
Microsoft is going to publicly release some of its threat indicators, the company pointed out that its users are already protected against these attacks by Microsoft Threat Protection (MTP).
Cyber Articles - H 2020 1 2 CyberCrime CyberSpy Cyber Articles - H 2021 2020 2019 2018 2017 1 Cyber blog Cyber blog
Creating an emergency ready cybersecurity program
27.5.2020 Net-Security Cyber
A large part of the world’s workforce has transitioned to working remotely, but as plans are being drawn up to reopen economies, the security industry is being challenged to develop stronger screening practices, emergency operations planning, and to deploy tools to detect and minimize the impact that future pandemics, natural disasters and cyberattacks can have on a company.
emergency ready cybersecurity program
Things like global security operation centers (SOCs), managed security services, thermal imaging and temperature screening for on-site visitors and employees and enhanced employee tracking capabilities are new areas of increased focus.
As security professionals are forced to reassess how the systems they monitor are working in this new environment, companies and organizations must still deal with day-to-day operations that are now more likely to occur on unsecured wireless networks. From data loss prevention and email spam protection to denial of service and data breach or leakage, there’s a large number of challenges to address as more and more workers work from home. So, what should businesses focus on to ensure security and safety?
The greatest vulnerabilities
One major cybersecurity shortcoming of companies is just how much of their network is accessible, both within an office and externally. As technology has advanced, the need for a secure network infrastructure is of the utmost importance to protect all company assets. That need is even more acute now, with many workers currently working from home on personal devices and unsecure wireless networks.
With the likely shift towards a more remote workforce in the coming years, across industries, wireless networks will need to be designed and revamped with security in mind.
Beyond the COVID-19 impact, IT teams still face non-standard deployments of technology in regard to security devices, as well as “bring your own device” options that are currently being used in every aspect of the IT world. IT groups also currently deal with a great deal of infrastructure that is aging without a replacement and/or a life-cycle management plan.
Additionally, “flat networks”, which were originally designed just to make sure everything could communicate, are still common. These networks were designed with very little regard for the security of edge devices and all other endpoints. Many enterprise customers are now retrofitting these networks to meet current cybersecurity requirements and recommendations. It is clear that security issues extend beyond our current, unforeseen circumstances and must still be dealt with promptly.
A strong incident response program
The success of security policies and systems depends on their proper implementation and a continuous improvement process to sustain the security program on a day-to-day basis. The program must meet business needs and appropriately mitigate security risks. By implementing an effective incident response program, a company will be able to use information generated from things like access control and video systems and ensure that a company’s security events are “real” and not falsely positives due to technological problems. Any strong IR program should be quick and accurate and with workers spread out around the globe.
Technology plays a growing role in almost all security programs but cannot be the ultimate factor when it comes to deciding which incidents require a response. As information becomes more integrated and easier to reach, successful IR programs ensure that the information delivered is accurate, relevant and actionable to security personnel. Technology may be providing the information avalanche, but it can also be used to effectively cull through the information and make sure the human operators only see what they are supposed to see.
The automation of security
How much of the world’s security can really be automated? Many simple tasks with access control and video systems are becoming more and more automated by the day. For example, video analytics are becoming more common on even the most basic security cameras and are less dependent on high-end servers than in the past.
Today, identification of people and vehicles can be accomplished through automation, rather than through human interaction. With remote workers, this is crucial. Many companies are now facing unexpected financial pressures and security budgets are being tightened. As such, automated processes for sending alerts and warnings have also taken on a larger role.
It is now expected, at the enterprise level, that every system should be able to auto-generate reports. Future deployment of all security-related technologies will further shrink the possibility of human error and the risk associated with those events, while providing a greater view for all stakeholders.
It goes without saying that we are in uncharted territory. As security experts work to shift security systems to accommodate the new reality we are living in, companies must find new ways to ensure the safety of their employees and their work – not just from COVID-19, but from additional challenges that come along with it.
As businesses across the world start to reopen, executives should be thinking about their cybersecurity protocols, and the best ways to utilize technology to their advantage. The most successful businesses will have strong, uniform IT standards and will be able to conduct their security work from any location, with a quick response.
The dark web is flooded with offers to purchase corporate network access
22.5.2020 Net-security Cyber
There is a flood of interest in accessing corporate networks on the dark web, according to Positive Technologies.
access dark web
In Q1 2020, the number of postings advertising access to these networks increased by 69 percent compared to the previous quarter. This may pose a significant risk to corporate infrastructure, especially now that many employees are working remotely.
“Access for sale” on the dark web is a generic term, referring to software, exploits, credentials, or anything else that allows illicitly controlling one or more remote computers.
In Q4 2019, over 50 access points to the networks of major companies from all over the world were publicly available for sale – the same number as during all of 2018. In Q1 2020, this number rose to 80.
Criminals mostly sell access to industrial companies, professional services companies, finance, science and education, and IT (together accounting for 58 percent of these offers).
Criminals targeting major companies
Only a year ago, criminals seemed to be more interested in trading in individual servers. Access to them was sold on the dark web for as little as to $20. However, in the second half of 2019, there has been an increasing interest in the purchase of access to local corporate networks.
Prices have also skyrocketed: we’ve seen hackers offer a commission of up to 30 percent of the potential profit from a hack of a company’s infrastructure – with annual income exceeding $500 million. The average cost of privileged access to a single local network is in the range of $5,000.
Some major companies become the victims of these crimes, with annual incomes running into the hundreds of millions or even billions of dollars. In terms of location, hackers’ primary target is U.S. companies (more than a third of the total), followed by Italy and the United Kingdom (5.2 percent each), Brazil (4.4 percent), and Germany (3.1 percent).
In the U.S., criminals predominately sell access to professional services companies (20 percent), industrial companies (18 percent), and government institutions (14 percent). In Italy, industrial companies lead (25 percent), followed by professional services (17 percent).
In the United Kingdom, science and educational organizations account for 25 percent, and finance for 17 percent. In Germany, IT and professional services each account for 29 percent of access points for sale.
Network access sold to other dark web criminals
In most cases, access to these networks is sold to other dark web criminals. They either develop an attack on business systems themselves or hire a team of more skilled hackers to escalate network privileges and infect critical hosts in the victim’s infrastructure with malware. Ransomware operators were among the first to use this scheme.
