 2022, it said it staved off a 15.3 million RPS HTTPS DDoS attack aimed at a customer operating a crypto launchpad.
According to the company's DDoS attack trends report for Q1 2022, volumetric DDoS attacks over 100 gigabits per second (gbps) surged by up to 645% quarter-on-quarter.
"Attacks with high bit rates attempt to cause a denial-of-service event by clogging the Internet link, while attacks with high packet rates attempt to overwhelm the servers, routers, or other in-line hardware appliances," the researchers said.
"In such a case, packets are 'dropped,' i.e., the appliance is unable to process them. For users, this results in service disruptions and denial of service."
Iranian Hackers Spotted Using a new DNS Hijacking Malware in Recent Attacks
13.6.22 Attack Thehackernews
The Iranian state-sponsored threat actor tracked under the moniker Lyceum has turned to using a new custom .NET-based backdoor in recent campaigns directed against the Middle East.
"The new malware is a .NET based DNS Backdoor which is a customized version of the open source tool 'DIG.net,'" Zscaler ThreatLabz researchers Niraj Shivtarkar and Avinash Kumar said in a report published last week.
"The malware leverages a DNS attack technique called 'DNS Hijacking' in which an attacker-controlled DNS server manipulates the response of DNS queries and resolves them as per their malicious requirements."
DNS hijacking is a redirection attack in which DNS queries to genuine websites are intercepted to take an unsuspecting user to fraudulent pages under an adversary's control. Unlike cache poisoning, DNS hijacking targets the DNS record of the website on the nameserver, rather than a resolver's cache.

Lyceum, also known as Hexane, Spirlin, or Siamesekitten, is primarily known for its cyber attacks in the Middle East and Africa. Earlier this year, Slovak cybersecurity firm ESET tied its activities to another threat actor called OilRig (aka APT34).
The latest infection chain involves the use of a macro-laced Microsoft Document downloaded from a domain named "news-spot[.]live," impersonating a legitimate news report from Radio Free Europe/Radio Liberty about Iran's drone strikes in December 2021.
Enabling the macro results in the execution of a malicious code that drops the implant to the Windows Startup folder to establish persistence and ensure it automatically runs every time the system is restarted.
The .NET DNS backdoor, dubbed DnsSystem, is a reworked variant of the open-source DIG.net DNS resolver tool, enabling the Lyceum actor to parse DNS responses issued from the DNS server ("cyberclub[.]one") and carry out its nefarious goals.
In addition to abusing the DNS protocol for command-and-control (C2) communications to evade detection, the malware is equipped to upload and download arbitrary files to and from the remote server as well as execute malicious system commands remotely on the compromised host.
"APT threat actors are continuously evolving their tactics and malware to successfully carry out attacks against their targets," the researchers said. "Attackers continuously embrace new anti-analysis tricks to evade security solutions; re-packaging of malware makes static analysis even more challenging."
MIT Researchers Discover New Flaw in Apple M1 CPUs That Can't Be Patched
11.6.22 Attack Thehackernews
A novel hardware attack dubbed PACMAN has been demonstrated against Apple's M1 processor chipsets, potentially arming a malicious actor with the capability to gain arbitrary code execution on macOS systems.
It leverages "speculative execution attacks to bypass an important memory protection mechanism, ARM Pointer Authentication, a security feature that is used to enforce pointer integrity," MIT researchers Joseph Ravichandran, Weon Taek Na, Jay Lang, and Mengjia Yan said in a new paper.
What's more concerning is that "while the hardware mechanisms used by PACMAN cannot be patched with software features, memory corruption bugs can be," the researchers added.
The vulnerability is rooted in pointer authentication codes (PACs), a line of defense introduced in arm64e architecture that aims to detect and secure against unexpected changes to pointers — objects that store a memory address — in memory.
PACs aim to solve a common problem in software security, such as memory corruption vulnerabilities, which are often exploited by overwriting control data in memory (i.e., pointers) to redirect code execution to an arbitrary location controlled by the attacker.
While strategies like Address Space Layout Randomization (ASLR) have been devised to increase the difficulty of performing buffer overflow attacks, the goal of PACs is to ascertain the "validity of pointers with minimal size and performance impact," effectively preventing an adversary from creating valid pointers for use in an exploit.
This is achieved by protecting a pointer with a cryptographic hash — called a Pointer Authentication Code (PAC) — to ensure its integrity. Apple explains PACs as follows -
Pointer authentication works by offering a special CPU instruction to add a cryptographic signature — or PAC — to unused high-order bits of a pointer before storing the pointer. Another instruction removes and authenticates the signature after reading the pointer back from memory. Any change to the stored value between the write and the read invalidates the signature. The CPU interprets authentication failure as memory corruption and sets a high-order bit in the pointer, making the pointer invalid and causing the app to crash.

But PACMAN "removes the primary barrier to conducting control-flow hijacking attacks on a platform protected using pointer authentication." It combines memory corruption and speculative execution to circumvent the security feature, leaking "PAC verification results via microarchitectural side channels without causing any crashes."