Positive Technologies senior analyst Vadim Solovyov said: “Large companies stand to become a source of easy money for low-skilled hackers. Now that so many employees are working from home, hackers will look for any and all security lapses on the network perimeter. The larger the hacked company is, and the higher the obtained privileges, the more profitable the attack becomes.
“To stay safe, companies should ensure comprehensive infrastructure protection, both on the network perimeter and within the local network. Make sure that all services on the perimeter are protected and security events on the local network are properly monitored to detect intruders in time.
“Regular retrospective analysis of security events allows teams to discover previously undetected attacks and address threats before criminals can steal data or disrupt business processes.”
Smarsh Adds Cybersecurity and Compliance to Archiving with Acquisition of Entreda
21.5.2020 Securityweek Cyber
Information archiving firm Smarsh has acquired cybersecurity and compliance firm Entreda. The acquisition adds Entreda's 300 clients from the enterprise wealth management market to Smarsh's 6,000 financial services clients, while bringing new cybersecurity expertise to the secure collection, storage and management of enterprise data.
Financial details of the acquisition have not been disclosed. Santa Clara, Calif-based Entreda (founded in 2010) will continue to operate under its own name as a wholly-owned subsidiary of Portland, Oregon-based Smarsh (founded in 2001).
The two firms offer complementary services. Entreda brings new cybersecurity risk and compliance capabilities to Smarsh's capture, archiving and monitoring of information across the breadth of corporate communication channels (such as email, voice, social media, collaboration tools and more).
The timing is judicious. The long-term slow advance of remote working has been propelled into the standard method of work by the sudden pandemic lockdown -- a state that many analysts believe will be irreversible. "In the past few months, more and more companies have asked for our help in addressing the regulatory, compliance and cybersecurity risks associated with the move to long-term remote-work models and the expanded use of mobile and collaborative communications technology, such as Microsoft Teams, Slack and Zoom," said Brian Cramer, CEO at Smarsh.
Enterprises are being forced into a new normal rather than being allowed to evolve towards it. The threat landscape has suddenly expanded dramatically, and data protection, privacy and finance compliance has become more complex. With the information managed by Smarsh increasingly being collected from outside the corporate network, the need for additional cybersecurity and compliance solutions is self-evident. "With the acquisition [of Entreda]," Cramer added, "Smarsh can now offer our customers cutting-edge device, network and user level cybersecurity risk and compliance management capabilities."
Stephen Marsh, founder and chairman at Smarsh, told SecurityWeek, "Through our conversations with customers and regulators, it has become clear that firms need a cybersecurity compliance partner like Entreda. Entreda's Unify platform is a comprehensive, easy-to-use cybersecurity command center, monitoring multiple mission-critical threat vectors behind a single pane of glass. Similar to the Smarsh Connected Archive offerings, the product was purpose-built to help broker-dealers and registered investment advisories efficiently meet their regulatory requirements. Now customers can get compliance solutions for cybersecurity and electronic communications in one place."
Both firms will continue to operate as they are, but with the ability to enhance integrated product offerings from the other's portfolio. It's business as usual, commented, Sid Yenamandra, CEO and co-founder of Entreda, but customers can "look forward to the many exciting product enhancements and new solutions that we can roll out, more expeditiously than ever, in partnership with Smarsh."
How Cybersecurity Enables Government, Health, EduTech Cope With COVID-19
21.5.2020 Thehackernews Cyber
The advent of the Covid-19 pandemic and the impact on our society has resulted in many dramatic changes to how people are traveling, interacting with each other, and collaborating at work.
There are several trends taking place as a consequence of the outbreak, which has only continued to heighten the need for the tightest possible cybersecurity.
Tools for Collaboration
There has been a massive spike in the adoption of Tools for Collaboration as a consequence of COVID-19.
Concerns about the coronavirus have caused an enormous increase in remote working, with many organizations requiring or at least encouraging their workers to stay at home—especially when cities, states, and even some entire nations are ultimately into lock down in a bid to spread the stem of the disease.
Meanwhile, with millions working from home for many weeks now, there has been a spike in the video conferencing and online collaboration software, many of which are fortunately entirely free, allowing organizations to integrate them with their internal apps for better performance.
Working from home can initially be a bit of the challenge. But it's also true that many organizations that have previously been reluctant to adopt remote working as a practice have now had little option but to embrace it.
remote work
There have been long many misconceptions in regards to remote working, but the worldwide pandemic has resulted in universal adoption of the practice that has forced previously dubious managers and executives to realize that remote working can actually have a massively positive impact on employee productivity, mental health, the environment, work-life balance, and expenses.
As a result, many organizations have already started planning to incorporate flexible and remote working models into their schedules on a more permanent basis—even after the Covid-19 crisis is over.
According to recent research published by global research and advisory company Gartner, the work culture move could be permanent for nearly half the workforce.
Remote working applications
Apparently, the number of applications needed to enable more remote working—especially on a more permanent basis—is clearly going to increase, and so will the number of customers and partners focused on Internet-facing applications.
remote work
Therefore, the availability and criticality of these applications will be extremely crucial for the future sustainability of the remote working practice, as well as enable businesses to collaborate and share information with their stakeholders, something that is only going to grow in importance.
Because there is inevitably going to be a massive spike in internet-facing applications that will be of vital importance for such businesses, there will be an even greater focus on ensuring security is tight enough to make certain business continuity.
The Increasing Importance of Cybersecurity
Many serious businesses have already long-held cybersecurity as one of the most important issues that they face in the modern age, but with the increasing importance of remote working, it is only going to become an even more integral aspect of the future planning process for companies.
cybersecurity code of practice
Having the best cybersecurity in place will allow quickly launching of a higher number of applications, ensuring that a business is better placed to cope not only with the current Covid-19 crisis but also to ensure the sustainability of future behavior after the pandemic has run its course.
There are several essential verticals that businesses will need to learn to cope with as quickly as possible due to many factors resulting from Covid-19, including:
the need for government to provide consumers more digital services,
the quick adoption of remote learning by the education sector, and
the need for the health system to develop innovative methods to deal with capacity problems.
The Solution
The solution to these problems will be greater collaboration and digitization and the embracing of focused consumer apps within these sectors.
Cybersecurity needs to be seen as a method to quickly achieve these goals without any compromises to safety or the benefits that it is actually intended to deliver.
How to Approach the Cybersecurity Issue
Several things need to be provided by any approach to cybersecurity, including:
Making exploitable risks to applications visible regularly.
Providing businesses with the capability of mitigating such risks in real-time to ensure business continuity is maintained, given that a breach can have severe costs besides transactional and brand loss, including a loss of productivity when teams rely on such applications to successfully complete their work.
Partnering with sector experts and businesses that provide these services, with the increase in demand, is likely to result in faster innovation that will make adoption more straightforward for companies without the need to create in-house expertise.
Approach Cybersecurity as an enabler for businesses, allowing organizations to be more agile, faster, and fearless being digital while mitigating the continuity risks.
Several services, including the Indusface app known as AppTrana, provide fully managed application security that allows businesses to move faster and remain sustainable during and after the Covid-19 crisis.
Microsoft is open-sourcing COVID-19 threat intelligence
17.5.2020 Securityaffairs Cyber
Microsoft has recently announced that it has made some of its COVID-19 threat intelligence open-source.
While the number of Coronavirus-themed attacks continues to increase increased Microsoft announced it is open-sourcing its COVID-19 threat intelligence to help organizations to repeal these threats.
“Microsoft processes trillions of signals each day across identities, endpoint, cloud, applications, and email, which provides visibility into a broad range of COVID-19-themed attacks, allowing us to detect, protect, and respond to them across our entire security stack.” reads a post published by Microsoft. “Today, we take our COVID-19 threat intelligence sharing a step further by making some of our own indicators available publicly for those that are not already protected by our solutions. “
Sharing information could offer the community a more complete view of attackers’ tactics, techniques, and procedures.
Microsoft experts have already been sharing examples of malicious lures and have provided guided hunting of COVID-themed attacks through Azure Sentinel Notebooks.

Microsoft is going to publicly release some of its threat indicators, the company pointed out that its users are already protected against these attacks by Microsoft Threat Protection (MTP).
Microsoft has made available the indicators both in the Azure Sentinel GitHub repo, and through the Microsoft Graph Security API.
“These indicators are now available in two ways. They are available in the Azure Sentinel GitHub and through the Microsoft Graph Security API. For enterprise customers who use MISP for storing and sharing threat intelligence, these indicators can easily be consumed via a MISP feed.” continues Microsoft.
“This threat intelligence is provided for use by the wider security community, as well as customers who would like to perform additional hunting, as we all defend against malicious actors seeking to exploit the COVID crisis.”
This is just the beginning of the threat intelligence sharing of Coronavirus-related IOCs that will be offered through the peak of the outbreak.
Microsoft is releasing file hash indicators related to malicious email attachments employed in the campaigns.
Azure Sentinel customers can import the indicators using a Playbook or access them directly from queries. Microsoft added that both Office 365 ATP and Microsoft Defender ATP already block the attacks associated with the above indicators.
Microsoft Open-Sources COVID-19 Threat Intelligence
16.5.2020 Securityweek Cyber
Microsoft this week announced that it has made some of its COVID-19 threat intelligence available to the public.
The number of attacks targeting organizations and individuals worldwide using coronavirus lures has increased dramatically over the past several months, and Microsoft says it wants to help even those who do not use its threat protection solutions.
The company says it processes “trillions of signals each day across identities, endpoint, cloud, applications, and email,” thus having broad visibility into a variety of COVID-19-themed attacks.
Microsoft has been sharing examples of malicious lures and has provided guided hunting of COVID-themed threats through Azure Sentinel Notebooks, but has decided to take things one step further.
For that, the tech company is making some of its threat indicators available publicly. Microsoft Threat Protection (MTP) can already keep customers safe from the threats identified by these indicators, but those who do not use the solution are not protected.
By publishing these indicators, Microsoft aims to raise awareness of the shift in attackers’ techniques and help detect them.
The indicators were made available both in the Azure Sentinel GitHub repo, and through the Microsoft Graph Security API. Enterprise customers that use MISP for storing and sharing threat intelligence can leverage these indicators via a MISP feed.
“This threat intelligence is provided for use by the wider security community, as well as customers who would like to perform additional hunting, as we all defend against malicious actors seeking to exploit the COVID crisis,” Microsoft says.
The company says this is only the beginning of its sharing of COVID-related IOCs, but underlines that this is a time-limited feed, maintained “through the peak of the outbreak to help organizations focus on recovery.”
What the company released today includes file hash indicators related to email attachments that were deemed malicious.
Azure Sentinel customers can import these indicators using a Playbook or access them directly from queries. Both Office 365 ATP and Microsoft Defender ATP block attacks that employ these indicators, Microsoft says.
Utah Says No to Apple/Google COVID-19 Tracing; Debuts Startup App
15.5.20 Threatpost Cyber
“Healthy Together” app uses a raft of location data, including GPS, cell tower triangulation and Bluetooth, to pinpoint users and ID coronavirus hotspots.
The state of Utah has settled on a contact-tracing mobile app that collects detailed user location information to track the spread of COVID-19 among citizens – eschewing the API model proposed by Apple and Google in April.
The app is called “Healthy Together” and it was created by a startup called Twenty Holdings – best-known for making a social app that allows users to “See who’s around. See who’s down. Hang out.” In other words, the company specializes in enabling physical, in-person connections.
It’s perhaps no surprise then that Twenty’s coronavirus app for Utah uses a raft of location data, including GPS, cell tower triangulation and Bluetooth, to pinpoint users.
The idea is to provide public health workers “with a faster and more accurate picture of where and how the virus is spreading in our community to focus public health efforts,” according to a notice on Utah’s official website.
The information collected by the app will be shared with public health officials (as expected) as well as a “limited number” of Twenty employees. Speaking to CNBC, Twenty chief strategy officer Jared Allgood explained how the state would use the data.
“Jeff and Sarah are two individuals in this example who don’t know each other but they both have the app on their phones,” he told the outlet. “And so both phones are emitting Bluetooth and GPS signals,” Allgood said. “Through that data we can identify whether or not two people have spent some time together.” From there, contact tracers can swing into action, making calls and contacting infected and exposed persons’ other contacts.
Armed with the data from the app, contact tracers and the patient “together can step through his list of location history,” Allgood said.
In marked contrast, Apple and Google’s API allows public health officials to build apps that have no centralized data collection on citizens. It makes use of an anonymous identifier beacon, which will be transmitted to other nearby devices via Bluetooth. When two people who have opted into contact tracing are in close contact for a certain period of time, their phones will exchange their anonymous identifier beacons. When people find out they’re infected, they can choose to upload the last 14 days of their broadcast beacons to the cloud. Any other person who has been in close proximity to someone infected will then be notified via the phone that an exposure to someone who has tested positive for coronavirus took place.