The attack method, in a nutshell, makes it possible to distinguish between a correct PAC and incorrect hash, permitting a bad actor to "brute-force the correct PAC value while suppressing crashes and construct a control-flow hijacking attack on a PA-enabled victim program or operating system."
The crash prevention, for its part, succeeds because each PAC value is speculatively guessed by exploiting a timing-based side channel via the translation look-aside buffer (TLB) using a Prime+Probe attack.
Speculative execution vulnerabilities, as observed in the case of Spectre and Meltdown, weaponize out-of-order execution, a technique that's used to bring about a performance improvement in modern microprocessors by predicting the most likely path of a program's execution flow.
However, it's worth noting that the threat model presumes that there already exists an exploitable memory corruption vulnerability in a victim program (kernel), which, in turn, allows the unprivileged attacker (a malicious app) to inject rogue code into certain memory locations in the victim process.
"This attack has important implications for designers looking to implement future processors featuring pointer authentication, and has broad implications for the security of future control-flow integrity primitives," the researchers concluded.
Attackers Can Use Electromagnetic Signals to Control Touchscreens Remotely
28.5.22 Attack Thehackernews
Researchers have demonstrated what they call the "first active contactless attack against capacitive touchscreens."
GhostTouch, as it's called, "uses electromagnetic interference (EMI) to inject fake touch points into a touchscreen without the need to physically touch it," a group of academics from Zhejiang University and Technical University of Darmstadt said in a new research paper.
The core idea is to take advantage of the electromagnetic signals to execute basic touch events such as taps and swipes into targeted locations of the touchscreen with the goal of taking over remote control and manipulating the underlying device.
The attack, which works from a distance of up to 40mm, hinges on the fact that capacitive touchscreens are sensitive to EMI, leveraging it to inject electromagnetic signals into transparent electrodes that are built into the touchscreen so as to register them as touch events.
The experimental setup involves an electrostatic gun to generate a strong pulse signal that's then sent to an antenna to transmit an electromagnetic field to the phone's touchscreen, thereby causing the electrodes — which act as antennas themselves — to pick up the EMI.
This can be further fine-tuned by tweaking the signal and the antenna to induce a variety of touch behaviors, such as press and hold and swipe to select, depending on the device model targeted.
In a real-world scenario, this could play out in different ways, including swiping up to unlock a phone, connecting to a rogue Wi-Fi network, stealthily clicking on a malicious link containing malware, and even answering a phone call on the victim's behalf.

"In places like a cafe, library, meeting room, or conference lobbies, people might place their smartphone face-down on the table," the researchers said. "An attacker may embed the attack equipment under the table and launch attacks remotely."
As many as nine different smartphone models have been found vulnerable to GhostTouch, including Galaxy A10s, Huawei P30 Lite, Honor View 10, Galaxy S20 FE 5G, Nexus 5X, Redmi Note 9S, Nokia 7.2, Redmi 8, and an iPhone SE (2020), the latter of which was used to establish a malicious Bluetooth connection.
To counteract the threat, the researchers recommend adding electromagnetic shielding to block EMI, improving the detection algorithm of the touchscreen, and prompting users to enter the phone's PIN or verify their faces or fingerprints prior to executing high-risk actions.
"GhostTouch controls and shapes the near-field electromagnetic signal, and injects touch events into the targeted area on the touchscreen, without the need for physical touch or access to the victim's device," the researchers said.
Researchers Uncover Rust Supply-Chain Attack Targeting Cloud CI Pipelines
20.5.22 Attack Thehackernews
A case of software supply chain attack has been observed in the Rust programming language's crate registry that leveraged typosquatting techniques to publish a rogue library containing malware.
Cybersecurity firm SentinelOne dubbed the attack "CrateDepression."
Typosquatting attacks take place when an adversary mimics the name of a popular package on a public registry in hopes that developers will accidentally download the malicious package instead of the legitimate library.
In this case, the crate in question is "rustdecimal," a typosquat of the real "rust_decimal" package that's been downloaded over 3.5 million times to date. The package was flagged earlier this month on May 3 by Askar Safin, a Moscow-based developer.
According to an advisory published by the Rust maintainers, the crate is said to have been first pushed on March 25, 2022, attracting fewer than 500 downloads before it was permanently removed from the repository.
Like prior typosquatting attacks of this kind, the misspelled library replicates the entire functionality of the original library while also introducing a malicious function that's designed to retrieve a Golang binary hosted on a remote URL.
Specifically, the new function checks if the "GITLAB_CI" environment variable is set, suggesting a "singular interest in GitLab continuous integration (CI) pipelines," SentinelOne noted.
The payload, which is equipped to capture screenshots, log keystrokes, and download arbitrary files, is capable of running on both Linux and macOS, but not Windows systems. The ultimate goals of the campaign are unknown as yet.
While typosquatting attacks have been previously documented against NPM (JavaScript), PyPi (Python), and RubyGems (Ruby), the development marks an uncommon instance where such an incident has been discovered in the Rust ecosystem.
"Software supply-chain attacks have gone from a rare occurrence to a highly desirable approach for attackers to 'fish with dynamite' in an attempt to infect entire user populations at once," SentinelOne researchers said.
"In the case of CrateDepression, the targeting interest in cloud software build environments suggests that the attackers could attempt to leverage these infections for larger scale supply-chain attacks."
DDoS attacks in Q1 2022
29.4.22 Attack Securelist
The DDoS landscape in Q1 2022 was shaped by the ongoing conflict between Russia and Ukraine: a significant part of all DDoS-related news concerned these countries. In mid-January, the website of Kyiv Mayor Vitali Klitschko was hit by a DDoS attack, and the websites of a number of Ukrainian ministries were defaced. In mid-February, DDoS attacks affected the website of Ukraine’s Ministry of Defense, online services of Oschadbank and PrivatBank, as well as the hosting provider Mirohost. Around the same time, PrivatBank customers received fake text messages about out-of-service ATMs, seemingly intended to sow panic. Another wave of DDoS engulfed Ukrainian government resources on February 23, while the State Service of Special Communication and Information Protection of Ukraine reported a series of continuous attacks in late February and early March. Although the volume of junk traffic exceeded 100 GB/s at peak onslaught, that pales in comparison to the attacks of 1 TB/s capacity or more that occured repeatedly last year.
In early March, researchers at Zscaler published an analysis of attacks on Ukrainian resources carried out by a DanaBot operator. This banking Trojan spreads via the malware-as-a-service (MaaS) model. The buyer used DanaBot to download onto infected devices a DDoS bot whose sole function was to attack a hard-coded domain. The initial target was the mail server of the Ukrainian Ministry of Defense. The attacks on this resource continued from March 2 through March 7, after which the cybercriminals switched to the page of the National Security and Defense Council of Ukraine website dedicated to information about Russian prisoners of war.
The information resource LiveUAMap, which provides real-time monitoring of the Russian-Ukrainian conflict, also became a DDoS target. This website is used by reporters and charities as a source of up-to-date information. In addition, Ukrainian media and information resources of NATO countries were subjected to attacks. In particular, the Ukrainian portal Espreso suffered a DDoS strike. According to Ukrainian providers, they faced DDoS attacks on certain resources throughout the whole of March.
Starting February 24, a spate of DDoS attacks hit Russian websites. The targets included media, government authorities at the regional (for example, in Yugra) and federal levels, Roscosmos, Russian Railways (RZD), the State Services (Gosuslugi) portal, telcos and other organizations. At the end of March, DDoSers went after the Russian domain registrar Ru-Center, disabling the websites of its customers for some time. According to RBC, at least some of the attacks targeting media were carried out from websites calling for an end to misinformation. The hacktivist group Anonymous, having declared war on Russia over Ukraine, claimed responsibility for several attacks, including a DDoS against the news station Russia Today.
Anonymous is not the only hacktivist group to come out in support of Ukraine. The country’s government called upon volunteers to join the “IT army,” whose tasks include DDoS attacks. Such attacks were coordinated primarily through Telegram, where the organizers posted lists of targets. Moreover, multiple websites appeared inviting sympathizers with any level of IT literacy to join the DDoS offensive against Russian organizations. All the user had to do was open the website in a browser for it to start sending junk requests to a given list of web resources. And to make it more entertaining, some stresser websites, for example, gamified the process.
Hacktivists also distributed apps allowing ordinary users to take part in DDoS attacks. As with the websites, their developers advertised them as tools for attacking Russian resources. According to Avast, one such app was downloaded by at least 900 users from Ukraine. Such apps do not just carry out attacks on behalf of users, but collect data about them, such as IP address, approximate location, username, system information, time zone, language, etc.
In response to the DDoS attacks, many Russian resources have employed geofencing to temporarily restrict access from abroad. In addition, Russia’s National Coordination Center for Computer Incidents published lists of IP addresses and domains from which attacks were allegedly launched, plus security recommendations for organizations. The list of DDoS sources included, inter alia, the domains of US intelligence agencies, as well as some media outlets.
Besides Russian and Ukrainian resources, North Korean websites also became unavailable several times. The country first went offline in mid-January after a series of missile tests, cutting access to most North Korean websites and mail servers. Researcher Junade Ali, who monitors the North Korean internet, said the incident resembled a DDoS attack. On January 26, the story repeated itself — after more tests. Connectivity disruptions were observed in the country at the end of the month, too. Although many initially attributed the incidents to North Korea’s increased military activity, it was an American infosec expert nicknamed P4x who claimed responsibility. In his own words, he acted in response to a series of cyberattacks by North Korean hackers against security experts. Seeing no reaction from the US authorities, P4x decided to take matters into his own hands: he found several vulnerabilities in North Korean network equipment which he used to overload critical routers and servers in the country.
In March, the Israeli ISP Cellcom was the target of a large-scale DDoS attack. The incident took government resources, in particular ministry websites, offline for some time. The attack also hit another major Israeli provider, Bezeq. The Israel National Cyber Directorate (INCD) believes that Iran was behind the attack.