Utah officials said that the Apple/Google reliance on Bluetooth alone gives a less accurate picture of where disease hotspots are.
“Bluetooth helps us understand person-to-person transmission, while location/GPS data helps us understand transmission zones — having both of these important data points provides a more effective picture of how COVID-19 spreads,” according to the site FAQ. “This data helps policy makers make the best possible decisions about how and where we begin to relax and modify restrictions as our community and economy begin to reactivate.”
In terms of privacy protections, Healthy Together is an opt-in scheme, and users can limit location services if they choose. “While the State will have access to your symptom data, location and Bluetooth data will only be released to the state should you test positive for COVID-19,” according to the official website. And according to the app’s privacy policy, the data is stored on Twenty’s servers for 30 days, after which it’s deleted.
Healthy Together is in beta testing and is not yet using live data. Besides contact tracing, the app offers a symptom checker, the ability to find the nearest COVID-19 testing center and access test results.
Contact-tracing apps have set off a slew of controversy over privacy concerns, even as contact tracing has emerged as a top idea for dealing with the coronavirus pandemic and is considered by many to be an important step towards reopening economies worldwide.
The National Health Service (NHS) in the U.K. is test-driving its own app on the Isle of Wight, also rejecting the Apple/Google approach. Recent leaked documents showed that roadmap features for the app include the ability for people to upload their health “status” on a self-reporting basis, with options that could include labeling oneself: Quarantine, self-isolating, social distancing, shielding and none. Future plans also indicate the integration of granular location data; and, future versions of the app could also “collect self-reported data from the public like post code, demographic information and co-location status to enable more effective resource planning for NHS,” the documents reveal.
While that level of data collection worries privacy advocates, the concerns go further. The documents also showed that the officials behind the NHS initiative are concerned about how unverified information could be used. Because the information would be self-reported, the data collected by the app could include unverified diagnoses – and could be open to abuse or lead to unjustified “public panic,” according to the documents.
Any approach to app-based contact tracing comes with potential problems, Paul Bischoff, privacy advocate with Comparitech, told Threatpost. For instance, the Apple/Google decentralized model is more private and less prone to developer abuse and data breaches than using centralized GPS tracking like Healthy Together – however, it makes it more difficult to verify diagnoses without users’ identities.
It’s also vulnerable to attacks, he explained. “The most private method combines a decentralized model that keeps users’ identities anonymous with Bluetooth for proximity checking [like Google and Apple],” he said. “Bluetooth offers more accurate real-time proximity tracking than GPS and the data is easier to anonymize, though…it’s more prone to trolling, and a well-resourced adversary could track users with linkage attacks.”
Cyberthreats on lockdown
14.5.2020 Securelist Cyber
Every year, our anti-malware research team releases a series of reports on various cyberthreats: financial malware, web attacks, exploits, etc. As we monitor the increase, or decrease, in the number of certain threats, we do not usually associate these changes with concurrent world events – unless these events have a direct relation to the cyberthreats, that is: for example, the closure of a large botnet and arrest of its owners result in a decrease in web attacks.
However, the COVID-19 pandemic has affected us all in some way, so it would be surprising if cybercriminals were an exception. Spammers and phishers were naturally the trailblazers in this – look for details in the next quarterly report – but the entire cybercrime landscape has changed in the last few months. Before we discuss the subject, let us get something out of the way: it would be farfetched to attribute all of the changes mentioned below to the pandemic. However, certain connections can be traced.
Remote work
The first thing that caught our attention was remote work. From an information security standpoint, an employee within the office network and an employee connecting to the same network from home are two completely different users. It seems cybercriminals share this view, as the number of attacks on servers and remote access tools has increased as their usage has grown. In particular, the average daily number of bruteforce attacks on database servers in April 2020 was up by 23% from January.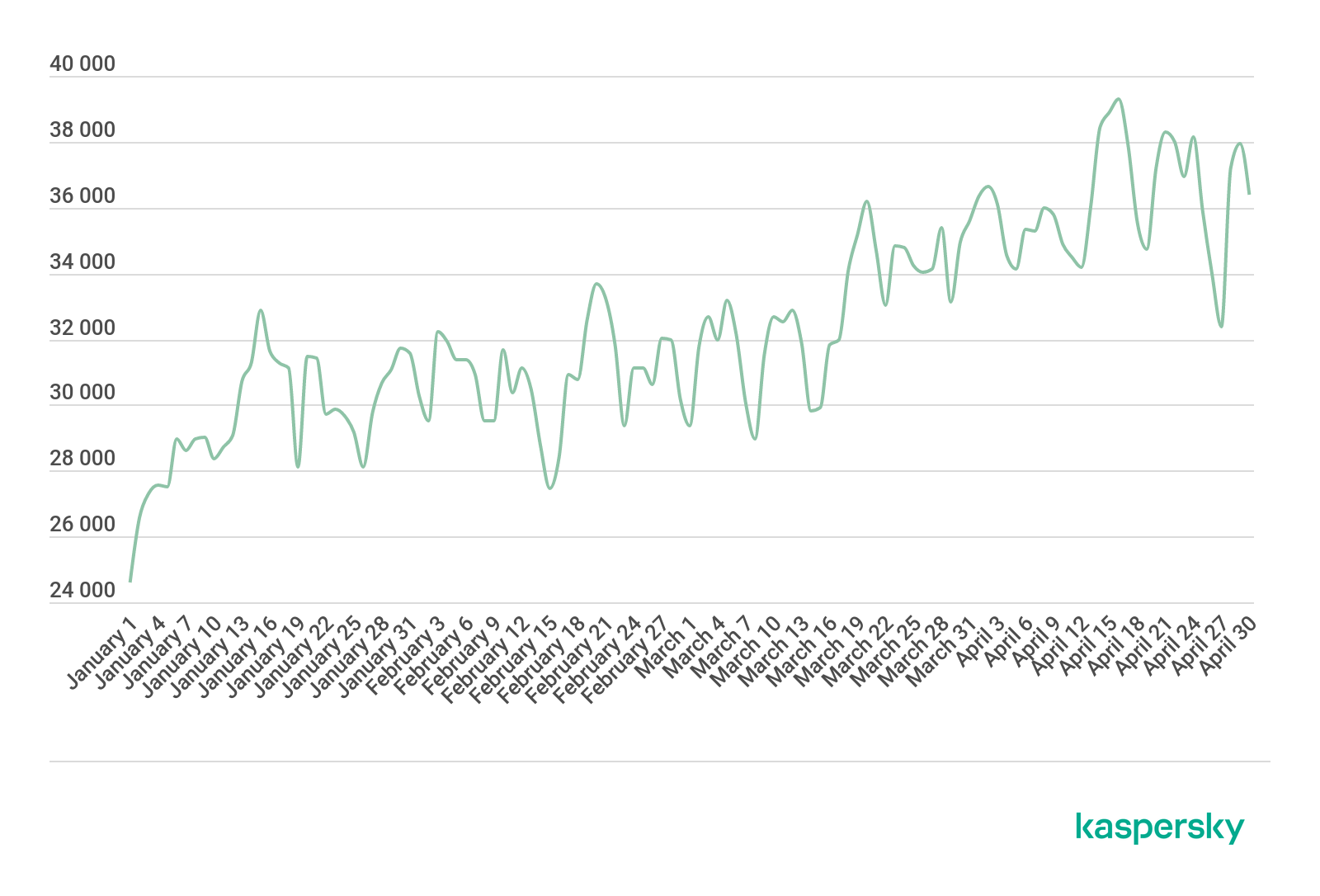
Distribution of botnet C&C servers by country, Q1 2020 (download)
Unique computers subjected to bruteforce attacks, January through April 2020
Cybercriminals use brute force to penetrate a company’s network and subsequently launch malware inside its infrastructure. We are monitoring several cybercrime groups that rely on the scheme. The payload is usually ransomware, mostly from the Trojan-Ransom.Win32.Crusis, Trojan-Ransom.Win32.Phobos and Trojan-Ransom.Win32.Cryakl families.