Another DDoS-hit country is Andorra. The targeting of Andorra Telecom, the only local ISP, temporarily cut off communications for everyone in the country. The attackers’ motive was far from political: the target seemed to be participants in the Twitch Rivals Squidcraft Games, a Minecraft tournament based on Squid Game. The tournament was for Spanish-speaking streamers in Europe and Latin America, and the top prize was $100,000. Among the players were many Spaniards living in Andorra — the attackers most likely wanted to disconnect them from the game. But because the country is small, its entire infrastructure was affected.
Q1 was not without DDoS attacks on suppliers of the popular technologies of blockchain and NFT. Right at the start of the year, the Solana platform, after repeated DDoS attacks in 2021, was hit again. The attackers disabled the platform using its own functionality by “spamming” the blockchain with empty transactions, causing the core network to overload and stop responding. This latest DDoS attack enraged users, who accused the developers of failing to secure the system.
No sooner had it opened than the new NFT marketplace LooksRare was DDoSed. The platform’s website was temporarily down, and users had trouble connecting wallets and getting information about purchased tokens. The problems with wallets persisted for some time, even after access to the website was restored.
DDoS extortionists, posing as the infamous REvil group, not only continued to attack companies, but displayed creativity. Imperva reported attacks in which a ransom note was included in requests to the targeted website. What’s more, if previously the attackers wanted a one-time ransom, they now demand 1 BTC per day in exchange for “protecting” the victim company from their attacks. Researchers note that the capacity of some attacks stretched to hundreds of thousands and even millions of requests per second. They also report that the attackers most likely used the Mēris botnet, discovered in Q3 2021.
In addition to requests carrying ransom notes, DDoS operators added another string to their virtual bow in Q1. Cybercriminals started using misconfigured Mitel MiCollab and MiVoice Business Express collaboration solutions to amplify attacks by more than 4 million times. Both solutions feature a TP-240 interface for VoIP. Acting as a bridge for interaction with this interface is the tp240dvr driver, whose tasks include receiving a command to generate huge amounts of traffic for the purpose of debugging and testing system performance. Normally this driver should not be available from the internet, but around 2,600 Mitel systems were found to accept commands from outside. The attackers forced vulnerable systems to send stress tests to the victim, thereby achieving manifold amplification. These attacks have been observed since mid-February and have targeted ISPs and financial, logistics and other organizations.
To combat DDoS and other cyberattacks, British authorities launched an initiative aimed at preventing child cybercrime. Students searching for suspicious terms on school computers see a warning page with a suggested redirection to information about cybercrime, its consequences and the Computer Misuse Act 1990. The pilot showed that in just four weeks children had become far less likely to search for “stressers” and “booters” (websites for carrying out DDoS attacks).
Quarter trends
Before evaluating the Q1 2022 data, it is worth recalling that our previous quarter report mentioned a record number of DDoS attacks. This quarter, we saw an almost 1.5-fold (46%) increase in the number of attacks relative to the record, and a 4.5-fold rise compared to the same period last year.
Comparative number of DDoS attacks, Q1 2022, Q1 and Q4 2021. Q1 2021 data is taken as 100% (download)
The reason for this growth is obvious: the crisis in Ukraine led to a cyberwar, which could hardly fail to impact the statistics. Looking at the distribution of DDoS attacks by week, we see that the peak of new attacks occurred in the eighth week of 2022, that is, February 21–27, and we repelled the largest number of DDoS attacks that week on February 25.
Comparative number of DDoS attacks by week, April 2021–March 2022 (download)
That said, there were relatively few attacks before late February, and without the spike in DDoS activity at the end of the month we would have seen a drop relative to the previous quarter. It is interesting to note that very many of the attacks in late February/early March were organized by hacktivists and carried out from personal devices that users voluntarily connected to the botnet (for example, by opening a stresser website in their browser).
Share of smart attacks, Q1 2022, Q1 and Q4 2021. The Q1 2022 decrease in this value is due to the surge in hacktivism (download)
The hacktivist nature of the attacks was also responsible for the sharp decline in their number towards mid-March: those initially driven by emotion had calmed down, and infosec companies published warnings against taking part in such attacks. As a result, the number of hacktivists decreased. Whereas in late February/early March we saw an unusually high number of amateurs involved in the attacks, by the end of March their relative number had almost returned to normal levels. In absolute terms, there are still more of them than usual, as well as of DDoS attacks, but the difference is not so great.
But the most curious thing has to do with the data not on the number of attacks, but on their duration. In Q1 we saw an increase in this indicator by two orders of magnitude. If previous attacks were measured in minutes, now the average attack is measured in hours, and many go on for several days. We detected the longest attack on March 29, which lasted a little over 177 hours, that is, more than a week.
DDoS attack duration, Q1 2022, Q1 and Q4 2021. Q1 2021 data is taken as 100% (download)
This is extremely uncharacteristic of DDoS attacks, especially ones filtered by security solutions. Attacks of this length are expensive and expose the botnet, since active nodes are easier to detect and disable. So professional DDoSers always try to stop an ineffective attack as quickly as possible so as not to waste money. Now, however, we are seeing the opposite: attacks continue regardless of their effectiveness. At the same time, the overwhelming majority of targets of ultra-long (more than a day) attacks are government agencies and banks. All of this underscores once more that many of the DDoS attacks this quarter were not financially motivated.