RDP-attacks and ways to counter these were recently covered in detail by Dmitry Galov in his blog post, “Remote spring: the rise of RDP bruteforce attacks“.
Remote entertainment
Online entertainment activity increased as users transitioned to a “remote” lifestyle. The increase was so pronounced that some video streaming services, such as YouTube, announced that they were changing their default video quality to help with reducing traffic. The cybercriminal world responded by stepping up web threats: the average daily number of attacks blocked by Kaspersky Web Anti-Virus increased by 25% from January 2020.
Web-based attacks blocked, January through April 2020 (download)
It is hard to single out one specific web threat as the driver – all of the threats grew more or less proportionally. Most web attacks that were blocked originated with resources that redirected users to all kinds of malicious websites. Some of these were phishing resources and websites that subscribed visitors to unsolicited push notifications or tried to scare them with fake system error warnings.
We also noticed an increase in Trojan-PSW browser script modifications that could be found on various infected sites. Their main task was to capture bank card credentials entered by users while shopping online and transfer these to cybercriminals.
Websites capable of silently installing cookie files on users’ computers (cookie stuffing) and resources that injected advertising scripts into users’ traffic together accounted for a significant share of the web threats.
Crooks continues to use COVID-19 lures, Microsoft warns
14.5.2020 Securityaffairs Cyber
Microsoft discovered a new phishing campaign using COVID-19 lures to target businesses with the infamous LokiBot information-stealer.
Microsoft has discovered a new COVID-19 themed phishing campaign targeting businesses with the LokiBot Trojan.
Lokibot was already employed in Coronavirus-themed campaigns, early of April, security experts at FortiGuard Labs discovered phishing attacks using alleged messages from the World Health Organization (WHO) to deliver the LokiBot trojan.
COVID-19 themed phishing campaigns recently observed by Microsoft was using messages with subject lines like “BUSINESS CONTINUITY PLAN ANNOUNCEMENT STARTING MAY 2020.”
Recent campaigns that deliver Lokibot, one of the first malware families to use COVID-19 lures, are showing a slight shift in tone reflecting current conversations, with subject lines like "BUSINESS CONTINUITY PLAN ANNOUNCEMENT STARTING MAY 2020" pic.twitter.com/vahi8VAsry
— Microsoft Security Intelligence (@MsftSecIntel) May 13, 2020
The LokiBot data stealer is able to collect information from tens of different web browsers, access to browsing data, locate the credentials for more than 15 different email and file transfer clients, and check for the presence of popular remote admin tools like SSH, VNC and RDP.
One of the phishing campaigns observed by Microsoft sees attackers pretending to be from the Centers for Disease Control (CDC), the messages promise latest information on the COVID-19 pandemic and a new “BUSINESS CONTINUITY PLAN ANNOUNCEMENT STARTING MAY 2020”.
Another campaign use messages that pretend to be from a vendor asking for updated banking information to process payments due to the COVID-19 virus lockdown.
The emails in both campaigns use ARJ attachments that contain malicious executables disguised as PDF files.
The choice of password-protected ARJ files aims at bypassing some security solutions. Upon opening the enclosed files, the infection process will start to finally deliver the LokiBot Trojan.
Microsoft pointed out that its Microsoft Threat Protection’s machine learning algorithms were able to detect the campaign, Microsoft users are automatically protected by the Microsoft Defender.
“Microsoft Defender’s advanced detection technologies, including behavior learning and machine learning, started blocking this attack right away. We used deeper analysis of the blocked attacks, which helped us to identify the end-to-end campaign detailed,” Tanmay Ganacharya, director of security research of Microsoft Threat Protection, told BleepingComputer.
“We see a lot of benefits of leveraging machine learning and we are in a very unique position here at Microsoft because of the quality and diversity of our 8.2 trillion signals we process daily through the Microsoft Intelligent Security Graph.”
5 easy steps to immediately bolster cybersecurity during the pandemic
14.5.2020 Net-security Cyber
Cyber attacks have increased exponentially since the start of the pandemic, with AT&T Alien Labs Open Threat Exchange (OTX) finding 419,643 indicators of compromise (IOC) related to COVID-19 from January to March, with a 2,000% month-over-month increase from February to March.
bolster cybersecurity
Rush to bolster cybersecurity
Companies of all sizes and in all sectors have been forced to adapt to a remote work environment overnight, regardless of whether they were ready or not. As this fast-moving shift to virtual business occurred, cybercriminals also adjusted their strategy to take advantage of the expanded attack surface, with the volume of attacks up by nearly 40% in the last month and COVID-19-themed phishing attacks jumping by 500%. The current situation is an IT manager’s worst nightmare.
This new remote work environment ushers in an entirely new security landscape and in record-time. Long-term solutions can be found in zero trust models and cloud security adoption, but time is of the essence. Organizations should act now.
The following are a few short-term, easy-to-implement actions that IT managers can take now to bolster cybersecurity amid the current pandemic.
1. Apply “social distancing” to home networks
Traditionally, home Wi-Fi networks are used for less sensitive tasks, often unrelated to work: children play games on their tablet, voice assistants are activated to display the weather, and movies are streamed on smart TVs. Fast forward to today, and employees are now connecting to the office through this same network, leaving gaps for children or non-working adults who may also be accessing the internet via the same network. Lines are blurred, and so is security.
Just as social distancing is encouraged to limit the potential spread of COVID-19, the same should apply digitally to our home networks. IT managers can encourage employees to partition their home internet access. This means trying to block children and non-working adults from using the same network connection that is used to log into the office. This step alone helps prevent a tidal wave of unknown vulnerabilities.
One doesn’t need to have extensive IT skills in order to isolate a home network, which saves IT managers valuable time and resources. On the market today, there are several home and small office routers, costing around $100, that offer VLAN support, and most Wi-Fi kits offer the ability to set up a “guest” network. As an IT manager, it’s important to provide step-by-step instructions on how to set this up on common routers, while communicating the importance of taking this small step to greatly boost security.
2. Encourage the use of lightweight mobile devices
BYOD brings immense security risk. What types of malware exist on your employees’ home devices? Have they completed recent software updates? It’s a gamble not worth taking.
If possible, IT managers should provide employees with company-owned lightweight devices, like smartphones and tablets. For one, in most of the country, you can use mobile broadband capabilities to avoid home networks altogether. Additionally, these devices are designed to be managed remotely. Users are essentially teaming up with the manufacturers’ security teams in keeping the devices secure, as well as the mobile operators in ensuring a secure connection. Attach a quality keyboard to such lightweight devices, and employees will not miss their PCs.
3. Move to the cloud… now!
On-premise software is outdated and often ineffective. If your organization has not moved to the cloud yet, let this be the forcing function for that change. Customer relationship management systems, office productivity apps and even creative design platforms are all available now as SaaS offerings, and outperform their traditional software equivalents. With cloud solutions, organizations are working with the SaaS provider’s security teams to help keep vulnerabilities away.
Once employees have transitioned to lightweight devices operating SaaS applications in the cloud, the attack surface is reduced exponentially.
4. Secure employee remote access
Employees will be connecting devices to several service connections, so many that it makes it difficult to manage on an ongoing, individual basis. Invest in secure remote access tools such as a strong endpoint security solution and a cloud security gateway. This will allow IT managers to set policies and monitor company-wide activity, even while the workforce is widely dispersed.
5. Brush up on password hygiene
I’m willing to bet that employees are logging into the office right now using poor passwords. They’re inputting passwords based on their children’s names, anniversary dates or, the worst, “password123.”
IT managers need to immediately (and regularly!) teach employees how to improve their security posture. One of the easiest ways to do that is to start with password hygiene. Insist that staff create long, complex, and unique passwords for every device and connection they use to access the office. Encourage the use of password managers to keep track of all logins. Staff should also set up two-factor authentication across the board, from the CEO down to the seasonal intern. This behavioral shift costs nothing and makes it significantly harder for cybercriminals to win.
We are all vulnerable to this pandemic. IT managers traditionally shoulder a tremendous amount of responsibility, but now with a remote work environment, that burden has quadrupled. While the to-do list may look exhaustive, try to focus on a few short-term actions that will bring peace of mind and bolstered security… right now.
Cybersecurity Threats to the Food Supply Chain
12.5.2020 Securityweek Cyber
Cyber Brings the Opportunity of Large-scale Adversarial Interference in Food Supplies
When Smithfield Foods closed its Sioux Falls pork processing plant – joining other meat and poultry closures from Tyson Foods, Cargill and JBS USA – headlines suggested that the country was ‘perilously close to the edge’ of food shortages. So, just how safe is the food supply?
The recent closures have been forced by the COVID-19 pandemic. This is likely to be a transient risk, but all modern plants face an ever-present consistent risk from cyber-attack. COVID-19 has merely focused minds on an under-considered risk: how safe is the food supply chain?
It’s a question that needs to be asked. Food supply is a fundamental pillar of ordered societies, and a catastrophic lack of food would rapidly lead to social disorder. This would likely be more rapid and severe in the western democracies that have not experienced serious food shortages for more than 70 years since the end of World War II.
Cyber risk and threat
There is no risk if there is no threat. The first question, then, is whether there is a cyber threat to food supply. Are cyber criminals likely to attack the food industry?
The answer is clearly ‘yes’; and there are at least three obvious channels: hacktivists, cyber-criminal gangs, and nation states. And a fourth, that needs to be mentioned: competitors. “Increased levels of espionage and sabotage from competitors will also heighten as organizations do battle for technological supremacy in this space,” warns Daniel Norman, research analyst with the Information Security Forum (ISF).
Hacktivists
There is a growing social movement to use the re-emergence from the COVID lockdown as an opportunity to ‘reboot’ the way society operates. Environmental pollution has dropped rapidly, and nature has recovered from its effects quickly. Environmental activists are calling for governments to invest in green technology as a post-pandemic economic stimulus.
Where this does not happen, and where the old polluting industries revert to their traditional practices, activists are likely to ‘punish’ the worst offenders. This is likely to be two-pronged: environmentalists concerned about increasing pollution, and animal rights activists objecting to the return to mass animal slaughter.
This punishment may come in the form of large-scale DDoS attacks, or even direct attacks against individual plants.
Cyber-criminal gangs
Criminal gangs are driven by two related issues – opportunity and money. The pandemic will have focused attention on the food supply chain, and both issues are apparent. The pandemic will be followed by recession, which could potentially be followed by a deeper depression. Even in the best scenario, there will be many areas of society operating on drastically reduced incomes in the foreseeable future.
The threat is not new. Theft of food has always existed: those who have none are forced to steal from those who have plenty. In the distant past, this was small-scale – effectively petty theft. In the more recent past, criminal gangs have become involved in more large-scale theft from distribution (cargo theft) and warehouses.