Average DDoS attack duration by week, April 2021–March 2022. A sharp increase occurs in the last third of February (download)
The upswing in DDoS attacks in Q1 2022 led to another significant trend: many Russian organizations were unprepared for being targeted. As a result, both we and other anti-DDoS protection providers received a huge number of requests in a short space of time from companies already under attack.
DDoS attack statistics
Methodology
Kaspersky has a long history of combating cyberthreats, including DDoS attacks of any type and complexity. Company experts monitor botnets using the Kaspersky DDoS Intelligence system.
A part of Kaspersky DDoS Protection, the DDoS Intelligence system intercepts and analyzes commands received by bots from C2 servers. The system is proactive, not reactive, meaning that it does not wait for a user device to get infected or a command to be executed.
This report contains DDoS Intelligence statistics for Q1 2022.
In the context of this report, the incident is counted as a single DDoS-attack only if the interval between botnet activity periods does not exceed 24 hours. For example, if the same resource is attacked by the same botnet after an interval of 24 hours or more, two attacks will be counted. Bot requests originating from different botnets but directed at one resource also count as separate attacks.
The geographic locations of DDoS-attack victims and C2 servers used to send commands are determined by their respective IP addresses. The number of unique targets of DDoS attacks in this report is counted by the number of unique IP addresses in the quarterly statistics.
DDoS Intelligence statistics are limited to botnets detected and analyzed by Kaspersky. Note that botnets are just one of the tools used for DDoS attacks, and that this section does not cover every single DDoS attack that occurred during the review period.
Quarter summary
In Q1 2022:
Kaspersky DDoS Intelligence system detected 91,052 DDoS attacks.
44.34% of attacks were directed at targets located in USA, which comprised 45.02% of all targets.
The largest number of DDoS-attacks (16.35%) come on Sundays.
Most attacks (94.95%) lasted less than 4 hours, but the longest attack continued for 549 hours (nearly 23 days).
53.64% of attacks were UDP flood.
55.53% of C&C servers were located in USA.
China accounted for 20.41% of bots attacking our SSH honeypots and 41.21% of those attacking Telnet traps.
DDoS attack geography
In Q1 2022, US-based resources were most frequently hit by DDoS attacks (44.34%). Their share increased slightly against the previous reporting period. In second place remains China (11.60%), whose share also rose slightly, and Germany (5.06%) moved into third.
Distribution of DDoS attacks by country and territory, Q4 2021 and Q1 2022 (download)
The Hong Kong SAR (3.71%) saw its share more than halve, taking fifth place by number of DDoS attacks in Q1. The UK (3.89%), which added 0.68 p.p., finished fourth. France (3.65%) and Canada (3.37%) dropped to sixth and seventh, respectively, while the Netherlands (2.36%) remained in eighth position. Brazil (2.24%) and Singapore (1.86%) swapped places, coming in ninth and tenth, respectively. Overall, the geographical distribution of DDoS attacks changed little compared to Q4 2021.
The distribution of unique targets by country and territory traditionally mirrors the attack geography — only the bottom of the TOP 10 differs. Most targets in Q1 were located in the US (45.02%), followed by China (9.34%) and Germany (4.95%). The shares of the three countries have seen slight growth since the end of 2021. In fourth place is the UK (4.30%), and in fifth is Hong Kong (4.00%), whose share more than halved.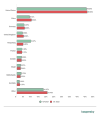
Distribution of unique targets by country and territory, Q4 2021 and Q1 2022 (download)
France (3.31%) and Canada (2.93%) remained in sixth and seventh positions, respectively, while Brazil (2.44%) moved up to eighth. By contrast, the Netherlands dropped to ninth place (2.32%). Australia (1.90%) rounds out the TOP 10.
Dynamics of the number of DDoS attacks
In Q1 2022, our DDoS Intelligence system detected 91,052 DDoS attacks. Throughout January and most of February, we saw an average of 1,406 attacks per day. The calmest day of this period was February 2, when DDoS Intelligence detected 809 attacks, and the stormiest was January 19, when 2,250 DDoS attacks were recorded. Since February 26, the average number of DDoS attacks per day has halved to 697. The most active day at the end of the quarter was February 28 with 1,362 attacks, and the quietest was March 3 with 479. Note that attacks by spontaneous hacktivist botnets, which happened to surge in late February and March, are not monitored by DDoS Intelligence.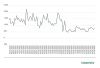
Dynamics of the number of DDoS attacks, Q1 2022 (download)
The distribution of DDoS attacks by day of the week is slightly more evenly spread than in Q4 2021. The difference between the most active and the quietest days was 2.72 p.p. The largest share of attacks, as in the previous reporting period, came on Sunday (16.35%), and the lowest on Friday (12.77%), which in late 2021 was quite an active day. The shares of both days of the week fell.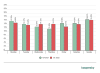
Distribution of DDoS attacks by day of the week, Q1 2022 (download)
Besides Friday and Sunday, Monday (14.83%), Tuesday (13.63%) and Saturday (14.09%) were calmer, while the shares of Wednesday (14.12%) and Thursday (14.21%) increased.