This is continuing: recent data from Transported Asset Protection Association (TAPA) suggests that cargo theft has increased by 114% over the last 12 months. On May 3, 2020, FreightWaves reported, “Trucks carrying food and other essentials have been popular with thieves along Mexico’s highways in recent weeks. Cargo theft of trucks has increased 25% during the coronavirus pandemic period, according to a survey conducted by LoJack Mexico.”
Cybercrime, however, could take this to a new level. Entire shipments of food could be redirected and stolen. Entire food companies can be extorted for large sums of money. IT and OT networks can be compromised by ransomware, and the rapid spoilage of food in production would be an incentive to pay the ransom. With much of the food industry comprising small local businesses, it will often become a question of paying up or going under – and this equation will attract additional attackers.
Nation states
The importance of the food supply chain is not lost on the military. In 1812, when Napoleon invaded Russia, the Russian army withdrew but operated a scorched earth policy to deny food supplies to Napoleon’s army. Without supplies, Napoleon was forced to retreat from Moscow, which arguably and ultimately led to his downfall.
“It is a well-known fact,” comments the ISF’s Norman, “that during times of conflict, the party that can destroy the food supply chain will inevitably win. It is therefore conceivable that cyber-attacks from nation state-backed actors and terrorist groups will begin targeting organizations dependent on new technologies, disrupting global supply chains.”
Cyber brings the opportunity of large-scale adversarial interference in food supplies. In military terms this could be a precursor to kinetic warfare, but the cyber age has introduced a new style of cyberwar. The U.S. experienced it in 2016 with Russian interference in the presidential election. The purpose may not have been to directly influence the outcome of the election, but to demoralize the American population. With a demoralized population, a nation’s effectiveness on the world stage is inevitably weakened.
“One way to weaken your adversary is to cause internal conflict,” added IOActive’s Sheehy. “Well, you can survive about three minutes without air, three days without water, and about three weeks without food. People will riot very quickly if they cannot get food. Even in this relatively civilized COVID lockdown, the stresses on the food supply chain have caused very high tensions among people.”
Continued interruption to the food supply chain would inevitably demoralize the population. In extreme circumstances it would lead to rioting in the streets and food looting. The possibility of such a threat from an adversarial nation should not be ignored.
The security of the food supply chain
The food industry is no different to any other industry – it has undergone rapid evolution into the fourth industrial revolution. IT and OT are being converged, and OT uses the same ICS devices with the same vulnerabilities as other industries. The same priority of continued production over updating systems prevails, and continued use of Windows 98 is still found. But just as older, vulnerable systems continue to be used, the industry is adopting new and not yet battle-tested technology with advanced sensors, robotics, drones and autonomous vehicles.
“One of the trends we see broadly in the food industry,” comments Sheehy, “is a move towards more automation. Partly this is a response to the pandemic – robots won't be sent home in any similar or repeated scenario. Labor is more of a business risk than robots. However, moving to more significant automation is going to change the risk profile in a way that a lot of organizations haven't formerly had to manage – operational technology has not been considered a high-risk priority.”
It's exacerbated, added Matt Rahman (IOActive’s COO), “by the structure of the industry. About 74% of food manufacturers have less than 20 employees. About 97% have fewer than 500 employees. They don't have the staff nor expertise to properly manage their cyber security.”
It is also worth noting that the food supply chain is more complex than the supply chains for most industries. Elsewhere, the supply chain primarily comprises third-party suppliers, product or parts delivery, and the manufacturer. With food it is third party suppliers (normally farmers), product delivery, food processing (the manufacturer), and then a further complex distribution to groceries/supermarkets and/or consumer. Each stage of this chain can be threatened.
“Technology adoption has skyrocketed in virtually every segment of our agriculture sector including food production, processing, and distribution,” comments Parham Eftekhari, founder and chairman of the Institute for Critical Infrastructure Technology (ICIT), “and experts predict this trend to continue with robotics and self-driving freight carriers paving the way for an autonomous future. This creates significant opportunity for disruption to our supply chain and food safety concerns.”
He continued, “Today, we are already hearing stories of processing plants shutting down and the potential of food shortages. What if manufacturing and storage facilities of perishable food products have their cooling systems hacked during a time of a national food shortage? It would only take a handful of high-profile attacks to create panic among citizens that could lead to a rush on grocery stores and threaten an already fragile food supply.”
The food industry supply chain is vulnerable at every stage. “Farmers are using GPS technology and robotics to custom fertilize and plant their land to optimize yield,” said Eftekhari. What if these systems are hacked – without their knowledge – resulting in crops that underperform expectations across the nation.”
Norman added, “5G environments will enable precision agriculture and farming at the individual crop or livestock level but will use poorly secured IoT devices and drones to monitor soil fertilization, nitrogen levels, pest control, water and sunlight requirements. Automated robotic combine harvesters will operate on private 5G networks, with machine learning systems calculating and monitoring optimum conditions across larger and interconnected ecosystems. The danger of attacks on the integrity of information could significantly alter the production process.”
At a local level, this could be a punitive attack by a hacktivist group objecting to use of certain pesticides, or genetically modified crops in general. “The agricultural industry is one of the biggest contributors to greenhouse gas emissions in the world,” says Norman. “Extreme levels of methane, nitrous oxide output and water usage consistently make them a prime target for activism. With greater dependency on technology, hacktivists will turn their attention to disrupting the technology underpinning the supply chain.”
At a national level, as part of modern geopolitical disruption, the aim could be to reduce yields in complete crops – shortages in wheat, corn and soybean crops would be both economically and socially damaging.
Distribution, both from farmer to processor and from processor to distributor, has long been subject to cargo theft by criminals – and the cyber element is growing. “Criminals hack into distribution firms,” comments IOActive’s Rahman, “to learn about shipments, create false invoices, bills of lading and manifests to falsify delivery/collection times when they can simply pick up the stolen cargo.”
The food processing plant is the obvious primary target for cyber criminals, especially for extortion. Ransomware is already targeting manufacturing. “Today, we are hearing stories of processing plants shutting down and the potential of food shortages,” said Eftekhari. “What if manufacturing and storage facilities of perishable food products have their cooling systems hacked during a time of a national food shortage? It would only take a handful of high-profile attacks to create panic among citizens that could lead to a rush on grocery stores and threaten an already fragile food supply.”
Here the worst scenario might come from terrorist groups rather than nation-states or criminal gangs. The motivation would be to seek harm rather than sow discord or acquire money. Such groups would be worried about neither attribution nor retribution, but could seek to break into processing plants either to damage equipment or poison supplies.