Duration and types of DDoS attacks
The average DDoS attack duration in the first three months of 2022 remained at the same level as in Q4 2021 — just under two hours. At the same time, the proportion of both very short (94.95%) and long attacks increased: DDoS attacks lasting more than 140 hours accounted for 0.03%, as did those lasting 100–139 hours. The share of attacks lasting 50–99 hours climbed to 0.15%. The duration of the quarter’s longest attack also increased: from 218 to 549 hours. Conversely, the share of moderately short attacks (5–49 hours) decreased.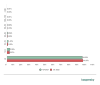
Distribution of DDoS attacks by duration, Q4 2021 and Q1 2022 (download)
UDP flooding (53.64%) constituted more than half of all DDoS attacks in Q1, adding 3.33 p.p. SYN flooding (22.37%) moved up to second, adding 6.08 p.p., while TCP flooding (20.17%) saw its share cut by a third, relegating this type of DDoS to third place. HTTP flooding (2.42%) and GRE flooding (1.41%) marginally increased their shares, but remained in fourth and fifth, respectively.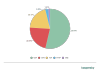
Distribution of DDoS attacks by type, Q1 2022 (download)
Geographic distribution of botnets
Glancing at the geographic distribution of botnet C&Cs, we see that more than half of those active in Q1 were located in the US (55.53%), up 9.04 p.p. from the end of 2021. Germany (8.30%) moved into second place (8.30%), followed by the Netherlands (8.09%). The Czech Republic (4.68%) and Russia (4.68%) share fourth place.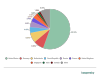
Distribution of C&C botnet servers by country, Q1 2022 (download)
In sixth place by number of C&C servers in Q1 is France (3.40%), in seventh is the UK (2.77%), and propping up the TOP 10 is Canada (1.06%). Eighth and ninth positions were taken by countries that did not make the TOP 10 last quarter: Singapore (1.91%) and India (1.49%).
Attacks on IoT honeypots
The largest share of bots trying to hack into our SSH honeypots in Q1 fell to China (20.41%). That said, the country’s share decreased compared to the previous reporting period by 6.32 p.p.; meanwhile, the share of the US rose from 11.20 to 15.24%. In third place in the list of countries and territories from which attacks originated is Germany (7.05%), followed by Brazil (4.91%) and Hong Kong (4.79%). However, not all bots were equally active. For instance, almost half of the attacks on our honeypots came from Russia (47.23%), despite accounting for just 3.40% of the total number of bots. In turn, China and the US were responsible for 9.01% and 8.16% of attacks, respectively.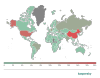
Geographic distribution of devices from which attempts were made to attack Kaspersky SSH honeypots, Q1 2022 (download)
The ranking of countries and territories with the most devices trying to hack into our Telnet honeypots is likewise headed by China (41.21%). Its share dropped since the last quarter, but remains significantly higher than that of other countries. India (8.44%) and Russia (6.15%) remained second and third, followed by Brazil (5.36%) and the US (3.95%). Meanwhile, Chinese bots were responsible for almost two-thirds (65.48%) of all attacks on Telnet honeypots, and another 12.02% of attacks came from inside the US.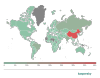
Geographic distribution of devices from which attempts were made to attack Kaspersky Telnet honeypots, Q1 2022 (download)
Conclusion
The DDoS attack landscape in Q1 was strongly influenced by the geopolitical situation: since the end of February, we have seen a surge in hacktivist activity and the emergence of a large number of spontaneous botnets that users connected to voluntarily. Hacktivist attacks were notable for their length, even if security solutions successfully filtered out the junk traffic. At the same time, known botnets, which we have long been monitoring, became far less active from late February, while in terms of duration, the number of both long and very short attacks of these botnets increased against the previous reporting period.
The Q1 situation with anti-DDoS protection in Russia warrants a separate mention. As we have said repeatedly, cyberdefenses need deploying in advance, because when an attack comes, it will be too late. This is precisely what very many owners of Russian network resources encountered at the end of February. The wave of new customers overwhelmed anti-DDoS services in the country. There was simply not enough time to set up protection, which led to long downtime for many resources. You never know when emergency occurs, so if you have yet to take care of anti-DDoS protection, we recommend that you start today.
It is very hard to predict anything in the current climate. The only certainty is that the state of the DDoS market in Q2 will depend directly and primarily on geopolitics. It is highly unlikely that we will see a decline in DDoS activity before the end of hostilities in Ukraine. Yet neither do we expect growth in Q2: for there to be a DDoS surge like we observed in late February/early March, a new shock of global proportions is needed.
Cloudflare Thwarts Record DDoS Attack Peaking at 15 Million Requests Per Second
29.4.22 Attack Thehackernews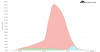
Cloudflare on Wednesday disclosed that it acted to mitigate a 15.3 million request-per-second (RPS) distributed denial-of-service (DDoS) attack. The web infrastructure and website security company called it one of the "largest HTTPS DDoS attacks on record."
"HTTPS DDoS attacks are more expensive in terms of required computational resources because of the higher cost of establishing a secure TLS encrypted connection," Cloudflare's Omer Yoachimik and Julien Desgats said. "Therefore it costs the attacker more to launch the attack, and for the victim to mitigate it."
The volumetric DDoS attack is said to have lasted less than 15 seconds and targeted an unnamed Cloudflare customer operating a crypto launchpad.
Volumetric DDoS attacks are designed to overwhelm a target network/service with significantly high volumes of malicious traffic, which typically originate from a botnet under a threat actor's control.
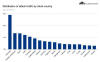
Cloudflare said the latest attack was launched from a botnet consisting of roughly 6,000 unique compromised devices, with 15% of the attack traffic emanating from Indonesia, followed by Russia, Brazil, India, Colombia, and the U.S.
"What's interesting is that the attack mostly came from data centers," Yoachimik and Desgats noted. "We're seeing a big move from residential network Internet Service Providers (ISPs) to cloud compute ISPs."
Record-setting DDoS attacks have become increasingly common in recent months. In August 2021, Cloudflare disclosed what it characterized as the largest application-layer attack ever seen, and, earlier this year, Microsoft revealed that it had prevented multiple DDoS attacks that crossed 2.4 terabits per second (Tbps).
In addition, cybersecurity firm Kaspersky revealed this week that the number of DDoS attacks hit an all-time high in the first quarter of 2022, jumping 4.5 times year-over-year, largely driven by Russia's invasion of Ukraine.
"The DDoS attack landscape in Q1 was strongly influenced by the geopolitical situation: since the end of February, we have seen a surge in hacktivist activity and the emergence of a large number of spontaneous botnets that users connected to voluntarily," the Russian company said.
FIN7 Hackers Leveraging Password Reuse and Software Supply Chain Attacks
5.4.22 Attack Thehackernews
The notorious cybercrime group known as FIN7 has diversified its initial access vectors to incorporate software supply chain compromise and the use of stolen credentials, new research has revealed.
"Data theft extortion or ransomware deployment following FIN7-attributed activity at multiple organizations, as well as technical overlaps, suggests that FIN7 actors have been associated with various ransomware operations over time," incident response firm Mandiant said in a Monday analysis.
The cybercriminal group, since its emergence in the mid-2010s, has gained notoriety for large-scale malware campaigns targeting the point-of-sale (POS) systems aimed at restaurant, gambling, and hospitality industries with credit card-stealing malware.
FIN7's shift in monetization strategy towards ransomware follows an October 2021 report from Recorded Future's Gemini Advisory unit, which found the adversary setting up a fake front company named Bastion Secure to recruit unwitting penetration testers in a lead up to a ransomware attack.
Then earlier this January, the U.S. Federal Bureau of Investigation (FBI) issued a Flash Alert warning organizations that the financially motivated gang was sending malicious USB drives (aka BadUSB) to U.S. business targets in the transportation, insurance, and defense industries to infect systems with malware, including ransomware.
Recent intrusions staged by the actor since 2020 have involved the deployment of a vast PowerShell backdoor framework called POWERPLANT, continuing the group's penchant for using PowerShell-based malware for its offensive operations.
"There is no doubt about it, PowerShell is FIN7's love language," Mandiant researchers said.
In one of the attacks, FIN7 was observed compromising a website that sells digital products in order to tweak multiple download links to make them point to an Amazon S3 bucket hosting trojanized versions that contained Atera Agent, a legitimate remote management tool, which then delivered POWERPLANT to the victim's system.
The supply chain attack also marks the group's evolving tradecraft for initial access and the deployment of first-stage malware payloads, which have typically centered around phishing schemes.
Other tools used by the group to facilitate its infiltrations include EASYLOOK, a reconnaissance utility; BOATLAUNCH, a helper module designed to bypass Windows AntiMalware Scan Interface (AMSI); and BIRDWATCH, a .NET-based downloader employed to fetch and execute next-stage binaries received over HTTP.
"Despite indictments of members of FIN7 in 2018 and a related sentencing in 2021 announced by the U.S. Department of Justice, at least some members of FIN7 have remained active and continue to evolve their criminal operations over time," Mandiant researchers said.
"Throughout their evolution, FIN7 has increased the speed of their operational tempo, the scope of their targeting, and even possibly their relationships with other ransomware operations in the cybercriminal underground."
Beastmode DDoS Botnet Exploiting New TOTOLINK Bugs to Enslave More Routers
5.4.22 Attack Thehackernews
A variant of the Mirai botnet called Beastmode has been observed adopting newly disclosed vulnerabilities in TOTOLINK routers between February and March 2022 to infect unpatched devices and expand its reach potentially.
"The Beastmode (aka B3astmode) Mirai-based DDoS campaign has aggressively updated its arsenal of exploits," Fortinet's FortiGuard Labs Research team said. "Five new exploits were added within a month, with three targeting various models of TOTOLINK routers."