Beyond the processing plant, the food supply chain continues to the sales outlets. For now, the threat is physical redirection or old-fashioned cargo theft. This will change in future years as more and more supplies are delivered by autonomous trucks. Autonomous vehicles are proven to be hackable. Experts expect the recent trend of the food industry adopting new technology to continue, warns Eftekhari, “with robotics and self-driving freight carriers paving the way for an autonomous future. This creates significant opportunity for disruption to our supply chain and food safety concerns.”
But the threat already exists with current connected trucks. “The heavy vehicle cabs are exposed to potential cyber-attack,” warns Sheehy, “as well as their refrigerated trailers. The more modern refrigerated trailers often have their own monitoring systems which can be remotely accessible over mobile networks. They are also often attached to the controller area network (CAN bus) of the vehicle, providing a potential attack point to compromise the overall security of the vehicle.”
The COVID-19 pandemic has highlighted the fragility of the global food chain. This fragility will not be lost on cyber criminals. As the world moves from pandemic lockdown to economic recession, criminals will almost certainly look closely at the food supply chain as a means of making money. The risk is not to any one specific part of the chain nor any one type of criminal – the whole chain is at risk.
“If an attacker wants to provide some type of disruption to the food supply, one area could be transportation; a second is in food processing; but a third would be in food safety,” says Sheehy. “If the cold storage facility is not kept at the appropriate temperature, products will spoil. Even though different parts of the supply chain may have successfully done the production, the transportation and processing securely, you may still be in a situation where you have a constraint on supply due to a compromise in the integrity of the safety processes."
Rail vehicle manufacturer Stadler hit by cyberattack, blackmailed
10.5.2020 Bleepingcomputer Cyber
International rail vehicle construction company, Stadler, disclosed that it was the victim of a cyberattack which might have also allowed the attackers to steal company and employee data.
Stadler manufactures a wide range of railway vehicles from high-speed trains to tramways and trams, and it is the world’s leading service provider in the rack-and-pinion rail vehicle industry.
The Swiss-based company has a workforce of roughly 11,000 employees based in 7 production locations, 5 component manufacturing sites, and 40 service locations around the world.
Data leak threats
Stadler announced on Thursday evening that attackers managed to infiltrate its IT network and infect some of its machines with malware and, most probably, to collect and exfiltrate data from the compromised devices in the process.
"Stadler's internal monitoring services have established that the company's IT network was attacked with malware and that it is highly probable that an outflow of data of an as yet unknown extent has occurred," the company said.
After the attack was discovered and Stadler took measures to contain it, the threat actors behind this security incident also asked for a large ransom and are attempting to blackmail the company by threatening to leak stolen data.
The unknown perpetrators are attempting to blackmail Stadler, demanding large sums of money, and to put pressure on Stadler with the possible publication of data in order to harm the company and thus also its employees. - Stadler
The rail vehicle manufacturer said that it took the steps needed to secure its computing systems immediately after and it also hired a team of external security experts to help with the incident's investigation.
Stadler also stated that it has backups for the affected data and that it is working on restarting and, potentially, restoring the impacted systems.
While the company does not explicitly call it a ransomware attack, all the signs of one are there: attackers asking for a ransom under the threat of leaking sensitive data stolen before encrypting the systems and the mention of data backups which directly implies that its systems were encrypted (or wiped) during the attack.
The entire Stadler group impacted by the attack
Although the incident announcement doesn't disclose the number of locations and systems affected, Swiss media says that the entire Stadler group was impacted by this cyberattack, including locations from Switzerland and abroad.
Stadler also said in a statement that the company has filed a complaint with the Thurgau public prosecutor and that an investigation is ongoing.
"Despite the corona pandemic and cyber attacks, the continuation of the production of new trains and Stadler's services is guaranteed," the train manufacture emphasizes.
BleepingComputer has reached out to a Stadler spokesperson for additional details but had not heard back at the time of this publication.
Cyber volunteers release blocklists for 26,000 COVID-19 threats
10.5.2020 Bleepingcomputer Cyber
The COVID-19 Cyber Threat Coalition has released a block list of known URLs and domain names associated with Coronavirus-themed scams, phishing attacks, and malware threats.
The coalition is a volunteer organization created towards the end of March 2020 to disseminate information about new threats trying to take advantage of the Coronavirus pandemic.
This COVID-19 Cyber Threat Coalition consists of members from the cybersecurity community, large companies, cyber intelligence firms, and antivirus vendors who use the collected information to protect businesses, consumers, government, and healthcare organizations from online attacks.
Blocklists released to protect enterprises and consumers
As part of this project, the group has created two blocklists containing URLs or domain names that are known to be associated with attacks on healthcare, government, and enterprise organizations or are related to Coronavirus "themed" scams, phishing attacks, and malware.
The URL blocklist currently consists of 13,863 malicious URLs that have been seen in attacks, and the domain blocklist now contains 12,258 malicious domains and hostnames.
Current URL blocklist
Both consumers and the enterprise can use these blocklists in locally run DNS sinkhole solutions such as Pi-Hole, by feeding them into firewalls or secure gateways, or using them in other security solutions.
Local users who want to use the domain blocklist to protect a single machine can also convert it into a HOSTS file by simply adding 127.0.0.1 in front of each hostname, as shown below.
Converted into a HOSTS file
With the current list of domains, this would generate a 452KB file, which may cause performance issues in Windows 10.
If you do create a HOSTS file from these blocklists, let us know how it goes and if you see any performance issues.
As both of these blocklists are refreshed every ten minutes if you use them to increase your security, be sure to update them at least twice a day.
Introduce Kids to Cybersecurity With This Free Activity Book
4.4.2020 Bleepingcomputer Cyber
Security company Balbix has released a 12-page printable activity book for children that introduces them to cybersecurity in a fun way.
With schools closed and parents working from home, it can be hard sometimes to find free time while keeping younger kids engaged in a fun activity.
To get some free time to do chores or to just relax while offering younger children a fun activity, parents can print out a free 12-page Cybersecurity activity book from Balbix that contains coloring pages, games, and puzzles.
"We have created a 12-page printable activity book for your kids. This book has cybersecurity themed coloring pages, puzzles, games, and other activities that they can enjoy," Balbix states on their download page.

Example game in the activity book
If this activity book was finished too fast, the Audible Stories is also providing a wide selection of free audiobooks for children and teens.