The list of exploited vulnerabilities in TOTOLINK routers is as follows -
CVE-2022-26210 (CVSS score: 9.8) - A command injection vulnerability that could be exploited to gain arbitrary code execution
CVE-2022-26186 (CVSS score: 9.8) - A command injection vulnerability affecting TOTOLINK N600R and A7100RU routers, and
CVE-2022-25075 to CVE-2022-25084 (CVSS scores: 9.8) - A command injection vulnerability impacting multiple TOTOLINK routers, leading to code execution
The other exploits targeted by Beastmode include flaws in TP-Link Tapo C200 IP camera (CVE-2021-4045, CVSS score: 9.8), Huawei HG532 routers (CVE-2017-17215, CVSS score: 8.8), video surveillance solutions from NUUO and Netgear (CVE-2016-5674, CVSS score: 9.8), and discontinued D-Link products (CVE-2021-45382, CVSS score: 9.8).

To prevent affected models from being taken over by the botnet, users are strongly recommended to update their devices to the latest firmware.
"Even though the original Mirai author was arrested in fall 2018, [the latest campaign] highlights how threat actors, such as those behind the Beastmode campaign, continue to rapidly incorporate newly published exploit code to infect unpatched devices using the Mirai malware," the researchers said.
15-Year-Old Bug in PEAR PHP Repository Could've Enabled Supply Chain Attacks
2.4.22 Attack Thehackernews
A 15-year-old security vulnerability has been disclosed in the PEAR PHP repository that could permit an attacker to carry out a supply chain attack, including obtaining unauthorized access to publish rogue packages and execute arbitrary code.
"An attacker exploiting the first one could take over any developer account and publish malicious releases, while the second bug would allow the attacker to gain persistent access to the central PEAR server," SonarSource vulnerability researcher Thomas Chauchefoin said in a write-up published this week.
PEAR, short for PHP Extension and Application Repository, is a framework and distribution system for reusable PHP components.
One of the issues, introduced in a code commit made in March 2007 when the feature was originally implemented, relates to the use of the cryptographically insecure mt_rand() PHP function in the password reset functionality that could allow an attacker to "discover a valid password reset token in less than 50 tries."
Armed with this exploit, a bad actor could target existing developer or administrator accounts to hijack them and publish new trojanized versions of packages already maintained by the developers, resulting in a widespread supply chain compromise.
The second vulnerability, which requires the adversary to chain it with the aforementioned flaw to attain initial access, stems from pearweb's reliance on an older version of Archive_Tar, which is susceptible to a high-severity directory traversal bug (CVE-2020-36193, CVSS score: 7.5), leading to arbitrary code execution.
"These vulnerabilities have been present for more than a decade and were trivial to identify and exploit, raising questions about the lack of security contributions from companies relying on it," Chauchefoin said.
The findings mark the second time security issues have been uncovered in the PHP supply chain in less than a year. In late April 2021, critical vulnerabilities were divulged in the Composer PHP package manager that could enable an adversary to execute arbitrary commands.
With software supply chain attacks emerging as a dangerous threat in the wake of protestware incidents aimed at widely-used libraries in the NPM ecosystem, security issues tied to code dependencies in software are back in the spotlight, prompting the Open Source Initiative to call the "weaponization of open source" an act of cyber vandalism that "outweigh[s] any possible benefit."
Hackers Target Real Estate Websites with Skimmer in Latest Supply Chain Attack
5.1.2022 Attack Thehackernews
Threat actors leveraged a cloud video hosting service to carry out a supply chain attack on more than 100 real estate websites operated by Sotheby's Realty that involved injecting malicious skimmers to steal sensitive personal information.
"The attacker injected the skimmer JavaScript codes into video, so whenever others import the video, their websites get embedded with skimmer codes as well," Palo Alto Networks' Unit 42 researchers said in a report published this week.
The skimmer attacks, also called formjacking, relates to a type of cyber attack wherein bad actors insert malicious JavaScript code into the target website, most often to checkout or payment pages on shopping and e-commerce portals, to harvest valuable information such as credit card details entered by users.

In the latest incarnation of the Magecart attacks, the operators behind the campaign breached the Brightcove account of Sotheby's and deployed malicious code into the player of the cloud video platform by tampering with a script that can be uploaded to add JavaScript customizations to the video player.
"The attacker altered the static script at its hosted location by attaching skimmer code. Upon the next player update, the video platform re-ingested the compromised file and served it along with the impacted player," the researchers said, adding it worked with the video service and the real estate company to help remove the malware.
The campaign is said to have begun as early as January 2021, according to MalwareBytes, with the harvested information — names, emails, phone numbers, credit card data — exfiltrated to a remote server "cdn-imgcloud[.]com" that also functioned as a collection domain for a Magecart attack targeting Amazon CloudFront CDN in June 2019.
To detect and prevent injection of malicious code into online sites, it's recommended to conduct web content integrity checks on a periodic basis, not to mention safeguard accounts from takeover attempts and watch out for potential social engineering schemes.
"The skimmer itself is highly polymorphic, elusive and continuously evolving," the researchers said. "When combined with cloud distribution platforms, the impact of a skimmer of this type could be very large."